Quick Enquiry Form
Categories
- Agile and Scrum (166)
- BigData (9)
- Business Analysis (66)
- Cirtix Client Administration (33)
- Cisco (39)
- Cloud Technology (43)
- Cyber Security (20)
- Data Science and Business Intelligence (18)
- Developement Courses (18)
- DevOps (13)
- Digital Marketing (36)
- Emerging Technology (143)
- IT Service Management (59)
- Microsoft (39)
- Other (393)
- Project Management (446)
- Quality Management (99)
- salesforce (47)
Latest posts
Using Lean Management to Boost..
The Future of Self Service..
CISSP Influence on Cybersecurity Duties..
Free Resources
Subscribe to Newsletter
ITIL 2011 Foundation Workshop incl Certification Exam
Information Technology Infrastructure Library (ITIL) is a set of globally recognized best practices for IT Service Management that can be tailored to any organization. ITIL provides the foundation for quality IT Service Management through documented, proven processes that cover the entire Service Lifecycle. It is easy for organizations to learn, tailor, and implement ITIL to suit their environment. A complete ITIL philosophy has grown around the guidance contained within the ITIL books and the supporting certification and qualification scheme.
ITIL is the most widely adopted approach for IT Service Management in the world. It provides a practical, no-nonsense framework for identifying, planning, delivering and supporting IT services to the business.
The ITIL Foundation Course is an entry-level certification. It introduces the Lifecycle of managing IT Services to deliver to business expectations and provides an approach to learning the core disciplines of ITIL best practices.
The ITIL Foundation Course is a stepping-stone for everyone who is interested in learning more about ITIL best practices. The audience includes all IT professionals who work in or plan to work in an ITIL supported environment as well as in key business areas.
images courtesy: goo.gl/HFDBU3
Read More
images courtesy: goo.gl/HFDBU3
ITIL training in Bangalore
Enroll for ITIL training in Bangalore..!!! Contact info@icertglobal.com
with your Name and Phone Number.. Hurry UP ..Limited Slots..
Enroll for ITIL training in Bangalore..!!! Contact info@icertglobal.com
with your Name and Phone Number.. Hurry UP ..Limited dates..
Read More
ITIL Service Operation Certification
ITIL Service Operation
Purpose of Service Operation:
Purpose of Service Operation is to make sure services are delivered at agreed levels. Its purpose is to also manage the technology, infrastructure and applications implemented in organization in order to meet customers' needs.
In fact this is the the stage in the whole life cycle where services basically deliver the value to the business because from business point of view this stage has the highest visibility. It is Service Operation staff responsibility to ensure that the value to the business is delivered.
At this stage there may be some conflicting goals appear and it is important to know how to balance this. Some examples are:
- technological, internal IT perception versus external business point of view.
- stability versus responsiveness.
- quality versus time to deliver versus cost of service.
- reactive attitude to support services versus proactive activities.
All the conflicts mentioned above are just examples. In practice there are much more of them and each one has to be balanced and maintained by the Service Operation staff. Excessive focus on one side without balancing another side will result in poor service.
images courtesy:goo.gl/fMKeZL
Read More
images courtesy:goo.gl/fMKeZL
ITIL Qualification Scheme
ITIL Qualification Scheme
The ITIL Qualifications scheme provides a modular approach to the ITIL framework, and is comprised of a series of qualifications focused on different aspects of ITIL Best Practice, to various degrees of depth and detail.
These are the levels of qualifications within the scheme:
ITIL Foundation
ITIL Intermediate Level
ITIL Managing Across the Life cycle
ITIL Expert Level
ITIL Master Qualification
The modular, tiered structure of the qualification not only offers candidates the flexibility in relating to the different disciplines and areas of ITIL, but generally makes ITIL qualifications more accessible and achievable.
images courtesy: goo.gl/asmH3z
Read More
images courtesy: goo.gl/asmH3z
IT Service Management
ITIL Foundation
The Foundation Level is the entry level qualification which offers candidates a general awareness of the key elements, concepts and terminology used in the ITIL Service Life cycle, including the linkages between Life cycle stages, the processes used and their contribution to Service Management practices.
Why should I take ITIL Foundation?
Upon successful completion of the education and examination components related to this qualification, candidates can expect to gain a general overview, and basic knowledge and understanding of ITIL.
Successful completion of the Foundation qualification also fulfils the prerequisite entry criteria for the next level of study within the ITIL qualifications scheme, the ITIL Intermediate Level .
images courtesy: goo.gl/LFf5uh
Read More
images courtesy: goo.gl/LFf5uh
ITIL Foundation Certification and Training
ITIL® Foundation
The Foundation Level is the entry level qualification which offers candidates a general awareness of the key elements, concepts and terminology used in the ITIL® Service Lifecycle, including the linkages between Lifecycle stages, the processes used and their contribution to Service Management practices.
Why should I take ITIL® Foundation?
Upon successful completion of the education and examination components related to this qualification, candidates can expect to gain a general overview, and basic knowledge and understanding of ITIL®.
qualification also fulfils the prerequisite entry criteria for the next level of study within the ITIL® qualifications scheme, the ITIL® Intermediate Level .
Is it right for me?
This qualification is primarily aimed towards:
those who require a basic understanding of the ITIL® framework;
those who need understanding of how ITIL® can be used to enhance the quality of IT service management within an organization;
IT professionals or others working within an organization that has adopted and adapted ITIL® who need to be informed about, or contribute to an ongoing service improvement programme.
The ITIL® qualification is open to any individuals who may have an interest in the subject.
The ITIL® Foundation qualification is not intended to enable the holders of the qualification to apply the ITIL® practices for Service Management without further guidance.
For more information and register for ITIL Foundation courset Please click on below register button.
images courtesy : goo.gl/NVVU7g
Read More
images courtesy : goo.gl/NVVU7g
Agile complements traditional project management but how
Agile doesn’t trade places with traditional project management which is centered around water-fall methodology. Hence Agile doesn’t counter against PMI®, long known for its project management credentials through PMP, rather it complements… Let’s get the insight on why do we recommend Agile. It is to be noted that PMI features PMI-ACP® as one of its flagship certification which is fast gaining grounds, if the traction is any indicator. We are one of the leading lights in knowledge and certification of PMI-ACP® and regularly conduct training and workshops on key locations around the globe. Let’s move on to the narrative.
Cost/Schedule Creep…
Agile talks about how we can be adaptive for changes for the projects which doesn’t have clear scope or which has evolving scope. However Agile doesn’t address about how one should manage the cost/effort against the change and in nutshell Agile talks/encourages the changes of the scope, Cost, effort and in reality as the project runs based on the budget and cost in most cases. Agile can complement within the schedule/cost however there needs a cap for the cost and schedule to avoid the major creeps on the same. PMI standards protect the projects from these variances or it gives us the better predictability on the same.
Big Picture Vs Progressive evolution
One should have big picture in mind which is very important to achieve the final goal. While agile emphasize on changes and adaptiveness, it doesn’t define the boundary wherein PMI plays a key role . We can be adaptive to changes as long as it is within the final goal of big picture. Without having final frame in mind, one cannot evolve in the right direction which means PMI gives you the right direction to evolve rightly. To my view without high level plan in hand, running the project in agile may never predict any time. We need a high level plan to assess ourselves on where do we stand in terms of goal achievements.
Agility within the project (Scope, Cost & Schedule) is always recommendable so that we always have grip on the project. Project should aim for success and that success is defined based on Scope achievement within agreed time and cost factors.
Read More
Risks Vs. Opportunities
Risks Vs. Opportunities What is Risk?
Risk is an uncertainty which could lead to an impact (positive or negative) to the project. When we mention uncertainty, it is related to probability. When the impact of the probable event is positive we call that as opportunity and when it turns negative, we term that traditionally as “Risk” (Negative impact).
Does it mean should we care about only negative impacts or Risks? As much as Risks are important to monitor to minimize the probability and impact, its equally important to maximize the opportunity and the impact of positive impact.
Risk à Reduce Probability à Reduce the impact
Opportunity à Increase the Probability à Maximize the impact
Example, we send the RFP (Request for Proposal) to our customer to get the deal which definitely is very uncertain to get the deal and make the profit out of that.
What are the threats?
Competitors are our threat who have same level of competency or more
What are the Risks and Opportunities?
commercially, if we spend money on developing prototype and the deal doesn’t materialize then it’s a loss to us. Hence developing prototype can be considered as Risk/Opportunity.
hence, we should try to maximize the probability to get the deal .
What are the Risks involved?
The Risks (Negative Impacts) as identified can be
Loss in profit
How to reduce the Negative Impact ? Have alternate business plans Credibility with employees Have the backup plan for the resources
What are the Opportunities (positive Impact)?
High chances to get the deal as we have all things ready
Team motivation
How to increase the Positive Impact ?
Create a prototype Resource Plan
People, Software & Hardware Have the ramp up plan ready and it will be easy to kick off the project on time
Learn more about Risk and Opportunities by visiting our Project Management certification courses http://goo.gl/fbuV2m
Read More
Quality Management a test of the Tester
The iron triangle of project management has scope+ time+ cost and at the core rests the Quality. Meaning none of the axes can be compromised, which consequently impact Quality adversely. So what’s about Quality? Well, everything boils down to Quality. Standards are Quality measure. High standards attributes to High Quality. Well, when thoughts transcend from personal experience as Project Manager, I always ensured the quality team has the final word on everything shipped much to the chagrin of the development team. They often sparred as to ‘who called the shots?’ and I will put my best foot forward “I do” to the eerie silence of the team. A team is a bunch of individuals with their own talent, and that’s why we refer recruitment more as Talent Acquisition. No matter the nomenclature associated, no two individuals are going to be the same. Like-minded perhaps, but unlikely twins in thoughts. So it’s a mixed pool. Fundamentally its still the make, sell, support, and the Quality team falls under the support bucket while developers act as the breadwinners in the ‘make’ stream, and hence feel privileged and even entitled. At the inception of the project, when the Developers roll up the sleeves and get busy writing Unit Cases, testers too are full of activity preparing test cases. So the any claim of entitlement is very juvenile in judgement and I dare say never to expect anything additional other than the allocated. One incident always enlivens and worth narrating. He was a super-duper geek that touching his code is deemed an insult. It’s like rinsed with Listerine mouth freshener every five minutes that the teeth are sparkling white and fragrant. One should marvel at the pride taken in their work that they come down to challenge “check my code and any bug, I am toasted else you are roasted”. I found a demure girl, belying her age, walking up to the rock star “I am sorry but there seems to be a bug”. A volcano just erupted. When the pride is pricked, what else can you expect? Fireworks. I was observing the exchange from a distance but didn't intervene. They are professionals and ought to conduct like one. A dent to his dignity, he mounts a ferocious attack justifying every nook and corner while the tester patiently hears him out. After a full fifteen minutes of explanation, the girl calmly states “I understand but it’s a bug”. The developer slams his forehead and unloads a heap of curses in which one expletive burst out unbeknown. Now discipline and decorum can never be conceded at any cost. Since the unfortunate exchange happened on the floor, the shrill pitch made heads turn around. The lady was unmoved and strangely didn't emote at all but retained her composure. The developer, in sharp contrast, was belligerent and a nervous wreck. However sharp you might be, team play takes prominence and position. Both approached my desk and my silence spelled ANGER. My glare at nowhere but all ears, I wanted to hear one word ‘sorry’ instead he defied everything that’s sacrosanct and conduct hardly propriety. I demanded ‘Apologize. Now’. It was not a counsel but a command, and reluctantly he budged and muttered the apology. He might be a rock star but that lady’s attitude made her much taller and he dwarfed in stature. I then requested the tester to walk through the bug and she clearly made her case which was watertight. Confounded with the bug and confused as how his code can be cracked, the developer was at his wits ends and close to tears. Passion is different to taking things personal. After all to err is human. Managing people is far too different and difficult than project. My call still remained unaltered ‘the tester will have the final word’ and pausing “if the client finds fault in the UAT [User Acceptance Testing], it will the tester who will be taken to task”. Even that developer smiled. Much rests on the shoulders of the tester who are gate-keepers. Nothing can or should slip or creep between their legs. With an eye for details and investigating instincts to sniff something unusual, they treat every test case as a suspect and once convinced of merits pass it for clearance. That tester demonstrated typical traits expected – the poise, politeness, profound knowledge, patience, perseverance, while the other (Developer) displayed pettiness. Her signature statement was bereft of sentiment but well stated “I am more concerned about the Quality of the Project just as you are about the principles of Project Management.” Well said! Quality Management is a key knowledge area in PMP® Certification exam. For more details visit http://goo.gl/U4Rtez
images courtesy: goo.gl/FtgC51
Read More
The iron triangle of project management has scope+ time+ cost and at the core rests the Quality. Meaning none of the axes can be compromised, which consequently impact Quality adversely. So what’s about Quality? Well, everything boils down to Quality. Standards are Quality measure. High standards attributes to High Quality. Well, when thoughts transcend from personal experience as Project Manager, I always ensured the quality team has the final word on everything shipped much to the chagrin of the development team. They often sparred as to ‘who called the shots?’ and I will put my best foot forward “I do” to the eerie silence of the team. A team is a bunch of individuals with their own talent, and that’s why we refer recruitment more as Talent Acquisition. No matter the nomenclature associated, no two individuals are going to be the same. Like-minded perhaps, but unlikely twins in thoughts. So it’s a mixed pool. Fundamentally its still the make, sell, support, and the Quality team falls under the support bucket while developers act as the breadwinners in the ‘make’ stream, and hence feel privileged and even entitled. At the inception of the project, when the Developers roll up the sleeves and get busy writing Unit Cases, testers too are full of activity preparing test cases. So the any claim of entitlement is very juvenile in judgement and I dare say never to expect anything additional other than the allocated. One incident always enlivens and worth narrating. He was a super-duper geek that touching his code is deemed an insult. It’s like rinsed with Listerine mouth freshener every five minutes that the teeth are sparkling white and fragrant. One should marvel at the pride taken in their work that they come down to challenge “check my code and any bug, I am toasted else you are roasted”. I found a demure girl, belying her age, walking up to the rock star “I am sorry but there seems to be a bug”. A volcano just erupted. When the pride is pricked, what else can you expect? Fireworks. I was observing the exchange from a distance but didn't intervene. They are professionals and ought to conduct like one. A dent to his dignity, he mounts a ferocious attack justifying every nook and corner while the tester patiently hears him out. After a full fifteen minutes of explanation, the girl calmly states “I understand but it’s a bug”. The developer slams his forehead and unloads a heap of curses in which one expletive burst out unbeknown. Now discipline and decorum can never be conceded at any cost. Since the unfortunate exchange happened on the floor, the shrill pitch made heads turn around. The lady was unmoved and strangely didn't emote at all but retained her composure. The developer, in sharp contrast, was belligerent and a nervous wreck. However sharp you might be, team play takes prominence and position. Both approached my desk and my silence spelled ANGER. My glare at nowhere but all ears, I wanted to hear one word ‘sorry’ instead he defied everything that’s sacrosanct and conduct hardly propriety. I demanded ‘Apologize. Now’. It was not a counsel but a command, and reluctantly he budged and muttered the apology. He might be a rock star but that lady’s attitude made her much taller and he dwarfed in stature. I then requested the tester to walk through the bug and she clearly made her case which was watertight. Confounded with the bug and confused as how his code can be cracked, the developer was at his wits ends and close to tears. Passion is different to taking things personal. After all to err is human. Managing people is far too different and difficult than project. My call still remained unaltered ‘the tester will have the final word’ and pausing “if the client finds fault in the UAT [User Acceptance Testing], it will the tester who will be taken to task”. Even that developer smiled. Much rests on the shoulders of the tester who are gate-keepers. Nothing can or should slip or creep between their legs. With an eye for details and investigating instincts to sniff something unusual, they treat every test case as a suspect and once convinced of merits pass it for clearance. That tester demonstrated typical traits expected – the poise, politeness, profound knowledge, patience, perseverance, while the other (Developer) displayed pettiness. Her signature statement was bereft of sentiment but well stated “I am more concerned about the Quality of the Project just as you are about the principles of Project Management.” Well said! Quality Management is a key knowledge area in PMP® Certification exam. For more details visit http://goo.gl/U4Rtez
images courtesy: goo.gl/FtgC51
Emotional intelligence (EI) and its effect on Management
Many of us are familiar with AI [Artificial Intelligence] but what is Emotional Intelligence? And its relevance in Management, especially people management? One respondent quipped ‘ego’. Though not entirely off the mark, it addresses just an aspect. Look before you leap; right. Do you think before acting?
Emotional intelligence (EI) is a term used to describe the ability of an individual to recognize their own and other people's emotions, to discriminate between different feelings and label them appropriately, and to use emotional information to guide thinking and behaviour [courtesy: wiki]. The term EI gained recognition in 1995 and thereafter evolved as a model, namely ability and trait model.
So far we have studied human behaviour, but seldom self-behaviour consciously. As individuals, we often introspect about our actions, and those who dig deeper to understand emotions and then associate with actions to adjust and adapt are better as decision-makers states studies.
How effective as Managers? More than anything and anywhere, Emotional Intelligence most needed when negotiating with a colleague or peer or team or superior. Man exhibits myriad emotions. To handle and navigate needs successful soft skills for our decision ought to be rationale, objective and holistic. In a chaotic world with its cacophony like – snarls created after caught in traffic jams or embroiled in a heated exchange - it can be anything trivial to most trying of circumstance. Conflict is common occurrence but the choice to respond rest with us. Calm, collected and composed even in the wake of a storm can’t be seen in everyone. It’s a calling at a very high level and hence those who EI is way above are really adept in adjusting response/reaction and revel at interpersonal relations. The ability to recognize, relate, identify, empathize with others plight, connecting with others, commendable communication and control crisis are typical traits. In other words, high Emotional intelligence (EI) proves very effective in man-Management.
Emotionally intelligent leadership are recognized by strong sense of self-awareness whereby that can detect one’s emotion and direct appropriate response mechanism. That call is critical. As highlighted above how we choose to respond is always our choice. Failure to manage might prove to fatal to one and all involved. Develop skills to be aware and evaluate the emotions of others, so as to react suitably to the situation. Leaders’ hallmark lies in this reception/response that has a direct impact on gaining confidence enhance performance, Employee retention to total satisfaction. They speak less and listen a lot. Not hear but listen to understand the underlying emotions. The tone, tenor, language, gestures gives scope to study and gauge emotions. Leaders always choose the words and measure before delivery – again in the right tone and tenor. These are exceptional skills to anticipate and in some case pre-empt – emotional intelligence is all about this and such Leaders prove to be remarkable in management.
It might sound new to some or even niche, but make no mistake - only the fittest survive. Emotional intelligence is treated as a critical factor in assessing your management skills complementing human capital [education, certification] and fitness aspects. Yes, very much!
Project Managers are expected to have a high emotional intelligence, as important and credible as the Project Management certification. One is a testament about your psyche and other about education, expertise and experience.
Please visit our http://goo.gl/IRCmJz to know more of our offerings.
Read More
PMP One of The Possible Pitfalls is Procrastination Project Management
Many talented professionals who are capable of cracking the PMP® exam at their first attempt fail to do so for a number of reasons ranging from domestic to demand of the day. But the most common amongst the reasons attributed is ‘Procrastination’.
“No Time” is the often heard refrain. Whether they develop cold feet or deeply immersed in their work to take shift their attention, the PMP Exam is given a pass and pushed to another day.
Some of the professionals interviewed cited reasons that might sound unbelievable, but then that’s their version. We have listed some for your reference as a precautionary note not to delay or defer in taking up the exam. Every single day you lose is something lost forever. On case your mind is set in appearing for the exam and obstacles of any kind can appear as stumbling blocks, you still can overcome the odds and not use or search for excuses.
Here are some reasons listed for Procrastination:
“It’s too tough” - of course, it’s tough. PMP® actually moderates from average to tough and calls for dedicated study and determined efforts. The view from the top is terrific but you got to toil to get to the top.
“I AM BUSY. I don’t have time” – No one has the time to spare. Try checking with anyone and a volley of reasons backed with rationale will be thrown in return. MAKE TIME. You can always apportion time. You really don’t consume all the 24 hours. So late nights, early mornings, and of obviously, the weekend is all yours to prepare for PMP. We do find time to make ourselves free for occasions and get-together by freeing up bandwidth. Studies are a struggle since childhood and in adulthood with more responsibilities sagging the shoulder, and hence it’s no easy feat to sit and burn the midnight oil. ‘Nothing great was ever accomplished without making sacrifices.’
“The Job Pressure is too much” – agreed. We all have gone through the grind and it’s difficult to focus when your mind is constantly analysing multiple scenarios and multitasking. Despite the pressure, can you rise up to meet the challenge? Determination. When the traffic too much, do you just reverse the vehicle and go back home or maneuver to find way to office? Studying despite the hardships is likewise. Most succeed because they are determined.
“May be next month” – the worst excuse. If something is to be done, better do it immediately. Tomorrow never comes, so how will next month? We only avoid accepting to spell the truth and instead pretend using the pretext of ‘another day’. As it is written, ‘If we wait until we are ready, we will be waiting for the rest of our lives’.
“I am not good enough” – that’s accepting defeat even before the fight. How would you know unless you attempted. So, all those appear for the PMP exam pass? There are no failures? Wrong. Even those failed should be applauded for their audacity to make an attempt, and failure will push them further to fare better. So long you qualify with the prerequisites set by PMI®, you are as good as any applicant. Just that you are poor on confidence. Build self-confidence and go for it. You will emerge triumphant.
The reasons to slow you down or stop may be innumerable. Bear in mind that it’s the strong that survives and succeeds. SO DO IT NOW.
“Its not the mountains we conquer, but ourselves.” – Edmund Hillary
Read More
Enroll for Upcoming 4 Days PMP Certification Training Courses Workshop with 100precent MoneyBack Assurance in US by iCertGlobal
PMP Certification Training Course Boot-Camp with 100% Money Back Assurance in US-iCertGlobal | PMP Training Course Workshop | PMP Classroom Training Workshop Course with 100% Money Back Assurance | PMP Boot Camp Workshop Training in US | Get trained on the latest PMBOK 5th edition by our industry-renowned trainers, who are veterans in their own right with years of working experience in the industry & training PMP aspirants.
We are a Global Registered professional certification organization in the areas of Project Management [PMI®, PRINCE2, MSP], Service management [ITIL Foundation, Intermediate, MALC and Expert Track], Quality Management [Six Sigma Green Belt & Lean Six Sigma Black Belt], Agile & Scrum [CSM, PMI-ACP, CSPO], Citrix, Cisco and Emerging Technologies.
Benefits of being PMP Certified
• Be able to pass the PMP® Exam and become a certified Project Management Professional (PMP®)
• Apply Project Management techniques useful in the real world
• Share a common lexicon of Project Management terms and principles
• Gain International Recognition
• Establish Credibility
Note: In case you are unable to attend classroom training, attend our Live Virtual Class (LVC) Session, as per your convenience.
Register Now! in upcoming workshop training to avail early bird offers.
E-mail: - info@icertglobal.com
Phone: +1 (713)-287-1252
For Live Chat:- http://goo.gl/wD0U0b
For more detail visit our site:- http://www.icertglobal.com/
Read More
Register Now For 4 Days PMP Certification Training Course with 100percet MoneyBack Assurance in India at iCertGlobal
PMPCertification Training Course with 100% Money Back Assurance in India at iCertGlobal | PMPTraining | PMP Classroom Course with 100% Money Back Assurance | PMP Boot CampWorkshop Training, India | Get trained on the latest PMBOK 5th edition by our industry-renowned trainers, who are veterans in their own right with years of working experience in the industry & training PMP aspirants.
We are a Global Registered professional certification organization in the areas of Project Management [PMI®, PRINCE2, MSP], Service management [ITIL Foundation, Intermediate, MALC and Expert Track], Quality Management [Six Sigma Green Belt & Lean Six Sigma Black Belt], Agile & Scrum [CSM, PMI-ACP, CSPO], Citrix, Cisco and Emerging Technologies.
At the end of this course, you will:
• Be able to pass the PMP® Exam and become a certified Project Management Professional (PMP®)
• Gain the skills and knowledge of project management based on the PMBOK® Guide and real-life project management practices
• Apply project management techniques useful in the real world
• Share a common lexicon of project management terms and principles
• Contribute to Better Job
• Open Doors to New Clients
• Gain International Recognition
• Establish Credibility
Note: In case you are unable to attend classroom training, attend our Live Virtual Class (LVC) Session, as per your convenience.
Register Now in upcoming workshop training to avail early bird offers!
E-mail: - info@icertglobal.com
Phone: +91 (80) 65370333
For Live Chat:- http://goo.gl/wD0U0b
For more detail visit our site:- http://www.icertglobal.com/
Read More
May2015 Workshop Schedule for PRINCE2 Foundation And Practitioner Classroom Training Certification Course by iCert Global
PRINCE2 Certification Training Course Workshop with 100% MoneyBack Assurance by iCert Global in India | PRINCE2 Certification Training Course Workshop with 100% MoneyBack Assurance by iCert Global in Australia | PRINCE2 Certification Training Course Workshop with 100% Money Back Assurance by iCert Global in United Kingdom(UK) | PRINCE2 Foundation and Practitioner Certification Training Workshop | PRINCE2 Foundation Classroom Training Workshop Courses with 100% Money Back Assurance | PRINCE2 Practitioner Certification Training Courses
Read More
PMP Certification do You have IT
There are currently 658,523 active PMP certified individuals. In the year 2010, there were roughly about 360000 plus. So in 5 years the number almost has doubled. Surely the demand in the market too has surged with projects on the rise and technology taking off to unknown horizons. Mobile is the device now – clearly wasn’t so 5 years back. Tabs just touched the table [iPad was released in 2010] and became a novelty.
A PMP certification was certainly niche a decade ago. Experience was given more weightage and with that the accrued skills and services. When the need for quality managers proved to be vital and critical, recognition of some sorts that underpins one’s prowess professionally became the most sought out factor in filtering the fine from the grainer like sifting stones from wheat. Positions high up in the ladder are few and far in between and hence in the rat-race to reach to the top, there is a scurry amongst qualified to find a seat in the front. And by virtue of? Apparently, meeting the requirement for the Job – vide education, and experience [as applicable]. In the context of Project Manager, many aspirants couldn’t just sneak through or gate-crash but cut teeth in the grinding many project before positing a claim for the position. A justification for the coronation ought to be proved by data points. And it was conventional wisdom that weighs experience prima facie in plucking the ripe fruit in filling a slot, and never the low hanging ones.
As the number of PMPs soared in numbers, the de facto certification in Project Management seems, experience proved vital a component to be COMPLEMENTED. To be fair, PMP is no walk in the park. To appear for a PMP exam, it mandates both education and experience as prerequisite on top of which 35 Professional Development Units (PDU) is imposed. The PDUs cover the 10 knowledge areas especially scope, cost, time and other core management of risk, human resources, communication, stakeholders. It’s a complete nine-yard drill packed with ‘all you need to know about project management’ with scintillating depth. Thus passing the exam proves the possession of collective wisdom. Thus PMP exam equates education, experience and expertise. More so, the Project Managers with hands-on experience gain to understand the science behind the learning making them more ‘informed and learned’. Well, if the odds are so heavy and certification makes you the elite amongst the eligible, does the rise in certified professionals raises your eyebrows?
Admirably the numbers lends credibility to the claim. With more certification as supply, the demand too is growing steady as forecasts reveal. The perk associated with the certification is the key differentiator amongst the crowd to make your profile stand out. Besides, HR uses sophisticated software in filtering to weed out potential candidates without certification based on key words, namely PMP. So non-PMP holders are denied an opportunity to be short-listed and decided at face value as ‘knowledge deficit’ (contentious one right?). And it’s been proved more than once the PMP holders are ‘pick of the lot’ as PMI raises the bar in clearing the certification which by now is the benchmark. The question posed to the professionals is: Do you have IT?
We would love to listen to your comments…..
Read More
Risk Mitigation
Risk Mitigation is to pre-empt and be prepared to respond to unexpected or anticipated issues that might spring up in course of development. Risk mitigation is not about developing the solution for anticipated issues all the time and at times, it also depends on how we would respond to an issue to reduce the impact of the same. Another perspective is to identify as to who needs to respond and how to respond in mitigating the issue.
Who should respond? The person who will be owning the Risk. This is what we classify as transfer of Risk. There are times we will not be able to respond to all the issue and we may need to direct to the right person.
Alternatively, identifying the dependencies is also another way of mitigating risks
Identifying Dependencies è Risk Transfer è Risk Mitigation
How to respond?
There are 2 types of risks we may come across
1. Issues which we need to address with solution
2. Issues for which we may not have solution with us
So how do we respond the above 2 scenarios.
In the first case, we have 2 options
Identify the solution è Reduce the impact (Risk still exists with less impact)
Identify the solution è Remove the impact (Risk is nullified)
In the second case
Accept the Risks è Plan for the impact
ð Adapt the impact in the scope/plan (Plan for the Risk impact)
Avoid the Risk è Change the scope to exclude the risk
ð Change the scope in such a way the risk is excluded
Transfer the Risk è Identify the right owner of the issue
ð Assign the responsibility/ownership to the right person
When to respond? In general, risks and its impacts ought to be reviewed/assessed periodically with the respective mitigation plan which may necessitate changes which have to be factored and plan updated accordingly. Depending on the duration, impact also may vary.
Example, during the planning phase, we might have identified the Dependency of external platform as a Risk. If that exists even during Design phase, impact will be more as right after development we may need the access to the external platform to do the validation.
Learn more about Risk Mitigation by enrolling in our PMP® Training. For more details, do click http://goo.gl/MPBy1r
Read More
The year 2016 closed on a high note 2017 is greeted with high hopes
The year 2016 closed on a high note. The low-profile CEO of iCert Global went on stage to receive the “Arch of Excellence” award from AIAC. Collecting the award, he commented on the sidelines that, “the key behind the success is our openness to ideas and innovations, especially with customer is in the center stage. Expect the unexpected – be prepared always. Learn from the defense services – why do they do the drill day in and day out? That’s preparedness. Keep educating yourself. Reinventing – is learning new things and innovation is about ideation and iterations. Figure out your strength and try channeling in many ways – that’s what makes you versatile.”
True. It was a fitting finale to a trying year filled with uncertainties and yet we prevailed.
“Energy can neither be created nor destroyed; rather, it transforms from one form to another.” So, the ultimate test will be who is the beneficiary of the training? Only when the customer is enabled through education, business grows, and not the other way around. The motive of any venture, undoubtedly, is to make money unless it is philanthropy. Absolutely. It’s the goal of any enterprise to make profit. But how do you make money matters? Money sounds crude, so replace with bottom-line to mask. But whatever words you wish to use, one can’t erase the ultimate objective of making dollars and cents in every engagement. So, how different are we then? Fair enough to question. We exist because of our customers. And the growth is synergetic. But who first? Customer always comes first. It might sound clichéd but that’s the age old truth which has stood the test of time.
At the end of the day, if you have successfully transformed an individual life positively, that’s an incredible feat. Something to feel immensely proud as achievement. At iCert Global, our endeavor is to transform as many lives as possible. We must be futurist in our thoughts, take and toil. Complete customer satisfaction, prompt service, on-schedule and within-budget delivery are the company’s guiding principles.
The soft-spoken, hands-on and low profile CEO signs off in a classic statement that’s inimitable. ‘The award makes us more conscious, now that we have been recognized for excellence. It motivates us to better ourselves, and strive to deliver more than we did before. There is always room for improvement and our performance will pay off eventually in the form of recognition. That’s as important and outstanding as this award. We have very high hopes of outperforming ourselves in 2017. Wish you all a prosperous New Year and success in all your undertakings.”
Happy New Year – 2017 to one and all.
Read More
How to prepare for an ITIL Foundation Certification
Want to get certified in first attempt in ITIL Foundation certification exam? Well then, how do you prepare for the exam? This article will walk you through some insights considered critical and vital to successfully crack the exam.
ITIL is considered as the best-practice service management framework across the industry, especially for IT service and governance. If your field of interest and area of expertise happens to center around IT services management, and serious about shaping a career, then we strongly recommend you to take up ITIL® certification. The certification will accelerate your career path and professional advancement.
Now that you are sure of your interest and inclination, the stepping stone towards the ITIL® certification is the ITIL Foundation.
Start your research
Before enrolling to ITIL Foundation course, do a bit of research to gain a basic understanding about ITIL Foundation. This will help you to assess and analyze the knowledge gap as some topics might be familiar, which is a shot in the arm and makes you more confident. It presents an idea of your own appetite as well.
Scout for a good learning providerExtend your research to check the available learning academies in and around your place. Alternatively, check and confirm if other modes of learning like instructor-led online class or e-learning can take the place of physical classroom. If your employment comes in the way of attending regular classroom training, other options should be open for consideration. So factor these aspects in your search ad don’t prioritize based on just proximity hoping to catch up on shortfall later. It should be well searched and informed decision before you can make your move.
Sign up
Once you screen and settle on a service provider, sign up after checking your calendar to ensure there are no planned events that might impact or interfere with your training dates. A dedicated effort always calls for a detailed plan. A systematic approach and meticulous plan and good balance bring in the much desired discipline. Make sure everything in its place before the course begins. There are tons of literatures available in the public domain. Read and upgrade.
Study
The relentless pursuit of learning leaves you rich and rewarding. So scratching the surface won’t suffice, instead dig deep and deeper and find roots. Study every chapter and summarize your learning. The Foundation course will be more about terminology, core concepts, process, lifecycles stages and links within. The course summary for every chapter will help you in identifying the learned and missed. If required, start all over again until you are satisfied and confident to close. Always question and seek greater clarity through illustration and examples. Try to reinforce learning through workplace experience and scenarios. After the completion of every chapter, attempt without fail the chapter test as this exercise will help you close the gaps that may exist and provide you the opportunity to assess your own standing based on the test outcome.
Self-study
Classroom study must be supplemented with self-study. The chapter tests taken in classroom can be replicated through tests available online. Today, the internet presents a wealth of information and poses hundreds of questions to test your skills and strength and as part of self-study, attempt as many as you can in the time available – that’s why the need for the systematic study and meticulous plan to apportion time accordingly. Usually, candidates are provided some time after the course completion to schedule the exam. Use this time effectively.
Self-assessment
The mock-exam or final test will be a comprehensive question papers simulating the severity of the Certification exam. You must endeavor to take as many as possible. Further, the official site hosts mock exam for participants to prepare themselves. Become conversant with course by scoring more than 90% in your mock exam. The ITIL Foundation is an objective-type 40 questions, and its possible to get all 40 correct. Your score above 90 must become a pattern from the series of mock exam attended. The score is a clear indicator of your learning and in case the score dips below 90, then restart by revisiting the chapters where the marks went missing. It’s plugging the holes and closing gaps that one scales. It’s very much possible and, with effort, achievable.
Sit for the examination
With the kind of strenuous preparation, just keep your cool and calmly appear for the exam. Make sure you read all the answers and most importantly understand the answers from the perspective of the question, and not misunderstand with your professional experience. Often candidates confuse the questions with scenarios experience in their professional front and as a result get sidetracked and struggle to find our way back.
The percentage of pass is 65% which is answering 26 question correctly out of 40. The insistence in scoring 90 and above successively in a series of mock exam is to make oneself fluent and assure a safe passage to the subsequent level of certification exam, namely ITIL Intermediate. Wish you well in your endeavors. As the next step in your professional ITIL certification, you can either opt for Intermediate-Lifecycle modules for those wanting to pursue managerial openings or Intermediate-Capability modules for those who wish to involve with process or mix of both Lifecycle and Capability.
About ITIL®
ITIL®, an acronym of Information Technology Infrastructure Library, is a collection of best practice in IT service management. ITIL is considered as the best-practice service management framework across the industry, especially for IT service and governance. If your area field of interest and area of expertise happens to center around IT services management, then we strongly recommend you to take up ITIL certification.
There are currently six levels for the ITIL® Qualification Scheme (ITIL® Certification):
§ ITIL® Foundation Level
§ ITIL® Practitioner (newly added in 2016)
§ ITIL® Intermediate Level (Lifecycle Stream / Capability Stream)
§ ITIL® Managing Across the Lifecycle
§ ITIL® Expert
§ ITIL® Master
The ITIL certification is a platform independent, vendor neutral and non-prescriptive credential, that’s widely accepted and recognized across the industry with regard to IT management and service advancement initiatives.
Read More
Certification Competency Enablement Makes You Elite and Eligible
The more the merrier. Just as our quest is insatiable so are the expectations. Try meeting a hiring head or a business investor and you will be questioned more about your skillset. Yes! Your primary skills are a given. While the focus on primary skills is paramount, the stress is always about developing additional abilities considered vital in competitive analysis. Those interested in your profile would want to know ‘more’. It’s the additional information that elicits more interest. A quintessential professional is versatile – like a player on the field ready to be placed in any position. So possessing the technical skill (read primary skill) wouldn’t provide that edge over peers, rather when supplemented and complimented with strategic and leadership traits places you in a formidable position clearly pushing your boundary further.
With business needs growing with greater unpredictability and technology advancement defying expectation through groundbreaking innovations, the landscape seems to be shifting perpetually, and hence there is admittedly a paradigm shift from the professional perspective without an exception. With time Individual assessment has changed. The organization is looking to fill the slot as Musterberg stated “finding the best possible man, how to produce the best possible work, and how to secure the best possible effects”. What it takes to become top performer with top potential. Potential is the possibility of an individual to do more than current contribution. Aon Hewitt defines potential as the assessment of an employee’s ability to rise to and succeed in a more senior or expanded role. Potential considers individuals’ performance, character, capability and motivation.
Today, the critical talent is evaluated in terms of knowledge, skills and abilities. The PMI Talent Triangle™ clearly lays emphasis on ‘more than’ technical skills by subscribing to Leadership and strategic & Business Management As inferred from the PMI’s ‘Pulse of the Profession 2016’, the most successful organizations seek added skills in leadership and business—competencies that support and sustain long-range strategic objectives. The ideal skill set—a combination of technical, leadership, and strategic and business management expertise—is embodied in the PMI Talent Triangle™. When organizations focus on all three skill sets, 40 percent more of their projects meet goals and original business intent.
As one of the leading educational powerhouse enabling to become professionally trained and certified, especially PMP®, PRINCE2, ITIL, Six Sigma, we interact with professionals on a daily basis. They are the folks wanting to stand out in their sphere of work. And we regularly hear how ‘Certification’ validates competency and enables your candidature as ‘eligible’.
What is the value add You bring to the table? Your bona fide already vetted, increased scrutiny would be on the ‘what else’ as the key differentiator. It’s always about ‘what more do I get’ and it applies to one and all. With the raw aggression witnessed like never before, it will be hard sell in promoting your profile given the spiraling number of applicants competing alongside and here is where ‘the more you have’ makes you leapfrog into the short list – a short one.
So dear Professional, what makes you so elite and eligible? Is the spotlight on you to single out in a crowded room? How do you distinguish yourself to differentiate? We, at iCert Global, besides the benchmarked certification courses also offer career counseling whereby our expert panel will engage with you to chalk out the future course of action to steer ahead the crowd and cacophony. We conduct exciting programs that shape your personality and profile to become more competitive and complete . Follow the link http://www.icertglobal.com/all-courses.php to get a glimpse of our offering and feel free to schedule a call with us.
Together We Win!
Read More
Are you Reading the Risks Right or Is It Target Missed a Case Study Project Management
Profile
A high-tech company in the travel industry has bagged a contract from a reputed Client for data migration with phased delivery over a period of ten quarters.
The project plan was created based on the requirements available. Since the project spanned in time, the data points presented covered only a year, which was deemed good to start by stakeholders. The visibility was for only one year and hence the limitation with data available – which is expected and accepted in this kind of engagement. The budget for the said timeline was apportioned. The team identified to undertake the project was present in different locations as a strategic call.
The Pain Point
It will be the assumptions that will turn out to be the worst of risks. The stakeholders agreed it was a long tunnel but not quite certain about the length. Since it was a time bound, the requirement gathering was focused for the first quarter as agreed by the stakeholders and signed-off.
Assumptions can become one of the major risks. The team initially settled on a framework only to change after the first sprint. The change would impact the team composition calling for ‘sourcing’ soon after launch that sent the human resources scrambling for talent. The need of the hour is never met and that’s the lesson learnt and hence due diligence paid to the selection from talent pool.
With new resources inducted, there was already burn on time and cost, the knowledge transfer turned out to be to be too steep and the project plan revisited to factor the changes. There were different verticals within the team which started concurrently, and it was the approach of the scheduled milestone that sent the alarm bells ringing as one of the core development team failed in meeting the deadline and thereby derailed further developments adversely impacting other teams as the output will be the primary feed for them to move forward. It had a typical domino effect shaking the entire team.
When the causal analysis was conducted, the results unearthed many issues that seemed to be swept under the carpet. Communication weren’t open and transparent; accountability absent and leadership clueless as team members tried passing the buck and concerned about safeguarding their position. The most baffling will be the lack of attention to basic details. There should have been a single point of contact for escalation; People Management and Stakeholder management. The root cause clearly spells poor communication and lack in understanding. The bottleneck undoubtedly was communication management. Clearly the opportunity would have been squandered if not for the milestone. It was the worst wake-up call for a company known for its intellectual capital and track record.
Analysis revealed that the actual against planned in the project plan left a gaping hole and lacked foresight for risk mitigation particularly to problem faced as such a scenario was never contemplated. How? That’s why the absence to attention on basic details. Too much rode on assumptions.
The impacts due to the imbalance resulted in
# changes in the team composition which proved too expensive at that point in time as investment and Knowledge Transition and team ramp-up
# Conflicts in the mid-management
The squabbles stressed the need for conflict resolution through effective people management and stakeholder management.
Troubleshooting
It was back to basics about team-building with open communication, more transparency and greater accountability. The team met frequently till all onboard were on the same page. Having ceded grounds, it’s more prudent to save and salvage and move on. Since it was the first milestone, the impact on the short-term goal was severe and long-term could be contained. The positive impact can be captured as
# Commitment from the stakeholders on requirements and delivery
# Transparency /Clarity to all the stakeholders
Recommendations
The Plan B that somehow missed the plan should be prepared.
The alternate scenario for worst cases should be assessed and addressed.
The assumptions must be studied again and stakeholders should provide clarity in closure.
The team should be cohesive and engage effectively to expedite delivery.
The Start of the Day and End of Day of meeting must analyze the day’s target and plan for next day deliverables.
The leadership to introduce SPOC and take stock at regular intervals (smaller intervals as possible) till things are streamlined and then schedule the standard stand-up meetings
Read More
What does it serve to hold a Professional Training
It’s a well beaten track, and oft-walked path and probably worn out. Even after it goes a full circle, sometimes we are back at square one. So what does it serve to hold a professional certification/training?
Maslow postulated that ‘when one need is met, another arises’. It’s a two way street between employers and employees. While one is on the lookout for extraordinary skills offering position and perks, the other is on the pursuit of offering its services to best bidder. The employer-employee relationship is reciprocal. ‘How can I help you’ to ‘what do you have to offer me’. As a professional aspiring to move ahead in the corporate ladder, what are the expectations from an individual standpoint as well as collective?
Skills Specialisation
Show uncommon skill.
It will become banal if you could do the math with the headcount, out of which how many really can be counted in?
“According to a report by Talent Sprint in 2014, only 27 per cent of the 7, 50, 00,000 fresh graduates would be employable by 2020. “
So the number of candidates who actually make it to the talent pool is disproportionate to talent available. Employers are really vetting a recruit’ worth because getting a new hire onboard is expensive and cumbersome. The trail of links from start to closure can be long and winding. So how does professional training help developing skills? Expectedly, your knowledge base should be broad and it’s strongly recommended to specialize. Academic knowledge is acknowledged and professional development will complement in carving your professional profile. Capabilities in line with the current standards, relevant knowledge about the changing trends and times in your track; closing your knowledge gaps and help you become a potential contributor.
Non-professionals as active participants
How do non-professionals get in? That’s an interesting poser. There are prospects in the industry which facilitates non-actors in to active participants through professional development programs. For instance, you have enlisted for Arts but interested in design, or your major is Math and penchant for Analytics, and the industry will surprise with the opportunities abound. There I nothing non-inclusive.
In fact, heavyweights and bellwether companies have opted to look beyond the conventional method even in campus selection shifting primary focus on skills. Those who have the appetite to ‘go beyond’ is succinctly encapsulated in this crisp comment “people who like figuring out stuff where there is no obvious answer”.
More than academic, it will be the analytic, innovative, think out-of-box approach that draws more eyeballs. Every player is deemed to have traits and skill primary followed by secondary. It will be through honing and fine-tuning, especially when professional migrate from their line of practice. And that’s when and how training, workshop or certification courses actually lend merit to improve skills in a planned and structured way.
International acceptance and recognition
With economy opening up profiles today are pancontinental. When visibility is high, the stakes too are high and hence it’s significant that your credentials take center stage or go places – literally. Some niche certification is renowned for its compelling grip to hold international audience. A professional certification course is a key enabler in making your profile visible and far reaching – by speaking in the same language that’s universally understood and upheld. When you can demonstrate with the expected skill, expertise and authorized by a professional governing or certifying body, it not only recognizes but endorses your commitment in a global business analysis community.
Job opportunities world-wide
Job opportunities will be a corollary to international recognition. Once the threshold is reached, doors are opened. The industry is not short of opportunities. There is a dearth of quality and qualified professional and this supply vs demand is grossly skewed underscoring the need for skilled personnel. Interestingly, professional training enabled many non-actors to get into the fray and find a place in the workforce.
The 74 million next-generation workforce of 15- to 24-year-olds who are unemployed are not skilled to fill the skills .
Ant crisis presents an opportunity and how can you capitalize the chance by leveraging on your knowledge and understanding. For a power-packed performance, you need support in the form of grooming and guidance and perhaps where professional training will pitch.
Career-path accelerator
The total costs of replacement can reach 200% of an employee’s annual salary.
Now that’s huge. A certification can ensure consideration, if not confirmation. Building your career will depend much on your personal branding. Just as in any job search, distinguish yourself head-over shoulder by positioning yourself. There are programs conceived and delivered to help you progress faster and further in your career with promotions and compensation. How does training impact career advancement? In addition they can provide linkage to training in the right modality to facilitate development, It’s not enough for you do good. You have to take control of career and make it happen.
We engage in knowledge transfer in the form of professional training and certification courses. You may please call on us or email at info@icertglobal.com to discuss more about career-building counseling offered as courtesy.
images courtesy: goo.gl/CFW9ka
Read More
Challenges with Project Management
The iron triangle is too tough to balance. Too often or not, it was observed that one axis is either long or short compared to the other two. And it might be near perfection to maintain equidistant axes. Project stakeholders are left perplexed tearing the hair wondering what went wrong, and ‘how didn’t we see that coming? We failed to detect and decipher the warning. Did we throw caution to the wind?’ that will sound too critical as due diligence is done through detailed discussion and deliberation before inking the contract, yet, projects going off the rails poses serious threats in damage control and contingency measures. What went wrong should be a lesson learnt for the next or projects in pipeline, yet projects seems to stumble in the same spot flummoxes and shakes the foundation. It might sound clichéd or routinely repetitive but professionals tread on a beaten track and worn out path, and ironically can’t sight the pitfalls and potholes? What possible oversights that project suffer – that are ‘known’ knowns and still found wanting on action and remedy.
Identify Project Objective and Goals:
The stakeholders stating the objective should make sure that project goals are identified and make sure the message reaches out to the team. Chances of disconnect is disturbingly high when objective isn’t clear or communication incoherent. Minor addition to the original scope will result in a major reshuffle, transfiguring the original requirements. Consequently, the project fails to progress on expected lines. It can be any field and platform independent and technology agnostic as project is a temporary endeavor with a start and end date. The dates differ because the project team plays a different wherein goal posts keeps keep shifting.
Determine the Project Scope:
Always the slippery slope. The in-scope and out-of-scope tends to blur and blend, and the risk is inherent. Is it easier for a camel to go through the eye of a needle? It might be appear as exaggeration expression. Most experienced project managers would agree that ‘admission and accommodation’ that starts as a trickle is difficult to stem as a tide. Nudge here and poke there and scope is nowhere near the ‘original’ scope.
Emphasize Project Communication across Stakeholders:
Stepping up communication will set the expectation right. The fundamental reason for any misunderstanding is poor communication. In a technology advance professional work environment, gap due to improper communication is unacceptable hampering hampers productivity and performance. Be it manual or electronic exchange, there will be greater degree of transparency and accountability only when communication between stakeholders is crystal clear and timely on delivery.
Prepare proper Project Deadlines:
Delivery deadlines must be realistic. Setting up unreasonable timeline is self-destructive. It can lead to serious issues running your project progress and workforce morale. Raising the bar is good to groom but poor governance to reflect in the target. The date of completion can be setting after taking stock of the soft skills and availability. The resources pose an intrinsic risk, admittedly, and hence there is a standby or fall back provisions made in the ‘resource plan’ but the usual practice of engaging someone on something is strictly on ‘evaluation of excellence’ and securing confidence.
Evaluate Talent Pool:
Expectation are always high – be it employer or employee but rising up to it and staying in ‘top of form’ consistently is breaking grounds in terms of performance. Team, inevitably, will be a mix of talent pool. Any shortcoming or deficit will be offset by outstanding performance and that’s how it becomes teamwork. The delivery and deadline should be worked out only after factoring your Talent Pool. Assessing your resources becomes critical before committing about the possible time of completion. Besides, it strongly recommended conducting the SWOT analysis on every team member to evaluate the team’s strength and weakness. Sometimes there is too much of reliance on a particular resource that can lead too much ‘burn’, and ‘wear’. There is only so much a resource can perform and efforts are to optimize. Beyond that the very resource is put in peril – too much of a risk.
To know more about Project Management programs, please click http://goo.gl/Vt0ZL1 or visit our website www.icertglobal.com
Read More
The PRINCE2 Practitioner Open Book Exam General Tips
The PRINCE2 Practitioner exam is an open-book format which enables those taking the exam to access Book(s) prescribed by Axelos.
PRINCE2 Practitioner Examination format . Objective testing . 8 questions - 10 question items per question, each worth one mark . 44 marks or more required to pass (out of 80 available) - 55% . Two-and-a-half hours (150 minutes) duration, no additional reading time . Open-book exam (official PRINCE2 manual only)
Open-Book -General Tips. Open-book – is in support and not as main ‘source’ It’s easy to be misled that answers are inserted in the book and all one has to do open and everything will unfold. Progress is based on preparation. So an unprepared attempt relying on the open-book completely will expectedly make no headway as the exam is not about rote learning or remembering and recalling answers. In a scenario-based exam, the challenge lies in applying the learning in the given context for which the open-book can serve as ‘aid’ and can never replace the hard hours bunt to bridge the knowledge gap. So open-book serves more as pointers and reference and surely not the study-material during the exam.
Well-versed with core concepts and subject matter.
The recommendation is to become conversant with core concepts like reading the back of your palm. How else you would able to know what lies where. In the pile of information, searching for the reference to the untrained eye is like being blindsided. The open-book will act as a guide in offering direction to look for material that can be useful while attempting on the answers. The more conversant, the easier it is to track and trace, which saves you time to spare while attempting the hard questions. Besides, you can check and confirm the probable answer by verifying the open-book, provided the answers were known prior and not by chance or second-guess.
Read, and read again.
the question
If you can’t get it in the first read, try again. The instinct is to eyeball or examine hastily the exam paper to run through all the questions. Understanding the question is the key in answering, and scenarios, in particular, poses the need to read the finer details for better grasp and reach. It is very much possible to miss out on some information or become confused. Enhanceyour comprehension.
Engage. The exam is not extempore effort.
Participation without prior preparation results in poor performance. Exceptions aside, it will be ill-advised to attempt an exam without the groundwork and grooming. One has to engage with the exam planning and readiness to clear the exam in the first attempt. There are mock exams, study aids available, and sample papers similar to that of the final exam. Attempt as many to empower with the relevant knowledge and understanding so as to acquaint and anticipate. It’s never extempore.
Don’t overestimate or oversimplify.
The confident mind can feel supremely strong and takes it easy and consequnetly, complacent. It is not the same as being cool before an exam. A sense of caution is expected than fear or foreboding, at the same time lethargic and laidback attitude will not take you far. Human, by nature, assume the worst and hence overestimate – which impedes progress and success. Open-book, as stated above, is again reiterated not to be interpreted as book of answers. This might make the 'smarts' ones to oversimplify or the 'unprepared' fraught with exam fear to overestimate. Attempt on its merit.
DOs and Don’ts.
DOs,You are allowed the access of the Axelos-approved manual. You can mark or add handwritten notes on the manual that can be referred. You can also use post-it notes for identifying sections or jumpstart to a page.
You have to validate the admission of the referenced book by clearly by presenting to the webcam. Open-Book should be emptied of any material concealed intentionally or inadvertently.
You need to open the book and flip pages in front of the camera to ascertain about hidden notes or papers.
You can take the exam from an authorized examination center or your training provider or online. In case, you are doing it online from a place of your choice, ensure complete compliance.
Don’ts,You cannot attach or affix any sheet or papers other than the allowed ‘book’. Any inserts or attachments or pullout that violates the rules and guidelines will disqualify your candidature.
You cannot have hidden notes inside the book, and hence a prerequisite that the ‘Open-book’ should be subject to inspection of the web camera before the start of exam.
You cannot use any additional information, like sheets or papers other than the book
You can always call on us to clarify any doubts or queries about PRINCE2 exams. For contact information, please click the link http://www.icertglobal.com/contact-us or visit our website www.icertglobal.com
Read More
PRINCE2 PRACTITIONER QUESTION PAPER PATTERNS
If you have PRINCE2 Foundation certification, then the calling is to commit to the next level and complete - The PRINCE2 Practitioner certification.
As a PRINCE2 Practitioner certified professional, you are empowered with the knowledge and understanding in applying your learning to a real-time situation or scenario, and expected to lead and manage projects in an environment that supports PRINCE2.
Prerequisites
The prerequisite to appear for the PRINCE2 Practitioner examination, as stated by the governing body Axelos, is to possess
a ‘proof of passing’ from one of the following:
PRINCE2 Foundation
Project Management Professional (PMP) . Certified Associate in Project Management (CAPM). PMA Level A® (Certified Projects Director)
. IPMA Level B® (Certified Senior Project Manager) . IPMA Level C® (Certified Project Manager). IPMA Level D® (Certified Project Management Associate)
Exam Format
The exam format is as follows:Objective testing8 questions - 10 question items per question, each worth one mark44 marks or more required to pass (out of 80 available) - 55%Two-and-a-half hours (150 minutes) duration, no additional reading time Open book exam (official PRINCE2 manual only).
PRINCE2 PRACTITIONER QUESTION PAPER PATTERNS Please note that this exam is available for participants registered Accredited Training Organization.
Sample Paper,
Having completed the certification course, it is strongly recommended that you try the ‘free Sample PRINCE2 Practitioner Exam’, offered by Axelos. This will present an overview and help you become familiar with the exam pattern, type of questions, severity of questions and so on. It arms with you awareness and helps you to prepare with a sense of anticipation. You have the option to take the test soon after completing the course to assess you own level of understanding and knowledge transfer or you can prepare prior to the test to get a first-hand evaluation of your own competence in cracking the exam.
Objective Test ,
The objective test will vary slightly from the usual objective answers, wherein, one correct answer needs to be selected. PRINCE2 Foundation follows this pattern of answering. However, in PRINCE2 Practitioner, there might be questions that may have more than 1 correct answer, and hence be informed about this departure from the tradition ‘objective answers’.
Knowledge Areas,
There will be eighty questions in all and each carry 1 mark. You have to score a minimum 44 to clear the certification exam, which is 55%. The question will be posed from knowledge areas and hence it’s imperative that you cover all topics and become conversant with the syllabus areas.The PRINCE2 Syllabus contains 15 defined syllabus areas covering each of the seven themes, each of the seven processes and an overview area also covering the principles and tailoring PRINCE2 to a project environment.Within the Practitioner Examination, there will be 6 “theme” questions, each testing one of the 7 themes, and 2 “process group” questions, which will test 2 of the 3 groups of processes as identified below.Each of the eight questions will test a minimum of 2 syllabus topics from within the syllabus area.
Syllabus Area,Business Case theme ,Organization theme ,Quality theme, Plans theme ,Risk theme ,Change theme ,Progress theme ,Starting up a Project and Initiating a Project Processes,Directing a Project, Managing a Stage Boundary and Closing a Project Processes,Controlling a Stage and Managing Product Delivery Processes.
Open Book,
Within each question the syllabus area to which the question refers is clearly stated.
The exam is to be taken with the support of the PRINCE2 Manual only. Remember, you cannot use any other book or resource, that is i.e. no material other than the Question Booklet, the Scenario Booklet, the Answer Booklet and the PRINCE2 Manual is to be used and ‘Open Book’ conditions as have to be complied. We will discuss about open book more in detail as a blog post.
Types of Questions
You can expect the 80 question posed in the certification exam. And they are presented in 5 different formats as detailed below.
Classic Multiple Choice Questions: the typical objective-type question wherein you need to select a right answer from the given choices
Multiple Response: you have to select 2 options from the list of 5 options. This marks the exception in the pattern by prompting for more than 1 answer.
Matching: the options on the left column need to be mapped to the correct answer in the right. Please note that there is only one match and there are possibilities of multiple matches. Meaning for 5 options on the left column, it is entirely possible that option 1, 2 and 3 can have the same mapping on the right column.
Sequencing: ‘position events in a sequence’. You need to answer the options like stacking in a sequence.
Assertion/Reason: You need to evaluate two statements a (an assertion and a reason) and confirm if they either, or both or neither with the help of reasons detailed in the question.
Capturing the Answer
In the answer leaflet, make sure the oval shapes are completely filled with PENCIL only. You have 150 minutes to answer questions. Hence your time management and answering ways should be 100% fill. Its an electronic submission and correction and hence filling the oval shapes that you find as the correct answer should be neatly and completely is the compelling factor. Failure in doing so may result in the making the answer null and void as system will be unable to ‘read’.
Read More
Areas of Improvement for the ITSM IT Service Management Sector
The Internet growth has reshaped service and its outlook. The ITSM best practices and processes put in place so that organization can step-up potential, performance and profit. The service aspect, unlike the software, is not the cynosure yet the product lifecycle will be incomplete, if not, stunted without service in its place. More often, repeat orders [read as customers] are the key business drivers, and in order to gain confidence and increase traction, improve service. In the ITSM realm, the stress of service is on information and technology (IT) – as the definition states design, delivery, manage and improve IT services within an organization to meet its business goals.
Process optimization:
The most pressing issue as highlighted by a number of service management experts is Process Optimization. How can you maximize efficiency at minimum cost? Process Optimization. The key is to identify the areas which have the best impossible impact to effect. A typical scenario to understand optimization is automation. Setting auto-response to any query, instead of acknowledging receipt manually is the basic automation that goes unnoticed but very effective. Process optimization will ensure compliance adherence, increased accountability and avoid wastage.
Self-service:
Self-service is a hard-biting issue that still finds itself lagging and lacking for want of a better system. ITSM should be optimized to offer the experience of self-satisfaction. While customer-satisfaction is paramount, the interest of the self shouldn’t be delayed or discarded. The Self-service issue was a priority in the previous year 2015 which went unaddressed as expected and given the lacuna, the need to close the gap and plug holes took precedence over other priorities for 2016. Any issue important can be read as a good opportunity to make the most and hence focus is on improving the service standards.
IT – business alignment:
The synergy between IT and Business always results in a greater yield. to understand IT-Business alignment, you need to understand how and where does IT and Business connect. How are your meeting with customer captured? And how does technology enable business? You might want to look at dashboards that typically summarize the events and present critical information to empower informed decision-making. Its very much a strategic call, like IT Governance with risk and compliance management.
The insights posited as trends or ‘Opportunities’ for 2016 is more of reflection from the remnant and projections for future. While Process Optimization was closely followed by self-service, the value of aligning business needs to increased customer satisfaction too was a pronounced call for action. Strong indication was sounded for Automation mainly to streamline process and resources and avoid waste of time and material. The list also featured Budgets, Digitization ESM and ITAM. While Budget and Digitization are prospects, ESM and ITAM stem from the remnants of 2015.
The Status of 2015:
The trends of 2015 was studied to understand the reach and addressal; and the understanding is that Services found wanting and fell short on Self-service, Service beyond management and IT Asset Management. The table below depicts the findings.
Self Service:
When user is self-empowered, the dependence on others can be cut down to improve productivity. Usually time-chokers, when issues have to be resolved by ‘someone’ always burdens the user with increased reliance on resources. Instances when access to a particular site is blocked that not only interrupts your work but arrests the thought flow, scuttling spontaneity and slowing work as a result, all in the aspect of security? There is always a better way to get things done without compromising security and still serving the self-service. The ITSM can step-in to sort out the mess and streamline flow to avoid interruption and enhance engagement. The service desk inexplicably, fails to empower self-service
Service management beyond IT:
It is also known as Enterprise Service Management (ESM), which can optimize service management to pass on benefits to other departments like Human Resources, Finance, to improve delivery. If you have to follow-up on a leave request or a loan applied, will it not be necessary to touch base with HR for eligibility and approval, and pass the request to Finance to disbursement? The services that can make the entire process seamless, cutting out the delay and accelerating the request-response will result in greater satisfaction.
IT Asset Management (ITAM):
Software management is significant because of its need and value, and also the adherence, compliance and audit check makes it increasingly important to manage your assets. Its observed from industry practice and use that aligning asset management with service management will result in substantial cost reduction. You will be able to better control and become cost-effective through screening and shortlisting to prioritize and take preventive measures to ac\void any attack or breaches in safeguarding your assets and value.
Some of the critical shortcoming in 2015 were lined up for redressal and remedy in 2016 and prominently featured were self-service and IT Asset Management.
You may please access the white paper which requires registration.
For more information about our ITSM programs, we request you to visit our website http://www.icertglobal.com/ all-courses or call the nearest branch close to your locality.
Read More
Its the way you type not what you type the amazing development with Artificial Intelligence
Password could be a pain, particularly when you have multiple web sites to access many sites. The consumer complains that passwords are fast becoming a psychological burden – an albatross that weighs down the person with too much data dumped in the head that’s hard to decipher. And apparently one can sense discomfort and disconnect. It’s like having too many keys to open one room and woefully, you can’t pick out the right one which will unlock. And the real hassle is when password is forgotten and the allowed number of ‘attempts’ gets exhausted, the system locks, leaving you stranded but the chore running back and forth with the back-office executive walking-through the password retrieval process leaves you fuming ‘is technology a boon or bane’. Anything will have its downside – including technology. You might want to have a turnkey system that does the trick and get you going.
Password, PIN and BreachRecent times have witnessed worst security breaches because of weak passwords. How private information lands in the public domain makes it a necessity to ensure that safety mechanism are in place and hence stronger password. But too many passwords? Why? Google has single sign-on to access all its application. Why can’t life be simpler? Or are we complicating in the name of security? The easy way out would be to have one password for all sites so that you really don’t squeeze hard your memory like sifting sand from grains. If it makes your life easier, then think about the breach and there it goes – with one key all of yours is ‘gone for good’. It was this paradox that actually turned out to be the problem statement. Single-point of entry is swift but so would be the theft. In this era of technology, and digitalization, all access points are fortified through authentication. Multi-tier security system or secured transaction or secured authentication service. Still, we are not done with the password for an alternate method that’s more convenient and confident. Almost everyone with digital experience would have yearned for that day they could dispense with password or PIN (Personal Identification Number) which earlier was recommended to be bolstered from breach by creating an alpha-numeric string with a heady mix of special characters to safeguard from sabotage, and now some institutions like Banks make the usage of special characters mandatory visualizing that invincible predator preying on vulnerable victims, and soon emerged phishing as one the worst attack on data integrity. With reputation in ruins, name in tatters and business rocked in its very foundation, damage control and image building exercises not only resulted in spiraling costs with a dent on the bottom-line, but kept the stakeholders on tenterhooks. So it would, by no stretch of imagination, become too much to bear for all the stakeholders and so far the necessity of the hour and lack of alternative left the end-user with no choice but coin the Password or PIN as complex as possible and remember it for good and retrieve on-demand. Further, it was strongly discouraged in storing the information in hard or soft copies, and science dealing with encryption and decryption made it even more mystique and technology related to secured socket layer took over.
Abacus – the painkiller? It is possible to solve every puzzle? At least, for the password related problem Google believes it can achieve a breakthrough by getting rid of the stiff impositions of barriers – NO PASSWORD.
How in the world would you access your information whether it’s an email or your bank account? Google assures that there is a ‘fix’ and will test with bank first and based on its success, offer for others.
Dan Kaufman, Head of advanced technology and projects at Google, commented at the company’s I/O developer conference “We have a phone, and these phones have all these sensors in them. Why couldn't it just know who I was, so I don't need a password? I should just be able to work,"
How does it work? The technology uses biometric data and supporting information to identify and authenticate access. It uses Trust API to determine ‘trust score’ by employing and engaging different parameters like facial recognition, location, typing styles to ascertain the identity of the user. To access sensitive information, the ‘trust score’ should be high, and that’s the reason the testing begins with a financial institution. The higher the score, clearer is the identification and access provided, else, denied. Interestingly, Kaufman, has this to say about authentication "What we're going to do with this is be able to get rid of the awkwardness of second-factor authentication,"
Google assured to introduce this ‘password-free’ feature to every android developer by this year-end.
Is there a Precedent for ‘No-Password’?The answer is in the affirmative. Yes. Let’s not take away the shine off Abacus and assess on its own merit. Scandinavians will be familiar with this concept of logging into their bank accounts using behavioral biometrics and not a password. The password is queried only when the usual signs and symptoms fail to be detected and is treated as a legitimate case in validating the customer identification . In Norway and Sweden, major banks employ BankID for doing daily banking transaction to booking tickets or applying loan or paying taxes online. It was estimated that by 2014, BankID is used by over 3 million Norwegians (over 75% of the adult population(pdf).
BankID can identify the user through a combination of factors like assessing the way the screen is swiped, the pace at which data is keyed – meaning the pressure with which you punch-in data is critical to analyze and evaluate your identity. It is behavioral science at an advanced level that any change in pattern or shift in style will trigger the system to confirm with a ‘password’ prompt. The system has studies the user to identify as its customer. This is made possible by behavioral biometrics layer of BankID.
So Behavioral Biometrics is nothing new; the anticipation is the evolution of technology in this space of biometrics in the context of identity crisis. We may to have wait till the year-end to see what the future unfolds.
Read More
Maslows theory of needs rewritten Needs and wants intertwine But wants outshine Professional Certification
Expectations are always high. One of Abraham Lincoln’s letters goes like this :
“Let Him Have The Courage To Be Impatient, Let Him Have The Patience To Be Brave.”
In changing times, especially in the IT realm surrounded by gadgets and flooded with apps [to the point that alert about rogue apps are being circulated], the millennial and iGen just can’t be restrained by patience. They are already pampered with the luxury of living that one hears the lament of ‘I want it and I want it now.” Cost isn’t the criterion; it’s the catch – what’s new and exciting. Inventive and innovative. It’s the desire to stand alone by owning either that’s something new to the market or that has something better than existing. The glint of pride lies in the possession. Try with a kid and it could be anything from a tablet or the latest game to greet the market. One wonders the psyche of long queue to get hold the new gadget. People lining up for apple’s products are legendary. Their needs long met, kids are screaming about wants.
The adults fare no better.
Oversupply and undervalue
The market is skewed when it comes to skilled professionals. We have an oversupply and hence undervalue, which is inevitable. The Asian sub-continent is known to roll out hundreds of thousands of engineers and yet recruiters are finding it a hard time in zeroing on the ‘right’ candidate. Why? Those who line up for openings somehow fails to measure up to the expectation. In the milieu that’s driving professional mad with its demands and infinite possibilities NEEDS no longer suffice. It’s the WANTS.
For instance, how many certified PMP®s are available to be engaged in typical waterfall methodology? It may not be surplus, but let’s say, sufficient enough or barely adequate. Alright, assuming the same professional is expected to work in an agile environment, and the norm is to possess a PMI-ACP® certification, now check your human capital that holds these two certifications? What’s the count? Professionals holding a dual certification of PMP® and PMI-ACP® are much less in numbers that recruiters would have to really look into the talent bucket to scrounge and scrape. What’s now a ‘good to have’ in your resume will become a mandate as ‘must have’. So brace yourself, as times ahead aren’t going to be any easier.
Get certifications, get higher salaries
Globally renowned and internationally acclaimed certification, especially in niche technologies like social, mobile, analytics, cloud including big data and internet of things, is a clear recognition of acquired skill, and when they address the mission critical initiatives , then their ‘ worthiness’ will soar for sure, commanding attractive compensation. It’s becoming passé to excel in a particular field or specific area of interest. Professionals these days are expected to be more fluid, without bracketing into a particular bucket, but to meet ever changing and evolving needs. They need to be flexible enough to accommodate as many tasks as possible - is the minimum expectation. In how many possible ways can I use the same resource to increase the ROI - yes, multitasking and that translates as 'monetising'. You are an asset and there is substantial investment. And as an investor, it’s only fair to expect an enhanced return on investment. Here again, the need is replaced with want.
Let’s accept that not everyone becomes an entrepreneur. Segment the society and sift the populace and find out how many families run on salary as bread-winning source. Most remain salaried. So your job matters. Disruption in technology is understandable but automation is not only perceived as a mere threat of disturbance but uprooting your livelihood .
Why is that threat real? Because the same skills don’t serve all time always. Like system upgrade, human capital too should reboot and reinvent.
When one need is met, another arises. Redefining Maslow in the present, would it be off the target to postulate when one want is met, one more emerges.
Needs and wants intertwine. But wants outshine.
Read More
ITIL Certification Credit and Career Advancement
According to information published in 2012 by the U.S. Bureau of Labor Statistics, the job outlook for computer and information systems managers is projected to increase by 15% through 2022.
ITIL® (IT Service Management) is the most recognized framework for IT service management in the world.
The opportunities presented are plenty – and subjective to a professional’s preference. Professionals inclined more towards managing and leading teams are recommended to pursue the Lifecycle Modules; for those who are process oriented and wish to play an active in service management then it is strongly suggested to take up Capability modules.
Certification & Credits
ITIL® is undoubtedly one of the most recognized and accredited IT Service framework and helps professionals to pursue career goals. More often not, ITIL certification is understood for service management exclusively. While that’s true, ITIL also complements Project Management. So the scope is quite broad and left to the individual’s preference about career path.
How many Credits do I need to become ITIL® Expert?
ITIL® certification commences with Foundation and moves forward with Lifecycle or Capability Modules, which eventually will make you qualify to appear for the MALC certification.
You need 22 credits to qualify for the expert level – which is usually achieved by becoming certified as Foundation level and earn 2 credit followed by Intermediate Modules and then MALC.
Foundation (2 credits) + 5 Lifecycle Modules (each module is worth 3 credits and hence 5 x 3 =15 credits) + MALC (5 credits) =22 credits.
Or
Foundation (2 credits) + 4 Capability Modules (each module is worth 4 credits and hence 4x4 =16 credits) + MALC (5 credits)=23 credits.
The criteria set are to earn 22 credit to become an Expert.
You can learn more about the Credit system , please visit Axelos link.
Career Advancement
Excellent. For a qualified professional, the prospects can be just amazing. Evaluating studies from payscale.com offer valuable insights about the Employees with a Information Technology Infrastructure Library (ITIL) Expert Level Certification:
There is an increasing need and growing demand for this certification and indicators from the public domain forecast a trend of capitalizing on IT Service Management.
ITIL professionals with more certifications earn on average 13% more in US, according to the ITSM Salary Survey by Plexent. According to the survey, certifications really do pay: in 2011, an ITIL Expert made on average $122,000 and an ITIL Service Manager $125,000 in US.
Read More
Bring Work Life Balance with Disciplined Project Management
There seems to be early burn-out in IT professionals. Doctors are appalled at the heart-risks and related ailments; whenever a young person wheeled into the emergency ward, the first question invariably is “are you working in IT?” why is it so? Job pressure, peer pressure, management pressure – the stress is too much. A number of factors collide and contribute to this havoc wreaked on youngsters. Heart attack in the forties or fifties doesn’t shock or surprise but in late twenties and early thirties psyches the physicians, who are perplexed dealing with the predicament. Such is the severity, and cut-throat the companies, employees either by choice or force end up staying late at their desk ‘burning the midnight oil’.
Does the number of hours clocked or the contributions count? The misconception in the market is that one who spends long hours in the office is deemed ‘hard working’. Anything less and your talent is questionable or the workload is not just enough to justify your paycheck. So some just pretend to stretch or ‘kill’ time by indulging in other activity instead of freeing up bandwidth to take up additional tasks. “If I do this task or accommodate more chores in addition, will the amount in the salary credited change?” this reflects not just the individual lack of commitment, but reflects poorly on the leadership as well.
Devotion to work should be wilful, lest it leaves one dissatisfied and disgruntled. Once resourceful, now turned rebels are primarily due to poor people management. Long and late nights are part of the daily rigor of an IT Professional. Time consumed at office leaves with less for family. Everything ought to be balanced – including work.
A project manager, whom I used to report, will sit beside me and plan the ‘tasks for the week’ taking my inputs for the ‘hours allocated’ and sometime let me estimate the ‘number of hours’. Effort estimation is both critical and crucial. Bagging the project by heck or crook, and later slogging the days, night and weekend are typical signs of burnout. It’s like cutting the foot to match the boot. That’s not project management. Weekends usually act as buffer and my manager managed on the maxim of “if you can’t get the work done in eight hour, either you are inefficient or incompetent." People also tend to procrastinate – another malaise with no medicine in sight. Hence there is no blaming the managers alone. Both sides suffer from their own shortcoming and apparently there has to be a middle ground.
The 40 hour week
Any project manager with appreciable knowledge and experience will not estimate more than 8-hours as man day in the project plan. How many hours does the team work is another question but for the record its 8 hours, and usually the weekends are not factored – and mostly serve as buffers. Remember time is money and hence any inflation in your estimation will have an adverse implication on your cost estimation. If the budget balloons, the project will slip out of your hands. It’s a typical trapeze act or skating on thin ice. So balancing the 40-hour and keeping the project within cost calls for a skilled and smart time management.
Performance and productivity
No matter how many hours you clock, you are most productive for the first 4 hours. The body might be willing but the mind simply is not up to it. Exhaustion,and fatigue hampers performance. Your ability to concentrate ebbs with passage of time. There should be a reason why Henry For came out with the brilliant strategy of ‘weekend’ so as to boost morale, improve productivity and increase time spent with family. Sources from public domain cite that working fewer hours increase productivity and thereafter tend to wane.
Work-life balance
“I am too busy at work” is the usual refrain. You start before the kids awake and return after the fast asleep. Many professionals itinerary falls in to this pattern. Genuine cases of work chewing and even gobbling time is a possibility but that can’t become the norm. Its not family first or work at any cost. One has to strike a balance to do justice to both – stakeholder management. Your internal and external client included, family too is part of stakeholders. And its important to attend on everyone, and if possible satisfy.
A gallup study revealed that we work 47 hours – which is 7 hours more. What will all the dollars, incentive, promotions and perks amount when you compromise your health for career. Think about it.
Read More
AI is another Competitor not Your Counterpart
Yet another splash of the waves. The news is about AI. Again.
All along, the news beamed over the web had to stress this message to drive home the hard fact that machines are here to replace professionals.
It sounds so artificial. Want your business to boom, add on AI.
We can argue all day about the robots coming to the rescue, but replacing jobs altogether is something we can agree to disagree.
Industrialization introduced the concept of automation – the first of the threat to replace human workforce. Before computers became really personal, typist was a typical occupation. That has been taken over or obliterated by software. Weren’t the threat of AI perceived real then? Yes, just that the impact was less, and man moved on.
Today the business runs on a different lane. Cross-selling and upselling is rampant. Technology is making business thrive. A cancer patient can know the course of treatment, courtesy not a doctor but a biotech company. So, software coding for cancer cure? Well, Microsoft too has stated as its long term goals.
Wakeup call
At some point in time, we all tend to become complacent by becoming too comfortable at workplace – the cushion factor. And it takes something like that of a threat to shake us out of the comfort zone – competition is the ultimate threat. AI is another competitor, not your counterpart.
How did farming take place before the advent of tractor? More hands in the field, and more time to till. The tractor proved to be a game changer. Was it warded off as a threat to uproot livelihood?
Why is that robots would act as our replacement and wipe out employment? What happens if robots fail to function or malfunction? Even in the worst of cases, it’s the repetitive work that can be automated. What about creative?
All your bets on an algorithm. Then try this read. It might help you to revise your opinion. Nothing like your instincts. And who is going to replace that as well? Certainly not algorithms – which has its pros and cons.
AI and Writing
The writing is on the wall about man’s dependence on AI but not its dominance. In fact, word from the industry has hinted instead of competing, AI can utilize the service of the human mind to complement.
“When you talk to an AI chatbot, who do you think writes those professional, peppy responses?” was an interesting read. AI didn’t appear intimidating, rather impressing the significance of the mind power as if to suggest ‘ we can compete against each other and also co-exist.’
Read More
Why You want to wait till they walk out Effective Leadership
As much as companies expect employees to upskill, the attrition rate in recent times has rocked the boat, and almost ran the ship aground. A large IT firm considered a bellwether in the Asian-pacific region witnessed unprecedented exits, especially in the upper management. Sources within cite “performance related issues’ for the departure. With so many legs to march out the door apparently was too much of a jolt, that the leadership itself came in to question as why talent, that too at the top of the pyramid, are hitting the bricks? Resignation are rampant. Job-hopping seems to be most happening that it is no longer a shocker to screen a resume with several companies chequered in the career path.
Why?
While the companies quote ,b>‘performance’, the employees have a different perspective that paints a different picture altogether. Expected and evident. Both parties need justification and play it out for the records. But the crux of the matter is ‘leadership failed’. Either it didn’t see it coming or perhaps caught off-guarded. Either ways, the executive cant be excused or exempted.
Observations made from the key trends of human capital mention that ‘Only 30% of CEOs said they were confident that they would have the talent they needed to grow their organisation in the near future’.
Companies have little idea or limited information behind the reasons of resignation of high-profiles despite digging on data available. At best, they turn out as conjectures and not conclusions. HBR.org offers insights in why employees choose to leave. Some of them aren’t sure of their call to quit, some chose to get out and some shunted out.
If innovations are the guiding force of the future, then the best and brightest can’t be possibly let go just like that – which does happen when paths collide or for the sheer pride.
Effective leadership is to know when to reign in and when to cut loose. Stop the flow and stem the tide. To influence beliefs and behavior to beget the best in result.
Read More
Has Trust lost its Trust Stakeholder Management
The word is abuzz about funds being embezzled or malpractice within company. Recent news about controversies and scandals are doing the rounds and ties that were painstakingly built appears so fragile. In the past days a CEO has stepped down, misuse of money in a blue chip company, and non-conformance of standards spells disaster in the parlance of people management.
Governance by every company is based on strong ethics and values and yet incidents like these rock the boats, sending shivers down the spine. Many exclaimed in disbelief ‘It’s just not possible”, and yet that’s exactly what happened – trust deficit.
It’s in good faith and belief that something is entrusted, but when the person manning the gate gives up blowing the cover then it’s a classic case of the ‘cats guarding the chickens.” Stakeholder Management is proving to be more critical. One might wonder if the company or the whole crew or the entire block that bungled, but all it takes is one rotten apple that makes the basket stink. And despite the foolproof security measures put in place, failure like the incidents cited can not only be frustrating but erode the confidence misplacing the faith. The murky matters cast a long shadow sparing none from suspicion. Paradoxically, the benefit of doubt cannot be passed and things have worsened to a state where one has to prove innocence. So where went the ‘you are innocent unless proven guilty’. We live in different times that demands drastic changes and impose difficult compliances lest we face dire consequences.
What makes one misbehave? Chances, conditions, circumstances, or plainly greed. Whatever might be the motive, it shatters everything the individual stood for, and along with brings down the whole house. Integrity is imperative. Character is what you do in the dark – when no one is noticing. Integrity plainly put is ‘do what you say and say what you do’. Hence, it becomes critical that we pay more attention to our human assets by studying behavioral aspects and identify scope for improvement. Not everyone is strong; some are susceptible. It’s up to the management to identify the grey areas and iron out the weakness. A SWOT generally helps – especially from an ethical standpoint.
Stakeholder Management involves your internal partners as well, whom at times, are overlooked. Build trust. It works both ways – employers and employees. It is incumbent on an individual to be accountable. You are answerable to your actions. So, the choice is clearly yours.
We will like to hear your thoughts about this subject. Please do share and we welcome your inputs.
Read More
Marketing Traditional Touch to Technology Transformation Digital Marketi
With the advent of internet originality became the first casualty? it might be contested, even disputed, but difficult to dismiss.
Lets look at the brighter side – which is broadening. Internet ignited the creativity in a way as no other force before. Check out the innovations and the improvisation.
Consequently marketing and promotion are also undergoing radical changes. Now direct marketing is addressed as ‘organic’ and referral leads as ‘inorganic’. The online presence used to complement’ brick and mortar’ or structural outlets. There are shops set up exclusively online with no ‘offline’ presence, meaning there is no shop or outlet to purchase. The only way is ‘shop online’. Of course, the fly-by-night operators might still exists, credibility counts. Integrity is at stake and also offered the best collateral to the customer. Customer comments or complaints can make or mar business. Reviews are treated respectfully
When and where did the diversion happen?
It would be interesting to note that the introduction and adaptation of plastic money was the game changer. This was even before Google became a juggernaut. But people stuck to traditional and conventional mode of shopping. The online ‘effect’ at its infancy didn’t promise much given the inexperience of the customer compounded with the insecurity. Online shopping was provided more ‘as a service’ initially as compared to the fast growing present day eCommerce, which is proving to be indispensable.
Why the surge in online shopping? Anecdotal Narration.
Today, the customer is spoilt for choices, and there are more areas and avenues opening. Competition always favors the customer. To generate traffic to the website, companies go all out …when we take pride in ‘eye for details’, marketing is driven on this paradigm of publishing details that will grab your attention – whichever way that will direct you to the company’s products or services or both. So you can avail by landing on the company’s home page or led from other sites by means of advertisement, usually stunning banners or striking slogans.
An executive in our workforce applied for an unplanned leave. Surprised by the move, and all the more intrigued, the team queried “what happened?”
“I am taking a vacation.”
That’s like snow in summer. Thrilled, the team pushed “but then it seems unplanned?”
“well”, said the executive “my wife just spotted this awesome offer of plane tickets that covers the hotel accommodation as well. The price is like a steal. Incredible. So we decided to jump on it and just booked the tickets“
“which website?”
“its some advertisement that came upon while she was surfing for shopping. The travel portal is reliable and we checked the review comments and also visited the carrier’s home page but the discount offered wasn’t direct. The offer is valid when you book from the travel portal only.”
He had the team's undivided attention now.
“The carrier might be a no-frill carrier offering dirt cheap prices but numbers of visitors are comparably less to their website and hence, they smartly advertised in a portal where traffic is heavy and also tied up with hotels. If not now, then when? Can’t wait till the next one rolls out. So we decided to go for it. Time is money, in fact, that is the premium. So seize the moment. Make the most of the deal.”
The offer is open to all, but not all can cash in the opportunity, and those could, they really would. It’s not serendipity but some smart marketing manoeuvring. Organic or inorganic, the sale was closed. Mission accomplished.
We will cover more about Digital Marketing in subsequent posting. Stay tuned.
Read More
The 5 Whys and Root Cause Analysis Quality Management
Mostly employed in root cause analysis, 5 Whys prominently appears in the Analyze phase of DMAIC in Six Sigma. This technique iteratively interrogative in nature, mainly used to identify to the root cause or defect, was developed by Sakichi Toyoda and used in the Toyota Motor Corporation. [source: wiki]
Experts have varied opinions about this methodology which is often performed by a fish-bone diagram. There is no single root cause, if observed closely. Usually, it is a chain of events or combination of factors. Identification of the bug is a critical challenge and there are various methods and techniques. One such identified method is 5-why. This helps to understand the top 5 root causes which predominantly contribute to the problem .
The method might sound basic but very effective. The question is often posed from the answer received and it’s an iterative model. You can try and picture as some day-to-day issues you find yourself troubleshooting by find the root cause, like the scores of your child in a recently held d test paper. It’s as much questioning your child “why did you grades dip?” and from response offered by your child, there is a counter question –answer, till you are convinced one way or the other.
Why did your grades dip?
I didn’t do the exam properly.
Why didn’t you do the exam properly?
I couldn’t answer most of the questions.
Why couldn’t you answer most of the questions?
The questions were not familiar.
Why weren’t the questions familiar?
I had not prepared well enough.
Why didn’t you prepare?
Because I was playing and missed on the time to prepare.
Finally, it’s the lack of preparation that led to the poor performance. This might be your conclusion drawn from the conversation. And the advice or course of action is to ‘gear up well and be more prepared to face the next test.’
Here is another example from a professional backdrop:
Apply the same to a project to analyze about a failure – which we call it the root cause analysis.
There is no rule to stop the questioning at 5-level. It can go further. General studies reveal that ‘5 why’ usually lead to the main reason(s) of failure.
To illustrate further the 5 Whys, take a look at the image :
Limitation
This method suffers from its own share of shortfalls. The technique stops at the symptoms level and fails to dig deeper at the lower-level root causes. The results not being repeatable is a major constraint in this method. Besides, ‘Why’ can lead to multiple root causes but there is an inclination to isolate a single root cause and stick to it.
The limitations aside, 5 Whys is nevertheless is significantly used in Root Cause Analysis (RCA).
Read More
Now that you filled the PMP Examination forms What next Write the PMP Exam
As a prelude to appearing for the PMP® Certification exam, few pointers worth to ponder.
1. Fill the PMP® application form
Filling the form can be time consuming and extensive in preparation with an eye for details.
Please be informed that PMI® will provide 90 days to fill your form online during which you can edit and make changes but cannot cancel the application. PMI® will post a mail to your valid email about the completeness of application.
2. Response from PMI® about Application’s completeness
Once you submit the PMP® application, PMI will get back in about 5 days about the ‘Application Completeness Review’.
Soon after you submit the PMP® application, it becomes mandate to appear for the examination within one year of submission. This is again for the benefit of the participants to stay concentrated about the exam. A lot many aspirants develop cold feet due lack of time constraints, unexpected events, and hectic work schedule or plainly lack of preparation.
Also, some aspirants wait to become completely conversant and extremely confident before they can start filling the form. These are exceptional cases, besides PMI offers you enough time for the kind of confidence and conversance one can work upon and build in due course of time.
3. Make the Payment
This is the third step. Once your application is vetted for veracity, reviewed and ratified, the PM will post a send you a confirmation email with an advise to make the payment towards the PMP® examination fee.
Now you can make the payment. You can visit ww.pmi.org and become a member by paying fee of $139 which can save $11 and also provide soft copy of PMBOK and study aids.
4. Scheduling the Exam
After the form is submitted, you will receive a mail from PMI® stating ,Your application is approved ,You will receive confirmation that your application is approved. Further, the email will provide the payment link to pay the exam fees. For PMP® certification fee, PMI members will have to pay USD $405 while for non-members, it will cost SD $555. Or The application is under Audit process.
The PMI audit will seek to substantiate certain details recorded in the application form. The applicant will receive an audit document which needs to be printed, verified and signed by the supervisor/manager as mentioned in the application form with the respective company seal. The printed hard copies need to be posted through ‘traceable’ post.
Note: there is no need to get worked-up or become anxious. It’s just PMI is cross-checking with the information provided in the application and validating any gaps observed. It can happen due to oversight despite checking and double-checking some information or may be certain data failed to capture. PMI will provide 90 days for you to post the required documents back to its head office. Its advised that you always you’re your superiors informed about your certification endeavor and they will do the needful when taken into confidence. PMI will require 7 days to approve your application, subject to the orderliness of the submitted hard copies, and will mail you the link to make the payment and schedule PMP® Examination date.
5. Appear for the Exam
The PMP® certification prep courses, multiple model papers, study aids, Resources available and the numbers of hour spent preparing will definitely make a difference. As stressed in our previous blog posting, preparation stress the need of heightened anticipation – which is what we meant as ‘state of readiness’ so that the date scheduled by PMI will not take you by surprise, and also you can keep sharpening axe. Practice and preparation are the keys.
NOTE: You must retain the unique PMI Eligibility ID located on your scheduling notification. This number will be required to register for the examination. [courtesy: www.pmi.org. to read more, click here}
“I try to prepare for everything beyond the extent of preparation. Taylor Swift”
We wish you success!!
images courtesy: goo.gl/f6SME8
Read More
The 7 Habits of Highly Effective People a Project Manager s perspective
Penned by a Project Manager
When my friend passed this book, it had a sacred aura as if a parchment of scriptures was being handed. Amused thoroughly by this hand-over ceremony, I was more intrigued to read the title “The 7 Habits of Highly Effective People.” Another Motivational book? Perhaps. But I have seen guys hooked to 'Good to Great' by Jim Collins like a manual even citing page numbers and personally enthralled with sheer statistics in Malcolm McDowell’s ‘Outliers’. Come on, to quote Beatles were ‘also a band’ that did the gig and grind in German clubs for hours before they achieved the cult status made my eyes blink with disbelief.
So in a way, Stephen Covey’ 7 Habits as its referred by my contemporaries made me feel nervous like holding Fluid Mechanics by PK Bhansal or Thermodynamics that did give the jitters then, when we were new and naïve as newcomers. The fear is either misplaced or we reel locked up in a panic room. As Truman said ‘we have nothing to fear but fear itself.’ The title alone was enough to get me going because it doesn’t assure to make you successful but to succeed follow the 7 habits.
The more I read, the more I wanted to apply the learning to my professional sphere and as a Project Manager, Interestingly, we can apply the 7 habits into project management practice. Socrates said ““I cannot teach anybody anything. I can only make them think.” So a book that makes one think is an amazing resource of education – the eternal spring of knowledge. Louis L'Amour was exquisite “Reading without thinking is nothing, for a book is less important for what it says than for what it makes you think.”
Without much ado, here are the 7 habits BE PROACTIVE, BEGIN WITH THE END IN MIND, PUT FIRST THINGS FIRST, THINK WIN-WIN, SEEK FIRST TO UNDERSTAND, THEN TO BE UNDERSTOOD, SYNERGIZE, SHARPEN THE SAW.
Proactive:
It’s all about ownership and shouldering responsibilities. It’s the reactive that are influenced by other factors to indulge in blame game. It will be pertinent to point L'Amour to stress about being proactive
“Up to a point a man’s life is shaped by environment, heredity, and movements and changes in the world about him; then there comes a time when it lies within his grasp to shape the clay of his life into the sort of thing he wishes to be. Only the weak blame parents, their race, their times, lack of good fortune, or the quirks of fate. Everyone has it within his power to say, this I am today, that I shall be tomorrow.”
You can only manage things that are under your control. The proactive persons devote their time and effort on things that can be controlled., primarily through Circle of Influence
·
These are the group of the people who will focus on issues in take care of things those are under their control
·
They don’t blame other for the actions as their focus is more on the solving and resolving. Basically solutioning.
à You can relate this with Risk Management & Stakeholder Management,
Begin End in Mind
It’s the ability to vision objective with action plan. Every organization has a mission statement and any undertaking (read as Project) will have its goals and mission. The prototype or blueprint is basically the model of the end-product. If development is connecting the dots, then planning is all about creating and placing and positioning the dots. Begin End in Mind typically stresses on the scope. You should know what needs to be done and also what is NOT to be accomodated. You can plan on your resources and apportion tasks and assign by preparing the project plan.
à Relate this with Overall Project Plan – (Scope, Quality, Time & Cost)
Put First Things First
Plan all the tasks that can be done first by specifying the severity and assigning priority. It’s about organization, management and execution. Balance it out. You don’t have to burn out. Revisit your project plan for prioritization as some developments might mandate that some tasks take precedence as against the planned action item or a resource originally delegated for a particular requirement need to be deployed elsewhere.
à Review of the Project Plan and Execution
Think WIN-WIN
Spell success mutually. It has to work both ways. We are all in together and so should the benefits that are accrued as a result of the association. The budgeting must ensure the project doesn’t bleed and scope should be contained from bloating. It wouldn’t be fair-game if the vendor emerges as the victor at the cost of customer as a victim. Don’t over-price or undervalue. Be reasonable so that it’s a collaborative and co-operative effort wherein all the stakeholders involved share the results to realize the returns on investment.
à Relate with Communication Plan
SEEK FIRST TO UNDERSTAND, THEN TO BE UNDERSTOOD
Perhaps the toughest. We seek to be heard before hearing. The loudest is one who is heard, lest voices are drowned in the din. We are quick to judge than reason; prejudice prevails above principle. We want to have the last word and have to be right always. Learn. And for that listen first. A willful listener who is genuinely interested and not merely pretending to hear. There are instance we hear with the sole intent to give it back not as a reply or response but retort. Also, there is the element of sub-conscious bias that creeps unnoticed and adversely influences our decision and deliberation. The essence of communication is to understand as well as to be understood.
à Relate with Conflict Management
SYNERGIZE
Fundamentally teamwork. Synergy by definition is “the working together of two things to produce an effect greater than the sum of their individual effects”. It is indeed true that “The whole is more than the sum of its parts.” Meaning we draw strength from each other that makes us formidable team and a force to reckon. It would be a mistake to obscure an individual’s contribution – there are some stars that shine brightly. How the individual contribution broadens the funnel of opportunities and possibilities for team members makes it even more significant. Some team members come forward to wear multiple hats or some are made to multi task to further project’s progress and team’s interest. Synergy is the collective strength and combined effort expending in achieving a common goal.
à Relate with Conflict Management and People Management
SHARPEN THE SAW
It was Abraham Lincoln’ who famously quoted “Give me six hours to chop down a tree and I will spend the first four sharpening the axe.” Work smart. It’s wise to invest time in figuring out the best possible ways to get the work done efficiently so as to enhance productivity. The best output in the given timeline, sometimes limited time always calls for smart work. Its left to you in managing the given time and to optimize, you must reinvent yourself and be at it. Its always about conserving your energy to combat challenges and crisis that comes in the way of work. The monotony of work – to be at the desk from dawn to dusk drains you down. Wont you feel weak and worn out? You want capitalize on newer opportunities or crash out because of overdoing? Try to lead a balanced life. Take your mind off by mediation or relaxation or spiritual activity. It helps to unplug once in a while to recharge and revitalize yourself.
à Relate with Monitoring and Control The above article was penned by one of the panel members who is an active and experienced Project Manager. iCert Global is a global learning provider specializing in the fields of Project Management amongst other offerings. You can learn more about Project management by signing up for our PMP® or PRINCE2 programs. We wish to thank you for visiting our blog and hope your stay was productive and purposeful.
images courtesy: goo.gl/R9UsNt
Read More
Advance your Career with Certified Business Analysis Professional CBAP Certification
There was an interesting and exciting write about Business Analysts - The 21st century business analyst is a liaison, bridge and diplomat who balances the oftentimes incongruous supply of IT resources and demands of the business. Forrester's research found that those business analysts who were most successful were the ones who could "communicate, facilitate and analyze."
Business Analyst, as a role and title, is often connected with IT industry given its dominating presence and dependence in the scope of business. This is not to discount or discredit Business Analysis in other industries but this article’s premise is clearly IT.
It’s the customer who drives the business. The stakeholders help create the ecosystem and the principal players play their part to progress and ensure profit. The endeavor should end in business value. The eyes are set at the topline and bottom line, and any business venture should demonstrate capabilities to monetize. The bottom line is the backbone. We have always toiled to profit in any profession and in software parlance Solution, as a way of business, is created based on the customer’s problem statement.
In business, the most difficult part is to please is your customer. Try as you might, they are never content. It’s an uphill task and times, unreasonable too. It’s unwise and unfair to expect the customer will record the requirement in their Business Requirement specification. The specification is subject to change as it evolving in nature but the scope should be pinned right at the start for change in scope can prove catastrophic.
Who is a business analyst and the importance of business analysis?
Mind Is always applying to matters and in that sense we are all analysts. Business Analysts is a specialized skill wherein a smart combination of strategic smartness as that of a diplomat and analytical approach of an intelligence community.
A Business Analyst should be able to handle aspects of both functional solution and technical solution in response to the business need in proposing a solution that s holistic and realistic.
Requirement gathering can be done through conventional ways like elicitation, ideation, brainstorming, or employ modern tools like prototyping, wireframing drawing the big picture or the end-product.
Who knows the scope better than a Business Analyst?
Business Analysts are not just touch points but the interface between the organization and the customer, translating business needs and providing feasible solutions that can be implemented at the agreed cost – which effectively contains scope. As the primary window for requirement gathering the Business Analyst is better placed at a vantage point in assessing and analyzing the scope better. Continuous dialogue and constant touch helps in shaping up the specification to systematically document the scope and bring on record ‘the out-of scope’ aspects as well. The customer of today is more empowered with data points at their fingertips and fluent in system architecture and talk technology as good as your technocrat. So quintessentially Business Analyst ought to be 2 steps ahead to preempt the perils and possible scenarios. Its that sense of anticipation that heightens the alertness which really sells. In case of scope creeps, it will become an undersell. Therefore, the best to identify the scope is left to the Business Analyst and contain will become imperative upon the executor (Project Manager). Why Certified Business Analysis Professional (CBAP®)?
As a professional, you need to establish credibility and build trust. CBAP® certification criteria make it a mandate to possess 7500 hours of hands-on business experience which makes it extensive in terms of learning in terms of time and talent. Its given to understand that CBAP® certified professionals are ‘experts in identifying the business needs of an organization in order to determine the best solutions’ as stated in iiba.org. Just like PMP® for Project Management following the Project Management Body of Knowledge (PMBOK® ) Guide, organization these days are stressing on the significant of a CBAP® certification for Business Analyst which follows The Business Analysis Body of Knowledge (BABOK® Guide V2.0.) and is fast gaining currency as one of the best known benchmark for business analysis. CBAP certification enhances the human capital of an organization and builds competency in business analysis practice. Also the recognition and career advancement potential for the professional makes it a synergetic growth for the organization. It enables effective work with stakeholders associated and helps better understand the profession as an expert.
As mentioned by iiba.org, CBAP® trained managers or provide CBAP trainings enjoy following benefits:
• CBAPs are acknowledged as competent individuals who perform a role which is increasingly recognized as a vital component of any successful project. • CBAP can be identified as individuals with an advanced level of knowledge and qualifications • CBAP follow established standards as outlined in the IIBA BABOK® Guide V2.0. • CBAPs produce reliable, quality results with increased efficiency and consistency
Records sourced from IIBA.org states that there 6208 registered professionals and the number is growing at a staggering pace. There are 6 knowledge areas as prescribed in the BABOK® Guide V2.0.which you will have to become proficient to pass the certification. Our CBAP® certification course will provide the necessary training and learning based on BABOK® Guide V2.0.Some key modules are listed below for reference as part of the course agenda:
.Introduction to CBAP .Enterprise Architecture .Developing A Solution Scope .Developing A Business Case .Stakeholder Roles and Responsibilities, .Elicitation Techniques
· Requirements Planning .Risk Analysis and Management Enterprise Analysis/Business Case .Enterprise Analysis Tasks .Requirements Management and Communication .Managing the Solution Scope Requirements .Traceability .Inputs to the Solution Scope .Managing Requirements Changes .Risk Analysis .SWOT Analysis
images courtesy: goo.gl/W37UgV
Read More
Manage Multiple Projects Effectively with a MSP Certification
Amazing. Astounding. Awe-inspiring. The technology revolution has taken the industry by storm and dazzles with “disruptive technology “ or ‘creative destruction. Buzz words by the horde appear on the headlines startling you by its sheer ‘sentence-construct’. Many couldn’t decipher disruptive technology then but we are now used to and even conversant to the point of expecting more. If you are someone juggling with more than one assignment – then talk of multi-tasking. Now when its managing multi-projects, then the unknowns and unexpected changes complicates to a severity hitherto undefined.
So as one entrusted with the Program management, how do you anticipate the unexpected and negotiate the unforeseen changes? Please note that a program is a portfolio comprised of multiple projects. Its common knowledge that managing large-scale programme can be very complex in terms of planning, organizing and execution. The business environment has changed drastically with the advent of mobile apps in every sphere of life and digitization of every dot, which demands completion at a pace that’s fast and yet cost-effective. While the scale and size in project and programs are growing, qualified professionals who can consistently perform and contribute are found wanting.
We recommend MSP® ( Managing Successful Programs). Your organization would want to continually improve, manage multiple projects to the minute detail, manage stakeholder expectation, provide value for investment, capitalize on business opportunities and become an enabler of change – which is why MSP® is strongly proposed to be pursued by your Personnel managing programs. MSP’s framework enables organization to break down complex programs in to manageable interrelated projects, balancing on the budget and staying on time without compromising the quality. Thus it’s a strategic approach to accomplish a complex engagement through transformation activities whereby a file is split as dossiers, organized, implemented and executed to achieve the intended outcome or business result, in other words, business value.
MSP® sets out successful programs
Pcubed has found MSP to be an effective platform upon which to develop a program or assess the effectiveness of those already underway. MSP® sets out how successful programs - portfolios of projects - can and should be accomplished. It emphasizes that a program will involve considerable resource commitment from a number of areas: "a significant budget, lengthy timescales, potential disruption of extant projects or programs, and major business or organizational change."
MSP® helps in delivering business outcome/output
MSP® is a flexible though not prescriptive business framework and best practice that helps organization with its pragmatic approach to realize present project objectives and enhances its business operation and processes. It enhances organization efficiency, makes resources effective and encourages innovation. The business goals, objectives are strategically aligned so as to improve operational efficiency, and act as a catalyst for delivery capabilities. Since MSP is developed from collective experience and expertise, it adds tremendous value, and benefits largely from the insights from experience.
MSP® is good enough for any type of organization
Big or small – the size is no constraint at all. So long the senior professionals, usually mid-level managers or higher are trained in MSP , preferably Practitioners will serve well to measure up to the organization’s expectations in terms of yield. the certified MSP Practitioners are adept in handling exigencies and resolving issues with enhance decision-making prowess. MSP certification is globally recognized and hence the talent pool of any organization with certified practitioners enhances its image and builds trust and credibility about the workforce.
It must be acknowledged that given global competition, compounded by other factors internal and external, one cannot completely insulate from failure but MSP helps organization to stay as competitive with its cutting edge a fair chance to succeed in the most demanding market that offers little latitude.
images courtesy: goo.gl/n9BBdt
Read More
Communicate with Clarity Stakeholder Management
All us will agree to the need for greater clarity in communication – be it any form, verbal, or written. We say a lot and
really don't mean anything much.
Conflicts arise mainly due to poor communication. When words are minced, message loses its meaning. Basically, we failed to
make sense, and probably never realized. Confusion is otherwise called as noise.
Let’s look into some real-time scenarios:
Despite a set agenda, meetings, at times, drag for hours not deliberating the issues tabled, rather a stray thought entertained finds resonance with someone seated and soon the discussion veers off in a direction that’s tangential. When the meeting is concluded, everyone leaves learning a lesson not to get distracted but fall into the same trap that was supposed to be safeguarded.
Likewise, a client call to collect requirements goes into an infinite loop of ‘back and forth’. Why? Either the message is
not clear or the stakeholders are not in the same page for the lack of understanding. It’s as if the conversation is taking
place in a language that the attendees in the call are absolutely clueless. This, when Language is no longer a limitation
can be so ironical.
Or, the instance when a simple mail intended to communicate a message can be so misleading.
So, how do you bring clarity in communication?
You don’t have to be poetic. Just be precise.
There is no need to compose an essay. A 2-liner will be enough if the message can be conveyed.
Be verbal, not verbose. Compose crisp concise message using shorter sentences.
The second paragraph is this post itself is typical disclaimer as to ‘how not to write’. Rather, simplify. Make it easier
for the reader to understand. It should not be a test on IQ. Is your message easy to understand? Assess the easiness. If
yes, post. If not, rewrite.
Clarity means simplicity. We often confuse that word as a business jargon. The challenge today that 'you might be possess
the knowledge of a professor' but can you explain in a way that a third-grade kid can understand?
There should not be any confusion at all; nor the need to refer the dictionary. Prose that is plain yet elegant; correct in
its context brings out greater clarity in communication.
It can be challenging. So is clarity in communication.
Read More
really don't mean anything much.
Conflicts arise mainly due to poor communication. When words are minced, message loses its meaning. Basically, we failed to
make sense, and probably never realized. Confusion is otherwise called as noise.
Let’s look into some real-time scenarios:
Despite a set agenda, meetings, at times, drag for hours not deliberating the issues tabled, rather a stray thought entertained finds resonance with someone seated and soon the discussion veers off in a direction that’s tangential. When the meeting is concluded, everyone leaves learning a lesson not to get distracted but fall into the same trap that was supposed to be safeguarded.
Likewise, a client call to collect requirements goes into an infinite loop of ‘back and forth’. Why? Either the message is
not clear or the stakeholders are not in the same page for the lack of understanding. It’s as if the conversation is taking
place in a language that the attendees in the call are absolutely clueless. This, when Language is no longer a limitation
can be so ironical.
Or, the instance when a simple mail intended to communicate a message can be so misleading.
So, how do you bring clarity in communication?
You don’t have to be poetic. Just be precise.
There is no need to compose an essay. A 2-liner will be enough if the message can be conveyed.
Be verbal, not verbose. Compose crisp concise message using shorter sentences.
The second paragraph is this post itself is typical disclaimer as to ‘how not to write’. Rather, simplify. Make it easier
for the reader to understand. It should not be a test on IQ. Is your message easy to understand? Assess the easiness. If
yes, post. If not, rewrite.
Clarity means simplicity. We often confuse that word as a business jargon. The challenge today that 'you might be possess
the knowledge of a professor' but can you explain in a way that a third-grade kid can understand?
There should not be any confusion at all; nor the need to refer the dictionary. Prose that is plain yet elegant; correct in
its context brings out greater clarity in communication.
It can be challenging. So is clarity in communication.
Turn the Threats to Opportunities Risk Management
Sometime back GE’ CEO hit headlines with a zinger that threw even the reader off the rails.”If you are joining the company in your 20s, unlike when I joined, you’re going to learn to code, "GE CEO Jeff Immelt wrote in a LinkedIn post on Thursday. "It doesn’t matter whether you are in sales, finance or operations. You may not end up being a programmer, but you will know how to code. We are also changing the plumbing inside the company to connect everyone and make the culture change possible. This is existential and we’re committed to this."
Become multi-skilled. Expand career options.
One can’t figure out the relevance of code with someone handling compensation or making cold calls in the hope of a prospect. How does coding propel a career in finance, HR or Sales? It’s hard to connect and yet the call is to ‘code.’ Is that a threat or opportunity? Look at the plus side; if you become competent to code, hailing from a finance background or pursuing a sales career, isn’t that a shot in the arm, with ‘soft skills” making your profile more sophisticated. Besides, in terms of career choice, you have more than one option. The choices presented upfront are just wide and varied. Turn that threat to an opportunity.
Don’t rely on one individual. Transition.
From newly found start-ups to deep grounded companies, this curse of leaving the core knowledge in the hands of very few, or someone reliable and then totally rely on that person is a paradox that remains unsolved till date. Can Manager code? It could be the pitch to the millennial, but from experience, can senior-level managers ask the programmers to move aside and start coding? Then who will manage?
Some of the tools and even languages that were potent and popular during their times have either faded or obliterated, distanced or disappeared. You don’t get to hear about BASIC or FORTRAN or Pascal. Where are they today? They had their hour of glory, shone in limelight and stepped offstage for some other language to become prominent. The show goes on; the actors change and so does the costume.
Besides, Managers have a higher calling than coding. They have to manage overruns and burn rate, keep cost within budget, cope with scope, rein risk and always an eye on the bottom-line. Leaders are expected to extract the best/optimal outcome from the team. Lead the team with strategic vision. As long as leader keeps their next level or second-in-command motivated to take care of things, they can focus on other responsibilities.
Today Leadership is about connecting with everyone and not the peers and reporting heads. That aside, isn’t it a threat to depend on someone or identified few? Over-dependence or too much reliance is harmful to the interest of any organization. It is a threat. Pooling all information in one server or maintaining multiple mirror servers spread across different geographical locations so that they will come in handy should one server crash - which makes more sense? Knowledge in the hands of one or concentrated few is a serious threat. To mitigate this threat, start transitioning. Disseminate. Distribute. Decentralize.
image courtesy:goo.gl/xYdeKD
Read More
Become multi-skilled. Expand career options.
One can’t figure out the relevance of code with someone handling compensation or making cold calls in the hope of a prospect. How does coding propel a career in finance, HR or Sales? It’s hard to connect and yet the call is to ‘code.’ Is that a threat or opportunity? Look at the plus side; if you become competent to code, hailing from a finance background or pursuing a sales career, isn’t that a shot in the arm, with ‘soft skills” making your profile more sophisticated. Besides, in terms of career choice, you have more than one option. The choices presented upfront are just wide and varied. Turn that threat to an opportunity.
Don’t rely on one individual. Transition.
From newly found start-ups to deep grounded companies, this curse of leaving the core knowledge in the hands of very few, or someone reliable and then totally rely on that person is a paradox that remains unsolved till date. Can Manager code? It could be the pitch to the millennial, but from experience, can senior-level managers ask the programmers to move aside and start coding? Then who will manage?
Some of the tools and even languages that were potent and popular during their times have either faded or obliterated, distanced or disappeared. You don’t get to hear about BASIC or FORTRAN or Pascal. Where are they today? They had their hour of glory, shone in limelight and stepped offstage for some other language to become prominent. The show goes on; the actors change and so does the costume.
Besides, Managers have a higher calling than coding. They have to manage overruns and burn rate, keep cost within budget, cope with scope, rein risk and always an eye on the bottom-line. Leaders are expected to extract the best/optimal outcome from the team. Lead the team with strategic vision. As long as leader keeps their next level or second-in-command motivated to take care of things, they can focus on other responsibilities.
Today Leadership is about connecting with everyone and not the peers and reporting heads. That aside, isn’t it a threat to depend on someone or identified few? Over-dependence or too much reliance is harmful to the interest of any organization. It is a threat. Pooling all information in one server or maintaining multiple mirror servers spread across different geographical locations so that they will come in handy should one server crash - which makes more sense? Knowledge in the hands of one or concentrated few is a serious threat. To mitigate this threat, start transitioning. Disseminate. Distribute. Decentralize.
image courtesy:goo.gl/xYdeKD
Attrition Has Never Been An Issue To This EdTech Company - iCertGlobal
People are leaving. Dropping off like nine pins. According to the Bureau of Labor Statistics, stating he the people who quit was at 2.2% which translates to 3.22 million Americans. The highest seen since February 2001.
Does it impact the companies when employees leave? It depends on who is leaving. If it is a top performer, then it might rock the boat
No Scarcity In Skills
iCertGlobal has faced a number of challenges, but never struggled with talent erosion. The ability to anticipate and manage expectations is one of its cornerstones. The company has risen in headcount steadily – not in leaps and bounds, but steady growth, just as their bottom line. “From that simple set-up with few heads” acknowledged their CEO Irfan Sharief “to where we stand today, I would say we have grown in numbers, increased our technology space but never compromised on core principles.”
Attrition Low. So what’s the big deal? That speaks a lot that fails to meet the eye. For an industry that’s known for poaching talent, it speaks a lot about the stability of the company.
It’s not a story by luck or chance that a company is started and survives and thrives in the digital transformation age when competition is fierce and you need to more than firefighting tactics. It’s one of audacity and ambition.
So, the challenge always is to enroll the employees in your mission. Unless, there is a buy-in from the staff, things will stall.
Pay, Passion, Or Profession
Why do employees stay or quit? The same reason can be cited for staying or leaving – the corporate culture, may be suiting or stifling. Again, subjective. The likes and dislikes vary from person to person. As a professional, what drives you to work? Pay, passion, policies, principle, or perks or any other factor. It could also be the same for you to stick on. It may be difficult to pinpoint. It is imperative to retain key talent. Looking at workforce, some have chosen to stay since inception.remain since inception.
What makes them stay? This is a place wherein every hand is ‘deemed’ indispensable and the philosophy of the ‘leader is as good as the team” is perfectly embodied in spirit and letter.
The vision is to reach out to everyone wanting education – the level doesn’t matter. It’s the willingness to learn. One of the reasons to switch the knowledge transfer to electronic mode apart from connectivity is cost. When education became expensive, affordability raised too many concerns and the drop-out rate increased. To curb this drop rate and encourage to enrol, e-Learning met many objectives. It was swift in reach, affordable in cost, and powerful as a platform. And who will deliver them? Not robots? So, it becomes even more important to retain the staff. Never undermine the check on attrition. When you take care of your employees, they will take care of business.
image courtesy: goo.gl/KnjbPz
Read More
People are leaving. Dropping off like nine pins. According to the Bureau of Labor Statistics, stating he the people who quit was at 2.2% which translates to 3.22 million Americans. The highest seen since February 2001.
Does it impact the companies when employees leave? It depends on who is leaving. If it is a top performer, then it might rock the boat
No Scarcity In Skills
iCertGlobal has faced a number of challenges, but never struggled with talent erosion. The ability to anticipate and manage expectations is one of its cornerstones. The company has risen in headcount steadily – not in leaps and bounds, but steady growth, just as their bottom line. “From that simple set-up with few heads” acknowledged their CEO Irfan Sharief “to where we stand today, I would say we have grown in numbers, increased our technology space but never compromised on core principles.”
Attrition Low. So what’s the big deal? That speaks a lot that fails to meet the eye. For an industry that’s known for poaching talent, it speaks a lot about the stability of the company.
It’s not a story by luck or chance that a company is started and survives and thrives in the digital transformation age when competition is fierce and you need to more than firefighting tactics. It’s one of audacity and ambition.
So, the challenge always is to enroll the employees in your mission. Unless, there is a buy-in from the staff, things will stall.
Pay, Passion, Or Profession
Why do employees stay or quit? The same reason can be cited for staying or leaving – the corporate culture, may be suiting or stifling. Again, subjective. The likes and dislikes vary from person to person. As a professional, what drives you to work? Pay, passion, policies, principle, or perks or any other factor. It could also be the same for you to stick on. It may be difficult to pinpoint. It is imperative to retain key talent. Looking at workforce, some have chosen to stay since inception.remain since inception.
What makes them stay? This is a place wherein every hand is ‘deemed’ indispensable and the philosophy of the ‘leader is as good as the team” is perfectly embodied in spirit and letter.
Quality Management - Six Sigma
Automation is almost everywhere, and head more in the IT sphere. Of course it started from there and soon spread to other industries. It wasn’t a question when they are introduced in software industry, especially in testing. It was more about the replacement skilled hands good at manual testing. No matter how good you are testing, there is a slack on everyone as the day wears out, human fatigue, wear and tear is all part of the daily rigor, but for a machine that’s lifeless and programmed to perform complex and complicated work, there is no such fatigue except the glitch, which the engineers anticipate, preempt before deploying into production.
There is flip side into automation but the benefits far overweigh manual testing and hence the job loss. With automation taking over as a technological drive, it was only a matter of time before manual testing would replace men with machines. That’s the reality and sooner one reconciles and find alternatives to stay relevant, and required there is less to worry about pink slips.
It is a technique that was devised way back in 1990s by two engineers working in Motorola to improve the quality by decreasing the numbers of errors that might occur. It is basically about identifying the causes of the errors, and systematically removing there errors, so that there will be not any recurrence. The quality engineer follows management methods based on experimentation and observation and analyse their findings through statistical methods.
The higher the probability of reducing the errors, then higher will the profitability to the organization. This was the underlying principle. This practice created a specialized pool of talented people who have an eye of detecting the flaws and direction solutions to fix.
They follow a step of methods that sequential in inspecting and identifying the defect to create a defect-free product. Statistically speaking 3.4 defective features per million opportunities means 99.99966% of all opportunities to produce some feature of a part that are free from defects. That is six sigma in a nut shell.
Six Sigma Green Belt Certification
Couresty:wiki
DPMO is Defect Per Million Opportunities. From the chart, it is evident the desired six sigma level is 6.
Along with the various level of identification came the expertise with in a person to handle six-sigma related projects and to evaluate their expertise, karate belts like yellow, black were used to identify the skillset of the six sigma professionals.
The Six Sigma Green Belt professionals are generally employees who are involved with maintenance of Six-Sigma as part of their job responsibilities. This does mean that this is their only job but one among many parts of their line of work. Six Sigma Certification Online is very much possible as training centers provide different modes of imparting knowledge transfer: Instructor-led Classroom, Instructor-Led Online Class and E-Learning.
There are many benefits of Sig Sigma testing, some of which are highlighted below:
Improved quality: when Motorola initiated in early 90s, it almost went unnoticed. Jack Welch made it popular when he announced the annual results and heads started turns to Six Sigma and more companies followed suit.
Increased ROI: As mentioned above, higher probability of reducing the errors leads to greater profitability to the organization.
Greater Customer Satisfaction: It’s a win-win where both the stakeholders are happy: the client and vendor.
Employee Recognition. The employees who worked in bringing the turnaround by tightly controlling the defects deserve due appreciation and accolade.
image courtesy: goo.gl/sfgsje
Read More
Automation is almost everywhere, and head more in the IT sphere. Of course it started from there and soon spread to other industries. It wasn’t a question when they are introduced in software industry, especially in testing. It was more about the replacement skilled hands good at manual testing. No matter how good you are testing, there is a slack on everyone as the day wears out, human fatigue, wear and tear is all part of the daily rigor, but for a machine that’s lifeless and programmed to perform complex and complicated work, there is no such fatigue except the glitch, which the engineers anticipate, preempt before deploying into production.
There is flip side into automation but the benefits far overweigh manual testing and hence the job loss. With automation taking over as a technological drive, it was only a matter of time before manual testing would replace men with machines. That’s the reality and sooner one reconciles and find alternatives to stay relevant, and required there is less to worry about pink slips.
It is a technique that was devised way back in 1990s by two engineers working in Motorola to improve the quality by decreasing the numbers of errors that might occur. It is basically about identifying the causes of the errors, and systematically removing there errors, so that there will be not any recurrence. The quality engineer follows management methods based on experimentation and observation and analyse their findings through statistical methods.
The higher the probability of reducing the errors, then higher will the profitability to the organization. This was the underlying principle. This practice created a specialized pool of talented people who have an eye of detecting the flaws and direction solutions to fix.
They follow a step of methods that sequential in inspecting and identifying the defect to create a defect-free product. Statistically speaking 3.4 defective features per million opportunities means 99.99966% of all opportunities to produce some feature of a part that are free from defects. That is six sigma in a nut shell.
Six Sigma Green Belt Certification
Couresty:wiki
DPMO is Defect Per Million Opportunities. From the chart, it is evident the desired six sigma level is 6.
Along with the various level of identification came the expertise with in a person to handle six-sigma related projects and to evaluate their expertise, karate belts like yellow, black were used to identify the skillset of the six sigma professionals.
The Six Sigma Green Belt professionals are generally employees who are involved with maintenance of Six-Sigma as part of their job responsibilities. This does mean that this is their only job but one among many parts of their line of work. Six Sigma Certification Online is very much possible as training centers provide different modes of imparting knowledge transfer: Instructor-led Classroom, Instructor-Led Online Class and E-Learning.
There are many benefits of Sig Sigma testing, some of which are highlighted below:
Improved quality: when Motorola initiated in early 90s, it almost went unnoticed. Jack Welch made it popular when he announced the annual results and heads started turns to Six Sigma and more companies followed suit.
Increased ROI: As mentioned above, higher probability of reducing the errors leads to greater profitability to the organization.
Greater Customer Satisfaction: It’s a win-win where both the stakeholders are happy: the client and vendor.
Employee Recognition. The employees who worked in bringing the turnaround by tightly controlling the defects deserve due appreciation and accolade.
image courtesy: goo.gl/sfgsje
The Importance Of IT Service Management.
Does artificial intelligence fall under the ambit of IT services? Yes, so long they are used for IT related projects and programs. Automation is again big time in the software industry. Check out and you will find them more IT-services based.
Failed computer replaced during U.S. astronauts' spacewalk [source- Reuters]that doesn’t speak of IT Service Management? News like and a horde of such articles and news items in the public domain only stresses the importance of IT Service management.
Who will manage the IT Services?Of course, IT Service Management team, that could include IT System Managers, IT Administrators, System Administrators, IT Quality Specialists, IT Audit, IT System Analysts and Quality Control who are either responsible for streamlining the IT Systems or part of IT Service Management team, Quality Assurance teams responsible for software and infrastructure.
Who will manage the people handling IT Services?The reiteration IT Service management is because there is no sphere of our life which IT has not shaped up. IT is ubiquitous. It’s almost everywhere. So you need people who are skilled in managing and handling IT systems. The need for ITIL® Certifications is more as a test of competency and validation expertise in handling critical scenarios. IT Service setup can be simple or complicated, and more often not, the complexity varies in severity, and you can take it for granted that any IT System will be complex. Hence, most companies prefer skilled people with experience and rich expertise in entrusting the systems. Just like mirror servers, company don’t prefer to depend on any particular team, rather they prefer a mix of teams who can be deployed and pressed in to service should a situation warrant. This is the very reason why the ITIL® Certifications have gained prominence in the recent times as professionals start at foundation level and then move on to the intermediate modules – which can be either Lifecycle modules best suited for professional pursuing management of services and the other is capability modules, which is apt for professionals preferring the process, and the next level of certification is the MALC ( Managing Across the Lifecycle) and clearance will lead to ITIL Expert. So given the mix of management and process in the intermediate levels, companies also use a judicious mix of people capable of handling scenarios pertaining to management or process or both.
Who will maintain the IT Systems?It is an interesting poser. Maintenance of IT Systems need not be the same as the one managing the IT Systems. There can be a dedicated team exclusively for IT system maintenance. The prerequisites, qualifications, certification and validation in terms of capability and competency remain the same. Maintenance is a critical and crucial as managing. In case of any faulty issues or malfunction, troubleshooting will be taken care by the maintenance crew who are always on standby. Expecting the unexpected is a good maxim and mostly follow b all the companies that have deployed IT Systems. There is also a misconception that IT Systems pertains to the software industry. The perception should ‘wherever IT Systems are deployed’, it calls for managing and maintenance of IT Systems.
Read More
The Sixth Edition of PMBOK® Guide Will Be Soon Out
The Sixth Edition of PMBOK® Guide Will Be Soon Out | Project Management
PMI (Project Management Institute) is expected to roll out the Project Management Body of Knowledge (PMBOK® Guide) – Sixth Edition by the third quarter of 2017. It is expected that the draft version of the Sixth Edition is ready by the first or second quarter, and the final version of the Sixth Edition should be available by mid-2017, if things go as planned.
What are the changes expected in the Sixth Edition?
>> The size of the book. Presently, the fifth edition PMBOK® Guide, has 13 chapters that spans 415 pages. The sixth edition is expected to be quarter the size of the 5th edition, which means it should be close to 84 pages and the number of chapters too have come down to 10. So, sixth edition should be 10 chapters with 84 pages in the draft version. By the time sixth edition gets published, PMI possibly will add more pages. The final number of pages for now is unknown.
>> Inputs, Tools & Techniques, Outputs (ITTOs) – the sixth edition will not dwell deep into ITTOs, rather it will be covered at a high level.
>> The first version of the PMBOK 6th edition is ¼ the size of the PMBOK 5th edition. The 6th editions currently has 10 chapters and 84 pages, while the 5th edition had 13 chapters and 415 pages.
>> Alignment with Process Groups: the sixth edition will be divided based on the 5 process groups, and not the 10 knowledge areas. This is considered a major change as the Role Delineation Study (RDS) conducted by PMI has presented its findings and proposed the changed to be aligned with process groups.
>> Combination of first three chapters. In the sixth edition, the first three chapters will be combined as one – the interpersonal skills of the project manager and organizational skills will be merged in to one.
>>Two processes are expected to be deleted. The Close Procurements process and Estimate Activities Resources are more likely to be deleted.
>>Two knowledge areas to be renamed; Time Management and Human Resource Management to be renamed. Time management will be renamed Schedule management, while human resource management becomes Resource Management
>> Knowledge Areas to feature four section. Every knowledge areas will have four new sections, namely, Key Concepts, Trends and Emerging Practices, Tailoring Considerations and Considerations for Agile/Adaptive Environments.
>> An exclusive chapter on role of Project manager. This chapter on Project Manager will cover the key concepts about core competencies, expertise, leadership skills expected in leading a project.
>> Approaches for Agile : every knowledge area will be inclusive of a section with approaches to Agile, Iterative and Adaptive Environments’. This section will detail the integration of agile practices in project backgrounds.
>> PMI Talent Triangle™: PMI spells the details about the technical skills, business intelligence , and leadership considered the key skills for success. It is also known as Talent triangle.
Reference source: http://www.examspm.com/2016/07/16/pmbok-6th-edition-release-date-changes/
https://www.pmi.org/pmbok-guide-standards/about/current-projects
http://www.pmi.org/certifications/types/project-management-pmp/update
https://www.pmi.org/pmbok-guide-standards/foundational-standards-exposure-draft
https://www.pmi.org/learning/training-development/talent-triangle
image courtesy: goo.gl/D9V6Rb
Read More
The Sixth Edition of PMBOK® Guide Will Be Soon Out | Project Management
PMI (Project Management Institute) is expected to roll out the Project Management Body of Knowledge (PMBOK® Guide) – Sixth Edition by the third quarter of 2017. It is expected that the draft version of the Sixth Edition is ready by the first or second quarter, and the final version of the Sixth Edition should be available by mid-2017, if things go as planned.
What are the changes expected in the Sixth Edition?
>> The size of the book. Presently, the fifth edition PMBOK® Guide, has 13 chapters that spans 415 pages. The sixth edition is expected to be quarter the size of the 5th edition, which means it should be close to 84 pages and the number of chapters too have come down to 10. So, sixth edition should be 10 chapters with 84 pages in the draft version. By the time sixth edition gets published, PMI possibly will add more pages. The final number of pages for now is unknown.
>> Inputs, Tools & Techniques, Outputs (ITTOs) – the sixth edition will not dwell deep into ITTOs, rather it will be covered at a high level.
>> The first version of the PMBOK 6th edition is ¼ the size of the PMBOK 5th edition. The 6th editions currently has 10 chapters and 84 pages, while the 5th edition had 13 chapters and 415 pages.
>> Alignment with Process Groups: the sixth edition will be divided based on the 5 process groups, and not the 10 knowledge areas. This is considered a major change as the Role Delineation Study (RDS) conducted by PMI has presented its findings and proposed the changed to be aligned with process groups.
>> Combination of first three chapters. In the sixth edition, the first three chapters will be combined as one – the interpersonal skills of the project manager and organizational skills will be merged in to one.
>>Two processes are expected to be deleted. The Close Procurements process and Estimate Activities Resources are more likely to be deleted.
>>Two knowledge areas to be renamed; Time Management and Human Resource Management to be renamed. Time management will be renamed Schedule management, while human resource management becomes Resource Management
>> Knowledge Areas to feature four section. Every knowledge areas will have four new sections, namely, Key Concepts, Trends and Emerging Practices, Tailoring Considerations and Considerations for Agile/Adaptive Environments.
>> An exclusive chapter on role of Project manager. This chapter on Project Manager will cover the key concepts about core competencies, expertise, leadership skills expected in leading a project.
>> Approaches for Agile : every knowledge area will be inclusive of a section with approaches to Agile, Iterative and Adaptive Environments’. This section will detail the integration of agile practices in project backgrounds.
>> PMI Talent Triangle™: PMI spells the details about the technical skills, business intelligence , and leadership considered the key skills for success. It is also known as Talent triangle.
Reference source: http://www.examspm.com/2016/07/16/pmbok-6th-edition-release-date-changes/
https://www.pmi.org/pmbok-guide-standards/about/current-projects
http://www.pmi.org/certifications/types/project-management-pmp/update
https://www.pmi.org/pmbok-guide-standards/foundational-standards-exposure-draft
https://www.pmi.org/learning/training-development/talent-triangle
Data is the new Oil | Digital Marketing
The most powerful mode of marketing is the word of mouth.
Is Digital marketing same as word-of-mouth marketing? Yes or no? Well, what do you call ‘thing going viral on the social media’. The word spreads faster than a forest fire. We bank on referrals and trust the testimonies of our contacts before deciding on a service provider or business provider.
Today, it’s too expensive to try out the trial and error, and hence we follow footprints to be better safe and sure. Check and double-check. And that’s the reason why the online reviews are attached too much importance because you can’t collect all the information from your known sources, and hence, need to rely on unknown sources as well. Be it a travel or hotel booking or buying a car, we need to arm ourselves with facts, figures and Opinions. It matters more these days on others’ experience to get a perspective of ‘how it will be’, before doing it on our own for the ‘self-experience.’ Isn’t it? How many times have you checked a restaurant‘s reputation online before booking a table? And scrolled down all the way to sniff out foul smell? Yes, that one star rating which makes your face frown. Yes!
Word of mouth is more personalized. But in this digital era, where time is money, it’s impossible to knock on every door to get first-hand feedback. Technology has advanced. We speak of being ahead or behind the curve in technology. So the best way to pool in people’s views in one place would be the internet. And if that be, what’s stopping you from marketing using internet as a channel.
This could be the genesis of digital marketing. People prefer both brick and mortar shops and online shopping too. There exists a market share for both, and if you consider convenience, comfort, choice, online shopping is head over shoulder.
Times have changed and it’s wise to turn along the tide. So hoardings which do exist have shrunk in number and instead the online banners have risen exponentially in numbers. The medium of sale has shifted. Online transactions have spiked in numbers. Marketing of products and services using technologies through internet is otherwise known as Digital marketing, wherein the online space is used to provide the user experience to the best extent possible in promotions and pushing sales.
‘data is the new oil’
Why? Because that’s the most valuable resource. What moves the needle? Sales. And sales to happen, you need data. Refined. There, indeed, is an information overload. Looks like there is a data dump, and that’s why refined.
Transparency is the key. Be it a website or a product/service promoted in a website. ‘how many users? how many likes? how many new users? And that leads to the next poser ‘do you have the resource to refine?’
People are crunching the numbers and scrambling for data to dissect the demography in order to study and better understand the market conditions and customer behavior. Anything that cannot be backed up with data becomes merely an opinion. Credibility is the cornerstone. Data integrity. Everything centers on it.
Know your customer.
When a customer shops for a book, or a perfume or a laptop, or holiday vacation or anything for that matter, it gives a glimpse of the customer in terms of taste and take. Next time when the same customer visits the page, there will be “you might also like” with several allied products or services listed. If that can bring a smile on customer’s face, then its good user experience.
Now this can be made possible only we have credible data. Don’t let data sound so technical. It is information. How much you know about your customer to serve better and thereby improve your relationship. Relationship building is the ultimate key because that's how you earn the customer’s confidence.
Data is the decisive factor.
Image credit: goo.gl/WmYFDt
We will discuss more about this subject in the week to come. Stay tuned.
Read More
The most powerful mode of marketing is the word of mouth.
Is Digital marketing same as word-of-mouth marketing? Yes or no? Well, what do you call ‘thing going viral on the social media’. The word spreads faster than a forest fire. We bank on referrals and trust the testimonies of our contacts before deciding on a service provider or business provider.
Today, it’s too expensive to try out the trial and error, and hence we follow footprints to be better safe and sure. Check and double-check. And that’s the reason why the online reviews are attached too much importance because you can’t collect all the information from your known sources, and hence, need to rely on unknown sources as well. Be it a travel or hotel booking or buying a car, we need to arm ourselves with facts, figures and Opinions. It matters more these days on others’ experience to get a perspective of ‘how it will be’, before doing it on our own for the ‘self-experience.’ Isn’t it? How many times have you checked a restaurant‘s reputation online before booking a table? And scrolled down all the way to sniff out foul smell? Yes, that one star rating which makes your face frown. Yes!
Word of mouth is more personalized. But in this digital era, where time is money, it’s impossible to knock on every door to get first-hand feedback. Technology has advanced. We speak of being ahead or behind the curve in technology. So the best way to pool in people’s views in one place would be the internet. And if that be, what’s stopping you from marketing using internet as a channel.
This could be the genesis of digital marketing. People prefer both brick and mortar shops and online shopping too. There exists a market share for both, and if you consider convenience, comfort, choice, online shopping is head over shoulder.
Times have changed and it’s wise to turn along the tide. So hoardings which do exist have shrunk in number and instead the online banners have risen exponentially in numbers. The medium of sale has shifted. Online transactions have spiked in numbers. Marketing of products and services using technologies through internet is otherwise known as Digital marketing, wherein the online space is used to provide the user experience to the best extent possible in promotions and pushing sales.
‘data is the new oil’
Why? Because that’s the most valuable resource. What moves the needle? Sales. And sales to happen, you need data. Refined. There, indeed, is an information overload. Looks like there is a data dump, and that’s why refined.
Transparency is the key. Be it a website or a product/service promoted in a website. ‘how many users? how many likes? how many new users? And that leads to the next poser ‘do you have the resource to refine?’
People are crunching the numbers and scrambling for data to dissect the demography in order to study and better understand the market conditions and customer behavior. Anything that cannot be backed up with data becomes merely an opinion. Credibility is the cornerstone. Data integrity. Everything centers on it.
Know your customer.
When a customer shops for a book, or a perfume or a laptop, or holiday vacation or anything for that matter, it gives a glimpse of the customer in terms of taste and take. Next time when the same customer visits the page, there will be “you might also like” with several allied products or services listed. If that can bring a smile on customer’s face, then its good user experience.
Now this can be made possible only we have credible data. Don’t let data sound so technical. It is information. How much you know about your customer to serve better and thereby improve your relationship. Relationship building is the ultimate key because that's how you earn the customer’s confidence.
Data is the decisive factor.
Image credit: goo.gl/WmYFDt
We will discuss more about this subject in the week to come. Stay tuned.
Work-life Balance with Discipline | Project Management
There seems to be early burn-out in IT professionals. Doctors are appalled at the heart-risks and related ailments that when wheeled a young person into the emergency ward, the first question invariably is “are you working in IT?” why is too so? Job pressure, peer pressure, management pressure – the stress is too much. a number of factors collide and contribute to this havoc wreaked on youngsters. Heart attack in the forties or fifties doesn’t shock or surprise but in late twenties and early thirties psyches the physicians, who are perplexed dealing with the predicament. Such is the severity, and cut-throat the companies, work force either by choice or force end up staying late at their desk ‘burning the midnight oil’.
Does the number of hours clocked or the contributions made in fewer count. The misconception in the market is one who spends long hours in the office is deemed ‘hard working’. Anything less and your talent is questionable or the workload is not just enough to justify your paycheck. So some just pretend to stretch or ‘kill’ time by indulging in other activity instead of freeing up bandwidth to take up additional tasks. “If I do this task or accommodate more chores in addition, will the amount in the salary credited change?” this reflects not just the individual lack of commitment, but reflects poorly on the leadership as well.
Devotion to work should be willful lest its leaves one dissatisfied and disgruntled. Once resourceful, now turned rebels are primarily due to poor people management. Hours makes one hardworking? Then at what cost? Tradeoff at the cost of health? Everything ought to be balanced – including work.
A project manager, whom I used to report, will sit beside me and plan the ‘tasks for the week’ taking my inputs for the ‘hours allocated’ and sometimes let me estimate the ‘number of hours’. Effort estimation is both critical and crucial. Bagging the project by heck or crook, and later slogging the days, night and weekend are typical signs of burnout. It’s like cutting the foot to match the boot. That’s not project management. Weekends usually act as buffer and my manager maxim of “if you can’t get the work done in eight hour, either you are inefficient or incompetent.’ People also tend to procrastinate – another malaise with no medicine in sight. Hence there is blaming the managers. There has to be a middle ground.
The 40 hour week
Any project manager with appreciable knowledge and experience will not estimate more than 8-hours as man day in the project plan. How many hours do the team work is another question but for the record its hours, and usually the weekends are not factored – and mostly serve as buffers. Remember time is money and hence any inflation in your estimation will have an adverse implication on your cost estimation. The budget balloons and the project just slipped out of your hands. It’s a typical trapeze act or skating on thin ice. So balancing the 40-hour and keeping the project within cost calls for a skilled and smart time management.
Performance and Productivity
No matter how many hours you clock, its 4 hours spread across 8. The body might be willing but the mind simply is not up to it. Exhaustion, fatigue leads to failure. Your ability to concentrate ebb s with passage of time. There should be a reason why Henry For came out with the brilliant strategy of ‘weekend’ so as to boost morale, improve productivity and increase time spent with family. Sources from public domain cite that working fewer hours increase productivity and thereafter tend to wane.
Work-Life balance
“I am too busy at work” is the usual refrain. You start before the kids awake and return after the fast asleep. Many professionals itinerary falls in to this pattern. Genuine cases of work chewing and even gobbling time is a possibility but that can’t become the norm. Its not family first or work at any cost. One has to strike a balance to do justice to both – stakeholder management. Your internal and external client included family too is part of stakeholders. And its important to attend on everyone, and if possible content.
A gallup study revealed that we work 47 hours – which is 7 hours more. What will all the dollars, incentive, promotions and perks amount when the people you value the most – your family aren’t there to share your moment to happiness and bask in glory.
image courtesy: goo.gl/vbW3j5
Read More
There seems to be early burn-out in IT professionals. Doctors are appalled at the heart-risks and related ailments that when wheeled a young person into the emergency ward, the first question invariably is “are you working in IT?” why is too so? Job pressure, peer pressure, management pressure – the stress is too much. a number of factors collide and contribute to this havoc wreaked on youngsters. Heart attack in the forties or fifties doesn’t shock or surprise but in late twenties and early thirties psyches the physicians, who are perplexed dealing with the predicament. Such is the severity, and cut-throat the companies, work force either by choice or force end up staying late at their desk ‘burning the midnight oil’.
Does the number of hours clocked or the contributions made in fewer count. The misconception in the market is one who spends long hours in the office is deemed ‘hard working’. Anything less and your talent is questionable or the workload is not just enough to justify your paycheck. So some just pretend to stretch or ‘kill’ time by indulging in other activity instead of freeing up bandwidth to take up additional tasks. “If I do this task or accommodate more chores in addition, will the amount in the salary credited change?” this reflects not just the individual lack of commitment, but reflects poorly on the leadership as well.
Devotion to work should be willful lest its leaves one dissatisfied and disgruntled. Once resourceful, now turned rebels are primarily due to poor people management. Hours makes one hardworking? Then at what cost? Tradeoff at the cost of health? Everything ought to be balanced – including work.
A project manager, whom I used to report, will sit beside me and plan the ‘tasks for the week’ taking my inputs for the ‘hours allocated’ and sometimes let me estimate the ‘number of hours’. Effort estimation is both critical and crucial. Bagging the project by heck or crook, and later slogging the days, night and weekend are typical signs of burnout. It’s like cutting the foot to match the boot. That’s not project management. Weekends usually act as buffer and my manager maxim of “if you can’t get the work done in eight hour, either you are inefficient or incompetent.’ People also tend to procrastinate – another malaise with no medicine in sight. Hence there is blaming the managers. There has to be a middle ground.
The 40 hour week
Any project manager with appreciable knowledge and experience will not estimate more than 8-hours as man day in the project plan. How many hours do the team work is another question but for the record its hours, and usually the weekends are not factored – and mostly serve as buffers. Remember time is money and hence any inflation in your estimation will have an adverse implication on your cost estimation. The budget balloons and the project just slipped out of your hands. It’s a typical trapeze act or skating on thin ice. So balancing the 40-hour and keeping the project within cost calls for a skilled and smart time management.
Performance and Productivity
No matter how many hours you clock, its 4 hours spread across 8. The body might be willing but the mind simply is not up to it. Exhaustion, fatigue leads to failure. Your ability to concentrate ebb s with passage of time. There should be a reason why Henry For came out with the brilliant strategy of ‘weekend’ so as to boost morale, improve productivity and increase time spent with family. Sources from public domain cite that working fewer hours increase productivity and thereafter tend to wane.
Work-Life balance
“I am too busy at work” is the usual refrain. You start before the kids awake and return after the fast asleep. Many professionals itinerary falls in to this pattern. Genuine cases of work chewing and even gobbling time is a possibility but that can’t become the norm. Its not family first or work at any cost. One has to strike a balance to do justice to both – stakeholder management. Your internal and external client included family too is part of stakeholders. And its important to attend on everyone, and if possible content.
A gallup study revealed that we work 47 hours – which is 7 hours more. What will all the dollars, incentive, promotions and perks amount when the people you value the most – your family aren’t there to share your moment to happiness and bask in glory.
The Reputation and Recognition…….| Stakeholder Management
Reputation management is critical to business interest. Customer experience is THE differentiator in moving the needles. Ensure the user experience in the superlative, lest your business interest would be superseded. Bad user experience is more than a frown. It can beat your bottom-line so hard to mark it purple and bleed crimson. You don’t need others to wreck your image: your action or inaction will do the damage, sometimes beyond repair.
Googled is an acceptable word today replacing ‘searched’. Adults to kids are aware and even decided that the search engine has an answer for every query posed. Remarkable, more than a search engine, it becomes kind of a genie ‘to fetch the answer at your beck and call’. It’s no more an illusion of the Alibaba ‘open sesame’. But every tidbit pooled as and served as ‘information’ – whether phony or perfect, anything on the net leaves a digital imprint. So it is imperative to be on your toes when it comes to customer service –regardless of the domain or industry as a customer is a customer. In as many languages possible. Period.
What rattles a service provider – it’s the review. For 100 positive reviews, it just takes one nasty one to make you feel so negative. Like a pin-prick to a blown-up balloon. Why? Is it because bade vibes spread fast and leaves distaste? From your personal experience, checks out how many time you have searched for ‘any negative comments’. Because we tend to believe others’ experience. Because we lend credibility to the bitter cry of wrong customer, without even validating the statement, assuming everything typed by an individual is true to the last letter. Because we are too lenient to offer ‘the customer’s experience the benefit of doubt’ rather than question the authenticity of the statement.
If one cares to notice, more than ever new business boom big with growing interest and alarming consumption of the internet that people’s lives are impacted by internet, Google and social media – which seem inevitable and indispensable. Gone is a single day without a shy at the social media and as consumers, our appetite is insatiable. Our hunger to know is fuelled all the more. Our thirst for knowledge is never quenched. It’s for the good? No one is competent to address that poser, but admittedly inadequate to come out with a convincing answer.
When business depends on the customer, then make sure the deal is fair, engagement positive and memories pleasant, else it will boomerang and knock you out of your senses. For the best brand out there, their best ambassador is the customer. The unofficial spokesperson. Any word spoken out of place from that spokesperson can erode your company’s credibility and cast you into infamy , We weigh in too much about the personal experience and too much reliance on anecdotes, which can be figment of imagination or statement of exaggeration or just someone settling scores. Words can be far from the truth, but who validates before your reputation is already in ruins.
Modern economy is way much different as plastic money and e-wallets are highly innovative when it comes to transaction. It’s a huge leap from the barter system, but what happens if there is a shutdown of services, including the internet. And growing dependence on the internet also makes it vulnerable for cyber-attacks throwing the reputation on the line. The best adocates are the rocogntion and repuation, so protect and preserve it.
image courtesy: goo.gl/NtH2Dq
Read More
Reputation management is critical to business interest. Customer experience is THE differentiator in moving the needles. Ensure the user experience in the superlative, lest your business interest would be superseded. Bad user experience is more than a frown. It can beat your bottom-line so hard to mark it purple and bleed crimson. You don’t need others to wreck your image: your action or inaction will do the damage, sometimes beyond repair.
Googled is an acceptable word today replacing ‘searched’. Adults to kids are aware and even decided that the search engine has an answer for every query posed. Remarkable, more than a search engine, it becomes kind of a genie ‘to fetch the answer at your beck and call’. It’s no more an illusion of the Alibaba ‘open sesame’. But every tidbit pooled as and served as ‘information’ – whether phony or perfect, anything on the net leaves a digital imprint. So it is imperative to be on your toes when it comes to customer service –regardless of the domain or industry as a customer is a customer. In as many languages possible. Period.
What rattles a service provider – it’s the review. For 100 positive reviews, it just takes one nasty one to make you feel so negative. Like a pin-prick to a blown-up balloon. Why? Is it because bade vibes spread fast and leaves distaste? From your personal experience, checks out how many time you have searched for ‘any negative comments’. Because we tend to believe others’ experience. Because we lend credibility to the bitter cry of wrong customer, without even validating the statement, assuming everything typed by an individual is true to the last letter. Because we are too lenient to offer ‘the customer’s experience the benefit of doubt’ rather than question the authenticity of the statement.
If one cares to notice, more than ever new business boom big with growing interest and alarming consumption of the internet that people’s lives are impacted by internet, Google and social media – which seem inevitable and indispensable. Gone is a single day without a shy at the social media and as consumers, our appetite is insatiable. Our hunger to know is fuelled all the more. Our thirst for knowledge is never quenched. It’s for the good? No one is competent to address that poser, but admittedly inadequate to come out with a convincing answer.
When business depends on the customer, then make sure the deal is fair, engagement positive and memories pleasant, else it will boomerang and knock you out of your senses. For the best brand out there, their best ambassador is the customer. The unofficial spokesperson. Any word spoken out of place from that spokesperson can erode your company’s credibility and cast you into infamy , We weigh in too much about the personal experience and too much reliance on anecdotes, which can be figment of imagination or statement of exaggeration or just someone settling scores. Words can be far from the truth, but who validates before your reputation is already in ruins.
Modern economy is way much different as plastic money and e-wallets are highly innovative when it comes to transaction. It’s a huge leap from the barter system, but what happens if there is a shutdown of services, including the internet. And growing dependence on the internet also makes it vulnerable for cyber-attacks throwing the reputation on the line. The best adocates are the rocogntion and repuation, so protect and preserve it.
image courtesy: goo.gl/NtH2Dq
Effective Communication - Clarity With a Purpose
All us will agree to the need for greater clarity in communication – be it any form, verbal, or written.
A sales person to software analyst - communication is critical and crucial.
Despite a set agenda, meetings, at times, drag for hours not deliberating the issues tabled. When a stray thought entertained finds resonance with someone seated and soon the discussion veers off in a direction that’s tangential. When the meeting is concluded, everyone leaves learning a lesson not to get distracted but fall into the same trap that was supposed to be safeguarded.
Likewise, a client call to collect requirements goes nowhere because of the lack of connectivity. The stakeholders are not in the same page for the lack of understanding. It’s as if the conversation is taking place in a foreign tongue that the attendees in the call are absolutely clueless.
Or, the instance when a simple mail intended to communicate a message can be so misleading.You don’t have to be poetic. Just be precise.
There is no need to compose an essay. A 2-liner will be enough if the message can be conveyed.
Be verbal, not verbose. Compose crisp concise message that usually are shorter sentences. Rather, simplify. Make it easier for the reader to understand. It should not be a test on IQ. Is your message universally understandable? Clarity means simplicity. We often confuse that word as a business jargon. The challenge of a learned mind is to communicate to a third-grade kid or a professor with absolute clarity. There should not be any confusion at all; nor the need to refer the dictionary. Prose that is polished, professional and stay simple, correct in its context brings out greater clarity in communication.
It can be challenging. So is communication.
image courtesy: goo.gl/QEqJ5Q
Read More
ITIL® - Define IT Success Through Service
A gaze into the future. That sounds exciting in terms of prospects and expectation. We seem to be advancing at an incredible speed. Technology is spearheading and impacting our lives in ways we would have imagined. According to Gartner’s prediction for 2016, some interesting insights that probably upped the ante would be
• By 2018, 6 billion connected things will be requesting support.• In Gartner's IoT forecast, by 2020, more than 35 billion things will be connected to the Internet • by 2021, 1 million IoT devices will be purchased and installed every single hour.
Of course, we expect smartness not just from people but in the products made by the people. When a solution is proposed, we pay attention and give equal weightage to the service aspect as well. Going by the statistics presented, there is going to an increased dependence on human intervention.
The stress on system and humans is significant to assess the way things will turnaround tomorrow. And that suggests the need of qualified professionals in ITSM. If the numbers in the forecasts are mind boggling, think about the demand that will be generated as a result and in terms of readiness what it takes to be prepared to face the challenges ahead. Looking forward, specialization and skills in service management will prove crucial and critical.
The advice to aspirants, especially those engaged in handling and managing of IT systems is to step out of the comfort zone and step up their credentials, wherein training and certification will establish credibility. ITIL and COBIT come across as commendable certification that should bolster your candidature. The digital divide is blurred and soon the switch to digital is expected to be complete attributing to the spike in the number presented.
By 2018, 2 million employees will be required to wear health and fitness tracking devices as a condition of employment.’ From a service perspective, for the system to be up and running, downtime is just unthinkable and SLAs charted will determine the uptime expected, which should be '200%'. So where are we heading? And how are we placed should the prediction come true? It might be baffling but to disbelieve would be disastrous.
It’s a clear indicator that systems would go up and so will the coordination to streamline. IT Services would hold a prominent portfolio. And if you are service personnel, its time to roll up your sleeves and start preparing to face tomorrow.
image courtesy: goo.gl/YX82HX
Read More
The Sixth Edition of PMBOK | Project Management
PMI (Project Management Institute) was expected to roll out the Project Management Body of Knowledge (PMBOK® Guide) – Sixth Edition by the third quarter of 2017. AND IT IS OUT.
What are the changes in the Sixth Edition?
>> Approaches to Agile.
Every knowledge area will be inclusive of approaches to Agile, Iterative and Adaptive Environments’. This section will detail the integration of agile practices in project backgrounds.
>> PMI Talent Triangle™.
PMI spells the details about the technical skills, business intelligence, and leadership considered the key skills for success. It is also known as Talent triangle.
>> The size of the book.
The fifth edition PMBOK® Guide, has 13 chapters that spans 415 pages. The sixth edition is expected to be quarter the size of the 5th edition, which means it should be close to 84 pages and the number of chapters too have come down to 10. So, sixth edition should be 10 chapters with 84 pages in the draft version.
>> Inputs, Tools & Techniques, Outputs (ITTOs).
The sixth edition will not dwell deep into ITTOs, rather it will be covered at a high level.
>> Alignment with Process Groups.
The sixth edition will be divided based on the 5 process groups, and not the 10 knowledge areas. This is considered as a major change. The Role Delineation Study (RDS) conducted by PMI has presented its findings and proposed the changed to be aligned with process groups.
>> Combination of first three chapters.
In the sixth edition, the first three chapters combined as one – the interpersonal skills of the project manager and organizational skills will be merged in to one.
>>Two processes are expected to be deleted.
The Close Procurement process and Estimate Activities Resources are more likely to be deleted.
>>Two knowledge areas to be renamed.
Time Management and Human Resource Management to be renamed. Time management will be renamed Schedule management, while Human Resource Management becomes Resource Management.
>> Knowledge Areas to feature four section.
Every knowledge areas will have four new sections, namely, Key Concepts, Trends and Emerging Practices, Tailoring Considerations and Considerations for Agile/Adaptive Environments.
>> An exclusive chapter on role of Project Manager.
This chapter on Project Manager will cover the key concepts about core competencies, expertise, leadership skills expected in leading a project.
Reference source: http://www.examspm.com/2016/07/16/pmbok-6th-edition-release-date-changes/
https://www.pmi.org/pmbok-guide-standards/about/current-projects
http://www.pmi.org/certifications/types/project-management-pmp/update
https://www.pmi.org/pmbok-guide-standards/foundational-standards-exposure-draft
https://www.pmi.org/learning/training-development/talent-triangle
image courtesy: https://www.pmi.org/pmbok-guide-standards
Read More
PMI (Project Management Institute) was expected to roll out the Project Management Body of Knowledge (PMBOK® Guide) – Sixth Edition by the third quarter of 2017. AND IT IS OUT.
What are the changes in the Sixth Edition?
>> Approaches to Agile.
Every knowledge area will be inclusive of approaches to Agile, Iterative and Adaptive Environments’. This section will detail the integration of agile practices in project backgrounds.
>> PMI Talent Triangle™.
PMI spells the details about the technical skills, business intelligence, and leadership considered the key skills for success. It is also known as Talent triangle.
>> The size of the book.
The fifth edition PMBOK® Guide, has 13 chapters that spans 415 pages. The sixth edition is expected to be quarter the size of the 5th edition, which means it should be close to 84 pages and the number of chapters too have come down to 10. So, sixth edition should be 10 chapters with 84 pages in the draft version.
>> Inputs, Tools & Techniques, Outputs (ITTOs).
The sixth edition will not dwell deep into ITTOs, rather it will be covered at a high level.
>> Alignment with Process Groups.
The sixth edition will be divided based on the 5 process groups, and not the 10 knowledge areas. This is considered as a major change. The Role Delineation Study (RDS) conducted by PMI has presented its findings and proposed the changed to be aligned with process groups.
>> Combination of first three chapters.
In the sixth edition, the first three chapters combined as one – the interpersonal skills of the project manager and organizational skills will be merged in to one.
>>Two processes are expected to be deleted.
The Close Procurement process and Estimate Activities Resources are more likely to be deleted.
>>Two knowledge areas to be renamed.
Time Management and Human Resource Management to be renamed. Time management will be renamed Schedule management, while Human Resource Management becomes Resource Management.
>> Knowledge Areas to feature four section.
Every knowledge areas will have four new sections, namely, Key Concepts, Trends and Emerging Practices, Tailoring Considerations and Considerations for Agile/Adaptive Environments.
>> An exclusive chapter on role of Project Manager.
This chapter on Project Manager will cover the key concepts about core competencies, expertise, leadership skills expected in leading a project.
Reference source: http://www.examspm.com/2016/07/16/pmbok-6th-edition-release-date-changes/
https://www.pmi.org/pmbok-guide-standards/about/current-projects
http://www.pmi.org/certifications/types/project-management-pmp/update
https://www.pmi.org/pmbok-guide-standards/foundational-standards-exposure-draft
https://www.pmi.org/learning/training-development/talent-triangle
image courtesy: https://www.pmi.org/pmbok-guide-standards
What’s New In Tthe PMBOK® Guide – Sixth Edition?
Project management as a discipline is evolving, and so is PMP® exam. PMBOK® is changing its version, from PMBOK® fifth to Sixth edition. Some of the leading lights in project management and active practitioners from around the world underscored the need to introduce agile approach based on research carried out by PMI. This led to the release of PMBOK® Sixth edition last September 2017, ensuring PMP® certification stays relevant to the changing trends of present times.
For the first time, implementation in agile environment is included in PMBOK® Guide – Sixth Edition. This is an important announcement weighed in the context of how waterfall and agile approaches can be bridged. As a result PMBOK® is aligned with Agile Practice Guide. PMI partnered with Agile Alliance® for developing the Agile Practice Guide.
So, will this impact the PMP® certification exam? When will the PMBOK® Guide – Sixth Edition be released? When will the PMP® Exam change in 2018?For the uninitiated, please be informed that PMBOK® Guide – Sixth Edition was released on 6th September, 2017, and books are available in different formats. If you are a PMI member, please visit the website and download relevant study materials in pdf format.PMP® Exam will change on 26 March, 2018. Candidates who take up the exam before 25th March, 2018, the exam reference material will be PMBOK® Guide – Fifth Edition. And, for those who take the exam on or after 26 March, 2018, the exam reference material will be PMBOK® Guide – Sixth Edition. Kindly note that that the PMP® certification exam is not solely based on PMBOK® Guide. It is one of the key reference materials to prepare for the exam.
You might want to know what are the other changes in PMBOK® Guide – Sixth Edition?The role of Project Manager is studied more prominently. A dedicated chapter deals Project Manager focusing on leaderships, skills, competency, and experience in effectively leading and managing a project. .There will be 49 processes. 3 new processes have been added and one deleted. The newly inducted processes are:• "Manage Project Knowledge"• "Control Resources"• "Implement Risk Responses"Close Procurements process has been removed.
Two Knowledge Areas have been renamed. • Time Management is renamed as Schedule Management • Human Resource Management is renamed as Resource Management
The Knowledge Area will feature four sections, namely,• Key Concepts• Trends and Emerging Practices• Tailoring Considerations• Considerations for Agile/Adaptive Environments
Other additions include:• Trends and emerging practices• Tailoring considerations• A greater emphasis on Strategic and Business Knowledge
Read More
Advance Your Career with PRINCE2® Certification
We have moved past the times when experience was enough for an audience with the HR, if not an offer.
Present times have a different kind of poser. Experience needs to be backed up with a certification. There isn't much of a choice. Credential is a key differentiator. This paper will discuss the prospects of PRINCE2® shaping up your profile as that consummate project management professional.
PRINCE2® is a major prerequisite for Project Management
In UK, PRINCE2® (Projects in Controlled Environments) is considered de facto standard for IT project management. PRINCE2 doesn’t define project as temporary endeavor, rather as a project management method it delivers based on a business case. The progress of the project is measured and monitored through periodical review of the business case so as not to deviate from the business outcome, and thus the situation at the ground level is assessed and addressed with a greater control and clarity. PRINCE2 can be used for any kind of project cutting across culture and setting aside geographic barriers. It is an effective process method, also easy to learn and the ease of use of framework makes it more favorable with newcomers to PRINCE2®. The merits of PRINCE2® are phenomenal that more companies consider as a major requisite in shortlisting and selection process.
PRINCE2® helps the Managing Project Management
In PRINCE2 methodology, the decision making doesn’t rest with the project manager, rather the functional and financial authority is with the senior executive. The project manager will help in managing and administering he project by directing resources on behalf of the board and primarily the reason why government sector prefer this program due to its standardized approach.
PRINCE2® improves employment opportunities.
The mind has never been at such a premium and to those talented, corporate are just waiting to tap to make it a win-win. . It’s very mutual. But how does PRINCE2 can turn out to be an asset? Its world class and widely renowned and increasing number want to be certified, especially the PRINCE2 Practitioner. You can go global for opportunities and show you got it what it takes with your PRINCE2 credential. Just check the stats at the top which is a clear indicator in the surge for the demand for qualified and PRINCE2® certified project managers.
You can reach us at info@icertglobal to know more PRINCE2® certification program.
image courtesy: goo.gl/41ogs
Read More
We have moved past the times when experience was enough for an audience with the HR, if not an offer.
Present times have a different kind of poser. Experience needs to be backed up with a certification. There isn't much of a choice. Credential is a key differentiator. This paper will discuss the prospects of PRINCE2® shaping up your profile as that consummate project management professional.
PRINCE2® is a major prerequisite for Project Management
In UK, PRINCE2® (Projects in Controlled Environments) is considered de facto standard for IT project management. PRINCE2 doesn’t define project as temporary endeavor, rather as a project management method it delivers based on a business case. The progress of the project is measured and monitored through periodical review of the business case so as not to deviate from the business outcome, and thus the situation at the ground level is assessed and addressed with a greater control and clarity. PRINCE2 can be used for any kind of project cutting across culture and setting aside geographic barriers. It is an effective process method, also easy to learn and the ease of use of framework makes it more favorable with newcomers to PRINCE2®. The merits of PRINCE2® are phenomenal that more companies consider as a major requisite in shortlisting and selection process.
PRINCE2® helps the Managing Project Management
In PRINCE2 methodology, the decision making doesn’t rest with the project manager, rather the functional and financial authority is with the senior executive. The project manager will help in managing and administering he project by directing resources on behalf of the board and primarily the reason why government sector prefer this program due to its standardized approach.
PRINCE2® improves employment opportunities.
The mind has never been at such a premium and to those talented, corporate are just waiting to tap to make it a win-win. . It’s very mutual. But how does PRINCE2 can turn out to be an asset? Its world class and widely renowned and increasing number want to be certified, especially the PRINCE2 Practitioner. You can go global for opportunities and show you got it what it takes with your PRINCE2 credential. Just check the stats at the top which is a clear indicator in the surge for the demand for qualified and PRINCE2® certified project managers.
You can reach us at info@icertglobal to know more PRINCE2® certification program.
image courtesy: goo.gl/41ogs
Can I apply for the PMP® Exam even if my title is not “Project Manager”?
This is a very common question heard in the corridors treaded too often by the Information Technology professionals, while other verticals and domains are following suit. And the answer is: Yes, you can.
Enroll for Project Management Professional (PMP) with a reputed education provider to earn 35 Contact Hours which is mandatory as prerequisite for taking up the PMP exam. You must possess the major prerequisite in terms of education and experience: Secondary degree (High School) and 60 months spent leading and directing project tasks [or] Four-year degree(Bachelor's) with 36 months unique, non-overlapping professional project management experience leading and directing project tasks.
The 4-day program will enable you to become proficient with the Principles of Project Management, mainly the 47 project management processes and 10 knowledge areas – this will be the curriculum or syllabus. The trainer, at best, can take you through the topics by apportioning time required to spend on modules as careful analysis has defined the hours to be dedicated to a particular module and they greatly differ from one to another.
The basic training must be supplemented through self-study by diving deep into the 10 knowledge areas as detailed in ‘PMBOK Guide- A guide to the Project Management Body of Knowledge’ as key reference and the course materials provided by the education provider. It’s to be noted that PMBOK will be offered by the PMI (Project Management Institute). as part of your registration exam fees as a soft copy.
How the 4-day training can be taken is matter of choice and convenience, be it classroom or virtual classroom or e-Learning. End of the day, much depends about your competency and capability in cracking the PMP certification examination. So far the answer is academic. Now from a practical perspective, your performance in the final exam boils down to the preparation. The better prepared you are, best are chances of making it big at the first attempt. Every institution’s bet is to equip their participants to pass PMP, and this is the differentiator for iCertGlobal to be one of the most sought after destination in preparing for professional certification.
We offer, in addition to the well-planned and well-structured schedule classroom or LVC {Live Virtual Classroom] training, other notables that prove to be the key ingredients to our immense success and popularity:
Exemplary course materials prepared by Industry experts who are PMP certified with hands-on experience in project management and training. Hence they bring tremendous inputs in terms of experience and expertise in carving out the course related resources like Books, Quiz, Practice Questionnaire, Case Studies, and real-time scenario analysis.
Exam Simulator with more than 6000 questions. The questions are created in the same complexity as it would be in the final PMP exam. The pattern and population of questions drawn for various modules will be of the same density as expected in the PMP exam.
Refreshing sessions are for those, on request, to brush up the lessons already learnt to brace for the final race.
Participants are encouraged to stay in touch and maintain contact through the 24x7 support to enhance improved communication. They can create as many opportunities at every turn to learn in as many forms to sharpen the skills in gaining the edge. A repository of resources is available for online access anytime, more as a supplementary link.
Moreover, we follow-up with every participant to sense their progress understand and offer services wherever struggle is detected or discovered.
Of course, the growing testimonies speak for itself!!
image:https://www.freeimages.com/photo/my-tools-1239864
Read More
This is a very common question heard in the corridors treaded too often by the Information Technology professionals, while other verticals and domains are following suit. And the answer is: Yes, you can.
Enroll for Project Management Professional (PMP) with a reputed education provider to earn 35 Contact Hours which is mandatory as prerequisite for taking up the PMP exam. You must possess the major prerequisite in terms of education and experience: Secondary degree (High School) and 60 months spent leading and directing project tasks [or] Four-year degree(Bachelor's) with 36 months unique, non-overlapping professional project management experience leading and directing project tasks.
The 4-day program will enable you to become proficient with the Principles of Project Management, mainly the 47 project management processes and 10 knowledge areas – this will be the curriculum or syllabus. The trainer, at best, can take you through the topics by apportioning time required to spend on modules as careful analysis has defined the hours to be dedicated to a particular module and they greatly differ from one to another.
The basic training must be supplemented through self-study by diving deep into the 10 knowledge areas as detailed in ‘PMBOK Guide- A guide to the Project Management Body of Knowledge’ as key reference and the course materials provided by the education provider. It’s to be noted that PMBOK will be offered by the PMI (Project Management Institute). as part of your registration exam fees as a soft copy.
How the 4-day training can be taken is matter of choice and convenience, be it classroom or virtual classroom or e-Learning. End of the day, much depends about your competency and capability in cracking the PMP certification examination. So far the answer is academic. Now from a practical perspective, your performance in the final exam boils down to the preparation. The better prepared you are, best are chances of making it big at the first attempt. Every institution’s bet is to equip their participants to pass PMP, and this is the differentiator for iCertGlobal to be one of the most sought after destination in preparing for professional certification.
We offer, in addition to the well-planned and well-structured schedule classroom or LVC {Live Virtual Classroom] training, other notables that prove to be the key ingredients to our immense success and popularity:
Exemplary course materials prepared by Industry experts who are PMP certified with hands-on experience in project management and training. Hence they bring tremendous inputs in terms of experience and expertise in carving out the course related resources like Books, Quiz, Practice Questionnaire, Case Studies, and real-time scenario analysis.
Exam Simulator with more than 6000 questions. The questions are created in the same complexity as it would be in the final PMP exam. The pattern and population of questions drawn for various modules will be of the same density as expected in the PMP exam.
Refreshing sessions are for those, on request, to brush up the lessons already learnt to brace for the final race.
Participants are encouraged to stay in touch and maintain contact through the 24x7 support to enhance improved communication. They can create as many opportunities at every turn to learn in as many forms to sharpen the skills in gaining the edge. A repository of resources is available for online access anytime, more as a supplementary link.
Moreover, we follow-up with every participant to sense their progress understand and offer services wherever struggle is detected or discovered.
Of course, the growing testimonies speak for itself!!
image:https://www.freeimages.com/photo/my-tools-1239864
ITSM - More Than Service
There is also a misconception that IT Systems pertains to the software industry. The perception should ‘wherever IT Systems are deployed’; it calls for managing and maintenance of IT Systems. Automation is again big time in the software industry. Check out and you will find them more IT-services based.
Who will manage the IT Services?Of course, IT Service Management team, that could include IT System Managers, IT Administrators, System Administrators, IT Quality Specialists, IT Audit, IT System Analysts and Quality Control who are either responsible for streamlining the IT Systems or part of IT Service Management team, Quality Assurance teams responsible for software and infrastructure.
Who will manage the people handling IT Services?IT is ubiquitous. It’s almost everywhere. So, IT Service management is indispensable because there is no sphere of our life which IT has not shaped up. So you need people who are skilled in managing and handling IT systems. The need for ITIL® Certifications is more as a test of competency and validation of expertise in handling critical scenarios.
Why ITIL® Certifications IT Service setup can be simple or complicated, and more often not, the complexity varies in severity. Hence, most companies prefer skilled people with experience and rich expertise in entrusting the systems. Just like mirror servers, company don’t prefer to depend on any particular team, rather they prefer a mix of teams who can be deployed and pressed in to service should a situation arise. This is the very reason why the ITIL® Certifications have gained prominence in the recent times as professionals start at foundation level and then move on to the intermediate modules – which can be either lifecycle modules best suited for professional pursuing management of services and the other is capability modules, which is apt for professionals preferring the process, and the next level of certification is the MALC ( Managing Across the Lifecycle) and clearance will lead to ITIL Expert. So given the mix of management and process in the intermediate levels, companies also use a judicious mix of people capable of handling management or process related issues.
In case of any faulty issues or malfunction, the troubleshooting will be addressed by the maintenance crew who are always on standby. Expecting the unexpected is a good maxim and mostly followed by all the companies that have deployed IT Systems. Maintenance is a critical and crucial as managing project. The prerequisites, qualifications, certification and validation in terms of capability and competency remain the same.
image:http://www.web-techsupport.com/images/ourservices.jpg
Read More
Our Tailor-Made Training Are Unique And Inimitable
This might be a regular word in the IT industry offering products and solutions. The definition states “made or done to order for a particular customer.” Today, custom-made is cut across the industry fitting to customer specifics.
Just imagine a customer walking into a restaurant and reading through the menu, and calls on the waiter to order something that’s not part of the menu. The Customer doesn’t take NO for an answer if you are really keen on customer service. If it is not listed on the menu, then better cook it – that’s the sense of service in the industry. This is just an analogy that can be applied to any vertical or horizontal.
There is no ‘one size fits for all’ – all these might sound cliches, but the spotlight is back on the customer beaming more brightly than ever before. The customer is king. True, if not for the customer, what will happen to business eco-system? Who drives business? If not for the patronage of the customer, who pays the bills – and that includes salaries.
“We got to think more along the lines of doing something exclusively for the customer.”
The distinct factor and differentiator in an industry dominated by the best in business is your ability to make the customer feel special. Right from sundry stuff to sophisticated schooling, think more along the lines of doing something different that is exciting and exactly meets the customer's requirement.
Interestingly, training too have seen the swing when institutions go out of the way to offer tailor-made training, which is unique and inimitable to the customer in the picture.
The engagement has gone one-notch above. Now customers brief a scenario to exact a solution. It’s like turning a use case into an application – which may sound like an exaggeration. Not anymore. In a recent inquiry, a customer came out with a specific need that was not part of our offering. In fact, they pinned the scope so neatly that the subject sought was close to 'cherry picking' and bundled as one course, and refusal to entertain their inquiry will make them shift and shop elsewhere. So, what do we do? Either make them understand, which they wont or find some middle ground where both of our objectives are met.
“You must be willing to go as far as you can”
Today, the choice for a customer has grown manifold. If you aren’t ready, move aside, and the next one in line will be inquired. So to a bag a business order, that connects directly or loosely, it’s both important and imperative to make most of the opportunity and drive hard for a closure. It will be foolhardy to dismiss with a ‘sorry, we don’t have that in our catalog”. The missed opportunity could cost us dear. From experience, its always the missed opportunity prove to be the worst casualties. Unless it's completely beyond your strength, you must be willing to go as far as you can. Chances aren’t easy to come by these days with competition throttling and scuttling at the first instant possible. Customer service is evolving. The service provided will be the game changer and excellence will result in the clincher.
One of our customers had an interesting anecdote. He was visiting a gift shop to buy something in particular. The shop owner heard his order, and declared his helplessness as “not available’ and turned his attention to the news on television. The customer moved on to the next door, which too was a gift shop, and that owner too didn’t have the article, but instead of flatly refusing with a ‘No’, he was interested to offer the customer with alternatives of ‘maybe you would like this or try that one.” The spirit of engagement impressed the customer, and even more impressive were the choices presented that the customer never thought of, and in the end, he purchased one and promised to come back. While leaving the shop, he looked at the previous shop and noticed the distinct difference in entrepreneurship. One was willing to go way go way beyond, while the other just sat and did nothing much. The customer left a thank you note to the shopkeeper saying “that looks like it’s just made for me”.
Custom-made, perhaps.
Read More
One Skill Is Not Enough. The Opportunities Are More.
The human capital, with the exponential growth in population, is immeasurably huge. Today the talent pool is just terrific. Paradoxically, the skill gap persists despite the overwhelming numbers of resources. The issue, as always, is the fitment. The question is: do you fit?
An organization needs vary from time to time, and that’s why the insistence of skills upgrades. Stopping at a place in today’s pace Is walking backward. That spells something about the competition – which means you have to have always in your guard, keep your eyes and ears open and be ready on your toes.
The physical attributes aside, the mental faculty needs to be brushed up and stepped up. Now comes the key question? What are your skills? Everyone is gifted with a primary skill. Problem is we don’t know what we are good at. We just follow the crowd and flow with the tide and knock on doors that have good opportunities – that pays you well offering good positions. So it’s more about aligning your skills towards the direction of boom and bucks.
Win-win for You and your CompanyThese days, a company is known for its workforce. Clients are setting the minimum requirement of ‘PMP certified’ for a manager, and hiring companies either enforce or set as their basic requirement even at the shortlisting stage. Hence, the certification on your profile is not only a value-add to your person but with the company, you are associated as well. That said, when one key certification used to suffice, today along with the demand, the expectations too have spiraled. “what else?” this goes both ways for the employers and employees. For the investment made on an asset, in the forms of pay and perks, what are the returns on investment (ROI) is a claim rightfully stated by the employer. Likewise, for investing so many hard hours and armed with skillsets, ‘what do I stand to gain in terms of compensation and growth?’. So, it’s a fair expectation both sides with an eye on the bottom-line.
Multifaceted Profile.There are many a professional who despite experience are unable to stand out for the fact that they aren’t certified. Hence, there is ‘that’ distinguished factor that sets one apart. So, a professional certification can make a huge difference. Compare a PMP certified with that of a non-certified professional/ doesn’t it make a difference. Now add more certifications to your profile aligned with your skill set. Maybe PgMP or PMI-ACP.
Job OpportunitiesMany doors will be opened. The job market is skewed with an imbalance in supply versus demand. Skilled professionals are scarce in the industry, and hence the difficulty in sourcing. The niche professional certification holders are fewer in the industry.
Career AdvancementThe competitive edge, undoubtedly, stems from the knowledge acquisition. Advanced certification is the measure of depth and applied across a domain. The principles and concepts are applicable to varied industry. You can move places and scale up the ladder, and always the threshold will be an acclaimed and accepted qualification and certification.
There are many such professional certifications depending on the subject matter and areas of interest. The common thread that sews up is the success factor: professionally certified profiles are head above shoulders.
image: www.pexels.com
Read More
The Top 15 High Paying IT Certification Courses | Professional Certification
The Top 15 High Paying IT Certification Courses | Professional Certification
Fast track your career by enrolling in one of the top 15 courses identified as the “highest paying” certification courses. Professionals, professional certification and pat are closely connected and interrelated.
According to the 15 Top Paying IT Certifications In 2019 listed in forbes .com, here there are some of the highest paid certification
• Google Cloud Certified Professional Cloud Architect is the highest paying certification of 2019, paying an average salary of $139,529.
• Certifications in virtualization and cloud computing pay an average salary of $127,494 this year, up from $112,955 in 2018, a 12.8% increase in just one year.
• Five of the top 15 highest paying certifications of 2019 are for cybersecurity expertise, and they pay an average of $115,867.
• Project Management Professional (PMP®) certifications increased in value by 18.6%, jumping from a median salary of $114,473 in 2018 to $135,798 in 2019.
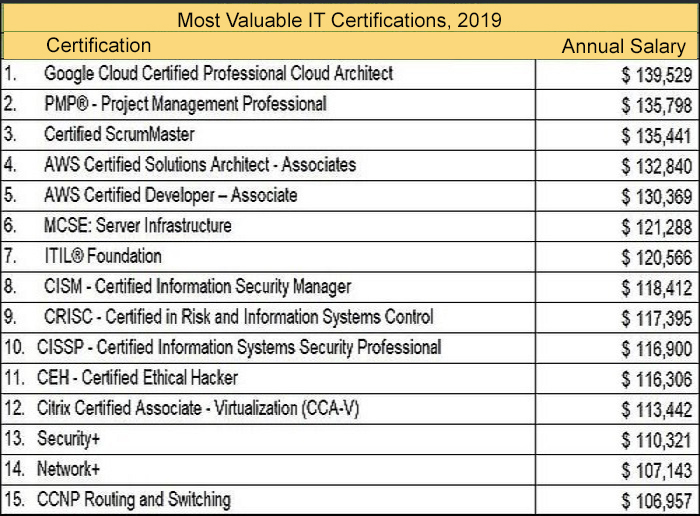
Key insights on the 15 top paying IT certifications in 2019 include the following:
• Average salary across all 15 certifications is $121,514 for 2019. Virtualization and cloud computing certifications pay an average salary of $127,494 in 2019, soaring over the median salary of $112,955 in 2018.
• The five cybersecurity certifications pay an average salary of $115,867.
• Network certifications pay an average salary of $111,555.
• Google Cloud Certified Professional Cloud Architect, Project Management Professional (PMP), Certified ScrumMaster, AWS Certified Solutions Architect – Associate and AWS Certified Developer – Associate all have salaries above the median of $121,514.
• Microsoft Certified Solutions Expert (MCSE) – Server Infrastructure certification pays an average salary of $121,288, up from $100,656 in 2018.
• The two highest-paying AWS certifications in 2019 have an average salary of $131,605, $6K higher than $125,591 which is the average of the five highest-paying AWS certifications of 2018. The following table provides a breakout of the top 15 IT certifications in 2019 according to latest survey.
Here are some of the top fifteen courses that you can select in propelling in your professional growth.
1.Artificial Intelligence (AI)
2. PMP
3.Google Cloud Certified Professional
4.Certified Scrum Master
5. ITIL Foundation
6.Machine Learning
7.Robotic Process Automation or RPA
8. Blockchain
9. Internet of Things
10. Data science
11. Cyber Security
12. Edge Computing
13. Big Data Certifications
14. Virtual Reality and Augmented Reality
15. Networking
1. Artificial Intelligence

What is Artificial Intelligence (AI)?
Artificial intelligence (AI) is an area of computer science that emphasizes the creation of intelligent machines that work and react like humans. Some of the activities computers with artificial intelligence are designed for include: Speech recognition. Learning.
Who should take this Artificial intelligence (AI)?
Software analysts and developers.
Computer scientists and computer engineers.
Algorithm specialists.
Research scientists and engineering consultants.
Mechanical engineers and maintenance technicians.
Manufacturing and electrical engineers.
How much Salary can I Expect once I am a Certified Artificial intelligence (AI)?
According to Indeed.com, the average IT salary – the keyword is "artificial intelligence engineer" – in the San Francisco area ranges from approximately $134,135 per year for software engineer to $169,930 per year for machine learning engineer.
What are the Top Companies hiring Certified Artificial intelligence (AI )?
The Top 15 Employers Hiring Artificial Intelligence Talent
1. Amazon
2. Nvidia
3. Microsoft
4. IBM
5. Accenture
6. Facebook
7. Intel
8. Samsung
9. Lenovo
10. Adobe
11. MoTek Technologies
12. Uber
13. PCO Innovation
14. Rakuten Marketing
15. Wells Fargo
What are the Top Industries Hiring Certified Artificial Intelligence?
E-commerce, Health and Power industries, Logistics, Mobility Solutions, Computer and computer related.
What's the Career Path to Become Artificial intelligence (AI) Professional?
6 Easy Steps To Get Started Learning Artificial Intelligence
STEP 1.) Learn Python & SQL
STEP 2.) Learn Machine Learning from some of the below courses.
STEP 3.) Learn basics of probability theory, statistics, and Maths.
STEP 4.) RECOMMENDED BOOKS to READ
STEP 5.) PRACTICE FEW EXERCISES
STEP 6.) Practice—Learn—Practice on your own, step by step you will slowly become AI programmer.
What's the Demand for Certified Artificial Intelligence Professionals by 2020?
With AI projected to create 2.3 million jobs by 2020, according to a Gartner report, it's safe to assume that machine learning will remain an in-demand skill for the foreseeable future.
Artificial intelligence (AI) skills dominated the list of the fastest-growing jobs in 2018—a trend that is expected only to grow in the future. Machines and algorithms are predicted to create 133 million new jobs by 2022,
Where can I get trained for the Artificial Intelligence?
You can get trained at iCertGlobal. They offer one of the best courses on ARTIFICIAL INTELLIGENCE AND DEEP LEARNING CERTIFICATION, MACHINE LEARNING AND ROBOTIC PROCESS AUTOMATION
What are the eligibility requirements to take up this Certified Artificial Intelligence?
Educational Requirements for Careers in Artificial Intelligence
• Various level of math, including probability, statistics, algebra, calculus, logic and algorithms.
• Bayesian networking or graphical modeling, including neural nets.
• Physics, engineering and robotics.
• Computer science, programming languages and coding.
How much does the Exam Cost?
Artificial Intelligence at Columbia University (Price: Content is FREE; Certificate Is $300) Machine Learning at Columbia University (Price: Content is FREE; Certificate Is $300)
Why do Companies Hire Artificial Intelligence Professionals?
The followings are the reasons companies hire Artificial Intelligence:
• Encourage more creative artistic jobs
• New customers means more jobs
• More data analysis
• Encourage entrepreneurship
• Programming.
Roles and responsibilities of Certified Artificial Intelligence professional
The roles and responsibilities of Artificial Intelligence are:
1. AI architect
This position focuses on individual business operations—along with the big picture—to determine where AI can be most successfully executed, the report said. The person in this role is responsible for measuring AI performance and maintaining AI sustainability.
2. AI product manager
Working alongside the AI architect, the AI product manager coordinates between business teams to make sure solutions are integrated correctly, according to the report. They also determine what organizational changes need to be made for optimal performance between employees and AI.
3. Data scientist
Data scientists have consistently appeared on top AI jobs lists, and these professionals typically earn an impressive salary. These employees are experts in analyzing data and gaining meaningful insights from the information for the business, said the report.
4. Software engineer
Scalable deployment is one of the biggest obstacles in AI adoption, according to the report. Software engineers are the ones working directly with data scientists to execute AI in a way that best works towards the company's goals.
5. AI ethicist
AI brings about many ethical and social issues, especially in regards to bias and taking jobs away from human workers. AI ethicists are the designated representatives who establish AI plans that align with the company's codes of ethics and standards, the report noted.
2. PMP

What is PMP?
Project Management Professional is an internationally recognized professional designation offered by the Project Management Institute
Who should take PMP?
Project Manager, (Unspecified Type / General)
Project Manager, Construction.
Operations Manager.
Project Manager, Information Technology (IT)
Project Engineer.
Construction Project Manager.
Senior Project Manager, IT.
How much Salary can I Expect once I am a Certified PMP?
At the lower end, a travel services PMP project manager in 2017 can expect to make $83,000-$90,000, according to PayScale. In the financial and insurance industries, PMPs typically make between $114,000 and $144,000. Both salary ranges represent a 20-22 percent increase over non-PMP project manager salaries.
To provide an idea of how lucrative this field can be, take a look at these job titles and average salaries for these project management jobs, collected from a leading online job website:
Job Title Average Salary
IT Project Manager $113,038
Senior Project Manager $111,691
Construction Project Manager $110,988
Technical Project Manager $113,276
Project Manager $110,342
What are the Top Companies hiring PMP?
These five jobs for project management professionals pay the most.
1. Pharmaceutical project management professional
Average U.S. salary: $131,833
Globally, the pharmaceutical industry is expected to breach $1.1 trillion in sales by 2022. So it’s no wonder that pharmaceutical project management professionals make more money, on average, than in any other industry.
The job: Pharmaceutical PMs work with doctors, researchers, and engineers to ensure that research and development stay on schedule and on budget. A successful project means overseeing the development of new medication for the treatment of diseases or other health problems.
Pros/cons: A pharmaceutical project manager can literally help find a cure for cancer and save millions of lives. Talk about a rewarding career! On the flip side, pharmaceutical PMPs will need an advanced healthcare degree or experience to approach top-tier salaries. Also, pharmaceutical research can move at a frustratingly slow pace to ensure compliance with necessary quality and safety regulations.
Top pharmaceutical companies:
1. Roche
2. Pfizer
3. AbbVie
2. Resources project management professional
Average U.S. salary: $129,368
Resources project managers work in industries such as mining, petroleum, and agriculture that extract and grow natural resources.
The job: Resources PMs work with farmers, mining, and oil companies to make the process of extracting and growing natural resources as efficient as possible by eliminating waste and improving communication. A successful project means overseeing the procurement of natural resources for efficient delivery to end consumers.
Pros/cons: Resources project management offers plenty of opportunities to travel and be outdoors. Because of the specific processes related to each natural resource, background as an engineer in a given field (farming, mining, drilling) may be required to become a resources project manager.
Top resources companies:
1. ExxonMobil (oil)
2. BHP Billiton (mining)
3. Cargill (agriculture)
3. Consulting project management professional
Average U.S. salary: $129,208
A consulting project management professional is different from a project management consultant—the first works as a project manager for a consulting company while the second works as a consultant who specializes in project management. We’re talking about the first of the two.
The job: A consulting project manager is the chameleon of the project management universe. The consulting PM could work with environmental engineers one month, and sales managers the next. A consulting project manager’s goal depends on the industry of the company they are working with on a case-to-case basis. In general, the goal is to furnish industry expertise and advanced knowledge to the client so that they can be successful in their project.
Pros/cons: A career as a consulting project manager is especially rewarding for someone who enjoys variety, as they will be asked to wear every hat from a construction helmet to a computer technician’s computer hat? However, that same unpredictability could be dizzying for someone who works best in a defined environment.
Top consulting firms:
1. McKinsey & Company
2. The Boston Consulting Group
3. Bain & Company
4. Aerospace project management professional
Average U.S. salary: $121,923
If you were the kind of kid who built model airplanes and dreamed of flying, but became a project manager instead, a job as an aerospace project management professional might be what you’re looking for.
The job: Aerospace PMs work with engineers and designers to make sure that new aircraft is delivered on time and on budget. Focus areas include risk management and quality control. A successful project means overseeing proposals leading to the development of new aircraft and aerospace systems.
Pros/cons: An aerospace project manager gets to work with airplanes and some of the most advanced technology on the planet. Because aerospace projects have a lot of moving parts (like, a lot) there are lots of opportunities for something to go wrong if something is missed.
Top aerospace companies:
1. Boeing
2. Airbus
3. Lockheed Martin
5. Engineering project management professional
Average U.S. salary: $121,769
Anyone who knows an engineer knows that they are some of the smartest people on the planet, but they can sometimes get caught up in the minutiae. An engineering project management professional is responsible for keeping the engineers focused.
The job: Engineering PMs work with, you guessed it, engineers. They also communicate with clients to make sure that the end product is what the client wants. A successful project means guiding the development of a product (often a complicated product) to completion within a specified timeline and budget.
Pros/cons: An engineering project manager has the satisfaction of seeing something very real, useful, and tangible at the end of their project—a large bridge, a new computer chip, or a satellite. On the other hand, the engineering PM must have extensive knowledge of the product they are overseeing, so experience as an engineer in that field is a prerequisite.
Top engineering companies:
1. Google Inc.
2. Microsoft
3. Apple
What are the Top Industries Hiring Certified PMP?
E-commerce, EdTech, Engineering, IT, BFSI, Pharmaceuticals, Health and Power industries, Logistics, Mobility Solutions, Computer and computer related. PMP is applicable across all verticals and platform or domain independent.
What's the Career Path to Become PMP Professional?
PMP® CERTIFICATION REQUIREMENTS
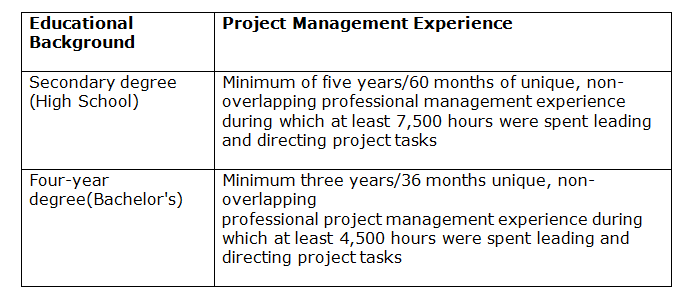
What's the Demand for Certified PMP Professionals by 2020?
The Project Management Institute (PMI) expects the future to be bright, with the global gross domestic product (GDP) in projectized industry anticipated to increase in the United States by $4.5 trillion by 2016.
Where can I get trained for PMP?
You can get trained at iCertGlobal. They offer one of the best courses on PMP .
What are the eligibility requirements to take up this Certified PMP?
The criteria stipulated by PMI ® clearly states the education background and number of hours of experience required in order to become eligible to apply for PMP ® exam.
How much does the Exam Cost?
The PMP Certification exam fee is 555 USD for the people who are not a member of PMI and for the members it is 405 USD. If you choose to become a PMI member at the time of your application, you will just have to pay 555 USD for the exam fee and the membership fee combined.
Why do Companies Hire PMP Professionals?
The followings are the reasons companies hire PMP:
• Encourage more creative artistic jobs
• New customers means more jobs
• More data analysis
• Encourage entrepreneurship
• Programming.
Roles and responsibilities of PMP
The roles and responsibilities of PMP can be explained with some examples:
• Launching a new product for a pharmaceutical firm
• Developing a new mobile application for a telecommunications company
• Implementing an internet-based banking system for a financial institution
• Standardizing testing procedures for an environmental organization
• Rolling out a new brand for a global retailer
Project manager job descriptions will reflect the specific needs of the company, the project manager will generally plan, coordinate, implement and finalize projects according to the specifications and deadlines, all while keeping the project within budget.
Depending on the industry and specific initiative, project managers may put together teams of personnel from a number of departments, such as information technology, purchasing, product development, marketing or distribution.
Project management professionals oversee projects from the planning stage through implementation, testing and reporting. They typically choose and manage the project team members, and are ultimately responsible for the project’s success or failure, based on objectives set by project stakeholders. Success may depend on whether the project is completed within the financial budget allocated or the established time frame – or whether it is completed at all.
3. GOOGLE CLOUD CERTIFIED Professional Cloud Architect

What is GOOGLE CLOUD CERTIFIED Professional Cloud Architect?
A Professional Cloud Architect enables organizations to leverage Google Cloud technologies. With a thorough understanding of cloud architecture and Google Cloud Platform, this individual can design, develop, and manage robust, secure, scalable, highly available, and dynamic solutions to drive business objectives.
How much Salary can I Expect once I am a GOOGLE CLOUD CERTIFIED Professional Cloud Architect?
The average pay for a Cloud Architect is $129,171 per year as per payscale.com
What are the Top Companies hiring GOOGLE CLOUD CERTIFIED Professional Cloud Architect?
Cloud Platform Architect - Google
IBM - United States 3.9
Consult with clients on how to best design Cloud High Performance and High Throughput Computing in the Google Cloud Platform.
Estimated: $120,000 - $170,000 a year 10d
Cloud Systems Architect - Connected Aircraft
Honeywell - Atlanta, GA 3.8
Amazon, Google, or Microsoft). 25 Connected Aircraft Cloud Architecture. Join a team assessing and driving cloud enabled initiatives within Honeywell's.
Estimated: $110,000 - $160,000 a year
Google Cloud Architect
Arth Consulting - New York, NY +3 locations
Google Certified Professional – Cloud Architect or Azure, AWS equivalent preferred. Amazon, Google, or Microsoft).
Estimated: $130,000 - $180,000 a year 5d
Cloud Solutions Architect
Center For Internet Security - Remote 4.6
The Cloud Solutions Architect position will work closely with the Cloud Product Owner (PO). Develop and implement cloud migration strategies.
Estimated: $120,000 - $160,000 a year
Solutions Architect, Healthcare and Life Sciences, Google Cloud
Google - San Francisco, CA +2 locations4.3
Your relationships with customers are crucial in helping Google grow its Google Cloud business and in bringing our product portfolio into companies around the.
Estimated: $120,000 - $170,000 a year
Cloud Architect - AWS / Google Cloud
Slalom Consulting - Silicon Valley, CA 3.7
Microsoft Azure, AWS, Google Cloud. Be versed in Google Cloud Platform and/or Amazon Web Services cloud solution, architecture, related technologies and their.
Estimated: $120,000 - $160,000 a year
Google Cloud Infrastructure Architect
Neudesic LLC - United States +2 locations
We are currently seeking a Google Cloud Infrastructure Architect, to become a member of Neudesic’s Cloud Infrastructure Team.
Estimated: $120,000 - $170,000 a year
Cloud Integration Architect
Sierra-Cedar - Remote 4.0
Hands-on Public Cloud (IaaS) – One or more of AWS, Google, Azure, OCI, etc. Sierra-Cedar is seeking a bright and motivated Cloud Automation Architect.
Estimated: $130,000 - $160,000 a year 12d
Google Cloud Platform Architect
Nerdery - Chicago, IL +2 locations3.3
Experience with at least one cloud orchestration tool such as Terraform or Google Deployment Manager Templates.
Estimated: $140,000 - $180,000 a year
Partner Engagement Manager, Google Cloud
Google - New York, NY 4.3
Provide best practices and accelerated support for Google Cloud Platform and G Suite Solutions. Google Cloud helps millions of employees and organizations.
Estimated: $110,000 - $160,000 a year
Multi-Cloud Solutions Architect
World Wide Technology, Inc. - Remote 3.6
Mid-Level Industry Certifications such as AWS Associate Level, MCSA - Cloud Platform or Google Associate Cloud Engineer.
Estimated: $130,000 - $170,000 a year
What are the Top Industries Hiring GOOGLE CLOUD CERTIFIED Professional Cloud Architect?
Telecommunication, Analytics, Pharmaceutical, Security, Networking
What's the Career Path to GOOGLE CLOUD CERTIFIED Professional Cloud Architect?
Required Education. Individuals will need a bachelor's degree in computer science or a related discipline to work as a cloud architect.
Required Skills. Excellent technical abilities are the most vital asset for cloud architects.
What's the Demand for GOOGLE CLOUD CERTIFIED Professional Cloud Architect by 2020?
It’s estimated that by 2025 the datasphere will grow to an incredible 163ZB, that’s over a trillion gigabytes! With such an enormous amount of data being created it needs to be stored somewhere for people to access. In recent years, cloud computing has become a popular data storage solution for both personal and business use.
Unfold Labs, an innovative product and service company based in San Diego, predicts that ‘in 2018 at least half of IT spending will be cloud-based and that by 2020 roughly 60-70% of all software, services and technology will be cloud based.’
Where can I get trained for GOOGLE CLOUD CERTIFIED Professional Cloud Architect?
You can get trained at iCertGlobal.
What are the eligibility requirements to take up this GOOGLE CLOUD CERTIFIED Professional Cloud Architect?
Career Requirements
STEP 1.) Earn a Degree. Systems architects usually need a bachelor's degree or higher related to information technology, software engineering or computer science.
STEP 2.) Consider Certification.
STEP 3.) Obtain Relevant Experience and Advance Your Career.
How much does the Exam Cost?
About this certification exam
This exam objectively measures an individual’s ability to demonstrate the critical job skills for the role. To earn this certification you must pass the Professional Cloud Architect exam. The format is multiple choice and multiple select. The exam has no prerequisites. This exam must be taken in-person at one of our testing center locations.
Locate a test center near you.
Length: 2 hours
Registration fee: USD $200
Language: English, Japanese, Spanish, Portuguese
Why do Companies Hire GOOGLE CLOUD CERTIFIED Professional Cloud Architect?
According to CRN, Apple will pay Google between $400 and $600 million for access to the platform. In other words, Apple is spending big with a company typically thought of as its chief rival.
Now, if a company of Apple’s magnitude will pair up with a direct competitor to power its own services, it’s a pretty good sign that cloud adoption is growing at a breakneck pace. Which means: jobs in cloud computing are a hot prospect right now (they pay well too, with a median salary of $124,300)
You could still be a cloud computing analyst or engineer for a traditional organization. Banks, IT companies and automotive manufacturers, as well as the government and military, are looking to hire cloud specialists in roles like cloud computing analyst, cloud administrator, cloud architect and cloud engineers.
These positions often demand ability with specific programming languages like Python, Java and Ruby on Rails, as well as experience with different operating systems (specifically Linux), and a database querying language like SQL. A company may already be committed to a specific cloud provider, so your resume may need to show you already have experience working with Amazon Web Services, Google Cloud Platform or another product in their vein.
Roles and responsibilities of GOOGLE CLOUD CERTIFIED Professional Cloud Architect
A Cloud Architect is an IT specialist who is responsible for deploying overseeing a company's cloud computing strategy. This includes cloud adoption plans, cloud application design, and cloud management and monitoring. Cloud architects oversee application architecture and deployment in cloud environments.
4. Agile Certified Scrum Master
What is Agile Certified Scrum Master?
An Agile Scrum Master certification is a designation given to Scrum Masters who understands the agile project methodology and scrum practices.
Who should take this Certified Scrum Master?
The Agile Scrum Master Certification course is recommended for:
• Project Managers
• Team leaders
• Scrum Team Managers
• Scrum Masters
• Developers and Product Owners.
How much Salary can I Expect once I am a Certified Scrum Master?
The annual average salary of a Certified Agile Scrum Master salary is $86,305 per year.
What are the Top Companies hiring Certified Scrum Master?
Many companies all over the world are using Agile to react to change, develop collaboration, raise the quality bar and produce happier employees. Such companies include Banks, Data services, IT companies, Energy supply firms, Marketing firm, etc.
What are the Top Industries Hiring Certified Scrum Master?
The top industries hiring Agile Scrum Masters are the Tech industry, Finance industry, and banking industry.
What's the Career Path to Certified Scrum Master?
To become an agile scrum master, you must have:
• 3+ years of experience in implementing Scrum for organizations
• Over 6 years of overall project management experience
• Attend a Certified Scrum master training program
• Take the exam, pass and get certified as an Agile Scrum Master.
What's the Demand for Certified Scrum Master by 2020?
The PMI® Talent Gap Report showed close to 16 million new project management jobs will be created by 2020 in 7 project-intensive industries. Since Agile Scrum Master is part of project management, there will a huge demand for Agile Scrum Master professionals with certification.
Where can I get trained for Certified Scrum Master?
You can get trained at iCertGlobal. It is a detailed course that teaches you how to:
• Become skillful in Scrum applications
• Organize daily Scrums, sprint planning and reviews
• Produce different Scrum artifacts, spring and product backlog
• Get the ultimate benefit from the Scrum methodology ntrol
• Create and carry out projects on a JIRA cloud site.
What are the eligibility requirements to take up this Certified Scrum Master?
There is no requirement to take the Agile Scrum Master certification. It is designed for any professional who wants to undertake a career in management.
How much does the Exam Cost?
The cost of the Agile Scrum Master exam is included in the course fee.
Why do Companies Hire Certified Scrum Master?
Companies hire Agile Scrum Master professionals because:
• Scrum masters improve customer satisfaction
• They improve organizational processes to lessen time to market.
• They ensure that better quality products are developed
• They improve progress visibility
• They improve team participation and ownership of tasks to establish a secure environment for teams to work.
Roles and responsibilities of Certified Scrum Master
The Agile Scrum Master takes care of development process and also serve the business, product owner, team, and individuals.
The roles and responsibilities include:
• The scrum master creates a safe environment that encourages collaboration.
• The scrum master helps in product planning and ensure that scrum techniques and practices are adhered to.
• The scrum master guide, coach, support and help to get rid of any stumbling block that teams may face along the line.
• The scrum master backs up individual efforts, solve any issues and get rid of problems that individuals may face
5. ITIL Foundation

What is ITIL Foundation?
ITIL, formerly an acronym for Information Technology Infrastructure Library, is a set of detailed practices for IT service management (ITSM) that focuses on aligning IT services with the needs of business.
The Foundation level is the entry level certification which offers you a general awareness of the key elements, concepts and terminology used in the ITIL service lifecycle, including the links between lifecycle stages, the processes used and their contribution to service management practices.
Who should take this ITIL Foundation?
• IT Managers/Support Teams
• IT Architects, Planners and Consultants
• System Administrators/Analysts
• Operations Managers
• Database Administrators
• Service Delivery Professionals
• Quality Analysts
• Application Management Team/Development Team
• Process Owners/Practitioners.
How much Salary can I Expect once I am a ITIL Foundation certified professional?
The average pay range for an ITIL Foundation varies modestly (up to $66,000) per year.
What are the Top Companies hiring ITIL Foundation certified professional?
Intel
McAfee
AT&T
Urbanpro.com
Computer Power Inc
HCL
British Telecom
Hitachi Consulting
American Express
Capgemini
What are the Top Industries Hiring ITIL Foundation certified professional?
The top industries include Telecommunication, BFSI, Service based industry, Operations, Manufacturing, computer and computer related, Analytics, any industry where service is a critical facet in running an opereation.
What's the Career Path to ITIL Foundation certified professional?
Achieve AXELOS-accredited ITIL® Foundation certification by following these steps:
STEP 1.) Appear for the ITIL Foundation exam after completing the training
STEP 2.) Score 65% on the exam [i.e. 26 out of 40 questions] in 60 minutes
STEP 3.) Earn two ITIL credits on successful completion of ITIL Foundation exam
What's the Demand for ITIL Foundation certified professional by 2020?
Businesswire predicted that the ITSM (IT service management) industry will increase from $4.4 billion in 2016 to $8.78 billion in 2021.
Where can I get trained for ITIL Foundation certified professional?
You can get trained at iCertGlobal. It is a detailed course that teaches using the IT Resources (IT Professionals, IT Infrastructure) in such a way that the customers get better service and the business gets profit out of it.
What are the eligibility requirements to take up this ITIL Foundation certified professional course?
There is no defined eligibility criterion for the ITIL Foundation exam. ITIL Foundation certification is in itself a prerequisite for other levels of ITIL certifications.
How much does the Exam Cost?
As of Dec'17, the costs for the exams for ITIL Foundation level is about $250 (about INR 15500/- or 210 EURO).
ITIL (foundation) certification costs
Country ITIL-F Certification exam fee
United States US $314
United Kingdom £269.00
Canada US $314.00
Australia AU $395
Why Companies Hire ITIL Foundation certified professional?
ITIL Foundation certified professional have a solid understanding in
• IT service management best practices, concepts and principles
• The purpose, aim, and scope of the service strategy, service design, service transition, service operations and continual service improvement
• Application of lean principles and automation of standard tasks to enhance efficiency of ITSM processes.
• Cost reduction by centralizing activities and teams using the right processes.
• Using ITIL® services to meet the needs of your organizations.
Roles and responsibilities of ITIL Foundation certified professional
Increase your contribution to ITSM in your organization by: automating standard tasks; identifying alignment opportunities of IT services with the business; cost optimization; taking a customer-centric approach to ITSM; and more.
6. Machine Learning

What is Machine Learning?
Machine Learning is the learning in which machine can learn by its own without being explicitly programmed. It is an application of AI that provide system the ability to automatically learn and improve from experience.
A definition. Machine learning is an application of artificial intelligence (AI) that provides systems the ability to automatically learn and improve from experience without being explicitly programmed.
The basics of machine learning:
Machine Learning algorithms can be classified into: Supervised Algorithms – Linear Regression, Logistic Regression, Support Vector Machine (SVM), Decision Trees, Random Forest. Unsupervised Algorithms – K Means Clustering. Reinforcement Algorithm.
Who should take this Machine Learning?
• Programmers, Developers, Architects, Technical Leads
• Developers who want to be a ‘Machine Learning Engineer’
• Analytics Managers leading a team of analysts
• Business Analysts who want to understand Machine Learning (ML) Techniques
• Business Analysts who want to understand Artificial Intelligence (AI) Techniques
• Information Architects who want to gain expertise in Predictive Analytics
• ‘Python’ professionals who want to design automatic predictive models
How much Salary can I Expect once I do Machine Learning?
The average pay for a Machine Learning Engineer is $42.50 per hour. The median Machine Learning Engineer has a base pay of $111,453. Salaries generally range from $76k to $153k as per payscale.com
What are the Top Companies hiring Machine Learning?
10. Salesforce – Intelligent CRMs
9. IBM – Better Healthcare
8. HubSpot – Smarter Sales
7. Baidu – The Future of Voice Search
6. Edgecase – Improving Ecommerce Conversion Rates
5. Google – Neural Networks and ‘Machines That Dream
4. Twitter – Curated Timelines
3. Facebook – Chatbot Army
2. Pinterest – Improved Content Discovery
1. Yelp – Image Curation at Scale
What are the Top Industries Hiring Machine Learning?
Telecom, Healthcare, Social Media, Analytics, Search Engines, neural Networks, e-Commerce
What's the Career Path to Machine Learning?
Here are the skills needed to begin and advance your machine learning career path:
• Basic Skills. As a conglomeration of math, data science and software engineering, machine learning will require you to be proficient in all three fields.
• Programming Skills.
• ML Programming Languages.
What is the best language for machine learning?
Top 5 best Programming Languages for Artificial Intelligence
1. Python. Python is considered to be in the first place in the list of all AI development languages due to the simplicity.
2. R. R is one of the most effective language and environment for analyzing and manipulating the data for statistical purposes.
3. Lisp.
4. Prolog.
5. Java
What's the Demand for Machine Learning by 2020?
Machine Learning focuses on the development of computer programs, and the primary aim is to allow computers to learn automatically without human intervention. Google says "Machine Learning is the future," and the future of Machine Learning is going to be very bright.
Where can I get trained for Machine Learning?
You can get trained at iCertGlobal, which offers Machine Learning, Artificial Intelligence and Robotic Process Automation.
What are the eligibility requirements to take up this Machine Learning?
Prerequisites
• Mastery of intro-level algebra. You should be comfortable with variables and coefficients, linear equations, graphs of functions, and histograms.
• Proficiency in programming basics, and some experience coding in Python. Programming exercises in Machine Learning Crash Course are coded in Python using TensorFlow.
How much does the Exam Cost?
Machines Learning with Python will costs you less than $400.
Why Companies Hire Machine Learning?
Machine Learning Engineer responsibilities include: Designing and developing machine learning and deep learning systems. Running machine learning tests and experiments. Implementing appropriate ML algorithms.
Roles and responsibilities of Machine Learning
Machine Learning Engineer responsibilities include: Designing and developing machine learning and deep learning systems. Running machine learning tests and experiments. Implementing appropriate ML algorithms.
7. Robotic Process Automation

What is Robotic Process Automation or RPA?
Robotic process automation (RPA) is the application of technology that allows employees in a company to configure computer software or a “robot” to capture and interpret existing applications for processing a transaction, manipulating data, triggering responses and communicating with other digital systems.
Robotic process automation (or RPA) is an emerging form of business process automation technology based on the notion of software robots or artificial intelligence (AI) workers. These tools also automate interactions with the GUI, and often do so by repeating a set of demonstration actions performed by a user.
Who should take this Robotic Process Automation or RPA?
There are no such prerequisites to learn RPA. From freshers to experienced professional, this technology is open for all. To master the concept of RPA, you need to have basic understanding of:
• Basic programming knowledge of using if/else and switch conditions
• Logical thinking ability
How much Salary can I Expect once I do Robotic Process Automation or RPA?
Average Salary of Robotic Process Automation Specialist is $126,094 (Indeed.com salary data)
What are the Top Companies hiring Robotic Process Automation or RPA?
Leading Players involved in the development of Robotic Process Automation:
• Automation Anywhere (U.S.)
• UiPath (Romania)
• Blue Prism (U.K.)
• Celaton Ltd (U.K.)
• IPSoft (U.S.)
• Nice Systems Ltd. (Israel)
• Pegasystems (U.S.)
• Redwood Software (U.S.)
• Verint (U.S.)
What's the Career Path to Machine Learning?
One of the most straightforward careers for an RPA expert is to become an RPA developer. With all the training and skills that one gain in their programs, this might be the best option for anyone.
The job of an RPA Developer is to build systems that can help to get a complete Robotics process automation work. For any professional, this would be something that they have trained in for months. These types of jobs pay well but sure they are time-consuming too. The projects are lengthy but all things considered being an RPA developer pays off well.
What's the Demand for Robotic Process Automation or RPA by 2020?
According to Forrester wave Q1 2017 Report, RPA Market Will Reach $2.9 Billion By 2021
Where can I get trained for Robotic Process Automation or RPA?
You can get trained at iCertGlobal.
What are the eligibility requirements to take up this Robotic Process Automation or RPA?
Prerequisites.
There are no such prerequisites to learn RPA. You don’t need any knowledge of programming language to use it to implement RPA.
How much does the Exam Cost?
RPA certification training costs $300.
Why Companies Hire Robotic Process Automation or RPA?
Here, we list top-5 benefits of implementing RPA software for your company.
1.) Reduced costs: By automating tasks, cost savings of nearly 30% can be achieved over the output of productivity. Software robots also cost less than a full time employee.
2.) Better customer experience: Deploying RPA frees up your high-value resources for them to be put back on the front line defining your customer success.
3.) Lower operational risk: By eliminating human errors such as tiredness or lack of knowledge, RPA reduces the rate of errors thereby providing a lower level of operational risk.
4.) Improved internal processes: In order to leverage AI and RPA, companies are forced to define clear governance procedures. This in turn, allows for faster internal reporting, on-boarding and other internal activities.
5.) Does not replace existing IT systems: One of the biggest advantages of using a virtual workforce, or an RPA bot is that it does not require you to replace your existing systems. Instead, RPA can leverage your existing systems, the same way a human employee can.
Roles and responsibilities of Robotic Process Automation or RPA
An RPA approach to streamline internal processes, where people and technology play their part in synchrony, enables better insight into trends and opportunities for business. Robotics process automation (RPA) works best with rule-based, regular tasks that require manual inputs.
8. Blockchain
.jpg)
What is Blockchain?
A global network of computers uses blockchain technology to jointly manage the database that records Bitcoin transactions. That is, Bitcoin is managed by its network, and not any one central authority.
Who should take this Blockchain?
Software Developers, IT Professionals, Engineers, Analysts, Technical Leads
How much Salary can I Expect once I do Blockchain?
Average yearly salary for "Blockchain Developer" ranges from $85k for Application Developer to $115k for Sr. Software Engineer as per indeed.com
What are the Top Companies hiring Blockchain?
Dell, vmware, Cisco, Honeywell, wipro.
What are the Top Industries Hiring Blockchain?
Telecom, Healthcare, Social Media, Analytics, Search Engines, neural Networks, e-Commerce
What's the Career Path to Blockchain?
For a Blockchain Developer, technical skills in the distributed ledger technology form the backbone of their career. A good place to start is Solidity for the development of Smart Contracts, and JavaScript for the development of a website.
What's the Demand for Blockchain by 2020?
According to the World Economic Forum, 18% of the world's GDP will be on Blockchain related technologies by 2025
Where can I get trained for Blockchain?
You can get trained at iCertGlobal.com.
What are the eligibility requirements to take up this Blockchain?
There are no prerequisites as such for this Blockchain Online Course. However, development experience on an object-oriented language, fundamentals of networking, and basic knowledge of command line & Linux would be advantageous. Further to brush up your skills,
How much does the Exam Cost?
The exam cost is $299 and it tests participants based on 100 questions spread across topics such as technical understanding, monetary implications, practical use, and regulations of cryptocurrencies. If you wish to take the training for this certification before you take the test, then it will cost you $2,995.
Why Companies Hire Blockchain?
Many industry leaders have already achieved significant business benefits, including greater transparency, enhanced security, improved traceability, increased efficiency and speed of transactions, and reduced costs. Read how blockchain provides these benefits to learn more about using blockchain in your industry
Roles and responsibilities of Blockchain
Responsibilities may include developing and implementing items like accelerators and assets, assisting with an organization's infrastructure setups utilizing technologies like Ethereum, and ensuring applications are secure. Blockchain engineers may analyze code artifacts and provide training to junior personnel.
9. Internet of Things
What is Internet of Things (IoT)?
The Internet of Things, commonly referred to as IoT, is the network of physical objects, devices, vehicles, buildings, and other items that's been integrated into the technology of modern electronics, software, sensors, and other “things” with network connectivity that enables them to collect and exchange data.
Who should take this Internet of Things (IoT)?
Software Developers, Engineers, Data Analysts, Big Data Professionals
How much Salary can I Expect once I do Internet of Things (IoT)?
Average salary of IoT Developer is $150k - Glassdoor.com
What are the Top Companies hiring Internet of Things (IoT)?
Dell, VMware, Cisco, Honeywell,
What are the Top Industries Hiring Internet of Things (IoT)?
Sensing — IoT endpoints
Communicating — IoT communications
Securing — IoT security
Understanding — IoT data and analytics
Acting — IoT artificial intelligence (AI)
What's the Demand for Internet of Things (IoT) by 2020?
By 2020, we will have over 50 billion devices connected to the Internet of Things.
The IoT will have an economic impact of up to $11 trillion by 2025 – McKinsey Global Institute.
There will be 250 million IoT connected automobiles creating new advancements in transportation by 2020.
Where can I get trained for the Internet of Things (IoT)?
You can get trained at iCertGlobal.com.
What are the eligibility requirements to take up this Internet of Things (IoT)?
There are no prerequisites for taking up this IoT training course.
IoT Certification Training on Azure demands an intermediate knowledge of the following:
Linux Fundamentals
Basic Python Programming
Working Knowledge of Azure IoT Hub and Azure Storage
How much does the Exam Cost?
The training cost works out to $400
Why Companies Hire Internet of Things (IoT)?
Internet of Things IoT for Businesses. Internet of things (IoT) is emerging as the next big revolution in the world of technology. A place where devices are smartly connected to communicate with each other. It can be anything; your smart phones, smart TVs, smart watches and smart homes.
Much of the IoT information will be stored in the cloud, so experts in providing cloud-based solutions will need to create storage big enough to host this volume of data, as well as enabling accessibility to facilitate a two-way process so that the provider of the data (you or me) is also able to consume the data. Hence, we will see an increase in SAN and server consultants.
Security professionals will be needed to guard against breaches in data protection, and to offer us some peace of mind that our data is not being accessed by those we would prefer not to access it.
Back-end developers will be required with skills in languages like NoSQL and, as we accumulate greater amounts of unstructured data in the form of sensory information, in developing non-relational databases.
Mobile app developers will have the opportunity to create apps that can harness data to provide live, up-to-date information that can inform our daily decision making.
Drones are set to be central to IoT, replacing sensors that would have been at rest on buildings, bridges or other infrastructure. Drones offer flexibility in information gathering due to their mobility. They have data collection and processing software, and GPS, built in for geo-processing. They are of huge benefit to organisations in the utility, transport, mining, mapping and energy sectors. They will require infrastructure to host data – usually in the cloud – which in turn will generate more work for the aforementioned storage and server consultants.
Roles and responsibilities of Internet of Things (IoT)
Dashboards play a big role in the internet of things. An IoT developer will be responsible for data processing, data storage, data preparation and dashboard development. A huge amount of data on countless different formats will be the standard in the world of an IoT developer.
Since Internet of Things involves communication between applications and physical devices, an IoT development team tends to be large, and different developers are assigned in different areas, among these software programming, hardware programming, security implementation, networking, and systems engineering.
10. Data science

What is Data science?
Data science is a field of Big Data geared toward providing meaningful information based on large amounts of complex data. Data science, or data-driven science, combines different fields of work in statistics and computation in order to interpret data for the purpose of decision making.
Who should take this Data science ?
Software Developers, Engineers, Data Analysts, Big Data Professionals
How much Salary can I Expect once I do Data science?
Despite a recent influx of early-career professionals, the median starting salary for a data scientist remains high at $95,000. Mid-level data scientist salary. The median salary for a mid-level data scientist is $128,750. If this data scientist is also in a managerial role, the median salary rises to $185,000.
What are the Top Companies hiring Data science ?
Angel Broking, Deloitte, HDFC, Ford Automotive, VM Ware, Exponentia, Clover Infotech, Value Direct, Virtusa, Credit Vidya, Guppy Media, Shzertech, Loginext, Persistent, L & T Finance, Whizminds, Mii app, K2 Analytics, Eclerx, Mobiliya, Emmfer, Suzlon, Infrasoft, Impact Analytics, IBM, Eigen Technologies, Intelenet, Pentation, Light app, Ixsight, Aangan NGO, Softcell, Nelsen etc.
What are the Top Industries Hiring Data science?
Make sure you don't overlook compact online Data Science courses that will provide exactly what you need to start your career in Data Science.
5 career options for graduates of Data Science.
Statistician.
Business intelligence reporting professional.
Data Analyst.
Data Mining or Big Data Engineer.
Program/Project Manager.
What's the Demand for Data science by 2020?
The number of Data Science and Analytics job listings is projected to grow by nearly 364,000 listings by 2020 - Forbes.
Where can I get trained for Data science?
You can get trained at iCertGlobal.com.
What are the eligibility requirements to take up Data science?
The prerequisites to learn data science:
You will find many data scientists with a bachelor's degree in statistics and machine learning but it is not a requirement to learn data science. However, having familiarity with the basic concepts of Math and Statistics like Linear Algebra, Calculus, Probability, etc. is important to learn data science.
Technical Skills: Computer Science
Python Coding. Python is the most common coding language I typically see required in data science roles, along with Java, Perl, or C/C++.
Hadoop Platform.
SQL Database/Coding.
Apache Spark.
Machine Learning and AI.
Data Visualization.
Unstructured data.
How much does the Exam Cost?
The training costs is around $300.
What is the career path to become a Data Scientist?
There are three general steps to becoming a data scientist:
1.) Earn a bachelor's degree in IT, computer science, math, physics, or another related field.
2.) Earn a master's degree in data or related field.
3.) Gain experience in the field you intend to work in (ex: healthcare, physics, business).
Why Companies Hire Data science?
Data Science and Its Growing Importance – An interdisciplinary field, data science deals with processes and systems that are used to extract knowledge or insights from large amounts of data. With advancements of so much of data, many aspects of data science are gaining immense importance, especially big data.
Roles and responsibilities of Data science
A data scientist is someone who makes value out ofdata. Data scientist duties typically include creating various machine learning-based tools or processes within the company, such as recommendation engines or automated lead scoring systems. People within this role should also be able to perform statistical analysis.
When it comes to programming, here are the list of courses are that quite in demand that draws attractive pay too.
Programming:
Most popular programming languages certification:
• Python
• Java
• C#
• Swift
• Scala
• R
• SAS
• JavaScript
• Typescript
We, at iCert Global offer you a wide array of courses and our Lead- Sales Consultants would be more than happy to clarify any concern you might have with regard to course offerings. We request you to spend time in checking our course catalog . www.icertglobal.com
Read More
The Top 15 High Paying IT Certification Courses | Professional Certification
Fast track your career by enrolling in one of the top 15 courses identified as the “highest paying” certification courses. Professionals, professional certification and pat are closely connected and interrelated.
According to the 15 Top Paying IT Certifications In 2019 listed in forbes .com, here there are some of the highest paid certification
• Google Cloud Certified Professional Cloud Architect is the highest paying certification of 2019, paying an average salary of $139,529.
• Certifications in virtualization and cloud computing pay an average salary of $127,494 this year, up from $112,955 in 2018, a 12.8% increase in just one year.
• Five of the top 15 highest paying certifications of 2019 are for cybersecurity expertise, and they pay an average of $115,867.
• Project Management Professional (PMP®) certifications increased in value by 18.6%, jumping from a median salary of $114,473 in 2018 to $135,798 in 2019.

Key insights on the 15 top paying IT certifications in 2019 include the following:
• Average salary across all 15 certifications is $121,514 for 2019. Virtualization and cloud computing certifications pay an average salary of $127,494 in 2019, soaring over the median salary of $112,955 in 2018.
• The five cybersecurity certifications pay an average salary of $115,867.
• Network certifications pay an average salary of $111,555.
• Google Cloud Certified Professional Cloud Architect, Project Management Professional (PMP), Certified ScrumMaster, AWS Certified Solutions Architect – Associate and AWS Certified Developer – Associate all have salaries above the median of $121,514.
• Microsoft Certified Solutions Expert (MCSE) – Server Infrastructure certification pays an average salary of $121,288, up from $100,656 in 2018.
• The two highest-paying AWS certifications in 2019 have an average salary of $131,605, $6K higher than $125,591 which is the average of the five highest-paying AWS certifications of 2018. The following table provides a breakout of the top 15 IT certifications in 2019 according to latest survey.
Here are some of the top fifteen courses that you can select in propelling in your professional growth.
1.Artificial Intelligence (AI)
2. PMP
3.Google Cloud Certified Professional
4.Certified Scrum Master
5. ITIL Foundation
6.Machine Learning
7.Robotic Process Automation or RPA
8. Blockchain
9. Internet of Things
10. Data science
11. Cyber Security
12. Edge Computing
13. Big Data Certifications
14. Virtual Reality and Augmented Reality
15. Networking
1. Artificial Intelligence

What is Artificial Intelligence (AI)?
Artificial intelligence (AI) is an area of computer science that emphasizes the creation of intelligent machines that work and react like humans. Some of the activities computers with artificial intelligence are designed for include: Speech recognition. Learning.
Who should take this Artificial intelligence (AI)?
Software analysts and developers.
Computer scientists and computer engineers.
Algorithm specialists.
Research scientists and engineering consultants.
Mechanical engineers and maintenance technicians.
Manufacturing and electrical engineers.
How much Salary can I Expect once I am a Certified Artificial intelligence (AI)?
According to Indeed.com, the average IT salary – the keyword is "artificial intelligence engineer" – in the San Francisco area ranges from approximately $134,135 per year for software engineer to $169,930 per year for machine learning engineer.
What are the Top Companies hiring Certified Artificial intelligence (AI )?
The Top 15 Employers Hiring Artificial Intelligence Talent
1. Amazon
2. Nvidia
3. Microsoft
4. IBM
5. Accenture
6. Facebook
7. Intel
8. Samsung
9. Lenovo
10. Adobe
11. MoTek Technologies
12. Uber
13. PCO Innovation
14. Rakuten Marketing
15. Wells Fargo
What are the Top Industries Hiring Certified Artificial Intelligence?
E-commerce, Health and Power industries, Logistics, Mobility Solutions, Computer and computer related.
What's the Career Path to Become Artificial intelligence (AI) Professional?
6 Easy Steps To Get Started Learning Artificial Intelligence
STEP 1.) Learn Python & SQL
STEP 2.) Learn Machine Learning from some of the below courses.
STEP 3.) Learn basics of probability theory, statistics, and Maths.
STEP 4.) RECOMMENDED BOOKS to READ
STEP 5.) PRACTICE FEW EXERCISES
STEP 6.) Practice—Learn—Practice on your own, step by step you will slowly become AI programmer.
What's the Demand for Certified Artificial Intelligence Professionals by 2020?
With AI projected to create 2.3 million jobs by 2020, according to a Gartner report, it's safe to assume that machine learning will remain an in-demand skill for the foreseeable future.
Artificial intelligence (AI) skills dominated the list of the fastest-growing jobs in 2018—a trend that is expected only to grow in the future. Machines and algorithms are predicted to create 133 million new jobs by 2022,
Where can I get trained for the Artificial Intelligence?
You can get trained at iCertGlobal. They offer one of the best courses on ARTIFICIAL INTELLIGENCE AND DEEP LEARNING CERTIFICATION, MACHINE LEARNING AND ROBOTIC PROCESS AUTOMATION
What are the eligibility requirements to take up this Certified Artificial Intelligence?
Educational Requirements for Careers in Artificial Intelligence
• Various level of math, including probability, statistics, algebra, calculus, logic and algorithms.
• Bayesian networking or graphical modeling, including neural nets.
• Physics, engineering and robotics.
• Computer science, programming languages and coding.
How much does the Exam Cost?
Artificial Intelligence at Columbia University (Price: Content is FREE; Certificate Is $300) Machine Learning at Columbia University (Price: Content is FREE; Certificate Is $300)
Why do Companies Hire Artificial Intelligence Professionals?
The followings are the reasons companies hire Artificial Intelligence:
• Encourage more creative artistic jobs
• New customers means more jobs
• More data analysis
• Encourage entrepreneurship
• Programming.
Roles and responsibilities of Certified Artificial Intelligence professional
The roles and responsibilities of Artificial Intelligence are:
1. AI architect
This position focuses on individual business operations—along with the big picture—to determine where AI can be most successfully executed, the report said. The person in this role is responsible for measuring AI performance and maintaining AI sustainability.
2. AI product manager
Working alongside the AI architect, the AI product manager coordinates between business teams to make sure solutions are integrated correctly, according to the report. They also determine what organizational changes need to be made for optimal performance between employees and AI.
3. Data scientist
Data scientists have consistently appeared on top AI jobs lists, and these professionals typically earn an impressive salary. These employees are experts in analyzing data and gaining meaningful insights from the information for the business, said the report.
4. Software engineer
Scalable deployment is one of the biggest obstacles in AI adoption, according to the report. Software engineers are the ones working directly with data scientists to execute AI in a way that best works towards the company's goals.
5. AI ethicist
AI brings about many ethical and social issues, especially in regards to bias and taking jobs away from human workers. AI ethicists are the designated representatives who establish AI plans that align with the company's codes of ethics and standards, the report noted.
2. PMP

What is PMP?
Project Management Professional is an internationally recognized professional designation offered by the Project Management Institute
Who should take PMP?
Project Manager, (Unspecified Type / General)
Project Manager, Construction.
Operations Manager.
Project Manager, Information Technology (IT)
Project Engineer.
Construction Project Manager.
Senior Project Manager, IT.
How much Salary can I Expect once I am a Certified PMP?
At the lower end, a travel services PMP project manager in 2017 can expect to make $83,000-$90,000, according to PayScale. In the financial and insurance industries, PMPs typically make between $114,000 and $144,000. Both salary ranges represent a 20-22 percent increase over non-PMP project manager salaries.
To provide an idea of how lucrative this field can be, take a look at these job titles and average salaries for these project management jobs, collected from a leading online job website:
Job Title Average Salary
IT Project Manager $113,038
Senior Project Manager $111,691
Construction Project Manager $110,988
Technical Project Manager $113,276
Project Manager $110,342
What are the Top Companies hiring PMP?
These five jobs for project management professionals pay the most.
1. Pharmaceutical project management professional
Average U.S. salary: $131,833
Globally, the pharmaceutical industry is expected to breach $1.1 trillion in sales by 2022. So it’s no wonder that pharmaceutical project management professionals make more money, on average, than in any other industry.
The job: Pharmaceutical PMs work with doctors, researchers, and engineers to ensure that research and development stay on schedule and on budget. A successful project means overseeing the development of new medication for the treatment of diseases or other health problems.
Pros/cons: A pharmaceutical project manager can literally help find a cure for cancer and save millions of lives. Talk about a rewarding career! On the flip side, pharmaceutical PMPs will need an advanced healthcare degree or experience to approach top-tier salaries. Also, pharmaceutical research can move at a frustratingly slow pace to ensure compliance with necessary quality and safety regulations.
Top pharmaceutical companies:
1. Roche
2. Pfizer
3. AbbVie
2. Resources project management professional
Average U.S. salary: $129,368
Resources project managers work in industries such as mining, petroleum, and agriculture that extract and grow natural resources.
The job: Resources PMs work with farmers, mining, and oil companies to make the process of extracting and growing natural resources as efficient as possible by eliminating waste and improving communication. A successful project means overseeing the procurement of natural resources for efficient delivery to end consumers.
Pros/cons: Resources project management offers plenty of opportunities to travel and be outdoors. Because of the specific processes related to each natural resource, background as an engineer in a given field (farming, mining, drilling) may be required to become a resources project manager.
Top resources companies:
1. ExxonMobil (oil)
2. BHP Billiton (mining)
3. Cargill (agriculture)
3. Consulting project management professional
Average U.S. salary: $129,208
A consulting project management professional is different from a project management consultant—the first works as a project manager for a consulting company while the second works as a consultant who specializes in project management. We’re talking about the first of the two.
The job: A consulting project manager is the chameleon of the project management universe. The consulting PM could work with environmental engineers one month, and sales managers the next. A consulting project manager’s goal depends on the industry of the company they are working with on a case-to-case basis. In general, the goal is to furnish industry expertise and advanced knowledge to the client so that they can be successful in their project.
Pros/cons: A career as a consulting project manager is especially rewarding for someone who enjoys variety, as they will be asked to wear every hat from a construction helmet to a computer technician’s computer hat? However, that same unpredictability could be dizzying for someone who works best in a defined environment.
Top consulting firms:
1. McKinsey & Company
2. The Boston Consulting Group
3. Bain & Company
4. Aerospace project management professional
Average U.S. salary: $121,923
If you were the kind of kid who built model airplanes and dreamed of flying, but became a project manager instead, a job as an aerospace project management professional might be what you’re looking for.
The job: Aerospace PMs work with engineers and designers to make sure that new aircraft is delivered on time and on budget. Focus areas include risk management and quality control. A successful project means overseeing proposals leading to the development of new aircraft and aerospace systems.
Pros/cons: An aerospace project manager gets to work with airplanes and some of the most advanced technology on the planet. Because aerospace projects have a lot of moving parts (like, a lot) there are lots of opportunities for something to go wrong if something is missed.
Top aerospace companies:
1. Boeing
2. Airbus
3. Lockheed Martin
5. Engineering project management professional
Average U.S. salary: $121,769
Anyone who knows an engineer knows that they are some of the smartest people on the planet, but they can sometimes get caught up in the minutiae. An engineering project management professional is responsible for keeping the engineers focused.
The job: Engineering PMs work with, you guessed it, engineers. They also communicate with clients to make sure that the end product is what the client wants. A successful project means guiding the development of a product (often a complicated product) to completion within a specified timeline and budget.
Pros/cons: An engineering project manager has the satisfaction of seeing something very real, useful, and tangible at the end of their project—a large bridge, a new computer chip, or a satellite. On the other hand, the engineering PM must have extensive knowledge of the product they are overseeing, so experience as an engineer in that field is a prerequisite.
Top engineering companies:
1. Google Inc.
2. Microsoft
3. Apple
What are the Top Industries Hiring Certified PMP?
E-commerce, EdTech, Engineering, IT, BFSI, Pharmaceuticals, Health and Power industries, Logistics, Mobility Solutions, Computer and computer related. PMP is applicable across all verticals and platform or domain independent.
What's the Career Path to Become PMP Professional?
PMP® CERTIFICATION REQUIREMENTS

What's the Demand for Certified PMP Professionals by 2020?
The Project Management Institute (PMI) expects the future to be bright, with the global gross domestic product (GDP) in projectized industry anticipated to increase in the United States by $4.5 trillion by 2016.
Where can I get trained for PMP?
You can get trained at iCertGlobal. They offer one of the best courses on PMP .
What are the eligibility requirements to take up this Certified PMP?
The criteria stipulated by PMI ® clearly states the education background and number of hours of experience required in order to become eligible to apply for PMP ® exam.
How much does the Exam Cost?
The PMP Certification exam fee is 555 USD for the people who are not a member of PMI and for the members it is 405 USD. If you choose to become a PMI member at the time of your application, you will just have to pay 555 USD for the exam fee and the membership fee combined.
Why do Companies Hire PMP Professionals?
The followings are the reasons companies hire PMP:
• Encourage more creative artistic jobs
• New customers means more jobs
• More data analysis
• Encourage entrepreneurship
• Programming.
Roles and responsibilities of PMP
The roles and responsibilities of PMP can be explained with some examples:
• Launching a new product for a pharmaceutical firm
• Developing a new mobile application for a telecommunications company
• Implementing an internet-based banking system for a financial institution
• Standardizing testing procedures for an environmental organization
• Rolling out a new brand for a global retailer
Project manager job descriptions will reflect the specific needs of the company, the project manager will generally plan, coordinate, implement and finalize projects according to the specifications and deadlines, all while keeping the project within budget.
Depending on the industry and specific initiative, project managers may put together teams of personnel from a number of departments, such as information technology, purchasing, product development, marketing or distribution.
Project management professionals oversee projects from the planning stage through implementation, testing and reporting. They typically choose and manage the project team members, and are ultimately responsible for the project’s success or failure, based on objectives set by project stakeholders. Success may depend on whether the project is completed within the financial budget allocated or the established time frame – or whether it is completed at all.
3. GOOGLE CLOUD CERTIFIED Professional Cloud Architect

What is GOOGLE CLOUD CERTIFIED Professional Cloud Architect?
A Professional Cloud Architect enables organizations to leverage Google Cloud technologies. With a thorough understanding of cloud architecture and Google Cloud Platform, this individual can design, develop, and manage robust, secure, scalable, highly available, and dynamic solutions to drive business objectives.
How much Salary can I Expect once I am a GOOGLE CLOUD CERTIFIED Professional Cloud Architect?
The average pay for a Cloud Architect is $129,171 per year as per payscale.com
What are the Top Companies hiring GOOGLE CLOUD CERTIFIED Professional Cloud Architect?
Cloud Platform Architect - Google
IBM - United States 3.9
Consult with clients on how to best design Cloud High Performance and High Throughput Computing in the Google Cloud Platform.
Estimated: $120,000 - $170,000 a year 10d
Cloud Systems Architect - Connected Aircraft
Honeywell - Atlanta, GA 3.8
Amazon, Google, or Microsoft). 25 Connected Aircraft Cloud Architecture. Join a team assessing and driving cloud enabled initiatives within Honeywell's.
Estimated: $110,000 - $160,000 a year
Google Cloud Architect
Arth Consulting - New York, NY +3 locations
Google Certified Professional – Cloud Architect or Azure, AWS equivalent preferred. Amazon, Google, or Microsoft).
Estimated: $130,000 - $180,000 a year 5d
Cloud Solutions Architect
Center For Internet Security - Remote 4.6
The Cloud Solutions Architect position will work closely with the Cloud Product Owner (PO). Develop and implement cloud migration strategies.
Estimated: $120,000 - $160,000 a year
Solutions Architect, Healthcare and Life Sciences, Google Cloud
Google - San Francisco, CA +2 locations4.3
Your relationships with customers are crucial in helping Google grow its Google Cloud business and in bringing our product portfolio into companies around the.
Estimated: $120,000 - $170,000 a year
Cloud Architect - AWS / Google Cloud
Slalom Consulting - Silicon Valley, CA 3.7
Microsoft Azure, AWS, Google Cloud. Be versed in Google Cloud Platform and/or Amazon Web Services cloud solution, architecture, related technologies and their.
Estimated: $120,000 - $160,000 a year
Google Cloud Infrastructure Architect
Neudesic LLC - United States +2 locations
We are currently seeking a Google Cloud Infrastructure Architect, to become a member of Neudesic’s Cloud Infrastructure Team.
Estimated: $120,000 - $170,000 a year
Cloud Integration Architect
Sierra-Cedar - Remote 4.0
Hands-on Public Cloud (IaaS) – One or more of AWS, Google, Azure, OCI, etc. Sierra-Cedar is seeking a bright and motivated Cloud Automation Architect.
Estimated: $130,000 - $160,000 a year 12d
Google Cloud Platform Architect
Nerdery - Chicago, IL +2 locations3.3
Experience with at least one cloud orchestration tool such as Terraform or Google Deployment Manager Templates.
Estimated: $140,000 - $180,000 a year
Partner Engagement Manager, Google Cloud
Google - New York, NY 4.3
Provide best practices and accelerated support for Google Cloud Platform and G Suite Solutions. Google Cloud helps millions of employees and organizations.
Estimated: $110,000 - $160,000 a year
Multi-Cloud Solutions Architect
World Wide Technology, Inc. - Remote 3.6
Mid-Level Industry Certifications such as AWS Associate Level, MCSA - Cloud Platform or Google Associate Cloud Engineer.
Estimated: $130,000 - $170,000 a year
What are the Top Industries Hiring GOOGLE CLOUD CERTIFIED Professional Cloud Architect?
Telecommunication, Analytics, Pharmaceutical, Security, Networking
What's the Career Path to GOOGLE CLOUD CERTIFIED Professional Cloud Architect?
Required Education. Individuals will need a bachelor's degree in computer science or a related discipline to work as a cloud architect.
Required Skills. Excellent technical abilities are the most vital asset for cloud architects.
What's the Demand for GOOGLE CLOUD CERTIFIED Professional Cloud Architect by 2020?
It’s estimated that by 2025 the datasphere will grow to an incredible 163ZB, that’s over a trillion gigabytes! With such an enormous amount of data being created it needs to be stored somewhere for people to access. In recent years, cloud computing has become a popular data storage solution for both personal and business use.
Unfold Labs, an innovative product and service company based in San Diego, predicts that ‘in 2018 at least half of IT spending will be cloud-based and that by 2020 roughly 60-70% of all software, services and technology will be cloud based.’
Where can I get trained for GOOGLE CLOUD CERTIFIED Professional Cloud Architect?
You can get trained at iCertGlobal.
What are the eligibility requirements to take up this GOOGLE CLOUD CERTIFIED Professional Cloud Architect?
Career Requirements
STEP 1.) Earn a Degree. Systems architects usually need a bachelor's degree or higher related to information technology, software engineering or computer science.
STEP 2.) Consider Certification.
STEP 3.) Obtain Relevant Experience and Advance Your Career.
How much does the Exam Cost?
About this certification exam
This exam objectively measures an individual’s ability to demonstrate the critical job skills for the role. To earn this certification you must pass the Professional Cloud Architect exam. The format is multiple choice and multiple select. The exam has no prerequisites. This exam must be taken in-person at one of our testing center locations.
Locate a test center near you.
Length: 2 hours
Registration fee: USD $200
Language: English, Japanese, Spanish, Portuguese
Why do Companies Hire GOOGLE CLOUD CERTIFIED Professional Cloud Architect?
According to CRN, Apple will pay Google between $400 and $600 million for access to the platform. In other words, Apple is spending big with a company typically thought of as its chief rival.
Now, if a company of Apple’s magnitude will pair up with a direct competitor to power its own services, it’s a pretty good sign that cloud adoption is growing at a breakneck pace. Which means: jobs in cloud computing are a hot prospect right now (they pay well too, with a median salary of $124,300)
You could still be a cloud computing analyst or engineer for a traditional organization. Banks, IT companies and automotive manufacturers, as well as the government and military, are looking to hire cloud specialists in roles like cloud computing analyst, cloud administrator, cloud architect and cloud engineers.
These positions often demand ability with specific programming languages like Python, Java and Ruby on Rails, as well as experience with different operating systems (specifically Linux), and a database querying language like SQL. A company may already be committed to a specific cloud provider, so your resume may need to show you already have experience working with Amazon Web Services, Google Cloud Platform or another product in their vein.
Roles and responsibilities of GOOGLE CLOUD CERTIFIED Professional Cloud Architect
A Cloud Architect is an IT specialist who is responsible for deploying overseeing a company's cloud computing strategy. This includes cloud adoption plans, cloud application design, and cloud management and monitoring. Cloud architects oversee application architecture and deployment in cloud environments.
4. Agile Certified Scrum Master

What is Agile Certified Scrum Master?
An Agile Scrum Master certification is a designation given to Scrum Masters who understands the agile project methodology and scrum practices.
Who should take this Certified Scrum Master?
The Agile Scrum Master Certification course is recommended for:
• Project Managers
• Team leaders
• Scrum Team Managers
• Scrum Masters
• Developers and Product Owners.
How much Salary can I Expect once I am a Certified Scrum Master?
The annual average salary of a Certified Agile Scrum Master salary is $86,305 per year.
What are the Top Companies hiring Certified Scrum Master?
Many companies all over the world are using Agile to react to change, develop collaboration, raise the quality bar and produce happier employees. Such companies include Banks, Data services, IT companies, Energy supply firms, Marketing firm, etc.
What are the Top Industries Hiring Certified Scrum Master?
The top industries hiring Agile Scrum Masters are the Tech industry, Finance industry, and banking industry.
What's the Career Path to Certified Scrum Master?
To become an agile scrum master, you must have:
• 3+ years of experience in implementing Scrum for organizations
• Over 6 years of overall project management experience
• Attend a Certified Scrum master training program
• Take the exam, pass and get certified as an Agile Scrum Master.
What's the Demand for Certified Scrum Master by 2020?
The PMI® Talent Gap Report showed close to 16 million new project management jobs will be created by 2020 in 7 project-intensive industries. Since Agile Scrum Master is part of project management, there will a huge demand for Agile Scrum Master professionals with certification.
Where can I get trained for Certified Scrum Master?
You can get trained at iCertGlobal. It is a detailed course that teaches you how to:
• Become skillful in Scrum applications
• Organize daily Scrums, sprint planning and reviews
• Produce different Scrum artifacts, spring and product backlog
• Get the ultimate benefit from the Scrum methodology ntrol
• Create and carry out projects on a JIRA cloud site.
What are the eligibility requirements to take up this Certified Scrum Master?
There is no requirement to take the Agile Scrum Master certification. It is designed for any professional who wants to undertake a career in management.
How much does the Exam Cost?
The cost of the Agile Scrum Master exam is included in the course fee.
Why do Companies Hire Certified Scrum Master?
Companies hire Agile Scrum Master professionals because:
• Scrum masters improve customer satisfaction
• They improve organizational processes to lessen time to market.
• They ensure that better quality products are developed
• They improve progress visibility
• They improve team participation and ownership of tasks to establish a secure environment for teams to work.
Roles and responsibilities of Certified Scrum Master
The Agile Scrum Master takes care of development process and also serve the business, product owner, team, and individuals.
The roles and responsibilities include:
• The scrum master creates a safe environment that encourages collaboration.
• The scrum master helps in product planning and ensure that scrum techniques and practices are adhered to.
• The scrum master guide, coach, support and help to get rid of any stumbling block that teams may face along the line.
• The scrum master backs up individual efforts, solve any issues and get rid of problems that individuals may face
5. ITIL Foundation

What is ITIL Foundation?
ITIL, formerly an acronym for Information Technology Infrastructure Library, is a set of detailed practices for IT service management (ITSM) that focuses on aligning IT services with the needs of business.
The Foundation level is the entry level certification which offers you a general awareness of the key elements, concepts and terminology used in the ITIL service lifecycle, including the links between lifecycle stages, the processes used and their contribution to service management practices.
Who should take this ITIL Foundation?
• IT Managers/Support Teams
• IT Architects, Planners and Consultants
• System Administrators/Analysts
• Operations Managers
• Database Administrators
• Service Delivery Professionals
• Quality Analysts
• Application Management Team/Development Team
• Process Owners/Practitioners.
How much Salary can I Expect once I am a ITIL Foundation certified professional?
The average pay range for an ITIL Foundation varies modestly (up to $66,000) per year.
What are the Top Companies hiring ITIL Foundation certified professional?
Intel
McAfee
AT&T
Urbanpro.com
Computer Power Inc
HCL
British Telecom
Hitachi Consulting
American Express
Capgemini
What are the Top Industries Hiring ITIL Foundation certified professional?
The top industries include Telecommunication, BFSI, Service based industry, Operations, Manufacturing, computer and computer related, Analytics, any industry where service is a critical facet in running an opereation.
What's the Career Path to ITIL Foundation certified professional?
Achieve AXELOS-accredited ITIL® Foundation certification by following these steps:
STEP 1.) Appear for the ITIL Foundation exam after completing the training
STEP 2.) Score 65% on the exam [i.e. 26 out of 40 questions] in 60 minutes
STEP 3.) Earn two ITIL credits on successful completion of ITIL Foundation exam
What's the Demand for ITIL Foundation certified professional by 2020?
Businesswire predicted that the ITSM (IT service management) industry will increase from $4.4 billion in 2016 to $8.78 billion in 2021.
Where can I get trained for ITIL Foundation certified professional?
You can get trained at iCertGlobal. It is a detailed course that teaches using the IT Resources (IT Professionals, IT Infrastructure) in such a way that the customers get better service and the business gets profit out of it.
What are the eligibility requirements to take up this ITIL Foundation certified professional course?
There is no defined eligibility criterion for the ITIL Foundation exam. ITIL Foundation certification is in itself a prerequisite for other levels of ITIL certifications.
How much does the Exam Cost?
As of Dec'17, the costs for the exams for ITIL Foundation level is about $250 (about INR 15500/- or 210 EURO).
ITIL (foundation) certification costs
Country ITIL-F Certification exam fee
United States US $314
United Kingdom £269.00
Canada US $314.00
Australia AU $395
Why Companies Hire ITIL Foundation certified professional?
ITIL Foundation certified professional have a solid understanding in
• IT service management best practices, concepts and principles
• The purpose, aim, and scope of the service strategy, service design, service transition, service operations and continual service improvement
• Application of lean principles and automation of standard tasks to enhance efficiency of ITSM processes.
• Cost reduction by centralizing activities and teams using the right processes.
• Using ITIL® services to meet the needs of your organizations.
Roles and responsibilities of ITIL Foundation certified professional
Increase your contribution to ITSM in your organization by: automating standard tasks; identifying alignment opportunities of IT services with the business; cost optimization; taking a customer-centric approach to ITSM; and more.
6. Machine Learning

What is Machine Learning?
Machine Learning is the learning in which machine can learn by its own without being explicitly programmed. It is an application of AI that provide system the ability to automatically learn and improve from experience.
A definition. Machine learning is an application of artificial intelligence (AI) that provides systems the ability to automatically learn and improve from experience without being explicitly programmed.
The basics of machine learning:
Machine Learning algorithms can be classified into: Supervised Algorithms – Linear Regression, Logistic Regression, Support Vector Machine (SVM), Decision Trees, Random Forest. Unsupervised Algorithms – K Means Clustering. Reinforcement Algorithm.
Who should take this Machine Learning?
• Programmers, Developers, Architects, Technical Leads
• Developers who want to be a ‘Machine Learning Engineer’
• Analytics Managers leading a team of analysts
• Business Analysts who want to understand Machine Learning (ML) Techniques
• Business Analysts who want to understand Artificial Intelligence (AI) Techniques
• Information Architects who want to gain expertise in Predictive Analytics
• ‘Python’ professionals who want to design automatic predictive models
How much Salary can I Expect once I do Machine Learning?
The average pay for a Machine Learning Engineer is $42.50 per hour. The median Machine Learning Engineer has a base pay of $111,453. Salaries generally range from $76k to $153k as per payscale.com
What are the Top Companies hiring Machine Learning?
10. Salesforce – Intelligent CRMs
9. IBM – Better Healthcare
8. HubSpot – Smarter Sales
7. Baidu – The Future of Voice Search
6. Edgecase – Improving Ecommerce Conversion Rates
5. Google – Neural Networks and ‘Machines That Dream
4. Twitter – Curated Timelines
3. Facebook – Chatbot Army
2. Pinterest – Improved Content Discovery
1. Yelp – Image Curation at Scale
What are the Top Industries Hiring Machine Learning?
Telecom, Healthcare, Social Media, Analytics, Search Engines, neural Networks, e-Commerce
What's the Career Path to Machine Learning?
Here are the skills needed to begin and advance your machine learning career path:
• Basic Skills. As a conglomeration of math, data science and software engineering, machine learning will require you to be proficient in all three fields.
• Programming Skills.
• ML Programming Languages.
What is the best language for machine learning?
Top 5 best Programming Languages for Artificial Intelligence
1. Python. Python is considered to be in the first place in the list of all AI development languages due to the simplicity.
2. R. R is one of the most effective language and environment for analyzing and manipulating the data for statistical purposes.
3. Lisp.
4. Prolog.
5. Java
What's the Demand for Machine Learning by 2020?
Machine Learning focuses on the development of computer programs, and the primary aim is to allow computers to learn automatically without human intervention. Google says "Machine Learning is the future," and the future of Machine Learning is going to be very bright.
Where can I get trained for Machine Learning?
You can get trained at iCertGlobal, which offers Machine Learning, Artificial Intelligence and Robotic Process Automation.
What are the eligibility requirements to take up this Machine Learning?
Prerequisites
• Mastery of intro-level algebra. You should be comfortable with variables and coefficients, linear equations, graphs of functions, and histograms.
• Proficiency in programming basics, and some experience coding in Python. Programming exercises in Machine Learning Crash Course are coded in Python using TensorFlow.
How much does the Exam Cost?
Machines Learning with Python will costs you less than $400.
Why Companies Hire Machine Learning?
Machine Learning Engineer responsibilities include: Designing and developing machine learning and deep learning systems. Running machine learning tests and experiments. Implementing appropriate ML algorithms.
Roles and responsibilities of Machine Learning
Machine Learning Engineer responsibilities include: Designing and developing machine learning and deep learning systems. Running machine learning tests and experiments. Implementing appropriate ML algorithms.
7. Robotic Process Automation

What is Robotic Process Automation or RPA?
Robotic process automation (RPA) is the application of technology that allows employees in a company to configure computer software or a “robot” to capture and interpret existing applications for processing a transaction, manipulating data, triggering responses and communicating with other digital systems.
Robotic process automation (or RPA) is an emerging form of business process automation technology based on the notion of software robots or artificial intelligence (AI) workers. These tools also automate interactions with the GUI, and often do so by repeating a set of demonstration actions performed by a user.
Who should take this Robotic Process Automation or RPA?
There are no such prerequisites to learn RPA. From freshers to experienced professional, this technology is open for all. To master the concept of RPA, you need to have basic understanding of:
• Basic programming knowledge of using if/else and switch conditions
• Logical thinking ability
How much Salary can I Expect once I do Robotic Process Automation or RPA?
Average Salary of Robotic Process Automation Specialist is $126,094 (Indeed.com salary data)
What are the Top Companies hiring Robotic Process Automation or RPA?
Leading Players involved in the development of Robotic Process Automation:
• Automation Anywhere (U.S.)
• UiPath (Romania)
• Blue Prism (U.K.)
• Celaton Ltd (U.K.)
• IPSoft (U.S.)
• Nice Systems Ltd. (Israel)
• Pegasystems (U.S.)
• Redwood Software (U.S.)
• Verint (U.S.)
What's the Career Path to Machine Learning?
One of the most straightforward careers for an RPA expert is to become an RPA developer. With all the training and skills that one gain in their programs, this might be the best option for anyone.
The job of an RPA Developer is to build systems that can help to get a complete Robotics process automation work. For any professional, this would be something that they have trained in for months. These types of jobs pay well but sure they are time-consuming too. The projects are lengthy but all things considered being an RPA developer pays off well.
What's the Demand for Robotic Process Automation or RPA by 2020?
According to Forrester wave Q1 2017 Report, RPA Market Will Reach $2.9 Billion By 2021
Where can I get trained for Robotic Process Automation or RPA?
You can get trained at iCertGlobal.
What are the eligibility requirements to take up this Robotic Process Automation or RPA?
Prerequisites.
There are no such prerequisites to learn RPA. You don’t need any knowledge of programming language to use it to implement RPA.
How much does the Exam Cost?
RPA certification training costs $300.
Why Companies Hire Robotic Process Automation or RPA?
Here, we list top-5 benefits of implementing RPA software for your company.
1.) Reduced costs: By automating tasks, cost savings of nearly 30% can be achieved over the output of productivity. Software robots also cost less than a full time employee.
2.) Better customer experience: Deploying RPA frees up your high-value resources for them to be put back on the front line defining your customer success.
3.) Lower operational risk: By eliminating human errors such as tiredness or lack of knowledge, RPA reduces the rate of errors thereby providing a lower level of operational risk.
4.) Improved internal processes: In order to leverage AI and RPA, companies are forced to define clear governance procedures. This in turn, allows for faster internal reporting, on-boarding and other internal activities.
5.) Does not replace existing IT systems: One of the biggest advantages of using a virtual workforce, or an RPA bot is that it does not require you to replace your existing systems. Instead, RPA can leverage your existing systems, the same way a human employee can.
Roles and responsibilities of Robotic Process Automation or RPA
An RPA approach to streamline internal processes, where people and technology play their part in synchrony, enables better insight into trends and opportunities for business. Robotics process automation (RPA) works best with rule-based, regular tasks that require manual inputs.
8. Blockchain
.jpg)
What is Blockchain?
A global network of computers uses blockchain technology to jointly manage the database that records Bitcoin transactions. That is, Bitcoin is managed by its network, and not any one central authority.
Who should take this Blockchain?
Software Developers, IT Professionals, Engineers, Analysts, Technical Leads
How much Salary can I Expect once I do Blockchain?
Average yearly salary for "Blockchain Developer" ranges from $85k for Application Developer to $115k for Sr. Software Engineer as per indeed.com
What are the Top Companies hiring Blockchain?
Dell, vmware, Cisco, Honeywell, wipro.
What are the Top Industries Hiring Blockchain?
Telecom, Healthcare, Social Media, Analytics, Search Engines, neural Networks, e-Commerce
What's the Career Path to Blockchain?
For a Blockchain Developer, technical skills in the distributed ledger technology form the backbone of their career. A good place to start is Solidity for the development of Smart Contracts, and JavaScript for the development of a website.
What's the Demand for Blockchain by 2020?
According to the World Economic Forum, 18% of the world's GDP will be on Blockchain related technologies by 2025
Where can I get trained for Blockchain?
You can get trained at iCertGlobal.com.
What are the eligibility requirements to take up this Blockchain?
There are no prerequisites as such for this Blockchain Online Course. However, development experience on an object-oriented language, fundamentals of networking, and basic knowledge of command line & Linux would be advantageous. Further to brush up your skills,
How much does the Exam Cost?
The exam cost is $299 and it tests participants based on 100 questions spread across topics such as technical understanding, monetary implications, practical use, and regulations of cryptocurrencies. If you wish to take the training for this certification before you take the test, then it will cost you $2,995.
Why Companies Hire Blockchain?
Many industry leaders have already achieved significant business benefits, including greater transparency, enhanced security, improved traceability, increased efficiency and speed of transactions, and reduced costs. Read how blockchain provides these benefits to learn more about using blockchain in your industry
Roles and responsibilities of Blockchain
Responsibilities may include developing and implementing items like accelerators and assets, assisting with an organization's infrastructure setups utilizing technologies like Ethereum, and ensuring applications are secure. Blockchain engineers may analyze code artifacts and provide training to junior personnel.
9. Internet of Things

What is Internet of Things (IoT)?
The Internet of Things, commonly referred to as IoT, is the network of physical objects, devices, vehicles, buildings, and other items that's been integrated into the technology of modern electronics, software, sensors, and other “things” with network connectivity that enables them to collect and exchange data.
Who should take this Internet of Things (IoT)?
Software Developers, Engineers, Data Analysts, Big Data Professionals
How much Salary can I Expect once I do Internet of Things (IoT)?
Average salary of IoT Developer is $150k - Glassdoor.com
What are the Top Companies hiring Internet of Things (IoT)?
Dell, VMware, Cisco, Honeywell,
What are the Top Industries Hiring Internet of Things (IoT)?
Sensing — IoT endpoints
Communicating — IoT communications
Securing — IoT security
Understanding — IoT data and analytics
Acting — IoT artificial intelligence (AI)
What's the Demand for Internet of Things (IoT) by 2020?
By 2020, we will have over 50 billion devices connected to the Internet of Things.
The IoT will have an economic impact of up to $11 trillion by 2025 – McKinsey Global Institute.
There will be 250 million IoT connected automobiles creating new advancements in transportation by 2020.
Where can I get trained for the Internet of Things (IoT)?
You can get trained at iCertGlobal.com.
What are the eligibility requirements to take up this Internet of Things (IoT)?
There are no prerequisites for taking up this IoT training course.
IoT Certification Training on Azure demands an intermediate knowledge of the following:
Linux Fundamentals
Basic Python Programming
Working Knowledge of Azure IoT Hub and Azure Storage
How much does the Exam Cost?
The training cost works out to $400
Why Companies Hire Internet of Things (IoT)?
Internet of Things IoT for Businesses. Internet of things (IoT) is emerging as the next big revolution in the world of technology. A place where devices are smartly connected to communicate with each other. It can be anything; your smart phones, smart TVs, smart watches and smart homes.
Much of the IoT information will be stored in the cloud, so experts in providing cloud-based solutions will need to create storage big enough to host this volume of data, as well as enabling accessibility to facilitate a two-way process so that the provider of the data (you or me) is also able to consume the data. Hence, we will see an increase in SAN and server consultants.
Security professionals will be needed to guard against breaches in data protection, and to offer us some peace of mind that our data is not being accessed by those we would prefer not to access it.
Back-end developers will be required with skills in languages like NoSQL and, as we accumulate greater amounts of unstructured data in the form of sensory information, in developing non-relational databases.
Mobile app developers will have the opportunity to create apps that can harness data to provide live, up-to-date information that can inform our daily decision making.
Drones are set to be central to IoT, replacing sensors that would have been at rest on buildings, bridges or other infrastructure. Drones offer flexibility in information gathering due to their mobility. They have data collection and processing software, and GPS, built in for geo-processing. They are of huge benefit to organisations in the utility, transport, mining, mapping and energy sectors. They will require infrastructure to host data – usually in the cloud – which in turn will generate more work for the aforementioned storage and server consultants.
Roles and responsibilities of Internet of Things (IoT)
Dashboards play a big role in the internet of things. An IoT developer will be responsible for data processing, data storage, data preparation and dashboard development. A huge amount of data on countless different formats will be the standard in the world of an IoT developer.
Since Internet of Things involves communication between applications and physical devices, an IoT development team tends to be large, and different developers are assigned in different areas, among these software programming, hardware programming, security implementation, networking, and systems engineering.
10. Data science

What is Data science?
Data science is a field of Big Data geared toward providing meaningful information based on large amounts of complex data. Data science, or data-driven science, combines different fields of work in statistics and computation in order to interpret data for the purpose of decision making.
Who should take this Data science ?
Software Developers, Engineers, Data Analysts, Big Data Professionals
How much Salary can I Expect once I do Data science?
Despite a recent influx of early-career professionals, the median starting salary for a data scientist remains high at $95,000. Mid-level data scientist salary. The median salary for a mid-level data scientist is $128,750. If this data scientist is also in a managerial role, the median salary rises to $185,000.
What are the Top Companies hiring Data science ?
Angel Broking, Deloitte, HDFC, Ford Automotive, VM Ware, Exponentia, Clover Infotech, Value Direct, Virtusa, Credit Vidya, Guppy Media, Shzertech, Loginext, Persistent, L & T Finance, Whizminds, Mii app, K2 Analytics, Eclerx, Mobiliya, Emmfer, Suzlon, Infrasoft, Impact Analytics, IBM, Eigen Technologies, Intelenet, Pentation, Light app, Ixsight, Aangan NGO, Softcell, Nelsen etc.
What are the Top Industries Hiring Data science?
Make sure you don't overlook compact online Data Science courses that will provide exactly what you need to start your career in Data Science.
5 career options for graduates of Data Science.
Statistician.
Business intelligence reporting professional.
Data Analyst.
Data Mining or Big Data Engineer.
Program/Project Manager.
What's the Demand for Data science by 2020?
The number of Data Science and Analytics job listings is projected to grow by nearly 364,000 listings by 2020 - Forbes.
Where can I get trained for Data science?
You can get trained at iCertGlobal.com.
What are the eligibility requirements to take up Data science?
The prerequisites to learn data science:
You will find many data scientists with a bachelor's degree in statistics and machine learning but it is not a requirement to learn data science. However, having familiarity with the basic concepts of Math and Statistics like Linear Algebra, Calculus, Probability, etc. is important to learn data science.
Technical Skills: Computer Science
Python Coding. Python is the most common coding language I typically see required in data science roles, along with Java, Perl, or C/C++.
Hadoop Platform.
SQL Database/Coding.
Apache Spark.
Machine Learning and AI.
Data Visualization.
Unstructured data.
How much does the Exam Cost?
The training costs is around $300.
What is the career path to become a Data Scientist?
There are three general steps to becoming a data scientist:
1.) Earn a bachelor's degree in IT, computer science, math, physics, or another related field.
2.) Earn a master's degree in data or related field.
3.) Gain experience in the field you intend to work in (ex: healthcare, physics, business).
Why Companies Hire Data science?
Data Science and Its Growing Importance – An interdisciplinary field, data science deals with processes and systems that are used to extract knowledge or insights from large amounts of data. With advancements of so much of data, many aspects of data science are gaining immense importance, especially big data.
Roles and responsibilities of Data science
A data scientist is someone who makes value out ofdata. Data scientist duties typically include creating various machine learning-based tools or processes within the company, such as recommendation engines or automated lead scoring systems. People within this role should also be able to perform statistical analysis.
When it comes to programming, here are the list of courses are that quite in demand that draws attractive pay too.
Programming:
Most popular programming languages certification:
• Python
• Java
• C#
• Swift
• Scala
• R
• SAS
• JavaScript
• Typescript
We, at iCert Global offer you a wide array of courses and our Lead- Sales Consultants would be more than happy to clarify any concern you might have with regard to course offerings. We request you to spend time in checking our course catalog . www.icertglobal.com
ITIL is updating Version 3 to V4 ITIL
ITIL is updating! Version 3 to V4 | ITIL
So, ITIL is upgrading to V4
ITIL 4 is an evolution from ITIL v3, providing a practical and flexible transition that allows organizations
to adopt the new ways of working required by the modern digital world.
What’s different in ITIL 4
ITIL 4 reflects and introduces the modern methods of digital transformation like DevOps, Agile and Lean IT.
The ITIL version 3 has a different lifecycle and credit system as compared to the newly launched version
4. The ITIL 4 Foundation was successfully launched in the month of February 2019 as per Axelos release statement.
ITIL evolution
ITIL ® V1
– Focus on systems Mgmt
– Business support focus
ITIL ® V2
– Focus on processes Mgmt for IT Services
– Business alignment focus
ITIL ® V3
– Focus on service lifecycle Mgmt with the help of processes
– Business Integration focus
ITIL ® V4
– Focus Digital transformation & New ways of working
– Integration & Coordination Focus
ITIL 3
ITIL Qualification Structure
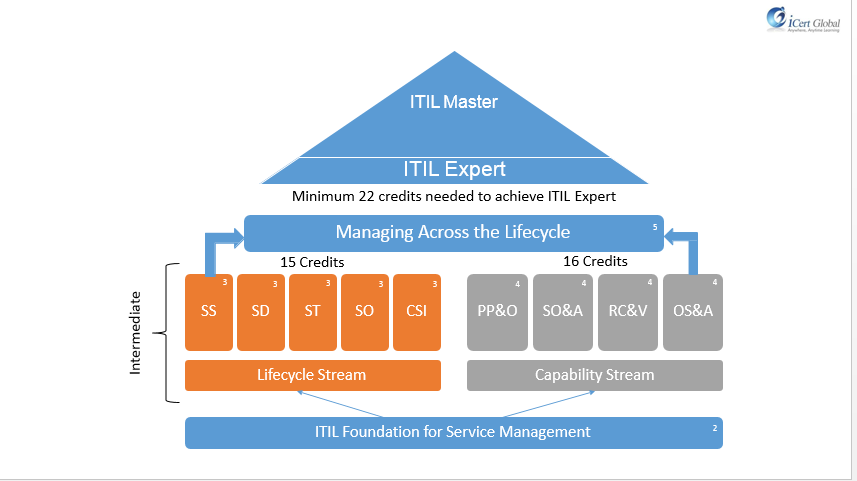
ITIL 4
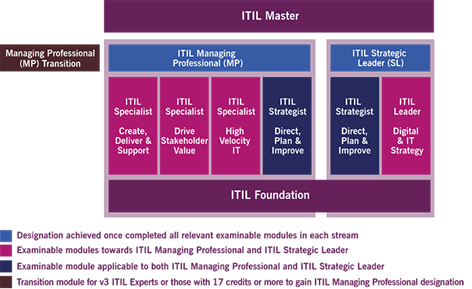
ITIL V4 Certification
In case you are doing ITIL V3, do not worry as your learning will be still be valuable but just hold it a
moment in pursuing further as ITIL 4 has a different pathway altogether. Remember, regardless of
ITIL V3 or V4, the core remains the same as we start off with Foundation Module and end up in Masters.
The modules in between changes.
As per the Axelos in their official page have reported that ITIL 4 expands on previous versions and
provides an end-to-end IT/digital operating model for the delivery and operation of tech-enabled
products and services.
Read More
ITIL is updating! Version 3 to V4 | ITIL
So, ITIL is upgrading to V4
ITIL 4 is an evolution from ITIL v3, providing a practical and flexible transition that allows organizations
to adopt the new ways of working required by the modern digital world.
What’s different in ITIL 4
ITIL 4 reflects and introduces the modern methods of digital transformation like DevOps, Agile and Lean IT.
The ITIL version 3 has a different lifecycle and credit system as compared to the newly launched version
4. The ITIL 4 Foundation was successfully launched in the month of February 2019 as per Axelos release statement.
ITIL evolution
ITIL ® V1
– Focus on systems Mgmt
– Business support focus
ITIL ® V2
– Focus on processes Mgmt for IT Services
– Business alignment focus
ITIL ® V3
– Focus on service lifecycle Mgmt with the help of processes
– Business Integration focus
ITIL ® V4
– Focus Digital transformation & New ways of working
– Integration & Coordination Focus
ITIL 3
ITIL Qualification Structure

ITIL 4

ITIL V4 Certification
In case you are doing ITIL V3, do not worry as your learning will be still be valuable but just hold it a
moment in pursuing further as ITIL 4 has a different pathway altogether. Remember, regardless of
ITIL V3 or V4, the core remains the same as we start off with Foundation Module and end up in Masters.
The modules in between changes.
As per the Axelos in their official page have reported that ITIL 4 expands on previous versions and
provides an end-to-end IT/digital operating model for the delivery and operation of tech-enabled
products and services.
PMP Exam Prep Certification Training Classroom Course in New York City, NY
iCert Global is conducting 4-day PMP® Certification Training courses in New York City. Our PMP certification training course is created by subject matter experts and delivered by experienced trainers. Enroll now for this PMP® Exam Prep Certification training course and accelerate the scope of your career as a certified project management professional.
Key Features of PMP® Certification Training in New York City (NYC)
- Comprehensive PMP Exam Prep Class- 4-day full-time intensive PMP Boot Camp- PMP classroom workshop conducted by an expert instructor- 35 Contact Hours Certificate- 2000+ PMP exam prep practice questions- 5 full-length PMP practice exams- Complimentary access to PMP E-learning- PMP® Program Handbook based on PMBOK® Guide - 6th Edition- Help with PMP Exam Application Process- Interactive PMP training workshop - Weekend and Weekday- Chapter-wise practice questions- Instructor-led Live-Online Training also available on demand
Benefits of PMP® Certification Training includes:
- Demonstrate your Project Management knowledge, experience, and skills to potential employers and clients - Provide professional skills necessary to lead project teams and bring projects to successful completion- Command higher salaries than non-certified individuals by showcasing competency in leading and directing projects with a PMP Certification- Accelerate your career to greater heights with a globally recognized Project Management certification- Improve your chances of growth by demonstrating your Project Management knowledge through an international certification- Get a globally recognized Project Management Certificate that is in-demand worldwide
The PMP Certification Training is an approach towards providing training for the project lifecycle, process groups, providing functional knowledge, business insights and techniques of managing projects effectively.
We provide the following options for you to choose your PMP Certification Training:
1. Instructor-led 4-day PMP Boot Camp in New York City for $1699 - Project Management Training Classroom Course
This 4-day instructor-led classroom training course in New York City will be conducted by an expert trainer with mock tests, practice questions, interactive sessions, and free e-learning.
The course also provides 35 contact hours, which is a mandatory requirement for applying for the PMP Examination.
2. PMP Training and PMI Membership for $1899 - Project Management Training and PMI Membership
This 4-day instructor-led PMP training classroom course includes annual Membership of the Project Management Institute, Inc.
3. PMP Training with PMI Membership and PMP Exam Fees Included $2299 - PMP Training, Membership, and PMP Exam Fees
This PMP training course includes 4-day PMP classroom training session, annual Membership to the Project Management Institute, Inc and the PMP Exam Fees. This is ideal for those that are looking at taking the PMP Exam at the earliest and this combination package provides access to 4 days of PMP training along with PMI Membership and PMP Exam fees and support for filling the PMP application form.
4. PMP Training Weekend Batch $1699 - PMP Boot Camp – Special Weekend Batches for Working Professionals
Weekend batches provide working professionals the time to enroll for intensive PMP training without compromising on their existing work commitments. This 4-day PMP certification training classroom course is spread over two weekends and includes interactive sessions by an expert trainer along with mock tests, practice questions and free e-learning.
5. PMP Training Live Virtual Class (LVC) Live Online Training $1099
4-day Instructor-led Live Online Training course conducted through Citrix GoToMeeting. This live virtual training class prepares you for the PMP Exam without the need to be physically present at a location. You can enroll for this training from the comfort of your home or office as per your convenience. Training is imparted by an experienced trainer in a live virtual setting through Citrix GoToMeeting with facilities for asking questions, clearing doubts, taking practice tests and learning in an interactive session without the compulsion of physically attending a classroom course. Live Virtual Class (LVC) is ideal for those working professionals who are unable to set a fixed schedule to attend a classroom training session. Learn from an expert trainer in a live online environment and prepare for the PMP Examination.
For more information on how iCert Global can help you to accelerate your career with a Project Management Professional certification, please e-mail info {at} icertglobal {dot} org or call now on +1-713-287-1213/ 1214 / 1053 / 1355.
We also provide complimentary PMP e-learning access through a Learning Management System for learners that book their seats for our PMP Classroom certification training courses.
For more information about our PMP Exam Prep certification training courses in New York City please fill-in the form on this page to contact our team or Call Now! on +1-713-287-1213/1214/1053/1355. You may also email us at info {at} icertglobal {dot} com.
About iCert Global:
iCert Global is an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide providing training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses. The organization has successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers. Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies.
Visit us at https://www.icertglobal.com for more information about our professional certification training courses in your location.
Read More
Enterprise Training | Corporate Training | Onsite Instructor-Led Classroom Training for Enterprise Learning Worldwide
Professional Certification Training courses worldwide for enterprises to empower their workforce.
iCert Global provides professional certification training courses in Project Management, Quality Management, Business Analysis, DevOps, Agile and Scrum, Cloud Computing, Data Analytics and more. The company's Enterprise Training portfolio encompasses 75+ courses across 15+ categories. Download Enterprise Training Brochure
Professional Certification Training Courses in Project Management, Quality Management, Business Analysis, Agile and Scrum, DevOps, Cloud Computing, Data Analytics and more. More than 75+ courses across 15+ categories. Download our Enterprise Training Brochure. Onsite instructor-led classroom training in your office premises.
Corporate training to upskill your employees. Instructor-led training classes for Project Management, Quality Management, Business Analysis, DevOps, Agile and Scrum, Cloud Computing and more. Live Online Training also available on demand as per your training schedule.
Onsite Classroom and Live Online Training. Multiple modes of training to achieve your company's learning and development objectives. Enterprise Workforce Development that accelerates growth by preparing your employees for professional certification exams.
Choose from 75+ courses across 15+ categories. Popular corporate training courses include PMP®, Lean Six Sigma Black Belt, Lean Six Sigma Green Belt, CBAP®, CCBA®, CAPM®, PMI-ACP®, Agile and Scrum, DevOps, and Cloud Computing among others.
Impart consistent training from certified trainers and accredited courseware created by subject matter experts. Onsite classroom training provided at your office premises across the globe.
Certify your employees and upgrade their skills to bag more projects and get more client wins by showcasing qualified resources with globally recognised certifications to potential clients to win those important projects.
Our course content is created by Subject Matter Experts and our professional certification trainings are conducted by certified instructors with training and real-life consulting experience.
Enable your employees to gain knowledge and also prepare for International certifications through a mix of in-house instructor-led classroom training and e-learning to practice and reinforce the concepts learnt in class. Learn from certified trainers and engage your employees in interactive training sessions that develops their intellectual curiosity.
Motivate your employees by providing them opportunities of upskilling themselves and as a by-product get qualified professionals with globally recognised certifications to showcase in your team when bidding for innovative and challenging projects.
Enable Enterprise Workforce Development to accelerate company and employee growth.
For more information about our instructor-led classroom and live online training professional certification Corporate Training courses worldwide, please fill-in the form from the link below.
Read More
Test Your PMP® Exam Preparation with these 30 PMP® (Project Management Professional) Exam Prep Practice Questions
PMP® certification is the most prestigious and premier certification in Project Management that is widely acclaimed and globally renowned. Let’s face it – the PMP exam is the perhaps the toughest to pass in the first attempt and hence calls for a great commitment and rigorous preparation through study and practice tests.
The preparatory questions presented below can be attempted by project management professionals, aspirants including those who are already PMP certified.
1. Aspiring Professionals who plan to take up the PMP® ExamThis test of Project Management skills in a 30-question format will serve as a prelude to the PMP exam you plan to take up in the immediate future. It’s a test of your proficiency with project management concepts, methodologies and practices. Make an attempt to find out how you fare in the first try and figure out your strength and shortcomings. This will prove to be a stepping stone for the success to come in becoming PMP certified.
2. Professionals who wish to sign-up for PMP® ExaminationCandidates considering to crack the PMP exam based on 6th edition will find the preparatory questions listed below as a curtain raiser as the questions are framed more in the lines of the actual PMP Exam. The structure and severity of questions are very similar to the final PMP exam conducted by PMI. Treat these 30 questions as a preview to the 200-exam PMP exam that will help you to identify your core strength and weakness with Project Management. Forewarned is forearmed. So when you know what’s that lacking and wanting will help you prepare the gap analysis of your project management skills to both sign-up and sit for the PMP exam.
3. Professionals who are already PMP® CertifiedChances are that you might have appeared for the PMP Exam based on the PMBOK® Guide - Fifth Edition, or earlier and hence might be a bit rusty. This test will help you to assess your standing with regard to the PMBOK® Guide - Sixth Edition. You can brush up your skills and sharpen the saw by upgrading yourself with the latest project management practice as prescribed in the PMP training. Professionals armed with a PMP certification can treat this questionnaire as a revision and the results will reflect your competency in being conversant with the current trends and practices in Project Management.
PMP Exam Prep - 30 Sample PMP Exam Questions based on the PMBOK Guide - Sixth Edition
If you are interested in attempting more questions, please follow link below to Download Free Full-Length PMP Practice Test with 200 questions.
1. Project management is:
A. The integration of the critical path method and the Earned ValueManagement system.B. The application of knowledge, skills, tools, and techniques to projectactivities to meet the project requirements.C. The application of knowledge, skills, wisdom, science, and art toorganizational activities to achieve operational excellence.D. A subset of most engineering and other technical disciplines.
2. A Project is:
A. A set of sequential activities performed in a process or system.B. A revenue-generating activity that needs to be accomplished whileachieving customer satisfaction.C. An ongoing endeavor undertaken to meet customer or marketrequirements.D. A temporary endeavor undertaken to create a unique product,service, or result.
3. Portfolio management refers to:
A. Managing various contents of the project file.B. Managing the levels of the levels of financial authority to facilitateproject decision makingC. The centralized management of one or more portfolios to achievestrategic objectives.D. Applying resource leveling heuristics across all the organization’sstrategic objectives.
4. All of the following are true about projects and operations EXCEPT:
A. Operations are ongoing endeavors that produce repetitive outputs,with resources assigned to do basically the same set of tasksaccording to the standards institutionalized in a product life cycle,whereas projects are temporary endeavors.B. Projects require project management activities and skill sets,whereas operations require business process management,operations management activities, and skill sets.C. Projects can intersect with operations at various points duringthe product life cycle. At each point, deliverables and knowledge aretransferred between the project and operations for implementationof the delivered work.D. Because of their temporary nature, projects cannot help achievean organization’s long-term goals. Therefore, strategic activities inthe organization can be generally addressed within theorganization’s normal operations.
5. A Program is a:
A. Group of related tasks lasting one year or less.B. Group of related projects, subsidiary programs, and programactivities managed in a coordinated manner.C. Large projects with significant cost and resource requirements.D. Sequence of activities constituting a major project.
6. All of the following are questions that the key stakeholders andproject managers should answer to develop the project successmeasures EXCEPT:
A. What does success look like for the project?B. How will success be measured?C. What are the communication requirements?D. What factors may impact success?
7. Your job responsibility is to align components (projects, programs,or related operations) to the organizational strategy, organizedinto portfolios or subsidiary portfolios to optimize project orprogram objectives, dependencies, costs, timelines, benefits,resources, and risks. This is known as:
A. Components management.B. Process management.C. Program management.D. Portfolio management.
8. The collection of generally sequential and sometimes overlappingproject phases, whose name and number are determined by themanagement and control needs of the organization ororganizations involved in the project, is known as the:
A. Project waterfall.B. Project life cycle.C. Project life stages.D. Project Management Process Groups.
9. The PMBOK® Guide (The Project Management Body of Knowledge Guide) is the standard for:
A. Managing all projects all of the time,B. Managing all projects most of the time.C. Managing most projects most of the time.D. Managing some projects some of the time.
10. All of the following are true about project phases and the projectlife cycle EXCEPT:
A. Stakeholder influences, risk, and uncertainty are greatest at the startof the project. These factors decrease over the life of the project.B. The ability to influence the final characteristics of the project’sproduct, without significantly impacting cost, is highest at thestart of the project and decreases as the project progresses towardcompletion.C. The cost of changes and correcting errors typically increasessubstantially as the project approaches completion.D. Cost and staffing levels are generally steady throughout the projectlife cycle .
11. You are managing a project in which you intend to respond to highlevels of change and ongoing stakeholder involvement. The mostsuitable project life cycle for your project is the:
A. Predictive life cycle.B. Adaptive life cycle.C. Waterfall life cycle.D. Configuration management life cycle.
12. All of the following statements about the project life cycle and theproduct life cycle are true EXCEPT:
A. In the project predictive life cycle, the project scope and the timeand cost required to deliver that scope are determined as early inthe project life cycle as practically possible.B. In the project iterative and incremental life cycles, project phasesintentionally repeat one or more project activities as the projectteam’s understanding of the product increases.C. The product life cycle is the series of phases that represent theevolution of a product, from concept through delivery, growth,maturity, and to retirementD. The product life cycle is contained within the predictive project lifecycle.
13. Project Management Processes:
A. May be overlapping activities that occur throughout the project.B. May be overlapping activities that generally occur at the same levelof intensity within each phase of the project.C. Are generally discrete, one-time events.D. Are discrete, repetitive events that occur generally at the same levelof intensity throughout each phase of the project
14. The five Project Management Process Groups are:
A. Planning, Checking, Directing, Monitoring, and Recording.B. Initiating, Planning, Executing, Monitoring and Controlling & Closing.C. Planning, Executing, Directing, Closing, and Commissioning.D. Initiating, Executing, Monitoring, Evaluating & Closing.
15. For a project to be successful, the project should generallyachieve all of the following EXCEPT:
A. Achieving stakeholder satisfaction.B. Striving to obtain acceptable customer/end-user adoption.C. Appling knowledge, skills, and processes within the ProjectManagement Process Groups uniformly to meet the projectobjectives.D. Fulfilling other agreed-upon success measures or criteria.
16. The project business case is all of the following EXCEPT:
A. Documented economic feasibility study used to establish the validityof the benefits of a selected component lacking sufficient definitionand that is used as a basis for the authorization of further projectmanagement activities.B. A document that lists the objectives and reasons for projectinitiation.C. A document that serves as an important input to the projectinitiation and is seldom used after the project is approved.D. An important document that may result in a go/no-go decision forthe project.
17. The key elements of the benefits management plan are all of thefollowing EXCEPT:
A. Work Breakdown Structure.B. Benefits owner.C. Assumptions.D. Strategic alignment.
18. The linkages between project management processes are bestdescribed by the following:
A. The work breakdown structure links processes.B. Processes are linked by their planned objectives-the summaryobjective of one often becomes the detailed action plan for anotherwithin the project, sub-project, or project phase.C. Processes are linked by the outputs that are produced-the outputof one process generally becomes an input to another process or isa deliverable of the project, sub-project, or project phase.D. There are no significant links between discrete processes.
19. Project tailoring is an important consideration for most projects.Which of the following is the least likely project consideration?
A. Project manager’s skills and competency.B. Each project is unique.C. Addressing competing constraints.D. Level of project governance varies.
20. A significant amount of data is collected and analyzed throughoutthe project. All of the following are examples of project data andinformation EXCEPT:
A. Work performance data.B. Work performance analysis.C. Work performance information.D. Work performance reports.
21. All of the following are true about the statement of work (SOW)for a procurement EXCEPT:
A. It describes the procurement item in sufficient detail to allowprospective sellers to determine if theyB. Are capable of providing the products, services, or results.C. It should be as ambiguous, incomplete, and wordy as possible toallow for future negotiations.D. It can include specifications, quantity desired, quality levels,performance data, period of performance, work location, and otherrequirements.E. It can be revised and refined as required as it moves through theprocurement process until incorporated into a signed agreement.
22. Source selection criteria are developed and used to rate or scoreseller proposals. These criteria generally have all of the followingcharacteristics EXCEPT:
A. They are often included as a part of the procurement documents.B. They can be objective or subjective.C. They may be limited to only the purchase price if the procurementitem is readily available from a number of acceptable sellers.D. They generally require specification of the name of thetransportation organization responsible for delivery of procuredproducts.
23. All legal contractual relationships generally fall into one of thefollowing broad categories EXCEPT:
A. Request For Proposal (RFP).B. Fixed-price contracts.C. Cost-reimbursable contracts.D. Time And Material Contracts (T&M).
24. All of the following are tools and techniques of the ConductProcurements process EXCEPT:A. Interpersonal and team skills.B. Bidder conferences.C. Expert judgment.D. Proposal evaluation techniques.
25. Which of the following is NOT a process in Project StakeholderManagement?
A. Identify Stakeholders.B. Control Stakeholder Engagement.C. Monitor Stakeholder Engagement.D. Manage Stakeholder Engagement.
26. In developing a stakeholder register, you need to include all of thefollowing EXCEPT:
A. Identification information.B. Assessment information.C. Stakeholder classification.D. Project risk information.
27. All of the following are external environmental factors EXCEPT:
A. Legal restrictions.B. Organizational values and principles.C. Competitive movements.D. Economic conditions.
28. All of the following are potential information in organizationalknowledge repositories EXCEPT:
A. Metrics used to collect and make available measurement data onprocesses and products.B. Configuration management.C. Tacit knowledge of previous projects such as project performancedata and lessons learned.D. Issue and defect management data.
29. A primary function of a Project Management Office (PMO) is tosupport project managers in a variety of ways, which may includeall of the following EXCEPT:
A. Intervening in project execution directly and without involving theproject manager.B. Managing shared resources across all projects administered by thePMO.C. Identifying and developing project management methodology, bestpractices, and standards.D. Coaching, mentoring, training, and oversight.
30. The types of Project Management Office (PMO) structures inorganizations include all of the following EXCEPT:
A. Supportive PMOs that provide a consultative role to projects bysupplying templates, best practices, training, access to information,and lessons learned from other projects.B. Controlling PMOs that provide support and require compliancethrough various means.C. Harmonizing PMOs that strive to reduce conflict and improveharmony among project team members.D. Directive PMOs that take control of the projects by directly managingthe projects.
Please provide your answers in the Comments section below. First 10 all correct answers will receive a 10% discount code on our upcoming PMP Exam Prep Certification Training classes at a location near you.
If you found these 30 sample PMP practice questions interesting, please follow link below to Download full-length PMP Exam Practice Test with 200 questions.
iCert Global is a leading provider of Professional Certification training courses worldwide. Our endeavor is to enable working professionals to expand the scope of their career through professional certification training courses.
Visit www.icertglobal.com for more information about our PMP Exam Prep Certification Training Courses courses worldwide
PMI®, PMP®, PMBOK® are registered marks of the Project Management Institute, Inc.
Read More
Top 10 High Paying Certifications to Target in 2020 | Cyber Security, AWS, Google Cloud, Data Science, PMP, CSM
10 Top Paying Certifications To Target In 2020
2019 has been a great year so far! Many new technologies grabbed a lot of attention this year. It will continue to shape up the future and beyond. Cloud Computing, Internet of Things(IoT), Big Data, Cyber Security, and other emerging technologies are changing the way companies do business and taking technology innovation to a higher level.
In this highly competitive and technology-driven world, wherein everyone is giving their best to prove their excellence and stand out in the crowd. Professional certification helps to scale up and stay updated with the latest technology trending in the industry. Along with many job opportunities for candidates, Professional Certifications also helps employers to select the potential candidate.
The 10 top-paying certifications to target in 2020 are:
1. Certified Information Systems Security Professional® (CISSP)
2. AWS Certified Solutions Architect
3. Google Certified Professional Cloud Architect
4. Big Data Certification
5. Data Science Certification
6. Certified In Risk And Information Systems Control (CRISC)
7. Certified Information Security Manager(CISM)
8. Project Management Professional (PMP)® Certification
9. Certified Ethical Hacker (CEH)
10. Certified Scrum Master (CSM)
Search queries for the term 'cyber security certifications' over the past five years, as per Google Trends.
Data dt. 8th November 2019.
Search queries for the term, 'scrum certification' over the past five years, as per Google Trends.
Data as of 8th November 2019.
Comparison of Cyber Security courses search queries (CISSP, CEH, CISM, and CRISC), over the past five years from 2014 onwards until date, as per Google Trends. Data dt. 8th November 2019.
1. Certified Information System Security Professional® (CISSP)
The Certified Information Systems Security Professional (CISSP), a certification accredited by International Information Systems Security Certification Consortium, (ISC)², is one of the world's largest IT security organizations. CISSP certified professionals are considered specialists on key security issues. This includes mobile security, risk management, application development security, cloud computing, among others.
According to Cybercrime Magazine, Cybersecurity Ventures predicted that cybercrime damages will cost the world $6 trillion annually by 2021. To mitigate these damages, there will be 3.5 million unfilled cybersecurity jobs globally by 2021.
· They also predict that there will be 6 billion Internet users by 2022 (75 percent of the projected world population of 8 billion) — and more than 7.5 billion Internet users by 2030 (90 percent of the projected world population of 8.5 billion, 6 years of age and older).
According to ziprecuriter.com, the Certified Information Systems Security Professional (CISSP) salary can go as high as $171,000
CISSP Average Annual Salary in the United States
Data as of 1st November 2019.
Eligibility criteria:
- Have a minimum 5 years of cumulative paid full-time work experience in two or more of the 8 domains of the (ISC)² CISSP Common Body of Knowledge (CBK)
- One-year experience waiver can be earned with a 4-year college degree, or regional equivalent or additional credential from the (ISC)² approved list.
How to become a Certified Information System Security Professional®( CISSP)?
Get trained for CISSP which validates your knowledge on information security. Apply for CISSP online, clear the exam, and you must ask an (ISC)² credential holder who can attest to your industry experience to complete an endorsement form for you if (ISC)² randomly selects(ISC)² -certified individuals for auditing. Successful completion of the certification entitles to automatic membership to the International Information Systems Security Certification Consortium (ISC)² Membership. The CISSP certification has a three-year validity. You need 120 continuing professional education (CPE) credits for renewal.
2. AWS Certified Solution Architect
AWS Certified Solutions Architects are one of the leading professionals in cloud computing. This certification is accredited by Amazon Web Services. AWS architect is someone who can evaluate an organization's requirements in cloud computing and make architectural recommendations for implementing and deploying applications on AWS.
· Currently, 69% of businesses are already utilising cloud technology and it is predicted that 83% of enterprise workloads will be in the Cloud by 2020.
· The public cloud market is expected to reach $236 billion by 2020, and AWS is the topmost cloud computing player with a 43% yearly growth.
According to ziprecruiter.com, AWS Certified Solutions Architect’s salary can go as high as $202,000
AWS Certified Solutions Architect - Average Annual Salary in the United States
Data as of 1st November 2019.
Cloud services such as Amazon Web Services (AWS), Google Cloud, and Microsoft Azure appeal to many organizations because of their stated features, such as pay per use, ability to scale up or down based on usage, high resiliency, and self-service. All these benefits are expected to lead to much lower IT costs, faster time to market, and better service quality compared with traditional IT offerings.
Eligibility criteria:
- At least one-year hands-on experience in cloud and AWS. These professionals should know about topics such as business continuity, deployment management, network design, data storage, security, scalability and elasticity, cloud migration and hybrid architecture.
How to become an AWS Certified Solution Architect?
First, you will need to set up an AWS Account. All AWS certifications are conducted at PSI test-taking facilities—typically a local community college. By taking up AWS Solution Architect training course you get well-versed with concepts, fundamentals, architectural best practices, designs and deployment of scalable systems on AWS.
3. Google Certified Professional Cloud Architect
Google Certified Professional Cloud Architect certification is currently the industry standard to help you emerge above the rest in this cloud job world. Google Cloud Platform (GCP) has evolved from being a niche player to a serious competitor to Amazon Web Services and Microsoft Azure. According to Fiormarkets, Global cloud computing market is expected to reach USD 712.83 Billion by 2025, at a CAGR of 18.46% from 2018 to 2025.
As per an article on Dataversity.net, according to Gartner TalentNeuron, an online real-time labour market insight portal, “there are about 50,248 cloud computing positions available in the U.S. from 3,701 employers, and 101,913 open positions worldwide.”
According to ziprecuriter.com, the Google Certified Professional Cloud Architect‘s salary can go as high as $201,500/year.
Google Cloud Platform - Average Annual Salary in the United States
Data as of 1st November 2019.
Eligibility Criteria:
The Cloud Architect should have 3+ years of industry experience as well as 1-year designing and building solutions on Google Cloud Platform.
How to become a Google Certified Professional Cloud Architect?
Register with Google cloud, Enhance your skill in Cloud adoption plans, Cloud application design, Cloud management and monitoring, Application architecture, Deployment strategies and get certified.
4. Big Data Certification
"Big Data" is a field that treats ways to analyze, systematically extract information from, or otherwise deal with data sets that are too large or complex to be dealt with by traditional data-processing application software.
A Big Data Certification will equip you with the skills and knowledge to tackle the 3 Vs of Big Data - Volume, Velocity, and Variety.
For professionals, who are skilled in Big Data Analytics, there is an ocean of opportunities out there. There is a huge demand for big data professionals in industries like entertainment, automobile, government, education etc. According to Forbes, IBM stated that by 2020, the number of jobs for all US data professionals will increase by 364,000 openings to 2,720,000.
According to ziprecuriter.com, Big Data Certified professional's salary can go as high as $196,000/year
Big Data Analytics - Average Annual Salary in the United States
Data as of 1st November 2019.
Eligibility criteria:
There is no such eligibility criteria to take up Big Data Certification. Preferable to be acquainted with the Core Java and SQL.
How to get certified in big data?
Enhance your skill by enrolling in Big data certification course. Prepare yourselves with quality study material and attempt as many mock exams to check and confirm your proficiency in the subject matter.
5. Data Science Certification:
Data science is a multi-disciplinary field that uses scientific methods, processes, algorithms and systems to extract knowledge and insights from structured and unstructured data.
The Data Scientist certification is a certification which validates data scientist’s knowledge on SAS, R, Hadoop, Python and Spark and how to use data concepts such as data exploration, visualization hypothesis testing, and predictive analytics. There is a huge demand for Data Scientists in industries like Aerospace industry, IT industry, e-commerce industry and healthcare industry. According to Forbes, IBM predicts that demand for Data Scientists will increase by 28% by 2020. IBM also predicts that 59% of all Data Science and Analytics (DSA) job demand is in Finance and Insurance, Professional Services, and IT.
According to ziprecuriter.com, the Data Science Certified professional's salary can go as high as $185,000/year
Data Scientist - Average Annual Salary in the United States
Data as of 1st November 2019.
Eligibility Criteria:
There are no prerequisites for this data science online training course.
How to get certified in Data Science?
Go for the Data scientist training course. Gain well-versed knowledge on using tools such as statistic hypothesis testing, clustering, decision trees, linear and logistic regression, R studio and Data Visualization. Pass the exam and get certified as a Data Scientist.
6. Certified In Risk And Information Systems Control (CRISC)
The Certified in Risk and Information Systems Control (CRISC) is the certification accredited by Information Systems Audit and Control Association (ISACA) which engages in the development, adoption and use of globally accepted, industry-leading knowledge and practices for information systems. CRISC professionals are one of of the highest-paid employee. The curriculum is based on 4 domains prescribed by ISACA.
Domain 01 - Risk Identification
Domain 02 - Risk Assessment
Domain 03 - Risk Response
Domain 04 - Risk and Control Monitoring and Reporting
· More than 20,000 professionals worldwide have earned the CRISC to affirm their business and IT risk management competence, and their ability to design, implement, monitor and maintain effective, risk-based information systems controls.
· More than 1,300 CRISC holders are CIOs, CISOs, or chief compliance, risk or privacy officers and over 600 are CEOs, CFOs or equivalent executives.
CRISC certification makes you highly valuable to enterprises seeking to manage IT risk as a critical component of the innovation process.
According to ziprecuriter.com, the Certified in Risk and Information Systems Control (CRISC) salary can go as high as $143,000/year
CRISC Average Annual Salary in the United States
Data as of 1st November 2019.
Eligibility Criteria:
According to ISACA, The requirements for CRISC Certification – 2015 exams and later are:
- Successful completion of the CRISC examination
- Three (3) or more years of cumulative work experience performing the tasks of a CRISC professional across at least two (2) CRISC domains, of which one must be in Domain 1 or 2, is required for certification. There are no substitutions or experience waivers.
- This experience must have been gained within the 10-year period preceding the application date for certification or within five years of passing the examination.
- A completed application must be submitted within 5 years from the date of initially passing the examination.
How to become a Certified In Risk And Information Systems Control (CRISC)?
First, candidates must register and pay a non-refundable and non-transferable fee prior to becoming eligible to schedule their test. To register for the CRISC exam, candidates must create an ISACA profile at www.isaca.org. After the login, candidates can schedule the exam. Candidates who clear the examination need to pay a maintenance fee and earn a minimum of 20 contact hours of CPE annually. Additionally, a minimum of 120 contact hours is required during a fixed 3-year period.
7. Certified Information Security Manager (CISM)
Data as of 1st November 2019.
Certified information security manager (CISM) is accredited by the Information Systems Audit and Control Association (ISACA). CISM supervises enterprise information security. As recommended by ISACA, There are 4 primary domains to be focused on to get CISM Certification:
· Information Security Governance.
· Information Risk Management.
· Information Security Program Development and Management.
· Information Security Incident Management.
According to ziprecuriter.com, the Certified information security manager (CISM) salaries can reach up to $216,000 per year.
CISM Average Annual Salary in the United States
Eligibility criteria:
- A completed application must be submitted within 5 years from the date of initially passing the examination.
- All experience must be verified independently with employers.
- This experience must have been gained within the 10-year period preceding the application date for certification or within five years of passing the examination.
- Three (3) years of the five (5) years of work experience must be gained performing the role of an information security manager
- In addition, this work experience must be broad and gained in three (3) of the four (4) CISMR domains
How to become a certified information security manager (CISM)?
Take up the course, gain knowledge on four domains and register with ISACA or exam locator. Every year, the exam is offered by ISACA during the designated testing of windows. Clear the exam and get credentials. Continuing education credits are required each year to maintain your certification.
8. Project Management Professional (PMP)® Certification
Data as of 1st November 2019.
Project Management Professional (PMP) accredited by Project Management Institute (PMI) is an industry-standard certification which is globally recognized. According to the PMI (2013). Talent Gap: Project Management through 2020 article by the Project Management Institute, Inc. - Through the decade ending in 2020, 15.7 million new project management roles will be created. The profession is expected to grow by US$6.61 trillion. Now is the time for professionals and job-seekers to build project management skills, as demand for these skills outstrips supply.
The PMP Certification has consistently been among the top ranked certifications worldwide and according to the 10th edition of PMI’s Project Management Salary Survey, Project Management Institute’s (PMI) Earning Power Report reveals a significant advantage in earning potential for PMP® certified practitioners. Survey respondents holding the Project Management Professional (PMP)® certification reported higher median salaries than those without a PMP certification―23% higher on average across the 37 countries surveyed.
A PMP certification demonstrates your Project Management knowledge, experience, and skills to potential employers and clients. It also provides professional skills necessary to lead project teams and bring projects to successful completion. A PMP certification will enable you to command higher salaries than non-certified individuals by showcasing competencies in leading and directing projects. Accelerate and expand the scope of your career with a globally recognized and in-demand certification. Know more about our PMP Exam Prep Certification Training courses at a location near you.
According to ziprecruiter.com, Project Management Professional's salary can go as high as $172,000
PMP - Average Annual Salary in the United States
Eligibility criteria:
For Graduates:
- 3 years or 4,500 hours of project management experience
- 35 hours of project management education
For non-graduates
- 5 years or 7,500 hours of project management experience
- 35 hours of project management education
How to become a Project Management Professional (PMP) ®?
Create a professional profile by signing up at PMI.org. Take 35 hours of PMP® Certification training course. For a special discount on PMP exam application fee and the access to a free PDF copy of the PMBOK Guide, apply for PMI membership. Fill the online application within 90 days. You can schedule the exam at your nearest test centres. Once you qualify the test, get PMP® certification. Your credentials are valid for only three years. You need to maintain your PMP® certification by earning 60 PDUs to fulfil the Continuing Certification Requirements (CCR).
Test your level of preparation for the PMP (Project Management Professional) Examination.
Free Download full-length PMP Exam Practice Test with 200 PMP Questions.
9. Certified Ethical Hacker (CEH)
Certified Ethical Hacker, accredited by EC-Council(The international council of E-Commerce consultants), validates the baseline knowledge on five phases of ethical hacking. These are:
· Reconnaissance,
· Gaining Access,
· Enumeration,
· Maintaining Access,
· Covering your tracks.
CEH Stimulates the real-time threats, counter-defensive mechanisms to eliminate threats and protective measures to prevent attacks. CEH simulates real-time threats, counter-defensive mechanisms to eliminate threats and protective measures to prevent attacks and breaches. There is a difference between Hacker and ethical hacker. Hacker hacks the system and steals the information, while CEH defends attacks and threats using the same techniques the hacker used. CEH professionals are in-demand and are internationally recognized because of the continuous updates of tools and techniques.
According to ziprecuriter.com, Certified Ethical Hacker salaries can go up to $220,000 per year.
CEH - Average Annual Salary in the United States
Eligibility criteria:
There are no such eligibility criteria to take up CEH. Basic knowledge of Transmission Control Protocol/Internet Protocol (TCP/IP) is advised.
How to become a Certified Ethical Hacker?
Take up training on CEH to learn tools and programs used for security, ethics, network security etc. With the knowledge of the above mentioned skills, you can pass the exam. The CEH certification is valid for three years and can be renewed by earning 120 continuing education credits within the three-year period.
10. Certified Scrum Master (CSM)
Certified Scrum Master, accredited by Scrum Alliance validates the knowledge of Agile principles and practices and makes you more noticeable than others. According to the State of Agile report, the Scrum Methodology is most widely used amongst software development creating many job opportunities.
According to ziprecruiter.com, Certified Scrum Master Salary can reach from median of $118,353/year to $160,000/year.
CSM - Average Annual Salary in the United States
Data as of 1st November 2019.
Eligibility criteria:
There is no such eligibility criteria to take up CSM. You can become a Certified Scrum Master regardless of your educational background.
How to become a Certified Scrum Master?
To become a certified Scrum Master, you need to take the Certified Scrum Master course from Certified Scrum Trainer (CST) or Scrum Alliance Authorized Trainer. Scrum Alliance will send you a link to create login credentials after completion of course. Clear the exam and get certified along with two-year membership with Scrum Alliance.
For more information on how you can accelerate your career with these certifications, visit us at https://www.icertglobal.com/ or call now on +1-713-287-1213 / 1214 or e-mail us at info {at} icertglobal {dot} com.
Know more about our Professional Certification Training Courses for preparing for the above certifications.
CISSP Certification Training Courses
AWS Certified Solutions Architect Certification Training Courses
Google Cloud Platform Fundamentals Certification Training Courses
Big Data Certification Training Courses
Data Science Certification Training Courses
CRISC Certification Training Courses
CISM Certification Training Courses
PMP Certification Training Courses
Free Download: PMP Practice Test with 200 Questions
CEH Certification Training Courses
CSM Certification Training Courses
We provide instructor-led classroom and instructor-led live online training across the globe. We also provide Corporate Training for enterprise workforce development.
Connect with us:
- Subscribe to our YouTube Channel
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
- PMP Certification Training
- CAPM Certification Training
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
iCert Global both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in 2020? Let us know your thoughts in the 'Comments' section below.
Thank you for reading this blog post. Hope you found it useful and interesting. Team iCert Global wishes you all the best for your learning endeavors.
Read More
10 Top Paying Certifications To Target In 2020
2019 has been a great year so far! Many new technologies grabbed a lot of attention this year. It will continue to shape up the future and beyond. Cloud Computing, Internet of Things(IoT), Big Data, Cyber Security, and other emerging technologies are changing the way companies do business and taking technology innovation to a higher level.
In this highly competitive and technology-driven world, wherein everyone is giving their best to prove their excellence and stand out in the crowd. Professional certification helps to scale up and stay updated with the latest technology trending in the industry. Along with many job opportunities for candidates, Professional Certifications also helps employers to select the potential candidate.
The 10 top-paying certifications to target in 2020 are:
1. Certified Information Systems Security Professional® (CISSP)
2. AWS Certified Solutions Architect
3. Google Certified Professional Cloud Architect
4. Big Data Certification
5. Data Science Certification
6. Certified In Risk And Information Systems Control (CRISC)
7. Certified Information Security Manager(CISM)
8. Project Management Professional (PMP)® Certification
9. Certified Ethical Hacker (CEH)
10. Certified Scrum Master (CSM)
Search queries for the term 'cyber security certifications' over the past five years, as per Google Trends.
Data dt. 8th November 2019.
Search queries for the term, 'scrum certification' over the past five years, as per Google Trends.
Data as of 8th November 2019.
Comparison of Cyber Security courses search queries (CISSP, CEH, CISM, and CRISC), over the past five years from 2014 onwards until date, as per Google Trends. Data dt. 8th November 2019.
1. Certified Information System Security Professional® (CISSP)
The Certified Information Systems Security Professional (CISSP), a certification accredited by International Information Systems Security Certification Consortium, (ISC)², is one of the world's largest IT security organizations. CISSP certified professionals are considered specialists on key security issues. This includes mobile security, risk management, application development security, cloud computing, among others.
According to Cybercrime Magazine, Cybersecurity Ventures predicted that cybercrime damages will cost the world $6 trillion annually by 2021. To mitigate these damages, there will be 3.5 million unfilled cybersecurity jobs globally by 2021.
· They also predict that there will be 6 billion Internet users by 2022 (75 percent of the projected world population of 8 billion) — and more than 7.5 billion Internet users by 2030 (90 percent of the projected world population of 8.5 billion, 6 years of age and older).
According to ziprecuriter.com, the Certified Information Systems Security Professional (CISSP) salary can go as high as $171,000
CISSP Average Annual Salary in the United States
Data as of 1st November 2019.
Eligibility criteria:
- Have a minimum 5 years of cumulative paid full-time work experience in two or more of the 8 domains of the (ISC)² CISSP Common Body of Knowledge (CBK)
- One-year experience waiver can be earned with a 4-year college degree, or regional equivalent or additional credential from the (ISC)² approved list.
How to become a Certified Information System Security Professional®( CISSP)?
Get trained for CISSP which validates your knowledge on information security. Apply for CISSP online, clear the exam, and you must ask an (ISC)² credential holder who can attest to your industry experience to complete an endorsement form for you if (ISC)² randomly selects(ISC)² -certified individuals for auditing. Successful completion of the certification entitles to automatic membership to the International Information Systems Security Certification Consortium (ISC)² Membership. The CISSP certification has a three-year validity. You need 120 continuing professional education (CPE) credits for renewal.
2. AWS Certified Solution Architect
AWS Certified Solutions Architects are one of the leading professionals in cloud computing. This certification is accredited by Amazon Web Services. AWS architect is someone who can evaluate an organization's requirements in cloud computing and make architectural recommendations for implementing and deploying applications on AWS.
· Currently, 69% of businesses are already utilising cloud technology and it is predicted that 83% of enterprise workloads will be in the Cloud by 2020.
· The public cloud market is expected to reach $236 billion by 2020, and AWS is the topmost cloud computing player with a 43% yearly growth.
According to ziprecruiter.com, AWS Certified Solutions Architect’s salary can go as high as $202,000
AWS Certified Solutions Architect - Average Annual Salary in the United States
Data as of 1st November 2019.
Cloud services such as Amazon Web Services (AWS), Google Cloud, and Microsoft Azure appeal to many organizations because of their stated features, such as pay per use, ability to scale up or down based on usage, high resiliency, and self-service. All these benefits are expected to lead to much lower IT costs, faster time to market, and better service quality compared with traditional IT offerings.
Eligibility criteria:
- At least one-year hands-on experience in cloud and AWS. These professionals should know about topics such as business continuity, deployment management, network design, data storage, security, scalability and elasticity, cloud migration and hybrid architecture.
How to become an AWS Certified Solution Architect?
First, you will need to set up an AWS Account. All AWS certifications are conducted at PSI test-taking facilities—typically a local community college. By taking up AWS Solution Architect training course you get well-versed with concepts, fundamentals, architectural best practices, designs and deployment of scalable systems on AWS.
3. Google Certified Professional Cloud Architect
Google Certified Professional Cloud Architect certification is currently the industry standard to help you emerge above the rest in this cloud job world. Google Cloud Platform (GCP) has evolved from being a niche player to a serious competitor to Amazon Web Services and Microsoft Azure. According to Fiormarkets, Global cloud computing market is expected to reach USD 712.83 Billion by 2025, at a CAGR of 18.46% from 2018 to 2025.
As per an article on Dataversity.net, according to Gartner TalentNeuron, an online real-time labour market insight portal, “there are about 50,248 cloud computing positions available in the U.S. from 3,701 employers, and 101,913 open positions worldwide.”
According to ziprecuriter.com, the Google Certified Professional Cloud Architect‘s salary can go as high as $201,500/year.
Google Cloud Platform - Average Annual Salary in the United States
Data as of 1st November 2019.
Eligibility Criteria:
The Cloud Architect should have 3+ years of industry experience as well as 1-year designing and building solutions on Google Cloud Platform.
How to become a Google Certified Professional Cloud Architect?
Register with Google cloud, Enhance your skill in Cloud adoption plans, Cloud application design, Cloud management and monitoring, Application architecture, Deployment strategies and get certified.
4. Big Data Certification
"Big Data" is a field that treats ways to analyze, systematically extract information from, or otherwise deal with data sets that are too large or complex to be dealt with by traditional data-processing application software.
A Big Data Certification will equip you with the skills and knowledge to tackle the 3 Vs of Big Data - Volume, Velocity, and Variety.
For professionals, who are skilled in Big Data Analytics, there is an ocean of opportunities out there. There is a huge demand for big data professionals in industries like entertainment, automobile, government, education etc. According to Forbes, IBM stated that by 2020, the number of jobs for all US data professionals will increase by 364,000 openings to 2,720,000.
According to ziprecuriter.com, Big Data Certified professional's salary can go as high as $196,000/year
Big Data Analytics - Average Annual Salary in the United States
Data as of 1st November 2019.
Eligibility criteria:
There is no such eligibility criteria to take up Big Data Certification. Preferable to be acquainted with the Core Java and SQL.
How to get certified in big data?
Enhance your skill by enrolling in Big data certification course. Prepare yourselves with quality study material and attempt as many mock exams to check and confirm your proficiency in the subject matter.
5. Data Science Certification:
Data science is a multi-disciplinary field that uses scientific methods, processes, algorithms and systems to extract knowledge and insights from structured and unstructured data.
The Data Scientist certification is a certification which validates data scientist’s knowledge on SAS, R, Hadoop, Python and Spark and how to use data concepts such as data exploration, visualization hypothesis testing, and predictive analytics. There is a huge demand for Data Scientists in industries like Aerospace industry, IT industry, e-commerce industry and healthcare industry. According to Forbes, IBM predicts that demand for Data Scientists will increase by 28% by 2020. IBM also predicts that 59% of all Data Science and Analytics (DSA) job demand is in Finance and Insurance, Professional Services, and IT.
According to ziprecuriter.com, the Data Science Certified professional's salary can go as high as $185,000/year
Data Scientist - Average Annual Salary in the United States
Data as of 1st November 2019.
Eligibility Criteria:
There are no prerequisites for this data science online training course.
How to get certified in Data Science?
Go for the Data scientist training course. Gain well-versed knowledge on using tools such as statistic hypothesis testing, clustering, decision trees, linear and logistic regression, R studio and Data Visualization. Pass the exam and get certified as a Data Scientist.
6. Certified In Risk And Information Systems Control (CRISC)
The Certified in Risk and Information Systems Control (CRISC) is the certification accredited by Information Systems Audit and Control Association (ISACA) which engages in the development, adoption and use of globally accepted, industry-leading knowledge and practices for information systems. CRISC professionals are one of of the highest-paid employee. The curriculum is based on 4 domains prescribed by ISACA.
Domain 01 - Risk Identification
Domain 02 - Risk Assessment
Domain 03 - Risk Response
Domain 04 - Risk and Control Monitoring and Reporting
· More than 20,000 professionals worldwide have earned the CRISC to affirm their business and IT risk management competence, and their ability to design, implement, monitor and maintain effective, risk-based information systems controls.
· More than 1,300 CRISC holders are CIOs, CISOs, or chief compliance, risk or privacy officers and over 600 are CEOs, CFOs or equivalent executives.
CRISC certification makes you highly valuable to enterprises seeking to manage IT risk as a critical component of the innovation process.
According to ziprecuriter.com, the Certified in Risk and Information Systems Control (CRISC) salary can go as high as $143,000/year
CRISC Average Annual Salary in the United States
Data as of 1st November 2019.
Eligibility Criteria:
According to ISACA, The requirements for CRISC Certification – 2015 exams and later are:
- Successful completion of the CRISC examination
- Three (3) or more years of cumulative work experience performing the tasks of a CRISC professional across at least two (2) CRISC domains, of which one must be in Domain 1 or 2, is required for certification. There are no substitutions or experience waivers.
- This experience must have been gained within the 10-year period preceding the application date for certification or within five years of passing the examination.
- A completed application must be submitted within 5 years from the date of initially passing the examination.
How to become a Certified In Risk And Information Systems Control (CRISC)?
First, candidates must register and pay a non-refundable and non-transferable fee prior to becoming eligible to schedule their test. To register for the CRISC exam, candidates must create an ISACA profile at www.isaca.org. After the login, candidates can schedule the exam. Candidates who clear the examination need to pay a maintenance fee and earn a minimum of 20 contact hours of CPE annually. Additionally, a minimum of 120 contact hours is required during a fixed 3-year period.
7. Certified Information Security Manager (CISM)
Data as of 1st November 2019.
Certified information security manager (CISM) is accredited by the Information Systems Audit and Control Association (ISACA). CISM supervises enterprise information security. As recommended by ISACA, There are 4 primary domains to be focused on to get CISM Certification:
· Information Security Governance.
· Information Risk Management.
· Information Security Program Development and Management.
· Information Security Incident Management.
According to ziprecuriter.com, the Certified information security manager (CISM) salaries can reach up to $216,000 per year.
CISM Average Annual Salary in the United States
Eligibility criteria:
- A completed application must be submitted within 5 years from the date of initially passing the examination.
- All experience must be verified independently with employers.
- This experience must have been gained within the 10-year period preceding the application date for certification or within five years of passing the examination.
- Three (3) years of the five (5) years of work experience must be gained performing the role of an information security manager
- In addition, this work experience must be broad and gained in three (3) of the four (4) CISMR domains
How to become a certified information security manager (CISM)?
Take up the course, gain knowledge on four domains and register with ISACA or exam locator. Every year, the exam is offered by ISACA during the designated testing of windows. Clear the exam and get credentials. Continuing education credits are required each year to maintain your certification.
8. Project Management Professional (PMP)® Certification
Data as of 1st November 2019.
Project Management Professional (PMP) accredited by Project Management Institute (PMI) is an industry-standard certification which is globally recognized. According to the PMI (2013). Talent Gap: Project Management through 2020 article by the Project Management Institute, Inc. - Through the decade ending in 2020, 15.7 million new project management roles will be created. The profession is expected to grow by US$6.61 trillion. Now is the time for professionals and job-seekers to build project management skills, as demand for these skills outstrips supply.
The PMP Certification has consistently been among the top ranked certifications worldwide and according to the 10th edition of PMI’s Project Management Salary Survey, Project Management Institute’s (PMI) Earning Power Report reveals a significant advantage in earning potential for PMP® certified practitioners. Survey respondents holding the Project Management Professional (PMP)® certification reported higher median salaries than those without a PMP certification―23% higher on average across the 37 countries surveyed.
A PMP certification demonstrates your Project Management knowledge, experience, and skills to potential employers and clients. It also provides professional skills necessary to lead project teams and bring projects to successful completion. A PMP certification will enable you to command higher salaries than non-certified individuals by showcasing competencies in leading and directing projects. Accelerate and expand the scope of your career with a globally recognized and in-demand certification. Know more about our PMP Exam Prep Certification Training courses at a location near you.
According to ziprecruiter.com, Project Management Professional's salary can go as high as $172,000
PMP - Average Annual Salary in the United States
Eligibility criteria:
For Graduates:
- 3 years or 4,500 hours of project management experience
- 35 hours of project management education
For non-graduates
- 5 years or 7,500 hours of project management experience
- 35 hours of project management education
How to become a Project Management Professional (PMP) ®?
Create a professional profile by signing up at PMI.org. Take 35 hours of PMP® Certification training course. For a special discount on PMP exam application fee and the access to a free PDF copy of the PMBOK Guide, apply for PMI membership. Fill the online application within 90 days. You can schedule the exam at your nearest test centres. Once you qualify the test, get PMP® certification. Your credentials are valid for only three years. You need to maintain your PMP® certification by earning 60 PDUs to fulfil the Continuing Certification Requirements (CCR).
Test your level of preparation for the PMP (Project Management Professional) Examination.
Free Download full-length PMP Exam Practice Test with 200 PMP Questions.
9. Certified Ethical Hacker (CEH)
Certified Ethical Hacker, accredited by EC-Council(The international council of E-Commerce consultants), validates the baseline knowledge on five phases of ethical hacking. These are:
· Reconnaissance,
· Gaining Access,
· Enumeration,
· Maintaining Access,
· Covering your tracks.
CEH Stimulates the real-time threats, counter-defensive mechanisms to eliminate threats and protective measures to prevent attacks. CEH simulates real-time threats, counter-defensive mechanisms to eliminate threats and protective measures to prevent attacks and breaches. There is a difference between Hacker and ethical hacker. Hacker hacks the system and steals the information, while CEH defends attacks and threats using the same techniques the hacker used. CEH professionals are in-demand and are internationally recognized because of the continuous updates of tools and techniques.
According to ziprecuriter.com, Certified Ethical Hacker salaries can go up to $220,000 per year.
CEH - Average Annual Salary in the United States
Eligibility criteria:
There are no such eligibility criteria to take up CEH. Basic knowledge of Transmission Control Protocol/Internet Protocol (TCP/IP) is advised.
How to become a Certified Ethical Hacker?
Take up training on CEH to learn tools and programs used for security, ethics, network security etc. With the knowledge of the above mentioned skills, you can pass the exam. The CEH certification is valid for three years and can be renewed by earning 120 continuing education credits within the three-year period.
10. Certified Scrum Master (CSM)
Certified Scrum Master, accredited by Scrum Alliance validates the knowledge of Agile principles and practices and makes you more noticeable than others. According to the State of Agile report, the Scrum Methodology is most widely used amongst software development creating many job opportunities.
According to ziprecruiter.com, Certified Scrum Master Salary can reach from median of $118,353/year to $160,000/year.
CSM - Average Annual Salary in the United States
Data as of 1st November 2019.
Eligibility criteria:
There is no such eligibility criteria to take up CSM. You can become a Certified Scrum Master regardless of your educational background.
How to become a Certified Scrum Master?
To become a certified Scrum Master, you need to take the Certified Scrum Master course from Certified Scrum Trainer (CST) or Scrum Alliance Authorized Trainer. Scrum Alliance will send you a link to create login credentials after completion of course. Clear the exam and get certified along with two-year membership with Scrum Alliance.
For more information on how you can accelerate your career with these certifications, visit us at https://www.icertglobal.com/ or call now on +1-713-287-1213 / 1214 or e-mail us at info {at} icertglobal {dot} com.
Know more about our Professional Certification Training Courses for preparing for the above certifications.
CISSP Certification Training Courses
AWS Certified Solutions Architect Certification Training Courses
Google Cloud Platform Fundamentals Certification Training Courses
Big Data Certification Training Courses
Data Science Certification Training Courses
CRISC Certification Training Courses
CISM Certification Training Courses
PMP Certification Training Courses
Free Download: PMP Practice Test with 200 Questions
CEH Certification Training Courses
CSM Certification Training Courses
We provide instructor-led classroom and instructor-led live online training across the globe. We also provide Corporate Training for enterprise workforce development.
Connect with us:
- Subscribe to our YouTube Channel
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
- PMP Certification Training
- CAPM Certification Training
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
iCert Global both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in 2020? Let us know your thoughts in the 'Comments' section below.
Thank you for reading this blog post. Hope you found it useful and interesting. Team iCert Global wishes you all the best for your learning endeavors.
Top 10 Most Important IT Skills In Demand For 2020 | Fast Track Your Career With These IT Skills
The 10 Most Important IT Skills For 2020
“Skills matter the most and we actually value skills over experience in the grand scheme of things,” says Janelle Gale, Facebook’s vice president of Human Resources to CNBC Make It.
In this blog, let's know more about the 10 Most Important IT skills that are most in-demand and that help you to fast-track your career in the year 2020.
-
Artificial Intelligence (AI) and Machine Learning (ML)
-
Big Data Analytics
-
Cloud Computing
-
Cyber Security
-
Project Management
-
Agile and Scrum
-
DevOps
-
Business Analysis
-
Digital Marketing
-
Networking
It is always a smart move to expand your skillset to be on top of your career in a fast-changing world where each day brings forward innovations that are changing the professional landscape at the workplace. Each day that you spend in learning is preparing for a better tomorrow for yourself and also for your family.
Learning new skills opens doors, more often than not;
-
To an increase in remuneration,
-
Greater recognition at work,
-
More lucrative job assignments,
-
Paves the way for career acceleration through greater visibility and demand from employers, peers, and potential recruiters.
-
Artificial Intelligence (AI) and Machine Learning (ML)
‘Machines with intelligence.' AI -Artificial Intelligence is a concept of machines being able to carry out tasks in terms of natural intelligence or stimulation of human behavior.
ML-Machine Learning is an application of AI Machine learning is the study of computer algorithms that allow computer programs to automatically improve through experience.
Demand for AI and ML:
According to McKinsey, Artificial Intelligence promises to boost profits and transform industries.
Amazon has achieved impressive results from its $775 million acquisition of Kiva, a robotics company that automates picking and packing. Netflix has also achieved impressive results from the algorithm it uses to personalize recommendations to its 100 million subscribers worldwide.
Sectors leading to AI adoption today also intend to grow their investment the most.
The below data represents the leading sectors adopting AI.
Average Annual Salaries of AI and ML:
According to neuvoo.com,

How AI and ML are shaping the world?
According to Microsoft,
Biggest environmental challenges can be faced when human ingenuity and technology meet.
-
Farmers use AI to scale the growth of crops
-
Physics-enabled AI models help everyone understand the climate-related risk at the hyper-local level.
-
Collecting farmland data in the cloud and making it available to farmers to enable precision agriculture.
-
Using satellites and AI to preserve biodiversity, protect livelihoods, and prevent slavery in the seafood industry.
-
AI and citizen scientists work together to fight extinction.
-
Protection Assistant for Wildlife Security (PAWS) uses AI to aid conservationists in the fight against poaching by utilizing machine learning, AI planning, and behavior modeling.
For more information on how iCert Global can help you to achieve your Artificial Intelligence (AI) and Machine Learning (ML) certification goals, please visit our Artificial Intelligence and Deep Learning Certification Training Course and Machine Learning Certification Training Course on our website.
2. Big Data Analytics
Big Data Analytics is a process of examining a large set of data to uncover hidden patterns, correlations and other insights. It helps to identify new opportunities and guide to smarter business moves.
Demand for Data Science and Big Data Analytics:
According to Market Expert24,
Data Science Platform Market is expected to grow from USD +19 Billion in 2016 to USD +101 billion by 2021, at a CAGR of +38% from 2019 to 2025.
According to IBM, by 2020 the number of positions for data and analytics talent in the United States will increase by 364,000 openings, to 2,720,000.
Average Annual Salaries of Data Scientists:
According to Neuvoo.com,

How Data Science and Big Data Analytics are shaping the world?
-
According to CIO.com, Data science helped Zoomcar (Self Driven Service) capture 75% of Indian market.
-
According to GCN.com, Data science could help Californians battle future wildfires.
For more information on how iCert Global can help you to achieve your Data Science Certification goals, please visit our Data Science Certification Training Courses on our website.
3. Cloud Computing
Cloud Computing is the delivery of on-demand computing services over the Internet (the cloud) offering faster innovation, flexible resources and economies of scale. The computing services include storage, servers, software, analytics, databases, networking, and intelligence.
Demand for Cloud Computing: There is a huge demand for cloud computing services. According to Forbes, IDC predicted that by 2022, 70% of enterprises will integrate cloud management.
Average Annual Salary of Cloud Architect: According to Nevuoo.com,

For more information on how iCert Global can help you to achieve your Cloud Computing Certification goals, please visit our website.
4. Cyber Security
Cyber Security is a practice of protecting data from malicious attacks or unauthorized access. It ensures integrity, confidentiality, and availability (ICA) of information.
Demand for Cyber Security:
According to Cybercrime Magazine, Cybersecurity Ventures predicted that cybercrime damages will cost the world $6 trillion annually by 2021. To mitigate these damages, there will be 3.5 million unfilled cybersecurity jobs globally by 2021.
Average Annual Salary of Cyber Security Professionals:
According to Neuvoo.com,

For more information on how iCert Global can help you to achieve your Cyber Security Certification goals, please visit our website.
5. Project Management
Project management is the practice of initiating, planning, executing, controlling, and closing of projects to achieve business goals within a constrained time.
Demand for Project management:
According to PMI.org,
By 2027, employers will need 87.7 million individuals working in project management-oriented roles.
Attrition, particularly as seasoned practitioners reach retirement age, is creating many project-related job openings. Leading sectors with job openings due to attrition are shown in the image below:

(Source: Project Management Job Growth and Talent Gap 2017–2027)
Average Annual Salary of Certified Project Management Professionals:
According to Neuvoo.com,

For more information on how iCert Global can help you to achieve your Project Management Certification goals, please visit our website.
6. Agile and Scrum
Agile is an iterative method to develop software step by step taking frequent reassessment whenever required, instead of delivering the whole product after completion. Agile is a framework and there are various approaches to implement agile. Scrum is one of the most popular ways to implement agile.
According to the 12th Annual State of Agile Report, The Scrum Methodology is most widely used amongst software development teams as it divides complicated tasks to user stories.
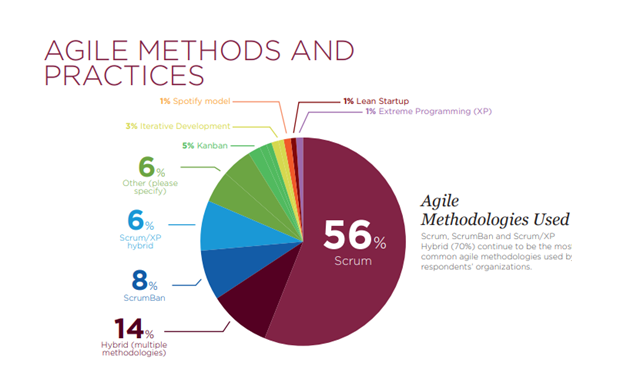
Demand for Agile and Scrum:
According to the report by EY: Digital Transformation for 2020 and beyond, Global Telecommunications Study, improved organizational agility is at the heart of successful digital transformation.
Average Annual salary of Agile Coach Scrum Master
According to Neuvoo.com,

For more information on how iCert Global can help you to achieve your Agile and Scrum Certification goals, please visit our website.
7. DevOps
DevOps is a collaborative approach of Software Development (Dev), Technology Operations (Ops), and Quality Assurance. This enables businesses to build, test, iterate and release software faster and in a more efficient manner.
Demand and Scope for DevOps:
According to IDC.com,
The worldwide DevOps software tools market achieved a level of $5.2 billion in 2018. The market is forecast to reach $15 billion in 2023.
Average Annual salary of DevOps Engineer
According to Nevuoo.com,

For more information on how iCert Global can help you to achieve your DevOps Certification goals, please visit our website.
8. Business Analysis
"Business analysis is the practice of enabling change in an enterprise by defining needs and recommending solutions that deliver value to clients".
Demand and Scope for Business Analysis:
According to IIBA 2018 Annual Business Analysis Salary Survey Summary Report,
The U.S. Bureau of labor indicates that Business Analysis is one of the highest growing occupations, with 14% growth projected between 2014-2024.
Average Annual Salary of Certified Business Analysts:
According to Nevuoo.com,

For more information on how iCert Global can help you to achieve your Business Analysis Certification goals, please visit our website.
9. Digital Marketing
-
Digital Marketing is implementing marketing strategies through digital channels like Search, Performance Marketing, Social Media Marketing, Mobile and Video Marketing, Content Marketing, and Web Analytics to increase brand recall, leads, sales, and business for organizations.
What separates digital marketing from traditional marketing is that it is:
-
Scalable: You can scale your marketing initiatives across geographies and digital has the ability to allow marketers to implement their strategies across the globe through various media as mentioned above.
-
Measurable: Each click, lead, enquiry, and sale is measurable giving superior insights on Return on Investment for better business monitoring and performance.
-
Targeted: Digital marketing is targeted and focused and can be used across countries and languages and also pinpointed to within a certain radius.
-
Granular: The granularity of drilling down on data, analytics and metrics that count for the business make it a must implement marketing strategy for companies and businesses looking to win in a fast-changing digital world.
Demand and Scope for Digital Marketing:
According to the report by Market Hiring Trends,
There is a considerable gap between the supply and demand of digital marketing professionals. The demand stood at around 59%, but the supply was only 19%.
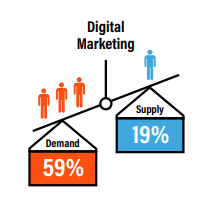
Taking up an in-demand Digital Marketing Certification Course will help you increase employability.
Average Annual Salary of Digital Marketing Manager:
According to Nevuoo.com, Average Annual Salary of Digital Marketing Manager can go as high as, $127,690/year.
For more information on how iCert Global can help you to achieve your Digital Marketing Certification goals, please visit our website.
10. Networking
Networking is the practice of exchanging or transporting data between nodes in an information system through a shared medium. Devices are connected through switches, routers and wireless access points.
Demand for Networking:
The companies have expanded their IT networks over the last decade resulting in high demand for network engineers.
Popular certifications in Networking are Cisco Certified Network Professional (CCNP) and Cisco Certified Network Professional (CCNA)
Average Annual Salary of Certified Network Engineers:
According to Ziprecuriter.com,
The average annual salary of CCNP Professional is $108,474/year.
The average annual salary of CCNA Professional is $84,424/year.
For more information on how iCert Global can help you to achieve your Networking Certification goals, please visit our website.
For more information on how you can accelerate your career with these certifications, visit us at https://www.icertglobal.com/ or call now on +1-713-287-1213 / 1214 or e-mail us at info {at} icertglobal {dot} com.
Know more about our Professional Certification Training Courses for preparing for the below mentioned recommended certifications.
Recommended Courses:
-
Artificial Intelligence and Deep Learning Certification Training Course
-
-
-
-
AWS Certified Solutions Architect Certification Training Courses
-
Google Cloud Platform Fundamentals Certification Training Courses
-
-
-
-
-
-
-
-
-
AWS Solution Architect Certification Training Course
Footnotes:
-
-
12th Annual State of Agile ReportEY: Digital Transformation for 2020 and beyond, Global Telecommunications Study
-
-
IIBA 2018 Annual Business Analysis Salary Survey Summary Report
-
United States Department of Labor: Bureau Of Labor Statistics
Read More
The 10 Most Important IT Skills For 2020
“Skills matter the most and we actually value skills over experience in the grand scheme of things,” says Janelle Gale, Facebook’s vice president of Human Resources to CNBC Make It.
In this blog, let's know more about the 10 Most Important IT skills that are most in-demand and that help you to fast-track your career in the year 2020.
-
Artificial Intelligence (AI) and Machine Learning (ML)
-
Big Data Analytics
-
Cloud Computing
-
Cyber Security
-
Project Management
-
Agile and Scrum
-
DevOps
-
Business Analysis
-
Digital Marketing
-
Networking
It is always a smart move to expand your skillset to be on top of your career in a fast-changing world where each day brings forward innovations that are changing the professional landscape at the workplace. Each day that you spend in learning is preparing for a better tomorrow for yourself and also for your family.
Learning new skills opens doors, more often than not;
-
To an increase in remuneration,
-
Greater recognition at work,
-
More lucrative job assignments,
-
Paves the way for career acceleration through greater visibility and demand from employers, peers, and potential recruiters.
-
Artificial Intelligence (AI) and Machine Learning (ML)
‘Machines with intelligence.' AI -Artificial Intelligence is a concept of machines being able to carry out tasks in terms of natural intelligence or stimulation of human behavior.
ML-Machine Learning is an application of AI Machine learning is the study of computer algorithms that allow computer programs to automatically improve through experience.
Demand for AI and ML:
According to McKinsey, Artificial Intelligence promises to boost profits and transform industries.
Amazon has achieved impressive results from its $775 million acquisition of Kiva, a robotics company that automates picking and packing. Netflix has also achieved impressive results from the algorithm it uses to personalize recommendations to its 100 million subscribers worldwide.
Sectors leading to AI adoption today also intend to grow their investment the most.
The below data represents the leading sectors adopting AI.

Average Annual Salaries of AI and ML:
According to neuvoo.com,
How AI and ML are shaping the world?
According to Microsoft,
Biggest environmental challenges can be faced when human ingenuity and technology meet.
-
Farmers use AI to scale the growth of crops
-
Physics-enabled AI models help everyone understand the climate-related risk at the hyper-local level.
-
Collecting farmland data in the cloud and making it available to farmers to enable precision agriculture.
-
Using satellites and AI to preserve biodiversity, protect livelihoods, and prevent slavery in the seafood industry.
-
AI and citizen scientists work together to fight extinction.
-
Protection Assistant for Wildlife Security (PAWS) uses AI to aid conservationists in the fight against poaching by utilizing machine learning, AI planning, and behavior modeling.
For more information on how iCert Global can help you to achieve your Artificial Intelligence (AI) and Machine Learning (ML) certification goals, please visit our Artificial Intelligence and Deep Learning Certification Training Course and Machine Learning Certification Training Course on our website.
2. Big Data Analytics
Big Data Analytics is a process of examining a large set of data to uncover hidden patterns, correlations and other insights. It helps to identify new opportunities and guide to smarter business moves.
Demand for Data Science and Big Data Analytics:
According to Market Expert24,
Data Science Platform Market is expected to grow from USD +19 Billion in 2016 to USD +101 billion by 2021, at a CAGR of +38% from 2019 to 2025.
According to IBM, by 2020 the number of positions for data and analytics talent in the United States will increase by 364,000 openings, to 2,720,000.
Average Annual Salaries of Data Scientists:
According to Neuvoo.com,
How Data Science and Big Data Analytics are shaping the world?
-
According to CIO.com, Data science helped Zoomcar (Self Driven Service) capture 75% of Indian market.
-
According to GCN.com, Data science could help Californians battle future wildfires.
For more information on how iCert Global can help you to achieve your Data Science Certification goals, please visit our Data Science Certification Training Courses on our website.
3. Cloud Computing
Cloud Computing is the delivery of on-demand computing services over the Internet (the cloud) offering faster innovation, flexible resources and economies of scale. The computing services include storage, servers, software, analytics, databases, networking, and intelligence.
Demand for Cloud Computing: There is a huge demand for cloud computing services. According to Forbes, IDC predicted that by 2022, 70% of enterprises will integrate cloud management.
Average Annual Salary of Cloud Architect: According to Nevuoo.com,
For more information on how iCert Global can help you to achieve your Cloud Computing Certification goals, please visit our website.
4. Cyber Security
Cyber Security is a practice of protecting data from malicious attacks or unauthorized access. It ensures integrity, confidentiality, and availability (ICA) of information.
Demand for Cyber Security:
According to Cybercrime Magazine, Cybersecurity Ventures predicted that cybercrime damages will cost the world $6 trillion annually by 2021. To mitigate these damages, there will be 3.5 million unfilled cybersecurity jobs globally by 2021.
Average Annual Salary of Cyber Security Professionals:
According to Neuvoo.com,
For more information on how iCert Global can help you to achieve your Cyber Security Certification goals, please visit our website.
5. Project Management
Project management is the practice of initiating, planning, executing, controlling, and closing of projects to achieve business goals within a constrained time.
Demand for Project management:
According to PMI.org,
By 2027, employers will need 87.7 million individuals working in project management-oriented roles.
Attrition, particularly as seasoned practitioners reach retirement age, is creating many project-related job openings. Leading sectors with job openings due to attrition are shown in the image below:
(Source: Project Management Job Growth and Talent Gap 2017–2027)
Average Annual Salary of Certified Project Management Professionals:
According to Neuvoo.com,
For more information on how iCert Global can help you to achieve your Project Management Certification goals, please visit our website.
6. Agile and Scrum
Agile is an iterative method to develop software step by step taking frequent reassessment whenever required, instead of delivering the whole product after completion. Agile is a framework and there are various approaches to implement agile. Scrum is one of the most popular ways to implement agile.
According to the 12th Annual State of Agile Report, The Scrum Methodology is most widely used amongst software development teams as it divides complicated tasks to user stories.

Demand for Agile and Scrum:
According to the report by EY: Digital Transformation for 2020 and beyond, Global Telecommunications Study, improved organizational agility is at the heart of successful digital transformation.
Average Annual salary of Agile Coach Scrum Master
According to Neuvoo.com,
For more information on how iCert Global can help you to achieve your Agile and Scrum Certification goals, please visit our website.
7. DevOps
DevOps is a collaborative approach of Software Development (Dev), Technology Operations (Ops), and Quality Assurance. This enables businesses to build, test, iterate and release software faster and in a more efficient manner.
Demand and Scope for DevOps:
According to IDC.com,
The worldwide DevOps software tools market achieved a level of $5.2 billion in 2018. The market is forecast to reach $15 billion in 2023.
Average Annual salary of DevOps Engineer
According to Nevuoo.com,
For more information on how iCert Global can help you to achieve your DevOps Certification goals, please visit our website.
8. Business Analysis
"Business analysis is the practice of enabling change in an enterprise by defining needs and recommending solutions that deliver value to clients".
Demand and Scope for Business Analysis:
According to IIBA 2018 Annual Business Analysis Salary Survey Summary Report,
The U.S. Bureau of labor indicates that Business Analysis is one of the highest growing occupations, with 14% growth projected between 2014-2024.
Average Annual Salary of Certified Business Analysts:
According to Nevuoo.com,
For more information on how iCert Global can help you to achieve your Business Analysis Certification goals, please visit our website.
9. Digital Marketing
-
Digital Marketing is implementing marketing strategies through digital channels like Search, Performance Marketing, Social Media Marketing, Mobile and Video Marketing, Content Marketing, and Web Analytics to increase brand recall, leads, sales, and business for organizations.
What separates digital marketing from traditional marketing is that it is: -
Scalable: You can scale your marketing initiatives across geographies and digital has the ability to allow marketers to implement their strategies across the globe through various media as mentioned above.
-
Measurable: Each click, lead, enquiry, and sale is measurable giving superior insights on Return on Investment for better business monitoring and performance.
-
Targeted: Digital marketing is targeted and focused and can be used across countries and languages and also pinpointed to within a certain radius.
-
Granular: The granularity of drilling down on data, analytics and metrics that count for the business make it a must implement marketing strategy for companies and businesses looking to win in a fast-changing digital world.
Demand and Scope for Digital Marketing:
According to the report by Market Hiring Trends,
There is a considerable gap between the supply and demand of digital marketing professionals. The demand stood at around 59%, but the supply was only 19%.

Taking up an in-demand Digital Marketing Certification Course will help you increase employability.
Average Annual Salary of Digital Marketing Manager:
According to Nevuoo.com, Average Annual Salary of Digital Marketing Manager can go as high as, $127,690/year.
For more information on how iCert Global can help you to achieve your Digital Marketing Certification goals, please visit our website.
10. Networking
Networking is the practice of exchanging or transporting data between nodes in an information system through a shared medium. Devices are connected through switches, routers and wireless access points.
Demand for Networking:
The companies have expanded their IT networks over the last decade resulting in high demand for network engineers.
Popular certifications in Networking are Cisco Certified Network Professional (CCNP) and Cisco Certified Network Professional (CCNA)
Average Annual Salary of Certified Network Engineers:
According to Ziprecuriter.com,
The average annual salary of CCNP Professional is $108,474/year.
The average annual salary of CCNA Professional is $84,424/year.
For more information on how iCert Global can help you to achieve your Networking Certification goals, please visit our website.
For more information on how you can accelerate your career with these certifications, visit us at https://www.icertglobal.com/ or call now on +1-713-287-1213 / 1214 or e-mail us at info {at} icertglobal {dot} com.
Know more about our Professional Certification Training Courses for preparing for the below mentioned recommended certifications.
Recommended Courses:
-
Artificial Intelligence and Deep Learning Certification Training Course
-
AWS Certified Solutions Architect Certification Training Courses
-
Google Cloud Platform Fundamentals Certification Training Courses
-
AWS Solution Architect Certification Training Course
Footnotes: -
12th Annual State of Agile ReportEY: Digital Transformation for 2020 and beyond, Global Telecommunications Study
-
IIBA 2018 Annual Business Analysis Salary Survey Summary Report
-
United States Department of Labor: Bureau Of Labor Statistics
The Benefits Of Getting a CAPM Certification
The Benefits Of Getting a CAPM Certification
The Certified Associate in Project Management (CAPM®) is a globally recognized entry-level certification accredited by the Project Management Institute, Inc. (PMI®).
If you are a junior level Project Manager and want to set the stage for a glittering career, then CAPM is the right credential to pursue to take you on the path of success and progress.
CAPM provides the fundamental knowledge on all the aspects of project management including Project Management Phases, Knowledge Areas and Processes.
Why get CAPM Certified?
There is a huge demand for Project Managers in all sectors.
Did you know, according to PMI’s Project Management Job Growth and Talent Gap Report (2017-2027),
by 2027, employers will need 87.7 million individuals working in project management-oriented role.
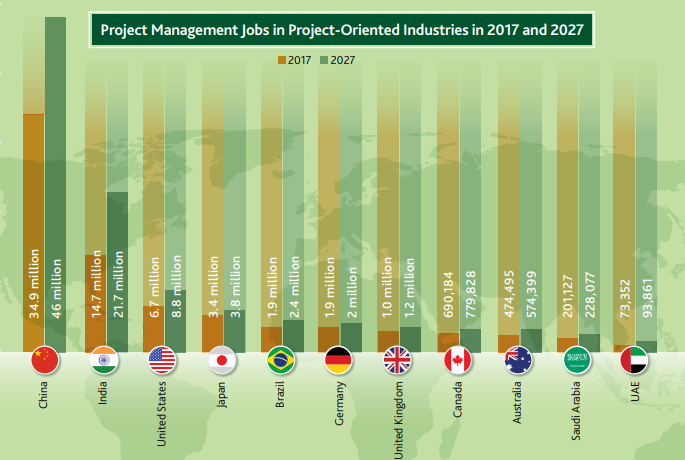
(Source: Project Management Job Growth and Talent Gap 2017–2027)
To meet this demand and skill gap, many professionals are taking up industry-recognized Project Management certifications to enhance their skills and stand out from the crowd.
What is the eligibility criteria for CAPM?
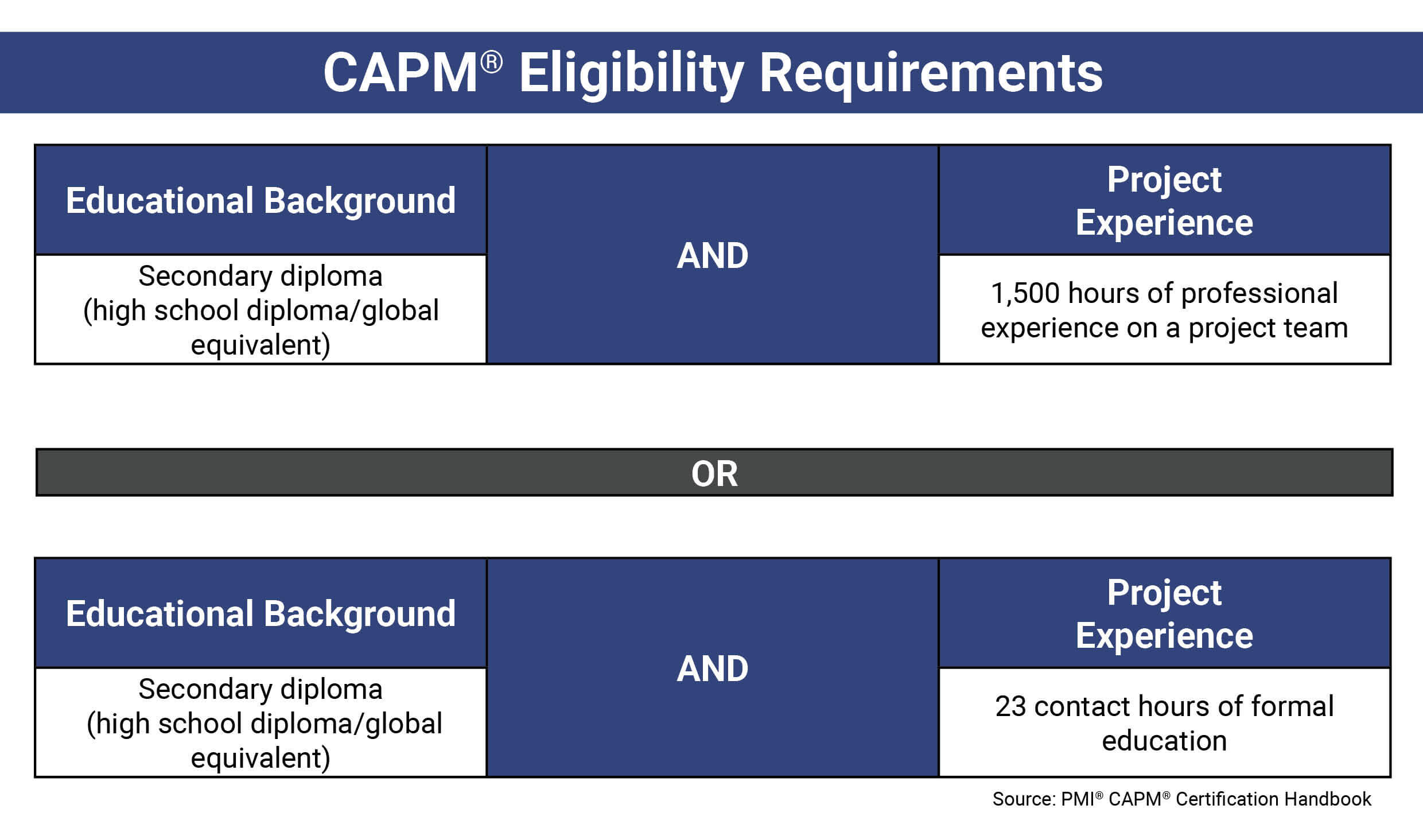
What is the CAPM Certification Exam Fees?
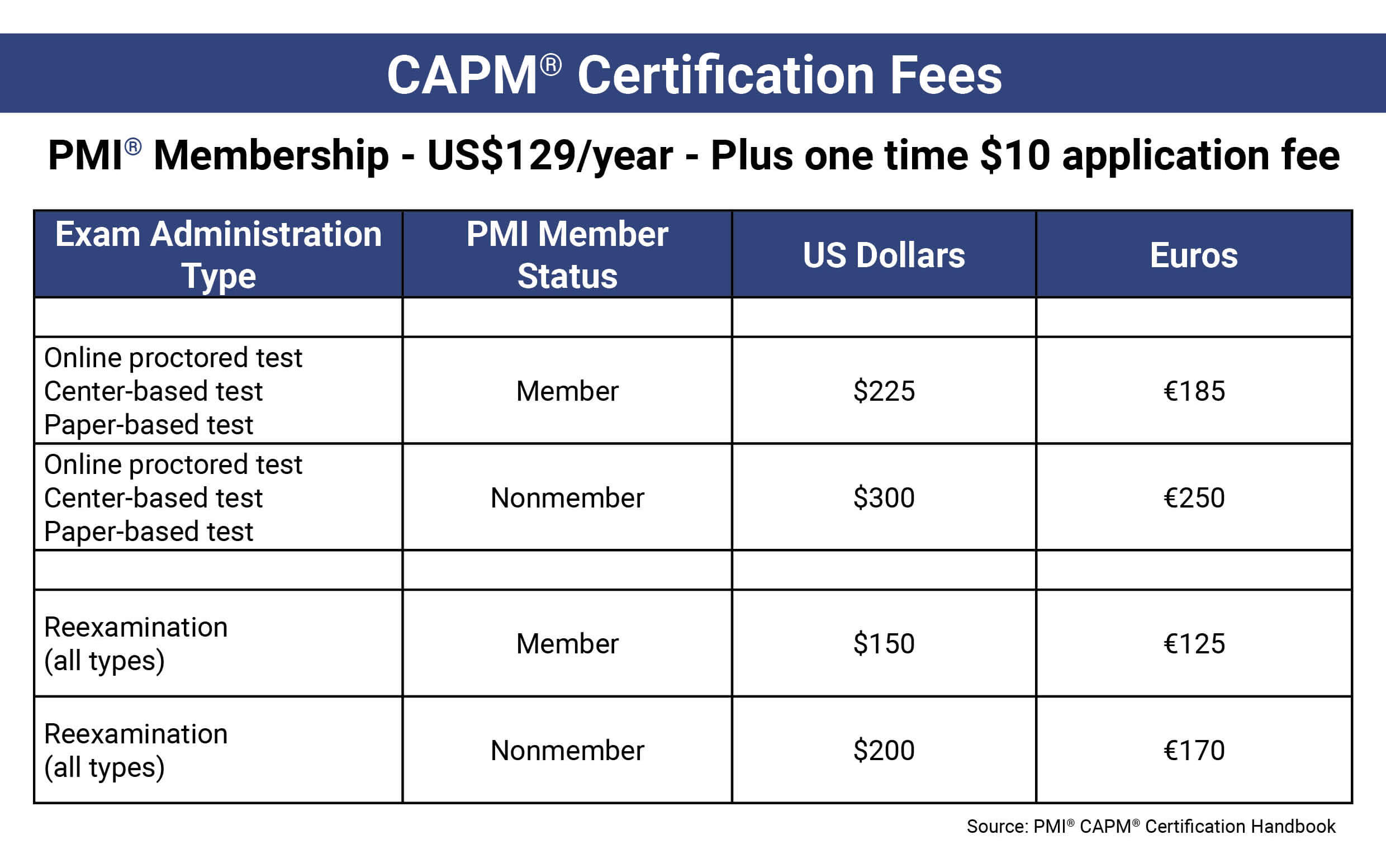
What is the CAPM certification course outline?
CAPM certification is designed based on the PMI framework and follows the standards as mentioned in the PMBOK Guide (A Guide to the Project Management Body of Knowledge).
Knowledge Areas Covered
Percentage of Exam
Introduction to Project Management
6%
Project Environment
6%
Role of the Project Manager
7%
Project Integration Management
9%
Project Scope Management
9%
Project Schedule Management
9%
Project Cost Management
8%
Project Quality Management
7%
Project Resource Management
8%
Project Communication Management
10%
Project Risk Management
8%
Project Procurement Management
4%
Project Stakeholder Management
9%
What are the Benefits of getting CAPM Certified?
- Professional Credibility: Thorough Understanding of the fundamental concepts through CAPM makes an individual highly proficient and boosts professional credibility.
- Global Recognition: Credentials from PMI is considered as industry- standard in-demand certification which validates the knowledge on project management.
- Stepping stone for PMP Exam Preparation: The familiarity with PMBOK and the experience you gain after implementing the skills acquired from CAPM Certification will act as a strong footing for PMP examination preparation.
- Enhance Project Management Skills: CAPM Certification not only enhances your knowledge of Project Management, but it also helps to attain leadership quality and team management quality.
- Career Advancement: CAPM accelerates the scope of your career as a Certified Associate Project Management professional with career advancement, professional growth, increase in salary and earning potential.
- Higher Recruiter Visibility: Getting globally recognized professional certification captures the recruiter’s attention for a potential hiring requirement. The certification at the early stage of your career will make a path for better job opportunities.
- Higher Pay:
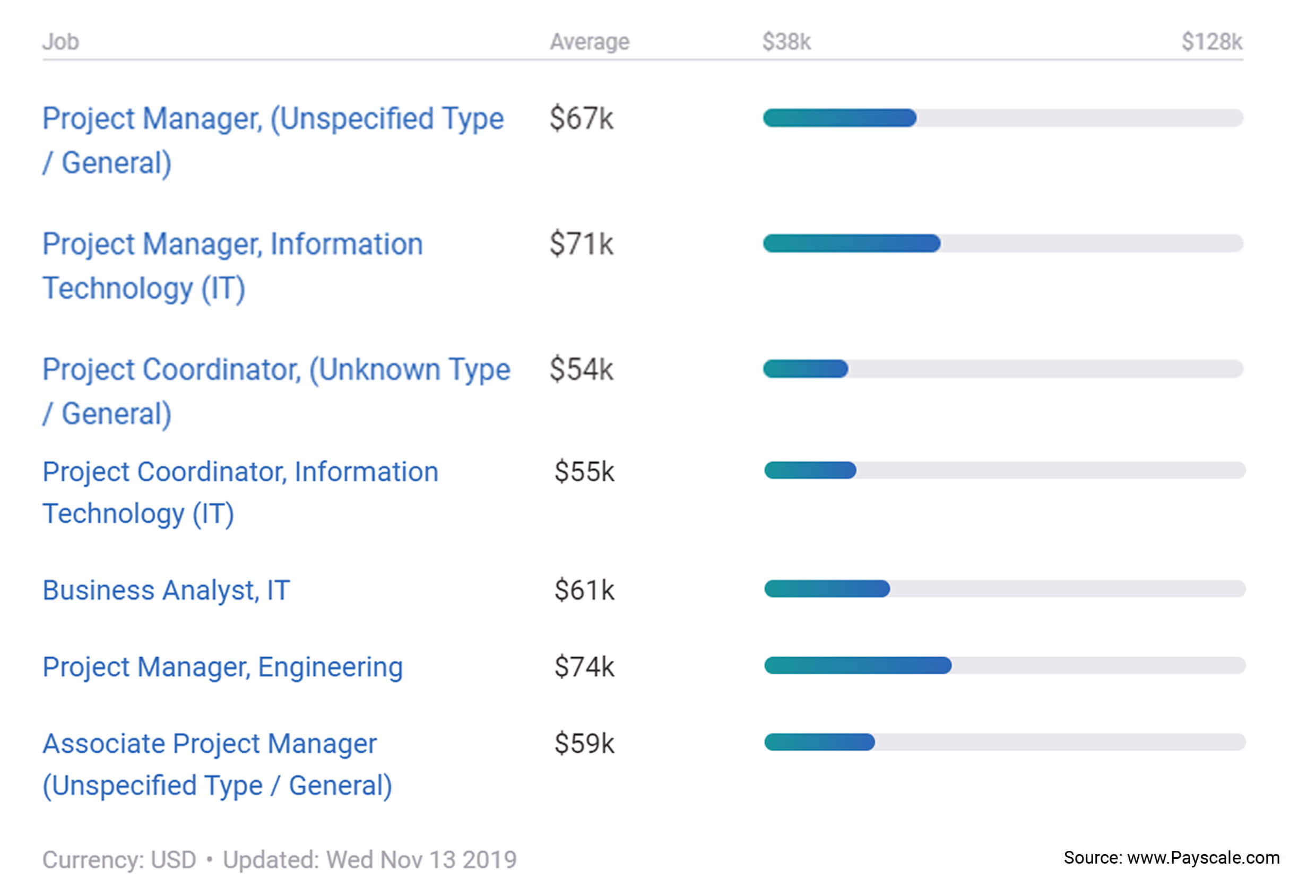
8. Get more lucrative assignments: Certified professionals are more likely to get challenging Projects and opportunity to handle valued projects.
9. Professional Versatility: As a certified professional you might get a chance to lead the team, work in different projects and enhance your project management skill.
10. Recession-Proof your career: CAPM certification helps you stand out as an accomplished professional as compared to other non-certified peers in your field. During an economic crisis or in a period of slow growth or recession, non-certified project managers are more likely to come in the line of fire than their certified peers.
What next?
- If you are planning to crack the PMP Certification exam in the first attempt, then having CAPM Credentials will prove to be an asset and help you for PMP exam preparation.
- The job profiles that CAPM certified professionals can apply for are:
- Consultants
- Business Analyst
- Relational Administrator
- Operational Support associate
- PMO
- Senior Project Manager in IT
- Marketing Coordinator for Communications
Take the first step towards exploring an opportunity to be a global project management professional. Prepare for the CAPM® certification exam and fast track your career as a project management professional. Join Now! Please fill in the enquiry form or call now on +1(713)-287-1355 or e-mail info {at} icertglobal {dot} com for our training consultant to understand your training requirements and guide you with an optimum way to achieve your learning objectives.
You may also be interested in attending a 2-hour Webinar on 'An Introduction to the PMP Certification'.
For more information about our Certified Associate in Project Management (CAPM®) Training Course, please visit us at https://www.icertglobal.com/
Read More
The Benefits Of Getting a CAPM Certification
The Certified Associate in Project Management (CAPM®) is a globally recognized entry-level certification accredited by the Project Management Institute, Inc. (PMI®).
If you are a junior level Project Manager and want to set the stage for a glittering career, then CAPM is the right credential to pursue to take you on the path of success and progress.
CAPM provides the fundamental knowledge on all the aspects of project management including Project Management Phases, Knowledge Areas and Processes.
Why get CAPM Certified?
There is a huge demand for Project Managers in all sectors.
Did you know, according to PMI’s Project Management Job Growth and Talent Gap Report (2017-2027),
by 2027, employers will need 87.7 million individuals working in project management-oriented role.

(Source: Project Management Job Growth and Talent Gap 2017–2027)
To meet this demand and skill gap, many professionals are taking up industry-recognized Project Management certifications to enhance their skills and stand out from the crowd.
What is the eligibility criteria for CAPM?

What is the CAPM Certification Exam Fees?

What is the CAPM certification course outline?
CAPM certification is designed based on the PMI framework and follows the standards as mentioned in the PMBOK Guide (A Guide to the Project Management Body of Knowledge).
|
Knowledge Areas Covered |
Percentage of Exam |
|
Introduction to Project Management |
6% |
|
Project Environment |
6% |
|
Role of the Project Manager |
7% |
|
Project Integration Management |
9% |
|
Project Scope Management |
9% |
|
Project Schedule Management |
9% |
|
Project Cost Management |
8% |
|
Project Quality Management |
7% |
|
Project Resource Management |
8% |
|
Project Communication Management |
10% |
|
Project Risk Management |
8% |
|
Project Procurement Management |
4% |
|
Project Stakeholder Management |
9% |
What are the Benefits of getting CAPM Certified?
- Professional Credibility: Thorough Understanding of the fundamental concepts through CAPM makes an individual highly proficient and boosts professional credibility.
- Global Recognition: Credentials from PMI is considered as industry- standard in-demand certification which validates the knowledge on project management.
- Stepping stone for PMP Exam Preparation: The familiarity with PMBOK and the experience you gain after implementing the skills acquired from CAPM Certification will act as a strong footing for PMP examination preparation.
- Enhance Project Management Skills: CAPM Certification not only enhances your knowledge of Project Management, but it also helps to attain leadership quality and team management quality.
- Career Advancement: CAPM accelerates the scope of your career as a Certified Associate Project Management professional with career advancement, professional growth, increase in salary and earning potential.
- Higher Recruiter Visibility: Getting globally recognized professional certification captures the recruiter’s attention for a potential hiring requirement. The certification at the early stage of your career will make a path for better job opportunities.
- Higher Pay:

8. Get more lucrative assignments: Certified professionals are more likely to get challenging Projects and opportunity to handle valued projects.
9. Professional Versatility: As a certified professional you might get a chance to lead the team, work in different projects and enhance your project management skill.
10. Recession-Proof your career: CAPM certification helps you stand out as an accomplished professional as compared to other non-certified peers in your field. During an economic crisis or in a period of slow growth or recession, non-certified project managers are more likely to come in the line of fire than their certified peers.
What next?
- If you are planning to crack the PMP Certification exam in the first attempt, then having CAPM Credentials will prove to be an asset and help you for PMP exam preparation.
- The job profiles that CAPM certified professionals can apply for are:
- Consultants
- Business Analyst
- Relational Administrator
- Operational Support associate
- PMO
- Senior Project Manager in IT
- Marketing Coordinator for Communications
Take the first step towards exploring an opportunity to be a global project management professional. Prepare for the CAPM® certification exam and fast track your career as a project management professional. Join Now! Please fill in the enquiry form or call now on +1(713)-287-1355 or e-mail info {at} icertglobal {dot} com for our training consultant to understand your training requirements and guide you with an optimum way to achieve your learning objectives.
You may also be interested in attending a 2-hour Webinar on 'An Introduction to the PMP Certification'.
For more information about our Certified Associate in Project Management (CAPM®) Training Course, please visit us at https://www.icertglobal.com/
What Is The Average Salary Of A PMP Certified Professional In The United States?
What Is The Average Salary Of A PMP Certified Professional In The United States?
The average salary of a PMP Certified Professional is $80,000 – $110,000
Some of the factors that influence PMP salary
- Number of years of experience in project management
- Roles and responsibilities
- Position /designation
- Certification status
PMP Salary Based on Experience
- Project Manager with less than 3 years experience: $75,000
- Project Manager with 5-10 years: $100,000
- Top experienced Project Manager with 10 years: $130,000
PMP Salaries Based on Job Position
- Director of Project Management: $130,000 – $150,000
- Portfolio Manager: $130,000
- Program Manager: $120,000
- Project manager: $100,000 – $110,000
What do you think a PMP certified professional draws as salary in United Sates?
PMI’s Project Management Salary Survey 10th edition, states that the salary can anywhere between $80,000 – $110,000 in the United States depending upon the number of years in experience, job position, location, and certification status. There are other factors that will influence your pay and perks like your employer and employment.
Look at the infographic to draw insights about the salary and various factors that influence and impact the figure that you carry home.
Factors that influence PMP salary
Experience, Roles & Responsibilities, Position and Certification status:
The salary will always vary as the composition of the team is never uniform. Even with Project Managers who have the same experience, the pay can be different and that’s where you factor the PMP Certification.
According to PMI, a PMP certified project manager draws 23% more than non-certified peers. That’s the earning power of PMP certification, considered a gold standard in project management that makes the Project Management Professional (PMP) ® certification holders stand out. It’s a great differentiator and decider too.
The roles and responsibilities assigned as part of your job description have a significant bearing on the salary. And so does experience - the more in experience draws more.
The PMP certification is valid for 3 years. Many professionals after the euphoria of passing the PMP exam and joining the elite professionals tend to overlook and some even forget to maintain their PMP credentials. To maintain your PMP credentials, you will have to recertify by earning 60 PDUs every three years. There is no need to write the exam for renewal. This is to ensure you are in touch with your profession and stay abreast of the prevailing best practices and changes across the world. By renewal, your status of PMP will reflect as “‘PMP with good standing.” And this ‘active’ status of PMP does impact your compensation, especially the 5-10 years or Top experienced Project Manager with more than 10 years.
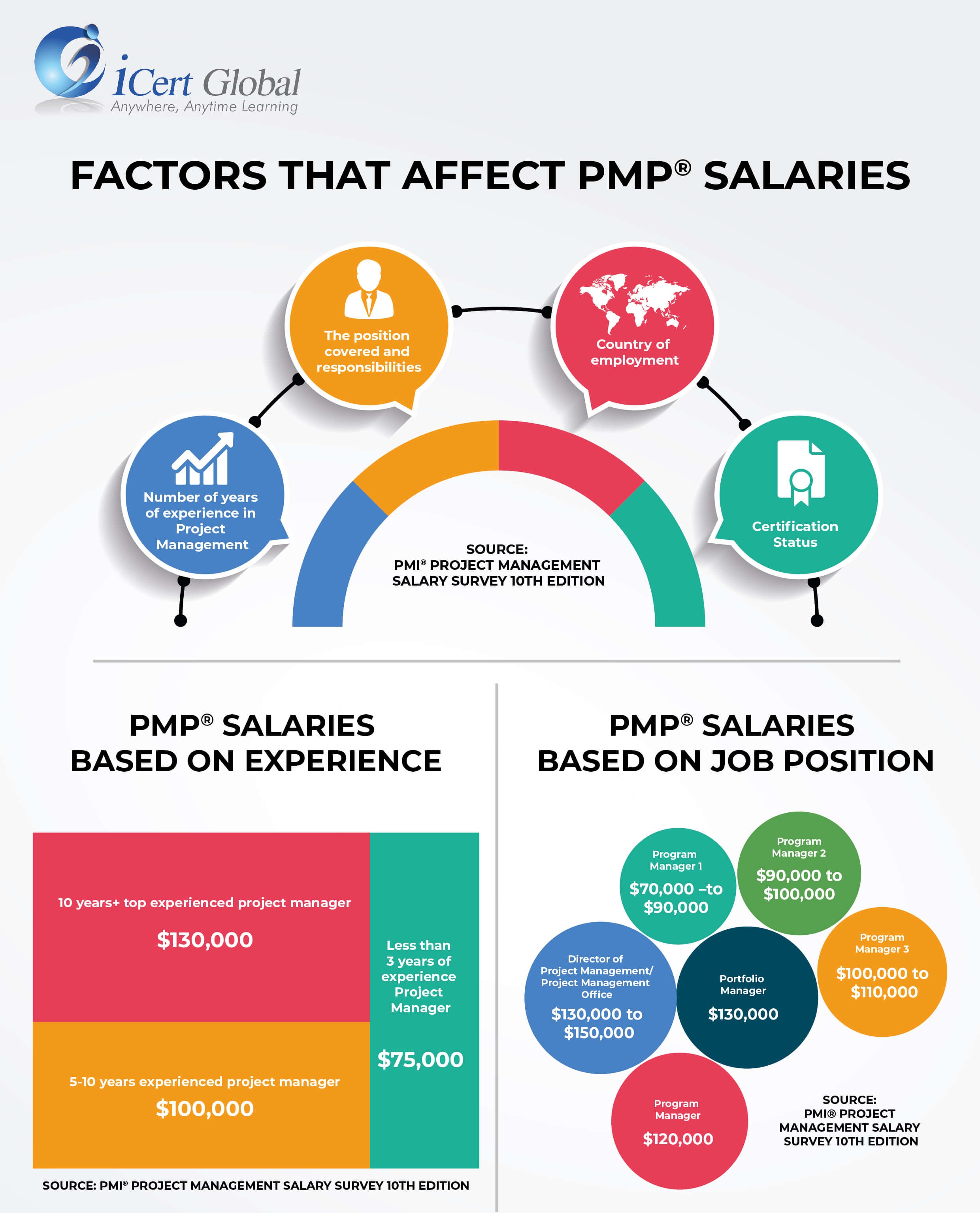
PMP – Supply vs. Demand
How many active PMPs are there in the world? The official number as released by PMI is 1 million.

(source: www.pmi.org)
What is the market demand for PMP professionals? About 2.2 million per year as per the PMI-commissioned talent gap analysis. The job opportunities project a positive outlook for PMP certified professionals.
At the same time, the report highlights a critical deficit in Project talent as the need for skilled professionals has increased phenomenally in numbers, but the availability of the resources is abysmally low. 1 million is hardly a number when the need is more than twice the figure. It's no wonder PMP is at a premium and hence the pay difference between the certified and non-certified stands at a substantial 23%.
PMP – Return on Investment (ROI)
How much does it cost you to get PMP certified?
The cost involved in getting the PMP certificate:
- PMI membership – non-negotiable, costs $139
- PMP exam fee: for a member, it costs $405. Non-member, the cost will be $555
- The cost of PMP certification training to gain 35 PDUs
- The cost of buying study materials.
Now add them up. It is going to be a little over $1000.
Check the statistic: PMP holder median pay is $111,000 as against $91,000 for a non-certified professional in the United States.
So over a $1000 investment, you could potentially earn $111,000 per year, and the returns will be recurring.
One of the factors influencing your salary will be the employer or the company as observed in the infographic. It is so because there are companies that do reimburse the employers for the exam and membership fees - which make the ROI, go higher.
Hence, as a project manager, your salary will increase when you are PMP certified and helps you to contribute to your profession with remuneration inline experience and position.
For more information about professional certification, please visit us at https://www.icertglobal.com or call now on +1-713-287-1213 / 1214 or e-mail us at info {at} icertglobal {dot} com.
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
For more information about our PMP (Project Management Professional) exam prep certification training courses, visit us at https://www.icertglobal.com/
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
Download our Free PMP Brochure for more information.
Read More
What Is The Average Salary Of A PMP Certified Professional In The United States?
|
The average salary of a PMP Certified Professional is $80,000 – $110,000 Some of the factors that influence PMP salary
PMP Salary Based on Experience
PMP Salaries Based on Job Position
|
What do you think a PMP certified professional draws as salary in United Sates?
PMI’s Project Management Salary Survey 10th edition, states that the salary can anywhere between $80,000 – $110,000 in the United States depending upon the number of years in experience, job position, location, and certification status. There are other factors that will influence your pay and perks like your employer and employment.
Look at the infographic to draw insights about the salary and various factors that influence and impact the figure that you carry home.
Factors that influence PMP salary
Experience, Roles & Responsibilities, Position and Certification status:
The salary will always vary as the composition of the team is never uniform. Even with Project Managers who have the same experience, the pay can be different and that’s where you factor the PMP Certification.
According to PMI, a PMP certified project manager draws 23% more than non-certified peers. That’s the earning power of PMP certification, considered a gold standard in project management that makes the Project Management Professional (PMP) ® certification holders stand out. It’s a great differentiator and decider too.
The roles and responsibilities assigned as part of your job description have a significant bearing on the salary. And so does experience - the more in experience draws more.
The PMP certification is valid for 3 years. Many professionals after the euphoria of passing the PMP exam and joining the elite professionals tend to overlook and some even forget to maintain their PMP credentials. To maintain your PMP credentials, you will have to recertify by earning 60 PDUs every three years. There is no need to write the exam for renewal. This is to ensure you are in touch with your profession and stay abreast of the prevailing best practices and changes across the world. By renewal, your status of PMP will reflect as “‘PMP with good standing.” And this ‘active’ status of PMP does impact your compensation, especially the 5-10 years or Top experienced Project Manager with more than 10 years.

PMP – Supply vs. Demand
How many active PMPs are there in the world? The official number as released by PMI is 1 million.

(source: www.pmi.org)
What is the market demand for PMP professionals? About 2.2 million per year as per the PMI-commissioned talent gap analysis. The job opportunities project a positive outlook for PMP certified professionals.
At the same time, the report highlights a critical deficit in Project talent as the need for skilled professionals has increased phenomenally in numbers, but the availability of the resources is abysmally low. 1 million is hardly a number when the need is more than twice the figure. It's no wonder PMP is at a premium and hence the pay difference between the certified and non-certified stands at a substantial 23%.
PMP – Return on Investment (ROI)
How much does it cost you to get PMP certified?
The cost involved in getting the PMP certificate:
- PMI membership – non-negotiable, costs $139
- PMP exam fee: for a member, it costs $405. Non-member, the cost will be $555
- The cost of PMP certification training to gain 35 PDUs
- The cost of buying study materials.
Now add them up. It is going to be a little over $1000.
Check the statistic: PMP holder median pay is $111,000 as against $91,000 for a non-certified professional in the United States.
So over a $1000 investment, you could potentially earn $111,000 per year, and the returns will be recurring.
One of the factors influencing your salary will be the employer or the company as observed in the infographic. It is so because there are companies that do reimburse the employers for the exam and membership fees - which make the ROI, go higher.
Hence, as a project manager, your salary will increase when you are PMP certified and helps you to contribute to your profession with remuneration inline experience and position.
For more information about professional certification, please visit us at https://www.icertglobal.com or call now on +1-713-287-1213 / 1214 or e-mail us at info {at} icertglobal {dot} com.
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
For more information about our PMP (Project Management Professional) exam prep certification training courses, visit us at https://www.icertglobal.com/
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
Download our Free PMP Brochure for more information.
PMP Exam Guidance With PMP Exam Format
PMP Exam Guidance With PMP Exam Format
PMP Exam based Questions
FORMULA based questions
SITUATIONAL based questions
DEFINITION based questions
KNOWLEDGE based questions
INTERPRETATIONAL based questions
SPECIFIC TECHNIQUE based questions
PMBOK GUIDE KNOWLEDGE based questions
ITTO (Inputs, Tools, Techniques & Outputs) based questions
Professional and Social Responsibility based questions.
Combination questions
Preparation is fundamental to PASS.
Agreed PMP is tough. The reading required is rigorous and effort tremendous. But nothing comes easy and if you wish to crack the coveted PMP exam, then preparation and practice are decisive to pass.
First, let us learn about the Pre-Requisite Qualifications for PMP certification.
It’s important to keep in mind that you must fulfill the eligibility criteria to take the PMP exam. The pre-requisites for the PMP exam are detailed below:
Education and Experience
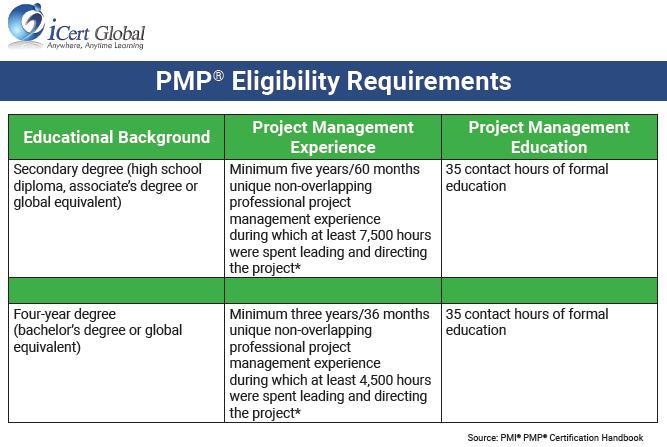
If you meet the above requirements, then you are qualified to appear for the PMP exam.
FEES
The examination fee is $405 for registered members and $555 for non-registered members.
PDUs
The 35 hours of Professional Development Units (PDUs) is MANDATORY to meet the requirements prescribed by PMI to sit for the PMP exam. You can gain the 35 PDUs by attending workshop sessions, coursework, and training through a globally registered PMI Education Provider. Please note that one PDU is equal to one hour of training.
PMP Examination Structure
Become familiar with the structure of the PMP exam before you begin your preparation. The PMP exam conducted by PMI will be difficult and demanding. So, get a good head start
It is essential to understand the basic structure of a PMP exam before starting to prepare for, or before sitting the exam. Being familiar with the structure will put you at an advantage.
PMP has the following phases with a breakdown of questions in percentage:
I. Initiating
13%
II. Planning
24%
III. Executing
31%
IV. Monitoring and Controlling
25%
V. Closing
7%
Total
100%
Each phase is significant. The PMP exam will test your knowledge in each phase. All the phases are related from the start of the project to the end. The first four phases are high in percentage because they are the most complex phases of the project.
PMP Exam Questions
- The PMP exam consists of 200 items, out of which 25 are pre-test questions.
- The pretest questions have no score.
- Only 175 will get the score.
- You will not know which question is a pre-test question. You need to answer all the 200 questions.
- The duration of the exam will be 4 hours. And there are no breaks.
PMP Passing Score
- PMP is no longer publishing the passing score.
- The outcome of the exam is indicated by pass or fail. The performance rating of the domains and the overall exam are also published.
- PMI uses “sound psychometric analysis” to calculate the passing figure.
- For each question, a point is awarded, and the subject matter experts selected by PMI will decide the number of right answers to pass the PMP exam.
PMP Exam Preparation
You can confidently sit for the exam and move forward with confidence: check out these four ways wth which project management professionals commonly tackle the exam prep process.
1. Picture the final line
Write down a mission and vision statement clearly spelling the importance of achieving the PMP credential. State the reasons why PMP is important to accelerate your career and increasing your earning potential. Read it, again and again, to stay motivated.
- Prepare a study plan that fills the weeks and months ahead of the exam day.
- Make the schedule after careful consideration balancing the work and family obligation.
- Stay on track by sharing the goal with friends, colleagues, other PMP aspirants and PMP professionals known to you that will help in ascertaining your course path.
2. Walk the PMP path
- You have to become familiar with the PMP exam pattern of 200 questions.
- Read and review the course outline and pay attention to the knowledge areas covered.
- Try to get an idea about the different formats of 200 questions by visiting some sample papers.
3. Chart out the course of action
- Execute your plan and start your study based on the schedule prepared.
- Find out the prep resources collected by you – it can be the PMBOK-6th edition, study materials provided by the training institutes where you earned the 35 PDUs and other relevant and required books and literature.
- Attempt as many practice tests and mock exams. These exams are available online and offline as well. Check with your training institute who might offer a question bank or simulator to help you practice. Preparation is the key.
- Get guidance from PMI chapter members and recommendations from PMP professionals.
4. Become a part of the community
- Get connected with the PMP community wherein you can benefit from the experience and wisdom of Project professionals who advise and keep you motivated.
- Join the discussions of professional groups, like PMI’s LinkedIn group that centres around PMP certifications. You can get to know the challenges and seek professional help in overcoming the odds.
- Become active in other PMP communities. Post a question, provide answers that you might know and engage in that thread. It's good to stay connected.
PMP Exam Question Format and Types
The PMP exam is composed of 200 multiple-choice questions.
The different types of questions that appear in the PMP certification exam are listed below
- FORMULA based questions
- SITUATIONAL based questions
- DEFINITION based questions
- KNOWLEDGE based questions
- INTERPRETATIONAL based questions
- SPECIFIC TECHNIQUE based questions
- PMBOK GUIDE KNOWLEDGE based questions
- ITTO (Inputs, Tools, Techniques & Outputs) based questions
- Professional and Social Responsibility based questions.
- Combination questions
1. FORMULA based questions
- In order to pass the PMP exam, it is critical you will have to be well-versed with the definitions, concepts, all the formuals, processes and knowledge areas.
- There are 49 PMP exam formulas which you should know like the back of the palm. It can range from averages to probability to forward pass or backward pass.
- You need these formulas to answer all the mathematical or formula-based questions.
- Get to know the formulas and their application. You must be good at knowing which formula to be used for what situation.
- Questions posed in this set of questions include concepts like critical path method, PERT, EVM (Eearned Value Management) and so on.
2. Situational PMP Exam Questions
- Most of the questions posed are situational in nature. It can be as high as 60%. The questions are long with too many words packed.
- These questions test your competence to apply your knowledge in real-lifetime scenarios and situations.
- You will be tested in identifying what's important and discard the ones that don’t matter. Its easier said than done as you need an eye for details to spot the right from wrong.
- The choices presented for this set of questions are “what is the Best Choice” or what is the only answer” or “except”. Mind you, situational questions can be tricky. Expect choices as NOT or EXCEPT or ONLY or ALWAYS which can alter the meaning of the question.
3. DEFINITION based questions for PMP
- These questions cover the definitions of the PMP certification exam, like definitions of project, risk, scope, etc.
- This set of questions can be easily answered if you are clear and conversant with the concepts and definitions detailed in the PMBOK and project management.
4. Knowledge-Based PMP Exam Questions
- You will have to analyze the data provided to arrive at the right answer. Your proficiency to understand a concept will be tested, and the ability to chart the right course of action.
- The questions asked might be about identifying the right process attached to the knowledge areas or the correct Inputs, Tools & Techniques or Outputs that are mapped to the process.
5. INTERPRETATIONAL based questions for PMP
- Interpretational questions test your ability to decode a situation or condition based on your understanding of the description of the problem.
- You will be presented with some data to analyze and interpret the right answer.
- You will have to infer the situation based on the information provided, and answer correctly. The questions analyze your awareness.
6. SPECIFIC TECHNIQUE based questions for PMP
- You will be presented with the details about a specific situation and asked to answer question-based on the situation. Say something like a network diagram or a flow chart.
- Sometimes, you will be asked to provide information that’s essential to the situation.
- The response you provide should directly relate to a component in the situation.
7. PMBOK GUIDE KNOWLEDGE based questions for PMP
- The questions in this type will probe your knowledge and understanding of the 10 knowledge areas and 49 processes.
- You will be tested about the ability to the application of the Processes and Knowledge Areas. Specifically, your proficiency in the concepts, processes as to how they are related, where do they occur and what do they consist.
8. ITTO based questions for PMP
- According to the PMBOK® Guide – Sixth Edition, there are 49 processes and each process features and input, tools & techniques and Outputs.
- You need to know about each input, Tools, Techniques & Output for every process, meaning, which ITTO belongs to what process and how can it be applied.
- Typically, the questions presented in this type will be the selection of the right correct Input, Tool & Technique, or Output for the given process.
9. Professional Social Responsibility based questions for PMP
- There are ethics and professional conduct prescribed by PMI, as part of becoming certified.
- The questions will be in line with professional and social conduct.
- These questions will check your knowledge about adherence to standards and ethics in doing what is right and honourable as sted by PMI
10. COMBINATION based questions for PMP
- The questions posed will be a combination of any of the above-mentioned types.
- You need to be proficient in all the formats or types of questions to answer correctly.
- Proficiency comes from practice. when the frequency of taking up practice tests and mock exams increases, you become more familiar with the formulas, situations, definitions interpretations, ITTO, and concepts.
- This not only prepares but boosts your confidence in cracking the PMP exam. Of course, in the first attempt.
For more information on PMP Exam, visit: https://www.pmi.org/
Recommended posts:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
For more information about PMP® Certification Training courses worldwide, please visit us at https://www.icertglobal.com or
Call Now! on +1-713-287-1213 / 1214 / 1053 / 1355 or e-mail us at info {at} icertglobal {dot} com.
Read More
PMP Exam Guidance With PMP Exam Format
PMP Exam based Questions
FORMULA based questions
SITUATIONAL based questions
DEFINITION based questions
KNOWLEDGE based questions
INTERPRETATIONAL based questions
SPECIFIC TECHNIQUE based questions
PMBOK GUIDE KNOWLEDGE based questions
ITTO (Inputs, Tools, Techniques & Outputs) based questions
Professional and Social Responsibility based questions.
Combination questions
Preparation is fundamental to PASS.
Agreed PMP is tough. The reading required is rigorous and effort tremendous. But nothing comes easy and if you wish to crack the coveted PMP exam, then preparation and practice are decisive to pass.
First, let us learn about the Pre-Requisite Qualifications for PMP certification.
It’s important to keep in mind that you must fulfill the eligibility criteria to take the PMP exam. The pre-requisites for the PMP exam are detailed below:
Education and Experience

If you meet the above requirements, then you are qualified to appear for the PMP exam.
FEES
The examination fee is $405 for registered members and $555 for non-registered members.
PDUs
The 35 hours of Professional Development Units (PDUs) is MANDATORY to meet the requirements prescribed by PMI to sit for the PMP exam. You can gain the 35 PDUs by attending workshop sessions, coursework, and training through a globally registered PMI Education Provider. Please note that one PDU is equal to one hour of training.
PMP Examination Structure
Become familiar with the structure of the PMP exam before you begin your preparation. The PMP exam conducted by PMI will be difficult and demanding. So, get a good head start
It is essential to understand the basic structure of a PMP exam before starting to prepare for, or before sitting the exam. Being familiar with the structure will put you at an advantage.
PMP has the following phases with a breakdown of questions in percentage:
|
I. Initiating |
13% |
|
II. Planning |
24% |
|
III. Executing |
31% |
|
IV. Monitoring and Controlling |
25% |
|
V. Closing |
7% |
|
Total |
100% |
Each phase is significant. The PMP exam will test your knowledge in each phase. All the phases are related from the start of the project to the end. The first four phases are high in percentage because they are the most complex phases of the project.
PMP Exam Questions
- The PMP exam consists of 200 items, out of which 25 are pre-test questions.
- The pretest questions have no score.
- Only 175 will get the score.
- You will not know which question is a pre-test question. You need to answer all the 200 questions.
- The duration of the exam will be 4 hours. And there are no breaks.
PMP Passing Score
- PMP is no longer publishing the passing score.
- The outcome of the exam is indicated by pass or fail. The performance rating of the domains and the overall exam are also published.
- PMI uses “sound psychometric analysis” to calculate the passing figure.
- For each question, a point is awarded, and the subject matter experts selected by PMI will decide the number of right answers to pass the PMP exam.
PMP Exam Preparation
You can confidently sit for the exam and move forward with confidence: check out these four ways wth which project management professionals commonly tackle the exam prep process.
1. Picture the final line
Write down a mission and vision statement clearly spelling the importance of achieving the PMP credential. State the reasons why PMP is important to accelerate your career and increasing your earning potential. Read it, again and again, to stay motivated.
- Prepare a study plan that fills the weeks and months ahead of the exam day.
- Make the schedule after careful consideration balancing the work and family obligation.
- Stay on track by sharing the goal with friends, colleagues, other PMP aspirants and PMP professionals known to you that will help in ascertaining your course path.
2. Walk the PMP path
- You have to become familiar with the PMP exam pattern of 200 questions.
- Read and review the course outline and pay attention to the knowledge areas covered.
- Try to get an idea about the different formats of 200 questions by visiting some sample papers.
3. Chart out the course of action
- Execute your plan and start your study based on the schedule prepared.
- Find out the prep resources collected by you – it can be the PMBOK-6th edition, study materials provided by the training institutes where you earned the 35 PDUs and other relevant and required books and literature.
- Attempt as many practice tests and mock exams. These exams are available online and offline as well. Check with your training institute who might offer a question bank or simulator to help you practice. Preparation is the key.
- Get guidance from PMI chapter members and recommendations from PMP professionals.
4. Become a part of the community
- Get connected with the PMP community wherein you can benefit from the experience and wisdom of Project professionals who advise and keep you motivated.
- Join the discussions of professional groups, like PMI’s LinkedIn group that centres around PMP certifications. You can get to know the challenges and seek professional help in overcoming the odds.
- Become active in other PMP communities. Post a question, provide answers that you might know and engage in that thread. It's good to stay connected.
PMP Exam Question Format and Types
The PMP exam is composed of 200 multiple-choice questions.
The different types of questions that appear in the PMP certification exam are listed below
- FORMULA based questions
- SITUATIONAL based questions
- DEFINITION based questions
- KNOWLEDGE based questions
- INTERPRETATIONAL based questions
- SPECIFIC TECHNIQUE based questions
- PMBOK GUIDE KNOWLEDGE based questions
- ITTO (Inputs, Tools, Techniques & Outputs) based questions
- Professional and Social Responsibility based questions.
- Combination questions
1. FORMULA based questions
- In order to pass the PMP exam, it is critical you will have to be well-versed with the definitions, concepts, all the formuals, processes and knowledge areas.
- There are 49 PMP exam formulas which you should know like the back of the palm. It can range from averages to probability to forward pass or backward pass.
- You need these formulas to answer all the mathematical or formula-based questions.
- Get to know the formulas and their application. You must be good at knowing which formula to be used for what situation.
- Questions posed in this set of questions include concepts like critical path method, PERT, EVM (Eearned Value Management) and so on.
2. Situational PMP Exam Questions
- Most of the questions posed are situational in nature. It can be as high as 60%. The questions are long with too many words packed.
- These questions test your competence to apply your knowledge in real-lifetime scenarios and situations.
- You will be tested in identifying what's important and discard the ones that don’t matter. Its easier said than done as you need an eye for details to spot the right from wrong.
- The choices presented for this set of questions are “what is the Best Choice” or what is the only answer” or “except”. Mind you, situational questions can be tricky. Expect choices as NOT or EXCEPT or ONLY or ALWAYS which can alter the meaning of the question.
3. DEFINITION based questions for PMP
- These questions cover the definitions of the PMP certification exam, like definitions of project, risk, scope, etc.
- This set of questions can be easily answered if you are clear and conversant with the concepts and definitions detailed in the PMBOK and project management.
4. Knowledge-Based PMP Exam Questions
- You will have to analyze the data provided to arrive at the right answer. Your proficiency to understand a concept will be tested, and the ability to chart the right course of action.
- The questions asked might be about identifying the right process attached to the knowledge areas or the correct Inputs, Tools & Techniques or Outputs that are mapped to the process.
5. INTERPRETATIONAL based questions for PMP
- Interpretational questions test your ability to decode a situation or condition based on your understanding of the description of the problem.
- You will be presented with some data to analyze and interpret the right answer.
- You will have to infer the situation based on the information provided, and answer correctly. The questions analyze your awareness.
6. SPECIFIC TECHNIQUE based questions for PMP
- You will be presented with the details about a specific situation and asked to answer question-based on the situation. Say something like a network diagram or a flow chart.
- Sometimes, you will be asked to provide information that’s essential to the situation.
- The response you provide should directly relate to a component in the situation.
7. PMBOK GUIDE KNOWLEDGE based questions for PMP
- The questions in this type will probe your knowledge and understanding of the 10 knowledge areas and 49 processes.
- You will be tested about the ability to the application of the Processes and Knowledge Areas. Specifically, your proficiency in the concepts, processes as to how they are related, where do they occur and what do they consist.
8. ITTO based questions for PMP
- According to the PMBOK® Guide – Sixth Edition, there are 49 processes and each process features and input, tools & techniques and Outputs.
- You need to know about each input, Tools, Techniques & Output for every process, meaning, which ITTO belongs to what process and how can it be applied.
- Typically, the questions presented in this type will be the selection of the right correct Input, Tool & Technique, or Output for the given process.
9. Professional Social Responsibility based questions for PMP
- There are ethics and professional conduct prescribed by PMI, as part of becoming certified.
- The questions will be in line with professional and social conduct.
- These questions will check your knowledge about adherence to standards and ethics in doing what is right and honourable as sted by PMI
10. COMBINATION based questions for PMP
- The questions posed will be a combination of any of the above-mentioned types.
- You need to be proficient in all the formats or types of questions to answer correctly.
- Proficiency comes from practice. when the frequency of taking up practice tests and mock exams increases, you become more familiar with the formulas, situations, definitions interpretations, ITTO, and concepts.
- This not only prepares but boosts your confidence in cracking the PMP exam. Of course, in the first attempt.
For more information on PMP Exam, visit: https://www.pmi.org/
Recommended posts:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
For more information about PMP® Certification Training courses worldwide, please visit us at https://www.icertglobal.com or
Call Now! on +1-713-287-1213 / 1214 / 1053 / 1355 or e-mail us at info {at} icertglobal {dot} com.
Benefits Of Getting A PMI-ACP Agile Certified Practitioner Certification.
Benefits Of Getting A PMI-ACP Agile Certified Practitioner Certification
#1 Global Recognition
#2 Enhances Agile Skills
#3 Increases Professional Credibility
#4 Higher Job Opportunities
#5 Higher Pay
#6 Career Advancement
#7 Professional Versatility
#8 Expands Market Reach
#9 Get More Lucrative Assignments
#10 Recession-Proof Career:
Project Management Institute (PMI®) – Agile Certified Practitioner Certification (ACP) is a globally recognized and in-demand certification in the field of agile project management accredited by PMI. Agile is an iterative method to develop software step by step taking frequent reassessment whenever required, instead of delivering the whole product after completion. PMI-ACP validates your knowledge and experience on agile principles and hands-on agile techniques. PMI-ACP is based on different frameworks and agile approaches such as:
- Scrum
- Kanban
- Lean-Agile Practices
- Extreme programming (XP)
- Test-driven development (TDD.)
Prerequisites for PMI-ACP:
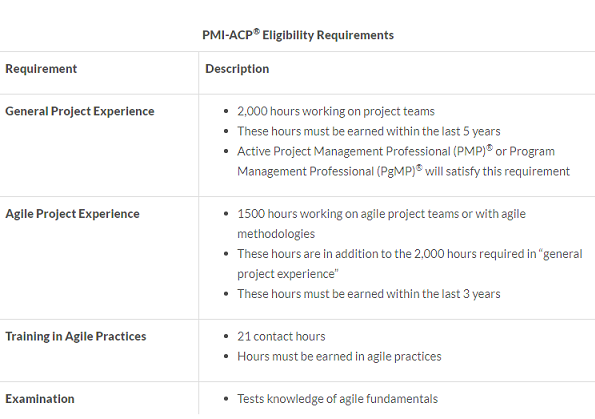
For more information on eligibility criteria refer PMI-ACP Handbook
Certification fee:
PMI Membership
Fee
Member
$435
Non-Member
$495
Target Audience:
- Project Managers
- Scrum Masters
- Scrum P
- product owners
- Program managers
- Project team members
- Professionals aspiring to shift from waterfall methodology to agile methodology
Demand and Scope for Agile certified practitioners:
According to the 13th State of Agile Survey Report (2019),
- 71% of respondents adopted agile because it reduces project cost
- 74% of respondents adopted agile as it accelerates the software delivery
- 51% of respondents claim that adopting agile increases productivity
- 43% of respondents stated adopting agile enhances the product quality
Benefits of getting PMI-ACP certified:
- Global recognition: PMI-ACP is globally recognized and in-demand certification by PMI.
- Enhances agile skills: Gain expertise in using agile practices in your projects and get hands-on agile experiences.
- Increases professional credibility: Carries a higher level of professional credibility as it requires a combination of agile training, and work experience in agile projects and knowledge.
- Higher Job Opportunities: As the adoption of agile methodology is increasing day by day, job opportunities are also increasing.
- Higher pay: Certified PMI-ACP professionals get a 28% higher salary than non-certified professionals. According to payscale.com, the average annual salary for certified PMI-ACP professionals is $108k/year.
- Career advancement: PMI-ACP certification allows you to advance your career in organizations practicing agile. Certified PMI-ACP professionals can become agile trainers and agile coaches.
- Professional Versatility: As a certified professional you might get a chance to lead the team, work in different projects and enhance your project management skills with agile tools and techniques.
- Expands market reach: Certification in PMI-ACP expands your market reach as an agile certified professional and provides you with an opportunity to network with a vibrant community of agile professionals, related organizations, and experts worldwide.
- Get more lucrative assignments: Certified professionals are more likely to get challenging projects and opportunities to handle valued projects.
- Recession-proof career: Invest in your future with PMI-AC certification. Agile professionals would retain their value even during a recession due to their strong and highly transferable core competencies.
Career opportunities after PMI-ACP certification:
- PMP Scrum master
- Technical business analyst
- Agile trainer
- Project Manager
- Digital Channel planner
- Deputy Project Manager
- Director - planning and Project management
- Business Analyst
- Agile Project Manager
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
iCert Global offers Agile based Certification:
Download our Free PMI-ACP Brochure for more information.
For more information on how iCert Global can help you to accelerate your career with Agile certification, please e-mail info {at} icertglobal {dot} org or call now on +1-713-287-1213/ 1214 / 1053 / 1355. Visit us at https://www.icertglobal.com/
Read More
Benefits Of Getting A PMI-ACP Agile Certified Practitioner Certification
#1 Global Recognition
#2 Enhances Agile Skills
#3 Increases Professional Credibility
#4 Higher Job Opportunities
#5 Higher Pay
#6 Career Advancement
#7 Professional Versatility
#8 Expands Market Reach
#9 Get More Lucrative Assignments
#10 Recession-Proof Career:
Project Management Institute (PMI®) – Agile Certified Practitioner Certification (ACP) is a globally recognized and in-demand certification in the field of agile project management accredited by PMI. Agile is an iterative method to develop software step by step taking frequent reassessment whenever required, instead of delivering the whole product after completion. PMI-ACP validates your knowledge and experience on agile principles and hands-on agile techniques. PMI-ACP is based on different frameworks and agile approaches such as:
- Scrum
- Kanban
- Lean-Agile Practices
- Extreme programming (XP)
- Test-driven development (TDD.)
Prerequisites for PMI-ACP:

For more information on eligibility criteria refer PMI-ACP Handbook
Certification fee:
|
PMI Membership |
Fee |
|
Member |
$435 |
|
Non-Member |
$495 |
Target Audience:
- Project Managers
- Scrum Masters
- Scrum P
- product owners
- Program managers
- Project team members
- Professionals aspiring to shift from waterfall methodology to agile methodology
Demand and Scope for Agile certified practitioners:
According to the 13th State of Agile Survey Report (2019),
- 71% of respondents adopted agile because it reduces project cost
- 74% of respondents adopted agile as it accelerates the software delivery
- 51% of respondents claim that adopting agile increases productivity
- 43% of respondents stated adopting agile enhances the product quality
Benefits of getting PMI-ACP certified:
- Global recognition: PMI-ACP is globally recognized and in-demand certification by PMI.
- Enhances agile skills: Gain expertise in using agile practices in your projects and get hands-on agile experiences.
- Increases professional credibility: Carries a higher level of professional credibility as it requires a combination of agile training, and work experience in agile projects and knowledge.
- Higher Job Opportunities: As the adoption of agile methodology is increasing day by day, job opportunities are also increasing.
- Higher pay: Certified PMI-ACP professionals get a 28% higher salary than non-certified professionals. According to payscale.com, the average annual salary for certified PMI-ACP professionals is $108k/year.
- Career advancement: PMI-ACP certification allows you to advance your career in organizations practicing agile. Certified PMI-ACP professionals can become agile trainers and agile coaches.
- Professional Versatility: As a certified professional you might get a chance to lead the team, work in different projects and enhance your project management skills with agile tools and techniques.
- Expands market reach: Certification in PMI-ACP expands your market reach as an agile certified professional and provides you with an opportunity to network with a vibrant community of agile professionals, related organizations, and experts worldwide.
- Get more lucrative assignments: Certified professionals are more likely to get challenging projects and opportunities to handle valued projects.
- Recession-proof career: Invest in your future with PMI-AC certification. Agile professionals would retain their value even during a recession due to their strong and highly transferable core competencies.
Career opportunities after PMI-ACP certification:
- PMP Scrum master
- Technical business analyst
- Agile trainer
- Project Manager
- Digital Channel planner
- Deputy Project Manager
- Director - planning and Project management
- Business Analyst
- Agile Project Manager
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
iCert Global offers Agile based Certification:
Download our Free PMI-ACP Brochure for more information.
For more information on how iCert Global can help you to accelerate your career with Agile certification, please e-mail info {at} icertglobal {dot} org or call now on +1-713-287-1213/ 1214 / 1053 / 1355. Visit us at https://www.icertglobal.com/
How Long Does It Take To Get A PMP® Certification?
How Long Does It Take To Get A PMP® Certification?
Preparation is the most critical factor in becoming a certified Project Management Professional (PMP). Depending on the prerequisites and preparedness it is possible to get a PMP certification in 8 to 12 weeks after applying to PMI.
Project Management Professional (PMP®) certification is a benchmark for project management. The PMP certification validates the experience, knowledge, expertise, capability, competency and required skills to lead and manage projects. PMP certification is the most recognized and sought after project management certification. The PMP certification is compelling in its benefits and considered to be lucrative as it increases the earning potential. PMI’s PMBOK (Product Management Body of Knowledge) Guide is one of the reference books for PMP certification.
PMP Pre-requisites:
You need 4500 or 7500 hours of project management experience to fulfil the eligibility.
You can use the following calculation to record your experience in hours:
Project hours = Average number of working days in a month x Average number of productive hours a day x Number of months worked on that project
- There are only 8 hours in a day.
- Five days and therefore 40 hours in a workweek
- Deducting the vacations thats around 2 weeks in a calendar year leaves us with 50 workweeks.
- 50 workweeks translate to 2000 hours in a year.
- PMI recognizes only the first 40 hours each week.
- Non-overlapping hours cannot be accounted for.
- Therefore, the total experience required works out to 4500 hours or 3 years.
After meeting the eligibility criteria, You need to apply for PMP application by registering with PMI.
(Source: PMI’s PMP Handbook)
PMP Application and PMI's Notifications
- PMI provides 90 days to fill the application form from the time you start filling the application. The step by step procedure to fill PMP application is in reference to PMI’s PMP Handbook. You need to incorporate project management experience in PMP application form which can be time-consuming.
- During those 90 days, PMI will send you reminders to submit the application form in case it is incomplete.
- Once you submit the application online, PMI takes 5 calendar days to confirm the receipt and completeness of the PMP application form. You can also submit the application by post.
- If your application is selected for the audit process, you have 90 days to send audit materials.
During an audit, you will be asked to submit supporting documentation such as:
- Copies of your diploma/global equivalent
- Signatures from your supervisor(s) or manager(s) from the project(s) recorded in the experience verification section of the application
- Copies of certificates and/or letters from the training institute(s) for each course recorded on the application to meet the required contact hours of project management education
- Once you send the audit materials to PMI via postal mail or express courier service, PMI takes 5 to 7 business days to complete the audit process after receiving all the supporting documents at once.
Note: If you fail the audit process, there is a one-year suspension period to apply for that certification again.
- If you pass the audit process, PMI will send you a notification mail to submit the payment.
- Once you submit the payment, PMI will notify you with confirmation of application approval.
You have one-year time period from the date of application approval to take up the exam. You have three attempts to pass the examination.
If you fail the PMP examination in the first attempt, you can apply for re-examination by submitting the following payment:
If you fail the PMP exam in all 3 attempts, you must wait one year from the date of the last examination you took to reapply for the certification.
Preparation is the most critical factor in becoming a certified Project Management Professional (PMP). Depending on the prerequisites and preparedness it is possible to get a PMP certification in 8 to 12 weeks after applying to PMI.
Please read this blog from an information perspective and do not be discouraged at all. PMP might be tough but with dedicated effort and disciplined approach, you can pass in the first attempt.
Recommended post:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
For more information about PMP® Certification Training courses worldwide, please visit us at https://www.icertglobal.com
or
Call Now! on +1-713-287-1213 / 1214 / 1053 / 1355 or e-mail us at info {at} icertglobal {dot} com.
Read More
How Long Does It Take To Get A PMP® Certification?
Preparation is the most critical factor in becoming a certified Project Management Professional (PMP). Depending on the prerequisites and preparedness it is possible to get a PMP certification in 8 to 12 weeks after applying to PMI.
Project Management Professional (PMP®) certification is a benchmark for project management. The PMP certification validates the experience, knowledge, expertise, capability, competency and required skills to lead and manage projects. PMP certification is the most recognized and sought after project management certification. The PMP certification is compelling in its benefits and considered to be lucrative as it increases the earning potential. PMI’s PMBOK (Product Management Body of Knowledge) Guide is one of the reference books for PMP certification.
PMP Pre-requisites:
You need 4500 or 7500 hours of project management experience to fulfil the eligibility.
You can use the following calculation to record your experience in hours:
Project hours = Average number of working days in a month x Average number of productive hours a day x Number of months worked on that project
- There are only 8 hours in a day.
- Five days and therefore 40 hours in a workweek
- Deducting the vacations thats around 2 weeks in a calendar year leaves us with 50 workweeks.
- 50 workweeks translate to 2000 hours in a year.
- PMI recognizes only the first 40 hours each week.
- Non-overlapping hours cannot be accounted for.
- Therefore, the total experience required works out to 4500 hours or 3 years.
After meeting the eligibility criteria, You need to apply for PMP application by registering with PMI.
(Source: PMI’s PMP Handbook)
PMP Application and PMI's Notifications
- PMI provides 90 days to fill the application form from the time you start filling the application. The step by step procedure to fill PMP application is in reference to PMI’s PMP Handbook. You need to incorporate project management experience in PMP application form which can be time-consuming.
- During those 90 days, PMI will send you reminders to submit the application form in case it is incomplete.
- Once you submit the application online, PMI takes 5 calendar days to confirm the receipt and completeness of the PMP application form. You can also submit the application by post.
- If your application is selected for the audit process, you have 90 days to send audit materials.
During an audit, you will be asked to submit supporting documentation such as:
- Copies of your diploma/global equivalent
- Signatures from your supervisor(s) or manager(s) from the project(s) recorded in the experience verification section of the application
- Copies of certificates and/or letters from the training institute(s) for each course recorded on the application to meet the required contact hours of project management education
- Once you send the audit materials to PMI via postal mail or express courier service, PMI takes 5 to 7 business days to complete the audit process after receiving all the supporting documents at once.
Note: If you fail the audit process, there is a one-year suspension period to apply for that certification again.
- If you pass the audit process, PMI will send you a notification mail to submit the payment.
- Once you submit the payment, PMI will notify you with confirmation of application approval.
You have one-year time period from the date of application approval to take up the exam. You have three attempts to pass the examination.
If you fail the PMP examination in the first attempt, you can apply for re-examination by submitting the following payment:
If you fail the PMP exam in all 3 attempts, you must wait one year from the date of the last examination you took to reapply for the certification.
Preparation is the most critical factor in becoming a certified Project Management Professional (PMP). Depending on the prerequisites and preparedness it is possible to get a PMP certification in 8 to 12 weeks after applying to PMI.
Please read this blog from an information perspective and do not be discouraged at all. PMP might be tough but with dedicated effort and disciplined approach, you can pass in the first attempt.
Recommended post:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
For more information about PMP® Certification Training courses worldwide, please visit us at https://www.icertglobal.com
or
Call Now! on +1-713-287-1213 / 1214 / 1053 / 1355 or e-mail us at info {at} icertglobal {dot} com.
Comparison of Popular Professional Certification Search Trends in 2019 in the United States
Comparison of Popular Professional Certifications Search Trends in the Year 2019 in the United States.
Google Trends data from 1st January 2019 until date (12th December 2019) for the following professional certification search terms across the United States.
- PMP Certification
- Six Sigma Certification
- Scrum Certification
- Agile Certification
- DevOps Certification
1. Google Search Trends (1st January 2019 to 12th December 2019)
Popular Professional Certification Training Courses in the United States.
2. PMP Certification - Top (related) Search Queries in the United States
Top search queries related to the search term pmp certification.
3. Six Sigma Certification - Top (related) Search Queries in the United States
Top search queries related to the search term six sigma certification.
4. Scrum Certification - Top (related) Search Queries in the United States
Top search queries related to the term scrum certification.
5. Agile Certification - Top (related) Search Queries in the United States
Top search queries related to the term agile certification.
6. DevOps Certification - Top (related) Search Queries in the United States
Top search queries related to the term devops certification.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
- PMP Certification Training
- CAPM Certification Training
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
Comparison of Popular Professional Certifications Search Trends in the Year 2019 in the United States.
Google Trends data from 1st January 2019 until date (12th December 2019) for the following professional certification search terms across the United States.- PMP Certification
- Six Sigma Certification
- Scrum Certification
- Agile Certification
- DevOps Certification
1. Google Search Trends (1st January 2019 to 12th December 2019)
Popular Professional Certification Training Courses in the United States.
2. PMP Certification - Top (related) Search Queries in the United States
Top search queries related to the search term pmp certification.
3. Six Sigma Certification - Top (related) Search Queries in the United States
Top search queries related to the search term six sigma certification.
4. Scrum Certification - Top (related) Search Queries in the United States
Top search queries related to the term scrum certification.
5. Agile Certification - Top (related) Search Queries in the United States
Top search queries related to the term agile certification.
6. DevOps Certification - Top (related) Search Queries in the United States
Top search queries related to the term devops certification.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
- PMP Certification Training
- CAPM Certification Training
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Can I take the PMP® exam without experience?
Can I take the PMP® exam without experience?
No. You cannot take the PMP exam without the required project management experience and education.
Project Management Professional (PMP®) certification is one of the prestigious and globally recognized certifications offered by the Project Management Institute (PMI®). According to PMI,s PMP handbook the prerequisites for PMP clearly states that you must have a minimum of 3 years of experience in leading and directing projects.
Eligibility criteria for applying PMP® certification:
- Secondary degree (high school diploma, associate’s degree or the global equivalent)
- 7,500 hours leading and directing projects
- 35 hours of project management education OR CAPM certification
OR
- Four-year degree
- 4,500 hours leading and directing projects
- 35 hours of project management education OR CAPM certification
What are 4500 or 7500 hours of leading and directing projects?
A Guide to the Project Management Body of Knowledge (PMBOK® Guide) defines a project as “a temporary endeavor undertaken to create a unique product or service.”
“Leading and directing” projects is any experience that falls under five processes of project management. The work in all the five project management processes includes:
-
Initiating
Initiating any project or sharing your ideas, creating the objective of the project or part of project management.
-
Planning
Converting the idea into proper work structure, creating Work Breakdown Structure (WBS), creating blueprints, resource planning, building, communication strategy.
-
Executing
Executing the project scope within a constrained timeframe, solving problems, quality management, cost management, and risk management.
-
Monitoring and Controlling
Tracking the project, reporting the project update and changes required, performance analysis, fixing problems, resource management, stakeholder management, cost management etc.
-
Closing
- Handing over, reviewing, documentation, finalizing and managing the final project report, etc.
- It is not necessary to have” Project Manager” designation in all the projects you worked on.
- 4500 or 7500 hours of experience can include all the experience you worked in project management processes. For every project, you do not need to have experience in all five process groups.
- In PMI’s PMP handbook, it is mentioned that the experience does not necessarily have to be paid work, but it does need to be in a professional setting.
What designation can be considered as a Project Management experience?
4500 or 7500 hours in leading and directing projects can be defined as an experience in any role which falls under project management processes.
A leading or directing role can be,
- Supervisor
- Team leader
- Assistant project manager
- Project Manager
- Project coordinators
- Any role participating in project management processes
You need reference related to all the projects and validation by your reporting manager to experience and description to qualify the audit process.
If you fail the audit process, there is a one-year suspension period to apply for that certification again.
How to get Project Management Experience?
- Step up the ladder along with your company to get project management experience. Take up a small project to lead and get experience in any of the five project management processes as mentioned above, PMI does not necessarily look for “Project manager” job title.
- To qualify PM experience, you have to keep a record of your work which includes initiating, planning, executing, managing and controlling, and closing such. Document your work with the information:
- Industry you worked
- Start and end date of the project
- Reporting manager
- Experience summary
Consider the past work experience which holds good for the definition of the project “a temporary endeavor was undertaken to create a unique product or service.” Keep a track of your work which comes with a specific deliverable and deadline.
- As mentioned above, the project management experience need not be paid work. You can take up volunteering projects to get PM experience in any of the five processes of project management.
- Create opportunities to lead the project by taking up other project management courses. Certified Associate Project Management Certification (CAPM) is one of the best project management certifications to start with. CAPM certification will help you to understand the fundamentals of the PMBOK Guide.
Recommended post:
- What is PMP?
- Key Features of PMP® Certification Training
- Top 10 Reasons to Get PMP® Certified
- How To Qualify PM Experience In PMP Application Form
- The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
For more information about PMP® Certification Training courses worldwide, please visit us at https://www.icertglobal.com
or
Call Now! on +1-713-287-1213 / 1214 / 1053 / 1355 or e-mail us at info {at} icertglobal {dot} com.
Read More
Can I take the PMP® exam without experience?
No. You cannot take the PMP exam without the required project management experience and education.
Project Management Professional (PMP®) certification is one of the prestigious and globally recognized certifications offered by the Project Management Institute (PMI®). According to PMI,s PMP handbook the prerequisites for PMP clearly states that you must have a minimum of 3 years of experience in leading and directing projects.
Eligibility criteria for applying PMP® certification:
- Secondary degree (high school diploma, associate’s degree or the global equivalent)
- 7,500 hours leading and directing projects
- 35 hours of project management education OR CAPM certification
OR
- Four-year degree
- 4,500 hours leading and directing projects
- 35 hours of project management education OR CAPM certification
What are 4500 or 7500 hours of leading and directing projects?
A Guide to the Project Management Body of Knowledge (PMBOK® Guide) defines a project as “a temporary endeavor undertaken to create a unique product or service.”
“Leading and directing” projects is any experience that falls under five processes of project management. The work in all the five project management processes includes:
-
Initiating
Initiating any project or sharing your ideas, creating the objective of the project or part of project management.
-
Planning
Converting the idea into proper work structure, creating Work Breakdown Structure (WBS), creating blueprints, resource planning, building, communication strategy.
-
Executing
Executing the project scope within a constrained timeframe, solving problems, quality management, cost management, and risk management.
-
Monitoring and Controlling
Tracking the project, reporting the project update and changes required, performance analysis, fixing problems, resource management, stakeholder management, cost management etc.
-
Closing
- Handing over, reviewing, documentation, finalizing and managing the final project report, etc.
- It is not necessary to have” Project Manager” designation in all the projects you worked on.
- 4500 or 7500 hours of experience can include all the experience you worked in project management processes. For every project, you do not need to have experience in all five process groups.
- In PMI’s PMP handbook, it is mentioned that the experience does not necessarily have to be paid work, but it does need to be in a professional setting.
What designation can be considered as a Project Management experience?
4500 or 7500 hours in leading and directing projects can be defined as an experience in any role which falls under project management processes.
A leading or directing role can be,
- Supervisor
- Team leader
- Assistant project manager
- Project Manager
- Project coordinators
- Any role participating in project management processes
You need reference related to all the projects and validation by your reporting manager to experience and description to qualify the audit process.
If you fail the audit process, there is a one-year suspension period to apply for that certification again.
How to get Project Management Experience?
- Step up the ladder along with your company to get project management experience. Take up a small project to lead and get experience in any of the five project management processes as mentioned above, PMI does not necessarily look for “Project manager” job title.
- To qualify PM experience, you have to keep a record of your work which includes initiating, planning, executing, managing and controlling, and closing such. Document your work with the information:
- Industry you worked
- Start and end date of the project
- Reporting manager
- Experience summary
Consider the past work experience which holds good for the definition of the project “a temporary endeavor was undertaken to create a unique product or service.” Keep a track of your work which comes with a specific deliverable and deadline.
- As mentioned above, the project management experience need not be paid work. You can take up volunteering projects to get PM experience in any of the five processes of project management.
- Create opportunities to lead the project by taking up other project management courses. Certified Associate Project Management Certification (CAPM) is one of the best project management certifications to start with. CAPM certification will help you to understand the fundamentals of the PMBOK Guide.
Recommended post:
- What is PMP?
- Key Features of PMP® Certification Training
- Top 10 Reasons to Get PMP® Certified
- How To Qualify PM Experience In PMP Application Form
- The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
For more information about PMP® Certification Training courses worldwide, please visit us at https://www.icertglobal.com
or
Call Now! on +1-713-287-1213 / 1214 / 1053 / 1355 or e-mail us at info {at} icertglobal {dot} com.
Is It Worth Getting a PMP (Project Management Professional) Certification?
Is It Worth Getting PMP Certification?
Yes, it is definitely worth getting PMP certification. It is worth the hard work, effort, time and money.
First let us know,
What is PMP all about?
Project Management Professional (PMP®) certification is a globally recognized certification accredited by the Project Management Institute (PMI®)- globally recognized organization in the field of project management.
PMP credential is an industry-recognized standard certification for project managers worldwide. Project managers having PMP credentials can witness their career growth as soon as they get certified. It validates their experience, knowledge, capability, and required skills to lead and manage complex projects.
Professionals who meet the following criteria can apply for prestigious PMP certification and take their career to a higher level:
- Secondary degree (high school diploma, associate’s degree or the global equivalent)
- 5 years or 7,500 hours leading and directing projects
- 35 hours of project management education OR CAPM certification
OR
- Four-year degree
- 3 years or 4,500 hours leading and directing projects
- 35 hours of project management education OR CAPM certification
PMP certification is aligned to the reference guide PMBOK- 6th edition released by PMI. It is the fundamental resource for the PMP credential aspirants. PMBOK-6th edition is developed by subject matter experts and reviewed by PMI’s Project management community. PMBOK guide is available in English and 11 other languages (Arabic, Chinese [simplified], French, German, Hindi, Italian, Japanese, Korean, Portuguese Brazilian, Russian and Spanish).
PMP examination is based on five domains mentioned in PMBOK-6 edition
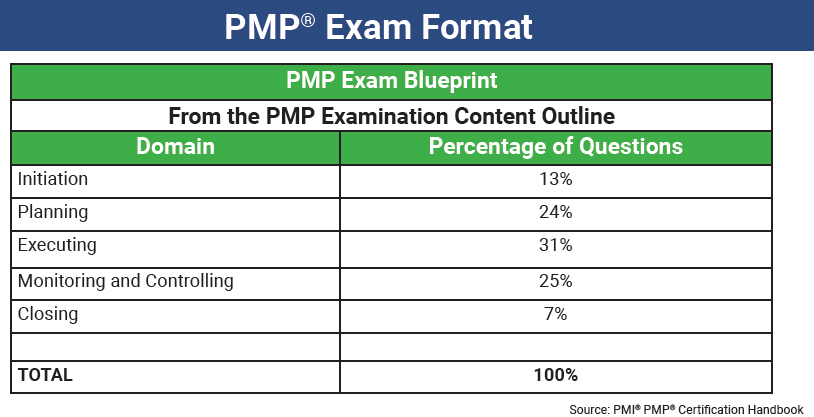
Let us know why getting PMP certification is worthy.
Adds value to your career
PMP credential definitely adds value to your career as it validates your competency and knowledge in the field of project management. It provides an opportunity to handle complex projects in the organization. PMP certification helps you to gain trust from the employers
The credentials from PMI prove that your knowledge is up to date as PMI course content is based on the current industry situation. It includes:
- Trends and emerging practices
- Tailoring considerations
- A greater emphasis on Strategic and Business Knowledge
- A new section on the role of the project manager
You can apply your project management skills according to the newest project management trends.
According to the statistics report by WRIKE,
“80 percent of high-performing projects are led by a certified project manager”.
Job opportunities worldwide
There are ocean-like opportunities in the field of project management for PMP certified professional.
According to PMI’s Talent Gap: Project management through 2020,

Project-intensive industries: The industries with a high level of project-oriented work. These industries are:
- Information services
- Manufacturing
- Business services
- Finance and insurance
- Oil and Gas
- Construction
- Utilities
The project management profession is expected to grow by US$6.61 trillion.
In the countries like Australia, Brazil, Canada, China, Germany, India, Japan, Saudi Arabia, United Arab Emirates and the United Kingdom, project management roles are expected to grow by 13.4 million through 2020.
Build network globally
Credentials from PMI is not just certification. It also gives opportunities to meet active practitioners and subject matter experts under one roof.
The PMI serves more than 2.9 million professionals including over 500,000 members in 208 countries and territories around the world, with 300 chapters and 10,000 volunteers serving local members in over 80 countries.
Though it is not mandatory to take PMI membership for PMP certification but it is recommended to take PMI membership for a discount on exam fee, opportunity to join local PMI chapter, free access to PMBOK guide etc.
If you are a member of PMI, PMI arranges frequent meetings, global conferences for members across the globe and speak common language of project management.
You can also access to online communities, templates, member-only webinars, virtual events etc. It will help you to build your network.
Higher earning potential
The earning potential increases with experience and progress of knowledge. According to Earning Power: Project Management Salary Survey, 10th Edition, certified PMP professionals earn 23% higher salary on average across 37 countries surveyed.
The countries with higher increase in the median salary of certified professionals are:
Country
Earning advantage
South Africa
58%
Ecuador
53%
Colombia
48%
Chile
43%
Mexico
43%
In the United States the median salary of Certified PMP professionals among survey respondents was 25% higher than the median salary of those without the PMP certification ($115,000 versus $92,000).
Continuous learning
Even after you get PMP certified once you get PMP certified you need to maintain your certification by earning Professional Development Units (PDUs) as a part of the Continuing Certification Requirement (CCR) Program.
1 PDU= 1 hour of learning activity
This allows you to gain knowledge on a continuous basis. You can earn PDU’s by attending webinars, joining the discussion thread, volunteering for local PMI chapter or by completing relevant educational courses by training organizations.
The Global Project Management community helps you to stay updated with recent methodologies and techniques.
Validates dedication towards a career
Getting PMP certification is not an easy task. Once you get PMP certified you will experience confidence to handle any kind of projects and increases the project success rate. It requires a lot of effort and commitment towards the goal.
The employee with continuous learning and dedicated to professional growth is an asset to the company.
The employers know the importance of trainings on project management.
According to PMI’s Pulse Of The Profession,
Three in five organizations provide training on project management tools and techniques.
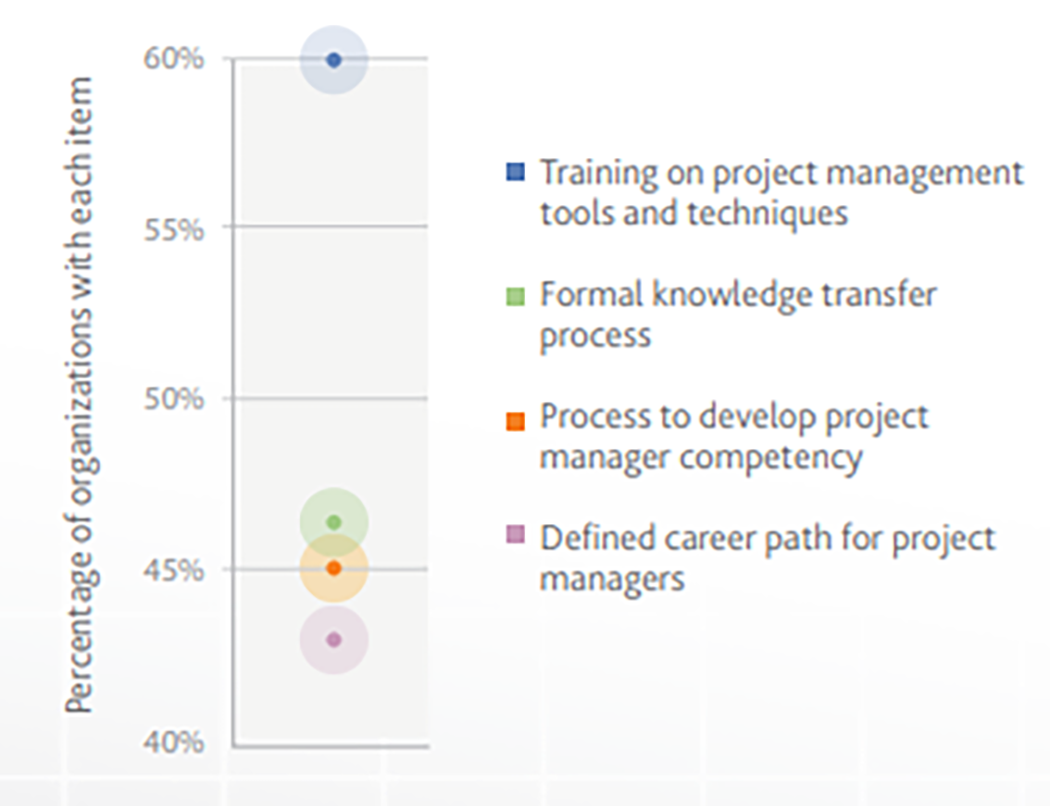
Conclusion
By knowing all the perks of getting PMP certified we can conclude that “yes” it is indeed worth all the efforts, money and time.
RECOMMENDED POST:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
For more information about PMP® Certification Training courses worldwide, please visit us at https://www.icertglobal.com
or
Call Now! on +1-713-287-1213 / 1214 / 1053 / 1355 or e-mail us at info {at} icertglobal {dot} com.
Read More
Is It Worth Getting PMP Certification?
Yes, it is definitely worth getting PMP certification. It is worth the hard work, effort, time and money.
First let us know,
What is PMP all about?
Project Management Professional (PMP®) certification is a globally recognized certification accredited by the Project Management Institute (PMI®)- globally recognized organization in the field of project management.
PMP credential is an industry-recognized standard certification for project managers worldwide. Project managers having PMP credentials can witness their career growth as soon as they get certified. It validates their experience, knowledge, capability, and required skills to lead and manage complex projects.
Professionals who meet the following criteria can apply for prestigious PMP certification and take their career to a higher level:
- Secondary degree (high school diploma, associate’s degree or the global equivalent)
- 5 years or 7,500 hours leading and directing projects
- 35 hours of project management education OR CAPM certification
OR
- Four-year degree
- 3 years or 4,500 hours leading and directing projects
- 35 hours of project management education OR CAPM certification
PMP certification is aligned to the reference guide PMBOK- 6th edition released by PMI. It is the fundamental resource for the PMP credential aspirants. PMBOK-6th edition is developed by subject matter experts and reviewed by PMI’s Project management community. PMBOK guide is available in English and 11 other languages (Arabic, Chinese [simplified], French, German, Hindi, Italian, Japanese, Korean, Portuguese Brazilian, Russian and Spanish).
PMP examination is based on five domains mentioned in PMBOK-6 edition

Let us know why getting PMP certification is worthy.
Adds value to your career
PMP credential definitely adds value to your career as it validates your competency and knowledge in the field of project management. It provides an opportunity to handle complex projects in the organization. PMP certification helps you to gain trust from the employers
The credentials from PMI prove that your knowledge is up to date as PMI course content is based on the current industry situation. It includes:
- Trends and emerging practices
- Tailoring considerations
- A greater emphasis on Strategic and Business Knowledge
- A new section on the role of the project manager
You can apply your project management skills according to the newest project management trends.
According to the statistics report by WRIKE,
“80 percent of high-performing projects are led by a certified project manager”.
Job opportunities worldwide
There are ocean-like opportunities in the field of project management for PMP certified professional.
According to PMI’s Talent Gap: Project management through 2020,

Project-intensive industries: The industries with a high level of project-oriented work. These industries are:
- Information services
- Manufacturing
- Business services
- Finance and insurance
- Oil and Gas
- Construction
- Utilities
The project management profession is expected to grow by US$6.61 trillion.
In the countries like Australia, Brazil, Canada, China, Germany, India, Japan, Saudi Arabia, United Arab Emirates and the United Kingdom, project management roles are expected to grow by 13.4 million through 2020.
Build network globally
Credentials from PMI is not just certification. It also gives opportunities to meet active practitioners and subject matter experts under one roof.
The PMI serves more than 2.9 million professionals including over 500,000 members in 208 countries and territories around the world, with 300 chapters and 10,000 volunteers serving local members in over 80 countries.
Though it is not mandatory to take PMI membership for PMP certification but it is recommended to take PMI membership for a discount on exam fee, opportunity to join local PMI chapter, free access to PMBOK guide etc.
If you are a member of PMI, PMI arranges frequent meetings, global conferences for members across the globe and speak common language of project management.
You can also access to online communities, templates, member-only webinars, virtual events etc. It will help you to build your network.
Higher earning potential
The earning potential increases with experience and progress of knowledge. According to Earning Power: Project Management Salary Survey, 10th Edition, certified PMP professionals earn 23% higher salary on average across 37 countries surveyed.
The countries with higher increase in the median salary of certified professionals are:
|
Country |
Earning advantage |
|
South Africa |
58% |
|
Ecuador |
53% |
|
Colombia |
48% |
|
Chile |
43% |
|
Mexico |
43% |
In the United States the median salary of Certified PMP professionals among survey respondents was 25% higher than the median salary of those without the PMP certification ($115,000 versus $92,000).
Continuous learning
Even after you get PMP certified once you get PMP certified you need to maintain your certification by earning Professional Development Units (PDUs) as a part of the Continuing Certification Requirement (CCR) Program.
1 PDU= 1 hour of learning activity
This allows you to gain knowledge on a continuous basis. You can earn PDU’s by attending webinars, joining the discussion thread, volunteering for local PMI chapter or by completing relevant educational courses by training organizations.
The Global Project Management community helps you to stay updated with recent methodologies and techniques.
Validates dedication towards a career
Getting PMP certification is not an easy task. Once you get PMP certified you will experience confidence to handle any kind of projects and increases the project success rate. It requires a lot of effort and commitment towards the goal.
The employee with continuous learning and dedicated to professional growth is an asset to the company.
The employers know the importance of trainings on project management.
According to PMI’s Pulse Of The Profession,
Three in five organizations provide training on project management tools and techniques.

Conclusion
By knowing all the perks of getting PMP certified we can conclude that “yes” it is indeed worth all the efforts, money and time.
RECOMMENDED POST:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
For more information about PMP® Certification Training courses worldwide, please visit us at https://www.icertglobal.com
or
Call Now! on +1-713-287-1213 / 1214 / 1053 / 1355 or e-mail us at info {at} icertglobal {dot} com.
What Are The Target Audience And Eligibility Criteria For Doing A PMP® Certification?
Project Management Professional (PMP®) certification is the benchmark for professional certification offered by the Project Management Institute. The professionals who successfully pass the PMP exam enter the elite club of PMP certification holders. There are just 1 million PMP certified professionals globally. PMP certification features in the ‘Top 10 Highest Paying Certifications.”
The PMP® certification demonstrates professionals’ knowledge and experience in project management including the five processes and ten knowledge areas of project management, and PMP® certification is renowned and recognized worldwide and applicable to all the verticals in the industry.
The average salary of a PMP certified professional in the United States is $80,000 – $110,000 according to PMI’s Project Management Salary Survey 10th edition. You can also visit our blog to know more about the average salary of a PMP (Project Management Professional) certified project manager worldwide.
The benefits of a PMP certification in terms of career advancement, global recognition, prominence, job opportunities, compensation are just great – but are you PMP certified?
If the answer is NO, then find out if you are eligible.
Eligibility criteria for PMP® certification:

To become eligible for PMP certification, you need to satisfy the education, project experience, and project management education criteria.
- Secondary degree (high school diploma, associate’s degree or the global equivalent)
- 7,500 hours leading and directing projects
- 35 hours of project management education
OR
- Four-year degree
- 4,500 hours leading and directing projects
- 35 hours of project management education
Note: “Can I take the PMP® exam without experience?” – is that your question? Why don’t you visit our article to find out more about it?
Almost everyone understands the education qualification aspect. But what is meant by project management experience and project management education?
Project Management Experience
Project management as a profession is all about delivery based on the agreed scope of work, execution, and communication with respective stakeholders to ensure a successful outcome. Communication is the cornerstone for a project manager to delegate, coordinate, manage and mitigate (risks) in each and every phase all the way to closure and handover of the project. This is the fundamental why Project Management experience matters so much and carries weightage.
In case you have a secondary degree, all the 7500 hours need not be in actual project management. The experience in a project environment is also counted. You don’t have to be a project manager at all times. A leading or directing role like that of a Project Lead, or Assitant Supervisor or team member will do. The title doesn’t count as much as the experience. Bottom line: You must have 3.5 years of experience in leading and managing projects.
Likewise, you hold an under-graduation credential, then 2 years of experience in leading and managing projects is absolutely mandatory.
The roles can be:
- Supervisor
- Team leader
- Assistant project manager
- Project Manager
- Project coordinators
- Any role participating in project management processes
Project Management Education
The PMP certification exam is aligned with the PMI’s reference guide PMBOK- 6th edition This reference book is the core material about the principles and practices of project management covering 10 knowledge areas and 49 processes that a project manager must be proficient. The questions of the PMP exam is based on the 5 domains with differing percentage as detailed in the table.
Experience for “Leading and directing” projects will fall under five processes of project management: Initiation, Planning, Execution, Monitoring and Controlling and Closing.
PMP exam will test your knowledge areas are in five different project domains with differing percentages as detailed in the table. In order to pass, you must be strong in the subject matter to score well and clear the exam in your first attempt.

You need 35 contact hours of PMP Training to satisfy the project management education requirement as prescribed by PMI.
You can earn these 35 hours through our PMP certification program which is conducted in 3 different modes of training :
- Instructor- LED Classroom Training
- Instructor- LED Live Online Training (Live or Virtual Training)
- Self-paced Online Training or E-Learning
If you want to know “How do you Get 35 Contact Hours Of Project Management Education In PMP?”, please visit our blog to learn more about “What counts as contact hours for PMP”.
Target Audience
PMP exam is best suited for professionals with at least three (3) years of project management experience. They include:
- Program managers,
- Project managers, and
- Project leaders
- PMO leaders,
- Project Executives
- Project Engineers
- Associate Project Managers
- Team Managers
- Team Leads/
- Aspirants in the field of project management.
The target audiences must possess at least 2 years experience at least two (2) years of experience managing projects, including experience performing ALL of the following activities:
- Project scope definition
- Stakeholder management
- Development of project plan and schedule
- Project communications coordination
- Managing Project Team
- Cost Estimation
- Monitoring of resources and project progress based on milestones
- Risk assessment and mitigation
- Evaluation of project performance
- Quality management
-
Note: The PMP Exam will change on July 1, 2020
The Project Management Institute (PMI®) has decided to the Course Outline based on its survey and expert opinion from its Subject Matter Experts panel. The PMP exam will change on July 1, 2020.
The present PMP course outline is based on 5 main domains, and the new course outline of PMP exam effect from July 2020 will focus on 3 new domains:
- People – Skills and knowledge (42%)
- Process- Technical aspects of handling projects (50%)
- Business Environment- Strategical aspects between the project and the organization (8%)
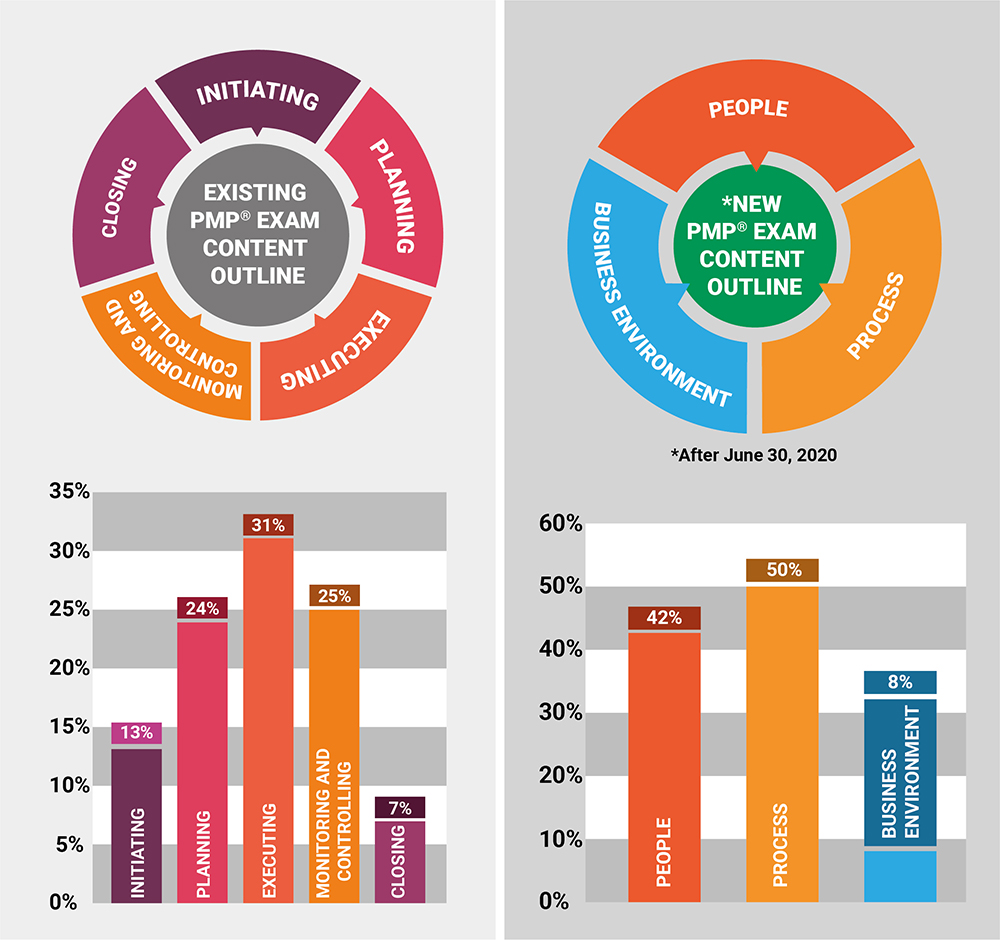
The new detailed framework of the content outline is based on predictive (approximately 50%), agile/hybrid (approximately 50%) approaches.
It will be a wise move to get your PMP certified as soon as possible before the PMP® Exam Changes on 1st July 2020.
RECOMMENDED POST:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
- PMP Certification Training
- CAPM Certification Training
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
Project Management Professional (PMP®) certification is the benchmark for professional certification offered by the Project Management Institute. The professionals who successfully pass the PMP exam enter the elite club of PMP certification holders. There are just 1 million PMP certified professionals globally. PMP certification features in the ‘Top 10 Highest Paying Certifications.”
The PMP® certification demonstrates professionals’ knowledge and experience in project management including the five processes and ten knowledge areas of project management, and PMP® certification is renowned and recognized worldwide and applicable to all the verticals in the industry.
The average salary of a PMP certified professional in the United States is $80,000 – $110,000 according to PMI’s Project Management Salary Survey 10th edition. You can also visit our blog to know more about the average salary of a PMP (Project Management Professional) certified project manager worldwide.
The benefits of a PMP certification in terms of career advancement, global recognition, prominence, job opportunities, compensation are just great – but are you PMP certified?
If the answer is NO, then find out if you are eligible.
Eligibility criteria for PMP® certification:

To become eligible for PMP certification, you need to satisfy the education, project experience, and project management education criteria.
- Secondary degree (high school diploma, associate’s degree or the global equivalent)
- 7,500 hours leading and directing projects
- 35 hours of project management education
OR
- Four-year degree
- 4,500 hours leading and directing projects
- 35 hours of project management education
Note: “Can I take the PMP® exam without experience?” – is that your question? Why don’t you visit our article to find out more about it?
Almost everyone understands the education qualification aspect. But what is meant by project management experience and project management education?
Project Management Experience
Project management as a profession is all about delivery based on the agreed scope of work, execution, and communication with respective stakeholders to ensure a successful outcome. Communication is the cornerstone for a project manager to delegate, coordinate, manage and mitigate (risks) in each and every phase all the way to closure and handover of the project. This is the fundamental why Project Management experience matters so much and carries weightage.
In case you have a secondary degree, all the 7500 hours need not be in actual project management. The experience in a project environment is also counted. You don’t have to be a project manager at all times. A leading or directing role like that of a Project Lead, or Assitant Supervisor or team member will do. The title doesn’t count as much as the experience. Bottom line: You must have 3.5 years of experience in leading and managing projects.
Likewise, you hold an under-graduation credential, then 2 years of experience in leading and managing projects is absolutely mandatory.
The roles can be:
- Supervisor
- Team leader
- Assistant project manager
- Project Manager
- Project coordinators
- Any role participating in project management processes
Project Management Education
The PMP certification exam is aligned with the PMI’s reference guide PMBOK- 6th edition This reference book is the core material about the principles and practices of project management covering 10 knowledge areas and 49 processes that a project manager must be proficient. The questions of the PMP exam is based on the 5 domains with differing percentage as detailed in the table.
Experience for “Leading and directing” projects will fall under five processes of project management: Initiation, Planning, Execution, Monitoring and Controlling and Closing.
PMP exam will test your knowledge areas are in five different project domains with differing percentages as detailed in the table. In order to pass, you must be strong in the subject matter to score well and clear the exam in your first attempt.

You need 35 contact hours of PMP Training to satisfy the project management education requirement as prescribed by PMI.
You can earn these 35 hours through our PMP certification program which is conducted in 3 different modes of training :
- Instructor- LED Classroom Training
- Instructor- LED Live Online Training (Live or Virtual Training)
- Self-paced Online Training or E-Learning
If you want to know “How do you Get 35 Contact Hours Of Project Management Education In PMP?”, please visit our blog to learn more about “What counts as contact hours for PMP”.
Target Audience
PMP exam is best suited for professionals with at least three (3) years of project management experience. They include:
- Program managers,
- Project managers, and
- Project leaders
- PMO leaders,
- Project Executives
- Project Engineers
- Associate Project Managers
- Team Managers
- Team Leads/
- Aspirants in the field of project management.
The target audiences must possess at least 2 years experience at least two (2) years of experience managing projects, including experience performing ALL of the following activities:
- Project scope definition
- Stakeholder management
- Development of project plan and schedule
- Project communications coordination
- Managing Project Team
- Cost Estimation
- Monitoring of resources and project progress based on milestones
- Risk assessment and mitigation
- Evaluation of project performance
- Quality management
Note: The PMP Exam will change on July 1, 2020
The Project Management Institute (PMI®) has decided to the Course Outline based on its survey and expert opinion from its Subject Matter Experts panel. The PMP exam will change on July 1, 2020.
The present PMP course outline is based on 5 main domains, and the new course outline of PMP exam effect from July 2020 will focus on 3 new domains:
- People – Skills and knowledge (42%)
- Process- Technical aspects of handling projects (50%)
- Business Environment- Strategical aspects between the project and the organization (8%)

The new detailed framework of the content outline is based on predictive (approximately 50%), agile/hybrid (approximately 50%) approaches.
It will be a wise move to get your PMP certified as soon as possible before the PMP® Exam Changes on 1st July 2020.
RECOMMENDED POST:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
- PMP Certification Training
- CAPM Certification Training
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
What are the Project Manager Roles and Responsibilities?
:
What are the Project Manager Roles and Responsibilities?
Project Manager – How was the role created?
It was during the creation of Microsoft Excel, the role ‘Project Manager” was created
During the late eighties, Microsoft was attempting to create something to the equivalent to that of the Lots spreadsheet, which was popular at that point in time. The project turned out to be chaotic as too many departments gt involved without any proper coordination. It proved to be an innovative and ideal solution as the team engaged seamlessly and the final product was launched as Excel.
The ingenious role created was the project manager.
The basic principles in project management have continued to be the same: manage scope, schedule costs resources, activities, and tasks.
The role of a project manager has evolved. There are different approaches to project management and project managers should be skilled and familiar with the project management system.
The project manager is responsible for leading and managing project teams leading to the successful delivery of the project. But before that, is a project manager really required?
Is the Project Manager really needed?
Time-bound and cost-bound projects require a project manager to plan, track, monitor, evaluate and work out the roadmap for successful closure and handover.
Does your project need a project manager? 89% of high performing organizations with large and demanding projects require a reliable project manager proficient in project management. The business has necessitated the need for Project Leader with strong leadership skills to consistently maintain efficiency and productivity.
From a small setup where a handful of projects are handled by one project manager to MNCs who hire domain specialists and verticals heads as project managers, it has become evident that Project manager is indispensable to project management and becomes an integral part of the business. The biggest challenge is to find a project manager with the right vision, skills, and knowledge to plan, coordinate, and deliver projects on schedule and within budget.
Let's take a look at key project manager roles and responsibilities.
Responsibilities of a Project Manager.

A Project which has a definite start and end with specific goals to achieve needs the direction and leadership of a Project Manager. Project Managers are the bridge between top management and project delivery team as they make sure the scope of the project is clear, monitors and reports regularly on the progress of the project that is in line with the defined cost, schedule, and quality. Therefore, Project Managers are accountable for all the tasks that are within the project right from inception till the completion.
They are expected to perform the following key tasks
Project Initiation
Project managers assess the proposed scope with a defined timeline, Budget and expected quality by engaging all relevant stakeholders to ensure that the expected outcome of the project is clear with the given timeline and cost. Project Manager performs the below activities to ensure the same
- Evaluate project/business requirements
- Identify the required assets and resources
- Determine dependencies / Make assumptions if any
- Assess the Risks / Issues if any
- Estimate Costs & Efforts
Preparation of Project Plan
A project plan is a strategic document that specifies goals, team, timing, and deliverables. It also establishes the scope and defines the objectives as in time, cost, quality, benefits realization which has to be monitored and assessed during regular intervals for a successful project outcome.
- Define the Scope, Goals, and Deliverables
- Project Key Stakeholder’s expectations and any cost/time-bound implications
- Definition of Project Organization
- Cost and Time Estimations
- Define the Tasks with required Resource Plan
- Definition of intermediate milestones (With respect to Deliverables, Cost, Schedule & Quality)
- Communication Plan
- Success Criteria against each milestoneCommunication of Project Plan
Once the project plan is formulated, the next step is to communicate the same to all relevant stakeholders and Project Team. This is to clearly set the right expectations for everyone involved in the project.
- Kick-off the project with all stakeholders to bring all in the same the expectations
- Follow the communication plan from hereon for reporting
The workspace creation
The project teams can be managed locally on-site, or it can be a virtual setup connecting the teams spread globally, It requires the team to enabled with the right tools and channels for communication in order to get the work done.
- Prepare or procure necessary resources, systems, and tools
- Provide access to and ensure the availability of relevant tools and resources
Creation of the team to complete the project
People are the heart of a project. Treat people right and your project is halfway done.
- Clarify tasks and roles
- Promote collaboration/relationship-building
- Recognize the achievements and appreciate (Set the standards for recognition)
- Monitor/Review the Risks, Issues, Assumptions, and Dependencies regularly
Execution of the project plan
When the team is on the same page, clear about all the parameters, the project team can begin the task of execution
- Monitor the Project Plan
- Resolve any blockers, Dependencies
- Review the Plan regularly and assess Scope, Cost, Schedule
Evaluation of the project’s progress
Project managers can utilize tools Using tools such as Microsoft Project to gain a high-level drilled-down view of every task of the project. Monitoring is helpful to mitigate risks, enhance gains, and make everyone involved stay focused.
- Conflicts resolution
- Address the open issues and risks
- Recognize achievement and reward
- Keep all stakeholders updated with regular reports
Close the project
Successful Closure ends on a congratulatory note. The celebrations aside, the takeaways must be recorded as lessons learned from the projects, especially handling of scope, identification of risk, allocation of resources, stretching of budget, slippage in the schedule, missed milestones, cost overrun – there could be instances in some phases during the course of development
- Thank the team for their contribution and highlight teamwork
- Congratulate the team for a job well done
- Spend time on the lessons that can be learned especially the loopholes.
Recommend action items to be worked on so as to avert recurrence of mistakes in future projects and also create awareness of any shortcomings suffered during the course of project development.
What makes a good Project Manager?

A matrix of technical, business, and leadership skills is critical to the making of a good project manager, and in which soft skills are a key aspect of leadership. Good business acumen with an entrepreneurial mindset to draw the big picture is one trait that makes a project manager outstanding. It is the influence wielded by the project manager to inspire the team to go far and beyond the call of duty that makes the project manager as a huge asset. That’s how project managers earn the trust of the team, and the progress of development wins the confidence of the stakeholders not throughout the project and futuristic engagements as well. The managerial skills, soft skills, technical skills, seamless transition of knowledge and information, effective combination to all stakeholders involved at a regular and required time are the combination of the most competent project manager. Project managers need the technical knowledge to assign tasks and managerial skills to get the tasks done and soft skills to keep the team motivated at all times.
It is imperative for a project manager to deliver everything signed off as in-scope, on time, within budget with the quality at benchmarked standards.
A good project manager aims to exceed the stakeholder’s expectations and strives to tie the project to its business goals.
Good project managers use communication as a cornerstone by keeping the stakeholders updated about the project’s progress right from kick-off to closure. Communicating the actual status – even in case of missed milestone or some slippage in schedule with proactive plans to bring the project on track is the hallmark of effective communication expected in a good project manager.
some of the qualities that make for a good project manager are an eye for detail, a sense of anticipation, an appetite for risk coupled with risk management capabilities, the ability to draw the big picture, excellent communication skills, resourcefulness, ability to think on their feet, attitude to achieve, critical thinking and the talent to lead the team from front.
The Project Management Institute attributed self-assessment and re-evaluation can make a huge difference in the reshaping of a successful project manager successful.
RECOMMENDED POST:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
:
What are the Project Manager Roles and Responsibilities?
Project Manager – How was the role created?
It was during the creation of Microsoft Excel, the role ‘Project Manager” was created
During the late eighties, Microsoft was attempting to create something to the equivalent to that of the Lots spreadsheet, which was popular at that point in time. The project turned out to be chaotic as too many departments gt involved without any proper coordination. It proved to be an innovative and ideal solution as the team engaged seamlessly and the final product was launched as Excel.
The ingenious role created was the project manager.
The basic principles in project management have continued to be the same: manage scope, schedule costs resources, activities, and tasks.
The role of a project manager has evolved. There are different approaches to project management and project managers should be skilled and familiar with the project management system.
The project manager is responsible for leading and managing project teams leading to the successful delivery of the project. But before that, is a project manager really required?
Is the Project Manager really needed?
Time-bound and cost-bound projects require a project manager to plan, track, monitor, evaluate and work out the roadmap for successful closure and handover.
Does your project need a project manager? 89% of high performing organizations with large and demanding projects require a reliable project manager proficient in project management. The business has necessitated the need for Project Leader with strong leadership skills to consistently maintain efficiency and productivity.
From a small setup where a handful of projects are handled by one project manager to MNCs who hire domain specialists and verticals heads as project managers, it has become evident that Project manager is indispensable to project management and becomes an integral part of the business. The biggest challenge is to find a project manager with the right vision, skills, and knowledge to plan, coordinate, and deliver projects on schedule and within budget.
Let's take a look at key project manager roles and responsibilities.
Responsibilities of a Project Manager.
A Project which has a definite start and end with specific goals to achieve needs the direction and leadership of a Project Manager. Project Managers are the bridge between top management and project delivery team as they make sure the scope of the project is clear, monitors and reports regularly on the progress of the project that is in line with the defined cost, schedule, and quality. Therefore, Project Managers are accountable for all the tasks that are within the project right from inception till the completion.
They are expected to perform the following key tasks
Project Initiation
Project managers assess the proposed scope with a defined timeline, Budget and expected quality by engaging all relevant stakeholders to ensure that the expected outcome of the project is clear with the given timeline and cost. Project Manager performs the below activities to ensure the same
- Evaluate project/business requirements
- Identify the required assets and resources
- Determine dependencies / Make assumptions if any
- Assess the Risks / Issues if any
- Estimate Costs & Efforts
Preparation of Project Plan
A project plan is a strategic document that specifies goals, team, timing, and deliverables. It also establishes the scope and defines the objectives as in time, cost, quality, benefits realization which has to be monitored and assessed during regular intervals for a successful project outcome.
- Define the Scope, Goals, and Deliverables
- Project Key Stakeholder’s expectations and any cost/time-bound implications
- Definition of Project Organization
- Cost and Time Estimations
- Define the Tasks with required Resource Plan
- Definition of intermediate milestones (With respect to Deliverables, Cost, Schedule & Quality)
- Communication Plan
- Success Criteria against each milestoneCommunication of Project Plan
Once the project plan is formulated, the next step is to communicate the same to all relevant stakeholders and Project Team. This is to clearly set the right expectations for everyone involved in the project.
- Kick-off the project with all stakeholders to bring all in the same the expectations
- Follow the communication plan from hereon for reporting
The workspace creation
The project teams can be managed locally on-site, or it can be a virtual setup connecting the teams spread globally, It requires the team to enabled with the right tools and channels for communication in order to get the work done.
- Prepare or procure necessary resources, systems, and tools
- Provide access to and ensure the availability of relevant tools and resources
Creation of the team to complete the project
People are the heart of a project. Treat people right and your project is halfway done.
- Clarify tasks and roles
- Promote collaboration/relationship-building
- Recognize the achievements and appreciate (Set the standards for recognition)
- Monitor/Review the Risks, Issues, Assumptions, and Dependencies regularly
Execution of the project plan
When the team is on the same page, clear about all the parameters, the project team can begin the task of execution
- Monitor the Project Plan
- Resolve any blockers, Dependencies
- Review the Plan regularly and assess Scope, Cost, Schedule
Evaluation of the project’s progress
Project managers can utilize tools Using tools such as Microsoft Project to gain a high-level drilled-down view of every task of the project. Monitoring is helpful to mitigate risks, enhance gains, and make everyone involved stay focused.
- Conflicts resolution
- Address the open issues and risks
- Recognize achievement and reward
- Keep all stakeholders updated with regular reports
Close the project
Successful Closure ends on a congratulatory note. The celebrations aside, the takeaways must be recorded as lessons learned from the projects, especially handling of scope, identification of risk, allocation of resources, stretching of budget, slippage in the schedule, missed milestones, cost overrun – there could be instances in some phases during the course of development
- Thank the team for their contribution and highlight teamwork
- Congratulate the team for a job well done
- Spend time on the lessons that can be learned especially the loopholes.
Recommend action items to be worked on so as to avert recurrence of mistakes in future projects and also create awareness of any shortcomings suffered during the course of project development.
What makes a good Project Manager?
A matrix of technical, business, and leadership skills is critical to the making of a good project manager, and in which soft skills are a key aspect of leadership. Good business acumen with an entrepreneurial mindset to draw the big picture is one trait that makes a project manager outstanding. It is the influence wielded by the project manager to inspire the team to go far and beyond the call of duty that makes the project manager as a huge asset. That’s how project managers earn the trust of the team, and the progress of development wins the confidence of the stakeholders not throughout the project and futuristic engagements as well. The managerial skills, soft skills, technical skills, seamless transition of knowledge and information, effective combination to all stakeholders involved at a regular and required time are the combination of the most competent project manager. Project managers need the technical knowledge to assign tasks and managerial skills to get the tasks done and soft skills to keep the team motivated at all times.
It is imperative for a project manager to deliver everything signed off as in-scope, on time, within budget with the quality at benchmarked standards.
A good project manager aims to exceed the stakeholder’s expectations and strives to tie the project to its business goals.
Good project managers use communication as a cornerstone by keeping the stakeholders updated about the project’s progress right from kick-off to closure. Communicating the actual status – even in case of missed milestone or some slippage in schedule with proactive plans to bring the project on track is the hallmark of effective communication expected in a good project manager.
some of the qualities that make for a good project manager are an eye for detail, a sense of anticipation, an appetite for risk coupled with risk management capabilities, the ability to draw the big picture, excellent communication skills, resourcefulness, ability to think on their feet, attitude to achieve, critical thinking and the talent to lead the team from front.
The Project Management Institute attributed self-assessment and re-evaluation can make a huge difference in the reshaping of a successful project manager successful.
RECOMMENDED POST:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
What are the Benefits of Project Cost Management?
:
What are the Benefits of Project Cost Management?
The benefits of Project Cost Management are:
1. Accountability
2. Lowers Expenses leads to lower project costs
3. Enhanced Efficiency
4. Financial Planning
5. Savings
6. Stress Relief
7. Operational Efficiency
8. Procurement Value
9. Systematize Technology
10. Prioritization
Project Cost Management
According to PMBOK® Guide – Sixth Edition Project cost management is defined as Project cost management includes the processes involved in planning, estimating, budgeting, financing, funding, managing, and controlling costs so the project can be completed within the approved budget.
Cost management is the process of estimating, apportioning, and controlling the costs in a project. A project manager should possess a strong sense of anticipation – even in cost estimation. Any change translates to cost and obviously out of scope. It is a matter of discretion to entertain the change at no cost or ‘at cost’ and a project manager is expected to have a sixth sense to see it coming. Usually what appears as cosmetics with little impact on scope and cost are the ones that derail the project slipping on schedule, resulting in cost overrun and scope creep. So, Predicting and preempting costs to factor during estimation and budgeting will prove critical to the project making a profit or bleed red.
Project cost management is used to forecast costs and manage them effectively. Projects can be challenging and if unchecked and uncontrolled, go over the budget. A good Project Cost Management can keep the project under check and well within budget.
For all the project costs, it is the Project cost management that determines the baseline. Effective and efficient cost management makes sure the project runs on track within budget and as per planned scope. Without Cost Management, the project can bleed, costs can go above project profit and result in a loss.
The project manager must have a strong grip on the cost, hence cost control is one of the most crucial aspects of project management. Time, scope and resource management are as important in achieving the goal, but cost management will have the ultimate bearing on a project’s outcome. The project manager’s prowess lies in organizing tasks with an eye on the cost to stay within the estimates.
Cost Management
Cost Management helps the project manager in foreseeing expenses and prepare to act accordingly by putting in place precautionary measures. To reduce the overall costs of a project, Cost Management is assigned the highest priority. Cost Management starts right from the initial planning phase and goes all the way to project completion and handover.
A project manager must exercise strict control over the cost to manage the project budget. The project manager at all times should be conscious about the costs incurred and the funds allocated to maintain and manage the project’s cost-expense within budget. There can be no lapse as it will lead to stretching the project estimate and consequently the project goes over the budget. To effectively control the cost, the project manager must recognize the needs for which funds have to be allocated. This is required for estimation and also study the allocated versus actual cost. The balance in the allocated and actuals costs will determine the cost overrun. These are the aspects a project manager must always focus on: the estimated cost, approved cost, the budget sanctioned, allocated versus actual cost.
What is Project cost?
It is during the project planning phase, cost estimation is done and the estimation needs approval from the stakeholders - the client or customer or upper management. It is only after the approval, the project execution begins.
The project manager records all the expenses incurred as the project moves in phases and keeps track of all the expenditures to monitor and control so that the project is maintained within the estimate. All the expenses are documented to study for any deviations during the project. The study becomes useful references while estimating costs and preparing cost management plans for other or future projects.
The project cost is the sum of the costs incurred to procure the necessary resources and services required to execute the project successfully to completion.
There is no project without a budget. Time, Scope and cost are the critical components of project management, and directly proportionate. Impact on anyone will affect the other two. If the project cannot be completed within the project cost, it’s a failure. There are tolerance levels set but if the costs climb higher and exceed the estimation, the project is set for failure. Therefore, it is imperative to get the cost estimation correct. To work out the accurate estimation, it is essential to understand the different types of project costs. By strategically reducing the cost spending in acquiring the required resources will result in significant benefits.
What are the Types of Project Costs?
There are 5 types of project costs incurred in any project. They are
- Fixed Cost - any Cost which is fixed throughout the project and does not fluctuate.
- Variable Cost – any cost which changes in proportion to a product or has a high tendency to variate
- Direct Costs - Costs that are directly linked to the budget of the project.
- Indirect Costs - costs that are not particularly connected to the project but shared across multiple projects.
- Sunk Cost - Sunk Costs are costs which are already spent, but have failed to generate any business value for the project.
Total Project Cost:
The Total Project Cost (TPC) is calculated by putting together the fixed cost and variable cost and Other Project Costs (OPC). It is important to get the total project cost accurate or close to the accurate figure with minimal tolerance as it would severely impact the project scope and schedule resulting in cost overrun.
The Benefits Of Project Cost Management
Some of the benefits of cost control management are compiled below.
1. Accountability
Cost management leads to the accountability of the people engaged in a project. The people or team are assigned tasks with a definite deadline and any delay in completion would become an additional cost. Slippage in the schedule is actually cost accrued which is not healthy for the project’s profit. Thus accounting for billable hours leads to impacts productivity. The person or team member completing on time accounts for the billable hours scheduled.
2. Lowers Expenses leads to lower project costs
Effective cost management lowers the overall expenses. By defining proper procedures, the company can save on spending, thus lowering the expenses and use the saved funds for procuring other resources or services. This, in turn, contributes to the overall growth of the company.
3. Enhanced Efficiency
Cost management helps to identify the tasks that are running as scheduled within the budget and those tasks that are exceeding the allocated budget. The project manager can take a call about the contingency plans to control keep the cost breach.
4. Financial Planning
One of the main objectives of cost management is organized spending through a disciplined approach in financial planning and accounting. The project manager can create a better budget once the requirement on the various resource is known, so as to invest in the right resources at the right hour. The plan also sets up boundaries as upper limits on spending.
5. Savings
A dollar saved is a dollar earned. By savings, the funds that sometimes get spent on the unresourceful tasks can be identified and redirected to other activities purposeful. This can be achieved by carefully defining the cost control procedures to close the plug on leaking money, which positively reflects on the fiscal goals.
6. Stress Relief
When managed well, cost and time management reduces stress. Effective cost control enhances the discipline in spending that lessens the worries about the expenses that may have to be met. It provides a buffer and eases the pressure on payments.
7. Operational Efficiency
Cost Management helps in enhancing Operational Efficiency by tracking the activities that have breakdowns and consumes funds far more than allocated. It provides visibility to the project manager to focus on those activities in line with the budget and act upon those that exceed the estimated amount.
8. Procurement Value
Cost management helps in the review of goods and services offered by vendors and empowers the project manager the width to bargain and arrive at a figure that’s an advantage to the company. It is about getting the value for the money invested.
9. Systematize Technology
Every project or business process involves technology and companies need to invest, like automation or tools, sometimes the choice of technology can be questionable as companies overspend or invest in technology that’s not necessary. Cost management imposes budget constraints which makes the project manager more conscious about making the right choice: either step-up technology or just simplify.
10. Prioritization
If there are multiple projects that mostly engage in time and cost management, not all the projects can be engaged as proposed. So, which project to fund first? Cost management helps in prioritizing the projects that deserve the funds.
RECOMMENDED POST:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
:
What are the Benefits of Project Cost Management?
The benefits of Project Cost Management are:
1. Accountability
2. Lowers Expenses leads to lower project costs
3. Enhanced Efficiency
4. Financial Planning
5. Savings
6. Stress Relief
7. Operational Efficiency
8. Procurement Value
9. Systematize Technology
10. Prioritization
Project Cost Management
According to PMBOK® Guide – Sixth Edition Project cost management is defined as Project cost management includes the processes involved in planning, estimating, budgeting, financing, funding, managing, and controlling costs so the project can be completed within the approved budget.
Cost management is the process of estimating, apportioning, and controlling the costs in a project. A project manager should possess a strong sense of anticipation – even in cost estimation. Any change translates to cost and obviously out of scope. It is a matter of discretion to entertain the change at no cost or ‘at cost’ and a project manager is expected to have a sixth sense to see it coming. Usually what appears as cosmetics with little impact on scope and cost are the ones that derail the project slipping on schedule, resulting in cost overrun and scope creep. So, Predicting and preempting costs to factor during estimation and budgeting will prove critical to the project making a profit or bleed red.
Project cost management is used to forecast costs and manage them effectively. Projects can be challenging and if unchecked and uncontrolled, go over the budget. A good Project Cost Management can keep the project under check and well within budget.
For all the project costs, it is the Project cost management that determines the baseline. Effective and efficient cost management makes sure the project runs on track within budget and as per planned scope. Without Cost Management, the project can bleed, costs can go above project profit and result in a loss.
The project manager must have a strong grip on the cost, hence cost control is one of the most crucial aspects of project management. Time, scope and resource management are as important in achieving the goal, but cost management will have the ultimate bearing on a project’s outcome. The project manager’s prowess lies in organizing tasks with an eye on the cost to stay within the estimates.
Cost Management
Cost Management helps the project manager in foreseeing expenses and prepare to act accordingly by putting in place precautionary measures. To reduce the overall costs of a project, Cost Management is assigned the highest priority. Cost Management starts right from the initial planning phase and goes all the way to project completion and handover.
A project manager must exercise strict control over the cost to manage the project budget. The project manager at all times should be conscious about the costs incurred and the funds allocated to maintain and manage the project’s cost-expense within budget. There can be no lapse as it will lead to stretching the project estimate and consequently the project goes over the budget. To effectively control the cost, the project manager must recognize the needs for which funds have to be allocated. This is required for estimation and also study the allocated versus actual cost. The balance in the allocated and actuals costs will determine the cost overrun. These are the aspects a project manager must always focus on: the estimated cost, approved cost, the budget sanctioned, allocated versus actual cost.
What is Project cost?
It is during the project planning phase, cost estimation is done and the estimation needs approval from the stakeholders - the client or customer or upper management. It is only after the approval, the project execution begins.
The project manager records all the expenses incurred as the project moves in phases and keeps track of all the expenditures to monitor and control so that the project is maintained within the estimate. All the expenses are documented to study for any deviations during the project. The study becomes useful references while estimating costs and preparing cost management plans for other or future projects.
The project cost is the sum of the costs incurred to procure the necessary resources and services required to execute the project successfully to completion.
There is no project without a budget. Time, Scope and cost are the critical components of project management, and directly proportionate. Impact on anyone will affect the other two. If the project cannot be completed within the project cost, it’s a failure. There are tolerance levels set but if the costs climb higher and exceed the estimation, the project is set for failure. Therefore, it is imperative to get the cost estimation correct. To work out the accurate estimation, it is essential to understand the different types of project costs. By strategically reducing the cost spending in acquiring the required resources will result in significant benefits.
What are the Types of Project Costs?
There are 5 types of project costs incurred in any project. They are
- Fixed Cost - any Cost which is fixed throughout the project and does not fluctuate.
- Variable Cost – any cost which changes in proportion to a product or has a high tendency to variate
- Direct Costs - Costs that are directly linked to the budget of the project.
- Indirect Costs - costs that are not particularly connected to the project but shared across multiple projects.
- Sunk Cost - Sunk Costs are costs which are already spent, but have failed to generate any business value for the project.
Total Project Cost:
The Total Project Cost (TPC) is calculated by putting together the fixed cost and variable cost and Other Project Costs (OPC). It is important to get the total project cost accurate or close to the accurate figure with minimal tolerance as it would severely impact the project scope and schedule resulting in cost overrun.
The Benefits Of Project Cost Management
Some of the benefits of cost control management are compiled below.
1. Accountability
Cost management leads to the accountability of the people engaged in a project. The people or team are assigned tasks with a definite deadline and any delay in completion would become an additional cost. Slippage in the schedule is actually cost accrued which is not healthy for the project’s profit. Thus accounting for billable hours leads to impacts productivity. The person or team member completing on time accounts for the billable hours scheduled.
2. Lowers Expenses leads to lower project costs
Effective cost management lowers the overall expenses. By defining proper procedures, the company can save on spending, thus lowering the expenses and use the saved funds for procuring other resources or services. This, in turn, contributes to the overall growth of the company.
3. Enhanced Efficiency
Cost management helps to identify the tasks that are running as scheduled within the budget and those tasks that are exceeding the allocated budget. The project manager can take a call about the contingency plans to control keep the cost breach.
4. Financial Planning
One of the main objectives of cost management is organized spending through a disciplined approach in financial planning and accounting. The project manager can create a better budget once the requirement on the various resource is known, so as to invest in the right resources at the right hour. The plan also sets up boundaries as upper limits on spending.
5. Savings
A dollar saved is a dollar earned. By savings, the funds that sometimes get spent on the unresourceful tasks can be identified and redirected to other activities purposeful. This can be achieved by carefully defining the cost control procedures to close the plug on leaking money, which positively reflects on the fiscal goals.
6. Stress Relief
When managed well, cost and time management reduces stress. Effective cost control enhances the discipline in spending that lessens the worries about the expenses that may have to be met. It provides a buffer and eases the pressure on payments.
7. Operational Efficiency
Cost Management helps in enhancing Operational Efficiency by tracking the activities that have breakdowns and consumes funds far more than allocated. It provides visibility to the project manager to focus on those activities in line with the budget and act upon those that exceed the estimated amount.
8. Procurement Value
Cost management helps in the review of goods and services offered by vendors and empowers the project manager the width to bargain and arrive at a figure that’s an advantage to the company. It is about getting the value for the money invested.
9. Systematize Technology
Every project or business process involves technology and companies need to invest, like automation or tools, sometimes the choice of technology can be questionable as companies overspend or invest in technology that’s not necessary. Cost management imposes budget constraints which makes the project manager more conscious about making the right choice: either step-up technology or just simplify.
10. Prioritization
If there are multiple projects that mostly engage in time and cost management, not all the projects can be engaged as proposed. So, which project to fund first? Cost management helps in prioritizing the projects that deserve the funds.
RECOMMENDED POST:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
How To Claim PMP Professional Development Units (PDUs)?
:
How To Claim PMP Professional Development Units (PDUs)?
What are PDUs?
Professional Development Units (PDUs) are part of the Continuing Certification Requirements (CCR) program from PMI and are earned in order to maintain the certification.
PMI’s Continuing Certification Requirements (CCR) program supports the ongoing educational and professional development of our certification holders so they are always prepared to meet the demands of today’s complex business environment
Project Management Institute (PMI®) defines PDUs as:
“PDUs are the measuring unit used to quantify approved learning and professional service activities.”
Professional Development Units (PDUs) are one-hour blocks of time that you spend learning, teaching others or volunteering
All the certifications accredited by PMI requires you to earn PDUs except for CAPM certification.
Project Management Professional (PMP®️) certification needs 60 PDUs within 3 years to maintain the credentials.
PDUs can be earned in two different categories.
- Education PDUs:
Education PDUs can be earned by attending professional seminars, classes, webinars or self-directed learning.
- Giving Back PDUs:
Giving Back PDUs can be earned by volunteering, mentoring, working with professional groups.
What are the requirements to earn PDUs?
To maintain the PMP Credentials, you need to earn 60 PDUs in the 3-year cycle. The 60 PDUs are then broken down into two categories:
- 35 Minimum Education PDUs aligned with PMI talent triangle

- 25 Maximum Giving Back PDUs (Optional)
60 PDUs are required to renew the PMP certification. The 60 PDUs can be achieved by meeting the following requirements of PDU.
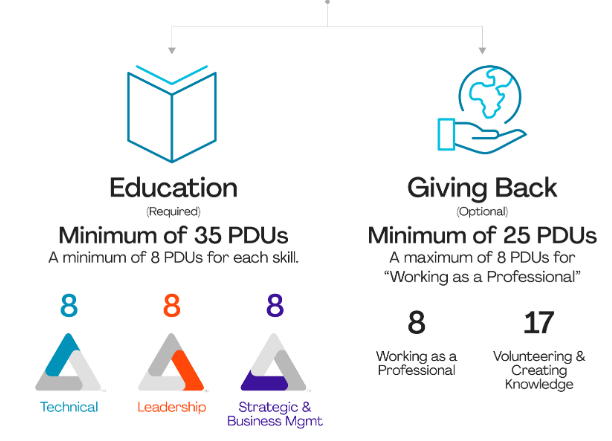
You must earn a minimum of 8 PDUs in each skill of PMI Talent Triangle- Technical, Leadership, Strategic and Business Management.
The purpose of earning PDUs aligned with PMI Talent Triangle is to make the certified professional more skilled and attain equal balance on all the updated skills- technical, leadership and strategic and business management skills.
It is not mandatory to earn PDUs by giving back through volunteering or mentoring. You can earn all the 60 PDUs through education aligned with a PMI Talent Triangle
You have to earn a minimum of 35 PDUs in education and you can earn a maximum of 25 PDUs in Giving Back.
In giving away PDUs, you can earn a maximum of 8 PDUs by applying skills and contributing to the profession.
You can earn 17PDUs by sharing knowledge, conducting seminars, volunteering with PMI.
What are the ways to earn educational PDUs?
In the ever-changing field of project management, it is very important to keep your knowledge up-to-date. In order to maintain PMP credential, you need to earn 60 PDUs out of which you must earn a minimum of 35 educational PDUs. The following are the ways to earn educational PDUs:
1. Course: Take a course relevant to the subject by education providers, training companies or PMI R.E.Ps.
Same as contact hour, one hour of instruction equals to 1 PDU
2. Meetings: Attend educational sessions organized by the company. You can also attend PMI chapters to earn PDUs. Typically limited to 1-2 PDUs
3. Online: Self-paced e-learning, watching videos or webinars can earn PDUs. Any content relevant to PMI Talent Triangles skill area topic can be valid to earn PDUs
4. Read: Reading articles, blogs or whitepapers relevant to the subject can also be considered as PDUs
5. Informal learning: You can earn PDUs by engaging in structured professional discussions with others or any interactive sessions relevant to PMI Talent Triangle. For example, while you’re being mentored or participating in a “lunch and learn” session with your organization.
What are the ways to earn Giving Back PDUs?
Sharing knowledge or giving back to the profession is a great way to expand your skills and knowledge. PMI is providing this opportunity to all the PMP holders. The following are the ways to earn educational PDUs:
1. Work as a Practitioner: You can earn PDUs by applying knowledge and skills in a practical setting relevant to the certification.
This activity has a maximum number of PDUs that can be claimed per cycle: 8 PDUs for PMP Certified professional.
2. Create Content: You can earn PDUs by creating content such as articles, blogs, webinars, videos or any content relevant to the subject.
3. Give a Presentation: If you give a presentation in PMI chapter or your organization, you can claim PDUs.
4. Share Knowledge: The time spent in teaching, mentoring can be claimed for PDUs.
5. Volunteer: Become a volunteer in PMI and other organization who relies on volunteers and earn PDUs
Note: All the ways of earning PDUs need supporting document to present if you get selected for the audit process.
How to renew the certification through CCRS?
The time you start earning your PDUs, record your PDUs in the Continuing Certification Requirements System (CCRS). CCRS helps you to track your progress against CCR requirements. The fractions of PDU can also be reported in CCRS. The process of the CCR system is as follows:
After PMI confirms that you have met the PDU requirements, PMI will notify you to submit the renewal payment.
The renewal fees are as follows:
*Note: PMI’s membership renewal fee is different and separate than the certification renewal fee.
After processing the completed application and the renewal payment, PMI will send you an updated certificate with the new active certification/CCR cycle dates.
If you do not satisfy the CCR program requirements within your current cycle dates, you will be placed in suspended status. The suspension period lasts one year (12 months).
Is there any audit process for renewal of PMP certification?
Yes, there is an audit process. It is important to keep all the documentation related to PDUs for at least 18 months after the CCR cycle has ended.
The documents required for each way of earning PDU is given in the CCR Handbook.
Note: If you earn more than the required PDUs in your CCR cycle, you may apply a portion of the PDUs to your next cycle. Only PDUs earned in the final year (12 months) of your certification cycle can be applied to a future cycle.
RECOMMENDED POST:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
:
How To Claim PMP Professional Development Units (PDUs)?
What are PDUs?
Professional Development Units (PDUs) are part of the Continuing Certification Requirements (CCR) program from PMI and are earned in order to maintain the certification.
PMI’s Continuing Certification Requirements (CCR) program supports the ongoing educational and professional development of our certification holders so they are always prepared to meet the demands of today’s complex business environment
Project Management Institute (PMI®) defines PDUs as:
“PDUs are the measuring unit used to quantify approved learning and professional service activities.”
Professional Development Units (PDUs) are one-hour blocks of time that you spend learning, teaching others or volunteering
All the certifications accredited by PMI requires you to earn PDUs except for CAPM certification.
Project Management Professional (PMP®️) certification needs 60 PDUs within 3 years to maintain the credentials.
PDUs can be earned in two different categories.
- Education PDUs:
Education PDUs can be earned by attending professional seminars, classes, webinars or self-directed learning.
- Giving Back PDUs:
Giving Back PDUs can be earned by volunteering, mentoring, working with professional groups.
What are the requirements to earn PDUs?
To maintain the PMP Credentials, you need to earn 60 PDUs in the 3-year cycle. The 60 PDUs are then broken down into two categories:
- 35 Minimum Education PDUs aligned with PMI talent triangle

- 25 Maximum Giving Back PDUs (Optional)
60 PDUs are required to renew the PMP certification. The 60 PDUs can be achieved by meeting the following requirements of PDU.

You must earn a minimum of 8 PDUs in each skill of PMI Talent Triangle- Technical, Leadership, Strategic and Business Management.
The purpose of earning PDUs aligned with PMI Talent Triangle is to make the certified professional more skilled and attain equal balance on all the updated skills- technical, leadership and strategic and business management skills.
It is not mandatory to earn PDUs by giving back through volunteering or mentoring. You can earn all the 60 PDUs through education aligned with a PMI Talent Triangle
You have to earn a minimum of 35 PDUs in education and you can earn a maximum of 25 PDUs in Giving Back.
In giving away PDUs, you can earn a maximum of 8 PDUs by applying skills and contributing to the profession.
You can earn 17PDUs by sharing knowledge, conducting seminars, volunteering with PMI.
What are the ways to earn educational PDUs?
In the ever-changing field of project management, it is very important to keep your knowledge up-to-date. In order to maintain PMP credential, you need to earn 60 PDUs out of which you must earn a minimum of 35 educational PDUs. The following are the ways to earn educational PDUs:
1. Course: Take a course relevant to the subject by education providers, training companies or PMI R.E.Ps.
Same as contact hour, one hour of instruction equals to 1 PDU
2. Meetings: Attend educational sessions organized by the company. You can also attend PMI chapters to earn PDUs. Typically limited to 1-2 PDUs
3. Online: Self-paced e-learning, watching videos or webinars can earn PDUs. Any content relevant to PMI Talent Triangles skill area topic can be valid to earn PDUs
4. Read: Reading articles, blogs or whitepapers relevant to the subject can also be considered as PDUs
5. Informal learning: You can earn PDUs by engaging in structured professional discussions with others or any interactive sessions relevant to PMI Talent Triangle. For example, while you’re being mentored or participating in a “lunch and learn” session with your organization.
What are the ways to earn Giving Back PDUs?
Sharing knowledge or giving back to the profession is a great way to expand your skills and knowledge. PMI is providing this opportunity to all the PMP holders. The following are the ways to earn educational PDUs:
1. Work as a Practitioner: You can earn PDUs by applying knowledge and skills in a practical setting relevant to the certification.
This activity has a maximum number of PDUs that can be claimed per cycle: 8 PDUs for PMP Certified professional.
2. Create Content: You can earn PDUs by creating content such as articles, blogs, webinars, videos or any content relevant to the subject.
3. Give a Presentation: If you give a presentation in PMI chapter or your organization, you can claim PDUs.
4. Share Knowledge: The time spent in teaching, mentoring can be claimed for PDUs.
5. Volunteer: Become a volunteer in PMI and other organization who relies on volunteers and earn PDUs
Note: All the ways of earning PDUs need supporting document to present if you get selected for the audit process.
How to renew the certification through CCRS?
The time you start earning your PDUs, record your PDUs in the Continuing Certification Requirements System (CCRS). CCRS helps you to track your progress against CCR requirements. The fractions of PDU can also be reported in CCRS. The process of the CCR system is as follows:

After PMI confirms that you have met the PDU requirements, PMI will notify you to submit the renewal payment.
The renewal fees are as follows:

*Note: PMI’s membership renewal fee is different and separate than the certification renewal fee.
After processing the completed application and the renewal payment, PMI will send you an updated certificate with the new active certification/CCR cycle dates.
If you do not satisfy the CCR program requirements within your current cycle dates, you will be placed in suspended status. The suspension period lasts one year (12 months).
Is there any audit process for renewal of PMP certification?
Yes, there is an audit process. It is important to keep all the documentation related to PDUs for at least 18 months after the CCR cycle has ended.
The documents required for each way of earning PDU is given in the CCR Handbook.
Note: If you earn more than the required PDUs in your CCR cycle, you may apply a portion of the PDUs to your next cycle. Only PDUs earned in the final year (12 months) of your certification cycle can be applied to a future cycle.
RECOMMENDED POST:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Project Scope Management And Its Benefits
:
PROJECT SCOPE MANAGEMENT AND ITS BENEFITS
What is Project Scope?
In project management, scope sets the boundaries to the project within which it can extend. The scope details the deliverables to the as a result of the project initiative.
The project scope determines the work and activities. The project manager must understand the scope clearly and correctly to determine what falls within the boundaries. Those activities that fall inside the boundary become “in scope” and those outside are stricken down as “not in scope”. Only the ‘in-scope” activities are planned for development.
The project scope is the first phase of project planning. The project scope forms the project objectives, the deliverables that include features and functions, limitations, assumptions, and project dependencies. Upon acceptance of the project, the scope management forms the first step in planning.
Why Project Scope is So Important
The question often asked is “Why Project Scope is important?”
Every project has to be delivered on time, within scope, within budget and yet lot many projects fail on these aspects – and the reason: the project scope was not captured correctly
A successful project manager will understand exactly whats to be achieved as a project objective also called scope. For a project manager to stay on track the entire time, regardless of size or complexity, it is important to read the scope right. And that means defining the scope which makes it simple to stay on schedule.
Expectations management is the most difficult and complex task for a project manager as it involves Managing clients' and stakeholders’ hopes and beliefs. A definitive and distinct scope brings everyone on the same page and helps to avoid often cited problems like
- changing requirements,
- or mid-project changes
- budget overspend
- slippage in schedule
- the final outcome contested by client
Without Project scope, the project manager will be left clueless about the time, cost and schedule and resources. The scope influences and forms the basis for every decision made by the project manager.
Project Scope Management
Even before the project begins, Project scope management is initiated. Scope Management is the collection of processes that captures the work to be undertaken in the project and also records the work that is not required. How to manage scope? Through a use case which clearly in writing defines the scope of the project. The business case is closely monitored throughout the project lifecycle.
Project scope states the whole work to be done to deliver the product or services with the agreed features and functions. The scope covers everything that goes into a project.
The Project Scope Management Plan
The Scope Management Plan specifies the scope’s definition, development, and verification. It also defines the responsibilities in managing the project’s scope and guides in scope control. The project scope management plan is one of the most critical and crucial aspects of a project’s success. It identifies the right work needs to be done. According to PMBOK, Guide to the Project Management Body of Knowledge, there are five processes for effective scope management: Collect Requirements, Define Scope. Create Work Breakdown Structure (WBS), Verify Scope and Control Scope.
- Collect Requirements – in this process the requirements that meet the objectives of the project are defined and documented. The documentation will include status updates and final deliverables. Project charter and stakeholder register are the foundation of this process. This process will help in understanding and managing to present the stakeholders’ expectations.
The documentation of this process will serve as an input to the next process, which is Define Scope.
- Define Scope – this step is the most important as it creates the scope statement and helps in understanding the expected deliverables. In this process, the ‘in scope’ and ‘out of scope’ are clearly defined. The project scope statement will guide the team members throughout the project. The define scope process is decisive to the project’s success as it includes the deliverables, assumptions, and constraints within which the project must be engaged, and executed and delivered. Define Scope works as a referral guide to the project and forms the statement that becomes the basis for all project activity.
- Create WBS – in this process, the deliverables are broken down into smaller individual tasks based on the project scope statement and requirement gathering documents. The deliverables are streamlined and the hierarchical structure makes it simpler to schedule, monitor and control. It also makes it easy to standardize and automate workflows.
- Verify Scope – In this process, the scope is formally accepted for all the deliverables documented by all the stakeholders involved, mainly the customer or sponsor.
- Control Scope – In this process, the scope of the project or product is monitored and controlled and any changes in the scope baseline are managed. Changes become inevitable despite capturing everything in the scope but the changes must be controlled to avoid scope creep.
Components of a Scope Management Plan
The Scope management ascertains that the scope of the project is defined accurately. This helps the project manager to assign resources to the tasks factoring the costs involved in completing the project. So it all starts with the scope, especially what is in-scope and out-of-scope. There are three processes involved in scope management. They are planning, controlling and closing.
- Planning: This step captures and defines the work to be undertaken.
- Controlling: the scope creep, change tracking, approval or disapproval of changes and documentation takes place in this step.
- Closing: All the project deliverables are audited in this step and the outcome of the project is assessed against the original plan.
The project scope statement is fundamental to the scope management plan. One more critical document associated with scope management is defining the scope in a statement. To delineate the project, a document is drawn after understanding all the processes.
Scope Statement
What is a Project Scope Statement?
The project regardless of size or duration or cost will include a Project Scope Statement. Project Scope Statement is created even before the project work commences. Project Managers use Project Scope Statement to map and confirm the expected results, constraints, limitations, assumptions, exclusions, justification based on which project work will be undertaken. All the stakeholders must agree upon the project scope statement.
What does a Project Scope Statement Include?
The scope statement creates an outline of the project objectives, goals, relationships, deadlines and other specific elements that minimize the risk due to disruptions or changes. The scope statement contains the following.
Business Case– this document presents the requirement of the project and the possible benefits that can be delivered.
Project Description– presents an overview of the final deliverables.
Success Criteria- The pre-agreed criteria with the stakeholders in determining the project’s success. These are specific conditions that have to be met before any deliverables are accepted by stakeholders.
Deliverables: The expected results that the project will produce upon completion are called as deliverables.
Project Exclusions: the part of the work excluded and will not be done as part of the project. Its called scoping out and is important to include so as to clarify and confirm the assumptions and uncertainties.
Limitations– Anything that can limit the project’s progress. It can be resources or technology or infrastructure related issues
Assumptions– Any assumptions made during the course of the project that may impact the final outcome of the project.
Define the Scope of a Project
To ensure the success of the project, a well-defined scope is an absolute must. Without a well-documented and defined scope in place, no matter how hardworking are your resources are efficient the project plan, the project just can't succeed in achieving its intended goals.
A clear vision of the project’ requirement – not at a higher level – but right down to gritty nitty details at a granular level capturing all the specific project goals, deliverables, features, functions, tasks, deadlines, and ultimately costs constitutes a good scope document and helps in defining the project scope.
So how do you define a project scope?
The following steps help to define the scope of a project:
1. Identify the project needs
It is important to understand the identify the project needs to understand the scope better. Identifying the needs provides the best beginning. It enables us to set groundwork, goals, and objectives. It will help in preparing the groundwork for the tasks to be created and the tasks to follow and execution of the tasks.
2. Confirm the objectives and goals of the Project
The objectives and goals of the Project must follow a SMART guideline. By SMART, the objectives and goals of the project ought to be Specific, Measurable, Achievable, Realistic and met within a time frame.
3. Project Scope description
The scope must clearly describe the features and functionalities as part of the project work. The clarity will have its bearing on the project’s success.
4. Expectations and acceptance
The project scope should be fine-tuned to favor an outcome that meets the expectations of the customer or stakeholders and result in the acceptance of deliverables by end-users.
The projects that meet the customer’s approval and earn their recognition and satisfaction are considered to be successful.
5. Identify constraints
Any project will face constraints, which are as inevitable as changes. There are possibilities or limitations, roadblocks that impede the progress and come in the way of achieving the desired results. But when these constraints are identified, then they can be tackled and the roadblocks cleared making way for smooth passage. It helps in minimizing the problems which otherwise would derail or delay the project.
6. Identify necessary changes
There is nothing more expensive than rework. The time, money and material invested would rise exponentially in case of rework and hence its best to avoid reworking the scope of your project. It will burn all available bandwidth. but there are instances when changes become necessary in which case, settle for the minimal change by making all the stakeholders involved to understand the consequence, especially delay and the additional cost.
How to Identify Scope Risks
A successful project manager must manage scope risks.
What is Scope Risk?
According to PMBOK® Guide—6th Edition, Risk is defined as "an uncertain event or condition that, if it occurs, has a positive or negative effect on one or more project objectives". Scope risks then are the uncertain events or conditions related to the project scope.
How do these scope risks arise? The out-of-scope are clearly identified and placed outside the boundaries of project work and yet they somehow sneak their way inside bloating the project scope. That’s what is called scope creep and these are requirements that weren’t factored as part of the agreed scope. It is a scope risk.
But how to identify the Scope Risk?
There are a few methods that can help to Identify Scope Risks.
Interviews
Prepare a set of questions specifically related to scope, and schedule an interview select stakeholders to clarify and confirm the deliverables, assumptions, exclusions, and constraints. It is advisable to document the results and secure a sign-off.
Brainstorming
Pick out the most significant risk that can impair the project deliverables and make a list of questions and use the same for a brainstorming session. With several minds applying their mind to matter, the outcome can be significant in identifying the scope risks.
Checklists
A project ought to have a check-list. Inspect if there are any scope-related risks. If not, create one. There must be a post-review conducted after every project to record the risks. It must be understood that all the risks cannot be captured in a checklist.
Assumption Analysis
Any Assumptions made in the project are sources of risk. These assumptions must be studied for the associated risks and documented.
Cause and Effect Diagrams
Cause and Effect diagrams are very effective in identifying the cause of risks. Once the cause is identified and addressed, the risk gets reduced.
Nominal Group Technique (NGT)
Nominal Group Technique is a kind of brainstorming where the Inputs are collected and prioritized. And the output of NGT is a prioritized list. The risk can be identified from the result of a prioritized list of risks.
Work Breakdown Structure (WBS)
Work Breakdown Structure (WBS) is one of the most powerful tools for identifying scope risk. A WBS with project team whereby they walk through the lowest elements —or work packages as they are called commonly referred. The participants are asked to identify risks.
What are the benefits of Project Scope Management?
Good project scope management will
- Help to understand what is in-scope of the project
- Help to understand the deliverables of the project
- help to make informed decision making during the project
- helps to identify risks and plans steps to mitigate
- helps in setting the right expectations to the stakeholders
- helps in planning on time money, manpower, material
- eases the scope related stress on project manager
- prioritizes tasks to keep the project on track and reduces unplanned work to save on time and expenses
- Enable effective communications between stakeholders by bringing everyone on the same page
- support successful project delivery
The most critical aspect to the success of a project is the project scope, and the project manager has to stay on top not to lose track or focus on the scope.
RECOMMENDED POST:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
:
PROJECT SCOPE MANAGEMENT AND ITS BENEFITS
What is Project Scope?
In project management, scope sets the boundaries to the project within which it can extend. The scope details the deliverables to the as a result of the project initiative.
The project scope determines the work and activities. The project manager must understand the scope clearly and correctly to determine what falls within the boundaries. Those activities that fall inside the boundary become “in scope” and those outside are stricken down as “not in scope”. Only the ‘in-scope” activities are planned for development.
The project scope is the first phase of project planning. The project scope forms the project objectives, the deliverables that include features and functions, limitations, assumptions, and project dependencies. Upon acceptance of the project, the scope management forms the first step in planning.
Why Project Scope is So Important
The question often asked is “Why Project Scope is important?”
Every project has to be delivered on time, within scope, within budget and yet lot many projects fail on these aspects – and the reason: the project scope was not captured correctly
A successful project manager will understand exactly whats to be achieved as a project objective also called scope. For a project manager to stay on track the entire time, regardless of size or complexity, it is important to read the scope right. And that means defining the scope which makes it simple to stay on schedule.
Expectations management is the most difficult and complex task for a project manager as it involves Managing clients' and stakeholders’ hopes and beliefs. A definitive and distinct scope brings everyone on the same page and helps to avoid often cited problems like
- changing requirements,
- or mid-project changes
- budget overspend
- slippage in schedule
- the final outcome contested by client
Without Project scope, the project manager will be left clueless about the time, cost and schedule and resources. The scope influences and forms the basis for every decision made by the project manager.
Project Scope Management
Even before the project begins, Project scope management is initiated. Scope Management is the collection of processes that captures the work to be undertaken in the project and also records the work that is not required. How to manage scope? Through a use case which clearly in writing defines the scope of the project. The business case is closely monitored throughout the project lifecycle.
Project scope states the whole work to be done to deliver the product or services with the agreed features and functions. The scope covers everything that goes into a project.
The Project Scope Management Plan
The Scope Management Plan specifies the scope’s definition, development, and verification. It also defines the responsibilities in managing the project’s scope and guides in scope control. The project scope management plan is one of the most critical and crucial aspects of a project’s success. It identifies the right work needs to be done. According to PMBOK, Guide to the Project Management Body of Knowledge, there are five processes for effective scope management: Collect Requirements, Define Scope. Create Work Breakdown Structure (WBS), Verify Scope and Control Scope.
- Collect Requirements – in this process the requirements that meet the objectives of the project are defined and documented. The documentation will include status updates and final deliverables. Project charter and stakeholder register are the foundation of this process. This process will help in understanding and managing to present the stakeholders’ expectations.
The documentation of this process will serve as an input to the next process, which is Define Scope.
- Define Scope – this step is the most important as it creates the scope statement and helps in understanding the expected deliverables. In this process, the ‘in scope’ and ‘out of scope’ are clearly defined. The project scope statement will guide the team members throughout the project. The define scope process is decisive to the project’s success as it includes the deliverables, assumptions, and constraints within which the project must be engaged, and executed and delivered. Define Scope works as a referral guide to the project and forms the statement that becomes the basis for all project activity.
- Create WBS – in this process, the deliverables are broken down into smaller individual tasks based on the project scope statement and requirement gathering documents. The deliverables are streamlined and the hierarchical structure makes it simpler to schedule, monitor and control. It also makes it easy to standardize and automate workflows.
- Verify Scope – In this process, the scope is formally accepted for all the deliverables documented by all the stakeholders involved, mainly the customer or sponsor.
- Control Scope – In this process, the scope of the project or product is monitored and controlled and any changes in the scope baseline are managed. Changes become inevitable despite capturing everything in the scope but the changes must be controlled to avoid scope creep.
Components of a Scope Management Plan
The Scope management ascertains that the scope of the project is defined accurately. This helps the project manager to assign resources to the tasks factoring the costs involved in completing the project. So it all starts with the scope, especially what is in-scope and out-of-scope. There are three processes involved in scope management. They are planning, controlling and closing.
- Planning: This step captures and defines the work to be undertaken.
- Controlling: the scope creep, change tracking, approval or disapproval of changes and documentation takes place in this step.
- Closing: All the project deliverables are audited in this step and the outcome of the project is assessed against the original plan.
The project scope statement is fundamental to the scope management plan. One more critical document associated with scope management is defining the scope in a statement. To delineate the project, a document is drawn after understanding all the processes.
Scope Statement
What is a Project Scope Statement?
The project regardless of size or duration or cost will include a Project Scope Statement. Project Scope Statement is created even before the project work commences. Project Managers use Project Scope Statement to map and confirm the expected results, constraints, limitations, assumptions, exclusions, justification based on which project work will be undertaken. All the stakeholders must agree upon the project scope statement.
What does a Project Scope Statement Include?
The scope statement creates an outline of the project objectives, goals, relationships, deadlines and other specific elements that minimize the risk due to disruptions or changes. The scope statement contains the following.
Business Case– this document presents the requirement of the project and the possible benefits that can be delivered.
Project Description– presents an overview of the final deliverables.
Success Criteria- The pre-agreed criteria with the stakeholders in determining the project’s success. These are specific conditions that have to be met before any deliverables are accepted by stakeholders.
Deliverables: The expected results that the project will produce upon completion are called as deliverables.
Project Exclusions: the part of the work excluded and will not be done as part of the project. Its called scoping out and is important to include so as to clarify and confirm the assumptions and uncertainties.
Limitations– Anything that can limit the project’s progress. It can be resources or technology or infrastructure related issues
Assumptions– Any assumptions made during the course of the project that may impact the final outcome of the project.
Define the Scope of a Project
To ensure the success of the project, a well-defined scope is an absolute must. Without a well-documented and defined scope in place, no matter how hardworking are your resources are efficient the project plan, the project just can't succeed in achieving its intended goals.
A clear vision of the project’ requirement – not at a higher level – but right down to gritty nitty details at a granular level capturing all the specific project goals, deliverables, features, functions, tasks, deadlines, and ultimately costs constitutes a good scope document and helps in defining the project scope.
So how do you define a project scope?
The following steps help to define the scope of a project:
1. Identify the project needs
It is important to understand the identify the project needs to understand the scope better. Identifying the needs provides the best beginning. It enables us to set groundwork, goals, and objectives. It will help in preparing the groundwork for the tasks to be created and the tasks to follow and execution of the tasks.
2. Confirm the objectives and goals of the Project
The objectives and goals of the Project must follow a SMART guideline. By SMART, the objectives and goals of the project ought to be Specific, Measurable, Achievable, Realistic and met within a time frame.
3. Project Scope description
The scope must clearly describe the features and functionalities as part of the project work. The clarity will have its bearing on the project’s success.
4. Expectations and acceptance
The project scope should be fine-tuned to favor an outcome that meets the expectations of the customer or stakeholders and result in the acceptance of deliverables by end-users.
The projects that meet the customer’s approval and earn their recognition and satisfaction are considered to be successful.
5. Identify constraints
Any project will face constraints, which are as inevitable as changes. There are possibilities or limitations, roadblocks that impede the progress and come in the way of achieving the desired results. But when these constraints are identified, then they can be tackled and the roadblocks cleared making way for smooth passage. It helps in minimizing the problems which otherwise would derail or delay the project.
6. Identify necessary changes
There is nothing more expensive than rework. The time, money and material invested would rise exponentially in case of rework and hence its best to avoid reworking the scope of your project. It will burn all available bandwidth. but there are instances when changes become necessary in which case, settle for the minimal change by making all the stakeholders involved to understand the consequence, especially delay and the additional cost.
How to Identify Scope Risks
A successful project manager must manage scope risks.
What is Scope Risk?
According to PMBOK® Guide—6th Edition, Risk is defined as "an uncertain event or condition that, if it occurs, has a positive or negative effect on one or more project objectives". Scope risks then are the uncertain events or conditions related to the project scope.
How do these scope risks arise? The out-of-scope are clearly identified and placed outside the boundaries of project work and yet they somehow sneak their way inside bloating the project scope. That’s what is called scope creep and these are requirements that weren’t factored as part of the agreed scope. It is a scope risk.
But how to identify the Scope Risk?
There are a few methods that can help to Identify Scope Risks.
Interviews
Prepare a set of questions specifically related to scope, and schedule an interview select stakeholders to clarify and confirm the deliverables, assumptions, exclusions, and constraints. It is advisable to document the results and secure a sign-off.
Brainstorming
Pick out the most significant risk that can impair the project deliverables and make a list of questions and use the same for a brainstorming session. With several minds applying their mind to matter, the outcome can be significant in identifying the scope risks.
Checklists
A project ought to have a check-list. Inspect if there are any scope-related risks. If not, create one. There must be a post-review conducted after every project to record the risks. It must be understood that all the risks cannot be captured in a checklist.
Assumption Analysis
Any Assumptions made in the project are sources of risk. These assumptions must be studied for the associated risks and documented.
Cause and Effect Diagrams
Cause and Effect diagrams are very effective in identifying the cause of risks. Once the cause is identified and addressed, the risk gets reduced.
Nominal Group Technique (NGT)
Nominal Group Technique is a kind of brainstorming where the Inputs are collected and prioritized. And the output of NGT is a prioritized list. The risk can be identified from the result of a prioritized list of risks.
Work Breakdown Structure (WBS)
Work Breakdown Structure (WBS) is one of the most powerful tools for identifying scope risk. A WBS with project team whereby they walk through the lowest elements —or work packages as they are called commonly referred. The participants are asked to identify risks.
What are the benefits of Project Scope Management?
Good project scope management will
- Help to understand what is in-scope of the project
- Help to understand the deliverables of the project
- help to make informed decision making during the project
- helps to identify risks and plans steps to mitigate
- helps in setting the right expectations to the stakeholders
- helps in planning on time money, manpower, material
- eases the scope related stress on project manager
- prioritizes tasks to keep the project on track and reduces unplanned work to save on time and expenses
- Enable effective communications between stakeholders by bringing everyone on the same page
- support successful project delivery
The most critical aspect to the success of a project is the project scope, and the project manager has to stay on top not to lose track or focus on the scope.
RECOMMENDED POST:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
What are the Roles and Responsibilities of a PRINCE2 Certified Professional?
:
What are the Roles and Responsibilities of a PRINCE2 Certified Professional?
What is Prince2 Certification?
PRINCE2 stands for PRojects IN Controlled Environments. PRINCE2 is regarded as a common standard that enables both public and private sector projects to be executed with a common understanding of the processes.
PRINCE2 is one of the leading and popular project management professional certification course that is highly recognized and widely used. PRINCE2 is applicable to any project regardless of the scale, type, geography, organization or culture.
The delivery of products is focused on PRINCE2 more than carrying out activities. There must be a business vase and plan in PRINCE which have to be reviewed periodically.
PRINCE2 is a non-proprietary process-based methodology that is in the public domain and hence not therefore, users are not attached to any single organization for training, consultancy and support.
The structure of PRINCE2 includes:
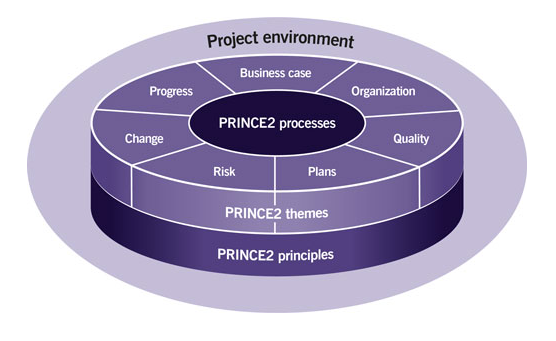
7 Principles of PRINCE2
- Continued business justification.
- Learn from experience.
- Defined roles and responsibilities.
- Manage by stages.
- Manage by exception.
- Focus on products.
- Tailor to suit the environment
7 Themes of PRINCE2
- Business case.
- Organization.
- Quality.
- Plans.
- Risk.
- Change.
- Progress.
7 Processes of PRINCE2
- Starting up a project.
- Directing a project.
- Initiating a project.
- Controlling a stage.
- Managing product delivery.
- Managing a stage boundary.
- Closing a project.
Roles of PRINCE2 Certified Professional
The jobs are not defined in PRINCE2, instead, the roles are defined detailed with responsibilities and it is not necessary that an individual is assigned to a role. There can be more than a person playing that role.
The important criteria are choosing the right person for the roles that come with its responsibilities and the person with the required skill set, knowledge, experience, expertise, leadership, competency, credibility and authority is the best fit.
There is an exclusive term in PRINCE2that comprises of the project manager, the project board and other roles that are optional. It is called Project Management Team.
For a project to be successful in PRINCE2, there must be three categories of stakeholders with a set of roles and responsibilities.
The project board roles and responsibilities are made up of three primary interests.
The Business interest – the value for the money is provided by the Business Case,
the User interest –project’s outputs are used to realize the benefits, or the user interest used to operate, maintain or support the project outputs.
The Supplier interest – the resources and skills are supplied to produce a project’s products.
The PRINCE2 project organization roles and responsibilities include 4 levels, which are,
1. Corporate or program management,
They are responsible for the Project Mandate, project-level tolerance definition, and identifying the executive. They are not apart of the project management team and are outside of it.
2. The Project Board
They are accountable for the success of the project by providing guidance and overall direction. The Project Board is also accountable for the project’s success or failure of the project, by supplying the required resources, approving the project funding and facilitating effective decision-making. The Project Board must possess the right level of authority, credibility, and ability to delegate. The Project Board Executive has the veto power on any decision making and is primarily responsible for the Business Case.
3. The Project Manager
The day-to-day management of the project is the responsibility of the Project Manager. The project board will lay down the constraints within which the Project Manager must manage within the project.
4. Team members
They are responsible for project delivery on time, within cost and desired quality.
Roles & Responsibilities of PRINCE2 Certified Professional
The Senior User roles and responsibilities
Who will use the project’s products will be represented by the Senior User. This also includes how the products will be to achieve an objective. The Senior User stipulates the benefits and held accountable by corporate or program management.
The Senior Supplier roles and responsibilities
The design, development, facilitate, procurement and implementation of the project’s products are represented by the Senior Supplier. The technical integrity of the project is the main responsibility of the Senior Supplier.
The Project Board
It is responsible for Project Assurance which comprises of assurance, business, user and supplier. Project Assurance can be performed by each project board member who may choose to delegate it. Project Assurance is not dependent on the Project Manager, rather it is independent. Project Assurance offers guidance and counsel to the Project Manager in managing the project. In the case of change requests, the Project Board should decide during the initiation stage if there is time to take up the changes or set up Change Authority who will own up the responsibility on their behalf. The Project Board should ideally comprise of six to eight members for effective decision making. If the number of persons shoots up, then it slows down the decision making process.
The Project Manager roles and responsibilities
is responsible for the project management, the delegation of responsibility to the team members and specialists for the creation of products. The project manager will assign work packages to the team which will be handled through a team manager.
The Team Manager roles and responsibilities
The Team Manager will assign the Work Packages to the team members and present the Project Manager with regular updates and Checkpoint Reports. It is the Team Manager who will manage the team members on a day-to-day basis.
Project Support
It is an optional role whose main roles and responsibilities are to provide administrative services to the project. Whenever required, it provides direction and guidance about the use of project management tools. It also provides configuration management. In the absence of Project Support, then the Project manager will have to manage by themselves.
Demand for PRINCE2 Certified Professionals
The PRINCE2 certification is an important asset to accelerate your career growth in project management.
A 2016 AXELOS survey interviewed project management professionals and other roles, like IT systems and operations and reported their findings as "regardless of function, candidates do find that PRINCE2 is valuable to their career".
According to Payscale.com, the average annual salaries for certified PRINCE2 professionals in the United States are shown below which was last updated on Nov 11, 2019
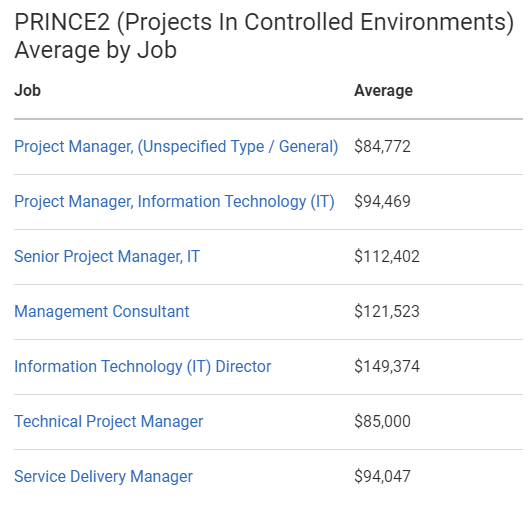
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
:
What are the Roles and Responsibilities of a PRINCE2 Certified Professional?
What is Prince2 Certification?
PRINCE2 stands for PRojects IN Controlled Environments. PRINCE2 is regarded as a common standard that enables both public and private sector projects to be executed with a common understanding of the processes.
PRINCE2 is one of the leading and popular project management professional certification course that is highly recognized and widely used. PRINCE2 is applicable to any project regardless of the scale, type, geography, organization or culture.
The delivery of products is focused on PRINCE2 more than carrying out activities. There must be a business vase and plan in PRINCE which have to be reviewed periodically.
PRINCE2 is a non-proprietary process-based methodology that is in the public domain and hence not therefore, users are not attached to any single organization for training, consultancy and support.
The structure of PRINCE2 includes:

7 Principles of PRINCE2
- Continued business justification.
- Learn from experience.
- Defined roles and responsibilities.
- Manage by stages.
- Manage by exception.
- Focus on products.
- Tailor to suit the environment
7 Themes of PRINCE2
- Business case.
- Organization.
- Quality.
- Plans.
- Risk.
- Change.
- Progress.
7 Processes of PRINCE2
- Starting up a project.
- Directing a project.
- Initiating a project.
- Controlling a stage.
- Managing product delivery.
- Managing a stage boundary.
- Closing a project.
Roles of PRINCE2 Certified Professional
The jobs are not defined in PRINCE2, instead, the roles are defined detailed with responsibilities and it is not necessary that an individual is assigned to a role. There can be more than a person playing that role.
The important criteria are choosing the right person for the roles that come with its responsibilities and the person with the required skill set, knowledge, experience, expertise, leadership, competency, credibility and authority is the best fit.
There is an exclusive term in PRINCE2that comprises of the project manager, the project board and other roles that are optional. It is called Project Management Team.
For a project to be successful in PRINCE2, there must be three categories of stakeholders with a set of roles and responsibilities.
The project board roles and responsibilities are made up of three primary interests.
The Business interest – the value for the money is provided by the Business Case,
the User interest –project’s outputs are used to realize the benefits, or the user interest used to operate, maintain or support the project outputs.
The Supplier interest – the resources and skills are supplied to produce a project’s products.
The PRINCE2 project organization roles and responsibilities include 4 levels, which are,
1. Corporate or program management,
They are responsible for the Project Mandate, project-level tolerance definition, and identifying the executive. They are not apart of the project management team and are outside of it.
2. The Project Board
They are accountable for the success of the project by providing guidance and overall direction. The Project Board is also accountable for the project’s success or failure of the project, by supplying the required resources, approving the project funding and facilitating effective decision-making. The Project Board must possess the right level of authority, credibility, and ability to delegate. The Project Board Executive has the veto power on any decision making and is primarily responsible for the Business Case.
3. The Project Manager
The day-to-day management of the project is the responsibility of the Project Manager. The project board will lay down the constraints within which the Project Manager must manage within the project.
4. Team members
They are responsible for project delivery on time, within cost and desired quality.
Roles & Responsibilities of PRINCE2 Certified Professional
The Senior User roles and responsibilities
Who will use the project’s products will be represented by the Senior User. This also includes how the products will be to achieve an objective. The Senior User stipulates the benefits and held accountable by corporate or program management.
The Senior Supplier roles and responsibilities
The design, development, facilitate, procurement and implementation of the project’s products are represented by the Senior Supplier. The technical integrity of the project is the main responsibility of the Senior Supplier.
The Project Board
It is responsible for Project Assurance which comprises of assurance, business, user and supplier. Project Assurance can be performed by each project board member who may choose to delegate it. Project Assurance is not dependent on the Project Manager, rather it is independent. Project Assurance offers guidance and counsel to the Project Manager in managing the project. In the case of change requests, the Project Board should decide during the initiation stage if there is time to take up the changes or set up Change Authority who will own up the responsibility on their behalf. The Project Board should ideally comprise of six to eight members for effective decision making. If the number of persons shoots up, then it slows down the decision making process.
The Project Manager roles and responsibilities
is responsible for the project management, the delegation of responsibility to the team members and specialists for the creation of products. The project manager will assign work packages to the team which will be handled through a team manager.
The Team Manager roles and responsibilities
The Team Manager will assign the Work Packages to the team members and present the Project Manager with regular updates and Checkpoint Reports. It is the Team Manager who will manage the team members on a day-to-day basis.
Project Support
It is an optional role whose main roles and responsibilities are to provide administrative services to the project. Whenever required, it provides direction and guidance about the use of project management tools. It also provides configuration management. In the absence of Project Support, then the Project manager will have to manage by themselves.
Demand for PRINCE2 Certified Professionals
The PRINCE2 certification is an important asset to accelerate your career growth in project management.
A 2016 AXELOS survey interviewed project management professionals and other roles, like IT systems and operations and reported their findings as "regardless of function, candidates do find that PRINCE2 is valuable to their career".
According to Payscale.com, the average annual salaries for certified PRINCE2 professionals in the United States are shown below which was last updated on Nov 11, 2019

Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Improve Project Success With These Project Management Skills
:
Improve Project Success With These Project Management Skills
Project’s success highly depends on project managers and their skill sets to manage the project effectively. In today’s competitive talent pool, you need to acquire all the project management skills to become a successful project manager.
There is a thin line between a qualified project manager and a certified project manager. Qualified professionals possess all the skills required but certification validates their skills, education, experience, and expertise. Project Management Professional (PMP) Certification helps in improving the skills required to manage all types of projects. It opens the doors to go ahead in the career. The project management skills to be improved for project success are:
- Leadership
- Communication skills
- Time management
- Negotiation skills
- Decision-making skills
- Risk management
1. Leadership
A good leader has the ability to bring the best out of the team with soft skills. The motivated team always gives the best result. A project manager with great leadership qualities lead the team, manage a team, motivate the team and get the work done in an effective manner. The team should be led in both strategic and operation’s perspective.
Project managers can possess effective leadership quality by the following ways that can improve the success rate of the project:
- Social- Influence: The performance of the team can be influenced by conformity, socialization, obedience and peer pressure. The productivity of the team can be improved by improvement in work culture. The opinions, emotions, and behavior team members are affected by the project managers.
- Clarity: Clear vision towards goal. Without a clear vision of the consequences, the team cannot be led by the project manager effectively.
- Inspire team members: Project managers should make things happen. The inspiring team is making team members work willingly.
- Motivate team: The motivated team always gives the best result. The team can be motivated by appreciation, opportunities, and rewards.
- Guidance: Project managers guide the team by providing all the required information clearly.
- Setting Measurable goals: The common goals are to be set by project managers. The timeframe required to reach the objective is set to accomplish the common goals.
2. Communication skills
The impact of communication is very high in project success. Communication is one of the most essential skills required to improve the success rate of the project. The effect of the project manager’s communication has an impact not only on the project but also on clients and stakeholders. Communicating clearly is one of the primary responsibilities of project managers. The changes are to be communicated to all the team members. The following skills include the best practice of communication skills:
The following modes of communication can help in improving the success rate of the project:
- Group meetings
- Email
- One-on-one meetings
- Status reports
- Updates
- Telephonic call
Great communication skills include:
- Active listening
- Clarity in discussion
- Confidence
- Responsiveness
- Respect
- Reach on agreements
- Result oriented
- Addressing important issues
- Resolving issues
Poor communication can mislead the project and result in project failure or delay.
3. Time management
Time management is the most important aspect of project management. Planning helps in setting goals and provide a definite path to reach the project objective. A strategic mindset is important for effective planning. Planning includes defining the project activities of each team member to achieve the project objective in constrained time without any obstacle.
It is completely project manager’s responsibility to deliver the project on time.
Keeping track on the project status and individual project activities helps in proper time management
The standardized time tracking tools and schedule templates are used to keep the transparency of the project.
4. Negotiation skills
Bringing a group of people to settle the differences in order to accomplish the common goal with the agreed resource, budget and time. A good project manager is always a good negotiator. Negotiation always comes with a settlement. In any disagreement, people bring out the best possible outcome. The project manager achieves a desirable outcome of the discussion if PM is a good negotiator. There are two types of negotiation
- competitive negotiation
- collaborative negotiation
The negotiation skills a project manager should possess to improve the rate of project success are:
- An ability to set goals and limits in order to reduce conflict management
- Excellent listening skills
- Effective verbal communication skills
- knowledge of when and how to close the negotiation.
- Reducing misunderstandings is a key part of effective negotiation
- Rapport Building.
- Problem Solving.
- Decision Making.
- Assertiveness.
- Dealing with Difficult Situations.
5. Decision-making skill
Decision making skill is the most important skill a project manager should possess. Some decisions on a daily basis are not much important but there are some critical decisions that lead the project to be successful. The character of the decision should be:
- Rational
- Unbiased decisions
The decision can be taken in the following steps:
- Identify the problem – Recognize the problem in the project process and gather all the information required to take the rational and unbiased decision.
- Summarize all the information
- Figure out all the possible solutions– find all the possible solutions and ideal way to resolve preferably in a group. Consider all the points and do not ignore anything
- Produce objective criteria – generate the measurement criteria to check the feasibility of the solutions.
- Decide what is best – Make a decision based on what is best for the successful completion of the project within a constrained time.
- Implement the solution – implement the solution decided
- Track the results – Track the outcome of the implemented solution.
6. Risk Management
The project manager identifies the risk at an early stage to avoid the impact of risk on project progress later. To predict the uncertainties, the streamlined risk management process is carried out. Risk identification and analysis are done throughout the project lifecycle to reduce the impact on the resource, processes, technology, and schedule.
In risk management,
Identifying the source of risk - The potential risks are listed out based on the previous projects.
Risks identified are categorized in:
- Technical
- External
- Organizational
Risk Analysis is done by performing two processes:
The qualitative Risk Analysis process
In order to set the risk priorities, the analysis is done on the probability of the risk, the impact of the risk on the project and other risk parameters affecting the project deliverables. The main objective of performing qualitative analysis is to predict and reduce the uncertainty of the risks.
The quantitative Risk Analysis process
Performing quantitative risk analysis is the process of numerically analyzing the effect parameters of identified risks on overall project activities. This process helps in further prioritization of risks, reducing the uncertainty.
Risk Responses are planned against the identified risk:
The process of developing action plans against the identified risks to reduce the overall impact on the project. Planning the risk responses involves selecting strategies and agreeing on the actions developed.
Implement Risk Responses process
The process of implementing risk responses involves executing all the actions planned against identified risks to reduce the uncertainty of the project.
Monitor Risks process
The process involves monitoring the implemented action plans against risk identified. This process involves tracking risk responses, analyzing new risks and reducing the risk factor throughout the project.
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
:
Improve Project Success With These Project Management Skills
Project’s success highly depends on project managers and their skill sets to manage the project effectively. In today’s competitive talent pool, you need to acquire all the project management skills to become a successful project manager.
There is a thin line between a qualified project manager and a certified project manager. Qualified professionals possess all the skills required but certification validates their skills, education, experience, and expertise. Project Management Professional (PMP) Certification helps in improving the skills required to manage all types of projects. It opens the doors to go ahead in the career. The project management skills to be improved for project success are:
- Leadership
- Communication skills
- Time management
- Negotiation skills
- Decision-making skills
- Risk management
1. Leadership
A good leader has the ability to bring the best out of the team with soft skills. The motivated team always gives the best result. A project manager with great leadership qualities lead the team, manage a team, motivate the team and get the work done in an effective manner. The team should be led in both strategic and operation’s perspective.
Project managers can possess effective leadership quality by the following ways that can improve the success rate of the project:
- Social- Influence: The performance of the team can be influenced by conformity, socialization, obedience and peer pressure. The productivity of the team can be improved by improvement in work culture. The opinions, emotions, and behavior team members are affected by the project managers.
- Clarity: Clear vision towards goal. Without a clear vision of the consequences, the team cannot be led by the project manager effectively.
- Inspire team members: Project managers should make things happen. The inspiring team is making team members work willingly.
- Motivate team: The motivated team always gives the best result. The team can be motivated by appreciation, opportunities, and rewards.
- Guidance: Project managers guide the team by providing all the required information clearly.
- Setting Measurable goals: The common goals are to be set by project managers. The timeframe required to reach the objective is set to accomplish the common goals.
2. Communication skills
The impact of communication is very high in project success. Communication is one of the most essential skills required to improve the success rate of the project. The effect of the project manager’s communication has an impact not only on the project but also on clients and stakeholders. Communicating clearly is one of the primary responsibilities of project managers. The changes are to be communicated to all the team members. The following skills include the best practice of communication skills:
The following modes of communication can help in improving the success rate of the project:
- Group meetings
- One-on-one meetings
- Status reports
- Updates
- Telephonic call
Great communication skills include:
- Active listening
- Clarity in discussion
- Confidence
- Responsiveness
- Respect
- Reach on agreements
- Result oriented
- Addressing important issues
- Resolving issues
Poor communication can mislead the project and result in project failure or delay.
3. Time management
Time management is the most important aspect of project management. Planning helps in setting goals and provide a definite path to reach the project objective. A strategic mindset is important for effective planning. Planning includes defining the project activities of each team member to achieve the project objective in constrained time without any obstacle.
It is completely project manager’s responsibility to deliver the project on time.
Keeping track on the project status and individual project activities helps in proper time management
The standardized time tracking tools and schedule templates are used to keep the transparency of the project.
4. Negotiation skills
Bringing a group of people to settle the differences in order to accomplish the common goal with the agreed resource, budget and time. A good project manager is always a good negotiator. Negotiation always comes with a settlement. In any disagreement, people bring out the best possible outcome. The project manager achieves a desirable outcome of the discussion if PM is a good negotiator. There are two types of negotiation
- competitive negotiation
- collaborative negotiation
The negotiation skills a project manager should possess to improve the rate of project success are:
- An ability to set goals and limits in order to reduce conflict management
- Excellent listening skills
- Effective verbal communication skills
- knowledge of when and how to close the negotiation.
- Reducing misunderstandings is a key part of effective negotiation
- Rapport Building.
- Problem Solving.
- Decision Making.
- Assertiveness.
- Dealing with Difficult Situations.
5. Decision-making skill
Decision making skill is the most important skill a project manager should possess. Some decisions on a daily basis are not much important but there are some critical decisions that lead the project to be successful. The character of the decision should be:
- Rational
- Unbiased decisions
The decision can be taken in the following steps:
- Identify the problem – Recognize the problem in the project process and gather all the information required to take the rational and unbiased decision.
- Summarize all the information
- Figure out all the possible solutions– find all the possible solutions and ideal way to resolve preferably in a group. Consider all the points and do not ignore anything
- Produce objective criteria – generate the measurement criteria to check the feasibility of the solutions.
- Decide what is best – Make a decision based on what is best for the successful completion of the project within a constrained time.
- Implement the solution – implement the solution decided
- Track the results – Track the outcome of the implemented solution.
6. Risk Management
The project manager identifies the risk at an early stage to avoid the impact of risk on project progress later. To predict the uncertainties, the streamlined risk management process is carried out. Risk identification and analysis are done throughout the project lifecycle to reduce the impact on the resource, processes, technology, and schedule.
In risk management,
Identifying the source of risk - The potential risks are listed out based on the previous projects.
Risks identified are categorized in:
- Technical
- External
- Organizational
Risk Analysis is done by performing two processes:
The qualitative Risk Analysis process
In order to set the risk priorities, the analysis is done on the probability of the risk, the impact of the risk on the project and other risk parameters affecting the project deliverables. The main objective of performing qualitative analysis is to predict and reduce the uncertainty of the risks.
The quantitative Risk Analysis process
Performing quantitative risk analysis is the process of numerically analyzing the effect parameters of identified risks on overall project activities. This process helps in further prioritization of risks, reducing the uncertainty.
Risk Responses are planned against the identified risk:
The process of developing action plans against the identified risks to reduce the overall impact on the project. Planning the risk responses involves selecting strategies and agreeing on the actions developed.
Implement Risk Responses process
The process of implementing risk responses involves executing all the actions planned against identified risks to reduce the uncertainty of the project.
Monitor Risks process
The process involves monitoring the implemented action plans against risk identified. This process involves tracking risk responses, analyzing new risks and reducing the risk factor throughout the project.
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
What are the Benefits of using the Gantt Chart in Project Management?
:
What are the Benefits of using the Gantt Chart in Project Management?
It’s never easy managing a project. In fact, it is very challenging and the project manager is the important driver for the project’s success. Project Manager will require all the resources possible and that includes tools and techniques in achieving the positive outcome for the project. There are a lot many tools employed by the project manager and this blog will deal with one of the significant and specialty tools called Gantt Chart.
What is the Gantt Chart in Project Management?
Wikipedia describes the Gantt Chart as a “ type of bar chart that illustrates a project schedule and shows the dependency relationships between activities and current schedule status.”
Gantt Chart, in simpler terms, is a Data visualization tool that depicts in a graphical format by mapping the tasks and activities of a project against time. All the activities performed in a project are outlined in the chart in an organized order displaying critical information.
The information presented on the Gantt Chart specifies the tasks of the project, the resources assigned to the task, duration of the task, and also the activities that might overlap. Gantt Chart helps the Project Manager to plan, schedule, track, and manage all the tasks effectively.
What is the History of Gantt Chart
Joseph Priestly in his “Charts of Biography” introduced the idea of bar charts in 1765. William Playfair in 1786 pioneered the Gantt Chart in his Commercial and Political Atlas. Karol Adamiecki, a Polish engineer built something close to Gantt Chart in his construction project in the year 1896. Then came an American Engineer named Henry Gantt introduced his version somewhere between 1910 to 1925 that rose to prominence and became popular in the form of mass adoption in a very short span of time. Gantt Charts were used in wartime during 1917-18 for the tracking of arms and ammunitions. Wallace Clark’s book named “The Gantt Chart – A Working Tool of Management“ released in the year 1923 mentioned Gantt Chart, which by then became an official term. With the passage of time, the adoption of the Gantt Chart kept growing in a wide range of domains and fields.
What is Gantt Chart Elements?

A typical Gantt chart is made up of several elements. The various elements in a Gantt Chart are detailed below:
Tasklist: depicted on the extreme left of the Gantt chart, the task list that runs down vertically describes the project work. The tasks can be grouped together and it is possible to create sub-groups.
Timeline: depicted as the horizontal bar that runs on top of the Gantt Chart. In order to keep track, the time is displayed in terms of months, weeks, days, and years
Dateline: depicted as a vertical line on the Gantt chart. that highlights the current date
Bars: depicted on the right side of the Gantt Chart. as horizontal markers, the bars display the tasks, duration, progress, tasks’ start dates and end dates for project completion.
Milestones: depicted as yellow diamonds, Milestones show up between the Bars denote an important achievement in a project especially dates, goals, events and deliverables.
Dependencies: depicted as the light gray lines linking tasks, Dependencies specify the relationships between tasks and the execution of tasks in a specific order.
Progress: depicted as a percentage of completion in the form of shading in the bar indicating the progress made in the project work.
The resource assigned: depicted the resource (team member) or the team assigned to complete the task.
Benefits of Gantt Chart in Project Management
1. Get to know your projects
Gantt charts acts as a great visualization and prioritization tool as it provides the total overview of the project and presents critical information like resources deployed in the project, the tasks and its orders, the duration, the start and end dates, the dependencies, and progress made in the project at any given point in time. Hence, it’s a great tool for project managers to equip themselves with the information to plan, coordinate and manage the project.
2. Enhance communication and team organization
Communication is critical to the success of a project. A study observed in the public domain revealed that 86% of employees cited the communication gap and issues are the worst reasons for the failure of the project. With regard to ti communication Gantt Chart as very effective as it provides clarity in communication. Project managers use the Gantt Chart to find out ‘who is working on what tasks’, secure information and provide inputs in getting the tasks completed. The communication with the team members is enhanced as the same tool can be used for both communication and tracking, resulting in a better relationship as a team.
3. Eliminate resource overload
There could instances when resources could be tasked with more than the permissible bandwidth. It does happen in a project wherein resources could be overloaded or stretched out. Effective use of resources is facilitated by Gantt Chart that aligns with the project timeline. Resources can be delegated tasks without saddling with too much work, which helps the project manager in proper and effective utilization of resources.
4. Assess the progress of projects
Gantt chart helps in scheduling and also tracks the project’s tasks. This assists the project manager in keeping under check the progress made in the project and also enables in shifting strategy to introduce necessary changes in case of slippage of schedule or if the project is lagging behind in timeline. Gantt Chart can be used by the project members to update the percentage of work completed, which is useful to the project manager in making the whole team stay on one page and also ensure the project is making progress rightly as planned.
5. Monitor task dependencies and overlapping activities
The dependencies can at times slow down or even derail as some tasks are dependent to start only upon the closure of another task. Dependencies make project development difficult and complex to manage. Gantt Chart presents the dependencies of the tasks and helps in scheduling in such a manner that the overlapping can be totally eliminated. This ensures that there is no adverse impact execution of the tasks and the overall progress of the project.
6. Experience more clarity
It's easy to get lost in the maze of numbers or stuck in the project details to lose sight of where the project is heading. Gantt Chart provides clarity by enabling to see instantly the progress made in the tasks and also of the team members involved in the project. It builds a better understanding of how the project is shaping out and brings more clarity about the project’s outcome.
7. Practice better time management
Time is an integral and critical component of project management. The biggest benefit of using a Gantt Chart is scheduling. The Gantt Chart plays a significant role by helping the team members recognize the severity of their tasks and realize the impact in case of delay. Gantt Chart presents the big picture of the overall progress to plan better on the allocation of time on every task and get it done within the scheduled timeline.
8. Create a sense of accountability
Gantt charts highlight the milestones achieved, big wins scored, deadlines met and the deliverables, slippage in schedule, failures which allow the project manager and team members to keep a track of the progress made. It creates a sense of accountability is created in the workplace with the help of the Gantt Chart, thus enabling the project manager and team members to work out solutions in closing the gaps and work towards exceeding the expectations of the stakeholders.
RECOMMENDED POST:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
:
What are the Benefits of using the Gantt Chart in Project Management?
It’s never easy managing a project. In fact, it is very challenging and the project manager is the important driver for the project’s success. Project Manager will require all the resources possible and that includes tools and techniques in achieving the positive outcome for the project. There are a lot many tools employed by the project manager and this blog will deal with one of the significant and specialty tools called Gantt Chart.
What is the Gantt Chart in Project Management?
Wikipedia describes the Gantt Chart as a “ type of bar chart that illustrates a project schedule and shows the dependency relationships between activities and current schedule status.”
Gantt Chart, in simpler terms, is a Data visualization tool that depicts in a graphical format by mapping the tasks and activities of a project against time. All the activities performed in a project are outlined in the chart in an organized order displaying critical information.
The information presented on the Gantt Chart specifies the tasks of the project, the resources assigned to the task, duration of the task, and also the activities that might overlap. Gantt Chart helps the Project Manager to plan, schedule, track, and manage all the tasks effectively.
What is the History of Gantt Chart
Joseph Priestly in his “Charts of Biography” introduced the idea of bar charts in 1765. William Playfair in 1786 pioneered the Gantt Chart in his Commercial and Political Atlas. Karol Adamiecki, a Polish engineer built something close to Gantt Chart in his construction project in the year 1896. Then came an American Engineer named Henry Gantt introduced his version somewhere between 1910 to 1925 that rose to prominence and became popular in the form of mass adoption in a very short span of time. Gantt Charts were used in wartime during 1917-18 for the tracking of arms and ammunitions. Wallace Clark’s book named “The Gantt Chart – A Working Tool of Management“ released in the year 1923 mentioned Gantt Chart, which by then became an official term. With the passage of time, the adoption of the Gantt Chart kept growing in a wide range of domains and fields.
What is Gantt Chart Elements?
A typical Gantt chart is made up of several elements. The various elements in a Gantt Chart are detailed below:
Tasklist: depicted on the extreme left of the Gantt chart, the task list that runs down vertically describes the project work. The tasks can be grouped together and it is possible to create sub-groups.
Timeline: depicted as the horizontal bar that runs on top of the Gantt Chart. In order to keep track, the time is displayed in terms of months, weeks, days, and years
Dateline: depicted as a vertical line on the Gantt chart. that highlights the current date
Bars: depicted on the right side of the Gantt Chart. as horizontal markers, the bars display the tasks, duration, progress, tasks’ start dates and end dates for project completion.
Milestones: depicted as yellow diamonds, Milestones show up between the Bars denote an important achievement in a project especially dates, goals, events and deliverables.
Dependencies: depicted as the light gray lines linking tasks, Dependencies specify the relationships between tasks and the execution of tasks in a specific order.
Progress: depicted as a percentage of completion in the form of shading in the bar indicating the progress made in the project work.
The resource assigned: depicted the resource (team member) or the team assigned to complete the task.
Benefits of Gantt Chart in Project Management
1. Get to know your projects
Gantt charts acts as a great visualization and prioritization tool as it provides the total overview of the project and presents critical information like resources deployed in the project, the tasks and its orders, the duration, the start and end dates, the dependencies, and progress made in the project at any given point in time. Hence, it’s a great tool for project managers to equip themselves with the information to plan, coordinate and manage the project.
2. Enhance communication and team organization
Communication is critical to the success of a project. A study observed in the public domain revealed that 86% of employees cited the communication gap and issues are the worst reasons for the failure of the project. With regard to ti communication Gantt Chart as very effective as it provides clarity in communication. Project managers use the Gantt Chart to find out ‘who is working on what tasks’, secure information and provide inputs in getting the tasks completed. The communication with the team members is enhanced as the same tool can be used for both communication and tracking, resulting in a better relationship as a team.
3. Eliminate resource overload
There could instances when resources could be tasked with more than the permissible bandwidth. It does happen in a project wherein resources could be overloaded or stretched out. Effective use of resources is facilitated by Gantt Chart that aligns with the project timeline. Resources can be delegated tasks without saddling with too much work, which helps the project manager in proper and effective utilization of resources.
4. Assess the progress of projects
Gantt chart helps in scheduling and also tracks the project’s tasks. This assists the project manager in keeping under check the progress made in the project and also enables in shifting strategy to introduce necessary changes in case of slippage of schedule or if the project is lagging behind in timeline. Gantt Chart can be used by the project members to update the percentage of work completed, which is useful to the project manager in making the whole team stay on one page and also ensure the project is making progress rightly as planned.
5. Monitor task dependencies and overlapping activities
The dependencies can at times slow down or even derail as some tasks are dependent to start only upon the closure of another task. Dependencies make project development difficult and complex to manage. Gantt Chart presents the dependencies of the tasks and helps in scheduling in such a manner that the overlapping can be totally eliminated. This ensures that there is no adverse impact execution of the tasks and the overall progress of the project.
6. Experience more clarity
It's easy to get lost in the maze of numbers or stuck in the project details to lose sight of where the project is heading. Gantt Chart provides clarity by enabling to see instantly the progress made in the tasks and also of the team members involved in the project. It builds a better understanding of how the project is shaping out and brings more clarity about the project’s outcome.
7. Practice better time management
Time is an integral and critical component of project management. The biggest benefit of using a Gantt Chart is scheduling. The Gantt Chart plays a significant role by helping the team members recognize the severity of their tasks and realize the impact in case of delay. Gantt Chart presents the big picture of the overall progress to plan better on the allocation of time on every task and get it done within the scheduled timeline.
8. Create a sense of accountability
Gantt charts highlight the milestones achieved, big wins scored, deadlines met and the deliverables, slippage in schedule, failures which allow the project manager and team members to keep a track of the progress made. It creates a sense of accountability is created in the workplace with the help of the Gantt Chart, thus enabling the project manager and team members to work out solutions in closing the gaps and work towards exceeding the expectations of the stakeholders.
RECOMMENDED POST:
Key Features of PMP® Certification Training
Top 10 Reasons to Get PMP® Certified
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
What are the Benefits of Project Time Management?
:
What are the Benefits of Project Time Management?
What Is Time Management?
Can you get more done in less time?
That’s the challenge in present times when there are always more things to do and time is always at a shortfall.
The process of organizing and dividing the time between activities through an effective plan is called Time Management. Effective Time Management enables smart work to accomplish more work in the given time despite the mounting pressure and tighter deadlines.
Those who are hailed as high achievers are the ones who manage their time exceedingly well to accommodate more in the timeline provided. More often than not being busy is interpreted as being effective but its not the efforts but the results that count. Hence time management is critical to be fiercely competent and productive.
It's poor time management that results in missed deadlines, poor quality of work, higher stress, inefficiency, poor professional reputation stunted career growth and Work and life imbalance.
Proper time management is about managing time efficiently to actually save time. It provides space to be proactive and creative in completing tasks. Strong time-management skills are one of the critical factors in achieving key goals of the organization by providing a clear picture of what needs to be completed within the given timeline boosting productivity.
Why Time Management Is Important?
Good time management ensures more work is accomplished in a shorter time period that frees up more time or bandwidth, which can be leveraged in taking up additional tasks. It opens up opportunities as the additional time can be utilized to the project’s advantage that essentially eases the pressure on the schedule, relaxes the crew, lowers the stress and strengthens the focus – eventually resulting in the successful outcome of the project.
Here are 5 reasons time management is crucial:
1. Time is limited
Divide it in any which ways, but a day has only 24 hours. You cant stretch it any further. So it is important to acknowledge that constraint and plan the day effectively to make the most of the hours through smart work. Innovation and improvisation in getting things done will help to rise through the ranks and effectively manage and utilize limited resources -in this case, time too is a limitation.
2. Accomplish more with less effort
the ability to focus is strengthened through effective control of time. And that enables the ability to focus which bolsters momentum and enhances efficiency. The net result is the completion of the task at a quicker turnaround in time much faster than anticipated.
3. Improved decision-making ability
When hard-pressed for time, the decision-making ability gets impaired as the pressure is piling making it difficult to arrive at an informed decision. Good time management skills eliminate the pressure that stems from the inadequacy of time, calms the mind to be more in control to carefully examine all the options in making the right decision.
4. Become more successful in your career
One of the keys to success is Time management which lets you take control of yourself rather than follow others. When the decisions are sound, the results will get recognized. The people around will notice and frontrunners will approach you for assistance in completing the tasks or activities, that shifts the spotlight on your profile and helps to accelerate your career.
5. Reduce stress
Lack of control of time can lead to complications as the deadlines might be delayed or milestone missed. Effective management of time helps you to take control and negotiate with the constraints and demands on time through proper estimation and completion of the given task within the timeline. This essentially lowers the level of stress as you are in control of the schedule and confident in delivery as planned.
What are the Project Schedule Management Processes?
There are six processes in Project Schedule Management:
- Plan Schedule Management
- Define Activities
- Sequence Activities
- Estimate Activity Durations
- Develop Schedule
- Control Schedule
1. Plan Schedule Management
Plan schedule management is the first process of Schedule Management in which various policies and procedures are established. The information about planning, developing, managing, executing and controlling of the project schedule is documented to minute details. This provides direction to the project manager in managing the project from initiation to final delivery. This process is executed once or predefined points in the entire project management lifecycle.
2. Define Activities
In the Define Activities process, all the actions required to prepare the final deliverables identified and documented. The work packages are broken down into smaller tasks. These smaller tasks act as the baseline for estimation, scheduling, execution, monitor, and control of the overall project work.
3. Sequence Activities
All the relationship among various project activities is identified and documented in Sequence Activities. This process defines the logical sequence of work which helps in gaining maximum efficiency despite the constraints. This process is executed throughout the project lifecycle.
4. Estimate Activity Durations
Estimate Activity Durations estimates the number of work periods needed to complete a single activity documented in the project schedule along with necessary and sufficient resources. The estimated time required to complete the individual activities are calculated in this process. This process is executed throughout the project lifecycle
5. Develop Schedule
In Develop Schedule process the schedule model is created to execute, monitor, manage and control the project. The finer details of the project activities are analyzed in terms of sequence, duration, resource requirement, constraints. Develop Schedule process and produces a model schedule complete with dates of various project activities and is executed throughout the project lifecycle.
6. Control Schedule
The last process of the Project Schedule Management, Control Schedule is executed throughout the project lifecycle. Based on the status of the project, the project schedule is updated in this process and as a result, the changes are incorporated into the schedule baseline. Because of this process, the schedule baseline is maintained throughout the project development.
What are the Benefits Of Time Management?
Proper management of time has its own benefits. Listed are some benefits of Time Management:
1. On-time delivery
To complete work on time, a definite time should be allocated, which will also help to manage the workload. When there are time-boxed tasks, achieving the target on the set timeline is possible through a structured schedule. Managing time effectively results in delivery on time.
2. Better quality of work
Proper utilization of time and effective use of resources, it is possible to deliver work of expected quality and standards. The focus can be shifted to important tasks that are of the highest priority in the list of activities with undivided attention and dedication resulting in improved quality of work.
3. Productivity and efficiency
Effective and efficient time management skills help in completing the tasks adhering to the highest standards m- and it requires proper planning and scheduling. when urgent tasks are taken on priority and identifying those tasks that are unimportant thus balancing the time and sticking to the schedule without slippage increases overall productivity.
4. Much less procrastination
Deferring the work to “sometime later” is not only the worst excuse but proves too costly in consequences as the postponed work will have a cascading effect adversely impacting the progress of the project. Applying good time management is necessary to motivate the employees in closing the tasks and removes the roadblock in the form of procrastination.
5. Less stress and anxiety
Difficult times are always a result f poor time management. When there is excessive work on the schedule, then time estimation has not been properly thought through, which can unnecessarily burden the employee. This inevitably adds to the stress and anxiety given the unreasonable deadlines that lead to depression, hypertension, and other illness.
6. Improved quality of life
Time management skills not only benefit professional life but it helps balances personal life too. The work-life balance is very much possible if the right balance is struck in apportioning time accordingly. Effective time management ensures tasks are on track which in turn provides time to focus on personal needs. This harmony improves the quality of life.
7. More opportunities and career growth
When tasks are completed on time, it becomes noteworthy and good work is always appreciated and complimented. Those who can get the work done consistently with a quicker turnaround in time are ‘achievers’ who are assigned more work. The one who gets work done always gets promotional opportunities at work that help up walk up the ladder.
What are The 4 Ds Of Effective Time Management?
Project managers often struggle with time management due to various reasons – maybe the client wasn’t clear about the specifications or introduction of last-minute changes or resource crunches or it can be anything. Managing time is not easy. One of the most popular productivity strategies for effective time management is known as “four Ds”.
Delete it.
It is very important to identify the task or activity that needs to concentrate. Confirm if that needs your full focus and attention. If it is not worth your time, better to delete it. Pareto principle (80/20 rule) in this context states that people spend 80% of their on activities either unproductive or a total waste.
Delegate it.
Delegation is a great way to save time to spend on critical tasks that are your responsibility. Delegation should not be misunderstood or just assigning tasks to subordinates. Work can be delegated across, upwards or even other departments. It's about the identification of accountability and the right fitment to do the particular task. A project manager doesn’t have to manage financial accounting and hence delegate to an accountant. Delegation doesn’t mean shaking off the responsibility. It’s the fine art of getting work done.
Do it.
If a task is very important and can be done you and there is time left, without deferring, deleting or delegating, then it's better to do it. It avoids postponement or procrastination. It helps to stay focused and not get sidetracked. If it is worth your time, and efforts on that task, then do it and move on.
Defer it.
There are some tasks that can wait. If there is no urgency or if it can be dealt with later, then Defer it. It might not be important during the working day, but still, it is important to get it done. For example, it can be an email that doesn’t need your immediate attention – defer it till you get some free time. Those that do not call for immediate action and can be taken up at a later point in time can be deferred but should be done eventually.
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
:
What are the Benefits of Project Time Management?
What Is Time Management?
Can you get more done in less time?
That’s the challenge in present times when there are always more things to do and time is always at a shortfall.
The process of organizing and dividing the time between activities through an effective plan is called Time Management. Effective Time Management enables smart work to accomplish more work in the given time despite the mounting pressure and tighter deadlines.
Those who are hailed as high achievers are the ones who manage their time exceedingly well to accommodate more in the timeline provided. More often than not being busy is interpreted as being effective but its not the efforts but the results that count. Hence time management is critical to be fiercely competent and productive.
It's poor time management that results in missed deadlines, poor quality of work, higher stress, inefficiency, poor professional reputation stunted career growth and Work and life imbalance.
Proper time management is about managing time efficiently to actually save time. It provides space to be proactive and creative in completing tasks. Strong time-management skills are one of the critical factors in achieving key goals of the organization by providing a clear picture of what needs to be completed within the given timeline boosting productivity.
Why Time Management Is Important?
Good time management ensures more work is accomplished in a shorter time period that frees up more time or bandwidth, which can be leveraged in taking up additional tasks. It opens up opportunities as the additional time can be utilized to the project’s advantage that essentially eases the pressure on the schedule, relaxes the crew, lowers the stress and strengthens the focus – eventually resulting in the successful outcome of the project.
Here are 5 reasons time management is crucial:
1. Time is limited
Divide it in any which ways, but a day has only 24 hours. You cant stretch it any further. So it is important to acknowledge that constraint and plan the day effectively to make the most of the hours through smart work. Innovation and improvisation in getting things done will help to rise through the ranks and effectively manage and utilize limited resources -in this case, time too is a limitation.
2. Accomplish more with less effort
the ability to focus is strengthened through effective control of time. And that enables the ability to focus which bolsters momentum and enhances efficiency. The net result is the completion of the task at a quicker turnaround in time much faster than anticipated.
3. Improved decision-making ability
When hard-pressed for time, the decision-making ability gets impaired as the pressure is piling making it difficult to arrive at an informed decision. Good time management skills eliminate the pressure that stems from the inadequacy of time, calms the mind to be more in control to carefully examine all the options in making the right decision.
4. Become more successful in your career
One of the keys to success is Time management which lets you take control of yourself rather than follow others. When the decisions are sound, the results will get recognized. The people around will notice and frontrunners will approach you for assistance in completing the tasks or activities, that shifts the spotlight on your profile and helps to accelerate your career.
5. Reduce stress
Lack of control of time can lead to complications as the deadlines might be delayed or milestone missed. Effective management of time helps you to take control and negotiate with the constraints and demands on time through proper estimation and completion of the given task within the timeline. This essentially lowers the level of stress as you are in control of the schedule and confident in delivery as planned.
What are the Project Schedule Management Processes?
There are six processes in Project Schedule Management:
- Plan Schedule Management
- Define Activities
- Sequence Activities
- Estimate Activity Durations
- Develop Schedule
- Control Schedule
1. Plan Schedule Management
Plan schedule management is the first process of Schedule Management in which various policies and procedures are established. The information about planning, developing, managing, executing and controlling of the project schedule is documented to minute details. This provides direction to the project manager in managing the project from initiation to final delivery. This process is executed once or predefined points in the entire project management lifecycle.
2. Define Activities
In the Define Activities process, all the actions required to prepare the final deliverables identified and documented. The work packages are broken down into smaller tasks. These smaller tasks act as the baseline for estimation, scheduling, execution, monitor, and control of the overall project work.
3. Sequence Activities
All the relationship among various project activities is identified and documented in Sequence Activities. This process defines the logical sequence of work which helps in gaining maximum efficiency despite the constraints. This process is executed throughout the project lifecycle.
4. Estimate Activity Durations
Estimate Activity Durations estimates the number of work periods needed to complete a single activity documented in the project schedule along with necessary and sufficient resources. The estimated time required to complete the individual activities are calculated in this process. This process is executed throughout the project lifecycle
5. Develop Schedule
In Develop Schedule process the schedule model is created to execute, monitor, manage and control the project. The finer details of the project activities are analyzed in terms of sequence, duration, resource requirement, constraints. Develop Schedule process and produces a model schedule complete with dates of various project activities and is executed throughout the project lifecycle.
6. Control Schedule
The last process of the Project Schedule Management, Control Schedule is executed throughout the project lifecycle. Based on the status of the project, the project schedule is updated in this process and as a result, the changes are incorporated into the schedule baseline. Because of this process, the schedule baseline is maintained throughout the project development.
What are the Benefits Of Time Management?
Proper management of time has its own benefits. Listed are some benefits of Time Management:
1. On-time delivery
To complete work on time, a definite time should be allocated, which will also help to manage the workload. When there are time-boxed tasks, achieving the target on the set timeline is possible through a structured schedule. Managing time effectively results in delivery on time.
2. Better quality of work
Proper utilization of time and effective use of resources, it is possible to deliver work of expected quality and standards. The focus can be shifted to important tasks that are of the highest priority in the list of activities with undivided attention and dedication resulting in improved quality of work.
3. Productivity and efficiency
Effective and efficient time management skills help in completing the tasks adhering to the highest standards m- and it requires proper planning and scheduling. when urgent tasks are taken on priority and identifying those tasks that are unimportant thus balancing the time and sticking to the schedule without slippage increases overall productivity.
4. Much less procrastination
Deferring the work to “sometime later” is not only the worst excuse but proves too costly in consequences as the postponed work will have a cascading effect adversely impacting the progress of the project. Applying good time management is necessary to motivate the employees in closing the tasks and removes the roadblock in the form of procrastination.
5. Less stress and anxiety
Difficult times are always a result f poor time management. When there is excessive work on the schedule, then time estimation has not been properly thought through, which can unnecessarily burden the employee. This inevitably adds to the stress and anxiety given the unreasonable deadlines that lead to depression, hypertension, and other illness.
6. Improved quality of life
Time management skills not only benefit professional life but it helps balances personal life too. The work-life balance is very much possible if the right balance is struck in apportioning time accordingly. Effective time management ensures tasks are on track which in turn provides time to focus on personal needs. This harmony improves the quality of life.
7. More opportunities and career growth
When tasks are completed on time, it becomes noteworthy and good work is always appreciated and complimented. Those who can get the work done consistently with a quicker turnaround in time are ‘achievers’ who are assigned more work. The one who gets work done always gets promotional opportunities at work that help up walk up the ladder.
What are The 4 Ds Of Effective Time Management?
Project managers often struggle with time management due to various reasons – maybe the client wasn’t clear about the specifications or introduction of last-minute changes or resource crunches or it can be anything. Managing time is not easy. One of the most popular productivity strategies for effective time management is known as “four Ds”.
Delete it.
It is very important to identify the task or activity that needs to concentrate. Confirm if that needs your full focus and attention. If it is not worth your time, better to delete it. Pareto principle (80/20 rule) in this context states that people spend 80% of their on activities either unproductive or a total waste.
Delegate it.
Delegation is a great way to save time to spend on critical tasks that are your responsibility. Delegation should not be misunderstood or just assigning tasks to subordinates. Work can be delegated across, upwards or even other departments. It's about the identification of accountability and the right fitment to do the particular task. A project manager doesn’t have to manage financial accounting and hence delegate to an accountant. Delegation doesn’t mean shaking off the responsibility. It’s the fine art of getting work done.
Do it.
If a task is very important and can be done you and there is time left, without deferring, deleting or delegating, then it's better to do it. It avoids postponement or procrastination. It helps to stay focused and not get sidetracked. If it is worth your time, and efforts on that task, then do it and move on.
Defer it.
There are some tasks that can wait. If there is no urgency or if it can be dealt with later, then Defer it. It might not be important during the working day, but still, it is important to get it done. For example, it can be an email that doesn’t need your immediate attention – defer it till you get some free time. Those that do not call for immediate action and can be taken up at a later point in time can be deferred but should be done eventually.
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
What is Project Quality Management?
:
What is Project Quality Management?
What is Project Quality?
The measure of how accurate the results are from the project deliverables in order to meet the customer needs and is suitable for its intended purpose is Project Quality. Project quality is nothing but the quality assurance given to the customers through its output.
Project quality can be defined in the following terms:
- Validation: The assurance to meet the satisfactory results.
- Verification: The compliance required to meet project requirements.
- Precision: The condition of being exact.
- Accuracy: The degree or measure of the closeness
- Tolerance: The range of the acceptable results
When the project is initiated, the main aim is to deliver quality deliverables throughout the project life cycle within the constrained budget and schedule.
In simple terms, project quality is “fit for use”.
According to PMBOK-6th edition,
“Quality- The degree to which a set of inherent characteristics fulfill requirements”
What is Project Quality Management?
Project Quality Management is the process or activity that ensures to meet the stakeholder’s expectations through effective and efficient project deliverables. The performance of an organization is measured, monitored and controlled through quality policies, standards, guidelines, and procedures.
Project quality management is performed throughout the project. It aims to maintain the quality through obtaining optimum results from all the project activities performed.
Project quality management is one of the 10 knowledge areas of project management. The process of quality management is in three phases of project management: Planning, execution, and monitoring and controlling.
What are the processes involved in Project Quality Management?
There are three processes involved in Project Quality Management in three phases: planning, execution, and monitoring and controlling.
Plan Quality Management process
Plan Quality Management is the process of identifying the quality requirements and quality standards relevant to the project output. The document of a set of quality standards is prepared for each project activities. The methodology used, the resource assigned, the cost and the time allocated are the major factors affecting quality.
Manage Quality process
Manage Quality is the process of managing all the project activities according to the quality management plan while executing. The main objective of managing the quality process is to integrate all the quality policies in the project activities to maintain the quality plan management.
Control Quality process
Control Quality process is the process of monitoring and controlling the executed project activities according to quality management. The main objective of this process is to ensure the project output is correct, complete and meet the expectations of the customer and the quality plan. This process also includes the documentation of results obtained during the control quality process.
Why Project Quality Management is important?
Project Quality Management is very important in order to avoid defects and re-work. The cost and schedule baseline will be affected due to poor quality management.
The organization’s reputation will be harmed if the quality is not up to the mark.
Project Quality Management is important due to the following reasons:
- Customer satisfaction
- It enhances the understanding between the internal processes
- Identifying and reducing risk at an early stage
- Higher efficiency of project deliverables
- Maintains consistent performance of the resources.
- Chances of getting other projects or references for the same.
What are the characteristics of project quality to be maintained?
The common characteristics of project quality defined by stakeholders are:
- Performance: The act of performing a task or project activity.
- Sustainability: The ability to be maintained at a certain level.
- Functionality: The purpose of the task or activity to be fulfilled
- Suitanbility: The quality of being an appropriate choice to perform a task
- Reliability: The measure of being trust-worthy
- Consistency: The evenness in the performance
- Timeliness: The measure to finish the project task in the allotted time.
- Completeness: The quality of finishing the specified task to meet the project scope.
What are the elements of Project Quality Management?
There are elements of the modern Project Quality Management based on ISO (International Organization for Standardization) quality standards. The five elements are:
Customer Satisfaction
The process of understanding, evaluating, defining and managing the requirements and expectations to meet the customer’s needs. Customer satisfaction is a key measure of project quality management. There are two main requirements to achieve great quality:
- Conformance
- Fit for use
Note: Meeting the agreed customer’s requirement is not the same as meeting the expectations. If the requirements are met and the results are not satisfactory, then the main cause is poor quality management.
Prevention over Inspection
The cost of preventing a mistake is comparatively lesser than correcting a mistake during execution. In quality management, quality is desired quality is achieved by planning but it is not inspected. Mistakes or re-work effects cost, schedule, and scope. In quality management, the Cost of Quality (COQ) is the money spent dealing with the issues related to quality.
The COQ is divided into two categories:
- Cost of conformance: Preventive cost
- Cost of nonconformance: Quality failure cost
The cost of conformance can be document process, training, equipment, and time.
The cost of non-conformance can be time spent on rework or scrap work.
Continuous Improvement
Continuous improvement is the on-going effort to improve product quality and services. It can be carried out through Six Sigma or Total Quality Management (TQM). TQM is the key concept of continuous improvement.
The continuous improvement can be done by analyzing the issues faced during the lesson learned after finishing the project activity and which can be used for future projects.
The main aim of continuous improvement is to avoid repeating the same mistakes.
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
:
What is Project Quality Management?
What is Project Quality?
The measure of how accurate the results are from the project deliverables in order to meet the customer needs and is suitable for its intended purpose is Project Quality. Project quality is nothing but the quality assurance given to the customers through its output.
Project quality can be defined in the following terms:
- Validation: The assurance to meet the satisfactory results.
- Verification: The compliance required to meet project requirements.
- Precision: The condition of being exact.
- Accuracy: The degree or measure of the closeness
- Tolerance: The range of the acceptable results
When the project is initiated, the main aim is to deliver quality deliverables throughout the project life cycle within the constrained budget and schedule.
In simple terms, project quality is “fit for use”.
According to PMBOK-6th edition,
“Quality- The degree to which a set of inherent characteristics fulfill requirements”
What is Project Quality Management?
Project Quality Management is the process or activity that ensures to meet the stakeholder’s expectations through effective and efficient project deliverables. The performance of an organization is measured, monitored and controlled through quality policies, standards, guidelines, and procedures.
Project quality management is performed throughout the project. It aims to maintain the quality through obtaining optimum results from all the project activities performed.
Project quality management is one of the 10 knowledge areas of project management. The process of quality management is in three phases of project management: Planning, execution, and monitoring and controlling.
What are the processes involved in Project Quality Management?
There are three processes involved in Project Quality Management in three phases: planning, execution, and monitoring and controlling.
Plan Quality Management process
Plan Quality Management is the process of identifying the quality requirements and quality standards relevant to the project output. The document of a set of quality standards is prepared for each project activities. The methodology used, the resource assigned, the cost and the time allocated are the major factors affecting quality.
Manage Quality process
Manage Quality is the process of managing all the project activities according to the quality management plan while executing. The main objective of managing the quality process is to integrate all the quality policies in the project activities to maintain the quality plan management.
Control Quality process
Control Quality process is the process of monitoring and controlling the executed project activities according to quality management. The main objective of this process is to ensure the project output is correct, complete and meet the expectations of the customer and the quality plan. This process also includes the documentation of results obtained during the control quality process.
Why Project Quality Management is important?
Project Quality Management is very important in order to avoid defects and re-work. The cost and schedule baseline will be affected due to poor quality management.
The organization’s reputation will be harmed if the quality is not up to the mark.
Project Quality Management is important due to the following reasons:
- Customer satisfaction
- It enhances the understanding between the internal processes
- Identifying and reducing risk at an early stage
- Higher efficiency of project deliverables
- Maintains consistent performance of the resources.
- Chances of getting other projects or references for the same.
What are the characteristics of project quality to be maintained?
The common characteristics of project quality defined by stakeholders are:
- Performance: The act of performing a task or project activity.
- Sustainability: The ability to be maintained at a certain level.
- Functionality: The purpose of the task or activity to be fulfilled
- Suitanbility: The quality of being an appropriate choice to perform a task
- Reliability: The measure of being trust-worthy
- Consistency: The evenness in the performance
- Timeliness: The measure to finish the project task in the allotted time.
- Completeness: The quality of finishing the specified task to meet the project scope.
What are the elements of Project Quality Management?
There are elements of the modern Project Quality Management based on ISO (International Organization for Standardization) quality standards. The five elements are:
Customer Satisfaction
The process of understanding, evaluating, defining and managing the requirements and expectations to meet the customer’s needs. Customer satisfaction is a key measure of project quality management. There are two main requirements to achieve great quality:
- Conformance
- Fit for use
Note: Meeting the agreed customer’s requirement is not the same as meeting the expectations. If the requirements are met and the results are not satisfactory, then the main cause is poor quality management.
Prevention over Inspection
The cost of preventing a mistake is comparatively lesser than correcting a mistake during execution. In quality management, quality is desired quality is achieved by planning but it is not inspected. Mistakes or re-work effects cost, schedule, and scope. In quality management, the Cost of Quality (COQ) is the money spent dealing with the issues related to quality.
The COQ is divided into two categories:
- Cost of conformance: Preventive cost
- Cost of nonconformance: Quality failure cost
The cost of conformance can be document process, training, equipment, and time.
The cost of non-conformance can be time spent on rework or scrap work.
Continuous Improvement
Continuous improvement is the on-going effort to improve product quality and services. It can be carried out through Six Sigma or Total Quality Management (TQM). TQM is the key concept of continuous improvement.
The continuous improvement can be done by analyzing the issues faced during the lesson learned after finishing the project activity and which can be used for future projects.
The main aim of continuous improvement is to avoid repeating the same mistakes.
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
What is the Difference Between PRINCE2 Foundation and PRINCE2 Practitioner Certifications?
:
What is the Difference Between PRINCE2 Foundation and PRINCE2 Practitioner Certifications?
PRINCE2® is an acronym for PRojects IN Controlled Environments and the "2" refers to its relaunch in October 1996. It is the non-proprietary process-based project management methodology. PRINCE2 is mainly focused to establish,
- Control at the commencement.
- Progression of the project.
- Termination of projects.
PRINCE2 is one of the most globally accepted project management methods. It can be applied to any kind of project irrespective of scale, type, geography, organization or culture.
In the UK, PRINCE2® (Projects in Controlled Environments) is considered the de facto standard for IT project management. PRINCE2 doesn’t define the project as a temporary endeavor, rather as a project management method it delivers based on a business case.
The PRINCE2 method is in the public domain therefore, users are not tied to any single organization for consultancy, training, and support.
PRINCE2 is widely regarded as a common standard that enables projects in the public or private sector to be executed with a common understanding of the processes and terminology used.
PRINCE2 is a certification program owned by AXELOS and this method is sustained by a scheme that offers four levels of certification:
- PRINCE2 Foundation
- PRINCE2 Practitioner
- PRINCE2 Agile Foundation
- PRINCE2 Agile Practitioner.
There are two levels of PRINCE2 Certification:
- PRINCE2 Foundation: Entry-level certification
- PRINCE2 Practitioner: Certification for project managers working on running projects
Before we get to know the differences, it is important to know what includes in PRINCE2.
The structure of PRINCE2 includes:

7 Principles of PRINCE2
- Continued business justification.
- Learn from experience.
- Defined roles and responsibilities.
- Manage by stages.
- Manage by exception.
- Focus on products.
- Tailor to suit the environment
7 Themes of PRINCE2
- Business case.
- Organization.
- Quality.
- Plans.
- Risk.
- Change.
- Progress.
7 Processes of PRINCE2
- Starting up a project.
- Directing a project.
- Initiating a project.
- Controlling a stage.
- Managing product delivery.
- Managing a stage boundary.
- Closing a project.
There are many differences between PRINCE2 Foundation certification and PRINCE2 Practitioner Certification in terms of syllabus, eligibility criteria, target audience, exam pattern, career path, demand, and scope.
Eligibility Criteria:
PRINCE2 Foundation certification: There is no formal prerequisite to take up PRINCE2 Foundation Certification. But having a basic knowledge of project management will be an advantage.
PRINCE2 Practitioner certification: To take-up PRINCE2 Practitioner Certification, you should have any one of the following certifications.
- PRINCE2 Foundation
- Project Management Professional (PMP)®
- Certified Associate in Project Management (CAPM)®
- IPMA Level A (Certified Projects Director)
- IPMA Level B® (Certified Senior Project Manager)
- IPMA Level C® (Certified Project Manager)
- IPMA Level D® (Certified Project Management Associate)
Syllabus
PRINCE2 Foundation Certification:
- PRINCE2 Foundation is the basic level of certification.
- The PRINCE2 method is introduced in the PRINCE2 Foundation Level. The PRINCE2 Foundation certification establishes your credentials in the knowledge and understanding of the PRINCE2 method.
- The PRINCE2 Foundation qualification will impart knowledge about the PRINCE2 principles, themes, and processes, and terminology and when qualified you will be able to act as an informed member of a project management team using the PRINCE2 methodology within a project environment supporting PRINCE2.
- The PRINCE2 Foundation certification endorses your credibility to engage as an informed team member to work on projects in an environment supporting PRINCE2.
PRINCE2 Practitioner Certification:
- The Practitioner certification validates your knowledge and understanding of PRINCE2 concepts and principles. It includes detailed explanations about PRINCE2 principles, themes, and processes.
- The Practitioner certification assesses your capability in applying and tailoring the PRINCE2 project management method in different project environments and scenarios.
Target Audience
Target audiences are those who are best suited for taking up PRINCE2 certifications:
PRINCE2 Foundation Certification
PRINCE2 Foundation certification is recommended for current and aspiring project managers. It is applicable for:
- Team Managers
- Project Board members
- Project Support
- Operation Managers
- Professionals who manage projects
PRINCE2 Practitioner Certification
This certification is best suitable for project managers, professionals involved with managing projects and aspiring project managers. It is also applicable for:
- Team Managers
- Project Board members
- Project Support
- Operation Managers
Exam Pattern
PRINCE2 Foundation Certification:
- Multiple-choice questions
- 60-minute duration
- 60 questions
- Closed book
- 33/60 required to pass = 55% passing score
- The exam can be taken in any of the 5 languages
PRINCE2 Practitioner Certification:
- Multiple-choice questions
- 150-minute exam duration
- 68 questions
- 38/68 required to pass = 55% passing score
- Open book exam (official PRINCE2 manual only)
Cost
According to AXELOS,
“AXELOS is not a training organization or exam body and so prices for training courses and exams are set by our partners and will vary.”
The cost of PRINCE2 Practitioner Certification fees will be higher compared to the PRINCE2 Foundation Certification cost.
Demand and Scope
PRINCE2 certification proves to be an asset as it accelerates your career in the field of project management.
A 2016 AXELOS survey questioned individuals in project management and other roles, such as IT, senior management and operations. They reported that "regardless of function, candidates do find that PRINCE2 is valuable to their career".
According to Payscale.com,
The average annual salaries for certified PRINCE2 professionals in the United States are shown below.
Currency: USD, Updated: Mon Nov 11 2019
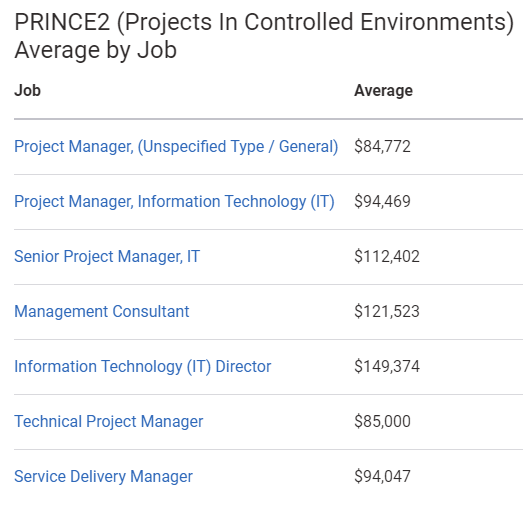
According to payscale, the salary of a PRINCE2® Practitioner ranges from $97,000 per year.
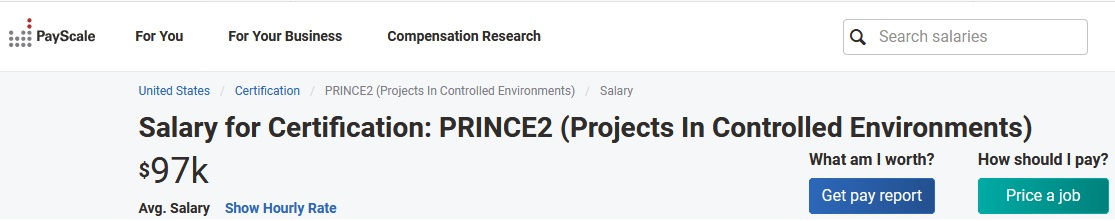
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
What is the Difference Between PRINCE2 Foundation and PRINCE2 Practitioner Certifications?
PRINCE2® is an acronym for PRojects IN Controlled Environments and the "2" refers to its relaunch in October 1996. It is the non-proprietary process-based project management methodology. PRINCE2 is mainly focused to establish,
- Control at the commencement.
- Progression of the project.
- Termination of projects.
PRINCE2 is one of the most globally accepted project management methods. It can be applied to any kind of project irrespective of scale, type, geography, organization or culture.
In the UK, PRINCE2® (Projects in Controlled Environments) is considered the de facto standard for IT project management. PRINCE2 doesn’t define the project as a temporary endeavor, rather as a project management method it delivers based on a business case.
The PRINCE2 method is in the public domain therefore, users are not tied to any single organization for consultancy, training, and support.
PRINCE2 is widely regarded as a common standard that enables projects in the public or private sector to be executed with a common understanding of the processes and terminology used.
PRINCE2 is a certification program owned by AXELOS and this method is sustained by a scheme that offers four levels of certification:
- PRINCE2 Foundation
- PRINCE2 Practitioner
- PRINCE2 Agile Foundation
- PRINCE2 Agile Practitioner.
There are two levels of PRINCE2 Certification:
- PRINCE2 Foundation: Entry-level certification
- PRINCE2 Practitioner: Certification for project managers working on running projects
Before we get to know the differences, it is important to know what includes in PRINCE2.
The structure of PRINCE2 includes:

7 Principles of PRINCE2
- Continued business justification.
- Learn from experience.
- Defined roles and responsibilities.
- Manage by stages.
- Manage by exception.
- Focus on products.
- Tailor to suit the environment
7 Themes of PRINCE2
- Business case.
- Organization.
- Quality.
- Plans.
- Risk.
- Change.
- Progress.
7 Processes of PRINCE2
- Starting up a project.
- Directing a project.
- Initiating a project.
- Controlling a stage.
- Managing product delivery.
- Managing a stage boundary.
- Closing a project.
There are many differences between PRINCE2 Foundation certification and PRINCE2 Practitioner Certification in terms of syllabus, eligibility criteria, target audience, exam pattern, career path, demand, and scope.
Eligibility Criteria:
PRINCE2 Foundation certification: There is no formal prerequisite to take up PRINCE2 Foundation Certification. But having a basic knowledge of project management will be an advantage.
PRINCE2 Practitioner certification: To take-up PRINCE2 Practitioner Certification, you should have any one of the following certifications.
- PRINCE2 Foundation
- Project Management Professional (PMP)®
- Certified Associate in Project Management (CAPM)®
- IPMA Level A (Certified Projects Director)
- IPMA Level B® (Certified Senior Project Manager)
- IPMA Level C® (Certified Project Manager)
- IPMA Level D® (Certified Project Management Associate)
Syllabus
PRINCE2 Foundation Certification:
- PRINCE2 Foundation is the basic level of certification.
- The PRINCE2 method is introduced in the PRINCE2 Foundation Level. The PRINCE2 Foundation certification establishes your credentials in the knowledge and understanding of the PRINCE2 method.
- The PRINCE2 Foundation qualification will impart knowledge about the PRINCE2 principles, themes, and processes, and terminology and when qualified you will be able to act as an informed member of a project management team using the PRINCE2 methodology within a project environment supporting PRINCE2.
- The PRINCE2 Foundation certification endorses your credibility to engage as an informed team member to work on projects in an environment supporting PRINCE2.
PRINCE2 Practitioner Certification:
- The Practitioner certification validates your knowledge and understanding of PRINCE2 concepts and principles. It includes detailed explanations about PRINCE2 principles, themes, and processes.
- The Practitioner certification assesses your capability in applying and tailoring the PRINCE2 project management method in different project environments and scenarios.
Target Audience
Target audiences are those who are best suited for taking up PRINCE2 certifications:
PRINCE2 Foundation Certification
PRINCE2 Foundation certification is recommended for current and aspiring project managers. It is applicable for:
- Team Managers
- Project Board members
- Project Support
- Operation Managers
- Professionals who manage projects
PRINCE2 Practitioner Certification
This certification is best suitable for project managers, professionals involved with managing projects and aspiring project managers. It is also applicable for:
- Team Managers
- Project Board members
- Project Support
- Operation Managers
Exam Pattern
PRINCE2 Foundation Certification:
- Multiple-choice questions
- 60-minute duration
- 60 questions
- Closed book
- 33/60 required to pass = 55% passing score
- The exam can be taken in any of the 5 languages
PRINCE2 Practitioner Certification:
- Multiple-choice questions
- 150-minute exam duration
- 68 questions
- 38/68 required to pass = 55% passing score
- Open book exam (official PRINCE2 manual only)
Cost
According to AXELOS,
“AXELOS is not a training organization or exam body and so prices for training courses and exams are set by our partners and will vary.”
The cost of PRINCE2 Practitioner Certification fees will be higher compared to the PRINCE2 Foundation Certification cost.
Demand and Scope
PRINCE2 certification proves to be an asset as it accelerates your career in the field of project management.
A 2016 AXELOS survey questioned individuals in project management and other roles, such as IT, senior management and operations. They reported that "regardless of function, candidates do find that PRINCE2 is valuable to their career".
According to Payscale.com,
The average annual salaries for certified PRINCE2 professionals in the United States are shown below.
Currency: USD, Updated: Mon Nov 11 2019

According to payscale, the salary of a PRINCE2® Practitioner ranges from $97,000 per year.

Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Top 20 Brainstorming Activities For Your Project Team To Think Out of the Box
Here is a List of Top 20 Brainstorming Activities for a Project Team to Think Out Of The Box:
- End in Mind
- Marshmallow Spaghetti Tower
- Frostbite
- A shrinking vessel
- Ad Game
- Idea Mock-ups
- Brainstorm ideas
- Egg Drop
- Dumbest Idea First
- Stranded
- Reverse Pyramid
- Legoman
- Idea Trial
- Escape
- Gamification
- Find the Funny
- Be a Character
- Move It!
- Word on the Street
- Human Knot
Brainstorming is a technique where ideas are collected to solve a specific problem. The team-based activities are conducted to enhance the ability to bring out innovative and unique ideas. The brainstorming activities are a structured approach to increase their thinking based skills. The activities are based on the following principle:
- Discover new ideas as much as possible
- Equal participation
- Share ideas irrespective of being judged
- Recording all the ideas
- No criticism
- Combine the ideas
- Improvise the ideas
The 20 brainstorming activities are:
1. End In Mind
End in Mind activity is a backtrack way to find the solution. This activity allows a team to start thinking from the end of the task. The milestones, finishing dates are established in reverse order.
2. Marshmallow Spaghetti Tower
Marshmallow Spaghetti Tower is a collaborative activity among teams.
According to Peter Senge,
“Collectively, we can be more insightful, more intelligent than we can possibly be individual”.
In this activity, you will need,
- 20 sticks of uncooked spaghetti
- Marshmallow
- Masking tape
- A yard of String
The teams have to utilize the above materials to construct a tower at a specific time range. This activity enhances the team’s spirit to work together and collaboratively build a solid foundation for their respective activities.
3. Frostbite
This brainstorming activity is to enhance decision-making skills and adaptability.
The required materials to perform this activity are:
- An electric fan
- Rubber bands and sticky notes
- Clothes table, cardboard, masking tape, etc.
- A blindfold
The instructions to be followed:
- Two teams are made of 5members each.
- Each team has to construct a shelter using a cloth table, cardboard, mask tapes, etc
- Except for team leaders, all the team members should be blindfolded to construct a shelter in 30 minutes.
- The hands of the leader are tied throughout the construction of shelter.
- After 30 minutes, the fan is turned on to check which shelter is strong to hold the storm i.e wind from the fan.
4. A shrinking vessel
A shrinking vessel is a technique to overcome the adaptability issues in the team. This activity is conducted using a string or a rope.
- A random shape is made on the floor using a rope.
- The shape should be big enough to fit all the team members in it.
- The size of the shape is reduced gradually
- The team members have to adapt to the shrinking area.
5. Ad Game
Ad Game activity is conducted to enhance communication and collaboration. In this activity, everyone is said to give one idea and everyone has to chant “yes”. The team members are free to give their ideas without having a fear of facing negativity or disagreements. The main aim of this activity is to be positive about all the suggestions given.
6. Idea Mockups
The mock-ups are conducted to bring out the different solutions for the same problem. This will help you to find the perfect solution to your problem.
7. Brainstorm Ideas
Brainstorming ideas are the simplest activity where the teams bring out their solutions on their own and help in choosing the right one. Brainstorming activities are carried out to resolve the common problems in a team. This activity is similar to Idea-Mockups.
8. Egg Drop
Egg Drop activity is conducted to increase the collaboration and decision-making skills among the team. In this activity, the following materials are required:
- Carton of eggs
- Materials to prepare a carrier: Plastic wrap, balloons, rubber bands, etc.
The game is carried out as follows:
- The team is formed and an egg is given to each team
- The team has to protect the egg by constructing a carrier for an egg given to them.
- Once the team has constructed the carriers, The eggs are dropped from the ledge or balcony.
- The team which successfully protects the egg wins the game.
9. Dumbest Idea First
Dumbest Idea First activity is carried out to find out the effective way out of the silliest ideas. Sometimes the solution of the problem lies in simple common sense. The team members are asked to quickly think of the dumbest and silliest idea popping in their minds. Once the team members give all the ideas, an effective solution can be produced by combining the ideas.
10. Stranded
Stranded activity is carried out to enhance the communication and collaboration between the team. In this activity,
The team is locked in the room
They will be given 30 minutes to choose 10 items for their survival
The team is supposed to choose items and rank in order of importance.
Each team member should agree on the items selected. The team members should also agree on the ranking order.
This activity builds a strong bond between team members and the collaboration and communication reflect in work.
11. Reverse Pyramid
Reverse Pyramid activity helps the team to enhance their adaptability and collaboration.
The team is made to stand in a pyramid shape
Only three people are allowed to move and flip the base and apex of the pyramid
This activity encourages collaboration and adaptability
12. Legoman
Legoman activity will enhance the communication between the team members using Lego.
In this activity,
The team of 2 or more members is made.
An impartial individual is selected to draw any structure using Lego within 10 mins
The team competing in this activity has to recreate the exact structure in 15 minutes in which only one member is allowed to see the structure.
The team member allowed to see the structure should explain the other team member on the basis of color, shape, and size.
13. Idea Trial
Idea Trial is a fun activity where mock trials of the problems are carried out in a court-type scenario. In this activity, all the team members project their ideas in court. They give opening and closing statements of all the problems. They can also call the team member as a witness for support.
14. Escape
Escape activity is conducted to build collaboration between teams using,
- Room
- Key
- Rope
- Clues for Puzzles
In this activity,
The key is hidden in the lockable room.
The clues to find the key are also hidden in the same room.
The team members are locked in the room.
The team is supposed to find the key using all the clues.
15. Gamification
Gamification is a fun game to solve the problems. In this game, problems are solved among the teams where different problems are set as an objective of the game. The team has to earn skill points by following all the rules set.
16. Find the Funny
In this activity, the monologue is created for every problem. The funny moments during the work are shared with all the other team members. This activity is a stress buster for everyone and lets them relax for some time.
17. Be a Character
Be a Character is conducted to add fun in the work environment. In this activity, the solutions to the problems are executed by as if you are an imaginary character. This will help you to think in a different perspective and get the solution.
18. Move It!
Move It is a fun activity conducted to enhance collaboration and adaptability. In this activity, the teams are split into two. This activity requires a large space.
The teams are made to stand in a line facing each other’s shoulders.
A boundary is drawn using chalk or tape for the team to stand.
The extra space is left between two facing rows.
The team has to switch their places where only one person is allowed to move at a time.
A player is not allowed to move backward and move around anyone if they are facing in the same direction.
They are allowed to move only once at a time around people from other teams.
19. Word on the Street
Word on a street is a technique to understand the perspective of others. In this activity, each team member will be interviewed by the head of the team about the solutions. The head will try to understand how the team members feel about the solution.
20. Human Knot
A human knot is a fun activity to enhance adaptability and collaboration in the team. In this activity, the team is made to form a big circle
The hands are held cross-connected with the next member
The challenge is to untangle the structure without letting go of anyone’s hand.
This activity will help the team to interact with each other and enhance collaboration.
For more information on how you can accelerate your career with these certifications, visit us at https://www.icertglobal.com/ or call now on +1-713-287-1213 / 1214 or email us at info {at} icertglobal {dot} com.
Know more about our Professional Certification Training Courses for preparing for the below mentioned recommended certifications.
Recommended Courses:
- Artificial Intelligence and Deep Learning Certification Training Course
- Machine Learning Certification Training Course
- Big Data Certification Training Courses
- Agile and Scrum
- Data Science Certification Training Courses
- AWS Certified Solutions Architect Certification Training Courses
- Google Cloud Platform Fundamentals Certification Training Courses
- CISSP Certification Training Courses
- CEH Certification Training Courses
- CSM Certification Training Courses
- CRISC Certification Training Courses
- CISM Certification Training Courses
- PMP Certification Training Courses
- CAPM Certification Training Course
- CompTIA Cloud Essentials Certification Training Course
- AWS Solution Architect Certification Training Course
We provide instructor-led classroom and instructor-led live online training across the globe. We also provide Corporate Training for enterprise workforce development.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
iCert Global both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in 2020? Let us know your thoughts in the 'Comments' section below.
Thank you for reading this blog post. Hope you found it useful and interesting. Team iCert Global wishes you all the best for your learning endeavors.
Read More
Here is a List of Top 20 Brainstorming Activities for a Project Team to Think Out Of The Box:
- End in Mind
- Marshmallow Spaghetti Tower
- Frostbite
- A shrinking vessel
- Ad Game
- Idea Mock-ups
- Brainstorm ideas
- Egg Drop
- Dumbest Idea First
- Stranded
- Reverse Pyramid
- Legoman
- Idea Trial
- Escape
- Gamification
- Find the Funny
- Be a Character
- Move It!
- Word on the Street
- Human Knot
Brainstorming is a technique where ideas are collected to solve a specific problem. The team-based activities are conducted to enhance the ability to bring out innovative and unique ideas. The brainstorming activities are a structured approach to increase their thinking based skills. The activities are based on the following principle:
- Discover new ideas as much as possible
- Equal participation
- Share ideas irrespective of being judged
- Recording all the ideas
- No criticism
- Combine the ideas
- Improvise the ideas
The 20 brainstorming activities are:
1. End In Mind
End in Mind activity is a backtrack way to find the solution. This activity allows a team to start thinking from the end of the task. The milestones, finishing dates are established in reverse order.
2. Marshmallow Spaghetti Tower
Marshmallow Spaghetti Tower is a collaborative activity among teams.
According to Peter Senge,
“Collectively, we can be more insightful, more intelligent than we can possibly be individual”.
In this activity, you will need,
- 20 sticks of uncooked spaghetti
- Marshmallow
- Masking tape
- A yard of String
The teams have to utilize the above materials to construct a tower at a specific time range. This activity enhances the team’s spirit to work together and collaboratively build a solid foundation for their respective activities.
3. Frostbite
This brainstorming activity is to enhance decision-making skills and adaptability.
The required materials to perform this activity are:
- An electric fan
- Rubber bands and sticky notes
- Clothes table, cardboard, masking tape, etc.
- A blindfold
The instructions to be followed:
- Two teams are made of 5members each.
- Each team has to construct a shelter using a cloth table, cardboard, mask tapes, etc
- Except for team leaders, all the team members should be blindfolded to construct a shelter in 30 minutes.
- The hands of the leader are tied throughout the construction of shelter.
- After 30 minutes, the fan is turned on to check which shelter is strong to hold the storm i.e wind from the fan.
4. A shrinking vessel
A shrinking vessel is a technique to overcome the adaptability issues in the team. This activity is conducted using a string or a rope.
- A random shape is made on the floor using a rope.
- The shape should be big enough to fit all the team members in it.
- The size of the shape is reduced gradually
- The team members have to adapt to the shrinking area.
5. Ad Game
Ad Game activity is conducted to enhance communication and collaboration. In this activity, everyone is said to give one idea and everyone has to chant “yes”. The team members are free to give their ideas without having a fear of facing negativity or disagreements. The main aim of this activity is to be positive about all the suggestions given.
6. Idea Mockups
The mock-ups are conducted to bring out the different solutions for the same problem. This will help you to find the perfect solution to your problem.
7. Brainstorm Ideas
Brainstorming ideas are the simplest activity where the teams bring out their solutions on their own and help in choosing the right one. Brainstorming activities are carried out to resolve the common problems in a team. This activity is similar to Idea-Mockups.
8. Egg Drop
Egg Drop activity is conducted to increase the collaboration and decision-making skills among the team. In this activity, the following materials are required:
- Carton of eggs
- Materials to prepare a carrier: Plastic wrap, balloons, rubber bands, etc.
The game is carried out as follows:
- The team is formed and an egg is given to each team
- The team has to protect the egg by constructing a carrier for an egg given to them.
- Once the team has constructed the carriers, The eggs are dropped from the ledge or balcony.
- The team which successfully protects the egg wins the game.
9. Dumbest Idea First
Dumbest Idea First activity is carried out to find out the effective way out of the silliest ideas. Sometimes the solution of the problem lies in simple common sense. The team members are asked to quickly think of the dumbest and silliest idea popping in their minds. Once the team members give all the ideas, an effective solution can be produced by combining the ideas.
10. Stranded
Stranded activity is carried out to enhance the communication and collaboration between the team. In this activity,
The team is locked in the room
They will be given 30 minutes to choose 10 items for their survival
The team is supposed to choose items and rank in order of importance.
Each team member should agree on the items selected. The team members should also agree on the ranking order.
This activity builds a strong bond between team members and the collaboration and communication reflect in work.
11. Reverse Pyramid
Reverse Pyramid activity helps the team to enhance their adaptability and collaboration.
The team is made to stand in a pyramid shape
Only three people are allowed to move and flip the base and apex of the pyramid
This activity encourages collaboration and adaptability
12. Legoman
Legoman activity will enhance the communication between the team members using Lego.
In this activity,
The team of 2 or more members is made.
An impartial individual is selected to draw any structure using Lego within 10 mins
The team competing in this activity has to recreate the exact structure in 15 minutes in which only one member is allowed to see the structure.
The team member allowed to see the structure should explain the other team member on the basis of color, shape, and size.
13. Idea Trial
Idea Trial is a fun activity where mock trials of the problems are carried out in a court-type scenario. In this activity, all the team members project their ideas in court. They give opening and closing statements of all the problems. They can also call the team member as a witness for support.
14. Escape
Escape activity is conducted to build collaboration between teams using,
- Room
- Key
- Rope
- Clues for Puzzles
In this activity,
The key is hidden in the lockable room.
The clues to find the key are also hidden in the same room.
The team members are locked in the room.
The team is supposed to find the key using all the clues.
15. Gamification
Gamification is a fun game to solve the problems. In this game, problems are solved among the teams where different problems are set as an objective of the game. The team has to earn skill points by following all the rules set.
16. Find the Funny
In this activity, the monologue is created for every problem. The funny moments during the work are shared with all the other team members. This activity is a stress buster for everyone and lets them relax for some time.
17. Be a Character
Be a Character is conducted to add fun in the work environment. In this activity, the solutions to the problems are executed by as if you are an imaginary character. This will help you to think in a different perspective and get the solution.
18. Move It!
Move It is a fun activity conducted to enhance collaboration and adaptability. In this activity, the teams are split into two. This activity requires a large space.
The teams are made to stand in a line facing each other’s shoulders.
A boundary is drawn using chalk or tape for the team to stand.
The extra space is left between two facing rows.
The team has to switch their places where only one person is allowed to move at a time.
A player is not allowed to move backward and move around anyone if they are facing in the same direction.
They are allowed to move only once at a time around people from other teams.
19. Word on the Street
Word on a street is a technique to understand the perspective of others. In this activity, each team member will be interviewed by the head of the team about the solutions. The head will try to understand how the team members feel about the solution.
20. Human Knot
A human knot is a fun activity to enhance adaptability and collaboration in the team. In this activity, the team is made to form a big circle
The hands are held cross-connected with the next member
The challenge is to untangle the structure without letting go of anyone’s hand.
This activity will help the team to interact with each other and enhance collaboration.
For more information on how you can accelerate your career with these certifications, visit us at https://www.icertglobal.com/ or call now on +1-713-287-1213 / 1214 or email us at info {at} icertglobal {dot} com.
Know more about our Professional Certification Training Courses for preparing for the below mentioned recommended certifications.
Recommended Courses:
- Artificial Intelligence and Deep Learning Certification Training Course
- Machine Learning Certification Training Course
- Big Data Certification Training Courses
- Agile and Scrum
- Data Science Certification Training Courses
- AWS Certified Solutions Architect Certification Training Courses
- Google Cloud Platform Fundamentals Certification Training Courses
- CISSP Certification Training Courses
- CEH Certification Training Courses
- CSM Certification Training Courses
- CRISC Certification Training Courses
- CISM Certification Training Courses
- PMP Certification Training Courses
- CAPM Certification Training Course
- CompTIA Cloud Essentials Certification Training Course
- AWS Solution Architect Certification Training Course
We provide instructor-led classroom and instructor-led live online training across the globe. We also provide Corporate Training for enterprise workforce development.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
iCert Global both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in 2020? Let us know your thoughts in the 'Comments' section below.
Thank you for reading this blog post. Hope you found it useful and interesting. Team iCert Global wishes you all the best for your learning endeavors.
Top 7 Project Management Software Tools For Enhancing Project Productivity
:
Here is the list of project management software tools to enhance project productivity.
- Trello
- Wrike
- Basecamp
- Zoho Projects
- LiquidPlanner
- Microsoft Project
- Teamwork Projects
Project management software tools lend a helpful hand to project managers. The software makes day-to-day work in a structured manner. There is a huge range of project management tools available to fulfill all the requirements of project managers. The software tools are used for the following benefits:
- Accuracy in estimation
- Optimization of resources
- Tracking the progress of the project
- Planning
- Budget tracking
- Risk assessment
- Automated reporting
Choosing the right tool for the project is very important. Depending on the features required, project management software is chosen.
According to Capterra,
70% of the users are satisfied with the performance of the project management software tool.
According to Capterra,
The impact of a project management software tool is shown in the below image:
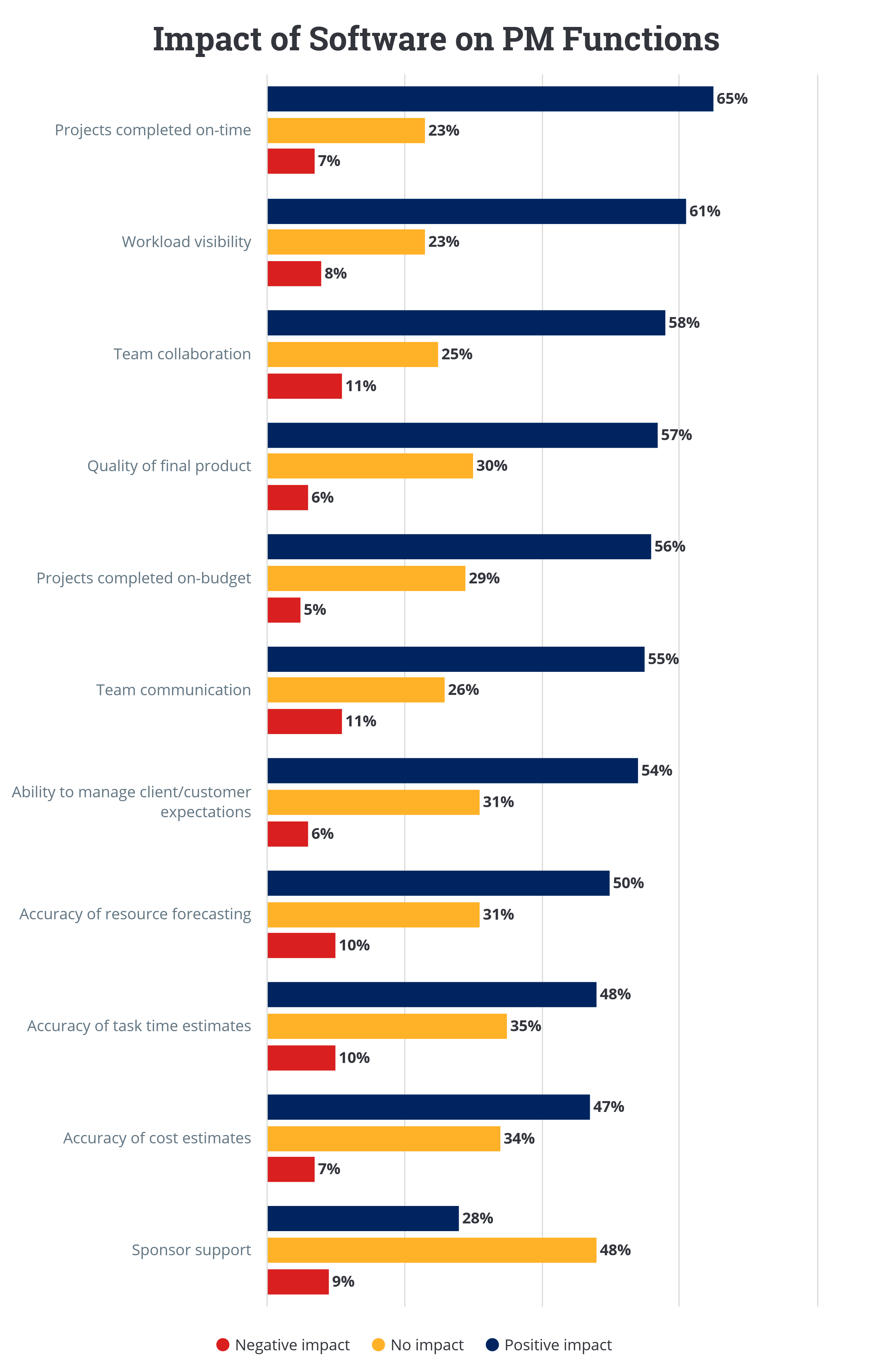
Here is the list of project management software tools to enhance project productivity.
- Trello
- Wrike
- Basecamp
- Zoho Projects
- LiquidPlanner
- Microsoft Project
- Teamwork Projects
1. Trello
Trello is based on Kanban card-based management system. It has a collaborative approach with Trello’s cards, boards, and lists which enables the user to organize and prioritize the projects and tasks. It is more free-form and flexible and easy to understand.
It enables even small teams to get started with basic project management.
Trello provides 3 pricing tiers:
- Free
- Business
- Enterprise
Free tiers require signup and give access to unlimited boards, lists, cards members, checklists and attachments but have restrictions on file size.
Business tiers - $9.99/user/month. The user is able to access the full range of integrations with tools such as Slack, Salesforce, GitHub and others. In this tier, the tool allows 250 MB file size for an attachment.
Enterprise tier pricing plan depends on the number of users. It starts at $20.83/user/month.
Trello is the best app to get started.
2. Wrike
Wrike is also a project management tool for collaboration. Wrike includes built-in standard features of project management like Gantt Charts, dashboards, time tracking tool and reporting suite.
Wrike mostly concentrates on time tracking but manages with the basic requirement of project management.
The free plan is available in Wrike- Unlimited projects can be created but a number of users and availability of features are limited.
Wrike is available in all the versions- website, android, and iOS.
The paid version of Wrike starts from - $9.80/user/month.
Wrike is known for its speedy setup.
3. Basecamp
Basecamp is one of the old project management tools available for over a decade. Basecamp includes,
- Scheduling and calendars,
- Real-time chat
- File Storage
- Private messaging etc.
Basecamp makes finding a file easy with powerful search tools and owns uncluttered interface, email integration, filesharing, notification customization.
The pricing of Basecamp is fixed: $99/month.
Basecamp provides free 30-days trial
Supported in web, desktop, and mobile versions.
Basecamp is best suitable for collaboration in larger organizations.
4. Zoho Projects
Zoho Projects is a cloud-based project management software tool. It consists of all the standard project management features. It possesses features like,
- Access control
- Revision tracking
- Document management
- File sharing
- Issue management
- Search
- Retrieval
Zoho Projects has integration with other services like Google and Microsoft.
The free tier is available for unlimited users but for a single project and limited storage.
The free tier of Zoho Projects offers only 10MB of storage.
Zoho pricing is based on features.
The pricing starts from $20/month
5. LiquidPlanner
LiquidPlanner is one of the best tools for organizations practicing traditional methodologies. LiquidPlanner includes,
Resource management
Issue tracking- Helpdesk style
Integration with cloud storage providers
Zapier support- Automated connections with other tools
LiquidPlanner is suitable for larger organizations with larger teams.
LiquidPlanner doesn’t provide free-tier pricing. The trial version of the tool is available for two weeks. The paid version of the tool starts from $45/user/month.
LiquidPlanner has a wide range of project management features.
6. Microsoft Project
Microsoft is one of the oldest project management tools running in all types of industries from the past 30 years. It is used by many senior project managers to manage complex projects. Microsoft Project appears similar to other Microsoft Office applications.
All the information about tasks and resources can be tracked in a detailed manner.
In Microsoft Project, the reports can be easily exported to Microsoft PowerPoint and other apps.
The integration with the tools other than Microsoft is limited.
There are different prices on different versions of Microsoft Project. The features also differ based on versions.
In order to use Microsoft Project, the subscription for Office365 is mandatory. The Microsoft Project plans start from $30/user/month.
7. Teamwork Projects
Known for its “easy to use” funtionality, Teamwork Projects offers a wide range of features required to run a project successfully. Teamwork Projects help to enhance collaboration, transparency, and accountability of the user. Without using any complex lists or charts, Teamwork Projects surf all the information very easily. Similar to Trello, it uses Kanban Boards and lists. The integration is within the app which is very helpful.
The free tier of Teamwork Project is available with limited storage space for 5 users and 2 projects.
The paid version of the tool has different price plans For 5 users with 100GB storage space, 300 Projects, 50 users at $9/user/month.
The tool is also available in the Premium and Enterprise plan.
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
:
Here is the list of project management software tools to enhance project productivity.
- Trello
- Wrike
- Basecamp
- Zoho Projects
- LiquidPlanner
- Microsoft Project
- Teamwork Projects
Project management software tools lend a helpful hand to project managers. The software makes day-to-day work in a structured manner. There is a huge range of project management tools available to fulfill all the requirements of project managers. The software tools are used for the following benefits:
- Accuracy in estimation
- Optimization of resources
- Tracking the progress of the project
- Planning
- Budget tracking
- Risk assessment
- Automated reporting
Choosing the right tool for the project is very important. Depending on the features required, project management software is chosen.
According to Capterra,
70% of the users are satisfied with the performance of the project management software tool.
According to Capterra,
The impact of a project management software tool is shown in the below image:

Here is the list of project management software tools to enhance project productivity.
- Trello
- Wrike
- Basecamp
- Zoho Projects
- LiquidPlanner
- Microsoft Project
- Teamwork Projects
1. Trello
Trello is based on Kanban card-based management system. It has a collaborative approach with Trello’s cards, boards, and lists which enables the user to organize and prioritize the projects and tasks. It is more free-form and flexible and easy to understand.
It enables even small teams to get started with basic project management.
Trello provides 3 pricing tiers:
- Free
- Business
- Enterprise
Free tiers require signup and give access to unlimited boards, lists, cards members, checklists and attachments but have restrictions on file size.
Business tiers - $9.99/user/month. The user is able to access the full range of integrations with tools such as Slack, Salesforce, GitHub and others. In this tier, the tool allows 250 MB file size for an attachment.
Enterprise tier pricing plan depends on the number of users. It starts at $20.83/user/month.
Trello is the best app to get started.
2. Wrike
Wrike is also a project management tool for collaboration. Wrike includes built-in standard features of project management like Gantt Charts, dashboards, time tracking tool and reporting suite.
Wrike mostly concentrates on time tracking but manages with the basic requirement of project management.
The free plan is available in Wrike- Unlimited projects can be created but a number of users and availability of features are limited.
Wrike is available in all the versions- website, android, and iOS.
The paid version of Wrike starts from - $9.80/user/month.
Wrike is known for its speedy setup.
3. Basecamp
Basecamp is one of the old project management tools available for over a decade. Basecamp includes,
- Scheduling and calendars,
- Real-time chat
- File Storage
- Private messaging etc.
Basecamp makes finding a file easy with powerful search tools and owns uncluttered interface, email integration, filesharing, notification customization.
The pricing of Basecamp is fixed: $99/month.
Basecamp provides free 30-days trial
Supported in web, desktop, and mobile versions.
Basecamp is best suitable for collaboration in larger organizations.
4. Zoho Projects
Zoho Projects is a cloud-based project management software tool. It consists of all the standard project management features. It possesses features like,
- Access control
- Revision tracking
- Document management
- File sharing
- Issue management
- Search
- Retrieval
Zoho Projects has integration with other services like Google and Microsoft.
The free tier is available for unlimited users but for a single project and limited storage.
The free tier of Zoho Projects offers only 10MB of storage.
Zoho pricing is based on features.
The pricing starts from $20/month
5. LiquidPlanner
LiquidPlanner is one of the best tools for organizations practicing traditional methodologies. LiquidPlanner includes,
Resource management
Issue tracking- Helpdesk style
Integration with cloud storage providers
Zapier support- Automated connections with other tools
LiquidPlanner is suitable for larger organizations with larger teams.
LiquidPlanner doesn’t provide free-tier pricing. The trial version of the tool is available for two weeks. The paid version of the tool starts from $45/user/month.
LiquidPlanner has a wide range of project management features.
6. Microsoft Project
Microsoft is one of the oldest project management tools running in all types of industries from the past 30 years. It is used by many senior project managers to manage complex projects. Microsoft Project appears similar to other Microsoft Office applications.
All the information about tasks and resources can be tracked in a detailed manner.
In Microsoft Project, the reports can be easily exported to Microsoft PowerPoint and other apps.
The integration with the tools other than Microsoft is limited.
There are different prices on different versions of Microsoft Project. The features also differ based on versions.
In order to use Microsoft Project, the subscription for Office365 is mandatory. The Microsoft Project plans start from $30/user/month.
7. Teamwork Projects
Known for its “easy to use” funtionality, Teamwork Projects offers a wide range of features required to run a project successfully. Teamwork Projects help to enhance collaboration, transparency, and accountability of the user. Without using any complex lists or charts, Teamwork Projects surf all the information very easily. Similar to Trello, it uses Kanban Boards and lists. The integration is within the app which is very helpful.
The free tier of Teamwork Project is available with limited storage space for 5 users and 2 projects.
The paid version of the tool has different price plans For 5 users with 100GB storage space, 300 Projects, 50 users at $9/user/month.
The tool is also available in the Premium and Enterprise plan.
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
What is Project Quality Management and What are the Processes in Project Quality Management?
:
Project quality is the degree of excellence of the deliverables to meet the customers’ requirements and satisfaction. The project outcome should fulfill the suitability for its intended purpose. The common characteristics of project quality are:
- Consistency: The evenness in the performance and services are delivered in the same way to all the beneficiaries.
- Suitability: The quality of being an appropriate choice to perform a task
- Completeness: The quality of finishing the specified task to meet the project scope.
- Sustainability: The ability to be maintained at a certain level.
- Functionality: The purpose of the task or activity to be fulfilled
- Reliability: The measure of being trust-worthy
- Performance: The act of performing a task or project activity.
- Timeliness: The measure to finish the project task in the allotted time.
The quality of the project is defined in the following terms:
- Validation: The assurance to meet the satisfactory results.
- Verification: The compliance required to meet project requirements.
- Precision: The condition of being exact.
- Accuracy: The degree or measure of the closeness
- Tolerance: The range of the acceptable results
Six Sigma and Lean Six Sigma are implemented in an organization to maintain the desired quality. Elimination of errors and continuous improvement is the main aim of implementing Lean Six Sigma.
There are many quality management software in the market to maintain the quality of the organization.
According to Transparency Market Research,
“Quality Management Software Market to Rise at a Stellar 13.20% CAGR, with Rising Demand for Maintaining Product Quality”.
What is Project Quality Management?
Project Quality Management is a continuous process to prevent, avoid and fix the poor quality issue in order to meet or exceed customer satisfaction. The performance of an organization is measured, monitored and controlled through quality policies, standards, guidelines, and procedures.
Project Quality Management is important due to the following reasons:
- Customer satisfaction
- Consistent performance
- Higher efficiency
- Enhance understanding between the internal processes
- Risk Reduction at an early stage
- References to secure other projects
Project Quality Management is one of the 10 knowledge areas of project management.
What are the processes in Project Quality Management?
There are three processes involved in Project Quality Management in three phases: Planning, Execution, and Monitoring and Controlling.
Plan Quality Management process
In order to maintain the desired quality, inspecting the quality is not the only solution. Preventing poor quality issues through effective planning and foresight is a regular practice in the organization. Plan Quality Management is the process of identifying the quality requirements and quality standards relevant to the project output. The quality plan is developed in such a way that it does not affect project scope, time and cost.
The document of a set of quality standards is prepared for each project's activities. The methodology used, the resource assigned, the cost and the time allocated are the major factors affecting quality.
There are several tools used to plan the quality process. There are some tools used for both planning and controlling quality:
- Cause and Effect diagram – helps to find the various factors related to the potential problems.
- Flowchart – Displays the logical steps in the project and various elements related to the system. Used to analyze the potential problems.
- Pareto Diagram – Used to identify the frequent small problems causing the big problem. The graph is used to define the percentage of defects against the number of causes.
- Histogram – Used to identify common problems.
- Control chart – Determines whether the cost and schedule are within statistical control
- Scatter diagram – tracks two variables and determines their relationship.
Manage Quality process
Manage Quality is the process of managing all the project activities according to the Quality Management plan while executing. To manage the quality, the following inputs are required
- Project Management Plan
- Project Documents like Lessons Learned, Quality Metrics
- Organizational Process Assets
The tools and techniques used to manage the quality are:
- Data Gathering - Checklists
- Data Analysis- Process Analysis, Root Cause Analysis
- Decision Making- Multi-Criteria Decision Analysis
- Data Representation- Histogram, graphs, and flowcharts
- Audits- Determining if the project activities comply with organizational policies, procedures, and processes.
- Design for X- Set of technical guidelines
- Problem-Solving- Solved through set of solutions
- Quality Improvement Methods- Plan-Do-Check-Act (PDCA) cycle or Six Sigma
The output of managing the quality process is:
- Quality reports
- Test and evaluation documents
- Change Requests
- Project Management Plan Updates
- Project Document Updates
The main objective of managing the quality process is to integrate all the quality policies in the project activities to maintain the Quality Plan Management.
Control Quality Process
The Control Quality Process is the process of inspecting and verifying the executed project activities according to quality management. The main objective of this process is to ensure the project output is correct, complete and meet the expectations of the customer and the quality plan. This process also includes the documentation of results obtained during the control quality process.
To manage the quality, the following inputs are required
- Project Management Plan
- Project Documents like Lessons Learned, Quality Metrics
- Approved change requests
- Deliverables
- Work Performance data
- Enterprise Environmental Factors
- Organizational Process Assets
The outputs of the Perform Quality Control process are:
- Measurements
- Validated changes
- Updates to the project management plan and project documents
- Change requests
- Lessons learned
- Validated deliverables
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
:
Project quality is the degree of excellence of the deliverables to meet the customers’ requirements and satisfaction. The project outcome should fulfill the suitability for its intended purpose. The common characteristics of project quality are:
- Consistency: The evenness in the performance and services are delivered in the same way to all the beneficiaries.
- Suitability: The quality of being an appropriate choice to perform a task
- Completeness: The quality of finishing the specified task to meet the project scope.
- Sustainability: The ability to be maintained at a certain level.
- Functionality: The purpose of the task or activity to be fulfilled
- Reliability: The measure of being trust-worthy
- Performance: The act of performing a task or project activity.
- Timeliness: The measure to finish the project task in the allotted time.
The quality of the project is defined in the following terms:
- Validation: The assurance to meet the satisfactory results.
- Verification: The compliance required to meet project requirements.
- Precision: The condition of being exact.
- Accuracy: The degree or measure of the closeness
- Tolerance: The range of the acceptable results
Six Sigma and Lean Six Sigma are implemented in an organization to maintain the desired quality. Elimination of errors and continuous improvement is the main aim of implementing Lean Six Sigma.
There are many quality management software in the market to maintain the quality of the organization.
According to Transparency Market Research,
“Quality Management Software Market to Rise at a Stellar 13.20% CAGR, with Rising Demand for Maintaining Product Quality”.
What is Project Quality Management?
Project Quality Management is a continuous process to prevent, avoid and fix the poor quality issue in order to meet or exceed customer satisfaction. The performance of an organization is measured, monitored and controlled through quality policies, standards, guidelines, and procedures.
Project Quality Management is important due to the following reasons:
- Customer satisfaction
- Consistent performance
- Higher efficiency
- Enhance understanding between the internal processes
- Risk Reduction at an early stage
- References to secure other projects
Project Quality Management is one of the 10 knowledge areas of project management.
What are the processes in Project Quality Management?
There are three processes involved in Project Quality Management in three phases: Planning, Execution, and Monitoring and Controlling.

Plan Quality Management process
In order to maintain the desired quality, inspecting the quality is not the only solution. Preventing poor quality issues through effective planning and foresight is a regular practice in the organization. Plan Quality Management is the process of identifying the quality requirements and quality standards relevant to the project output. The quality plan is developed in such a way that it does not affect project scope, time and cost.
The document of a set of quality standards is prepared for each project's activities. The methodology used, the resource assigned, the cost and the time allocated are the major factors affecting quality.
There are several tools used to plan the quality process. There are some tools used for both planning and controlling quality:
- Cause and Effect diagram – helps to find the various factors related to the potential problems.
- Flowchart – Displays the logical steps in the project and various elements related to the system. Used to analyze the potential problems.
- Pareto Diagram – Used to identify the frequent small problems causing the big problem. The graph is used to define the percentage of defects against the number of causes.
- Histogram – Used to identify common problems.
- Control chart – Determines whether the cost and schedule are within statistical control
- Scatter diagram – tracks two variables and determines their relationship.
Manage Quality process
Manage Quality is the process of managing all the project activities according to the Quality Management plan while executing. To manage the quality, the following inputs are required
- Project Management Plan
- Project Documents like Lessons Learned, Quality Metrics
- Organizational Process Assets
The tools and techniques used to manage the quality are:
- Data Gathering - Checklists
- Data Analysis- Process Analysis, Root Cause Analysis
- Decision Making- Multi-Criteria Decision Analysis
- Data Representation- Histogram, graphs, and flowcharts
- Audits- Determining if the project activities comply with organizational policies, procedures, and processes.
- Design for X- Set of technical guidelines
- Problem-Solving- Solved through set of solutions
- Quality Improvement Methods- Plan-Do-Check-Act (PDCA) cycle or Six Sigma
The output of managing the quality process is:
- Quality reports
- Test and evaluation documents
- Change Requests
- Project Management Plan Updates
- Project Document Updates
The main objective of managing the quality process is to integrate all the quality policies in the project activities to maintain the Quality Plan Management.
Control Quality Process
The Control Quality Process is the process of inspecting and verifying the executed project activities according to quality management. The main objective of this process is to ensure the project output is correct, complete and meet the expectations of the customer and the quality plan. This process also includes the documentation of results obtained during the control quality process.
To manage the quality, the following inputs are required
- Project Management Plan
- Project Documents like Lessons Learned, Quality Metrics
- Approved change requests
- Deliverables
- Work Performance data
- Enterprise Environmental Factors
- Organizational Process Assets
The outputs of the Perform Quality Control process are:
- Measurements
- Validated changes
- Updates to the project management plan and project documents
- Change requests
- Lessons learned
- Validated deliverables
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
What is Project Quality Management and What are the Processes in Project Quality Management?
:
Project quality is the degree of excellence of the deliverables to meet the customers’ requirements and satisfaction. The project outcome should fulfill the suitability for its intended purpose. The common characteristics of project quality are:
- Consistency: The evenness in the performance and services are delivered in the same way to all the beneficiaries.
- Suitability: The quality of being an appropriate choice to perform a task
- Completeness: The quality of finishing the specified task to meet the project scope.
- Sustainability: The ability to be maintained at a certain level.
- Functionality: The purpose of the task or activity to be fulfilled
- Reliability: The measure of being trust-worthy
- Performance: The act of performing a task or project activity.
- Timeliness: The measure to finish the project task in the allotted time.
The quality of the project is defined in the following terms:
- Validation: The assurance to meet the satisfactory results.
- Verification: The compliance required to meet project requirements.
- Precision: The condition of being exact.
- Accuracy: The degree or measure of the closeness
- Tolerance: The range of the acceptable results
Six Sigma and Lean Six Sigma are implemented in an organization to maintain the desired quality. Elimination of errors and continuous improvement is the main aim of implementing Lean Six Sigma.
There are many quality management software in the market to maintain the quality of the organization.
According to Transparency Market Research,
“Quality Management Software Market to Rise at a Stellar 13.20% CAGR, with Rising Demand for Maintaining Product Quality”.
What is Project Quality Management?
Project Quality Management is a continuous process to prevent, avoid and fix the poor quality issue in order to meet or exceed customer satisfaction. The performance of an organization is measured, monitored and controlled through quality policies, standards, guidelines, and procedures.
Project Quality Management is important due to the following reasons:
- Customer satisfaction
- Consistent performance
- Higher efficiency
- Enhance understanding between the internal processes
- Risk Reduction at an early stage
- References to secure other projects
Project Quality Management is one of the 10 knowledge areas of project management.
What are the processes in Project Quality Management?
There are three processes involved in Project Quality Management in three phases: Planning, Execution, and Monitoring and Controlling.

Plan Quality Management process
In order to maintain the desired quality, inspecting the quality is not the only solution. Preventing poor quality issues through effective planning and foresight is a regular practice in the organization. Plan Quality Management is the process of identifying the quality requirements and quality standards relevant to the project output. The quality plan is developed in such a way that it does not affect project scope, time and cost.
The document of a set of quality standards is prepared for each project's activities. The methodology used, the resource assigned, the cost and the time allocated are the major factors affecting quality.
There are several tools used to plan the quality process. There are some tools used for both planning and controlling quality:
- Cause and Effect diagram – helps to find the various factors related to the potential problems.
- Flowchart – Displays the logical steps in the project and various elements related to the system. Used to analyze the potential problems.
- Pareto Diagram – Used to identify the frequent small problems causing the big problem. The graph is used to define the percentage of defects against the number of causes.
- Histogram – Used to identify common problems.
- Control chart – Determines whether the cost and schedule are within statistical control
- Scatter diagram – tracks two variables and determines their relationship.
Manage Quality process
Manage Quality is the process of managing all the project activities according to the Quality Management plan while executing. To manage the quality, the following inputs are required
- Project Management Plan
- Project Documents like Lessons Learned, Quality Metrics
- Organizational Process Assets
The tools and techniques used to manage the quality are:
- Data Gathering - Checklists
- Data Analysis- Process Analysis, Root Cause Analysis
- Decision Making- Multi-Criteria Decision Analysis
- Data Representation- Histogram, graphs, and flowcharts
- Audits- Determining if the project activities comply with organizational policies, procedures, and processes.
- Design for X- Set of technical guidelines
- Problem-Solving- Solved through set of solutions
- Quality Improvement Methods- Plan-Do-Check-Act (PDCA) cycle or Six Sigma
The output of managing the quality process is:
- Quality reports
- Test and evaluation documents
- Change Requests
- Project Management Plan Updates
- Project Document Updates
The main objective of managing the quality process is to integrate all the quality policies in the project activities to maintain the Quality Plan Management.
Control Quality Process
The Control Quality Process is the process of inspecting and verifying the executed project activities according to quality management. The main objective of this process is to ensure the project output is correct, complete and meet the expectations of the customer and the quality plan. This process also includes the documentation of results obtained during the control quality process.
To manage the quality, the following inputs are required
- Project Management Plan
- Project Documents like Lessons Learned, Quality Metrics
- Approved change requests
- Deliverables
- Work Performance data
- Enterprise Environmental Factors
- Organizational Process Assets
The outputs of the Perform Quality Control process are:
- Measurements
- Validated changes
- Updates to the project management plan and project documents
- Change requests
- Lessons learned
- Validated deliverables
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
:
Project quality is the degree of excellence of the deliverables to meet the customers’ requirements and satisfaction. The project outcome should fulfill the suitability for its intended purpose. The common characteristics of project quality are:
- Consistency: The evenness in the performance and services are delivered in the same way to all the beneficiaries.
- Suitability: The quality of being an appropriate choice to perform a task
- Completeness: The quality of finishing the specified task to meet the project scope.
- Sustainability: The ability to be maintained at a certain level.
- Functionality: The purpose of the task or activity to be fulfilled
- Reliability: The measure of being trust-worthy
- Performance: The act of performing a task or project activity.
- Timeliness: The measure to finish the project task in the allotted time.
The quality of the project is defined in the following terms:
- Validation: The assurance to meet the satisfactory results.
- Verification: The compliance required to meet project requirements.
- Precision: The condition of being exact.
- Accuracy: The degree or measure of the closeness
- Tolerance: The range of the acceptable results
Six Sigma and Lean Six Sigma are implemented in an organization to maintain the desired quality. Elimination of errors and continuous improvement is the main aim of implementing Lean Six Sigma.
There are many quality management software in the market to maintain the quality of the organization.
According to Transparency Market Research,
“Quality Management Software Market to Rise at a Stellar 13.20% CAGR, with Rising Demand for Maintaining Product Quality”.
What is Project Quality Management?
Project Quality Management is a continuous process to prevent, avoid and fix the poor quality issue in order to meet or exceed customer satisfaction. The performance of an organization is measured, monitored and controlled through quality policies, standards, guidelines, and procedures.
Project Quality Management is important due to the following reasons:
- Customer satisfaction
- Consistent performance
- Higher efficiency
- Enhance understanding between the internal processes
- Risk Reduction at an early stage
- References to secure other projects
Project Quality Management is one of the 10 knowledge areas of project management.
What are the processes in Project Quality Management?
There are three processes involved in Project Quality Management in three phases: Planning, Execution, and Monitoring and Controlling.

Plan Quality Management process
In order to maintain the desired quality, inspecting the quality is not the only solution. Preventing poor quality issues through effective planning and foresight is a regular practice in the organization. Plan Quality Management is the process of identifying the quality requirements and quality standards relevant to the project output. The quality plan is developed in such a way that it does not affect project scope, time and cost.
The document of a set of quality standards is prepared for each project's activities. The methodology used, the resource assigned, the cost and the time allocated are the major factors affecting quality.
There are several tools used to plan the quality process. There are some tools used for both planning and controlling quality:
- Cause and Effect diagram – helps to find the various factors related to the potential problems.
- Flowchart – Displays the logical steps in the project and various elements related to the system. Used to analyze the potential problems.
- Pareto Diagram – Used to identify the frequent small problems causing the big problem. The graph is used to define the percentage of defects against the number of causes.
- Histogram – Used to identify common problems.
- Control chart – Determines whether the cost and schedule are within statistical control
- Scatter diagram – tracks two variables and determines their relationship.
Manage Quality process
Manage Quality is the process of managing all the project activities according to the Quality Management plan while executing. To manage the quality, the following inputs are required
- Project Management Plan
- Project Documents like Lessons Learned, Quality Metrics
- Organizational Process Assets
The tools and techniques used to manage the quality are:
- Data Gathering - Checklists
- Data Analysis- Process Analysis, Root Cause Analysis
- Decision Making- Multi-Criteria Decision Analysis
- Data Representation- Histogram, graphs, and flowcharts
- Audits- Determining if the project activities comply with organizational policies, procedures, and processes.
- Design for X- Set of technical guidelines
- Problem-Solving- Solved through set of solutions
- Quality Improvement Methods- Plan-Do-Check-Act (PDCA) cycle or Six Sigma
The output of managing the quality process is:
- Quality reports
- Test and evaluation documents
- Change Requests
- Project Management Plan Updates
- Project Document Updates
The main objective of managing the quality process is to integrate all the quality policies in the project activities to maintain the Quality Plan Management.
Control Quality Process
The Control Quality Process is the process of inspecting and verifying the executed project activities according to quality management. The main objective of this process is to ensure the project output is correct, complete and meet the expectations of the customer and the quality plan. This process also includes the documentation of results obtained during the control quality process.
To manage the quality, the following inputs are required
- Project Management Plan
- Project Documents like Lessons Learned, Quality Metrics
- Approved change requests
- Deliverables
- Work Performance data
- Enterprise Environmental Factors
- Organizational Process Assets
The outputs of the Perform Quality Control process are:
- Measurements
- Validated changes
- Updates to the project management plan and project documents
- Change requests
- Lessons learned
- Validated deliverables
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Top 10 Leadership Skills and Traits of Successful Project Managers
Here is the list of leadership qualities and traits a successful project manager possess:
- Confidence
- Decision making
- Honesty and integrity
- Communication
- Vision
- Delegation
- Empathy
- Resilience
- Emotional Intelligence
- Accountability
The success of the project is highly dependent on project managers. Behavioral traits are very important when it comes to managing projects and people. Nowadays, projects are complex and the team size is bigger. Leadership attributes, traits, characteristics, and skills can be attained through practice. According to Project Management Talent Triangle, leadership is one of the most important skills sought by employers.
According to CIO,
PMI stated that,
“By 2020, reports estimate that there will be 700,000 new project management jobs in the United States and 66 percent of organizations rate leadership skills as the most valuable trait of a successful PM.”
Here are the list of leadership qualities and traits a successful project manager possess:
- Confidence
- Decision making
- Honesty and integrity
- Communication
- Vision
- Delegation
- Empathy
- Resilience
- Emotional Intelligence
- Accountability
1. Confidence
Confidence is the most important skill to lead a team. The more you believe in your abilities as a project manager the more you feel confident. In order to empower a team, confidence in yourself and the team is very essential. The productivity of the team is higher when you guide them with confidence. The ways to build confidence as a project manager are:
- Empower your knowledge
- Take Project Management Professional Certification
- Prepare yourself before going to any discussion
- Exude confidence and exhibit positive body language
The project manager with great confidence can address the problems in an effective way. The flow of the project becomes smooth with a confident project manager.
2. Decision making
The decision-making abilities of a project manager make a direct impact on the project. Successful project managers possess high decision-making skills. It is not always possible to make the best decision. A good leader takes responsibility for the decision and is accountable.
To be a strong decision-maker, you must possess high knowledge about the subject and be able to see the consequences of the decision made.
3. Honesty and integrity
Honesty and Integrity are the bottom line of ethics. You are recognized as an honest professional when you adhere to both ethical values and individual morality. Integrity means honesty with strong moral values. It requires professionals to always be clear and truthful. Honesty and integrity build trust between the stakeholders which makes the project highly successful.
“The supreme quality of leadership is unquestionably integrity”
-Dwight.D.Eisenhower
Integrity involves:
- Apologizing for the mistakes
- When issues are unclear, giving them a benefit of doubt
- Appreciating time.
4. Communication
Effective communication skills are very important to run the project smoothly. The successful project manager clearly communicates the vision, goals, guidelines, expectations to the other stakeholders.
Listening is the most important part of communication. Being able to speak effectively is the foundation of effective leadership.
According to Forbes Insights 2010 Strategic Initiatives report,
- 88% of the strategists say that communications are critical to the success of their strategic initiatives
- 46% that communications are an integral and active component of the strategic planning and execution process.
The list of tools for effective communication are:
- Project Management Tools: Proofhub
- Real-Time Chat Tools: Microsoft Teams, HipChat
- Voice and Video Conferencing tools: Zoom, Skype
- Document Collaboration tools: Office365, G Suite
- Internal Communication Tools: Jive, Yammer
5. Vision
Successful project managers have great vision and purpose at the initiation stage of the project. They make their team members visualize their vision and make them understand the strategy and action plan to reach the goal.
When a project manager implements ideas, the chances of failure also exist. A good leader understands the changes, practices adaptability and becomes agile to reach the goal.
The project managers with great visionary skills will ensure the team members share the same goal and abe to see the bigger picture.
6. Delegation
Delegation is when you share the responsibility to perform a specific task. It is one of the important qualities a project manager possesses. Based on the positive attitude and willingness, the project manager selects the people to delegate the task.
Project Manager delegates the task for two reasons:
- To make the best use of team
- To be able to focus on the other tasks based on priority
The successful project manager picks the right person, matches the requirements, sets realistic goals, gives all the necessary information and delegates the task.
7. Empathy
The successful project manager possesses the ability to understand the team member’s aspirations, hopes, expectations, and problems. The dictatorial style of management doesn’t hold good in the current era of project management. A good leader has open-mindedness to understand the situation and not just be a nice person. Empathy enables a project manager to:
- Build a strong bond with team members
- Communicate work strategies effectively
- Make team members win the trust
- Be creative
8. Resilience
Resilience is a positive attitude of project managers to lead and manage the team no matter the circumstances. A great leader focuses on solutions rather than problems.
Resilience is a leadership quality that comes with experience. The changes are uncertain. Project managers with resilience will manage the change effectively with a positive attitude and are generally resourceful and agile in nature. The project managers exhibit resilience when the project goes through change and uncertainties.
9. Emotional Intelligence
Emotions can influence many aspects of leadership traits such as communication and decision-making skills. Projects involve a lot of face to face communications and discussions. In order to make team members accept the ideas of leaders, project managers should connect with team members through emotional intelligence. The ability to sense and understand emotions and act accordingly in order to manage the team with emotions and empathy is called emotional intelligence in project management.
According to HR Daily,
According to HR managers, the greatest benefit of hiring an employee with the highest emotional intelligence is increasing morale.
10. Accountability
Good leaders make sure the team members working are accountable for what they are doing. Making team members accountable creates a sense of responsibility among themselves to perform better.
“A good leader takes little more than his share of the blame and little less than his share of the credit.”
-Arnold H Glaso
Being accountable is the best way to build trust with team members.
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
Here is the list of leadership qualities and traits a successful project manager possess:
- Confidence
- Decision making
- Honesty and integrity
- Communication
- Vision
- Delegation
- Empathy
- Resilience
- Emotional Intelligence
- Accountability
The success of the project is highly dependent on project managers. Behavioral traits are very important when it comes to managing projects and people. Nowadays, projects are complex and the team size is bigger. Leadership attributes, traits, characteristics, and skills can be attained through practice. According to Project Management Talent Triangle, leadership is one of the most important skills sought by employers.
According to CIO,
PMI stated that,
“By 2020, reports estimate that there will be 700,000 new project management jobs in the United States and 66 percent of organizations rate leadership skills as the most valuable trait of a successful PM.”
Here are the list of leadership qualities and traits a successful project manager possess:
- Confidence
- Decision making
- Honesty and integrity
- Communication
- Vision
- Delegation
- Empathy
- Resilience
- Emotional Intelligence
- Accountability
1. Confidence
Confidence is the most important skill to lead a team. The more you believe in your abilities as a project manager the more you feel confident. In order to empower a team, confidence in yourself and the team is very essential. The productivity of the team is higher when you guide them with confidence. The ways to build confidence as a project manager are:
- Empower your knowledge
- Take Project Management Professional Certification
- Prepare yourself before going to any discussion
- Exude confidence and exhibit positive body language
The project manager with great confidence can address the problems in an effective way. The flow of the project becomes smooth with a confident project manager.
2. Decision making
The decision-making abilities of a project manager make a direct impact on the project. Successful project managers possess high decision-making skills. It is not always possible to make the best decision. A good leader takes responsibility for the decision and is accountable.
To be a strong decision-maker, you must possess high knowledge about the subject and be able to see the consequences of the decision made.
3. Honesty and integrity
Honesty and Integrity are the bottom line of ethics. You are recognized as an honest professional when you adhere to both ethical values and individual morality. Integrity means honesty with strong moral values. It requires professionals to always be clear and truthful. Honesty and integrity build trust between the stakeholders which makes the project highly successful.
“The supreme quality of leadership is unquestionably integrity”
-Dwight.D.Eisenhower
Integrity involves:
- Apologizing for the mistakes
- When issues are unclear, giving them a benefit of doubt
- Appreciating time.
4. Communication
Effective communication skills are very important to run the project smoothly. The successful project manager clearly communicates the vision, goals, guidelines, expectations to the other stakeholders.
Listening is the most important part of communication. Being able to speak effectively is the foundation of effective leadership.
According to Forbes Insights 2010 Strategic Initiatives report,
- 88% of the strategists say that communications are critical to the success of their strategic initiatives
- 46% that communications are an integral and active component of the strategic planning and execution process.
The list of tools for effective communication are:
- Project Management Tools: Proofhub
- Real-Time Chat Tools: Microsoft Teams, HipChat
- Voice and Video Conferencing tools: Zoom, Skype
- Document Collaboration tools: Office365, G Suite
- Internal Communication Tools: Jive, Yammer
5. Vision
Successful project managers have great vision and purpose at the initiation stage of the project. They make their team members visualize their vision and make them understand the strategy and action plan to reach the goal.
When a project manager implements ideas, the chances of failure also exist. A good leader understands the changes, practices adaptability and becomes agile to reach the goal.
The project managers with great visionary skills will ensure the team members share the same goal and abe to see the bigger picture.
6. Delegation
Delegation is when you share the responsibility to perform a specific task. It is one of the important qualities a project manager possesses. Based on the positive attitude and willingness, the project manager selects the people to delegate the task.
Project Manager delegates the task for two reasons:
- To make the best use of team
- To be able to focus on the other tasks based on priority
The successful project manager picks the right person, matches the requirements, sets realistic goals, gives all the necessary information and delegates the task.
7. Empathy
The successful project manager possesses the ability to understand the team member’s aspirations, hopes, expectations, and problems. The dictatorial style of management doesn’t hold good in the current era of project management. A good leader has open-mindedness to understand the situation and not just be a nice person. Empathy enables a project manager to:
- Build a strong bond with team members
- Communicate work strategies effectively
- Make team members win the trust
- Be creative
8. Resilience
Resilience is a positive attitude of project managers to lead and manage the team no matter the circumstances. A great leader focuses on solutions rather than problems.
Resilience is a leadership quality that comes with experience. The changes are uncertain. Project managers with resilience will manage the change effectively with a positive attitude and are generally resourceful and agile in nature. The project managers exhibit resilience when the project goes through change and uncertainties.
9. Emotional Intelligence
Emotions can influence many aspects of leadership traits such as communication and decision-making skills. Projects involve a lot of face to face communications and discussions. In order to make team members accept the ideas of leaders, project managers should connect with team members through emotional intelligence. The ability to sense and understand emotions and act accordingly in order to manage the team with emotions and empathy is called emotional intelligence in project management.
According to HR Daily,
According to HR managers, the greatest benefit of hiring an employee with the highest emotional intelligence is increasing morale.
10. Accountability
Good leaders make sure the team members working are accountable for what they are doing. Making team members accountable creates a sense of responsibility among themselves to perform better.
“A good leader takes little more than his share of the blame and little less than his share of the credit.”
-Arnold H Glaso
Being accountable is the best way to build trust with team members.
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve? Let us know your thoughts in the 'Comments' section below. Thank you.
What is Data Science and Its Importance in 2021
What is Data Science and Its Importance in 2021
Introduction
Given the vast volumes of data created nowadays, data science is important and is a crucial aspect of any industry. Data science is currently one of the most hotly disputed subjects in the industry. Its popularity has expanded over time, and businesses have begun to use data science approaches to expand their operations and improve customer happiness.
This article will discuss the importance of Data Science in the year 2021 by defining Data Science, Why it is helpful, what is a Data Scientist, ways in which data science can add value to the business, Applications of Data Science and finally, Data Science as a Career.
What is Data Science?
Data science is a field of study that works with large amounts of facts and uses cutting-edge tools and techniques to uncover hidden patterns, extract useful data, and make business decisions. To create prediction models, data scientists use complicated machine learning algorithms. Data for analysis can come from a variety of sources and be in a variety of formats.
In other words, data science is important as it is the process of extracting knowledge from data collected through various approaches. As a data scientist, you take a difficult business problem, gather information, turn it into data, and then utilise that data to solve it.
Why is Data Science Helpful?
Any organization's data is a valuable asset. It assists businesses in better understanding and improving their processes, resulting in time and cost savings. Waste of time and money, such as a poor advertising decision, depletes resources and has a negative influence on a company. Businesses can reduce waste by examining the success of various marketing channels and focusing on those that provide the best return on investment. As a result, a business can produce more leads without spending more money on advertising.
Data is pointless until it is transformed into useful information. Mining massive datasets containing structured and unstructured data and uncovering hidden patterns to derive relevant insights is what Data Science is all about. The value of Data Science can be seen in its numerous applications, which vary from simple tasks like asking Siri or Alexa for recommendations to more complicated ones like piloting a self-driving car. Better decision-making, predictive analysis, and pattern finding are all aided by data science or data-driven science. It's beneficial because:
- By asking the appropriate questions, you can determine the root cause of an issue.
- Conduct an exploratory analysis of the data.
- Various algorithms are used to model the data.
- Graphs, dashboards, and other visual aids can be used to communicate and visualise the results.
In practice, data science is already assisting the airline sector in predicting flight interruptions to help both airlines and customers avoid misery. Airlines may improve their operations in a variety of ways with the help of data science, including:
- Plan your itineraries and decide whether to fly direct or connect.
- To predict flight delays, create predictive analytics algorithms.
- Provide clients with customised promotional offers depending on their booking patterns.
- Choose which plane class to buy for better overall performance.
Data science is important in every aspect of digital as well as offline recurring data methods. Its existence has solved major flaws in human society and continues to do so.
Data Science Prerequisites
Here are some technical terms you should be familiar with before diving into the world of data science.
1. Machine Learning
The backbone of data science is machine learning. Data scientists must have a strong understanding of machine learning (ML) as well as a fundamental understanding of statistics.
2. Statistics
The foundation of data science is statistics. With a firm grasp of statistics, you can extract more intelligence and produce more relevant results.
3. Modelling
Based on what you already know about the data, mathematical models allow you to make quick calculations and predictions. Modelling is another aspect of machine learning, and it entails determining which algorithm is best for solving a specific problem and how to train these models.
4. Databases
You must grasp how databases function, how to maintain them, and how to extract data from them in order to be a competent data scientist.
5. Programming
A successful data science project necessitates some level of programming. Python and R are the most widely used programming languages. Python is particularly popular because it is simple to learn and supports a variety of data science and machine learning libraries.
What is a Data Scientist?
Data scientists are particularly interested in fraud, particularly online fraud. Data scientists use their abilities to design algorithms to detect and prevent fraud. Data scientists are employed in a wide range of fields. Each is critical to problem-solving and necessitates specialised knowledge. Data capture, preparation, mining and modelling, and model maintenance are among these fields. Data scientists take raw data and convert it into a wealth of knowledge using machine learning algorithms to provide answers to questions posed by businesses.
A data scientist examines corporate data in order to derive actionable insights. To put it another way, a data scientist solves business challenges by following a set of procedures, which include:
- Obtain data from a variety of sources, including company data, public data, and so on.
- Process raw data and turn it into an analysis-ready format.
- Feed the data into the analytic system, which could be a machine learning algorithm or a statistical model.
- Prepare the findings and conclusions to be shared with the relevant parties.
Five Ways Data Science can Add value to Businesses in 2021
1. Providing management and officers with the tools they need to make better decisions.
By ensuring that the staff's analytics capabilities are maximised, an experienced data scientist is likely to be a valued advisor and strategic partner to the organization's higher management. Through measuring, tracking, and documenting performance metrics and other information, a data scientist conveys and illustrates the value of the institution's data to support improved decision-making processes across the entire company.
2. Trends are used to guide actions, which in turn aid in the definition of goals.
A data scientist evaluates and explores an organization's data before recommending and prescribing specific measures that would help the institution enhance its performance, better engage customers, and increase profitability.
3. Encouraging Employees to Adopt Best Practices and Concentrate on Critical Issues
One of a data scientist's responsibilities is to guarantee that the company's analytics product is well-known and understood by its employees. They set the team up for success by demonstrating how to use the system effectively to extract insights and drive action. After the team has a good understanding of the product's capabilities, they may work on solving significant business problems.
4. Locating Possibilities
Incorporating data science evaluates existing procedures and assumptions while interacting with the organization's present analytics system in order to build new methodologies and analytical algorithms. Data science improves the value obtained from the organization's data on a continuous basis.
5. Target Audiences: Identifying and Refining
Most businesses will collect consumer data from a variety of sources, including Google Analytics and customer surveys. However, data is useless if it isn't used properly, such as to identify demographics. The value of data science is predicated on the capacity to connect existing data that isn't always relevant on its own with other data points to develop insights that a company can use to learn more about its customers and audience.
A data scientist can assist in the precise identification of significant groups through a thorough investigation of diverse data sources. Organizations may personalise services and goods to specific consumer groups and increase profit margins with this in-depth knowledge.
Lifecycle of Data Science projects
A full overview of the stages involved in a data science project's lifetime can be found in the following:
Study of the Concept
The idea research is the first step in every data science project. The purpose of this step is to figure out what's wrong by looking at the business model. Let's imagine you're attempting to forecast the price of a 1.35-carat diamond. In this situation, you must first learn the industry's vocabulary as well as the business challenge, and then gather enough relevant data about the industry.
Preparation of Data
Data preparation is the most important part of the data science lifecycle because raw data may not be usable. A data scientist must first look over the data to see if there are any gaps or data that isn't useful. Several steps must be completed during this procedure, including:
- Integration of data: Remove any redundancy from the dataset by resolving any conflicts.
- Transformation of data: ETL (extract, transform, load) procedures can be used to normalise, transform, and aggregate data.
- Reduction of data: Reduce the size of data without sacrificing quality or outcome by employing a variety of tactics.
- Cleaning of data: Fill in missing numbers and smooth out noisy data to fix inconsistencies.
Model Preparation
After you've cleaned up the data, you'll need to pick a model that fits your needs. Is it a regression problem or a classification problem? The model you choose must reflect the nature of the problem. Exploratory Data Examination (EDA) is also used in this step to give a more in-depth analysis of the data and to better understand the link between the variables. Histograms, box plots, trend analysis, and other EDA techniques are employed.
Model Construction
Building the model is the next step in the lifecycle. You can alter the data with various analytical tools and approaches in order to ‘discover' important information.
Communication
The next stage is to obtain the study's major findings and communicate them to the stakeholders. A good scientist should be able to explain his findings to a business audience, outlining the processes required to solve the problem in detail.
Operationalize
They are launched once all parties have agreed to the findings. Stakeholders also receive final reports, code, and technical papers during this phase.
Applications of Data Science
Data science is now being used in practically every business such as:
Gaming
Data science is currently being used to build video and computer games, which has elevated the gaming experience to new heights.
Recognition of images
One of the most prominent data science applications is detecting objects in photos and identifying patterns in them.
Healthcare
Data science is being used by healthcare companies to develop advanced medical tools that can identify and cure ailments.
Systems of Recommendation
Netflix and Amazon make movie and product suggestions based on your viewing, purchasing, and browsing habits on their platforms.
Logistics
Organisations employ data science to optimise routes in order to assure faster product delivery and increase operational efficiency.
Detection of Fraud
Data science and related algorithms are used by banking and financial institutions to detect fraudulent activities.
Data Science as a Profession
Data science and associated disciplines have seen a large increase in job openings over the previous five years. According to the 2021 forecast, the number one job in the United States is data scientist. Data Scientist, Machine Learning Engineer, Data Consultant, Data Analyst, and others are some of the significant career roles.
Conclusion
Data is essential for any company because it allows them to make decisions based on trends, statistics, and facts. Because of the importance of data, data science is important as it has evolved into a multi-disciplinary profession. To extract insight from a large amount of data, it employs scientific methodologies, frameworks, algorithms, and procedures. Data science is the backbone of any enterprise these days, and current trends indicate that it will become much more important.
In the future decade, data will be the oil for businesses. Companies may now estimate future growth and assess potential dangers by incorporating data science techniques into their operations. Any company that can effectively use its data can benefit from data science. Data science is valuable to any organization in any industry, from statistics and insights throughout workflows and hiring new applicants to assist senior employees in making better-informed decisions.
We provide instructor-led classroom and instructor-led live online training across the globe. We also provide Corporate Training for enterprise workforce development.
Connect with us:
- Subscribe to our YouTube Channel
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
For more information about our professional certification training courses Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Read More
What is Data Science and Its Importance in 2021
Introduction
Given the vast volumes of data created nowadays, data science is important and is a crucial aspect of any industry. Data science is currently one of the most hotly disputed subjects in the industry. Its popularity has expanded over time, and businesses have begun to use data science approaches to expand their operations and improve customer happiness.
This article will discuss the importance of Data Science in the year 2021 by defining Data Science, Why it is helpful, what is a Data Scientist, ways in which data science can add value to the business, Applications of Data Science and finally, Data Science as a Career.
What is Data Science?
Data science is a field of study that works with large amounts of facts and uses cutting-edge tools and techniques to uncover hidden patterns, extract useful data, and make business decisions. To create prediction models, data scientists use complicated machine learning algorithms. Data for analysis can come from a variety of sources and be in a variety of formats.
In other words, data science is important as it is the process of extracting knowledge from data collected through various approaches. As a data scientist, you take a difficult business problem, gather information, turn it into data, and then utilise that data to solve it.
Why is Data Science Helpful?
Any organization's data is a valuable asset. It assists businesses in better understanding and improving their processes, resulting in time and cost savings. Waste of time and money, such as a poor advertising decision, depletes resources and has a negative influence on a company. Businesses can reduce waste by examining the success of various marketing channels and focusing on those that provide the best return on investment. As a result, a business can produce more leads without spending more money on advertising.
Data is pointless until it is transformed into useful information. Mining massive datasets containing structured and unstructured data and uncovering hidden patterns to derive relevant insights is what Data Science is all about. The value of Data Science can be seen in its numerous applications, which vary from simple tasks like asking Siri or Alexa for recommendations to more complicated ones like piloting a self-driving car. Better decision-making, predictive analysis, and pattern finding are all aided by data science or data-driven science. It's beneficial because:
- By asking the appropriate questions, you can determine the root cause of an issue.
- Conduct an exploratory analysis of the data.
- Various algorithms are used to model the data.
- Graphs, dashboards, and other visual aids can be used to communicate and visualise the results.
In practice, data science is already assisting the airline sector in predicting flight interruptions to help both airlines and customers avoid misery. Airlines may improve their operations in a variety of ways with the help of data science, including:
- Plan your itineraries and decide whether to fly direct or connect.
- To predict flight delays, create predictive analytics algorithms.
- Provide clients with customised promotional offers depending on their booking patterns.
- Choose which plane class to buy for better overall performance.
Data science is important in every aspect of digital as well as offline recurring data methods. Its existence has solved major flaws in human society and continues to do so.
Data Science Prerequisites
Here are some technical terms you should be familiar with before diving into the world of data science.
1. Machine Learning
The backbone of data science is machine learning. Data scientists must have a strong understanding of machine learning (ML) as well as a fundamental understanding of statistics.
2. Statistics
The foundation of data science is statistics. With a firm grasp of statistics, you can extract more intelligence and produce more relevant results.
3. Modelling
Based on what you already know about the data, mathematical models allow you to make quick calculations and predictions. Modelling is another aspect of machine learning, and it entails determining which algorithm is best for solving a specific problem and how to train these models.
4. Databases
You must grasp how databases function, how to maintain them, and how to extract data from them in order to be a competent data scientist.
5. Programming
A successful data science project necessitates some level of programming. Python and R are the most widely used programming languages. Python is particularly popular because it is simple to learn and supports a variety of data science and machine learning libraries.
What is a Data Scientist?
Data scientists are particularly interested in fraud, particularly online fraud. Data scientists use their abilities to design algorithms to detect and prevent fraud. Data scientists are employed in a wide range of fields. Each is critical to problem-solving and necessitates specialised knowledge. Data capture, preparation, mining and modelling, and model maintenance are among these fields. Data scientists take raw data and convert it into a wealth of knowledge using machine learning algorithms to provide answers to questions posed by businesses.
A data scientist examines corporate data in order to derive actionable insights. To put it another way, a data scientist solves business challenges by following a set of procedures, which include:
- Obtain data from a variety of sources, including company data, public data, and so on.
- Process raw data and turn it into an analysis-ready format.
- Feed the data into the analytic system, which could be a machine learning algorithm or a statistical model.
- Prepare the findings and conclusions to be shared with the relevant parties.
Five Ways Data Science can Add value to Businesses in 2021
1. Providing management and officers with the tools they need to make better decisions.
By ensuring that the staff's analytics capabilities are maximised, an experienced data scientist is likely to be a valued advisor and strategic partner to the organization's higher management. Through measuring, tracking, and documenting performance metrics and other information, a data scientist conveys and illustrates the value of the institution's data to support improved decision-making processes across the entire company.
2. Trends are used to guide actions, which in turn aid in the definition of goals.
A data scientist evaluates and explores an organization's data before recommending and prescribing specific measures that would help the institution enhance its performance, better engage customers, and increase profitability.
3. Encouraging Employees to Adopt Best Practices and Concentrate on Critical Issues
One of a data scientist's responsibilities is to guarantee that the company's analytics product is well-known and understood by its employees. They set the team up for success by demonstrating how to use the system effectively to extract insights and drive action. After the team has a good understanding of the product's capabilities, they may work on solving significant business problems.
4. Locating Possibilities
Incorporating data science evaluates existing procedures and assumptions while interacting with the organization's present analytics system in order to build new methodologies and analytical algorithms. Data science improves the value obtained from the organization's data on a continuous basis.
5. Target Audiences: Identifying and Refining
Most businesses will collect consumer data from a variety of sources, including Google Analytics and customer surveys. However, data is useless if it isn't used properly, such as to identify demographics. The value of data science is predicated on the capacity to connect existing data that isn't always relevant on its own with other data points to develop insights that a company can use to learn more about its customers and audience.
A data scientist can assist in the precise identification of significant groups through a thorough investigation of diverse data sources. Organizations may personalise services and goods to specific consumer groups and increase profit margins with this in-depth knowledge.
Lifecycle of Data Science projects
A full overview of the stages involved in a data science project's lifetime can be found in the following:
Study of the Concept
The idea research is the first step in every data science project. The purpose of this step is to figure out what's wrong by looking at the business model. Let's imagine you're attempting to forecast the price of a 1.35-carat diamond. In this situation, you must first learn the industry's vocabulary as well as the business challenge, and then gather enough relevant data about the industry.
Preparation of Data
Data preparation is the most important part of the data science lifecycle because raw data may not be usable. A data scientist must first look over the data to see if there are any gaps or data that isn't useful. Several steps must be completed during this procedure, including:
- Integration of data: Remove any redundancy from the dataset by resolving any conflicts.
- Transformation of data: ETL (extract, transform, load) procedures can be used to normalise, transform, and aggregate data.
- Reduction of data: Reduce the size of data without sacrificing quality or outcome by employing a variety of tactics.
- Cleaning of data: Fill in missing numbers and smooth out noisy data to fix inconsistencies.
Model Preparation
After you've cleaned up the data, you'll need to pick a model that fits your needs. Is it a regression problem or a classification problem? The model you choose must reflect the nature of the problem. Exploratory Data Examination (EDA) is also used in this step to give a more in-depth analysis of the data and to better understand the link between the variables. Histograms, box plots, trend analysis, and other EDA techniques are employed.
Model Construction
Building the model is the next step in the lifecycle. You can alter the data with various analytical tools and approaches in order to ‘discover' important information.
Communication
The next stage is to obtain the study's major findings and communicate them to the stakeholders. A good scientist should be able to explain his findings to a business audience, outlining the processes required to solve the problem in detail.
Operationalize
They are launched once all parties have agreed to the findings. Stakeholders also receive final reports, code, and technical papers during this phase.
Applications of Data Science
Data science is now being used in practically every business such as:
Gaming
Data science is currently being used to build video and computer games, which has elevated the gaming experience to new heights.
Recognition of images
One of the most prominent data science applications is detecting objects in photos and identifying patterns in them.
Healthcare
Data science is being used by healthcare companies to develop advanced medical tools that can identify and cure ailments.
Systems of Recommendation
Netflix and Amazon make movie and product suggestions based on your viewing, purchasing, and browsing habits on their platforms.
Logistics
Organisations employ data science to optimise routes in order to assure faster product delivery and increase operational efficiency.
Detection of Fraud
Data science and related algorithms are used by banking and financial institutions to detect fraudulent activities.
Data Science as a Profession
Data science and associated disciplines have seen a large increase in job openings over the previous five years. According to the 2021 forecast, the number one job in the United States is data scientist. Data Scientist, Machine Learning Engineer, Data Consultant, Data Analyst, and others are some of the significant career roles.
Conclusion
Data is essential for any company because it allows them to make decisions based on trends, statistics, and facts. Because of the importance of data, data science is important as it has evolved into a multi-disciplinary profession. To extract insight from a large amount of data, it employs scientific methodologies, frameworks, algorithms, and procedures. Data science is the backbone of any enterprise these days, and current trends indicate that it will become much more important.
In the future decade, data will be the oil for businesses. Companies may now estimate future growth and assess potential dangers by incorporating data science techniques into their operations. Any company that can effectively use its data can benefit from data science. Data science is valuable to any organization in any industry, from statistics and insights throughout workflows and hiring new applicants to assist senior employees in making better-informed decisions.
We provide instructor-led classroom and instructor-led live online training across the globe. We also provide Corporate Training for enterprise workforce development.
Connect with us:
- Subscribe to our YouTube Channel
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
For more information about our professional certification training courses Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Scrum Master Roles and Responsibilities
In this blog we cover the typical tasks, responsibilities, skills, problems, qualities, and benefits of the Scrum Master role in Scrum.
What is a scrum master?
Scrum Master is often the term used for this role, even by teams that do not explicitly follow Scrum. Other terms that are rarely used are iteration manager, agile coach, or team coach. The Scrum Master cleverly removes obstacles and distractions that could prevent the team from achieving its goals. This person is the connection between the Scrum Team and the people or teams outside of the Scrum Team. The Scrum Master is a service leader for the Scrum Team who helps the Scrum Team and its environment work together and interact to maximize the value delivered by the Scrum Team. Article - Scrum master roles and responsibilities will give you a brief knowledge about how Scrum Master works. Scrum Master is also responsible for helping people to understand Scrum theory, its practices, rules and values.

Imagesource - https://www.lucidchart.com/blog/scrum-master-skills-and-responsibilities
Skills defined for scrum master -
While there are no officially defined skill levels for Scrum Masters, there are different levels of experience in practice:
- Rotating scrum master - Members of a team rotate Scrum Master responsibilities (primarily administrative) among themselves on a sprint-by-sprint basis.
- Part time scrum master - In addition to other tasks on the same team, one person on the team assumes the Scrum Master tasks.
- Full time scrum master - The sole responsibility of an individual is to be a Scrum Master at one time or another. This model is the best for a team that is learning agilely.
- Full time scrum master with more than one team - This model is often used when a person's only responsibility is to be a Scrum Master, but they are working with more than one team.
- Agile Coach - A person does not have a specially assigned team, but works with several teams and only on certain needs.
Benefits as a scrum master
The overall benefit one expects from a Scrum Master in a team is to provide a self-organizing team with constant access to someone who has used Agile and especially Scrum in a different environment and can help the team find the best way to apply it. in your situation.
Another expected benefit is that the Scrum Master is someone who can address distractions, interruptions, and obstacles so that the rest of the team can focus on work to produce results that produce the desired result.
Common problems as a scrum master
While there are several advantages to being a Scrum Master, several problems arise from improper use of the role. These problems include:
- Suppose you can only slide project managers that are used to command and control the guide guide guide in a scrum Master role and expect it to be effective.
- Asking someone to fill the role of Scrum Master with no experience in an agile environment.
- Expect a Scrum Master's workload to be the same across teams, regardless of how long they have worked as a team, how they understand Agile values and principles, and what domain expertise they have.
- A well-functioning team will likely need much less training from a Scrum Master than a team that is new to working with Agile values and principles.
7 Key scrum master’s responsibilities
Despite the word "Master" in the title, the Scrum Master is not responsible for the project or the development team. Instead, a scrum masterpiece works with the product owner and the scrum team to refine and improve processes where it makes sense.
A Scrum Master role may include, but is not limited to, the following responsibilities.
- Teach Scrum practices and principles - To ensure that the work does not decrease the speed, an important role of Scrum Master is a mentor and a teacher to provide new employees and new team members. As a teacher, Scrum Manager helps new team members understand the scope and vision of a product and ensures that team members understand Scrum theory and adhere to Scrum rules and practices. The Scrum Master teaches the team to organize and stay focused.
Scrum Master qualifications do not include personnel management. Furthermore, the Scrum Master is not individually responsible for the results of the project; Instead, the scrum team as a whole is responsible for the results. The Scrum Master has the authority to ensure that the team implements and adheres to the Scrum values, principles, and practices. Whenever they are lacking as a teacher, the Scrum Master will help them understand the scope and vision and adhere to Scrum rules and practices.
- Host daily stand-up meetings - Daily scrum or standup meetings last no more than 15 minutes and allow each team member to answer these questions:
- What will you do today?
- What is hindering your progress?
- What did you do yesterday?
Team members can be asked to estimate how long they will need to complete certain tasks. The Scrum Master moderates this meeting, tracks the team's progress, and takes note of obstacles that could prevent the team from completing tasks.
The Scrum Master ensures that all team members, including those who work remotely, can attend and participate in the daily meeting. They also make sure the meeting stays focused and ends on time.
- Remove roadblocks - To help the team focus on the tasks that need to be accomplished during each iteration, the Scrum Master looks for distractions and obstacles that may hinder progress. For example, if team members are involved in too many unimportant meetings, the Scrum Master can work with the meeting organizers to determine who should attend the meetings.
Or if a team member is drawn in too many directions and tasks are assigned to multiple teams, the Scrum Master can work with Product Owners and other stakeholders to redistribute the workload.
Again, there could be internal disagreements in the team about their individual work styles or disagreements about the Scrum process itself. The Scrum Master can have a one-on-one interaction with members of the development team to understand the same and resolve such conflicts before they turn into full-blown disagreements.
- Coach team members - The Scrum Master ensures that team members are well trained and understand agile processes. The Scrum Master also ensures that team members know their respective roles, that they have a sense of responsibility for the project, that processes are followed, and that teams are self-managed.
- Assist the product owner with the product backlog - The product owner is responsible for creating and maintaining the product backlog. The Product Backlog is a list of the work that the team must do. The Scrum Master helps the Product Owner to refine and maintain the Product Backlog with information from daily meetings. The product backlog is a live document that changes based on current status and development needs. The Scrum Master can help with the Product Backlog by planning meetings and writing user stories.
- Keep all parties on track and informed:- The Scrum Master conducts daily team meetings to learn about the project's progress, resolve potential obstacles, and make sure the project is on track. They also hold regular meetings to share with product stakeholders about the project's progress (or not). Ultimately, it is the job of a Scrum Master to make sure the team is on schedule with the desired outcome.
- Protect the team from outside interference - The Scrum Master acts as a protector and assists the team by shielding it from outside interference that gets in the way of realizing business value during each sprint.
Interference can come from many sources; for example, by managers who want to divert team members in the middle of a sprint. Regardless of the source of the interruption, the Scrum Master acts as an interceptor and solves the problem amicably.
This role includes more scrum master’s responsibilities like:-
- Overcoming obstacles
- Protect the team from external disturbances and distractions.
- Ensuring a good relationship between the team and the product owner and others outside the team.
- Create an environment in which the team can be effective.
- Dynamic team management.
Do you want to pursue your career as a scrum master?
Typically, most Scrum Masters skill job descriptions require applicants to have at least a bachelor's degree in computer science or a related field to become a Scrum Master. Also, you need some experience as an agile software developer. One of the most important Scrum Master skills you will need is communication.
As part of your Scrum Master roles, you will be the primary communicator between project owners and other key stakeholders.
If you do not have good oral and written communication skills, or if you feel uncomfortable interacting with One-on-One or in groups, this may not be the job for you.
Earning a Scrum Master’s certification can increase your chances of landing a higher paying job as it confirms that you have the right skills.
Scrum master’s certification programme
There are also a number of other Scrum certification programs that may interest you, including:
- Scrum Developer
- Scrum Coach
- Scrum Trainer
- Scrum Professional
- Scrum Product owner
A Scrum Masters certification in any of these disciplines can boost your career and mean significant salary increases. The possibilities are open.
Qualities of a scrum master
- Observant:- The Scrum Master is not a manager, but a team member and a moderator. They must be good listeners and be aware of the challenges the project team faces at every step. The Scrum Master must also be alert and aware of the daily activities of the team to have a clear view of the roles and contributions of the members in the sprint sessions.
- Collaborative - The Scrum Master forms an essential link between the product owner and the project team. While the Product Owner drives the overall initiative, the Scrum Master maintains the team. An effective collaboration between Scrum Master and Product Owner ultimately leads to successful products that meet the organization's requirements. A good Scrum Master should be able to find creative ways to increase organization, collaboration, and productivity to deliver the product that the business unit owner has requested.
- Influential - A Scrum Master leads different teams working on a project to achieve certain milestones and results. He must be able to motivate multiple groups and stakeholders at the organizational level and maximize the potential of everyone involved. As a team leader, the Scrum Master must bridge the gap between the project concept and the steps required to complete it. The Scrum Master must have strong organizational and leadership skills.
- Knowledgeable - In addition to solving problems and problems that arise, the Scrum Master must also proactively prevent potential problems. This requires a thorough knowledge of the product and the process. The Scrum Master's experience allows the team to avoid obstacles. The Scrum Master must have knowledge of various agile work formats and methods such as XP, Lean, and Kanban.
- Transparent - Last but not least, the Scrum Master must be transparent in all forms of communication. There should be no hidden intentions when working with team members; What you see and hear from the Scrum Master has to be what you get. People expect no less from a leader in service.
The Scrum Master also promotes transparent communication outside of the Scrum team. Without transparency, it is difficult for the organization to use Scrum to review and adjust the desired business results.
Different tasks for a Scrum Master
Organizations often find a way to implement the Scrum Master role and therefore there are many types of Scrum Masters. There are Scrum Masters who mainly focus on the development team and support them during Scrum events and in their work. This is often the result of implementing the Scrum Master role as a part-time role. In other organizations, Scrum Masters act more like agile change agents who change the organization, advise top management, and implement change.
The following list is not complete, but some typical scrum masters tasks include:
- Employee training and workshop moderation to gain a better understanding and better application of the Scrum framework.
- Support, training, coaching and support of the product owner, the development team and the organization if it is necessary or demanded to continually improve and become more self-organized.
- Moderation of Scrum events if required or requested by the Scrum team.
- Prepare and carry out the Sprint Retrospective by collecting data and observations during the Sprint.
- Train stakeholders (including clients, Clevel, top management, and other stakeholders) on agility and understanding of the Scrum framework to effectively interact with the Scrum team; and,
- Solve obstacles if necessary and / or teach the Scrum team how to solve obstacles themselves.
Traits of the Scrum Master
- Empathy:- Being able to feel what is happening in a group of people is critical to the success of Scrum Masters. The most valuable things are often said between the lines or can be gleaned from non-verbal communication. This is often used for the Scrum Master to train and train people to maximize the value of Scrum.
- Courage:- There are many important skills and traits for Scrum Masters, but if you make it to the top three, you must have "courage." As explained in the "Skills" section, the Scrum Master is a servant leader. Many organizations are "damaged" in some way. In many organizations, people are afraid to speak up, make mistakes and, for example, take responsibility. The Scrum Master as a leader plays an important role in showing people the courage to follow him and act boldly.
- Openness:- Transparency, necessary for review and adjustment, is one of the pillars of Scrum. Openness is an extremely important value in Scrum. Both are critical to the success of Scrum. However, for many people it is terrifying to be completely open and transparent. Therefore, the Scrum Master must be open and honest and be an example to follow for others.
Wrapping up
As a reminder: the Scrum methodology is a subset of agile software development, in which a development team sets goals to provide new software features and functions in clearly defined iterative cycles. Each iteration delivers small but significant parts of an overall project every two to four weeks. Whether you're interested in becoming a Scrum Master or want to make sure you establish best practices in your Scrum team, learn about these important Scrum Master skills and responsibilities that come with the job. This Scrum Master role is responsible for ensuring that the project runs smoothly within the guidelines of the Scrum methodology. By implementing these tips and working through the requirements, you are on your way to becoming the master of your scrum.
“Scrum master roles and responsibilities” - this elaborated article will help you to grow in your organization and will help you to learn more about teamwork and team management.
The Scrum Framework consists of three roles, the Product Owner, the Scrum Master, and the Development Team. Together they make up the Scrum team. This elaborated article titled Scrum master roles and responsibilities will help you to grow in a professional manner.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
In this blog we cover the typical tasks, responsibilities, skills, problems, qualities, and benefits of the Scrum Master role in Scrum.
What is a scrum master?
Scrum Master is often the term used for this role, even by teams that do not explicitly follow Scrum. Other terms that are rarely used are iteration manager, agile coach, or team coach. The Scrum Master cleverly removes obstacles and distractions that could prevent the team from achieving its goals. This person is the connection between the Scrum Team and the people or teams outside of the Scrum Team. The Scrum Master is a service leader for the Scrum Team who helps the Scrum Team and its environment work together and interact to maximize the value delivered by the Scrum Team. Article - Scrum master roles and responsibilities will give you a brief knowledge about how Scrum Master works. Scrum Master is also responsible for helping people to understand Scrum theory, its practices, rules and values.
Imagesource - https://www.lucidchart.com/blog/scrum-master-skills-and-responsibilities
Skills defined for scrum master -
While there are no officially defined skill levels for Scrum Masters, there are different levels of experience in practice:
- Rotating scrum master - Members of a team rotate Scrum Master responsibilities (primarily administrative) among themselves on a sprint-by-sprint basis.
- Part time scrum master - In addition to other tasks on the same team, one person on the team assumes the Scrum Master tasks.
- Full time scrum master - The sole responsibility of an individual is to be a Scrum Master at one time or another. This model is the best for a team that is learning agilely.
- Full time scrum master with more than one team - This model is often used when a person's only responsibility is to be a Scrum Master, but they are working with more than one team.
- Agile Coach - A person does not have a specially assigned team, but works with several teams and only on certain needs.
Benefits as a scrum master
The overall benefit one expects from a Scrum Master in a team is to provide a self-organizing team with constant access to someone who has used Agile and especially Scrum in a different environment and can help the team find the best way to apply it. in your situation.
Another expected benefit is that the Scrum Master is someone who can address distractions, interruptions, and obstacles so that the rest of the team can focus on work to produce results that produce the desired result.
Common problems as a scrum master
While there are several advantages to being a Scrum Master, several problems arise from improper use of the role. These problems include:
- Suppose you can only slide project managers that are used to command and control the guide guide guide in a scrum Master role and expect it to be effective.
- Asking someone to fill the role of Scrum Master with no experience in an agile environment.
- Expect a Scrum Master's workload to be the same across teams, regardless of how long they have worked as a team, how they understand Agile values and principles, and what domain expertise they have.
- A well-functioning team will likely need much less training from a Scrum Master than a team that is new to working with Agile values and principles.
7 Key scrum master’s responsibilities
Despite the word "Master" in the title, the Scrum Master is not responsible for the project or the development team. Instead, a scrum masterpiece works with the product owner and the scrum team to refine and improve processes where it makes sense.
A Scrum Master role may include, but is not limited to, the following responsibilities.
- Teach Scrum practices and principles - To ensure that the work does not decrease the speed, an important role of Scrum Master is a mentor and a teacher to provide new employees and new team members. As a teacher, Scrum Manager helps new team members understand the scope and vision of a product and ensures that team members understand Scrum theory and adhere to Scrum rules and practices. The Scrum Master teaches the team to organize and stay focused.
Scrum Master qualifications do not include personnel management. Furthermore, the Scrum Master is not individually responsible for the results of the project; Instead, the scrum team as a whole is responsible for the results. The Scrum Master has the authority to ensure that the team implements and adheres to the Scrum values, principles, and practices. Whenever they are lacking as a teacher, the Scrum Master will help them understand the scope and vision and adhere to Scrum rules and practices.
- Host daily stand-up meetings - Daily scrum or standup meetings last no more than 15 minutes and allow each team member to answer these questions:
- What will you do today?
- What is hindering your progress?
- What did you do yesterday?
Team members can be asked to estimate how long they will need to complete certain tasks. The Scrum Master moderates this meeting, tracks the team's progress, and takes note of obstacles that could prevent the team from completing tasks.
The Scrum Master ensures that all team members, including those who work remotely, can attend and participate in the daily meeting. They also make sure the meeting stays focused and ends on time.
- Remove roadblocks - To help the team focus on the tasks that need to be accomplished during each iteration, the Scrum Master looks for distractions and obstacles that may hinder progress. For example, if team members are involved in too many unimportant meetings, the Scrum Master can work with the meeting organizers to determine who should attend the meetings.
Or if a team member is drawn in too many directions and tasks are assigned to multiple teams, the Scrum Master can work with Product Owners and other stakeholders to redistribute the workload.
Again, there could be internal disagreements in the team about their individual work styles or disagreements about the Scrum process itself. The Scrum Master can have a one-on-one interaction with members of the development team to understand the same and resolve such conflicts before they turn into full-blown disagreements.
- Coach team members - The Scrum Master ensures that team members are well trained and understand agile processes. The Scrum Master also ensures that team members know their respective roles, that they have a sense of responsibility for the project, that processes are followed, and that teams are self-managed.
- Assist the product owner with the product backlog - The product owner is responsible for creating and maintaining the product backlog. The Product Backlog is a list of the work that the team must do. The Scrum Master helps the Product Owner to refine and maintain the Product Backlog with information from daily meetings. The product backlog is a live document that changes based on current status and development needs. The Scrum Master can help with the Product Backlog by planning meetings and writing user stories.
- Keep all parties on track and informed:- The Scrum Master conducts daily team meetings to learn about the project's progress, resolve potential obstacles, and make sure the project is on track. They also hold regular meetings to share with product stakeholders about the project's progress (or not). Ultimately, it is the job of a Scrum Master to make sure the team is on schedule with the desired outcome.
- Protect the team from outside interference - The Scrum Master acts as a protector and assists the team by shielding it from outside interference that gets in the way of realizing business value during each sprint.
Interference can come from many sources; for example, by managers who want to divert team members in the middle of a sprint. Regardless of the source of the interruption, the Scrum Master acts as an interceptor and solves the problem amicably.
This role includes more scrum master’s responsibilities like:-
- Overcoming obstacles
- Protect the team from external disturbances and distractions.
- Ensuring a good relationship between the team and the product owner and others outside the team.
- Create an environment in which the team can be effective.
- Dynamic team management.
Do you want to pursue your career as a scrum master?
Typically, most Scrum Masters skill job descriptions require applicants to have at least a bachelor's degree in computer science or a related field to become a Scrum Master. Also, you need some experience as an agile software developer. One of the most important Scrum Master skills you will need is communication.
As part of your Scrum Master roles, you will be the primary communicator between project owners and other key stakeholders.
If you do not have good oral and written communication skills, or if you feel uncomfortable interacting with One-on-One or in groups, this may not be the job for you.
Earning a Scrum Master’s certification can increase your chances of landing a higher paying job as it confirms that you have the right skills.
Scrum master’s certification programme
There are also a number of other Scrum certification programs that may interest you, including:
- Scrum Developer
- Scrum Coach
- Scrum Trainer
- Scrum Professional
- Scrum Product owner
A Scrum Masters certification in any of these disciplines can boost your career and mean significant salary increases. The possibilities are open.
Qualities of a scrum master
- Observant:- The Scrum Master is not a manager, but a team member and a moderator. They must be good listeners and be aware of the challenges the project team faces at every step. The Scrum Master must also be alert and aware of the daily activities of the team to have a clear view of the roles and contributions of the members in the sprint sessions.
- Collaborative - The Scrum Master forms an essential link between the product owner and the project team. While the Product Owner drives the overall initiative, the Scrum Master maintains the team. An effective collaboration between Scrum Master and Product Owner ultimately leads to successful products that meet the organization's requirements. A good Scrum Master should be able to find creative ways to increase organization, collaboration, and productivity to deliver the product that the business unit owner has requested.
- Influential - A Scrum Master leads different teams working on a project to achieve certain milestones and results. He must be able to motivate multiple groups and stakeholders at the organizational level and maximize the potential of everyone involved. As a team leader, the Scrum Master must bridge the gap between the project concept and the steps required to complete it. The Scrum Master must have strong organizational and leadership skills.
- Knowledgeable - In addition to solving problems and problems that arise, the Scrum Master must also proactively prevent potential problems. This requires a thorough knowledge of the product and the process. The Scrum Master's experience allows the team to avoid obstacles. The Scrum Master must have knowledge of various agile work formats and methods such as XP, Lean, and Kanban.
- Transparent - Last but not least, the Scrum Master must be transparent in all forms of communication. There should be no hidden intentions when working with team members; What you see and hear from the Scrum Master has to be what you get. People expect no less from a leader in service.
The Scrum Master also promotes transparent communication outside of the Scrum team. Without transparency, it is difficult for the organization to use Scrum to review and adjust the desired business results.
Different tasks for a Scrum Master
Organizations often find a way to implement the Scrum Master role and therefore there are many types of Scrum Masters. There are Scrum Masters who mainly focus on the development team and support them during Scrum events and in their work. This is often the result of implementing the Scrum Master role as a part-time role. In other organizations, Scrum Masters act more like agile change agents who change the organization, advise top management, and implement change.
The following list is not complete, but some typical scrum masters tasks include:
- Employee training and workshop moderation to gain a better understanding and better application of the Scrum framework.
- Support, training, coaching and support of the product owner, the development team and the organization if it is necessary or demanded to continually improve and become more self-organized.
- Moderation of Scrum events if required or requested by the Scrum team.
- Prepare and carry out the Sprint Retrospective by collecting data and observations during the Sprint.
- Train stakeholders (including clients, Clevel, top management, and other stakeholders) on agility and understanding of the Scrum framework to effectively interact with the Scrum team; and,
- Solve obstacles if necessary and / or teach the Scrum team how to solve obstacles themselves.
Traits of the Scrum Master
- Empathy:- Being able to feel what is happening in a group of people is critical to the success of Scrum Masters. The most valuable things are often said between the lines or can be gleaned from non-verbal communication. This is often used for the Scrum Master to train and train people to maximize the value of Scrum.
- Courage:- There are many important skills and traits for Scrum Masters, but if you make it to the top three, you must have "courage." As explained in the "Skills" section, the Scrum Master is a servant leader. Many organizations are "damaged" in some way. In many organizations, people are afraid to speak up, make mistakes and, for example, take responsibility. The Scrum Master as a leader plays an important role in showing people the courage to follow him and act boldly.
- Openness:- Transparency, necessary for review and adjustment, is one of the pillars of Scrum. Openness is an extremely important value in Scrum. Both are critical to the success of Scrum. However, for many people it is terrifying to be completely open and transparent. Therefore, the Scrum Master must be open and honest and be an example to follow for others.
Wrapping up
As a reminder: the Scrum methodology is a subset of agile software development, in which a development team sets goals to provide new software features and functions in clearly defined iterative cycles. Each iteration delivers small but significant parts of an overall project every two to four weeks. Whether you're interested in becoming a Scrum Master or want to make sure you establish best practices in your Scrum team, learn about these important Scrum Master skills and responsibilities that come with the job. This Scrum Master role is responsible for ensuring that the project runs smoothly within the guidelines of the Scrum methodology. By implementing these tips and working through the requirements, you are on your way to becoming the master of your scrum.
“Scrum master roles and responsibilities” - this elaborated article will help you to grow in your organization and will help you to learn more about teamwork and team management.
The Scrum Framework consists of three roles, the Product Owner, the Scrum Master, and the Development Team. Together they make up the Scrum team. This elaborated article titled Scrum master roles and responsibilities will help you to grow in a professional manner.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Top 10 Cyber Security Trends
Technology is rapidly advancing and transforming the way businesses work. Cloud computing, artificial intelligence (AI), automation, and the Internet of Things (IoT) are all emerging technologies that are giving businesses unprecedented opportunities to generate new value. This value, however, is not guaranteed. Organizations must negotiate a changing cyberthreat landscape as technology advances. In fact, it is anticipated that by 2020, the global cyber threat would have slowed the pace of technological innovation by USD 3 trillion in lost economic value. The most pressing ongoing cyber security concerns are a scarcity of qualified security staff, complex compliance requirements, the constant evolution of cyber attacks, and dangerous insider threats.
With the digital revolution sweeping the globe, all businesses, large and small, corporations, organisations, and even governments are relying on computerised systems to manage their day-to-day operations, making cyber security a top priority to protect data from online attacks and unauthorised access. As news of data breaches, ransomware, and hacking becomes the norm, constant development in technology necessitates a matching shift in cybersecurity practices.
The topic of cyber security, in particular, can be difficult to manage. Many firms' perspectives on cyber security have shifted as a result of the new remote-work-focused environment. Furthermore, many of the latest and future cybersecurity solutions are buried in technical specs and industry jargon while researching them.
Top 10 Cyber Security Trends to Watch For!
1. Integrating Artificial Intelligence and Cyber security
With AI being implemented across all market areas, this technology, together with machine learning, has resulted in significant improvements in cyber security. In the development of automated security systems, natural language processing, facial detection, and autonomous threat detection, AI has played a critical role. It's also being used to create smart malware and attacks to get around the most up-to-date data protection protocols. Artificial intelligence-enabled threat detection systems can predict new assaults and alert administrators to any data breaches immediately.
Artificial Intelligence (AI) will help under-resourced security teams stay ahead of the dangers as cyber attacks become more intense and frequent. AI delivers threat intelligence by evaluating huge amounts of risk data from structured and unstructured resources, lowering the time it takes for the security team to make crucial decisions and respond to the threat.
2. The New Target Is Mobile
In 2019, cyber security trends predict a significant increase (50 per cent) in mobile banking malware or attacks, making our mobile devices a target for hackers. Individuals are more at risk from all of our images, financial transactions, emails, and communications. In 2021, a smartphone virus or malware may attract the attention of cyber security trends.
With increased concerns about data management and security, data privacy is set to become a more major, defined discipline on its own, rather than just a part of compliance requirements. Data privacy affects practically every area of a business as a separate discipline, from co-directing corporate strategy to closely aligning with security, HR, governance, and procurement.
3. The Internet of Things and 5G Networks: A New Era of Technology and Risks
IoT with 5G networks is the next big cyber security trend for 2021. With 5G networks slated to launch globally in 2020, the Internet of Things will usher in a new era of interconnectivity (IoT). This communication across numerous devices exposes them to outside influence, attacks, or an unknown software defect, exposing them to vulnerabilities. Even Google Chrome, the world's most popular browser, was proven to have major problems. 5G design is still relatively new in the market, and it will take a lot of investigation to uncover flaws that will allow the system to be secure against external assault.
Every stage of the 5G network could result in a slew of network assaults that we are unaware of. To prevent data breaches, manufacturers must create sophisticated 5G hardware and software with extreme caution. The internet of things (IoT) refers to all internet-connected products and gadgets that make our life easier. Everything from smart speakers to thermostats (think Nest), watches, doorbells, lightbulbs, water metres, and manufacturing equipment is included in this category, and the list is constantly growing. These gadgets, despite their small size, convey a large amount of data. They also save data that you presumably don't want to give to anyone who can break into your network.
4. Edge of Secure Access Service (SASE)
The coronavirus epidemic has prompted a shift toward remote working, cloud usage, and online collaboration, and this trend is expected to continue. As a result, network security in enterprises is shifting away from LAN-based appliance models and toward cloud-native security service models, such as Secure Access Service Edge (SASE).
By routing the network traffic through a cloud-based security stack, SASE technology allows enterprises to secure their remote workforce and cloud applications.
5. Integration and Automation
Here's the next cyber security trend: as data grows in bulk every day, it's imperative that automation be implemented to provide more sophisticated management over the data. Professionals and engineers are under increasing pressure to produce rapid and effective solutions in today's demanding work environment, making automation more useful than ever.
To design more safe software in every element, security metrics are incorporated within the agile process. Large and complicated web applications are even more difficult to secure, making automation and cyber security a critical notion in the software development process.
6. Threats from Within
One of the most common causes of data breaches is human mistakes. A single bad day or purposeful loophole can bring a whole corporation down, resulting in millions of dollars in stolen data. Verizon's data breach report provides strategic insights into cyber security trends, revealing that workers were directly or indirectly responsible for 34% of all attacks. As a result, be sure to raise awareness among employees to ensure that data is protected in every way possible.
Unauthorized remote access, weak passwords, insecure networks, and the misuse of personal devices have left multinational firms unable to monitor or identify internal threats as a result of the extraordinary shift to remote work. These trends are projected to persist, if not accelerate, in 2021 and beyond.
7. Plans for Long-Distance Remote Working
Many firms hurried to put together emergency work from home strategies when the coronavirus outbreak broke out. There is now a trend toward more permanent work from home or flexible remote work arrangements.
When employees are dispersed across offices, states, and time zones, technology demands in terms of software, hardware, cyber security, and support appear different. Of course, technology is essential for businesses to stay connected, complete tasks, and provide support to their staff. More companies are rethinking their haphazard work from home programmes in favour of building long-term remote workplaces or hybrid remote work plans.
8. Access to a Network with Zero Trust (ZTNA)
Previously, IT departments used Virtual Private Networks (VPNs) to allow distant workers access to the corporate network. VPNs were tragically inadequate when COVID-19 forced practically all staff to work remotely.
Zero-Trust Network Access (ZTNA) has evolved as a more secure method of controlling remote access to certain apps for enterprises.
By 2020, ZTNA will be used to access 80 percent of new digital business apps, and by 2023, 60 percent of businesses will have switched from remote-access VPNs to ZTNA.
9. Detection and Response to Endpoints (EDR)
There are more devices, or endpoints, out in the field away from the office in a work-from-home economy. EDR focuses on securing and safeguarding individual devices deployed over an organization's virtual network, regardless of where they are situated, rather than protecting devices behind a firewall in a physical location.
EDR uses advanced technologies like artificial intelligence and machine learning to monitor the business's devices in real-time for unusual behaviour in order to detect cyber attacks, isolate infected workstations, alert administrators, and remove cyber threats. Before the entire business network is hacked, cyber security specialists may monitor alarms and quarantine individual devices using EDR.
10. MFA (Multi-Factor Authentication)
More businesses are transacting business online, from shopping and banking to acquiring solutions such as phone systems and cyber security services. When accessing information online, MFA adds an extra layer of security by authenticating your identity with a different touchpoint.
You're probably aware of the most common MFA scenario: you input your username and password, and then you must enter an extra code that's normally given through text message or email to your mobile device after your login information has been confirmed. This extra layer of protection helps prevent fraudulent people from gaining access to accounts and private information.
Conclusion
Organizations will be more afraid to stack their security measures in 2021 as a result of these cyber security trends. Organizations are likely to spend more than ever on asset protection this year, with estimates of $100 billion or more.
With infrastructure security playing such an important role in practically every firm today, it would be a wise decision to begin their cyber security education today in order to become specialists in the future. Cyber security specialists who are skilled and experienced are among the highest-paid in the IT business.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
Technology is rapidly advancing and transforming the way businesses work. Cloud computing, artificial intelligence (AI), automation, and the Internet of Things (IoT) are all emerging technologies that are giving businesses unprecedented opportunities to generate new value. This value, however, is not guaranteed. Organizations must negotiate a changing cyberthreat landscape as technology advances. In fact, it is anticipated that by 2020, the global cyber threat would have slowed the pace of technological innovation by USD 3 trillion in lost economic value. The most pressing ongoing cyber security concerns are a scarcity of qualified security staff, complex compliance requirements, the constant evolution of cyber attacks, and dangerous insider threats.
With the digital revolution sweeping the globe, all businesses, large and small, corporations, organisations, and even governments are relying on computerised systems to manage their day-to-day operations, making cyber security a top priority to protect data from online attacks and unauthorised access. As news of data breaches, ransomware, and hacking becomes the norm, constant development in technology necessitates a matching shift in cybersecurity practices.
The topic of cyber security, in particular, can be difficult to manage. Many firms' perspectives on cyber security have shifted as a result of the new remote-work-focused environment. Furthermore, many of the latest and future cybersecurity solutions are buried in technical specs and industry jargon while researching them.
Top 10 Cyber Security Trends to Watch For!
1. Integrating Artificial Intelligence and Cyber security
With AI being implemented across all market areas, this technology, together with machine learning, has resulted in significant improvements in cyber security. In the development of automated security systems, natural language processing, facial detection, and autonomous threat detection, AI has played a critical role. It's also being used to create smart malware and attacks to get around the most up-to-date data protection protocols. Artificial intelligence-enabled threat detection systems can predict new assaults and alert administrators to any data breaches immediately.
Artificial Intelligence (AI) will help under-resourced security teams stay ahead of the dangers as cyber attacks become more intense and frequent. AI delivers threat intelligence by evaluating huge amounts of risk data from structured and unstructured resources, lowering the time it takes for the security team to make crucial decisions and respond to the threat.
2. The New Target Is Mobile
In 2019, cyber security trends predict a significant increase (50 per cent) in mobile banking malware or attacks, making our mobile devices a target for hackers. Individuals are more at risk from all of our images, financial transactions, emails, and communications. In 2021, a smartphone virus or malware may attract the attention of cyber security trends.
With increased concerns about data management and security, data privacy is set to become a more major, defined discipline on its own, rather than just a part of compliance requirements. Data privacy affects practically every area of a business as a separate discipline, from co-directing corporate strategy to closely aligning with security, HR, governance, and procurement.
3. The Internet of Things and 5G Networks: A New Era of Technology and Risks
IoT with 5G networks is the next big cyber security trend for 2021. With 5G networks slated to launch globally in 2020, the Internet of Things will usher in a new era of interconnectivity (IoT). This communication across numerous devices exposes them to outside influence, attacks, or an unknown software defect, exposing them to vulnerabilities. Even Google Chrome, the world's most popular browser, was proven to have major problems. 5G design is still relatively new in the market, and it will take a lot of investigation to uncover flaws that will allow the system to be secure against external assault.
Every stage of the 5G network could result in a slew of network assaults that we are unaware of. To prevent data breaches, manufacturers must create sophisticated 5G hardware and software with extreme caution. The internet of things (IoT) refers to all internet-connected products and gadgets that make our life easier. Everything from smart speakers to thermostats (think Nest), watches, doorbells, lightbulbs, water metres, and manufacturing equipment is included in this category, and the list is constantly growing. These gadgets, despite their small size, convey a large amount of data. They also save data that you presumably don't want to give to anyone who can break into your network.
4. Edge of Secure Access Service (SASE)
The coronavirus epidemic has prompted a shift toward remote working, cloud usage, and online collaboration, and this trend is expected to continue. As a result, network security in enterprises is shifting away from LAN-based appliance models and toward cloud-native security service models, such as Secure Access Service Edge (SASE).
By routing the network traffic through a cloud-based security stack, SASE technology allows enterprises to secure their remote workforce and cloud applications.
5. Integration and Automation
Here's the next cyber security trend: as data grows in bulk every day, it's imperative that automation be implemented to provide more sophisticated management over the data. Professionals and engineers are under increasing pressure to produce rapid and effective solutions in today's demanding work environment, making automation more useful than ever.
To design more safe software in every element, security metrics are incorporated within the agile process. Large and complicated web applications are even more difficult to secure, making automation and cyber security a critical notion in the software development process.
6. Threats from Within
One of the most common causes of data breaches is human mistakes. A single bad day or purposeful loophole can bring a whole corporation down, resulting in millions of dollars in stolen data. Verizon's data breach report provides strategic insights into cyber security trends, revealing that workers were directly or indirectly responsible for 34% of all attacks. As a result, be sure to raise awareness among employees to ensure that data is protected in every way possible.
Unauthorized remote access, weak passwords, insecure networks, and the misuse of personal devices have left multinational firms unable to monitor or identify internal threats as a result of the extraordinary shift to remote work. These trends are projected to persist, if not accelerate, in 2021 and beyond.
7. Plans for Long-Distance Remote Working
Many firms hurried to put together emergency work from home strategies when the coronavirus outbreak broke out. There is now a trend toward more permanent work from home or flexible remote work arrangements.
When employees are dispersed across offices, states, and time zones, technology demands in terms of software, hardware, cyber security, and support appear different. Of course, technology is essential for businesses to stay connected, complete tasks, and provide support to their staff. More companies are rethinking their haphazard work from home programmes in favour of building long-term remote workplaces or hybrid remote work plans.
8. Access to a Network with Zero Trust (ZTNA)
Previously, IT departments used Virtual Private Networks (VPNs) to allow distant workers access to the corporate network. VPNs were tragically inadequate when COVID-19 forced practically all staff to work remotely.
Zero-Trust Network Access (ZTNA) has evolved as a more secure method of controlling remote access to certain apps for enterprises.
By 2020, ZTNA will be used to access 80 percent of new digital business apps, and by 2023, 60 percent of businesses will have switched from remote-access VPNs to ZTNA.
9. Detection and Response to Endpoints (EDR)
There are more devices, or endpoints, out in the field away from the office in a work-from-home economy. EDR focuses on securing and safeguarding individual devices deployed over an organization's virtual network, regardless of where they are situated, rather than protecting devices behind a firewall in a physical location.
EDR uses advanced technologies like artificial intelligence and machine learning to monitor the business's devices in real-time for unusual behaviour in order to detect cyber attacks, isolate infected workstations, alert administrators, and remove cyber threats. Before the entire business network is hacked, cyber security specialists may monitor alarms and quarantine individual devices using EDR.
10. MFA (Multi-Factor Authentication)
More businesses are transacting business online, from shopping and banking to acquiring solutions such as phone systems and cyber security services. When accessing information online, MFA adds an extra layer of security by authenticating your identity with a different touchpoint.
You're probably aware of the most common MFA scenario: you input your username and password, and then you must enter an extra code that's normally given through text message or email to your mobile device after your login information has been confirmed. This extra layer of protection helps prevent fraudulent people from gaining access to accounts and private information.
Conclusion
Organizations will be more afraid to stack their security measures in 2021 as a result of these cyber security trends. Organizations are likely to spend more than ever on asset protection this year, with estimates of $100 billion or more.
With infrastructure security playing such an important role in practically every firm today, it would be a wise decision to begin their cyber security education today in order to become specialists in the future. Cyber security specialists who are skilled and experienced are among the highest-paid in the IT business.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Top 10 Network Security Certifications
The first line of protection against hackers and other cyber dangers is network security. We can see why network security has become more important, given estimates that cybercrime would cause $6 trillion in global damage by 2021. However, just as there are numerous types of assaults, there is a bewildering assortment of cybersecurity certificates from which to pick.
While having so many cybersecurity options is undoubtedly beneficial, the sheer number and range of options also present a hurdle. It's easy to become overwhelmed by the number of options available, to the point where you don't make a decision at all.
What are the most important network security credentials? Which one(s) is/are the best fit for you and your company? Is there any cyber security certification that is generally applicable?
What is the Definition of Network Security?
Most experts define network security as policies and practices for preventing trespassing, unlawful access, alteration, misuse, change, destruction, or the unauthorised gathering and dissemination of data on network infrastructure. A combination of hardware devices, security software, and user understanding of security processes and approaches is required for the entire process.
Employees who have been instructed on correct security measures, as well as experts who have completed network security training, are examples of the latter part.
What is the Purpose of Network Security?
Many parts of our lives have made the transition to the digital realm. We utilise the internet to conduct financial transactions, interact with family and coworkers, shop, entertain ourselves, and conduct research. Everything from birth dates, Social Security (or other identification numbers), health history, credit history, bank accounts, utility bills, and a variety of other things can be found online.
Hackers and cybercriminals have access to all of that information and transactions. The more time we devote to the internet, the greater the chance of being hacked. Furthermore, as the Internet of Things (IoT) grows in prominence, so does reliance on wireless networks, which only adds to the threat picture by giving criminals more ways and opportunities to commit fraud. There is far too much at stake in our personal and professional lives for network security to be compromised. So, what are the different types of network security?
What Are the Different Network Security Types?
Cybersecurity specialists have access to a vast array of network security technologies, methodologies, and practices. Here's a high-level summary:
Software
Anti-virus, anti-malware, and anti-spyware are examples of security software. These tools are offered as suites or as subscriptions, and the hosting provider updates them on a regular basis to stay on top of the current threats. These programmes keep an eye on your network and thwart intruders, spyware, and viruses.
Aside from that, it's far better to purchase a security subscription rather than buying a suite and installing it yourself. Subscription providers/vendors are better equipped to deal with the cybersecurity landscape's continual changes. Every day, it seems like a new cyber threat or virus emerges, and your software won't be able to protect you from threats it isn't aware of. That's why it's best to let the subscription provider handle the heavy job.
Firewalls
If your network were a posh nightclub, the firewall would be the bouncer, guarding the entrance and keeping intruders out. They block unwanted users by filtering traffic (both incoming and outgoing) based on established policies. Anyone who has attempted to work remotely but been barred out of their company's core systems due to a lack of authorisation knows how powerful a firewall can be.
Security Software for Email
In any network, email is a particularly vulnerable point. Cybercriminals enjoy sending phoney emails that appear to be from respectable businesses and financial institutions.
However, a single click on a link hidden in these phishing emails could damage your machine. To that purpose, email security software can not only filter out incoming threats but can also block the transmission of particular types of data.
Password Security
This is such a basic measure, but it is crucial. Strong passwords are a low-cost but effective approach to keep systems, apps, and networks secure, and you don't need to be a cybersecurity expert to use them. We don't mean passwords like "password" or "99999" when we mention "strong" passwords.
Networks that are Segmented
This method sorts and separates traffic according to predetermined parameters. Segmented networks are particularly effective for confining users to a single area, namely the one in which they need to complete their work, while keeping them away from material that isn't relevant to them. Restricting users in this way helps to reduce the network's overall weak points.
Top 10 Network Security Certifications
Before you can make a lot of money in network security, you must first understand the tools and abilities. This is where network security education comes into play. Network security certifications courses not only provide you with the necessary information for these professions, but they also provide you with a useful credential that verifies your qualifications to potential employers.
1. CEH: "Certified Ethical Hacker."
Ethical hacking, also known as white hat hacking, penetration testing, or red team hacking, is the practice of legitimately hacking businesses in order to find weaknesses before harmful actors do. The CEH Certified Ethical Hacker certification is offered by the EC-Council. To demonstrate your knowledge of penetration testing, attack detection, vectors, and prevention, earn this badge.
These are IT security professionals, also known as "white hat hackers," whose duty is to try to breach systems and uncover weaknesses. They are hired by businesses and organisations to uncover flaws in the system and figure out how to remedy them. When you consider how vital cybersecurity has become, it's no surprise that this certification is so valuable.
The CEH certification teaches you how to think like a hacker and how to be more proactive when it comes to cybersecurity. Consider this qualification if you want to work in the following fields:
- $104,116 for a penetration tester
- $86,454 for a cyber incident analyst
- $90,269 for a threat intelligence analyst
- $158,536 for a cloud security architect
- $100,636 for a cybersecurity engineer
Requirements: You can take the CEH test if you have two years of information security job experience or if you have completed an authorised EC-Council programme.
Cost: Depending on the testing location, costs range from $950 to $1,199.
2. CISSP: (Certified Information Systems Security Professional)
This certification is for experienced security professionals who are in charge of developing and managing security processes, policies, and standards for their firm. It is ideal for IT security professionals who are looking to advance their careers.
The cybersecurity professional organisation (ISC) ranks among the top. CISSP certification is one of the most sought-after qualifications in the business. Earning a CISSP validates your knowledge of IT security and your ability to design, implement, and monitor a cybersecurity programme.
This advanced certification is for security professionals with expertise who want to further their careers in roles such as:
- $170,793 for Chief Information Security Officer
- $85,742 for a security administrator
- $100,605 for an IT security engineer
- $111,250 for a senior security consultant
- $82,070 for an information assurance analyst
Requirements: You must have five or more years of cumulative work experience in at least two of the eight cybersecurity domains to take the CISSP exam. Security and Risk Management, Asset Security, Security Architecture and Engineering, Communication and Network Security, Identity and Access Management, Security Assessment and Testing, Security Operations, and Software Development Security are just a few of the topics covered.
You can still take the exam to become an Associate of (ISC)2 if you're new to cybersecurity and don't have the required experience. After passing the exam, you'll have six years to gain the necessary experience to achieve full CISSP certification.
One year of labour is satisfied by a four-year degree in computer science. Part-time jobs and paid internships are also valid options.
Cost: $749
3. CISA: (Certified Information Systems Auditor)
This certification is aimed at information security professionals who work primarily in the areas of audit control, assurance, and security. It equips you with the knowledge and skills needed to manage and control enterprise IT and conduct a thorough security audit. ISACA allows you to demonstrate your experience in identifying security vulnerabilities, devising and implementing controls, and tracking compliance. It's one of the most well-known qualifications in the field of cybersecurity auditing.
The CISA is for IT professionals in their mid-career who want to develop into positions such as:
- $122,254 for an IT audit manager
- $69,083 for a cybersecurity auditor
- $99,372 for an information security analyst
- $93,526 - IT security engineer
- $102,743 for IT project manager
- Manager of Compliance Programs - $92,829
Requirements: At least five years of expertise in IT or IS audit, control, security, or assurance is required. One or two years of experience can be substituted for a two- or four-year degree, respectively.
Cost: Members pay $575, while non-members pay $760.
4. Manager of Information Security Certification (CISM)
You can certify your knowledge in the management side of information security with the CISM certification from ISACA, which covers issues like governance, programme creation, and programme, incident, and risk management.
Earning your CISM could be a smart choice if you want to go from the technical to the managerial side of cybersecurity. The CISM is used in the following jobs:
- $108,353 for an IT manager
- Security officer for information systems - $96,568
- $92,624 - Information Risk Consultant
- $173,387 Director of Information Security
- $119,816 for a data governance manager
Requirements: You must have at least five years of experience in information security management to take the CISM exam. With general information security experience, you can satisfy up to two years of this prerequisite. With another valid certification or a graduate degree in an information security-related discipline, you can also skip one or two years.
Cost: Members pay $575, while non-members pay $760.
5. CompTIA Security+
CompTIA Security+ is a certification programme that certifies you as a security expert. Cryptography, threat management, identity management, network access control, security systems, risk identification, and mitigation are all covered in this certification. It is aimed towards people who are just starting out in the field of information technology.
The certifications you choose will be determined by where you are in your profession, and each person's ideal list will be unique. The final two certificates, for example, are best suited for entry-level IT employees, whereas the CISM and CISSP are designed for more seasoned security experts. There is no better method for an IT professional to become well-rounded than to gradually earn certification in all of the above fields. Even the most seasoned cybersecurity professionals might benefit from a refresher course. Whether it's a newly found cyber threat or a new strategy to combat it, there's always something new to learn. Upskilling not only elevates your status within your company, but it also makes you a more marketable candidate if you decide to move on. Expertise, leverage, and independence are all benefits of upskilling.
The CompTIA Security+ certification is an entry-level security certification that verifies the essential abilities required in any cybersecurity position. Demonstrate your ability to assess an organization's security, monitor and secure cloud, mobile, and internet of things (IoT) environments, comprehend risk and compliance rules and regulations, and identify and respond to security issues with this certification.
Obtaining your Security+ certification can assist you in a variety of positions, including:
- $74,086 for a systems administrator
- $70,531 for a help desk manager
- $109,863 for a security engineer
- $110,152 for a cloud engineer
- $85,742 for a security administrator
- $78,633 for an IT auditor
- $107,597 for a software developer
Requirements: While there are no mandatory prerequisites for taking the Security+ test, it is recommended that you first acquire your Network+ certification and gain at least two years of IT experience with a security focus.
Cost: $370
6. Security Essentials Certification by GIAC (GSEC)
This entry-level security accreditation from the Global Information Assurance Certification (GIAC) is for persons with a background in information systems and networking. This certification verifies your knowledge of active defence, network security, cryptography, incident response, and cloud security.
If you have some IT experience and want to move into cybersecurity, consider taking the GSEC exam. The skills indicated by the GSEC are used in the following job roles:
- $124,638 for IT security manager
- $85,121 for a computer forensic analyst
- $104,116 for a penetration tester
- $85,742 for a security administrator
- $78,633 for an IT auditor
- $116,252 for a software development engineer
Requirements: There are no specific prerequisites for taking the GSEC exam. Get some experience with information systems or computer networking to set yourself up for success.
Cost: $2,499 (includes two practise tests)
7. Certified Systems Security Practitioner (SSCP)
Employers will be able to see that you have the abilities to design, deploy, and maintain a secure IT infrastructure if you have this intermediate security certificate from (ISC)2. The exam assesses knowledge of access controls, risk identification and analysis, security administration, incident response, cryptography, and network, communications, systems, and application security, as well as network, communications, systems, and application security.
The SSCP is for IT professionals who work directly with a company's security systems or assets. This accreditation is suitable for jobs such as:
- $95,997 for a network security engineer
- $74,086 for a system administrator
- $76,112 for a systems engineer
- $77,662 for a security analyst
- $82,167 for database administrator
- $97,516 for a security consultant
Requirements: Candidates must have at least one year of paid job experience in one or more of the testing areas to be eligible for the SSCP. A bachelor's or master's degree in a cybersecurity-related programme can also satisfy this requirement.
Cost: $249
8. Advanced Security Practitioner (CASP+)
It is a certification offered by CompTIA. The CASP+ is for cybersecurity professionals who have demonstrated advanced skills but want to stay in the industry (as opposed to management). Enterprise security domain, risk analysis, software vulnerability, safeguarding cloud and virtualization technologies, and cryptographic approaches are among the advanced subjects covered in the test.
Advanced responsibilities in architecture, risk management, and enterprise security integration may become available as a result of the CASP+. The following are examples of possible job titles:
- $152,732 for a security architect
- $109,863 for a security engineer
- $110,660 for an application security engineer
- $109,766 for technical lead analyst
- $80,475 for a vulnerability analyst
Requirements: There are no formal prerequisites for taking the CASP+ examination. Only experienced cybersecurity workers with at least 10 years of IT administration expertise should take it, according to CompTIA (including five years of broad hands-on experience with security).
Cost: $466
9. Incident Handler with GIAC Certification (GCIH)
The GCIH certifies your knowledge of offensive operations, including as common attack strategies and vectors, as well as your ability to identify, respond, and defend against attacks. Incident handling, computer crime investigation, hacker exploits, and hacker tools are all included in the certification test.
Anyone who works in incident response will benefit from this certification. The following are examples of job titles:
- $92,833 for incident handler
- $152,732 for a security architect
- $74,086 for a system administrator
Requirements:There are no specific prerequisites for taking the GCIH exam, however having a working knowledge of security principles, networking protocols, and the Windows Command Line is a good idea.
Cost: $2,499 (includes two practise tests)
10. Certified Professional in Offensive Security (OSCP)
One of the most sought-after credentials for penetration testers is the OSCP from Offensive Security. The exam assesses your ability to compromise a number of target devices using a variety of exploitation techniques and provide detailed penetration test reports for each attack.
The OSCP is an excellent choice for jobs such as:
- $104,116 for a penetration tester
- $100,742 for ethical hacker
- $65,148 for a threat researcher
- $92,005 for an application security analyst
Requirements: There are no official exam requirements. Networking, Linux, Bash scripting, Perl or Python knowledge, as well as completion of the Penetration Testing with Kali course, are all recommended by Offensive Security.
Cost: $999. (Penetration Testing with Kali Linux (PWK/PEN-200) training, 30 days of lab access, and one test attempt are included in the basic package.)
How to Choose the Right One for You?
Earning a cybersecurity certification can help you authenticate your hard-won abilities and boost your career. When deciding whether certification is best for you, keep the following points in mind.
Your level of knowledge: Begin by obtaining a certification that corresponds to your present skill set. Invest in a certification that you know you'll be able to complete and utilise it to progress to more difficult certifications later in your career. If you're fresh to the field of information technology,
Cost: Obtaining certification often costs several hundred dollars (or more), plus ongoing fees. The correct certification can lead to improved career opportunities and more pay, but it's crucial to invest carefully.
It's always a good idea to ask ahead of time if your employer would assist pay for your certification. According to the (ISC)2 survey, 40% of respondents stated that their company paid for their courses, exams, and fees.
Area of focus: A more generic certification can be a suitable alternative if you're just getting started in cybersecurity or want to progress into a management position. You might decide to specialise as your career progresses. A certification in your concentration area will help potential employers recognise your abilities.
Potential employers: Employers who might be interested: Examine the job descriptions of potential companies (or the job titles you intend to apply for) to determine what certifications are typically required.
Having the correct certifications might help you find work in the field of information security (InfoSec). If you work in information security or cybersecurity, you should be aware of the top network security certifications. Gaining these credentials can help you to achieve success in your career.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
The first line of protection against hackers and other cyber dangers is network security. We can see why network security has become more important, given estimates that cybercrime would cause $6 trillion in global damage by 2021. However, just as there are numerous types of assaults, there is a bewildering assortment of cybersecurity certificates from which to pick.
While having so many cybersecurity options is undoubtedly beneficial, the sheer number and range of options also present a hurdle. It's easy to become overwhelmed by the number of options available, to the point where you don't make a decision at all.
What are the most important network security credentials? Which one(s) is/are the best fit for you and your company? Is there any cyber security certification that is generally applicable?
What is the Definition of Network Security?
Most experts define network security as policies and practices for preventing trespassing, unlawful access, alteration, misuse, change, destruction, or the unauthorised gathering and dissemination of data on network infrastructure. A combination of hardware devices, security software, and user understanding of security processes and approaches is required for the entire process.
Employees who have been instructed on correct security measures, as well as experts who have completed network security training, are examples of the latter part.
What is the Purpose of Network Security?
Many parts of our lives have made the transition to the digital realm. We utilise the internet to conduct financial transactions, interact with family and coworkers, shop, entertain ourselves, and conduct research. Everything from birth dates, Social Security (or other identification numbers), health history, credit history, bank accounts, utility bills, and a variety of other things can be found online.
Hackers and cybercriminals have access to all of that information and transactions. The more time we devote to the internet, the greater the chance of being hacked. Furthermore, as the Internet of Things (IoT) grows in prominence, so does reliance on wireless networks, which only adds to the threat picture by giving criminals more ways and opportunities to commit fraud. There is far too much at stake in our personal and professional lives for network security to be compromised. So, what are the different types of network security?
What Are the Different Network Security Types?
Cybersecurity specialists have access to a vast array of network security technologies, methodologies, and practices. Here's a high-level summary:
Software
Anti-virus, anti-malware, and anti-spyware are examples of security software. These tools are offered as suites or as subscriptions, and the hosting provider updates them on a regular basis to stay on top of the current threats. These programmes keep an eye on your network and thwart intruders, spyware, and viruses.
Aside from that, it's far better to purchase a security subscription rather than buying a suite and installing it yourself. Subscription providers/vendors are better equipped to deal with the cybersecurity landscape's continual changes. Every day, it seems like a new cyber threat or virus emerges, and your software won't be able to protect you from threats it isn't aware of. That's why it's best to let the subscription provider handle the heavy job.
Firewalls
If your network were a posh nightclub, the firewall would be the bouncer, guarding the entrance and keeping intruders out. They block unwanted users by filtering traffic (both incoming and outgoing) based on established policies. Anyone who has attempted to work remotely but been barred out of their company's core systems due to a lack of authorisation knows how powerful a firewall can be.
Security Software for Email
In any network, email is a particularly vulnerable point. Cybercriminals enjoy sending phoney emails that appear to be from respectable businesses and financial institutions.
However, a single click on a link hidden in these phishing emails could damage your machine. To that purpose, email security software can not only filter out incoming threats but can also block the transmission of particular types of data.
Password Security
This is such a basic measure, but it is crucial. Strong passwords are a low-cost but effective approach to keep systems, apps, and networks secure, and you don't need to be a cybersecurity expert to use them. We don't mean passwords like "password" or "99999" when we mention "strong" passwords.
Networks that are Segmented
This method sorts and separates traffic according to predetermined parameters. Segmented networks are particularly effective for confining users to a single area, namely the one in which they need to complete their work, while keeping them away from material that isn't relevant to them. Restricting users in this way helps to reduce the network's overall weak points.
Top 10 Network Security Certifications
Before you can make a lot of money in network security, you must first understand the tools and abilities. This is where network security education comes into play. Network security certifications courses not only provide you with the necessary information for these professions, but they also provide you with a useful credential that verifies your qualifications to potential employers.
1. CEH: "Certified Ethical Hacker."
Ethical hacking, also known as white hat hacking, penetration testing, or red team hacking, is the practice of legitimately hacking businesses in order to find weaknesses before harmful actors do. The CEH Certified Ethical Hacker certification is offered by the EC-Council. To demonstrate your knowledge of penetration testing, attack detection, vectors, and prevention, earn this badge.
These are IT security professionals, also known as "white hat hackers," whose duty is to try to breach systems and uncover weaknesses. They are hired by businesses and organisations to uncover flaws in the system and figure out how to remedy them. When you consider how vital cybersecurity has become, it's no surprise that this certification is so valuable.
The CEH certification teaches you how to think like a hacker and how to be more proactive when it comes to cybersecurity. Consider this qualification if you want to work in the following fields:
- $104,116 for a penetration tester
- $86,454 for a cyber incident analyst
- $90,269 for a threat intelligence analyst
- $158,536 for a cloud security architect
- $100,636 for a cybersecurity engineer
Requirements: You can take the CEH test if you have two years of information security job experience or if you have completed an authorised EC-Council programme.
Cost: Depending on the testing location, costs range from $950 to $1,199.
2. CISSP: (Certified Information Systems Security Professional)
This certification is for experienced security professionals who are in charge of developing and managing security processes, policies, and standards for their firm. It is ideal for IT security professionals who are looking to advance their careers.
The cybersecurity professional organisation (ISC) ranks among the top. CISSP certification is one of the most sought-after qualifications in the business. Earning a CISSP validates your knowledge of IT security and your ability to design, implement, and monitor a cybersecurity programme.
This advanced certification is for security professionals with expertise who want to further their careers in roles such as:
- $170,793 for Chief Information Security Officer
- $85,742 for a security administrator
- $100,605 for an IT security engineer
- $111,250 for a senior security consultant
- $82,070 for an information assurance analyst
Requirements: You must have five or more years of cumulative work experience in at least two of the eight cybersecurity domains to take the CISSP exam. Security and Risk Management, Asset Security, Security Architecture and Engineering, Communication and Network Security, Identity and Access Management, Security Assessment and Testing, Security Operations, and Software Development Security are just a few of the topics covered.
You can still take the exam to become an Associate of (ISC)2 if you're new to cybersecurity and don't have the required experience. After passing the exam, you'll have six years to gain the necessary experience to achieve full CISSP certification.
One year of labour is satisfied by a four-year degree in computer science. Part-time jobs and paid internships are also valid options.
Cost: $749
3. CISA: (Certified Information Systems Auditor)
This certification is aimed at information security professionals who work primarily in the areas of audit control, assurance, and security. It equips you with the knowledge and skills needed to manage and control enterprise IT and conduct a thorough security audit. ISACA allows you to demonstrate your experience in identifying security vulnerabilities, devising and implementing controls, and tracking compliance. It's one of the most well-known qualifications in the field of cybersecurity auditing.
The CISA is for IT professionals in their mid-career who want to develop into positions such as:
- $122,254 for an IT audit manager
- $69,083 for a cybersecurity auditor
- $99,372 for an information security analyst
- $93,526 - IT security engineer
- $102,743 for IT project manager
- Manager of Compliance Programs - $92,829
Requirements: At least five years of expertise in IT or IS audit, control, security, or assurance is required. One or two years of experience can be substituted for a two- or four-year degree, respectively.
Cost: Members pay $575, while non-members pay $760.
4. Manager of Information Security Certification (CISM)
You can certify your knowledge in the management side of information security with the CISM certification from ISACA, which covers issues like governance, programme creation, and programme, incident, and risk management.
Earning your CISM could be a smart choice if you want to go from the technical to the managerial side of cybersecurity. The CISM is used in the following jobs:
- $108,353 for an IT manager
- Security officer for information systems - $96,568
- $92,624 - Information Risk Consultant
- $173,387 Director of Information Security
- $119,816 for a data governance manager
Requirements: You must have at least five years of experience in information security management to take the CISM exam. With general information security experience, you can satisfy up to two years of this prerequisite. With another valid certification or a graduate degree in an information security-related discipline, you can also skip one or two years.
Cost: Members pay $575, while non-members pay $760.
5. CompTIA Security+
CompTIA Security+ is a certification programme that certifies you as a security expert. Cryptography, threat management, identity management, network access control, security systems, risk identification, and mitigation are all covered in this certification. It is aimed towards people who are just starting out in the field of information technology.
The certifications you choose will be determined by where you are in your profession, and each person's ideal list will be unique. The final two certificates, for example, are best suited for entry-level IT employees, whereas the CISM and CISSP are designed for more seasoned security experts. There is no better method for an IT professional to become well-rounded than to gradually earn certification in all of the above fields. Even the most seasoned cybersecurity professionals might benefit from a refresher course. Whether it's a newly found cyber threat or a new strategy to combat it, there's always something new to learn. Upskilling not only elevates your status within your company, but it also makes you a more marketable candidate if you decide to move on. Expertise, leverage, and independence are all benefits of upskilling.
The CompTIA Security+ certification is an entry-level security certification that verifies the essential abilities required in any cybersecurity position. Demonstrate your ability to assess an organization's security, monitor and secure cloud, mobile, and internet of things (IoT) environments, comprehend risk and compliance rules and regulations, and identify and respond to security issues with this certification.
Obtaining your Security+ certification can assist you in a variety of positions, including:
- $74,086 for a systems administrator
- $70,531 for a help desk manager
- $109,863 for a security engineer
- $110,152 for a cloud engineer
- $85,742 for a security administrator
- $78,633 for an IT auditor
- $107,597 for a software developer
Requirements: While there are no mandatory prerequisites for taking the Security+ test, it is recommended that you first acquire your Network+ certification and gain at least two years of IT experience with a security focus.
Cost: $370
6. Security Essentials Certification by GIAC (GSEC)
This entry-level security accreditation from the Global Information Assurance Certification (GIAC) is for persons with a background in information systems and networking. This certification verifies your knowledge of active defence, network security, cryptography, incident response, and cloud security.
If you have some IT experience and want to move into cybersecurity, consider taking the GSEC exam. The skills indicated by the GSEC are used in the following job roles:
- $124,638 for IT security manager
- $85,121 for a computer forensic analyst
- $104,116 for a penetration tester
- $85,742 for a security administrator
- $78,633 for an IT auditor
- $116,252 for a software development engineer
Requirements: There are no specific prerequisites for taking the GSEC exam. Get some experience with information systems or computer networking to set yourself up for success.
Cost: $2,499 (includes two practise tests)
7. Certified Systems Security Practitioner (SSCP)
Employers will be able to see that you have the abilities to design, deploy, and maintain a secure IT infrastructure if you have this intermediate security certificate from (ISC)2. The exam assesses knowledge of access controls, risk identification and analysis, security administration, incident response, cryptography, and network, communications, systems, and application security, as well as network, communications, systems, and application security.
The SSCP is for IT professionals who work directly with a company's security systems or assets. This accreditation is suitable for jobs such as:
- $95,997 for a network security engineer
- $74,086 for a system administrator
- $76,112 for a systems engineer
- $77,662 for a security analyst
- $82,167 for database administrator
- $97,516 for a security consultant
Requirements: Candidates must have at least one year of paid job experience in one or more of the testing areas to be eligible for the SSCP. A bachelor's or master's degree in a cybersecurity-related programme can also satisfy this requirement.
Cost: $249
8. Advanced Security Practitioner (CASP+)
It is a certification offered by CompTIA. The CASP+ is for cybersecurity professionals who have demonstrated advanced skills but want to stay in the industry (as opposed to management). Enterprise security domain, risk analysis, software vulnerability, safeguarding cloud and virtualization technologies, and cryptographic approaches are among the advanced subjects covered in the test.
Advanced responsibilities in architecture, risk management, and enterprise security integration may become available as a result of the CASP+. The following are examples of possible job titles:
- $152,732 for a security architect
- $109,863 for a security engineer
- $110,660 for an application security engineer
- $109,766 for technical lead analyst
- $80,475 for a vulnerability analyst
Requirements: There are no formal prerequisites for taking the CASP+ examination. Only experienced cybersecurity workers with at least 10 years of IT administration expertise should take it, according to CompTIA (including five years of broad hands-on experience with security).
Cost: $466
9. Incident Handler with GIAC Certification (GCIH)
The GCIH certifies your knowledge of offensive operations, including as common attack strategies and vectors, as well as your ability to identify, respond, and defend against attacks. Incident handling, computer crime investigation, hacker exploits, and hacker tools are all included in the certification test.
Anyone who works in incident response will benefit from this certification. The following are examples of job titles:
- $92,833 for incident handler
- $152,732 for a security architect
- $74,086 for a system administrator
Requirements:There are no specific prerequisites for taking the GCIH exam, however having a working knowledge of security principles, networking protocols, and the Windows Command Line is a good idea.
Cost: $2,499 (includes two practise tests)
10. Certified Professional in Offensive Security (OSCP)
One of the most sought-after credentials for penetration testers is the OSCP from Offensive Security. The exam assesses your ability to compromise a number of target devices using a variety of exploitation techniques and provide detailed penetration test reports for each attack.
The OSCP is an excellent choice for jobs such as:
- $104,116 for a penetration tester
- $100,742 for ethical hacker
- $65,148 for a threat researcher
- $92,005 for an application security analyst
Requirements: There are no official exam requirements. Networking, Linux, Bash scripting, Perl or Python knowledge, as well as completion of the Penetration Testing with Kali course, are all recommended by Offensive Security.
Cost: $999. (Penetration Testing with Kali Linux (PWK/PEN-200) training, 30 days of lab access, and one test attempt are included in the basic package.)
How to Choose the Right One for You?
Earning a cybersecurity certification can help you authenticate your hard-won abilities and boost your career. When deciding whether certification is best for you, keep the following points in mind.
Your level of knowledge: Begin by obtaining a certification that corresponds to your present skill set. Invest in a certification that you know you'll be able to complete and utilise it to progress to more difficult certifications later in your career. If you're fresh to the field of information technology,
Cost: Obtaining certification often costs several hundred dollars (or more), plus ongoing fees. The correct certification can lead to improved career opportunities and more pay, but it's crucial to invest carefully.
It's always a good idea to ask ahead of time if your employer would assist pay for your certification. According to the (ISC)2 survey, 40% of respondents stated that their company paid for their courses, exams, and fees.
Area of focus: A more generic certification can be a suitable alternative if you're just getting started in cybersecurity or want to progress into a management position. You might decide to specialise as your career progresses. A certification in your concentration area will help potential employers recognise your abilities.
Potential employers: Employers who might be interested: Examine the job descriptions of potential companies (or the job titles you intend to apply for) to determine what certifications are typically required.
Having the correct certifications might help you find work in the field of information security (InfoSec). If you work in information security or cybersecurity, you should be aware of the top network security certifications. Gaining these credentials can help you to achieve success in your career.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Career Progression With PMP For Non Project Managers
Today, the Project Management Profession (PMP) is becoming the most inspiring endeavor for professionals. If you are ready to do something innovative, choosing this profession is an ideal decision. Due to the market demand for this occupation, it is now considered one of the most acceptable occupations. Freshmen in particular who have just finished their studies are more interested in taking advantage of these opportunities; as they like to explore their careers in the most lucrative and challenging way possible.
If you are interested in project management, you can start your career in any area; because project management is necessary for all industries.
If you are looking for job openings in project management in various industries, you have come to the right place. In this article we will discuss the professional perspective of PMPs. Surprisingly, there are a variety of project management career opportunities in major industries such as information technology, banking, construction, IT-based services, and more. The decision is up to the candidates to choose one of these areas based on their choice.
Requirement for PMP, when working in a non-project environment
PMI does not require you to be formally associated with a project to gain the 4500 and 7500 hour project experience. It would be sufficient if you have dealt with various aspects of project management, even non-project work.

Components of Project Management in a Non-Project Environment
Let's learn this with an example. Assuming you are a pure business economist in the IT industry, his day at the office might include:
- Resource planning
- Business planning
- Quality planning
- Cost optimization
- Automation
- Process Improvement
- Benchmark Analysis
- Training new employees
The good news is that any time you spend on these assignments can be documented as project experience, increasing your eligibility for the PMP exam. All you have to do is assign these tasks to the appropriate buckets in the 5 phases of project management. PMI does not verify each candidate's credentials prior to the exam. From all applications received, PMI randomly selects 20% of the applications and reviews them. If your application is selected for an audit, you will need to provide your educational evidence and have your project-related experience validated by a stakeholder involved in the project or work area in the case of an off-project scenario.
Career progression with PMP for non-project managers
Even in a project-free environment, the PMP certification ensures healthy professional development by helping you align company goals with client goals. In PMP training, you will also learn to speak a language that resonates with both your stakeholders and your team members. It also helps you articulate specific aspects of your job responsibilities, such as making the best use of resources and dealing with risks and limitations.
Job opportunities with PMP certification for Non Project Managers
PMP is one of the best certifications that can be obtained regardless of the candidate's industry and employment background. PMP continues to be popular with professionals as it continues to be the high-paying position. Regardless of gender, women who are PMP certified earn more than women who are certified in other fields.
The project management approach requires constant change; Therefore, a company creating projects requires the use of standard and formal project management approaches. Furthermore, the abundance of projects, whether small or large, is continually increasing. For these two reasons, the demands of these skilled workers in the labor market will remain high for a long time to come.
Certified PMPs can be paid up to an average salary of $ 109,405. The most common questions asked by most professions are: "Will the PMP certification support a well-paying job?" Today, recruiters and candidates see PMP certification as a huge benefit. A growing number of applicants have started to enroll in PMP certification courses, showing that they understand the immense value of these certifications and that recruiters prefer their candidacy to non-certified professionals.
Project Management Skills for Non-Project Managers
It is common for professionals who are asked to complete projects to do so in their normal work environment, regardless of whether they have the necessary skills and formal training, such as project managers, to manage and streamline projects in a more efficient way. structured. Managers and knowledge workers unexpectedly slipped into the role of project manager.
Of course, even a layman may know that project management is the process and discipline of end-to-end management tasks within the project life cycle. The project life cycle includes activities such as:-
- Monitoring
- Controlling
- Budgeting
- Planning
- Resource Managing
- Keeping the morale among the project team
It is also difficult that all the activities mentioned above need to be done at the same time to achieve the project objectives on time and with the specified quality. It is also essential to ensure quality and performance with the strategic definition of the organization.
In addition to responsible factors such as project completion and execution, the success of a project also depends on how it was carried out.
Therefore, non-project managers who do not have enough experience as a project manager should be properly trained to become familiar with the tools and techniques necessary to efficiently manage, direct, execute and control projects in the analysis of operations of the day to day.
In general, managers who are not project managers lack the following qualities:
- Scope Creep
- Time Management
- Formal Process or Project Training
- Persuasion skills
The lack of the above attributes increases the potential for project disappointments that cost companies money, time and morale. Therefore, managing projects without the right skills leads to speeches and frustrations. If you plan to manage your projects in a systematic way, knowledge of project management is essential. The PMP certification is the best option to simplify your project management process.
Without the proper project management skills, organizations and managers would find themselves in a chaotic and unpredictable environment over which they have little control. Therefore, the project management certification is essential and necessary for the success of the project.
Benefits as PMP to get an amazing job
- Make your resume more impressive:- Because the PMP certification is widely recognized, candidates must meet certain requirements to become certified. Employers consider achieving these basic principles high, as it requires effort, time and commitment. Therefore, the PMP certification will add astonishing value to the resume of candidates who are PMP certified and planning to pursue a career in project management. In addition, this certification also brings the career of candidates who are already involved in project management and includes the necessary track of experience in the following area.
Most recruiters refer to the PMP certification through the master's degree.
While a master's degree is valuable, the certified recruiter demonstrates that the candidate has proven experience and has passed strict criteria. The PMP qualification provides training in project management in the industry with extensive experience in industrial projects. For this reason, most industries place more importance on this certification than others.
Below are some of the industries that only consider candidates with basic certifications:
- Defense
- Pharmaceuticals
- Financial Services
- Aerospace
PMP Project managers have put in a significant amount of effort and time to obtain PMP certification, which means they are qualified for project management commitment as a profession. Even if you do not want to work as a project manager for the rest of your life, understanding the significance of this certification will help you advance in your career. This demonstrates that there are regulated opportunities for project management available these days, necessitating the PMP certification.
2. Earn Higher Salaries:- Once a certified professional has passed the interview stage, he has a good chance because he will earn more than someone who does not have certification. According to a 2011 survey of thirty thousand project management professionals, PMP professionals in the United States earned an average annual salary of $111, 824, while project managers without the PMP certification earned $97,829 on average. Surprisingly, there is a $14,000 difference.

Image source:- Salary Survey of Project Management Institute, 7th edition
The salary of project management professionals is shown in the table above. In addition, project management professionals with the certification also feel secure and comfortable in their earning capability. According to one study, 76 percent of professionals with certification expected their pay to increase in the coming year, while only 2 percent expected it to decrease. This demonstrates that PMP certification can be sufficient to increase a person's salary range. Some professionals report that their salary was immediately doubled after completing the PMP training course.
Conclusion
In today's industry, project managers can no longer ignore the practise of project management. Even if your present job does not contain project management, having a PMP credential to your name can help you advance your career. However, there is a common misperception that you must be a project manager or at the very least be involved in any project in some way.
They are in charge of establishing the foundations of what is achieved throughout the project lifecycle. In most industries, PMP certification is becoming increasingly important. Since then, it has become a long-term career investment. As discussed above, Project management abilities are in high demand in a variety of industries, including information technology, banking, construction, information technology-enabled services, and much more. Candidates have the option of selecting any of these areas based on their preferences.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
Today, the Project Management Profession (PMP) is becoming the most inspiring endeavor for professionals. If you are ready to do something innovative, choosing this profession is an ideal decision. Due to the market demand for this occupation, it is now considered one of the most acceptable occupations. Freshmen in particular who have just finished their studies are more interested in taking advantage of these opportunities; as they like to explore their careers in the most lucrative and challenging way possible.
If you are interested in project management, you can start your career in any area; because project management is necessary for all industries.
If you are looking for job openings in project management in various industries, you have come to the right place. In this article we will discuss the professional perspective of PMPs. Surprisingly, there are a variety of project management career opportunities in major industries such as information technology, banking, construction, IT-based services, and more. The decision is up to the candidates to choose one of these areas based on their choice.
Requirement for PMP, when working in a non-project environment
PMI does not require you to be formally associated with a project to gain the 4500 and 7500 hour project experience. It would be sufficient if you have dealt with various aspects of project management, even non-project work.
Components of Project Management in a Non-Project Environment
Let's learn this with an example. Assuming you are a pure business economist in the IT industry, his day at the office might include:
- Resource planning
- Business planning
- Quality planning
- Cost optimization
- Automation
- Process Improvement
- Benchmark Analysis
- Training new employees
The good news is that any time you spend on these assignments can be documented as project experience, increasing your eligibility for the PMP exam. All you have to do is assign these tasks to the appropriate buckets in the 5 phases of project management. PMI does not verify each candidate's credentials prior to the exam. From all applications received, PMI randomly selects 20% of the applications and reviews them. If your application is selected for an audit, you will need to provide your educational evidence and have your project-related experience validated by a stakeholder involved in the project or work area in the case of an off-project scenario.
Career progression with PMP for non-project managers
Even in a project-free environment, the PMP certification ensures healthy professional development by helping you align company goals with client goals. In PMP training, you will also learn to speak a language that resonates with both your stakeholders and your team members. It also helps you articulate specific aspects of your job responsibilities, such as making the best use of resources and dealing with risks and limitations.
Job opportunities with PMP certification for Non Project Managers
PMP is one of the best certifications that can be obtained regardless of the candidate's industry and employment background. PMP continues to be popular with professionals as it continues to be the high-paying position. Regardless of gender, women who are PMP certified earn more than women who are certified in other fields.
The project management approach requires constant change; Therefore, a company creating projects requires the use of standard and formal project management approaches. Furthermore, the abundance of projects, whether small or large, is continually increasing. For these two reasons, the demands of these skilled workers in the labor market will remain high for a long time to come.
Certified PMPs can be paid up to an average salary of $ 109,405. The most common questions asked by most professions are: "Will the PMP certification support a well-paying job?" Today, recruiters and candidates see PMP certification as a huge benefit. A growing number of applicants have started to enroll in PMP certification courses, showing that they understand the immense value of these certifications and that recruiters prefer their candidacy to non-certified professionals.
Project Management Skills for Non-Project Managers
It is common for professionals who are asked to complete projects to do so in their normal work environment, regardless of whether they have the necessary skills and formal training, such as project managers, to manage and streamline projects in a more efficient way. structured. Managers and knowledge workers unexpectedly slipped into the role of project manager.
Of course, even a layman may know that project management is the process and discipline of end-to-end management tasks within the project life cycle. The project life cycle includes activities such as:-
- Monitoring
- Controlling
- Budgeting
- Planning
- Resource Managing
- Keeping the morale among the project team
It is also difficult that all the activities mentioned above need to be done at the same time to achieve the project objectives on time and with the specified quality. It is also essential to ensure quality and performance with the strategic definition of the organization.
In addition to responsible factors such as project completion and execution, the success of a project also depends on how it was carried out.
Therefore, non-project managers who do not have enough experience as a project manager should be properly trained to become familiar with the tools and techniques necessary to efficiently manage, direct, execute and control projects in the analysis of operations of the day to day.
In general, managers who are not project managers lack the following qualities:
- Scope Creep
- Time Management
- Formal Process or Project Training
- Persuasion skills
The lack of the above attributes increases the potential for project disappointments that cost companies money, time and morale. Therefore, managing projects without the right skills leads to speeches and frustrations. If you plan to manage your projects in a systematic way, knowledge of project management is essential. The PMP certification is the best option to simplify your project management process.
Without the proper project management skills, organizations and managers would find themselves in a chaotic and unpredictable environment over which they have little control. Therefore, the project management certification is essential and necessary for the success of the project.
Benefits as PMP to get an amazing job
- Make your resume more impressive:- Because the PMP certification is widely recognized, candidates must meet certain requirements to become certified. Employers consider achieving these basic principles high, as it requires effort, time and commitment. Therefore, the PMP certification will add astonishing value to the resume of candidates who are PMP certified and planning to pursue a career in project management. In addition, this certification also brings the career of candidates who are already involved in project management and includes the necessary track of experience in the following area.
Most recruiters refer to the PMP certification through the master's degree.
While a master's degree is valuable, the certified recruiter demonstrates that the candidate has proven experience and has passed strict criteria. The PMP qualification provides training in project management in the industry with extensive experience in industrial projects. For this reason, most industries place more importance on this certification than others.
Below are some of the industries that only consider candidates with basic certifications:
- Defense
- Pharmaceuticals
- Financial Services
- Aerospace
PMP Project managers have put in a significant amount of effort and time to obtain PMP certification, which means they are qualified for project management commitment as a profession. Even if you do not want to work as a project manager for the rest of your life, understanding the significance of this certification will help you advance in your career. This demonstrates that there are regulated opportunities for project management available these days, necessitating the PMP certification.
2. Earn Higher Salaries:- Once a certified professional has passed the interview stage, he has a good chance because he will earn more than someone who does not have certification. According to a 2011 survey of thirty thousand project management professionals, PMP professionals in the United States earned an average annual salary of $111, 824, while project managers without the PMP certification earned $97,829 on average. Surprisingly, there is a $14,000 difference.
Image source:- Salary Survey of Project Management Institute, 7th edition
The salary of project management professionals is shown in the table above. In addition, project management professionals with the certification also feel secure and comfortable in their earning capability. According to one study, 76 percent of professionals with certification expected their pay to increase in the coming year, while only 2 percent expected it to decrease. This demonstrates that PMP certification can be sufficient to increase a person's salary range. Some professionals report that their salary was immediately doubled after completing the PMP training course.
Conclusion
In today's industry, project managers can no longer ignore the practise of project management. Even if your present job does not contain project management, having a PMP credential to your name can help you advance your career. However, there is a common misperception that you must be a project manager or at the very least be involved in any project in some way.
They are in charge of establishing the foundations of what is achieved throughout the project lifecycle. In most industries, PMP certification is becoming increasingly important. Since then, it has become a long-term career investment. As discussed above, Project management abilities are in high demand in a variety of industries, including information technology, banking, construction, information technology-enabled services, and much more. Candidates have the option of selecting any of these areas based on their preferences.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Feasibility Study and Its Importance In Project Management
A Quick Guide to Feasibility Study
A feasibility study is conducted to determine whether or not a given project or system is economically viable. Before embarking on a project involving thousands of resources and costing millions of dollars, executives and the board of directors want to see a feasibility study report. If a large error is made during the decision-making process, it may have an impact on the organization's future performance. As a result, preparing a feasibility study report is essential for determining the project's viability. The sorts of feasibility studies used in project management will be discussed in this article.
A well-designed study should include information such as a description of the product or service, accounting statements, details of operations and management, marketing research and policies, financial data, legal requirements, and tax obligations, as well as a historical background of the business or project. Technical development and project implementation are usually preceded by such research.
Major benefits that feasibility study in project management can provide you
- Project teams' focus is improved.
- Provides pertinent information that aids in making a decision on whether or not to proceed.
- Finds a convincing cause to continue with the project.
- Assists in the decision-making process for projects.
- Determines why proceeding is not a good idea.
- It boosts the success rate by considering numerous parameters.
- The number of company possibilities is reduced.
- New possibilities are discovered.
- Measures a project's ability and likelihood of being completed effectively.
- Potential issues are highlighted.
5 types of Feasibility study in project management
Because a feasibility analysis assesses a project's chances of success, perceived neutrality is a critical aspect in the study's credibility with possible investors and lenders. There are five different types of feasibility studies, each of which examines a different topic, as stated below.
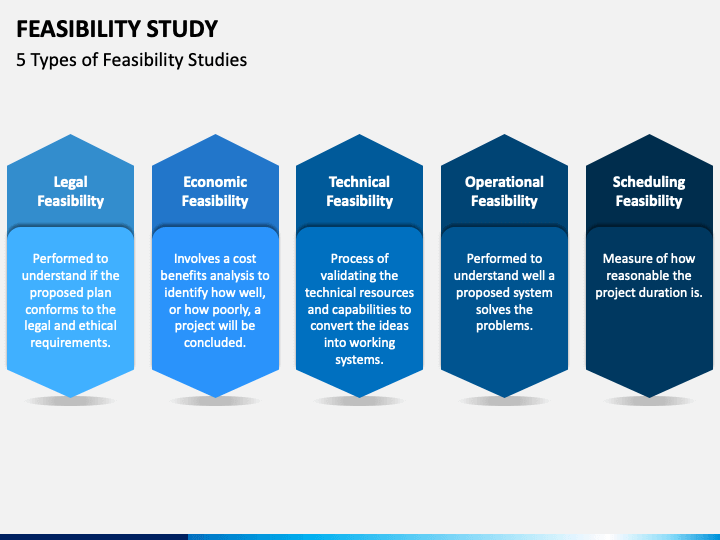
Image Source - https://www.sketchbubble.com/en/presentation-feasibility-study.html
- Legal Feasibility:- This assessment looks into if any component of the proposed project violates any regulations, such as zoning rules, data protection legislation, or social media laws. Assume a company wishes to develop a new office building at a specified location. A feasibility study may discover that the desired location for the company is not designated for that sort of business. That organisation has just saved a lot of time and effort by discovering early on that their idea was not feasible.
- Economic Feasibility:- This evaluation typically includes a cost-benefit analysis of the project, which aids firms in determining the project's viability, cost, and benefits before spending financial resources. It also acts as an objective project review, boosting project credibility by assisting decision-makers in identifying the proposed project's beneficial economic benefits to the organisation.
- Technical Feasibility:- The technological resources accessible to the organisation are the subject of this examination. It aids companies in determining whether technical resources are adequate for the job and whether the technical team is capable of turning concepts into operational systems. The proposed system's hardware, software, and other technical needs are also evaluated for technical viability. An organisation, for example, would not want to try to install Star Trek's transporters in their facility because it is currently not technically feasible.
- Operational Feasibility:- This evaluation entails conducting research to evaluate whether—and to what extent—the organization's needs can be addressed by completing the project. Operational feasibility studies also look at how a project plan meets the requirements specified during the system development requirements analysis phase.
- Scheduling Feasibility:- Scheduling a feasibility evaluation is critical to project success; after all, if the project is not completed on time, it will fail. When scheduling feasibility, a corporation estimates the length of time it will take to complete a project. Following the consideration of all of these elements, the feasibility study can assist in identifying any potential project restrictions, such as:
- External restrictions include logistics, the environment, rules and regulations, and so on.
- Technological, financial, and resource restrictions are examples of internal project constraints.
- Technological, financial, and resource constraints are among the project's internal constraints.
Steps for - How to conduct a feasibility study in Project management
When doing a feasibility study, there are several procedures to take.
- Conduct an introductory analysis - Before making an investment, a preliminary analysis is used to summarise project concepts, outline market circumstances, and identify potential hurdles. You can determine whether the proposal has promise based on the facts gathered in this step. If there are no big stumbling barriers, you can move on to the following phase.
- Define the scope - It's vital to define the project's scope in order to determine the feasibility study's scope. The project's scope will also evaluate the influence it will have on internal stakeholders as well as external clients or customers. It's crucial to think about how the project might affect different parts of the firm.
- Develop a projected income statement - Estimate how much money the project will make and how much money it will take to make that money. The first step in producing a projected income statement is to figure out how much money you have. Analyze and calculate the cost of the required services in order to create income.
- Conduct a market research - One of the most critical phases in a feasibility study is to do market research. A market research project might be carried out by an internal specialist or by an outside agency. The goal of conducting a good survey is to establish accurate revenue projections. Market research is a comprehensive study that includes population trends, demographic characteristics, market volume, opportunity, location, and other factors.
- Roadblocks and alternative solutions - It will research measures to assure the project's success if any potential barriers develop during the investigation.
- Plan business organization and operations - At this stage, corporate organisations and operations are designed in sufficient detail to identify the organization's technological capabilities and operational costs.
- Develop an opening day balance sheet - An opening day balance sheet is a chart that calculates total assets and liabilities on the first day of the firm before it earns money, using Prepaid Expenses, Other Assets, Current Liabilities, and Owners' Equity. The complete capital structure of your company is shown on the opening day balance sheet. Financial ratios are used to measure the project's financial situation.
- Review and analyze - Review all of the work from the previous steps to ensure that you have included all of the relevant information and that nothing needs to be changed. Make a comparison of the charts and information from the previous steps to ensure that everything is in order. Examine the potential dangers that may arise during the project.
- Make a final decision - Make a decision regarding whether the option is viable or not based on the information supplied in the previous steps. You will have adequate inputs to support your decision-making process if all of the preceding phases have been completely completed.
Key Features of a feasibility study for a good project
A project feasibility study evaluates the following topics in project management:
- Time - How long do you think it'll take to finish?
- Risk - What are the dangers of finishing this project? Based on the predicted rewards, is the risk worth the company's money and time?
- Legality - Is the company well-equipped to complete the project in terms of technical resources?
- Budget - Is the organisation financially capable of completing the project, and does the cost-benefit analysis justify proceeding?
- Operational Feasibility - Is the project addressing the organization's needs in its intended scope by resolving issues and/or capturing opportunities?
- Technical capability - Is the company well-equipped to complete the project in terms of technical resources?
Importance of Feasibility study in Project Management
The value of a feasibility study stems from the goal of an organisation to "get it right" before investing resources, time, or money. A feasibility study may unearth fresh ideas that totally alter the scope of a project. It's preferable to make these decisions ahead of time rather than rushing into a project only to discover that it won't work. A feasibility study is usually advantageous to a project since it provides you and other stakeholders with a clear picture of what is being proposed.
Suggestions - Some best practices to conduct project feasibility study
Feasibility studies are unique in that they represent the project's goals and requirements. The following recommendations, on the other hand, can be employed in any feasibility assessment. You might want to try the following, for example:
- Make a preliminary choice about whether or not to go ahead with the strategy.
- Prepare a balance sheet forecast.
- Make an income statement that is projected.
- Make plans for your business, organisation, or operations.
- Conduct a market survey or market research to aid with data collection.
- Analyze and test your data to make sure it's accurate.
- Obtain input on the new concept from the appropriate stakeholders.
Conclusion
Many companies make the mistake of skipping the "feasibility analysis" process and jumping right into the project. In the vast majority of situations, this results in the project's failure. It's important to keep in mind that it's impossible to avoid potential losses if a choice to proceed has been taken without a thorough feasibility analysis. As a result, doing a feasibility study and creating a report for any sort of project that entails risks and uncertainties is a sound business practice.
We hope that this article titled “Importance of Feasibility study in Project Management” has clarified the concept of a feasibility study for you. Explore our library of Project Management articles for additional information, or enroll in our Project Management programme, which covers new trends, developing practises, customised considerations, and fundamental capabilities required of a Project Management expert.
Good luck with your reading!
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
A Quick Guide to Feasibility Study
A feasibility study is conducted to determine whether or not a given project or system is economically viable. Before embarking on a project involving thousands of resources and costing millions of dollars, executives and the board of directors want to see a feasibility study report. If a large error is made during the decision-making process, it may have an impact on the organization's future performance. As a result, preparing a feasibility study report is essential for determining the project's viability. The sorts of feasibility studies used in project management will be discussed in this article.
A well-designed study should include information such as a description of the product or service, accounting statements, details of operations and management, marketing research and policies, financial data, legal requirements, and tax obligations, as well as a historical background of the business or project. Technical development and project implementation are usually preceded by such research.
Major benefits that feasibility study in project management can provide you
- Project teams' focus is improved.
- Provides pertinent information that aids in making a decision on whether or not to proceed.
- Finds a convincing cause to continue with the project.
- Assists in the decision-making process for projects.
- Determines why proceeding is not a good idea.
- It boosts the success rate by considering numerous parameters.
- The number of company possibilities is reduced.
- New possibilities are discovered.
- Measures a project's ability and likelihood of being completed effectively.
- Potential issues are highlighted.
5 types of Feasibility study in project management
Because a feasibility analysis assesses a project's chances of success, perceived neutrality is a critical aspect in the study's credibility with possible investors and lenders. There are five different types of feasibility studies, each of which examines a different topic, as stated below.
Image Source - https://www.sketchbubble.com/en/presentation-feasibility-study.html
- Legal Feasibility:- This assessment looks into if any component of the proposed project violates any regulations, such as zoning rules, data protection legislation, or social media laws. Assume a company wishes to develop a new office building at a specified location. A feasibility study may discover that the desired location for the company is not designated for that sort of business. That organisation has just saved a lot of time and effort by discovering early on that their idea was not feasible.
- Economic Feasibility:- This evaluation typically includes a cost-benefit analysis of the project, which aids firms in determining the project's viability, cost, and benefits before spending financial resources. It also acts as an objective project review, boosting project credibility by assisting decision-makers in identifying the proposed project's beneficial economic benefits to the organisation.
- Technical Feasibility:- The technological resources accessible to the organisation are the subject of this examination. It aids companies in determining whether technical resources are adequate for the job and whether the technical team is capable of turning concepts into operational systems. The proposed system's hardware, software, and other technical needs are also evaluated for technical viability. An organisation, for example, would not want to try to install Star Trek's transporters in their facility because it is currently not technically feasible.
- Operational Feasibility:- This evaluation entails conducting research to evaluate whether—and to what extent—the organization's needs can be addressed by completing the project. Operational feasibility studies also look at how a project plan meets the requirements specified during the system development requirements analysis phase.
- Scheduling Feasibility:- Scheduling a feasibility evaluation is critical to project success; after all, if the project is not completed on time, it will fail. When scheduling feasibility, a corporation estimates the length of time it will take to complete a project. Following the consideration of all of these elements, the feasibility study can assist in identifying any potential project restrictions, such as:
- External restrictions include logistics, the environment, rules and regulations, and so on.
- Technological, financial, and resource restrictions are examples of internal project constraints.
- Technological, financial, and resource constraints are among the project's internal constraints.
Steps for - How to conduct a feasibility study in Project management
When doing a feasibility study, there are several procedures to take.
- Conduct an introductory analysis - Before making an investment, a preliminary analysis is used to summarise project concepts, outline market circumstances, and identify potential hurdles. You can determine whether the proposal has promise based on the facts gathered in this step. If there are no big stumbling barriers, you can move on to the following phase.
- Define the scope - It's vital to define the project's scope in order to determine the feasibility study's scope. The project's scope will also evaluate the influence it will have on internal stakeholders as well as external clients or customers. It's crucial to think about how the project might affect different parts of the firm.
- Develop a projected income statement - Estimate how much money the project will make and how much money it will take to make that money. The first step in producing a projected income statement is to figure out how much money you have. Analyze and calculate the cost of the required services in order to create income.
- Conduct a market research - One of the most critical phases in a feasibility study is to do market research. A market research project might be carried out by an internal specialist or by an outside agency. The goal of conducting a good survey is to establish accurate revenue projections. Market research is a comprehensive study that includes population trends, demographic characteristics, market volume, opportunity, location, and other factors.
- Roadblocks and alternative solutions - It will research measures to assure the project's success if any potential barriers develop during the investigation.
- Plan business organization and operations - At this stage, corporate organisations and operations are designed in sufficient detail to identify the organization's technological capabilities and operational costs.
- Develop an opening day balance sheet - An opening day balance sheet is a chart that calculates total assets and liabilities on the first day of the firm before it earns money, using Prepaid Expenses, Other Assets, Current Liabilities, and Owners' Equity. The complete capital structure of your company is shown on the opening day balance sheet. Financial ratios are used to measure the project's financial situation.
- Review and analyze - Review all of the work from the previous steps to ensure that you have included all of the relevant information and that nothing needs to be changed. Make a comparison of the charts and information from the previous steps to ensure that everything is in order. Examine the potential dangers that may arise during the project.
- Make a final decision - Make a decision regarding whether the option is viable or not based on the information supplied in the previous steps. You will have adequate inputs to support your decision-making process if all of the preceding phases have been completely completed.
Key Features of a feasibility study for a good project
A project feasibility study evaluates the following topics in project management:
- Time - How long do you think it'll take to finish?
- Risk - What are the dangers of finishing this project? Based on the predicted rewards, is the risk worth the company's money and time?
- Legality - Is the company well-equipped to complete the project in terms of technical resources?
- Budget - Is the organisation financially capable of completing the project, and does the cost-benefit analysis justify proceeding?
- Operational Feasibility - Is the project addressing the organization's needs in its intended scope by resolving issues and/or capturing opportunities?
- Technical capability - Is the company well-equipped to complete the project in terms of technical resources?
Importance of Feasibility study in Project Management
The value of a feasibility study stems from the goal of an organisation to "get it right" before investing resources, time, or money. A feasibility study may unearth fresh ideas that totally alter the scope of a project. It's preferable to make these decisions ahead of time rather than rushing into a project only to discover that it won't work. A feasibility study is usually advantageous to a project since it provides you and other stakeholders with a clear picture of what is being proposed.
Suggestions - Some best practices to conduct project feasibility study
Feasibility studies are unique in that they represent the project's goals and requirements. The following recommendations, on the other hand, can be employed in any feasibility assessment. You might want to try the following, for example:
- Make a preliminary choice about whether or not to go ahead with the strategy.
- Prepare a balance sheet forecast.
- Make an income statement that is projected.
- Make plans for your business, organisation, or operations.
- Conduct a market survey or market research to aid with data collection.
- Analyze and test your data to make sure it's accurate.
- Obtain input on the new concept from the appropriate stakeholders.
Conclusion
Many companies make the mistake of skipping the "feasibility analysis" process and jumping right into the project. In the vast majority of situations, this results in the project's failure. It's important to keep in mind that it's impossible to avoid potential losses if a choice to proceed has been taken without a thorough feasibility analysis. As a result, doing a feasibility study and creating a report for any sort of project that entails risks and uncertainties is a sound business practice.
We hope that this article titled “Importance of Feasibility study in Project Management” has clarified the concept of a feasibility study for you. Explore our library of Project Management articles for additional information, or enroll in our Project Management programme, which covers new trends, developing practises, customised considerations, and fundamental capabilities required of a Project Management expert.
Good luck with your reading!
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
How to Handle Project Monitoring and Controlling Processes Perfectly
An organization's project manager is in charge of planning, organising, and steering a project to completion. Before a project can begin, the management must assess the final outcome and estimate the necessary resources and costs, as well as create a budget, assign work, and set a deadline. The project can only begin after the pre-planning phase has been drawn out and completed.
Nowadays, successfully monitoring and controlling a project is a difficult endeavour. I'm sure each of us uses a variety of approaches to maintain project control. However, without this control, about 70% of the project fails catastrophically. And if the project is done effectively, either you spent more money (i.e., over-budgeted) or you spent more time (i.e., under-budgeted) (i.e., behind schedule). Both of these scenarios are bad for a project manager. So, the bottom line is, what should the project manager do to save the project from this awful situation? Controlling the project's pricing, schedule, and scope is a difficult task. These three project restrictions will inevitably cause issues for your project. Be on the lookout! You're doing fantastic if you can keep these three baselines (scope baselines, schedule baselines, and cost performance baselines) in good shape.
Handle Project Monitoring and Controlling Processes:
As a project manager, you take on a significant amount of responsibility that can feel more daunting than rewarding at times. When successful project monitoring and control are a crucial component of your job responsibilities, however, it's critical to develop and refine project monitoring and control best practises.

- Control risk -
Risk can occur at any time and in any part of your project. You can't state as a project manager that you'll solely check risk during the monitoring and controlling stage. Clearly not!!! Risk should be assessed as soon as the project is launched. For the project manager, it is a never-ending task.
- Control schedule and control cost -
You should be able to regulate the schedule and expense of your project using Earned Value Management (EVM). You know your CPI (Cost Performance Index) and SPI (Schedule Performance Index), and you can monitor and control the project based on the CPI and SPI results. If your CPI is positive or greater than 1, you are doing well in terms of project costs, and if your SPI is positive or greater than 1, you are doing well in terms of schedule.
- Perform quality control -
Before sending the product to the customer, double-check that you are delivering the goods in the quality that the consumer expects. You can use a variety of quality tools or processes to accomplish this, such as Root Cause Analysis, Pareto Chart, Control Chart, Histograms, and so on.
- Administer Procurement -
You must keep every relevant stakeholder up to speed on the project status because you are managing a major project with many stakeholders. Specifically, you must update the project progress report with information such as: where are you in the project's development? What are the projections for your project?
- Report Performance -
You must keep every relevant stakeholder up to speed on the project status because you are managing a major project with many stakeholders. Specifically, you must update the project progress report with information such as: where are you in the project's development? What are the projections for your project?
- Verify scope and control scope -
In most cases, scope verification happens after quality control. When quality control approves your project deliverable, it will be moved to the verify scope step. Your customer will check the scope to see if the deliverable meets all of the requirements, and if it does, the deliverable will be moved to the customer's site. If not, the deliverable will have to be revisited throughout the production stage. You should maintain scope control throughout the project life cycle as a project manager. It's not as if you start controlling the product once the deliverable is complete; it's an ongoing process. You should take extra precautions to ensure that the scope requirement does not escape your grasp.
- Perform integrated change control & Monitor and Control Project work -
ollowing project planning, you must begin working on the project in accordance with the plan, and it is now imperative that you double-check that you are working in the same manner as intended. Because you planned your project based on the information you had at the time (Rolling Wave Planning), it's inevitable that it will alter as work goes (which is why planning is iterative and gradually elaborated). Good project managers usually try to avoid modifications and, if they do occur, govern them efficiently by balancing the baselines. Discuss your options with the consultants, other SMEs, senior management, or any other project stakeholders, including your customer. Change is necessary, but it is not always essential. Change requests that have nothing to do with the project's requirements should be ignored.
- Find out the exceptions -
Finding any deviations from established processes would be simple with the right monitoring tools. However, relying too heavily on these technologies might lead to blind spots, allowing potential dangers and concerns to go unnoticed. So be on the alert for any problems and have a solid contingency plan in place, because despite thorough monitoring and control, unexpected events can occur.
- Try to be flexible -
It's pointless to monitor a project if you're unwilling to make changes to the original goals. These modifications may be minor or, depending on the circumstances, may require you to re-plan the entire project. The fundamental goal in either scenario is to complete the project and the duties as efficiently as feasible.
- Use correct tools -
Using project management software is the most effective way to apply project monitoring and control techniques. The ideal way to go is to use Earned Value Analysis (EVA), Project Evaluation and Review Technique (PERT), Gantt Charts, and other tools early on in the project. Tools for project collaboration and secure communications can also help with project monitoring and control.
- Make the project more engaging -
With visual clues, better engagement, and collaboration, tools may make the tedious process of monitoring and regulating more appealing. The use of Kanban can aid in project management efficiency. The emphasis on visual involvement can help both the workers and the project manager participate more actively. Because, let's face it, who has time to read long, cluttered reports?
- Setup project parameters -
icromanaging every facet of a project is difficult, if not impossible. What you require is a method for determining when you must intervene. Setting up monitoring milestones with tools like CPM or Gantt Charts can help you set up goalposts from which you can track the project's overall development.
- Make budgets and forecast -
For milestone management and project monitoring, project forecasting and budgeting are useful tools. You can use forecasting to answer a variety of key issues, such as when the best time is to complete a project, how much a specific activity will cost, and how long it will take. Furthermore, with proper forecasting, you'll know ahead of time what kind of adjustments you'll need to make in terms of human resources, optimal workstations, and so on during a project. Going into a project blind might leave your project insecure and without a context to monitor and measure its progress against. You'll be able to prioritise key actions if you have precisely defined deliverables and know how much slake time you'll have.
Why is it so important to control and monitor projects?
When it comes to project management, any competent project manager will tell you that fulfilling deadlines isn't the only factor to consider. It's just as crucial how you meet deadlines as it is how you achieve them. Monitoring and controlling are the most effective tools for assessing real performance and making informed decisions to guarantee quality standards are met. Managers can take decisive and corrective action with updated information to avoid a crisis and be aware of any potential opportunity that may arise during the work process. This is accomplished by providing project managers with status updates and overseeing project operations, allowing them to achieve a balance between time, cost, quality, and budget.
Conclusion
In an ideal world, all of your projects would run smoothly. Everything would be finished on schedule and on budget. In reality, however, employees may miss deadlines due to personal emergencies, external stakeholders may withdraw without explanation, and so on. You can discover and minimise concerns that could affect the project scope, quality, timetable, or budget by using project monitoring and assessment. After that, you can utilise the information to improve processes for future projects. Monitoring and controlling project work entails comparing actual project performance to project management activities that have been planned. It can primarily be seen as a control function that occurs at all stages of a project, from inception to completion. Monitoring and controlling project activities is a relatively simple undertaking for small projects. Project Management, on the other hand, is more stringently necessary for major projects, where the project manager must make a systematic effort to monitor and regulate how the processes are progressing. In huge projects, he or she will not be personally involved in project activities.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
An organization's project manager is in charge of planning, organising, and steering a project to completion. Before a project can begin, the management must assess the final outcome and estimate the necessary resources and costs, as well as create a budget, assign work, and set a deadline. The project can only begin after the pre-planning phase has been drawn out and completed.
Nowadays, successfully monitoring and controlling a project is a difficult endeavour. I'm sure each of us uses a variety of approaches to maintain project control. However, without this control, about 70% of the project fails catastrophically. And if the project is done effectively, either you spent more money (i.e., over-budgeted) or you spent more time (i.e., under-budgeted) (i.e., behind schedule). Both of these scenarios are bad for a project manager. So, the bottom line is, what should the project manager do to save the project from this awful situation? Controlling the project's pricing, schedule, and scope is a difficult task. These three project restrictions will inevitably cause issues for your project. Be on the lookout! You're doing fantastic if you can keep these three baselines (scope baselines, schedule baselines, and cost performance baselines) in good shape.
Handle Project Monitoring and Controlling Processes:
As a project manager, you take on a significant amount of responsibility that can feel more daunting than rewarding at times. When successful project monitoring and control are a crucial component of your job responsibilities, however, it's critical to develop and refine project monitoring and control best practises.
- Control risk -
Risk can occur at any time and in any part of your project. You can't state as a project manager that you'll solely check risk during the monitoring and controlling stage. Clearly not!!! Risk should be assessed as soon as the project is launched. For the project manager, it is a never-ending task.
- Control schedule and control cost -
You should be able to regulate the schedule and expense of your project using Earned Value Management (EVM). You know your CPI (Cost Performance Index) and SPI (Schedule Performance Index), and you can monitor and control the project based on the CPI and SPI results. If your CPI is positive or greater than 1, you are doing well in terms of project costs, and if your SPI is positive or greater than 1, you are doing well in terms of schedule.
- Perform quality control -
Before sending the product to the customer, double-check that you are delivering the goods in the quality that the consumer expects. You can use a variety of quality tools or processes to accomplish this, such as Root Cause Analysis, Pareto Chart, Control Chart, Histograms, and so on.
- Administer Procurement -
You must keep every relevant stakeholder up to speed on the project status because you are managing a major project with many stakeholders. Specifically, you must update the project progress report with information such as: where are you in the project's development? What are the projections for your project?
- Report Performance -
You must keep every relevant stakeholder up to speed on the project status because you are managing a major project with many stakeholders. Specifically, you must update the project progress report with information such as: where are you in the project's development? What are the projections for your project?
- Verify scope and control scope -
In most cases, scope verification happens after quality control. When quality control approves your project deliverable, it will be moved to the verify scope step. Your customer will check the scope to see if the deliverable meets all of the requirements, and if it does, the deliverable will be moved to the customer's site. If not, the deliverable will have to be revisited throughout the production stage. You should maintain scope control throughout the project life cycle as a project manager. It's not as if you start controlling the product once the deliverable is complete; it's an ongoing process. You should take extra precautions to ensure that the scope requirement does not escape your grasp.
- Perform integrated change control & Monitor and Control Project work -
ollowing project planning, you must begin working on the project in accordance with the plan, and it is now imperative that you double-check that you are working in the same manner as intended. Because you planned your project based on the information you had at the time (Rolling Wave Planning), it's inevitable that it will alter as work goes (which is why planning is iterative and gradually elaborated). Good project managers usually try to avoid modifications and, if they do occur, govern them efficiently by balancing the baselines. Discuss your options with the consultants, other SMEs, senior management, or any other project stakeholders, including your customer. Change is necessary, but it is not always essential. Change requests that have nothing to do with the project's requirements should be ignored.
- Find out the exceptions -
Finding any deviations from established processes would be simple with the right monitoring tools. However, relying too heavily on these technologies might lead to blind spots, allowing potential dangers and concerns to go unnoticed. So be on the alert for any problems and have a solid contingency plan in place, because despite thorough monitoring and control, unexpected events can occur.
- Try to be flexible -
It's pointless to monitor a project if you're unwilling to make changes to the original goals. These modifications may be minor or, depending on the circumstances, may require you to re-plan the entire project. The fundamental goal in either scenario is to complete the project and the duties as efficiently as feasible.
- Use correct tools -
Using project management software is the most effective way to apply project monitoring and control techniques. The ideal way to go is to use Earned Value Analysis (EVA), Project Evaluation and Review Technique (PERT), Gantt Charts, and other tools early on in the project. Tools for project collaboration and secure communications can also help with project monitoring and control.
- Make the project more engaging -
With visual clues, better engagement, and collaboration, tools may make the tedious process of monitoring and regulating more appealing. The use of Kanban can aid in project management efficiency. The emphasis on visual involvement can help both the workers and the project manager participate more actively. Because, let's face it, who has time to read long, cluttered reports?
- Setup project parameters -
icromanaging every facet of a project is difficult, if not impossible. What you require is a method for determining when you must intervene. Setting up monitoring milestones with tools like CPM or Gantt Charts can help you set up goalposts from which you can track the project's overall development.
- Make budgets and forecast -
For milestone management and project monitoring, project forecasting and budgeting are useful tools. You can use forecasting to answer a variety of key issues, such as when the best time is to complete a project, how much a specific activity will cost, and how long it will take. Furthermore, with proper forecasting, you'll know ahead of time what kind of adjustments you'll need to make in terms of human resources, optimal workstations, and so on during a project. Going into a project blind might leave your project insecure and without a context to monitor and measure its progress against. You'll be able to prioritise key actions if you have precisely defined deliverables and know how much slake time you'll have.
Why is it so important to control and monitor projects?
When it comes to project management, any competent project manager will tell you that fulfilling deadlines isn't the only factor to consider. It's just as crucial how you meet deadlines as it is how you achieve them. Monitoring and controlling are the most effective tools for assessing real performance and making informed decisions to guarantee quality standards are met. Managers can take decisive and corrective action with updated information to avoid a crisis and be aware of any potential opportunity that may arise during the work process. This is accomplished by providing project managers with status updates and overseeing project operations, allowing them to achieve a balance between time, cost, quality, and budget.
Conclusion
In an ideal world, all of your projects would run smoothly. Everything would be finished on schedule and on budget. In reality, however, employees may miss deadlines due to personal emergencies, external stakeholders may withdraw without explanation, and so on. You can discover and minimise concerns that could affect the project scope, quality, timetable, or budget by using project monitoring and assessment. After that, you can utilise the information to improve processes for future projects. Monitoring and controlling project work entails comparing actual project performance to project management activities that have been planned. It can primarily be seen as a control function that occurs at all stages of a project, from inception to completion. Monitoring and controlling project activities is a relatively simple undertaking for small projects. Project Management, on the other hand, is more stringently necessary for major projects, where the project manager must make a systematic effort to monitor and regulate how the processes are progressing. In huge projects, he or she will not be personally involved in project activities.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
The Importance of Defining Project Acceptance Criteria in Your Projects
Acceptance criteria are a formal list that fully narrates user requirements as well as all product scenarios considered. It clearly describes the conditions under which the user requirements are desired, removing any uncertainty about the client's expectations and misunderstandings.
This approach states the client's intent rather than the solution; it is up to the team to understand them, ask for clarification where necessary, and find the solution.
What is a project acceptance criteria?
Performance requirements and necessary conditions must be completed before project deliverables are accepted, according to project acceptance standards. They specify the circumstances under which the user will accept the project's final output. They are benchmarks against which we may assess, attain, and demonstrate to our clients that our task is finished.

Examples of Project Acceptance criteria
- The testing of backups and restores has been done successfully.
- The user acceptability testing (UAT) has been completed, and the Senior User/Project Executive has given his approval.
- All of the specifications have been legally approved.
- The Business Continuity Plan (BCP) is in place to be used in the event that the IT system goes down for any reason.
What Are the Benefits of a Well-Defined Set of Acceptance Criteria in Your Projects?
- Avoid miscommunication on internal projects -
If the client is internal, developing a clearly defined set of acceptance criteria will allow you to avoid political maneuvering and miscommunication. I had the opportunity to manage an application development project for our organization's testing horizon a few years ago. The web application was created to provide clients and senior management with a wealth of information about the business of this particular horizontal. One of the most difficult aspects of these projects was managing communications with a geographically dispersed team based in different cities' development centers. The majority of the Stakeholders on this project (including myself) volunteered for this project in addition to our regular responsibilities. As a result, many stakeholders found it difficult to contribute to the project while working full-time. As a result, gaining a common, clear, and shared understanding among the stakeholders on several issues in the project, including requirements gathering, was difficult. This was one of the reasons it took us nearly a month to gather a clear set of requirements and acceptance criteria, then get it approved by the project's VP, who was also the project sponsor. Another issue was that the end product was perceived differently by all of the primary stakeholders, including business analysts, testing experts, and testing managers.
- Set the client’s expectation level -
Your project's success or failure is determined by the team's ability to meet the clients' documented or perceived acceptance criteria. You will be able to set the client's expectation level and lay the groundwork for their perception of the completed product if you have a clearly defined set of acceptance criteria. Inadequate or missing acceptance criteria can result in low customer satisfaction, missed delivery dates, and cost overruns during development. For example, on the previously mentioned project, one of the acceptance criteria we worked on was whether performance testing was performed to evaluate the SharePoint application against the agreed-upon performance criteria. This would determine whether or not the expected response time was met. Despite a slight increase in the number of users worldwide, the SharePoint application's response times have been drastically reduced in recent years. For example, on the previously mentioned project, one of the acceptance criteria we worked on was whether performance testing was performed to evaluate the SharePoint application against the agreed-upon performance criteria. This would determine whether or not the expected response time was met. Despite a slight increase in the number of users worldwide, the SharePoint application's response times have been drastically reduced in recent years.
- Make the difference between getting paid and not getting paid on projects where the client pays for deliverables -
Acceptance criteria are commonly used in projects where the client pays for deliverables or the completion of project phases. You should make sure that the acceptance criteria you develop are relevant to the deliverables, binary (either acceptable or not), measurable or tangible (whenever possible), and tied to payments (whenever appropriate). Clients have been known to refuse to sign off on deliverables for two legitimate reasons: either the project results did not meet their needs, or they were unclear about their needs. You will protect yourself, your project team, and your company by working toward a clearly defined set of acceptance criteria before beginning work on your deliverables. Because the project sponsor is in charge of approving the final product, they are also in charge of approving the acceptance criteria. If the acceptance criteria are met, there should be no reason for the sponsor not to approve and accept the final product.
Importance of Acceptance criteria
Acceptance criteria are an essential component of every user story on which an agile team works. It clearly defines the scope, desired outcomes, and testing criteria for pieces of functionality being worked on by the delivery team. The process of developing and agreeing on acceptance criteria is also a valuable opportunity for developers and product to communicate.
What exactly does the Acceptance Criteria Specification entail?
If you want to properly define the described concept, keep in mind that the end product should be as expected by the client and meet the primary requirements. As a result, it must be executable, and in order for this to happen, it must be written in clear and simple language that can be easily translated to manual or automated test cases with no ambiguity about the expected output.
How will you document project acceptance criteria?
The acceptance criteria are contained in the project scope statement and the requirements document. Acceptance criteria are frequently regarded as a critical component of contract agreements for external projects.
How to write criteria for Acceptance?
Because this management technique is primarily concerned with the client and the team, it is expected to be written by one of them. However, the client is the one who writes the majority of the time, especially if they have adequate knowledge of software development and writing sustainability criteria. Then a team member reviews it to ensure that it is well-documented and that there are no technical misunderstandings that could impede proper software development. In the event that a client is unfamiliar with criteria writing or software development, they can delegate the task to a technical expert such as a project manager, requirements analyst, or product owner. It would be confusing to write acceptance criteria after development has begun. Before the project begins, requirements are documented and completed, and the team and the client agree on the lowest yield that will meet the client's needs.
Suggestions on writing -
- You must begin by describing achievable and sensible information, just as you would with any process's goal. It should provide the bare minimum of functionality for the product while leaving room for outcome flexibility. User acceptance criteria should not be overestimated or underestimated, but should be set at a reasonable level.
- The main points are well detailed and defined so that team members can easily understand what is expected of them and apply the information in the development.
- Project acceptance criteria should include a proper perceived measurement that will be used to track the progress of product development.
- Every criterion should be agreed upon by the client and the team. The two parties would have different solutions to the same problem, but this approach requires both to agree on a single solution.
- In the same way that the project is divided into tasks using the sustainability criteria, you should have a reference checklist to ensure that the user story is covered.
The Impact of Acceptance Criteria on the Development Process
It is uncommon for the software development process to proceed as planned from start to finish, especially for complex products. Nonetheless, making numerous changes to the process can result in a significant increase in costs and the consumption of more time than anticipated. However, with the help of the product acceptance criteria, the team is able to move more quickly and fluidly because the project scope and end product are well documented. The team and the client can easily assess the software development progress and look for any errors, which they can easily correct if any exist.
Conclusion
Acceptance criteria are a set of conditions that must be met before a project can be considered complete and the client accepts the project deliverables. The project team can benefit from clearly established acceptance criteria in a variety of ways, including:
- Defining the client's expectations for the final output.
- Measuring, achieving, and demonstrating that the work is finished to your clients.
- Obtaining formal signatures from the client on the project's deliverables.
- Protecting yourself and your business from concerns such as client non-payment.
Internal projects might also benefit from clearly stated acceptance criteria to avoid misinterpretation and political manipulation. Now you know why they're included in the project scope statement and requirement documents, as well as in the contractual agreement with clients.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
Acceptance criteria are a formal list that fully narrates user requirements as well as all product scenarios considered. It clearly describes the conditions under which the user requirements are desired, removing any uncertainty about the client's expectations and misunderstandings.
This approach states the client's intent rather than the solution; it is up to the team to understand them, ask for clarification where necessary, and find the solution.
What is a project acceptance criteria?
Performance requirements and necessary conditions must be completed before project deliverables are accepted, according to project acceptance standards. They specify the circumstances under which the user will accept the project's final output. They are benchmarks against which we may assess, attain, and demonstrate to our clients that our task is finished.
Examples of Project Acceptance criteria
- The testing of backups and restores has been done successfully.
- The user acceptability testing (UAT) has been completed, and the Senior User/Project Executive has given his approval.
- All of the specifications have been legally approved.
- The Business Continuity Plan (BCP) is in place to be used in the event that the IT system goes down for any reason.
What Are the Benefits of a Well-Defined Set of Acceptance Criteria in Your Projects?
- Avoid miscommunication on internal projects -
If the client is internal, developing a clearly defined set of acceptance criteria will allow you to avoid political maneuvering and miscommunication. I had the opportunity to manage an application development project for our organization's testing horizon a few years ago. The web application was created to provide clients and senior management with a wealth of information about the business of this particular horizontal. One of the most difficult aspects of these projects was managing communications with a geographically dispersed team based in different cities' development centers. The majority of the Stakeholders on this project (including myself) volunteered for this project in addition to our regular responsibilities. As a result, many stakeholders found it difficult to contribute to the project while working full-time. As a result, gaining a common, clear, and shared understanding among the stakeholders on several issues in the project, including requirements gathering, was difficult. This was one of the reasons it took us nearly a month to gather a clear set of requirements and acceptance criteria, then get it approved by the project's VP, who was also the project sponsor. Another issue was that the end product was perceived differently by all of the primary stakeholders, including business analysts, testing experts, and testing managers.
- Set the client’s expectation level -
Your project's success or failure is determined by the team's ability to meet the clients' documented or perceived acceptance criteria. You will be able to set the client's expectation level and lay the groundwork for their perception of the completed product if you have a clearly defined set of acceptance criteria. Inadequate or missing acceptance criteria can result in low customer satisfaction, missed delivery dates, and cost overruns during development. For example, on the previously mentioned project, one of the acceptance criteria we worked on was whether performance testing was performed to evaluate the SharePoint application against the agreed-upon performance criteria. This would determine whether or not the expected response time was met. Despite a slight increase in the number of users worldwide, the SharePoint application's response times have been drastically reduced in recent years. For example, on the previously mentioned project, one of the acceptance criteria we worked on was whether performance testing was performed to evaluate the SharePoint application against the agreed-upon performance criteria. This would determine whether or not the expected response time was met. Despite a slight increase in the number of users worldwide, the SharePoint application's response times have been drastically reduced in recent years.
- Make the difference between getting paid and not getting paid on projects where the client pays for deliverables -
Acceptance criteria are commonly used in projects where the client pays for deliverables or the completion of project phases. You should make sure that the acceptance criteria you develop are relevant to the deliverables, binary (either acceptable or not), measurable or tangible (whenever possible), and tied to payments (whenever appropriate). Clients have been known to refuse to sign off on deliverables for two legitimate reasons: either the project results did not meet their needs, or they were unclear about their needs. You will protect yourself, your project team, and your company by working toward a clearly defined set of acceptance criteria before beginning work on your deliverables. Because the project sponsor is in charge of approving the final product, they are also in charge of approving the acceptance criteria. If the acceptance criteria are met, there should be no reason for the sponsor not to approve and accept the final product.
Importance of Acceptance criteria
Acceptance criteria are an essential component of every user story on which an agile team works. It clearly defines the scope, desired outcomes, and testing criteria for pieces of functionality being worked on by the delivery team. The process of developing and agreeing on acceptance criteria is also a valuable opportunity for developers and product to communicate.
What exactly does the Acceptance Criteria Specification entail?
If you want to properly define the described concept, keep in mind that the end product should be as expected by the client and meet the primary requirements. As a result, it must be executable, and in order for this to happen, it must be written in clear and simple language that can be easily translated to manual or automated test cases with no ambiguity about the expected output.
How will you document project acceptance criteria?
The acceptance criteria are contained in the project scope statement and the requirements document. Acceptance criteria are frequently regarded as a critical component of contract agreements for external projects.
How to write criteria for Acceptance?
Because this management technique is primarily concerned with the client and the team, it is expected to be written by one of them. However, the client is the one who writes the majority of the time, especially if they have adequate knowledge of software development and writing sustainability criteria. Then a team member reviews it to ensure that it is well-documented and that there are no technical misunderstandings that could impede proper software development. In the event that a client is unfamiliar with criteria writing or software development, they can delegate the task to a technical expert such as a project manager, requirements analyst, or product owner. It would be confusing to write acceptance criteria after development has begun. Before the project begins, requirements are documented and completed, and the team and the client agree on the lowest yield that will meet the client's needs.
Suggestions on writing -
- You must begin by describing achievable and sensible information, just as you would with any process's goal. It should provide the bare minimum of functionality for the product while leaving room for outcome flexibility. User acceptance criteria should not be overestimated or underestimated, but should be set at a reasonable level.
- The main points are well detailed and defined so that team members can easily understand what is expected of them and apply the information in the development.
- Project acceptance criteria should include a proper perceived measurement that will be used to track the progress of product development.
- Every criterion should be agreed upon by the client and the team. The two parties would have different solutions to the same problem, but this approach requires both to agree on a single solution.
- In the same way that the project is divided into tasks using the sustainability criteria, you should have a reference checklist to ensure that the user story is covered.
The Impact of Acceptance Criteria on the Development Process
It is uncommon for the software development process to proceed as planned from start to finish, especially for complex products. Nonetheless, making numerous changes to the process can result in a significant increase in costs and the consumption of more time than anticipated. However, with the help of the product acceptance criteria, the team is able to move more quickly and fluidly because the project scope and end product are well documented. The team and the client can easily assess the software development progress and look for any errors, which they can easily correct if any exist.
Conclusion
Acceptance criteria are a set of conditions that must be met before a project can be considered complete and the client accepts the project deliverables. The project team can benefit from clearly established acceptance criteria in a variety of ways, including:
- Defining the client's expectations for the final output.
- Measuring, achieving, and demonstrating that the work is finished to your clients.
- Obtaining formal signatures from the client on the project's deliverables.
- Protecting yourself and your business from concerns such as client non-payment.
Internal projects might also benefit from clearly stated acceptance criteria to avoid misinterpretation and political manipulation. Now you know why they're included in the project scope statement and requirement documents, as well as in the contractual agreement with clients.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Top 10 Reasons Why You Should Learn Cyber Security
In recent years, cybersecurity has emerged as a crucial sector of job growth, owing to an inflow of people interested in pursuing a career in the field. Even so, some people are still debating whether or not they should plunge into the unknown waters of Cybersecurity as a career. This blog, which addresses the "Top 10 Reasons To Learn Cybersecurity," should undoubtedly assist you in making your decision.
Here are Top 10 Reasons to learn Cyber Security:
- Fat Pay Cheques -
'Money makes the world go round,' I believe we can all agree. With tales of new cyber attacks in the news virtually every week, the world has understood the critical relevance of cybersecurity. Faced with cybercrime, businesses and government organisations are looking for professionals who can defend their systems from hackers – and they're willing to pay top dollar and provide extensive training and development. Anyone interested in pursuing a career in cybersecurity should consider the following:
- Cyber security salaries have a higher growth potential than salaries in 90% of other businesses.
- Senior security experts can earn significantly more than the average median.
- Earnings are determined by merit rather than your gender, age, or race.

- A job that is never dull -
A job in cybersecurity is not and cannot be static and stale due to the uncertain nature of the future. On a regular basis, you will be tested. There will be fresh and unexpected setbacks, as well as incredible and unexpected discoveries. One thing is certain: attackers will continue to develop new exploits on a regular basis, and it is your obligation to come up with innovative and efficient solutions to the problems that arise. You'll be solving new riddles, fighting new monsters, and supporting new activities on a regular basis as a cybersecurity professional. So, if you become bored easily when things become tedious, fear not: Cybersecurity is never dull!

- A mixed bag of industries to select -
Unlike the majority of the professional world, you are not limited to a single industry as a cybersecurity specialist. Many sectors are undergoing digital transformation. We are in the midst of a digital revolution, thanks to breakthroughs in the fields of IoT, Big Data, Automation, and Cloud Computing. As a result, becoming a cybersecurity expert does not preclude you from working in a hospital, school, government agency, or top-secret military organisation. Almost everyone wants to be secure on the digital front, thus the gates are wide open.
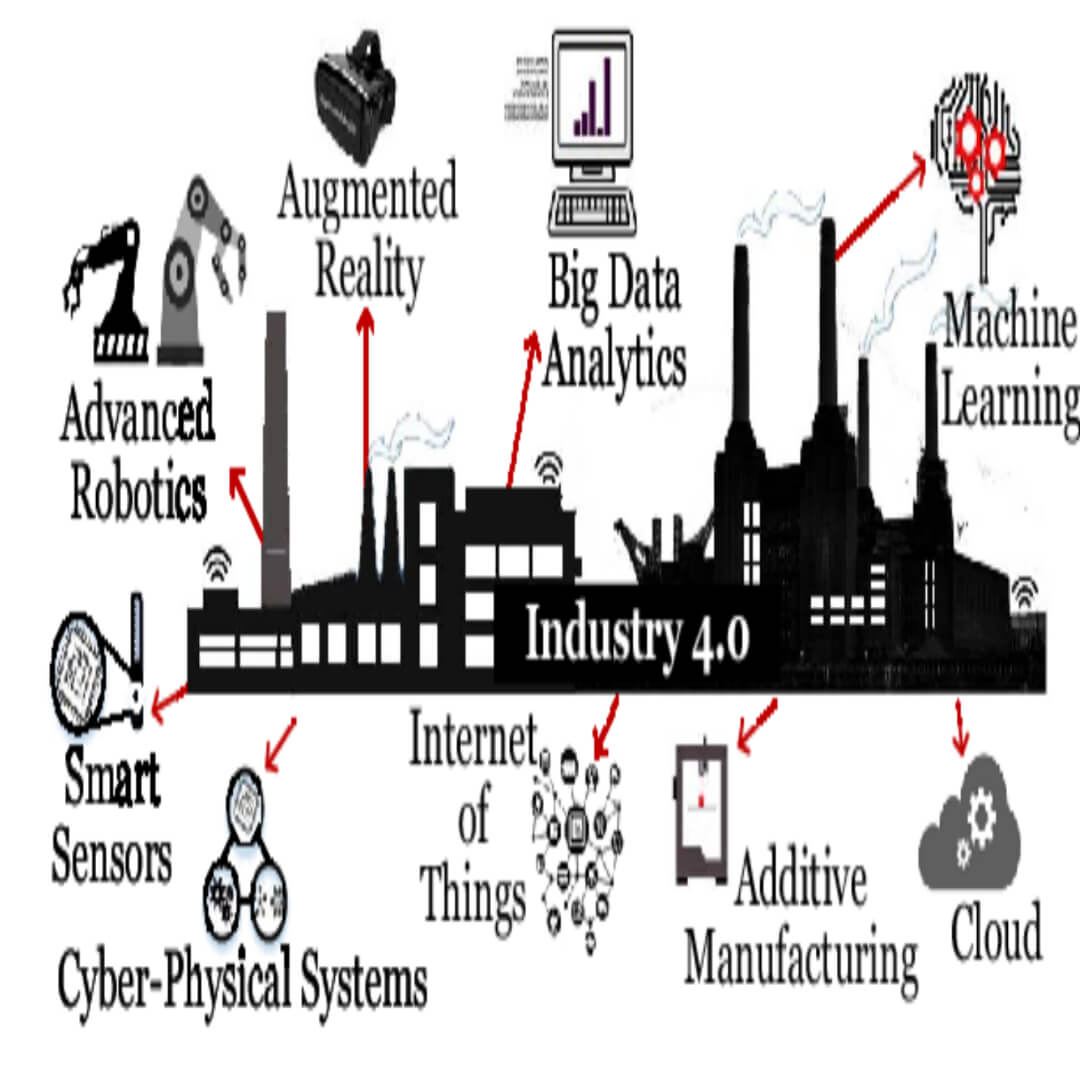
- Innumerable Opportunities -
There are over a million businesses in the world, spanning across a wide range of sectors and industries, and the majority of them now have one thing in common: the necessity for an internet connection. The information security industry employs approximately 400,000 people, and demand for cyber capabilities is increasing rapidly in all types of businesses and government agencies. So, whether you want to work in sports or fashion, media or emergency services, banking or retail, cyber skills could be your ticket to success. After all, everyone needs someone to protect their critical data.

- Limitless potential for personal growth -
Cyber attacks are becoming increasingly sophisticated. Cybersecurity specialists are always working to outsmart black hat hackers, fix vulnerabilities, and assess an organization's risk. In an ever-changing sector, combating such attacks requires constant study and thorough investigation. This implies that after you learn cybersecurity and begin working, your knowledge will continue to increase, and your wisdom will continue to sharpen as you gain experience. As a result, the sky's the limit when it comes to personal growth in the cybersecurity business.

- No mathematics required -
It's a well-known reality that not everyone has the same enthusiasm for mathematics as other people appear to have. A job in cybersecurity should be exactly up your alley if you've always had a dislike for numbers. Mathematics is not required in cybersecurity courses. Instead, you devote your time to improving abilities such as programming and networking, allowing you to develop a career-specific skill set!

- An opportunity to work with secretive agencies -
It's undeniable that Cybersecurity Professionals have a strong chance of landing jobs with prestigious Fortune 500 businesses like Dell, Accenture, and InfoTech, but the opportunities don't stop there. Experts who demonstrate their worth may be given the opportunity to work with top-secret government agencies and intelligence agencies such as MI6, Mossad, and the National Security Agency (NSA). As a result, if you understand cybersecurity, you could end up as a top-secret agent!

- Travel around the world with Cyber security -
Cybersecurity may be the ideal job option for those of you who want to travel the world. Thousands of cybersecurity specialists from the United States are striving to protect businesses, government institutions, and ordinary citizens. The surge in cyber-attacks is exceeding the supply of cyber-defenders on a global scale. As a result, there are several chances for cybersecurity professionals and specialists to go internationally to service their in-demand expertise. As a result, if you've ever desired to work in a different country, a career in cybersecurity could be the ticket to success!

- A profession that contributes to the greater good -
Cybersecurity Companies have repeatedly protected us against a wide range of cyber threats aimed at jeopardising our confidentiality, availability, and integrity. Despite this, the number of online crimes is steadily increasing. Phishing schemes, ransomware and spyware, and DDoS attacks are all affecting millions of people. The cyber threat to businesses, large and small, as well as individuals, is significant and growing. National Crime Agencies, Police Forces, and Company Security Teams are all tackling this threat around the world — but they need additional aid. They are in desperate need of people like you. Learn cybersecurity and join industry if you desire the satisfaction of a lucrative profession and the opportunity to make a meaningful difference.

- Cyber Security - A never ending industry -
Cybersecurity has gradually evolved into a sustainable sector. Cyber attacks are a by-product of the digital revolution, much like air pollution was a by-product of the industrial revolution. With this in mind, and considering the progress we've achieved as a society since the internet's inception, I believe it's a foregone conclusion that cybersecurity as a viable career option is here to stay. With the introduction of issues such as Big Data, Internet of Things, and Cloud Computing, Cybersecurity's permanent status and magnitude of relevance have been thoroughly established. So, if you want to understand cybersecurity in this day and age, it's a great idea.
4 Reasons to consider cyber security as your career:
Here are the top four reasons to seek a career in cybersecurity.
- The capability to solve puzzles -
When you consider the evolution of technology and its diversity, you can begin to see the various types of puzzles that cybersecurity specialists may solve. When you consider the evolution of technology and its diversity, you can begin to see the various types of puzzles that cybersecurity specialists may solve. Each new wave of technology introduces new dangers. It is the responsibility of security professionals to identify, comprehend, and then assist in the mitigation of these risks. When defending a website hosted in the cloud vs a pacemaker implanted in an old patient, the situation changes dramatically. Each event presents a new puzzle to solve and a new opportunity to rise to the occasion.
- The job has a real impact -
Last but not least, defending a pacemaker in an elderly patient is a real scenario. A major recall of pacemakers was recently issued owing to a security risk. The Equifax data breach affected 145 million people in the United States. Cybersecurity is crucial. It has ramifications that go beyond the digital realm into the actual realm. That's both a terrible and exciting proposition, emphasising its significance.Cybersecurity may be the discipline for you if you want to work on IT challenges that have a real-world impact.
- Unlimited Growth -
With its ever-expanding breadth, cybersecurity offers limitless prospects for advancement, both professionally and educationally. We teach security as a separate discipline, yet it is intertwined with all other IT skills. A smart cybersecurity expert tries to learn everything he or she can about how technologies and organisations work. A competent cybersecurity expert understands that there is always more to learn. That's a huge opportunity to keep challenged and involved. When security teams first began, they were made up of "jack-of-all-trades" individuals. Specialties in forensics, application security, and incident response were yet to emerge in the discipline. Due to the current demand, security teams have been compelled to scale up and out quickly. Professionals that are willing to take on new challenges will have the opportunity to do so. Whether you want to work your way up to Chief Information Security Officer (CISO) status or work with cutting-edge technologies, the only thing stopping you is your drive. That's an enticing prospect in and of itself, and a compelling reason to pursue a career in cybersecurity.
- Various Variety -
The range of technology and scenarios that security professionals must deal with are related to all of the prospects for advancement. It has a cybersecurity component if it uses ones and zeros (and certain roles even extend to physical security!). Security professionals have the opportunity to work directly with teams on technologies and systems that they could never have imagined. The diversity is nearly unlimited, from robots to cars to websites serving millions of visitors. That's a fascinating employment opportunity. You won't use the word "bored" very much. This diversity has an interesting side effect: cybersecurity experts come from a wide range of backgrounds due to the broad skill set required to effectively comprehend modern security threats. In fact, the more diverse your experience, the better a security professional you will be! There is no one-size-fits-all approach to becoming a cybersecurity expert.
The benefits of getting a degree in Cyber Security:
There are various advantages to earning a cybersecurity degree, which are outlined below.
- Qualified cybersecurity specialists are in high demand right now.
- Employees in this field have limitless opportunities for advancement.
- Employees can work as consultants either full-time or part-time.
- Cybersecurity specialists can earn a lot of money and have great benefits.
- Employees will be able to choose from a wide range of job opportunities all over the world.
- People in this sector will be able to make a positive difference in their clients' lives and careers.
- Cybersecurity specialists will be continually acquiring new skills and tactics to help them defeat cyber attackers, thanks to regular technological breakthroughs.
Job Responsibilities:
- Information security for both the corporation and the employees
- Preventing the downtime of websites preventing spyware from being installed on workplace systems
- Adware has given us the ability to combat possibly virus-infected advertisements.
- Security against ransomware
- Providing customers with the features and assistance they require to protect themselves from cyber predators.
- Hackers must have the knowledge and skills to beat them at their own game.
- In the case of a data breach, a plan of action is in place to assist customers in recovering promptly.
- Possibilities to assist a company or organisation in improving their rank, credentials, and professional reputation.
Types of Cyber security for organizational safety:
As a result, a strategic method to prevent cyber-attacks must be developed. In this post, we'll look at five different sorts of cybersecurity tactics that can help businesses and organisations protect themselves against cyber attacks.
- Network Security -
Network security is a method for protecting computer networks from unauthorised access, targeted attacks, and opportunistic viruses. Because the Internet contains a variety of networks linked to many websites, it is common to see businesses targeted for unwanted intrusion and malevolent intent. Users' activity are also recorded because many websites utilise third-party cookies. This can be beneficial to businesses in terms of expanding their operations, but it also exposes clients to fraud and sexual exploitation. As a result, enterprises must implement a security programme to monitor the internal network and infrastructure in order to combat cyber attacks and viruses linked with the network. Machine learning technology, according to experts, might be used to inform authorities in the event of unusual traffic. Organizations must continue to improve their network security by enacting policies that can protect them from cyber-attacks. For improved network security, experts recommend the following methods:
- Extra Logins
- Firewalls
- Incognito mode
- Encryption
- Antivirus Programs
- Monitored Internet Access
- New Passwords
- Application Security -
Users become enamoured with a variety of applications, including hardware, software, and devices. However, just like networks, an application can be hacked or infected with malware. Application security thwarts cyber-security breaches by implementing hardware and software methods during the project's development phase. Companies and organisations can discover sensitive data sets and secure them with specialised applications regarding the datasets using an application security network. The following are some of the application security methods:
- Antivirus Program
- Encryption Program
- Firewalls
- Cloud Security -
Artificial intelligence is increasingly being used by businesses to improve their enterprises, improve customer experiences, and run more efficiently. It is challenging for companies to retain data in tangible form due to the abundance of data accessible at each stage of organisational setup. Furthermore, it has been found that most of this data is unstructured and obtained from unknown sources, posing a risk to the organization's network. As a result, Amazon Web Services, Microsoft Azure, and Google Cloud provide their customers with a cloud computing platform on which they may store data and monitor it using a security tool. According to reports, on-premises environments are particularly vulnerable to cyber virus. Users will be provided with protected data after integrating the system with a cloud security platform, reducing the risk of a cyber-attack.
- Internet of Things (IoT) -
The Internet of Things is thought to be the next technology revolution's tool. According to a forecast by Bain and Company, the IoT market will grow by 520 billion dollars by 2021. IoT provides the user with a variety of important and non-critical equipment, such as appliances, sensors, printers, and wifi-routers, among other routers, through its security network. According to the survey, one of the most significant barriers to deploying IoT in any firm is the security risk. Organizations get insightful analytics, legacy embedded systems, and a secure network by connecting the system with IoT security.
- Critical Infrastructure Cyber Security -
The critical infrastructure cybersecurity technique is used to protect the critical infrastructure systems. They are systems that societies rely greatly on. Electricity grids, water purification, traffic lights, shopping malls, and hospitals are among them. They are not directly tied to a potential cyber breach, but they can serve as a platform for cyber malware to infect the endpoints to which these systems are connected. To lessen the risk of cyber infection or cyber assaults, companies in charge of key infrastructure must gain access to weak areas in order to secure the businesses they are responsible for. Organizations that rely on vital infrastructure must assess the extent of the damage caused by cyber assaults. These firms must have a contingency plan in place to ensure that they do not bear the brunt of cyber-attacks.
Skills required in Cyber Security:
- Communication skills -
You'll be working directly with people in various positions and departments as a cybersecurity professional, so you'll need to be able to effectively communicate and explain your discoveries, concerns, and solutions to others. It's critical to be able to talk effectively and simply about cybersecurity strategy and policy, as well as to convey technical knowledge to people with varying levels of technical understanding.
- Technical Aptitude -
As the name suggests, cybersecurity is a technology-focused area, and you'll most likely be entrusted with diagnosing, maintaining, and updating information security systems, as well as performing continuous network monitoring and offering real-time security solutions. To conduct the daily responsibilities of a cybersecurity expert, you must be digitally savvy.
- Problem Solving skills -
Problem-solving will be a big part of your day-to-day work as a cybersecurity practitioner. Those working in the field must think of new approaches to tackle and solve difficult information security problems in a variety of present and developing technologies and digital environments.
- Eye for Detail -
To properly uncover vulnerabilities and hazards and defend an organisation from cyber breaches, you must be extremely alert and detail-oriented. You'll be in charge of constant network monitoring, and you'll need to be able to spot problems immediately and devise real-time security solutions to handle them.
- Keen learner -
Cybersecurity, like any other technical sector, is always evolving. Anyone working in the sector will need to be dedicated to staying up to date on best practises and developing industry trends, as well as be constantly learning and self-educating - both on and off the job.
- Ability to understand hacking -
To defend an organization's network and infrastructure efficiently, you must first understand how they might be attacked, which is why most cybersecurity experts must learn how to "ethically hack." To properly grasp how a system might be infiltrated and, in turn, design efficient solutions to counter these attacks, you need to have the same abilities as a hacker.
- Skills for Fundamental Computer Forensics -
While computer forensics and cybersecurity are two distinct areas, they are intertwined, and a foundation in computer forensics can help you succeed in your cybersecurity career. You'll need a thorough grasp of what happens if your efforts fail and how compromised data is recovered to be able to properly secure organisations' digital assets and avoid security breaches. For this reason, most cybersecurity degree programmes will include a computer forensics component.
- Knowledge of Security through several platforms -
You'll need to be familiar with a range of operating systems, computer systems, mobile devices, cloud networks, and wireless networks, as well as stay up with innovations in the field for each of them.
Conclusion
Do you think you'd be interested in a job in cybersecurity? Cybersecurity is a high-demand, fast-growing area with a high demand for qualified individuals, with high median wages, career opportunities across a wide range of industries, and a tough, fast-paced work environment.
If you're interested in safeguarding organisations' digital assets and intelligence from security breaches but aren't sure if you're qualified, conduct some research into the area, find out what typical cybersecurity jobs include, and discover more about the skills required for cybersecurity positions. A comprehensive mix of technical, professional, and functional skills, as well as the specific cybersecurity skills and critical soft skills in demand by companies, will set you apart from the competition. To help you understand what it takes to be a professional in the cybersecurity area, we've compiled a list of top cybersecurity talents.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
In recent years, cybersecurity has emerged as a crucial sector of job growth, owing to an inflow of people interested in pursuing a career in the field. Even so, some people are still debating whether or not they should plunge into the unknown waters of Cybersecurity as a career. This blog, which addresses the "Top 10 Reasons To Learn Cybersecurity," should undoubtedly assist you in making your decision.
Here are Top 10 Reasons to learn Cyber Security:
- Fat Pay Cheques -
'Money makes the world go round,' I believe we can all agree. With tales of new cyber attacks in the news virtually every week, the world has understood the critical relevance of cybersecurity. Faced with cybercrime, businesses and government organisations are looking for professionals who can defend their systems from hackers – and they're willing to pay top dollar and provide extensive training and development. Anyone interested in pursuing a career in cybersecurity should consider the following:
- Cyber security salaries have a higher growth potential than salaries in 90% of other businesses.
- Senior security experts can earn significantly more than the average median.
- Earnings are determined by merit rather than your gender, age, or race.
- A job that is never dull -
A job in cybersecurity is not and cannot be static and stale due to the uncertain nature of the future. On a regular basis, you will be tested. There will be fresh and unexpected setbacks, as well as incredible and unexpected discoveries. One thing is certain: attackers will continue to develop new exploits on a regular basis, and it is your obligation to come up with innovative and efficient solutions to the problems that arise. You'll be solving new riddles, fighting new monsters, and supporting new activities on a regular basis as a cybersecurity professional. So, if you become bored easily when things become tedious, fear not: Cybersecurity is never dull!
- A mixed bag of industries to select -
Unlike the majority of the professional world, you are not limited to a single industry as a cybersecurity specialist. Many sectors are undergoing digital transformation. We are in the midst of a digital revolution, thanks to breakthroughs in the fields of IoT, Big Data, Automation, and Cloud Computing. As a result, becoming a cybersecurity expert does not preclude you from working in a hospital, school, government agency, or top-secret military organisation. Almost everyone wants to be secure on the digital front, thus the gates are wide open.
- Innumerable Opportunities -
There are over a million businesses in the world, spanning across a wide range of sectors and industries, and the majority of them now have one thing in common: the necessity for an internet connection. The information security industry employs approximately 400,000 people, and demand for cyber capabilities is increasing rapidly in all types of businesses and government agencies. So, whether you want to work in sports or fashion, media or emergency services, banking or retail, cyber skills could be your ticket to success. After all, everyone needs someone to protect their critical data.
- Limitless potential for personal growth -
Cyber attacks are becoming increasingly sophisticated. Cybersecurity specialists are always working to outsmart black hat hackers, fix vulnerabilities, and assess an organization's risk. In an ever-changing sector, combating such attacks requires constant study and thorough investigation. This implies that after you learn cybersecurity and begin working, your knowledge will continue to increase, and your wisdom will continue to sharpen as you gain experience. As a result, the sky's the limit when it comes to personal growth in the cybersecurity business.
- No mathematics required -
It's a well-known reality that not everyone has the same enthusiasm for mathematics as other people appear to have. A job in cybersecurity should be exactly up your alley if you've always had a dislike for numbers. Mathematics is not required in cybersecurity courses. Instead, you devote your time to improving abilities such as programming and networking, allowing you to develop a career-specific skill set!
- An opportunity to work with secretive agencies -
It's undeniable that Cybersecurity Professionals have a strong chance of landing jobs with prestigious Fortune 500 businesses like Dell, Accenture, and InfoTech, but the opportunities don't stop there. Experts who demonstrate their worth may be given the opportunity to work with top-secret government agencies and intelligence agencies such as MI6, Mossad, and the National Security Agency (NSA). As a result, if you understand cybersecurity, you could end up as a top-secret agent!
- Travel around the world with Cyber security -
Cybersecurity may be the ideal job option for those of you who want to travel the world. Thousands of cybersecurity specialists from the United States are striving to protect businesses, government institutions, and ordinary citizens. The surge in cyber-attacks is exceeding the supply of cyber-defenders on a global scale. As a result, there are several chances for cybersecurity professionals and specialists to go internationally to service their in-demand expertise. As a result, if you've ever desired to work in a different country, a career in cybersecurity could be the ticket to success!
- A profession that contributes to the greater good -
Cybersecurity Companies have repeatedly protected us against a wide range of cyber threats aimed at jeopardising our confidentiality, availability, and integrity. Despite this, the number of online crimes is steadily increasing. Phishing schemes, ransomware and spyware, and DDoS attacks are all affecting millions of people. The cyber threat to businesses, large and small, as well as individuals, is significant and growing. National Crime Agencies, Police Forces, and Company Security Teams are all tackling this threat around the world — but they need additional aid. They are in desperate need of people like you. Learn cybersecurity and join industry if you desire the satisfaction of a lucrative profession and the opportunity to make a meaningful difference.
- Cyber Security - A never ending industry -
Cybersecurity has gradually evolved into a sustainable sector. Cyber attacks are a by-product of the digital revolution, much like air pollution was a by-product of the industrial revolution. With this in mind, and considering the progress we've achieved as a society since the internet's inception, I believe it's a foregone conclusion that cybersecurity as a viable career option is here to stay. With the introduction of issues such as Big Data, Internet of Things, and Cloud Computing, Cybersecurity's permanent status and magnitude of relevance have been thoroughly established. So, if you want to understand cybersecurity in this day and age, it's a great idea.
4 Reasons to consider cyber security as your career:
Here are the top four reasons to seek a career in cybersecurity.
- The capability to solve puzzles -
When you consider the evolution of technology and its diversity, you can begin to see the various types of puzzles that cybersecurity specialists may solve. When you consider the evolution of technology and its diversity, you can begin to see the various types of puzzles that cybersecurity specialists may solve. Each new wave of technology introduces new dangers. It is the responsibility of security professionals to identify, comprehend, and then assist in the mitigation of these risks. When defending a website hosted in the cloud vs a pacemaker implanted in an old patient, the situation changes dramatically. Each event presents a new puzzle to solve and a new opportunity to rise to the occasion.
- The job has a real impact -
Last but not least, defending a pacemaker in an elderly patient is a real scenario. A major recall of pacemakers was recently issued owing to a security risk. The Equifax data breach affected 145 million people in the United States. Cybersecurity is crucial. It has ramifications that go beyond the digital realm into the actual realm. That's both a terrible and exciting proposition, emphasising its significance.Cybersecurity may be the discipline for you if you want to work on IT challenges that have a real-world impact.
- Unlimited Growth -
With its ever-expanding breadth, cybersecurity offers limitless prospects for advancement, both professionally and educationally. We teach security as a separate discipline, yet it is intertwined with all other IT skills. A smart cybersecurity expert tries to learn everything he or she can about how technologies and organisations work. A competent cybersecurity expert understands that there is always more to learn. That's a huge opportunity to keep challenged and involved. When security teams first began, they were made up of "jack-of-all-trades" individuals. Specialties in forensics, application security, and incident response were yet to emerge in the discipline. Due to the current demand, security teams have been compelled to scale up and out quickly. Professionals that are willing to take on new challenges will have the opportunity to do so. Whether you want to work your way up to Chief Information Security Officer (CISO) status or work with cutting-edge technologies, the only thing stopping you is your drive. That's an enticing prospect in and of itself, and a compelling reason to pursue a career in cybersecurity.
- Various Variety -
The range of technology and scenarios that security professionals must deal with are related to all of the prospects for advancement. It has a cybersecurity component if it uses ones and zeros (and certain roles even extend to physical security!). Security professionals have the opportunity to work directly with teams on technologies and systems that they could never have imagined. The diversity is nearly unlimited, from robots to cars to websites serving millions of visitors. That's a fascinating employment opportunity. You won't use the word "bored" very much. This diversity has an interesting side effect: cybersecurity experts come from a wide range of backgrounds due to the broad skill set required to effectively comprehend modern security threats. In fact, the more diverse your experience, the better a security professional you will be! There is no one-size-fits-all approach to becoming a cybersecurity expert.
The benefits of getting a degree in Cyber Security:
There are various advantages to earning a cybersecurity degree, which are outlined below.
- Qualified cybersecurity specialists are in high demand right now.
- Employees in this field have limitless opportunities for advancement.
- Employees can work as consultants either full-time or part-time.
- Cybersecurity specialists can earn a lot of money and have great benefits.
- Employees will be able to choose from a wide range of job opportunities all over the world.
- People in this sector will be able to make a positive difference in their clients' lives and careers.
- Cybersecurity specialists will be continually acquiring new skills and tactics to help them defeat cyber attackers, thanks to regular technological breakthroughs.
Job Responsibilities:
- Information security for both the corporation and the employees
- Preventing the downtime of websites preventing spyware from being installed on workplace systems
- Adware has given us the ability to combat possibly virus-infected advertisements.
- Security against ransomware
- Providing customers with the features and assistance they require to protect themselves from cyber predators.
- Hackers must have the knowledge and skills to beat them at their own game.
- In the case of a data breach, a plan of action is in place to assist customers in recovering promptly.
- Possibilities to assist a company or organisation in improving their rank, credentials, and professional reputation.
Types of Cyber security for organizational safety:
As a result, a strategic method to prevent cyber-attacks must be developed. In this post, we'll look at five different sorts of cybersecurity tactics that can help businesses and organisations protect themselves against cyber attacks.
- Network Security -
Network security is a method for protecting computer networks from unauthorised access, targeted attacks, and opportunistic viruses. Because the Internet contains a variety of networks linked to many websites, it is common to see businesses targeted for unwanted intrusion and malevolent intent. Users' activity are also recorded because many websites utilise third-party cookies. This can be beneficial to businesses in terms of expanding their operations, but it also exposes clients to fraud and sexual exploitation. As a result, enterprises must implement a security programme to monitor the internal network and infrastructure in order to combat cyber attacks and viruses linked with the network. Machine learning technology, according to experts, might be used to inform authorities in the event of unusual traffic. Organizations must continue to improve their network security by enacting policies that can protect them from cyber-attacks. For improved network security, experts recommend the following methods:
- Extra Logins
- Firewalls
- Incognito mode
- Encryption
- Antivirus Programs
- Monitored Internet Access
- New Passwords
- Application Security -
Users become enamoured with a variety of applications, including hardware, software, and devices. However, just like networks, an application can be hacked or infected with malware. Application security thwarts cyber-security breaches by implementing hardware and software methods during the project's development phase. Companies and organisations can discover sensitive data sets and secure them with specialised applications regarding the datasets using an application security network. The following are some of the application security methods:
- Antivirus Program
- Encryption Program
- Firewalls
- Cloud Security -
Artificial intelligence is increasingly being used by businesses to improve their enterprises, improve customer experiences, and run more efficiently. It is challenging for companies to retain data in tangible form due to the abundance of data accessible at each stage of organisational setup. Furthermore, it has been found that most of this data is unstructured and obtained from unknown sources, posing a risk to the organization's network. As a result, Amazon Web Services, Microsoft Azure, and Google Cloud provide their customers with a cloud computing platform on which they may store data and monitor it using a security tool. According to reports, on-premises environments are particularly vulnerable to cyber virus. Users will be provided with protected data after integrating the system with a cloud security platform, reducing the risk of a cyber-attack.
- Internet of Things (IoT) -
The Internet of Things is thought to be the next technology revolution's tool. According to a forecast by Bain and Company, the IoT market will grow by 520 billion dollars by 2021. IoT provides the user with a variety of important and non-critical equipment, such as appliances, sensors, printers, and wifi-routers, among other routers, through its security network. According to the survey, one of the most significant barriers to deploying IoT in any firm is the security risk. Organizations get insightful analytics, legacy embedded systems, and a secure network by connecting the system with IoT security.
- Critical Infrastructure Cyber Security -
The critical infrastructure cybersecurity technique is used to protect the critical infrastructure systems. They are systems that societies rely greatly on. Electricity grids, water purification, traffic lights, shopping malls, and hospitals are among them. They are not directly tied to a potential cyber breach, but they can serve as a platform for cyber malware to infect the endpoints to which these systems are connected. To lessen the risk of cyber infection or cyber assaults, companies in charge of key infrastructure must gain access to weak areas in order to secure the businesses they are responsible for. Organizations that rely on vital infrastructure must assess the extent of the damage caused by cyber assaults. These firms must have a contingency plan in place to ensure that they do not bear the brunt of cyber-attacks.
Skills required in Cyber Security:
- Communication skills -
You'll be working directly with people in various positions and departments as a cybersecurity professional, so you'll need to be able to effectively communicate and explain your discoveries, concerns, and solutions to others. It's critical to be able to talk effectively and simply about cybersecurity strategy and policy, as well as to convey technical knowledge to people with varying levels of technical understanding.
- Technical Aptitude -
As the name suggests, cybersecurity is a technology-focused area, and you'll most likely be entrusted with diagnosing, maintaining, and updating information security systems, as well as performing continuous network monitoring and offering real-time security solutions. To conduct the daily responsibilities of a cybersecurity expert, you must be digitally savvy.
- Problem Solving skills -
Problem-solving will be a big part of your day-to-day work as a cybersecurity practitioner. Those working in the field must think of new approaches to tackle and solve difficult information security problems in a variety of present and developing technologies and digital environments.
- Eye for Detail -
To properly uncover vulnerabilities and hazards and defend an organisation from cyber breaches, you must be extremely alert and detail-oriented. You'll be in charge of constant network monitoring, and you'll need to be able to spot problems immediately and devise real-time security solutions to handle them.
- Keen learner -
Cybersecurity, like any other technical sector, is always evolving. Anyone working in the sector will need to be dedicated to staying up to date on best practises and developing industry trends, as well as be constantly learning and self-educating - both on and off the job.
- Ability to understand hacking -
To defend an organization's network and infrastructure efficiently, you must first understand how they might be attacked, which is why most cybersecurity experts must learn how to "ethically hack." To properly grasp how a system might be infiltrated and, in turn, design efficient solutions to counter these attacks, you need to have the same abilities as a hacker.
- Skills for Fundamental Computer Forensics -
While computer forensics and cybersecurity are two distinct areas, they are intertwined, and a foundation in computer forensics can help you succeed in your cybersecurity career. You'll need a thorough grasp of what happens if your efforts fail and how compromised data is recovered to be able to properly secure organisations' digital assets and avoid security breaches. For this reason, most cybersecurity degree programmes will include a computer forensics component.
- Knowledge of Security through several platforms -
You'll need to be familiar with a range of operating systems, computer systems, mobile devices, cloud networks, and wireless networks, as well as stay up with innovations in the field for each of them.
Conclusion
Do you think you'd be interested in a job in cybersecurity? Cybersecurity is a high-demand, fast-growing area with a high demand for qualified individuals, with high median wages, career opportunities across a wide range of industries, and a tough, fast-paced work environment.
If you're interested in safeguarding organisations' digital assets and intelligence from security breaches but aren't sure if you're qualified, conduct some research into the area, find out what typical cybersecurity jobs include, and discover more about the skills required for cybersecurity positions. A comprehensive mix of technical, professional, and functional skills, as well as the specific cybersecurity skills and critical soft skills in demand by companies, will set you apart from the competition. To help you understand what it takes to be a professional in the cybersecurity area, we've compiled a list of top cybersecurity talents.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Project Integration Management and Its Process Groups
Every firm is currently employing the most up-to-date and successful Project Management practises to ensure that its projects and processes are managed consistently throughout the organisation. When it comes to consistency, the emergence of organisational business demands, individual preferences, and team differences will lead to judgments that aren't in the company's long-term best interests. To achieve their long-term strategic goals, the business must ensure that a high level of integration is adopted in Project Management techniques if such challenges develop.
A Guide to Integration Management
Integration Management is the process of delegating authority to the project manager to monitor and coordinate the operations and activities occurring at various levels of the company. The goal of the integration is to ensure that the team works together to complete the project by ensuring that the scope, budget, and timeline are all met. The project manager's ability to execute integration management effectively is recognised as a significant success factor.

Understand the meaning of Project Integration Management:
According to the Project Management Institute, the first knowledge group is Project Integration Management. As a project manager, you're responsible for integrating, articulating, and unifying all sub-processes into a unified whole, and that's all there is to project management. To execute a successful project as a project manager, you must be an exceptional integrator. If you are a PMP certified project manager or have attended a project management training session, you should be familiar with the terms used in today's project management. As a project manager, you are aware that you must monitor the activity of the process groups (i.e., Initiation, Planning, Executing, Monitoring and Controlling, and Closing). As Integration is one of the knowledge domains, you must now understand what work you must perform in each process group, from Initiation to Closure, in order to manage integration.
Project Integration Management and its Process Groups:
The project integration management knowledge area is further separated into smaller procedures that serve as access points for the Project Manager. Each of these procedures is an important aspect of project management and contributes to project success. These are the procedures:

- Initiation Process Group
You create a project charter in the Integration knowledge area at the beginning stage. A project charter is nothing more than a necessary paper/document/authorization letter to begin and plan a project. Let me give you an example of what the project charter might include:
- The project's business need – What are the benefits of this initiative for the organisation?
- The project's objectives - What is the ultimate goal of this project?
- What work do you need to do to meet the customer's target? High-level product and project scope — what work do you need to do to meet the customer's target?
- Budget information at a high level — what would the project's high-level cost be?
- Schedule information at a high level — Information on the project's completion at a high level.
- Risk information at a high level – Project-related opportunities and threats
- Acceptance criteria for projects — parameters that determine whether or not a project is considered successful.
- Name of the Signatory Authority — The financing authority's name and signature (Maybe customer itself or Project Sponsor)
- Name of the project manager – The name of the project manager who has been authorised (if decided earlier)
- Project manager's authoritative power - How and to what extent will the project manager be involved in project activities?
- Pre-assigned team members — Names of Subject Matter Experts, if previously decided
- Names of major stakeholders, such as the financing authority, the client, and so on.
You create the project charter by putting all of the aforementioned material in front of you. You plan your project based on the information provided in the project charter. The information in the project charter serves as the foundation for project planning.
- Planning Process Group
You plan your project based on the information provided in the project charter. A planning process group is nothing more than an amalgamation of all sub-planning activities such as scope management, cost management, schedule management, quality management, human resource planning, communication planning, risk management, procurement planning, requirement management planning, stakeholder management planning, and so on. To produce final project management planning, you must trigger all sub-processes into a coherent whole as a project manager. This is the most important process group since it has an impact on all knowledge domains. When working on the planning process group as a project manager, you must be more focused.
- Execution Process Group
Your project planning is complete, and your team will begin work as soon as your planning is authorised and you receive the work authorization letter to begin the project. As scheduled, your team will begin working on the project. After getting approval from the change control board or configuration management, you'll generate the deliverables and, if any changes are discovered, you'll align the baselines (scope baselines, cost performance baselines, and schedule baselines).
- Monitoring & Controlling Process Group
This process group is where you keep track of your work performance to see if there are any deviations from the original plan. You can compare them to the real baselines set in the planning based on the work performance report. You may observe some variations or deviations and believe that you need to revisit some processes; as a result, you seek project modification. If the approved adjustments are performed in the project to address the deviations, your project management planning and associated documents may need to be revised. This process group functions similarly to a hawk's eye, in that it is responsible for monitoring and controlling project operations throughout the project life cycle.
- Closing Process Group
If the customer has successfully received the product or deliverables, acknowledged them, and signed off on them, the project can be considered finished. After the project is completed, you must close the procurement agreement and release the project's resources. To be used in the future, you must complete the archive project process with the assistance of other stakeholders.
Importance of Project Integration Management:
Multiple teams and organisational procedures are frequently involved in projects, making them dynamic and complicated. Project integration management is required to guarantee that all aspects are working together toward the same end goal. Here are some of the advantages of this method.
- Organizes and coordinates the project from start to finish -
Project integration management functions as an instruction manual for steering the project in the right direction and ensuring that all processes are in sync. As the project progresses, it ensures that the outputs and papers are in order so that the following phase may proceed successfully.
- Ascertains that everyone is aware of their obligations -
All stakeholders and team members will have a clear grasp of their roles and duties thanks to project integration management. You'll be able to address questions from teams or stakeholders if there are any points of uncertainty or concerns if you keep a close eye on the project.
- Keeps the project on schedule -
Project integration management ensures that projects are completed on time and within budget. It also ensures that the project stays on track with the project management plan in order to achieve the desired outcomes. Project integration management aids in the resolution of disagreements or adjustments while minimising the overall project's impact.
- Maintains open lines of communication with all parties involved -
Stakeholders are regularly informed about project progress thanks to integrated project management. It enables you to set up a method for informing stakeholders about project modifications, whether they're authorised or not. It also underlines the significance of attending a wrap-up meeting once the project is concluded to ensure that everything is in order.
- Makes decisions easier to understand -
The goals and outcomes of each step in project integration management are clearly specified. You'll have a better understanding of the appropriate course of action for each project phase if you walk through all of the phases. You'll be able to properly express the reasons behind the ideas if you create detailed project documentation.
How do you go about putting project integration management into practise?
Project integration management necessitates a mix of technical and leadership abilities. Here are some pointers to help you get started managing project integration.
- Oversee integrated project management with the help of a project manager -
Project managers must have a solid awareness of how each aspect interacts with the others and the project's ultimate impact. Integrated project management entails the project manager keeping track of a process, phase, and output.
- Use a team communication tool to collaborate -
Use a communication strategy to identify the channels teams should use to share information, resources, and project status updates to avoid miscommunication or a lack of communication between teams. You won't have to function as an intermediary because teams will be able to speak directly with one another.
- To save time, use project templates -
Creating project plans and materials can take a long time, especially when there are so many of them for a single project. Use project templates, either from prior projects or readymade ones, rather than creating them from scratch.
- Make sure your project teams are well-rounded -
A strong project team can make all the difference in the success of a project. It's your responsibility to assemble a well-balanced project team and allocate assignments that are appropriate for each team member's talents and experience. Ensure that everyone receives the resources they require and that communication between the various teams is coordinated.
- Keep meticulous time records -
Implementing time-tracking software, if you haven't previously, could be advantageous not only for billing but also for future project scheduling. While team calendars provide a high-level perspective of how time will be allocated, tracking the amount of hours spent on assignments provides more detailed information.
Conclusion
Project integration management is all about ensuring that all project activities are integrated and that all the pieces are put together to complete the jigsaw. When it comes to project integration management, executing all of the essential processes and their process groups will ensure project success. I hope that this Project Integration Management article has cleared any misconceptions you may have about Project Integration Management. If not, feel free to leave a comment below with any questions you have on the topic.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
Every firm is currently employing the most up-to-date and successful Project Management practises to ensure that its projects and processes are managed consistently throughout the organisation. When it comes to consistency, the emergence of organisational business demands, individual preferences, and team differences will lead to judgments that aren't in the company's long-term best interests. To achieve their long-term strategic goals, the business must ensure that a high level of integration is adopted in Project Management techniques if such challenges develop.
A Guide to Integration Management
Integration Management is the process of delegating authority to the project manager to monitor and coordinate the operations and activities occurring at various levels of the company. The goal of the integration is to ensure that the team works together to complete the project by ensuring that the scope, budget, and timeline are all met. The project manager's ability to execute integration management effectively is recognised as a significant success factor.
Understand the meaning of Project Integration Management:
According to the Project Management Institute, the first knowledge group is Project Integration Management. As a project manager, you're responsible for integrating, articulating, and unifying all sub-processes into a unified whole, and that's all there is to project management. To execute a successful project as a project manager, you must be an exceptional integrator. If you are a PMP certified project manager or have attended a project management training session, you should be familiar with the terms used in today's project management. As a project manager, you are aware that you must monitor the activity of the process groups (i.e., Initiation, Planning, Executing, Monitoring and Controlling, and Closing). As Integration is one of the knowledge domains, you must now understand what work you must perform in each process group, from Initiation to Closure, in order to manage integration.
Project Integration Management and its Process Groups:
The project integration management knowledge area is further separated into smaller procedures that serve as access points for the Project Manager. Each of these procedures is an important aspect of project management and contributes to project success. These are the procedures:
- Initiation Process Group
You create a project charter in the Integration knowledge area at the beginning stage. A project charter is nothing more than a necessary paper/document/authorization letter to begin and plan a project. Let me give you an example of what the project charter might include:
- The project's business need – What are the benefits of this initiative for the organisation?
- The project's objectives - What is the ultimate goal of this project?
- What work do you need to do to meet the customer's target? High-level product and project scope — what work do you need to do to meet the customer's target?
- Budget information at a high level — what would the project's high-level cost be?
- Schedule information at a high level — Information on the project's completion at a high level.
- Risk information at a high level – Project-related opportunities and threats
- Acceptance criteria for projects — parameters that determine whether or not a project is considered successful.
- Name of the Signatory Authority — The financing authority's name and signature (Maybe customer itself or Project Sponsor)
- Name of the project manager – The name of the project manager who has been authorised (if decided earlier)
- Project manager's authoritative power - How and to what extent will the project manager be involved in project activities?
- Pre-assigned team members — Names of Subject Matter Experts, if previously decided
- Names of major stakeholders, such as the financing authority, the client, and so on.
You create the project charter by putting all of the aforementioned material in front of you. You plan your project based on the information provided in the project charter. The information in the project charter serves as the foundation for project planning.
- Planning Process Group
You plan your project based on the information provided in the project charter. A planning process group is nothing more than an amalgamation of all sub-planning activities such as scope management, cost management, schedule management, quality management, human resource planning, communication planning, risk management, procurement planning, requirement management planning, stakeholder management planning, and so on. To produce final project management planning, you must trigger all sub-processes into a coherent whole as a project manager. This is the most important process group since it has an impact on all knowledge domains. When working on the planning process group as a project manager, you must be more focused.
- Execution Process Group
Your project planning is complete, and your team will begin work as soon as your planning is authorised and you receive the work authorization letter to begin the project. As scheduled, your team will begin working on the project. After getting approval from the change control board or configuration management, you'll generate the deliverables and, if any changes are discovered, you'll align the baselines (scope baselines, cost performance baselines, and schedule baselines).
- Monitoring & Controlling Process Group
This process group is where you keep track of your work performance to see if there are any deviations from the original plan. You can compare them to the real baselines set in the planning based on the work performance report. You may observe some variations or deviations and believe that you need to revisit some processes; as a result, you seek project modification. If the approved adjustments are performed in the project to address the deviations, your project management planning and associated documents may need to be revised. This process group functions similarly to a hawk's eye, in that it is responsible for monitoring and controlling project operations throughout the project life cycle.
- Closing Process Group
If the customer has successfully received the product or deliverables, acknowledged them, and signed off on them, the project can be considered finished. After the project is completed, you must close the procurement agreement and release the project's resources. To be used in the future, you must complete the archive project process with the assistance of other stakeholders.
Importance of Project Integration Management:
Multiple teams and organisational procedures are frequently involved in projects, making them dynamic and complicated. Project integration management is required to guarantee that all aspects are working together toward the same end goal. Here are some of the advantages of this method.
- Organizes and coordinates the project from start to finish -
Project integration management functions as an instruction manual for steering the project in the right direction and ensuring that all processes are in sync. As the project progresses, it ensures that the outputs and papers are in order so that the following phase may proceed successfully.
- Ascertains that everyone is aware of their obligations -
All stakeholders and team members will have a clear grasp of their roles and duties thanks to project integration management. You'll be able to address questions from teams or stakeholders if there are any points of uncertainty or concerns if you keep a close eye on the project.
- Keeps the project on schedule -
Project integration management ensures that projects are completed on time and within budget. It also ensures that the project stays on track with the project management plan in order to achieve the desired outcomes. Project integration management aids in the resolution of disagreements or adjustments while minimising the overall project's impact.
- Maintains open lines of communication with all parties involved -
Stakeholders are regularly informed about project progress thanks to integrated project management. It enables you to set up a method for informing stakeholders about project modifications, whether they're authorised or not. It also underlines the significance of attending a wrap-up meeting once the project is concluded to ensure that everything is in order.
- Makes decisions easier to understand -
The goals and outcomes of each step in project integration management are clearly specified. You'll have a better understanding of the appropriate course of action for each project phase if you walk through all of the phases. You'll be able to properly express the reasons behind the ideas if you create detailed project documentation.
How do you go about putting project integration management into practise?
Project integration management necessitates a mix of technical and leadership abilities. Here are some pointers to help you get started managing project integration.
- Oversee integrated project management with the help of a project manager -
Project managers must have a solid awareness of how each aspect interacts with the others and the project's ultimate impact. Integrated project management entails the project manager keeping track of a process, phase, and output.
- Use a team communication tool to collaborate -
Use a communication strategy to identify the channels teams should use to share information, resources, and project status updates to avoid miscommunication or a lack of communication between teams. You won't have to function as an intermediary because teams will be able to speak directly with one another.
- To save time, use project templates -
Creating project plans and materials can take a long time, especially when there are so many of them for a single project. Use project templates, either from prior projects or readymade ones, rather than creating them from scratch.
- Make sure your project teams are well-rounded -
A strong project team can make all the difference in the success of a project. It's your responsibility to assemble a well-balanced project team and allocate assignments that are appropriate for each team member's talents and experience. Ensure that everyone receives the resources they require and that communication between the various teams is coordinated.
- Keep meticulous time records -
Implementing time-tracking software, if you haven't previously, could be advantageous not only for billing but also for future project scheduling. While team calendars provide a high-level perspective of how time will be allocated, tracking the amount of hours spent on assignments provides more detailed information.
Conclusion
Project integration management is all about ensuring that all project activities are integrated and that all the pieces are put together to complete the jigsaw. When it comes to project integration management, executing all of the essential processes and their process groups will ensure project success. I hope that this Project Integration Management article has cleared any misconceptions you may have about Project Integration Management. If not, feel free to leave a comment below with any questions you have on the topic.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
IT Security Roles and Responsibilities of Cyber Security Professionals
Technology has intertwined our personal and professional lives in ways that were inconceivable just a few decades ago. Cloud computing, mobility, and the sophisticated devices most of us carry in our pockets enable a culture of ease as well as the opportunity to collaborate and be more productive. While this convenience may make our lives easier, it also makes it easier for cybercriminals to access our sensitive personal information no matter where it resides or travels across the network. There is a huge market for the sale and exploitation of that data, so these bad actors have plenty of reason. Hackers and cybercriminals will eventually find a method to access your data, even if you have the greatest Cyber Security Professional on your side. That isn't to argue that everything is bleak. IT security professionals fight on the front lines of this war to keep up with the ever-changing threat landscape.
Important skills for Cyber security professionals
More than technical capabilities are required of successful IT security experts. To make real progress in the sector, these professionals should be able to:

- Learners - Technical proficiency is another essential skill. With the rapid pace of change in IT security, this necessitates continual study, training, and certification. To be able to tackle complicated security challenges, these specialists need to be constantly learning new advanced technology skills.
- Communicators - Effective coordination with teams and clients is ensured through management and communication abilities. Every employee in an organisation is affected by technology and security. By teaching and empowering people to assist secure systems, security professionals must interact in meaningful ways.
- Strategists - Professionals in cyber security should be able to proactively deploy security measures and controls within enterprises while assessing the implications of every action. Workflows, dependencies, finances, and resources must all be evaluated tactically and strategically in order to implement advanced security processes. Because new ways to hack information are appearing all the time, specialists must stay one step ahead of the game, learning how hackers get into networks and how to stop them.
Responsibilities of the cyber security professional
New security risks emerge on a regular basis, and IT security experts must keep up with the current strategies used by hackers in the field. In addition to the high-level roles listed above, IT security teams also do the following tasks:
- Set up and use identity and access management systems, as well as user access controls.
- To detect and prevent abnormal activity, keep an eye on network and application performance.
- Conduct regular audits to ensure that security procedures are in compliance.
- To thwart malicious hacks, use endpoint detection and prevention solutions.
- Set up patch management systems to automatically update software.
- Implement comprehensive vulnerability management systems across all assets, including on-premises and in the cloud.
- And collaborate with IT operations to create a single disaster recovery/business continuity strategy.
- Educate staff on how to spot suspicious conduct in collaboration with HR and/or team leads.
Salary for cyber security professional

Cyber security professionals, for example, earn an average of $116,000 per year or $55.77 per hour, according to CIO, but PayScale estimates that the average wage for computer security specialists is around $74,000, with geography being a big role in pay structure.
Different roles in Cyber Security
Starting as a generalist and then specialising in an area of interest or strength might assist cyber security professionals. These are some of the possibilities:
- Application Security
- Data loss prevention
- Forensics
- Network Security
- Security Architecture
- Threat Intelligence
- Incident response
- Vulnerability management
Job growth in Cyber Security

Professionals in cyber security work in practically every area and industry – public and private, for-profit and charity – and at both large and small enterprises and organisations, including:
- Government
- Finance and Banking
- Health Care
- Insurance
- Technology
- Government
- Telecommunications
- Law enforcement
What are Cyber Security people known as?
Cyber security specialists go by a variety of names, but their work titles or descriptions "usually" include the terms "information security," "cyber security," or "similar terms." Here are several examples:
- Cyber Security Specialists
- Penetration Testers
- Cyber Security or Security Administrators
- Cyber Security or Security Principals
- Cyber Security or Security Technicians
- Cyber Security Specialists
- Cyber Security Technical Architects
- Information Security, Cyber Security or Vulnerable Analysts
Roles of Cyber Security Professionals
Cybersecurity experts are in charge of protecting IT infrastructure, edge devices, networks, and data at a high level. They are in charge of preventing data breaches as well as monitoring and responding to attacks. Many come from programming, systems or network administration, as well as math and statistics backgrounds. Those skills are unquestionably important in the role of an IT security expert, but equally important are the qualities that cannot be taught: critical thinking, curiosity, and a desire to learn and explore. Companies should not limit themselves to a small pool of candidates because those attributes exist in people from all walks of life. Hackers are also naturally creative. To outwit them, security professionals must be as well.
Common skills that are required in this field
Not sure if a career in cyber security is right for you? If the prospect of working as an information security analyst, penetration tester, or computer forensics investigator has piqued your interest, you may already have a few skills required for one of these positions.

A qualified information security practitioner will require the following skills:
- Ability to work in a challenging environment.
- Should be analytical.
- Should be logical.
- Should have a strong background in Information Security (IT).
- Should have proper knowledge of Networking, database and Systems.
- Should be aware of the developments in Cyber Security.
- Should have experience with Web Proxy Management and Antivirus Software.
- Should know about the UK Laws and Regulations which are applicable in relation to IT Security.
- Strong communication abilities, as well as the capacity to change communication techniques to meet the needs of various audiences.
- Strong analytical abilities and a keen eye for data trends are required.
What does it involve?
The primary purpose of IT security, as well as the primary job of an IT security expert, is to:
- Create barriers to external access to computer systems to protect them.
- Recognize faults within systems by looking for unusual activities.
- Examine the present state of network security and conduct audits.
- Implement enhancements where necessary, and keep users informed by submitting performance reports on a regular basis to communicate system security status.
An IT Security specialist's regular working hours will be 37 or 40 hours per week. However, you will very certainly be required to remain on call 24 hours a day, seven days a week in the event of a security breach. This is something you should be aware of.
Qualifications for Cyber Security Professionals
If you believe you have some of the abilities listed above plus a strong interest in information security, you should consider pursuing a career in cyber security. If you're just starting out in your career, a suitable degree subject is one of the finest methods to break into the information security field.

- IT
- Physics, Mathematics and other STEM subjects
- Forensic Computing
- Network Engineering
- Networks and Security
- Computer Science
- Cyber Security
Some Certification Courses for Cyber Security Professionals
If you're already employed in the cyber security field, you might want to pursue a few additional certifications to advance your career. With so many industry-related certifications available, it's critical that professionals only take modules that pertain to their area of expertise.

There are a few other qualifications available for cyber security experts to consider:
- Certified Information Systems Security Professionals (CISSP) -
The CISSP is the most widely held certification among information security professionals, and it is frequently required for advancement in this field. Individuals must have four or more years of experience and typically work as consultants or managers. Before ending in a six-hour exam, the qualification covers eight cyber security topics, including asset security, security engineering, and identity and access management. The certification is a worldwide recognised mark of quality and one of the requirements of the ISO/IEC Standard 17024.
- Certified Information Security Manager (CISM) -
The CISM certification is an excellent approach to advance your career for people with at least five years of experience working in the sector. Before you may receive the certification, you must have completed the requisite five years of work experience, including at least three years in an information security management position. To be eligible for accreditation, you must have completed your work experience within the previous ten years before applying.
- Systems Security Certified Practitioner (SSCP) -
This accreditation, which only requires one year of experience and provides the ideal opportunity for individuals to demonstrate their technical abilities and security expertise, is ideal for professionals just starting out in cyber security. Individuals who want to get the SSCP must have a thorough understanding of all the skills and information needed to succeed in this sector, with modules covering topics like risk identification and cryptography. Finally, a three-hour exam will be used to evaluate individuals studying for the SSCP.
Importance of Cyber Security

Everyone benefits from improved cyberdefense strategies in today's linked society. A cybersecurity attack on an individual level can result in everything from identity theft to extortion attempts to the loss of crucial data such as family photos. Critical infrastructure, such as power plants, hospitals, and financial services organisations, is used by everyone. It is critical to keep these and other institutions secure in order for our society to function. Cyberthreat researchers, such as the team of 250 threat researchers at Talos, who analyse new and emerging dangers and cyber assault techniques, help everyone. They expose new vulnerabilities, raise public awareness about the need of cybersecurity, and improve open source tools. Their efforts help to make the Internet a safer place for everyone.
Cyber Security Threats

- Mobile Security Threats -
Businesses can benefit from mobile technology, but it also exposes them to the risk of cyber security breaches. According to the findings of a recent mobile security survey, one out of every five enterprises has experienced a mobile security breach. Malware and malicious Wifi were responsible for the majority of these attacks.
- Outdated Hardware -
Software isn't the only source of cyber security problems. The rapid distribution of software updates might make it difficult for hardware to keep up. As a result, there are exposures that can put a company's data at risk. Many antiquated devices will not allow updates with the most recent patches and security measures when hardware becomes obsolete. Devices that run on older software are more vulnerable to cyber attacks, posing a significant risk. It's critical to keep an eye on this and respond immediately if equipment becomes obsolete. You should keep your hardware up to date in the same way that you keep your software up to date.
- Internet of things (IoT) -
The Internet of Things (IoT) uses the internet to connect gadgets from all around the world. This enables for the creation of a network of data-storage, data-transmission, and data-receiving devices. Many individuals and businesses take advantage of it because of its convenience. However, the exact thing that makes them useful also exposes them to danger. Hackers can use internet connectivity as a point of entry to steal information. Many experts believe that as firms increasingly rely on IoT devices, this will be one of the most serious cyber dangers in the future years.
- Third Party Exposure -
Many retailers outsource services like payment processing to third parties. As a result, they frequently feel they are immune from culpability for a third-party breach. In actuality, enlisting the help of a third-party vendor does not absolve them of liability in the event of a data breach. Even if a corporation does not handle personal data directly, such as social security numbers or credit card numbers, a third party can compromise them. Hackers can steal data from third-party vendors via malware, as they did with the Target malware attack in 2013. Even if the assault was carried out by a third party, the company that hired the third party vendor is still liable and legally compelled to notify their clients and regulators if a data breach occurs. Fines and penalties can be substantial, ranging from tens of thousands of dollars to millions of dollars depending on the circumstances.
- Social Engineering -
Social engineering assaults take advantage of social interactions to get access to sensitive information. Deception is at the heart of all social engineering attacks. Cyber thieves use deception and manipulation to persuade their victims to take specific activities, such as circumventing security measures or releasing sensitive information. Because the target lets the hacker inside the system, even the strongest cyber security systems can't stop a social engineering attack. Social engineering attacks are on the rise, according to experts, which is why we've included it as a top danger.
- Patch Management -
Many cyber-attacks begin with out-of-date software. As a result, failing to keep up with software patches leaves businesses open to a variety of data security breaches. As soon as an attacker discovers a software flaw, they might use it to launch a cyber attack. This trend in cyber security is illustrated by two large-scale cyber attacks that began in May 2018. The attacks took advantage of Eternal Blue, a serious flaw in the Windows operating system. Microsoft had, crucially, provided a patch for the Eternal Blue flaw two months prior. Organizations who did not keep their software up to date were left vulnerable. Millions of dollars were wasted due to a simple software update failure.
- BYOD (Bring Your Own Device) Policy -
As part of their Bring Your Own Device (BYOD) policies, several organisations encourage employees to use personal devices at work. This provides a number of advantages, including more flexibility and convenience. It's even been said that it boosts productivity and morale. While BYOD policies have many advantages, they can also expose businesses to major cyber security risks. Hacking personal devices is easier than hacking corporate devices, allowing attackers to infiltrate networks and expose data. To reduce the associated cyber risks, it's critical to review these policies and ensure that employees are properly trained.
Conclusion
Security specialists with advanced training are in high demand. Because no firm is immune to cybercrime, IT security must be a key priority for all. Finding the most qualified professionals to lead the way is the first step.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
Technology has intertwined our personal and professional lives in ways that were inconceivable just a few decades ago. Cloud computing, mobility, and the sophisticated devices most of us carry in our pockets enable a culture of ease as well as the opportunity to collaborate and be more productive. While this convenience may make our lives easier, it also makes it easier for cybercriminals to access our sensitive personal information no matter where it resides or travels across the network. There is a huge market for the sale and exploitation of that data, so these bad actors have plenty of reason. Hackers and cybercriminals will eventually find a method to access your data, even if you have the greatest Cyber Security Professional on your side. That isn't to argue that everything is bleak. IT security professionals fight on the front lines of this war to keep up with the ever-changing threat landscape.
Important skills for Cyber security professionals
More than technical capabilities are required of successful IT security experts. To make real progress in the sector, these professionals should be able to:
- Learners - Technical proficiency is another essential skill. With the rapid pace of change in IT security, this necessitates continual study, training, and certification. To be able to tackle complicated security challenges, these specialists need to be constantly learning new advanced technology skills.
- Communicators - Effective coordination with teams and clients is ensured through management and communication abilities. Every employee in an organisation is affected by technology and security. By teaching and empowering people to assist secure systems, security professionals must interact in meaningful ways.
- Strategists - Professionals in cyber security should be able to proactively deploy security measures and controls within enterprises while assessing the implications of every action. Workflows, dependencies, finances, and resources must all be evaluated tactically and strategically in order to implement advanced security processes. Because new ways to hack information are appearing all the time, specialists must stay one step ahead of the game, learning how hackers get into networks and how to stop them.
Responsibilities of the cyber security professional
New security risks emerge on a regular basis, and IT security experts must keep up with the current strategies used by hackers in the field. In addition to the high-level roles listed above, IT security teams also do the following tasks:
- Set up and use identity and access management systems, as well as user access controls.
- To detect and prevent abnormal activity, keep an eye on network and application performance.
- Conduct regular audits to ensure that security procedures are in compliance.
- To thwart malicious hacks, use endpoint detection and prevention solutions.
- Set up patch management systems to automatically update software.
- Implement comprehensive vulnerability management systems across all assets, including on-premises and in the cloud.
- And collaborate with IT operations to create a single disaster recovery/business continuity strategy.
- Educate staff on how to spot suspicious conduct in collaboration with HR and/or team leads.
Salary for cyber security professional
Cyber security professionals, for example, earn an average of $116,000 per year or $55.77 per hour, according to CIO, but PayScale estimates that the average wage for computer security specialists is around $74,000, with geography being a big role in pay structure.
Different roles in Cyber Security
Starting as a generalist and then specialising in an area of interest or strength might assist cyber security professionals. These are some of the possibilities:
- Application Security
- Data loss prevention
- Forensics
- Network Security
- Security Architecture
- Threat Intelligence
- Incident response
- Vulnerability management
Job growth in Cyber Security
Professionals in cyber security work in practically every area and industry – public and private, for-profit and charity – and at both large and small enterprises and organisations, including:
- Government
- Finance and Banking
- Health Care
- Insurance
- Technology
- Government
- Telecommunications
- Law enforcement
What are Cyber Security people known as?
Cyber security specialists go by a variety of names, but their work titles or descriptions "usually" include the terms "information security," "cyber security," or "similar terms." Here are several examples:
- Cyber Security Specialists
- Penetration Testers
- Cyber Security or Security Administrators
- Cyber Security or Security Principals
- Cyber Security or Security Technicians
- Cyber Security Specialists
- Cyber Security Technical Architects
- Information Security, Cyber Security or Vulnerable Analysts
Roles of Cyber Security Professionals
Cybersecurity experts are in charge of protecting IT infrastructure, edge devices, networks, and data at a high level. They are in charge of preventing data breaches as well as monitoring and responding to attacks. Many come from programming, systems or network administration, as well as math and statistics backgrounds. Those skills are unquestionably important in the role of an IT security expert, but equally important are the qualities that cannot be taught: critical thinking, curiosity, and a desire to learn and explore. Companies should not limit themselves to a small pool of candidates because those attributes exist in people from all walks of life. Hackers are also naturally creative. To outwit them, security professionals must be as well.
Common skills that are required in this field
Not sure if a career in cyber security is right for you? If the prospect of working as an information security analyst, penetration tester, or computer forensics investigator has piqued your interest, you may already have a few skills required for one of these positions.
A qualified information security practitioner will require the following skills:
- Ability to work in a challenging environment.
- Should be analytical.
- Should be logical.
- Should have a strong background in Information Security (IT).
- Should have proper knowledge of Networking, database and Systems.
- Should be aware of the developments in Cyber Security.
- Should have experience with Web Proxy Management and Antivirus Software.
- Should know about the UK Laws and Regulations which are applicable in relation to IT Security.
- Strong communication abilities, as well as the capacity to change communication techniques to meet the needs of various audiences.
- Strong analytical abilities and a keen eye for data trends are required.
What does it involve?
The primary purpose of IT security, as well as the primary job of an IT security expert, is to:
- Create barriers to external access to computer systems to protect them.
- Recognize faults within systems by looking for unusual activities.
- Examine the present state of network security and conduct audits.
- Implement enhancements where necessary, and keep users informed by submitting performance reports on a regular basis to communicate system security status.
An IT Security specialist's regular working hours will be 37 or 40 hours per week. However, you will very certainly be required to remain on call 24 hours a day, seven days a week in the event of a security breach. This is something you should be aware of.
Qualifications for Cyber Security Professionals
If you believe you have some of the abilities listed above plus a strong interest in information security, you should consider pursuing a career in cyber security. If you're just starting out in your career, a suitable degree subject is one of the finest methods to break into the information security field.
- IT
- Physics, Mathematics and other STEM subjects
- Forensic Computing
- Network Engineering
- Networks and Security
- Computer Science
- Cyber Security
Some Certification Courses for Cyber Security Professionals
If you're already employed in the cyber security field, you might want to pursue a few additional certifications to advance your career. With so many industry-related certifications available, it's critical that professionals only take modules that pertain to their area of expertise.
There are a few other qualifications available for cyber security experts to consider:
- Certified Information Systems Security Professionals (CISSP) -
The CISSP is the most widely held certification among information security professionals, and it is frequently required for advancement in this field. Individuals must have four or more years of experience and typically work as consultants or managers. Before ending in a six-hour exam, the qualification covers eight cyber security topics, including asset security, security engineering, and identity and access management. The certification is a worldwide recognised mark of quality and one of the requirements of the ISO/IEC Standard 17024.
- Certified Information Security Manager (CISM) -
The CISM certification is an excellent approach to advance your career for people with at least five years of experience working in the sector. Before you may receive the certification, you must have completed the requisite five years of work experience, including at least three years in an information security management position. To be eligible for accreditation, you must have completed your work experience within the previous ten years before applying.
- Systems Security Certified Practitioner (SSCP) -
This accreditation, which only requires one year of experience and provides the ideal opportunity for individuals to demonstrate their technical abilities and security expertise, is ideal for professionals just starting out in cyber security. Individuals who want to get the SSCP must have a thorough understanding of all the skills and information needed to succeed in this sector, with modules covering topics like risk identification and cryptography. Finally, a three-hour exam will be used to evaluate individuals studying for the SSCP.
Importance of Cyber Security
Everyone benefits from improved cyberdefense strategies in today's linked society. A cybersecurity attack on an individual level can result in everything from identity theft to extortion attempts to the loss of crucial data such as family photos. Critical infrastructure, such as power plants, hospitals, and financial services organisations, is used by everyone. It is critical to keep these and other institutions secure in order for our society to function. Cyberthreat researchers, such as the team of 250 threat researchers at Talos, who analyse new and emerging dangers and cyber assault techniques, help everyone. They expose new vulnerabilities, raise public awareness about the need of cybersecurity, and improve open source tools. Their efforts help to make the Internet a safer place for everyone.
Cyber Security Threats
- Mobile Security Threats -
Businesses can benefit from mobile technology, but it also exposes them to the risk of cyber security breaches. According to the findings of a recent mobile security survey, one out of every five enterprises has experienced a mobile security breach. Malware and malicious Wifi were responsible for the majority of these attacks.
- Outdated Hardware -
Software isn't the only source of cyber security problems. The rapid distribution of software updates might make it difficult for hardware to keep up. As a result, there are exposures that can put a company's data at risk. Many antiquated devices will not allow updates with the most recent patches and security measures when hardware becomes obsolete. Devices that run on older software are more vulnerable to cyber attacks, posing a significant risk. It's critical to keep an eye on this and respond immediately if equipment becomes obsolete. You should keep your hardware up to date in the same way that you keep your software up to date.
- Internet of things (IoT) -
The Internet of Things (IoT) uses the internet to connect gadgets from all around the world. This enables for the creation of a network of data-storage, data-transmission, and data-receiving devices. Many individuals and businesses take advantage of it because of its convenience. However, the exact thing that makes them useful also exposes them to danger. Hackers can use internet connectivity as a point of entry to steal information. Many experts believe that as firms increasingly rely on IoT devices, this will be one of the most serious cyber dangers in the future years.
- Third Party Exposure -
Many retailers outsource services like payment processing to third parties. As a result, they frequently feel they are immune from culpability for a third-party breach. In actuality, enlisting the help of a third-party vendor does not absolve them of liability in the event of a data breach. Even if a corporation does not handle personal data directly, such as social security numbers or credit card numbers, a third party can compromise them. Hackers can steal data from third-party vendors via malware, as they did with the Target malware attack in 2013. Even if the assault was carried out by a third party, the company that hired the third party vendor is still liable and legally compelled to notify their clients and regulators if a data breach occurs. Fines and penalties can be substantial, ranging from tens of thousands of dollars to millions of dollars depending on the circumstances.
- Social Engineering -
Social engineering assaults take advantage of social interactions to get access to sensitive information. Deception is at the heart of all social engineering attacks. Cyber thieves use deception and manipulation to persuade their victims to take specific activities, such as circumventing security measures or releasing sensitive information. Because the target lets the hacker inside the system, even the strongest cyber security systems can't stop a social engineering attack. Social engineering attacks are on the rise, according to experts, which is why we've included it as a top danger.
- Patch Management -
Many cyber-attacks begin with out-of-date software. As a result, failing to keep up with software patches leaves businesses open to a variety of data security breaches. As soon as an attacker discovers a software flaw, they might use it to launch a cyber attack. This trend in cyber security is illustrated by two large-scale cyber attacks that began in May 2018. The attacks took advantage of Eternal Blue, a serious flaw in the Windows operating system. Microsoft had, crucially, provided a patch for the Eternal Blue flaw two months prior. Organizations who did not keep their software up to date were left vulnerable. Millions of dollars were wasted due to a simple software update failure.
- BYOD (Bring Your Own Device) Policy -
As part of their Bring Your Own Device (BYOD) policies, several organisations encourage employees to use personal devices at work. This provides a number of advantages, including more flexibility and convenience. It's even been said that it boosts productivity and morale. While BYOD policies have many advantages, they can also expose businesses to major cyber security risks. Hacking personal devices is easier than hacking corporate devices, allowing attackers to infiltrate networks and expose data. To reduce the associated cyber risks, it's critical to review these policies and ensure that employees are properly trained.
Conclusion
Security specialists with advanced training are in high demand. Because no firm is immune to cybercrime, IT security must be a key priority for all. Finding the most qualified professionals to lead the way is the first step.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Fundamentals of Project Sustainability
Sustainable development is a notion that refers to the continuity of human society's economic, social, institutional, and environmental components, as well as the non-human environment. The ability to sustain a business at a specific level indefinitely is a property of a process or situation. Project sustainability is currently a typical approach to the management of projects, programmes, institutions, organisations, individuals, and other entities that require effective and efficient product and service creation, marketing, distribution, and delivery.
From project discovery to feasibility studies, conceptualization, design, appraisal, funding, execution, monitoring, and evaluation, specific metrics and criteria must be established in order for initiatives to be sustained. It is a well-known fact that most projects fail due to a lack of a suitable sustainability plan. For project execution, a thorough examination of the social, economic, legal, cultural, educational, and political surroundings is required.
The plan should completely describe and state the project philosophy, mission, vision, values, goals, and objectives. The involvement of stakeholders and advocates is critical since it allows for some logistical planning. Beneficiary analysis, legal and regulatory framework studies, marketing and competitive analysis, partnership creation, and institutional analysis all help to ensure that projects are implemented effectively and efficiently.
Characteristics of Project Sustainability
Project sustainability management (PSM) is gaining traction in project management and is altering the dynamics of a range of projects' execution. Business sustainability refers to a situation in which people and commerce impose demands on the environment that may be met without compromising the environment's ability to provide for future generations. The main premise is for businesses to offer tasks and services that are successful and efficient while also promoting societal sustainability.
Services and products should have minimal or no competition in terms of image, power, quality, packaging, prices, and so on, in order for a firm to be viable in the marketplace. Instead, products and services should be delivered in such a way that they reduce consumption, energy consumption, distribution costs, economic concentration, and other forms of business and environmental harm.
Following are the Characteristics of Project Sustainability:
1) Adaptability
Adaptability in organisational management refers to the ability to adjust something or oneself to accommodate changing circumstances and cope with unforeseen disruptions in any context. It is a system's ability to adapt efficiently and quickly enough to changing circumstances. As a result, a sustainable project should be adaptable and able to fit into any changing environment or system.
2) Auditing Capability
A person, organisation, system, process, enterprise, project, or product is frequently the subject of an audit. This notion, however, can be applied to project management, quality control, and energy conservation. Audits are conducted to determine the quality and reliability of data in order to offer an opinion on a subject under consideration and to establish an internal control system. Organizations are using risk-based audits to cover different regulations and standards in order to assure credibility, good governance, and sustainability as a result of increased regulations and the requirement for operational transparency.
3) Ability to Implement
One of the most important principles in project management is that it must be reasonable, feasible, attainable, and, most importantly, implementable in order to be marketable.
4) Scalability
Scalability refers to a project's ability to expand its scope of operation and accommodate additional capacity or capabilities. It also addresses the project's potential to expand in size, volume, number, or scope in order to accommodate unforeseen extra components or features.
5) Extensibility
This refers to the ability to expand the project by adding new functions or modifying current ones in order to impact change while keeping existing project functions to a minimum.
6) Maintainability
When errors can be repaired, new requirements can be met, future maintenance is simplified, and the project can adapt to changing conditions, it is considered sustainable.
7) Manageability
A long-term project should have a clear organisational structure that defines roles, responsibilities, and responsibilities. This will make project management easier and increase its long-term viability.
Implementation of the Strategic Plan
In ministries and related departments and divisions, public, non-governmental organisations, parastatal organisations, international organisations, and private enterprises, a strategic plan is created to ensure that services are delivered effectively and efficiently. Small and large firms, agro-industrial complexes, pharmaceutical industries, and a variety of other businesses that require quality in their products and services, as well as their general operation, can benefit from this implementation plan.
This plan includes seventeen important implementation steps, including top management commitment, the development of a corporate strategic plan, the development of an organisational structure, the development of an implementation budget, the formation of a quality council, teams, and panels, the beginning of an awareness plan, the training of team leaders and facilitators, the conduct of an initial survey, the documentation of the implementation plan, the documentation of the quality system, the documentation control, and the act.
Because it will result in a "paradigm shift" and "culture transition," the implementation affects the entire company from the start and is pushed with zeal. The complexity of the process is determined by the sophistication of the society and organisation, as well as the size of the organisation. Identifying programme goals to be addressed in the identified time period, determining programme logic, targeting specific audiences, specifying desired outcomes, determining the current situation, identifying sequenced learning strategies, determining resource needs, and selecting specific marketing strategies are all basic elements of implementation planning.
The following are some of the advantages of effective implementation planning:
- Possibilities for greater programme impact, Sequence and continuity in educational programmes
- Clarification of the actions and resources required to carry out a programme,
- Program marketing is being planned.
- enhanced evaluation and accountability,
- Improved time management and scheduling, as well as increased personal satisfaction from a sense of progress and accomplishment.
Project Management for Longevity (Project Sustainability Management)
Project sustainability management is a novel idea born from the requirement for project sustainability (PSM). This is a complex mix of systems, structures, plans, resources, laws, regulations, technology, and other processes put in place to manage the sustainability process of any project effectively and efficiently. The project sustainability management process is intended to tailor sustainable development project goals and indicators to local conditions and priorities, as well as to guarantee that project sustainability goals are linked to societal goals and objectives.
A project sustainability management system identifies the relevant issues, objectives, and performance levels that must be met; it also establishes an ethical framework as the foundation for establishing policies and codes of conduct, consults with and maintains a dialogue with stakeholders, and accounts for the results achieved.
The following are the global principles of sustainable development:
- This is a concern for the future. This entails a variety of innovations to create and improve for the future, anticipating what may occur, and enabling information through sharing and increased interaction. Innovation also improves the gathering and assimilation of information about new products and processes.
- Participation refers to the involvement of stakeholders in project decision making. This necessitates a significant amount of education and trust in order to engage stakeholders and build their capacity to identify issues, incorporate local values, and communicate their experiences.
- Resources—This is the concern for equitability in resource consumption and improvement in resource utilisation. This necessitates continuous improvement in methods for identifying and managing resources, as well as seeking new knowledge and information about them.
- Concern for the quality and integrity of the environment necessitates the adaptation of global standards to local conditions. This entails using a variety of indicators to match project aims with global goals while also taking into account local circumstances.
Conclusion
A project must always have the rationale, demand and supply basis, expenses, expected outcomes or outputs, and performance metrics, all of which must be met in order for it to be funded. In order to assess affordability, demographic studies examine needs, income, interests, cultures, education, and other humans, social, and economic characteristics. The legal and regulatory framework deals with licences and authorizations, as well as the many rules, regulations, bylaws, and procedures that are necessary by law for project implementation in that environment.
Technically, the project's information, communication, and technology (ICT) infrastructure, particularly access to modern technology and systems, should be properly assessed.
Sustainability's philosophical and analytical framework draws on and connects with many different disciplines and fields, and it has tended to be problem-driven and oriented toward guiding decision-making.
The emphasis shifts from the total carrying capacity (sustainability) of the planet to the sustainability of economic and social sectors, ecosystems, countries, municipalities, neighbourhoods, home gardens, individual lives, individual goods and services, occupations, lifestyles, behaviour patterns, academic and research institutions, political institutions, and business operations.
Sustainable development is a situation in which human and commercial demands on the environment can be addressed without compromising the environment's ability to provide for future generations. The main premise is for businesses to offer tasks and services that are successful and efficient while also promoting societal sustainability.
Services and products should have minimal or no competition in terms of image, power, quality, packaging, prices, and so on, in order for a firm to be viable in the marketplace. Instead, products and services should be delivered in such a way that they reduce consumption, energy consumption, distribution costs, economic concentration, and other forms of business and environmental harm. Stakeholder analysis, policy development, and objective and design are the major ways for operating an organisation according to sustainable development principles.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
Sustainable development is a notion that refers to the continuity of human society's economic, social, institutional, and environmental components, as well as the non-human environment. The ability to sustain a business at a specific level indefinitely is a property of a process or situation. Project sustainability is currently a typical approach to the management of projects, programmes, institutions, organisations, individuals, and other entities that require effective and efficient product and service creation, marketing, distribution, and delivery.
From project discovery to feasibility studies, conceptualization, design, appraisal, funding, execution, monitoring, and evaluation, specific metrics and criteria must be established in order for initiatives to be sustained. It is a well-known fact that most projects fail due to a lack of a suitable sustainability plan. For project execution, a thorough examination of the social, economic, legal, cultural, educational, and political surroundings is required.
The plan should completely describe and state the project philosophy, mission, vision, values, goals, and objectives. The involvement of stakeholders and advocates is critical since it allows for some logistical planning. Beneficiary analysis, legal and regulatory framework studies, marketing and competitive analysis, partnership creation, and institutional analysis all help to ensure that projects are implemented effectively and efficiently.
Characteristics of Project Sustainability
Project sustainability management (PSM) is gaining traction in project management and is altering the dynamics of a range of projects' execution. Business sustainability refers to a situation in which people and commerce impose demands on the environment that may be met without compromising the environment's ability to provide for future generations. The main premise is for businesses to offer tasks and services that are successful and efficient while also promoting societal sustainability.
Services and products should have minimal or no competition in terms of image, power, quality, packaging, prices, and so on, in order for a firm to be viable in the marketplace. Instead, products and services should be delivered in such a way that they reduce consumption, energy consumption, distribution costs, economic concentration, and other forms of business and environmental harm.
Following are the Characteristics of Project Sustainability:
1) Adaptability
Adaptability in organisational management refers to the ability to adjust something or oneself to accommodate changing circumstances and cope with unforeseen disruptions in any context. It is a system's ability to adapt efficiently and quickly enough to changing circumstances. As a result, a sustainable project should be adaptable and able to fit into any changing environment or system.
2) Auditing Capability
A person, organisation, system, process, enterprise, project, or product is frequently the subject of an audit. This notion, however, can be applied to project management, quality control, and energy conservation. Audits are conducted to determine the quality and reliability of data in order to offer an opinion on a subject under consideration and to establish an internal control system. Organizations are using risk-based audits to cover different regulations and standards in order to assure credibility, good governance, and sustainability as a result of increased regulations and the requirement for operational transparency.
3) Ability to Implement
One of the most important principles in project management is that it must be reasonable, feasible, attainable, and, most importantly, implementable in order to be marketable.
4) Scalability
Scalability refers to a project's ability to expand its scope of operation and accommodate additional capacity or capabilities. It also addresses the project's potential to expand in size, volume, number, or scope in order to accommodate unforeseen extra components or features.
5) Extensibility
This refers to the ability to expand the project by adding new functions or modifying current ones in order to impact change while keeping existing project functions to a minimum.
6) Maintainability
When errors can be repaired, new requirements can be met, future maintenance is simplified, and the project can adapt to changing conditions, it is considered sustainable.
7) Manageability
A long-term project should have a clear organisational structure that defines roles, responsibilities, and responsibilities. This will make project management easier and increase its long-term viability.
Implementation of the Strategic Plan
In ministries and related departments and divisions, public, non-governmental organisations, parastatal organisations, international organisations, and private enterprises, a strategic plan is created to ensure that services are delivered effectively and efficiently. Small and large firms, agro-industrial complexes, pharmaceutical industries, and a variety of other businesses that require quality in their products and services, as well as their general operation, can benefit from this implementation plan.
This plan includes seventeen important implementation steps, including top management commitment, the development of a corporate strategic plan, the development of an organisational structure, the development of an implementation budget, the formation of a quality council, teams, and panels, the beginning of an awareness plan, the training of team leaders and facilitators, the conduct of an initial survey, the documentation of the implementation plan, the documentation of the quality system, the documentation control, and the act.
Because it will result in a "paradigm shift" and "culture transition," the implementation affects the entire company from the start and is pushed with zeal. The complexity of the process is determined by the sophistication of the society and organisation, as well as the size of the organisation. Identifying programme goals to be addressed in the identified time period, determining programme logic, targeting specific audiences, specifying desired outcomes, determining the current situation, identifying sequenced learning strategies, determining resource needs, and selecting specific marketing strategies are all basic elements of implementation planning.
The following are some of the advantages of effective implementation planning:
- Possibilities for greater programme impact, Sequence and continuity in educational programmes
- Clarification of the actions and resources required to carry out a programme,
- Program marketing is being planned.
- enhanced evaluation and accountability,
- Improved time management and scheduling, as well as increased personal satisfaction from a sense of progress and accomplishment.
Project Management for Longevity (Project Sustainability Management)
Project sustainability management is a novel idea born from the requirement for project sustainability (PSM). This is a complex mix of systems, structures, plans, resources, laws, regulations, technology, and other processes put in place to manage the sustainability process of any project effectively and efficiently. The project sustainability management process is intended to tailor sustainable development project goals and indicators to local conditions and priorities, as well as to guarantee that project sustainability goals are linked to societal goals and objectives.
A project sustainability management system identifies the relevant issues, objectives, and performance levels that must be met; it also establishes an ethical framework as the foundation for establishing policies and codes of conduct, consults with and maintains a dialogue with stakeholders, and accounts for the results achieved.
The following are the global principles of sustainable development:
- This is a concern for the future. This entails a variety of innovations to create and improve for the future, anticipating what may occur, and enabling information through sharing and increased interaction. Innovation also improves the gathering and assimilation of information about new products and processes.
- Participation refers to the involvement of stakeholders in project decision making. This necessitates a significant amount of education and trust in order to engage stakeholders and build their capacity to identify issues, incorporate local values, and communicate their experiences.
- Resources—This is the concern for equitability in resource consumption and improvement in resource utilisation. This necessitates continuous improvement in methods for identifying and managing resources, as well as seeking new knowledge and information about them.
- Concern for the quality and integrity of the environment necessitates the adaptation of global standards to local conditions. This entails using a variety of indicators to match project aims with global goals while also taking into account local circumstances.
Conclusion
A project must always have the rationale, demand and supply basis, expenses, expected outcomes or outputs, and performance metrics, all of which must be met in order for it to be funded. In order to assess affordability, demographic studies examine needs, income, interests, cultures, education, and other humans, social, and economic characteristics. The legal and regulatory framework deals with licences and authorizations, as well as the many rules, regulations, bylaws, and procedures that are necessary by law for project implementation in that environment.
Technically, the project's information, communication, and technology (ICT) infrastructure, particularly access to modern technology and systems, should be properly assessed.
Sustainability's philosophical and analytical framework draws on and connects with many different disciplines and fields, and it has tended to be problem-driven and oriented toward guiding decision-making.
The emphasis shifts from the total carrying capacity (sustainability) of the planet to the sustainability of economic and social sectors, ecosystems, countries, municipalities, neighbourhoods, home gardens, individual lives, individual goods and services, occupations, lifestyles, behaviour patterns, academic and research institutions, political institutions, and business operations.
Sustainable development is a situation in which human and commercial demands on the environment can be addressed without compromising the environment's ability to provide for future generations. The main premise is for businesses to offer tasks and services that are successful and efficient while also promoting societal sustainability.
Services and products should have minimal or no competition in terms of image, power, quality, packaging, prices, and so on, in order for a firm to be viable in the marketplace. Instead, products and services should be delivered in such a way that they reduce consumption, energy consumption, distribution costs, economic concentration, and other forms of business and environmental harm. Stakeholder analysis, policy development, and objective and design are the major ways for operating an organisation according to sustainable development principles.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Pros and Cons of Enlisting AI for Cyber Security
Year after year, the technology industry expands at a breakneck pace, resulting in increased data transmission. Software engineers and cyber security analysts rely on artificial intelligence and machine learning algorithms to better defend against hackers due to the vast data size.
By analysing the flow of online traffic, this ground-breaking technology will be able to predict cyberattacks before they happen. And, if AI can predict future threats, it will be better able to protect against them and eradicate them before they cause havoc. What if, on the other hand, hackers can use artificial intelligence to generate more powerful malware capable of breaching even the most sophisticated cyber security systems?
Artificial intelligence is being used by increasing cyber security organisations for a variety of reasons. In this essay, I'll discuss the benefits and drawbacks of AI in cyber security.
AI in Cyber security
Machine learning offers a wide range of uses. It's used by researchers and IT professionals in fields as diverse as medicine, mechanical engineering, marketing, astronomy, and more. The number of users is increasing as devices become more networked and reliant on the internet.
Hackers now have access to more data through destructive activity. They frequently employ AI technologies to limit the number of times malware is exploited.
The Android apps on the Google Play Store, for example, use adware to gain access to your phone. When users launch an app, the latter is software that automatically downloads advertising to their devices. AI is frequently used in such apps to create customised advertising content. On a daily basis, a typical mid-sized organisation receives up to 200,000 security threats. Even the most skilled experts will find it difficult to track because of this. Each analyst would have to go over each threat separately.
However, by repeating the process, more dangers and assaults may go unreported.
Pros of enlisting AI for cyber security
By predicting and preventing threats, artificial intelligence can help to improve cyber security and provide greater protection.

- Processes that are duplicated are reduced -
Detecting possible risks is a process that is repeated and duplicated. Analysts can save a lot of time by using AI-driven algorithms instead of repeating the same process on millions of datasets. In the meantime, cyber security specialists can work on improving algorithms or learning more about new threats on the internet.
- Machine Learning Aids in the Fight Against Scams -
To avoid spam emails and phishing scams, Google employs machine learning algorithms. Phishing is a technique in which hackers trick consumers into clicking on a link that appears to be a popular website such as Facebook or PayPal. Google's algorithms aid in the detection of dangerous emails, allowing users to be warned and protected.
- AI is capable of handling Large Amounts of Data -
Cyber security automation aids businesses in managing massive amounts of data on a regular basis. A robust machine learning algorithm, on the other hand, can predict risks before they occur. It can also quickly skim through a large amount of data to find them. In a sea of chaotic data, the automated procedure streamlines the practise of assessing each cyber security occurrence.
- Algorithms improve their Learning Capacity Over Time -
Machine learning and deep learning algorithms are used by AI-driven applications to learn. They are able to discern patterns and predict changes. The algorithm groups them together once they've been recognised, allowing for the detection and removal of prospective threats with comparable characteristics.
Furthermore, AI cyber security solutions become familiar with typical network activity and can immediately identify any changes before taking action to eliminate threats. Such algorithms can also aid IT security experts in identifying hazards and resolving problems.
- Threats that aren't well-known are easy to spot -
Every day, hackers release millions of pieces of harmful software. According to G Data Software's study, 7.41 million new malware samples were discovered per day in 2017. That number far outnumbers the abilities of professional hackers who frequently play hide-and-seek with the most recent virus.
Instead, automated cyber security looks for changes in the network to spot new threats.
- Improved adaptability -
Machine learning algorithms and deep learning are used by AI-driven applications and systems to learn. AI can readily grasp various IT trends and make modifications to its algorithms based on the most up-to-date data or information using these techniques. In the same way, AI in cyber security is conversant with complex data networks that can swiftly discover and eradicate security problems with minimal human participation.
Cons of enlisting AI for Cyber security
While automated cyber security has a number of advantages, it also has a number of drawbacks. Here's a list of them.

- AI is costly -
The growth of artificial intelligence is primarily due to data science and big data. As a result, experts in this subject are few or impossible to come by. Many businesses are at risk of overspending due to the scarcity of cyber security AI solutions.
- Unemployment -
Automated cyber security, like other AI-driven solutions, poses a risk of job loss. Many businesses do not require IT experts to manually test their networks. Artificial intelligence, on the other hand, is capable of completing the task.
- Evolvement of cyber threats -
Artificial intelligence, as previously said, can process a big amount of data and swiftly recognise a threat in the midst of turmoil. AI-driven solutions, on the other hand, require continual upgrades and improvements to stay up with evolving threats. Hackers can be resourceful and create a variety of changes to mislead a programme.
Before becoming available to the general public, AI systems are frequently subjected to extensive testing. Researchers open-source their work and publish it in open-access journals so that anybody can see it. That includes hackers, who can use such data to plan assaults ahead of time.
- Cybercriminals are also well-versed in Artificial Intelligence -
Everyone has access to AI knowledge. As a result, fraudsters can easily obtain AI-generated cyber security solutions and utilise them to exploit malware. They can construct malevolent, AI-proof applications that can breach websites and organisations more effectively.
Machine learning is used by cybercriminals to discover how AI-based cyber solutions are trained. They can also learn how to work together to avoid cyber threats. This technique will also be used by hackers to contaminate malware and make it appear innocent. IT security professionals will not focus on a "harmless" danger in such a case. They'll concentrate on what they consider to be the more dangerous threat, while the masked threat continues to harm your data.
- The invasion of privacy -
Biometric systems and other AI-powered technologies may pose a threat to our sensitive and secret data. These devices have the ability to send our data to third-party providers, who may then misuse it, infringing on the privacy of both individuals and businesses.
Today's Major Cyber security Challenges
Despite cyber security breakthroughs, internet attacks are getting increasingly deadly. And the challenges that the industry is facing aren't helping matters.
- There are far too many IT systems spread out throughout the globe, making manual tracking more challenging. Despite the fact that many of them have successful manual monitoring, the entire procedure is difficult. Experts in cyber security must overcome infrastructure differences.
- Threat-tracking by hand can be costly and time-consuming. As a result, more attacks may go undetected or untreated in a timely manner.
- Because of the reactive nature of cyber security, we can only tackle problems after they've occurred. For security specialists, predicting threats before they cause damage to IT systems is a huge task.
- To conduct a cyberattack, hackers frequently modify and mask their IP addresses using various methods. They use VPNs (Virtual Private Networks), proxy servers, TOR browsers, and other tools. These methods allow hackers to remain anonymous and undiscovered. As a result, in order to safeguard your data, you must equip your smartphone with these vital tools.
Role of Microsoft in the evolution of AI in Cyber security
In 2017, the evolution of AI in cyber security began. Microsoft announced the acquisition of Hexadite, an artificial intelligence cyber security firm based in the United States and Israel. That's when many businesses understood that the only way to deal with massive amounts of data was to use an efficient algorithm.
The company's cutting-edge technology was one of the key reasons Microsoft purchased it. That technology will be used in Windows Defender's Advanced Threat Protection functionality. It will be able to predict zero-day assaults, ransomware, and other threats thanks to the AI-driven upgrade.
Final thoughts
AI continues to be integrated into futuristic cyber security solutions by cyber security companies and organisations. That trend was expedited by Microsoft's game-changing acquisition. In the battle against cybercrime, AI technologies will improve and become even more effective.
For every firm to run successfully, the interaction between AI and cyber security is critical. It's a proactive method that gives you insight into the ongoing operation so you can anticipate and respond to threats. It encourages the use of artificial intelligence to make data-driven judgments. To comprehend the relationship between AI and cyber security methods, protocols, rules, procedures, and strict measures are required. This gives you control over your risk management system and aids in the development of a cyber security strategy.
With that in mind, there will be a slew of additional benefits to adopting automated methods to combat hackers.
Do you believe that Artificial Intelligence will be able to eliminate cyber threats? In the comments section below, express your thoughts on the subject.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
Year after year, the technology industry expands at a breakneck pace, resulting in increased data transmission. Software engineers and cyber security analysts rely on artificial intelligence and machine learning algorithms to better defend against hackers due to the vast data size.
By analysing the flow of online traffic, this ground-breaking technology will be able to predict cyberattacks before they happen. And, if AI can predict future threats, it will be better able to protect against them and eradicate them before they cause havoc. What if, on the other hand, hackers can use artificial intelligence to generate more powerful malware capable of breaching even the most sophisticated cyber security systems?
Artificial intelligence is being used by increasing cyber security organisations for a variety of reasons. In this essay, I'll discuss the benefits and drawbacks of AI in cyber security.
AI in Cyber security
Machine learning offers a wide range of uses. It's used by researchers and IT professionals in fields as diverse as medicine, mechanical engineering, marketing, astronomy, and more. The number of users is increasing as devices become more networked and reliant on the internet.
Hackers now have access to more data through destructive activity. They frequently employ AI technologies to limit the number of times malware is exploited.
The Android apps on the Google Play Store, for example, use adware to gain access to your phone. When users launch an app, the latter is software that automatically downloads advertising to their devices. AI is frequently used in such apps to create customised advertising content. On a daily basis, a typical mid-sized organisation receives up to 200,000 security threats. Even the most skilled experts will find it difficult to track because of this. Each analyst would have to go over each threat separately.
However, by repeating the process, more dangers and assaults may go unreported.
Pros of enlisting AI for cyber security
By predicting and preventing threats, artificial intelligence can help to improve cyber security and provide greater protection.
- Processes that are duplicated are reduced -
Detecting possible risks is a process that is repeated and duplicated. Analysts can save a lot of time by using AI-driven algorithms instead of repeating the same process on millions of datasets. In the meantime, cyber security specialists can work on improving algorithms or learning more about new threats on the internet.
- Machine Learning Aids in the Fight Against Scams -
To avoid spam emails and phishing scams, Google employs machine learning algorithms. Phishing is a technique in which hackers trick consumers into clicking on a link that appears to be a popular website such as Facebook or PayPal. Google's algorithms aid in the detection of dangerous emails, allowing users to be warned and protected.
- AI is capable of handling Large Amounts of Data -
Cyber security automation aids businesses in managing massive amounts of data on a regular basis. A robust machine learning algorithm, on the other hand, can predict risks before they occur. It can also quickly skim through a large amount of data to find them. In a sea of chaotic data, the automated procedure streamlines the practise of assessing each cyber security occurrence.
- Algorithms improve their Learning Capacity Over Time -
Machine learning and deep learning algorithms are used by AI-driven applications to learn. They are able to discern patterns and predict changes. The algorithm groups them together once they've been recognised, allowing for the detection and removal of prospective threats with comparable characteristics.
Furthermore, AI cyber security solutions become familiar with typical network activity and can immediately identify any changes before taking action to eliminate threats. Such algorithms can also aid IT security experts in identifying hazards and resolving problems.
- Threats that aren't well-known are easy to spot -
Every day, hackers release millions of pieces of harmful software. According to G Data Software's study, 7.41 million new malware samples were discovered per day in 2017. That number far outnumbers the abilities of professional hackers who frequently play hide-and-seek with the most recent virus.
Instead, automated cyber security looks for changes in the network to spot new threats.
- Improved adaptability -
Machine learning algorithms and deep learning are used by AI-driven applications and systems to learn. AI can readily grasp various IT trends and make modifications to its algorithms based on the most up-to-date data or information using these techniques. In the same way, AI in cyber security is conversant with complex data networks that can swiftly discover and eradicate security problems with minimal human participation.
Cons of enlisting AI for Cyber security
While automated cyber security has a number of advantages, it also has a number of drawbacks. Here's a list of them.
- AI is costly -
The growth of artificial intelligence is primarily due to data science and big data. As a result, experts in this subject are few or impossible to come by. Many businesses are at risk of overspending due to the scarcity of cyber security AI solutions.
- Unemployment -
Automated cyber security, like other AI-driven solutions, poses a risk of job loss. Many businesses do not require IT experts to manually test their networks. Artificial intelligence, on the other hand, is capable of completing the task.
- Evolvement of cyber threats -
Artificial intelligence, as previously said, can process a big amount of data and swiftly recognise a threat in the midst of turmoil. AI-driven solutions, on the other hand, require continual upgrades and improvements to stay up with evolving threats. Hackers can be resourceful and create a variety of changes to mislead a programme.
Before becoming available to the general public, AI systems are frequently subjected to extensive testing. Researchers open-source their work and publish it in open-access journals so that anybody can see it. That includes hackers, who can use such data to plan assaults ahead of time.
- Cybercriminals are also well-versed in Artificial Intelligence -
Everyone has access to AI knowledge. As a result, fraudsters can easily obtain AI-generated cyber security solutions and utilise them to exploit malware. They can construct malevolent, AI-proof applications that can breach websites and organisations more effectively.
Machine learning is used by cybercriminals to discover how AI-based cyber solutions are trained. They can also learn how to work together to avoid cyber threats. This technique will also be used by hackers to contaminate malware and make it appear innocent. IT security professionals will not focus on a "harmless" danger in such a case. They'll concentrate on what they consider to be the more dangerous threat, while the masked threat continues to harm your data.
- The invasion of privacy -
Biometric systems and other AI-powered technologies may pose a threat to our sensitive and secret data. These devices have the ability to send our data to third-party providers, who may then misuse it, infringing on the privacy of both individuals and businesses.
Today's Major Cyber security Challenges
Despite cyber security breakthroughs, internet attacks are getting increasingly deadly. And the challenges that the industry is facing aren't helping matters.
- There are far too many IT systems spread out throughout the globe, making manual tracking more challenging. Despite the fact that many of them have successful manual monitoring, the entire procedure is difficult. Experts in cyber security must overcome infrastructure differences.
- Threat-tracking by hand can be costly and time-consuming. As a result, more attacks may go undetected or untreated in a timely manner.
- Because of the reactive nature of cyber security, we can only tackle problems after they've occurred. For security specialists, predicting threats before they cause damage to IT systems is a huge task.
- To conduct a cyberattack, hackers frequently modify and mask their IP addresses using various methods. They use VPNs (Virtual Private Networks), proxy servers, TOR browsers, and other tools. These methods allow hackers to remain anonymous and undiscovered. As a result, in order to safeguard your data, you must equip your smartphone with these vital tools.
Role of Microsoft in the evolution of AI in Cyber security
In 2017, the evolution of AI in cyber security began. Microsoft announced the acquisition of Hexadite, an artificial intelligence cyber security firm based in the United States and Israel. That's when many businesses understood that the only way to deal with massive amounts of data was to use an efficient algorithm.
The company's cutting-edge technology was one of the key reasons Microsoft purchased it. That technology will be used in Windows Defender's Advanced Threat Protection functionality. It will be able to predict zero-day assaults, ransomware, and other threats thanks to the AI-driven upgrade.
Final thoughts
AI continues to be integrated into futuristic cyber security solutions by cyber security companies and organisations. That trend was expedited by Microsoft's game-changing acquisition. In the battle against cybercrime, AI technologies will improve and become even more effective.
For every firm to run successfully, the interaction between AI and cyber security is critical. It's a proactive method that gives you insight into the ongoing operation so you can anticipate and respond to threats. It encourages the use of artificial intelligence to make data-driven judgments. To comprehend the relationship between AI and cyber security methods, protocols, rules, procedures, and strict measures are required. This gives you control over your risk management system and aids in the development of a cyber security strategy.
With that in mind, there will be a slew of additional benefits to adopting automated methods to combat hackers.
Do you believe that Artificial Intelligence will be able to eliminate cyber threats? In the comments section below, express your thoughts on the subject.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
10 Traits of Highly Effective Project Managers
Every project manager understands the importance of completing projects on time and on budget. Good project managers also go to great lengths to ensure that project criteria are met on a consistent basis. Great project managers, on the other hand, go above and above. Not only do they complete projects on time and on budget, but they are also accountable, strategic business partners who are invested in the organization's success.
What is a Project Manager?
A project manager is a person who is in charge of all parts of a project from beginning to end. Project managers are in charge of planning, executing, and overseeing projects, and they are frequently the first point of contact for any concerns that may develop. As a project manager, you will most likely be in charge of a team of people to whom you will delegate and allocate duties in order to execute a project.
Common responsibilities
A project manager's typical responsibilities include:
- Identifying and conveying project goals
- Obtaining any project requirements, such as materials, teams, and technology
- Creating timetables and schedules for the project's completion
- Managing the project's quality, timeliness, and cost
- Keeping track of every work completed as part of the project
- Stakeholder identification and management
- Bringing the project to a close and confirming that all goals have been satisfied
Highly effective 10 traits of Project Managers
In the year 2020, a lot has changed. As a result of COVID-19, project management has grown more difficult. The following attributes of highly effective project managers will show you the way if you want to stand out and take your project management career to the next level.

These qualities, when combined with the appropriate technical skills, will put you in higher demand as a project manager, giving a solid foundation that will allow you to react to the project's constantly changing dynamics while prioritising the demands of your stakeholders.
- A skilled communicator -
Communication is the most important skill because it plays such an important role in managing projects, teams, and other stakeholders. Communication does not just include being an excellent facilitator, speaker, or writer; it also necessitates excellent listening abilities. It's beneficial to actively listen to what's being said — and not stated — and to consider context. Listening to others' perspectives and taking into consideration their experiences and knowledge can assist to avoid possible conflict and hazards caused by blind spots, as well as boost project success.
- Accountable and trustworthy -
On a project, not everything will go as to plan. Mistakes are to be expected, but it's critical to always recognise when you're wrong and learn from them. It's critical to take responsibility for your decisions and actions, since it sends a powerful message to the rest of the team. "Integrity, decisiveness, sound judgement, the capacity to establish a vision and execute it, confidence in your own competence" are trademarks of extremely effective project managers, according to Paul Dillon, founder of Dillon Consulting Services.
- Working amid the gloom -
All of the previously described qualities stand out, but the ability to work in the grey area is what truly distinguishes a project manager. Because the majority of projects, regardless of type, industry, size, or complexity, will include grey regions that you will need to negotiate at some point, this is a must-have ability. External limits and complications, remote project limitations, disagreement and uncertainty – all of these and other unknowns will very likely arise. When you combine those skills with the ability to work in the grey, you've got yourself a highly capable project manager.
- A catalyst for change - If the year 2020 has taught us anything, it is that change is unavoidable and can be extremely disruptive in many aspects of business and personal life, including project management. Highly effective project managers are aware of this, embrace it, and include elements of risk into their project planning. They also understand the importance of collaborating closely with change management professionals to assist stakeholders in adapting to change and better preparing for the future state of affairs — as well as functioning in the grey.
- Stakeholder-focused -
COVID-19 has wreaked havoc on businesses and individuals around the world, making it impossible to prioritise stakeholder demands over personal and family concerns. Good project managers, on the other hand, can separate their own requirements from those of project stakeholders as professionals. Regardless of personal bias or needs, they give their best effort at all times. This is the amount of focus that organisations have grown to expect from project managers, and it is what distinguishes excellent candidates.
- Giving credit to others in a generous manner -
Others' contributions have a significant impact on a project leader's ability to lead his or her team. Project managers that are very effective share credit for good work and encourage all team members to participate and contribute to their full potential. Rather than trying to be a jack of all trades, make use of the team's collective knowledge and talents. This simple but effective strategy can dramatically boost your chances of attaining your objectives.
- A capable motivator -
The ability of a project manager to communicate with and influence a wide range of stakeholders is critical to project success. After all, you must discover ways to encourage employees over whom you have no direct control but who have the power to make or break a project. It's critical to instil confidence in the minds of stakeholders and sponsors, especially if and when it's required to approach them with adjustments to the project's scope. If you want to be respected by your teammates, stakeholders, and sponsors, you must treat them with respect at all times. Without respect and motivation, especially from sponsors and stakeholders, it's nearly impossible for projects to develop in the proper direction and on time.
- Fully committed to success -
Highly effective project managers are passionate about their profession and are invested in seeing a project through from start to finish. This mentality aids in achieving the finest results possible throughout the project. Participate fully in all professional aspects of the project, including its operations and people. If you want to maintain professional ethics and stakeholder satisfaction, don't overextend yourself. Engagement, resilience, and the ability to sustain a high level of client and team satisfaction, according to John Paul Engel, president of Knowledge Capital Consulting, are the keys to delivering success.
- A well-liked and respected leader -
Although you can't please everyone, having a well-respected leadership reputation usually signifies you've earned it via hard effort. This will take some time if you're new to project management. Working to improve your communication skills, investing in your stakeholders' success, and preserving accountability and integrity, among other things, will help you get there faster. Once you've arrived, it's much easier to lead projects and teams with ease.
- A strategic business partner -
Project managers who can deliver higher-level strategic leadership skills, rather than merely technical management skills, benefit firms of all sizes significantly. Since the epidemic began in early 2020, there have been significantly more complex internal and external issues that might negatively affect initiatives of all kinds. The triple bottom line (economic, ecological, and social consequences), legal and legislative limits, remote project challenges, international and cultural factors, as well as severe resource constraints and delays, are all examples of such factors. Factors like this contribute to the challenges that a project manager must overcome. You greatly reduce your chances of producing good outcomes if you don't have a strong understanding of how your project fits into the overarching company-wide strategic goals. EPMOs (executive project management offices) concentrate on this link to boost project, programme, and portfolio success rates.
How can these qualities help to tackle the project hindrances?
Before we go any further, let's go over the limits that a project manager should be aware of. The following are the limitations:
- SCOPE - It specifies the customers' wants as well as the explicit and implicit requirements.
- TIME - Customers want their projects to be completed by a certain deadline.
- QUALITY - It is the standard to which a project is anticipated to be completed.
- RESOURCE - This refers to the quantity of money, budget, or resources allocated to the project.
- RISK - Specifies what might happen to throw the plan off track and what will be done to get it back on track.
These aren't the only limitations that a project may face. The following are some of the major reasons for the project's failure:
- User interaction is lacking.
- Timescales that are too long or too short.
- Poor or non-existent requirements.
- Creep in the scope.
- There is no change management mechanism in place.
- Inadequate testing.
The suggested attributes work together to assist a project manager avoid all of these stumbling blocks and move the project forward successfully.
Final thoughts
When using various project management systems to keep all elements of their projects organised, a project manager should have specific features and characteristics. These qualities enable a project manager to address each project as though it were its own distinct entity.
Furthermore, with the increasing need for project managers around the world, the traits listed above will undoubtedly aid you in gaining a foothold in the fast-paced market. I wish you the best of luck in your project management endeavours!
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
Every project manager understands the importance of completing projects on time and on budget. Good project managers also go to great lengths to ensure that project criteria are met on a consistent basis. Great project managers, on the other hand, go above and above. Not only do they complete projects on time and on budget, but they are also accountable, strategic business partners who are invested in the organization's success.
What is a Project Manager?
A project manager is a person who is in charge of all parts of a project from beginning to end. Project managers are in charge of planning, executing, and overseeing projects, and they are frequently the first point of contact for any concerns that may develop. As a project manager, you will most likely be in charge of a team of people to whom you will delegate and allocate duties in order to execute a project.
Common responsibilities
A project manager's typical responsibilities include:
- Identifying and conveying project goals
- Obtaining any project requirements, such as materials, teams, and technology
- Creating timetables and schedules for the project's completion
- Managing the project's quality, timeliness, and cost
- Keeping track of every work completed as part of the project
- Stakeholder identification and management
- Bringing the project to a close and confirming that all goals have been satisfied
Highly effective 10 traits of Project Managers
In the year 2020, a lot has changed. As a result of COVID-19, project management has grown more difficult. The following attributes of highly effective project managers will show you the way if you want to stand out and take your project management career to the next level.
These qualities, when combined with the appropriate technical skills, will put you in higher demand as a project manager, giving a solid foundation that will allow you to react to the project's constantly changing dynamics while prioritising the demands of your stakeholders.
- A skilled communicator -
Communication is the most important skill because it plays such an important role in managing projects, teams, and other stakeholders. Communication does not just include being an excellent facilitator, speaker, or writer; it also necessitates excellent listening abilities. It's beneficial to actively listen to what's being said — and not stated — and to consider context. Listening to others' perspectives and taking into consideration their experiences and knowledge can assist to avoid possible conflict and hazards caused by blind spots, as well as boost project success.
- Accountable and trustworthy -
On a project, not everything will go as to plan. Mistakes are to be expected, but it's critical to always recognise when you're wrong and learn from them. It's critical to take responsibility for your decisions and actions, since it sends a powerful message to the rest of the team. "Integrity, decisiveness, sound judgement, the capacity to establish a vision and execute it, confidence in your own competence" are trademarks of extremely effective project managers, according to Paul Dillon, founder of Dillon Consulting Services.
- Working amid the gloom -
All of the previously described qualities stand out, but the ability to work in the grey area is what truly distinguishes a project manager. Because the majority of projects, regardless of type, industry, size, or complexity, will include grey regions that you will need to negotiate at some point, this is a must-have ability. External limits and complications, remote project limitations, disagreement and uncertainty – all of these and other unknowns will very likely arise. When you combine those skills with the ability to work in the grey, you've got yourself a highly capable project manager.
- A catalyst for change - If the year 2020 has taught us anything, it is that change is unavoidable and can be extremely disruptive in many aspects of business and personal life, including project management. Highly effective project managers are aware of this, embrace it, and include elements of risk into their project planning. They also understand the importance of collaborating closely with change management professionals to assist stakeholders in adapting to change and better preparing for the future state of affairs — as well as functioning in the grey.
- Stakeholder-focused -
COVID-19 has wreaked havoc on businesses and individuals around the world, making it impossible to prioritise stakeholder demands over personal and family concerns. Good project managers, on the other hand, can separate their own requirements from those of project stakeholders as professionals. Regardless of personal bias or needs, they give their best effort at all times. This is the amount of focus that organisations have grown to expect from project managers, and it is what distinguishes excellent candidates.
- Giving credit to others in a generous manner -
Others' contributions have a significant impact on a project leader's ability to lead his or her team. Project managers that are very effective share credit for good work and encourage all team members to participate and contribute to their full potential. Rather than trying to be a jack of all trades, make use of the team's collective knowledge and talents. This simple but effective strategy can dramatically boost your chances of attaining your objectives.
- A capable motivator -
The ability of a project manager to communicate with and influence a wide range of stakeholders is critical to project success. After all, you must discover ways to encourage employees over whom you have no direct control but who have the power to make or break a project. It's critical to instil confidence in the minds of stakeholders and sponsors, especially if and when it's required to approach them with adjustments to the project's scope. If you want to be respected by your teammates, stakeholders, and sponsors, you must treat them with respect at all times. Without respect and motivation, especially from sponsors and stakeholders, it's nearly impossible for projects to develop in the proper direction and on time.
- Fully committed to success -
Highly effective project managers are passionate about their profession and are invested in seeing a project through from start to finish. This mentality aids in achieving the finest results possible throughout the project. Participate fully in all professional aspects of the project, including its operations and people. If you want to maintain professional ethics and stakeholder satisfaction, don't overextend yourself. Engagement, resilience, and the ability to sustain a high level of client and team satisfaction, according to John Paul Engel, president of Knowledge Capital Consulting, are the keys to delivering success.
- A well-liked and respected leader -
Although you can't please everyone, having a well-respected leadership reputation usually signifies you've earned it via hard effort. This will take some time if you're new to project management. Working to improve your communication skills, investing in your stakeholders' success, and preserving accountability and integrity, among other things, will help you get there faster. Once you've arrived, it's much easier to lead projects and teams with ease.
- A strategic business partner -
Project managers who can deliver higher-level strategic leadership skills, rather than merely technical management skills, benefit firms of all sizes significantly. Since the epidemic began in early 2020, there have been significantly more complex internal and external issues that might negatively affect initiatives of all kinds. The triple bottom line (economic, ecological, and social consequences), legal and legislative limits, remote project challenges, international and cultural factors, as well as severe resource constraints and delays, are all examples of such factors. Factors like this contribute to the challenges that a project manager must overcome. You greatly reduce your chances of producing good outcomes if you don't have a strong understanding of how your project fits into the overarching company-wide strategic goals. EPMOs (executive project management offices) concentrate on this link to boost project, programme, and portfolio success rates.
How can these qualities help to tackle the project hindrances?
Before we go any further, let's go over the limits that a project manager should be aware of. The following are the limitations:
- SCOPE - It specifies the customers' wants as well as the explicit and implicit requirements.
- TIME - Customers want their projects to be completed by a certain deadline.
- QUALITY - It is the standard to which a project is anticipated to be completed.
- RESOURCE - This refers to the quantity of money, budget, or resources allocated to the project.
- RISK - Specifies what might happen to throw the plan off track and what will be done to get it back on track.
These aren't the only limitations that a project may face. The following are some of the major reasons for the project's failure:
- User interaction is lacking.
- Timescales that are too long or too short.
- Poor or non-existent requirements.
- Creep in the scope.
- There is no change management mechanism in place.
- Inadequate testing.
The suggested attributes work together to assist a project manager avoid all of these stumbling blocks and move the project forward successfully.
Final thoughts
When using various project management systems to keep all elements of their projects organised, a project manager should have specific features and characteristics. These qualities enable a project manager to address each project as though it were its own distinct entity.
Furthermore, with the increasing need for project managers around the world, the traits listed above will undoubtedly aid you in gaining a foothold in the fast-paced market. I wish you the best of luck in your project management endeavours!
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Best Practices To Embed Security Into Your DevOps
More and more businesses are realising that DevOps, as a software development methodology, can transform the way they innovate and deliver high-quality products. Shorter delivery cycles and speedier time-to-market are further advantages of teams working together and bridging the gap between development and operations.

However, with the growing data and cybersecurity concerns of the day, industry experts have recognized the need to embed security into the very fabric of DevOps. Traditional security techniques are becoming obsolete and, sometimes, even seen as hurdles to the speed and effectiveness expected from DevOps.
18 Top Practices which are recommended to Embed Security into your DevOps:

Here are a few best practises that will assist you with this:
- Establish governance structures -
The first step in implementing security into DevOps is to prepare your team. Begin by establishing simple cybersecurity regulations and clear governance procedures aimed at increasing the DevOps environment's overall security. Then, properly express them to your staff and gain their approval. As a result, developing high-quality codes that fulfil your standards becomes much easier for them.
- Make security procedures more automated -
Automate procedures like patching and vulnerability management, code analysis, configuration management, privileged identity management, and so on with automated security technologies. This will assist you in keeping security on pace with the DevOps process's speed. Because DevOps is a highly automated process in and of itself, failing to embrace automation in security might cause the entire process to slow down.
- Make a list of everything -
Because cloud subscriptions are so easy to set up, it might be difficult to apply security standards to all of them if there isn't a proper inventory of what resources are available and to which teams. It's also crucial to keep track of all your devices, tools, and accounts so that you can verify compliance with your cybersecurity policy and scan for threats and vulnerabilities on a regular basis.
- Segment your DevOps Network -
Hackers' line-of-sight is mitigated by network segmentation, which stops them from getting access to the full programme. Even if a single segment is compromised, the hacker will be unable to access the rest of the application due to the protection measures in place. By default, application servers, resource servers, and other assets must be grouped into logical units that are not trusted by one another. Multi-factor authentication, adaptive access authorisation, and session monitoring should all be implemented to allow authorised users to acquire access.
- Continuous vulnerability management should be implemented -
Vulnerabilities must be identified and corrected on a regular basis. Preemptively scanning and assessing codes in development and integration environments so that they can be fixed before being deployed to production is part of the process. This procedure should be used in conjunction with the continuous testing procedure, in which codes are examined for flaws and patches are applied.
- Using specialist tools, you can manage your credentials -
Because access credentials can be readily fished out and misused by hackers, never incorporate them in code or keep them in files or devices. Instead, use a password management application or a password safe to keep them distinct. Developers and anyone who utilises such a tool will be able to request credential use from the tool whenever they need it, without having to know the credentials themselves.
- Control how privileged accounts are used -
Review the permissions and access granted to "privileged" users and grant the fewest privileges possible based on the needs of each user. Internal and external attackers will be less likely to abuse privileged access as a result of this. Keep an eye on what's going on with those privileged accounts to make sure the sessions are legal and compliance with regulations. To assist you with all of the aforementioned tasks, consider using a privileged access management (PAM) solution.
- Standards for Secure Coding -
Because security is not a top priority for developers, they focus solely on the application's capabilities and ignore the security parameters. However, with the rise of cyber-threats, you must ensure that your development staff is aware of the best security measures when coding for the app. They should be aware of security technologies that can assist them in identifying vulnerabilities in their code as it is being developed, allowing developers to quickly adjust the code and correct the flaws.
- Security training for the development team -
You should also train the development team on security best practises as part of the security requirements. So, if a new developer joins the team and is unfamiliar with SQL injection, you must ensure that the developer understands what SQL injection is, what it accomplishes, and the potential damage it can cause to the programme. You might not want to get into the nitty-gritty of it. Nonetheless, you must guarantee that the development team is up to date on the latest security regulations, guidelines, and best practises.
- Process of Change Management Implementation -
A change management strategy should be implemented. You don't want developers to keep updating code or adding or removing functionality to the programme that is currently in the deployment stage as changes occur. As a result, at this point, the only thing that can help you is to apply the change management approach. As a result, every modification to the application that needs to be made should go through the change management procedure. After it has been accepted, the developer should be able to make changes.
- Configuration Management should be implemented -
Configuration management should also be implemented. Configuration management includes the change management process, which I discussed earlier. As a result, you must ensure that you know what configuration you're working with, what modifications are being made to the application, and who is allowing and approving them. All of this will be managed through configuration management.
- Develop and Implement Security Procedures -
Security cannot function without processes; you must first develop and implement certain security processes in your firm. After the implementation, there's a chance you'll need to alter the processes since certain things didn't work out as planned or the process was too cumbersome. There could be any number of reasons for this, so you'll need to change your security procedures. Whatever you do, be sure that security processes are monitored and audited after they've been implemented.
- The Least Privilege Model should be implemented -
One of the most important thumb rules in DevOps security is to use the least privilege paradigm. Never give somebody more power than they need. If a developer doesn't need ROOT or Admin access, for example, you can give them standard user access so they can work on the application modules they need.
- Audit and review should be implemented -
Continuous auditing and review should also be implemented. Regular audits of the application's code, the environment of the security procedures, and the data it collects should be performed.
- Use the DevSecOps model -
Another popular word in the DevOps world is DevSecOps. It is a basic security procedure in divorce that every IT business has begun to implement. It is a combination of development, security, and operations, as the name implies. DevSecOps is a DevOps paradigm for incorporating security tools into the development process. As a result, security must be a part of the application development process from the start. Integrating the DevOps approach with security allows businesses to create secure applications that are free of risks. This methodology also aids in the dismantling of organisational silos between development operations and security teams. In the DevSecOps model, there are a few key practises that must be implemented:
- In the development integration process, use security tools like Snyk and Checkmarx.
- All automated testing must be reviewed by security professionals.
- To establish threat models, development and security teams must work together.
- In the product backlog, security concerns must be given top priority.
- Before deployment, all infrastructure security policies must be examined.
- Make use of a password manager -
Excel should not be used to store credentials. Use a centralised password manager instead. Individual passwords should not be shared among users under any circumstances. It's recommended to keep the credentials in a secure, centralised area where only the appropriate team has access to perform API requests and use the credentials.
- Examine the Code in a Smaller Font Size -
You should look over the code in a smaller font. It is never a good idea to evaluate large amounts of code, and it is also not a good idea to review the entire application at once. Review the programmes in small chunks so that you can go over them thoroughly.
- Continue to evaluate applications in the field -
When an application is live in production, many firms overlook security. You should keep an eye on the application at all times. To verify that no new security flaws have been introduced, you should keep analysing its code and performing frequent security tests.
Conclusion
These are some of the most important DevOps security best practises that a company should follow when developing secure applications and software. Implementing security standards as part of the DevOps process can save a company millions of dollars. So, for a secure and speedier release of the application, start adopting the security measures outlined in this article.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
More and more businesses are realising that DevOps, as a software development methodology, can transform the way they innovate and deliver high-quality products. Shorter delivery cycles and speedier time-to-market are further advantages of teams working together and bridging the gap between development and operations.
However, with the growing data and cybersecurity concerns of the day, industry experts have recognized the need to embed security into the very fabric of DevOps. Traditional security techniques are becoming obsolete and, sometimes, even seen as hurdles to the speed and effectiveness expected from DevOps.
18 Top Practices which are recommended to Embed Security into your DevOps:
Here are a few best practises that will assist you with this:
- Establish governance structures -
The first step in implementing security into DevOps is to prepare your team. Begin by establishing simple cybersecurity regulations and clear governance procedures aimed at increasing the DevOps environment's overall security. Then, properly express them to your staff and gain their approval. As a result, developing high-quality codes that fulfil your standards becomes much easier for them.
- Make security procedures more automated -
Automate procedures like patching and vulnerability management, code analysis, configuration management, privileged identity management, and so on with automated security technologies. This will assist you in keeping security on pace with the DevOps process's speed. Because DevOps is a highly automated process in and of itself, failing to embrace automation in security might cause the entire process to slow down.
- Make a list of everything -
Because cloud subscriptions are so easy to set up, it might be difficult to apply security standards to all of them if there isn't a proper inventory of what resources are available and to which teams. It's also crucial to keep track of all your devices, tools, and accounts so that you can verify compliance with your cybersecurity policy and scan for threats and vulnerabilities on a regular basis.
- Segment your DevOps Network -
Hackers' line-of-sight is mitigated by network segmentation, which stops them from getting access to the full programme. Even if a single segment is compromised, the hacker will be unable to access the rest of the application due to the protection measures in place. By default, application servers, resource servers, and other assets must be grouped into logical units that are not trusted by one another. Multi-factor authentication, adaptive access authorisation, and session monitoring should all be implemented to allow authorised users to acquire access.
- Continuous vulnerability management should be implemented -
Vulnerabilities must be identified and corrected on a regular basis. Preemptively scanning and assessing codes in development and integration environments so that they can be fixed before being deployed to production is part of the process. This procedure should be used in conjunction with the continuous testing procedure, in which codes are examined for flaws and patches are applied.
- Using specialist tools, you can manage your credentials -
Because access credentials can be readily fished out and misused by hackers, never incorporate them in code or keep them in files or devices. Instead, use a password management application or a password safe to keep them distinct. Developers and anyone who utilises such a tool will be able to request credential use from the tool whenever they need it, without having to know the credentials themselves.
- Control how privileged accounts are used -
Review the permissions and access granted to "privileged" users and grant the fewest privileges possible based on the needs of each user. Internal and external attackers will be less likely to abuse privileged access as a result of this. Keep an eye on what's going on with those privileged accounts to make sure the sessions are legal and compliance with regulations. To assist you with all of the aforementioned tasks, consider using a privileged access management (PAM) solution.
- Standards for Secure Coding -
Because security is not a top priority for developers, they focus solely on the application's capabilities and ignore the security parameters. However, with the rise of cyber-threats, you must ensure that your development staff is aware of the best security measures when coding for the app. They should be aware of security technologies that can assist them in identifying vulnerabilities in their code as it is being developed, allowing developers to quickly adjust the code and correct the flaws.
- Security training for the development team -
You should also train the development team on security best practises as part of the security requirements. So, if a new developer joins the team and is unfamiliar with SQL injection, you must ensure that the developer understands what SQL injection is, what it accomplishes, and the potential damage it can cause to the programme. You might not want to get into the nitty-gritty of it. Nonetheless, you must guarantee that the development team is up to date on the latest security regulations, guidelines, and best practises.
- Process of Change Management Implementation -
A change management strategy should be implemented. You don't want developers to keep updating code or adding or removing functionality to the programme that is currently in the deployment stage as changes occur. As a result, at this point, the only thing that can help you is to apply the change management approach. As a result, every modification to the application that needs to be made should go through the change management procedure. After it has been accepted, the developer should be able to make changes.
- Configuration Management should be implemented -
Configuration management should also be implemented. Configuration management includes the change management process, which I discussed earlier. As a result, you must ensure that you know what configuration you're working with, what modifications are being made to the application, and who is allowing and approving them. All of this will be managed through configuration management.
- Develop and Implement Security Procedures -
Security cannot function without processes; you must first develop and implement certain security processes in your firm. After the implementation, there's a chance you'll need to alter the processes since certain things didn't work out as planned or the process was too cumbersome. There could be any number of reasons for this, so you'll need to change your security procedures. Whatever you do, be sure that security processes are monitored and audited after they've been implemented.
- The Least Privilege Model should be implemented -
One of the most important thumb rules in DevOps security is to use the least privilege paradigm. Never give somebody more power than they need. If a developer doesn't need ROOT or Admin access, for example, you can give them standard user access so they can work on the application modules they need.
- Audit and review should be implemented -
Continuous auditing and review should also be implemented. Regular audits of the application's code, the environment of the security procedures, and the data it collects should be performed.
- Use the DevSecOps model -
Another popular word in the DevOps world is DevSecOps. It is a basic security procedure in divorce that every IT business has begun to implement. It is a combination of development, security, and operations, as the name implies. DevSecOps is a DevOps paradigm for incorporating security tools into the development process. As a result, security must be a part of the application development process from the start. Integrating the DevOps approach with security allows businesses to create secure applications that are free of risks. This methodology also aids in the dismantling of organisational silos between development operations and security teams. In the DevSecOps model, there are a few key practises that must be implemented:
- In the development integration process, use security tools like Snyk and Checkmarx.
- All automated testing must be reviewed by security professionals.
- To establish threat models, development and security teams must work together.
- In the product backlog, security concerns must be given top priority.
- Before deployment, all infrastructure security policies must be examined.
- Make use of a password manager -
Excel should not be used to store credentials. Use a centralised password manager instead. Individual passwords should not be shared among users under any circumstances. It's recommended to keep the credentials in a secure, centralised area where only the appropriate team has access to perform API requests and use the credentials.
- Examine the Code in a Smaller Font Size -
You should look over the code in a smaller font. It is never a good idea to evaluate large amounts of code, and it is also not a good idea to review the entire application at once. Review the programmes in small chunks so that you can go over them thoroughly.
- Continue to evaluate applications in the field -
When an application is live in production, many firms overlook security. You should keep an eye on the application at all times. To verify that no new security flaws have been introduced, you should keep analysing its code and performing frequent security tests.
Conclusion
These are some of the most important DevOps security best practises that a company should follow when developing secure applications and software. Implementing security standards as part of the DevOps process can save a company millions of dollars. So, for a secure and speedier release of the application, start adopting the security measures outlined in this article.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
The Real World of Quality Management
Organizations throughout the world are increasingly resorting to the tried-and-true bastions of quality control and quality management as they strive to perfect their operations and stay competitive. Lean Six Sigma (LSS) has long been a cornerstone of quality management best practices, with impressive results across a wide range of sectors and critical business processes.
It is a data-driven business management methodology that aims to improve product quality and process excellence by decreasing waste and increasing the value of every stage of the product or service lifecycle.

According to a recent study, about 20% of companies intend to use cross-functional quality processes and teams across design, manufacturing and service. For years, practitioners of Lean Six Sigma and other quality management methodologies have prospered.
To understand Real-world quality management, consider the following:
- The act of managing all activities and duties required to achieve a specified degree of perfection is known as quality management.
- Quality management entails establishing a quality strategy, developing and implementing quality assurance and planning, as well as quality control and improvement.
- Total Quality Management (TQM) necessitates collaboration among all stakeholders in a business to improve processes, products, services and the company's culture.
The overall quality approach explains the culture, mindset and organization that commits to providing better products and services that meet the needs of customers. Total quality management is a management technique that entails the process of improving employer-employee connections and consumer-business relationships in order to achieve better results in the production of goods and services. Let's take a look, how the concepts are managed in real-world situations.
What is the concept of quality management?
The act of overseeing various operations and duties inside a company to guarantee that the products and services given, as well as the means employed to produce them, are consistent is known as quality management. It assists the company in achieving and maintaining a targeted level of quality.

There are four main components to quality management, which are as follows:
- Quality Planning - The process of determining the project's quality criteria and determining how to meet them.
- Quality Improvement - The deliberate alteration of a process in order to improve the outcome confidence or reliability.
- Quality Control - The ongoing endeavor to maintain the integrity and dependability of a process in reaching a goal.
- Quality Assurance - The systematic or planned actions required to provide sufficient reliability so that a certain service or product meets the defined requirements.
Quality management is to guarantee that all stakeholders in an organization collaborate to improve the company's procedures, products, services and culture in order to achieve long-term success based on customer satisfaction.
Quality management is a set of guidelines produced by a team to ensure that the products and services they produce meet the appropriate standards or are suitable for a certain purpose.
- The process begins when the organization establishes quality goals that are agreed upon by both the client and the organization.
- After that, the organization determines how the goals will be measured. It performs the steps required to assess quality. It then finds and corrects any quality concerns that have arisen.
- The final step is to report on the overall degree of quality that has been attained.
The procedure ensures that the team's products and services meet the consumers' expectations.
Methods for Improving Quality
Product improvement, process improvement and people-based improvement are the three components of quality improvement approaches. There are a variety of quality management strategies and procedures that can be used.

Kaizen, Zero Defect Programs, Six Sigma, Quality Circle, Taguchi Methods, Toyota Production System, Kansei Engineering, TRIZ, BPR, OQRM, ISO and Top-Down & Bottom-Up methodologies are just a few of them.
Example of Quality Management
Toyota Corporation's application of the Kanban system is a shining example of excellent quality management. Kanban is an inventory control technique created by Taiichi Ohno to assist in minimizing the accumulation of surplus inventory on the manufacturing line at any given time by providing visibility to both suppliers and purchasers.
Toyota adopted the notion to implement their Just-in-Time (JIT) system, which lets suppliers synchronize raw material orders with production schedules directly. Toyota's manufacturing line improved efficiency by ensuring that the corporation had just enough inventory on hand to match client orders as they came in.
Improving the quality of manufacturing and the supply chain
Manufacturing enterprises are among the best examples of how Lean Six Sigma can aid in the development of high-quality products. For example, in North America, 3M recently used LSS principles in their design and manufacturing capabilities for compressed natural gas systems.
They used cutting-edge materials, technology and Lean Six Sigma experience to improve the overall quality and durability of their natural gas tanks, making them 30% lighter and with 10% more storage than competing tank types. 3M has also devised a long-term strategy to accomplish financial and customer goals by using Lean Six Sigma across manufacturing, supply chain and even customer service.
Manufacturers benefit not only from supplying higher-quality products to customers (with fewer flaws to rectify) but also from the speed with which they can handle issues that arise once they reach the end consumer. This ongoing plan includes quality management as a key component.
The Construction Industry's Quality Management
Construction is a one-time yet creative activity, therefore it's important to keep in mind that it's costly and time-consuming to reproduce a structure (or similar). TQM is used to reduce costs and increase productivity and it is possible to track efforts if results improve. Quality in the construction sector is determined by the level of satisfaction of the designer, builder and homeowners.
Getting Rid of Defects in Pharmaceuticals
Companies that create products that have an influence on the health and safety of daily consumers have a responsibility to ensure that the creation and testing of these items are done in a way that minimizes risk.
Pharmaceutical companies come under this group and they are required by law to ensure that their products are safe. Lean Six Sigma concepts, according to a recent LinkedIn article, may help firms attain this level of confidence in their processes to the point where they are nearly error-free.
LSS is used by pharmaceutical companies to implement end-to-end product testing, predict and eliminate errors during the development and testing life cycles and, as a result, improve product quality and meet compliance requirements. LSS assists them in reducing the risk of passing on tainted or ineffective medications, which can have serious health consequences for patients.
Onboarding Procedures in Healthcare
Long and complicated business processes are well-known in the healthcare industry. One example is Johns Hopkins All Children's Hospital (JHACH), which had a slow and inefficient provider enrollment process (taking up to six months to onboard providers).
JHACH patients who rely on those providers have had their visits with physicians delayed or they have had to see a whole new physician, resulting in dissatisfied patients and low customer satisfaction with the process.
JHACH boosted the number of hospital-employed providers who are active with health plans by nearly 30% by using the Lean Six Sigma workflow, consolidating departments and building a monitoring tool to monitor every stage of the process.
In the long run, the key to hospital business is cost and quality treatment. These principles should be followed by organizations for the best results.
- The patient should come first and the organization should prioritize the customer's needs; treatment should be the top priority.
- A good and engaging leader is in demand and a good leader should always be cautious and able to keep employees engaged in the organization's goals.
- Employee participation means that each employee, even doctors, should feel responsible for their work and become involved in it; only then can the organization benefit from the business.
- The organization must prioritize improvement and conduct regular audits in order to improve the environment.
Software Products of Higher Quality
Software quality assurance (QA) engineers play a critical role in ensuring that software solutions meet stringent quality standards and perform as expected. Certification as a Certified Tester Foundation Level (CTFL) is a requirement for anyone working in the software development and testing industry.
However, actions can be taken to increase quality earlier in the development lifecycle. Lean Six Sigma can assist businesses in reducing waste and superfluous cycles, allowing them to produce items faster and with higher quality.
Among the most essential areas where LSS can help are:
- Value stream analysis is used to discover and eliminate non-value contributed operations.
- Establishing a strategy for obtaining customer feedback and approval on requirements prior to the commencement of development work.
- Establishing a knowledge management system in which all reusable components are stored in a knowledge base and can be accessed later.
- Benchmarking with other team members in order to implement best practices without having to reinvent the wheel every time.
- Resource usage to determine what is being overused and underutilized and to take corrective or preventive measures.
Quality Oriented Culture
Total Quality Management (TQM) is a phrase used by quality experts to describe the use of quality concepts at all levels of a business. While TQM has typically implied widespread use of process tools and analytical procedures, the definition has broadened to include the entire organization's larger cultural norms.
The extension of TQM to cover both explicit efforts by people to enhance Quality and the underlying beliefs, philosophies and behaviors on which those efforts are based are referred to as Culture of Quality.

A successful Quality Culture is one in which the organization's core Quality values, such as a focus on responding to customer needs and the importance of data-based decision-making and workers' basic assumptions about the nature of human relationships and their places in the world, such as the value of collaborative relationships among people with common goals and the importance of developing long-term personal connections, are closely integrated.
Because core values are overtly expressed and understood at all levels of the organization, they are relatively easy to measure. Even the people who hold basic ideas typically resist explicit analysis, making participation at this level challenging.
A Culture of Quality can only be achieved when leaders and employees have a common understanding of not only the core values and processes they utilize and promote but also their underlying assumptions about the nature of work and human interactions on which those core values are based.
Quality Management Principles
The International Standard for Quality Management adheres to a number of quality management concepts. Top management uses these ideas to guide an organization's procedures toward higher performance. They are as follows:

1) Customer Service Focus
The fundamental goal of every firm should be to satisfy and surpass the expectations and needs of its consumers. When a company can understand and cater to its consumers' current and future demands, it builds client loyalty, which leads to increased income.
The company is also capable of identifying and satisfying new consumer opportunities. When business operations are more efficient, quality improves and more customers are able to be satisfied.
2) People's Participation
Another important aspect is employee involvement. Whether full-time, part-time, outsourced, or in-house, management engages employees in developing and delivering value. Employees should be encouraged to continually develop their abilities and maintain consistency in their work.
Empowering employees, including them in decision-making and acknowledging their accomplishments are all part of this philosophy. People work to their full potential when they feel valued, as it enhances their confidence and motivation. Employees feel empowered and accountable for their actions when they are fully involved.
3) Leadership
Good leadership leads to the success of an organization. Great leadership creates a sense of purpose and togetherness among employees and shareholders. Creating a vibrant corporate culture creates an internal climate in which people may completely fulfill their potential and actively participate in attaining company goals.
Employees should be involved in the development of clear organizational goals and objectives by leaders. Employees are motivated as a result and their productivity and loyalty may improve dramatically.
4) Approach to the Process
According to the process approach principle, an organization's performance is critical. The approach principle focuses on improving organizational processes' efficiency and effectiveness.
The concept assumes that good processes lead to increased consistency, faster actions, lower costs, waste elimination and continual improvement. When leaders can manage and control the organization's inputs and outputs, as well as the processes that produce the outputs, the organization benefits.
5) Continuous Enhancement
Every organization should have a goal to actively participate in continuous development. Businesses that continuously improve see a higher performance, organizational flexibility and the ability to seize new possibilities. Businesses should be able to constantly establish new procedures and adapt to changing market conditions.
6) Making Decisions Based on Evidence
Businesses should use a data-driven approach to decision-making. Businesses that base their decisions on verified and studied data have a better understanding of the market. They may complete tasks that provide the necessary results and justify their previous actions.
Factual decision making is critical for understanding the cause-and-effect relationships of various things and explaining probable unintended repercussions and results.
7) Management of Relationships
Creating mutually beneficial relationships with suppliers and retailers is the goal of relationship management. A company's performance can be influenced by a variety of stakeholders.
To maximize their impact on the company's success, the organization should manage the supply chain process well and enhance the relationship between the organization and its suppliers. When an organization effectively manages its relationships with interested parties, it is more likely to achieve long-term business success and collaboration.
The Advantages of Quality Management

- It assists an organization in achieving more consistency in the tasks and activities associated with the production of products and services.
- It enhances process efficiency, minimizes waste and makes better use of time and other resources.
- It contributes to increased consumer satisfaction.
- It enables enterprises to efficiently sell their products and enter new markets.
- It makes it easier for organizations to integrate new personnel, allowing them to manage growth more smoothly.
- It enables a company to constantly enhance its goods, processes and systems.
Conclusion
Customers understand the importance of quality in products and services. Suppliers know that quality can be a key differentiator between their own and competitors' offers (quality differentiation is also called the quality gap).
The quality gap between competing products and services has narrowed dramatically during the last two decades. This is due in part to manufacturing contracting (also known as outsourcing) to nations such as China and India, as well as the internationalization of commerce and competition.
In order to fulfill worldwide standards and client needs, these countries, among many others, have upgraded their own quality requirements. Quality culture, the relevance of knowledge management and the role of leadership in promoting and achieving high quality have all become more prominent themes.
Systems thinking, for example, is bringing more holistic methods to quality management, in which people, processes and products are all examined together rather than as separate components in quality management.
Quality culture has been acknowledged by government agencies and industrial organizations that regulate products as a way to help enterprises develop those items. According to a survey of more than 60 global organizations, companies with a bad quality culture had increased costs of $67 million per year for every 5000 employees compared to companies with a good quality culture.
iCert Global will help you to find best related certifications courses under Quality Management.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
Organizations throughout the world are increasingly resorting to the tried-and-true bastions of quality control and quality management as they strive to perfect their operations and stay competitive. Lean Six Sigma (LSS) has long been a cornerstone of quality management best practices, with impressive results across a wide range of sectors and critical business processes.
It is a data-driven business management methodology that aims to improve product quality and process excellence by decreasing waste and increasing the value of every stage of the product or service lifecycle.
According to a recent study, about 20% of companies intend to use cross-functional quality processes and teams across design, manufacturing and service. For years, practitioners of Lean Six Sigma and other quality management methodologies have prospered.
To understand Real-world quality management, consider the following:
- The act of managing all activities and duties required to achieve a specified degree of perfection is known as quality management.
- Quality management entails establishing a quality strategy, developing and implementing quality assurance and planning, as well as quality control and improvement.
- Total Quality Management (TQM) necessitates collaboration among all stakeholders in a business to improve processes, products, services and the company's culture.
The overall quality approach explains the culture, mindset and organization that commits to providing better products and services that meet the needs of customers. Total quality management is a management technique that entails the process of improving employer-employee connections and consumer-business relationships in order to achieve better results in the production of goods and services. Let's take a look, how the concepts are managed in real-world situations.
What is the concept of quality management?
The act of overseeing various operations and duties inside a company to guarantee that the products and services given, as well as the means employed to produce them, are consistent is known as quality management. It assists the company in achieving and maintaining a targeted level of quality.
There are four main components to quality management, which are as follows:
- Quality Planning - The process of determining the project's quality criteria and determining how to meet them.
- Quality Improvement - The deliberate alteration of a process in order to improve the outcome confidence or reliability.
- Quality Control - The ongoing endeavor to maintain the integrity and dependability of a process in reaching a goal.
- Quality Assurance - The systematic or planned actions required to provide sufficient reliability so that a certain service or product meets the defined requirements.
Quality management is to guarantee that all stakeholders in an organization collaborate to improve the company's procedures, products, services and culture in order to achieve long-term success based on customer satisfaction.
Quality management is a set of guidelines produced by a team to ensure that the products and services they produce meet the appropriate standards or are suitable for a certain purpose.
- The process begins when the organization establishes quality goals that are agreed upon by both the client and the organization.
- After that, the organization determines how the goals will be measured. It performs the steps required to assess quality. It then finds and corrects any quality concerns that have arisen.
- The final step is to report on the overall degree of quality that has been attained.
The procedure ensures that the team's products and services meet the consumers' expectations.
Methods for Improving Quality
Product improvement, process improvement and people-based improvement are the three components of quality improvement approaches. There are a variety of quality management strategies and procedures that can be used.
Kaizen, Zero Defect Programs, Six Sigma, Quality Circle, Taguchi Methods, Toyota Production System, Kansei Engineering, TRIZ, BPR, OQRM, ISO and Top-Down & Bottom-Up methodologies are just a few of them.
Example of Quality Management
Toyota Corporation's application of the Kanban system is a shining example of excellent quality management. Kanban is an inventory control technique created by Taiichi Ohno to assist in minimizing the accumulation of surplus inventory on the manufacturing line at any given time by providing visibility to both suppliers and purchasers.
Toyota adopted the notion to implement their Just-in-Time (JIT) system, which lets suppliers synchronize raw material orders with production schedules directly. Toyota's manufacturing line improved efficiency by ensuring that the corporation had just enough inventory on hand to match client orders as they came in.
Improving the quality of manufacturing and the supply chain
Manufacturing enterprises are among the best examples of how Lean Six Sigma can aid in the development of high-quality products. For example, in North America, 3M recently used LSS principles in their design and manufacturing capabilities for compressed natural gas systems.
They used cutting-edge materials, technology and Lean Six Sigma experience to improve the overall quality and durability of their natural gas tanks, making them 30% lighter and with 10% more storage than competing tank types. 3M has also devised a long-term strategy to accomplish financial and customer goals by using Lean Six Sigma across manufacturing, supply chain and even customer service.
Manufacturers benefit not only from supplying higher-quality products to customers (with fewer flaws to rectify) but also from the speed with which they can handle issues that arise once they reach the end consumer. This ongoing plan includes quality management as a key component.
The Construction Industry's Quality Management
Construction is a one-time yet creative activity, therefore it's important to keep in mind that it's costly and time-consuming to reproduce a structure (or similar). TQM is used to reduce costs and increase productivity and it is possible to track efforts if results improve. Quality in the construction sector is determined by the level of satisfaction of the designer, builder and homeowners.
Getting Rid of Defects in Pharmaceuticals
Companies that create products that have an influence on the health and safety of daily consumers have a responsibility to ensure that the creation and testing of these items are done in a way that minimizes risk.
Pharmaceutical companies come under this group and they are required by law to ensure that their products are safe. Lean Six Sigma concepts, according to a recent LinkedIn article, may help firms attain this level of confidence in their processes to the point where they are nearly error-free.
LSS is used by pharmaceutical companies to implement end-to-end product testing, predict and eliminate errors during the development and testing life cycles and, as a result, improve product quality and meet compliance requirements. LSS assists them in reducing the risk of passing on tainted or ineffective medications, which can have serious health consequences for patients.
Onboarding Procedures in Healthcare
Long and complicated business processes are well-known in the healthcare industry. One example is Johns Hopkins All Children's Hospital (JHACH), which had a slow and inefficient provider enrollment process (taking up to six months to onboard providers).
JHACH patients who rely on those providers have had their visits with physicians delayed or they have had to see a whole new physician, resulting in dissatisfied patients and low customer satisfaction with the process.
JHACH boosted the number of hospital-employed providers who are active with health plans by nearly 30% by using the Lean Six Sigma workflow, consolidating departments and building a monitoring tool to monitor every stage of the process.
In the long run, the key to hospital business is cost and quality treatment. These principles should be followed by organizations for the best results.
- The patient should come first and the organization should prioritize the customer's needs; treatment should be the top priority.
- A good and engaging leader is in demand and a good leader should always be cautious and able to keep employees engaged in the organization's goals.
- Employee participation means that each employee, even doctors, should feel responsible for their work and become involved in it; only then can the organization benefit from the business.
- The organization must prioritize improvement and conduct regular audits in order to improve the environment.
Software Products of Higher Quality
Software quality assurance (QA) engineers play a critical role in ensuring that software solutions meet stringent quality standards and perform as expected. Certification as a Certified Tester Foundation Level (CTFL) is a requirement for anyone working in the software development and testing industry.
However, actions can be taken to increase quality earlier in the development lifecycle. Lean Six Sigma can assist businesses in reducing waste and superfluous cycles, allowing them to produce items faster and with higher quality.
Among the most essential areas where LSS can help are:
- Value stream analysis is used to discover and eliminate non-value contributed operations.
- Establishing a strategy for obtaining customer feedback and approval on requirements prior to the commencement of development work.
- Establishing a knowledge management system in which all reusable components are stored in a knowledge base and can be accessed later.
- Benchmarking with other team members in order to implement best practices without having to reinvent the wheel every time.
- Resource usage to determine what is being overused and underutilized and to take corrective or preventive measures.
Quality Oriented Culture
Total Quality Management (TQM) is a phrase used by quality experts to describe the use of quality concepts at all levels of a business. While TQM has typically implied widespread use of process tools and analytical procedures, the definition has broadened to include the entire organization's larger cultural norms.
The extension of TQM to cover both explicit efforts by people to enhance Quality and the underlying beliefs, philosophies and behaviors on which those efforts are based are referred to as Culture of Quality.
A successful Quality Culture is one in which the organization's core Quality values, such as a focus on responding to customer needs and the importance of data-based decision-making and workers' basic assumptions about the nature of human relationships and their places in the world, such as the value of collaborative relationships among people with common goals and the importance of developing long-term personal connections, are closely integrated.
Because core values are overtly expressed and understood at all levels of the organization, they are relatively easy to measure. Even the people who hold basic ideas typically resist explicit analysis, making participation at this level challenging.
A Culture of Quality can only be achieved when leaders and employees have a common understanding of not only the core values and processes they utilize and promote but also their underlying assumptions about the nature of work and human interactions on which those core values are based.
Quality Management Principles
The International Standard for Quality Management adheres to a number of quality management concepts. Top management uses these ideas to guide an organization's procedures toward higher performance. They are as follows:
1) Customer Service Focus
The fundamental goal of every firm should be to satisfy and surpass the expectations and needs of its consumers. When a company can understand and cater to its consumers' current and future demands, it builds client loyalty, which leads to increased income.
The company is also capable of identifying and satisfying new consumer opportunities. When business operations are more efficient, quality improves and more customers are able to be satisfied.
2) People's Participation
Another important aspect is employee involvement. Whether full-time, part-time, outsourced, or in-house, management engages employees in developing and delivering value. Employees should be encouraged to continually develop their abilities and maintain consistency in their work.
Empowering employees, including them in decision-making and acknowledging their accomplishments are all part of this philosophy. People work to their full potential when they feel valued, as it enhances their confidence and motivation. Employees feel empowered and accountable for their actions when they are fully involved.
3) Leadership
Good leadership leads to the success of an organization. Great leadership creates a sense of purpose and togetherness among employees and shareholders. Creating a vibrant corporate culture creates an internal climate in which people may completely fulfill their potential and actively participate in attaining company goals.
Employees should be involved in the development of clear organizational goals and objectives by leaders. Employees are motivated as a result and their productivity and loyalty may improve dramatically.
4) Approach to the Process
According to the process approach principle, an organization's performance is critical. The approach principle focuses on improving organizational processes' efficiency and effectiveness.
The concept assumes that good processes lead to increased consistency, faster actions, lower costs, waste elimination and continual improvement. When leaders can manage and control the organization's inputs and outputs, as well as the processes that produce the outputs, the organization benefits.
5) Continuous Enhancement
Every organization should have a goal to actively participate in continuous development. Businesses that continuously improve see a higher performance, organizational flexibility and the ability to seize new possibilities. Businesses should be able to constantly establish new procedures and adapt to changing market conditions.
6) Making Decisions Based on Evidence
Businesses should use a data-driven approach to decision-making. Businesses that base their decisions on verified and studied data have a better understanding of the market. They may complete tasks that provide the necessary results and justify their previous actions.
Factual decision making is critical for understanding the cause-and-effect relationships of various things and explaining probable unintended repercussions and results.
7) Management of Relationships
Creating mutually beneficial relationships with suppliers and retailers is the goal of relationship management. A company's performance can be influenced by a variety of stakeholders.
To maximize their impact on the company's success, the organization should manage the supply chain process well and enhance the relationship between the organization and its suppliers. When an organization effectively manages its relationships with interested parties, it is more likely to achieve long-term business success and collaboration.
The Advantages of Quality Management
- It assists an organization in achieving more consistency in the tasks and activities associated with the production of products and services.
- It enhances process efficiency, minimizes waste and makes better use of time and other resources.
- It contributes to increased consumer satisfaction.
- It enables enterprises to efficiently sell their products and enter new markets.
- It makes it easier for organizations to integrate new personnel, allowing them to manage growth more smoothly.
- It enables a company to constantly enhance its goods, processes and systems.
Conclusion
Customers understand the importance of quality in products and services. Suppliers know that quality can be a key differentiator between their own and competitors' offers (quality differentiation is also called the quality gap).
The quality gap between competing products and services has narrowed dramatically during the last two decades. This is due in part to manufacturing contracting (also known as outsourcing) to nations such as China and India, as well as the internationalization of commerce and competition.
In order to fulfill worldwide standards and client needs, these countries, among many others, have upgraded their own quality requirements. Quality culture, the relevance of knowledge management and the role of leadership in promoting and achieving high quality have all become more prominent themes.
Systems thinking, for example, is bringing more holistic methods to quality management, in which people, processes and products are all examined together rather than as separate components in quality management.
Quality culture has been acknowledged by government agencies and industrial organizations that regulate products as a way to help enterprises develop those items. According to a survey of more than 60 global organizations, companies with a bad quality culture had increased costs of $67 million per year for every 5000 employees compared to companies with a good quality culture.
iCert Global will help you to find best related certifications courses under Quality Management.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
20 Exciting Technology Trends That Might Attract an Eye in 2022
2020 has been a year full of technological transformations. But a drastic tech change was seen in 2020, a year none of us were prepared for with an uninvited guest – disrupting the seamless workflow of businesses. The covid-19 outbreak has made IT experts realize that their role won't remain the same in tomorrow's contactless world.
Numerous promotions and extensive technologies amid the early 2000s had gradually ceased to exist, and new-flanged ones came to light. Several exciting technology trends have come up in 2022 that are most likely to attract an eye and perhaps reach the common man's hands.
In this blog, we will dive into 20 fascinating technology trends this year and some of the technology certifications offered by iCert Global.
2022's Exciting 20 Technology Trends
- AI & ML
Over the past few decades, Artificial Intelligence (AI) has received several buzzes. However, it is still one of the top technology trends due to tremendous impacts on our lifestyle, workspace and games.
AI has proven dominance in personal assistants (Alexa, Siri and Google Assistant), image and speech recognition, ride-sharing apps (Uber, Ola, Lyft and more) and navigation apps (Google Maps, Apple Maps).
Between the years 2019 and 2020, AI practitioners' or specialists' recruitments were seen to increase by 32%, and in LinkedIn's emerging job report 2020, the role of an AI specialist was ranked #1.
Machine Learning (ML) is a subset of AI that predicts future data based on previously generated data. It is widely practised in various industries such as logistics, healthcare, manufacturing and more, creating a massive demand for adept.
Both these technology trends need profound knowledge of statistics, aiding us to identify the outcomes generated by the algorithm for a particular dataset.
Some of the highest-paying jobs in the AI & ML field include:
- ML Engineer
- AI Architect
- Robotics Scientists
- Big Data Engineering
- Data Science & Analytics
From the beginning of the 21st century, both Data Science & Analytics were known to be breakthrough technology. Analyzing data has been crucial for organizations, educational systems, governments, and departments for a long time.
What exactly is the difference between both the technology trends?
Data Analytics focuses on particular areas with specific targets, while Data Science focuses on determining new questions that we might not realize to drive innovation. It helps build connections and shapes the questions to answer them for future requirements.
Data analysis helps us gain insight into process efficacy, employee surveys, and compute people's everyday moods. However, as 2020 has been a new year for digital growth, data analysis also turned digital.
With the swift growth of computational tech, the potentials of data analysis are set to rise further. The good side of having a job in the data science field is that you are the central part of the company's overall venture.
Career opportunities in the new technology trend are:
- Business Intelligence (BI) Analyst
- Data Engineer
- Operations Analyst
- Statistician
- VR & AR
The next-generation technology trends are often Virtual Reality (VR) & Augmented Reality (AR); these technologies play a minimal role in our lives. However, they are hyped in the industry.
VR engages the users in an environment while AR amplifies their environment. These technologies had been superior in the gaming industry; however, they have been widely used to train US Navy, Army and Coast Guard ship captains using simulation software – VirtualShip.
Usually working in pairs with other evolved technologies, VR & AR has a wide range of marketing, entertainment, rehabilitation, and education applications. We have recently come across a new where VR provides experiences to museum-goers in India, taking us on an inside tour seemingly like flipping a book.
A point to keep in mind is that the average salary of an AR Engineer is above 6 lakhs per annum. Awe-stricken by the engineer's salary? What say about offering a hand to these technologies in 2022?
In-demand AR & VR jobs include:
- Amazon - Graphics Engineer
- Facebook - VR/AR Graphics Engineer
- Apple - 3D Graphics Software Engineer
- Spatial - AR Engineer (SF)
- IoT
The Internet of Things (IoT) - physical objects are embedded with software, sensors, processing ability and other technologies that link and exchange data with other system devices over the internet or other networks.
This technology trend is the futuristic trend that has proven its superiority in devices, home appliances, vehicles and many more. The IoT is safe efficient and enables business decision-making as data is collected and analyzed. It also helps in quicker medical care predictive maintenance, offers benefits, and enhances customer services.
In an article by Cisco - by 2025, more than 75Bn IoT devices will be connected to the internet, thus expanding the tech applications. We are familiar with an IoT device 'Fitbits' which tracks the calories we burn. Another added advantage of the device is remote locking our doors, preheating our ovens on our way back home and a smart voice assistant.
IoT career opportunities include:
- Cell & User Interface Development
- Embedded Program Engineer
- Professional in Sensors & Actuators
- Network & the Networking Structure
- 5G
5th Generation (5G) of the mobile network is a much-awaited call for the 2022 technology trend - offering a high-speed network capable of connecting multiple objects at a timeframe. Faster than 4G, this technology delivers 20Gbps peak data rates and more than 100Mbps average data rates.
While the 5G was estimated to launch worldwide in 2021 with 50+ operators providing services in 30 countries by last year, the technology is in its developing phase. It is available only to a limited extent and is relatively pricey. The leading countries employing 5G are South Korea, the US and China.
As the technology has become more extensive, it has led to the need for an enormous workforce focused on creating and launching 5G networks.
- Blockchain
Blockchain technology has been a hot topic for a while. Most people think the technology concerning bitcoin is a cryptocurrency. However, this technology trends have several other applications offered with utmost security.
The essential factor about Blockchain is that the recorded data can't be changed. Due to the security offered by it, the data can be shared among parties without complications.
Since the systems are consensus-driven, no one entity can completely control the data. Thanks to Blockchain, we don't require a 3rd-party to validate transactions. Moreover, we could real-time track the product status in a supply chain.
Being a Blockchain expert can help in scaling your profile in different sectors:
- Crypto Community Manager
- Risk Analyst
- Front-end Engineer
- Tech Architect
- RPA
Robotic Process Automation (RPA) is a lot more than just robots. Like AI & ML, this technology trend is software - leveraged to automate business workflows such as email replying, interpretation of applications, transaction processing and association with data.
Before the invention of computers, most processes, be it in IT or manufacturing fields are done by humans. Once technology started revolutionizing and workflows started digitizing, the amount of human intervention drastically reduced.
A career in RPA involves substantial coding knowledge, where one has to write codes for a process to be automated. In financial sectors, the automation process reduces the time intended to speed the online tractions, thereby enhancing the overall productivity of the company and its connected ventures.
Some of the opportunities for people with RPA skills are:
- Project Manager
- Business Analyst
- Solution Architect
- RPA Developer
- DevOps
DevOps is a set of practices that merges IT operations and software development to advance - business value, continuous delivery and software quality. This technology trend is complementary with Agile Software development.
To implement the technology, Netflix has developed a suite of programs known as the Simian Army, creating deliberate latency issues between services, random shutting down of servers, and more. This helped their team develop fault-tolerant and scalable systems to achieve the DevOps principles.
ML and data engineering processes can be automated by leveraging the same principles in DevOps. This, in turn, creates a hybrid network known as MLOps and DataOps.
Some of the diverse roles in DevOps career paths are:
- Integration Specialist
- Release Manager
- Automation Engineer
- DevOps Architect
- Edge Computing
During the initial part of the 21st century, cloud computing was hyped to be the next-generation technology. Around 2010, computing technology started showing up in advent, and by the time it was 2022, the technology had become a mere thing.
In 2022, cloud computing is no longer a technology trend that paved the way for the next big thing - Edge Computing. The technology is developed to help solve latency issues caused by cloud computing and acquire data to the data centre for processing.
Edge Computing is an excellent approach in IoT, allowing data to remain at the edge of the cloud and the device for processing so that commands are followed at a short turn-around time.
In line with cloud computing, some of the career opportunities you might get with Edge Computing are:
- Cloud Infrastructure Engineer
- DevOps Cloud Engineer
- Cloud and Security Architect
- Cloud Reliability Engineer
- Cyber Security
Cyber Security might not seem like a trending technology, as it has been lingering around for a while, but it is also evolving just like other technology trends. Once the pandemic set in, almost every industrial sector started shifting to the digital world. It is one of the main reasons why awareness regarding cyberattacks began rising, and the technology continues to be an organization's top concern.
Most frequent cyberattacks occur in storage facilities of giant firms and government data repositories. Simple antivirus software is not enough to protect your systems from malicious attacks. Hence, better and robust technologies are of utmost importance, as malevolent hackers are not going to stop soon.
As the need for Cyber Security professionals increases, the jobs in this field started growing 3 times faster than other technology jobs. Some of the jobs that offer lucrative 6-figure incomes are:
- Security Engineer
- Ethical Hacker
- Chief Security Officer
- Malware Analyst
- Full Stack Development
Full Stack Development means the development of both front-end (client-side) and back-end (server-side) portions of web applications and is known to be one of the exciting trending technologies of 2022.
According to Forbes, over the last 2 years, internet usage has significantly increased by 70 percent, creating ways for online ventures shortly. The primary responsibility of a Full Stack developer includes server development, mobile platform coding, design UI on websites and databases for website functionality.
The front-end generally needs knowledge of Bootstrap, HTML and CSS. The back-end side requires knowledge of C++, PHP and ASP.
Career opportunities in Full Stack Development include:
- Web Developer
- Front-end and Back-end Developer
- Web Designer
- Full-Stack Developer
- Quantum Computing
The next big thing of 2022 in the technological field is Quantum Computing, which takes advantage of quantum phenomena like quantum entanglement and superposition.
This technology trend also had a significant role in preventing the covid-19 spread and potential vaccine development because of its ability to query, monitor, analyze and act on information.
Another area where Quantum Computing proved its dominance is finance and banking, to control credit risk for high-frequency fraud and trading identification. To shine in the latest trend, one must have experience with ML, linear algebra, information theory, quantum mechanics and probability.
Career opportunities in Quantum Computing are:
- Software Developer
- Computer Architects
- Algorithm Researcher
- Snowflake
Snowflake is a cloud data warehouse that enables data storage, analytic solutions, and processing that are quicker, easier to leverage, and more flexible than typical offerings. Its data platform is not developed on existing database technology or platforms like Hadoop.
This technology trend that stands out from the crowd is its ability to scale, compute and store independently. It has 4,900+ customers, including 212 of Fortune 500 and the average salary of Snowflake data warehouse engineer is 15 Lakh per annum (INR).
- IoB
The Internet of Behaviors (IoB) is an area of research and development (R&D) that seeks to understand when, how and why people use technology to make decisions before purchasing. It combines 3 fields of study - IoT, behavioural science and edge analytics.
Have you wondered how Facebook and Google display ads according to our needs? Well, it is through IoB. This technology trend helps ventures connect with their audience and track their advertising behaviours via click-through rate.
- Predictive Analytics
Predictive Analytics is a branch of advanced analytics that predicts future results using historical data associated with ML, statistical modelling and data mining. Companies leverage the tool to find data patterns to identify risks and opportunities.
Companies seek to develop services and products in crowded markets with increasing competition. This technology trend creates more precise forecasts, enabling efficient resource planning.
Career opportunities in the Predictive Analytics field are as follows:
- Marketing Operations Specialist
- Research Analyst
- Associate Decision Science
- Data Scientist
- Autonomous Vehicles
2020 has been a year of the self-driving or, in other words, Autonomous Vehicles, with large companies continuing to update their algorithms to develop cars that do away with drivers ultimately.
The technology trend has 5 levels of driving that range from no to full automation. Levels 0 to 2 need human observation, while Levels 3 to 5 depend on algorithms to observe the environment. Tesla has been the leading Autonomous Vehicle manufacturing company, though the driving levels are 3 & 4.
It is estimated that by 2025, the driving range will be 5. But even if the level is reached, it will not replace the cars; instead, it will create particular roads and spaces for Autonomous Vehicles.
- Metaverse
Metaverse is a digital universe in which virtual and physical worlds are merged in a shared online space that will entirely change how we communicate, work and shop.
This technology trend will offer more choices for organizations, ranging from an increase in the social presence to office work, product purchase, payments and healthcare. Tech giants such as Microsoft, Facebook and Epic Games are some companies that have joined the Metaverse concept.
- Smart Homes
The AI trend in our homes is ongoing and will only accelerate over the next 3 to 4 years. We have already adjusted to such a transformation with Amazon's Alexa and Google's Nest.
With the most internet-related things, Smart Homes are benefitted from network impacts. They will eventually acquire customer trust when more functions are added, from brewing coffee while opening the blinds to the bathroom temperature rise when someone senses getting up.
- Mega-constellation Satellites
Over the next few years, Elon Musk-owned company SpaceX plans to deploy 42,000 satellites to develop an internet connection from any part of our planet.
Other companies that have joined the technology trend are Amazon. They plan to introduce 3,236 low-orbit satellites to cover white areas, and the OneWeb constellation planning to launch 600 satellites by this year.
Mega-constellation of satellites has been made possible by low-cost nano-satellite launch. However, the deployment of several objects in space might create an issue in terms of collision risk, weather and disturbance of astronomical observation.
- Cryptocurrency
Cryptocurrency is a tradable digital asset built on blockchain technology. Though many people say the technology trend is the future of finance, it poses 2 major problems.
Its primary appeal is that Cryptocurrencies are trendy, but they never meant to sustain the attention they received in 2017. The technology might work, but there's just no mass market. The second issue is that its value is subjective and always in pre-bubble or bubble territory. Hence banks and governments will seek to discredit.
iCert Global Certification
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and worldwide.
- AI & ML
AI and Deep Learning Certification Training Course
ML Certification Training Course
- RPA
RPA Certification Training Course
- Blockchain
Blockchain Certification Training Course
- IoT
IoT Certification Training Course
- Cyber Security
Ethical Hacking Certification Training Course
CISSP Training Course
CRISC Training Course
CISM Training Course
CISA Training Course
- Data Science
Data Science with R Programming Certification Training Course
- DevOps
DevOps Certification Training Course
Conclusion
Although technologies are evolving around us and in the year 2022, we will see the world economy's transformation. Our lives will transform entirely shortly with the promising technology trends mentioned above. Jobs and skills in these technologies will be invaluable, and gaining education related to the trends will help you in your career over the long run.
Choosing and being an expert in the right trend will make you more dominant in the technological field, and you will be the future proof of it.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
2020 has been a year full of technological transformations. But a drastic tech change was seen in 2020, a year none of us were prepared for with an uninvited guest – disrupting the seamless workflow of businesses. The covid-19 outbreak has made IT experts realize that their role won't remain the same in tomorrow's contactless world.
Numerous promotions and extensive technologies amid the early 2000s had gradually ceased to exist, and new-flanged ones came to light. Several exciting technology trends have come up in 2022 that are most likely to attract an eye and perhaps reach the common man's hands.
In this blog, we will dive into 20 fascinating technology trends this year and some of the technology certifications offered by iCert Global.
2022's Exciting 20 Technology Trends
- AI & ML
Over the past few decades, Artificial Intelligence (AI) has received several buzzes. However, it is still one of the top technology trends due to tremendous impacts on our lifestyle, workspace and games.
AI has proven dominance in personal assistants (Alexa, Siri and Google Assistant), image and speech recognition, ride-sharing apps (Uber, Ola, Lyft and more) and navigation apps (Google Maps, Apple Maps).
Between the years 2019 and 2020, AI practitioners' or specialists' recruitments were seen to increase by 32%, and in LinkedIn's emerging job report 2020, the role of an AI specialist was ranked #1.
Machine Learning (ML) is a subset of AI that predicts future data based on previously generated data. It is widely practised in various industries such as logistics, healthcare, manufacturing and more, creating a massive demand for adept.
Both these technology trends need profound knowledge of statistics, aiding us to identify the outcomes generated by the algorithm for a particular dataset.
Some of the highest-paying jobs in the AI & ML field include:
- ML Engineer
- AI Architect
- Robotics Scientists
- Big Data Engineering
- Data Science & Analytics
From the beginning of the 21st century, both Data Science & Analytics were known to be breakthrough technology. Analyzing data has been crucial for organizations, educational systems, governments, and departments for a long time.
What exactly is the difference between both the technology trends?
Data Analytics focuses on particular areas with specific targets, while Data Science focuses on determining new questions that we might not realize to drive innovation. It helps build connections and shapes the questions to answer them for future requirements.
Data analysis helps us gain insight into process efficacy, employee surveys, and compute people's everyday moods. However, as 2020 has been a new year for digital growth, data analysis also turned digital.
With the swift growth of computational tech, the potentials of data analysis are set to rise further. The good side of having a job in the data science field is that you are the central part of the company's overall venture.
Career opportunities in the new technology trend are:
- Business Intelligence (BI) Analyst
- Data Engineer
- Operations Analyst
- Statistician
- VR & AR
The next-generation technology trends are often Virtual Reality (VR) & Augmented Reality (AR); these technologies play a minimal role in our lives. However, they are hyped in the industry.
VR engages the users in an environment while AR amplifies their environment. These technologies had been superior in the gaming industry; however, they have been widely used to train US Navy, Army and Coast Guard ship captains using simulation software – VirtualShip.
Usually working in pairs with other evolved technologies, VR & AR has a wide range of marketing, entertainment, rehabilitation, and education applications. We have recently come across a new where VR provides experiences to museum-goers in India, taking us on an inside tour seemingly like flipping a book.
A point to keep in mind is that the average salary of an AR Engineer is above 6 lakhs per annum. Awe-stricken by the engineer's salary? What say about offering a hand to these technologies in 2022?
In-demand AR & VR jobs include:
- Amazon - Graphics Engineer
- Facebook - VR/AR Graphics Engineer
- Apple - 3D Graphics Software Engineer
- Spatial - AR Engineer (SF)
- IoT
The Internet of Things (IoT) - physical objects are embedded with software, sensors, processing ability and other technologies that link and exchange data with other system devices over the internet or other networks.
This technology trend is the futuristic trend that has proven its superiority in devices, home appliances, vehicles and many more. The IoT is safe efficient and enables business decision-making as data is collected and analyzed. It also helps in quicker medical care predictive maintenance, offers benefits, and enhances customer services.
In an article by Cisco - by 2025, more than 75Bn IoT devices will be connected to the internet, thus expanding the tech applications. We are familiar with an IoT device 'Fitbits' which tracks the calories we burn. Another added advantage of the device is remote locking our doors, preheating our ovens on our way back home and a smart voice assistant.
IoT career opportunities include:
- Cell & User Interface Development
- Embedded Program Engineer
- Professional in Sensors & Actuators
- Network & the Networking Structure
- 5G
5th Generation (5G) of the mobile network is a much-awaited call for the 2022 technology trend - offering a high-speed network capable of connecting multiple objects at a timeframe. Faster than 4G, this technology delivers 20Gbps peak data rates and more than 100Mbps average data rates.
While the 5G was estimated to launch worldwide in 2021 with 50+ operators providing services in 30 countries by last year, the technology is in its developing phase. It is available only to a limited extent and is relatively pricey. The leading countries employing 5G are South Korea, the US and China.
As the technology has become more extensive, it has led to the need for an enormous workforce focused on creating and launching 5G networks.
- Blockchain
Blockchain technology has been a hot topic for a while. Most people think the technology concerning bitcoin is a cryptocurrency. However, this technology trends have several other applications offered with utmost security.
The essential factor about Blockchain is that the recorded data can't be changed. Due to the security offered by it, the data can be shared among parties without complications.
Since the systems are consensus-driven, no one entity can completely control the data. Thanks to Blockchain, we don't require a 3rd-party to validate transactions. Moreover, we could real-time track the product status in a supply chain.
Being a Blockchain expert can help in scaling your profile in different sectors:
- Crypto Community Manager
- Risk Analyst
- Front-end Engineer
- Tech Architect
- RPA
Robotic Process Automation (RPA) is a lot more than just robots. Like AI & ML, this technology trend is software - leveraged to automate business workflows such as email replying, interpretation of applications, transaction processing and association with data.
Before the invention of computers, most processes, be it in IT or manufacturing fields are done by humans. Once technology started revolutionizing and workflows started digitizing, the amount of human intervention drastically reduced.
A career in RPA involves substantial coding knowledge, where one has to write codes for a process to be automated. In financial sectors, the automation process reduces the time intended to speed the online tractions, thereby enhancing the overall productivity of the company and its connected ventures.
Some of the opportunities for people with RPA skills are:
- Project Manager
- Business Analyst
- Solution Architect
- RPA Developer
- DevOps
DevOps is a set of practices that merges IT operations and software development to advance - business value, continuous delivery and software quality. This technology trend is complementary with Agile Software development.
To implement the technology, Netflix has developed a suite of programs known as the Simian Army, creating deliberate latency issues between services, random shutting down of servers, and more. This helped their team develop fault-tolerant and scalable systems to achieve the DevOps principles.
ML and data engineering processes can be automated by leveraging the same principles in DevOps. This, in turn, creates a hybrid network known as MLOps and DataOps.
Some of the diverse roles in DevOps career paths are:
- Integration Specialist
- Release Manager
- Automation Engineer
- DevOps Architect
- Edge Computing
During the initial part of the 21st century, cloud computing was hyped to be the next-generation technology. Around 2010, computing technology started showing up in advent, and by the time it was 2022, the technology had become a mere thing.
In 2022, cloud computing is no longer a technology trend that paved the way for the next big thing - Edge Computing. The technology is developed to help solve latency issues caused by cloud computing and acquire data to the data centre for processing.
Edge Computing is an excellent approach in IoT, allowing data to remain at the edge of the cloud and the device for processing so that commands are followed at a short turn-around time.
In line with cloud computing, some of the career opportunities you might get with Edge Computing are:
- Cloud Infrastructure Engineer
- DevOps Cloud Engineer
- Cloud and Security Architect
- Cloud Reliability Engineer
- Cyber Security
Cyber Security might not seem like a trending technology, as it has been lingering around for a while, but it is also evolving just like other technology trends. Once the pandemic set in, almost every industrial sector started shifting to the digital world. It is one of the main reasons why awareness regarding cyberattacks began rising, and the technology continues to be an organization's top concern.
Most frequent cyberattacks occur in storage facilities of giant firms and government data repositories. Simple antivirus software is not enough to protect your systems from malicious attacks. Hence, better and robust technologies are of utmost importance, as malevolent hackers are not going to stop soon.
As the need for Cyber Security professionals increases, the jobs in this field started growing 3 times faster than other technology jobs. Some of the jobs that offer lucrative 6-figure incomes are:
- Security Engineer
- Ethical Hacker
- Chief Security Officer
- Malware Analyst
- Full Stack Development
Full Stack Development means the development of both front-end (client-side) and back-end (server-side) portions of web applications and is known to be one of the exciting trending technologies of 2022.
According to Forbes, over the last 2 years, internet usage has significantly increased by 70 percent, creating ways for online ventures shortly. The primary responsibility of a Full Stack developer includes server development, mobile platform coding, design UI on websites and databases for website functionality.
The front-end generally needs knowledge of Bootstrap, HTML and CSS. The back-end side requires knowledge of C++, PHP and ASP.
Career opportunities in Full Stack Development include:
- Web Developer
- Front-end and Back-end Developer
- Web Designer
- Full-Stack Developer
- Quantum Computing
The next big thing of 2022 in the technological field is Quantum Computing, which takes advantage of quantum phenomena like quantum entanglement and superposition.
This technology trend also had a significant role in preventing the covid-19 spread and potential vaccine development because of its ability to query, monitor, analyze and act on information.
Another area where Quantum Computing proved its dominance is finance and banking, to control credit risk for high-frequency fraud and trading identification. To shine in the latest trend, one must have experience with ML, linear algebra, information theory, quantum mechanics and probability.
Career opportunities in Quantum Computing are:
- Software Developer
- Computer Architects
- Algorithm Researcher
- Snowflake
Snowflake is a cloud data warehouse that enables data storage, analytic solutions, and processing that are quicker, easier to leverage, and more flexible than typical offerings. Its data platform is not developed on existing database technology or platforms like Hadoop.
This technology trend that stands out from the crowd is its ability to scale, compute and store independently. It has 4,900+ customers, including 212 of Fortune 500 and the average salary of Snowflake data warehouse engineer is 15 Lakh per annum (INR).
- IoB
The Internet of Behaviors (IoB) is an area of research and development (R&D) that seeks to understand when, how and why people use technology to make decisions before purchasing. It combines 3 fields of study - IoT, behavioural science and edge analytics.
Have you wondered how Facebook and Google display ads according to our needs? Well, it is through IoB. This technology trend helps ventures connect with their audience and track their advertising behaviours via click-through rate.
- Predictive Analytics
Predictive Analytics is a branch of advanced analytics that predicts future results using historical data associated with ML, statistical modelling and data mining. Companies leverage the tool to find data patterns to identify risks and opportunities.
Companies seek to develop services and products in crowded markets with increasing competition. This technology trend creates more precise forecasts, enabling efficient resource planning.
Career opportunities in the Predictive Analytics field are as follows:
- Marketing Operations Specialist
- Research Analyst
- Associate Decision Science
- Data Scientist
- Autonomous Vehicles
2020 has been a year of the self-driving or, in other words, Autonomous Vehicles, with large companies continuing to update their algorithms to develop cars that do away with drivers ultimately.
The technology trend has 5 levels of driving that range from no to full automation. Levels 0 to 2 need human observation, while Levels 3 to 5 depend on algorithms to observe the environment. Tesla has been the leading Autonomous Vehicle manufacturing company, though the driving levels are 3 & 4.
It is estimated that by 2025, the driving range will be 5. But even if the level is reached, it will not replace the cars; instead, it will create particular roads and spaces for Autonomous Vehicles.
- Metaverse
Metaverse is a digital universe in which virtual and physical worlds are merged in a shared online space that will entirely change how we communicate, work and shop.
This technology trend will offer more choices for organizations, ranging from an increase in the social presence to office work, product purchase, payments and healthcare. Tech giants such as Microsoft, Facebook and Epic Games are some companies that have joined the Metaverse concept.
- Smart Homes
The AI trend in our homes is ongoing and will only accelerate over the next 3 to 4 years. We have already adjusted to such a transformation with Amazon's Alexa and Google's Nest.
With the most internet-related things, Smart Homes are benefitted from network impacts. They will eventually acquire customer trust when more functions are added, from brewing coffee while opening the blinds to the bathroom temperature rise when someone senses getting up.
- Mega-constellation Satellites
Over the next few years, Elon Musk-owned company SpaceX plans to deploy 42,000 satellites to develop an internet connection from any part of our planet.
Other companies that have joined the technology trend are Amazon. They plan to introduce 3,236 low-orbit satellites to cover white areas, and the OneWeb constellation planning to launch 600 satellites by this year.
Mega-constellation of satellites has been made possible by low-cost nano-satellite launch. However, the deployment of several objects in space might create an issue in terms of collision risk, weather and disturbance of astronomical observation.
- Cryptocurrency
Cryptocurrency is a tradable digital asset built on blockchain technology. Though many people say the technology trend is the future of finance, it poses 2 major problems.
Its primary appeal is that Cryptocurrencies are trendy, but they never meant to sustain the attention they received in 2017. The technology might work, but there's just no mass market. The second issue is that its value is subjective and always in pre-bubble or bubble territory. Hence banks and governments will seek to discredit.
iCert Global Certification
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and worldwide.
- AI & ML
AI and Deep Learning Certification Training Course
ML Certification Training Course
- RPA
RPA Certification Training Course
- Blockchain
Blockchain Certification Training Course
- IoT
IoT Certification Training Course
- Cyber Security
Ethical Hacking Certification Training Course
CISSP Training Course
CRISC Training Course
CISM Training Course
CISA Training Course
- Data Science
Data Science with R Programming Certification Training Course
- DevOps
DevOps Certification Training Course
Conclusion
Although technologies are evolving around us and in the year 2022, we will see the world economy's transformation. Our lives will transform entirely shortly with the promising technology trends mentioned above. Jobs and skills in these technologies will be invaluable, and gaining education related to the trends will help you in your career over the long run.
Choosing and being an expert in the right trend will make you more dominant in the technological field, and you will be the future proof of it.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1187 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Gain Visibility into Your Company's Cyber Risk with Cyber Security Engineering
What's stopping you from safeguarding your company from HACKERS? Resource inadequacy.... or fear of accepting challenges?
Cyber Security is a niche area, dealing with different methods for protecting computer systems, networks and data from malicious attacks. As today's world lingers more on mobile computing and the internet to achieve everyday tasks, so are the bad guys. Hence, the urgency of security protection becomes more.
This is where the demand for Cyber Security Engineers comes into play. If you are among those who enjoy challenges, then a Cyber Security career is for you.
The field is fresh with potential, and in today's blog, we shall see why a Cyber Security Engineering career is a rewarding choice. So, let's dive in, shall we?
Cyber Security Engineer…? What is it?
Data privacy is our right and belongs to us, so let's protect it with all our will!!!!
The cyber or malicious attack is like a natural disaster. There is no way to put a stop to an earthquake or flood from hitting your town, but you can certainly prepare for it.
The digital attacks try to manipulate or access crucial company data and sometimes force money from users by stealing their private information. To prevent these from happening, Cyber Security Engineer steps in.
Cyber Security Engineers shield your company from these internet attacks by designing and executing secure network solutions. They monitor and test these networks to ensure that all of the defence mechanisms are up-to-date and working efficiently.
They form a part of the IT team in any organization and work in sequential with other departments to identify and fix any security issues and glitches arising from security lapses.
Often these engineers are known to be Web Security Engineer, Data Security Engineer or IT Security Engineer. In smaller firms where they can't afford to hire a Cyber Security expert, security engineers roll into different IT positions.
How's the Job Market Growth of Cyber Security Engineers?

3.5 million Cybersecurity job vacancy as per 2021 report
According to Cybrary's job outlook report, the demand for Cyber Security Engineers is estimated to grow 12% between 2016 and 2026 - a faster-growing market compared to all other jobs. In the coming years, the need for these engineers is never going in vain as governments, businesses, and other technology giants depend more on digital platforms.
The world's leading technology association - CompTIA, highlighted that people with strong communication skills, a passion for teamwork and genuine interest are ultimate candidates to join the ranks of the nation's Cyber Security personnel.
The demands in this job market are soaring while the supply is low. Though these engineers are of significant importance in today's digital world, cybersecurity experts have a corresponding widening skill gap.
As per the professional industry report, by 2021, there will be 3.5Mn unfilled jobs for Cyber Security posts worldwide, and here we are in 2022, where the situation is only getting worse.
Regarding cyber-based crimes, Cyber Security Ventures prognosticated that the annual rate of these crime damages will drastically increase, going from $3 trillion in 2015 to $6 trillion by last year.
The demand makes it difficult for Chief Information Security Officer (CISO) to captivate and reserve experienced engineers who can find and fix threats. As a result of solid engineer demands and shortage of qualified experts - the career outlooks, salaries and job opportunities are beyond our imaginations.
Some of the leading companies that are looking for qualified Cyber Security Engineers with attractive salary packages are:
- CyberArk Software
- Amazon (AWS)
- Symantec
- Microsoft
- BAE Systems
- IBM
- Cisco
Roles and Responsibilities of Cyber Security Engineers
Does developing secure systems & solutions, managing security & audit systems, and performing assessments & penetration testing sound like your interest challenges? Then it's time for you to explore the career advancement in Cyber Security Engineer profession.
Cyber engineers' merges computer science and electrical engineering to understand cyberspace and leverage potentials developed in network defence, digital forensics and security policy to implement Cyber Security works.
Let's have a quick peek into the roles and responsibilities of Cyber Security Engineers:
- Evaluating a company's requirements and building ideal methodologies and standards.
- Plan, design, implement, control, monitor and upgrade all security approaches required to safeguard the company's systems, networks and data.
- Regular conduction of penetration testing
- Active participation in management procedural transformation
- Responding to all security violations or threats to the network and other linked systems.
- Helping in any security breach probes
- Troubleshooting all security and internet situations and problems.
- Tackling daily administration works like reporting and maintaining open communication lines with the company's related departments.
- Taking significant security standards to ensure that the company's existing data and infrastructure are safe.
The engineering job and roles come hand-in-hand with those of a security analyst. A Cyber Security Engineer designs and establishes systems, while the analyst focuses on putting the system through its paces and finding means to break it.
Since most security engineers conduct regular stress tests and strive to find the weak points and test them.
Cyber Security Job Opportunities
Though many Cyber Security Engineer posts are vacant due to soring engineering demands, the job opportunities in these fields are like a vast ocean, and so are its demand.
Here are some of the jobs that are relevant for Cyber Security Engineers:
- Information assurance engineer
- IT security engineer
- Information system security engineer
People with Cyber Security engineering experience can look for the following:
- Cyber security consultant
- CISO
- Cyber security architect
- Cyber security director
A recent search for Cyber Security Engineer jobs in LinkedIn unveiled numerous opportunities put forward by wide-range of companies worldwide, and some of them are:
- Mobile application security engineer Booz Allen Hamilton, MD
- Privacy engineer, tech audit (University Grad), Meta Inc., Seattle
- Cyber security engineer, JP Morgan Chase & Co., OH
- Jr. security engineer, Barclays, NJ
- Cyber security engineer, Motorola Solutions, Vancouver, BC
- Application security engineer - Xcode Cloud, Apple Inc., BC
Cyber Security Engineer Skills
To ensure success in cyberspace, an engineer must exhibit a few outstanding skills of technology frameworks, including:
- Ethical hacking
- IDS/IDP, penetration and vulnerability test
- MySQL/MSSQL database networks
- Application security and encryption techs
- Subnetting, VPNs, VoIP, DNS and other network routing approaches
- Windows, Linux and UNIX OS
- Adroitness in C++, Node, Power Shell, Python, Java, Ruby and Go
How Much Does Cyber Security Engineer Make?
According to Glassdoor.com, the average salary for a Cyber Security Engineer is $1,01,548 (INR 6 Lakhs) yearly. But these are not fixed salary rates, and they will vary depending on several factors like employer, location, educational qualification and experience. But regardless of the elements, the security engineer can earn serious pay.
Timeline To be a Cyber Security Engineer
Wondering how long it will take to be a successful Cyber Security Engineer? Well… you can relax a bit.
The actual timeline to be a Cyber Security Engineer depends on your educational qualification, certification and experience. Most people make their way into entry-level security engineer positions within 2 or 4 years, depending on their experience progress.
But if you are already working in an IT field and have adequate experience, a certification in Cyber Security Engineering is sure to lift you into the field at a swift pace.
Closure Call
The future in cyberspace or cyber-related fields are thriving, especially in today's world, where businesses started transforming into digital ventures, resulting in frequent ransomware trap fall. Data breaches and malevolent attacks are a threat that organizations and whatnot say, Government to face regularly. Hence, Cyber Security Engineers have become a central part of the companies.
The career is in-demand and overwhelmed by all of the choices, but not knowing which certification offering company to choose, you are in the right place.
iCert Global is a one-stop solution offering certification training courses in a wide variety of techniques that will give you a head start in this competitive world. Visit our website to find out the different Cyber Security courses provided.
About Us
Our company conducts both Instructor-led Live Online Training sessions and Instructor-led Classroom training workshops for learners across the globe.
We also provide Corporate Training for enterprise workforce development
Project Management Courses
Cloud Technology
- AWS Solution Architect Certification
- Google Cloud Certification
- Developing Microsoft Azure Solutions 70 532 Certification
Cyber Security
Quality Management Training
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Read More
What's stopping you from safeguarding your company from HACKERS? Resource inadequacy.... or fear of accepting challenges?
Cyber Security is a niche area, dealing with different methods for protecting computer systems, networks and data from malicious attacks. As today's world lingers more on mobile computing and the internet to achieve everyday tasks, so are the bad guys. Hence, the urgency of security protection becomes more.
This is where the demand for Cyber Security Engineers comes into play. If you are among those who enjoy challenges, then a Cyber Security career is for you.
The field is fresh with potential, and in today's blog, we shall see why a Cyber Security Engineering career is a rewarding choice. So, let's dive in, shall we?
Cyber Security Engineer…? What is it?
Data privacy is our right and belongs to us, so let's protect it with all our will!!!!
The cyber or malicious attack is like a natural disaster. There is no way to put a stop to an earthquake or flood from hitting your town, but you can certainly prepare for it.
The digital attacks try to manipulate or access crucial company data and sometimes force money from users by stealing their private information. To prevent these from happening, Cyber Security Engineer steps in.
Cyber Security Engineers shield your company from these internet attacks by designing and executing secure network solutions. They monitor and test these networks to ensure that all of the defence mechanisms are up-to-date and working efficiently.
They form a part of the IT team in any organization and work in sequential with other departments to identify and fix any security issues and glitches arising from security lapses.
Often these engineers are known to be Web Security Engineer, Data Security Engineer or IT Security Engineer. In smaller firms where they can't afford to hire a Cyber Security expert, security engineers roll into different IT positions.
How's the Job Market Growth of Cyber Security Engineers?
3.5 million Cybersecurity job vacancy as per 2021 report
According to Cybrary's job outlook report, the demand for Cyber Security Engineers is estimated to grow 12% between 2016 and 2026 - a faster-growing market compared to all other jobs. In the coming years, the need for these engineers is never going in vain as governments, businesses, and other technology giants depend more on digital platforms.
The world's leading technology association - CompTIA, highlighted that people with strong communication skills, a passion for teamwork and genuine interest are ultimate candidates to join the ranks of the nation's Cyber Security personnel.
The demands in this job market are soaring while the supply is low. Though these engineers are of significant importance in today's digital world, cybersecurity experts have a corresponding widening skill gap.
As per the professional industry report, by 2021, there will be 3.5Mn unfilled jobs for Cyber Security posts worldwide, and here we are in 2022, where the situation is only getting worse.
Regarding cyber-based crimes, Cyber Security Ventures prognosticated that the annual rate of these crime damages will drastically increase, going from $3 trillion in 2015 to $6 trillion by last year.
The demand makes it difficult for Chief Information Security Officer (CISO) to captivate and reserve experienced engineers who can find and fix threats. As a result of solid engineer demands and shortage of qualified experts - the career outlooks, salaries and job opportunities are beyond our imaginations.
Some of the leading companies that are looking for qualified Cyber Security Engineers with attractive salary packages are:
- CyberArk Software
- Amazon (AWS)
- Symantec
- Microsoft
- BAE Systems
- IBM
- Cisco
Roles and Responsibilities of Cyber Security Engineers
Does developing secure systems & solutions, managing security & audit systems, and performing assessments & penetration testing sound like your interest challenges? Then it's time for you to explore the career advancement in Cyber Security Engineer profession.
Cyber engineers' merges computer science and electrical engineering to understand cyberspace and leverage potentials developed in network defence, digital forensics and security policy to implement Cyber Security works.
Let's have a quick peek into the roles and responsibilities of Cyber Security Engineers:
- Evaluating a company's requirements and building ideal methodologies and standards.
- Plan, design, implement, control, monitor and upgrade all security approaches required to safeguard the company's systems, networks and data.
- Regular conduction of penetration testing
- Active participation in management procedural transformation
- Responding to all security violations or threats to the network and other linked systems.
- Helping in any security breach probes
- Troubleshooting all security and internet situations and problems.
- Tackling daily administration works like reporting and maintaining open communication lines with the company's related departments.
- Taking significant security standards to ensure that the company's existing data and infrastructure are safe.
The engineering job and roles come hand-in-hand with those of a security analyst. A Cyber Security Engineer designs and establishes systems, while the analyst focuses on putting the system through its paces and finding means to break it.
Since most security engineers conduct regular stress tests and strive to find the weak points and test them.
Cyber Security Job Opportunities
Though many Cyber Security Engineer posts are vacant due to soring engineering demands, the job opportunities in these fields are like a vast ocean, and so are its demand.
Here are some of the jobs that are relevant for Cyber Security Engineers:
- Information assurance engineer
- IT security engineer
- Information system security engineer
People with Cyber Security engineering experience can look for the following:
- Cyber security consultant
- CISO
- Cyber security architect
- Cyber security director
A recent search for Cyber Security Engineer jobs in LinkedIn unveiled numerous opportunities put forward by wide-range of companies worldwide, and some of them are:
- Mobile application security engineer Booz Allen Hamilton, MD
- Privacy engineer, tech audit (University Grad), Meta Inc., Seattle
- Cyber security engineer, JP Morgan Chase & Co., OH
- Jr. security engineer, Barclays, NJ
- Cyber security engineer, Motorola Solutions, Vancouver, BC
- Application security engineer - Xcode Cloud, Apple Inc., BC
Cyber Security Engineer Skills
To ensure success in cyberspace, an engineer must exhibit a few outstanding skills of technology frameworks, including:
- Ethical hacking
- IDS/IDP, penetration and vulnerability test
- MySQL/MSSQL database networks
- Application security and encryption techs
- Subnetting, VPNs, VoIP, DNS and other network routing approaches
- Windows, Linux and UNIX OS
- Adroitness in C++, Node, Power Shell, Python, Java, Ruby and Go
How Much Does Cyber Security Engineer Make?
According to Glassdoor.com, the average salary for a Cyber Security Engineer is $1,01,548 (INR 6 Lakhs) yearly. But these are not fixed salary rates, and they will vary depending on several factors like employer, location, educational qualification and experience. But regardless of the elements, the security engineer can earn serious pay.
Timeline To be a Cyber Security Engineer
Wondering how long it will take to be a successful Cyber Security Engineer? Well… you can relax a bit.
The actual timeline to be a Cyber Security Engineer depends on your educational qualification, certification and experience. Most people make their way into entry-level security engineer positions within 2 or 4 years, depending on their experience progress.
But if you are already working in an IT field and have adequate experience, a certification in Cyber Security Engineering is sure to lift you into the field at a swift pace.
Closure Call
The future in cyberspace or cyber-related fields are thriving, especially in today's world, where businesses started transforming into digital ventures, resulting in frequent ransomware trap fall. Data breaches and malevolent attacks are a threat that organizations and whatnot say, Government to face regularly. Hence, Cyber Security Engineers have become a central part of the companies.
The career is in-demand and overwhelmed by all of the choices, but not knowing which certification offering company to choose, you are in the right place.
iCert Global is a one-stop solution offering certification training courses in a wide variety of techniques that will give you a head start in this competitive world. Visit our website to find out the different Cyber Security courses provided.
About Us
Our company conducts both Instructor-led Live Online Training sessions and Instructor-led Classroom training workshops for learners across the globe.
We also provide Corporate Training for enterprise workforce development
Project Management Courses
Cloud Technology
- AWS Solution Architect Certification
- Google Cloud Certification
- Developing Microsoft Azure Solutions 70 532 Certification
Cyber Security
Quality Management Training
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
6 Things You Need to Know Why PMP Is Worth It
We have seen people raising questions on Quora.com about the worthiness of PMP, like Why PMP Certification? Is it a valuable course for my career advancement? What is the pay scale once I am a certified PMP professional? Why should IT professionals opt for PMP certification? and many more.
We would have taken a second to think while looking at these questions: what is this course? Is it the new market trend?
PMP certification is undoubtedly the forever's market trend. We can say the demand for PMP professionals will not fade, not any time soon at least. They always stay on demand, taking into account any industry vertical. Hence the course is beneficial both for your career advancement and future.
In this blog, let's see what PMP certification, its goals, exam requirement, worthiness and not least, its cons are. Come on, everything has a negative side; not all things are perfect.
Let's not waste time and dive into the topic, shall we?
What is PMP Certification?

One of the most prestigious and globally known professional qualifications for project managers is the Project Management Professional (PMP) certification. A US non-profit professional organization, Project Management Institute (PMI), offers this certification.
This well-known credential is essential for those who wish to advance their career for a bright future.
Performance Domain of PMP Certification
Project Management Body of Knowledge (PMBoK) is leveraged as the guide for candidates. The examination validates the aspirants on tasks out of 5 performance domains:
- Project initialization (13%)
- Project planning (24%)
- Project execution (31%)
- Project controlling and management (25%)
- Project completion (7%)
Objectives of PMP Certification
The Project Management Institute's - A Guide to the Project Management Body of Knowledge (PMBoK) is the basis for the PMP training programme. PMP trainers or coaches will teach you about the project lifecycle, process groups, and knowledge domains and provide you with the functional expertise and business insights for effective project management.
The project manager's job is to ensure that the project is completed on time and on budget while meeting all requirements.
PMP Certification course will thoroughly prepare you to pass your certification exam and provide you with an in-depth understanding of varied and best Project Management best practices.
Prerequisites of PMP Examination
If you are a skillful project manager responsible for project delivery, directing and leading multi-functional teams, then the PMP is for you. Before taking the PMP certification exam, you must know the test requirements.
Participants must have one among two of the following:
- 4-year degree
- Project leading and directing hours: 4,500
- Project management education hours: 35
OR
- High school diploma, affiliated degree or any other secondary degree
- Project leading and directing hours: 7,500
- Project management education hours: 35
Should You Get PMP Certification?
As we got a basic outline on the term PMP certification, its exam requirements and objectives, let's get to the actual play. Is PMP Certification fruitful?
As the blog's beginning, everything has its own pros and cons, which applies to PMP. But many recruiting proficient and certified experts agree that the pros far outweigh the cons.
PMP Certification Cons
-
Time-consuming Factor
Several people complain about the cost of the time it needs to be a certified PMP professional. As the PMP examination is strenuous, you will need to allot some daily time to be proficient in the PMBoK Guide. Hence a part of the time goes into exam preparation.
But, that’s not all - you will have to read lots of other guides, join preparatory sessions and attend sample tests as a part of PMP preparation. These tasks do take a lot of time. Since most candidates are currently employed, they feel even more frustrated.
Moreover, PMP applications require the documentation of all projects that you perform. Writing even the minutest detail can consume more time than you think it would. Since PMI conducts an audit process to indicate application authenticity.
-
Expensive
The cost of PMP certification is less for PMI members than for non-PMI members. Though PMI membership seems expensive, other benefits associated with it seem to outweigh. Hence, it would be apt to become a PMI member before registering for the exam.
Taking into account the worst scenario where you failed in your first attempt and decided to retake the exam. The cost of retaking the test is quite expensive. So, it's always better to clear it in the first attempt by seeking help from PMP experts to cut down the unnecessary re-examination costs.
Other costs include PMP training classes, preparation resource materials, and sample questions, apart from test costs.
-
Strenuous
Most people argue that the PMP Certification examination is the hardest. The strenuous task is not only the concept memory but also the practical applications. But the cracking of exams truly depends on each individual. Some may take 2 to 3 months, while others can't get certified even after preparing for years.
If the exam was a piece of cake, then there won't be any global value as it has now. This certification's prosperity lies in the rigid standards that are needed to clear and maintain the PMP.
PMP Certification Pros

- Industry Recognition
PMP is a globally recognized certificate. According to several reports, as the number of certified project managers in a company increases, the profit or success rate of the project also increases.
Also, organizations recognize that certified managers are better at project completion on time and within the budget. If you are about to start a career in project management, then this certificate will make up for your lack of experience.
- Networking Opportunities
According to PMI, there are 16.5Mn PMP-certified professionals around the globe. When you sign in as a PMI member, congratulations you become part of PMI. It holds frequent member meetings in major cities.
These are arranged to assist the members in earning Professional Development Units (PDUs) - needed to fulfil Continuous Credential Requirements (CCRs). Benefits of networking - by constant meetings, one could learn about the new project manager job opportunities.
The meetings allow specific time for job adverts. There are several online and offline mode communities where the PMPs communicate. Hence, we could say these communities can help create a professional network.
- Adds Value to Resume
There is a wide array of professional certificates that you can obtain for career advancement. But PMP always shines brighter than the rest, making it the most valuable certification.
Anyone can be applicable for project managers, but recruiters who are trying to fill in a position of project managers always prioritize profiles with PMP certifications over the one which doesn't.
Recruiters often find the potential assessment process daunting, with numerous applications reaching their days each day. The PMP certification leads, as it is one of the most targeted methods to shortlist the candidates.
Some companies make it mandatory to have a PMP certification before applying, making the skimming process much more manageable. The certification can be worth it if you plan to advance in your current company. Moreover, a certified manager can handle an exhausting project management interview much better than a non-certified individual.
- Higher Pay-scale
Another central point of being a certified PMP professional is the cash flow. Across the industry, the average salary of certified project managers is significantly higher.
This has consistently been the highest-paid IT certification that will continue to grow shortly. The accreditation also improves job security. Some organizations value the core competencies learned through PMP during downtime. Therefore, the credential aids in fighting a potential lay-off better than a non-certified one.
Country-wise PMP salary in 2021
Country
Salary
US
US $120,000
India
INR 2,000,000
UK
GBP 60,000
Singapore
SG $96,000
Canada
CAD 93,000
Germany
EUR 79,000
Australia
AU $130,000
PMP salary according to job roles
Job Roles
Yearly Salary (in USD)
Project Manager
60K - 87K
Sr. Project Manager
65K - 115K
Director of Operations
77K - 109K
Project Manager, Engineering
64K - 105K
IT Director
80K - 143K
- Validates Job Dedications
There are specific requirements needed to be fulfilled before being a PMP certified professional. If you are an associate, you need a working experience of 60 months to be eligible.
If a person has a Bachelor's degree, his work experience must be 36 months to be eligible. Since the certification has high standards, clearing the exam takes dedication to the job.
It highlights that you are serious about making project management your ultimate moto and long-term career. A workforce that invests in learning is a significant company asset.
The certification indicates your drive to enhance professional potential, knowledge, and credentials. It helps you to command respect among co-workers and team members.
- Learning Significant Skills
To make you an exceptional case, PMBoK certification teaches you practical skills to excel in your career, and they are:
- The exam preparation course has been updated to reflect the PMP exam.
- Gain project management expertise based on the PMBoK and real-world project management techniques.
- Understand how to put the tools and strategies you learned while studying for the PMP test to good use.
- Use project management strategies that are applicable in the actual world.
- Establish a consistent vocabulary of project management terms and principles.
- Apply project management ideas and terminologies.
- Lead Provides clients with quicker solutions and maintains open communication lines between stakeholders and team members.
- Motivate and lead your team to more tremendous success.
- Ensure compliance, lower risks, and save time and money.
- Study for the PMI Project Management Professional (PMP) Certification Exam and attempt a first-time pass. The Five Process Groups, Ten Knowledge Areas, and Professional and Social Responsibility Area of the PMBoK Guide.
Conclusion
Some people might say PMP certification is time-consuming, complex and even expensive. But many recruiting proficient treat the certification as a crucial credential that adds credential to your resume. Moreover, helps you to build essential skills required to pave the way to future career advancement.
So yes, PMP certification is fruitful and worth the effort.
About Us
iCert Global is a one-stop solution offering certification training courses in a wide variety of techniques that will give you a head start in this competitive world. Visit our website to find out the different Project management courses.
Our company conducts both Instructor-led Live Online Training sessions and Instructor-led Classroom training workshops for learners across the globe.
We also provide Corporate Training for enterprise workforce development
Project Management courses
Quality Management Training
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
DevOps Training
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Read More
We have seen people raising questions on Quora.com about the worthiness of PMP, like Why PMP Certification? Is it a valuable course for my career advancement? What is the pay scale once I am a certified PMP professional? Why should IT professionals opt for PMP certification? and many more.
We would have taken a second to think while looking at these questions: what is this course? Is it the new market trend?
PMP certification is undoubtedly the forever's market trend. We can say the demand for PMP professionals will not fade, not any time soon at least. They always stay on demand, taking into account any industry vertical. Hence the course is beneficial both for your career advancement and future.
In this blog, let's see what PMP certification, its goals, exam requirement, worthiness and not least, its cons are. Come on, everything has a negative side; not all things are perfect.
Let's not waste time and dive into the topic, shall we?
What is PMP Certification?
One of the most prestigious and globally known professional qualifications for project managers is the Project Management Professional (PMP) certification. A US non-profit professional organization, Project Management Institute (PMI), offers this certification.
This well-known credential is essential for those who wish to advance their career for a bright future.
Performance Domain of PMP Certification
Project Management Body of Knowledge (PMBoK) is leveraged as the guide for candidates. The examination validates the aspirants on tasks out of 5 performance domains:
- Project initialization (13%)
- Project planning (24%)
- Project execution (31%)
- Project controlling and management (25%)
- Project completion (7%)
Objectives of PMP Certification
The Project Management Institute's - A Guide to the Project Management Body of Knowledge (PMBoK) is the basis for the PMP training programme. PMP trainers or coaches will teach you about the project lifecycle, process groups, and knowledge domains and provide you with the functional expertise and business insights for effective project management.
The project manager's job is to ensure that the project is completed on time and on budget while meeting all requirements.
PMP Certification course will thoroughly prepare you to pass your certification exam and provide you with an in-depth understanding of varied and best Project Management best practices.
Prerequisites of PMP Examination
If you are a skillful project manager responsible for project delivery, directing and leading multi-functional teams, then the PMP is for you. Before taking the PMP certification exam, you must know the test requirements.
Participants must have one among two of the following:
- 4-year degree
- Project leading and directing hours: 4,500
- Project management education hours: 35
OR
- High school diploma, affiliated degree or any other secondary degree
- Project leading and directing hours: 7,500
- Project management education hours: 35
Should You Get PMP Certification?
As we got a basic outline on the term PMP certification, its exam requirements and objectives, let's get to the actual play. Is PMP Certification fruitful?
As the blog's beginning, everything has its own pros and cons, which applies to PMP. But many recruiting proficient and certified experts agree that the pros far outweigh the cons.
PMP Certification Cons
-
Time-consuming Factor
Several people complain about the cost of the time it needs to be a certified PMP professional. As the PMP examination is strenuous, you will need to allot some daily time to be proficient in the PMBoK Guide. Hence a part of the time goes into exam preparation.
But, that’s not all - you will have to read lots of other guides, join preparatory sessions and attend sample tests as a part of PMP preparation. These tasks do take a lot of time. Since most candidates are currently employed, they feel even more frustrated.
Moreover, PMP applications require the documentation of all projects that you perform. Writing even the minutest detail can consume more time than you think it would. Since PMI conducts an audit process to indicate application authenticity.
-
Expensive
The cost of PMP certification is less for PMI members than for non-PMI members. Though PMI membership seems expensive, other benefits associated with it seem to outweigh. Hence, it would be apt to become a PMI member before registering for the exam.
Taking into account the worst scenario where you failed in your first attempt and decided to retake the exam. The cost of retaking the test is quite expensive. So, it's always better to clear it in the first attempt by seeking help from PMP experts to cut down the unnecessary re-examination costs.
Other costs include PMP training classes, preparation resource materials, and sample questions, apart from test costs.
-
Strenuous
Most people argue that the PMP Certification examination is the hardest. The strenuous task is not only the concept memory but also the practical applications. But the cracking of exams truly depends on each individual. Some may take 2 to 3 months, while others can't get certified even after preparing for years.
If the exam was a piece of cake, then there won't be any global value as it has now. This certification's prosperity lies in the rigid standards that are needed to clear and maintain the PMP.
PMP Certification Pros
- Industry Recognition
PMP is a globally recognized certificate. According to several reports, as the number of certified project managers in a company increases, the profit or success rate of the project also increases.
Also, organizations recognize that certified managers are better at project completion on time and within the budget. If you are about to start a career in project management, then this certificate will make up for your lack of experience.
- Networking Opportunities
According to PMI, there are 16.5Mn PMP-certified professionals around the globe. When you sign in as a PMI member, congratulations you become part of PMI. It holds frequent member meetings in major cities.
These are arranged to assist the members in earning Professional Development Units (PDUs) - needed to fulfil Continuous Credential Requirements (CCRs). Benefits of networking - by constant meetings, one could learn about the new project manager job opportunities.
The meetings allow specific time for job adverts. There are several online and offline mode communities where the PMPs communicate. Hence, we could say these communities can help create a professional network.
- Adds Value to Resume
There is a wide array of professional certificates that you can obtain for career advancement. But PMP always shines brighter than the rest, making it the most valuable certification.
Anyone can be applicable for project managers, but recruiters who are trying to fill in a position of project managers always prioritize profiles with PMP certifications over the one which doesn't.
Recruiters often find the potential assessment process daunting, with numerous applications reaching their days each day. The PMP certification leads, as it is one of the most targeted methods to shortlist the candidates.
Some companies make it mandatory to have a PMP certification before applying, making the skimming process much more manageable. The certification can be worth it if you plan to advance in your current company. Moreover, a certified manager can handle an exhausting project management interview much better than a non-certified individual.
- Higher Pay-scale
Another central point of being a certified PMP professional is the cash flow. Across the industry, the average salary of certified project managers is significantly higher.
This has consistently been the highest-paid IT certification that will continue to grow shortly. The accreditation also improves job security. Some organizations value the core competencies learned through PMP during downtime. Therefore, the credential aids in fighting a potential lay-off better than a non-certified one.
Country-wise PMP salary in 2021
|
Country |
Salary |
|
US |
US $120,000 |
|
India |
INR 2,000,000 |
|
UK |
GBP 60,000 |
|
Singapore |
SG $96,000 |
|
Canada |
CAD 93,000 |
|
Germany |
EUR 79,000 |
|
Australia |
AU $130,000 |
PMP salary according to job roles
|
Job Roles |
Yearly Salary (in USD) |
|
Project Manager |
60K - 87K |
|
Sr. Project Manager |
65K - 115K |
|
Director of Operations |
77K - 109K |
|
Project Manager, Engineering |
64K - 105K |
|
IT Director |
80K - 143K |
- Validates Job Dedications
There are specific requirements needed to be fulfilled before being a PMP certified professional. If you are an associate, you need a working experience of 60 months to be eligible.
If a person has a Bachelor's degree, his work experience must be 36 months to be eligible. Since the certification has high standards, clearing the exam takes dedication to the job.
It highlights that you are serious about making project management your ultimate moto and long-term career. A workforce that invests in learning is a significant company asset.
The certification indicates your drive to enhance professional potential, knowledge, and credentials. It helps you to command respect among co-workers and team members.
- Learning Significant Skills
To make you an exceptional case, PMBoK certification teaches you practical skills to excel in your career, and they are:
- The exam preparation course has been updated to reflect the PMP exam.
- Gain project management expertise based on the PMBoK and real-world project management techniques.
- Understand how to put the tools and strategies you learned while studying for the PMP test to good use.
- Use project management strategies that are applicable in the actual world.
- Establish a consistent vocabulary of project management terms and principles.
- Apply project management ideas and terminologies.
- Lead Provides clients with quicker solutions and maintains open communication lines between stakeholders and team members.
- Motivate and lead your team to more tremendous success.
- Ensure compliance, lower risks, and save time and money.
- Study for the PMI Project Management Professional (PMP) Certification Exam and attempt a first-time pass. The Five Process Groups, Ten Knowledge Areas, and Professional and Social Responsibility Area of the PMBoK Guide.
Conclusion
Some people might say PMP certification is time-consuming, complex and even expensive. But many recruiting proficient treat the certification as a crucial credential that adds credential to your resume. Moreover, helps you to build essential skills required to pave the way to future career advancement.
So yes, PMP certification is fruitful and worth the effort.
About Us
iCert Global is a one-stop solution offering certification training courses in a wide variety of techniques that will give you a head start in this competitive world. Visit our website to find out the different Project management courses.
Our company conducts both Instructor-led Live Online Training sessions and Instructor-led Classroom training workshops for learners across the globe.
We also provide Corporate Training for enterprise workforce development
Project Management courses
Quality Management Training
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
DevOps Training
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Roles and Responsibilities of Hadoop Administrators
In recent years, there has been a massive advancement in both data and technology, opening new doors to accommodate the growing demands of the industry vertical. System administration is one of the areas that might affect business performance. The job performance relates to system performance either it can improve or play havoc with the version.
Like system admins, Hadoop admins are a trending job in the big data domain. As the volume of data generated worldwide keeps on increasing, open-source processing systems such as Hadoop are gaining immense popularity in the industry.
With the rising adoption of Hadoop across various industry verticals due to its potential to scale and process the colossal amount of data, organizations require Hadoop admins to take care of the Hadoop clusters.
Who is Hadoop Admin?
A Hadoop admin is a core part of the Hadoop implementation procedure, where they are responsible for maintaining the Hadoop clusters running seamlessly in production. They are in charge of clusters and other resources in the Hadoop ecosystem.
The job of Hadoop admins is not visible to other clients or IT groups. They are responsible for developing and formulating the architecture, development, and engineering of big data. These admins must ensure that there are no flaws in the cluster installation. They must alleviate issues and improve the overall cluster performance.
Why Hadoop Admin?
Hadoop has become a top-notch priority in the IT sectors worldwide. Probably, the execution has a production of vast clusters with a more significant number of nodes, and they need an admin to manage and monitor their performance.
Their routine programs involve the tracking of entire Hadoop jobs which is scheduled. Clusters are activated towards failures offered and given test performance, and the admin must keep track of the cluster workflows.
This procedure makes the business sector obtain accurate data regarding the nodes with the help of the interface.
Roles and Responsibilities of Hadoop Admins
Administrating Hadoop clusters introduces numerous challenges to the Hadoop admins with running data tests via several machines. Hadoop deployment often fails as the admins attempt to replicate the procedures tested on one or two different devices across complex clusters.
Let us see the roles and responsibilities of Hadoop admins in an organization.
DBA responsibilities include:
- Managing and optimizing disk space for data handling
- Backup and recovery procedure of database
- Performance observation and fine-tuning on the data pattern changes
- Software installation and configuration
- Data modeling, design and execution of data based on recognized practices
- Checking the connectivity and security measurements of data
- Automating manual tasks for swift performance
- Installing patches and upgrading software
The task of Hadoop admin covers batch works as part of data warehousing - involving the development, testing, and monitoring, which are:
- Loading of colossal amount of data in a timely manner
- Performing primary key execution
- Ensuring referential integrity
- Accomplishments of data restatements
Now, let us see the routine work done by a Hadoop administrator in an organization.
The key activities include:
- Configuring NameNode to ensure high availability
- Analysis of storage data volume and assigning the space in HDFS
- Required software and hardware deployment in the Hadoop ecosystem, and the expansion of existing ones
- Implementation in a Hadoop cluster and its maintenance
- Deployment and management of Hadoop infrastructure on a current basis
- Installing of Hadoop in Linux
- Monitoring the Hadoop cluster to check whether it is up-to-date and constantly running
- Management of resources in a cluster ecosystem - new node development and eradication of non-functioning ones
Other activities of the admins include:
- Checking the connectivity and security of cluster
- Operating as a central person for Vendor escalation
- Capacity planning
- HDFS file system management and monitoring
- Coordinating with application teams, installing the OS and Hadoop-related updates
- Troubleshooting
- User creation in Linux and its components in the ecosystem, and also setting up Kerberos principles
- Effective communication with organizational-level teams such as application, BI, database, infrastructure and network teams
- Managing and reviewing log files
- Administrating HDFS and offering significant supports
Essential Skills to be a Hadoop Admin
- The potential to install and execute the Hadoop cluster, add and eradicate nodes, monitor workflows and all the critical parts of the cluster, configuration of name-node, recovery of backups and many more.
- In-depth knowledge of Unix based file infrastructure
- The expertise of general operations, including troubleshooting and sound understanding of network and system.
- Networking proficiency
- Experience with open-source configuration deployment and management tools such as Chef, Puppet, etc.
- Strong fundamental knowledge of the operating system – Linux
- Understanding Core Java is a plus point for efficient job performance
Hadoop Admin Career Path
Today, Hadoop has become the talk of the town, with global companies readily adopting Hadoop and its related big data solutions, irrespective of their humungous size.
Due to a significant increase in big data and data analytics, the demand for big data skillsets is growing. Several job profiles come within the Hadoop admin career path, some of which are:
- Data analytics administrator
- IT Hadoop administrator
- Hadoop system admin
- Web engineer
- Cluster admin
- Hadoop architect
- Data engineer
- Data science tools & application engineer
- Data management analyst
- IT storage admin
- Tech support admin and many more.
These careers and roles can differ depending on the business size and job role. Moreover, the salary of a Hadoop admin makes a considerable difference in their presence in the company. Many experienced admins receive the best pay scale; hence, the Hadoop admin gets handsome money.
Potential Problems with Hadoop Admin Job
Few potential issues associated with Hadoop admin task on a company’s routine operation include:
- Hardware: Since Hadoop tackles a vast among of data, however, over the period, storage infrastructure fails to perform as expected. Hence a close watching of HDFS prevents data loss.
- Human error: While handling complex systems like Hadoop, man-made fallacies are common. A minor flaw can create a huge problem, making a day in Hadoop admin life tiresome. Hence, establishing preventive measures is an add-on work.
- Resource Exhaustion: It is a crucial factor used to estimate the task failure, identify users and correct the procedures. Repetitive failure of tasks is a drain on the capacity.
- Configuration issue: If you dealing with Hadoop, then configuration issues sum up to 80 percent. Hence, the performance may have a lot to pay because of configuration flaws.
Future Scope of Hadoop Admin
Being a Hadoop admin isn't rocket science, and neither is a cakewalk. Individuals who have a fundamental understanding of statistics, computation and programming languages are good to go. Taking a comprehensive data course is beneficial as it offers you complete knowledge and is not just limited to Hadoop.
Apart from aspirants, IT professionals such as software architects, IT managers, Java developers, DBAs and many more who are interested in Hadoop admin can take up the big data courses, as these courses provide an ocean of job opportunities and are one of the most searched terms on leading job websites.
Final Call
Hadoop administration is a rewarding career, opening to plenty of job opportunities in today's big data market such as Yahoo, Facebook, Quantcast, netseer, etc.
The core objective of Hadoop admins is to understand the concept of big data and Hadoop distributions. Several other factors must be considered when these admins are involved in business performance. Though they aren't limited, their works are not visible to other IT sectors. Moreover, it helps to continue the safety of Hadoop clusters.
If you are looking for up-skilling with the Hadoop administration, this is the right choice. Don't let this moment go in vain.
About Us
iCert Global is a one-stop solution offering certification training courses in a wide variety of techniques that will give you a head start in this competitive world.
Visit our website to find out more about the course.
Our company conducts both Instructor-led Live Online Training sessions and Instructor-led Classroom training workshops for learners across the globe.
We also provide Corporate Training for enterprise workforce development
Data Science & BI courses
Quality Management Training
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
DevOps Training
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Read More
In recent years, there has been a massive advancement in both data and technology, opening new doors to accommodate the growing demands of the industry vertical. System administration is one of the areas that might affect business performance. The job performance relates to system performance either it can improve or play havoc with the version.
Like system admins, Hadoop admins are a trending job in the big data domain. As the volume of data generated worldwide keeps on increasing, open-source processing systems such as Hadoop are gaining immense popularity in the industry.
With the rising adoption of Hadoop across various industry verticals due to its potential to scale and process the colossal amount of data, organizations require Hadoop admins to take care of the Hadoop clusters.
Who is Hadoop Admin?
A Hadoop admin is a core part of the Hadoop implementation procedure, where they are responsible for maintaining the Hadoop clusters running seamlessly in production. They are in charge of clusters and other resources in the Hadoop ecosystem.
The job of Hadoop admins is not visible to other clients or IT groups. They are responsible for developing and formulating the architecture, development, and engineering of big data. These admins must ensure that there are no flaws in the cluster installation. They must alleviate issues and improve the overall cluster performance.
Why Hadoop Admin?
Hadoop has become a top-notch priority in the IT sectors worldwide. Probably, the execution has a production of vast clusters with a more significant number of nodes, and they need an admin to manage and monitor their performance.
Their routine programs involve the tracking of entire Hadoop jobs which is scheduled. Clusters are activated towards failures offered and given test performance, and the admin must keep track of the cluster workflows.
This procedure makes the business sector obtain accurate data regarding the nodes with the help of the interface.
Roles and Responsibilities of Hadoop Admins
Administrating Hadoop clusters introduces numerous challenges to the Hadoop admins with running data tests via several machines. Hadoop deployment often fails as the admins attempt to replicate the procedures tested on one or two different devices across complex clusters.
Let us see the roles and responsibilities of Hadoop admins in an organization.
DBA responsibilities include:
- Managing and optimizing disk space for data handling
- Backup and recovery procedure of database
- Performance observation and fine-tuning on the data pattern changes
- Software installation and configuration
- Data modeling, design and execution of data based on recognized practices
- Checking the connectivity and security measurements of data
- Automating manual tasks for swift performance
- Installing patches and upgrading software
The task of Hadoop admin covers batch works as part of data warehousing - involving the development, testing, and monitoring, which are:
- Loading of colossal amount of data in a timely manner
- Performing primary key execution
- Ensuring referential integrity
- Accomplishments of data restatements
Now, let us see the routine work done by a Hadoop administrator in an organization.
The key activities include:
- Configuring NameNode to ensure high availability
- Analysis of storage data volume and assigning the space in HDFS
- Required software and hardware deployment in the Hadoop ecosystem, and the expansion of existing ones
- Implementation in a Hadoop cluster and its maintenance
- Deployment and management of Hadoop infrastructure on a current basis
- Installing of Hadoop in Linux
- Monitoring the Hadoop cluster to check whether it is up-to-date and constantly running
- Management of resources in a cluster ecosystem - new node development and eradication of non-functioning ones
Other activities of the admins include:
- Checking the connectivity and security of cluster
- Operating as a central person for Vendor escalation
- Capacity planning
- HDFS file system management and monitoring
- Coordinating with application teams, installing the OS and Hadoop-related updates
- Troubleshooting
- User creation in Linux and its components in the ecosystem, and also setting up Kerberos principles
- Effective communication with organizational-level teams such as application, BI, database, infrastructure and network teams
- Managing and reviewing log files
- Administrating HDFS and offering significant supports
Essential Skills to be a Hadoop Admin
- The potential to install and execute the Hadoop cluster, add and eradicate nodes, monitor workflows and all the critical parts of the cluster, configuration of name-node, recovery of backups and many more.
- In-depth knowledge of Unix based file infrastructure
- The expertise of general operations, including troubleshooting and sound understanding of network and system.
- Networking proficiency
- Experience with open-source configuration deployment and management tools such as Chef, Puppet, etc.
- Strong fundamental knowledge of the operating system – Linux
- Understanding Core Java is a plus point for efficient job performance
Hadoop Admin Career Path
Today, Hadoop has become the talk of the town, with global companies readily adopting Hadoop and its related big data solutions, irrespective of their humungous size.
Due to a significant increase in big data and data analytics, the demand for big data skillsets is growing. Several job profiles come within the Hadoop admin career path, some of which are:
- Data analytics administrator
- IT Hadoop administrator
- Hadoop system admin
- Web engineer
- Cluster admin
- Hadoop architect
- Data engineer
- Data science tools & application engineer
- Data management analyst
- IT storage admin
- Tech support admin and many more.
These careers and roles can differ depending on the business size and job role. Moreover, the salary of a Hadoop admin makes a considerable difference in their presence in the company. Many experienced admins receive the best pay scale; hence, the Hadoop admin gets handsome money.
Potential Problems with Hadoop Admin Job
Few potential issues associated with Hadoop admin task on a company’s routine operation include:
- Hardware: Since Hadoop tackles a vast among of data, however, over the period, storage infrastructure fails to perform as expected. Hence a close watching of HDFS prevents data loss.
- Human error: While handling complex systems like Hadoop, man-made fallacies are common. A minor flaw can create a huge problem, making a day in Hadoop admin life tiresome. Hence, establishing preventive measures is an add-on work.
- Resource Exhaustion: It is a crucial factor used to estimate the task failure, identify users and correct the procedures. Repetitive failure of tasks is a drain on the capacity.
- Configuration issue: If you dealing with Hadoop, then configuration issues sum up to 80 percent. Hence, the performance may have a lot to pay because of configuration flaws.
Future Scope of Hadoop Admin
Being a Hadoop admin isn't rocket science, and neither is a cakewalk. Individuals who have a fundamental understanding of statistics, computation and programming languages are good to go. Taking a comprehensive data course is beneficial as it offers you complete knowledge and is not just limited to Hadoop.
Apart from aspirants, IT professionals such as software architects, IT managers, Java developers, DBAs and many more who are interested in Hadoop admin can take up the big data courses, as these courses provide an ocean of job opportunities and are one of the most searched terms on leading job websites.
Final Call
Hadoop administration is a rewarding career, opening to plenty of job opportunities in today's big data market such as Yahoo, Facebook, Quantcast, netseer, etc.
The core objective of Hadoop admins is to understand the concept of big data and Hadoop distributions. Several other factors must be considered when these admins are involved in business performance. Though they aren't limited, their works are not visible to other IT sectors. Moreover, it helps to continue the safety of Hadoop clusters.
If you are looking for up-skilling with the Hadoop administration, this is the right choice. Don't let this moment go in vain.
About Us
iCert Global is a one-stop solution offering certification training courses in a wide variety of techniques that will give you a head start in this competitive world.
Visit our website to find out more about the course.
Our company conducts both Instructor-led Live Online Training sessions and Instructor-led Classroom training workshops for learners across the globe.
We also provide Corporate Training for enterprise workforce development
Data Science & BI courses
Quality Management Training
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
DevOps Training
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Concepts of Zero Defects in Quality Management
Quality defects can have significant costs associated with them: money, resources, time, and reputation. The programs leveraged by organizations to eradicate quality flaws can be big-budget and time-consuming.
During these times, organizations have a hard time maintaining their quality to stay competitive in their field; that’s when quality management tools come into action. These tools are productive approaches to streamlining business practices to offer better quality and swifter outcomes.
More than 91 percent of companies saw an increase in their operating income after successfully executing a quality management tool. Quality handling is one of the fastest ways to increase production returns.
The Zero Defects approach in quality management works to minimize the flaws to imaginary and, as a result, create better value.
Introduction to the Concept of Zero Defects
The Zero Defects concept was first coined by Mr. Philip Crosby in "Absolutes of Quality Management" and is widely adopted by Six Sigma methodologies as one of its theories. However, the concept also had a fair share of criticism, with some debating about the non-existence of Zero Defects.
Others have struggled hard to prove that Zero Defects in quality management don't mean perfect; instead, a method for eradicating waste and minimization flaws.
What is Zero Defects?
Quality management talks about practices that ensure that the outputs produced are suitable. But to attain zero defects in the deliverable production is technically nearly impossible as complex projects, irrespective of the size, will have some flaws.
According to Six Sigma, Zero Defects are defined as 3.4 defects per million opportunities (DPMO), permitting a 1.5 sigma process transition. To enhance the quality of manufacturing or developing procedures, the Zero Defects concepts can be considered a perfection quest.
Though true perfection might not be obtainable, the pursuit will push quality and enhancements to the point that is acceptable even under rigorous metrics.
Application of Zero Defects
Automotive sectors use Zero Defects to handle and enhance quality problems. It targets reducing the number of flaws in manufactured services and products without the need for specific rules to follow.
This makes the organizations customize how they want the management tool to work for themselves, which is why Zero Defects can be so effective.
It is leveraged in Six Sigma methodologies to minimize the variation and standard deviation, which will indirectly reduce the flaws and bring them near zero.
Principles of Zero Defects
The principles of Zero Defects, according to Philip Crosby, are:
- Quality is the accordance to requirements
Each product has a requirement, and it defines what end-users expect to see. A particular service or product is said to attain the utmost quality when it meets customer prerequisites. This should not be confused with the highest product standards. For example, it will be unrealistic if we say the old mobile phones lack quality compared to the latest smartphone. They both must meet different quality standards to pass the quality test irrespective of their model, size or other internal/external features.
Suppose we visualize the above scenario with the Zero Defects case. In that case, the primary mobile phone version is a quality product if it meets the fundamental customer requirements such as making phone calls and sending and receiving messages. The product is said to accord to the quality and has near to Zero Defects.
- Defect prevention
Here, the top priority is the quality management of the product or service; hence, flaw prevention is made a part of the company procedure. It should be in practice rather than in quality scrutiny and rectification. This is why because Zero Defects management is always less tiring and strenuous. It is more accurate and budget-oriented, as it targets preventing fallacies than identifying and rectifying them later.
- Quality benchmark means zero defects
The following principle of Zero Defects depends on the nature of demands. A demand highlights what the customer or the product itself is needed. Every service and product unit that does not meet the request will not satisfy the prerequisites and is nowhere near the word excellence. But, in some scenarios, the teams that do not meet the conditions could still satisfy the customer demands, so these requirements must be reviewed and modified accordingly to reflect reality.
- Quality measurements in terms of money
Mr. Crosby expects that every flaw indicates a personal expense, including inspection time, rework procedures, and overall budget or revenue. Being extra to the list includes the cost of discarded materials, customer dissatisfactions and labour. When the defects are identified accurately, and appropriate measures are taken, the impact of these costs can be made precise.
This, in turn, offers a clear-cut justification on expense leading to a step forward for quality enhancement. Companies must find a method to estimate a Zero Defects management procedure that aids in maintaining management commitment, employee encouragement or rewarding, and ensuring organizational targets are made measurable. Keeping these in mind, the practices can be made solid, thus helping in making genuine decisions on relative returns.
Theory & Execution of Zero Defects
Zero Defects methodology ensures that there is no waste accumulation in a project. The procedure eradicates unproductive and is of no value to a project, thereby creating process enhancements and lower costs.
The motto of the Zero Defects theory is 'Doing it right the first time, that eventually helps eliminate expensive and time-consuming resolutions later in the project management practice.
Generally, the methodology is based on 4 elements for its execution in an actual project are they are:
- Quality is a state of accordance with requirements. Hence Zero Defects in a project mean the satisfaction of prerequisites at that period.
- Right the first time means that quality must be merged into the project process at the initial phase than keeping it aside and solving it later.
- Quality measure in terms of money means that individuals in charge of the project must consider waste, production, and revenue in terms of economic impact.
- Performance must be considered by the accepted procedures, as near to perfection as possible.
How to Achieve Zero Defects?
There are no magic procedures in achieving Zero Defects; however, there are some techniques to use if you are ready to introduce the concept in an organization, and they are:
- Manage process transitions efficiently.
- Acknowledgment on customer expectations about product or service quality
- Prioritizing continuous enhancement and efficacy
- Introduce and learn Japanese system of Poka-Yoke (prevention of inadvertent flaws).
- Monitor your progress.
- Estimate your quality efforts.
- Develop quality into performance expectations.
Advantage & Disadvantage of Zero Defects
One of the top advantages of attaining a zero-defect phase is minimizing cost and waste when manufacturing products according to customer demands. Zero Defects mean higher user satisfaction and enhanced customer loyalty that consistently results in better profits and sales.
The concept target might lead to a situation where a team is attempting a perfect practice that cannot realistically be obtained. The resources and time allocated on reaching Zero Defects may negatively affect the project performance and strain workforce satisfaction and confidence.
Moreover, there can also be negative suggestions when you ponder the entire supply chain. Other industrialists might have a different viewpoint on the Zero Defects concept.
Ultimately, the pursuit for Zero Defects is a prime target in itself, and many organizations find that merits exceed the demerits. By attempting for rigorous but accepted defects practices, they can develop reasonable procedures and build an ecosystem of continuous service enhancement.
Conclusion
Implementing the Zero Defects concept in an organization allows them to understand and streamline their production workflow to very minor detail. The minimal expense and maximum revenue on implementations make it suitable for any company seeking to launch a new business practice without any training and recalibration investment.
It is essential for company employees and other individuals to get trained and certified in popular quality management courses to properly acknowledge the Zero Defects approach and how it adds value to your company.
About Us
iCert Global is a one-stop solution offering certification training courses in a wide variety of techniques that will give you a head start in this competitive world.
Visit our website to find out more about the course.
Our company conducts both Instructor-led Live Online Training sessions and Instructor-led Classroom training workshops for learners across the globe.
We also provide Corporate Training for enterprise workforce development
Data Science & BI courses
Quality Management Training
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
DevOps Training
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Read More
Quality defects can have significant costs associated with them: money, resources, time, and reputation. The programs leveraged by organizations to eradicate quality flaws can be big-budget and time-consuming.
During these times, organizations have a hard time maintaining their quality to stay competitive in their field; that’s when quality management tools come into action. These tools are productive approaches to streamlining business practices to offer better quality and swifter outcomes.
More than 91 percent of companies saw an increase in their operating income after successfully executing a quality management tool. Quality handling is one of the fastest ways to increase production returns.
The Zero Defects approach in quality management works to minimize the flaws to imaginary and, as a result, create better value.
Introduction to the Concept of Zero Defects
The Zero Defects concept was first coined by Mr. Philip Crosby in "Absolutes of Quality Management" and is widely adopted by Six Sigma methodologies as one of its theories. However, the concept also had a fair share of criticism, with some debating about the non-existence of Zero Defects.
Others have struggled hard to prove that Zero Defects in quality management don't mean perfect; instead, a method for eradicating waste and minimization flaws.
What is Zero Defects?
Quality management talks about practices that ensure that the outputs produced are suitable. But to attain zero defects in the deliverable production is technically nearly impossible as complex projects, irrespective of the size, will have some flaws.
According to Six Sigma, Zero Defects are defined as 3.4 defects per million opportunities (DPMO), permitting a 1.5 sigma process transition. To enhance the quality of manufacturing or developing procedures, the Zero Defects concepts can be considered a perfection quest.
Though true perfection might not be obtainable, the pursuit will push quality and enhancements to the point that is acceptable even under rigorous metrics.
Application of Zero Defects
Automotive sectors use Zero Defects to handle and enhance quality problems. It targets reducing the number of flaws in manufactured services and products without the need for specific rules to follow.
This makes the organizations customize how they want the management tool to work for themselves, which is why Zero Defects can be so effective.
It is leveraged in Six Sigma methodologies to minimize the variation and standard deviation, which will indirectly reduce the flaws and bring them near zero.
Principles of Zero Defects
The principles of Zero Defects, according to Philip Crosby, are:
- Quality is the accordance to requirements
Each product has a requirement, and it defines what end-users expect to see. A particular service or product is said to attain the utmost quality when it meets customer prerequisites. This should not be confused with the highest product standards. For example, it will be unrealistic if we say the old mobile phones lack quality compared to the latest smartphone. They both must meet different quality standards to pass the quality test irrespective of their model, size or other internal/external features.
Suppose we visualize the above scenario with the Zero Defects case. In that case, the primary mobile phone version is a quality product if it meets the fundamental customer requirements such as making phone calls and sending and receiving messages. The product is said to accord to the quality and has near to Zero Defects.
- Defect prevention
Here, the top priority is the quality management of the product or service; hence, flaw prevention is made a part of the company procedure. It should be in practice rather than in quality scrutiny and rectification. This is why because Zero Defects management is always less tiring and strenuous. It is more accurate and budget-oriented, as it targets preventing fallacies than identifying and rectifying them later.
- Quality benchmark means zero defects
The following principle of Zero Defects depends on the nature of demands. A demand highlights what the customer or the product itself is needed. Every service and product unit that does not meet the request will not satisfy the prerequisites and is nowhere near the word excellence. But, in some scenarios, the teams that do not meet the conditions could still satisfy the customer demands, so these requirements must be reviewed and modified accordingly to reflect reality.
- Quality measurements in terms of money
Mr. Crosby expects that every flaw indicates a personal expense, including inspection time, rework procedures, and overall budget or revenue. Being extra to the list includes the cost of discarded materials, customer dissatisfactions and labour. When the defects are identified accurately, and appropriate measures are taken, the impact of these costs can be made precise.
This, in turn, offers a clear-cut justification on expense leading to a step forward for quality enhancement. Companies must find a method to estimate a Zero Defects management procedure that aids in maintaining management commitment, employee encouragement or rewarding, and ensuring organizational targets are made measurable. Keeping these in mind, the practices can be made solid, thus helping in making genuine decisions on relative returns.
Theory & Execution of Zero Defects
Zero Defects methodology ensures that there is no waste accumulation in a project. The procedure eradicates unproductive and is of no value to a project, thereby creating process enhancements and lower costs.
The motto of the Zero Defects theory is 'Doing it right the first time, that eventually helps eliminate expensive and time-consuming resolutions later in the project management practice.
Generally, the methodology is based on 4 elements for its execution in an actual project are they are:
- Quality is a state of accordance with requirements. Hence Zero Defects in a project mean the satisfaction of prerequisites at that period.
- Right the first time means that quality must be merged into the project process at the initial phase than keeping it aside and solving it later.
- Quality measure in terms of money means that individuals in charge of the project must consider waste, production, and revenue in terms of economic impact.
- Performance must be considered by the accepted procedures, as near to perfection as possible.
How to Achieve Zero Defects?
There are no magic procedures in achieving Zero Defects; however, there are some techniques to use if you are ready to introduce the concept in an organization, and they are:
- Manage process transitions efficiently.
- Acknowledgment on customer expectations about product or service quality
- Prioritizing continuous enhancement and efficacy
- Introduce and learn Japanese system of Poka-Yoke (prevention of inadvertent flaws).
- Monitor your progress.
- Estimate your quality efforts.
- Develop quality into performance expectations.
Advantage & Disadvantage of Zero Defects
One of the top advantages of attaining a zero-defect phase is minimizing cost and waste when manufacturing products according to customer demands. Zero Defects mean higher user satisfaction and enhanced customer loyalty that consistently results in better profits and sales.
The concept target might lead to a situation where a team is attempting a perfect practice that cannot realistically be obtained. The resources and time allocated on reaching Zero Defects may negatively affect the project performance and strain workforce satisfaction and confidence.
Moreover, there can also be negative suggestions when you ponder the entire supply chain. Other industrialists might have a different viewpoint on the Zero Defects concept.
Ultimately, the pursuit for Zero Defects is a prime target in itself, and many organizations find that merits exceed the demerits. By attempting for rigorous but accepted defects practices, they can develop reasonable procedures and build an ecosystem of continuous service enhancement.
Conclusion
Implementing the Zero Defects concept in an organization allows them to understand and streamline their production workflow to very minor detail. The minimal expense and maximum revenue on implementations make it suitable for any company seeking to launch a new business practice without any training and recalibration investment.
It is essential for company employees and other individuals to get trained and certified in popular quality management courses to properly acknowledge the Zero Defects approach and how it adds value to your company.
About Us
iCert Global is a one-stop solution offering certification training courses in a wide variety of techniques that will give you a head start in this competitive world.
Visit our website to find out more about the course.
Our company conducts both Instructor-led Live Online Training sessions and Instructor-led Classroom training workshops for learners across the globe.
We also provide Corporate Training for enterprise workforce development
Data Science & BI courses
Quality Management Training
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
DevOps Training
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
What an Artificial Intelligence (AI) Benefits in Today’s World
What an Artificial Intelligence (AI) Benefits in Today’s World
Over the past few decades, Artificial Intelligence (AI) has received several buzzes. However, it is still one of the top technology trends due to tremendous impacts on our lifestyle, workspace and games.
AI has proven dominance in personal assistants (Alexa, Siri and Google Assistant), image and speech recognition, ride-sharing apps (Uber, Ola, Lyft and more) and navigation apps (Google Maps, Apple Maps).
Between the years 2019 and 2020, AI practitioners' or specialists' recruitments were seen to increase by 32%, and in LinkedIn's emerging job report 2020, the role of an AI specialist was ranked #1.
This tech trend needs profound knowledge of statistics, helping us to identify the outcomes generated by the algorithm for a particular dataset.
Some of the highest-paying jobs in the AI field include AI Architect, Robotics Scientists and Big Data Engineering.
What AI Actually Means?
When time travelled to the 1950s, Minsky and McCarthy described the tech trend as any task executed by a machine that was previously considered to need human intelligence.
However, according to modern definition, AI is the ability of a digital computer to execute tasks that are associated with skillsets. It is often applied to the developing system projects invested with the intellectual method characteristics of humans like the potential to reason, identify insights, or learn from prior experience.
The History of AI

Artificial and intelligent bots first appeared in ancient Greek myths of Antiquity. Aristotle's syllogism development and its use of deductive reasoning was a crucial point in a human's quest to gain insights into its own intelligence.
Following are significant event timelines in AI:
1943 - 1949
In 1943, Walter Pits and Warren McCulloch released 'A Logical Calculus of Ideas Immanent in Nervous Activity,' the first work on AI in that year. The paper suggested the first mathematical model for developing a neural network.
In 1949, in his book 'The Organization of Behavior: A Neuropsychological Theory, Donald Hebb proposed that neural pathways are developed from experience and connections between neurons become firmer the more frequently they are used.
1950 - 1959
In 1950, Alan Turing published a theory 'Computing Machinery and Intelligence' proposed a test called Turin Test that identifies whether a machine has the potential to exhibit human behaviour or not. The same year, Marvin Minsky and Dean Edmonds, Harvard graduates, developed their first neural network computer named SNARC.
In 1952, Arthur Samuel built a self-learning algorithm to play checkers.
In 1954, the Georgetown-IBM machine translation test automatically translated 60 Russian sentences into English.
In 1956, Allen Newell and Herbert A. Simon developed the first AI program called Logic Theorist that verified 38 of 52 math theorems, followed by discovering new and more proofs. The same year, AI was first adopted by John McCarthy at the Dartmouth Conference, which defined the scope of AI, and is widely considered the birth of tech trend as we know it now.
In 1958, John McCarthy built the AI programming language - Lisp and published 'Programs with Common Sense.'
In 1959, J.C. Shaw and Newell and Simon created the General Problem Solver (GPS) - designed to mimic human problem-solving. The same year, Herbert Gelernter created the Geometry Theorem Prover program, Arthur Samuel coined Machine Learning (ML) while at IBM, and McCarthy and Marvin Minsky founded the MIT AI Project.
1963 - 1969
In 1963, McCarthy established the AI Lab at Stanford.
In 1966, Joseph Weizenbaum developed the first-ever chatbot - ELIZA.
In 1969, the first successful proficient systems were created in DENDRAL, a XX program, and MYCIN, developed to determine blood infections, were made at Stanford.
1972 - 1980
In 1972, the PROLOG, a logic programming language, was created. In Japan, the first humanoid bot - WABOT-1 was built the same year.
From 1974 to 1980 was known to be the first AI winter period, where researchers couldn't pursue their studies to the best extent as they were short of funds from the govt, resulting in a gradual decrease of AI interests.
In 1980, AI came back with much greater force. The first successful commercial proficient system - R1, was developed by Digital Equipment Corp. The same year, the national conference of the American Association of AI was organized at Stanford Univ.
1982 - 1997
In 1982, the Japan Ministry of International Trade and Industry introduced the 5th Gen Computer System (FGCS) project for developing supercomputer and AI development platforms.
From 1987 to 1993, AI entered the second winter period; as an emerging computer tech and inexpensive alternatives, investors and the govt stopped funding for AI research.
In 1997, the machine took a significant twist, with IBM's Deep Blue defeating world chess champion - Gary Kasparov, thus becoming the first computer to do so.
2002 - 2020
In 2002, The introduction of vacuum cleaners made way for AI to enter our households.
In 2005, an autonomous car - STANLEY won the DARPA Grand Challenge. The same year, the US military started investing in robots like iRobot's PackBot and Boston Dynamics' Big Dog.
In 2006, tech giants such as Google, Netflix, Facebook and Twitter started leveraging AI.
In 2008, US tech giant - Google made an innovation in speech recognition and launched the feature in the iPhone app.
In 2011, an IBM computer - Watson won Jeopardy, a game show that solved complex riddles. The computer displayed it could comprehend plain language and solve complicated questions quickly.
In 2014, Google made the first autonomous car which passed the driving test. The same year, Alexa - an Amazon product, was launched.
In 2016, Hanson Robotics developed the first robot citizen - Sophia, capable of reading facial emotion, verbal conversation and face recognition.
In 2018, Google launched the NLP engine - BERT, which minimized translation and understanding barriers by ML applications. Waymo introduced its One Service the same year, allowing individuals to request a pick-up.
In 2020, Baidu introduced its LinearFold AI algorithm to medical and research teams working to create a vaccine during the early phase of the SARS-CoV-2 pandemic.
Why AI?
The significance of AI is to help us make an advanced decisions with profound scenarios. Moreover, the tech trend can assist us in having a meaningful life without hard labour and managing a complex web of interconnected individuals.
Let’s see why AI is so important these days:
Existing Product Improvements
AI adds intelligence to the existing services and products. Several products that we come across or use in our routine life are being enhanced with AI potentials, much like Alexa and Siri, which were added as virtual voice assistant features.
To enhance technologies, automation, transforming platforms, intelligent machines, and bots can be incorporated with massive data. If you look at your workplace and home, AI has upgraded the range from security intelligence and intelligent cameras to investment analysis.
Deeper Data Analysis
Leveraging neural networks with several hidden layers, AI will analyze more and deeper data. Developing a fraud detecting system with five hidden layers was once impossible, but not anymore, thanks to supercomputer power and big data.
To train a deep learning algorithm, you need massive data sets to gain insight directly from data.
Automates Iteration Learning
Instead of automating manual works, AI executes frequent, massive, computerized ones. Though humans are vital for the system set-up and queries, AI needs automating iteration learning and discovery through data.
Progressive Learning Algorithms
To enable the data to do all the programming work, AI modifies through advanced learning algorithms. AI finds data regularities and structures so that algorithms can obtain skills. Like an algorithm undergoing self-study to play chess, it can teach itself what product to recommend following online.
Top-notch Accuracy
Through deep neural networks, AI obtains top-notch accuracy. For instance, your interactions with Google and Alexa are based on Deep Learning (DL). These products are getting more precise when leveraged regularly.
In the medical industry, AI methods from DL and object recognition can be leveraged to determine cancer on medical images with enhanced precision.
What are the Different Types of AI?

It is significant to note that AI has enabled robots to differentiate images and texts, understand vocal commands, and much more than a person can do. For instance, Alexa from Amazon, Siri from Apple, and Hello Google from Google are AI applications that can easily understand and perform vocal commands.
Given the rate at which ML, DL, NLP, predictive AI, and other related concepts are emerging, it isn't a little dream to expect that a day would arrive when machines would walk among us, seamlessly offering all human actions.
Current AI systems can do complex calculations at a high rate, followed by the ability to process large data sets and generate precise predictions.
In terms of development, AI is divided into four parts:
Reactive Machines
This type of AI is solely reactive, without developing memories or creating judgments based on prior experiences. These devices are designed to execute specific duties. Programmable coffeemakers and washing machines, for example, are built to fulfil particular functions but lack memory.
Let's take the example of IBM's Deep Blue chess computer. It defeated international grandmaster Garry Kasparov six times in a row. The technology could recognize chess board pieces and understand how they moved.
Its superior intelligence allows it to guess all of the opponent's possible movements far faster than a human opponent. As a result, it could compute the best moves for each scenario.
AI with a limited memory
This type of AI makes decisions based on previous experiences and present data. These machines have limited memory and integrated a memory-running application; they cannot generate new concepts.
Modifications in these machines demand re-programming. Limited memory AI is exemplified by self-driving automobiles, where they can monitor the speed and direction of other vehicles.
Mind-Body Theory
These AI computers can socialize and understand human emotions and a cognitive understanding of people based on their surroundings, facial traits, and other factors.
Such powers have yet to be developed in machines. This sort of AI is the subject of a lot of research.
Self-Awareness
This is a type of AI where machines will be equipped with technologies to be self-aware of their surroundings. This phase is also a continuation of the Mind-body Theory phase, in which devices will be aware of themselves for a reason.
This will elevate the machine's intellect to an entirely different level. Though AI researchers have a long way to travel before these machines are in practical use; however, present AI scientists are focusing on enhancing these computers' ML potentials. The potential of devices to respond similarly to humans is increasing each day.
What are the Benefits of AI?

AI has been lingering around us for quite a while now and is a part of our routine life - including web search recommendations to robot attendants at shopping malls.
By integrating AI into every organizational aspect, businesses are getting optimized, gaining a competitive edge, and finally leading to successful profit growth.
AI in business has numerous innovation potential and will continue to transform the world we know today in a wide range of ways.
The top 10 benefits of AI in business are as follows:
1. Global Defense
The most innovative and advanced robots across the globe are being developed with global defence applications. This is one of the reasons why breakthrough techs get first implemented in the military. However, most of them don't see astronomical days.
One example of it is the AnBot, a Chinese developed AI bot with the potential to reach a maximum of 11mph. The idea behind this tech is to patrol areas, and in case a danger spurs up, this bot can deploy an electrically charged riot control tool.
The 1.6m height AnBot can identify individuals having criminal backgrounds. It has contributed to the improvement of security by maintaining a track of malevolent acts around its territory.
2. Solve Complex Issues
Over the years, the AI tech trend has evolved from a basic ML algorithm to an advanced level such as deep learning. The expansion of AI has helped organizations solve complex problems like weather forecasting, cybercrimes, malevolent activity detection, medical diagnosis and many more.
An example of leveraging AI for fraud detection is PayPal, and you may be wondering how?
Well, because of a breakthrough technique - deep learning (DL), the US multinational financial tech giant can now find out the possible suspicious activities accurately. The company processed around $235Bn payments from 4Bn transactions by more than 170Mn users.
ML and DL algorithms do data mining of users' purchase history to determine possible fraud patterns stored in its databases and can tell whether a transaction is deceitful or not.
3. Automation
From tasks involving strenuous labour to hiring procedures, AI can be leveraged to automate nearly anything. There is infinite count to AI-related applications that can be leveraged to automate the hiring process.
Such a system will assist in freeing the workforce from hectic manual tasks and schedules and allow them to shift their attention to complex tasks such as decision-making and strategizing.
A classic example of this type of recruitment is the conversational AI recruiter MYA, which focuses on automating monotonous parts of the hiring procedure, such as candidate screening and sourcing. This technology is trained by advanced ML algorithms and leverages NLP to acquire conversational details.
MYA is also accountable for creating candidate portfolios, executing analytics, and, lastly, shortlisting applicants.
4. Repetitive Task Management
Executing iteration tasks can be a tedious and time-consuming procedure. Leveraging AI for these routine tasks helps us focus on essential tasks requiring immediate actions.
An example is the Virtual Financial Assistant named Erica, used by the Bank of America. This technology implements ML and AI methodologies to serve the customer service demands. Erica does this by developing credit report updates, assisting bill payments and aiding customers with streamlined transactions.
Recently, Erica's potential has been expanded to help end-users make better financial choices by offering them customized insights.
5. Disaster Management
Precise weather forecasting allows farmers to make critical choices about farming and harvesting. It makes shipping seamless and secure. Most significantly, accurate weather forecasting can be used to predict natural calamities that take a toll on millions.
After much research, IBM collaborated with the Weather Company and obtained massive data sets. This alliance gave IBM the chance to access the Weather Company's predictive models, thus offering numerous data to feed into IBM's AI - Watson for prediction enhancement.
The product of this alliance is IBM Deep Thunder, which generates highly personalized data for business clients.
6. Economy
Though AI has been a criticism victim; however, according to the PwC report, it is estimated that AI will contribute around $15Tr to the global economy. By 2030, AI’s continuous advancement will maximize the global GDP by 14 percent.
The report also highlighted that approx $6.6Tr of the expected GDP growth will come from productivity gains of routine task automation and innovative bot developments.
7. Lifestyle Improvements
Since AI's emergence in the 1950s, we have witnessed significant growth in its offerings. We leverage AI-based virtual assistants to interact with other devices to diagnose deadly diseases.
The online shopping platform - Amazon and Flipkart monitors our browsing habits and serves up products it thinks we'd buy. Even Google decides what outcomes to offer us based on our search activity.
8. Productivity
In recent years, AI has been necessary to control highly computing tasks that need maximum time and effort. Businesses these days rely on AI-based applications to increase their productivity and growth.
An example is a Legal Robot that used ML techniques to gain insight and analyze legal documents, find and resolve legal errors, partner with experienced proficient, and many more. It also allows us to compare our contract with others in the same sector to ensure yours is standard.
9. Personalization
Brands that master personalization delivery results in the improved sale by more than 10 percent than other organizations that don't personalize. Personalization can be a tedious and time-consuming task for an individual, but with machines and technologies, these tasks can be simplified.
An example of personalization is the UK-based fashion firm Thread, which utilizes AI to offer personalized clothing suggestions for each customer.
Each week, customers get personalized suggestions that they can vote accordingly. The company uses an ML algorithm called Thimble that utilizes user data to determine patterns and understand buyers' likes.
10. Decision-making
One of the crucial factors that AI must focus on is intelligent decision-making. The technology must help businesses or organizations to make wiser decisions regarding their offered products and services.
A comprehensive AI for CRM - Salesforce Einstein has managed to do effective decision-making. It eradicates the complexity of AI and enables companies to offer personalized customer experiences.
Driven by DL, ML, NLP, and predictive modelling, Einstein is implemented in extensive businesses to identify relevant insights, forecast market behaviour, and make intelligent decisions.
What are AI Applications?

Some of the applications of AI are as follows:
Medical Industry
Medical care is a basic service for all citizens around the world. While doctors and scientists work hard from time to time to bring about a medical revolution, AI does its part by offering great contributions to the sector. The role of AI in healthcare enables machines to interpret the patient’s medical history and predict possible diseases that individuals may be susceptible to in the next few years.
In addition, AI facilitates drug discovery and the development of drugs that can cure harmful and even fatal diseases.
An example of AI in medical industry is IBM Watson Health, a medical company that actively integrates AI into the healthcare industry. It assists in research, data analysis and offers clients with medical solutions.
Customer Service
AI makes it easier to integrate machines into customer service. A computer that is designed to record feedback from various customers visiting major brand stores, shopping centres or showrooms.
ML chatbot technology is one of the best AI applications that simulates the human behaviour and dialogue methods of marketers. The chatbots communicate with customers through online platforms to clear their queries to an extent.
For example, the e-commerce platform Amazon incorporated chatbots into its customer service department. This is where customers are tricked into chatting with bots who want to resolve issues or disagreements related to purchases, orders, etc.
Finance and Stock Market
With the help of AI algorithms, machines can now interpret past stock market developments, analyze the profit and loss of related stocks, and even predict future stock market developments.
The tech been a major contributor in the financial field recently, one of the financial companies, Nomura Group, has successfully implemented AI technology.
In addition, AI is seeking different methods to enter financial processes, such as payment transfers, e-commerce platforms, and many other.
Fitness Apps
Fitness is everything that people desire in the modern world. From the number of steps, you walk in a day to the number of calories you burn, fitness plays a huge role in our lives.
AI has formed an alliance with fitness to promote the launch of fitness equipment, such as fitness bracelets and watches, to help people recognize their health, boost their physical fitness, and achieve goals.
The role of AI is to interpret the data that occurs every day and predict future data based on the data analysis. An example is Fitbit, that trades with fitness bands powered by AI.
About Us
iCert Global is a one-stop solution offering certification training courses in a wide variety of techniques that will give you a head start in this competitive world.
For more information on how iCert Global can help you to achieve your ML, AI and Deep Learning (DL) Certification goals, please visit our website.
We provide instructor-led classroom and online training across the globe, followed by Corporate Training for enterprise workforce development.
Read More
What an Artificial Intelligence (AI) Benefits in Today’s World
Over the past few decades, Artificial Intelligence (AI) has received several buzzes. However, it is still one of the top technology trends due to tremendous impacts on our lifestyle, workspace and games.
AI has proven dominance in personal assistants (Alexa, Siri and Google Assistant), image and speech recognition, ride-sharing apps (Uber, Ola, Lyft and more) and navigation apps (Google Maps, Apple Maps).
Between the years 2019 and 2020, AI practitioners' or specialists' recruitments were seen to increase by 32%, and in LinkedIn's emerging job report 2020, the role of an AI specialist was ranked #1.
This tech trend needs profound knowledge of statistics, helping us to identify the outcomes generated by the algorithm for a particular dataset.
Some of the highest-paying jobs in the AI field include AI Architect, Robotics Scientists and Big Data Engineering.
What AI Actually Means?
When time travelled to the 1950s, Minsky and McCarthy described the tech trend as any task executed by a machine that was previously considered to need human intelligence.
However, according to modern definition, AI is the ability of a digital computer to execute tasks that are associated with skillsets. It is often applied to the developing system projects invested with the intellectual method characteristics of humans like the potential to reason, identify insights, or learn from prior experience.
The History of AI

Artificial and intelligent bots first appeared in ancient Greek myths of Antiquity. Aristotle's syllogism development and its use of deductive reasoning was a crucial point in a human's quest to gain insights into its own intelligence.
Following are significant event timelines in AI:
1943 - 1949
In 1943, Walter Pits and Warren McCulloch released 'A Logical Calculus of Ideas Immanent in Nervous Activity,' the first work on AI in that year. The paper suggested the first mathematical model for developing a neural network.
In 1949, in his book 'The Organization of Behavior: A Neuropsychological Theory, Donald Hebb proposed that neural pathways are developed from experience and connections between neurons become firmer the more frequently they are used.
1950 - 1959
In 1950, Alan Turing published a theory 'Computing Machinery and Intelligence' proposed a test called Turin Test that identifies whether a machine has the potential to exhibit human behaviour or not. The same year, Marvin Minsky and Dean Edmonds, Harvard graduates, developed their first neural network computer named SNARC.
In 1952, Arthur Samuel built a self-learning algorithm to play checkers.
In 1954, the Georgetown-IBM machine translation test automatically translated 60 Russian sentences into English.
In 1956, Allen Newell and Herbert A. Simon developed the first AI program called Logic Theorist that verified 38 of 52 math theorems, followed by discovering new and more proofs. The same year, AI was first adopted by John McCarthy at the Dartmouth Conference, which defined the scope of AI, and is widely considered the birth of tech trend as we know it now.
In 1958, John McCarthy built the AI programming language - Lisp and published 'Programs with Common Sense.'
In 1959, J.C. Shaw and Newell and Simon created the General Problem Solver (GPS) - designed to mimic human problem-solving. The same year, Herbert Gelernter created the Geometry Theorem Prover program, Arthur Samuel coined Machine Learning (ML) while at IBM, and McCarthy and Marvin Minsky founded the MIT AI Project.
1963 - 1969
In 1963, McCarthy established the AI Lab at Stanford.
In 1966, Joseph Weizenbaum developed the first-ever chatbot - ELIZA.
In 1969, the first successful proficient systems were created in DENDRAL, a XX program, and MYCIN, developed to determine blood infections, were made at Stanford.
1972 - 1980
In 1972, the PROLOG, a logic programming language, was created. In Japan, the first humanoid bot - WABOT-1 was built the same year.
From 1974 to 1980 was known to be the first AI winter period, where researchers couldn't pursue their studies to the best extent as they were short of funds from the govt, resulting in a gradual decrease of AI interests.
In 1980, AI came back with much greater force. The first successful commercial proficient system - R1, was developed by Digital Equipment Corp. The same year, the national conference of the American Association of AI was organized at Stanford Univ.
1982 - 1997
In 1982, the Japan Ministry of International Trade and Industry introduced the 5th Gen Computer System (FGCS) project for developing supercomputer and AI development platforms.
From 1987 to 1993, AI entered the second winter period; as an emerging computer tech and inexpensive alternatives, investors and the govt stopped funding for AI research.
In 1997, the machine took a significant twist, with IBM's Deep Blue defeating world chess champion - Gary Kasparov, thus becoming the first computer to do so.
2002 - 2020
In 2002, The introduction of vacuum cleaners made way for AI to enter our households.
In 2005, an autonomous car - STANLEY won the DARPA Grand Challenge. The same year, the US military started investing in robots like iRobot's PackBot and Boston Dynamics' Big Dog.
In 2006, tech giants such as Google, Netflix, Facebook and Twitter started leveraging AI.
In 2008, US tech giant - Google made an innovation in speech recognition and launched the feature in the iPhone app.
In 2011, an IBM computer - Watson won Jeopardy, a game show that solved complex riddles. The computer displayed it could comprehend plain language and solve complicated questions quickly.
In 2014, Google made the first autonomous car which passed the driving test. The same year, Alexa - an Amazon product, was launched.
In 2016, Hanson Robotics developed the first robot citizen - Sophia, capable of reading facial emotion, verbal conversation and face recognition.
In 2018, Google launched the NLP engine - BERT, which minimized translation and understanding barriers by ML applications. Waymo introduced its One Service the same year, allowing individuals to request a pick-up.
In 2020, Baidu introduced its LinearFold AI algorithm to medical and research teams working to create a vaccine during the early phase of the SARS-CoV-2 pandemic.
Why AI?

The significance of AI is to help us make an advanced decisions with profound scenarios. Moreover, the tech trend can assist us in having a meaningful life without hard labour and managing a complex web of interconnected individuals.
Let’s see why AI is so important these days:
Existing Product Improvements
AI adds intelligence to the existing services and products. Several products that we come across or use in our routine life are being enhanced with AI potentials, much like Alexa and Siri, which were added as virtual voice assistant features.
To enhance technologies, automation, transforming platforms, intelligent machines, and bots can be incorporated with massive data. If you look at your workplace and home, AI has upgraded the range from security intelligence and intelligent cameras to investment analysis.
Deeper Data Analysis
Leveraging neural networks with several hidden layers, AI will analyze more and deeper data. Developing a fraud detecting system with five hidden layers was once impossible, but not anymore, thanks to supercomputer power and big data.
To train a deep learning algorithm, you need massive data sets to gain insight directly from data.
Automates Iteration Learning
Instead of automating manual works, AI executes frequent, massive, computerized ones. Though humans are vital for the system set-up and queries, AI needs automating iteration learning and discovery through data.
Progressive Learning Algorithms
To enable the data to do all the programming work, AI modifies through advanced learning algorithms. AI finds data regularities and structures so that algorithms can obtain skills. Like an algorithm undergoing self-study to play chess, it can teach itself what product to recommend following online.
Top-notch Accuracy
Through deep neural networks, AI obtains top-notch accuracy. For instance, your interactions with Google and Alexa are based on Deep Learning (DL). These products are getting more precise when leveraged regularly.
In the medical industry, AI methods from DL and object recognition can be leveraged to determine cancer on medical images with enhanced precision.
What are the Different Types of AI?

It is significant to note that AI has enabled robots to differentiate images and texts, understand vocal commands, and much more than a person can do. For instance, Alexa from Amazon, Siri from Apple, and Hello Google from Google are AI applications that can easily understand and perform vocal commands.
Given the rate at which ML, DL, NLP, predictive AI, and other related concepts are emerging, it isn't a little dream to expect that a day would arrive when machines would walk among us, seamlessly offering all human actions.
Current AI systems can do complex calculations at a high rate, followed by the ability to process large data sets and generate precise predictions.
In terms of development, AI is divided into four parts:
Reactive Machines
This type of AI is solely reactive, without developing memories or creating judgments based on prior experiences. These devices are designed to execute specific duties. Programmable coffeemakers and washing machines, for example, are built to fulfil particular functions but lack memory.
Let's take the example of IBM's Deep Blue chess computer. It defeated international grandmaster Garry Kasparov six times in a row. The technology could recognize chess board pieces and understand how they moved.
Its superior intelligence allows it to guess all of the opponent's possible movements far faster than a human opponent. As a result, it could compute the best moves for each scenario.
AI with a limited memory
This type of AI makes decisions based on previous experiences and present data. These machines have limited memory and integrated a memory-running application; they cannot generate new concepts.
Modifications in these machines demand re-programming. Limited memory AI is exemplified by self-driving automobiles, where they can monitor the speed and direction of other vehicles.
Mind-Body Theory
These AI computers can socialize and understand human emotions and a cognitive understanding of people based on their surroundings, facial traits, and other factors.
Such powers have yet to be developed in machines. This sort of AI is the subject of a lot of research.
Self-Awareness
This is a type of AI where machines will be equipped with technologies to be self-aware of their surroundings. This phase is also a continuation of the Mind-body Theory phase, in which devices will be aware of themselves for a reason.
This will elevate the machine's intellect to an entirely different level. Though AI researchers have a long way to travel before these machines are in practical use; however, present AI scientists are focusing on enhancing these computers' ML potentials. The potential of devices to respond similarly to humans is increasing each day.
What are the Benefits of AI?

AI has been lingering around us for quite a while now and is a part of our routine life - including web search recommendations to robot attendants at shopping malls.
By integrating AI into every organizational aspect, businesses are getting optimized, gaining a competitive edge, and finally leading to successful profit growth.
AI in business has numerous innovation potential and will continue to transform the world we know today in a wide range of ways.
The top 10 benefits of AI in business are as follows:
1. Global Defense
The most innovative and advanced robots across the globe are being developed with global defence applications. This is one of the reasons why breakthrough techs get first implemented in the military. However, most of them don't see astronomical days.
One example of it is the AnBot, a Chinese developed AI bot with the potential to reach a maximum of 11mph. The idea behind this tech is to patrol areas, and in case a danger spurs up, this bot can deploy an electrically charged riot control tool.
The 1.6m height AnBot can identify individuals having criminal backgrounds. It has contributed to the improvement of security by maintaining a track of malevolent acts around its territory.
2. Solve Complex Issues
Over the years, the AI tech trend has evolved from a basic ML algorithm to an advanced level such as deep learning. The expansion of AI has helped organizations solve complex problems like weather forecasting, cybercrimes, malevolent activity detection, medical diagnosis and many more.
An example of leveraging AI for fraud detection is PayPal, and you may be wondering how?
Well, because of a breakthrough technique - deep learning (DL), the US multinational financial tech giant can now find out the possible suspicious activities accurately. The company processed around $235Bn payments from 4Bn transactions by more than 170Mn users.
ML and DL algorithms do data mining of users' purchase history to determine possible fraud patterns stored in its databases and can tell whether a transaction is deceitful or not.
3. Automation
From tasks involving strenuous labour to hiring procedures, AI can be leveraged to automate nearly anything. There is infinite count to AI-related applications that can be leveraged to automate the hiring process.
Such a system will assist in freeing the workforce from hectic manual tasks and schedules and allow them to shift their attention to complex tasks such as decision-making and strategizing.
A classic example of this type of recruitment is the conversational AI recruiter MYA, which focuses on automating monotonous parts of the hiring procedure, such as candidate screening and sourcing. This technology is trained by advanced ML algorithms and leverages NLP to acquire conversational details.
MYA is also accountable for creating candidate portfolios, executing analytics, and, lastly, shortlisting applicants.
4. Repetitive Task Management
Executing iteration tasks can be a tedious and time-consuming procedure. Leveraging AI for these routine tasks helps us focus on essential tasks requiring immediate actions.
An example is the Virtual Financial Assistant named Erica, used by the Bank of America. This technology implements ML and AI methodologies to serve the customer service demands. Erica does this by developing credit report updates, assisting bill payments and aiding customers with streamlined transactions.
Recently, Erica's potential has been expanded to help end-users make better financial choices by offering them customized insights.
5. Disaster Management
Precise weather forecasting allows farmers to make critical choices about farming and harvesting. It makes shipping seamless and secure. Most significantly, accurate weather forecasting can be used to predict natural calamities that take a toll on millions.
After much research, IBM collaborated with the Weather Company and obtained massive data sets. This alliance gave IBM the chance to access the Weather Company's predictive models, thus offering numerous data to feed into IBM's AI - Watson for prediction enhancement.
The product of this alliance is IBM Deep Thunder, which generates highly personalized data for business clients.
6. Economy
Though AI has been a criticism victim; however, according to the PwC report, it is estimated that AI will contribute around $15Tr to the global economy. By 2030, AI’s continuous advancement will maximize the global GDP by 14 percent.
The report also highlighted that approx $6.6Tr of the expected GDP growth will come from productivity gains of routine task automation and innovative bot developments.
7. Lifestyle Improvements
Since AI's emergence in the 1950s, we have witnessed significant growth in its offerings. We leverage AI-based virtual assistants to interact with other devices to diagnose deadly diseases.
The online shopping platform - Amazon and Flipkart monitors our browsing habits and serves up products it thinks we'd buy. Even Google decides what outcomes to offer us based on our search activity.
8. Productivity
In recent years, AI has been necessary to control highly computing tasks that need maximum time and effort. Businesses these days rely on AI-based applications to increase their productivity and growth.
An example is a Legal Robot that used ML techniques to gain insight and analyze legal documents, find and resolve legal errors, partner with experienced proficient, and many more. It also allows us to compare our contract with others in the same sector to ensure yours is standard.
9. Personalization
Brands that master personalization delivery results in the improved sale by more than 10 percent than other organizations that don't personalize. Personalization can be a tedious and time-consuming task for an individual, but with machines and technologies, these tasks can be simplified.
An example of personalization is the UK-based fashion firm Thread, which utilizes AI to offer personalized clothing suggestions for each customer.
Each week, customers get personalized suggestions that they can vote accordingly. The company uses an ML algorithm called Thimble that utilizes user data to determine patterns and understand buyers' likes.
10. Decision-making
One of the crucial factors that AI must focus on is intelligent decision-making. The technology must help businesses or organizations to make wiser decisions regarding their offered products and services.
A comprehensive AI for CRM - Salesforce Einstein has managed to do effective decision-making. It eradicates the complexity of AI and enables companies to offer personalized customer experiences.
Driven by DL, ML, NLP, and predictive modelling, Einstein is implemented in extensive businesses to identify relevant insights, forecast market behaviour, and make intelligent decisions.
What are AI Applications?

Some of the applications of AI are as follows:
Medical Industry
Medical care is a basic service for all citizens around the world. While doctors and scientists work hard from time to time to bring about a medical revolution, AI does its part by offering great contributions to the sector. The role of AI in healthcare enables machines to interpret the patient’s medical history and predict possible diseases that individuals may be susceptible to in the next few years.
In addition, AI facilitates drug discovery and the development of drugs that can cure harmful and even fatal diseases.
An example of AI in medical industry is IBM Watson Health, a medical company that actively integrates AI into the healthcare industry. It assists in research, data analysis and offers clients with medical solutions.
Customer Service
AI makes it easier to integrate machines into customer service. A computer that is designed to record feedback from various customers visiting major brand stores, shopping centres or showrooms.
ML chatbot technology is one of the best AI applications that simulates the human behaviour and dialogue methods of marketers. The chatbots communicate with customers through online platforms to clear their queries to an extent.
For example, the e-commerce platform Amazon incorporated chatbots into its customer service department. This is where customers are tricked into chatting with bots who want to resolve issues or disagreements related to purchases, orders, etc.
Finance and Stock Market
With the help of AI algorithms, machines can now interpret past stock market developments, analyze the profit and loss of related stocks, and even predict future stock market developments.
The tech been a major contributor in the financial field recently, one of the financial companies, Nomura Group, has successfully implemented AI technology.
In addition, AI is seeking different methods to enter financial processes, such as payment transfers, e-commerce platforms, and many other.
Fitness Apps
Fitness is everything that people desire in the modern world. From the number of steps, you walk in a day to the number of calories you burn, fitness plays a huge role in our lives.
AI has formed an alliance with fitness to promote the launch of fitness equipment, such as fitness bracelets and watches, to help people recognize their health, boost their physical fitness, and achieve goals.
The role of AI is to interpret the data that occurs every day and predict future data based on the data analysis. An example is Fitbit, that trades with fitness bands powered by AI.
About Us
iCert Global is a one-stop solution offering certification training courses in a wide variety of techniques that will give you a head start in this competitive world.
For more information on how iCert Global can help you to achieve your ML, AI and Deep Learning (DL) Certification goals, please visit our website.
We provide instructor-led classroom and online training across the globe, followed by Corporate Training for enterprise workforce development.
Can You Get PMP Certification Without Experience?
Can You Get PMP Certification Without Experience?
The answer is NO.
Why?!
Simple, you are not fit for taking the PMP certification exam as you lack project management experience and education, which means the certification isn’t for the freshers.
You can pursue CAPM Certification, which can become a step ahead of passing the PMP credential test.
Now, if the question is ‘Whether you can get project management experience without PMP certification’? Then the answer is YES.
Find out why the first question is a big NO and the second one a YES in this blog. Make sure you read till the end!!! So, let’s get started.
Table of Contents
Eligibility Criteria to Apply for PMP Exam
PMP Experience Criteria
What are the Leading and Directing Project Experience?
How to Get Project Management Experience?
Designations that Offer Project Management Experience
Validation of Project Management Experience
Project Management Professional (PMP®) Certification is a worldwide renowned and prestigious certification awarded by the Project Management Institute (PMI®). If you've set your eye on obtaining PMP certification for a project management career, it may seem like a mind-boggling situation due to its prerequisites.
According to PMI's PMP handbook, the requirement for PMP highlights that you must have a minimum experience of 3 years in leading and directing projects. It is one of the reasons why PMP certification holds a significant weightage in the industry. Individuals with this badge are proficient project managers having all the needed education, including relevant credentials and ample training.
Eligibility Criteria to Apply for PMP Exam
The PMP certification being highly valued, its requirements get even more rigorous.
PMI needs exam appearing candidates to have project management experience of at least 36 months (3 years), extending to 60 months (5 years) for those who don’t hold either a 4-year UG degree or a global equivalent.
Additionally, to be exam-fit, you are required to have 35 contact hours of project management education. This condition, however, is waived off for CAPM-certified professionals.
You may also like: 10 Tips to Crack CAPM Exam in First Try
The eligibility criteria for applying for PMP, according to PMI, are given below:
- Secondary degree (high school diploma, associate’s degree or the global equivalent)
- 7,500 hours leading and directing projects
- 35 hours of project management education or CAPM certification
OR
- 4-year degree (bachelor’s degree or global equivalent)
- 4,500 hours leading and directing projects
- 35 hours of project management education or CAPM certification
According to pmi.org - examination content outline 2021:

PMP Experience Criteria
What is meant by project management experience?
An experience in project management means the time spent executing or performing numerous project management tasks during the complete project duration.
Until 2020, PMI demanded that professionals have a minimum of 7,500 and 4,500 hours of project management experience appear for the PMP certification exam. However, according to the exam content outline 2021 of PMI, the institute doesn't specify any minimum hours; instead shows professionals must have a minimum experience of 3 and 5 years.

©2019 Project Management Institute, Inc. All rights reserved. PMI PMP Examination Content Outline – January 2021
Though PMI hasn't disclosed removing the minimum number of hours from its system, we as the audience shall wait for any further updates. We shall consider the older version of 4500 or 7500 hours until then.
Below given are a few cases where you can obtain the required hours:
- You have done project management activities equal in value to 4500 or 7500-hours in a single project.
- You worked in multiple sequential projects and gained project management activities worth 4500 or 7500-hours.
- You worked in multiple simultaneous projects and done activities worth 4500 or 7500-hours.

What are the Leading and Directing Project?
A Guide to the Project Management Body of Knowledge (PMBOK Guide®) 4th Edition coins a project as a "temporary endeavor undertaken to create a unique product or service."
Leading and directing projects refers to any experience that falls under five project management activities, that are:
1. Initiation
Initiating any project or sharing your ideas and defining project goals.
2. Planning
Here, we identify the project's scope and create a Work Breakdown Structure (WBS), the project plan (cost, quality, resources and duration) and communication strategy.
3. Execution
This stage includes executing project scope within real-time, solving issues and managing quality, cost, and risk.
4. Monitoring & Controlling
The project progress and performance are measured during the execution phase and at the phase end. It includes project tracking, reporting the project update and changes needed, troubleshooting issues, stakeholder management, resource management, and more.
5. Closing
Lastly, the project closing. Here processes such as reviewing, documentation, finalizing and maintaining the final project report, handing over the deliverables, etc., are done.
According to PMI's PMP Handbook, the experience doesn't necessarily have to be paid one but must be in a professional setting. Moreover, it isn't necessary to have a Project Manager title in all the projects you worked on to qualify for program management activities experience hours.
How to Get Project Management Experience?
Take up small projects to lead and gain experience in any of the five project management activities said earlier, as PMI doesn't look for the candidate who carries the Project Manager designation. Hence step up the business ladder together with your organization to gain project management experience.
To qualify the criteria for appearing PMP exam, you must maintain a record of work with information like:
- The industry you worked with
- Project date (Start to finish)
- Reporting manager and finally,
- Experience overview or summary.
You must keep track of your work with specific deadlines and deliverables. Remember, project management experience is not about obtaining paid project work but working in a professional environment.
Pave ways to lead projects by taking any of the project management courses. Certified Associate Project Management (CAPM) is one of the best stepping stones towards PMP as it covers the fundamental of the PMBOK Guide.
Designations that Offer Project Management Experience
If you in search of a career change, consider roles that have project management roles and responsibilities, but without project manager designations, and they are:
Business Analyst (BA)
BAs get assigned with the accumulation of requirements that significantly become part of the project or provide tasks during project execution.
Training Organizer
As a training organizer or coordinator, you have the advantage of being both parts of a vast project and managing your own. On massive projects, training allows individuals to participate in a project. Creating a training plan for a team is visualized as a project requiring skills similar to a project manager.
Personal Assistant
Being a personal assistant will attain time management and organization skills. You will likely end up in multiple minor projects that need the right project managing responsibilities and works.
Office Admin or Manager
Now, both roles have different roles and responsibilities, mostly resembling the project manager. To be an office admin or manager requires proficiency in communication and organization skills, followed by the potential to plan and perform more significant activities. Here too, you will lead minor projects that will help you achieve project management skills.
Other leading or directing role includes supervisor, project coordinators, team luminary or leader, assistant project manager, etc.
Validation of Project Management Experience
It's not just about you gaining PM experiences. PMP credential is prestigious for project management skills and knowledge. Hence it is no surprise that PMI undergoes stringent policies to verify the applications.
They randomly review the applications before you appear for the credential test. If your application comes under audit, PMI can ask for validations regarding educational qualification or contact hours.
If you fail the audit process, there is a suspension period of 1-year to apply for that certification again.
Enrol Now for Project Management Experience
To meet the prerequisites of getting a PMP certification takes two to four years. As you move ahead with your plan on achieving the goal, ensure you maintain an accurate record of project experience hours and track them accordingly. This additional effort will help you complete the application seamlessly.
If you have the required project management experience and are looking for training, then you can check out iCert Global’s 35 contact hours of PMP training course.
In this course, you will have:

If you still have doubts about PMP prerequisites, you can Contact Us with your query, and we will answer it for you.
Recommended Post:
- Top 50 PMP Exam Questions for 2022
- Top 10 Roles of Project Managers
- Widely Adopted Steps in Creating Project Communication Plan
- A Step-by-step Beginner's Guide to Project Management
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions. You may also be interested in Top 50 PMP Exam Questions for 2022 before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
For more information about PMP® Certification Training courses worldwide, please visit us at https://www.icertglobal.com
or
Call Now!
USA: +1-713-287-1213 / 1214 / 1053 / 1355
UK: +44-2038689013
AUS: +61 272019662
SG: +65 3158 8869
BHR: +973-16-196142
IND: +91 988-620-5050
OR
E-mail Us: info@icertglobal.com
Read More
Can You Get PMP Certification Without Experience?
The answer is NO.
Why?!
Simple, you are not fit for taking the PMP certification exam as you lack project management experience and education, which means the certification isn’t for the freshers.
You can pursue CAPM Certification, which can become a step ahead of passing the PMP credential test.
Now, if the question is ‘Whether you can get project management experience without PMP certification’? Then the answer is YES.
Find out why the first question is a big NO and the second one a YES in this blog. Make sure you read till the end!!! So, let’s get started.
|
Table of Contents Eligibility Criteria to Apply for PMP Exam PMP Experience Criteria What are the Leading and Directing Project Experience? How to Get Project Management Experience? Designations that Offer Project Management Experience Validation of Project Management Experience |
Project Management Professional (PMP®) Certification is a worldwide renowned and prestigious certification awarded by the Project Management Institute (PMI®). If you've set your eye on obtaining PMP certification for a project management career, it may seem like a mind-boggling situation due to its prerequisites.
According to PMI's PMP handbook, the requirement for PMP highlights that you must have a minimum experience of 3 years in leading and directing projects. It is one of the reasons why PMP certification holds a significant weightage in the industry. Individuals with this badge are proficient project managers having all the needed education, including relevant credentials and ample training.
Eligibility Criteria to Apply for PMP Exam
The PMP certification being highly valued, its requirements get even more rigorous.
PMI needs exam appearing candidates to have project management experience of at least 36 months (3 years), extending to 60 months (5 years) for those who don’t hold either a 4-year UG degree or a global equivalent.
Additionally, to be exam-fit, you are required to have 35 contact hours of project management education. This condition, however, is waived off for CAPM-certified professionals.
You may also like: 10 Tips to Crack CAPM Exam in First Try
The eligibility criteria for applying for PMP, according to PMI, are given below:
- Secondary degree (high school diploma, associate’s degree or the global equivalent)
- 7,500 hours leading and directing projects
- 35 hours of project management education or CAPM certification
OR
- 4-year degree (bachelor’s degree or global equivalent)
- 4,500 hours leading and directing projects
- 35 hours of project management education or CAPM certification
According to pmi.org - examination content outline 2021:
PMP Experience Criteria
What is meant by project management experience?
An experience in project management means the time spent executing or performing numerous project management tasks during the complete project duration.
Until 2020, PMI demanded that professionals have a minimum of 7,500 and 4,500 hours of project management experience appear for the PMP certification exam. However, according to the exam content outline 2021 of PMI, the institute doesn't specify any minimum hours; instead shows professionals must have a minimum experience of 3 and 5 years.
©2019 Project Management Institute, Inc. All rights reserved. PMI PMP Examination Content Outline – January 2021
Though PMI hasn't disclosed removing the minimum number of hours from its system, we as the audience shall wait for any further updates. We shall consider the older version of 4500 or 7500 hours until then.
Below given are a few cases where you can obtain the required hours:
- You have done project management activities equal in value to 4500 or 7500-hours in a single project.
- You worked in multiple sequential projects and gained project management activities worth 4500 or 7500-hours.
- You worked in multiple simultaneous projects and done activities worth 4500 or 7500-hours.
What are the Leading and Directing Project?
A Guide to the Project Management Body of Knowledge (PMBOK Guide®) 4th Edition coins a project as a "temporary endeavor undertaken to create a unique product or service."
Leading and directing projects refers to any experience that falls under five project management activities, that are:
1. Initiation
Initiating any project or sharing your ideas and defining project goals.
2. Planning
Here, we identify the project's scope and create a Work Breakdown Structure (WBS), the project plan (cost, quality, resources and duration) and communication strategy.
3. Execution
This stage includes executing project scope within real-time, solving issues and managing quality, cost, and risk.
4. Monitoring & Controlling
The project progress and performance are measured during the execution phase and at the phase end. It includes project tracking, reporting the project update and changes needed, troubleshooting issues, stakeholder management, resource management, and more.
5. Closing
Lastly, the project closing. Here processes such as reviewing, documentation, finalizing and maintaining the final project report, handing over the deliverables, etc., are done.
According to PMI's PMP Handbook, the experience doesn't necessarily have to be paid one but must be in a professional setting. Moreover, it isn't necessary to have a Project Manager title in all the projects you worked on to qualify for program management activities experience hours.
How to Get Project Management Experience?
Take up small projects to lead and gain experience in any of the five project management activities said earlier, as PMI doesn't look for the candidate who carries the Project Manager designation. Hence step up the business ladder together with your organization to gain project management experience.
To qualify the criteria for appearing PMP exam, you must maintain a record of work with information like:
- The industry you worked with
- Project date (Start to finish)
- Reporting manager and finally,
- Experience overview or summary.
You must keep track of your work with specific deadlines and deliverables. Remember, project management experience is not about obtaining paid project work but working in a professional environment.
Pave ways to lead projects by taking any of the project management courses. Certified Associate Project Management (CAPM) is one of the best stepping stones towards PMP as it covers the fundamental of the PMBOK Guide.
Designations that Offer Project Management Experience
If you in search of a career change, consider roles that have project management roles and responsibilities, but without project manager designations, and they are:
Business Analyst (BA)
BAs get assigned with the accumulation of requirements that significantly become part of the project or provide tasks during project execution.
Training Organizer
As a training organizer or coordinator, you have the advantage of being both parts of a vast project and managing your own. On massive projects, training allows individuals to participate in a project. Creating a training plan for a team is visualized as a project requiring skills similar to a project manager.
Personal Assistant
Being a personal assistant will attain time management and organization skills. You will likely end up in multiple minor projects that need the right project managing responsibilities and works.
Office Admin or Manager
Now, both roles have different roles and responsibilities, mostly resembling the project manager. To be an office admin or manager requires proficiency in communication and organization skills, followed by the potential to plan and perform more significant activities. Here too, you will lead minor projects that will help you achieve project management skills.
Other leading or directing role includes supervisor, project coordinators, team luminary or leader, assistant project manager, etc.
Validation of Project Management Experience
It's not just about you gaining PM experiences. PMP credential is prestigious for project management skills and knowledge. Hence it is no surprise that PMI undergoes stringent policies to verify the applications.
They randomly review the applications before you appear for the credential test. If your application comes under audit, PMI can ask for validations regarding educational qualification or contact hours.
If you fail the audit process, there is a suspension period of 1-year to apply for that certification again.
Enrol Now for Project Management Experience
To meet the prerequisites of getting a PMP certification takes two to four years. As you move ahead with your plan on achieving the goal, ensure you maintain an accurate record of project experience hours and track them accordingly. This additional effort will help you complete the application seamlessly.
If you have the required project management experience and are looking for training, then you can check out iCert Global’s 35 contact hours of PMP training course.
In this course, you will have:
If you still have doubts about PMP prerequisites, you can Contact Us with your query, and we will answer it for you.
Recommended Post:
- Top 50 PMP Exam Questions for 2022
- Top 10 Roles of Project Managers
- Widely Adopted Steps in Creating Project Communication Plan
- A Step-by-step Beginner's Guide to Project Management
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions. You may also be interested in Top 50 PMP Exam Questions for 2022 before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
For more information about PMP® Certification Training courses worldwide, please visit us at https://www.icertglobal.com
or
Call Now!
USA: +1-713-287-1213 / 1214 / 1053 / 1355
UK: +44-2038689013
AUS: +61 272019662
SG: +65 3158 8869
BHR: +973-16-196142
IND: +91 988-620-5050
OR
E-mail Us: info@icertglobal.com
What are the Prerequisites to Satisfy PMP?
What are the Prerequisites to Satisfy PMP?
In Quora.com, we have come across a common yet significant quest lingering on PMP aspirants "What are the prerequisites to satisfy PMP?" Therefore, we, iCert Global, have come up with today's blog to put an end to your queries right then and there.
As mentioned in yesterday's blog, PMP is a prestigious certification for project enthusiasts across different industry verticals to get a hold on. This highly valued certification allows aspirants to lead projects in almost every country.
Without further delay, let's get into the main topic: What are the requirements to appear for PMP or the requirements for gaining a PMP certification? This blog will also solve your query regarding examination cost, its format, and other PMP-related topics.
The Eligibility Criteria for PMP Certification
PMP Certification criteria are a ranked validation structure that ensures you have the needed educational qualifications and work experience. Earning this credential means you must qualify for the prerequisites put forward by Project Management Institute (PMI®) in addition to appearing for the PMP test. Meeting these prerequisites is the first stepping stone to your PMP certification.
You can check PMI set credential requirements in PMI's PMP Handbook. You can now download a free version of this handbook from their official website: http://www.pmi.org
It will help you clear your quest regarding PMP certification, such as who is eligible and how to apply.
The eligibility criteria for PMP certification are tabulated below according to the PMI’s requirement 2021:
Eligibility Criteria
Leading and Directing Project Experiences
Project Management Education
Secondary degree (high school diploma, associate degree or global equivalent)
5 years
35 contact hours
4-year undergraduate degree
3 years
35 contact hours
4-year or post-grad degree from GAC accredited program
2 years
35 contact hours
Though the institute hasn’t mentioned the hours of leading and directing project experience nor waived off in PMI's PMP certification criteria from 2021, let's consider who knows what happens at the last moment.
As per PMI's prerequisites till 2020:
- Secondary degree (high school diploma, associate’s degree or the global equivalent)
- 7,500 hours leading and directing projects
- 35 hours of project management education or CAPM certification
OR
- 4-year degree (bachelor’s degree or global equivalent)
- 4,500 hours leading and directing projects
- 35 hours of project management education or CAPM certification
You may also like: Can You Take PMP Without Experience?
How to Gather Experience of PMP?
Suppose you are a full-time project manager or have a similar role of full-time handling project leading and directing. In that case, it's easy for you to gather the required number of hours. In case you don't have enough hours, don't be overwhelmed. You can go ahead with the current position, and with time you will gather adequate hours.
For those, not full-time project managers, earning PMI-required experience can be challenging. Suppose you are managing projects part-time or not all. In that case, your speed of collecting experience hours will be less compared to a full-time project manager.
Here are the different ways you can increase the rate of gaining experience to:
Changing Organization
Suppose you are not getting an opportunity to shift to a project managing area or similar field in your present organization. In that case, it is time for you to change the firm you are working for. Finding a suitable organization with experience uplifting opportunities earns you the required experience hours - with a quicker demand meeting.
Changing Role
The number of hours spent managing projects can increase with the change of your role. Hence go for a broader discussion regarding career development with your manager by a clear briefing on how you would like to offer more value to your employer by leading and directing projects.
By changing your role and ending up being a full-time project manager, then you can gather the required hours swiftly.
Volunteering
If you are a PMI Member and want to meet other PMI experts, join a local PMI Chapter. You can always check for any volunteering in it, exposing you to other benefits such as building your project management network and attending PMI events.
With volunteering, you can earn enough to meet the eligibility demand of PMI's PMP credential.
PMP Credential Cost
Apart from the PMP certification prerequisites, the credential exam does have specific costs. However, you will save more costs in the long-term if you are a PMI member and want to maintain your credential renewal continuously.
Cost
PMI Member
Non-PMI Member
PMI membership fee
$139
n/a
PMP exam fee
$405
$555
PMP re-exam fee
$275
$375
Certification renewal fee
$60
$150
TOTAL
$879
$1,080
Content and Format Outline
According to pmi.org, the proportion of question from each domain that appear for PMP credential test:
Domain
% Of Items on Test
People
42%
Process
50%
Business Environment
8%
TOTAL
100%
The exam consists of 180 questions out of these domains, and you will have 230 minutes to finish the test. If you are worried about not passing on the first try, do not worry. You can take the credential re-exam up to 3 times a year.
Once you pass the test, your PMP certification will be valid for the next three years. You will have to earn 60 Professional Development Units (PDUs) during that period, collaborating with project management education and activities that offer a profession to maintain your credential.
Meet One of Your PMP Requirements Today!
You need to meet one of the eligibility criteria put ahead by PMI to qualify for PMP certification. However, it is also essential for aspirants to finish 35 project management education experiences to appear for the credential exam.
However, questioning yourself on how to earn it? Enrol in PMP Certification training course to earn 35 hours of project management education criteria. With training, you get entirely prepared for the PMP exam and receive support from experts to pass the credential in one shot.
Want to get hands-on project management expertise? Enrol for the PMP training course iCert Global offers and be fit to appear for the credential test. Our experts help you finish the projects on time and within budget without much effort. We also help you track significant PMP credentials tasks, so nothing goes in vain.
So, what are you waiting for? Enrol Now!
In this course, you will have:

If you still have doubts about PMP prerequisites, you can Contact Us with your query, and we will answer it for you.
Recommended Post:
- Can You Take PMP Certification Without Experience?
- Top 50 PMP Exam Questions for 2022
- Top 10 Roles of Project Managers
- Widely Adopted Steps in Creating Project Communication Plan
- A Step-by-step Beginner's Guide to Project Management
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions. You may also be interested in Top 50 PMP Exam Questions for 2022 before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
For more information about PMP® Certification Training courses worldwide, please visit us at https://www.icertglobal.com
or
Call Now!
USA: +1-713-287-1213 / 1214 / 1053 / 1355
UK: +44-2038689013
AUS: +61 272019662
SG: +65 3158 8869
BHR: +973-16-196142
IND: +91 988-620-5050
OR
E-mail Us: info@icertglobal.com
Read More
What are the Prerequisites to Satisfy PMP?
In Quora.com, we have come across a common yet significant quest lingering on PMP aspirants "What are the prerequisites to satisfy PMP?" Therefore, we, iCert Global, have come up with today's blog to put an end to your queries right then and there.
As mentioned in yesterday's blog, PMP is a prestigious certification for project enthusiasts across different industry verticals to get a hold on. This highly valued certification allows aspirants to lead projects in almost every country.
Without further delay, let's get into the main topic: What are the requirements to appear for PMP or the requirements for gaining a PMP certification? This blog will also solve your query regarding examination cost, its format, and other PMP-related topics.
The Eligibility Criteria for PMP Certification
PMP Certification criteria are a ranked validation structure that ensures you have the needed educational qualifications and work experience. Earning this credential means you must qualify for the prerequisites put forward by Project Management Institute (PMI®) in addition to appearing for the PMP test. Meeting these prerequisites is the first stepping stone to your PMP certification.
You can check PMI set credential requirements in PMI's PMP Handbook. You can now download a free version of this handbook from their official website: http://www.pmi.org
It will help you clear your quest regarding PMP certification, such as who is eligible and how to apply.
The eligibility criteria for PMP certification are tabulated below according to the PMI’s requirement 2021:
|
Eligibility Criteria |
Leading and Directing Project Experiences |
Project Management Education |
|
Secondary degree (high school diploma, associate degree or global equivalent) |
5 years |
35 contact hours |
|
4-year undergraduate degree |
3 years |
35 contact hours |
|
4-year or post-grad degree from GAC accredited program |
2 years |
35 contact hours |
Though the institute hasn’t mentioned the hours of leading and directing project experience nor waived off in PMI's PMP certification criteria from 2021, let's consider who knows what happens at the last moment.
As per PMI's prerequisites till 2020:
- Secondary degree (high school diploma, associate’s degree or the global equivalent)
- 7,500 hours leading and directing projects
- 35 hours of project management education or CAPM certification
OR
- 4-year degree (bachelor’s degree or global equivalent)
- 4,500 hours leading and directing projects
- 35 hours of project management education or CAPM certification
You may also like: Can You Take PMP Without Experience?
How to Gather Experience of PMP?
Suppose you are a full-time project manager or have a similar role of full-time handling project leading and directing. In that case, it's easy for you to gather the required number of hours. In case you don't have enough hours, don't be overwhelmed. You can go ahead with the current position, and with time you will gather adequate hours.
For those, not full-time project managers, earning PMI-required experience can be challenging. Suppose you are managing projects part-time or not all. In that case, your speed of collecting experience hours will be less compared to a full-time project manager.
Here are the different ways you can increase the rate of gaining experience to:
Changing Organization
Suppose you are not getting an opportunity to shift to a project managing area or similar field in your present organization. In that case, it is time for you to change the firm you are working for. Finding a suitable organization with experience uplifting opportunities earns you the required experience hours - with a quicker demand meeting.
Changing Role
The number of hours spent managing projects can increase with the change of your role. Hence go for a broader discussion regarding career development with your manager by a clear briefing on how you would like to offer more value to your employer by leading and directing projects.
By changing your role and ending up being a full-time project manager, then you can gather the required hours swiftly.
Volunteering
If you are a PMI Member and want to meet other PMI experts, join a local PMI Chapter. You can always check for any volunteering in it, exposing you to other benefits such as building your project management network and attending PMI events.
With volunteering, you can earn enough to meet the eligibility demand of PMI's PMP credential.
PMP Credential Cost
Apart from the PMP certification prerequisites, the credential exam does have specific costs. However, you will save more costs in the long-term if you are a PMI member and want to maintain your credential renewal continuously.
|
Cost |
PMI Member |
Non-PMI Member |
|
PMI membership fee |
$139 |
n/a |
|
PMP exam fee |
$405 |
$555 |
|
PMP re-exam fee |
$275 |
$375 |
|
Certification renewal fee |
$60 |
$150 |
|
TOTAL |
$879 |
$1,080 |
Content and Format Outline
According to pmi.org, the proportion of question from each domain that appear for PMP credential test:
|
Domain |
% Of Items on Test |
|
People |
42% |
|
Process |
50% |
|
Business Environment |
8% |
|
TOTAL |
100% |
The exam consists of 180 questions out of these domains, and you will have 230 minutes to finish the test. If you are worried about not passing on the first try, do not worry. You can take the credential re-exam up to 3 times a year.
Once you pass the test, your PMP certification will be valid for the next three years. You will have to earn 60 Professional Development Units (PDUs) during that period, collaborating with project management education and activities that offer a profession to maintain your credential.
Meet One of Your PMP Requirements Today!
You need to meet one of the eligibility criteria put ahead by PMI to qualify for PMP certification. However, it is also essential for aspirants to finish 35 project management education experiences to appear for the credential exam.
However, questioning yourself on how to earn it? Enrol in PMP Certification training course to earn 35 hours of project management education criteria. With training, you get entirely prepared for the PMP exam and receive support from experts to pass the credential in one shot.
Want to get hands-on project management expertise? Enrol for the PMP training course iCert Global offers and be fit to appear for the credential test. Our experts help you finish the projects on time and within budget without much effort. We also help you track significant PMP credentials tasks, so nothing goes in vain.
So, what are you waiting for? Enrol Now!
In this course, you will have:
If you still have doubts about PMP prerequisites, you can Contact Us with your query, and we will answer it for you.
Recommended Post:
- Can You Take PMP Certification Without Experience?
- Top 50 PMP Exam Questions for 2022
- Top 10 Roles of Project Managers
- Widely Adopted Steps in Creating Project Communication Plan
- A Step-by-step Beginner's Guide to Project Management
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions. You may also be interested in Top 50 PMP Exam Questions for 2022 before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
For more information about PMP® Certification Training courses worldwide, please visit us at https://www.icertglobal.com
or
Call Now!
USA: +1-713-287-1213 / 1214 / 1053 / 1355
UK: +44-2038689013
AUS: +61 272019662
SG: +65 3158 8869
BHR: +973-16-196142
IND: +91 988-620-5050
OR
E-mail Us: info@icertglobal.com
Find Out What Happened to Architects with PMP Certification
Find Out What Happened to Architects with PMP Certification
TABLE OF CONTENTS
What is an Architectural Project Manager?
What You Need to Know About Being PMP Architects?
Duties of Architectural Project Manager
Education Required for Architectural Project Manager
Skills for Architectural Project Manager
How to Become an Architectural Project Manager?
Is PMP Good for Architects?
Concluding Thoughts
Commercial project performance has significantly increased across the globe yearly. For example, the 2018 report of PMI shows that 71% of projects have met their actual objectives and business demands compared to 68% in 2016.
Project managers have continued to be a greater force behind this change, and they are in high demand. The Project Management Institute (PMI) also reported the requirement of 97.7Mn project professionals by 2027.
Without experts in project management roles, a business could crumble up with a loss of billion dollars. It is one of the main reasons why companies are turning to architects. They bring in a unique set of potentials that result in the successful management of projects.
In earlier ages of businesses, Architects only dealt with the creative and design sides of the building project. However, with the companies and technologies evolving consistently, architectural organizations have started realizing the significance of being a part of projects' delivery, expense control, and construction quality.
Moreover, as the PMP architect offers more opportunities to improve their skills for managing massive projects, your architectural background can lead to greater career height with the collaboration of design with management skills.
Today's topic might be new, though it's not a new trend. However, few aren't familiar with the term Architectural Project Managers. Most often, we only hear about the business analyst, project manager, Sr. program managers, and PMP-related roles.
Therefore, here we are with today's blog on Architectural Project Managers.
What is an Architectural Project Manager?
These individuals are licensed architects who have advanced to senior-level positions. In addition, the architectural project managers are responsible for overseeing groups of other architects while planning and building architectural projects.
They are the shoulder of the architectural project sector - organizing and leading their groups through various job procedures while keeping them motivated.
These managers' duties include meeting up between clients and architects, creating project teams, scheduling, budgeting, and starting building designs.
In the specialized media of our world today, it becomes an additional benefit to nurture the skill and gain insight, similar to a project manager. However, architectural project management has a higher degree of uncertainty and complexity than other project management fields due to several factors involved.
What You Need to Know About Being PMP Architects?
Required Degree Background
Bachelor of Architecture (B. Arch) or Masters of Architecture (M. Arch)
Training
Must take internship for licensure
Responsibilities
- Supervising teams and projects
- Client management
- Project scheduling
- Budgeting
- Project design creation
Licensure
Must pass the Architect Registration Exam to obtain licensure
Job Growth (till 2030 as per PayScale.com)
3% (for all architects)
Average Salary (2022 Glassdoor.com)
- India - INR 14L
- US - $84,456
- UK - £46,191
- Canada - CAD 75,786
Duties of Architectural Project Manager
As an architectural project manager, your primary focus or role will be to manage the development of architectural projects. In addition, you often work within an architectural organization. Therefore, you must handle all of the practical and organizational information related to the project.
Moreover, you will be responsible for the overall success of architectural projects.
For instance, you are an architectural project manager of a company. What will be your roles and responsibilities in the firm?
There are various roles out of which a few essential steps are listed below you as an architectural project manager will follow on a somewhat routine basis:
- Schedule meetings between clients and architects
- Develop project plans
- Assemble and manage architect teams
- Guide the creation of architectural designs
- Strategizing project schedules
- Creating a project budget
- Motivate and manage a team of assistants
But can you walk into a company with a fake thought of being an architectural project manager?
No, that's right.
So, what do you need?
Exactly, education and experience.
You have to be a licensed architect to acquire the position of an architectural project manager. In addition, you must have several years of experience working in architectural design before proceeding to a project management role.
Education Required for Architectural Project Manager
Most countries need you to have a professional degree in architecture before obtaining licensure and start working in the architectural area. You can either enroll in Bachelor of Architecture (B. Arch), a 5-year program or complete a related Bachelor's degree program and architecture graduation program.
What do you learn in a professional architecture program?
- Construction methods and materials
- Building designs
- Mathematics
- Architecture
- Drafting
- Building structures
- Computer-aided design
If you want to go for an architectural project manager, choose to minor or focus on management, business, or urban planning.
Skills for Architectural Project Manager
Personal Management
The personal management skill of these project managers involves managing others by supervising particular skillsets or acting as a guide to other team members.
Problem-solving
These managers can quickly identify issues and develop solutions that positively impact or minimize the adverse effects. They use critical thinking, decision-making, and analysis for issue resolution.
Understanding of Building and Zoning Codes
This manager aids in ensuring compliance with local building codes. Therefore, they need to know both industry standards and geographic codes.
Project Management
As an architectural project manager, you need to have the logistical and organizational skills to follow a project from beginning to the end - including scheduling, planning, budgeting, designing, and expense control.
Computer-aided Design
To finish the design components, the architectural project managers must be experts in leveraging top-notch software - REVIT (building modeling software) and AutoCAD (design and drafting software).
Knowledge of Drafting & Architectural Engineering
These involve reviewing technical project elements and inspecting and approving plans.
How to Become an Architectural Project Manager?
- Degree completion: If you're looking for a Bachelor of Architecture (B Arch) Degree, you have two options:
- 5-year B. Arch from a program provided by the National Architecture Accrediting Board (NAAB) offers all the needed schooling to become a fully licensed architect.
- The 4-year pre-professional degree can be paired with a 2-year M. Arch program to be a licensed practitioner.
- Individuals having Bachelor's degree in an unrelated field - opt for a more extended M. Arch program (3-4 years program) accredited by NAAB
- Complete the training: From B. Arch/M. Arch to complete the formal training to become fully licensed is an added advantage for architectural project manager interviews. It means completing the Architectural Experience Program (AXP), taking the Architecture Registration Examination (ARE), and getting a license.
- Project management certification: Some job listing for architectural project management role seeks the specific certifications:
- Certified construction manager: This accreditation is from the Construction Management Association of America. It is particular to the construction sector and must undergo an exam to be a certified construction manager.
- Project Management Professional (PMP): Accredited by the PMI is a globally renowned certification that involves taking courses and passing the credential test. The first level of the certificate is CAPM. PMP is an advanced-level credential that needs the CAPM and specific project management experience.
- Project management degree: Bachelor's and Master's degree programs in project management can be completed online or in person. These being a widely focused area, they may be the right option if the project management aspect of this role is more appealing to you than the architectural specialization.
- Maintain Relevant Certification: If you have a project management certification or an architect license, you must renew them periodically. These renewals usually need extra coursework, which is a great choice to update your skills and knowledge.
Is PMP Good for Architects?
As an architect, you will bring a wide range of skills to project management position, and they are:
- Bring in strong negotiation skills by offering great experience and advice across the building project process.
- You can maintain records and monitor all variables across your team's work. Your business stays within budget control, thus making sure shareholders get paid within the time.
- You can help with the design process to ensure the project is created and built by mitigating risks. With your architectural knowledge, you can better understand which contractors are a suitable fit.
- One of the crucial factors of being a good project manager is team communication. The architects are made project-ready by using existing stakeholder management experience and building companies and clients.
- Your architectural knowledge provides you with decision-making skills, which can significantly benefit your future career in project management. As a project manager, you can confidently make decisions - help in establishing construction sites, developing a quality control system, coordinating equipment, and arrangement for infrastructural needs.
- Architects have a creative mindset to solve critical problems in project management. Not only are they adept at handling structural details, but also come up with unique solutions.
Concluding Thoughts
Learning project management skills can enable you to expand your architecture career. It opens up a wide range of job opportunities. However, it will also help increase your analytical and reporting expertise while allowing you to grow as a successful project leader.
If you're an architect looking for project management education, oceanic opportunities await you at undergraduate and postgraduate levels. One of the plus points is that you can study, and at the same time work, with online study materials offered by reputed and NAAB accredited institutions.
The project management course will help you expand your current architectural experience into a fantastic salary perk career. Balancing online education with practical work, the 16-month program includes six flexible preparation periods for seven weeks. It will put you in the best position to take a leadership position in a significantly growing sector, resulting in exciting personal growth.
Recommended posts
How Can I Prepare for PMP in 30 Days?
What are PMP Certification Fees?
Can I Take the PMP Certification Test at Home?
To know more, Visit our website:
Read More
Find Out What Happened to Architects with PMP Certification
|
TABLE OF CONTENTS What is an Architectural Project Manager? What You Need to Know About Being PMP Architects? Duties of Architectural Project Manager Education Required for Architectural Project Manager Skills for Architectural Project Manager How to Become an Architectural Project Manager? Is PMP Good for Architects? Concluding Thoughts |
Commercial project performance has significantly increased across the globe yearly. For example, the 2018 report of PMI shows that 71% of projects have met their actual objectives and business demands compared to 68% in 2016.
Project managers have continued to be a greater force behind this change, and they are in high demand. The Project Management Institute (PMI) also reported the requirement of 97.7Mn project professionals by 2027.
Without experts in project management roles, a business could crumble up with a loss of billion dollars. It is one of the main reasons why companies are turning to architects. They bring in a unique set of potentials that result in the successful management of projects.
In earlier ages of businesses, Architects only dealt with the creative and design sides of the building project. However, with the companies and technologies evolving consistently, architectural organizations have started realizing the significance of being a part of projects' delivery, expense control, and construction quality.
Moreover, as the PMP architect offers more opportunities to improve their skills for managing massive projects, your architectural background can lead to greater career height with the collaboration of design with management skills.
Today's topic might be new, though it's not a new trend. However, few aren't familiar with the term Architectural Project Managers. Most often, we only hear about the business analyst, project manager, Sr. program managers, and PMP-related roles.
Therefore, here we are with today's blog on Architectural Project Managers.
What is an Architectural Project Manager?
These individuals are licensed architects who have advanced to senior-level positions. In addition, the architectural project managers are responsible for overseeing groups of other architects while planning and building architectural projects.
They are the shoulder of the architectural project sector - organizing and leading their groups through various job procedures while keeping them motivated.
These managers' duties include meeting up between clients and architects, creating project teams, scheduling, budgeting, and starting building designs.
In the specialized media of our world today, it becomes an additional benefit to nurture the skill and gain insight, similar to a project manager. However, architectural project management has a higher degree of uncertainty and complexity than other project management fields due to several factors involved.
What You Need to Know About Being PMP Architects?
|
Required Degree Background |
Bachelor of Architecture (B. Arch) or Masters of Architecture (M. Arch) |
|
Training |
Must take internship for licensure |
|
Responsibilities |
|
|
Licensure |
Must pass the Architect Registration Exam to obtain licensure |
|
Job Growth (till 2030 as per PayScale.com) |
3% (for all architects) |
|
Average Salary (2022 Glassdoor.com) |
|
Duties of Architectural Project Manager
As an architectural project manager, your primary focus or role will be to manage the development of architectural projects. In addition, you often work within an architectural organization. Therefore, you must handle all of the practical and organizational information related to the project.
Moreover, you will be responsible for the overall success of architectural projects.
For instance, you are an architectural project manager of a company. What will be your roles and responsibilities in the firm?
There are various roles out of which a few essential steps are listed below you as an architectural project manager will follow on a somewhat routine basis:
- Schedule meetings between clients and architects
- Develop project plans
- Assemble and manage architect teams
- Guide the creation of architectural designs
- Strategizing project schedules
- Creating a project budget
- Motivate and manage a team of assistants
But can you walk into a company with a fake thought of being an architectural project manager?
No, that's right.
So, what do you need?
Exactly, education and experience.
You have to be a licensed architect to acquire the position of an architectural project manager. In addition, you must have several years of experience working in architectural design before proceeding to a project management role.
Education Required for Architectural Project Manager
Most countries need you to have a professional degree in architecture before obtaining licensure and start working in the architectural area. You can either enroll in Bachelor of Architecture (B. Arch), a 5-year program or complete a related Bachelor's degree program and architecture graduation program.
What do you learn in a professional architecture program?
- Construction methods and materials
- Building designs
- Mathematics
- Architecture
- Drafting
- Building structures
- Computer-aided design
If you want to go for an architectural project manager, choose to minor or focus on management, business, or urban planning.
Skills for Architectural Project Manager
Personal Management
The personal management skill of these project managers involves managing others by supervising particular skillsets or acting as a guide to other team members.
Problem-solving
These managers can quickly identify issues and develop solutions that positively impact or minimize the adverse effects. They use critical thinking, decision-making, and analysis for issue resolution.
Understanding of Building and Zoning Codes
This manager aids in ensuring compliance with local building codes. Therefore, they need to know both industry standards and geographic codes.
Project Management
As an architectural project manager, you need to have the logistical and organizational skills to follow a project from beginning to the end - including scheduling, planning, budgeting, designing, and expense control.
Computer-aided Design
To finish the design components, the architectural project managers must be experts in leveraging top-notch software - REVIT (building modeling software) and AutoCAD (design and drafting software).
Knowledge of Drafting & Architectural Engineering
These involve reviewing technical project elements and inspecting and approving plans.
How to Become an Architectural Project Manager?
- Degree completion: If you're looking for a Bachelor of Architecture (B Arch) Degree, you have two options:
- 5-year B. Arch from a program provided by the National Architecture Accrediting Board (NAAB) offers all the needed schooling to become a fully licensed architect.
- The 4-year pre-professional degree can be paired with a 2-year M. Arch program to be a licensed practitioner.
- Individuals having Bachelor's degree in an unrelated field - opt for a more extended M. Arch program (3-4 years program) accredited by NAAB
- Complete the training: From B. Arch/M. Arch to complete the formal training to become fully licensed is an added advantage for architectural project manager interviews. It means completing the Architectural Experience Program (AXP), taking the Architecture Registration Examination (ARE), and getting a license.
- Project management certification: Some job listing for architectural project management role seeks the specific certifications:
- Certified construction manager: This accreditation is from the Construction Management Association of America. It is particular to the construction sector and must undergo an exam to be a certified construction manager.
- Project Management Professional (PMP): Accredited by the PMI is a globally renowned certification that involves taking courses and passing the credential test. The first level of the certificate is CAPM. PMP is an advanced-level credential that needs the CAPM and specific project management experience.
- Project management degree: Bachelor's and Master's degree programs in project management can be completed online or in person. These being a widely focused area, they may be the right option if the project management aspect of this role is more appealing to you than the architectural specialization.
- Maintain Relevant Certification: If you have a project management certification or an architect license, you must renew them periodically. These renewals usually need extra coursework, which is a great choice to update your skills and knowledge.
Is PMP Good for Architects?
As an architect, you will bring a wide range of skills to project management position, and they are:
- Bring in strong negotiation skills by offering great experience and advice across the building project process.
- You can maintain records and monitor all variables across your team's work. Your business stays within budget control, thus making sure shareholders get paid within the time.
- You can help with the design process to ensure the project is created and built by mitigating risks. With your architectural knowledge, you can better understand which contractors are a suitable fit.
- One of the crucial factors of being a good project manager is team communication. The architects are made project-ready by using existing stakeholder management experience and building companies and clients.
- Your architectural knowledge provides you with decision-making skills, which can significantly benefit your future career in project management. As a project manager, you can confidently make decisions - help in establishing construction sites, developing a quality control system, coordinating equipment, and arrangement for infrastructural needs.
- Architects have a creative mindset to solve critical problems in project management. Not only are they adept at handling structural details, but also come up with unique solutions.
Concluding Thoughts
Learning project management skills can enable you to expand your architecture career. It opens up a wide range of job opportunities. However, it will also help increase your analytical and reporting expertise while allowing you to grow as a successful project leader.
If you're an architect looking for project management education, oceanic opportunities await you at undergraduate and postgraduate levels. One of the plus points is that you can study, and at the same time work, with online study materials offered by reputed and NAAB accredited institutions.
The project management course will help you expand your current architectural experience into a fantastic salary perk career. Balancing online education with practical work, the 16-month program includes six flexible preparation periods for seven weeks. It will put you in the best position to take a leadership position in a significantly growing sector, resulting in exciting personal growth.
Recommended posts
How Can I Prepare for PMP in 30 Days?
What are PMP Certification Fees?
Can I Take the PMP Certification Test at Home?
To know more, Visit our website:
PMP Certification Exam Eligibility You Need to Know Before Scheduling
PMP Certification Exam Eligibility You Need to Know Before Scheduling
Have you ever asked yourself, "What is the PMP certification for project managers?" When it comes to the PMP® Certification, the answer is simple.
With PMP certification, you can work on projects all over the globe, no matter what sector you are in or which project management methodology you choose.
To sit for the Project Management Professional (PMP) ® exam, you must meet specific education and experience requirements.
In particular, you need to have at least five years of project management experience to appear for the exam. This shows that you have enough soft skills (knowledge of project management theory) to manage a project.
And PMI, to accept your application, you need to prove that you have a specific educational background—either a bachelor's degree or an equivalent combination of education and experience.
PMP Exam Eligibility Requirement

If you are wondering where to find out about the requirements for taking the PMP® exam, then you can download the free PMP® Credential Handbook from PMI's Web site. The handbook contains details about becoming certified, including eligibility information.
Identify PMP Eligibility
To determine if you are eligible to take the PMP® exam, follow the simple 4-step approach outlined here:
Go through the PMP handbook
Click here to read the PMP handbook
Eligibility requirements in this section of the PMI website under "Project Management Professional," you will be able to find the required information for determining your eligibility for taking the PMP® exam.
In addition, you will be able to start your application and request more information on how to prepare for the exam if necessary.
You must read this page very carefully, especially if you are starting. It will provide you with the information you need to help plan and execute your next steps in achieving accreditation.
Read Examination Content Outline (ECO)
Based on the tasks identified in the outline, you should recognize many of them as tasks you typically complete as part of your work in managing projects. The system covers what a Project Manager does, which would make you eligible to take the PMP® exam.
Analyze
You worked hard to gain the skills and experience to qualify for the PMP® exam.
Now review your responsibilities to identify areas of overlap with the responsibility requirements for Certification.
After identifying those areas, update your resume to provide specific examples of projects where you gained the experience required for Certification.
Get in touch with PMI customer care
Don't worry about eligibility. PMI's customer care department is happy to assist you with any queries. Visit the website PMI
What happens if the PMP certificate expires?
PMP credential holders must earn 60 PDUs every three years to maintain active Certification.
If they do not earn the required 60 PDUs during the three-year certification cycle, their Certification will be suspended.
To retain the suspended PMP certification, you have to submit 60 additional PDUs and pay the annual credential fee within one year of the suspension date.
Failure to do so will result in their Certification being placed on Terminated status. Having a certification on suspended status means that the individual may not.
(1) Call himself a certification holder
(2) Use the certification designation.
The whole recertification process must be completed within one year of suspension to regain benefits.
Skills Needed for PMP
Many organizations hire project managers to oversee and help monitor projects.
Getting a project management certification is good if you want your project management career to take off.
Skills needed are –
Risk Management and Analysis
Outsourcing enables industries to complete projects more quickly with greater flexibility, including hiring employees from other areas.
Outsourcing tasks require much coordination among teams in different locations.
Project managers need to be vigilant about the potential for miscommunication or supply chain management problems.
To monitor and control project risks, qualitative and quantitative risk analysis techniques and predictive risk responses are used.
Cost Management
Starting with a clearly defined scope of work will help you plan a realistic budget, and setting achievable milestones will make it easier to estimate costs and stick to a budget.
A project manager's role is to determine how much money a particular project phase requires and ensure that the stakeholder's budget is not exceeded.
Once the project has started, it is essential to keep close track of how much money each milestone is costing—and be prepared to adjust your plans if they start exceeding your budget.
Communication Skills
Proper communication between the various teams and the stakeholders will significantly determine the success of an entire project. Each unit has to know its expected deliverables, budget, and time constraints.
A project manager should be aware of any scope changes or work lag that could affect the overall progress of the project and resolve any conflicts that may arise.
Organizing one-to-one interactions and team meetings with a goal, proper documentation of the conclusions, and using the right communication channel for each issue is essential for keeping all parties informed.
Managing Time
Creating an activity list based on a clearly defined scope—the things you and your team will do to reach your goal—will help you estimate how long it will take to finish the project.
A time plan can involve creating milestones, which are essential pauses in your project that allow you to celebrate what you've done so far and plan for what's ahead.
To create good milestones, think about the goals of the project and what your team can accomplish within a certain amount of time.
Leadership skills
A project manager's role is to manage a project and oversee its progress.
A good project manager needs to set the vision for the entire project, initiate it in the right direction, control its flow by inspiring the team to achieve their targets, and coordinate with other groups working on different parts of the project.
Checking all deliverables at various times and ensuring that they adhere to the standards laid out early on help ensure a quality product.
Management of Product Quality
It's essential to define the project guidelines in the beginning stages to ensure that all stakeholders are satisfied with the results.
Documentation of each step of a project milestone, in conjunction with regular stakeholder communication, will help prevent setbacks that could slow down the project's progress.
Expert project management professionals who can demonstrate an ability to put previous lessons learned into practice by creating comprehensive business case studies for projects will be able to enhance their resumes further.
What does PMP mean in the real world?
Project Management Professional Certification from the Project Management Institute or PMI is one of the best ways to prepare yourself for a project management career.
This Certification will help you learn how to plan, manage resources and successfully execute a project on time and budget.
Project Management Institute or PMI offers PMP Certification, which has been around for over four decades and is the leading authority in the project management industry.
It provides rigorous programs to introduce people to the field's basics and helps experienced managers increase their effectiveness.
Project Management is the collection and application of skills, knowledge, processes, and activities to acquire specific project goals according to the project acceptance criteria within agreed parameters.
Project management has final deliverables constrained to a finite timescale and budget.
Day to Day responsibilities of the Project Manager is:
· Cost Estimation
· Analysis and design of project goals
· Risk Assessment and Management
· Ensuring the project is completed in a given timeline and directing the work as a whole.
· Sending out the reports and tracking progress on a regular system through Management Information System
· Maintaining coordination between the different departments and Defining Project Timeline
· Organizing human and material resources
· Project Closure and Communicating to Stakeholders
· Resource Estimation and Allocation of Work
· Quality Management and Resolution of Issues
· Forecasting future trends, analyzing results and developing future strategies based on these results and trends.
· Maintaining the Six Sigma Quality
Can you pass PMP without experience?
You cannot appear for the credential test without relevant experience.
The project management experience refers to time spent performing various project management tasks during the entire duration.
You can apply the knowledge you had while working with (or on) your PMP exam application.
Why is experience needed?
PMI clearly says that a certified Project manager will deliver the desired result that he has learned from his experience.
Many PMPs have achieved their Certification based on their actual project management experience.
However, passing the PMP exam confirms that you have studied all the inputs and tools of project management.
You will not just be able to work in a world-class environment but also have the edge over your peers who do not hold a PMP certification.
Experience Proof
Project Management Professional (PMP®) credential is for project manager's competency and experience.
Hence it goes without surprise that PMI undergoes extensive measures to verify the applications. In addition, random audits are done to ensure the skills and knowledge of the applicants.
The demand of Projects Managers
Since project managers can work in just about any industry you can imagine, they're always in demand.
They also have quite a bit of flexibility regarding their career path.
If you're considering studying towards a project management degree, here are four industries where project managers are always in demand.
IT industry
Always wanted to be an IT project manager? Sure, it can be heavy lifting, but it's a dynamic field that offers a chance to work with some of the newest and most exciting technologies.
You'll have the opportunity to work with teams, leadership training and presentations, monitor progress, and develop long-term relationships with clients from different industries.
Finance
Global finance represents one of the most dynamic and fastest-growing industries today.
It also offers tremendous opportunities for trained and certified project managers with experience in the industry.
Project managers in this field perform various business risk identification, mergers and acquisitions, and everything in between.
However, they all have one thing in common: they can apply their understanding of both business processes and regulatory structures to the benefit of their employers.
Construction
Construction, infrastructure, and engineering industries are booming across the globe – so project managers are in high demand.
Earning a PMP certification can give you the skills to take advantage of this growing field.
Construction project managers are needed everywhere globally to find themselves out of work.
Construction projects remain necessary, regardless of economic conditions, making for a stable career option for those starting in the workforce.
Flexible Job profile
Project managers have a unique advantage in finding "the right fit." Those who choose to pursue degrees in project management often find that they can work as freelancers, moving from project to project. Or, they can focus on a particular industry to build experience.
The variety of options that project managers have in finding the right career is endless.
The bottom line is that those choosing to pursue degrees in project management will be granting themselves entry to one of the most exciting and rewarding professions anywhere. In addition, they will be able to find a path they love without fear of getting stranded in a job they don't enjoy.
For more information regarding PMP, do visit the website iCert Global
Recommended posts
Why is PMP a great deal in today’s business?
How can I prepare for PMP in 30 days?
Find Out What Happened to Architects with PMP Certification.
Read More
PMP Certification Exam Eligibility You Need to Know Before Scheduling
Have you ever asked yourself, "What is the PMP certification for project managers?" When it comes to the PMP® Certification, the answer is simple.
With PMP certification, you can work on projects all over the globe, no matter what sector you are in or which project management methodology you choose.
To sit for the Project Management Professional (PMP) ® exam, you must meet specific education and experience requirements.
In particular, you need to have at least five years of project management experience to appear for the exam. This shows that you have enough soft skills (knowledge of project management theory) to manage a project.
And PMI, to accept your application, you need to prove that you have a specific educational background—either a bachelor's degree or an equivalent combination of education and experience.
PMP Exam Eligibility Requirement
If you are wondering where to find out about the requirements for taking the PMP® exam, then you can download the free PMP® Credential Handbook from PMI's Web site. The handbook contains details about becoming certified, including eligibility information.
Identify PMP Eligibility
To determine if you are eligible to take the PMP® exam, follow the simple 4-step approach outlined here:
Go through the PMP handbook
Click here to read the PMP handbook
Eligibility requirements in this section of the PMI website under "Project Management Professional," you will be able to find the required information for determining your eligibility for taking the PMP® exam.
In addition, you will be able to start your application and request more information on how to prepare for the exam if necessary.
You must read this page very carefully, especially if you are starting. It will provide you with the information you need to help plan and execute your next steps in achieving accreditation.
Read Examination Content Outline (ECO)
Based on the tasks identified in the outline, you should recognize many of them as tasks you typically complete as part of your work in managing projects. The system covers what a Project Manager does, which would make you eligible to take the PMP® exam.
Analyze
You worked hard to gain the skills and experience to qualify for the PMP® exam.
Now review your responsibilities to identify areas of overlap with the responsibility requirements for Certification.
After identifying those areas, update your resume to provide specific examples of projects where you gained the experience required for Certification.
Get in touch with PMI customer care
Don't worry about eligibility. PMI's customer care department is happy to assist you with any queries. Visit the website PMI
What happens if the PMP certificate expires?
PMP credential holders must earn 60 PDUs every three years to maintain active Certification.
If they do not earn the required 60 PDUs during the three-year certification cycle, their Certification will be suspended.
To retain the suspended PMP certification, you have to submit 60 additional PDUs and pay the annual credential fee within one year of the suspension date.
Failure to do so will result in their Certification being placed on Terminated status. Having a certification on suspended status means that the individual may not.
(1) Call himself a certification holder
(2) Use the certification designation.
The whole recertification process must be completed within one year of suspension to regain benefits.
Skills Needed for PMP
Many organizations hire project managers to oversee and help monitor projects.
Getting a project management certification is good if you want your project management career to take off.
Skills needed are –
Risk Management and Analysis
Outsourcing enables industries to complete projects more quickly with greater flexibility, including hiring employees from other areas.
Outsourcing tasks require much coordination among teams in different locations.
Project managers need to be vigilant about the potential for miscommunication or supply chain management problems.
To monitor and control project risks, qualitative and quantitative risk analysis techniques and predictive risk responses are used.
Cost Management
Starting with a clearly defined scope of work will help you plan a realistic budget, and setting achievable milestones will make it easier to estimate costs and stick to a budget.
A project manager's role is to determine how much money a particular project phase requires and ensure that the stakeholder's budget is not exceeded.
Once the project has started, it is essential to keep close track of how much money each milestone is costing—and be prepared to adjust your plans if they start exceeding your budget.
Communication Skills
Proper communication between the various teams and the stakeholders will significantly determine the success of an entire project. Each unit has to know its expected deliverables, budget, and time constraints.
A project manager should be aware of any scope changes or work lag that could affect the overall progress of the project and resolve any conflicts that may arise.
Organizing one-to-one interactions and team meetings with a goal, proper documentation of the conclusions, and using the right communication channel for each issue is essential for keeping all parties informed.
Managing Time
Creating an activity list based on a clearly defined scope—the things you and your team will do to reach your goal—will help you estimate how long it will take to finish the project.
A time plan can involve creating milestones, which are essential pauses in your project that allow you to celebrate what you've done so far and plan for what's ahead.
To create good milestones, think about the goals of the project and what your team can accomplish within a certain amount of time.
Leadership skills
A project manager's role is to manage a project and oversee its progress.
A good project manager needs to set the vision for the entire project, initiate it in the right direction, control its flow by inspiring the team to achieve their targets, and coordinate with other groups working on different parts of the project.
Checking all deliverables at various times and ensuring that they adhere to the standards laid out early on help ensure a quality product.
Management of Product Quality
It's essential to define the project guidelines in the beginning stages to ensure that all stakeholders are satisfied with the results.
Documentation of each step of a project milestone, in conjunction with regular stakeholder communication, will help prevent setbacks that could slow down the project's progress.
Expert project management professionals who can demonstrate an ability to put previous lessons learned into practice by creating comprehensive business case studies for projects will be able to enhance their resumes further.
What does PMP mean in the real world?
Project Management Professional Certification from the Project Management Institute or PMI is one of the best ways to prepare yourself for a project management career.
This Certification will help you learn how to plan, manage resources and successfully execute a project on time and budget.
Project Management Institute or PMI offers PMP Certification, which has been around for over four decades and is the leading authority in the project management industry.
It provides rigorous programs to introduce people to the field's basics and helps experienced managers increase their effectiveness.
Project Management is the collection and application of skills, knowledge, processes, and activities to acquire specific project goals according to the project acceptance criteria within agreed parameters.
Project management has final deliverables constrained to a finite timescale and budget.
Day to Day responsibilities of the Project Manager is:
· Cost Estimation
· Analysis and design of project goals
· Risk Assessment and Management
· Ensuring the project is completed in a given timeline and directing the work as a whole.
· Sending out the reports and tracking progress on a regular system through Management Information System
· Maintaining coordination between the different departments and Defining Project Timeline
· Organizing human and material resources
· Project Closure and Communicating to Stakeholders
· Resource Estimation and Allocation of Work
· Quality Management and Resolution of Issues
· Forecasting future trends, analyzing results and developing future strategies based on these results and trends.
· Maintaining the Six Sigma Quality
Can you pass PMP without experience?
You cannot appear for the credential test without relevant experience.
The project management experience refers to time spent performing various project management tasks during the entire duration.
You can apply the knowledge you had while working with (or on) your PMP exam application.
Why is experience needed?
PMI clearly says that a certified Project manager will deliver the desired result that he has learned from his experience.
Many PMPs have achieved their Certification based on their actual project management experience.
However, passing the PMP exam confirms that you have studied all the inputs and tools of project management.
You will not just be able to work in a world-class environment but also have the edge over your peers who do not hold a PMP certification.
Experience Proof
Project Management Professional (PMP®) credential is for project manager's competency and experience.
Hence it goes without surprise that PMI undergoes extensive measures to verify the applications. In addition, random audits are done to ensure the skills and knowledge of the applicants.
The demand of Projects Managers
Since project managers can work in just about any industry you can imagine, they're always in demand.
They also have quite a bit of flexibility regarding their career path.
If you're considering studying towards a project management degree, here are four industries where project managers are always in demand.
IT industry
Always wanted to be an IT project manager? Sure, it can be heavy lifting, but it's a dynamic field that offers a chance to work with some of the newest and most exciting technologies.
You'll have the opportunity to work with teams, leadership training and presentations, monitor progress, and develop long-term relationships with clients from different industries.
Finance
Global finance represents one of the most dynamic and fastest-growing industries today.
It also offers tremendous opportunities for trained and certified project managers with experience in the industry.
Project managers in this field perform various business risk identification, mergers and acquisitions, and everything in between.
However, they all have one thing in common: they can apply their understanding of both business processes and regulatory structures to the benefit of their employers.
Construction
Construction, infrastructure, and engineering industries are booming across the globe – so project managers are in high demand.
Earning a PMP certification can give you the skills to take advantage of this growing field.
Construction project managers are needed everywhere globally to find themselves out of work.
Construction projects remain necessary, regardless of economic conditions, making for a stable career option for those starting in the workforce.
Flexible Job profile
Project managers have a unique advantage in finding "the right fit." Those who choose to pursue degrees in project management often find that they can work as freelancers, moving from project to project. Or, they can focus on a particular industry to build experience.
The variety of options that project managers have in finding the right career is endless.
The bottom line is that those choosing to pursue degrees in project management will be granting themselves entry to one of the most exciting and rewarding professions anywhere. In addition, they will be able to find a path they love without fear of getting stranded in a job they don't enjoy.
For more information regarding PMP, do visit the website iCert Global
Recommended posts
Why is PMP a great deal in today’s business?
How can I prepare for PMP in 30 days?
Find Out What Happened to Architects with PMP Certification.
Is It worth Getting PMP certification?
Is It worth Getting PMP certification?
Suppose you're currently working as a Project Manager and looking to get certified. In that case, it's crucial to know if the Project Management Professional (PMP) certification is worth it.
Yes, PMP is worth doing if you plan to have a better career path in the Project Management field.
Leading employers prefer the PMP certification, which validates a manager's knowledge of managing projects and your professional career. It is also a great way to improve your project management skills, including time, costs, risks, quality, and people.
The PMP® certification is universally valued in the project management profession and is known worldwide.
Professionals who become certified as PMP® increase their market value, improve their professional recognition, and gain credibility. The PMP® has proven to be a valuable asset for those who have achieved it.
Companies search for PMP-certified professionals to benefit from their knowledge and experience. In addition, training programs, job rotation, and opportunities for advancement promote personal growth.
PMP is based on the PMBOK guide, a guide that PMI creates and updates every 4-5 years. The purpose of the PMBOK guide is to recognize and explain Good Practices.
Is it worth getting a PMP certification?
Yes! PMP is worth it. According to different studies, almost 2.2 million project management jobs will be needed globally through 2027, and employers will prioritize PMP-certified professionals as they hire.
Business is more challenging than ever before, thanks to the increasingly competitive and globalized markets.
Today, many companies are adopting project-based business strategies to improve performance and ensure that they remain aligned with the company's strategy.
Companies are becoming more demanding of their Project Managers in terms of certification. In addition, clients ask for qualified and specialized personnel to manage their projects.
The merit of PMP Certification
Numerous benefits to becoming PMP certified include career growth, high pay, and skills that make you stand out from the competition.
Suppose you can successfully pass the PMP exam. In that case, you won't be able to ignore the benefits you'll have, some of which are unlimited opportunities and considerable amounts of money.
PMP certification shows your Knowledge of Project management
To become certified as a PMP (Project Management Professional), you'll need experience leading and directing projects.
The requirement is 4,500 hours of experience.
The PMI (Project Management Institute) applies an audit process to ensure that you tell the truth when submitting your project experience history.
The CAPM certification can always be an alternative for those who don't have enough experience. And it allows you to climb an essential step in the future, obtaining the PMP certification.
Add value to the CV
The Project Management Professional (PMP) certification can benefit those holding it.
First, many companies and organizations require certification from the project managers they hire.
Second, it can strengthen one's resume and demonstrate to others that you are serious about your work.
Third, it stands as a way to earn a better paycheck and greater credibility with peers, colleagues, and potential employers.
Pay is more than non-PMP certified
PMP accreditation is a vital resource for advancing your career in project management. A PMP certification gives you a competitive edge.
Increases professional network
As a Project Management Professional (PMP), you can attend the Project Management Institute (PMI).
You can meet and share experiences with other PMPs and non-certified project managers. You can also learn about advanced project management techniques.
Does becoming a PMP increase your value as a project manager? Yes. Think about it: by becoming a PMP, you are saying that you are committed to your career. And, if you're committed to your job, it shows that you're committed to excellence in your profession.
Shows responsibility toward the profession
PMPs have a degree of commitment to Project Management, so they've invested time and effort in obtaining their PMP certification.
As part of that commitment, they know that the PMP certification is an essential aspect of their professional lives, so they do what's necessary to maintain their certification.
Should Technical professionals get PMP certified?
If you want to move up in the engineering world, particularly into leadership positions on more complex projects, consider getting your Project Management Professional Certification (PMP).
After five years of work experience in the engineering field, leadership roles may be given to you.
Getting the Project Management Professional certification is a good idea to prove your project management knowledge and prove that you're qualified for a more advanced position.
The certificate will also provide a globally-recognized, industry-spanning measure of your experience and skill.
Research can help expand your knowledge of risk management about infrastructure projects and resiliency and mitigation work.
PMP scope in India?
PMP certification is the number one choice for professionals working in project management. Here's a look at what makes it so popular:
- When Indian companies hire at least one-third of project managers with PMP certification, they see a noticeable improvement in their project delivery, budget management, and goal meetings.
- PMP-certified professionals communicate with a global audience and are competent in project management.
- The job market is thriving because of the current state of the economy. PMP will help you stand out among other job candidates and get the most out of your career.
- Because employers who hire PMPs get a guarantee that the graduates have completed all the requirements. There are prerequisites for obtaining PMP certification.
- A thorough audit is a part of earning a PMP certification from the Project Management Institute (PMI). The audit ensures that candidates are committed to their profession and have a solid foundation, which they can showcase on their resumes.
- Interacting with a diverse group of professionals can be highly beneficial. It can make you much more marketable in your current company or to companies in other countries.
Although it's difficult and expensive to get your PMP certification, the benefits of doing so far outweigh the costs. Suppose you want to set yourself apart, especially in an ever-competitive job market. In that case, you will have to do something special.
Will PMP help you get a job?
PMP certification is globally recognized, so the certification will surely get you a job.
Aside from a higher income, getting your PMP certification improves job security. Some companies value that their employees are certified.
Jobs you can get with PMP certification:
Project Consultant- A project consultant is responsible for managing different aspects of a project. Some examples include budgeting, scheduling, and marketing. If the project has other project managers, a PMP manager leads and guides the rest on moving the project forward.
A PMP certification indicates that you are certified as a project manager and can work as a consultant for an organization or independently and offer support to organizations that need help with project management.
Project Director- A project director supervises all projects in a company, whether they are upcoming or already underway. They record completed projects and develop strategies for managing multiple projects, overseeing their progress to completion.
Getting a PMP credential is one way to ensure that you are prepared to manage projects in today's competitive job market.
Project owner- The product owner is responsible for managing the product backlog, making it easier for the development team to complete the project on time.
They set the overall goal for the final product and regularly motivate the team toward that goal. Suppose the client needs to know anything about what the team is working on. In that case, they facilitate communication between the client and the product owner.
Engineering project manager- These professionals use the skills of engineering, mathematics, and technology. They collaborate with project managers to solve real-life challenges by managing a product throughout its development and delivery.
On a typical day, their work involves communication between clients and experts so that the product meets their specifications. One expert they work with is the project manager.
They help them by guiding the development of a product from the start to the end and providing contact with clients.
Program Manager- As a project portfolio manager, you're responsible for creating a plan to complete projects and monitoring their progress. Executives give you instructions on specific tasks, and you merge all of them into one solution.
Since the PM is often in charge of the governance structure, they usually task you with running the executives' oversight of issues that need executive leadership.
Project Coordination- A project coordinator helps project managers support their teams' performance and monitor their projects' status. Project coordinators often use tracking tools like spreadsheets for this purpose. Again, the PMP certification is recommended for enhancing your chances of landing this job.
Although PMP Certification is essential for a Project Manager, it is not the certification itself that determines success. Instead, the knowledge goes into preparing for the certificate that helps make a project manager successful.
PMP certification is no longer for beginners. It is only required of experienced project managers because it is hard to pass the exam without previous project management experience.
PMP certification improves your salary
When you pursue a career in project management and get a PMP certificate, you can expect significant salary increases.
Suppose you are PMP certified and hold a position as a project manager in the financial and insurance industries. In that case, you can expect to make between $114,000 and $144,000 annually, which is roughly 20-22% more than non-PMP project managers.
Why does PMP earn more?
The PMP certification is the one to get. It develops your project management skills to do your job better and make sure you consistently deliver on time.
There are five distinct phases in the project management process:
Initiation: The project manager prepares the entire work needed for a project before the start of the project and leads the team at the beginning of a project.
Planning: The project manager plans the entire life of the project and identifies all resources, such as supplies, labor, space, and funding needed for the project to complete on time.
Execution: The project manager facilitates the team's goals by ensuring everyone knows what to expect.
Monitoring and Controlling: The project manager takes responsibility for delivering all aspects of a project, handling changes as they occur, and dealing with any unexpected roadblocks.
Closing: The project manager communicates with all team members and is there to help if there are questions or concerns. They work to ensure that each project completes on time and that all final details are as they should be before presenting the project.
The PMP certification ensures that you know what you are doing through the five stages of a project (conceptualization, planning, implementation, monitoring and control, and closing).
You don't have to be PMP certified to work as a project manager. Instead, having the accreditation shows employers that you have the skills, knowledge, and experience to complete projects to a certain standard.
Final Thoughts
Project management is an integral part of a company's success. As a result, the demand for project managers is rising, especially in countries like India, where more and more companies are running their projects.
Becoming a project manager certified with PMI is no longer a suggestion; it's necessary. There are several advantages to certification, including job opportunities, career advancement, and salary growth.
If you don't get certified, you will find yourself at a competitive disadvantage when getting the best job, advancing the fastest, and earning the highest salary.
Because of the high demand for PMP certification, many job applicants must pass a rigorous exam. Those who don't become certified may miss out on jobs or future careers.
The Project Management Institute recognizes the Project Management Professional certification as the standard for professional project managers. It can be the key to a successful career.
Recommended post
PMP Certification Hard to Obtain?
PMP Certification Exam Eligibility You Need to Know Before Scheduling
Why is PMP a Great Deal in Today's Businesses?
Read More
Is It worth Getting PMP certification?
Suppose you're currently working as a Project Manager and looking to get certified. In that case, it's crucial to know if the Project Management Professional (PMP) certification is worth it.
Yes, PMP is worth doing if you plan to have a better career path in the Project Management field.
Leading employers prefer the PMP certification, which validates a manager's knowledge of managing projects and your professional career. It is also a great way to improve your project management skills, including time, costs, risks, quality, and people.
The PMP® certification is universally valued in the project management profession and is known worldwide.
Professionals who become certified as PMP® increase their market value, improve their professional recognition, and gain credibility. The PMP® has proven to be a valuable asset for those who have achieved it.
Companies search for PMP-certified professionals to benefit from their knowledge and experience. In addition, training programs, job rotation, and opportunities for advancement promote personal growth.
PMP is based on the PMBOK guide, a guide that PMI creates and updates every 4-5 years. The purpose of the PMBOK guide is to recognize and explain Good Practices.
Is it worth getting a PMP certification?
Yes! PMP is worth it. According to different studies, almost 2.2 million project management jobs will be needed globally through 2027, and employers will prioritize PMP-certified professionals as they hire.
Business is more challenging than ever before, thanks to the increasingly competitive and globalized markets.
Today, many companies are adopting project-based business strategies to improve performance and ensure that they remain aligned with the company's strategy.
Companies are becoming more demanding of their Project Managers in terms of certification. In addition, clients ask for qualified and specialized personnel to manage their projects.
The merit of PMP Certification
Numerous benefits to becoming PMP certified include career growth, high pay, and skills that make you stand out from the competition.
Suppose you can successfully pass the PMP exam. In that case, you won't be able to ignore the benefits you'll have, some of which are unlimited opportunities and considerable amounts of money.
PMP certification shows your Knowledge of Project management
To become certified as a PMP (Project Management Professional), you'll need experience leading and directing projects.
The requirement is 4,500 hours of experience.
The PMI (Project Management Institute) applies an audit process to ensure that you tell the truth when submitting your project experience history.
The CAPM certification can always be an alternative for those who don't have enough experience. And it allows you to climb an essential step in the future, obtaining the PMP certification.
Add value to the CV
The Project Management Professional (PMP) certification can benefit those holding it.
First, many companies and organizations require certification from the project managers they hire.
Second, it can strengthen one's resume and demonstrate to others that you are serious about your work.
Third, it stands as a way to earn a better paycheck and greater credibility with peers, colleagues, and potential employers.
Pay is more than non-PMP certified
PMP accreditation is a vital resource for advancing your career in project management. A PMP certification gives you a competitive edge.
Increases professional network
As a Project Management Professional (PMP), you can attend the Project Management Institute (PMI).
You can meet and share experiences with other PMPs and non-certified project managers. You can also learn about advanced project management techniques.
Does becoming a PMP increase your value as a project manager? Yes. Think about it: by becoming a PMP, you are saying that you are committed to your career. And, if you're committed to your job, it shows that you're committed to excellence in your profession.
Shows responsibility toward the profession
PMPs have a degree of commitment to Project Management, so they've invested time and effort in obtaining their PMP certification.
As part of that commitment, they know that the PMP certification is an essential aspect of their professional lives, so they do what's necessary to maintain their certification.
Should Technical professionals get PMP certified?
If you want to move up in the engineering world, particularly into leadership positions on more complex projects, consider getting your Project Management Professional Certification (PMP).
After five years of work experience in the engineering field, leadership roles may be given to you.
Getting the Project Management Professional certification is a good idea to prove your project management knowledge and prove that you're qualified for a more advanced position.
The certificate will also provide a globally-recognized, industry-spanning measure of your experience and skill.
Research can help expand your knowledge of risk management about infrastructure projects and resiliency and mitigation work.
PMP scope in India?
PMP certification is the number one choice for professionals working in project management. Here's a look at what makes it so popular:
- When Indian companies hire at least one-third of project managers with PMP certification, they see a noticeable improvement in their project delivery, budget management, and goal meetings.
- PMP-certified professionals communicate with a global audience and are competent in project management.
- The job market is thriving because of the current state of the economy. PMP will help you stand out among other job candidates and get the most out of your career.
- Because employers who hire PMPs get a guarantee that the graduates have completed all the requirements. There are prerequisites for obtaining PMP certification.
- A thorough audit is a part of earning a PMP certification from the Project Management Institute (PMI). The audit ensures that candidates are committed to their profession and have a solid foundation, which they can showcase on their resumes.
- Interacting with a diverse group of professionals can be highly beneficial. It can make you much more marketable in your current company or to companies in other countries.
Although it's difficult and expensive to get your PMP certification, the benefits of doing so far outweigh the costs. Suppose you want to set yourself apart, especially in an ever-competitive job market. In that case, you will have to do something special.
Will PMP help you get a job?
PMP certification is globally recognized, so the certification will surely get you a job.
Aside from a higher income, getting your PMP certification improves job security. Some companies value that their employees are certified.
Jobs you can get with PMP certification:
Project Consultant- A project consultant is responsible for managing different aspects of a project. Some examples include budgeting, scheduling, and marketing. If the project has other project managers, a PMP manager leads and guides the rest on moving the project forward.
A PMP certification indicates that you are certified as a project manager and can work as a consultant for an organization or independently and offer support to organizations that need help with project management.
Project Director- A project director supervises all projects in a company, whether they are upcoming or already underway. They record completed projects and develop strategies for managing multiple projects, overseeing their progress to completion.
Getting a PMP credential is one way to ensure that you are prepared to manage projects in today's competitive job market.
Project owner- The product owner is responsible for managing the product backlog, making it easier for the development team to complete the project on time.
They set the overall goal for the final product and regularly motivate the team toward that goal. Suppose the client needs to know anything about what the team is working on. In that case, they facilitate communication between the client and the product owner.
Engineering project manager- These professionals use the skills of engineering, mathematics, and technology. They collaborate with project managers to solve real-life challenges by managing a product throughout its development and delivery.
On a typical day, their work involves communication between clients and experts so that the product meets their specifications. One expert they work with is the project manager.
They help them by guiding the development of a product from the start to the end and providing contact with clients.
Program Manager- As a project portfolio manager, you're responsible for creating a plan to complete projects and monitoring their progress. Executives give you instructions on specific tasks, and you merge all of them into one solution.
Since the PM is often in charge of the governance structure, they usually task you with running the executives' oversight of issues that need executive leadership.
Project Coordination- A project coordinator helps project managers support their teams' performance and monitor their projects' status. Project coordinators often use tracking tools like spreadsheets for this purpose. Again, the PMP certification is recommended for enhancing your chances of landing this job.
Although PMP Certification is essential for a Project Manager, it is not the certification itself that determines success. Instead, the knowledge goes into preparing for the certificate that helps make a project manager successful.
PMP certification is no longer for beginners. It is only required of experienced project managers because it is hard to pass the exam without previous project management experience.
PMP certification improves your salary
When you pursue a career in project management and get a PMP certificate, you can expect significant salary increases.
Suppose you are PMP certified and hold a position as a project manager in the financial and insurance industries. In that case, you can expect to make between $114,000 and $144,000 annually, which is roughly 20-22% more than non-PMP project managers.
Why does PMP earn more?
The PMP certification is the one to get. It develops your project management skills to do your job better and make sure you consistently deliver on time.
There are five distinct phases in the project management process:
Initiation: The project manager prepares the entire work needed for a project before the start of the project and leads the team at the beginning of a project.
Planning: The project manager plans the entire life of the project and identifies all resources, such as supplies, labor, space, and funding needed for the project to complete on time.
Execution: The project manager facilitates the team's goals by ensuring everyone knows what to expect.
Monitoring and Controlling: The project manager takes responsibility for delivering all aspects of a project, handling changes as they occur, and dealing with any unexpected roadblocks.
Closing: The project manager communicates with all team members and is there to help if there are questions or concerns. They work to ensure that each project completes on time and that all final details are as they should be before presenting the project.
The PMP certification ensures that you know what you are doing through the five stages of a project (conceptualization, planning, implementation, monitoring and control, and closing).
You don't have to be PMP certified to work as a project manager. Instead, having the accreditation shows employers that you have the skills, knowledge, and experience to complete projects to a certain standard.
Final Thoughts
Project management is an integral part of a company's success. As a result, the demand for project managers is rising, especially in countries like India, where more and more companies are running their projects.
Becoming a project manager certified with PMI is no longer a suggestion; it's necessary. There are several advantages to certification, including job opportunities, career advancement, and salary growth.
If you don't get certified, you will find yourself at a competitive disadvantage when getting the best job, advancing the fastest, and earning the highest salary.
Because of the high demand for PMP certification, many job applicants must pass a rigorous exam. Those who don't become certified may miss out on jobs or future careers.
The Project Management Institute recognizes the Project Management Professional certification as the standard for professional project managers. It can be the key to a successful career.
Recommended post
PMP Certification Hard to Obtain?
PMP Certification Exam Eligibility You Need to Know Before Scheduling
Why is PMP a Great Deal in Today's Businesses?
Career Opportunities in Six Sigma Green Belt
The Six Sigma Green Belt Certification is a highly-prized qualification prerequisite to many Six Sigma Black Belt projects. The Green Belt denotes that an employee has the necessary skill sets to implement the Six Sigma methodology.
Green Belt certification educates professionals on the tools necessary to implement a proven improvement methodology called “Define-Measure-Analyze-Improve-Control.”
In addition, the individual earning a Green Belt certification is recognized as someone who can effectively use Lean and Six Sigma to streamline processes and reduce waste and variances.
Professionals with a Six Sigma Green Belt certification should have a solid understanding of the fundamental principles of Six Sigma and be able to apply those principles daily.
Mid-level project managers, process engineers, specialists, and industrial engineers are all positions suitable for Green Belts.
The Six Sigma Green Belt is an expert in applying daily concepts to improve business operations. Many firms have found that the Green Belt can help improve many different areas of their business operations.
In addition, there are many career opportunities for the Six Sigma Green Belt because many companies hire people who can apply Six Sigma approaches to improve productivity and save money.
What is Lean Six Sigma Certification?
Six Sigma describes a Six Sigma Green Belt as someone who “has been trained on the improvement methodology of Six Sigma and will lead a process improvement or quality improvement team as part of their full-time job.”
Green Belt certification has significant value in the workplace. Certified professionals should take advantage of their position to enhance customer satisfaction and improve processes.
Companies may elect to promote Green Belt certification employees to a Black Belt position. However, professionals typically fill these positions with Six Sigma Black Belt certification.
The Need for Lean Six Sigma Green Belts
The Society for Human Resource Management says that Six Sigma data processing and process evaluation can help minimize HR costs and can be used to attract employees or optimize workplace satisfaction.
Employers seeking people with Six Sigma skills include many in the automotive, electronics, healthcare, manufacturing, and logistics fields.
In addition, green Belt certification is a must for many workers in process engineering, quality control, and exhibition careers. Some of the top companies looking to fill Six Sigma positions include Hershey Company, IBM, Wells Fargo, Siemens, etc.
Six Sigma Green Belt Careers by Job Title
Green Belts are problem-solvers who focus on quality, cost-effectiveness, and efficiency. Green Belt jobs involve analyzing data and improving processes. Jobs for professionals with Six Sigma Green Belt certification include:
Process engineers support a company's leadership in evaluating internal processes. Their goal is to make processes more efficient so their organization can produce high-quality products. The median salary for a process engineer in 2016 was $70,876.
Continuous improvement specialists collect data and conduct root cause analysis to identify and coordinate ongoing improvement initiatives. Then, they make recommendations and share their findings with senior management.
Six Sigma consultants use project management skills and business acumen to analyze current processes, challenge business assumptions, and recommend changes to improve workflow and reduce waste.
Operational excellence managers work with team members to manage an organization's Lean Six Sigma initiatives. As a result, they play an essential role in the success of improvement projects.
Quality engineers are responsible for ensuring that the products their companies manufacture meet customer standards. In addition, they usually take part in day-to-day operations and long-term improvement planning.
Industrial engineers help companies streamline their production processes, increase employee productivity and reduce costs by identifying ways to use employees, equipment, and other resources more efficiently.
Manufacturing engineers develop and optimize the processes used to design, build, and ship products such as cars and electronics. They use their knowledge of lean methodology to troubleshoot problems and continuously improve the manufacturing process.
Project managers track schedules, budgets, and other project statuses. They also use Six Sigma knowledge to ensure that projects are completed effectively and efficiently.
Mechanical engineers focus on new product development and the improvement of existing products. They use their knowledge of Six Sigma to create product concepts, design equipment, and test products.
As a Reliability Engineer, you will be working on developing reliability test plans for a company's products and working with internal teams and customers to remedy any reliability concerns.
Conclusion
A Six Sigma Green Belt can use its skills to take on a wide range of quality management roles in many fields. Many experienced quality professionals are looking for jobs as Green Belts because they know they will be able to make a meaningful difference in an organization, doing projects that create real company-wide impact.
People with Six Sigma Green Belt certification enhance their job prospects by demonstrating that they have the skills and training to help businesses lower costs and improve performance across departments and locations.
Six Sigma is an advanced application of statistical methods that allows you to test and improve your processes' quality.
Although it does require a particular skill set, it offers better opportunities for employment for people who already have relevant experience and want to advance in their careers.
Innovation and improvement are on the rise. Driven by customers who want better products and services, companies are starting to figure out ways to create better performance.
In addition, many companies want their employees to understand why it is essential to measure and improve performance.
This is a demanding job; being a sigma green belt, you will get to work on anything and everything about project management.
But the pay and the experience of working in such a big organization will be rewarding. I suggest studying hard and getting into one of the best colleges. You can only get a job in six sigma green belt after graduation.
Recommended Posts
Project Manager & Product Manager: What's the Difference?
How much time do you need to study for the PMP Exam?
PMP Certification: Course Details & Exam Costs
Is PMP the Right Choice for the Construction Industry?
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and worldwide.
Don't hesitate to get in touch with Us for more information about our professional certification training courses to accelerate your career in the best possible way.
Connect with iCert Global on:
LinkedIn | Facebook | Twitter | Instagram | YouTube | Pinterest
Subscribe to our YouTube Channel | Subscribe to our Telegram Channel
Professional Certification Training Courses from iCert Global
Quality Management Training by iCert Global:
-Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
-Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
-Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
-CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
-DevOps Certification Training Courses
Business Analysis Training by iCert Global:
-ECBA (Entry Certificate in Business Analysis) Certification Training Courses
-CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
-CBAP (Certified Business Analysis Professional) Certification Training Courses
Read More
The Six Sigma Green Belt Certification is a highly-prized qualification prerequisite to many Six Sigma Black Belt projects. The Green Belt denotes that an employee has the necessary skill sets to implement the Six Sigma methodology.
Green Belt certification educates professionals on the tools necessary to implement a proven improvement methodology called “Define-Measure-Analyze-Improve-Control.”
In addition, the individual earning a Green Belt certification is recognized as someone who can effectively use Lean and Six Sigma to streamline processes and reduce waste and variances.
Professionals with a Six Sigma Green Belt certification should have a solid understanding of the fundamental principles of Six Sigma and be able to apply those principles daily.
Mid-level project managers, process engineers, specialists, and industrial engineers are all positions suitable for Green Belts.
The Six Sigma Green Belt is an expert in applying daily concepts to improve business operations. Many firms have found that the Green Belt can help improve many different areas of their business operations.
In addition, there are many career opportunities for the Six Sigma Green Belt because many companies hire people who can apply Six Sigma approaches to improve productivity and save money.
What is Lean Six Sigma Certification?
Six Sigma describes a Six Sigma Green Belt as someone who “has been trained on the improvement methodology of Six Sigma and will lead a process improvement or quality improvement team as part of their full-time job.”
Green Belt certification has significant value in the workplace. Certified professionals should take advantage of their position to enhance customer satisfaction and improve processes.
Companies may elect to promote Green Belt certification employees to a Black Belt position. However, professionals typically fill these positions with Six Sigma Black Belt certification.
The Need for Lean Six Sigma Green Belts
The Society for Human Resource Management says that Six Sigma data processing and process evaluation can help minimize HR costs and can be used to attract employees or optimize workplace satisfaction.
Employers seeking people with Six Sigma skills include many in the automotive, electronics, healthcare, manufacturing, and logistics fields.
In addition, green Belt certification is a must for many workers in process engineering, quality control, and exhibition careers. Some of the top companies looking to fill Six Sigma positions include Hershey Company, IBM, Wells Fargo, Siemens, etc.
Six Sigma Green Belt Careers by Job Title
Green Belts are problem-solvers who focus on quality, cost-effectiveness, and efficiency. Green Belt jobs involve analyzing data and improving processes. Jobs for professionals with Six Sigma Green Belt certification include:
Process engineers support a company's leadership in evaluating internal processes. Their goal is to make processes more efficient so their organization can produce high-quality products. The median salary for a process engineer in 2016 was $70,876.
Continuous improvement specialists collect data and conduct root cause analysis to identify and coordinate ongoing improvement initiatives. Then, they make recommendations and share their findings with senior management.
Six Sigma consultants use project management skills and business acumen to analyze current processes, challenge business assumptions, and recommend changes to improve workflow and reduce waste.
Operational excellence managers work with team members to manage an organization's Lean Six Sigma initiatives. As a result, they play an essential role in the success of improvement projects.
Quality engineers are responsible for ensuring that the products their companies manufacture meet customer standards. In addition, they usually take part in day-to-day operations and long-term improvement planning.
Industrial engineers help companies streamline their production processes, increase employee productivity and reduce costs by identifying ways to use employees, equipment, and other resources more efficiently.
Manufacturing engineers develop and optimize the processes used to design, build, and ship products such as cars and electronics. They use their knowledge of lean methodology to troubleshoot problems and continuously improve the manufacturing process.
Project managers track schedules, budgets, and other project statuses. They also use Six Sigma knowledge to ensure that projects are completed effectively and efficiently.
Mechanical engineers focus on new product development and the improvement of existing products. They use their knowledge of Six Sigma to create product concepts, design equipment, and test products.
As a Reliability Engineer, you will be working on developing reliability test plans for a company's products and working with internal teams and customers to remedy any reliability concerns.
Conclusion
A Six Sigma Green Belt can use its skills to take on a wide range of quality management roles in many fields. Many experienced quality professionals are looking for jobs as Green Belts because they know they will be able to make a meaningful difference in an organization, doing projects that create real company-wide impact.
People with Six Sigma Green Belt certification enhance their job prospects by demonstrating that they have the skills and training to help businesses lower costs and improve performance across departments and locations.
Six Sigma is an advanced application of statistical methods that allows you to test and improve your processes' quality.
Although it does require a particular skill set, it offers better opportunities for employment for people who already have relevant experience and want to advance in their careers.
Innovation and improvement are on the rise. Driven by customers who want better products and services, companies are starting to figure out ways to create better performance.
In addition, many companies want their employees to understand why it is essential to measure and improve performance.
This is a demanding job; being a sigma green belt, you will get to work on anything and everything about project management.
But the pay and the experience of working in such a big organization will be rewarding. I suggest studying hard and getting into one of the best colleges. You can only get a job in six sigma green belt after graduation.
Recommended Posts
Project Manager & Product Manager: What's the Difference?
How much time do you need to study for the PMP Exam?
PMP Certification: Course Details & Exam Costs
Is PMP the Right Choice for the Construction Industry?
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and worldwide.
Don't hesitate to get in touch with Us for more information about our professional certification training courses to accelerate your career in the best possible way.
Connect with iCert Global on:
LinkedIn | Facebook | Twitter | Instagram | YouTube | Pinterest
Subscribe to our YouTube Channel | Subscribe to our Telegram Channel
Professional Certification Training Courses from iCert Global
Quality Management Training by iCert Global:
-Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
-Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
-Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
-CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
-DevOps Certification Training Courses
Business Analysis Training by iCert Global:
-ECBA (Entry Certificate in Business Analysis) Certification Training Courses
-CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
-CBAP (Certified Business Analysis Professional) Certification Training Courses
Prepare for Project Manager Interview | Top Questions with Answers 2022
Prepare for Project Manager Interview | Top Questions with Answers 2022
A project manager interview can be strenuous, especially when the participants aren't familiar with or unsure what to expect. There are many unknowns; however, focusing on critical areas and providing accurate solutions to the questions based on them during the procedure helps you get selected.
HR managers and senior heads acknowledge project management as crucial to business success. They understand that potential and approved project managers are among their most essential assets.
The Project Management Institute (PMI) reports that in the US, around $122Mn gets wasted for every $1Bn invested because of poor project management. However, when recruiting certified project managers, things get a bit challenging, and participants are reviewed in various methods.
Here are the top project manager interview questions that recruitments are sure to ask, followed by how to answer - helping you be the right fit for the role.
Project Manager Interview Questions 2022
Q1. How will you define an ideal project?
One of the most significant project management questions often asked during the interviews is to get an idea of the projects you wish to take up.
By answering the question, you will create a new door of opportunities to manage projects that fascinate you or those you are proficient in.
While answering, ensure you add multiple relevant points such as whether you're interested in working as a team or alone, the type of timelines you prefer, whether you like creative projects, and more.
Q2. How do you prioritize project tasks?
Irrespective of a project's scope and size, prioritization is crucial in determining a project's success and timely completion. Therefore, this type of question tests your adaptability and flexibility in managing a project.
When the interviewer asks you to define task prioritizing, your answer must include how you differentiate significance and short turnaround time. You can elaborate on what is essential and what not to consider.
Q3. Describe a scenario where the project you were managing underwent a downfall.
Downfalls are common when managing a project. Therefore, recruiting managers will want to know how you overcome such a scenario.
Since dealing with unpredictable situations is a central part of project management, you can highlight a few instances and mention how you include change methods in the project.
First of all, start with the facts of the scenario and why it happened. Secondly, explain what tasks you were expected to do to solve the situation. Next, describe what your role was and how you solved the issue. Last but not least, share the result, and explain what you learned from the experience.
Q4. According to you, what is the most desired skill a successful project manager must have?
If you're expertise in the project management field, you may know that no single skill is enough to become successful in the industry.
To become a successful project manager, one must possess several skills like communication, negotiation, time management, and leadership.
To give an accurate answer, you must justify why you choose a specific skill - including a few examples to state your answer.
Q5. How will you resolve internal team member conflicts?
By asking this question, the interviewer is trying to understand your mediation skills and how unbiased you're while making decisions to deal with internal conflicts.
You can describe why listening to both parties and understanding their vision is necessary. Your answer must include how you will convince either to reach the best conclusion for the project at hand.
Q6. Can you distinguish risk from issues? What are the different kinds of risks we come across in a project?
Risk is an uncertain future event that will either positively or negatively affect the project objectives. Issues indicate any scenario that currently involves the project goals. In a more straightforward form, risks target future events, while the issue is all about present occurrences that are often negative.
The major types of risks are:
- Cost
- Strategic
- Technology
- Market
- External
- Operational
- Resource
Q7. What are the approaches you may use to define a project scope?
Here, the interviewer tries to understand your insight on the concerned area. You can highlight various approaches involved in defining project scope, such as:
- Requirement analysis
- Alternatives analysis
- System analysis
- Product breakdown
- Value analysis
- Systems engineering
- Value engineering
Q8. When would you escalate an issue?
An escalation of an issue take place, if:
- The issue creates a project delay or budget overrun.
- Attempting to reach a deal and develop a common ground with concerned authority.
- Previous leveraging of trial and fail approach to solve the issue with several approaches.
- Due to issue, you or other team members are forces to accept massive work.
Q9. Describe your experience in budget management.
Recruiting managers may ask questions on various skills such as budget management. In most cases, it's not a deal-breaker if you've no prior experience; they're just trying to understand where you stand.
Budget management includes estimating the cost, allocating funds, maintaining expense records, and planning unexpected expenses.
If you have experience in budget management, it's great to pitch in a few scenarios. If you don't have much experience, you can share what you know of budget planning or speak about an experience you had in your personal life of managing expenses, if relevant. It's also good to highlight that you're good to go with new skills.
Q10. How will you describe a project plan?
For this type of question, start with explaining crucial factors for a project plan, such as team members, targets, and tasks. You can go further in-depth by stating a few examples of how you implemented the elements in the past.
Q11. State some communication challenges you faced on the last project?
For a successful project completion, project managers must communicate with team members. Unfortunately, during this process, the chances of misinformation or other communication-related issues are enormous.
The hiring manager wants to see how you tackled these challenges seamlessly and effectively as a project manager. It needs to be clear that you were able to work with your team efficiently with these obstacles, and the project outcome came out pretty good.
Q12. What are your project and career objectives for the next 6 months?
If you've any short-term project objectives, speak about them, as it shows the hiring manager that you're a dedicated and goal-oriented professional. When it comes to career objectives, ensure that you include the organization you're interviewing with as part of your targets.
If the interview is with a job placement recruiter, you might not have a particular firm in mind, and that's fine. You need to be honest and transparent about what type of role you will like to see yourself in the next six months or more.
Q13. How will ensure that the project is on track?
The recruiters might want to know how you track the project progress and whether you’re detailed-oriented.
Therefore, you will have to describe how you monitor a project from beginning to end. For instance, you will have to highlight that effective communication is a key to ensuring projects are on track.
Q14. How do you monitor and control changes to your project?
Some levels of change are inexorable. However, as a project manager, it's crucial to acclimatize those alterations rapidly. Explain to the hiring managers how you continue to maintain your team on track whenever a change occurs.
Q15. Mention some best practices you have leveraged to build top-notch customer relations?
Current clients make the best loyal customers, and it's vital to keep superior relationships beyond just offering them what they paid for. The interviewer wants to know you feel the same, so as you describe the methods you have maintained superior customer relations, ensure to weigh the significance of having delightful customers.
Conclusion
Project management sometimes needs a good judgment call in a limited period. Therefore, though the questions mentioned above are short-numbered; however, we have selected the top and often asked interview questions for the project manager post.
Nonetheless, the interview questions cover the most effective project management skills and competencies that the participant will be tested on during a hiring procedure and will need to succeed as a project manager.
Read More
Prepare for Project Manager Interview | Top Questions with Answers 2022
A project manager interview can be strenuous, especially when the participants aren't familiar with or unsure what to expect. There are many unknowns; however, focusing on critical areas and providing accurate solutions to the questions based on them during the procedure helps you get selected.
HR managers and senior heads acknowledge project management as crucial to business success. They understand that potential and approved project managers are among their most essential assets.
The Project Management Institute (PMI) reports that in the US, around $122Mn gets wasted for every $1Bn invested because of poor project management. However, when recruiting certified project managers, things get a bit challenging, and participants are reviewed in various methods.
Here are the top project manager interview questions that recruitments are sure to ask, followed by how to answer - helping you be the right fit for the role.
Project Manager Interview Questions 2022
Q1. How will you define an ideal project?
One of the most significant project management questions often asked during the interviews is to get an idea of the projects you wish to take up.
By answering the question, you will create a new door of opportunities to manage projects that fascinate you or those you are proficient in.
While answering, ensure you add multiple relevant points such as whether you're interested in working as a team or alone, the type of timelines you prefer, whether you like creative projects, and more.
Q2. How do you prioritize project tasks?
Irrespective of a project's scope and size, prioritization is crucial in determining a project's success and timely completion. Therefore, this type of question tests your adaptability and flexibility in managing a project.
When the interviewer asks you to define task prioritizing, your answer must include how you differentiate significance and short turnaround time. You can elaborate on what is essential and what not to consider.
Q3. Describe a scenario where the project you were managing underwent a downfall.
Downfalls are common when managing a project. Therefore, recruiting managers will want to know how you overcome such a scenario.
Since dealing with unpredictable situations is a central part of project management, you can highlight a few instances and mention how you include change methods in the project.
First of all, start with the facts of the scenario and why it happened. Secondly, explain what tasks you were expected to do to solve the situation. Next, describe what your role was and how you solved the issue. Last but not least, share the result, and explain what you learned from the experience.
Q4. According to you, what is the most desired skill a successful project manager must have?
If you're expertise in the project management field, you may know that no single skill is enough to become successful in the industry.
To become a successful project manager, one must possess several skills like communication, negotiation, time management, and leadership.
To give an accurate answer, you must justify why you choose a specific skill - including a few examples to state your answer.
Q5. How will you resolve internal team member conflicts?
By asking this question, the interviewer is trying to understand your mediation skills and how unbiased you're while making decisions to deal with internal conflicts.
You can describe why listening to both parties and understanding their vision is necessary. Your answer must include how you will convince either to reach the best conclusion for the project at hand.
Q6. Can you distinguish risk from issues? What are the different kinds of risks we come across in a project?
Risk is an uncertain future event that will either positively or negatively affect the project objectives. Issues indicate any scenario that currently involves the project goals. In a more straightforward form, risks target future events, while the issue is all about present occurrences that are often negative.
The major types of risks are:
- Cost
- Strategic
- Technology
- Market
- External
- Operational
- Resource
Q7. What are the approaches you may use to define a project scope?
Here, the interviewer tries to understand your insight on the concerned area. You can highlight various approaches involved in defining project scope, such as:
- Requirement analysis
- Alternatives analysis
- System analysis
- Product breakdown
- Value analysis
- Systems engineering
- Value engineering
Q8. When would you escalate an issue?
An escalation of an issue take place, if:
- The issue creates a project delay or budget overrun.
- Attempting to reach a deal and develop a common ground with concerned authority.
- Previous leveraging of trial and fail approach to solve the issue with several approaches.
- Due to issue, you or other team members are forces to accept massive work.
Q9. Describe your experience in budget management.
Recruiting managers may ask questions on various skills such as budget management. In most cases, it's not a deal-breaker if you've no prior experience; they're just trying to understand where you stand.
Budget management includes estimating the cost, allocating funds, maintaining expense records, and planning unexpected expenses.
If you have experience in budget management, it's great to pitch in a few scenarios. If you don't have much experience, you can share what you know of budget planning or speak about an experience you had in your personal life of managing expenses, if relevant. It's also good to highlight that you're good to go with new skills.
Q10. How will you describe a project plan?
For this type of question, start with explaining crucial factors for a project plan, such as team members, targets, and tasks. You can go further in-depth by stating a few examples of how you implemented the elements in the past.
Q11. State some communication challenges you faced on the last project?
For a successful project completion, project managers must communicate with team members. Unfortunately, during this process, the chances of misinformation or other communication-related issues are enormous.
The hiring manager wants to see how you tackled these challenges seamlessly and effectively as a project manager. It needs to be clear that you were able to work with your team efficiently with these obstacles, and the project outcome came out pretty good.
Q12. What are your project and career objectives for the next 6 months?
If you've any short-term project objectives, speak about them, as it shows the hiring manager that you're a dedicated and goal-oriented professional. When it comes to career objectives, ensure that you include the organization you're interviewing with as part of your targets.
If the interview is with a job placement recruiter, you might not have a particular firm in mind, and that's fine. You need to be honest and transparent about what type of role you will like to see yourself in the next six months or more.
Q13. How will ensure that the project is on track?
The recruiters might want to know how you track the project progress and whether you’re detailed-oriented.
Therefore, you will have to describe how you monitor a project from beginning to end. For instance, you will have to highlight that effective communication is a key to ensuring projects are on track.
Q14. How do you monitor and control changes to your project?
Some levels of change are inexorable. However, as a project manager, it's crucial to acclimatize those alterations rapidly. Explain to the hiring managers how you continue to maintain your team on track whenever a change occurs.
Q15. Mention some best practices you have leveraged to build top-notch customer relations?
Current clients make the best loyal customers, and it's vital to keep superior relationships beyond just offering them what they paid for. The interviewer wants to know you feel the same, so as you describe the methods you have maintained superior customer relations, ensure to weigh the significance of having delightful customers.
Conclusion
Project management sometimes needs a good judgment call in a limited period. Therefore, though the questions mentioned above are short-numbered; however, we have selected the top and often asked interview questions for the project manager post.
Nonetheless, the interview questions cover the most effective project management skills and competencies that the participant will be tested on during a hiring procedure and will need to succeed as a project manager.
Is It Worth Acquiring a Project Management Certification?
Is It Worth Acquiring a Project Management Certification?
Whether or not you should acquire a project management certification depends on where you want to head with your career. Generally, project management is practiced as a discipline within a former position, i.e., project managers are rarely just project managers. Instead, they may be IT experts or external contractors who assist in managing projects in addition to their actual crucial roles.
Project management roles gradually develop out of your current job position most of the time. For instance, you are working for a print publication, where you must ensure that the marketing department has placed the advertisements correctly. You might not consider yourself a project manager; however, prompting prerequisites is a massive part of what project managers execute.
If you can determine tasks in your existing working environment that qualify as project management responsibilities and precisely communicate how they might aid you in a full-time position, you will impress hiring managers.
Some qualifications such as Project Management Professional (PMP) and PRINCE 2 are considered renowned and industry standards. You will be at a disadvantage if you don't possess one.
If nothing else, a certification in any project management course is a seamless method of showing the recruiters that you got both - the skills and knowledge needed to oversee projects and complete them within the timeline and budget.
Can I Get a Job with Project Management Certification?
Demonstrating your abilities is significant to set yourself apart from other peers or participants in the corporate world. Even if you have the necessary experience in project management, undergoing a certification course in the field will undoubtedly improve your current skills and knowledge.
The enhanced skill sets will increase your career prospects and help you create a rapid shift to the project manager role. In addition, the organizations prefer these managers with accreditation from a reputed training institute or college and are given ample remuneration for their potential to derive critical business values.
Project managers with a valid certification earn 16% more than their non-certified peers.
There are many scopes for career development for beginners and senior personnel by acquiring the proper project management credential.
After achieving the credentials, let us see some of the project management designations you acquire.
- Project coordinator
- Project manager (construction, engineering, healthcare, law, IT, environmental research, and architecture)
- Chief operation manager
- Social media manager
- Marketing manager'
- Operations manager
- Program manager
- Portfolio manager
If you don't have any relevant experience in the project management industry, don't worry. You can still find roles in the field that might not need special training.
These roles will be of low risk, i.e., you will have to manage small teams, and the only resource you receive is the skills brought in by your teammates. It's not much; however, working your way up will guarantee by the time you start managing challenging projects.
How Long is Project Management Course?
The duration of project management programs depends on what level of accreditation you're striving for. Most courses might take over a week, including the examination. Then, depending on the qualification, you might choose to opt for an online program.
Some advanced programs need routine peer-review or tests by an external board. In these scenarios, the procedure can take at least a month. However, these advanced courses aren't mandatory for most industry verticals but are suited to project managers interested in management theory.
Are Project Managers on Demand?
The demand for project managers is sky-rocketing. According to the Project Management Institute (PMI) report, there will be 22Mn new project management job openings through 2027.
One of the reasons why project managers are in demand is their ability to switch jobs almost at will. The wide range of options that project managers have in finding the right fit is never-ending. Qualified professionals can work as freelancers, shifting from one project to the next, or can focus on a particular sector to build experience.
Hence, project managers are required in a wide range of industry verticals. Although there are pretty popular in the IT sector, project-related work is also common in finance, manufacturing, business service, construction, oil & gas, and utility sectors across the globe.
To build a career in the project management field and develop your skills, enroll in the iCert Global PMP Certification Training Program, a PMI-approved training provider. The course will teach you how to plan, organize, execute, and direct successful projects irrespective of the scale or complexity.
Recommended Post
How Business Process Management (BPM) Relates to Six Sigma?
PMP Certification: Course Details & Exam Costs
Is PMP the Right Choice for the Construction Industry?
Read More
Is It Worth Acquiring a Project Management Certification?
Whether or not you should acquire a project management certification depends on where you want to head with your career. Generally, project management is practiced as a discipline within a former position, i.e., project managers are rarely just project managers. Instead, they may be IT experts or external contractors who assist in managing projects in addition to their actual crucial roles.
Project management roles gradually develop out of your current job position most of the time. For instance, you are working for a print publication, where you must ensure that the marketing department has placed the advertisements correctly. You might not consider yourself a project manager; however, prompting prerequisites is a massive part of what project managers execute.
If you can determine tasks in your existing working environment that qualify as project management responsibilities and precisely communicate how they might aid you in a full-time position, you will impress hiring managers.
Some qualifications such as Project Management Professional (PMP) and PRINCE 2 are considered renowned and industry standards. You will be at a disadvantage if you don't possess one.
If nothing else, a certification in any project management course is a seamless method of showing the recruiters that you got both - the skills and knowledge needed to oversee projects and complete them within the timeline and budget.
Can I Get a Job with Project Management Certification?
Demonstrating your abilities is significant to set yourself apart from other peers or participants in the corporate world. Even if you have the necessary experience in project management, undergoing a certification course in the field will undoubtedly improve your current skills and knowledge.
The enhanced skill sets will increase your career prospects and help you create a rapid shift to the project manager role. In addition, the organizations prefer these managers with accreditation from a reputed training institute or college and are given ample remuneration for their potential to derive critical business values.
Project managers with a valid certification earn 16% more than their non-certified peers.
There are many scopes for career development for beginners and senior personnel by acquiring the proper project management credential.
After achieving the credentials, let us see some of the project management designations you acquire.
- Project coordinator
- Project manager (construction, engineering, healthcare, law, IT, environmental research, and architecture)
- Chief operation manager
- Social media manager
- Marketing manager'
- Operations manager
- Program manager
- Portfolio manager
If you don't have any relevant experience in the project management industry, don't worry. You can still find roles in the field that might not need special training.
These roles will be of low risk, i.e., you will have to manage small teams, and the only resource you receive is the skills brought in by your teammates. It's not much; however, working your way up will guarantee by the time you start managing challenging projects.
How Long is Project Management Course?
The duration of project management programs depends on what level of accreditation you're striving for. Most courses might take over a week, including the examination. Then, depending on the qualification, you might choose to opt for an online program.
Some advanced programs need routine peer-review or tests by an external board. In these scenarios, the procedure can take at least a month. However, these advanced courses aren't mandatory for most industry verticals but are suited to project managers interested in management theory.
Are Project Managers on Demand?
The demand for project managers is sky-rocketing. According to the Project Management Institute (PMI) report, there will be 22Mn new project management job openings through 2027.
One of the reasons why project managers are in demand is their ability to switch jobs almost at will. The wide range of options that project managers have in finding the right fit is never-ending. Qualified professionals can work as freelancers, shifting from one project to the next, or can focus on a particular sector to build experience.
Hence, project managers are required in a wide range of industry verticals. Although there are pretty popular in the IT sector, project-related work is also common in finance, manufacturing, business service, construction, oil & gas, and utility sectors across the globe.
To build a career in the project management field and develop your skills, enroll in the iCert Global PMP Certification Training Program, a PMI-approved training provider. The course will teach you how to plan, organize, execute, and direct successful projects irrespective of the scale or complexity.
Recommended Post
How Business Process Management (BPM) Relates to Six Sigma?
PMP Certification: Course Details & Exam Costs
Is PMP the Right Choice for the Construction Industry?
How does PMP Training of Employees Benefit Organizations?
How does PMP Training of Employees Benefit Organizations?
Project management is an in-demand career field as it's not bound to a certain industry and has an exponential increase in job opportunities across various sectors worldwide.
If you want to benefit from the ocean of opportunities, you will have to put your best. Certification in project management can help the professional become fruitful in the work and organization they work for.
A stepping stone toward a project management career is Project Management Professional (PMP) certification offered by PMI, a globally renowned and prestigious credential that benefits employees and organizations.
If you are a manager in education, construction, healthcare, IT, and more, you should go for a PMP training program to gain a competitive edge at your workplace. Being an international recognition credential, the PMP exam is not a piece of cake to crack, but it's never impossible with adequate support.
PMP Training Benefits to the Workforces
1. Global Recognition: If you want the freedom of choice to work in any part of the world with your current educational certification, PMP is the right path for you. It is one of the globally recognized credentials by PMI with an excellent reputation and handsome remuneration for the project managers in any industry vertical.
2. Salary Perks: Through PMP training and certification, professionals can earn a higher salary package. In addition, the training offers insights and expertise to professionals, which they can leverage to stay ahead in the career race. A PMP-certified holder earns over 22% more than their non-certified peer.
3. Credibility: If you want to create an impression among your peers and employers, your resumes need to be eye-catching. With the PMP credential badge, you leave a mark even before appearing for the interview. In every industry vertical, there is a criterion of professionals who constantly upgrade their knowledge and potential. PMP is a first step that can drastically change your management and technical career.
4. Challenging Tasks and Projects: If you're a project manager looking for challenges at work, you need to start working to achieve your PMP accreditation. With the credential, you get the opportunity to face novel challenges in your work area. The training program aids in building up the potential to tackle these challenges efficiently.
5. Meet the Industry Criteria: All industries have project managers, IT, automobiles, construction, or healthcare. In all these verticals, there is always a demand for skilled and qualified managers who can efficiently oversee business operations. PMP credential training conveys valuable knowledge to individuals, beneficial in significant industries.
6. Job Security: If you ask any industrial professional, 'What is your biggest concern working in the specific industry?' their answer will be job security. There are several reasons why the workforce lost their jobs, especially during the COVID-19 pandemic. One of the main reasons is 'Automation.' Despite everything else, a wide gap exists between the demand and availability of skilled professionals. Though there is no specific percentage of job security for managers; however, PMP certified holders have a better job position and safety than non-holders.
PMP Training Benefits to Companies
All organizations wish to excel their competitors, and there is a constant demand to recruit skilled professionals. A company that hires PMP-certified holders gets the following advantages:
1. More Value: A manager who has taken a PMP training program adds more value to the organization they are working for. In addition, recruiting certified professionals assures the organizations that their business projects are with the right person.
2. Deliver Successful Projects: A project may fail for several reasons, such as the inability to meet customers' demands, unrealistic schedules, insufficient resources, monetary concerns, etc. However, with a PMP training program, individuals get to tackle projects with top-notch efficiency, insights, and acuteness. This gives the project to be managed with few errors and greater responsibility
3. Enhanced Work Culture: With certified holders leading and directing projects in a company, the workforces working under them get to acquire many experiences and knowledge. In addition, the approaches adopted by these managers to tackle projects offer an excellent example for their peers, thereby enhancing the work culture overall.
PMP certification is a resource that benefits the people acquiring the credential and the companies recruiting these individuals, as the certification does offer tremendous value in the project management world.
To build a career in the project management field and develop your skills, enroll in the iCert Global PMP Certification Training Program, a PMI-approved training provider. The course will teach you how to plan, organize, execute, and direct successful projects irrespective of the scale or complexity.
Recommended Post
Is It Worth Acquiring a Project Management Certification?
How Business Process Management (BPM) Relates to Six Sigma?
Prepare for Project Manager Interview | Top Questions with Answers 2022
Read More
How does PMP Training of Employees Benefit Organizations?
Project management is an in-demand career field as it's not bound to a certain industry and has an exponential increase in job opportunities across various sectors worldwide.
If you want to benefit from the ocean of opportunities, you will have to put your best. Certification in project management can help the professional become fruitful in the work and organization they work for.
A stepping stone toward a project management career is Project Management Professional (PMP) certification offered by PMI, a globally renowned and prestigious credential that benefits employees and organizations.
If you are a manager in education, construction, healthcare, IT, and more, you should go for a PMP training program to gain a competitive edge at your workplace. Being an international recognition credential, the PMP exam is not a piece of cake to crack, but it's never impossible with adequate support.
PMP Training Benefits to the Workforces
1. Global Recognition: If you want the freedom of choice to work in any part of the world with your current educational certification, PMP is the right path for you. It is one of the globally recognized credentials by PMI with an excellent reputation and handsome remuneration for the project managers in any industry vertical.
2. Salary Perks: Through PMP training and certification, professionals can earn a higher salary package. In addition, the training offers insights and expertise to professionals, which they can leverage to stay ahead in the career race. A PMP-certified holder earns over 22% more than their non-certified peer.
3. Credibility: If you want to create an impression among your peers and employers, your resumes need to be eye-catching. With the PMP credential badge, you leave a mark even before appearing for the interview. In every industry vertical, there is a criterion of professionals who constantly upgrade their knowledge and potential. PMP is a first step that can drastically change your management and technical career.
4. Challenging Tasks and Projects: If you're a project manager looking for challenges at work, you need to start working to achieve your PMP accreditation. With the credential, you get the opportunity to face novel challenges in your work area. The training program aids in building up the potential to tackle these challenges efficiently.
5. Meet the Industry Criteria: All industries have project managers, IT, automobiles, construction, or healthcare. In all these verticals, there is always a demand for skilled and qualified managers who can efficiently oversee business operations. PMP credential training conveys valuable knowledge to individuals, beneficial in significant industries.
6. Job Security: If you ask any industrial professional, 'What is your biggest concern working in the specific industry?' their answer will be job security. There are several reasons why the workforce lost their jobs, especially during the COVID-19 pandemic. One of the main reasons is 'Automation.' Despite everything else, a wide gap exists between the demand and availability of skilled professionals. Though there is no specific percentage of job security for managers; however, PMP certified holders have a better job position and safety than non-holders.
PMP Training Benefits to Companies
All organizations wish to excel their competitors, and there is a constant demand to recruit skilled professionals. A company that hires PMP-certified holders gets the following advantages:
1. More Value: A manager who has taken a PMP training program adds more value to the organization they are working for. In addition, recruiting certified professionals assures the organizations that their business projects are with the right person.
2. Deliver Successful Projects: A project may fail for several reasons, such as the inability to meet customers' demands, unrealistic schedules, insufficient resources, monetary concerns, etc. However, with a PMP training program, individuals get to tackle projects with top-notch efficiency, insights, and acuteness. This gives the project to be managed with few errors and greater responsibility
3. Enhanced Work Culture: With certified holders leading and directing projects in a company, the workforces working under them get to acquire many experiences and knowledge. In addition, the approaches adopted by these managers to tackle projects offer an excellent example for their peers, thereby enhancing the work culture overall.
PMP certification is a resource that benefits the people acquiring the credential and the companies recruiting these individuals, as the certification does offer tremendous value in the project management world.
To build a career in the project management field and develop your skills, enroll in the iCert Global PMP Certification Training Program, a PMI-approved training provider. The course will teach you how to plan, organize, execute, and direct successful projects irrespective of the scale or complexity.
Recommended Post
Is It Worth Acquiring a Project Management Certification?
How Business Process Management (BPM) Relates to Six Sigma?
Prepare for Project Manager Interview | Top Questions with Answers 2022
MBA Or PMP: Which Do You Think is Profitable in 2022?
MBA Or PMP: Which Do You Think is Profitable in 2022?
A common question we might have heard recruiters asking the candidates: Where do you see yourself 5 years from now? And it’s high time we start asking ourselves where we would like to land in 5- or 10-years’ time.
A professional designation such as PMP or MBA certification is supposed to assist us in gaining a competitive edge in our career; hence, it should satisfy the below-given criteria:
- Make you more worthy for the job market
- Must have short and long-term benefits
- Should aid you in earning more.
Any kind of designation you consider must be evaluated based on these points. Ultimately, the answer will depend on your personal career preference, though there are a few facts a professional must consider before making a decision.
An Ocean of MBA Graduates
There was a time when an MBA degree was sporadic, a 2-year graduation degree that not many acquired. Moreover, there weren't many universities or colleges that provided the degree program.
But as the demand for MBA courses sky-rocketed, several education providers started providing short executive MBA courses, making it easier for a working person to get the degree and for those who could afford one.
At present, MBA courses are more surplus than ever before. This is because every college/institution has hoped into the MBA drive. Adding to this, the online education choice looks like an ocean of MBA graduates and courses.
However, is the sector all set for the massive wave of professionals? Apparently not. Professionals realize that their careers are static even after investing thousands of dollars and time to gain an MBA degree.
On the contrary, PMP works according to the industry requirements. Therefore, you get trained in the sector of your choice to fulfill a specific need of the vertical. Indeed, a PMP accreditation helps professionals develop their skills while working in the industry.
Another fact to consider - PMP is relatively a new program, and there aren't many PMP professionals in the job market compared to MBAs.
Stereotyping MBA Programs
MBA degrees are created to develop managers. Therefore, an MBA program can be stereotyped, hardly targeted on a specific vertical or functional field, which is its superior strength. Preferably, an MBA degree can find jobs in any industry vertical.
However, companies, especially technology giants, have recognized that they require more than just managers. They need professionals who understand and work with technologies.
So, what’s the solution that organizations have come upon? Will they hire professionals with a solid technical background and lack leadership and management potential?
The answer to this is the PMP credential, where individuals attain technical knowledge and managerial skills. Professionals with the certification are immediately recognizable to recruiters as someone with actual skills. In addition, the PMP certification training offers specialized expertise that an MBA lacks and has a higher value in the job market.
MBAs Cost a Fortune
How much does an MBA degree cost? Probably worth a king's ransom. A good grade MBA course can cost you around $100,000.
However, when we compare PMP and MBA costs of education, PMP certification turns out to be relatively budget-oriented. The average expense of PMP is $2,000.
Another thing to consider is that MBA takes more educational hours than a PMP certification. Moreover, the average salary of an MBA in the US is $105,684, while that of a PMP is around $112,000.
Once the professionals are done with their PMP training, the certification holders get more handsome remuneration than an MBA holder at 1/50th the price.
The State of the Economy
The last decade has been a white knuckle, and the organizations have been pressurized to evolve for survival. As a result, many companies have become leaner, meaner firms, while those who failed to make changes have fallen out.
That being the case, recruiters are looking for professionals suitable for their company's portfolio, individuals with hard-earned competency who can exhibit leadership in their selected areas. Hence, it's not surprising why organizations recruit PMP-certified project managers these days.
What Do You Think: PMP, MBA, or Both?
Now that you've got an idea of why PMP is more advantageous than an MBA in an organization, the ultimate choice to decide is yours.
But there are few benefits to an MBA that a PMP certification can't match. For example, MBA programs teach business theories and practices that aren't covered in a PMP certification training. Moreover, if you acquire an MBA degree from a reputed college/university, you get access to good networking opportunities.
In contrast, obtaining a PMP credential prepares the candidate for what is known as the rapidly growing profession in the modern world. It needs a professional to have sound work experience, which the accreditation then builds upon. As a result, the certification makes you job-ready.
In the Erewhon world, you should aim for both the credentials, and this is the choice several individuals are making - MBAs are acquiring PMP accreditation and vice versa. Having both is sure to make you an all-rounder in any verticals.
About US
If you're looking for PMP certification training, explore iCert Global's training courses to aid you prepare for the PMP credential test. Our courses are conducted by certified lecturers and they are designed to help you pass the exam on the first attempt.
Gain an in-depth understanding of project management and learn how to manage challenging ones with our Project Management Training course now.
Read More
MBA Or PMP: Which Do You Think is Profitable in 2022?
A common question we might have heard recruiters asking the candidates: Where do you see yourself 5 years from now? And it’s high time we start asking ourselves where we would like to land in 5- or 10-years’ time.
A professional designation such as PMP or MBA certification is supposed to assist us in gaining a competitive edge in our career; hence, it should satisfy the below-given criteria:
- Make you more worthy for the job market
- Must have short and long-term benefits
- Should aid you in earning more.
Any kind of designation you consider must be evaluated based on these points. Ultimately, the answer will depend on your personal career preference, though there are a few facts a professional must consider before making a decision.
An Ocean of MBA Graduates
There was a time when an MBA degree was sporadic, a 2-year graduation degree that not many acquired. Moreover, there weren't many universities or colleges that provided the degree program.
But as the demand for MBA courses sky-rocketed, several education providers started providing short executive MBA courses, making it easier for a working person to get the degree and for those who could afford one.
At present, MBA courses are more surplus than ever before. This is because every college/institution has hoped into the MBA drive. Adding to this, the online education choice looks like an ocean of MBA graduates and courses.
However, is the sector all set for the massive wave of professionals? Apparently not. Professionals realize that their careers are static even after investing thousands of dollars and time to gain an MBA degree.
On the contrary, PMP works according to the industry requirements. Therefore, you get trained in the sector of your choice to fulfill a specific need of the vertical. Indeed, a PMP accreditation helps professionals develop their skills while working in the industry.
Another fact to consider - PMP is relatively a new program, and there aren't many PMP professionals in the job market compared to MBAs.
Stereotyping MBA Programs
MBA degrees are created to develop managers. Therefore, an MBA program can be stereotyped, hardly targeted on a specific vertical or functional field, which is its superior strength. Preferably, an MBA degree can find jobs in any industry vertical.
However, companies, especially technology giants, have recognized that they require more than just managers. They need professionals who understand and work with technologies.
So, what’s the solution that organizations have come upon? Will they hire professionals with a solid technical background and lack leadership and management potential?
The answer to this is the PMP credential, where individuals attain technical knowledge and managerial skills. Professionals with the certification are immediately recognizable to recruiters as someone with actual skills. In addition, the PMP certification training offers specialized expertise that an MBA lacks and has a higher value in the job market.
MBAs Cost a Fortune
How much does an MBA degree cost? Probably worth a king's ransom. A good grade MBA course can cost you around $100,000.
However, when we compare PMP and MBA costs of education, PMP certification turns out to be relatively budget-oriented. The average expense of PMP is $2,000.
Another thing to consider is that MBA takes more educational hours than a PMP certification. Moreover, the average salary of an MBA in the US is $105,684, while that of a PMP is around $112,000.
Once the professionals are done with their PMP training, the certification holders get more handsome remuneration than an MBA holder at 1/50th the price.
The State of the Economy
The last decade has been a white knuckle, and the organizations have been pressurized to evolve for survival. As a result, many companies have become leaner, meaner firms, while those who failed to make changes have fallen out.
That being the case, recruiters are looking for professionals suitable for their company's portfolio, individuals with hard-earned competency who can exhibit leadership in their selected areas. Hence, it's not surprising why organizations recruit PMP-certified project managers these days.
What Do You Think: PMP, MBA, or Both?
Now that you've got an idea of why PMP is more advantageous than an MBA in an organization, the ultimate choice to decide is yours.
But there are few benefits to an MBA that a PMP certification can't match. For example, MBA programs teach business theories and practices that aren't covered in a PMP certification training. Moreover, if you acquire an MBA degree from a reputed college/university, you get access to good networking opportunities.
In contrast, obtaining a PMP credential prepares the candidate for what is known as the rapidly growing profession in the modern world. It needs a professional to have sound work experience, which the accreditation then builds upon. As a result, the certification makes you job-ready.
In the Erewhon world, you should aim for both the credentials, and this is the choice several individuals are making - MBAs are acquiring PMP accreditation and vice versa. Having both is sure to make you an all-rounder in any verticals.
About US
If you're looking for PMP certification training, explore iCert Global's training courses to aid you prepare for the PMP credential test. Our courses are conducted by certified lecturers and they are designed to help you pass the exam on the first attempt.
Gain an in-depth understanding of project management and learn how to manage challenging ones with our Project Management Training course now.
Syllabus and Criteria for PMP Exam Preparation
The Project Management Professional (PMP) is the most renowned and globally valued individual accreditation awarded by the Project Management Institute (PMI).
In some cases, it's a necessary qualification for a project management career. A project manager with a PMP credential can work as a project manager in any industry vertical worldwide.
PMP Exam Criteria
Anyone can sign up for the PMP examination considering the candidates satisfy the PMI-set criteria.
Let's see what those prerequisites for the PMP exam are:
Eligibility Criteria
Leading and Directing Project Experiences
Project Management Education
Secondary degree (high school diploma, associate degree or global equivalent)
5 years
35 contact hours
4-year undergraduate degree
3 years
35 contact hours
4-year or post-grad degree from GAC accredited program
2 years
35 contact hours
PMP Exam Syllabus and Format Outline
PMP Exam Syllabus
According to the 2019 PMP Examination Content Outline (ECO), the credential covers three domains based on the PMBOK Guide latest edition by PMI. This structure came into effect in January 2021.
Later, PMI has announced that the examination would be based on PMBOK Ed 6. However, the Guide latest edition (PMBOK Guide Ed 7) is available.
DOMAIN
CONTENT WEIGHTAGE (%)
People
42%
Process
50%
Business Environment
8%
TOTAL
100%
About half of the credential tests will have predictive project management methodologies, and the other half will have agile or hybrid methods.
The PMP knowledge domains cover many essentials and understand concepts such as managing business environment changes, continuous improvement, and process analysis.
The PMP credential test doesn't need mathematical knowledge to a more significant extent. However, participants must be average in the calculation present value, performing PERT analysis, and schedule variance.
The arduous part of the test is that understanding terminologies and concepts are never enough. The candidates must use that knowledge for complex scenarios mimicking real-life project situations.
Designed by project professionals, the PMP credential validates that you are among the top-notch skillset in:
PEOPLE (42%)
The 'People' domain emphasizes the soft skills you require to lead a project team in the changing business environment efficiently.
Some of the tasks in this domain include:
- Conflict management
- Team leadership
- Supporting team performance
- Ensuring adequate training for team members
- Project negotiation
- Stakeholder collaboration, and more.
PROCESS (50%)
The 'Process' domain strengthens the technical aspects of successful project management.
Some of the tasks in this domain include:
- Communication management
- Risk assessment and management
- Project execution to deliver business value
- Budgeting planning
- Plan and manage schedule, and more.
BUSINESS ENVIRONMENT (8%)
The 'Business Environment' domain displays the relation between projects and organizational strategy.
Some of the tasks in this domain include:
- Plan and manage project compliance
- Determine project value and benefits
- Supporting organizational change
- Addressing external business changes
Read to know more on domain tasks: What are the Domains in Project Management Professional (PMP)?
PMP Exam Format
- Total no. of questions: 180
- Question types: Combination questions (MCQs, fill-in-the-blanks, hotspot, etc.)
- No. of scored questions: 175
- No. of pre-test questions: 5
- Duration of the exam: 230 minutes (approx 4 hours)
- Exam mode: Online and offline
For the PMP test, there are two 10-minutes breaks. The first break appears when you complete questions 1-60 and review all the answers. Then, after you are done with 120 questions and confirm that all the responses are checked, you can take the next 10-minute break.
With so much new content to focus on, it's understandable that the new PMP test will facilitate a broader study scope to cover everything. However, there is much more to learn and outshine; therefore, the credential test will be more difficult.
Passing Score for the PMP Exam
PMI has never disclosed the actual passing score or the percentage one needs to get to be PMP-certified. Therefore, we as training providers often suggest our students aim for more than 70 percent, or 126 questions, to get right out of 180.
As the exam is scored based on the difficulty of the questions, PMI uses psychometric analysis. Since the questions will be randomly placed, candidates can't find which one is difficult, pre-test, or easy. Hence, we recommend that you answer all the questions with equal seriousness.
Retaking PMP Examination
PMI offers you three chances to pass the PMP examination within an eligibility period of one year. Now there are two scenarios:
- If the one-year eligibility period expires without you taking the examination, you must reapply for the certification.
- Suppose the candidate fails in all three attempts. In that case, they will undergo a suspension period of one year from the last examination date before reapplying for the certification.
Remember, during the suspension period, you can apply for any other PMI certification.
Final Thoughts
We know that PMP is the most challenging certification test, as it covers a wide range of concepts on project management. Moreover, one needs to have hands-on expertise of these concepts and terminologies.
However, with the best exam prep plans and resource materials, any individual can crack the exam on the first attempt.
Read More
The Project Management Professional (PMP) is the most renowned and globally valued individual accreditation awarded by the Project Management Institute (PMI).
In some cases, it's a necessary qualification for a project management career. A project manager with a PMP credential can work as a project manager in any industry vertical worldwide.
PMP Exam Criteria
Anyone can sign up for the PMP examination considering the candidates satisfy the PMI-set criteria.
Let's see what those prerequisites for the PMP exam are:
|
Eligibility Criteria |
Leading and Directing Project Experiences |
Project Management Education |
|
Secondary degree (high school diploma, associate degree or global equivalent) |
5 years |
35 contact hours |
|
4-year undergraduate degree |
3 years |
35 contact hours |
|
4-year or post-grad degree from GAC accredited program |
2 years |
35 contact hours |
PMP Exam Syllabus and Format Outline
PMP Exam Syllabus
According to the 2019 PMP Examination Content Outline (ECO), the credential covers three domains based on the PMBOK Guide latest edition by PMI. This structure came into effect in January 2021.
Later, PMI has announced that the examination would be based on PMBOK Ed 6. However, the Guide latest edition (PMBOK Guide Ed 7) is available.
|
DOMAIN |
CONTENT WEIGHTAGE (%) |
|
People |
42% |
|
Process |
50% |
|
Business Environment |
8% |
|
TOTAL |
100% |
About half of the credential tests will have predictive project management methodologies, and the other half will have agile or hybrid methods.
The PMP knowledge domains cover many essentials and understand concepts such as managing business environment changes, continuous improvement, and process analysis.
The PMP credential test doesn't need mathematical knowledge to a more significant extent. However, participants must be average in the calculation present value, performing PERT analysis, and schedule variance.
The arduous part of the test is that understanding terminologies and concepts are never enough. The candidates must use that knowledge for complex scenarios mimicking real-life project situations.
Designed by project professionals, the PMP credential validates that you are among the top-notch skillset in:
PEOPLE (42%)
The 'People' domain emphasizes the soft skills you require to lead a project team in the changing business environment efficiently.
Some of the tasks in this domain include:
- Conflict management
- Team leadership
- Supporting team performance
- Ensuring adequate training for team members
- Project negotiation
- Stakeholder collaboration, and more.
PROCESS (50%)
The 'Process' domain strengthens the technical aspects of successful project management.
Some of the tasks in this domain include:
- Communication management
- Risk assessment and management
- Project execution to deliver business value
- Budgeting planning
- Plan and manage schedule, and more.
BUSINESS ENVIRONMENT (8%)
The 'Business Environment' domain displays the relation between projects and organizational strategy.
Some of the tasks in this domain include:
- Plan and manage project compliance
- Determine project value and benefits
- Supporting organizational change
- Addressing external business changes
Read to know more on domain tasks: What are the Domains in Project Management Professional (PMP)?
PMP Exam Format
- Total no. of questions: 180
- Question types: Combination questions (MCQs, fill-in-the-blanks, hotspot, etc.)
- No. of scored questions: 175
- No. of pre-test questions: 5
- Duration of the exam: 230 minutes (approx 4 hours)
- Exam mode: Online and offline
For the PMP test, there are two 10-minutes breaks. The first break appears when you complete questions 1-60 and review all the answers. Then, after you are done with 120 questions and confirm that all the responses are checked, you can take the next 10-minute break.
With so much new content to focus on, it's understandable that the new PMP test will facilitate a broader study scope to cover everything. However, there is much more to learn and outshine; therefore, the credential test will be more difficult.
Passing Score for the PMP Exam
PMI has never disclosed the actual passing score or the percentage one needs to get to be PMP-certified. Therefore, we as training providers often suggest our students aim for more than 70 percent, or 126 questions, to get right out of 180.
As the exam is scored based on the difficulty of the questions, PMI uses psychometric analysis. Since the questions will be randomly placed, candidates can't find which one is difficult, pre-test, or easy. Hence, we recommend that you answer all the questions with equal seriousness.
Retaking PMP Examination
PMI offers you three chances to pass the PMP examination within an eligibility period of one year. Now there are two scenarios:
- If the one-year eligibility period expires without you taking the examination, you must reapply for the certification.
- Suppose the candidate fails in all three attempts. In that case, they will undergo a suspension period of one year from the last examination date before reapplying for the certification.
Remember, during the suspension period, you can apply for any other PMI certification.
Final Thoughts
We know that PMP is the most challenging certification test, as it covers a wide range of concepts on project management. Moreover, one needs to have hands-on expertise of these concepts and terminologies.
However, with the best exam prep plans and resource materials, any individual can crack the exam on the first attempt.
Does It Pay to Earn a PM Certification After One Year?
Does It Pay to Earn a PM Certification After One Year?
There has always been a discussion regarding professional credentials, and we often see many recruiters seeking specific accreditations in their job listings. However, is a professional certification required to get a job? Does it increase my salary?
We have conducted a survey where the results for the post-Project Management (PM) certifications are captivating. So let’s see, read till the end.
First Attempt PM Exam Pass Rate
iCert Global candidates have around 98% first-attempt success rate.
Based on the survey, over 95% of the candidates who appeared for the exam have succeeded in the first attempt. The rest of the individuals are those preparing for their credential exam and couldn't sit for the test in one year.
The prep process for the certification exam differs from one individual to the next. As iCert Global, we provide 100% self-paced and online training courses for PM certifications such as PMP, CAPM, PgMP, and PMI-RMP.
If you opt for a self-paced program, it's entirely up to you how much time you dedicate to completing the course training. Moreover, we always suggest that the candidates support their study schedule with various materials like flashcards or sample tests.
If you are a working professional with a tight schedule, the entire study period required to complete will be longer.
If you're looking to obtain a certification in PMP, refer to our PMP training program - Corporate, e-learning, and Instructor-led live online classes.
Promotion or Found New Jobs
Achieving a certification increases the pay scale; instead, it brings new opportunities. Around 40% of the participants who earned a project management credential in one year stated that they either found a new job or got a promotion in their present company.
If you're already working or want to start a career in the project management field, acquiring yourself a professional accreditation is highly beneficial. You can either get a promotion in the existing firm or get a brand-new job role.
Salary Increase by More Than 10% or Maybe 20%
There is much debate circulating whether achieving a credential increases the pay scale.
Over 30% of our candidates who earned a project management accreditation in one year had a salary increase of 10%, and about 12% of them had more than 20%.
Considering the present pandemic scenario and financial turmoil globally, workforces with professional certification earn more than non-certified peers.
There are many professional credentials that you can achieve, out of which PRINCE2 certification is popular in countries like Australia, the UK, and New Zealand, whereas PMP certification is popular in the USA, Germany, UAE, India, and others.
Here is a list of average income received by professionals with PMP certification in different countries:
COUNTRY
SALARY
US
USD 112,000
India
INR 2,000,000
UAE
AED 312,000
Germany
EUR 82,000
Helping Professionals in the Early Years of Career
When it comes to years of experience, employees who have experience of less than 5 years receive handsome remuneration when they achieve certification. Around 35% with a minimum of 5 years have salary raise of 10% or more, while over 20% increased their pay scale by 20%.
Around 13% of individuals with more than 5 years of experience said they increased their pay scale by 20% after obtaining a professional credential.
This shows that achieving an accreditation significantly boosts if you're a newcomer in the project management industry, as recruits look for more evidence that you're qualified to execute specific tasks offered.
Starting a career is not easy, as many good positions often need significant experience. But you can handle this barrier by acquiring a professional certification.
Concluding Thoughts
Organizations want to keep up with the swift transforming global environment in today's corporate world. To do so, they have to deliver more innovative services and products to satisfy customer demands. This makes PM skills highly valuable as it's the projects that add to new services and products.
Getting a PM certification differentiates you from other skillsets competing for the same jobs.
PMI's PMP certification has global recognition and demand. Hence, it's the most recognized accreditation for project managers. But like, stated, PRINCE2 might be more beneficial if you're working in New Zealand, UK, or Australia. You can begin your PM career with PRINCE2 Foundation certification and develop your skills with PRINCE2 Agile Practitioner credential.
Read More
Does It Pay to Earn a PM Certification After One Year?
There has always been a discussion regarding professional credentials, and we often see many recruiters seeking specific accreditations in their job listings. However, is a professional certification required to get a job? Does it increase my salary?
We have conducted a survey where the results for the post-Project Management (PM) certifications are captivating. So let’s see, read till the end.
First Attempt PM Exam Pass Rate
iCert Global candidates have around 98% first-attempt success rate.
Based on the survey, over 95% of the candidates who appeared for the exam have succeeded in the first attempt. The rest of the individuals are those preparing for their credential exam and couldn't sit for the test in one year.
The prep process for the certification exam differs from one individual to the next. As iCert Global, we provide 100% self-paced and online training courses for PM certifications such as PMP, CAPM, PgMP, and PMI-RMP.
If you opt for a self-paced program, it's entirely up to you how much time you dedicate to completing the course training. Moreover, we always suggest that the candidates support their study schedule with various materials like flashcards or sample tests.
If you are a working professional with a tight schedule, the entire study period required to complete will be longer.
If you're looking to obtain a certification in PMP, refer to our PMP training program - Corporate, e-learning, and Instructor-led live online classes.
Promotion or Found New Jobs
Achieving a certification increases the pay scale; instead, it brings new opportunities. Around 40% of the participants who earned a project management credential in one year stated that they either found a new job or got a promotion in their present company.
If you're already working or want to start a career in the project management field, acquiring yourself a professional accreditation is highly beneficial. You can either get a promotion in the existing firm or get a brand-new job role.
Salary Increase by More Than 10% or Maybe 20%
There is much debate circulating whether achieving a credential increases the pay scale.
Over 30% of our candidates who earned a project management accreditation in one year had a salary increase of 10%, and about 12% of them had more than 20%.
Considering the present pandemic scenario and financial turmoil globally, workforces with professional certification earn more than non-certified peers.
There are many professional credentials that you can achieve, out of which PRINCE2 certification is popular in countries like Australia, the UK, and New Zealand, whereas PMP certification is popular in the USA, Germany, UAE, India, and others.
Here is a list of average income received by professionals with PMP certification in different countries:
|
COUNTRY |
SALARY |
|
US |
USD 112,000 |
|
India |
INR 2,000,000 |
|
UAE |
AED 312,000 |
|
Germany |
EUR 82,000 |
Helping Professionals in the Early Years of Career
When it comes to years of experience, employees who have experience of less than 5 years receive handsome remuneration when they achieve certification. Around 35% with a minimum of 5 years have salary raise of 10% or more, while over 20% increased their pay scale by 20%.
Around 13% of individuals with more than 5 years of experience said they increased their pay scale by 20% after obtaining a professional credential.
This shows that achieving an accreditation significantly boosts if you're a newcomer in the project management industry, as recruits look for more evidence that you're qualified to execute specific tasks offered.
Starting a career is not easy, as many good positions often need significant experience. But you can handle this barrier by acquiring a professional certification.
Concluding Thoughts
Organizations want to keep up with the swift transforming global environment in today's corporate world. To do so, they have to deliver more innovative services and products to satisfy customer demands. This makes PM skills highly valuable as it's the projects that add to new services and products.
Getting a PM certification differentiates you from other skillsets competing for the same jobs.
PMI's PMP certification has global recognition and demand. Hence, it's the most recognized accreditation for project managers. But like, stated, PRINCE2 might be more beneficial if you're working in New Zealand, UK, or Australia. You can begin your PM career with PRINCE2 Foundation certification and develop your skills with PRINCE2 Agile Practitioner credential.
What You Need to Know About PMP Accreditation?
What You Need to Know About PMP Accreditation?
In recent years, project management has evolved as one of the globe’s triumphing new professions. According to the PMI survey, employers will need to fill over 2.2Mn new project roles each year through 2027, meaning project managers are in high demand.
This swift development, coupled with competitive industry remuneration, has encouraged many workforces and students to consider a career in project management.
But with so many novel arrivals to the industry, incentivized project managers are looking for different ways to distinguish them from the crowd. The Project Management Professional (PMP) accreditation holds the key for many.
What is PMP Certification?
PMP credential is a globally renowned accreditation for project managers awarded by Project Management Institute (PMI). Though the credential isn't required to work as a project manager in most roles, PMP reflects a person's technical skills and instills trust in future workforces and clients - serving as justification for promotion and handsome salary.
The average salary of project managers with a PMP certification is the US $112,000, and according to the PMI salary survey, the median salary for PMP holders in the US is 25% higher than those without the certification.
Prerequisites of PMP Certification Exam

Syllabus of PMP Exam
About half of the PMP certification exam will have predictive project management methodologies, and the other half will have agile or hybrid methods.
The PMP knowledge domains cover many essentials and understand concepts such as managing business environment changes, continuous improvement, and process analysis.
According to the 2019 PMP Examination Content Outline (ECO), the credential covers three domains:
PEOPLE (42%)
The 'People' domain emphasizes the soft skills you require to lead a project team in the changing business environment efficiently.
Some of the tasks in this domain include:
- Conflict management
- Team leadership
- Supporting team performance
- Ensuring adequate training for team members
- Project negotiation
- Stakeholder collaboration, and more.
PROCESS (50%)
The 'Process' domain strengthens the technical aspects of successful project management.
Some of the tasks in this domain include:
- Communication management
- Risk assessment and management
- Project execution to deliver business value
- Budgeting planning
- Plan and manage schedule, and more.
BUSINESS ENVIRONMENT (8%)
The 'Business Environment' domain displays the relation between projects and organizational strategy.
- Some of the tasks in this domain include:
- Plan and manage project compliance
- Determine project value and benefits
- Supporting organizational change
- Addressing external business changes
PMP Exam Format & Cost
- Total no. of questions: 180
- Question types: Combination questions (MCQs, fill-in-the-blanks, hotspot, etc.)
- No. of scored questions: 175
- No. of pre-test questions: 5
- Duration of the exam: 230 minutes (approx 4 hours)
- Exam mode: Online and offline
For the PMP test, there are two 10-minutes breaks. The first break appears when you complete questions 1-60 and review all the answers. Then, after you are done with 120 questions and confirm that all the responses are checked, you can take the next 10-minute break.
With so much new content to focus on, it's understandable that the new PMP test will facilitate a broader study scope to cover everything. However, there is much more to learn and outshine; therefore, the credential test will be more difficult.
The PMP certification exam costs for PMI members and non-members are as follows:
PMP CERTIFICATION
PMI MEMBERS
NON-PMI MEMBERS
Exam
$405
$555
Re-examination
$275
$375
Renewal
$60
$150
PMP Certification Renewal
Once you receive the PMP credential badge, ensure that you maintain the same by earning 35 PDUs over three years. After PMI confirms that you have met the PDU prerequisites, you'll receive a mail/message to apply for PMP certification renewal – asking you to make payments through the online certification system.
PMI will send the individual an updated certificate with new CCR cycle dates after processing the application and renewal fees. This usually takes around 6-8 weeks to get delivered through postal.
The credential holders must agree to comply with the terms of use, including audit norms agreements. The participant can renew the accreditation only after completing the audit and agreeing with all the terms and conditions during an audit.
The auditing done by PMI is random, i.e., PMI selects a group of PMI certification holders randomly, where they must submit supporting documentation to prove PDUs.
Therefore, credential holders must keep these PDU claiming materials for 18 months after the end of the CCR Cycle.
Conclusion
A PMP certification is a stepping stone to other project management accreditation, offering you a competitive edge in the market, a source of pride among peers, and several other perks.
Whether looking for marketability to workforces, clientele reputations, or annual income, the PMP credential is the best choice for project management enthusiasts globally.
To build a career in the project management field and develop your skills, enroll in the iCert Global PMP Certification Training Program, a PMI-approved training provider. The course will teach you how to plan, organize, execute, and direct successful projects irrespective of the scale or complexity.
Read More
What You Need to Know About PMP Accreditation?
In recent years, project management has evolved as one of the globe’s triumphing new professions. According to the PMI survey, employers will need to fill over 2.2Mn new project roles each year through 2027, meaning project managers are in high demand.
This swift development, coupled with competitive industry remuneration, has encouraged many workforces and students to consider a career in project management.
But with so many novel arrivals to the industry, incentivized project managers are looking for different ways to distinguish them from the crowd. The Project Management Professional (PMP) accreditation holds the key for many.
What is PMP Certification?
PMP credential is a globally renowned accreditation for project managers awarded by Project Management Institute (PMI). Though the credential isn't required to work as a project manager in most roles, PMP reflects a person's technical skills and instills trust in future workforces and clients - serving as justification for promotion and handsome salary.
The average salary of project managers with a PMP certification is the US $112,000, and according to the PMI salary survey, the median salary for PMP holders in the US is 25% higher than those without the certification.
Prerequisites of PMP Certification Exam
Syllabus of PMP Exam
About half of the PMP certification exam will have predictive project management methodologies, and the other half will have agile or hybrid methods.
The PMP knowledge domains cover many essentials and understand concepts such as managing business environment changes, continuous improvement, and process analysis.
According to the 2019 PMP Examination Content Outline (ECO), the credential covers three domains:
PEOPLE (42%)
The 'People' domain emphasizes the soft skills you require to lead a project team in the changing business environment efficiently.
Some of the tasks in this domain include:
- Conflict management
- Team leadership
- Supporting team performance
- Ensuring adequate training for team members
- Project negotiation
- Stakeholder collaboration, and more.
PROCESS (50%)
The 'Process' domain strengthens the technical aspects of successful project management.
Some of the tasks in this domain include:
- Communication management
- Risk assessment and management
- Project execution to deliver business value
- Budgeting planning
- Plan and manage schedule, and more.
BUSINESS ENVIRONMENT (8%)
The 'Business Environment' domain displays the relation between projects and organizational strategy.
- Some of the tasks in this domain include:
- Plan and manage project compliance
- Determine project value and benefits
- Supporting organizational change
- Addressing external business changes
PMP Exam Format & Cost
- Total no. of questions: 180
- Question types: Combination questions (MCQs, fill-in-the-blanks, hotspot, etc.)
- No. of scored questions: 175
- No. of pre-test questions: 5
- Duration of the exam: 230 minutes (approx 4 hours)
- Exam mode: Online and offline
For the PMP test, there are two 10-minutes breaks. The first break appears when you complete questions 1-60 and review all the answers. Then, after you are done with 120 questions and confirm that all the responses are checked, you can take the next 10-minute break.
With so much new content to focus on, it's understandable that the new PMP test will facilitate a broader study scope to cover everything. However, there is much more to learn and outshine; therefore, the credential test will be more difficult.
The PMP certification exam costs for PMI members and non-members are as follows:
|
PMP CERTIFICATION |
PMI MEMBERS |
NON-PMI MEMBERS |
|
Exam |
$405 |
$555 |
|
Re-examination |
$275 |
$375 |
|
Renewal |
$60 |
$150 |
PMP Certification Renewal
Once you receive the PMP credential badge, ensure that you maintain the same by earning 35 PDUs over three years. After PMI confirms that you have met the PDU prerequisites, you'll receive a mail/message to apply for PMP certification renewal – asking you to make payments through the online certification system.
PMI will send the individual an updated certificate with new CCR cycle dates after processing the application and renewal fees. This usually takes around 6-8 weeks to get delivered through postal.
The credential holders must agree to comply with the terms of use, including audit norms agreements. The participant can renew the accreditation only after completing the audit and agreeing with all the terms and conditions during an audit.
The auditing done by PMI is random, i.e., PMI selects a group of PMI certification holders randomly, where they must submit supporting documentation to prove PDUs.
Therefore, credential holders must keep these PDU claiming materials for 18 months after the end of the CCR Cycle.
Conclusion
A PMP certification is a stepping stone to other project management accreditation, offering you a competitive edge in the market, a source of pride among peers, and several other perks.
Whether looking for marketability to workforces, clientele reputations, or annual income, the PMP credential is the best choice for project management enthusiasts globally.
To build a career in the project management field and develop your skills, enroll in the iCert Global PMP Certification Training Program, a PMI-approved training provider. The course will teach you how to plan, organize, execute, and direct successful projects irrespective of the scale or complexity.
Top 30 Lean Six Sigma Black Belt Certification Exam Questions with Answers
Top 30 Lean Six Sigma Black Belt Certification Exam Questions with Answers
Six Sigma is a group of methods and tools employed for process enhancement. It focuses on enhancing the overall quality by estimating the defects present within a process and eradicating those through a systematic technique.
The Lean Six Sigma Black Belt certification will offer you proficiency in Lean Six Sigma methods of DMAIC. Here, we have a collection of top 30 exam questions of the certifications with solutions that will help you gain confidence to appear for the test.
Q1. What does DMADV stands for:
- Design, Measure, Analyze, Define, Validate
- Develop Measurement and Analysis Department for Verification
- Define, Measure, Analyze, Define, Verify
ANSWER: (A)
Q2. What does P stand in the acronym of a process map, SIPOC. What does the P stand for in this acronym?
- Product
- Process
- Preliminary
- Population
ANSWER: (B)
Q3. The practice of using specific points in its storage area to indicate when products need to be ordered.
- Poka-yoke
- Checkpoints
- Hoshin
- Kanban
ANSWER: (D)
Q4. Which of the following techniques dramatically shortens changeover times?
- Work in process (WIP)
- Continuous flow
- Single minute exchange of dies (SMED)
- Standard work
ANSWER: (C)
Q5. Which of the following tools can be used to identify waste or non-value-added activities?
- Process map
- Force yield analysis
- Scatter diagram
- Pareto analysis
ANSWER: (A)
Q6. The purpose of Toll Gate review is to:
- Review progress and kick off the next phase
- Confirm if the earlier phase was completed successfully
- Get a formal sign-off from the stakeholders
- All of the above
ANSWER: (D)
Q7. A Black Belt is expected to deliver what types of results from Six Sigma projects?
- Large projects
- A minimum 200K USD as annual benefit
- Defects reduction projects
- Have everybody in the organization trained on Six Sigma
ANSWER: (B)
Q8. The purpose of capturing Voice of Customer (VoC) is to:
- Capture stated or unstated customer requirements
- Have a sampling exercise
- Collect customer feedback
- Ensure there is no confusion between the contract and delivery
ANSWER: (A)
Q9. Which of the control charts must have at least 20 subgroups of observed values to judge whether a process is in control or not?
- R-Chart
- P-Chart
- C-Chart
- Y-Chart
ANSWER: (A)
Q10. An advanced quantitative analysis to optimize business or industrial processes through process mapping and modelling using multiple variables. This tool is referred as:
- Capability-requirements analysis
- C&E Analysis
- Capability-complexity analysis
- FMEA analysis
ANSWER: (C)
Q11. Correction, over-production, inventory, and motion are all examples of:
- Waste
- Noise
- 5S target areas
- Value-added activities
ANSWER: (A)
Q12. What tool did Kaoru Ishikawa develop?
- CTQ Diagram
- FMEA Tool
- SWAT Analysis Tool
- Cause and Effect Diagram
ANSWER: (D)
Q13. Which tool is used to assess the significance of factors in either a fractional or a full-factorial experiment structure?
- Analysis of variance (ANOVA)
- Fault tree analysis (FTA)
- Failure mode and effects analysis (FMEA)
- Evolutionary operation (EVOP)
ANSWER: (A)
Q14. Which of the following methods is used to develop an exhaustive list of ideas about a subject?
- Benchmarking
- Brainstorming
- Goal-setting
- Problem-solving
ANSWER: (B)
Q15. A company wishes to compare the expected mileage of eight different types of car tires. Which of the following statistical tests is best suited for the analysis?
- Multiple regression
- ANOVA
- Paired-difference test
- Z-test
ANSWER: (B)
Q16. A company has installed a system that prevents orders with incorrect information from being forwarded to production scheduling. This is an example of which of the following lean tools?
- Standard work
- Kanban
- Poka-Yoke
- Visual factory
ANSWER: (C)
Q17. SMED is a lean manufacturing concept that is used to reduce waste in the manufacturing process. What does the E stand for?
- Exchange
- Error
- Estimate
- Expected
ANSWER: (A)
Q18. Which of the following tools is appropriate to use with multiple criteria requiring a single option to be selected?
- Pugh matrix
- Kano model
- Hypothesis testing
- PDCA
ANSWER: (A)
Q19. The process developing a problem statement by a Six Sigma team will help to:
- Agree on key dates associated with completing major project phases
- Achieve consensus and ownership of the process
- Determine solutions
- Determine how often it should meet.
ANSWER: (B)
Q20. Which of the following is the correct formula for DPMO?
- D/TOP
- DPO×1,000,000
- D×U×OP
- DPU/DPO
ANSWER: (B)
Q21. A method that changes data without significantly reducing accuracy or precision is known as:
- Bias adjustment
- Statistical efficiency
- Blocking
- Coding
ANSWER: (D)
Q22. When the sampling method used creates a difference between the result obtained from the sample and the actual population value, the difference is known as:
- Correlation
- Precision
- Accuracy
- Bias
ANSWER: (D)
Q23. A technique for demonstrating the connection between customer needs and features on the product is:
- Flow charts and process maps
- Relationship matrix
- Cause and effect diagrams
- Pareto chart
ANSWER: (B)
Q24. The workers of a manufacturing unit want to maintain cleanliness on a daily basis. Which approach is most apt?
- 5S
- Poka-yoke
- Kaizen
- PDCA
ANSWER: (A)
Q25. Which of the following best describes a team that has members with different skills or roles from different areas within the organization?
- Self-directed
- Cross-functional
- Parallel
- Process
ANSWER: (B)
Q26. An important aspect of data collection is that the data collector should:
- Determine the dispersion of the data
- Know how the data are to be used
- Use a control chart to analyze the data
- Use stratified sampling plan
ANSWER: (B)
Q27. When the variation cause is a cluttered workstation which technique helps to increase the process stability?
- 5S
- SMED
- Preventive maintenance
- Visual factory
ANSWER: (A)
Q28. Which of the following is an important responsibility of a project champion?
- Leading the team
- Documenting the overall progress of the team
- Allocating resources to support the team
- Coaching the team in DMAIC process
ANSWER: (C)
Q29. Positional, cyclical, and temporal variations are most commonly analyzed in:
- SPC charts
- Multi-vary charts
- Cause and effect diagrams
- Run charts
ANSWER: (B)
Q30. Which one of the following is an inventive methodology for problem-solving?
- BPR
- TPM
- TRIZ
- BMP
ANSWER: (C)
Read More
Top 30 Lean Six Sigma Black Belt Certification Exam Questions with Answers
Six Sigma is a group of methods and tools employed for process enhancement. It focuses on enhancing the overall quality by estimating the defects present within a process and eradicating those through a systematic technique.
The Lean Six Sigma Black Belt certification will offer you proficiency in Lean Six Sigma methods of DMAIC. Here, we have a collection of top 30 exam questions of the certifications with solutions that will help you gain confidence to appear for the test.
Q1. What does DMADV stands for:
- Design, Measure, Analyze, Define, Validate
- Develop Measurement and Analysis Department for Verification
- Define, Measure, Analyze, Define, Verify
ANSWER: (A)
Q2. What does P stand in the acronym of a process map, SIPOC. What does the P stand for in this acronym?
- Product
- Process
- Preliminary
- Population
ANSWER: (B)
Q3. The practice of using specific points in its storage area to indicate when products need to be ordered.
- Poka-yoke
- Checkpoints
- Hoshin
- Kanban
ANSWER: (D)
Q4. Which of the following techniques dramatically shortens changeover times?
- Work in process (WIP)
- Continuous flow
- Single minute exchange of dies (SMED)
- Standard work
ANSWER: (C)
Q5. Which of the following tools can be used to identify waste or non-value-added activities?
- Process map
- Force yield analysis
- Scatter diagram
- Pareto analysis
ANSWER: (A)
Q6. The purpose of Toll Gate review is to:
- Review progress and kick off the next phase
- Confirm if the earlier phase was completed successfully
- Get a formal sign-off from the stakeholders
- All of the above
ANSWER: (D)
Q7. A Black Belt is expected to deliver what types of results from Six Sigma projects?
- Large projects
- A minimum 200K USD as annual benefit
- Defects reduction projects
- Have everybody in the organization trained on Six Sigma
ANSWER: (B)
Q8. The purpose of capturing Voice of Customer (VoC) is to:
- Capture stated or unstated customer requirements
- Have a sampling exercise
- Collect customer feedback
- Ensure there is no confusion between the contract and delivery
ANSWER: (A)
Q9. Which of the control charts must have at least 20 subgroups of observed values to judge whether a process is in control or not?
- R-Chart
- P-Chart
- C-Chart
- Y-Chart
ANSWER: (A)
Q10. An advanced quantitative analysis to optimize business or industrial processes through process mapping and modelling using multiple variables. This tool is referred as:
- Capability-requirements analysis
- C&E Analysis
- Capability-complexity analysis
- FMEA analysis
ANSWER: (C)
Q11. Correction, over-production, inventory, and motion are all examples of:
- Waste
- Noise
- 5S target areas
- Value-added activities
ANSWER: (A)
Q12. What tool did Kaoru Ishikawa develop?
- CTQ Diagram
- FMEA Tool
- SWAT Analysis Tool
- Cause and Effect Diagram
ANSWER: (D)
Q13. Which tool is used to assess the significance of factors in either a fractional or a full-factorial experiment structure?
- Analysis of variance (ANOVA)
- Fault tree analysis (FTA)
- Failure mode and effects analysis (FMEA)
- Evolutionary operation (EVOP)
ANSWER: (A)
Q14. Which of the following methods is used to develop an exhaustive list of ideas about a subject?
- Benchmarking
- Brainstorming
- Goal-setting
- Problem-solving
ANSWER: (B)
Q15. A company wishes to compare the expected mileage of eight different types of car tires. Which of the following statistical tests is best suited for the analysis?
- Multiple regression
- ANOVA
- Paired-difference test
- Z-test
ANSWER: (B)
Q16. A company has installed a system that prevents orders with incorrect information from being forwarded to production scheduling. This is an example of which of the following lean tools?
- Standard work
- Kanban
- Poka-Yoke
- Visual factory
ANSWER: (C)
Q17. SMED is a lean manufacturing concept that is used to reduce waste in the manufacturing process. What does the E stand for?
- Exchange
- Error
- Estimate
- Expected
ANSWER: (A)
Q18. Which of the following tools is appropriate to use with multiple criteria requiring a single option to be selected?
- Pugh matrix
- Kano model
- Hypothesis testing
- PDCA
ANSWER: (A)
Q19. The process developing a problem statement by a Six Sigma team will help to:
- Agree on key dates associated with completing major project phases
- Achieve consensus and ownership of the process
- Determine solutions
- Determine how often it should meet.
ANSWER: (B)
Q20. Which of the following is the correct formula for DPMO?
- D/TOP
- DPO×1,000,000
- D×U×OP
- DPU/DPO
ANSWER: (B)
Q21. A method that changes data without significantly reducing accuracy or precision is known as:
- Bias adjustment
- Statistical efficiency
- Blocking
- Coding
ANSWER: (D)
Q22. When the sampling method used creates a difference between the result obtained from the sample and the actual population value, the difference is known as:
- Correlation
- Precision
- Accuracy
- Bias
ANSWER: (D)
Q23. A technique for demonstrating the connection between customer needs and features on the product is:
- Flow charts and process maps
- Relationship matrix
- Cause and effect diagrams
- Pareto chart
ANSWER: (B)
Q24. The workers of a manufacturing unit want to maintain cleanliness on a daily basis. Which approach is most apt?
- 5S
- Poka-yoke
- Kaizen
- PDCA
ANSWER: (A)
Q25. Which of the following best describes a team that has members with different skills or roles from different areas within the organization?
- Self-directed
- Cross-functional
- Parallel
- Process
ANSWER: (B)
Q26. An important aspect of data collection is that the data collector should:
- Determine the dispersion of the data
- Know how the data are to be used
- Use a control chart to analyze the data
- Use stratified sampling plan
ANSWER: (B)
Q27. When the variation cause is a cluttered workstation which technique helps to increase the process stability?
- 5S
- SMED
- Preventive maintenance
- Visual factory
ANSWER: (A)
Q28. Which of the following is an important responsibility of a project champion?
- Leading the team
- Documenting the overall progress of the team
- Allocating resources to support the team
- Coaching the team in DMAIC process
ANSWER: (C)
Q29. Positional, cyclical, and temporal variations are most commonly analyzed in:
- SPC charts
- Multi-vary charts
- Cause and effect diagrams
- Run charts
ANSWER: (B)
Q30. Which one of the following is an inventive methodology for problem-solving?
- BPR
- TPM
- TRIZ
- BMP
ANSWER: (C)
Top 30 Scrum Exam Questions with Answers
Top 30 Scrum Exam Questions
- Which of the following is NOT an objective of a Retrospect Sprint Meeting?
- Identify Process Improvements.
- Identify Feature Improvements.
- Identify Best Practices.
- Identify Process problems and bottlenecks.
Ans-B
- Which of the following is a responsibility of the Scrum Master in the context of change in Scrum?
- Eliminating all changes that may affect the quality of deliverables and processes
- Facilitating the identification of Change Requests by the Scrum Team and their assessment and prioritization by the Product Owner.
- Providing requests for changes in a project.
- Approving amended, removed, or added changes according to project requirements and communicating to the Scrum Team.
Ans-B
- Which of the following are roles in the Scrum framework?
- Product Owner
- Project Manager
- Lead Developer
- Business Analyst
Ans-A
- What is most important in all Scrum Teams? A) Self-management B) Clear hierarchies C) Communication D) Continuous improvement
- A, B, C, D
- A, C, D
- A, D
- A, B
Ans-B
- The primary purpose of the daily scrum (daily stand-up) is:
- To give a status report to the ScrumMaster
- To give a status report to the product owner
- Developers inspect how progress is made towards the Sprint Goal and adapt how the remaining work is done accordingly.
- To give team members a chance to take a break from their tasks
Ans-C
- Which one of the following is NOT traditionally an activity of the Scrum framework?
- Sprint planning
- Sprint review
- Sprint retrospective
- Weekly inspection
Ans-D
- The primary purpose of the daily scrum (daily stand-up) is:
- To give a status report to the ScrumMaster
- To give a status report to the product owner
- Developers inspect how progress is made towards the Sprint Goal and adapt how the remaining work is done accordingly.
- To give team members a chance to take a break from their tasks
Ans- C
- Which statement of the following is the best description for sprint?
- A sprint is a condensed amount of time where developers work as many hours as they need to finish the work assigned to them.
- A sprint is a pre-specified amount of time in which the developer’s team works at a sustained pace to complete a chosen set of items from the Product Backlog.
- A sprint is a fixed amount of time set aside for the team to run tests and resolve any outstanding bugs right before the product ships
- A sprint is a pre-specified period during which team members choose individual items from the product backlog to work on. A new article is brought into the sprint as each item is completed.
Ans- B
- What is the Scrum approach to doing design early in a project?
- Having the design up front is always a good idea
- Much design can be done in parallel with implementation because, ideally, both design and implementation are done by the same Scrum Team.
- Design should be done by a separate team from the Scrum team.
- Design has no place in an Agile project
Ans- B
- How can software development projects be executed by implementing the Scrum Framework?
- Complete software packages
- Customer projects
- All kinds of software development projects
- Sub-systems, components, or parts of more extensive systems
Ans- C
- An excellent approach to documentation in Scrum is:
- Do no documentation because it is a waste of time
- Do the necessary documentation to support the development and use of the product
- Do sufficient documentation to prove you have done an excellent job
- Do more documentation than usual because Agile is risky
Ans-B
- Which of the following best describes the approach for determining the Sprint length?
- Sprint should always be 30 days
- The team determines Sprint length by dividing the total number of story points by the average velocity of the team
- Sprint should always be two weeks
- The team should agree on a fixed length of the Sprint, of one month or less
Ans-D
- What should the developers do if the product owner is repeatedly too busy to be available?
- Continue the work, record the assumptions and ask the customer later for input
- Send the customer a written warning that the end product will be completed on time but may not meet their needs
- Allow the Business Analyst to take on the role of Proxy Product Owner
- Draw the problem to the attention of the Scrum Master
Ans-D
- An excellent approach to documentation in Scrum is:
- Do no documentation because it is a waste of time
- Do the necessary documentation to support the development and use of the product
- Do sufficient documentation to prove you have done an excellent job
- Do more documentation than usual because Agile is risky
Ans- B
- Why is it important to trust the team?
- High trust teams do not have to be accountable to each other
- High trust teams do not require a user representative
- The Project Manager does not then have to keep a project schedule
- The presence of trust is positively correlated with the team performance
Ans-D
- In a Scrum Team, we “learn as we go” because
- Planning gets more reliable over time
- Requirements evolve over time
- The collaboration within the team gets better over time
- All of the above
Ans-D
- What are the two primary artifacts of a sprint planning meeting, and what is the related commitment?
- A sprint backlog and sprint goal
- A requirements documents and a Gantt chart
- A requirements documents and a test plan
- A test plan and a Gantt chart
Ans-A
- Which of these statements best describes the Agile approach to teamwork?
- The team should plan to work overtime regularly throughout the project
- The team should expect to work longer hours towards the end of the project to deliver all that was committed to
- The team should strive for a sustainable pace that they can maintain potentially for a long time
- The team will regularly need to work many hours overtime but can compensate for this during periods of less intensity
Ans-C
- Who ultimately decides when the team has enough work for the sprint in planning?
- The ScrumMaster
- The product owner
- The team Developers
- The product owner, ScrumMaster, and team vote to determine when the sprint backlog is full
Ans-C
- Which of the following is the most characteristic of a ScrumMaster?
- Task focused
- Process-oriented
- Supportive
- Disengaged
Ans-C
- The Agile Manifesto states the following values:
- People are more important than contracts
- Working software is valued over comprehensive documentation
- Plans should have priority over the ability to respond
- Contracts should be negotiated which allow control over the people
Ans-B
- The “ MoSCoW “ technique is a popular prioritization technique, where the "M" stands for ...
- May have
- Major
- Must Have
- Mandatory
Ans- C
- The product owner role in a Scrum Teams…
- Has no control over the prioritization of delivered features
- Is accountable for the ordering of items on the Product Backlog
- Collaborates with the developers over the prioritization of features, but the developers have the final decision
- Collaborates with the developers over the prioritization of features, but the business has the final decision
Ans- B
- When handling team dynamics, the ScrumMaster should ......
- Empower the team members within appropriate limits
- Encourage an environment of competition and personal advantage
- Give clear directives to the team about what they should do and how
- Expect team members to be proactive and each work to their priorities and objectives
Ans- A
- Once an Agile project is underway, what should the approach to planning be?
- Should be able to demonstrate control of its progress
- Should have no control over its progress
- Is always out of control
- Is controlled by the velocity of the most junior team member
Ans-A
- What does Scrum advise a team to do with the product backlog items it chooses to bring into the sprint?
- The team should break each product backlog item into work items that preferably take no more than a day.
- The product owner assigns each product backlog item to the specialist best suited to carry the work.
- The team asks the ScrumMaster to research the product backlog items and decide who should work on each one.
- The team doesn't do anything with the product backlog items. Scrum doesn’t use tasks or task lists.
Ans-A
- As per Scrum, which one of the following is an essential feature of the daily stand-up (daily Scrum) meeting?
- The meeting should ensure that it is clear to all which team members are not performing
- All Developers participate every day and are willing to help each other in completing the work of the Sprint
- Everyone is required to report how much time was spent on each work item
- No one is allowed to leave the stand-up meeting until all problems raised have been solved
Ans-B
- How could the maintainability of the developing product be improved in a team?
- Apply standard design patterns
- Make refactoring a common practice
- Ensure unit testing is included in the sprint
- All of these
Ans-D
- An Agile project should have ...
- Occasional early deliveries if the business is prepared to accept lower quality
- A regular pattern of delivery of developer-focused products
- A regular pattern of delivery of business-valued increments
- An irregular and unpredictable delivery of products
Ans-C
- How could maintainability of the developing product be improved in a team?
- Apply standard design patterns
- Make refactoring a common practice
- Ensure unit testing is included in the sprint
- All of these
Ans- D
Read More
Top 30 Scrum Exam Questions
- Which of the following is NOT an objective of a Retrospect Sprint Meeting?
- Identify Process Improvements.
- Identify Feature Improvements.
- Identify Best Practices.
- Identify Process problems and bottlenecks.
Ans-B
- Which of the following is a responsibility of the Scrum Master in the context of change in Scrum?
- Eliminating all changes that may affect the quality of deliverables and processes
- Facilitating the identification of Change Requests by the Scrum Team and their assessment and prioritization by the Product Owner.
- Providing requests for changes in a project.
- Approving amended, removed, or added changes according to project requirements and communicating to the Scrum Team.
Ans-B
- Which of the following are roles in the Scrum framework?
- Product Owner
- Project Manager
- Lead Developer
- Business Analyst
Ans-A
- What is most important in all Scrum Teams? A) Self-management B) Clear hierarchies C) Communication D) Continuous improvement
- A, B, C, D
- A, C, D
- A, D
- A, B
Ans-B
- The primary purpose of the daily scrum (daily stand-up) is:
- To give a status report to the ScrumMaster
- To give a status report to the product owner
- Developers inspect how progress is made towards the Sprint Goal and adapt how the remaining work is done accordingly.
- To give team members a chance to take a break from their tasks
Ans-C
- Which one of the following is NOT traditionally an activity of the Scrum framework?
- Sprint planning
- Sprint review
- Sprint retrospective
- Weekly inspection
Ans-D
- The primary purpose of the daily scrum (daily stand-up) is:
- To give a status report to the ScrumMaster
- To give a status report to the product owner
- Developers inspect how progress is made towards the Sprint Goal and adapt how the remaining work is done accordingly.
- To give team members a chance to take a break from their tasks
Ans- C
- Which statement of the following is the best description for sprint?
- A sprint is a condensed amount of time where developers work as many hours as they need to finish the work assigned to them.
- A sprint is a pre-specified amount of time in which the developer’s team works at a sustained pace to complete a chosen set of items from the Product Backlog.
- A sprint is a fixed amount of time set aside for the team to run tests and resolve any outstanding bugs right before the product ships
- A sprint is a pre-specified period during which team members choose individual items from the product backlog to work on. A new article is brought into the sprint as each item is completed.
Ans- B
- What is the Scrum approach to doing design early in a project?
- Having the design up front is always a good idea
- Much design can be done in parallel with implementation because, ideally, both design and implementation are done by the same Scrum Team.
- Design should be done by a separate team from the Scrum team.
- Design has no place in an Agile project
Ans- B
- How can software development projects be executed by implementing the Scrum Framework?
- Complete software packages
- Customer projects
- All kinds of software development projects
- Sub-systems, components, or parts of more extensive systems
Ans- C
- An excellent approach to documentation in Scrum is:
- Do no documentation because it is a waste of time
- Do the necessary documentation to support the development and use of the product
- Do sufficient documentation to prove you have done an excellent job
- Do more documentation than usual because Agile is risky
Ans-B
- Which of the following best describes the approach for determining the Sprint length?
- Sprint should always be 30 days
- The team determines Sprint length by dividing the total number of story points by the average velocity of the team
- Sprint should always be two weeks
- The team should agree on a fixed length of the Sprint, of one month or less
Ans-D
- What should the developers do if the product owner is repeatedly too busy to be available?
- Continue the work, record the assumptions and ask the customer later for input
- Send the customer a written warning that the end product will be completed on time but may not meet their needs
- Allow the Business Analyst to take on the role of Proxy Product Owner
- Draw the problem to the attention of the Scrum Master
Ans-D
- An excellent approach to documentation in Scrum is:
- Do no documentation because it is a waste of time
- Do the necessary documentation to support the development and use of the product
- Do sufficient documentation to prove you have done an excellent job
- Do more documentation than usual because Agile is risky
Ans- B
- Why is it important to trust the team?
- High trust teams do not have to be accountable to each other
- High trust teams do not require a user representative
- The Project Manager does not then have to keep a project schedule
- The presence of trust is positively correlated with the team performance
Ans-D
- In a Scrum Team, we “learn as we go” because
- Planning gets more reliable over time
- Requirements evolve over time
- The collaboration within the team gets better over time
- All of the above
Ans-D
- What are the two primary artifacts of a sprint planning meeting, and what is the related commitment?
- A sprint backlog and sprint goal
- A requirements documents and a Gantt chart
- A requirements documents and a test plan
- A test plan and a Gantt chart
Ans-A
- Which of these statements best describes the Agile approach to teamwork?
- The team should plan to work overtime regularly throughout the project
- The team should expect to work longer hours towards the end of the project to deliver all that was committed to
- The team should strive for a sustainable pace that they can maintain potentially for a long time
- The team will regularly need to work many hours overtime but can compensate for this during periods of less intensity
Ans-C
- Who ultimately decides when the team has enough work for the sprint in planning?
- The ScrumMaster
- The product owner
- The team Developers
- The product owner, ScrumMaster, and team vote to determine when the sprint backlog is full
Ans-C
- Which of the following is the most characteristic of a ScrumMaster?
- Task focused
- Process-oriented
- Supportive
- Disengaged
Ans-C
- The Agile Manifesto states the following values:
- People are more important than contracts
- Working software is valued over comprehensive documentation
- Plans should have priority over the ability to respond
- Contracts should be negotiated which allow control over the people
Ans-B
- The “ MoSCoW “ technique is a popular prioritization technique, where the "M" stands for ...
- May have
- Major
- Must Have
- Mandatory
Ans- C
- The product owner role in a Scrum Teams…
- Has no control over the prioritization of delivered features
- Is accountable for the ordering of items on the Product Backlog
- Collaborates with the developers over the prioritization of features, but the developers have the final decision
- Collaborates with the developers over the prioritization of features, but the business has the final decision
Ans- B
- When handling team dynamics, the ScrumMaster should ......
- Empower the team members within appropriate limits
- Encourage an environment of competition and personal advantage
- Give clear directives to the team about what they should do and how
- Expect team members to be proactive and each work to their priorities and objectives
Ans- A
- Once an Agile project is underway, what should the approach to planning be?
- Should be able to demonstrate control of its progress
- Should have no control over its progress
- Is always out of control
- Is controlled by the velocity of the most junior team member
Ans-A
- What does Scrum advise a team to do with the product backlog items it chooses to bring into the sprint?
- The team should break each product backlog item into work items that preferably take no more than a day.
- The product owner assigns each product backlog item to the specialist best suited to carry the work.
- The team asks the ScrumMaster to research the product backlog items and decide who should work on each one.
- The team doesn't do anything with the product backlog items. Scrum doesn’t use tasks or task lists.
Ans-A
- As per Scrum, which one of the following is an essential feature of the daily stand-up (daily Scrum) meeting?
- The meeting should ensure that it is clear to all which team members are not performing
- All Developers participate every day and are willing to help each other in completing the work of the Sprint
- Everyone is required to report how much time was spent on each work item
- No one is allowed to leave the stand-up meeting until all problems raised have been solved
Ans-B
- How could the maintainability of the developing product be improved in a team?
- Apply standard design patterns
- Make refactoring a common practice
- Ensure unit testing is included in the sprint
- All of these
Ans-D
- An Agile project should have ...
- Occasional early deliveries if the business is prepared to accept lower quality
- A regular pattern of delivery of developer-focused products
- A regular pattern of delivery of business-valued increments
- An irregular and unpredictable delivery of products
Ans-C
- How could maintainability of the developing product be improved in a team?
- Apply standard design patterns
- Make refactoring a common practice
- Ensure unit testing is included in the sprint
- All of these
Ans- D
What is Project Scope Management & How It’s Important in 2022?
What is Project Scope Management & How It’s Important in 2022?
Project scope management indicates a set of procedures that ensure project scope is precisely defined and mapped. The scope management methods enable project professionals to allocate the appropriate number of tasks necessary to complete a project, concerned primarily with controlling what is and what isn't a part of the scope.
The scope knowledge domain is crucial for a project professional, and the PMI also highlights this.
What is Project Scope?
Scope refers to the detailed set of project deliverables. These deliverables are produced from a project's prerequisite. According to PMI PMBOK, the scope is the work that needs to be obtained to deliver a service, product, or outcome with the particular functions and features.
There are three processes for a Project Scope Management which are:
- Planning – happens when an attempt is made to achieve and define the work that requires to be completed.
- Controlling & Monitoring - Focus on document tracking, approving/disapproving project shifts, scope creep, and tracking.
- Closing - includes project deliverable audits and outcome assessment against the actual plan.
Significance of Project Scope Management
If you’re managing a project, observing the expectations of clients and stakeholders can be one of the most strenuous tasks. But with an accurate scope and set deadline, a project professional can seamlessly ensure that timelines are met and time is efficiently utilized throughout the project lifecycle.
The scope management helps in avoiding several common issues like re-examining the budget discussion, regular criteria changing, failure to meet the project timelines, and many more.
Scope management is vital for a long-term project, as it allows measurement of how much labor, cost, and time is required for executing the project. The scope is a crucial factor of project management, and it sets parameters for the shifting features of the project lifecycle.
Steps Involved in Project Scope Management
As a project manager, you have to define scope no matter what practice you select. Let's the steps involved in the project scope management:
Step 1: Define project requirement
Step 2: Understand the objectives of a project
Step 3: Define the project scope
For Step 3, following parameters have to be identified:
- Project objectives
- Goals
- Sub-phases
- Tasks
- Resources
- Budget
- Schedule
Once these specifications are established, the project limitation must be clarified, and the factors not included in the project are identified. Finally, the scope will explain what will and won't be included in the final service/product to team members, stakeholders, and senior executives.
Moreover, the project scope should have a tactile goal for the company undertaking the project. This is central to the project scope as it will play an essential role in how project practices are applied to complete it.
Project Scope Management Processes
1. Plan Scope Management
It's the first process that creates the scope management plan. This plan explains the scope and documents how it will be defined, validated, and controlled. It also includes data on scope creep, tackling change requests, the escalation path for any scope factor disagreement between clients, the process for the scope statement creation, WBS, and how the deliverables will be accepted.
2. Collect Requirements
This involves the documenting of stakeholder's criteria with the stated intent of meeting the project's goals. Here, professionals leverage several tools and practices for collecting project needs from stakeholders.
If this approach is accurately performed, it can drastically minimize the possibility of vexatious surprises as the project moves towards successful completion.
3. Define Project Scope
Here, a detailed description of the project and its relevant deliverables are prepared. The scope correctly states what the project goal is and what it can't achieve.
The supporting documents are verified to ensure that the project will deliver work in line with the stated objectives. The scope that results state the client's requirements and communicates expectations for project execution.
4. Create WBS
The Work Breakdown Structure (WBS) is an essential factor of the scope management process, while many project professionals often skip this procedure - leading to inaccurate project planning.
The WBS offers the project professional and the team with the choice to break down a top-notch scope statement to manageable units of works, known as work packages.
5. Scope Validation
This process focuses mainly on customer acceptance of all the project deliverables. The validate scope happens at the end of each stage; where the customer gives feedback on the tasks performed.
6. Scope Control
This is the last process group of project scope management that involves the monitoring of project status and managing of scope changes. This method involves assessing extra needs from the customer or proactively overlooking scope of the project.
Read More
What is Project Scope Management & How It’s Important in 2022?
Project scope management indicates a set of procedures that ensure project scope is precisely defined and mapped. The scope management methods enable project professionals to allocate the appropriate number of tasks necessary to complete a project, concerned primarily with controlling what is and what isn't a part of the scope.
The scope knowledge domain is crucial for a project professional, and the PMI also highlights this.
What is Project Scope?
Scope refers to the detailed set of project deliverables. These deliverables are produced from a project's prerequisite. According to PMI PMBOK, the scope is the work that needs to be obtained to deliver a service, product, or outcome with the particular functions and features.
There are three processes for a Project Scope Management which are:
- Planning – happens when an attempt is made to achieve and define the work that requires to be completed.
- Controlling & Monitoring - Focus on document tracking, approving/disapproving project shifts, scope creep, and tracking.
- Closing - includes project deliverable audits and outcome assessment against the actual plan.
Significance of Project Scope Management
If you’re managing a project, observing the expectations of clients and stakeholders can be one of the most strenuous tasks. But with an accurate scope and set deadline, a project professional can seamlessly ensure that timelines are met and time is efficiently utilized throughout the project lifecycle.
The scope management helps in avoiding several common issues like re-examining the budget discussion, regular criteria changing, failure to meet the project timelines, and many more.
Scope management is vital for a long-term project, as it allows measurement of how much labor, cost, and time is required for executing the project. The scope is a crucial factor of project management, and it sets parameters for the shifting features of the project lifecycle.
Steps Involved in Project Scope Management
As a project manager, you have to define scope no matter what practice you select. Let's the steps involved in the project scope management:
Step 1: Define project requirement
Step 2: Understand the objectives of a project
Step 3: Define the project scope
For Step 3, following parameters have to be identified:
- Project objectives
- Goals
- Sub-phases
- Tasks
- Resources
- Budget
- Schedule
Once these specifications are established, the project limitation must be clarified, and the factors not included in the project are identified. Finally, the scope will explain what will and won't be included in the final service/product to team members, stakeholders, and senior executives.
Moreover, the project scope should have a tactile goal for the company undertaking the project. This is central to the project scope as it will play an essential role in how project practices are applied to complete it.
Project Scope Management Processes
1. Plan Scope Management
It's the first process that creates the scope management plan. This plan explains the scope and documents how it will be defined, validated, and controlled. It also includes data on scope creep, tackling change requests, the escalation path for any scope factor disagreement between clients, the process for the scope statement creation, WBS, and how the deliverables will be accepted.
2. Collect Requirements
This involves the documenting of stakeholder's criteria with the stated intent of meeting the project's goals. Here, professionals leverage several tools and practices for collecting project needs from stakeholders.
If this approach is accurately performed, it can drastically minimize the possibility of vexatious surprises as the project moves towards successful completion.
3. Define Project Scope
Here, a detailed description of the project and its relevant deliverables are prepared. The scope correctly states what the project goal is and what it can't achieve.
The supporting documents are verified to ensure that the project will deliver work in line with the stated objectives. The scope that results state the client's requirements and communicates expectations for project execution.
4. Create WBS
The Work Breakdown Structure (WBS) is an essential factor of the scope management process, while many project professionals often skip this procedure - leading to inaccurate project planning.
The WBS offers the project professional and the team with the choice to break down a top-notch scope statement to manageable units of works, known as work packages.
5. Scope Validation
This process focuses mainly on customer acceptance of all the project deliverables. The validate scope happens at the end of each stage; where the customer gives feedback on the tasks performed.
6. Scope Control
This is the last process group of project scope management that involves the monitoring of project status and managing of scope changes. This method involves assessing extra needs from the customer or proactively overlooking scope of the project.
Why Leadership a Necessity in Today's Digital Era?
Why Leadership a Necessity in Today's Digital Era?
The world as we witness today has seen a drastic transformation towards the digital era. The companies have highlighted more on digital shift to keep pace with the change all around.
Digital transformation can be disorienting and can cause panic. However, successful luminaries realize that 'Digital' isn't so much a thing to get hold of within an industry or a company; instead, an era needs an ever-evolving mindset and intentional investment in the suitable potential.
Famous business leaders such as Steve Jobs, Elon Musk, and Bill Gates have accepted the digital shift and adapted to it quickly with their top-notch leadership skills, making them stand out as leaders.
With the advent of technology, these leaders have upgraded their skills that go hand-in-hand with the relevant transformation. Enhanced skills have enabled the belief of doing things by the influential luminaries of today.
What exactly are these digital era leadership skills that set the leaders apart from the rest?
Leadership skills are required to interact, encourage, and persuade individuals to align with a goal or vision. As leaders look for long-term, they must create conditions that enable digital maturity, attract the best talent, and bring out the best in the talent pool they captivate.
Before diving into the skills that make you a standout leader, let's look at the characteristics of a good leader.
The Characteristic of a Good Leader
1. Dedication to the Organizational Mission
Being dedicated to the goal and purpose of a company takes a lot of effort and strong commitment, and it's this dedication that will make you different from others.
They introduce effective communication and an exuberant willingness in everyone that improve organizational and personal development. Proficient luminaries develop this readiness through trust and understanding of the member's perspective of the company.
2. The Wish to Lead
It's a known fact that leaders always pave the path for their followers, and they wish to lead is a leadership characteristic of utmost importance. Without the readiness to lead, it becomes strenuous to become a luminary of your team or company.
Without the desire, you won't be able to pitch in the effort to attain the skills for the modern digital era to encourage others and complete the tasks.
3. Integrity
A successful leader always has the characteristic of integrity. Integrity is defined as being true to their word, being authentic, and having behavioral power you might want to see in your workforce.
Leaders with integrity traits are sincere, maintain consistency in their work, and accept responsibility for their errors.
The Leadership Skills You Require in Digital Reign
Now that we have discusses the three main characteristics of a leader, let's see leadership skills that will aid you in becoming a great leader:
1. Possessing Creative Edge
Creativity has no boundaries and offers everyone several choices to explore things. But, when it comes to the creative leader, they're those who think out of the box, has emotional intelligence, and develop possibilities that fit right in with the enormous technological phase change.
As a leader, getting creative at work empowers your workforce to be more open regarding ideas and thoughts upfront. This leader characteristic offers more credible odds to your company to merge well with the transformations.
2. Proficiency in Technology
As our world keeps transforming swiftly, technology has taken over everything - enhancing every sector of business. Technically proficient leaders see the big picture that technology can play in a company.
It's one of the vital skills a leader must have that help them gain knowledge on organization strength, the products/services, and the potential to solve technical problems.
Technological proficiency will also help you display yourself as a leader for the future who is well-equipped with ideas with problem-solving expertise.
3. Learning & Re-learning
With the pace at which our world is transforming, adaptability remains the best deal for leaders in the current business situation. Digital disruption has been rising, and flexible leaders understand the significance of being relevant in the game and keeping their career curve steady.
Leaders must understand the new work process tactic and behaviors to learn business and workflows in the modern digital era. In the same way, it's essential that you go back to the fundamentals, re-learn and start new with fresh tactics and techniques that have given the digital change.
This will offer you a new perspective on the current transformations and aid you in dealing with the phase shift.
4. Agility
Agility means the ability of a person to think and understand rapidly. In today's swift-paced corporate and evolving digital environment, it has become crucial for anyone to adapt quickly. However, this is only possible if leaders are open to changes and have an agile mind.
The sound and clear mind of a leader can work well across cultures and encourage employees. Hence leadership agility offers you the skill to make wise and effective decisions in swiftly changing tech lives.
5. Collaborative
Individual contributors and talent can turn out to be crucial across any company. However, when there is a team play, it becomes daunting for your competitors to take you down. But this sense of collaboration comes into action only from your leadership trait.
It's central to employ a team that works cohesively, creating an environment where collaboration is present. You, as a leader, have to do more than tell employees what they require to operate.
It's no piece of cake to develop any skill overnight. Patience, communication, hard work, and perseverance are the essentials here. Just give yourself some time to process the shifts going around you.
Learn from it, explore and welcome the infinite potential you will achieve as a leader. You can create opportunities for your workforce with these flourishing skills and prepare them for their future development.
Read More
Why Leadership a Necessity in Today's Digital Era?
The world as we witness today has seen a drastic transformation towards the digital era. The companies have highlighted more on digital shift to keep pace with the change all around.
Digital transformation can be disorienting and can cause panic. However, successful luminaries realize that 'Digital' isn't so much a thing to get hold of within an industry or a company; instead, an era needs an ever-evolving mindset and intentional investment in the suitable potential.
Famous business leaders such as Steve Jobs, Elon Musk, and Bill Gates have accepted the digital shift and adapted to it quickly with their top-notch leadership skills, making them stand out as leaders.
With the advent of technology, these leaders have upgraded their skills that go hand-in-hand with the relevant transformation. Enhanced skills have enabled the belief of doing things by the influential luminaries of today.
What exactly are these digital era leadership skills that set the leaders apart from the rest?
Leadership skills are required to interact, encourage, and persuade individuals to align with a goal or vision. As leaders look for long-term, they must create conditions that enable digital maturity, attract the best talent, and bring out the best in the talent pool they captivate.
Before diving into the skills that make you a standout leader, let's look at the characteristics of a good leader.
The Characteristic of a Good Leader
1. Dedication to the Organizational Mission
Being dedicated to the goal and purpose of a company takes a lot of effort and strong commitment, and it's this dedication that will make you different from others.
They introduce effective communication and an exuberant willingness in everyone that improve organizational and personal development. Proficient luminaries develop this readiness through trust and understanding of the member's perspective of the company.
2. The Wish to Lead
It's a known fact that leaders always pave the path for their followers, and they wish to lead is a leadership characteristic of utmost importance. Without the readiness to lead, it becomes strenuous to become a luminary of your team or company.
Without the desire, you won't be able to pitch in the effort to attain the skills for the modern digital era to encourage others and complete the tasks.
3. Integrity
A successful leader always has the characteristic of integrity. Integrity is defined as being true to their word, being authentic, and having behavioral power you might want to see in your workforce.
Leaders with integrity traits are sincere, maintain consistency in their work, and accept responsibility for their errors.
The Leadership Skills You Require in Digital Reign
Now that we have discusses the three main characteristics of a leader, let's see leadership skills that will aid you in becoming a great leader:
1. Possessing Creative Edge
Creativity has no boundaries and offers everyone several choices to explore things. But, when it comes to the creative leader, they're those who think out of the box, has emotional intelligence, and develop possibilities that fit right in with the enormous technological phase change.
As a leader, getting creative at work empowers your workforce to be more open regarding ideas and thoughts upfront. This leader characteristic offers more credible odds to your company to merge well with the transformations.
2. Proficiency in Technology
As our world keeps transforming swiftly, technology has taken over everything - enhancing every sector of business. Technically proficient leaders see the big picture that technology can play in a company.
It's one of the vital skills a leader must have that help them gain knowledge on organization strength, the products/services, and the potential to solve technical problems.
Technological proficiency will also help you display yourself as a leader for the future who is well-equipped with ideas with problem-solving expertise.
3. Learning & Re-learning
With the pace at which our world is transforming, adaptability remains the best deal for leaders in the current business situation. Digital disruption has been rising, and flexible leaders understand the significance of being relevant in the game and keeping their career curve steady.
Leaders must understand the new work process tactic and behaviors to learn business and workflows in the modern digital era. In the same way, it's essential that you go back to the fundamentals, re-learn and start new with fresh tactics and techniques that have given the digital change.
This will offer you a new perspective on the current transformations and aid you in dealing with the phase shift.
4. Agility
Agility means the ability of a person to think and understand rapidly. In today's swift-paced corporate and evolving digital environment, it has become crucial for anyone to adapt quickly. However, this is only possible if leaders are open to changes and have an agile mind.
The sound and clear mind of a leader can work well across cultures and encourage employees. Hence leadership agility offers you the skill to make wise and effective decisions in swiftly changing tech lives.
5. Collaborative
Individual contributors and talent can turn out to be crucial across any company. However, when there is a team play, it becomes daunting for your competitors to take you down. But this sense of collaboration comes into action only from your leadership trait.
It's central to employ a team that works cohesively, creating an environment where collaboration is present. You, as a leader, have to do more than tell employees what they require to operate.
It's no piece of cake to develop any skill overnight. Patience, communication, hard work, and perseverance are the essentials here. Just give yourself some time to process the shifts going around you.
Learn from it, explore and welcome the infinite potential you will achieve as a leader. You can create opportunities for your workforce with these flourishing skills and prepare them for their future development.
How Extended Reality (XR) Enhance the Visual Learning Process?
How Extended Reality (XR) Enhance the Visual Learning Process?
Is there a role for Virtual Reality (VR) and Augmented Reality (AR) in the visual learning process? From a particular perspective, when we leverage modern technology, we learn new and different things, from how to chance on an electronic originator.
You might be an IT, education manager, or both and are interested in finding modern VR and AR technologies that can speed up learning in any sector. And it's just to say that numerous teaching methods are based on presenting learners with facts.
Students who can retain facts seamlessly are successful, while those who struggle to process massive information at once can become disengaged. This applies to all sorts of students - school environment, workplace training program, or a lifelong education.
Some people are visual learners, which means the potential to see a process rather than read or hear about it. This is where AR and VR add value to the education process.
As technological change advances in the education sector, the Extended Reality (XR), the next big thing in the EdTech sector, creates immersive worlds where students can visualize concepts and interactively learn new information and skills.
Educators worldwide are beginning to realize the surplus benefits of leveraging XR technology in education, and a study predicts the worldwide AR/VR market in learning to reach $22.7Bn by 2027.
In this article, we will see five main reasons to be optimistic about the revolutionization of future education by XR technology.
5 Ways XR Could Transform Visual Learning Process
1. Creating an Immersive Classroom Experience
Adopting XR tech in education can significantly transform how we teach and learn. What sounds more captivating - learning from a book or putting on a VR headset to visualize concepts?
The second choice rings a bell, doesn't it?
Most students are visual learners, so they get more out of XR technology than traditional spoon-feeding knowledge techniques. Moreover, studies show retention rates are more significant for students who learn through immersive sessions.
2. Redefining Hands-on Learning
Observational learning is an engaged learning procedure in which students learn through experimenting and reflecting on the experience. However, several schools don't have the budget to build labs or afford modern lab devices.
Moreover, amid the pandemic, institutions are shifting to online education, which lacks practical aspects. Merging XR technology in learning provides a realistic, practical learning procedure.
AR/VR presents a secure setting for learners to practice high-risk experiments. Thus, students can experiment with critical tasks such as medical operations, machinery training, and more.
A secure virtual setting ensures students can commit mistakes and learn from those without the concern of real-life scenarios.
3. Enhancing Learning Outcomes
Adopting XR technology in schools needs drastic funding, which has people concerned about the effectiveness of XR in education. However, XR is not just a hot buzzword in the industry that will fade away when given the time. Reports and experiments back up the claim that VR can transform the way we learn and teach.
In recent research, Google Daydream Labs taught two groups to operate an espresso machine, one with YouTube videos and another with VR tech. The outcomes from the experiment displayed that VR learners understood quicker and made few mistakes.
Stanford University and Technical University Demarked revealed that merging XR tech-enhanced memory retention rates by 76 percent compared to routine learning procedures.
This shows that XR has the power to become the new norm in education.
4. Social and Collaborative Learning
Whether earning a career choice, growing your network, or enhancing customer experience, knowing how to interact is the main factor. Unfortunately, in traditional or online learning, students often don't get the opportunity to interact with individuals from different parts of the world.
However, XR takes social collaboration to the next level, as learners can interact with others through virtual conferences, VR avatars, and more, leading to increased diversity and enabling them to join virtual events.
5. Long-term Learning Experience
Education doesn't have a limit, so your learning won't cease after college graduation. XR tech can aid individuals of all ages to keep learning and expanding their knowledge - learning a new language, other soft skills, or practicing public speaking.
Today, XR is also offering benefits to corporate training. With the technology, workforces can practice risky tasks in an AR/VR setting. Whether school, college, or corporate training, XR tech can make learning fun, engaging, and interactive.
There are several perks to adopting XR tech into the learning process. Leveraging XR is a promising method for delivering an innovative, engaging learning experience. Given the current state of rapid tech developments, XR will become more accessible and budget-oriented.
Read More
How Extended Reality (XR) Enhance the Visual Learning Process?
Is there a role for Virtual Reality (VR) and Augmented Reality (AR) in the visual learning process? From a particular perspective, when we leverage modern technology, we learn new and different things, from how to chance on an electronic originator.
You might be an IT, education manager, or both and are interested in finding modern VR and AR technologies that can speed up learning in any sector. And it's just to say that numerous teaching methods are based on presenting learners with facts.
Students who can retain facts seamlessly are successful, while those who struggle to process massive information at once can become disengaged. This applies to all sorts of students - school environment, workplace training program, or a lifelong education.
Some people are visual learners, which means the potential to see a process rather than read or hear about it. This is where AR and VR add value to the education process.
As technological change advances in the education sector, the Extended Reality (XR), the next big thing in the EdTech sector, creates immersive worlds where students can visualize concepts and interactively learn new information and skills.
Educators worldwide are beginning to realize the surplus benefits of leveraging XR technology in education, and a study predicts the worldwide AR/VR market in learning to reach $22.7Bn by 2027.
In this article, we will see five main reasons to be optimistic about the revolutionization of future education by XR technology.
5 Ways XR Could Transform Visual Learning Process
1. Creating an Immersive Classroom Experience
Adopting XR tech in education can significantly transform how we teach and learn. What sounds more captivating - learning from a book or putting on a VR headset to visualize concepts?
The second choice rings a bell, doesn't it?
Most students are visual learners, so they get more out of XR technology than traditional spoon-feeding knowledge techniques. Moreover, studies show retention rates are more significant for students who learn through immersive sessions.
2. Redefining Hands-on Learning
Observational learning is an engaged learning procedure in which students learn through experimenting and reflecting on the experience. However, several schools don't have the budget to build labs or afford modern lab devices.
Moreover, amid the pandemic, institutions are shifting to online education, which lacks practical aspects. Merging XR technology in learning provides a realistic, practical learning procedure.
AR/VR presents a secure setting for learners to practice high-risk experiments. Thus, students can experiment with critical tasks such as medical operations, machinery training, and more.
A secure virtual setting ensures students can commit mistakes and learn from those without the concern of real-life scenarios.
3. Enhancing Learning Outcomes
Adopting XR technology in schools needs drastic funding, which has people concerned about the effectiveness of XR in education. However, XR is not just a hot buzzword in the industry that will fade away when given the time. Reports and experiments back up the claim that VR can transform the way we learn and teach.
In recent research, Google Daydream Labs taught two groups to operate an espresso machine, one with YouTube videos and another with VR tech. The outcomes from the experiment displayed that VR learners understood quicker and made few mistakes.
Stanford University and Technical University Demarked revealed that merging XR tech-enhanced memory retention rates by 76 percent compared to routine learning procedures.
This shows that XR has the power to become the new norm in education.
4. Social and Collaborative Learning
Whether earning a career choice, growing your network, or enhancing customer experience, knowing how to interact is the main factor. Unfortunately, in traditional or online learning, students often don't get the opportunity to interact with individuals from different parts of the world.
However, XR takes social collaboration to the next level, as learners can interact with others through virtual conferences, VR avatars, and more, leading to increased diversity and enabling them to join virtual events.
5. Long-term Learning Experience
Education doesn't have a limit, so your learning won't cease after college graduation. XR tech can aid individuals of all ages to keep learning and expanding their knowledge - learning a new language, other soft skills, or practicing public speaking.
Today, XR is also offering benefits to corporate training. With the technology, workforces can practice risky tasks in an AR/VR setting. Whether school, college, or corporate training, XR tech can make learning fun, engaging, and interactive.
There are several perks to adopting XR tech into the learning process. Leveraging XR is a promising method for delivering an innovative, engaging learning experience. Given the current state of rapid tech developments, XR will become more accessible and budget-oriented.
Top 10 Machine Learning Algorithms You Need to Know in 2022
Top 10 Machine Learning Algorithms You Need to Know in 2022
In a world where the definition of manual is transforming to automation, the Machine Learning (ML) algorithm makes the word 'Impossible' a reality. Technology can help computers play chess, perform surgeries, and even become more personal and innovative.
Living in a period of constant technological progress, computing has evolved drastically over the years; hence, we can predict what's to come shortly.
A primary aspect of this upgrade is how computing tools and methods have been democratized. Over the last five years, data scientists have built trailblazing data-crunching machines by optimally functioning advanced techniques. The results have been phenomenal.
If you're one of the data scientists or ML aspirants, then you should get a catch of Machine Learning algorithms.
In this article, we'll discuss the top 10 Machine Learning Algorithms you need to know in 2022, so let's get started.
Top 10 Machine Learning Algorithms
1. Linear Regression
This process establishes the relationship between dependent and independent variables by fitting them to a line. This line is called the regression line and is represented using an equation:
Y= a *X + b
Where,
Y = Dependent Variable
a = Slope
X = Independent variable
b = Intercept
The coefficients a & b are derived by minimizing the sum of the squared difference of distance between data points and regression line.
2. Logistic Regression
This process estimates the discrete values from an independent variable set. It helps predict the probability of an event by fitting data to a logit function, called logit regression.
The methods that can help enhance the logistic regression include interaction terms, a non-linear model, eradicating features, and regularizing techniques.
3. Decision Tree
This is one of the widely popular and used algorithms of Machine learning. It's a supervised learning algorithm that is used for classifying problems. It works with the classification of both continuous and categorical dependent variables.
In the Decision Tree algorithm, we split the population into two/more homogeneous sets based on the relevant attributes.
4. Support Vector Machine (SVM)
This process is used to classify algorithms in which you plot raw data as points in an n-dimensional space. The value of each attribute is then tied to a specific coordinate, making it seamless to classify the data.
Lines known as classifiers can be leveraged to plot the data and plot them on a graph.
5. Naïve Bayes
This classifier assumes that the presence of a specific feature in a class is unrelated to the presence of any other attribute. Even if these features are related, a Naive Bayes algorithm would consider all of these factors independently when calculating the probability of a specific outcome.
Moreover, this algorithm is easy to develop and is helpful for colossal datasets. A simple Naive Bayesian model is known to outperform highly sophisticated classification techniques.
6. K-Nearest Neighbors (KNN)
KNN is a more widely leveraged algorithm to solve classification problems; however, this technique can also be applied to regression problems. This simple algorithm stores all available cases and classifies new cases by taking a majority vote of its k-neighbors.
The case is then given to the class with the most similarity. Finally, a distance function executes this measurement.
Though the KNN has some perks; however, you must be exceptionally considerate on selecting KNN as they're computationally expensive, its variables must be normalized (else higher range variables can bias the model), and the data requires pre-processing.
7. K-Means
K-Means is an unsupervised learning algorithm that solves clustering problems. Datasets are classified into a certain number of clusters so that all the data points within a cluster are hetero and homogeneous from other cluster data.
Let's see how K-Means form clusters.
- The K-Means algorithm picks the 'k' number of points known as centroid for each cluster.
- Each data point forms a cluster with the nearest centroids (K clusters)
- Now, it creates new centroids based on the existing cluster members.
- The nearest distance for each data point is estimated with the new centroids. This process continues until the centroids don't change.
8. Random Forest Algorithm
A collective of decision trees is known as a Random Forest, which is leveraged to classify a new object based on its attributes, where each tree is classified, and the tree votes for that class. The forest selects the classification having the most votes.
How are these trees planted and grown?
- If the number of cases is 'N' in the training set, the sample of N cases is taken randomly. This sample will be the training set for tree growing.
- Suppose there are 'M' input variables, a number m << M is specified such that at each node, 'm' variables are chosen randomly from the 'M,' and the best split on this 'm' is leveraged to split the node. The value of 'm' is held constant during this process.
- Each tree is grown to the most substantial extent possible, and there's no pruning.
9. Dimensionality Reduction
In the modern world, a massive amount of data is being analyzed and stored by govt agencies, research organizations, and corporates. If you're a data scientist, you know that this raw data contains several pieces of information, and the quest is to determine relevant patterns and variables.
To determine essential details, Dimensionality Reduction such as Factor Analysis, Random Forest, Decision Tree, and Missing Value Ration can be helpful.
10. Gradient Boosting & AdaBoosting
These boosting algorithms are leveraged when colossal data loads have to be handled to create predictions with top-notch accuracy. Boosting is an ensemble learning algorithm that merges the predictive power of many base estimators to enhance robustness.
These algorithms work top-class in data science competitions such as CrowdAnalytix, Kaggle, and AV Hackathon. These are the most preferred ML algorithms today and can be leveraged along with R Codes and Python to achieve precise results.
Concluding Thoughts
If you want to develop a career in ML, start now. The field is sky-rocketing, and the sooner you understand the scope of ML techniques, the better you'll be able to offer solutions to challenging workplace issues.
However, if you're looking forward to becoming one, enroll in our ML certification training course to learn new software trends, emerging techniques, customizing considerations, and core competencies needed by a Machine Learning expert.
By opting for iCert Global's certification training course, we ensure that you ace the role of a Machine Learning professional in any organization.
Read More
Top 10 Machine Learning Algorithms You Need to Know in 2022
In a world where the definition of manual is transforming to automation, the Machine Learning (ML) algorithm makes the word 'Impossible' a reality. Technology can help computers play chess, perform surgeries, and even become more personal and innovative.
Living in a period of constant technological progress, computing has evolved drastically over the years; hence, we can predict what's to come shortly.
A primary aspect of this upgrade is how computing tools and methods have been democratized. Over the last five years, data scientists have built trailblazing data-crunching machines by optimally functioning advanced techniques. The results have been phenomenal.
If you're one of the data scientists or ML aspirants, then you should get a catch of Machine Learning algorithms.
In this article, we'll discuss the top 10 Machine Learning Algorithms you need to know in 2022, so let's get started.
Top 10 Machine Learning Algorithms
1. Linear Regression
This process establishes the relationship between dependent and independent variables by fitting them to a line. This line is called the regression line and is represented using an equation:
Y= a *X + b
Where,
Y = Dependent Variable
a = Slope
X = Independent variable
b = Intercept
The coefficients a & b are derived by minimizing the sum of the squared difference of distance between data points and regression line.
2. Logistic Regression
This process estimates the discrete values from an independent variable set. It helps predict the probability of an event by fitting data to a logit function, called logit regression.
The methods that can help enhance the logistic regression include interaction terms, a non-linear model, eradicating features, and regularizing techniques.
3. Decision Tree
This is one of the widely popular and used algorithms of Machine learning. It's a supervised learning algorithm that is used for classifying problems. It works with the classification of both continuous and categorical dependent variables.
In the Decision Tree algorithm, we split the population into two/more homogeneous sets based on the relevant attributes.
4. Support Vector Machine (SVM)
This process is used to classify algorithms in which you plot raw data as points in an n-dimensional space. The value of each attribute is then tied to a specific coordinate, making it seamless to classify the data.
Lines known as classifiers can be leveraged to plot the data and plot them on a graph.
5. Naïve Bayes
This classifier assumes that the presence of a specific feature in a class is unrelated to the presence of any other attribute. Even if these features are related, a Naive Bayes algorithm would consider all of these factors independently when calculating the probability of a specific outcome.
Moreover, this algorithm is easy to develop and is helpful for colossal datasets. A simple Naive Bayesian model is known to outperform highly sophisticated classification techniques.
6. K-Nearest Neighbors (KNN)
KNN is a more widely leveraged algorithm to solve classification problems; however, this technique can also be applied to regression problems. This simple algorithm stores all available cases and classifies new cases by taking a majority vote of its k-neighbors.
The case is then given to the class with the most similarity. Finally, a distance function executes this measurement.
Though the KNN has some perks; however, you must be exceptionally considerate on selecting KNN as they're computationally expensive, its variables must be normalized (else higher range variables can bias the model), and the data requires pre-processing.
7. K-Means
K-Means is an unsupervised learning algorithm that solves clustering problems. Datasets are classified into a certain number of clusters so that all the data points within a cluster are hetero and homogeneous from other cluster data.
Let's see how K-Means form clusters.
- The K-Means algorithm picks the 'k' number of points known as centroid for each cluster.
- Each data point forms a cluster with the nearest centroids (K clusters)
- Now, it creates new centroids based on the existing cluster members.
- The nearest distance for each data point is estimated with the new centroids. This process continues until the centroids don't change.
8. Random Forest Algorithm
A collective of decision trees is known as a Random Forest, which is leveraged to classify a new object based on its attributes, where each tree is classified, and the tree votes for that class. The forest selects the classification having the most votes.
How are these trees planted and grown?
- If the number of cases is 'N' in the training set, the sample of N cases is taken randomly. This sample will be the training set for tree growing.
- Suppose there are 'M' input variables, a number m << M is specified such that at each node, 'm' variables are chosen randomly from the 'M,' and the best split on this 'm' is leveraged to split the node. The value of 'm' is held constant during this process.
- Each tree is grown to the most substantial extent possible, and there's no pruning.
9. Dimensionality Reduction
In the modern world, a massive amount of data is being analyzed and stored by govt agencies, research organizations, and corporates. If you're a data scientist, you know that this raw data contains several pieces of information, and the quest is to determine relevant patterns and variables.
To determine essential details, Dimensionality Reduction such as Factor Analysis, Random Forest, Decision Tree, and Missing Value Ration can be helpful.
10. Gradient Boosting & AdaBoosting
These boosting algorithms are leveraged when colossal data loads have to be handled to create predictions with top-notch accuracy. Boosting is an ensemble learning algorithm that merges the predictive power of many base estimators to enhance robustness.
These algorithms work top-class in data science competitions such as CrowdAnalytix, Kaggle, and AV Hackathon. These are the most preferred ML algorithms today and can be leveraged along with R Codes and Python to achieve precise results.
Concluding Thoughts
If you want to develop a career in ML, start now. The field is sky-rocketing, and the sooner you understand the scope of ML techniques, the better you'll be able to offer solutions to challenging workplace issues.
However, if you're looking forward to becoming one, enroll in our ML certification training course to learn new software trends, emerging techniques, customizing considerations, and core competencies needed by a Machine Learning expert.
By opting for iCert Global's certification training course, we ensure that you ace the role of a Machine Learning professional in any organization.
Project scope management and its importance in 2022
Project scope management and its importance in 2022
Project scope management has always been one of the most challenging tasks for project managers, and it's getting even more difficult. Today, more and more businesses are asking for better project scope management tools due to the continuous growth of software projects.
Project scope management is one of the essential tasks in an entire project plan. A team must manage all critical aspects of the project and ensure it is completed successfully.
The term project scope management has been getting much attention lately. This is new, but it's becoming popular in architecture and construction. However, many questions about it have been raised by people unaware of its importance or how it works. People may ask some honest answers about this method for planning projects, but for now, let's start looking at what that means and how to use it.
What is project scope management?
Project scope management is the systematic process of defining project objectives, assigning responsibilities, and making decisions to ensure that a project stays within the defined boundaries.
Project scope management is an essential aspect of project management because it defines the boundaries of a project and ensures that the team members stay within those boundaries throughout their work. In this way, it helps to ensure that budget, time, and other resources are used appropriately and effectively.
It provides a framework for managing projects by defining what needs to be done and setting realistic expectations about how long it will take. It also identifies risks associated with the project. Finally, it makes sure that these risks are adequately managed so as not to affect other aspects of the project's execution.
How do you define the scope of a project?
The scope is the range of activity within which a project team is responsible for working. All projects have content, but not all projects have an area that is clearly defined to all stakeholders.
The project manager and sponsor define the scope in response to stakeholder input, such as user requirements, organizational goals, project constraints, and risk factors.
From the beginning of a project, it should be clear to all involved stakeholders to work together toward delivering a successful solution using agreed-upon processes and methods.
Why is scope management critical?
Scope management is about managing the work scope, which is the amount of work that needs to be done and by when.
Scope management is essential because it allows you to deliver the right product on time and within budget. Without scope management, you could end up having a product that doesn't meet your requirements or doesn't meet your customers' expectations.
Project scope management process

Planning scope management
Planning scope management is a process that enables the project manager to have a clear view of the overall project, including its objectives and end-states. The planning scope management process is the process whereby a project scope is developed and managed. Planning scope management includes:
- Defining and documenting the goals, objectives, and constraints of the project.
- Estimating key performance indicators (KPIs) for each phase of the project.
- We are defining the boundaries of each phase of the project.
- It identifies risks associated with each phase of the project.
Collecting requirements
Collecting requirements is the second step of the project scope management process. The requirements are collected from all stakeholders, including customers, end-users, and your staff. The requirements should be documented in a clear, concise, and unambiguous format. The requirements document should include:
- Project objectives
- Scope statement
- Billing information for each procedure
- Technical design specification (TDS)
Defining the scope
When it comes to managing the scope of your project, there are many different ways to go about it.
One way is to define what you want in detail and then ensure that the person doing the work defines their scope based on that. This is a widespread practice and one which works very well for projects with tight deadlines and limited budgets.
However, in more complex situations, this can be not easy because there might be more than one person working on a project, and they may not all agree on how things should be done. In these situations, it's usually better to let them work out their scopes and then provide feedback after the fact.
This ensures that everyone understands what needs to be done and when it needs to happen, which can help avoid confusion later on down the line.
Making a project breakdown structure
A project breakdown structure (PBS) is a model that describes all the components of a project, including their dependencies and relationships.
The purpose of a PBS is to show clearly how each part of a project fits together and relates to other factors. The PBS can be used as a reference when trying to figure out where something belongs in your project or if you need to revise your plan. A good PBS should have the following characteristics:
- It should be easy to understand. It shouldn't contain too many details and focus on the key issues.
- It should be clear how each component fits together with other features and with the overall goal of your project.
- It should be easy for people working on your team to understand what's happening in different parts of your project — mainly because people often don't know much about technology or business concepts at first!
Validating scope
The most critical part of project scope management is validating the scope. It's not enough to know what you're supposed to do; you need to ensure you can do it. The process should involve several steps:
Define the scope. This is the most crucial step since it helps you define what your project is supposed to accomplish. You should determine the content as clearly as possible so that everyone involved understands exactly what needs to be done and how long it will take.
Identify dependencies. Many factors can affect your ability to deliver on time or under budget. Still, one of the biggest is having too much work or too little time. For example, suppose your company has an aggressive sales goal for this quarter. In that case, it's going to be difficult for anyone on your team if they have only two weeks' worth of work left before being unable to meet their goals – but if they have nine months' worth of work left, then they could easily fit everything in those extra three weeks and still hit their goals.
Identify risks and constraints. Risk management is about identifying potential problems before they occur so that you can prevent them from happening by taking action now rather than later. This can include identifying.
Controlling scope
By controlling scope, you ensure that the project is on track and within budget. You can do this by developing a detailed plan with accurate estimates of all costs associated with the project. The client and stakeholders should approve this plan before you begin work.
For example, suppose you are working on a new website for your company. In that case, you will need to determine what features will be included in the final product (such as additional pages or functionality).
Once you have determined what features are needed, you can create a list of tasks that will be completed during the next development phase. By controlling the scope at this point, you ensure everything is done correctly and on time.
Another way to control scope is by creating multiple product versions before launch. This allows you to test different features and see which ones work best before launching them publicly.
Why is project scope management important in 2022 and beyond?
For 2022 and beyond, Project scope management is critical because it helps ensure that the project objective is met. In other words, it provides that the project will not be over budget or take longer than expected. It also ensures that the project will be completed on time and with as few resources as possible.
Another reason is that it helps avoid costly rework later in the project. For example, if there are changes to the scope of a project, it often means that work will have to start again from scratch. This can be very costly for businesses and organizations because it takes time to build up the skills needed for a new project. This lost time can't be used on something else productive.
Scope management is essential when many stakeholders are involved in a project, such as when evaluating an environmental impact study or building an oil refinery plant. Stakeholders want to know what needs to be done to participate in decision-making processes and make informed decisions about how their projects should go forward with minimal risk of negative consequences.
Conclusion
Like its big brother, PDM (Project Data Management), Project Scope Management has many benefits for both organizations and project managers. A full 20% percent of global project management budgets would be allocated to scope management, and why not? The scope of any project is arguably the most important thing that any project manager has to deal with; it makes sense.
Read More
Project scope management and its importance in 2022
Project scope management has always been one of the most challenging tasks for project managers, and it's getting even more difficult. Today, more and more businesses are asking for better project scope management tools due to the continuous growth of software projects.
Project scope management is one of the essential tasks in an entire project plan. A team must manage all critical aspects of the project and ensure it is completed successfully.
The term project scope management has been getting much attention lately. This is new, but it's becoming popular in architecture and construction. However, many questions about it have been raised by people unaware of its importance or how it works. People may ask some honest answers about this method for planning projects, but for now, let's start looking at what that means and how to use it.
What is project scope management?
Project scope management is the systematic process of defining project objectives, assigning responsibilities, and making decisions to ensure that a project stays within the defined boundaries.
Project scope management is an essential aspect of project management because it defines the boundaries of a project and ensures that the team members stay within those boundaries throughout their work. In this way, it helps to ensure that budget, time, and other resources are used appropriately and effectively.
It provides a framework for managing projects by defining what needs to be done and setting realistic expectations about how long it will take. It also identifies risks associated with the project. Finally, it makes sure that these risks are adequately managed so as not to affect other aspects of the project's execution.
How do you define the scope of a project?
The scope is the range of activity within which a project team is responsible for working. All projects have content, but not all projects have an area that is clearly defined to all stakeholders.
The project manager and sponsor define the scope in response to stakeholder input, such as user requirements, organizational goals, project constraints, and risk factors.
From the beginning of a project, it should be clear to all involved stakeholders to work together toward delivering a successful solution using agreed-upon processes and methods.
Why is scope management critical?
Scope management is about managing the work scope, which is the amount of work that needs to be done and by when.
Scope management is essential because it allows you to deliver the right product on time and within budget. Without scope management, you could end up having a product that doesn't meet your requirements or doesn't meet your customers' expectations.
Project scope management process
Planning scope management
Planning scope management is a process that enables the project manager to have a clear view of the overall project, including its objectives and end-states. The planning scope management process is the process whereby a project scope is developed and managed. Planning scope management includes:
- Defining and documenting the goals, objectives, and constraints of the project.
- Estimating key performance indicators (KPIs) for each phase of the project.
- We are defining the boundaries of each phase of the project.
- It identifies risks associated with each phase of the project.
Collecting requirements
Collecting requirements is the second step of the project scope management process. The requirements are collected from all stakeholders, including customers, end-users, and your staff. The requirements should be documented in a clear, concise, and unambiguous format. The requirements document should include:
- Project objectives
- Scope statement
- Billing information for each procedure
- Technical design specification (TDS)
Defining the scope
When it comes to managing the scope of your project, there are many different ways to go about it.
One way is to define what you want in detail and then ensure that the person doing the work defines their scope based on that. This is a widespread practice and one which works very well for projects with tight deadlines and limited budgets.
However, in more complex situations, this can be not easy because there might be more than one person working on a project, and they may not all agree on how things should be done. In these situations, it's usually better to let them work out their scopes and then provide feedback after the fact.
This ensures that everyone understands what needs to be done and when it needs to happen, which can help avoid confusion later on down the line.
Making a project breakdown structure
A project breakdown structure (PBS) is a model that describes all the components of a project, including their dependencies and relationships.
The purpose of a PBS is to show clearly how each part of a project fits together and relates to other factors. The PBS can be used as a reference when trying to figure out where something belongs in your project or if you need to revise your plan. A good PBS should have the following characteristics:
- It should be easy to understand. It shouldn't contain too many details and focus on the key issues.
- It should be clear how each component fits together with other features and with the overall goal of your project.
- It should be easy for people working on your team to understand what's happening in different parts of your project — mainly because people often don't know much about technology or business concepts at first!
Validating scope
The most critical part of project scope management is validating the scope. It's not enough to know what you're supposed to do; you need to ensure you can do it. The process should involve several steps:
Define the scope. This is the most crucial step since it helps you define what your project is supposed to accomplish. You should determine the content as clearly as possible so that everyone involved understands exactly what needs to be done and how long it will take.
Identify dependencies. Many factors can affect your ability to deliver on time or under budget. Still, one of the biggest is having too much work or too little time. For example, suppose your company has an aggressive sales goal for this quarter. In that case, it's going to be difficult for anyone on your team if they have only two weeks' worth of work left before being unable to meet their goals – but if they have nine months' worth of work left, then they could easily fit everything in those extra three weeks and still hit their goals.
Identify risks and constraints. Risk management is about identifying potential problems before they occur so that you can prevent them from happening by taking action now rather than later. This can include identifying.
Controlling scope
By controlling scope, you ensure that the project is on track and within budget. You can do this by developing a detailed plan with accurate estimates of all costs associated with the project. The client and stakeholders should approve this plan before you begin work.
For example, suppose you are working on a new website for your company. In that case, you will need to determine what features will be included in the final product (such as additional pages or functionality).
Once you have determined what features are needed, you can create a list of tasks that will be completed during the next development phase. By controlling the scope at this point, you ensure everything is done correctly and on time.
Another way to control scope is by creating multiple product versions before launch. This allows you to test different features and see which ones work best before launching them publicly.
Why is project scope management important in 2022 and beyond?
For 2022 and beyond, Project scope management is critical because it helps ensure that the project objective is met. In other words, it provides that the project will not be over budget or take longer than expected. It also ensures that the project will be completed on time and with as few resources as possible.
Another reason is that it helps avoid costly rework later in the project. For example, if there are changes to the scope of a project, it often means that work will have to start again from scratch. This can be very costly for businesses and organizations because it takes time to build up the skills needed for a new project. This lost time can't be used on something else productive.
Scope management is essential when many stakeholders are involved in a project, such as when evaluating an environmental impact study or building an oil refinery plant. Stakeholders want to know what needs to be done to participate in decision-making processes and make informed decisions about how their projects should go forward with minimal risk of negative consequences.
Conclusion
Like its big brother, PDM (Project Data Management), Project Scope Management has many benefits for both organizations and project managers. A full 20% percent of global project management budgets would be allocated to scope management, and why not? The scope of any project is arguably the most important thing that any project manager has to deal with; it makes sense.
Top 16 Qualities of a Good Manager and a Leader
Top 16 Qualities of a Good Manager and a Leader
What are the qualities of a good manager? A leader, for that matter? How about someone who both manages and leads? You don't often find a single person who excels in both, but it happens. So if you work and want to develop skills in either of these two areas, this article is for you.
Vision
A good manager and leader have a vision for the future of their business or the world. They see where they want to go and understand what it will take to get there. They also have a clear idea of how they will get there. This is important because it allows them to make decisions based on facts, not wishful thinking.
Vision doesn't mean that you have to be able to predict precisely what will happen in the future; it just means that you know where you're going and why. For example, knowing where your company should go next is essential when deciding what technology to use or how much money to spend on marketing.
Positive
A good manager can identify and understand the needs of the people they manage. They should also be able to motivate employees to seek out opportunities to improve their skills and performance. A good manager will also help you find ways to work together as a team, be flexible, and deal with problems when they arise.
A good leader has all these qualities but doesn't just tell people what to do; instead, they inspire them by making them feel like they have the best interests.
Leadership
A good manager is a leader. A great manager is an exceptional leader. A great leader can inspire others and help them to reach their full potential while at the same time encouraging them to work together in a positive environment.
Leadership is about being able to motivate people and get them excited about achieving something significant. A good manager will be able to help you manage your time effectively and make sure that you have the resources available for you to achieve your goals.
Confidence
Confidence is a quality that most people desire in their managers and leaders, and it's one of the top qualities of a good manager. Confidence comes from knowing what you're doing, having experience, and having the ability to do it well. Great managers know they have the skills to lead, and they use those skills to help their team succeed.
When you're confident about your decision-making abilities and leadership skills, it makes things easier for others on the team. They know that if they ask for help or advice, they will get it without hesitation or fear of being judged as incompetent or weak.
Communication
Communication is critical in any workplace. A good manager or leader can help employees feel respected and understood while providing feedback and guidance.
Communication should be open and honest, with a positive tone. If you are communicating with your team members, try to avoid using words such as "must," "have," or "have to." Instead, use positive words like "I would like" or "I think."
Honesty
Being a good manager and a leader means being honest with your employees and your team. This doesn't come naturally to everyone, but it is an essential quality for a great leader. Honesty is one of the most critical skills as a manager.
Honesty also means being honest with yourself. It would help if you didn't deceive yourself when deciding how to lead your team or manage their performance. If you constantly lie to yourself about whether or not something is working out or if there are other options available, then you're doomed from the start because nobody will ever believe anything you say!
Open-mindedness
A good manager needs to be able to listen, think and learn. He needs to be open-minded to be receptive to new ideas and ways of doing things. The best managers are open-minded enough to accept new ideas from their employees. They also should be able to see the strengths in their employees and recognize their weaknesses, so they can work together to improve on those weaknesses.
Sense of humor
A sense of humor is an essential quality in a manager. People need to be able to laugh at themselves and their mistakes and also laugh at others' jokes. This is a great way to build co-workers' trust, morale, and camaraderie.
When you're having fun with your team, they're probably having fun too. This can lead to a more productive work environment and a better team overall.
Team player
A good manager and leader put the needs of their team above her own needs. They are always thinking of ways to improve their team and know how to get the best out of their team members.
A good manager and leader is also someone with strong leadership skills, which means they can make decisions confidently and handle conflict well.
Creativity
Creativity is one of the most essential and exciting qualities of a good manager and leader. A great manager and leader not only knows how to manage but also knows how to inspire other people to do their best work. In addition, a creative manager can develop new ideas for improving processes and procedures or making the workplace more attractive for employees. This can improve productivity, morale, and employee satisfaction.
Decision-making ability
The ability to make decisions is an essential quality for a manager. A good decision-maker understands what needs to be done, when, and how it should be done. As a result, the best manager can make the right decisions for the organization and its people.
A good leader also has an excellent decision-making ability. They can see the big picture and how all parts of the organization fit together to reach a common goal. This ability enables leaders to understand problems from different angles and develop solutions that will benefit everyone involved in the organization.
Willingness to learn new things, adaptability to change, and flexibility.
Great managers are willing to learn new things, adapt to change, and be flexible.
They have the ability and willingness to do whatever it takes to get the job done. They are not afraid of failure or doing things differently than what has been done before. Leaders can see past their ego and focus on what is best for the company or team they lead.
Optimism for the future
Optimism is a good quality to have as a manager and leader. Seeing the glass half full and being optimistic about your team and the future will help you get the best out of them.
One of the biggest problems with managers is that they can be negative about everything, which can cause them to lose their employees' faith. This can lead to poor performance, disengagement, and ultimately dismissal.
Do not underestimate the power of optimism in your life and your business.
Commitment to the organization and its staff members
The best managers and leaders can be committed to their organization and its staff members. But, to be successful, they must be able to inspire others through their words, actions, and deeds.
Good managers and leaders are committed to the organization's goals, mission, vision, and values. In addition, they take pride in their work, which is evident in how they present themselves in front of others.
A good manager and leader delegate assignments for growth and development
A good manager and leader is a good listener and understands the need of employees to grow professionally. In addition, good managers and leaders are transparent with their employees and keep them informed about their role in the organization.
A good manager and leader have integrity which means they follow ethical conduct in/her work environment. They do not compromise with any unethical behavior in/her organization or workplace. A good manager and leader always try to keep things on track by following the rules of the organization that they work for.
A good manager and a leader reward and recognize accomplishments
A good manager and a leader treat all employees equally regardless of their position or level in the company. A good leader knows their team members well enough to recognize who is doing well and who needs help improving on something.
A good manager knows how to delegate tasks effectively and efficiently because he understands his employee's strengths and weaknesses, while a suitable leader delegates tasks based on their ability to do them correctly without having to be coached every step.
Conclusion
To be an effective manager and leader, you must have unique qualities that separate you from the rest. You're responsible for leading a group of people. As such, your leadership skills will dictate whether or not you can effectively do your job. So, what are some key characteristics that make a good manager and leader? As with most things, knowing yourself and understanding your strengths and weaknesses is essential. Move through each of these characteristics, then decide which ones would make you a better manager and leader, given who you already are in today's business world.
Read More
Top 16 Qualities of a Good Manager and a Leader
What are the qualities of a good manager? A leader, for that matter? How about someone who both manages and leads? You don't often find a single person who excels in both, but it happens. So if you work and want to develop skills in either of these two areas, this article is for you.
Vision
A good manager and leader have a vision for the future of their business or the world. They see where they want to go and understand what it will take to get there. They also have a clear idea of how they will get there. This is important because it allows them to make decisions based on facts, not wishful thinking.
Vision doesn't mean that you have to be able to predict precisely what will happen in the future; it just means that you know where you're going and why. For example, knowing where your company should go next is essential when deciding what technology to use or how much money to spend on marketing.
Positive
A good manager can identify and understand the needs of the people they manage. They should also be able to motivate employees to seek out opportunities to improve their skills and performance. A good manager will also help you find ways to work together as a team, be flexible, and deal with problems when they arise.
A good leader has all these qualities but doesn't just tell people what to do; instead, they inspire them by making them feel like they have the best interests.
Leadership
A good manager is a leader. A great manager is an exceptional leader. A great leader can inspire others and help them to reach their full potential while at the same time encouraging them to work together in a positive environment.
Leadership is about being able to motivate people and get them excited about achieving something significant. A good manager will be able to help you manage your time effectively and make sure that you have the resources available for you to achieve your goals.
Confidence
Confidence is a quality that most people desire in their managers and leaders, and it's one of the top qualities of a good manager. Confidence comes from knowing what you're doing, having experience, and having the ability to do it well. Great managers know they have the skills to lead, and they use those skills to help their team succeed.
When you're confident about your decision-making abilities and leadership skills, it makes things easier for others on the team. They know that if they ask for help or advice, they will get it without hesitation or fear of being judged as incompetent or weak.
Communication
Communication is critical in any workplace. A good manager or leader can help employees feel respected and understood while providing feedback and guidance.
Communication should be open and honest, with a positive tone. If you are communicating with your team members, try to avoid using words such as "must," "have," or "have to." Instead, use positive words like "I would like" or "I think."
Honesty
Being a good manager and a leader means being honest with your employees and your team. This doesn't come naturally to everyone, but it is an essential quality for a great leader. Honesty is one of the most critical skills as a manager.
Honesty also means being honest with yourself. It would help if you didn't deceive yourself when deciding how to lead your team or manage their performance. If you constantly lie to yourself about whether or not something is working out or if there are other options available, then you're doomed from the start because nobody will ever believe anything you say!
Open-mindedness
A good manager needs to be able to listen, think and learn. He needs to be open-minded to be receptive to new ideas and ways of doing things. The best managers are open-minded enough to accept new ideas from their employees. They also should be able to see the strengths in their employees and recognize their weaknesses, so they can work together to improve on those weaknesses.
Sense of humor
A sense of humor is an essential quality in a manager. People need to be able to laugh at themselves and their mistakes and also laugh at others' jokes. This is a great way to build co-workers' trust, morale, and camaraderie.
When you're having fun with your team, they're probably having fun too. This can lead to a more productive work environment and a better team overall.
Team player
A good manager and leader put the needs of their team above her own needs. They are always thinking of ways to improve their team and know how to get the best out of their team members.
A good manager and leader is also someone with strong leadership skills, which means they can make decisions confidently and handle conflict well.
Creativity
Creativity is one of the most essential and exciting qualities of a good manager and leader. A great manager and leader not only knows how to manage but also knows how to inspire other people to do their best work. In addition, a creative manager can develop new ideas for improving processes and procedures or making the workplace more attractive for employees. This can improve productivity, morale, and employee satisfaction.
Decision-making ability
The ability to make decisions is an essential quality for a manager. A good decision-maker understands what needs to be done, when, and how it should be done. As a result, the best manager can make the right decisions for the organization and its people.
A good leader also has an excellent decision-making ability. They can see the big picture and how all parts of the organization fit together to reach a common goal. This ability enables leaders to understand problems from different angles and develop solutions that will benefit everyone involved in the organization.
Willingness to learn new things, adaptability to change, and flexibility.
Great managers are willing to learn new things, adapt to change, and be flexible.
They have the ability and willingness to do whatever it takes to get the job done. They are not afraid of failure or doing things differently than what has been done before. Leaders can see past their ego and focus on what is best for the company or team they lead.
Optimism for the future
Optimism is a good quality to have as a manager and leader. Seeing the glass half full and being optimistic about your team and the future will help you get the best out of them.
One of the biggest problems with managers is that they can be negative about everything, which can cause them to lose their employees' faith. This can lead to poor performance, disengagement, and ultimately dismissal.
Do not underestimate the power of optimism in your life and your business.
Commitment to the organization and its staff members
The best managers and leaders can be committed to their organization and its staff members. But, to be successful, they must be able to inspire others through their words, actions, and deeds.
Good managers and leaders are committed to the organization's goals, mission, vision, and values. In addition, they take pride in their work, which is evident in how they present themselves in front of others.
A good manager and leader delegate assignments for growth and development
A good manager and leader is a good listener and understands the need of employees to grow professionally. In addition, good managers and leaders are transparent with their employees and keep them informed about their role in the organization.
A good manager and leader have integrity which means they follow ethical conduct in/her work environment. They do not compromise with any unethical behavior in/her organization or workplace. A good manager and leader always try to keep things on track by following the rules of the organization that they work for.
A good manager and a leader reward and recognize accomplishments
A good manager and a leader treat all employees equally regardless of their position or level in the company. A good leader knows their team members well enough to recognize who is doing well and who needs help improving on something.
A good manager knows how to delegate tasks effectively and efficiently because he understands his employee's strengths and weaknesses, while a suitable leader delegates tasks based on their ability to do them correctly without having to be coached every step.
Conclusion
To be an effective manager and leader, you must have unique qualities that separate you from the rest. You're responsible for leading a group of people. As such, your leadership skills will dictate whether or not you can effectively do your job. So, what are some key characteristics that make a good manager and leader? As with most things, knowing yourself and understanding your strengths and weaknesses is essential. Move through each of these characteristics, then decide which ones would make you a better manager and leader, given who you already are in today's business world.
Understanding the Estimation of Activity Duration in Project Management
Understanding the Estimation of Activity Duration in Project Management
Pursuing project managers must understand how to perform various tasks to get a project started, and estimation of activity duration is one among them.
It isn't always a seamless activity to estimate project duration, as doing so requires a project manager's knowledge of a few theories, along with applying a few top techniques and practices.
Estimating activity duration is a daunting procedure that takes time for a long-term project. Ideally, it would be best to involve your core team in the estimation process.
It would help if you involved them, who will work on the project to attain the goal, the project management team, and all identified stakeholders to make a consensus on the target dates, and delivery schedules.
Estimating activity duration can be transformed as work progresses and as new activities of the projects are identified. Firstly, you can evaluate your project depending on the network diagram and can be further changed based on project changes done during the execution, controlling, and monitoring of the process.
According to the Project Management Institute (PMI), there are some project management practices, techniques, and tools to estimate the activity duration, and they are as follows:
Parametric Estimating
Parametric Estimating is more precise and is based on a statistical calculation of historical data and other variables. For instance, in the design stage of a construction project, you may already have the activity duration, i.e., cutting 1,000 stones will take 8 hours.
If your project is similar to one executed before, it's worth your while to determine existing activity duration estimates and previous data from the past project.
Heuristic Estimating
Heuristic Estimating is called Rule of Thumb, where you can roughly guess that the whole design stage can take 45% off your entire project time. This is a fruitful method for knowing factors where you can place an imaginary figure depending on the experience.
Analogous Estimating
Analogous Estimating is a vital technique that offers you the whole duration estimation. Depending on similar projects, you can attain a ballpark view of the entire duration estimation.
You can also get this data from the Project Management Office or other project managers and use this template for your existing project. Though this estimation practice isn't so precise in nature; however, it's less expensive and less time-consuming than other techniques.
You can often leverage Analogous Estimating when you don't have enough time to undergo a proper estimation and have a timeline. This can be a part of the project, so you don't need to estimate the whole project.
You can estimate the activity duration for a single stage if the phase requirement is identical to the last processed project.
Three-point Estimating
Three-point estimating depends on considering several choices such as resource assignments, uncertainty, and the associated risk like the best and worst scenario-based. This estimating technique originated from PERT, and through PERT, we estimate three kinds of estimation:
- Most Likely (M)
- Optimistic (O)
- Pessimistic (P)
Most Likely is based on the resources assigned, Optimistic is based on the best scenario-based analysis, and Pessimistic is based on the worst scenario-based analysis. Once you have these three durations, you can leverage some valuable formulas to derive the expected duration, i.e.,
TE = (O + 4M + P) ÷ 6
Where, TE = expected time
In this way, you can understand the significance of PERT in estimating the duration of the project.
Reserve Analysis
This is a type of contingency reserve, where after fixing a schedule for each activity level based on the activity features, you can create reserve timing by adding a few percent to the derived program of each activity. It can be modified as work progresses, minimizing or maximizing depending on the scenario.
Final Call
Estimating project activity duration can help you manage the project that comes in on time and within budget. Understand from the lessons your company has already dissolved to save yourself time when doing duration estimates.
To learn more about successful project management, look to iCert Global's online PMP certification training course.
Read More
Understanding the Estimation of Activity Duration in Project Management
Pursuing project managers must understand how to perform various tasks to get a project started, and estimation of activity duration is one among them.
It isn't always a seamless activity to estimate project duration, as doing so requires a project manager's knowledge of a few theories, along with applying a few top techniques and practices.
Estimating activity duration is a daunting procedure that takes time for a long-term project. Ideally, it would be best to involve your core team in the estimation process.
It would help if you involved them, who will work on the project to attain the goal, the project management team, and all identified stakeholders to make a consensus on the target dates, and delivery schedules.
Estimating activity duration can be transformed as work progresses and as new activities of the projects are identified. Firstly, you can evaluate your project depending on the network diagram and can be further changed based on project changes done during the execution, controlling, and monitoring of the process.
According to the Project Management Institute (PMI), there are some project management practices, techniques, and tools to estimate the activity duration, and they are as follows:
Parametric Estimating
Parametric Estimating is more precise and is based on a statistical calculation of historical data and other variables. For instance, in the design stage of a construction project, you may already have the activity duration, i.e., cutting 1,000 stones will take 8 hours.
If your project is similar to one executed before, it's worth your while to determine existing activity duration estimates and previous data from the past project.
Heuristic Estimating
Heuristic Estimating is called Rule of Thumb, where you can roughly guess that the whole design stage can take 45% off your entire project time. This is a fruitful method for knowing factors where you can place an imaginary figure depending on the experience.
Analogous Estimating
Analogous Estimating is a vital technique that offers you the whole duration estimation. Depending on similar projects, you can attain a ballpark view of the entire duration estimation.
You can also get this data from the Project Management Office or other project managers and use this template for your existing project. Though this estimation practice isn't so precise in nature; however, it's less expensive and less time-consuming than other techniques.
You can often leverage Analogous Estimating when you don't have enough time to undergo a proper estimation and have a timeline. This can be a part of the project, so you don't need to estimate the whole project.
You can estimate the activity duration for a single stage if the phase requirement is identical to the last processed project.
Three-point Estimating
Three-point estimating depends on considering several choices such as resource assignments, uncertainty, and the associated risk like the best and worst scenario-based. This estimating technique originated from PERT, and through PERT, we estimate three kinds of estimation:
- Most Likely (M)
- Optimistic (O)
- Pessimistic (P)
Most Likely is based on the resources assigned, Optimistic is based on the best scenario-based analysis, and Pessimistic is based on the worst scenario-based analysis. Once you have these three durations, you can leverage some valuable formulas to derive the expected duration, i.e.,
TE = (O + 4M + P) ÷ 6
Where, TE = expected time
In this way, you can understand the significance of PERT in estimating the duration of the project.
Reserve Analysis
This is a type of contingency reserve, where after fixing a schedule for each activity level based on the activity features, you can create reserve timing by adding a few percent to the derived program of each activity. It can be modified as work progresses, minimizing or maximizing depending on the scenario.
Final Call
Estimating project activity duration can help you manage the project that comes in on time and within budget. Understand from the lessons your company has already dissolved to save yourself time when doing duration estimates.
To learn more about successful project management, look to iCert Global's online PMP certification training course.
Top 25 Productivity Tools to Maximize Your Time in 2022
Top 25 Productivity Tools to Maximize Your Time in 2022
Everyone is constantly trying to be more productive. We all strive hard to get more done at home and work while working less. However, staying effective can be a massive order in this reign of remote working, with diversions in the digital and personal space.
It can take more than a person's effort to remain effective. That is why it makes sense to take the aid of productivity techniques and tools.
Today's blog will highlight the top 25 productivity tools and how executing them can maximize your time in 2022.
Before jumping into our main topic, let us first see what are productivity tools and how increased productivity enhance our life?
What is a Productivity Tool?
Productivity is an estimation of how efficient you're at what you do. Productivity tools are software created to simplify tasks, streamline work procedures, and often include factors that let us access documents swiftly, design graphs and charts for project plan visualization, progress, and more.
How Increased Productivity Enhance our Life?
It isn't confidential that productivity is a necessity for career success and personal happiness. Productive individuals are prized assets in the professional environment, while productivity brings content and a sense of achievement to a person.
However, productivity is hard to accomplish factor. A primary reason is that our brain is wired to diversion, making our minds travel to dreamland easily, and our focus span is shorter than ever.
25 Best Productivity Tools you can Leverage
1. Infinity
Keep your team in sync and on the same page with Infinity which expands daily productivity. Few key benefits include efficient task management, better team collaboration, and time tracking with Clockify.
2. Shift
Shift is a desktop app that is build to streamline your accounts, workflows, and apps. Switching between multiple accounts has never been an easier task. Two of its best aspects are cross-platform support and unified search across multiple Google accounts.
3. Toggl
It's a time-saver app that easy to leverage and can merge various tools to increase functionality. Two of its top aspects are offline time tracking and the instant overview of team growth and time.
4. Microsoft OneNote
Microsoft OneNote is a digital note-taking application that is build to operate on any platform/device such as smartphones or laptops. This app can be used to write, type, and draw with a pen-to-paper sense. Handy for taking notes, it features audio/video recording and real-time collaboration.
5. Skype
One of the most famous apps for communication over video calls is Skype, that has merged tons of new aspects to aid you stay connected.
6. ProofHub
ProofHub is a comprehensive project and task management tool that helps maintain things organized, improves accountability, and facilitates efficient communication.
By leveraging the tool, you can assign activities to certain individual, organize work procedures by uploading file/documents, and check the time spent at each project stage.
7. Everhour
Everhour is an intuitive time-tracking app that enables teams to reach their targets swiftly. It aids in sticking to project estimates, ensuring that you're with your task all the time.
8. Box Notes
It's an online note-taking software which allows real-time collaboration so you can share views with colleagues or share notes with others without having to worry on security. The living edit aspect allows real-time collaboration.
9. nTask
It's complicated to remain productive while working on massive projects where you've to keep dot on every detail. With productivity tools such as nTask, you can stay on the top of every project feature without losing time and hampering productivity. This tool is great for team collaboration, creating to-do lists, and merging time-tracking tools with workforce worksheets, among other things.
10. Slack
It's a popular team collaboration app to join all team communications. Besides its much-appreciated chat and team communication aspects, Slack lets us track documents, share files and update, and set reminders for meetings and tasks. This app fits in which app such as Dropbox and Google Drive.
11. GoToMeeting
GoToMeeting is an online video conferencing app that allows meetings to be turned into conference calls, share screens, and schedule meetings.
12. Time Doctor
If you want to know where your team is spending their time, even when remotely working, then Time Doctor app is for you. This productivity and time-tracking tool is created specifically for remote teams.
13. Simplenote
This app simplifies note-taking, assisting you to maintain your notes specific, accessible, and accurate. There is no need to waste time while identifying files, just type your search item, and your list instantly updates, and the notes are backed up. You only require to leverage the version slider to switch between versions.
14. GanttPro
GanttPro is an online app that ensure you maintain a track of activity of all teammates. Its key aspects include deadline management, export and sharing files via public URLs, task management, and more.
15. Chanty
Chanty is an easy and fast team chat app that can help improve communication between teams. Its crucial aspects include the potential to make video/audio calls, voice messages within the app, and integrated task management.
16. Hubstaff
Hubstaff is a time-tracking software that can run on your mobile as an app or on your desktop. Once the time is tracked, people get options for paying workforces, invoicing clients, checking in-depth reporting, and more.
17. Calendar
The AI-enabled calendar focuses on your schedule and performs booking, event and meeting organization based on your calendar. The app merges with various digital calendars such as Outlook and Google Calendar. You can even share your calendar with others in your team.
18. Bit.ai
Bit.ai is a document management and collaboration tool that is top choice for collaborating with teams, sharing, tracking, and managing documents at a single place.
19. Harvest
Harvest is a time-tracking software that lets people to track their time on any given activity from the web, phone or any other application.
20. HubSpot's Marketing Hub
One of the top team collaboration tools, HubSpot's Marketing Hub is the finest software to release, manage and sustain your promotional campaigns and techniques. The key aspects of this software include easy contact management, a contact database, and the potential to sync data across sales teams, marketing, and customer service.
21. Paymo
A productivity tool that takes care of planning, scheduling, time-tracking, invoicing, and task management, Paymo is ideal for getting a synopsis of team performance.
22. Google Docs
Google Docs is a popular document storage and task management software that lets users to access, create, collaborate, and edit from anywhere, using their computer, phone, or tablet even when there's no connectivity.
23. Evernote
A note-making app helps you remember everything. Evernote is a perfect app to stay organized and get job done. Gather, organize and share notes from anywhere, so things are more accessible.
24. Zoom
It's a widely leveraged tool that offer cloud-based remote conferencing services, where over 500 people can participate in Zoom meetings.
25. Free
Free is a flexible messenger that can be merged with email and leveraged to share and store files seamlessly.
Read More
Top 25 Productivity Tools to Maximize Your Time in 2022
Everyone is constantly trying to be more productive. We all strive hard to get more done at home and work while working less. However, staying effective can be a massive order in this reign of remote working, with diversions in the digital and personal space.
It can take more than a person's effort to remain effective. That is why it makes sense to take the aid of productivity techniques and tools.
Today's blog will highlight the top 25 productivity tools and how executing them can maximize your time in 2022.
Before jumping into our main topic, let us first see what are productivity tools and how increased productivity enhance our life?
What is a Productivity Tool?
Productivity is an estimation of how efficient you're at what you do. Productivity tools are software created to simplify tasks, streamline work procedures, and often include factors that let us access documents swiftly, design graphs and charts for project plan visualization, progress, and more.
How Increased Productivity Enhance our Life?
It isn't confidential that productivity is a necessity for career success and personal happiness. Productive individuals are prized assets in the professional environment, while productivity brings content and a sense of achievement to a person.
However, productivity is hard to accomplish factor. A primary reason is that our brain is wired to diversion, making our minds travel to dreamland easily, and our focus span is shorter than ever.
25 Best Productivity Tools you can Leverage
1. Infinity
Keep your team in sync and on the same page with Infinity which expands daily productivity. Few key benefits include efficient task management, better team collaboration, and time tracking with Clockify.
2. Shift
Shift is a desktop app that is build to streamline your accounts, workflows, and apps. Switching between multiple accounts has never been an easier task. Two of its best aspects are cross-platform support and unified search across multiple Google accounts.
3. Toggl
It's a time-saver app that easy to leverage and can merge various tools to increase functionality. Two of its top aspects are offline time tracking and the instant overview of team growth and time.
4. Microsoft OneNote
Microsoft OneNote is a digital note-taking application that is build to operate on any platform/device such as smartphones or laptops. This app can be used to write, type, and draw with a pen-to-paper sense. Handy for taking notes, it features audio/video recording and real-time collaboration.
5. Skype
One of the most famous apps for communication over video calls is Skype, that has merged tons of new aspects to aid you stay connected.
6. ProofHub
ProofHub is a comprehensive project and task management tool that helps maintain things organized, improves accountability, and facilitates efficient communication.
By leveraging the tool, you can assign activities to certain individual, organize work procedures by uploading file/documents, and check the time spent at each project stage.
7. Everhour
Everhour is an intuitive time-tracking app that enables teams to reach their targets swiftly. It aids in sticking to project estimates, ensuring that you're with your task all the time.
8. Box Notes
It's an online note-taking software which allows real-time collaboration so you can share views with colleagues or share notes with others without having to worry on security. The living edit aspect allows real-time collaboration.
9. nTask
It's complicated to remain productive while working on massive projects where you've to keep dot on every detail. With productivity tools such as nTask, you can stay on the top of every project feature without losing time and hampering productivity. This tool is great for team collaboration, creating to-do lists, and merging time-tracking tools with workforce worksheets, among other things.
10. Slack
It's a popular team collaboration app to join all team communications. Besides its much-appreciated chat and team communication aspects, Slack lets us track documents, share files and update, and set reminders for meetings and tasks. This app fits in which app such as Dropbox and Google Drive.
11. GoToMeeting
GoToMeeting is an online video conferencing app that allows meetings to be turned into conference calls, share screens, and schedule meetings.
12. Time Doctor
If you want to know where your team is spending their time, even when remotely working, then Time Doctor app is for you. This productivity and time-tracking tool is created specifically for remote teams.
13. Simplenote
This app simplifies note-taking, assisting you to maintain your notes specific, accessible, and accurate. There is no need to waste time while identifying files, just type your search item, and your list instantly updates, and the notes are backed up. You only require to leverage the version slider to switch between versions.
14. GanttPro
GanttPro is an online app that ensure you maintain a track of activity of all teammates. Its key aspects include deadline management, export and sharing files via public URLs, task management, and more.
15. Chanty
Chanty is an easy and fast team chat app that can help improve communication between teams. Its crucial aspects include the potential to make video/audio calls, voice messages within the app, and integrated task management.
16. Hubstaff
Hubstaff is a time-tracking software that can run on your mobile as an app or on your desktop. Once the time is tracked, people get options for paying workforces, invoicing clients, checking in-depth reporting, and more.
17. Calendar
The AI-enabled calendar focuses on your schedule and performs booking, event and meeting organization based on your calendar. The app merges with various digital calendars such as Outlook and Google Calendar. You can even share your calendar with others in your team.
18. Bit.ai
Bit.ai is a document management and collaboration tool that is top choice for collaborating with teams, sharing, tracking, and managing documents at a single place.
19. Harvest
Harvest is a time-tracking software that lets people to track their time on any given activity from the web, phone or any other application.
20. HubSpot's Marketing Hub
One of the top team collaboration tools, HubSpot's Marketing Hub is the finest software to release, manage and sustain your promotional campaigns and techniques. The key aspects of this software include easy contact management, a contact database, and the potential to sync data across sales teams, marketing, and customer service.
21. Paymo
A productivity tool that takes care of planning, scheduling, time-tracking, invoicing, and task management, Paymo is ideal for getting a synopsis of team performance.
22. Google Docs
Google Docs is a popular document storage and task management software that lets users to access, create, collaborate, and edit from anywhere, using their computer, phone, or tablet even when there's no connectivity.
23. Evernote
A note-making app helps you remember everything. Evernote is a perfect app to stay organized and get job done. Gather, organize and share notes from anywhere, so things are more accessible.
24. Zoom
It's a widely leveraged tool that offer cloud-based remote conferencing services, where over 500 people can participate in Zoom meetings.
25. Free
Free is a flexible messenger that can be merged with email and leveraged to share and store files seamlessly.
Best Professional Benefits of the CAPM Certification 2022
Best Professional Benefits of the CAPM Certification 2022
The Certified Associate in Project Management (CAPM) is a certification that recognizes professionals new to the project management domain. The Project Management Institute (PMI) certifies that aspirants have in-depth expertise in the techniques and principles defined by the PMBOK Guide and all the globally recognized project management methodologies.
CAPM is specially created for enthusiasts with minimum experience in the project management domain, thus, offering them a fundamental understanding of the topic. One of the benefits of a credential is that it gives the highest value to your resume and skills.
In today’s blog, we will discuss the following topics, exploring the advantages of CAPM accreditation.
TABLE OF CONTENTS
What's in CAPM Certification?
The CAPM Certification Exam Format
CAPM Certification Eligibility Criteria
Top Advantages of CAPM Certification
CAPM: A Path to the PMP Certification
Job Opportunities for CAPM Certification
What's in CAPM Certification?
With CAPM certification, professionals will learn to organize their work with the norms needed by project management teams. People with this credential get higher credibility among peers, PMP certified-holders, employers, and project managers.
Let's see few basic topics you must learn in CAPM credential.
- Project and organization lifecycle
- Project scope management
- Quality management
- Communications management
- Time and cost management
- Stakeholder management
- Project management processes
- Project risk management
Format of CAPM Certification Exam
The CAPM certification test comprises 150 MCQ-type questions, and you have three hours to complete them. The accreditations provided by PMI, including CAPM, are de facto standards and validate a person's skills in initiating, planning, managing, and running massive projects.
CAPM certification professionals can display competency, education, and learning experience to potential peers. In addition, achieving this credential opens up various opportunities for individuals.
CAPM Certification Eligibility Criteria
Like any other credential, there are eligibility requirements. CAPM aspirants must have:
- Secondary degree (high school diploma, associate's degree, or any global equivalent).
- Project experience: 1500 hours
- Project management training: 23 hours prior to CAPM certification exam.
Top Advantages of CAPM Certification
The CAPM credential is a popular requirement that aids recruiters find the professionals most suited to satisfy specific roles in their companies. The credential validates a person's knowledge and experience, followed by their skills to take on significant responsibilities.
Project professionals are required in almost every sector, such as IT, engineering, construction, and more. Therefore, achieving the CAPM credential opens up various choices, including:
Global Opportunities
Among the advantages of CAPM certification, global recognition is first on the benefits list. You will be able to work worldwide, bringing you the choice to travel across the globe to places with more projects. Even within organizations, management may be more willing to transfer a certified professional to international locations if they feel it's in their best interest.
Handsome Remuneration
Project management is one of the best-paying jobs on many professional surveys. Project managers can earn between $90K-$150K per year. CAPM salary for certified holders averages $92K. The top-paying IT sector often pays salaries above $100K.s
Career Incentives
In several scenarios, the CAPM accreditation is a requirement that will help land your career as you shift into new roles and increased responsibilities in a company. Employers trust this certification, and CAPM professionals have proven they can tackle increased responsibility.
Personal Development
Interviewees are often more confident than the competition in their learning while earning their CAPM credentials, making them knowledgeable of the best project management techniques and tools. It isn't just textbook material but a real-life experience that earns one the CAPM credential.
Job Profiles
CAPM for beginners is an entry-level course created for those with little experience in project management. It educates candidates on the basics of project management, including its methodologies, knowledge, and practical techniques.
CAPM professionals can look at job profiles are Sr. IT technical project manager, member relations administrator, PMO operational support analyst, business analyst consultants, and more.
CAPM: A Path to the PMP Certification
Attaining your CAPM certification can be a path to becoming a certified PMP. The PMP certification is a globally renowned and prestigious project management accreditation by PMI. Earning PMP certification can help you:
- Display that you've the experience, education and competency to direct and lead projects
- Improve your career choices by offering you a competitive edge amid job applications
- Increase your earnings potential by earning a handsome remuneration than non-certified peers.
- Enhance your credibility by holding a globally recognized project management certification.
Job Opportunities for CAPM Certification
You'll be qualified to work as a CAPM-certified holder in various project management roles. Some of the most common designations are project analyst, assistant project manager, project scheduler, project manager, and project coordinator.
With a CAPM accreditation, you'll have the significant skills and knowledge to manage projects irrespective of size and complexity efficiently. This credential opens up several doors for your career in this domain.
Besides, from the standard roles you land with a CAPM credential, a CAPM certification professional has a lot more options to select from, some of which are:
- Program Manager
- IT Project Manager
- Construction Project Manager
- Event Planner
- Human Resources Manager
- Recruitment Manager
- Training Manager
- Organizational Development Manager
- Business Process Analyst
- Quality Assurance Manager
- Sales Manager
Project management is a well-established domain. However, the recent developments in job technicalities and the increasing responsibilities make the position more demanding and highly flexible.
It makes CAPM accreditation a benchmark for recruiters seeking to hire suitable professionals. If you're looking for significant career development, CAPM is ideal.
Read More
Best Professional Benefits of the CAPM Certification 2022
The Certified Associate in Project Management (CAPM) is a certification that recognizes professionals new to the project management domain. The Project Management Institute (PMI) certifies that aspirants have in-depth expertise in the techniques and principles defined by the PMBOK Guide and all the globally recognized project management methodologies.
CAPM is specially created for enthusiasts with minimum experience in the project management domain, thus, offering them a fundamental understanding of the topic. One of the benefits of a credential is that it gives the highest value to your resume and skills.
In today’s blog, we will discuss the following topics, exploring the advantages of CAPM accreditation.
|
TABLE OF CONTENTS What's in CAPM Certification? The CAPM Certification Exam Format CAPM Certification Eligibility Criteria Top Advantages of CAPM Certification CAPM: A Path to the PMP Certification Job Opportunities for CAPM Certification |
What's in CAPM Certification?
With CAPM certification, professionals will learn to organize their work with the norms needed by project management teams. People with this credential get higher credibility among peers, PMP certified-holders, employers, and project managers.
Let's see few basic topics you must learn in CAPM credential.
- Project and organization lifecycle
- Project scope management
- Quality management
- Communications management
- Time and cost management
- Stakeholder management
- Project management processes
- Project risk management
Format of CAPM Certification Exam
The CAPM certification test comprises 150 MCQ-type questions, and you have three hours to complete them. The accreditations provided by PMI, including CAPM, are de facto standards and validate a person's skills in initiating, planning, managing, and running massive projects.
CAPM certification professionals can display competency, education, and learning experience to potential peers. In addition, achieving this credential opens up various opportunities for individuals.
CAPM Certification Eligibility Criteria
Like any other credential, there are eligibility requirements. CAPM aspirants must have:
- Secondary degree (high school diploma, associate's degree, or any global equivalent).
- Project experience: 1500 hours
- Project management training: 23 hours prior to CAPM certification exam.
Top Advantages of CAPM Certification
The CAPM credential is a popular requirement that aids recruiters find the professionals most suited to satisfy specific roles in their companies. The credential validates a person's knowledge and experience, followed by their skills to take on significant responsibilities.
Project professionals are required in almost every sector, such as IT, engineering, construction, and more. Therefore, achieving the CAPM credential opens up various choices, including:
Global Opportunities
Among the advantages of CAPM certification, global recognition is first on the benefits list. You will be able to work worldwide, bringing you the choice to travel across the globe to places with more projects. Even within organizations, management may be more willing to transfer a certified professional to international locations if they feel it's in their best interest.
Handsome Remuneration
Project management is one of the best-paying jobs on many professional surveys. Project managers can earn between $90K-$150K per year. CAPM salary for certified holders averages $92K. The top-paying IT sector often pays salaries above $100K.s
Career Incentives
In several scenarios, the CAPM accreditation is a requirement that will help land your career as you shift into new roles and increased responsibilities in a company. Employers trust this certification, and CAPM professionals have proven they can tackle increased responsibility.
Personal Development
Interviewees are often more confident than the competition in their learning while earning their CAPM credentials, making them knowledgeable of the best project management techniques and tools. It isn't just textbook material but a real-life experience that earns one the CAPM credential.
Job Profiles
CAPM for beginners is an entry-level course created for those with little experience in project management. It educates candidates on the basics of project management, including its methodologies, knowledge, and practical techniques.
CAPM professionals can look at job profiles are Sr. IT technical project manager, member relations administrator, PMO operational support analyst, business analyst consultants, and more.
CAPM: A Path to the PMP Certification
Attaining your CAPM certification can be a path to becoming a certified PMP. The PMP certification is a globally renowned and prestigious project management accreditation by PMI. Earning PMP certification can help you:
- Display that you've the experience, education and competency to direct and lead projects
- Improve your career choices by offering you a competitive edge amid job applications
- Increase your earnings potential by earning a handsome remuneration than non-certified peers.
- Enhance your credibility by holding a globally recognized project management certification.
Job Opportunities for CAPM Certification
You'll be qualified to work as a CAPM-certified holder in various project management roles. Some of the most common designations are project analyst, assistant project manager, project scheduler, project manager, and project coordinator.
With a CAPM accreditation, you'll have the significant skills and knowledge to manage projects irrespective of size and complexity efficiently. This credential opens up several doors for your career in this domain.
Besides, from the standard roles you land with a CAPM credential, a CAPM certification professional has a lot more options to select from, some of which are:
- Program Manager
- IT Project Manager
- Construction Project Manager
- Event Planner
- Human Resources Manager
- Recruitment Manager
- Training Manager
- Organizational Development Manager
- Business Process Analyst
- Quality Assurance Manager
- Sales Manager
Project management is a well-established domain. However, the recent developments in job technicalities and the increasing responsibilities make the position more demanding and highly flexible.
It makes CAPM accreditation a benchmark for recruiters seeking to hire suitable professionals. If you're looking for significant career development, CAPM is ideal.
Project Documentation and Its Importance in 2022
Project Documentation and Its Importance in 2022
Project documentation is something that we usually ignore. But why? Project documentation plays a vital role in the success and failure of the project completion itself. It acts as a guideline to efficiently manage the project and gives precise estimates of its cost. It is also an asset to the project owners, vendors, and team members.
A web application or an IT project should be adequately documented with well-designed documentation to minimize the risk of failure and improve user knowledge.
In addition, having clear and comprehensive documentation helps in easy and accurate appraisals of the work performed. Unfortunately, however, many IT projects fail because of mismanagement.
One of the key reasons for such failures is improper documentation by the project managers. Therefore, any project manager must understand how vital quality documentation is for successful projects.
Why is Project Documentation necessary?
Project documentation is the backbone of any project. It helps stakeholders understand the purpose and goals of the project, how it will be executed, and what resources are needed.
It is an essential part of every project management process. Creating a document helps you manage your project by providing specific details about what needs to be done and when. The paper also acts as a roadmap to help you track what has been completed and what remains to be done.
Project documentation is often overlooked, but it should not be underestimated because it can help you save time and money.
In addition, you can avoid mistakes by referring back to your documents if, at any point, you feel like something is not going according to plan or if there is a change in direction due to unforeseen circumstances or changes in requirements.
What are some examples of project documentation?
Project documentation is a set of documents describing a project's process and outcomes. The documentation may be in reports, memos, or other written documents.
Having proper documentation for all your projects is essential because it helps you track and manage your work better. It also allows you to determine what has been achieved and what remains to be done.
The following are some examples of project documentation:
Project Charter: This document describes the scope, purpose, and objectives of the project, along with the deliverables required from your team members. This document will help you to develop an overall vision for your project and set goals for your team members based on their performance.
Project Plan: This document contains all the activities required to complete each milestone successfully within its timeframe. It also includes specific details about how your team members will carry out each exercise and how long it will take them to complete each activity.
Project Proposal: A document gives a clear overview of a project's goals, requirements, and value proposition. It highlights the number of resources that will work on the project, the budget allocation, timelines, and the key deliverables.
Project Evaluation: It is essential to document how a project performed – what went well and what didn't meet your expectations. Your team can use this as a reference for their next project to avoid repeating mistakes and improve on successes.
Project Progress Report: To keep everyone on the same page, you will update the project's progress regularly. This report shows how far you've come since the start of the project. In addition, it identifies any obstacles that may have prevented you from moving forward as quickly as you'd hoped. It will also outline your next steps to keep things moving as smoothly as possible.
Benefits of Project Documentation
Project documentation is the process of recording and storing information about a project. The information gathered can be used for future reference and to communicate with other project stakeholders.
The benefits of project documentation include the following:
- It helps ensure the team can work together effectively and efficiently.
- It records what has been done and what remains to be completed.
- It serves as evidence that critical decisions were made and the reasoning behind those decisions.
- It provides an overview of what was done and what remains to be done at any given time during a project's lifecycle.
- Project documentation is also essential for ensuring compliance with regulatory requirements.
Documentation helps everyone stay on the same page.
Project documentation is essential as it helps keep everyone on the same page. It's also a way to ensure that everyone involved in a project is privy to any changes that happen during the project. So, what are some of how you can use project documentation?
Project Management Documentation: This type of documentation is used by project managers to track progress and keep track of all related tasks and issues.
The data collected through such documentation is then analyzed to see whether or not they have been completed successfully.
Suppose there are any issues with completing these tasks. In that case, this information can be shared with other team members to take appropriate action.
Communication Documentation: Communication documents are used for sharing information about projects with team members, clients, and stakeholders.
Communication documents should contain all relevant information about a project in an organized manner so that people can understand them easily without much effort.
These communication documents include minutes from meetings and emails exchanged between different parties involved in a project.
Financial Documentation: Financial documents are used for recording financial information related to a particular project, like the budget allocated for it and how much has been spent on various aspects of the project.
Conclusion
Writing good project documentation is a necessity in the field of project management and execution.
As per experts, a standard project documentation template or format includes all crucial details of the project along with its objectives, requirements, deliverables, risks, assumptions, etc.
It also has a perfect platform for discussing between the client and project manager the changes in conditions, budget, etc.
Comprehensive documentation helps everyone know the project's objective and how to accomplish it on time. Note all small details while working on the documentation to avoid miscommunication between stakeholders later.
Read More
Project Documentation and Its Importance in 2022
Project documentation is something that we usually ignore. But why? Project documentation plays a vital role in the success and failure of the project completion itself. It acts as a guideline to efficiently manage the project and gives precise estimates of its cost. It is also an asset to the project owners, vendors, and team members.
A web application or an IT project should be adequately documented with well-designed documentation to minimize the risk of failure and improve user knowledge.
In addition, having clear and comprehensive documentation helps in easy and accurate appraisals of the work performed. Unfortunately, however, many IT projects fail because of mismanagement.
One of the key reasons for such failures is improper documentation by the project managers. Therefore, any project manager must understand how vital quality documentation is for successful projects.
Why is Project Documentation necessary?
Project documentation is the backbone of any project. It helps stakeholders understand the purpose and goals of the project, how it will be executed, and what resources are needed.
It is an essential part of every project management process. Creating a document helps you manage your project by providing specific details about what needs to be done and when. The paper also acts as a roadmap to help you track what has been completed and what remains to be done.
Project documentation is often overlooked, but it should not be underestimated because it can help you save time and money.
In addition, you can avoid mistakes by referring back to your documents if, at any point, you feel like something is not going according to plan or if there is a change in direction due to unforeseen circumstances or changes in requirements.
What are some examples of project documentation?
Project documentation is a set of documents describing a project's process and outcomes. The documentation may be in reports, memos, or other written documents.
Having proper documentation for all your projects is essential because it helps you track and manage your work better. It also allows you to determine what has been achieved and what remains to be done.
The following are some examples of project documentation:
Project Charter: This document describes the scope, purpose, and objectives of the project, along with the deliverables required from your team members. This document will help you to develop an overall vision for your project and set goals for your team members based on their performance.
Project Plan: This document contains all the activities required to complete each milestone successfully within its timeframe. It also includes specific details about how your team members will carry out each exercise and how long it will take them to complete each activity.
Project Proposal: A document gives a clear overview of a project's goals, requirements, and value proposition. It highlights the number of resources that will work on the project, the budget allocation, timelines, and the key deliverables.
Project Evaluation: It is essential to document how a project performed – what went well and what didn't meet your expectations. Your team can use this as a reference for their next project to avoid repeating mistakes and improve on successes.
Project Progress Report: To keep everyone on the same page, you will update the project's progress regularly. This report shows how far you've come since the start of the project. In addition, it identifies any obstacles that may have prevented you from moving forward as quickly as you'd hoped. It will also outline your next steps to keep things moving as smoothly as possible.
Benefits of Project Documentation
Project documentation is the process of recording and storing information about a project. The information gathered can be used for future reference and to communicate with other project stakeholders.
The benefits of project documentation include the following:
- It helps ensure the team can work together effectively and efficiently.
- It records what has been done and what remains to be completed.
- It serves as evidence that critical decisions were made and the reasoning behind those decisions.
- It provides an overview of what was done and what remains to be done at any given time during a project's lifecycle.
- Project documentation is also essential for ensuring compliance with regulatory requirements.
Documentation helps everyone stay on the same page.
Project documentation is essential as it helps keep everyone on the same page. It's also a way to ensure that everyone involved in a project is privy to any changes that happen during the project. So, what are some of how you can use project documentation?
Project Management Documentation: This type of documentation is used by project managers to track progress and keep track of all related tasks and issues.
The data collected through such documentation is then analyzed to see whether or not they have been completed successfully.
Suppose there are any issues with completing these tasks. In that case, this information can be shared with other team members to take appropriate action.
Communication Documentation: Communication documents are used for sharing information about projects with team members, clients, and stakeholders.
Communication documents should contain all relevant information about a project in an organized manner so that people can understand them easily without much effort.
These communication documents include minutes from meetings and emails exchanged between different parties involved in a project.
Financial Documentation: Financial documents are used for recording financial information related to a particular project, like the budget allocated for it and how much has been spent on various aspects of the project.
Conclusion
Writing good project documentation is a necessity in the field of project management and execution.
As per experts, a standard project documentation template or format includes all crucial details of the project along with its objectives, requirements, deliverables, risks, assumptions, etc.
It also has a perfect platform for discussing between the client and project manager the changes in conditions, budget, etc.
Comprehensive documentation helps everyone know the project's objective and how to accomplish it on time. Note all small details while working on the documentation to avoid miscommunication between stakeholders later.
Requirements Traceability Matrix (RTM): Templates, Types, and Tools for 2022
Requirements Traceability Matrix (RTM): Templates, Types, and Tools for 2022
If you are searching for "Requirements Traceability Matrix" templates, this is the right place. This post will detail all kinds of templates, types, and tools that will help you use RTM to trace your requirements.
What is Requirements Traceability Matrix (RTM)?
Requirements traceability is the process that tracks requirements as they move into design and development and where they go when they are checked in to the appropriate locations.
Having an RTM also allows you to monitor the amount of work taken up by the various groups and how much work remains. This helps you evaluate how efficiently your team is functioning.
The following requirements traceability matrix templates, types, and tools allow a more efficient and effective workflow for your company's requirements management.
Requirements Traceability Matrix (RTM) Essentials
Requirements traceability matrix (RTM) is a diagrammatic representation of functional requirements, showing how they relate to one another.
It helps trace each requirement back to its originator(s). In addition, it serves as a guide for identifying missing information or defects at any stage of the development process.
The matrixes can be used at different levels – from project level down to component level and even individual requirement level – depending on the number of stakeholders involved and their role in the project life cycle.
Why Requirements Traceability Matrix (RTM) Needed?
The main objective of RTM is to provide traceability between different elements of a project like projects, requirements, defects, test cases, etc. The below-mentioned points show why RTM is needed:
- It helps link all related documents together in one place to make it easy for anyone to access the required information at any time.
- It makes it easier for testers to understand how they can use this information while testing and what they should not do while trying.
- It helps testers identify gaps between documents such as requirements and test cases which may result in missing functionality during the testing phase.
Requirements Traceability Matrix (RTM) Types
Following are the types of RTM:
Forward traceability: Forwards traceability is proper when there are many revisions and a large backlog. It traces the product requirements from the definition phase to the testing phase.
Backward traceability: Backwards traceability works in the opposite direction as compared to Forwarding traceability. Backward traceability traces the validation of the product from testing to the requirement definition phase.
Bidirectional traceability: Bidirectional traceability supports both backward and forward tracing. It is often used in large projects with multiple development cycles. Bidirectional RTM covers all aspects of the development cycle, from the requirements gathering process to the testing cycle.
Benefits of RTM
The benefits of using a traceability matrix are numerous. It can help:
- Improve the quality of products and services.
- Reduce the time required to find information and resolve issues.
- Identify relationships between different parts of a product or service.
- Make it easier to identify problems and solve them more quickly.
Requirements Traceability Matrix (RTM) Tools
A Requirements Traceability Matrix (RTM) tool is software that automates the creation and maintenance of RTMs. It typically allows users to perform search queries on their RTMs, allowing them to see which documents contain which requirements or vice versa.
Modern Requirements4DevOps: Modern Requirements4DevOps integrates with Microsoft's Azure DevOps, TFS, and VSTS and provides project managers with traceability through every stage of the process
Visure Requirements: Visure Requirements is a tool that tracks changes made during the development process, providing complete traceability.
ReQtest: ReQtest is cloud-based and customizable; it provides traceability from project start to finish.
Requirements Traceability Matrix (RTM) Template

Conclusion
This article has tried to cover all aspects of RTM tool development. However, there are times when you would need to have an urgent requirement change, or if you have to make a hotfix, you can make it with the help of RTM.
Nonetheless, RTM helps in preventing any dissociation between requirement and code. An RTM is a one-stop solution for the testers and the developers. Further, it determines the bugs that programmers need to fix as soon as possible to eliminate them.
Of course, you can also use the requirements traceability matrix as a standalone solution to identify a mapping between test cases and requirements.
Read More
Requirements Traceability Matrix (RTM): Templates, Types, and Tools for 2022
If you are searching for "Requirements Traceability Matrix" templates, this is the right place. This post will detail all kinds of templates, types, and tools that will help you use RTM to trace your requirements.
What is Requirements Traceability Matrix (RTM)?
Requirements traceability is the process that tracks requirements as they move into design and development and where they go when they are checked in to the appropriate locations.
Having an RTM also allows you to monitor the amount of work taken up by the various groups and how much work remains. This helps you evaluate how efficiently your team is functioning.
The following requirements traceability matrix templates, types, and tools allow a more efficient and effective workflow for your company's requirements management.
Requirements Traceability Matrix (RTM) Essentials
Requirements traceability matrix (RTM) is a diagrammatic representation of functional requirements, showing how they relate to one another.
It helps trace each requirement back to its originator(s). In addition, it serves as a guide for identifying missing information or defects at any stage of the development process.
The matrixes can be used at different levels – from project level down to component level and even individual requirement level – depending on the number of stakeholders involved and their role in the project life cycle.
Why Requirements Traceability Matrix (RTM) Needed?
The main objective of RTM is to provide traceability between different elements of a project like projects, requirements, defects, test cases, etc. The below-mentioned points show why RTM is needed:
- It helps link all related documents together in one place to make it easy for anyone to access the required information at any time.
- It makes it easier for testers to understand how they can use this information while testing and what they should not do while trying.
- It helps testers identify gaps between documents such as requirements and test cases which may result in missing functionality during the testing phase.
Requirements Traceability Matrix (RTM) Types
Following are the types of RTM:
Forward traceability: Forwards traceability is proper when there are many revisions and a large backlog. It traces the product requirements from the definition phase to the testing phase.
Backward traceability: Backwards traceability works in the opposite direction as compared to Forwarding traceability. Backward traceability traces the validation of the product from testing to the requirement definition phase.
Bidirectional traceability: Bidirectional traceability supports both backward and forward tracing. It is often used in large projects with multiple development cycles. Bidirectional RTM covers all aspects of the development cycle, from the requirements gathering process to the testing cycle.
Benefits of RTM
The benefits of using a traceability matrix are numerous. It can help:
- Improve the quality of products and services.
- Reduce the time required to find information and resolve issues.
- Identify relationships between different parts of a product or service.
- Make it easier to identify problems and solve them more quickly.
Requirements Traceability Matrix (RTM) Tools
A Requirements Traceability Matrix (RTM) tool is software that automates the creation and maintenance of RTMs. It typically allows users to perform search queries on their RTMs, allowing them to see which documents contain which requirements or vice versa.
Modern Requirements4DevOps: Modern Requirements4DevOps integrates with Microsoft's Azure DevOps, TFS, and VSTS and provides project managers with traceability through every stage of the process
Visure Requirements: Visure Requirements is a tool that tracks changes made during the development process, providing complete traceability.
ReQtest: ReQtest is cloud-based and customizable; it provides traceability from project start to finish.
Requirements Traceability Matrix (RTM) Template
Conclusion
This article has tried to cover all aspects of RTM tool development. However, there are times when you would need to have an urgent requirement change, or if you have to make a hotfix, you can make it with the help of RTM.
Nonetheless, RTM helps in preventing any dissociation between requirement and code. An RTM is a one-stop solution for the testers and the developers. Further, it determines the bugs that programmers need to fix as soon as possible to eliminate them.
Of course, you can also use the requirements traceability matrix as a standalone solution to identify a mapping between test cases and requirements.
Project Quality Management: Cost of Quality
Project Quality Management: Cost of Quality
Cost of quality is a significant concept in the project quality management knowledge area. However, it's also misinterpreted by several PMP credential exam-takers. A strong understanding of this concept can help increase a participant's score as there're very few questions on the exam based on it.
Let's take a quick and profound journey into the cost of quality concept.
If a product meets/exceeds its design features and is null-defect, it's said to have a top-notch conformance quality. So, for example, if a steel watch has zero defects, it can have a high conformance quality as a zero-defect diamond-studded watch. The steel one may not be attractive or expensive as the diamond, but you can expect it to be free of defects.
The prevention, identification, and handling of defects incur costs of quality. The term indicates total costs incurred to prevent product defects or costs that result from product defects.
Quality costs don't just relate to manufacturing but all the tasks from research and development (R&D) to customer services. So, the whole product life-cycle is included while deriving quality costs.
The quality cost is reviewed as a part of project management to make crucial decisions on how much to invest in quality.
When it comes to the definition of quality cost, there are two categories:
Cost of Conformance
These costs are incurred to maintain defective products from falling into customers' hands. The cost of conformance is made of:
1. Appraisal Costs
These are also known as inspection costs incurred to determine defective products before they're shipped to consumers. However, performing appraisal tasks doesn't prevent defects from happening. Most managers realize that keeping a team of inspectors isn't an effective way to control quality.
A better method is to ask employees to be responsible for their quality control, followed by creating designs for how to manufacture a zero-defect product. This method enables quality to be built into the product, rather than depending on inspections to determine defects.
2. Prevention Costs
These costs include all those expenses incurred for tasks mainly designed to prevent the low-quality product from occurring. It's much less expensive to prevent an issue than to identify and rectify the problem after its occurrence.
Prevention costs are incurred for activities that minimize the defects number. Companies employ several practices to prevent them, including statistical process control, quality engineering, and training.
Cost of Non-conformance
These costs are incurred due to defects generated despite efforts by a company to prevent them. Hence, these costs are also called costs of poor quality. These failure expenses are incurred when a product fails to conform to its design properties.
The non-conformance costs consist of 2 categories:
1. Internal Failure Costs
These costs result from defects found before they are shipped to consumers. They are determined within the project scope. Internal failure costs include rejected products, downtime, and reworking detective systems caused by quality issues.
It also includes costs if an organization has to reject and throw units of their project work, called scrap. If the company's appraisal activities are productive, it has a good chance of identifying defects internally; thus increasing the internal failure cost level.
2. External Failure Costs
These costs are an outcome of delivering a defective product to the consumer. The external failure costs include many sales arising from a poor-quality reputation, repairs and replacements, product recalls, warranty, and liabilities arising from legal action against a firm. Such expenses can even reduce a business's profit.
These costs also give rise to intangible expenses. For example, a company may lose its future venture with its existing consumer for delivering a poor-quality product. These expenses aren't there on the balance sheet; instead, they significantly impact the income statement.
The best method a company can follow amid these scenarios is to ensure the defective products never reach the consumer.
By minimizing internal loss, one can ensure they don't slip through to become external failures. Even if they have an external failure, one should act quickly and resolve the customer problem. This is the benchmark of good customer service.
Hence, the cost of quality includes costs of conformance and non-conformance. This method helps us estimate the amount we spend to assure quality. It also involves looking at the conformance and non-conformance costs of the project and creating a suitable balance.
Read More
Project Quality Management: Cost of Quality
Cost of quality is a significant concept in the project quality management knowledge area. However, it's also misinterpreted by several PMP credential exam-takers. A strong understanding of this concept can help increase a participant's score as there're very few questions on the exam based on it.
Let's take a quick and profound journey into the cost of quality concept.
If a product meets/exceeds its design features and is null-defect, it's said to have a top-notch conformance quality. So, for example, if a steel watch has zero defects, it can have a high conformance quality as a zero-defect diamond-studded watch. The steel one may not be attractive or expensive as the diamond, but you can expect it to be free of defects.
The prevention, identification, and handling of defects incur costs of quality. The term indicates total costs incurred to prevent product defects or costs that result from product defects.
Quality costs don't just relate to manufacturing but all the tasks from research and development (R&D) to customer services. So, the whole product life-cycle is included while deriving quality costs.
The quality cost is reviewed as a part of project management to make crucial decisions on how much to invest in quality.
When it comes to the definition of quality cost, there are two categories:
Cost of Conformance
These costs are incurred to maintain defective products from falling into customers' hands. The cost of conformance is made of:
1. Appraisal Costs
These are also known as inspection costs incurred to determine defective products before they're shipped to consumers. However, performing appraisal tasks doesn't prevent defects from happening. Most managers realize that keeping a team of inspectors isn't an effective way to control quality.
A better method is to ask employees to be responsible for their quality control, followed by creating designs for how to manufacture a zero-defect product. This method enables quality to be built into the product, rather than depending on inspections to determine defects.
2. Prevention Costs
These costs include all those expenses incurred for tasks mainly designed to prevent the low-quality product from occurring. It's much less expensive to prevent an issue than to identify and rectify the problem after its occurrence.
Prevention costs are incurred for activities that minimize the defects number. Companies employ several practices to prevent them, including statistical process control, quality engineering, and training.
Cost of Non-conformance
These costs are incurred due to defects generated despite efforts by a company to prevent them. Hence, these costs are also called costs of poor quality. These failure expenses are incurred when a product fails to conform to its design properties.
The non-conformance costs consist of 2 categories:
1. Internal Failure Costs
These costs result from defects found before they are shipped to consumers. They are determined within the project scope. Internal failure costs include rejected products, downtime, and reworking detective systems caused by quality issues.
It also includes costs if an organization has to reject and throw units of their project work, called scrap. If the company's appraisal activities are productive, it has a good chance of identifying defects internally; thus increasing the internal failure cost level.
2. External Failure Costs
These costs are an outcome of delivering a defective product to the consumer. The external failure costs include many sales arising from a poor-quality reputation, repairs and replacements, product recalls, warranty, and liabilities arising from legal action against a firm. Such expenses can even reduce a business's profit.
These costs also give rise to intangible expenses. For example, a company may lose its future venture with its existing consumer for delivering a poor-quality product. These expenses aren't there on the balance sheet; instead, they significantly impact the income statement.
The best method a company can follow amid these scenarios is to ensure the defective products never reach the consumer.
By minimizing internal loss, one can ensure they don't slip through to become external failures. Even if they have an external failure, one should act quickly and resolve the customer problem. This is the benchmark of good customer service.
Hence, the cost of quality includes costs of conformance and non-conformance. This method helps us estimate the amount we spend to assure quality. It also involves looking at the conformance and non-conformance costs of the project and creating a suitable balance.
Critical Chain Project Management
Critical Chain Project Management
What is Critical Chain Project Management?
Critical Chain Project Management is a project management methodology that focuses on managing the critical path of a project. This is done by reducing the time spent on non-critical tasks and ensuring that resources are allocated to jobs so they will not delay the project's completion date.
There are two main concepts associated with Critical Chain Project Management:
Critical Path Method: This refers to a schedule management tool used to determine which tasks must be completed first for the project to be completed on time. This is done by analyzing dependencies between functions and deciding which ones are necessary for completion first.
Project Buffer: A project buffer refers to any amount of time added onto the critical path which does not contribute directly towards completing a task but would help prevent delays caused by other factors such as resource availability or weather conditions.
Using Critical Chain to Improve Project Performance
The critical chain is defined as the longest path through the network of activities in the project schedule. Any delay in moving along this path increases the overall project duration. In other words, Critical Chain is also the most extended sequence of dependent activities without a float (i.e., without slack).
The float associated with each activity determines its position in the critical path (or critical chain). Activities with zero float are always on the essential way; activities with positive float are never on the critical path, and activities with negative float may or may not be on it depending upon whether there are other higher priority zero-float activities ahead of them in the schedule.
For Critical Chain Project Management to work effectively, you need first to identify your key activities and then determine if they require more resources or not.
Application of critical chain in project management
It aims to improve the performance of projects by managing their schedules according to the critical path method and ensuring that all activities are completed in the most efficient manner possible.
The critical difference between CCPM and other project management approaches is that it does not rely on resource leveling but instead determines the critical path for each activity and ensures that resources are applied to those activities first. This helps prevent resource bottlenecks, which can lead to project delays.
Resource Management in CCPM
Resource management in critical chain project management is assigning resources to tasks and projects.
The resource management process involves four steps:
- First, select the right resources for your project or task. Then, the right help can do the job, have the required skills and experience, and are available when needed. This step is crucial for successful critical chain project management.
- Allocating resources to tasks. Once you've selected the right resources, you must assign them to tasks using a fair method that doesn't favor one study over another. For example, you might want to use an algorithm like shortest job first (SJF) or longest job first (LJF). Both methods are discussed below.
- You are monitoring resource utilization against capacity constraints. This step helps ensure that your resources aren't over-allocated and that your projects stay on track for completion dates. Suppose your projects fall behind schedule or use more than their allocated capacity. In that case, you should take corrective action immediately so as not to affect other projects in production.
- Managing unplanned work by ensuring it doesn't impact scheduled work or delay delivery dates.
Advantages of Critical Chain Project Management (CCPM)
- It offers a more realistic way of scheduling projects.
- It helps you use project controls to make better decisions, so you have a clear idea of each project's scope, cost, and schedule.
- It'll help you predict, plan and manage your projects better.
- It helps prevent you from having too much or too little slack in a project.
- It lets you more easily plan your schedule to get work done on time.
- It helps project managers to stay on task.
Conclusion
Critical Chain Project Management, or CCPM, is a type of project management methodology that analyzes tasks and breaks them into smaller, less complex chunks called critical path method projects or CPM.
Critical Chain Project Management then tries to reduce or eliminate the lag time of task completion as much as possible to get work done faster. Additionally, it prioritizes the parts of a project that are most important to the outcome of a goal.
Read More
Critical Chain Project Management
What is Critical Chain Project Management?
Critical Chain Project Management is a project management methodology that focuses on managing the critical path of a project. This is done by reducing the time spent on non-critical tasks and ensuring that resources are allocated to jobs so they will not delay the project's completion date.
There are two main concepts associated with Critical Chain Project Management:
Critical Path Method: This refers to a schedule management tool used to determine which tasks must be completed first for the project to be completed on time. This is done by analyzing dependencies between functions and deciding which ones are necessary for completion first.
Project Buffer: A project buffer refers to any amount of time added onto the critical path which does not contribute directly towards completing a task but would help prevent delays caused by other factors such as resource availability or weather conditions.
Using Critical Chain to Improve Project Performance
The critical chain is defined as the longest path through the network of activities in the project schedule. Any delay in moving along this path increases the overall project duration. In other words, Critical Chain is also the most extended sequence of dependent activities without a float (i.e., without slack).
The float associated with each activity determines its position in the critical path (or critical chain). Activities with zero float are always on the essential way; activities with positive float are never on the critical path, and activities with negative float may or may not be on it depending upon whether there are other higher priority zero-float activities ahead of them in the schedule.
For Critical Chain Project Management to work effectively, you need first to identify your key activities and then determine if they require more resources or not.
Application of critical chain in project management
It aims to improve the performance of projects by managing their schedules according to the critical path method and ensuring that all activities are completed in the most efficient manner possible.
The critical difference between CCPM and other project management approaches is that it does not rely on resource leveling but instead determines the critical path for each activity and ensures that resources are applied to those activities first. This helps prevent resource bottlenecks, which can lead to project delays.
Resource Management in CCPM
Resource management in critical chain project management is assigning resources to tasks and projects.
The resource management process involves four steps:
- First, select the right resources for your project or task. Then, the right help can do the job, have the required skills and experience, and are available when needed. This step is crucial for successful critical chain project management.
- Allocating resources to tasks. Once you've selected the right resources, you must assign them to tasks using a fair method that doesn't favor one study over another. For example, you might want to use an algorithm like shortest job first (SJF) or longest job first (LJF). Both methods are discussed below.
- You are monitoring resource utilization against capacity constraints. This step helps ensure that your resources aren't over-allocated and that your projects stay on track for completion dates. Suppose your projects fall behind schedule or use more than their allocated capacity. In that case, you should take corrective action immediately so as not to affect other projects in production.
- Managing unplanned work by ensuring it doesn't impact scheduled work or delay delivery dates.
Advantages of Critical Chain Project Management (CCPM)
- It offers a more realistic way of scheduling projects.
- It helps you use project controls to make better decisions, so you have a clear idea of each project's scope, cost, and schedule.
- It'll help you predict, plan and manage your projects better.
- It helps prevent you from having too much or too little slack in a project.
- It lets you more easily plan your schedule to get work done on time.
- It helps project managers to stay on task.
Conclusion
Critical Chain Project Management, or CCPM, is a type of project management methodology that analyzes tasks and breaks them into smaller, less complex chunks called critical path method projects or CPM.
Critical Chain Project Management then tries to reduce or eliminate the lag time of task completion as much as possible to get work done faster. Additionally, it prioritizes the parts of a project that are most important to the outcome of a goal.
Understanding the Difference between ROM Estimate Vs Definitive Estimate
Understanding the Difference between ROM Estimate Vs Definitive Estimate
Table of Content
What is a ROM Estimate?
Components of a ROM Estimate
Advantages of ROM Estimates
What is a Definitive Estimate?
Components of a Definitive Estimate
Advantages of Definitive Estimates
Difference between ROM Estimate and Definitive Estimates
What is a ROM Estimate?
ROM Estimate is a project estimate that summarizes the work required to complete a project. It gives an idea of the major activities and tasks involved in the project, along with the effort and resources needed for them.
The ROM Estimate is used to calculate the size of work packages (WP) and duration. It also determines whether other elements must be considered in the estimation process, such as cost drivers and resource requirements.
Components of a ROM Estimate
The Following are the component of the ROM Estimate
- Relevant work is defined and quantified.
- A schedule is created based on the tasks, resources, and other relevant factors required to complete the project.
- The process of creating and updating this schedule is known as Project Management.
- The project manager or the team leads define their scope of work and then assign tasks to various group members.
- The scope of work can be divided into many other sub-tasks. Each sub-task has a set of resources that are required to complete it. These resources include human resources and the funds needed to pay them.
Advantages of ROM Estimates
In project management, the ROM estimate determines the time and money needed to complete a project. This is done by calculating the total cost for all activities (from start to finish) in one specific calendar year. Advantages of ROM are:
- Comparing projects with different scopes, sizes, and complexity is more manageable.
- Comparing projects with similar scope, size, and complexity is easier.
- It's more accurate than using detailed cost breakdowns.
- It's more flexible than using detailed cost breakdowns.
- It can negotiate price or scope changes with customers or vendors.
What is a Definitive Estimate?
A definitive estimate is an estimate that the project manager has confidence in because it has undergone a process of review, revision, and consensus. A final assessment is based on analyzing all relevant factors and includes the best information available at the estimation time.
A definitive estimate provides a more accurate view of what can be achieved than an estimate derived from preliminary data. This is because it takes into account all known facts, as well as assumptions about future events. These assumptions are based on current performance trends and experience with similar projects.
Suppose a project's budget is not updated in line with actual costs incurred. In that case, it will be challenging to manage effectively over time.
For example, if a company expects to spend $1 million on a project which costs $1 million to complete but then discovers that it costs $2 million to build, then this discrepancy between budgeted and actual costs will affect future business decisions by management.
Components of a Definitive Estimate
The components of a definitive estimate include:
- Cost baseline -Defines all costs associated with the project, including personnel costs and subcontractor fees. This component also includes any expenses related to the acquisition of the work.
- Activity list- Provides details about each activity required during the life cycle of your project.
- Resource requirements -Provides details about each resource needed to execute your project plan.
Advantages of Definitive Estimates
The advantages of definitive estimates are:
- Definitive estimates are more accurate than ROM estimates. This is because they include all the inputs and assumptions used to determine the original ROM estimate.
- Definitive estimates are easier to verify because they include all of the information used to make the previous estimates so that you can double-check them more easily.
- Definitive estimates are more detailed and comprehensive than ROM estimates. For example, they describe what the project will cost, how long it will take, how much it will cost, how much it will take to complete, etc., making it easier to manage and plan for.
Difference between ROM Estimate and Definitive Estimates
The main difference between a ROM estimate and a definitive estimate is that with a ROM estimate, you have to make sure that the project's scope is defined correctly. In contrast, with a final estimate, you must ensure that enough information has been gathered to go ahead with your project without any significant problems.
The ROM estimate will have more variables than a definitive estimate. For example, in a ROM estimate, you will include how much time it takes to develop the product, how much time it takes to test the product, and how long it takes to launch the product.
Suppose you include all these variables in your ROM estimate. In that case, you can quickly get an accurate idea of how long your project will take to complete according to your schedule.
Conclusion
The estimate for a project is a culmination of the various data and information gathered about the project. When sourcing quotes and compiling data or information, it is easy to make mistakes.
Understanding the difference between ROM estimates and definitive estimates will therefore be crucial in minimizing the possibility of making errors in predictive analysis.
Read More
Understanding the Difference between ROM Estimate Vs Definitive Estimate
Table of Content
What is a ROM Estimate?
Components of a ROM Estimate
Advantages of ROM Estimates
What is a Definitive Estimate?
Components of a Definitive Estimate
Advantages of Definitive Estimates
Difference between ROM Estimate and Definitive Estimates
What is a ROM Estimate?
ROM Estimate is a project estimate that summarizes the work required to complete a project. It gives an idea of the major activities and tasks involved in the project, along with the effort and resources needed for them.
The ROM Estimate is used to calculate the size of work packages (WP) and duration. It also determines whether other elements must be considered in the estimation process, such as cost drivers and resource requirements.
Components of a ROM Estimate
The Following are the component of the ROM Estimate
- Relevant work is defined and quantified.
- A schedule is created based on the tasks, resources, and other relevant factors required to complete the project.
- The process of creating and updating this schedule is known as Project Management.
- The project manager or the team leads define their scope of work and then assign tasks to various group members.
- The scope of work can be divided into many other sub-tasks. Each sub-task has a set of resources that are required to complete it. These resources include human resources and the funds needed to pay them.
Advantages of ROM Estimates
In project management, the ROM estimate determines the time and money needed to complete a project. This is done by calculating the total cost for all activities (from start to finish) in one specific calendar year. Advantages of ROM are:
- Comparing projects with different scopes, sizes, and complexity is more manageable.
- Comparing projects with similar scope, size, and complexity is easier.
- It's more accurate than using detailed cost breakdowns.
- It's more flexible than using detailed cost breakdowns.
- It can negotiate price or scope changes with customers or vendors.
What is a Definitive Estimate?
A definitive estimate is an estimate that the project manager has confidence in because it has undergone a process of review, revision, and consensus. A final assessment is based on analyzing all relevant factors and includes the best information available at the estimation time.
A definitive estimate provides a more accurate view of what can be achieved than an estimate derived from preliminary data. This is because it takes into account all known facts, as well as assumptions about future events. These assumptions are based on current performance trends and experience with similar projects.
Suppose a project's budget is not updated in line with actual costs incurred. In that case, it will be challenging to manage effectively over time.
For example, if a company expects to spend $1 million on a project which costs $1 million to complete but then discovers that it costs $2 million to build, then this discrepancy between budgeted and actual costs will affect future business decisions by management.
Components of a Definitive Estimate
The components of a definitive estimate include:
- Cost baseline -Defines all costs associated with the project, including personnel costs and subcontractor fees. This component also includes any expenses related to the acquisition of the work.
- Activity list- Provides details about each activity required during the life cycle of your project.
- Resource requirements -Provides details about each resource needed to execute your project plan.
Advantages of Definitive Estimates
The advantages of definitive estimates are:
- Definitive estimates are more accurate than ROM estimates. This is because they include all the inputs and assumptions used to determine the original ROM estimate.
- Definitive estimates are easier to verify because they include all of the information used to make the previous estimates so that you can double-check them more easily.
- Definitive estimates are more detailed and comprehensive than ROM estimates. For example, they describe what the project will cost, how long it will take, how much it will cost, how much it will take to complete, etc., making it easier to manage and plan for.
Difference between ROM Estimate and Definitive Estimates
The main difference between a ROM estimate and a definitive estimate is that with a ROM estimate, you have to make sure that the project's scope is defined correctly. In contrast, with a final estimate, you must ensure that enough information has been gathered to go ahead with your project without any significant problems.
The ROM estimate will have more variables than a definitive estimate. For example, in a ROM estimate, you will include how much time it takes to develop the product, how much time it takes to test the product, and how long it takes to launch the product.
Suppose you include all these variables in your ROM estimate. In that case, you can quickly get an accurate idea of how long your project will take to complete according to your schedule.
Conclusion
The estimate for a project is a culmination of the various data and information gathered about the project. When sourcing quotes and compiling data or information, it is easy to make mistakes.
Understanding the difference between ROM estimates and definitive estimates will therefore be crucial in minimizing the possibility of making errors in predictive analysis.
How to Monitor and Control Project Work: PMP Processes
How to Monitor and Control Project Work: PMP Processes
Table of Content
Monitor and Control Project Work
Project Management Processes
Control Scope
Schedule Progress Control
Costs Control
Quality Control
Risk Management
Why Is It Important to Monitor And Control Projects?
Monitoring and Control Method
Conclusion
Monitor and Control Project Work
Monitoring and controlling project work is an essential and integral part of the PMP Process. PMP Preparing a project plan, preparing a project schedule, monitoring and controlling project work, and monitoring and controlling the quality of work are the processes included in PMP Processes.
The process of monitoring and controlling project work involves following the procedures for monitoring and controlling project work systematically.
Monitoring and controlling the progress of significant activities is done by following the system for monitoring and controlling gain.
There are several ways to monitor and control project work:
- For example, using time-tracking software or a task management system helps you manage your time effectively.
- By creating schedules based on time-based estimates.
- By creating reports based on data collected from various sources.
- By performing post-activity reviews.
Project Management Processes
To monitor and control project work, it is necessary to have a good understanding of the Project Management Processes. The following are some of the key PMP processes:
Project Initiation: This process is where you start working on projects. It includes preparation and definition of scope, resources, team, etc., so the project can begin.
Project Planning: In this process, you plan for all activities performed during a project. This includes estimating the time required for each activity and determining how much time will be needed from different resources such as cost, labor, and equipment.
Project Execution: In this process, you carry out all tasks assigned to you by your supervisor or your manager in accordance with the plan you created in the previous phases of planning and initiation.
Project Closing: In this phase, all tasks assigned to people working on a project should be completed successfully according to your schedule. Also, all costs should have been collected by individuals involved in these tasks.
Control Scope
The primary purpose of the control scope process is to ensure that each project has a specific and well-defined scope. The method also helps to ensure that the project is on track and stays on track.
The control scope process involves defining, monitoring, and controlling. The first step is to determine what it means for the project to be on track. This can be done by considering how much work has been done so far, how much work is left, what resources are required, and when they need to be delivered.
Schedule Progress Control
The Schedule Progress Control process helps you stay on top of your deadlines by ensuring that all tasks are completed on time. This ensures that there are no delays in meeting milestones or deadlines for deliverables, which could cause problems for stakeholders who depend on those deliverables for their workflows or decisions.
When used correctly, this process allows you to spot potential problems early on so that they can be resolved before they become major issues that could derail the entire project.
Costs Control
The Cost Control Process is a part of the Monitoring and Controlling process group. It determines whether the project is within budget and whether it will be completed on time. This process ensures that the project's costs are monitored, controlled, and reported throughout the life cycle.
Cost control involves:
- Monitoring actual cost performance against baseline estimates.
- Take corrective action when needed.
- Assessing variances between actual costs and baseline estimates (at least monthly).
- Based on current performance trends, develop an estimate of total project costs at completion (TPC).
Quality Control
The quality control process is a systematic way of monitoring and controlling the project work. Quality control is a set of activities that help ensure that the product or service delivered to the customer meets the requirements specified in the project plan.
Quality control activities include:
- Planning for quality control.
- Performing quality audits.
- Identifying nonconformities and their root causes.
- Resolving nonconformities and recommending actions to prevent a recurrence.
Risk Management
Risk management is a process that helps project managers to identify, assess and manage risks. In addition, it helps to ensure that the project is completed within time and budget constraints.
The risk management process consists of the following steps:
Identification of Risks: In this step, you need to identify all possible threats that might impact the project, such as financial risks, technical risks, human resource risks, etc.
Assessment of Risks: After identifying the risks, you need to evaluate them based on their probability and impact on project success. You may also need to assess how serious each risk may be or how likely it is to occur.
Response Planning: Based on the risk assessment results, you can decide which risks are high priority and require immediate action or response planning (which includes preventive measures). It would help if you also considered taking preventive measures for high-priority risks by implementing risk responses that could prevent their occurrence from happening in the future.
Monitoring: You should monitor your response plans regularly until they are no longer required or until they have been successfully implemented with no failures reported at any point in time during the monitoring period.
Why Is It Important to Monitor and Control Projects?
The purpose of monitoring and controlling projects is to ensure that the project meets the specified objectives and targets. It also helps you ensure the project is on track, within budget, and under control.
Therefore, monitoring and controlling projects are essential for ensuring the smooth completion of a project. You can monitor your projects with different tools available in the market for this purpose. For this purpose, you can use Excel spreadsheets, Gantt charts, PERT charts, etc.
Monitoring and Control Method
The monitoring and controlling process is the main activity of quality control. It is performed by the project manager or a person who reports to them.
This process aims to provide information about the current status of work, problems, and risks so that the project manager can take appropriate actions to correct the situation.
The project manager must use various techniques to monitor and control project activities. Some examples include:
- Inspecting deliverables and completed work products (including reviewing documentation).
- Interview team members as needed.
- Reviewing progress reports prepared by team members.
- Meeting with team members as needed to discuss their progress on their assigned tasks or subtasks (as well as other aspects of the project).
Conclusion
The PMP Processes help one accurately monitor and control project work. These processes should be applied at the right time in the project to ensure that all tasks are being performed according to plan, that delays are quickly discovered and controlled, and that the project is ultimately completed on time and within budget
Read More
How to Monitor and Control Project Work: PMP Processes
Table of Content
Monitor and Control Project Work
Project Management Processes
Control Scope
Schedule Progress Control
Costs Control
Quality Control
Risk Management
Why Is It Important to Monitor And Control Projects?
Monitoring and Control Method
Conclusion
Monitor and Control Project Work
Monitoring and controlling project work is an essential and integral part of the PMP Process. PMP Preparing a project plan, preparing a project schedule, monitoring and controlling project work, and monitoring and controlling the quality of work are the processes included in PMP Processes.
The process of monitoring and controlling project work involves following the procedures for monitoring and controlling project work systematically.
Monitoring and controlling the progress of significant activities is done by following the system for monitoring and controlling gain.
There are several ways to monitor and control project work:
- For example, using time-tracking software or a task management system helps you manage your time effectively.
- By creating schedules based on time-based estimates.
- By creating reports based on data collected from various sources.
- By performing post-activity reviews.
Project Management Processes
To monitor and control project work, it is necessary to have a good understanding of the Project Management Processes. The following are some of the key PMP processes:
Project Initiation: This process is where you start working on projects. It includes preparation and definition of scope, resources, team, etc., so the project can begin.
Project Planning: In this process, you plan for all activities performed during a project. This includes estimating the time required for each activity and determining how much time will be needed from different resources such as cost, labor, and equipment.
Project Execution: In this process, you carry out all tasks assigned to you by your supervisor or your manager in accordance with the plan you created in the previous phases of planning and initiation.
Project Closing: In this phase, all tasks assigned to people working on a project should be completed successfully according to your schedule. Also, all costs should have been collected by individuals involved in these tasks.
Control Scope
The primary purpose of the control scope process is to ensure that each project has a specific and well-defined scope. The method also helps to ensure that the project is on track and stays on track.
The control scope process involves defining, monitoring, and controlling. The first step is to determine what it means for the project to be on track. This can be done by considering how much work has been done so far, how much work is left, what resources are required, and when they need to be delivered.
Schedule Progress Control
The Schedule Progress Control process helps you stay on top of your deadlines by ensuring that all tasks are completed on time. This ensures that there are no delays in meeting milestones or deadlines for deliverables, which could cause problems for stakeholders who depend on those deliverables for their workflows or decisions.
When used correctly, this process allows you to spot potential problems early on so that they can be resolved before they become major issues that could derail the entire project.
Costs Control
The Cost Control Process is a part of the Monitoring and Controlling process group. It determines whether the project is within budget and whether it will be completed on time. This process ensures that the project's costs are monitored, controlled, and reported throughout the life cycle.
Cost control involves:
- Monitoring actual cost performance against baseline estimates.
- Take corrective action when needed.
- Assessing variances between actual costs and baseline estimates (at least monthly).
- Based on current performance trends, develop an estimate of total project costs at completion (TPC).
Quality Control
The quality control process is a systematic way of monitoring and controlling the project work. Quality control is a set of activities that help ensure that the product or service delivered to the customer meets the requirements specified in the project plan.
Quality control activities include:
- Planning for quality control.
- Performing quality audits.
- Identifying nonconformities and their root causes.
- Resolving nonconformities and recommending actions to prevent a recurrence.
Risk Management
Risk management is a process that helps project managers to identify, assess and manage risks. In addition, it helps to ensure that the project is completed within time and budget constraints.
The risk management process consists of the following steps:
Identification of Risks: In this step, you need to identify all possible threats that might impact the project, such as financial risks, technical risks, human resource risks, etc.
Assessment of Risks: After identifying the risks, you need to evaluate them based on their probability and impact on project success. You may also need to assess how serious each risk may be or how likely it is to occur.
Response Planning: Based on the risk assessment results, you can decide which risks are high priority and require immediate action or response planning (which includes preventive measures). It would help if you also considered taking preventive measures for high-priority risks by implementing risk responses that could prevent their occurrence from happening in the future.
Monitoring: You should monitor your response plans regularly until they are no longer required or until they have been successfully implemented with no failures reported at any point in time during the monitoring period.
Why Is It Important to Monitor and Control Projects?
The purpose of monitoring and controlling projects is to ensure that the project meets the specified objectives and targets. It also helps you ensure the project is on track, within budget, and under control.
Therefore, monitoring and controlling projects are essential for ensuring the smooth completion of a project. You can monitor your projects with different tools available in the market for this purpose. For this purpose, you can use Excel spreadsheets, Gantt charts, PERT charts, etc.
Monitoring and Control Method
The monitoring and controlling process is the main activity of quality control. It is performed by the project manager or a person who reports to them.
This process aims to provide information about the current status of work, problems, and risks so that the project manager can take appropriate actions to correct the situation.
The project manager must use various techniques to monitor and control project activities. Some examples include:
- Inspecting deliverables and completed work products (including reviewing documentation).
- Interview team members as needed.
- Reviewing progress reports prepared by team members.
- Meeting with team members as needed to discuss their progress on their assigned tasks or subtasks (as well as other aspects of the project).
Conclusion
The PMP Processes help one accurately monitor and control project work. These processes should be applied at the right time in the project to ensure that all tasks are being performed according to plan, that delays are quickly discovered and controlled, and that the project is ultimately completed on time and within budget
The Affinity Diagram: PMP Planning Tools that You Should Know
The Affinity Diagram: PMP Planning Tools that You Should Know
Are you looking for a focus tool to help with your PMP exams? As someone who managed projects daily, prioritized cost reduction and faster delivery. However, other things became my focus, especially when preparing for the PMP certification exam.
The product manager's job is not just about managing the team and timelines but also ensuring that each project has the necessary budget allocated to meet quality standards. The only way to go about this process is what's known as the Affinity Diagram, which offers a variety of planning tools that can help you achieve optimum results.
What is the Affinity Diagram?
An affinity diagram is a process-mapping tool that helps you organize your ideas and identify relationships between them. This can be applied to project planning, for example, where you might locate all the inputs and outputs of a project and then determine the activities between these elements.
The affinity diagram is one of several tools in the PMBOK Guide (Project Management Body of Knowledge) that can help you plan your projects.
It's a visual representation of how people think about the project based on their input or output. It's useful because it lets you look at different aspects of your project and get an overall view of where everything fits together.
The affinity diagram can be used for the following purposes:
- First, to identify relationships between items in a list.
- To organize thoughts into groups related to similar concepts or ideas.
- To prioritize items in each group so they can be easily understood when viewing them side by side.
How can we use this tool?
In project management, affinity diagrams are used at the start of any project to identify key relationships between different elements of the project (such as tasks). This helps you understand how various tasks relate and how they might impact each other's completion time or cost.
Using an affinity diagram can help you:
- Understand how different tasks relate to each other (and how they might impact each other's completion time or cost)
- Identify which tasks need more attention than others (and why)
- The affinity diagram enables you to classify ideas and gather them into groups based on common characteristics. This helps you gain insight into the project's structure or process and make improvements based on what you find out.
Why Use an Affinity Diagram?
An affinity diagram can be used for brainstorming during problem-solving sessions. It helps you organize your thoughts before deciding how to solve problems within projects/programs/portfolios and how they relate to each other.
For example, if you are trying to determine how many people should be assigned to a project, instead of listing all possible options and then making a decision based on that list, use an affinity diagram first so that you can see which ones are more likely than others before making a final decision.
Here are reasons why you should use an affinity:
The Affinity Diagram Helps You Understand Your Audience
It's easy to get lost in the weeds when developing a project plan. Using an affinity diagram helps you understand what your audience needs from the project and what they don't need from it. This will help you create a better plan that covers all of their needs while not wasting time on things that don't matter.
The Affinity Diagram Helps You Prioritize Your Ideas
Once you've figured out what your audience wants and doesn't want, it's easier to prioritize your ideas and determine which ones matter most and which can wait until later in the process (or maybe never). This will help streamline your planning process so that you don't waste time on things that don't matter now and can focus on what matters most.
It helps you to identify themes and group similar ideas together
An affinity diagram allows you to group similar concepts so that you can easily see the most common types of solutions. This makes it easier for you to choose the best answers from all the possible solutions.
It helps teams come together around a common goal
One of the main benefits of using an affinity diagram is that it forces team members to collaborate. When everyone has input into the process and contributes their ideas, it creates a sense of ownership within the team. It helps them feel more engaged with each other's work.
What are the benefits of using an affinity diagram?
- A great benefit of using this tool is its ability to organize ideas. It will help you become more organized with your thoughts, which will help you make better decisions.
- It allows you to devise solutions for problems by grouping them so they can be dealt with efficiently. For example, suppose the problem is on one side. In that case, it will be easier for you to solve it because they are all together in one place instead of being scattered around different parts of your mind.
- An affinity diagram helps you identify all possible relationships between your tasks to determine how they should be sequenced or linked together with dependencies. Doing this will ensure that there are no gaps or overlaps in your project plan. In other words, this tool allows you to create a solid and robust schedule with no holes!
Affinity diagram is used in many PMP exams.
Affinity diagram is one of the planning tools in the PMBOK® Guide. It lists ideas or concepts and then organizes them into logical groups. The affinity diagram is also known as a Cluster Diagram or KJ Method.
An affinity diagram consists of two steps: identifying key characteristics and grouping similar items together. Once you have your list of ideas, you can use an affinity diagram to organize them into similar groups based on common characteristics.
Affinity diagrams are often used during project planning because they help identify different aspects of a project and group them according to their relationships. This helps decision-makers understand how various parts of a project work together, which can be very useful when deciding how best to proceed with your project plan.
While most people who use affinity diagrams do not refer to them as such, there are many similarities between this tool and mind mapping techniques like concept maps or mind maps. Both methods identify key traits among items considered for inclusion in a group.
Conclusion
As it turns out, the PMP is all about planning. In many ways, my favorite concept in project management is one called an affinity diagram.
That's where you get all the team members together and work with them to sort and group your ideas. This tool is helpful for planning because it helps you build a plan even if you don't have every detail of what you'll be doing until the end of your project.
Read More
The Affinity Diagram: PMP Planning Tools that You Should Know
Are you looking for a focus tool to help with your PMP exams? As someone who managed projects daily, prioritized cost reduction and faster delivery. However, other things became my focus, especially when preparing for the PMP certification exam.
The product manager's job is not just about managing the team and timelines but also ensuring that each project has the necessary budget allocated to meet quality standards. The only way to go about this process is what's known as the Affinity Diagram, which offers a variety of planning tools that can help you achieve optimum results.
What is the Affinity Diagram?
An affinity diagram is a process-mapping tool that helps you organize your ideas and identify relationships between them. This can be applied to project planning, for example, where you might locate all the inputs and outputs of a project and then determine the activities between these elements.
The affinity diagram is one of several tools in the PMBOK Guide (Project Management Body of Knowledge) that can help you plan your projects.
It's a visual representation of how people think about the project based on their input or output. It's useful because it lets you look at different aspects of your project and get an overall view of where everything fits together.
The affinity diagram can be used for the following purposes:
- First, to identify relationships between items in a list.
- To organize thoughts into groups related to similar concepts or ideas.
- To prioritize items in each group so they can be easily understood when viewing them side by side.
How can we use this tool?
In project management, affinity diagrams are used at the start of any project to identify key relationships between different elements of the project (such as tasks). This helps you understand how various tasks relate and how they might impact each other's completion time or cost.
Using an affinity diagram can help you:
- Understand how different tasks relate to each other (and how they might impact each other's completion time or cost)
- Identify which tasks need more attention than others (and why)
- The affinity diagram enables you to classify ideas and gather them into groups based on common characteristics. This helps you gain insight into the project's structure or process and make improvements based on what you find out.
Why Use an Affinity Diagram?
An affinity diagram can be used for brainstorming during problem-solving sessions. It helps you organize your thoughts before deciding how to solve problems within projects/programs/portfolios and how they relate to each other.
For example, if you are trying to determine how many people should be assigned to a project, instead of listing all possible options and then making a decision based on that list, use an affinity diagram first so that you can see which ones are more likely than others before making a final decision.
Here are reasons why you should use an affinity:
The Affinity Diagram Helps You Understand Your Audience
It's easy to get lost in the weeds when developing a project plan. Using an affinity diagram helps you understand what your audience needs from the project and what they don't need from it. This will help you create a better plan that covers all of their needs while not wasting time on things that don't matter.
The Affinity Diagram Helps You Prioritize Your Ideas
Once you've figured out what your audience wants and doesn't want, it's easier to prioritize your ideas and determine which ones matter most and which can wait until later in the process (or maybe never). This will help streamline your planning process so that you don't waste time on things that don't matter now and can focus on what matters most.
It helps you to identify themes and group similar ideas together
An affinity diagram allows you to group similar concepts so that you can easily see the most common types of solutions. This makes it easier for you to choose the best answers from all the possible solutions.
It helps teams come together around a common goal
One of the main benefits of using an affinity diagram is that it forces team members to collaborate. When everyone has input into the process and contributes their ideas, it creates a sense of ownership within the team. It helps them feel more engaged with each other's work.
What are the benefits of using an affinity diagram?
- A great benefit of using this tool is its ability to organize ideas. It will help you become more organized with your thoughts, which will help you make better decisions.
- It allows you to devise solutions for problems by grouping them so they can be dealt with efficiently. For example, suppose the problem is on one side. In that case, it will be easier for you to solve it because they are all together in one place instead of being scattered around different parts of your mind.
- An affinity diagram helps you identify all possible relationships between your tasks to determine how they should be sequenced or linked together with dependencies. Doing this will ensure that there are no gaps or overlaps in your project plan. In other words, this tool allows you to create a solid and robust schedule with no holes!
Affinity diagram is used in many PMP exams.
Affinity diagram is one of the planning tools in the PMBOK® Guide. It lists ideas or concepts and then organizes them into logical groups. The affinity diagram is also known as a Cluster Diagram or KJ Method.
An affinity diagram consists of two steps: identifying key characteristics and grouping similar items together. Once you have your list of ideas, you can use an affinity diagram to organize them into similar groups based on common characteristics.
Affinity diagrams are often used during project planning because they help identify different aspects of a project and group them according to their relationships. This helps decision-makers understand how various parts of a project work together, which can be very useful when deciding how best to proceed with your project plan.
While most people who use affinity diagrams do not refer to them as such, there are many similarities between this tool and mind mapping techniques like concept maps or mind maps. Both methods identify key traits among items considered for inclusion in a group.
Conclusion
As it turns out, the PMP is all about planning. In many ways, my favorite concept in project management is one called an affinity diagram.
That's where you get all the team members together and work with them to sort and group your ideas. This tool is helpful for planning because it helps you build a plan even if you don't have every detail of what you'll be doing until the end of your project.
Cost of Quality: PMP Topics to Learn for the Exam
Cost of Quality: PMP Topics to Learn for the Exam
Cost of Quality
The Cost of Quality is an essential topic for the PMP exam. The Cost of Quality is a management accounting concept that can help you measure the cost of defects or poor quality in your project, product, or service. This information can improve quality and reduce costs in future projects.
The PMBOK® Guide defines the Cost of Quality as: "The cost required by a company to prevent poor quality and implement good quality in products, services, and processes."
You can calculate the cost of poor quality using two approaches: Cost of Conformance and Cost of Non-Conformance.
Cost of Conformance
These are the costs incurred when a product, service, or process does not meet specifications. This may include costs for rework and the use of defective materials. The Cost of Conformance is made up of Preventions costs and Appraisal costs.
Prevention Costs
Prevention is the most effective means of preventing defects. These costs include all those incurred for activities specifically designed to avoid poor product quality from happening in the first place. Preventing mistakes is much less costly than fixing them after they have been made. For example, organizations use statistical process control (SPC), Quality engineering, training, and more advanced techniques like Lean Manufacturing or Six Sigma to help prevent defects from occurring in the first place.
Appraisal Costs
Appraisal costs are also referred to as inspection costs. These costs encompass the cost of inspecting a product before it is shipped to customers. In most cases, an appraisal does not prevent defects from occurring but instead identifies these defects before the customer receives their order. Therefore, appraisal activities should be performed by employees responsible for quality control and designing defect-free products from the beginning.
Cost of Non-Conformance
These are the costs incurred when a product, service, or process does not meet customer requirements. These may include lost sales and customer dissatisfaction due to product or service errors. The cost of non-conformance is made up of internal and external failure costs.
Internal Failure Costs
Internal failure costs result from identifying defects before they are shipped to customers. If flaws are detected internally, it is more likely that the organization will be able to correct them before they are sent to customers. This leads to a reduction in the external failure costs that arise from the production of defective units.
External Failure Costs
A company incurs external failure costs when delivering damaged or defective products to the end customer. These costs include warranty, repairs, and replacements, product recalls, liabilities arising from legal action against a company, and lost sales stemming from a reputation for poor quality. They are not included in an income statement, but they can have an adverse impact on it.
If you haven't already started studying for the PMP exam, consider reading through this infographic to help guide your studies. Please start with the fundamentals and work your way up to more complicated topics as you become familiar with them. The goal here is not just to give you a list of issues but to help you learn methodically from the ground up.
Read More
Cost of Quality: PMP Topics to Learn for the Exam
Cost of Quality
The Cost of Quality is an essential topic for the PMP exam. The Cost of Quality is a management accounting concept that can help you measure the cost of defects or poor quality in your project, product, or service. This information can improve quality and reduce costs in future projects.
The PMBOK® Guide defines the Cost of Quality as: "The cost required by a company to prevent poor quality and implement good quality in products, services, and processes."
You can calculate the cost of poor quality using two approaches: Cost of Conformance and Cost of Non-Conformance.
Cost of Conformance
These are the costs incurred when a product, service, or process does not meet specifications. This may include costs for rework and the use of defective materials. The Cost of Conformance is made up of Preventions costs and Appraisal costs.
Prevention Costs
Prevention is the most effective means of preventing defects. These costs include all those incurred for activities specifically designed to avoid poor product quality from happening in the first place. Preventing mistakes is much less costly than fixing them after they have been made. For example, organizations use statistical process control (SPC), Quality engineering, training, and more advanced techniques like Lean Manufacturing or Six Sigma to help prevent defects from occurring in the first place.
Appraisal Costs
Appraisal costs are also referred to as inspection costs. These costs encompass the cost of inspecting a product before it is shipped to customers. In most cases, an appraisal does not prevent defects from occurring but instead identifies these defects before the customer receives their order. Therefore, appraisal activities should be performed by employees responsible for quality control and designing defect-free products from the beginning.
Cost of Non-Conformance
These are the costs incurred when a product, service, or process does not meet customer requirements. These may include lost sales and customer dissatisfaction due to product or service errors. The cost of non-conformance is made up of internal and external failure costs.
Internal Failure Costs
Internal failure costs result from identifying defects before they are shipped to customers. If flaws are detected internally, it is more likely that the organization will be able to correct them before they are sent to customers. This leads to a reduction in the external failure costs that arise from the production of defective units.
External Failure Costs
A company incurs external failure costs when delivering damaged or defective products to the end customer. These costs include warranty, repairs, and replacements, product recalls, liabilities arising from legal action against a company, and lost sales stemming from a reputation for poor quality. They are not included in an income statement, but they can have an adverse impact on it.
If you haven't already started studying for the PMP exam, consider reading through this infographic to help guide your studies. Please start with the fundamentals and work your way up to more complicated topics as you become familiar with them. The goal here is not just to give you a list of issues but to help you learn methodically from the ground up.
Quality Management: PMP Questions to Review
Quality Management: PMP Questions to Review
Q1. Experienced project managers always tell that accuracy and precision are not the same. Precise measurements may not be accurate and accurate measurements may not be precise. Which of the following statement about precision and accuracy is CORRECT?
- Precision means the values of repeated measurements are clustered and Accuracy means the measured value is close to the actual value
- Accuracy means the degree to which a set of inherent characteristics fulfill requirements and Precision means a category assigned to products or services having the same functional use but different technical characteristics
- Precision means the degree to which a set of inherent characteristics fulfill requirements and Accuracy means a category assigned to products or services having the same functional use but different technical characteristics
- Accuracy means the values of repeated measurements are clustered and Precision means the measured value is close to the actual value
Q2. A project management team came up with certain metrics such as defect frequency, failure rate, availability, and reliability. These are usually defined as an output of what process?
- Manage Quality
- Define Scope
- Plan Quality Management
- Collect Requirements
Q3. Which of these statements is accurate regarding quality management?
- Project requirements are turned into customer needs, wants, and expectations
- Quality and grade are essentially the same
- Modern quality management complements project management
- Overworking the team to meet requirements is not likely to increase attrition and rework
Q4. Which of these tools is NOT a part of the Seven Basic Tools of Quality?
- Scatter Diagram
- Control Chart
- Flowcharting
- Statistical Sampling
Q5. A control chart is used to determine whether or not a process is stable or has predictable performance. When a process is within acceptable limits, the process need not be adjusted. What are the upper and lower control limits usually set as?
- + / – 2 sigma
- + / – 3 sigma
- + / – 1 sigma
- + / – 6 sigma
Q6. A project manager used a control chart to determine whether a process was stable or not, and to determine if its performance was predictable. He determined the upper and lower specification limits based on the contractual requirements. A set of eighteen data points were taken. Of these, 8 consecutive data points were above the mean. What can you say about such a process?
- A process is considered as being within control if less than half the data points are above or below the mean. Hence the process is within control.
- A process is considered as out of control if five consecutive data points are above or below the mean. Hence the process is out of control.
- A process is considered as out of control if seven consecutive data points are above or below the mean. Hence the process is out of control.
- A process is considered as out of control if six consecutive data points are above or below the mean. Hence the process is within control.
Q7. Which quality control technique or tool should be used when trying to determine the cause of a major defect?
- Control Chart
- Fishbone diagram
- Pareto Chart
- Histogram
Q8. The term ____________ indicates the degree to which a particular product or service meets requirements, while ____________ indicates a category or rank used to distinguish that item from other similar items.
- Grade, quality
- Quality, grade
- Quality, standard
- Grade, standard
Q9. You work at a software company that authors Material Safety Data Sheets (MSDS) for chemical companies. Prior to releasing the MSDS to the company you have created a list of items to be reviewed to see that they appear on the document such as: chemical name, CAS#, protection required, what to do an emergency, etc. This is an example of what type of tool?
- Quality Metrics
- Process Improvement Plan
- Quality Management Plan
- Checklist
Q10. The process of auditing the quality requirements and the results from quality control measurements to ensure appropriate quality standards and operational definitions are used is the definition of: _____________
- Scope validation
- Quality planning
- Quality control
- Quality assurance
Q11. A good quality audit should be:
- informal and internal
- structured and independent
- structured and internal
- informal and independent
Q12. In order to keep costs low, a project management team decided to apply statistical sampling while inspecting some of the work products. They decided to select 10 out of 50 engineering drawings for inspection. During which process should the sample frequency and sample size be determined?
- Control Quality
- Collect Requirements
- Plan Quality Management
- Manage Quality
Q13. You are in the execution stage of your project and you have been informed that “corporate” will be sending in a team of consultants to review whether your project activities comply with the company’s and PMI’s policies, standards, and procedures. This is an example of?
- Recommended Corrective Actions
- Organizational Process Assets
- Process Analysis
- Quality Audit
Q14. Select the best answer: Continuous process improvement reduces ___________ and ___________ , which allows processes to operate at increased levels of efficiency and effectiveness.
- Departmental and organization processes
- Process and policy overhead.
- Waste and non-value added activities.
- Cost and scope
Q15. A project manager used a control chart to determine whether a process was stable or not, and to determine if its performance was predictable. He determined the upper and lower specification limits based on the contractual requirements. A set of eighteen data points were taken. Of these, 8 consecutive data points were above the mean. What can you say about such a process?
- A process is considered as out of control if five consecutive data points are above or below the mean. Hence the process is out of control.
- A process is considered as out of control if seven consecutive data points are above or below the mean. Hence the process is out of control.
- A process is considered as out of control if six consecutive data points are above or below the mean. Hence the process is within control.
- A process is considered as being within control if less than half the data points are above or below the mean. Hence the process is within control.
Q16. A team of engineers is reviewing a scatter diagram to determine how the changes in two variables in a new type of automobile tire are related. The closer points on the diagram are to a diagonal line, ______________ .
- the less likely a control group will be required
- the more likely a control group will be required
- the less likely they are to be related
- the more closely they are related
Q17. On a control chart, if six consecutive plot points are above the mean, then what can be established about the process?
- The process is out of control
- Nothing can be established
- The process is in control
- The process will be out of control after plotting the seventh point.
Q18. Which of the following tools would be most appropriate for collecting data to study the symptoms of a problem?
- Checklist
- Histogram
- Check Sheet
- Control Chart
Q19. The cost of scrap rework, in a product quality cost system, is categorized as a:
- Appraisal costs
- External failure costs
- Prevention costs
- Internal failure costs
Q20. The four categories of costs associated with product quality costs are:
- External failure, internal failure, prevention, and inspection
- External failure, internal failure, repair, and appraisal
- Warranty, product liability, training, and appraisal
- External failure, internal failure, prevention, and appraisal
Q21. Which of the following quality costs are failure costs?
- Pre-dispatch inspection costs
- Customer satisfaction survey costs
- Product recall costs
- Equipment calibration costs
Q22. In which of the following control chart the control limits will vary from subgroup to subgroup?
- Xbar-R Chart
- c Chart
- p Chart
- np Chart
Q23. If there are seven data points either above or below the mean, but still within the control limits, what should you do?
- Reinspect the product
- Ignore it and continue to measure the process
- Find the cause because this means that the process is out of control
- Reject the product
Q24. Two variables, x and y, are related. Variable x increases or decreases with y. Which of the following tools could best be used to graphically show this relationship?
- Histogram
- Scatter Plot
- Control Charts
- Control Charts
Q25. Which of these quality gurus introduced the concept of Control Charts?
- Crosby
- Taguchi
- Juran
- Shewhart
Q26. Control Limits are the same are Specifications Limits.
- True
- False
Q27. What does COQ stand for?
- Cost of Quality
- Carry on Quality
- Cost Oriented Quality
- Corporate Quality
Read More
Quality Management: PMP Questions to Review
Q1. Experienced project managers always tell that accuracy and precision are not the same. Precise measurements may not be accurate and accurate measurements may not be precise. Which of the following statement about precision and accuracy is CORRECT?
- Precision means the values of repeated measurements are clustered and Accuracy means the measured value is close to the actual value
- Accuracy means the degree to which a set of inherent characteristics fulfill requirements and Precision means a category assigned to products or services having the same functional use but different technical characteristics
- Precision means the degree to which a set of inherent characteristics fulfill requirements and Accuracy means a category assigned to products or services having the same functional use but different technical characteristics
- Accuracy means the values of repeated measurements are clustered and Precision means the measured value is close to the actual value
Q2. A project management team came up with certain metrics such as defect frequency, failure rate, availability, and reliability. These are usually defined as an output of what process?
- Manage Quality
- Define Scope
- Plan Quality Management
- Collect Requirements
Q3. Which of these statements is accurate regarding quality management?
- Project requirements are turned into customer needs, wants, and expectations
- Quality and grade are essentially the same
- Modern quality management complements project management
- Overworking the team to meet requirements is not likely to increase attrition and rework
Q4. Which of these tools is NOT a part of the Seven Basic Tools of Quality?
- Scatter Diagram
- Control Chart
- Flowcharting
- Statistical Sampling
Q5. A control chart is used to determine whether or not a process is stable or has predictable performance. When a process is within acceptable limits, the process need not be adjusted. What are the upper and lower control limits usually set as?
- + / – 2 sigma
- + / – 3 sigma
- + / – 1 sigma
- + / – 6 sigma
Q6. A project manager used a control chart to determine whether a process was stable or not, and to determine if its performance was predictable. He determined the upper and lower specification limits based on the contractual requirements. A set of eighteen data points were taken. Of these, 8 consecutive data points were above the mean. What can you say about such a process?
- A process is considered as being within control if less than half the data points are above or below the mean. Hence the process is within control.
- A process is considered as out of control if five consecutive data points are above or below the mean. Hence the process is out of control.
- A process is considered as out of control if seven consecutive data points are above or below the mean. Hence the process is out of control.
- A process is considered as out of control if six consecutive data points are above or below the mean. Hence the process is within control.
Q7. Which quality control technique or tool should be used when trying to determine the cause of a major defect?
- Control Chart
- Fishbone diagram
- Pareto Chart
- Histogram
Q8. The term ____________ indicates the degree to which a particular product or service meets requirements, while ____________ indicates a category or rank used to distinguish that item from other similar items.
- Grade, quality
- Quality, grade
- Quality, standard
- Grade, standard
Q9. You work at a software company that authors Material Safety Data Sheets (MSDS) for chemical companies. Prior to releasing the MSDS to the company you have created a list of items to be reviewed to see that they appear on the document such as: chemical name, CAS#, protection required, what to do an emergency, etc. This is an example of what type of tool?
- Quality Metrics
- Process Improvement Plan
- Quality Management Plan
- Checklist
Q10. The process of auditing the quality requirements and the results from quality control measurements to ensure appropriate quality standards and operational definitions are used is the definition of: _____________
- Scope validation
- Quality planning
- Quality control
- Quality assurance
Q11. A good quality audit should be:
- informal and internal
- structured and independent
- structured and internal
- informal and independent
Q12. In order to keep costs low, a project management team decided to apply statistical sampling while inspecting some of the work products. They decided to select 10 out of 50 engineering drawings for inspection. During which process should the sample frequency and sample size be determined?
- Control Quality
- Collect Requirements
- Plan Quality Management
- Manage Quality
Q13. You are in the execution stage of your project and you have been informed that “corporate” will be sending in a team of consultants to review whether your project activities comply with the company’s and PMI’s policies, standards, and procedures. This is an example of?
- Recommended Corrective Actions
- Organizational Process Assets
- Process Analysis
- Quality Audit
Q14. Select the best answer: Continuous process improvement reduces ___________ and ___________ , which allows processes to operate at increased levels of efficiency and effectiveness.
- Departmental and organization processes
- Process and policy overhead.
- Waste and non-value added activities.
- Cost and scope
Q15. A project manager used a control chart to determine whether a process was stable or not, and to determine if its performance was predictable. He determined the upper and lower specification limits based on the contractual requirements. A set of eighteen data points were taken. Of these, 8 consecutive data points were above the mean. What can you say about such a process?
- A process is considered as out of control if five consecutive data points are above or below the mean. Hence the process is out of control.
- A process is considered as out of control if seven consecutive data points are above or below the mean. Hence the process is out of control.
- A process is considered as out of control if six consecutive data points are above or below the mean. Hence the process is within control.
- A process is considered as being within control if less than half the data points are above or below the mean. Hence the process is within control.
Q16. A team of engineers is reviewing a scatter diagram to determine how the changes in two variables in a new type of automobile tire are related. The closer points on the diagram are to a diagonal line, ______________ .
- the less likely a control group will be required
- the more likely a control group will be required
- the less likely they are to be related
- the more closely they are related
Q17. On a control chart, if six consecutive plot points are above the mean, then what can be established about the process?
- The process is out of control
- Nothing can be established
- The process is in control
- The process will be out of control after plotting the seventh point.
Q18. Which of the following tools would be most appropriate for collecting data to study the symptoms of a problem?
- Checklist
- Histogram
- Check Sheet
- Control Chart
Q19. The cost of scrap rework, in a product quality cost system, is categorized as a:
- Appraisal costs
- External failure costs
- Prevention costs
- Internal failure costs
Q20. The four categories of costs associated with product quality costs are:
- External failure, internal failure, prevention, and inspection
- External failure, internal failure, repair, and appraisal
- Warranty, product liability, training, and appraisal
- External failure, internal failure, prevention, and appraisal
Q21. Which of the following quality costs are failure costs?
- Pre-dispatch inspection costs
- Customer satisfaction survey costs
- Product recall costs
- Equipment calibration costs
Q22. In which of the following control chart the control limits will vary from subgroup to subgroup?
- Xbar-R Chart
- c Chart
- p Chart
- np Chart
Q23. If there are seven data points either above or below the mean, but still within the control limits, what should you do?
- Reinspect the product
- Ignore it and continue to measure the process
- Find the cause because this means that the process is out of control
- Reject the product
Q24. Two variables, x and y, are related. Variable x increases or decreases with y. Which of the following tools could best be used to graphically show this relationship?
- Histogram
- Scatter Plot
- Control Charts
- Control Charts
Q25. Which of these quality gurus introduced the concept of Control Charts?
- Crosby
- Taguchi
- Juran
- Shewhart
Q26. Control Limits are the same are Specifications Limits.
- True
- False
Q27. What does COQ stand for?
- Cost of Quality
- Carry on Quality
- Cost Oriented Quality
- Corporate Quality
What is Six Sigma: Everything You Need to know about it
What is Six Sigma: Everything You Need to know about it
Six Sigma is one of the six types of processes to achieve excellence. Six Sigma is an applied process to understand what works and goes wrong. It is a concept used in many companies around the globe to understand how an organization can perform and the steps that need to be taken.
Hence, it is a methodology that offers a very big framework that helps understand Six Sigma and how it would be implemented to handle any issues or situations that may occur in the organizational culture.
What is Six Sigma?
Six Sigma is a set of tools, techniques, and methodologies used in Quality Control (QC) to improve the quality of products or services. Motorola developed it in 1986.
Six Sigma aims to eliminate defects at any stage of a process, from design to production and delivery, while providing superior customer satisfaction through improved quality.
It involves systematically identifying problems and their root causes, implementation of countermeasures, and continual improvement through analysis of results.
Why does Six Sigma Matter?
Six Sigma is an approach to quality management that emphasizes prevention over detection, which results in fewer defects and less waste (or rework). It also helps companies improve their processes and become more competitive in their industries.
By using Six Sigma analytics and tools, organizations can identify areas where improvements can be made within their business processes — which ultimately leads to increased profitability.
Achieving Six Sigma certification indicates that a company has committed to its goal of producing only 3.4 defects per million opportunities (DPMO).
Is Six Sigma different from lean?
While lean focuses on reducing waste and optimizing processes, Six Sigma focuses on improving quality. So you can think of it this way: Lean seeks to maximize efficiency by eliminating waste.
In contrast, Six Sigma seeks to optimize quality by minimizing variation in any given process or system.
How does Six Sigma Differ from Other Management Standards and Methodologies?
Six Sigma differs from other management standards and methodologies in the following ways:
- It's a business process improvement methodology rather than a management system or compliance program; it provides tools for improving processes to produce higher quality results but doesn't mandate specific actions in each area where improvement is needed.
- It focuses on process improvement rather than fixing problems after they occur — this means implementing changes before defects occur rather than afterward.
- It focuses on identifying, measuring, and improving processes that add value to the customer by reducing variation in products and services.
What are the Key Elements of Six Sigma?
Six Sigma uses DMAIC methodologies to achieve its goals, which stand for:
Define: The first step in DMAIC is to define the problem or opportunity that needs to be addressed. This can be done through brainstorming or other techniques.
Measure: Once the problem has been defined, it needs to be measured to make improvements. This step requires collecting data on key factors related to the improved process and analyzing it using statistical techniques such as regression analysis and ANOVA (analysis of variance).
Analyze: After measuring the process, you should analyze your data using statistical techniques like regression analysis and ANOVA (analysis of variance). These techniques allow you to determine whether your measurements are within acceptable limits or if any patterns in them may help with future improvements.
Improve: This step includes developing new processes or improving existing ones by identifying opportunities for improvement through brainstorming sessions with employees from all levels of the organization.
Control: In the final phase of Six Sigma, you create a control plan, a set of procedures that ensures your new standardized process works smoothly and meets quality standards.
Why is Six Sigma Important for Businesses?
The Six Sigma methodology is a set of tools and techniques that help businesses improve their processes, thereby enhancing their customer experience.
It is an improvement strategy that helps companies achieve consistent perfection in their processes. It aims to reduce the variability in business activities, products, and services. This helps in eliminating defects and improving quality while also reducing costs.
There are many benefits to adopting a Six Sigma approach, including:
- Reduces waste and variation through structured processes.
- Improves product quality and customer satisfaction.
- Increases revenues by reducing costs.
Six Sigma Benefits:
Cost Reduction: Six Sigma helps reduce costs by identifying key areas where costs can be reduced by improving efficiency and reducing waste. The focus is on the elimination of destruction rather than just cutting costs.
Improved Quality: By reducing variability in processes and products, you can ensure that your customers get a consistent, high-quality product or service every time they interact with you or use your product or service. This will also help retain existing customers, attract new ones, and increase customer loyalty towards your brand because of a better experience!
Innovation: By identifying critical variables within processes and then optimizing them based on data analysis, Six Sigma ensures that innovation is focused on areas where it matters most – driving ROI for your business!
Conclusion
Six Sigma is the process behind some of the business' most reliable innovations. It's more than just a methodology, however, with plenty of training and courses available to help companies put it into practice.
And while small companies can implement it, it's also been used to great success on a massive scale, with proven results in quality control. As a result, six Sigma is more relevant today than ever before.
Read More
What is Six Sigma: Everything You Need to know about it
Six Sigma is one of the six types of processes to achieve excellence. Six Sigma is an applied process to understand what works and goes wrong. It is a concept used in many companies around the globe to understand how an organization can perform and the steps that need to be taken.
Hence, it is a methodology that offers a very big framework that helps understand Six Sigma and how it would be implemented to handle any issues or situations that may occur in the organizational culture.
What is Six Sigma?
Six Sigma is a set of tools, techniques, and methodologies used in Quality Control (QC) to improve the quality of products or services. Motorola developed it in 1986.
Six Sigma aims to eliminate defects at any stage of a process, from design to production and delivery, while providing superior customer satisfaction through improved quality.
It involves systematically identifying problems and their root causes, implementation of countermeasures, and continual improvement through analysis of results.
Why does Six Sigma Matter?
Six Sigma is an approach to quality management that emphasizes prevention over detection, which results in fewer defects and less waste (or rework). It also helps companies improve their processes and become more competitive in their industries.
By using Six Sigma analytics and tools, organizations can identify areas where improvements can be made within their business processes — which ultimately leads to increased profitability.
Achieving Six Sigma certification indicates that a company has committed to its goal of producing only 3.4 defects per million opportunities (DPMO).
Is Six Sigma different from lean?
While lean focuses on reducing waste and optimizing processes, Six Sigma focuses on improving quality. So you can think of it this way: Lean seeks to maximize efficiency by eliminating waste.
In contrast, Six Sigma seeks to optimize quality by minimizing variation in any given process or system.
How does Six Sigma Differ from Other Management Standards and Methodologies?
Six Sigma differs from other management standards and methodologies in the following ways:
- It's a business process improvement methodology rather than a management system or compliance program; it provides tools for improving processes to produce higher quality results but doesn't mandate specific actions in each area where improvement is needed.
- It focuses on process improvement rather than fixing problems after they occur — this means implementing changes before defects occur rather than afterward.
- It focuses on identifying, measuring, and improving processes that add value to the customer by reducing variation in products and services.
What are the Key Elements of Six Sigma?
Six Sigma uses DMAIC methodologies to achieve its goals, which stand for:
Define: The first step in DMAIC is to define the problem or opportunity that needs to be addressed. This can be done through brainstorming or other techniques.
Measure: Once the problem has been defined, it needs to be measured to make improvements. This step requires collecting data on key factors related to the improved process and analyzing it using statistical techniques such as regression analysis and ANOVA (analysis of variance).
Analyze: After measuring the process, you should analyze your data using statistical techniques like regression analysis and ANOVA (analysis of variance). These techniques allow you to determine whether your measurements are within acceptable limits or if any patterns in them may help with future improvements.
Improve: This step includes developing new processes or improving existing ones by identifying opportunities for improvement through brainstorming sessions with employees from all levels of the organization.
Control: In the final phase of Six Sigma, you create a control plan, a set of procedures that ensures your new standardized process works smoothly and meets quality standards.
Why is Six Sigma Important for Businesses?
The Six Sigma methodology is a set of tools and techniques that help businesses improve their processes, thereby enhancing their customer experience.
It is an improvement strategy that helps companies achieve consistent perfection in their processes. It aims to reduce the variability in business activities, products, and services. This helps in eliminating defects and improving quality while also reducing costs.
There are many benefits to adopting a Six Sigma approach, including:
- Reduces waste and variation through structured processes.
- Improves product quality and customer satisfaction.
- Increases revenues by reducing costs.
Six Sigma Benefits:
Cost Reduction: Six Sigma helps reduce costs by identifying key areas where costs can be reduced by improving efficiency and reducing waste. The focus is on the elimination of destruction rather than just cutting costs.
Improved Quality: By reducing variability in processes and products, you can ensure that your customers get a consistent, high-quality product or service every time they interact with you or use your product or service. This will also help retain existing customers, attract new ones, and increase customer loyalty towards your brand because of a better experience!
Innovation: By identifying critical variables within processes and then optimizing them based on data analysis, Six Sigma ensures that innovation is focused on areas where it matters most – driving ROI for your business!
Conclusion
Six Sigma is the process behind some of the business' most reliable innovations. It's more than just a methodology, however, with plenty of training and courses available to help companies put it into practice.
And while small companies can implement it, it's also been used to great success on a massive scale, with proven results in quality control. As a result, six Sigma is more relevant today than ever before.
Feasibility Study and Its Importance in Project Management
Table of Content
What is a Feasibility Study?
Why is it important?
What do the results of a feasibility study show?
Benefits of a Feasibility Study
Phases of a Feasibility Study
When to Conduct a Feasibility Study?
What are the steps in a feasibility study?
Purpose of a Feasibility Study?
Conclusion
What is a Feasibility Study?
A feasibility study is a business plan that describes how a new idea will be implemented, what resources are needed, and how much it will cost. The term "feasibility" means the study has been done, and the project is possible.
A feasibility study can evaluate an idea's viability before investing substantial time and money into developing it further.
For example, suppose a company has an idea for a new product or service but does not have enough information to make a business case for its development. In that case, it may need to conduct feasibility studies first.
A feasibility study will typically include:
- An evaluation of existing products and services in your market space
- A description of existing clientele and target audience
- Existing competition in your market space (if any)
- Current market conditions and trends (e.g., economic conditions)
- The results from previous feasibility studies on similar projects (if any)
Why is it important?
- A feasibility study is an essential part of project management. It helps in determining whether a project will be successful or not.
- A feasibility study also determines the cost and time element of the project, which are essential to determine whether a project is feasible.
- A feasibility study is essential to determine if a project can be completed on time, within budget, and within scope.
- It also helps determine the number of resources required to complete the project.
What do the results of a feasibility study show?
The results of a feasibility study can show project managers what the project will cost, how long it will take, and which products or services they should produce.
The results give you an idea of what it will take to produce the project, and whether it is worth doing it's not worth doing; There is no point in continuing with it.
If the company wants to build a new factory, it must consider cost, time, and quality before making any decisions. The feasibility study will give them the necessary information to make those decisions.
Benefits of a Feasibility Study
Feasibility studies are essential to project management because they help you evaluate your project against the criteria in your project plan.
A feasibility study is a process that involves evaluating your project against the criteria set out in your project plan. It helps you determine whether the risks and rewards of starting or continuing a project outweigh any potential benefits or costs.
Benefits of Using Feasibility Study in Project Management:
- Feasibility Studies help predict the results of a business, financial or operational activity.
- Feasibility studies help determine whether a business, financial or operational activity can be implemented successfully.
- The results from feasibility studies are used as inputs when making project decisions.
- A feasibility study helps determine whether there would be an increase in profits by implementing a new product line or service offered by an organization.
Phases of a Feasibility Study
The phases of a feasibility study are:
Pre-Feasibility Study
In this stage, you will need to establish the project objectives and determine if it is possible to achieve them. This is done by gathering information about the market, competitors, customers, and other relevant information. It would help if you also considered the financial implications of your project and how best to finance it.
Feasibility Study
The feasibility study phase looks at your proposed project's feasibility from an economic point of view, considering such things as investment costs, financing arrangements, technical specifications, and related costs. You can also conduct surveys with potential partners or suppliers for their opinions on whether or not they would participate in the project.
Scoping Study
The scoping study phase involves gathering information about your proposed project and identifying all its essential aspects. Then, it determines the scope and cost of each component of the project. The purpose of this phase is to provide you with a clear idea of how much time and effort you need to put into each component of the project so that you can ensure that everything fits into one schedule as far as possible.
Detailed Feasibility Study
A detailed feasibility study is a process that helps you to understand the pros and cons of your idea. In this study, you will be able to identify whether your idea is financially viable or not.
You can use this study as a guide for future projects. By doing this, you will be able to plan and avoid unnecessary expenses in the future.
When to Conduct a Feasibility Study?
It is essential to conduct feasibility studies, especially when starting a new project. This is because the availability of resources and the costs will determine whether the project can be completed successfully.
Projects that are too big, too high-risk, or too complex for the budget cannot be carried out successfully. A feasibility study will help you establish whether or not your project has been planned correctly and how it can be achieved based on available resources.
You should also conduct feasibility studies if you want to implement new technology, such as a new software application or web platform. In this case, you need to determine whether or not your business can adopt this new technology and if it meets your needs.
What are the steps in a feasibility study?
The steps in a feasibility study are:
Conduct a Preliminary Analysis
The purpose of this step is to identify the need for further investigation. You need to determine if the project will be profitable or if it will have a negative impact on your company's finances. The reason that you should conduct a preliminary analysis is that you want to make sure that any project will have a positive impact on your company's bottom line.
Prepare a Projected Income Statement
The projected income statement shows what you expect to earn from the completed project and how much of that you expect to spend on materials, labor, and other costs. If you're going to spend $10,000 on materials but only expect $6,000 in revenue from selling the completed product, then your projected income statement would look like this:
$10,000 - $6,000 = $4,000
You can use this projected income statement later in the planning process when it comes time to determine how much money is available for spending on additional projects.
Conduct a Market Survey
The first step in a feasibility study is to conduct market research. This will help you understand your customers, competitors, and the market as a whole. You can also use this information to determine how much of your business you can expect to generate and how much it will cost to produce.
Plan Business Organization and Operations
Once you have gathered all the information you need, you must decide on the business model for your new venture. This involves determining what type of organization will work best for your experience. Combining two or more models may be necessary to create a successful business plan.
Determine Marketing and Sales Strategies
Your next step is determining how much money you need for marketing and sales strategies. It would help if you also considered how much money will be required for advertising and other promotional activities. Once you have determined these numbers, it's time to develop marketing strategies that will help drive sales and maximize profits at launch time.
Review and Analyze All Data
The most important part of your feasibility study is to review and analyze all your data. You want to ensure that you have collected enough data, that the data are correct and that there are no missing or incorrect pieces of information in your information collection process. This can be done by using a checklist or by having someone else review the data with you and ensure that everything is accurate and up-to-date.
Make a Go/No-Go Decision
After reviewing all your data, it's time to decide whether or not this idea will work for your business plan. You may determine that this project does not fit your current schedule or budget. Still, you do want to keep it on file as an option for future consideration. For example, suppose this project does not fit your current schedule, budget, or timeline. In that case, you should move on with another idea (or ideas).
Purpose of a Feasibility Study
The purpose of a feasibility study is to analyze the business and technical requirements of an idea. In addition, the study helps determine if there is a market for the developed product or service.
A feasibility study also looks at all aspects of the project, including finances and management skills.
The feasibility study should be performed by someone who knows about the particular field and industry.
The person conducting the survey should be able to answer questions like "What are the advantages of this particular idea?" and "Is this something that people will want?"
Conclusion
A feasibility study is a preliminary assessment to determine if the project can succeed. This usually involves a thorough analysis of the objectives and requirements, examining the available resources and constraints, and some financial assessment or projection.
In most cases, a feasibility study will identify potential problems before they occur, saving valuable time and money in the long run. After all, with so many options on the table, it's always better to make an educated decision than risk a potentially poor or unsuccessful outcome.
Read More
Table of Content
What is a Feasibility Study?
Why is it important?
What do the results of a feasibility study show?
Benefits of a Feasibility Study
Phases of a Feasibility Study
When to Conduct a Feasibility Study?
What are the steps in a feasibility study?
Purpose of a Feasibility Study?
Conclusion
What is a Feasibility Study?
A feasibility study is a business plan that describes how a new idea will be implemented, what resources are needed, and how much it will cost. The term "feasibility" means the study has been done, and the project is possible.
A feasibility study can evaluate an idea's viability before investing substantial time and money into developing it further.
For example, suppose a company has an idea for a new product or service but does not have enough information to make a business case for its development. In that case, it may need to conduct feasibility studies first.
A feasibility study will typically include:
- An evaluation of existing products and services in your market space
- A description of existing clientele and target audience
- Existing competition in your market space (if any)
- Current market conditions and trends (e.g., economic conditions)
- The results from previous feasibility studies on similar projects (if any)
Why is it important?
- A feasibility study is an essential part of project management. It helps in determining whether a project will be successful or not.
- A feasibility study also determines the cost and time element of the project, which are essential to determine whether a project is feasible.
- A feasibility study is essential to determine if a project can be completed on time, within budget, and within scope.
- It also helps determine the number of resources required to complete the project.
What do the results of a feasibility study show?
The results of a feasibility study can show project managers what the project will cost, how long it will take, and which products or services they should produce.
The results give you an idea of what it will take to produce the project, and whether it is worth doing it's not worth doing; There is no point in continuing with it.
If the company wants to build a new factory, it must consider cost, time, and quality before making any decisions. The feasibility study will give them the necessary information to make those decisions.
Benefits of a Feasibility Study
Feasibility studies are essential to project management because they help you evaluate your project against the criteria in your project plan.
A feasibility study is a process that involves evaluating your project against the criteria set out in your project plan. It helps you determine whether the risks and rewards of starting or continuing a project outweigh any potential benefits or costs.
Benefits of Using Feasibility Study in Project Management:
- Feasibility Studies help predict the results of a business, financial or operational activity.
- Feasibility studies help determine whether a business, financial or operational activity can be implemented successfully.
- The results from feasibility studies are used as inputs when making project decisions.
- A feasibility study helps determine whether there would be an increase in profits by implementing a new product line or service offered by an organization.
Phases of a Feasibility Study
The phases of a feasibility study are:
Pre-Feasibility Study
In this stage, you will need to establish the project objectives and determine if it is possible to achieve them. This is done by gathering information about the market, competitors, customers, and other relevant information. It would help if you also considered the financial implications of your project and how best to finance it.
Feasibility Study
The feasibility study phase looks at your proposed project's feasibility from an economic point of view, considering such things as investment costs, financing arrangements, technical specifications, and related costs. You can also conduct surveys with potential partners or suppliers for their opinions on whether or not they would participate in the project.
Scoping Study
The scoping study phase involves gathering information about your proposed project and identifying all its essential aspects. Then, it determines the scope and cost of each component of the project. The purpose of this phase is to provide you with a clear idea of how much time and effort you need to put into each component of the project so that you can ensure that everything fits into one schedule as far as possible.
Detailed Feasibility Study
A detailed feasibility study is a process that helps you to understand the pros and cons of your idea. In this study, you will be able to identify whether your idea is financially viable or not.
You can use this study as a guide for future projects. By doing this, you will be able to plan and avoid unnecessary expenses in the future.
When to Conduct a Feasibility Study?
It is essential to conduct feasibility studies, especially when starting a new project. This is because the availability of resources and the costs will determine whether the project can be completed successfully.
Projects that are too big, too high-risk, or too complex for the budget cannot be carried out successfully. A feasibility study will help you establish whether or not your project has been planned correctly and how it can be achieved based on available resources.
You should also conduct feasibility studies if you want to implement new technology, such as a new software application or web platform. In this case, you need to determine whether or not your business can adopt this new technology and if it meets your needs.
What are the steps in a feasibility study?
The steps in a feasibility study are:
Conduct a Preliminary Analysis
The purpose of this step is to identify the need for further investigation. You need to determine if the project will be profitable or if it will have a negative impact on your company's finances. The reason that you should conduct a preliminary analysis is that you want to make sure that any project will have a positive impact on your company's bottom line.
Prepare a Projected Income Statement
The projected income statement shows what you expect to earn from the completed project and how much of that you expect to spend on materials, labor, and other costs. If you're going to spend $10,000 on materials but only expect $6,000 in revenue from selling the completed product, then your projected income statement would look like this:
$10,000 - $6,000 = $4,000
You can use this projected income statement later in the planning process when it comes time to determine how much money is available for spending on additional projects.
Conduct a Market Survey
The first step in a feasibility study is to conduct market research. This will help you understand your customers, competitors, and the market as a whole. You can also use this information to determine how much of your business you can expect to generate and how much it will cost to produce.
Plan Business Organization and Operations
Once you have gathered all the information you need, you must decide on the business model for your new venture. This involves determining what type of organization will work best for your experience. Combining two or more models may be necessary to create a successful business plan.
Determine Marketing and Sales Strategies
Your next step is determining how much money you need for marketing and sales strategies. It would help if you also considered how much money will be required for advertising and other promotional activities. Once you have determined these numbers, it's time to develop marketing strategies that will help drive sales and maximize profits at launch time.
Review and Analyze All Data
The most important part of your feasibility study is to review and analyze all your data. You want to ensure that you have collected enough data, that the data are correct and that there are no missing or incorrect pieces of information in your information collection process. This can be done by using a checklist or by having someone else review the data with you and ensure that everything is accurate and up-to-date.
Make a Go/No-Go Decision
After reviewing all your data, it's time to decide whether or not this idea will work for your business plan. You may determine that this project does not fit your current schedule or budget. Still, you do want to keep it on file as an option for future consideration. For example, suppose this project does not fit your current schedule, budget, or timeline. In that case, you should move on with another idea (or ideas).
Purpose of a Feasibility Study
The purpose of a feasibility study is to analyze the business and technical requirements of an idea. In addition, the study helps determine if there is a market for the developed product or service.
A feasibility study also looks at all aspects of the project, including finances and management skills.
The feasibility study should be performed by someone who knows about the particular field and industry.
The person conducting the survey should be able to answer questions like "What are the advantages of this particular idea?" and "Is this something that people will want?"
Conclusion
A feasibility study is a preliminary assessment to determine if the project can succeed. This usually involves a thorough analysis of the objectives and requirements, examining the available resources and constraints, and some financial assessment or projection.
In most cases, a feasibility study will identify potential problems before they occur, saving valuable time and money in the long run. After all, with so many options on the table, it's always better to make an educated decision than risk a potentially poor or unsuccessful outcome.
Quality Management Plan: What It Is & Why It Matters
Quality Management Plan: What It Is & Why It Matters
Table of Content
What is Quality Management Plan?
Why Quality Management Plan?
Quality Management Plan Tools
Steps to a Successful Quality Plan
How to make Quality Management Plan
Benefits of a Quality Plan
Conclusion
What is Quality Management Plan?
A quality management plan is a document that describes the organization's approach to quality. It also serves as a communication tool and a guide to help you manage your company's processes for achieving customer satisfaction.
The quality management plan will identify your company's goals and objectives, how you intend to achieve those goals, how you will measure whether you've achieved them, and any relevant information about your employees.
It will also include information about existing policies and procedures related to quality management.
Why Quality Management Plan?
The quality management plan is a document that outlines the steps required to achieve the desired level of excellence in your organization. This can be as simple as having a quality assurance plan for your production line or as complex as an entire project management system that covers all aspects of an organization. In any case, you must have a plan in place to know where you're going, what needs to be done, and when.
It helps communicate with employees about their role in achieving the company's goals. When employees know their roles and responsibilities, they can more easily understand what it means for them if they don't meet those expectations. This helps them feel more invested in their work and makes them more likely to perform at an exceptional level because they know they're part of something bigger than themselves.
It allows for regular communication between departments that may not always need to talk directly.
Quality Management Plan Tools
Quality management plan tools can help you identify quality issues at the earliest stages of a project.
Many different types of quality management plan tools are available to help you manage your project's quality. The following is an overview of some of the most common ones:
Affinity diagrams: Affinity diagrams involve grouping ideas into categories based on their similarities. They help team members discover and examine potential causes of problems within your organization.
Interrelationship diagrams: Interrelationship diagrams involve connecting ideas with arrows to show how they interact and influence each other. They're often used with affinity diagrams to provide a more detailed view of how systems work together.
Process Decision Program Charts (PDPC): This is one of the most commonly used tools in quality management. It helps in identifying non-value-added activities and eliminating them from your process. This tool also helps in generating new ideas for process improvement.
Matrix Diagrams: These diagrams are used to analyze factors that affect the quality of a product, service, or process. These diagrams help identify relationships between various factors and how they influence each other. This is especially useful when too many variables are involved in analyzing individually.
Prioritization matrices: In a quality management plan, you can use prioritization matrices to define what should be done first, second and third. They can help define objectives, set priorities, make trade-offs, and choose courses of action.
Network diagrams: Network diagrams illustrate how data flows through an organization so that employees can identify potential issues that may lead to poor quality. These diagrams also help employees understand their roles and responsibilities within their teams, allowing them to focus on their tasks instead of trying to do everything themselves.
Steps to a Successful Quality Plan
- The first step to a successful quality plan is to define what quality means to your organization.
- Write down the vision and values of your company. This will help you focus on the company's mission and how you can provide value for customers.
- Understand that all customers are not created equal. Each customer has different needs, wants, and desires, which should be addressed accordingly.
- Identify the processes critical to your business success and those not so essential (non-value-added activities). If you have inefficiencies or waste in your processes, eliminate them immediately!
- Create performance measures for each process so you can measure performance against goals, objectives, and benchmarks set forth by management. This allows us as leaders to see if our employees are doing their jobs effectively and efficiently – it also helps us see where we need to make improvements to become more efficient overall as an organization.
- Analyze your processes regularly using statistical tools such as Pareto analysis or cause-and-effect diagrams (fishbone diagrams). These tools allow us as leaders to identify areas where we may need to improve efficiency or effectiveness within our organization to reduce costs.
How to make Quality Management Plan
The quality management plan is a document that describes how the company is going to ensure that the product or service meets customer requirements and expectations.
It is essential for any organization as it helps identify the risks involved in producing a product or providing a service. It also helps develop strategies to eliminate or reduce those risks.
Quality management plans can be developed in various ways depending on your organization's needs. However, they all share some common elements:
Product quality policy defines why you are doing this and what you hope to achieve by implementing a quality system.
Product quality objective sets out what level of quality you want to achieve with your product or service. For example, suppose you want to ensure that no defects occur in your products. In that case, this might be reflected in an objective such as "controlling the number of defects per million opportunities."
Quality control procedures specify how you will control quality throughout the production process. For example, you may have different strategies for different parts of your business or other products within your company. Sometimes, these will be documented as part of your standard operating procedures (SOPs).
Quality assurance procedures describe how you will monitor and measure the success of your quality control measures so that they are practical and efficient.
Benefits of a Quality Plan
The benefits of a quality management plan are numerous. The following are just a few of the many benefits of implementing a quality management plan.
- It helps companies to reduce costs by reducing waste and errors, which in turn reduces overhead costs.
- It makes your company more efficient, which will help you increase your profits.
- It lets customers know they can rely on your company to deliver quality products and services.
- It allows employees to feel confident in their abilities and more comfortable working at their job.
- A good quality management plan will ensure customers receive high-quality products or services every time they order from your company.
- A quality management plan allows you to identify areas where productivity can be increased. It also lets you know which processes need improvement to make them more efficient in the long run.
- Implementing a QMP helps you identify the root cause of problems or defects in your products or services. This allows you to develop strategies to eliminate them quickly.
Conclusion
Every company, large or small, has adopted the practice of launching a quality management plan. Most companies see it as a way to improve their processes and reduce costs. But what is a QMP? As you will see, a QMP is much more than just a document that outlines the steps to be carried out during the production of a product or service.
Because so many aspects go into developing a quality management system, it is not a simple undertaking by any means. It requires you to document each step of your process, from incoming material examination to customer service. So put, if you have planned for every conceivable contingency during your manufacturing process, a quality management plan will help ensure every product or service your company provides is manufactured according to your high standards and to the highest specifications possible.
Read More
Quality Management Plan: What It Is & Why It Matters
Table of Content
What is Quality Management Plan?
Why Quality Management Plan?
Quality Management Plan Tools
Steps to a Successful Quality Plan
How to make Quality Management Plan
Benefits of a Quality Plan
Conclusion
What is Quality Management Plan?
A quality management plan is a document that describes the organization's approach to quality. It also serves as a communication tool and a guide to help you manage your company's processes for achieving customer satisfaction.
The quality management plan will identify your company's goals and objectives, how you intend to achieve those goals, how you will measure whether you've achieved them, and any relevant information about your employees.
It will also include information about existing policies and procedures related to quality management.
Why Quality Management Plan?
The quality management plan is a document that outlines the steps required to achieve the desired level of excellence in your organization. This can be as simple as having a quality assurance plan for your production line or as complex as an entire project management system that covers all aspects of an organization. In any case, you must have a plan in place to know where you're going, what needs to be done, and when.
It helps communicate with employees about their role in achieving the company's goals. When employees know their roles and responsibilities, they can more easily understand what it means for them if they don't meet those expectations. This helps them feel more invested in their work and makes them more likely to perform at an exceptional level because they know they're part of something bigger than themselves.
It allows for regular communication between departments that may not always need to talk directly.
Quality Management Plan Tools
Quality management plan tools can help you identify quality issues at the earliest stages of a project.
Many different types of quality management plan tools are available to help you manage your project's quality. The following is an overview of some of the most common ones:
Affinity diagrams: Affinity diagrams involve grouping ideas into categories based on their similarities. They help team members discover and examine potential causes of problems within your organization.
Interrelationship diagrams: Interrelationship diagrams involve connecting ideas with arrows to show how they interact and influence each other. They're often used with affinity diagrams to provide a more detailed view of how systems work together.
Process Decision Program Charts (PDPC): This is one of the most commonly used tools in quality management. It helps in identifying non-value-added activities and eliminating them from your process. This tool also helps in generating new ideas for process improvement.
Matrix Diagrams: These diagrams are used to analyze factors that affect the quality of a product, service, or process. These diagrams help identify relationships between various factors and how they influence each other. This is especially useful when too many variables are involved in analyzing individually.
Prioritization matrices: In a quality management plan, you can use prioritization matrices to define what should be done first, second and third. They can help define objectives, set priorities, make trade-offs, and choose courses of action.
Network diagrams: Network diagrams illustrate how data flows through an organization so that employees can identify potential issues that may lead to poor quality. These diagrams also help employees understand their roles and responsibilities within their teams, allowing them to focus on their tasks instead of trying to do everything themselves.
Steps to a Successful Quality Plan
- The first step to a successful quality plan is to define what quality means to your organization.
- Write down the vision and values of your company. This will help you focus on the company's mission and how you can provide value for customers.
- Understand that all customers are not created equal. Each customer has different needs, wants, and desires, which should be addressed accordingly.
- Identify the processes critical to your business success and those not so essential (non-value-added activities). If you have inefficiencies or waste in your processes, eliminate them immediately!
- Create performance measures for each process so you can measure performance against goals, objectives, and benchmarks set forth by management. This allows us as leaders to see if our employees are doing their jobs effectively and efficiently – it also helps us see where we need to make improvements to become more efficient overall as an organization.
- Analyze your processes regularly using statistical tools such as Pareto analysis or cause-and-effect diagrams (fishbone diagrams). These tools allow us as leaders to identify areas where we may need to improve efficiency or effectiveness within our organization to reduce costs.
How to make Quality Management Plan
The quality management plan is a document that describes how the company is going to ensure that the product or service meets customer requirements and expectations.
It is essential for any organization as it helps identify the risks involved in producing a product or providing a service. It also helps develop strategies to eliminate or reduce those risks.
Quality management plans can be developed in various ways depending on your organization's needs. However, they all share some common elements:
Product quality policy defines why you are doing this and what you hope to achieve by implementing a quality system.
Product quality objective sets out what level of quality you want to achieve with your product or service. For example, suppose you want to ensure that no defects occur in your products. In that case, this might be reflected in an objective such as "controlling the number of defects per million opportunities."
Quality control procedures specify how you will control quality throughout the production process. For example, you may have different strategies for different parts of your business or other products within your company. Sometimes, these will be documented as part of your standard operating procedures (SOPs).
Quality assurance procedures describe how you will monitor and measure the success of your quality control measures so that they are practical and efficient.
Benefits of a Quality Plan
The benefits of a quality management plan are numerous. The following are just a few of the many benefits of implementing a quality management plan.
- It helps companies to reduce costs by reducing waste and errors, which in turn reduces overhead costs.
- It makes your company more efficient, which will help you increase your profits.
- It lets customers know they can rely on your company to deliver quality products and services.
- It allows employees to feel confident in their abilities and more comfortable working at their job.
- A good quality management plan will ensure customers receive high-quality products or services every time they order from your company.
- A quality management plan allows you to identify areas where productivity can be increased. It also lets you know which processes need improvement to make them more efficient in the long run.
- Implementing a QMP helps you identify the root cause of problems or defects in your products or services. This allows you to develop strategies to eliminate them quickly.
Conclusion
Every company, large or small, has adopted the practice of launching a quality management plan. Most companies see it as a way to improve their processes and reduce costs. But what is a QMP? As you will see, a QMP is much more than just a document that outlines the steps to be carried out during the production of a product or service.
Because so many aspects go into developing a quality management system, it is not a simple undertaking by any means. It requires you to document each step of your process, from incoming material examination to customer service. So put, if you have planned for every conceivable contingency during your manufacturing process, a quality management plan will help ensure every product or service your company provides is manufactured according to your high standards and to the highest specifications possible.
Quality Assurance vs Quality Management - Similarities & Differences
Quality Assurance vs Quality Management - Similarities & Differences
Quality assurance and quality management are terms that are often heard but not well understood. Sometimes they refer to the same thing, but at other times they might mean different things.
In order to prevent themselves from falling deeper into the confusion surrounding these two terms, many business owners have turned to online resources to learn about their differences.
Quality assurance vs Quality management
The primary difference between quality management and quality assurance is the scale of their operations:
Quality management applies to an entire organization or department. For example, it can describe how a whole company manages its customer service or how a software development team works its coding standards.
Quality assurance applies to specific functions within an organization or department. For example, it can describe how an engineering team ensures that new products meet technical requirements before they are released into production.
What is Quality Assurance?
Quality assurance (QA) is the part of quality control focused on fulfilling quality requirements. Its purpose is to ensure that a product or service is of the desired quality and satisfies given customer requirements. There are three types of QA processes:
Pre-production QA: Ensuring that all processes, documentation, tools, and resources are in place for an effective start of production.
Production QA: Monitoring the production process to ensure that products conform to requirements.
Post-production QA: Checking the finished product against specifications, standards, and regulatory requirements.
The main goals of quality assurance are:
- To ensure that the quality of your products or services meets your customers' needs and expectations.
- To reduce the number of defects in your products or services.
- To improve the efficiency and effectiveness of your product or service development process.
Benefits of Quality Assurance
The main benefit of quality assurance is that it helps to ensure that your product is delivered as expected. In addition, quality assurance ensures that the final product matches the requirements in the engineering specifications.
Quality assurance can also help to eliminate waste and errors, which would otherwise be expensive to correct in production. For example, suppose a supplier fails to deliver on time or produces an inferior product. In that case, this can lead to delays in production and may ultimately cause you to lose customers.
Another benefit of quality assurance is that it helps you to identify any potential issues with your product before they become an issue for your customers. This prevents customers from getting dissatisfied with their purchases because they are not working correctly or have other defects.
Quality assurance also helps businesses improve their processes and make them more efficient at delivering high-quality products or services.
The most significant benefit of quality assurance is that it improves customer satisfaction with your service or product. If you want happy customers, then there are few things better than ensuring they get exactly what they expect when they buy something from you!
Why Quality Assurance?
The purpose of QA is to ensure that all the processes involved in the production or delivery of goods or services are done correctly to achieve the desired standard or goal. The show involves many functions, such as purchasing materials, inventory management, designing products/services, etc., which need proper planning and execution to achieve good results.
What is Quality Management?
Quality management is a process that ensures the products and services that a company provides meet customer requirements. It involves measuring the quality of products and services, identifying where improvements are needed, and implementing solutions to improve quality.
Quality management is an ongoing process that includes planning, organizing, directing, and controlling activities to ensure that the methods used in creating products or services meet customer requirements.
The goal of quality management is to provide consistent product quality at all levels of production.
In addition, it seeks to continuously improve the processes used to create products or deliver services by identifying problems early in the production cycle to correct them before they become significant problems.
Benefits of Quality Management
The benefits of quality management are many. Quality management is not only beneficial to the overall health of an organization, but it can also improve its financial status. In addition, quality management provides several benefits for businesses, including:
Reduced costs: Companies implementing quality management systems often find that they save money in the long run. This is because they can identify problems early on and fix them before they become too expensive to fix. By catching issues before they become significant, companies can avoid paying for costly repairs or replacements later.
Increased productivity: A sound quality management system can help businesses increase their productivity by reducing errors and preventing defects in the first place. In addition, if a company has a high level of employee satisfaction, this will also lead to increased productivity because satisfied employees tend to be more productive than unhappy ones.
Improved customer service: A company with an effective quality management system will provide better customer service than one without one because it will be able to identify problems quickly and fix them before they become serious issues that upset customers or result in expensive recalls. Since customers expect high service levels these days, any service failure can negatively affect your reputation and bottom line.
Why Quality Management?
Quality management ensures that businesses continually assess their performance and make necessary improvements. By focusing on continuous improvement rather than perfection, companies can avoid investing too much time, money and effort into getting something right from scratch before moving on to something else. This approach also helps them retain their competitive edge in a fast-changing environment.
Conclusion
Hopefully, the above definitions and explanations have cleared up any questions you might have had about quality assurance and quality management. The two concepts are closely related but are not entirely the same.
Quality management focuses more on the broader picture, while quality assurance is more hands-on. Quality management is also organizational, while quality assurance is more often individualized. The takeaway here? Quality management refers to an overall system or framework to ensure high-quality standards. In contrast, quality assurance relates to the personal actions involved in providing those standards are met.
Read More
Quality Assurance vs Quality Management - Similarities & Differences
Quality assurance and quality management are terms that are often heard but not well understood. Sometimes they refer to the same thing, but at other times they might mean different things.
In order to prevent themselves from falling deeper into the confusion surrounding these two terms, many business owners have turned to online resources to learn about their differences.
Quality assurance vs Quality management
The primary difference between quality management and quality assurance is the scale of their operations:
Quality management applies to an entire organization or department. For example, it can describe how a whole company manages its customer service or how a software development team works its coding standards.
Quality assurance applies to specific functions within an organization or department. For example, it can describe how an engineering team ensures that new products meet technical requirements before they are released into production.
What is Quality Assurance?
Quality assurance (QA) is the part of quality control focused on fulfilling quality requirements. Its purpose is to ensure that a product or service is of the desired quality and satisfies given customer requirements. There are three types of QA processes:
Pre-production QA: Ensuring that all processes, documentation, tools, and resources are in place for an effective start of production.
Production QA: Monitoring the production process to ensure that products conform to requirements.
Post-production QA: Checking the finished product against specifications, standards, and regulatory requirements.
The main goals of quality assurance are:
- To ensure that the quality of your products or services meets your customers' needs and expectations.
- To reduce the number of defects in your products or services.
- To improve the efficiency and effectiveness of your product or service development process.
Benefits of Quality Assurance
The main benefit of quality assurance is that it helps to ensure that your product is delivered as expected. In addition, quality assurance ensures that the final product matches the requirements in the engineering specifications.
Quality assurance can also help to eliminate waste and errors, which would otherwise be expensive to correct in production. For example, suppose a supplier fails to deliver on time or produces an inferior product. In that case, this can lead to delays in production and may ultimately cause you to lose customers.
Another benefit of quality assurance is that it helps you to identify any potential issues with your product before they become an issue for your customers. This prevents customers from getting dissatisfied with their purchases because they are not working correctly or have other defects.
Quality assurance also helps businesses improve their processes and make them more efficient at delivering high-quality products or services.
The most significant benefit of quality assurance is that it improves customer satisfaction with your service or product. If you want happy customers, then there are few things better than ensuring they get exactly what they expect when they buy something from you!
Why Quality Assurance?
The purpose of QA is to ensure that all the processes involved in the production or delivery of goods or services are done correctly to achieve the desired standard or goal. The show involves many functions, such as purchasing materials, inventory management, designing products/services, etc., which need proper planning and execution to achieve good results.
What is Quality Management?
Quality management is a process that ensures the products and services that a company provides meet customer requirements. It involves measuring the quality of products and services, identifying where improvements are needed, and implementing solutions to improve quality.
Quality management is an ongoing process that includes planning, organizing, directing, and controlling activities to ensure that the methods used in creating products or services meet customer requirements.
The goal of quality management is to provide consistent product quality at all levels of production.
In addition, it seeks to continuously improve the processes used to create products or deliver services by identifying problems early in the production cycle to correct them before they become significant problems.
Benefits of Quality Management
The benefits of quality management are many. Quality management is not only beneficial to the overall health of an organization, but it can also improve its financial status. In addition, quality management provides several benefits for businesses, including:
Reduced costs: Companies implementing quality management systems often find that they save money in the long run. This is because they can identify problems early on and fix them before they become too expensive to fix. By catching issues before they become significant, companies can avoid paying for costly repairs or replacements later.
Increased productivity: A sound quality management system can help businesses increase their productivity by reducing errors and preventing defects in the first place. In addition, if a company has a high level of employee satisfaction, this will also lead to increased productivity because satisfied employees tend to be more productive than unhappy ones.
Improved customer service: A company with an effective quality management system will provide better customer service than one without one because it will be able to identify problems quickly and fix them before they become serious issues that upset customers or result in expensive recalls. Since customers expect high service levels these days, any service failure can negatively affect your reputation and bottom line.
Why Quality Management?
Quality management ensures that businesses continually assess their performance and make necessary improvements. By focusing on continuous improvement rather than perfection, companies can avoid investing too much time, money and effort into getting something right from scratch before moving on to something else. This approach also helps them retain their competitive edge in a fast-changing environment.
Conclusion
Hopefully, the above definitions and explanations have cleared up any questions you might have had about quality assurance and quality management. The two concepts are closely related but are not entirely the same.
Quality management focuses more on the broader picture, while quality assurance is more hands-on. Quality management is also organizational, while quality assurance is more often individualized. The takeaway here? Quality management refers to an overall system or framework to ensure high-quality standards. In contrast, quality assurance relates to the personal actions involved in providing those standards are met.
Quality Improvement in Six Sigma
Quality Improvement in Six Sigma
Quality improvement is a key component of Six Sigma. It's a continuous process designed to produce more consistent and reliable results, ultimately leading to higher customer satisfaction.
Quality improvement is integral to Six Sigma because it helps organizations identify problems before they become significant. The goal is to eliminate or reduce defects per million opportunities (DPMO).
There are six steps in the quality improvement process:
First, define the problem: Determine what needs fixing by understanding why customers aren't satisfied with your product or service.
Measure performance: Set up metrics to track key performance indicators (KPIs) such as repeat purchases, customer complaints, and returns.
Analyze data: Look at your KPIs to see if there are any patterns or trends you can use to improve your product or service.
Define the solution: Develop ideas for making changes based on your analysis so you can fix specific problems related to DPMO.
Implement improvements: Create new processes or systems for implementing change throughout the organization so everyone works toward the same goal — reducing errors and improving customer satisfaction.
Evaluate results: Monitor all improvements closely after implementation to ensure they achieve their desired outcomes.
Importance of Quality Improvement
Quality improvement is an essential part of the Six Sigma methodology. It is the area of a company where employees are responsible for improving the quality of the product or service. It involves continuous improvement in all parts of a business, from manufacturing to sales, customer service, and administration. Quality improvement is a constant process and not a one-time event. Therefore, it has to be managed continuously throughout the organization.
The most important aspect of quality improvement is quality standardization. Quality standards help in identifying defects and creating a quality management system.
Quality improvement is an activity that focuses on improving products or services, processes, or customer satisfaction by identifying areas for improvement, implementing solutions, and monitoring results. Quality improvement activities may include:
Identification of problems: Identifying problems with the current state of affairs, considering the reasons behind them, and determining their effects on customers or internal operations
Possible solutions: Developing plans for dealing with problems, such as introducing new products, changing policies or procedures, enhancing training programs or employee performance evaluations
Implementation: Implementing solutions through action plans that address identified problems within specific time frames (typically 6-9 months)
Monitoring results: Evaluating whether changes made have improved performance and whether they lead to customer satisfaction.
Six Sigma Methodology
Six Sigma uses DMAIC methodologies to achieve its goals, which stand for:
Define: The first step in DMAIC is to define the problem or opportunity that needs to be addressed. This can be done through brainstorming or other techniques.
Measure: Once the problem has been defined, it needs to be measured to make improvements. This step requires collecting data on key factors related to the improved process and analyzing it using statistical techniques such as regression analysis and ANOVA (analysis of variance).
Analyze: After measuring the process, you should analyze your data using statistical techniques like regression analysis and ANOVA (analysis of variance). These techniques allow you to determine whether your measurements are within acceptable limits or if any patterns in them may help with future improvements.
Improve: This step includes developing new processes or improving existing ones by identifying opportunities for improvement through brainstorming sessions with employees from all levels of the organization.
Control: In the final phase of Six Sigma, you create a control plan, a set of procedures that ensures your new standardized process works smoothly and meets quality standards.
Benefits of Quality Improvement
Quality management has been a significant focus for Six Sigma for many years. This is not surprising because quality is the basis of all business activity and, in particular, customer satisfaction. As a result, quality improvement has become a central tenet of Six Sigma's philosophy.
The benefits of quality improvement include:
Reduced costs: Reductions in product defects and errors lead to reduced production costs. This is particularly significant in the case of products where quality control costs can be very high.
Improved customer satisfaction: Improved product quality leads to improved customer satisfaction, measured using customer surveys or other electronic commerce (e-commerce) techniques.
Increased market share: Improved product quality ensures more customers are satisfied with their purchases, which increases the company's market share.
Increased Productivity: Productivity increases when employees can perform their duties efficiently and correctly without making mistakes, leading to fewer rework activities and reduced costs associated with correcting errors.
Improved Quality: Six sigma provides organizations with a way to improve their processes. This will result in more satisfying customers who will give positive feedback to the organization.
Increased employee job satisfaction: It improves employee morale because employees are happier knowing they are helping their company achieve its goals.
Once you put a Six Sigma quality improvement plan into action, you will see how much of an impact it can have on your company's work. So don't wait—start today!
Read More
Quality Improvement in Six Sigma
Quality improvement is a key component of Six Sigma. It's a continuous process designed to produce more consistent and reliable results, ultimately leading to higher customer satisfaction.
Quality improvement is integral to Six Sigma because it helps organizations identify problems before they become significant. The goal is to eliminate or reduce defects per million opportunities (DPMO).
There are six steps in the quality improvement process:
First, define the problem: Determine what needs fixing by understanding why customers aren't satisfied with your product or service.
Measure performance: Set up metrics to track key performance indicators (KPIs) such as repeat purchases, customer complaints, and returns.
Analyze data: Look at your KPIs to see if there are any patterns or trends you can use to improve your product or service.
Define the solution: Develop ideas for making changes based on your analysis so you can fix specific problems related to DPMO.
Implement improvements: Create new processes or systems for implementing change throughout the organization so everyone works toward the same goal — reducing errors and improving customer satisfaction.
Evaluate results: Monitor all improvements closely after implementation to ensure they achieve their desired outcomes.
Importance of Quality Improvement
Quality improvement is an essential part of the Six Sigma methodology. It is the area of a company where employees are responsible for improving the quality of the product or service. It involves continuous improvement in all parts of a business, from manufacturing to sales, customer service, and administration. Quality improvement is a constant process and not a one-time event. Therefore, it has to be managed continuously throughout the organization.
The most important aspect of quality improvement is quality standardization. Quality standards help in identifying defects and creating a quality management system.
Quality improvement is an activity that focuses on improving products or services, processes, or customer satisfaction by identifying areas for improvement, implementing solutions, and monitoring results. Quality improvement activities may include:
Identification of problems: Identifying problems with the current state of affairs, considering the reasons behind them, and determining their effects on customers or internal operations
Possible solutions: Developing plans for dealing with problems, such as introducing new products, changing policies or procedures, enhancing training programs or employee performance evaluations
Implementation: Implementing solutions through action plans that address identified problems within specific time frames (typically 6-9 months)
Monitoring results: Evaluating whether changes made have improved performance and whether they lead to customer satisfaction.
Six Sigma Methodology
Six Sigma uses DMAIC methodologies to achieve its goals, which stand for:
Define: The first step in DMAIC is to define the problem or opportunity that needs to be addressed. This can be done through brainstorming or other techniques.
Measure: Once the problem has been defined, it needs to be measured to make improvements. This step requires collecting data on key factors related to the improved process and analyzing it using statistical techniques such as regression analysis and ANOVA (analysis of variance).
Analyze: After measuring the process, you should analyze your data using statistical techniques like regression analysis and ANOVA (analysis of variance). These techniques allow you to determine whether your measurements are within acceptable limits or if any patterns in them may help with future improvements.
Improve: This step includes developing new processes or improving existing ones by identifying opportunities for improvement through brainstorming sessions with employees from all levels of the organization.
Control: In the final phase of Six Sigma, you create a control plan, a set of procedures that ensures your new standardized process works smoothly and meets quality standards.
Benefits of Quality Improvement
Quality management has been a significant focus for Six Sigma for many years. This is not surprising because quality is the basis of all business activity and, in particular, customer satisfaction. As a result, quality improvement has become a central tenet of Six Sigma's philosophy.
The benefits of quality improvement include:
Reduced costs: Reductions in product defects and errors lead to reduced production costs. This is particularly significant in the case of products where quality control costs can be very high.
Improved customer satisfaction: Improved product quality leads to improved customer satisfaction, measured using customer surveys or other electronic commerce (e-commerce) techniques.
Increased market share: Improved product quality ensures more customers are satisfied with their purchases, which increases the company's market share.
Increased Productivity: Productivity increases when employees can perform their duties efficiently and correctly without making mistakes, leading to fewer rework activities and reduced costs associated with correcting errors.
Improved Quality: Six sigma provides organizations with a way to improve their processes. This will result in more satisfying customers who will give positive feedback to the organization.
Increased employee job satisfaction: It improves employee morale because employees are happier knowing they are helping their company achieve its goals.
Once you put a Six Sigma quality improvement plan into action, you will see how much of an impact it can have on your company's work. So don't wait—start today!
Why Choose Quality Management
Why Choose Quality Management
Quality management is a vast area of management thinking and strategy. It is a systematic approach to identifying and monitoring processes to ensure that they produce products and services that meet customer expectations, cost targets, and other standards.
A Quality Management System (QMS) helps businesses implement best practices for measuring quality, monitoring performance, and reporting on results. A Quality Management system has several components that work together to help an organization adopt best practices for measuring quality, monitoring performance, and reporting on results.
Each element of the QMS has a different scope, function, and set of activities. Some are more visible than others because they involve creating new policies or assigning responsibilities to various departments within the company. Here’s everything you need to know about quality management to choose whether it makes sense for your business:
Ensures All Products and Services Are Consistent
A quality management system ensures that all products and services are consistent. What does this mean? Each time a product or service is created or delivered, it should be compatible with the standard that has been agreed upon in your organization. That standard could be required to be safe, meet a particular set of features or functionalities, or be completed by a specific date.
Often, the standard will be determined by the customer and be agreed upon by the manufacturer or service provider and the customer beforehand. This is especially important for industries like food and healthcare, where the quality standard is critical for customers’ health and safety.
If the quality management system is well-designed and implemented, it will ensure that the company meets these requirements every time.
Improves Communication
A quality management system promotes communication. Communication is critical to the success of any organization. People must learn what they do and how they fit into the company’s operations, communicate to one another when their work has been completed, and communicate with customers and stakeholders to understand their needs and expectations.
Communication is the act of sharing information with others. It could be verbal or written, face-to-face, or in a meeting. Communication also includes listening and understanding what others have communicated to you. Communication is critical to the success of any organization.
Communication is the system by which information is shared in an organization. A quality management system promotes communication by creating a platform for people to share information. This could be within the department, customer service, or management.
It is necessary for people to learn what they do and how they fit into the company’s operations; communicate to one another when their work has been completed, and communicate with customers and stakeholders to understand their needs and expectations.
Reduces Waste
A quality management system reduces waste. Waste can cost an organization in many ways, including time, effort, money, and other resources. In some organizations, waste can cause health and safety issues, too. Where does this happen? Waste usually occurs when a process takes longer than it should or when something is created but is not needed.
For example, you may have a complex system for ordering and delivering your products. If a customer asks for a change to be made, it can add time to the process. That’s why a quality management system is helpful. It helps you quickly see where waste occurs, decide what to do about it, and put a plan to stop it from happening again.
Helps You Identify and Reduce Errors
A quality management system helps you identify and reduce errors. What are the most common errors?
An error could be as simple as the printer being out of ink when a report is due or a machine producing parts with the wrong measurements. Higher costs and lower customer satisfaction are possible outcomes of too many errors in your company.
A quality management system helps you identify and reduce errors in several ways:
- Understanding customer requirements and expectations helps you know what kind of work you do. What do customers expect? How should the work be done?
- Having clear procedures and expectations for employees will help avoid simple errors, such as changing the wrong settings on a machine or not completing the correct paperwork.
- Having quality checks ensures that the product or service meets the customer’s requirements and has been completed correctly.
Increases Customer Satisfaction
A quality management system increases customer satisfaction by improving the quality of products and services. Customer satisfaction is about meeting and exceeding expectations. It’s about exceeding quality standards and giving customers what they want and need.
How can you increase customer satisfaction with your products, services, and operations?
- Understanding how customers use your products or services helps you identify any issues with the product or service and the quality of the experience.
- Analyzing defects and errors - This helps you to identify what is causing the problems and correct them.
- Using quality checklists - Quality checklists help you to confirm that the product or service has been completed according to the agreed-upon quality standards.
Manage Risks Effectively
A quality management system can help you manage risks effectively. It allows you to take a broader view of the business, identify potential risks, and implement plans to prevent them from happening.
A quality management system helps you to put together a risk management plan that follows three steps:
- Identify the risks: What are the most significant risks to your business? What might happen if you don’t address them?
- Analyze the risks: How likely are they to happen? What would be the impact if they did occur?
- Reduce the risks: What steps can you take to prevent the risks from happening?
Conclusion
Quality management makes sense for companies that want to produce consistent, high-quality products and services. Quality management systems help organizations prevent defects, reduce errors, and improve communication between employees and customers.
A quality management system achieves this by having clearly defined goals, metrics for success, and a method for problem-solving when problems arise. If your company is considering implementing a quality management system, ensure it is the right time. Then, please choose the right plan for your organization and partner with the right partner to help you implement it successfully.
Read More
Why Choose Quality Management
Quality management is a vast area of management thinking and strategy. It is a systematic approach to identifying and monitoring processes to ensure that they produce products and services that meet customer expectations, cost targets, and other standards.
A Quality Management System (QMS) helps businesses implement best practices for measuring quality, monitoring performance, and reporting on results. A Quality Management system has several components that work together to help an organization adopt best practices for measuring quality, monitoring performance, and reporting on results.
Each element of the QMS has a different scope, function, and set of activities. Some are more visible than others because they involve creating new policies or assigning responsibilities to various departments within the company. Here’s everything you need to know about quality management to choose whether it makes sense for your business:
Ensures All Products and Services Are Consistent
A quality management system ensures that all products and services are consistent. What does this mean? Each time a product or service is created or delivered, it should be compatible with the standard that has been agreed upon in your organization. That standard could be required to be safe, meet a particular set of features or functionalities, or be completed by a specific date.
Often, the standard will be determined by the customer and be agreed upon by the manufacturer or service provider and the customer beforehand. This is especially important for industries like food and healthcare, where the quality standard is critical for customers’ health and safety.
If the quality management system is well-designed and implemented, it will ensure that the company meets these requirements every time.
Improves Communication
A quality management system promotes communication. Communication is critical to the success of any organization. People must learn what they do and how they fit into the company’s operations, communicate to one another when their work has been completed, and communicate with customers and stakeholders to understand their needs and expectations.
Communication is the act of sharing information with others. It could be verbal or written, face-to-face, or in a meeting. Communication also includes listening and understanding what others have communicated to you. Communication is critical to the success of any organization.
Communication is the system by which information is shared in an organization. A quality management system promotes communication by creating a platform for people to share information. This could be within the department, customer service, or management.
It is necessary for people to learn what they do and how they fit into the company’s operations; communicate to one another when their work has been completed, and communicate with customers and stakeholders to understand their needs and expectations.
Reduces Waste
A quality management system reduces waste. Waste can cost an organization in many ways, including time, effort, money, and other resources. In some organizations, waste can cause health and safety issues, too. Where does this happen? Waste usually occurs when a process takes longer than it should or when something is created but is not needed.
For example, you may have a complex system for ordering and delivering your products. If a customer asks for a change to be made, it can add time to the process. That’s why a quality management system is helpful. It helps you quickly see where waste occurs, decide what to do about it, and put a plan to stop it from happening again.
Helps You Identify and Reduce Errors
A quality management system helps you identify and reduce errors. What are the most common errors?
An error could be as simple as the printer being out of ink when a report is due or a machine producing parts with the wrong measurements. Higher costs and lower customer satisfaction are possible outcomes of too many errors in your company.
A quality management system helps you identify and reduce errors in several ways:
- Understanding customer requirements and expectations helps you know what kind of work you do. What do customers expect? How should the work be done?
- Having clear procedures and expectations for employees will help avoid simple errors, such as changing the wrong settings on a machine or not completing the correct paperwork.
- Having quality checks ensures that the product or service meets the customer’s requirements and has been completed correctly.
Increases Customer Satisfaction
A quality management system increases customer satisfaction by improving the quality of products and services. Customer satisfaction is about meeting and exceeding expectations. It’s about exceeding quality standards and giving customers what they want and need.
How can you increase customer satisfaction with your products, services, and operations?
- Understanding how customers use your products or services helps you identify any issues with the product or service and the quality of the experience.
- Analyzing defects and errors - This helps you to identify what is causing the problems and correct them.
- Using quality checklists - Quality checklists help you to confirm that the product or service has been completed according to the agreed-upon quality standards.
Manage Risks Effectively
A quality management system can help you manage risks effectively. It allows you to take a broader view of the business, identify potential risks, and implement plans to prevent them from happening.
A quality management system helps you to put together a risk management plan that follows three steps:
- Identify the risks: What are the most significant risks to your business? What might happen if you don’t address them?
- Analyze the risks: How likely are they to happen? What would be the impact if they did occur?
- Reduce the risks: What steps can you take to prevent the risks from happening?
Conclusion
Quality management makes sense for companies that want to produce consistent, high-quality products and services. Quality management systems help organizations prevent defects, reduce errors, and improve communication between employees and customers.
A quality management system achieves this by having clearly defined goals, metrics for success, and a method for problem-solving when problems arise. If your company is considering implementing a quality management system, ensure it is the right time. Then, please choose the right plan for your organization and partner with the right partner to help you implement it successfully.
All You Need to Learn About Cyber Security
All You Need to Learn About Cyber Security
Cyber Security is one of the world's fastest-growing fields, and it's no wonder why. With more and more people, businesses, and even homes having access to the Internet, there is a growing concern that these digital spaces are vulnerable to cyber criminals and malicious hackers. Whether you're interested in becoming a cyber-security professional or want to be better informed about this critical topic, this article will provide you with everything you need to know about cyber security.
What is cyber security?
Cyber security is the collection of methods used to protect networks, computers, programs, and data from threats such as malicious software, identity theft, and damage to critical infrastructure.
Speaking more generally, cyber security is the protection of computers and digital networks from all forms of cyber-attacks. This includes protecting against attempts to steal or damage data, disrupt operations, or otherwise interrupt service.
Cyber security is a growing field that spans multiple disciplines, including computer science, engineering, and criminal justice. The Internet of Things and people's dependence on technology has grown exponentially with increased connectivity. While this has made life easier in many ways, it has also introduced new security risks that did not exist before.
Cyber security professionals are charged with addressing these risks and keeping systems secure. The field is ever-evolving as new threats and vulnerabilities are discovered, and new technologies are created.
Is cyber security suitable for me?
Suppose you are interested in a constantly changing career that offers plenty of variety and helps people in need. In that case, cyber security may be the perfect fit for you. This is because cyber security protects computers, data, networks, and people from cyber-attacks. This can include everything from updating existing security systems to developing new tools to defend against threats.
The field is constantly evolving and changing, so you will likely have various daily tasks and an ever-growing skill set. Additionally, you will get to help people in need, protect critical infrastructure, and be part of a team that works towards a common goal.
What skills will I need to have?
Almost anyone interested in a career in cyber security can find a place in the field. However, specific skills make you more attractive in the job market.
Computer Security: If you want to work in computer security, you will need to thoroughly understand how computer systems function. This means knowing how hardware, software, networks, etc. all work together. If this sounds like a lot, don't worry, computer science is constantly evolving. You may want to consider staying up-to-date on the latest developments in the field.
Digital Forensics: If you're going to work in digital forensics, you will need to know how to collect and preserve evidence from computers and other digital devices. You will likely work closely with law enforcement or government agencies in these situations.
Network Security: If you want to work in network security, you will need to understand the different types of networks (e.g., LAN, WAN, etc.), how they work, and how to protect them from other attacks. Network engineers are responsible for designing and maintaining networks.
Importance of cyber security
Without cyber security, computers, networks, and other digital devices would be incredibly susceptible to attacks. Hackers could access your information without issues and even take over your device. This could have devastating effects, especially if the hack involves critical infrastructure, such as power grids or transportation systems.
Suppose you are ever worried about the state of cyber security in your country. In that case, you can do your part by taking steps to protect yourself and your devices. Additionally, suppose you are interested in a career in cyber security. In that case, you can help protect others from cyber-attacks by learning how to defend against them.
What Are Cyber Attacks?
Cyber-attacks are attempts to disrupt or damage computers or computer networks. They can be used for various malicious purposes, including stealing information or money or disrupting a person's or company's ability to function. Cyber-attacks can come in many forms, each with its threat level and consequences.
For example, denial-of-service attacks can be used to shut down computer networks. In contrast, ransomware attacks are used to encrypt computer files until a ransom is paid. Cyber-attacks can be targeted at individuals and organizations and may happen at any time. At times of the year, such as Black Friday, retail networks experience a high volume of cyber-attacks.
Different Types of Attacks
There are many types of cyber-attacks, each of which poses different threats to you and your data. You can defend yourself against these attacks by regularly updating your software, installing anti-virus software, and being careful about what websites you visit. These attacks include denial-of-service, ransomware, viruses, social engineering, and spoofing.
Denial-of-service Attack: A denial-of-service attack floods a computer network with requests. This attempt to overload computer systems often originates with a single computer.
Ransomware Attack: A type of malware that encrypts your computer files and holds them hostage until a ransom is paid.
Virus Attack: A type of malware that copies itself and spreads to computers by other means, such as email or social media.
Social Engineering: An attempt to trick people into revealing sensitive information, clicking on malicious links, or taking other action that damages computer systems.
Spoofing Attack: A type of cyber-attack that tricks a computer system into thinking it is coming from a trusted source.
What are the Different Types of Cybersecurity Threats
There are many different types of cyber security threats. The most common types include computer viruses, malware, identity theft, spam.
Computer Viruses: Computer viruses are malicious software (or malware) designed to damage computer systems. They can spread from computer to computer and sometimes be difficult to remove.
Malware: A type of software designed to disrupt computer systems or steal information. There are several different types of malwares, but they are often disguised as legitimate software.
Identity Theft: Identity theft occurs when someone uses your identity for their benefit. This can happen in various ways but most commonly with stolen credit cards or banking information.
Spam: Unsolicited email or message sent to a large number of people. Spam is often used to distribute malware or trick people into clicking on links that take them to fake websites.
Risks of Having Poor Cybersecurity
Suppose you have poor cybersecurity and don't take the necessary precautions to protect yourself. In that case, you are at risk of a cyber-attack. Hackers can steal your personal information, including banking and credit card information, Social Security Number, and other sensitive data. This can put your finances and personal information at risk, and it can take a long time to repair the damage.
Suppose you have poor cybersecurity and are connected to critical infrastructure. In that case, you could be responsible for a cyber-attack that causes harm to others. This could include hacking into a power grid and causing blackouts or hacking into an airplane control system and causing a plane to crash.
Finally, suppose you have poor cybersecurity and work for a company. In that case, you could be responsible for a cyber-attack that damages your company. This could include allowing hackers to steal sensitive information or disrupt operations.
Summary
Computer networks, programs, and data risk being hacked or attacked by malicious software at any time. It would help if you had strong cybersecurity measures to protect yourself against these threats.
Cyber-attacks include denial-of-service, ransomware, viruses, social engineering, and spoofing. You can defend yourself against these attacks by regularly updating your software, installing anti-virus software, and being careful about what websites you visit.
Read More
All You Need to Learn About Cyber Security
Cyber Security is one of the world's fastest-growing fields, and it's no wonder why. With more and more people, businesses, and even homes having access to the Internet, there is a growing concern that these digital spaces are vulnerable to cyber criminals and malicious hackers. Whether you're interested in becoming a cyber-security professional or want to be better informed about this critical topic, this article will provide you with everything you need to know about cyber security.
What is cyber security?
Cyber security is the collection of methods used to protect networks, computers, programs, and data from threats such as malicious software, identity theft, and damage to critical infrastructure.
Speaking more generally, cyber security is the protection of computers and digital networks from all forms of cyber-attacks. This includes protecting against attempts to steal or damage data, disrupt operations, or otherwise interrupt service.
Cyber security is a growing field that spans multiple disciplines, including computer science, engineering, and criminal justice. The Internet of Things and people's dependence on technology has grown exponentially with increased connectivity. While this has made life easier in many ways, it has also introduced new security risks that did not exist before.
Cyber security professionals are charged with addressing these risks and keeping systems secure. The field is ever-evolving as new threats and vulnerabilities are discovered, and new technologies are created.
Is cyber security suitable for me?
Suppose you are interested in a constantly changing career that offers plenty of variety and helps people in need. In that case, cyber security may be the perfect fit for you. This is because cyber security protects computers, data, networks, and people from cyber-attacks. This can include everything from updating existing security systems to developing new tools to defend against threats.
The field is constantly evolving and changing, so you will likely have various daily tasks and an ever-growing skill set. Additionally, you will get to help people in need, protect critical infrastructure, and be part of a team that works towards a common goal.
What skills will I need to have?
Almost anyone interested in a career in cyber security can find a place in the field. However, specific skills make you more attractive in the job market.
Computer Security: If you want to work in computer security, you will need to thoroughly understand how computer systems function. This means knowing how hardware, software, networks, etc. all work together. If this sounds like a lot, don't worry, computer science is constantly evolving. You may want to consider staying up-to-date on the latest developments in the field.
Digital Forensics: If you're going to work in digital forensics, you will need to know how to collect and preserve evidence from computers and other digital devices. You will likely work closely with law enforcement or government agencies in these situations.
Network Security: If you want to work in network security, you will need to understand the different types of networks (e.g., LAN, WAN, etc.), how they work, and how to protect them from other attacks. Network engineers are responsible for designing and maintaining networks.
Importance of cyber security
Without cyber security, computers, networks, and other digital devices would be incredibly susceptible to attacks. Hackers could access your information without issues and even take over your device. This could have devastating effects, especially if the hack involves critical infrastructure, such as power grids or transportation systems.
Suppose you are ever worried about the state of cyber security in your country. In that case, you can do your part by taking steps to protect yourself and your devices. Additionally, suppose you are interested in a career in cyber security. In that case, you can help protect others from cyber-attacks by learning how to defend against them.
What Are Cyber Attacks?
Cyber-attacks are attempts to disrupt or damage computers or computer networks. They can be used for various malicious purposes, including stealing information or money or disrupting a person's or company's ability to function. Cyber-attacks can come in many forms, each with its threat level and consequences.
For example, denial-of-service attacks can be used to shut down computer networks. In contrast, ransomware attacks are used to encrypt computer files until a ransom is paid. Cyber-attacks can be targeted at individuals and organizations and may happen at any time. At times of the year, such as Black Friday, retail networks experience a high volume of cyber-attacks.
Different Types of Attacks
There are many types of cyber-attacks, each of which poses different threats to you and your data. You can defend yourself against these attacks by regularly updating your software, installing anti-virus software, and being careful about what websites you visit. These attacks include denial-of-service, ransomware, viruses, social engineering, and spoofing.
Denial-of-service Attack: A denial-of-service attack floods a computer network with requests. This attempt to overload computer systems often originates with a single computer.
Ransomware Attack: A type of malware that encrypts your computer files and holds them hostage until a ransom is paid.
Virus Attack: A type of malware that copies itself and spreads to computers by other means, such as email or social media.
Social Engineering: An attempt to trick people into revealing sensitive information, clicking on malicious links, or taking other action that damages computer systems.
Spoofing Attack: A type of cyber-attack that tricks a computer system into thinking it is coming from a trusted source.
What are the Different Types of Cybersecurity Threats
There are many different types of cyber security threats. The most common types include computer viruses, malware, identity theft, spam.
Computer Viruses: Computer viruses are malicious software (or malware) designed to damage computer systems. They can spread from computer to computer and sometimes be difficult to remove.
Malware: A type of software designed to disrupt computer systems or steal information. There are several different types of malwares, but they are often disguised as legitimate software.
Identity Theft: Identity theft occurs when someone uses your identity for their benefit. This can happen in various ways but most commonly with stolen credit cards or banking information.
Spam: Unsolicited email or message sent to a large number of people. Spam is often used to distribute malware or trick people into clicking on links that take them to fake websites.
Risks of Having Poor Cybersecurity
Suppose you have poor cybersecurity and don't take the necessary precautions to protect yourself. In that case, you are at risk of a cyber-attack. Hackers can steal your personal information, including banking and credit card information, Social Security Number, and other sensitive data. This can put your finances and personal information at risk, and it can take a long time to repair the damage.
Suppose you have poor cybersecurity and are connected to critical infrastructure. In that case, you could be responsible for a cyber-attack that causes harm to others. This could include hacking into a power grid and causing blackouts or hacking into an airplane control system and causing a plane to crash.
Finally, suppose you have poor cybersecurity and work for a company. In that case, you could be responsible for a cyber-attack that damages your company. This could include allowing hackers to steal sensitive information or disrupt operations.
Summary
Computer networks, programs, and data risk being hacked or attacked by malicious software at any time. It would help if you had strong cybersecurity measures to protect yourself against these threats.
Cyber-attacks include denial-of-service, ransomware, viruses, social engineering, and spoofing. You can defend yourself against these attacks by regularly updating your software, installing anti-virus software, and being careful about what websites you visit.
Security Risk Management
Security Risk Management
Security risk management is identifying vulnerabilities, prioritizing and implementing procedures to defend against them, and maintaining constant awareness. Security risk management is more than just about electronic security. It is about managing the risks within your organization and how to mitigate them.
Understanding Security Risk Management
Security Risk Management is identifying and evaluating security risks in your business. It is a systematic way of analyzing, assessing, and prioritizing threats to your organization. It involves specifying your security infrastructure's "loose ends" and then implementing controls to address them.
Security risk management should be viewed as a continuous process involving a series of decisions about managing risk based on threat intelligence, available resources, and other factors. The key steps are:
- Identify vulnerabilities
- Assess impact
- Create an action plan
- Implement controls or mitigate vulnerabilities (if possible)
The Importance of Security Risk Management
Although security risk management is a relatively new concept and the field of risk management has a relatively short history, it has already become an essential aspect of any company's IT security strategy.
The importance of security risk management is closely related to the fact that it allows companies to protect themselves against cyberattacks and other vulnerabilities. Therefore, the main goal of this process is to reduce the likelihood of adverse events occurring in the future and thus help prevent them from happening.
In addition, companies that apply security risk management can develop measures for preventing damage caused by accidents, theft, or other events. Moreover, they can also use these methods to improve their overall security posture.
In addition, companies may choose to establish a dedicated team or department within their organization that focuses exclusively on this particular aspect of their business. This team will be responsible for developing policies and procedures that ensure compliance with all relevant regulations and standards and with other internal policies and procedures.
The role of security risk management specialists is vital for organizations because they have access to information about potential threats and vulnerabilities at all times. They can also provide recommendations on how best to address these issues.
Objectives of Security Risk Management
There are several objectives of security risk management.
The first is to protect your business from any potential cyber-attacks by ensuring that all systems are secured and up to date.
The second objective is to protect employees from potential threats, such as identity theft, data breaches, and fraud.
Finally, you want to ensure that your partners and customers are protected.
Why Security Risk Management?
Security risk management helps in the following ways:
- It ensures that the system complies with regulatory agencies and industry standards.
- It helps to protect your organization from data breaches.
- It ensures that your staff is not wasting time on low-priority tasks and instead working on high-priority issues.
- It helps to identify and understand the risks involved in a project and take steps to reduce them.
- It ensures that your resources are used more efficiently.
Risk Assessment
A Risk assessment is a method of evaluating and quantifying the likelihood that a specific threat will occur and the potential impact if it does. If a threat is high, then appropriate steps can be taken to lower the risk through risk mitigation.
A risk assessment should consider various factors, such as the type and nature of the threat, vulnerability, and impact on the business if the threat is realized. Several steps should be taken when performing a risk assessment.
The first is to identify and list all existing threats. The next step is to assess the likelihood that each threat will occur, followed by an assessment of the threat's impact if it happens. Finally, risk mitigation strategies can be developed and implemented to reduce risk.
Risk Mitigation
Risk mitigation reduces the risk associated with a specific threat, such as a cyber-attack. There are several ways to mitigate risk.
The first is identifying and listing all existing threats and their potential severity. Once the threats are known, mitigation strategies can be developed to reduce the risk.
For example, several strategies can be implemented when it comes to mitigating the risk of cyber-attacks. The first is to ensure that all software is up to date and patched and that firewalls are installed and properly configured. Other strategies include installing malware detection and prevention software and hiring a cyber-security firm to regularly test and scan your network.
Risk Monitoring
Risk monitoring is keeping track of potential threats to your organization and ensuring that they are managed and that a mitigation strategy is in place. This is not only useful for risk assessment but also all other elements of security risk management.
When monitoring risk, you want to ensure that you know everything happening within your organization. This includes new threats that may be emerging, changes in regulatory requirements, changes in technology, and changes in your organization's structure. If a threat is identified, the appropriate mitigation strategies can be implemented.
Conclusion
The security risk management process is vital to any organization's success, both in the digital and physical world. If you want to protect your business and your customers, then this is something that you need to be doing.
Additionally, it is essential to protect your employees as well. There are many different things to consider regarding security risk management. You may encounter many risks, and you need to be prepared to deal with them. If you want to be successful, then security risk management is something you need to do.
Read More
Security Risk Management
Security risk management is identifying vulnerabilities, prioritizing and implementing procedures to defend against them, and maintaining constant awareness. Security risk management is more than just about electronic security. It is about managing the risks within your organization and how to mitigate them.
Understanding Security Risk Management
Security Risk Management is identifying and evaluating security risks in your business. It is a systematic way of analyzing, assessing, and prioritizing threats to your organization. It involves specifying your security infrastructure's "loose ends" and then implementing controls to address them.
Security risk management should be viewed as a continuous process involving a series of decisions about managing risk based on threat intelligence, available resources, and other factors. The key steps are:
- Identify vulnerabilities
- Assess impact
- Create an action plan
- Implement controls or mitigate vulnerabilities (if possible)
The Importance of Security Risk Management
Although security risk management is a relatively new concept and the field of risk management has a relatively short history, it has already become an essential aspect of any company's IT security strategy.
The importance of security risk management is closely related to the fact that it allows companies to protect themselves against cyberattacks and other vulnerabilities. Therefore, the main goal of this process is to reduce the likelihood of adverse events occurring in the future and thus help prevent them from happening.
In addition, companies that apply security risk management can develop measures for preventing damage caused by accidents, theft, or other events. Moreover, they can also use these methods to improve their overall security posture.
In addition, companies may choose to establish a dedicated team or department within their organization that focuses exclusively on this particular aspect of their business. This team will be responsible for developing policies and procedures that ensure compliance with all relevant regulations and standards and with other internal policies and procedures.
The role of security risk management specialists is vital for organizations because they have access to information about potential threats and vulnerabilities at all times. They can also provide recommendations on how best to address these issues.
Objectives of Security Risk Management
There are several objectives of security risk management.
The first is to protect your business from any potential cyber-attacks by ensuring that all systems are secured and up to date.
The second objective is to protect employees from potential threats, such as identity theft, data breaches, and fraud.
Finally, you want to ensure that your partners and customers are protected.
Why Security Risk Management?
Security risk management helps in the following ways:
- It ensures that the system complies with regulatory agencies and industry standards.
- It helps to protect your organization from data breaches.
- It ensures that your staff is not wasting time on low-priority tasks and instead working on high-priority issues.
- It helps to identify and understand the risks involved in a project and take steps to reduce them.
- It ensures that your resources are used more efficiently.
Risk Assessment
A Risk assessment is a method of evaluating and quantifying the likelihood that a specific threat will occur and the potential impact if it does. If a threat is high, then appropriate steps can be taken to lower the risk through risk mitigation.
A risk assessment should consider various factors, such as the type and nature of the threat, vulnerability, and impact on the business if the threat is realized. Several steps should be taken when performing a risk assessment.
The first is to identify and list all existing threats. The next step is to assess the likelihood that each threat will occur, followed by an assessment of the threat's impact if it happens. Finally, risk mitigation strategies can be developed and implemented to reduce risk.
Risk Mitigation
Risk mitigation reduces the risk associated with a specific threat, such as a cyber-attack. There are several ways to mitigate risk.
The first is identifying and listing all existing threats and their potential severity. Once the threats are known, mitigation strategies can be developed to reduce the risk.
For example, several strategies can be implemented when it comes to mitigating the risk of cyber-attacks. The first is to ensure that all software is up to date and patched and that firewalls are installed and properly configured. Other strategies include installing malware detection and prevention software and hiring a cyber-security firm to regularly test and scan your network.
Risk Monitoring
Risk monitoring is keeping track of potential threats to your organization and ensuring that they are managed and that a mitigation strategy is in place. This is not only useful for risk assessment but also all other elements of security risk management.
When monitoring risk, you want to ensure that you know everything happening within your organization. This includes new threats that may be emerging, changes in regulatory requirements, changes in technology, and changes in your organization's structure. If a threat is identified, the appropriate mitigation strategies can be implemented.
Conclusion
The security risk management process is vital to any organization's success, both in the digital and physical world. If you want to protect your business and your customers, then this is something that you need to be doing.
Additionally, it is essential to protect your employees as well. There are many different things to consider regarding security risk management. You may encounter many risks, and you need to be prepared to deal with them. If you want to be successful, then security risk management is something you need to do.
Cloud Storage and its Importance
Cloud Storage and its Importance
Cloud storage plays a vital role in our day-to-day lives. This is evident from the rapid growth of cloud storage providers. Cloud-based storage providers have transformed how we save data, store private information, and transfer files to other locations. Cloud storage is the new hot sector, with all the companies jumping on the bandwagon. In this digital age, where everything is online, we want to save and keep all our data safe. Unfortunately, there are many instances in which we might lose all our files or data if we don't have a good backup in place! But what exactly is cloud storage? How does it work? Continue the blog to learn about these.
What is Cloud Storage?
Cloud storage is a type of computer storage that is accessible over the Internet. It is part of the cloud computing industry, including server hosting, network storage, and data management. Cloud storage differs from file servers and other types of centralized storage in that it is not owned by an organization or group but rather by a third-party provider who has access to your data as needed for their business purpose.
Cloud storage services typically allow users to store files in one place to access them anywhere on any device. They may also provide tools such as email, instant messaging, and calendars. Cloud storage can be accessed through web browsers or mobile apps on multiple computers and smartphones.
Cloud services are convenient because they allow you to store large amounts of data without worrying about maintaining physical space or spending money on hardware upgrades. Users can also pay only for what they use, unlike traditional methods where they purchase hard drives or other components upfront and pay for additional space yearly as their needs grow.
What is Cloud?
A cloud is a large data center that can be accessed remotely. It allows your application to run without the need for you to be physically present at a particular location.
For example, your software may only be used at home or work. You don't need to worry about transporting or storing data locally since it will all be stored in the cloud.
The benefit of using cloud computing is that you don't need to worry about storage space or maintenance costs since the company handling the storage and care will do it for you.
The Importance of Cloud Storage
Cloud data storage is generally less expensive than on-premises data storage. This is one of the most significant advantages of cloud data storage.
In addition, cloud data storage offers scalability for your business as your data storage needs increase. This also depends on which provider you choose to store your data. There are various storage options to choose from in cloud data storage. Cloud data storage can store and transfer multiple business data, including sensitive data.
In addition, cloud data storage offers data accessibility from any device connected to the internet. This can be particularly useful for businesses that want to give their employees the freedom to work remotely.
How does Cloud Storage work?
Cloud storage works on a different mechanism as compared to traditional data storage. Cloud-based storage works on a multi-tenant architecture, meaning they have multiple clients accessing their servers from a shared environment. This can be compared to a hotel where all the guests have access to the same kitchen and dining area.
Cloud storage uses a single system for storing, managing, and protecting data for multiple clients. The system is highly scalable and can quickly expand to accommodate increased customer demand.
There are different types of storage offered by cloud providers. While some offer only storage services, others also provide backup services.
The General Architecture of Cloud Storage
Cloud storage architecture comprises applications, networks, operating systems, hypervisors, and storage.
Applications consist of software used in storing and managing data.
The network is the interconnection between the client, application, and data center.
Operating systems are software that controls the hardware and software of the computer.
Hypervisors are software applications that manage virtual machines. Finally, storage is the place where data is stored.
Types of Cloud Service
There are many cloud storage services:
Software as a Service (SaaS): This service is used for business software. The software is hosted in the cloud and accessed over the internet by users. Software as a Service (SaaS) includes marketing and sales automation, human resource software, financial management software, etc.
Platform as a Service (PaaS): PaaS is a cloud service that gives all the tools one needs to build and run an application. This includes a programming language, a code editor, a runtime, a database, a file system, and an execution environment.
Infrastructure as a Service (IaaS): IaaS is a cloud service that provides the infrastructure needed to run an application. This includes virtual machines, networks, storage, and load balancers.
Cloud Storage Providers
Google - The most popular cloud storage service is Google Drive. Google Drive comes with 15 GB of free cloud storage. Many users use Google Drive because of its simplicity and ease of use.
Amazon - Amazon comes with free cloud storage with 5 GB of free space for users. It also allows you to earn more free Amazon Drive space. You can earn up to 50 GB of free Amazon Drive space by participating in their referral program.
Microsoft - Microsoft OneDrive comes with 15 GB of free cloud storage space. You can refer your friends and earn an additional 5 GB of space.
Advantages of Cloud Storage
Cost Effective - Cloud storage can be much less expensive than traditional data storage.
Scalability - Cloud storage can scale as your needs change.
Convenience - Cloud storage can be accessed from any device.
Security - Cloud storage offers a high level of security and compliance with industry standards.
No upfront cost - You don't have to spend money to implement an effective backup.
Available as a service - Companies that provide cloud storage services make their product available, so you only pay for what you use.
Offsite backup - Cloud storage offers a convenient way to keep your essential files safe during a natural disaster.
No equipment - You don't have to purchase the hardware to store data onsite.
No technical knowledge - You don't have to have any special knowledge to use cloud storage.
Safety - Cloud storage services keep your data in a remote location. Hence, they're safe in case of a fire or other disaster at your business.
Variety of providers - A variety of providers offer cloud storage services, so you have many options when choosing a provider.
Conclusion
Cloud storage has become an essential part of business operations. It has proven a reliable and cost-effective way to store and share data. The wide range of providers and the growing demand for cloud storage are indicators of the growth of this sector.
Cloud storage offers an easy way to share data with partners and co-workers. It also makes it easier for remote employees to access files from home. Cloud storage is helpful for businesses that need extra storage space, but don-t have room for servers.
It's also beneficial for people who need to store sensitive information on an external server. Cloud storage is widely used for storing personal data like photos, videos, and emails. In addition, cloud storage lets you access your data from anywhere, on any device. These benefits make cloud storage an excellent choice for anyone who needs to store data online.
Read More
Cloud Storage and its Importance
Cloud storage plays a vital role in our day-to-day lives. This is evident from the rapid growth of cloud storage providers. Cloud-based storage providers have transformed how we save data, store private information, and transfer files to other locations. Cloud storage is the new hot sector, with all the companies jumping on the bandwagon. In this digital age, where everything is online, we want to save and keep all our data safe. Unfortunately, there are many instances in which we might lose all our files or data if we don't have a good backup in place! But what exactly is cloud storage? How does it work? Continue the blog to learn about these.
What is Cloud Storage?
Cloud storage is a type of computer storage that is accessible over the Internet. It is part of the cloud computing industry, including server hosting, network storage, and data management. Cloud storage differs from file servers and other types of centralized storage in that it is not owned by an organization or group but rather by a third-party provider who has access to your data as needed for their business purpose.
Cloud storage services typically allow users to store files in one place to access them anywhere on any device. They may also provide tools such as email, instant messaging, and calendars. Cloud storage can be accessed through web browsers or mobile apps on multiple computers and smartphones.
Cloud services are convenient because they allow you to store large amounts of data without worrying about maintaining physical space or spending money on hardware upgrades. Users can also pay only for what they use, unlike traditional methods where they purchase hard drives or other components upfront and pay for additional space yearly as their needs grow.
What is Cloud?
A cloud is a large data center that can be accessed remotely. It allows your application to run without the need for you to be physically present at a particular location.
For example, your software may only be used at home or work. You don't need to worry about transporting or storing data locally since it will all be stored in the cloud.
The benefit of using cloud computing is that you don't need to worry about storage space or maintenance costs since the company handling the storage and care will do it for you.
The Importance of Cloud Storage
Cloud data storage is generally less expensive than on-premises data storage. This is one of the most significant advantages of cloud data storage.
In addition, cloud data storage offers scalability for your business as your data storage needs increase. This also depends on which provider you choose to store your data. There are various storage options to choose from in cloud data storage. Cloud data storage can store and transfer multiple business data, including sensitive data.
In addition, cloud data storage offers data accessibility from any device connected to the internet. This can be particularly useful for businesses that want to give their employees the freedom to work remotely.
How does Cloud Storage work?
Cloud storage works on a different mechanism as compared to traditional data storage. Cloud-based storage works on a multi-tenant architecture, meaning they have multiple clients accessing their servers from a shared environment. This can be compared to a hotel where all the guests have access to the same kitchen and dining area.
Cloud storage uses a single system for storing, managing, and protecting data for multiple clients. The system is highly scalable and can quickly expand to accommodate increased customer demand.
There are different types of storage offered by cloud providers. While some offer only storage services, others also provide backup services.
The General Architecture of Cloud Storage
Cloud storage architecture comprises applications, networks, operating systems, hypervisors, and storage.
Applications consist of software used in storing and managing data.
The network is the interconnection between the client, application, and data center.
Operating systems are software that controls the hardware and software of the computer.
Hypervisors are software applications that manage virtual machines. Finally, storage is the place where data is stored.
Types of Cloud Service
There are many cloud storage services:
Software as a Service (SaaS): This service is used for business software. The software is hosted in the cloud and accessed over the internet by users. Software as a Service (SaaS) includes marketing and sales automation, human resource software, financial management software, etc.
Platform as a Service (PaaS): PaaS is a cloud service that gives all the tools one needs to build and run an application. This includes a programming language, a code editor, a runtime, a database, a file system, and an execution environment.
Infrastructure as a Service (IaaS): IaaS is a cloud service that provides the infrastructure needed to run an application. This includes virtual machines, networks, storage, and load balancers.
Cloud Storage Providers
Google - The most popular cloud storage service is Google Drive. Google Drive comes with 15 GB of free cloud storage. Many users use Google Drive because of its simplicity and ease of use.
Amazon - Amazon comes with free cloud storage with 5 GB of free space for users. It also allows you to earn more free Amazon Drive space. You can earn up to 50 GB of free Amazon Drive space by participating in their referral program.
Microsoft - Microsoft OneDrive comes with 15 GB of free cloud storage space. You can refer your friends and earn an additional 5 GB of space.
Advantages of Cloud Storage
Cost Effective - Cloud storage can be much less expensive than traditional data storage.
Scalability - Cloud storage can scale as your needs change.
Convenience - Cloud storage can be accessed from any device.
Security - Cloud storage offers a high level of security and compliance with industry standards.
No upfront cost - You don't have to spend money to implement an effective backup.
Available as a service - Companies that provide cloud storage services make their product available, so you only pay for what you use.
Offsite backup - Cloud storage offers a convenient way to keep your essential files safe during a natural disaster.
No equipment - You don't have to purchase the hardware to store data onsite.
No technical knowledge - You don't have to have any special knowledge to use cloud storage.
Safety - Cloud storage services keep your data in a remote location. Hence, they're safe in case of a fire or other disaster at your business.
Variety of providers - A variety of providers offer cloud storage services, so you have many options when choosing a provider.
Conclusion
Cloud storage has become an essential part of business operations. It has proven a reliable and cost-effective way to store and share data. The wide range of providers and the growing demand for cloud storage are indicators of the growth of this sector.
Cloud storage offers an easy way to share data with partners and co-workers. It also makes it easier for remote employees to access files from home. Cloud storage is helpful for businesses that need extra storage space, but don-t have room for servers.
It's also beneficial for people who need to store sensitive information on an external server. Cloud storage is widely used for storing personal data like photos, videos, and emails. In addition, cloud storage lets you access your data from anywhere, on any device. These benefits make cloud storage an excellent choice for anyone who needs to store data online.
Software Quality Assurance
Software Quality Assurance
Quality assurance is one of the most important aspects of any software development project. But you might be skeptical about how important it is to have a QA team for your assignments because you think there are too many other things on your plate. Moreover, it would add more work to your team, which could cause you sleepless nights. Well, it's time to stop with all this thinking and start with proper planning for software testing to ensure that each of your projects will be delivered as expected by its customers/users.
Software QA professionals face a constantly changing landscape, making their job difficult because many products are never released. Still, QA professionals must remain persistent and take risks that can lead to failure. Still, they must never forget what matters: satisfying customers!
What is Software Quality Assurance?
Software quality assurance (SQA) is a process that helps to ensure the correctness, reliability, usability, and maintainability of software. If a program works correctly, the user will experience a satisfaction. If it does not work correctly, users will experience frustration. The process includes several activities: planning, analysis, design, testing, and documentation.
Software must be constructed so that it can be used by people who are not technical experts to operate it. This requires that the software be designed to be easy to use and understand. In addition, it must run on various platforms and systems. Finally, it must also be able to function as expected when all these factors are considered.
The goal of SQA is to make sure that your products meet their customers' expectations. This can be done in several ways:
- By ensuring that the requirements are understood and well-defined by all involved parties, including you and your stakeholders.
- By ensuring that there are no errors or omissions in the code.
- By performing regression testing to detect any new bugs that may have been introduced over time.
- Testing with real users and discovering if they have any concerns about your product.
Software Quality Assurance Importance
Quality assurance is an essential part of any software development process. In software development, quality assurance is the process of ensuring that a product meets its specified requirements. It involves many aspects, including testing, documentation and documentation review, regression testing, and others.
When developing a software product, it's not just about creating something that works - it's also about testing it to ensure it works properly. This requires you to test how well the software works, how well it performs under various conditions, and how robust it is against unexpected errors or bugs.
There are three main quality assurance tests: unit tests (end-to-end tests), integration tests, and system tests.
Unit tests check that each component works as expected.
Integration tests check whether multiple components work together correctly.
System tests check if all components work together as expected in a real-world scenario.
Software Quality Assurance Plan
A software quality assurance plan (SQAP) is a statement of how an organization ensures that its software product or system meets applicable standards. An SQAP should be developed for each product or system being developed, maintained, and operated.
The purpose of an SQAP is to provide clear direction on what needs to be done to ensure that the end product or system conforms to applicable standards. The plan documents and defines the roles and responsibilities of all parties involved in developing and implementing the program. The SQAP also describes the types of evidence required for meeting compliance requirements and maintenance activities necessary to maintain compliance.
The primary purpose of an SQAP is to provide direction on what needs to be done to ensure that products or systems meet applicable standards. An SQAP is a document that describes how an organization ensures that its products or systems meet applicable standards through testing processes, audits, reviews, and other means.
How Professionals Implement SAQ
Software quality assurance professionals implement software quality assurance processes to ensure the software quality produced by a software development organization. They evaluate, improve and extend the quality of software. They also help ensure that the requirements are met during the development process.
The role of a software quality assurance professional is to verify that a product meets its specifications and requirements before it is released to customers. This process includes reviewing documents such as test plans and cases to ensure they match the conditions. They may also check code for defects and fix them if necessary.
Software quality assurance professionals should know all phases of software development, including requirements gathering, design, coding, testing, and maintenance. This process is implemented through various methods, including testing, debugging, and documentation.
Software quality assurance involves the following steps:
First, identifying defects in software products using tests.
Analyzing data collected from tests to identify patterns that indicate the presence of defects.
Fixing defects identified by data analysis.
Documenting any changes made to the software during testing or after completion of testing.
Conclusion
Software quality assurance is, at its most basic level, a job that involves keeping an eye on the creation, modification, and usage of the software. There are many ways to accomplish this task from a structural standpoint. One way to ensure the quality of the software is by creating a software test plan. This is the first step in ensuring things work out for the best of your project. A comprehensive test plan can protect against pitfalls resulting from inferior code or poor development processes.
Without QA, the software risks not being fit for purpose and, therefore, not meeting the requirements. QA must test software and expose flaws so they can be corrected. The tests are created based on Test Requirements derived from the User Story or Feature Description. Tests must cover all of the specified features. Without comprehensive coverage, bugs will likely be missed resulting in poor-quality software. Setting up the environment for automated testing is a complex process. To support deployment, it requires a significant amount of stakeholder engagement to agree on the testing approach, test cases, and acceptance criteria.
Read More
Software Quality Assurance
Quality assurance is one of the most important aspects of any software development project. But you might be skeptical about how important it is to have a QA team for your assignments because you think there are too many other things on your plate. Moreover, it would add more work to your team, which could cause you sleepless nights. Well, it's time to stop with all this thinking and start with proper planning for software testing to ensure that each of your projects will be delivered as expected by its customers/users.
Software QA professionals face a constantly changing landscape, making their job difficult because many products are never released. Still, QA professionals must remain persistent and take risks that can lead to failure. Still, they must never forget what matters: satisfying customers!
What is Software Quality Assurance?
Software quality assurance (SQA) is a process that helps to ensure the correctness, reliability, usability, and maintainability of software. If a program works correctly, the user will experience a satisfaction. If it does not work correctly, users will experience frustration. The process includes several activities: planning, analysis, design, testing, and documentation.
Software must be constructed so that it can be used by people who are not technical experts to operate it. This requires that the software be designed to be easy to use and understand. In addition, it must run on various platforms and systems. Finally, it must also be able to function as expected when all these factors are considered.
The goal of SQA is to make sure that your products meet their customers' expectations. This can be done in several ways:
- By ensuring that the requirements are understood and well-defined by all involved parties, including you and your stakeholders.
- By ensuring that there are no errors or omissions in the code.
- By performing regression testing to detect any new bugs that may have been introduced over time.
- Testing with real users and discovering if they have any concerns about your product.
Software Quality Assurance Importance
Quality assurance is an essential part of any software development process. In software development, quality assurance is the process of ensuring that a product meets its specified requirements. It involves many aspects, including testing, documentation and documentation review, regression testing, and others.
When developing a software product, it's not just about creating something that works - it's also about testing it to ensure it works properly. This requires you to test how well the software works, how well it performs under various conditions, and how robust it is against unexpected errors or bugs.
There are three main quality assurance tests: unit tests (end-to-end tests), integration tests, and system tests.
Unit tests check that each component works as expected.
Integration tests check whether multiple components work together correctly.
System tests check if all components work together as expected in a real-world scenario.
Software Quality Assurance Plan
A software quality assurance plan (SQAP) is a statement of how an organization ensures that its software product or system meets applicable standards. An SQAP should be developed for each product or system being developed, maintained, and operated.
The purpose of an SQAP is to provide clear direction on what needs to be done to ensure that the end product or system conforms to applicable standards. The plan documents and defines the roles and responsibilities of all parties involved in developing and implementing the program. The SQAP also describes the types of evidence required for meeting compliance requirements and maintenance activities necessary to maintain compliance.
The primary purpose of an SQAP is to provide direction on what needs to be done to ensure that products or systems meet applicable standards. An SQAP is a document that describes how an organization ensures that its products or systems meet applicable standards through testing processes, audits, reviews, and other means.
How Professionals Implement SAQ
Software quality assurance professionals implement software quality assurance processes to ensure the software quality produced by a software development organization. They evaluate, improve and extend the quality of software. They also help ensure that the requirements are met during the development process.
The role of a software quality assurance professional is to verify that a product meets its specifications and requirements before it is released to customers. This process includes reviewing documents such as test plans and cases to ensure they match the conditions. They may also check code for defects and fix them if necessary.
Software quality assurance professionals should know all phases of software development, including requirements gathering, design, coding, testing, and maintenance. This process is implemented through various methods, including testing, debugging, and documentation.
Software quality assurance involves the following steps:
First, identifying defects in software products using tests.
Analyzing data collected from tests to identify patterns that indicate the presence of defects.
Fixing defects identified by data analysis.
Documenting any changes made to the software during testing or after completion of testing.
Conclusion
Software quality assurance is, at its most basic level, a job that involves keeping an eye on the creation, modification, and usage of the software. There are many ways to accomplish this task from a structural standpoint. One way to ensure the quality of the software is by creating a software test plan. This is the first step in ensuring things work out for the best of your project. A comprehensive test plan can protect against pitfalls resulting from inferior code or poor development processes.
Without QA, the software risks not being fit for purpose and, therefore, not meeting the requirements. QA must test software and expose flaws so they can be corrected. The tests are created based on Test Requirements derived from the User Story or Feature Description. Tests must cover all of the specified features. Without comprehensive coverage, bugs will likely be missed resulting in poor-quality software. Setting up the environment for automated testing is a complex process. To support deployment, it requires a significant amount of stakeholder engagement to agree on the testing approach, test cases, and acceptance criteria.
Top Machine Learning Algorithms
Top Machine Learning Algorithms
Finding a suitable algorithm can take hours or even days. As they say, the best algorithm is the one that doesn't exist yet. There's a lot of big data in computer science and machine learning —we aren't just talking about your data. Programmers often feel overwhelmed by all the decisions to make when creating new algorithms. In this article, we'll show you some standard machine-learning algorithms you should know about to be an influential data scientist!
Support Vector Machines (SVM)
Support vector machines (SVM) are machine learning algorithm that maps arbitrary data to high-dimensional spaces, finding a hyperplane (a line separating two classes) that maximizes the margin between the hyperplane and the nearest data point. The SVM is an iterative method that can be trained by repeatedly approximating the optimal solution for small steps.
SVM is a non-linear classifier that takes advantage of the structure of high-dimensional spaces to find optimal discriminants between different classes. It is one of several non-linear kernel methods for multilabel classification.
Linear Regression
Linear regression is a technique used to predict continuous numerical outcomes based on independent variables. It is a supervised learning algorithm in which we want to make predictions on new data that we have not used to train the model. There are two types of linear regression, Simple Linear Regression, and Multiple Linear Regression.
In simple linear regression, we have one continuous independent variable and one continuous dependent variable.
In multiple regression, we have more than one continuous independent variable and one continuous dependent variable.
Logistic Regression
Logistic regression is a classification algorithm, which means that it will predict a discrete outcome. There are two types of logistic regression, binary logistic regression, and multinomial logistic regression.
Binary logistic regression is used when we have two discrete effects: pass or fail, fraud or not fraud, and so on.
Multinomial logistic regression is used when we have more than two discrete outcomes.
Decision Tree
The decision tree algorithm is a machine learning technique that makes predictions by analyzing the information in a set of observations.
The algorithm can predict the probability of an event occurring or the likelihood that a specific outcome will happen. It works by creating a tree structure based on the data and then using it to find general rules that can be applied to more complex situations.
In its simplest form, decision trees work by finding patterns in data. For example, suppose you have a database of customers who bought products from different stores and have demographic information about them. In that case, you could create a decision tree that predicts whether or not they would return for another purchase.
Naive Bayes
Naive Bayes machine learning algorithm is a supervised learning algorithm for classification. It can be used for prediction, estimation, and various continuous variables.
This algorithm uses the Bayes theorem to estimate the probability of an event given some evidence. The result of this estimation is called a posteriori probability (PP) or probability assigned to an event or label given a set of observations. Naive Bayes machine learning algorithm is one of the most popular machine learning algorithms used in many fields, including marketing, finance, text mining, etc.
KNN (K- Nearest Neighbors)
KNN (K-Nearest Neighbors) is an algorithm that learns a mapping from an input to a target. It is based on the concept of nearest neighbors, which means that if you know something about your closest neighbors, then you can use that information to predict what will happen next in the training data. This is called a "compound document" problem.
The KNN algorithm works by training a model to find the closest possible matches for a query document. Then, it uses the records most relative to the query as training examples and the rest as test data.
This is achieved using a metric called "distance" between two documents (or, more generally, between two instances). There are many different methods for calculating this distance: Euclidean distance, cosine similarity, etc., but they all have similar properties: they measure how far apart two objects are in terms of the number of links between them (or in terms of how many words they share). The larger this number gets compared to 1 (the ideal case), the better match we have found!
K-Means
K-means is an unsupervised learning algorithm that uses the principle of minimum distance to cluster data points into groups. It works by assigning each point in the data set to a group, or cluster, whose center is the point with the fewest total distances from each end. Then, the algorithm iteratively adjusts each point's location to maximize the within-cluster sum of squares (WCS) and minimize the between-clusters sum of squares (BSS).
K-means clustering involves calculating the centroid for each point by finding its distance to each other in its cluster and then adjusting that point's position to minimize its distance from all other issues in its collection. This can be done with a single weighted average or another function of all individual measures for each point.
K-means has been used extensively in many fields, including computer vision, machine learning, and pattern recognition. It's considered one of the simplest methods for clustering data due to its intuitive nature; however, it can be inefficient if implemented poorly due to overfitting problems that arise when using training data samples from only one class (such as all red dots).
Random Forest
The Random Forest Machine Learning Algorithms are a set of methods to predict future events' outcomes. The method is based on the idea that many decision trees are created using random subsets of training data. Then, these subsets are combined to produce new sets containing more information than any individual decision tree. This allows for better prediction because each tree has access to more information than previous ones, making finding patterns in the data more accessible.
Random Forest Algorithms can be used in numerous areas of business and technology, including marketing, finance, and e-commerce. They're particularly useful when applied to data sets that are difficult or expensive to analyze in other ways. For example, they could help companies understand consumer behavior by analyzing purchases made at different locations over time or across different demographics.
Dimensionality Reduction Algorithms
With all this data, we must be careful about how much of it we use. Using all of your information is called a full-data approach. Using too much data can slow down your algorithm or even cause it to crash, and that's not a good thing. You want to use as little data as possible to predict accurately. Dimensionality reduction algorithms are used when you want to reduce the amount of data used to train an algorithm. You can use these algorithms when you have a lot of data, but your algorithm might be too slow. There are many different dimensionality reduction algorithms, but three popular ones.
- Principal Component Analysis (PCA)
- Singular Value Decomposition (SVD)
- Random Forest.
Gradient Boosting algorithms
Gradient boosting is an ensemble technique. The idea of an ensemble is to create a team of algorithms. Then each algorithm will specialize in predicting certain types of errors that the others aren't as good at predicting. When you combine them, you get a more accurate model. There are many different types of gradient-boosting algorithms that you can use in your models. Three of the most popular ones are
- Gradient boosting trees (GBTs)
- Adaptive gradient boosting trees (Ada Grad)
- Stochastic gradient boosting (SGDB)
Conclusion
Machine learning algorithms are a valuable tool to use when working with data. When choosing the correct machine learning algorithm, selecting an appropriate algorithm for your data and problem is essential. Many different types of machine learning algorithms are available for various tasks, such as regression, clustering, and classification. If you want to become a data scientist, you have to understand how machine learning algorithms work. In addition, different algorithms are best for other problems, so it is essential to have a broad knowledge of the different algorithms and when to use them.
Read More
Top Machine Learning Algorithms
Finding a suitable algorithm can take hours or even days. As they say, the best algorithm is the one that doesn't exist yet. There's a lot of big data in computer science and machine learning —we aren't just talking about your data. Programmers often feel overwhelmed by all the decisions to make when creating new algorithms. In this article, we'll show you some standard machine-learning algorithms you should know about to be an influential data scientist!
Support Vector Machines (SVM)
Support vector machines (SVM) are machine learning algorithm that maps arbitrary data to high-dimensional spaces, finding a hyperplane (a line separating two classes) that maximizes the margin between the hyperplane and the nearest data point. The SVM is an iterative method that can be trained by repeatedly approximating the optimal solution for small steps.
SVM is a non-linear classifier that takes advantage of the structure of high-dimensional spaces to find optimal discriminants between different classes. It is one of several non-linear kernel methods for multilabel classification.
Linear Regression
Linear regression is a technique used to predict continuous numerical outcomes based on independent variables. It is a supervised learning algorithm in which we want to make predictions on new data that we have not used to train the model. There are two types of linear regression, Simple Linear Regression, and Multiple Linear Regression.
In simple linear regression, we have one continuous independent variable and one continuous dependent variable.
In multiple regression, we have more than one continuous independent variable and one continuous dependent variable.
Logistic Regression
Logistic regression is a classification algorithm, which means that it will predict a discrete outcome. There are two types of logistic regression, binary logistic regression, and multinomial logistic regression.
Binary logistic regression is used when we have two discrete effects: pass or fail, fraud or not fraud, and so on.
Multinomial logistic regression is used when we have more than two discrete outcomes.
Decision Tree
The decision tree algorithm is a machine learning technique that makes predictions by analyzing the information in a set of observations.
The algorithm can predict the probability of an event occurring or the likelihood that a specific outcome will happen. It works by creating a tree structure based on the data and then using it to find general rules that can be applied to more complex situations.
In its simplest form, decision trees work by finding patterns in data. For example, suppose you have a database of customers who bought products from different stores and have demographic information about them. In that case, you could create a decision tree that predicts whether or not they would return for another purchase.
Naive Bayes
Naive Bayes machine learning algorithm is a supervised learning algorithm for classification. It can be used for prediction, estimation, and various continuous variables.
This algorithm uses the Bayes theorem to estimate the probability of an event given some evidence. The result of this estimation is called a posteriori probability (PP) or probability assigned to an event or label given a set of observations. Naive Bayes machine learning algorithm is one of the most popular machine learning algorithms used in many fields, including marketing, finance, text mining, etc.
KNN (K- Nearest Neighbors)
KNN (K-Nearest Neighbors) is an algorithm that learns a mapping from an input to a target. It is based on the concept of nearest neighbors, which means that if you know something about your closest neighbors, then you can use that information to predict what will happen next in the training data. This is called a "compound document" problem.
The KNN algorithm works by training a model to find the closest possible matches for a query document. Then, it uses the records most relative to the query as training examples and the rest as test data.
This is achieved using a metric called "distance" between two documents (or, more generally, between two instances). There are many different methods for calculating this distance: Euclidean distance, cosine similarity, etc., but they all have similar properties: they measure how far apart two objects are in terms of the number of links between them (or in terms of how many words they share). The larger this number gets compared to 1 (the ideal case), the better match we have found!
K-Means
K-means is an unsupervised learning algorithm that uses the principle of minimum distance to cluster data points into groups. It works by assigning each point in the data set to a group, or cluster, whose center is the point with the fewest total distances from each end. Then, the algorithm iteratively adjusts each point's location to maximize the within-cluster sum of squares (WCS) and minimize the between-clusters sum of squares (BSS).
K-means clustering involves calculating the centroid for each point by finding its distance to each other in its cluster and then adjusting that point's position to minimize its distance from all other issues in its collection. This can be done with a single weighted average or another function of all individual measures for each point.
K-means has been used extensively in many fields, including computer vision, machine learning, and pattern recognition. It's considered one of the simplest methods for clustering data due to its intuitive nature; however, it can be inefficient if implemented poorly due to overfitting problems that arise when using training data samples from only one class (such as all red dots).
Random Forest
The Random Forest Machine Learning Algorithms are a set of methods to predict future events' outcomes. The method is based on the idea that many decision trees are created using random subsets of training data. Then, these subsets are combined to produce new sets containing more information than any individual decision tree. This allows for better prediction because each tree has access to more information than previous ones, making finding patterns in the data more accessible.
Random Forest Algorithms can be used in numerous areas of business and technology, including marketing, finance, and e-commerce. They're particularly useful when applied to data sets that are difficult or expensive to analyze in other ways. For example, they could help companies understand consumer behavior by analyzing purchases made at different locations over time or across different demographics.
Dimensionality Reduction Algorithms
With all this data, we must be careful about how much of it we use. Using all of your information is called a full-data approach. Using too much data can slow down your algorithm or even cause it to crash, and that's not a good thing. You want to use as little data as possible to predict accurately. Dimensionality reduction algorithms are used when you want to reduce the amount of data used to train an algorithm. You can use these algorithms when you have a lot of data, but your algorithm might be too slow. There are many different dimensionality reduction algorithms, but three popular ones.
- Principal Component Analysis (PCA)
- Singular Value Decomposition (SVD)
- Random Forest.
Gradient Boosting algorithms
Gradient boosting is an ensemble technique. The idea of an ensemble is to create a team of algorithms. Then each algorithm will specialize in predicting certain types of errors that the others aren't as good at predicting. When you combine them, you get a more accurate model. There are many different types of gradient-boosting algorithms that you can use in your models. Three of the most popular ones are
- Gradient boosting trees (GBTs)
- Adaptive gradient boosting trees (Ada Grad)
- Stochastic gradient boosting (SGDB)
Conclusion
Machine learning algorithms are a valuable tool to use when working with data. When choosing the correct machine learning algorithm, selecting an appropriate algorithm for your data and problem is essential. Many different types of machine learning algorithms are available for various tasks, such as regression, clustering, and classification. If you want to become a data scientist, you have to understand how machine learning algorithms work. In addition, different algorithms are best for other problems, so it is essential to have a broad knowledge of the different algorithms and when to use them.
What is Capacity Planning?
What is Capacity Planning?
If you want to manage your tasks most efficiently, it's essential to have a clear plan for how much capacity your project requires. Capacity planning is of utmost importance if you want to implement project management on a large scale. It helps you evaluate the resources necessary for the successful completion of the project and calculate various project management metrics such as Projected Cost and Schedule, Startup Time, and the Critical Path Method.
Definition: Capacity Planning
Capacity planning is determining all the resources, activities, and costs required to complete a project. The goal of capacity planning is to ensure that the required resources for a project are available at the start of the project and throughout its life cycle.
Capacity planning should be performed when a new project starts or when an existing project needs to be modified to meet new requirements or challenges. It can also be performed at any point to determine how much work is completed and how much remains before completion.
Capacity planning is essential because it informs management about the effort required to complete projects on time and within budget. It allows managers to better allocate their resources and ensures that they have adequate financial controls to stay within budget constraints.
Types of Capacity Planning
Capacity planning is an essential step in project management as it helps determine the effort required to complete tasks or projects. The purpose of capacity planning is to identify all critical systems, personnel, equipment, and services needed by a project at various stages throughout the life cycle.
Capacity planning helps ensure that all resources are available when needed by the project team, preventing delays due to unforeseen circumstances or equipment failures. Capacity planning also ensures that the correct amount of money has been allocated for each task within a particular budget.
There are three significant types of capacity planning:
Business case analysis
This is the essential type of capacity planning because it determines whether or not a project is worthwhile and should be undertaken. In addition, it determines the resources required and prepares a plan for those resources.
Capacity planning for management
This analysis determines what skills, tools, and equipment are available within a project's organization. It also determines whether or not these resources are adequate to support the project, especially if there are unforeseen delays or problems along the way.
Capacity planning for human resources
This type of analysis determines how many people will be needed to complete a project and the skills they need to have to do so successfully. It also helps determine how much training will be required to become proficient with new technology or procedures that may be introduced during a project."
Technical Capacity Planning
This extends organizational capacity planning, where organizations identify the skills required to perform a specific task or project.
Financial Capacity Planning
This involves identifying how much money will be needed for a particular task or project so that you can plan your budget accordingly.
Benefits of Capacity Planning
Capacity plans are created using a simple formula that determines the required resources, such as employees, equipment, materials, and time spent on each task. This information is then used to calculate how many people or items will be needed for each job. For example, if you have 10 employees working on your project, you would need 1 person who can handle every task and another responsible for scheduling meetings with other team members.
There are many benefits of capacity planning in project management. Some of the significant benefits include the following:
- It can be used for project risk assessment and risk mitigation.
- The capacity planning results can estimate future demand, which can help reduce costs and increase profits.
- It helps identify problem areas before they become critical by informing them about their current capacities and future needs so that they can take action to address them.
- Capacity planning helps stakeholders to understand their specific roles in providing services or products that are required by the company or organization, thus helping them to understand their responsibilities towards it.
- Providing an accurate estimate of costs
- Ensuring that all tasks are completed before the deadlines
- Identifying any potential risks associated with larger projects
When Capacity Planning is required
Capacity planning is a continuous process throughout the project life cycle. This means that it is vital that all project managers and senior management keep their staff informed of any changes in their workloads, as well as any new requirements or constraints that might affect their ability to deliver the project successfully.
The size of your team will have a significant impact on how you manage your capacity planning process. For example, suppose you have a small group. In that case, they may only be able to handle some of the work required by the project with additional resources. If this is the case, then it is likely that you will need to outsource some work or consider hiring other staff who can help support your team on this particular project.
Even with larger teams, however, there must be no bottlenecks in your delivery processes or areas where there are delays due to poor communication or mismanagement. This could lead to problems such as missed deadlines and delayed payments from clients, resulting in lost revenue and damage to reputation - both financially and publicly!
Capacity planning is a skill that we, as project managers, need to have to complete our projects ahead of the deadline and under budget. Unfortunately, we could only meet all deadlines with proper capacity planning, causing costly delays and missed opportunities.
Read More
What is Capacity Planning?
If you want to manage your tasks most efficiently, it's essential to have a clear plan for how much capacity your project requires. Capacity planning is of utmost importance if you want to implement project management on a large scale. It helps you evaluate the resources necessary for the successful completion of the project and calculate various project management metrics such as Projected Cost and Schedule, Startup Time, and the Critical Path Method.
Definition: Capacity Planning
Capacity planning is determining all the resources, activities, and costs required to complete a project. The goal of capacity planning is to ensure that the required resources for a project are available at the start of the project and throughout its life cycle.
Capacity planning should be performed when a new project starts or when an existing project needs to be modified to meet new requirements or challenges. It can also be performed at any point to determine how much work is completed and how much remains before completion.
Capacity planning is essential because it informs management about the effort required to complete projects on time and within budget. It allows managers to better allocate their resources and ensures that they have adequate financial controls to stay within budget constraints.
Types of Capacity Planning
Capacity planning is an essential step in project management as it helps determine the effort required to complete tasks or projects. The purpose of capacity planning is to identify all critical systems, personnel, equipment, and services needed by a project at various stages throughout the life cycle.
Capacity planning helps ensure that all resources are available when needed by the project team, preventing delays due to unforeseen circumstances or equipment failures. Capacity planning also ensures that the correct amount of money has been allocated for each task within a particular budget.
There are three significant types of capacity planning:
Business case analysis
This is the essential type of capacity planning because it determines whether or not a project is worthwhile and should be undertaken. In addition, it determines the resources required and prepares a plan for those resources.
Capacity planning for management
This analysis determines what skills, tools, and equipment are available within a project's organization. It also determines whether or not these resources are adequate to support the project, especially if there are unforeseen delays or problems along the way.
Capacity planning for human resources
This type of analysis determines how many people will be needed to complete a project and the skills they need to have to do so successfully. It also helps determine how much training will be required to become proficient with new technology or procedures that may be introduced during a project."
Technical Capacity Planning
This extends organizational capacity planning, where organizations identify the skills required to perform a specific task or project.
Financial Capacity Planning
This involves identifying how much money will be needed for a particular task or project so that you can plan your budget accordingly.
Benefits of Capacity Planning
Capacity plans are created using a simple formula that determines the required resources, such as employees, equipment, materials, and time spent on each task. This information is then used to calculate how many people or items will be needed for each job. For example, if you have 10 employees working on your project, you would need 1 person who can handle every task and another responsible for scheduling meetings with other team members.
There are many benefits of capacity planning in project management. Some of the significant benefits include the following:
- It can be used for project risk assessment and risk mitigation.
- The capacity planning results can estimate future demand, which can help reduce costs and increase profits.
- It helps identify problem areas before they become critical by informing them about their current capacities and future needs so that they can take action to address them.
- Capacity planning helps stakeholders to understand their specific roles in providing services or products that are required by the company or organization, thus helping them to understand their responsibilities towards it.
- Providing an accurate estimate of costs
- Ensuring that all tasks are completed before the deadlines
- Identifying any potential risks associated with larger projects
When Capacity Planning is required
Capacity planning is a continuous process throughout the project life cycle. This means that it is vital that all project managers and senior management keep their staff informed of any changes in their workloads, as well as any new requirements or constraints that might affect their ability to deliver the project successfully.
The size of your team will have a significant impact on how you manage your capacity planning process. For example, suppose you have a small group. In that case, they may only be able to handle some of the work required by the project with additional resources. If this is the case, then it is likely that you will need to outsource some work or consider hiring other staff who can help support your team on this particular project.
Even with larger teams, however, there must be no bottlenecks in your delivery processes or areas where there are delays due to poor communication or mismanagement. This could lead to problems such as missed deadlines and delayed payments from clients, resulting in lost revenue and damage to reputation - both financially and publicly!
Capacity planning is a skill that we, as project managers, need to have to complete our projects ahead of the deadline and under budget. Unfortunately, we could only meet all deadlines with proper capacity planning, causing costly delays and missed opportunities.
Scrum Master Role and Responsibilities
Scrum Master Role and Responsibilities
Scrum Master is a multifaceted role. In fact, there are many different ways to define what it means to be a Scrum Master. However, regardless of how you define the role and responsibilities, everyone who plays a part in creating an agile project will be called upon to fill the Scrum Master shoes – regardless of their experience level or current project responsibilities.
What is a Scrum Master?
The Scrum Master is a person who helps the Product Owner, Development Team, and the Team to work together efficiently and effectively. The Scrum Master maintains a common understanding of the Scrum process and ensures that it is followed.
In addition, they act as a neutral facilitator for all meetings, remove impediments to progress, and provide coaching and training to help the team become more effective.
The Scrum Master guides how to adapt the Scrum process to their organization's specific needs. They also help teams improve their practices by providing feedback and education on best practices.
Scrum Master Roles and Responsibilities
- Facilitate the Scrum Teams in their work.
- Ensure that the teams understand all requirements and that they can meet them.
- Ensure that all communication between the teams is effective and efficient.
- Provide any additional training required for the team members to perform their work effectively.
- Understanding the teams' context and situation and their goals and objectives.
- Ensuring that each team member clearly understands who they are working with, their work roles, and any special requirements they may have (e.g., accessibility).
- Ensuring all team members understand how they can contribute to the product vision and strategy.
- Facilitating frequent interactions among all team members so that commitments are met, risks are shared, and progress is made (e.g., daily stand-up meetings).
Why Do Teams Need a Scrum Master?
There are many reasons why the Scrum Master needs to be a part of the Scrum team. The Scrum Master is not just another person on the team but an integral part.
The Scrum Master's role on a Scrum team is to help ensure that everyone on the team has access to information about what is going on at all times, as well as make sure that people are working together in a way that will help them achieve their goals. This role's goal is also to ensure whoever may need help has access to it as quickly as possible. This can be done by ensuring that everyone understands how they should interact with each other and how they should handle their tasks within their roles. It also means ensuring there are clear understandings and communication within the team.
This is important because there could be confusion over who should do what or how something should be done. As well as this, if you need someone who can participate in meetings and get everyone involved in discussions around what needs to happen next about your project or task, then it will take longer than necessary for things to get done.
Scrum Master vs. Product Manager
- Scrum master and product manager are two different titles. The main difference between the two is that one oversees the development activities of a team, and the other manages the overall business objectives of an organization.
- Scrum masters help teams deliver products, while product managers help organizations deliver products. Both roles involve collaborating with people from different departments to build and deliver software.
- Scrum masters create software, while product managers focus on its delivery.
- A scrum master guides a team through an iterative process that involves breaking down features into small increments and regularly testing them against user needs before releasing them to production. The product manager is responsible for managing this entire process, which involves coming up with business requirements and then helping teams develop software based on those requirements.
- The scrum master is responsible for the overall success of the project and the product. The product manager is responsible for the development of a specific product.
- A scrum master oversees the full sprint and ensures that all teams work together effectively. Finally, a product manager leads a particular team and oversees daily work.
- The main difference between these two roles is that a scrum master focuses more on long-term planning. In contrast, a product manager focuses more on short-term planning.
Scrum Master vs. Project Manager
- Scrum Master is a person who leads the Scrum process.
- He is responsible for ensuring that all scrum team members can work effectively together and that they clearly understand the roles they are required to perform.
- The Scrum Master also maintains a good working relationship with the product owner and stakeholders by acting as their agent during the development phase of an Agile project.
- In contrast, a Project Manager is responsible for managing projects within or between organizations.
- The manager’s job is to prepare the project plan, manage the resources (managers and staff) involved in implementing that plan, monitor progress toward completion of objectives and ensure that budgeted funds are available to fulfill tasks assigned to team members.
Qualities of a Successful Scrum Master
The qualities of a successful Scrum Master include:
- A good understanding of the Agile development process's principles, values, and practices.
- Understanding the individuals involved with the project and their roles and responsibilities.
- Knowledge of product management, design, development, and customer services.
- An ability to communicate effectively both verbally and in writing.
- The ability to influence change without being confrontational or confrontational; this includes dealing with difficult situations professionally and tactfully.
Conclusion
As for the future, Scrum Master is a profession just like every other programming job, and it might get fully independent shortly. However, lately, there has been an increased demand for Scrum Masters, and salaries are much higher than before.
Read More
Scrum Master Role and Responsibilities
Scrum Master is a multifaceted role. In fact, there are many different ways to define what it means to be a Scrum Master. However, regardless of how you define the role and responsibilities, everyone who plays a part in creating an agile project will be called upon to fill the Scrum Master shoes – regardless of their experience level or current project responsibilities.
What is a Scrum Master?
The Scrum Master is a person who helps the Product Owner, Development Team, and the Team to work together efficiently and effectively. The Scrum Master maintains a common understanding of the Scrum process and ensures that it is followed.
In addition, they act as a neutral facilitator for all meetings, remove impediments to progress, and provide coaching and training to help the team become more effective.
The Scrum Master guides how to adapt the Scrum process to their organization's specific needs. They also help teams improve their practices by providing feedback and education on best practices.
Scrum Master Roles and Responsibilities
- Facilitate the Scrum Teams in their work.
- Ensure that the teams understand all requirements and that they can meet them.
- Ensure that all communication between the teams is effective and efficient.
- Provide any additional training required for the team members to perform their work effectively.
- Understanding the teams' context and situation and their goals and objectives.
- Ensuring that each team member clearly understands who they are working with, their work roles, and any special requirements they may have (e.g., accessibility).
- Ensuring all team members understand how they can contribute to the product vision and strategy.
- Facilitating frequent interactions among all team members so that commitments are met, risks are shared, and progress is made (e.g., daily stand-up meetings).
Why Do Teams Need a Scrum Master?
There are many reasons why the Scrum Master needs to be a part of the Scrum team. The Scrum Master is not just another person on the team but an integral part.
The Scrum Master's role on a Scrum team is to help ensure that everyone on the team has access to information about what is going on at all times, as well as make sure that people are working together in a way that will help them achieve their goals. This role's goal is also to ensure whoever may need help has access to it as quickly as possible. This can be done by ensuring that everyone understands how they should interact with each other and how they should handle their tasks within their roles. It also means ensuring there are clear understandings and communication within the team.
This is important because there could be confusion over who should do what or how something should be done. As well as this, if you need someone who can participate in meetings and get everyone involved in discussions around what needs to happen next about your project or task, then it will take longer than necessary for things to get done.
Scrum Master vs. Product Manager
- Scrum master and product manager are two different titles. The main difference between the two is that one oversees the development activities of a team, and the other manages the overall business objectives of an organization.
- Scrum masters help teams deliver products, while product managers help organizations deliver products. Both roles involve collaborating with people from different departments to build and deliver software.
- Scrum masters create software, while product managers focus on its delivery.
- A scrum master guides a team through an iterative process that involves breaking down features into small increments and regularly testing them against user needs before releasing them to production. The product manager is responsible for managing this entire process, which involves coming up with business requirements and then helping teams develop software based on those requirements.
- The scrum master is responsible for the overall success of the project and the product. The product manager is responsible for the development of a specific product.
- A scrum master oversees the full sprint and ensures that all teams work together effectively. Finally, a product manager leads a particular team and oversees daily work.
- The main difference between these two roles is that a scrum master focuses more on long-term planning. In contrast, a product manager focuses more on short-term planning.
Scrum Master vs. Project Manager
- Scrum Master is a person who leads the Scrum process.
- He is responsible for ensuring that all scrum team members can work effectively together and that they clearly understand the roles they are required to perform.
- The Scrum Master also maintains a good working relationship with the product owner and stakeholders by acting as their agent during the development phase of an Agile project.
- In contrast, a Project Manager is responsible for managing projects within or between organizations.
- The manager’s job is to prepare the project plan, manage the resources (managers and staff) involved in implementing that plan, monitor progress toward completion of objectives and ensure that budgeted funds are available to fulfill tasks assigned to team members.
Qualities of a Successful Scrum Master
The qualities of a successful Scrum Master include:
- A good understanding of the Agile development process's principles, values, and practices.
- Understanding the individuals involved with the project and their roles and responsibilities.
- Knowledge of product management, design, development, and customer services.
- An ability to communicate effectively both verbally and in writing.
- The ability to influence change without being confrontational or confrontational; this includes dealing with difficult situations professionally and tactfully.
Conclusion
As for the future, Scrum Master is a profession just like every other programming job, and it might get fully independent shortly. However, lately, there has been an increased demand for Scrum Masters, and salaries are much higher than before.
Certified Scrum Master Certification Benefits 2023
Certified Scrum Master Certification Benefits 2023
The Certified ScrumMaster (CSM) is a beginner’s certification to offer new Scrum enthusiasts an idea of project management techniques. The credential is a globally renowned course provided by the prestigious Scrum Alliance. This program is offered to individuals who prove their skills in Scrum techniques, principles, and terminologies in the CSM test.
Certified Scrum Master Certification: Explain
A Scrum Master credential pinpoints your competency in the principles of Scrum Project management. Scrum Masters are project managers who leverage Scrum as their project management practice.
People who achieve CSM credential shows tangible proof to the recruiter that they possess the accurate skills and training for the job. Moreover, accreditation is an excellent source, regardless of your chosen field.
When it comes to Scrum Masters, part of your credential procedure is achieving the knowledge required for the position. Scrum teams need leaders; else, the whole practice is a waste of energy and time.
In addition, Scrum Master is the most sought-after career today, making recruiters choose candidates with CSM certification.
Roles of Scrum Masters
In general, the roles of a Scrum Master include the following:
- Eradicate organizational challenges, remove outdated procedures, and train new Scrum leaders
- Schedule Scrum meetings more efficiently, aiding team members to focus on the concept driving Scrum.
- Resolve problems that stand in the way of project progress.
- Leverages daily challenges as a learning technique for the team to help them improve significantly.
- Helps team members to upskill self-organizing skills.
Benefits of CSM Certification
CSM credentials help you stand out, showcasing your leadership skills far beyond what a typical project manager could offer.
A significant benefit of a CSM credential is that it proves your potential to organizations looking for Scrum Masters. In addition, there's a drastic increase in demands for Scrum Masters as every team needs a committed person to perform different Agile projects.
Some benefits of CSM certification are:
- If you're a Scrum professional with prior experience, a credential in Scrum expands your knowledge and helps you overcome hardships. It's an added benefit when you manage massive cross-functional teams leveraging the same framework.
- Being a CSM professional can encourage and lead your teammates. You will direct them and help the team work efficiently. The CSM certification displays your potential to recruiters, thus having the edge over your counterparts.
- Becoming a CSM can drastically expand your career opportunities. This credential will make you more relevant in your field - leading to handsome remuneration compared to your counterparts. It also equips you with the accurate skills required to fulfill the enterprise's objectives.
The Certified Scrum Master Exam
Certified Scrum Master individuals must undergo CSM training by CST trainers and will have to CST trainers and will have to take and pass an online test after the training to get certified. Like Agile and Scrum, credential enables experts to improve their excellence in agile and Scrum techniques and gives them a chance to be a member of the Scrum Alliance for two years.
CSM exam syllabus includes:
- Scrum overview
- Scrum project overview
- The Scrum teams
- Product backlog
- The product owner
- Releases
- Sprints
- The Scrum Master
- Enterprise transformation
Read More
Certified Scrum Master Certification Benefits 2023
The Certified ScrumMaster (CSM) is a beginner’s certification to offer new Scrum enthusiasts an idea of project management techniques. The credential is a globally renowned course provided by the prestigious Scrum Alliance. This program is offered to individuals who prove their skills in Scrum techniques, principles, and terminologies in the CSM test.
Certified Scrum Master Certification: Explain
A Scrum Master credential pinpoints your competency in the principles of Scrum Project management. Scrum Masters are project managers who leverage Scrum as their project management practice.
People who achieve CSM credential shows tangible proof to the recruiter that they possess the accurate skills and training for the job. Moreover, accreditation is an excellent source, regardless of your chosen field.
When it comes to Scrum Masters, part of your credential procedure is achieving the knowledge required for the position. Scrum teams need leaders; else, the whole practice is a waste of energy and time.
In addition, Scrum Master is the most sought-after career today, making recruiters choose candidates with CSM certification.
Roles of Scrum Masters
In general, the roles of a Scrum Master include the following:
- Eradicate organizational challenges, remove outdated procedures, and train new Scrum leaders
- Schedule Scrum meetings more efficiently, aiding team members to focus on the concept driving Scrum.
- Resolve problems that stand in the way of project progress.
- Leverages daily challenges as a learning technique for the team to help them improve significantly.
- Helps team members to upskill self-organizing skills.
Benefits of CSM Certification
CSM credentials help you stand out, showcasing your leadership skills far beyond what a typical project manager could offer.
A significant benefit of a CSM credential is that it proves your potential to organizations looking for Scrum Masters. In addition, there's a drastic increase in demands for Scrum Masters as every team needs a committed person to perform different Agile projects.
Some benefits of CSM certification are:
- If you're a Scrum professional with prior experience, a credential in Scrum expands your knowledge and helps you overcome hardships. It's an added benefit when you manage massive cross-functional teams leveraging the same framework.
- Being a CSM professional can encourage and lead your teammates. You will direct them and help the team work efficiently. The CSM certification displays your potential to recruiters, thus having the edge over your counterparts.
- Becoming a CSM can drastically expand your career opportunities. This credential will make you more relevant in your field - leading to handsome remuneration compared to your counterparts. It also equips you with the accurate skills required to fulfill the enterprise's objectives.
The Certified Scrum Master Exam
Certified Scrum Master individuals must undergo CSM training by CST trainers and will have to CST trainers and will have to take and pass an online test after the training to get certified. Like Agile and Scrum, credential enables experts to improve their excellence in agile and Scrum techniques and gives them a chance to be a member of the Scrum Alliance for two years.
CSM exam syllabus includes:
- Scrum overview
- Scrum project overview
- The Scrum teams
- Product backlog
- The product owner
- Releases
- Sprints
- The Scrum Master
- Enterprise transformation
Strengthen Your Job Application with Project Management Certification
Strengthen Your Job Application with Project Management Certification
Today, Project Management is the most demanding professional accreditation, guaranteeing personal and professional achievements. As a result, we have often seen vacancy adverts for Project Management, where recruiters mention Project Management Certification as mandatory or preferred.
Over a decade, Project Management credentials have achieved global acceptance, with several companies recruiting candidates with certifications or pursuing the same.
Some of the popular Project Management Accreditations offering handsome remunerations are:
- Project Management Professional (PMP)
- Prince2
- Managing Successful Programmes (MSP)
- Risk Management Professional (RMP)
- PMI-ACP
- PgMP
- CAPM
Software Estimation Certification & Business Analysis (BA) Certification is also significant credential in Project Management.
Irrespective of large/small-scale companies, skilled and trained Project Management certification holders are in great demand. A globally-renowned credential highlights that a person fulfills the needs of being a great project manager. However, let's get the point clear: these certifications aren't only for project managers but for those associated with a project at any time.
Now, what counts is competency, and the days when someone got promoted to a project manager position for being loyal for years have long gone. What does an organization look for in a person for project manager position?
- Are you capable enough to take project charge?
- What are your necessary qualifications?
- Can you make use of all your given resources efficiently?
Let’s looks at some benefits of Project Management Certifications.
- Adds value to your resume
- Develops international recognition
- Increase customer satisfaction
- Successful completion of projects
- Handsome remunerations
- Validates your skills, knowledge and potential in project execution
- Client preferences
Here, we come to the conclusion that to have a distinct position in a competitive world, individuals must remain marketable. Project Management credentials act as a significant barrier in this regard. Being professionally certified after a particular age might be daunting; however, gaining an outstanding balance in your work career is always possible.
Read More
Strengthen Your Job Application with Project Management Certification
Today, Project Management is the most demanding professional accreditation, guaranteeing personal and professional achievements. As a result, we have often seen vacancy adverts for Project Management, where recruiters mention Project Management Certification as mandatory or preferred.
Over a decade, Project Management credentials have achieved global acceptance, with several companies recruiting candidates with certifications or pursuing the same.
Some of the popular Project Management Accreditations offering handsome remunerations are:
- Project Management Professional (PMP)
- Prince2
- Managing Successful Programmes (MSP)
- Risk Management Professional (RMP)
- PMI-ACP
- PgMP
- CAPM
Software Estimation Certification & Business Analysis (BA) Certification is also significant credential in Project Management.
Irrespective of large/small-scale companies, skilled and trained Project Management certification holders are in great demand. A globally-renowned credential highlights that a person fulfills the needs of being a great project manager. However, let's get the point clear: these certifications aren't only for project managers but for those associated with a project at any time.
Now, what counts is competency, and the days when someone got promoted to a project manager position for being loyal for years have long gone. What does an organization look for in a person for project manager position?
- Are you capable enough to take project charge?
- What are your necessary qualifications?
- Can you make use of all your given resources efficiently?
Let’s looks at some benefits of Project Management Certifications.
- Adds value to your resume
- Develops international recognition
- Increase customer satisfaction
- Successful completion of projects
- Handsome remunerations
- Validates your skills, knowledge and potential in project execution
- Client preferences
Here, we come to the conclusion that to have a distinct position in a competitive world, individuals must remain marketable. Project Management credentials act as a significant barrier in this regard. Being professionally certified after a particular age might be daunting; however, gaining an outstanding balance in your work career is always possible.
Trends to Look Forward in Business Agility 2023
Trends to Look Forward in Business Agility 2023
Business Agility has taken a whole new round for organizations amid the pandemic forcing businesses to simplify development operations. As a result, enterprises seek to become dependent on Agile-based project management techniques to maintain their ventures' adaptability.
The Agile principle focuses on streamlining challenging operational procedures, enabling project professionals to deliver projects in operational phases, where modifications are made more quickly.
Agile allows project teams to utilize solutions and determine issues in the development phase, focusing on customer requirements. First, let us see how trends affect organizations the most.
Scaled Agile & Scrum Techniques
The Scrum development technique accredits project professionals to proficiently coordinate the activities of cross-functional teams and generate working code at the end of each sprint. Organizations these days are leaping onto scaling their Scrum activities to offer more excellent value and enhanced partnership.
According to a recent survey, the most popular framework, SAFe, is rated as the top-scaled agile technique. Leading SAFe practices are the most comprehensive for massive Agile projects and support a successful change of companies into Lean-Agile companies.
SAFe Scrum Masters are highly cherished as they're trained to plan and perform projects in the context of the business, not just individual sprints.
Business Agility and Design Thinking
The design thinking technique exposes customer requirements on a human level by creating solid user empathy and experimenting in stages to make a design right. Design thinking and agile have a lot in common. For instance, a project team can build additional time into sprint activities to better understand customer facts and enhance their overall satisfaction.
Taking the time upfront to establish user empathy and getting design feedback will help streamline modeling and testing, followed by visualizing a solution that can guide the team on the right path.
Within the Agile space, organizations should ponder staggered sprints that include user feedback loops, empathy, and ideation of the Agile process.
Machine Learning and Artificial Intelligence Supporting Agile
Machine Learning and Artificial Intelligence are the greatest booms in data analysis in the project and development environments. For instance, they offer real-time data and swift analytical capabilities to provide precise predictions of when project stages will be complete. That's significant when projects get close to the ending stage, and the eyes of various executive constituents are fixed on the schedules.
Additional benefits offered to Agile by ML and AI are:
- We offer accurate insights and transparent procedures for developing and testing programming code.
- Reviewing code with better precision to determine and eradicate bugs.
- Merging with innovative techs such as RPA, Quantum Computing, IoT devices, and intelligent techs to swift development time and get products to market faster.
Project management professionals leverage their resources to maintain their teams for optimum running, including Agile Scrums that scale to business criteria, design thinking techniques to merge customer requirements early on the lifecycle, and cutting-edge techs like ML and AI to fasten testing and market time.
Read More
Trends to Look Forward in Business Agility 2023
Business Agility has taken a whole new round for organizations amid the pandemic forcing businesses to simplify development operations. As a result, enterprises seek to become dependent on Agile-based project management techniques to maintain their ventures' adaptability.
The Agile principle focuses on streamlining challenging operational procedures, enabling project professionals to deliver projects in operational phases, where modifications are made more quickly.
Agile allows project teams to utilize solutions and determine issues in the development phase, focusing on customer requirements. First, let us see how trends affect organizations the most.
Scaled Agile & Scrum Techniques
The Scrum development technique accredits project professionals to proficiently coordinate the activities of cross-functional teams and generate working code at the end of each sprint. Organizations these days are leaping onto scaling their Scrum activities to offer more excellent value and enhanced partnership.
According to a recent survey, the most popular framework, SAFe, is rated as the top-scaled agile technique. Leading SAFe practices are the most comprehensive for massive Agile projects and support a successful change of companies into Lean-Agile companies.
SAFe Scrum Masters are highly cherished as they're trained to plan and perform projects in the context of the business, not just individual sprints.
Business Agility and Design Thinking
The design thinking technique exposes customer requirements on a human level by creating solid user empathy and experimenting in stages to make a design right. Design thinking and agile have a lot in common. For instance, a project team can build additional time into sprint activities to better understand customer facts and enhance their overall satisfaction.
Taking the time upfront to establish user empathy and getting design feedback will help streamline modeling and testing, followed by visualizing a solution that can guide the team on the right path.
Within the Agile space, organizations should ponder staggered sprints that include user feedback loops, empathy, and ideation of the Agile process.
Machine Learning and Artificial Intelligence Supporting Agile
Machine Learning and Artificial Intelligence are the greatest booms in data analysis in the project and development environments. For instance, they offer real-time data and swift analytical capabilities to provide precise predictions of when project stages will be complete. That's significant when projects get close to the ending stage, and the eyes of various executive constituents are fixed on the schedules.
Additional benefits offered to Agile by ML and AI are:
- We offer accurate insights and transparent procedures for developing and testing programming code.
- Reviewing code with better precision to determine and eradicate bugs.
- Merging with innovative techs such as RPA, Quantum Computing, IoT devices, and intelligent techs to swift development time and get products to market faster.
Project management professionals leverage their resources to maintain their teams for optimum running, including Agile Scrums that scale to business criteria, design thinking techniques to merge customer requirements early on the lifecycle, and cutting-edge techs like ML and AI to fasten testing and market time.
Introduction to Digital Marketing
Introduction to Digital Marketing
In the past, digital marketing was something that only large companies could afford to do. However, today this is changing, as thousands of small business owners are adopting digital marketing into their businesses. And with the power of social media, word-of-mouth advertising, and data collection, you can see how concerned small business owners should be about using these resources to reach their targeted customers and build a profitable brand.
What is Digital Marketing?
Digital marketing uses digital technology and other strategies to address an organization's business objectives. It is a strategic approach that incorporates all aspects of a business, including branding, retailing, direct marketing, public relations, and advertising.
Digital marketing encompasses all technologies that can be used to deliver content to achieve these goals. These include web design, search engine optimization (SEO), online advertising (search ads, display ads), email marketing/remarketing, affiliate marketing/referral programs, paid search, and mobile apps.
Why is Digital Marketing Important?
Digital marketing is the most important way to reach your customers. It's often called 'marketing in a box' because it provides everything you need to run your business online.
Digital marketing is essential for any business owner who wants to connect with their audience, drive traffic and increase sales. Digital marketing helps you sell more products or services by building trust with your target audience and building an audience of loyal customers who come back again and again.
Types of Digital Marketing
There are many types of digital marketing, but each class can be broken down into a few core elements. Each element is designed to accomplish a specific task in driving online traffic and leads to your website.
Search Engine Optimization (SEO)
SEO is optimizing your website for search engines like Google and Bing. Search engines use algorithms to determine which sites are most relevant to users based on their search terms, keywords, and other factors. The goal of SEO is to get your site listed as high up in the search results as possible.
Social Media Marketing (SMM)
Social media marketing involves using platforms such as Facebook, Instagram, Twitter, or LinkedIn to promote your brand or business. It's also known as social media advertising or SMO. Content sharing and engagement are two important factors in this marketing strategy because they allow you to build relationships with people who might become customers. In addition, social media platforms enable businesses to collaborate with their customers to create content that can be shared with others in their network and across the web.
Content marketing
Content marketing is about producing valuable information for your audience relevant to their needs and interests. You can make this content yourself or hire writers specializing in content creation. The goal is to attract new audience members and build trust with existing ones through original, quality content available for free on websites like Medium or YouTube.
E-commerce
With e-commerce, you can sell products and services online. This includes shopping carts that allow consumers to buy online, websites that list products and services for sale, and sites where consumers can purchase items from third-party vendors (e.g., Amazon.com). In addition to selling products and services, e-commerce companies may provide other value-added services such as shipping and returns.
Mobile Marketing
Mobile marketing is using portable devices to deliver digital content, including advertisements. Mobile marketing began as a way for advertisers to reach potential customers on their phones. Still, it has now evolved into a full-fledged marketing channel with an entire ecosystem of apps, content, and services designed to help marketers reach potential customers through mobile devices and applications.
Email marketing
Email marketing is one part of digital marketing where you get paid directly by the company or company owner. You promote your service or product through email campaigns like newsletters or blasts. You can send notifications about new products or services available at certain time intervals or when there is some special event in the industry related to your niche if you are an expert in that area or have expertise in that industry.
Affiliate Marketing
Affiliate marketing is a method of marketing that pays website owners and publishers based on the performance of their advertisements and sales. Affiliate marketers use special links called affiliate codes to identify themselves and the products they are promoting. When potential customers click on those links, they are taken to the merchant's site, where they can purchase if they wish.
Digital Marketing Benefits
There are many benefits to digital marketing, which include:
- Leverage Search Engine Optimization (SEO) to attract traffic, leads, and sales.
- Create content that people will want to read and share on social media.
- Automate your email marketing campaigns so you can focus on growing your business.
- Measure the effectiveness of your digital marketing campaigns by tracking ROI, conversions, and other KPIs.
- It's easy to use.
- You don't risk getting sued by a customer or consumer who feels you have misled them or made a false claim about your product or service.
- You can target specific groups of people with digital marketing campaigns that will appeal to their interests, lifestyle, and even psychology (for example, they may be interested in products that are related to their interests).
- Digital marketing is effective because it reaches people when they are using their mobile devices (or computers) on the go - which means that they are more likely to see it than other forms of advertising, such as TV or billboard ads would be!
Future of Digital Marketing
In the last few years, digital marketing has become a significant part of businesses' growth strategies. In fact, according to Statista, digital marketing expenditure is expected to reach $1 trillion by 2020 and $5 trillion by 2025.
Digital marketing is not just about online advertising anymore. Nowadays, it's also about social media marketing, email marketing, content marketing, and many other channels integrated into a single package.
The future of digital marketing is bright because there are so many different aspects that can be used to reach your target audience and generate leads for you or your business.
Your job as a digital marketer is to create new and innovative ways for people to interact with your brand and purchase your products or services. So you have to get creative and think of new ways to deliver value so that your customers don't feel like they are just another number on someone's list.
This introduction to digital marketing has opened a few doors for you. You might not know much about it now, but at least you know what goes into digital marketing and why it's there.
Read More
Introduction to Digital Marketing
In the past, digital marketing was something that only large companies could afford to do. However, today this is changing, as thousands of small business owners are adopting digital marketing into their businesses. And with the power of social media, word-of-mouth advertising, and data collection, you can see how concerned small business owners should be about using these resources to reach their targeted customers and build a profitable brand.
What is Digital Marketing?
Digital marketing uses digital technology and other strategies to address an organization's business objectives. It is a strategic approach that incorporates all aspects of a business, including branding, retailing, direct marketing, public relations, and advertising.
Digital marketing encompasses all technologies that can be used to deliver content to achieve these goals. These include web design, search engine optimization (SEO), online advertising (search ads, display ads), email marketing/remarketing, affiliate marketing/referral programs, paid search, and mobile apps.
Why is Digital Marketing Important?
Digital marketing is the most important way to reach your customers. It's often called 'marketing in a box' because it provides everything you need to run your business online.
Digital marketing is essential for any business owner who wants to connect with their audience, drive traffic and increase sales. Digital marketing helps you sell more products or services by building trust with your target audience and building an audience of loyal customers who come back again and again.
Types of Digital Marketing
There are many types of digital marketing, but each class can be broken down into a few core elements. Each element is designed to accomplish a specific task in driving online traffic and leads to your website.
Search Engine Optimization (SEO)
SEO is optimizing your website for search engines like Google and Bing. Search engines use algorithms to determine which sites are most relevant to users based on their search terms, keywords, and other factors. The goal of SEO is to get your site listed as high up in the search results as possible.
Social Media Marketing (SMM)
Social media marketing involves using platforms such as Facebook, Instagram, Twitter, or LinkedIn to promote your brand or business. It's also known as social media advertising or SMO. Content sharing and engagement are two important factors in this marketing strategy because they allow you to build relationships with people who might become customers. In addition, social media platforms enable businesses to collaborate with their customers to create content that can be shared with others in their network and across the web.
Content marketing
Content marketing is about producing valuable information for your audience relevant to their needs and interests. You can make this content yourself or hire writers specializing in content creation. The goal is to attract new audience members and build trust with existing ones through original, quality content available for free on websites like Medium or YouTube.
E-commerce
With e-commerce, you can sell products and services online. This includes shopping carts that allow consumers to buy online, websites that list products and services for sale, and sites where consumers can purchase items from third-party vendors (e.g., Amazon.com). In addition to selling products and services, e-commerce companies may provide other value-added services such as shipping and returns.
Mobile Marketing
Mobile marketing is using portable devices to deliver digital content, including advertisements. Mobile marketing began as a way for advertisers to reach potential customers on their phones. Still, it has now evolved into a full-fledged marketing channel with an entire ecosystem of apps, content, and services designed to help marketers reach potential customers through mobile devices and applications.
Email marketing
Email marketing is one part of digital marketing where you get paid directly by the company or company owner. You promote your service or product through email campaigns like newsletters or blasts. You can send notifications about new products or services available at certain time intervals or when there is some special event in the industry related to your niche if you are an expert in that area or have expertise in that industry.
Affiliate Marketing
Affiliate marketing is a method of marketing that pays website owners and publishers based on the performance of their advertisements and sales. Affiliate marketers use special links called affiliate codes to identify themselves and the products they are promoting. When potential customers click on those links, they are taken to the merchant's site, where they can purchase if they wish.
Digital Marketing Benefits
There are many benefits to digital marketing, which include:
- Leverage Search Engine Optimization (SEO) to attract traffic, leads, and sales.
- Create content that people will want to read and share on social media.
- Automate your email marketing campaigns so you can focus on growing your business.
- Measure the effectiveness of your digital marketing campaigns by tracking ROI, conversions, and other KPIs.
- It's easy to use.
- You don't risk getting sued by a customer or consumer who feels you have misled them or made a false claim about your product or service.
- You can target specific groups of people with digital marketing campaigns that will appeal to their interests, lifestyle, and even psychology (for example, they may be interested in products that are related to their interests).
- Digital marketing is effective because it reaches people when they are using their mobile devices (or computers) on the go - which means that they are more likely to see it than other forms of advertising, such as TV or billboard ads would be!
Future of Digital Marketing
In the last few years, digital marketing has become a significant part of businesses' growth strategies. In fact, according to Statista, digital marketing expenditure is expected to reach $1 trillion by 2020 and $5 trillion by 2025.
Digital marketing is not just about online advertising anymore. Nowadays, it's also about social media marketing, email marketing, content marketing, and many other channels integrated into a single package.
The future of digital marketing is bright because there are so many different aspects that can be used to reach your target audience and generate leads for you or your business.
Your job as a digital marketer is to create new and innovative ways for people to interact with your brand and purchase your products or services. So you have to get creative and think of new ways to deliver value so that your customers don't feel like they are just another number on someone's list.
This introduction to digital marketing has opened a few doors for you. You might not know much about it now, but at least you know what goes into digital marketing and why it's there.
Become an Information Security Analyst 2023
Become an Information Security Analyst 2023
With networked computing becoming a trend even in a small-scale company and the development of the internet and cloud solutions, accessing advanced data to solve business challenges has never been widespread.
As data systems are universal, data has become less secure, where more companies manage a colossal amount of data, making it an easier target for cybercriminals. Often smaller organizations need IT the experience to keep data safe. Over the last decade, more companies have dealt with high-profile data breaches.
As a result, the role of Information Security (IS) Analyst has advanced to a most sought-after position across industry verticals.
What is an IS Analyst?
An Information Security (IS) Analyst defends computer networks performed by private businesses, nonprofit organizations, and government organizations. However, there are a few domains where an IS Analyst can't find work relying on data security.
As ML and predictive modeling illustrate their investment returns, more enterprises need the skills of a competent IS Analyst. The sole responsibility of an Information Security Analyst is to develop scalable security apparatuses to address and prevent threats.
The job's criteria depend on the sector; however, an IS Analyst is often reserved in case of data breaches, hacking, or other crises based on tech asset security.
An analyst generates reports that IT admins and business professionals leverage to assess the practicality of their security systems. Depending on the Analyst's suggestions, organizations will modify security networks to ensure data is inaccessible to unauthorized people.
Developing and delivering educational courses is also a part of their work, as it's adequate to aid workforces in maintaining solid security practices.
Roles of Information Security Analysts
An IS Analyst is responsible for the following:
- Maintain data encryption and firewalls to safeguard sensitive data.
- Establish security standards
- Investigate security breaches on their company's networks.
- Ensure that senior IT staff is aware of security improvements
- Help users with learning and installation of new security products
- Staying updated on the latest advancements in IT security
Information Security Analysts: Job Prospects & Certification Requirement
According to BLS, IS Analyst job scope is projected to rise to 28% from 2016-2026, considerably more rapidly than other occupations' average growth. In addition, according to US News, IS Analyst is listed as the fourth best IT job in 2019, attributing to a wide variety of ventures looking for data security solutions.
According to Indeed, the average IS Analyst salary is $81,065 annually, which may increase as per expertise and knowledge.
An IS accreditation comprises a collection of credentials that set up foundational knowledge in different topics.
ICert Global helps people excel in the skills required for network security. Our security programs and certifications help participants to spot vulnerabilities, immediately respond to emergencies, and fend off attacks.
Some of the top-notch security certifications are as follows:
- Certified Ethical Hacker (CEH)
- Cyber Security Expert
- Certified Information Systems Auditor (CISA)
- CompTIA Security+
- Certified Information Systems Security Professional (CISSP)
Read More
Become an Information Security Analyst 2023
With networked computing becoming a trend even in a small-scale company and the development of the internet and cloud solutions, accessing advanced data to solve business challenges has never been widespread.
As data systems are universal, data has become less secure, where more companies manage a colossal amount of data, making it an easier target for cybercriminals. Often smaller organizations need IT the experience to keep data safe. Over the last decade, more companies have dealt with high-profile data breaches.
As a result, the role of Information Security (IS) Analyst has advanced to a most sought-after position across industry verticals.
What is an IS Analyst?
An Information Security (IS) Analyst defends computer networks performed by private businesses, nonprofit organizations, and government organizations. However, there are a few domains where an IS Analyst can't find work relying on data security.
As ML and predictive modeling illustrate their investment returns, more enterprises need the skills of a competent IS Analyst. The sole responsibility of an Information Security Analyst is to develop scalable security apparatuses to address and prevent threats.
The job's criteria depend on the sector; however, an IS Analyst is often reserved in case of data breaches, hacking, or other crises based on tech asset security.
An analyst generates reports that IT admins and business professionals leverage to assess the practicality of their security systems. Depending on the Analyst's suggestions, organizations will modify security networks to ensure data is inaccessible to unauthorized people.
Developing and delivering educational courses is also a part of their work, as it's adequate to aid workforces in maintaining solid security practices.
Roles of Information Security Analysts
An IS Analyst is responsible for the following:
- Maintain data encryption and firewalls to safeguard sensitive data.
- Establish security standards
- Investigate security breaches on their company's networks.
- Ensure that senior IT staff is aware of security improvements
- Help users with learning and installation of new security products
- Staying updated on the latest advancements in IT security
Information Security Analysts: Job Prospects & Certification Requirement
According to BLS, IS Analyst job scope is projected to rise to 28% from 2016-2026, considerably more rapidly than other occupations' average growth. In addition, according to US News, IS Analyst is listed as the fourth best IT job in 2019, attributing to a wide variety of ventures looking for data security solutions.
According to Indeed, the average IS Analyst salary is $81,065 annually, which may increase as per expertise and knowledge.
An IS accreditation comprises a collection of credentials that set up foundational knowledge in different topics.
ICert Global helps people excel in the skills required for network security. Our security programs and certifications help participants to spot vulnerabilities, immediately respond to emergencies, and fend off attacks.
Some of the top-notch security certifications are as follows:
- Certified Ethical Hacker (CEH)
- Cyber Security Expert
- Certified Information Systems Auditor (CISA)
- CompTIA Security+
- Certified Information Systems Security Professional (CISSP)
Productivity Management and Its Importance
Productivity Management and Its Importance
Table of Content
Why Does Productivity Matter?
What is productivity management?
Why is productivity management important?
What Are Some Effective Ways to Manage Productivity?
Productivity is Essential for Today's Companies
Why Does Productivity Matter?
The productivity of a project is the amount of work that can be done in a given period. The productivity of a project will vary depending on many factors. Still, one of the most important is the quality of the team. A good team will provide better results, which means their productivity increases. Productivity matters in any project because it's a key driver for success. If you don't produce enough value, you won't be able to provide a good return on your investment.
What is Productivity Management?
Productivity management is a strategic management process that helps an organization achieve its goals by reducing waste and increasing the efficiency of business operations. Productivity management focuses on all aspects of the business, including sales, service, marketing, and financial results. Productivity management aims to create the highest level of value for the customer while minimizing costs or any other negative impact on the organization's bottom line.
Productivity management can be applied to any business or organization, whether a small business or a large corporation. Many companies use productivity management as one of their top priorities because it positively impacts their bottom line.
Why is Productivity Management Important?
The ability to manage productivity is an essential part of business success.
Productivity measures the amount of output produced by a worker over a specific period. In simple terms, it is the amount of work done per unit of time.
There are many reasons why productivity management is essential:
- It allows you to control costs.
- It helps you make better decisions about how you spend your money.
- It helps keep workloads down and staff happy.
- Setting goals for each employee so that they know what to work towards.
- Strategizing how to reach those goals.
- Measuring how well each employee is doing toward those goals.
- Maintaining consistent communication between all employees involved in the project or task.
What Are Some Effective Ways to Manage Productivity?
Productivity is the amount of work you get done in a day or week. The most effective way to manage productivity is by setting goals and keeping track of your progress toward those goals.
Here are some practical ways to manage productivity:
- Set realistic goals
Goals should be SMART (specific, measurable, action-oriented, realistic, and time-bound). You must set your goals based on your current level and what you are willing to do to achieve them.
- Track your progress
Once you have set your goals and recorded them in a place where you will constantly see them (such as a calendar), make sure that you keep track of how well you are doing each week or month.
- Take Advantage of Technology
Technology has become an integral part of our daily lives. It helps us stay connected and get things done faster. You can use technology to make managing your time easier by using app such as Google Calendar. This will help you keep track of the time you spend doing things and how much time it takes to complete them. For example, if you find that it takes 15 minutes to complete a task, to your calendar so they don't get forgotten about later on during the day when it would be too late to do anything about it!
- Create a Schedule
Creating a schedule for yourself is essential to get things done on time. It will help you organize your life around important tasks and juggle all the other stuff in between them. Schedule everything from work-related tasks like meetings, lunches with clients, or even just random errands.
- Set boundaries for yourself
When you have a lot of work, it can be easy to lose track of time. That's why it's important to set boundaries for yourself. If you know exactly when you will stop working on a project, you won't have any trouble staying focused until that time. Of course, you should also set these boundaries in advance so there are no surprises.
- Turn off distracting notifications.
It's easy to get distracted by notifications while working on something important. If you don't want to miss any important messages or alerts, turn them off while working on something else and then turn them back on when it's time for that project again. This way, all distractions will be behind closed doors and out of sight so that nothing distracts from what needs doing at that moment (and vice versa).
Productivity is Essential for Today's Companies
The world has become where we need to be productive to survive. The faster we can be effective, the more time we will have for ourselves and our loved ones.
Productivity is essential for today's companies because it allows them to operate at a higher efficiency level. However, suppose you are not able to produce your products or services at a quick rate. In that case, your company might not be able to stay competitive in the marketplace.
Productivity is also important because it allows us to get ahead and meet our financial obligations on time. However, when you cannot produce as much as possible within a given period, it can cause many problems with your finances and other aspects of your life.
Takeaway: How to Improve Productivity
There are many ways to improve productivity. Here are a few tips:
- Have a clear vision of what you want to achieve.
- Do not let yourself get distracted by other things in the project.
- Have a set of standards for what good looks like.
- Reward yourself for small victories along the way.
- Set deadlines and enforce them as necessary.
Conclusion
Productivity management is a broad term and can refer to several different things. However, the concept of "productivity" is simple to understand-it and deals with the quantity and quality of work output. That's not to say that it's easy to implement in the workplace. While it may seem like a simple issue on paper, getting employees to be productive at work can be far more complex than it looks. Nevertheless, here's hoping for a successful implementation for all!
Read More
Productivity Management and Its Importance
Table of Content
Why Does Productivity Matter?
What is productivity management?
Why is productivity management important?
What Are Some Effective Ways to Manage Productivity?
Productivity is Essential for Today's Companies
Why Does Productivity Matter?
The productivity of a project is the amount of work that can be done in a given period. The productivity of a project will vary depending on many factors. Still, one of the most important is the quality of the team. A good team will provide better results, which means their productivity increases. Productivity matters in any project because it's a key driver for success. If you don't produce enough value, you won't be able to provide a good return on your investment.
What is Productivity Management?
Productivity management is a strategic management process that helps an organization achieve its goals by reducing waste and increasing the efficiency of business operations. Productivity management focuses on all aspects of the business, including sales, service, marketing, and financial results. Productivity management aims to create the highest level of value for the customer while minimizing costs or any other negative impact on the organization's bottom line.
Productivity management can be applied to any business or organization, whether a small business or a large corporation. Many companies use productivity management as one of their top priorities because it positively impacts their bottom line.
Why is Productivity Management Important?
The ability to manage productivity is an essential part of business success.
Productivity measures the amount of output produced by a worker over a specific period. In simple terms, it is the amount of work done per unit of time.
There are many reasons why productivity management is essential:
- It allows you to control costs.
- It helps you make better decisions about how you spend your money.
- It helps keep workloads down and staff happy.
- Setting goals for each employee so that they know what to work towards.
- Strategizing how to reach those goals.
- Measuring how well each employee is doing toward those goals.
- Maintaining consistent communication between all employees involved in the project or task.
What Are Some Effective Ways to Manage Productivity?
Productivity is the amount of work you get done in a day or week. The most effective way to manage productivity is by setting goals and keeping track of your progress toward those goals.
Here are some practical ways to manage productivity:
- Set realistic goals
Goals should be SMART (specific, measurable, action-oriented, realistic, and time-bound). You must set your goals based on your current level and what you are willing to do to achieve them.
- Track your progress
Once you have set your goals and recorded them in a place where you will constantly see them (such as a calendar), make sure that you keep track of how well you are doing each week or month.
- Take Advantage of Technology
Technology has become an integral part of our daily lives. It helps us stay connected and get things done faster. You can use technology to make managing your time easier by using app such as Google Calendar. This will help you keep track of the time you spend doing things and how much time it takes to complete them. For example, if you find that it takes 15 minutes to complete a task, to your calendar so they don't get forgotten about later on during the day when it would be too late to do anything about it!
- Create a Schedule
Creating a schedule for yourself is essential to get things done on time. It will help you organize your life around important tasks and juggle all the other stuff in between them. Schedule everything from work-related tasks like meetings, lunches with clients, or even just random errands.
- Set boundaries for yourself
When you have a lot of work, it can be easy to lose track of time. That's why it's important to set boundaries for yourself. If you know exactly when you will stop working on a project, you won't have any trouble staying focused until that time. Of course, you should also set these boundaries in advance so there are no surprises.
- Turn off distracting notifications.
It's easy to get distracted by notifications while working on something important. If you don't want to miss any important messages or alerts, turn them off while working on something else and then turn them back on when it's time for that project again. This way, all distractions will be behind closed doors and out of sight so that nothing distracts from what needs doing at that moment (and vice versa).
Productivity is Essential for Today's Companies
The world has become where we need to be productive to survive. The faster we can be effective, the more time we will have for ourselves and our loved ones.
Productivity is essential for today's companies because it allows them to operate at a higher efficiency level. However, suppose you are not able to produce your products or services at a quick rate. In that case, your company might not be able to stay competitive in the marketplace.
Productivity is also important because it allows us to get ahead and meet our financial obligations on time. However, when you cannot produce as much as possible within a given period, it can cause many problems with your finances and other aspects of your life.
Takeaway: How to Improve Productivity
There are many ways to improve productivity. Here are a few tips:
- Have a clear vision of what you want to achieve.
- Do not let yourself get distracted by other things in the project.
- Have a set of standards for what good looks like.
- Reward yourself for small victories along the way.
- Set deadlines and enforce them as necessary.
Conclusion
Productivity management is a broad term and can refer to several different things. However, the concept of "productivity" is simple to understand-it and deals with the quantity and quality of work output. That's not to say that it's easy to implement in the workplace. While it may seem like a simple issue on paper, getting employees to be productive at work can be far more complex than it looks. Nevertheless, here's hoping for a successful implementation for all!
Information Security Management
Information Security Management
The wave of cyberattacks is increasing in number and complexity, with perpetrators taking advantage of the latest tools and technologies. The number of victims is growing exponentially, too, affecting a wide variety of organizations, from large corporations to small businesses, government agencies, and even individuals. These attacks are also getting more sophisticated by the day. A straightforward way to protect your network and information is mastering information security management, a core part of any comprehensive IT security strategy.
What is Information Security Management?
Information security management ensures that information assets are protected from loss, unauthorized access, misuse, and destruction. Information security management involves a systematic information security approach applied throughout an organization. This includes policies, procedures, and standards for safeguarding data; hiring qualified staff; establishing processes for detecting, reporting, responding to, and managing incidents involving information systems or when unauthorized users gain access to sensitive data, and maintaining a program that communicates information security expectations to employees.
Information security management is an ongoing process that begins with establishing policies and procedures but continues throughout the life cycle of an organization's information assets. The goal of information security management is not only to protect assets but also to help companies be more competitive in their markets by assisting them in understanding how their competitors are doing business.
Goal of ISM
Information security management aims to reduce the likelihood of a data breach or other security incident occurring by identifying vulnerabilities before attackers can exploit them. In addition, the aim is to prevent attackers from gaining access to sensitive data to steal money or information that could be used for illegal purposes.
Steps Involve in ISM
The steps involved in information security management are:
- First, identify the potential threats to your business or organization.
- Devise a plan to prevent and minimize these threats.
- Ensure compliance with security policies and procedures that address these risks.
- Implement monitoring systems to detect unauthorized access, use, and disclosure of information assets or activities that may adversely affect the confidentiality and integrity of information systems and data.
- Develop and implement measures to protect information assets through physical, technical, and administrative actions by the appropriate provisions of relevant laws and regulations.
Why Should You Care About Information Security Management?
If your organization is not concerned with information security management, you must do it right.
Information security is a critical function of any business. Therefore, it is essential to understand what makes your organization values and how to protect it from external threats.
As a senior leader, you should care about information security management because:
- It will help you understand your organization's risks and set goals for improving them over time.
- It will help you identify areas where your organization is at risk and give you the tools to mitigate them.
- It will help you build a culture of cybersecurity in your organization so that everyone understands how important it is to be vigilant about information security.
What are the Benefits of Information Security Management (ISM)?
Information Security Management (ISM) is a process that requires identifying, analyzing, and mitigating risks to organizations from unauthorized access to or acquisition of their information systems.
The benefits of Information Security Management (ISM) include:
- Reduced risk of data breaches.
- Improved customer confidence in the organization.
- Enhanced reputation as an ethical business.
- Increased profitability and profitability.
- It helps to identify and manage risks effectively.
- It improves the security of information assets by ensuring that it is stored. securely and protected from unauthorized access or disclosure.
Difference Between Information Security, Computer Security, and Information Assurance
Information security protects information assets from threats and vulnerabilities. The goal is to keep information assets safe from unauthorized access, use, disclosure, or modification. This means that your organization must have a comprehensive plan to protect your data from external threats and internal fraud/error.
Computer security refers to the protection of computers against external attacks. Computer attacks can come from human attackers or malicious software (malware) programs. Malware is a software developed by hackers and then distributed on the Internet for illegal purposes. Computer security aims to limit the damage caused by malware infections so that they do not impact productivity or compromise users' privacy.
Information assurance ensures the availability, integrity, and confidentiality of information and computer systems. Information assurance goals are to prevent and mitigate information-related risks, reduce impact when risks occur, and help ensure that business activities continue to be performed without interruption.
Conclusion
The threat of information security breaches is a growing concern for businesses and individuals alike. As technology advances, our information becomes more vulnerable, and we must take appropriate measures to protect ourselves from malicious threats. An excellent place to start is by educating yourself about the basics of Information Security Management and then adopting actions to protect your personal information.
Read More
Information Security Management
The wave of cyberattacks is increasing in number and complexity, with perpetrators taking advantage of the latest tools and technologies. The number of victims is growing exponentially, too, affecting a wide variety of organizations, from large corporations to small businesses, government agencies, and even individuals. These attacks are also getting more sophisticated by the day. A straightforward way to protect your network and information is mastering information security management, a core part of any comprehensive IT security strategy.
What is Information Security Management?
Information security management ensures that information assets are protected from loss, unauthorized access, misuse, and destruction. Information security management involves a systematic information security approach applied throughout an organization. This includes policies, procedures, and standards for safeguarding data; hiring qualified staff; establishing processes for detecting, reporting, responding to, and managing incidents involving information systems or when unauthorized users gain access to sensitive data, and maintaining a program that communicates information security expectations to employees.
Information security management is an ongoing process that begins with establishing policies and procedures but continues throughout the life cycle of an organization's information assets. The goal of information security management is not only to protect assets but also to help companies be more competitive in their markets by assisting them in understanding how their competitors are doing business.
Goal of ISM
Information security management aims to reduce the likelihood of a data breach or other security incident occurring by identifying vulnerabilities before attackers can exploit them. In addition, the aim is to prevent attackers from gaining access to sensitive data to steal money or information that could be used for illegal purposes.
Steps Involve in ISM
The steps involved in information security management are:
- First, identify the potential threats to your business or organization.
- Devise a plan to prevent and minimize these threats.
- Ensure compliance with security policies and procedures that address these risks.
- Implement monitoring systems to detect unauthorized access, use, and disclosure of information assets or activities that may adversely affect the confidentiality and integrity of information systems and data.
- Develop and implement measures to protect information assets through physical, technical, and administrative actions by the appropriate provisions of relevant laws and regulations.
Why Should You Care About Information Security Management?
If your organization is not concerned with information security management, you must do it right.
Information security is a critical function of any business. Therefore, it is essential to understand what makes your organization values and how to protect it from external threats.
As a senior leader, you should care about information security management because:
- It will help you understand your organization's risks and set goals for improving them over time.
- It will help you identify areas where your organization is at risk and give you the tools to mitigate them.
- It will help you build a culture of cybersecurity in your organization so that everyone understands how important it is to be vigilant about information security.
What are the Benefits of Information Security Management (ISM)?
Information Security Management (ISM) is a process that requires identifying, analyzing, and mitigating risks to organizations from unauthorized access to or acquisition of their information systems.
The benefits of Information Security Management (ISM) include:
- Reduced risk of data breaches.
- Improved customer confidence in the organization.
- Enhanced reputation as an ethical business.
- Increased profitability and profitability.
- It helps to identify and manage risks effectively.
- It improves the security of information assets by ensuring that it is stored. securely and protected from unauthorized access or disclosure.
Difference Between Information Security, Computer Security, and Information Assurance
Information security protects information assets from threats and vulnerabilities. The goal is to keep information assets safe from unauthorized access, use, disclosure, or modification. This means that your organization must have a comprehensive plan to protect your data from external threats and internal fraud/error.
Computer security refers to the protection of computers against external attacks. Computer attacks can come from human attackers or malicious software (malware) programs. Malware is a software developed by hackers and then distributed on the Internet for illegal purposes. Computer security aims to limit the damage caused by malware infections so that they do not impact productivity or compromise users' privacy.
Information assurance ensures the availability, integrity, and confidentiality of information and computer systems. Information assurance goals are to prevent and mitigate information-related risks, reduce impact when risks occur, and help ensure that business activities continue to be performed without interruption.
Conclusion
The threat of information security breaches is a growing concern for businesses and individuals alike. As technology advances, our information becomes more vulnerable, and we must take appropriate measures to protect ourselves from malicious threats. An excellent place to start is by educating yourself about the basics of Information Security Management and then adopting actions to protect your personal information.
Data Acquisition in Machine learning
Data Acquisition in Machine learning
Data acquisition in machine learning can significantly widen your knowledge of a particular topic. For example, suppose you are planning to analyze your website's data. In that case, it can help you find out what features and functions on your site work well and which ones don't appeal to the customers. During data collection, you might also be required to collect website domain names or page titles. Let’s know more about data acquisition.
What is Data Acquisition?
Data acquisition is one of the most important steps in a machine learning algorithm. It's used to collect data on how your model performs on new datasets.
Data acquisition is simply collecting new data and transforming it into a format your machine learning algorithm can use. Once you've acquired some training data, your model can learn from it and improve its performance on new tasks.
Why do we need Data Acquisition?
For most machine learning algorithms, you need to acquire training data before using them for prediction. This training data can be provided by humans or other machines (e.g., from web scraping). The goal is to have a large enough sample size that your model can learn from effectively but not so large that it takes too much time to train (and possibly overfit) the available data.
Components of Data Acquisition System
The Data Acquisition System (DAS) is a set of components that perform data acquisition. The components are:
Sensor: A sensor converts physical properties into electrical signals, which a DAS can use to acquire data. A sensor may be a simple device like an inductive proximity sensor or an expensive instrument with many channels and options.
Signal Conditioner: The signal conditioning system converts the analog signals from the sensor into digital form. It provides gain, offset, and trim controls for each channel on the DAS. It also filters out noise from external sources, such as motors or other electronics that generate electromagnetic interference.
Analog-to-Digital Converter (ADC): The ADC converts the analog signal from the signal conditioner into a digital format for processing by a computer or other processor.
Importance of Data Acquisition System
The most important aspect of data acquisition systems is the ability to record and analyze data. This includes both the hardware and software aspects. The hardware consists of the devices that collect data, including sensors and radio frequency identification (RFID) devices. The software aspect includes the software used to collect, store and process the data.
The purpose of a data acquisition system is to automate processes. Automating an approach means that it can be done without human intervention. This can reduce the time needed for a specific task or improve overall efficiency in performing tasks that require human intervention.
In addition to automating processes, a good data acquisition system will provide information about what went wrong when something does go wrong during an automated procedure. For example, suppose a computerized process fails several times in a row. In that case, something may be wrong with the program or one of its components. A good data acquisition system will alert users to potential problems before they cause severe damage to equipment (or humans).
Purposes of Data Acquisition
The most important purposes of data acquisition are:
First, data acquisition helps to understand the behavior of the system.
Data acquisition helps to develop a model for the system.
Finally, data acquisition helps to improve the performance of the system.
What Does a DAQ System Measure?
The DAQ system measures a variety of parameters, including:
- Temperature
- Pressure
- Voltage
- Current flow through an electrical circuit
- Power usage of a piece of equipment
A data acquisition system (DAS) measures various parameters that can be used to control and analyze equipment. The DAS is typically connected to the electrical system and can be programmed, via a web browser, for specific functions and tasks.
The following are some common uses for a DAQ system:
- Control of electronic devices such as motors, valves, and pumps
- Measuring variable parameters of temperature, pressure, or flow rate
- Monitoring vibration levels in air conditioning systems
- Providing feedback to users through visual displays or audible alarm tones
With that, we have finished our exploration of topics relevant to Data Acquisition in machine learning. I hope you learned a lot and enjoyed the read! Please leave any thoughts or questions you may have (along with any suggestions) in the comments section below.
Read More
Data Acquisition in Machine learning
Data acquisition in machine learning can significantly widen your knowledge of a particular topic. For example, suppose you are planning to analyze your website's data. In that case, it can help you find out what features and functions on your site work well and which ones don't appeal to the customers. During data collection, you might also be required to collect website domain names or page titles. Let’s know more about data acquisition.
What is Data Acquisition?
Data acquisition is one of the most important steps in a machine learning algorithm. It's used to collect data on how your model performs on new datasets.
Data acquisition is simply collecting new data and transforming it into a format your machine learning algorithm can use. Once you've acquired some training data, your model can learn from it and improve its performance on new tasks.
Why do we need Data Acquisition?
For most machine learning algorithms, you need to acquire training data before using them for prediction. This training data can be provided by humans or other machines (e.g., from web scraping). The goal is to have a large enough sample size that your model can learn from effectively but not so large that it takes too much time to train (and possibly overfit) the available data.
Components of Data Acquisition System
The Data Acquisition System (DAS) is a set of components that perform data acquisition. The components are:
Sensor: A sensor converts physical properties into electrical signals, which a DAS can use to acquire data. A sensor may be a simple device like an inductive proximity sensor or an expensive instrument with many channels and options.
Signal Conditioner: The signal conditioning system converts the analog signals from the sensor into digital form. It provides gain, offset, and trim controls for each channel on the DAS. It also filters out noise from external sources, such as motors or other electronics that generate electromagnetic interference.
Analog-to-Digital Converter (ADC): The ADC converts the analog signal from the signal conditioner into a digital format for processing by a computer or other processor.
Importance of Data Acquisition System
The most important aspect of data acquisition systems is the ability to record and analyze data. This includes both the hardware and software aspects. The hardware consists of the devices that collect data, including sensors and radio frequency identification (RFID) devices. The software aspect includes the software used to collect, store and process the data.
The purpose of a data acquisition system is to automate processes. Automating an approach means that it can be done without human intervention. This can reduce the time needed for a specific task or improve overall efficiency in performing tasks that require human intervention.
In addition to automating processes, a good data acquisition system will provide information about what went wrong when something does go wrong during an automated procedure. For example, suppose a computerized process fails several times in a row. In that case, something may be wrong with the program or one of its components. A good data acquisition system will alert users to potential problems before they cause severe damage to equipment (or humans).
Purposes of Data Acquisition
The most important purposes of data acquisition are:
First, data acquisition helps to understand the behavior of the system.
Data acquisition helps to develop a model for the system.
Finally, data acquisition helps to improve the performance of the system.
What Does a DAQ System Measure?
The DAQ system measures a variety of parameters, including:
- Temperature
- Pressure
- Voltage
- Current flow through an electrical circuit
- Power usage of a piece of equipment
A data acquisition system (DAS) measures various parameters that can be used to control and analyze equipment. The DAS is typically connected to the electrical system and can be programmed, via a web browser, for specific functions and tasks.
The following are some common uses for a DAQ system:
- Control of electronic devices such as motors, valves, and pumps
- Measuring variable parameters of temperature, pressure, or flow rate
- Monitoring vibration levels in air conditioning systems
- Providing feedback to users through visual displays or audible alarm tones
With that, we have finished our exploration of topics relevant to Data Acquisition in machine learning. I hope you learned a lot and enjoyed the read! Please leave any thoughts or questions you may have (along with any suggestions) in the comments section below.
What Is a Project Management Plan ,Certifation Eligibility & How to Obtain PMP?
Project management is a complex process that involves careful planning, execution, monitoring, and control to ensure that projects are completed on time, within budget, and to the satisfaction of stakeholders. One essential component of project management is the project management plan. A project management plan is a comprehensive document that outlines how a project will be executed, monitored, and controlled. It includes information on project scope, schedule, budget, risk management, communication, quality management, and other aspects of the project. In this topic, we will explore what a project management plan is, why it is important, and how to create one. We will also discuss some key elements of a project management plan that you should include to ensure project success.
Table of Contents
What Is a Project Management Plan?
What Is a Project Management Plan Used For?
What are the Components of a Project Management Plan?
The Importance of Project Management Planning
Things You Need to Know Before Writing a Project Plan
Creating a Project Management Plan
PMP Certification Eligibility?
How to Create a Project Management Plan? [ Explained in 6 Steps]
How to Turn Your Project Management Plan Into a Plan of Action
Project Management Plan Approval
How Is Project Management Different From Financial Management?
Conclusion
What Is a Project Management Plan?
A project management plan is a formal document that outlines how a project will be executed, monitored, and controlled. It is a comprehensive document that serves as a roadmap for the project and provides a detailed understanding of how the project will be managed from start to finish.
The project management plan outlines the project's scope, objectives, schedule, budget, quality management, risk management, communication plan, and other key aspects. It describes the processes and procedures that will be used to manage the project and provides a framework for decision-making throughout the project's lifecycle.
The project management plan is typically created during the planning phase of the project, and it serves as a reference document throughout the project's execution. It provides a baseline against which project progress can be measured, and it helps to ensure that the project remains aligned with its goals, scope, and constraints.
What Is a Project Management Plan Used For?
A project management plan serves as a roadmap for the project and provides a detailed understanding of how the project will be managed from start to finish. It is a critical document that is used to ensure that the project remains on track and aligned with its goals, scope, and constraints.
The project management plan is used for several purposes, including:
- Defining project scope: The project management plan outlines the project's scope, objectives, and deliverables, helping to ensure that all stakeholders have a clear understanding of the project's goals and expectations.
- Managing project schedule and budget: The project management plan includes a detailed schedule and budget, which helps to ensure that the project is completed on time and within budget.
- Managing project risks: The project management plan includes a risk management plan that identifies potential risks and outlines strategies for mitigating or avoiding them.
- Managing project quality: The project management plan includes a quality management plan that outlines the processes and procedures for ensuring that project deliverables meet the required quality standards.
- Managing project communications: The project management plan includes a communication plan that outlines how project information will be shared among stakeholders.
What are the Components of a Project Management Plan?
- Project Scope Management Plan: This outlines the project's scope, objectives, and deliverables, and provides a detailed understanding of what will be accomplished.
- Project Schedule Management Plan: This outlines the project schedule, including key milestones, timelines, and dependencies, and helps to ensure that the project is completed on time.
- Project Cost Management Plan: This outlines the project budget, including costs for resources, materials, and other expenses, and helps to ensure that the project is completed within budget.
- Project Quality Management Plan: This outlines the processes and procedures for ensuring that project deliverables meet the required quality standards.
- Project Resource Management Plan: This outlines how project resources will be managed, including roles, responsibilities, and staffing.
- Project Communication Management Plan: This outlines how project information will be shared among stakeholders, including the frequency and format of communication.
- Project Risk Management Plan: This outlines potential project risks and outlines strategies for mitigating or avoiding them.
- Project Procurement Management Plan: This outlines how project resources and materials will be procured and managed, including contracting and vendor management.
- Project Stakeholder Management Plan: This outlines how project stakeholders will be identified, managed, and engaged throughout the project's lifecycle.
The Importance of Project Management Planning .
Project management planning is essential for the success of any project. It is the process of defining project objectives, determining project goals, outlining project deliverables, and creating a roadmap for how the project will be executed, monitored, and controlled.
The importance of project management planning can be summarized in the following points:
- Establishes clear project goals and objectives: A well-planned project management plan provides a clear definition of project goals and objectives, which helps stakeholders understand what the project will accomplish.
- Provides a roadmap for project execution: A project management plan outlines the steps that need to be taken to achieve project objectives, providing a roadmap for project execution.
- Helps to manage project risks: A project management plan includes a risk management plan that identifies potential risks and outlines strategies for mitigating or avoiding them.
- Ensures project quality: A project management plan includes a quality management plan that outlines the processes and procedures for ensuring that project deliverables meet the required quality standards.
- Helps to manage project resources: A project management plan includes a resource management plan that outlines how project resources will be managed, including roles, responsibilities, and staffing.
- Provides a baseline for measuring progress: A project management plan provides a baseline against which project progress can be measured, helping to ensure that the project remains on track and aligned with its goals, scope, and constraints.
Things You Need to Know Before Writing a Project Plan
- Project goals and objectives: Understand the purpose of the project and its intended outcomes. Clearly define project goals and objectives to guide the planning process.
- Project scope: Define the boundaries of the project, including what's included and excluded. Understand the project's requirements, deliverables, timelines, and budget.
- Project constraints: Identify any limitations that may impact the project's success, including resource availability, technology limitations, regulatory requirements, and budget constraints.
- Stakeholders: Identify all stakeholders who will be affected by the project, including project sponsors, team members, customers, and end-users. Understand their needs and expectations to ensure they are properly addressed in the project plan.
- Project team: Identify the project team and their roles and responsibilities. Ensure that the team is properly trained and equipped to execute the project plan.
- Project risks: Identify potential project risks and develop a risk management plan to mitigate or avoid them.
- Communication plan: Develop a communication plan that outlines how project information will be shared among stakeholders, including the frequency and format of communication.
- Project management methodology: Choose a project management methodology that aligns with the project's goals, scope, and constraints.
- Project management tools: Select appropriate project management tools to support the planning and execution of the project.
PMP Certification Eligibility?
To be eligible for the Project Management Professional (PMP) certification, you need to fulfill certain requirements set by the Project Management Institute (PMI). The eligibility criteria for the PMP certification are as follows:
- Education: You must have a secondary degree (high school diploma, associate's degree, or the global equivalent) or a four-year degree (bachelor's degree or the global equivalent).
- Project Management Experience: You need to have project management experience, which varies depending on your educational background:
- If you have a secondary degree, you should have at least five years (60 months) of non-overlapping project management experience, with a minimum of 7,500 hours leading and directing projects.
- If you have a four-year degree, you should have at least three years (36 months) of non-overlapping project management experience, with a minimum of 4,500 hours leading and directing projects.
- Project Management Education: In addition to project management experience, you must have completed 35 hours of formal project management education. This requirement can be fulfilled through formal project management training courses, such as PMP exam preparation courses.
Creating a Project Management Plan
- Define project goals and objectives: Clearly define the purpose and outcomes of the project, including its scope and deliverables.
- Develop a project scope statement: Define the boundaries of the project, including what's included and excluded. This will help to prevent scope creep and ensure that project goals are achievable.
- Create a work breakdown structure (WBS): Break down the project into smaller, manageable tasks to help with resource allocation and project scheduling.
- Develop a project schedule: Define the project timeline, including key milestones and deadlines. Use project management tools such as Gantt charts to help visualize the project schedule.
- Identify project resources: Identify the people, equipment, and materials needed to complete the project. Develop a resource management plan that outlines how resources will be allocated and managed throughout the project.
- Develop a risk management plan: Identify potential risks and develop strategies to mitigate or avoid them. This will help to minimize project delays and cost overruns.
- Define project quality standards: Establish the quality standards that must be met to ensure project success. Develop a quality management plan that outlines the processes and procedures for ensuring that project deliverables meet these standards.
- Develop a communication plan: Define the project communication plan, including how information will be shared among stakeholders and the frequency and format of communication.
- Define project roles and responsibilities: Clearly define the roles and responsibilities of project team members, stakeholders, and sponsors. This will help to ensure that everyone knows what's expected of them and can work effectively together.
How to Create a Project Management Plan? [ Explained in 6 Steps]
Creating a project management plan can be broken down into six key steps:
- Define project scope and objectives: Clearly define the purpose, goals, and deliverables of the project, including its scope and limitations. This will help to ensure that all stakeholders have a clear understanding of what the project entails.
- Develop a project schedule: Create a timeline for the project that includes all the tasks, milestones, and deadlines. Use project management tools such as Gantt charts to help visualize the project schedule and identify any potential bottlenecks or scheduling conflicts.
- Identify project resources: Determine the resources needed to complete the project, including people, equipment, and materials. Develop a resource management plan that outlines how resources will be allocated and managed throughout the project.
- Develop a risk management plan: Identify potential risks and develop strategies to mitigate or avoid them. This will help to minimize project delays and cost overruns.
- Define project quality standards: Establish the quality standards that must be met to ensure project success. Develop a quality management plan that outlines the processes and procedures for ensuring that project deliverables meet these standards.
- Develop a communication plan: Define the project communication plan, including how information will be shared among stakeholders and the frequency and format of communication. This will help to ensure that everyone is kept informed about the project's progress and can provide feedback or input as needed.
How to Turn Your Project Management Plan Into a Plan of Action
Assign roles and responsibilities: Assign specific roles and responsibilities to team members, and ensure that everyone understands their role in the project. This will help to ensure that everyone is clear on what they need to do and who is responsible for what.
- Develop a detailed work breakdown structure (WBS): Create a detailed WBS that breaks down the project into smaller, more manageable tasks. Assign deadlines and dependencies to each task to ensure that they are completed in the correct order and on time.
- Establish a project management system: Set up a project management system that allows you to track progress, monitor performance, and make adjustments as needed. Use project management tools such as task lists, calendars, and dashboards to help you stay organized and on track.
- Develop a change management plan: Develop a plan for managing changes to the project scope, schedule, or budget. Establish a formal change management process that includes review and approval procedures to ensure that changes are properly documented and communicated.
- Monitor progress and adjust as needed: Regularly monitor project progress against the plan, and make adjustments as needed. Use project management metrics such as earned value, schedule variance, and cost variance to help you identify potential issues and take corrective action.
Project Management Plan Approval
Project management plan approval is a critical step in the project management process. It is the process of obtaining formal approval of the project management plan from stakeholders, sponsors, and other relevant parties. The approval process is important because it ensures that everyone is on the same page about the project and its objectives, and that there is agreement on how the project will be executed, monitored, and controlled.
To obtain project management plan approval, you should:
- Identify the stakeholders: Identify all stakeholders who have a vested interest in the project, such as sponsors, customers, team members, and regulatory bodies.
- Present the plan: Present the project management plan to the stakeholders in a clear and concise manner. Be prepared to answer any questions or concerns they may have.
- Obtain feedback: Solicit feedback from stakeholders to ensure that their expectations and concerns have been addressed in the plan.
- Revise the plan: Revise the project management plan based on feedback received from stakeholders.
- Obtain formal approval: Once the plan has been revised, obtain formal approval from stakeholders. This approval may be in the form of a signed document, email approval, or verbal confirmation.
How Is Project Management Different From Financial Management?
Project management and financial management are two distinct disciplines that have different goals, objectives, and tools. While both are important for the success of an organization, there are some fundamental differences between them.
Project management is focused on the planning, execution, and control of projects to achieve specific objectives. Project managers are responsible for managing resources, timelines, budgets, risks, and stakeholders to deliver a project on time, within budget, and with the desired quality.
On the other hand, financial management is focused on managing the financial resources of an organization to achieve its strategic goals. Financial managers are responsible for managing cash flow, analyzing financial statements, forecasting, budgeting, and investment decisions.
Some key differences between project management and financial management are:
- Objectives: The objective of project management is to deliver a specific project with specific goals and objectives, while the objective of financial management is to manage financial resources to achieve the overall strategic goals of the organization.
- Time horizon: Project management is generally short-term in nature and has a specific timeline, while financial management is a long-term process that involves managing the financial health of the organization over time.
- Tools and techniques: Project managers use tools and techniques such as Gantt charts, project schedules, risk management plans, and quality control plans to manage projects, while financial managers use financial statements, budgeting tools, and financial ratios to manage financial resources.
- Focus: Project management is focused on achieving specific project objectives, while financial management is focused on the overall financial health and sustainability of the organization.
How to obtain the PMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM
- Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
Conclusion
In conclusion, project management and financial management are two essential functions in any organization, but they have different objectives, time horizons, tools, and focuses. Project management is focused on delivering specific projects within a defined timeline, budget, and quality, while financial management is focused on managing financial resources to achieve the overall strategic goals of the organization. Understanding the differences between these two disciplines is important for managers to allocate resources, manage risks, and achieve their organizational objectives. By leveraging the right tools and techniques, project managers and financial managers can work together to ensure the success of their organization.
Read More
Project management is a complex process that involves careful planning, execution, monitoring, and control to ensure that projects are completed on time, within budget, and to the satisfaction of stakeholders. One essential component of project management is the project management plan. A project management plan is a comprehensive document that outlines how a project will be executed, monitored, and controlled. It includes information on project scope, schedule, budget, risk management, communication, quality management, and other aspects of the project. In this topic, we will explore what a project management plan is, why it is important, and how to create one. We will also discuss some key elements of a project management plan that you should include to ensure project success.
Table of Contents
What Is a Project Management Plan?
What Is a Project Management Plan Used For?
What are the Components of a Project Management Plan?
The Importance of Project Management Planning
Things You Need to Know Before Writing a Project Plan
Creating a Project Management Plan
PMP Certification Eligibility?
How to Create a Project Management Plan? [ Explained in 6 Steps]
How to Turn Your Project Management Plan Into a Plan of Action
Project Management Plan Approval
How Is Project Management Different From Financial Management?
Conclusion
What Is a Project Management Plan?
A project management plan is a formal document that outlines how a project will be executed, monitored, and controlled. It is a comprehensive document that serves as a roadmap for the project and provides a detailed understanding of how the project will be managed from start to finish.
The project management plan outlines the project's scope, objectives, schedule, budget, quality management, risk management, communication plan, and other key aspects. It describes the processes and procedures that will be used to manage the project and provides a framework for decision-making throughout the project's lifecycle.
The project management plan is typically created during the planning phase of the project, and it serves as a reference document throughout the project's execution. It provides a baseline against which project progress can be measured, and it helps to ensure that the project remains aligned with its goals, scope, and constraints.
What Is a Project Management Plan Used For?
A project management plan serves as a roadmap for the project and provides a detailed understanding of how the project will be managed from start to finish. It is a critical document that is used to ensure that the project remains on track and aligned with its goals, scope, and constraints.
The project management plan is used for several purposes, including:
- Defining project scope: The project management plan outlines the project's scope, objectives, and deliverables, helping to ensure that all stakeholders have a clear understanding of the project's goals and expectations.
- Managing project schedule and budget: The project management plan includes a detailed schedule and budget, which helps to ensure that the project is completed on time and within budget.
- Managing project risks: The project management plan includes a risk management plan that identifies potential risks and outlines strategies for mitigating or avoiding them.
- Managing project quality: The project management plan includes a quality management plan that outlines the processes and procedures for ensuring that project deliverables meet the required quality standards.
- Managing project communications: The project management plan includes a communication plan that outlines how project information will be shared among stakeholders.
What are the Components of a Project Management Plan?
- Project Scope Management Plan: This outlines the project's scope, objectives, and deliverables, and provides a detailed understanding of what will be accomplished.
- Project Schedule Management Plan: This outlines the project schedule, including key milestones, timelines, and dependencies, and helps to ensure that the project is completed on time.
- Project Cost Management Plan: This outlines the project budget, including costs for resources, materials, and other expenses, and helps to ensure that the project is completed within budget.
- Project Quality Management Plan: This outlines the processes and procedures for ensuring that project deliverables meet the required quality standards.
- Project Resource Management Plan: This outlines how project resources will be managed, including roles, responsibilities, and staffing.
- Project Communication Management Plan: This outlines how project information will be shared among stakeholders, including the frequency and format of communication.
- Project Risk Management Plan: This outlines potential project risks and outlines strategies for mitigating or avoiding them.
- Project Procurement Management Plan: This outlines how project resources and materials will be procured and managed, including contracting and vendor management.
- Project Stakeholder Management Plan: This outlines how project stakeholders will be identified, managed, and engaged throughout the project's lifecycle.
The Importance of Project Management Planning .
Project management planning is essential for the success of any project. It is the process of defining project objectives, determining project goals, outlining project deliverables, and creating a roadmap for how the project will be executed, monitored, and controlled.
The importance of project management planning can be summarized in the following points:
- Establishes clear project goals and objectives: A well-planned project management plan provides a clear definition of project goals and objectives, which helps stakeholders understand what the project will accomplish.
- Provides a roadmap for project execution: A project management plan outlines the steps that need to be taken to achieve project objectives, providing a roadmap for project execution.
- Helps to manage project risks: A project management plan includes a risk management plan that identifies potential risks and outlines strategies for mitigating or avoiding them.
- Ensures project quality: A project management plan includes a quality management plan that outlines the processes and procedures for ensuring that project deliverables meet the required quality standards.
- Helps to manage project resources: A project management plan includes a resource management plan that outlines how project resources will be managed, including roles, responsibilities, and staffing.
- Provides a baseline for measuring progress: A project management plan provides a baseline against which project progress can be measured, helping to ensure that the project remains on track and aligned with its goals, scope, and constraints.
Things You Need to Know Before Writing a Project Plan
- Project goals and objectives: Understand the purpose of the project and its intended outcomes. Clearly define project goals and objectives to guide the planning process.
- Project scope: Define the boundaries of the project, including what's included and excluded. Understand the project's requirements, deliverables, timelines, and budget.
- Project constraints: Identify any limitations that may impact the project's success, including resource availability, technology limitations, regulatory requirements, and budget constraints.
- Stakeholders: Identify all stakeholders who will be affected by the project, including project sponsors, team members, customers, and end-users. Understand their needs and expectations to ensure they are properly addressed in the project plan.
- Project team: Identify the project team and their roles and responsibilities. Ensure that the team is properly trained and equipped to execute the project plan.
- Project risks: Identify potential project risks and develop a risk management plan to mitigate or avoid them.
- Communication plan: Develop a communication plan that outlines how project information will be shared among stakeholders, including the frequency and format of communication.
- Project management methodology: Choose a project management methodology that aligns with the project's goals, scope, and constraints.
- Project management tools: Select appropriate project management tools to support the planning and execution of the project.
PMP Certification Eligibility?
To be eligible for the Project Management Professional (PMP) certification, you need to fulfill certain requirements set by the Project Management Institute (PMI). The eligibility criteria for the PMP certification are as follows:
- Education: You must have a secondary degree (high school diploma, associate's degree, or the global equivalent) or a four-year degree (bachelor's degree or the global equivalent).
- Project Management Experience: You need to have project management experience, which varies depending on your educational background:
- If you have a secondary degree, you should have at least five years (60 months) of non-overlapping project management experience, with a minimum of 7,500 hours leading and directing projects.
- If you have a four-year degree, you should have at least three years (36 months) of non-overlapping project management experience, with a minimum of 4,500 hours leading and directing projects.
- Project Management Education: In addition to project management experience, you must have completed 35 hours of formal project management education. This requirement can be fulfilled through formal project management training courses, such as PMP exam preparation courses.
Creating a Project Management Plan
- Define project goals and objectives: Clearly define the purpose and outcomes of the project, including its scope and deliverables.
- Develop a project scope statement: Define the boundaries of the project, including what's included and excluded. This will help to prevent scope creep and ensure that project goals are achievable.
- Create a work breakdown structure (WBS): Break down the project into smaller, manageable tasks to help with resource allocation and project scheduling.
- Develop a project schedule: Define the project timeline, including key milestones and deadlines. Use project management tools such as Gantt charts to help visualize the project schedule.
- Identify project resources: Identify the people, equipment, and materials needed to complete the project. Develop a resource management plan that outlines how resources will be allocated and managed throughout the project.
- Develop a risk management plan: Identify potential risks and develop strategies to mitigate or avoid them. This will help to minimize project delays and cost overruns.
- Define project quality standards: Establish the quality standards that must be met to ensure project success. Develop a quality management plan that outlines the processes and procedures for ensuring that project deliverables meet these standards.
- Develop a communication plan: Define the project communication plan, including how information will be shared among stakeholders and the frequency and format of communication.
- Define project roles and responsibilities: Clearly define the roles and responsibilities of project team members, stakeholders, and sponsors. This will help to ensure that everyone knows what's expected of them and can work effectively together.
How to Create a Project Management Plan? [ Explained in 6 Steps]
Creating a project management plan can be broken down into six key steps:
- Define project scope and objectives: Clearly define the purpose, goals, and deliverables of the project, including its scope and limitations. This will help to ensure that all stakeholders have a clear understanding of what the project entails.
- Develop a project schedule: Create a timeline for the project that includes all the tasks, milestones, and deadlines. Use project management tools such as Gantt charts to help visualize the project schedule and identify any potential bottlenecks or scheduling conflicts.
- Identify project resources: Determine the resources needed to complete the project, including people, equipment, and materials. Develop a resource management plan that outlines how resources will be allocated and managed throughout the project.
- Develop a risk management plan: Identify potential risks and develop strategies to mitigate or avoid them. This will help to minimize project delays and cost overruns.
- Define project quality standards: Establish the quality standards that must be met to ensure project success. Develop a quality management plan that outlines the processes and procedures for ensuring that project deliverables meet these standards.
- Develop a communication plan: Define the project communication plan, including how information will be shared among stakeholders and the frequency and format of communication. This will help to ensure that everyone is kept informed about the project's progress and can provide feedback or input as needed.
How to Turn Your Project Management Plan Into a Plan of Action
Assign roles and responsibilities: Assign specific roles and responsibilities to team members, and ensure that everyone understands their role in the project. This will help to ensure that everyone is clear on what they need to do and who is responsible for what.
- Develop a detailed work breakdown structure (WBS): Create a detailed WBS that breaks down the project into smaller, more manageable tasks. Assign deadlines and dependencies to each task to ensure that they are completed in the correct order and on time.
- Establish a project management system: Set up a project management system that allows you to track progress, monitor performance, and make adjustments as needed. Use project management tools such as task lists, calendars, and dashboards to help you stay organized and on track.
- Develop a change management plan: Develop a plan for managing changes to the project scope, schedule, or budget. Establish a formal change management process that includes review and approval procedures to ensure that changes are properly documented and communicated.
- Monitor progress and adjust as needed: Regularly monitor project progress against the plan, and make adjustments as needed. Use project management metrics such as earned value, schedule variance, and cost variance to help you identify potential issues and take corrective action.
Project Management Plan Approval
Project management plan approval is a critical step in the project management process. It is the process of obtaining formal approval of the project management plan from stakeholders, sponsors, and other relevant parties. The approval process is important because it ensures that everyone is on the same page about the project and its objectives, and that there is agreement on how the project will be executed, monitored, and controlled.
To obtain project management plan approval, you should:
- Identify the stakeholders: Identify all stakeholders who have a vested interest in the project, such as sponsors, customers, team members, and regulatory bodies.
- Present the plan: Present the project management plan to the stakeholders in a clear and concise manner. Be prepared to answer any questions or concerns they may have.
- Obtain feedback: Solicit feedback from stakeholders to ensure that their expectations and concerns have been addressed in the plan.
- Revise the plan: Revise the project management plan based on feedback received from stakeholders.
- Obtain formal approval: Once the plan has been revised, obtain formal approval from stakeholders. This approval may be in the form of a signed document, email approval, or verbal confirmation.
How Is Project Management Different From Financial Management?
Project management and financial management are two distinct disciplines that have different goals, objectives, and tools. While both are important for the success of an organization, there are some fundamental differences between them.
Project management is focused on the planning, execution, and control of projects to achieve specific objectives. Project managers are responsible for managing resources, timelines, budgets, risks, and stakeholders to deliver a project on time, within budget, and with the desired quality.
On the other hand, financial management is focused on managing the financial resources of an organization to achieve its strategic goals. Financial managers are responsible for managing cash flow, analyzing financial statements, forecasting, budgeting, and investment decisions.
Some key differences between project management and financial management are:
- Objectives: The objective of project management is to deliver a specific project with specific goals and objectives, while the objective of financial management is to manage financial resources to achieve the overall strategic goals of the organization.
- Time horizon: Project management is generally short-term in nature and has a specific timeline, while financial management is a long-term process that involves managing the financial health of the organization over time.
- Tools and techniques: Project managers use tools and techniques such as Gantt charts, project schedules, risk management plans, and quality control plans to manage projects, while financial managers use financial statements, budgeting tools, and financial ratios to manage financial resources.
- Focus: Project management is focused on achieving specific project objectives, while financial management is focused on the overall financial health and sustainability of the organization.
How to obtain the PMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM
- Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
Conclusion
In conclusion, project management and financial management are two essential functions in any organization, but they have different objectives, time horizons, tools, and focuses. Project management is focused on delivering specific projects within a defined timeline, budget, and quality, while financial management is focused on managing financial resources to achieve the overall strategic goals of the organization. Understanding the differences between these two disciplines is important for managers to allocate resources, manage risks, and achieve their organizational objectives. By leveraging the right tools and techniques, project managers and financial managers can work together to ensure the success of their organization.
What is CAPM Certification ? , Benefits of CAPM Certification & CAPM Certification Training Options
The CAPM Certification, which stands for Certified Associate in Project Management, is a highly recognized credential offered by the Project Management Institute (PMI). It is designed for individuals who are interested in pursuing a career in project management or wish to demonstrate their foundational knowledge and understanding of project management principles. The CAPM certification serves as a stepping stone for professionals who are starting their journey in the field of project management. It validates their ability to contribute effectively to project teams and demonstrates their commitment to enhancing their project management skills. To earn the CAPM certification, candidates need to meet specific eligibility requirements and pass the CAPM exam, which covers essential project management topics such as project lifecycle, scope management, schedule management, cost management, risk management, and more. Achieving the CAPM certification not only enhances one's professional credibility but also opens up new job opportunities and provides access to a global network of project management professionals. It is an investment in one's career growth and can lead to further certifications and advancement in the project management field.
Table of Contents
- Introduction to CAPM Certification:
- Understanding the CAPM Exam:
- CAPM Exam Preparation Tips:
- Key Concepts and Knowledge Areas Covered in CAPM:
- Benefits of CAPM Certification:
- CAPM Certification Training Options:
- Maintaining and Renewing CAPM Certification:
- Conclusion:
Introduction to CAPM Certification
The Certified Associate in Project Management (CAPM) certification is a valuable credential offered by the Project Management Institute (PMI). It is designed for individuals who are new to project management or who are looking to establish a solid foundation in this field. Whether you are a recent graduate, a career changer, or a professional seeking to enhance your project management skills, CAPM certification can open doors to exciting opportunities.
What is CAPM?
CAPM stands for Certified Associate in Project Management. It is a globally recognized certification that validates your understanding of fundamental project management concepts, terminology, and processes. The CAPM certification demonstrates your commitment to professional growth and showcases your ability to contribute effectively to project teams.
Importance and Benefits of CAPM Certification
Obtaining CAPM certification offers several benefits that can boost your career in project management:
- Establishing Credibility: CAPM certification validates your knowledge and expertise in project management, which can enhance your credibility among employers, colleagues, and clients. It demonstrates your commitment to professional development and adherence to industry standards.
- Widening Career Opportunities: CAPM certification expands your career options in various industries and sectors that require skilled project managers. It serves as a valuable asset when applying for project management positions, enabling you to stand out from other candidates.
- Building a Strong Foundation: CAPM provides you with a comprehensive understanding of project management principles, best practices, and processes. It equips you with the knowledge and skills necessary to contribute effectively to project teams and execute projects successfully.
- Networking Opportunities: CAPM certification connects you with a global community of project management professionals. You gain access to PMI's extensive network, allowing you to collaborate, share experiences, and learn from seasoned project managers.
Target Audience for CAPM Certification
CAPM certification is ideal for individuals who are at the early stages of their project management careers, including:
- Entry-Level Project Managers: CAPM certification serves as an excellent starting point for those aspiring to become project managers. It provides a solid foundation and validates their understanding of project management principles.
- Project Team Members: If you are currently working as part of a project team and want to enhance your project management knowledge and contribute more effectively, CAPM certification can be a valuable asset.
- Career Changers: If you are transitioning into project management from another field, CAPM certification can help you acquire the necessary knowledge and skills to make a successful switch.
- Recent Graduates: CAPM certification offers recent graduates an opportunity to differentiate themselves in a competitive job market. It demonstrates their commitment to professional growth and prepares them for project management roles.
Understanding the CAPM Exam
To pursue CAPM certification, it is important to have a clear understanding of the CAPM exam. This section will provide an overview of the exam, including its requirements, format, and key details, to help candidates prepare effectively.
Exam Requirements and Eligibility Criteria: To be eligible for the CAPM exam, candidates must meet the following requirements:
- Secondary Education: Candidates should have a high school diploma, an associate's degree, or an equivalent global qualification.
- Project Management Education: Completion of 23 hours of formal project management education is required. This can be fulfilled through PMI-approved training courses or educational programs.
Exam Format and Structure: The CAPM exam is a computer-based test consisting of 150 multiple-choice questions. Among these questions, 15 are pretest questions that are not scored and are used for future exam development. The remaining 135 questions contribute to the final score. The exam covers ten knowledge areas from the Project Management Body of Knowledge (PMBOK® Guide).
Registration Process and Fees: To register for the CAPM exam, follow these steps:
- Create a PMI Account: Visit the official PMI website and create an account.
- Complete the Application: Fill out the CAPM certification application, providing information about your educational background and project management education.
- Application Review: PMI will review your application, and upon approval, you will receive instructions for exam payment.
- Schedule the Exam: After payment, you can schedule the exam at a Prometric testing center or choose the online proctored exam option.
- Exam Fee: The exam fee varies for PMI members and non-members, with PMI members receiving a discounted rate.
Exam Preparation: To prepare for the CAPM exam, candidates can utilize various resources such as study guides, practice exams, and online training courses. It is important to create a study plan, allocate sufficient time for each knowledge area, and practice answering sample questions to become familiar with the exam format and content.
Exam Scoring and Passing Criteria: The CAPM exam is scored on a scale of 0-500, with 300 considered the passing score. Candidates receive the pass/fail result immediately upon completion of the exam. Those who pass the exam will be awarded the CAPM certification.
Understanding the CAPM exam's requirements, format, registration process, and preparation strategies is vital for candidates aiming to achieve CAPM certification. By familiarizing themselves with these aspects, candidates can approach the exam with confidence and increase their chances of success.
CAPM Exam Preparation Tips
Preparing for the CAPM exam requires a structured and focused approach. Here are some tips to help you effectively prepare for the exam:
- Understand the Exam Content: Familiarize yourself with the CAPM exam content outline and the ten knowledge areas covered in the PMBOK® Guide. Understand the key processes, concepts, and terms associated with each knowledge area.
- Create a Study Plan: Develop a study plan that outlines your preparation timeline, study materials, and dedicated study hours. Breaking down the content into manageable sections and setting specific goals for each study session will help you stay organized and focused.
- Utilize Study Resources: Make use of CAPM exam study guides, reference books, online courses, and practice exams. PMI provides official study resources, including the CAPM Exam Content Outline and the CAPM Handbook, which are valuable references for exam preparation.
- Practice with Sample Questions: Solve sample questions and practice exams to become familiar with the exam format and question types. This will help you identify areas where you need to improve and enhance your understanding of the content. Analyze the explanations for both correct and incorrect answers to deepen your knowledge.
- Join Study Groups or Forums: Engage with fellow CAPM candidates by joining study groups or online forums. Discussion and collaboration can provide different perspectives and help reinforce your understanding of the concepts. It also offers an opportunity to share tips, resources, and exam experiences.
- Take Mock Exams: Simulate the exam experience by taking mock exams under timed conditions. This will help you assess your readiness, build your exam stamina, and identify areas where you need further improvement.
- Review and Reinforce: Regularly review the material you have studied to reinforce your understanding and retention. Focus on areas that you find challenging or need further clarification. Consider creating flashcards or summaries to aid in revision.
- Understand PMI's Approach: Familiarize yourself with PMI's project management methodology and approach, as outlined in the PMBOK® Guide. Understand how PMI expects project managers to apply the knowledge and processes in real-world scenarios.
- Time Management: Develop effective time management strategies for the exam. Understand the time constraints for each question and allocate your time accordingly. If you encounter a challenging question, mark it for review and move on to avoid getting stuck.
- Take Care of Yourself: Maintain a healthy lifestyle during your exam preparation. Get adequate sleep, eat well, exercise, and manage stress. A well-rested and focused mind will help you retain information better and perform optimally during the exam.
Key Concepts and Knowledge Areas Covered in CAPM
The CAPM certification covers essential project management concepts and knowledge areas. Here are the key knowledge areas that you should focus on during your CAPM exam preparation:
- Project Integration Management:
- Developing project charters and project management plans.
- Directing and managing project work.
- Monitoring and controlling project work.
- Performing integrated change control.
- Closing project or phase.
- Project Scope Management:
- Planning scope management.
- Collecting project requirements.
- Defining project scope.
- Creating a work breakdown structure (WBS).
- Validating and controlling project scope.
- Project Schedule Management:
- Defining project activities.
- Sequencing activities.
- Estimating activity resources and durations.
- Developing and controlling the project schedule.
- Project Cost Management:
- Estimating costs.
- Determining the project budget.
- Controlling project costs.
- Project Quality Management:
- Planning quality management.
- Performing quality assurance.
- Controlling project quality.
- Project Resource Management:
- Planning resource management.
- Estimating resource requirements.
- Acquiring, developing, and managing project teams.
- Controlling project resources.
- Project Communications Management:
- Planning communications management.
- Managing and controlling project communications.
- Project Risk Management:
- Planning risk management.
- Identifying project risks.
- Performing qualitative and quantitative risk analysis.
- Planning risk responses.
- Monitoring and controlling project risks.
- Project Procurement Management:
- Planning procurement management.
- Conducting procurement.
- Controlling procurement.
- Project Stakeholder Management:
- Identifying stakeholders.
- Planning stakeholder engagement.
- Managing stakeholder engagement.
- Monitoring stakeholder engagement.
These knowledge areas, as outlined in the Project Management Body of Knowledge (PMBOK® Guide), provide a comprehensive framework for understanding project management processes, practices, and terminology. By developing a solid understanding of these knowledge areas and their interrelationships, you will be well-equipped to handle project management challenges and contribute effectively to project teams.
Benefits of CAPM Certification
Obtaining CAPM (Certified Associate in Project Management) certification offers numerous benefits for individuals in their project management careers. Here are some key benefits of CAPM certification:
- Enhanced Career Opportunities: CAPM certification provides a competitive edge in the job market. It demonstrates your commitment to professional development and validates your knowledge of project management principles and practices. Many organizations specifically look for CAPM-certified professionals when hiring for entry-level project management positions.
- Widened Skill Set: CAPM certification equips you with a solid foundation in project management. It covers essential knowledge areas, processes, and terminology, enabling you to understand and contribute effectively to project teams. The certification enhances your ability to initiate, plan, execute, monitor, control, and close projects, boosting your overall skill set.
- Global Recognition: CAPM is a globally recognized certification offered by the Project Management Institute (PMI), a renowned professional association in the field of project management. The certification is recognized and respected across industries and countries, providing you with credibility and mobility in your career.
- Networking Opportunities: CAPM certification connects you with a vast network of project management professionals. You gain access to PMI's global community, including local chapters and online forums, where you can interact, collaborate, and learn from experienced project managers. Networking can lead to valuable connections, job opportunities, and professional growth.
- Improved Project Performance: The knowledge gained through CAPM certification enables you to apply project management best practices, methodologies, and tools. This can lead to improved project planning, execution, and control, resulting in enhanced project performance, increased efficiency, and successful project outcomes.
- Professional Development: CAPM certification demonstrates your commitment to continuous learning and professional development. It showcases your dedication to staying updated with industry standards and practices. As a CAPM-certified professional, you are encouraged to pursue further certifications, such as the Project Management Professional (PMP) certification, to advance your career.
- Increased Earning Potential: CAPM certification can positively impact your earning potential. Certified professionals often command higher salaries than their non-certified counterparts. The certification serves as evidence of your expertise and can be a decisive factor in negotiations and promotions.
- Transferable Skills: The skills acquired through CAPM certification are transferable across industries and sectors. Project management is applicable in various domains, making CAPM certification valuable in diverse career paths, from IT to construction, healthcare to finance.
CAPM Certification Training Options
When it comes to CAPM certification training, you have several options to choose from based on your learning preferences, schedule, and budget. Here are some popular CAPM certification training options:
- Instructor-Led Classroom Training: Many training providers offer instructor-led classroom training for CAPM certification. These training sessions are typically conducted by experienced instructors who guide you through the CAPM exam content, knowledge areas, and provide interactive learning experiences. This option allows for direct interaction with the instructor and fellow participants, facilitating discussion and knowledge sharing.
- Online Instructor-Led Training: Online instructor-led training provides the flexibility of attending CAPM certification courses remotely. These virtual training sessions are conducted in real-time, allowing you to interact with the instructor and other participants through video conferencing or collaboration tools. Online training offers convenience, as you can attend from anywhere with an internet connection.
- Self-Paced Online Courses: Self-paced online courses provide flexibility in terms of study schedule. You can access pre-recorded video lessons, study materials, and practice exams at your own pace. These courses often include interactive elements and quizzes to reinforce learning. Self-paced courses are suitable for individuals who prefer independent study and have a busy schedule.
- Boot Camps: CAPM certification boot camps are intensive training programs designed to accelerate your exam preparation. These boot camps typically span a few days and offer comprehensive coverage of the CAPM exam content. Boot camps often involve a combination of classroom instruction, group activities, and practice exams to maximize learning in a condensed timeframe.
- Study Guides and Books: CAPM certification study guides and books are valuable self-study resources. These publications are specifically tailored to the CAPM exam content, providing in-depth coverage of the knowledge areas and practice questions. They serve as a comprehensive reference and can supplement other training options.
- Online Learning Platforms: Online learning platforms, such as Udemy, Coursera, and LinkedIn Learning, offer a variety of CAPM certification courses. These platforms provide a range of options, including video-based courses, practice exams, and supplementary materials. You can choose courses based on user ratings, reviews, and specific learning objectives.
How to obtain the CAPM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM
- Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
Maintaining and Renewing CAPM Certification
Maintaining and renewing your CAPM (Certified Associate in Project Management) certification is essential to ensure its validity and demonstrate your commitment to ongoing professional development. Here are the key steps and requirements for maintaining and renewing your CAPM certification:
- Continuing Education:
- CAPM certification requires you to engage in ongoing professional development activities to earn Professional Development Units (PDUs). PDUs are units that reflect the time and effort you dedicate to learning, growing, and staying current in the field of project management.
- As a CAPM holder, you need to earn 15 PDUs every three years to maintain your certification. These PDUs can be obtained through various activities, such as attending project management seminars, webinars, conferences, training courses, or engaging in self-directed learning.
- Reporting PDUs:
- You must track and report your earned PDUs through the PMI Continuing Certification Requirements System (CCRS). This online system allows you to log your PDUs and submit them for review and approval.
- PDUs can be reported under different categories, such as Education, Giving Back, and Working as a Professional. Each category has specific requirements and limitations, so ensure that you understand and comply with the guidelines when reporting your PDUs.
- CAPM Certification Renewal:
- CAPM certification is valid for five years from the date of certification. To renew your CAPM certification, you need to meet the continuing education requirements and submit the renewal application.
- Before your certification expires, you should gather the necessary documentation and evidence of your earned PDUs. The PMI audit process randomly selects a percentage of CAPM holders for audit, requiring them to provide supporting documentation for their reported PDUs.
- After successfully completing the renewal application and any required audits, you will receive notification of your CAPM certification renewal.
- Transitioning to PMP Certification:
- As a CAPM holder, you may choose to transition to the Project Management Professional (PMP) certification as you gain the necessary experience. The PMP certification requires a higher level of project management experience and has its own set of requirements and renewal criteria.
- If you decide to pursue the PMP certification, the PDUs you earned for maintaining your CAPM certification can be applied towards the PMP renewal requirements.
Conclusion
In conclusion, obtaining the CAPM certification offers numerous benefits for individuals interested in pursuing a career in project management. It demonstrates your knowledge and understanding of project management principles, enhances your career opportunities, and provides global recognition. The CAPM exam covers essential knowledge areas, and with proper exam preparation, you can increase your chances of success.
To effectively prepare for the CAPM exam, it is important to understand the exam content, create a study plan, utilize study resources, practice with sample questions, and join study groups or forums. Taking mock exams and reviewing the material regularly will help reinforce your understanding and identify areas for improvement. Additionally, understanding PMI's project management approach and practicing effective time management are crucial for success.
Once you obtain the CAPM certification, it is important to maintain and renew it by earning PDUs through ongoing professional development activities. Reporting your PDUs and complying with the renewal requirements will ensure the validity and continued relevance of your certification.
By investing in CAPM certification and maintaining your professional development, you can establish yourself as a competent project management professional, increase your career prospects, and contribute to successful project outcomes. Remember to stay engaged, continue learning, and adapt to the evolving project management landscape to excel in your project management journey.
Read More
The CAPM Certification, which stands for Certified Associate in Project Management, is a highly recognized credential offered by the Project Management Institute (PMI). It is designed for individuals who are interested in pursuing a career in project management or wish to demonstrate their foundational knowledge and understanding of project management principles. The CAPM certification serves as a stepping stone for professionals who are starting their journey in the field of project management. It validates their ability to contribute effectively to project teams and demonstrates their commitment to enhancing their project management skills. To earn the CAPM certification, candidates need to meet specific eligibility requirements and pass the CAPM exam, which covers essential project management topics such as project lifecycle, scope management, schedule management, cost management, risk management, and more. Achieving the CAPM certification not only enhances one's professional credibility but also opens up new job opportunities and provides access to a global network of project management professionals. It is an investment in one's career growth and can lead to further certifications and advancement in the project management field.
Table of Contents
- Introduction to CAPM Certification:
- Understanding the CAPM Exam:
- CAPM Exam Preparation Tips:
- Key Concepts and Knowledge Areas Covered in CAPM:
- Benefits of CAPM Certification:
- CAPM Certification Training Options:
- Maintaining and Renewing CAPM Certification:
- Conclusion:
Introduction to CAPM Certification
The Certified Associate in Project Management (CAPM) certification is a valuable credential offered by the Project Management Institute (PMI). It is designed for individuals who are new to project management or who are looking to establish a solid foundation in this field. Whether you are a recent graduate, a career changer, or a professional seeking to enhance your project management skills, CAPM certification can open doors to exciting opportunities.
What is CAPM?
CAPM stands for Certified Associate in Project Management. It is a globally recognized certification that validates your understanding of fundamental project management concepts, terminology, and processes. The CAPM certification demonstrates your commitment to professional growth and showcases your ability to contribute effectively to project teams.
Importance and Benefits of CAPM Certification
Obtaining CAPM certification offers several benefits that can boost your career in project management:
- Establishing Credibility: CAPM certification validates your knowledge and expertise in project management, which can enhance your credibility among employers, colleagues, and clients. It demonstrates your commitment to professional development and adherence to industry standards.
- Widening Career Opportunities: CAPM certification expands your career options in various industries and sectors that require skilled project managers. It serves as a valuable asset when applying for project management positions, enabling you to stand out from other candidates.
- Building a Strong Foundation: CAPM provides you with a comprehensive understanding of project management principles, best practices, and processes. It equips you with the knowledge and skills necessary to contribute effectively to project teams and execute projects successfully.
- Networking Opportunities: CAPM certification connects you with a global community of project management professionals. You gain access to PMI's extensive network, allowing you to collaborate, share experiences, and learn from seasoned project managers.
Target Audience for CAPM Certification
CAPM certification is ideal for individuals who are at the early stages of their project management careers, including:
- Entry-Level Project Managers: CAPM certification serves as an excellent starting point for those aspiring to become project managers. It provides a solid foundation and validates their understanding of project management principles.
- Project Team Members: If you are currently working as part of a project team and want to enhance your project management knowledge and contribute more effectively, CAPM certification can be a valuable asset.
- Career Changers: If you are transitioning into project management from another field, CAPM certification can help you acquire the necessary knowledge and skills to make a successful switch.
- Recent Graduates: CAPM certification offers recent graduates an opportunity to differentiate themselves in a competitive job market. It demonstrates their commitment to professional growth and prepares them for project management roles.
Understanding the CAPM Exam
To pursue CAPM certification, it is important to have a clear understanding of the CAPM exam. This section will provide an overview of the exam, including its requirements, format, and key details, to help candidates prepare effectively.
Exam Requirements and Eligibility Criteria: To be eligible for the CAPM exam, candidates must meet the following requirements:
- Secondary Education: Candidates should have a high school diploma, an associate's degree, or an equivalent global qualification.
- Project Management Education: Completion of 23 hours of formal project management education is required. This can be fulfilled through PMI-approved training courses or educational programs.
Exam Format and Structure: The CAPM exam is a computer-based test consisting of 150 multiple-choice questions. Among these questions, 15 are pretest questions that are not scored and are used for future exam development. The remaining 135 questions contribute to the final score. The exam covers ten knowledge areas from the Project Management Body of Knowledge (PMBOK® Guide).
Registration Process and Fees: To register for the CAPM exam, follow these steps:
- Create a PMI Account: Visit the official PMI website and create an account.
- Complete the Application: Fill out the CAPM certification application, providing information about your educational background and project management education.
- Application Review: PMI will review your application, and upon approval, you will receive instructions for exam payment.
- Schedule the Exam: After payment, you can schedule the exam at a Prometric testing center or choose the online proctored exam option.
- Exam Fee: The exam fee varies for PMI members and non-members, with PMI members receiving a discounted rate.
Exam Preparation: To prepare for the CAPM exam, candidates can utilize various resources such as study guides, practice exams, and online training courses. It is important to create a study plan, allocate sufficient time for each knowledge area, and practice answering sample questions to become familiar with the exam format and content.
Exam Scoring and Passing Criteria: The CAPM exam is scored on a scale of 0-500, with 300 considered the passing score. Candidates receive the pass/fail result immediately upon completion of the exam. Those who pass the exam will be awarded the CAPM certification.
Understanding the CAPM exam's requirements, format, registration process, and preparation strategies is vital for candidates aiming to achieve CAPM certification. By familiarizing themselves with these aspects, candidates can approach the exam with confidence and increase their chances of success.
CAPM Exam Preparation Tips
Preparing for the CAPM exam requires a structured and focused approach. Here are some tips to help you effectively prepare for the exam:
- Understand the Exam Content: Familiarize yourself with the CAPM exam content outline and the ten knowledge areas covered in the PMBOK® Guide. Understand the key processes, concepts, and terms associated with each knowledge area.
- Create a Study Plan: Develop a study plan that outlines your preparation timeline, study materials, and dedicated study hours. Breaking down the content into manageable sections and setting specific goals for each study session will help you stay organized and focused.
- Utilize Study Resources: Make use of CAPM exam study guides, reference books, online courses, and practice exams. PMI provides official study resources, including the CAPM Exam Content Outline and the CAPM Handbook, which are valuable references for exam preparation.
- Practice with Sample Questions: Solve sample questions and practice exams to become familiar with the exam format and question types. This will help you identify areas where you need to improve and enhance your understanding of the content. Analyze the explanations for both correct and incorrect answers to deepen your knowledge.
- Join Study Groups or Forums: Engage with fellow CAPM candidates by joining study groups or online forums. Discussion and collaboration can provide different perspectives and help reinforce your understanding of the concepts. It also offers an opportunity to share tips, resources, and exam experiences.
- Take Mock Exams: Simulate the exam experience by taking mock exams under timed conditions. This will help you assess your readiness, build your exam stamina, and identify areas where you need further improvement.
- Review and Reinforce: Regularly review the material you have studied to reinforce your understanding and retention. Focus on areas that you find challenging or need further clarification. Consider creating flashcards or summaries to aid in revision.
- Understand PMI's Approach: Familiarize yourself with PMI's project management methodology and approach, as outlined in the PMBOK® Guide. Understand how PMI expects project managers to apply the knowledge and processes in real-world scenarios.
- Time Management: Develop effective time management strategies for the exam. Understand the time constraints for each question and allocate your time accordingly. If you encounter a challenging question, mark it for review and move on to avoid getting stuck.
- Take Care of Yourself: Maintain a healthy lifestyle during your exam preparation. Get adequate sleep, eat well, exercise, and manage stress. A well-rested and focused mind will help you retain information better and perform optimally during the exam.
Key Concepts and Knowledge Areas Covered in CAPM
The CAPM certification covers essential project management concepts and knowledge areas. Here are the key knowledge areas that you should focus on during your CAPM exam preparation:
- Project Integration Management:
- Developing project charters and project management plans.
- Directing and managing project work.
- Monitoring and controlling project work.
- Performing integrated change control.
- Closing project or phase.
- Project Scope Management:
- Planning scope management.
- Collecting project requirements.
- Defining project scope.
- Creating a work breakdown structure (WBS).
- Validating and controlling project scope.
- Project Schedule Management:
- Defining project activities.
- Sequencing activities.
- Estimating activity resources and durations.
- Developing and controlling the project schedule.
- Project Cost Management:
- Estimating costs.
- Determining the project budget.
- Controlling project costs.
- Project Quality Management:
- Planning quality management.
- Performing quality assurance.
- Controlling project quality.
- Project Resource Management:
- Planning resource management.
- Estimating resource requirements.
- Acquiring, developing, and managing project teams.
- Controlling project resources.
- Project Communications Management:
- Planning communications management.
- Managing and controlling project communications.
- Project Risk Management:
- Planning risk management.
- Identifying project risks.
- Performing qualitative and quantitative risk analysis.
- Planning risk responses.
- Monitoring and controlling project risks.
- Project Procurement Management:
- Planning procurement management.
- Conducting procurement.
- Controlling procurement.
- Project Stakeholder Management:
- Identifying stakeholders.
- Planning stakeholder engagement.
- Managing stakeholder engagement.
- Monitoring stakeholder engagement.
These knowledge areas, as outlined in the Project Management Body of Knowledge (PMBOK® Guide), provide a comprehensive framework for understanding project management processes, practices, and terminology. By developing a solid understanding of these knowledge areas and their interrelationships, you will be well-equipped to handle project management challenges and contribute effectively to project teams.
Benefits of CAPM Certification
Obtaining CAPM (Certified Associate in Project Management) certification offers numerous benefits for individuals in their project management careers. Here are some key benefits of CAPM certification:
- Enhanced Career Opportunities: CAPM certification provides a competitive edge in the job market. It demonstrates your commitment to professional development and validates your knowledge of project management principles and practices. Many organizations specifically look for CAPM-certified professionals when hiring for entry-level project management positions.
- Widened Skill Set: CAPM certification equips you with a solid foundation in project management. It covers essential knowledge areas, processes, and terminology, enabling you to understand and contribute effectively to project teams. The certification enhances your ability to initiate, plan, execute, monitor, control, and close projects, boosting your overall skill set.
- Global Recognition: CAPM is a globally recognized certification offered by the Project Management Institute (PMI), a renowned professional association in the field of project management. The certification is recognized and respected across industries and countries, providing you with credibility and mobility in your career.
- Networking Opportunities: CAPM certification connects you with a vast network of project management professionals. You gain access to PMI's global community, including local chapters and online forums, where you can interact, collaborate, and learn from experienced project managers. Networking can lead to valuable connections, job opportunities, and professional growth.
- Improved Project Performance: The knowledge gained through CAPM certification enables you to apply project management best practices, methodologies, and tools. This can lead to improved project planning, execution, and control, resulting in enhanced project performance, increased efficiency, and successful project outcomes.
- Professional Development: CAPM certification demonstrates your commitment to continuous learning and professional development. It showcases your dedication to staying updated with industry standards and practices. As a CAPM-certified professional, you are encouraged to pursue further certifications, such as the Project Management Professional (PMP) certification, to advance your career.
- Increased Earning Potential: CAPM certification can positively impact your earning potential. Certified professionals often command higher salaries than their non-certified counterparts. The certification serves as evidence of your expertise and can be a decisive factor in negotiations and promotions.
- Transferable Skills: The skills acquired through CAPM certification are transferable across industries and sectors. Project management is applicable in various domains, making CAPM certification valuable in diverse career paths, from IT to construction, healthcare to finance.
CAPM Certification Training Options
When it comes to CAPM certification training, you have several options to choose from based on your learning preferences, schedule, and budget. Here are some popular CAPM certification training options:
- Instructor-Led Classroom Training: Many training providers offer instructor-led classroom training for CAPM certification. These training sessions are typically conducted by experienced instructors who guide you through the CAPM exam content, knowledge areas, and provide interactive learning experiences. This option allows for direct interaction with the instructor and fellow participants, facilitating discussion and knowledge sharing.
- Online Instructor-Led Training: Online instructor-led training provides the flexibility of attending CAPM certification courses remotely. These virtual training sessions are conducted in real-time, allowing you to interact with the instructor and other participants through video conferencing or collaboration tools. Online training offers convenience, as you can attend from anywhere with an internet connection.
- Self-Paced Online Courses: Self-paced online courses provide flexibility in terms of study schedule. You can access pre-recorded video lessons, study materials, and practice exams at your own pace. These courses often include interactive elements and quizzes to reinforce learning. Self-paced courses are suitable for individuals who prefer independent study and have a busy schedule.
- Boot Camps: CAPM certification boot camps are intensive training programs designed to accelerate your exam preparation. These boot camps typically span a few days and offer comprehensive coverage of the CAPM exam content. Boot camps often involve a combination of classroom instruction, group activities, and practice exams to maximize learning in a condensed timeframe.
- Study Guides and Books: CAPM certification study guides and books are valuable self-study resources. These publications are specifically tailored to the CAPM exam content, providing in-depth coverage of the knowledge areas and practice questions. They serve as a comprehensive reference and can supplement other training options.
- Online Learning Platforms: Online learning platforms, such as Udemy, Coursera, and LinkedIn Learning, offer a variety of CAPM certification courses. These platforms provide a range of options, including video-based courses, practice exams, and supplementary materials. You can choose courses based on user ratings, reviews, and specific learning objectives.
How to obtain the CAPM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM
- Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
Maintaining and Renewing CAPM Certification
Maintaining and renewing your CAPM (Certified Associate in Project Management) certification is essential to ensure its validity and demonstrate your commitment to ongoing professional development. Here are the key steps and requirements for maintaining and renewing your CAPM certification:
- Continuing Education:
- CAPM certification requires you to engage in ongoing professional development activities to earn Professional Development Units (PDUs). PDUs are units that reflect the time and effort you dedicate to learning, growing, and staying current in the field of project management.
- As a CAPM holder, you need to earn 15 PDUs every three years to maintain your certification. These PDUs can be obtained through various activities, such as attending project management seminars, webinars, conferences, training courses, or engaging in self-directed learning.
- Reporting PDUs:
- You must track and report your earned PDUs through the PMI Continuing Certification Requirements System (CCRS). This online system allows you to log your PDUs and submit them for review and approval.
- PDUs can be reported under different categories, such as Education, Giving Back, and Working as a Professional. Each category has specific requirements and limitations, so ensure that you understand and comply with the guidelines when reporting your PDUs.
- CAPM Certification Renewal:
- CAPM certification is valid for five years from the date of certification. To renew your CAPM certification, you need to meet the continuing education requirements and submit the renewal application.
- Before your certification expires, you should gather the necessary documentation and evidence of your earned PDUs. The PMI audit process randomly selects a percentage of CAPM holders for audit, requiring them to provide supporting documentation for their reported PDUs.
- After successfully completing the renewal application and any required audits, you will receive notification of your CAPM certification renewal.
- Transitioning to PMP Certification:
- As a CAPM holder, you may choose to transition to the Project Management Professional (PMP) certification as you gain the necessary experience. The PMP certification requires a higher level of project management experience and has its own set of requirements and renewal criteria.
- If you decide to pursue the PMP certification, the PDUs you earned for maintaining your CAPM certification can be applied towards the PMP renewal requirements.
Conclusion
In conclusion, obtaining the CAPM certification offers numerous benefits for individuals interested in pursuing a career in project management. It demonstrates your knowledge and understanding of project management principles, enhances your career opportunities, and provides global recognition. The CAPM exam covers essential knowledge areas, and with proper exam preparation, you can increase your chances of success.
To effectively prepare for the CAPM exam, it is important to understand the exam content, create a study plan, utilize study resources, practice with sample questions, and join study groups or forums. Taking mock exams and reviewing the material regularly will help reinforce your understanding and identify areas for improvement. Additionally, understanding PMI's project management approach and practicing effective time management are crucial for success.
Once you obtain the CAPM certification, it is important to maintain and renew it by earning PDUs through ongoing professional development activities. Reporting your PDUs and complying with the renewal requirements will ensure the validity and continued relevance of your certification.
By investing in CAPM certification and maintaining your professional development, you can establish yourself as a competent project management professional, increase your career prospects, and contribute to successful project outcomes. Remember to stay engaged, continue learning, and adapt to the evolving project management landscape to excel in your project management journey.
What is Risk Management Professional Certification , overview ,Eligibility ,Requirement, Benefits and Tips
The Risk Management Professional (RMP) Certification is a highly esteemed credential offered by the Project Management Institute (PMI) that focuses on the field of risk management. The RMP certification equips professionals with the knowledge and skills necessary to identify, assess, and mitigate risks effectively within projects and organizations. It provides a comprehensive overview of risk management principles, frameworks, and best practices. To be eligible for the RMP certification, candidates must meet specific requirements, including a combination of education and professional experience in risk management. The certification process involves passing the RMP exam, which covers various areas such as risk identification, risk assessment, risk response planning, and risk monitoring and control. Obtaining the RMP certification brings numerous benefits, including enhanced career prospects, recognition of expertise in risk management, and the ability to contribute effectively to risk management strategies within organizations. To succeed in earning the RMP certification, it is advisable to engage in thorough exam preparation, leverage study materials and resources, and actively apply risk management principles in real-world projects. The RMP certification sets professionals apart in the field of risk management, validating their proficiency and commitment to delivering successful projects while effectively managing risks.
Table of contents
- Introduction to Risk Management:
- Overview of Risk Management Certifications:
- Eligibility and Requirements:
- Exam Structure and Preparation Tips:
- Benefits of Risk Management Certification::
- Conclusion:
Introduction to Risk Management:
Risk management is a crucial process that organizations undertake to identify, assess, and mitigate potential risks that could impact their objectives. It is a systematic approach to analyzing and addressing uncertainties and threats that may hinder the achievement of business goals. By implementing effective risk management practices, businesses can proactively identify vulnerabilities, minimize losses, and seize opportunities.
In today's dynamic and complex business environment, risk management has become increasingly important across industries such as finance, healthcare, construction, IT, and more. Risks can arise from various sources, including financial uncertainties, operational inefficiencies, regulatory compliance issues, natural disasters, cybersecurity threats, and market volatility. Organizations need skilled professionals who can navigate these risks and develop strategies to manage them effectively.
Risk management professionals play a vital role in identifying potential risks, analyzing their potential impact, and devising risk mitigation plans. They apply a structured and disciplined approach to evaluate risks, considering factors such as likelihood, impact, and timeframes. By implementing risk management frameworks, methodologies, and tools, these professionals help organizations make informed decisions, protect their assets, and safeguard their reputation.
The primary objective of risk management is not to eliminate risks entirely, but rather to manage them in a way that aligns with the organization's risk appetite and tolerance. Through risk assessment and prioritization, risk management professionals identify the critical risks that require immediate attention and allocate resources accordingly. This proactive approach helps organizations minimize potential losses, protect stakeholders' interests, and ensure the sustainability of their operations.
Overview of Risk Management Certifications:
Risk management certifications are professional credentials that validate the knowledge, skills, and expertise of individuals in the field of risk management. These certifications provide professionals with a recognized standard of competency and demonstrate their commitment to excellence in managing and mitigating risks. They are offered by various certification bodies and are highly regarded within the risk management industry.
Here are some popular risk management certifications:
- Project Management Institute - Risk Management Professional (PMI-RMP): The PMI-RMP certification is offered by the Project Management Institute (PMI) and focuses on risk management within the project management context. It validates professionals' ability to identify, assess, and mitigate project risks. PMI-RMP holders demonstrate their expertise in risk planning, risk monitoring and control, and risk response strategies.
- Certified Risk Manager (CRM): The Certified Risk Manager designation is offered by the National Alliance for Insurance Education and Research. This certification emphasizes risk management in the insurance industry. CRM holders are well-versed in identifying and analyzing risks, implementing risk management strategies, and developing effective insurance programs to mitigate risks.
- Certified in Risk and Information Systems Control (CRISC): CRISC is a certification offered by ISACA (Information Systems Audit and Control Association) and focuses on risk management in information systems and IT environments. CRISC professionals possess knowledge and expertise in identifying and managing IT risks, implementing information systems controls, and aligning risk management with business objectives.
- Certified Risk Analyst (CRA): The Certified Risk Analyst designation is offered by the Global Association of Risk Professionals (GARP). CRA certification validates professionals' knowledge and understanding of risk assessment and management techniques across various industries. It covers topics such as quantitative risk analysis, risk modeling, and risk mitigation strategies.
- Financial Risk Manager (FRM): The Financial Risk Manager certification is also offered by GARP and is geared towards professionals working in the financial industry. FRM certification focuses on financial risk management, including topics such as market risk, credit risk, operational risk, and risk modeling and measurement techniques.
These certifications typically require candidates to meet specific eligibility criteria, including educational qualifications, professional experience, and passing a rigorous examination. They often have ongoing professional development requirements to ensure that certified professionals stay up-to-date with the latest practices and trends in risk management.
Obtaining a risk management certification can provide several benefits, including enhanced career opportunities, increased marketability, and greater credibility in the field. It demonstrates a commitment to professional growth and can open doors to higher-level positions and increased responsibilities within organizations.
Eligibility and Requirements for Risk Management Certifications:
To pursue a risk management certification, candidates are generally required to meet specific eligibility criteria set by the certifying organization. These criteria ensure that individuals possess the necessary educational background, professional experience, and knowledge to successfully undertake the certification process. While the specific requirements may vary depending on the certification, here are some common eligibility criteria and requirements:
- Educational Background:
- Many risk management certifications require a minimum educational qualification, such as a high school diploma, bachelor's degree, or equivalent.
- Some certifications may have specific educational requirements related to the field of risk management or a related discipline (e.g., finance, project management, information systems).
- Professional Experience:
- Risk management certifications often have experience requirements to ensure candidates have practical exposure to risk management practices.
- The experience requirements may be specified in terms of the number of years of relevant work experience or a combination of education and experience.
- The experience may need to be in a specific industry or role related to risk management.
- Preparatory Courses and Training:
- Some certifications may recommend or require candidates to complete preparatory courses or training programs.
- These courses can provide candidates with the necessary knowledge and skills to succeed in the certification process.
- Preparatory courses may be offered by the certifying organization or by authorized training providers.
- Adherence to a Code of Ethics:
- Many certification programs require candidates to adhere to a code of ethics or professional conduct.
- Candidates may be asked to confirm their commitment to ethical practices in their work as risk management professionals.
- Certification Examination:
- A key requirement for most risk management certifications is passing a certification examination.
- The examination evaluates candidates' knowledge and understanding of risk management principles, frameworks, and practices.
- The format of the examination may vary, but it often consists of multiple-choice questions, scenario-based questions, or a combination of both.
It's important to note that meeting the eligibility criteria does not guarantee certification. Candidates must demonstrate their competence by successfully completing the examination or any other requirements specified by the certifying organization.
Additionally, some risk management certifications require ongoing professional development and continuing education to maintain the certification. This ensures that certified professionals stay updated with the evolving practices and trends in risk management.
Before pursuing a specific risk management certification, it's recommended to thoroughly review the eligibility criteria and requirements provided by the certifying organization. This will help ensure that you meet the necessary qualifications and understand the steps involved in obtaining and maintaining the certification.
Exam Structure and Preparation Tips for Risk Management Certifications:
Understanding the structure of the certification exam and having a solid preparation strategy are crucial for success. While the specific exam structure may vary depending on the certification, here are some general exam structure elements and preparation tips for risk management certifications:
- Familiarize Yourself with the Exam Format:
- Start by thoroughly reviewing the exam structure and format provided by the certifying organization.
- Understand the types of questions you can expect, such as multiple-choice, scenario-based, or essay questions.
- Take note of the allotted time for the exam and any specific instructions or guidelines.
- Review the Exam Content Outline:
- Obtain the exam content outline or syllabus, which highlights the topics and knowledge areas covered in the exam.
- Use the content outline as a guide to identify the areas where you need to focus your studies.
- Create a Study Plan:
- Develop a study plan that outlines your study schedule, topics to cover, and milestones leading up to the exam date.
- Break down the content into manageable sections and allocate sufficient time to review each topic.
- Consider your personal learning style and preferences when designing your study plan.
- Utilize Available Study Materials:
- Take advantage of study materials provided by the certifying organization, such as official textbooks, study guides, or practice exams.
- Seek out additional resources such as online courses, video tutorials, or reference books to supplement your understanding of key concepts.
- Engage in Active Learning:
- Actively engage with the study material rather than passively reading or memorizing.
- Take notes, summarize key points, and create flashcards or study aids to reinforce your understanding.
- Seek opportunities to apply the concepts through practice questions, case studies, or real-life examples.
- Practice with Sample Exams:
- Practice exams are invaluable in familiarizing yourself with the exam format and assessing your knowledge and readiness.
- Take advantage of any sample exams or practice questions provided by the certifying organization or available from reputable sources.
- Analyze your performance, identify areas of weakness, and focus on improving those areas.
- Join Study Groups or Discussion Forums:
- Engage with other candidates preparing for the same certification by joining study groups or participating in online discussion forums.
- Collaborating with others can help clarify doubts, share study strategies, and gain different perspectives on the exam content.
- Simulate Exam Conditions:
- As the exam date approaches, simulate exam conditions during your practice sessions.
- Set a timer and attempt full-length practice exams to build endurance and improve time management skills.
- Mimicking exam conditions will help reduce anxiety and increase your confidence on the actual exam day.
- Review and Revise:
- Allocate sufficient time for comprehensive review and revision before the exam.
- Focus on consolidating your understanding of key concepts, reinforcing weak areas, and clarifying any remaining doubts.
- Use revision techniques that work best for you, such as summarizing notes, creating visual aids, or teaching concepts to someone else.
- Take Care of Yourself:
- Prioritize your well-being and maintain a healthy balance between studying and self-care.
- Get adequate rest, eat nutritious meals, exercise, and manage stress effectively.
- Taking care of your physical and mental well-being will optimize your focus, concentration, and overall performance during the exam.
Benefits of Risk Management Certification:
Obtaining a risk management certification can bring numerous benefits to professionals in the field. Here are some key advantages of earning a risk management certification:
- Enhanced Career Opportunities:
- Risk management certifications provide a competitive edge in the job market by demonstrating your specialized knowledge and expertise.
- Certification can open doors to a wider range of career opportunities, including higher-level positions, leadership roles, and specialized risk management positions.
- Many employers prefer or require risk management certifications when hiring for risk management positions, giving certified professionals a distinct advantage.
- Increased Marketability:
- Risk management certifications enhance your professional credibility and marketability.
- Certified professionals are recognized as having met rigorous standards and demonstrated competence in risk management.
- The certification logo or designation on your resume, LinkedIn profile, or business card serves as a tangible proof of your qualifications, attracting potential employers and clients.
- Demonstrated Commitment to Excellence:
- Earning a risk management certification showcases your commitment to professional growth and continuous learning in the field.
- It demonstrates your dedication to staying updated with the latest risk management practices, industry trends, and emerging technologies.
- Employers value candidates who invest in their professional development, and certification is a tangible representation of that commitment.
- Expanded Knowledge and Skill Set:
- Risk management certifications provide a comprehensive understanding of risk management principles, frameworks, and methodologies.
- Certified professionals acquire in-depth knowledge of risk assessment techniques, risk mitigation strategies, and risk management best practices.
- The certification process often involves extensive study and preparation, enabling professionals to broaden their skill set and deepen their expertise.
- Recognition within the Industry:
- Risk management certifications are widely recognized and respected within the industry.
- Being certified establishes your professional credibility among peers, employers, and clients.
- Certification demonstrates that you have met the industry-recognized standards and have the necessary skills to effectively manage risks in various contexts.
- Networking Opportunities:
- Certification programs often provide access to professional networks, events, and communities.
- Connecting with other certified professionals, industry experts, and thought leaders can expand your professional network and facilitate knowledge sharing.
- Networking opportunities may lead to collaborations, career advancements, and exposure to new job opportunities.
- Continuous Professional Development:
- Many risk management certifications have ongoing professional development requirements, encouraging certified professionals to stay updated and relevant.
- These requirements often involve completing continuing education courses, attending conferences, participating in webinars, or engaging in other learning activities.
- Continuous professional development ensures that certified professionals stay current with evolving risk management practices and maintain their certification status.
How to obtain the PMI RMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
Conclusion
In conclusion, risk management certifications play a vital role in the professional development of individuals in the field of risk management. These certifications provide a recognized standard of competency, demonstrating expertise in identifying, assessing, and mitigating risks. By earning a risk management certification, professionals can enjoy a range of benefits.
First and foremost, certifications enhance career opportunities by opening doors to higher-level positions, specialized roles, and leadership positions. They make professionals more marketable, as employers often prefer or require certifications when hiring for risk management positions. The certification designation on resumes and profiles serves as a tangible proof of qualifications and credibility.
Risk management certifications also demonstrate a commitment to excellence and continuous learning. They show that professionals have met rigorous standards and are dedicated to staying updated with the latest practices and trends. This dedication to professional growth is highly valued by employers and clients alike.
Earning a risk management certification expands professionals' knowledge and skill set. The certification process involves in-depth study and preparation, providing a comprehensive understanding of risk management principles, frameworks, and methodologies. This knowledge equips professionals with the ability to assess risks, develop effective risk mitigation strategies, and make informed decisions.
Certifications are widely recognized within the industry, enhancing professionals' credibility and recognition among peers, employers, and clients. They establish professionals as trusted experts who have met industry-recognized standards. Additionally, certifications provide networking opportunities, allowing professionals to connect with other certified individuals, industry experts, and thought leaders, fostering collaboration and career advancement.
Furthermore, risk management certifications often have ongoing professional development requirements, ensuring that certified professionals stay updated and relevant. This continuous learning helps professionals remain at the forefront of risk management practices, enabling them to adapt to evolving challenges and technologies.
In summary, risk management certifications offer a range of benefits, including enhanced career opportunities, increased marketability, and recognition within the industry. By earning a certification, professionals demonstrate their expertise, expand their knowledge, and gain a competitive edge in the field of risk management.
Read More
The Risk Management Professional (RMP) Certification is a highly esteemed credential offered by the Project Management Institute (PMI) that focuses on the field of risk management. The RMP certification equips professionals with the knowledge and skills necessary to identify, assess, and mitigate risks effectively within projects and organizations. It provides a comprehensive overview of risk management principles, frameworks, and best practices. To be eligible for the RMP certification, candidates must meet specific requirements, including a combination of education and professional experience in risk management. The certification process involves passing the RMP exam, which covers various areas such as risk identification, risk assessment, risk response planning, and risk monitoring and control. Obtaining the RMP certification brings numerous benefits, including enhanced career prospects, recognition of expertise in risk management, and the ability to contribute effectively to risk management strategies within organizations. To succeed in earning the RMP certification, it is advisable to engage in thorough exam preparation, leverage study materials and resources, and actively apply risk management principles in real-world projects. The RMP certification sets professionals apart in the field of risk management, validating their proficiency and commitment to delivering successful projects while effectively managing risks.
Table of contents
- Introduction to Risk Management:
- Overview of Risk Management Certifications:
- Eligibility and Requirements:
- Exam Structure and Preparation Tips:
- Benefits of Risk Management Certification::
- Conclusion:
Introduction to Risk Management:
Risk management is a crucial process that organizations undertake to identify, assess, and mitigate potential risks that could impact their objectives. It is a systematic approach to analyzing and addressing uncertainties and threats that may hinder the achievement of business goals. By implementing effective risk management practices, businesses can proactively identify vulnerabilities, minimize losses, and seize opportunities.
In today's dynamic and complex business environment, risk management has become increasingly important across industries such as finance, healthcare, construction, IT, and more. Risks can arise from various sources, including financial uncertainties, operational inefficiencies, regulatory compliance issues, natural disasters, cybersecurity threats, and market volatility. Organizations need skilled professionals who can navigate these risks and develop strategies to manage them effectively.
Risk management professionals play a vital role in identifying potential risks, analyzing their potential impact, and devising risk mitigation plans. They apply a structured and disciplined approach to evaluate risks, considering factors such as likelihood, impact, and timeframes. By implementing risk management frameworks, methodologies, and tools, these professionals help organizations make informed decisions, protect their assets, and safeguard their reputation.
The primary objective of risk management is not to eliminate risks entirely, but rather to manage them in a way that aligns with the organization's risk appetite and tolerance. Through risk assessment and prioritization, risk management professionals identify the critical risks that require immediate attention and allocate resources accordingly. This proactive approach helps organizations minimize potential losses, protect stakeholders' interests, and ensure the sustainability of their operations.
Overview of Risk Management Certifications:
Risk management certifications are professional credentials that validate the knowledge, skills, and expertise of individuals in the field of risk management. These certifications provide professionals with a recognized standard of competency and demonstrate their commitment to excellence in managing and mitigating risks. They are offered by various certification bodies and are highly regarded within the risk management industry.
Here are some popular risk management certifications:
- Project Management Institute - Risk Management Professional (PMI-RMP): The PMI-RMP certification is offered by the Project Management Institute (PMI) and focuses on risk management within the project management context. It validates professionals' ability to identify, assess, and mitigate project risks. PMI-RMP holders demonstrate their expertise in risk planning, risk monitoring and control, and risk response strategies.
- Certified Risk Manager (CRM): The Certified Risk Manager designation is offered by the National Alliance for Insurance Education and Research. This certification emphasizes risk management in the insurance industry. CRM holders are well-versed in identifying and analyzing risks, implementing risk management strategies, and developing effective insurance programs to mitigate risks.
- Certified in Risk and Information Systems Control (CRISC): CRISC is a certification offered by ISACA (Information Systems Audit and Control Association) and focuses on risk management in information systems and IT environments. CRISC professionals possess knowledge and expertise in identifying and managing IT risks, implementing information systems controls, and aligning risk management with business objectives.
- Certified Risk Analyst (CRA): The Certified Risk Analyst designation is offered by the Global Association of Risk Professionals (GARP). CRA certification validates professionals' knowledge and understanding of risk assessment and management techniques across various industries. It covers topics such as quantitative risk analysis, risk modeling, and risk mitigation strategies.
- Financial Risk Manager (FRM): The Financial Risk Manager certification is also offered by GARP and is geared towards professionals working in the financial industry. FRM certification focuses on financial risk management, including topics such as market risk, credit risk, operational risk, and risk modeling and measurement techniques.
These certifications typically require candidates to meet specific eligibility criteria, including educational qualifications, professional experience, and passing a rigorous examination. They often have ongoing professional development requirements to ensure that certified professionals stay up-to-date with the latest practices and trends in risk management.
Obtaining a risk management certification can provide several benefits, including enhanced career opportunities, increased marketability, and greater credibility in the field. It demonstrates a commitment to professional growth and can open doors to higher-level positions and increased responsibilities within organizations.
Eligibility and Requirements for Risk Management Certifications:
To pursue a risk management certification, candidates are generally required to meet specific eligibility criteria set by the certifying organization. These criteria ensure that individuals possess the necessary educational background, professional experience, and knowledge to successfully undertake the certification process. While the specific requirements may vary depending on the certification, here are some common eligibility criteria and requirements:
- Educational Background:
- Many risk management certifications require a minimum educational qualification, such as a high school diploma, bachelor's degree, or equivalent.
- Some certifications may have specific educational requirements related to the field of risk management or a related discipline (e.g., finance, project management, information systems).
- Professional Experience:
- Risk management certifications often have experience requirements to ensure candidates have practical exposure to risk management practices.
- The experience requirements may be specified in terms of the number of years of relevant work experience or a combination of education and experience.
- The experience may need to be in a specific industry or role related to risk management.
- Preparatory Courses and Training:
- Some certifications may recommend or require candidates to complete preparatory courses or training programs.
- These courses can provide candidates with the necessary knowledge and skills to succeed in the certification process.
- Preparatory courses may be offered by the certifying organization or by authorized training providers.
- Adherence to a Code of Ethics:
- Many certification programs require candidates to adhere to a code of ethics or professional conduct.
- Candidates may be asked to confirm their commitment to ethical practices in their work as risk management professionals.
- Certification Examination:
- A key requirement for most risk management certifications is passing a certification examination.
- The examination evaluates candidates' knowledge and understanding of risk management principles, frameworks, and practices.
- The format of the examination may vary, but it often consists of multiple-choice questions, scenario-based questions, or a combination of both.
It's important to note that meeting the eligibility criteria does not guarantee certification. Candidates must demonstrate their competence by successfully completing the examination or any other requirements specified by the certifying organization.
Additionally, some risk management certifications require ongoing professional development and continuing education to maintain the certification. This ensures that certified professionals stay updated with the evolving practices and trends in risk management.
Before pursuing a specific risk management certification, it's recommended to thoroughly review the eligibility criteria and requirements provided by the certifying organization. This will help ensure that you meet the necessary qualifications and understand the steps involved in obtaining and maintaining the certification.
Exam Structure and Preparation Tips for Risk Management Certifications:
Understanding the structure of the certification exam and having a solid preparation strategy are crucial for success. While the specific exam structure may vary depending on the certification, here are some general exam structure elements and preparation tips for risk management certifications:
- Familiarize Yourself with the Exam Format:
- Start by thoroughly reviewing the exam structure and format provided by the certifying organization.
- Understand the types of questions you can expect, such as multiple-choice, scenario-based, or essay questions.
- Take note of the allotted time for the exam and any specific instructions or guidelines.
- Review the Exam Content Outline:
- Obtain the exam content outline or syllabus, which highlights the topics and knowledge areas covered in the exam.
- Use the content outline as a guide to identify the areas where you need to focus your studies.
- Create a Study Plan:
- Develop a study plan that outlines your study schedule, topics to cover, and milestones leading up to the exam date.
- Break down the content into manageable sections and allocate sufficient time to review each topic.
- Consider your personal learning style and preferences when designing your study plan.
- Utilize Available Study Materials:
- Take advantage of study materials provided by the certifying organization, such as official textbooks, study guides, or practice exams.
- Seek out additional resources such as online courses, video tutorials, or reference books to supplement your understanding of key concepts.
- Engage in Active Learning:
- Actively engage with the study material rather than passively reading or memorizing.
- Take notes, summarize key points, and create flashcards or study aids to reinforce your understanding.
- Seek opportunities to apply the concepts through practice questions, case studies, or real-life examples.
- Practice with Sample Exams:
- Practice exams are invaluable in familiarizing yourself with the exam format and assessing your knowledge and readiness.
- Take advantage of any sample exams or practice questions provided by the certifying organization or available from reputable sources.
- Analyze your performance, identify areas of weakness, and focus on improving those areas.
- Join Study Groups or Discussion Forums:
- Engage with other candidates preparing for the same certification by joining study groups or participating in online discussion forums.
- Collaborating with others can help clarify doubts, share study strategies, and gain different perspectives on the exam content.
- Simulate Exam Conditions:
- As the exam date approaches, simulate exam conditions during your practice sessions.
- Set a timer and attempt full-length practice exams to build endurance and improve time management skills.
- Mimicking exam conditions will help reduce anxiety and increase your confidence on the actual exam day.
- Review and Revise:
- Allocate sufficient time for comprehensive review and revision before the exam.
- Focus on consolidating your understanding of key concepts, reinforcing weak areas, and clarifying any remaining doubts.
- Use revision techniques that work best for you, such as summarizing notes, creating visual aids, or teaching concepts to someone else.
- Take Care of Yourself:
- Prioritize your well-being and maintain a healthy balance between studying and self-care.
- Get adequate rest, eat nutritious meals, exercise, and manage stress effectively.
- Taking care of your physical and mental well-being will optimize your focus, concentration, and overall performance during the exam.
Benefits of Risk Management Certification:
Obtaining a risk management certification can bring numerous benefits to professionals in the field. Here are some key advantages of earning a risk management certification:
- Enhanced Career Opportunities:
- Risk management certifications provide a competitive edge in the job market by demonstrating your specialized knowledge and expertise.
- Certification can open doors to a wider range of career opportunities, including higher-level positions, leadership roles, and specialized risk management positions.
- Many employers prefer or require risk management certifications when hiring for risk management positions, giving certified professionals a distinct advantage.
- Increased Marketability:
- Risk management certifications enhance your professional credibility and marketability.
- Certified professionals are recognized as having met rigorous standards and demonstrated competence in risk management.
- The certification logo or designation on your resume, LinkedIn profile, or business card serves as a tangible proof of your qualifications, attracting potential employers and clients.
- Demonstrated Commitment to Excellence:
- Earning a risk management certification showcases your commitment to professional growth and continuous learning in the field.
- It demonstrates your dedication to staying updated with the latest risk management practices, industry trends, and emerging technologies.
- Employers value candidates who invest in their professional development, and certification is a tangible representation of that commitment.
- Expanded Knowledge and Skill Set:
- Risk management certifications provide a comprehensive understanding of risk management principles, frameworks, and methodologies.
- Certified professionals acquire in-depth knowledge of risk assessment techniques, risk mitigation strategies, and risk management best practices.
- The certification process often involves extensive study and preparation, enabling professionals to broaden their skill set and deepen their expertise.
- Recognition within the Industry:
- Risk management certifications are widely recognized and respected within the industry.
- Being certified establishes your professional credibility among peers, employers, and clients.
- Certification demonstrates that you have met the industry-recognized standards and have the necessary skills to effectively manage risks in various contexts.
- Networking Opportunities:
- Certification programs often provide access to professional networks, events, and communities.
- Connecting with other certified professionals, industry experts, and thought leaders can expand your professional network and facilitate knowledge sharing.
- Networking opportunities may lead to collaborations, career advancements, and exposure to new job opportunities.
- Continuous Professional Development:
- Many risk management certifications have ongoing professional development requirements, encouraging certified professionals to stay updated and relevant.
- These requirements often involve completing continuing education courses, attending conferences, participating in webinars, or engaging in other learning activities.
- Continuous professional development ensures that certified professionals stay current with evolving risk management practices and maintain their certification status.
How to obtain the PMI RMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
Conclusion
In conclusion, risk management certifications play a vital role in the professional development of individuals in the field of risk management. These certifications provide a recognized standard of competency, demonstrating expertise in identifying, assessing, and mitigating risks. By earning a risk management certification, professionals can enjoy a range of benefits.
First and foremost, certifications enhance career opportunities by opening doors to higher-level positions, specialized roles, and leadership positions. They make professionals more marketable, as employers often prefer or require certifications when hiring for risk management positions. The certification designation on resumes and profiles serves as a tangible proof of qualifications and credibility.
Risk management certifications also demonstrate a commitment to excellence and continuous learning. They show that professionals have met rigorous standards and are dedicated to staying updated with the latest practices and trends. This dedication to professional growth is highly valued by employers and clients alike.
Earning a risk management certification expands professionals' knowledge and skill set. The certification process involves in-depth study and preparation, providing a comprehensive understanding of risk management principles, frameworks, and methodologies. This knowledge equips professionals with the ability to assess risks, develop effective risk mitigation strategies, and make informed decisions.
Certifications are widely recognized within the industry, enhancing professionals' credibility and recognition among peers, employers, and clients. They establish professionals as trusted experts who have met industry-recognized standards. Additionally, certifications provide networking opportunities, allowing professionals to connect with other certified individuals, industry experts, and thought leaders, fostering collaboration and career advancement.
Furthermore, risk management certifications often have ongoing professional development requirements, ensuring that certified professionals stay updated and relevant. This continuous learning helps professionals remain at the forefront of risk management practices, enabling them to adapt to evolving challenges and technologies.
In summary, risk management certifications offer a range of benefits, including enhanced career opportunities, increased marketability, and recognition within the industry. By earning a certification, professionals demonstrate their expertise, expand their knowledge, and gain a competitive edge in the field of risk management.
What is CBAP Certification ? ,Overview , Benefits & Maintaining CBAP Certifictation.
The Certified Business Analysis Professional (CBAP) is a highly regarded certification program designed for professionals in the field of business analysis. Offered by the International Institute of Business Analysis (IIBA), the CBAP certification signifies an individual's expertise and proficiency in various aspects of business analysis.
Business analysis plays a crucial role in organizations, acting as a bridge between stakeholders and the IT department. It involves identifying business needs, eliciting requirements, and developing solutions to address those needs. A certified business analysis professional possesses the knowledge and skills necessary to effectively navigate these complex processes and deliver value to the organization.
To obtain the CBAP certification, individuals must meet specific eligibility criteria, including a minimum number of years of professional business analysis experience, adherence to the IIBA's code of conduct, and successful completion of the CBAP examination. The examination covers a wide range of knowledge areas, including business analysis planning and monitoring, requirements analysis and design definition, solution evaluation, and many others.
By achieving the CBAP certification, professionals demonstrate their commitment to continuous learning and professional development in the field of business analysis. It serves as a recognized industry standard and distinguishes individuals as competent and qualified practitioners in their field.
CBAP-certified professionals possess a deep understanding of business analysis methodologies, tools, and best practices. They excel in requirements gathering, stakeholder management, and business process improvement, enabling them to identify opportunities for innovation and drive positive change within organizations.
With the CBAP certification, individuals gain enhanced credibility and recognition within the business analysis community. It opens doors to exciting career opportunities, improves earning potential, and establishes a foundation for continued growth and advancement in the field.
In summary, the Certified Business Analysis Professional (CBAP) certification validates the expertise and competence of professionals in the field of business analysis. It demonstrates a commitment to industry best practices and provides a competitive edge in a rapidly evolving business landscape. CBAP-certified professionals are equipped with the skills and knowledge necessary to drive successful outcomes and deliver value to organizations worldwide.
Table of contents
- Introduction to CBAP Certification
- Overview of Business Analysis
- Understanding the CBAP Certification Process
- Benefits of CBAP Certification Training
- CBAP Exam Preparation Tips
- Maintaining CBAP Certification and Continuing Professional Development
- Conclusion
Introduction to CBAP Certification
The Certified Business Analysis Professional (CBAP) certification is a globally recognized credential that validates the skills and expertise of professionals in the field of business analysis. Awarded by the International Institute of Business Analysis (IIBA), the CBAP certification signifies a high level of proficiency in the discipline of business analysis and serves as a testament to an individual's commitment to professional growth and excellence.
Business analysis plays a vital role in today's dynamic business environment, where organizations are constantly striving to identify and implement effective solutions to address their challenges and achieve their goals. A business analyst serves as a bridge between business stakeholders and IT professionals, ensuring that the needs and requirements of the business are clearly understood and translated into practical solutions.
CBAP certification is designed for experienced business analysts who have a solid understanding of the principles and practices of business analysis. It demonstrates mastery of a comprehensive body of knowledge and signifies a high level of competency in the field. By obtaining the CBAP certification, professionals can enhance their career prospects, gain recognition in the industry, and access a wide range of exciting opportunities.
The CBAP certification is renowned for its rigorous requirements, which ensure that certified professionals possess the necessary knowledge and skills to excel in their roles. To be eligible for the CBAP exam, candidates must meet certain criteria, including a minimum number of years of work experience in business analysis, adherence to the IIBA's Business Analysis Body of Knowledge (BABOK), and the endorsement of professional references.
Earning the CBAP certification involves successfully passing a comprehensive examination that tests candidates on various knowledge areas, such as business analysis planning and monitoring, requirements management and communication, enterprise analysis, and solution assessment and validation. The exam assesses not only theoretical knowledge but also the practical application of business analysis principles and techniques.
By investing time and effort into CBAP certification training, professionals can deepen their understanding of the core concepts, tools, and techniques of business analysis. A comprehensive CBAP training course covers all the knowledge areas outlined in the BABOK, equipping participants with the necessary skills to excel in their roles as business analysts. These training programs often include interactive lectures, case studies, hands-on exercises, and practice exams to ensure a well-rounded learning experience.
In summary, the CBAP certification is a prestigious credential that showcases a business analyst's expertise and dedication to the field. It provides professionals with a competitive edge in the job market and opens doors to new career opportunities. By undergoing the rigorous training and examination process, individuals can enhance their knowledge, credibility, and value as business analysis professionals.
Overview of Business Analysis
Business analysis is a critical discipline that focuses on understanding and solving business problems and identifying opportunities for improvement within organizations. It involves analyzing business processes, systems, and strategies to help companies achieve their goals, increase efficiency, and drive innovation.
The role of a business analyst is to bridge the gap between business stakeholders and technology professionals. They work closely with stakeholders from various departments, including management, operations, finance, and IT, to gather requirements, define objectives, and develop solutions that align with the organization's overall strategy.
Here are some key aspects of business analysis:
- Understanding Business Needs: Business analysts are responsible for identifying and understanding the needs and goals of the organization. This involves conducting thorough research, engaging with stakeholders, and analyzing business processes to determine the underlying challenges and opportunities.
- Requirements Elicitation and Management: Business analysts play a crucial role in eliciting and managing requirements. They work closely with stakeholders to gather, document, and prioritize requirements, ensuring that they are clear, concise, and aligned with the organization's objectives. Effective requirements management involves capturing changes, conducting impact analysis, and maintaining traceability throughout the project lifecycle.
- Business Process Analysis: Analyzing and improving business processes is a key area of focus for business analysts. They evaluate existing processes, identify bottlenecks and inefficiencies, and propose optimized workflows that enhance productivity and effectiveness. Process modeling techniques, such as flowcharts and process maps, are often used to visualize and communicate process improvements.
- Data Analysis: Business analysts work with data to derive insights and support decision-making. They analyze trends, patterns, and metrics to identify areas of improvement, make data-driven recommendations, and measure the success of implemented solutions. Data analysis techniques, such as statistical analysis, data visualization, and predictive modeling, are employed to uncover valuable insights.
- Solution Evaluation: Business analysts are involved in the evaluation of proposed solutions to ensure they meet the desired objectives and requirements. They assess the feasibility, cost-effectiveness, and potential risks associated with implementing a solution. This includes conducting user acceptance testing, evaluating performance metrics, and gathering feedback to refine and optimize the solution.
- Stakeholder Management and Communication: Effective communication and stakeholder management are crucial skills for business analysts. They facilitate collaboration among diverse stakeholders, manage expectations, and ensure that all parties have a clear understanding of the project scope, objectives, and deliverables. Strong communication skills are essential for conducting interviews, facilitating workshops, and presenting findings and recommendations.
Business analysis is a dynamic field that requires continuous learning and adaptation to changing business environments. Professionals in this role often pursue certifications, such as the Certified Business Analysis Professional (CBAP), to validate their knowledge and expertise.
Understanding the CBAP Certification Process
The Certified Business Analysis Professional (CBAP) certification process is a comprehensive and structured approach that validates the knowledge, skills, and experience of professionals in the field of business analysis. It is administered by the International Institute of Business Analysis (IIBA) and is globally recognized as a prestigious credential in the industry. Here's an overview of the CBAP certification process:
- Eligibility Requirements: To be eligible for the CBAP certification, candidates must meet specific criteria set by the IIBA. These requirements include:
- Minimum 7,500 hours of business analysis work experience, aligned with the BABOK Guide (Business Analysis Body of Knowledge) within the last 10 years.
- A minimum of 35 hours of professional development in business analysis.
- A minimum of 900 hours of work experience in at least four of the six BABOK Guide knowledge areas or 500 hours in at least four of the six knowledge areas with a minimum of 21 hours of professional development in business analysis.
- Application Process: Once the eligibility criteria are met, candidates can proceed with the application process. This involves providing details about their work experience, educational background, and professional development hours. The application is submitted online through the IIBA website.
- Application Review and Approval: The submitted application goes through a review process by the IIBA. The review ensures that the provided information aligns with the CBAP certification requirements. If any clarifications or additional documentation is needed, candidates will be notified. Once the application is approved, candidates can proceed to the next step.
- Exam Preparation: After the application is approved, candidates can start preparing for the CBAP exam. The exam is based on the BABOK Guide, which is the globally recognized standard for the practice of business analysis. It covers various knowledge areas, tasks, and techniques related to business analysis. Candidates are advised to thoroughly study the BABOK Guide and other recommended study materials to ensure they have a solid understanding of the content.
- CBAP Exam: The CBAP exam is a 3.5-hour, scenario-based examination that consists of 120 multiple-choice questions. The exam assesses a candidate's knowledge and application of business analysis concepts and techniques. It tests their ability to analyze scenarios, identify the appropriate business analysis approach, and make informed decisions. The exam is conducted at designated testing centers or online, depending on the availability and options provided by the IIBA.
- Exam Results: After completing the exam, candidates receive immediate preliminary results indicating whether they have passed or failed. The official exam results, including a detailed score report, are typically available within a few weeks of completing the exam.
- Certification Maintenance: Once a candidate successfully passes the CBAP exam and earns the certification, they must maintain their CBAP credential by fulfilling the IIBA's recertification requirements. This includes earning Continuing Development Units (CDUs) through professional development activities, such as attending conferences, training programs, or participating in relevant business analysis activities. Recertification is required every three years to ensure that CBAP-certified professionals stay updated with evolving industry practices and continue to demonstrate their commitment to professional growth.
Benefits of CBAP Certification Training
CBAP (Certified Business Analysis Professional) certification training offers several benefits to professionals in the field of business analysis. Here are some key advantages of undergoing CBAP certification training:
- Enhanced Career Prospects: CBAP certification is globally recognized and highly valued by employers in the business analysis field. It serves as a testament to your expertise, competence, and commitment to professional growth. CBAP certification training equips you with the knowledge and skills necessary to excel in business analysis roles, making you more competitive in the job market and increasing your chances of career advancement.
- Industry Recognition and Credibility: CBAP certification is awarded by the International Institute of Business Analysis (IIBA), a leading professional association for business analysts. By earning the certification, you gain recognition and credibility within the industry. Employers and clients have confidence in your abilities and trust your expertise, which can lead to better career opportunities and higher-value projects.
- Expanded Job Opportunities: CBAP certification opens doors to a wide range of job opportunities. Many organizations prioritize hiring CBAP-certified professionals for business analysis roles, especially for complex projects or strategic initiatives. The certification demonstrates your ability to handle challenging business analysis tasks and positions you as a qualified candidate for positions such as business analyst, senior business analyst, business systems analyst, or requirements manager.
- Higher Earning Potential: CBAP certification often correlates with higher earning potential. Certified professionals typically command higher salaries compared to their non-certified counterparts. The specialized knowledge and expertise gained through CBAP training, coupled with the industry recognition, can justify higher compensation for your skills and contributions as a business analyst.
- Up-to-Date Knowledge and Best Practices: CBAP certification training ensures that you stay updated with the latest trends, techniques, and best practices in the field of business analysis. The training programs are designed to align with the current version of the BABOK Guide (Business Analysis Body of Knowledge) and cover the latest industry standards. This helps you refine your skills, expand your knowledge base, and stay ahead of emerging practices, giving you a competitive edge in the industry.
- Networking and Professional Development: CBAP certification training provides opportunities for networking and professional development. Training programs often involve interactions with industry experts, experienced instructors, and fellow business analysis professionals. This enables you to connect with like-minded individuals, share experiences, and build a professional network that can be beneficial for future collaborations, knowledge sharing, and career growth.
- Continuous Learning and Growth: CBAP certification is not a one-time achievement. It signifies a commitment to ongoing professional development and continuous learning. By pursuing CBAP certification training, you cultivate a mindset of lifelong learning and stay updated with evolving industry practices. The training programs often include resources and materials that can be referred to even after certification, serving as a valuable reference for future projects and endeavors.
CBAP Exam Preparation Tips
Preparing for the CBAP (Certified Business Analysis Professional) exam requires a focused and strategic approach to ensure success. Here are some valuable tips to help you prepare effectively for the CBAP exam:
- Understand the Exam Blueprint: Familiarize yourself with the CBAP exam blueprint, which outlines the knowledge areas and their respective weights in the exam. This will help you allocate your study time and resources accordingly, focusing on areas that carry more weight in the exam.
- Study the BABOK Guide: The BABOK Guide is the primary reference for the CBAP exam. Thoroughly study the guide, understand its concepts, and become familiar with the tasks, techniques, and knowledge areas covered in each chapter. Pay attention to the underlying principles and best practices outlined in the guide.
- Create a Study Plan: Develop a study plan that outlines your study goals, timelines, and resources. Break down the content into manageable sections and allocate specific study time for each knowledge area. Consider your personal learning style and create a plan that works best for you. Set realistic targets and adhere to the study schedule.
- Utilize Additional Study Materials: Supplement your study with additional resources such as study guides, practice exams, online forums, and training courses. These materials can provide further insights, explanations, and practice questions to reinforce your understanding of the content. Seek out reputable resources that align with the BABOK Guide and the CBAP exam syllabus.
- Join Study Groups or Forums: Engage with other CBAP aspirants by joining study groups or online forums dedicated to CBAP exam preparation. Collaborating with peers allows you to discuss concepts, share study techniques, and clarify doubts. It also provides an opportunity to learn from others' experiences and gain valuable insights.
- Take Practice Exams: Practice exams are an essential part of CBAP exam preparation. They simulate the exam environment and help you become familiar with the format and types of questions you may encounter. Practice exams also identify your strengths and weaknesses, enabling you to focus your revision efforts on areas that require more attention. Analyze your performance in practice exams and use them as a learning tool.
- Analyze and Review: After taking practice exams, thoroughly review both the correct and incorrect answers. Understand the reasoning behind each answer choice and identify any knowledge gaps. Focus on understanding the underlying concepts rather than memorizing answers. Review the BABOK Guide chapters related to questions you answered incorrectly to strengthen your understanding.
- Hands-on Experience: Apply your knowledge and skills in practical scenarios by working on real-world business analysis projects, if possible. Hands-on experience enhances your understanding of concepts and helps you relate theory to practice. If you lack practical experience, consider working on case studies or simulations that replicate real-world scenarios.
- Time Management and Exam Strategies: Develop effective time management and exam strategies to maximize your performance during the actual exam. Practice time management techniques while taking practice exams to ensure you complete all questions within the allotted time. Familiarize yourself with the exam format, review the instructions, and strategize how you will tackle different question types.
- Stay Calm and Confident: On the day of the exam, stay calm, well-rested, and confident in your preparation. Trust in your abilities and the efforts you have put into studying. Manage exam stress by practicing relaxation techniques, such as deep breathing or visualization exercises. Read each question carefully, analyze options, and choose the best answer based on your knowledge and reasoning.
Maintaining CBAP Certification and Continuing Professional Development
Maintaining CBAP (Certified Business Analysis Professional) certification and engaging in continuing professional development (CPD) is crucial to staying relevant, expanding your skills, and demonstrating your commitment to the field of business analysis. Here are some important aspects of maintaining CBAP certification and participating in CPD:
- Recertification Requirements: CBAP certification is valid for three years. To maintain your certification, you must meet the recertification requirements set by the International Institute of Business Analysis (IIBA). These requirements typically include earning a specified number of Continuing Development Units (CDUs) and adhering to the IIBA Code of Conduct.
- Continuing Development Units (CDUs): CDUs are a measure of professional development and learning activities recognized by the IIBA. To maintain your CBAP certification, you must accumulate a certain number of CDUs within the recertification period. CDUs can be earned through various activities, such as attending conferences, workshops, training programs, webinars, and participating in professional associations or business analysis communities.
- CPD Planning: It's important to plan your CPD activities strategically. Assess your professional development needs and interests, and identify areas where you would like to expand your knowledge or skills. Create a CPD plan that outlines specific activities, timelines, and CDU targets. This will help you stay organized and focused on achieving your CPD goals.
- Participation in Professional Associations: Joining professional associations, such as the IIBA or other business analysis organizations, provides access to a wealth of resources, networking opportunities, and CPD activities. Engage with these associations by attending events, joining discussion groups, and contributing to the community. Many of these activities can earn you CDUs and enhance your professional network.
- Industry Conferences and Events: Attend industry conferences, seminars, and workshops related to business analysis. These events offer valuable insights into emerging trends, best practices, and innovative approaches in the field. They also provide opportunities to connect with industry experts, share experiences, and expand your professional network.
- Self-Study and Research: Allocate time for self-study and independent research to stay updated with the latest developments in business analysis. Explore industry publications, blogs, whitepapers, and research papers. This self-directed learning can help you deepen your knowledge, gain new perspectives, and identify areas for professional growth.
- Mentoring and Coaching: Seek opportunities for mentoring or coaching relationships with experienced business analysis professionals. Mentors can provide guidance, share their insights, and offer advice based on their own experiences. Engaging in mentorship programs can contribute to your professional development and expose you to different perspectives and approaches in the field.
- Volunteering and Giving Back: Consider volunteering your time and expertise to contribute to the business analysis community. Participate in initiatives, such as speaking at conferences, writing articles, mentoring aspiring business analysts, or serving on committees. Volunteering not only allows you to give back to the profession but also helps you develop leadership skills and expand your network.
- Embrace New Technologies and Methodologies: Stay abreast of new technologies, methodologies, and tools that impact the practice of business analysis. Be open to learning and adapting to industry advancements, such as agile methodologies, data analytics, or process automation. Seek out relevant training opportunities to enhance your skills in these areas.
- Reflect and Evaluate: Periodically reflect on your professional development journey and evaluate the effectiveness of your CPD activities. Assess the impact of your learning efforts on your career progression, job performance, and overall professional growth. Identify areas for improvement and adjust your CPD plan accordingly.
How to obtain the CBAP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
Conclusion
In conclusion, pursuing the CBAP (Certified Business Analysis Professional) certification and engaging in continuing professional development (CPD) are essential for business analysts who seek to excel in their careers. The CBAP certification validates your expertise, enhances your marketability, and opens doors to exciting job opportunities. By understanding the core knowledge areas covered in CBAP training, you can develop a strong foundation in business analysis principles and practices.
Throughout your career, maintaining CBAP certification requires active participation in CPD activities. By accumulating Continuing Development Units (CDUs) through various learning opportunities, you stay up to date with industry trends, expand your knowledge and skills, and remain relevant in a rapidly evolving profession. Participation in professional associations, attending industry conferences, self-study, mentoring, and embracing new technologies are all integral parts of CPD.
Commitment to CPD demonstrates your dedication to professional growth and lifelong learning. It positions you as a trusted and competent business analysis professional, capable of navigating complex projects and delivering value to organizations. Additionally, CPD activities provide opportunities for networking, collaboration, and contributing to the business analysis community.
As you embark on your CBAP certification journey and embrace the path of continuous professional development, remember that staying curious, adaptable, and proactive in seeking new learning experiences will set you apart in the field of business analysis. By investing in your professional development, you invest in your future success and contribute to the advancement of the business analysis profession as a whole.
Read More
The Certified Business Analysis Professional (CBAP) is a highly regarded certification program designed for professionals in the field of business analysis. Offered by the International Institute of Business Analysis (IIBA), the CBAP certification signifies an individual's expertise and proficiency in various aspects of business analysis.
Business analysis plays a crucial role in organizations, acting as a bridge between stakeholders and the IT department. It involves identifying business needs, eliciting requirements, and developing solutions to address those needs. A certified business analysis professional possesses the knowledge and skills necessary to effectively navigate these complex processes and deliver value to the organization.
To obtain the CBAP certification, individuals must meet specific eligibility criteria, including a minimum number of years of professional business analysis experience, adherence to the IIBA's code of conduct, and successful completion of the CBAP examination. The examination covers a wide range of knowledge areas, including business analysis planning and monitoring, requirements analysis and design definition, solution evaluation, and many others.
By achieving the CBAP certification, professionals demonstrate their commitment to continuous learning and professional development in the field of business analysis. It serves as a recognized industry standard and distinguishes individuals as competent and qualified practitioners in their field.
CBAP-certified professionals possess a deep understanding of business analysis methodologies, tools, and best practices. They excel in requirements gathering, stakeholder management, and business process improvement, enabling them to identify opportunities for innovation and drive positive change within organizations.
With the CBAP certification, individuals gain enhanced credibility and recognition within the business analysis community. It opens doors to exciting career opportunities, improves earning potential, and establishes a foundation for continued growth and advancement in the field.
In summary, the Certified Business Analysis Professional (CBAP) certification validates the expertise and competence of professionals in the field of business analysis. It demonstrates a commitment to industry best practices and provides a competitive edge in a rapidly evolving business landscape. CBAP-certified professionals are equipped with the skills and knowledge necessary to drive successful outcomes and deliver value to organizations worldwide.
Table of contents
- Introduction to CBAP Certification
- Overview of Business Analysis
- Understanding the CBAP Certification Process
- Benefits of CBAP Certification Training
- CBAP Exam Preparation Tips
- Maintaining CBAP Certification and Continuing Professional Development
- Conclusion
Introduction to CBAP Certification
The Certified Business Analysis Professional (CBAP) certification is a globally recognized credential that validates the skills and expertise of professionals in the field of business analysis. Awarded by the International Institute of Business Analysis (IIBA), the CBAP certification signifies a high level of proficiency in the discipline of business analysis and serves as a testament to an individual's commitment to professional growth and excellence.
Business analysis plays a vital role in today's dynamic business environment, where organizations are constantly striving to identify and implement effective solutions to address their challenges and achieve their goals. A business analyst serves as a bridge between business stakeholders and IT professionals, ensuring that the needs and requirements of the business are clearly understood and translated into practical solutions.
CBAP certification is designed for experienced business analysts who have a solid understanding of the principles and practices of business analysis. It demonstrates mastery of a comprehensive body of knowledge and signifies a high level of competency in the field. By obtaining the CBAP certification, professionals can enhance their career prospects, gain recognition in the industry, and access a wide range of exciting opportunities.
The CBAP certification is renowned for its rigorous requirements, which ensure that certified professionals possess the necessary knowledge and skills to excel in their roles. To be eligible for the CBAP exam, candidates must meet certain criteria, including a minimum number of years of work experience in business analysis, adherence to the IIBA's Business Analysis Body of Knowledge (BABOK), and the endorsement of professional references.
Earning the CBAP certification involves successfully passing a comprehensive examination that tests candidates on various knowledge areas, such as business analysis planning and monitoring, requirements management and communication, enterprise analysis, and solution assessment and validation. The exam assesses not only theoretical knowledge but also the practical application of business analysis principles and techniques.
By investing time and effort into CBAP certification training, professionals can deepen their understanding of the core concepts, tools, and techniques of business analysis. A comprehensive CBAP training course covers all the knowledge areas outlined in the BABOK, equipping participants with the necessary skills to excel in their roles as business analysts. These training programs often include interactive lectures, case studies, hands-on exercises, and practice exams to ensure a well-rounded learning experience.
In summary, the CBAP certification is a prestigious credential that showcases a business analyst's expertise and dedication to the field. It provides professionals with a competitive edge in the job market and opens doors to new career opportunities. By undergoing the rigorous training and examination process, individuals can enhance their knowledge, credibility, and value as business analysis professionals.
Overview of Business Analysis
Business analysis is a critical discipline that focuses on understanding and solving business problems and identifying opportunities for improvement within organizations. It involves analyzing business processes, systems, and strategies to help companies achieve their goals, increase efficiency, and drive innovation.
The role of a business analyst is to bridge the gap between business stakeholders and technology professionals. They work closely with stakeholders from various departments, including management, operations, finance, and IT, to gather requirements, define objectives, and develop solutions that align with the organization's overall strategy.
Here are some key aspects of business analysis:
- Understanding Business Needs: Business analysts are responsible for identifying and understanding the needs and goals of the organization. This involves conducting thorough research, engaging with stakeholders, and analyzing business processes to determine the underlying challenges and opportunities.
- Requirements Elicitation and Management: Business analysts play a crucial role in eliciting and managing requirements. They work closely with stakeholders to gather, document, and prioritize requirements, ensuring that they are clear, concise, and aligned with the organization's objectives. Effective requirements management involves capturing changes, conducting impact analysis, and maintaining traceability throughout the project lifecycle.
- Business Process Analysis: Analyzing and improving business processes is a key area of focus for business analysts. They evaluate existing processes, identify bottlenecks and inefficiencies, and propose optimized workflows that enhance productivity and effectiveness. Process modeling techniques, such as flowcharts and process maps, are often used to visualize and communicate process improvements.
- Data Analysis: Business analysts work with data to derive insights and support decision-making. They analyze trends, patterns, and metrics to identify areas of improvement, make data-driven recommendations, and measure the success of implemented solutions. Data analysis techniques, such as statistical analysis, data visualization, and predictive modeling, are employed to uncover valuable insights.
- Solution Evaluation: Business analysts are involved in the evaluation of proposed solutions to ensure they meet the desired objectives and requirements. They assess the feasibility, cost-effectiveness, and potential risks associated with implementing a solution. This includes conducting user acceptance testing, evaluating performance metrics, and gathering feedback to refine and optimize the solution.
- Stakeholder Management and Communication: Effective communication and stakeholder management are crucial skills for business analysts. They facilitate collaboration among diverse stakeholders, manage expectations, and ensure that all parties have a clear understanding of the project scope, objectives, and deliverables. Strong communication skills are essential for conducting interviews, facilitating workshops, and presenting findings and recommendations.
Business analysis is a dynamic field that requires continuous learning and adaptation to changing business environments. Professionals in this role often pursue certifications, such as the Certified Business Analysis Professional (CBAP), to validate their knowledge and expertise.
Understanding the CBAP Certification Process
The Certified Business Analysis Professional (CBAP) certification process is a comprehensive and structured approach that validates the knowledge, skills, and experience of professionals in the field of business analysis. It is administered by the International Institute of Business Analysis (IIBA) and is globally recognized as a prestigious credential in the industry. Here's an overview of the CBAP certification process:
- Eligibility Requirements: To be eligible for the CBAP certification, candidates must meet specific criteria set by the IIBA. These requirements include:
- Minimum 7,500 hours of business analysis work experience, aligned with the BABOK Guide (Business Analysis Body of Knowledge) within the last 10 years.
- A minimum of 35 hours of professional development in business analysis.
- A minimum of 900 hours of work experience in at least four of the six BABOK Guide knowledge areas or 500 hours in at least four of the six knowledge areas with a minimum of 21 hours of professional development in business analysis.
- Application Process: Once the eligibility criteria are met, candidates can proceed with the application process. This involves providing details about their work experience, educational background, and professional development hours. The application is submitted online through the IIBA website.
- Application Review and Approval: The submitted application goes through a review process by the IIBA. The review ensures that the provided information aligns with the CBAP certification requirements. If any clarifications or additional documentation is needed, candidates will be notified. Once the application is approved, candidates can proceed to the next step.
- Exam Preparation: After the application is approved, candidates can start preparing for the CBAP exam. The exam is based on the BABOK Guide, which is the globally recognized standard for the practice of business analysis. It covers various knowledge areas, tasks, and techniques related to business analysis. Candidates are advised to thoroughly study the BABOK Guide and other recommended study materials to ensure they have a solid understanding of the content.
- CBAP Exam: The CBAP exam is a 3.5-hour, scenario-based examination that consists of 120 multiple-choice questions. The exam assesses a candidate's knowledge and application of business analysis concepts and techniques. It tests their ability to analyze scenarios, identify the appropriate business analysis approach, and make informed decisions. The exam is conducted at designated testing centers or online, depending on the availability and options provided by the IIBA.
- Exam Results: After completing the exam, candidates receive immediate preliminary results indicating whether they have passed or failed. The official exam results, including a detailed score report, are typically available within a few weeks of completing the exam.
- Certification Maintenance: Once a candidate successfully passes the CBAP exam and earns the certification, they must maintain their CBAP credential by fulfilling the IIBA's recertification requirements. This includes earning Continuing Development Units (CDUs) through professional development activities, such as attending conferences, training programs, or participating in relevant business analysis activities. Recertification is required every three years to ensure that CBAP-certified professionals stay updated with evolving industry practices and continue to demonstrate their commitment to professional growth.
Benefits of CBAP Certification Training
CBAP (Certified Business Analysis Professional) certification training offers several benefits to professionals in the field of business analysis. Here are some key advantages of undergoing CBAP certification training:
- Enhanced Career Prospects: CBAP certification is globally recognized and highly valued by employers in the business analysis field. It serves as a testament to your expertise, competence, and commitment to professional growth. CBAP certification training equips you with the knowledge and skills necessary to excel in business analysis roles, making you more competitive in the job market and increasing your chances of career advancement.
- Industry Recognition and Credibility: CBAP certification is awarded by the International Institute of Business Analysis (IIBA), a leading professional association for business analysts. By earning the certification, you gain recognition and credibility within the industry. Employers and clients have confidence in your abilities and trust your expertise, which can lead to better career opportunities and higher-value projects.
- Expanded Job Opportunities: CBAP certification opens doors to a wide range of job opportunities. Many organizations prioritize hiring CBAP-certified professionals for business analysis roles, especially for complex projects or strategic initiatives. The certification demonstrates your ability to handle challenging business analysis tasks and positions you as a qualified candidate for positions such as business analyst, senior business analyst, business systems analyst, or requirements manager.
- Higher Earning Potential: CBAP certification often correlates with higher earning potential. Certified professionals typically command higher salaries compared to their non-certified counterparts. The specialized knowledge and expertise gained through CBAP training, coupled with the industry recognition, can justify higher compensation for your skills and contributions as a business analyst.
- Up-to-Date Knowledge and Best Practices: CBAP certification training ensures that you stay updated with the latest trends, techniques, and best practices in the field of business analysis. The training programs are designed to align with the current version of the BABOK Guide (Business Analysis Body of Knowledge) and cover the latest industry standards. This helps you refine your skills, expand your knowledge base, and stay ahead of emerging practices, giving you a competitive edge in the industry.
- Networking and Professional Development: CBAP certification training provides opportunities for networking and professional development. Training programs often involve interactions with industry experts, experienced instructors, and fellow business analysis professionals. This enables you to connect with like-minded individuals, share experiences, and build a professional network that can be beneficial for future collaborations, knowledge sharing, and career growth.
- Continuous Learning and Growth: CBAP certification is not a one-time achievement. It signifies a commitment to ongoing professional development and continuous learning. By pursuing CBAP certification training, you cultivate a mindset of lifelong learning and stay updated with evolving industry practices. The training programs often include resources and materials that can be referred to even after certification, serving as a valuable reference for future projects and endeavors.
CBAP Exam Preparation Tips
Preparing for the CBAP (Certified Business Analysis Professional) exam requires a focused and strategic approach to ensure success. Here are some valuable tips to help you prepare effectively for the CBAP exam:
- Understand the Exam Blueprint: Familiarize yourself with the CBAP exam blueprint, which outlines the knowledge areas and their respective weights in the exam. This will help you allocate your study time and resources accordingly, focusing on areas that carry more weight in the exam.
- Study the BABOK Guide: The BABOK Guide is the primary reference for the CBAP exam. Thoroughly study the guide, understand its concepts, and become familiar with the tasks, techniques, and knowledge areas covered in each chapter. Pay attention to the underlying principles and best practices outlined in the guide.
- Create a Study Plan: Develop a study plan that outlines your study goals, timelines, and resources. Break down the content into manageable sections and allocate specific study time for each knowledge area. Consider your personal learning style and create a plan that works best for you. Set realistic targets and adhere to the study schedule.
- Utilize Additional Study Materials: Supplement your study with additional resources such as study guides, practice exams, online forums, and training courses. These materials can provide further insights, explanations, and practice questions to reinforce your understanding of the content. Seek out reputable resources that align with the BABOK Guide and the CBAP exam syllabus.
- Join Study Groups or Forums: Engage with other CBAP aspirants by joining study groups or online forums dedicated to CBAP exam preparation. Collaborating with peers allows you to discuss concepts, share study techniques, and clarify doubts. It also provides an opportunity to learn from others' experiences and gain valuable insights.
- Take Practice Exams: Practice exams are an essential part of CBAP exam preparation. They simulate the exam environment and help you become familiar with the format and types of questions you may encounter. Practice exams also identify your strengths and weaknesses, enabling you to focus your revision efforts on areas that require more attention. Analyze your performance in practice exams and use them as a learning tool.
- Analyze and Review: After taking practice exams, thoroughly review both the correct and incorrect answers. Understand the reasoning behind each answer choice and identify any knowledge gaps. Focus on understanding the underlying concepts rather than memorizing answers. Review the BABOK Guide chapters related to questions you answered incorrectly to strengthen your understanding.
- Hands-on Experience: Apply your knowledge and skills in practical scenarios by working on real-world business analysis projects, if possible. Hands-on experience enhances your understanding of concepts and helps you relate theory to practice. If you lack practical experience, consider working on case studies or simulations that replicate real-world scenarios.
- Time Management and Exam Strategies: Develop effective time management and exam strategies to maximize your performance during the actual exam. Practice time management techniques while taking practice exams to ensure you complete all questions within the allotted time. Familiarize yourself with the exam format, review the instructions, and strategize how you will tackle different question types.
- Stay Calm and Confident: On the day of the exam, stay calm, well-rested, and confident in your preparation. Trust in your abilities and the efforts you have put into studying. Manage exam stress by practicing relaxation techniques, such as deep breathing or visualization exercises. Read each question carefully, analyze options, and choose the best answer based on your knowledge and reasoning.
Maintaining CBAP Certification and Continuing Professional Development
Maintaining CBAP (Certified Business Analysis Professional) certification and engaging in continuing professional development (CPD) is crucial to staying relevant, expanding your skills, and demonstrating your commitment to the field of business analysis. Here are some important aspects of maintaining CBAP certification and participating in CPD:
- Recertification Requirements: CBAP certification is valid for three years. To maintain your certification, you must meet the recertification requirements set by the International Institute of Business Analysis (IIBA). These requirements typically include earning a specified number of Continuing Development Units (CDUs) and adhering to the IIBA Code of Conduct.
- Continuing Development Units (CDUs): CDUs are a measure of professional development and learning activities recognized by the IIBA. To maintain your CBAP certification, you must accumulate a certain number of CDUs within the recertification period. CDUs can be earned through various activities, such as attending conferences, workshops, training programs, webinars, and participating in professional associations or business analysis communities.
- CPD Planning: It's important to plan your CPD activities strategically. Assess your professional development needs and interests, and identify areas where you would like to expand your knowledge or skills. Create a CPD plan that outlines specific activities, timelines, and CDU targets. This will help you stay organized and focused on achieving your CPD goals.
- Participation in Professional Associations: Joining professional associations, such as the IIBA or other business analysis organizations, provides access to a wealth of resources, networking opportunities, and CPD activities. Engage with these associations by attending events, joining discussion groups, and contributing to the community. Many of these activities can earn you CDUs and enhance your professional network.
- Industry Conferences and Events: Attend industry conferences, seminars, and workshops related to business analysis. These events offer valuable insights into emerging trends, best practices, and innovative approaches in the field. They also provide opportunities to connect with industry experts, share experiences, and expand your professional network.
- Self-Study and Research: Allocate time for self-study and independent research to stay updated with the latest developments in business analysis. Explore industry publications, blogs, whitepapers, and research papers. This self-directed learning can help you deepen your knowledge, gain new perspectives, and identify areas for professional growth.
- Mentoring and Coaching: Seek opportunities for mentoring or coaching relationships with experienced business analysis professionals. Mentors can provide guidance, share their insights, and offer advice based on their own experiences. Engaging in mentorship programs can contribute to your professional development and expose you to different perspectives and approaches in the field.
- Volunteering and Giving Back: Consider volunteering your time and expertise to contribute to the business analysis community. Participate in initiatives, such as speaking at conferences, writing articles, mentoring aspiring business analysts, or serving on committees. Volunteering not only allows you to give back to the profession but also helps you develop leadership skills and expand your network.
- Embrace New Technologies and Methodologies: Stay abreast of new technologies, methodologies, and tools that impact the practice of business analysis. Be open to learning and adapting to industry advancements, such as agile methodologies, data analytics, or process automation. Seek out relevant training opportunities to enhance your skills in these areas.
- Reflect and Evaluate: Periodically reflect on your professional development journey and evaluate the effectiveness of your CPD activities. Assess the impact of your learning efforts on your career progression, job performance, and overall professional growth. Identify areas for improvement and adjust your CPD plan accordingly.
How to obtain the CBAP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
Conclusion
In conclusion, pursuing the CBAP (Certified Business Analysis Professional) certification and engaging in continuing professional development (CPD) are essential for business analysts who seek to excel in their careers. The CBAP certification validates your expertise, enhances your marketability, and opens doors to exciting job opportunities. By understanding the core knowledge areas covered in CBAP training, you can develop a strong foundation in business analysis principles and practices.
Throughout your career, maintaining CBAP certification requires active participation in CPD activities. By accumulating Continuing Development Units (CDUs) through various learning opportunities, you stay up to date with industry trends, expand your knowledge and skills, and remain relevant in a rapidly evolving profession. Participation in professional associations, attending industry conferences, self-study, mentoring, and embracing new technologies are all integral parts of CPD.
Commitment to CPD demonstrates your dedication to professional growth and lifelong learning. It positions you as a trusted and competent business analysis professional, capable of navigating complex projects and delivering value to organizations. Additionally, CPD activities provide opportunities for networking, collaboration, and contributing to the business analysis community.
As you embark on your CBAP certification journey and embrace the path of continuous professional development, remember that staying curious, adaptable, and proactive in seeking new learning experiences will set you apart in the field of business analysis. By investing in your professional development, you invest in your future success and contribute to the advancement of the business analysis profession as a whole.
What is CCBA Certification ? ,Exam Overview, Requirements & Benefits
The CCBA (Certification of Capability in Business Analysis) is a professional certification that recognizes individuals who possess a solid foundation and practical experience in the field of business analysis. The CCBA certification is offered by the International Institute of Business Analysis (IIBA) and is designed for business analysts who are early in their careers or have a moderate level of experience.
Business analysis is a critical discipline that focuses on understanding business needs, defining requirements, and facilitating solutions to improve organizational performance. The CCBA certification establishes a standard of knowledge and expertise in these areas, validating an individual's ability to effectively contribute to business analysis initiatives.
To be eligible for the CCBA certification, candidates must meet specific criteria, including a minimum number of hours of business analysis work experience, adherence to the IIBA's code of conduct, and successful completion of the CCBA examination. The exam covers various knowledge areas, including business analysis planning and monitoring, requirements elicitation and analysis, solution evaluation, and more.
By attaining the CCBA certification, professionals demonstrate their commitment to ongoing professional development and a dedication to honing their business analysis skills. It signifies a level of competence and proficiency in core business analysis practices and methodologies.
CCBA-certified professionals possess a strong understanding of business analysis techniques, tools, and best practices. They excel in requirements gathering, documentation, and stakeholder communication, enabling them to contribute effectively to projects and deliver valuable outcomes.
The CCBA certification provides numerous benefits to professionals seeking to advance their careers in business analysis. It enhances their credibility, distinguishes them from their peers, and expands their professional network within the business analysis community. Additionally, the CCBA certification opens doors to new career opportunities, helps professionals command higher salaries, and provides a pathway for further growth and specialization in the field.
In summary, the CCBA (Certification of Capability in Business Analysis) is a valuable certification that recognizes the knowledge and practical skills of business analysts early in their careers or with moderate experience. It signifies a commitment to excellence in business analysis practices, enhances professional credibility, and unlocks opportunities for career advancement. CCBA-certified professionals play a vital role in driving successful business outcomes and contribute to the growth and success of organizations across industries.
Table of Contents
- Introduction to CCBA Certification:
- CCBA Certification Requirements:
- CCBA Certification Exam Overview:
- Benefits of CCBA Certification Training:
- Continuing Education and Recertification:
- Conclusion
Introduction to CCBA Certification:
CCBA (Certification of Capability in Business Analysis) is a globally recognized certification offered by the International Institute of Business Analysis (IIBA). It is specifically designed for business analysts who want to demonstrate their knowledge, skills, and expertise in the field of business analysis. The CCBA Certification is a valuable credential that signifies a professional's ability to effectively analyze and solve business problems, contribute to successful project outcomes, and drive business improvements.
Why is CCBA Certification important for business analysts?
CCBA Certification holds significant importance for business analysts for several reasons:
- Recognition and Credibility: CCBA Certification provides recognition and credibility within the industry. It demonstrates that you have met the rigorous standards set by the IIBA and have a comprehensive understanding of business analysis principles and practices.
- Enhanced Professional Competence: The CCBA Certification process involves a thorough examination of your knowledge and skills in various business analysis areas. By earning the certification, you showcase your competence and expertise, which can boost your confidence and enhance your job performance.
- Career Advancement: CCBA Certification opens up new avenues for career advancement. Many organizations value and seek professionals with CCBA Certification for their business analysis roles, leading to increased job opportunities and the potential for higher salaries and promotions.
- Global Recognition: The CCBA Certification is recognized globally, allowing you to stand out in a competitive job market and potentially pursue opportunities internationally. It signifies that you possess a standardized skill set that is relevant across industries and geographies.
- Networking Opportunities: Becoming CCBA certified provides access to a vast network of professionals in the business analysis field. You can connect with like-minded individuals, attend industry events, and participate in forums and communities dedicated to business analysis, fostering valuable relationships and knowledge sharing.
Benefits of earning a CCBA Certification:
- Comprehensive Business Analysis Knowledge: The CCBA Certification process ensures that you have a strong foundation in all aspects of business analysis, including requirements planning and management, enterprise analysis, solution assessment and validation, and more. This knowledge equips you to tackle complex business challenges effectively.
- Professional Growth and Development: The CCBA Certification journey involves studying and preparing for the exam, which expands your knowledge and skills. Additionally, maintaining the certification requires ongoing professional development, enabling you to stay current with the latest trends, methodologies, and best practices in business analysis.
- Increased Marketability: CCBA Certification enhances your marketability and differentiates you from other business analysts. It demonstrates to employers and clients that you have the necessary expertise and commitment to excel in your role, making you a valuable asset to any organization.
- Higher Earning Potential: With CCBA Certification, you may have the opportunity to negotiate higher salaries and compensation packages. The certification serves as evidence of your proficiency and can contribute to your overall value as a business analyst.
CCBA Certification Requirements:
To become CCBA (Certification of Capability in Business Analysis) certified, candidates must meet specific eligibility criteria set by the International Institute of Business Analysis (IIBA). These requirements ensure that individuals possess the necessary education, work experience, and knowledge to pursue and obtain the CCBA Certification. The requirements include:
- Education Requirement:
- High School Diploma, General Education Development (GED), or global equivalent
- Work Experience Requirement:
- A minimum of 3,750 hours of business analysis work experience in the last seven years.
- This work experience should cover activities related to the business analysis knowledge areas defined in the BABOK® Guide (Business Analysis Body of Knowledge), including requirements analysis and design, elicitation and collaboration, solution assessment and validation, strategy analysis, and more.
- Professional Development Requirement:
- A minimum of 21 hours of professional development in the last four years.
- These professional development hours should be specifically focused on business analysis-related topics and can include workshops, courses, conferences, and other learning activities.
- References:
- Two references from a career manager, client, or Certified Business Analysis Professional (CBAP®) recipient are required to validate the work experience.
It's important to note that the CCBA Certification requirements are subject to change, and it's recommended to refer to the official IIBA website or the current CCBA Certification Handbook for the most up-to-date information.
Application Process:
Once you have met the eligibility requirements, you can proceed with the CCBA Certification application process, which typically involves the following steps:
- Create an Account: Visit the IIBA website and create an account to access the CCBA Certification application portal.
- Complete the Application Form: Fill out the CCBA Certification application form, providing accurate details about your education, work experience, professional development hours, and references.
- Application Review: The IIBA will review your application to ensure you meet the eligibility requirements. They may contact you for additional information or clarification if needed.
- Pay the Application Fee: Once your application is approved, you will be required to pay the application fee. The fee amount may vary and is subject to change, so refer to the IIBA website for the current fee structure.
- Schedule and Prepare for the Exam: After your application is accepted and the fee is paid, you will receive instructions on how to schedule your CCBA Certification exam. Prepare for the exam by studying the BABOK® Guide and utilizing additional study materials and resources.
CCBA Certification Exam Overview:
The CCBA (Certification of Capability in Business Analysis) exam is designed to assess the knowledge, skills, and competencies of business analysts based on the BABOK® Guide (Business Analysis Body of Knowledge). Understanding the exam structure, format, duration, and passing score is crucial for effective preparation. Here is an overview of the CCBA Certification exam:
- Exam Structure:
- The CCBA Certification exam consists of multiple-choice questions.
- The exam is based on the BABOK® Guide version specified by the International Institute of Business Analysis (IIBA).
- Exam Format:
- The CCBA Certification exam is computer-based and delivered through designated test centers or online proctoring, depending on the available options in your region.
- The questions are presented as multiple-choice with four answer options, out of which you need to select the most appropriate response.
- Exam Duration:
- The duration of the CCBA Certification exam is typically 3.5 hours (210 minutes).
- This duration includes the time for reading and accepting the exam agreement, as well as the actual time allocated for answering the questions.
- Number of Questions:
- The CCBA Certification exam consists of a fixed number of questions.
- The exact number of questions may vary, but it is generally around 130 questions.
- Question Types:
- The CCBA Certification exam includes different types of questions to assess various aspects of business analysis knowledge and skills.
- These question types may include scenario-based questions, knowledge-based questions, and application-based questions.
- Passing Score:
- The passing score for the CCBA Certification exam is not disclosed by the IIBA.
- The exam is scored on a scaled basis, taking into account the difficulty level of the questions.
- You will receive a pass or fail result after completing the exam.
- Exam Syllabus:
- The CCBA Certification exam covers the knowledge areas and tasks outlined in the BABOK® Guide.
- The BABOK® Guide defines the key concepts, techniques, and best practices relevant to business analysis, and serves as the primary study resource for the exam.
- Exam Preparation:
- Effective exam preparation is crucial to succeed in the CCBA Certification exam.
- Study the BABOK® Guide thoroughly, understanding the knowledge areas, tasks, and techniques.
- Utilize additional study materials, such as practice exams, sample questions, study guides, and online resources.
- Consider attending CCBA Certification training courses to enhance your understanding and preparation.
Benefits of CCBA Certification Training
CCBA Certification training offers numerous benefits to aspiring business analysts who are preparing for the CCBA (Certification of Capability in Business Analysis) exam. Here are some key benefits of undergoing CCBA Certification training:
- Comprehensive Exam Preparation: CCBA Certification training courses are specifically designed to cover all the knowledge areas, tasks, and techniques outlined in the BABOK® Guide (Business Analysis Body of Knowledge). These courses provide a structured and comprehensive approach to exam preparation, ensuring that candidates have a thorough understanding of the subject matter.
- Mastery of Business Analysis Concepts: CCBA training helps candidates deepen their knowledge and mastery of business analysis concepts, methodologies, and best practices. It covers a wide range of topics, including requirements planning and management, enterprise analysis, solution assessment and validation, business analysis planning and monitoring, and more. This in-depth understanding enhances the capabilities of business analysts and prepares them for real-world challenges.
- Application of BABOK® Guide Principles: The BABOK® Guide serves as the primary reference for the CCBA Certification exam, and CCBA training courses provide practical guidance on how to apply the principles outlined in the guide. Training helps candidates understand how to analyze business problems, elicit and manage requirements, develop business solutions, and ensure stakeholder satisfaction.
- Real-World Case Studies and Examples: CCBA training often includes real-world case studies and examples that illustrate the application of business analysis techniques in different scenarios. These case studies provide valuable insights into the challenges faced by business analysts and demonstrate how to effectively analyze and solve complex business problems. By studying and analyzing these cases, candidates gain practical knowledge and learn from industry best practices.
- Interactive Learning Environment: CCBA training courses are typically conducted in an interactive learning environment, allowing candidates to engage in discussions, ask questions, and collaborate with fellow participants. This interactive approach fosters a deeper understanding of the subject matter through shared experiences and perspectives, enhancing the overall learning experience.
- Experienced and Certified Instructors: CCBA training is usually delivered by experienced instructors who hold CCBA or other relevant certifications themselves. These instructors bring their expertise and real-world knowledge to the training sessions, providing valuable insights and guidance to candidates. They can clarify doubts, share practical tips, and offer exam-specific guidance based on their own experiences.
- Exam Preparation Strategies: CCBA training courses provide candidates with strategies and techniques to effectively prepare for the certification exam. This includes guidance on creating study plans, time management techniques, understanding the exam structure and question types, and practicing with sample questions and mock exams. These exam-specific preparation strategies increase candidates' confidence and readiness for the actual exam.
- Networking Opportunities: CCBA training brings together aspiring business analysts from various backgrounds, industries, and organizations. This provides an excellent opportunity for networking and building professional connections within the business analysis community. Networking with fellow professionals can lead to valuable collaborations, knowledge sharing, and future career opportunities.
Continuing Education and Recertification for CCBA Certification:
Once you have achieved CCBA (Certification of Capability in Business Analysis) certification, it is important to stay updated with evolving industry practices and maintain your professional competence. The International Institute of Business Analysis (IIBA) has established continuing education and recertification requirements to ensure that CCBA certified professionals remain current and relevant in the field of business analysis. Here's an overview of continuing education and recertification for CCBA Certification:
- Recertification Cycle:
- The recertification cycle for CCBA Certification is three years.
- It begins on the date of your initial certification and ends three years later.
- Continuing Development Units (CDUs):
- To maintain CCBA Certification, you are required to earn and report a specific number of Continuing Development Units (CDUs) during each recertification cycle.
- CDUs are professional development units that represent the amount of time spent on continuing education activities related to business analysis.
- 1 CDU is equivalent to 1 hour of professional development activity.
- CDU Requirements:
- As of my knowledge cutoff in September 2021, CCBA certified professionals need to earn 60 CDUs during each three-year recertification cycle.
- CDUs can be earned through a variety of activities, such as attending training programs, workshops, conferences, webinars, and seminars related to business analysis.
- Other activities that contribute to CDU requirements may include presenting or writing articles on business analysis topics, volunteering for the IIBA, or participating in relevant professional activities.
- Recertification Application:
- At the end of your three-year recertification cycle, you are required to submit a recertification application to the IIBA.
- The recertification application includes reporting the CDUs you have earned during the cycle and providing relevant supporting documentation, such as certificates of completion or attendance.
- Recertification Fee:
- There is a recertification fee associated with maintaining CCBA Certification.
- The fee amount is subject to change, and it is advisable to refer to the IIBA website or the CCBA Certification Handbook for the most up-to-date information regarding the recertification fee.
- Audits:
- The IIBA conducts random audits to ensure compliance with the recertification requirements.
- If selected for an audit, you will be required to provide documentation as evidence of the CDUs you have claimed during the recertification cycle.
It's important to note that the specific recertification requirements and processes may change over time. Therefore, it is crucial to refer to the official IIBA website and the current CCBA Certification Handbook for the most accurate and up-to-date information regarding continuing education and recertification.
How to obtain the CCBA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
Conclusion
In conclusion, CCBA (Certification of Capability in Business Analysis) Certification is a valuable credential for business analysts seeking to demonstrate their knowledge, skills, and expertise in the field of business analysis. Through the CCBA Certification, professionals can enhance their marketability, open doors to new career opportunities, and gain recognition within the industry.
In this blog, we explored various aspects related to CCBA Certification, including an introduction to the certification, its importance for business analysts, the certification requirements, an overview of the certification exam, and the benefits of CCBA Certification training. We also touched upon the significance of continuing education and recertification to maintain the CCBA Certification and stay updated with industry practices.
By pursuing CCBA Certification, business analysts can deepen their understanding of business analysis principles and practices, demonstrate their competence to employers and clients, and gain access to a global network of professionals in the field. The certification serves as a validation of their expertise and commitment to professional growth.
It's important to stay informed about the current requirements and guidelines set by the International Institute of Business Analysis (IIBA) for CCBA Certification. It's recommended to regularly refer to the official IIBA website and the CCBA Certification Handbook for the latest information and updates.
Embarking on the journey to become CCBA certified requires dedication, preparation, and ongoing commitment to professional development. However, the rewards are worth it, as CCBA Certification can significantly contribute to the advancement of your business analysis career and open doors to exciting opportunities in the field.
Remember, CCBA Certification is not only a one-time achievement but a continuous process of learning and growth. By staying current with industry trends, expanding your knowledge through continuing education, and maintaining your certification through recertification, you can ensure that you remain at the forefront of the business analysis profession.
So, if you aspire to excel in the field of business analysis and establish yourself as a trusted and skilled professional, consider pursuing CCBA Certification and embark on a rewarding journey of professional growth and success.
Read More
The CCBA (Certification of Capability in Business Analysis) is a professional certification that recognizes individuals who possess a solid foundation and practical experience in the field of business analysis. The CCBA certification is offered by the International Institute of Business Analysis (IIBA) and is designed for business analysts who are early in their careers or have a moderate level of experience.
Business analysis is a critical discipline that focuses on understanding business needs, defining requirements, and facilitating solutions to improve organizational performance. The CCBA certification establishes a standard of knowledge and expertise in these areas, validating an individual's ability to effectively contribute to business analysis initiatives.
To be eligible for the CCBA certification, candidates must meet specific criteria, including a minimum number of hours of business analysis work experience, adherence to the IIBA's code of conduct, and successful completion of the CCBA examination. The exam covers various knowledge areas, including business analysis planning and monitoring, requirements elicitation and analysis, solution evaluation, and more.
By attaining the CCBA certification, professionals demonstrate their commitment to ongoing professional development and a dedication to honing their business analysis skills. It signifies a level of competence and proficiency in core business analysis practices and methodologies.
CCBA-certified professionals possess a strong understanding of business analysis techniques, tools, and best practices. They excel in requirements gathering, documentation, and stakeholder communication, enabling them to contribute effectively to projects and deliver valuable outcomes.
The CCBA certification provides numerous benefits to professionals seeking to advance their careers in business analysis. It enhances their credibility, distinguishes them from their peers, and expands their professional network within the business analysis community. Additionally, the CCBA certification opens doors to new career opportunities, helps professionals command higher salaries, and provides a pathway for further growth and specialization in the field.
In summary, the CCBA (Certification of Capability in Business Analysis) is a valuable certification that recognizes the knowledge and practical skills of business analysts early in their careers or with moderate experience. It signifies a commitment to excellence in business analysis practices, enhances professional credibility, and unlocks opportunities for career advancement. CCBA-certified professionals play a vital role in driving successful business outcomes and contribute to the growth and success of organizations across industries.
Table of Contents
- Introduction to CCBA Certification:
- CCBA Certification Requirements:
- CCBA Certification Exam Overview:
- Benefits of CCBA Certification Training:
- Continuing Education and Recertification:
- Conclusion
Introduction to CCBA Certification:
CCBA (Certification of Capability in Business Analysis) is a globally recognized certification offered by the International Institute of Business Analysis (IIBA). It is specifically designed for business analysts who want to demonstrate their knowledge, skills, and expertise in the field of business analysis. The CCBA Certification is a valuable credential that signifies a professional's ability to effectively analyze and solve business problems, contribute to successful project outcomes, and drive business improvements.
Why is CCBA Certification important for business analysts?
CCBA Certification holds significant importance for business analysts for several reasons:
- Recognition and Credibility: CCBA Certification provides recognition and credibility within the industry. It demonstrates that you have met the rigorous standards set by the IIBA and have a comprehensive understanding of business analysis principles and practices.
- Enhanced Professional Competence: The CCBA Certification process involves a thorough examination of your knowledge and skills in various business analysis areas. By earning the certification, you showcase your competence and expertise, which can boost your confidence and enhance your job performance.
- Career Advancement: CCBA Certification opens up new avenues for career advancement. Many organizations value and seek professionals with CCBA Certification for their business analysis roles, leading to increased job opportunities and the potential for higher salaries and promotions.
- Global Recognition: The CCBA Certification is recognized globally, allowing you to stand out in a competitive job market and potentially pursue opportunities internationally. It signifies that you possess a standardized skill set that is relevant across industries and geographies.
- Networking Opportunities: Becoming CCBA certified provides access to a vast network of professionals in the business analysis field. You can connect with like-minded individuals, attend industry events, and participate in forums and communities dedicated to business analysis, fostering valuable relationships and knowledge sharing.
Benefits of earning a CCBA Certification:
- Comprehensive Business Analysis Knowledge: The CCBA Certification process ensures that you have a strong foundation in all aspects of business analysis, including requirements planning and management, enterprise analysis, solution assessment and validation, and more. This knowledge equips you to tackle complex business challenges effectively.
- Professional Growth and Development: The CCBA Certification journey involves studying and preparing for the exam, which expands your knowledge and skills. Additionally, maintaining the certification requires ongoing professional development, enabling you to stay current with the latest trends, methodologies, and best practices in business analysis.
- Increased Marketability: CCBA Certification enhances your marketability and differentiates you from other business analysts. It demonstrates to employers and clients that you have the necessary expertise and commitment to excel in your role, making you a valuable asset to any organization.
- Higher Earning Potential: With CCBA Certification, you may have the opportunity to negotiate higher salaries and compensation packages. The certification serves as evidence of your proficiency and can contribute to your overall value as a business analyst.
CCBA Certification Requirements:
To become CCBA (Certification of Capability in Business Analysis) certified, candidates must meet specific eligibility criteria set by the International Institute of Business Analysis (IIBA). These requirements ensure that individuals possess the necessary education, work experience, and knowledge to pursue and obtain the CCBA Certification. The requirements include:
- Education Requirement:
- High School Diploma, General Education Development (GED), or global equivalent
- Work Experience Requirement:
- A minimum of 3,750 hours of business analysis work experience in the last seven years.
- This work experience should cover activities related to the business analysis knowledge areas defined in the BABOK® Guide (Business Analysis Body of Knowledge), including requirements analysis and design, elicitation and collaboration, solution assessment and validation, strategy analysis, and more.
- Professional Development Requirement:
- A minimum of 21 hours of professional development in the last four years.
- These professional development hours should be specifically focused on business analysis-related topics and can include workshops, courses, conferences, and other learning activities.
- References:
- Two references from a career manager, client, or Certified Business Analysis Professional (CBAP®) recipient are required to validate the work experience.
It's important to note that the CCBA Certification requirements are subject to change, and it's recommended to refer to the official IIBA website or the current CCBA Certification Handbook for the most up-to-date information.
Application Process:
Once you have met the eligibility requirements, you can proceed with the CCBA Certification application process, which typically involves the following steps:
- Create an Account: Visit the IIBA website and create an account to access the CCBA Certification application portal.
- Complete the Application Form: Fill out the CCBA Certification application form, providing accurate details about your education, work experience, professional development hours, and references.
- Application Review: The IIBA will review your application to ensure you meet the eligibility requirements. They may contact you for additional information or clarification if needed.
- Pay the Application Fee: Once your application is approved, you will be required to pay the application fee. The fee amount may vary and is subject to change, so refer to the IIBA website for the current fee structure.
- Schedule and Prepare for the Exam: After your application is accepted and the fee is paid, you will receive instructions on how to schedule your CCBA Certification exam. Prepare for the exam by studying the BABOK® Guide and utilizing additional study materials and resources.
CCBA Certification Exam Overview:
The CCBA (Certification of Capability in Business Analysis) exam is designed to assess the knowledge, skills, and competencies of business analysts based on the BABOK® Guide (Business Analysis Body of Knowledge). Understanding the exam structure, format, duration, and passing score is crucial for effective preparation. Here is an overview of the CCBA Certification exam:
- Exam Structure:
- The CCBA Certification exam consists of multiple-choice questions.
- The exam is based on the BABOK® Guide version specified by the International Institute of Business Analysis (IIBA).
- Exam Format:
- The CCBA Certification exam is computer-based and delivered through designated test centers or online proctoring, depending on the available options in your region.
- The questions are presented as multiple-choice with four answer options, out of which you need to select the most appropriate response.
- Exam Duration:
- The duration of the CCBA Certification exam is typically 3.5 hours (210 minutes).
- This duration includes the time for reading and accepting the exam agreement, as well as the actual time allocated for answering the questions.
- Number of Questions:
- The CCBA Certification exam consists of a fixed number of questions.
- The exact number of questions may vary, but it is generally around 130 questions.
- Question Types:
- The CCBA Certification exam includes different types of questions to assess various aspects of business analysis knowledge and skills.
- These question types may include scenario-based questions, knowledge-based questions, and application-based questions.
- Passing Score:
- The passing score for the CCBA Certification exam is not disclosed by the IIBA.
- The exam is scored on a scaled basis, taking into account the difficulty level of the questions.
- You will receive a pass or fail result after completing the exam.
- Exam Syllabus:
- The CCBA Certification exam covers the knowledge areas and tasks outlined in the BABOK® Guide.
- The BABOK® Guide defines the key concepts, techniques, and best practices relevant to business analysis, and serves as the primary study resource for the exam.
- Exam Preparation:
- Effective exam preparation is crucial to succeed in the CCBA Certification exam.
- Study the BABOK® Guide thoroughly, understanding the knowledge areas, tasks, and techniques.
- Utilize additional study materials, such as practice exams, sample questions, study guides, and online resources.
- Consider attending CCBA Certification training courses to enhance your understanding and preparation.
Benefits of CCBA Certification Training
CCBA Certification training offers numerous benefits to aspiring business analysts who are preparing for the CCBA (Certification of Capability in Business Analysis) exam. Here are some key benefits of undergoing CCBA Certification training:
- Comprehensive Exam Preparation: CCBA Certification training courses are specifically designed to cover all the knowledge areas, tasks, and techniques outlined in the BABOK® Guide (Business Analysis Body of Knowledge). These courses provide a structured and comprehensive approach to exam preparation, ensuring that candidates have a thorough understanding of the subject matter.
- Mastery of Business Analysis Concepts: CCBA training helps candidates deepen their knowledge and mastery of business analysis concepts, methodologies, and best practices. It covers a wide range of topics, including requirements planning and management, enterprise analysis, solution assessment and validation, business analysis planning and monitoring, and more. This in-depth understanding enhances the capabilities of business analysts and prepares them for real-world challenges.
- Application of BABOK® Guide Principles: The BABOK® Guide serves as the primary reference for the CCBA Certification exam, and CCBA training courses provide practical guidance on how to apply the principles outlined in the guide. Training helps candidates understand how to analyze business problems, elicit and manage requirements, develop business solutions, and ensure stakeholder satisfaction.
- Real-World Case Studies and Examples: CCBA training often includes real-world case studies and examples that illustrate the application of business analysis techniques in different scenarios. These case studies provide valuable insights into the challenges faced by business analysts and demonstrate how to effectively analyze and solve complex business problems. By studying and analyzing these cases, candidates gain practical knowledge and learn from industry best practices.
- Interactive Learning Environment: CCBA training courses are typically conducted in an interactive learning environment, allowing candidates to engage in discussions, ask questions, and collaborate with fellow participants. This interactive approach fosters a deeper understanding of the subject matter through shared experiences and perspectives, enhancing the overall learning experience.
- Experienced and Certified Instructors: CCBA training is usually delivered by experienced instructors who hold CCBA or other relevant certifications themselves. These instructors bring their expertise and real-world knowledge to the training sessions, providing valuable insights and guidance to candidates. They can clarify doubts, share practical tips, and offer exam-specific guidance based on their own experiences.
- Exam Preparation Strategies: CCBA training courses provide candidates with strategies and techniques to effectively prepare for the certification exam. This includes guidance on creating study plans, time management techniques, understanding the exam structure and question types, and practicing with sample questions and mock exams. These exam-specific preparation strategies increase candidates' confidence and readiness for the actual exam.
- Networking Opportunities: CCBA training brings together aspiring business analysts from various backgrounds, industries, and organizations. This provides an excellent opportunity for networking and building professional connections within the business analysis community. Networking with fellow professionals can lead to valuable collaborations, knowledge sharing, and future career opportunities.
Continuing Education and Recertification for CCBA Certification:
Once you have achieved CCBA (Certification of Capability in Business Analysis) certification, it is important to stay updated with evolving industry practices and maintain your professional competence. The International Institute of Business Analysis (IIBA) has established continuing education and recertification requirements to ensure that CCBA certified professionals remain current and relevant in the field of business analysis. Here's an overview of continuing education and recertification for CCBA Certification:
- Recertification Cycle:
- The recertification cycle for CCBA Certification is three years.
- It begins on the date of your initial certification and ends three years later.
- Continuing Development Units (CDUs):
- To maintain CCBA Certification, you are required to earn and report a specific number of Continuing Development Units (CDUs) during each recertification cycle.
- CDUs are professional development units that represent the amount of time spent on continuing education activities related to business analysis.
- 1 CDU is equivalent to 1 hour of professional development activity.
- CDU Requirements:
- As of my knowledge cutoff in September 2021, CCBA certified professionals need to earn 60 CDUs during each three-year recertification cycle.
- CDUs can be earned through a variety of activities, such as attending training programs, workshops, conferences, webinars, and seminars related to business analysis.
- Other activities that contribute to CDU requirements may include presenting or writing articles on business analysis topics, volunteering for the IIBA, or participating in relevant professional activities.
- Recertification Application:
- At the end of your three-year recertification cycle, you are required to submit a recertification application to the IIBA.
- The recertification application includes reporting the CDUs you have earned during the cycle and providing relevant supporting documentation, such as certificates of completion or attendance.
- Recertification Fee:
- There is a recertification fee associated with maintaining CCBA Certification.
- The fee amount is subject to change, and it is advisable to refer to the IIBA website or the CCBA Certification Handbook for the most up-to-date information regarding the recertification fee.
- Audits:
- The IIBA conducts random audits to ensure compliance with the recertification requirements.
- If selected for an audit, you will be required to provide documentation as evidence of the CDUs you have claimed during the recertification cycle.
It's important to note that the specific recertification requirements and processes may change over time. Therefore, it is crucial to refer to the official IIBA website and the current CCBA Certification Handbook for the most accurate and up-to-date information regarding continuing education and recertification.
How to obtain the CCBA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
Conclusion
In conclusion, CCBA (Certification of Capability in Business Analysis) Certification is a valuable credential for business analysts seeking to demonstrate their knowledge, skills, and expertise in the field of business analysis. Through the CCBA Certification, professionals can enhance their marketability, open doors to new career opportunities, and gain recognition within the industry.
In this blog, we explored various aspects related to CCBA Certification, including an introduction to the certification, its importance for business analysts, the certification requirements, an overview of the certification exam, and the benefits of CCBA Certification training. We also touched upon the significance of continuing education and recertification to maintain the CCBA Certification and stay updated with industry practices.
By pursuing CCBA Certification, business analysts can deepen their understanding of business analysis principles and practices, demonstrate their competence to employers and clients, and gain access to a global network of professionals in the field. The certification serves as a validation of their expertise and commitment to professional growth.
It's important to stay informed about the current requirements and guidelines set by the International Institute of Business Analysis (IIBA) for CCBA Certification. It's recommended to regularly refer to the official IIBA website and the CCBA Certification Handbook for the latest information and updates.
Embarking on the journey to become CCBA certified requires dedication, preparation, and ongoing commitment to professional development. However, the rewards are worth it, as CCBA Certification can significantly contribute to the advancement of your business analysis career and open doors to exciting opportunities in the field.
Remember, CCBA Certification is not only a one-time achievement but a continuous process of learning and growth. By staying current with industry trends, expanding your knowledge through continuing education, and maintaining your certification through recertification, you can ensure that you remain at the forefront of the business analysis profession.
So, if you aspire to excel in the field of business analysis and establish yourself as a trusted and skilled professional, consider pursuing CCBA Certification and embark on a rewarding journey of professional growth and success.
ECBA Certification: Is it Worth it?
The ECBA (Entry Certificate in Business Analysis) certification is a professional credential offered by the International Institute of Business Analysis (IIBA) that recognizes individuals with foundational knowledge and understanding of business analysis principles and practices. The ECBA certification is specifically designed for individuals who are new to the field of business analysis or have limited work experience in the role.
Business analysis is a discipline that focuses on identifying business needs, defining requirements, and facilitating the development of effective solutions to address those needs. The ECBA certification serves as a validation of an individual's knowledge and understanding of fundamental concepts and techniques in business analysis.
To be eligible for the ECBA certification, candidates must meet specific criteria, including a minimum number of hours of professional development training in business analysis, adherence to the IIBA's code of conduct, and successful completion of the ECBA examination. The exam covers various knowledge areas, such as business analysis planning and monitoring, requirements elicitation and analysis, solution evaluation, and more.
Attaining the ECBA certification demonstrates an individual's commitment to professional growth and development in the field of business analysis. It signifies a solid foundation in essential business analysis practices, methodologies, and techniques.
ECBA-certified professionals possess a basic understanding of business analysis concepts and can contribute effectively to business analysis activities within their organizations. They are equipped with the skills to gather and document requirements, analyze business processes, and communicate effectively with stakeholders.
The ECBA certification offers several benefits to individuals seeking to establish themselves in the field of business analysis. It enhances their credibility and demonstrates their commitment to ongoing professional development. It also provides a pathway for career advancement by opening doors to entry-level business analysis roles and enabling professionals to build a solid foundation for further specialization and growth.
In summary, the ECBA (Entry Certificate in Business Analysis) certification is a valuable credential for individuals new to the field of business analysis or with limited experience. It validates foundational knowledge and understanding of core business analysis principles and practices. ECBA-certified professionals contribute effectively to business analysis initiatives, possess the skills to gather and analyze requirements, and establish a strong base for further career growth in the field of business analysis.
In this article
- What Is ECBA Certification?
- Is The ECBA Certification Worth It?
- Value Of ECBA Certification
- How To Become A Certified Business Analyst?
- Here Are Five Great Reasons to earn your ECBA Certificate
- Is The ECBA Difficult?
- Which Is The Best Certification For A Business Analyst?
- Final Thoughts
Business analysis is a field that requires specialized skills and knowledge to help organizations make informed decisions and achieve their goals. As such, professionals in this field often seek to demonstrate their expertise through certifications. One such certification is the Entry Certificate in Business Analysis (ECBA), offered by the International Institute of Business Analysis (IIBA). However, with the time and cost associated with obtaining the ECBA, many individuals may wonder if it is truly worth it. In this article, we will explore the benefits of obtaining the ECBA certification and help you decide whether pursuing it is the right choice for you.
What Is ECBA Certification?
The Entry Certificate in Business Analysis (ECBA) is a certification offered by the International Institute of Business Analysis (IIBA) to individuals who are starting their careers in business analysis or are interested in transitioning to this field. The ECBA certification is the first level in the IIBA's certification program and provides a solid foundation in the core concepts of business analysis. It covers topics such as business analysis planning and monitoring, elicitation and collaboration, requirements life cycle management, strategy analysis, and solution evaluation. The ECBA certification is designed to demonstrate that an individual has a fundamental understanding of business analysis principles and practices and is committed to professional development in this field.
Is The ECBA Certification Worth It?
Whether or not the ECBA certification is worth it depends on your individual career goals and circumstances. However, there are several benefits to obtaining the ECBA certification that may make it a worthwhile investment for many individuals.
Firstly, the ECBA certification provides a recognized standard of knowledge and expertise in the field of business analysis. This can be particularly valuable for individuals who are starting their careers in this field or who are looking to make a transition into business analysis from another discipline. The certification can serve as a way to demonstrate to employers and peers that you have a fundamental understanding of business analysis principles and practices.
Secondly, obtaining the ECBA certification can provide opportunities for career advancement and increased earning potential. Many organizations look for individuals with certifications to fill business analysis roles and may offer higher salaries or promotions to those with certification credentials.
Lastly, pursuing the ECBA certification can be a valuable learning experience. The certification program covers a wide range of topics and provides a structured approach to developing a comprehensive understanding of business analysis principles and practices. Even if you ultimately decide not to pursue the certification, the knowledge and skills gained through the program can be beneficial for your career development.
Value Of ECBA Certification
The value of the Entry Certificate in Business Analysis (ECBA) certification lies in the recognition it provides for individuals who are starting their careers in business analysis or transitioning into this field. Here are some key benefits of obtaining the ECBA certification:
- Demonstrates a foundational understanding of business analysis: The ECBA certification provides a recognized standard of knowledge and expertise in the field of business analysis. This can be particularly valuable for individuals who are new to the field and want to demonstrate their understanding of core concepts.
- Enhances job prospects: Many organizations look for individuals with certification credentials to fill business analysis roles. Having the ECBA certification on your resume can set you apart from other candidates and increase your chances of being selected for job interviews.
- Opens up opportunities for career advancement: Obtaining the ECBA certification can lead to higher salaries and promotions within the field of business analysis. Employers often offer salary increases or promotions to individuals who have demonstrated their commitment to professional development by obtaining certification credentials.
- Provides a structured approach to learning: The ECBA certification program covers a wide range of topics and provides a structured approach to developing a comprehensive understanding of business analysis principles and practices. This can be beneficial for individuals who want to gain a solid foundation in the field or those who are looking to expand their knowledge and skills.
- Demonstrates a commitment to professional development: Pursuing the ECBA certification demonstrates a commitment to professional development and a desire to stay up-to-date with industry trends and best practices. This can be valuable to employers and peers alike, as it shows that you are committed to your career and take your profession seriously.
How To Become A Certified Business Analyst?
To become a certified business analyst, follow these general steps:
- Meet the eligibility requirements: Most certification programs have eligibility requirements, such as a minimum level of education or work experience in the field. For example, to obtain the Entry Certificate in Business Analysis (ECBA) certification offered by the International Institute of Business Analysis (IIBA), you need to have at least 21 hours of professional development training in the field of business analysis.
- Choose a certification program: There are several certification programs available for business analysts, including the ECBA, CCBA, CBAP, and PMI-PBA. Research the different certification programs and choose one that aligns with your career goals and interests.
- Prepare for the exam: Certification exams typically cover a wide range of topics, so it's important to prepare thoroughly. This may include taking training courses, reviewing study materials, and practicing sample exam questions.
- Schedule and take the exam: Once you feel prepared, schedule a date and time to take the certification exam. The format and length of the exam will depend on the specific certification program.
- Maintain your certification: Most certification programs require individuals to maintain their certification through ongoing professional development and/or recertification exams. Stay up-to-date with industry trends and best practices to maintain your certification and continue to advance your career as a business analyst.
It's important to note that the specific steps and requirements for becoming a certified business analyst may vary depending on the certification program and your individual circumstances. Be sure to thoroughly research the certification program you are interested in and follow their specific requirements and guidelines.
Here Are Five Great Reasons to earn your ECBA Certificate
- Establish your foundational knowledge: The Entry Certificate in Business Analysis (ECBA) certification will provide you with a foundational understanding of business analysis principles and practices, making you a more effective and confident practitioner in this field.
- Boost your career prospects: The ECBA certification is recognized and respected by employers around the world, and earning this certification can increase your chances of being hired for business analysis roles or being promoted within your current organization.
- Enhance your earning potential: Individuals with ECBA certification tend to earn more than those without certification. According to the International Institute of Business Analysis (IIBA), individuals with ECBA certification earn an average of 13% more than those without certification.
- Stay up-to-date with industry best practices: The ECBA certification requires ongoing professional development to maintain, which ensures that certified individuals stay up-to-date with the latest trends, practices, and technologies in the field of business analysis.
- Join a global community of business analysts: Earning the ECBA certification will give you access to a global community of business analysts and professionals. This community can provide you with valuable networking opportunities, resources, and support throughout your career in business analysis.
Is The ECBA Difficult?
The difficulty of the Entry Certificate in Business Analysis (ECBA) certification exam may vary from person to person, depending on their background, experience, and familiarity with the topics covered in the exam. However, the ECBA certification is designed to be an entry-level certification, meaning that it is intended for individuals who are new to the field of business analysis or who have limited experience in this area.
The ECBA certification exam consists of 50 multiple-choice questions and has a duration of one hour. The questions are designed to test the candidate's understanding of fundamental concepts in business analysis, such as requirements analysis, modeling, and stakeholder engagement. The exam is based on the Business Analysis Body of Knowledge (BABOK) guide, which is a comprehensive guide to the practice of business analysis.
To prepare for the ECBA certification exam, candidates can take training courses, review study materials, and practice sample exam questions. The International Institute of Business Analysis (IIBA), which offers the ECBA certification, also provides study materials and resources to help candidates prepare for the exam.
Which Is The Best Certification For A Business Analyst?
There are several certifications available for business analysts, and the best certification for a business analyst will depend on their individual career goals and the specific needs of their organization or industry. Here are some of the most widely recognized and respected certifications for business analysts:
- Entry Certificate in Business Analysis (ECBA): This is an entry-level certification offered by the International Institute of Business Analysis (IIBA) and is intended for individuals who are new to the field of business analysis.
- Certification of Competency in Business Analysis (CCBA): This certification, also offered by the IIBA, is intended for business analysts with two to three years of experience in the field.
- Certified Business Analysis Professional (CBAP): This certification, also offered by the IIBA, is intended for business analysts with five or more years of experience in the field and who are looking to demonstrate their advanced knowledge and skills.
- Professional in Business Analysis (PMI-PBA): This certification is offered by the Project Management Institute (PMI) and is intended for business analysts who work in a project management environment.
- Certified Analytics Professional (CAP): This certification is offered by the International Institute for Analytics (IIA) and is intended for individuals who work in data and analytics, which is closely related to business analysis.
How to obtain the ECBA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
Final Thoughts
In conclusion, the Entry Certificate in Business Analysis (ECBA) certification can be a valuable credential for individuals looking to establish their foundational knowledge and skills in the field of business analysis. The ECBA certification can help boost your career prospects, enhance your earning potential, and keep you up-to-date with the latest trends and practices in business analysis.
While the difficulty of the ECBA certification exam may vary, with proper preparation and study, most individuals should be able to pass the exam and earn their certification. Additionally, there are several other certifications available for business analysts, and the best certification for you will depend on your individual career goals and experience level.
Read More
The ECBA (Entry Certificate in Business Analysis) certification is a professional credential offered by the International Institute of Business Analysis (IIBA) that recognizes individuals with foundational knowledge and understanding of business analysis principles and practices. The ECBA certification is specifically designed for individuals who are new to the field of business analysis or have limited work experience in the role.
Business analysis is a discipline that focuses on identifying business needs, defining requirements, and facilitating the development of effective solutions to address those needs. The ECBA certification serves as a validation of an individual's knowledge and understanding of fundamental concepts and techniques in business analysis.
To be eligible for the ECBA certification, candidates must meet specific criteria, including a minimum number of hours of professional development training in business analysis, adherence to the IIBA's code of conduct, and successful completion of the ECBA examination. The exam covers various knowledge areas, such as business analysis planning and monitoring, requirements elicitation and analysis, solution evaluation, and more.
Attaining the ECBA certification demonstrates an individual's commitment to professional growth and development in the field of business analysis. It signifies a solid foundation in essential business analysis practices, methodologies, and techniques.
ECBA-certified professionals possess a basic understanding of business analysis concepts and can contribute effectively to business analysis activities within their organizations. They are equipped with the skills to gather and document requirements, analyze business processes, and communicate effectively with stakeholders.
The ECBA certification offers several benefits to individuals seeking to establish themselves in the field of business analysis. It enhances their credibility and demonstrates their commitment to ongoing professional development. It also provides a pathway for career advancement by opening doors to entry-level business analysis roles and enabling professionals to build a solid foundation for further specialization and growth.
In summary, the ECBA (Entry Certificate in Business Analysis) certification is a valuable credential for individuals new to the field of business analysis or with limited experience. It validates foundational knowledge and understanding of core business analysis principles and practices. ECBA-certified professionals contribute effectively to business analysis initiatives, possess the skills to gather and analyze requirements, and establish a strong base for further career growth in the field of business analysis.
In this article
- What Is ECBA Certification?
- Is The ECBA Certification Worth It?
- Value Of ECBA Certification
- How To Become A Certified Business Analyst?
- Here Are Five Great Reasons to earn your ECBA Certificate
- Is The ECBA Difficult?
- Which Is The Best Certification For A Business Analyst?
- Final Thoughts
Business analysis is a field that requires specialized skills and knowledge to help organizations make informed decisions and achieve their goals. As such, professionals in this field often seek to demonstrate their expertise through certifications. One such certification is the Entry Certificate in Business Analysis (ECBA), offered by the International Institute of Business Analysis (IIBA). However, with the time and cost associated with obtaining the ECBA, many individuals may wonder if it is truly worth it. In this article, we will explore the benefits of obtaining the ECBA certification and help you decide whether pursuing it is the right choice for you.
What Is ECBA Certification?
The Entry Certificate in Business Analysis (ECBA) is a certification offered by the International Institute of Business Analysis (IIBA) to individuals who are starting their careers in business analysis or are interested in transitioning to this field. The ECBA certification is the first level in the IIBA's certification program and provides a solid foundation in the core concepts of business analysis. It covers topics such as business analysis planning and monitoring, elicitation and collaboration, requirements life cycle management, strategy analysis, and solution evaluation. The ECBA certification is designed to demonstrate that an individual has a fundamental understanding of business analysis principles and practices and is committed to professional development in this field.
Is The ECBA Certification Worth It?
Whether or not the ECBA certification is worth it depends on your individual career goals and circumstances. However, there are several benefits to obtaining the ECBA certification that may make it a worthwhile investment for many individuals.
Firstly, the ECBA certification provides a recognized standard of knowledge and expertise in the field of business analysis. This can be particularly valuable for individuals who are starting their careers in this field or who are looking to make a transition into business analysis from another discipline. The certification can serve as a way to demonstrate to employers and peers that you have a fundamental understanding of business analysis principles and practices.
Secondly, obtaining the ECBA certification can provide opportunities for career advancement and increased earning potential. Many organizations look for individuals with certifications to fill business analysis roles and may offer higher salaries or promotions to those with certification credentials.
Lastly, pursuing the ECBA certification can be a valuable learning experience. The certification program covers a wide range of topics and provides a structured approach to developing a comprehensive understanding of business analysis principles and practices. Even if you ultimately decide not to pursue the certification, the knowledge and skills gained through the program can be beneficial for your career development.
Value Of ECBA Certification
The value of the Entry Certificate in Business Analysis (ECBA) certification lies in the recognition it provides for individuals who are starting their careers in business analysis or transitioning into this field. Here are some key benefits of obtaining the ECBA certification:
- Demonstrates a foundational understanding of business analysis: The ECBA certification provides a recognized standard of knowledge and expertise in the field of business analysis. This can be particularly valuable for individuals who are new to the field and want to demonstrate their understanding of core concepts.
- Enhances job prospects: Many organizations look for individuals with certification credentials to fill business analysis roles. Having the ECBA certification on your resume can set you apart from other candidates and increase your chances of being selected for job interviews.
- Opens up opportunities for career advancement: Obtaining the ECBA certification can lead to higher salaries and promotions within the field of business analysis. Employers often offer salary increases or promotions to individuals who have demonstrated their commitment to professional development by obtaining certification credentials.
- Provides a structured approach to learning: The ECBA certification program covers a wide range of topics and provides a structured approach to developing a comprehensive understanding of business analysis principles and practices. This can be beneficial for individuals who want to gain a solid foundation in the field or those who are looking to expand their knowledge and skills.
- Demonstrates a commitment to professional development: Pursuing the ECBA certification demonstrates a commitment to professional development and a desire to stay up-to-date with industry trends and best practices. This can be valuable to employers and peers alike, as it shows that you are committed to your career and take your profession seriously.
How To Become A Certified Business Analyst?
To become a certified business analyst, follow these general steps:
- Meet the eligibility requirements: Most certification programs have eligibility requirements, such as a minimum level of education or work experience in the field. For example, to obtain the Entry Certificate in Business Analysis (ECBA) certification offered by the International Institute of Business Analysis (IIBA), you need to have at least 21 hours of professional development training in the field of business analysis.
- Choose a certification program: There are several certification programs available for business analysts, including the ECBA, CCBA, CBAP, and PMI-PBA. Research the different certification programs and choose one that aligns with your career goals and interests.
- Prepare for the exam: Certification exams typically cover a wide range of topics, so it's important to prepare thoroughly. This may include taking training courses, reviewing study materials, and practicing sample exam questions.
- Schedule and take the exam: Once you feel prepared, schedule a date and time to take the certification exam. The format and length of the exam will depend on the specific certification program.
- Maintain your certification: Most certification programs require individuals to maintain their certification through ongoing professional development and/or recertification exams. Stay up-to-date with industry trends and best practices to maintain your certification and continue to advance your career as a business analyst.
It's important to note that the specific steps and requirements for becoming a certified business analyst may vary depending on the certification program and your individual circumstances. Be sure to thoroughly research the certification program you are interested in and follow their specific requirements and guidelines.
Here Are Five Great Reasons to earn your ECBA Certificate
- Establish your foundational knowledge: The Entry Certificate in Business Analysis (ECBA) certification will provide you with a foundational understanding of business analysis principles and practices, making you a more effective and confident practitioner in this field.
- Boost your career prospects: The ECBA certification is recognized and respected by employers around the world, and earning this certification can increase your chances of being hired for business analysis roles or being promoted within your current organization.
- Enhance your earning potential: Individuals with ECBA certification tend to earn more than those without certification. According to the International Institute of Business Analysis (IIBA), individuals with ECBA certification earn an average of 13% more than those without certification.
- Stay up-to-date with industry best practices: The ECBA certification requires ongoing professional development to maintain, which ensures that certified individuals stay up-to-date with the latest trends, practices, and technologies in the field of business analysis.
- Join a global community of business analysts: Earning the ECBA certification will give you access to a global community of business analysts and professionals. This community can provide you with valuable networking opportunities, resources, and support throughout your career in business analysis.
Is The ECBA Difficult?
The difficulty of the Entry Certificate in Business Analysis (ECBA) certification exam may vary from person to person, depending on their background, experience, and familiarity with the topics covered in the exam. However, the ECBA certification is designed to be an entry-level certification, meaning that it is intended for individuals who are new to the field of business analysis or who have limited experience in this area.
The ECBA certification exam consists of 50 multiple-choice questions and has a duration of one hour. The questions are designed to test the candidate's understanding of fundamental concepts in business analysis, such as requirements analysis, modeling, and stakeholder engagement. The exam is based on the Business Analysis Body of Knowledge (BABOK) guide, which is a comprehensive guide to the practice of business analysis.
To prepare for the ECBA certification exam, candidates can take training courses, review study materials, and practice sample exam questions. The International Institute of Business Analysis (IIBA), which offers the ECBA certification, also provides study materials and resources to help candidates prepare for the exam.
Which Is The Best Certification For A Business Analyst?
There are several certifications available for business analysts, and the best certification for a business analyst will depend on their individual career goals and the specific needs of their organization or industry. Here are some of the most widely recognized and respected certifications for business analysts:
- Entry Certificate in Business Analysis (ECBA): This is an entry-level certification offered by the International Institute of Business Analysis (IIBA) and is intended for individuals who are new to the field of business analysis.
- Certification of Competency in Business Analysis (CCBA): This certification, also offered by the IIBA, is intended for business analysts with two to three years of experience in the field.
- Certified Business Analysis Professional (CBAP): This certification, also offered by the IIBA, is intended for business analysts with five or more years of experience in the field and who are looking to demonstrate their advanced knowledge and skills.
- Professional in Business Analysis (PMI-PBA): This certification is offered by the Project Management Institute (PMI) and is intended for business analysts who work in a project management environment.
- Certified Analytics Professional (CAP): This certification is offered by the International Institute for Analytics (IIA) and is intended for individuals who work in data and analytics, which is closely related to business analysis.
How to obtain the ECBA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
Final Thoughts
In conclusion, the Entry Certificate in Business Analysis (ECBA) certification can be a valuable credential for individuals looking to establish their foundational knowledge and skills in the field of business analysis. The ECBA certification can help boost your career prospects, enhance your earning potential, and keep you up-to-date with the latest trends and practices in business analysis.
While the difficulty of the ECBA certification exam may vary, with proper preparation and study, most individuals should be able to pass the exam and earn their certification. Additionally, there are several other certifications available for business analysts, and the best certification for you will depend on your individual career goals and experience level.
What is COBIT? Understanding the COBIT Framework
The COBIT® 5 Foundation Certification is a highly recognized credential in the field of IT governance and management. It signifies an individual's understanding and proficiency in utilizing the COBIT® 5 framework for effective governance and control of information and technology within organizations.
COBIT® (Control Objectives for Information and Related Technology) is a globally accepted framework developed by ISACA (Information Systems Audit and Control Association) for guiding the governance and management of enterprise IT. The COBIT® 5 Foundation Certification serves as an entry-level qualification that equips professionals with the fundamental knowledge and skills necessary to apply COBIT® 5 principles and practices.
The COBIT® 5 Foundation Certification provides individuals with a comprehensive understanding of IT governance domains, processes, and enablers. It covers various aspects of IT management, including strategic alignment, risk management, performance measurement, and process improvement. By obtaining this certification, individuals demonstrate their ability to effectively govern and control IT resources and align them with organizational goals and objectives.
To achieve the COBIT® 5 Foundation Certification, candidates must successfully pass an examination that tests their knowledge of key COBIT® 5 concepts, principles, and terminology. This certification is beneficial for professionals involved in IT governance, IT management, IT assurance, and IT risk management roles, as well as individuals aspiring to enhance their career prospects in these areas.
By earning the COBIT® 5 Foundation Certification, professionals gain a competitive advantage in the job market. The certification enhances their credibility, demonstrating their commitment to best practices in IT governance and management. It equips them with the necessary skills to contribute effectively to organizations' strategic decision-making processes, risk management practices, and value delivery mechanisms.
The COBIT® 5 Foundation Certification not only validates an individual's knowledge and expertise but also provides them with a practical framework for managing IT resources and improving organizational performance. It offers a common language and set of principles for IT professionals to align their efforts with business objectives and drive sustainable success.
In summary, the COBIT® 5 Foundation Certification is a highly regarded qualification that establishes individuals as proficient practitioners in IT governance and management. It equips professionals with the necessary skills and knowledge to implement effective controls, enhance IT processes, and align IT strategies with organizational goals. COBIT® 5-certified professionals play a vital role in ensuring efficient and secure management of IT resources, driving value for organizations in today's rapidly evolving digital landscape.
Table of Contents
What is COBIT?
What is ISACA?
What is the History of COBIT?
Why Is COBIT Important?
What Is COBIT Framework?
What Are the COBIT Framework Basics?
What Are the Principles of COBIT?
What Do You Need to Know Before Using COBIT?
What is the Difference Between COBIT 5 and COBIT 2019?
How Does COBIT Compare With Other Governance Frameworks?
The Various COBIT Components
Why Is COBIT 5.0 the Most Celebrated Version?
The Advantages of COBIT 5.0 Certification
Benefits of COBIT
Goals of the COBIT Framework
Meeting Stakeholder Needs
Taking a Holistic Approach to Governance
Conclusion
COBIT is a widely recognized and respected framework that is used to help organizations govern and manage their information technology (IT) systems. COBIT, which stands for Control Objectives for Information and Related Technology, was first introduced in the mid-1990s by the Information Systems Audit and Control Association (ISACA). Since then, it has become a well-established standard for IT governance and management, with a focus on providing a comprehensive framework for ensuring that IT systems align with business goals, comply with regulations and standards, and operate effectively and efficiently. This article will explore the basics of the COBIT framework, including its history, key concepts, and benefits, to help you understand how it can be used to improve your organization's IT governance and management.
What is COBIT?
COBIT (Control Objectives for Information and Related Technology) is a widely recognized and respected framework that provides a comprehensive set of guidelines for governing and managing enterprise information technology (IT) systems. Developed by the Information Systems Audit and Control Association (ISACA), COBIT is designed to help organizations align their IT strategy with their business goals, optimize the use of IT resources, ensure compliance with laws and regulations, and manage IT risks effectively. The framework provides a set of best practices and standards for IT governance and management, including a comprehensive set of control objectives, metrics, and maturity models that can be used to assess and improve an organization's IT processes and capabilities. COBIT is used by businesses, government agencies, and other organizations around the world to improve the effectiveness and efficiency of their IT operations, reduce risk, and improve overall business performance.
What is ISACA?
ISACA stands for Information Systems Audit and Control Association. It is an international professional association that provides knowledge, tools, and networking opportunities to information technology (IT) professionals and organizations around the world. ISACA was founded in 1969 and currently has over 150,000 members in more than 180 countries. The association offers a range of professional development and certification programs, including the Certified Information Systems Auditor (CISA), Certified Information Security Manager (CISM), and Certified in Risk and Information Systems Control (CRISC) certifications. ISACA also develops and maintains several widely used frameworks and standards related to IT governance, including COBIT (Control Objectives for Information and Related Technology), which is a framework for IT governance and management. ISACA plays an important role in advancing the field of IT governance, risk management, and compliance by providing guidance and resources to IT professionals and organizations worldwide.
What is the History of COBIT?
COBIT (Control Objectives for Information and Related Technology) was first developed in 1996 by the Information Systems Audit and Control Association (ISACA) as a framework to help IT professionals govern and manage IT systems more effectively. The original version of COBIT was focused on IT auditing and control, with a focus on providing a set of control objectives and best practices to help organizations improve the reliability, security, and integrity of their IT systems.
Over the years, COBIT has evolved to become a more comprehensive framework for IT governance and management, incorporating best practices from other frameworks such as ITIL (Information Technology Infrastructure Library) and ISO/IEC 27001 (Information Security Management System). Today, COBIT is widely recognized as a leading framework for IT governance and management, with a focus on providing a comprehensive set of guidelines and best practices for managing IT systems in a way that supports business objectives, meets regulatory requirements, and optimizes IT investments.
COBIT is regularly updated to reflect changes in the IT landscape, such as the increasing importance of cybersecurity and the growing use of cloud computing and other emerging technologies. The latest version of COBIT, COBIT 2019, was released in 2018 and represents the most up-to-date and comprehensive set of guidelines for IT governance and management available today.
Why Is COBIT Important?
COBIT (Control Objectives for Information and Related Technology) is important for several reasons:
- Provides a comprehensive framework for IT governance and management: COBIT provides a comprehensive set of guidelines and best practices for managing IT systems in a way that supports business objectives, meets regulatory requirements, and optimizes IT investments. This makes it an essential tool for IT professionals and organizations that want to improve their IT governance and management capabilities.
- Helps organizations comply with laws and regulations: COBIT helps organizations ensure that their IT systems comply with laws, regulations, and industry standards. By following the COBIT framework, organizations can reduce the risk of non-compliance and avoid legal and regulatory penalties.
- Supports effective risk management: COBIT includes a comprehensive set of controls and metrics that can be used to assess and manage IT-related risks. This helps organizations identify and mitigate risks before they become major issues, reducing the risk of IT-related incidents and their impact on business operations.
- Improves business performance: COBIT helps organizations align their IT strategy with their business goals, optimizing the use of IT resources and improving overall business performance. By improving IT governance and management, organizations can reduce costs, improve efficiency, and gain a competitive advantage.
What Is COBIT Framework?
The COBIT (Control Objectives for Information and Related Technology) framework is a set of guidelines, best practices, and standards for IT governance and management. It is designed to help organizations ensure that their IT systems align with business goals, comply with laws and regulations, and operate effectively and efficiently. The COBIT framework provides a comprehensive set of control objectives, metrics, and maturity models that can be used to assess and improve an organization's IT processes and capabilities.
The COBIT framework is organized into five key domains:
- Evaluate, Direct, and Monitor (EDM): This domain provides guidance on how to ensure that IT governance is effective, efficient, and responsive to business needs. It includes best practices for setting IT policies and strategies, defining IT objectives, and monitoring IT performance.
- Align, Plan, and Organize (APO): This domain focuses on how to align IT with business objectives, plan and manage IT projects, and organize IT resources effectively. It includes best practices for IT portfolio management, IT budgeting, and IT organizational design.
- Build, Acquire, and Implement (BAI): This domain provides guidance on how to build, acquire, and implement IT systems and solutions that meet business needs and comply with regulations and standards. It includes best practices for project management, system development, and change management.
- Deliver, Service, and Support (DSS): This domain focuses on how to deliver IT services and support to end-users, ensuring that IT systems operate effectively and efficiently. It includes best practices for IT service management, IT operations management, and IT asset management.
- Monitor, Evaluate, and Assess (MEA): This domain provides guidance on how to monitor and assess IT performance, compliance, and risk. It includes best practices for IT audit, IT risk management, and IT performance management.
What Are the COBIT Framework Basics?
The COBIT (Control Objectives for Information and Related Technology) framework is based on five core principles that provide a foundation for effective IT governance and management:
- Meeting stakeholder needs: IT systems should be designed and operated to meet the needs of stakeholders, including customers, regulators, shareholders, and employees.
- Covering the enterprise end-to-end: IT governance and management should cover the entire enterprise, including all IT systems and processes.
- Applying a single integrated framework: Organizations should use a single integrated framework to manage their IT systems, rather than relying on multiple frameworks or ad-hoc approaches.
- Enabling a holistic approach: IT governance and management should be approached holistically, considering all aspects of IT, including people, processes, and technology.
- Separating governance from management: IT governance should be separate from IT management, with clear roles and responsibilities defined for each.
In addition to these core principles, the COBIT framework provides a set of control objectives, metrics, and maturity models that can be used to assess and improve an organization's IT governance and management capabilities. These are organized into five domains, as described in my previous answer: Evaluate, Direct, and Monitor (EDM); Align, Plan, and Organize (APO); Build, Acquire, and Implement (BAI); Deliver, Service, and Support (DSS); and Monitor, Evaluate, and Assess (MEA).
The COBIT framework also includes a set of enablers, such as processes, organizational structures, information, and technology, which can be used to support the implementation of the framework and the achievement of IT governance and management objectives.
What Are the Principles of COBIT?
The COBIT (Control Objectives for Information and Related Technology) framework is based on a set of five principles that provide a foundation for effective IT governance and management. These principles are as follows:
- Meeting Stakeholder Needs: The first principle of COBIT is to meet the needs of stakeholders, which includes customers, regulators, shareholders, and employees. IT systems should be designed and operated to meet these needs, and organizations should prioritize their IT investments accordingly.
- Covering the Enterprise End-to-End: The second principle of COBIT is to cover the entire enterprise, including all IT systems and processes. IT governance and management should be integrated across the enterprise and should consider all aspects of IT, including people, processes, and technology.
- Applying a Single, Integrated Framework: The third principle of COBIT is to apply a single, integrated framework for IT governance and management. This helps organizations to avoid inconsistencies and gaps in their IT processes and ensures that all stakeholders are working toward the same objectives.
- Enabling a Holistic Approach: The fourth principle of COBIT is to enable a holistic approach to IT governance and management. This means considering all aspects of IT in an integrated manner, and ensuring that all stakeholders are working together to achieve common objectives.
- Separating Governance from Management: The final principle of COBIT is to separate IT governance from IT management. Governance is responsible for setting direction and ensuring compliance, while management is responsible for implementing and executing the IT strategy. This helps to ensure clear accountability and avoid conflicts of interest.
What Do You Need to Know Before Using COBIT?
Before using COBIT (Control Objectives for Information and Related Technology), there are several key things you should know:
- Understand your organization's objectives: Before implementing the COBIT framework, it's important to understand your organization's objectives, including its mission, values, and strategic goals. This will help you tailor the framework to meet your organization's specific needs.
- Identify key stakeholders: Identify the key stakeholders involved in your organization's IT governance and management processes, including customers, regulators, shareholders, and employees. Understanding their needs and expectations is essential for designing an effective IT governance and management strategy.
- Establish clear roles and responsibilities: It's important to establish clear roles and responsibilities for IT governance and management, including who is responsible for setting strategy, making decisions, and executing on that strategy. This helps to ensure accountability and avoid confusion.
- Assess your organization's current state: Before implementing the COBIT framework, assess your organization's current state of IT governance and management. This will help you identify areas of strength and weakness, and tailor your approach accordingly.
- Determine which COBIT version to use: COBIT has evolved over time, with different versions available for different purposes. It's important to determine which version of COBIT is best suited to your organization's needs.
- Define metrics and measurement criteria: Define metrics and measurement criteria to evaluate the effectiveness of your IT governance and management processes. This will help you track progress over time and identify areas for improvement.
What is the Difference Between COBIT 5 and COBIT 2019?
COBIT 5 and COBIT 2019 are two different versions of the COBIT (Control Objectives for Information and Related Technology) framework. While both versions share many similarities, there are some key differences between the two:
- Scope: COBIT 5 has a broader scope than COBIT 2019, as it covers not only IT governance but also enterprise governance and management. COBIT 2019 focuses specifically on IT governance and management.
- Structure: COBIT 5 is structured around five governance and management domains, while COBIT 2019 is structured around four focus areas. The domains in COBIT 5 are governance, strategy, acquisition, delivery, and monitoring, while the focus areas in COBIT 2019 are governance, management, alignment, and assurance.
- Framework components: COBIT 2019 has several new components that were not present in COBIT 5, including design factors, implementation guidance, and performance management.
- Updated content: COBIT 2019 includes updated content to reflect changes in the IT landscape since the release of COBIT 5, including new technologies and emerging trends.
- Implementation approach: COBIT 2019 provides a more flexible implementation approach than COBIT 5, with guidance on how to tailor the framework to meet an organization's specific needs.
How Does COBIT Compare With Other Governance Frameworks?
COBIT (Control Objectives for Information and Related Technology) is one of several governance frameworks that organizations can use to guide their IT governance and management practices. Here are some ways that COBIT compares with other popular frameworks:
- ITIL (Information Technology Infrastructure Library): ITIL is a framework that focuses on IT service management. While COBIT covers a broad range of IT governance and management topics, including IT service management, ITIL provides a more detailed set of best practices for delivering IT services.
- ISO/IEC 27001: ISO/IEC 27001 is a standard that outlines requirements for information security management systems. While COBIT includes information security as part of its overall governance and management framework, ISO/IEC 27001 provides more detailed guidance on how to establish and maintain an information security management system.
- NIST Cybersecurity Framework: The NIST Cybersecurity Framework provides a set of guidelines for improving cybersecurity risk management. While COBIT includes guidance on managing IT risks, the NIST Cybersecurity Framework provides more detailed guidance on how to assess and manage cybersecurity risks.
- COSO (Committee of Sponsoring Organizations of the Treadway Commission): COSO provides a framework for enterprise risk management. While COBIT includes risk management as part of its overall governance and management framework, COSO provides a more detailed set of best practices for managing risks across the enterprise.
How Does COBIT Compare With Other Governance Frameworks?
COBIT (Control Objectives for Information and Related Technology) is one of several governance frameworks that organizations can use to guide their IT governance and management practices. Here are some ways that COBIT compares with other popular frameworks:
- ITIL (Information Technology Infrastructure Library): ITIL is a framework that focuses on IT service management. While COBIT covers a broad range of IT governance and management topics, including IT service management, ITIL provides a more detailed set of best practices for delivering IT services.
- ISO/IEC 27001: ISO/IEC 27001 is a standard that outlines requirements for information security management systems. While COBIT includes information security as part of its overall governance and management framework, ISO/IEC 27001 provides more detailed guidance on how to establish and maintain an information security management system.
- NIST Cybersecurity Framework: The NIST Cybersecurity Framework provides a set of guidelines for improving cybersecurity risk management. While COBIT includes guidance on managing IT risks, the NIST Cybersecurity Framework provides more detailed guidance on how to assess and manage cybersecurity risks.
- COSO (Committee of Sponsoring Organizations of the Treadway Commission): COSO provides a framework for enterprise risk management. While COBIT includes risk management as part of its overall governance and management framework, COSO provides a more detailed set of best practices for managing risks across the enterprise.
The Various COBIT Components
The COBIT (Control Objectives for Information and Related Technology) framework is comprised of several components that work together to provide a comprehensive approach to IT governance and management. Here are the main components of COBIT:
- Governance objectives: COBIT defines governance as the set of practices and processes that ensure that an organization's IT investments support its overall business goals and objectives. COBIT includes a set of governance objectives that provide a high-level overview of the key areas that organizations need to focus on to achieve effective IT governance.
- Governance and management domains: COBIT is structured around five governance and management domains: governance, strategy, acquisition, delivery, and monitoring. Each domain includes a set of processes and practices that organizations can use to manage and govern their IT operations.
- Process reference model: COBIT provides a process reference model that defines the processes and activities involved in each of the five domains. The process reference model includes a set of generic processes that can be tailored to meet an organization's specific needs.
- Control objectives: COBIT includes a set of control objectives that provide detailed guidance on how to achieve specific outcomes within each process. Control objectives are used to define the specific requirements that need to be met to achieve effective IT governance.
- Management guidelines: COBIT provides a set of management guidelines that organizations can use to implement the framework. The guidelines include practical advice and guidance on how to implement COBIT in a way that is tailored to an organization's specific needs.
- Maturity models: COBIT includes a set of maturity models that organizations can use to assess their current level of IT governance maturity and identify areas for improvement. The maturity models provide a roadmap for organizations to follow as they work to improve their IT governance and management practices.
Why Is COBIT 5.0 the Most Celebrated Version?
COBIT 5.0 is often considered the most celebrated version of the COBIT framework due to several reasons:
- Broad scope: COBIT 5.0 has a broad scope that covers all aspects of IT governance and management. This makes it a comprehensive framework that can be used by organizations of all sizes and across all industries.
- Alignment with other frameworks: COBIT 5.0 is designed to be compatible with other frameworks, such as ITIL and ISO/IEC 27001, making it easier for organizations to integrate it into their existing IT governance and management practices.
- Focus on business value: COBIT 5.0 places a strong emphasis on delivering business value through effective IT governance and management. This helps organizations to align their IT investments with their overall business objectives and achieve better outcomes.
- Maturity models: COBIT 5.0 includes maturity models that organizations can use to assess their current level of IT governance and management maturity and identify areas for improvement. This helps organizations to take a more strategic approach to IT governance and management and improve their overall performance.
- User-friendly: COBIT 5.0 is designed to be user-friendly, with clear and concise language and a straightforward structure that makes it easy to navigate and implement.
The Advantages of COBIT 5.0 Certification
There are several advantages of COBIT 5.0 certification, including:
- Industry recognition: COBIT 5.0 is widely recognized as a leading framework for IT governance and management. Achieving COBIT 5.0 certification demonstrates a high level of knowledge and expertise in this field and can enhance your professional reputation.
- Career advancement: COBIT 5.0 certification can help you to advance your career in the IT governance and management field. It demonstrates to employers that you have the skills and knowledge needed to contribute to the success of their organization.
- Improved job performance: COBIT 5.0 certification can improve your job performance by providing you with a deeper understanding of IT governance and management principles, processes, and practices. This can help you to make better decisions and deliver better outcomes for your organization.
- Competitive advantage: COBIT 5.0 certification can give you a competitive advantage in the job market by setting you apart from other candidates who do not have this certification. It can help you to stand out and demonstrate your commitment to professional development and excellence.
- Personal growth: COBIT 5.0 certification can provide you with personal growth and development opportunities. It can help you to expand your knowledge and skills and take on new challenges in your career.
Benefits of COBIT
The COBIT framework offers several benefits for organizations, including:
- Improved IT governance: COBIT provides a structured approach to IT governance that helps organizations to align their IT strategy with their business goals and objectives. This ensures that IT investments are focused on delivering value and that IT risks are managed effectively.
- Better risk management: COBIT helps organizations to identify and manage IT-related risks more effectively. By providing a framework for risk management, COBIT enables organizations to assess the impact of IT risks on their business operations and take appropriate measures to mitigate them.
- Increased efficiency and effectiveness: COBIT promotes best practices for IT management and governance, which can help organizations to improve their operational efficiency and effectiveness. By standardizing processes and procedures, COBIT enables organizations to reduce errors and improve service delivery.
- Improved stakeholder confidence: COBIT provides a transparent and auditable approach to IT governance that can help to improve stakeholder confidence. By demonstrating a commitment to effective IT management and governance, organizations can build trust with their stakeholders and enhance their reputation.
- Better compliance: COBIT can help organizations to comply with regulatory and legal requirements related to IT governance and management. By providing a framework for compliance, COBIT enables organizations to ensure that they are meeting their obligations and avoiding potential legal and financial risks.
How to obtain the COBIT Framewordk certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- IT Service Management & Governance: COBIT, ISO
Goals of the COBIT Framework
The goals of the COBIT framework are to:
- Provide a comprehensive framework: COBIT aims to provide a comprehensive framework for IT governance and management that covers all aspects of IT operations, from strategy development to day-to-day operations.
- Ensure alignment between IT and business objectives: COBIT emphasizes the importance of aligning IT objectives with business objectives to ensure that IT investments are focused on delivering value to the organization.
- Promote best practices: COBIT promotes best practices for IT governance and management that are based on industry standards and frameworks.
- Provide a common language: COBIT provides a common language and terminology for IT governance and management that can be understood by all stakeholders, including business leaders, IT professionals, and auditors.
- Enable effective risk management: COBIT provides a structured approach to IT risk management that enables organizations to identify, assess, and manage IT-related risks more effectively.
- Ensure compliance: COBIT helps organizations to comply with regulatory and legal requirements related to IT governance and management by providing a framework for compliance.
Meeting Stakeholder Needs
Meeting stakeholder needs is a key component of the COBIT framework. COBIT defines stakeholders as individuals or groups that have an interest in or are affected by an organization's IT operations. This can include internal stakeholders, such as business leaders and IT professionals, as well as external stakeholders, such as customers, regulators, and investors.
To meet stakeholder needs, COBIT emphasizes the importance of understanding stakeholder expectations and ensuring that IT operations are aligned with these expectations. This requires a structured approach to IT governance and management that takes into account the needs and expectations of all stakeholders.
COBIT provides a framework for IT governance and management that enables organizations to:
- Define stakeholder expectations: COBIT helps organizations to identify and understand the needs and expectations of all stakeholders, including business leaders, IT professionals, customers, and regulators.
- Align IT with business objectives: COBIT emphasizes the importance of aligning IT objectives with business objectives to ensure that IT investments are focused on delivering value to the organization and meeting stakeholder needs.
- Manage IT-related risks: COBIT provides a structured approach to IT risk management that enables organizations to identify, assess, and manage IT-related risks that could impact stakeholders.
- Ensure compliance with regulatory and legal requirements: COBIT helps organizations to comply with regulatory and legal requirements related to IT governance and management, which can help to build stakeholder confidence and trust.
Taking a Holistic Approach to Governance
Taking a holistic approach to governance is a fundamental concept of the COBIT framework. Holistic governance means that organizations should view IT as an integral part of their overall business strategy, and that IT governance should be integrated with overall organizational governance.
COBIT emphasizes that effective IT governance requires a holistic approach that encompasses all aspects of IT operations, including people, processes, and technology. This approach enables organizations to achieve the following:
- Alignment with business objectives: A holistic approach to governance ensures that IT operations are aligned with the overall business objectives of the organization. This alignment is critical to ensure that IT investments are focused on delivering value to the organization.
- Integration with overall governance: A holistic approach to governance integrates IT governance with overall organizational governance. This integration ensures that IT governance is aligned with the overall governance framework and helps to avoid silos and fragmentation.
- Comprehensive coverage: A holistic approach to governance provides comprehensive coverage of all aspects of IT operations, including people, processes, and technology. This coverage ensures that all aspects of IT operations are governed and managed effectively.
- Effective risk management: A holistic approach to governance enables effective risk management by ensuring that all aspects of IT operations are considered when assessing and managing risks.
- Continual improvement: A holistic approach to governance emphasizes the importance of continual improvement. This ensures that organizations are constantly seeking to improve their IT operations to meet the evolving needs of the business.
Conclusion
In conclusion, COBIT is a comprehensive framework that provides organizations with a structured approach to IT governance and management. The framework is designed to help organizations meet stakeholder needs, align IT with business objectives, manage IT-related risks, and ensure compliance with regulatory and legal requirements.
COBIT emphasizes the importance of taking a holistic approach to governance that encompasses all aspects of IT operations, including people, processes, and technology. This approach enables organizations to achieve effective IT governance and management that is integrated with overall organizational governance.
COBIT has evolved over time, with each version bringing improvements and updates to the framework. The most celebrated version of COBIT is COBIT 5.0, which provides organizations with a comprehensive approach to IT governance and management.
In addition to providing a framework for IT governance and management, COBIT also offers certification programs that enable IT professionals to demonstrate their knowledge and expertise in the framework. COBIT certification can provide professionals with a competitive edge in the job market and help organizations to build a team of skilled IT professionals who can effectively implement and manage the COBIT framework.
Read More
The COBIT® 5 Foundation Certification is a highly recognized credential in the field of IT governance and management. It signifies an individual's understanding and proficiency in utilizing the COBIT® 5 framework for effective governance and control of information and technology within organizations.
COBIT® (Control Objectives for Information and Related Technology) is a globally accepted framework developed by ISACA (Information Systems Audit and Control Association) for guiding the governance and management of enterprise IT. The COBIT® 5 Foundation Certification serves as an entry-level qualification that equips professionals with the fundamental knowledge and skills necessary to apply COBIT® 5 principles and practices.
The COBIT® 5 Foundation Certification provides individuals with a comprehensive understanding of IT governance domains, processes, and enablers. It covers various aspects of IT management, including strategic alignment, risk management, performance measurement, and process improvement. By obtaining this certification, individuals demonstrate their ability to effectively govern and control IT resources and align them with organizational goals and objectives.
To achieve the COBIT® 5 Foundation Certification, candidates must successfully pass an examination that tests their knowledge of key COBIT® 5 concepts, principles, and terminology. This certification is beneficial for professionals involved in IT governance, IT management, IT assurance, and IT risk management roles, as well as individuals aspiring to enhance their career prospects in these areas.
By earning the COBIT® 5 Foundation Certification, professionals gain a competitive advantage in the job market. The certification enhances their credibility, demonstrating their commitment to best practices in IT governance and management. It equips them with the necessary skills to contribute effectively to organizations' strategic decision-making processes, risk management practices, and value delivery mechanisms.
The COBIT® 5 Foundation Certification not only validates an individual's knowledge and expertise but also provides them with a practical framework for managing IT resources and improving organizational performance. It offers a common language and set of principles for IT professionals to align their efforts with business objectives and drive sustainable success.
In summary, the COBIT® 5 Foundation Certification is a highly regarded qualification that establishes individuals as proficient practitioners in IT governance and management. It equips professionals with the necessary skills and knowledge to implement effective controls, enhance IT processes, and align IT strategies with organizational goals. COBIT® 5-certified professionals play a vital role in ensuring efficient and secure management of IT resources, driving value for organizations in today's rapidly evolving digital landscape.
Table of Contents
What is COBIT?
What is ISACA?
What is the History of COBIT?
Why Is COBIT Important?
What Is COBIT Framework?
What Are the COBIT Framework Basics?
What Are the Principles of COBIT?
What Do You Need to Know Before Using COBIT?
What is the Difference Between COBIT 5 and COBIT 2019?
How Does COBIT Compare With Other Governance Frameworks?
The Various COBIT Components
Why Is COBIT 5.0 the Most Celebrated Version?
The Advantages of COBIT 5.0 Certification
Benefits of COBIT
Goals of the COBIT Framework
Meeting Stakeholder Needs
Taking a Holistic Approach to Governance
Conclusion
COBIT is a widely recognized and respected framework that is used to help organizations govern and manage their information technology (IT) systems. COBIT, which stands for Control Objectives for Information and Related Technology, was first introduced in the mid-1990s by the Information Systems Audit and Control Association (ISACA). Since then, it has become a well-established standard for IT governance and management, with a focus on providing a comprehensive framework for ensuring that IT systems align with business goals, comply with regulations and standards, and operate effectively and efficiently. This article will explore the basics of the COBIT framework, including its history, key concepts, and benefits, to help you understand how it can be used to improve your organization's IT governance and management.
What is COBIT?
COBIT (Control Objectives for Information and Related Technology) is a widely recognized and respected framework that provides a comprehensive set of guidelines for governing and managing enterprise information technology (IT) systems. Developed by the Information Systems Audit and Control Association (ISACA), COBIT is designed to help organizations align their IT strategy with their business goals, optimize the use of IT resources, ensure compliance with laws and regulations, and manage IT risks effectively. The framework provides a set of best practices and standards for IT governance and management, including a comprehensive set of control objectives, metrics, and maturity models that can be used to assess and improve an organization's IT processes and capabilities. COBIT is used by businesses, government agencies, and other organizations around the world to improve the effectiveness and efficiency of their IT operations, reduce risk, and improve overall business performance.
What is ISACA?
ISACA stands for Information Systems Audit and Control Association. It is an international professional association that provides knowledge, tools, and networking opportunities to information technology (IT) professionals and organizations around the world. ISACA was founded in 1969 and currently has over 150,000 members in more than 180 countries. The association offers a range of professional development and certification programs, including the Certified Information Systems Auditor (CISA), Certified Information Security Manager (CISM), and Certified in Risk and Information Systems Control (CRISC) certifications. ISACA also develops and maintains several widely used frameworks and standards related to IT governance, including COBIT (Control Objectives for Information and Related Technology), which is a framework for IT governance and management. ISACA plays an important role in advancing the field of IT governance, risk management, and compliance by providing guidance and resources to IT professionals and organizations worldwide.
What is the History of COBIT?
COBIT (Control Objectives for Information and Related Technology) was first developed in 1996 by the Information Systems Audit and Control Association (ISACA) as a framework to help IT professionals govern and manage IT systems more effectively. The original version of COBIT was focused on IT auditing and control, with a focus on providing a set of control objectives and best practices to help organizations improve the reliability, security, and integrity of their IT systems.
Over the years, COBIT has evolved to become a more comprehensive framework for IT governance and management, incorporating best practices from other frameworks such as ITIL (Information Technology Infrastructure Library) and ISO/IEC 27001 (Information Security Management System). Today, COBIT is widely recognized as a leading framework for IT governance and management, with a focus on providing a comprehensive set of guidelines and best practices for managing IT systems in a way that supports business objectives, meets regulatory requirements, and optimizes IT investments.
COBIT is regularly updated to reflect changes in the IT landscape, such as the increasing importance of cybersecurity and the growing use of cloud computing and other emerging technologies. The latest version of COBIT, COBIT 2019, was released in 2018 and represents the most up-to-date and comprehensive set of guidelines for IT governance and management available today.
Why Is COBIT Important?
COBIT (Control Objectives for Information and Related Technology) is important for several reasons:
- Provides a comprehensive framework for IT governance and management: COBIT provides a comprehensive set of guidelines and best practices for managing IT systems in a way that supports business objectives, meets regulatory requirements, and optimizes IT investments. This makes it an essential tool for IT professionals and organizations that want to improve their IT governance and management capabilities.
- Helps organizations comply with laws and regulations: COBIT helps organizations ensure that their IT systems comply with laws, regulations, and industry standards. By following the COBIT framework, organizations can reduce the risk of non-compliance and avoid legal and regulatory penalties.
- Supports effective risk management: COBIT includes a comprehensive set of controls and metrics that can be used to assess and manage IT-related risks. This helps organizations identify and mitigate risks before they become major issues, reducing the risk of IT-related incidents and their impact on business operations.
- Improves business performance: COBIT helps organizations align their IT strategy with their business goals, optimizing the use of IT resources and improving overall business performance. By improving IT governance and management, organizations can reduce costs, improve efficiency, and gain a competitive advantage.
What Is COBIT Framework?
The COBIT (Control Objectives for Information and Related Technology) framework is a set of guidelines, best practices, and standards for IT governance and management. It is designed to help organizations ensure that their IT systems align with business goals, comply with laws and regulations, and operate effectively and efficiently. The COBIT framework provides a comprehensive set of control objectives, metrics, and maturity models that can be used to assess and improve an organization's IT processes and capabilities.
The COBIT framework is organized into five key domains:
- Evaluate, Direct, and Monitor (EDM): This domain provides guidance on how to ensure that IT governance is effective, efficient, and responsive to business needs. It includes best practices for setting IT policies and strategies, defining IT objectives, and monitoring IT performance.
- Align, Plan, and Organize (APO): This domain focuses on how to align IT with business objectives, plan and manage IT projects, and organize IT resources effectively. It includes best practices for IT portfolio management, IT budgeting, and IT organizational design.
- Build, Acquire, and Implement (BAI): This domain provides guidance on how to build, acquire, and implement IT systems and solutions that meet business needs and comply with regulations and standards. It includes best practices for project management, system development, and change management.
- Deliver, Service, and Support (DSS): This domain focuses on how to deliver IT services and support to end-users, ensuring that IT systems operate effectively and efficiently. It includes best practices for IT service management, IT operations management, and IT asset management.
- Monitor, Evaluate, and Assess (MEA): This domain provides guidance on how to monitor and assess IT performance, compliance, and risk. It includes best practices for IT audit, IT risk management, and IT performance management.
What Are the COBIT Framework Basics?
The COBIT (Control Objectives for Information and Related Technology) framework is based on five core principles that provide a foundation for effective IT governance and management:
- Meeting stakeholder needs: IT systems should be designed and operated to meet the needs of stakeholders, including customers, regulators, shareholders, and employees.
- Covering the enterprise end-to-end: IT governance and management should cover the entire enterprise, including all IT systems and processes.
- Applying a single integrated framework: Organizations should use a single integrated framework to manage their IT systems, rather than relying on multiple frameworks or ad-hoc approaches.
- Enabling a holistic approach: IT governance and management should be approached holistically, considering all aspects of IT, including people, processes, and technology.
- Separating governance from management: IT governance should be separate from IT management, with clear roles and responsibilities defined for each.
In addition to these core principles, the COBIT framework provides a set of control objectives, metrics, and maturity models that can be used to assess and improve an organization's IT governance and management capabilities. These are organized into five domains, as described in my previous answer: Evaluate, Direct, and Monitor (EDM); Align, Plan, and Organize (APO); Build, Acquire, and Implement (BAI); Deliver, Service, and Support (DSS); and Monitor, Evaluate, and Assess (MEA).
The COBIT framework also includes a set of enablers, such as processes, organizational structures, information, and technology, which can be used to support the implementation of the framework and the achievement of IT governance and management objectives.
What Are the Principles of COBIT?
The COBIT (Control Objectives for Information and Related Technology) framework is based on a set of five principles that provide a foundation for effective IT governance and management. These principles are as follows:
- Meeting Stakeholder Needs: The first principle of COBIT is to meet the needs of stakeholders, which includes customers, regulators, shareholders, and employees. IT systems should be designed and operated to meet these needs, and organizations should prioritize their IT investments accordingly.
- Covering the Enterprise End-to-End: The second principle of COBIT is to cover the entire enterprise, including all IT systems and processes. IT governance and management should be integrated across the enterprise and should consider all aspects of IT, including people, processes, and technology.
- Applying a Single, Integrated Framework: The third principle of COBIT is to apply a single, integrated framework for IT governance and management. This helps organizations to avoid inconsistencies and gaps in their IT processes and ensures that all stakeholders are working toward the same objectives.
- Enabling a Holistic Approach: The fourth principle of COBIT is to enable a holistic approach to IT governance and management. This means considering all aspects of IT in an integrated manner, and ensuring that all stakeholders are working together to achieve common objectives.
- Separating Governance from Management: The final principle of COBIT is to separate IT governance from IT management. Governance is responsible for setting direction and ensuring compliance, while management is responsible for implementing and executing the IT strategy. This helps to ensure clear accountability and avoid conflicts of interest.
What Do You Need to Know Before Using COBIT?
Before using COBIT (Control Objectives for Information and Related Technology), there are several key things you should know:
- Understand your organization's objectives: Before implementing the COBIT framework, it's important to understand your organization's objectives, including its mission, values, and strategic goals. This will help you tailor the framework to meet your organization's specific needs.
- Identify key stakeholders: Identify the key stakeholders involved in your organization's IT governance and management processes, including customers, regulators, shareholders, and employees. Understanding their needs and expectations is essential for designing an effective IT governance and management strategy.
- Establish clear roles and responsibilities: It's important to establish clear roles and responsibilities for IT governance and management, including who is responsible for setting strategy, making decisions, and executing on that strategy. This helps to ensure accountability and avoid confusion.
- Assess your organization's current state: Before implementing the COBIT framework, assess your organization's current state of IT governance and management. This will help you identify areas of strength and weakness, and tailor your approach accordingly.
- Determine which COBIT version to use: COBIT has evolved over time, with different versions available for different purposes. It's important to determine which version of COBIT is best suited to your organization's needs.
- Define metrics and measurement criteria: Define metrics and measurement criteria to evaluate the effectiveness of your IT governance and management processes. This will help you track progress over time and identify areas for improvement.
What is the Difference Between COBIT 5 and COBIT 2019?
COBIT 5 and COBIT 2019 are two different versions of the COBIT (Control Objectives for Information and Related Technology) framework. While both versions share many similarities, there are some key differences between the two:
- Scope: COBIT 5 has a broader scope than COBIT 2019, as it covers not only IT governance but also enterprise governance and management. COBIT 2019 focuses specifically on IT governance and management.
- Structure: COBIT 5 is structured around five governance and management domains, while COBIT 2019 is structured around four focus areas. The domains in COBIT 5 are governance, strategy, acquisition, delivery, and monitoring, while the focus areas in COBIT 2019 are governance, management, alignment, and assurance.
- Framework components: COBIT 2019 has several new components that were not present in COBIT 5, including design factors, implementation guidance, and performance management.
- Updated content: COBIT 2019 includes updated content to reflect changes in the IT landscape since the release of COBIT 5, including new technologies and emerging trends.
- Implementation approach: COBIT 2019 provides a more flexible implementation approach than COBIT 5, with guidance on how to tailor the framework to meet an organization's specific needs.
How Does COBIT Compare With Other Governance Frameworks?
COBIT (Control Objectives for Information and Related Technology) is one of several governance frameworks that organizations can use to guide their IT governance and management practices. Here are some ways that COBIT compares with other popular frameworks:
- ITIL (Information Technology Infrastructure Library): ITIL is a framework that focuses on IT service management. While COBIT covers a broad range of IT governance and management topics, including IT service management, ITIL provides a more detailed set of best practices for delivering IT services.
- ISO/IEC 27001: ISO/IEC 27001 is a standard that outlines requirements for information security management systems. While COBIT includes information security as part of its overall governance and management framework, ISO/IEC 27001 provides more detailed guidance on how to establish and maintain an information security management system.
- NIST Cybersecurity Framework: The NIST Cybersecurity Framework provides a set of guidelines for improving cybersecurity risk management. While COBIT includes guidance on managing IT risks, the NIST Cybersecurity Framework provides more detailed guidance on how to assess and manage cybersecurity risks.
- COSO (Committee of Sponsoring Organizations of the Treadway Commission): COSO provides a framework for enterprise risk management. While COBIT includes risk management as part of its overall governance and management framework, COSO provides a more detailed set of best practices for managing risks across the enterprise.
How Does COBIT Compare With Other Governance Frameworks?
COBIT (Control Objectives for Information and Related Technology) is one of several governance frameworks that organizations can use to guide their IT governance and management practices. Here are some ways that COBIT compares with other popular frameworks:
- ITIL (Information Technology Infrastructure Library): ITIL is a framework that focuses on IT service management. While COBIT covers a broad range of IT governance and management topics, including IT service management, ITIL provides a more detailed set of best practices for delivering IT services.
- ISO/IEC 27001: ISO/IEC 27001 is a standard that outlines requirements for information security management systems. While COBIT includes information security as part of its overall governance and management framework, ISO/IEC 27001 provides more detailed guidance on how to establish and maintain an information security management system.
- NIST Cybersecurity Framework: The NIST Cybersecurity Framework provides a set of guidelines for improving cybersecurity risk management. While COBIT includes guidance on managing IT risks, the NIST Cybersecurity Framework provides more detailed guidance on how to assess and manage cybersecurity risks.
- COSO (Committee of Sponsoring Organizations of the Treadway Commission): COSO provides a framework for enterprise risk management. While COBIT includes risk management as part of its overall governance and management framework, COSO provides a more detailed set of best practices for managing risks across the enterprise.
The Various COBIT Components
The COBIT (Control Objectives for Information and Related Technology) framework is comprised of several components that work together to provide a comprehensive approach to IT governance and management. Here are the main components of COBIT:
- Governance objectives: COBIT defines governance as the set of practices and processes that ensure that an organization's IT investments support its overall business goals and objectives. COBIT includes a set of governance objectives that provide a high-level overview of the key areas that organizations need to focus on to achieve effective IT governance.
- Governance and management domains: COBIT is structured around five governance and management domains: governance, strategy, acquisition, delivery, and monitoring. Each domain includes a set of processes and practices that organizations can use to manage and govern their IT operations.
- Process reference model: COBIT provides a process reference model that defines the processes and activities involved in each of the five domains. The process reference model includes a set of generic processes that can be tailored to meet an organization's specific needs.
- Control objectives: COBIT includes a set of control objectives that provide detailed guidance on how to achieve specific outcomes within each process. Control objectives are used to define the specific requirements that need to be met to achieve effective IT governance.
- Management guidelines: COBIT provides a set of management guidelines that organizations can use to implement the framework. The guidelines include practical advice and guidance on how to implement COBIT in a way that is tailored to an organization's specific needs.
- Maturity models: COBIT includes a set of maturity models that organizations can use to assess their current level of IT governance maturity and identify areas for improvement. The maturity models provide a roadmap for organizations to follow as they work to improve their IT governance and management practices.
Why Is COBIT 5.0 the Most Celebrated Version?
COBIT 5.0 is often considered the most celebrated version of the COBIT framework due to several reasons:
- Broad scope: COBIT 5.0 has a broad scope that covers all aspects of IT governance and management. This makes it a comprehensive framework that can be used by organizations of all sizes and across all industries.
- Alignment with other frameworks: COBIT 5.0 is designed to be compatible with other frameworks, such as ITIL and ISO/IEC 27001, making it easier for organizations to integrate it into their existing IT governance and management practices.
- Focus on business value: COBIT 5.0 places a strong emphasis on delivering business value through effective IT governance and management. This helps organizations to align their IT investments with their overall business objectives and achieve better outcomes.
- Maturity models: COBIT 5.0 includes maturity models that organizations can use to assess their current level of IT governance and management maturity and identify areas for improvement. This helps organizations to take a more strategic approach to IT governance and management and improve their overall performance.
- User-friendly: COBIT 5.0 is designed to be user-friendly, with clear and concise language and a straightforward structure that makes it easy to navigate and implement.
The Advantages of COBIT 5.0 Certification
There are several advantages of COBIT 5.0 certification, including:
- Industry recognition: COBIT 5.0 is widely recognized as a leading framework for IT governance and management. Achieving COBIT 5.0 certification demonstrates a high level of knowledge and expertise in this field and can enhance your professional reputation.
- Career advancement: COBIT 5.0 certification can help you to advance your career in the IT governance and management field. It demonstrates to employers that you have the skills and knowledge needed to contribute to the success of their organization.
- Improved job performance: COBIT 5.0 certification can improve your job performance by providing you with a deeper understanding of IT governance and management principles, processes, and practices. This can help you to make better decisions and deliver better outcomes for your organization.
- Competitive advantage: COBIT 5.0 certification can give you a competitive advantage in the job market by setting you apart from other candidates who do not have this certification. It can help you to stand out and demonstrate your commitment to professional development and excellence.
- Personal growth: COBIT 5.0 certification can provide you with personal growth and development opportunities. It can help you to expand your knowledge and skills and take on new challenges in your career.
Benefits of COBIT
The COBIT framework offers several benefits for organizations, including:
- Improved IT governance: COBIT provides a structured approach to IT governance that helps organizations to align their IT strategy with their business goals and objectives. This ensures that IT investments are focused on delivering value and that IT risks are managed effectively.
- Better risk management: COBIT helps organizations to identify and manage IT-related risks more effectively. By providing a framework for risk management, COBIT enables organizations to assess the impact of IT risks on their business operations and take appropriate measures to mitigate them.
- Increased efficiency and effectiveness: COBIT promotes best practices for IT management and governance, which can help organizations to improve their operational efficiency and effectiveness. By standardizing processes and procedures, COBIT enables organizations to reduce errors and improve service delivery.
- Improved stakeholder confidence: COBIT provides a transparent and auditable approach to IT governance that can help to improve stakeholder confidence. By demonstrating a commitment to effective IT management and governance, organizations can build trust with their stakeholders and enhance their reputation.
- Better compliance: COBIT can help organizations to comply with regulatory and legal requirements related to IT governance and management. By providing a framework for compliance, COBIT enables organizations to ensure that they are meeting their obligations and avoiding potential legal and financial risks.
How to obtain the COBIT Framewordk certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- IT Service Management & Governance: COBIT, ISO
Goals of the COBIT Framework
The goals of the COBIT framework are to:
- Provide a comprehensive framework: COBIT aims to provide a comprehensive framework for IT governance and management that covers all aspects of IT operations, from strategy development to day-to-day operations.
- Ensure alignment between IT and business objectives: COBIT emphasizes the importance of aligning IT objectives with business objectives to ensure that IT investments are focused on delivering value to the organization.
- Promote best practices: COBIT promotes best practices for IT governance and management that are based on industry standards and frameworks.
- Provide a common language: COBIT provides a common language and terminology for IT governance and management that can be understood by all stakeholders, including business leaders, IT professionals, and auditors.
- Enable effective risk management: COBIT provides a structured approach to IT risk management that enables organizations to identify, assess, and manage IT-related risks more effectively.
- Ensure compliance: COBIT helps organizations to comply with regulatory and legal requirements related to IT governance and management by providing a framework for compliance.
Meeting Stakeholder Needs
Meeting stakeholder needs is a key component of the COBIT framework. COBIT defines stakeholders as individuals or groups that have an interest in or are affected by an organization's IT operations. This can include internal stakeholders, such as business leaders and IT professionals, as well as external stakeholders, such as customers, regulators, and investors.
To meet stakeholder needs, COBIT emphasizes the importance of understanding stakeholder expectations and ensuring that IT operations are aligned with these expectations. This requires a structured approach to IT governance and management that takes into account the needs and expectations of all stakeholders.
COBIT provides a framework for IT governance and management that enables organizations to:
- Define stakeholder expectations: COBIT helps organizations to identify and understand the needs and expectations of all stakeholders, including business leaders, IT professionals, customers, and regulators.
- Align IT with business objectives: COBIT emphasizes the importance of aligning IT objectives with business objectives to ensure that IT investments are focused on delivering value to the organization and meeting stakeholder needs.
- Manage IT-related risks: COBIT provides a structured approach to IT risk management that enables organizations to identify, assess, and manage IT-related risks that could impact stakeholders.
- Ensure compliance with regulatory and legal requirements: COBIT helps organizations to comply with regulatory and legal requirements related to IT governance and management, which can help to build stakeholder confidence and trust.
Taking a Holistic Approach to Governance
Taking a holistic approach to governance is a fundamental concept of the COBIT framework. Holistic governance means that organizations should view IT as an integral part of their overall business strategy, and that IT governance should be integrated with overall organizational governance.
COBIT emphasizes that effective IT governance requires a holistic approach that encompasses all aspects of IT operations, including people, processes, and technology. This approach enables organizations to achieve the following:
- Alignment with business objectives: A holistic approach to governance ensures that IT operations are aligned with the overall business objectives of the organization. This alignment is critical to ensure that IT investments are focused on delivering value to the organization.
- Integration with overall governance: A holistic approach to governance integrates IT governance with overall organizational governance. This integration ensures that IT governance is aligned with the overall governance framework and helps to avoid silos and fragmentation.
- Comprehensive coverage: A holistic approach to governance provides comprehensive coverage of all aspects of IT operations, including people, processes, and technology. This coverage ensures that all aspects of IT operations are governed and managed effectively.
- Effective risk management: A holistic approach to governance enables effective risk management by ensuring that all aspects of IT operations are considered when assessing and managing risks.
- Continual improvement: A holistic approach to governance emphasizes the importance of continual improvement. This ensures that organizations are constantly seeking to improve their IT operations to meet the evolving needs of the business.
Conclusion
In conclusion, COBIT is a comprehensive framework that provides organizations with a structured approach to IT governance and management. The framework is designed to help organizations meet stakeholder needs, align IT with business objectives, manage IT-related risks, and ensure compliance with regulatory and legal requirements.
COBIT emphasizes the importance of taking a holistic approach to governance that encompasses all aspects of IT operations, including people, processes, and technology. This approach enables organizations to achieve effective IT governance and management that is integrated with overall organizational governance.
COBIT has evolved over time, with each version bringing improvements and updates to the framework. The most celebrated version of COBIT is COBIT 5.0, which provides organizations with a comprehensive approach to IT governance and management.
In addition to providing a framework for IT governance and management, COBIT also offers certification programs that enable IT professionals to demonstrate their knowledge and expertise in the framework. COBIT certification can provide professionals with a competitive edge in the job market and help organizations to build a team of skilled IT professionals who can effectively implement and manage the COBIT framework.
What is ISOO 20000 IT service Management certification? Benefits and Maintaining.
ISO/IEC 20000 is an internationally recognized standard for IT service management (ITSM) that provides organizations with a framework to effectively deliver and manage their IT services. It outlines the best practices and requirements for establishing, implementing, and maintaining a service management system. By achieving ISO/IEC 20000 certification, organizations demonstrate their commitment to delivering high-quality IT services and meeting customer expectations.
The ISO/IEC 20000 certification specifically focuses on IT service management, which involves the design, delivery, and continuous improvement of IT services to support business objectives. It encompasses various processes and activities, such as incident management, problem management, service design, service transition, and service operation. These processes are aimed at ensuring that IT services are delivered efficiently, effectively, and in alignment with the organization's overall goals.
Obtaining the ISO/IEC 20000 certification is not only a testament to an organization's dedication to excellence in IT service management but also provides several benefits. It helps organizations enhance their service quality, improve customer satisfaction, and establish a culture of continual improvement. Additionally, ISO/IEC 20000 certification can enhance the organization's reputation, increase its competitive edge, and provide a basis for establishing service level agreements with customers.
To achieve ISO/IEC 20000 certification, organizations must undergo a thorough assessment of their IT service management practices and demonstrate compliance with the standard's requirements. This assessment is typically conducted by an independent certification body, ensuring objectivity and impartiality in evaluating the organization's IT service management system.
In summary, ISO/IEC 20000 IT Service Management certification is a prestigious recognition that signifies an organization's adherence to internationally recognized best practices in IT service delivery. It helps organizations improve their service quality, enhance customer satisfaction, and establish a strong foundation for effective IT service management.
Table of contents
-
Introduction to ISO 20000 Certification:
-
Understanding the ISO 20000 Framework:
-
Benefits of ISO 20000 Certification:
-
Steps to Achieve ISO 20000 Certification:
-
ISO 20000 Certification and IT Service Providers:
-
Maintaining ISO 20000 Certification:
-
Conlusion
1. Introduction to ISO 20000 Certification:
ISO 20000 is an international standard that outlines the requirements for an organization's IT service management (ITSM) system. It provides a framework for effectively managing and delivering IT services to meet customer requirements and improve overall service quality.
-
What is ISO 20000?
-
Definition: ISO 20000, also known as ISO/IEC 20000, is the international standard for IT service management systems.
-
Background: It was first published in 2005 by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC).
-
Scope: ISO 20000 covers all aspects of IT service management, including service design, transition, delivery, and improvement.
-
Importance of ISO 20000 Certification
-
Customer Confidence: ISO 20000 certification demonstrates an organization's commitment to delivering high-quality IT services and meeting customer requirements.
-
Industry Recognition: It provides recognition and credibility in the IT service management industry, distinguishing certified organizations from their competitors.
-
Compliance: ISO 20000 certification ensures compliance with internationally recognized best practices for IT service management.
-
Continuous Improvement: It promotes a culture of continual improvement, driving organizations to enhance their IT service delivery processes and customer satisfaction.
-
Benefits of Achieving ISO 20000 Certification
-
Service Quality Improvement: ISO 20000 helps organizations establish robust processes and procedures to consistently deliver high-quality IT services.
-
Customer Satisfaction: By meeting ISO 20000 requirements, organizations can enhance customer satisfaction by meeting their service expectations and requirements.
-
Operational Efficiency: ISO 20000 provides guidelines for efficient service management practices, leading to improved operational efficiency and cost-effectiveness.
-
Risk Management: It helps organizations identify and mitigate risks associated with IT service management, ensuring business continuity and minimizing service disruptions.
-
Competitive Advantage: ISO 20000 certification sets organizations apart from their competitors, giving them a competitive edge in the market.
2. Understanding the ISO 20000 Framework.
ISO 20000 is a comprehensive framework that outlines the requirements for implementing and maintaining an effective IT service management system. Familiarizing yourself with the key components and sections of the ISO 20000 standard will help you understand how it supports IT service management best practices.
-
Overview of the ISO 20000 Standard
-
Structure: ISO 20000 is divided into two parts - Part 1: Service management system requirements (SMSR) and Part 2: Guidance on the application of SMSR.
-
Part 1: This section defines the requirements that organizations need to meet to achieve ISO 20000 certification.
-
Part 2: It provides guidance on implementing the requirements specified in Part 1 and offers additional insights into interpreting and applying the standard.
-
Key Components of ISO 20000
-
Service Management System (SMS): ISO 20000 emphasizes the establishment of a service management system, which serves as the foundation for effective IT service delivery.
-
Service Management Processes: The standard outlines specific processes that organizations should implement to manage IT services, including incident management, problem management, change management, and service level management.
-
Documentation Requirements: ISO 20000 defines the documentation necessary to demonstrate compliance, such as service management plans, policies, procedures, and records.
-
ISO 20000 Sections and Requirements
-
Context of the Organization: This section focuses on understanding the organization's context and identifying the scope of the IT service management system.
-
Leadership: It emphasizes the involvement and commitment of top management in establishing and maintaining the service management system.
-
Planning: This section covers activities related to risk management, service planning, and service design and transition.
-
Support: It outlines the requirements for resource management, competency and awareness, communication, and document management.
-
Operation: This section addresses the execution of service management processes, including service delivery, service control, and resolution of incidents and service requests.
-
Performance Evaluation: It specifies the requirements for monitoring, measurement, analysis, and evaluation of the service management system and services.
-
Improvement: This section focuses on continual improvement of the service management system and the services provided.
-
Alignment with ITIL (Information Technology Infrastructure Library)
-
Relationship with ITIL: ISO 20000 and ITIL are closely related, with ISO 20000 incorporating many ITIL best practices into its framework.
-
ITIL Processes in ISO 20000: ISO 20000 recognizes and aligns with various ITIL processes, such as incident management, problem management, change management, and service level management.
-
Synergies and Enhancements: Implementing ISO 20000 can help organizations enhance their ITIL implementation and vice versa, as both frameworks share common goals and principles.
3. Benefits of ISO 20000 Certification
Obtaining ISO 20000 certification brings numerous advantages to organizations in terms of service quality, operational efficiency, and credibility. Here are some key benefits that organizations can experience:
-
Improved Service Quality and Customer Satisfaction
-
Standardized Processes: ISO 20000 requires organizations to establish and follow standardized processes for IT service management, ensuring consistent and reliable service delivery.
-
Service Level Management: Implementing ISO 20000 helps organizations effectively manage service level agreements (SLAs), resulting in improved service performance and meeting customer expectations.
-
Incident and Problem Management: ISO 20000 provides guidelines for incident and problem management, enabling organizations to respond to and resolve issues promptly, minimizing service disruptions and enhancing customer satisfaction.
-
Enhanced Operational Efficiency and Cost-effectiveness
-
Streamlined Processes: ISO 20000 encourages organizations to streamline their IT service management processes, eliminating redundancies and improving efficiency.
-
Resource Optimization: By implementing ISO 20000, organizations can optimize their resource allocation, ensuring that resources are utilized effectively and reducing unnecessary costs.
-
Change Management: ISO 20000 emphasizes proper change management practices, reducing the risk of errors, service disruptions, and costly rollbacks.
-
Increased Credibility and Competitive Advantage
-
International Recognition: ISO 20000 is an internationally recognized standard for IT service management, providing organizations with credibility and demonstrating their commitment to quality.
-
Competitive Differentiation: ISO 20000 certification sets organizations apart from their competitors, particularly when bidding for contracts or providing services to clients who prioritize certified providers.
-
Trust and Confidence: Customers and stakeholders have increased trust and confidence in organizations that have achieved ISO 20000 certification, knowing that their IT services are managed according to globally accepted best practices.
-
Compliance with Best Practices and Regulations
-
Alignment with ITIL: ISO 20000 aligns with ITIL, incorporating many ITIL best practices into its framework. This alignment ensures compliance with widely recognized IT service management principles.
-
Regulatory Compliance: Achieving ISO 20000 certification helps organizations demonstrate compliance with regulatory requirements related to IT service management, enhancing their reputation and credibility.
-
Continual Service Improvement
-
Continuous Improvement Culture: ISO 20000 promotes a culture of continual service improvement, encouraging organizations to monitor, measure, and evaluate their IT services to identify areas for enhancement.
-
Proactive Problem Resolution: Through ISO 20000, organizations can implement proactive problem management practices, identifying and addressing underlying issues before they impact service quality.
4.Steps to Achieve ISO 20000 Certification
-
Familiarize Yourself with ISO 20000:
-
Understand the requirements and key components of the ISO 20000 standard.
-
Familiarize yourself with the structure and sections of the standard to gain a comprehensive understanding.
-
Conduct a Gap Analysis:
-
Evaluate your organization's current IT service management practices against the requirements specified in the ISO 20000 standard.
-
Identify areas where your organization already complies with the standard and areas that require improvement or alignment.
-
Develop an Implementation Plan:
-
Create a detailed plan that outlines the necessary actions, resources, and timelines for implementing ISO 20000 within your organization.
-
Define roles and responsibilities for the implementation team members.
-
Establish the Service Management System (SMS):
-
Develop and document the service management system, which will serve as the foundation for implementing ISO 20000 requirements.
-
Define the scope of your SMS, considering the services, processes, and organizational units covered by the certification.
-
Implement Required Processes and Procedures:
-
Implement the specific processes and procedures outlined in the ISO 20000 standard, such as incident management, problem management, change management, and service level management.
-
Align your existing processes with the ISO 20000 requirements or establish new ones where necessary.
-
Document the SMS:
-
Develop the required documentation to demonstrate compliance with ISO 20000.
-
Document policies, procedures, work instructions, and records necessary to support the implementation and operation of the SMS.
-
Conduct Internal Audits:
-
Perform internal audits to assess the effectiveness and compliance of your SMS with ISO 20000 requirements.
-
Identify any non-conformities and take corrective actions to address them.
-
Management Review:
-
Conduct a management review to evaluate the performance of the SMS and the progress towards ISO 20000 certification.
-
Ensure that top management is actively involved in reviewing the SMS and providing necessary support.
-
Select an Accredited Certification Body:
-
Choose an accredited certification body to perform the final certification audit.
-
Verify that the certification body has experience and expertise in ISO 20000 certification.
-
External Certification Audit:
-
The certification body will conduct an on-site audit to assess your organization's compliance with ISO 20000 requirements.
-
The audit will typically involve interviews, documentation reviews, and observations of your IT service management practices.
-
Corrective Actions and Finalization:
-
Address any non-conformities identified during the certification audit and implement corrective actions.
-
Provide necessary evidence of compliance to the certification body.
-
Once all non-conformities are resolved, the certification body will issue the ISO 20000 certification.
-
Continual Improvement:
-
Embrace a culture of continual improvement by monitoring, measuring, and evaluating your IT service management practices.
-
Implement processes to ensure ongoing compliance with ISO 20000 requirements and drive continuous enhancement of your services.
5.ISO 20000 Certification and IT Service Providers
ISO 20000 certification holds significant benefits for IT service providers, helping them enhance their service delivery, gain customer trust, and establish a competitive edge. Here are some key aspects of ISO 20000 certification for IT service providers:
-
Customer Confidence and Trust:
-
ISO 20000 certification demonstrates an IT service provider's commitment to delivering high-quality services that meet customer requirements and expectations.
-
Certified providers are seen as more reliable, trustworthy, and capable of delivering consistent and efficient IT services.
-
Differentiation and Competitive Advantage:
-
ISO 20000 certification sets IT service providers apart from their competitors in a crowded market.
-
Certification can serve as a unique selling point and a competitive advantage, helping providers attract new customers and win contracts.
-
Improved Service Delivery:
-
ISO 20000 provides guidelines for effective service management processes, ensuring IT service providers have well-defined processes in place.
-
By implementing ISO 20000 requirements, providers can enhance their service delivery, resulting in improved customer satisfaction and loyalty.
-
Enhanced Operational Efficiency:
-
ISO 20000 encourages IT service providers to streamline their processes, eliminate redundancies, and optimize resource allocation.
-
By aligning with ISO 20000, providers can improve operational efficiency, reduce costs, and deliver services more effectively.
-
Alignment with Customer Requirements:
-
ISO 20000 certification ensures that IT service providers align with internationally recognized best practices and standards for IT service management.
-
Many customers and organizations specifically require ISO 20000 certification when selecting service providers, making it essential for business opportunities.
-
Compliance with Service Level Agreements (SLAs):
-
ISO 20000 helps IT service providers effectively manage and fulfill SLAs with their customers.
-
It provides guidelines for defining, monitoring, and reporting on service levels, ensuring providers meet their contractual obligations.
-
Continual Improvement:
-
ISO 20000 promotes a culture of continual service improvement within IT service providers.
-
By monitoring and evaluating service performance, providers can identify areas for enhancement and implement proactive measures for ongoing improvement.
-
Vendor and Partner Relationships:
-
ISO 20000 certification can be advantageous when working with vendors or partners, as it demonstrates a provider's commitment to quality and adherence to best practices.
-
It enhances the provider's credibility and strengthens their relationships with vendors and partners.
6.Maintaining ISO 20000 Certification
Achieving ISO 20000 certification is a significant accomplishment, but it's essential to continuously maintain compliance with the standard's requirements to preserve the benefits it offers. Here are key aspects to consider for maintaining ISO 20000 certification:
-
Regular Internal Audits:
-
Conduct internal audits at regular intervals to assess the effectiveness and compliance of your IT service management system (SMS).
-
Internal audits help identify any non-conformities or areas that need improvement, allowing you to take corrective actions proactively.
-
Corrective Actions and Preventive Measures:
-
Address any non-conformities identified during internal audits promptly.
-
Implement corrective actions and preventive measures to prevent the recurrence of non-conformities and improve the effectiveness of your SMS.
-
Ongoing Monitoring and Measurement:
-
Continuously monitor and measure key performance indicators (KPIs) related to IT service management.
-
Regularly review and analyze data to identify trends, areas for improvement, and potential risks.
-
Management Review:
-
Conduct periodic management reviews to evaluate the performance of the SMS and the effectiveness of your IT service management processes.
-
Involve top management in the review process to ensure ongoing commitment and support.
-
Employee Training and Awareness:
-
Provide regular training and awareness programs to employees on the requirements of ISO 20000 and their roles in maintaining compliance.
-
Ensure employees are familiar with the processes, procedures, and policies related to IT service management.
-
Document Control and Record Keeping:
-
Maintain proper document control processes to ensure the accuracy, availability, and relevance of documented information.
-
Keep records of key activities, such as incidents, problem resolutions, changes, and service level agreements (SLAs).
-
External Audits and Surveillance Visits:
-
The certification body may conduct surveillance visits or periodic audits to assess ongoing compliance with ISO 20000 requirements.
-
Prepare for these audits by ensuring all necessary documentation and records are up to date and readily available.
-
Continual Improvement:
-
Foster a culture of continual improvement within your organization.
-
Encourage employees to provide suggestions for enhancing the IT service management processes and implementing improvements.
-
Stay Updated with Changes:
-
Stay informed about any updates or revisions to the ISO 20000 standard.
-
Ensure your SMS remains aligned with the latest requirements and best practices.
-
Customer Feedback and Satisfaction:
-
Regularly seek customer feedback and monitor customer satisfaction levels.
-
Use customer feedback to identify areas for improvement and make necessary adjustments to enhance service delivery.
How to obtain the IS20000 certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
IT Service Management & Governance :COBIT , ISO
7.Conclusion
In conclusion, ISO 20000 IT Service Management Certification holds significant value for organizations and IT service providers. Throughout this blog, we explored various subtopics related to ISO 20000 certification, providing insights into its framework, benefits, steps to achieve certification, and maintenance strategies.
ISO 20000 certification provides a structured approach to IT service management, enabling organizations to establish and maintain effective service delivery processes. It enhances service quality, customer satisfaction, and operational efficiency while demonstrating compliance with internationally recognized best practices. By aligning with ISO 20000, organizations can gain a competitive advantage, build customer trust, and differentiate themselves in the market.
The steps to achieve ISO 20000 certification involve understanding the standard, conducting a gap analysis, implementing required processes, documenting the service management system, and undergoing internal and external audits. Once certified, organizations must maintain compliance through regular audits, corrective actions, ongoing monitoring, and employee training.
The benefits of ISO 20000 certification are numerous, including improved service quality, enhanced operational efficiency, increased credibility, and compliance with regulations and customer requirements. IT service providers, in particular, can leverage certification to differentiate themselves, gain customer confidence, and optimize their service delivery.
By adhering to ISO 20000 requirements and continually striving for improvement, organizations can maximize the value of their certification and ensure the consistent delivery of high-quality IT services. ISO 20000 serves as a valuable framework for organizations seeking to enhance their IT service management practices and establish themselves as reliable and trusted providers in the industry.
Read More
ISO/IEC 20000 is an internationally recognized standard for IT service management (ITSM) that provides organizations with a framework to effectively deliver and manage their IT services. It outlines the best practices and requirements for establishing, implementing, and maintaining a service management system. By achieving ISO/IEC 20000 certification, organizations demonstrate their commitment to delivering high-quality IT services and meeting customer expectations.
The ISO/IEC 20000 certification specifically focuses on IT service management, which involves the design, delivery, and continuous improvement of IT services to support business objectives. It encompasses various processes and activities, such as incident management, problem management, service design, service transition, and service operation. These processes are aimed at ensuring that IT services are delivered efficiently, effectively, and in alignment with the organization's overall goals.
Obtaining the ISO/IEC 20000 certification is not only a testament to an organization's dedication to excellence in IT service management but also provides several benefits. It helps organizations enhance their service quality, improve customer satisfaction, and establish a culture of continual improvement. Additionally, ISO/IEC 20000 certification can enhance the organization's reputation, increase its competitive edge, and provide a basis for establishing service level agreements with customers.
To achieve ISO/IEC 20000 certification, organizations must undergo a thorough assessment of their IT service management practices and demonstrate compliance with the standard's requirements. This assessment is typically conducted by an independent certification body, ensuring objectivity and impartiality in evaluating the organization's IT service management system.
In summary, ISO/IEC 20000 IT Service Management certification is a prestigious recognition that signifies an organization's adherence to internationally recognized best practices in IT service delivery. It helps organizations improve their service quality, enhance customer satisfaction, and establish a strong foundation for effective IT service management.
Table of contents
-
Introduction to ISO 20000 Certification:
-
Understanding the ISO 20000 Framework:
-
Benefits of ISO 20000 Certification:
-
Steps to Achieve ISO 20000 Certification:
-
ISO 20000 Certification and IT Service Providers:
-
Maintaining ISO 20000 Certification:
-
Conlusion
1. Introduction to ISO 20000 Certification:
ISO 20000 is an international standard that outlines the requirements for an organization's IT service management (ITSM) system. It provides a framework for effectively managing and delivering IT services to meet customer requirements and improve overall service quality.
-
What is ISO 20000?
-
Definition: ISO 20000, also known as ISO/IEC 20000, is the international standard for IT service management systems.
-
Background: It was first published in 2005 by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC).
-
Scope: ISO 20000 covers all aspects of IT service management, including service design, transition, delivery, and improvement.
-
-
Importance of ISO 20000 Certification
-
Customer Confidence: ISO 20000 certification demonstrates an organization's commitment to delivering high-quality IT services and meeting customer requirements.
-
Industry Recognition: It provides recognition and credibility in the IT service management industry, distinguishing certified organizations from their competitors.
-
Compliance: ISO 20000 certification ensures compliance with internationally recognized best practices for IT service management.
-
Continuous Improvement: It promotes a culture of continual improvement, driving organizations to enhance their IT service delivery processes and customer satisfaction.
-
-
Benefits of Achieving ISO 20000 Certification
-
Service Quality Improvement: ISO 20000 helps organizations establish robust processes and procedures to consistently deliver high-quality IT services.
-
Customer Satisfaction: By meeting ISO 20000 requirements, organizations can enhance customer satisfaction by meeting their service expectations and requirements.
-
Operational Efficiency: ISO 20000 provides guidelines for efficient service management practices, leading to improved operational efficiency and cost-effectiveness.
-
Risk Management: It helps organizations identify and mitigate risks associated with IT service management, ensuring business continuity and minimizing service disruptions.
-
Competitive Advantage: ISO 20000 certification sets organizations apart from their competitors, giving them a competitive edge in the market.
-
2. Understanding the ISO 20000 Framework.
ISO 20000 is a comprehensive framework that outlines the requirements for implementing and maintaining an effective IT service management system. Familiarizing yourself with the key components and sections of the ISO 20000 standard will help you understand how it supports IT service management best practices.
-
Overview of the ISO 20000 Standard
-
Structure: ISO 20000 is divided into two parts - Part 1: Service management system requirements (SMSR) and Part 2: Guidance on the application of SMSR.
-
Part 1: This section defines the requirements that organizations need to meet to achieve ISO 20000 certification.
-
Part 2: It provides guidance on implementing the requirements specified in Part 1 and offers additional insights into interpreting and applying the standard.
-
-
Key Components of ISO 20000
-
Service Management System (SMS): ISO 20000 emphasizes the establishment of a service management system, which serves as the foundation for effective IT service delivery.
-
Service Management Processes: The standard outlines specific processes that organizations should implement to manage IT services, including incident management, problem management, change management, and service level management.
-
Documentation Requirements: ISO 20000 defines the documentation necessary to demonstrate compliance, such as service management plans, policies, procedures, and records.
-
-
ISO 20000 Sections and Requirements
-
Context of the Organization: This section focuses on understanding the organization's context and identifying the scope of the IT service management system.
-
Leadership: It emphasizes the involvement and commitment of top management in establishing and maintaining the service management system.
-
Planning: This section covers activities related to risk management, service planning, and service design and transition.
-
Support: It outlines the requirements for resource management, competency and awareness, communication, and document management.
-
Operation: This section addresses the execution of service management processes, including service delivery, service control, and resolution of incidents and service requests.
-
Performance Evaluation: It specifies the requirements for monitoring, measurement, analysis, and evaluation of the service management system and services.
-
Improvement: This section focuses on continual improvement of the service management system and the services provided.
-
-
Alignment with ITIL (Information Technology Infrastructure Library)
-
Relationship with ITIL: ISO 20000 and ITIL are closely related, with ISO 20000 incorporating many ITIL best practices into its framework.
-
ITIL Processes in ISO 20000: ISO 20000 recognizes and aligns with various ITIL processes, such as incident management, problem management, change management, and service level management.
-
Synergies and Enhancements: Implementing ISO 20000 can help organizations enhance their ITIL implementation and vice versa, as both frameworks share common goals and principles.
-
3. Benefits of ISO 20000 Certification
Obtaining ISO 20000 certification brings numerous advantages to organizations in terms of service quality, operational efficiency, and credibility. Here are some key benefits that organizations can experience:
-
Improved Service Quality and Customer Satisfaction
-
Standardized Processes: ISO 20000 requires organizations to establish and follow standardized processes for IT service management, ensuring consistent and reliable service delivery.
-
Service Level Management: Implementing ISO 20000 helps organizations effectively manage service level agreements (SLAs), resulting in improved service performance and meeting customer expectations.
-
Incident and Problem Management: ISO 20000 provides guidelines for incident and problem management, enabling organizations to respond to and resolve issues promptly, minimizing service disruptions and enhancing customer satisfaction.
-
-
Enhanced Operational Efficiency and Cost-effectiveness
-
Streamlined Processes: ISO 20000 encourages organizations to streamline their IT service management processes, eliminating redundancies and improving efficiency.
-
Resource Optimization: By implementing ISO 20000, organizations can optimize their resource allocation, ensuring that resources are utilized effectively and reducing unnecessary costs.
-
Change Management: ISO 20000 emphasizes proper change management practices, reducing the risk of errors, service disruptions, and costly rollbacks.
-
-
Increased Credibility and Competitive Advantage
-
International Recognition: ISO 20000 is an internationally recognized standard for IT service management, providing organizations with credibility and demonstrating their commitment to quality.
-
Competitive Differentiation: ISO 20000 certification sets organizations apart from their competitors, particularly when bidding for contracts or providing services to clients who prioritize certified providers.
-
Trust and Confidence: Customers and stakeholders have increased trust and confidence in organizations that have achieved ISO 20000 certification, knowing that their IT services are managed according to globally accepted best practices.
-
-
Compliance with Best Practices and Regulations
-
Alignment with ITIL: ISO 20000 aligns with ITIL, incorporating many ITIL best practices into its framework. This alignment ensures compliance with widely recognized IT service management principles.
-
Regulatory Compliance: Achieving ISO 20000 certification helps organizations demonstrate compliance with regulatory requirements related to IT service management, enhancing their reputation and credibility.
-
-
Continual Service Improvement
-
Continuous Improvement Culture: ISO 20000 promotes a culture of continual service improvement, encouraging organizations to monitor, measure, and evaluate their IT services to identify areas for enhancement.
-
Proactive Problem Resolution: Through ISO 20000, organizations can implement proactive problem management practices, identifying and addressing underlying issues before they impact service quality.
-
4.Steps to Achieve ISO 20000 Certification
-
Familiarize Yourself with ISO 20000:
-
Understand the requirements and key components of the ISO 20000 standard.
-
Familiarize yourself with the structure and sections of the standard to gain a comprehensive understanding.
-
-
Conduct a Gap Analysis:
-
Evaluate your organization's current IT service management practices against the requirements specified in the ISO 20000 standard.
-
Identify areas where your organization already complies with the standard and areas that require improvement or alignment.
-
-
Develop an Implementation Plan:
-
Create a detailed plan that outlines the necessary actions, resources, and timelines for implementing ISO 20000 within your organization.
-
Define roles and responsibilities for the implementation team members.
-
-
Establish the Service Management System (SMS):
-
Develop and document the service management system, which will serve as the foundation for implementing ISO 20000 requirements.
-
Define the scope of your SMS, considering the services, processes, and organizational units covered by the certification.
-
-
Implement Required Processes and Procedures:
-
Implement the specific processes and procedures outlined in the ISO 20000 standard, such as incident management, problem management, change management, and service level management.
-
Align your existing processes with the ISO 20000 requirements or establish new ones where necessary.
-
-
Document the SMS:
-
Develop the required documentation to demonstrate compliance with ISO 20000.
-
Document policies, procedures, work instructions, and records necessary to support the implementation and operation of the SMS.
-
-
Conduct Internal Audits:
-
Perform internal audits to assess the effectiveness and compliance of your SMS with ISO 20000 requirements.
-
Identify any non-conformities and take corrective actions to address them.
-
-
Management Review:
-
Conduct a management review to evaluate the performance of the SMS and the progress towards ISO 20000 certification.
-
Ensure that top management is actively involved in reviewing the SMS and providing necessary support.
-
-
Select an Accredited Certification Body:
-
Choose an accredited certification body to perform the final certification audit.
-
Verify that the certification body has experience and expertise in ISO 20000 certification.
-
-
External Certification Audit:
-
The certification body will conduct an on-site audit to assess your organization's compliance with ISO 20000 requirements.
-
The audit will typically involve interviews, documentation reviews, and observations of your IT service management practices.
-
-
Corrective Actions and Finalization:
-
Address any non-conformities identified during the certification audit and implement corrective actions.
-
Provide necessary evidence of compliance to the certification body.
-
Once all non-conformities are resolved, the certification body will issue the ISO 20000 certification.
-
-
Continual Improvement:
-
Embrace a culture of continual improvement by monitoring, measuring, and evaluating your IT service management practices.
-
Implement processes to ensure ongoing compliance with ISO 20000 requirements and drive continuous enhancement of your services.
-
5.ISO 20000 Certification and IT Service Providers
ISO 20000 certification holds significant benefits for IT service providers, helping them enhance their service delivery, gain customer trust, and establish a competitive edge. Here are some key aspects of ISO 20000 certification for IT service providers:
-
Customer Confidence and Trust:
-
ISO 20000 certification demonstrates an IT service provider's commitment to delivering high-quality services that meet customer requirements and expectations.
-
Certified providers are seen as more reliable, trustworthy, and capable of delivering consistent and efficient IT services.
-
-
Differentiation and Competitive Advantage:
-
ISO 20000 certification sets IT service providers apart from their competitors in a crowded market.
-
Certification can serve as a unique selling point and a competitive advantage, helping providers attract new customers and win contracts.
-
-
Improved Service Delivery:
-
ISO 20000 provides guidelines for effective service management processes, ensuring IT service providers have well-defined processes in place.
-
By implementing ISO 20000 requirements, providers can enhance their service delivery, resulting in improved customer satisfaction and loyalty.
-
-
Enhanced Operational Efficiency:
-
ISO 20000 encourages IT service providers to streamline their processes, eliminate redundancies, and optimize resource allocation.
-
By aligning with ISO 20000, providers can improve operational efficiency, reduce costs, and deliver services more effectively.
-
-
Alignment with Customer Requirements:
-
ISO 20000 certification ensures that IT service providers align with internationally recognized best practices and standards for IT service management.
-
Many customers and organizations specifically require ISO 20000 certification when selecting service providers, making it essential for business opportunities.
-
-
Compliance with Service Level Agreements (SLAs):
-
ISO 20000 helps IT service providers effectively manage and fulfill SLAs with their customers.
-
It provides guidelines for defining, monitoring, and reporting on service levels, ensuring providers meet their contractual obligations.
-
-
Continual Improvement:
-
ISO 20000 promotes a culture of continual service improvement within IT service providers.
-
By monitoring and evaluating service performance, providers can identify areas for enhancement and implement proactive measures for ongoing improvement.
-
-
Vendor and Partner Relationships:
-
ISO 20000 certification can be advantageous when working with vendors or partners, as it demonstrates a provider's commitment to quality and adherence to best practices.
-
It enhances the provider's credibility and strengthens their relationships with vendors and partners.
-
6.Maintaining ISO 20000 Certification
Achieving ISO 20000 certification is a significant accomplishment, but it's essential to continuously maintain compliance with the standard's requirements to preserve the benefits it offers. Here are key aspects to consider for maintaining ISO 20000 certification:
-
Regular Internal Audits:
-
Conduct internal audits at regular intervals to assess the effectiveness and compliance of your IT service management system (SMS).
-
Internal audits help identify any non-conformities or areas that need improvement, allowing you to take corrective actions proactively.
-
-
Corrective Actions and Preventive Measures:
-
Address any non-conformities identified during internal audits promptly.
-
Implement corrective actions and preventive measures to prevent the recurrence of non-conformities and improve the effectiveness of your SMS.
-
-
Ongoing Monitoring and Measurement:
-
Continuously monitor and measure key performance indicators (KPIs) related to IT service management.
-
Regularly review and analyze data to identify trends, areas for improvement, and potential risks.
-
-
Management Review:
-
Conduct periodic management reviews to evaluate the performance of the SMS and the effectiveness of your IT service management processes.
-
Involve top management in the review process to ensure ongoing commitment and support.
-
-
Employee Training and Awareness:
-
Provide regular training and awareness programs to employees on the requirements of ISO 20000 and their roles in maintaining compliance.
-
Ensure employees are familiar with the processes, procedures, and policies related to IT service management.
-
-
Document Control and Record Keeping:
-
Maintain proper document control processes to ensure the accuracy, availability, and relevance of documented information.
-
Keep records of key activities, such as incidents, problem resolutions, changes, and service level agreements (SLAs).
-
-
External Audits and Surveillance Visits:
-
The certification body may conduct surveillance visits or periodic audits to assess ongoing compliance with ISO 20000 requirements.
-
Prepare for these audits by ensuring all necessary documentation and records are up to date and readily available.
-
-
Continual Improvement:
-
Foster a culture of continual improvement within your organization.
-
Encourage employees to provide suggestions for enhancing the IT service management processes and implementing improvements.
-
-
Stay Updated with Changes:
-
Stay informed about any updates or revisions to the ISO 20000 standard.
-
Ensure your SMS remains aligned with the latest requirements and best practices.
-
-
Customer Feedback and Satisfaction:
-
Regularly seek customer feedback and monitor customer satisfaction levels.
-
Use customer feedback to identify areas for improvement and make necessary adjustments to enhance service delivery.
-
How to obtain the IS20000 certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
IT Service Management & Governance :COBIT , ISO
7.Conclusion
In conclusion, ISO 20000 IT Service Management Certification holds significant value for organizations and IT service providers. Throughout this blog, we explored various subtopics related to ISO 20000 certification, providing insights into its framework, benefits, steps to achieve certification, and maintenance strategies.
ISO 20000 certification provides a structured approach to IT service management, enabling organizations to establish and maintain effective service delivery processes. It enhances service quality, customer satisfaction, and operational efficiency while demonstrating compliance with internationally recognized best practices. By aligning with ISO 20000, organizations can gain a competitive advantage, build customer trust, and differentiate themselves in the market.
The steps to achieve ISO 20000 certification involve understanding the standard, conducting a gap analysis, implementing required processes, documenting the service management system, and undergoing internal and external audits. Once certified, organizations must maintain compliance through regular audits, corrective actions, ongoing monitoring, and employee training.
The benefits of ISO 20000 certification are numerous, including improved service quality, enhanced operational efficiency, increased credibility, and compliance with regulations and customer requirements. IT service providers, in particular, can leverage certification to differentiate themselves, gain customer confidence, and optimize their service delivery.
By adhering to ISO 20000 requirements and continually striving for improvement, organizations can maximize the value of their certification and ensure the consistent delivery of high-quality IT services. ISO 20000 serves as a valuable framework for organizations seeking to enhance their IT service management practices and establish themselves as reliable and trusted providers in the industry.
Six Sigma Black Belt :Achieving Your Goals with Understanding
The Six Sigma Black Belt certification represents the pinnacle of expertise in process improvement and quality management. It is a highly coveted credential that signifies an individual's mastery of Lean Six Sigma methodologies and their ability to lead complex improvement initiatives within organizations. In this article, we will explore the significance of achieving a Six Sigma Black Belt and how it empowers individuals to effectively drive change and achieve their goals.
The journey to becoming a Six Sigma Black Belt requires a deep understanding of the DMAIC (Define, Measure, Analyze, Improve, Control) methodology and the application of advanced statistical analysis and problem-solving techniques. Black Belts possess the skills to lead cross-functional teams, manage projects, and orchestrate process improvements that yield substantial results.
With a Black Belt certification, individuals gain the capability to identify root causes of problems, analyze data-driven insights, and implement sustainable solutions. Black Belts excel in driving process optimization, reducing defects, enhancing productivity, and ultimately improving the bottom line. Their advanced problem-solving skills enable them to tackle complex challenges and overcome organizational barriers to change.
Moreover, Six Sigma Black Belts play a pivotal role in driving organizational excellence. They are equipped to align process improvement initiatives with business strategies, ensuring that efforts are focused on achieving the organization's goals. Black Belts are effective change agents, driving cultural transformation and fostering a mindset of continuous improvement throughout the organization.
Achieving a Six Sigma Black Belt is a testament to an individual's dedication to personal and professional growth. It opens doors to new career opportunities, as organizations across various industries recognize the value of individuals who possess the expertise to deliver significant improvements in quality, efficiency, and customer satisfaction. Additionally, Black Belts often serve as mentors and trainers for Green Belts and Yellow Belts, sharing their knowledge and guiding others on their journey to process excellence.
In conclusion, the Six Sigma Black Belt certification represents the highest level of proficiency in Lean Six Sigma methodologies. Black Belts possess the knowledge and skills to drive substantial process improvements and achieve organizational goals. Their expertise in advanced problem-solving, data analysis, and project management enables them to lead impactful change initiatives. By obtaining a Six Sigma Black Belt, individuals position themselves as catalysts for transformation, driving success in organizations and achieving their own professional aspirations.
Table of contents
- Introduction to Six Sigma Black Belt
- Requirements for Six Sigma Black Belt Certification:
- DMAIC Methodology:
- Leadership and Change Management:
- Certification Process and Examination:
- Benefits and Career Opportunities:
- Conclusion
Introduction to Six Sigma Black Belt:
Six Sigma, a renowned methodology for process improvement and quality management, has revolutionized the way organizations operate. At the heart of Six Sigma lies the role of a Black Belt, a highly skilled professional responsible for leading improvement projects and driving significant results. A Six Sigma Black Belt possesses a deep understanding of statistical analysis, problem-solving techniques, and project management. Their expertise enables them to identify process inefficiencies, reduce variation, and enhance overall organizational performance. Obtaining a Six Sigma Black Belt certification showcases a commitment to excellence and signifies mastery of the methodology. In this blog post, we will explore the significance of Six Sigma Black Belt certification, its requirements, and the essential skills it encompasses, shedding light on the value these professionals bring to organizations seeking continuous improvement and success.
Requirements for Six Sigma Black Belt Certification:
To earn a Six Sigma Black Belt certification, individuals are required to meet certain prerequisites that ensure they possess the necessary knowledge, skills, and experience to effectively lead process improvement initiatives. The specific requirements may vary depending on the certifying body or organization offering the certification. Here are some common requirements:
- Education and Experience:
- A minimum educational qualification, such as a bachelor's degree, is often required. The field of study may vary, but degrees in engineering, business, mathematics, or statistics are commonly preferred.
- Several years of professional work experience in a relevant field are typically expected. This experience should involve exposure to process improvement, project management, or quality management responsibilities.
- Completion of Green Belt Certification:
- Many certifying bodies require candidates to have already earned a Six Sigma Green Belt certification. This ensures a solid foundation in the principles, tools, and techniques of Six Sigma methodology.
- Green Belt certification demonstrates practical experience in executing process improvement projects and serves as a stepping stone to the more advanced Black Belt level.
- Training and Professional Development:
- Completion of a comprehensive Black Belt training program is usually mandatory. This training covers advanced statistical analysis, project management, process mapping, and other specialized Six Sigma tools and techniques.
- The training may be conducted in a classroom setting or through online courses. It is essential to choose an accredited program that aligns with recognized Six Sigma methodologies.
- Demonstrated Application of Six Sigma:
- Candidates are typically required to showcase their practical application of Six Sigma principles and methodologies in real-world projects.
- This may involve providing evidence of successfully completed improvement projects, including project charters, data analysis, process documentation, and measurable outcomes.
- Written Examination:
- Candidates are generally required to pass a written examination to demonstrate their understanding of Six Sigma concepts, tools, and methodologies.
- The exam may include multiple-choice questions, case studies, and scenario-based assessments.
- Adequate preparation through self-study, review of course materials, and practice exams is essential to perform well in the certification exam.
GET COURSE
DMAIC Methodology
The DMAIC methodology is a core component of Six Sigma and serves as a systematic framework for problem-solving and process improvement. DMAIC stands for Define, Measure, Analyze, Improve, and Control, representing the five distinct phases of the methodology. Each phase plays a vital role in identifying and eliminating process deficiencies to achieve enhanced performance and customer satisfaction. Let's explore each phase of the DMAIC methodology in detail:
- Define:
- In the Define phase, the project team clarifies the problem or opportunity for improvement, establishes project goals, and defines customer requirements and expectations.
- Key activities in this phase include developing a project charter, identifying stakeholders, and defining the project scope and boundaries.
- The goal is to ensure a clear understanding of the problem to be addressed and align project objectives with the overall organizational goals.
- Measure:
- The Measure phase focuses on collecting data and measuring the current state of the process under study.
- The team identifies and selects relevant process metrics and establishes a baseline for performance.
- Data collection methods, such as sampling, surveys, or direct measurements, are employed to quantify process performance and identify sources of variation.
- Analyze:
- In the Analyze phase, the collected data is analyzed to identify root causes of process variation and performance gaps.
- Statistical tools and techniques, such as hypothesis testing, regression analysis, and Pareto charts, are utilized to identify factors that significantly impact the process outcomes.
- The goal is to gain insights into the underlying causes of problems and prioritize improvement opportunities.
- Improve:
- The Improve phase focuses on developing and implementing solutions to address the identified root causes and improve process performance.
- The team generates potential solutions, evaluates their feasibility, and selects the most promising ones.
- These solutions are then tested on a small scale through pilots or simulations before being implemented fully.
- The objective is to implement changes that result in significant process improvement and meet the desired goals.
- Control:
- The Control phase involves establishing control mechanisms to sustain the improvements achieved and prevent a return to the previous state.
- Process controls, such as standard operating procedures, statistical process control charts, and training programs, are put in place.
- The team develops a monitoring and feedback system to track ongoing process performance and ensure that any deviations are promptly addressed.
- The aim is to create a culture of continuous improvement and ensure that the gains achieved through the project are maintained over time.
By following the DMAIC methodology, organizations can systematically approach process improvement, driving data-driven decision-making and achieving measurable results. It provides a structured approach for tackling complex problems, identifying opportunities for improvement, and implementing effective solutions. DMAIC serves as a powerful tool for organizations seeking to enhance quality, reduce costs, and improve customer satisfaction.
Leadership and Change Management:
In the context of Six Sigma Black Belt certification, leadership and change management skills play a critical role in driving successful process improvement initiatives. As a Six Sigma Black Belt, you are not only responsible for applying technical tools and methodologies but also for leading teams, influencing stakeholders, and managing the change associated with process improvements. Let's explore the importance of leadership and change management in the Six Sigma Black Belt role:
- Leading Teams:
- Effective leadership is crucial for guiding project teams through the various phases of the DMAIC methodology.
- As a Black Belt, you need to inspire and motivate team members, set clear expectations, and foster a collaborative and productive team environment.
- Strong leadership skills enable you to delegate tasks, resolve conflicts, and ensure that team members are aligned and focused on achieving project goals.
- Influencing Stakeholders:
- Change within an organization often encounters resistance from stakeholders who may be skeptical or hesitant to adopt new processes or methods.
- As a Black Belt, you must possess influential communication and persuasion skills to engage stakeholders, build trust, and communicate the benefits of process improvements.
- By effectively engaging stakeholders, you can gain their support, address concerns, and drive organizational buy-in for the proposed changes.
- Change Management Expertise:
- Change management is a critical aspect of successful process improvement initiatives. It involves preparing individuals and the organization for the changes that will result from implementing new processes or procedures.
- Black Belts must be skilled in change management principles, including assessing the impact of changes, developing change management plans, and addressing resistance to change.
- By applying change management methodologies, such as creating communication plans, conducting training sessions, and providing ongoing support, Black Belts can facilitate smooth transitions and ensure sustainable results.
- Creating a Culture of Continuous Improvement:
- Black Belts are instrumental in fostering a culture of continuous improvement within their organizations.
- By leading by example, promoting a mindset of learning and innovation, and recognizing and celebrating successes, Black Belts can inspire others to embrace a continuous improvement mindset.
- This cultural shift encourages employees at all levels to proactively identify opportunities for improvement and participate in the ongoing enhancement of processes and operations.
- Project Management Skills:
- Effective project management is essential for successful process improvement initiatives.
- Black Belts must possess project management skills, including defining project scopes, setting realistic timelines, managing resources, and monitoring progress.
- By applying project management principles and practices, Black Belts can ensure that projects stay on track, are completed within specified timelines, and achieve the desired outcomes.
Leadership and change management skills are integral to the Six Sigma Black Belt role, as they enable Black Belts to guide teams, navigate organizational dynamics, and ensure the successful implementation of process improvements. By combining technical expertise with strong leadership and change management capabilities, Black Belts can drive sustainable change and make a significant impact on organizational performance and customer satisfaction.
Certification Process and Examination:
The certification process for Six Sigma Black Belt is an essential step for individuals aspiring to validate their expertise in process improvement and quality management. The process typically involves meeting certain requirements and successfully completing an examination. Here's an overview of the certification process and examination for Six Sigma Black Belt:
- Eligibility and Prerequisites:
- Before pursuing Six Sigma Black Belt certification, individuals must typically meet specific prerequisites set by the certifying body or organization offering the certification.
- Common prerequisites may include having a certain level of education (e.g., bachelor's degree) and relevant work experience in process improvement, quality management, or related fields.
- It is important to review and ensure that you meet the specific eligibility criteria before proceeding with the certification process.
- Training and Preparation:
- Black Belt candidates are often required to undergo comprehensive training to acquire the necessary knowledge and skills.
- Training programs can be offered by accredited institutions, training providers, or organizations specializing in Six Sigma methodologies.
- These training programs cover advanced topics such as statistical analysis, project management, process improvement tools, and Six Sigma principles.
- Candidates should carefully select a reputable training program that aligns with recognized Six Sigma methodologies and provides adequate preparation for the certification examination.
- Certification Examination:
- The certification examination is designed to assess candidates' understanding of Six Sigma concepts, methodologies, and their ability to apply them in real-world scenarios.
- The format and structure of the examination may vary depending on the certifying body or organization offering the certification.
- The examination typically consists of multiple-choice questions, scenario-based questions, or case studies that require candidates to demonstrate their problem-solving skills and application of Six Sigma tools and techniques.
- It is crucial to familiarize yourself with the exam format, content areas, and time constraints to adequately prepare for the examination.
- Exam Preparation:
- Adequate preparation is essential to increase the chances of success in the certification examination.
- Reviewing course materials, studying textbooks, practicing with sample questions, and taking mock exams can help candidates become familiar with the content and format of the exam.
- It is recommended to allocate dedicated study time, create a study plan, and leverage additional resources such as reference books, online tutorials, and study guides.
- Certification Renewal and Maintenance:
- Some certifying bodies may require individuals to renew their Six Sigma Black Belt certification periodically to ensure ongoing professional development and staying up-to-date with industry best practices.
- Renewal requirements may include earning continuing education credits, completing professional development activities, or participating in relevant projects.
- It is important to understand the specific renewal and maintenance requirements associated with the certification obtained.
How to obtain the Six Sigma Black Belt certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- IT Service Management & Governance: COBIT, ISO
Benefits and Career Opportunities:
Obtaining a Six Sigma Black Belt certification offers numerous benefits and opens up exciting career opportunities for professionals in various industries. Let's explore the key benefits and career opportunities associated with Six Sigma Black Belt certification:
- Enhanced Problem-Solving Skills:
- Six Sigma Black Belt certification equips individuals with advanced problem-solving techniques and tools.
- The certification emphasizes the use of data-driven analysis and statistical methods to identify and address process inefficiencies and quality issues.
- Black Belts gain the ability to analyze complex problems, identify root causes, and implement effective solutions, leading to improved organizational performance.
- Increased Employability:
- Six Sigma Black Belt certification is widely recognized and valued by organizations across industries.
- Holding this certification demonstrates a high level of competence in process improvement and quality management, making individuals highly sought after by employers.
- Certified Black Belts have a competitive edge in the job market and often enjoy better career prospects and higher earning potential.
- Leadership and Management Opportunities:
- Six Sigma Black Belt certification prepares individuals to lead and manage process improvement initiatives within organizations.
- Black Belts possess the skills to effectively lead cross-functional teams, influence stakeholders, and drive organizational change.
- They are well-positioned for roles such as Process Improvement Managers, Quality Managers, or Operations Managers, where they can spearhead continuous improvement efforts and contribute to overall business success.
- Cost Savings and Efficiency Gains:
- Six Sigma methodologies focus on reducing process variation, eliminating defects, and improving operational efficiency.
- Black Belts are trained to identify and eliminate waste, streamline processes, and optimize resource utilization.
- By implementing Six Sigma principles, organizations can achieve significant cost savings, improved productivity, and enhanced customer satisfaction.
- Career Advancement and Professional Growth:
- Six Sigma Black Belt certification provides a solid foundation for career advancement and professional growth.
- Black Belts are equipped with skills that are highly transferrable across industries and can lead to opportunities in various sectors such as manufacturing, healthcare, finance, and IT.
- Continuous learning and application of Six Sigma principles enable Black Belts to take on more challenging projects and assume leadership roles within their organizations.
- Contributing to Organizational Success:
- Six Sigma Black Belts play a pivotal role in driving organizational success by improving processes, reducing defects, and enhancing customer satisfaction.
- Their efforts result in tangible and measurable outcomes that directly contribute to business goals, performance, and profitability.
- Black Belts have the opportunity to make a significant impact on their organizations' bottom line, reputation, and competitive advantage.
Conclusion
In conclusion, Six Sigma Black Belt certification holds significant value for professionals seeking to excel in process improvement and quality management. Throughout this blog, we have explored various aspects related to Six Sigma Black Belt certification, including an introduction to the role, requirements for certification, the DMAIC methodology, the importance of leadership and change management, and the certification process and examination. We have also highlighted the benefits and career opportunities that come with earning this certification.
By obtaining Six Sigma Black Belt certification, individuals gain expertise in problem-solving, data analysis, project management, and change management. They become equipped to lead teams, influence stakeholders, and drive impactful process improvements within organizations. This certification enhances employability, opens doors to leadership roles, and offers opportunities for career advancement and professional growth.
Moreover, Six Sigma Black Belts contribute to the success of their organizations by improving efficiency, reducing costs, and enhancing customer satisfaction. Their ability to apply data-driven approaches and implement sustainable solutions leads to tangible and measurable results.
In a highly competitive business landscape, organizations are increasingly recognizing the value of professionals with Six Sigma Black Belt certification. As a certified Black Belt, individuals can make a significant impact, drive continuous improvement, and contribute to the overall success of their organizations.
In summary, Six Sigma Black Belt certification offers a pathway to excellence in process improvement, leadership, and career advancement. It is a valuable asset for professionals seeking to make a difference and excel in their chosen fields.
Read More
The Six Sigma Black Belt certification represents the pinnacle of expertise in process improvement and quality management. It is a highly coveted credential that signifies an individual's mastery of Lean Six Sigma methodologies and their ability to lead complex improvement initiatives within organizations. In this article, we will explore the significance of achieving a Six Sigma Black Belt and how it empowers individuals to effectively drive change and achieve their goals.
The journey to becoming a Six Sigma Black Belt requires a deep understanding of the DMAIC (Define, Measure, Analyze, Improve, Control) methodology and the application of advanced statistical analysis and problem-solving techniques. Black Belts possess the skills to lead cross-functional teams, manage projects, and orchestrate process improvements that yield substantial results.
With a Black Belt certification, individuals gain the capability to identify root causes of problems, analyze data-driven insights, and implement sustainable solutions. Black Belts excel in driving process optimization, reducing defects, enhancing productivity, and ultimately improving the bottom line. Their advanced problem-solving skills enable them to tackle complex challenges and overcome organizational barriers to change.
Moreover, Six Sigma Black Belts play a pivotal role in driving organizational excellence. They are equipped to align process improvement initiatives with business strategies, ensuring that efforts are focused on achieving the organization's goals. Black Belts are effective change agents, driving cultural transformation and fostering a mindset of continuous improvement throughout the organization.
Achieving a Six Sigma Black Belt is a testament to an individual's dedication to personal and professional growth. It opens doors to new career opportunities, as organizations across various industries recognize the value of individuals who possess the expertise to deliver significant improvements in quality, efficiency, and customer satisfaction. Additionally, Black Belts often serve as mentors and trainers for Green Belts and Yellow Belts, sharing their knowledge and guiding others on their journey to process excellence.
In conclusion, the Six Sigma Black Belt certification represents the highest level of proficiency in Lean Six Sigma methodologies. Black Belts possess the knowledge and skills to drive substantial process improvements and achieve organizational goals. Their expertise in advanced problem-solving, data analysis, and project management enables them to lead impactful change initiatives. By obtaining a Six Sigma Black Belt, individuals position themselves as catalysts for transformation, driving success in organizations and achieving their own professional aspirations.
Table of contents
- Introduction to Six Sigma Black Belt
- Requirements for Six Sigma Black Belt Certification:
- DMAIC Methodology:
- Leadership and Change Management:
- Certification Process and Examination:
- Benefits and Career Opportunities:
- Conclusion
Introduction to Six Sigma Black Belt:
Six Sigma, a renowned methodology for process improvement and quality management, has revolutionized the way organizations operate. At the heart of Six Sigma lies the role of a Black Belt, a highly skilled professional responsible for leading improvement projects and driving significant results. A Six Sigma Black Belt possesses a deep understanding of statistical analysis, problem-solving techniques, and project management. Their expertise enables them to identify process inefficiencies, reduce variation, and enhance overall organizational performance. Obtaining a Six Sigma Black Belt certification showcases a commitment to excellence and signifies mastery of the methodology. In this blog post, we will explore the significance of Six Sigma Black Belt certification, its requirements, and the essential skills it encompasses, shedding light on the value these professionals bring to organizations seeking continuous improvement and success.
Requirements for Six Sigma Black Belt Certification:
To earn a Six Sigma Black Belt certification, individuals are required to meet certain prerequisites that ensure they possess the necessary knowledge, skills, and experience to effectively lead process improvement initiatives. The specific requirements may vary depending on the certifying body or organization offering the certification. Here are some common requirements:
- Education and Experience:
- A minimum educational qualification, such as a bachelor's degree, is often required. The field of study may vary, but degrees in engineering, business, mathematics, or statistics are commonly preferred.
- Several years of professional work experience in a relevant field are typically expected. This experience should involve exposure to process improvement, project management, or quality management responsibilities.
- Completion of Green Belt Certification:
- Many certifying bodies require candidates to have already earned a Six Sigma Green Belt certification. This ensures a solid foundation in the principles, tools, and techniques of Six Sigma methodology.
- Green Belt certification demonstrates practical experience in executing process improvement projects and serves as a stepping stone to the more advanced Black Belt level.
- Training and Professional Development:
- Completion of a comprehensive Black Belt training program is usually mandatory. This training covers advanced statistical analysis, project management, process mapping, and other specialized Six Sigma tools and techniques.
- The training may be conducted in a classroom setting or through online courses. It is essential to choose an accredited program that aligns with recognized Six Sigma methodologies.
- Demonstrated Application of Six Sigma:
- Candidates are typically required to showcase their practical application of Six Sigma principles and methodologies in real-world projects.
- This may involve providing evidence of successfully completed improvement projects, including project charters, data analysis, process documentation, and measurable outcomes.
- Written Examination:
- Candidates are generally required to pass a written examination to demonstrate their understanding of Six Sigma concepts, tools, and methodologies.
- The exam may include multiple-choice questions, case studies, and scenario-based assessments.
- Adequate preparation through self-study, review of course materials, and practice exams is essential to perform well in the certification exam.
GET COURSE
DMAIC Methodology
The DMAIC methodology is a core component of Six Sigma and serves as a systematic framework for problem-solving and process improvement. DMAIC stands for Define, Measure, Analyze, Improve, and Control, representing the five distinct phases of the methodology. Each phase plays a vital role in identifying and eliminating process deficiencies to achieve enhanced performance and customer satisfaction. Let's explore each phase of the DMAIC methodology in detail:
- Define:
- In the Define phase, the project team clarifies the problem or opportunity for improvement, establishes project goals, and defines customer requirements and expectations.
- Key activities in this phase include developing a project charter, identifying stakeholders, and defining the project scope and boundaries.
- The goal is to ensure a clear understanding of the problem to be addressed and align project objectives with the overall organizational goals.
- Measure:
- The Measure phase focuses on collecting data and measuring the current state of the process under study.
- The team identifies and selects relevant process metrics and establishes a baseline for performance.
- Data collection methods, such as sampling, surveys, or direct measurements, are employed to quantify process performance and identify sources of variation.
- Analyze:
- In the Analyze phase, the collected data is analyzed to identify root causes of process variation and performance gaps.
- Statistical tools and techniques, such as hypothesis testing, regression analysis, and Pareto charts, are utilized to identify factors that significantly impact the process outcomes.
- The goal is to gain insights into the underlying causes of problems and prioritize improvement opportunities.
- Improve:
- The Improve phase focuses on developing and implementing solutions to address the identified root causes and improve process performance.
- The team generates potential solutions, evaluates their feasibility, and selects the most promising ones.
- These solutions are then tested on a small scale through pilots or simulations before being implemented fully.
- The objective is to implement changes that result in significant process improvement and meet the desired goals.
- Control:
- The Control phase involves establishing control mechanisms to sustain the improvements achieved and prevent a return to the previous state.
- Process controls, such as standard operating procedures, statistical process control charts, and training programs, are put in place.
- The team develops a monitoring and feedback system to track ongoing process performance and ensure that any deviations are promptly addressed.
- The aim is to create a culture of continuous improvement and ensure that the gains achieved through the project are maintained over time.
By following the DMAIC methodology, organizations can systematically approach process improvement, driving data-driven decision-making and achieving measurable results. It provides a structured approach for tackling complex problems, identifying opportunities for improvement, and implementing effective solutions. DMAIC serves as a powerful tool for organizations seeking to enhance quality, reduce costs, and improve customer satisfaction.
Leadership and Change Management:
In the context of Six Sigma Black Belt certification, leadership and change management skills play a critical role in driving successful process improvement initiatives. As a Six Sigma Black Belt, you are not only responsible for applying technical tools and methodologies but also for leading teams, influencing stakeholders, and managing the change associated with process improvements. Let's explore the importance of leadership and change management in the Six Sigma Black Belt role:
- Leading Teams:
- Effective leadership is crucial for guiding project teams through the various phases of the DMAIC methodology.
- As a Black Belt, you need to inspire and motivate team members, set clear expectations, and foster a collaborative and productive team environment.
- Strong leadership skills enable you to delegate tasks, resolve conflicts, and ensure that team members are aligned and focused on achieving project goals.
- Influencing Stakeholders:
- Change within an organization often encounters resistance from stakeholders who may be skeptical or hesitant to adopt new processes or methods.
- As a Black Belt, you must possess influential communication and persuasion skills to engage stakeholders, build trust, and communicate the benefits of process improvements.
- By effectively engaging stakeholders, you can gain their support, address concerns, and drive organizational buy-in for the proposed changes.
- Change Management Expertise:
- Change management is a critical aspect of successful process improvement initiatives. It involves preparing individuals and the organization for the changes that will result from implementing new processes or procedures.
- Black Belts must be skilled in change management principles, including assessing the impact of changes, developing change management plans, and addressing resistance to change.
- By applying change management methodologies, such as creating communication plans, conducting training sessions, and providing ongoing support, Black Belts can facilitate smooth transitions and ensure sustainable results.
- Creating a Culture of Continuous Improvement:
- Black Belts are instrumental in fostering a culture of continuous improvement within their organizations.
- By leading by example, promoting a mindset of learning and innovation, and recognizing and celebrating successes, Black Belts can inspire others to embrace a continuous improvement mindset.
- This cultural shift encourages employees at all levels to proactively identify opportunities for improvement and participate in the ongoing enhancement of processes and operations.
- Project Management Skills:
- Effective project management is essential for successful process improvement initiatives.
- Black Belts must possess project management skills, including defining project scopes, setting realistic timelines, managing resources, and monitoring progress.
- By applying project management principles and practices, Black Belts can ensure that projects stay on track, are completed within specified timelines, and achieve the desired outcomes.
Leadership and change management skills are integral to the Six Sigma Black Belt role, as they enable Black Belts to guide teams, navigate organizational dynamics, and ensure the successful implementation of process improvements. By combining technical expertise with strong leadership and change management capabilities, Black Belts can drive sustainable change and make a significant impact on organizational performance and customer satisfaction.
Certification Process and Examination:
The certification process for Six Sigma Black Belt is an essential step for individuals aspiring to validate their expertise in process improvement and quality management. The process typically involves meeting certain requirements and successfully completing an examination. Here's an overview of the certification process and examination for Six Sigma Black Belt:
- Eligibility and Prerequisites:
- Before pursuing Six Sigma Black Belt certification, individuals must typically meet specific prerequisites set by the certifying body or organization offering the certification.
- Common prerequisites may include having a certain level of education (e.g., bachelor's degree) and relevant work experience in process improvement, quality management, or related fields.
- It is important to review and ensure that you meet the specific eligibility criteria before proceeding with the certification process.
- Training and Preparation:
- Black Belt candidates are often required to undergo comprehensive training to acquire the necessary knowledge and skills.
- Training programs can be offered by accredited institutions, training providers, or organizations specializing in Six Sigma methodologies.
- These training programs cover advanced topics such as statistical analysis, project management, process improvement tools, and Six Sigma principles.
- Candidates should carefully select a reputable training program that aligns with recognized Six Sigma methodologies and provides adequate preparation for the certification examination.
- Certification Examination:
- The certification examination is designed to assess candidates' understanding of Six Sigma concepts, methodologies, and their ability to apply them in real-world scenarios.
- The format and structure of the examination may vary depending on the certifying body or organization offering the certification.
- The examination typically consists of multiple-choice questions, scenario-based questions, or case studies that require candidates to demonstrate their problem-solving skills and application of Six Sigma tools and techniques.
- It is crucial to familiarize yourself with the exam format, content areas, and time constraints to adequately prepare for the examination.
- Exam Preparation:
- Adequate preparation is essential to increase the chances of success in the certification examination.
- Reviewing course materials, studying textbooks, practicing with sample questions, and taking mock exams can help candidates become familiar with the content and format of the exam.
- It is recommended to allocate dedicated study time, create a study plan, and leverage additional resources such as reference books, online tutorials, and study guides.
- Certification Renewal and Maintenance:
- Some certifying bodies may require individuals to renew their Six Sigma Black Belt certification periodically to ensure ongoing professional development and staying up-to-date with industry best practices.
- Renewal requirements may include earning continuing education credits, completing professional development activities, or participating in relevant projects.
- It is important to understand the specific renewal and maintenance requirements associated with the certification obtained.
How to obtain the Six Sigma Black Belt certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- IT Service Management & Governance: COBIT, ISO
Benefits and Career Opportunities:
Obtaining a Six Sigma Black Belt certification offers numerous benefits and opens up exciting career opportunities for professionals in various industries. Let's explore the key benefits and career opportunities associated with Six Sigma Black Belt certification:
- Enhanced Problem-Solving Skills:
- Six Sigma Black Belt certification equips individuals with advanced problem-solving techniques and tools.
- The certification emphasizes the use of data-driven analysis and statistical methods to identify and address process inefficiencies and quality issues.
- Black Belts gain the ability to analyze complex problems, identify root causes, and implement effective solutions, leading to improved organizational performance.
- Increased Employability:
- Six Sigma Black Belt certification is widely recognized and valued by organizations across industries.
- Holding this certification demonstrates a high level of competence in process improvement and quality management, making individuals highly sought after by employers.
- Certified Black Belts have a competitive edge in the job market and often enjoy better career prospects and higher earning potential.
- Leadership and Management Opportunities:
- Six Sigma Black Belt certification prepares individuals to lead and manage process improvement initiatives within organizations.
- Black Belts possess the skills to effectively lead cross-functional teams, influence stakeholders, and drive organizational change.
- They are well-positioned for roles such as Process Improvement Managers, Quality Managers, or Operations Managers, where they can spearhead continuous improvement efforts and contribute to overall business success.
- Cost Savings and Efficiency Gains:
- Six Sigma methodologies focus on reducing process variation, eliminating defects, and improving operational efficiency.
- Black Belts are trained to identify and eliminate waste, streamline processes, and optimize resource utilization.
- By implementing Six Sigma principles, organizations can achieve significant cost savings, improved productivity, and enhanced customer satisfaction.
- Career Advancement and Professional Growth:
- Six Sigma Black Belt certification provides a solid foundation for career advancement and professional growth.
- Black Belts are equipped with skills that are highly transferrable across industries and can lead to opportunities in various sectors such as manufacturing, healthcare, finance, and IT.
- Continuous learning and application of Six Sigma principles enable Black Belts to take on more challenging projects and assume leadership roles within their organizations.
- Contributing to Organizational Success:
- Six Sigma Black Belts play a pivotal role in driving organizational success by improving processes, reducing defects, and enhancing customer satisfaction.
- Their efforts result in tangible and measurable outcomes that directly contribute to business goals, performance, and profitability.
- Black Belts have the opportunity to make a significant impact on their organizations' bottom line, reputation, and competitive advantage.
Conclusion
In conclusion, Six Sigma Black Belt certification holds significant value for professionals seeking to excel in process improvement and quality management. Throughout this blog, we have explored various aspects related to Six Sigma Black Belt certification, including an introduction to the role, requirements for certification, the DMAIC methodology, the importance of leadership and change management, and the certification process and examination. We have also highlighted the benefits and career opportunities that come with earning this certification.
By obtaining Six Sigma Black Belt certification, individuals gain expertise in problem-solving, data analysis, project management, and change management. They become equipped to lead teams, influence stakeholders, and drive impactful process improvements within organizations. This certification enhances employability, opens doors to leadership roles, and offers opportunities for career advancement and professional growth.
Moreover, Six Sigma Black Belts contribute to the success of their organizations by improving efficiency, reducing costs, and enhancing customer satisfaction. Their ability to apply data-driven approaches and implement sustainable solutions leads to tangible and measurable results.
In a highly competitive business landscape, organizations are increasingly recognizing the value of professionals with Six Sigma Black Belt certification. As a certified Black Belt, individuals can make a significant impact, drive continuous improvement, and contribute to the overall success of their organizations.
In summary, Six Sigma Black Belt certification offers a pathway to excellence in process improvement, leadership, and career advancement. It is a valuable asset for professionals seeking to make a difference and excel in their chosen fields.
A Comprehensive Guide to Minitab,benifits,vs Excel
In the realm of statistical analysis and data management, professionals are often faced with the choice between using dedicated statistical software like Minitab or relying on the familiar Excel spreadsheet tool. "A Comprehensive Guide to Minitab: Benefits vs Excel" aims to provide a comprehensive resource that explores the capabilities, advantages, and key differences between these two powerful tools.
Minitab is a specialized statistical software designed specifically for data analysis, quality improvement, and process optimization. With its robust features and extensive range of statistical techniques, Minitab offers professionals a dedicated platform to perform complex statistical analyses, conduct hypothesis testing, create visualizations, build predictive models, and more. This guide will delve into the various functionalities and features of Minitab, offering step-by-step instructions and practical examples to help users leverage its power effectively.
On the other hand, Excel, a widely used spreadsheet software, also offers some basic statistical functions and data analysis capabilities. With its familiarity and ease of use, Excel has become a popular choice for handling data and conducting simple analyses. However, when it comes to advanced statistical analysis and specialized techniques, Excel may have limitations compared to Minitab.
This comprehensive guide will delve into the benefits and advantages of using Minitab over Excel for statistical analysis tasks. It will explore the statistical accuracy, user-friendliness, automation and customization options, collaboration features, and integration capabilities that set Minitab apart. Additionally, it will address the training and support available for Minitab users and provide insights into the cost-effectiveness of utilizing Minitab in comparison to Excel.
Whether you are a quality professional, data analyst, researcher, or anyone involved in statistical analysis and data-driven decision making, this guide will equip you with the knowledge and understanding needed to make an informed choice between Minitab and Excel. Prepare to explore the depths of Minitab's capabilities and discover how it can empower you to unlock greater insights, drive quality improvements, and make more informed decisions based on data.
Embark on your journey to mastering Minitab and gaining a comprehensive understanding of its benefits over Excel with "A Comprehensive Guide to Minitab: Benefits vs Excel."
Table of Contents
MiniTab in Six Sigma
Benefits of MiniTab
MiniTab vs. Excel
Key Features of Minitab
Our Learners Also Asked
Conclusion
Minitab is a powerful statistical software package widely used by researchers, analysts, and data scientists to perform data analysis, process improvement, and quality control. This software provides a user-friendly interface and a comprehensive set of tools for data analysis, visualization, and modeling. With its vast collection of statistical techniques, Minitab has become an indispensable tool for professionals working in various fields, including healthcare, manufacturing, engineering, and finance. In this article, we will explore the features and benefits of Minitab, and explain how it can be used to perform various statistical analyses and process improvements. Whether you are a seasoned data analyst or a beginner, this introduction to Minitab will provide you with the knowledge and skills necessary to leverage this software for your data analysis needs.
MiniTab in Six Sigma
Minitab is a statistical software package that is widely used in the field of Six Sigma, a methodology for process improvement that aims to reduce defects and variations in production processes. With its comprehensive set of statistical tools and data analysis capabilities, Minitab is an essential tool for Six Sigma practitioners, helping them to identify and analyze critical factors that impact the quality of products or services. Some of the key features of Minitab that are particularly useful for Six Sigma include hypothesis testing, statistical process control, design of experiments, and regression analysis. By leveraging Minitab, Six Sigma professionals can make data-driven decisions and optimize their processes, resulting in increased efficiency, cost savings, and improved customer satisfaction. Whether you are a Six Sigma practitioner or a quality control professional, Minitab can help you achieve your goals and drive continuous improvement in your organization.
Benefits of MiniTab
Minitab is a powerful statistical software package that provides numerous benefits to data analysts, researchers, and quality control professionals. Its comprehensive set of tools and user-friendly interface make it an indispensable tool for data analysis, visualization, and modeling. Some of the key benefits of Minitab include:
- Improved efficiency: Minitab's automation and streamlined workflows allow users to quickly and easily perform data analysis, saving time and improving productivity.
- Accurate data analysis: Minitab's advanced statistical techniques and data visualization tools enable users to accurately analyze and interpret data, leading to more informed decision-making.
- Process improvement: Minitab's statistical process control, design of experiments, and quality tools enable users to identify and improve critical factors that impact the quality of products and services, leading to process improvements and cost savings.
- Flexibility: Minitab is compatible with a wide range of data formats and can be used for data analysis in various fields, including healthcare, manufacturing, engineering, and finance.
- User-friendly interface: Minitab's intuitive interface and easy-to-use features make it accessible to users of all levels of expertise, from beginners to advanced data analysts.
MiniTab vs. Excel
Minitab and Excel are both powerful tools for data analysis, but they differ in terms of their capabilities, features, and intended use. While Excel is a widely used spreadsheet software that provides basic data analysis and visualization capabilities, Minitab is a specialized statistical software package that offers a more comprehensive set of tools for data analysis and process improvement.
Some of the key differences between Minitab and Excel include:
- Statistical analysis: Minitab offers a wide range of statistical techniques and data analysis tools that are specifically designed for data analysis and process improvement, including statistical process control, design of experiments, and regression analysis. Excel, on the other hand, provides limited statistical capabilities, which are mostly limited to basic descriptive statistics and data visualization.
- Ease of use: Minitab is designed to be user-friendly and intuitive, with a streamlined interface and clear workflows. Excel can be more complex to use, particularly for users who are not familiar with its advanced features.
- Data visualization: Minitab provides a comprehensive set of data visualization tools, including scatterplots, histograms, boxplots, and control charts, which can be used to analyze data and communicate insights effectively. While Excel also provides basic data visualization capabilities, it may not be as powerful or flexible as Minitab.
- Process improvement: Minitab offers a range of process improvement tools, including process mapping, failure mode and effects analysis, and design of experiments, which are not available in Excel. These tools are designed to help organizations identify and eliminate sources of process variation, leading to improved quality and efficiency.
Key Features of Minitab , with long-tailed keywords
Minitab is a comprehensive statistical software package that provides a wide range of tools for data analysis, visualization, and modeling. Some of the key features of Minitab include:
- Statistical analysis: Minitab offers a comprehensive set of statistical techniques, including hypothesis testing, regression analysis, analysis of variance (ANOVA), and time series analysis. These tools enable users to accurately analyze and interpret data and make data-driven decisions.
- Data visualization: Minitab provides a range of data visualization tools, including scatterplots, histograms, boxplots, and control charts, which enable users to effectively analyze and communicate insights from their data.
- Process improvement: Minitab offers a range of process improvement tools, including statistical process control (SPC), design of experiments (DOE), and quality tools, which are specifically designed to help organizations identify and eliminate sources of process variation, leading to improved quality and efficiency.
- Automation: Minitab provides automation features that enable users to perform repetitive tasks quickly and easily, saving time and improving productivity.
- Compatibility: Minitab is compatible with a wide range of data formats, including Excel, CSV, and text files, and can be used on both Windows and Mac operating systems.
- User-friendly interface: Minitab's intuitive interface and easy-to-use features make it accessible to users of all levels of expertise, from beginners to advanced data analysts.
- Customization: Minitab allows users to customize their analysis and reporting workflows to meet their specific needs, enabling them to tailor the software to their unique requirements.
How to obtain the Minitab certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- IT Service Management & Governance: COBIT, ISO
Our Learners Also Asked
What is Minitab Software used for?
Minitab is a statistical software package that is used for data analysis, process improvement, and quality control. It provides a wide range of statistical techniques and data analysis tools, including descriptive statistics, hypothesis testing, regression analysis, design of experiments (DOE), statistical process control (SPC), and quality control charts. Minitab is commonly used in industries such as manufacturing, healthcare, and engineering to analyze data and identify sources of variation in processes. The software also provides tools for process improvement, including Lean Six Sigma methodologies, to help organizations streamline processes, improve quality, and reduce costs. With its user-friendly interface, Minitab enables users to easily import data, perform statistical analyses, and visualize the results, allowing them to make data-driven decisions. Overall, Minitab is a powerful tool that provides statistical solutions to problems in many industries.
Is minitab same as excel?
Minitab and Excel are both software packages used for data analysis, but Minitab is a more specialized statistical software package, while Excel is a spreadsheet software. Minitab is designed specifically for statistical analysis and process improvement, providing a wide range of statistical techniques, user-friendly interfaces, and specialized process improvement tools. Excel, on the other hand, provides basic data analysis capabilities, limited statistical capabilities, and some data visualization tools, but it lacks the specialized tools and advanced statistical techniques that Minitab provides. Overall, Minitab is a more powerful and comprehensive tool for users in fields such as manufacturing, healthcare, and engineering, while Excel is more suitable for basic data analysis and visualization tasks.
What type of software is minitab?
Minitab is a statistical software package that is used for data analysis, process improvement, and quality control. It is a specialized software that provides a wide range of statistical tools and techniques to analyze and interpret data. Minitab is designed to assist professionals in various industries, such as manufacturing, healthcare, and engineering, to improve their processes and products by identifying and eliminating sources of variation. With its user-friendly interface, Minitab enables users to easily import data, perform statistical analyses, and visualize the results, allowing them to make data-driven decisions. Overall, Minitab is a powerful tool that provides statistical solutions to problems in many industries.
What Is The Difference Between Minitab and SPSS?
Minitab and SPSS are both statistical software packages used for data analysis, but they differ in their focus, features, and intended use. Minitab is specialized in process improvement and quality control, providing tools such as Statistical Process Control (SPC) and Design of Experiments (DOE), while SPSS is geared towards social science research and provides specialized tools such as factor analysis, cluster analysis, and categorical data analysis. Minitab has a more user-friendly interface, whereas SPSS provides a more comprehensive set of data management tools. Minitab is generally less expensive than SPSS, making it more accessible for small businesses or individuals who need statistical analysis tools. The choice between Minitab and SPSS ultimately depends on the user's needs and the type of data analysis tasks they are working on.
Is minitab a programming language?
No, Minitab is not a programming language, but rather a statistical software package that provides a user-friendly interface for statistical analysis and data visualization. It provides a wide range of statistical tools and techniques that can be used by professionals in various industries to analyze and interpret data, and make data-driven decisions. Minitab does not require users to write programming code, but it provides a command-line interface that allows users to execute statistical analyses and produce reports. Users can also use macros in Minitab, which are pre-programmed sets of commands that automate repetitive tasks. However, Minitab is primarily designed to be a point-and-click software, so users can perform most of the analyses and operations by selecting the appropriate menus and options from the user interface.
Conclusion
In conclusion, Minitab is a powerful statistical software package that provides a wide range of data analysis and process improvement tools. It is specialized in process improvement and quality control and is commonly used in industries such as manufacturing, healthcare, and engineering. Minitab provides a user-friendly interface that allows users to easily import data, perform statistical analyses, and visualize the results, without requiring them to write programming code. While Minitab and SPSS are both statistical software packages, they differ in their focus, features, and intended use. Minitab is less expensive than SPSS and is an excellent choice for small businesses or individuals who need statistical analysis tools. Overall, Minitab is a versatile tool that can help organizations streamline processes, improve quality, and reduce costs by making data-driven decisions.
Read More
In the realm of statistical analysis and data management, professionals are often faced with the choice between using dedicated statistical software like Minitab or relying on the familiar Excel spreadsheet tool. "A Comprehensive Guide to Minitab: Benefits vs Excel" aims to provide a comprehensive resource that explores the capabilities, advantages, and key differences between these two powerful tools.
Minitab is a specialized statistical software designed specifically for data analysis, quality improvement, and process optimization. With its robust features and extensive range of statistical techniques, Minitab offers professionals a dedicated platform to perform complex statistical analyses, conduct hypothesis testing, create visualizations, build predictive models, and more. This guide will delve into the various functionalities and features of Minitab, offering step-by-step instructions and practical examples to help users leverage its power effectively.
On the other hand, Excel, a widely used spreadsheet software, also offers some basic statistical functions and data analysis capabilities. With its familiarity and ease of use, Excel has become a popular choice for handling data and conducting simple analyses. However, when it comes to advanced statistical analysis and specialized techniques, Excel may have limitations compared to Minitab.
This comprehensive guide will delve into the benefits and advantages of using Minitab over Excel for statistical analysis tasks. It will explore the statistical accuracy, user-friendliness, automation and customization options, collaboration features, and integration capabilities that set Minitab apart. Additionally, it will address the training and support available for Minitab users and provide insights into the cost-effectiveness of utilizing Minitab in comparison to Excel.
Whether you are a quality professional, data analyst, researcher, or anyone involved in statistical analysis and data-driven decision making, this guide will equip you with the knowledge and understanding needed to make an informed choice between Minitab and Excel. Prepare to explore the depths of Minitab's capabilities and discover how it can empower you to unlock greater insights, drive quality improvements, and make more informed decisions based on data.
Embark on your journey to mastering Minitab and gaining a comprehensive understanding of its benefits over Excel with "A Comprehensive Guide to Minitab: Benefits vs Excel."
Table of Contents
MiniTab in Six Sigma
Benefits of MiniTab
MiniTab vs. Excel
Key Features of Minitab
Our Learners Also Asked
Conclusion
Minitab is a powerful statistical software package widely used by researchers, analysts, and data scientists to perform data analysis, process improvement, and quality control. This software provides a user-friendly interface and a comprehensive set of tools for data analysis, visualization, and modeling. With its vast collection of statistical techniques, Minitab has become an indispensable tool for professionals working in various fields, including healthcare, manufacturing, engineering, and finance. In this article, we will explore the features and benefits of Minitab, and explain how it can be used to perform various statistical analyses and process improvements. Whether you are a seasoned data analyst or a beginner, this introduction to Minitab will provide you with the knowledge and skills necessary to leverage this software for your data analysis needs.
MiniTab in Six Sigma
Minitab is a statistical software package that is widely used in the field of Six Sigma, a methodology for process improvement that aims to reduce defects and variations in production processes. With its comprehensive set of statistical tools and data analysis capabilities, Minitab is an essential tool for Six Sigma practitioners, helping them to identify and analyze critical factors that impact the quality of products or services. Some of the key features of Minitab that are particularly useful for Six Sigma include hypothesis testing, statistical process control, design of experiments, and regression analysis. By leveraging Minitab, Six Sigma professionals can make data-driven decisions and optimize their processes, resulting in increased efficiency, cost savings, and improved customer satisfaction. Whether you are a Six Sigma practitioner or a quality control professional, Minitab can help you achieve your goals and drive continuous improvement in your organization.
Benefits of MiniTab
Minitab is a powerful statistical software package that provides numerous benefits to data analysts, researchers, and quality control professionals. Its comprehensive set of tools and user-friendly interface make it an indispensable tool for data analysis, visualization, and modeling. Some of the key benefits of Minitab include:
- Improved efficiency: Minitab's automation and streamlined workflows allow users to quickly and easily perform data analysis, saving time and improving productivity.
- Accurate data analysis: Minitab's advanced statistical techniques and data visualization tools enable users to accurately analyze and interpret data, leading to more informed decision-making.
- Process improvement: Minitab's statistical process control, design of experiments, and quality tools enable users to identify and improve critical factors that impact the quality of products and services, leading to process improvements and cost savings.
- Flexibility: Minitab is compatible with a wide range of data formats and can be used for data analysis in various fields, including healthcare, manufacturing, engineering, and finance.
- User-friendly interface: Minitab's intuitive interface and easy-to-use features make it accessible to users of all levels of expertise, from beginners to advanced data analysts.
MiniTab vs. Excel
Minitab and Excel are both powerful tools for data analysis, but they differ in terms of their capabilities, features, and intended use. While Excel is a widely used spreadsheet software that provides basic data analysis and visualization capabilities, Minitab is a specialized statistical software package that offers a more comprehensive set of tools for data analysis and process improvement.
Some of the key differences between Minitab and Excel include:
- Statistical analysis: Minitab offers a wide range of statistical techniques and data analysis tools that are specifically designed for data analysis and process improvement, including statistical process control, design of experiments, and regression analysis. Excel, on the other hand, provides limited statistical capabilities, which are mostly limited to basic descriptive statistics and data visualization.
- Ease of use: Minitab is designed to be user-friendly and intuitive, with a streamlined interface and clear workflows. Excel can be more complex to use, particularly for users who are not familiar with its advanced features.
- Data visualization: Minitab provides a comprehensive set of data visualization tools, including scatterplots, histograms, boxplots, and control charts, which can be used to analyze data and communicate insights effectively. While Excel also provides basic data visualization capabilities, it may not be as powerful or flexible as Minitab.
- Process improvement: Minitab offers a range of process improvement tools, including process mapping, failure mode and effects analysis, and design of experiments, which are not available in Excel. These tools are designed to help organizations identify and eliminate sources of process variation, leading to improved quality and efficiency.
Key Features of Minitab , with long-tailed keywords
Minitab is a comprehensive statistical software package that provides a wide range of tools for data analysis, visualization, and modeling. Some of the key features of Minitab include:
- Statistical analysis: Minitab offers a comprehensive set of statistical techniques, including hypothesis testing, regression analysis, analysis of variance (ANOVA), and time series analysis. These tools enable users to accurately analyze and interpret data and make data-driven decisions.
- Data visualization: Minitab provides a range of data visualization tools, including scatterplots, histograms, boxplots, and control charts, which enable users to effectively analyze and communicate insights from their data.
- Process improvement: Minitab offers a range of process improvement tools, including statistical process control (SPC), design of experiments (DOE), and quality tools, which are specifically designed to help organizations identify and eliminate sources of process variation, leading to improved quality and efficiency.
- Automation: Minitab provides automation features that enable users to perform repetitive tasks quickly and easily, saving time and improving productivity.
- Compatibility: Minitab is compatible with a wide range of data formats, including Excel, CSV, and text files, and can be used on both Windows and Mac operating systems.
- User-friendly interface: Minitab's intuitive interface and easy-to-use features make it accessible to users of all levels of expertise, from beginners to advanced data analysts.
- Customization: Minitab allows users to customize their analysis and reporting workflows to meet their specific needs, enabling them to tailor the software to their unique requirements.
How to obtain the Minitab certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- IT Service Management & Governance: COBIT, ISO
Our Learners Also Asked
What is Minitab Software used for?
Minitab is a statistical software package that is used for data analysis, process improvement, and quality control. It provides a wide range of statistical techniques and data analysis tools, including descriptive statistics, hypothesis testing, regression analysis, design of experiments (DOE), statistical process control (SPC), and quality control charts. Minitab is commonly used in industries such as manufacturing, healthcare, and engineering to analyze data and identify sources of variation in processes. The software also provides tools for process improvement, including Lean Six Sigma methodologies, to help organizations streamline processes, improve quality, and reduce costs. With its user-friendly interface, Minitab enables users to easily import data, perform statistical analyses, and visualize the results, allowing them to make data-driven decisions. Overall, Minitab is a powerful tool that provides statistical solutions to problems in many industries.
Is minitab same as excel?
Minitab and Excel are both software packages used for data analysis, but Minitab is a more specialized statistical software package, while Excel is a spreadsheet software. Minitab is designed specifically for statistical analysis and process improvement, providing a wide range of statistical techniques, user-friendly interfaces, and specialized process improvement tools. Excel, on the other hand, provides basic data analysis capabilities, limited statistical capabilities, and some data visualization tools, but it lacks the specialized tools and advanced statistical techniques that Minitab provides. Overall, Minitab is a more powerful and comprehensive tool for users in fields such as manufacturing, healthcare, and engineering, while Excel is more suitable for basic data analysis and visualization tasks.
What type of software is minitab?
Minitab is a statistical software package that is used for data analysis, process improvement, and quality control. It is a specialized software that provides a wide range of statistical tools and techniques to analyze and interpret data. Minitab is designed to assist professionals in various industries, such as manufacturing, healthcare, and engineering, to improve their processes and products by identifying and eliminating sources of variation. With its user-friendly interface, Minitab enables users to easily import data, perform statistical analyses, and visualize the results, allowing them to make data-driven decisions. Overall, Minitab is a powerful tool that provides statistical solutions to problems in many industries.
What Is The Difference Between Minitab and SPSS?
Minitab and SPSS are both statistical software packages used for data analysis, but they differ in their focus, features, and intended use. Minitab is specialized in process improvement and quality control, providing tools such as Statistical Process Control (SPC) and Design of Experiments (DOE), while SPSS is geared towards social science research and provides specialized tools such as factor analysis, cluster analysis, and categorical data analysis. Minitab has a more user-friendly interface, whereas SPSS provides a more comprehensive set of data management tools. Minitab is generally less expensive than SPSS, making it more accessible for small businesses or individuals who need statistical analysis tools. The choice between Minitab and SPSS ultimately depends on the user's needs and the type of data analysis tasks they are working on.
Is minitab a programming language?
No, Minitab is not a programming language, but rather a statistical software package that provides a user-friendly interface for statistical analysis and data visualization. It provides a wide range of statistical tools and techniques that can be used by professionals in various industries to analyze and interpret data, and make data-driven decisions. Minitab does not require users to write programming code, but it provides a command-line interface that allows users to execute statistical analyses and produce reports. Users can also use macros in Minitab, which are pre-programmed sets of commands that automate repetitive tasks. However, Minitab is primarily designed to be a point-and-click software, so users can perform most of the analyses and operations by selecting the appropriate menus and options from the user interface.
Conclusion
In conclusion, Minitab is a powerful statistical software package that provides a wide range of data analysis and process improvement tools. It is specialized in process improvement and quality control and is commonly used in industries such as manufacturing, healthcare, and engineering. Minitab provides a user-friendly interface that allows users to easily import data, perform statistical analyses, and visualize the results, without requiring them to write programming code. While Minitab and SPSS are both statistical software packages, they differ in their focus, features, and intended use. Minitab is less expensive than SPSS and is an excellent choice for small businesses or individuals who need statistical analysis tools. Overall, Minitab is a versatile tool that can help organizations streamline processes, improve quality, and reduce costs by making data-driven decisions.
A Comprehensive Overview of Google Cloud Certification: Core Services, Benifits
In today's rapidly evolving technological landscape, cloud computing has become the cornerstone of digital transformation for businesses worldwide. Among the leading providers in the cloud industry, Google Cloud Platform (GCP) has emerged as a prominent player, offering a vast array of services and solutions to cater to diverse business needs. To validate and showcase their expertise in utilizing Google Cloud's core services, professionals often pursue Google Cloud Certification.
This comprehensive overview aims to shed light on the Google Cloud Certification program, its core services, and the benefits it brings to individuals and organizations. Whether you are an aspiring cloud professional, a seasoned IT expert, or a business owner seeking to leverage the power of Google Cloud, understanding the intricacies of certification and its value can significantly contribute to your success in the cloud domain.
Throughout this guide, we will explore the different certification tracks available, delve into the core services offered by Google Cloud, and highlight the advantages of becoming a certified professional. From foundational knowledge to specialized skills, Google Cloud Certification equips individuals with the expertise required to design, build, and manage secure and scalable cloud solutions.
By gaining a comprehensive understanding of the Google Cloud Certification program and its associated benefits, you will be able to make informed decisions regarding your professional development, unlocking exciting opportunities in the cloud job market. So, let us embark on this journey to explore the world of Google Cloud Certification and discover how it can propel your career and transform your organization's cloud capabilities.
Table of contents
- Introduction to Google Cloud Certification
- Available Google Cloud Certifications
- Benefits of Google Cloud Certification
- Preparing for Google Cloud Certification Exams
- Tips for Success in Google Cloud Certification Exams
- Maintaining and Renewing Google Cloud Certification
- Conclusion
Introduction to Google Cloud Certification
Google Cloud Certification is a credential that validates an individual's knowledge and skills in utilizing Google Cloud Platform (GCP) services. As more businesses migrate their infrastructure and applications to the cloud, the demand for professionals proficient in GCP continues to grow. Google Cloud Certification serves as a credible and recognized way to demonstrate expertise in working with GCP.
GCP offers a wide range of cloud services, including computing, storage, networking, machine learning, data analytics, and more. Google Cloud Certification is designed to assess proficiency in using these services effectively, enabling individuals to showcase their expertise to potential employers, clients, and peers.
By earning a Google Cloud Certification, professionals can enhance their career prospects, gain a competitive edge in the job market, and establish themselves as trusted experts in cloud computing. These certifications validate both theoretical knowledge and practical skills, ensuring that certified individuals are capable of successfully designing, implementing, and managing cloud solutions using GCP.
Google offers a variety of certification paths to cater to different roles and expertise levels. The certifications are categorized into three main levels:
- Associate-level certifications: These certifications validate foundational knowledge and skills for specific roles within GCP. They include the Associate Cloud Engineer, Associate Cloud Developer, and Associate Cloud Data Engineer certifications.
- Professional-level certifications: These certifications validate advanced knowledge and skills required for specialized roles, such as Cloud Architect, Data Engineer, and DevOps Engineer.
- Specialty certifications: These certifications focus on specific domains or technologies, such as machine learning, security, networking, and more. They enable professionals to showcase their expertise in these niche areas.
To earn a Google Cloud Certification, individuals are required to pass a rigorous exam that assesses their understanding of GCP services, best practices, and real-world application scenarios. The exams typically consist of a combination of multiple-choice questions, scenario-based questions, and hands-on tasks that simulate real-world scenarios.
Preparing for the exams involves a combination of self-study, hands-on experience with GCP, practice exams, and utilizing various learning resources provided by Google. The Google Cloud documentation, online courses, and official exam guides serve as valuable study materials.
Once certified, individuals can enjoy several benefits, including increased job opportunities, recognition in the industry, and access to a network of professionals within the Google Cloud community. However, it's important to note that certifications require ongoing maintenance and renewal to stay relevant in the ever-evolving cloud landscape.
In conclusion, Google Cloud Certification offers a pathway for professionals to demonstrate their expertise in working with GCP. It provides tangible evidence of their skills and knowledge, boosting their credibility and career prospects in the cloud computing industry. Whether you're an aspiring cloud engineer, architect, data engineer, or any other cloud-related role, Google Cloud Certification can be a valuable investment in your professional growth and success.
Available Google Cloud Certifications
Google offers a range of certifications under its Google Cloud Certification program. These certifications cover different roles and expertise levels within Google Cloud Platform (GCP). Here are the main categories of Google Cloud Certifications:
- Associate-level Certifications:
a. Associate Cloud Engineer: This certification is designed for individuals who have foundational knowledge of GCP and can deploy, monitor, and manage GCP projects. It validates skills related to cloud infrastructure, networking, storage, security, and application deployment using GCP services.
b. Associate Cloud Developer: The Associate Cloud Developer certification is for individuals who have experience in developing, deploying, and monitoring applications on GCP. It covers topics such as cloud-native application development, GCP services integration, and application deployment using App Engine, Compute Engine, and other GCP tools.
c. Associate Cloud Data Engineer: This certification focuses on validating skills related to data engineering and data analytics using GCP. It covers topics such as data ingestion, transformation, storage, processing, and analysis using GCP's data analytics and machine learning services.
- Professional-level Certifications:
a. Professional Cloud Architect: The Professional Cloud Architect certification is designed for experienced cloud architects who can design and manage scalable, secure, and highly available solutions on GCP. It validates skills in solution design, infrastructure architecture, security, data management, and business continuity planning.
b. Professional Data Engineer: This certification is intended for data engineers who design and build data processing systems, manage and analyze large-scale datasets, and implement data solutions using GCP services. It covers topics such as data ingestion, processing, storage, analysis, and machine learning.
c. Professional Cloud DevOps Engineer: The Professional Cloud DevOps Engineer certification targets professionals who specialize in DevOps practices on GCP. It validates skills in continuous integration and delivery (CI/CD), automation, infrastructure management, and optimizing performance and scalability of applications on GCP.
- Specialty Certifications:
a. Cloud Architect: The Cloud Architect certification is for individuals who demonstrate expertise in designing and managing cloud architecture within specific industry domains, such as healthcare, finance, retail, and more. It validates skills in developing scalable and reliable solutions that meet industry-specific requirements.
b. Data Engineer: The Data Engineer certification focuses on data engineering and analytics within specific industry domains. It validates skills in designing and building data processing systems, managing and analyzing data, and implementing data solutions using GCP services in industry-specific contexts.
c. Machine Learning Engineer: The Machine Learning Engineer certification is for professionals who specialize in designing, building, and deploying machine learning models using GCP's machine learning services. It validates skills in data preprocessing, model development, optimization, and deployment.
Each certification requires passing a specific exam that tests the candidate's knowledge and skills related to the respective role or domain. Google Cloud Certifications provide professionals with industry-recognized credentials that showcase their expertise and competence in utilizing GCP services effectively.
Benefits of Google Cloud Certification
Obtaining a Google Cloud Certification can offer numerous benefits to individuals in their careers and professional development. Here are some key advantages of earning a Google Cloud Certification:
- Career Advancement Opportunities: Google Cloud Certifications can significantly enhance career prospects. They demonstrate your expertise and proficiency in working with Google Cloud Platform (GCP), making you a valuable asset to organizations seeking cloud professionals. Certified individuals often have a competitive edge when applying for job roles or promotions within their current organizations.
- Industry Recognition and Credibility: Google Cloud Certifications are recognized and respected in the industry. They validate your knowledge and skills in using GCP services effectively, providing third-party verification of your expertise. Employers and clients are more likely to trust your abilities when you hold a reputable certification from a recognized provider like Google.
- Enhanced Skills and Knowledge: Preparing for a Google Cloud Certification requires comprehensive study and hands-on experience with GCP. The certification process enables you to deepen your understanding of cloud concepts, best practices, and the implementation of cloud solutions. Through the certification journey, you gain valuable skills and knowledge that can be immediately applied to real-world scenarios.
- Access to Exclusive Resources: Google Cloud Certifications grant access to exclusive resources provided by Google. Certified individuals often gain access to private forums, online communities, and networking opportunities where they can connect with other certified professionals, share insights, and learn from each other's experiences. These resources can foster continuous learning and professional growth.
- Validation of Specialized Expertise: Google offers specialty certifications that focus on specific domains or technologies, such as machine learning, data engineering, and cloud architecture. These certifications validate your specialized expertise in these areas, allowing you to differentiate yourself from general cloud professionals and showcase your proficiency in specific industry domains.
- Confidence in Decision-Making: Google Cloud Certifications provide a comprehensive understanding of GCP services, best practices, and architectural considerations. With this knowledge, you can make informed decisions regarding infrastructure design, service selection, data management, and security. The certification instills confidence in your ability to architect and implement effective cloud solutions.
- Networking and Collaboration Opportunities: Being part of the Google Cloud Certification community offers opportunities to network and collaborate with like-minded professionals. You can engage in discussions, seek advice, and share ideas with others who have similar interests and experiences. This network can lead to valuable connections, career opportunities, and collaborative projects.
- Demonstrated Commitment to Professional Development: Earning a Google Cloud Certification demonstrates your commitment to continuous learning and professional development. It showcases your dedication to staying up-to-date with the latest cloud technologies and industry trends. Employers value individuals who invest in their professional growth and show a willingness to adapt to the evolving cloud landscape.
Preparing for Google Cloud Certification Exams
Preparing for Google Cloud Certification exams requires a systematic approach and dedication to studying and hands-on practice. Here are some steps to help you prepare effectively:
- Understand the Exam Objectives: Familiarize yourself with the exam objectives and the topics that will be covered. Google provides detailed exam guides for each certification, outlining the knowledge and skills required. Read through the exam guide to gain clarity on what to expect and what areas to focus on during your preparation.
- Create a Study Plan: Develop a study plan that suits your schedule and allows for consistent and organized studying. Break down the exam objectives into smaller topics and allocate specific study time for each. Set realistic goals and milestones to track your progress. Ensure that you allocate enough time for hands-on practice to reinforce your theoretical knowledge.
- Utilize Official Study Resources: Google offers official study resources, including documentation, whitepapers, tutorials, and online courses specifically designed to prepare you for the certification exams. Review the recommended resources provided in the exam guide and make use of them during your preparation. These resources are comprehensive and cover the topics in-depth.
- Hands-on Practice: Practical experience is crucial for success in Google Cloud Certification exams. Set up a practice environment using the Google Cloud Console and experiment with various services and configurations. Implement sample projects, follow tutorials, and work on real-world scenarios. Hands-on practice helps solidify your understanding of GCP services and their practical applications.
- Take Advantage of Practice Exams: Practice exams are invaluable for assessing your knowledge and identifying areas that require further study. Google provides sample questions and practice exams that simulate the actual exam environment. Take these practice exams under timed conditions to get a feel for the pace and structure of the real exam. Analyze your results to identify weak areas and focus your study efforts accordingly.
- Join Study Groups and Online Communities: Engaging with others who are also preparing for Google Cloud Certification exams can provide valuable insights and support. Join study groups or online communities where you can discuss exam topics, ask questions, and learn from each other's experiences. Collaborating with peers can enhance your understanding and help you approach challenges from different perspectives.
- Review Documentation and Best Practices: Google Cloud documentation contains detailed information about each GCP service. Familiarize yourself with the documentation for the services relevant to your certification. Pay attention to recommended best practices, design patterns, and use cases. Understanding the nuances of GCP services and their optimal usage can greatly benefit you during the exam.
- Time Management and Exam Strategies: During the exam, time management is crucial. Understand the exam structure and allocate appropriate time to each section or question. Read the questions carefully and ensure you understand the requirements before providing your answer. If you encounter challenging questions, mark them for review and come back to them later. Maintain a calm and focused mindset throughout the exam.
- Continuous Learning and Iterative Preparation: Google Cloud technologies evolve rapidly, and new features and services are introduced regularly. Stay updated with the latest developments by following relevant blogs, attending webinars, and exploring additional resources beyond the exam requirements. Treat your certification journey as a continuous learning process, even after passing the exam.
Tips for Success in Google Cloud Certification Exams
To increase your chances of success in Google Cloud Certification exams, consider the following tips:
- Understand the Exam Format: Familiarize yourself with the format of the exam, including the number of questions, time limit, and question types (multiple-choice, scenario-based, etc.). Understanding the exam structure will help you manage your time effectively during the test.
- Review the Exam Guide: Read the exam guide provided by Google. It outlines the topics and skills that will be assessed in the exam. Use it as a blueprint for your preparation and ensure you have a solid understanding of each objective.
- Focus on Hands-on Practice: Google Cloud Certification exams often include hands-on tasks or scenario-based questions. Practice using the Google Cloud Console and work on real-world projects to gain practical experience with GCP services. This will help you apply your knowledge effectively during the exam.
- Study Official Documentation: Google Cloud documentation is a valuable resource. Review the documentation for GCP services covered in the exam to understand their features, capabilities, best practices, and use cases. This will enhance your understanding and help you answer questions more accurately.
- Take Practice Exams: Google provides sample questions and practice exams that simulate the actual exam environment. Take advantage of these resources to familiarize yourself with the question format and assess your readiness. Analyze your performance and focus on improving weak areas.
- Join Study Groups and Online Communities: Engaging with others who are also preparing for the same exam can provide valuable insights and support. Join study groups, participate in forums, or connect with fellow learners online. Discussing exam topics and sharing experiences can help solidify your understanding and clarify any doubts.
- Emphasize Key Concepts and Services: Identify the key concepts and GCP services emphasized in the exam guide. Allocate more study time to these areas and ensure you have a thorough understanding of their functionalities, use cases, and associated best practices.
- Practice Time Management: Time management is crucial during the exam. Practice answering questions under timed conditions during your preparation to improve your speed and efficiency. Allocate appropriate time to each question or section based on its weightage and difficulty level.
- Read Questions Carefully: Carefully read each question and understand its requirements before selecting your answer. Pay attention to any specific constraints or conditions mentioned in the question. Avoid rushing through questions and take the time to analyze and think through your answers.
- Stay Calm and Confident: Exam anxiety can hinder your performance. Stay calm, confident, and focused throughout the exam. If you encounter challenging questions, don't panic. Take a deep breath, mark them for review, and move on. Trust in your preparation and believe in your abilities.
- Review and Revise: If time allows, review your answers before submitting the exam. Double-check for any errors or omissions. In scenario-based questions, ensure you have considered all relevant factors and provided a comprehensive solution.
- Stay Updated: Google Cloud technologies evolve, and new features and services are introduced regularly. Stay updated with the latest advancements by following official Google Cloud blogs, attending webinars, and exploring additional resources beyond the exam requirements.
Maintaining and Renewing Google Cloud Certification
Once you have earned a Google Cloud Certification, it's important to maintain and renew it to demonstrate your continued expertise and stay up to date with the evolving Google Cloud Platform (GCP). Here are some key aspects to consider for maintaining and renewing your Google Cloud Certification:
- Stay Updated with GCP: Google Cloud technologies and services evolve over time. Stay informed about the latest updates, new features, and best practices by regularly reviewing the official Google Cloud documentation, attending webinars, and participating in relevant training sessions or events. This will help you stay current with GCP and ensure your certification remains relevant.
- Follow Certification Renewal Requirements: Each Google Cloud Certification has specific renewal requirements, which typically involve meeting certain criteria within a specified period. Review the renewal requirements for your certification and ensure you understand what is expected. Familiarize yourself with the renewal process and any associated fees, if applicable.
- Earn Recertification Exams or Achievements: To maintain your certification, you may be required to pass a recertification exam or earn specific achievements within a given timeframe. Google may introduce recertification exams or provide alternative pathways to demonstrate your ongoing expertise. Stay updated with the recertification options and plan accordingly to meet the renewal requirements.
- Participate in Continuing Education: Google offers various opportunities for continuing education, such as webinars, online courses, and training programs. Participate in these educational resources to expand your knowledge, deepen your expertise, and earn relevant continuing education credits. These activities not only contribute to your professional growth but also help you meet the renewal requirements.
- Engage with the Google Cloud Community: Actively engage with the Google Cloud community, including forums, user groups, and online communities. Share your knowledge, contribute to discussions, and learn from other professionals in the field. Networking with peers and staying connected to the community can provide valuable insights, support, and access to new opportunities.
- Maintain Hands-on Experience: Regularly practice your skills and maintain hands-on experience with GCP. Stay engaged with real-world projects, experiment with new services and features, and leverage the cloud console to reinforce your practical knowledge. Continuously applying your skills in real-life scenarios helps you stay proficient and adapt to changing industry needs.
- Explore Advanced Certifications: Consider pursuing advanced certifications or specialty certifications within your area of interest or expertise. Advanced certifications can demonstrate your deeper knowledge and proficiency in specific domains of GCP. They can further enhance your professional profile and open doors to more advanced roles or opportunities.
- Track Certification Expiration Dates: Keep track of your certification expiration dates to ensure timely renewal. Set up reminders or alerts to notify you in advance so that you can plan and complete the necessary renewal activities without any last-minute rush or potential lapse in certification.
- Update Your Professional Profiles: Once you renew your certification, update your professional profiles, such as LinkedIn, resume, and online portfolios, to reflect your current certification status. This helps showcase your ongoing commitment to professional development and keeps your profile up to date for potential employers or clients.
Remember, maintaining and renewing your Google Cloud Certification requires a proactive approach. Stay engaged with the GCP ecosystem, continuously learn, and participate in relevant activities to ensure that your certification remains current and valuable in the ever-evolving cloud industry.
How to obtain Google Cloud Certifications Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Microsoft Azure Solutions 70 532 Certification
Conclusion
In conclusion, obtaining a Google Cloud Certification can significantly benefit your career in the cloud computing industry. It demonstrates your expertise and proficiency in working with Google Cloud Platform (GCP) and provides you with a competitive edge in the job market. Throughout this blog, we have explored various aspects related to Google Cloud Certification.
We began by introducing the concept of Google Cloud Certification, highlighting its importance in validating your knowledge and skills in using GCP effectively. We then discussed the available Google Cloud Certifications, which cover a wide range of roles and specializations, allowing you to choose the certification that aligns with your career goals.
Next, we delved into the benefits of earning a Google Cloud Certification. These advantages include career advancement opportunities, industry recognition and credibility, enhanced skills and knowledge, access to exclusive resources, validation of specialized expertise, confidence in decision-making, networking and collaboration opportunities, and a demonstration of commitment to professional development.
To help you succeed in Google Cloud Certification exams, we provided tips for effective preparation. These tips emphasized understanding the exam format, utilizing official study resources, hands-on practice, joining study groups and online communities, and practicing time management and exam strategies.
Furthermore, we highlighted the importance of maintaining and renewing your Google Cloud Certification. This involves staying updated with GCP, following certification renewal requirements, earning recertification exams or achievements, participating in continuing education, engaging with the Google Cloud community, maintaining hands-on experience, exploring advanced certifications, and tracking certification expiration dates.
By continuously investing in your professional development, staying current with the latest cloud technologies, and actively participating in the Google Cloud community, you can maximize the value of your Google Cloud Certification and advance your career in the dynamic and rapidly growing field of cloud computing.
Obtaining a Google Cloud Certification is not only a testament to your skills but also a commitment to excellence and continuous learning. So, take the first step, embark on your certification journey, and unlock new opportunities in the exciting world of Google Cloud Platform.
Read More
In today's rapidly evolving technological landscape, cloud computing has become the cornerstone of digital transformation for businesses worldwide. Among the leading providers in the cloud industry, Google Cloud Platform (GCP) has emerged as a prominent player, offering a vast array of services and solutions to cater to diverse business needs. To validate and showcase their expertise in utilizing Google Cloud's core services, professionals often pursue Google Cloud Certification.
This comprehensive overview aims to shed light on the Google Cloud Certification program, its core services, and the benefits it brings to individuals and organizations. Whether you are an aspiring cloud professional, a seasoned IT expert, or a business owner seeking to leverage the power of Google Cloud, understanding the intricacies of certification and its value can significantly contribute to your success in the cloud domain.
Throughout this guide, we will explore the different certification tracks available, delve into the core services offered by Google Cloud, and highlight the advantages of becoming a certified professional. From foundational knowledge to specialized skills, Google Cloud Certification equips individuals with the expertise required to design, build, and manage secure and scalable cloud solutions.
By gaining a comprehensive understanding of the Google Cloud Certification program and its associated benefits, you will be able to make informed decisions regarding your professional development, unlocking exciting opportunities in the cloud job market. So, let us embark on this journey to explore the world of Google Cloud Certification and discover how it can propel your career and transform your organization's cloud capabilities.
Table of contents
- Introduction to Google Cloud Certification
- Available Google Cloud Certifications
- Benefits of Google Cloud Certification
- Preparing for Google Cloud Certification Exams
- Tips for Success in Google Cloud Certification Exams
- Maintaining and Renewing Google Cloud Certification
- Conclusion
Introduction to Google Cloud Certification
Google Cloud Certification is a credential that validates an individual's knowledge and skills in utilizing Google Cloud Platform (GCP) services. As more businesses migrate their infrastructure and applications to the cloud, the demand for professionals proficient in GCP continues to grow. Google Cloud Certification serves as a credible and recognized way to demonstrate expertise in working with GCP.
GCP offers a wide range of cloud services, including computing, storage, networking, machine learning, data analytics, and more. Google Cloud Certification is designed to assess proficiency in using these services effectively, enabling individuals to showcase their expertise to potential employers, clients, and peers.
By earning a Google Cloud Certification, professionals can enhance their career prospects, gain a competitive edge in the job market, and establish themselves as trusted experts in cloud computing. These certifications validate both theoretical knowledge and practical skills, ensuring that certified individuals are capable of successfully designing, implementing, and managing cloud solutions using GCP.
Google offers a variety of certification paths to cater to different roles and expertise levels. The certifications are categorized into three main levels:
- Associate-level certifications: These certifications validate foundational knowledge and skills for specific roles within GCP. They include the Associate Cloud Engineer, Associate Cloud Developer, and Associate Cloud Data Engineer certifications.
- Professional-level certifications: These certifications validate advanced knowledge and skills required for specialized roles, such as Cloud Architect, Data Engineer, and DevOps Engineer.
- Specialty certifications: These certifications focus on specific domains or technologies, such as machine learning, security, networking, and more. They enable professionals to showcase their expertise in these niche areas.
To earn a Google Cloud Certification, individuals are required to pass a rigorous exam that assesses their understanding of GCP services, best practices, and real-world application scenarios. The exams typically consist of a combination of multiple-choice questions, scenario-based questions, and hands-on tasks that simulate real-world scenarios.
Preparing for the exams involves a combination of self-study, hands-on experience with GCP, practice exams, and utilizing various learning resources provided by Google. The Google Cloud documentation, online courses, and official exam guides serve as valuable study materials.
Once certified, individuals can enjoy several benefits, including increased job opportunities, recognition in the industry, and access to a network of professionals within the Google Cloud community. However, it's important to note that certifications require ongoing maintenance and renewal to stay relevant in the ever-evolving cloud landscape.
In conclusion, Google Cloud Certification offers a pathway for professionals to demonstrate their expertise in working with GCP. It provides tangible evidence of their skills and knowledge, boosting their credibility and career prospects in the cloud computing industry. Whether you're an aspiring cloud engineer, architect, data engineer, or any other cloud-related role, Google Cloud Certification can be a valuable investment in your professional growth and success.
Available Google Cloud Certifications
Google offers a range of certifications under its Google Cloud Certification program. These certifications cover different roles and expertise levels within Google Cloud Platform (GCP). Here are the main categories of Google Cloud Certifications:
- Associate-level Certifications:
a. Associate Cloud Engineer: This certification is designed for individuals who have foundational knowledge of GCP and can deploy, monitor, and manage GCP projects. It validates skills related to cloud infrastructure, networking, storage, security, and application deployment using GCP services.
b. Associate Cloud Developer: The Associate Cloud Developer certification is for individuals who have experience in developing, deploying, and monitoring applications on GCP. It covers topics such as cloud-native application development, GCP services integration, and application deployment using App Engine, Compute Engine, and other GCP tools.
c. Associate Cloud Data Engineer: This certification focuses on validating skills related to data engineering and data analytics using GCP. It covers topics such as data ingestion, transformation, storage, processing, and analysis using GCP's data analytics and machine learning services.
- Professional-level Certifications:
a. Professional Cloud Architect: The Professional Cloud Architect certification is designed for experienced cloud architects who can design and manage scalable, secure, and highly available solutions on GCP. It validates skills in solution design, infrastructure architecture, security, data management, and business continuity planning.
b. Professional Data Engineer: This certification is intended for data engineers who design and build data processing systems, manage and analyze large-scale datasets, and implement data solutions using GCP services. It covers topics such as data ingestion, processing, storage, analysis, and machine learning.
c. Professional Cloud DevOps Engineer: The Professional Cloud DevOps Engineer certification targets professionals who specialize in DevOps practices on GCP. It validates skills in continuous integration and delivery (CI/CD), automation, infrastructure management, and optimizing performance and scalability of applications on GCP.
- Specialty Certifications:
a. Cloud Architect: The Cloud Architect certification is for individuals who demonstrate expertise in designing and managing cloud architecture within specific industry domains, such as healthcare, finance, retail, and more. It validates skills in developing scalable and reliable solutions that meet industry-specific requirements.
b. Data Engineer: The Data Engineer certification focuses on data engineering and analytics within specific industry domains. It validates skills in designing and building data processing systems, managing and analyzing data, and implementing data solutions using GCP services in industry-specific contexts.
c. Machine Learning Engineer: The Machine Learning Engineer certification is for professionals who specialize in designing, building, and deploying machine learning models using GCP's machine learning services. It validates skills in data preprocessing, model development, optimization, and deployment.
Each certification requires passing a specific exam that tests the candidate's knowledge and skills related to the respective role or domain. Google Cloud Certifications provide professionals with industry-recognized credentials that showcase their expertise and competence in utilizing GCP services effectively.
Benefits of Google Cloud Certification
Obtaining a Google Cloud Certification can offer numerous benefits to individuals in their careers and professional development. Here are some key advantages of earning a Google Cloud Certification:
- Career Advancement Opportunities: Google Cloud Certifications can significantly enhance career prospects. They demonstrate your expertise and proficiency in working with Google Cloud Platform (GCP), making you a valuable asset to organizations seeking cloud professionals. Certified individuals often have a competitive edge when applying for job roles or promotions within their current organizations.
- Industry Recognition and Credibility: Google Cloud Certifications are recognized and respected in the industry. They validate your knowledge and skills in using GCP services effectively, providing third-party verification of your expertise. Employers and clients are more likely to trust your abilities when you hold a reputable certification from a recognized provider like Google.
- Enhanced Skills and Knowledge: Preparing for a Google Cloud Certification requires comprehensive study and hands-on experience with GCP. The certification process enables you to deepen your understanding of cloud concepts, best practices, and the implementation of cloud solutions. Through the certification journey, you gain valuable skills and knowledge that can be immediately applied to real-world scenarios.
- Access to Exclusive Resources: Google Cloud Certifications grant access to exclusive resources provided by Google. Certified individuals often gain access to private forums, online communities, and networking opportunities where they can connect with other certified professionals, share insights, and learn from each other's experiences. These resources can foster continuous learning and professional growth.
- Validation of Specialized Expertise: Google offers specialty certifications that focus on specific domains or technologies, such as machine learning, data engineering, and cloud architecture. These certifications validate your specialized expertise in these areas, allowing you to differentiate yourself from general cloud professionals and showcase your proficiency in specific industry domains.
- Confidence in Decision-Making: Google Cloud Certifications provide a comprehensive understanding of GCP services, best practices, and architectural considerations. With this knowledge, you can make informed decisions regarding infrastructure design, service selection, data management, and security. The certification instills confidence in your ability to architect and implement effective cloud solutions.
- Networking and Collaboration Opportunities: Being part of the Google Cloud Certification community offers opportunities to network and collaborate with like-minded professionals. You can engage in discussions, seek advice, and share ideas with others who have similar interests and experiences. This network can lead to valuable connections, career opportunities, and collaborative projects.
- Demonstrated Commitment to Professional Development: Earning a Google Cloud Certification demonstrates your commitment to continuous learning and professional development. It showcases your dedication to staying up-to-date with the latest cloud technologies and industry trends. Employers value individuals who invest in their professional growth and show a willingness to adapt to the evolving cloud landscape.
Preparing for Google Cloud Certification Exams
Preparing for Google Cloud Certification exams requires a systematic approach and dedication to studying and hands-on practice. Here are some steps to help you prepare effectively:
- Understand the Exam Objectives: Familiarize yourself with the exam objectives and the topics that will be covered. Google provides detailed exam guides for each certification, outlining the knowledge and skills required. Read through the exam guide to gain clarity on what to expect and what areas to focus on during your preparation.
- Create a Study Plan: Develop a study plan that suits your schedule and allows for consistent and organized studying. Break down the exam objectives into smaller topics and allocate specific study time for each. Set realistic goals and milestones to track your progress. Ensure that you allocate enough time for hands-on practice to reinforce your theoretical knowledge.
- Utilize Official Study Resources: Google offers official study resources, including documentation, whitepapers, tutorials, and online courses specifically designed to prepare you for the certification exams. Review the recommended resources provided in the exam guide and make use of them during your preparation. These resources are comprehensive and cover the topics in-depth.
- Hands-on Practice: Practical experience is crucial for success in Google Cloud Certification exams. Set up a practice environment using the Google Cloud Console and experiment with various services and configurations. Implement sample projects, follow tutorials, and work on real-world scenarios. Hands-on practice helps solidify your understanding of GCP services and their practical applications.
- Take Advantage of Practice Exams: Practice exams are invaluable for assessing your knowledge and identifying areas that require further study. Google provides sample questions and practice exams that simulate the actual exam environment. Take these practice exams under timed conditions to get a feel for the pace and structure of the real exam. Analyze your results to identify weak areas and focus your study efforts accordingly.
- Join Study Groups and Online Communities: Engaging with others who are also preparing for Google Cloud Certification exams can provide valuable insights and support. Join study groups or online communities where you can discuss exam topics, ask questions, and learn from each other's experiences. Collaborating with peers can enhance your understanding and help you approach challenges from different perspectives.
- Review Documentation and Best Practices: Google Cloud documentation contains detailed information about each GCP service. Familiarize yourself with the documentation for the services relevant to your certification. Pay attention to recommended best practices, design patterns, and use cases. Understanding the nuances of GCP services and their optimal usage can greatly benefit you during the exam.
- Time Management and Exam Strategies: During the exam, time management is crucial. Understand the exam structure and allocate appropriate time to each section or question. Read the questions carefully and ensure you understand the requirements before providing your answer. If you encounter challenging questions, mark them for review and come back to them later. Maintain a calm and focused mindset throughout the exam.
- Continuous Learning and Iterative Preparation: Google Cloud technologies evolve rapidly, and new features and services are introduced regularly. Stay updated with the latest developments by following relevant blogs, attending webinars, and exploring additional resources beyond the exam requirements. Treat your certification journey as a continuous learning process, even after passing the exam.
Tips for Success in Google Cloud Certification Exams
To increase your chances of success in Google Cloud Certification exams, consider the following tips:
- Understand the Exam Format: Familiarize yourself with the format of the exam, including the number of questions, time limit, and question types (multiple-choice, scenario-based, etc.). Understanding the exam structure will help you manage your time effectively during the test.
- Review the Exam Guide: Read the exam guide provided by Google. It outlines the topics and skills that will be assessed in the exam. Use it as a blueprint for your preparation and ensure you have a solid understanding of each objective.
- Focus on Hands-on Practice: Google Cloud Certification exams often include hands-on tasks or scenario-based questions. Practice using the Google Cloud Console and work on real-world projects to gain practical experience with GCP services. This will help you apply your knowledge effectively during the exam.
- Study Official Documentation: Google Cloud documentation is a valuable resource. Review the documentation for GCP services covered in the exam to understand their features, capabilities, best practices, and use cases. This will enhance your understanding and help you answer questions more accurately.
- Take Practice Exams: Google provides sample questions and practice exams that simulate the actual exam environment. Take advantage of these resources to familiarize yourself with the question format and assess your readiness. Analyze your performance and focus on improving weak areas.
- Join Study Groups and Online Communities: Engaging with others who are also preparing for the same exam can provide valuable insights and support. Join study groups, participate in forums, or connect with fellow learners online. Discussing exam topics and sharing experiences can help solidify your understanding and clarify any doubts.
- Emphasize Key Concepts and Services: Identify the key concepts and GCP services emphasized in the exam guide. Allocate more study time to these areas and ensure you have a thorough understanding of their functionalities, use cases, and associated best practices.
- Practice Time Management: Time management is crucial during the exam. Practice answering questions under timed conditions during your preparation to improve your speed and efficiency. Allocate appropriate time to each question or section based on its weightage and difficulty level.
- Read Questions Carefully: Carefully read each question and understand its requirements before selecting your answer. Pay attention to any specific constraints or conditions mentioned in the question. Avoid rushing through questions and take the time to analyze and think through your answers.
- Stay Calm and Confident: Exam anxiety can hinder your performance. Stay calm, confident, and focused throughout the exam. If you encounter challenging questions, don't panic. Take a deep breath, mark them for review, and move on. Trust in your preparation and believe in your abilities.
- Review and Revise: If time allows, review your answers before submitting the exam. Double-check for any errors or omissions. In scenario-based questions, ensure you have considered all relevant factors and provided a comprehensive solution.
- Stay Updated: Google Cloud technologies evolve, and new features and services are introduced regularly. Stay updated with the latest advancements by following official Google Cloud blogs, attending webinars, and exploring additional resources beyond the exam requirements.
Maintaining and Renewing Google Cloud Certification
Once you have earned a Google Cloud Certification, it's important to maintain and renew it to demonstrate your continued expertise and stay up to date with the evolving Google Cloud Platform (GCP). Here are some key aspects to consider for maintaining and renewing your Google Cloud Certification:
- Stay Updated with GCP: Google Cloud technologies and services evolve over time. Stay informed about the latest updates, new features, and best practices by regularly reviewing the official Google Cloud documentation, attending webinars, and participating in relevant training sessions or events. This will help you stay current with GCP and ensure your certification remains relevant.
- Follow Certification Renewal Requirements: Each Google Cloud Certification has specific renewal requirements, which typically involve meeting certain criteria within a specified period. Review the renewal requirements for your certification and ensure you understand what is expected. Familiarize yourself with the renewal process and any associated fees, if applicable.
- Earn Recertification Exams or Achievements: To maintain your certification, you may be required to pass a recertification exam or earn specific achievements within a given timeframe. Google may introduce recertification exams or provide alternative pathways to demonstrate your ongoing expertise. Stay updated with the recertification options and plan accordingly to meet the renewal requirements.
- Participate in Continuing Education: Google offers various opportunities for continuing education, such as webinars, online courses, and training programs. Participate in these educational resources to expand your knowledge, deepen your expertise, and earn relevant continuing education credits. These activities not only contribute to your professional growth but also help you meet the renewal requirements.
- Engage with the Google Cloud Community: Actively engage with the Google Cloud community, including forums, user groups, and online communities. Share your knowledge, contribute to discussions, and learn from other professionals in the field. Networking with peers and staying connected to the community can provide valuable insights, support, and access to new opportunities.
- Maintain Hands-on Experience: Regularly practice your skills and maintain hands-on experience with GCP. Stay engaged with real-world projects, experiment with new services and features, and leverage the cloud console to reinforce your practical knowledge. Continuously applying your skills in real-life scenarios helps you stay proficient and adapt to changing industry needs.
- Explore Advanced Certifications: Consider pursuing advanced certifications or specialty certifications within your area of interest or expertise. Advanced certifications can demonstrate your deeper knowledge and proficiency in specific domains of GCP. They can further enhance your professional profile and open doors to more advanced roles or opportunities.
- Track Certification Expiration Dates: Keep track of your certification expiration dates to ensure timely renewal. Set up reminders or alerts to notify you in advance so that you can plan and complete the necessary renewal activities without any last-minute rush or potential lapse in certification.
- Update Your Professional Profiles: Once you renew your certification, update your professional profiles, such as LinkedIn, resume, and online portfolios, to reflect your current certification status. This helps showcase your ongoing commitment to professional development and keeps your profile up to date for potential employers or clients.
Remember, maintaining and renewing your Google Cloud Certification requires a proactive approach. Stay engaged with the GCP ecosystem, continuously learn, and participate in relevant activities to ensure that your certification remains current and valuable in the ever-evolving cloud industry.
How to obtain Google Cloud Certifications Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Microsoft Azure Solutions 70 532 Certification
Conclusion
In conclusion, obtaining a Google Cloud Certification can significantly benefit your career in the cloud computing industry. It demonstrates your expertise and proficiency in working with Google Cloud Platform (GCP) and provides you with a competitive edge in the job market. Throughout this blog, we have explored various aspects related to Google Cloud Certification.
We began by introducing the concept of Google Cloud Certification, highlighting its importance in validating your knowledge and skills in using GCP effectively. We then discussed the available Google Cloud Certifications, which cover a wide range of roles and specializations, allowing you to choose the certification that aligns with your career goals.
Next, we delved into the benefits of earning a Google Cloud Certification. These advantages include career advancement opportunities, industry recognition and credibility, enhanced skills and knowledge, access to exclusive resources, validation of specialized expertise, confidence in decision-making, networking and collaboration opportunities, and a demonstration of commitment to professional development.
To help you succeed in Google Cloud Certification exams, we provided tips for effective preparation. These tips emphasized understanding the exam format, utilizing official study resources, hands-on practice, joining study groups and online communities, and practicing time management and exam strategies.
Furthermore, we highlighted the importance of maintaining and renewing your Google Cloud Certification. This involves staying updated with GCP, following certification renewal requirements, earning recertification exams or achievements, participating in continuing education, engaging with the Google Cloud community, maintaining hands-on experience, exploring advanced certifications, and tracking certification expiration dates.
By continuously investing in your professional development, staying current with the latest cloud technologies, and actively participating in the Google Cloud community, you can maximize the value of your Google Cloud Certification and advance your career in the dynamic and rapidly growing field of cloud computing.
Obtaining a Google Cloud Certification is not only a testament to your skills but also a commitment to excellence and continuous learning. So, take the first step, embark on your certification journey, and unlock new opportunities in the exciting world of Google Cloud Platform.
DevOps Certification: Core Services and Benifits Explained
DevOps certification holds significant importance in today's technology-driven landscape. It provides professionals with a tangible validation of their skills and expertise in implementing DevOps practices. By obtaining certification, individuals gain industry recognition and enhance their career prospects. Certification demonstrates a commitment to continuous learning and improvement, allowing professionals to stay updated with the latest tools and methodologies. It also opens doors to new job opportunities and potential career growth. Moreover, certified DevOps professionals contribute to fostering a culture of collaboration, automation, and continuous delivery within organizations, resulting in streamlined software development and deployment processes. Ultimately, DevOps certification empowers individuals to make a meaningful impact in their roles and adds value to the organizations they work with.
Table of contents
- Introduction to DevOps Certification
- Popular DevOps Certification Programs
- Preparing for DevOps Certification
- DevOps Certification Exam Structure
- Real-World Benefits of DevOps Certification
- Maintaining DevOps Certification
- Challenges and Tips for DevOps Certification
- Conclusion
Popular DevOps Certification Programs
Several popular DevOps certification programs are available, offered by reputable providers. These certifications validate an individual's skills and knowledge in various aspects of DevOps practices and tools. Here are some of the widely recognized and sought-after DevOps certification programs:
- AWS Certified DevOps Engineer: This certification, offered by Amazon Web Services (AWS), validates expertise in deploying, operating, and managing applications on the AWS platform using DevOps practices. It covers topics such as continuous delivery, automation, monitoring, and security.
- Microsoft Certified: Azure DevOps Engineer Expert: Provided by Microsoft, this certification demonstrates proficiency in implementing DevOps practices using Azure DevOps tools and services. It focuses on topics like source control, continuous integration, continuous delivery, and infrastructure as code.
- Docker Certified Associate: Offered by Docker, this certification assesses an individual's understanding of Docker containerization technology and its role in DevOps workflows. It covers areas such as Docker installation and configuration, container management, networking, and security.
- Puppet Certified Professional: Puppet's certification program validates skills in using Puppet's infrastructure automation tools for configuration management and orchestration. It includes topics like Puppet architecture, module development, resource management, and troubleshooting.
- Google Cloud Certified - Professional Cloud DevOps Engineer: This certification, provided by Google Cloud, evaluates proficiency in implementing DevOps practices on the Google Cloud Platform (GCP). It covers topics like continuous integration and delivery, infrastructure automation, site reliability engineering, and security.
These certifications are highly regarded within the industry and can enhance job prospects, validate expertise, and open doors to exciting career opportunities in the field of DevOps. It is essential to explore the specific requirements and objectives of each certification program to choose the one that aligns best with individual career goals and interests.
Preparing for DevOps Certification
Preparing for a DevOps certification requires a systematic approach and dedicated effort. Here are some essential steps to help you effectively prepare for your DevOps certification:
- Understand the Certification Exam: Familiarize yourself with the structure, format, and objectives of the certification exam. Review the official certification documentation, including exam guidelines, topics covered, and question types. This will give you a clear understanding of what to expect and how to focus your preparation.
- Identify Knowledge Gaps: Assess your existing knowledge and identify areas where you need improvement. Compare the certification exam objectives with your current skills to determine the gaps. This will guide your study plan and help you allocate more time to areas that require more attention.
- Create a Study Plan: Develop a study plan that outlines your study schedule, goals, and milestones. Break down the exam objectives into manageable study topics and allocate dedicated time for each. Establish a realistic timeline to ensure steady progress leading up to the exam date.
- Utilize Official Study Materials: Take advantage of official study materials provided by the certification program. These materials may include documentation, study guides, recommended reading lists, and practice exams. Use them as primary resources for your preparation.
- Explore Additional Learning Resources: Supplement your study materials with additional resources like online courses, tutorials, video lectures, and blogs. Look for reputable platforms and educational websites that offer DevOps-related content. These resources can provide different perspectives and further enhance your understanding.
- Hands-on Experience: Gain practical experience by working on real-world projects or using DevOps tools and technologies. Hands-on practice allows you to apply your knowledge, reinforce concepts, and gain valuable insights into the practical implementation of DevOps practices.
- Join Study Groups or Forums: Engage in study groups, forums, or online communities dedicated to the specific certification you're pursuing. Collaborating with fellow learners can provide support, share resources, and clarify doubts. It also offers an opportunity to discuss and debate concepts, enhancing your understanding.
- Practice Mock Exams: Take advantage of practice exams and sample questions. These simulate the actual exam environment and help you assess your readiness. Analyze your performance, identify weak areas, and focus your study efforts accordingly.
- Review and Revise: Regularly review and revise the topics you've covered. Create flashcards, summaries, or mind maps to consolidate key concepts and ensure they stay fresh in your memory. Repetition and reinforcement are crucial for retaining information.
- Test Yourself: Test your knowledge periodically by taking practice tests or quizzes. This allows you to evaluate your progress, identify areas of improvement, and gain confidence in your abilities.
- Stay Updated: Keep up with the latest industry trends, emerging technologies, and evolving DevOps practices. Follow reputable blogs, attend webinars, and subscribe to newsletters to stay informed about advancements in the field.
- Take Care of Yourself: Remember to maintain a healthy balance between studying and taking care of your well-being. Get adequate rest, exercise regularly, and manage your stress levels. A refreshed mind and body will contribute to better focus and retention during your preparation.
By following these steps and maintaining discipline in your study routine, you can effectively prepare for your DevOps certification and increase your chances of success. Best of luck in your certification journey!
DevOps Certification Exam Structure
The structure of DevOps certification exams can vary depending on the specific certification program and provider. However, there are some common elements and considerations to be aware of. Here's an overview of the typical components of a DevOps certification exam:
- Exam Format: DevOps certification exams are often conducted in a computer-based format, where you are presented with a series of questions to answer within a designated time frame.
- Question Types: The exam may include various question types to assess your knowledge and understanding. Common question types include:
- Multiple Choice: You are presented with a question and a set of options, and you must select the correct answer(s).
- True/False: You are provided with statements, and you need to determine whether they are true or false.
- Fill in the Blanks: You are given a sentence or phrase with missing words, and you must fill in the correct words.
- Matching: You are required to match items from two columns, such as terms and their definitions.
- Scenario-based: You are presented with a real-world scenario or problem and asked to apply your knowledge to analyze and provide a solution.
- Exam Duration: The duration of DevOps certification exams can vary, typically ranging from one to three hours. The allotted time is usually sufficient to complete the exam, but time management is crucial. Be mindful of the time and allocate it appropriately to each question.
- Passing Criteria: Certification exams have a passing score or percentage that you need to achieve to pass the exam. The passing criteria are typically established by the certification provider. It's important to understand the passing score requirement before taking the exam.
- Scoring System: DevOps certification exams may employ different scoring systems. Some exams follow a straightforward scoring method where each correctly answered question contributes to your overall score. Other exams may have weighted scoring, giving more value to certain question types or topics.
- Exam Syllabus and Objectives: Certification exams are designed based on a predefined syllabus or set of objectives. The certification provider outlines the topics and areas that the exam will cover. Review the syllabus and ensure your preparation aligns with the stated objectives.
- Exam Registration and Proctoring: Certification exams typically require registration and may involve proctoring to ensure exam integrity. Proctoring can be conducted either in-person at a testing center or online remotely. Follow the registration instructions provided by the certification provider.
Before taking the exam, carefully read and understand the guidelines, policies, and rules provided by the certification program. Familiarize yourself with the exam structure and question types through practice exams or sample questions. This will help you become comfortable with the format and prepare accordingly.
Real-World Benefits of DevOps Certification
DevOps certification offers several real-world benefits for professionals in the technology and software development industry. Here are some key advantages of obtaining DevOps certification:
- Enhanced Career Opportunities: DevOps certification can significantly expand your career prospects. Certified professionals often have a competitive edge in the job market, as certification validates your skills and knowledge in DevOps practices. It opens doors to a wide range of job opportunities, including roles such as DevOps engineer, automation architect, release manager, and site reliability engineer.
- Industry Recognition and Credibility: DevOps certifications are recognized and respected within the IT industry. They provide a tangible proof of your expertise and demonstrate your commitment to professional growth. Certification adds credibility to your resume and establishes you as a qualified professional in the eyes of employers and peers.
- Skill Validation and Personal Growth: Pursuing DevOps certification requires comprehensive knowledge and understanding of DevOps principles, practices, and tools. The certification process validates your skills, ensuring you possess the necessary expertise to contribute effectively to DevOps initiatives. It also encourages continuous learning, as you need to stay updated with the latest industry trends and advancements to maintain your certification.
- Increased Earning Potential: Certified DevOps professionals often enjoy higher earning potential compared to non-certified counterparts. Employers value certified professionals and are willing to offer competitive compensation packages for their skills and expertise. Certification can lead to better job opportunities and salary negotiations.
- Improved Collaboration and Teamwork: DevOps emphasizes collaboration and cross-functional teamwork. By pursuing DevOps certification, you gain a deeper understanding of collaboration methodologies, communication practices, and tools that promote effective teamwork. This knowledge helps you foster better collaboration among teams, resulting in improved productivity and streamlined software delivery processes.
- Faster Career Advancement: DevOps certification can accelerate your career growth. Certified professionals are often considered for leadership positions or more senior roles within organizations. Certification demonstrates your dedication to professional development and continuous learning, which are qualities that employers value when identifying candidates for promotions and higher-level responsibilities.
- Networking and Community Engagement: DevOps certifications provide opportunities to engage with a community of certified professionals. Networking with peers, attending industry events, and participating in forums or user groups can expand your professional network, facilitate knowledge sharing, and provide a platform for collaboration and career growth.
In summary, DevOps certification offers tangible benefits that can positively impact your career trajectory. From expanded job opportunities and increased earning potential to industry recognition and personal growth, DevOps certification validates your skills, enhances your credibility, and opens doors to new possibilities in the rapidly evolving world of technology and software development.
Maintaining DevOps Certification
Once you have obtained your DevOps certification, it's important to maintain it to ensure its relevance and value over time. Here are some key strategies for maintaining your DevOps certification:
- Stay Updated with Industry Trends: DevOps practices and tools evolve rapidly. Stay current with the latest industry trends, emerging technologies, and best practices. Follow industry blogs, attend webinars, participate in conferences, and engage with online communities to stay informed about advancements in the DevOps field.
- Continuous Learning: Embrace a mindset of continuous learning. DevOps certification is not a one-time achievement but a commitment to ongoing professional development. Engage in continuous learning activities such as attending workshops, taking relevant courses, reading books, and exploring new tools and techniques.
- Engage in Practical Application: Apply the knowledge and skills gained from your certification in real-world scenarios. Seek opportunities to implement DevOps practices, tools, and methodologies in your work projects. Practical application helps reinforce your understanding, identifies challenges, and provides insights for improvement.
- Join Professional Communities: Join DevOps-related professional communities, forums, and user groups. Engage in discussions, share experiences, and learn from other professionals in the field. Networking with like-minded individuals can foster knowledge exchange, collaboration, and provide valuable insights into industry trends and best practices.
- Seek Additional Certifications: Consider pursuing additional certifications in related areas to broaden your skill set and deepen your expertise. Look for certifications that complement your DevOps certification, such as cloud platforms, automation tools, or specific DevOps methodologies. This demonstrates your commitment to continuous learning and expands your knowledge base.
- Attend Continuing Education Programs: Some certification providers offer continuing education programs or additional modules to keep your certification up to date. Take advantage of these programs to refresh your knowledge, learn new features or updates, and maintain your certification status.
- Contribute to the Community: Share your knowledge and experiences with the DevOps community. Write blog posts, contribute to open-source projects, deliver presentations, or participate in webinars. Sharing your expertise not only helps others but also solidifies your understanding of the subject matter.
- Renew Your Certification: DevOps certifications typically have an expiration date. Be aware of the renewal requirements and ensure you meet them on time. This may involve completing a certain number of continuing education hours, passing a recertification exam, or submitting proof of professional development activities. Stay proactive and plan ahead to avoid certification lapses.
- Document Your Professional Development: Keep a record of your professional development activities, including courses completed, workshops attended, and relevant work projects. This documentation can be helpful when renewing your certification or updating your resume.
By actively maintaining your DevOps certification, you demonstrate your commitment to staying relevant in the field and continuously improving your skills. It enhances your professional credibility, keeps you abreast of industry trends, and ensures your certification remains valuable in a dynamic and ever-evolving DevOps landscape.
Challenges and Tips for DevOps Certification
DevOps certification can be a rewarding journey, but it also comes with its own set of challenges. Here are some common challenges that individuals may face while pursuing DevOps certification, along with tips to overcome them:
- Vast and Rapidly Changing Landscape: DevOps encompasses a broad range of tools, practices, and methodologies. Keeping up with the rapidly evolving DevOps landscape can be challenging. Stay focused on the certification objectives and prioritize your study topics based on their relevance to your current role or career goals. Regularly review industry blogs, attend webinars, and engage in continuous learning to stay updated with the latest trends.
- Balancing Work and Study: Balancing work commitments with certification preparation can be demanding. Create a study schedule that aligns with your work schedule and commitments. Dedicate specific time slots for studying and stick to them. Break down the certification objectives into smaller, manageable topics and cover them incrementally. Prioritize your study time effectively and leverage weekends or downtime to concentrate on more intensive study sessions.
- Practical Experience: While certifications validate theoretical knowledge, practical experience is equally important in the DevOps field. Gain hands-on experience by working on real-world projects, contributing to open-source projects, or exploring personal projects. Seek opportunities within your organization to apply DevOps practices and tools. Practical experience enhances your understanding, reinforces concepts, and provides valuable insights during the certification process.
- Complex Concepts and Tools: DevOps certifications often cover complex concepts and a variety of tools and technologies. Break down complex topics into smaller, manageable parts. Start with foundational concepts and gradually build upon them. Utilize multiple learning resources such as study guides, online courses, and video tutorials to reinforce your understanding. Practice using relevant tools in a lab environment or through virtual machines to gain familiarity.
- Exam Anxiety and Time Management: Exam anxiety and time management can be common challenges during certification exams. Familiarize yourself with the exam structure and question types through practice exams or sample questions. Simulate the exam environment by setting time limits and practicing under similar conditions. Develop strategies to manage your time effectively during the exam, such as allocating specific time for each question and flagging difficult questions for review.
- Lack of Guidance: Sometimes, individuals may feel a lack of guidance or mentorship during their certification journey. Seek support from experienced professionals in the DevOps community. Join study groups, forums, or online communities dedicated to the certification you're pursuing. Engage in discussions, ask questions, and leverage the collective knowledge and experiences of others. Consider connecting with individuals who have already obtained the certification for tips and insights.
- Motivation and Persistence: Certification journeys can be lengthy and require perseverance. Set clear goals and remind yourself of the benefits and opportunities that come with certification. Break down your study plan into achievable milestones and celebrate small victories along the way. Find a study buddy or accountability partner to keep each other motivated and accountable. Regularly assess your progress and adjust your study plan if necessary.
How to obtain Devops certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Devops Certifiction
Conclusion
In conclusion, DevOps certification holds significant value for professionals in the technology and software development industry. It provides tangible benefits such as expanded career opportunities, industry recognition, increased earning potential, and improved collaboration and teamwork. DevOps certification validates your skills and knowledge in DevOps practices, tools, and methodologies, and demonstrates your commitment to professional growth and continuous learning.
Choosing the right DevOps certification requires careful consideration of your career goals, the specific areas of DevOps that interest you, and the industry trends. Preparing for DevOps certification involves studying the relevant concepts, gaining practical experience, and utilizing available resources such as study guides and practice exams. Understanding the exam structure is crucial for success.
Once certified, it is important to maintain your DevOps certification by staying updated with industry trends, engaging in continuous learning, and actively applying your knowledge in real-world scenarios. Maintaining certification helps you stay relevant and ensures its ongoing value in the dynamic DevOps landscape.
DevOps certification comes with its challenges, including the vast and rapidly changing landscape, balancing work and study, and mastering complex concepts and tools. However, these challenges can be overcome with effective time management, practical experience, seeking guidance from the community, and maintaining motivation and persistence.
Looking to the future, specialized certifications, automation and AI, security and compliance, multi-cloud and hybrid environments, industry-specific certifications, and soft skills development may emerge as prominent trends in DevOps certification.
In summary, DevOps certification offers professionals the opportunity to enhance their careers, gain industry recognition, and contribute to the advancement of DevOps practices. By pursuing certification, maintaining it, and staying updated with emerging trends, you can position yourself as a skilled and sought-after professional in the ever-evolving field of DevOps.
Read More
DevOps certification holds significant importance in today's technology-driven landscape. It provides professionals with a tangible validation of their skills and expertise in implementing DevOps practices. By obtaining certification, individuals gain industry recognition and enhance their career prospects. Certification demonstrates a commitment to continuous learning and improvement, allowing professionals to stay updated with the latest tools and methodologies. It also opens doors to new job opportunities and potential career growth. Moreover, certified DevOps professionals contribute to fostering a culture of collaboration, automation, and continuous delivery within organizations, resulting in streamlined software development and deployment processes. Ultimately, DevOps certification empowers individuals to make a meaningful impact in their roles and adds value to the organizations they work with.
Table of contents
- Introduction to DevOps Certification
- Popular DevOps Certification Programs
- Preparing for DevOps Certification
- DevOps Certification Exam Structure
- Real-World Benefits of DevOps Certification
- Maintaining DevOps Certification
- Challenges and Tips for DevOps Certification
- Conclusion
Popular DevOps Certification Programs
Several popular DevOps certification programs are available, offered by reputable providers. These certifications validate an individual's skills and knowledge in various aspects of DevOps practices and tools. Here are some of the widely recognized and sought-after DevOps certification programs:
- AWS Certified DevOps Engineer: This certification, offered by Amazon Web Services (AWS), validates expertise in deploying, operating, and managing applications on the AWS platform using DevOps practices. It covers topics such as continuous delivery, automation, monitoring, and security.
- Microsoft Certified: Azure DevOps Engineer Expert: Provided by Microsoft, this certification demonstrates proficiency in implementing DevOps practices using Azure DevOps tools and services. It focuses on topics like source control, continuous integration, continuous delivery, and infrastructure as code.
- Docker Certified Associate: Offered by Docker, this certification assesses an individual's understanding of Docker containerization technology and its role in DevOps workflows. It covers areas such as Docker installation and configuration, container management, networking, and security.
- Puppet Certified Professional: Puppet's certification program validates skills in using Puppet's infrastructure automation tools for configuration management and orchestration. It includes topics like Puppet architecture, module development, resource management, and troubleshooting.
- Google Cloud Certified - Professional Cloud DevOps Engineer: This certification, provided by Google Cloud, evaluates proficiency in implementing DevOps practices on the Google Cloud Platform (GCP). It covers topics like continuous integration and delivery, infrastructure automation, site reliability engineering, and security.
These certifications are highly regarded within the industry and can enhance job prospects, validate expertise, and open doors to exciting career opportunities in the field of DevOps. It is essential to explore the specific requirements and objectives of each certification program to choose the one that aligns best with individual career goals and interests.
Preparing for DevOps Certification
Preparing for a DevOps certification requires a systematic approach and dedicated effort. Here are some essential steps to help you effectively prepare for your DevOps certification:
- Understand the Certification Exam: Familiarize yourself with the structure, format, and objectives of the certification exam. Review the official certification documentation, including exam guidelines, topics covered, and question types. This will give you a clear understanding of what to expect and how to focus your preparation.
- Identify Knowledge Gaps: Assess your existing knowledge and identify areas where you need improvement. Compare the certification exam objectives with your current skills to determine the gaps. This will guide your study plan and help you allocate more time to areas that require more attention.
- Create a Study Plan: Develop a study plan that outlines your study schedule, goals, and milestones. Break down the exam objectives into manageable study topics and allocate dedicated time for each. Establish a realistic timeline to ensure steady progress leading up to the exam date.
- Utilize Official Study Materials: Take advantage of official study materials provided by the certification program. These materials may include documentation, study guides, recommended reading lists, and practice exams. Use them as primary resources for your preparation.
- Explore Additional Learning Resources: Supplement your study materials with additional resources like online courses, tutorials, video lectures, and blogs. Look for reputable platforms and educational websites that offer DevOps-related content. These resources can provide different perspectives and further enhance your understanding.
- Hands-on Experience: Gain practical experience by working on real-world projects or using DevOps tools and technologies. Hands-on practice allows you to apply your knowledge, reinforce concepts, and gain valuable insights into the practical implementation of DevOps practices.
- Join Study Groups or Forums: Engage in study groups, forums, or online communities dedicated to the specific certification you're pursuing. Collaborating with fellow learners can provide support, share resources, and clarify doubts. It also offers an opportunity to discuss and debate concepts, enhancing your understanding.
- Practice Mock Exams: Take advantage of practice exams and sample questions. These simulate the actual exam environment and help you assess your readiness. Analyze your performance, identify weak areas, and focus your study efforts accordingly.
- Review and Revise: Regularly review and revise the topics you've covered. Create flashcards, summaries, or mind maps to consolidate key concepts and ensure they stay fresh in your memory. Repetition and reinforcement are crucial for retaining information.
- Test Yourself: Test your knowledge periodically by taking practice tests or quizzes. This allows you to evaluate your progress, identify areas of improvement, and gain confidence in your abilities.
- Stay Updated: Keep up with the latest industry trends, emerging technologies, and evolving DevOps practices. Follow reputable blogs, attend webinars, and subscribe to newsletters to stay informed about advancements in the field.
- Take Care of Yourself: Remember to maintain a healthy balance between studying and taking care of your well-being. Get adequate rest, exercise regularly, and manage your stress levels. A refreshed mind and body will contribute to better focus and retention during your preparation.
By following these steps and maintaining discipline in your study routine, you can effectively prepare for your DevOps certification and increase your chances of success. Best of luck in your certification journey!
DevOps Certification Exam Structure
The structure of DevOps certification exams can vary depending on the specific certification program and provider. However, there are some common elements and considerations to be aware of. Here's an overview of the typical components of a DevOps certification exam:
- Exam Format: DevOps certification exams are often conducted in a computer-based format, where you are presented with a series of questions to answer within a designated time frame.
- Question Types: The exam may include various question types to assess your knowledge and understanding. Common question types include:
- Multiple Choice: You are presented with a question and a set of options, and you must select the correct answer(s).
- True/False: You are provided with statements, and you need to determine whether they are true or false.
- Fill in the Blanks: You are given a sentence or phrase with missing words, and you must fill in the correct words.
- Matching: You are required to match items from two columns, such as terms and their definitions.
- Scenario-based: You are presented with a real-world scenario or problem and asked to apply your knowledge to analyze and provide a solution.
- Exam Duration: The duration of DevOps certification exams can vary, typically ranging from one to three hours. The allotted time is usually sufficient to complete the exam, but time management is crucial. Be mindful of the time and allocate it appropriately to each question.
- Passing Criteria: Certification exams have a passing score or percentage that you need to achieve to pass the exam. The passing criteria are typically established by the certification provider. It's important to understand the passing score requirement before taking the exam.
- Scoring System: DevOps certification exams may employ different scoring systems. Some exams follow a straightforward scoring method where each correctly answered question contributes to your overall score. Other exams may have weighted scoring, giving more value to certain question types or topics.
- Exam Syllabus and Objectives: Certification exams are designed based on a predefined syllabus or set of objectives. The certification provider outlines the topics and areas that the exam will cover. Review the syllabus and ensure your preparation aligns with the stated objectives.
- Exam Registration and Proctoring: Certification exams typically require registration and may involve proctoring to ensure exam integrity. Proctoring can be conducted either in-person at a testing center or online remotely. Follow the registration instructions provided by the certification provider.
Before taking the exam, carefully read and understand the guidelines, policies, and rules provided by the certification program. Familiarize yourself with the exam structure and question types through practice exams or sample questions. This will help you become comfortable with the format and prepare accordingly.
Real-World Benefits of DevOps Certification
DevOps certification offers several real-world benefits for professionals in the technology and software development industry. Here are some key advantages of obtaining DevOps certification:
- Enhanced Career Opportunities: DevOps certification can significantly expand your career prospects. Certified professionals often have a competitive edge in the job market, as certification validates your skills and knowledge in DevOps practices. It opens doors to a wide range of job opportunities, including roles such as DevOps engineer, automation architect, release manager, and site reliability engineer.
- Industry Recognition and Credibility: DevOps certifications are recognized and respected within the IT industry. They provide a tangible proof of your expertise and demonstrate your commitment to professional growth. Certification adds credibility to your resume and establishes you as a qualified professional in the eyes of employers and peers.
- Skill Validation and Personal Growth: Pursuing DevOps certification requires comprehensive knowledge and understanding of DevOps principles, practices, and tools. The certification process validates your skills, ensuring you possess the necessary expertise to contribute effectively to DevOps initiatives. It also encourages continuous learning, as you need to stay updated with the latest industry trends and advancements to maintain your certification.
- Increased Earning Potential: Certified DevOps professionals often enjoy higher earning potential compared to non-certified counterparts. Employers value certified professionals and are willing to offer competitive compensation packages for their skills and expertise. Certification can lead to better job opportunities and salary negotiations.
- Improved Collaboration and Teamwork: DevOps emphasizes collaboration and cross-functional teamwork. By pursuing DevOps certification, you gain a deeper understanding of collaboration methodologies, communication practices, and tools that promote effective teamwork. This knowledge helps you foster better collaboration among teams, resulting in improved productivity and streamlined software delivery processes.
- Faster Career Advancement: DevOps certification can accelerate your career growth. Certified professionals are often considered for leadership positions or more senior roles within organizations. Certification demonstrates your dedication to professional development and continuous learning, which are qualities that employers value when identifying candidates for promotions and higher-level responsibilities.
- Networking and Community Engagement: DevOps certifications provide opportunities to engage with a community of certified professionals. Networking with peers, attending industry events, and participating in forums or user groups can expand your professional network, facilitate knowledge sharing, and provide a platform for collaboration and career growth.
In summary, DevOps certification offers tangible benefits that can positively impact your career trajectory. From expanded job opportunities and increased earning potential to industry recognition and personal growth, DevOps certification validates your skills, enhances your credibility, and opens doors to new possibilities in the rapidly evolving world of technology and software development.
Maintaining DevOps Certification
Once you have obtained your DevOps certification, it's important to maintain it to ensure its relevance and value over time. Here are some key strategies for maintaining your DevOps certification:
- Stay Updated with Industry Trends: DevOps practices and tools evolve rapidly. Stay current with the latest industry trends, emerging technologies, and best practices. Follow industry blogs, attend webinars, participate in conferences, and engage with online communities to stay informed about advancements in the DevOps field.
- Continuous Learning: Embrace a mindset of continuous learning. DevOps certification is not a one-time achievement but a commitment to ongoing professional development. Engage in continuous learning activities such as attending workshops, taking relevant courses, reading books, and exploring new tools and techniques.
- Engage in Practical Application: Apply the knowledge and skills gained from your certification in real-world scenarios. Seek opportunities to implement DevOps practices, tools, and methodologies in your work projects. Practical application helps reinforce your understanding, identifies challenges, and provides insights for improvement.
- Join Professional Communities: Join DevOps-related professional communities, forums, and user groups. Engage in discussions, share experiences, and learn from other professionals in the field. Networking with like-minded individuals can foster knowledge exchange, collaboration, and provide valuable insights into industry trends and best practices.
- Seek Additional Certifications: Consider pursuing additional certifications in related areas to broaden your skill set and deepen your expertise. Look for certifications that complement your DevOps certification, such as cloud platforms, automation tools, or specific DevOps methodologies. This demonstrates your commitment to continuous learning and expands your knowledge base.
- Attend Continuing Education Programs: Some certification providers offer continuing education programs or additional modules to keep your certification up to date. Take advantage of these programs to refresh your knowledge, learn new features or updates, and maintain your certification status.
- Contribute to the Community: Share your knowledge and experiences with the DevOps community. Write blog posts, contribute to open-source projects, deliver presentations, or participate in webinars. Sharing your expertise not only helps others but also solidifies your understanding of the subject matter.
- Renew Your Certification: DevOps certifications typically have an expiration date. Be aware of the renewal requirements and ensure you meet them on time. This may involve completing a certain number of continuing education hours, passing a recertification exam, or submitting proof of professional development activities. Stay proactive and plan ahead to avoid certification lapses.
- Document Your Professional Development: Keep a record of your professional development activities, including courses completed, workshops attended, and relevant work projects. This documentation can be helpful when renewing your certification or updating your resume.
By actively maintaining your DevOps certification, you demonstrate your commitment to staying relevant in the field and continuously improving your skills. It enhances your professional credibility, keeps you abreast of industry trends, and ensures your certification remains valuable in a dynamic and ever-evolving DevOps landscape.
Challenges and Tips for DevOps Certification
DevOps certification can be a rewarding journey, but it also comes with its own set of challenges. Here are some common challenges that individuals may face while pursuing DevOps certification, along with tips to overcome them:
- Vast and Rapidly Changing Landscape: DevOps encompasses a broad range of tools, practices, and methodologies. Keeping up with the rapidly evolving DevOps landscape can be challenging. Stay focused on the certification objectives and prioritize your study topics based on their relevance to your current role or career goals. Regularly review industry blogs, attend webinars, and engage in continuous learning to stay updated with the latest trends.
- Balancing Work and Study: Balancing work commitments with certification preparation can be demanding. Create a study schedule that aligns with your work schedule and commitments. Dedicate specific time slots for studying and stick to them. Break down the certification objectives into smaller, manageable topics and cover them incrementally. Prioritize your study time effectively and leverage weekends or downtime to concentrate on more intensive study sessions.
- Practical Experience: While certifications validate theoretical knowledge, practical experience is equally important in the DevOps field. Gain hands-on experience by working on real-world projects, contributing to open-source projects, or exploring personal projects. Seek opportunities within your organization to apply DevOps practices and tools. Practical experience enhances your understanding, reinforces concepts, and provides valuable insights during the certification process.
- Complex Concepts and Tools: DevOps certifications often cover complex concepts and a variety of tools and technologies. Break down complex topics into smaller, manageable parts. Start with foundational concepts and gradually build upon them. Utilize multiple learning resources such as study guides, online courses, and video tutorials to reinforce your understanding. Practice using relevant tools in a lab environment or through virtual machines to gain familiarity.
- Exam Anxiety and Time Management: Exam anxiety and time management can be common challenges during certification exams. Familiarize yourself with the exam structure and question types through practice exams or sample questions. Simulate the exam environment by setting time limits and practicing under similar conditions. Develop strategies to manage your time effectively during the exam, such as allocating specific time for each question and flagging difficult questions for review.
- Lack of Guidance: Sometimes, individuals may feel a lack of guidance or mentorship during their certification journey. Seek support from experienced professionals in the DevOps community. Join study groups, forums, or online communities dedicated to the certification you're pursuing. Engage in discussions, ask questions, and leverage the collective knowledge and experiences of others. Consider connecting with individuals who have already obtained the certification for tips and insights.
- Motivation and Persistence: Certification journeys can be lengthy and require perseverance. Set clear goals and remind yourself of the benefits and opportunities that come with certification. Break down your study plan into achievable milestones and celebrate small victories along the way. Find a study buddy or accountability partner to keep each other motivated and accountable. Regularly assess your progress and adjust your study plan if necessary.
How to obtain Devops certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Devops Certifiction
Conclusion
In conclusion, DevOps certification holds significant value for professionals in the technology and software development industry. It provides tangible benefits such as expanded career opportunities, industry recognition, increased earning potential, and improved collaboration and teamwork. DevOps certification validates your skills and knowledge in DevOps practices, tools, and methodologies, and demonstrates your commitment to professional growth and continuous learning.
Choosing the right DevOps certification requires careful consideration of your career goals, the specific areas of DevOps that interest you, and the industry trends. Preparing for DevOps certification involves studying the relevant concepts, gaining practical experience, and utilizing available resources such as study guides and practice exams. Understanding the exam structure is crucial for success.
Once certified, it is important to maintain your DevOps certification by staying updated with industry trends, engaging in continuous learning, and actively applying your knowledge in real-world scenarios. Maintaining certification helps you stay relevant and ensures its ongoing value in the dynamic DevOps landscape.
DevOps certification comes with its challenges, including the vast and rapidly changing landscape, balancing work and study, and mastering complex concepts and tools. However, these challenges can be overcome with effective time management, practical experience, seeking guidance from the community, and maintaining motivation and persistence.
Looking to the future, specialized certifications, automation and AI, security and compliance, multi-cloud and hybrid environments, industry-specific certifications, and soft skills development may emerge as prominent trends in DevOps certification.
In summary, DevOps certification offers professionals the opportunity to enhance their careers, gain industry recognition, and contribute to the advancement of DevOps practices. By pursuing certification, maintaining it, and staying updated with emerging trends, you can position yourself as a skilled and sought-after professional in the ever-evolving field of DevOps.
The Essential Guide to Digital Marketing Certification
The Essential Guide to Digital Marketing Certification" is a comprehensive resource designed to equip aspiring digital marketers with the knowledge and skills necessary to excel in the dynamic world of online advertising and promotion. In today's digitally-driven era, businesses of all sizes recognize the importance of establishing a strong online presence to reach their target audience effectively. This guide serves as a roadmap to navigate the intricacies of digital marketing, providing valuable insights and practical advice to help individuals obtain the coveted digital marketing certification.
From understanding the fundamental concepts of digital marketing to mastering advanced strategies, this guide covers a wide range of topics essential for success in the field. Whether you are a marketing professional seeking to expand your skill set or a newcomer eager to embark on a career in digital marketing, this guide offers a comprehensive overview of the industry, backed by the latest insights and industry best practices.
Throughout the guide, you will discover in-depth explanations of various digital marketing disciplines, including social media marketing, search engine optimization (SEO), content marketing, email marketing, data analytics, and more. By exploring these key areas, you will gain a solid foundation and learn how to leverage them to create effective marketing campaigns that generate tangible results.
In addition to exploring the core concepts, this guide provides practical tips on selecting the right digital marketing certification program and preparing for the certification exam. It delves into the benefits of certification, such as increased job prospects, industry recognition, and enhanced credibility in the competitive digital marketing landscape.
With a strong emphasis on actionable insights and real-world examples, "The Essential Guide to Digital Marketing Certification" empowers readers to apply their newfound knowledge to real-world scenarios and challenges. By combining theoretical principles with practical application, this guide enables individuals to develop a holistic understanding of digital marketing and cultivate the skills needed to thrive in this rapidly evolving industry.
Whether you are a marketing professional aiming to advance your career or an entrepreneur seeking to leverage digital channels for business growth, this guide will serve as your trusted companion on the path to digital marketing certification excellence. Get ready to unlock new opportunities, broaden your horizons, and make a meaningful impact in the exciting world of digital marketing.
In this blog
- Digital Marketing Definition
- Inbound vs Digital Marketing
- B2B vs B2C Digital Marketing
- History of Digital Marketing
- Why should you learn Digital Marketing?
- Digital Marketing Types
- The benefits of digital marketing
- Digital Marketing Scope
- Conclusion
Digital Marketing Defination
Digital marketing refers to the practice of promoting products, services, or brands using digital channels, such as search engines, social media platforms, email, mobile applications, websites, and other digital media. It involves leveraging various digital marketing strategies and tactics, such as search engine optimization (SEO), pay-per-click (PPC) advertising, social media marketing, content marketing, email marketing, and mobile marketing, to reach and engage with potential customers and drive business growth. Digital marketing offers businesses a cost-effective and measurable way to connect with their target audience, build brand awareness, and ultimately drive sales and revenue.
Inbound vs Digital Marketing
Inbound marketing and digital marketing are often used interchangeably, but they are not the same thing.
Inbound marketing refers to a marketing methodology that focuses on attracting customers by providing them with valuable content and experiences, rather than interrupting them with ads. Inbound marketing is all about creating a meaningful connection with potential customers by providing helpful information, solving their problems, and addressing their needs.
Digital marketing, on the other hand, refers to the use of digital channels and tactics, such as SEO, PPC advertising, social media marketing, email marketing, and mobile marketing, to promote products, services, or brands to potential customers.
While inbound marketing is a subset of digital marketing, it differs in its approach and focus. Inbound marketing is focused on attracting, engaging, and delighting customers through valuable content and experiences, while digital marketing is focused on using digital channels and tactics to promote products or services and drive business growth.
In summary, inbound marketing is a methodology that emphasizes creating meaningful connections with potential customers, while digital marketing is a set of tactics used to promote products, services, or brands through digital channels.
B2B vs B2C Digital Marketing
B2B (business-to-business) and B2C (business-to-consumer) digital marketing differ in their target audience, strategies, and tactics.
B2B digital marketing targets businesses and other organizations as customers, while B2C digital marketing targets individual consumers. In B2B marketing, the goal is to create demand for products or services among business customers and build relationships with them. In B2C marketing, the goal is to generate immediate sales by targeting consumers with compelling offers and promotions.
The strategies and tactics used in B2B digital marketing are often focused on building long-term relationships with customers. Content marketing, search engine optimization (SEO), social media marketing, and email marketing are all commonly used strategies in B2B marketing. The focus is on providing valuable information and resources that can help businesses solve their problems and meet their needs.
In contrast, B2C digital marketing strategies and tactics are often more transactional in nature, with a focus on generating immediate sales. Paid advertising, influencer marketing, social media advertising, and retargeting campaigns are all common tactics used in B2C marketing. The goal is to create a compelling message that resonates with individual consumers and drives them to make a purchase.
Overall, the primary difference between B2B and B2C digital marketing is the target audience and the approach to building relationships with them. B2B marketing is focused on building long-term relationships with businesses, while B2C marketing is focused on generating immediate sales from individual consumers.
History of Digital Marketing
The history of digital marketing can be traced back to the late 1970s and early 1980s when the first personal computers were introduced. The emergence of the internet in the early 1990s revolutionized the way people communicated, worked, and shopped, creating new opportunities for businesses to connect with customers.
In the mid-1990s, the first search engine, called Archie, was created, followed by Yahoo and Google in the late 1990s. This gave rise to search engine optimization (SEO) as a critical digital marketing strategy, as businesses began optimizing their websites to rank higher in search engine results pages (SERPs).
The early 2000s saw the rise of social media platforms, such as MySpace and LinkedIn, followed by Facebook and Twitter in the mid-2000s. This gave businesses new opportunities to reach and engage with customers through social media marketing.
The introduction of smartphones in the late 2000s led to the emergence of mobile marketing, as businesses began creating mobile-friendly websites and developing mobile apps to connect with customers on-the-go.
In the 2010s, the explosion of big data and analytics tools enabled businesses to better understand customer behavior and preferences, leading to the rise of targeted advertising and personalized marketing.
Today, digital marketing continues to evolve with the emergence of new technologies, such as artificial intelligence (AI) and virtual reality (VR), creating new opportunities for businesses to connect with customers in innovative and engaging ways.
Why should you learn Digital Marketing?
There are several reasons why learning digital marketing can be beneficial, both for personal and professional development. Here are some of the key reasons why you should consider learning digital marketing:
- High demand for digital marketing skills: With the increasing use of digital channels and the growing importance of online marketing, the demand for digital marketing skills is on the rise. Learning digital marketing can give you a competitive edge in the job market and open up new career opportunities.
- Cost-effective marketing: Digital marketing is often more cost-effective than traditional marketing methods, making it an attractive option for businesses of all sizes. Learning digital marketing can help you develop skills and strategies to effectively promote products and services on a tight budget.
- Measurable results: Digital marketing allows for the measurement of the effectiveness of campaigns in real-time, enabling marketers to quickly make adjustments and optimize their strategies for better results. Learning digital marketing can help you develop skills to track and analyze campaign performance to drive business growth.
- Creative expression: Digital marketing allows for creative expression and innovation, offering marketers the opportunity to experiment with new ideas and approaches to engage with customers. Learning digital marketing can help you develop skills to create engaging content, design effective campaigns, and leverage new technologies to connect with customers.
- Business growth: Digital marketing can help businesses of all sizes reach a wider audience, increase brand awareness, and drive sales and revenue growth. Learning digital marketing can provide you with the knowledge and skills to help businesses achieve their marketing goals and drive growth.
Digital Marketing Types
There are several types of digital marketing, each with its own set of strategies and tactics. Here are some of the most common types of digital marketing:
- Search engine optimization (SEO): SEO involves optimizing your website and content to improve your search engine ranking and drive organic traffic to your website.
- Pay-per-click advertising (PPC): PPC involves placing ads on search engine results pages or other websites, with advertisers paying a fee each time their ad is clicked.
- Social media marketing: Social media marketing involves using social media platforms, such as Facebook, Instagram, Twitter, and LinkedIn, to engage with customers and promote products or services.
- Content marketing: Content marketing involves creating valuable and informative content, such as blog posts, videos, and infographics, to attract and engage with customers.
- Email marketing: Email marketing involves sending promotional emails to customers and prospects to promote products or services, build relationships, and drive sales.
- Influencer marketing: Influencer marketing involves partnering with influential people in your industry or niche to promote your products or services to their followers.
- Affiliate marketing: Affiliate marketing involves partnering with other businesses or individuals to promote your products or services in exchange for a commission on sales.
- Video marketing: Video marketing involves creating and sharing videos to promote products or services, build brand awareness, and engage with customers.
The benefits of digital marketing
Digital marketing has several benefits for businesses of all sizes. Here are some of the key benefits of digital marketing:
- Increased visibility: Digital marketing can help increase your online visibility, making it easier for potential customers to find your business when searching for products or services online.
- Cost-effective: Digital marketing is often more cost-effective than traditional marketing methods, making it an attractive option for businesses of all sizes, especially those with limited budgets.
- Targeted advertising: Digital marketing allows you to target specific audiences based on demographics, interests, and behaviors, enabling you to reach the right people with the right message at the right time.
- Measurable results: Digital marketing allows you to track and measure the effectiveness of your campaigns in real-time, enabling you to make adjustments and optimize your strategies for better results.
- Increased engagement: Digital marketing allows you to engage with your customers through social media, email marketing, and other channels, enabling you to build relationships and improve customer loyalty.
- Brand awareness: Digital marketing can help increase your brand awareness, making your business more visible and recognizable to potential customers.
- Improved customer experience: Digital marketing can help you provide a better customer experience by delivering personalized and relevant content, responding to customer inquiries and feedback, and providing a seamless online experience.
- Competitive advantage: Digital marketing can help you stay ahead of the competition by reaching customers through new and innovative channels and leveraging new technologies to improve your marketing efforts.
Digital Marketing Scope
The scope of digital marketing is vast and continues to evolve with advancements in technology and changes in consumer behavior. Here are some of the key areas of digital marketing scope:
- Search engine optimization (SEO): SEO involves optimizing your website and content to improve your search engine ranking and drive organic traffic to your website.
- Pay-per-click advertising (PPC): PPC involves placing ads on search engine results pages or other websites, with advertisers paying a fee each time their ad is clicked.
- Social media marketing: Social media marketing involves using social media platforms, such as Facebook, Instagram, Twitter, and LinkedIn, to engage with customers and promote products or services.
- Content marketing: Content marketing involves creating valuable and informative content, such as blog posts, videos, and infographics, to attract and engage with customers.
- Email marketing: Email marketing involves sending promotional emails to customers and prospects to promote products or services, build relationships, and drive sales.
- Influencer marketing: Influencer marketing involves partnering with influential people in your industry or niche to promote your products or services to their followers.
- Affiliate marketing: Affiliate marketing involves partnering with other businesses or individuals to promote your products or services in exchange for a commission on sales.
- Video marketing: Video marketing involves creating and sharing videos to promote products or services, build brand awareness, and engage with customers.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: SMAC Certication
- Big Data: Big Data and Hadoop Administrator
- Digital Marketing : Digital Marketing Certification
Conclusion
Digital marketing has become an essential component of modern business, as more and more consumers turn to online channels to research and purchase products and services. From SEO and PPC advertising to social media marketing, content marketing, email marketing, influencer marketing, affiliate marketing, and video marketing, digital marketing offers a wide range of tools and techniques for businesses to reach and engage with customers across multiple channels. By leveraging digital marketing, businesses can increase their visibility, target specific audiences, measure the effectiveness of their campaigns, build brand awareness, improve the customer experience, and gain a competitive advantage. As technology continues to evolve and consumer behavior changes, the scope of digital marketing is expected to expand, offering new opportunities for businesses to connect with customers and drive growth and profitability.
Read More
The Essential Guide to Digital Marketing Certification" is a comprehensive resource designed to equip aspiring digital marketers with the knowledge and skills necessary to excel in the dynamic world of online advertising and promotion. In today's digitally-driven era, businesses of all sizes recognize the importance of establishing a strong online presence to reach their target audience effectively. This guide serves as a roadmap to navigate the intricacies of digital marketing, providing valuable insights and practical advice to help individuals obtain the coveted digital marketing certification.
From understanding the fundamental concepts of digital marketing to mastering advanced strategies, this guide covers a wide range of topics essential for success in the field. Whether you are a marketing professional seeking to expand your skill set or a newcomer eager to embark on a career in digital marketing, this guide offers a comprehensive overview of the industry, backed by the latest insights and industry best practices.
Throughout the guide, you will discover in-depth explanations of various digital marketing disciplines, including social media marketing, search engine optimization (SEO), content marketing, email marketing, data analytics, and more. By exploring these key areas, you will gain a solid foundation and learn how to leverage them to create effective marketing campaigns that generate tangible results.
In addition to exploring the core concepts, this guide provides practical tips on selecting the right digital marketing certification program and preparing for the certification exam. It delves into the benefits of certification, such as increased job prospects, industry recognition, and enhanced credibility in the competitive digital marketing landscape.
With a strong emphasis on actionable insights and real-world examples, "The Essential Guide to Digital Marketing Certification" empowers readers to apply their newfound knowledge to real-world scenarios and challenges. By combining theoretical principles with practical application, this guide enables individuals to develop a holistic understanding of digital marketing and cultivate the skills needed to thrive in this rapidly evolving industry.
Whether you are a marketing professional aiming to advance your career or an entrepreneur seeking to leverage digital channels for business growth, this guide will serve as your trusted companion on the path to digital marketing certification excellence. Get ready to unlock new opportunities, broaden your horizons, and make a meaningful impact in the exciting world of digital marketing.
In this blog
- Digital Marketing Definition
- Inbound vs Digital Marketing
- B2B vs B2C Digital Marketing
- History of Digital Marketing
- Why should you learn Digital Marketing?
- Digital Marketing Types
- The benefits of digital marketing
- Digital Marketing Scope
- Conclusion
Digital Marketing Defination
Digital marketing refers to the practice of promoting products, services, or brands using digital channels, such as search engines, social media platforms, email, mobile applications, websites, and other digital media. It involves leveraging various digital marketing strategies and tactics, such as search engine optimization (SEO), pay-per-click (PPC) advertising, social media marketing, content marketing, email marketing, and mobile marketing, to reach and engage with potential customers and drive business growth. Digital marketing offers businesses a cost-effective and measurable way to connect with their target audience, build brand awareness, and ultimately drive sales and revenue.
Inbound vs Digital Marketing
Inbound marketing and digital marketing are often used interchangeably, but they are not the same thing.
Inbound marketing refers to a marketing methodology that focuses on attracting customers by providing them with valuable content and experiences, rather than interrupting them with ads. Inbound marketing is all about creating a meaningful connection with potential customers by providing helpful information, solving their problems, and addressing their needs.
Digital marketing, on the other hand, refers to the use of digital channels and tactics, such as SEO, PPC advertising, social media marketing, email marketing, and mobile marketing, to promote products, services, or brands to potential customers.
While inbound marketing is a subset of digital marketing, it differs in its approach and focus. Inbound marketing is focused on attracting, engaging, and delighting customers through valuable content and experiences, while digital marketing is focused on using digital channels and tactics to promote products or services and drive business growth.
In summary, inbound marketing is a methodology that emphasizes creating meaningful connections with potential customers, while digital marketing is a set of tactics used to promote products, services, or brands through digital channels.
B2B vs B2C Digital Marketing
B2B (business-to-business) and B2C (business-to-consumer) digital marketing differ in their target audience, strategies, and tactics.
B2B digital marketing targets businesses and other organizations as customers, while B2C digital marketing targets individual consumers. In B2B marketing, the goal is to create demand for products or services among business customers and build relationships with them. In B2C marketing, the goal is to generate immediate sales by targeting consumers with compelling offers and promotions.
The strategies and tactics used in B2B digital marketing are often focused on building long-term relationships with customers. Content marketing, search engine optimization (SEO), social media marketing, and email marketing are all commonly used strategies in B2B marketing. The focus is on providing valuable information and resources that can help businesses solve their problems and meet their needs.
In contrast, B2C digital marketing strategies and tactics are often more transactional in nature, with a focus on generating immediate sales. Paid advertising, influencer marketing, social media advertising, and retargeting campaigns are all common tactics used in B2C marketing. The goal is to create a compelling message that resonates with individual consumers and drives them to make a purchase.
Overall, the primary difference between B2B and B2C digital marketing is the target audience and the approach to building relationships with them. B2B marketing is focused on building long-term relationships with businesses, while B2C marketing is focused on generating immediate sales from individual consumers.
History of Digital Marketing
The history of digital marketing can be traced back to the late 1970s and early 1980s when the first personal computers were introduced. The emergence of the internet in the early 1990s revolutionized the way people communicated, worked, and shopped, creating new opportunities for businesses to connect with customers.
In the mid-1990s, the first search engine, called Archie, was created, followed by Yahoo and Google in the late 1990s. This gave rise to search engine optimization (SEO) as a critical digital marketing strategy, as businesses began optimizing their websites to rank higher in search engine results pages (SERPs).
The early 2000s saw the rise of social media platforms, such as MySpace and LinkedIn, followed by Facebook and Twitter in the mid-2000s. This gave businesses new opportunities to reach and engage with customers through social media marketing.
The introduction of smartphones in the late 2000s led to the emergence of mobile marketing, as businesses began creating mobile-friendly websites and developing mobile apps to connect with customers on-the-go.
In the 2010s, the explosion of big data and analytics tools enabled businesses to better understand customer behavior and preferences, leading to the rise of targeted advertising and personalized marketing.
Today, digital marketing continues to evolve with the emergence of new technologies, such as artificial intelligence (AI) and virtual reality (VR), creating new opportunities for businesses to connect with customers in innovative and engaging ways.
Why should you learn Digital Marketing?
There are several reasons why learning digital marketing can be beneficial, both for personal and professional development. Here are some of the key reasons why you should consider learning digital marketing:
- High demand for digital marketing skills: With the increasing use of digital channels and the growing importance of online marketing, the demand for digital marketing skills is on the rise. Learning digital marketing can give you a competitive edge in the job market and open up new career opportunities.
- Cost-effective marketing: Digital marketing is often more cost-effective than traditional marketing methods, making it an attractive option for businesses of all sizes. Learning digital marketing can help you develop skills and strategies to effectively promote products and services on a tight budget.
- Measurable results: Digital marketing allows for the measurement of the effectiveness of campaigns in real-time, enabling marketers to quickly make adjustments and optimize their strategies for better results. Learning digital marketing can help you develop skills to track and analyze campaign performance to drive business growth.
- Creative expression: Digital marketing allows for creative expression and innovation, offering marketers the opportunity to experiment with new ideas and approaches to engage with customers. Learning digital marketing can help you develop skills to create engaging content, design effective campaigns, and leverage new technologies to connect with customers.
- Business growth: Digital marketing can help businesses of all sizes reach a wider audience, increase brand awareness, and drive sales and revenue growth. Learning digital marketing can provide you with the knowledge and skills to help businesses achieve their marketing goals and drive growth.
Digital Marketing Types
There are several types of digital marketing, each with its own set of strategies and tactics. Here are some of the most common types of digital marketing:
- Search engine optimization (SEO): SEO involves optimizing your website and content to improve your search engine ranking and drive organic traffic to your website.
- Pay-per-click advertising (PPC): PPC involves placing ads on search engine results pages or other websites, with advertisers paying a fee each time their ad is clicked.
- Social media marketing: Social media marketing involves using social media platforms, such as Facebook, Instagram, Twitter, and LinkedIn, to engage with customers and promote products or services.
- Content marketing: Content marketing involves creating valuable and informative content, such as blog posts, videos, and infographics, to attract and engage with customers.
- Email marketing: Email marketing involves sending promotional emails to customers and prospects to promote products or services, build relationships, and drive sales.
- Influencer marketing: Influencer marketing involves partnering with influential people in your industry or niche to promote your products or services to their followers.
- Affiliate marketing: Affiliate marketing involves partnering with other businesses or individuals to promote your products or services in exchange for a commission on sales.
- Video marketing: Video marketing involves creating and sharing videos to promote products or services, build brand awareness, and engage with customers.
The benefits of digital marketing
Digital marketing has several benefits for businesses of all sizes. Here are some of the key benefits of digital marketing:
- Increased visibility: Digital marketing can help increase your online visibility, making it easier for potential customers to find your business when searching for products or services online.
- Cost-effective: Digital marketing is often more cost-effective than traditional marketing methods, making it an attractive option for businesses of all sizes, especially those with limited budgets.
- Targeted advertising: Digital marketing allows you to target specific audiences based on demographics, interests, and behaviors, enabling you to reach the right people with the right message at the right time.
- Measurable results: Digital marketing allows you to track and measure the effectiveness of your campaigns in real-time, enabling you to make adjustments and optimize your strategies for better results.
- Increased engagement: Digital marketing allows you to engage with your customers through social media, email marketing, and other channels, enabling you to build relationships and improve customer loyalty.
- Brand awareness: Digital marketing can help increase your brand awareness, making your business more visible and recognizable to potential customers.
- Improved customer experience: Digital marketing can help you provide a better customer experience by delivering personalized and relevant content, responding to customer inquiries and feedback, and providing a seamless online experience.
- Competitive advantage: Digital marketing can help you stay ahead of the competition by reaching customers through new and innovative channels and leveraging new technologies to improve your marketing efforts.
Digital Marketing Scope
The scope of digital marketing is vast and continues to evolve with advancements in technology and changes in consumer behavior. Here are some of the key areas of digital marketing scope:
- Search engine optimization (SEO): SEO involves optimizing your website and content to improve your search engine ranking and drive organic traffic to your website.
- Pay-per-click advertising (PPC): PPC involves placing ads on search engine results pages or other websites, with advertisers paying a fee each time their ad is clicked.
- Social media marketing: Social media marketing involves using social media platforms, such as Facebook, Instagram, Twitter, and LinkedIn, to engage with customers and promote products or services.
- Content marketing: Content marketing involves creating valuable and informative content, such as blog posts, videos, and infographics, to attract and engage with customers.
- Email marketing: Email marketing involves sending promotional emails to customers and prospects to promote products or services, build relationships, and drive sales.
- Influencer marketing: Influencer marketing involves partnering with influential people in your industry or niche to promote your products or services to their followers.
- Affiliate marketing: Affiliate marketing involves partnering with other businesses or individuals to promote your products or services in exchange for a commission on sales.
- Video marketing: Video marketing involves creating and sharing videos to promote products or services, build brand awareness, and engage with customers.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: SMAC Certication
- Big Data: Big Data and Hadoop Administrator
- Digital Marketing : Digital Marketing Certification
Conclusion
Digital marketing has become an essential component of modern business, as more and more consumers turn to online channels to research and purchase products and services. From SEO and PPC advertising to social media marketing, content marketing, email marketing, influencer marketing, affiliate marketing, and video marketing, digital marketing offers a wide range of tools and techniques for businesses to reach and engage with customers across multiple channels. By leveraging digital marketing, businesses can increase their visibility, target specific audiences, measure the effectiveness of their campaigns, build brand awareness, improve the customer experience, and gain a competitive advantage. As technology continues to evolve and consumer behavior changes, the scope of digital marketing is expected to expand, offering new opportunities for businesses to connect with customers and drive growth and profitability.
Data Science with R Programming Certification Training: A Comprehensive Guide
Welcome to the comprehensive guide on "Data Science with R Programming Certification Training." In today's data-driven world, organizations across industries are increasingly recognizing the importance of data science in gaining valuable insights, making informed decisions, and driving innovation. Data science, with its powerful techniques and tools, plays a crucial role in extracting knowledge and meaningful patterns from vast amounts of data.
This guide aims to provide you with a comprehensive understanding of data science using the R programming language. R is a popular open-source programming language known for its extensive libraries and packages specifically designed for data analysis, statistical modeling, and visualization. By mastering R programming in the context of data science, you can unlock a wide range of possibilities for exploring and harnessing the potential of data.
Throughout this certification training, you will delve into various aspects of data science, including data manipulation, exploratory data analysis, statistical modeling, predictive analytics, machine learning, and data visualization. You will also learn how to apply these techniques to real-world datasets and solve complex problems.
The comprehensive nature of this guide ensures that beginners in data science, as well as those with some prior knowledge, can benefit from it. Whether you are a student, a professional looking to upskill, or an aspiring data scientist, this training will equip you with the necessary knowledge and skills to excel in the field of data science with R programming.
By the end of this certification training, you will have a solid foundation in R programming and a deep understanding of the data science workflow. Moreover, you will be prepared to tackle data-driven challenges, develop models for predictive analysis, and present your findings effectively through data visualization.
Embark on this exciting journey into the world of data science with R programming, and unlock the power of data to drive insights and innovation. Let's dive in and explore the fascinating realm of data science together!
Table of contents
- Introduction to Data Science and R Programming
- Understanding the Fundamentals of R Programming
- Data Preprocessing and Feature Engineering in R
- Advanced Topics in Data Science with R
- R Packages and Libraries for Data Science
- Building Data Science Projects with R
- Tips for Success in Data Science with R Certification
- Conclusion
Introduction to Data Science and R Programming
In today's data-driven world, the field of data science has gained tremendous significance. Data science involves extracting meaningful insights and knowledge from vast amounts of data using various statistical and computational techniques. One of the most popular and powerful programming languages used in data science is R.
R is an open-source programming language specifically designed for statistical computing and graphics. It provides a comprehensive set of tools and libraries that enable data scientists to analyze, visualize, and model data effectively. R has gained widespread adoption in the data science community due to its flexibility, extensive package ecosystem, and robust statistical capabilities.
The combination of data science and R programming offers a powerful toolkit for solving complex problems, making data-driven decisions, and deriving actionable insights from data. By mastering R programming for data science, professionals can enhance their analytical skills, expand their career opportunities, and contribute to the advancement of various industries.
Benefits of pursuing a certification in data science with R programming are:
- Industry Relevance: Data science with R programming is highly sought after in industries such as finance, healthcare, e-commerce, marketing, and more. A certification in this field demonstrates your proficiency and makes you stand out in the job market.
- Comprehensive Skill Set: The certification training covers a wide range of topics, including data preprocessing, exploratory data analysis, machine learning algorithms, and advanced data analytics techniques. It equips you with the skills needed to handle real-world data science projects.
- Hands-on Experience: Certification programs often include practical exercises and projects that provide hands-on experience in applying R programming to real data sets. This practical exposure enhances your ability to tackle data-related challenges effectively.
- Networking Opportunities: Certification programs often provide opportunities to connect with fellow data science professionals, instructors, and industry experts. Networking can lead to collaborations, mentorships, and job referrals, expanding your professional network.
- Career Advancement: Data science professionals with R programming skills are in high demand. A certification can boost your career prospects, increase job opportunities, and potentially lead to higher salaries and more challenging roles.
In summary, a certification in data science with R programming offers a pathway to gain expertise in a widely-used programming language for data analysis and empowers you with the necessary skills to succeed in the data science field. It is a valuable investment for both aspiring and experienced data professionals looking to excel in their careers.
Understanding the Fundamentals of R Programming
To excel in data science with R programming, it's crucial to have a strong foundation in the fundamentals of R programming. This section will introduce you to the essential aspects of R programming and its key components. Let's dive into the fundamentals:
- Installing R and RStudio:
-
- Start by downloading and installing R, which is available for Windows, macOS, and Linux platforms. Visit the official R website (https://www.r-project.org/) for the installation package.
- RStudio is an integrated development environment (IDE) for R programming that provides a user-friendly interface. Install RStudio to enhance your coding experience and productivity.
- R Syntax and Data Structures:
-
- R uses a straightforward syntax that allows you to perform computations, manipulate data, and create visualizations. Familiarize yourself with basic R syntax, such as variable assignments, arithmetic operations, and function calls.
- R supports various data structures, including vectors, matrices, data frames, and lists. Understand the characteristics and usage of each data structure to effectively handle data in R.
- Variables and Data Types:
-
- In R, variables are used to store and manipulate data. Learn how to assign values to variables, choose appropriate variable names, and access their contents.
- R supports several data types, such as numeric, character, logical, and factors. Understand how to work with different data types and convert between them as needed.
- Control Structures:
-
- Control structures allow you to control the flow of execution in your R programs. Familiarize yourself with key control structures like if-else statements, for loops, while loops, and switch statements.
- Understand how to use conditional statements and looping constructs to perform repetitive tasks or make decisions based on specific conditions.
- Functions in R:
-
- Functions are a fundamental part of R programming and enable you to encapsulate reusable code. Learn how to define and call functions, pass arguments, and return values.
- Explore built-in functions in R and understand how to create custom functions to perform specific tasks or calculations.
- Packages and Libraries:
-
- R has a vast collection of packages and libraries that extend its functionality. Explore popular packages such as dplyr, ggplot2, and tidyr, which offer powerful tools for data manipulation, visualization, and tidying.
- Learn how to install packages from the Comprehensive R Archive Network (CRAN) or other repositories and load them into your R session to leverage their capabilities.
- File Input and Output:
-
- R provides several functions to read data from external files, such as CSV, Excel, and text files. Familiarize yourself with functions like read.csv(), read_excel(), and readLines() to import data into R.
- Similarly, learn how to export data from R to different file formats using functions like write.csv(), write.xlsx(), and writeLines().
Data Preprocessing and Feature Engineering in R
Data preprocessing and feature engineering play a crucial role in data science projects. They involve transforming raw data into a format suitable for analysis and building models. In this section, we will explore various techniques for data preprocessing and feature engineering using R.
- Handling Missing Data:
-
- Identify missing values in the dataset using functions like is.na() or complete.cases().
- Impute missing data using techniques such as mean imputation, median imputation, or predictive imputation.
- Consider the impact of missing data on the analysis and decide whether to remove or impute missing values based on the context.
- Dealing with Outliers:
-
- Detect outliers using statistical measures such as z-scores, box plots, or Mahalanobis distance.
- Decide whether to remove outliers based on their impact on the analysis or apply outlier treatment techniques such as winsorization or robust methods.
- Handling Categorical Variables:
-
- Encode categorical variables into numerical representations using techniques like one-hot encoding, label encoding, or target encoding.
- Consider the appropriate encoding strategy based on the nature of the categorical variable and its relationship with the target variable.
- Feature Scaling and Normalization:
-
- Normalize numerical features to a common scale using techniques like min-max scaling or z-score normalization.
- Ensure that features have similar ranges and distributions to avoid biases in the analysis and model training.
- Handling Skewed Data:
-
- Identify skewed distributions in the data using measures like skewness or visual inspection.
- Apply transformations such as log transformation, square root transformation, or Box-Cox transformation to reduce skewness and achieve a more symmetric distribution.
- Feature Extraction:
-
- Extract new features from existing ones to capture additional information or reduce dimensionality.
- Techniques like principal component analysis (PCA), factor analysis, or feature selection methods can be used for feature extraction.
- Handling Time Series Data:
-
- Preprocess time series data by converting it into a suitable format, such as creating a time index or resampling.
- Handle missing values and outliers in time series data using specific techniques designed for time-dependent data.
- Data Normalization:
-
- Normalize data to ensure that different variables are on a comparable scale.
- Techniques such as min-max scaling, z-score normalization, or robust normalization can be applied to normalize data.
- Handling Imbalanced Data:
-
- Address class imbalance issues in the dataset, especially in classification tasks.
- Techniques such as oversampling, undersampling, or generating synthetic samples using methods like SMOTE (Synthetic Minority Over-sampling Technique) can be employed to handle imbalanced data.
- Data Partitioning:
-
- Split the dataset into training, validation, and testing sets to evaluate the model's performance.
- Utilize functions like createDataPartition() or train_test_split() to split the data based on various strategies (e.g., random sampling or stratified sampling).
Advanced Topics in Data Science with R
Once you have a solid understanding of the fundamentals of R programming and data preprocessing, you can explore advanced topics in data science that can further enhance your skills and capabilities. Here are some advanced topics in data science with R that you can delve into:
- Text Mining and Natural Language Processing (NLP):
-
- Learn how to process and analyze text data using R.
- Explore techniques such as text cleaning, tokenization, stemming, and sentiment analysis.
- Apply natural language processing (NLP) techniques, including topic modeling and named entity recognition.
- Time Series Analysis and Forecasting:
-
- Gain expertise in handling time-dependent data and perform time series analysis in R.
- Understand concepts such as autocorrelation, stationarity, and seasonality.
- Learn time series forecasting techniques, including ARIMA models, exponential smoothing, and state space models.
- Deep Learning with R:
-
- Explore the world of deep learning using R and frameworks like TensorFlow and Keras.
- Build and train deep neural networks for tasks such as image recognition, natural language processing, and time series forecasting.
- Understand concepts like convolutional neural networks (CNNs), recurrent neural networks (RNNs), and generative adversarial networks (GANs).
- Big Data Analytics with R:
-
- Learn how to handle and analyze large-scale datasets using R.
- Utilize distributed computing frameworks like Apache Spark with R to perform big data analytics.
- Explore techniques for parallel processing, distributed machine learning, and handling data in a distributed environment.
- Spatial Data Analysis:
-
- Analyze and visualize spatial data using R's spatial packages, such as sp and sf.
- Perform spatial data manipulation, geostatistics, and spatial interpolation.
- Build spatial models and perform spatial regression analysis.
- Recommender Systems:
-
- Understand the principles behind recommender systems and their applications.
- Implement collaborative filtering and content-based recommendation algorithms in R.
- Evaluate and fine-tune recommender systems for improved accuracy.
- Bayesian Data Analysis:
-
- Learn Bayesian statistics and its application in data analysis.
- Utilize R packages like rstan and brms for Bayesian modeling.
- Perform inference, model comparison, and prediction using Bayesian methods.
- Ensemble Methods and Model Stacking:
-
- Explore ensemble learning techniques such as bagging, boosting, and random forests in R.
- Understand the concept of model stacking and how to combine predictions from multiple models.
- Apply ensemble methods to improve the accuracy and robustness of predictive models.
- Interfacing R with Other Technologies:
-
- Integrate R with other technologies, such as databases (e.g., SQL), web applications, and cloud services.
- Learn how to connect R with databases, perform SQL queries, and extract data for analysis.
- Develop interactive web-based dashboards and visualizations using R and frameworks like Shiny.
- Advanced Visualization Techniques:
-
- Explore advanced visualization libraries and techniques in R, such as ggplot2, plotly, and lattice.
- Create interactive and dynamic visualizations that go beyond basic charts and graphs.
- Use advanced plotting functions to convey complex information effectively.
R Packages and Libraries for Data Science
R offers a rich ecosystem of packages and libraries that extend its functionality for data science tasks. These packages provide pre-built functions, tools, and algorithms that can significantly enhance your productivity and enable you to tackle various data science challenges. Here are some popular R packages and libraries for data science:
- tidyverse: The tidyverse is a collection of packages that includes dplyr, ggplot2, tidyr, readr, and other packages. It provides a cohesive and consistent set of tools for data manipulation, data visualization, and data tidying.
- caret: The caret (Classification And REgression Training) package offers a unified interface for training and evaluating machine learning models in R. It provides a wide range of algorithms, automated pre-processing, model tuning, and feature selection capabilities.
- randomForest: The randomForest package implements the random forest algorithm, a powerful ensemble learning method for classification and regression tasks. It can handle large datasets, detect variable importance, and handle missing data.
- xgboost: The xgboost package provides an implementation of the gradient boosting algorithm, which is known for its efficiency and high predictive performance. It supports various machine learning tasks and has become popular in many data science competitions.
- keras and tensorflow: The keras and tensorflow packages enable deep learning in R. They provide interfaces to the TensorFlow library, allowing you to build and train neural networks for tasks such as image classification, natural language processing, and more.
- data.table: The data.table package offers an enhanced data manipulation framework that provides fast and efficient operations on large datasets. It extends the functionality of base R's data.frame and offers additional features like fast aggregation, indexing, and joins.
- dplyr: The dplyr package provides a set of intuitive and efficient functions for data manipulation. It includes functions like filter, select, mutate, and summarize, which allow you to perform data transformations and manipulations easily.
- ggplot2: The ggplot2 package is a powerful data visualization library that follows the grammar of graphics paradigm. It allows you to create sophisticated and publication-quality plots with a high level of customization.
- caretEnsemble: The caretEnsemble package combines multiple machine learning models into an ensemble, allowing you to benefit from the predictive power of multiple models. It supports various ensemble methods and provides tools for model selection and combination.
- shiny: The shiny package enables you to create interactive web applications and dashboards directly from R. It allows you to build interactive visualizations and provide user-friendly interfaces to showcase your data analysis and models.
These are just a few examples of the numerous packages available in the R ecosystem for data science. Depending on your specific needs and tasks, you can explore additional packages tailored to specialized areas such as natural language processing (NLP), time series analysis, spatial data analysis, and more.
To install and use R packages, you can use the install.packages() function to install them, and then load the packages into your R session using the library() function. Make sure to check the documentation and examples provided by each package to learn how to effectively use their functions and take advantage of their features.
Remember to stay up-to-date with the latest package versions and explore new packages that are constantly being developed in the R community.
Building Data Science Projects with R
Building data science projects with R allows you to apply your knowledge and skills to real-world scenarios and gain hands-on experience. Here is a step-by-step guide on how to approach building data science projects with R:
- Define the Problem:
-
- Start by clearly defining the problem or objective of your data science project. Understand what you want to achieve and the questions you want to answer through your analysis.
- Gather and Explore Data:
-
- Identify and gather relevant data for your project. This can include public datasets, data from APIs, or data from internal sources.
- Perform exploratory data analysis (EDA) to understand the structure, patterns, and relationships within the data. Use visualizations, summary statistics, and data profiling techniques to gain insights.
- Data Preprocessing:
-
- Preprocess the data to ensure it is in a suitable format for analysis.
- Clean the data by handling missing values, outliers, and inconsistencies.
- Perform data transformations, scaling, or normalization as needed.
- Split the data into training and testing sets for model evaluation.
- Feature Engineering:
-
- Engineer new features from the existing data to improve model performance.
- Create new variables, combine or transform existing variables, and extract relevant information from the data.
- Consider domain knowledge and feature selection techniques to identify the most informative features for your analysis.
- Model Selection and Training:
-
- Choose appropriate machine learning algorithms or statistical models based on the problem type (classification, regression, clustering, etc.) and data characteristics.
- Train the selected models using the training dataset.
- Evaluate model performance using appropriate evaluation metrics and techniques, such as cross-validation or hold-out validation.
- Model Tuning and Optimization:
-
- Fine-tune the model hyperparameters to improve its performance.
- Use techniques like grid search, random search, or Bayesian optimization to find optimal hyperparameter values.
- Validate the tuned model to ensure the improvements generalize well to unseen data.
- Model Evaluation and Interpretation:
-
- Assess the performance of the final model using evaluation metrics specific to your problem (e.g., accuracy, precision, recall, R-squared, etc.).
- Interpret the model results and analyze the impact of different features on the predictions.
- Communicate the findings effectively, using visualizations, summaries, and insights.
- Deployment and Visualization:
-
- Create interactive visualizations, dashboards, or reports to present your results and insights.
- Use packages like Shiny to build interactive web applications to showcase your analysis and allow others to explore the results.
- Deploy the model in a production environment, if applicable, to make predictions on new data.
- Documentation and Collaboration:
-
- Document your project thoroughly, including the problem statement, data sources, preprocessing steps, model selection, evaluation, and key findings.
- Collaborate with others by sharing your code, documentation, and findings through version control systems (e.g., Git) and collaboration platforms.
- Continual Learning and Iteration:
-
- Reflect on your project and identify areas for improvement.
- Seek feedback from peers or experts to enhance your analysis, modeling techniques, or presentation.
- Stay updated with the latest advancements in data science, tools, and techniques to continually enhance your skills.
Tips for Success in Data Science with R Certification
Obtaining a data science certification in R can be a valuable asset to showcase your skills and expertise in the field. Here are some tips to help you succeed in your data science certification journey with R:
- Master the Fundamentals: Ensure you have a strong foundation in R programming and the fundamental concepts of data science. Familiarize yourself with data manipulation, visualization, statistical analysis, and machine learning algorithms commonly used in R.
- Practice with Real-world Projects: Work on real-world data science projects to gain hands-on experience. Practice applying your R skills to solve problems, preprocess data, build models, and analyze results. The more projects you work on, the better you'll understand the practical aspects of data science.
- Explore R Packages and Libraries: Familiarize yourself with popular R packages and libraries specific to data science, such as tidyverse, caret, ggplot2, and dplyr. Learn how to leverage their functionalities to streamline your workflows and perform various data science tasks efficiently.
- Take Advantage of Online Resources: Utilize online tutorials, courses, and forums to enhance your knowledge and skills in R for data science. Platforms like Coursera, DataCamp, and Kaggle offer a wide range of data science courses and challenges specifically focused on R.
- Participate in Data Science Competitions: Engage in data science competitions hosted on platforms like Kaggle. These competitions allow you to work on real-world problems, explore different datasets, and benchmark your skills against other data scientists. It's an excellent opportunity to learn from others, experiment with different techniques, and gain exposure.
- Build a Portfolio: Showcase your data science projects and achievements in a portfolio. Create a dedicated GitHub repository or personal website where you can share your projects, code, visualizations, and insights. A portfolio demonstrates your practical skills and provides tangible evidence of your expertise.
- Collaborate and Network: Engage with the data science community by joining relevant forums, attending meetups, and participating in online communities. Collaborate with other data scientists, seek feedback on your work, and learn from their experiences. Networking can lead to valuable connections and opportunities in the field.
- Review Certification Exam Guidelines: Familiarize yourself with the certification exam guidelines and syllabus. Understand the topics covered, the format of the exam, and the time constraints. This will help you structure your preparation and focus on the areas that carry more weight in the certification.
- Take Practice Exams: Practice exams can help you familiarize yourself with the exam format, time management, and the types of questions you might encounter. Seek out sample questions or practice exams related to your data science certification in R.
- Stay Updated and Keep Learning: Data science is a rapidly evolving field. Stay updated with the latest developments in R, data science techniques, and best practices. Read research papers, follow data science blogs, and attend webinars or conferences to stay at the forefront of the field.
How to obtain Data Science with R Programming certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: SMAC Certication
- Big Data: Big Data and Hadoop Administrator
- Digital Marketing : Digital Marketing Certification
- Data Science : Data Science with R programming
Conclusion
In conclusion, pursuing a data science certification in R programming can significantly enhance your skills and open up new opportunities in the field of data science. By mastering the fundamentals of R, exploring advanced topics, and building practical projects, you can demonstrate your proficiency and expertise in data science with R.
Throughout your certification journey, it is essential to practice and work on real-world projects to apply your knowledge effectively. Leveraging the wide range of R packages and libraries specific to data science, such as tidyverse, caret, and ggplot2, can streamline your workflows and improve your productivity.
Engaging with the data science community, collaborating with others, and participating in competitions can help you grow and learn from peers. Building a portfolio to showcase your projects and accomplishments allows you to present tangible evidence of your skills and expertise.
To succeed in your data science certification, it is crucial to review the exam guidelines, take practice exams, and focus on the areas covered in the certification syllabus. Continual learning, staying updated with the latest trends and techniques, and networking with professionals in the field will further enhance your knowledge and keep you at the forefront of data science.
Remember, obtaining a data science certification is a milestone, but it is equally important to keep learning, exploring new challenges, and refining your skills beyond certification. Embrace a growth mindset, stay curious, and enjoy the exciting and ever-evolving world of data science with R.
Read More
Welcome to the comprehensive guide on "Data Science with R Programming Certification Training." In today's data-driven world, organizations across industries are increasingly recognizing the importance of data science in gaining valuable insights, making informed decisions, and driving innovation. Data science, with its powerful techniques and tools, plays a crucial role in extracting knowledge and meaningful patterns from vast amounts of data.
This guide aims to provide you with a comprehensive understanding of data science using the R programming language. R is a popular open-source programming language known for its extensive libraries and packages specifically designed for data analysis, statistical modeling, and visualization. By mastering R programming in the context of data science, you can unlock a wide range of possibilities for exploring and harnessing the potential of data.
Throughout this certification training, you will delve into various aspects of data science, including data manipulation, exploratory data analysis, statistical modeling, predictive analytics, machine learning, and data visualization. You will also learn how to apply these techniques to real-world datasets and solve complex problems.
The comprehensive nature of this guide ensures that beginners in data science, as well as those with some prior knowledge, can benefit from it. Whether you are a student, a professional looking to upskill, or an aspiring data scientist, this training will equip you with the necessary knowledge and skills to excel in the field of data science with R programming.
By the end of this certification training, you will have a solid foundation in R programming and a deep understanding of the data science workflow. Moreover, you will be prepared to tackle data-driven challenges, develop models for predictive analysis, and present your findings effectively through data visualization.
Embark on this exciting journey into the world of data science with R programming, and unlock the power of data to drive insights and innovation. Let's dive in and explore the fascinating realm of data science together!
Table of contents
- Introduction to Data Science and R Programming
- Understanding the Fundamentals of R Programming
- Data Preprocessing and Feature Engineering in R
- Advanced Topics in Data Science with R
- R Packages and Libraries for Data Science
- Building Data Science Projects with R
- Tips for Success in Data Science with R Certification
- Conclusion
Introduction to Data Science and R Programming
In today's data-driven world, the field of data science has gained tremendous significance. Data science involves extracting meaningful insights and knowledge from vast amounts of data using various statistical and computational techniques. One of the most popular and powerful programming languages used in data science is R.
R is an open-source programming language specifically designed for statistical computing and graphics. It provides a comprehensive set of tools and libraries that enable data scientists to analyze, visualize, and model data effectively. R has gained widespread adoption in the data science community due to its flexibility, extensive package ecosystem, and robust statistical capabilities.
The combination of data science and R programming offers a powerful toolkit for solving complex problems, making data-driven decisions, and deriving actionable insights from data. By mastering R programming for data science, professionals can enhance their analytical skills, expand their career opportunities, and contribute to the advancement of various industries.
Benefits of pursuing a certification in data science with R programming are:
- Industry Relevance: Data science with R programming is highly sought after in industries such as finance, healthcare, e-commerce, marketing, and more. A certification in this field demonstrates your proficiency and makes you stand out in the job market.
- Comprehensive Skill Set: The certification training covers a wide range of topics, including data preprocessing, exploratory data analysis, machine learning algorithms, and advanced data analytics techniques. It equips you with the skills needed to handle real-world data science projects.
- Hands-on Experience: Certification programs often include practical exercises and projects that provide hands-on experience in applying R programming to real data sets. This practical exposure enhances your ability to tackle data-related challenges effectively.
- Networking Opportunities: Certification programs often provide opportunities to connect with fellow data science professionals, instructors, and industry experts. Networking can lead to collaborations, mentorships, and job referrals, expanding your professional network.
- Career Advancement: Data science professionals with R programming skills are in high demand. A certification can boost your career prospects, increase job opportunities, and potentially lead to higher salaries and more challenging roles.
In summary, a certification in data science with R programming offers a pathway to gain expertise in a widely-used programming language for data analysis and empowers you with the necessary skills to succeed in the data science field. It is a valuable investment for both aspiring and experienced data professionals looking to excel in their careers.
Understanding the Fundamentals of R Programming
To excel in data science with R programming, it's crucial to have a strong foundation in the fundamentals of R programming. This section will introduce you to the essential aspects of R programming and its key components. Let's dive into the fundamentals:
- Installing R and RStudio:
-
- Start by downloading and installing R, which is available for Windows, macOS, and Linux platforms. Visit the official R website (https://www.r-project.org/) for the installation package.
- RStudio is an integrated development environment (IDE) for R programming that provides a user-friendly interface. Install RStudio to enhance your coding experience and productivity.
- R Syntax and Data Structures:
-
- R uses a straightforward syntax that allows you to perform computations, manipulate data, and create visualizations. Familiarize yourself with basic R syntax, such as variable assignments, arithmetic operations, and function calls.
- R supports various data structures, including vectors, matrices, data frames, and lists. Understand the characteristics and usage of each data structure to effectively handle data in R.
- Variables and Data Types:
-
- In R, variables are used to store and manipulate data. Learn how to assign values to variables, choose appropriate variable names, and access their contents.
- R supports several data types, such as numeric, character, logical, and factors. Understand how to work with different data types and convert between them as needed.
- Control Structures:
-
- Control structures allow you to control the flow of execution in your R programs. Familiarize yourself with key control structures like if-else statements, for loops, while loops, and switch statements.
- Understand how to use conditional statements and looping constructs to perform repetitive tasks or make decisions based on specific conditions.
- Functions in R:
-
- Functions are a fundamental part of R programming and enable you to encapsulate reusable code. Learn how to define and call functions, pass arguments, and return values.
- Explore built-in functions in R and understand how to create custom functions to perform specific tasks or calculations.
- Packages and Libraries:
-
- R has a vast collection of packages and libraries that extend its functionality. Explore popular packages such as dplyr, ggplot2, and tidyr, which offer powerful tools for data manipulation, visualization, and tidying.
- Learn how to install packages from the Comprehensive R Archive Network (CRAN) or other repositories and load them into your R session to leverage their capabilities.
- File Input and Output:
-
- R provides several functions to read data from external files, such as CSV, Excel, and text files. Familiarize yourself with functions like read.csv(), read_excel(), and readLines() to import data into R.
- Similarly, learn how to export data from R to different file formats using functions like write.csv(), write.xlsx(), and writeLines().
Data Preprocessing and Feature Engineering in R
Data preprocessing and feature engineering play a crucial role in data science projects. They involve transforming raw data into a format suitable for analysis and building models. In this section, we will explore various techniques for data preprocessing and feature engineering using R.
- Handling Missing Data:
-
- Identify missing values in the dataset using functions like is.na() or complete.cases().
- Impute missing data using techniques such as mean imputation, median imputation, or predictive imputation.
- Consider the impact of missing data on the analysis and decide whether to remove or impute missing values based on the context.
- Dealing with Outliers:
-
- Detect outliers using statistical measures such as z-scores, box plots, or Mahalanobis distance.
- Decide whether to remove outliers based on their impact on the analysis or apply outlier treatment techniques such as winsorization or robust methods.
- Handling Categorical Variables:
-
- Encode categorical variables into numerical representations using techniques like one-hot encoding, label encoding, or target encoding.
- Consider the appropriate encoding strategy based on the nature of the categorical variable and its relationship with the target variable.
- Feature Scaling and Normalization:
-
- Normalize numerical features to a common scale using techniques like min-max scaling or z-score normalization.
- Ensure that features have similar ranges and distributions to avoid biases in the analysis and model training.
- Handling Skewed Data:
-
- Identify skewed distributions in the data using measures like skewness or visual inspection.
- Apply transformations such as log transformation, square root transformation, or Box-Cox transformation to reduce skewness and achieve a more symmetric distribution.
- Feature Extraction:
-
- Extract new features from existing ones to capture additional information or reduce dimensionality.
- Techniques like principal component analysis (PCA), factor analysis, or feature selection methods can be used for feature extraction.
- Handling Time Series Data:
-
- Preprocess time series data by converting it into a suitable format, such as creating a time index or resampling.
- Handle missing values and outliers in time series data using specific techniques designed for time-dependent data.
- Data Normalization:
-
- Normalize data to ensure that different variables are on a comparable scale.
- Techniques such as min-max scaling, z-score normalization, or robust normalization can be applied to normalize data.
- Handling Imbalanced Data:
-
- Address class imbalance issues in the dataset, especially in classification tasks.
- Techniques such as oversampling, undersampling, or generating synthetic samples using methods like SMOTE (Synthetic Minority Over-sampling Technique) can be employed to handle imbalanced data.
- Data Partitioning:
-
- Split the dataset into training, validation, and testing sets to evaluate the model's performance.
- Utilize functions like createDataPartition() or train_test_split() to split the data based on various strategies (e.g., random sampling or stratified sampling).
Advanced Topics in Data Science with R
Once you have a solid understanding of the fundamentals of R programming and data preprocessing, you can explore advanced topics in data science that can further enhance your skills and capabilities. Here are some advanced topics in data science with R that you can delve into:
- Text Mining and Natural Language Processing (NLP):
-
- Learn how to process and analyze text data using R.
- Explore techniques such as text cleaning, tokenization, stemming, and sentiment analysis.
- Apply natural language processing (NLP) techniques, including topic modeling and named entity recognition.
- Time Series Analysis and Forecasting:
-
- Gain expertise in handling time-dependent data and perform time series analysis in R.
- Understand concepts such as autocorrelation, stationarity, and seasonality.
- Learn time series forecasting techniques, including ARIMA models, exponential smoothing, and state space models.
- Deep Learning with R:
-
- Explore the world of deep learning using R and frameworks like TensorFlow and Keras.
- Build and train deep neural networks for tasks such as image recognition, natural language processing, and time series forecasting.
- Understand concepts like convolutional neural networks (CNNs), recurrent neural networks (RNNs), and generative adversarial networks (GANs).
- Big Data Analytics with R:
-
- Learn how to handle and analyze large-scale datasets using R.
- Utilize distributed computing frameworks like Apache Spark with R to perform big data analytics.
- Explore techniques for parallel processing, distributed machine learning, and handling data in a distributed environment.
- Spatial Data Analysis:
-
- Analyze and visualize spatial data using R's spatial packages, such as sp and sf.
- Perform spatial data manipulation, geostatistics, and spatial interpolation.
- Build spatial models and perform spatial regression analysis.
- Recommender Systems:
-
- Understand the principles behind recommender systems and their applications.
- Implement collaborative filtering and content-based recommendation algorithms in R.
- Evaluate and fine-tune recommender systems for improved accuracy.
- Bayesian Data Analysis:
-
- Learn Bayesian statistics and its application in data analysis.
- Utilize R packages like rstan and brms for Bayesian modeling.
- Perform inference, model comparison, and prediction using Bayesian methods.
- Ensemble Methods and Model Stacking:
-
- Explore ensemble learning techniques such as bagging, boosting, and random forests in R.
- Understand the concept of model stacking and how to combine predictions from multiple models.
- Apply ensemble methods to improve the accuracy and robustness of predictive models.
- Interfacing R with Other Technologies:
-
- Integrate R with other technologies, such as databases (e.g., SQL), web applications, and cloud services.
- Learn how to connect R with databases, perform SQL queries, and extract data for analysis.
- Develop interactive web-based dashboards and visualizations using R and frameworks like Shiny.
- Advanced Visualization Techniques:
-
- Explore advanced visualization libraries and techniques in R, such as ggplot2, plotly, and lattice.
- Create interactive and dynamic visualizations that go beyond basic charts and graphs.
- Use advanced plotting functions to convey complex information effectively.
R Packages and Libraries for Data Science
R offers a rich ecosystem of packages and libraries that extend its functionality for data science tasks. These packages provide pre-built functions, tools, and algorithms that can significantly enhance your productivity and enable you to tackle various data science challenges. Here are some popular R packages and libraries for data science:
- tidyverse: The tidyverse is a collection of packages that includes dplyr, ggplot2, tidyr, readr, and other packages. It provides a cohesive and consistent set of tools for data manipulation, data visualization, and data tidying.
- caret: The caret (Classification And REgression Training) package offers a unified interface for training and evaluating machine learning models in R. It provides a wide range of algorithms, automated pre-processing, model tuning, and feature selection capabilities.
- randomForest: The randomForest package implements the random forest algorithm, a powerful ensemble learning method for classification and regression tasks. It can handle large datasets, detect variable importance, and handle missing data.
- xgboost: The xgboost package provides an implementation of the gradient boosting algorithm, which is known for its efficiency and high predictive performance. It supports various machine learning tasks and has become popular in many data science competitions.
- keras and tensorflow: The keras and tensorflow packages enable deep learning in R. They provide interfaces to the TensorFlow library, allowing you to build and train neural networks for tasks such as image classification, natural language processing, and more.
- data.table: The data.table package offers an enhanced data manipulation framework that provides fast and efficient operations on large datasets. It extends the functionality of base R's data.frame and offers additional features like fast aggregation, indexing, and joins.
- dplyr: The dplyr package provides a set of intuitive and efficient functions for data manipulation. It includes functions like filter, select, mutate, and summarize, which allow you to perform data transformations and manipulations easily.
- ggplot2: The ggplot2 package is a powerful data visualization library that follows the grammar of graphics paradigm. It allows you to create sophisticated and publication-quality plots with a high level of customization.
- caretEnsemble: The caretEnsemble package combines multiple machine learning models into an ensemble, allowing you to benefit from the predictive power of multiple models. It supports various ensemble methods and provides tools for model selection and combination.
- shiny: The shiny package enables you to create interactive web applications and dashboards directly from R. It allows you to build interactive visualizations and provide user-friendly interfaces to showcase your data analysis and models.
These are just a few examples of the numerous packages available in the R ecosystem for data science. Depending on your specific needs and tasks, you can explore additional packages tailored to specialized areas such as natural language processing (NLP), time series analysis, spatial data analysis, and more.
To install and use R packages, you can use the install.packages() function to install them, and then load the packages into your R session using the library() function. Make sure to check the documentation and examples provided by each package to learn how to effectively use their functions and take advantage of their features.
Remember to stay up-to-date with the latest package versions and explore new packages that are constantly being developed in the R community.
Building Data Science Projects with R
Building data science projects with R allows you to apply your knowledge and skills to real-world scenarios and gain hands-on experience. Here is a step-by-step guide on how to approach building data science projects with R:
- Define the Problem:
-
- Start by clearly defining the problem or objective of your data science project. Understand what you want to achieve and the questions you want to answer through your analysis.
- Gather and Explore Data:
-
- Identify and gather relevant data for your project. This can include public datasets, data from APIs, or data from internal sources.
- Perform exploratory data analysis (EDA) to understand the structure, patterns, and relationships within the data. Use visualizations, summary statistics, and data profiling techniques to gain insights.
- Data Preprocessing:
-
- Preprocess the data to ensure it is in a suitable format for analysis.
- Clean the data by handling missing values, outliers, and inconsistencies.
- Perform data transformations, scaling, or normalization as needed.
- Split the data into training and testing sets for model evaluation.
- Feature Engineering:
-
- Engineer new features from the existing data to improve model performance.
- Create new variables, combine or transform existing variables, and extract relevant information from the data.
- Consider domain knowledge and feature selection techniques to identify the most informative features for your analysis.
- Model Selection and Training:
-
- Choose appropriate machine learning algorithms or statistical models based on the problem type (classification, regression, clustering, etc.) and data characteristics.
- Train the selected models using the training dataset.
- Evaluate model performance using appropriate evaluation metrics and techniques, such as cross-validation or hold-out validation.
- Model Tuning and Optimization:
-
- Fine-tune the model hyperparameters to improve its performance.
- Use techniques like grid search, random search, or Bayesian optimization to find optimal hyperparameter values.
- Validate the tuned model to ensure the improvements generalize well to unseen data.
- Model Evaluation and Interpretation:
-
- Assess the performance of the final model using evaluation metrics specific to your problem (e.g., accuracy, precision, recall, R-squared, etc.).
- Interpret the model results and analyze the impact of different features on the predictions.
- Communicate the findings effectively, using visualizations, summaries, and insights.
- Deployment and Visualization:
-
- Create interactive visualizations, dashboards, or reports to present your results and insights.
- Use packages like Shiny to build interactive web applications to showcase your analysis and allow others to explore the results.
- Deploy the model in a production environment, if applicable, to make predictions on new data.
- Documentation and Collaboration:
-
- Document your project thoroughly, including the problem statement, data sources, preprocessing steps, model selection, evaluation, and key findings.
- Collaborate with others by sharing your code, documentation, and findings through version control systems (e.g., Git) and collaboration platforms.
- Continual Learning and Iteration:
-
- Reflect on your project and identify areas for improvement.
- Seek feedback from peers or experts to enhance your analysis, modeling techniques, or presentation.
- Stay updated with the latest advancements in data science, tools, and techniques to continually enhance your skills.
Tips for Success in Data Science with R Certification
Obtaining a data science certification in R can be a valuable asset to showcase your skills and expertise in the field. Here are some tips to help you succeed in your data science certification journey with R:
- Master the Fundamentals: Ensure you have a strong foundation in R programming and the fundamental concepts of data science. Familiarize yourself with data manipulation, visualization, statistical analysis, and machine learning algorithms commonly used in R.
- Practice with Real-world Projects: Work on real-world data science projects to gain hands-on experience. Practice applying your R skills to solve problems, preprocess data, build models, and analyze results. The more projects you work on, the better you'll understand the practical aspects of data science.
- Explore R Packages and Libraries: Familiarize yourself with popular R packages and libraries specific to data science, such as tidyverse, caret, ggplot2, and dplyr. Learn how to leverage their functionalities to streamline your workflows and perform various data science tasks efficiently.
- Take Advantage of Online Resources: Utilize online tutorials, courses, and forums to enhance your knowledge and skills in R for data science. Platforms like Coursera, DataCamp, and Kaggle offer a wide range of data science courses and challenges specifically focused on R.
- Participate in Data Science Competitions: Engage in data science competitions hosted on platforms like Kaggle. These competitions allow you to work on real-world problems, explore different datasets, and benchmark your skills against other data scientists. It's an excellent opportunity to learn from others, experiment with different techniques, and gain exposure.
- Build a Portfolio: Showcase your data science projects and achievements in a portfolio. Create a dedicated GitHub repository or personal website where you can share your projects, code, visualizations, and insights. A portfolio demonstrates your practical skills and provides tangible evidence of your expertise.
- Collaborate and Network: Engage with the data science community by joining relevant forums, attending meetups, and participating in online communities. Collaborate with other data scientists, seek feedback on your work, and learn from their experiences. Networking can lead to valuable connections and opportunities in the field.
- Review Certification Exam Guidelines: Familiarize yourself with the certification exam guidelines and syllabus. Understand the topics covered, the format of the exam, and the time constraints. This will help you structure your preparation and focus on the areas that carry more weight in the certification.
- Take Practice Exams: Practice exams can help you familiarize yourself with the exam format, time management, and the types of questions you might encounter. Seek out sample questions or practice exams related to your data science certification in R.
- Stay Updated and Keep Learning: Data science is a rapidly evolving field. Stay updated with the latest developments in R, data science techniques, and best practices. Read research papers, follow data science blogs, and attend webinars or conferences to stay at the forefront of the field.
How to obtain Data Science with R Programming certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: SMAC Certication
- Big Data: Big Data and Hadoop Administrator
- Digital Marketing : Digital Marketing Certification
- Data Science : Data Science with R programming
Conclusion
In conclusion, pursuing a data science certification in R programming can significantly enhance your skills and open up new opportunities in the field of data science. By mastering the fundamentals of R, exploring advanced topics, and building practical projects, you can demonstrate your proficiency and expertise in data science with R.
Throughout your certification journey, it is essential to practice and work on real-world projects to apply your knowledge effectively. Leveraging the wide range of R packages and libraries specific to data science, such as tidyverse, caret, and ggplot2, can streamline your workflows and improve your productivity.
Engaging with the data science community, collaborating with others, and participating in competitions can help you grow and learn from peers. Building a portfolio to showcase your projects and accomplishments allows you to present tangible evidence of your skills and expertise.
To succeed in your data science certification, it is crucial to review the exam guidelines, take practice exams, and focus on the areas covered in the certification syllabus. Continual learning, staying updated with the latest trends and techniques, and networking with professionals in the field will further enhance your knowledge and keep you at the forefront of data science.
Remember, obtaining a data science certification is a milestone, but it is equally important to keep learning, exploring new challenges, and refining your skills beyond certification. Embrace a growth mindset, stay curious, and enjoy the exciting and ever-evolving world of data science with R.
How to Get Started with Apache Kafka Certification Training
Are you eager to become a certified Apache Kafka professional and gain expertise in real-time data streaming and distributed messaging systems? Getting started with Apache Kafka certification training is the perfect way to achieve your goals. Apache Kafka has become a popular platform for handling high-volume, real-time data streams, and organizations are increasingly seeking skilled Kafka professionals. By obtaining a certification, you validate your understanding of Kafka's core concepts and demonstrate your ability to design, develop, and manage Kafka-based solutions effectively. Through comprehensive training, you will learn essential topics such as Kafka fundamentals, architecture, producers and consumers, connectors, streams, administration, and the broader Kafka ecosystem. By completing the certification, you not only acquire valuable knowledge and skills but also enhance your professional profile and open doors to exciting career opportunities in the field of data engineering and real-time analytics.
Table of contents
-
Introduction to Apache Kafka
-
Understanding Kafka Certification
-
Getting Started with Kafka
-
Working with Kafka Producers
-
Kafka Streams and Real-time Processing
-
Best Practices for Kafka Development
-
Preparing for Kafka Certification Exam
-
Conclusion
Introduction to Apache Kafka
Apache Kafka is an open-source distributed event streaming platform that is widely used for building real-time data pipelines and streaming applications. It was initially developed by LinkedIn and later open-sourced in 2011. Kafka is designed to handle high-throughput, fault-tolerant, and scalable streaming of data across different systems and applications.
Key Features and Benefits of Kafka:
-
Publish-Subscribe Messaging: Kafka follows the publish-subscribe messaging model, where producers publish messages to specific topics, and consumers subscribe to those topics to receive the messages.
-
Fault-Tolerant Architecture: Kafka is designed to be highly fault-tolerant and durable. It persists messages to disk and replicates them across multiple brokers to ensure data reliability even in the case of failures.
-
Scalability and High Throughput: Kafka can handle high message throughput and supports horizontal scalability by allowing the distribution of topics and partitions across multiple brokers.
-
Real-Time Stream Processing: Kafka enables real-time processing of data streams. It allows applications to consume and process data as soon as it becomes available, enabling near real-time analytics, monitoring, and decision-making.
-
Data Retention and Durability: Kafka provides configurable retention policies, allowing messages to be stored for a specific duration or size. This feature makes Kafka suitable for building data pipelines and replaying events for data analysis.
-
Stream Partitioning and Parallel Processing: Kafka partitions data across multiple brokers, allowing parallel processing of messages within a topic. This enables efficient handling of large data volumes and enables horizontal scaling of consumers.
-
Integration with Ecosystem: Kafka integrates seamlessly with various data systems, including Apache Spark, Apache Storm, Apache Hadoop, and databases, making it a versatile platform for building complex data processing workflows.
Kafka Architecture and Components:
The core architecture of Kafka consists of the following components:
-
Topics: Topics represent a specific category or feed name to which producers publish messages. They act as channels for organizing and segregating data streams.
-
Producers: Producers are responsible for publishing messages to Kafka topics. They write data to a specific topic, which is then made available for consumption by consumers.
-
Consumers: Consumers are applications or services that subscribe to Kafka topics and retrieve messages for processing. They read data from one or more partitions within a topic.
-
Brokers: Brokers form the Kafka cluster and are responsible for storing and replicating the published messages. Each broker can handle a certain amount of data and provides the necessary infrastructure for message storage and retrieval.
-
Partitions: Kafka topics are divided into partitions to enable parallelism and scalability. Each partition is an ordered and immutable sequence of messages. The number of partitions determines the level of parallelism for message consumption.
-
ZooKeeper: ZooKeeper is used by Kafka for maintaining cluster coordination, managing metadata, and detecting failures. It helps in maintaining the availability and reliability of the Kafka cluster.
Understanding the fundamentals of Apache Kafka sets the stage for diving deeper into its various components, features, and use cases. It serves as a robust foundation for building real-time data processing systems and enables the creation of scalable and fault-tolerant streaming applications.
Understanding Kafka Certification
Kafka certification is a validation of one's knowledge and expertise in working with Apache Kafka. It demonstrates proficiency in various aspects of Kafka, including its architecture, components, operations, and best practices. Kafka certification can enhance your credibility as a Kafka professional and open up new career opportunities in the field of data streaming and real-time analytics.
Different Types of Kafka Certifications Available:
-
Confluent Certified Developer for Apache Kafka (CCDAK): This certification focuses on the development aspects of Kafka, including building and managing Kafka producers, consumers, and streams applications. It validates skills related to Kafka APIs, message serialization, stream processing, and error handling.
-
Confluent Certified Operator for Apache Kafka (CCOAK): This certification is targeted towards individuals responsible for operating and managing Kafka clusters in production environments. It covers topics such as cluster setup, configuration, monitoring, security, and troubleshooting.
Certification Prerequisites and Exam Details:
To pursue Kafka certification, it is essential to have a solid understanding of Kafka concepts, architecture, and core components. Familiarity with programming languages like Java, Python, or Scala can also be beneficial, especially for the developer-focused certification.
The exact prerequisites and exam details may vary depending on the certification provider. However, in general, the certification process typically involves the following steps:
-
Exam Registration: Register for the Kafka certification exam through the official certification provider's website. Pay attention to the registration deadlines and any specific requirements.
-
Exam Format: Kafka certification exams are usually conducted online and consist of multiple-choice questions, hands-on exercises, and scenario-based problems. The format may differ based on the certification type and level.
-
Exam Preparation: Prepare for the certification exam by studying relevant Kafka documentation, official study guides, and recommended reading materials. Hands-on experience with Kafka and practical exercises can also enhance your preparation.
-
Exam Duration and Passing Score: The duration of the Kafka certification exam can vary, typically ranging from a few hours to half a day. The passing score requirement may also differ based on the certification level and difficulty.
-
Certification Validity and Renewal: Kafka certifications are typically valid for a certain period, such as two years. To maintain an active certification status, you may need to renew it by meeting certain criteria, such as earning continuing education credits or retaking the exam.
Preparing for and obtaining Kafka certification not only validates your Kafka skills but also demonstrates your commitment to professional growth in the field of real-time data streaming and processing.
Note: While Confluent is a prominent provider of Kafka certifications, other organizations or platforms may offer their own Kafka-related certifications. It's essential to research and choose a certification that aligns with your goals and is recognized within the industry.
By obtaining Kafka certification, you can enhance your career prospects, demonstrate your expertise to potential employers or clients, and gain a competitive edge in the evolving landscape of data streaming and event-driven architectures.
Getting Started with Kafka
If you're new to Apache Kafka, getting started with this powerful distributed streaming platform can seem daunting. However, with the right guidance, you can quickly grasp the fundamentals and begin building your own Kafka-based applications. Here are the essential steps to get started with Kafka:
-
Understanding Kafka Basics:
-
-
Familiarize yourself with the core concepts of Kafka, such as topics, partitions, producers, consumers, and brokers. Understanding these fundamental building blocks is crucial for working effectively with Kafka.
-
Install Kafka:
-
-
Download and install Apache Kafka on your local machine or set up a Kafka cluster on multiple servers for production environments. Kafka is written in Java, so ensure you have Java installed and configured on your machine.
-
Start ZooKeeper:
-
-
Kafka relies on Apache ZooKeeper for cluster coordination. Start ZooKeeper by running the ZooKeeper server and configuring the necessary properties. ZooKeeper must be running before starting Kafka.
-
Configure Kafka:
-
-
Kafka provides various configuration options. Familiarize yourself with the configuration files, such as server.properties and producer.properties, and make any necessary modifications to suit your requirements.
-
Create a Topic:
-
-
A Kafka topic is a category or feed name to which messages are published. Use the Kafka command-line tools to create a topic, specifying the topic name, number of partitions, and replication factor. For example:
-
Produce Messages:
-
-
Kafka producers write messages to topics. Create a simple producer application using the Kafka client libraries (e.g., Java, Python) and start publishing messages to your topic. Include the necessary configuration for connecting to the Kafka cluster, specifying the topic, and sending messages.
-
Consume Messages:
-
-
Kafka consumers read messages from topics. Develop a consumer application using the Kafka client libraries and configure it to subscribe to the topic you created. Retrieve and process messages received from the Kafka cluster.
-
Explore Advanced Features:
-
-
Once you have the basic Kafka setup running, explore additional features like message serialization (e.g., Avro, JSON), message partitioning strategies, fault-tolerance mechanisms, and advanced configurations for optimizing performance.
-
Experiment with Kafka Streams:
-
-
Kafka Streams is a powerful stream processing library that allows you to process and analyze data in real-time. Learn how to build stream processing applications using Kafka Streams and integrate them into your Kafka-based ecosystem.
-
Join the Kafka Community:
-
-
Engage with the vibrant Kafka community, including forums, mailing lists, and social media channels. Participate in discussions, ask questions, and learn from experienced Kafka users and contributors.
-
Explore Kafka Ecosystem:
-
-
Dive into the broader Kafka ecosystem, including connectors like Kafka Connect for integrating Kafka with external systems, monitoring tools, and frameworks like Apache Spark or Apache Flink for advanced data processing.
Working with Kafka Producers
Kafka producers are responsible for publishing messages to Kafka topics. They play a crucial role in the data pipeline, enabling data producers to send messages to be consumed by one or more consumers. Here are the key aspects to consider when working with Kafka producers:
-
Producer Configuration:
-
-
Configure the producer properties to establish a connection with the Kafka cluster. Set properties such as bootstrap servers (the list of Kafka broker addresses), message serialization settings (key and value serializers), acknowledgments, retries, and batch sizes. Proper configuration ensures reliable and efficient message publishing.
-
Creating a Kafka Producer:
-
-
Create an instance of the Kafka producer by instantiating the appropriate Kafka client library (e.g., KafkaProducer in Java). Pass the relevant configuration properties to the producer constructor.
-
Producing Messages:
-
-
Use the producer's send() method to publish messages to Kafka topics. Messages consist of a key and a value. The key is optional and is used for partitioning purposes. The value represents the actual content of the message. Send messages synchronously or asynchronously, depending on your application's requirements.
-
Message Serialization:
-
-
Serialize data into the appropriate format before sending it to Kafka. Kafka handles byte arrays as messages, so use serializers to convert your data objects into byte arrays. Common serialization formats include Avro, JSON, or plain text. Ensure that you configure the appropriate key and value serializers based on your data format.
-
Message Partitioning:
-
-
Kafka partitions messages within a topic. By default, Kafka uses a round-robin approach to distribute messages evenly among partitions. However, you can also specify a key when sending a message to ensure that all messages with the same key go to the same partition. Understand your data distribution and key selection criteria to optimize message distribution across partitions.
-
Message Routing and Topic Selection:
-
-
Select the appropriate Kafka topic to publish your messages based on your application's data organization and processing requirements. Consider creating separate topics for different data sources or different types of events to maintain logical separation and enable efficient message processing.
-
Message Retries and Error Handling:
-
-
Handle failures and errors gracefully when producing messages. Configure appropriate retry mechanisms to handle transient failures such as network issues or temporary unavailability of brokers. Implement error handlers to catch and handle any exceptions that occur during message publication.
-
Message Compression:
-
-
Enable compression to reduce the size of messages being sent to Kafka, especially if your messages are large or if you have a high message throughput. Kafka supports various compression codecs (e.g., gzip, Snappy, LZ4) that can be configured on the producer to reduce network bandwidth and storage requirements.
-
Monitoring and Metrics:
-
-
Monitor the producer's performance and track relevant metrics. Kafka provides metrics such as message send rate, message delivery latency, and request response times. Leverage monitoring tools and frameworks like Kafka's built-in metrics or external tools to gain insights into the producer's behavior and performance.
-
Security Considerations:
-
-
Ensure that appropriate security measures are in place when producing messages to Kafka. This may include authentication and authorization mechanisms, encryption of data in transit, and securing access to the Kafka cluster. Consult Kafka's security documentation and best practices for implementing a secure producer setup.
Kafka Streams and Real-time Processing
Kafka Streams is a powerful Java library provided by Apache Kafka that enables real-time processing and analysis of data streams. It allows developers to build scalable and fault-tolerant stream processing applications that can ingest, transform, and aggregate data in real-time. Here's an overview of Kafka Streams and its role in real-time processing:
-
Introduction to Kafka Streams:
-
-
Kafka Streams provides a high-level, easy-to-use API for building real-time stream processing applications. It is built on top of Kafka, leveraging its distributed architecture, fault-tolerance, and scalability features. Kafka Streams allows developers to focus on writing stream processing logic without worrying about infrastructure complexities.
-
Stream Processing Basics:
-
-
In Kafka Streams, data is processed in the form of continuous streams of records. Streams can be derived from Kafka topics, and processing tasks are defined as a series of transformations applied to the input streams. Each transformation produces an output stream, allowing for a chain of processing steps.
-
Stream-Table Duality:
-
-
Kafka Streams introduces the concept of stream-table duality, which means that a stream can be treated as a continuously updating table and vice versa. This duality allows developers to perform joins, aggregations, and other operations on streams and tables seamlessly.
-
Stream Processing Operations:
-
-
Kafka Streams provides a rich set of operations for transforming and manipulating data streams. These operations include filtering, mapping, flat-mapping, grouping, aggregating, joining, windowing, and more. These operations can be combined to perform complex data processing tasks.
-
Windowing and Time-based Operations:
-
-
Kafka Streams supports windowing operations, allowing you to define time-based windows over data streams. Windowing operations enable calculations over fixed-duration windows, sliding windows, and tumbling windows. This feature is useful for computing real-time analytics and aggregations.
-
Stateful Stream Processing:
-
-
Kafka Streams provides state stores that allow stream processing applications to maintain and update state information. State stores enable tasks like maintaining counts, aggregating values, and tracking session information. Kafka Streams manages state store replication and fault-tolerance automatically.
-
Exactly-once Processing Semantics:
-
-
Kafka Streams guarantees exactly-once processing semantics, ensuring that each input record is processed exactly once, even in the presence of failures and system restarts. This reliability is achieved through the use of Kafka's transactional messaging and internal state management.
-
Integration with External Systems:
-
-
Kafka Streams provides connectors and integration capabilities with various external systems and libraries. These include integration with databases, key-value stores, message queues, and analytics frameworks like Apache Spark and Apache Flink. This allows you to easily integrate stream processing with other components of your data ecosystem.
-
Interactive Queries:
-
-
Kafka Streams enables interactive queries, allowing you to retrieve aggregated results and query the state maintained by the stream processing application. Interactive queries enable real-time access to the processed data, facilitating the development of interactive dashboards, APIs, and real-time analytics applications.
-
Scalability and Fault-tolerance:
-
-
Kafka Streams leverages Kafka's distributed architecture, allowing applications to scale horizontally by adding more instances. Kafka Streams automatically rebalances the workload across instances, ensuring fault-tolerance and high availability of the stream processing application.
-
Monitoring and Management:
-
-
Kafka Streams provides monitoring capabilities and integration with monitoring tools like Kafka's built-in metrics, JMX, and third-party monitoring systems. These tools enable you to monitor the health, performance, and throughput of your stream processing applications.
Best Practices for Kafka Development
Developing applications using Apache Kafka requires careful consideration of various aspects to ensure optimal performance, reliability, and scalability. Here are some best practices to follow when working with Kafka:
-
Design Data Schema and Message Formats:
-
-
Plan and design your data schema and message formats carefully. Choose appropriate serialization formats (such as Avro, JSON, or Protobuf) that strike a balance between data size and ease of processing. Ensure backward compatibility as your data schema evolves.
-
Topic Naming and Organization:
-
-
Establish a consistent and meaningful naming convention for your Kafka topics. Consider organizing topics based on data sources, data types, or event types to maintain logical separation and ease of management. Avoid creating a large number of unnecessary topics.
-
Proper Partitioning Strategy:
-
-
Choose an effective partitioning strategy for your topics. Consider factors such as data distribution, message ordering requirements, and scalability. Distribute messages evenly across partitions to ensure balanced workloads and avoid hotspots.
-
Sizing and Resource Allocation:
-
-
Estimate the expected message throughput, data volume, and retention policy to determine the appropriate sizing and resource allocation for your Kafka cluster. Consider factors such as CPU, memory, and disk space to handle the anticipated workload effectively.
-
Use Compression:
-
-
Enable compression for message payloads, especially if your messages are large or if you have a high message throughput. Compression reduces network bandwidth usage, improves throughput, and reduces storage requirements.
-
Configure Replication:
-
-
Set an appropriate replication factor for your topics. Replicating data across multiple brokers ensures fault-tolerance and high availability. Consider the trade-off between durability and resource utilization when configuring replication.
-
Monitor Consumer Lag:
-
-
Keep track of consumer lag, which measures the delay between producing messages and consuming them. Monitor lag metrics to identify any performance bottlenecks or issues with consumer processing. Lag can be monitored using Kafka consumer offsets and Kafka monitoring tools.
-
Handle Consumer Offset Management:
-
-
Manage consumer offsets properly to ensure message ordering and avoid data duplication. Use Kafka's built-in offset management or external offset management systems like Apache Kafka's Consumer Offset Committer API. Handle offset commits based on your application's processing guarantees.
-
Implement Error Handling and Retry Mechanisms:
-
-
Build robust error handling and retry mechanisms in your Kafka applications. Handle exceptions and errors gracefully to ensure reliable message processing. Implement retry strategies for transient failures, such as network errors or temporary unavailability of brokers.
-
Security Considerations:
-
-
Implement appropriate security measures to protect your Kafka cluster and data. Secure network connections with SSL/TLS encryption, authenticate clients, and authorize access to topics and resources. Follow Kafka's security best practices to prevent unauthorized access and data breaches.
-
Monitor and Tune Performance:
-
-
Implement monitoring and performance tuning practices to optimize the performance of your Kafka cluster. Monitor key metrics such as message throughput, latency, disk usage, and resource utilization. Tune Kafka configurations based on workload patterns and requirements.
-
Test and Validate:
-
-
Thoroughly test your Kafka applications before deploying them to production. Conduct load testing, performance testing, and end-to-end testing to validate the behavior and performance of your applications under various scenarios. Use tools like Kafka's integrated testing framework or external testing frameworks.
-
Upgrade and Maintain:
-
-
Keep your Kafka cluster up to date by regularly upgrading to the latest stable version. Stay informed about bug fixes, performance improvements, and new features. Monitor release notes and follow upgrade best practices to ensure a smooth upgrade process.
Preparing for Kafka Certification Exam
Preparing for a Kafka certification exam requires a comprehensive understanding of Kafka's concepts, features, architecture, and practical use cases. Here are some steps you can follow to prepare effectively:
-
Review Kafka Documentation:
-
-
Start by thoroughly reading the official Apache Kafka documentation. Familiarize yourself with the core concepts, terminology, and components of Kafka. Pay close attention to topics such as producers, consumers, brokers, topics, partitions, replication, and fault-tolerance.
-
Understand Kafka Architecture:
-
-
Dive deep into Kafka's architecture and how it works. Study the role of ZooKeeper in Kafka, the responsibilities of brokers, and the interaction between producers and consumers. Understand how Kafka handles data storage, partitioning, and replication for high availability and fault tolerance.
-
Learn Kafka APIs and Tools:
-
-
Gain hands-on experience with Kafka's APIs and command-line tools. Practice using the Kafka Producer API and Consumer API to publish and consume messages. Familiarize yourself with the Kafka Streams API for stream processing. Explore tools like Kafka Connect for data integration and Kafka MirrorMaker for replication.
-
Explore Real-World Use Cases:
-
-
Study real-world use cases and architectural patterns where Kafka is commonly used. Understand how Kafka facilitates event streaming, data pipelines, real-time analytics, microservices communication, and log aggregation. Learn how to design Kafka-based solutions for various scenarios.
-
Practice with Kafka Cluster Setup:
-
-
Set up a Kafka cluster on your local machine or a test environment. Configure brokers, ZooKeeper, and topics. Experiment with different configurations, replication factors, and partitioning strategies. Practice scaling the cluster, handling failures, and managing topics and consumer groups.
-
Study Kafka Streams and Stream Processing:
-
-
Explore Kafka Streams and its APIs for stream processing. Understand windowing operations, stateful processing, aggregations, and joins. Study the concepts of stream-table duality and interactive queries. Practice building simple stream processing applications with Kafka Streams.
-
Review Kafka Security:
-
-
Familiarize yourself with Kafka's security features and best practices. Learn about authentication, authorization, SSL/TLS encryption, and encryption at rest. Understand how to configure and secure your Kafka cluster to protect against unauthorized access and data breaches.
-
Take Sample Exams and Practice Tests:
-
-
Look for sample Kafka certification exams or practice tests available online. These resources can help you assess your knowledge and identify areas that require further study. Practice answering exam-style questions to get familiar with the exam format and time management.
-
Join Kafka Communities and Forums:
-
-
Engage with the Kafka community by joining forums, discussion groups, and mailing lists. Participate in discussions, ask questions, and learn from experienced Kafka users and experts. Collaborating with others can enhance your understanding and provide valuable insights.
-
Hands-on Projects and Practical Experience:
-
-
Gain practical experience by working on Kafka projects or contributing to open-source Kafka-related initiatives. Implement end-to-end Kafka solutions, build data pipelines, and develop stream processing applications. Practical experience will solidify your understanding and improve your problem-solving skills.
How to obtain Apache Kafka certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: SMAC Certication
-
Big Data: Big Data and Hadoop Administrator
-
Digital Marketing : Digital Marketing Certification
-
Data Science : Apache Kafka Certification
Conclusion
In conclusion, Apache Kafka is a powerful distributed streaming platform that enables reliable and scalable real-time data processing. Whether you're a developer, architect, or data professional, gaining expertise in Kafka can significantly enhance your skills and open up new opportunities in the world of data streaming and event-driven architectures.
Throughout this blog, we have explored various subtopics related to Apache Kafka certification training. We covered essential areas such as an introduction to Apache Kafka, understanding Kafka certification, getting started with Kafka, Kafka messaging concepts, Kafka cluster setup and configuration, working with Kafka producers, Kafka Streams and real-time processing, and best practices for Kafka development. Each subtopic provides valuable insights and knowledge to help you excel in your Kafka journey.
By familiarizing yourself with Kafka's core concepts, architecture, and practical aspects, you can confidently navigate Kafka's ecosystem and effectively leverage its capabilities. Whether it's understanding Kafka's messaging model, designing Kafka-based solutions, or optimizing performance and scalability, a strong foundation in Kafka is crucial.
Remember to supplement your learning with hands-on experience, practical projects, and engaging with the Kafka community. Continuous learning, staying updated with the latest features and enhancements, and exploring real-world use cases will help you master Kafka and succeed in your Kafka certification exam.
Embrace the power of Kafka as you embark on your certification journey, and leverage its capabilities to build robust data pipelines, real-time analytics, and event-driven applications. With Kafka's scalability, fault-tolerance, and high-throughput capabilities, you can unlock the potential of real-time data processing and create innovative solutions that drive your organization forward.
Best of luck in your Kafka certification training and future endeavors with Apache Kafka!
Read More
Are you eager to become a certified Apache Kafka professional and gain expertise in real-time data streaming and distributed messaging systems? Getting started with Apache Kafka certification training is the perfect way to achieve your goals. Apache Kafka has become a popular platform for handling high-volume, real-time data streams, and organizations are increasingly seeking skilled Kafka professionals. By obtaining a certification, you validate your understanding of Kafka's core concepts and demonstrate your ability to design, develop, and manage Kafka-based solutions effectively. Through comprehensive training, you will learn essential topics such as Kafka fundamentals, architecture, producers and consumers, connectors, streams, administration, and the broader Kafka ecosystem. By completing the certification, you not only acquire valuable knowledge and skills but also enhance your professional profile and open doors to exciting career opportunities in the field of data engineering and real-time analytics.
Table of contents
-
Introduction to Apache Kafka
-
Understanding Kafka Certification
-
Getting Started with Kafka
-
Working with Kafka Producers
-
Kafka Streams and Real-time Processing
-
Best Practices for Kafka Development
-
Preparing for Kafka Certification Exam
-
Conclusion
Introduction to Apache Kafka
Apache Kafka is an open-source distributed event streaming platform that is widely used for building real-time data pipelines and streaming applications. It was initially developed by LinkedIn and later open-sourced in 2011. Kafka is designed to handle high-throughput, fault-tolerant, and scalable streaming of data across different systems and applications.
Key Features and Benefits of Kafka:
-
Publish-Subscribe Messaging: Kafka follows the publish-subscribe messaging model, where producers publish messages to specific topics, and consumers subscribe to those topics to receive the messages.
-
Fault-Tolerant Architecture: Kafka is designed to be highly fault-tolerant and durable. It persists messages to disk and replicates them across multiple brokers to ensure data reliability even in the case of failures.
-
Scalability and High Throughput: Kafka can handle high message throughput and supports horizontal scalability by allowing the distribution of topics and partitions across multiple brokers.
-
Real-Time Stream Processing: Kafka enables real-time processing of data streams. It allows applications to consume and process data as soon as it becomes available, enabling near real-time analytics, monitoring, and decision-making.
-
Data Retention and Durability: Kafka provides configurable retention policies, allowing messages to be stored for a specific duration or size. This feature makes Kafka suitable for building data pipelines and replaying events for data analysis.
-
Stream Partitioning and Parallel Processing: Kafka partitions data across multiple brokers, allowing parallel processing of messages within a topic. This enables efficient handling of large data volumes and enables horizontal scaling of consumers.
-
Integration with Ecosystem: Kafka integrates seamlessly with various data systems, including Apache Spark, Apache Storm, Apache Hadoop, and databases, making it a versatile platform for building complex data processing workflows.
Kafka Architecture and Components:
The core architecture of Kafka consists of the following components:
-
Topics: Topics represent a specific category or feed name to which producers publish messages. They act as channels for organizing and segregating data streams.
-
Producers: Producers are responsible for publishing messages to Kafka topics. They write data to a specific topic, which is then made available for consumption by consumers.
-
Consumers: Consumers are applications or services that subscribe to Kafka topics and retrieve messages for processing. They read data from one or more partitions within a topic.
-
Brokers: Brokers form the Kafka cluster and are responsible for storing and replicating the published messages. Each broker can handle a certain amount of data and provides the necessary infrastructure for message storage and retrieval.
-
Partitions: Kafka topics are divided into partitions to enable parallelism and scalability. Each partition is an ordered and immutable sequence of messages. The number of partitions determines the level of parallelism for message consumption.
-
ZooKeeper: ZooKeeper is used by Kafka for maintaining cluster coordination, managing metadata, and detecting failures. It helps in maintaining the availability and reliability of the Kafka cluster.
Understanding the fundamentals of Apache Kafka sets the stage for diving deeper into its various components, features, and use cases. It serves as a robust foundation for building real-time data processing systems and enables the creation of scalable and fault-tolerant streaming applications.
Understanding Kafka Certification
Kafka certification is a validation of one's knowledge and expertise in working with Apache Kafka. It demonstrates proficiency in various aspects of Kafka, including its architecture, components, operations, and best practices. Kafka certification can enhance your credibility as a Kafka professional and open up new career opportunities in the field of data streaming and real-time analytics.
Different Types of Kafka Certifications Available:
-
Confluent Certified Developer for Apache Kafka (CCDAK): This certification focuses on the development aspects of Kafka, including building and managing Kafka producers, consumers, and streams applications. It validates skills related to Kafka APIs, message serialization, stream processing, and error handling.
-
Confluent Certified Operator for Apache Kafka (CCOAK): This certification is targeted towards individuals responsible for operating and managing Kafka clusters in production environments. It covers topics such as cluster setup, configuration, monitoring, security, and troubleshooting.
Certification Prerequisites and Exam Details:
To pursue Kafka certification, it is essential to have a solid understanding of Kafka concepts, architecture, and core components. Familiarity with programming languages like Java, Python, or Scala can also be beneficial, especially for the developer-focused certification.
The exact prerequisites and exam details may vary depending on the certification provider. However, in general, the certification process typically involves the following steps:
-
Exam Registration: Register for the Kafka certification exam through the official certification provider's website. Pay attention to the registration deadlines and any specific requirements.
-
Exam Format: Kafka certification exams are usually conducted online and consist of multiple-choice questions, hands-on exercises, and scenario-based problems. The format may differ based on the certification type and level.
-
Exam Preparation: Prepare for the certification exam by studying relevant Kafka documentation, official study guides, and recommended reading materials. Hands-on experience with Kafka and practical exercises can also enhance your preparation.
-
Exam Duration and Passing Score: The duration of the Kafka certification exam can vary, typically ranging from a few hours to half a day. The passing score requirement may also differ based on the certification level and difficulty.
-
Certification Validity and Renewal: Kafka certifications are typically valid for a certain period, such as two years. To maintain an active certification status, you may need to renew it by meeting certain criteria, such as earning continuing education credits or retaking the exam.
Preparing for and obtaining Kafka certification not only validates your Kafka skills but also demonstrates your commitment to professional growth in the field of real-time data streaming and processing.
Note: While Confluent is a prominent provider of Kafka certifications, other organizations or platforms may offer their own Kafka-related certifications. It's essential to research and choose a certification that aligns with your goals and is recognized within the industry.
By obtaining Kafka certification, you can enhance your career prospects, demonstrate your expertise to potential employers or clients, and gain a competitive edge in the evolving landscape of data streaming and event-driven architectures.
Getting Started with Kafka
If you're new to Apache Kafka, getting started with this powerful distributed streaming platform can seem daunting. However, with the right guidance, you can quickly grasp the fundamentals and begin building your own Kafka-based applications. Here are the essential steps to get started with Kafka:
-
Understanding Kafka Basics:
-
-
Familiarize yourself with the core concepts of Kafka, such as topics, partitions, producers, consumers, and brokers. Understanding these fundamental building blocks is crucial for working effectively with Kafka.
-
-
Install Kafka:
-
-
Download and install Apache Kafka on your local machine or set up a Kafka cluster on multiple servers for production environments. Kafka is written in Java, so ensure you have Java installed and configured on your machine.
-
-
Start ZooKeeper:
-
-
Kafka relies on Apache ZooKeeper for cluster coordination. Start ZooKeeper by running the ZooKeeper server and configuring the necessary properties. ZooKeeper must be running before starting Kafka.
-
-
Configure Kafka:
-
-
Kafka provides various configuration options. Familiarize yourself with the configuration files, such as server.properties and producer.properties, and make any necessary modifications to suit your requirements.
-
-
Create a Topic:
-
-
A Kafka topic is a category or feed name to which messages are published. Use the Kafka command-line tools to create a topic, specifying the topic name, number of partitions, and replication factor. For example:
-
-
Produce Messages:
-
-
Kafka producers write messages to topics. Create a simple producer application using the Kafka client libraries (e.g., Java, Python) and start publishing messages to your topic. Include the necessary configuration for connecting to the Kafka cluster, specifying the topic, and sending messages.
-
-
Consume Messages:
-
-
Kafka consumers read messages from topics. Develop a consumer application using the Kafka client libraries and configure it to subscribe to the topic you created. Retrieve and process messages received from the Kafka cluster.
-
-
Explore Advanced Features:
-
-
Once you have the basic Kafka setup running, explore additional features like message serialization (e.g., Avro, JSON), message partitioning strategies, fault-tolerance mechanisms, and advanced configurations for optimizing performance.
-
-
Experiment with Kafka Streams:
-
-
Kafka Streams is a powerful stream processing library that allows you to process and analyze data in real-time. Learn how to build stream processing applications using Kafka Streams and integrate them into your Kafka-based ecosystem.
-
-
Join the Kafka Community:
-
-
Engage with the vibrant Kafka community, including forums, mailing lists, and social media channels. Participate in discussions, ask questions, and learn from experienced Kafka users and contributors.
-
-
Explore Kafka Ecosystem:
-
-
Dive into the broader Kafka ecosystem, including connectors like Kafka Connect for integrating Kafka with external systems, monitoring tools, and frameworks like Apache Spark or Apache Flink for advanced data processing.
-
Working with Kafka Producers
Kafka producers are responsible for publishing messages to Kafka topics. They play a crucial role in the data pipeline, enabling data producers to send messages to be consumed by one or more consumers. Here are the key aspects to consider when working with Kafka producers:
-
Producer Configuration:
-
-
Configure the producer properties to establish a connection with the Kafka cluster. Set properties such as bootstrap servers (the list of Kafka broker addresses), message serialization settings (key and value serializers), acknowledgments, retries, and batch sizes. Proper configuration ensures reliable and efficient message publishing.
-
-
Creating a Kafka Producer:
-
-
Create an instance of the Kafka producer by instantiating the appropriate Kafka client library (e.g., KafkaProducer in Java). Pass the relevant configuration properties to the producer constructor.
-
-
Producing Messages:
-
-
Use the producer's send() method to publish messages to Kafka topics. Messages consist of a key and a value. The key is optional and is used for partitioning purposes. The value represents the actual content of the message. Send messages synchronously or asynchronously, depending on your application's requirements.
-
-
Message Serialization:
-
-
Serialize data into the appropriate format before sending it to Kafka. Kafka handles byte arrays as messages, so use serializers to convert your data objects into byte arrays. Common serialization formats include Avro, JSON, or plain text. Ensure that you configure the appropriate key and value serializers based on your data format.
-
-
Message Partitioning:
-
-
Kafka partitions messages within a topic. By default, Kafka uses a round-robin approach to distribute messages evenly among partitions. However, you can also specify a key when sending a message to ensure that all messages with the same key go to the same partition. Understand your data distribution and key selection criteria to optimize message distribution across partitions.
-
-
Message Routing and Topic Selection:
-
-
Select the appropriate Kafka topic to publish your messages based on your application's data organization and processing requirements. Consider creating separate topics for different data sources or different types of events to maintain logical separation and enable efficient message processing.
-
-
Message Retries and Error Handling:
-
-
Handle failures and errors gracefully when producing messages. Configure appropriate retry mechanisms to handle transient failures such as network issues or temporary unavailability of brokers. Implement error handlers to catch and handle any exceptions that occur during message publication.
-
-
Message Compression:
-
-
Enable compression to reduce the size of messages being sent to Kafka, especially if your messages are large or if you have a high message throughput. Kafka supports various compression codecs (e.g., gzip, Snappy, LZ4) that can be configured on the producer to reduce network bandwidth and storage requirements.
-
-
Monitoring and Metrics:
-
-
Monitor the producer's performance and track relevant metrics. Kafka provides metrics such as message send rate, message delivery latency, and request response times. Leverage monitoring tools and frameworks like Kafka's built-in metrics or external tools to gain insights into the producer's behavior and performance.
-
-
Security Considerations:
-
-
Ensure that appropriate security measures are in place when producing messages to Kafka. This may include authentication and authorization mechanisms, encryption of data in transit, and securing access to the Kafka cluster. Consult Kafka's security documentation and best practices for implementing a secure producer setup.
-
Kafka Streams and Real-time Processing
Kafka Streams is a powerful Java library provided by Apache Kafka that enables real-time processing and analysis of data streams. It allows developers to build scalable and fault-tolerant stream processing applications that can ingest, transform, and aggregate data in real-time. Here's an overview of Kafka Streams and its role in real-time processing:
-
Introduction to Kafka Streams:
-
-
Kafka Streams provides a high-level, easy-to-use API for building real-time stream processing applications. It is built on top of Kafka, leveraging its distributed architecture, fault-tolerance, and scalability features. Kafka Streams allows developers to focus on writing stream processing logic without worrying about infrastructure complexities.
-
-
Stream Processing Basics:
-
-
In Kafka Streams, data is processed in the form of continuous streams of records. Streams can be derived from Kafka topics, and processing tasks are defined as a series of transformations applied to the input streams. Each transformation produces an output stream, allowing for a chain of processing steps.
-
-
Stream-Table Duality:
-
-
Kafka Streams introduces the concept of stream-table duality, which means that a stream can be treated as a continuously updating table and vice versa. This duality allows developers to perform joins, aggregations, and other operations on streams and tables seamlessly.
-
-
Stream Processing Operations:
-
-
Kafka Streams provides a rich set of operations for transforming and manipulating data streams. These operations include filtering, mapping, flat-mapping, grouping, aggregating, joining, windowing, and more. These operations can be combined to perform complex data processing tasks.
-
-
Windowing and Time-based Operations:
-
-
Kafka Streams supports windowing operations, allowing you to define time-based windows over data streams. Windowing operations enable calculations over fixed-duration windows, sliding windows, and tumbling windows. This feature is useful for computing real-time analytics and aggregations.
-
-
Stateful Stream Processing:
-
-
Kafka Streams provides state stores that allow stream processing applications to maintain and update state information. State stores enable tasks like maintaining counts, aggregating values, and tracking session information. Kafka Streams manages state store replication and fault-tolerance automatically.
-
-
Exactly-once Processing Semantics:
-
-
Kafka Streams guarantees exactly-once processing semantics, ensuring that each input record is processed exactly once, even in the presence of failures and system restarts. This reliability is achieved through the use of Kafka's transactional messaging and internal state management.
-
-
Integration with External Systems:
-
-
Kafka Streams provides connectors and integration capabilities with various external systems and libraries. These include integration with databases, key-value stores, message queues, and analytics frameworks like Apache Spark and Apache Flink. This allows you to easily integrate stream processing with other components of your data ecosystem.
-
-
Interactive Queries:
-
-
Kafka Streams enables interactive queries, allowing you to retrieve aggregated results and query the state maintained by the stream processing application. Interactive queries enable real-time access to the processed data, facilitating the development of interactive dashboards, APIs, and real-time analytics applications.
-
-
Scalability and Fault-tolerance:
-
-
Kafka Streams leverages Kafka's distributed architecture, allowing applications to scale horizontally by adding more instances. Kafka Streams automatically rebalances the workload across instances, ensuring fault-tolerance and high availability of the stream processing application.
-
-
Monitoring and Management:
-
-
Kafka Streams provides monitoring capabilities and integration with monitoring tools like Kafka's built-in metrics, JMX, and third-party monitoring systems. These tools enable you to monitor the health, performance, and throughput of your stream processing applications.
-
Best Practices for Kafka Development
Developing applications using Apache Kafka requires careful consideration of various aspects to ensure optimal performance, reliability, and scalability. Here are some best practices to follow when working with Kafka:
-
Design Data Schema and Message Formats:
-
-
Plan and design your data schema and message formats carefully. Choose appropriate serialization formats (such as Avro, JSON, or Protobuf) that strike a balance between data size and ease of processing. Ensure backward compatibility as your data schema evolves.
-
-
Topic Naming and Organization:
-
-
Establish a consistent and meaningful naming convention for your Kafka topics. Consider organizing topics based on data sources, data types, or event types to maintain logical separation and ease of management. Avoid creating a large number of unnecessary topics.
-
-
Proper Partitioning Strategy:
-
-
Choose an effective partitioning strategy for your topics. Consider factors such as data distribution, message ordering requirements, and scalability. Distribute messages evenly across partitions to ensure balanced workloads and avoid hotspots.
-
-
Sizing and Resource Allocation:
-
-
Estimate the expected message throughput, data volume, and retention policy to determine the appropriate sizing and resource allocation for your Kafka cluster. Consider factors such as CPU, memory, and disk space to handle the anticipated workload effectively.
-
-
Use Compression:
-
-
Enable compression for message payloads, especially if your messages are large or if you have a high message throughput. Compression reduces network bandwidth usage, improves throughput, and reduces storage requirements.
-
-
Configure Replication:
-
-
Set an appropriate replication factor for your topics. Replicating data across multiple brokers ensures fault-tolerance and high availability. Consider the trade-off between durability and resource utilization when configuring replication.
-
-
Monitor Consumer Lag:
-
-
Keep track of consumer lag, which measures the delay between producing messages and consuming them. Monitor lag metrics to identify any performance bottlenecks or issues with consumer processing. Lag can be monitored using Kafka consumer offsets and Kafka monitoring tools.
-
-
Handle Consumer Offset Management:
-
-
Manage consumer offsets properly to ensure message ordering and avoid data duplication. Use Kafka's built-in offset management or external offset management systems like Apache Kafka's Consumer Offset Committer API. Handle offset commits based on your application's processing guarantees.
-
-
Implement Error Handling and Retry Mechanisms:
-
-
Build robust error handling and retry mechanisms in your Kafka applications. Handle exceptions and errors gracefully to ensure reliable message processing. Implement retry strategies for transient failures, such as network errors or temporary unavailability of brokers.
-
-
Security Considerations:
-
-
Implement appropriate security measures to protect your Kafka cluster and data. Secure network connections with SSL/TLS encryption, authenticate clients, and authorize access to topics and resources. Follow Kafka's security best practices to prevent unauthorized access and data breaches.
-
-
Monitor and Tune Performance:
-
-
Implement monitoring and performance tuning practices to optimize the performance of your Kafka cluster. Monitor key metrics such as message throughput, latency, disk usage, and resource utilization. Tune Kafka configurations based on workload patterns and requirements.
-
-
Test and Validate:
-
-
Thoroughly test your Kafka applications before deploying them to production. Conduct load testing, performance testing, and end-to-end testing to validate the behavior and performance of your applications under various scenarios. Use tools like Kafka's integrated testing framework or external testing frameworks.
-
-
Upgrade and Maintain:
-
-
Keep your Kafka cluster up to date by regularly upgrading to the latest stable version. Stay informed about bug fixes, performance improvements, and new features. Monitor release notes and follow upgrade best practices to ensure a smooth upgrade process.
-
Preparing for Kafka Certification Exam
Preparing for a Kafka certification exam requires a comprehensive understanding of Kafka's concepts, features, architecture, and practical use cases. Here are some steps you can follow to prepare effectively:
-
Review Kafka Documentation:
-
-
Start by thoroughly reading the official Apache Kafka documentation. Familiarize yourself with the core concepts, terminology, and components of Kafka. Pay close attention to topics such as producers, consumers, brokers, topics, partitions, replication, and fault-tolerance.
-
-
Understand Kafka Architecture:
-
-
Dive deep into Kafka's architecture and how it works. Study the role of ZooKeeper in Kafka, the responsibilities of brokers, and the interaction between producers and consumers. Understand how Kafka handles data storage, partitioning, and replication for high availability and fault tolerance.
-
-
Learn Kafka APIs and Tools:
-
-
Gain hands-on experience with Kafka's APIs and command-line tools. Practice using the Kafka Producer API and Consumer API to publish and consume messages. Familiarize yourself with the Kafka Streams API for stream processing. Explore tools like Kafka Connect for data integration and Kafka MirrorMaker for replication.
-
-
Explore Real-World Use Cases:
-
-
Study real-world use cases and architectural patterns where Kafka is commonly used. Understand how Kafka facilitates event streaming, data pipelines, real-time analytics, microservices communication, and log aggregation. Learn how to design Kafka-based solutions for various scenarios.
-
-
Practice with Kafka Cluster Setup:
-
-
Set up a Kafka cluster on your local machine or a test environment. Configure brokers, ZooKeeper, and topics. Experiment with different configurations, replication factors, and partitioning strategies. Practice scaling the cluster, handling failures, and managing topics and consumer groups.
-
-
Study Kafka Streams and Stream Processing:
-
-
Explore Kafka Streams and its APIs for stream processing. Understand windowing operations, stateful processing, aggregations, and joins. Study the concepts of stream-table duality and interactive queries. Practice building simple stream processing applications with Kafka Streams.
-
-
Review Kafka Security:
-
-
Familiarize yourself with Kafka's security features and best practices. Learn about authentication, authorization, SSL/TLS encryption, and encryption at rest. Understand how to configure and secure your Kafka cluster to protect against unauthorized access and data breaches.
-
-
Take Sample Exams and Practice Tests:
-
-
Look for sample Kafka certification exams or practice tests available online. These resources can help you assess your knowledge and identify areas that require further study. Practice answering exam-style questions to get familiar with the exam format and time management.
-
-
Join Kafka Communities and Forums:
-
-
Engage with the Kafka community by joining forums, discussion groups, and mailing lists. Participate in discussions, ask questions, and learn from experienced Kafka users and experts. Collaborating with others can enhance your understanding and provide valuable insights.
-
-
Hands-on Projects and Practical Experience:
-
-
Gain practical experience by working on Kafka projects or contributing to open-source Kafka-related initiatives. Implement end-to-end Kafka solutions, build data pipelines, and develop stream processing applications. Practical experience will solidify your understanding and improve your problem-solving skills.
-
How to obtain Apache Kafka certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: SMAC Certication
-
Big Data: Big Data and Hadoop Administrator
-
Digital Marketing : Digital Marketing Certification
-
Data Science : Apache Kafka Certification
Conclusion
In conclusion, Apache Kafka is a powerful distributed streaming platform that enables reliable and scalable real-time data processing. Whether you're a developer, architect, or data professional, gaining expertise in Kafka can significantly enhance your skills and open up new opportunities in the world of data streaming and event-driven architectures.
Throughout this blog, we have explored various subtopics related to Apache Kafka certification training. We covered essential areas such as an introduction to Apache Kafka, understanding Kafka certification, getting started with Kafka, Kafka messaging concepts, Kafka cluster setup and configuration, working with Kafka producers, Kafka Streams and real-time processing, and best practices for Kafka development. Each subtopic provides valuable insights and knowledge to help you excel in your Kafka journey.
By familiarizing yourself with Kafka's core concepts, architecture, and practical aspects, you can confidently navigate Kafka's ecosystem and effectively leverage its capabilities. Whether it's understanding Kafka's messaging model, designing Kafka-based solutions, or optimizing performance and scalability, a strong foundation in Kafka is crucial.
Remember to supplement your learning with hands-on experience, practical projects, and engaging with the Kafka community. Continuous learning, staying updated with the latest features and enhancements, and exploring real-world use cases will help you master Kafka and succeed in your Kafka certification exam.
Embrace the power of Kafka as you embark on your certification journey, and leverage its capabilities to build robust data pipelines, real-time analytics, and event-driven applications. With Kafka's scalability, fault-tolerance, and high-throughput capabilities, you can unlock the potential of real-time data processing and create innovative solutions that drive your organization forward.
Best of luck in your Kafka certification training and future endeavors with Apache Kafka!
The Essential Guide to Becoming a Certified Information Systems Security Professional
In today's digital age, information security has become a critical concern for businesses and organizations of all sizes. As technology continues to evolve, so do the threats to data security, making it essential to have professionals who can protect against these risks. One such professional certification is the Certified Information Systems Security Professional (CISSP), which is globally recognized as a standard for information security expertise. The CISSP certification provides numerous benefits, including career advancement opportunities, increased earning potential, and enhanced credibility within the information security industry. In this topic, we will explore the various advantages of the CISSP certification in detail, giving you a comprehensive understanding of the benefits it provides to both individuals and organizations.
Table of Contents
CISSP Exam
CISSP Exam Eligibility Criteria
CISSP Exam Course Syllabus
CISSP Exam Preparation
Maintaining CISSP Certificatrion
Benefits of CISSP Certification
Conclusion
CISSP Exam
The CISSP exam is a globally recognized certification examination for information security professionals. It is designed to test the knowledge and skills required to effectively design, implement, and manage an organization's information security program. The exam covers a wide range of topics, including security and risk management, asset security, security architecture and engineering, communication and network security, identity and access management, security assessment and testing, security operations, and software development security.
The CISSP exam consists of 250 multiple-choice questions, and candidates have six hours to complete it. To pass the exam, candidates must score at least 700 out of 1000 points. The exam is computer-based and is administered by Pearson VUE testing centers globally.
Obtaining the CISSP certification requires more than just passing the exam. Candidates must also meet specific experience and educational requirements and agree to abide by the (ISC)² code of ethics. Once certified, individuals must maintain their certification by earning Continuing Professional Education (CPE) credits and paying an annual maintenance fee.
The CISSP certification is widely recognized as a mark of excellence in the information security industry and is highly valued by employers. It can lead to increased job opportunities, higher salaries, and greater credibility as an information security professional.
CISSP Exam Eligibility Criteria
To be eligible to take the CISSP exam, candidates must meet specific experience and educational requirements. The International Information System Security Certification Consortium, or (ISC)², is responsible for administering the CISSP exam and setting the eligibility criteria. The following are the eligibility criteria for the CISSP exam:
- Work Experience: Candidates must have a minimum of five years of professional work experience in two or more of the eight domains of the CISSP Common Body of Knowledge (CBK). Candidates with a four-year college degree or regional equivalent or higher can substitute one year of experience for the five-year requirement.
- Educational Background: Candidates must have a four-year college degree or regional equivalent or higher, or an additional credential from (ISC)² approved list that satisfies the one-year experience requirement. If the candidate does not have a four-year college degree, then he/she must have a minimum of six years of professional work experience in two or more of the eight domains of the CISSP CBK.
- Code of Ethics: Candidates must subscribe to the (ISC)² code of ethics and agree to abide by it.
- Endorsement: Candidates must be endorsed by an (ISC)² member in good standing who can attest to their professional experience and ethics.
CISSP Exam Course Syllabus
The CISSP exam covers a wide range of topics related to information security. The following is the official CISSP course syllabus, which outlines the eight domains of the CISSP Common Body of Knowledge (CBK):
- Security and Risk Management: This domain covers topics such as security governance, compliance, legal and regulatory issues, risk management, and business continuity.
- Asset Security: This domain covers topics such as data classification, privacy protection, asset retention, and secure handling.
- Security Architecture and Engineering: This domain covers topics such as system architecture design, security models, security capabilities, and secure design principles.
- Communication and Network Security: This domain covers topics such as network protocols, network devices, secure communication channels, and network architecture.
- Identity and Access Management: This domain covers topics such as access control, identity verification, authentication, and authorization.
- Security Assessment and Testing: This domain covers topics such as security assessment, vulnerability testing, penetration testing, and security audit.
- Security Operations: This domain covers topics such as incident response, disaster recovery, security operations center, and physical security.
- Software Development Security: This domain covers topics such as software development life cycle, secure coding practices, software testing, and software deployment.
The CISSP exam requires candidates to have a comprehensive understanding of each domain, including the relevant concepts, principles, and best practices. It is essential to study the syllabus thoroughly and supplement it with additional study materials to prepare effectively for the exam.
CISSP Exam Preparation:
- Understanding the CISSP Exam:
-
- Overview of the CISSP exam structure, format, and duration
- Number of questions and passing score requirements
- Importance of understanding the exam domains and objectives
- Creating a Study Plan:
-
- Developing a personalized study plan based on your strengths and weaknesses
- Setting realistic goals and milestones for exam preparation
- Allocating time for each CISSP domain and topic
- Recommended Study Resources:
-
- Reviewing official CISSP study materials and guides
- Exploring CISSP textbooks, reference books, and online resources
- Utilizing CISSP exam prep courses and boot camps
- Practice Exams and Mock Tests:
-
- Importance of practicing with sample questions and mock exams
- Accessing CISSP practice tests and exam simulators
- Analyzing and understanding the rationale behind correct and incorrect answers
- Domains and Knowledge Areas:
-
- Breaking down each CISSP domain and its subtopics
- Identifying key concepts, theories, and best practices within each domain
- Strategies for comprehending and retaining complex information
- Study Techniques and Strategies:
-
- Effective note-taking methods during study sessions
- Utilizing flashcards and mnemonic devices to aid memorization
- Developing critical thinking and problem-solving skills for scenario-based questions
- Time Management Tips:
-
- Allocating study time based on the weightage of each CISSP domain
- Balancing study commitments with work and personal life
- Techniques for maintaining focus and avoiding distractions
- Joining Study Groups and Communities:
-
- Benefits of studying with peers and sharing knowledge
- Online forums, social media groups, and CISSP study communities
- Engaging in discussions and exchanging insights and resources
- Seeking Professional Guidance:
-
- Engaging with CISSP-certified professionals for mentorship and advice
- Attending local CISSP study groups or networking events
- Connecting with industry experts through online platforms
Maintaining CISSP Certification:
Maintaining CISSP certification requires ongoing professional development and active engagement in the field of information security. Here are some key points to cover when discussing how to maintain CISSP certification:
- Continuing Professional Education (CPE) Requirements:
-
- Overview of the CPE program and its purpose
- Explanation of the CPE credit system
- Required number of CPE credits for CISSP maintenance
- Different categories of CPE activities (e.g., education, professional contributions)
- Guidelines for earning and reporting CPE credits
- Types of CPE Activities:
-
- Participating in information security conferences, seminars, and workshops
- Completing relevant training courses and certifications
- Writing articles, books, or blog posts on information security topics
- Presenting or speaking at industry events or webinars
- Contributing to information security research or publications
- Engaging in professional mentoring or coaching activities
- Recording and Documenting CPE Activities:
-
- Keeping track of CPE activities and documentation
- Understanding the CPE submission and audit process
- Recommended tools or systems for tracking CPE credits
- Importance of maintaining accurate records for audit purposes
- Staying Current with Industry Developments:
-
- Importance of staying updated with emerging trends and technologies
- Engaging in continuous learning through reading industry publications and research papers
- Following reputable information security blogs, forums, and online communities
- Subscribing to industry newsletters or mailing lists
- Joining professional organizations or associations related to information security
- Engaging in Professional Networking:
-
- Participating in local or virtual information security groups or chapters
- Attending industry conferences and events
- Joining online communities or forums to connect with peers
- Engaging in discussions on social media platforms
- Building professional relationships and sharing knowledge with other CISSP-certified professionals
- Renewal Process and Timelines:
-
- Understanding the renewal process and deadlines for CISSP certification
- Explaining the importance of timely renewal to maintain active status
- Tips for planning and managing the renewal process effectively
- Benefits of Maintaining CISSP Certification:
-
- Professional credibility and recognition in the field of information security
- Enhanced career opportunities and advancement
- Access to a network of CISSP-certified professionals for collaboration and support
- Continued access to valuable resources and updates from (ISC)²
Benefits of CISSP Certification
The CISSP (Certified Information Systems Security Professional) certification is globally recognized as a standard for information security expertise. Obtaining the CISSP certification provides numerous benefits, including:
- Career Advancement: The CISSP certification is highly valued by employers and can lead to career advancement opportunities. It demonstrates a high level of expertise in information security and can make you stand out in a crowded job market.
- Higher Earning Potential: Certified professionals typically earn higher salaries than non-certified professionals. According to (ISC)², CISSP certified professionals earn an average salary of $131,030 per year, making it one of the most lucrative certifications in the information security industry.
- Enhanced Credibility: The CISSP certification is widely recognized as a mark of excellence in the information security industry. It enhances your credibility as an information security professional and can lead to increased respect from colleagues and peers.
- Global Recognition: The CISSP certification is recognized globally and is highly valued by employers and organizations worldwide. It can lead to job opportunities in different countries and can make you an attractive candidate for international assignments.
- Continuing Professional Education: Once certified, individuals must maintain their certification by earning Continuing Professional Education (CPE) credits. This ensures that certified professionals stay up-to-date with the latest developments and trends in information security, enhancing their knowledge and skills.
- Membership to Professional Network: The CISSP certification provides access to a global network of information security professionals through membership to (ISC)². This allows you to connect with peers, share knowledge, and stay current with industry best practices.
In conclusion, obtaining the CISSP certification provides numerous benefits that can enhance your career, increase your earning potential, and improve your credibility as an information security professional. It is a valuable investment that can pay off in the long run and open up a world of opportunities in the information security industry.
Renewal Process and Timelines
The renewal process for CISSP certification involves meeting certain requirements and submitting the necessary documentation to maintain an active certification status. Here's an overview of the renewal process and timelines:
- Certification Cycle:
-
- CISSP certification is valid for three years.
- The certification cycle begins on the date when you pass the CISSP exam.
- Continuing Professional Education (CPE) Requirements:
-
- CISSP-certified professionals must earn and report a specific number of CPE credits within the three-year certification cycle to renew their certification.
- The exact number of required CPE credits may vary based on your geographic location and any additional (ISC)² policies.
- CPE Credit Requirements:
-
- CISSP holders must earn a total of 120 CPE credits over the three-year certification cycle.
- At least 20 CPE credits must be earned each year of the cycle to meet the annual minimum requirement.
- Of the 120 total credits, a minimum of 40 credits must be earned from Group A activities, which are related to CISSP domains.
- The remaining credits can be earned from Group A or Group B activities, which are broader professional development activities.
- Group A and Group B Activities:
-
- Group A activities are directly related to the CISSP Common Body of Knowledge (CBK) domains and include activities such as attending training courses, conferences, webinars, or writing articles focused on CISSP topics.
- Group B activities are more general professional development activities and may include attending general industry conferences, completing non-CISSP certifications, or teaching information security courses.
- Documenting and Reporting CPE Credits:
-
- CISSP-certified professionals are responsible for maintaining accurate records of their CPE activities.
- (ISC)² provides an online tool called the Continuing Professional Education (CPE) portal where you can log your activities and submit CPE credits.
- Documentation such as certificates of completion, attendance records, or other supporting evidence may be required during audits.
- Renewal Application and Fees:
-
- At the end of the three-year certification cycle, CISSP holders must submit a renewal application to (ISC)² and pay the applicable renewal fee.
- The renewal application typically includes confirming adherence to the (ISC)² Code of Ethics and submitting the CPE credits earned during the certification cycle.
- Timelines:
-
- It is important to plan ahead and monitor the expiration date of your CISSP certification to ensure a smooth renewal process.
- (ISC)² allows CISSP holders to begin earning CPE credits as soon as they pass the exam, even before the official certification is granted.
- (ISC)² provides a grace period of up to 90 days after the certification expiration date to complete the renewal process, but during this period, your certification status is considered inactive.
How to obtain Certified Information Systems Security certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: SMAC Certication
- Big Data: Big Data and Hadoop Administrator
- Digital Marketing : Digital Marketing Certification
- Data Science : Power BI Certification
- Cyber Security : Certified information systems security Profession Certification
Conclusion
In conclusion, "The Essential Guide to Becoming a Certified Information Systems Security Professional" provides a comprehensive and invaluable resource for individuals aiming to pursue the CISSP certification. This guide not only covers the essential knowledge required to pass the CISSP exam but also delves into the eligibility criteria, course syllabus, and preparation strategies necessary to excel in the certification process. It emphasizes the importance of maintaining the CISSP certification through continuous professional development, keeping up with the evolving field of information security. Moreover, the guide highlights the numerous benefits of obtaining the CISSP certification, including increased career opportunities, industry recognition, and the ability to effectively safeguard organizations from cyber threats. By utilizing this guide, individuals can confidently embark on their journey to become a Certified Information Systems Security Professional and unlock the many advantages that this certification offers.
Read More
In today's digital age, information security has become a critical concern for businesses and organizations of all sizes. As technology continues to evolve, so do the threats to data security, making it essential to have professionals who can protect against these risks. One such professional certification is the Certified Information Systems Security Professional (CISSP), which is globally recognized as a standard for information security expertise. The CISSP certification provides numerous benefits, including career advancement opportunities, increased earning potential, and enhanced credibility within the information security industry. In this topic, we will explore the various advantages of the CISSP certification in detail, giving you a comprehensive understanding of the benefits it provides to both individuals and organizations.
Table of Contents
CISSP Exam
CISSP Exam Eligibility Criteria
CISSP Exam Course Syllabus
CISSP Exam Preparation
Maintaining CISSP Certificatrion
Benefits of CISSP Certification
Conclusion
CISSP Exam
The CISSP exam is a globally recognized certification examination for information security professionals. It is designed to test the knowledge and skills required to effectively design, implement, and manage an organization's information security program. The exam covers a wide range of topics, including security and risk management, asset security, security architecture and engineering, communication and network security, identity and access management, security assessment and testing, security operations, and software development security.
The CISSP exam consists of 250 multiple-choice questions, and candidates have six hours to complete it. To pass the exam, candidates must score at least 700 out of 1000 points. The exam is computer-based and is administered by Pearson VUE testing centers globally.
Obtaining the CISSP certification requires more than just passing the exam. Candidates must also meet specific experience and educational requirements and agree to abide by the (ISC)² code of ethics. Once certified, individuals must maintain their certification by earning Continuing Professional Education (CPE) credits and paying an annual maintenance fee.
The CISSP certification is widely recognized as a mark of excellence in the information security industry and is highly valued by employers. It can lead to increased job opportunities, higher salaries, and greater credibility as an information security professional.
CISSP Exam Eligibility Criteria
To be eligible to take the CISSP exam, candidates must meet specific experience and educational requirements. The International Information System Security Certification Consortium, or (ISC)², is responsible for administering the CISSP exam and setting the eligibility criteria. The following are the eligibility criteria for the CISSP exam:
- Work Experience: Candidates must have a minimum of five years of professional work experience in two or more of the eight domains of the CISSP Common Body of Knowledge (CBK). Candidates with a four-year college degree or regional equivalent or higher can substitute one year of experience for the five-year requirement.
- Educational Background: Candidates must have a four-year college degree or regional equivalent or higher, or an additional credential from (ISC)² approved list that satisfies the one-year experience requirement. If the candidate does not have a four-year college degree, then he/she must have a minimum of six years of professional work experience in two or more of the eight domains of the CISSP CBK.
- Code of Ethics: Candidates must subscribe to the (ISC)² code of ethics and agree to abide by it.
- Endorsement: Candidates must be endorsed by an (ISC)² member in good standing who can attest to their professional experience and ethics.
CISSP Exam Course Syllabus
The CISSP exam covers a wide range of topics related to information security. The following is the official CISSP course syllabus, which outlines the eight domains of the CISSP Common Body of Knowledge (CBK):
- Security and Risk Management: This domain covers topics such as security governance, compliance, legal and regulatory issues, risk management, and business continuity.
- Asset Security: This domain covers topics such as data classification, privacy protection, asset retention, and secure handling.
- Security Architecture and Engineering: This domain covers topics such as system architecture design, security models, security capabilities, and secure design principles.
- Communication and Network Security: This domain covers topics such as network protocols, network devices, secure communication channels, and network architecture.
- Identity and Access Management: This domain covers topics such as access control, identity verification, authentication, and authorization.
- Security Assessment and Testing: This domain covers topics such as security assessment, vulnerability testing, penetration testing, and security audit.
- Security Operations: This domain covers topics such as incident response, disaster recovery, security operations center, and physical security.
- Software Development Security: This domain covers topics such as software development life cycle, secure coding practices, software testing, and software deployment.
The CISSP exam requires candidates to have a comprehensive understanding of each domain, including the relevant concepts, principles, and best practices. It is essential to study the syllabus thoroughly and supplement it with additional study materials to prepare effectively for the exam.
CISSP Exam Preparation:
- Understanding the CISSP Exam:
-
- Overview of the CISSP exam structure, format, and duration
- Number of questions and passing score requirements
- Importance of understanding the exam domains and objectives
- Creating a Study Plan:
-
- Developing a personalized study plan based on your strengths and weaknesses
- Setting realistic goals and milestones for exam preparation
- Allocating time for each CISSP domain and topic
- Recommended Study Resources:
-
- Reviewing official CISSP study materials and guides
- Exploring CISSP textbooks, reference books, and online resources
- Utilizing CISSP exam prep courses and boot camps
- Practice Exams and Mock Tests:
-
- Importance of practicing with sample questions and mock exams
- Accessing CISSP practice tests and exam simulators
- Analyzing and understanding the rationale behind correct and incorrect answers
- Domains and Knowledge Areas:
-
- Breaking down each CISSP domain and its subtopics
- Identifying key concepts, theories, and best practices within each domain
- Strategies for comprehending and retaining complex information
- Study Techniques and Strategies:
-
- Effective note-taking methods during study sessions
- Utilizing flashcards and mnemonic devices to aid memorization
- Developing critical thinking and problem-solving skills for scenario-based questions
- Time Management Tips:
-
- Allocating study time based on the weightage of each CISSP domain
- Balancing study commitments with work and personal life
- Techniques for maintaining focus and avoiding distractions
- Joining Study Groups and Communities:
-
- Benefits of studying with peers and sharing knowledge
- Online forums, social media groups, and CISSP study communities
- Engaging in discussions and exchanging insights and resources
- Seeking Professional Guidance:
-
- Engaging with CISSP-certified professionals for mentorship and advice
- Attending local CISSP study groups or networking events
- Connecting with industry experts through online platforms
Maintaining CISSP Certification:
Maintaining CISSP certification requires ongoing professional development and active engagement in the field of information security. Here are some key points to cover when discussing how to maintain CISSP certification:
- Continuing Professional Education (CPE) Requirements:
-
- Overview of the CPE program and its purpose
- Explanation of the CPE credit system
- Required number of CPE credits for CISSP maintenance
- Different categories of CPE activities (e.g., education, professional contributions)
- Guidelines for earning and reporting CPE credits
- Types of CPE Activities:
-
- Participating in information security conferences, seminars, and workshops
- Completing relevant training courses and certifications
- Writing articles, books, or blog posts on information security topics
- Presenting or speaking at industry events or webinars
- Contributing to information security research or publications
- Engaging in professional mentoring or coaching activities
- Recording and Documenting CPE Activities:
-
- Keeping track of CPE activities and documentation
- Understanding the CPE submission and audit process
- Recommended tools or systems for tracking CPE credits
- Importance of maintaining accurate records for audit purposes
- Staying Current with Industry Developments:
-
- Importance of staying updated with emerging trends and technologies
- Engaging in continuous learning through reading industry publications and research papers
- Following reputable information security blogs, forums, and online communities
- Subscribing to industry newsletters or mailing lists
- Joining professional organizations or associations related to information security
- Engaging in Professional Networking:
-
- Participating in local or virtual information security groups or chapters
- Attending industry conferences and events
- Joining online communities or forums to connect with peers
- Engaging in discussions on social media platforms
- Building professional relationships and sharing knowledge with other CISSP-certified professionals
- Renewal Process and Timelines:
-
- Understanding the renewal process and deadlines for CISSP certification
- Explaining the importance of timely renewal to maintain active status
- Tips for planning and managing the renewal process effectively
- Benefits of Maintaining CISSP Certification:
-
- Professional credibility and recognition in the field of information security
- Enhanced career opportunities and advancement
- Access to a network of CISSP-certified professionals for collaboration and support
- Continued access to valuable resources and updates from (ISC)²
Benefits of CISSP Certification
The CISSP (Certified Information Systems Security Professional) certification is globally recognized as a standard for information security expertise. Obtaining the CISSP certification provides numerous benefits, including:
- Career Advancement: The CISSP certification is highly valued by employers and can lead to career advancement opportunities. It demonstrates a high level of expertise in information security and can make you stand out in a crowded job market.
- Higher Earning Potential: Certified professionals typically earn higher salaries than non-certified professionals. According to (ISC)², CISSP certified professionals earn an average salary of $131,030 per year, making it one of the most lucrative certifications in the information security industry.
- Enhanced Credibility: The CISSP certification is widely recognized as a mark of excellence in the information security industry. It enhances your credibility as an information security professional and can lead to increased respect from colleagues and peers.
- Global Recognition: The CISSP certification is recognized globally and is highly valued by employers and organizations worldwide. It can lead to job opportunities in different countries and can make you an attractive candidate for international assignments.
- Continuing Professional Education: Once certified, individuals must maintain their certification by earning Continuing Professional Education (CPE) credits. This ensures that certified professionals stay up-to-date with the latest developments and trends in information security, enhancing their knowledge and skills.
- Membership to Professional Network: The CISSP certification provides access to a global network of information security professionals through membership to (ISC)². This allows you to connect with peers, share knowledge, and stay current with industry best practices.
In conclusion, obtaining the CISSP certification provides numerous benefits that can enhance your career, increase your earning potential, and improve your credibility as an information security professional. It is a valuable investment that can pay off in the long run and open up a world of opportunities in the information security industry.
Renewal Process and Timelines
The renewal process for CISSP certification involves meeting certain requirements and submitting the necessary documentation to maintain an active certification status. Here's an overview of the renewal process and timelines:
- Certification Cycle:
-
- CISSP certification is valid for three years.
- The certification cycle begins on the date when you pass the CISSP exam.
- Continuing Professional Education (CPE) Requirements:
-
- CISSP-certified professionals must earn and report a specific number of CPE credits within the three-year certification cycle to renew their certification.
- The exact number of required CPE credits may vary based on your geographic location and any additional (ISC)² policies.
- CPE Credit Requirements:
-
- CISSP holders must earn a total of 120 CPE credits over the three-year certification cycle.
- At least 20 CPE credits must be earned each year of the cycle to meet the annual minimum requirement.
- Of the 120 total credits, a minimum of 40 credits must be earned from Group A activities, which are related to CISSP domains.
- The remaining credits can be earned from Group A or Group B activities, which are broader professional development activities.
- Group A and Group B Activities:
-
- Group A activities are directly related to the CISSP Common Body of Knowledge (CBK) domains and include activities such as attending training courses, conferences, webinars, or writing articles focused on CISSP topics.
- Group B activities are more general professional development activities and may include attending general industry conferences, completing non-CISSP certifications, or teaching information security courses.
- Documenting and Reporting CPE Credits:
-
- CISSP-certified professionals are responsible for maintaining accurate records of their CPE activities.
- (ISC)² provides an online tool called the Continuing Professional Education (CPE) portal where you can log your activities and submit CPE credits.
- Documentation such as certificates of completion, attendance records, or other supporting evidence may be required during audits.
- Renewal Application and Fees:
-
- At the end of the three-year certification cycle, CISSP holders must submit a renewal application to (ISC)² and pay the applicable renewal fee.
- The renewal application typically includes confirming adherence to the (ISC)² Code of Ethics and submitting the CPE credits earned during the certification cycle.
- Timelines:
-
- It is important to plan ahead and monitor the expiration date of your CISSP certification to ensure a smooth renewal process.
- (ISC)² allows CISSP holders to begin earning CPE credits as soon as they pass the exam, even before the official certification is granted.
- (ISC)² provides a grace period of up to 90 days after the certification expiration date to complete the renewal process, but during this period, your certification status is considered inactive.
How to obtain Certified Information Systems Security certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: SMAC Certication
- Big Data: Big Data and Hadoop Administrator
- Digital Marketing : Digital Marketing Certification
- Data Science : Power BI Certification
- Cyber Security : Certified information systems security Profession Certification
Conclusion
In conclusion, "The Essential Guide to Becoming a Certified Information Systems Security Professional" provides a comprehensive and invaluable resource for individuals aiming to pursue the CISSP certification. This guide not only covers the essential knowledge required to pass the CISSP exam but also delves into the eligibility criteria, course syllabus, and preparation strategies necessary to excel in the certification process. It emphasizes the importance of maintaining the CISSP certification through continuous professional development, keeping up with the evolving field of information security. Moreover, the guide highlights the numerous benefits of obtaining the CISSP certification, including increased career opportunities, industry recognition, and the ability to effectively safeguard organizations from cyber threats. By utilizing this guide, individuals can confidently embark on their journey to become a Certified Information Systems Security Professional and unlock the many advantages that this certification offers.
CRISC Certification Training: A Comprehensive Overview of Benefits and Career Paths
In today's digital age, organizations are constantly facing new and complex information security challenges. To mitigate these risks, they need skilled professionals who can identify and manage these risks effectively. This is where the Certified in Risk and Information Systems Control (CRISC) certification comes in.
CRISC is a globally recognized certification that validates an individual's expertise in identifying, assessing, and evaluating information systems and technology risks. It is awarded by the Information Systems Audit and Control Association (ISACA) and is designed for IT professionals who are responsible for managing IT and business risks.
In this article, we will provide an overview of CRISC certification training, including its benefits and the career path it can lead to. Whether you're an experienced IT professional or just starting out in your career, understanding the value of CRISC certification can help you take your career to the next level.
Table of Contents
What Is a CRISC Certification?
Why Is CRISC Important?
How Do You Get CRISC Certification?
How Much Is the CRISC Exam?
What Are the Domains in the Context of the CRISC Exam? How Hard is the CRISC Exam?
CRISC Job Opportunities and Salary
Some Useful Certifications for CRISC
Conclusion
What Is a CRISC Certification?
The Certified in Risk and Information Systems Control (CRISC) certification is a globally recognized certification awarded by the Information Systems Audit and Control Association (ISACA). The certification validates an individual's expertise in identifying, assessing, and evaluating information systems and technology risks.
To earn the CRISC certification, an individual must pass a rigorous exam that covers four domains:
- IT Risk Identification
- IT Risk Assessment
- Risk Response and Mitigation
- Risk and Control Monitoring and Reporting
In addition to passing the exam, individuals must also have at least three years of relevant work experience in at least two of the four CRISC domains, with at least one year of experience in the CRISC focus area. They must also adhere to the ISACA Code of Professional Ethics.
The CRISC certification is designed for IT professionals who are responsible for managing IT and business risks, including IT auditors, risk management professionals, business analysts, compliance professionals, and security professionals. It is recognized globally and can help individuals advance their careers in IT risk management.
Why Is CRISC Important?
The Certified in Risk and Information Systems Control (CRISC) certification is important for several reasons:
- Validates expertise in IT risk management: CRISC certification validates an individual's expertise in identifying, assessing, and evaluating information systems and technology risks. It demonstrates that the individual has a strong understanding of the principles and practices of IT risk management and can effectively manage risks in an organization.
- Globally recognized: CRISC certification is globally recognized and respected in the field of IT risk management. It is awarded by the Information Systems Audit and Control Association (ISACA), which is a well-respected professional organization for IT auditors and security professionals.
- Competitive advantage: CRISC certification can give IT professionals a competitive advantage in the job market. It demonstrates to employers that the individual has the skills and knowledge needed to effectively manage IT risks and can provide value to the organization.
- Improved career prospects: CRISC certification can open up new career opportunities for IT professionals. It can lead to higher-paying jobs and positions with greater responsibility, such as IT risk managers or IT security directors.
- Risk management best practices: CRISC certification provides individuals with a deep understanding of IT risk management best practices. This knowledge can help individuals improve their organization's risk management processes and better protect their organization's information assets.
How Do You Get CRISC Certification?
To obtain the Certified in Risk and Information Systems Control (CRISC) certification, individuals must follow the certification process established by the Information Systems Audit and Control Association (ISACA), which includes the following steps:
- Meet the eligibility requirements: To be eligible for CRISC certification, individuals must have at least three years of relevant work experience in at least two of the four CRISC domains, with at least one year of experience in the CRISC focus area. Alternatively, individuals can substitute certain educational or other professional experience for up to two years of work experience.
- Register for the CRISC exam: Once eligible, individuals can register for the CRISC exam through the ISACA website. The exam consists of 150 multiple-choice questions and covers the four CRISC domains: IT Risk Identification, IT Risk Assessment, Risk Response and Mitigation, and Risk and Control Monitoring and Reporting.
- Prepare for the exam: ISACA provides various resources to help individuals prepare for the CRISC exam, including study materials, review courses, and practice exams. Individuals can also choose to attend a CRISC training course provided by an ISACA-accredited training provider.
- Pass the exam: To obtain CRISC certification, individuals must pass the CRISC exam with a score of at least 450 out of 800.
- Adhere to the Code of Professional Ethics: CRISC certification holders must adhere to the ISACA Code of Professional Ethics, which includes standards of conduct, integrity, and objectivity.
- Maintain the certification: CRISC certification holders must maintain their certification by earning and reporting continuing professional education (CPE) credits. They must earn and report 20 CPE credits annually and 120 CPE credits over a three-year reporting period.
How Much Is the CRISC Exam?
The cost of the Certified in Risk and Information Systems Control (CRISC) exam varies depending on whether an individual is a member of the Information Systems Audit and Control Association (ISACA) and when they register for the exam. As of May 2023, the exam fees are:
- Early registration exam fee for ISACA members: $660
- Early registration exam fee for non-ISACA members: $925
- Standard registration exam fee for ISACA members: $760
- Standard registration exam fee for non-ISACA members: $1,025
ISACA offers early registration discounts to individuals who register for the exam early. Early registration typically begins in late January or early February for the May-June exam window and in late July or early August for the September-October exam window. Standard registration typically begins about two weeks after early registration ends.
It's important to note that these fees are subject to change, and individuals should check the ISACA website for the most up-to-date information on exam fees and registration deadlines. Additionally, there may be additional costs associated with preparing for the exam, such as study materials, training courses, and practice exams.
What Are the Domains in the Context of the CRISC Exam? How Hard is the CRISC Exam?
The Certified in Risk and Information Systems Control (CRISC) exam covers four domains related to IT risk management. These domains are:
- IT Risk Identification: This domain covers the process of identifying and assessing IT risks, including the identification of assets, vulnerabilities, threats, and impacts.
- IT Risk Assessment: This domain covers the process of assessing and evaluating IT risks, including the use of risk assessment techniques and the analysis of risk scenarios.
- Risk Response and Mitigation: This domain covers the process of developing and implementing risk response and mitigation strategies, including risk acceptance, risk avoidance, risk mitigation, and risk transfer.
- Risk and Control Monitoring and Reporting: This domain covers the process of monitoring and reporting on IT risks and controls, including the establishment of key risk indicators (KRIs) and the use of metrics to measure the effectiveness of risk management.
The CRISC exam is generally considered to be a challenging exam that requires a thorough understanding of IT risk management principles and practices. The exam consists of 150 multiple-choice questions and must be completed within four hours. The questions are designed to test an individual's knowledge of the four CRISC domains and their ability to apply this knowledge to real-world scenarios. The passing score for the CRISC exam is 450 out of a possible 800 points.
To prepare for the exam, individuals should take advantage of the study materials, review courses, and practice exams provided by the Information Systems Audit and Control Association (ISACA), as well as other resources available through accredited training providers and industry associations. With diligent preparation and a solid understanding of the CRISC domains, individuals can increase their chances of passing the exam and obtaining CRISC certification.
CRISC Job Opportunities and Salary
Individuals who hold the Certified in Risk and Information Systems Control (CRISC) certification may be qualified for a wide range of job opportunities in the field of IT risk management. Some common job titles for CRISC certified professionals include:
- IT Risk Manager
- Information Security Manager
- Compliance Manager
- IT Audit Manager
- Business Continuity Manager
- IT Governance Manager
These professionals may work in a variety of industries, including finance, healthcare, government, and technology.
According to the job website Indeed, the average salary for an IT Risk Manager in the United States is $116,215 per year. However, salaries can vary depending on factors such as location, industry, and experience. For example, IT Risk Managers in New York City, San Francisco, and Washington DC tend to earn higher salaries than those in other cities. Additionally, individuals with advanced degrees, certifications, or specialized skills may be able to command higher salaries.
Some Useful Certifications for CRISC
There are several certifications that can be useful for individuals who hold the Certified in Risk and Information Systems Control (CRISC) certification, as they can help to further enhance their knowledge and skills in related areas. Some of these certifications include:
- Certified Information Systems Security Professional (CISSP): This certification is offered by the International Information System Security Certification Consortium (ISC)² and is designed for information security professionals who want to demonstrate their expertise in the field.
- Certified Information Systems Auditor (CISA): This certification is also offered by ISACA and is designed for professionals who want to demonstrate their knowledge and expertise in information systems auditing, control, and security.
- Certified in the Governance of Enterprise IT (CGEIT): This certification, also offered by ISACA, is designed for professionals who are responsible for managing IT governance processes within their organizations.
- Project Management Professional (PMP): This certification, offered by the Project Management Institute (PMI), is designed for professionals who want to demonstrate their knowledge and expertise in project management.
- Certified Fraud Examiner (CFE): This certification, offered by the Association of Certified Fraud Examiners (ACFE), is designed for professionals who want to demonstrate their knowledge and expertise in preventing, detecting, and investigating fraud.
By obtaining one or more of these certifications, CRISC certified professionals can demonstrate their commitment to ongoing professional development and enhance their knowledge and skills in related areas, which can help them to excel in their careers and take on more challenging roles.
How to obtain Certified in Risk and Information Systems Control Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: SMAC Certication
- Big Data: Big Data and Hadoop Administrator
- Digital Marketing : Digital Marketing Certification
- Data Science : Power BI Certification
- Cyber Security : CRISC Certification
Conclusion
In conclusion, the Certified in Risk and Information Systems Control (CRISC) certification is an important credential for IT professionals who want to demonstrate their knowledge and expertise in IT risk management. The certification covers four domains related to IT risk management, including IT risk identification, assessment, response and mitigation, and risk and control monitoring and reporting. The CRISC exam is considered challenging and requires a thorough understanding of the CRISC domains and their practical application.
CRISC certified professionals may be qualified for a wide range of job opportunities in IT risk management, including roles such as IT Risk Manager, Information Security Manager, Compliance Manager, and IT Audit Manager. The CRISC certification can also be complemented by other certifications such as CISSP, CISA, CGEIT, PMP, and CFE, which can help to further enhance their knowledge and skills in related areas.
Overall, obtaining the CRISC certification can be a valuable asset for IT professionals seeking to advance their careers in IT risk management and demonstrate their commitment to ongoing professional development.
Read More
In today's digital age, organizations are constantly facing new and complex information security challenges. To mitigate these risks, they need skilled professionals who can identify and manage these risks effectively. This is where the Certified in Risk and Information Systems Control (CRISC) certification comes in.
CRISC is a globally recognized certification that validates an individual's expertise in identifying, assessing, and evaluating information systems and technology risks. It is awarded by the Information Systems Audit and Control Association (ISACA) and is designed for IT professionals who are responsible for managing IT and business risks.
In this article, we will provide an overview of CRISC certification training, including its benefits and the career path it can lead to. Whether you're an experienced IT professional or just starting out in your career, understanding the value of CRISC certification can help you take your career to the next level.
Table of Contents
What Is a CRISC Certification?
Why Is CRISC Important?
How Do You Get CRISC Certification?
How Much Is the CRISC Exam?
What Are the Domains in the Context of the CRISC Exam? How Hard is the CRISC Exam?
CRISC Job Opportunities and Salary
Some Useful Certifications for CRISC
Conclusion
What Is a CRISC Certification?
The Certified in Risk and Information Systems Control (CRISC) certification is a globally recognized certification awarded by the Information Systems Audit and Control Association (ISACA). The certification validates an individual's expertise in identifying, assessing, and evaluating information systems and technology risks.
To earn the CRISC certification, an individual must pass a rigorous exam that covers four domains:
- IT Risk Identification
- IT Risk Assessment
- Risk Response and Mitigation
- Risk and Control Monitoring and Reporting
In addition to passing the exam, individuals must also have at least three years of relevant work experience in at least two of the four CRISC domains, with at least one year of experience in the CRISC focus area. They must also adhere to the ISACA Code of Professional Ethics.
The CRISC certification is designed for IT professionals who are responsible for managing IT and business risks, including IT auditors, risk management professionals, business analysts, compliance professionals, and security professionals. It is recognized globally and can help individuals advance their careers in IT risk management.
Why Is CRISC Important?
The Certified in Risk and Information Systems Control (CRISC) certification is important for several reasons:
- Validates expertise in IT risk management: CRISC certification validates an individual's expertise in identifying, assessing, and evaluating information systems and technology risks. It demonstrates that the individual has a strong understanding of the principles and practices of IT risk management and can effectively manage risks in an organization.
- Globally recognized: CRISC certification is globally recognized and respected in the field of IT risk management. It is awarded by the Information Systems Audit and Control Association (ISACA), which is a well-respected professional organization for IT auditors and security professionals.
- Competitive advantage: CRISC certification can give IT professionals a competitive advantage in the job market. It demonstrates to employers that the individual has the skills and knowledge needed to effectively manage IT risks and can provide value to the organization.
- Improved career prospects: CRISC certification can open up new career opportunities for IT professionals. It can lead to higher-paying jobs and positions with greater responsibility, such as IT risk managers or IT security directors.
- Risk management best practices: CRISC certification provides individuals with a deep understanding of IT risk management best practices. This knowledge can help individuals improve their organization's risk management processes and better protect their organization's information assets.
How Do You Get CRISC Certification?
To obtain the Certified in Risk and Information Systems Control (CRISC) certification, individuals must follow the certification process established by the Information Systems Audit and Control Association (ISACA), which includes the following steps:
- Meet the eligibility requirements: To be eligible for CRISC certification, individuals must have at least three years of relevant work experience in at least two of the four CRISC domains, with at least one year of experience in the CRISC focus area. Alternatively, individuals can substitute certain educational or other professional experience for up to two years of work experience.
- Register for the CRISC exam: Once eligible, individuals can register for the CRISC exam through the ISACA website. The exam consists of 150 multiple-choice questions and covers the four CRISC domains: IT Risk Identification, IT Risk Assessment, Risk Response and Mitigation, and Risk and Control Monitoring and Reporting.
- Prepare for the exam: ISACA provides various resources to help individuals prepare for the CRISC exam, including study materials, review courses, and practice exams. Individuals can also choose to attend a CRISC training course provided by an ISACA-accredited training provider.
- Pass the exam: To obtain CRISC certification, individuals must pass the CRISC exam with a score of at least 450 out of 800.
- Adhere to the Code of Professional Ethics: CRISC certification holders must adhere to the ISACA Code of Professional Ethics, which includes standards of conduct, integrity, and objectivity.
- Maintain the certification: CRISC certification holders must maintain their certification by earning and reporting continuing professional education (CPE) credits. They must earn and report 20 CPE credits annually and 120 CPE credits over a three-year reporting period.
How Much Is the CRISC Exam?
The cost of the Certified in Risk and Information Systems Control (CRISC) exam varies depending on whether an individual is a member of the Information Systems Audit and Control Association (ISACA) and when they register for the exam. As of May 2023, the exam fees are:
- Early registration exam fee for ISACA members: $660
- Early registration exam fee for non-ISACA members: $925
- Standard registration exam fee for ISACA members: $760
- Standard registration exam fee for non-ISACA members: $1,025
ISACA offers early registration discounts to individuals who register for the exam early. Early registration typically begins in late January or early February for the May-June exam window and in late July or early August for the September-October exam window. Standard registration typically begins about two weeks after early registration ends.
It's important to note that these fees are subject to change, and individuals should check the ISACA website for the most up-to-date information on exam fees and registration deadlines. Additionally, there may be additional costs associated with preparing for the exam, such as study materials, training courses, and practice exams.
What Are the Domains in the Context of the CRISC Exam? How Hard is the CRISC Exam?
The Certified in Risk and Information Systems Control (CRISC) exam covers four domains related to IT risk management. These domains are:
- IT Risk Identification: This domain covers the process of identifying and assessing IT risks, including the identification of assets, vulnerabilities, threats, and impacts.
- IT Risk Assessment: This domain covers the process of assessing and evaluating IT risks, including the use of risk assessment techniques and the analysis of risk scenarios.
- Risk Response and Mitigation: This domain covers the process of developing and implementing risk response and mitigation strategies, including risk acceptance, risk avoidance, risk mitigation, and risk transfer.
- Risk and Control Monitoring and Reporting: This domain covers the process of monitoring and reporting on IT risks and controls, including the establishment of key risk indicators (KRIs) and the use of metrics to measure the effectiveness of risk management.
The CRISC exam is generally considered to be a challenging exam that requires a thorough understanding of IT risk management principles and practices. The exam consists of 150 multiple-choice questions and must be completed within four hours. The questions are designed to test an individual's knowledge of the four CRISC domains and their ability to apply this knowledge to real-world scenarios. The passing score for the CRISC exam is 450 out of a possible 800 points.
To prepare for the exam, individuals should take advantage of the study materials, review courses, and practice exams provided by the Information Systems Audit and Control Association (ISACA), as well as other resources available through accredited training providers and industry associations. With diligent preparation and a solid understanding of the CRISC domains, individuals can increase their chances of passing the exam and obtaining CRISC certification.
CRISC Job Opportunities and Salary
Individuals who hold the Certified in Risk and Information Systems Control (CRISC) certification may be qualified for a wide range of job opportunities in the field of IT risk management. Some common job titles for CRISC certified professionals include:
- IT Risk Manager
- Information Security Manager
- Compliance Manager
- IT Audit Manager
- Business Continuity Manager
- IT Governance Manager
These professionals may work in a variety of industries, including finance, healthcare, government, and technology.
According to the job website Indeed, the average salary for an IT Risk Manager in the United States is $116,215 per year. However, salaries can vary depending on factors such as location, industry, and experience. For example, IT Risk Managers in New York City, San Francisco, and Washington DC tend to earn higher salaries than those in other cities. Additionally, individuals with advanced degrees, certifications, or specialized skills may be able to command higher salaries.
Some Useful Certifications for CRISC
There are several certifications that can be useful for individuals who hold the Certified in Risk and Information Systems Control (CRISC) certification, as they can help to further enhance their knowledge and skills in related areas. Some of these certifications include:
- Certified Information Systems Security Professional (CISSP): This certification is offered by the International Information System Security Certification Consortium (ISC)² and is designed for information security professionals who want to demonstrate their expertise in the field.
- Certified Information Systems Auditor (CISA): This certification is also offered by ISACA and is designed for professionals who want to demonstrate their knowledge and expertise in information systems auditing, control, and security.
- Certified in the Governance of Enterprise IT (CGEIT): This certification, also offered by ISACA, is designed for professionals who are responsible for managing IT governance processes within their organizations.
- Project Management Professional (PMP): This certification, offered by the Project Management Institute (PMI), is designed for professionals who want to demonstrate their knowledge and expertise in project management.
- Certified Fraud Examiner (CFE): This certification, offered by the Association of Certified Fraud Examiners (ACFE), is designed for professionals who want to demonstrate their knowledge and expertise in preventing, detecting, and investigating fraud.
By obtaining one or more of these certifications, CRISC certified professionals can demonstrate their commitment to ongoing professional development and enhance their knowledge and skills in related areas, which can help them to excel in their careers and take on more challenging roles.
How to obtain Certified in Risk and Information Systems Control Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: SMAC Certication
- Big Data: Big Data and Hadoop Administrator
- Digital Marketing : Digital Marketing Certification
- Data Science : Power BI Certification
- Cyber Security : CRISC Certification
Conclusion
In conclusion, the Certified in Risk and Information Systems Control (CRISC) certification is an important credential for IT professionals who want to demonstrate their knowledge and expertise in IT risk management. The certification covers four domains related to IT risk management, including IT risk identification, assessment, response and mitigation, and risk and control monitoring and reporting. The CRISC exam is considered challenging and requires a thorough understanding of the CRISC domains and their practical application.
CRISC certified professionals may be qualified for a wide range of job opportunities in IT risk management, including roles such as IT Risk Manager, Information Security Manager, Compliance Manager, and IT Audit Manager. The CRISC certification can also be complemented by other certifications such as CISSP, CISA, CGEIT, PMP, and CFE, which can help to further enhance their knowledge and skills in related areas.
Overall, obtaining the CRISC certification can be a valuable asset for IT professionals seeking to advance their careers in IT risk management and demonstrate their commitment to ongoing professional development.
A Step-by-Step Guide to Certification as an Information Security Manager
In today's digital age, information security has become a top priority for businesses of all sizes. With the increasing number of cyber-attacks, organizations need professionals who can effectively manage and secure their information assets. This is where the Certified Information Security Manager (CISM) certification comes in.
CISM is a globally recognized certification for information security professionals who want to demonstrate their expertise in managing, designing, and assessing information security programs. It is offered by the Information Systems Audit and Control Association (ISACA), a non-profit organization that provides guidance and certification in information security, IT governance, and assurance.
Holding a CISM certification validates an individual's knowledge and skills in critical areas such as risk management, incident management, governance, and compliance. It also demonstrates an individual's commitment to the information security profession and to staying current with the latest industry trends and best practices.
In this blog post, we will explore the various aspects of the CISM certification, including its benefits, exam format, preparation strategies, and recertification requirements. Whether you are an aspiring information security professional or an experienced practitioner looking to enhance your career, the CISM certification can provide you with the knowledge and credentials you need to succeed in this rapidly evolving field.
Table of contents
- What is CISM?
- The CISM Exam
- How to Prepare for the CISM Exam
- The Value of CISM Certification
- CISM vs. Other Security Certifications
- CISM Exam Tips from Successful Candidates
- CISM Recertification
- CISM Exam Eligibility Criteria
- Benefits of CISM Certification
- Conclusion
What is CISM?
CISM stands for Certified Information Security Manager, which is a globally recognized certification for information security professionals. The certification is awarded by the Information Systems Audit and Control Association (ISACA), a non-profit organization that provides guidance and certification in information security, IT governance, and assurance.
The CISM certification is designed to validate the expertise of individuals in managing, designing, and assessing information security programs. It is intended for professionals who are responsible for developing, implementing, and managing information security programs in their organizations. CISM focuses on four key domains: Information Security Governance, Risk Management, Information Security Program Development and Management, and Incident Management.
To earn the CISM certification, candidates must pass a comprehensive exam that tests their knowledge and skills in these domains. The exam is designed to assess a candidate's ability to manage and secure information assets and to align information security programs with business goals and objectives.
Holding a CISM certification demonstrates an individual's commitment to the information security profession and to staying current with the latest industry trends and best practices. It also provides a competitive advantage in the job market and can lead to career advancement opportunities.
The CISM Exam
The CISM (Certified Information Security Manager) exam is a comprehensive test designed to assess an individual's knowledge and skills in managing, designing, and assessing information security programs. The exam is offered by the Information Systems Audit and Control Association (ISACA), and passing it is a requirement for obtaining the CISM certification.
The CISM exam consists of 150 multiple-choice questions and is administered over a four-hour period. The questions are based on the four domains of the CISM job practice areas, which are:
- Information Security Governance
- Risk Management
- Information Security Program Development and Management
- Incident Management
The exam is designed to test a candidate's ability to align information security programs with business goals and objectives, manage and secure information assets, and assess and mitigate risks.
The exam questions are developed by a committee of subject matter experts and are regularly updated to reflect changes in the industry. The passing score for the CISM exam is 450 out of a possible 800 points.
Candidates can register for the CISM exam online through the ISACA website. The exam fee varies by location and ISACA membership status. ISACA members receive a discount on the exam fee.
To prepare for the CISM exam, candidates can take advantage of study materials and resources provided by ISACA, such as the CISM Review Manual, online courses, and practice exams. Candidates can also form study groups or attend review courses to help them prepare for the exam. It is recommended that candidates spend at least 120 hours of study time to adequately prepare for the exam.
How to Prepare for the CISM Exam
Preparing for the CISM (Certified Information Security Manager) exam requires dedication, hard work, and a solid study plan. Here are some tips on how to prepare for the CISM exam:
- Familiarize yourself with the exam format: The CISM exam consists of 150 multiple-choice questions that you must answer within a four-hour time frame. Understanding the exam format will help you manage your time effectively during the exam.
- Review the CISM Job Practice Areas: The CISM exam is based on the four domains of the CISM Job Practice Areas. Reviewing the domains will help you identify areas where you need to focus your study efforts.
- Use ISACA Study Materials: The Information Systems Audit and Control Association (ISACA) provides a variety of study materials to help you prepare for the exam. The CISM Review Manual, practice questions, and online courses are just a few examples of the study materials that ISACA offers.
- Join a Study Group: Studying with a group of peers can be a great way to stay motivated and share knowledge. Joining a study group can also help you identify areas where you need to focus your study efforts.
- Take Practice Exams: Taking practice exams can help you assess your knowledge and identify areas where you need to improve. ISACA provides a variety of practice exams that you can use to test your knowledge.
- Attend Review Courses: Review courses can help you prepare for the exam by providing you with a structured study plan, expert instruction, and an opportunity to interact with other candidates.
- Dedicate Sufficient Study Time: The CISM exam requires a significant amount of study time. Plan your study schedule in advance and make sure to dedicate sufficient time to each domain.
The Value of CISM Certification
The Certified Information Security Manager (CISM) certification is highly valued in the field of information security. Here are some reasons why:
- Demonstrates Expertise: Holding a CISM certification demonstrates an individual's expertise in managing, designing, and assessing information security programs. It validates that an individual has the knowledge and skills required to align information security programs with business goals and objectives, manage and secure information assets, and assess and mitigate risks.
- Career Advancement: The CISM certification provides a competitive advantage in the job market and can lead to career advancement opportunities. Employers recognize the value of the CISM certification and often require it for senior-level information security positions.
- Professional Development: Maintaining a CISM certification requires continuing education, which ensures that certified professionals stay up-to-date with the latest industry trends and best practices. This commitment to professional development enhances an individual's credibility and reputation in the industry.
- Networking Opportunities: ISACA, the organization that awards the CISM certification, provides networking opportunities for certified professionals. These opportunities allow individuals to connect with peers in the industry, share knowledge, and stay up-to-date with the latest industry trends and best practices.
- International Recognition: The CISM certification is recognized globally as a standard for information security professionals. It provides international recognition of an individual's knowledge and skills in managing, designing, and assessing information security programs.
CISM vs. Other Security Certifications
There are several security certifications available in the industry, and choosing the right one can be challenging. Here are some comparisons between the Certified Information Security Manager (CISM) certification and other popular security certifications:
- CISM vs. CISSP: The Certified Information Systems Security Professional (CISSP) certification is focused on technical security knowledge and is geared towards security professionals who work with technology. The CISM certification, on the other hand, is focused on managing and designing security programs and is geared towards security professionals who have a more strategic role. Both certifications are highly valued in the industry, and the choice between them depends on an individual's career goals and job requirements.
- CISM vs. CISA: The Certified Information Systems Auditor (CISA) certification is focused on auditing and assessing information systems. The CISM certification, on the other hand, is focused on managing and designing security programs. Both certifications are valuable in the industry, and the choice between them depends on an individual's career goals and job requirements.
- CISM vs. Security+: The CompTIA Security+ certification is an entry-level certification that provides a foundation in security concepts and best practices. The CISM certification, on the other hand, is a more advanced certification that is focused on managing and designing security programs. The choice between these certifications depends on an individual's level of experience and career goals.
- CISM vs. CCSP: The Certified Cloud Security Professional (CCSP) certification is focused on cloud security. The CISM certification, on the other hand, is focused on managing and designing security programs. Both certifications are valuable in the industry, and the choice between them depends on an individual's job requirements and level of experience.
CISM Exam Tips from Successful Candidates
Here are some tips from successful candidates who have passed the Certified Information Security Manager (CISM) exam:
- Understand the Exam Content: Spend time studying the exam content outline and understand the specific domains, tasks, and knowledge areas that will be covered on the exam.
- Use Official Study Materials: Utilize official study materials from ISACA, including review manuals, practice exams, and online courses. These materials are designed to provide valuable insights into the exam content and structure.
- Practice with Sample Questions: Practice as many sample questions as possible, including official practice exams from ISACA, to familiarize yourself with the exam format and types of questions.
- Manage Your Time: During the exam, manage your time carefully and allocate enough time to answer each question. Don't spend too much time on difficult questions and ensure that you answer all questions within the allocated time limit.
- Read Questions Carefully: Carefully read each exam question and ensure that you understand the requirements and any specific details provided.
- Apply Your Knowledge: The CISM exam is not about memorization, but about applying knowledge to real-world scenarios. Focus on understanding key concepts and how they apply in different situations.
- Stay Calm and Focused: The CISM exam can be stressful, but it's essential to stay calm and focused throughout the exam. Take breaks when needed, stay hydrated, and practice relaxation techniques to manage stress.
- Join a Study Group: Joining a study group can provide a supportive environment where you can collaborate with other exam candidates, share knowledge, and ask questions.
- Utilize Exam Resources: ISACA offers a range of exam resources, including study materials, exam prep courses, and practice exams. Utilize these resources to prepare effectively for the exam.
- Review Your Results: After completing the exam, review your results and identify any areas where you need to improve. This will help you prepare more effectively if you need to retake the exam.
CISM Recertification
Certified Information Security Manager (CISM) certification is valid for three years. To maintain your CISM certification, you must recertify every three years by earning and reporting the required number of continuing education units (CEUs) and paying the recertification fee.
To recertify, you must earn a minimum of 20 CISM CEUs annually, with a total of 60 CEUs over the three-year certification period. CEUs can be earned through various activities, including attending educational events, publishing articles or books, completing online training courses, and participating in professional development activities.
You must report your CEUs using the ISACA online certification system. ISACA randomly audits a percentage of CISM holders to ensure that they have met the continuing education requirements. You must retain documentation to support your CEU claims for at least five years after the recertification cycle.
If you do not recertify within the three-year period, your CISM certification will expire, and you will need to retake and pass the CISM exam to regain certification. Therefore, it's crucial to plan ahead and ensure that you earn the required CEUs to recertify in time.
CISM Exam Eligibility Criteria
To be eligible to take the Certified Information Security Manager (CISM) exam, you must meet the following requirements:
- Information Security Experience: You must have at least five years of experience in information security, with a minimum of three years in information security management. Alternatively, you may substitute two years of general information security experience with a degree in information security management or a related field.
- Adherence to ISACA Code of Ethics: You must agree to abide by the ISACA Code of Ethics, which requires you to uphold high standards of professional conduct and maintain confidentiality and integrity in all your work.
- Pass the Exam: You must pass the CISM exam with a minimum score of 450 out of 800. The exam consists of 150 multiple-choice questions and covers four domains of information security management.
ISACA periodically audits the exam results and may require candidates to provide documentation to verify their work experience. Therefore, it's crucial to ensure that you meet the eligibility criteria and have the necessary documentation to support your experience before registering for the exam.
Benefits of CISM Certification
There are many benefits to earning the Certified Information Security Manager (CISM) certification, including:
- Demonstrated Expertise: CISM certification demonstrates that you have the knowledge and expertise to develop and manage an information security program. It shows that you have a comprehensive understanding of information security management, risk management, and governance.
- Career Advancement: CISM certification is highly valued by employers and can open up new career opportunities. It demonstrates that you have the skills and knowledge to effectively manage information security programs, and can lead to job titles such as information security manager, IT security director, and chief information security officer (CISO).
- Higher Earnings: According to ISACA's 2020 IT Audit, Assurance, Risk and Governance Salary Survey, CISM holders earn an average of 28% more than their non-certified counterparts. CISM certification can lead to higher salaries, better job opportunities, and increased job security.
- International Recognition: CISM certification is recognized globally as a standard for information security management. It's highly respected in the industry and is often required for positions with international organizations.
- Networking Opportunities: CISM certification provides opportunities for networking with other information security professionals. ISACA offers local chapter meetings, online forums, and other events where you can connect with others in the field, share ideas, and stay up-to-date with the latest trends and best practices.
How to obtain CISM Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: SMAC Certication
- Big Data: Big Data and Hadoop Administrator
- Digital Marketing : Digital Marketing Certification
- Data Science : Power BI Certification
- Cyber Security : CISM Certification
Conclusion
In conclusion, the Certified Information Security Manager (CISM) certification is a highly respected credential for professionals who manage, design, and oversee information security programs. CISM certification demonstrates that you have a comprehensive understanding of information security management, risk management, and governance. It can lead to new career opportunities, higher earnings, and international recognition. To earn CISM certification, you must meet eligibility criteria and pass the CISM exam. Once certified, you must recertify every three years by earning and reporting the required number of continuing education units (CEUs) and paying the recertification fee. CISM certification offers numerous benefits for information security professionals looking to advance their careers and demonstrate their expertise in the field.
Read More
In today's digital age, information security has become a top priority for businesses of all sizes. With the increasing number of cyber-attacks, organizations need professionals who can effectively manage and secure their information assets. This is where the Certified Information Security Manager (CISM) certification comes in.
CISM is a globally recognized certification for information security professionals who want to demonstrate their expertise in managing, designing, and assessing information security programs. It is offered by the Information Systems Audit and Control Association (ISACA), a non-profit organization that provides guidance and certification in information security, IT governance, and assurance.
Holding a CISM certification validates an individual's knowledge and skills in critical areas such as risk management, incident management, governance, and compliance. It also demonstrates an individual's commitment to the information security profession and to staying current with the latest industry trends and best practices.
In this blog post, we will explore the various aspects of the CISM certification, including its benefits, exam format, preparation strategies, and recertification requirements. Whether you are an aspiring information security professional or an experienced practitioner looking to enhance your career, the CISM certification can provide you with the knowledge and credentials you need to succeed in this rapidly evolving field.
Table of contents
- What is CISM?
- The CISM Exam
- How to Prepare for the CISM Exam
- The Value of CISM Certification
- CISM vs. Other Security Certifications
- CISM Exam Tips from Successful Candidates
- CISM Recertification
- CISM Exam Eligibility Criteria
- Benefits of CISM Certification
- Conclusion
What is CISM?
CISM stands for Certified Information Security Manager, which is a globally recognized certification for information security professionals. The certification is awarded by the Information Systems Audit and Control Association (ISACA), a non-profit organization that provides guidance and certification in information security, IT governance, and assurance.
The CISM certification is designed to validate the expertise of individuals in managing, designing, and assessing information security programs. It is intended for professionals who are responsible for developing, implementing, and managing information security programs in their organizations. CISM focuses on four key domains: Information Security Governance, Risk Management, Information Security Program Development and Management, and Incident Management.
To earn the CISM certification, candidates must pass a comprehensive exam that tests their knowledge and skills in these domains. The exam is designed to assess a candidate's ability to manage and secure information assets and to align information security programs with business goals and objectives.
Holding a CISM certification demonstrates an individual's commitment to the information security profession and to staying current with the latest industry trends and best practices. It also provides a competitive advantage in the job market and can lead to career advancement opportunities.
The CISM Exam
The CISM (Certified Information Security Manager) exam is a comprehensive test designed to assess an individual's knowledge and skills in managing, designing, and assessing information security programs. The exam is offered by the Information Systems Audit and Control Association (ISACA), and passing it is a requirement for obtaining the CISM certification.
The CISM exam consists of 150 multiple-choice questions and is administered over a four-hour period. The questions are based on the four domains of the CISM job practice areas, which are:
- Information Security Governance
- Risk Management
- Information Security Program Development and Management
- Incident Management
The exam is designed to test a candidate's ability to align information security programs with business goals and objectives, manage and secure information assets, and assess and mitigate risks.
The exam questions are developed by a committee of subject matter experts and are regularly updated to reflect changes in the industry. The passing score for the CISM exam is 450 out of a possible 800 points.
Candidates can register for the CISM exam online through the ISACA website. The exam fee varies by location and ISACA membership status. ISACA members receive a discount on the exam fee.
To prepare for the CISM exam, candidates can take advantage of study materials and resources provided by ISACA, such as the CISM Review Manual, online courses, and practice exams. Candidates can also form study groups or attend review courses to help them prepare for the exam. It is recommended that candidates spend at least 120 hours of study time to adequately prepare for the exam.
How to Prepare for the CISM Exam
Preparing for the CISM (Certified Information Security Manager) exam requires dedication, hard work, and a solid study plan. Here are some tips on how to prepare for the CISM exam:
- Familiarize yourself with the exam format: The CISM exam consists of 150 multiple-choice questions that you must answer within a four-hour time frame. Understanding the exam format will help you manage your time effectively during the exam.
- Review the CISM Job Practice Areas: The CISM exam is based on the four domains of the CISM Job Practice Areas. Reviewing the domains will help you identify areas where you need to focus your study efforts.
- Use ISACA Study Materials: The Information Systems Audit and Control Association (ISACA) provides a variety of study materials to help you prepare for the exam. The CISM Review Manual, practice questions, and online courses are just a few examples of the study materials that ISACA offers.
- Join a Study Group: Studying with a group of peers can be a great way to stay motivated and share knowledge. Joining a study group can also help you identify areas where you need to focus your study efforts.
- Take Practice Exams: Taking practice exams can help you assess your knowledge and identify areas where you need to improve. ISACA provides a variety of practice exams that you can use to test your knowledge.
- Attend Review Courses: Review courses can help you prepare for the exam by providing you with a structured study plan, expert instruction, and an opportunity to interact with other candidates.
- Dedicate Sufficient Study Time: The CISM exam requires a significant amount of study time. Plan your study schedule in advance and make sure to dedicate sufficient time to each domain.
The Value of CISM Certification
The Certified Information Security Manager (CISM) certification is highly valued in the field of information security. Here are some reasons why:
- Demonstrates Expertise: Holding a CISM certification demonstrates an individual's expertise in managing, designing, and assessing information security programs. It validates that an individual has the knowledge and skills required to align information security programs with business goals and objectives, manage and secure information assets, and assess and mitigate risks.
- Career Advancement: The CISM certification provides a competitive advantage in the job market and can lead to career advancement opportunities. Employers recognize the value of the CISM certification and often require it for senior-level information security positions.
- Professional Development: Maintaining a CISM certification requires continuing education, which ensures that certified professionals stay up-to-date with the latest industry trends and best practices. This commitment to professional development enhances an individual's credibility and reputation in the industry.
- Networking Opportunities: ISACA, the organization that awards the CISM certification, provides networking opportunities for certified professionals. These opportunities allow individuals to connect with peers in the industry, share knowledge, and stay up-to-date with the latest industry trends and best practices.
- International Recognition: The CISM certification is recognized globally as a standard for information security professionals. It provides international recognition of an individual's knowledge and skills in managing, designing, and assessing information security programs.
CISM vs. Other Security Certifications
There are several security certifications available in the industry, and choosing the right one can be challenging. Here are some comparisons between the Certified Information Security Manager (CISM) certification and other popular security certifications:
- CISM vs. CISSP: The Certified Information Systems Security Professional (CISSP) certification is focused on technical security knowledge and is geared towards security professionals who work with technology. The CISM certification, on the other hand, is focused on managing and designing security programs and is geared towards security professionals who have a more strategic role. Both certifications are highly valued in the industry, and the choice between them depends on an individual's career goals and job requirements.
- CISM vs. CISA: The Certified Information Systems Auditor (CISA) certification is focused on auditing and assessing information systems. The CISM certification, on the other hand, is focused on managing and designing security programs. Both certifications are valuable in the industry, and the choice between them depends on an individual's career goals and job requirements.
- CISM vs. Security+: The CompTIA Security+ certification is an entry-level certification that provides a foundation in security concepts and best practices. The CISM certification, on the other hand, is a more advanced certification that is focused on managing and designing security programs. The choice between these certifications depends on an individual's level of experience and career goals.
- CISM vs. CCSP: The Certified Cloud Security Professional (CCSP) certification is focused on cloud security. The CISM certification, on the other hand, is focused on managing and designing security programs. Both certifications are valuable in the industry, and the choice between them depends on an individual's job requirements and level of experience.
CISM Exam Tips from Successful Candidates
Here are some tips from successful candidates who have passed the Certified Information Security Manager (CISM) exam:
- Understand the Exam Content: Spend time studying the exam content outline and understand the specific domains, tasks, and knowledge areas that will be covered on the exam.
- Use Official Study Materials: Utilize official study materials from ISACA, including review manuals, practice exams, and online courses. These materials are designed to provide valuable insights into the exam content and structure.
- Practice with Sample Questions: Practice as many sample questions as possible, including official practice exams from ISACA, to familiarize yourself with the exam format and types of questions.
- Manage Your Time: During the exam, manage your time carefully and allocate enough time to answer each question. Don't spend too much time on difficult questions and ensure that you answer all questions within the allocated time limit.
- Read Questions Carefully: Carefully read each exam question and ensure that you understand the requirements and any specific details provided.
- Apply Your Knowledge: The CISM exam is not about memorization, but about applying knowledge to real-world scenarios. Focus on understanding key concepts and how they apply in different situations.
- Stay Calm and Focused: The CISM exam can be stressful, but it's essential to stay calm and focused throughout the exam. Take breaks when needed, stay hydrated, and practice relaxation techniques to manage stress.
- Join a Study Group: Joining a study group can provide a supportive environment where you can collaborate with other exam candidates, share knowledge, and ask questions.
- Utilize Exam Resources: ISACA offers a range of exam resources, including study materials, exam prep courses, and practice exams. Utilize these resources to prepare effectively for the exam.
- Review Your Results: After completing the exam, review your results and identify any areas where you need to improve. This will help you prepare more effectively if you need to retake the exam.
CISM Recertification
Certified Information Security Manager (CISM) certification is valid for three years. To maintain your CISM certification, you must recertify every three years by earning and reporting the required number of continuing education units (CEUs) and paying the recertification fee.
To recertify, you must earn a minimum of 20 CISM CEUs annually, with a total of 60 CEUs over the three-year certification period. CEUs can be earned through various activities, including attending educational events, publishing articles or books, completing online training courses, and participating in professional development activities.
You must report your CEUs using the ISACA online certification system. ISACA randomly audits a percentage of CISM holders to ensure that they have met the continuing education requirements. You must retain documentation to support your CEU claims for at least five years after the recertification cycle.
If you do not recertify within the three-year period, your CISM certification will expire, and you will need to retake and pass the CISM exam to regain certification. Therefore, it's crucial to plan ahead and ensure that you earn the required CEUs to recertify in time.
CISM Exam Eligibility Criteria
To be eligible to take the Certified Information Security Manager (CISM) exam, you must meet the following requirements:
- Information Security Experience: You must have at least five years of experience in information security, with a minimum of three years in information security management. Alternatively, you may substitute two years of general information security experience with a degree in information security management or a related field.
- Adherence to ISACA Code of Ethics: You must agree to abide by the ISACA Code of Ethics, which requires you to uphold high standards of professional conduct and maintain confidentiality and integrity in all your work.
- Pass the Exam: You must pass the CISM exam with a minimum score of 450 out of 800. The exam consists of 150 multiple-choice questions and covers four domains of information security management.
ISACA periodically audits the exam results and may require candidates to provide documentation to verify their work experience. Therefore, it's crucial to ensure that you meet the eligibility criteria and have the necessary documentation to support your experience before registering for the exam.
Benefits of CISM Certification
There are many benefits to earning the Certified Information Security Manager (CISM) certification, including:
- Demonstrated Expertise: CISM certification demonstrates that you have the knowledge and expertise to develop and manage an information security program. It shows that you have a comprehensive understanding of information security management, risk management, and governance.
- Career Advancement: CISM certification is highly valued by employers and can open up new career opportunities. It demonstrates that you have the skills and knowledge to effectively manage information security programs, and can lead to job titles such as information security manager, IT security director, and chief information security officer (CISO).
- Higher Earnings: According to ISACA's 2020 IT Audit, Assurance, Risk and Governance Salary Survey, CISM holders earn an average of 28% more than their non-certified counterparts. CISM certification can lead to higher salaries, better job opportunities, and increased job security.
- International Recognition: CISM certification is recognized globally as a standard for information security management. It's highly respected in the industry and is often required for positions with international organizations.
- Networking Opportunities: CISM certification provides opportunities for networking with other information security professionals. ISACA offers local chapter meetings, online forums, and other events where you can connect with others in the field, share ideas, and stay up-to-date with the latest trends and best practices.
How to obtain CISM Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: SMAC Certication
- Big Data: Big Data and Hadoop Administrator
- Digital Marketing : Digital Marketing Certification
- Data Science : Power BI Certification
- Cyber Security : CISM Certification
Conclusion
In conclusion, the Certified Information Security Manager (CISM) certification is a highly respected credential for professionals who manage, design, and oversee information security programs. CISM certification demonstrates that you have a comprehensive understanding of information security management, risk management, and governance. It can lead to new career opportunities, higher earnings, and international recognition. To earn CISM certification, you must meet eligibility criteria and pass the CISM exam. Once certified, you must recertify every three years by earning and reporting the required number of continuing education units (CEUs) and paying the recertification fee. CISM certification offers numerous benefits for information security professionals looking to advance their careers and demonstrate their expertise in the field.
How to Become a Certified Information Systems Auditor (CISA)
Welcome to the world of information systems auditing! If you have a passion for technology, a keen eye for detail, and a desire to protect valuable data and systems, then becoming a Certified Information Systems Auditor (CISA) might be the ideal career path for you. In today's digital age, where cyber threats loom large, organizations are increasingly reliant on skilled professionals who can ensure the integrity and security of their information systems. This comprehensive guide will walk you through the process of becoming a CISA, providing valuable insights into the certification requirements, exam preparation strategies, and the rewarding opportunities that await those who embark on this fulfilling journey. Whether you are a seasoned IT professional seeking career advancement or a tech enthusiast starting afresh, this guide will equip you with the knowledge and resources needed to excel in the field of information systems auditing and gain the prestigious CISA designation. So, let's dive in and discover how you can pave your way to becoming a Certified Information Systems Auditor!
Table of Contents
-
What is the CISA certification and why is it important?
-
Requirements for obtaining the CISA certification.
-
Benefits of becoming a CISA-certified professional.
-
Job prospects and career opportunities for CISA-certified professionals.
-
How to prepare for the CISA exam: study materials, tips, and resources.
-
Exam structure and format: what to expect on the day of the exam.
-
CISA exam eligibility and registration process.
-
Renewal requirements for CISA certification.
-
Conclusion.
The Certified Information Systems Auditor (CISA) certification is a globally recognized credential for professionals who audit, control, monitor, and assess information technology and business systems. This certification is awarded by the Information Systems Audit and Control Association (ISACA), a professional organization that provides knowledge, certifications, and networking opportunities to IT and information security professionals. The CISA certification is designed to validate a candidate's knowledge and expertise in information systems auditing, control, and security. It is considered one of the most prestigious and in-demand certifications in the field of information technology, with the potential to open up career opportunities and enhance professional credibility. In this topic, we will discuss the benefits of obtaining a CISA certification, the exam requirements, and how to prepare for the exam.
What is the CISA certification and why is it important?
The Certified Information Systems Auditor (CISA) certification is a professional certification that validates a candidate's knowledge and expertise in information systems auditing, control, and security. It is awarded by the Information Systems Audit and Control Association (ISACA), a professional organization that provides knowledge, certifications, and networking opportunities to IT and information security professionals.
The CISA certification is globally recognized and highly respected in the field of information technology and information security. It is designed for professionals who are responsible for auditing, monitoring, controlling, and assessing information technology and business systems. This certification is important because it provides a comprehensive understanding of the principles, practices, and standards involved in auditing and assessing information systems, including risk management, governance, and compliance.
Becoming a CISA-certified professional demonstrates that you possess the knowledge, skills, and experience required to audit and control information systems effectively. It also highlights your commitment to professional development and your willingness to stay up-to-date with the latest industry trends and practices.
Additionally, the CISA certification can lead to greater job opportunities, higher salaries, and career advancement in fields such as auditing, security, risk management, and compliance. It is recognized by many organizations, including government agencies, financial institutions, and consulting firms, as a mark of excellence and a requirement for certain positions.
Requirements for obtaining the CISA certification.
To obtain the CISA certification, candidates must meet the following requirements:
-
Education: Candidates must have a minimum of a bachelor's degree from an accredited college or university or have equivalent work experience. Two years of work experience can be substituted for one year of education, up to a maximum of five years.
-
Work Experience: Candidates must have a minimum of five years of professional information systems auditing, control, or security work experience. Work experience must be gained within the ten-year period preceding the application date for certification or within five years from the date of passing the CISA exam.
-
Adherence to the ISACA Code of Professional Ethics: Candidates must agree to abide by the ISACA Code of Professional Ethics.
-
Exam: Candidates must pass the CISA exam, which is a 150-question, multiple-choice exam that covers five domains related to information systems auditing:
-
Domain 1: Information System Auditing Process
-
Domain 2: Governance and Management of IT
-
Domain 3: Information Systems Acquisition, Development, and Implementation
-
Domain 4: Information Systems Operations, Maintenance, and Support
-
Domain 5: Protection of Information Assets
The CISA exam is offered three times a year and is administered at various testing centers worldwide.
-
Continuing Professional Education: After obtaining the CISA certification, candidates must complete a minimum of 20 continuing professional education (CPE) hours annually and 120 CPE hours in a three-year period.
Benefits of becoming a CISA-certified professional.
Becoming a Certified Information Systems Auditor (CISA) certified professional offers numerous benefits, including:
-
Career Advancement: Obtaining the CISA certification demonstrates your knowledge and skills in information systems auditing and security, which can lead to better job opportunities and career advancement in fields such as auditing, security, risk management, and compliance.
-
Industry Recognition: The CISA certification is globally recognized and highly respected in the field of information technology and information security. It is recognized by many organizations, including government agencies, financial institutions, and consulting firms, as a mark of excellence and a requirement for certain positions.
-
Competitive Advantage: The CISA certification gives you a competitive advantage over non-certified professionals in the job market. It shows that you have demonstrated your expertise, commitment to professional development, and willingness to stay up-to-date with the latest industry trends and practices.
-
Increased Salary: CISA-certified professionals are typically paid more than non-certified professionals in similar roles. According to the 2020 ISACA Salary Survey, CISA-certified professionals earn an average of $148,622 per year.
-
Professional Network: Becoming a CISA-certified professional provides access to a professional network of other CISA-certified professionals, as well as other ISACA members. This can be valuable for networking, career development, and staying up-to-date with industry news and trends.
-
Improved Job Performance: The knowledge and skills gained through obtaining the CISA certification can help you perform your job more effectively and efficiently, which can benefit your organization and contribute to your personal and professional growth.
Job prospects and career opportunities for CISA-certified professionals.
The Certified Information Systems Auditor (CISA) certification is highly respected and globally recognized in the field of information technology and information security. It is a valuable credential for professionals seeking to advance their careers in fields such as auditing, security, risk management, and compliance. Here are some job prospects and career opportunities for CISA-certified professionals:
-
Information Systems Auditor: The most common career path for CISA-certified professionals is working as an information systems auditor. They are responsible for auditing, monitoring, and assessing an organization's information technology and business systems to ensure they are secure, efficient, and effective.
-
Information Security Manager: CISA-certified professionals can also pursue a career as an information security manager. They are responsible for developing and implementing information security policies and procedures to protect an organization's information systems and assets.
-
IT Risk Manager: CISA-certified professionals can work as IT risk managers, responsible for identifying and mitigating IT risks that may impact an organization's operations, reputation, or financial performance.
-
Compliance Manager: CISA-certified professionals can also work as compliance managers, responsible for ensuring an organization complies with relevant laws, regulations, and industry standards related to information systems and security.
-
Consultant: CISA-certified professionals can work as consultants, providing advice and guidance to organizations on information systems auditing, control, and security.
-
Chief Information Security Officer (CISO): CISA-certified professionals with extensive experience and leadership skills can pursue a career as a CISO, responsible for developing and implementing an organization's overall information security strategy and program.
How to prepare for the CISA exam: study materials, tips, and resources.
Preparing for the Certified Information Systems Auditor (CISA) exam can be a challenging but rewarding experience. Here are some study materials, tips, and resources to help you prepare for the exam:
-
ISACA Study Materials: ISACA, the organization that offers the CISA certification, provides study materials to help candidates prepare for the exam. These include the CISA Review Manual, the CISA Review Questions, Answers & Explanations Database, and the CISA Virtual Instructor-Led Training.
-
Exam Preparation Courses: Many training providers offer CISA exam preparation courses, both in-person and online. These courses cover the exam content and provide practice questions, study materials, and guidance from experienced instructors.
-
Practice Questions: Practicing with sample questions and mock exams is an essential part of exam preparation. ISACA offers an official CISA practice exam and other sample questions and mock exams are available from various sources, including online forums, study groups, and exam preparation courses.
-
Time Management: The CISA exam consists of 150 multiple-choice questions to be completed in four hours. Time management is crucial to passing the exam, so it is essential to practice answering questions within the time limit. You can use a timer to practice answering questions within the allocated time.
-
Focus on Weak Areas: Identify your weak areas and focus on them during your study sessions. Focus on the domains where you scored the lowest in your practice exams and review the related study materials.
-
Join Study Groups: Joining a study group can be helpful for sharing study materials, discussing difficult concepts, and providing support and motivation. Study groups can be found online or in-person.
-
Stay Up-to-Date: Stay up-to-date with the latest industry trends and practices related to information systems auditing and security. Read industry publications, attend webinars, and network with other professionals to stay informed.
Exam structure and format: what to expect on the day of the exam.
The Certified Information Systems Auditor (CISA) exam is a four-hour, computer-based exam that consists of 150 multiple-choice questions. The exam is offered in multiple languages, including English, Chinese Simplified, French, German, Hebrew, Italian, Japanese, Korean, Spanish, and Turkish.
Here's what you can expect on the day of the CISA exam:
-
Arrival: Arrive at the exam center at least 30 minutes before the scheduled exam time. Bring your admission ticket, government-issued identification with a photo, and any other necessary items as specified by the exam center.
-
Check-in: Check in at the exam center and follow the procedures specified by the exam center. This may include a fingerprint scan, photo, or other identification methods.
-
Exam Format: The CISA exam consists of 150 multiple-choice questions. The questions are presented one at a time, and you must select the best answer from the four choices provided. You can flag questions for review and return to them later.
-
Exam Domains: The exam covers five domains:
-
Domain 1: Information System Auditing Process (21%)
-
Domain 2: Governance and Management of IT (16%)
-
Domain 3: Information Systems Acquisition, Development, and Implementation (18%)
-
Domain 4: Information Systems Operations and Business Resilience (20%)
-
Domain 5: Protection of Information Assets (25%)
-
Breaks: You can take a break during the exam, but the exam clock will continue to run. You must return to your seat before the break time is over.
-
Completion: When you have completed the exam, you will receive a preliminary score report indicating whether you have passed or failed. The official score report will be available within 10 business days of the exam.
CISA exam eligibility and registration process.
To be eligible for the Certified Information Systems Auditor (CISA) exam, you must meet certain requirements. Here are the eligibility requirements and the registration process for the CISA exam:
Eligibility Requirements:
-
Work Experience: You must have a minimum of five years of professional information systems auditing, control, or security work experience. Alternatively, you can substitute up to three years of experience with certain educational or professional certifications.
-
Adherence to Code of Ethics: You must adhere to the ISACA Code of Professional Ethics.
-
Agreement to the Terms and Conditions: You must agree to the terms and conditions of the CISA certification.
Registration Process:
-
Create an Account: Create an account on the ISACA website and complete your profile.
-
Submit the Application: Complete the CISA application, including details of your work experience and education. If you are substituting experience with education or certifications, provide the necessary documentation.
-
Pay the Fees: Pay the CISA exam fee, which varies depending on your ISACA membership status and location.
-
Receive Confirmation: Once your application and payment have been processed, you will receive confirmation of your eligibility to take the exam.
-
Schedule the Exam: Schedule your exam appointment with the designated testing provider. You can choose to take the exam at a testing center or via remote proctoring.
-
Prepare for the Exam: Use the study materials and resources provided by ISACA to prepare for the exam.
-
Take the Exam: On the exam day, arrive at the testing center or log in for remote proctoring at least 30 minutes before the scheduled exam time.
-
Receive the Results: You will receive a preliminary score report on the exam day. The official score report will be available within 10 business days.
Renewal requirements for CISA certification.
To maintain your Certified Information Systems Auditor (CISA) certification, you must renew it every three years. The renewal process is designed to ensure that CISA-certified professionals stay current with the latest developments in the field. Here are the requirements for renewing your CISA certification:
-
Continuing Professional Education (CPE): You must earn a minimum of 120 CPE credits during the three-year renewal period. At least 20 of these credits must be earned each year, and at least 60 must be related to information security, IT audit, or information technology.
-
Compliance with ISACA Code of Professional Ethics: You must comply with the ISACA Code of Professional Ethics during the renewal period.
-
Payment of the Annual Maintenance Fee: You must pay an annual maintenance fee to maintain your membership and CISA certification.
-
Submission of CPE Documentation: You must document and report your CPE activities to ISACA. ISACA provides a CPE reporting tool for this purpose. You can submit your CPE documentation as you earn the credits or at the end of the three-year renewal period.
-
Compliance with Audit Requirements: You may be selected for a random audit to ensure that you have met the CPE requirements. If you are selected for an audit, you will be required to provide documentation of your CPE activities.
How to obtain CISA Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: SMAC Certication
-
Big Data: Big Data and Hadoop Administrator
-
Digital Marketing : Digital Marketing Certification
-
Data Science : Power BI Certification
-
Cyber Security : CISA Certification
Conclusion
In conclusion, obtaining the Certified Information Systems Auditor (CISA) certification can be a significant step for professionals seeking to enhance their career in information systems auditing and security. The CISA certification validates the skills and knowledge necessary to effectively audit, control, monitor, and assess an organization's information technology and business systems. The certification provides benefits such as career advancement, increased salary, and improved marketability. Additionally, complementing the CISA certification with other relevant certifications can further enhance one's skillset and provide additional career opportunities. While preparing for the CISA exam can be challenging, there are many resources available to help individuals succeed, and the investment in obtaining the certification can be well worth it in the long run.
Read More
Welcome to the world of information systems auditing! If you have a passion for technology, a keen eye for detail, and a desire to protect valuable data and systems, then becoming a Certified Information Systems Auditor (CISA) might be the ideal career path for you. In today's digital age, where cyber threats loom large, organizations are increasingly reliant on skilled professionals who can ensure the integrity and security of their information systems. This comprehensive guide will walk you through the process of becoming a CISA, providing valuable insights into the certification requirements, exam preparation strategies, and the rewarding opportunities that await those who embark on this fulfilling journey. Whether you are a seasoned IT professional seeking career advancement or a tech enthusiast starting afresh, this guide will equip you with the knowledge and resources needed to excel in the field of information systems auditing and gain the prestigious CISA designation. So, let's dive in and discover how you can pave your way to becoming a Certified Information Systems Auditor!
Table of Contents
-
What is the CISA certification and why is it important?
-
Requirements for obtaining the CISA certification.
-
Benefits of becoming a CISA-certified professional.
-
Job prospects and career opportunities for CISA-certified professionals.
-
How to prepare for the CISA exam: study materials, tips, and resources.
-
Exam structure and format: what to expect on the day of the exam.
-
CISA exam eligibility and registration process.
-
Renewal requirements for CISA certification.
-
Conclusion.
The Certified Information Systems Auditor (CISA) certification is a globally recognized credential for professionals who audit, control, monitor, and assess information technology and business systems. This certification is awarded by the Information Systems Audit and Control Association (ISACA), a professional organization that provides knowledge, certifications, and networking opportunities to IT and information security professionals. The CISA certification is designed to validate a candidate's knowledge and expertise in information systems auditing, control, and security. It is considered one of the most prestigious and in-demand certifications in the field of information technology, with the potential to open up career opportunities and enhance professional credibility. In this topic, we will discuss the benefits of obtaining a CISA certification, the exam requirements, and how to prepare for the exam.
What is the CISA certification and why is it important?
The Certified Information Systems Auditor (CISA) certification is a professional certification that validates a candidate's knowledge and expertise in information systems auditing, control, and security. It is awarded by the Information Systems Audit and Control Association (ISACA), a professional organization that provides knowledge, certifications, and networking opportunities to IT and information security professionals.
The CISA certification is globally recognized and highly respected in the field of information technology and information security. It is designed for professionals who are responsible for auditing, monitoring, controlling, and assessing information technology and business systems. This certification is important because it provides a comprehensive understanding of the principles, practices, and standards involved in auditing and assessing information systems, including risk management, governance, and compliance.
Becoming a CISA-certified professional demonstrates that you possess the knowledge, skills, and experience required to audit and control information systems effectively. It also highlights your commitment to professional development and your willingness to stay up-to-date with the latest industry trends and practices.
Additionally, the CISA certification can lead to greater job opportunities, higher salaries, and career advancement in fields such as auditing, security, risk management, and compliance. It is recognized by many organizations, including government agencies, financial institutions, and consulting firms, as a mark of excellence and a requirement for certain positions.
Requirements for obtaining the CISA certification.
To obtain the CISA certification, candidates must meet the following requirements:
-
Education: Candidates must have a minimum of a bachelor's degree from an accredited college or university or have equivalent work experience. Two years of work experience can be substituted for one year of education, up to a maximum of five years.
-
Work Experience: Candidates must have a minimum of five years of professional information systems auditing, control, or security work experience. Work experience must be gained within the ten-year period preceding the application date for certification or within five years from the date of passing the CISA exam.
-
Adherence to the ISACA Code of Professional Ethics: Candidates must agree to abide by the ISACA Code of Professional Ethics.
-
Exam: Candidates must pass the CISA exam, which is a 150-question, multiple-choice exam that covers five domains related to information systems auditing:
-
Domain 1: Information System Auditing Process
-
Domain 2: Governance and Management of IT
-
Domain 3: Information Systems Acquisition, Development, and Implementation
-
Domain 4: Information Systems Operations, Maintenance, and Support
-
Domain 5: Protection of Information Assets
The CISA exam is offered three times a year and is administered at various testing centers worldwide.
-
Continuing Professional Education: After obtaining the CISA certification, candidates must complete a minimum of 20 continuing professional education (CPE) hours annually and 120 CPE hours in a three-year period.
Benefits of becoming a CISA-certified professional.
Becoming a Certified Information Systems Auditor (CISA) certified professional offers numerous benefits, including:
-
Career Advancement: Obtaining the CISA certification demonstrates your knowledge and skills in information systems auditing and security, which can lead to better job opportunities and career advancement in fields such as auditing, security, risk management, and compliance.
-
Industry Recognition: The CISA certification is globally recognized and highly respected in the field of information technology and information security. It is recognized by many organizations, including government agencies, financial institutions, and consulting firms, as a mark of excellence and a requirement for certain positions.
-
Competitive Advantage: The CISA certification gives you a competitive advantage over non-certified professionals in the job market. It shows that you have demonstrated your expertise, commitment to professional development, and willingness to stay up-to-date with the latest industry trends and practices.
-
Increased Salary: CISA-certified professionals are typically paid more than non-certified professionals in similar roles. According to the 2020 ISACA Salary Survey, CISA-certified professionals earn an average of $148,622 per year.
-
Professional Network: Becoming a CISA-certified professional provides access to a professional network of other CISA-certified professionals, as well as other ISACA members. This can be valuable for networking, career development, and staying up-to-date with industry news and trends.
-
Improved Job Performance: The knowledge and skills gained through obtaining the CISA certification can help you perform your job more effectively and efficiently, which can benefit your organization and contribute to your personal and professional growth.
Job prospects and career opportunities for CISA-certified professionals.
The Certified Information Systems Auditor (CISA) certification is highly respected and globally recognized in the field of information technology and information security. It is a valuable credential for professionals seeking to advance their careers in fields such as auditing, security, risk management, and compliance. Here are some job prospects and career opportunities for CISA-certified professionals:
-
Information Systems Auditor: The most common career path for CISA-certified professionals is working as an information systems auditor. They are responsible for auditing, monitoring, and assessing an organization's information technology and business systems to ensure they are secure, efficient, and effective.
-
Information Security Manager: CISA-certified professionals can also pursue a career as an information security manager. They are responsible for developing and implementing information security policies and procedures to protect an organization's information systems and assets.
-
IT Risk Manager: CISA-certified professionals can work as IT risk managers, responsible for identifying and mitigating IT risks that may impact an organization's operations, reputation, or financial performance.
-
Compliance Manager: CISA-certified professionals can also work as compliance managers, responsible for ensuring an organization complies with relevant laws, regulations, and industry standards related to information systems and security.
-
Consultant: CISA-certified professionals can work as consultants, providing advice and guidance to organizations on information systems auditing, control, and security.
-
Chief Information Security Officer (CISO): CISA-certified professionals with extensive experience and leadership skills can pursue a career as a CISO, responsible for developing and implementing an organization's overall information security strategy and program.
How to prepare for the CISA exam: study materials, tips, and resources.
Preparing for the Certified Information Systems Auditor (CISA) exam can be a challenging but rewarding experience. Here are some study materials, tips, and resources to help you prepare for the exam:
-
ISACA Study Materials: ISACA, the organization that offers the CISA certification, provides study materials to help candidates prepare for the exam. These include the CISA Review Manual, the CISA Review Questions, Answers & Explanations Database, and the CISA Virtual Instructor-Led Training.
-
Exam Preparation Courses: Many training providers offer CISA exam preparation courses, both in-person and online. These courses cover the exam content and provide practice questions, study materials, and guidance from experienced instructors.
-
Practice Questions: Practicing with sample questions and mock exams is an essential part of exam preparation. ISACA offers an official CISA practice exam and other sample questions and mock exams are available from various sources, including online forums, study groups, and exam preparation courses.
-
Time Management: The CISA exam consists of 150 multiple-choice questions to be completed in four hours. Time management is crucial to passing the exam, so it is essential to practice answering questions within the time limit. You can use a timer to practice answering questions within the allocated time.
-
Focus on Weak Areas: Identify your weak areas and focus on them during your study sessions. Focus on the domains where you scored the lowest in your practice exams and review the related study materials.
-
Join Study Groups: Joining a study group can be helpful for sharing study materials, discussing difficult concepts, and providing support and motivation. Study groups can be found online or in-person.
-
Stay Up-to-Date: Stay up-to-date with the latest industry trends and practices related to information systems auditing and security. Read industry publications, attend webinars, and network with other professionals to stay informed.
Exam structure and format: what to expect on the day of the exam.
The Certified Information Systems Auditor (CISA) exam is a four-hour, computer-based exam that consists of 150 multiple-choice questions. The exam is offered in multiple languages, including English, Chinese Simplified, French, German, Hebrew, Italian, Japanese, Korean, Spanish, and Turkish.
Here's what you can expect on the day of the CISA exam:
-
Arrival: Arrive at the exam center at least 30 minutes before the scheduled exam time. Bring your admission ticket, government-issued identification with a photo, and any other necessary items as specified by the exam center.
-
Check-in: Check in at the exam center and follow the procedures specified by the exam center. This may include a fingerprint scan, photo, or other identification methods.
-
Exam Format: The CISA exam consists of 150 multiple-choice questions. The questions are presented one at a time, and you must select the best answer from the four choices provided. You can flag questions for review and return to them later.
-
Exam Domains: The exam covers five domains:
-
Domain 1: Information System Auditing Process (21%)
-
Domain 2: Governance and Management of IT (16%)
-
Domain 3: Information Systems Acquisition, Development, and Implementation (18%)
-
Domain 4: Information Systems Operations and Business Resilience (20%)
-
Domain 5: Protection of Information Assets (25%)
-
Breaks: You can take a break during the exam, but the exam clock will continue to run. You must return to your seat before the break time is over.
-
Completion: When you have completed the exam, you will receive a preliminary score report indicating whether you have passed or failed. The official score report will be available within 10 business days of the exam.
CISA exam eligibility and registration process.
To be eligible for the Certified Information Systems Auditor (CISA) exam, you must meet certain requirements. Here are the eligibility requirements and the registration process for the CISA exam:
Eligibility Requirements:
-
Work Experience: You must have a minimum of five years of professional information systems auditing, control, or security work experience. Alternatively, you can substitute up to three years of experience with certain educational or professional certifications.
-
Adherence to Code of Ethics: You must adhere to the ISACA Code of Professional Ethics.
-
Agreement to the Terms and Conditions: You must agree to the terms and conditions of the CISA certification.
Registration Process:
-
Create an Account: Create an account on the ISACA website and complete your profile.
-
Submit the Application: Complete the CISA application, including details of your work experience and education. If you are substituting experience with education or certifications, provide the necessary documentation.
-
Pay the Fees: Pay the CISA exam fee, which varies depending on your ISACA membership status and location.
-
Receive Confirmation: Once your application and payment have been processed, you will receive confirmation of your eligibility to take the exam.
-
Schedule the Exam: Schedule your exam appointment with the designated testing provider. You can choose to take the exam at a testing center or via remote proctoring.
-
Prepare for the Exam: Use the study materials and resources provided by ISACA to prepare for the exam.
-
Take the Exam: On the exam day, arrive at the testing center or log in for remote proctoring at least 30 minutes before the scheduled exam time.
-
Receive the Results: You will receive a preliminary score report on the exam day. The official score report will be available within 10 business days.
Renewal requirements for CISA certification.
To maintain your Certified Information Systems Auditor (CISA) certification, you must renew it every three years. The renewal process is designed to ensure that CISA-certified professionals stay current with the latest developments in the field. Here are the requirements for renewing your CISA certification:
-
Continuing Professional Education (CPE): You must earn a minimum of 120 CPE credits during the three-year renewal period. At least 20 of these credits must be earned each year, and at least 60 must be related to information security, IT audit, or information technology.
-
Compliance with ISACA Code of Professional Ethics: You must comply with the ISACA Code of Professional Ethics during the renewal period.
-
Payment of the Annual Maintenance Fee: You must pay an annual maintenance fee to maintain your membership and CISA certification.
-
Submission of CPE Documentation: You must document and report your CPE activities to ISACA. ISACA provides a CPE reporting tool for this purpose. You can submit your CPE documentation as you earn the credits or at the end of the three-year renewal period.
-
Compliance with Audit Requirements: You may be selected for a random audit to ensure that you have met the CPE requirements. If you are selected for an audit, you will be required to provide documentation of your CPE activities.
How to obtain CISA Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: SMAC Certication
-
Big Data: Big Data and Hadoop Administrator
-
Digital Marketing : Digital Marketing Certification
-
Data Science : Power BI Certification
-
Cyber Security : CISA Certification
Conclusion
In conclusion, obtaining the Certified Information Systems Auditor (CISA) certification can be a significant step for professionals seeking to enhance their career in information systems auditing and security. The CISA certification validates the skills and knowledge necessary to effectively audit, control, monitor, and assess an organization's information technology and business systems. The certification provides benefits such as career advancement, increased salary, and improved marketability. Additionally, complementing the CISA certification with other relevant certifications can further enhance one's skillset and provide additional career opportunities. While preparing for the CISA exam can be challenging, there are many resources available to help individuals succeed, and the investment in obtaining the certification can be well worth it in the long run.
Navigating Digital Marketing Diversity: Optimal Applications of 10 Distinct Strategies
In the rapidly evolving landscape of digital marketing, success is no longer achieved through a one-size-fits-all approach. The diverse range of strategies available has transformed the way businesses engage with audiences, build brand identity, and drive growth. "Navigating Digital Marketing Diversity: Optimal Applications of 10 Distinct Strategies" delves into the dynamic world of modern marketing, uncovering the unique strengths and applications of ten key strategies. From the timeless power of SEO and the immediate impact of PPC to the engaging realms of social media, influencer collaborations, and beyond, this exploration guides you through the intricacies of each strategy, empowering you to make informed decisions and chart a course towards digital marketing excellence. Join us on this journey to discover how the convergence of these strategies can shape your business's success in the ever-expanding digital landscape.
Table of Contents
What is Digital Marketing?
10 Types of Digital Marketing
-
Content Marketing
-
Search Engine Optimization
-
Search Engine Marketing/Pay-per-Click
-
Social Media Marketing
-
Affiliate and Influencer Marketing
-
Email Marketing
-
Mobile Marketing
-
Video Marketing
-
Audio Marketing
-
Chatbot Marketing
When and How to Use Different Types of Marketing?
What Types of Digital Marketing are Best for Your Business?
Want to Get a Jumpstart on your Digital Marketing Career?
Conclusion
What is Digital Marketing?
Digital marketing refers to the practice of promoting products, services, or brands using digital channels and technologies. It encompasses a wide range of strategies and tactics that leverage the internet, electronic devices, and various online platforms to connect with potential customers and engage with existing ones. The goal of digital marketing is to reach a targeted audience, build brand awareness, drive traffic, and ultimately achieve business objectives, such as generating leads, increasing sales, or improving customer retention.
Digital marketing takes advantage of the digital landscape to create personalized and interactive experiences for consumers. It includes a variety of channels and methods, such as search engines, social media, email, content creation, advertising, and more. The effectiveness of digital marketing campaigns can often be tracked and measured in real-time, allowing marketers to make data-driven decisions and optimize their strategies for better results.
As technology continues to evolve, digital marketing methods also continue to evolve, offering new and innovative ways to connect with audiences. It has become an essential component of modern marketing efforts, allowing businesses of all sizes to reach global audiences and engage with customers on a more personalized level.
10 Types of Digital Marketing
Here are 10 types of digital marketing, each focusing on different strategies and channels to reach and engage audiences:
Content Marketing
It is a digital marketing strategy focused on creating and distributing valuable, relevant, and consistent content to attract and engage a target audience. The content can take various forms, such as blog posts, articles, videos, infographics, podcasts, and more. Here are the pros and cons of content marketing:
Pros:
-
Builds Authority and Credibility: Creating high-quality content showcases your expertise in your industry, establishing you as a knowledgeable authority and building trust with your audience.
-
Attracts Targeted Traffic: Well-optimized content can drive organic traffic from search engines, increasing your website's visibility and potentially attracting valuable leads.
Cons:
-
Time-Consuming: Content creation requires time and effort, from brainstorming ideas to creating, editing, and optimizing the content for distribution.
-
Results Aren't Immediate: Content marketing typically requires consistent efforts over time to yield significant results, making it less suitable for businesses seeking quick returns.
Search Engine Optimization (SEO)
It is a digital marketing strategy aimed at improving a website's visibility in search engine results pages (SERPs) organically. The goal is to increase the quantity and quality of organic (non-paid) traffic to a website. Here are the pros and cons of SEO:
Pros:
1. Increased Organic Traffic: Optimizing your website for relevant keywords and user intent can lead to higher rankings in search results, driving more organic traffic to your site.
2. Long-Term Results: Once you achieve higher rankings, they can be relatively stable, leading to ongoing traffic and exposure without continual advertising costs.
Cons:
-
Time-Consuming: SEO is a long-term strategy that requires patience, as it can take several months to see significant improvements in rankings and traffic.
-
Algorithm Changes: Search engines frequently update their algorithms, which can impact your rankings. Staying current with these changes can be challenging.
Search Engine Marketing (SEM)
Its often referred to in the context of "Pay-per-Click (PPC)" advertising, is a digital marketing strategy that involves placing advertisements on search engine results pages (SERPs) or other platforms. In SEM, advertisers bid on specific keywords that users might enter into search engines like Google or Bing. When users search for these keywords, the ads appear at the top or bottom of the search results. Here's an explanation of SEM/PPC with its pros and cons:
Pros:
-
Immediate Visibility: Ads are displayed as soon as the campaign is set up, providing instant visibility for your products or services.
-
Highly Targeted: You can choose specific keywords, demographics, locations, and even device types to target your ads to a relevant audience.
Cons:
-
Costs Can Add Up: While you have control over your budget, clicks can be expensive, especially for competitive keywords, and costs can escalate quickly if not managed effectively.
-
Dependent on Bidding: Higher bids can lead to better ad placements, but the competition for popular keywords can make bidding competitive and costly.
Social Media Marketing (SMM)
It is a digital marketing strategy that involves using social media platforms to connect, engage, and interact with your target audience. SMM aims to build brand awareness, drive website traffic, and achieve specific marketing goals through both organic (unpaid) and paid efforts. Here's an explanation of Social Media Marketing along with its pros and cons:
Pros:
-
Broad Audience Reach: Social media platforms have billions of active users, allowing you to connect with a vast and diverse audience.
-
Audience Targeting: Platforms offer advanced targeting options based on demographics, interests, behaviors, and more, ensuring your content reaches the right people.
Cons:
-
Time-Consuming: Managing multiple social media accounts, creating content, and engaging with followers can be time-intensive.
-
Algorithm Changes: Social media algorithms change frequently, affecting the reach and visibility of your posts.
Affiliate Marketing and Influencer Marketing
These are two distinct digital marketing strategies that involve partnering with external individuals or entities to promote products or services. Here's an explanation of both, along with their pros and cons:
Affiliate Marketing:
Affiliate marketing is a performance-based strategy where businesses partner with affiliates who promote their products or services. Affiliates earn a commission for each sale, click, or lead generated through their marketing efforts.
Pros:
-
Cost-Effective: You pay only for results (sales, clicks, etc.), making it a cost-effective way to reach a broader audience.
-
Risk Mitigation: Since affiliates are rewarded for conversions, there's a shared interest in driving actual sales.
cons
-
Management Complexity: Managing relationships, tracking conversions, and ensuring fairness can be complex, especially with a large affiliate network.
-
Quality Control: You have limited control over how affiliates promote your products, which could impact your brand's image.
Influencer Marketing:
Influencer marketing involves collaborating with individuals who have a significant online following and can influence their audience's purchasing decisions. Influencers create content that features or promotes your products.
Pros:
-
Authenticity: Influencers' genuine endorsements can resonate with their followers, creating more authentic connections.
-
Niche Audiences: Influencers often have highly targeted audiences, allowing you to reach specific segments effectively.
-
Creativity: Influencers can showcase your products in creative and relatable ways that appeal to their followers.
-
Brand Exposure: Working with influencers exposes your brand to a wider audience, increasing brand awareness.
Cons:
-
Cost Variability: Influencers' rates can vary widely based on their following, making budgeting challenging.
-
Vetting Process: Finding influencers who align with your brand values and audience can be time-consuming.
-
Influencer Misalignment: If an influencer's actions or content deviate from your brand values, it could negatively impact your brand.
Email Marketing
Email Marketing is a digital marketing strategy that involves sending targeted emails to a group of recipients with the aim of promoting products, services, or building relationships. It's a direct and personal way to communicate with your audience. Here's an explanation of email marketing along with its pros and cons:
Pros:
-
Direct Communication: Email allows you to reach your audience directly, often delivering messages right to their inbox.
-
Personalization: You can segment your email list based on various criteria (demographics, behavior, interests) and send personalized content that resonates with each segment.
Cons:
-
Deliverability Challenges: Emails might land in spam folders, limiting their visibility and effectiveness.
-
Overwhelm: Audiences receive a significant volume of emails daily, which can lead to inbox fatigue and reduced engagement.
Mobile Marketing
Mobile Marketing is a digital marketing strategy that focuses on reaching and engaging audiences through mobile devices, such as smartphones and tablets. Given the widespread use of mobile devices, mobile marketing aims to deliver content, promotions, and experiences that are optimized for smaller screens and cater to on-the-go users. Here's an explanation of mobile marketing along with its pros and cons:
Pros:
-
Widespread Reach: With the proliferation of mobile devices, mobile marketing enables you to reach a large and diverse audience.
-
Immediate Engagement: Mobile devices allow for instant interaction, enabling real-time communication and quick responses.
Cons:
-
Screen Size Limitations: The limited screen size of mobile devices can pose challenges in presenting comprehensive information.
-
Device Fragmentation: The variety of devices, operating systems, and screen sizes requires careful optimization for consistent user experience.
Video Marketing
Video Marketing is a digital marketing strategy that involves using videos to promote products, services, or brands. It leverages the power of visual and auditory content to engage and communicate with audiences. Video marketing can take various forms, including promotional videos, tutorials, explainer videos, testimonials, and more. Here's an explanation of video marketing along with its pros and cons:
Pros:
-
High Engagement: Videos have the ability to captivate audiences and convey information in a more engaging and memorable way compared to text-based content.
-
Versatility: Videos can be adapted to various platforms and formats, from social media posts to website content and email campaigns.
Cons:
-
Resource-Intensive: Creating high-quality videos requires time, effort, equipment, and often professional expertise.
-
Technical Challenges: Video production involves technical aspects like filming, editing, and post-production, which might be unfamiliar to some marketers.
Audio Marketing
Audio Marketing, also known as Audio Branding or Sonic Branding, is a digital marketing strategy that involves using sound and audio elements to create a consistent and memorable brand experience. It leverages auditory cues, such as jingles, sound effects, and even voiceovers, to establish a distinct brand identity and enhance the overall customer experience. Here's an explanation of audio marketing along with its pros and cons:
Pros:
-
Memorable Brand Identity: Audio elements like jingles or sonic logos can create a unique and recognizable brand identity that sticks in customers' minds.
-
Emotional Connection: Sound has the power to evoke emotions and create a deeper emotional connection with your audience.
Cons:
1. Complex Implementation: Crafting the right audio elements requires creativity and expertise, often involving professional musicians or audio experts.
2. Subjective Interpretation: Different people might interpret audio cues differently, leading to varied emotional responses.
Chatbot Marketing
Chatbot Marketing is a digital marketing strategy that involves the use of chatbots to interact with customers, answer their queries, provide information, and guide them through various stages of the customer journey. Chatbots are automated systems that simulate human conversations and can be integrated into websites, messaging apps, social media platforms, and more. Here's an explanation of chatbot marketing along with its pros and cons:
Pros:
-
24/7 Availability: Chatbots can provide instant responses and assistance to customers around the clock, enhancing user experience.
-
Efficient Customer Support: Chatbots can handle a high volume of inquiries simultaneously, reducing wait times and increasing customer satisfaction.
Cons:
-
Limited Understanding: Chatbots might struggle with understanding complex or nuanced queries, leading to frustration for users.
-
Lack of Empathy: Chatbots lack human emotions, which might not be ideal for handling sensitive or emotionally charged interactions.
When and How to Use Different Types of Marketing?
To use different types of marketing effectively, align your approach with your business objectives and audience preferences. Digital marketing encompasses various strategies such as SEO for long-term visibility, PPC for quick results, and content marketing to build authority. Leverage social media marketing for brand engagement, email marketing for personalized communication, and tap into wider audiences with influencer marketing and affiliate marketing. Engage visually with video marketing and target on-the-go users via mobile marketing. Lastly, enhance customer interactions through chatbot marketing. Continuously analyze results, adapting your strategies to optimize outcomes and maximize your marketing impact.
What Types of Digital Marketing are Best for Your Business?
The most effective types of digital marketing for your business depend on factors such as your industry, audience, and goals. If you're aiming to enhance your online visibility and credibility, SEO is crucial across industries. For immediate results and time-sensitive campaigns, consider PPC. Engaging with your audience and showcasing products is facilitated through social media marketing, while content marketing is ideal for establishing expertise. To nurture customer relationships and provide personalized communication, email marketing is valuable. Collaborating with influencers suits businesses looking for authentic endorsements, while affiliate marketing extends reach through partnerships. To convey complex information visually, explore video marketing, and target mobile users through mobile marketing. Finally, if you aim to enhance customer support and engagement, consider integrating chatbot marketing. Assess your business's specific needs to craft a tailored digital marketing approach.
Want to Get a Jumpstart on your Digital Marketing Career?
If you're eager to kickstart your digital marketing career, start by educating yourself through online courses and resources. Choose a specialization that aligns with your interests, build an online presence to showcase your skills, and gain practical experience through internships or freelance work. Obtain relevant certifications to boost your credibility, attend industry events to network, and stay updated on the latest trends. Experiment with strategies on personal projects, create a portfolio to showcase your work, and apply for entry-level positions or freelancing opportunities to gain real-world experience. Continuous learning and adaptability are crucial in this rapidly evolving field, so remain curious and persistent as you embark on your digital marketing journey.
Conclusion
In the ever-evolving landscape of digital marketing, the ability to navigate and harness the diversity of strategies is a cornerstone of success. As we've explored the optimal applications of 10 distinct strategies, from the enduring power of SEO and the immediacy of PPC to the engagement potential of social media and the authenticity of influencer marketing, it's clear that a holistic approach is key. Content marketing's authority-building, email marketing's personal touch, and the visual impact of video marketing all play vital roles. Moreover, mobile marketing's adaptability and chatbot marketing's efficiency address changing user habits. Through affiliate marketing's collaboration and the auditory identity of audio marketing, every facet has its place. Navigating this diversity requires a deep understanding of your business, audience, and goals. By skillfully blending these strategies, adapting to trends, and continually learning, you can chart a course for digital marketing success, fostering meaningful connections and driving sustainable growth in the digital realm.
Read More
In the rapidly evolving landscape of digital marketing, success is no longer achieved through a one-size-fits-all approach. The diverse range of strategies available has transformed the way businesses engage with audiences, build brand identity, and drive growth. "Navigating Digital Marketing Diversity: Optimal Applications of 10 Distinct Strategies" delves into the dynamic world of modern marketing, uncovering the unique strengths and applications of ten key strategies. From the timeless power of SEO and the immediate impact of PPC to the engaging realms of social media, influencer collaborations, and beyond, this exploration guides you through the intricacies of each strategy, empowering you to make informed decisions and chart a course towards digital marketing excellence. Join us on this journey to discover how the convergence of these strategies can shape your business's success in the ever-expanding digital landscape.
Table of Contents
What is Digital Marketing?
10 Types of Digital Marketing
-
Content Marketing
-
Search Engine Optimization
-
Search Engine Marketing/Pay-per-Click
-
Social Media Marketing
-
Affiliate and Influencer Marketing
-
Email Marketing
-
Mobile Marketing
-
Video Marketing
-
Audio Marketing
-
Chatbot Marketing
When and How to Use Different Types of Marketing?
What Types of Digital Marketing are Best for Your Business?
Want to Get a Jumpstart on your Digital Marketing Career?
Conclusion
What is Digital Marketing?
Digital marketing refers to the practice of promoting products, services, or brands using digital channels and technologies. It encompasses a wide range of strategies and tactics that leverage the internet, electronic devices, and various online platforms to connect with potential customers and engage with existing ones. The goal of digital marketing is to reach a targeted audience, build brand awareness, drive traffic, and ultimately achieve business objectives, such as generating leads, increasing sales, or improving customer retention.
Digital marketing takes advantage of the digital landscape to create personalized and interactive experiences for consumers. It includes a variety of channels and methods, such as search engines, social media, email, content creation, advertising, and more. The effectiveness of digital marketing campaigns can often be tracked and measured in real-time, allowing marketers to make data-driven decisions and optimize their strategies for better results.
As technology continues to evolve, digital marketing methods also continue to evolve, offering new and innovative ways to connect with audiences. It has become an essential component of modern marketing efforts, allowing businesses of all sizes to reach global audiences and engage with customers on a more personalized level.
10 Types of Digital Marketing
Here are 10 types of digital marketing, each focusing on different strategies and channels to reach and engage audiences:
Content Marketing
It is a digital marketing strategy focused on creating and distributing valuable, relevant, and consistent content to attract and engage a target audience. The content can take various forms, such as blog posts, articles, videos, infographics, podcasts, and more. Here are the pros and cons of content marketing:
Pros:
-
Builds Authority and Credibility: Creating high-quality content showcases your expertise in your industry, establishing you as a knowledgeable authority and building trust with your audience.
-
Attracts Targeted Traffic: Well-optimized content can drive organic traffic from search engines, increasing your website's visibility and potentially attracting valuable leads.
Cons:
-
Time-Consuming: Content creation requires time and effort, from brainstorming ideas to creating, editing, and optimizing the content for distribution.
-
Results Aren't Immediate: Content marketing typically requires consistent efforts over time to yield significant results, making it less suitable for businesses seeking quick returns.
Search Engine Optimization (SEO)
It is a digital marketing strategy aimed at improving a website's visibility in search engine results pages (SERPs) organically. The goal is to increase the quantity and quality of organic (non-paid) traffic to a website. Here are the pros and cons of SEO:
Pros:
1. Increased Organic Traffic: Optimizing your website for relevant keywords and user intent can lead to higher rankings in search results, driving more organic traffic to your site.
2. Long-Term Results: Once you achieve higher rankings, they can be relatively stable, leading to ongoing traffic and exposure without continual advertising costs.
Cons:
-
Time-Consuming: SEO is a long-term strategy that requires patience, as it can take several months to see significant improvements in rankings and traffic.
-
Algorithm Changes: Search engines frequently update their algorithms, which can impact your rankings. Staying current with these changes can be challenging.
Search Engine Marketing (SEM)
Its often referred to in the context of "Pay-per-Click (PPC)" advertising, is a digital marketing strategy that involves placing advertisements on search engine results pages (SERPs) or other platforms. In SEM, advertisers bid on specific keywords that users might enter into search engines like Google or Bing. When users search for these keywords, the ads appear at the top or bottom of the search results. Here's an explanation of SEM/PPC with its pros and cons:
Pros:
-
Immediate Visibility: Ads are displayed as soon as the campaign is set up, providing instant visibility for your products or services.
-
Highly Targeted: You can choose specific keywords, demographics, locations, and even device types to target your ads to a relevant audience.
Cons:
-
Costs Can Add Up: While you have control over your budget, clicks can be expensive, especially for competitive keywords, and costs can escalate quickly if not managed effectively.
-
Dependent on Bidding: Higher bids can lead to better ad placements, but the competition for popular keywords can make bidding competitive and costly.
Social Media Marketing (SMM)
It is a digital marketing strategy that involves using social media platforms to connect, engage, and interact with your target audience. SMM aims to build brand awareness, drive website traffic, and achieve specific marketing goals through both organic (unpaid) and paid efforts. Here's an explanation of Social Media Marketing along with its pros and cons:
Pros:
-
Broad Audience Reach: Social media platforms have billions of active users, allowing you to connect with a vast and diverse audience.
-
Audience Targeting: Platforms offer advanced targeting options based on demographics, interests, behaviors, and more, ensuring your content reaches the right people.
Cons:
-
Time-Consuming: Managing multiple social media accounts, creating content, and engaging with followers can be time-intensive.
-
Algorithm Changes: Social media algorithms change frequently, affecting the reach and visibility of your posts.
Affiliate Marketing and Influencer Marketing
These are two distinct digital marketing strategies that involve partnering with external individuals or entities to promote products or services. Here's an explanation of both, along with their pros and cons:
Affiliate Marketing:
Affiliate marketing is a performance-based strategy where businesses partner with affiliates who promote their products or services. Affiliates earn a commission for each sale, click, or lead generated through their marketing efforts.
Pros:
-
Cost-Effective: You pay only for results (sales, clicks, etc.), making it a cost-effective way to reach a broader audience.
-
Risk Mitigation: Since affiliates are rewarded for conversions, there's a shared interest in driving actual sales.
cons
-
Management Complexity: Managing relationships, tracking conversions, and ensuring fairness can be complex, especially with a large affiliate network.
-
Quality Control: You have limited control over how affiliates promote your products, which could impact your brand's image.
Influencer Marketing:
Influencer marketing involves collaborating with individuals who have a significant online following and can influence their audience's purchasing decisions. Influencers create content that features or promotes your products.
Pros:
-
Authenticity: Influencers' genuine endorsements can resonate with their followers, creating more authentic connections.
-
Niche Audiences: Influencers often have highly targeted audiences, allowing you to reach specific segments effectively.
-
Creativity: Influencers can showcase your products in creative and relatable ways that appeal to their followers.
-
Brand Exposure: Working with influencers exposes your brand to a wider audience, increasing brand awareness.
Cons:
-
Cost Variability: Influencers' rates can vary widely based on their following, making budgeting challenging.
-
Vetting Process: Finding influencers who align with your brand values and audience can be time-consuming.
-
Influencer Misalignment: If an influencer's actions or content deviate from your brand values, it could negatively impact your brand.
Email Marketing
Email Marketing is a digital marketing strategy that involves sending targeted emails to a group of recipients with the aim of promoting products, services, or building relationships. It's a direct and personal way to communicate with your audience. Here's an explanation of email marketing along with its pros and cons:
Pros:
-
Direct Communication: Email allows you to reach your audience directly, often delivering messages right to their inbox.
-
Personalization: You can segment your email list based on various criteria (demographics, behavior, interests) and send personalized content that resonates with each segment.
Cons:
-
Deliverability Challenges: Emails might land in spam folders, limiting their visibility and effectiveness.
-
Overwhelm: Audiences receive a significant volume of emails daily, which can lead to inbox fatigue and reduced engagement.
Mobile Marketing
Mobile Marketing is a digital marketing strategy that focuses on reaching and engaging audiences through mobile devices, such as smartphones and tablets. Given the widespread use of mobile devices, mobile marketing aims to deliver content, promotions, and experiences that are optimized for smaller screens and cater to on-the-go users. Here's an explanation of mobile marketing along with its pros and cons:
Pros:
-
Widespread Reach: With the proliferation of mobile devices, mobile marketing enables you to reach a large and diverse audience.
-
Immediate Engagement: Mobile devices allow for instant interaction, enabling real-time communication and quick responses.
Cons:
-
Screen Size Limitations: The limited screen size of mobile devices can pose challenges in presenting comprehensive information.
-
Device Fragmentation: The variety of devices, operating systems, and screen sizes requires careful optimization for consistent user experience.
Video Marketing
Video Marketing is a digital marketing strategy that involves using videos to promote products, services, or brands. It leverages the power of visual and auditory content to engage and communicate with audiences. Video marketing can take various forms, including promotional videos, tutorials, explainer videos, testimonials, and more. Here's an explanation of video marketing along with its pros and cons:
Pros:
-
High Engagement: Videos have the ability to captivate audiences and convey information in a more engaging and memorable way compared to text-based content.
-
Versatility: Videos can be adapted to various platforms and formats, from social media posts to website content and email campaigns.
Cons:
-
Resource-Intensive: Creating high-quality videos requires time, effort, equipment, and often professional expertise.
-
Technical Challenges: Video production involves technical aspects like filming, editing, and post-production, which might be unfamiliar to some marketers.
Audio Marketing
Audio Marketing, also known as Audio Branding or Sonic Branding, is a digital marketing strategy that involves using sound and audio elements to create a consistent and memorable brand experience. It leverages auditory cues, such as jingles, sound effects, and even voiceovers, to establish a distinct brand identity and enhance the overall customer experience. Here's an explanation of audio marketing along with its pros and cons:
Pros:
-
Memorable Brand Identity: Audio elements like jingles or sonic logos can create a unique and recognizable brand identity that sticks in customers' minds.
-
Emotional Connection: Sound has the power to evoke emotions and create a deeper emotional connection with your audience.
Cons:
1. Complex Implementation: Crafting the right audio elements requires creativity and expertise, often involving professional musicians or audio experts.
2. Subjective Interpretation: Different people might interpret audio cues differently, leading to varied emotional responses.
Chatbot Marketing
Chatbot Marketing is a digital marketing strategy that involves the use of chatbots to interact with customers, answer their queries, provide information, and guide them through various stages of the customer journey. Chatbots are automated systems that simulate human conversations and can be integrated into websites, messaging apps, social media platforms, and more. Here's an explanation of chatbot marketing along with its pros and cons:
Pros:
-
24/7 Availability: Chatbots can provide instant responses and assistance to customers around the clock, enhancing user experience.
-
Efficient Customer Support: Chatbots can handle a high volume of inquiries simultaneously, reducing wait times and increasing customer satisfaction.
Cons:
-
Limited Understanding: Chatbots might struggle with understanding complex or nuanced queries, leading to frustration for users.
-
Lack of Empathy: Chatbots lack human emotions, which might not be ideal for handling sensitive or emotionally charged interactions.
When and How to Use Different Types of Marketing?
To use different types of marketing effectively, align your approach with your business objectives and audience preferences. Digital marketing encompasses various strategies such as SEO for long-term visibility, PPC for quick results, and content marketing to build authority. Leverage social media marketing for brand engagement, email marketing for personalized communication, and tap into wider audiences with influencer marketing and affiliate marketing. Engage visually with video marketing and target on-the-go users via mobile marketing. Lastly, enhance customer interactions through chatbot marketing. Continuously analyze results, adapting your strategies to optimize outcomes and maximize your marketing impact.
What Types of Digital Marketing are Best for Your Business?
The most effective types of digital marketing for your business depend on factors such as your industry, audience, and goals. If you're aiming to enhance your online visibility and credibility, SEO is crucial across industries. For immediate results and time-sensitive campaigns, consider PPC. Engaging with your audience and showcasing products is facilitated through social media marketing, while content marketing is ideal for establishing expertise. To nurture customer relationships and provide personalized communication, email marketing is valuable. Collaborating with influencers suits businesses looking for authentic endorsements, while affiliate marketing extends reach through partnerships. To convey complex information visually, explore video marketing, and target mobile users through mobile marketing. Finally, if you aim to enhance customer support and engagement, consider integrating chatbot marketing. Assess your business's specific needs to craft a tailored digital marketing approach.
Want to Get a Jumpstart on your Digital Marketing Career?
If you're eager to kickstart your digital marketing career, start by educating yourself through online courses and resources. Choose a specialization that aligns with your interests, build an online presence to showcase your skills, and gain practical experience through internships or freelance work. Obtain relevant certifications to boost your credibility, attend industry events to network, and stay updated on the latest trends. Experiment with strategies on personal projects, create a portfolio to showcase your work, and apply for entry-level positions or freelancing opportunities to gain real-world experience. Continuous learning and adaptability are crucial in this rapidly evolving field, so remain curious and persistent as you embark on your digital marketing journey.
Conclusion
In the ever-evolving landscape of digital marketing, the ability to navigate and harness the diversity of strategies is a cornerstone of success. As we've explored the optimal applications of 10 distinct strategies, from the enduring power of SEO and the immediacy of PPC to the engagement potential of social media and the authenticity of influencer marketing, it's clear that a holistic approach is key. Content marketing's authority-building, email marketing's personal touch, and the visual impact of video marketing all play vital roles. Moreover, mobile marketing's adaptability and chatbot marketing's efficiency address changing user habits. Through affiliate marketing's collaboration and the auditory identity of audio marketing, every facet has its place. Navigating this diversity requires a deep understanding of your business, audience, and goals. By skillfully blending these strategies, adapting to trends, and continually learning, you can chart a course for digital marketing success, fostering meaningful connections and driving sustainable growth in the digital realm.
Exploring Data Encryption: Unveiling Types, Algorithms, Techniques, and Approaches
In an increasingly interconnected digital world, where data is both the lifeblood and the target of modern endeavors, the need for robust data protection has never been more critical. At the heart of this defense lies the art and science of data encryption—an intricate process that transforms information into an unreadable code, rendering it impervious to prying eyes. This exploration into the realm of data encryption aims to unravel its intricacies, unveiling the diverse types, sophisticated algorithms, ingenious techniques, and strategic approaches that together fortify the security of our digital landscape. From the symmetrical dance of keys to the asymmetric harmony of secure communications, from the impenetrable armor of Advanced Encryption Standard (AES) to the mathematical elegance of RSA and Elliptic Curve Cryptography (ECC), this journey will delve into the mechanisms that power our defenses against data breaches and unauthorized access. We will navigate through the labyrinth of encryption methods, discerning the nuanced interplay of confidentiality, integrity, and authenticity that they orchestrate. Whether you're a curious explorer of technology or an ardent guardian of data integrity, join us as we embark on an enlightening expedition into the world of data encryption, where each layer of knowledge adds another layer of protection.
Table of Contents
What is Data Encryption?
How Does Data Encryption Work?
Why Do We Need Data Encryption?
What are the 2 Types of Data Encryption Techniques?
What is Hashing?
What is an Encryption Algorithm?
Best Encryption Algorithms
3DES
The Future of Data Encryption
Should You Use Symmetric or Asymmetric Encryption?
Businesses Use Encryption For Many Purposes
Steps to Implement an Effective Encryption Strategy
What Is a Key in Cryptography?
Do You Want to Learn More About Cybersecurity?
FAQs
What is Data Encryption?
Data encryption is the process of converting understandable data into an unreadable form, known as ciphertext, using complex algorithms and a secret key. This transformation ensures that even if unauthorized parties gain access to the encrypted data, they cannot comprehend its original meaning without the corresponding decryption key. Encryption serves as a vital mechanism for safeguarding sensitive information during storage, transmission, and processing, thwarting unauthorized access and maintaining data confidentiality. It finds application in various realms such as online transactions, secure communication, and data protection, offering varying levels of security through different encryption methods and algorithms tailored to specific needs.
How Does Data Encryption Work?
Data encryption functions by utilizing complex algorithms to convert plain data into an unintelligible form known as ciphertext. This process involves an encryption key that serves as the foundation for the transformation. The chosen algorithm determines how the encryption and decryption keys interact. During encryption, the algorithm combines the encryption key with the plaintext, generating ciphertext that appears as random characters. This ciphertext can be safely transmitted or stored without revealing the original information. To reverse the process, decryption employs the corresponding decryption key, allowing the recipient to transform the ciphertext back into readable plaintext. The security of encrypted data hinges on robust algorithms, secure key management, and effective protection against unauthorized access to the encryption keys.
Why Do We Need Data Encryption?
Data encryption is a vital necessity due to its role in shielding sensitive information from unauthorized access and maintaining confidentiality. It acts as a bulwark against privacy breaches by converting data into an unreadable format, making it indecipherable without the appropriate decryption key. This protection is essential across diverse domains, from safeguarding personal data and financial records to upholding regulatory compliance and mitigating the impact of data breaches. Encryption not only secures communication over networks and cloud storage but also fortifies authentication procedures and shields intellectual property from prying eyes. In an era of global connectivity, encryption stands as a cornerstone of cybersecurity, ensuring the security and privacy of digital interactions and sensitive information.
What are the 2 Types of Data Encryption Techniques?
Data encryption techniques can be broadly categorized into two main types: Symmetric Encryption and Asymmetric Encryption.
-
Symmetric Encryption: In symmetric encryption, a single encryption key is used for both the encryption and decryption processes. The same key is shared between the sender and the recipient. The main advantage of symmetric encryption is its speed and efficiency, as the algorithms used are generally faster than their asymmetric counterparts. However, the challenge lies in securely exchanging the encryption key between parties without it being intercepted by unauthorized individuals. Common symmetric encryption algorithms include AES (Advanced Encryption Standard) and DES (Data Encryption Standard).
-
Asymmetric Encryption: Asymmetric encryption, also known as public-key encryption, employs a pair of keys: a public key and a private key. The public key is used for encryption, while the private key is used for decryption. The keys are mathematically related but cannot be practically derived from each other. This setup addresses the key exchange challenge of symmetric encryption, as the public key can be freely shared without compromising the security of the private key. Asymmetric encryption provides a higher level of security for tasks like secure communication and digital signatures. RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are examples of asymmetric encryption algorithms.
Both types of encryption techniques have their advantages and are often used together to address specific security needs. Symmetric encryption is suitable for encrypting large amounts of data quickly, while asymmetric encryption is valuable for secure key exchange and ensuring the authenticity of communication parties.
What is Hashing?
Hashing is a cryptographic technique that involves transforming input data into a fixed-length string of characters, known as a hash value. This process is designed to be fast and deterministic, meaning the same input will always produce the same hash value. Hashing serves various purposes, such as verifying data integrity and authenticity. It ensures data integrity by generating a unique representation of the input data, making it easy to detect even minor changes in the data. Hashing is commonly used for tasks like password storage, where passwords are hashed and stored to enhance security. Additionally, hashing underpins digital signatures, providing a way to confirm the authenticity of digital documents and messages. However, it's important to choose secure and collision-resistant hash functions to prevent vulnerabilities and ensure the reliability of hash-based applications.
What is an Encryption Algorithm?
An encryption algorithm is a set of mathematical rules and procedures used to transform data from its original, readable form (plaintext) into an unreadable and secure format (ciphertext) during encryption, and to revert it back to plaintext during decryption. It dictates how the encryption key interacts with the data to produce the ciphertext and how the decryption key is used to reverse the process. Encryption algorithms play a pivotal role in maintaining data security and confidentiality, ensuring that sensitive information remains protected from unauthorized access and interception. These algorithms come in two main types: symmetric, which use the same key for both encryption and decryption, and asymmetric (public-key), which employ a pair of keys for these operations. The selection of an encryption algorithm depends on factors such as security requirements, key management, and the specific application's needs.
Best Encryption Algorithms
The "best" encryption algorithm depends on the specific use case, security requirements, and the state of current cryptographic research. However, as of my last knowledge update in September 2021, I can mention some widely recognized and respected encryption algorithms that were considered strong at that time:
-
AES (Advanced Encryption Standard): AES is one of the most widely used symmetric encryption algorithms. It offers strong security and efficiency and is considered secure for a wide range of applications. AES operates with varying key lengths, including 128-bit, 192-bit, and 256-bit.
-
RSA (Rivest-Shamir-Adleman): RSA is a well-known asymmetric encryption algorithm used for secure key exchange, digital signatures, and other cryptographic tasks. It relies on the difficulty of factoring large prime numbers to provide security.
-
ECC (Elliptic Curve Cryptography): ECC is another asymmetric encryption algorithm known for its strong security and relatively shorter key lengths compared to RSA. It is particularly well-suited for resource-constrained environments, such as mobile devices.
-
SHA-256 (Secure Hash Algorithm 256-bit): While not an encryption algorithm per se, SHA-256 is a widely used cryptographic hash function. It's used for various purposes, including generating digital signatures and verifying data integrity.
-
ChaCha20 and Poly1305: These are modern cryptographic algorithms designed to provide encryption and data integrity in a combined mode. They are becoming popular choices, especially for use in stream cipher constructions.
It's important to note that cryptographic algorithms and best practices can evolve over time due to advances in technology and cryptanalysis. Organizations should stay updated with the latest recommendations from reputable sources, such as NIST (National Institute of Standards and Technology), to ensure they are using algorithms that meet current security standards. Additionally, the strength of encryption also relies on proper key management, implementation, and the overall security of the system in which it is used.
3DES
Triple Data Encryption Standard (3DES), also known as TDEA (Triple Data Encryption Algorithm), is a symmetric encryption algorithm that provides a higher level of security compared to the original Data Encryption Standard (DES) algorithm. 3DES applies the DES algorithm three times in a cascade, using multiple keys. This process significantly increases the effective key length and enhances security.
Here's how 3DES works:
-
Key Generation: Three separate keys are generated, often referred to as Key 1, Key 2, and Key 3.
-
Encryption: The plaintext data undergoes three consecutive rounds of encryption using the three keys. The data is first encrypted with Key 1, then decrypted using Key 2, and finally encrypted again using Key 3.
-
Decryption: To decrypt the data, the process is reversed. The ciphertext is decrypted with Key 3, then encrypted with Key 2, and finally decrypted using Key 1.
3DES provides an effective key length of 168 bits, as each of the three keys is 56 bits long. This makes it significantly more secure than the original DES, which had a 56-bit key length and became susceptible to brute-force attacks as computing power increased. However, it's worth noting that 3DES is not as efficient as more modern symmetric encryption algorithms like AES, which offer better performance and security with shorter key lengths.
3DES was widely adopted as an interim solution when transitioning from DES to more secure algorithms. However, due to its relatively slower performance and the availability of more efficient encryption algorithms, such as AES, it's recommended to use AES for new implementations requiring strong symmetric encryption.
The Future of Data Encryption
The future of data encryption holds several promising trends and challenges. Post-Quantum Cryptography is actively being researched to ensure encryption methods remain secure against the potential threat of quantum computers. Homomorphic encryption presents opportunities for processing data while it remains encrypted, enhancing privacy and security. Zero-knowledge proofs could revolutionize authentication and digital identity, while encryption's role in securing blockchain networks will continue to be paramount. Enhanced key management practices, such as hardware security modules and secure key distribution, will strengthen encryption protocols. Quantum Key Distribution offers ultra-secure methods for key exchange. The synergy of AI and encryption is likely to optimize processes and enhance overall security. As regulations evolve, encryption laws may adapt to balance security and law enforcement needs. Usability improvements and broader integration into applications and devices will be pivotal for increasing encryption adoption. Staying abreast of these developments will be essential as the landscape of data encryption continues to evolve dynamically.
Should You Use Symmetric or Asymmetric Encryption?
The decision to use symmetric or asymmetric encryption hinges on the context and security requirements of the scenario. Symmetric encryption offers speed and efficiency, making it suitable for encrypting large data volumes. However, it demands a secure method of distributing the shared key among parties. Asymmetric encryption, while slower, addresses the challenge of secure key exchange and is pivotal for scenarios where parties don't share a pre-established secret key. Asymmetric encryption's application extends to digital signatures and secure communication with key exchange. Often, a hybrid approach is employed, utilizing both encryption types to leverage their strengths. In such cases, asymmetric encryption may be used to securely establish a symmetric encryption key, enabling efficient data encryption. Ultimately, the choice should align with specific security needs, key management complexity, and the speed requirements of the given use case, ensuring an appropriate balance between security and practicality.
Businesses Use Encryption For Many Purposes
Businesses leverage encryption for a multitude of purposes to reinforce their data security measures and uphold the integrity of their operations. Encryption is extensively employed to shield sensitive customer data, proprietary information, and financial records, thereby thwarting unauthorized access and data breaches. It's pivotal in securing communication channels, such as emails and instant messaging, ensuring that confidential information remains private during transmission. Encryption also underpins secure financial transactions on e-commerce platforms and online banking systems. It bolsters password security by storing user credentials securely and helps businesses adhere to regulatory frameworks like GDPR and HIPAA, safeguarding them from legal consequences and maintaining customer trust. Additionally, encryption is paramount for cloud security, remote work scenarios, secure file sharing, digital signatures, IoT security, and preserving the confidentiality of sensitive data within supply chains. Overall, encryption is a cornerstone of modern business strategies, fostering data protection and bolstering organizational reputation.
Steps to Implement an Effective Encryption Strategy
Implementing an effective encryption strategy involves a systematic approach to ensure the security of sensitive data. Here are five key steps to guide the process:
-
Data Classification and Assessment: Begin by identifying and classifying the types of data that require encryption. Conduct a thorough assessment of your organization's data landscape to determine which data is sensitive and where it resides. This includes data at rest, in transit, and during processing.
-
Security Requirements Definition: Define your security requirements based on the sensitivity of the data. Determine which encryption algorithms and key lengths are appropriate for different data types and use cases. Consider compliance regulations and industry standards that apply to your organization.
-
Encryption Implementation: Select suitable encryption solutions and tools that align with your requirements. Implement encryption mechanisms for data at rest and in transit. For data at rest, utilize encryption features provided by databases, operating systems, or storage solutions. For data in transit, employ secure protocols such as TLS/SSL for network communication.
-
Key Management and Access Control: Develop a robust key management strategy. Establish procedures for generating, storing, rotating, and revoking encryption keys. Ensure that only authorized personnel have access to encryption keys. Implement strong access controls to prevent unauthorized users from accessing encrypted data.
-
Testing, Monitoring, and Compliance: Thoroughly test your encryption implementation to ensure its effectiveness and compatibility with your systems. Regularly monitor encryption processes, access logs, and audit trails to detect any anomalies or unauthorized access attempts. Conduct periodic security assessments and audits to ensure compliance with encryption policies and regulations.
By following these steps, you can create a structured and comprehensive encryption strategy that safeguards sensitive data, mitigates risks, and aligns with industry best practices and compliance standards.
What Is a Key in Cryptography?
In cryptography, a key refers to a specific piece of information, often a sequence of characters, numbers, or bits, that is used to control the encryption and decryption processes. Keys play a central role in cryptographic operations by determining how data is transformed from its original form (plaintext) to an encrypted form (ciphertext) and back to plaintext.
There are two main types of keys in cryptography:
-
Encryption Key: This key is used during the encryption process to convert plaintext into ciphertext. The encryption key is known only to authorized parties involved in secure communication or data protection.
-
Decryption Key: This key is used during the decryption process to revert the ciphertext back to its original plaintext. In symmetric encryption, the same key is used for both encryption and decryption. In asymmetric encryption (public-key cryptography), there is a pair of keys: a public key for encryption and a private key for decryption.
Keys are kept confidential to ensure the security of encrypted data. The strength and security of a cryptographic system often depend on the length and complexity of the encryption keys. Longer keys are generally more secure because they increase the number of possible combinations that an attacker would need to try in order to break the encryption.
Effective key management is essential to maintain the integrity of cryptographic systems. This includes secure key generation, distribution, storage, rotation, and disposal. In many cases, hardware security modules (HSMs) are used to securely store and manage encryption keys to prevent unauthorized access or theft.
Do You Want to Learn More About Cybersecurity?
Are you interested in delving deeper into the realm of cybersecurity? With the ever-growing importance of safeguarding digital systems and data, gaining expertise in this field is invaluable. Notable certifications such as Certified Information Security Manager (CISM), Certified Information Systems Security Professional (CISSP), Certified Information Systems Auditor (CISA), and CompTIA Security+ offer comprehensive knowledge and skills that can elevate your understanding of cybersecurity principles and practices. Furthermore, exploring frameworks like COBIT 2019 can provide you with a structured approach to governance and management of enterprise information technology. These certifications and frameworks encompass a wide range of topics, from risk management and security controls to compliance and governance. Whether you're just beginning your journey or seeking to advance your career, these resources can serve as essential guides on your path to becoming a proficient cybersecurity professional.
FAQs
-
What is Data Encryption?
Data encryption is the process of converting plaintext data into ciphertext using cryptographic algorithms. It ensures the confidentiality and security of sensitive information by rendering it unreadable to unauthorized parties.
-
Why is Data Encryption Important?
Data encryption is crucial for protecting sensitive information from unauthorized access and breaches. It helps maintain privacy, prevents data leaks, and ensures the integrity of transmitted and stored data.
-
What are the Types of Data Encryption?
There are two main types of data encryption: symmetric and asymmetric. Symmetric encryption uses a single key for both encryption and decryption, while asymmetric encryption employs a pair of keys: a public key for encryption and a private key for decryption.
-
What Are Some Common Symmetric Encryption Algorithms?
Common symmetric encryption algorithms include Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple DES (3DES). AES, in particular, is widely used due to its security and efficiency.
-
What Are Some Common Asymmetric Encryption Algorithms?
Well-known asymmetric encryption algorithms include RSA (Rivest-Shamir-Adleman) and Elliptic Curve Cryptography (ECC). These algorithms are used for secure key exchange, digital signatures, and ensuring data confidentiality.
-
How Does Data Encryption Work in Secure Communications?
In secure communications, asymmetric encryption is often used. The sender encrypts the data with the recipient's public key, and the recipient decrypts it using their private key. This ensures that only the intended recipient can read the message.
-
What is the Role of Data Encryption in Cloud Security?
Data encryption plays a vital role in cloud security by ensuring that data stored in cloud servers remains protected from unauthorized access. Encryption helps mitigate risks associated with data breaches and unauthorized data exposure.
-
Can Encrypted Data Be Hacked?
Encrypted data can be decrypted, but the process is highly complex and requires extensive computational resources and time. Strong encryption algorithms with long key lengths make it exceedingly difficult for attackers to break the encryption.
-
What is End-to-End Encryption?
End-to-end encryption is a form of communication encryption where data is encrypted on the sender's side and decrypted only on the recipient's side. This prevents intermediaries, including service providers, from accessing the plaintext data.
-
What Are the Best Practices for Data Encryption Implementation?
Effective data encryption implementation involves key management, using strong encryption algorithms, securing keys with hardware modules, regular security audits, and keeping up with advancements in encryption technologies.
-
Is Data Encryption Used Only for Confidentiality?
While confidentiality is a primary goal of data encryption, it also ensures data integrity, authenticity, and non-repudiation. Encryption plays a significant role in ensuring the overall security of digital transactions and communications.
Read More
In an increasingly interconnected digital world, where data is both the lifeblood and the target of modern endeavors, the need for robust data protection has never been more critical. At the heart of this defense lies the art and science of data encryption—an intricate process that transforms information into an unreadable code, rendering it impervious to prying eyes. This exploration into the realm of data encryption aims to unravel its intricacies, unveiling the diverse types, sophisticated algorithms, ingenious techniques, and strategic approaches that together fortify the security of our digital landscape. From the symmetrical dance of keys to the asymmetric harmony of secure communications, from the impenetrable armor of Advanced Encryption Standard (AES) to the mathematical elegance of RSA and Elliptic Curve Cryptography (ECC), this journey will delve into the mechanisms that power our defenses against data breaches and unauthorized access. We will navigate through the labyrinth of encryption methods, discerning the nuanced interplay of confidentiality, integrity, and authenticity that they orchestrate. Whether you're a curious explorer of technology or an ardent guardian of data integrity, join us as we embark on an enlightening expedition into the world of data encryption, where each layer of knowledge adds another layer of protection.
Table of Contents
What is Data Encryption?
How Does Data Encryption Work?
Why Do We Need Data Encryption?
What are the 2 Types of Data Encryption Techniques?
What is Hashing?
What is an Encryption Algorithm?
Best Encryption Algorithms
3DES
The Future of Data Encryption
Should You Use Symmetric or Asymmetric Encryption?
Businesses Use Encryption For Many Purposes
Steps to Implement an Effective Encryption Strategy
What Is a Key in Cryptography?
Do You Want to Learn More About Cybersecurity?
FAQs
What is Data Encryption?
Data encryption is the process of converting understandable data into an unreadable form, known as ciphertext, using complex algorithms and a secret key. This transformation ensures that even if unauthorized parties gain access to the encrypted data, they cannot comprehend its original meaning without the corresponding decryption key. Encryption serves as a vital mechanism for safeguarding sensitive information during storage, transmission, and processing, thwarting unauthorized access and maintaining data confidentiality. It finds application in various realms such as online transactions, secure communication, and data protection, offering varying levels of security through different encryption methods and algorithms tailored to specific needs.
How Does Data Encryption Work?
Data encryption functions by utilizing complex algorithms to convert plain data into an unintelligible form known as ciphertext. This process involves an encryption key that serves as the foundation for the transformation. The chosen algorithm determines how the encryption and decryption keys interact. During encryption, the algorithm combines the encryption key with the plaintext, generating ciphertext that appears as random characters. This ciphertext can be safely transmitted or stored without revealing the original information. To reverse the process, decryption employs the corresponding decryption key, allowing the recipient to transform the ciphertext back into readable plaintext. The security of encrypted data hinges on robust algorithms, secure key management, and effective protection against unauthorized access to the encryption keys.
Why Do We Need Data Encryption?
Data encryption is a vital necessity due to its role in shielding sensitive information from unauthorized access and maintaining confidentiality. It acts as a bulwark against privacy breaches by converting data into an unreadable format, making it indecipherable without the appropriate decryption key. This protection is essential across diverse domains, from safeguarding personal data and financial records to upholding regulatory compliance and mitigating the impact of data breaches. Encryption not only secures communication over networks and cloud storage but also fortifies authentication procedures and shields intellectual property from prying eyes. In an era of global connectivity, encryption stands as a cornerstone of cybersecurity, ensuring the security and privacy of digital interactions and sensitive information.
What are the 2 Types of Data Encryption Techniques?
Data encryption techniques can be broadly categorized into two main types: Symmetric Encryption and Asymmetric Encryption.
-
Symmetric Encryption: In symmetric encryption, a single encryption key is used for both the encryption and decryption processes. The same key is shared between the sender and the recipient. The main advantage of symmetric encryption is its speed and efficiency, as the algorithms used are generally faster than their asymmetric counterparts. However, the challenge lies in securely exchanging the encryption key between parties without it being intercepted by unauthorized individuals. Common symmetric encryption algorithms include AES (Advanced Encryption Standard) and DES (Data Encryption Standard).
-
Asymmetric Encryption: Asymmetric encryption, also known as public-key encryption, employs a pair of keys: a public key and a private key. The public key is used for encryption, while the private key is used for decryption. The keys are mathematically related but cannot be practically derived from each other. This setup addresses the key exchange challenge of symmetric encryption, as the public key can be freely shared without compromising the security of the private key. Asymmetric encryption provides a higher level of security for tasks like secure communication and digital signatures. RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are examples of asymmetric encryption algorithms.
Both types of encryption techniques have their advantages and are often used together to address specific security needs. Symmetric encryption is suitable for encrypting large amounts of data quickly, while asymmetric encryption is valuable for secure key exchange and ensuring the authenticity of communication parties.
What is Hashing?
Hashing is a cryptographic technique that involves transforming input data into a fixed-length string of characters, known as a hash value. This process is designed to be fast and deterministic, meaning the same input will always produce the same hash value. Hashing serves various purposes, such as verifying data integrity and authenticity. It ensures data integrity by generating a unique representation of the input data, making it easy to detect even minor changes in the data. Hashing is commonly used for tasks like password storage, where passwords are hashed and stored to enhance security. Additionally, hashing underpins digital signatures, providing a way to confirm the authenticity of digital documents and messages. However, it's important to choose secure and collision-resistant hash functions to prevent vulnerabilities and ensure the reliability of hash-based applications.
What is an Encryption Algorithm?
An encryption algorithm is a set of mathematical rules and procedures used to transform data from its original, readable form (plaintext) into an unreadable and secure format (ciphertext) during encryption, and to revert it back to plaintext during decryption. It dictates how the encryption key interacts with the data to produce the ciphertext and how the decryption key is used to reverse the process. Encryption algorithms play a pivotal role in maintaining data security and confidentiality, ensuring that sensitive information remains protected from unauthorized access and interception. These algorithms come in two main types: symmetric, which use the same key for both encryption and decryption, and asymmetric (public-key), which employ a pair of keys for these operations. The selection of an encryption algorithm depends on factors such as security requirements, key management, and the specific application's needs.
Best Encryption Algorithms
The "best" encryption algorithm depends on the specific use case, security requirements, and the state of current cryptographic research. However, as of my last knowledge update in September 2021, I can mention some widely recognized and respected encryption algorithms that were considered strong at that time:
-
AES (Advanced Encryption Standard): AES is one of the most widely used symmetric encryption algorithms. It offers strong security and efficiency and is considered secure for a wide range of applications. AES operates with varying key lengths, including 128-bit, 192-bit, and 256-bit.
-
RSA (Rivest-Shamir-Adleman): RSA is a well-known asymmetric encryption algorithm used for secure key exchange, digital signatures, and other cryptographic tasks. It relies on the difficulty of factoring large prime numbers to provide security.
-
ECC (Elliptic Curve Cryptography): ECC is another asymmetric encryption algorithm known for its strong security and relatively shorter key lengths compared to RSA. It is particularly well-suited for resource-constrained environments, such as mobile devices.
-
SHA-256 (Secure Hash Algorithm 256-bit): While not an encryption algorithm per se, SHA-256 is a widely used cryptographic hash function. It's used for various purposes, including generating digital signatures and verifying data integrity.
-
ChaCha20 and Poly1305: These are modern cryptographic algorithms designed to provide encryption and data integrity in a combined mode. They are becoming popular choices, especially for use in stream cipher constructions.
It's important to note that cryptographic algorithms and best practices can evolve over time due to advances in technology and cryptanalysis. Organizations should stay updated with the latest recommendations from reputable sources, such as NIST (National Institute of Standards and Technology), to ensure they are using algorithms that meet current security standards. Additionally, the strength of encryption also relies on proper key management, implementation, and the overall security of the system in which it is used.
3DES
Triple Data Encryption Standard (3DES), also known as TDEA (Triple Data Encryption Algorithm), is a symmetric encryption algorithm that provides a higher level of security compared to the original Data Encryption Standard (DES) algorithm. 3DES applies the DES algorithm three times in a cascade, using multiple keys. This process significantly increases the effective key length and enhances security.
Here's how 3DES works:
-
Key Generation: Three separate keys are generated, often referred to as Key 1, Key 2, and Key 3.
-
Encryption: The plaintext data undergoes three consecutive rounds of encryption using the three keys. The data is first encrypted with Key 1, then decrypted using Key 2, and finally encrypted again using Key 3.
-
Decryption: To decrypt the data, the process is reversed. The ciphertext is decrypted with Key 3, then encrypted with Key 2, and finally decrypted using Key 1.
3DES provides an effective key length of 168 bits, as each of the three keys is 56 bits long. This makes it significantly more secure than the original DES, which had a 56-bit key length and became susceptible to brute-force attacks as computing power increased. However, it's worth noting that 3DES is not as efficient as more modern symmetric encryption algorithms like AES, which offer better performance and security with shorter key lengths.
3DES was widely adopted as an interim solution when transitioning from DES to more secure algorithms. However, due to its relatively slower performance and the availability of more efficient encryption algorithms, such as AES, it's recommended to use AES for new implementations requiring strong symmetric encryption.
The Future of Data Encryption
The future of data encryption holds several promising trends and challenges. Post-Quantum Cryptography is actively being researched to ensure encryption methods remain secure against the potential threat of quantum computers. Homomorphic encryption presents opportunities for processing data while it remains encrypted, enhancing privacy and security. Zero-knowledge proofs could revolutionize authentication and digital identity, while encryption's role in securing blockchain networks will continue to be paramount. Enhanced key management practices, such as hardware security modules and secure key distribution, will strengthen encryption protocols. Quantum Key Distribution offers ultra-secure methods for key exchange. The synergy of AI and encryption is likely to optimize processes and enhance overall security. As regulations evolve, encryption laws may adapt to balance security and law enforcement needs. Usability improvements and broader integration into applications and devices will be pivotal for increasing encryption adoption. Staying abreast of these developments will be essential as the landscape of data encryption continues to evolve dynamically.
Should You Use Symmetric or Asymmetric Encryption?
The decision to use symmetric or asymmetric encryption hinges on the context and security requirements of the scenario. Symmetric encryption offers speed and efficiency, making it suitable for encrypting large data volumes. However, it demands a secure method of distributing the shared key among parties. Asymmetric encryption, while slower, addresses the challenge of secure key exchange and is pivotal for scenarios where parties don't share a pre-established secret key. Asymmetric encryption's application extends to digital signatures and secure communication with key exchange. Often, a hybrid approach is employed, utilizing both encryption types to leverage their strengths. In such cases, asymmetric encryption may be used to securely establish a symmetric encryption key, enabling efficient data encryption. Ultimately, the choice should align with specific security needs, key management complexity, and the speed requirements of the given use case, ensuring an appropriate balance between security and practicality.
Businesses Use Encryption For Many Purposes
Businesses leverage encryption for a multitude of purposes to reinforce their data security measures and uphold the integrity of their operations. Encryption is extensively employed to shield sensitive customer data, proprietary information, and financial records, thereby thwarting unauthorized access and data breaches. It's pivotal in securing communication channels, such as emails and instant messaging, ensuring that confidential information remains private during transmission. Encryption also underpins secure financial transactions on e-commerce platforms and online banking systems. It bolsters password security by storing user credentials securely and helps businesses adhere to regulatory frameworks like GDPR and HIPAA, safeguarding them from legal consequences and maintaining customer trust. Additionally, encryption is paramount for cloud security, remote work scenarios, secure file sharing, digital signatures, IoT security, and preserving the confidentiality of sensitive data within supply chains. Overall, encryption is a cornerstone of modern business strategies, fostering data protection and bolstering organizational reputation.
Steps to Implement an Effective Encryption Strategy
Implementing an effective encryption strategy involves a systematic approach to ensure the security of sensitive data. Here are five key steps to guide the process:
-
Data Classification and Assessment: Begin by identifying and classifying the types of data that require encryption. Conduct a thorough assessment of your organization's data landscape to determine which data is sensitive and where it resides. This includes data at rest, in transit, and during processing.
-
Security Requirements Definition: Define your security requirements based on the sensitivity of the data. Determine which encryption algorithms and key lengths are appropriate for different data types and use cases. Consider compliance regulations and industry standards that apply to your organization.
-
Encryption Implementation: Select suitable encryption solutions and tools that align with your requirements. Implement encryption mechanisms for data at rest and in transit. For data at rest, utilize encryption features provided by databases, operating systems, or storage solutions. For data in transit, employ secure protocols such as TLS/SSL for network communication.
-
Key Management and Access Control: Develop a robust key management strategy. Establish procedures for generating, storing, rotating, and revoking encryption keys. Ensure that only authorized personnel have access to encryption keys. Implement strong access controls to prevent unauthorized users from accessing encrypted data.
-
Testing, Monitoring, and Compliance: Thoroughly test your encryption implementation to ensure its effectiveness and compatibility with your systems. Regularly monitor encryption processes, access logs, and audit trails to detect any anomalies or unauthorized access attempts. Conduct periodic security assessments and audits to ensure compliance with encryption policies and regulations.
By following these steps, you can create a structured and comprehensive encryption strategy that safeguards sensitive data, mitigates risks, and aligns with industry best practices and compliance standards.
What Is a Key in Cryptography?
In cryptography, a key refers to a specific piece of information, often a sequence of characters, numbers, or bits, that is used to control the encryption and decryption processes. Keys play a central role in cryptographic operations by determining how data is transformed from its original form (plaintext) to an encrypted form (ciphertext) and back to plaintext.
There are two main types of keys in cryptography:
-
Encryption Key: This key is used during the encryption process to convert plaintext into ciphertext. The encryption key is known only to authorized parties involved in secure communication or data protection.
-
Decryption Key: This key is used during the decryption process to revert the ciphertext back to its original plaintext. In symmetric encryption, the same key is used for both encryption and decryption. In asymmetric encryption (public-key cryptography), there is a pair of keys: a public key for encryption and a private key for decryption.
Keys are kept confidential to ensure the security of encrypted data. The strength and security of a cryptographic system often depend on the length and complexity of the encryption keys. Longer keys are generally more secure because they increase the number of possible combinations that an attacker would need to try in order to break the encryption.
Effective key management is essential to maintain the integrity of cryptographic systems. This includes secure key generation, distribution, storage, rotation, and disposal. In many cases, hardware security modules (HSMs) are used to securely store and manage encryption keys to prevent unauthorized access or theft.
Do You Want to Learn More About Cybersecurity?
Are you interested in delving deeper into the realm of cybersecurity? With the ever-growing importance of safeguarding digital systems and data, gaining expertise in this field is invaluable. Notable certifications such as Certified Information Security Manager (CISM), Certified Information Systems Security Professional (CISSP), Certified Information Systems Auditor (CISA), and CompTIA Security+ offer comprehensive knowledge and skills that can elevate your understanding of cybersecurity principles and practices. Furthermore, exploring frameworks like COBIT 2019 can provide you with a structured approach to governance and management of enterprise information technology. These certifications and frameworks encompass a wide range of topics, from risk management and security controls to compliance and governance. Whether you're just beginning your journey or seeking to advance your career, these resources can serve as essential guides on your path to becoming a proficient cybersecurity professional.
FAQs
-
What is Data Encryption?
Data encryption is the process of converting plaintext data into ciphertext using cryptographic algorithms. It ensures the confidentiality and security of sensitive information by rendering it unreadable to unauthorized parties.
-
Why is Data Encryption Important?
Data encryption is crucial for protecting sensitive information from unauthorized access and breaches. It helps maintain privacy, prevents data leaks, and ensures the integrity of transmitted and stored data.
-
What are the Types of Data Encryption?
There are two main types of data encryption: symmetric and asymmetric. Symmetric encryption uses a single key for both encryption and decryption, while asymmetric encryption employs a pair of keys: a public key for encryption and a private key for decryption.
-
What Are Some Common Symmetric Encryption Algorithms?
Common symmetric encryption algorithms include Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple DES (3DES). AES, in particular, is widely used due to its security and efficiency.
-
What Are Some Common Asymmetric Encryption Algorithms?
Well-known asymmetric encryption algorithms include RSA (Rivest-Shamir-Adleman) and Elliptic Curve Cryptography (ECC). These algorithms are used for secure key exchange, digital signatures, and ensuring data confidentiality.
-
How Does Data Encryption Work in Secure Communications?
In secure communications, asymmetric encryption is often used. The sender encrypts the data with the recipient's public key, and the recipient decrypts it using their private key. This ensures that only the intended recipient can read the message.
-
What is the Role of Data Encryption in Cloud Security?
Data encryption plays a vital role in cloud security by ensuring that data stored in cloud servers remains protected from unauthorized access. Encryption helps mitigate risks associated with data breaches and unauthorized data exposure.
-
Can Encrypted Data Be Hacked?
Encrypted data can be decrypted, but the process is highly complex and requires extensive computational resources and time. Strong encryption algorithms with long key lengths make it exceedingly difficult for attackers to break the encryption.
-
What is End-to-End Encryption?
End-to-end encryption is a form of communication encryption where data is encrypted on the sender's side and decrypted only on the recipient's side. This prevents intermediaries, including service providers, from accessing the plaintext data.
-
What Are the Best Practices for Data Encryption Implementation?
Effective data encryption implementation involves key management, using strong encryption algorithms, securing keys with hardware modules, regular security audits, and keeping up with advancements in encryption technologies.
-
Is Data Encryption Used Only for Confidentiality?
While confidentiality is a primary goal of data encryption, it also ensures data integrity, authenticity, and non-repudiation. Encryption plays a significant role in ensuring the overall security of digital transactions and communications.
What is Big Data Analytics and What is Its Significance in the Modern World?
Welcome to our comprehensive guide on 'What is Big Data Analytics and What is Its Significance in the Modern World?' In this in-depth exploration, we delve into the realm of big data analytics, shedding light on its fundamental concepts, applications, and its paramount importance in our contemporary data-driven society. Join us as we unravel the intricacies of this transformative technology and unveil its profound impact on businesses, industries, and society as a whole.
Table of Contents
What is Big Data Analytics?
Why is big data analytics important?
What is Big Data?
Uses and Examples of Big Data Analytics
History of Big Data Analytics
Benefits and Advantages of Big Data Analytics
The Lifecycle Phases of Big Data Analytics
Different Types of Big Data Analytics
Big Data Analytics Tools
Big Data Industry Applications
FAQs
What is Big Data Analytics?
Big Data Analytics is the process of extracting valuable insights from vast and complex data sets, enabling organizations to make data-driven decisions, enhance operational efficiency, improve customer experiences, manage risks effectively, and foster innovation across various industries. This transformative discipline combines data collection, storage, processing, analysis, visualization, and the utilization of machine learning techniques, empowering businesses to thrive in our data-centric modern world by leveraging the wealth of information available to them.
Why is big data analytics important?
Big Data Analytics is vital in today's digital age because it provides organizations with the ability to extract valuable insights from the vast volumes of data generated daily. This data, often referred to as "big data," encompasses a wide range of information from various sources, such as customer transactions, social media interactions, sensor data, and more. Without effective analytics, this data would remain largely untapped potential. By employing advanced techniques and technologies, organizations can uncover hidden patterns, trends, and correlations within their data, allowing for informed decision-making, improved operational efficiency, and the ability to gain a competitive edge in rapidly evolving markets.
Furthermore, Big Data Analytics has a profound impact on innovation and problem-solving across industries. It enables businesses to innovate in their product offerings, marketing strategies, and operational processes by providing a data-driven foundation for experimentation and improvement. Moreover, it plays a critical role in fields like healthcare, where it can lead to advancements in patient care, drug discovery, and disease prevention. In essence, Big Data Analytics is essential because it transforms data into actionable knowledge, fostering smarter decisions, greater efficiency, and continuous innovation in both the private and public sectors.
What is Big Data?
Big Data refers to extremely large and complex sets of data that exceed the capabilities of traditional data processing tools and methods. These data sets are characterized by what is often referred to as the "3Vs": volume, velocity, and variety.
-
Volume: Big Data typically involves massive amounts of data, often ranging from terabytes to petabytes or more. This data can be generated from various sources, including sensors, social media, business transactions, and more.
-
Velocity: Data is generated at an unprecedented speed in today's digital world. This real-time or near-real-time data flow requires rapid processing and analysis to derive meaningful insights and make timely decisions.
-
Variety: Big Data comes in various formats, including structured data (such as databases and spreadsheets), semi-structured data (like XML and JSON files), and unstructured data (such as text documents, social media posts, and multimedia content). Analyzing and making sense of this diverse data landscape is a fundamental challenge in Big Data.
In addition to the 3Vs, Big Data is often associated with two more characteristics:
-
Variability: Data can be inconsistent and vary in its format and quality over time.
-
Veracity: Ensuring the accuracy and reliability of Big Data can be a challenge, as data may contain errors or inconsistencies.
Effectively managing, storing, processing, and analyzing Big Data is crucial for organizations looking to gain valuable insights, make data-driven decisions, and derive business value from this wealth of information. This has led to the development of specialized technologies and tools, such as distributed computing frameworks like Hadoop and advanced analytics techniques like machine learning, to handle the unique challenges posed by Big Data.
Uses and Examples of Big Data Analytics
Big Data Analytics serves as a powerful tool across various industries by harnessing the vast volumes of data generated in today's digital age. One of its primary applications is in the realm of business intelligence and analytics, where organizations leverage it to gain a deeper understanding of their operations, customers, and markets. For instance, retail companies employ Big Data Analytics to analyze sales data and customer purchase patterns, enabling them to optimize inventory management and design personalized marketing campaigns. This data-driven approach enhances decision-making, helping businesses remain competitive and agile in rapidly evolving markets.
Another significant use of Big Data Analytics is in healthcare, where it aids in patient care and disease management. By analyzing electronic health records and medical data, healthcare providers can make more accurate diagnoses, recommend tailored treatment plans, and predict disease outbreaks. This application not only improves patient outcomes but also contributes to the overall efficiency of healthcare systems. In essence, Big Data Analytics is a multidimensional tool that empowers organizations to transform raw data into actionable insights, driving innovation, efficiency, and informed decision-making across a wide spectrum of industries and sectors.
History of Big Data Analytics
The history of Big Data Analytics can be traced back to the early days of computing, but it has evolved significantly over time. Here's an overview of its key milestones:
-
1950s-1960s: The concept of data processing and analysis emerged with the advent of computers. Early mainframe computers were used for basic data processing tasks, such as sorting and aggregating large volumes of data.
-
1970s-1980s: The development of relational database management systems (RDBMS) marked a significant step forward. SQL (Structured Query Language) became the standard for querying and managing structured data. However, these systems had limitations in handling large and complex datasets.
-
1990s: Data warehousing gained prominence as organizations started collecting and storing vast amounts of data. Data warehousing solutions allowed for the consolidation of data from various sources, making it easier to analyze and report on.
-
Early 2000s: The term "Big Data" began to gain traction as companies like Google and Yahoo faced challenges in managing and analyzing massive datasets. Google's MapReduce and the Hadoop Distributed File System (HDFS) were pivotal in developing scalable solutions for processing Big Data.
-
Mid-2000s: Apache Hadoop, an open-source framework, emerged as a leading platform for processing and analyzing large datasets. It popularized the idea of distributed computing and laid the foundation for Big Data Analytics.
-
Late 2000s-2010s: As organizations generated more data from various sources, technologies for Big Data Analytics continued to advance. Companies like Amazon, Facebook, and Netflix demonstrated the power of data-driven decision-making and personalized user experiences.
-
2010s-Present: Machine learning and artificial intelligence (AI) have become integral to Big Data Analytics. These technologies enable predictive analytics, anomaly detection, and automation of data analysis tasks. Cloud computing services, such as Amazon Web Services (AWS) and Microsoft Azure, offer scalable platforms for Big Data processing and storage.
-
2020s: Big Data Analytics continues to evolve with a focus on real-time data processing, edge computing, and privacy considerations. Data governance and ethical use of data have also gained prominence.
Throughout its history, Big Data Analytics has transformed from a niche concept to a critical component of decision-making in various industries, ranging from finance and healthcare to e-commerce and entertainment. As data continues to grow in volume and complexity, the field of Big Data Analytics will likely continue to evolve and adapt to meet the ever-expanding demands of the digital age.
Benefits and Advantages of Big Data Analytics
Big Data Analytics offers numerous benefits and advantages to organizations across various industries. Here are some of the key advantages:
-
Data-Driven Decision-Making: Big Data Analytics empowers organizations to make informed decisions based on real data rather than intuition or guesswork. This leads to more accurate and effective choices in various aspects of business operations.
-
Competitive Advantage: Companies that leverage Big Data Analytics gain a competitive edge by identifying market trends, customer preferences, and emerging opportunities faster and more accurately than their competitors.
-
Improved Operational Efficiency: By analyzing processes and operations, organizations can identify bottlenecks, inefficiencies, and areas for improvement. This optimization leads to cost reduction and enhanced productivity.
-
Enhanced Customer Experiences: Understanding customer behavior and preferences allows businesses to personalize products, services, and marketing campaigns. This leads to higher customer satisfaction and loyalty.
-
Risk Management: In industries like finance and insurance, Big Data Analytics aids in assessing and mitigating risks more effectively. It can detect anomalies and potential issues early, helping prevent financial losses.
The Lifecycle Phases of Big Data Analytics
The eight key stages in the lifecycle of Big Data Analytics:
-
Data Collection: Gather data from various sources, such as databases, sensors, or social media.
-
Data Storage: Organize and store the data in suitable repositories like data lakes or warehouses.
-
Data Preprocessing: Clean, transform, and prepare the data for analysis to ensure quality and consistency.
-
Data Analysis: Apply statistical and machine learning techniques to extract insights from the data.
-
Data Visualization: Present the results through charts, graphs, and dashboards for better understanding.
-
Deployment: Implement analytical models into production systems for real-time decision-making.
-
Monitoring: Continuously oversee model performance and data quality.
-
Optimization: Fine-tune models and scale infrastructure to handle increased data demands.
Different Types of Big Data Analytics
Big Data Analytics encompasses various types of analytical approaches, each tailored to address specific business or data challenges. Here are different types of Big Data Analytics:
-
Descriptive Analytics:
-
Purpose: Descriptive analytics focuses on summarizing historical data to provide insights into past trends and events.
-
Use Cases: It helps organizations understand what has happened in the past, such as sales trends, customer behavior, or website traffic patterns.
-
Diagnostic Analytics:
-
Purpose: Diagnostic analytics aims to identify the reasons behind past events or trends.
-
Use Cases: It helps uncover the causes of specific outcomes, such as understanding why sales dropped in a particular region or why a marketing campaign failed.
-
Predictive Analytics:
-
Purpose: Predictive analytics uses historical data and statistical algorithms to forecast future outcomes or trends.
-
Use Cases: Organizations use predictive analytics for demand forecasting, customer churn prediction, fraud detection, and inventory optimization.
-
Prescriptive Analytics:
-
Purpose: Prescriptive analytics goes beyond prediction by suggesting the best course of action to optimize outcomes.
-
Use Cases: It helps organizations make data-driven decisions by recommending actions based on predictive models. For instance, it can suggest pricing strategies to maximize profits.
Top of Form
Big Data Analytics Tools
Big Data Analytics tools are essential for processing, analyzing, and deriving insights from large and complex datasets. There are numerous tools available, each with its own strengths and capabilities. Here's a list of some popular Big Data Analytics tools:
-
Hadoop:
-
Description: Hadoop is an open-source framework that facilitates distributed storage and processing of large datasets across clusters of commodity hardware.
-
Key Features: Hadoop includes the Hadoop Distributed File System (HDFS) for storage and MapReduce for parallel processing. Additionally, it offers various ecosystem components like Hive, Pig, and Spark for advanced analytics.
-
Apache Spark:
-
Description: Apache Spark is an open-source, distributed computing framework that provides high-speed, in-memory data processing capabilities.
-
Key Features: Spark offers libraries for machine learning (MLlib), graph processing (GraphX), and stream processing (Structured Streaming). It's known for its speed and versatility in processing both batch and real-time data.
-
Apache Flink:
-
Description: Apache Flink is an open-source stream processing framework designed for real-time data analytics.
-
Key Features: Flink provides event time processing, support for batch and stream processing, and stateful computations. It's commonly used in applications requiring low-latency, high-throughput data processing.
-
Apache Kafka:
-
Description: Apache Kafka is a distributed streaming platform used for building real-time data pipelines and event-driven applications.
-
Key Features: Kafka is known for its high throughput, fault tolerance, and scalability. It allows for the ingestion and processing of large volumes of streaming data.
-
Hive:
-
Description: Hive is a data warehousing and SQL-like query language system built on top of Hadoop for structured data analysis.
-
Key Features: Hive provides a familiar SQL interface for querying data stored in Hadoop, making it accessible to analysts and data scientists.
-
Pig:
-
Description: Apache Pig is a high-level scripting platform for data analysis and processing in Hadoop.
-
Key Features: Pig provides a simple scripting language called Pig Latin, which allows users to express data transformations and processing logic.
-
R and RStudio:
-
Description: R is a programming language and environment specifically designed for statistical analysis and data visualization.
-
Key Features: R, along with RStudio as an integrated development environment (IDE), offers a rich ecosystem of packages and libraries for data analysis, statistical modeling, and data visualization.
Big Data Industry Applications
The applications of Big Data analytics span across a wide range of industries, offering transformative solutions to various challenges. Here are some notable industry-specific applications:
-
Healthcare:
-
Electronic Health Records (EHRs): Analyzing patient data in EHRs to improve diagnoses, treatment plans, and patient outcomes.
-
Disease Prediction: Predicting disease outbreaks, identifying high-risk populations, and improving public health strategies.
-
Drug Discovery: Accelerating drug development by analyzing genomics data and identifying potential drug candidates.
-
Finance:
-
Risk Assessment: Using data analytics to assess credit risks, detect fraudulent transactions, and manage investment portfolios.
-
Algorithmic Trading: Employing data-driven algorithms to make real-time trading decisions in financial markets.
-
Customer Segmentation: Analyzing customer data to tailor financial products and services for different segments.
-
Retail and E-commerce:
-
Recommendation Systems: Offering personalized product recommendations based on customer behavior and preferences.
-
Inventory Management: Optimizing inventory levels to reduce costs and prevent stockouts.
-
Pricing Optimization: Dynamically adjusting prices based on demand and market conditions.
-
Manufacturing:
-
Predictive Maintenance: Monitoring equipment sensors to predict and prevent machine failures and reduce downtime.
-
Quality Control: Analyzing production data to identify defects and improve product quality.
-
Supply Chain Optimization: Optimizing logistics and supply chain operations to reduce costs and improve efficiency.
-
Telecommunications:
-
Network Optimization: Analyzing network data to improve network performance, reduce downtime, and enhance customer experiences.
-
Churn Prediction: Identifying and retaining at-risk customers by analyzing usage patterns and customer behavior.
FAQs
-
What is Big Data Analytics?
Big Data Analytics is the process of examining and deriving valuable insights from large and complex datasets, often referred to as "big data." It involves various techniques and technologies to uncover hidden patterns, trends, and valuable information within massive data sets.
-
Why is Big Data Analytics important in the modern world?
Big Data Analytics is crucial in the modern world because it empowers organizations to make data-driven decisions, improve operational efficiency, enhance customer experiences, manage risks effectively, and foster innovation. It enables businesses to thrive in a data-centric environment.
-
What are the key components of Big Data Analytics?
The key components of Big Data Analytics include data collection, storage, processing, analysis, visualization, machine learning and AI, scalability, real-time analytics, and more.
-
What industries benefit from Big Data Analytics?
Big Data Analytics is beneficial in various industries, including finance, healthcare, retail, manufacturing, marketing, transportation, government, and many others. It helps organizations across sectors make data-driven decisions and gain a competitive edge.
-
What are the challenges in implementing Big Data Analytics?
Challenges in implementing Big Data Analytics include data quality issues, data privacy and security concerns, the need for specialized skills and resources, and the complexity of managing and processing large volumes of data.
-
How does Big Data Analytics impact innovation?
Big Data Analytics can lead to innovation by uncovering insights, trends, and opportunities that drive new product development, marketing strategies, and business models. It fosters innovation through data-driven decision-making.
-
What role does machine learning play in Big Data Analytics?
Machine learning is a crucial component of Big Data Analytics. It automates and enhances data analysis, enabling predictive modeling, classification, and the discovery of patterns and anomalies in large datasets.
-
What is the significance of real-time analytics in Big Data?
Real-time analytics in Big Data enables organizations to analyze and act on data as it's generated, allowing for immediate decision-making, such as fraud detection, customer support, and monitoring of critical systems.
-
How can organizations get started with Big Data Analytics?
Organizations can start with Big Data Analytics by defining their goals, assessing data needs, building the necessary infrastructure, acquiring analytical tools and talent, and formulating a data strategy aligned with their business objectives.
-
What are the ethical considerations in Big Data Analytics?
Ethical considerations in Big Data Analytics include data privacy, transparency, fairness, and responsible data handling. Organizations should adhere to ethical guidelines to ensure the responsible use of data.
Read More
Welcome to our comprehensive guide on 'What is Big Data Analytics and What is Its Significance in the Modern World?' In this in-depth exploration, we delve into the realm of big data analytics, shedding light on its fundamental concepts, applications, and its paramount importance in our contemporary data-driven society. Join us as we unravel the intricacies of this transformative technology and unveil its profound impact on businesses, industries, and society as a whole.
Table of Contents
What is Big Data Analytics?
Why is big data analytics important?
What is Big Data?
Uses and Examples of Big Data Analytics
History of Big Data Analytics
Benefits and Advantages of Big Data Analytics
The Lifecycle Phases of Big Data Analytics
Different Types of Big Data Analytics
Big Data Analytics Tools
Big Data Industry Applications
FAQs
What is Big Data Analytics?
Big Data Analytics is the process of extracting valuable insights from vast and complex data sets, enabling organizations to make data-driven decisions, enhance operational efficiency, improve customer experiences, manage risks effectively, and foster innovation across various industries. This transformative discipline combines data collection, storage, processing, analysis, visualization, and the utilization of machine learning techniques, empowering businesses to thrive in our data-centric modern world by leveraging the wealth of information available to them.
Why is big data analytics important?
Big Data Analytics is vital in today's digital age because it provides organizations with the ability to extract valuable insights from the vast volumes of data generated daily. This data, often referred to as "big data," encompasses a wide range of information from various sources, such as customer transactions, social media interactions, sensor data, and more. Without effective analytics, this data would remain largely untapped potential. By employing advanced techniques and technologies, organizations can uncover hidden patterns, trends, and correlations within their data, allowing for informed decision-making, improved operational efficiency, and the ability to gain a competitive edge in rapidly evolving markets.
Furthermore, Big Data Analytics has a profound impact on innovation and problem-solving across industries. It enables businesses to innovate in their product offerings, marketing strategies, and operational processes by providing a data-driven foundation for experimentation and improvement. Moreover, it plays a critical role in fields like healthcare, where it can lead to advancements in patient care, drug discovery, and disease prevention. In essence, Big Data Analytics is essential because it transforms data into actionable knowledge, fostering smarter decisions, greater efficiency, and continuous innovation in both the private and public sectors.
What is Big Data?
Big Data refers to extremely large and complex sets of data that exceed the capabilities of traditional data processing tools and methods. These data sets are characterized by what is often referred to as the "3Vs": volume, velocity, and variety.
-
Volume: Big Data typically involves massive amounts of data, often ranging from terabytes to petabytes or more. This data can be generated from various sources, including sensors, social media, business transactions, and more.
-
Velocity: Data is generated at an unprecedented speed in today's digital world. This real-time or near-real-time data flow requires rapid processing and analysis to derive meaningful insights and make timely decisions.
-
Variety: Big Data comes in various formats, including structured data (such as databases and spreadsheets), semi-structured data (like XML and JSON files), and unstructured data (such as text documents, social media posts, and multimedia content). Analyzing and making sense of this diverse data landscape is a fundamental challenge in Big Data.
In addition to the 3Vs, Big Data is often associated with two more characteristics:
-
Variability: Data can be inconsistent and vary in its format and quality over time.
-
Veracity: Ensuring the accuracy and reliability of Big Data can be a challenge, as data may contain errors or inconsistencies.
Effectively managing, storing, processing, and analyzing Big Data is crucial for organizations looking to gain valuable insights, make data-driven decisions, and derive business value from this wealth of information. This has led to the development of specialized technologies and tools, such as distributed computing frameworks like Hadoop and advanced analytics techniques like machine learning, to handle the unique challenges posed by Big Data.
Uses and Examples of Big Data Analytics
Big Data Analytics serves as a powerful tool across various industries by harnessing the vast volumes of data generated in today's digital age. One of its primary applications is in the realm of business intelligence and analytics, where organizations leverage it to gain a deeper understanding of their operations, customers, and markets. For instance, retail companies employ Big Data Analytics to analyze sales data and customer purchase patterns, enabling them to optimize inventory management and design personalized marketing campaigns. This data-driven approach enhances decision-making, helping businesses remain competitive and agile in rapidly evolving markets.
Another significant use of Big Data Analytics is in healthcare, where it aids in patient care and disease management. By analyzing electronic health records and medical data, healthcare providers can make more accurate diagnoses, recommend tailored treatment plans, and predict disease outbreaks. This application not only improves patient outcomes but also contributes to the overall efficiency of healthcare systems. In essence, Big Data Analytics is a multidimensional tool that empowers organizations to transform raw data into actionable insights, driving innovation, efficiency, and informed decision-making across a wide spectrum of industries and sectors.
History of Big Data Analytics
The history of Big Data Analytics can be traced back to the early days of computing, but it has evolved significantly over time. Here's an overview of its key milestones:
-
1950s-1960s: The concept of data processing and analysis emerged with the advent of computers. Early mainframe computers were used for basic data processing tasks, such as sorting and aggregating large volumes of data.
-
1970s-1980s: The development of relational database management systems (RDBMS) marked a significant step forward. SQL (Structured Query Language) became the standard for querying and managing structured data. However, these systems had limitations in handling large and complex datasets.
-
1990s: Data warehousing gained prominence as organizations started collecting and storing vast amounts of data. Data warehousing solutions allowed for the consolidation of data from various sources, making it easier to analyze and report on.
-
Early 2000s: The term "Big Data" began to gain traction as companies like Google and Yahoo faced challenges in managing and analyzing massive datasets. Google's MapReduce and the Hadoop Distributed File System (HDFS) were pivotal in developing scalable solutions for processing Big Data.
-
Mid-2000s: Apache Hadoop, an open-source framework, emerged as a leading platform for processing and analyzing large datasets. It popularized the idea of distributed computing and laid the foundation for Big Data Analytics.
-
Late 2000s-2010s: As organizations generated more data from various sources, technologies for Big Data Analytics continued to advance. Companies like Amazon, Facebook, and Netflix demonstrated the power of data-driven decision-making and personalized user experiences.
-
2010s-Present: Machine learning and artificial intelligence (AI) have become integral to Big Data Analytics. These technologies enable predictive analytics, anomaly detection, and automation of data analysis tasks. Cloud computing services, such as Amazon Web Services (AWS) and Microsoft Azure, offer scalable platforms for Big Data processing and storage.
-
2020s: Big Data Analytics continues to evolve with a focus on real-time data processing, edge computing, and privacy considerations. Data governance and ethical use of data have also gained prominence.
Throughout its history, Big Data Analytics has transformed from a niche concept to a critical component of decision-making in various industries, ranging from finance and healthcare to e-commerce and entertainment. As data continues to grow in volume and complexity, the field of Big Data Analytics will likely continue to evolve and adapt to meet the ever-expanding demands of the digital age.
Benefits and Advantages of Big Data Analytics
Big Data Analytics offers numerous benefits and advantages to organizations across various industries. Here are some of the key advantages:
-
Data-Driven Decision-Making: Big Data Analytics empowers organizations to make informed decisions based on real data rather than intuition or guesswork. This leads to more accurate and effective choices in various aspects of business operations.
-
Competitive Advantage: Companies that leverage Big Data Analytics gain a competitive edge by identifying market trends, customer preferences, and emerging opportunities faster and more accurately than their competitors.
-
Improved Operational Efficiency: By analyzing processes and operations, organizations can identify bottlenecks, inefficiencies, and areas for improvement. This optimization leads to cost reduction and enhanced productivity.
-
Enhanced Customer Experiences: Understanding customer behavior and preferences allows businesses to personalize products, services, and marketing campaigns. This leads to higher customer satisfaction and loyalty.
-
Risk Management: In industries like finance and insurance, Big Data Analytics aids in assessing and mitigating risks more effectively. It can detect anomalies and potential issues early, helping prevent financial losses.
The Lifecycle Phases of Big Data Analytics
The eight key stages in the lifecycle of Big Data Analytics:
-
Data Collection: Gather data from various sources, such as databases, sensors, or social media.
-
Data Storage: Organize and store the data in suitable repositories like data lakes or warehouses.
-
Data Preprocessing: Clean, transform, and prepare the data for analysis to ensure quality and consistency.
-
Data Analysis: Apply statistical and machine learning techniques to extract insights from the data.
-
Data Visualization: Present the results through charts, graphs, and dashboards for better understanding.
-
Deployment: Implement analytical models into production systems for real-time decision-making.
-
Monitoring: Continuously oversee model performance and data quality.
-
Optimization: Fine-tune models and scale infrastructure to handle increased data demands.
Different Types of Big Data Analytics
Big Data Analytics encompasses various types of analytical approaches, each tailored to address specific business or data challenges. Here are different types of Big Data Analytics:
-
Descriptive Analytics:
-
Purpose: Descriptive analytics focuses on summarizing historical data to provide insights into past trends and events.
-
Use Cases: It helps organizations understand what has happened in the past, such as sales trends, customer behavior, or website traffic patterns.
-
-
Diagnostic Analytics:
-
Purpose: Diagnostic analytics aims to identify the reasons behind past events or trends.
-
Use Cases: It helps uncover the causes of specific outcomes, such as understanding why sales dropped in a particular region or why a marketing campaign failed.
-
-
Predictive Analytics:
-
Purpose: Predictive analytics uses historical data and statistical algorithms to forecast future outcomes or trends.
-
Use Cases: Organizations use predictive analytics for demand forecasting, customer churn prediction, fraud detection, and inventory optimization.
-
-
Prescriptive Analytics:
-
Purpose: Prescriptive analytics goes beyond prediction by suggesting the best course of action to optimize outcomes.
-
Use Cases: It helps organizations make data-driven decisions by recommending actions based on predictive models. For instance, it can suggest pricing strategies to maximize profits.
-
Top of Form
Big Data Analytics Tools
Big Data Analytics tools are essential for processing, analyzing, and deriving insights from large and complex datasets. There are numerous tools available, each with its own strengths and capabilities. Here's a list of some popular Big Data Analytics tools:
-
Hadoop:
-
Description: Hadoop is an open-source framework that facilitates distributed storage and processing of large datasets across clusters of commodity hardware.
-
Key Features: Hadoop includes the Hadoop Distributed File System (HDFS) for storage and MapReduce for parallel processing. Additionally, it offers various ecosystem components like Hive, Pig, and Spark for advanced analytics.
-
-
Apache Spark:
-
Description: Apache Spark is an open-source, distributed computing framework that provides high-speed, in-memory data processing capabilities.
-
Key Features: Spark offers libraries for machine learning (MLlib), graph processing (GraphX), and stream processing (Structured Streaming). It's known for its speed and versatility in processing both batch and real-time data.
-
-
Apache Flink:
-
Description: Apache Flink is an open-source stream processing framework designed for real-time data analytics.
-
Key Features: Flink provides event time processing, support for batch and stream processing, and stateful computations. It's commonly used in applications requiring low-latency, high-throughput data processing.
-
-
Apache Kafka:
-
Description: Apache Kafka is a distributed streaming platform used for building real-time data pipelines and event-driven applications.
-
Key Features: Kafka is known for its high throughput, fault tolerance, and scalability. It allows for the ingestion and processing of large volumes of streaming data.
-
-
Hive:
-
Description: Hive is a data warehousing and SQL-like query language system built on top of Hadoop for structured data analysis.
-
Key Features: Hive provides a familiar SQL interface for querying data stored in Hadoop, making it accessible to analysts and data scientists.
-
-
Pig:
-
Description: Apache Pig is a high-level scripting platform for data analysis and processing in Hadoop.
-
Key Features: Pig provides a simple scripting language called Pig Latin, which allows users to express data transformations and processing logic.
-
-
R and RStudio:
-
Description: R is a programming language and environment specifically designed for statistical analysis and data visualization.
-
Key Features: R, along with RStudio as an integrated development environment (IDE), offers a rich ecosystem of packages and libraries for data analysis, statistical modeling, and data visualization.
-
Big Data Industry Applications
The applications of Big Data analytics span across a wide range of industries, offering transformative solutions to various challenges. Here are some notable industry-specific applications:
-
Healthcare:
-
Electronic Health Records (EHRs): Analyzing patient data in EHRs to improve diagnoses, treatment plans, and patient outcomes.
-
Disease Prediction: Predicting disease outbreaks, identifying high-risk populations, and improving public health strategies.
-
Drug Discovery: Accelerating drug development by analyzing genomics data and identifying potential drug candidates.
-
-
Finance:
-
Risk Assessment: Using data analytics to assess credit risks, detect fraudulent transactions, and manage investment portfolios.
-
Algorithmic Trading: Employing data-driven algorithms to make real-time trading decisions in financial markets.
-
Customer Segmentation: Analyzing customer data to tailor financial products and services for different segments.
-
-
Retail and E-commerce:
-
Recommendation Systems: Offering personalized product recommendations based on customer behavior and preferences.
-
Inventory Management: Optimizing inventory levels to reduce costs and prevent stockouts.
-
Pricing Optimization: Dynamically adjusting prices based on demand and market conditions.
-
-
Manufacturing:
-
Predictive Maintenance: Monitoring equipment sensors to predict and prevent machine failures and reduce downtime.
-
Quality Control: Analyzing production data to identify defects and improve product quality.
-
Supply Chain Optimization: Optimizing logistics and supply chain operations to reduce costs and improve efficiency.
-
-
Telecommunications:
-
Network Optimization: Analyzing network data to improve network performance, reduce downtime, and enhance customer experiences.
-
Churn Prediction: Identifying and retaining at-risk customers by analyzing usage patterns and customer behavior.
-
FAQs
-
What is Big Data Analytics?
Big Data Analytics is the process of examining and deriving valuable insights from large and complex datasets, often referred to as "big data." It involves various techniques and technologies to uncover hidden patterns, trends, and valuable information within massive data sets.
-
Why is Big Data Analytics important in the modern world?
Big Data Analytics is crucial in the modern world because it empowers organizations to make data-driven decisions, improve operational efficiency, enhance customer experiences, manage risks effectively, and foster innovation. It enables businesses to thrive in a data-centric environment.
-
What are the key components of Big Data Analytics?
The key components of Big Data Analytics include data collection, storage, processing, analysis, visualization, machine learning and AI, scalability, real-time analytics, and more.
-
What industries benefit from Big Data Analytics?
Big Data Analytics is beneficial in various industries, including finance, healthcare, retail, manufacturing, marketing, transportation, government, and many others. It helps organizations across sectors make data-driven decisions and gain a competitive edge.
-
What are the challenges in implementing Big Data Analytics?
Challenges in implementing Big Data Analytics include data quality issues, data privacy and security concerns, the need for specialized skills and resources, and the complexity of managing and processing large volumes of data.
-
How does Big Data Analytics impact innovation?
Big Data Analytics can lead to innovation by uncovering insights, trends, and opportunities that drive new product development, marketing strategies, and business models. It fosters innovation through data-driven decision-making.
-
What role does machine learning play in Big Data Analytics?
Machine learning is a crucial component of Big Data Analytics. It automates and enhances data analysis, enabling predictive modeling, classification, and the discovery of patterns and anomalies in large datasets.
-
What is the significance of real-time analytics in Big Data?
Real-time analytics in Big Data enables organizations to analyze and act on data as it's generated, allowing for immediate decision-making, such as fraud detection, customer support, and monitoring of critical systems.
-
How can organizations get started with Big Data Analytics?
Organizations can start with Big Data Analytics by defining their goals, assessing data needs, building the necessary infrastructure, acquiring analytical tools and talent, and formulating a data strategy aligned with their business objectives.
-
What are the ethical considerations in Big Data Analytics?
Ethical considerations in Big Data Analytics include data privacy, transparency, fairness, and responsible data handling. Organizations should adhere to ethical guidelines to ensure the responsible use of data.
A Complete Guide to ITIL Concepts and Summary Process: What is ITIL?
Welcome to "A Complete Guide to ITIL Concepts and Summary Process: What is ITIL?" In this comprehensive exploration, we demystify ITIL, the Information Technology Infrastructure Library, offering you a compass to navigate the intricate realm of IT Service Management (ITSM). Discover the core concepts of ITIL, unravel its summary processes, and understand its pivotal role in optimizing IT service delivery, enhancing customer satisfaction, and reshaping modern business operations. Whether you're an IT professional, a business leader, or simply curious about ITIL's impact, this guide equips you with essential knowledge, transforming the way you perceive and implement IT service management practices, all within a single paragraph.
Table of Contents
What is ITIL?
What's in the ITIL?
Benefits of ITIL:
Drawbacks of ITIL:
What are the ITIL Concepts?
What are ITIL's Guiding Principles?
Key ITIL Terms
ITIL Framework
1. Service Strategy
2. Service Design
3. Service Transition
4. Service Operations
5. Continual Service Improvement (CSI)
How Do I Put ITIL into Practice?
What is ITIL Certification, and is it Worth it?
Major Differences Between ITIL® V3 vs. ITIL® V4 Certification
How Does ITIL Help Business?
What Will ITIL Cost?
How Does ITIL Reduce Costs?
ITIL Processes and Functions
History of ITIL
ITIL Processes and Stages: Summary
What is ITIL?
ITIL, or Information Technology Infrastructure Library, is a widely adopted framework for IT service management. It offers a structured approach to aligning IT services with business objectives and delivering high-quality services to customers. ITIL encompasses various phases, including service strategy, design, transition, operation, and continual service improvement. It provides best practices and guidelines to enhance the efficiency, reliability, and customer-centricity of IT processes and services, making it a valuable resource for organizations seeking to improve their IT operations.
What's in the ITIL?
ITIL consists of a structured framework for IT service management, including a service lifecycle with stages like Service Strategy, Design, Transition, Operation, and Continual Service Improvement. It defines processes, roles, and functions within IT organizations, guiding how services are designed, delivered, and improved. ITIL emphasizes aligning IT with business goals, offering best practices for incident and problem management, change control, and more. It also provides certification options for IT professionals to validate their expertise. Overall, ITIL offers a holistic approach to managing IT services effectively and efficiently.
Benefits of ITIL
Implementing ITIL (Information Technology Infrastructure Library) in an organization can bring several significant benefits, including:
-
Improved Service Quality: ITIL promotes best practices and standardized processes, leading to more consistent and reliable IT service delivery. This, in turn, enhances the overall quality of IT services, reducing downtime and customer dissatisfaction.
-
Better Alignment with Business Goals: ITIL encourages the alignment of IT services with the objectives and needs of the business. This ensures that IT investments and efforts contribute directly to the organization's success.
-
Cost Efficiency: By optimizing processes and resources, ITIL helps organizations reduce operational costs. Effective incident management, problem resolution, and resource allocation lead to cost savings.
-
Enhanced Customer Satisfaction: ITIL's customer-centric approach ensures that IT services are designed and delivered with the customer's experience in mind. Meeting or exceeding customer expectations leads to higher satisfaction levels.
-
Reduced Risk: ITIL's focus on change management and risk mitigation helps organizations minimize the potential for disruptions and security breaches during service transitions or changes.
Drawbacks of ITIL
While ITIL (Information Technology Infrastructure Library) offers many advantages, it also has some potential drawbacks and challenges:
-
Complexity: ITIL is a comprehensive framework with a multitude of processes, roles, and functions. Implementing the full framework can be complex and resource-intensive, especially for small organizations.
-
Cost: The implementation of ITIL may involve significant upfront costs, including training, software, and process redesign. These expenses can be a barrier for some organizations.
-
Resource Intensive: ITIL requires dedicated resources, including personnel, tools, and time for training and implementation. Smaller organizations may struggle to allocate these resources.
-
Resistance to Change: Employees may resist changes in processes and procedures that ITIL mandates, especially if they have been accustomed to their current ways of working. This can slow down adoption.
-
Overstandardization: In some cases, ITIL's emphasis on standardization can stifle innovation and adaptability. Organizations may become too rigid in their processes and struggle to respond to rapidly changing business needs.
What are the ITIL Concepts?
ITIL (Information Technology Infrastructure Library) encompasses several key concepts that form the foundation of its framework for IT service management. These concepts help organizations understand and implement effective IT service management practices. Here are the core ITIL concepts:
-
Service: ITIL views services as a means of delivering value to customers without the ownership of specific costs and risks.
-
Service Management: ITIL involves specialized organizational capabilities to deliver value through IT services, encompassing processes, functions, roles, and responsibilities.
-
Service Lifecycle: ITIL's framework revolves around five stages: Service Strategy, Design, Transition, Operation, and Continual Service Improvement.
-
Process: ITIL defines a set of processes, each with specific activities, inputs, outputs, and roles, essential for effective IT service management.
-
SLA and KPI: ITIL uses Service Level Agreements (SLAs) to define service quality and Key Performance Indicators (KPIs) to measure and monitor service performance and effectiveness.
What are ITIL's Guiding Principles?
Here are the seven simplified guiding principles of ITIL:
-
Value-Centric: Focus on delivering value to customers and the business.
-
Start Where You Are: Build on your existing processes and capabilities.
-
Feedback-Driven Progress: Continuously improve through feedback and small changes.
-
Collaborate and Communicate: Work together and share information for better results.
-
Think Holistically: Consider the big picture and interconnectedness of services.
-
Keep it Simple: Avoid complexity and prioritize practicality.
-
Optimize and Automate: Streamline processes and use automation to improve efficiency.
Key ITIL Terms
ITIL (Information Technology Infrastructure Library) uses specific terminology to describe its concepts and processes. Here are some key ITIL terms:
-
Service: The means by which value is delivered to customers, often in the form of intangible deliverables like email or network connectivity.
-
Service Management: The set of organizational capabilities for delivering value to customers in the form of services.
-
Service Lifecycle: The stages of a service's existence, including Service Strategy, Service Design, Service Transition, Service Operation, and Continual Service Improvement.
-
Process: A structured set of activities designed to accomplish a specific objective. ITIL defines numerous processes for IT service management.
-
Function: A team or group of people with specific skills and resources responsible for carrying out one or more processes or activities.
-
Role: A defined set of responsibilities and activities assigned to an individual or group, such as a Service Owner or Incident Manager.
-
Stakeholder: Individuals or groups with an interest in or an impact on the services provided by an organization. This can include customers, users, suppliers, and employees.
-
Service Provider: The organization delivering IT services to customers. It can be an internal IT department or an external service provider.
-
Customer: The person or group that defines requirements for IT services and receives the value provided by those services.
-
User: Individuals who utilize IT services to carry out their tasks and achieve their goals, which may or may not be the same as the customer.
ITIL Framework
The ITIL (Information Technology Infrastructure Library) framework is a comprehensive set of best practices and guidelines for IT service management (ITSM). It provides a structured approach for organizations to plan, design, deliver, operate, and continually improve their IT services. The framework is designed to align IT services with the needs of the business and ensure the efficient and effective delivery of those services. Here are the key components and aspects of the ITIL framework:
-
Service Strategy: Defining the organization's IT service strategy, considering business objectives and customer needs.
-
Service Design: Designing IT services, processes, and supporting infrastructure.
-
Service Transition: Managing the transition of new or changed services into the production environment.
-
Service Operation: Ensuring the day-to-day delivery and management of IT services.
-
Continual Service Improvement (CSI): Identifying and implementing improvements to services and processes.
Service Strategy
Service Strategy in ITIL is the critical phase where an organization aligns its IT services with its business objectives and needs. It involves defining a clear service strategy, managing a portfolio of IT services, ensuring financial viability, understanding and influencing customer demand, coordinating service design, managing risks, and nurturing strong business relationships. The goal is to create a roadmap that ensures IT services provide value to the business, support its success, and remain cost-effective, thus guiding subsequent phases of service management and helping the organization make informed decisions about service design, transition, and operation.
Service Design
Service Design, a pivotal phase within the ITIL service lifecycle, focuses on crafting IT services that are not only technically robust but also perfectly aligned with the organization's strategic goals and customer needs. It encompasses the meticulous planning and design of services, including service catalogs, service levels, capacity, availability, continuity, security, and supplier relationships. By adhering to ITIL principles and leveraging design coordination, it ensures that services are both cost-effective and poised for seamless transition into the operational environment. Service Design plays a vital role in delivering services that deliver value to the business while maintaining high levels of quality and customer satisfaction.
Service Transition
Service Transition, a critical phase within the ITIL service lifecycle, orchestrates the controlled and efficient movement of new or modified IT services from development and testing into the operational environment. It encompasses comprehensive change management, configuration control, rigorous testing and validation, and knowledge management to minimize risks and disruptions while maximizing the value and quality of services. By adhering to ITIL principles and detailed transition planning, it ensures that services meet customer expectations, business requirements, and service levels. Service Transition plays a pivotal role in the successful delivery of IT services, fostering agility and adaptability within the organization's IT landscape.
Service Operations
Service Operation, a pivotal phase within the ITIL service lifecycle, is responsible for the continuous and efficient delivery of IT services to meet agreed-upon service levels and customer needs. It encompasses incident and problem management to swiftly resolve issues, event management for proactive monitoring and response, request fulfillment, access management, and the critical role of the service desk as a central point of user support. Technical and IT operations management ensure infrastructure reliability, while application management oversees the lifecycle of business-critical software. By adhering to ITIL principles and promoting continual service improvement, Service Operation plays a vital role in maintaining service quality, minimizing disruptions, and contributing to overall customer satisfaction and business resilience.
Continual Service Improvement (CSI)
Continual Service Improvement (CSI) is a fundamental phase within the ITIL service lifecycle, dedicated to the ongoing enhancement of IT services and processes. It involves systematically measuring service performance, analyzing results, and identifying areas for improvement. By establishing clear metrics, conducting regular reviews, and creating action plans, organizations can drive efficiency, reduce costs, and align IT services with evolving business needs. CSI fosters a culture of continuous improvement, ensuring that IT services remain adaptable and responsive to changing customer requirements and market dynamics, ultimately delivering greater value and quality to the organization and its stakeholders.
How Do I Put ITIL into Practice?
-
Assessment and Alignment: Begin by assessing your organization's existing IT service management practices and identifying areas that need improvement. Determine how well your current practices align with ITIL principles and the organization's business objectives. This assessment provides a baseline for your ITIL implementation efforts.
-
Customization and Planning: ITIL is not a one-size-fits-all framework. Customize ITIL practices to match your organization's specific needs and constraints. Create a clear implementation plan that outlines objectives, milestones, roles, responsibilities, and timelines. Ensure that the plan aligns with your business's strategic goals and secures the necessary resources.
-
Education and Training: Equip your IT teams and staff with the knowledge and skills required for ITIL adoption. Offer training and awareness programs to help them understand the ITIL framework and its benefits. It's essential to create a shared understanding and commitment among team members.
-
Process Redesign and Automation: Redesign or adapt your IT service management processes to align with ITIL best practices. Ensure that these processes are well-documented and easily accessible to all relevant parties. Invest in IT service management tools and technologies that support ITIL processes and automate repetitive tasks to improve efficiency.
-
Continuous Improvement: ITIL is built on the concept of continual service improvement (CSI). Establish a culture of continuous improvement within your organization, where regular reviews and evaluations of ITIL implementation are conducted. Use performance metrics and feedback to identify areas for enhancement and make adjustments to your ITIL practices accordingly. CSI ensures that your IT services remain aligned with evolving business needs and industry best practices.
What is ITIL Certification, and is it Worth it?
ITIL certification is a valuable credential for individuals working in IT service management and related fields. It offers a structured and globally recognized framework for understanding and implementing best practices in IT service delivery and management. Achieving ITIL certification demonstrates your commitment to improving IT service quality and aligning IT with business goals. It can open doors to career advancement and higher earning potential, as many employers value ITIL certification when hiring or promoting IT professionals. However, it's important to consider the cost and time investment required for training and exams, as well as whether ITIL aligns with your specific career path and goals. Continuous learning and staying updated with the latest ITIL practices are also necessary for maintaining the certification's value. Ultimately, the worth of ITIL certification depends on your career aspirations and the relevance of IT service management in your professional journey.
Major Differences Between ITIL® V3 vs. ITIL® V4 Certification
ITIL V3 and ITIL V4 certifications represent two distinct iterations of the ITIL framework. While ITIL V3 followed a process-oriented service lifecycle model with a structured certification scheme, ITIL V4 introduced a more flexible and holistic approach to IT service management. V4 emphasizes value co-creation, incorporates guiding principles, and introduces a simplified certification structure with practical orientation. It addresses modern trends like digital transformation and agile practices, making it more adaptable to the evolving needs of organizations in the digital age. The transition from V3 to V4 signifies a shift from a process-centric framework to one that focuses on delivering value, enhancing customer experience, and embracing emerging practices, reflecting the changing landscape of IT service management.
Major Differences Between ITIL® V3 vs. ITIL® V4 Certification
-
Certification Structure:
-
ITIL® V3: V3 had a certification structure consisting of Foundation, Intermediate (Lifecycle and Capability modules), Expert, and Master levels.
-
ITIL® V4: V4 introduced a simplified certification scheme with four levels: Foundation, Practitioner, Specialist, and Strategist. The Master level remains the highest certification but is more accessible under V4.
-
Practical Orientation:
-
ITIL® V3: V3 certification focused on theoretical knowledge of ITIL processes and practices.
-
ITIL® V4: V4 places a stronger emphasis on practical application and adaptation of ITIL principles in real-world scenarios. The Practitioner and Specialist levels are designed to help professionals apply ITIL concepts effectively.
-
Guiding Principles:
-
ITIL® V3: V3 did not have a specific set of guiding principles.
-
ITIL® V4: V4 introduces seven guiding principles (e.g., Focus on Value, Start Where You Are, Collaborate and Promote Visibility) that underpin the framework and guide decision-making.
-
Service Value Chain:
-
ITIL® V3: V3 organized processes into a service lifecycle with five stages: Service Strategy, Service Design, Service Transition, Service Operation, and Continual Service Improvement (CSI).
-
ITIL® V4: V4 introduces the Service Value System, which includes the Service Value Chain (a set of interconnected activities) and emphasizes value co-creation with customers.
-
Flexibility and Adaptability:
-
ITIL® V3: V3 had a more rigid and process-centric approach.
-
ITIL® V4: V4 is designed to be more flexible and adaptable, allowing organizations to tailor ITIL practices to their unique needs and circumstances.
-
Digital Transformation and Agile Practices:
-
ITIL® V3: V3 did not specifically address emerging trends like digital transformation and agile practices.
-
ITIL® V4: V4 incorporates modern concepts and practices, making it more relevant in the digital age, including considerations for DevOps, Agile, and lean principles.
How Does ITIL Help Business?
ITIL benefits businesses by offering a structured framework for IT service management, resulting in improved service quality, cost efficiency, and alignment with business objectives. It reduces downtime, enhances change management, and facilitates effective risk mitigation. ITIL's customer-centric approach strengthens customer satisfaction, while its emphasis on continual improvement ensures adaptability and competitiveness in the evolving digital landscape. Additionally, it aids in regulatory compliance, fosters effective communication, and establishes transparent IT governance, ultimately contributing to business resilience, growth, and a competitive edge in the market.
What Will ITIL Cost?
The cost of ITIL can vary significantly depending on factors such as the level of certification, training format, study materials, and the size and complexity of ITIL implementation within an organization. ITIL certification exams range from $150 to $700 or more, with associated training and study materials adding to the expenses. Implementing ITIL practices within an organization involves costs related to training, consulting, process redesign, ITSM tools, and ongoing maintenance. It's crucial to budget carefully, considering both certification and implementation costs, while also weighing the long-term benefits of improved IT service quality, efficiency, and alignment with business objectives that ITIL can bring to the organization.
How Does ITIL Reduce Costs?
ITIL reduces costs for organizations by fostering efficiency, standardizing processes, and minimizing the risks and disruptions associated with IT service management. It achieves this through proactive problem management, rigorous change control, optimized resource allocation, meticulous documentation, and a continual focus on improvement. ITIL's emphasis on aligning IT services with business needs ensures that resources are directed towards activities that generate value, avoiding unnecessary expenses. By preventing service outages and incidents, streamlining workflows, and promoting cost transparency, ITIL helps organizations optimize their IT operations, resulting in significant cost reductions and improved cost-effectiveness.
ITIL Processes and Functions
In ITIL (Information Technology Infrastructure Library), processes and functions are key components of the framework, serving different roles in managing IT services effectively. Here's an overview of ITIL processes and functions:
ITIL Processes: ITIL defines several processes that are essential for IT service management. These processes are organized into five core lifecycle stages:
-
Service Strategy: This stage focuses on defining the overall strategy for IT services, including understanding customer needs, defining service portfolios, and aligning IT goals with business objectives. Key processes include Service Portfolio Management and Financial Management.
-
Service Design: In this stage, ITIL defines processes for designing IT services, ensuring they meet business requirements and are manageable. Processes include Service Catalog Management, Service Level Management, Capacity Management, and Availability Management.
-
Service Transition: This stage involves transitioning new or modified services into the production environment. Key processes include Change Management, Release and Deployment Management, and Service Validation and Testing.
-
Service Operation: Service Operation is responsible for the daily delivery and management of IT services to meet service levels and customer expectations. Processes here include Incident Management, Problem Management, Event Management, and Request Fulfillment.
-
Continual Service Improvement (CSI): CSI focuses on ongoing improvement of IT services and processes. It includes processes like Service Measurement and Reporting, Service Review, and Process Evaluation.
ITIL Functions: Functions in ITIL represent organizational units or groups responsible for specific activities or roles within the IT service management framework. While not all functions are required in every organization, they provide structure and accountability in managing IT services. Key ITIL functions include:
-
Service Desk: The Service Desk function acts as a central point of contact for users to report incidents, request services, and seek assistance. It plays a critical role in providing support and ensuring efficient communication.
-
Technical Management: This function provides technical expertise and support for IT infrastructure and services. It ensures that technical resources are available and properly maintained.
-
IT Operations Management: Responsible for the day-to-day operational activities required to deliver IT services. This includes data center management, network operations, and hardware maintenance.
-
Application Management: The Application Management function manages the lifecycle of applications, ensuring they are designed, developed, tested, and maintained to support business needs.
-
IT Security Management: While not always defined as a separate function, ITIL emphasizes the importance of security throughout the service lifecycle. This involves managing security policies, access controls, and compliance.
-
Supplier Management: Supplier Management ensures that external suppliers and vendors are effectively managed to deliver the required IT services and support.
These functions and processes work together to ensure that IT services are delivered efficiently, reliably, and in alignment with business goals and customer expectations. They provide a structured approach to managing IT services throughout their lifecycle, from strategy and design to operation and improvement.
History of ITIL
The history of ITIL (Information Technology Infrastructure Library) traces its origins to the late 1980s when it was developed by the UK's Central Computer and Telecommunications Agency (CCTA). Initially conceived to standardize and improve IT service management within the UK government, ITIL soon gained recognition for its best-practice guidelines. ITIL V1, released in the late 1980s and early 1990s, laid the foundation with a comprehensive set of 31 books. However, it was in 2000 with the launch of ITIL V2 that ITIL's global impact began to take shape. V2 consolidated the framework into eight core books and gained widespread adoption. ITIL V3, introduced in 2007 and updated in 2011 (ITIL 2011), brought a service lifecycle approach and a focus on aligning IT services with business processes. In 2019, ITIL V4 marked a major shift, emphasizing value co-creation, the Service Value System, and modern IT practices. It continues to evolve, reflecting the changing landscape of IT service management and digital transformation. Throughout its history, ITIL has become a globally recognized framework for enhancing IT service quality and alignment with business objectives.
ITIL Processes and Stages: Summary
ITIL, or the Information Technology Infrastructure Library, encompasses a set of well-defined processes and stages designed to help organizations manage their IT services effectively. The core processes include Service Strategy, which aligns IT services with business goals; Service Design, which focuses on designing services that meet business requirements; Service Transition, which ensures a smooth transition of services into the production environment; Service Operation, responsible for daily service delivery and support; and Continual Service Improvement, which drives ongoing enhancements in service quality and efficiency. These processes are organized into stages that reflect the IT service lifecycle, from aligning IT with business objectives to designing, transitioning, operating, and continually improving services. By following the ITIL framework, organizations can deliver IT services that are not only reliable and cost-effective but also aligned with evolving business needs and customer expectations, ultimately contributing to improved overall business performance and competitiveness.
Read More
Welcome to "A Complete Guide to ITIL Concepts and Summary Process: What is ITIL?" In this comprehensive exploration, we demystify ITIL, the Information Technology Infrastructure Library, offering you a compass to navigate the intricate realm of IT Service Management (ITSM). Discover the core concepts of ITIL, unravel its summary processes, and understand its pivotal role in optimizing IT service delivery, enhancing customer satisfaction, and reshaping modern business operations. Whether you're an IT professional, a business leader, or simply curious about ITIL's impact, this guide equips you with essential knowledge, transforming the way you perceive and implement IT service management practices, all within a single paragraph.
Table of Contents
What is ITIL?
What's in the ITIL?
Benefits of ITIL:
Drawbacks of ITIL:
What are the ITIL Concepts?
What are ITIL's Guiding Principles?
Key ITIL Terms
ITIL Framework
1. Service Strategy
2. Service Design
3. Service Transition
4. Service Operations
5. Continual Service Improvement (CSI)
How Do I Put ITIL into Practice?
What is ITIL Certification, and is it Worth it?
Major Differences Between ITIL® V3 vs. ITIL® V4 Certification
How Does ITIL Help Business?
What Will ITIL Cost?
How Does ITIL Reduce Costs?
ITIL Processes and Functions
History of ITIL
ITIL Processes and Stages: Summary
What is ITIL?
ITIL, or Information Technology Infrastructure Library, is a widely adopted framework for IT service management. It offers a structured approach to aligning IT services with business objectives and delivering high-quality services to customers. ITIL encompasses various phases, including service strategy, design, transition, operation, and continual service improvement. It provides best practices and guidelines to enhance the efficiency, reliability, and customer-centricity of IT processes and services, making it a valuable resource for organizations seeking to improve their IT operations.
What's in the ITIL?
ITIL consists of a structured framework for IT service management, including a service lifecycle with stages like Service Strategy, Design, Transition, Operation, and Continual Service Improvement. It defines processes, roles, and functions within IT organizations, guiding how services are designed, delivered, and improved. ITIL emphasizes aligning IT with business goals, offering best practices for incident and problem management, change control, and more. It also provides certification options for IT professionals to validate their expertise. Overall, ITIL offers a holistic approach to managing IT services effectively and efficiently.
Benefits of ITIL
Implementing ITIL (Information Technology Infrastructure Library) in an organization can bring several significant benefits, including:
-
Improved Service Quality: ITIL promotes best practices and standardized processes, leading to more consistent and reliable IT service delivery. This, in turn, enhances the overall quality of IT services, reducing downtime and customer dissatisfaction.
-
Better Alignment with Business Goals: ITIL encourages the alignment of IT services with the objectives and needs of the business. This ensures that IT investments and efforts contribute directly to the organization's success.
-
Cost Efficiency: By optimizing processes and resources, ITIL helps organizations reduce operational costs. Effective incident management, problem resolution, and resource allocation lead to cost savings.
-
Enhanced Customer Satisfaction: ITIL's customer-centric approach ensures that IT services are designed and delivered with the customer's experience in mind. Meeting or exceeding customer expectations leads to higher satisfaction levels.
-
Reduced Risk: ITIL's focus on change management and risk mitigation helps organizations minimize the potential for disruptions and security breaches during service transitions or changes.
Drawbacks of ITIL
While ITIL (Information Technology Infrastructure Library) offers many advantages, it also has some potential drawbacks and challenges:
-
Complexity: ITIL is a comprehensive framework with a multitude of processes, roles, and functions. Implementing the full framework can be complex and resource-intensive, especially for small organizations.
-
Cost: The implementation of ITIL may involve significant upfront costs, including training, software, and process redesign. These expenses can be a barrier for some organizations.
-
Resource Intensive: ITIL requires dedicated resources, including personnel, tools, and time for training and implementation. Smaller organizations may struggle to allocate these resources.
-
Resistance to Change: Employees may resist changes in processes and procedures that ITIL mandates, especially if they have been accustomed to their current ways of working. This can slow down adoption.
-
Overstandardization: In some cases, ITIL's emphasis on standardization can stifle innovation and adaptability. Organizations may become too rigid in their processes and struggle to respond to rapidly changing business needs.
What are the ITIL Concepts?
ITIL (Information Technology Infrastructure Library) encompasses several key concepts that form the foundation of its framework for IT service management. These concepts help organizations understand and implement effective IT service management practices. Here are the core ITIL concepts:
-
Service: ITIL views services as a means of delivering value to customers without the ownership of specific costs and risks.
-
Service Management: ITIL involves specialized organizational capabilities to deliver value through IT services, encompassing processes, functions, roles, and responsibilities.
-
Service Lifecycle: ITIL's framework revolves around five stages: Service Strategy, Design, Transition, Operation, and Continual Service Improvement.
-
Process: ITIL defines a set of processes, each with specific activities, inputs, outputs, and roles, essential for effective IT service management.
-
SLA and KPI: ITIL uses Service Level Agreements (SLAs) to define service quality and Key Performance Indicators (KPIs) to measure and monitor service performance and effectiveness.
What are ITIL's Guiding Principles?
Here are the seven simplified guiding principles of ITIL:
-
Value-Centric: Focus on delivering value to customers and the business.
-
Start Where You Are: Build on your existing processes and capabilities.
-
Feedback-Driven Progress: Continuously improve through feedback and small changes.
-
Collaborate and Communicate: Work together and share information for better results.
-
Think Holistically: Consider the big picture and interconnectedness of services.
-
Keep it Simple: Avoid complexity and prioritize practicality.
-
Optimize and Automate: Streamline processes and use automation to improve efficiency.
Key ITIL Terms
ITIL (Information Technology Infrastructure Library) uses specific terminology to describe its concepts and processes. Here are some key ITIL terms:
-
Service: The means by which value is delivered to customers, often in the form of intangible deliverables like email or network connectivity.
-
Service Management: The set of organizational capabilities for delivering value to customers in the form of services.
-
Service Lifecycle: The stages of a service's existence, including Service Strategy, Service Design, Service Transition, Service Operation, and Continual Service Improvement.
-
Process: A structured set of activities designed to accomplish a specific objective. ITIL defines numerous processes for IT service management.
-
Function: A team or group of people with specific skills and resources responsible for carrying out one or more processes or activities.
-
Role: A defined set of responsibilities and activities assigned to an individual or group, such as a Service Owner or Incident Manager.
-
Stakeholder: Individuals or groups with an interest in or an impact on the services provided by an organization. This can include customers, users, suppliers, and employees.
-
Service Provider: The organization delivering IT services to customers. It can be an internal IT department or an external service provider.
-
Customer: The person or group that defines requirements for IT services and receives the value provided by those services.
-
User: Individuals who utilize IT services to carry out their tasks and achieve their goals, which may or may not be the same as the customer.
ITIL Framework
The ITIL (Information Technology Infrastructure Library) framework is a comprehensive set of best practices and guidelines for IT service management (ITSM). It provides a structured approach for organizations to plan, design, deliver, operate, and continually improve their IT services. The framework is designed to align IT services with the needs of the business and ensure the efficient and effective delivery of those services. Here are the key components and aspects of the ITIL framework:
-
Service Strategy: Defining the organization's IT service strategy, considering business objectives and customer needs.
-
Service Design: Designing IT services, processes, and supporting infrastructure.
-
Service Transition: Managing the transition of new or changed services into the production environment.
-
Service Operation: Ensuring the day-to-day delivery and management of IT services.
-
Continual Service Improvement (CSI): Identifying and implementing improvements to services and processes.
Service Strategy
Service Strategy in ITIL is the critical phase where an organization aligns its IT services with its business objectives and needs. It involves defining a clear service strategy, managing a portfolio of IT services, ensuring financial viability, understanding and influencing customer demand, coordinating service design, managing risks, and nurturing strong business relationships. The goal is to create a roadmap that ensures IT services provide value to the business, support its success, and remain cost-effective, thus guiding subsequent phases of service management and helping the organization make informed decisions about service design, transition, and operation.
Service Design
Service Design, a pivotal phase within the ITIL service lifecycle, focuses on crafting IT services that are not only technically robust but also perfectly aligned with the organization's strategic goals and customer needs. It encompasses the meticulous planning and design of services, including service catalogs, service levels, capacity, availability, continuity, security, and supplier relationships. By adhering to ITIL principles and leveraging design coordination, it ensures that services are both cost-effective and poised for seamless transition into the operational environment. Service Design plays a vital role in delivering services that deliver value to the business while maintaining high levels of quality and customer satisfaction.
Service Transition
Service Transition, a critical phase within the ITIL service lifecycle, orchestrates the controlled and efficient movement of new or modified IT services from development and testing into the operational environment. It encompasses comprehensive change management, configuration control, rigorous testing and validation, and knowledge management to minimize risks and disruptions while maximizing the value and quality of services. By adhering to ITIL principles and detailed transition planning, it ensures that services meet customer expectations, business requirements, and service levels. Service Transition plays a pivotal role in the successful delivery of IT services, fostering agility and adaptability within the organization's IT landscape.
Service Operations
Service Operation, a pivotal phase within the ITIL service lifecycle, is responsible for the continuous and efficient delivery of IT services to meet agreed-upon service levels and customer needs. It encompasses incident and problem management to swiftly resolve issues, event management for proactive monitoring and response, request fulfillment, access management, and the critical role of the service desk as a central point of user support. Technical and IT operations management ensure infrastructure reliability, while application management oversees the lifecycle of business-critical software. By adhering to ITIL principles and promoting continual service improvement, Service Operation plays a vital role in maintaining service quality, minimizing disruptions, and contributing to overall customer satisfaction and business resilience.
Continual Service Improvement (CSI)
Continual Service Improvement (CSI) is a fundamental phase within the ITIL service lifecycle, dedicated to the ongoing enhancement of IT services and processes. It involves systematically measuring service performance, analyzing results, and identifying areas for improvement. By establishing clear metrics, conducting regular reviews, and creating action plans, organizations can drive efficiency, reduce costs, and align IT services with evolving business needs. CSI fosters a culture of continuous improvement, ensuring that IT services remain adaptable and responsive to changing customer requirements and market dynamics, ultimately delivering greater value and quality to the organization and its stakeholders.
How Do I Put ITIL into Practice?
-
Assessment and Alignment: Begin by assessing your organization's existing IT service management practices and identifying areas that need improvement. Determine how well your current practices align with ITIL principles and the organization's business objectives. This assessment provides a baseline for your ITIL implementation efforts.
-
Customization and Planning: ITIL is not a one-size-fits-all framework. Customize ITIL practices to match your organization's specific needs and constraints. Create a clear implementation plan that outlines objectives, milestones, roles, responsibilities, and timelines. Ensure that the plan aligns with your business's strategic goals and secures the necessary resources.
-
Education and Training: Equip your IT teams and staff with the knowledge and skills required for ITIL adoption. Offer training and awareness programs to help them understand the ITIL framework and its benefits. It's essential to create a shared understanding and commitment among team members.
-
Process Redesign and Automation: Redesign or adapt your IT service management processes to align with ITIL best practices. Ensure that these processes are well-documented and easily accessible to all relevant parties. Invest in IT service management tools and technologies that support ITIL processes and automate repetitive tasks to improve efficiency.
-
Continuous Improvement: ITIL is built on the concept of continual service improvement (CSI). Establish a culture of continuous improvement within your organization, where regular reviews and evaluations of ITIL implementation are conducted. Use performance metrics and feedback to identify areas for enhancement and make adjustments to your ITIL practices accordingly. CSI ensures that your IT services remain aligned with evolving business needs and industry best practices.
What is ITIL Certification, and is it Worth it?
ITIL certification is a valuable credential for individuals working in IT service management and related fields. It offers a structured and globally recognized framework for understanding and implementing best practices in IT service delivery and management. Achieving ITIL certification demonstrates your commitment to improving IT service quality and aligning IT with business goals. It can open doors to career advancement and higher earning potential, as many employers value ITIL certification when hiring or promoting IT professionals. However, it's important to consider the cost and time investment required for training and exams, as well as whether ITIL aligns with your specific career path and goals. Continuous learning and staying updated with the latest ITIL practices are also necessary for maintaining the certification's value. Ultimately, the worth of ITIL certification depends on your career aspirations and the relevance of IT service management in your professional journey.
Major Differences Between ITIL® V3 vs. ITIL® V4 Certification
ITIL V3 and ITIL V4 certifications represent two distinct iterations of the ITIL framework. While ITIL V3 followed a process-oriented service lifecycle model with a structured certification scheme, ITIL V4 introduced a more flexible and holistic approach to IT service management. V4 emphasizes value co-creation, incorporates guiding principles, and introduces a simplified certification structure with practical orientation. It addresses modern trends like digital transformation and agile practices, making it more adaptable to the evolving needs of organizations in the digital age. The transition from V3 to V4 signifies a shift from a process-centric framework to one that focuses on delivering value, enhancing customer experience, and embracing emerging practices, reflecting the changing landscape of IT service management.
Major Differences Between ITIL® V3 vs. ITIL® V4 Certification
-
Certification Structure:
-
ITIL® V3: V3 had a certification structure consisting of Foundation, Intermediate (Lifecycle and Capability modules), Expert, and Master levels.
-
ITIL® V4: V4 introduced a simplified certification scheme with four levels: Foundation, Practitioner, Specialist, and Strategist. The Master level remains the highest certification but is more accessible under V4.
-
-
Practical Orientation:
-
ITIL® V3: V3 certification focused on theoretical knowledge of ITIL processes and practices.
-
ITIL® V4: V4 places a stronger emphasis on practical application and adaptation of ITIL principles in real-world scenarios. The Practitioner and Specialist levels are designed to help professionals apply ITIL concepts effectively.
-
-
Guiding Principles:
-
ITIL® V3: V3 did not have a specific set of guiding principles.
-
ITIL® V4: V4 introduces seven guiding principles (e.g., Focus on Value, Start Where You Are, Collaborate and Promote Visibility) that underpin the framework and guide decision-making.
-
-
Service Value Chain:
-
ITIL® V3: V3 organized processes into a service lifecycle with five stages: Service Strategy, Service Design, Service Transition, Service Operation, and Continual Service Improvement (CSI).
-
ITIL® V4: V4 introduces the Service Value System, which includes the Service Value Chain (a set of interconnected activities) and emphasizes value co-creation with customers.
-
-
Flexibility and Adaptability:
-
ITIL® V3: V3 had a more rigid and process-centric approach.
-
ITIL® V4: V4 is designed to be more flexible and adaptable, allowing organizations to tailor ITIL practices to their unique needs and circumstances.
-
-
Digital Transformation and Agile Practices:
-
ITIL® V3: V3 did not specifically address emerging trends like digital transformation and agile practices.
-
ITIL® V4: V4 incorporates modern concepts and practices, making it more relevant in the digital age, including considerations for DevOps, Agile, and lean principles.
-
How Does ITIL Help Business?
ITIL benefits businesses by offering a structured framework for IT service management, resulting in improved service quality, cost efficiency, and alignment with business objectives. It reduces downtime, enhances change management, and facilitates effective risk mitigation. ITIL's customer-centric approach strengthens customer satisfaction, while its emphasis on continual improvement ensures adaptability and competitiveness in the evolving digital landscape. Additionally, it aids in regulatory compliance, fosters effective communication, and establishes transparent IT governance, ultimately contributing to business resilience, growth, and a competitive edge in the market.
What Will ITIL Cost?
The cost of ITIL can vary significantly depending on factors such as the level of certification, training format, study materials, and the size and complexity of ITIL implementation within an organization. ITIL certification exams range from $150 to $700 or more, with associated training and study materials adding to the expenses. Implementing ITIL practices within an organization involves costs related to training, consulting, process redesign, ITSM tools, and ongoing maintenance. It's crucial to budget carefully, considering both certification and implementation costs, while also weighing the long-term benefits of improved IT service quality, efficiency, and alignment with business objectives that ITIL can bring to the organization.
How Does ITIL Reduce Costs?
ITIL reduces costs for organizations by fostering efficiency, standardizing processes, and minimizing the risks and disruptions associated with IT service management. It achieves this through proactive problem management, rigorous change control, optimized resource allocation, meticulous documentation, and a continual focus on improvement. ITIL's emphasis on aligning IT services with business needs ensures that resources are directed towards activities that generate value, avoiding unnecessary expenses. By preventing service outages and incidents, streamlining workflows, and promoting cost transparency, ITIL helps organizations optimize their IT operations, resulting in significant cost reductions and improved cost-effectiveness.
ITIL Processes and Functions
In ITIL (Information Technology Infrastructure Library), processes and functions are key components of the framework, serving different roles in managing IT services effectively. Here's an overview of ITIL processes and functions:
ITIL Processes: ITIL defines several processes that are essential for IT service management. These processes are organized into five core lifecycle stages:
-
Service Strategy: This stage focuses on defining the overall strategy for IT services, including understanding customer needs, defining service portfolios, and aligning IT goals with business objectives. Key processes include Service Portfolio Management and Financial Management.
-
Service Design: In this stage, ITIL defines processes for designing IT services, ensuring they meet business requirements and are manageable. Processes include Service Catalog Management, Service Level Management, Capacity Management, and Availability Management.
-
Service Transition: This stage involves transitioning new or modified services into the production environment. Key processes include Change Management, Release and Deployment Management, and Service Validation and Testing.
-
Service Operation: Service Operation is responsible for the daily delivery and management of IT services to meet service levels and customer expectations. Processes here include Incident Management, Problem Management, Event Management, and Request Fulfillment.
-
Continual Service Improvement (CSI): CSI focuses on ongoing improvement of IT services and processes. It includes processes like Service Measurement and Reporting, Service Review, and Process Evaluation.
ITIL Functions: Functions in ITIL represent organizational units or groups responsible for specific activities or roles within the IT service management framework. While not all functions are required in every organization, they provide structure and accountability in managing IT services. Key ITIL functions include:
-
Service Desk: The Service Desk function acts as a central point of contact for users to report incidents, request services, and seek assistance. It plays a critical role in providing support and ensuring efficient communication.
-
Technical Management: This function provides technical expertise and support for IT infrastructure and services. It ensures that technical resources are available and properly maintained.
-
IT Operations Management: Responsible for the day-to-day operational activities required to deliver IT services. This includes data center management, network operations, and hardware maintenance.
-
Application Management: The Application Management function manages the lifecycle of applications, ensuring they are designed, developed, tested, and maintained to support business needs.
-
IT Security Management: While not always defined as a separate function, ITIL emphasizes the importance of security throughout the service lifecycle. This involves managing security policies, access controls, and compliance.
-
Supplier Management: Supplier Management ensures that external suppliers and vendors are effectively managed to deliver the required IT services and support.
These functions and processes work together to ensure that IT services are delivered efficiently, reliably, and in alignment with business goals and customer expectations. They provide a structured approach to managing IT services throughout their lifecycle, from strategy and design to operation and improvement.
History of ITIL
The history of ITIL (Information Technology Infrastructure Library) traces its origins to the late 1980s when it was developed by the UK's Central Computer and Telecommunications Agency (CCTA). Initially conceived to standardize and improve IT service management within the UK government, ITIL soon gained recognition for its best-practice guidelines. ITIL V1, released in the late 1980s and early 1990s, laid the foundation with a comprehensive set of 31 books. However, it was in 2000 with the launch of ITIL V2 that ITIL's global impact began to take shape. V2 consolidated the framework into eight core books and gained widespread adoption. ITIL V3, introduced in 2007 and updated in 2011 (ITIL 2011), brought a service lifecycle approach and a focus on aligning IT services with business processes. In 2019, ITIL V4 marked a major shift, emphasizing value co-creation, the Service Value System, and modern IT practices. It continues to evolve, reflecting the changing landscape of IT service management and digital transformation. Throughout its history, ITIL has become a globally recognized framework for enhancing IT service quality and alignment with business objectives.
ITIL Processes and Stages: Summary
ITIL, or the Information Technology Infrastructure Library, encompasses a set of well-defined processes and stages designed to help organizations manage their IT services effectively. The core processes include Service Strategy, which aligns IT services with business goals; Service Design, which focuses on designing services that meet business requirements; Service Transition, which ensures a smooth transition of services into the production environment; Service Operation, responsible for daily service delivery and support; and Continual Service Improvement, which drives ongoing enhancements in service quality and efficiency. These processes are organized into stages that reflect the IT service lifecycle, from aligning IT with business objectives to designing, transitioning, operating, and continually improving services. By following the ITIL framework, organizations can deliver IT services that are not only reliable and cost-effective but also aligned with evolving business needs and customer expectations, ultimately contributing to improved overall business performance and competitiveness.
Feasibility Study and Its Importance in Project Management
In the dynamic landscape of project management and business endeavors, the path to success is often paved with uncertainty. For every visionary project or entrepreneurial venture, there exists an inherent risk that can lead to unforeseen challenges, setbacks, or even failure. In this complex terrain, the beacon of clarity and guidance comes in the form of a "Feasibility Study." It is the compass that not only points to the direction of project viability but also illuminates the obstacles that lie ahead. This journey into the realm of feasibility studies unveils their pivotal role in project management, where informed decisions, meticulous analysis, and calculated risk mitigation converge to shape the destiny of projects and businesses. Join us as we delve into the significance of feasibility studies, understanding their multifaceted importance in steering the course of success.
Table of Contents
What is a Feasibility Study?
Understanding A Feasibility Study
Types of Feasibility Study
Importance of Feasibility Study
Benefits of a Feasibility Study
What Is Included in a Feasibility Study Report?
Tools for Conducting a Feasibility Study
Examples of a Feasibility Study
What is the Purpose of a Feasibility Study?
How Do You Write a Feasibility Study?
7 Steps to Do a Feasibility Study
How to Conduct a Feasibility Study
Feasibility Study vs. Business Plan
Reasons to Do or Not to Do a Feasibility Study
Conclusion
FAQs
What is a Feasibility Study?
A feasibility study is a thorough examination of whether a proposed project or business idea is practical and likely to succeed. It involves analyzing factors like market demand, technical capabilities, financial viability, operational logistics, legal requirements, environmental impact, and potential risks. The study helps decision-makers determine whether it's worth pursuing the project or if adjustments are needed. Ultimately, it provides a clear recommendation on whether to go ahead with the project or not, based on a comprehensive assessment of all relevant factors.
Understanding A Feasibility Study
A feasibility study is a comprehensive analysis conducted during the early stages of project planning to determine the practicality and viability of a proposed project or business endeavor. It involves assessing various factors such as market demand, technical feasibility, financial considerations, operational logistics, legal and regulatory requirements, environmental impacts, and potential risks. The goal is to answer the fundamental question of whether the project is feasible and worth pursuing. A well-executed feasibility study provides decision-makers with valuable insights to make informed choices about whether to invest resources, time, and effort into the project or explore alternative options. Ultimately, it helps prevent costly mistakes by identifying potential challenges and opportunities early in the project's development.
Types of Feasibility Study
-
Market Feasibility Study: This type of study is essential when considering a new product or service. It assesses whether there is enough demand in the market for the proposed offering. Market feasibility examines factors such as target demographics, customer preferences, market trends, competition, and potential market size. The goal is to determine if there is a substantial and sustainable market for the product or service.
-
Technical Feasibility Study: When a project relies on specific technology or technical processes, a technical feasibility study is conducted. It evaluates whether the required technology and expertise are available or can be developed within the project's scope. This study also looks at potential technical challenges and obstacles that might hinder project implementation.
-
Financial Feasibility Study: Financial feasibility is crucial to assess the project's profitability and financial viability. It involves estimating all costs associated with the project, including initial investments, operating expenses, and maintenance costs. Revenue projections and cash flow analysis are also conducted to determine if the project can generate a positive return on investment (ROI).
-
Operational Feasibility Study: This study focuses on how the proposed project will operate in practical terms. It assesses whether the project can be effectively integrated into existing operations or if it requires significant changes to processes, staffing, and logistics. Operational feasibility helps ensure that the project can be executed smoothly and efficiently.
-
Legal and Regulatory Feasibility Study: Projects often need to navigate complex legal and regulatory landscapes. A legal and regulatory feasibility study examines whether the project complies with all relevant laws, regulations, permits, and industry-specific requirements. It identifies potential legal obstacles and outlines the steps necessary for legal and regulatory compliance.
Importance of Feasibility Study
The importance of a feasibility study in the context of project management and business decision-making cannot be overstated. Here are several key reasons why conducting a feasibility study is crucial:
-
Risk Identification and Mitigation: A feasibility study helps identify potential risks and challenges associated with a project. By recognizing these risks early, project managers and stakeholders can develop strategies to mitigate them effectively. This proactive approach minimizes the likelihood of unforeseen issues derailing the project later on.
-
Cost-Benefit Analysis: One of the primary purposes of a feasibility study is to assess the financial feasibility of a project. It involves estimating the costs of implementing the project and comparing them to the expected benefits. This analysis helps in determining whether the project will yield a positive return on investment (ROI). If the costs outweigh the benefits, it may not be financially viable.
-
Resource Allocation: Resource allocation is a critical aspect of project management. A feasibility study outlines the resources required for the project, including manpower, equipment, and materials. This information allows project managers to allocate resources efficiently and ensure that they are available when needed, reducing delays and cost overruns.
-
Alignment with Strategic Goals: Projects should align with an organization's strategic goals and objectives. A feasibility study assesses how the proposed project aligns with these strategic goals. If there is a mismatch, it provides an opportunity to refine the project's scope or reconsider its importance in the context of the organization's overarching strategy.
-
Stakeholder Buy-In: Feasibility studies involve engaging with key stakeholders, including sponsors, investors, and end-users. These stakeholders play a crucial role in the success of the project. The study helps in gaining their buy-in and support by providing them with a clear understanding of the project's goals, benefits, and potential risks.
-
Decision-Making Tool: A feasibility study serves as a decision-making tool for project sponsors and stakeholders. It provides them with the information needed to make an informed decision about whether to proceed with the project, revise its scope, or abandon it altogether. This ensures that resources are allocated to projects with a higher likelihood of success.
-
Project Viability Assessment: Feasibility studies assess the overall viability of a project. They consider various aspects, including market demand, technical feasibility, financial considerations, and operational logistics. This comprehensive evaluation helps in determining whether the project is worth pursuing and has a realistic chance of success.
-
Cost Control: By estimating project costs and potential cost overruns during the feasibility study, project managers can develop effective cost control measures. This proactive approach allows for better financial management throughout the project's lifecycle.
-
Time Efficiency: A feasibility study helps in setting realistic project timelines. By identifying potential delays and obstacles early on, project managers can plan and allocate resources more effectively, reducing the likelihood of project schedule disruptions.
-
Alternative Evaluation: Feasibility studies often explore alternative solutions or approaches to achieve project objectives. This allows decision-makers to compare different options and select the most feasible and cost-effective one.
In conclusion, a well-conducted feasibility study is an indispensable tool in project management and business decision-making. It provides a structured and systematic approach to assess a project's feasibility, risks, costs, and benefits, ultimately leading to more informed and successful project outcomes.
Benefits of a Feasibility Study
A feasibility study offers a multitude of benefits that are invaluable to organizations and stakeholders contemplating new projects or business ventures. Firstly, it serves as a risk mitigation tool by uncovering potential challenges and obstacles early in the project's conceptualization phase, enabling the development of strategies to address these concerns proactively. Furthermore, a well-executed feasibility study empowers decision-makers with comprehensive information and data, facilitating informed choices regarding whether to proceed with the project, modify its scope, or abandon it altogether. Financial feasibility studies, a key component, provide financial clarity by estimating costs, revenue projections, and profitability prospects, ensuring alignment with budget constraints. Resource allocation becomes more efficient, as the study identifies the resources needed and helps prevent delays or shortages. Additionally, it ensures that the project aligns with an organization's strategic goals, fosters stakeholder buy-in, and assesses environmental and social responsibility. In essence, a feasibility study is an essential compass guiding project success by minimizing risks, optimizing resources, and ensuring strategic alignment.
What Is Included in a Feasibility Study Report?
A comprehensive feasibility study report typically includes the following key sections and information:
-
Executive Summary: This section provides a concise overview of the entire feasibility study, summarizing its main findings and recommendations. It is often the first section decision-makers read, so it should effectively convey the project's viability and key takeaways.
-
Introduction: The introduction sets the stage for the study by explaining the purpose, scope, and objectives of the feasibility study. It also introduces the project or business idea being evaluated.
-
Project Description: This section provides a detailed description of the proposed project, including its goals, objectives, and scope. It outlines what the project aims to achieve and its intended outcomes.
-
Market Analysis: In this section, the study delves into the market feasibility, examining factors such as market size, growth potential, target demographics, competition, and customer demand. It also assesses market trends and dynamics.
-
Technical Analysis: The technical analysis evaluates the technical feasibility of the project. It considers the technology, equipment, and infrastructure required, as well as potential technical challenges and solutions. It may also include information on suppliers and technology partners.
-
Financial Analysis: The financial analysis is a critical component. It includes detailed financial projections, cost estimates, revenue forecasts, and cash flow analysis. It assesses the project's financial feasibility, including its return on investment (ROI) and payback period.
-
Operational Analysis: This section focuses on the operational feasibility of the project. It looks at how the project will function in practical terms, including staffing requirements, processes, logistics, and supply chain considerations.
-
Legal and Regulatory Considerations: Here, the study addresses legal and regulatory feasibility by identifying the legal requirements, permits, licenses, and compliance issues relevant to the project. It also outlines strategies for ensuring compliance.
-
Environmental and Social Impact Assessment: This section assesses the potential environmental and social impacts of the project, including its sustainability, community acceptance, and corporate social responsibility considerations.
-
Risk Analysis: The risk analysis identifies potential risks and uncertainties associated with the project and provides recommendations for risk mitigation. It may include a risk matrix or assessment of key risks.
-
Alternative Solutions: Feasibility studies often explore alternative approaches or solutions to achieve the project's objectives. This section compares different options and provides rationale for the chosen approach.
-
Recommendations: Based on the analysis conducted throughout the study, this section presents clear and well-supported recommendations regarding whether to proceed with the project, make modifications, or abandon it. It outlines the rationale for the recommended course of action.
-
Appendices: The appendices contain supplementary information, such as detailed financial spreadsheets, market research data, technical specifications, and any other relevant documents that support the findings and conclusions of the feasibility study.
-
References: If the study includes external sources or references, a list of these sources should be provided in a reference section.
A well-structured feasibility study report serves as a comprehensive document that guides decision-makers in assessing the viability of a project or business venture. It should be clear, well-organized, and supported by data and analysis to ensure that stakeholders have the information needed to make informed decisions.
Tools for Conducting a Feasibility Study
-
Microsoft Excel: Use it for financial calculations and modeling.
-
Survey Software: Collect market data through tools like SurveyMonkey or Google Forms.
-
Market Research Tools: Access industry reports and trends with tools like Statista.
-
Project Management Software: Create timelines and track progress with tools like Trello.
-
Financial Software: For detailed financial projections, use QuickBooks or specialized financial modeling tools.
-
Research Databases: Access academic and industry data from online libraries and databases.
-
GIS Software: Analyze spatial data and site selection with tools like ArcGIS.
-
Risk Management Tools: Identify and manage project risks using tools like RiskWatch.
-
Business Plan Software: Structure your findings into a business plan with tools like LivePlan.
-
Presentation Tools: Communicate study results visually with software like PowerPoint.
-
Collaboration Tools: Facilitate teamwork with platforms like Microsoft Teams or Slack.
-
Document Management Systems: Organize and store project documents using software like SharePoint.
-
Decision Support Tools: Enhance decision-making with software like DecisionTools Suite for scenario analysis.
Examples of a Feasibility Study
Feasibility studies are conducted in various industries and for diverse purposes. Here are some examples of feasibility studies:
-
Real Estate Development: Before embarking on a real estate project, such as constructing a residential or commercial building, a feasibility study is conducted. It assesses the market demand for the property, construction costs, potential revenue from rentals or sales, and factors like zoning regulations and environmental impact.
-
Product Launch: When a company plans to launch a new product, a feasibility study is conducted to determine if there's a market for it. It includes market research to gauge customer interest, pricing strategies, manufacturing or production costs, and potential profitability.
-
Restaurant Opening: Before opening a new restaurant, a feasibility study is conducted to assess factors like location, target market, competition, menu pricing, and operating costs. It helps in understanding whether the restaurant can be profitable in a specific area.
-
Technology Start-up: Tech entrepreneurs often conduct feasibility studies to evaluate the viability of their software or app ideas. This includes assessing market demand, development costs, potential revenue streams, and competition in the tech sector.
-
Infrastructure Projects: Large-scale infrastructure projects like bridges, highways, or public transportation systems require feasibility studies to assess technical, financial, and environmental factors. These studies help determine if the project is practical and cost-effective.
-
Hotel Expansion: When a hotel chain plans to expand by building a new location, a feasibility study examines the market conditions, demand for hotel rooms in the area, construction and operational costs, and the potential return on investment.
-
Agricultural Ventures: Farmers and agricultural entrepreneurs may conduct feasibility studies before starting a new crop or livestock farming operation. The study evaluates factors like soil quality, market demand for the products, input costs, and expected yields.
-
Renewable Energy Projects: Feasibility studies are essential for renewable energy projects like wind farms or solar power plants. They assess factors such as available resources, technology feasibility, regulatory requirements, and financial viability.
-
Healthcare Facilities: Hospitals and healthcare organizations may conduct feasibility studies when planning to build new medical facilities. These studies analyze factors such as patient demand, location suitability, construction costs, and long-term operational expenses.
-
Manufacturing Plants: Before setting up a new manufacturing plant, businesses conduct feasibility studies to determine the feasibility of production, supply chain logistics, labor costs, and market demand for the products.
-
Educational Institutions: Feasibility studies are used by educational institutions to assess whether it's viable to expand or build new facilities, launch new academic programs, or enter new markets. These studies consider factors like enrollment projections, budget requirements, and competitive landscape.
-
Tourism and Hospitality: In the tourism sector, feasibility studies are conducted to evaluate the potential of opening new resorts, amusement parks, or tourist attractions. These studies analyze market demand, location, infrastructure requirements, and investment costs.
These are just a few examples of feasibility studies in different domains. The specific elements and focus of a feasibility study can vary widely depending on the nature of the project or business venture.
What is the Purpose of a Feasibility Study?
The primary purpose of a feasibility study is to comprehensively evaluate the viability and potential success of a proposed project or business endeavor. This study serves as a crucial decision-making tool, enabling stakeholders to assess the project's feasibility, risks, and financial viability. By identifying potential challenges and opportunities early on, a feasibility study helps mitigate risks and develop effective strategies for success. It aligns the project with an organization's strategic goals, facilitates resource allocation, and ensures that resources are directed toward projects with a high likelihood of achieving positive returns on investment. Additionally, it fosters stakeholder buy-in and provides a clear roadmap for project execution. Ultimately, the overarching goal of a feasibility study is to inform well-informed decisions about whether to pursue, modify, or abandon the project, thereby promoting efficiency, cost-effectiveness, and the likelihood of successful outcomes.
How Do You Write a Feasibility Study?
Writing a feasibility study involves a structured and systematic approach to assessing the viability of a proposed project or business venture. Here's a step-by-step guide on how to write a feasibility study:
-
Project Introduction:
-
Begin with an introduction that provides context for the study. Explain the purpose of the study, the project's objectives, and its significance.
-
Executive Summary:
-
Create an executive summary that offers a concise overview of the entire feasibility study, summarizing key findings, recommendations, and conclusions. This section should be clear and compelling as it's often the first part decision-makers read.
-
Background Information:
-
Provide background information on the project, including its history, the problem it aims to address, and any relevant historical data or context.
-
Scope of Work:
-
Clearly define the scope of the feasibility study. Specify the boundaries and limitations of the study, including what will and will not be included.
-
Methodology:
-
Explain the research methods and tools used to collect and analyze data. This section should outline the approach to market research, financial analysis, risk assessment, and other key aspects of the study.
-
Market Analysis:
-
Evaluate the market feasibility of the project by examining factors such as market size, growth potential, target demographics, competition, and customer demand. Present relevant market research data and trends.
-
Technical Analysis:
-
Assess the technical feasibility of the project, focusing on the required technology, equipment, and infrastructure. Address potential technical challenges and outline solutions.
-
Financial Analysis:
-
Conduct a detailed financial analysis, including cost estimations, revenue projections, cash flow analysis, and return on investment (ROI) calculations. Evaluate the project's financial viability.
-
Operational Analysis:
-
Evaluate the operational feasibility of the project by analyzing how it will function in practical terms. Consider staffing requirements, processes, logistics, and supply chain considerations.
-
Legal and Regulatory Assessment:
-
Examine legal and regulatory requirements relevant to the project. Identify permits, licenses, compliance issues, and strategies for ensuring legal conformity.
-
Environmental and Social Impact Assessment:
-
Assess the potential environmental and social impacts of the project, including sustainability considerations and community acceptance.
-
Risk Analysis:
-
Identify and evaluate potential risks and uncertainties associated with the project. Develop risk mitigation strategies and present them in this section.
-
Alternative Solutions:
-
Explore alternative approaches or solutions to achieve the project's objectives. Compare different options and provide a rationale for the chosen approach.
-
Recommendations:
-
Based on the analysis conducted throughout the study, present clear and well-supported recommendations regarding whether to proceed with the project, modify its scope, or abandon it. Provide a summary of the key findings that support the recommendations.
-
Appendices:
-
Include supplementary information in the appendices, such as detailed financial spreadsheets, market research data, technical specifications, and any other relevant documents that support the study's findings.
-
References:
-
If the study includes external sources or references, provide a list of these sources in a reference section.
-
Conclusion:
-
Conclude the feasibility study by summarizing the main findings, highlighting the recommended course of action, and reiterating the importance of the study's conclusions.
-
Final Review:
-
Before finalizing the report, conduct a thorough review for accuracy, clarity, and coherence. Ensure that the report is well-organized and follows a logical flow.
7 Steps to Do a Feasibility Study
Performing a feasibility study involves a systematic process to assess the viability of a project or business idea. Here are seven essential steps to conduct a feasibility study:
-
Define the Project Scope and Objectives:
-
Clearly outline the purpose, goals, and objectives of the feasibility study. Determine the specific questions the study should answer and the key aspects to be evaluated.
-
Gather Information and Data:
-
Collect all relevant data and information needed for the study. This includes market research, technical specifications, financial data, legal and regulatory requirements, and any other pertinent details.
-
Market Research and Analysis:
-
Evaluate the market feasibility by researching and analyzing factors like market size, growth trends, competition, customer preferences, and demand for the product or service.
-
Technical Analysis:
-
Assess the technical feasibility by examining the required technology, equipment, and infrastructure. Identify potential technical challenges and determine if they can be overcome.
-
Financial Analysis:
-
Conduct a comprehensive financial analysis, including cost estimations, revenue projections, cash flow analysis, and ROI calculations. Determine if the project is financially viable and can yield positive returns.
-
Operational Analysis:
-
Evaluate the operational feasibility of the project by analyzing how it will function in practical terms. Consider staffing needs, processes, logistics, and supply chain requirements.
-
Risk Assessment and Recommendations:
-
Identify and assess potential risks and uncertainties associated with the project. Develop strategies for risk mitigation. Based on the analysis, make clear and well-supported recommendations regarding whether to proceed with the project, make modifications, or abandon it. Summarize key findings and provide a concise roadmap for decision-makers.
How to Conduct a Feasibility Study
Performing a feasibility study involves a systematic process to assess the viability of a project or business idea. Here are seven essential steps to conduct a feasibility study:
-
Define the Project Scope and Objectives:
-
Clearly outline the purpose, goals, and objectives of the feasibility study. Determine the specific questions the study should answer and the key aspects to be evaluated.
-
Gather Information and Data:
-
Collect all relevant data and information needed for the study. This includes market research, technical specifications, financial data, legal and regulatory requirements, and any other pertinent details.
-
Market Research and Analysis:
-
Evaluate the market feasibility by researching and analyzing factors like market size, growth trends, competition, customer preferences, and demand for the product or service.
-
Technical Analysis:
-
Assess the technical feasibility by examining the required technology, equipment, and infrastructure. Identify potential technical challenges and determine if they can be overcome.
-
Financial Analysis:
-
Conduct a comprehensive financial analysis, including cost estimations, revenue projections, cash flow analysis, and ROI calculations. Determine if the project is financially viable and can yield positive returns.
-
Operational Analysis:
-
Evaluate the operational feasibility of the project by analyzing how it will function in practical terms. Consider staffing needs, processes, logistics, and supply chain requirements.
-
Risk Assessment and Recommendations:
-
Identify and assess potential risks and uncertainties associated with the project. Develop strategies for risk mitigation. Based on the analysis, make clear and well-supported recommendations regarding whether to proceed with the project, make modifications, or abandon it. Summarize key findings and provide a concise roadmap for decision-makers.
Feasibility Study vs. Business Plan
Feasibility Study vs. Business Plan:
Feasibility Study:
-
Purpose: The primary purpose of a feasibility study is to assess the viability and feasibility of a proposed project or business idea. It aims to answer the question, "Is this project or business concept feasible?"
-
Timing: Feasibility studies are typically conducted in the early stages of project development, often before significant resources are invested.
-
Scope: Feasibility studies have a broader scope and focus on evaluating various aspects of the project, including market feasibility, technical feasibility, financial feasibility, legal and regulatory considerations, operational feasibility, and risk assessment.
-
Analysis: Feasibility studies involve in-depth analysis of data and information related to the project, such as market research, cost estimation, revenue projections, and risk assessment.
-
Outcome: The primary outcome of a feasibility study is to provide stakeholders with a recommendation on whether to proceed with the project, modify its scope, or abandon it. It helps stakeholders make informed decisions.
Business Plan:
-
Purpose: A business plan serves as a detailed blueprint for the actual operation and management of a business. It outlines the goals, strategies, and operations of the business and provides a roadmap for its growth and development.
-
Timing: Business plans are typically developed after the feasibility study, once the decision to proceed with the project has been made. They are often used when seeking financing or as a guide for day-to-day operations.
-
Scope: Business plans focus on the specific strategies, tactics, and operations required to run the business successfully. They include detailed information on marketing, sales, organizational structure, funding requirements, revenue and expense projections, and long-term goals.
-
Analysis: While business plans incorporate the findings from the feasibility study, they go beyond feasibility analysis and delve into the practical aspects of running the business. Business plans include detailed financial projections and operational plans.
-
Outcome: The primary outcome of a business plan is to provide a comprehensive and actionable roadmap for the business. It is used for securing financing, attracting investors, guiding day-to-day operations, and measuring the business's performance against its objectives.
In summary, a feasibility study assesses the initial viability of a project or business idea and informs the decision to proceed or not, while a business plan is a detailed document that outlines how a business will operate, grow, and achieve its goals once the decision to move forward has been made. Both documents are crucial in the lifecycle of a business or project, with the feasibility study informing the business plan's foundation.
Reasons to Do or Not to Do a Feasibility Study
Reasons to Do a Feasibility Study:
-
Risk Assessment: A feasibility study helps identify potential risks and challenges associated with the project. It provides an opportunity to assess and mitigate these risks proactively.
-
Informed Decision-Making: Conducting a feasibility study ensures that decision-makers have comprehensive information to make informed choices about whether to proceed with the project, make modifications, or abandon it.
-
Financial Clarity: Financial feasibility studies estimate costs, revenue projections, and potential profitability. This clarity ensures that the project aligns with budget constraints and has a potential for positive returns on investment.
-
Resource Optimization: Feasibility studies outline the resources required for the project, such as personnel, equipment, materials, and technology. This allows for efficient resource allocation and prevents delays or resource shortages.
-
Strategic Alignment: Projects should align with an organization's strategic goals and objectives. A feasibility study assesses this alignment, ensuring that the project supports the organization's overarching strategy.
Reasons Not to Do a Feasibility Study:
-
Low Complexity: For very simple projects with minimal investment and known market demand, a full-scale feasibility study may be unnecessary. However, even small projects can benefit from some form of preliminary assessment.
-
Urgency: In cases where time is of the essence, such as responding to rapidly changing market conditions, conducting a lengthy feasibility study may not be feasible. In such situations, a rapid assessment or a simpler analysis may be more appropriate.
-
Cost Concerns: Some organizations may be hesitant to invest in a feasibility study due to budget constraints. However, failing to conduct a feasibility study can lead to much higher costs if the project encounters unforeseen issues.
-
Obvious Viability: In rare cases where the viability of a project is self-evident and unquestionable, skipping a feasibility study might be considered. However, a cursory assessment is still advisable to confirm assumptions.
Conclusion
In conclusion, a feasibility study is an indispensable tool in the process of evaluating the potential success and viability of a proposed project or business venture. It serves as a critical decision-making guide, providing stakeholders with a comprehensive understanding of the project's feasibility, risks, and financial viability. By identifying potential challenges and opportunities early on, a feasibility study enables proactive risk mitigation and the development of effective strategies for success. It aligns the project with an organization's strategic objectives, facilitates resource allocation, and ensures that resources are directed toward endeavors with a high likelihood of achieving positive returns. Furthermore, it fosters stakeholder buy-in and provides a clear roadmap for project execution. Ultimately, the overarching goal of a feasibility study is to inform well-informed decisions about whether to pursue, modify, or abandon the project, thereby promoting efficiency, cost-effectiveness, and the likelihood of successful outcomes. In essence, a well-executed feasibility study lays the foundation for a project's success and serves as a cornerstone for prudent decision-making in the world of business and project management.
FAQs
1. What is a feasibility study?
A feasibility study is an in-depth analysis and evaluation of a proposed project or business venture to determine its viability and potential for success. It assesses various aspects such as market feasibility, technical feasibility, financial feasibility, and operational feasibility.
2. Why is a feasibility study important?
A feasibility study is crucial because it helps stakeholders make informed decisions about whether to proceed with a project, modify its scope, or abandon it. It identifies risks, assesses costs, and evaluates the potential for profitability, thereby reducing uncertainty and minimizing the likelihood of project failure.
3. What are the key components of a feasibility study?
A feasibility study typically includes sections on market analysis, technical analysis, financial analysis, operational analysis, legal and regulatory considerations, environmental and social impact assessment, risk analysis, and recommendations.
4. How is a feasibility study different from a business plan?
A feasibility study assesses the initial viability of a project, while a business plan provides a detailed roadmap for running and growing a business after the decision to proceed has been made. Feasibility studies inform the foundation of a business plan.
5. When should you conduct a feasibility study?
Feasibility studies are typically conducted in the early stages of project development, before significant resources are invested. However, they can also be conducted at any point when there is uncertainty about the feasibility of a project.
6. What is the role of market research in a feasibility study?
Market research is a crucial component of a feasibility study as it assesses market demand, competition, customer preferences, and trends. It helps determine if there is a market for the project's products or services.
7. How do you assess financial feasibility in a feasibility study?
Financial feasibility is assessed by estimating project costs, revenue projections, cash flow analysis, and calculating metrics like return on investment (ROI) and payback period. It determines if the project is financially viable.
8. What are the benefits of conducting a feasibility study?
Benefits of a feasibility study include risk mitigation, informed decision-making, financial clarity, efficient resource allocation, strategic alignment, stakeholder buy-in, and the identification of potential issues early in the project.
9. Are there situations where a feasibility study may not be necessary?
In some cases, for very simple projects with minimal investment and known market demand, a full-scale feasibility study may be considered unnecessary. However, even small projects can benefit from a preliminary assessment.
10. How do you present the findings of a feasibility study to stakeholders? -
The findings of a feasibility study are typically presented in a structured report format, with clear sections covering each aspect of the study. An executive summary is often included to provide a concise overview of the key findings and recommendations. Presentations and discussions with stakeholders may also be part of the communication process.
Read More
In the dynamic landscape of project management and business endeavors, the path to success is often paved with uncertainty. For every visionary project or entrepreneurial venture, there exists an inherent risk that can lead to unforeseen challenges, setbacks, or even failure. In this complex terrain, the beacon of clarity and guidance comes in the form of a "Feasibility Study." It is the compass that not only points to the direction of project viability but also illuminates the obstacles that lie ahead. This journey into the realm of feasibility studies unveils their pivotal role in project management, where informed decisions, meticulous analysis, and calculated risk mitigation converge to shape the destiny of projects and businesses. Join us as we delve into the significance of feasibility studies, understanding their multifaceted importance in steering the course of success.
Table of Contents
What is a Feasibility Study?
Understanding A Feasibility Study
Types of Feasibility Study
Importance of Feasibility Study
Benefits of a Feasibility Study
What Is Included in a Feasibility Study Report?
Tools for Conducting a Feasibility Study
Examples of a Feasibility Study
What is the Purpose of a Feasibility Study?
How Do You Write a Feasibility Study?
7 Steps to Do a Feasibility Study
How to Conduct a Feasibility Study
Feasibility Study vs. Business Plan
Reasons to Do or Not to Do a Feasibility Study
Conclusion
FAQs
What is a Feasibility Study?
A feasibility study is a thorough examination of whether a proposed project or business idea is practical and likely to succeed. It involves analyzing factors like market demand, technical capabilities, financial viability, operational logistics, legal requirements, environmental impact, and potential risks. The study helps decision-makers determine whether it's worth pursuing the project or if adjustments are needed. Ultimately, it provides a clear recommendation on whether to go ahead with the project or not, based on a comprehensive assessment of all relevant factors.
Understanding A Feasibility Study
A feasibility study is a comprehensive analysis conducted during the early stages of project planning to determine the practicality and viability of a proposed project or business endeavor. It involves assessing various factors such as market demand, technical feasibility, financial considerations, operational logistics, legal and regulatory requirements, environmental impacts, and potential risks. The goal is to answer the fundamental question of whether the project is feasible and worth pursuing. A well-executed feasibility study provides decision-makers with valuable insights to make informed choices about whether to invest resources, time, and effort into the project or explore alternative options. Ultimately, it helps prevent costly mistakes by identifying potential challenges and opportunities early in the project's development.
Types of Feasibility Study
-
Market Feasibility Study: This type of study is essential when considering a new product or service. It assesses whether there is enough demand in the market for the proposed offering. Market feasibility examines factors such as target demographics, customer preferences, market trends, competition, and potential market size. The goal is to determine if there is a substantial and sustainable market for the product or service.
-
Technical Feasibility Study: When a project relies on specific technology or technical processes, a technical feasibility study is conducted. It evaluates whether the required technology and expertise are available or can be developed within the project's scope. This study also looks at potential technical challenges and obstacles that might hinder project implementation.
-
Financial Feasibility Study: Financial feasibility is crucial to assess the project's profitability and financial viability. It involves estimating all costs associated with the project, including initial investments, operating expenses, and maintenance costs. Revenue projections and cash flow analysis are also conducted to determine if the project can generate a positive return on investment (ROI).
-
Operational Feasibility Study: This study focuses on how the proposed project will operate in practical terms. It assesses whether the project can be effectively integrated into existing operations or if it requires significant changes to processes, staffing, and logistics. Operational feasibility helps ensure that the project can be executed smoothly and efficiently.
-
Legal and Regulatory Feasibility Study: Projects often need to navigate complex legal and regulatory landscapes. A legal and regulatory feasibility study examines whether the project complies with all relevant laws, regulations, permits, and industry-specific requirements. It identifies potential legal obstacles and outlines the steps necessary for legal and regulatory compliance.
Importance of Feasibility Study
The importance of a feasibility study in the context of project management and business decision-making cannot be overstated. Here are several key reasons why conducting a feasibility study is crucial:
-
Risk Identification and Mitigation: A feasibility study helps identify potential risks and challenges associated with a project. By recognizing these risks early, project managers and stakeholders can develop strategies to mitigate them effectively. This proactive approach minimizes the likelihood of unforeseen issues derailing the project later on.
-
Cost-Benefit Analysis: One of the primary purposes of a feasibility study is to assess the financial feasibility of a project. It involves estimating the costs of implementing the project and comparing them to the expected benefits. This analysis helps in determining whether the project will yield a positive return on investment (ROI). If the costs outweigh the benefits, it may not be financially viable.
-
Resource Allocation: Resource allocation is a critical aspect of project management. A feasibility study outlines the resources required for the project, including manpower, equipment, and materials. This information allows project managers to allocate resources efficiently and ensure that they are available when needed, reducing delays and cost overruns.
-
Alignment with Strategic Goals: Projects should align with an organization's strategic goals and objectives. A feasibility study assesses how the proposed project aligns with these strategic goals. If there is a mismatch, it provides an opportunity to refine the project's scope or reconsider its importance in the context of the organization's overarching strategy.
-
Stakeholder Buy-In: Feasibility studies involve engaging with key stakeholders, including sponsors, investors, and end-users. These stakeholders play a crucial role in the success of the project. The study helps in gaining their buy-in and support by providing them with a clear understanding of the project's goals, benefits, and potential risks.
-
Decision-Making Tool: A feasibility study serves as a decision-making tool for project sponsors and stakeholders. It provides them with the information needed to make an informed decision about whether to proceed with the project, revise its scope, or abandon it altogether. This ensures that resources are allocated to projects with a higher likelihood of success.
-
Project Viability Assessment: Feasibility studies assess the overall viability of a project. They consider various aspects, including market demand, technical feasibility, financial considerations, and operational logistics. This comprehensive evaluation helps in determining whether the project is worth pursuing and has a realistic chance of success.
-
Cost Control: By estimating project costs and potential cost overruns during the feasibility study, project managers can develop effective cost control measures. This proactive approach allows for better financial management throughout the project's lifecycle.
-
Time Efficiency: A feasibility study helps in setting realistic project timelines. By identifying potential delays and obstacles early on, project managers can plan and allocate resources more effectively, reducing the likelihood of project schedule disruptions.
-
Alternative Evaluation: Feasibility studies often explore alternative solutions or approaches to achieve project objectives. This allows decision-makers to compare different options and select the most feasible and cost-effective one.
In conclusion, a well-conducted feasibility study is an indispensable tool in project management and business decision-making. It provides a structured and systematic approach to assess a project's feasibility, risks, costs, and benefits, ultimately leading to more informed and successful project outcomes.
Benefits of a Feasibility Study
A feasibility study offers a multitude of benefits that are invaluable to organizations and stakeholders contemplating new projects or business ventures. Firstly, it serves as a risk mitigation tool by uncovering potential challenges and obstacles early in the project's conceptualization phase, enabling the development of strategies to address these concerns proactively. Furthermore, a well-executed feasibility study empowers decision-makers with comprehensive information and data, facilitating informed choices regarding whether to proceed with the project, modify its scope, or abandon it altogether. Financial feasibility studies, a key component, provide financial clarity by estimating costs, revenue projections, and profitability prospects, ensuring alignment with budget constraints. Resource allocation becomes more efficient, as the study identifies the resources needed and helps prevent delays or shortages. Additionally, it ensures that the project aligns with an organization's strategic goals, fosters stakeholder buy-in, and assesses environmental and social responsibility. In essence, a feasibility study is an essential compass guiding project success by minimizing risks, optimizing resources, and ensuring strategic alignment.
What Is Included in a Feasibility Study Report?
A comprehensive feasibility study report typically includes the following key sections and information:
-
Executive Summary: This section provides a concise overview of the entire feasibility study, summarizing its main findings and recommendations. It is often the first section decision-makers read, so it should effectively convey the project's viability and key takeaways.
-
Introduction: The introduction sets the stage for the study by explaining the purpose, scope, and objectives of the feasibility study. It also introduces the project or business idea being evaluated.
-
Project Description: This section provides a detailed description of the proposed project, including its goals, objectives, and scope. It outlines what the project aims to achieve and its intended outcomes.
-
Market Analysis: In this section, the study delves into the market feasibility, examining factors such as market size, growth potential, target demographics, competition, and customer demand. It also assesses market trends and dynamics.
-
Technical Analysis: The technical analysis evaluates the technical feasibility of the project. It considers the technology, equipment, and infrastructure required, as well as potential technical challenges and solutions. It may also include information on suppliers and technology partners.
-
Financial Analysis: The financial analysis is a critical component. It includes detailed financial projections, cost estimates, revenue forecasts, and cash flow analysis. It assesses the project's financial feasibility, including its return on investment (ROI) and payback period.
-
Operational Analysis: This section focuses on the operational feasibility of the project. It looks at how the project will function in practical terms, including staffing requirements, processes, logistics, and supply chain considerations.
-
Legal and Regulatory Considerations: Here, the study addresses legal and regulatory feasibility by identifying the legal requirements, permits, licenses, and compliance issues relevant to the project. It also outlines strategies for ensuring compliance.
-
Environmental and Social Impact Assessment: This section assesses the potential environmental and social impacts of the project, including its sustainability, community acceptance, and corporate social responsibility considerations.
-
Risk Analysis: The risk analysis identifies potential risks and uncertainties associated with the project and provides recommendations for risk mitigation. It may include a risk matrix or assessment of key risks.
-
Alternative Solutions: Feasibility studies often explore alternative approaches or solutions to achieve the project's objectives. This section compares different options and provides rationale for the chosen approach.
-
Recommendations: Based on the analysis conducted throughout the study, this section presents clear and well-supported recommendations regarding whether to proceed with the project, make modifications, or abandon it. It outlines the rationale for the recommended course of action.
-
Appendices: The appendices contain supplementary information, such as detailed financial spreadsheets, market research data, technical specifications, and any other relevant documents that support the findings and conclusions of the feasibility study.
-
References: If the study includes external sources or references, a list of these sources should be provided in a reference section.
A well-structured feasibility study report serves as a comprehensive document that guides decision-makers in assessing the viability of a project or business venture. It should be clear, well-organized, and supported by data and analysis to ensure that stakeholders have the information needed to make informed decisions.
Tools for Conducting a Feasibility Study
-
Microsoft Excel: Use it for financial calculations and modeling.
-
Survey Software: Collect market data through tools like SurveyMonkey or Google Forms.
-
Market Research Tools: Access industry reports and trends with tools like Statista.
-
Project Management Software: Create timelines and track progress with tools like Trello.
-
Financial Software: For detailed financial projections, use QuickBooks or specialized financial modeling tools.
-
Research Databases: Access academic and industry data from online libraries and databases.
-
GIS Software: Analyze spatial data and site selection with tools like ArcGIS.
-
Risk Management Tools: Identify and manage project risks using tools like RiskWatch.
-
Business Plan Software: Structure your findings into a business plan with tools like LivePlan.
-
Presentation Tools: Communicate study results visually with software like PowerPoint.
-
Collaboration Tools: Facilitate teamwork with platforms like Microsoft Teams or Slack.
-
Document Management Systems: Organize and store project documents using software like SharePoint.
-
Decision Support Tools: Enhance decision-making with software like DecisionTools Suite for scenario analysis.
Examples of a Feasibility Study
Feasibility studies are conducted in various industries and for diverse purposes. Here are some examples of feasibility studies:
-
Real Estate Development: Before embarking on a real estate project, such as constructing a residential or commercial building, a feasibility study is conducted. It assesses the market demand for the property, construction costs, potential revenue from rentals or sales, and factors like zoning regulations and environmental impact.
-
Product Launch: When a company plans to launch a new product, a feasibility study is conducted to determine if there's a market for it. It includes market research to gauge customer interest, pricing strategies, manufacturing or production costs, and potential profitability.
-
Restaurant Opening: Before opening a new restaurant, a feasibility study is conducted to assess factors like location, target market, competition, menu pricing, and operating costs. It helps in understanding whether the restaurant can be profitable in a specific area.
-
Technology Start-up: Tech entrepreneurs often conduct feasibility studies to evaluate the viability of their software or app ideas. This includes assessing market demand, development costs, potential revenue streams, and competition in the tech sector.
-
Infrastructure Projects: Large-scale infrastructure projects like bridges, highways, or public transportation systems require feasibility studies to assess technical, financial, and environmental factors. These studies help determine if the project is practical and cost-effective.
-
Hotel Expansion: When a hotel chain plans to expand by building a new location, a feasibility study examines the market conditions, demand for hotel rooms in the area, construction and operational costs, and the potential return on investment.
-
Agricultural Ventures: Farmers and agricultural entrepreneurs may conduct feasibility studies before starting a new crop or livestock farming operation. The study evaluates factors like soil quality, market demand for the products, input costs, and expected yields.
-
Renewable Energy Projects: Feasibility studies are essential for renewable energy projects like wind farms or solar power plants. They assess factors such as available resources, technology feasibility, regulatory requirements, and financial viability.
-
Healthcare Facilities: Hospitals and healthcare organizations may conduct feasibility studies when planning to build new medical facilities. These studies analyze factors such as patient demand, location suitability, construction costs, and long-term operational expenses.
-
Manufacturing Plants: Before setting up a new manufacturing plant, businesses conduct feasibility studies to determine the feasibility of production, supply chain logistics, labor costs, and market demand for the products.
-
Educational Institutions: Feasibility studies are used by educational institutions to assess whether it's viable to expand or build new facilities, launch new academic programs, or enter new markets. These studies consider factors like enrollment projections, budget requirements, and competitive landscape.
-
Tourism and Hospitality: In the tourism sector, feasibility studies are conducted to evaluate the potential of opening new resorts, amusement parks, or tourist attractions. These studies analyze market demand, location, infrastructure requirements, and investment costs.
These are just a few examples of feasibility studies in different domains. The specific elements and focus of a feasibility study can vary widely depending on the nature of the project or business venture.
What is the Purpose of a Feasibility Study?
The primary purpose of a feasibility study is to comprehensively evaluate the viability and potential success of a proposed project or business endeavor. This study serves as a crucial decision-making tool, enabling stakeholders to assess the project's feasibility, risks, and financial viability. By identifying potential challenges and opportunities early on, a feasibility study helps mitigate risks and develop effective strategies for success. It aligns the project with an organization's strategic goals, facilitates resource allocation, and ensures that resources are directed toward projects with a high likelihood of achieving positive returns on investment. Additionally, it fosters stakeholder buy-in and provides a clear roadmap for project execution. Ultimately, the overarching goal of a feasibility study is to inform well-informed decisions about whether to pursue, modify, or abandon the project, thereby promoting efficiency, cost-effectiveness, and the likelihood of successful outcomes.
How Do You Write a Feasibility Study?
Writing a feasibility study involves a structured and systematic approach to assessing the viability of a proposed project or business venture. Here's a step-by-step guide on how to write a feasibility study:
-
Project Introduction:
-
Begin with an introduction that provides context for the study. Explain the purpose of the study, the project's objectives, and its significance.
-
-
Executive Summary:
-
Create an executive summary that offers a concise overview of the entire feasibility study, summarizing key findings, recommendations, and conclusions. This section should be clear and compelling as it's often the first part decision-makers read.
-
-
Background Information:
-
Provide background information on the project, including its history, the problem it aims to address, and any relevant historical data or context.
-
-
Scope of Work:
-
Clearly define the scope of the feasibility study. Specify the boundaries and limitations of the study, including what will and will not be included.
-
-
Methodology:
-
Explain the research methods and tools used to collect and analyze data. This section should outline the approach to market research, financial analysis, risk assessment, and other key aspects of the study.
-
-
Market Analysis:
-
Evaluate the market feasibility of the project by examining factors such as market size, growth potential, target demographics, competition, and customer demand. Present relevant market research data and trends.
-
-
Technical Analysis:
-
Assess the technical feasibility of the project, focusing on the required technology, equipment, and infrastructure. Address potential technical challenges and outline solutions.
-
-
Financial Analysis:
-
Conduct a detailed financial analysis, including cost estimations, revenue projections, cash flow analysis, and return on investment (ROI) calculations. Evaluate the project's financial viability.
-
-
Operational Analysis:
-
Evaluate the operational feasibility of the project by analyzing how it will function in practical terms. Consider staffing requirements, processes, logistics, and supply chain considerations.
-
-
Legal and Regulatory Assessment:
-
Examine legal and regulatory requirements relevant to the project. Identify permits, licenses, compliance issues, and strategies for ensuring legal conformity.
-
-
Environmental and Social Impact Assessment:
-
Assess the potential environmental and social impacts of the project, including sustainability considerations and community acceptance.
-
-
Risk Analysis:
-
Identify and evaluate potential risks and uncertainties associated with the project. Develop risk mitigation strategies and present them in this section.
-
-
Alternative Solutions:
-
Explore alternative approaches or solutions to achieve the project's objectives. Compare different options and provide a rationale for the chosen approach.
-
-
Recommendations:
-
Based on the analysis conducted throughout the study, present clear and well-supported recommendations regarding whether to proceed with the project, modify its scope, or abandon it. Provide a summary of the key findings that support the recommendations.
-
-
Appendices:
-
Include supplementary information in the appendices, such as detailed financial spreadsheets, market research data, technical specifications, and any other relevant documents that support the study's findings.
-
-
References:
-
If the study includes external sources or references, provide a list of these sources in a reference section.
-
-
Conclusion:
-
Conclude the feasibility study by summarizing the main findings, highlighting the recommended course of action, and reiterating the importance of the study's conclusions.
-
-
Final Review:
-
Before finalizing the report, conduct a thorough review for accuracy, clarity, and coherence. Ensure that the report is well-organized and follows a logical flow.
-
7 Steps to Do a Feasibility Study
Performing a feasibility study involves a systematic process to assess the viability of a project or business idea. Here are seven essential steps to conduct a feasibility study:
-
Define the Project Scope and Objectives:
-
Clearly outline the purpose, goals, and objectives of the feasibility study. Determine the specific questions the study should answer and the key aspects to be evaluated.
-
-
Gather Information and Data:
-
Collect all relevant data and information needed for the study. This includes market research, technical specifications, financial data, legal and regulatory requirements, and any other pertinent details.
-
-
Market Research and Analysis:
-
Evaluate the market feasibility by researching and analyzing factors like market size, growth trends, competition, customer preferences, and demand for the product or service.
-
-
Technical Analysis:
-
Assess the technical feasibility by examining the required technology, equipment, and infrastructure. Identify potential technical challenges and determine if they can be overcome.
-
-
Financial Analysis:
-
Conduct a comprehensive financial analysis, including cost estimations, revenue projections, cash flow analysis, and ROI calculations. Determine if the project is financially viable and can yield positive returns.
-
-
Operational Analysis:
-
Evaluate the operational feasibility of the project by analyzing how it will function in practical terms. Consider staffing needs, processes, logistics, and supply chain requirements.
-
-
Risk Assessment and Recommendations:
-
Identify and assess potential risks and uncertainties associated with the project. Develop strategies for risk mitigation. Based on the analysis, make clear and well-supported recommendations regarding whether to proceed with the project, make modifications, or abandon it. Summarize key findings and provide a concise roadmap for decision-makers.
-
How to Conduct a Feasibility Study
Performing a feasibility study involves a systematic process to assess the viability of a project or business idea. Here are seven essential steps to conduct a feasibility study:
-
Define the Project Scope and Objectives:
-
Clearly outline the purpose, goals, and objectives of the feasibility study. Determine the specific questions the study should answer and the key aspects to be evaluated.
-
-
Gather Information and Data:
-
Collect all relevant data and information needed for the study. This includes market research, technical specifications, financial data, legal and regulatory requirements, and any other pertinent details.
-
-
Market Research and Analysis:
-
Evaluate the market feasibility by researching and analyzing factors like market size, growth trends, competition, customer preferences, and demand for the product or service.
-
-
Technical Analysis:
-
Assess the technical feasibility by examining the required technology, equipment, and infrastructure. Identify potential technical challenges and determine if they can be overcome.
-
-
Financial Analysis:
-
Conduct a comprehensive financial analysis, including cost estimations, revenue projections, cash flow analysis, and ROI calculations. Determine if the project is financially viable and can yield positive returns.
-
-
Operational Analysis:
-
Evaluate the operational feasibility of the project by analyzing how it will function in practical terms. Consider staffing needs, processes, logistics, and supply chain requirements.
-
-
Risk Assessment and Recommendations:
-
Identify and assess potential risks and uncertainties associated with the project. Develop strategies for risk mitigation. Based on the analysis, make clear and well-supported recommendations regarding whether to proceed with the project, make modifications, or abandon it. Summarize key findings and provide a concise roadmap for decision-makers.
-
Feasibility Study vs. Business Plan
Feasibility Study vs. Business Plan:
Feasibility Study:
-
Purpose: The primary purpose of a feasibility study is to assess the viability and feasibility of a proposed project or business idea. It aims to answer the question, "Is this project or business concept feasible?"
-
Timing: Feasibility studies are typically conducted in the early stages of project development, often before significant resources are invested.
-
Scope: Feasibility studies have a broader scope and focus on evaluating various aspects of the project, including market feasibility, technical feasibility, financial feasibility, legal and regulatory considerations, operational feasibility, and risk assessment.
-
Analysis: Feasibility studies involve in-depth analysis of data and information related to the project, such as market research, cost estimation, revenue projections, and risk assessment.
-
Outcome: The primary outcome of a feasibility study is to provide stakeholders with a recommendation on whether to proceed with the project, modify its scope, or abandon it. It helps stakeholders make informed decisions.
Business Plan:
-
Purpose: A business plan serves as a detailed blueprint for the actual operation and management of a business. It outlines the goals, strategies, and operations of the business and provides a roadmap for its growth and development.
-
Timing: Business plans are typically developed after the feasibility study, once the decision to proceed with the project has been made. They are often used when seeking financing or as a guide for day-to-day operations.
-
Scope: Business plans focus on the specific strategies, tactics, and operations required to run the business successfully. They include detailed information on marketing, sales, organizational structure, funding requirements, revenue and expense projections, and long-term goals.
-
Analysis: While business plans incorporate the findings from the feasibility study, they go beyond feasibility analysis and delve into the practical aspects of running the business. Business plans include detailed financial projections and operational plans.
-
Outcome: The primary outcome of a business plan is to provide a comprehensive and actionable roadmap for the business. It is used for securing financing, attracting investors, guiding day-to-day operations, and measuring the business's performance against its objectives.
In summary, a feasibility study assesses the initial viability of a project or business idea and informs the decision to proceed or not, while a business plan is a detailed document that outlines how a business will operate, grow, and achieve its goals once the decision to move forward has been made. Both documents are crucial in the lifecycle of a business or project, with the feasibility study informing the business plan's foundation.
Reasons to Do or Not to Do a Feasibility Study
Reasons to Do a Feasibility Study:
-
Risk Assessment: A feasibility study helps identify potential risks and challenges associated with the project. It provides an opportunity to assess and mitigate these risks proactively.
-
Informed Decision-Making: Conducting a feasibility study ensures that decision-makers have comprehensive information to make informed choices about whether to proceed with the project, make modifications, or abandon it.
-
Financial Clarity: Financial feasibility studies estimate costs, revenue projections, and potential profitability. This clarity ensures that the project aligns with budget constraints and has a potential for positive returns on investment.
-
Resource Optimization: Feasibility studies outline the resources required for the project, such as personnel, equipment, materials, and technology. This allows for efficient resource allocation and prevents delays or resource shortages.
-
Strategic Alignment: Projects should align with an organization's strategic goals and objectives. A feasibility study assesses this alignment, ensuring that the project supports the organization's overarching strategy.
Reasons Not to Do a Feasibility Study:
-
Low Complexity: For very simple projects with minimal investment and known market demand, a full-scale feasibility study may be unnecessary. However, even small projects can benefit from some form of preliminary assessment.
-
Urgency: In cases where time is of the essence, such as responding to rapidly changing market conditions, conducting a lengthy feasibility study may not be feasible. In such situations, a rapid assessment or a simpler analysis may be more appropriate.
-
Cost Concerns: Some organizations may be hesitant to invest in a feasibility study due to budget constraints. However, failing to conduct a feasibility study can lead to much higher costs if the project encounters unforeseen issues.
-
Obvious Viability: In rare cases where the viability of a project is self-evident and unquestionable, skipping a feasibility study might be considered. However, a cursory assessment is still advisable to confirm assumptions.
Conclusion
In conclusion, a feasibility study is an indispensable tool in the process of evaluating the potential success and viability of a proposed project or business venture. It serves as a critical decision-making guide, providing stakeholders with a comprehensive understanding of the project's feasibility, risks, and financial viability. By identifying potential challenges and opportunities early on, a feasibility study enables proactive risk mitigation and the development of effective strategies for success. It aligns the project with an organization's strategic objectives, facilitates resource allocation, and ensures that resources are directed toward endeavors with a high likelihood of achieving positive returns. Furthermore, it fosters stakeholder buy-in and provides a clear roadmap for project execution. Ultimately, the overarching goal of a feasibility study is to inform well-informed decisions about whether to pursue, modify, or abandon the project, thereby promoting efficiency, cost-effectiveness, and the likelihood of successful outcomes. In essence, a well-executed feasibility study lays the foundation for a project's success and serves as a cornerstone for prudent decision-making in the world of business and project management.
FAQs
1. What is a feasibility study?
A feasibility study is an in-depth analysis and evaluation of a proposed project or business venture to determine its viability and potential for success. It assesses various aspects such as market feasibility, technical feasibility, financial feasibility, and operational feasibility.
2. Why is a feasibility study important?
A feasibility study is crucial because it helps stakeholders make informed decisions about whether to proceed with a project, modify its scope, or abandon it. It identifies risks, assesses costs, and evaluates the potential for profitability, thereby reducing uncertainty and minimizing the likelihood of project failure.
3. What are the key components of a feasibility study?
A feasibility study typically includes sections on market analysis, technical analysis, financial analysis, operational analysis, legal and regulatory considerations, environmental and social impact assessment, risk analysis, and recommendations.
4. How is a feasibility study different from a business plan?
A feasibility study assesses the initial viability of a project, while a business plan provides a detailed roadmap for running and growing a business after the decision to proceed has been made. Feasibility studies inform the foundation of a business plan.
5. When should you conduct a feasibility study?
Feasibility studies are typically conducted in the early stages of project development, before significant resources are invested. However, they can also be conducted at any point when there is uncertainty about the feasibility of a project.
6. What is the role of market research in a feasibility study?
Market research is a crucial component of a feasibility study as it assesses market demand, competition, customer preferences, and trends. It helps determine if there is a market for the project's products or services.
7. How do you assess financial feasibility in a feasibility study?
Financial feasibility is assessed by estimating project costs, revenue projections, cash flow analysis, and calculating metrics like return on investment (ROI) and payback period. It determines if the project is financially viable.
8. What are the benefits of conducting a feasibility study?
Benefits of a feasibility study include risk mitigation, informed decision-making, financial clarity, efficient resource allocation, strategic alignment, stakeholder buy-in, and the identification of potential issues early in the project.
9. Are there situations where a feasibility study may not be necessary?
In some cases, for very simple projects with minimal investment and known market demand, a full-scale feasibility study may be considered unnecessary. However, even small projects can benefit from a preliminary assessment.
10. How do you present the findings of a feasibility study to stakeholders? -
The findings of a feasibility study are typically presented in a structured report format, with clear sections covering each aspect of the study. An executive summary is often included to provide a concise overview of the key findings and recommendations. Presentations and discussions with stakeholders may also be part of the communication process.
Digital Marketing Role in 2023: Responsibilities and Skill Requirements
Welcome to the ever-evolving landscape of digital marketing in 2023! In today's fast-paced, technology-driven world, the role of digital marketing has become more pivotal than ever for businesses seeking to thrive in the online realm. As we delve into the "Digital Marketing Job Description: Responsibilities and Skills in 2023," we will explore the dynamic and multifaceted nature of this profession. In this digital era, where consumers are increasingly connected, informed, and discerning, the demands on digital marketers have grown exponentially. This comprehensive guide will not only outline the core responsibilities of a digital marketer but also shed light on the essential skills and competencies required to excel in this exciting and competitive field. Whether you are a seasoned marketing professional looking to adapt to the latest trends or someone aspiring to launch a career in digital marketing, this exploration will serve as your compass through the ever-changing digital marketing landscape of 2023. Join us on this journey to discover what it takes to succeed in the world of digital marketing and stay ahead of the curve in this dynamic and ever-evolving industry.
Table of Contents
-
Growth of Digital Marketing Jobs
-
The Role of a Digital Marketer
-
Digital Marketing Job Description (Sample)
-
Specialist Digital Marketing Skills
-
The Common Elements of a Digital Marketing Job Description
-
Conclusion
Growth of Digital Marketing Jobs
The growth of digital marketing jobs over the past decade has been nothing short of remarkable. As the world becomes increasingly connected and reliant on digital technologies, the demand for skilled professionals in this field has surged. Several key factors can be attributed to this growth
-
Digital Transformation: Businesses across various industries are undergoing digital transformation efforts to stay competitive and reach their target audiences effectively. This has led to an increased demand for digital marketing professionals who can navigate and leverage the digital landscape.
-
Shift in Consumer Behavior: Consumers are spending more time online, from shopping and socializing to seeking information. Companies are keen to capitalize on this trend by employing digital marketing strategies to connect with their target customers where they spend the most time.
-
Data-Driven Decision-Making: The availability of vast amounts of data and analytics tools has made it possible for companies to measure the effectiveness of their marketing campaigns with precision. Digital marketing professionals who can analyze and interpret data are in high demand to drive data-driven decision-making.
-
E-commerce Boom: The growth of e-commerce has been exponential, especially in the wake of global events like the COVID-19 pandemic. Digital marketing plays a critical role in helping e-commerce businesses reach wider audiences, optimize their websites, and drive sales.
-
Social Media Dominance: Social media platforms have become powerful marketing tools. Companies are hiring digital marketers to create and execute social media strategies that engage audiences, build brand awareness, and drive conversions.
-
Search Engine Optimization (SEO): As the competition for online visibility intensifies, SEO expertise is invaluable. Digital marketers skilled in SEO are sought after to improve a website's ranking on search engines like Google.
-
Content Marketing: High-quality content is essential for online success. Content marketing professionals are needed to create compelling, relevant content that resonates with audiences and drives traffic.
-
Specialization: The field of digital marketing has diversified, with various specializations such as email marketing, influencer marketing, and affiliate marketing. This specialization has opened up more career opportunities for professionals with specific expertise.
-
Remote Work: The digital nature of these jobs has made remote work more feasible, allowing companies to tap into a global talent pool and professionals to work from virtually anywhere.
In summary, the growth of digital marketing jobs can be attributed to the ever-increasing importance of digital channels in reaching and engaging with consumers. As businesses continue to invest in their online presence and marketing efforts, the demand for skilled digital marketing professionals is expected to remain robust in the years to come.
The Role of a Digital Marketer
The role of a digital marketer is dynamic, multifaceted, and central to the success of businesses in the digital age. Digital marketers are responsible for developing, implementing, and managing online marketing strategies to achieve various business objectives. Here are some key aspects of the role of a digital marketer:
-
Strategy Development: Digital marketers begin by creating comprehensive digital marketing strategies tailored to their organization's goals. This involves identifying target audiences, defining key performance indicators (KPIs), and selecting the most suitable digital channels and tactics.
-
Content Creation: Content is at the heart of digital marketing. Digital marketers often create a wide range of content, including blog posts, social media updates, videos, infographics, and more. They ensure that content is engaging, relevant, and aligned with the brand's messaging.
-
Search Engine Optimization (SEO): Digital marketers optimize web content and websites to improve their visibility on search engines like Google. This involves keyword research, on-page optimization, and backlink building to drive organic traffic.
-
Social Media Management: Managing and growing a brand's presence on social media platforms is a critical aspect of the role. Digital marketers develop content calendars, engage with followers, run paid advertising campaigns, and track performance metrics.
-
Email Marketing: Email still stands as a potent marketing instrument. Digital marketers create and execute email campaigns to nurture leads, retain customers, and drive conversions. They also segment email lists for targeted messaging.
-
Paid Advertising: Digital marketers manage paid advertising campaigns on platforms like Google Ads, Facebook Ads, and LinkedIn Ads. They set budgets, create ad creatives, and continuously optimize campaigns to maximize ROI.
-
Analytics and Data Analysis: The foundation of digital marketing relies on data. Marketers use analytics tools to track website traffic, user behavior, and campaign performance. They analyze this data to make informed decisions and adjust strategies as needed.
-
Conversion Rate Optimization (CRO): Improving the conversion rate of website visitors into customers or leads is a key responsibility. Digital marketers conduct A/B testing and implement changes to enhance the user experience and drive conversions.
-
Affiliate Marketing: Some digital marketers work on affiliate marketing programs, where they collaborate with affiliates to promote products or services in exchange for commissions.
-
Influencer Marketing: Digital marketers identify and partner with influencers or industry experts to promote their brand or products to a wider audience.
-
Online Reputation Management: Monitoring and managing the online reputation of a brand is crucial. Digital marketers address negative feedback and promote positive reviews and content.
-
Marketing Automation: Digital marketers often use marketing automation tools to streamline repetitive tasks, such as email sending, lead nurturing, and campaign tracking.
-
Compliance and Privacy: Staying informed about digital marketing regulations and ensuring compliance with data privacy laws (e.g., GDPR, CCPA) is essential.
-
Continuous Learning: Given the rapidly evolving nature of digital marketing, professionals in this role must stay updated on industry trends, emerging technologies, and best practices.
In conclusion, the role of a digital marketer is multifaceted and ever-evolving. Success in this field requires a combination of creativity, analytical skills, adaptability, and a deep understanding of digital tools and platforms. Digital marketers play a pivotal role in helping businesses connect with their target audiences, drive growth, and stay competitive in the digital landscape.
Digital Marketing Job Description (Sample)
Job Title: Digital Marketer
Job Description:
As a Digital Marketing Specialist you will be responsible for planning, executing, and optimizing our digital marketing campaigns across various online platforms. Your goal will be to enhance our online presence, engage with our target audience, and ultimately drive business growth.
Key Responsibilities:
-
Digital Strategy: Develop and implement comprehensive digital marketing strategies that align with company goals and objectives.
-
Content Creation: Create, edit, and curate compelling and relevant content for various digital channels, including blog posts, social media updates, emails, and more.
-
SEO Optimization: Conduct keyword research, optimize website content, and monitor and improve search engine rankings to increase organic traffic.
-
Social Media Management: Manage and grow our social media presence by creating content calendars, running paid campaigns, and engaging with our online community.
-
Email Marketing: Plan and execute email marketing campaigns, segment audiences, create engaging email content, and monitor campaign performance.
-
Paid Advertising: Manage paid advertising campaigns on platforms like Google Ads, Facebook Ads, and others to drive traffic, conversions, and ROI.
-
Analytics and Reporting: Monitor website analytics, user behavior, and campaign performance using tools like Google Analytics. Offer consistent reports and insights to steer decision-making.
-
Conversion Rate Optimization (CRO): Identify opportunities to improve website conversion rates through A/B testing, user experience enhancements, and other strategies.
-
Affiliate Marketing: Collaborate with affiliates and partners to promote products or services and track affiliate performance.
-
Online Reputation Management: Monitor online reviews and comments, address negative feedback, and encourage positive reviews and brand mentions.
Qualifications:
-
A Bachelor's degree in Marketing, Digital Marketing, or a related field is required.
-
Demonstrated expertise in digital marketing, substantiated by a robust portfolio of successful campaigns.
-
Proficiency in utilizing digital marketing tools and platforms, such as Google Analytics, social media management tools, and email marketing software.
-
Profound knowledge of SEO best practices and strategies is essential.
-
Exceptional written and verbal communication skills are a must.
-
Capable of working autonomously and as part of a collaborative team.
-
Possesses an analytical mindset, enabling the interpretation of data and the formulation of data-driven decisions.
-
Certifications in digital marketing (e.g., Google Ads, HubSpot, or similar) are a plus.
Specialist Digital Marketing Skills
Specialist digital marketing skills are essential for professionals who want to excel in the field and stand out in an increasingly competitive landscape. Here are some specialized digital marketing skills that can make a significant difference in your career:
-
Search Engine Optimization (SEO):
-
Technical SEO: Understanding and optimizing website structure, crawlability, and performance.
-
On-Page SEO: Mastering keyword research, optimization, and content quality.
-
Off-Page SEO: Building high-quality backlinks and managing link-building strategies.
-
Content Marketing:
-
Content Strategy: Creating content strategies that align with business goals.
-
Content Creation: Writing, editing, and producing various content types, such as blog posts, videos, infographics, and eBooks.
-
Content Promotion: Effective distribution and promotion of content across channels.
-
Social Media Marketing:
-
Social Media Advertising: Creating and managing paid ad campaigns on platforms like Facebook Ads, Instagram Ads, and LinkedIn Ads.
-
Community Management: Engaging with the audience, responding to comments, and managing brand reputation.
-
Social Media Analytics: Analyzing and interpreting social media data to refine strategies.
-
Email Marketing:
-
Email Automation: Designing and implementing automated email campaigns.
-
Segmentation: Creating targeted email lists for personalized messaging.
-
A/B Testing: Experimenting with subject lines, content, and CTAs to optimize email performance.
-
Pay-Per-Click (PPC) Advertising:
-
Google Ads: Overseeing and enhancing Google Ads campaigns.
-
Display Advertising: Creating and optimizing banner ads for display networks.
-
Remarketing: Implementing strategies to target previous website visitors.
-
Analytics and Data Analysis:
-
Google Analytics: Proficiency in using Google Analytics to track website performance and user behavior.
-
Data Interpretation: Analyzing data to derive actionable insights and make data-driven decisions.
-
Conversion Rate Optimization (CRO): Optimizing websites and landing pages for improved conversion rates.
-
Marketing Automation:
-
Marketing Automation Platforms: Familiarity with tools like HubSpot, Marketo, or Salesforce for automated marketing workflows.
-
Lead Nurturing: Creating and managing lead nurturing campaigns to guide prospects through the sales funnel.
-
Affiliate Marketing:
-
Partner Outreach: Building and managing relationships with affiliate partners.
-
Program Management: Running affiliate marketing programs and tracking partner performance.
-
Influencer Marketing:
-
Influencer Selection: Identifying and partnering with influencers who align with the brand.
-
Campaign Management: Planning and executing influencer marketing campaigns.
-
E-commerce Optimization:
-
E-commerce SEO: Executing e-commerce website-focused SEO strategies.
-
Conversion Optimization: Enhancing product pages, checkout processes, and user experience to boost sales.
-
Mobile Marketing:
-
Mobile App Marketing: Promoting mobile apps through app stores and in-app advertising.
-
Mobile Website Optimization: Ensuring websites are mobile-friendly and load quickly on mobile devices.
-
Data Privacy and Compliance:
-
Comprehending and complying with data privacy regulations such as GDPR and CCPA.
-
Ensuring marketing practices comply with legal requirements.
Remember that digital marketing is a dynamic field, and staying updated with the latest trends, tools, and techniques is crucial to maintaining and enhancing your specialist skills in the long term. Continual learning and adaptation are key to success in digital marketing.
The Common Elements of a Digital Marketing Job Description
Digital marketing job descriptions typically share common elements that help define the role, responsibilities, qualifications, and expectations for candidates. Here are the common elements you can find in a digital marketing job description:
-
Job Title: The job title, such as "Digital Marketing Specialist," "Digital Marketing Manager," or "Digital Marketing Coordinator," indicates the specific role within the digital marketing field.
-
Company Overview: A brief introduction to the hiring company, including its industry, mission, and values, sets the context for the role.
-
Job Location: Specifies where the position is based, which can be in a specific city, state, or country, or may indicate whether it's a remote position.
-
Job Summary/Objective: A concise statement outlining the primary purpose of the role and what the candidate is expected to achieve in the position.
-
Responsibilities/Duties: A detailed list of the day-to-day tasks and responsibilities expected of the candidate. This section often includes items such as content creation, SEO optimization, social media management, and email marketing.
-
Qualifications/Skills: Lists the education, experience, and skills required or preferred for the role. This section may include qualifications like a bachelor's degree in marketing, proficiency in specific tools or platforms, and soft skills like communication and teamwork.
-
Experience: Often divided into "required experience" and "preferred experience," this section outlines the level of experience the company is seeking in candidates.
-
Certifications: If specific certifications (e.g., Google Ads, HubSpot, Facebook Blueprint) are required or preferred, they are listed here.
-
Competencies: Describes the competencies or attributes the ideal candidate should possess, such as analytical skills, creativity, adaptability, and attention to detail.
-
Work Environment: Provides information about the work environment, team size, and any unique aspects of the workplace.
-
Salary and Benefits: In some job descriptions, you may find information about the salary range or compensation package offered, as well as details about benefits like health insurance, retirement plans, and bonuses.
-
How to Apply: Instructions on how candidates should apply, which often include submitting a resume, cover letter, and portfolio, and providing contact details for application submission.
-
Application Deadline: If there's a specific deadline for applications, it's mentioned here.
-
Equal Opportunity Statement: Many job descriptions include a statement about the company's commitment to diversity and equal opportunity employment.
-
Contact Information: Provides contact details for inquiries or questions related to the job posting.
-
Company Culture: Some job descriptions may include information about the company's culture, values, or mission to help candidates understand the work environment and ethos.
These common elements help candidates understand the role, evaluate their qualifications, and prepare their applications accordingly. Employers use them to communicate their expectations clearly and attract candidates who are the best fit for the position and the company.
How to obtain Robotic Process Automation Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
Project Management: PMP, CAPM ,PMI RMP
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
Business Analysis: CBAP, CCBA, ECBA
Agile Training: PMI-ACP , CSM , CSPO
Scrum Training: CSM
DevOps
Program Management: PgMP
Cloud Technology: SMAC Certication
Big Data: Big Data and Hadoop Administrator
Digital Marketing : Digital Marketing Certification
Data Science : Power BI Certification
Cyber Security : CISA Certification
Emerging Technologies : Robotic Process Automation
Conclusion
The landscape of digital marketing in 2023 is more dynamic and critical than ever before. As this guide has illuminated, the responsibilities and skills required of digital marketers have evolved to meet the demands of a rapidly changing digital ecosystem. In a world where businesses are vying for online visibility and customer engagement, digital marketers play a pivotal role in shaping strategies that drive success. Whether it's mastering the intricacies of SEO, creating compelling content, or leveraging emerging technologies, the digital marketer of 2023 must be adaptable, data-savvy, and customer-centric. As we navigate this ever-shifting terrain, it becomes clear that digital marketing is not just a profession; it's an art and science, and those who embrace its challenges and opportunities will continue to be at the forefront of the digital revolution. So, whether you're a seasoned professional or just beginning your journey in this field, the world of digital marketing in 2023 is ripe with possibilities for those who are willing to learn, adapt, and innovate.
Read More
Welcome to the ever-evolving landscape of digital marketing in 2023! In today's fast-paced, technology-driven world, the role of digital marketing has become more pivotal than ever for businesses seeking to thrive in the online realm. As we delve into the "Digital Marketing Job Description: Responsibilities and Skills in 2023," we will explore the dynamic and multifaceted nature of this profession. In this digital era, where consumers are increasingly connected, informed, and discerning, the demands on digital marketers have grown exponentially. This comprehensive guide will not only outline the core responsibilities of a digital marketer but also shed light on the essential skills and competencies required to excel in this exciting and competitive field. Whether you are a seasoned marketing professional looking to adapt to the latest trends or someone aspiring to launch a career in digital marketing, this exploration will serve as your compass through the ever-changing digital marketing landscape of 2023. Join us on this journey to discover what it takes to succeed in the world of digital marketing and stay ahead of the curve in this dynamic and ever-evolving industry.
Table of Contents
-
Growth of Digital Marketing Jobs
-
The Role of a Digital Marketer
-
Digital Marketing Job Description (Sample)
-
Specialist Digital Marketing Skills
-
The Common Elements of a Digital Marketing Job Description
-
Conclusion
Growth of Digital Marketing Jobs
The growth of digital marketing jobs over the past decade has been nothing short of remarkable. As the world becomes increasingly connected and reliant on digital technologies, the demand for skilled professionals in this field has surged. Several key factors can be attributed to this growth
-
Digital Transformation: Businesses across various industries are undergoing digital transformation efforts to stay competitive and reach their target audiences effectively. This has led to an increased demand for digital marketing professionals who can navigate and leverage the digital landscape.
-
Shift in Consumer Behavior: Consumers are spending more time online, from shopping and socializing to seeking information. Companies are keen to capitalize on this trend by employing digital marketing strategies to connect with their target customers where they spend the most time.
-
Data-Driven Decision-Making: The availability of vast amounts of data and analytics tools has made it possible for companies to measure the effectiveness of their marketing campaigns with precision. Digital marketing professionals who can analyze and interpret data are in high demand to drive data-driven decision-making.
-
E-commerce Boom: The growth of e-commerce has been exponential, especially in the wake of global events like the COVID-19 pandemic. Digital marketing plays a critical role in helping e-commerce businesses reach wider audiences, optimize their websites, and drive sales.
-
Social Media Dominance: Social media platforms have become powerful marketing tools. Companies are hiring digital marketers to create and execute social media strategies that engage audiences, build brand awareness, and drive conversions.
-
Search Engine Optimization (SEO): As the competition for online visibility intensifies, SEO expertise is invaluable. Digital marketers skilled in SEO are sought after to improve a website's ranking on search engines like Google.
-
Content Marketing: High-quality content is essential for online success. Content marketing professionals are needed to create compelling, relevant content that resonates with audiences and drives traffic.
-
Specialization: The field of digital marketing has diversified, with various specializations such as email marketing, influencer marketing, and affiliate marketing. This specialization has opened up more career opportunities for professionals with specific expertise.
-
Remote Work: The digital nature of these jobs has made remote work more feasible, allowing companies to tap into a global talent pool and professionals to work from virtually anywhere.
In summary, the growth of digital marketing jobs can be attributed to the ever-increasing importance of digital channels in reaching and engaging with consumers. As businesses continue to invest in their online presence and marketing efforts, the demand for skilled digital marketing professionals is expected to remain robust in the years to come.
The Role of a Digital Marketer
The role of a digital marketer is dynamic, multifaceted, and central to the success of businesses in the digital age. Digital marketers are responsible for developing, implementing, and managing online marketing strategies to achieve various business objectives. Here are some key aspects of the role of a digital marketer:
-
Strategy Development: Digital marketers begin by creating comprehensive digital marketing strategies tailored to their organization's goals. This involves identifying target audiences, defining key performance indicators (KPIs), and selecting the most suitable digital channels and tactics.
-
Content Creation: Content is at the heart of digital marketing. Digital marketers often create a wide range of content, including blog posts, social media updates, videos, infographics, and more. They ensure that content is engaging, relevant, and aligned with the brand's messaging.
-
Search Engine Optimization (SEO): Digital marketers optimize web content and websites to improve their visibility on search engines like Google. This involves keyword research, on-page optimization, and backlink building to drive organic traffic.
-
Social Media Management: Managing and growing a brand's presence on social media platforms is a critical aspect of the role. Digital marketers develop content calendars, engage with followers, run paid advertising campaigns, and track performance metrics.
-
Email Marketing: Email still stands as a potent marketing instrument. Digital marketers create and execute email campaigns to nurture leads, retain customers, and drive conversions. They also segment email lists for targeted messaging.
-
Paid Advertising: Digital marketers manage paid advertising campaigns on platforms like Google Ads, Facebook Ads, and LinkedIn Ads. They set budgets, create ad creatives, and continuously optimize campaigns to maximize ROI.
-
Analytics and Data Analysis: The foundation of digital marketing relies on data. Marketers use analytics tools to track website traffic, user behavior, and campaign performance. They analyze this data to make informed decisions and adjust strategies as needed.
-
Conversion Rate Optimization (CRO): Improving the conversion rate of website visitors into customers or leads is a key responsibility. Digital marketers conduct A/B testing and implement changes to enhance the user experience and drive conversions.
-
Affiliate Marketing: Some digital marketers work on affiliate marketing programs, where they collaborate with affiliates to promote products or services in exchange for commissions.
-
Influencer Marketing: Digital marketers identify and partner with influencers or industry experts to promote their brand or products to a wider audience.
-
Online Reputation Management: Monitoring and managing the online reputation of a brand is crucial. Digital marketers address negative feedback and promote positive reviews and content.
-
Marketing Automation: Digital marketers often use marketing automation tools to streamline repetitive tasks, such as email sending, lead nurturing, and campaign tracking.
-
Compliance and Privacy: Staying informed about digital marketing regulations and ensuring compliance with data privacy laws (e.g., GDPR, CCPA) is essential.
-
Continuous Learning: Given the rapidly evolving nature of digital marketing, professionals in this role must stay updated on industry trends, emerging technologies, and best practices.
In conclusion, the role of a digital marketer is multifaceted and ever-evolving. Success in this field requires a combination of creativity, analytical skills, adaptability, and a deep understanding of digital tools and platforms. Digital marketers play a pivotal role in helping businesses connect with their target audiences, drive growth, and stay competitive in the digital landscape.
Digital Marketing Job Description (Sample)
Job Title: Digital Marketer
Job Description:
As a Digital Marketing Specialist you will be responsible for planning, executing, and optimizing our digital marketing campaigns across various online platforms. Your goal will be to enhance our online presence, engage with our target audience, and ultimately drive business growth.
Key Responsibilities:
-
Digital Strategy: Develop and implement comprehensive digital marketing strategies that align with company goals and objectives.
-
Content Creation: Create, edit, and curate compelling and relevant content for various digital channels, including blog posts, social media updates, emails, and more.
-
SEO Optimization: Conduct keyword research, optimize website content, and monitor and improve search engine rankings to increase organic traffic.
-
Social Media Management: Manage and grow our social media presence by creating content calendars, running paid campaigns, and engaging with our online community.
-
Email Marketing: Plan and execute email marketing campaigns, segment audiences, create engaging email content, and monitor campaign performance.
-
Paid Advertising: Manage paid advertising campaigns on platforms like Google Ads, Facebook Ads, and others to drive traffic, conversions, and ROI.
-
Analytics and Reporting: Monitor website analytics, user behavior, and campaign performance using tools like Google Analytics. Offer consistent reports and insights to steer decision-making.
-
Conversion Rate Optimization (CRO): Identify opportunities to improve website conversion rates through A/B testing, user experience enhancements, and other strategies.
-
Affiliate Marketing: Collaborate with affiliates and partners to promote products or services and track affiliate performance.
-
Online Reputation Management: Monitor online reviews and comments, address negative feedback, and encourage positive reviews and brand mentions.
Qualifications:
-
A Bachelor's degree in Marketing, Digital Marketing, or a related field is required.
-
Demonstrated expertise in digital marketing, substantiated by a robust portfolio of successful campaigns.
-
Proficiency in utilizing digital marketing tools and platforms, such as Google Analytics, social media management tools, and email marketing software.
-
Profound knowledge of SEO best practices and strategies is essential.
-
Exceptional written and verbal communication skills are a must.
-
Capable of working autonomously and as part of a collaborative team.
-
Possesses an analytical mindset, enabling the interpretation of data and the formulation of data-driven decisions.
-
Certifications in digital marketing (e.g., Google Ads, HubSpot, or similar) are a plus.
Specialist Digital Marketing Skills
Specialist digital marketing skills are essential for professionals who want to excel in the field and stand out in an increasingly competitive landscape. Here are some specialized digital marketing skills that can make a significant difference in your career:
-
Search Engine Optimization (SEO):
-
Technical SEO: Understanding and optimizing website structure, crawlability, and performance.
-
On-Page SEO: Mastering keyword research, optimization, and content quality.
-
Off-Page SEO: Building high-quality backlinks and managing link-building strategies.
-
-
Content Marketing:
-
Content Strategy: Creating content strategies that align with business goals.
-
Content Creation: Writing, editing, and producing various content types, such as blog posts, videos, infographics, and eBooks.
-
Content Promotion: Effective distribution and promotion of content across channels.
-
-
Social Media Marketing:
-
Social Media Advertising: Creating and managing paid ad campaigns on platforms like Facebook Ads, Instagram Ads, and LinkedIn Ads.
-
Community Management: Engaging with the audience, responding to comments, and managing brand reputation.
-
Social Media Analytics: Analyzing and interpreting social media data to refine strategies.
-
-
Email Marketing:
-
Email Automation: Designing and implementing automated email campaigns.
-
Segmentation: Creating targeted email lists for personalized messaging.
-
A/B Testing: Experimenting with subject lines, content, and CTAs to optimize email performance.
-
-
Pay-Per-Click (PPC) Advertising:
-
Google Ads: Overseeing and enhancing Google Ads campaigns.
-
Display Advertising: Creating and optimizing banner ads for display networks.
-
Remarketing: Implementing strategies to target previous website visitors.
-
-
Analytics and Data Analysis:
-
Google Analytics: Proficiency in using Google Analytics to track website performance and user behavior.
-
Data Interpretation: Analyzing data to derive actionable insights and make data-driven decisions.
-
Conversion Rate Optimization (CRO): Optimizing websites and landing pages for improved conversion rates.
-
-
Marketing Automation:
-
Marketing Automation Platforms: Familiarity with tools like HubSpot, Marketo, or Salesforce for automated marketing workflows.
-
Lead Nurturing: Creating and managing lead nurturing campaigns to guide prospects through the sales funnel.
-
-
Affiliate Marketing:
-
Partner Outreach: Building and managing relationships with affiliate partners.
-
Program Management: Running affiliate marketing programs and tracking partner performance.
-
-
Influencer Marketing:
-
Influencer Selection: Identifying and partnering with influencers who align with the brand.
-
Campaign Management: Planning and executing influencer marketing campaigns.
-
-
E-commerce Optimization:
-
E-commerce SEO: Executing e-commerce website-focused SEO strategies.
-
Conversion Optimization: Enhancing product pages, checkout processes, and user experience to boost sales.
-
-
Mobile Marketing:
-
Mobile App Marketing: Promoting mobile apps through app stores and in-app advertising.
-
Mobile Website Optimization: Ensuring websites are mobile-friendly and load quickly on mobile devices.
-
-
Data Privacy and Compliance:
-
Comprehending and complying with data privacy regulations such as GDPR and CCPA.
-
Ensuring marketing practices comply with legal requirements.
Remember that digital marketing is a dynamic field, and staying updated with the latest trends, tools, and techniques is crucial to maintaining and enhancing your specialist skills in the long term. Continual learning and adaptation are key to success in digital marketing.
The Common Elements of a Digital Marketing Job Description
Digital marketing job descriptions typically share common elements that help define the role, responsibilities, qualifications, and expectations for candidates. Here are the common elements you can find in a digital marketing job description:
-
Job Title: The job title, such as "Digital Marketing Specialist," "Digital Marketing Manager," or "Digital Marketing Coordinator," indicates the specific role within the digital marketing field.
-
Company Overview: A brief introduction to the hiring company, including its industry, mission, and values, sets the context for the role.
-
Job Location: Specifies where the position is based, which can be in a specific city, state, or country, or may indicate whether it's a remote position.
-
Job Summary/Objective: A concise statement outlining the primary purpose of the role and what the candidate is expected to achieve in the position.
-
Responsibilities/Duties: A detailed list of the day-to-day tasks and responsibilities expected of the candidate. This section often includes items such as content creation, SEO optimization, social media management, and email marketing.
-
Qualifications/Skills: Lists the education, experience, and skills required or preferred for the role. This section may include qualifications like a bachelor's degree in marketing, proficiency in specific tools or platforms, and soft skills like communication and teamwork.
-
Experience: Often divided into "required experience" and "preferred experience," this section outlines the level of experience the company is seeking in candidates.
-
Certifications: If specific certifications (e.g., Google Ads, HubSpot, Facebook Blueprint) are required or preferred, they are listed here.
-
Competencies: Describes the competencies or attributes the ideal candidate should possess, such as analytical skills, creativity, adaptability, and attention to detail.
-
Work Environment: Provides information about the work environment, team size, and any unique aspects of the workplace.
-
Salary and Benefits: In some job descriptions, you may find information about the salary range or compensation package offered, as well as details about benefits like health insurance, retirement plans, and bonuses.
-
How to Apply: Instructions on how candidates should apply, which often include submitting a resume, cover letter, and portfolio, and providing contact details for application submission.
-
Application Deadline: If there's a specific deadline for applications, it's mentioned here.
-
Equal Opportunity Statement: Many job descriptions include a statement about the company's commitment to diversity and equal opportunity employment.
-
Contact Information: Provides contact details for inquiries or questions related to the job posting.
-
Company Culture: Some job descriptions may include information about the company's culture, values, or mission to help candidates understand the work environment and ethos.
These common elements help candidates understand the role, evaluate their qualifications, and prepare their applications accordingly. Employers use them to communicate their expectations clearly and attract candidates who are the best fit for the position and the company.
How to obtain Robotic Process Automation Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
Project Management: PMP, CAPM ,PMI RMP
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
Business Analysis: CBAP, CCBA, ECBA
Agile Training: PMI-ACP , CSM , CSPO
Scrum Training: CSM
DevOps
Program Management: PgMP
Cloud Technology: SMAC Certication
Big Data: Big Data and Hadoop Administrator
Digital Marketing : Digital Marketing Certification
Data Science : Power BI Certification
Cyber Security : CISA Certification
Emerging Technologies : Robotic Process Automation
Conclusion
The landscape of digital marketing in 2023 is more dynamic and critical than ever before. As this guide has illuminated, the responsibilities and skills required of digital marketers have evolved to meet the demands of a rapidly changing digital ecosystem. In a world where businesses are vying for online visibility and customer engagement, digital marketers play a pivotal role in shaping strategies that drive success. Whether it's mastering the intricacies of SEO, creating compelling content, or leveraging emerging technologies, the digital marketer of 2023 must be adaptable, data-savvy, and customer-centric. As we navigate this ever-shifting terrain, it becomes clear that digital marketing is not just a profession; it's an art and science, and those who embrace its challenges and opportunities will continue to be at the forefront of the digital revolution. So, whether you're a seasoned professional or just beginning your journey in this field, the world of digital marketing in 2023 is ripe with possibilities for those who are willing to learn, adapt, and innovate.
Career Advancement Through Top Network Security Certifications
In today's digitally interconnected world, where data breaches and cyber threats have become increasingly prevalent, the demand for skilled network security professionals has never been higher. If you're looking to establish or advance your career in the field of network security, you'll find that acquiring relevant certifications is not just a valuable asset but often a necessity. These certifications not only validate your expertise but also serve as a testament to your commitment to maintaining the integrity and security of critical digital infrastructure.
In this comprehensive guide, we will delve into the realm of network security certifications, providing you with valuable insights into the top certifications that can propel your career to new heights. Whether you're an aspiring cybersecurity enthusiast, a seasoned professional looking to upskill, or simply someone intrigued by the dynamic world of network security, this exploration will shed light on the certifications that matter most, the skills they encompass, and how they can open doors to lucrative and fulfilling career opportunities. So, fasten your digital seatbelt as we embark on a journey through the realm of "Top Network Security Certifications for Career Advancement."
Table of Contents
-
What is Network Security?
-
Why is Network Security Needed?
-
What Are the Types of Network Security?
-
Which are the Best Network Security Certifications?
-
Conclusion
What is Network Security?
Network security is a critical aspect of modern computing and communications. It encompasses a wide range of measures and practices aimed at safeguarding the integrity, confidentiality, and availability of data and resources within a computer network. In an era where digital information plays an increasingly pivotal role in businesses, governments, and personal lives, the importance of network security cannot be overstated. It involves a multifaceted approach, incorporating both technological solutions and human behaviors, to protect against an ever-evolving landscape of cyber threats. Whether it's the protection of sensitive corporate data, the privacy of personal information, or the reliability of critical network services, network security serves as the frontline defense against malicious actors and potential disasters. It is a dynamic and continuously evolving field, driven by the need to stay one step ahead of those who seek to compromise the security and functionality of our interconnected world.
Why is Network Security Needed?
Network security is an indispensable element of our modern digital landscape for several compelling reasons. Firstly, it acts as a safeguard against data breaches, protecting valuable assets such as customer information, financial records, and intellectual property from unauthorized access and theft. In an era where data is a precious commodity, these protections are essential to mitigate the severe financial and reputational repercussions of a breach. Additionally, network security ensures the privacy of individuals and organizations, preventing the unauthorized interception of personal data and confidential business communications.
Secondly, network security is vital for business continuity. Cyberattacks, ranging from Distributed Denial of Service (DDoS) assaults to ransomware, can disrupt essential services and operations, causing significant downtime and financial losses. Network security measures help maintain the availability of critical systems and services, ensuring uninterrupted business operations and mitigating potential financial harm. Furthermore, network security is a key component of regulatory compliance, as many industries and jurisdictions have strict rules governing data security and privacy. Adherence to these regulations is imperative to avoid legal penalties and protect the reputation of organizations. In summary, network security is an essential bulwark against data breaches, preserves privacy, ensures business continuity, supports regulatory compliance, and helps organizations withstand the ever-evolving landscape of cyber threats.
What Are the Types of Network Security?
Network security encompasses various measures and strategies to safeguard computer networks from unauthorized access, data breaches, and other cyber threats. Here are the key types of network security:
-
Firewalls: Firewalls act as a barrier between a trusted internal network and untrusted external networks, such as the internet. They analyze incoming and outgoing traffic, based on predetermined security rules, to allow or block data packets.
-
Intrusion Prevention Systems (IPS): IPSs monitor network and/or system activities for malicious exploits or security policy violations. They can identify and block suspicious traffic in real-time.
-
Intrusion Detection Systems (IDS): IDSs detect and alert on suspicious activities or patterns within a network. They provide notifications about potential security breaches, but they do not actively prevent them.
-
Virtual Private Networks (VPNs): VPNs establish secure connections over the internet, allowing remote users or branch offices to access a private network securely. They use encryption protocols to ensure data confidentiality.
-
Access Control Lists (ACLs): ACLs are a set of rules defined on a network device (e.g., router, firewall) that dictate which types of traffic are allowed or denied based on factors like source, destination, and protocol.
-
Wireless Security: This includes measures like Wi-Fi Protected Access (WPA) and WPA2 protocols, which secure wireless networks from unauthorized access.
-
Network Segmentation: This involves dividing a network into smaller, isolated segments to limit the scope of a potential breach. Each segment may have its own security policies.
-
Anti-virus and Anti-malware Software: These programs detect, prevent, and remove malicious software (viruses, worms, Trojans, etc.) from devices and networks.
-
Email Security: This includes spam filters, antivirus scanning, and encryption to protect email communications from phishing attacks, malware, and other threats.
-
Web Security: Web security solutions filter and monitor web traffic, blocking access to malicious websites and scanning downloads for malware.
-
Security Information and Event Management (SIEM): SIEM tools aggregate and analyze data from various network and security devices to detect and respond to security incidents.
-
Data Loss Prevention (DLP): DLP solutions monitor and control data transfers to prevent unauthorized access or sharing of sensitive information.
-
Security Policies and Procedures: Establishing and enforcing security policies, along with educating employees on security best practices, are crucial elements of network security.
-
Biometric Authentication: This includes fingerprint scanning, facial recognition, and other biometric methods to ensure secure access to devices and networks.
-
Backup and Disaster Recovery: Regularly backing up data and having a robust disaster recovery plan in place helps mitigate the impact of data breaches or system failures.
Implementing a combination of these network security measures provides a layered defense against a wide range of cyber threats, helping to create a more resilient and secure network environment.
Which are the Best Network Security Certifications?
To unlock significant earning potential in the field of network security, a solid grasp of essential tools and skills is imperative. This is precisely where network security education assumes a pivotal role. Enrolling in network security certification courses not only equips you with the fundamental knowledge and skills required for these careers but also furnishes you with a valuable credential, serving as a tangible validation of your qualifications to prospective employers.
-
CEH: Certified Ethical Hacker
-
Also known as "white hat hacking," ethical hacking involves legally probing businesses to identify vulnerabilities before malicious actors do.
-
The CEH certification, offered by the EC-Council, validates your expertise in penetration testing, attack detection, vectors, and prevention.
-
Ethical hackers, or "white hat hackers," are hired to uncover system flaws and propose solutions, making this certification highly valuable in today's cybersecurity landscape.
-
CEH teaches you to think like a hacker, making it ideal for roles such as penetration testers, cyber incident analysts, threat intelligence analysts, and cloud security architects.
-
Requirements: Two years of information security job experience or completion of an authorized EC-Council program.
-
Cost: Varies between $950 and $1,199 depending on the testing location.
-
CISSP: Certified Information Systems Security Professional
-
CISSP, from (ISC)², is a prestigious certification for experienced security professionals responsible for developing and managing security processes, policies, and standards.
-
This certification is highly sought after in the industry, validating your expertise in IT security, cybersecurity program design, implementation, and monitoring.
-
CISSP is suitable for roles like Chief Information Security Officer, security administrators, IT security engineers, and senior security consultants.
-
Requirements: Five or more years of cumulative work experience in at least two of the eight cybersecurity domains or becoming an Associate of (ISC)² if you're new to cybersecurity.
-
Cost: $749
-
CISA: Certified Information Systems Auditor
-
CISA, offered by ISACA, is designed for information security professionals specializing in audit control, assurance, and security.
-
It equips you with the skills needed to manage IT, conduct comprehensive security audits, and identify vulnerabilities.
-
Valued in cybersecurity auditing, it's suitable for roles like IT audit managers, cybersecurity auditors, information security analysts, and IT security engineers.
-
Requirements: At least five years of experience in IT or IS audit, control, security, or assurance, with exceptions for degrees and certifications.
-
Cost: $575 for members, $760 for non-members.
-
CISM: Certified Information Security Manager
-
CISM, also from ISACA, focuses on the management aspects of information security, including governance, program creation, and risk management.
-
Ideal for transitioning from technical to managerial roles in cybersecurity.
-
Relevant for positions like IT managers, information risk consultants, directors of information security, and data governance managers.
-
Requirements: At least five years of information security management experience, with possible substitutions.
-
Cost: $575 for members, $760 for non-members.
-
CompTIA Security+
-
An entry-level certification covering essential cybersecurity skills.
-
Validates your ability to assess security, secure cloud and IoT environments, understand risk and compliance, and respond to security issues.
-
Suitable for roles like systems administrators, help desk managers, security engineers, and IT auditors.
-
Requirements: Recommended to have CompTIA Network+ and two years of IT experience with a security focus.
-
Cost: $370.
-
GIAC Security Essentials (GSEC)
-
An entry-level certification for individuals with a background in information systems and networking.
-
Validates skills in active defense, network security, cryptography, incident response, and cloud security.
-
Relevant for roles like IT security managers, computer forensic analysts, penetration testers, and security administrators.
-
Requirements: No specific prerequisites, but IT experience is beneficial.
-
Cost: $2,499 (includes two practice tests).
-
SSCP: Systems Security Certified Practitioner
-
Focuses on designing, deploying, and maintaining secure IT infrastructures.
-
Suitable for roles like network security engineers, system administrators, and security analysts.
-
Requirements: One year of work experience in one of the testing areas or relevant degrees or certifications.
-
Cost: $249.
-
CompTIA Advanced Security Practitioner (CASP+)
-
Covers advanced topics like enterprise security, risk analysis, and cryptographic approaches.
-
Relevant for positions such as security architects, security engineers, and IT project managers.
-
Requirements: CompTIA recommends ten years of IT experience with five years of hands-on security experience.
-
Cost: $466.
-
GIAC Certified Incident Handler (GCIH)
-
Focuses on identifying, responding to, and defending against cyberattacks.
-
Suitable for incident handlers, security analysts, and system administrators.
-
Requirements: No specific prerequisites, but familiarity with security principles and networking protocols is helpful.
-
Cost: $2,499 (includes two practice tests).
-
Offensive Security Certified Professional (OSCP)
-
A highly sought-after certification for penetration testers.
-
Requires compromising target devices using various exploitation techniques and providing detailed penetration test reports.
-
Relevant for roles like penetration testers, ethical hackers, and threat researchers.
-
Requirements: No formal prerequisites, but prior knowledge of networking and scripting is recommended.
-
Cost: $999 (includes training, lab access, and one test attempt).
Conclusion
In conclusion, the world of cybersecurity is dynamic and ever-evolving, and staying ahead of the curve is essential in defending against the ever-present threats in the digital realm. The array of certifications available provides a roadmap for professionals at every stage of their cybersecurity journey.
Whether you're a newcomer looking to establish a foothold or a seasoned expert seeking to advance your career, these certifications offer a structured path to sharpen your skills, validate your knowledge, and enhance your professional prospects. From ethical hacking to security management, each certification serves a specific purpose and opens doors to various rewarding roles within the cybersecurity landscape.
In this rapidly changing field, continuous learning is paramount, and acquiring certifications is not just a one-time achievement but an ongoing commitment to excellence. Regardless of where you are in your career, investing in these certifications not only elevates your expertise but also fortifies your ability to protect organizations and individuals from the ever-evolving threat landscape.
Remember that the ideal certification depends on your career goals, interests, and experience level. Combining multiple certifications can create a well-rounded skill set, making you a valuable asset in the ever-expanding realm of cybersecurity. So, choose wisely, invest in your professional development, and stay committed to the pursuit of knowledge in the ever-important field of cybersecurity.
How to obtain Robotic Process Automation Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Cyber Security Training:
- Certified Ethical Hacker Training Courses
- Certified Information Systems Security Professional Training Courses
- Certified inrisk and Information Systems Control Training Courses
- Certified Information Security Manager Training Courses
- Certified Information Systems Auditor
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1(713)-518-1187 / +1(713)-287-1214 or e-mail us at info@icertglobal.com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
In today's digitally interconnected world, where data breaches and cyber threats have become increasingly prevalent, the demand for skilled network security professionals has never been higher. If you're looking to establish or advance your career in the field of network security, you'll find that acquiring relevant certifications is not just a valuable asset but often a necessity. These certifications not only validate your expertise but also serve as a testament to your commitment to maintaining the integrity and security of critical digital infrastructure.
In this comprehensive guide, we will delve into the realm of network security certifications, providing you with valuable insights into the top certifications that can propel your career to new heights. Whether you're an aspiring cybersecurity enthusiast, a seasoned professional looking to upskill, or simply someone intrigued by the dynamic world of network security, this exploration will shed light on the certifications that matter most, the skills they encompass, and how they can open doors to lucrative and fulfilling career opportunities. So, fasten your digital seatbelt as we embark on a journey through the realm of "Top Network Security Certifications for Career Advancement."
Table of Contents
-
What is Network Security?
-
Why is Network Security Needed?
-
What Are the Types of Network Security?
-
Which are the Best Network Security Certifications?
-
Conclusion
What is Network Security?
Network security is a critical aspect of modern computing and communications. It encompasses a wide range of measures and practices aimed at safeguarding the integrity, confidentiality, and availability of data and resources within a computer network. In an era where digital information plays an increasingly pivotal role in businesses, governments, and personal lives, the importance of network security cannot be overstated. It involves a multifaceted approach, incorporating both technological solutions and human behaviors, to protect against an ever-evolving landscape of cyber threats. Whether it's the protection of sensitive corporate data, the privacy of personal information, or the reliability of critical network services, network security serves as the frontline defense against malicious actors and potential disasters. It is a dynamic and continuously evolving field, driven by the need to stay one step ahead of those who seek to compromise the security and functionality of our interconnected world.
Why is Network Security Needed?
Network security is an indispensable element of our modern digital landscape for several compelling reasons. Firstly, it acts as a safeguard against data breaches, protecting valuable assets such as customer information, financial records, and intellectual property from unauthorized access and theft. In an era where data is a precious commodity, these protections are essential to mitigate the severe financial and reputational repercussions of a breach. Additionally, network security ensures the privacy of individuals and organizations, preventing the unauthorized interception of personal data and confidential business communications.
Secondly, network security is vital for business continuity. Cyberattacks, ranging from Distributed Denial of Service (DDoS) assaults to ransomware, can disrupt essential services and operations, causing significant downtime and financial losses. Network security measures help maintain the availability of critical systems and services, ensuring uninterrupted business operations and mitigating potential financial harm. Furthermore, network security is a key component of regulatory compliance, as many industries and jurisdictions have strict rules governing data security and privacy. Adherence to these regulations is imperative to avoid legal penalties and protect the reputation of organizations. In summary, network security is an essential bulwark against data breaches, preserves privacy, ensures business continuity, supports regulatory compliance, and helps organizations withstand the ever-evolving landscape of cyber threats.
What Are the Types of Network Security?
Network security encompasses various measures and strategies to safeguard computer networks from unauthorized access, data breaches, and other cyber threats. Here are the key types of network security:
-
Firewalls: Firewalls act as a barrier between a trusted internal network and untrusted external networks, such as the internet. They analyze incoming and outgoing traffic, based on predetermined security rules, to allow or block data packets.
-
Intrusion Prevention Systems (IPS): IPSs monitor network and/or system activities for malicious exploits or security policy violations. They can identify and block suspicious traffic in real-time.
-
Intrusion Detection Systems (IDS): IDSs detect and alert on suspicious activities or patterns within a network. They provide notifications about potential security breaches, but they do not actively prevent them.
-
Virtual Private Networks (VPNs): VPNs establish secure connections over the internet, allowing remote users or branch offices to access a private network securely. They use encryption protocols to ensure data confidentiality.
-
Access Control Lists (ACLs): ACLs are a set of rules defined on a network device (e.g., router, firewall) that dictate which types of traffic are allowed or denied based on factors like source, destination, and protocol.
-
Wireless Security: This includes measures like Wi-Fi Protected Access (WPA) and WPA2 protocols, which secure wireless networks from unauthorized access.
-
Network Segmentation: This involves dividing a network into smaller, isolated segments to limit the scope of a potential breach. Each segment may have its own security policies.
-
Anti-virus and Anti-malware Software: These programs detect, prevent, and remove malicious software (viruses, worms, Trojans, etc.) from devices and networks.
-
Email Security: This includes spam filters, antivirus scanning, and encryption to protect email communications from phishing attacks, malware, and other threats.
-
Web Security: Web security solutions filter and monitor web traffic, blocking access to malicious websites and scanning downloads for malware.
-
Security Information and Event Management (SIEM): SIEM tools aggregate and analyze data from various network and security devices to detect and respond to security incidents.
-
Data Loss Prevention (DLP): DLP solutions monitor and control data transfers to prevent unauthorized access or sharing of sensitive information.
-
Security Policies and Procedures: Establishing and enforcing security policies, along with educating employees on security best practices, are crucial elements of network security.
-
Biometric Authentication: This includes fingerprint scanning, facial recognition, and other biometric methods to ensure secure access to devices and networks.
-
Backup and Disaster Recovery: Regularly backing up data and having a robust disaster recovery plan in place helps mitigate the impact of data breaches or system failures.
Implementing a combination of these network security measures provides a layered defense against a wide range of cyber threats, helping to create a more resilient and secure network environment.
Which are the Best Network Security Certifications?
To unlock significant earning potential in the field of network security, a solid grasp of essential tools and skills is imperative. This is precisely where network security education assumes a pivotal role. Enrolling in network security certification courses not only equips you with the fundamental knowledge and skills required for these careers but also furnishes you with a valuable credential, serving as a tangible validation of your qualifications to prospective employers.
-
CEH: Certified Ethical Hacker
-
Also known as "white hat hacking," ethical hacking involves legally probing businesses to identify vulnerabilities before malicious actors do.
-
The CEH certification, offered by the EC-Council, validates your expertise in penetration testing, attack detection, vectors, and prevention.
-
Ethical hackers, or "white hat hackers," are hired to uncover system flaws and propose solutions, making this certification highly valuable in today's cybersecurity landscape.
-
CEH teaches you to think like a hacker, making it ideal for roles such as penetration testers, cyber incident analysts, threat intelligence analysts, and cloud security architects.
-
Requirements: Two years of information security job experience or completion of an authorized EC-Council program.
-
Cost: Varies between $950 and $1,199 depending on the testing location.
-
-
CISSP: Certified Information Systems Security Professional
-
CISSP, from (ISC)², is a prestigious certification for experienced security professionals responsible for developing and managing security processes, policies, and standards.
-
This certification is highly sought after in the industry, validating your expertise in IT security, cybersecurity program design, implementation, and monitoring.
-
CISSP is suitable for roles like Chief Information Security Officer, security administrators, IT security engineers, and senior security consultants.
-
Requirements: Five or more years of cumulative work experience in at least two of the eight cybersecurity domains or becoming an Associate of (ISC)² if you're new to cybersecurity.
-
Cost: $749
-
-
CISA: Certified Information Systems Auditor
-
CISA, offered by ISACA, is designed for information security professionals specializing in audit control, assurance, and security.
-
It equips you with the skills needed to manage IT, conduct comprehensive security audits, and identify vulnerabilities.
-
Valued in cybersecurity auditing, it's suitable for roles like IT audit managers, cybersecurity auditors, information security analysts, and IT security engineers.
-
Requirements: At least five years of experience in IT or IS audit, control, security, or assurance, with exceptions for degrees and certifications.
-
Cost: $575 for members, $760 for non-members.
-
-
CISM: Certified Information Security Manager
-
CISM, also from ISACA, focuses on the management aspects of information security, including governance, program creation, and risk management.
-
Ideal for transitioning from technical to managerial roles in cybersecurity.
-
Relevant for positions like IT managers, information risk consultants, directors of information security, and data governance managers.
-
Requirements: At least five years of information security management experience, with possible substitutions.
-
Cost: $575 for members, $760 for non-members.
-
-
CompTIA Security+
-
An entry-level certification covering essential cybersecurity skills.
-
Validates your ability to assess security, secure cloud and IoT environments, understand risk and compliance, and respond to security issues.
-
Suitable for roles like systems administrators, help desk managers, security engineers, and IT auditors.
-
Requirements: Recommended to have CompTIA Network+ and two years of IT experience with a security focus.
-
Cost: $370.
-
-
GIAC Security Essentials (GSEC)
-
An entry-level certification for individuals with a background in information systems and networking.
-
Validates skills in active defense, network security, cryptography, incident response, and cloud security.
-
Relevant for roles like IT security managers, computer forensic analysts, penetration testers, and security administrators.
-
Requirements: No specific prerequisites, but IT experience is beneficial.
-
Cost: $2,499 (includes two practice tests).
-
-
SSCP: Systems Security Certified Practitioner
-
Focuses on designing, deploying, and maintaining secure IT infrastructures.
-
Suitable for roles like network security engineers, system administrators, and security analysts.
-
Requirements: One year of work experience in one of the testing areas or relevant degrees or certifications.
-
Cost: $249.
-
-
CompTIA Advanced Security Practitioner (CASP+)
-
Covers advanced topics like enterprise security, risk analysis, and cryptographic approaches.
-
Relevant for positions such as security architects, security engineers, and IT project managers.
-
Requirements: CompTIA recommends ten years of IT experience with five years of hands-on security experience.
-
Cost: $466.
-
-
GIAC Certified Incident Handler (GCIH)
-
Focuses on identifying, responding to, and defending against cyberattacks.
-
Suitable for incident handlers, security analysts, and system administrators.
-
Requirements: No specific prerequisites, but familiarity with security principles and networking protocols is helpful.
-
Cost: $2,499 (includes two practice tests).
-
-
Offensive Security Certified Professional (OSCP)
-
A highly sought-after certification for penetration testers.
-
Requires compromising target devices using various exploitation techniques and providing detailed penetration test reports.
-
Relevant for roles like penetration testers, ethical hackers, and threat researchers.
-
Requirements: No formal prerequisites, but prior knowledge of networking and scripting is recommended.
-
Cost: $999 (includes training, lab access, and one test attempt).
-
Conclusion
In conclusion, the world of cybersecurity is dynamic and ever-evolving, and staying ahead of the curve is essential in defending against the ever-present threats in the digital realm. The array of certifications available provides a roadmap for professionals at every stage of their cybersecurity journey.
Whether you're a newcomer looking to establish a foothold or a seasoned expert seeking to advance your career, these certifications offer a structured path to sharpen your skills, validate your knowledge, and enhance your professional prospects. From ethical hacking to security management, each certification serves a specific purpose and opens doors to various rewarding roles within the cybersecurity landscape.
In this rapidly changing field, continuous learning is paramount, and acquiring certifications is not just a one-time achievement but an ongoing commitment to excellence. Regardless of where you are in your career, investing in these certifications not only elevates your expertise but also fortifies your ability to protect organizations and individuals from the ever-evolving threat landscape.
Remember that the ideal certification depends on your career goals, interests, and experience level. Combining multiple certifications can create a well-rounded skill set, making you a valuable asset in the ever-expanding realm of cybersecurity. So, choose wisely, invest in your professional development, and stay committed to the pursuit of knowledge in the ever-important field of cybersecurity.
How to obtain Robotic Process Automation Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Cyber Security Training:
- Certified Ethical Hacker Training Courses
- Certified Information Systems Security Professional Training Courses
- Certified inrisk and Information Systems Control Training Courses
- Certified Information Security Manager Training Courses
- Certified Information Systems Auditor
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1(713)-518-1187 / +1(713)-287-1214 or e-mail us at info@icertglobal.com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Salesforce Pardot: A Complete Overview, Pricing Breakdown, and Benefits Analysis
In today's fast-paced business landscape, effective marketing automation has become the cornerstone of successful customer engagement and lead nurturing. Among the multitude of tools available, Salesforce Pardot stands out as a powerful and versatile solution for businesses seeking to streamline their marketing efforts, personalize customer interactions, and ultimately drive growth.
In this blog post, we'll take a deep dive into Salesforce Pardot, exploring what it is, its key features, and the benefits it offers to businesses of all sizes and industries. We'll also delve into the pricing structure, helping you understand the investment required for incorporating Pardot into your marketing strategy.
Whether you're a seasoned marketer looking to enhance your automation capabilities or a business owner curious about the potential of marketing automation, this comprehensive guide will provide you with valuable insights to make informed decisions. Let's embark on this journey to discover Salesforce Pardot's incredible potential and the advantages it can bring to your marketing efforts.
Table of Contents
-
What is Salesforce Pardot
-
Benefits of Using Salesforce Pardot
-
Salesforce Pardot Pricing
-
Use Cases and Success Stories
-
Getting Started with Salesforce Pardot
-
Alternatives to Salesforce Pardot
-
Conclusion
What is Salesforce Pardot
Salesforce Pardot is a versatile marketing automation solution that empowers businesses to streamline their marketing efforts and engage with leads more effectively. With its robust features, Pardot enables businesses to automate various marketing tasks, such as email marketing, lead nurturing, and lead scoring. It facilitates personalized communication with leads, ensuring that the right message reaches the right audience at the right time. Furthermore, its seamless integration with Salesforce CRM enhances collaboration between marketing and sales teams, enabling a smoother lead handoff process. Pardot's analytics and reporting capabilities provide valuable insights, helping businesses refine their marketing strategies and boost ROI. Whether you're a small startup or a large enterprise, Pardot offers scalability and customization to meet your unique marketing automation needs.
One of the key strengths of Salesforce Pardot is its ability to deliver tangible benefits to businesses. By automating repetitive marketing tasks, it saves valuable time and resources, allowing marketing teams to focus on strategic activities. Its lead scoring and nurturing features increase the efficiency of lead management, ensuring that sales teams engage with leads that are more likely to convert. Pardot's data-driven approach enhances decision-making, as businesses can analyze campaign performance and make adjustments in real-time. Additionally, its integration with Salesforce CRM enhances customer relationship management, promoting a unified and efficient sales and marketing process. Overall, Salesforce Pardot is a powerful tool for businesses looking to drive revenue and improve marketing effectiveness through automation and data-driven insights.
Benefits of Using Salesforce Pardot
Using Salesforce Pardot offers a wide range of benefits to businesses seeking to enhance their marketing efforts, improve lead management, and drive revenue growth. Here are some key advantages of incorporating Salesforce Pardot into your marketing strategy:
-
Efficient Lead Generation and Nurturing: Pardot enables businesses to capture leads seamlessly through web forms, landing pages, and other channels. It also automates lead nurturing through personalized email campaigns, ensuring that leads are engaged and nurtured at every stage of the buyer's journey.
-
Improved Lead Scoring: With Pardot's lead scoring capabilities, you can prioritize leads based on their behavior and engagement with your content. This ensures that your sales team focuses their efforts on the most qualified leads, increasing conversion rates and sales efficiency.
-
Personalization: Pardot allows you to create highly targeted and personalized marketing campaigns. You can segment your audience based on various criteria, ensuring that each lead receives content tailored to their interests and needs.
-
Seamless CRM Integration: As part of the Salesforce ecosystem, Pardot seamlessly integrates with Salesforce CRM. This integration ensures that all lead and customer data is synchronized, providing a 360-degree view of your customers and prospects. It also streamlines the lead handoff process between marketing and sales teams.
-
Automation and Efficiency: Pardot automates various marketing tasks, such as email marketing, lead scoring, and lead assignment. This automation saves time and reduces the risk of human errors, allowing your marketing team to focus on strategic initiatives.
-
Advanced Analytics and Reporting: Pardot provides in-depth analytics and reporting tools to track the performance of your marketing campaigns. You can measure key metrics, such as email open rates, click-through rates, and conversion rates, and use these insights to refine your marketing strategies for better results.
-
Scalability: Pardot is scalable, making it suitable for businesses of all sizes. Whether you're a small startup or a large enterprise, you can customize Pardot to meet your specific marketing automation needs and scale as your business grows.
-
Enhanced Social Media Engagement: Pardot helps you manage and track your social media marketing efforts, allowing you to monitor social engagement and incorporate it into your lead nurturing strategies.
-
Cost Savings: By automating marketing tasks and improving lead conversion rates, Pardot can lead to cost savings in both time and resources. It maximizes the efficiency of your marketing team while delivering tangible results.
-
Competitive Advantage: Leveraging Pardot's advanced features can give your business a competitive edge in a crowded marketplace. It enables you to stay ahead of the curve in terms of marketing automation and customer engagement.
Salesforce Pardot Pricing
Salesforce Pardot offers various pricing tiers to accommodate the needs and budgets of different businesses. The pricing structure is typically based on the number of users, the number of contacts or leads you want to manage, and the features you require. It's important to note that pricing may change over time, so it's advisable to visit the Salesforce Pardot website or contact their sales team for the most up-to-date information.
Pardot Edition
Features Included
Starting Price (Approximate)*
Growth Edition
- Basic marketing automation
Starting at $1,250/month
- Email marketing
- Lead scoring
- CRM integration
Plus Edition
- Advanced email analytics
Starting at $2,500/month
- Dynamic content
- A/B testing
- CRM integration
Advanced Edition
- AI-powered analytics
Custom pricing
- Custom user roles
- Marketing assets
- CRM integration
Premium Edition
- Custom analytics
Custom pricing
- Event-based segmentation
- Advanced features tailored to needs
Add-Ons
- B2B Marketing Analytics (Additional)
Custom pricing
- Engagement History (Additional)
- Additional services, training, and support
*Note: Pricing is typically based on factors such as the number of contacts or leads and additional features and services required. Actual prices may vary depending on specific business needs.
Use Cases and Success Stories
Use Cases and Success Stories of Salesforce Pardot
Salesforce Pardot has been employed by businesses across various industries to achieve marketing automation excellence and drive significant results. Below are some use cases and success stories that showcase the versatility and impact of Pardot:
1. Lead Nurturing and Conversion: A technology company that sells complex software solutions used Salesforce Pardot to nurture leads and increase conversions. By creating personalized email campaigns and automating lead scoring, they reduced the sales cycle by 30%. This resulted in a 20% increase in revenue in the first year of implementing Pardot.
2. B2B E-commerce: An e-commerce company specializing in B2B sales adopted Pardot to better understand its customers' needs. By tracking customer interactions and using Pardot's lead scoring, they were able to send targeted product recommendations, leading to a 15% increase in upsell and cross-sell revenue.
3. Event Promotion: An event management company utilized Pardot for event promotion. They automated email marketing campaigns and personalized event invitations based on attendee preferences. This resulted in a 40% increase in event attendance and a 25% boost in post-event engagement.
4. Higher Education: A university employed Pardot to streamline its student recruitment efforts. By automating email communication and tracking prospect engagement, they achieved a 50% increase in the number of enrolled students. Pardot's integration with Salesforce CRM also improved communication between admissions and academic departments.
5. Healthcare: A healthcare organization implemented Pardot to improve patient engagement and appointment scheduling. They sent automated appointment reminders and health tips to patients, resulting in a 25% reduction in missed appointments and improved patient satisfaction.
6. Manufacturing: A manufacturing company used Pardot to enhance its distributor engagement. By automating lead nurturing and providing distributors with tailored marketing collateral, they saw a 30% increase in distributor-generated sales leads within six months.
7. Non-Profit Fundraising: A non-profit organization leveraged Pardot for donor outreach and fundraising campaigns. They personalized donation requests and automated follow-up emails. As a result, they experienced a 40% increase in online donations and donor retention rates.
8. Financial Services: A financial services firm integrated Pardot with its CRM to improve lead management. They automated lead assignment to financial advisors, resulting in a 15% increase in lead conversion rates and a 20% reduction in response time.
These use cases highlight the adaptability of Salesforce Pardot across different industries and functions. Whether it's lead nurturing, event promotion, student recruitment, healthcare engagement, distributor management, non-profit fundraising, or financial services, Pardot has consistently delivered tangible benefits such as increased revenue, improved customer engagement, and enhanced operational efficiency. These success stories underscore the effectiveness of Pardot in helping businesses achieve their marketing and sales objectives.
Getting Started with Salesforce Pardot
Getting started with Salesforce Pardot involves several key steps to ensure a successful implementation of the marketing automation platform. Here's a step-by-step guide on how to get started with Salesforce Pardot:
1. Set Clear Goals and Objectives:
-
Define your marketing automation goals and objectives. What do you aim to achieve with Pardot? Whether it's lead generation, lead nurturing, improving conversions, or increasing ROI, having clear goals will guide your implementation.
2. Sign Up for Pardot:
-
Visit the Salesforce Pardot website and sign up for the edition that best suits your business needs. You may also request a demo or contact Salesforce for more information.
3. Assign an Administrator:
-
Designate an internal administrator or team responsible for managing Pardot. This individual should be trained in Pardot's features and functionality.
4. Set Up Salesforce Integration:
-
If you're already using Salesforce CRM, ensure that Pardot is properly integrated with Salesforce. This step is crucial for syncing data between the two platforms seamlessly.
5. Define Your Lead Scoring Model:
-
Develop a lead scoring model that assigns values to various lead interactions and behaviors. This model helps prioritize leads for your sales team.
6. Import Your Contacts and Data:
-
Import your existing leads and contacts into Pardot. Ensure that data is clean, accurate, and well-segmented for effective targeting.
7. Create Landing Pages and Forms:
-
Build custom landing pages and forms to capture lead information. Pardot provides templates and a user-friendly interface for this purpose.
8. Design Email Templates:
-
Create email templates that align with your branding and messaging. Pardot allows for responsive and personalized email design.
9. Set Up Drip Campaigns:
-
Create automated drip email campaigns for lead nurturing. Map out the content and timing of these campaigns based on your lead's journey.
10. Implement Lead Scoring and Grading: - Configure lead scoring rules and grading criteria to identify the most engaged and qualified leads.
11. Test Automation Workflows: - Before going live, thoroughly test your automation workflows, including email sequences and landing page forms, to ensure they function as intended.
12. Train Your Team: - Provide training to your marketing and sales teams on how to use Pardot effectively. Ensure they understand lead management processes and how to interpret lead scoring data.
13. Monitor and Analyze: - Regularly monitor the performance of your campaigns and use Pardot's analytics and reporting tools to gain insights into what's working and what needs improvement.
14. Optimize and Iterate: - Continuously optimize your marketing strategies based on data and feedback. Adjust your automation workflows, content, and targeting as needed to achieve better results.
15. Seek Professional Assistance: - If needed, consider consulting with Salesforce Pardot experts or attending training sessions to maximize the value of the platform.
Remember that Salesforce Pardot is a powerful marketing automation tool, and its effectiveness often grows over time as you become more familiar with its features and capabilities. Regularly reviewing your strategies and adapting to changing market conditions will help you get the most out of Pardot and drive success in your marketing efforts.
Alternatives to Salesforce Pardot
There are several alternatives to Salesforce Pardot, each offering its own set of features and capabilities for marketing automation and lead management. The choice of an alternative depends on your specific business needs, budget, and existing technology stack. Here are some popular alternatives to Salesforce Pardot:
-
HubSpot Marketing Hub:
-
HubSpot offers a comprehensive suite of marketing tools, including automation, email marketing, lead nurturing, and analytics. It's known for its user-friendly interface and is suitable for both small businesses and larger enterprises.
-
Marketo:
-
Marketo, now part of Adobe Experience Cloud, provides a robust marketing automation platform. It's ideal for B2B marketers and offers features such as lead scoring, advanced analytics, and integration with Adobe's creative tools.
-
Mailchimp:
-
While traditionally known for email marketing, Mailchimp has expanded its offerings to include marketing automation features. It's a cost-effective solution for small to medium-sized businesses.
-
ActiveCampaign:
-
ActiveCampaign combines email marketing, automation, and CRM capabilities. It's known for its advanced automation features and is suitable for businesses of all sizes.
-
Eloqua (Oracle Marketing Cloud):
-
Oracle Eloqua is a high-end marketing automation solution with a focus on enterprise-level marketing. It offers advanced lead scoring, campaign orchestration, and robust analytics.
-
SharpSpring:
-
SharpSpring is a marketing automation platform that caters to agencies and small to medium-sized businesses. It offers email marketing, CRM integration, and lead tracking features.
-
GetResponse:
-
GetResponse provides email marketing, automation, and landing page creation tools. It's a versatile solution for businesses looking to automate marketing tasks.
-
Infusionsoft by Keap:
-
Infusionsoft (now part of Keap) is a small business-focused marketing automation platform that offers CRM, email marketing, and automation capabilities.
-
Zoho MarketingHub:
-
Zoho MarketingHub is part of the Zoho suite of business tools and offers marketing automation features, email marketing, and CRM integration.
-
SendinBlue:
-
SendinBlue offers email marketing, marketing automation, and transactional email services. It's known for its affordability and ease of use.
-
Drip:
-
Drip is an e-commerce-focused marketing automation platform that specializes in personalized email marketing and automation for online retailers.
When evaluating alternatives to Salesforce Pardot, consider factors such as the size of your business, your budget, your specific marketing automation needs, and how well the platform integrates with your existing software stack, including your CRM. Additionally, take advantage of free trials and demos to test the platforms and see which one aligns best with your goals and workflows.
How to obtain Salesforce Certifications?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
Project Management: PMP, CAPM ,PMI RMP
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
Business Analysis: CBAP, CCBA, ECBA
Agile Training: PMI-ACP , CSM , CSPO
Scrum Training: CSM
DevOps
Program Management: PgMP
Cloud Technology: SMAC Certication
Big Data: Big Data and Hadoop Administrator
Digital Marketing : Digital Marketing Certification
Data Science : Power BI Certification
Cyber Security : CISA Certification
Emerging Technologies : Blockchain Certification
Salesforce : Salesforce Administration Certification
Conclusion
In conclusion, Salesforce Pardot presents a compelling solution for businesses seeking to elevate their marketing strategies through efficient automation. Its versatile feature set, encompassing lead generation, nurturing, and seamless CRM integration, offers tangible benefits such as increased lead conversion rates and streamlined processes. While Pardot's pricing structure varies to accommodate businesses of all sizes, its value lies in the potential for personalized engagement, data-driven insights, and scalable marketing campaigns, making it a noteworthy contender in the competitive landscape of marketing automation platforms.
Read More
In today's fast-paced business landscape, effective marketing automation has become the cornerstone of successful customer engagement and lead nurturing. Among the multitude of tools available, Salesforce Pardot stands out as a powerful and versatile solution for businesses seeking to streamline their marketing efforts, personalize customer interactions, and ultimately drive growth.
In this blog post, we'll take a deep dive into Salesforce Pardot, exploring what it is, its key features, and the benefits it offers to businesses of all sizes and industries. We'll also delve into the pricing structure, helping you understand the investment required for incorporating Pardot into your marketing strategy.
Whether you're a seasoned marketer looking to enhance your automation capabilities or a business owner curious about the potential of marketing automation, this comprehensive guide will provide you with valuable insights to make informed decisions. Let's embark on this journey to discover Salesforce Pardot's incredible potential and the advantages it can bring to your marketing efforts.
Table of Contents
-
What is Salesforce Pardot
-
Benefits of Using Salesforce Pardot
-
Salesforce Pardot Pricing
-
Use Cases and Success Stories
-
Getting Started with Salesforce Pardot
-
Alternatives to Salesforce Pardot
-
Conclusion
What is Salesforce Pardot
Salesforce Pardot is a versatile marketing automation solution that empowers businesses to streamline their marketing efforts and engage with leads more effectively. With its robust features, Pardot enables businesses to automate various marketing tasks, such as email marketing, lead nurturing, and lead scoring. It facilitates personalized communication with leads, ensuring that the right message reaches the right audience at the right time. Furthermore, its seamless integration with Salesforce CRM enhances collaboration between marketing and sales teams, enabling a smoother lead handoff process. Pardot's analytics and reporting capabilities provide valuable insights, helping businesses refine their marketing strategies and boost ROI. Whether you're a small startup or a large enterprise, Pardot offers scalability and customization to meet your unique marketing automation needs.
One of the key strengths of Salesforce Pardot is its ability to deliver tangible benefits to businesses. By automating repetitive marketing tasks, it saves valuable time and resources, allowing marketing teams to focus on strategic activities. Its lead scoring and nurturing features increase the efficiency of lead management, ensuring that sales teams engage with leads that are more likely to convert. Pardot's data-driven approach enhances decision-making, as businesses can analyze campaign performance and make adjustments in real-time. Additionally, its integration with Salesforce CRM enhances customer relationship management, promoting a unified and efficient sales and marketing process. Overall, Salesforce Pardot is a powerful tool for businesses looking to drive revenue and improve marketing effectiveness through automation and data-driven insights.
Benefits of Using Salesforce Pardot
Using Salesforce Pardot offers a wide range of benefits to businesses seeking to enhance their marketing efforts, improve lead management, and drive revenue growth. Here are some key advantages of incorporating Salesforce Pardot into your marketing strategy:
-
Efficient Lead Generation and Nurturing: Pardot enables businesses to capture leads seamlessly through web forms, landing pages, and other channels. It also automates lead nurturing through personalized email campaigns, ensuring that leads are engaged and nurtured at every stage of the buyer's journey.
-
Improved Lead Scoring: With Pardot's lead scoring capabilities, you can prioritize leads based on their behavior and engagement with your content. This ensures that your sales team focuses their efforts on the most qualified leads, increasing conversion rates and sales efficiency.
-
Personalization: Pardot allows you to create highly targeted and personalized marketing campaigns. You can segment your audience based on various criteria, ensuring that each lead receives content tailored to their interests and needs.
-
Seamless CRM Integration: As part of the Salesforce ecosystem, Pardot seamlessly integrates with Salesforce CRM. This integration ensures that all lead and customer data is synchronized, providing a 360-degree view of your customers and prospects. It also streamlines the lead handoff process between marketing and sales teams.
-
Automation and Efficiency: Pardot automates various marketing tasks, such as email marketing, lead scoring, and lead assignment. This automation saves time and reduces the risk of human errors, allowing your marketing team to focus on strategic initiatives.
-
Advanced Analytics and Reporting: Pardot provides in-depth analytics and reporting tools to track the performance of your marketing campaigns. You can measure key metrics, such as email open rates, click-through rates, and conversion rates, and use these insights to refine your marketing strategies for better results.
-
Scalability: Pardot is scalable, making it suitable for businesses of all sizes. Whether you're a small startup or a large enterprise, you can customize Pardot to meet your specific marketing automation needs and scale as your business grows.
-
Enhanced Social Media Engagement: Pardot helps you manage and track your social media marketing efforts, allowing you to monitor social engagement and incorporate it into your lead nurturing strategies.
-
Cost Savings: By automating marketing tasks and improving lead conversion rates, Pardot can lead to cost savings in both time and resources. It maximizes the efficiency of your marketing team while delivering tangible results.
-
Competitive Advantage: Leveraging Pardot's advanced features can give your business a competitive edge in a crowded marketplace. It enables you to stay ahead of the curve in terms of marketing automation and customer engagement.
Salesforce Pardot Pricing
Salesforce Pardot offers various pricing tiers to accommodate the needs and budgets of different businesses. The pricing structure is typically based on the number of users, the number of contacts or leads you want to manage, and the features you require. It's important to note that pricing may change over time, so it's advisable to visit the Salesforce Pardot website or contact their sales team for the most up-to-date information.
|
Pardot Edition |
Features Included |
Starting Price (Approximate)* |
|
Growth Edition |
- Basic marketing automation |
Starting at $1,250/month |
|
- Email marketing |
||
|
- Lead scoring |
||
|
- CRM integration |
||
|
Plus Edition |
- Advanced email analytics |
Starting at $2,500/month |
|
- Dynamic content |
||
|
- A/B testing |
||
|
- CRM integration |
||
|
Advanced Edition |
- AI-powered analytics |
Custom pricing |
|
- Custom user roles |
||
|
- Marketing assets |
||
|
- CRM integration |
||
|
Premium Edition |
- Custom analytics |
Custom pricing |
|
- Event-based segmentation |
||
|
- Advanced features tailored to needs |
||
|
Add-Ons |
- B2B Marketing Analytics (Additional) |
Custom pricing |
|
- Engagement History (Additional) |
||
|
- Additional services, training, and support |
*Note: Pricing is typically based on factors such as the number of contacts or leads and additional features and services required. Actual prices may vary depending on specific business needs.
Use Cases and Success Stories
Use Cases and Success Stories of Salesforce Pardot
Salesforce Pardot has been employed by businesses across various industries to achieve marketing automation excellence and drive significant results. Below are some use cases and success stories that showcase the versatility and impact of Pardot:
1. Lead Nurturing and Conversion: A technology company that sells complex software solutions used Salesforce Pardot to nurture leads and increase conversions. By creating personalized email campaigns and automating lead scoring, they reduced the sales cycle by 30%. This resulted in a 20% increase in revenue in the first year of implementing Pardot.
2. B2B E-commerce: An e-commerce company specializing in B2B sales adopted Pardot to better understand its customers' needs. By tracking customer interactions and using Pardot's lead scoring, they were able to send targeted product recommendations, leading to a 15% increase in upsell and cross-sell revenue.
3. Event Promotion: An event management company utilized Pardot for event promotion. They automated email marketing campaigns and personalized event invitations based on attendee preferences. This resulted in a 40% increase in event attendance and a 25% boost in post-event engagement.
4. Higher Education: A university employed Pardot to streamline its student recruitment efforts. By automating email communication and tracking prospect engagement, they achieved a 50% increase in the number of enrolled students. Pardot's integration with Salesforce CRM also improved communication between admissions and academic departments.
5. Healthcare: A healthcare organization implemented Pardot to improve patient engagement and appointment scheduling. They sent automated appointment reminders and health tips to patients, resulting in a 25% reduction in missed appointments and improved patient satisfaction.
6. Manufacturing: A manufacturing company used Pardot to enhance its distributor engagement. By automating lead nurturing and providing distributors with tailored marketing collateral, they saw a 30% increase in distributor-generated sales leads within six months.
7. Non-Profit Fundraising: A non-profit organization leveraged Pardot for donor outreach and fundraising campaigns. They personalized donation requests and automated follow-up emails. As a result, they experienced a 40% increase in online donations and donor retention rates.
8. Financial Services: A financial services firm integrated Pardot with its CRM to improve lead management. They automated lead assignment to financial advisors, resulting in a 15% increase in lead conversion rates and a 20% reduction in response time.
These use cases highlight the adaptability of Salesforce Pardot across different industries and functions. Whether it's lead nurturing, event promotion, student recruitment, healthcare engagement, distributor management, non-profit fundraising, or financial services, Pardot has consistently delivered tangible benefits such as increased revenue, improved customer engagement, and enhanced operational efficiency. These success stories underscore the effectiveness of Pardot in helping businesses achieve their marketing and sales objectives.
Getting Started with Salesforce Pardot
Getting started with Salesforce Pardot involves several key steps to ensure a successful implementation of the marketing automation platform. Here's a step-by-step guide on how to get started with Salesforce Pardot:
1. Set Clear Goals and Objectives:
-
Define your marketing automation goals and objectives. What do you aim to achieve with Pardot? Whether it's lead generation, lead nurturing, improving conversions, or increasing ROI, having clear goals will guide your implementation.
2. Sign Up for Pardot:
-
Visit the Salesforce Pardot website and sign up for the edition that best suits your business needs. You may also request a demo or contact Salesforce for more information.
3. Assign an Administrator:
-
Designate an internal administrator or team responsible for managing Pardot. This individual should be trained in Pardot's features and functionality.
4. Set Up Salesforce Integration:
-
If you're already using Salesforce CRM, ensure that Pardot is properly integrated with Salesforce. This step is crucial for syncing data between the two platforms seamlessly.
5. Define Your Lead Scoring Model:
-
Develop a lead scoring model that assigns values to various lead interactions and behaviors. This model helps prioritize leads for your sales team.
6. Import Your Contacts and Data:
-
Import your existing leads and contacts into Pardot. Ensure that data is clean, accurate, and well-segmented for effective targeting.
7. Create Landing Pages and Forms:
-
Build custom landing pages and forms to capture lead information. Pardot provides templates and a user-friendly interface for this purpose.
8. Design Email Templates:
-
Create email templates that align with your branding and messaging. Pardot allows for responsive and personalized email design.
9. Set Up Drip Campaigns:
-
Create automated drip email campaigns for lead nurturing. Map out the content and timing of these campaigns based on your lead's journey.
10. Implement Lead Scoring and Grading: - Configure lead scoring rules and grading criteria to identify the most engaged and qualified leads.
11. Test Automation Workflows: - Before going live, thoroughly test your automation workflows, including email sequences and landing page forms, to ensure they function as intended.
12. Train Your Team: - Provide training to your marketing and sales teams on how to use Pardot effectively. Ensure they understand lead management processes and how to interpret lead scoring data.
13. Monitor and Analyze: - Regularly monitor the performance of your campaigns and use Pardot's analytics and reporting tools to gain insights into what's working and what needs improvement.
14. Optimize and Iterate: - Continuously optimize your marketing strategies based on data and feedback. Adjust your automation workflows, content, and targeting as needed to achieve better results.
15. Seek Professional Assistance: - If needed, consider consulting with Salesforce Pardot experts or attending training sessions to maximize the value of the platform.
Remember that Salesforce Pardot is a powerful marketing automation tool, and its effectiveness often grows over time as you become more familiar with its features and capabilities. Regularly reviewing your strategies and adapting to changing market conditions will help you get the most out of Pardot and drive success in your marketing efforts.
Alternatives to Salesforce Pardot
There are several alternatives to Salesforce Pardot, each offering its own set of features and capabilities for marketing automation and lead management. The choice of an alternative depends on your specific business needs, budget, and existing technology stack. Here are some popular alternatives to Salesforce Pardot:
-
HubSpot Marketing Hub:
-
HubSpot offers a comprehensive suite of marketing tools, including automation, email marketing, lead nurturing, and analytics. It's known for its user-friendly interface and is suitable for both small businesses and larger enterprises.
-
-
Marketo:
-
Marketo, now part of Adobe Experience Cloud, provides a robust marketing automation platform. It's ideal for B2B marketers and offers features such as lead scoring, advanced analytics, and integration with Adobe's creative tools.
-
-
Mailchimp:
-
While traditionally known for email marketing, Mailchimp has expanded its offerings to include marketing automation features. It's a cost-effective solution for small to medium-sized businesses.
-
-
ActiveCampaign:
-
ActiveCampaign combines email marketing, automation, and CRM capabilities. It's known for its advanced automation features and is suitable for businesses of all sizes.
-
-
Eloqua (Oracle Marketing Cloud):
-
Oracle Eloqua is a high-end marketing automation solution with a focus on enterprise-level marketing. It offers advanced lead scoring, campaign orchestration, and robust analytics.
-
-
SharpSpring:
-
SharpSpring is a marketing automation platform that caters to agencies and small to medium-sized businesses. It offers email marketing, CRM integration, and lead tracking features.
-
-
GetResponse:
-
GetResponse provides email marketing, automation, and landing page creation tools. It's a versatile solution for businesses looking to automate marketing tasks.
-
-
Infusionsoft by Keap:
-
Infusionsoft (now part of Keap) is a small business-focused marketing automation platform that offers CRM, email marketing, and automation capabilities.
-
-
Zoho MarketingHub:
-
Zoho MarketingHub is part of the Zoho suite of business tools and offers marketing automation features, email marketing, and CRM integration.
-
-
SendinBlue:
-
SendinBlue offers email marketing, marketing automation, and transactional email services. It's known for its affordability and ease of use.
-
-
Drip:
-
Drip is an e-commerce-focused marketing automation platform that specializes in personalized email marketing and automation for online retailers.
-
When evaluating alternatives to Salesforce Pardot, consider factors such as the size of your business, your budget, your specific marketing automation needs, and how well the platform integrates with your existing software stack, including your CRM. Additionally, take advantage of free trials and demos to test the platforms and see which one aligns best with your goals and workflows.
How to obtain Salesforce Certifications?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
Project Management: PMP, CAPM ,PMI RMP
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
Business Analysis: CBAP, CCBA, ECBA
Agile Training: PMI-ACP , CSM , CSPO
Scrum Training: CSM
DevOps
Program Management: PgMP
Cloud Technology: SMAC Certication
Big Data: Big Data and Hadoop Administrator
Digital Marketing : Digital Marketing Certification
Data Science : Power BI Certification
Cyber Security : CISA Certification
Emerging Technologies : Blockchain Certification
Salesforce : Salesforce Administration Certification
Conclusion
In conclusion, Salesforce Pardot presents a compelling solution for businesses seeking to elevate their marketing strategies through efficient automation. Its versatile feature set, encompassing lead generation, nurturing, and seamless CRM integration, offers tangible benefits such as increased lead conversion rates and streamlined processes. While Pardot's pricing structure varies to accommodate businesses of all sizes, its value lies in the potential for personalized engagement, data-driven insights, and scalable marketing campaigns, making it a noteworthy contender in the competitive landscape of marketing automation platforms.
Lean Methodology Essentials: A Guide with Examples
Welcome to "Lean Methodology Essentials: A Guide with Examples." In a world where businesses must continually innovate, optimize, and adapt to remain competitive, Lean Methodology has emerged as a transformative approach to achieving operational excellence. This guide serves as your essential companion on a journey into the heart of Lean, offering a clear and practical understanding of its principles, techniques, and real-world applications.
Lean Methodology is more than a management philosophy; it's a mindset that emphasizes efficiency, waste reduction, and a relentless focus on delivering value to customers. In the pages that follow, we will break down the core tenets of Lean, demystify its terminology, and provide you with concrete examples that illustrate how Lean principles can be implemented across various industries. Whether you are a seasoned professional seeking to refine your Lean expertise or a newcomer eager to embrace its principles, this guide equips you with the knowledge and tools to embark on a journey of continuous improvement, setting you on the path to organizational excellence.
Table of Contents
-
What is Lean Methodology?
-
How Did Lean Methodology Originate?
-
Fundamentals of Lean Methodology
-
What Makes the Lean Methodology Unique?
-
Pillars of Lean Methodology
-
Why Should You Choose Lean Methodology?
-
Lean Methodology in Software Development
-
Lean Methodology Examples
-
Master the Concepts of Lean Methodology Today
-
Conclusion
What is Lean Methodology?
Lean Methodology is a systematic approach to process improvement that aims to maximize customer value while minimizing waste. Rooted in the principles of efficiency and continuous improvement, Lean emphasizes the identification and elimination of non-value-added activities, streamlining processes for smoother flow, adopting a pull system based on actual customer demand, and the relentless pursuit of perfection. By optimizing operations and reducing waste in industries ranging from manufacturing to healthcare and software development, Lean Methodology enhances quality, efficiency, and customer satisfaction, making it a cornerstone of modern business improvement strategies.
How Did Lean Methodology Originate?
Lean Methodology, originating in post-World War II Japan, owes its genesis to the innovative response of Japanese manufacturers, particularly Toyota, to the challenging economic environment of the time. Scarce resources, a damaged infrastructure, and a competitive landscape compelled Japanese companies to devise more efficient and economical production methods. Central to Lean's origins is the Toyota Production System (TPS), developed by Taiichi Ohno and Shigeo Shingo in the mid-20th century. TPS emphasized core Lean principles such as Just-In-Time (JIT) production, which aimed to reduce waste by producing only what was needed when it was needed. Another foundational concept was continuous improvement (Kaizen), which encouraged ongoing refinement of processes to enhance efficiency and quality. This systematic approach revolutionized manufacturing by minimizing waste, optimizing resource utilization, and improving product quality.
The adoption of Lean principles extended beyond manufacturing and became a global phenomenon in the late 20th century as Western companies recognized its effectiveness in improving operational efficiency and product quality. Lean's success in industries such as automotive manufacturing led to its widespread application across various sectors, including healthcare, services, and software development. Lean's ability to adapt and deliver results in diverse fields is a testament to its universal appeal and the enduring legacy of its Japanese origins, which continue to shape modern approaches to process optimization and waste reduction.
Fundamentals of Lean Methodology
The fundamentals of Lean Methodology are rooted in a set of core principles and practices that aim to maximize value while minimizing waste. These principles guide organizations in their pursuit of operational excellence and continuous improvement. Here are the key fundamentals of Lean Methodology:
-
Value: Identify what is valuable from the customer's perspective. Value represents any activity or process step that directly contributes to meeting customer needs or requirements.
-
Value Stream Mapping: Analyze and map the entire value stream, which is the end-to-end sequence of activities and processes that deliver a product or service to the customer. Value stream mapping helps identify bottlenecks, inefficiencies, and areas of waste.
-
Flow: Optimize the flow of work or materials through the value stream. This involves reducing interruptions, delays, and excess inventory that can hinder the smooth progression of tasks. Creating a continuous flow is a key objective.
-
Pull: Implement a pull system, where work is initiated or products are produced based on actual customer demand. This contrasts with a push system, where items are produced in anticipation of demand, often leading to overproduction and waste.
-
Perfection: Embrace a culture of continuous improvement (Kaizen) with the goal of achieving perfection, even though it may never be fully attainable. Continuously seek ways to eliminate waste, enhance processes, and deliver greater value to customers.
-
Customer Focus: Place the customer at the center of all decisions and activities. Understand customer needs and preferences to drive value creation.
-
Employee Involvement: Involve and empower employees at all levels of the organization to identify and solve problems, make improvements, and contribute to the Lean culture.
-
Standardization: Establish standardized work processes and procedures to ensure consistency, reduce variation, and enable easier identification of abnormalities.
-
Visual Management: Use visual cues and tools, such as Kanban boards and Andon systems, to make information and the status of processes readily visible, facilitating better communication and decision-making.
-
Waste Reduction: Identify and eliminate the eight types of waste in Lean, often remembered by the acronym "TIMWOODS":
-
Transportation
-
Inventory
-
Motion
-
Waiting
-
Overproduction
-
Overprocessing
-
Defects
-
Skills (underutilized)
-
Continuous Improvement: Promote a culture of continuous learning and improvement. Encourage teams to regularly assess processes, gather feedback, and make incremental changes to enhance efficiency and quality.
-
Respect for People: Recognize the value of every employee and treat them with respect. Lean encourages collaboration, teamwork, and the involvement of employees in decision-making.
By adhering to these fundamentals, organizations can achieve greater efficiency, improved quality, reduced costs, and increased customer satisfaction, making Lean Methodology a powerful approach for achieving operational excellence.
What Makes the Lean Methodology Unique?
The Lean Methodology is distinctive due to several key factors:
-
Customer-Centric Philosophy: Lean is fundamentally centered on delivering value to the customer. It places a primary focus on understanding and meeting customer needs, which drives all decision-making and process improvements.
-
Waste Elimination: A core principle of Lean is the systematic identification and elimination of waste in all forms, including overproduction, unnecessary inventory, defects, waiting times, and more. This relentless pursuit of waste reduction sets Lean apart from many other methodologies.
-
Continuous Improvement Culture: Lean fosters a culture of continuous improvement (Kaizen) throughout an organization. It encourages employees at all levels to continuously seek ways to enhance processes, products, and services, leading to ongoing innovation and optimization.
-
Pull System: Lean employs a pull system where work is initiated based on actual customer demand rather than pushing products or services onto the market. This minimizes overproduction and excess inventory, reducing waste and improving efficiency.
-
Visual Management: Lean uses visual tools like Kanban boards and Andon systems to make information and process status highly visible. This transparency enhances communication, problem-solving, and decision-making.
-
Respect for People: Lean places a strong emphasis on respecting and engaging employees. It recognizes that employees often hold valuable insights for process improvement and encourages their active participation in decision-making.
-
Standardization and Documentation: Lean promotes the development and documentation of standardized work processes and procedures. This ensures consistency, reduces variation, and simplifies problem identification and resolution.
-
Flow Optimization: Lean focuses on optimizing the flow of work or materials through a value stream. This minimizes interruptions, delays, and inefficiencies, creating a smoother and more efficient workflow.
-
Pursuit of Perfection: While perfection may be an aspirational goal, Lean embraces the concept as a continuous improvement objective. Organizations continually strive for higher levels of efficiency, quality, and customer satisfaction.
-
Global Applicability: Lean has transcended its origins in Japan and has been successfully applied across industries and geographies, demonstrating its universal applicability and effectiveness.
In summary, the Lean Methodology's unique characteristics include its customer-centricity, waste reduction focus, commitment to continuous improvement, pull-based systems, visual management practices, respect for people, and adaptability to various contexts. These features have contributed to Lean's widespread adoption and its reputation for driving efficiency, quality, and competitiveness in organizations worldwide.
Pillars of Lean Methodology
The "pillars" of Lean Methodology typically refer to the foundational principles and concepts that underpin the Lean approach to process improvement and waste reduction. While there isn't a universal agreement on a fixed set of pillars, the following are commonly recognized as the core pillars of Lean Methodology:
-
Value: Understanding and defining value from the customer's perspective is the first pillar of Lean. Value represents any activity or process step that directly contributes to meeting customer needs or requirements. Everything else is considered waste.
-
Value Stream Mapping: This pillar involves analyzing and mapping the entire value stream, which is the sequence of activities and processes that deliver a product or service to the customer. Value stream mapping helps identify bottlenecks, inefficiencies, and areas of waste.
-
Flow: The flow pillar emphasizes optimizing the flow of work or materials through the value stream. It aims to reduce interruptions, delays, and excess inventory that can impede the smooth progression of tasks.
-
Pull: The pull pillar involves implementing a pull system where work is initiated or products are produced based on actual customer demand. This contrasts with push systems, which produce items in anticipation of demand, often leading to overproduction and waste.
-
Perfection: Perfection is the continuous improvement pillar of Lean. While perfection may be an unattainable ideal, Lean encourages organizations to relentlessly pursue it by continuously seeking ways to eliminate waste, improve processes, and deliver greater value to customers.
These five pillars are often represented as the foundation of Lean Thinking and provide the guiding principles for organizations to achieve greater efficiency, reduce waste, and enhance customer satisfaction. Additional concepts and tools, such as standardized work, visual management, and respect for people, are integrated into Lean practices to support these pillars and drive continuous improvement.
Why Should You Choose Lean Methodology?
Choosing Lean Methodology is a strategic decision for organizations seeking to thrive in today's competitive landscape. Lean's central focus on waste reduction, coupled with a relentless commitment to improving processes and delivering customer value, positions companies for sustainable success. By minimizing non-value-added activities, Lean enhances efficiency, reduces costs, and bolsters quality. It fosters a culture of continuous improvement, empowering employees at all levels to identify and address operational inefficiencies, ultimately driving innovation and adaptability. Lean is not confined to a specific industry, making it versatile and adaptable to diverse organizational contexts, from manufacturing to healthcare, services, and software development. Its global recognition and proven track record of delivering tangible results underscore its status as a transformative methodology for organizations striving to achieve operational excellence, customer satisfaction, and a competitive edge.
Lean Methodology in Software Development
Lean Methodology, when applied to software development, is often referred to as "Lean Software Development." It adapts the principles and practices of Lean thinking to the unique challenges of creating software products and managing software projects. Here are key aspects of Lean Software Development:
-
Customer Value: Lean Software Development starts by identifying and prioritizing customer value. It involves understanding user needs and focusing on features or functionalities that directly contribute to customer satisfaction and business goals.
-
Eliminating Waste: Lean principles of waste reduction are applied rigorously in software development. This includes reducing unnecessary code complexity, eliminating duplication, and avoiding overproduction of features that may not be needed.
-
Pull System: Lean Software Development often employs a pull system, where features or tasks are pulled into the development process based on real customer demand or project priorities. This prevents overloading teams with excessive work.
-
Continuous Improvement: Like other Lean applications, Lean Software Development encourages continuous improvement. Teams regularly review their processes and seek ways to streamline workflows, enhance collaboration, and reduce cycle times.
-
Small Batch Sizes: Lean promotes working in small, manageable batches. This means breaking down large projects into smaller, deliverable units, allowing for quicker feedback and adjustment.
-
Visual Management: Visual tools like Kanban boards are frequently used to make the status of work visible, helping teams track progress, identify bottlenecks, and manage their work effectively.
-
Lean Metrics: Lean Software Development relies on key performance indicators (KPIs) that measure the flow of work, cycle times, and other relevant metrics to identify areas for improvement.
-
Empowering Teams: Lean principles emphasize giving teams autonomy and responsibility. Teams are encouraged to self-organize, make decisions, and take ownership of their work.
-
Minimal Viable Product (MVP): Lean encourages the development of Minimum Viable Products that can be quickly delivered to customers for feedback. This iterative approach allows for faster learning and adaptation.
-
Customer Feedback Loop: Lean Software Development relies on frequent customer feedback to validate assumptions, refine requirements, and make course corrections. This feedback loop is essential for delivering software that aligns with customer expectations.
-
Respect for People: As with all Lean applications, Lean Software Development places a strong emphasis on respecting and valuing the contributions of team members, recognizing that they are essential to the success of the project.
By applying Lean principles to software development, organizations can achieve greater efficiency, reduce the risk of building unnecessary features, and deliver software products that align more closely with customer needs. It's an adaptable and effective approach that has gained popularity in Agile development methodologies, such as Scrum and Kanban, which incorporate Lean principles to varying degrees.
Lean Methodology Examples
Lean Methodology is applied across various industries and functions to optimize processes, reduce waste, and enhance overall efficiency. Here are some examples of Lean Methodology in action:
-
Manufacturing:
-
Toyota Production System (TPS): Toyota is often credited as the originator of Lean principles. TPS emphasizes Just-In-Time (JIT) production, pull systems, and continuous improvement to minimize waste, reduce inventory, and enhance production efficiency.
-
Healthcare:
-
Reducing Patient Wait Times: Lean principles have been applied in hospitals to reduce patient wait times, optimize appointment scheduling, and improve the efficiency of healthcare delivery.
-
Software Development:
-
Kanban: Software development teams often use Kanban boards to visualize and manage their work, limit work in progress (WIP), and optimize workflow processes.
-
Service Industry:
-
Lean Banking: Banks have applied Lean principles to streamline processes such as loan approvals, customer service, and account management, reducing wait times and improving customer satisfaction.
-
Supply Chain Management:
-
Lean Supply Chain: Organizations apply Lean principles to supply chain management to reduce excess inventory, eliminate bottlenecks, and improve overall supply chain efficiency.
-
Retail:
-
Inventory Management: Retailers use Lean principles to optimize inventory management, reducing carrying costs, minimizing stockouts, and ensuring products are available when customers need them.
-
Education:
-
Lean Education: Lean principles have been adapted to education to improve classroom processes, curriculum development, and administrative tasks, resulting in more efficient and effective educational institutions.
-
Construction:
-
Lean Construction: The construction industry has adopted Lean principles to optimize project planning, reduce project delays, eliminate waste, and enhance overall project management.
-
Aerospace and Aviation:
-
Lean Aerospace: Companies in the aerospace and aviation sectors use Lean principles to improve manufacturing processes, reduce production lead times, and increase aircraft production efficiency.
-
Food Industry:
-
Lean in Restaurants: Restaurants have implemented Lean practices to optimize kitchen processes, reduce food waste, and improve customer service.
-
Government:
-
Lean Government: Some government agencies have adopted Lean principles to streamline administrative processes, reduce paperwork, and enhance citizen services.
-
Small Businesses:
-
Lean Startup: Small businesses and startups often use Lean principles to validate business ideas, develop minimal viable products (MVPs), and iterate based on customer feedback.
Master the Concepts of Lean Methodology Today
Mastering the concepts of Lean Methodology requires a combination of study, practical application, and continuous learning. Here's a step-by-step guide to help you get started:
-
Study Lean Principles:
-
Begin by reading books and articles on Lean Methodology to understand its core principles and concepts. Some recommended books include "The Lean Startup" by Eric Ries and "Lean Thinking" by James P. Womack and Daniel T. Jones.
-
Enroll in Lean Training:
-
Consider enrolling in Lean training programs or workshops offered by accredited organizations. These programs provide structured learning and often include real-world case studies and exercises.
-
Online Courses and Tutorials:
-
Many online platforms offer free and paid courses on Lean Methodology. Websites like Coursera, edX, and LinkedIn Learning provide access to comprehensive courses on Lean principles and their application.
-
Certification:
-
If you're looking to establish your expertise, consider pursuing Lean certification. Organizations like the Lean Enterprise Institute (LEI) offer certification programs, including Lean Green Belt and Lean Black Belt certifications.
-
Practice Lean Tools and Techniques:
-
To truly understand Lean, apply its tools and techniques in real-world scenarios. Implement practices like value stream mapping, Kanban, and 5S in your workplace or personal projects.
-
Join Lean Communities:
-
Participate in Lean forums, online communities, and social media groups. Engaging with Lean practitioners and enthusiasts can provide valuable insights and opportunities for discussion.
-
Read Case Studies:
-
Read case studies and success stories of organizations that have effectively implemented Lean Methodology. Analyze their experiences and learn from their challenges and solutions.
-
Continuous Improvement:
-
Embrace the Lean philosophy of continuous improvement. Regularly assess your own processes and workflows, and apply Lean principles to make incremental enhancements.
-
Lean Workshops and Seminars:
-
Attend Lean workshops, seminars, and conferences to gain exposure to the latest developments in Lean Methodology and learn from industry experts.
-
Teach Others:
-
Teaching Lean concepts to others can deepen your own understanding. Consider sharing your knowledge through presentations, workshops, or writing articles or blog posts.
-
Problem-Solving Practice:
-
Lean is fundamentally about problem-solving. Practice structured problem-solving techniques like the PDCA (Plan-Do-Check-Act) cycle to address challenges effectively.
-
Stay Informed:
-
Stay updated on Lean trends, research, and best practices through books, journals, blogs, and industry publications.
-
Networking:
-
Build a network of Lean professionals and mentors who can offer guidance and support in your Lean journey.
-
Apply Lean to Your Life:
-
Extend Lean principles beyond the workplace. Apply them to personal projects, time management, and daily routines to enhance your problem-solving skills and efficiency.
Remember that mastering Lean Methodology is an ongoing process. It requires a commitment to continuous learning, experimentation, and the application of Lean principles in various contexts. As you gain experience and expertise, you'll be better equipped to drive operational excellence and improve processes in your organization or projects.
How to obtain the Lean Six Sigma Green Belt certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Green Belt ,Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
IT Service Management & Governance: COBIT, ISO
Conclusion
In conclusion, the fundamentals of Lean Methodology represent a powerful framework for organizations seeking to thrive in today's dynamic and competitive landscape. By understanding and applying the principles of value, waste reduction, continuous improvement, and customer-centricity, businesses can unlock remarkable benefits. The real-world examples showcased in this blog highlight the versatility of Lean, demonstrating its effectiveness across diverse industries, from manufacturing and healthcare to software development and services.
As we wrap up our exploration of Lean, it's important to remember that Lean is not a one-time initiative but a journey of ongoing improvement. Embracing a Lean mindset, fostering a culture of innovation, and empowering employees to identify and eliminate waste are essential for sustained success. By integrating Lean into the DNA of your organization, you can optimize processes, reduce costs, enhance quality, and ultimately deliver greater value to your customers, setting the stage for a prosperous and efficient future.
Read More
Welcome to "Lean Methodology Essentials: A Guide with Examples." In a world where businesses must continually innovate, optimize, and adapt to remain competitive, Lean Methodology has emerged as a transformative approach to achieving operational excellence. This guide serves as your essential companion on a journey into the heart of Lean, offering a clear and practical understanding of its principles, techniques, and real-world applications.
Lean Methodology is more than a management philosophy; it's a mindset that emphasizes efficiency, waste reduction, and a relentless focus on delivering value to customers. In the pages that follow, we will break down the core tenets of Lean, demystify its terminology, and provide you with concrete examples that illustrate how Lean principles can be implemented across various industries. Whether you are a seasoned professional seeking to refine your Lean expertise or a newcomer eager to embrace its principles, this guide equips you with the knowledge and tools to embark on a journey of continuous improvement, setting you on the path to organizational excellence.
Table of Contents
-
What is Lean Methodology?
-
How Did Lean Methodology Originate?
-
Fundamentals of Lean Methodology
-
What Makes the Lean Methodology Unique?
-
Pillars of Lean Methodology
-
Why Should You Choose Lean Methodology?
-
Lean Methodology in Software Development
-
Lean Methodology Examples
-
Master the Concepts of Lean Methodology Today
-
Conclusion
What is Lean Methodology?
Lean Methodology is a systematic approach to process improvement that aims to maximize customer value while minimizing waste. Rooted in the principles of efficiency and continuous improvement, Lean emphasizes the identification and elimination of non-value-added activities, streamlining processes for smoother flow, adopting a pull system based on actual customer demand, and the relentless pursuit of perfection. By optimizing operations and reducing waste in industries ranging from manufacturing to healthcare and software development, Lean Methodology enhances quality, efficiency, and customer satisfaction, making it a cornerstone of modern business improvement strategies.
How Did Lean Methodology Originate?
Lean Methodology, originating in post-World War II Japan, owes its genesis to the innovative response of Japanese manufacturers, particularly Toyota, to the challenging economic environment of the time. Scarce resources, a damaged infrastructure, and a competitive landscape compelled Japanese companies to devise more efficient and economical production methods. Central to Lean's origins is the Toyota Production System (TPS), developed by Taiichi Ohno and Shigeo Shingo in the mid-20th century. TPS emphasized core Lean principles such as Just-In-Time (JIT) production, which aimed to reduce waste by producing only what was needed when it was needed. Another foundational concept was continuous improvement (Kaizen), which encouraged ongoing refinement of processes to enhance efficiency and quality. This systematic approach revolutionized manufacturing by minimizing waste, optimizing resource utilization, and improving product quality.
The adoption of Lean principles extended beyond manufacturing and became a global phenomenon in the late 20th century as Western companies recognized its effectiveness in improving operational efficiency and product quality. Lean's success in industries such as automotive manufacturing led to its widespread application across various sectors, including healthcare, services, and software development. Lean's ability to adapt and deliver results in diverse fields is a testament to its universal appeal and the enduring legacy of its Japanese origins, which continue to shape modern approaches to process optimization and waste reduction.
Fundamentals of Lean Methodology
The fundamentals of Lean Methodology are rooted in a set of core principles and practices that aim to maximize value while minimizing waste. These principles guide organizations in their pursuit of operational excellence and continuous improvement. Here are the key fundamentals of Lean Methodology:
-
Value: Identify what is valuable from the customer's perspective. Value represents any activity or process step that directly contributes to meeting customer needs or requirements.
-
Value Stream Mapping: Analyze and map the entire value stream, which is the end-to-end sequence of activities and processes that deliver a product or service to the customer. Value stream mapping helps identify bottlenecks, inefficiencies, and areas of waste.
-
Flow: Optimize the flow of work or materials through the value stream. This involves reducing interruptions, delays, and excess inventory that can hinder the smooth progression of tasks. Creating a continuous flow is a key objective.
-
Pull: Implement a pull system, where work is initiated or products are produced based on actual customer demand. This contrasts with a push system, where items are produced in anticipation of demand, often leading to overproduction and waste.
-
Perfection: Embrace a culture of continuous improvement (Kaizen) with the goal of achieving perfection, even though it may never be fully attainable. Continuously seek ways to eliminate waste, enhance processes, and deliver greater value to customers.
-
Customer Focus: Place the customer at the center of all decisions and activities. Understand customer needs and preferences to drive value creation.
-
Employee Involvement: Involve and empower employees at all levels of the organization to identify and solve problems, make improvements, and contribute to the Lean culture.
-
Standardization: Establish standardized work processes and procedures to ensure consistency, reduce variation, and enable easier identification of abnormalities.
-
Visual Management: Use visual cues and tools, such as Kanban boards and Andon systems, to make information and the status of processes readily visible, facilitating better communication and decision-making.
-
Waste Reduction: Identify and eliminate the eight types of waste in Lean, often remembered by the acronym "TIMWOODS":
-
Transportation
-
Inventory
-
Motion
-
Waiting
-
Overproduction
-
Overprocessing
-
Defects
-
Skills (underutilized)
-
-
Continuous Improvement: Promote a culture of continuous learning and improvement. Encourage teams to regularly assess processes, gather feedback, and make incremental changes to enhance efficiency and quality.
-
Respect for People: Recognize the value of every employee and treat them with respect. Lean encourages collaboration, teamwork, and the involvement of employees in decision-making.
By adhering to these fundamentals, organizations can achieve greater efficiency, improved quality, reduced costs, and increased customer satisfaction, making Lean Methodology a powerful approach for achieving operational excellence.
What Makes the Lean Methodology Unique?
The Lean Methodology is distinctive due to several key factors:
-
Customer-Centric Philosophy: Lean is fundamentally centered on delivering value to the customer. It places a primary focus on understanding and meeting customer needs, which drives all decision-making and process improvements.
-
Waste Elimination: A core principle of Lean is the systematic identification and elimination of waste in all forms, including overproduction, unnecessary inventory, defects, waiting times, and more. This relentless pursuit of waste reduction sets Lean apart from many other methodologies.
-
Continuous Improvement Culture: Lean fosters a culture of continuous improvement (Kaizen) throughout an organization. It encourages employees at all levels to continuously seek ways to enhance processes, products, and services, leading to ongoing innovation and optimization.
-
Pull System: Lean employs a pull system where work is initiated based on actual customer demand rather than pushing products or services onto the market. This minimizes overproduction and excess inventory, reducing waste and improving efficiency.
-
Visual Management: Lean uses visual tools like Kanban boards and Andon systems to make information and process status highly visible. This transparency enhances communication, problem-solving, and decision-making.
-
Respect for People: Lean places a strong emphasis on respecting and engaging employees. It recognizes that employees often hold valuable insights for process improvement and encourages their active participation in decision-making.
-
Standardization and Documentation: Lean promotes the development and documentation of standardized work processes and procedures. This ensures consistency, reduces variation, and simplifies problem identification and resolution.
-
Flow Optimization: Lean focuses on optimizing the flow of work or materials through a value stream. This minimizes interruptions, delays, and inefficiencies, creating a smoother and more efficient workflow.
-
Pursuit of Perfection: While perfection may be an aspirational goal, Lean embraces the concept as a continuous improvement objective. Organizations continually strive for higher levels of efficiency, quality, and customer satisfaction.
-
Global Applicability: Lean has transcended its origins in Japan and has been successfully applied across industries and geographies, demonstrating its universal applicability and effectiveness.
In summary, the Lean Methodology's unique characteristics include its customer-centricity, waste reduction focus, commitment to continuous improvement, pull-based systems, visual management practices, respect for people, and adaptability to various contexts. These features have contributed to Lean's widespread adoption and its reputation for driving efficiency, quality, and competitiveness in organizations worldwide.
Pillars of Lean Methodology
The "pillars" of Lean Methodology typically refer to the foundational principles and concepts that underpin the Lean approach to process improvement and waste reduction. While there isn't a universal agreement on a fixed set of pillars, the following are commonly recognized as the core pillars of Lean Methodology:
-
Value: Understanding and defining value from the customer's perspective is the first pillar of Lean. Value represents any activity or process step that directly contributes to meeting customer needs or requirements. Everything else is considered waste.
-
Value Stream Mapping: This pillar involves analyzing and mapping the entire value stream, which is the sequence of activities and processes that deliver a product or service to the customer. Value stream mapping helps identify bottlenecks, inefficiencies, and areas of waste.
-
Flow: The flow pillar emphasizes optimizing the flow of work or materials through the value stream. It aims to reduce interruptions, delays, and excess inventory that can impede the smooth progression of tasks.
-
Pull: The pull pillar involves implementing a pull system where work is initiated or products are produced based on actual customer demand. This contrasts with push systems, which produce items in anticipation of demand, often leading to overproduction and waste.
-
Perfection: Perfection is the continuous improvement pillar of Lean. While perfection may be an unattainable ideal, Lean encourages organizations to relentlessly pursue it by continuously seeking ways to eliminate waste, improve processes, and deliver greater value to customers.
These five pillars are often represented as the foundation of Lean Thinking and provide the guiding principles for organizations to achieve greater efficiency, reduce waste, and enhance customer satisfaction. Additional concepts and tools, such as standardized work, visual management, and respect for people, are integrated into Lean practices to support these pillars and drive continuous improvement.
Why Should You Choose Lean Methodology?
Choosing Lean Methodology is a strategic decision for organizations seeking to thrive in today's competitive landscape. Lean's central focus on waste reduction, coupled with a relentless commitment to improving processes and delivering customer value, positions companies for sustainable success. By minimizing non-value-added activities, Lean enhances efficiency, reduces costs, and bolsters quality. It fosters a culture of continuous improvement, empowering employees at all levels to identify and address operational inefficiencies, ultimately driving innovation and adaptability. Lean is not confined to a specific industry, making it versatile and adaptable to diverse organizational contexts, from manufacturing to healthcare, services, and software development. Its global recognition and proven track record of delivering tangible results underscore its status as a transformative methodology for organizations striving to achieve operational excellence, customer satisfaction, and a competitive edge.
Lean Methodology in Software Development
Lean Methodology, when applied to software development, is often referred to as "Lean Software Development." It adapts the principles and practices of Lean thinking to the unique challenges of creating software products and managing software projects. Here are key aspects of Lean Software Development:
-
Customer Value: Lean Software Development starts by identifying and prioritizing customer value. It involves understanding user needs and focusing on features or functionalities that directly contribute to customer satisfaction and business goals.
-
Eliminating Waste: Lean principles of waste reduction are applied rigorously in software development. This includes reducing unnecessary code complexity, eliminating duplication, and avoiding overproduction of features that may not be needed.
-
Pull System: Lean Software Development often employs a pull system, where features or tasks are pulled into the development process based on real customer demand or project priorities. This prevents overloading teams with excessive work.
-
Continuous Improvement: Like other Lean applications, Lean Software Development encourages continuous improvement. Teams regularly review their processes and seek ways to streamline workflows, enhance collaboration, and reduce cycle times.
-
Small Batch Sizes: Lean promotes working in small, manageable batches. This means breaking down large projects into smaller, deliverable units, allowing for quicker feedback and adjustment.
-
Visual Management: Visual tools like Kanban boards are frequently used to make the status of work visible, helping teams track progress, identify bottlenecks, and manage their work effectively.
-
Lean Metrics: Lean Software Development relies on key performance indicators (KPIs) that measure the flow of work, cycle times, and other relevant metrics to identify areas for improvement.
-
Empowering Teams: Lean principles emphasize giving teams autonomy and responsibility. Teams are encouraged to self-organize, make decisions, and take ownership of their work.
-
Minimal Viable Product (MVP): Lean encourages the development of Minimum Viable Products that can be quickly delivered to customers for feedback. This iterative approach allows for faster learning and adaptation.
-
Customer Feedback Loop: Lean Software Development relies on frequent customer feedback to validate assumptions, refine requirements, and make course corrections. This feedback loop is essential for delivering software that aligns with customer expectations.
-
Respect for People: As with all Lean applications, Lean Software Development places a strong emphasis on respecting and valuing the contributions of team members, recognizing that they are essential to the success of the project.
By applying Lean principles to software development, organizations can achieve greater efficiency, reduce the risk of building unnecessary features, and deliver software products that align more closely with customer needs. It's an adaptable and effective approach that has gained popularity in Agile development methodologies, such as Scrum and Kanban, which incorporate Lean principles to varying degrees.
Lean Methodology Examples
Lean Methodology is applied across various industries and functions to optimize processes, reduce waste, and enhance overall efficiency. Here are some examples of Lean Methodology in action:
-
Manufacturing:
-
Toyota Production System (TPS): Toyota is often credited as the originator of Lean principles. TPS emphasizes Just-In-Time (JIT) production, pull systems, and continuous improvement to minimize waste, reduce inventory, and enhance production efficiency.
-
-
Healthcare:
-
Reducing Patient Wait Times: Lean principles have been applied in hospitals to reduce patient wait times, optimize appointment scheduling, and improve the efficiency of healthcare delivery.
-
-
Software Development:
-
Kanban: Software development teams often use Kanban boards to visualize and manage their work, limit work in progress (WIP), and optimize workflow processes.
-
-
Service Industry:
-
Lean Banking: Banks have applied Lean principles to streamline processes such as loan approvals, customer service, and account management, reducing wait times and improving customer satisfaction.
-
-
Supply Chain Management:
-
Lean Supply Chain: Organizations apply Lean principles to supply chain management to reduce excess inventory, eliminate bottlenecks, and improve overall supply chain efficiency.
-
-
Retail:
-
Inventory Management: Retailers use Lean principles to optimize inventory management, reducing carrying costs, minimizing stockouts, and ensuring products are available when customers need them.
-
-
Education:
-
Lean Education: Lean principles have been adapted to education to improve classroom processes, curriculum development, and administrative tasks, resulting in more efficient and effective educational institutions.
-
-
Construction:
-
Lean Construction: The construction industry has adopted Lean principles to optimize project planning, reduce project delays, eliminate waste, and enhance overall project management.
-
-
Aerospace and Aviation:
-
Lean Aerospace: Companies in the aerospace and aviation sectors use Lean principles to improve manufacturing processes, reduce production lead times, and increase aircraft production efficiency.
-
-
Food Industry:
-
Lean in Restaurants: Restaurants have implemented Lean practices to optimize kitchen processes, reduce food waste, and improve customer service.
-
-
Government:
-
Lean Government: Some government agencies have adopted Lean principles to streamline administrative processes, reduce paperwork, and enhance citizen services.
-
-
Small Businesses:
-
Lean Startup: Small businesses and startups often use Lean principles to validate business ideas, develop minimal viable products (MVPs), and iterate based on customer feedback.
-
Master the Concepts of Lean Methodology Today
Mastering the concepts of Lean Methodology requires a combination of study, practical application, and continuous learning. Here's a step-by-step guide to help you get started:
-
Study Lean Principles:
-
Begin by reading books and articles on Lean Methodology to understand its core principles and concepts. Some recommended books include "The Lean Startup" by Eric Ries and "Lean Thinking" by James P. Womack and Daniel T. Jones.
-
-
Enroll in Lean Training:
-
Consider enrolling in Lean training programs or workshops offered by accredited organizations. These programs provide structured learning and often include real-world case studies and exercises.
-
-
Online Courses and Tutorials:
-
Many online platforms offer free and paid courses on Lean Methodology. Websites like Coursera, edX, and LinkedIn Learning provide access to comprehensive courses on Lean principles and their application.
-
-
Certification:
-
If you're looking to establish your expertise, consider pursuing Lean certification. Organizations like the Lean Enterprise Institute (LEI) offer certification programs, including Lean Green Belt and Lean Black Belt certifications.
-
-
Practice Lean Tools and Techniques:
-
To truly understand Lean, apply its tools and techniques in real-world scenarios. Implement practices like value stream mapping, Kanban, and 5S in your workplace or personal projects.
-
-
Join Lean Communities:
-
Participate in Lean forums, online communities, and social media groups. Engaging with Lean practitioners and enthusiasts can provide valuable insights and opportunities for discussion.
-
-
Read Case Studies:
-
Read case studies and success stories of organizations that have effectively implemented Lean Methodology. Analyze their experiences and learn from their challenges and solutions.
-
-
Continuous Improvement:
-
Embrace the Lean philosophy of continuous improvement. Regularly assess your own processes and workflows, and apply Lean principles to make incremental enhancements.
-
-
Lean Workshops and Seminars:
-
Attend Lean workshops, seminars, and conferences to gain exposure to the latest developments in Lean Methodology and learn from industry experts.
-
-
Teach Others:
-
Teaching Lean concepts to others can deepen your own understanding. Consider sharing your knowledge through presentations, workshops, or writing articles or blog posts.
-
-
Problem-Solving Practice:
-
Lean is fundamentally about problem-solving. Practice structured problem-solving techniques like the PDCA (Plan-Do-Check-Act) cycle to address challenges effectively.
-
-
Stay Informed:
-
Stay updated on Lean trends, research, and best practices through books, journals, blogs, and industry publications.
-
-
Networking:
-
Build a network of Lean professionals and mentors who can offer guidance and support in your Lean journey.
-
-
Apply Lean to Your Life:
-
Extend Lean principles beyond the workplace. Apply them to personal projects, time management, and daily routines to enhance your problem-solving skills and efficiency.
-
Remember that mastering Lean Methodology is an ongoing process. It requires a commitment to continuous learning, experimentation, and the application of Lean principles in various contexts. As you gain experience and expertise, you'll be better equipped to drive operational excellence and improve processes in your organization or projects.
How to obtain the Lean Six Sigma Green Belt certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Green Belt ,Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
IT Service Management & Governance: COBIT, ISO
Conclusion
In conclusion, the fundamentals of Lean Methodology represent a powerful framework for organizations seeking to thrive in today's dynamic and competitive landscape. By understanding and applying the principles of value, waste reduction, continuous improvement, and customer-centricity, businesses can unlock remarkable benefits. The real-world examples showcased in this blog highlight the versatility of Lean, demonstrating its effectiveness across diverse industries, from manufacturing and healthcare to software development and services.
As we wrap up our exploration of Lean, it's important to remember that Lean is not a one-time initiative but a journey of ongoing improvement. Embracing a Lean mindset, fostering a culture of innovation, and empowering employees to identify and eliminate waste are essential for sustained success. By integrating Lean into the DNA of your organization, you can optimize processes, reduce costs, enhance quality, and ultimately deliver greater value to your customers, setting the stage for a prosperous and efficient future.
What is Scrum Framework, and How Does it Work?
In the dynamic landscape of project management and software development, methodologies that foster flexibility, collaboration, and rapid adaptation are essential. One such methodology that has gained widespread recognition and adoption is the Scrum Framework. Born out of the Agile movement, Scrum has revolutionized the way teams tackle complex projects, enabling them to deliver high-quality results efficiently and with enhanced teamwork.
In this comprehensive guide, we will delve into the intricacies of the Scrum Framework, unraveling its core principles, methodologies, and the seamless interplay of its roles and rituals. Whether you're an aspiring project manager, a seasoned software developer, or simply curious about how Scrum works, join us on this journey as we explore the essence of Scrum and how it can transform the way you approach projects. From its foundational concepts to its practical implementation, you'll gain a solid understanding of what Scrum is and, more importantly, how it works to bring about unparalleled success in the world of project management and beyond.
Table of Contents
What is the Scrum Process Framework?
What Are Scrum Artifacts?
Benefits of Scrum Methodology
Scrum and Agile Relationship Explained
Scrum Ceremonies or Events
Scrum Pillars and Values
3 Essential Roles for Scrum Success
Scaling Scrum to Multiple Teams
Conclusion
What is the Scrum Process Framework?
The Scrum process framework is an agile project management approach designed to facilitate the iterative and incremental development of products. It is characterized by a set of defined roles, events, artifacts, and rules that guide a development team's work. Key roles include the Product Owner, Scrum Master, and Development Team, each with specific responsibilities. Scrum events, such as Sprint Planning, Daily Scrum, Sprint Review, and Sprint Retrospective, provide a structured rhythm to the development process. The Product Backlog, Sprint Backlog, and Increment are the essential artifacts used to manage work and track progress. Scrum emphasizes transparency, inspection, and adaptation, allowing teams to respond to changing requirements and deliver high-value product increments regularly.
One of Scrum's core principles is its focus on collaboration and adaptability. By breaking work into small, manageable iterations called sprints, teams can quickly respond to customer feedback and changing priorities. This iterative approach encourages continuous improvement, making Scrum an effective framework for complex projects where requirements may evolve over time. It promotes a sense of ownership and accountability among team members, leading to more efficient and productive development cycles. Scrum's simplicity and flexibility have made it a popular choice not only in software development but also in various industries seeking to deliver value to customers faster and with greater adaptability.
What Are Scrum Artifacts?
Scrum artifacts are essential documents or information sources that provide transparency and help in managing work within the Scrum framework. These artifacts are used to ensure that everyone involved in a Scrum project has a common understanding of the product being developed and the progress being made. There are three primary Scrum artifacts:
-
Product Backlog: The Product Backlog is a prioritized list of all the work that needs to be done to create and maintain the product. It is owned and managed by the Product Owner. The items in the Product Backlog can include features, user stories, bug fixes, technical tasks, and other work items. Each item is described in sufficient detail so that the development team understands what needs to be done. The Product Owner continuously refines and prioritizes the backlog based on changing requirements and feedback from stakeholders.
-
Sprint Backlog: The Sprint Backlog is a subset of the items from the Product Backlog that the development team commits to completing during a specific sprint. It is created during the Sprint Planning event, where the team selects the highest-priority items from the Product Backlog and decides how they will deliver them. The Sprint Backlog is a dynamic document that can be adjusted as the team gains a better understanding of the work during the sprint. It helps the team track progress toward the sprint goal.
-
Increment: The Increment is the sum of all the product backlog items that have been completed during a sprint. It represents a potentially shippable product or a product incrementally closer to the desired end state. At the end of each sprint, the development team delivers the Increment for review by stakeholders during the Sprint Review event. If accepted, the Increment can be released to users or customers. The goal is to have a potentially shippable product increment at the end of each sprint, although it may not include all desired features until subsequent sprints.
These Scrum artifacts serve to provide transparency, enable inspection, and support adaptation throughout the development process. They ensure that everyone involved in the project, including the development team, Product Owner, and stakeholders, has a clear understanding of what work is to be done, what has been completed, and the overall progress toward the product's goals.
Benefits of Scrum Methodology
The Scrum methodology offers several benefits, making it a popular choice for agile project management and product development. Some of the key advantages of Scrum include:
-
Flexibility and Adaptability: Scrum embraces change and allows teams to adapt to evolving requirements, market conditions, and customer feedback. It offers the flexibility to reprioritize work and make adjustments during short, time-boxed iterations called sprints.
-
Customer-Centric: Scrum places a strong emphasis on delivering value to the customer. The Product Owner is responsible for prioritizing the product backlog based on customer needs, ensuring that the most valuable features are built first.
-
Transparency: Scrum promotes transparency by making project information visible to all team members. This transparency encourages collaboration, accountability, and open communication among team members and stakeholders.
-
Increased Productivity: Scrum's iterative approach often leads to higher productivity because it focuses on delivering a potentially shippable product incrementally. Teams can release valuable features sooner, providing benefits to the end-users and stakeholders.
-
Early and Regular Feedback: Scrum encourages frequent feedback through events like Sprint Reviews and Daily Scrums. This continuous feedback loop helps identify and address issues early in the development process, reducing the risk of building the wrong product.
-
Improved Quality: Scrum places a strong emphasis on quality through practices like automated testing and continuous integration. The incremental development and regular inspections help maintain and improve product quality over time.
-
Empowered Teams: Scrum empowers development teams to self-organize and make decisions regarding how to achieve sprint goals. This autonomy and ownership often lead to more motivated and engaged team members.
-
Predictable Delivery: Scrum promotes predictability by establishing a consistent cadence of work through time-boxed sprints. This helps stakeholders understand when they can expect specific features or updates.
-
Reduced Risk: With its focus on frequent inspections and adaptations, Scrum helps mitigate risks by identifying and addressing issues early in the project. Teams can make informed decisions to course-correct as needed.
-
Enhanced Collaboration: Scrum fosters collaboration among cross-functional team members, including developers, testers, designers, and product managers. Regular meetings like the Daily Scrum promote communication and collaboration.
While Scrum offers numerous benefits, it's essential to recognize that its successful implementation requires a committed and well-trained team, adherence to Scrum principles, and continuous improvement to refine processes over time.
Scrum and Agile Relationship Explained
Scrum and Agile are closely related concepts in the world of project management and software development, with Scrum being one of the most popular frameworks within the broader Agile methodology. Here's an explanation of their relationship:
Agile:
-
Agile is a set of values and principles outlined in the Agile Manifesto, which was created in 2001 by a group of software developers. The manifesto emphasizes customer collaboration, responding to change, and delivering working software as primary goals.
-
Agile is not a specific framework or methodology but rather a mindset or philosophy that promotes flexibility, collaboration, and customer-centricity. It encourages teams to work iteratively and adapt to changing requirements and customer feedback.
Scrum:
-
Scrum is a specific framework for implementing Agile principles. It provides a structured approach to managing work within an Agile context.
-
Scrum prescribes a set of roles (Product Owner, Scrum Master, Development Team), events (Sprint, Sprint Planning, Daily Scrum, Sprint Review, Sprint Retrospective), and artifacts (Product Backlog, Sprint Backlog, Increment) that help teams organize their work, collaborate effectively, and deliver value to customers.
Relationship:
-
Scrum is a subset of Agile: Scrum falls under the umbrella of Agile methodologies. While Agile is a broader philosophy, Scrum is a specific approach that adheres to Agile principles.
-
Scrum operationalizes Agile: Scrum provides a practical framework for teams to implement Agile principles in a structured way. It defines roles, events, and artifacts that guide the development process, making Agile principles actionable.
-
Scrum is a popular choice for Agile: Many organizations adopt Scrum as their chosen methodology for implementing Agile practices. However, Agile is not limited to Scrum; there are other Agile frameworks like Kanban, Lean, and Extreme Programming (XP), each with its own set of principles and practices.
In summary, Agile is the overarching philosophy that emphasizes customer collaboration, flexibility, and iterative development, while Scrum is a specific framework that operationalizes Agile principles. Scrum provides a structured approach to managing work and is one of the most widely used methods for implementing Agile practices in software development and other project management contexts.
Scrum Ceremonies or Events
In Scrum, there are several ceremonies or events that provide structure and cadence to the development process. These events help teams collaborate, plan, inspect and adapt their work. The key Scrum ceremonies or events are:
-
Sprint Planning: This is a time-boxed event at the start of each sprint where the Product Owner and Development Team collaborate to select and commit to a set of product backlog items to be worked on during the sprint. The team also discusses how to achieve the sprint goal.
-
Daily Scrum (Daily Standup): A daily, time-boxed meeting where the Development Team synchronizes their work. Each team member answers three questions: What did I do yesterday? What will I do today? Are there any impediments or blockers? This meeting helps the team stay on track and adapt to changing circumstances.
-
Sprint Review: At the end of each sprint, there is a Sprint Review meeting where the Development Team demonstrates the work completed during the sprint to stakeholders, including the Product Owner and possibly customers. It's an opportunity to gather feedback and potentially adjust the product backlog based on new insights.
-
Sprint Retrospective: Also held at the end of each sprint, the Sprint Retrospective is a meeting for the Development Team to reflect on the sprint and identify improvements. It's a time to discuss what went well, what could be improved, and what action items the team will take in the next sprint.
-
Backlog Refinement (Grooming): While not a formal event, backlog refinement is an ongoing activity where the Product Owner and Development Team collaborate to clarify, estimate, and prioritize items in the product backlog. This ensures that the backlog is well-prepared for future sprints.
These Scrum ceremonies provide a structured framework for planning, communication, and continuous improvement within the Scrum process. They help teams stay focused on delivering value, adapt to changing requirements, and maintain transparency throughout the development process. The time-boxed nature of these events ensures that they are efficient and don't become overly time-consuming.
Scrum Pillars and Values
Scrum is guided by three pillars and five core values, which provide the foundation for the framework and help teams implement Scrum effectively. These pillars and values are integral to Scrum's success:
Pillars:
-
Transparency: Transparency is the first pillar of Scrum, emphasizing openness and visibility in all aspects of work. It means that all relevant information about the project, progress, and challenges should be easily accessible to all team members and stakeholders. Transparency promotes trust and helps teams make informed decisions.
-
Inspection: The second pillar is inspection, which encourages regular examination of the product, processes, and progress. Teams should inspect their work and the product increment continuously, identifying areas that need improvement. Inspection provides opportunities to adapt and make necessary changes to enhance product quality and efficiency.
-
Adaptation: The third pillar, adaptation, goes hand-in-hand with inspection. Once issues are identified through inspection, teams must take action to adapt and make improvements. Scrum encourages flexibility and adaptability in response to changing requirements, market conditions, or other factors. Adaptation is essential for delivering valuable products and continuously improving the development process.
Values:
-
Commitment: Scrum values commitment, particularly commitment to delivering value to the customer. The team commits to the goals of the sprint and works diligently to achieve them. Commitment also includes the commitment to quality and excellence in all aspects of the work.
-
Courage: Courage is the value that enables teams to confront challenges and take calculated risks. It means speaking up about issues, suggesting changes, and admitting when something isn't working as expected. Teams should have the courage to make tough decisions that are in the best interest of the product and the project.
-
Focus: Scrum encourages focus on the sprint goal and the highest-priority work. Teams should concentrate their efforts on completing the items in the sprint backlog and delivering a potentially shippable product increment. Distractions and scope changes should be minimized to maintain focus.
-
Openness: Openness is about fostering an environment where team members and stakeholders can communicate transparently. It means being receptive to feedback, actively listening, and promoting collaboration. Openness encourages the sharing of information and ideas to improve the project.
-
Respect: Respect is a fundamental value in Scrum, promoting respect for each team member's expertise, opinions, and contributions. It also extends to respecting the decisions of the team and stakeholders. A respectful environment supports effective teamwork and collaboration.
These pillars and values provide the underlying philosophy and principles that guide Scrum teams in their work. When teams and organizations embrace these pillars and values, they are better equipped to harness the power of Scrum to deliver high-quality products and adapt to changing demands effectively.
3 Essential Roles for Scrum Success
Scrum relies on three essential roles to ensure its success. These roles play distinct but interconnected functions in the Scrum framework:
Product Owner:
-
The Product Owner is a crucial role responsible for representing the interests of stakeholders, including customers and users. They are the primary decision-maker regarding the product's features, functionality, and priorities.
-
Responsibilities include creating and maintaining the product backlog, which is a prioritized list of work items (often user stories) that define what needs to be built or improved.
-
The Product Owner collaborates closely with the development team to clarify requirements, answer questions, and provide ongoing feedback.
-
Success in this role involves effectively balancing stakeholder needs, maintaining a clear product vision, and continuously prioritizing the backlog to maximize the product's value.
Scrum Master:
-
The Scrum Master is a servant-leader for the Scrum team, focused on facilitating and coaching the team to follow Scrum principles and practices.
-
Responsibilities include removing impediments or obstacles that hinder the team's progress, ensuring that Scrum events are conducted effectively, and promoting a collaborative and self-organizing team culture.
-
The Scrum Master fosters continuous improvement by facilitating the Sprint Retrospective and encouraging the team to reflect on their processes and make adjustments.
-
Success in this role involves guiding the team toward self-sufficiency, helping them improve their Scrum practices, and ensuring that Scrum values are upheld.
Development Team:
-
The Development Team consists of cross-functional individuals who work together to deliver a potentially shippable product increment during each sprint.
-
Responsibilities include selecting and committing to work items from the sprint backlog, designing, coding, testing, and delivering the product increment.
-
Development Teams are self-organizing, meaning they have the autonomy to determine how to complete the work and make decisions about how to meet the sprint goal.
-
Success of the Development Team is measured by their ability to consistently deliver high-quality, potentially shippable increments of the product and their commitment to continuous improvement.
These three roles are integral to the success of Scrum. The Product Owner ensures that the product meets customer needs, the Scrum Master enables the team to follow Scrum principles, and the Development Team is responsible for delivering the product increment. Effective collaboration and adherence to Scrum values and principles among these roles are essential for achieving Scrum's goal of delivering value to customers through iterative and incremental development.
Scaling Scrum to Multiple Teams
Scaling Scrum to multiple teams in five key points:
-
Choose a Scaling Framework: Select an appropriate scaling framework, such as SAFe, LeSS, or Nexus, that aligns with your organizational goals and context.
-
Coordinate Product Ownership: Ensure product ownership is well-coordinated across teams, either by creating a Product Owner team or designating a Chief Product Owner to maintain a unified product backlog.
-
Facilitate Cross-Team Collaboration: Organize regular Scrum of Scrums meetings to facilitate cross-team collaboration, share information, and address dependencies.
-
Implement Program Increment (PI) Planning: Conduct PI planning sessions to align the work of multiple teams for a set period (e.g., 8-12 weeks) and establish a shared vision.
-
Promote a Culture of Continuous Improvement: Foster a culture of continuous improvement, provide training and coaching, and regularly inspect and adapt at both the team and program levels to enhance collaboration and alignment among teams.
How to obtain the CSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
Conclusion
In conclusion, Scrum is a powerful framework for agile project management and product development that emphasizes transparency, inspection, and adaptation. Its three pillars of transparency, inspection, and adaptation, along with its five core values of commitment, courage, focus, openness, and respect, provide a strong foundation for teams to deliver value to customers effectively.
Scrum's essential roles, including the Product Owner, Scrum Master, and Development Team, play distinct but interconnected functions in ensuring project success. The ceremonies or events, such as Sprint Planning, Daily Scrum, Sprint Review, and Sprint Retrospective, provide structure and guidance throughout the development process.
When it comes to scaling Scrum to multiple teams, organizations have several frameworks and strategies to choose from, such as SAFe, Scrum of Scrums, and coordinated product ownership. These approaches enable large and complex organizations to maintain alignment, collaboration, and responsiveness as they deliver value to customers.
In essence, Scrum promotes a customer-centric, adaptable, and collaborative approach to project management, making it a valuable choice for a wide range of industries and project types. By embracing Scrum's principles, roles, values, and ceremonies, teams and organizations can increase their chances of delivering high-quality products and continuously improving their processes.
Read More
In the dynamic landscape of project management and software development, methodologies that foster flexibility, collaboration, and rapid adaptation are essential. One such methodology that has gained widespread recognition and adoption is the Scrum Framework. Born out of the Agile movement, Scrum has revolutionized the way teams tackle complex projects, enabling them to deliver high-quality results efficiently and with enhanced teamwork.
In this comprehensive guide, we will delve into the intricacies of the Scrum Framework, unraveling its core principles, methodologies, and the seamless interplay of its roles and rituals. Whether you're an aspiring project manager, a seasoned software developer, or simply curious about how Scrum works, join us on this journey as we explore the essence of Scrum and how it can transform the way you approach projects. From its foundational concepts to its practical implementation, you'll gain a solid understanding of what Scrum is and, more importantly, how it works to bring about unparalleled success in the world of project management and beyond.
Table of Contents
What is the Scrum Process Framework?
What Are Scrum Artifacts?
Benefits of Scrum Methodology
Scrum and Agile Relationship Explained
Scrum Ceremonies or Events
Scrum Pillars and Values
3 Essential Roles for Scrum Success
Scaling Scrum to Multiple Teams
Conclusion
What is the Scrum Process Framework?
The Scrum process framework is an agile project management approach designed to facilitate the iterative and incremental development of products. It is characterized by a set of defined roles, events, artifacts, and rules that guide a development team's work. Key roles include the Product Owner, Scrum Master, and Development Team, each with specific responsibilities. Scrum events, such as Sprint Planning, Daily Scrum, Sprint Review, and Sprint Retrospective, provide a structured rhythm to the development process. The Product Backlog, Sprint Backlog, and Increment are the essential artifacts used to manage work and track progress. Scrum emphasizes transparency, inspection, and adaptation, allowing teams to respond to changing requirements and deliver high-value product increments regularly.
One of Scrum's core principles is its focus on collaboration and adaptability. By breaking work into small, manageable iterations called sprints, teams can quickly respond to customer feedback and changing priorities. This iterative approach encourages continuous improvement, making Scrum an effective framework for complex projects where requirements may evolve over time. It promotes a sense of ownership and accountability among team members, leading to more efficient and productive development cycles. Scrum's simplicity and flexibility have made it a popular choice not only in software development but also in various industries seeking to deliver value to customers faster and with greater adaptability.
What Are Scrum Artifacts?
Scrum artifacts are essential documents or information sources that provide transparency and help in managing work within the Scrum framework. These artifacts are used to ensure that everyone involved in a Scrum project has a common understanding of the product being developed and the progress being made. There are three primary Scrum artifacts:
-
Product Backlog: The Product Backlog is a prioritized list of all the work that needs to be done to create and maintain the product. It is owned and managed by the Product Owner. The items in the Product Backlog can include features, user stories, bug fixes, technical tasks, and other work items. Each item is described in sufficient detail so that the development team understands what needs to be done. The Product Owner continuously refines and prioritizes the backlog based on changing requirements and feedback from stakeholders.
-
Sprint Backlog: The Sprint Backlog is a subset of the items from the Product Backlog that the development team commits to completing during a specific sprint. It is created during the Sprint Planning event, where the team selects the highest-priority items from the Product Backlog and decides how they will deliver them. The Sprint Backlog is a dynamic document that can be adjusted as the team gains a better understanding of the work during the sprint. It helps the team track progress toward the sprint goal.
-
Increment: The Increment is the sum of all the product backlog items that have been completed during a sprint. It represents a potentially shippable product or a product incrementally closer to the desired end state. At the end of each sprint, the development team delivers the Increment for review by stakeholders during the Sprint Review event. If accepted, the Increment can be released to users or customers. The goal is to have a potentially shippable product increment at the end of each sprint, although it may not include all desired features until subsequent sprints.
These Scrum artifacts serve to provide transparency, enable inspection, and support adaptation throughout the development process. They ensure that everyone involved in the project, including the development team, Product Owner, and stakeholders, has a clear understanding of what work is to be done, what has been completed, and the overall progress toward the product's goals.
Benefits of Scrum Methodology
The Scrum methodology offers several benefits, making it a popular choice for agile project management and product development. Some of the key advantages of Scrum include:
-
Flexibility and Adaptability: Scrum embraces change and allows teams to adapt to evolving requirements, market conditions, and customer feedback. It offers the flexibility to reprioritize work and make adjustments during short, time-boxed iterations called sprints.
-
Customer-Centric: Scrum places a strong emphasis on delivering value to the customer. The Product Owner is responsible for prioritizing the product backlog based on customer needs, ensuring that the most valuable features are built first.
-
Transparency: Scrum promotes transparency by making project information visible to all team members. This transparency encourages collaboration, accountability, and open communication among team members and stakeholders.
-
Increased Productivity: Scrum's iterative approach often leads to higher productivity because it focuses on delivering a potentially shippable product incrementally. Teams can release valuable features sooner, providing benefits to the end-users and stakeholders.
-
Early and Regular Feedback: Scrum encourages frequent feedback through events like Sprint Reviews and Daily Scrums. This continuous feedback loop helps identify and address issues early in the development process, reducing the risk of building the wrong product.
-
Improved Quality: Scrum places a strong emphasis on quality through practices like automated testing and continuous integration. The incremental development and regular inspections help maintain and improve product quality over time.
-
Empowered Teams: Scrum empowers development teams to self-organize and make decisions regarding how to achieve sprint goals. This autonomy and ownership often lead to more motivated and engaged team members.
-
Predictable Delivery: Scrum promotes predictability by establishing a consistent cadence of work through time-boxed sprints. This helps stakeholders understand when they can expect specific features or updates.
-
Reduced Risk: With its focus on frequent inspections and adaptations, Scrum helps mitigate risks by identifying and addressing issues early in the project. Teams can make informed decisions to course-correct as needed.
-
Enhanced Collaboration: Scrum fosters collaboration among cross-functional team members, including developers, testers, designers, and product managers. Regular meetings like the Daily Scrum promote communication and collaboration.
While Scrum offers numerous benefits, it's essential to recognize that its successful implementation requires a committed and well-trained team, adherence to Scrum principles, and continuous improvement to refine processes over time.
Scrum and Agile Relationship Explained
Scrum and Agile are closely related concepts in the world of project management and software development, with Scrum being one of the most popular frameworks within the broader Agile methodology. Here's an explanation of their relationship:
Agile:
-
Agile is a set of values and principles outlined in the Agile Manifesto, which was created in 2001 by a group of software developers. The manifesto emphasizes customer collaboration, responding to change, and delivering working software as primary goals.
-
Agile is not a specific framework or methodology but rather a mindset or philosophy that promotes flexibility, collaboration, and customer-centricity. It encourages teams to work iteratively and adapt to changing requirements and customer feedback.
Scrum:
-
Scrum is a specific framework for implementing Agile principles. It provides a structured approach to managing work within an Agile context.
-
Scrum prescribes a set of roles (Product Owner, Scrum Master, Development Team), events (Sprint, Sprint Planning, Daily Scrum, Sprint Review, Sprint Retrospective), and artifacts (Product Backlog, Sprint Backlog, Increment) that help teams organize their work, collaborate effectively, and deliver value to customers.
Relationship:
-
Scrum is a subset of Agile: Scrum falls under the umbrella of Agile methodologies. While Agile is a broader philosophy, Scrum is a specific approach that adheres to Agile principles.
-
Scrum operationalizes Agile: Scrum provides a practical framework for teams to implement Agile principles in a structured way. It defines roles, events, and artifacts that guide the development process, making Agile principles actionable.
-
Scrum is a popular choice for Agile: Many organizations adopt Scrum as their chosen methodology for implementing Agile practices. However, Agile is not limited to Scrum; there are other Agile frameworks like Kanban, Lean, and Extreme Programming (XP), each with its own set of principles and practices.
In summary, Agile is the overarching philosophy that emphasizes customer collaboration, flexibility, and iterative development, while Scrum is a specific framework that operationalizes Agile principles. Scrum provides a structured approach to managing work and is one of the most widely used methods for implementing Agile practices in software development and other project management contexts.
Scrum Ceremonies or Events
In Scrum, there are several ceremonies or events that provide structure and cadence to the development process. These events help teams collaborate, plan, inspect and adapt their work. The key Scrum ceremonies or events are:
-
Sprint Planning: This is a time-boxed event at the start of each sprint where the Product Owner and Development Team collaborate to select and commit to a set of product backlog items to be worked on during the sprint. The team also discusses how to achieve the sprint goal.
-
Daily Scrum (Daily Standup): A daily, time-boxed meeting where the Development Team synchronizes their work. Each team member answers three questions: What did I do yesterday? What will I do today? Are there any impediments or blockers? This meeting helps the team stay on track and adapt to changing circumstances.
-
Sprint Review: At the end of each sprint, there is a Sprint Review meeting where the Development Team demonstrates the work completed during the sprint to stakeholders, including the Product Owner and possibly customers. It's an opportunity to gather feedback and potentially adjust the product backlog based on new insights.
-
Sprint Retrospective: Also held at the end of each sprint, the Sprint Retrospective is a meeting for the Development Team to reflect on the sprint and identify improvements. It's a time to discuss what went well, what could be improved, and what action items the team will take in the next sprint.
-
Backlog Refinement (Grooming): While not a formal event, backlog refinement is an ongoing activity where the Product Owner and Development Team collaborate to clarify, estimate, and prioritize items in the product backlog. This ensures that the backlog is well-prepared for future sprints.
These Scrum ceremonies provide a structured framework for planning, communication, and continuous improvement within the Scrum process. They help teams stay focused on delivering value, adapt to changing requirements, and maintain transparency throughout the development process. The time-boxed nature of these events ensures that they are efficient and don't become overly time-consuming.
Scrum Pillars and Values
Scrum is guided by three pillars and five core values, which provide the foundation for the framework and help teams implement Scrum effectively. These pillars and values are integral to Scrum's success:
Pillars:
-
Transparency: Transparency is the first pillar of Scrum, emphasizing openness and visibility in all aspects of work. It means that all relevant information about the project, progress, and challenges should be easily accessible to all team members and stakeholders. Transparency promotes trust and helps teams make informed decisions.
-
Inspection: The second pillar is inspection, which encourages regular examination of the product, processes, and progress. Teams should inspect their work and the product increment continuously, identifying areas that need improvement. Inspection provides opportunities to adapt and make necessary changes to enhance product quality and efficiency.
-
Adaptation: The third pillar, adaptation, goes hand-in-hand with inspection. Once issues are identified through inspection, teams must take action to adapt and make improvements. Scrum encourages flexibility and adaptability in response to changing requirements, market conditions, or other factors. Adaptation is essential for delivering valuable products and continuously improving the development process.
Values:
-
Commitment: Scrum values commitment, particularly commitment to delivering value to the customer. The team commits to the goals of the sprint and works diligently to achieve them. Commitment also includes the commitment to quality and excellence in all aspects of the work.
-
Courage: Courage is the value that enables teams to confront challenges and take calculated risks. It means speaking up about issues, suggesting changes, and admitting when something isn't working as expected. Teams should have the courage to make tough decisions that are in the best interest of the product and the project.
-
Focus: Scrum encourages focus on the sprint goal and the highest-priority work. Teams should concentrate their efforts on completing the items in the sprint backlog and delivering a potentially shippable product increment. Distractions and scope changes should be minimized to maintain focus.
-
Openness: Openness is about fostering an environment where team members and stakeholders can communicate transparently. It means being receptive to feedback, actively listening, and promoting collaboration. Openness encourages the sharing of information and ideas to improve the project.
-
Respect: Respect is a fundamental value in Scrum, promoting respect for each team member's expertise, opinions, and contributions. It also extends to respecting the decisions of the team and stakeholders. A respectful environment supports effective teamwork and collaboration.
These pillars and values provide the underlying philosophy and principles that guide Scrum teams in their work. When teams and organizations embrace these pillars and values, they are better equipped to harness the power of Scrum to deliver high-quality products and adapt to changing demands effectively.
3 Essential Roles for Scrum Success
Scrum relies on three essential roles to ensure its success. These roles play distinct but interconnected functions in the Scrum framework:
Product Owner:
-
The Product Owner is a crucial role responsible for representing the interests of stakeholders, including customers and users. They are the primary decision-maker regarding the product's features, functionality, and priorities.
-
Responsibilities include creating and maintaining the product backlog, which is a prioritized list of work items (often user stories) that define what needs to be built or improved.
-
The Product Owner collaborates closely with the development team to clarify requirements, answer questions, and provide ongoing feedback.
-
Success in this role involves effectively balancing stakeholder needs, maintaining a clear product vision, and continuously prioritizing the backlog to maximize the product's value.
Scrum Master:
-
The Scrum Master is a servant-leader for the Scrum team, focused on facilitating and coaching the team to follow Scrum principles and practices.
-
Responsibilities include removing impediments or obstacles that hinder the team's progress, ensuring that Scrum events are conducted effectively, and promoting a collaborative and self-organizing team culture.
-
The Scrum Master fosters continuous improvement by facilitating the Sprint Retrospective and encouraging the team to reflect on their processes and make adjustments.
-
Success in this role involves guiding the team toward self-sufficiency, helping them improve their Scrum practices, and ensuring that Scrum values are upheld.
Development Team:
-
The Development Team consists of cross-functional individuals who work together to deliver a potentially shippable product increment during each sprint.
-
Responsibilities include selecting and committing to work items from the sprint backlog, designing, coding, testing, and delivering the product increment.
-
Development Teams are self-organizing, meaning they have the autonomy to determine how to complete the work and make decisions about how to meet the sprint goal.
-
Success of the Development Team is measured by their ability to consistently deliver high-quality, potentially shippable increments of the product and their commitment to continuous improvement.
These three roles are integral to the success of Scrum. The Product Owner ensures that the product meets customer needs, the Scrum Master enables the team to follow Scrum principles, and the Development Team is responsible for delivering the product increment. Effective collaboration and adherence to Scrum values and principles among these roles are essential for achieving Scrum's goal of delivering value to customers through iterative and incremental development.
Scaling Scrum to Multiple Teams
Scaling Scrum to multiple teams in five key points:
-
Choose a Scaling Framework: Select an appropriate scaling framework, such as SAFe, LeSS, or Nexus, that aligns with your organizational goals and context.
-
Coordinate Product Ownership: Ensure product ownership is well-coordinated across teams, either by creating a Product Owner team or designating a Chief Product Owner to maintain a unified product backlog.
-
Facilitate Cross-Team Collaboration: Organize regular Scrum of Scrums meetings to facilitate cross-team collaboration, share information, and address dependencies.
-
Implement Program Increment (PI) Planning: Conduct PI planning sessions to align the work of multiple teams for a set period (e.g., 8-12 weeks) and establish a shared vision.
-
Promote a Culture of Continuous Improvement: Foster a culture of continuous improvement, provide training and coaching, and regularly inspect and adapt at both the team and program levels to enhance collaboration and alignment among teams.
How to obtain the CSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
Conclusion
In conclusion, Scrum is a powerful framework for agile project management and product development that emphasizes transparency, inspection, and adaptation. Its three pillars of transparency, inspection, and adaptation, along with its five core values of commitment, courage, focus, openness, and respect, provide a strong foundation for teams to deliver value to customers effectively.
Scrum's essential roles, including the Product Owner, Scrum Master, and Development Team, play distinct but interconnected functions in ensuring project success. The ceremonies or events, such as Sprint Planning, Daily Scrum, Sprint Review, and Sprint Retrospective, provide structure and guidance throughout the development process.
When it comes to scaling Scrum to multiple teams, organizations have several frameworks and strategies to choose from, such as SAFe, Scrum of Scrums, and coordinated product ownership. These approaches enable large and complex organizations to maintain alignment, collaboration, and responsiveness as they deliver value to customers.
In essence, Scrum promotes a customer-centric, adaptable, and collaborative approach to project management, making it a valuable choice for a wide range of industries and project types. By embracing Scrum's principles, roles, values, and ceremonies, teams and organizations can increase their chances of delivering high-quality products and continuously improving their processes.
COBIT® 5 and IT Risk Management: A Powerful Combination
In today's ever-evolving digital landscape, organizations face a multitude of challenges when it comes to managing and mitigating IT risks. The rapid pace of technological advancements, the increasing complexity of IT environments, and the relentless onslaught of cyber threats have made effective risk management an imperative for businesses of all sizes and industries.
This blog post explores a powerful combination that has emerged to tackle these challenges head-on: COBIT® 5 and IT risk management. COBIT® 5, a globally recognized framework for IT governance and management, provides organizations with a structured approach to optimizing IT processes and aligning them with business goals. When integrated with robust IT risk management practices, COBIT® 5 becomes a formidable tool in helping organizations identify, assess, mitigate, and monitor IT risks effectively.
In this post, we will delve into the core concepts of COBIT® 5, emphasizing its principles and guidelines that support IT risk management. We will also discuss the benefits of combining COBIT® 5 with IT risk management, including improved visibility, enhanced decision-making, and better compliance. Additionally, we'll provide practical insights on how organizations can implement COBIT® 5 in their risk management processes and showcase real-world examples of its successful integration.
Table of Contents
-
Understanding COBIT® 5 in Brief
-
The Critical Role of IT Risk Management
-
COBIT® 5's Approach to IT Risk Management
-
Benefits of Integrating COBIT® 5 with IT Risk Management
-
COBIT® 5's Framework for IT Risk Management
-
Practical Implementation Steps
-
Real-world Examples
-
Challenges and Considerations
-
Conclusion
Understanding COBIT® 5 in Brief
COBIT® 5, which stands for Control Objectives for Information and Related Technologies, is a globally recognized framework developed by the Information Systems Audit and Control Association (ISACA) to guide organizations in effectively managing and governing their information technology (IT) processes. At its core, COBIT® 5 seeks to bridge the gap between business objectives and IT functions. It is a comprehensive framework that offers a structured approach to IT governance and management, ensuring that IT activities align with business goals and regulatory requirements.
Key Components of COBIT® 5:
COBIT® 5 is built on five fundamental principles that underpin its effectiveness. These principles include meeting stakeholder needs, covering the enterprise end-to-end, applying a single integrated framework, enabling a holistic approach, and separating governance from management. Within the framework, a set of processes is organized into five domains: Evaluate, Direct, and Monitor (EDM), Align, Plan, and Organize (APO), Build, Acquire, and Implement (BAI), Deliver, Service, and Support (DSS), and Monitor, Evaluate, and Assess (MEA). These processes provide guidance on various aspects of IT governance and management, from strategic planning to day-to-day operations.
Benefits of COBIT® 5:
Organizations that embrace COBIT® 5 gain several notable advantages. It enhances IT governance by establishing a robust framework that ensures IT investments and actions are in harmony with business objectives and compliance requirements. COBIT® 5 also plays a vital role in risk management, offering a structured approach to identify, assess, and mitigate IT-related risks. It aids in efficient resource allocation, enabling organizations to make informed decisions regarding IT investments. Moreover, COBIT® 5 promotes transparency and accountability in IT processes, facilitating areas of improvement identification and compliance demonstration. The framework's compatibility with various industry standards and frameworks, such as ITIL and ISO/IEC 27001, enhances its appeal as a versatile tool applicable to organizations of all sizes and industries. In summary, COBIT® 5 serves as an invaluable resource for organizations aspiring to elevate their IT governance and management practices, aligning IT with business objectives and enhancing overall efficiency and effectiveness.
The Critical Role of IT Risk Management
In today's digital-centric business landscape, the critical role of IT risk management cannot be overstated. As organizations increasingly rely on technology to drive their operations, serve customers, and manage data, they become more exposed to a wide array of IT-related risks. These risks can range from cybersecurity threats and data breaches to system failures and compliance violations. Effectively managing these risks is essential for business continuity, reputation preservation, and regulatory compliance.
IT risk management is a systematic and structured approach to identifying, assessing, mitigating, and monitoring IT-related risks. Its significance lies in its ability to proactively identify potential threats and vulnerabilities, allowing organizations to take preemptive action to reduce their impact. Here are several key aspects highlighting the critical role of IT risk management:
1. Protecting Business Assets: IT systems and digital assets are vital components of modern businesses. IT risk management safeguards these assets from a wide range of threats, including cyberattacks, unauthorized access, and data loss. By protecting these assets, organizations can ensure the uninterrupted flow of operations and maintain customer trust.
2. Safeguarding Reputation: A data breach or security incident can have severe consequences for an organization's reputation. IT risk management practices, including robust cybersecurity measures and incident response plans, help minimize the risk of reputational damage by preventing or mitigating the impact of such incidents.
3. Regulatory Compliance: Many industries are subject to stringent regulations related to data protection, privacy, and security. IT risk management ensures that organizations remain in compliance with these regulations, avoiding costly fines and legal repercussions.
4. Business Continuity: Effective risk management includes disaster recovery and business continuity planning. This ensures that in the event of IT disruptions, whether due to natural disasters or technical failures, organizations can continue to operate or quickly recover their operations.
5. Cost Reduction: Well-planned IT risk management can lead to cost savings. By identifying and mitigating risks, organizations can reduce the financial impact of potential incidents and allocate resources more efficiently.
6. Decision Support: IT risk assessments provide valuable insights into the vulnerabilities and threats an organization faces. This information aids in informed decision-making, such as prioritizing investments in security measures and risk mitigation strategies.
7. Competitive Advantage: Organizations that can demonstrate effective IT risk management practices often gain a competitive edge. Customers and partners are increasingly concerned about data security and compliance, making sound risk management a selling point.
COBIT® 5's Approach to IT Risk Management
COBIT® 5, the globally recognized framework for IT governance and management, offers a structured and effective approach to managing IT-related risks within organizations. Its approach can be summarized in a few key steps, making it accessible for organizations of various sizes and industries:
-
Understand Business Goals: First, know your organization's business objectives well. IT should support these goals.
-
Set Risk Tolerance: Decide how much risk you're willing to accept to achieve your business goals, like setting a limit on a game.
-
Identify IT Risks: Spot potential IT risks, such as cyber threats or software problems, just like noticing road obstacles.
-
Assess Risks: Estimate how big each risk is and how likely it is to happen, similar to evaluating the size of a road pothole and its likelihood of causing damage.
-
Respond to Risks: Decide what to do about each risk—avoid it, lessen its impact, transfer it (like getting insurance), or accept it, just as you choose to fix a pothole or take a different route.
-
Monitor Continuously: Keep an eye on risks all the time, like watching the road while driving, and adjust your plans if new risks appear.
-
Communicate Clearly: Make sure everyone in your organization understands the risks and what you're doing to manage them.
-
Report and Follow Rules: Share information about how you're handling risks with key people and stay in line with laws and standards.
-
Learn and Improve: Keep learning from your experiences with risk management to get better at it over time, like becoming a better driver after each trip.
In simple terms, COBIT® 5's approach to IT risk management is like planning a safe journey. You know where you want to go (business goals), identify potential roadblocks (IT risks), set limits on how risky you're willing to be, and use strategies to navigate safely. This helps organizations protect their IT systems and make smart choices in the digital world.
Benefits of Integrating COBIT® 5 with IT Risk Management
Integrating COBIT® 5, a comprehensive framework for IT governance and management, with IT risk management brings several significant benefits to organizations. This integration creates a powerful synergy that enhances an organization's ability to identify, assess, mitigate, and monitor IT-related risks effectively. Here are the key advantages:
-
Business Alignment: Aligns IT activities with what the organization wants to achieve, ensuring that IT supports business goals.
-
Proactive Risk Management: Helps spot and address IT risks before they become big problems.
-
Informed Decision-Making: Provides insights for smart decisions about IT investments and how to deal with risks.
-
Regulatory Compliance: Makes it easier to follow rules and regulations related to IT risk management.
-
Efficient Resource Use: Helps allocate resources wisely by focusing on the most important risks.
-
Clear Communication: Makes it easy to explain IT risks and how they're being managed to everyone in the organization.
-
Adaptation to Change: Keeps an eye on risks and adjusts strategies as needed to stay safe in a changing world.
-
Easier Audits: Simplifies the process of checking that risk management practices are working correctly.
-
Competitive Advantage: Organizations that do this well look better to customers and partners who care about data security and following the rules.
COBIT® 5's Framework for IT Risk Management
COBIT® 5 provides a structured and comprehensive framework for IT risk management within organizations. This framework offers a clear path to identify, assess, mitigate, and monitor IT-related risks effectively. Here are the key components and steps in COBIT® 5's framework for IT risk management:
-
Identify Risks: Find potential IT risks that could harm your organization, like cyber threats or data problems.
-
Assess Risks: Figure out how big each risk is and how likely it is to happen, so you know which ones need attention.
-
Manage Risks: Decide what to do about each risk—avoid it, lessen its impact, transfer it (like insurance), or accept it.
-
Keep an Eye Out: Continuously watch for changes in risks and adjust your plans accordingly.
-
Report Clearly: Share what you're doing about risks with everyone in your organization and make sure to document everything.
-
Follow the Rules: Make sure your risk management follows the laws and rules that apply to your business.
-
Learn and Get Better: Keep learning from your experiences with risk management to do it even better next time.
-
Integrate with Everything: Make sure risk management is part of all your IT decisions and fits with your overall goals.
In simple terms, COBIT® 5's framework for IT risk management is like a clear roadmap to help organizations handle IT risks wisely. It guides you in spotting risks, figuring out how to deal with them, and making sure you're following the rules and improving over time. This helps keep your organization safe and successful in the digital world.
Practical Implementation Steps
Implementing COBIT® 5's IT risk management framework involves practical steps to ensure a systematic and effective approach to managing IT-related risks within your organization. Here are the key implementation steps:
-
Assign Responsibilities: Appoint people to handle risk management tasks and make sure senior leaders support the process.
-
Set Risk Limits: Decide how much risk your organization can accept for different types of IT activities.
-
Spot Risks: Identify potential IT risks using your team's knowledge and available data.
-
Check Risks: Evaluate each risk to see how big it is and how likely it is to happen, and then prioritize them.
-
Make Risk Plans: Create plans to deal with the most important risks, deciding whether to avoid them, reduce their impact, transfer them (like buying insurance), or accept them.
-
Integrate with Everything: Make sure risk management is part of your regular IT processes and document it.
-
Keep Watch: Set up a system to keep an eye on how risks change and how your plans are working.
-
Tell Everyone: Regularly tell your team and leaders about the risks and what you're doing to manage them.
-
Keep Records: Write down everything you do related to risk management.
-
Train and Learn: Teach your team about risk management and learn from your experiences to get better over time.
-
Follow the Rules: Make sure your risk management meets the laws and rules that apply to your business.
-
Get Help If Needed: Consider getting outside experts to help or assess your risk management.
In simple terms, these steps help organizations manage IT risks effectively, aligning with their goals and complying with rules while learning and improving along the way.
Real-world Examples
Here are some real-world examples of organizations that have successfully implemented COBIT® 5's IT risk management framework:
-
JPMorgan Chase & Co.: JPMorgan Chase, one of the world's largest financial institutions, utilizes COBIT® 5's IT risk management framework to ensure the security and reliability of its IT systems. The framework helps them identify and assess risks associated with their extensive digital operations, including online banking and financial services. It enables them to proactively address cybersecurity threats, data breaches, and regulatory compliance challenges.
-
The World Bank: The World Bank, a global financial institution, leverages COBIT® 5 to manage IT risks across its diverse operations. They use the framework to identify and assess risks related to the implementation of technology in development projects. This helps them mitigate potential project delays, budget overruns, and data security issues.
-
Dubai Electricity and Water Authority (DEWA): DEWA, the utility provider for Dubai, uses COBIT® 5 to enhance IT risk management in the context of critical infrastructure. They apply the framework to identify and address risks associated with their energy and water supply systems. This ensures the reliability and resilience of their services, even in the face of IT-related challenges.
-
PwC (PricewaterhouseCoopers): As a leading global professional services firm, PwC employs COBIT® 5 for IT risk management to help their clients across various industries. They assist organizations in identifying and managing IT risks to enhance cybersecurity, regulatory compliance, and overall operational efficiency.
-
Nestlé: Nestlé, the multinational food and beverage company, uses COBIT® 5's IT risk management framework to ensure the integrity of its global IT systems. This includes managing risks related to data privacy, supply chain, and production systems. The framework helps Nestlé maintain the trust of its customers and regulators while ensuring the smooth operation of its business.
These real-world examples demonstrate how organizations across different sectors, including finance, development, utilities, and professional services, leverage COBIT® 5's IT risk management framework to enhance their IT governance and protect their operations from a wide range of IT-related risks. This illustrates the versatility and effectiveness of COBIT® 5 in managing IT risks in various contexts.
Challenges and Considerations
Implementing COBIT® 5's IT risk management framework comes with a set of challenges and considerations that organizations should carefully address. One significant challenge is resource allocation, involving finding the right personnel and financial investments for risk management initiatives. Changing the organizational culture to prioritize risk management can be a formidable hurdle, as it requires strong leadership support and effective communication to instill the importance of risk management across all levels of the organization. The complexity of modern IT environments, with their ever-evolving nature, presents another challenge, necessitating the use of advanced monitoring tools and regular risk assessments to keep up. Adhering to regulatory requirements is a critical consideration, especially as rules can change frequently, making it vital to stay informed and seek expert guidance when needed.
Safeguarding sensitive data from breaches and cyberattacks remains a constant challenge, demanding robust cybersecurity measures and well-defined incident response plans. Integrating COBIT® 5's IT risk management framework with existing IT governance processes may pose difficulties, necessitating expert guidance and a strategic approach to ensure seamless integration. Building and maintaining the necessary skills and knowledge within the organization for effective risk management requires investment in training and development programs. Overcoming resistance to change and managing organizational change effectively is essential, as implementing new risk management processes can meet with opposition. Finally, measuring the effectiveness of risk management efforts and reporting on them in a clear and meaningful way can be complex, requiring the definition of key performance indicators and metrics to evaluate success and communicate progress to stakeholders. Addressing these challenges and considerations strategically empowers organizations to protect their IT assets, align IT with business objectives, and ensure resilience in an ever-evolving digital landscape.
How to obtain the COBIT Foundation Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
IT Service Management & Governance: COBIT, ISO
Conclusion
In conclusion, COBIT® 5's IT risk management framework offers organizations a structured and comprehensive approach to navigate the complex landscape of IT-related risks. While it brings substantial benefits such as enhanced alignment with business goals, proactive risk identification, and improved decision-making, it also presents various challenges and considerations. These challenges include resource allocation, cultural change, the complexity of IT environments, regulatory compliance, data security, integration with existing processes, skills and training, change management, and effective measurement and reporting.
Despite these challenges, organizations that commit to implementing COBIT® 5's framework stand to gain in terms of better IT risk management, alignment with regulatory requirements, and enhanced data security. It empowers organizations to proactively identify and address risks, ultimately safeguarding their IT assets and ensuring their resilience in an ever-evolving digital landscape. Therefore, while the road to effective IT risk management may be challenging, the destination of a secure and well-aligned IT environment is well worth the journey.
Read More
In today's ever-evolving digital landscape, organizations face a multitude of challenges when it comes to managing and mitigating IT risks. The rapid pace of technological advancements, the increasing complexity of IT environments, and the relentless onslaught of cyber threats have made effective risk management an imperative for businesses of all sizes and industries.
This blog post explores a powerful combination that has emerged to tackle these challenges head-on: COBIT® 5 and IT risk management. COBIT® 5, a globally recognized framework for IT governance and management, provides organizations with a structured approach to optimizing IT processes and aligning them with business goals. When integrated with robust IT risk management practices, COBIT® 5 becomes a formidable tool in helping organizations identify, assess, mitigate, and monitor IT risks effectively.
In this post, we will delve into the core concepts of COBIT® 5, emphasizing its principles and guidelines that support IT risk management. We will also discuss the benefits of combining COBIT® 5 with IT risk management, including improved visibility, enhanced decision-making, and better compliance. Additionally, we'll provide practical insights on how organizations can implement COBIT® 5 in their risk management processes and showcase real-world examples of its successful integration.
Table of Contents
-
Understanding COBIT® 5 in Brief
-
The Critical Role of IT Risk Management
-
COBIT® 5's Approach to IT Risk Management
-
Benefits of Integrating COBIT® 5 with IT Risk Management
-
COBIT® 5's Framework for IT Risk Management
-
Practical Implementation Steps
-
Real-world Examples
-
Challenges and Considerations
-
Conclusion
Understanding COBIT® 5 in Brief
COBIT® 5, which stands for Control Objectives for Information and Related Technologies, is a globally recognized framework developed by the Information Systems Audit and Control Association (ISACA) to guide organizations in effectively managing and governing their information technology (IT) processes. At its core, COBIT® 5 seeks to bridge the gap between business objectives and IT functions. It is a comprehensive framework that offers a structured approach to IT governance and management, ensuring that IT activities align with business goals and regulatory requirements.
Key Components of COBIT® 5:
COBIT® 5 is built on five fundamental principles that underpin its effectiveness. These principles include meeting stakeholder needs, covering the enterprise end-to-end, applying a single integrated framework, enabling a holistic approach, and separating governance from management. Within the framework, a set of processes is organized into five domains: Evaluate, Direct, and Monitor (EDM), Align, Plan, and Organize (APO), Build, Acquire, and Implement (BAI), Deliver, Service, and Support (DSS), and Monitor, Evaluate, and Assess (MEA). These processes provide guidance on various aspects of IT governance and management, from strategic planning to day-to-day operations.
Benefits of COBIT® 5:
Organizations that embrace COBIT® 5 gain several notable advantages. It enhances IT governance by establishing a robust framework that ensures IT investments and actions are in harmony with business objectives and compliance requirements. COBIT® 5 also plays a vital role in risk management, offering a structured approach to identify, assess, and mitigate IT-related risks. It aids in efficient resource allocation, enabling organizations to make informed decisions regarding IT investments. Moreover, COBIT® 5 promotes transparency and accountability in IT processes, facilitating areas of improvement identification and compliance demonstration. The framework's compatibility with various industry standards and frameworks, such as ITIL and ISO/IEC 27001, enhances its appeal as a versatile tool applicable to organizations of all sizes and industries. In summary, COBIT® 5 serves as an invaluable resource for organizations aspiring to elevate their IT governance and management practices, aligning IT with business objectives and enhancing overall efficiency and effectiveness.
The Critical Role of IT Risk Management
In today's digital-centric business landscape, the critical role of IT risk management cannot be overstated. As organizations increasingly rely on technology to drive their operations, serve customers, and manage data, they become more exposed to a wide array of IT-related risks. These risks can range from cybersecurity threats and data breaches to system failures and compliance violations. Effectively managing these risks is essential for business continuity, reputation preservation, and regulatory compliance.
IT risk management is a systematic and structured approach to identifying, assessing, mitigating, and monitoring IT-related risks. Its significance lies in its ability to proactively identify potential threats and vulnerabilities, allowing organizations to take preemptive action to reduce their impact. Here are several key aspects highlighting the critical role of IT risk management:
1. Protecting Business Assets: IT systems and digital assets are vital components of modern businesses. IT risk management safeguards these assets from a wide range of threats, including cyberattacks, unauthorized access, and data loss. By protecting these assets, organizations can ensure the uninterrupted flow of operations and maintain customer trust.
2. Safeguarding Reputation: A data breach or security incident can have severe consequences for an organization's reputation. IT risk management practices, including robust cybersecurity measures and incident response plans, help minimize the risk of reputational damage by preventing or mitigating the impact of such incidents.
3. Regulatory Compliance: Many industries are subject to stringent regulations related to data protection, privacy, and security. IT risk management ensures that organizations remain in compliance with these regulations, avoiding costly fines and legal repercussions.
4. Business Continuity: Effective risk management includes disaster recovery and business continuity planning. This ensures that in the event of IT disruptions, whether due to natural disasters or technical failures, organizations can continue to operate or quickly recover their operations.
5. Cost Reduction: Well-planned IT risk management can lead to cost savings. By identifying and mitigating risks, organizations can reduce the financial impact of potential incidents and allocate resources more efficiently.
6. Decision Support: IT risk assessments provide valuable insights into the vulnerabilities and threats an organization faces. This information aids in informed decision-making, such as prioritizing investments in security measures and risk mitigation strategies.
7. Competitive Advantage: Organizations that can demonstrate effective IT risk management practices often gain a competitive edge. Customers and partners are increasingly concerned about data security and compliance, making sound risk management a selling point.
COBIT® 5's Approach to IT Risk Management
COBIT® 5, the globally recognized framework for IT governance and management, offers a structured and effective approach to managing IT-related risks within organizations. Its approach can be summarized in a few key steps, making it accessible for organizations of various sizes and industries:
-
Understand Business Goals: First, know your organization's business objectives well. IT should support these goals.
-
Set Risk Tolerance: Decide how much risk you're willing to accept to achieve your business goals, like setting a limit on a game.
-
Identify IT Risks: Spot potential IT risks, such as cyber threats or software problems, just like noticing road obstacles.
-
Assess Risks: Estimate how big each risk is and how likely it is to happen, similar to evaluating the size of a road pothole and its likelihood of causing damage.
-
Respond to Risks: Decide what to do about each risk—avoid it, lessen its impact, transfer it (like getting insurance), or accept it, just as you choose to fix a pothole or take a different route.
-
Monitor Continuously: Keep an eye on risks all the time, like watching the road while driving, and adjust your plans if new risks appear.
-
Communicate Clearly: Make sure everyone in your organization understands the risks and what you're doing to manage them.
-
Report and Follow Rules: Share information about how you're handling risks with key people and stay in line with laws and standards.
-
Learn and Improve: Keep learning from your experiences with risk management to get better at it over time, like becoming a better driver after each trip.
In simple terms, COBIT® 5's approach to IT risk management is like planning a safe journey. You know where you want to go (business goals), identify potential roadblocks (IT risks), set limits on how risky you're willing to be, and use strategies to navigate safely. This helps organizations protect their IT systems and make smart choices in the digital world.
Benefits of Integrating COBIT® 5 with IT Risk Management
Integrating COBIT® 5, a comprehensive framework for IT governance and management, with IT risk management brings several significant benefits to organizations. This integration creates a powerful synergy that enhances an organization's ability to identify, assess, mitigate, and monitor IT-related risks effectively. Here are the key advantages:
-
Business Alignment: Aligns IT activities with what the organization wants to achieve, ensuring that IT supports business goals.
-
Proactive Risk Management: Helps spot and address IT risks before they become big problems.
-
Informed Decision-Making: Provides insights for smart decisions about IT investments and how to deal with risks.
-
Regulatory Compliance: Makes it easier to follow rules and regulations related to IT risk management.
-
Efficient Resource Use: Helps allocate resources wisely by focusing on the most important risks.
-
Clear Communication: Makes it easy to explain IT risks and how they're being managed to everyone in the organization.
-
Adaptation to Change: Keeps an eye on risks and adjusts strategies as needed to stay safe in a changing world.
-
Easier Audits: Simplifies the process of checking that risk management practices are working correctly.
-
Competitive Advantage: Organizations that do this well look better to customers and partners who care about data security and following the rules.
COBIT® 5's Framework for IT Risk Management
COBIT® 5 provides a structured and comprehensive framework for IT risk management within organizations. This framework offers a clear path to identify, assess, mitigate, and monitor IT-related risks effectively. Here are the key components and steps in COBIT® 5's framework for IT risk management:
-
Identify Risks: Find potential IT risks that could harm your organization, like cyber threats or data problems.
-
Assess Risks: Figure out how big each risk is and how likely it is to happen, so you know which ones need attention.
-
Manage Risks: Decide what to do about each risk—avoid it, lessen its impact, transfer it (like insurance), or accept it.
-
Keep an Eye Out: Continuously watch for changes in risks and adjust your plans accordingly.
-
Report Clearly: Share what you're doing about risks with everyone in your organization and make sure to document everything.
-
Follow the Rules: Make sure your risk management follows the laws and rules that apply to your business.
-
Learn and Get Better: Keep learning from your experiences with risk management to do it even better next time.
-
Integrate with Everything: Make sure risk management is part of all your IT decisions and fits with your overall goals.
In simple terms, COBIT® 5's framework for IT risk management is like a clear roadmap to help organizations handle IT risks wisely. It guides you in spotting risks, figuring out how to deal with them, and making sure you're following the rules and improving over time. This helps keep your organization safe and successful in the digital world.
Practical Implementation Steps
Implementing COBIT® 5's IT risk management framework involves practical steps to ensure a systematic and effective approach to managing IT-related risks within your organization. Here are the key implementation steps:
-
Assign Responsibilities: Appoint people to handle risk management tasks and make sure senior leaders support the process.
-
Set Risk Limits: Decide how much risk your organization can accept for different types of IT activities.
-
Spot Risks: Identify potential IT risks using your team's knowledge and available data.
-
Check Risks: Evaluate each risk to see how big it is and how likely it is to happen, and then prioritize them.
-
Make Risk Plans: Create plans to deal with the most important risks, deciding whether to avoid them, reduce their impact, transfer them (like buying insurance), or accept them.
-
Integrate with Everything: Make sure risk management is part of your regular IT processes and document it.
-
Keep Watch: Set up a system to keep an eye on how risks change and how your plans are working.
-
Tell Everyone: Regularly tell your team and leaders about the risks and what you're doing to manage them.
-
Keep Records: Write down everything you do related to risk management.
-
Train and Learn: Teach your team about risk management and learn from your experiences to get better over time.
-
Follow the Rules: Make sure your risk management meets the laws and rules that apply to your business.
-
Get Help If Needed: Consider getting outside experts to help or assess your risk management.
In simple terms, these steps help organizations manage IT risks effectively, aligning with their goals and complying with rules while learning and improving along the way.
Real-world Examples
Here are some real-world examples of organizations that have successfully implemented COBIT® 5's IT risk management framework:
-
JPMorgan Chase & Co.: JPMorgan Chase, one of the world's largest financial institutions, utilizes COBIT® 5's IT risk management framework to ensure the security and reliability of its IT systems. The framework helps them identify and assess risks associated with their extensive digital operations, including online banking and financial services. It enables them to proactively address cybersecurity threats, data breaches, and regulatory compliance challenges.
-
The World Bank: The World Bank, a global financial institution, leverages COBIT® 5 to manage IT risks across its diverse operations. They use the framework to identify and assess risks related to the implementation of technology in development projects. This helps them mitigate potential project delays, budget overruns, and data security issues.
-
Dubai Electricity and Water Authority (DEWA): DEWA, the utility provider for Dubai, uses COBIT® 5 to enhance IT risk management in the context of critical infrastructure. They apply the framework to identify and address risks associated with their energy and water supply systems. This ensures the reliability and resilience of their services, even in the face of IT-related challenges.
-
PwC (PricewaterhouseCoopers): As a leading global professional services firm, PwC employs COBIT® 5 for IT risk management to help their clients across various industries. They assist organizations in identifying and managing IT risks to enhance cybersecurity, regulatory compliance, and overall operational efficiency.
-
Nestlé: Nestlé, the multinational food and beverage company, uses COBIT® 5's IT risk management framework to ensure the integrity of its global IT systems. This includes managing risks related to data privacy, supply chain, and production systems. The framework helps Nestlé maintain the trust of its customers and regulators while ensuring the smooth operation of its business.
These real-world examples demonstrate how organizations across different sectors, including finance, development, utilities, and professional services, leverage COBIT® 5's IT risk management framework to enhance their IT governance and protect their operations from a wide range of IT-related risks. This illustrates the versatility and effectiveness of COBIT® 5 in managing IT risks in various contexts.
Challenges and Considerations
Implementing COBIT® 5's IT risk management framework comes with a set of challenges and considerations that organizations should carefully address. One significant challenge is resource allocation, involving finding the right personnel and financial investments for risk management initiatives. Changing the organizational culture to prioritize risk management can be a formidable hurdle, as it requires strong leadership support and effective communication to instill the importance of risk management across all levels of the organization. The complexity of modern IT environments, with their ever-evolving nature, presents another challenge, necessitating the use of advanced monitoring tools and regular risk assessments to keep up. Adhering to regulatory requirements is a critical consideration, especially as rules can change frequently, making it vital to stay informed and seek expert guidance when needed.
Safeguarding sensitive data from breaches and cyberattacks remains a constant challenge, demanding robust cybersecurity measures and well-defined incident response plans. Integrating COBIT® 5's IT risk management framework with existing IT governance processes may pose difficulties, necessitating expert guidance and a strategic approach to ensure seamless integration. Building and maintaining the necessary skills and knowledge within the organization for effective risk management requires investment in training and development programs. Overcoming resistance to change and managing organizational change effectively is essential, as implementing new risk management processes can meet with opposition. Finally, measuring the effectiveness of risk management efforts and reporting on them in a clear and meaningful way can be complex, requiring the definition of key performance indicators and metrics to evaluate success and communicate progress to stakeholders. Addressing these challenges and considerations strategically empowers organizations to protect their IT assets, align IT with business objectives, and ensure resilience in an ever-evolving digital landscape.
How to obtain the COBIT Foundation Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
IT Service Management & Governance: COBIT, ISO
Conclusion
In conclusion, COBIT® 5's IT risk management framework offers organizations a structured and comprehensive approach to navigate the complex landscape of IT-related risks. While it brings substantial benefits such as enhanced alignment with business goals, proactive risk identification, and improved decision-making, it also presents various challenges and considerations. These challenges include resource allocation, cultural change, the complexity of IT environments, regulatory compliance, data security, integration with existing processes, skills and training, change management, and effective measurement and reporting.
Despite these challenges, organizations that commit to implementing COBIT® 5's framework stand to gain in terms of better IT risk management, alignment with regulatory requirements, and enhanced data security. It empowers organizations to proactively identify and address risks, ultimately safeguarding their IT assets and ensuring their resilience in an ever-evolving digital landscape. Therefore, while the road to effective IT risk management may be challenging, the destination of a secure and well-aligned IT environment is well worth the journey.
CMMI for Agile: Integrating Agile Practices with CMMI Certification
In today's fast-paced and ever-evolving business landscape, organizations are continually seeking ways to deliver high-quality products and services while remaining agile and responsive to customer needs. Agile methodologies have emerged as a beacon of adaptability and customer-centricity, empowering teams to iterate quickly and stay in tune with market demands. Simultaneously, the Capability Maturity Model Integration (CMMI) provides a structured framework for process improvement, ensuring consistency, reliability, and efficiency in operations.
But what happens when you bring these two seemingly contrasting worlds together? Can Agile practices and CMMI certification coexist harmoniously, allowing organizations to reap the benefits of both approaches? The answer is a resounding "yes." This blog explores the dynamic intersection of Agile and CMMI, shedding light on how organizations can successfully integrate Agile practices with CMMI certification, ultimately achieving a unique synergy that enhances both agility and process maturity. Join us on this journey of discovery as we uncover the strategies, challenges, and advantages of merging Agile with CMMI, ushering in a new era of process excellence and customer satisfaction.
Table of Contents
-
Understanding CMMI and Agile Methodologies
-
Benefits of Combining CMMI and Agile
-
Mapping Agile Practices to CMMI Framework
-
Tailoring CMMI for Agile Environments
-
Roles and Responsibilities in Agile CMMI Integration
-
Measuring Agile Performance with CMMI Metrics
-
Agile CMMI Certification Levels
-
Challenges in Integrating Agile and CMMI
-
Training and Skill Development for Agile CMMI
-
Continuous Improvement in Agile CMMI
-
Tools and Software for Agile CMMI Integration
-
Audit and Assessment for Agile CMMI Certification
-
Scaling Agile with CMMI
-
Future Trends in Agile CMMI Integration
-
Conclusion
Understanding CMMI and Agile Methodologies
CMMI (Capability Maturity Model Integration) is a framework that enables organizations to enhance their processes and consistently deliver high-quality products and services. It encompasses maturity levels and specific process areas to guide organizations towards process improvement and optimization. CMMI promotes a culture of continuous improvement, encouraging organizations to monitor, measure, and refine their processes over time. Organizations can undergo CMMI assessments to gauge their process maturity and, if they meet the criteria, seek formal certification.
On the other hand, Agile methodologies are a set of principles and practices for software development and project management that prioritize adaptability, collaboration, and customer feedback. Agile embraces iterative and incremental development, frequent customer involvement, and cross-functional teams. It relies on empirical data and regular inspections to make informed decisions and respond to changing requirements. Agile is guided by the Agile Manifesto and its principles, emphasizing customer collaboration and working solutions.
The relationship between CMMI and Agile involves integrating these approaches to achieve higher levels of process maturity while retaining the flexibility and customer-centric focus of Agile methodologies. This integration, known as "Agile CMMI" or "CMMI for Agile," allows organizations to improve their processes systematically while remaining agile and responsive in an ever-evolving business landscape. By combining the strengths of both CMMI and Agile, organizations can enhance their capabilities, deliver value more efficiently, and meet customer needs effectively.
Benefits of Combining CMMI and Agile
-
Better Processes: CMMI improves your organization's processes, making them more efficient and effective.
-
Flexibility: Agile's adaptability to change is retained, ensuring you can respond quickly to customer needs.
-
Quality: The integration enhances product quality and reduces defects.
-
Customer Satisfaction: Agile's customer focus, combined with CMMI, leads to higher customer satisfaction.
-
Risk Management: You can identify and manage risks more effectively, reducing project disruptions.
-
Resource Efficiency: It helps optimize resource allocation and utilization for dynamic projects.
-
Compliance: You can meet industry standards and compliance requirements while using Agile practices.
-
Culture of Improvement: It fosters a culture of continuous improvement within your organization.
-
Measurable Progress: You can measure and track your progress effectively.
-
Competitive Advantage: Successful integration can give you a competitive edge by delivering high-quality products or services faster and more efficiently.
Mapping Agile Practices to CMMI Framework
Mapping Agile practices to the CMMI (Capability Maturity Model Integration) framework is a strategic approach that enables organizations to combine the agility of Agile methodologies with the structured process improvement provided by CMMI. In this integration, Agile principles and practices align with specific CMMI process areas and goals. For instance, Agile's emphasis on customer collaboration and responsiveness can be linked to CMMI's objectives related to managing requirements effectively and handling change through configuration management. Sprints and iterations in Agile neatly correspond to CMMI's project planning and monitoring and control process areas, and Agile's focus on continuous integration aligns with CMMI's configuration management practices. By mapping these connections, organizations can ensure that their Agile practices contribute to meeting CMMI compliance requirements while still reaping the benefits of Agile's customer-centric, iterative approach to development.
Furthermore, mapping Agile practices to CMMI facilitates a data-driven approach to decision-making by connecting Agile metrics and practices with CMMI's measurement and analysis process area. Agile teams can use metrics like velocity and burndown charts in conjunction with CMMI's goals to continuously improve processes and product quality. This integration also helps organizations manage large-scale Agile projects by considering CMMI for Development, which extends CMMI's process areas to address scalability and complex development environments. Ultimately, the mapping of Agile practices to the CMMI framework empowers organizations to harmonize two powerful methodologies, enhancing both process maturity and agility in their software development and project management endeavors.
Tailoring CMMI for Agile Environments
Tailoring CMMI (Capability Maturity Model Integration) for Agile environments is a strategic approach that recognizes the unique characteristics of Agile methodologies while harnessing the structured process improvement capabilities of CMMI. In this adaptation, organizations embrace Agile's core values such as customer collaboration, responsiveness to change, and iterative development, while identifying the areas within CMMI that can support and enhance these principles. Agile's preference for working software over excessive documentation is met by streamlining documentation requirements, ensuring that any documentation created serves a meaningful purpose. Additionally, tailored metrics in Agile environments shift the focus towards velocity, burndown rates, and customer satisfaction, aligning more closely with Agile project goals and priorities. The synergy between Agile's iterative cycles and CMMI's process improvement cycles allows for continuous enhancements in Agile projects while maintaining the rigor of CMMI.
Moreover, effective tailoring encourages cross-functional collaboration between Agile teams and CMMI practitioners, fostering an environment where the strengths of both approaches are leveraged. This collaboration results in valuable insights, shared best practices, and a culture of ongoing process improvement. By documenting the tailoring decisions and promoting a culture of continuous improvement, organizations can ensure that their tailored CMMI-Agile framework remains flexible, adaptable, and aligned with the ever-evolving needs of Agile development projects. In essence, tailoring CMMI for Agile environments allows organizations to strike a harmonious balance between structured process improvement and the agile, customer-focused, and iterative nature of Agile methodologies, ultimately driving higher-quality outcomes in software development and project management.
Roles and Responsibilities in Agile CMMI Integration
-
Agile Coach:
-
Responsibilities: Guides Agile practices and helps teams understand how Agile aligns with CMMI.
-
CMMI Process Improvement Lead:
-
Responsibilities: Oversees CMMI process improvements and ensures they fit Agile environments.
-
Scrum Masters and Agile Team Members:
-
Responsibilities: Scrum Masters facilitate Agile processes, while team members adapt Agile practices for CMMI.
-
Product Owners and Business Analysts:
-
Responsibilities: Define and prioritize requirements, ensuring they align with Agile and CMMI standards.
-
Quality Assurance and Testing Specialists:
-
Responsibilities: Ensure product quality through testing, adapting to Agile iterations while following CMMI quality practices.
-
Project Managers or Release Managers:
-
Responsibilities: Oversee project or release planning, ensuring alignment with CMMI process areas.
-
Change Agents and Champions:
-
Responsibilities: Advocate for Agile CMMI integration, promote best practices, and encourage a culture of improvement.
-
Auditors and Assessors:
-
Responsibilities: Conduct CMMI assessments and audits to verify compliance and provide feedback for improvement.
Clear communication and collaboration among these roles are essential for successful Agile CMMI integration, enhancing the organization's ability to deliver high-quality products and services while maintaining Agile principles.
Measuring Agile Performance with CMMI Metrics
Measuring Agile performance with CMMI metrics is a strategic approach that bridges the gap between the Agile methodologies' iterative, customer-focused practices and CMMI's structured process improvement framework. These metrics provide organizations with valuable insights into their Agile processes, aligning them with CMMI's goals of efficiency, quality, and continuous improvement. Metrics such as velocity, cycle time, and burndown charts enable teams to monitor progress, identify bottlenecks, and optimize their workflow within the Agile framework. Customer satisfaction surveys and feedback response times ensure that Agile teams remain customer-centric, meeting the requirements of CMMI's customer focus. Additionally, defect density and work item aging metrics help maintain product quality while highlighting areas for improvement, aligning with CMMI's emphasis on quality management.
The integration of CMMI metrics into Agile environments promotes a culture of measurement and analysis, enabling organizations to make data-driven decisions. This not only enhances the organization's ability to deliver high-quality products and services but also ensures compliance with CMMI standards. Ultimately, measuring Agile performance with CMMI metrics empowers organizations to leverage the strengths of both approaches, fostering greater process maturity, efficiency, and customer satisfaction in Agile development and project management.
Agile CMMI Certification Levels
-
CMMI Maturity Levels: CMMI certification involves maturity levels, from Level 1 to Level 5, representing increasing process maturity and capability.
-
Agile Integration: Organizations can integrate Agile practices into these CMMI maturity levels to maintain flexibility while meeting CMMI requirements.
-
Certification Assessment: Certified appraisers or auditors assess an organization's processes, including the integration of Agile practices, to determine certification eligibility.
-
Tailored CMMI: Some organizations use tailored CMMI frameworks that provide specific guidance on incorporating Agile practices at different maturity levels.
-
Industry Requirements: Compliance with CMMI, Agile, or both may be necessary to meet industry standards and client expectations.
-
Consult Experts: Seek guidance from CMMI experts or certification authorities for the latest information and specific certification requirements related to Agile and CMMI integration.
Challenges in Integrating Agile and CMMI
-
Cultural Differences: Balancing Agile's flexibility with CMMI's structured approach can be a cultural challenge.
-
Documentation: Finding the right balance between extensive CMMI documentation and Agile's minimal documentation can be tricky.
-
Resistance to Change: Teams may resist shifting from traditional CMMI practices to Agile or adding perceived bureaucracy to Agile.
-
Mapping Practices: Aligning Agile practices with CMMI requirements and maturity levels requires careful mapping.
-
Process Tailoring: Customizing CMMI practices to fit Agile environments is challenging but necessary.
-
Metrics: Developing metrics that effectively measure performance in an integrated approach can be difficult.
-
Resource Allocation: Allocating resources for both Agile and CMMI efforts must be balanced.
-
Audit and Assessment: Preparing for CMMI assessments and audits in Agile settings requires planning.
-
Skills and Training: Ensuring that team members have the skills for the integrated approach is vital.
-
Sustainability: Maintaining the integration over time and preventing it from becoming a one-time effort is a challenge that requires ongoing commitment and adaptation.
Training and Skill Development for Agile CMMI
Training and skill development are fundamental pillars of achieving a successful integration of Agile and CMMI within an organization. In such an integrated environment, team members, leaders, and practitioners need a comprehensive understanding of both Agile methodologies and CMMI standards to effectively navigate the complexities of this hybrid approach. Initially, basic Agile training establishes a common foundation, fostering an understanding of Agile principles and practices, such as Scrum or Kanban. Concurrently, CMMI-specific training introduces the organization to the CMMI framework's concepts, maturity levels, and process areas.
The critical component lies in integration awareness, where dedicated training sessions and workshops enlighten participants about how Agile practices seamlessly align with CMMI goals while highlighting areas requiring adaptation. These sessions underscore the importance of tailoring CMMI processes to Agile settings, facilitating a smooth transition. Furthermore, training extends to leadership roles, equipping managers and executives with Agile leadership principles and the skills needed to support and lead in an Agile CMMI environment. Ultimately, a continuous learning culture, role-specific training, and feedback mechanisms ensure that individuals and teams stay agile in their approach to process improvement, product development, and compliance, thereby enhancing the organization's ability to excel in both agility and quality assurance.
Continuous Improvement in Agile CMMI
Continuous improvement in Agile CMMI environments represents an ongoing commitment to excellence in process, product, and service delivery. By seamlessly integrating Agile's iterative, customer-centric approach with CMMI's structured process improvement framework, organizations create a powerful engine for relentless enhancement. Agile retrospectives, data-driven decision-making, and Kaizen principles are instrumental in identifying and addressing areas for improvement at the team level. These practices dovetail with CMMI's emphasis on process optimization and quality assurance, resulting in a culture of constant self-assessment and refinement. Data collected through Agile practices, such as velocity and customer feedback, serves as a valuable input for CMMI-compliant measurement and analysis, further aligning the two methodologies.
Moreover, in Agile CMMI environments, continuous improvement extends beyond processes to encompass skill development and leadership support. By nurturing a culture of learning and adaptation, organizations empower their teams and leaders to stay agile in their approach to both product development and process maturity. The synergy between Agile's adaptability and CMMI's rigor creates an environment where innovation and efficiency thrive, ultimately enabling organizations to deliver high-quality products and services that meet customer needs while ensuring compliance with CMMI standards. Top of Form
Tools and Software for Agile CMMI Integration
Tools and software play a crucial role in facilitating the integration of Agile and CMMI methodologies within an organization. These tools bridge the gap between Agile's flexibility and CMMI's structured processes, aiding in the seamless coexistence of both approaches. Project management tools like Jira and Azure DevOps enable Agile teams to plan, track, and manage their work efficiently while accommodating CMMI process areas. Agile Lifecycle Management (ALM) tools such as VersionOne and Rally provide comprehensive support for Agile practices and can be customized to align with CMMI standards. Requirements management tools ensure traceability and compliance with CMMI requirements, while test management tools contribute to quality assurance, aligning with CMMI's focus on testing. Configuration management and version control tools help organizations meet CMMI's configuration management process area requirements. Collaboration and communication tools foster transparency and knowledge sharing among Agile teams, making it easier to document and communicate process improvements. Metrics and analytics tools enable organizations to collect and analyze data for both Agile and CMMI goals, facilitating data-driven process enhancements. DevOps and CI/CD tools automate and streamline development and deployment processes, aligning with CMMI's process automation practices. Specialized process improvement tools may also be employed to support the adoption and assessment of CMMI practices, ensuring continuous process maturity enhancements.
However, the success of these tools in Agile CMMI integration hinges on how they are configured, customized, and integrated into the organization's workflows. Additionally, tool selection should be based on the specific needs and objectives of Agile CMMI integration. The tools serve as enablers, helping organizations achieve the dual goals of delivering high-quality products or services through Agile practices while adhering to the structured process improvement framework of CMMI.
Audit and Assessment for Agile CMMI Certification
The audit and assessment process for Agile CMMI certification is a rigorous and comprehensive evaluation that determines an organization's adherence to both Agile methodologies and CMMI process improvement standards. The journey begins with careful preparation, where trained CMMI appraisers assess an organization's documentation, scrutinize Agile artifacts, and conduct a gap analysis to identify areas of alignment and potential deviations. On-site assessments involve in-depth interviews, observations, and artifact reviews to gauge how Agile practices are implemented in practice. Data collected during the assessment, including Agile-specific metrics and process performance, forms the basis for analysis, leading to documented findings and recommendations.
The ultimate goal of Agile CMMI certification is to demonstrate that an organization can balance the adaptability and customer-centricity of Agile with the structured process improvement focus of CMMI. The certification decision is made by an external body, based on the assessment results, and organizations may receive maturity or capability level ratings. Beyond certification, the process serves as a catalyst for ongoing improvement, as organizations develop action plans to address recommendations and engage in periodic follow-up assessments to ensure that the integrated Agile-CMMI framework remains effective and aligned with evolving goals. This holistic approach to assessment underscores the commitment to continuous improvement, quality, and process maturity in Agile development and project management.
Scaling Agile with CMMI
Scaling Agile with CMMI is a strategic approach that harmonizes the flexibility and customer-centricity of Agile methodologies with the structured process improvement framework of CMMI, allowing organizations to effectively manage larger and more complex projects and portfolios. This integration typically begins by selecting a suitable Agile scaling framework like SAFe or LeSS, which provides guidance on how to expand Agile practices while ensuring alignment with CMMI goals. Customization of the chosen framework is crucial to adapt CMMI process areas to Agile practices and vice versa, striking the right balance between Agile's adaptability and CMMI's process rigor.
Leadership support plays a pivotal role in fostering this integration, as leaders champion the effort, allocate necessary resources, and actively engage in aligning Agile and CMMI practices. Organizations must prioritize continuous improvement, regularly assessing the integration's effectiveness through metrics, feedback, and assessment processes. By promoting a culture of collaboration, providing training and skill development, and maintaining compliance with CMMI standards through periodic assessments, organizations can successfully scale Agile while achieving the desired levels of process maturity and product quality. The result is a dynamic and adaptable approach to project and product management that thrives in complex and evolving business landscapes.
Future Trends in Agile CMMI Integration
The future of Agile CMMI integration promises to be both dynamic and transformative, reflecting the ever-evolving landscape of software development and process improvement. One key trend is the increasing role of AI and automation in optimizing processes and decision-making. AI-driven tools will assist organizations in analyzing vast datasets, identifying patterns, and recommending improvements, making Agile CMMI integration more data-driven and efficient. Additionally, as Agile principles continue to resonate with organizations seeking agility and customer-centricity, scaling Agile practices beyond individual teams to the entire enterprise will remain a prominent trend. Frameworks like SAFe and LeSS will evolve to support larger and more complex organizations in their Agile journeys, allowing them to balance agility with the structured process improvement goals of CMMI.
Another critical trend is the integration of security and compliance practices into Agile CMMI environments. With cybersecurity concerns on the rise, organizations will work to harmonize Agile's rapid delivery with CMMI's focus on risk management and compliance, ensuring that security and regulatory requirements are seamlessly embedded into the development process. As remote and distributed work become increasingly prevalent, Agile CMMI integration will adapt to address the unique challenges of virtual collaboration and process adherence. This adaptability, along with a growing emphasis on cultural transformation, will be instrumental in organizations' efforts to foster a culture of innovation, collaboration, and continuous learning, ultimately driving successful Agile CMMI integration in the years to come.
How to obtain the CMMI certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab ,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
IT Service Management & Governance: COBIT, ISO
Conclusion
In conclusion, Agile CMMI integration represents a powerful approach for organizations seeking to balance the flexibility and customer-centricity of Agile methodologies with the structured process improvement framework of CMMI. This integration enables organizations to achieve high levels of process maturity while delivering high-quality products and services. The process involves careful customization of Agile practices and CMMI process areas, leadership support, continuous improvement efforts, and a commitment to aligning Agile and CMMI principles. As the business landscape evolves, the integration of Agile and CMMI will continue to adapt to meet new challenges and opportunities.
Future trends in Agile CMMI integration, including the use of AI, scaling Agile practices, and the integration of security and compliance, will shape the way organizations approach process improvement and Agile delivery. Cultural transformation and a focus on value stream management will also play critical roles in the success of Agile CMMI integration efforts. Overall, the integration of Agile and CMMI is a journey toward achieving process excellence and delivering exceptional value to customers, and it will remain a key strategy for organizations striving to excel in an ever-changing world.
Read More
In today's fast-paced and ever-evolving business landscape, organizations are continually seeking ways to deliver high-quality products and services while remaining agile and responsive to customer needs. Agile methodologies have emerged as a beacon of adaptability and customer-centricity, empowering teams to iterate quickly and stay in tune with market demands. Simultaneously, the Capability Maturity Model Integration (CMMI) provides a structured framework for process improvement, ensuring consistency, reliability, and efficiency in operations.
But what happens when you bring these two seemingly contrasting worlds together? Can Agile practices and CMMI certification coexist harmoniously, allowing organizations to reap the benefits of both approaches? The answer is a resounding "yes." This blog explores the dynamic intersection of Agile and CMMI, shedding light on how organizations can successfully integrate Agile practices with CMMI certification, ultimately achieving a unique synergy that enhances both agility and process maturity. Join us on this journey of discovery as we uncover the strategies, challenges, and advantages of merging Agile with CMMI, ushering in a new era of process excellence and customer satisfaction.
Table of Contents
-
Understanding CMMI and Agile Methodologies
-
Benefits of Combining CMMI and Agile
-
Mapping Agile Practices to CMMI Framework
-
Tailoring CMMI for Agile Environments
-
Roles and Responsibilities in Agile CMMI Integration
-
Measuring Agile Performance with CMMI Metrics
-
Agile CMMI Certification Levels
-
Challenges in Integrating Agile and CMMI
-
Training and Skill Development for Agile CMMI
-
Continuous Improvement in Agile CMMI
-
Tools and Software for Agile CMMI Integration
-
Audit and Assessment for Agile CMMI Certification
-
Scaling Agile with CMMI
-
Future Trends in Agile CMMI Integration
-
Conclusion
Understanding CMMI and Agile Methodologies
CMMI (Capability Maturity Model Integration) is a framework that enables organizations to enhance their processes and consistently deliver high-quality products and services. It encompasses maturity levels and specific process areas to guide organizations towards process improvement and optimization. CMMI promotes a culture of continuous improvement, encouraging organizations to monitor, measure, and refine their processes over time. Organizations can undergo CMMI assessments to gauge their process maturity and, if they meet the criteria, seek formal certification.
On the other hand, Agile methodologies are a set of principles and practices for software development and project management that prioritize adaptability, collaboration, and customer feedback. Agile embraces iterative and incremental development, frequent customer involvement, and cross-functional teams. It relies on empirical data and regular inspections to make informed decisions and respond to changing requirements. Agile is guided by the Agile Manifesto and its principles, emphasizing customer collaboration and working solutions.
The relationship between CMMI and Agile involves integrating these approaches to achieve higher levels of process maturity while retaining the flexibility and customer-centric focus of Agile methodologies. This integration, known as "Agile CMMI" or "CMMI for Agile," allows organizations to improve their processes systematically while remaining agile and responsive in an ever-evolving business landscape. By combining the strengths of both CMMI and Agile, organizations can enhance their capabilities, deliver value more efficiently, and meet customer needs effectively.
Benefits of Combining CMMI and Agile
-
Better Processes: CMMI improves your organization's processes, making them more efficient and effective.
-
Flexibility: Agile's adaptability to change is retained, ensuring you can respond quickly to customer needs.
-
Quality: The integration enhances product quality and reduces defects.
-
Customer Satisfaction: Agile's customer focus, combined with CMMI, leads to higher customer satisfaction.
-
Risk Management: You can identify and manage risks more effectively, reducing project disruptions.
-
Resource Efficiency: It helps optimize resource allocation and utilization for dynamic projects.
-
Compliance: You can meet industry standards and compliance requirements while using Agile practices.
-
Culture of Improvement: It fosters a culture of continuous improvement within your organization.
-
Measurable Progress: You can measure and track your progress effectively.
-
Competitive Advantage: Successful integration can give you a competitive edge by delivering high-quality products or services faster and more efficiently.
Mapping Agile Practices to CMMI Framework
Mapping Agile practices to the CMMI (Capability Maturity Model Integration) framework is a strategic approach that enables organizations to combine the agility of Agile methodologies with the structured process improvement provided by CMMI. In this integration, Agile principles and practices align with specific CMMI process areas and goals. For instance, Agile's emphasis on customer collaboration and responsiveness can be linked to CMMI's objectives related to managing requirements effectively and handling change through configuration management. Sprints and iterations in Agile neatly correspond to CMMI's project planning and monitoring and control process areas, and Agile's focus on continuous integration aligns with CMMI's configuration management practices. By mapping these connections, organizations can ensure that their Agile practices contribute to meeting CMMI compliance requirements while still reaping the benefits of Agile's customer-centric, iterative approach to development.
Furthermore, mapping Agile practices to CMMI facilitates a data-driven approach to decision-making by connecting Agile metrics and practices with CMMI's measurement and analysis process area. Agile teams can use metrics like velocity and burndown charts in conjunction with CMMI's goals to continuously improve processes and product quality. This integration also helps organizations manage large-scale Agile projects by considering CMMI for Development, which extends CMMI's process areas to address scalability and complex development environments. Ultimately, the mapping of Agile practices to the CMMI framework empowers organizations to harmonize two powerful methodologies, enhancing both process maturity and agility in their software development and project management endeavors.
Tailoring CMMI for Agile Environments
Tailoring CMMI (Capability Maturity Model Integration) for Agile environments is a strategic approach that recognizes the unique characteristics of Agile methodologies while harnessing the structured process improvement capabilities of CMMI. In this adaptation, organizations embrace Agile's core values such as customer collaboration, responsiveness to change, and iterative development, while identifying the areas within CMMI that can support and enhance these principles. Agile's preference for working software over excessive documentation is met by streamlining documentation requirements, ensuring that any documentation created serves a meaningful purpose. Additionally, tailored metrics in Agile environments shift the focus towards velocity, burndown rates, and customer satisfaction, aligning more closely with Agile project goals and priorities. The synergy between Agile's iterative cycles and CMMI's process improvement cycles allows for continuous enhancements in Agile projects while maintaining the rigor of CMMI.
Moreover, effective tailoring encourages cross-functional collaboration between Agile teams and CMMI practitioners, fostering an environment where the strengths of both approaches are leveraged. This collaboration results in valuable insights, shared best practices, and a culture of ongoing process improvement. By documenting the tailoring decisions and promoting a culture of continuous improvement, organizations can ensure that their tailored CMMI-Agile framework remains flexible, adaptable, and aligned with the ever-evolving needs of Agile development projects. In essence, tailoring CMMI for Agile environments allows organizations to strike a harmonious balance between structured process improvement and the agile, customer-focused, and iterative nature of Agile methodologies, ultimately driving higher-quality outcomes in software development and project management.
Roles and Responsibilities in Agile CMMI Integration
-
Agile Coach:
-
Responsibilities: Guides Agile practices and helps teams understand how Agile aligns with CMMI.
-
-
CMMI Process Improvement Lead:
-
Responsibilities: Oversees CMMI process improvements and ensures they fit Agile environments.
-
-
Scrum Masters and Agile Team Members:
-
Responsibilities: Scrum Masters facilitate Agile processes, while team members adapt Agile practices for CMMI.
-
-
Product Owners and Business Analysts:
-
Responsibilities: Define and prioritize requirements, ensuring they align with Agile and CMMI standards.
-
-
Quality Assurance and Testing Specialists:
-
Responsibilities: Ensure product quality through testing, adapting to Agile iterations while following CMMI quality practices.
-
-
Project Managers or Release Managers:
-
Responsibilities: Oversee project or release planning, ensuring alignment with CMMI process areas.
-
-
Change Agents and Champions:
-
Responsibilities: Advocate for Agile CMMI integration, promote best practices, and encourage a culture of improvement.
-
-
Auditors and Assessors:
-
Responsibilities: Conduct CMMI assessments and audits to verify compliance and provide feedback for improvement.
-
Clear communication and collaboration among these roles are essential for successful Agile CMMI integration, enhancing the organization's ability to deliver high-quality products and services while maintaining Agile principles.
Measuring Agile Performance with CMMI Metrics
Measuring Agile performance with CMMI metrics is a strategic approach that bridges the gap between the Agile methodologies' iterative, customer-focused practices and CMMI's structured process improvement framework. These metrics provide organizations with valuable insights into their Agile processes, aligning them with CMMI's goals of efficiency, quality, and continuous improvement. Metrics such as velocity, cycle time, and burndown charts enable teams to monitor progress, identify bottlenecks, and optimize their workflow within the Agile framework. Customer satisfaction surveys and feedback response times ensure that Agile teams remain customer-centric, meeting the requirements of CMMI's customer focus. Additionally, defect density and work item aging metrics help maintain product quality while highlighting areas for improvement, aligning with CMMI's emphasis on quality management.
The integration of CMMI metrics into Agile environments promotes a culture of measurement and analysis, enabling organizations to make data-driven decisions. This not only enhances the organization's ability to deliver high-quality products and services but also ensures compliance with CMMI standards. Ultimately, measuring Agile performance with CMMI metrics empowers organizations to leverage the strengths of both approaches, fostering greater process maturity, efficiency, and customer satisfaction in Agile development and project management.
Agile CMMI Certification Levels
-
CMMI Maturity Levels: CMMI certification involves maturity levels, from Level 1 to Level 5, representing increasing process maturity and capability.
-
Agile Integration: Organizations can integrate Agile practices into these CMMI maturity levels to maintain flexibility while meeting CMMI requirements.
-
Certification Assessment: Certified appraisers or auditors assess an organization's processes, including the integration of Agile practices, to determine certification eligibility.
-
Tailored CMMI: Some organizations use tailored CMMI frameworks that provide specific guidance on incorporating Agile practices at different maturity levels.
-
Industry Requirements: Compliance with CMMI, Agile, or both may be necessary to meet industry standards and client expectations.
-
Consult Experts: Seek guidance from CMMI experts or certification authorities for the latest information and specific certification requirements related to Agile and CMMI integration.
Challenges in Integrating Agile and CMMI
-
Cultural Differences: Balancing Agile's flexibility with CMMI's structured approach can be a cultural challenge.
-
Documentation: Finding the right balance between extensive CMMI documentation and Agile's minimal documentation can be tricky.
-
Resistance to Change: Teams may resist shifting from traditional CMMI practices to Agile or adding perceived bureaucracy to Agile.
-
Mapping Practices: Aligning Agile practices with CMMI requirements and maturity levels requires careful mapping.
-
Process Tailoring: Customizing CMMI practices to fit Agile environments is challenging but necessary.
-
Metrics: Developing metrics that effectively measure performance in an integrated approach can be difficult.
-
Resource Allocation: Allocating resources for both Agile and CMMI efforts must be balanced.
-
Audit and Assessment: Preparing for CMMI assessments and audits in Agile settings requires planning.
-
Skills and Training: Ensuring that team members have the skills for the integrated approach is vital.
-
Sustainability: Maintaining the integration over time and preventing it from becoming a one-time effort is a challenge that requires ongoing commitment and adaptation.
Training and Skill Development for Agile CMMI
Training and skill development are fundamental pillars of achieving a successful integration of Agile and CMMI within an organization. In such an integrated environment, team members, leaders, and practitioners need a comprehensive understanding of both Agile methodologies and CMMI standards to effectively navigate the complexities of this hybrid approach. Initially, basic Agile training establishes a common foundation, fostering an understanding of Agile principles and practices, such as Scrum or Kanban. Concurrently, CMMI-specific training introduces the organization to the CMMI framework's concepts, maturity levels, and process areas.
The critical component lies in integration awareness, where dedicated training sessions and workshops enlighten participants about how Agile practices seamlessly align with CMMI goals while highlighting areas requiring adaptation. These sessions underscore the importance of tailoring CMMI processes to Agile settings, facilitating a smooth transition. Furthermore, training extends to leadership roles, equipping managers and executives with Agile leadership principles and the skills needed to support and lead in an Agile CMMI environment. Ultimately, a continuous learning culture, role-specific training, and feedback mechanisms ensure that individuals and teams stay agile in their approach to process improvement, product development, and compliance, thereby enhancing the organization's ability to excel in both agility and quality assurance.
Continuous Improvement in Agile CMMI
Continuous improvement in Agile CMMI environments represents an ongoing commitment to excellence in process, product, and service delivery. By seamlessly integrating Agile's iterative, customer-centric approach with CMMI's structured process improvement framework, organizations create a powerful engine for relentless enhancement. Agile retrospectives, data-driven decision-making, and Kaizen principles are instrumental in identifying and addressing areas for improvement at the team level. These practices dovetail with CMMI's emphasis on process optimization and quality assurance, resulting in a culture of constant self-assessment and refinement. Data collected through Agile practices, such as velocity and customer feedback, serves as a valuable input for CMMI-compliant measurement and analysis, further aligning the two methodologies.
Moreover, in Agile CMMI environments, continuous improvement extends beyond processes to encompass skill development and leadership support. By nurturing a culture of learning and adaptation, organizations empower their teams and leaders to stay agile in their approach to both product development and process maturity. The synergy between Agile's adaptability and CMMI's rigor creates an environment where innovation and efficiency thrive, ultimately enabling organizations to deliver high-quality products and services that meet customer needs while ensuring compliance with CMMI standards. Top of Form
Tools and Software for Agile CMMI Integration
Tools and software play a crucial role in facilitating the integration of Agile and CMMI methodologies within an organization. These tools bridge the gap between Agile's flexibility and CMMI's structured processes, aiding in the seamless coexistence of both approaches. Project management tools like Jira and Azure DevOps enable Agile teams to plan, track, and manage their work efficiently while accommodating CMMI process areas. Agile Lifecycle Management (ALM) tools such as VersionOne and Rally provide comprehensive support for Agile practices and can be customized to align with CMMI standards. Requirements management tools ensure traceability and compliance with CMMI requirements, while test management tools contribute to quality assurance, aligning with CMMI's focus on testing. Configuration management and version control tools help organizations meet CMMI's configuration management process area requirements. Collaboration and communication tools foster transparency and knowledge sharing among Agile teams, making it easier to document and communicate process improvements. Metrics and analytics tools enable organizations to collect and analyze data for both Agile and CMMI goals, facilitating data-driven process enhancements. DevOps and CI/CD tools automate and streamline development and deployment processes, aligning with CMMI's process automation practices. Specialized process improvement tools may also be employed to support the adoption and assessment of CMMI practices, ensuring continuous process maturity enhancements.
However, the success of these tools in Agile CMMI integration hinges on how they are configured, customized, and integrated into the organization's workflows. Additionally, tool selection should be based on the specific needs and objectives of Agile CMMI integration. The tools serve as enablers, helping organizations achieve the dual goals of delivering high-quality products or services through Agile practices while adhering to the structured process improvement framework of CMMI.
Audit and Assessment for Agile CMMI Certification
The audit and assessment process for Agile CMMI certification is a rigorous and comprehensive evaluation that determines an organization's adherence to both Agile methodologies and CMMI process improvement standards. The journey begins with careful preparation, where trained CMMI appraisers assess an organization's documentation, scrutinize Agile artifacts, and conduct a gap analysis to identify areas of alignment and potential deviations. On-site assessments involve in-depth interviews, observations, and artifact reviews to gauge how Agile practices are implemented in practice. Data collected during the assessment, including Agile-specific metrics and process performance, forms the basis for analysis, leading to documented findings and recommendations.
The ultimate goal of Agile CMMI certification is to demonstrate that an organization can balance the adaptability and customer-centricity of Agile with the structured process improvement focus of CMMI. The certification decision is made by an external body, based on the assessment results, and organizations may receive maturity or capability level ratings. Beyond certification, the process serves as a catalyst for ongoing improvement, as organizations develop action plans to address recommendations and engage in periodic follow-up assessments to ensure that the integrated Agile-CMMI framework remains effective and aligned with evolving goals. This holistic approach to assessment underscores the commitment to continuous improvement, quality, and process maturity in Agile development and project management.
Scaling Agile with CMMI
Scaling Agile with CMMI is a strategic approach that harmonizes the flexibility and customer-centricity of Agile methodologies with the structured process improvement framework of CMMI, allowing organizations to effectively manage larger and more complex projects and portfolios. This integration typically begins by selecting a suitable Agile scaling framework like SAFe or LeSS, which provides guidance on how to expand Agile practices while ensuring alignment with CMMI goals. Customization of the chosen framework is crucial to adapt CMMI process areas to Agile practices and vice versa, striking the right balance between Agile's adaptability and CMMI's process rigor.
Leadership support plays a pivotal role in fostering this integration, as leaders champion the effort, allocate necessary resources, and actively engage in aligning Agile and CMMI practices. Organizations must prioritize continuous improvement, regularly assessing the integration's effectiveness through metrics, feedback, and assessment processes. By promoting a culture of collaboration, providing training and skill development, and maintaining compliance with CMMI standards through periodic assessments, organizations can successfully scale Agile while achieving the desired levels of process maturity and product quality. The result is a dynamic and adaptable approach to project and product management that thrives in complex and evolving business landscapes.
Future Trends in Agile CMMI Integration
The future of Agile CMMI integration promises to be both dynamic and transformative, reflecting the ever-evolving landscape of software development and process improvement. One key trend is the increasing role of AI and automation in optimizing processes and decision-making. AI-driven tools will assist organizations in analyzing vast datasets, identifying patterns, and recommending improvements, making Agile CMMI integration more data-driven and efficient. Additionally, as Agile principles continue to resonate with organizations seeking agility and customer-centricity, scaling Agile practices beyond individual teams to the entire enterprise will remain a prominent trend. Frameworks like SAFe and LeSS will evolve to support larger and more complex organizations in their Agile journeys, allowing them to balance agility with the structured process improvement goals of CMMI.
Another critical trend is the integration of security and compliance practices into Agile CMMI environments. With cybersecurity concerns on the rise, organizations will work to harmonize Agile's rapid delivery with CMMI's focus on risk management and compliance, ensuring that security and regulatory requirements are seamlessly embedded into the development process. As remote and distributed work become increasingly prevalent, Agile CMMI integration will adapt to address the unique challenges of virtual collaboration and process adherence. This adaptability, along with a growing emphasis on cultural transformation, will be instrumental in organizations' efforts to foster a culture of innovation, collaboration, and continuous learning, ultimately driving successful Agile CMMI integration in the years to come.
How to obtain the CMMI certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab ,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
IT Service Management & Governance: COBIT, ISO
Conclusion
In conclusion, Agile CMMI integration represents a powerful approach for organizations seeking to balance the flexibility and customer-centricity of Agile methodologies with the structured process improvement framework of CMMI. This integration enables organizations to achieve high levels of process maturity while delivering high-quality products and services. The process involves careful customization of Agile practices and CMMI process areas, leadership support, continuous improvement efforts, and a commitment to aligning Agile and CMMI principles. As the business landscape evolves, the integration of Agile and CMMI will continue to adapt to meet new challenges and opportunities.
Future trends in Agile CMMI integration, including the use of AI, scaling Agile practices, and the integration of security and compliance, will shape the way organizations approach process improvement and Agile delivery. Cultural transformation and a focus on value stream management will also play critical roles in the success of Agile CMMI integration efforts. Overall, the integration of Agile and CMMI is a journey toward achieving process excellence and delivering exceptional value to customers, and it will remain a key strategy for organizations striving to excel in an ever-changing world.
The Importance of AWS Solution Architects in Cloud Computing
In the ever-evolving landscape of cloud computing, where agility, scalability, and innovation reign supreme, there exists a key figure who plays a central role in shaping the digital destiny of organizations—AWS Solution Architects. These architects are the visionaries, the strategists, and the technical wizards who navigate the intricate web of Amazon Web Services (AWS) to design and orchestrate cloud solutions that power the modern enterprise.
Cloud computing has ushered in a new era of possibilities, revolutionizing the way businesses operate, innovate, and compete. Yet, harnessing the full potential of the cloud demands expertise and precision, and this is where AWS Solution Architects emerge as the unsung heroes. In this blog, we delve deep into the significance of AWS Solution Architects in the realm of cloud computing, uncovering their multifaceted roles, their impact on businesses, and the vital link they provide between technology and strategic success. Join us on a journey to understand why these architects are the linchpin in the cloud revolution and how their skills are reshaping the digital landscape.
Table of contents
-
Defining the Role of an AWS Solution Architect
-
The Growing Significance of Cloud Computing
-
Why Cloud Architecture Matters
-
AWS as a Leading Cloud Provider
-
The Challenges of Cloud Adoption
-
How AWS Solution Architects Address Business Needs
-
Cost Optimization and Efficiency
-
Security and Compliance in AWS Solutions
-
Scaling for Growth and Performance
-
Disaster Recovery and Business Continuity
-
Innovation and Future-Proofing
-
Certification and Training for AWS Solution Architects
-
Collaboration with Other IT Roles
-
The Role of AWS Partnerships
-
Conclusion
Defining the Role of an AWS Solution Architect
An AWS Solution Architect serves as a pivotal figure in the realm of cloud computing, tasked with the essential responsibility of designing, implementing, and optimizing cloud-based solutions tailored to meet the unique needs of organizations. At its core, this role revolves around crafting architectural blueprints that seamlessly integrate AWS services to build robust, scalable, secure, and cost-effective cloud infrastructures. With deep expertise in AWS services and best practices, Solution Architects act as the bridge between business objectives and technical execution. They collaborate closely with stakeholders, ensuring that every solution aligns with organizational goals while emphasizing security, compliance, and efficiency. Moreover, these professionals remain vigilant in their commitment to continuous learning, keeping pace with AWS's ever-evolving ecosystem to provide innovative, future-proof solutions.
The role of an AWS Solution Architect encompasses a multifaceted skill set, including cloud expertise, cost optimization, security prowess, and effective communication. Their role extends beyond technical implementation; it involves understanding the intricate nuances of an organization's operations and translating them into well-architected cloud solutions. Ultimately, AWS Solution Architects play a crucial role in driving business growth, innovation, and operational excellence through the harnessing of AWS's powerful cloud services, making them indispensable assets in today's cloud-centric world.
The Growing Significance of Cloud Computing
The growing significance of cloud computing represents a fundamental shift in the way businesses and individuals interact with technology. At its core, cloud computing offers unprecedented accessibility, scalability, and flexibility. Gone are the days of hefty upfront investments in on-premises infrastructure; instead, organizations can leverage cloud resources on-demand, enabling rapid adaptation to changing market dynamics. This agility is a game-changer, allowing businesses to pivot, scale, and innovate more swiftly than ever before. Furthermore, cloud computing has democratized access to advanced technologies like artificial intelligence, machine learning, and big data analytics, empowering businesses of all sizes to harness the power of these tools to drive growth and competitiveness.
Moreover, cloud computing has proven instrumental in facilitating remote work and collaboration. The COVID-19 pandemic underscored the essential role the cloud plays in enabling remote workforces and ensuring business continuity. It has become the backbone of modern collaboration tools, allowing teams to connect and work seamlessly regardless of geographical boundaries. Additionally, cloud providers have prioritized security, investing heavily in robust safeguards and compliance measures, assuaging concerns about data protection and privacy. As the cloud ecosystem continues to evolve, its significance will only intensify, serving as a catalyst for innovation, cost-efficiency, and strategic transformation in businesses and industries worldwide.
Why Cloud Architecture Matters
Cloud architecture is paramount in the modern business landscape for a multitude of reasons. Firstly, it serves as the blueprint for a company's digital infrastructure, determining how resources are provisioned, deployed, and managed in the cloud. This fundamental design impacts an organization's ability to scale rapidly in response to changing demands, control costs by efficiently allocating resources, and maintain the highest standards of security and compliance. Effective cloud architecture can make the difference between an agile, cost-effective, and secure operation and one that struggles to adapt to the fast-paced digital world.
Secondly, cloud architecture unlocks the potential for innovation and business agility. With the cloud's vast array of managed services, organizations can experiment and implement cutting-edge technologies like artificial intelligence, machine learning, and IoT without the burden of managing complex underlying infrastructure. Cloud-native development practices foster agility by enabling rapid development, testing, and deployment of applications. As remote work and global collaboration become the norm, the cloud also plays a pivotal role in providing accessibility to data and applications from anywhere, supporting businesses in their quest for operational continuity and growth. In essence, cloud architecture isn't just about IT; it's about the strategic foundation upon which businesses build their digital future.
AWS as a Leading Cloud Provider
Amazon Web Services (AWS) has solidified its position as the foremost cloud provider due to a combination of factors that set it apart in the industry. Its vast and constantly expanding service portfolio encompasses virtually every aspect of cloud computing, enabling businesses to not only migrate their existing infrastructure but also to innovate and transform their operations. This extensive range of services includes scalable computing resources, cutting-edge machine learning and analytics tools, secure storage options, and developer-friendly solutions like serverless computing, all backed by a global network of data centers. This versatility makes AWS suitable for startups, enterprises, government organizations, and virtually any industry seeking to harness the power of the cloud.
One of AWS's standout attributes is its relentless commitment to security and compliance. AWS invests heavily in advanced security features, encryption, and access controls, earning it the trust of highly regulated industries like healthcare and finance. Furthermore, AWS consistently obtains and maintains a broad array of compliance certifications, ensuring that customers can adhere to industry-specific regulations while leveraging the cloud's capabilities. This focus on security and compliance, combined with its innovation, reliability, and global reach, makes AWS not just a leading cloud provider but also a strategic partner for organizations worldwide as they navigate the complexities of the digital age.
The Challenges of Cloud Adoption
-
Security Concerns: Worries about data security and unauthorized access.
-
Compliance and Regulations: Meeting legal requirements and industry-specific regulations.
-
Data Migration: Moving existing data and applications to the cloud seamlessly.
-
Cost Management: Controlling cloud spending and optimizing costs.
-
Skills Gap: Lack of expertise in managing cloud environments.
-
Vendor Lock-In: Dependency on a single cloud provider.
-
Performance Issues: Ensuring consistent application performance.
-
Change Resistance: Employees resisting changes in processes and workflows.
-
Governance: Lack of clear policies for managing cloud resources.
-
Downtime and Availability: Dealing with occasional outages and downtime.
How AWS Solution Architects Address Business Needs Top of Form
AWS Solution Architects are instrumental in bridging the gap between an organization's business needs and the technological capabilities provided by Amazon Web Services. They start by deeply understanding the unique objectives and challenges faced by the business, working closely with stakeholders to align cloud solutions with these requirements. Whether it's optimizing costs, enhancing security, ensuring scalability, or addressing compliance concerns, Solution Architects craft tailored solutions that cater to these specific business needs. Their expertise in AWS services and best practices allows them to design robust architectures that not only meet current demands but also anticipate future growth and innovation.
Moreover, AWS Solution Architects provide a crucial layer of assurance and reliability to organizations. By prioritizing security measures and compliance, they ensure that data and operations are safeguarded, instilling confidence in cloud adoption. Their ability to create detailed technical documentation and collaborate effectively with cross-functional teams ensures the successful implementation of cloud solutions. In essence, AWS Solution Architects play a pivotal role in driving business success by leveraging AWS's powerful cloud capabilities to address the ever-evolving landscape of business needs, from cost efficiency and scalability to security and innovation.
Cost Optimization and Efficiency
Cost optimization and efficiency are paramount in the world of AWS as organizations seek to harness the cloud's power while keeping their budgets in check. AWS offers a multitude of tools and strategies to help businesses strike the right balance between performance and expenditure. One of the fundamental principles is resource optimization, where organizations carefully select the appropriate instance types, storage options, and services that align with their actual requirements. By avoiding overprovisioning and rightsizing their resources, businesses can prevent unnecessary spending and ensure that they pay only for what they use.
Furthermore, AWS provides advanced features like auto-scaling, which enables resources to automatically adapt to fluctuating workloads, optimizing both performance and costs. Reserved Instances and Spot Instances offer significant cost savings, allowing organizations to commit to long-term usage for predictable workloads or take advantage of surplus capacity for transient tasks. AWS's suite of monitoring and optimization tools empowers organizations to gain visibility into their cloud expenditure and make data-driven decisions to reduce costs. By continually reviewing and adjusting their cloud architecture, employing serverless computing for certain tasks, and educating teams on best practices, organizations can achieve a delicate balance between efficiency and cost control, ensuring that their AWS investments yield maximum value.
Security and Compliance in AWS Solutions
Security and compliance are foundational pillars in AWS solutions, reflecting the platform's unwavering commitment to safeguarding customer data and ensuring adherence to industry-specific regulations. AWS employs a multi-layered approach to security, starting with its shared responsibility model, which delineates responsibilities between AWS and its customers. AWS is responsible for securing the underlying infrastructure, while customers are tasked with securing their data, applications, and configurations. This model ensures that security is a collaborative effort, with AWS providing a secure cloud environment and customers implementing security best practices within it.
To bolster security, AWS offers a comprehensive suite of services, including IAM for access control, encryption for data protection, VPC for network isolation, and a range of monitoring and logging tools. AWS also invests heavily in compliance, obtaining and maintaining various certifications to meet the strictest regulatory requirements, such as HIPAA and GDPR. This commitment to security and compliance gives organizations the confidence to migrate sensitive workloads to the cloud while maintaining data integrity and adhering to industry-specific regulations. AWS's emphasis on security and compliance underscores its position as a trusted partner for businesses seeking to leverage the cloud's capabilities while mitigating potential risks.
Scaling for Growth and Performance
Scaling for growth and performance is a fundamental requirement in today's dynamic business landscape, and AWS provides organizations with a robust toolkit to achieve this scalability seamlessly. The heart of AWS's scaling capabilities lies in its auto-scaling features, which enable applications to dynamically adjust their compute resources in response to fluctuations in demand. This not only ensures that applications can handle sudden surges in traffic but also optimizes resource utilization during quieter periods, resulting in cost-effective operations.
Moreover, AWS promotes a serverless paradigm through services like AWS Lambda, allowing organizations to focus on code rather than infrastructure management. Serverless computing automatically scales resources in response to individual events, delivering exceptional performance and cost-efficiency without the need to provision or manage servers. Coupled with elastic load balancing, content delivery networks, and scalable databases, AWS empowers organizations to build resilient, high-performance applications that can seamlessly scale to accommodate growth while delivering optimal user experiences. Whether it's handling a sudden influx of customers or supporting continuous expansion, AWS's scaling capabilities are integral to modern businesses aiming for both agility and performance.
Disaster Recovery and Business Continuity
Disaster recovery and business continuity are foundational elements of AWS's cloud offerings, reflecting its commitment to ensuring the availability and resilience of critical business operations. AWS provides organizations with versatile tools and services to craft robust disaster recovery and business continuity strategies. This begins with AWS's high availability infrastructure, which spans multiple availability zones and regions, allowing businesses to deploy resources in geographically separate locations to guard against localized outages or disasters. Services like AWS Disaster Recovery (DR) as a Service (DRaaS) and AWS Site Recovery facilitate automated failover and replication of workloads, ensuring minimal downtime and seamless continuity in the event of a disaster or unforeseen event.
Moreover, AWS's backup solutions, such as Amazon S3 and Amazon EBS snapshots, enable organizations to create secure and scalable data backups, ensuring that critical information can be restored quickly and reliably. AWS's global content delivery network, Amazon CloudFront, accelerates content delivery, reducing latency and ensuring data remains accessible even during network disruptions. Additionally, the ability to simulate disaster scenarios and conduct testing exercises without impacting production environments empowers organizations to refine their disaster recovery and business continuity plans proactively. With these capabilities, AWS strengthens an organization's ability to navigate the unpredictable and safeguard its operations, data, and reputation in the face of adversity.
Innovation and Future-Proofing
Innovation and future-proofing are at the core of AWS solutions, allowing organizations to not only meet current challenges but also anticipate and adapt to future technological advancements. AWS's commitment to staying on the cutting edge of technology is evident through its constant introduction of new services and features that harness emerging trends like artificial intelligence, machine learning, IoT, and serverless computing. These innovations empower businesses to explore new frontiers, streamline operations, and enhance customer experiences. AWS's vast ecosystem of services provides organizations with the flexibility to experiment, iterate, and scale their solutions, fostering a culture of continuous innovation.
Furthermore, AWS's emphasis on cloud-native development practices, well-architected frameworks, and global infrastructure allows organizations to future-proof their operations. By adopting cloud-native principles such as microservices and DevOps, businesses can remain agile and responsive to changing market conditions. AWS's global reach ensures that organizations can expand their reach and serve customers globally, while the well-architected framework guides them in building resilient and efficient solutions that can withstand future challenges. With AWS, organizations have a partner that not only supports their current needs but also equips them with the tools and strategies to thrive in an ever-evolving digital landscape, positioning them for sustained success and innovation.
Certification and Training for AWS Solution Architects
-
Choose Your Certification Level: Start with the "AWS Certified Solutions Architect - Associate" certification, and you can progress to the "AWS Certified Solutions Architect - Professional" later.
-
Review Exam Objectives: Understand what topics are covered in the certification exam by reviewing the exam blueprint provided by AWS.
-
Access Training Resources: Utilize AWS's official training resources, including online courses and hands-on labs, available on the AWS Training and Certification portal.
-
Hands-On Practice: Gain practical experience by working on real AWS projects and experimenting with AWS services in a free-tier environment.
-
Practice Exams: Use practice exams and sample questions to test your knowledge and readiness for the certification exam.
-
Register for the Exam: Sign up for the certification exam through the AWS Certification portal.
-
Stay Updated: Keep yourself updated with the latest AWS services and best practices by attending webinars, reading documentation, and participating in the AWS community.
-
Recertify When Required: Be aware of recertification requirements and ensure you renew your certification when necessary to stay current.
By following these steps, you can work towards becoming a certified AWS Solutions Architect, demonstrating your expertise in designing and implementing AWS solutions.
Collaboration with Other IT Roles
Collaboration with various IT roles is a cornerstone of success for AWS Solution Architects in the complex world of cloud computing. Working closely with developers, architects help translate architectural designs into functional applications by providing guidance on best practices, security, and scalability. Collaboration with system administrators and DevOps engineers is essential to automate resource provisioning, implement CI/CD pipelines, and ensure the architecture's resilience. Solution Architects liaise with security specialists to embed security measures into the design, and with network engineers to configure networking components in line with performance and security needs. They also partner with database administrators to optimize database performance and with data scientists and analysts to create data solutions leveraging AWS's capabilities. Collaboration with project managers helps align architectural goals with project timelines and budgets, ensuring that cloud solutions are not only technically sound but also delivered on schedule and within budget.
This collaborative approach extends beyond technology, fostering a culture of teamwork and shared responsibility. It promotes effective communication and coordination among cross-functional teams, enabling them to collectively tackle challenges, make informed decisions, and deliver solutions that align with business objectives. In essence, AWS Solution Architects' ability to collaborate with a diverse set of IT roles is integral to their role as orchestrators of cloud excellence, ensuring that AWS solutions not only meet technical requirements but also drive business success.
The Role of AWS Partnerships
Here are the key points about the role of AWS partnerships in a simple format:
-
Expertise Access: AWS partnerships connect businesses with skilled professionals who have deep expertise in AWS technologies, helping organizations make informed decisions and optimize their cloud solutions.
-
Innovation Acceleration: Technology partners collaborate with AWS to create and integrate innovative products and services, allowing customers to harness cutting-edge technology without starting from scratch.
-
Enhanced Support: Consulting and managed service partners offer valuable support, acting as trusted advisors to guide businesses in adopting and managing AWS services effectively.
-
Global Presence: AWS partnerships provide access to AWS services and support in local regions, ensuring global reach and localized assistance for businesses with international operations.
-
Ecosystem Expansion: Partnerships contribute to an extensive ecosystem of third-party solutions that integrate seamlessly with AWS, offering a wide array of options to tailor cloud environments to specific needs.
-
Certified Solutions: AWS-certified partner solutions undergo rigorous testing and validation, ensuring compatibility, reliability, and quality for customers.
-
Resources and Support: AWS offers partners resources, training, marketing support, and co-selling opportunities, enabling them to better serve customers and grow their businesses.
AWS partnerships play a vital role in helping businesses leverage the full potential of AWS cloud services, providing expertise, innovation, and support to drive digital transformation and growth.
Conclusion
In conclusion, AWS Solution Architects hold a pivotal role in the realm of cloud computing, where businesses increasingly rely on AWS's vast array of services and infrastructure. These architects serve as the linchpin between technology and business, bridging the gap by designing, implementing, and optimizing cloud solutions that align with organizational goals. They navigate the complexities of AWS to create architectures that are secure, scalable, cost-efficient, and resilient.
The importance of AWS Solution Architects extends beyond technical prowess. They collaborate with diverse IT roles, facilitate innovation, and leverage AWS partnerships to enhance cloud capabilities. These architects play a key role in disaster recovery, business continuity, security, and compliance, safeguarding critical data and operations. They are instrumental in driving cost optimization, ensuring resources are used efficiently.
As businesses continue to embrace the cloud, AWS Solution Architects will remain essential in guiding these transformations. Their expertise, collaboration, and commitment to innovation enable organizations to thrive in the ever-evolving digital landscape, making them invaluable assets in the journey toward cloud excellence.
Read More
In the ever-evolving landscape of cloud computing, where agility, scalability, and innovation reign supreme, there exists a key figure who plays a central role in shaping the digital destiny of organizations—AWS Solution Architects. These architects are the visionaries, the strategists, and the technical wizards who navigate the intricate web of Amazon Web Services (AWS) to design and orchestrate cloud solutions that power the modern enterprise.
Cloud computing has ushered in a new era of possibilities, revolutionizing the way businesses operate, innovate, and compete. Yet, harnessing the full potential of the cloud demands expertise and precision, and this is where AWS Solution Architects emerge as the unsung heroes. In this blog, we delve deep into the significance of AWS Solution Architects in the realm of cloud computing, uncovering their multifaceted roles, their impact on businesses, and the vital link they provide between technology and strategic success. Join us on a journey to understand why these architects are the linchpin in the cloud revolution and how their skills are reshaping the digital landscape.
Table of contents
-
Defining the Role of an AWS Solution Architect
-
The Growing Significance of Cloud Computing
-
Why Cloud Architecture Matters
-
AWS as a Leading Cloud Provider
-
The Challenges of Cloud Adoption
-
How AWS Solution Architects Address Business Needs
-
Cost Optimization and Efficiency
-
Security and Compliance in AWS Solutions
-
Scaling for Growth and Performance
-
Disaster Recovery and Business Continuity
-
Innovation and Future-Proofing
-
Certification and Training for AWS Solution Architects
-
Collaboration with Other IT Roles
-
The Role of AWS Partnerships
-
Conclusion
Defining the Role of an AWS Solution Architect
An AWS Solution Architect serves as a pivotal figure in the realm of cloud computing, tasked with the essential responsibility of designing, implementing, and optimizing cloud-based solutions tailored to meet the unique needs of organizations. At its core, this role revolves around crafting architectural blueprints that seamlessly integrate AWS services to build robust, scalable, secure, and cost-effective cloud infrastructures. With deep expertise in AWS services and best practices, Solution Architects act as the bridge between business objectives and technical execution. They collaborate closely with stakeholders, ensuring that every solution aligns with organizational goals while emphasizing security, compliance, and efficiency. Moreover, these professionals remain vigilant in their commitment to continuous learning, keeping pace with AWS's ever-evolving ecosystem to provide innovative, future-proof solutions.
The role of an AWS Solution Architect encompasses a multifaceted skill set, including cloud expertise, cost optimization, security prowess, and effective communication. Their role extends beyond technical implementation; it involves understanding the intricate nuances of an organization's operations and translating them into well-architected cloud solutions. Ultimately, AWS Solution Architects play a crucial role in driving business growth, innovation, and operational excellence through the harnessing of AWS's powerful cloud services, making them indispensable assets in today's cloud-centric world.
The Growing Significance of Cloud Computing
The growing significance of cloud computing represents a fundamental shift in the way businesses and individuals interact with technology. At its core, cloud computing offers unprecedented accessibility, scalability, and flexibility. Gone are the days of hefty upfront investments in on-premises infrastructure; instead, organizations can leverage cloud resources on-demand, enabling rapid adaptation to changing market dynamics. This agility is a game-changer, allowing businesses to pivot, scale, and innovate more swiftly than ever before. Furthermore, cloud computing has democratized access to advanced technologies like artificial intelligence, machine learning, and big data analytics, empowering businesses of all sizes to harness the power of these tools to drive growth and competitiveness.
Moreover, cloud computing has proven instrumental in facilitating remote work and collaboration. The COVID-19 pandemic underscored the essential role the cloud plays in enabling remote workforces and ensuring business continuity. It has become the backbone of modern collaboration tools, allowing teams to connect and work seamlessly regardless of geographical boundaries. Additionally, cloud providers have prioritized security, investing heavily in robust safeguards and compliance measures, assuaging concerns about data protection and privacy. As the cloud ecosystem continues to evolve, its significance will only intensify, serving as a catalyst for innovation, cost-efficiency, and strategic transformation in businesses and industries worldwide.
Why Cloud Architecture Matters
Cloud architecture is paramount in the modern business landscape for a multitude of reasons. Firstly, it serves as the blueprint for a company's digital infrastructure, determining how resources are provisioned, deployed, and managed in the cloud. This fundamental design impacts an organization's ability to scale rapidly in response to changing demands, control costs by efficiently allocating resources, and maintain the highest standards of security and compliance. Effective cloud architecture can make the difference between an agile, cost-effective, and secure operation and one that struggles to adapt to the fast-paced digital world.
Secondly, cloud architecture unlocks the potential for innovation and business agility. With the cloud's vast array of managed services, organizations can experiment and implement cutting-edge technologies like artificial intelligence, machine learning, and IoT without the burden of managing complex underlying infrastructure. Cloud-native development practices foster agility by enabling rapid development, testing, and deployment of applications. As remote work and global collaboration become the norm, the cloud also plays a pivotal role in providing accessibility to data and applications from anywhere, supporting businesses in their quest for operational continuity and growth. In essence, cloud architecture isn't just about IT; it's about the strategic foundation upon which businesses build their digital future.
AWS as a Leading Cloud Provider
Amazon Web Services (AWS) has solidified its position as the foremost cloud provider due to a combination of factors that set it apart in the industry. Its vast and constantly expanding service portfolio encompasses virtually every aspect of cloud computing, enabling businesses to not only migrate their existing infrastructure but also to innovate and transform their operations. This extensive range of services includes scalable computing resources, cutting-edge machine learning and analytics tools, secure storage options, and developer-friendly solutions like serverless computing, all backed by a global network of data centers. This versatility makes AWS suitable for startups, enterprises, government organizations, and virtually any industry seeking to harness the power of the cloud.
One of AWS's standout attributes is its relentless commitment to security and compliance. AWS invests heavily in advanced security features, encryption, and access controls, earning it the trust of highly regulated industries like healthcare and finance. Furthermore, AWS consistently obtains and maintains a broad array of compliance certifications, ensuring that customers can adhere to industry-specific regulations while leveraging the cloud's capabilities. This focus on security and compliance, combined with its innovation, reliability, and global reach, makes AWS not just a leading cloud provider but also a strategic partner for organizations worldwide as they navigate the complexities of the digital age.
The Challenges of Cloud Adoption
-
Security Concerns: Worries about data security and unauthorized access.
-
Compliance and Regulations: Meeting legal requirements and industry-specific regulations.
-
Data Migration: Moving existing data and applications to the cloud seamlessly.
-
Cost Management: Controlling cloud spending and optimizing costs.
-
Skills Gap: Lack of expertise in managing cloud environments.
-
Vendor Lock-In: Dependency on a single cloud provider.
-
Performance Issues: Ensuring consistent application performance.
-
Change Resistance: Employees resisting changes in processes and workflows.
-
Governance: Lack of clear policies for managing cloud resources.
-
Downtime and Availability: Dealing with occasional outages and downtime.
How AWS Solution Architects Address Business Needs Top of Form
AWS Solution Architects are instrumental in bridging the gap between an organization's business needs and the technological capabilities provided by Amazon Web Services. They start by deeply understanding the unique objectives and challenges faced by the business, working closely with stakeholders to align cloud solutions with these requirements. Whether it's optimizing costs, enhancing security, ensuring scalability, or addressing compliance concerns, Solution Architects craft tailored solutions that cater to these specific business needs. Their expertise in AWS services and best practices allows them to design robust architectures that not only meet current demands but also anticipate future growth and innovation.
Moreover, AWS Solution Architects provide a crucial layer of assurance and reliability to organizations. By prioritizing security measures and compliance, they ensure that data and operations are safeguarded, instilling confidence in cloud adoption. Their ability to create detailed technical documentation and collaborate effectively with cross-functional teams ensures the successful implementation of cloud solutions. In essence, AWS Solution Architects play a pivotal role in driving business success by leveraging AWS's powerful cloud capabilities to address the ever-evolving landscape of business needs, from cost efficiency and scalability to security and innovation.
Cost Optimization and Efficiency
Cost optimization and efficiency are paramount in the world of AWS as organizations seek to harness the cloud's power while keeping their budgets in check. AWS offers a multitude of tools and strategies to help businesses strike the right balance between performance and expenditure. One of the fundamental principles is resource optimization, where organizations carefully select the appropriate instance types, storage options, and services that align with their actual requirements. By avoiding overprovisioning and rightsizing their resources, businesses can prevent unnecessary spending and ensure that they pay only for what they use.
Furthermore, AWS provides advanced features like auto-scaling, which enables resources to automatically adapt to fluctuating workloads, optimizing both performance and costs. Reserved Instances and Spot Instances offer significant cost savings, allowing organizations to commit to long-term usage for predictable workloads or take advantage of surplus capacity for transient tasks. AWS's suite of monitoring and optimization tools empowers organizations to gain visibility into their cloud expenditure and make data-driven decisions to reduce costs. By continually reviewing and adjusting their cloud architecture, employing serverless computing for certain tasks, and educating teams on best practices, organizations can achieve a delicate balance between efficiency and cost control, ensuring that their AWS investments yield maximum value.
Security and Compliance in AWS Solutions
Security and compliance are foundational pillars in AWS solutions, reflecting the platform's unwavering commitment to safeguarding customer data and ensuring adherence to industry-specific regulations. AWS employs a multi-layered approach to security, starting with its shared responsibility model, which delineates responsibilities between AWS and its customers. AWS is responsible for securing the underlying infrastructure, while customers are tasked with securing their data, applications, and configurations. This model ensures that security is a collaborative effort, with AWS providing a secure cloud environment and customers implementing security best practices within it.
To bolster security, AWS offers a comprehensive suite of services, including IAM for access control, encryption for data protection, VPC for network isolation, and a range of monitoring and logging tools. AWS also invests heavily in compliance, obtaining and maintaining various certifications to meet the strictest regulatory requirements, such as HIPAA and GDPR. This commitment to security and compliance gives organizations the confidence to migrate sensitive workloads to the cloud while maintaining data integrity and adhering to industry-specific regulations. AWS's emphasis on security and compliance underscores its position as a trusted partner for businesses seeking to leverage the cloud's capabilities while mitigating potential risks.
Scaling for Growth and Performance
Scaling for growth and performance is a fundamental requirement in today's dynamic business landscape, and AWS provides organizations with a robust toolkit to achieve this scalability seamlessly. The heart of AWS's scaling capabilities lies in its auto-scaling features, which enable applications to dynamically adjust their compute resources in response to fluctuations in demand. This not only ensures that applications can handle sudden surges in traffic but also optimizes resource utilization during quieter periods, resulting in cost-effective operations.
Moreover, AWS promotes a serverless paradigm through services like AWS Lambda, allowing organizations to focus on code rather than infrastructure management. Serverless computing automatically scales resources in response to individual events, delivering exceptional performance and cost-efficiency without the need to provision or manage servers. Coupled with elastic load balancing, content delivery networks, and scalable databases, AWS empowers organizations to build resilient, high-performance applications that can seamlessly scale to accommodate growth while delivering optimal user experiences. Whether it's handling a sudden influx of customers or supporting continuous expansion, AWS's scaling capabilities are integral to modern businesses aiming for both agility and performance.
Disaster Recovery and Business Continuity
Disaster recovery and business continuity are foundational elements of AWS's cloud offerings, reflecting its commitment to ensuring the availability and resilience of critical business operations. AWS provides organizations with versatile tools and services to craft robust disaster recovery and business continuity strategies. This begins with AWS's high availability infrastructure, which spans multiple availability zones and regions, allowing businesses to deploy resources in geographically separate locations to guard against localized outages or disasters. Services like AWS Disaster Recovery (DR) as a Service (DRaaS) and AWS Site Recovery facilitate automated failover and replication of workloads, ensuring minimal downtime and seamless continuity in the event of a disaster or unforeseen event.
Moreover, AWS's backup solutions, such as Amazon S3 and Amazon EBS snapshots, enable organizations to create secure and scalable data backups, ensuring that critical information can be restored quickly and reliably. AWS's global content delivery network, Amazon CloudFront, accelerates content delivery, reducing latency and ensuring data remains accessible even during network disruptions. Additionally, the ability to simulate disaster scenarios and conduct testing exercises without impacting production environments empowers organizations to refine their disaster recovery and business continuity plans proactively. With these capabilities, AWS strengthens an organization's ability to navigate the unpredictable and safeguard its operations, data, and reputation in the face of adversity.
Innovation and Future-Proofing
Innovation and future-proofing are at the core of AWS solutions, allowing organizations to not only meet current challenges but also anticipate and adapt to future technological advancements. AWS's commitment to staying on the cutting edge of technology is evident through its constant introduction of new services and features that harness emerging trends like artificial intelligence, machine learning, IoT, and serverless computing. These innovations empower businesses to explore new frontiers, streamline operations, and enhance customer experiences. AWS's vast ecosystem of services provides organizations with the flexibility to experiment, iterate, and scale their solutions, fostering a culture of continuous innovation.
Furthermore, AWS's emphasis on cloud-native development practices, well-architected frameworks, and global infrastructure allows organizations to future-proof their operations. By adopting cloud-native principles such as microservices and DevOps, businesses can remain agile and responsive to changing market conditions. AWS's global reach ensures that organizations can expand their reach and serve customers globally, while the well-architected framework guides them in building resilient and efficient solutions that can withstand future challenges. With AWS, organizations have a partner that not only supports their current needs but also equips them with the tools and strategies to thrive in an ever-evolving digital landscape, positioning them for sustained success and innovation.
Certification and Training for AWS Solution Architects
-
Choose Your Certification Level: Start with the "AWS Certified Solutions Architect - Associate" certification, and you can progress to the "AWS Certified Solutions Architect - Professional" later.
-
Review Exam Objectives: Understand what topics are covered in the certification exam by reviewing the exam blueprint provided by AWS.
-
Access Training Resources: Utilize AWS's official training resources, including online courses and hands-on labs, available on the AWS Training and Certification portal.
-
Hands-On Practice: Gain practical experience by working on real AWS projects and experimenting with AWS services in a free-tier environment.
-
Practice Exams: Use practice exams and sample questions to test your knowledge and readiness for the certification exam.
-
Register for the Exam: Sign up for the certification exam through the AWS Certification portal.
-
Stay Updated: Keep yourself updated with the latest AWS services and best practices by attending webinars, reading documentation, and participating in the AWS community.
-
Recertify When Required: Be aware of recertification requirements and ensure you renew your certification when necessary to stay current.
By following these steps, you can work towards becoming a certified AWS Solutions Architect, demonstrating your expertise in designing and implementing AWS solutions.
Collaboration with Other IT Roles
Collaboration with various IT roles is a cornerstone of success for AWS Solution Architects in the complex world of cloud computing. Working closely with developers, architects help translate architectural designs into functional applications by providing guidance on best practices, security, and scalability. Collaboration with system administrators and DevOps engineers is essential to automate resource provisioning, implement CI/CD pipelines, and ensure the architecture's resilience. Solution Architects liaise with security specialists to embed security measures into the design, and with network engineers to configure networking components in line with performance and security needs. They also partner with database administrators to optimize database performance and with data scientists and analysts to create data solutions leveraging AWS's capabilities. Collaboration with project managers helps align architectural goals with project timelines and budgets, ensuring that cloud solutions are not only technically sound but also delivered on schedule and within budget.
This collaborative approach extends beyond technology, fostering a culture of teamwork and shared responsibility. It promotes effective communication and coordination among cross-functional teams, enabling them to collectively tackle challenges, make informed decisions, and deliver solutions that align with business objectives. In essence, AWS Solution Architects' ability to collaborate with a diverse set of IT roles is integral to their role as orchestrators of cloud excellence, ensuring that AWS solutions not only meet technical requirements but also drive business success.
The Role of AWS Partnerships
Here are the key points about the role of AWS partnerships in a simple format:
-
Expertise Access: AWS partnerships connect businesses with skilled professionals who have deep expertise in AWS technologies, helping organizations make informed decisions and optimize their cloud solutions.
-
Innovation Acceleration: Technology partners collaborate with AWS to create and integrate innovative products and services, allowing customers to harness cutting-edge technology without starting from scratch.
-
Enhanced Support: Consulting and managed service partners offer valuable support, acting as trusted advisors to guide businesses in adopting and managing AWS services effectively.
-
Global Presence: AWS partnerships provide access to AWS services and support in local regions, ensuring global reach and localized assistance for businesses with international operations.
-
Ecosystem Expansion: Partnerships contribute to an extensive ecosystem of third-party solutions that integrate seamlessly with AWS, offering a wide array of options to tailor cloud environments to specific needs.
-
Certified Solutions: AWS-certified partner solutions undergo rigorous testing and validation, ensuring compatibility, reliability, and quality for customers.
-
Resources and Support: AWS offers partners resources, training, marketing support, and co-selling opportunities, enabling them to better serve customers and grow their businesses.
AWS partnerships play a vital role in helping businesses leverage the full potential of AWS cloud services, providing expertise, innovation, and support to drive digital transformation and growth.
Conclusion
In conclusion, AWS Solution Architects hold a pivotal role in the realm of cloud computing, where businesses increasingly rely on AWS's vast array of services and infrastructure. These architects serve as the linchpin between technology and business, bridging the gap by designing, implementing, and optimizing cloud solutions that align with organizational goals. They navigate the complexities of AWS to create architectures that are secure, scalable, cost-efficient, and resilient.
The importance of AWS Solution Architects extends beyond technical prowess. They collaborate with diverse IT roles, facilitate innovation, and leverage AWS partnerships to enhance cloud capabilities. These architects play a key role in disaster recovery, business continuity, security, and compliance, safeguarding critical data and operations. They are instrumental in driving cost optimization, ensuring resources are used efficiently.
As businesses continue to embrace the cloud, AWS Solution Architects will remain essential in guiding these transformations. Their expertise, collaboration, and commitment to innovation enable organizations to thrive in the ever-evolving digital landscape, making them invaluable assets in the journey toward cloud excellence.
How to Build a Career in Risk Management with PMI-RMP Certification
In a world marked by volatility, uncertainty, and complexity, risk management has emerged as a pivotal discipline, safeguarding organizations from unforeseen challenges and ensuring their sustainability. The role of risk managers has evolved into a cornerstone of modern business strategy, making it a highly sought-after and rewarding career path. One of the key milestones on the journey to becoming a proficient risk management professional is obtaining the PMI-RMP (Project Management Institute - Risk Management Professional) certification. This certification not only validates one's expertise in risk management but also opens doors to a realm of career opportunities across a myriad of industries and sectors.
In this blog, we will delve into the dynamic field of risk management and explore the steps to build a thriving career with the PMI-RMP certification. From understanding the fundamentals of risk management to meeting the eligibility requirements, preparing diligently for the certification exam, and navigating the intricacies of practical experience, this guide will serve as a compass for those embarking on a journey towards becoming a trusted guardian of organizations in an ever-changing world. So, fasten your seatbelts as we navigate the exciting terrain of building a career in risk management with the esteemed PMI-RMP certification.
Table of contents
-
Introduction to PMI-RMP Certification
-
Eligibility and Exam Requirements
-
Preparing for the PMI-RMP Exam
-
Benefits of PMI-RMP Certification
-
Career Opportunities in Risk Management
-
Gaining Practical Experience
-
Continuous Learning and Professional Development
-
Networking and Building Professional Relationships
-
Career Advancement with PMI-RMP
-
Conclusion
Introduction to PMI-RMP Certification
PMI-RMP (Project Management Institute - Risk Management Professional) certification is a prestigious credential recognized globally for its emphasis on risk management within the context of project management. This certification is designed for professionals who are involved in identifying, assessing, and mitigating risks to ensure successful project outcomes. It signifies an individual's specialized expertise in risk management processes, making them valuable assets to organizations across various industries.
PMI-RMP certification offers numerous benefits, including enhanced career prospects, increased earning potential, and a competitive edge in the job market. It is a testament to a professional's commitment to continuous learning and the highest standards of risk management practices. Furthermore, PMI-RMP certification connects individuals with a global network of like-minded professionals and provides access to valuable resources, enabling them to stay at the forefront of risk management innovation. In summary, PMI-RMP certification is an invaluable asset for anyone seeking a rewarding career in risk management and project management, offering recognition, expertise, and opportunities for growth.
Eligibility and Exam Requirements
Eligibility and exam requirements for PMI-RMP (Project Management Institute - Risk Management Professional) certification are essential aspects of the certification process. Here, we'll delve into the prerequisites and details you need to know to pursue this certification:
Eligibility Requirements: To be eligible for the PMI-RMP certification exam, candidates must meet certain educational and professional criteria. These include:
-
Educational Requirements:
-
A high school diploma or global equivalent.
-
Four years (or 4,500 hours) of project risk management experience within the last five years.
OR
-
A Bachelor's Degree or Higher:
-
A four-year degree (or global equivalent).
-
Three years (or 3,000 hours) of project risk management experience within the last five years.
Exam Requirements: Once you meet the eligibility criteria, you can proceed with the PMI-RMP certification process, which includes:
-
Exam Application: Candidates need to submit an application through the PMI website, providing details of their education and project risk management experience. The application is reviewed by PMI for completeness and accuracy.
-
Payment: You must pay the examination fee, which varies for PMI members and non-members. PMI members typically receive a discount on the exam fee.
-
Scheduling the Exam: After your application is approved, you can schedule the PMI-RMP exam at a Pearson VUE test center or, in some cases, take it online. PMI provides information on scheduling options and available exam centers.
-
Exam Format: The PMI-RMP exam is a computer-based exam consisting of 170 multiple-choice questions. Of these, 150 questions are scored, and 20 are pretest questions used for future exam development. Candidates have 3.5 hours to complete the exam.
-
Passing Score: PMI doesn't disclose the passing score for the PMI-RMP exam. It is based on a psychometric analysis of the questions and is not a fixed percentage.
-
Maintaining Certification: To maintain your PMI-RMP certification, you must earn 30 Professional Development Units (PDUs) in risk management-related activities every three years and retake the PMI-RMP exam every three years to renew your certification.
Understanding these eligibility and exam requirements is crucial for individuals looking to pursue PMI-RMP certification. Meeting the prerequisites and successfully passing the exam demonstrate your expertise in project risk management, enhancing your career prospects in this field.
Preparing for the PMI-RMP Exam
-
Understand the Exam Outline: Familiarize yourself with what the exam covers by reviewing the PMI-RMP Exam Content Outline.
-
Use Official Resources: Utilize PMI's official resources, like the PMI-RMP Handbook and Content Outline.
-
Study Materials: Invest in quality study materials such as books and online courses.
-
Create a Study Plan: Develop a study schedule that outlines what to study each day or week.
-
Practice with Sample Questions: Use practice exams to get comfortable with the exam format and types of questions.
-
Join a Study Group: Consider joining a study group or forum to discuss concepts and share resources.
-
Understand PMBOK Concepts: Have a strong grasp of PMBOK concepts, especially in the context of risk management.
-
Simulate Exam Conditions: Take practice exams under timed conditions to prepare for the real test.
-
Focus on Weak Areas: Identify and spend extra time on areas where you feel less confident.
-
Regular Review: Continuously review the material you've studied.
-
Stay Calm on Exam Day: Get enough rest, arrive early, and stay calm during the exam.
-
Read Questions Carefully: Pay attention to keywords in questions and eliminate incorrect options.
-
Flag and Review: Flag uncertain answers for review and revisit them later.
-
Manage Time: Keep track of time during the exam to answer all questions.
-
Submit Confidently: Submit your exam confidently, and await PMI's results notification.
By following these straightforward steps, you can effectively prepare for the PMI-RMP exam and increase your chances of success.
Benefits of PMI-RMP Certification
-
Expertise: Demonstrates your expertise in risk management.
-
Global Recognition: Respected worldwide by employers and peers.
-
Career Advancement: Opens doors to higher-paying roles.
-
Earning Potential: Can lead to higher salaries.
-
Competitive Advantage: Sets you apart in job applications.
-
Networking: Connects you with a global community of professionals.
-
Project Success: Contributes to on-time, on-budget project delivery.
-
Continuous Learning: Encourages ongoing skill development.
-
Ethical Standards: Emphasizes ethical practices in risk management.
-
Versatility: Applicable across various industries.
Career Opportunities in Risk Management
A career in risk management presents a wide array of opportunities across diverse industries. Risk analysts and managers play pivotal roles in identifying, assessing, and mitigating risks that organizations face, be they financial, operational, or strategic in nature. These professionals employ quantitative and qualitative methodologies to provide critical insights that enable companies to make informed decisions and protect their interests. Credit risk analysts work within financial institutions to assess borrowers' creditworthiness, while operational risk managers focus on operational threats and process efficiency. Compliance officers ensure organizations abide by regulatory guidelines, and enterprise risk managers oversee holistic risk management strategies. Additionally, careers in areas like cybersecurity, environmental risk, healthcare, and supply chain risk management have emerged as specialized fields, reflecting the evolving complexities and demands of modern business environments.
The significance of risk management in today's global and interconnected business landscape has elevated the demand for professionals in this field. With opportunities spanning from financial institutions to healthcare, construction, and cybersecurity, individuals entering risk management can tailor their careers to align with their interests and expertise. This diversity, coupled with the potential for career advancement and competitive compensation, makes risk management an appealing and rewarding career path for those with a penchant for critical thinking, analytical skills, and a desire to safeguard organizations from unforeseen challenges.
Gaining Practical Experience
Gaining practical experience in risk management is essential for developing the skills and expertise required to excel in this field. Entry-level positions, internships, and volunteer opportunities provide invaluable exposure to real-world risk scenarios, allowing individuals to apply theoretical knowledge in practical contexts. These hands-on roles often involve tasks such as risk assessment, mitigation strategy development, and collaboration with cross-functional teams to address organizational vulnerabilities. Furthermore, networking, professional development courses, and certifications like PMI-RMP can facilitate access to practical experience opportunities while providing structured learning pathways. Additionally, staying informed through continuous learning and seeking mentorship from experienced professionals can further enhance one's ability to navigate complex risk management challenges, making practical experience a cornerstone of a successful career in this dynamic field.
In summary, practical experience in risk management is not only a means to apply theoretical knowledge but also a pathway to gaining confidence and competence in addressing real-world risks. Whether through formal roles, volunteer work, or professional development, hands-on experience equips individuals with the practical skills and insights necessary to make informed decisions and contribute effectively to an organization's risk management efforts.
Continuous Learning and Professional Development
Continuous learning and professional development are vital for success in risk management and many other fields. Here are key points about their significance:
-
Adapting to Change: Continuous learning helps professionals stay updated with evolving industry trends, technologies, and best practices. In risk management, where threats and challenges constantly change, staying current is essential.
-
Skill Enhancement: It allows individuals to enhance their skills, whether in risk assessment, data analysis, or decision-making. These skills improvements can lead to more effective risk management.
-
Career Advancement: Continuous learning and professional development can open up new career opportunities and make you a more attractive candidate for promotions and leadership roles.
-
Risk Mitigation: Being well-informed and continuously learning helps organizations anticipate and mitigate risks effectively. Professionals can proactively identify emerging risks and develop strategies to address them.
-
Certifications: Pursuing certifications, such as PMI-RMP or CRM, demonstrates a commitment to ongoing professional development and can boost career prospects.
-
Networking: Learning opportunities, seminars, and conferences provide chances to network with peers and experts, leading to valuable knowledge sharing and potential collaborations.
-
Innovation: Staying current with the latest developments in risk management can spark innovative solutions and approaches to risk mitigation.
-
Resilience: Continuous learning builds resilience by ensuring that professionals are prepared to handle unexpected challenges and disruptions.
-
Ethical Practices: Learning about evolving ethical standards in risk management ensures that professionals maintain the highest ethical practices in their work.
-
Personal Growth: Beyond career benefits, continuous learning fosters personal growth, intellectual stimulation, and a sense of accomplishment.
In summary, continuous learning and professional development are integral to staying relevant, advancing one's career, and effectively managing risks in an ever-changing world. They empower professionals to adapt, innovate, and excel in the dynamic field of risk management.
Networking and Building Professional Relationships
Networking and cultivating professional relationships are cornerstone practices for success in risk management. In this field, where dynamic challenges often demand innovative solutions, connecting with peers, experts, and industry leaders is invaluable. Networking offers a platform to share insights, learn from others' experiences, and stay updated on the latest risk management trends and strategies. Whether through attending industry conferences, joining professional associations, or engaging in online forums, these interactions provide a continuous learning opportunity that can lead to better risk assessment and mitigation.
Moreover, building a robust professional network can lead to career advancement and collaboration opportunities. It can open doors to job referrals, mentorship from seasoned professionals, and access to a wider pool of talent for cross-functional risk management teams. In essence, networking is more than just exchanging business cards; it's about creating a support system, fostering collaboration, and expanding one's horizons in the dynamic world of risk management.
Career Advancement with PMI-RMP
PMI-RMP certification serves as a powerful catalyst for career advancement in the realm of risk management. It goes beyond just validating your skills; it showcases your specialized expertise in identifying, assessing, and mitigating risks, making you a sought-after professional in industries spanning from finance to healthcare and beyond. The competitive edge it provides cannot be understated, as it distinguishes you from your peers in a crowded job market and positions you for leadership roles in risk management departments. With PMI-RMP certification, you become a trusted resource for organizations looking to navigate complexities and uncertainties effectively, propelling your career into higher-paying positions and more significant responsibilities.
Moreover, PMI-RMP fosters continuous learning and development, ensuring that you remain at the forefront of industry trends and best practices. This commitment to lifelong learning not only boosts your competence but also keeps you adaptable and innovative in an ever-evolving field. Additionally, the global recognition PMI-RMP offers broadens your horizons, potentially leading to international career opportunities and a rich network of professionals who can provide mentorship and support. In essence, PMI-RMP is a pivotal stepping stone for those aspiring to not only succeed but excel in the dynamic domain of risk management, enabling you to become a key player in shaping an organization's future.
Conclusion
In conclusion, building a successful career in risk management with PMI-RMP certification is a strategic and rewarding journey. This certification not only validates your expertise in risk management but also opens doors to a wide range of career opportunities across diverse industries. As outlined in this blog, the path to PMI-RMP certification involves meeting eligibility requirements, preparing diligently for the exam, and continuously expanding your knowledge and practical experience.
Once you've earned your PMI-RMP certification, you become a sought-after professional equipped with the skills to identify, assess, and mitigate risks effectively. This credential can lead to career advancement, increased earning potential, and a deeper understanding of risk management principles. Moreover, it connects you with a global network of like-minded professionals, fostering collaboration and growth.
In the dynamic and ever-evolving world of risk management, PMI-RMP certification stands as a symbol of excellence and dedication. It empowers individuals to make informed decisions, protect their organizations from uncertainties, and embark on a fulfilling and prosperous career in risk management. So, take the first step, set your career goals, and embark on your journey to PMI-RMP certification and a rewarding career in risk management. Your future in this dynamic field awaits, full of opportunities to make a meaningful impact.
Read More
In a world marked by volatility, uncertainty, and complexity, risk management has emerged as a pivotal discipline, safeguarding organizations from unforeseen challenges and ensuring their sustainability. The role of risk managers has evolved into a cornerstone of modern business strategy, making it a highly sought-after and rewarding career path. One of the key milestones on the journey to becoming a proficient risk management professional is obtaining the PMI-RMP (Project Management Institute - Risk Management Professional) certification. This certification not only validates one's expertise in risk management but also opens doors to a realm of career opportunities across a myriad of industries and sectors.
In this blog, we will delve into the dynamic field of risk management and explore the steps to build a thriving career with the PMI-RMP certification. From understanding the fundamentals of risk management to meeting the eligibility requirements, preparing diligently for the certification exam, and navigating the intricacies of practical experience, this guide will serve as a compass for those embarking on a journey towards becoming a trusted guardian of organizations in an ever-changing world. So, fasten your seatbelts as we navigate the exciting terrain of building a career in risk management with the esteemed PMI-RMP certification.
Table of contents
-
Introduction to PMI-RMP Certification
-
Eligibility and Exam Requirements
-
Preparing for the PMI-RMP Exam
-
Benefits of PMI-RMP Certification
-
Career Opportunities in Risk Management
-
Gaining Practical Experience
-
Continuous Learning and Professional Development
-
Networking and Building Professional Relationships
-
Career Advancement with PMI-RMP
-
Conclusion
Introduction to PMI-RMP Certification
PMI-RMP (Project Management Institute - Risk Management Professional) certification is a prestigious credential recognized globally for its emphasis on risk management within the context of project management. This certification is designed for professionals who are involved in identifying, assessing, and mitigating risks to ensure successful project outcomes. It signifies an individual's specialized expertise in risk management processes, making them valuable assets to organizations across various industries.
PMI-RMP certification offers numerous benefits, including enhanced career prospects, increased earning potential, and a competitive edge in the job market. It is a testament to a professional's commitment to continuous learning and the highest standards of risk management practices. Furthermore, PMI-RMP certification connects individuals with a global network of like-minded professionals and provides access to valuable resources, enabling them to stay at the forefront of risk management innovation. In summary, PMI-RMP certification is an invaluable asset for anyone seeking a rewarding career in risk management and project management, offering recognition, expertise, and opportunities for growth.
Eligibility and Exam Requirements
Eligibility and exam requirements for PMI-RMP (Project Management Institute - Risk Management Professional) certification are essential aspects of the certification process. Here, we'll delve into the prerequisites and details you need to know to pursue this certification:
Eligibility Requirements: To be eligible for the PMI-RMP certification exam, candidates must meet certain educational and professional criteria. These include:
-
Educational Requirements:
-
A high school diploma or global equivalent.
-
Four years (or 4,500 hours) of project risk management experience within the last five years.
OR
-
A Bachelor's Degree or Higher:
-
A four-year degree (or global equivalent).
-
Three years (or 3,000 hours) of project risk management experience within the last five years.
Exam Requirements: Once you meet the eligibility criteria, you can proceed with the PMI-RMP certification process, which includes:
-
Exam Application: Candidates need to submit an application through the PMI website, providing details of their education and project risk management experience. The application is reviewed by PMI for completeness and accuracy.
-
Payment: You must pay the examination fee, which varies for PMI members and non-members. PMI members typically receive a discount on the exam fee.
-
Scheduling the Exam: After your application is approved, you can schedule the PMI-RMP exam at a Pearson VUE test center or, in some cases, take it online. PMI provides information on scheduling options and available exam centers.
-
Exam Format: The PMI-RMP exam is a computer-based exam consisting of 170 multiple-choice questions. Of these, 150 questions are scored, and 20 are pretest questions used for future exam development. Candidates have 3.5 hours to complete the exam.
-
Passing Score: PMI doesn't disclose the passing score for the PMI-RMP exam. It is based on a psychometric analysis of the questions and is not a fixed percentage.
-
Maintaining Certification: To maintain your PMI-RMP certification, you must earn 30 Professional Development Units (PDUs) in risk management-related activities every three years and retake the PMI-RMP exam every three years to renew your certification.
Understanding these eligibility and exam requirements is crucial for individuals looking to pursue PMI-RMP certification. Meeting the prerequisites and successfully passing the exam demonstrate your expertise in project risk management, enhancing your career prospects in this field.
Preparing for the PMI-RMP Exam
-
Understand the Exam Outline: Familiarize yourself with what the exam covers by reviewing the PMI-RMP Exam Content Outline.
-
Use Official Resources: Utilize PMI's official resources, like the PMI-RMP Handbook and Content Outline.
-
Study Materials: Invest in quality study materials such as books and online courses.
-
Create a Study Plan: Develop a study schedule that outlines what to study each day or week.
-
Practice with Sample Questions: Use practice exams to get comfortable with the exam format and types of questions.
-
Join a Study Group: Consider joining a study group or forum to discuss concepts and share resources.
-
Understand PMBOK Concepts: Have a strong grasp of PMBOK concepts, especially in the context of risk management.
-
Simulate Exam Conditions: Take practice exams under timed conditions to prepare for the real test.
-
Focus on Weak Areas: Identify and spend extra time on areas where you feel less confident.
-
Regular Review: Continuously review the material you've studied.
-
Stay Calm on Exam Day: Get enough rest, arrive early, and stay calm during the exam.
-
Read Questions Carefully: Pay attention to keywords in questions and eliminate incorrect options.
-
Flag and Review: Flag uncertain answers for review and revisit them later.
-
Manage Time: Keep track of time during the exam to answer all questions.
-
Submit Confidently: Submit your exam confidently, and await PMI's results notification.
By following these straightforward steps, you can effectively prepare for the PMI-RMP exam and increase your chances of success.
Benefits of PMI-RMP Certification
-
Expertise: Demonstrates your expertise in risk management.
-
Global Recognition: Respected worldwide by employers and peers.
-
Career Advancement: Opens doors to higher-paying roles.
-
Earning Potential: Can lead to higher salaries.
-
Competitive Advantage: Sets you apart in job applications.
-
Networking: Connects you with a global community of professionals.
-
Project Success: Contributes to on-time, on-budget project delivery.
-
Continuous Learning: Encourages ongoing skill development.
-
Ethical Standards: Emphasizes ethical practices in risk management.
-
Versatility: Applicable across various industries.
Career Opportunities in Risk Management
A career in risk management presents a wide array of opportunities across diverse industries. Risk analysts and managers play pivotal roles in identifying, assessing, and mitigating risks that organizations face, be they financial, operational, or strategic in nature. These professionals employ quantitative and qualitative methodologies to provide critical insights that enable companies to make informed decisions and protect their interests. Credit risk analysts work within financial institutions to assess borrowers' creditworthiness, while operational risk managers focus on operational threats and process efficiency. Compliance officers ensure organizations abide by regulatory guidelines, and enterprise risk managers oversee holistic risk management strategies. Additionally, careers in areas like cybersecurity, environmental risk, healthcare, and supply chain risk management have emerged as specialized fields, reflecting the evolving complexities and demands of modern business environments.
The significance of risk management in today's global and interconnected business landscape has elevated the demand for professionals in this field. With opportunities spanning from financial institutions to healthcare, construction, and cybersecurity, individuals entering risk management can tailor their careers to align with their interests and expertise. This diversity, coupled with the potential for career advancement and competitive compensation, makes risk management an appealing and rewarding career path for those with a penchant for critical thinking, analytical skills, and a desire to safeguard organizations from unforeseen challenges.
Gaining Practical Experience
Gaining practical experience in risk management is essential for developing the skills and expertise required to excel in this field. Entry-level positions, internships, and volunteer opportunities provide invaluable exposure to real-world risk scenarios, allowing individuals to apply theoretical knowledge in practical contexts. These hands-on roles often involve tasks such as risk assessment, mitigation strategy development, and collaboration with cross-functional teams to address organizational vulnerabilities. Furthermore, networking, professional development courses, and certifications like PMI-RMP can facilitate access to practical experience opportunities while providing structured learning pathways. Additionally, staying informed through continuous learning and seeking mentorship from experienced professionals can further enhance one's ability to navigate complex risk management challenges, making practical experience a cornerstone of a successful career in this dynamic field.
In summary, practical experience in risk management is not only a means to apply theoretical knowledge but also a pathway to gaining confidence and competence in addressing real-world risks. Whether through formal roles, volunteer work, or professional development, hands-on experience equips individuals with the practical skills and insights necessary to make informed decisions and contribute effectively to an organization's risk management efforts.
Continuous Learning and Professional Development
Continuous learning and professional development are vital for success in risk management and many other fields. Here are key points about their significance:
-
Adapting to Change: Continuous learning helps professionals stay updated with evolving industry trends, technologies, and best practices. In risk management, where threats and challenges constantly change, staying current is essential.
-
Skill Enhancement: It allows individuals to enhance their skills, whether in risk assessment, data analysis, or decision-making. These skills improvements can lead to more effective risk management.
-
Career Advancement: Continuous learning and professional development can open up new career opportunities and make you a more attractive candidate for promotions and leadership roles.
-
Risk Mitigation: Being well-informed and continuously learning helps organizations anticipate and mitigate risks effectively. Professionals can proactively identify emerging risks and develop strategies to address them.
-
Certifications: Pursuing certifications, such as PMI-RMP or CRM, demonstrates a commitment to ongoing professional development and can boost career prospects.
-
Networking: Learning opportunities, seminars, and conferences provide chances to network with peers and experts, leading to valuable knowledge sharing and potential collaborations.
-
Innovation: Staying current with the latest developments in risk management can spark innovative solutions and approaches to risk mitigation.
-
Resilience: Continuous learning builds resilience by ensuring that professionals are prepared to handle unexpected challenges and disruptions.
-
Ethical Practices: Learning about evolving ethical standards in risk management ensures that professionals maintain the highest ethical practices in their work.
-
Personal Growth: Beyond career benefits, continuous learning fosters personal growth, intellectual stimulation, and a sense of accomplishment.
In summary, continuous learning and professional development are integral to staying relevant, advancing one's career, and effectively managing risks in an ever-changing world. They empower professionals to adapt, innovate, and excel in the dynamic field of risk management.
Networking and Building Professional Relationships
Networking and cultivating professional relationships are cornerstone practices for success in risk management. In this field, where dynamic challenges often demand innovative solutions, connecting with peers, experts, and industry leaders is invaluable. Networking offers a platform to share insights, learn from others' experiences, and stay updated on the latest risk management trends and strategies. Whether through attending industry conferences, joining professional associations, or engaging in online forums, these interactions provide a continuous learning opportunity that can lead to better risk assessment and mitigation.
Moreover, building a robust professional network can lead to career advancement and collaboration opportunities. It can open doors to job referrals, mentorship from seasoned professionals, and access to a wider pool of talent for cross-functional risk management teams. In essence, networking is more than just exchanging business cards; it's about creating a support system, fostering collaboration, and expanding one's horizons in the dynamic world of risk management.
Career Advancement with PMI-RMP
PMI-RMP certification serves as a powerful catalyst for career advancement in the realm of risk management. It goes beyond just validating your skills; it showcases your specialized expertise in identifying, assessing, and mitigating risks, making you a sought-after professional in industries spanning from finance to healthcare and beyond. The competitive edge it provides cannot be understated, as it distinguishes you from your peers in a crowded job market and positions you for leadership roles in risk management departments. With PMI-RMP certification, you become a trusted resource for organizations looking to navigate complexities and uncertainties effectively, propelling your career into higher-paying positions and more significant responsibilities.
Moreover, PMI-RMP fosters continuous learning and development, ensuring that you remain at the forefront of industry trends and best practices. This commitment to lifelong learning not only boosts your competence but also keeps you adaptable and innovative in an ever-evolving field. Additionally, the global recognition PMI-RMP offers broadens your horizons, potentially leading to international career opportunities and a rich network of professionals who can provide mentorship and support. In essence, PMI-RMP is a pivotal stepping stone for those aspiring to not only succeed but excel in the dynamic domain of risk management, enabling you to become a key player in shaping an organization's future.
Conclusion
In conclusion, building a successful career in risk management with PMI-RMP certification is a strategic and rewarding journey. This certification not only validates your expertise in risk management but also opens doors to a wide range of career opportunities across diverse industries. As outlined in this blog, the path to PMI-RMP certification involves meeting eligibility requirements, preparing diligently for the exam, and continuously expanding your knowledge and practical experience.
Once you've earned your PMI-RMP certification, you become a sought-after professional equipped with the skills to identify, assess, and mitigate risks effectively. This credential can lead to career advancement, increased earning potential, and a deeper understanding of risk management principles. Moreover, it connects you with a global network of like-minded professionals, fostering collaboration and growth.
In the dynamic and ever-evolving world of risk management, PMI-RMP certification stands as a symbol of excellence and dedication. It empowers individuals to make informed decisions, protect their organizations from uncertainties, and embark on a fulfilling and prosperous career in risk management. So, take the first step, set your career goals, and embark on your journey to PMI-RMP certification and a rewarding career in risk management. Your future in this dynamic field awaits, full of opportunities to make a meaningful impact.
The Role of Minitab in Quality Control and Six Sigma
In an era where data is the lifeblood of informed decision-making, organizations across diverse industries strive for excellence in quality control and process improvement. Six Sigma, a methodology focused on minimizing defects and variations, stands as a beacon of efficiency and quality. At the heart of this data-driven revolution lies Minitab, a versatile statistical software package. In this blog, we embark on a journey to explore "The Role of Minitab in Quality Control and Six Sigma." We will unravel how Minitab empowers professionals and organizations to harness the power of data, streamline processes, and elevate quality standards. From hypothesis testing and control charts to regression analysis and root cause analysis, Minitab serves as an indispensable tool, enabling the pursuit of data-driven excellence and the achievement of Six Sigma's lofty goals. Join us as we delve into the essential role that Minitab plays in the world of quality control and process improvement, where data reigns supreme and continuous improvement is the ultimate objective.
Table of contents
-
Introduction to Minitab
-
How Minitab Facilitates Data Analysis in Six Sigma Projects
-
Minitab and DMAIC
-
Statistical Analysis with Minitab
-
Creating Control Charts with Minitab
-
Hypothesis Testing in Minitab
-
Regression Analysis in Minitab
-
Design of Experiments (DOE) Made Easy with Minitab
-
Using Minitab for Root Cause Analysis
-
Conclusion
Introduction to Minitab
Minitab is a versatile and powerful statistical software package used extensively in data analysis, quality control, and process improvement. With a user-friendly interface and a comprehensive set of statistical tools, Minitab enables professionals and organizations to analyze data, make data-driven decisions, and enhance the quality of products and services. It offers a wide range of features, including data import from various sources, hypothesis testing, regression analysis, control chart creation, and process capability analysis. Minitab's compatibility with Six Sigma methodologies further enhances its appeal as it aligns seamlessly with the DMAIC (Define, Measure, Analyze, Improve, Control) framework, making it a go-to tool for professionals aiming to optimize processes and achieve higher quality standards in various industries.
Professionals from diverse fields, including manufacturing, healthcare, finance, and education, rely on Minitab to uncover insights from data and drive continuous improvement. Minitab's accessibility through various licensing options, coupled with its extensive learning resources and tutorials, makes it suitable for both beginners and experienced statisticians. As data analysis continues to play a pivotal role in decision-making, Minitab remains a valuable asset, helping individuals and organizations harness the power of data to achieve their goals and maintain a competitive edge in their respective industries.
How Minitab Facilitates Data Analysis in Six Sigma Projects
Minitab plays a crucial role in facilitating data analysis within Six Sigma projects by providing a robust set of tools and features tailored to the methodology's DMAIC (Define, Measure, Analyze, Improve, Control) framework. Here's how Minitab contributes to each phase of a Six Sigma project:
-
Define Phase: Minitab assists in defining project goals, scope, and metrics by helping users collect and organize data. It can be used to create project charters and establish clear objectives. Additionally, it supports the creation of process maps and flowcharts, aiding in the identification of potential improvement areas.
-
Measure Phase: In this phase, Minitab enables users to collect and analyze data to quantify the current state of a process. It simplifies data entry, statistical calculations, and the creation of graphical representations such as histograms and box plots. Minitab's capabilities for measurement system analysis (MSA) ensure that data collection methods are reliable, a fundamental aspect of Six Sigma.
-
Analyze Phase: Minitab shines in the Analyze phase by offering a wide range of statistical tools. It simplifies hypothesis testing, regression analysis, and design of experiments (DOE), helping users identify the root causes of process issues and validate potential improvement factors. Users can also create various graphical representations to visualize data relationships, making it easier to pinpoint areas for improvement.
-
Improve Phase: Minitab supports users in implementing and testing improvement solutions. It assists in optimizing processes by conducting Monte Carlo simulations, which evaluate the impact of different variables on process performance. This phase also benefits from Minitab's capabilities for factorial experiments and response surface methodology (RSM).
-
Control Phase: Finally, in the Control phase, Minitab aids in establishing control mechanisms to sustain process improvements. Users can create control charts, set control limits, and monitor process stability over time. Minitab also helps in documenting standard operating procedures and creating visual aids for training and continuous monitoring.
Overall, Minitab's user-friendly interface, extensive statistical capabilities, and alignment with Six Sigma principles make it an indispensable tool for data analysis throughout the DMAIC framework. It empowers Six Sigma practitioners to make data-driven decisions, identify process improvements, and drive quality and efficiency enhancements in their organizations.
Minitab and DMAIC
Minitab and DMAIC are two pillars of success in Six Sigma methodology, working hand in hand to achieve process improvement and quality enhancement. Minitab, as a statistical software tool, is well-aligned with the DMAIC framework's five phases, from defining project objectives to controlling and maintaining process improvements. It simplifies data collection, organizes information, conducts robust statistical analyses, and assists in visualizing data relationships, enabling Six Sigma practitioners to make informed decisions at each stage of the project. Whether it's hypothesis testing in the Analyze phase or creating control charts in the Control phase, Minitab provides the necessary tools and features to drive data-driven excellence within a Six Sigma context.
The synergy between Minitab and DMAIC empowers organizations to identify and address process inefficiencies, reduce defects, and enhance overall quality. Minitab's user-friendly interface and comprehensive statistical capabilities streamline the application of Six Sigma principles, making it a vital asset for professionals and teams dedicated to process optimization and continuous improvement. By leveraging Minitab in conjunction with DMAIC, businesses can achieve higher quality standards, reduced variability, and increased customer satisfaction, ultimately leading to improved competitiveness and success in today's competitive marketplace.
Statistical Analysis with Minitab
Statistical analysis with Minitab is a dynamic and versatile process that empowers individuals and organizations to extract meaningful insights from data. Minitab's user-friendly interface simplifies the often complex world of statistics, enabling users to perform a wide range of statistical analyses with ease. From conducting hypothesis tests and regression analysis to creating control charts and designing experiments, Minitab provides a comprehensive suite of tools to address diverse analytical needs. Moreover, its ability to generate clear and compelling visualizations enhances the understanding and communication of statistical findings. Minitab's role extends beyond just number crunching; it fosters data-driven decision-making, supports quality control efforts, and aids in process optimization, ultimately contributing to improved outcomes and greater efficiency across various domains.
Whether in the realms of business, academia, healthcare, or manufacturing, statistical analysis with Minitab empowers professionals to uncover trends, identify patterns, and make informed choices based on data-driven evidence. Its widespread adoption in quality control, Six Sigma projects, research, and beyond underscores its importance as a valuable tool for data analysis and decision support. In an era where data is increasingly integral to success, Minitab remains a reliable and indispensable partner, ensuring that the power of statistics is accessible and actionable for individuals and organizations alike.
Creating Control Charts with Minitab
Creating control charts with Minitab is a cornerstone of effective quality control and process monitoring. Minitab's user-friendly interface and extensive charting capabilities make it accessible to both beginners and experienced quality professionals. With Minitab, users can effortlessly generate a variety of control charts, such as X-bar and R charts for continuous data or p-charts for attribute data, with just a few clicks. The software automatically calculates control limits, plots data points, and highlights potential issues in a visually intuitive manner.
Interpreting these control charts is equally straightforward; users can quickly identify trends, shifts, or outliers that might indicate process instability. Minitab empowers organizations to proactively address quality issues, reduce defects, and enhance process performance by providing a comprehensive solution for monitoring and maintaining control over critical processes. Its role in facilitating the creation and interpretation of control charts ensures that organizations can achieve and sustain the highest standards of quality control and efficiency, fostering continuous improvement in their operations.
Hypothesis Testing in Minitab
Here are the steps to perform hypothesis testing in Minitab in simple points:
-
Data Entry: Enter your data into Minitab.
-
Select Test: Choose the specific hypothesis test you need (e.g., t-test, ANOVA) from Minitab's menu.
-
Define Hypotheses: State your null hypothesis (H0) and alternative hypothesis (Ha).
-
Perform the Test: Minitab calculates the test statistic and p-value based on your data.
-
Interpret Results: If p-value is smaller than your chosen significance level, reject the null hypothesis. If not, fail to reject it.
-
Draw Conclusions: Make decisions based on the p-value and the specific hypothesis test.
-
Generate Reports: Create reports and visualizations of your results using Minitab's tools.
Minitab simplifies hypothesis testing, making it accessible for making data-driven decisions in various fields.
Regression Analysis in Minitab
Regression analysis in Minitab is a powerful tool for understanding and quantifying relationships between variables. With a straightforward interface, it enables users to perform a wide range of regression analyses, from simple linear regressions to more complex multiple regression models. Users begin by entering their data and specifying the response and predictor variables of interest. Minitab then runs the analysis, providing crucial statistics such as coefficients, p-values, and R-squared values that help assess the strength and significance of these relationships.
Interpreting the results is made accessible, allowing users to draw meaningful conclusions and make predictions based on their data. Whether it's uncovering the factors that impact sales figures, evaluating the effectiveness of marketing campaigns, or making informed decisions in research, Minitab's regression analysis capabilities simplify the process, making it an indispensable resource for professionals across diverse fields. Its ability to visualize data and generate comprehensive reports further enhances its utility, ensuring that organizations can harness the power of regression analysis for data-driven insights and improved decision-making.
Design of Experiments (DOE) Made Easy with Minitab
Design of Experiments (DOE) is a systematic approach for conducting experiments to optimize processes, improve products, and identify critical factors affecting outcomes. Minitab, a widely used statistical software, simplifies the entire DOE process, making it accessible to both beginners and experienced practitioners. Here's how Minitab makes DOE easy:
-
Experimental Design Wizard: Minitab offers an intuitive Experimental Design Wizard that guides users through the DOE process step by step. This tool helps users select the appropriate design type, define factors and responses, and choose the levels of these factors.
-
Design Selection: Minitab provides a variety of design types, including full factorial, fractional factorial, response surface, and mixture designs. Users can easily select the design that suits their specific experiment requirements.
-
Factorial and Fractional Factorial Designs: Minitab automatically generates the necessary experimental runs and assigns factor settings based on the chosen design. This simplifies the planning process and reduces the number of experimental trials needed, saving time and resources.
-
Response Optimization: Minitab helps users analyze the results of their experiments by fitting models and optimizing responses. It provides visualizations, contour plots, and response surface plots that aid in understanding the relationships between factors and responses.
-
Robust Parameter Design (RPD): Minitab includes tools for conducting robust parameter design, which allows users to optimize processes while considering variability and noise factors, ensuring robust and reliable outcomes.
-
Analysis of Variance (ANOVA): Minitab automates the ANOVA analysis, making it easy to identify significant factors and interactions in the experimental data.
-
Data Visualization: Minitab's graphical capabilities help users visualize the effects of factors on responses, facilitating the interpretation of results.
-
Statistical Output: The software generates comprehensive reports that summarize the experimental design, analysis, and optimization results, making it simple to communicate findings to stakeholders.
-
Quality Improvement: Minitab's DOE tools are particularly valuable in Six Sigma and quality improvement projects, as they enable practitioners to identify the optimal settings for process parameters that minimize defects and variation.
By providing a user-friendly interface, automated calculations, and comprehensive analysis and reporting capabilities, Minitab streamlines the design of experiments. This accessibility empowers organizations to conduct efficient and effective experiments, leading to improved processes, products, and overall quality while saving time and resources in the process.
Using Minitab for Root Cause Analysis
Minitab is a powerful ally in the process of root cause analysis, offering a comprehensive suite of statistical tools and data analysis capabilities. The journey begins by clearly defining the problem and gathering relevant data, which Minitab helps organize and prepare for analysis. Its intuitive graphical tools and descriptive statistics assist in exploring data distributions and patterns, providing valuable insights into the nature of the problem. Minitab's versatility shines during the brainstorming phase, as it aids in creating cause-and-effect diagrams to systematically identify potential causes across different categories. Once potential causes are identified, Minitab facilitates their prioritization through Pareto analysis, ensuring that the most significant factors are addressed first. Through hypothesis testing and regression analysis, Minitab helps validate hypotheses about the root causes, enabling data-driven decision-making.
Beyond analysis, Minitab supports corrective action planning and monitoring by helping organizations track the effectiveness of implemented solutions. Control charts and ongoing data analysis ensure that processes remain stable and that the identified root causes are genuinely mitigated. Finally, Minitab aids in documentation and reporting, allowing organizations to maintain a clear record of the root cause analysis process and communicate findings and actions effectively. In essence, Minitab serves as an indispensable tool for organizations committed to uncovering the underlying causes of problems and implementing data-driven solutions for process improvement and quality enhancement.
Conclusion
In conclusion, Minitab is a versatile and powerful statistical software package that plays a pivotal role in data analysis, quality control, Six Sigma projects, regression analysis, and root cause analysis. Its user-friendly interface, comprehensive statistical tools, and graphical capabilities make it accessible to both beginners and experienced professionals across various industries.
Minitab simplifies complex statistical processes, empowering users to make data-driven decisions, uncover insights from data, and optimize processes. Whether it's conducting hypothesis tests, creating control charts, designing experiments, or identifying root causes of problems, Minitab streamlines the analytical journey, saving time and resources while ensuring accurate results.
As organizations continue to rely on data-driven decision-making for success, Minitab remains a valuable asset, facilitating the pursuit of quality improvement, process optimization, and continuous excellence. Its role in supporting Six Sigma methodologies, conducting robust regression analyses, and aiding in root cause analysis positions it as a trusted partner for professionals and organizations dedicated to harnessing the power of data for growth and competitiveness.
Read More
In an era where data is the lifeblood of informed decision-making, organizations across diverse industries strive for excellence in quality control and process improvement. Six Sigma, a methodology focused on minimizing defects and variations, stands as a beacon of efficiency and quality. At the heart of this data-driven revolution lies Minitab, a versatile statistical software package. In this blog, we embark on a journey to explore "The Role of Minitab in Quality Control and Six Sigma." We will unravel how Minitab empowers professionals and organizations to harness the power of data, streamline processes, and elevate quality standards. From hypothesis testing and control charts to regression analysis and root cause analysis, Minitab serves as an indispensable tool, enabling the pursuit of data-driven excellence and the achievement of Six Sigma's lofty goals. Join us as we delve into the essential role that Minitab plays in the world of quality control and process improvement, where data reigns supreme and continuous improvement is the ultimate objective.
Table of contents
-
Introduction to Minitab
-
How Minitab Facilitates Data Analysis in Six Sigma Projects
-
Minitab and DMAIC
-
Statistical Analysis with Minitab
-
Creating Control Charts with Minitab
-
Hypothesis Testing in Minitab
-
Regression Analysis in Minitab
-
Design of Experiments (DOE) Made Easy with Minitab
-
Using Minitab for Root Cause Analysis
-
Conclusion
Introduction to Minitab
Minitab is a versatile and powerful statistical software package used extensively in data analysis, quality control, and process improvement. With a user-friendly interface and a comprehensive set of statistical tools, Minitab enables professionals and organizations to analyze data, make data-driven decisions, and enhance the quality of products and services. It offers a wide range of features, including data import from various sources, hypothesis testing, regression analysis, control chart creation, and process capability analysis. Minitab's compatibility with Six Sigma methodologies further enhances its appeal as it aligns seamlessly with the DMAIC (Define, Measure, Analyze, Improve, Control) framework, making it a go-to tool for professionals aiming to optimize processes and achieve higher quality standards in various industries.
Professionals from diverse fields, including manufacturing, healthcare, finance, and education, rely on Minitab to uncover insights from data and drive continuous improvement. Minitab's accessibility through various licensing options, coupled with its extensive learning resources and tutorials, makes it suitable for both beginners and experienced statisticians. As data analysis continues to play a pivotal role in decision-making, Minitab remains a valuable asset, helping individuals and organizations harness the power of data to achieve their goals and maintain a competitive edge in their respective industries.
How Minitab Facilitates Data Analysis in Six Sigma Projects
Minitab plays a crucial role in facilitating data analysis within Six Sigma projects by providing a robust set of tools and features tailored to the methodology's DMAIC (Define, Measure, Analyze, Improve, Control) framework. Here's how Minitab contributes to each phase of a Six Sigma project:
-
Define Phase: Minitab assists in defining project goals, scope, and metrics by helping users collect and organize data. It can be used to create project charters and establish clear objectives. Additionally, it supports the creation of process maps and flowcharts, aiding in the identification of potential improvement areas.
-
Measure Phase: In this phase, Minitab enables users to collect and analyze data to quantify the current state of a process. It simplifies data entry, statistical calculations, and the creation of graphical representations such as histograms and box plots. Minitab's capabilities for measurement system analysis (MSA) ensure that data collection methods are reliable, a fundamental aspect of Six Sigma.
-
Analyze Phase: Minitab shines in the Analyze phase by offering a wide range of statistical tools. It simplifies hypothesis testing, regression analysis, and design of experiments (DOE), helping users identify the root causes of process issues and validate potential improvement factors. Users can also create various graphical representations to visualize data relationships, making it easier to pinpoint areas for improvement.
-
Improve Phase: Minitab supports users in implementing and testing improvement solutions. It assists in optimizing processes by conducting Monte Carlo simulations, which evaluate the impact of different variables on process performance. This phase also benefits from Minitab's capabilities for factorial experiments and response surface methodology (RSM).
-
Control Phase: Finally, in the Control phase, Minitab aids in establishing control mechanisms to sustain process improvements. Users can create control charts, set control limits, and monitor process stability over time. Minitab also helps in documenting standard operating procedures and creating visual aids for training and continuous monitoring.
Overall, Minitab's user-friendly interface, extensive statistical capabilities, and alignment with Six Sigma principles make it an indispensable tool for data analysis throughout the DMAIC framework. It empowers Six Sigma practitioners to make data-driven decisions, identify process improvements, and drive quality and efficiency enhancements in their organizations.
Minitab and DMAIC
Minitab and DMAIC are two pillars of success in Six Sigma methodology, working hand in hand to achieve process improvement and quality enhancement. Minitab, as a statistical software tool, is well-aligned with the DMAIC framework's five phases, from defining project objectives to controlling and maintaining process improvements. It simplifies data collection, organizes information, conducts robust statistical analyses, and assists in visualizing data relationships, enabling Six Sigma practitioners to make informed decisions at each stage of the project. Whether it's hypothesis testing in the Analyze phase or creating control charts in the Control phase, Minitab provides the necessary tools and features to drive data-driven excellence within a Six Sigma context.
The synergy between Minitab and DMAIC empowers organizations to identify and address process inefficiencies, reduce defects, and enhance overall quality. Minitab's user-friendly interface and comprehensive statistical capabilities streamline the application of Six Sigma principles, making it a vital asset for professionals and teams dedicated to process optimization and continuous improvement. By leveraging Minitab in conjunction with DMAIC, businesses can achieve higher quality standards, reduced variability, and increased customer satisfaction, ultimately leading to improved competitiveness and success in today's competitive marketplace.
Statistical Analysis with Minitab
Statistical analysis with Minitab is a dynamic and versatile process that empowers individuals and organizations to extract meaningful insights from data. Minitab's user-friendly interface simplifies the often complex world of statistics, enabling users to perform a wide range of statistical analyses with ease. From conducting hypothesis tests and regression analysis to creating control charts and designing experiments, Minitab provides a comprehensive suite of tools to address diverse analytical needs. Moreover, its ability to generate clear and compelling visualizations enhances the understanding and communication of statistical findings. Minitab's role extends beyond just number crunching; it fosters data-driven decision-making, supports quality control efforts, and aids in process optimization, ultimately contributing to improved outcomes and greater efficiency across various domains.
Whether in the realms of business, academia, healthcare, or manufacturing, statistical analysis with Minitab empowers professionals to uncover trends, identify patterns, and make informed choices based on data-driven evidence. Its widespread adoption in quality control, Six Sigma projects, research, and beyond underscores its importance as a valuable tool for data analysis and decision support. In an era where data is increasingly integral to success, Minitab remains a reliable and indispensable partner, ensuring that the power of statistics is accessible and actionable for individuals and organizations alike.
Creating Control Charts with Minitab
Creating control charts with Minitab is a cornerstone of effective quality control and process monitoring. Minitab's user-friendly interface and extensive charting capabilities make it accessible to both beginners and experienced quality professionals. With Minitab, users can effortlessly generate a variety of control charts, such as X-bar and R charts for continuous data or p-charts for attribute data, with just a few clicks. The software automatically calculates control limits, plots data points, and highlights potential issues in a visually intuitive manner.
Interpreting these control charts is equally straightforward; users can quickly identify trends, shifts, or outliers that might indicate process instability. Minitab empowers organizations to proactively address quality issues, reduce defects, and enhance process performance by providing a comprehensive solution for monitoring and maintaining control over critical processes. Its role in facilitating the creation and interpretation of control charts ensures that organizations can achieve and sustain the highest standards of quality control and efficiency, fostering continuous improvement in their operations.
Hypothesis Testing in Minitab
Here are the steps to perform hypothesis testing in Minitab in simple points:
-
Data Entry: Enter your data into Minitab.
-
Select Test: Choose the specific hypothesis test you need (e.g., t-test, ANOVA) from Minitab's menu.
-
Define Hypotheses: State your null hypothesis (H0) and alternative hypothesis (Ha).
-
Perform the Test: Minitab calculates the test statistic and p-value based on your data.
-
Interpret Results: If p-value is smaller than your chosen significance level, reject the null hypothesis. If not, fail to reject it.
-
Draw Conclusions: Make decisions based on the p-value and the specific hypothesis test.
-
Generate Reports: Create reports and visualizations of your results using Minitab's tools.
Minitab simplifies hypothesis testing, making it accessible for making data-driven decisions in various fields.
Regression Analysis in Minitab
Regression analysis in Minitab is a powerful tool for understanding and quantifying relationships between variables. With a straightforward interface, it enables users to perform a wide range of regression analyses, from simple linear regressions to more complex multiple regression models. Users begin by entering their data and specifying the response and predictor variables of interest. Minitab then runs the analysis, providing crucial statistics such as coefficients, p-values, and R-squared values that help assess the strength and significance of these relationships.
Interpreting the results is made accessible, allowing users to draw meaningful conclusions and make predictions based on their data. Whether it's uncovering the factors that impact sales figures, evaluating the effectiveness of marketing campaigns, or making informed decisions in research, Minitab's regression analysis capabilities simplify the process, making it an indispensable resource for professionals across diverse fields. Its ability to visualize data and generate comprehensive reports further enhances its utility, ensuring that organizations can harness the power of regression analysis for data-driven insights and improved decision-making.
Design of Experiments (DOE) Made Easy with Minitab
Design of Experiments (DOE) is a systematic approach for conducting experiments to optimize processes, improve products, and identify critical factors affecting outcomes. Minitab, a widely used statistical software, simplifies the entire DOE process, making it accessible to both beginners and experienced practitioners. Here's how Minitab makes DOE easy:
-
Experimental Design Wizard: Minitab offers an intuitive Experimental Design Wizard that guides users through the DOE process step by step. This tool helps users select the appropriate design type, define factors and responses, and choose the levels of these factors.
-
Design Selection: Minitab provides a variety of design types, including full factorial, fractional factorial, response surface, and mixture designs. Users can easily select the design that suits their specific experiment requirements.
-
Factorial and Fractional Factorial Designs: Minitab automatically generates the necessary experimental runs and assigns factor settings based on the chosen design. This simplifies the planning process and reduces the number of experimental trials needed, saving time and resources.
-
Response Optimization: Minitab helps users analyze the results of their experiments by fitting models and optimizing responses. It provides visualizations, contour plots, and response surface plots that aid in understanding the relationships between factors and responses.
-
Robust Parameter Design (RPD): Minitab includes tools for conducting robust parameter design, which allows users to optimize processes while considering variability and noise factors, ensuring robust and reliable outcomes.
-
Analysis of Variance (ANOVA): Minitab automates the ANOVA analysis, making it easy to identify significant factors and interactions in the experimental data.
-
Data Visualization: Minitab's graphical capabilities help users visualize the effects of factors on responses, facilitating the interpretation of results.
-
Statistical Output: The software generates comprehensive reports that summarize the experimental design, analysis, and optimization results, making it simple to communicate findings to stakeholders.
-
Quality Improvement: Minitab's DOE tools are particularly valuable in Six Sigma and quality improvement projects, as they enable practitioners to identify the optimal settings for process parameters that minimize defects and variation.
By providing a user-friendly interface, automated calculations, and comprehensive analysis and reporting capabilities, Minitab streamlines the design of experiments. This accessibility empowers organizations to conduct efficient and effective experiments, leading to improved processes, products, and overall quality while saving time and resources in the process.
Using Minitab for Root Cause Analysis
Minitab is a powerful ally in the process of root cause analysis, offering a comprehensive suite of statistical tools and data analysis capabilities. The journey begins by clearly defining the problem and gathering relevant data, which Minitab helps organize and prepare for analysis. Its intuitive graphical tools and descriptive statistics assist in exploring data distributions and patterns, providing valuable insights into the nature of the problem. Minitab's versatility shines during the brainstorming phase, as it aids in creating cause-and-effect diagrams to systematically identify potential causes across different categories. Once potential causes are identified, Minitab facilitates their prioritization through Pareto analysis, ensuring that the most significant factors are addressed first. Through hypothesis testing and regression analysis, Minitab helps validate hypotheses about the root causes, enabling data-driven decision-making.
Beyond analysis, Minitab supports corrective action planning and monitoring by helping organizations track the effectiveness of implemented solutions. Control charts and ongoing data analysis ensure that processes remain stable and that the identified root causes are genuinely mitigated. Finally, Minitab aids in documentation and reporting, allowing organizations to maintain a clear record of the root cause analysis process and communicate findings and actions effectively. In essence, Minitab serves as an indispensable tool for organizations committed to uncovering the underlying causes of problems and implementing data-driven solutions for process improvement and quality enhancement.
Conclusion
In conclusion, Minitab is a versatile and powerful statistical software package that plays a pivotal role in data analysis, quality control, Six Sigma projects, regression analysis, and root cause analysis. Its user-friendly interface, comprehensive statistical tools, and graphical capabilities make it accessible to both beginners and experienced professionals across various industries.
Minitab simplifies complex statistical processes, empowering users to make data-driven decisions, uncover insights from data, and optimize processes. Whether it's conducting hypothesis tests, creating control charts, designing experiments, or identifying root causes of problems, Minitab streamlines the analytical journey, saving time and resources while ensuring accurate results.
As organizations continue to rely on data-driven decision-making for success, Minitab remains a valuable asset, facilitating the pursuit of quality improvement, process optimization, and continuous excellence. Its role in supporting Six Sigma methodologies, conducting robust regression analyses, and aiding in root cause analysis positions it as a trusted partner for professionals and organizations dedicated to harnessing the power of data for growth and competitiveness.
Lean Six Sigma Essentials: Definition, Methodology, Benefits
Navigating the realm of employee benefits and well-being, this guide focuses on "Lean Six Sigma Essentials: Definition, Methodology, Benefits." In the landscape of professional development, Lean Six Sigma stands as a crucial methodology, seamlessly blending Lean principles and Six Sigma techniques. As we explore the methodology encompassed by DMAIC — Define, Measure, Analyze, Improve, and Control — we draw parallels to the critical elements found in employee benefits. From the optimization principles of Lean Six Sigma to the benefits it brings to organizational efficiency, this guide delves into how methodologies akin to those in employee assistance programs (EAP), disability benefits, and dental plans contribute to holistic workplace well-being. Understanding the parallels between Lean Six Sigma and critical illness cover, Social Security benefits, and even the application process for disability benefits sheds light on the comprehensive approach organizations can adopt for both professional and personal development in the ever-evolving landscape of employee benefits.
Table of contents
-
Defining Lean Six Sigma
-
Methodology Deep Dive
-
Principles at the Core
-
Techniques and Tools of Lean Six Sigma
-
Realizing the Benefits
-
Conclusion
Defining Lean Six Sigma
Defining Lean Six Sigma encompasses unraveling a methodology that combines Lean principles and Six Sigma techniques, creating a comprehensive approach to process improvement. At its core, Lean Six Sigma is a data-driven strategy designed to enhance efficiency, reduce waste, and optimize organizational processes. It integrates the principles of Lean, which focuses on minimizing waste and maximizing value for the customer, with Six Sigma, a methodology centered on minimizing variability and defects. This dual approach aims to achieve operational excellence by systematically identifying and eliminating inefficiencies within processes. The definition of Lean Six Sigma not only involves understanding its foundational concepts but also acknowledges its adaptability across various industries and sectors. As a transformative methodology, Lean Six Sigma provides organizations with the tools and frameworks needed to foster a culture of continuous improvement and achieve sustainable success.
Methodology Deep Dive
The methodology at the heart of Lean Six Sigma is a structured and systematic approach known as DMAIC, representing Define, Measure, Analyze, Improve, and Control. This methodology serves as the cornerstone for Lean Six Sigma projects, guiding practitioners through a step-by-step process of process improvement. In the "Methodology Deep Dive," we explore each phase intricately. The Define phase involves clarifying project goals and scope, setting the foundation for subsequent stages. Measurement follows, where practitioners quantify existing processes to establish baselines and identify areas for improvement. Analysis involves a comprehensive examination of data to uncover root causes and inefficiencies. Subsequently, the Improve phase focuses on implementing solutions and innovations to enhance processes. Finally, the Control phase ensures that improvements are sustained by instituting measures to monitor and manage ongoing performance. This deep dive into the DMAIC methodology provides a nuanced understanding of Lean Six Sigma's systematic approach, making it a valuable resource for practitioners aiming to drive continuous improvement within their organizations.
Principles at the Core
At the core of Lean Six Sigma are fundamental principles that shape its philosophy and guide practitioners toward effective process improvement. These principles draw from both Lean and Six Sigma methodologies, emphasizing a customer-centric approach, process optimization, and data-driven decision-making. Customer focus entails understanding and meeting customer requirements, aligning processes with customer needs, and delivering maximum value. Process optimization involves the continuous pursuit of efficiency, minimizing waste, and streamlining operations. Data-driven decision-making underscores the importance of basing decisions on factual analysis rather than assumptions. Lean Six Sigma principles collectively contribute to a holistic understanding of how organizations can achieve excellence by aligning their processes with customer expectations, continuously improving efficiency, and fostering a culture of evidence-based decision-making. These core principles not only define the ethos of Lean Six Sigma but also guide its implementation across diverse industries and contexts.
Techniques and Tools of Lean Six Sigma
The effectiveness of Lean Six Sigma lies in its arsenal of techniques and tools specifically crafted for process improvement. These methodologies are instrumental in identifying and eliminating inefficiencies, reducing defects, and optimizing organizational processes. Techniques such as value stream mapping provide a visual representation of end-to-end processes, facilitating the identification of areas for improvement. Statistical process control ensures that processes operate within acceptable limits, minimizing variation. Root cause analysis allows practitioners to delve into the underlying issues causing defects or inefficiencies. Lean Six Sigma tools like Kaizen events, Pareto charts, and Fishbone diagrams offer structured approaches to problem-solving and continuous improvement. The utilization of these techniques and tools enables organizations to undertake data-driven, systematic approaches to enhance overall process performance. This comprehensive suite of methodologies contributes to the robustness of Lean Six Sigma as a transformative strategy for achieving excellence in diverse industries and operational contexts.
Realizing the Benefits
Realizing the benefits of Lean Six Sigma extends beyond a theoretical understanding, showcasing tangible improvements that organizations can achieve through its systematic application. By embracing Lean Six Sigma, companies can streamline their processes, resulting in enhanced efficiency, reduced operational costs, and heightened overall quality. The methodology's emphasis on data-driven decision-making ensures that organizations make informed choices, leading to a more optimized workflow. Furthermore, the customer-centric approach inherent in Lean Six Sigma often results in increased customer satisfaction as products and services align more closely with customer needs and expectations. Real-world examples and case studies provide evidence of successful Lean Six Sigma implementations, illustrating how organizations have achieved remarkable transformations in various industries, from manufacturing to healthcare and beyond. As organizations navigate the dynamic landscape of quality management, Lean Six Sigma stands out as a catalyst for continuous improvement, offering a pathway to sustained success by realizing quantifiable benefits and fostering a culture of excellence.
Conclusion
In conclusion, the exploration of Lean Six Sigma, spanning its definition, methodology, principles, techniques, and benefits, reveals a robust and transformative approach to organizational excellence. The synergy of Lean principles and Six Sigma techniques, as exemplified through the DMAIC methodology, provides a systematic framework for process improvement. Core principles, such as customer focus and data-driven decision-making, underscore the methodology's ethos, guiding organizations toward efficiency and continuous improvement. The array of techniques and tools available in Lean Six Sigma equips practitioners with the means to identify and address inefficiencies, ultimately leading to streamlined operations and improved quality. The realization of benefits, including enhanced efficiency, cost reduction, and heightened customer satisfaction, is substantiated by real-world case studies, underscoring the methodology's practical impact across diverse industries. As a comprehensive strategy for excellence, Lean Six Sigma emerges not merely as a set of principles but as a transformative force that empowers organizations to navigate challenges, optimize processes, and cultivate a culture of continuous improvement in the ever-evolving landscape of quality management.
Read More
Navigating the realm of employee benefits and well-being, this guide focuses on "Lean Six Sigma Essentials: Definition, Methodology, Benefits." In the landscape of professional development, Lean Six Sigma stands as a crucial methodology, seamlessly blending Lean principles and Six Sigma techniques. As we explore the methodology encompassed by DMAIC — Define, Measure, Analyze, Improve, and Control — we draw parallels to the critical elements found in employee benefits. From the optimization principles of Lean Six Sigma to the benefits it brings to organizational efficiency, this guide delves into how methodologies akin to those in employee assistance programs (EAP), disability benefits, and dental plans contribute to holistic workplace well-being. Understanding the parallels between Lean Six Sigma and critical illness cover, Social Security benefits, and even the application process for disability benefits sheds light on the comprehensive approach organizations can adopt for both professional and personal development in the ever-evolving landscape of employee benefits.
Table of contents
-
Defining Lean Six Sigma
-
Methodology Deep Dive
-
Principles at the Core
-
Techniques and Tools of Lean Six Sigma
-
Realizing the Benefits
-
Conclusion
Defining Lean Six Sigma
Defining Lean Six Sigma encompasses unraveling a methodology that combines Lean principles and Six Sigma techniques, creating a comprehensive approach to process improvement. At its core, Lean Six Sigma is a data-driven strategy designed to enhance efficiency, reduce waste, and optimize organizational processes. It integrates the principles of Lean, which focuses on minimizing waste and maximizing value for the customer, with Six Sigma, a methodology centered on minimizing variability and defects. This dual approach aims to achieve operational excellence by systematically identifying and eliminating inefficiencies within processes. The definition of Lean Six Sigma not only involves understanding its foundational concepts but also acknowledges its adaptability across various industries and sectors. As a transformative methodology, Lean Six Sigma provides organizations with the tools and frameworks needed to foster a culture of continuous improvement and achieve sustainable success.
Methodology Deep Dive
The methodology at the heart of Lean Six Sigma is a structured and systematic approach known as DMAIC, representing Define, Measure, Analyze, Improve, and Control. This methodology serves as the cornerstone for Lean Six Sigma projects, guiding practitioners through a step-by-step process of process improvement. In the "Methodology Deep Dive," we explore each phase intricately. The Define phase involves clarifying project goals and scope, setting the foundation for subsequent stages. Measurement follows, where practitioners quantify existing processes to establish baselines and identify areas for improvement. Analysis involves a comprehensive examination of data to uncover root causes and inefficiencies. Subsequently, the Improve phase focuses on implementing solutions and innovations to enhance processes. Finally, the Control phase ensures that improvements are sustained by instituting measures to monitor and manage ongoing performance. This deep dive into the DMAIC methodology provides a nuanced understanding of Lean Six Sigma's systematic approach, making it a valuable resource for practitioners aiming to drive continuous improvement within their organizations.
Principles at the Core
At the core of Lean Six Sigma are fundamental principles that shape its philosophy and guide practitioners toward effective process improvement. These principles draw from both Lean and Six Sigma methodologies, emphasizing a customer-centric approach, process optimization, and data-driven decision-making. Customer focus entails understanding and meeting customer requirements, aligning processes with customer needs, and delivering maximum value. Process optimization involves the continuous pursuit of efficiency, minimizing waste, and streamlining operations. Data-driven decision-making underscores the importance of basing decisions on factual analysis rather than assumptions. Lean Six Sigma principles collectively contribute to a holistic understanding of how organizations can achieve excellence by aligning their processes with customer expectations, continuously improving efficiency, and fostering a culture of evidence-based decision-making. These core principles not only define the ethos of Lean Six Sigma but also guide its implementation across diverse industries and contexts.
Techniques and Tools of Lean Six Sigma
The effectiveness of Lean Six Sigma lies in its arsenal of techniques and tools specifically crafted for process improvement. These methodologies are instrumental in identifying and eliminating inefficiencies, reducing defects, and optimizing organizational processes. Techniques such as value stream mapping provide a visual representation of end-to-end processes, facilitating the identification of areas for improvement. Statistical process control ensures that processes operate within acceptable limits, minimizing variation. Root cause analysis allows practitioners to delve into the underlying issues causing defects or inefficiencies. Lean Six Sigma tools like Kaizen events, Pareto charts, and Fishbone diagrams offer structured approaches to problem-solving and continuous improvement. The utilization of these techniques and tools enables organizations to undertake data-driven, systematic approaches to enhance overall process performance. This comprehensive suite of methodologies contributes to the robustness of Lean Six Sigma as a transformative strategy for achieving excellence in diverse industries and operational contexts.
Realizing the Benefits
Realizing the benefits of Lean Six Sigma extends beyond a theoretical understanding, showcasing tangible improvements that organizations can achieve through its systematic application. By embracing Lean Six Sigma, companies can streamline their processes, resulting in enhanced efficiency, reduced operational costs, and heightened overall quality. The methodology's emphasis on data-driven decision-making ensures that organizations make informed choices, leading to a more optimized workflow. Furthermore, the customer-centric approach inherent in Lean Six Sigma often results in increased customer satisfaction as products and services align more closely with customer needs and expectations. Real-world examples and case studies provide evidence of successful Lean Six Sigma implementations, illustrating how organizations have achieved remarkable transformations in various industries, from manufacturing to healthcare and beyond. As organizations navigate the dynamic landscape of quality management, Lean Six Sigma stands out as a catalyst for continuous improvement, offering a pathway to sustained success by realizing quantifiable benefits and fostering a culture of excellence.
Conclusion
In conclusion, the exploration of Lean Six Sigma, spanning its definition, methodology, principles, techniques, and benefits, reveals a robust and transformative approach to organizational excellence. The synergy of Lean principles and Six Sigma techniques, as exemplified through the DMAIC methodology, provides a systematic framework for process improvement. Core principles, such as customer focus and data-driven decision-making, underscore the methodology's ethos, guiding organizations toward efficiency and continuous improvement. The array of techniques and tools available in Lean Six Sigma equips practitioners with the means to identify and address inefficiencies, ultimately leading to streamlined operations and improved quality. The realization of benefits, including enhanced efficiency, cost reduction, and heightened customer satisfaction, is substantiated by real-world case studies, underscoring the methodology's practical impact across diverse industries. As a comprehensive strategy for excellence, Lean Six Sigma emerges not merely as a set of principles but as a transformative force that empowers organizations to navigate challenges, optimize processes, and cultivate a culture of continuous improvement in the ever-evolving landscape of quality management.
Azure data architect step-by-step guide!
Welcome to our comprehensive "Azure Data Architect Step-by-Step Guide!" In today's dynamic business landscape, harnessing the power of cloud-based data solutions is imperative, and Microsoft Azure stands at the forefront of this technological evolution. Whether you're an aspiring data architect or an experienced professional looking to enhance your skills, this guide is your roadmap to mastering the intricacies of architecting data solutions on the Azure platform.
As businesses increasingly migrate their data ecosystems to the cloud, the role of an Azure Data Architect has become instrumental in ensuring efficiency, scalability, and security. This step-by-step guide is crafted to empower you with the knowledge and practical know-how needed to navigate the Azure data landscape seamlessly.
Throughout this journey, we will explore key concepts such as data modeling, cloud data storage, and the implementation of best practices using Azure services. Dive into the world of Azure Data Services, including Azure SQL Database, Azure Data Factory, and Azure Synapse Analytics, and learn how to design and optimize data solutions tailored to your organization's unique needs.
Whether you're interested in building data pipelines, ensuring data governance, or implementing robust security measures, each chapter of this guide is dedicated to providing actionable insights and hands-on examples. By the end of this journey, you'll not only be well-versed in the principles of Azure data architecture but also equipped to tackle real-world challenges and contribute significantly to data-driven success in the cloud era.
Table of contents
-
Azure Data Modeling
-
Building Data Pipelines with Azure Data Factory
-
Optimizing Data Storage in Azure
-
Securing Data in Azure
-
Data Governance in Azure
-
Conclusion
Azure Data Modeling
Data modeling is a foundational aspect of effective data architecture, and within the Azure ecosystem, it plays a crucial role in shaping the structure and relationships of data. In this section of the guide, we explore the nuances of Azure Data Modeling, offering a step-by-step walkthrough on understanding the principles, methodologies, and tools involved. From conceptualizing entities and relationships to implementing various data modeling approaches, readers will gain insights into crafting a robust data model tailored for Azure environments. The guide also delves into leveraging Azure SQL Database for efficient data modeling, covering topics such as schema design, normalization, and indexing. Whether you're a beginner navigating the basics or an experienced professional seeking to optimize your data model, this section provides practical guidance and best practices to empower Azure Data Architects in designing scalable and well-organized data structures within the Azure cloud.
Building Data Pipelines with Azure Data Factory
In this segment of the guide, we delve into the critical realm of orchestrating data workflows with Azure Data Factory. As organizations increasingly adopt cloud-based data solutions, the creation of efficient and scalable data pipelines becomes paramount. This section offers a comprehensive, step-by-step guide to Azure Data Factory, beginning with an introduction to its key features and architecture. Readers will be guided through the process of designing, deploying, and managing data pipelines, exploring data movement, transformation, and integration techniques along the way. Practical insights into monitoring and optimizing data pipelines ensure that Azure Data Architects can not only build but also fine-tune pipelines for optimal performance. Whether you're new to Azure Data Factory or looking to enhance your skills, this section equips you with the knowledge and hands-on experience needed to leverage this powerful tool for seamless data integration and processing in the Azure cloud environment.
Optimizing Data Storage in Azure
Efficient data storage is a cornerstone of successful data architecture, and this section of the guide focuses on navigating the diverse landscape of Azure data storage options. From understanding the characteristics of Azure Data Storage solutions to selecting the right storage model for specific use cases, readers will embark on a step-by-step journey to optimize data storage in the Azure cloud. Covering key considerations such as data partitioning, indexing strategies, and performance optimization, the guide provides actionable insights to enhance storage efficiency. Whether it's leveraging Azure Blob Storage for scalability, Azure SQL Database for relational data, or Azure Data Lake Storage for big data analytics, this section equips Azure Data Architects with the knowledge and best practices to make informed decisions, ensuring their data storage solutions align seamlessly with the unique requirements of their projects.
Securing Data in Azure
In the ever-evolving landscape of cloud computing, ensuring the robust security of data is paramount, and this guide section focuses on fortifying data within the Azure environment. From fundamental principles to advanced strategies, readers will navigate through Azure Data Security, covering encryption methodologies, access controls, and compliance standards. The step-by-step approach guides Azure Data Architects in implementing comprehensive security measures, safeguarding sensitive information against potential threats. Whether it's understanding Azure's security fundamentals, encrypting data in transit and at rest, or adhering to regulatory compliance, this section provides practical insights and best practices to empower professionals in creating a secure data environment within Azure, instilling confidence in data integrity and confidentiality.
Data Governance in Azure
This section of the guide illuminates the critical domain of data governance within the Azure cloud, emphasizing the significance of maintaining data quality, integrity, and compliance. Readers will embark on a comprehensive journey through the principles and practices of data governance, covering essential aspects such as metadata management, data quality assurance, and the establishment of policies and standards. From defining data ownership and access controls to monitoring and auditing data governance processes, this step-by-step guide equips Azure Data Architects with the knowledge and tools to implement robust governance frameworks. Whether you're navigating the complexities of ensuring data reliability or striving to align with industry regulations, this section provides actionable insights and best practices to empower professionals in cultivating a culture of effective data governance within the Azure ecosystem.
Conclusion
In conclusion, this step-by-step guide on becoming an Azure Data Architect serves as a comprehensive roadmap for navigating the intricacies of data architecture within the Azure cloud environment. From mastering the art of data modeling to building efficient data pipelines with Azure Data Factory, optimizing data storage, securing sensitive information, and implementing robust data governance practices, each section provides practical insights and hands-on guidance. As organizations increasingly turn to Azure for their data solutions, this guide empowers both novice and seasoned professionals with the knowledge and skills needed to architect, implement, and manage data systems effectively. By embracing best practices, industry standards, and leveraging Azure's cutting-edge services, readers are well-equipped to contribute significantly to the success of data-driven initiatives in the cloud era. Whether you're embarking on a new project, seeking to enhance your existing skills, or aiming for Azure data architecture certification, this guide is your comprehensive companion in mastering the diverse facets of Azure data architecture. Let this journey inspire confidence as you navigate the evolving landscape of data management in the Azure cloud.
Read More
Welcome to our comprehensive "Azure Data Architect Step-by-Step Guide!" In today's dynamic business landscape, harnessing the power of cloud-based data solutions is imperative, and Microsoft Azure stands at the forefront of this technological evolution. Whether you're an aspiring data architect or an experienced professional looking to enhance your skills, this guide is your roadmap to mastering the intricacies of architecting data solutions on the Azure platform.
As businesses increasingly migrate their data ecosystems to the cloud, the role of an Azure Data Architect has become instrumental in ensuring efficiency, scalability, and security. This step-by-step guide is crafted to empower you with the knowledge and practical know-how needed to navigate the Azure data landscape seamlessly.
Throughout this journey, we will explore key concepts such as data modeling, cloud data storage, and the implementation of best practices using Azure services. Dive into the world of Azure Data Services, including Azure SQL Database, Azure Data Factory, and Azure Synapse Analytics, and learn how to design and optimize data solutions tailored to your organization's unique needs.
Whether you're interested in building data pipelines, ensuring data governance, or implementing robust security measures, each chapter of this guide is dedicated to providing actionable insights and hands-on examples. By the end of this journey, you'll not only be well-versed in the principles of Azure data architecture but also equipped to tackle real-world challenges and contribute significantly to data-driven success in the cloud era.
Table of contents
-
Azure Data Modeling
-
Building Data Pipelines with Azure Data Factory
-
Optimizing Data Storage in Azure
-
Securing Data in Azure
-
Data Governance in Azure
-
Conclusion
Azure Data Modeling
Data modeling is a foundational aspect of effective data architecture, and within the Azure ecosystem, it plays a crucial role in shaping the structure and relationships of data. In this section of the guide, we explore the nuances of Azure Data Modeling, offering a step-by-step walkthrough on understanding the principles, methodologies, and tools involved. From conceptualizing entities and relationships to implementing various data modeling approaches, readers will gain insights into crafting a robust data model tailored for Azure environments. The guide also delves into leveraging Azure SQL Database for efficient data modeling, covering topics such as schema design, normalization, and indexing. Whether you're a beginner navigating the basics or an experienced professional seeking to optimize your data model, this section provides practical guidance and best practices to empower Azure Data Architects in designing scalable and well-organized data structures within the Azure cloud.
Building Data Pipelines with Azure Data Factory
In this segment of the guide, we delve into the critical realm of orchestrating data workflows with Azure Data Factory. As organizations increasingly adopt cloud-based data solutions, the creation of efficient and scalable data pipelines becomes paramount. This section offers a comprehensive, step-by-step guide to Azure Data Factory, beginning with an introduction to its key features and architecture. Readers will be guided through the process of designing, deploying, and managing data pipelines, exploring data movement, transformation, and integration techniques along the way. Practical insights into monitoring and optimizing data pipelines ensure that Azure Data Architects can not only build but also fine-tune pipelines for optimal performance. Whether you're new to Azure Data Factory or looking to enhance your skills, this section equips you with the knowledge and hands-on experience needed to leverage this powerful tool for seamless data integration and processing in the Azure cloud environment.
Optimizing Data Storage in Azure
Efficient data storage is a cornerstone of successful data architecture, and this section of the guide focuses on navigating the diverse landscape of Azure data storage options. From understanding the characteristics of Azure Data Storage solutions to selecting the right storage model for specific use cases, readers will embark on a step-by-step journey to optimize data storage in the Azure cloud. Covering key considerations such as data partitioning, indexing strategies, and performance optimization, the guide provides actionable insights to enhance storage efficiency. Whether it's leveraging Azure Blob Storage for scalability, Azure SQL Database for relational data, or Azure Data Lake Storage for big data analytics, this section equips Azure Data Architects with the knowledge and best practices to make informed decisions, ensuring their data storage solutions align seamlessly with the unique requirements of their projects.
Securing Data in Azure
In the ever-evolving landscape of cloud computing, ensuring the robust security of data is paramount, and this guide section focuses on fortifying data within the Azure environment. From fundamental principles to advanced strategies, readers will navigate through Azure Data Security, covering encryption methodologies, access controls, and compliance standards. The step-by-step approach guides Azure Data Architects in implementing comprehensive security measures, safeguarding sensitive information against potential threats. Whether it's understanding Azure's security fundamentals, encrypting data in transit and at rest, or adhering to regulatory compliance, this section provides practical insights and best practices to empower professionals in creating a secure data environment within Azure, instilling confidence in data integrity and confidentiality.
Data Governance in Azure
This section of the guide illuminates the critical domain of data governance within the Azure cloud, emphasizing the significance of maintaining data quality, integrity, and compliance. Readers will embark on a comprehensive journey through the principles and practices of data governance, covering essential aspects such as metadata management, data quality assurance, and the establishment of policies and standards. From defining data ownership and access controls to monitoring and auditing data governance processes, this step-by-step guide equips Azure Data Architects with the knowledge and tools to implement robust governance frameworks. Whether you're navigating the complexities of ensuring data reliability or striving to align with industry regulations, this section provides actionable insights and best practices to empower professionals in cultivating a culture of effective data governance within the Azure ecosystem.
Conclusion
In conclusion, this step-by-step guide on becoming an Azure Data Architect serves as a comprehensive roadmap for navigating the intricacies of data architecture within the Azure cloud environment. From mastering the art of data modeling to building efficient data pipelines with Azure Data Factory, optimizing data storage, securing sensitive information, and implementing robust data governance practices, each section provides practical insights and hands-on guidance. As organizations increasingly turn to Azure for their data solutions, this guide empowers both novice and seasoned professionals with the knowledge and skills needed to architect, implement, and manage data systems effectively. By embracing best practices, industry standards, and leveraging Azure's cutting-edge services, readers are well-equipped to contribute significantly to the success of data-driven initiatives in the cloud era. Whether you're embarking on a new project, seeking to enhance your existing skills, or aiming for Azure data architecture certification, this guide is your comprehensive companion in mastering the diverse facets of Azure data architecture. Let this journey inspire confidence as you navigate the evolving landscape of data management in the Azure cloud.
Benefits of Microsoft Power BI Certification
Welcome to our exploration of the professional landscape where data meets insight – "Benefits of Microsoft Power BI Certification." In today's digital age, harnessing the power of data is not just a skill but a strategic advantage, and Microsoft Power BI has emerged as a frontrunner in the realm of business intelligence. In this episode, we uncover the myriad advantages and career-transforming benefits that come with earning a Microsoft Power BI Certification. From enhancing your analytics skills and gaining industry recognition to unlocking new career opportunities and positioning yourself as a proficient data analyst, we delve into the tangible impact this certification can have on your professional journey. Join us as we navigate through the keywords that define the landscape of Power BI certification, exploring the valuable insights, recognition, and career growth that await those who embark on this transformative learning journey. Whether you're considering certification or aiming to maximize its potential, this episode is your guide to unlocking the full spectrum of benefits that Microsoft Power BI Certification has to offer.
Table of contents
-
Enhanced Data Visualization Skills: Unleashing the Power of Insights
-
Career Advancement Opportunities: Powering Your Professional Growth
-
Industry Recognition and Credibility: Establishing Your Data Authority
-
Business Intelligence Excellence: Driving Organizational Impact
-
Continuous Learning and Community Engagement: The Power BI Network
-
Conclusion
Enhanced Data Visualization Skills: Unleashing the Power of Insights
In this segment of our exploration into the "Benefits of Microsoft Power BI Certification," we focus on the transformative impact of enhanced data visualization skills, truly unleashing the power of insights. Microsoft Power BI Certification stands as a beacon for professionals seeking to elevate their data visualization proficiency. We delve into how this certification refines and sharpens the ability to translate complex data sets into compelling visual narratives, enabling more effective communication and decision-making. Through real-world examples, we showcase the tangible difference in reporting and storytelling that comes with honing these skills through Power BI. Join us as we uncover the art and science behind data visualization, and how acquiring these advanced skills can not only set professionals apart but also empower them to convey data-driven insights in the most compelling and impactful ways.
Career Advancement Opportunities: Powering Your Professional Growth
In this segment of our exploration into the "Benefits of Microsoft Power BI Certification," we turn our focus to "Career Advancement Opportunities: Powering Your Professional Growth." Earning a Microsoft Power BI Certification is more than a validation of skills; it's a catalyst for unlocking new dimensions in one's professional journey. We delve into the direct correlation between Power BI Certification and expanded career opportunities, examining how certified professionals distinguish themselves in the competitive job market. Through compelling insights and success stories, we illustrate how individuals, armed with Power BI Certification, not only stand out to potential employers but also experience tangible career growth. Join us as we navigate the landscape of career advancement powered by Power BI, exploring how this certification becomes a strategic asset, propelling professionals towards new heights in the ever-evolving field of data analytics.
Industry Recognition and Credibility: Establishing Your Data Authority
In this episode dedicated to the "Benefits of Microsoft Power BI Certification," we delve into the critical realm of "Industry Recognition and Credibility: Establishing Your Data Authority." Microsoft Power BI Certification is not merely a credential; it serves as a powerful testament to one's expertise in the field of data analytics. We explore how this certification becomes a cornerstone in establishing credibility and recognition within the industry, shedding light on how employers and peers value the rigorous standards set by Power BI. Through discussions and examples, we uncover the pivotal role that certification plays in solidifying an individual's position as a trusted data authority, contributing to a heightened professional reputation and increased opportunities within the broader data analytics community. Join us as we unravel the dynamics of industry recognition and explore how Power BI Certification can elevate your standing in the ever-evolving landscape of data analytics.
Business Intelligence Excellence: Driving Organizational Impact
In this segment of our exploration into the "Benefits of Microsoft Power BI Certification," we delve into the realm of "Business Intelligence Excellence: Driving Organizational Impact." Microsoft Power BI Certification is not just an individual accomplishment; it's a catalyst for fostering business intelligence excellence within organizations. We examine how certified professionals contribute to the improvement of organizational decision-making processes through enhanced data analysis and reporting. Through insightful discussions and practical examples, we showcase the tangible impact of Power BI Certification on driving insights that directly influence strategic business decisions. Join us as we uncover the transformative role that certified professionals play in elevating business intelligence standards, ultimately shaping the success and competitive edge of organizations in today's data-driven landscape.
Continuous Learning and Community Engagement: The Power BI Network
In this installment of our exploration into the "Benefits of Microsoft Power BI Certification," we shine a spotlight on "Continuous Learning and Community Engagement: The Power BI Network." Beyond acquiring a certification, Microsoft Power BI fosters a culture of continuous learning and community engagement. We delve into the vibrant ecosystem surrounding Power BI, where certified professionals have access to ongoing resources, updates, and collaborative opportunities. From online forums to workshops and events, we discuss how being part of the Power BI community enhances the learning experience, encourages knowledge sharing, and provides valuable insights into emerging trends. Join us as we uncover the dynamic network that surrounds Power BI, illustrating how continuous learning and community engagement become integral components in the journey of professionals who seek not only to certify their skills but to thrive in a collaborative and ever-evolving landscape of data analytics.
Conclusion
As we bring this episode on the "Benefits of Microsoft Power BI Certification" to a close, the breadth of advantages and transformative potentials explored is a testament to the profound impact this certification can have on professionals in the realm of data analytics. From honing enhanced data visualization skills to leveraging career advancement opportunities, establishing industry recognition and credibility, contributing to business intelligence excellence, and engaging in continuous learning within the vibrant Power BI network, the journey has been enlightening. The Microsoft Power BI Certification emerges not only as a mark of proficiency but as a key to unlocking doors to new career horizons and contributing to organizational success. Whether you are considering certification, in pursuit of continuous learning, or seeking to make a mark in the dynamic field of data analytics, this episode has provided insights into how Power BI Certification can be a pivotal asset. Join us in the ongoing conversation about the dynamic intersection of skills, recognition, and community within the Power BI landscape. Until next time, may your journey in data analytics be enriched and empowered by the benefits of Microsoft Power BI Certification.
Read More
Welcome to our exploration of the professional landscape where data meets insight – "Benefits of Microsoft Power BI Certification." In today's digital age, harnessing the power of data is not just a skill but a strategic advantage, and Microsoft Power BI has emerged as a frontrunner in the realm of business intelligence. In this episode, we uncover the myriad advantages and career-transforming benefits that come with earning a Microsoft Power BI Certification. From enhancing your analytics skills and gaining industry recognition to unlocking new career opportunities and positioning yourself as a proficient data analyst, we delve into the tangible impact this certification can have on your professional journey. Join us as we navigate through the keywords that define the landscape of Power BI certification, exploring the valuable insights, recognition, and career growth that await those who embark on this transformative learning journey. Whether you're considering certification or aiming to maximize its potential, this episode is your guide to unlocking the full spectrum of benefits that Microsoft Power BI Certification has to offer.
Table of contents
-
Enhanced Data Visualization Skills: Unleashing the Power of Insights
-
Career Advancement Opportunities: Powering Your Professional Growth
-
Industry Recognition and Credibility: Establishing Your Data Authority
-
Business Intelligence Excellence: Driving Organizational Impact
-
Continuous Learning and Community Engagement: The Power BI Network
-
Conclusion
Enhanced Data Visualization Skills: Unleashing the Power of Insights
In this segment of our exploration into the "Benefits of Microsoft Power BI Certification," we focus on the transformative impact of enhanced data visualization skills, truly unleashing the power of insights. Microsoft Power BI Certification stands as a beacon for professionals seeking to elevate their data visualization proficiency. We delve into how this certification refines and sharpens the ability to translate complex data sets into compelling visual narratives, enabling more effective communication and decision-making. Through real-world examples, we showcase the tangible difference in reporting and storytelling that comes with honing these skills through Power BI. Join us as we uncover the art and science behind data visualization, and how acquiring these advanced skills can not only set professionals apart but also empower them to convey data-driven insights in the most compelling and impactful ways.
Career Advancement Opportunities: Powering Your Professional Growth
In this segment of our exploration into the "Benefits of Microsoft Power BI Certification," we turn our focus to "Career Advancement Opportunities: Powering Your Professional Growth." Earning a Microsoft Power BI Certification is more than a validation of skills; it's a catalyst for unlocking new dimensions in one's professional journey. We delve into the direct correlation between Power BI Certification and expanded career opportunities, examining how certified professionals distinguish themselves in the competitive job market. Through compelling insights and success stories, we illustrate how individuals, armed with Power BI Certification, not only stand out to potential employers but also experience tangible career growth. Join us as we navigate the landscape of career advancement powered by Power BI, exploring how this certification becomes a strategic asset, propelling professionals towards new heights in the ever-evolving field of data analytics.
Industry Recognition and Credibility: Establishing Your Data Authority
In this episode dedicated to the "Benefits of Microsoft Power BI Certification," we delve into the critical realm of "Industry Recognition and Credibility: Establishing Your Data Authority." Microsoft Power BI Certification is not merely a credential; it serves as a powerful testament to one's expertise in the field of data analytics. We explore how this certification becomes a cornerstone in establishing credibility and recognition within the industry, shedding light on how employers and peers value the rigorous standards set by Power BI. Through discussions and examples, we uncover the pivotal role that certification plays in solidifying an individual's position as a trusted data authority, contributing to a heightened professional reputation and increased opportunities within the broader data analytics community. Join us as we unravel the dynamics of industry recognition and explore how Power BI Certification can elevate your standing in the ever-evolving landscape of data analytics.
Business Intelligence Excellence: Driving Organizational Impact
In this segment of our exploration into the "Benefits of Microsoft Power BI Certification," we delve into the realm of "Business Intelligence Excellence: Driving Organizational Impact." Microsoft Power BI Certification is not just an individual accomplishment; it's a catalyst for fostering business intelligence excellence within organizations. We examine how certified professionals contribute to the improvement of organizational decision-making processes through enhanced data analysis and reporting. Through insightful discussions and practical examples, we showcase the tangible impact of Power BI Certification on driving insights that directly influence strategic business decisions. Join us as we uncover the transformative role that certified professionals play in elevating business intelligence standards, ultimately shaping the success and competitive edge of organizations in today's data-driven landscape.
Continuous Learning and Community Engagement: The Power BI Network
In this installment of our exploration into the "Benefits of Microsoft Power BI Certification," we shine a spotlight on "Continuous Learning and Community Engagement: The Power BI Network." Beyond acquiring a certification, Microsoft Power BI fosters a culture of continuous learning and community engagement. We delve into the vibrant ecosystem surrounding Power BI, where certified professionals have access to ongoing resources, updates, and collaborative opportunities. From online forums to workshops and events, we discuss how being part of the Power BI community enhances the learning experience, encourages knowledge sharing, and provides valuable insights into emerging trends. Join us as we uncover the dynamic network that surrounds Power BI, illustrating how continuous learning and community engagement become integral components in the journey of professionals who seek not only to certify their skills but to thrive in a collaborative and ever-evolving landscape of data analytics.
Conclusion
As we bring this episode on the "Benefits of Microsoft Power BI Certification" to a close, the breadth of advantages and transformative potentials explored is a testament to the profound impact this certification can have on professionals in the realm of data analytics. From honing enhanced data visualization skills to leveraging career advancement opportunities, establishing industry recognition and credibility, contributing to business intelligence excellence, and engaging in continuous learning within the vibrant Power BI network, the journey has been enlightening. The Microsoft Power BI Certification emerges not only as a mark of proficiency but as a key to unlocking doors to new career horizons and contributing to organizational success. Whether you are considering certification, in pursuit of continuous learning, or seeking to make a mark in the dynamic field of data analytics, this episode has provided insights into how Power BI Certification can be a pivotal asset. Join us in the ongoing conversation about the dynamic intersection of skills, recognition, and community within the Power BI landscape. Until next time, may your journey in data analytics be enriched and empowered by the benefits of Microsoft Power BI Certification.
COBIT® 5 Implementation Best Practices: Tips for Success
"COBIT® 5 Implementation Best Practices: Tips for Success" serves as a comprehensive guide for organizations looking to adopt and implement COBIT® 5, a globally recognized framework for enterprise IT governance. In the rapidly evolving landscape of information technology, effective governance is critical for ensuring that organizations achieve their strategic objectives while managing risks and optimizing resource utilization. This guide delves into the key principles and methodologies that underpin COBIT® 5, providing practical insights and best practices to facilitate a successful implementation process.
As organizations grapple with the complexities of IT governance, the COBIT® 5 framework emerges as a robust solution, offering a systematic approach to aligning business goals with IT processes. The guide not only introduces readers to the core concepts of COBIT® 5 but also provides actionable tips and strategies to overcome common challenges encountered during implementation. It emphasizes the importance of tailoring COBIT® 5 to the unique needs and context of each organization, ensuring a customized and effective application of the framework.
Readers will gain valuable insights into how COBIT® 5 can enhance overall business performance, drive innovation, and foster a culture of continuous improvement within their IT governance structures. With a focus on real-world scenarios and practical examples, the guide equips organizations with the knowledge and tools necessary to navigate the intricacies of COBIT® 5 implementation, promoting a seamless integration that maximizes benefits and minimizes disruptions. Whether an organization is embarking on its initial COBIT® 5 implementation or seeking to optimize existing processes, this guide serves as an invaluable resource for achieving success in the dynamic realmof IT governance.
Table of contents
-
Customization Strategies for COBIT® 5 Implementation
-
Overcoming Common Implementation Challenges
-
Effective Stakeholder Engagement in COBIT® 5 Implementation
-
Measuring and Monitoring Success Metrics
-
Integration of COBIT® 5 with Other IT Management Frameworks
-
Conclusion
Customization Strategies for COBIT® 5 Implementation
Customization is a pivotal aspect of successful COBIT® 5 implementation, recognizing that a one-size-fits-all approach may not align with the unique characteristics of every organization. This sub-topic delves into the strategies and considerations involved in tailoring COBIT® 5 to meet the specific needs and context of each organization. One essential element of customization is the acknowledgment of industry-specific requirements, understanding that different sectors may have distinct governance and compliance demands. This section will guide organizations in identifying these sector-specific nuances and adapting COBIT® 5 principles accordingly.
Additionally, organizational size plays a crucial role in customization strategies. Small and large enterprises may have different resource capabilities and structures, necessitating an adaptable approach to COBIT® 5 implementation. Practical tips will be provided on how organizations can scale and tailor the framework to suit their size, ensuring that it remains a practical and effective tool for governance in any organizational context.
Balancing adherence to COBIT® 5 principles with the flexibility to adapt to organizational goals is another critical consideration. This section will offer insights into finding the equilibrium between following the established framework and modifying it to address unique challenges or opportunities. Examples of successful customization efforts, drawn from diverse industries, will be explored to illustrate how organizations have effectively personalized COBIT® 5 to suit their specific needs without compromising its integrity.
Overcoming Common Implementation Challenges
The successful implementation of COBIT® 5 is not without its share of challenges, and this sub-topic addresses key obstacles that organizations commonly encounter during the implementation process. One prevalent challenge is the resistance to change, as employees may be accustomed to existing processes and may view the adoption of COBIT® 5 as disruptive. This section provides practical insights into fostering a positive attitude towards change, offering strategies to communicate the benefits of COBIT® 5 clearly and engage employees in the transition process.
Resource constraints represent another significant hurdle in COBIT® 5 implementation. Organizations often face limitations in terms of time, budget, and skilled personnel. Here, the discussion focuses on innovative approaches to maximize resources efficiently, such as prioritizing critical areas of implementation, leveraging existing skill sets, and exploring partnerships or collaborations. Real-world examples of organizations successfully navigating resource challenges during COBIT® 5 implementation will be explored to inspire effective strategies.
By addressing these common challenges head-on, organizations can better prepare for the hurdles associated with COBIT® 5 implementation. Practical tips, case studies, and lessons learned from organizations that have successfully navigated these challenges will provide valuable insights, offering a roadmap for others to overcome obstacles and ensure a smoother implementation journey for COBIT® 5.
Effective Stakeholder Engagement in COBIT® 5 Implementation
Effective stakeholder engagement is a critical element in the successful implementation of COBIT® 5, recognizing the importance of garnering support from key individuals and groups throughout the process. This sub-topic explores strategies for engaging stakeholders at various levels within the organization, starting with top-level executives. It emphasizes the need for executive buy-in, as their support is instrumental in providing the necessary resources and leadership to drive COBIT® 5 implementation. The discussion delves into effective communication strategies to convey the value proposition of COBIT® 5 to executives, aligning the framework with overarching business goals.
Moving beyond executives, this section also addresses the involvement of IT teams and other relevant stakeholders. It explores the creation of targeted training programs to enhance stakeholder understanding of COBIT® 5 principles and their role in the implementation journey. The importance of establishing clear lines of communication, feedback mechanisms, and collaborative decision-making processes is highlighted to foster a sense of ownership and commitment among stakeholders.
It discusses how effective stakeholder engagement can contribute to shaping a positive organizational culture that embraces the principles of COBIT® 5. Real-world examples of successful stakeholder engagement initiatives will be provided to illustrate how organizations have effectively mobilized support and collaboration across various levels, ensuring a collective effort towards COBIT® 5 implementation.
Measuring and Monitoring Success Metrics
Measuring and monitoring success metrics constitute a fundamental component of a robust COBIT® 5 implementation, serving as the compass to navigate the effectiveness and impact of the framework on an organization's IT governance. This sub-topic underscores the significance of methodically selecting key performance indicators (KPIs) that align with the organization's strategic objectives. By establishing clear, measurable goals, organizations can evaluate the tangible outcomes of COBIT® 5 implementation, ensuring a tangible link between IT governance practices and overarching business goals.
Continuous monitoring is pivotal in maintaining the health and efficacy of COBIT® 5 processes. This section advocates for a proactive and systematic approach to tracking performance, leveraging automated tools and reporting mechanisms to gather real-time data. Through diligent monitoring, organizations can identify deviations from expected outcomes, address potential issues promptly, and fine-tune processes to align with the evolving needs of the organization. Practical insights into setting up a robust monitoring framework within the COBIT® 5 context will be provided, drawing on successful examples of organizations that have effectively utilized monitoring mechanisms.
As organizational priorities shift, technological landscapes evolve, and industry standards change, the measurement framework should be flexible enough to accommodate these fluctuations. Organizations will gain insights into strategies for adjusting success metrics, ensuring their continued relevance in assessing the impact of COBIT® 5 on the IT governance landscape.
By implementing a comprehensive system for performance evaluation and remaining agile in adapting metrics, organizations can not only gauge the success of COBIT® 5 but also lay the groundwork for continuous improvement and strategic alignment with evolving business objectives.
Integration of COBIT® 5 with Other IT Management Frameworks
The integration of COBIT® 5 with other IT management frameworks represents a strategic approach to creating a cohesive and comprehensive governance structure within organizations. This sub-topic delves into the synergy between COBIT® 5 and other frameworks, such as ITIL (Information Technology Infrastructure Library) or ISO/IEC 27001. It acknowledges that organizations often leverage multiple frameworks to address various aspects of IT management and governance, and explores how COBIT® 5 can seamlessly complement and enhance existing practices.
The discussion highlights the importance of identifying areas of alignment and potential overlaps between COBIT® 5 and other frameworks. By recognizing the synergies, organizations can avoid duplication of efforts and create a unified governance framework that optimally addresses their unique needs. This involves a nuanced understanding of the strengths and focus areas of each framework, allowing for a harmonious integration that leverages the best aspects of each.
Practical guidance is provided on how organizations can navigate the integration process, emphasizing the need for collaboration among stakeholders involved in different frameworks. This collaboration ensures that integration efforts are well-coordinated, fostering a shared understanding of objectives and methodologies across the organization. Real-world examples will illustrate successful instances of organizations integrating COBIT® 5 with other frameworks, showcasing the positive outcomes and enhanced efficiency resulting from this holistic approach.
The integration of COBIT® 5 with other IT management frameworks is presented as a strategic imperative for organizations aiming to build a robust and harmonized governance ecosystem. Through careful consideration, collaboration, and a nuanced approach to integration, organizations can harness the collective strengths of multiple frameworks to achieve a more comprehensive and effective IT governance strategy.
How to obtain COBIT 5 Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, "COBIT® 5 Implementation Best Practices: Tips for Success" encapsulates a comprehensive guide for organizations navigating the intricacies of adopting and implementing the COBIT® 5 framework for IT governance. The exploration of customization strategies underscores the importance of tailoring COBIT® 5 to suit the unique needs and context of each organization, providing practical insights into industry-specific requirements and organizational size considerations. Recognizing and addressing common implementation challenges, from resistance to change to resource constraints, empowers organizations to navigate these hurdles effectively, drawing inspiration from real-world examples of successful implementations.
The sub-topic on effective stakeholder engagement establishes a crucial aspect of COBIT® 5 implementation by emphasizing the need for buy-in from top executives and active involvement of IT teams. Through clear communication, targeted training, and a collaborative approach, organizations can foster a positive organizational culture that aligns with COBIT® 5 principles. Measuring and monitoring success metrics form the backbone of the implementation journey, guiding organizations in selecting relevant KPIs, leveraging automation, and embracing adaptability to ensure continuous improvement and alignment with evolving business objectives.
Finally, the exploration of the integration of COBIT® 5 with other IT management frameworks highlights the strategic advantage of creating a unified governance structure. By identifying synergies and avoiding duplication, organizations can harness the strengths of multiple frameworks, resulting in improved risk management, streamlined processes, and enhanced overall IT governance.
Collectively, the insights provided in this guide empower organizations with the knowledge, strategies, and practical tips needed to navigate the multifaceted landscape of COBIT® 5 implementation. As organizations embark on this journey, the guide serves as a valuable resource, offering a roadmap for success and fostering a culture of continuous improvement within the realm of IT governance.
Read More
"COBIT® 5 Implementation Best Practices: Tips for Success" serves as a comprehensive guide for organizations looking to adopt and implement COBIT® 5, a globally recognized framework for enterprise IT governance. In the rapidly evolving landscape of information technology, effective governance is critical for ensuring that organizations achieve their strategic objectives while managing risks and optimizing resource utilization. This guide delves into the key principles and methodologies that underpin COBIT® 5, providing practical insights and best practices to facilitate a successful implementation process.
As organizations grapple with the complexities of IT governance, the COBIT® 5 framework emerges as a robust solution, offering a systematic approach to aligning business goals with IT processes. The guide not only introduces readers to the core concepts of COBIT® 5 but also provides actionable tips and strategies to overcome common challenges encountered during implementation. It emphasizes the importance of tailoring COBIT® 5 to the unique needs and context of each organization, ensuring a customized and effective application of the framework.
Readers will gain valuable insights into how COBIT® 5 can enhance overall business performance, drive innovation, and foster a culture of continuous improvement within their IT governance structures. With a focus on real-world scenarios and practical examples, the guide equips organizations with the knowledge and tools necessary to navigate the intricacies of COBIT® 5 implementation, promoting a seamless integration that maximizes benefits and minimizes disruptions. Whether an organization is embarking on its initial COBIT® 5 implementation or seeking to optimize existing processes, this guide serves as an invaluable resource for achieving success in the dynamic realmof IT governance.
Table of contents
-
Customization Strategies for COBIT® 5 Implementation
-
Overcoming Common Implementation Challenges
-
Effective Stakeholder Engagement in COBIT® 5 Implementation
-
Measuring and Monitoring Success Metrics
-
Integration of COBIT® 5 with Other IT Management Frameworks
-
Conclusion
Customization Strategies for COBIT® 5 Implementation
Customization is a pivotal aspect of successful COBIT® 5 implementation, recognizing that a one-size-fits-all approach may not align with the unique characteristics of every organization. This sub-topic delves into the strategies and considerations involved in tailoring COBIT® 5 to meet the specific needs and context of each organization. One essential element of customization is the acknowledgment of industry-specific requirements, understanding that different sectors may have distinct governance and compliance demands. This section will guide organizations in identifying these sector-specific nuances and adapting COBIT® 5 principles accordingly.
Additionally, organizational size plays a crucial role in customization strategies. Small and large enterprises may have different resource capabilities and structures, necessitating an adaptable approach to COBIT® 5 implementation. Practical tips will be provided on how organizations can scale and tailor the framework to suit their size, ensuring that it remains a practical and effective tool for governance in any organizational context.
Balancing adherence to COBIT® 5 principles with the flexibility to adapt to organizational goals is another critical consideration. This section will offer insights into finding the equilibrium between following the established framework and modifying it to address unique challenges or opportunities. Examples of successful customization efforts, drawn from diverse industries, will be explored to illustrate how organizations have effectively personalized COBIT® 5 to suit their specific needs without compromising its integrity.
Overcoming Common Implementation Challenges
The successful implementation of COBIT® 5 is not without its share of challenges, and this sub-topic addresses key obstacles that organizations commonly encounter during the implementation process. One prevalent challenge is the resistance to change, as employees may be accustomed to existing processes and may view the adoption of COBIT® 5 as disruptive. This section provides practical insights into fostering a positive attitude towards change, offering strategies to communicate the benefits of COBIT® 5 clearly and engage employees in the transition process.
Resource constraints represent another significant hurdle in COBIT® 5 implementation. Organizations often face limitations in terms of time, budget, and skilled personnel. Here, the discussion focuses on innovative approaches to maximize resources efficiently, such as prioritizing critical areas of implementation, leveraging existing skill sets, and exploring partnerships or collaborations. Real-world examples of organizations successfully navigating resource challenges during COBIT® 5 implementation will be explored to inspire effective strategies.
By addressing these common challenges head-on, organizations can better prepare for the hurdles associated with COBIT® 5 implementation. Practical tips, case studies, and lessons learned from organizations that have successfully navigated these challenges will provide valuable insights, offering a roadmap for others to overcome obstacles and ensure a smoother implementation journey for COBIT® 5.
Effective Stakeholder Engagement in COBIT® 5 Implementation
Effective stakeholder engagement is a critical element in the successful implementation of COBIT® 5, recognizing the importance of garnering support from key individuals and groups throughout the process. This sub-topic explores strategies for engaging stakeholders at various levels within the organization, starting with top-level executives. It emphasizes the need for executive buy-in, as their support is instrumental in providing the necessary resources and leadership to drive COBIT® 5 implementation. The discussion delves into effective communication strategies to convey the value proposition of COBIT® 5 to executives, aligning the framework with overarching business goals.
Moving beyond executives, this section also addresses the involvement of IT teams and other relevant stakeholders. It explores the creation of targeted training programs to enhance stakeholder understanding of COBIT® 5 principles and their role in the implementation journey. The importance of establishing clear lines of communication, feedback mechanisms, and collaborative decision-making processes is highlighted to foster a sense of ownership and commitment among stakeholders.
It discusses how effective stakeholder engagement can contribute to shaping a positive organizational culture that embraces the principles of COBIT® 5. Real-world examples of successful stakeholder engagement initiatives will be provided to illustrate how organizations have effectively mobilized support and collaboration across various levels, ensuring a collective effort towards COBIT® 5 implementation.
Measuring and Monitoring Success Metrics
Measuring and monitoring success metrics constitute a fundamental component of a robust COBIT® 5 implementation, serving as the compass to navigate the effectiveness and impact of the framework on an organization's IT governance. This sub-topic underscores the significance of methodically selecting key performance indicators (KPIs) that align with the organization's strategic objectives. By establishing clear, measurable goals, organizations can evaluate the tangible outcomes of COBIT® 5 implementation, ensuring a tangible link between IT governance practices and overarching business goals.
Continuous monitoring is pivotal in maintaining the health and efficacy of COBIT® 5 processes. This section advocates for a proactive and systematic approach to tracking performance, leveraging automated tools and reporting mechanisms to gather real-time data. Through diligent monitoring, organizations can identify deviations from expected outcomes, address potential issues promptly, and fine-tune processes to align with the evolving needs of the organization. Practical insights into setting up a robust monitoring framework within the COBIT® 5 context will be provided, drawing on successful examples of organizations that have effectively utilized monitoring mechanisms.
As organizational priorities shift, technological landscapes evolve, and industry standards change, the measurement framework should be flexible enough to accommodate these fluctuations. Organizations will gain insights into strategies for adjusting success metrics, ensuring their continued relevance in assessing the impact of COBIT® 5 on the IT governance landscape.
By implementing a comprehensive system for performance evaluation and remaining agile in adapting metrics, organizations can not only gauge the success of COBIT® 5 but also lay the groundwork for continuous improvement and strategic alignment with evolving business objectives.
Integration of COBIT® 5 with Other IT Management Frameworks
The integration of COBIT® 5 with other IT management frameworks represents a strategic approach to creating a cohesive and comprehensive governance structure within organizations. This sub-topic delves into the synergy between COBIT® 5 and other frameworks, such as ITIL (Information Technology Infrastructure Library) or ISO/IEC 27001. It acknowledges that organizations often leverage multiple frameworks to address various aspects of IT management and governance, and explores how COBIT® 5 can seamlessly complement and enhance existing practices.
The discussion highlights the importance of identifying areas of alignment and potential overlaps between COBIT® 5 and other frameworks. By recognizing the synergies, organizations can avoid duplication of efforts and create a unified governance framework that optimally addresses their unique needs. This involves a nuanced understanding of the strengths and focus areas of each framework, allowing for a harmonious integration that leverages the best aspects of each.
Practical guidance is provided on how organizations can navigate the integration process, emphasizing the need for collaboration among stakeholders involved in different frameworks. This collaboration ensures that integration efforts are well-coordinated, fostering a shared understanding of objectives and methodologies across the organization. Real-world examples will illustrate successful instances of organizations integrating COBIT® 5 with other frameworks, showcasing the positive outcomes and enhanced efficiency resulting from this holistic approach.
The integration of COBIT® 5 with other IT management frameworks is presented as a strategic imperative for organizations aiming to build a robust and harmonized governance ecosystem. Through careful consideration, collaboration, and a nuanced approach to integration, organizations can harness the collective strengths of multiple frameworks to achieve a more comprehensive and effective IT governance strategy.
How to obtain COBIT 5 Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, "COBIT® 5 Implementation Best Practices: Tips for Success" encapsulates a comprehensive guide for organizations navigating the intricacies of adopting and implementing the COBIT® 5 framework for IT governance. The exploration of customization strategies underscores the importance of tailoring COBIT® 5 to suit the unique needs and context of each organization, providing practical insights into industry-specific requirements and organizational size considerations. Recognizing and addressing common implementation challenges, from resistance to change to resource constraints, empowers organizations to navigate these hurdles effectively, drawing inspiration from real-world examples of successful implementations.
The sub-topic on effective stakeholder engagement establishes a crucial aspect of COBIT® 5 implementation by emphasizing the need for buy-in from top executives and active involvement of IT teams. Through clear communication, targeted training, and a collaborative approach, organizations can foster a positive organizational culture that aligns with COBIT® 5 principles. Measuring and monitoring success metrics form the backbone of the implementation journey, guiding organizations in selecting relevant KPIs, leveraging automation, and embracing adaptability to ensure continuous improvement and alignment with evolving business objectives.
Finally, the exploration of the integration of COBIT® 5 with other IT management frameworks highlights the strategic advantage of creating a unified governance structure. By identifying synergies and avoiding duplication, organizations can harness the strengths of multiple frameworks, resulting in improved risk management, streamlined processes, and enhanced overall IT governance.
Collectively, the insights provided in this guide empower organizations with the knowledge, strategies, and practical tips needed to navigate the multifaceted landscape of COBIT® 5 implementation. As organizations embark on this journey, the guide serves as a valuable resource, offering a roadmap for success and fostering a culture of continuous improvement within the realm of IT governance.
The Impact of Privacy Changes on Digital Marketing Strategies
In an era dominated by digital advancements and rapidly evolving technology, the landscape of digital marketing is continually shaped by various factors. One of the most influential and dynamic aspects currently affecting the digital marketing realm is the ongoing transformation in privacy policies and practices. As individuals become more conscientious about their online privacy, governments and technology companies are responding with heightened regulations and updates to safeguard personal information. These privacy changes, often implemented through legislation or platform updates, have profound implications for businesses and marketers who rely on digital channels to reach their target audiences.
The evolving privacy landscape is marked by significant shifts in consumer attitudes, regulatory frameworks, and technological innovations. With increasing awareness and concerns regarding data security, individuals are becoming more cautious about sharing their personal information online. Governments worldwide are responding to these concerns by introducing and updating privacy laws, such as the General Data Protection Regulation (GDPR) in Europe and similar initiatives in other regions. These regulations impose stricter requirements on how businesses collect, process, and store user data, forcing marketers to adapt their strategies to ensure compliance while still effectively reaching their audiences.
Moreover, major tech platforms are also playing a pivotal role in shaping the privacy narrative. Companies like Apple and Google have implemented changes to their operating systems and browser functionalities, emphasizing user privacy and giving individuals more control over their data. These alterations, while commendable in terms of user empowerment, pose challenges for digital marketers who heavily rely on targeted advertising and personalized campaigns. As tracking capabilities diminish and the collection of certain user data becomes more restricted, marketers must rethink their approaches to maintain the effectiveness of their digital marketing strategies.
In this complex and rapidly changing landscape, businesses find themselves at a crossroads, navigating the delicate balance between delivering personalized, targeted content and respecting user privacy. The impact of privacy changes on digital marketing strategies is multi-faceted, influencing not only how data is collected and utilized but also challenging marketers to explore innovative approaches that prioritize transparency, consent, and ethical practices. This evolving scenario prompts a critical examination of the strategies employed by businesses, encouraging them to adapt to the changing dynamics of digital marketing while upholding the principles of privacy and user trust.
Table of contents
-
Adaptation to Cookie-Free Environments
-
User-Centric Data Governance
-
Impact on Social Media Advertising
-
Emergence of Privacy-Focused Marketing Tools
-
Legal and Reputational Risks
-
Conclusion
Adaptation to Cookie-Free Environments
The transition towards a cookie-free environment represents a seismic shift in the digital marketing landscape, challenging businesses to reevaluate their strategies in the absence of traditional tracking mechanisms. With increasing privacy concerns and browser updates restricting the use of third-party cookies, marketers are compelled to adapt to a new era of data-driven advertising. The reliance on cookies for user tracking, retargeting, and personalized advertising is diminishing, necessitating innovative approaches to maintain effective audience targeting and campaign performance.
In response to the diminishing role of cookies, marketers are exploring alternative tracking methods that align with privacy regulations and user expectations. First-party data utilization has emerged as a key strategy, leveraging the direct information collected from users who willingly engage with a brand's platforms. This approach not only respects user privacy preferences but also enables businesses to create more personalized experiences based on the data voluntarily shared by their audience.
As digital marketers navigate the challenges of adapting to cookie-free environments, a fundamental rethinking of advertising strategies is underway. The emphasis on transparent data practices, user consent, and ethical data governance is not only a response to regulatory requirements but also a recognition of the growing demand for privacy-conscious digital experiences. In this evolving landscape, businesses that successfully navigate the transition to cookie-free environments stand to build stronger relationships with their audiences while ensuring compliance with the changing norms of digital privacy.
User-Centric Data Governance
The paradigm shift towards user-centric data governance is reshaping the landscape of digital marketing, placing the control and privacy of user data at the forefront. In response to heightened concerns over data security and privacy breaches, businesses are undergoing a fundamental transformation in their approach to data management. This shift emphasizes the empowerment of users in controlling their personal information and dictates a new set of standards for ethical and transparent data practices.
Central to user-centric data governance is the explicit and informed consent of individuals regarding the collection, processing, and utilization of their data. As privacy regulations become more stringent, businesses are reevaluating their data acquisition strategies to ensure compliance with these standards. This involves implementing robust consent mechanisms that clearly communicate the purpose of data collection and provide users with the ability to opt-in or opt-out of specific data processing activities.
The transition to user-centric data governance reflects a broader societal shift towards recognizing the importance of individual privacy rights. By placing users at the center of the data governance framework, businesses are not only ensuring compliance with evolving regulations but also fostering a culture of respect for user privacy, thus building a foundation for sustainable and trust-based digital interactions.
Impact on Social Media Advertising
The landscape of social media advertising is undergoing a profound transformation in response to the impactful changes in privacy policies and user preferences. Social media platforms, serving as vital hubs for digital marketing, are adapting to new privacy-centric paradigms that seek to strike a balance between targeted advertising and safeguarding user information. The evolving privacy landscape is compelling marketers to reevaluate their strategies as major platforms implement updates aimed at providing users with more control over their data.
The impact on social media advertising extends beyond targeting capabilities to the measurement and analysis of campaign effectiveness. As the availability of granular user data diminishes, businesses are exploring alternative methods for assessing the performance of their social media campaigns. Key performance indicators (KPIs) are being adjusted, and analytics tools are evolving to accommodate these changes, emphasizing the importance of engagement metrics and user interactions over traditional tracking metrics.
The impact of privacy changes on social media advertising necessitates a paradigm shift in how marketers approach audience engagement. The focus on user consent, transparency, and the exploration of alternative targeting methods is shaping a more privacy-conscious era for social media advertising. As marketers navigate this evolving landscape, they are compelled to strike a delicate balance between delivering effective campaigns and respecting the privacy expectations of their target audiences.
Emergence of Privacy-Focused Marketing Tools
The emergence of privacy-focused marketing tools is a direct response to the evolving landscape of digital marketing, where privacy considerations have taken center stage. As businesses navigate the complexities of data protection regulations and changing user expectations, a new generation of tools is evolving to help marketers maintain the effectiveness of their campaigns while prioritizing user privacy. These tools aim to strike a balance between data-driven insights and ethical, transparent practices.
One significant development in this space is the rise of privacy-focused analytics platforms. These tools are designed to provide marketers with valuable insights into user behavior without compromising individual privacy. By employing techniques such as aggregated data analysis and anonymized tracking, these platforms enable businesses to gather meaningful information about audience engagement while respecting user confidentiality and adhering to privacy regulations.
Consent management tools represent another pivotal aspect of the privacy-focused marketing toolkit. With regulations like GDPR emphasizing the importance of explicit user consent, these tools streamline the process of obtaining and managing user permissions for data processing. They empower businesses to implement clear and user-friendly consent mechanisms, fostering a more transparent and accountable approach to data collection.
The emergence of privacy-focused marketing tools signifies a conscientious shift within the industry towards ethical data practices and user-centricity. These tools empower marketers to navigate the challenges posed by evolving privacy regulations, enabling them to create targeted, effective campaigns without compromising the privacy and trust of their audiences. As businesses increasingly prioritize transparency and user consent, the adoption of privacy-focused marketing tools is becoming integral to maintaining a sustainable and responsible approach to digital marketing.
Legal and Reputational Risks
The evolving landscape of digital marketing in the context of privacy changes brings forth not only opportunities but also a set of profound legal and reputational risks that businesses must navigate with diligence. As governments worldwide enact stringent privacy regulations, non-compliance can expose companies to significant legal consequences. Privacy breaches, unauthorized data usage, or failure to adhere to regulatory standards may result in hefty fines, legal actions, and damaged reputations. In this scenario, staying abreast of and ensuring compliance with evolving privacy laws has become a paramount concern for businesses engaged in digital marketing.
Beyond the legal realm, the reputational risks associated with privacy lapses are equally formidable. In an era where consumer trust is a precious commodity, a single instance of mishandling personal data can lead to a severe erosion of brand credibility. Instances of data breaches or unethical data practices can quickly become public relations nightmares, causing lasting damage to a company's reputation and eroding the trust that consumers place in their chosen brands. Consequently, businesses operating in the digital sphere are compelled to prioritize stringent data protection measures to safeguard not only legal standing but also the trust and confidence of their customer base.
The potential legal and reputational risks amplify the importance of implementing robust data protection strategies and transparent communication. Businesses are investing in comprehensive privacy policies that not only adhere to legal standards but are also easily accessible and comprehensible for users. Clear articulation of data handling practices and a commitment to user privacy not only aids in compliance but also serves as a proactive measure to mitigate potential legal and reputational pitfalls.
How to obtain DIGITAL MARKETING Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the impact of privacy changes on digital marketing strategies is reshaping the landscape in profound ways, ushering in a new era where user privacy takes center stage. The evolving regulatory frameworks, technological shifts, and changing consumer attitudes have necessitated a fundamental reevaluation of how businesses approach digital marketing. As third-party cookies face restrictions and data tracking becomes more limited, marketers are challenged to adapt their strategies to maintain effectiveness while respecting user privacy preferences.
The emergence of privacy-focused marketing tools reflects a commitment to ethical data practices and transparent communication. From analytics platforms that prioritize user confidentiality to consent management tools that empower users with control over their data, businesses are navigating the complexities of a digital environment that demands privacy-conscious approaches. The shift towards user-centric data governance, overseen by data protection officers, underscores the importance of obtaining explicit user consent and fostering a culture of responsible data management.
Social media advertising, a cornerstone of digital marketing, is undergoing a transformation as platforms implement updates to provide users with more control over their data. Marketers are adjusting their strategies to align with these changes, focusing on contextual targeting and exploring innovative advertising formats that prioritize user privacy.
In this evolving digital marketing landscape, the convergence of legal, technological, and consumer-driven changes demands a holistic approach. By embracing privacy-focused tools, adhering to user-centric data governance, and proactively addressing legal and reputational risks, businesses can not only navigate the challenges but also position themselves as trustworthy stewards of user data. As the digital marketing realm continues to evolve, those who prioritize user privacy and ethical data practices will likely thrive in building lasting connections with their audiences.
Read More
In an era dominated by digital advancements and rapidly evolving technology, the landscape of digital marketing is continually shaped by various factors. One of the most influential and dynamic aspects currently affecting the digital marketing realm is the ongoing transformation in privacy policies and practices. As individuals become more conscientious about their online privacy, governments and technology companies are responding with heightened regulations and updates to safeguard personal information. These privacy changes, often implemented through legislation or platform updates, have profound implications for businesses and marketers who rely on digital channels to reach their target audiences.
The evolving privacy landscape is marked by significant shifts in consumer attitudes, regulatory frameworks, and technological innovations. With increasing awareness and concerns regarding data security, individuals are becoming more cautious about sharing their personal information online. Governments worldwide are responding to these concerns by introducing and updating privacy laws, such as the General Data Protection Regulation (GDPR) in Europe and similar initiatives in other regions. These regulations impose stricter requirements on how businesses collect, process, and store user data, forcing marketers to adapt their strategies to ensure compliance while still effectively reaching their audiences.
Moreover, major tech platforms are also playing a pivotal role in shaping the privacy narrative. Companies like Apple and Google have implemented changes to their operating systems and browser functionalities, emphasizing user privacy and giving individuals more control over their data. These alterations, while commendable in terms of user empowerment, pose challenges for digital marketers who heavily rely on targeted advertising and personalized campaigns. As tracking capabilities diminish and the collection of certain user data becomes more restricted, marketers must rethink their approaches to maintain the effectiveness of their digital marketing strategies.
In this complex and rapidly changing landscape, businesses find themselves at a crossroads, navigating the delicate balance between delivering personalized, targeted content and respecting user privacy. The impact of privacy changes on digital marketing strategies is multi-faceted, influencing not only how data is collected and utilized but also challenging marketers to explore innovative approaches that prioritize transparency, consent, and ethical practices. This evolving scenario prompts a critical examination of the strategies employed by businesses, encouraging them to adapt to the changing dynamics of digital marketing while upholding the principles of privacy and user trust.
Table of contents
-
Adaptation to Cookie-Free Environments
-
User-Centric Data Governance
-
Impact on Social Media Advertising
-
Emergence of Privacy-Focused Marketing Tools
-
Legal and Reputational Risks
-
Conclusion
Adaptation to Cookie-Free Environments
The transition towards a cookie-free environment represents a seismic shift in the digital marketing landscape, challenging businesses to reevaluate their strategies in the absence of traditional tracking mechanisms. With increasing privacy concerns and browser updates restricting the use of third-party cookies, marketers are compelled to adapt to a new era of data-driven advertising. The reliance on cookies for user tracking, retargeting, and personalized advertising is diminishing, necessitating innovative approaches to maintain effective audience targeting and campaign performance.
In response to the diminishing role of cookies, marketers are exploring alternative tracking methods that align with privacy regulations and user expectations. First-party data utilization has emerged as a key strategy, leveraging the direct information collected from users who willingly engage with a brand's platforms. This approach not only respects user privacy preferences but also enables businesses to create more personalized experiences based on the data voluntarily shared by their audience.
As digital marketers navigate the challenges of adapting to cookie-free environments, a fundamental rethinking of advertising strategies is underway. The emphasis on transparent data practices, user consent, and ethical data governance is not only a response to regulatory requirements but also a recognition of the growing demand for privacy-conscious digital experiences. In this evolving landscape, businesses that successfully navigate the transition to cookie-free environments stand to build stronger relationships with their audiences while ensuring compliance with the changing norms of digital privacy.
User-Centric Data Governance
The paradigm shift towards user-centric data governance is reshaping the landscape of digital marketing, placing the control and privacy of user data at the forefront. In response to heightened concerns over data security and privacy breaches, businesses are undergoing a fundamental transformation in their approach to data management. This shift emphasizes the empowerment of users in controlling their personal information and dictates a new set of standards for ethical and transparent data practices.
Central to user-centric data governance is the explicit and informed consent of individuals regarding the collection, processing, and utilization of their data. As privacy regulations become more stringent, businesses are reevaluating their data acquisition strategies to ensure compliance with these standards. This involves implementing robust consent mechanisms that clearly communicate the purpose of data collection and provide users with the ability to opt-in or opt-out of specific data processing activities.
The transition to user-centric data governance reflects a broader societal shift towards recognizing the importance of individual privacy rights. By placing users at the center of the data governance framework, businesses are not only ensuring compliance with evolving regulations but also fostering a culture of respect for user privacy, thus building a foundation for sustainable and trust-based digital interactions.
Impact on Social Media Advertising
The landscape of social media advertising is undergoing a profound transformation in response to the impactful changes in privacy policies and user preferences. Social media platforms, serving as vital hubs for digital marketing, are adapting to new privacy-centric paradigms that seek to strike a balance between targeted advertising and safeguarding user information. The evolving privacy landscape is compelling marketers to reevaluate their strategies as major platforms implement updates aimed at providing users with more control over their data.
The impact on social media advertising extends beyond targeting capabilities to the measurement and analysis of campaign effectiveness. As the availability of granular user data diminishes, businesses are exploring alternative methods for assessing the performance of their social media campaigns. Key performance indicators (KPIs) are being adjusted, and analytics tools are evolving to accommodate these changes, emphasizing the importance of engagement metrics and user interactions over traditional tracking metrics.
The impact of privacy changes on social media advertising necessitates a paradigm shift in how marketers approach audience engagement. The focus on user consent, transparency, and the exploration of alternative targeting methods is shaping a more privacy-conscious era for social media advertising. As marketers navigate this evolving landscape, they are compelled to strike a delicate balance between delivering effective campaigns and respecting the privacy expectations of their target audiences.
Emergence of Privacy-Focused Marketing Tools
The emergence of privacy-focused marketing tools is a direct response to the evolving landscape of digital marketing, where privacy considerations have taken center stage. As businesses navigate the complexities of data protection regulations and changing user expectations, a new generation of tools is evolving to help marketers maintain the effectiveness of their campaigns while prioritizing user privacy. These tools aim to strike a balance between data-driven insights and ethical, transparent practices.
One significant development in this space is the rise of privacy-focused analytics platforms. These tools are designed to provide marketers with valuable insights into user behavior without compromising individual privacy. By employing techniques such as aggregated data analysis and anonymized tracking, these platforms enable businesses to gather meaningful information about audience engagement while respecting user confidentiality and adhering to privacy regulations.
Consent management tools represent another pivotal aspect of the privacy-focused marketing toolkit. With regulations like GDPR emphasizing the importance of explicit user consent, these tools streamline the process of obtaining and managing user permissions for data processing. They empower businesses to implement clear and user-friendly consent mechanisms, fostering a more transparent and accountable approach to data collection.
The emergence of privacy-focused marketing tools signifies a conscientious shift within the industry towards ethical data practices and user-centricity. These tools empower marketers to navigate the challenges posed by evolving privacy regulations, enabling them to create targeted, effective campaigns without compromising the privacy and trust of their audiences. As businesses increasingly prioritize transparency and user consent, the adoption of privacy-focused marketing tools is becoming integral to maintaining a sustainable and responsible approach to digital marketing.
Legal and Reputational Risks
The evolving landscape of digital marketing in the context of privacy changes brings forth not only opportunities but also a set of profound legal and reputational risks that businesses must navigate with diligence. As governments worldwide enact stringent privacy regulations, non-compliance can expose companies to significant legal consequences. Privacy breaches, unauthorized data usage, or failure to adhere to regulatory standards may result in hefty fines, legal actions, and damaged reputations. In this scenario, staying abreast of and ensuring compliance with evolving privacy laws has become a paramount concern for businesses engaged in digital marketing.
Beyond the legal realm, the reputational risks associated with privacy lapses are equally formidable. In an era where consumer trust is a precious commodity, a single instance of mishandling personal data can lead to a severe erosion of brand credibility. Instances of data breaches or unethical data practices can quickly become public relations nightmares, causing lasting damage to a company's reputation and eroding the trust that consumers place in their chosen brands. Consequently, businesses operating in the digital sphere are compelled to prioritize stringent data protection measures to safeguard not only legal standing but also the trust and confidence of their customer base.
The potential legal and reputational risks amplify the importance of implementing robust data protection strategies and transparent communication. Businesses are investing in comprehensive privacy policies that not only adhere to legal standards but are also easily accessible and comprehensible for users. Clear articulation of data handling practices and a commitment to user privacy not only aids in compliance but also serves as a proactive measure to mitigate potential legal and reputational pitfalls.
How to obtain DIGITAL MARKETING Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the impact of privacy changes on digital marketing strategies is reshaping the landscape in profound ways, ushering in a new era where user privacy takes center stage. The evolving regulatory frameworks, technological shifts, and changing consumer attitudes have necessitated a fundamental reevaluation of how businesses approach digital marketing. As third-party cookies face restrictions and data tracking becomes more limited, marketers are challenged to adapt their strategies to maintain effectiveness while respecting user privacy preferences.
The emergence of privacy-focused marketing tools reflects a commitment to ethical data practices and transparent communication. From analytics platforms that prioritize user confidentiality to consent management tools that empower users with control over their data, businesses are navigating the complexities of a digital environment that demands privacy-conscious approaches. The shift towards user-centric data governance, overseen by data protection officers, underscores the importance of obtaining explicit user consent and fostering a culture of responsible data management.
Social media advertising, a cornerstone of digital marketing, is undergoing a transformation as platforms implement updates to provide users with more control over their data. Marketers are adjusting their strategies to align with these changes, focusing on contextual targeting and exploring innovative advertising formats that prioritize user privacy.
In this evolving digital marketing landscape, the convergence of legal, technological, and consumer-driven changes demands a holistic approach. By embracing privacy-focused tools, adhering to user-centric data governance, and proactively addressing legal and reputational risks, businesses can not only navigate the challenges but also position themselves as trustworthy stewards of user data. As the digital marketing realm continues to evolve, those who prioritize user privacy and ethical data practices will likely thrive in building lasting connections with their audiences.
7 Steps for AWS Solutions Architect Exam Success
Embarking on the journey to become an AWS Solutions Architect is an exciting venture, but navigating through the intricacies of the certification exam demands a well-defined strategy. In this guide, we will unveil the "7 Steps for AWS Solutions Architect Exam Success," offering you a comprehensive roadmap to triumph in this challenging endeavor. From crafting a meticulous study plan to implementing effective exam strategies, our insights cover key aspects such as AWS Certification preparation, study techniques, and best practices for ensuring your success. Whether you're a seasoned IT professional or a newcomer to the AWS ecosystem, these carefully curated steps will guide you towards conquering the AWS Solutions Architect Exam with confidence. Let's delve into the intricacies of this certification journey, unlocking the doors to a rewarding career in cloud computing.
Table of contents
-
Creating a Detailed Study Plan
-
Mastering Core AWS Services
-
Utilizing Practice Exams and Mock Tests
-
Developing Effective Exam Strategies
-
Staying Updated with AWS Documentation and Updates
-
Conclusion
Creating a Detailed Study Plan
Crafting a meticulous study plan is the foundational step toward achieving success in the AWS Solutions Architect Exam. Begin by breaking down the exam domains to understand the scope and weightage of each section. Allocate dedicated time to cover theoretical concepts and engage in hands-on practice. A well-structured study plan should include specific goals, milestones, and deadlines, ensuring that you cover all essential topics before the exam date. Consider the availability of study resources, such as official AWS documentation, online courses, and practice exams, and integrate them into your plan strategically. Tailor your study schedule to your individual learning style and pace, allowing for a balanced mix of theoretical understanding and practical application of AWS services. Regularly review and adapt your study plan based on your progress, ensuring that you stay on track and confidently approach the exam with a comprehensive understanding of the material.
Mastering Core AWS Services
Mastering core AWS services is a pivotal component in preparing for the AWS Solutions Architect Exam. Delve into an in-depth exploration of essential AWS services, including but not limited to compute, storage, database, networking, and security services. Engage in hands-on labs and practical exercises to reinforce your understanding and gain proficiency in deploying, configuring, and managing these services. Identify key AWS services that carry significant weight in the exam objectives, and prioritize your focus accordingly. Through practical application and experimentation, develop a comprehensive understanding of how these services interact within the AWS ecosystem. By mastering core AWS services, you not only enhance your theoretical knowledge but also build the practical skills necessary for success in the Solutions Architect Exam, where real-world scenarios and application play a crucial role in assessment.
Utilizing Practice Exams and Mock Tests
Utilizing practice exams and mock tests is a critical strategy to fortify your readiness for the AWS Solutions Architect Exam. These simulated assessments serve as invaluable tools to gauge your understanding of exam topics, identify areas of improvement, and familiarize yourself with the exam format and question types. Opt for reputable practice materials and resources, such as official AWS practice exams or well-established third-party providers, to ensure accuracy and relevance to the actual exam. Regularly integrate these practice sessions into your study routine, mimicking real exam conditions to enhance your time management skills and build confidence. Analyze your performance in practice exams, focusing on both correct and incorrect answers, to gain insights into your strengths and weaknesses. This iterative process of practicing and learning from mock tests contributes significantly to refining your exam-taking strategies and ultimately positions you for success on the day of the AWS Solutions Architect Exam.
Developing Effective Exam Strategies
Developing effective exam strategies is a crucial aspect of preparing for the AWS Solutions Architect Exam. Begin by familiarizing yourself with the exam structure, understanding different question formats, and recognizing the specific skills and knowledge areas that are assessed. Time management is paramount, so practice allocating your time wisely during practice exams to ensure you can answer all questions within the given timeframe. Explore techniques for approaching different types of questions, whether they involve scenario-based problem-solving or direct knowledge recall. Consider strategies such as flagging challenging questions for later review, answering known questions first, and maintaining a steady pace throughout the exam. Additionally, understand how to leverage the tools and resources provided during the exam effectively. Developing a well-thought-out exam strategy not only boosts your confidence but also enhances your overall performance, allowing you to navigate the exam with efficiency and precision.
Staying Updated with AWS Documentation and Updates
Staying updated with AWS documentation and keeping abreast of the latest platform updates is a pivotal aspect of effective preparation for the AWS Solutions Architect Exam. Integrating AWS documentation into your study routine provides a reliable and comprehensive source of information directly from the official channels. Regularly check for updates and announcements from AWS, ensuring that your study materials align with the most current exam objectives and content. This practice not only enhances your theoretical knowledge but also prepares you to tackle any new features or changes introduced by AWS. Embrace a proactive approach to learning by understanding how to navigate and leverage AWS documentation effectively during the exam. By staying informed about the evolving landscape of AWS services and technologies, you not only demonstrate a commitment to continuous learning but also position yourself for success in a dynamic and ever-changing cloud computing environment.
Conclusion
In conclusion, mastering the AWS Solutions Architect Exam requires a strategic and comprehensive approach. By following the "7 Steps for AWS Solutions Architect Exam Success," you can navigate this challenging certification journey with confidence. Crafting a detailed study plan sets the foundation, allowing you to allocate time efficiently and cover all essential exam domains. Delving into and mastering core AWS services through hands-on labs enhances your theoretical knowledge and practical skills, preparing you for real-world scenarios. Utilizing practice exams and mock tests becomes a vital tool, honing your exam-taking skills and providing valuable insights into your strengths and areas for improvement. Developing effective exam strategies ensures that you approach the exam with confidence, managing time wisely and navigating various question formats. Lastly, staying updated with AWS documentation and embracing continuous learning equips you to adapt to the evolving AWS landscape. Collectively, these steps form a holistic guide to success, empowering you to not only pass the AWS Solutions Architect Exam but also thrive in the dynamic and rapidly evolving world of cloud computing.
Read More
Embarking on the journey to become an AWS Solutions Architect is an exciting venture, but navigating through the intricacies of the certification exam demands a well-defined strategy. In this guide, we will unveil the "7 Steps for AWS Solutions Architect Exam Success," offering you a comprehensive roadmap to triumph in this challenging endeavor. From crafting a meticulous study plan to implementing effective exam strategies, our insights cover key aspects such as AWS Certification preparation, study techniques, and best practices for ensuring your success. Whether you're a seasoned IT professional or a newcomer to the AWS ecosystem, these carefully curated steps will guide you towards conquering the AWS Solutions Architect Exam with confidence. Let's delve into the intricacies of this certification journey, unlocking the doors to a rewarding career in cloud computing.
Table of contents
-
Creating a Detailed Study Plan
-
Mastering Core AWS Services
-
Utilizing Practice Exams and Mock Tests
-
Developing Effective Exam Strategies
-
Staying Updated with AWS Documentation and Updates
-
Conclusion
Creating a Detailed Study Plan
Crafting a meticulous study plan is the foundational step toward achieving success in the AWS Solutions Architect Exam. Begin by breaking down the exam domains to understand the scope and weightage of each section. Allocate dedicated time to cover theoretical concepts and engage in hands-on practice. A well-structured study plan should include specific goals, milestones, and deadlines, ensuring that you cover all essential topics before the exam date. Consider the availability of study resources, such as official AWS documentation, online courses, and practice exams, and integrate them into your plan strategically. Tailor your study schedule to your individual learning style and pace, allowing for a balanced mix of theoretical understanding and practical application of AWS services. Regularly review and adapt your study plan based on your progress, ensuring that you stay on track and confidently approach the exam with a comprehensive understanding of the material.
Mastering Core AWS Services
Mastering core AWS services is a pivotal component in preparing for the AWS Solutions Architect Exam. Delve into an in-depth exploration of essential AWS services, including but not limited to compute, storage, database, networking, and security services. Engage in hands-on labs and practical exercises to reinforce your understanding and gain proficiency in deploying, configuring, and managing these services. Identify key AWS services that carry significant weight in the exam objectives, and prioritize your focus accordingly. Through practical application and experimentation, develop a comprehensive understanding of how these services interact within the AWS ecosystem. By mastering core AWS services, you not only enhance your theoretical knowledge but also build the practical skills necessary for success in the Solutions Architect Exam, where real-world scenarios and application play a crucial role in assessment.
Utilizing Practice Exams and Mock Tests
Utilizing practice exams and mock tests is a critical strategy to fortify your readiness for the AWS Solutions Architect Exam. These simulated assessments serve as invaluable tools to gauge your understanding of exam topics, identify areas of improvement, and familiarize yourself with the exam format and question types. Opt for reputable practice materials and resources, such as official AWS practice exams or well-established third-party providers, to ensure accuracy and relevance to the actual exam. Regularly integrate these practice sessions into your study routine, mimicking real exam conditions to enhance your time management skills and build confidence. Analyze your performance in practice exams, focusing on both correct and incorrect answers, to gain insights into your strengths and weaknesses. This iterative process of practicing and learning from mock tests contributes significantly to refining your exam-taking strategies and ultimately positions you for success on the day of the AWS Solutions Architect Exam.
Developing Effective Exam Strategies
Developing effective exam strategies is a crucial aspect of preparing for the AWS Solutions Architect Exam. Begin by familiarizing yourself with the exam structure, understanding different question formats, and recognizing the specific skills and knowledge areas that are assessed. Time management is paramount, so practice allocating your time wisely during practice exams to ensure you can answer all questions within the given timeframe. Explore techniques for approaching different types of questions, whether they involve scenario-based problem-solving or direct knowledge recall. Consider strategies such as flagging challenging questions for later review, answering known questions first, and maintaining a steady pace throughout the exam. Additionally, understand how to leverage the tools and resources provided during the exam effectively. Developing a well-thought-out exam strategy not only boosts your confidence but also enhances your overall performance, allowing you to navigate the exam with efficiency and precision.
Staying Updated with AWS Documentation and Updates
Staying updated with AWS documentation and keeping abreast of the latest platform updates is a pivotal aspect of effective preparation for the AWS Solutions Architect Exam. Integrating AWS documentation into your study routine provides a reliable and comprehensive source of information directly from the official channels. Regularly check for updates and announcements from AWS, ensuring that your study materials align with the most current exam objectives and content. This practice not only enhances your theoretical knowledge but also prepares you to tackle any new features or changes introduced by AWS. Embrace a proactive approach to learning by understanding how to navigate and leverage AWS documentation effectively during the exam. By staying informed about the evolving landscape of AWS services and technologies, you not only demonstrate a commitment to continuous learning but also position yourself for success in a dynamic and ever-changing cloud computing environment.
Conclusion
In conclusion, mastering the AWS Solutions Architect Exam requires a strategic and comprehensive approach. By following the "7 Steps for AWS Solutions Architect Exam Success," you can navigate this challenging certification journey with confidence. Crafting a detailed study plan sets the foundation, allowing you to allocate time efficiently and cover all essential exam domains. Delving into and mastering core AWS services through hands-on labs enhances your theoretical knowledge and practical skills, preparing you for real-world scenarios. Utilizing practice exams and mock tests becomes a vital tool, honing your exam-taking skills and providing valuable insights into your strengths and areas for improvement. Developing effective exam strategies ensures that you approach the exam with confidence, managing time wisely and navigating various question formats. Lastly, staying updated with AWS documentation and embracing continuous learning equips you to adapt to the evolving AWS landscape. Collectively, these steps form a holistic guide to success, empowering you to not only pass the AWS Solutions Architect Exam but also thrive in the dynamic and rapidly evolving world of cloud computing.
Key Benefits of Achieving ISO 20000 Certification for Your IT Services
Achieving ISO 20000 certification for your IT services is a significant milestone that demonstrates your commitment to excellence in managing information technology processes. ISO 20000 is an international standard specifically designed for IT service management systems, providing a framework for organizations to establish, implement, maintain, and continually improve their IT service delivery. This certification not only signifies compliance with industry best practices but also brings forth a multitude of key benefits for businesses operating in the ever-evolving digital landscape.
ISO 20000 certification also promotes a culture of continual improvement within the organization. The standard emphasizes the importance of regularly monitoring and evaluating IT service management processes, fostering a mindset of adaptability and responsiveness to changing technological landscapes. This proactive approach not only ensures the alignment of IT services with business objectives but also equips organizations to stay ahead of industry trends and emerging technologies.
In summary, attaining ISO 20000 certification for your IT services is a strategic investment that goes beyond mere compliance. It serves as a powerful tool for enhancing service quality, fostering a culture of continual improvement, and gaining a competitive edge in the dynamic realm of IT service management. As organizations increasingly rely on technology for their operations, ISO 20000 certification stands as a testament to a commitment to excellence, reliability, and customer satisfaction in the provision of IT services.
Table of contents
-
Process Standardization and Consistency
-
Enhanced Service Delivery and Customer Confidence
-
Cost Savings and Resource Optimization
-
Alignment with Business Objectives
-
Market Recognition and Competitive Edge
-
Conclusion
Process Standardization and Consistency
Process Standardization and Consistency are pivotal benefits derived from achieving ISO 20000 certification for IT services. The certification instills a disciplined approach to IT service management, emphasizing the need for standardized processes across the organization. Standardization involves establishing uniform procedures, protocols, and guidelines, ensuring that every aspect of IT service delivery adheres to a consistent framework. This systematic approach not only minimizes the risk of errors but also promotes operational efficiency by streamlining workflows and eliminating redundancies.
Consistency is a key byproduct of process standardization within the ISO 20000 framework. It ensures that IT services are delivered in a uniform manner, regardless of the specific circumstances or individuals involved. This uniformity is crucial for fostering predictability and reliability in service delivery. Clients and stakeholders can have confidence that the IT services they receive will consistently meet or exceed established standards, leading to increased trust and satisfaction.
Moreover, process standardization and consistency contribute to improved communication and collaboration within the IT service management team. With everyone following the same set of procedures, there is a common language and understanding of how tasks should be executed. This not only reduces the likelihood of misunderstandings but also facilitates the seamless integration of new team members into existing workflows.
From a strategic perspective, the emphasis on process standardization and consistency aligns with the broader goal of achieving operational excellence. Organizations that attain ISO 20000 certification position themselves to operate more efficiently, respond more effectively to challenges, and adapt to evolving technological landscapes with agility. Ultimately, the benefits of process standardization and consistency extend beyond mere compliance; they lay the foundation for a resilient and high-performing IT service management system.
Enhanced Service Delivery and Customer Confidence
ISO 20000 certification plays a pivotal role in enhancing service delivery within IT organizations, leading to increased customer confidence and satisfaction. By adhering to the rigorous standards set by ISO 20000, organizations commit to a systematic and customer-focused approach to IT service management. This commitment translates into tangible improvements in the quality and reliability of services, directly impacting the overall customer experience.
Achieving enhanced service delivery begins with a comprehensive understanding of customer requirements and expectations. ISO 20000 encourages organizations to align their IT services with customer needs, ensuring that the delivered solutions are not only technically sound but also relevant and valuable to the end-users. This customer-centric approach fosters a culture of continuous improvement, with organizations actively seeking feedback to refine and optimize their service offerings.
The certification also emphasizes the establishment of service level agreements (SLAs) and key performance indicators (KPIs) to measure and monitor service delivery. This transparency in performance metrics not only allows organizations to track their own efficiency but also provides customers with clear insights into the quality and reliability of the services they are receiving. This increased transparency contributes to customer confidence, as clients can make informed decisions based on measurable and verifiable data.
The pursuit of ISO 20000 certification not only elevates the overall quality of service delivery but also establishes a foundation for building and maintaining customer confidence. By systematically aligning IT services with customer expectations, actively monitoring performance, and fostering a culture of continuous improvement, organizations can position themselves as reliable and customer-focused partners in the dynamic landscape of IT service management.
Cost Savings and Resource Optimization
ISO 20000 certification offers organizations a pathway to significant cost savings and resource optimization in the realm of IT services. The certification's emphasis on efficient IT service management processes directly contributes to streamlining operations and reducing unnecessary expenditures. Through the adoption of standardized procedures and the elimination of redundant activities, organizations can achieve notable improvements in resource utilization, ultimately leading to cost-effectiveness.
Cost savings are also realized through improved efficiency in service delivery processes. ISO 20000 encourages organizations to identify and eliminate inefficiencies, ensuring that tasks are completed with maximum productivity. This focus on efficiency not only saves time but also reduces operational costs, enhancing the overall cost-effectiveness of IT service management.
Resource optimization extends beyond the realm of technology to include human resources. ISO 20000 emphasizes training and development initiatives to enhance the skills and competencies of IT personnel. Well-trained teams are not only more productive but also better equipped to handle diverse challenges, reducing the likelihood of errors and costly rework.
Alignment with Business Objectives
ISO 20000 certification serves as a powerful catalyst for aligning IT services with the broader strategic objectives of an organization. One of the key benefits is the establishment of a seamless connection between IT processes and the overarching business goals. The certification framework emphasizes the need for a comprehensive understanding of the organization's objectives, enabling IT service providers to tailor their services to directly contribute to the achievement of those objectives.
By aligning IT services with business objectives, organizations can ensure that technology is not just a support function but a strategic enabler. ISO 20000 encourages IT service management to become an integral part of the business strategy, facilitating a collaborative approach that considers both technological and business perspectives. This alignment fosters a holistic understanding of how IT supports and enhances various business functions, ultimately driving overall organizational success.
ISO 20000's focus on alignment extends to the continuous monitoring and improvement of IT services in relation to changing business needs. Organizations that achieve and maintain certification demonstrate a commitment to staying adaptable and responsive to evolving business objectives. This adaptability is crucial in a dynamic business environment where technological advancements and market conditions can rapidly change, requiring IT services to evolve in tandem with organizational goals.
ISO 20000 certification serves as a guide for organizations seeking to align their IT services with overarching business objectives. This alignment ensures that IT is not a siloed function but an integral part of the organizational strategy, fostering collaboration, transparency, and continuous improvement in the pursuit of shared business goals.
Market Recognition and Competitive Edge
Market recognition stems from the credibility and prestige associated with ISO 20000 certification. Clients and businesses often view this certification as a validation of an organization's dedication to quality, reliability, and continuous improvement in delivering IT services. As a result, organizations that have achieved ISO 20000 certification are more likely to be recognized as reliable and trustworthy partners in the competitive IT services sector.
The competitive edge gained through ISO 20000 certification extends beyond mere recognition. It positions organizations to meet or exceed industry benchmarks, demonstrating a commitment to excellence that sets them apart from competitors. Clients, when faced with a choice between service providers, are more inclined to select those with a proven track record of adherence to international standards, viewing it as an assurance of superior service quality and reliability.
ISO 20000 certification not only enhances market recognition but also provides a tangible competitive edge in the dynamic and competitive field of IT services. It positions organizations as leaders who prioritize quality and efficiency, contributing to increased trust, customer loyalty, and ultimately, business success in a globally competitive market.
How to obtain ISO 20000 IT SERVICE MANAGEMENT CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, achieving ISO 20000 certification for IT services yields a spectrum of key benefits that extend far beyond compliance. The certification's emphasis on process standardization and consistency ensures a streamlined and error-resistant approach to IT service management, fostering operational efficiency. Enhanced service delivery, coupled with a customer-centric focus, elevates the overall customer experience, instilling confidence and loyalty.
Cost savings and resource optimization emerge as significant advantages, driven by the systematic and efficient processes encouraged by ISO 20000. Aligning IT services with business objectives not only positions technology as a strategic enabler but also strengthens collaboration between IT and other business functions. This alignment ensures that IT services are not just technically sound but actively contribute to the realization of broader organizational goals.
ISO 20000 certification transcends the realm of IT service management, becoming a strategic investment that positively impacts an organization's overall performance, client relationships, and competitive positioning. As businesses navigate the ever-evolving landscape of technology and service delivery, the benefits of ISO 20000 certification stand as a testament to an organization's commitment to excellence, adaptability, and long-term success in the dynamic field of IT services.
Read More
Achieving ISO 20000 certification for your IT services is a significant milestone that demonstrates your commitment to excellence in managing information technology processes. ISO 20000 is an international standard specifically designed for IT service management systems, providing a framework for organizations to establish, implement, maintain, and continually improve their IT service delivery. This certification not only signifies compliance with industry best practices but also brings forth a multitude of key benefits for businesses operating in the ever-evolving digital landscape.
ISO 20000 certification also promotes a culture of continual improvement within the organization. The standard emphasizes the importance of regularly monitoring and evaluating IT service management processes, fostering a mindset of adaptability and responsiveness to changing technological landscapes. This proactive approach not only ensures the alignment of IT services with business objectives but also equips organizations to stay ahead of industry trends and emerging technologies.
In summary, attaining ISO 20000 certification for your IT services is a strategic investment that goes beyond mere compliance. It serves as a powerful tool for enhancing service quality, fostering a culture of continual improvement, and gaining a competitive edge in the dynamic realm of IT service management. As organizations increasingly rely on technology for their operations, ISO 20000 certification stands as a testament to a commitment to excellence, reliability, and customer satisfaction in the provision of IT services.
Table of contents
-
Process Standardization and Consistency
-
Enhanced Service Delivery and Customer Confidence
-
Cost Savings and Resource Optimization
-
Alignment with Business Objectives
-
Market Recognition and Competitive Edge
-
Conclusion
Process Standardization and Consistency
Process Standardization and Consistency are pivotal benefits derived from achieving ISO 20000 certification for IT services. The certification instills a disciplined approach to IT service management, emphasizing the need for standardized processes across the organization. Standardization involves establishing uniform procedures, protocols, and guidelines, ensuring that every aspect of IT service delivery adheres to a consistent framework. This systematic approach not only minimizes the risk of errors but also promotes operational efficiency by streamlining workflows and eliminating redundancies.
Consistency is a key byproduct of process standardization within the ISO 20000 framework. It ensures that IT services are delivered in a uniform manner, regardless of the specific circumstances or individuals involved. This uniformity is crucial for fostering predictability and reliability in service delivery. Clients and stakeholders can have confidence that the IT services they receive will consistently meet or exceed established standards, leading to increased trust and satisfaction.
Moreover, process standardization and consistency contribute to improved communication and collaboration within the IT service management team. With everyone following the same set of procedures, there is a common language and understanding of how tasks should be executed. This not only reduces the likelihood of misunderstandings but also facilitates the seamless integration of new team members into existing workflows.
From a strategic perspective, the emphasis on process standardization and consistency aligns with the broader goal of achieving operational excellence. Organizations that attain ISO 20000 certification position themselves to operate more efficiently, respond more effectively to challenges, and adapt to evolving technological landscapes with agility. Ultimately, the benefits of process standardization and consistency extend beyond mere compliance; they lay the foundation for a resilient and high-performing IT service management system.
Enhanced Service Delivery and Customer Confidence
ISO 20000 certification plays a pivotal role in enhancing service delivery within IT organizations, leading to increased customer confidence and satisfaction. By adhering to the rigorous standards set by ISO 20000, organizations commit to a systematic and customer-focused approach to IT service management. This commitment translates into tangible improvements in the quality and reliability of services, directly impacting the overall customer experience.
Achieving enhanced service delivery begins with a comprehensive understanding of customer requirements and expectations. ISO 20000 encourages organizations to align their IT services with customer needs, ensuring that the delivered solutions are not only technically sound but also relevant and valuable to the end-users. This customer-centric approach fosters a culture of continuous improvement, with organizations actively seeking feedback to refine and optimize their service offerings.
The certification also emphasizes the establishment of service level agreements (SLAs) and key performance indicators (KPIs) to measure and monitor service delivery. This transparency in performance metrics not only allows organizations to track their own efficiency but also provides customers with clear insights into the quality and reliability of the services they are receiving. This increased transparency contributes to customer confidence, as clients can make informed decisions based on measurable and verifiable data.
The pursuit of ISO 20000 certification not only elevates the overall quality of service delivery but also establishes a foundation for building and maintaining customer confidence. By systematically aligning IT services with customer expectations, actively monitoring performance, and fostering a culture of continuous improvement, organizations can position themselves as reliable and customer-focused partners in the dynamic landscape of IT service management.
Cost Savings and Resource Optimization
ISO 20000 certification offers organizations a pathway to significant cost savings and resource optimization in the realm of IT services. The certification's emphasis on efficient IT service management processes directly contributes to streamlining operations and reducing unnecessary expenditures. Through the adoption of standardized procedures and the elimination of redundant activities, organizations can achieve notable improvements in resource utilization, ultimately leading to cost-effectiveness.
Cost savings are also realized through improved efficiency in service delivery processes. ISO 20000 encourages organizations to identify and eliminate inefficiencies, ensuring that tasks are completed with maximum productivity. This focus on efficiency not only saves time but also reduces operational costs, enhancing the overall cost-effectiveness of IT service management.
Resource optimization extends beyond the realm of technology to include human resources. ISO 20000 emphasizes training and development initiatives to enhance the skills and competencies of IT personnel. Well-trained teams are not only more productive but also better equipped to handle diverse challenges, reducing the likelihood of errors and costly rework.
Alignment with Business Objectives
ISO 20000 certification serves as a powerful catalyst for aligning IT services with the broader strategic objectives of an organization. One of the key benefits is the establishment of a seamless connection between IT processes and the overarching business goals. The certification framework emphasizes the need for a comprehensive understanding of the organization's objectives, enabling IT service providers to tailor their services to directly contribute to the achievement of those objectives.
By aligning IT services with business objectives, organizations can ensure that technology is not just a support function but a strategic enabler. ISO 20000 encourages IT service management to become an integral part of the business strategy, facilitating a collaborative approach that considers both technological and business perspectives. This alignment fosters a holistic understanding of how IT supports and enhances various business functions, ultimately driving overall organizational success.
ISO 20000's focus on alignment extends to the continuous monitoring and improvement of IT services in relation to changing business needs. Organizations that achieve and maintain certification demonstrate a commitment to staying adaptable and responsive to evolving business objectives. This adaptability is crucial in a dynamic business environment where technological advancements and market conditions can rapidly change, requiring IT services to evolve in tandem with organizational goals.
ISO 20000 certification serves as a guide for organizations seeking to align their IT services with overarching business objectives. This alignment ensures that IT is not a siloed function but an integral part of the organizational strategy, fostering collaboration, transparency, and continuous improvement in the pursuit of shared business goals.
Market Recognition and Competitive Edge
Market recognition stems from the credibility and prestige associated with ISO 20000 certification. Clients and businesses often view this certification as a validation of an organization's dedication to quality, reliability, and continuous improvement in delivering IT services. As a result, organizations that have achieved ISO 20000 certification are more likely to be recognized as reliable and trustworthy partners in the competitive IT services sector.
The competitive edge gained through ISO 20000 certification extends beyond mere recognition. It positions organizations to meet or exceed industry benchmarks, demonstrating a commitment to excellence that sets them apart from competitors. Clients, when faced with a choice between service providers, are more inclined to select those with a proven track record of adherence to international standards, viewing it as an assurance of superior service quality and reliability.
ISO 20000 certification not only enhances market recognition but also provides a tangible competitive edge in the dynamic and competitive field of IT services. It positions organizations as leaders who prioritize quality and efficiency, contributing to increased trust, customer loyalty, and ultimately, business success in a globally competitive market.
How to obtain ISO 20000 IT SERVICE MANAGEMENT CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, achieving ISO 20000 certification for IT services yields a spectrum of key benefits that extend far beyond compliance. The certification's emphasis on process standardization and consistency ensures a streamlined and error-resistant approach to IT service management, fostering operational efficiency. Enhanced service delivery, coupled with a customer-centric focus, elevates the overall customer experience, instilling confidence and loyalty.
Cost savings and resource optimization emerge as significant advantages, driven by the systematic and efficient processes encouraged by ISO 20000. Aligning IT services with business objectives not only positions technology as a strategic enabler but also strengthens collaboration between IT and other business functions. This alignment ensures that IT services are not just technically sound but actively contribute to the realization of broader organizational goals.
ISO 20000 certification transcends the realm of IT service management, becoming a strategic investment that positively impacts an organization's overall performance, client relationships, and competitive positioning. As businesses navigate the ever-evolving landscape of technology and service delivery, the benefits of ISO 20000 certification stand as a testament to an organization's commitment to excellence, adaptability, and long-term success in the dynamic field of IT services.
The Impact of Artificial Intelligence on Digital Marketing Campaigns
The rapid evolution of technology has ushered in an era where Artificial Intelligence (AI) plays a pivotal role in transforming various industries, and one such domain experiencing significant change is digital marketing. As businesses navigate the dynamic landscape of online interactions, consumer behavior, and data analytics, AI has emerged as a powerful ally in optimizing and enhancing digital marketing campaigns. This synergy between AI and digital marketing holds the potential to revolutionize the way companies connect with their target audiences, streamline processes, and achieve unprecedented levels of efficiency.
At its core, AI empowers digital marketers with the ability to leverage data-driven insights and predictive analytics, allowing for more accurate and personalized targeting. Through machine learning algorithms, AI analyzes vast datasets to discern patterns and trends, providing marketers with valuable information about consumer preferences, behaviors, and purchasing patterns. This newfound understanding enables businesses to create highly targeted and relevant content, delivering a more personalized and engaging experience to their audience. Consequently, AI-driven digital marketing campaigns have the potential to significantly improve customer satisfaction and loyalty.
As AI continues to evolve, the integration of technologies like natural language processing and chatbots further revolutionizes the way brands interact with consumers. Chatbots powered by AI can engage in real-time conversations, addressing customer queries, providing information, and even facilitating transactions. This not only enhances customer engagement but also ensures a seamless and responsive communication channel, fostering a positive brand image.
The impact of artificial intelligence on digital marketing campaigns is profound and multifaceted. From data-driven insights and predictive analytics to automation and personalized interactions, AI is reshaping the landscape of digital marketing, offering new possibilities and efficiencies for businesses. As the technology continues to advance, striking the right balance between innovation and ethical considerations will be key to unlocking the full potential of AI in digital marketing.
Table of contents
-
Personalization through AI in Digital Marketing
-
Automation and Operational Efficiency
-
Enhancing Customer Engagement with AI-Powered Chatbots
-
Ethical Considerations in AI-Driven Digital Marketing
-
Measuring and Analyzing AI-Enhanced Marketing Performance
-
Conclusion
Personalization through AI in Digital Marketing
The advent of Artificial Intelligence (AI) has ushered in a new era of personalization in the realm of digital marketing, fundamentally altering the way businesses engage with their target audiences. At the heart of this transformation lies the capability of AI, particularly machine learning algorithms, to analyze vast datasets and derive actionable insights about individual consumer behavior. This level of granular understanding enables marketers to create highly personalized and targeted content that resonates with the unique preferences and interests of each consumer.
AI-driven personalization in digital marketing goes beyond traditional demographic segmentation. Instead, it focuses on the analysis of real-time data, online behaviors, and previous interactions to tailor marketing messages at an individual level. Through predictive analytics, AI can anticipate consumer needs, preferences, and even the likelihood of specific actions, allowing marketers to deliver timely and relevant content that significantly enhances the user experience.
One of the key benefits of AI-powered personalization is the ability to create dynamic and adaptive content. By continuously learning from user interactions, AI algorithms can optimize content in real-time, ensuring that marketing messages remain current and resonate with the evolving preferences of the audience. This dynamic adaptation contributes to increased engagement and, ultimately, a higher likelihood of conversion.
Moreover, personalization through AI extends beyond content customization to include personalized recommendations and product offerings. E-commerce platforms, for example, leverage AI algorithms to analyze past purchase history and user behavior, providing customers with tailored product recommendations. This not only facilitates a more efficient and enjoyable shopping experience but also enhances the likelihood of cross-selling and upselling opportunities.
Automation and Operational Efficiency
The infusion of Artificial Intelligence (AI) into digital marketing has brought about a profound transformation in operational efficiency, reshaping the way marketing tasks are executed and optimizing resource allocation. At its core, AI-driven automation is revolutionizing how marketing teams handle repetitive and time-consuming tasks. This shift is particularly evident in data analysis, where machine learning algorithms can swiftly process vast datasets, providing real-time insights and empowering marketers to make informed decisions with unparalleled efficiency.
One of the central advantages of automation in digital marketing is its capacity to liberate marketing professionals from mundane activities, allowing them to redirect their focus toward strategic endeavors. Routine tasks such as email marketing, social media posting, and ad placement can be automated, enabling teams to dedicate more time and creativity to high-level aspects of campaign management. This not only enhances overall efficiency but also fosters an environment conducive to strategic thinking and innovation within marketing departments.
AI-driven automation not only expedites tasks but also enhances the agility and responsiveness of marketing campaigns. Machine learning algorithms adapt to changing market conditions and consumer behaviors in real-time, facilitating rapid adjustments to marketing strategies. In an era where the digital landscape evolves swiftly, this dynamic responsiveness ensures that campaigns remain relevant and effective.
Moreover, the impact of AI-driven automation extends to the realm of personalization, allowing marketers to tailor content and experiences for individual consumers. By analyzing user behaviors and preferences, AI algorithms can deliver highly targeted and relevant content, cultivating a more profound connection between brands and their audiences. This heightened level of personalization contributes not only to increased customer engagement but also to higher conversion rates.
As marketing campaigns become increasingly intricate, AI-driven automation facilitates comprehensive campaign orchestration. Marketers can seamlessly integrate various channels, ensuring a synchronized approach across platforms. This holistic perspective enables marketers to track the customer journey more accurately, identify crucial touchpoints, and allocate resources effectively.
The integration of AI-driven automation in digital marketing not only enhances operational efficiency but also redefines customer engagement and campaign management. A thoughtful and ethical approach ensures that AI becomes an enabler, fostering a harmonious relationship between human creativity and AI capabilities in the pursuit of marketing excellence.
Enhancing Customer Engagement with AI-Powered Chatbots
The landscape of customer engagement has undergone a transformative shift with the integration of Artificial Intelligence (AI), particularly through the implementation of AI-powered chatbots. These intelligent conversational agents are revolutionizing the way businesses interact with their customers, providing real-time communication and personalized assistance. At the forefront of this change is the ability of AI-powered chatbots to engage with users in natural language, facilitating seamless and instant communication.
One of the key contributions of AI-powered chatbots to customer engagement lies in their availability and responsiveness. Unlike traditional customer service channels that operate within specific hours, chatbots are available 24/7, providing customers with immediate assistance whenever they require it. This around-the-clock availability not only enhances customer satisfaction but also addresses issues promptly, contributing to a positive overall customer experience.
Moreover, AI-powered chatbots excel in handling routine and frequently asked queries, allowing human customer service representatives to focus on more complex and nuanced issues. By automating these routine tasks, chatbots streamline the customer support process, reducing response times and increasing efficiency. This ensures that customers receive quick and accurate information, leading to improved satisfaction and a more positive perception of the brand.
The personalization capabilities of AI-powered chatbots further elevate customer engagement. These chatbots can analyze customer data, past interactions, and preferences to tailor responses and recommendations. This level of personalization not only enhances the relevance of interactions but also contributes to a more individualized and customer-centric experience, fostering a deeper connection between the customer and the brand.
AI-powered chatbots are reshaping the landscape of customer engagement by providing instantaneous, personalized, and efficient interactions. As businesses continue to adopt these intelligent conversational agents, the focus remains on optimizing customer experiences, building brand loyalty, and staying at the forefront of technological advancements in customer service.
Ethical Considerations in AI-Driven Digital Marketing
As Artificial Intelligence (AI) becomes increasingly integrated into digital marketing strategies, a critical dimension that demands careful attention is the ethical considerations surrounding its implementation. Ethical concerns in AI-driven digital marketing encompass a range of issues, including user privacy, responsible data usage, and the potential biases embedded in algorithms.
One of the foremost ethical considerations is the protection of user privacy. As AI algorithms analyze vast amounts of data to generate insights and personalize marketing content, there is a heightened risk of infringing on individual privacy. Marketers must be vigilant in adhering to data protection regulations, obtaining informed consent, and ensuring that user information is handled with the utmost security to build and maintain trust with consumers.
Responsible data usage is another ethical imperative in AI-driven digital marketing. Collecting and utilizing consumer data should be done transparently and ethically. It is essential to strike a balance between personalization for improved user experiences and avoiding the exploitation of sensitive information. Marketers must communicate clearly about the data they collect, how it will be used, and provide users with options to control their preferences.
Biases in AI algorithms present a complex ethical challenge. Machine learning models learn from historical data, which may contain biases. If these biases are not identified and addressed, AI-driven marketing campaigns can inadvertently perpetuate or amplify existing societal prejudices. Businesses must invest in diverse and inclusive datasets, regularly audit algorithms for biases, and implement measures to correct and prevent discriminatory outcomes to ensure fair and equitable treatment for all users.
Transparency is a cornerstone of ethical AI in digital marketing. Marketers should be open about the use of AI in their campaigns, communicating to consumers how algorithms influence content recommendations, personalization, and decision-making processes. Transparent practices build trust, empowering users to make informed choices about their engagement with digital platforms.
Measuring and Analyzing AI-Enhanced Marketing Performance
The integration of Artificial Intelligence (AI) into digital marketing has ushered in a new era of sophisticated measurement and analysis of marketing performance. The capabilities of AI go beyond traditional metrics, offering marketers powerful tools to gain deeper insights into campaign effectiveness, consumer behavior, and overall ROI. The use of AI for measuring and analyzing marketing performance contributes to a more data-driven and strategic approach to decision-making.
One of the primary benefits of AI in marketing performance analysis is its ability to process and interpret vast datasets at an unprecedented speed. Machine learning algorithms can sift through large volumes of data, identifying patterns and correlations that may be elusive to human analysis. This enables marketers to gain a comprehensive understanding of consumer behavior, preferences, and the impact of various marketing initiatives on key performance indicators (KPIs).
Predictive analytics, powered by AI, plays a pivotal role in forecasting future trends and outcomes based on historical data. Marketers can leverage these insights to optimize campaign strategies, allocate resources more efficiently, and proactively address potential challenges. The predictive capabilities of AI contribute to a more agile and adaptive approach to marketing, ensuring that campaigns are not only responsive to current trends but also well-positioned for future success.
AI-enhanced marketing performance measurement represents a significant leap forward in the digital marketing landscape. The ability to harness the power of AI for data analysis and predictive insights empowers marketers to make informed decisions, optimize campaigns, and deliver more personalized and impactful experiences to their target audience. As technology continues to advance, the synergy between human expertise and AI capabilities will be essential for unlocking the full potential of data-driven marketing strategies.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
-
Digital Marketing : Digital Marketing Certification
Conclusion
In conclusion, the impact of Artificial Intelligence (AI) on digital marketing campaigns is undeniably transformative, touching various aspects of strategy, execution, and customer engagement. AI's ability to analyze vast datasets, personalize content, and automate tasks has ushered in a new era of efficiency and innovation in the digital marketing landscape.
Personalization through AI has elevated the customer experience, allowing businesses to tailor their content and recommendations with unprecedented precision. This not only enhances engagement but also contributes to building stronger and more meaningful connections with the target audience. The efficiency gains from automation have liberated marketers from routine tasks, enabling them to focus on strategic thinking and creative endeavors. From data analysis to social media management, AI-driven automation streamlines processes and ensures campaigns remain agile and responsive to dynamic market conditions.
The integration of AI-powered chatbots has revolutionized customer engagement by providing instant and personalized interactions. These intelligent conversational agents operate around the clock, offering real-time assistance and contributing to enhanced customer satisfaction. However, it is crucial to maintain a balance between automation and the human touch, preserving the authenticity that is vital for genuine customer relationships.
As AI becomes an integral part of digital marketing, ethical considerations take center stage. Protecting user privacy, ensuring responsible data usage, and addressing biases in algorithms are paramount. Transparent communication about AI usage and fostering a commitment to ethical practices are essential for building and maintaining trust with consumers.
Read More
The rapid evolution of technology has ushered in an era where Artificial Intelligence (AI) plays a pivotal role in transforming various industries, and one such domain experiencing significant change is digital marketing. As businesses navigate the dynamic landscape of online interactions, consumer behavior, and data analytics, AI has emerged as a powerful ally in optimizing and enhancing digital marketing campaigns. This synergy between AI and digital marketing holds the potential to revolutionize the way companies connect with their target audiences, streamline processes, and achieve unprecedented levels of efficiency.
At its core, AI empowers digital marketers with the ability to leverage data-driven insights and predictive analytics, allowing for more accurate and personalized targeting. Through machine learning algorithms, AI analyzes vast datasets to discern patterns and trends, providing marketers with valuable information about consumer preferences, behaviors, and purchasing patterns. This newfound understanding enables businesses to create highly targeted and relevant content, delivering a more personalized and engaging experience to their audience. Consequently, AI-driven digital marketing campaigns have the potential to significantly improve customer satisfaction and loyalty.
As AI continues to evolve, the integration of technologies like natural language processing and chatbots further revolutionizes the way brands interact with consumers. Chatbots powered by AI can engage in real-time conversations, addressing customer queries, providing information, and even facilitating transactions. This not only enhances customer engagement but also ensures a seamless and responsive communication channel, fostering a positive brand image.
The impact of artificial intelligence on digital marketing campaigns is profound and multifaceted. From data-driven insights and predictive analytics to automation and personalized interactions, AI is reshaping the landscape of digital marketing, offering new possibilities and efficiencies for businesses. As the technology continues to advance, striking the right balance between innovation and ethical considerations will be key to unlocking the full potential of AI in digital marketing.
Table of contents
-
Personalization through AI in Digital Marketing
-
Automation and Operational Efficiency
-
Enhancing Customer Engagement with AI-Powered Chatbots
-
Ethical Considerations in AI-Driven Digital Marketing
-
Measuring and Analyzing AI-Enhanced Marketing Performance
-
Conclusion
Personalization through AI in Digital Marketing
The advent of Artificial Intelligence (AI) has ushered in a new era of personalization in the realm of digital marketing, fundamentally altering the way businesses engage with their target audiences. At the heart of this transformation lies the capability of AI, particularly machine learning algorithms, to analyze vast datasets and derive actionable insights about individual consumer behavior. This level of granular understanding enables marketers to create highly personalized and targeted content that resonates with the unique preferences and interests of each consumer.
AI-driven personalization in digital marketing goes beyond traditional demographic segmentation. Instead, it focuses on the analysis of real-time data, online behaviors, and previous interactions to tailor marketing messages at an individual level. Through predictive analytics, AI can anticipate consumer needs, preferences, and even the likelihood of specific actions, allowing marketers to deliver timely and relevant content that significantly enhances the user experience.
One of the key benefits of AI-powered personalization is the ability to create dynamic and adaptive content. By continuously learning from user interactions, AI algorithms can optimize content in real-time, ensuring that marketing messages remain current and resonate with the evolving preferences of the audience. This dynamic adaptation contributes to increased engagement and, ultimately, a higher likelihood of conversion.
Moreover, personalization through AI extends beyond content customization to include personalized recommendations and product offerings. E-commerce platforms, for example, leverage AI algorithms to analyze past purchase history and user behavior, providing customers with tailored product recommendations. This not only facilitates a more efficient and enjoyable shopping experience but also enhances the likelihood of cross-selling and upselling opportunities.
Automation and Operational Efficiency
The infusion of Artificial Intelligence (AI) into digital marketing has brought about a profound transformation in operational efficiency, reshaping the way marketing tasks are executed and optimizing resource allocation. At its core, AI-driven automation is revolutionizing how marketing teams handle repetitive and time-consuming tasks. This shift is particularly evident in data analysis, where machine learning algorithms can swiftly process vast datasets, providing real-time insights and empowering marketers to make informed decisions with unparalleled efficiency.
One of the central advantages of automation in digital marketing is its capacity to liberate marketing professionals from mundane activities, allowing them to redirect their focus toward strategic endeavors. Routine tasks such as email marketing, social media posting, and ad placement can be automated, enabling teams to dedicate more time and creativity to high-level aspects of campaign management. This not only enhances overall efficiency but also fosters an environment conducive to strategic thinking and innovation within marketing departments.
AI-driven automation not only expedites tasks but also enhances the agility and responsiveness of marketing campaigns. Machine learning algorithms adapt to changing market conditions and consumer behaviors in real-time, facilitating rapid adjustments to marketing strategies. In an era where the digital landscape evolves swiftly, this dynamic responsiveness ensures that campaigns remain relevant and effective.
Moreover, the impact of AI-driven automation extends to the realm of personalization, allowing marketers to tailor content and experiences for individual consumers. By analyzing user behaviors and preferences, AI algorithms can deliver highly targeted and relevant content, cultivating a more profound connection between brands and their audiences. This heightened level of personalization contributes not only to increased customer engagement but also to higher conversion rates.
As marketing campaigns become increasingly intricate, AI-driven automation facilitates comprehensive campaign orchestration. Marketers can seamlessly integrate various channels, ensuring a synchronized approach across platforms. This holistic perspective enables marketers to track the customer journey more accurately, identify crucial touchpoints, and allocate resources effectively.
The integration of AI-driven automation in digital marketing not only enhances operational efficiency but also redefines customer engagement and campaign management. A thoughtful and ethical approach ensures that AI becomes an enabler, fostering a harmonious relationship between human creativity and AI capabilities in the pursuit of marketing excellence.
Enhancing Customer Engagement with AI-Powered Chatbots
The landscape of customer engagement has undergone a transformative shift with the integration of Artificial Intelligence (AI), particularly through the implementation of AI-powered chatbots. These intelligent conversational agents are revolutionizing the way businesses interact with their customers, providing real-time communication and personalized assistance. At the forefront of this change is the ability of AI-powered chatbots to engage with users in natural language, facilitating seamless and instant communication.
One of the key contributions of AI-powered chatbots to customer engagement lies in their availability and responsiveness. Unlike traditional customer service channels that operate within specific hours, chatbots are available 24/7, providing customers with immediate assistance whenever they require it. This around-the-clock availability not only enhances customer satisfaction but also addresses issues promptly, contributing to a positive overall customer experience.
Moreover, AI-powered chatbots excel in handling routine and frequently asked queries, allowing human customer service representatives to focus on more complex and nuanced issues. By automating these routine tasks, chatbots streamline the customer support process, reducing response times and increasing efficiency. This ensures that customers receive quick and accurate information, leading to improved satisfaction and a more positive perception of the brand.
The personalization capabilities of AI-powered chatbots further elevate customer engagement. These chatbots can analyze customer data, past interactions, and preferences to tailor responses and recommendations. This level of personalization not only enhances the relevance of interactions but also contributes to a more individualized and customer-centric experience, fostering a deeper connection between the customer and the brand.
AI-powered chatbots are reshaping the landscape of customer engagement by providing instantaneous, personalized, and efficient interactions. As businesses continue to adopt these intelligent conversational agents, the focus remains on optimizing customer experiences, building brand loyalty, and staying at the forefront of technological advancements in customer service.
Ethical Considerations in AI-Driven Digital Marketing
As Artificial Intelligence (AI) becomes increasingly integrated into digital marketing strategies, a critical dimension that demands careful attention is the ethical considerations surrounding its implementation. Ethical concerns in AI-driven digital marketing encompass a range of issues, including user privacy, responsible data usage, and the potential biases embedded in algorithms.
One of the foremost ethical considerations is the protection of user privacy. As AI algorithms analyze vast amounts of data to generate insights and personalize marketing content, there is a heightened risk of infringing on individual privacy. Marketers must be vigilant in adhering to data protection regulations, obtaining informed consent, and ensuring that user information is handled with the utmost security to build and maintain trust with consumers.
Responsible data usage is another ethical imperative in AI-driven digital marketing. Collecting and utilizing consumer data should be done transparently and ethically. It is essential to strike a balance between personalization for improved user experiences and avoiding the exploitation of sensitive information. Marketers must communicate clearly about the data they collect, how it will be used, and provide users with options to control their preferences.
Biases in AI algorithms present a complex ethical challenge. Machine learning models learn from historical data, which may contain biases. If these biases are not identified and addressed, AI-driven marketing campaigns can inadvertently perpetuate or amplify existing societal prejudices. Businesses must invest in diverse and inclusive datasets, regularly audit algorithms for biases, and implement measures to correct and prevent discriminatory outcomes to ensure fair and equitable treatment for all users.
Transparency is a cornerstone of ethical AI in digital marketing. Marketers should be open about the use of AI in their campaigns, communicating to consumers how algorithms influence content recommendations, personalization, and decision-making processes. Transparent practices build trust, empowering users to make informed choices about their engagement with digital platforms.
Measuring and Analyzing AI-Enhanced Marketing Performance
The integration of Artificial Intelligence (AI) into digital marketing has ushered in a new era of sophisticated measurement and analysis of marketing performance. The capabilities of AI go beyond traditional metrics, offering marketers powerful tools to gain deeper insights into campaign effectiveness, consumer behavior, and overall ROI. The use of AI for measuring and analyzing marketing performance contributes to a more data-driven and strategic approach to decision-making.
One of the primary benefits of AI in marketing performance analysis is its ability to process and interpret vast datasets at an unprecedented speed. Machine learning algorithms can sift through large volumes of data, identifying patterns and correlations that may be elusive to human analysis. This enables marketers to gain a comprehensive understanding of consumer behavior, preferences, and the impact of various marketing initiatives on key performance indicators (KPIs).
Predictive analytics, powered by AI, plays a pivotal role in forecasting future trends and outcomes based on historical data. Marketers can leverage these insights to optimize campaign strategies, allocate resources more efficiently, and proactively address potential challenges. The predictive capabilities of AI contribute to a more agile and adaptive approach to marketing, ensuring that campaigns are not only responsive to current trends but also well-positioned for future success.
AI-enhanced marketing performance measurement represents a significant leap forward in the digital marketing landscape. The ability to harness the power of AI for data analysis and predictive insights empowers marketers to make informed decisions, optimize campaigns, and deliver more personalized and impactful experiences to their target audience. As technology continues to advance, the synergy between human expertise and AI capabilities will be essential for unlocking the full potential of data-driven marketing strategies.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
-
Digital Marketing : Digital Marketing Certification
Conclusion
In conclusion, the impact of Artificial Intelligence (AI) on digital marketing campaigns is undeniably transformative, touching various aspects of strategy, execution, and customer engagement. AI's ability to analyze vast datasets, personalize content, and automate tasks has ushered in a new era of efficiency and innovation in the digital marketing landscape.
Personalization through AI has elevated the customer experience, allowing businesses to tailor their content and recommendations with unprecedented precision. This not only enhances engagement but also contributes to building stronger and more meaningful connections with the target audience. The efficiency gains from automation have liberated marketers from routine tasks, enabling them to focus on strategic thinking and creative endeavors. From data analysis to social media management, AI-driven automation streamlines processes and ensures campaigns remain agile and responsive to dynamic market conditions.
The integration of AI-powered chatbots has revolutionized customer engagement by providing instant and personalized interactions. These intelligent conversational agents operate around the clock, offering real-time assistance and contributing to enhanced customer satisfaction. However, it is crucial to maintain a balance between automation and the human touch, preserving the authenticity that is vital for genuine customer relationships.
As AI becomes an integral part of digital marketing, ethical considerations take center stage. Protecting user privacy, ensuring responsible data usage, and addressing biases in algorithms are paramount. Transparent communication about AI usage and fostering a commitment to ethical practices are essential for building and maintaining trust with consumers.
Understanding the Global Interpreter Lock GIL in Python Multithreading
Python is a versatile and widely-used programming language known for its simplicity, readability, and extensive standard libraries. However, when it comes to concurrent programming and multithreading, developers often encounter a significant challenge known as the Global Interpreter Lock (GIL). The GIL has been a topic of discussion and debate within the Python community for years, as it plays a crucial role in shaping the language's behavior in a multi-threaded environment.
At its core, the Global Interpreter Lock is a mechanism implemented in the CPython interpreter, which is the default and most widely used implementation of Python. The GIL ensures that only one thread executes Python bytecode at a time, effectively serializing the execution of threads. While this design simplifies memory management and makes certain aspects of programming more straightforward, it also introduces limitations and trade-offs, particularly in scenarios where parallelism is crucial for performance optimization.
In this exploration of the Global Interpreter Lock, we will delve into the reasons behind its existence, its impact on Python multithreading, and the implications for developers seeking to harness the power of concurrent processing. Understanding the nuances of the GIL is essential for Python developers aiming to build efficient and scalable applications, as it directly influences the language's ability to fully leverage the capabilities of modern multi-core processors. As we navigate through the complexities of the Global Interpreter Lock, we will uncover strategies, alternatives, and best practices for mitigating its effects and achieving better performance in multi-threaded Python programs.
Table of contents
-
The Role of the Global Interpreter Lock (GIL)
-
GIL Limitations and Performance Challenges
-
Strategies for GIL Mitigation
-
Concurrency Patterns and Best Practices
-
Future Directions: GIL and Python's Evolution
-
Conclusion
The Role of the Global Interpreter Lock (GIL)
The Global Interpreter Lock (GIL) serves as a critical component within the CPython interpreter, the default and most widely used implementation of the Python programming language. Its primary role is to safeguard access to Python objects, preventing multiple native threads from executing Python bytecode simultaneously. The GIL essentially acts as a mutex, ensuring that only one thread can execute Python bytecode within a single process at any given moment. This mechanism simplifies memory management and alleviates certain complexities associated with multithreading, as it helps avoid race conditions and ensures thread safety in the CPython interpreter.
While the GIL serves a valuable purpose in terms of simplicity and ease of memory management, it introduces limitations in scenarios where parallelism is a key consideration. In a multi-threaded environment, the GIL can become a bottleneck, hindering the effective utilization of multiple processor cores. This limitation is particularly noteworthy in performance-critical applications, such as those involving computationally intensive tasks or data processing, where the ability to leverage concurrent execution for improved speed is highly desirable.
The GIL's role extends beyond its technical aspects; it has become a topic of ongoing discussion and debate within the Python community. Developers and language designers grapple with the trade-offs associated with the GIL, weighing the benefits of simplicity against the drawbacks of restricted parallelism. As Python continues to evolve, so does the discourse around potential modifications to the GIL or the exploration of alternative strategies that could maintain simplicity while enhancing concurrency. Understanding the role of the GIL lays the foundation for comprehending its impact on multithreading in Python and motivates the exploration of strategies to optimize performance within its constraints.
GIL Limitations and Performance Challenges
The Global Interpreter Lock (GIL) in Python, while serving its purpose of simplifying memory management and ensuring thread safety, introduces significant limitations and performance challenges in the realm of multithreading. One of the key drawbacks of the GIL is its tendency to become a performance bottleneck, particularly in scenarios where parallelism is crucial for optimal execution. The GIL restricts the execution of Python bytecode to a single thread at a time, effectively serializing the operations even in the presence of multiple threads. As a consequence, the full potential of multi-core processors remains largely untapped, and applications may fail to achieve the expected performance gains through parallelism.
In performance-critical applications, such as scientific computing or data-intensive tasks, the GIL can pose substantial challenges. Computations that could otherwise benefit from concurrent execution are hindered by the lock, leading to suboptimal resource utilization. The limitations become particularly evident in applications that require extensive CPU-bound processing, where the inability to efficiently distribute work across multiple cores can result in slower execution times and decreased overall system performance.
Developers often encounter scenarios where the GIL's impact is felt acutely, prompting the exploration of alternative concurrency models or the adoption of strategies to mitigate its effects. While certain types of applications, such as those centered around I/O-bound tasks, may experience less pronounced limitations, the GIL remains a central consideration in the performance tuning and optimization of Python programs. As the Python community strives for both simplicity and improved parallelism, addressing the limitations and performance challenges posed by the GIL remains an ongoing area of exploration and innovation.
Strategies for GIL Mitigation
In response to the challenges posed by the Global Interpreter Lock (GIL) in Python multithreading, developers employ various strategies to mitigate its impact and enhance concurrency.One common approach involves leveraging the multiprocessing module instead of multithreading. Unlike threads, separate processes in Python run in their own interpreter and have independent memory space, circumventing the GIL limitations. While this introduces inter-process communication complexities, it allows for parallel execution of Python code on multi-core systems, enabling better utilization of available resources.
Another strategy involves adopting asynchronous programming, which utilizes coroutines and the asyncio library. Instead of relying on multiple threads, asynchronous programming allows a single thread to efficiently switch between different tasks when waiting for I/O operations. While this approach doesn't eliminate the GIL, it mitigates its impact by focusing on non-blocking I/O operations, making it particularly effective for I/O-bound tasks such as networking.
Furthermore, developers may explore alternative interpreters like Jython or IronPython, which are implementations of Python for the Java Virtual Machine (JVM) and the .NET Framework, respectively. These interpreters operate on different concurrency models and lack a GIL, offering an avenue for achieving better parallelism in specific environments.
Thread pools and parallel processing libraries, such as concurrent.futures, provide a higher-level abstraction for managing parallel tasks without directly dealing with threads. These abstractions allow developers to write concurrent code without the need to explicitly manage threads, offering a more straightforward approach to harnessing parallelism.
While each strategy has its merits and trade-offs, the choice depends on the specific requirements of the application. Successful GIL mitigation often involves a combination of these approaches, tailored to the characteristics of the workload and the desired performance outcomes. As Python evolves, the community continues to explore innovative ways to address GIL-related challenges, seeking a balance between simplicity and effective parallelism.
Concurrency Patterns and Best Practices
Navigating the intricacies of the Global Interpreter Lock (GIL) in Python multithreading necessitates the adoption of specific concurrency patterns and best practices. One fundamental approach involves the use of thread pools, which efficiently manage a pool of worker threads to execute tasks concurrently. Thread pools encapsulate the complexities of thread creation and management, providing a more controlled and scalable solution for applications that require parallelism.
Concurrency patterns such as the Producer-Consumer pattern can be beneficial in scenarios where multiple threads need to collaborate on shared resources. This pattern involves a producer thread generating data and placing it into a shared buffer, while one or more consumer threads retrieve and process the data. Careful synchronization mechanisms, such as locks or semaphores, can be employed to ensure the integrity of shared data structures.
Asynchronous programming, facilitated by the asyncio library, has become increasingly popular for managing concurrency in Python. By using coroutines and an event loop, asynchronous programming allows tasks to yield control to the event loop when waiting for external resources, maximizing the efficiency of single-threaded execution and reducing the impact of the GIL. This approach is particularly effective in I/O-bound scenarios, where threads spend a significant amount of time waiting for input or output operations to complete.
Thread-local storage is a crucial best practice for mitigating GIL-related challenges. By minimizing shared data between threads and utilizing thread-local storage for certain variables, developers can reduce contention for shared resources. This approach enhances thread isolation and minimizes the risk of race conditions, contributing to the overall reliability of multithreaded applications.
Effective concurrency patterns and best practices in Python involve a thoughtful combination of thread pools, synchronization mechanisms, asynchronous programming, thread-local storage, and judicious use of thread-safe data structures. Tailoring these techniques to the specific requirements of the application allows developers to create responsive, scalable, and reliable multithreaded Python applications, optimizing performance within the confines of the GIL.
Future Directions: GIL and Python's Evolution
The Global Interpreter Lock (GIL) in Python has long been a subject of discussion and debate within the programming community, prompting a keen interest in the future directions of Python's evolution and its relationship with the GIL. As Python continues to evolve as a language, developers and language designers are exploring avenues to address or potentially eliminate the limitations imposed by the GIL on concurrent execution.
One notable initiative in this context is the Global Interpreter Lock Removal (GILR) project. This ongoing effort seeks to explore the feasibility of removing the GIL from the CPython interpreter, thereby allowing multiple threads to execute Python bytecode simultaneously. While this endeavor presents numerous technical challenges, the potential benefits in terms of improved parallelism and performance have sparked enthusiasm within the Python community. Developers are closely monitoring the progress of the GILR project as it represents a significant step towards unlocking the full potential of Python in multi-core environments.
In addition to GIL removal efforts, other proposals and discussions revolve around alternative concurrency models that could coexist with or replace the GIL. These include exploring more fine-grained locking mechanisms, promoting the adoption of multiprocessing over multithreading, and enhancing support for asynchronous programming. The goal is to strike a delicate balance between simplicity, which has been a hallmark of Python, and providing developers with the tools needed to harness the power of modern hardware effectively.
The evolution of Python's concurrency capabilities is not only a technical consideration but also a reflection of the evolving landscape of computing architectures. As hardware trends emphasize increasing core counts and parallel processing capabilities, the Python community is driven to adapt the language to fully exploit these advancements. In the years to come, the trajectory of Python's evolution and its handling of concurrency will likely shape how developers approach parallelism, making it a pivotal aspect of the language's ongoing development. As these discussions unfold, the Python community remains committed to preserving the language's strengths while continually striving to enhance its concurrency features and mitigate the challenges posed by the Global Interpreter Lock.
How to obtain python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
Conclusion
In conclusion, the Global Interpreter Lock (GIL) stands as a double-edged sword in the realm of Python multithreading, offering simplicity in memory management while presenting challenges in achieving efficient parallelism. As we've explored the role of the GIL, its limitations, and various strategies for mitigation, it is evident that the Python community is actively engaged in addressing these challenges.
While the GIL has been a longstanding aspect of CPython, ongoing initiatives like the Global Interpreter Lock Removal (GILR) project signify a commitment to evolving Python's concurrency model. The pursuit of GIL removal underscores the community's dedication to unlocking the full potential of Python in the face of modern multi-core architectures.
In essence, the story of the GIL in Python is one of continuous adaptation and innovation. As Python evolves, so too will the strategies employed by developers to overcome the challenges posed by the GIL. The journey involves not only technical considerations but also a deeper exploration of how concurrency aligns with the broader goals and principles of the Python language. In this ever-evolving landscape, the Python community remains steadfast in its commitment to providing developers with tools that enable them to write efficient, scalable, and reliable code, even as it navigates the complexities of the Global Interpreter Lock.
Read More
Python is a versatile and widely-used programming language known for its simplicity, readability, and extensive standard libraries. However, when it comes to concurrent programming and multithreading, developers often encounter a significant challenge known as the Global Interpreter Lock (GIL). The GIL has been a topic of discussion and debate within the Python community for years, as it plays a crucial role in shaping the language's behavior in a multi-threaded environment.
At its core, the Global Interpreter Lock is a mechanism implemented in the CPython interpreter, which is the default and most widely used implementation of Python. The GIL ensures that only one thread executes Python bytecode at a time, effectively serializing the execution of threads. While this design simplifies memory management and makes certain aspects of programming more straightforward, it also introduces limitations and trade-offs, particularly in scenarios where parallelism is crucial for performance optimization.
In this exploration of the Global Interpreter Lock, we will delve into the reasons behind its existence, its impact on Python multithreading, and the implications for developers seeking to harness the power of concurrent processing. Understanding the nuances of the GIL is essential for Python developers aiming to build efficient and scalable applications, as it directly influences the language's ability to fully leverage the capabilities of modern multi-core processors. As we navigate through the complexities of the Global Interpreter Lock, we will uncover strategies, alternatives, and best practices for mitigating its effects and achieving better performance in multi-threaded Python programs.
Table of contents
-
The Role of the Global Interpreter Lock (GIL)
-
GIL Limitations and Performance Challenges
-
Strategies for GIL Mitigation
-
Concurrency Patterns and Best Practices
-
Future Directions: GIL and Python's Evolution
-
Conclusion
The Role of the Global Interpreter Lock (GIL)
The Global Interpreter Lock (GIL) serves as a critical component within the CPython interpreter, the default and most widely used implementation of the Python programming language. Its primary role is to safeguard access to Python objects, preventing multiple native threads from executing Python bytecode simultaneously. The GIL essentially acts as a mutex, ensuring that only one thread can execute Python bytecode within a single process at any given moment. This mechanism simplifies memory management and alleviates certain complexities associated with multithreading, as it helps avoid race conditions and ensures thread safety in the CPython interpreter.
While the GIL serves a valuable purpose in terms of simplicity and ease of memory management, it introduces limitations in scenarios where parallelism is a key consideration. In a multi-threaded environment, the GIL can become a bottleneck, hindering the effective utilization of multiple processor cores. This limitation is particularly noteworthy in performance-critical applications, such as those involving computationally intensive tasks or data processing, where the ability to leverage concurrent execution for improved speed is highly desirable.
The GIL's role extends beyond its technical aspects; it has become a topic of ongoing discussion and debate within the Python community. Developers and language designers grapple with the trade-offs associated with the GIL, weighing the benefits of simplicity against the drawbacks of restricted parallelism. As Python continues to evolve, so does the discourse around potential modifications to the GIL or the exploration of alternative strategies that could maintain simplicity while enhancing concurrency. Understanding the role of the GIL lays the foundation for comprehending its impact on multithreading in Python and motivates the exploration of strategies to optimize performance within its constraints.
GIL Limitations and Performance Challenges
The Global Interpreter Lock (GIL) in Python, while serving its purpose of simplifying memory management and ensuring thread safety, introduces significant limitations and performance challenges in the realm of multithreading. One of the key drawbacks of the GIL is its tendency to become a performance bottleneck, particularly in scenarios where parallelism is crucial for optimal execution. The GIL restricts the execution of Python bytecode to a single thread at a time, effectively serializing the operations even in the presence of multiple threads. As a consequence, the full potential of multi-core processors remains largely untapped, and applications may fail to achieve the expected performance gains through parallelism.
In performance-critical applications, such as scientific computing or data-intensive tasks, the GIL can pose substantial challenges. Computations that could otherwise benefit from concurrent execution are hindered by the lock, leading to suboptimal resource utilization. The limitations become particularly evident in applications that require extensive CPU-bound processing, where the inability to efficiently distribute work across multiple cores can result in slower execution times and decreased overall system performance.
Developers often encounter scenarios where the GIL's impact is felt acutely, prompting the exploration of alternative concurrency models or the adoption of strategies to mitigate its effects. While certain types of applications, such as those centered around I/O-bound tasks, may experience less pronounced limitations, the GIL remains a central consideration in the performance tuning and optimization of Python programs. As the Python community strives for both simplicity and improved parallelism, addressing the limitations and performance challenges posed by the GIL remains an ongoing area of exploration and innovation.
Strategies for GIL Mitigation
In response to the challenges posed by the Global Interpreter Lock (GIL) in Python multithreading, developers employ various strategies to mitigate its impact and enhance concurrency.One common approach involves leveraging the multiprocessing module instead of multithreading. Unlike threads, separate processes in Python run in their own interpreter and have independent memory space, circumventing the GIL limitations. While this introduces inter-process communication complexities, it allows for parallel execution of Python code on multi-core systems, enabling better utilization of available resources.
Another strategy involves adopting asynchronous programming, which utilizes coroutines and the asyncio library. Instead of relying on multiple threads, asynchronous programming allows a single thread to efficiently switch between different tasks when waiting for I/O operations. While this approach doesn't eliminate the GIL, it mitigates its impact by focusing on non-blocking I/O operations, making it particularly effective for I/O-bound tasks such as networking.
Furthermore, developers may explore alternative interpreters like Jython or IronPython, which are implementations of Python for the Java Virtual Machine (JVM) and the .NET Framework, respectively. These interpreters operate on different concurrency models and lack a GIL, offering an avenue for achieving better parallelism in specific environments.
Thread pools and parallel processing libraries, such as concurrent.futures, provide a higher-level abstraction for managing parallel tasks without directly dealing with threads. These abstractions allow developers to write concurrent code without the need to explicitly manage threads, offering a more straightforward approach to harnessing parallelism.
While each strategy has its merits and trade-offs, the choice depends on the specific requirements of the application. Successful GIL mitigation often involves a combination of these approaches, tailored to the characteristics of the workload and the desired performance outcomes. As Python evolves, the community continues to explore innovative ways to address GIL-related challenges, seeking a balance between simplicity and effective parallelism.
Concurrency Patterns and Best Practices
Navigating the intricacies of the Global Interpreter Lock (GIL) in Python multithreading necessitates the adoption of specific concurrency patterns and best practices. One fundamental approach involves the use of thread pools, which efficiently manage a pool of worker threads to execute tasks concurrently. Thread pools encapsulate the complexities of thread creation and management, providing a more controlled and scalable solution for applications that require parallelism.
Concurrency patterns such as the Producer-Consumer pattern can be beneficial in scenarios where multiple threads need to collaborate on shared resources. This pattern involves a producer thread generating data and placing it into a shared buffer, while one or more consumer threads retrieve and process the data. Careful synchronization mechanisms, such as locks or semaphores, can be employed to ensure the integrity of shared data structures.
Asynchronous programming, facilitated by the asyncio library, has become increasingly popular for managing concurrency in Python. By using coroutines and an event loop, asynchronous programming allows tasks to yield control to the event loop when waiting for external resources, maximizing the efficiency of single-threaded execution and reducing the impact of the GIL. This approach is particularly effective in I/O-bound scenarios, where threads spend a significant amount of time waiting for input or output operations to complete.
Thread-local storage is a crucial best practice for mitigating GIL-related challenges. By minimizing shared data between threads and utilizing thread-local storage for certain variables, developers can reduce contention for shared resources. This approach enhances thread isolation and minimizes the risk of race conditions, contributing to the overall reliability of multithreaded applications.
Effective concurrency patterns and best practices in Python involve a thoughtful combination of thread pools, synchronization mechanisms, asynchronous programming, thread-local storage, and judicious use of thread-safe data structures. Tailoring these techniques to the specific requirements of the application allows developers to create responsive, scalable, and reliable multithreaded Python applications, optimizing performance within the confines of the GIL.
Future Directions: GIL and Python's Evolution
The Global Interpreter Lock (GIL) in Python has long been a subject of discussion and debate within the programming community, prompting a keen interest in the future directions of Python's evolution and its relationship with the GIL. As Python continues to evolve as a language, developers and language designers are exploring avenues to address or potentially eliminate the limitations imposed by the GIL on concurrent execution.
One notable initiative in this context is the Global Interpreter Lock Removal (GILR) project. This ongoing effort seeks to explore the feasibility of removing the GIL from the CPython interpreter, thereby allowing multiple threads to execute Python bytecode simultaneously. While this endeavor presents numerous technical challenges, the potential benefits in terms of improved parallelism and performance have sparked enthusiasm within the Python community. Developers are closely monitoring the progress of the GILR project as it represents a significant step towards unlocking the full potential of Python in multi-core environments.
In addition to GIL removal efforts, other proposals and discussions revolve around alternative concurrency models that could coexist with or replace the GIL. These include exploring more fine-grained locking mechanisms, promoting the adoption of multiprocessing over multithreading, and enhancing support for asynchronous programming. The goal is to strike a delicate balance between simplicity, which has been a hallmark of Python, and providing developers with the tools needed to harness the power of modern hardware effectively.
The evolution of Python's concurrency capabilities is not only a technical consideration but also a reflection of the evolving landscape of computing architectures. As hardware trends emphasize increasing core counts and parallel processing capabilities, the Python community is driven to adapt the language to fully exploit these advancements. In the years to come, the trajectory of Python's evolution and its handling of concurrency will likely shape how developers approach parallelism, making it a pivotal aspect of the language's ongoing development. As these discussions unfold, the Python community remains committed to preserving the language's strengths while continually striving to enhance its concurrency features and mitigate the challenges posed by the Global Interpreter Lock.
How to obtain python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
Conclusion
In conclusion, the Global Interpreter Lock (GIL) stands as a double-edged sword in the realm of Python multithreading, offering simplicity in memory management while presenting challenges in achieving efficient parallelism. As we've explored the role of the GIL, its limitations, and various strategies for mitigation, it is evident that the Python community is actively engaged in addressing these challenges.
While the GIL has been a longstanding aspect of CPython, ongoing initiatives like the Global Interpreter Lock Removal (GILR) project signify a commitment to evolving Python's concurrency model. The pursuit of GIL removal underscores the community's dedication to unlocking the full potential of Python in the face of modern multi-core architectures.
In essence, the story of the GIL in Python is one of continuous adaptation and innovation. As Python evolves, so too will the strategies employed by developers to overcome the challenges posed by the GIL. The journey involves not only technical considerations but also a deeper exploration of how concurrency aligns with the broader goals and principles of the Python language. In this ever-evolving landscape, the Python community remains steadfast in its commitment to providing developers with tools that enable them to write efficient, scalable, and reliable code, even as it navigates the complexities of the Global Interpreter Lock.
3 Productivity Tips for Every Project Manager
In the dynamic realm of project management, where precision and efficiency are paramount, the role of a project manager extends far beyond overseeing tasks and timelines. In the ever-evolving landscape of project execution, leveraging advanced tools and methodologies is crucial for success. As the demands of the industry continue to grow, project managers find themselves relying on powerful solutions like Microsoft Project, Google Project Management, and a myriad of task and project management software to navigate the complexities of their projects.
This article unveils three indispensable productivity tips tailored for every project manager, emphasizing the strategic use of project management software to enhance overall efficiency. From unlocking the full potential of Microsoft Project to exploring the capabilities of Google Project Management and other innovative solutions, these tips aim to equip project managers with insights that transcend conventional approaches. Whether you're a seasoned project management professional or a newcomer to the field, these strategies will empower you to harness the best project management software available, optimize task management, and embrace agile methodologies, ultimately elevating your effectiveness in steering projects to success. Join us as we delve into the transformative tips that can redefine your project management approach in an ever-evolving landscape shaped by the Project Management Institute's best practices.
Table of contents
-
Maximizing Efficiency with Microsoft Project: Insider Tips and Tricks
-
Navigating the Landscape of Task and Project Management Software
-
Agile Project Management Strategies for Adaptive Leadership
-
Google Project Management: Unleashing Collaboration and Innovation
-
Professional Development with the Project Management Institute (PMI)
-
Conclusion
Maximizing Efficiency with Microsoft Project: Insider Tips and Tricks
In the realm of project management, where precision and efficiency are paramount, mastering the intricacies of software tools is essential. "Maximizing Efficiency with Microsoft Project: Insider Tips and Tricks" unveils a comprehensive guide to empower project managers in extracting the full potential of this powerful project management software. Delving into advanced features, this sub-topic explores insider tips and tricks to optimize project planning and execution. From resource allocation and timeline management to fostering effective collaboration, project managers will gain insights into leveraging Microsoft Project as a central hub for comprehensive project oversight. With a focus on practical applications, this segment aims to equip project managers with the skills needed to navigate the complexities of project management seamlessly, ensuring they harness the true capabilities of Microsoft Project for enhanced productivity and project success.
Navigating the Landscape of Task and Project Management Software
"Navigating the Landscape of Task and Project Management Software" serves as a compass for project managers seeking the most effective tools in an expansive and diverse digital landscape. This sub-topic delves into the intricacies of various task and project management software options, providing a comprehensive comparison to aid project managers in making informed choices. From highlighting the key features of popular software solutions to discussing essential considerations based on project requirements, this segment guides professionals in selecting the best project management software for their specific needs. Additionally, exploration of integration possibilities emphasizes creating a cohesive workflow across different tools, ensuring a seamless and efficient project management process. Whether a project manager is a seasoned veteran or a newcomer to the field, this sub-topic offers valuable insights to navigate the vast array of software options available, empowering them to make strategic decisions that enhance overall project productivity.
Agile Project Management Strategies for Adaptive Leadership
"Agile Project Management Strategies for Adaptive Leadership" presents a strategic roadmap for project managers aiming to thrive in dynamic and rapidly changing environments. This sub-topic explores the foundational principles of agile project management, offering practical insights and strategies to foster adaptability and responsiveness. From embracing iterative development cycles to quick response mechanisms for changing project requirements, the segment guides project managers through the implementation of agile methodologies in diverse project scenarios. Furthermore, it sheds light on the role of agile project management software in facilitating seamless collaboration and communication within agile teams. By emphasizing the importance of adaptability, this segment equips project managers with the tools and methodologies needed to lead with resilience and agility, ultimately enhancing project outcomes in today's dynamic project management landscape.
Google Project Management: Unleashing Collaboration and Innovation
"Google Project Management: Unleashing Collaboration and Innovation" offers a deep dive into the collaborative potential of Google's project management tools, providing project managers with insights into fostering creativity and innovation within their teams. This sub-topic explores the unique features of Google Project Management tools and their integration capabilities, showcasing how G Suite applications complement project management processes. From real-time collaboration on documents to efficient communication through tools like Google Meet, the segment highlights the collaborative power inherent in Google's suite. Strategies for leveraging Google Project Management alongside other tools for enhanced productivity are also discussed, emphasizing its role in streamlining workflows and driving innovation. For project managers seeking a holistic approach to collaboration and project execution, this segment serves as a guide to harnessing the collaborative and innovative capacities of Google Project Management.
Professional Development with the Project Management Institute (PMI)
"Professional Development with the Project Management Institute (PMI)" illuminates the pivotal role that the Project Management Institute plays in shaping the growth and proficiency of project managers. This sub-topic provides an insightful overview of PMI, underscoring its significance as a premier organization in the project management domain. Exploring the multitude of resources, certifications, and best practices offered by PMI, the segment encourages project managers to embark on a journey of continuous learning and skill enhancement. By delving into PMI's certifications and highlighting its commitment to professional development, the segment empowers project managers to stay abreast of industry trends, refine their skills, and align themselves with global standards. For project management professionals seeking to elevate their expertise and advance their careers, this segment serves as a compass for navigating the enriching landscape of opportunities provided by the Project Management Institute.
Conclusion
In conclusion, these five sub-topics collectively form a comprehensive guide for project managers aiming to enhance their efficiency and effectiveness in the ever-evolving landscape of project management. From unlocking the full potential of Microsoft Project to navigating the diverse world of task and project management software, adopting agile methodologies, leveraging Google Project Management for collaboration, and embracing continuous professional development with the Project Management Institute (PMI), each segment provides valuable insights and practical tips. By implementing the strategies outlined in these sub-topics, project managers can not only optimize their use of cutting-edge tools but also cultivate adaptive leadership skills, fostering innovation and resilience in the face of change. In the dynamic field of project management, staying informed, agile, and focused on professional development is key to achieving success, and this guide aims to empower project managers with the knowledge and strategies needed to navigate challenges and drive projects to successful outcomes.
Read More
In the dynamic realm of project management, where precision and efficiency are paramount, the role of a project manager extends far beyond overseeing tasks and timelines. In the ever-evolving landscape of project execution, leveraging advanced tools and methodologies is crucial for success. As the demands of the industry continue to grow, project managers find themselves relying on powerful solutions like Microsoft Project, Google Project Management, and a myriad of task and project management software to navigate the complexities of their projects.
This article unveils three indispensable productivity tips tailored for every project manager, emphasizing the strategic use of project management software to enhance overall efficiency. From unlocking the full potential of Microsoft Project to exploring the capabilities of Google Project Management and other innovative solutions, these tips aim to equip project managers with insights that transcend conventional approaches. Whether you're a seasoned project management professional or a newcomer to the field, these strategies will empower you to harness the best project management software available, optimize task management, and embrace agile methodologies, ultimately elevating your effectiveness in steering projects to success. Join us as we delve into the transformative tips that can redefine your project management approach in an ever-evolving landscape shaped by the Project Management Institute's best practices.
Table of contents
-
Maximizing Efficiency with Microsoft Project: Insider Tips and Tricks
-
Navigating the Landscape of Task and Project Management Software
-
Agile Project Management Strategies for Adaptive Leadership
-
Google Project Management: Unleashing Collaboration and Innovation
-
Professional Development with the Project Management Institute (PMI)
-
Conclusion
Maximizing Efficiency with Microsoft Project: Insider Tips and Tricks
In the realm of project management, where precision and efficiency are paramount, mastering the intricacies of software tools is essential. "Maximizing Efficiency with Microsoft Project: Insider Tips and Tricks" unveils a comprehensive guide to empower project managers in extracting the full potential of this powerful project management software. Delving into advanced features, this sub-topic explores insider tips and tricks to optimize project planning and execution. From resource allocation and timeline management to fostering effective collaboration, project managers will gain insights into leveraging Microsoft Project as a central hub for comprehensive project oversight. With a focus on practical applications, this segment aims to equip project managers with the skills needed to navigate the complexities of project management seamlessly, ensuring they harness the true capabilities of Microsoft Project for enhanced productivity and project success.
Navigating the Landscape of Task and Project Management Software
"Navigating the Landscape of Task and Project Management Software" serves as a compass for project managers seeking the most effective tools in an expansive and diverse digital landscape. This sub-topic delves into the intricacies of various task and project management software options, providing a comprehensive comparison to aid project managers in making informed choices. From highlighting the key features of popular software solutions to discussing essential considerations based on project requirements, this segment guides professionals in selecting the best project management software for their specific needs. Additionally, exploration of integration possibilities emphasizes creating a cohesive workflow across different tools, ensuring a seamless and efficient project management process. Whether a project manager is a seasoned veteran or a newcomer to the field, this sub-topic offers valuable insights to navigate the vast array of software options available, empowering them to make strategic decisions that enhance overall project productivity.
Agile Project Management Strategies for Adaptive Leadership
"Agile Project Management Strategies for Adaptive Leadership" presents a strategic roadmap for project managers aiming to thrive in dynamic and rapidly changing environments. This sub-topic explores the foundational principles of agile project management, offering practical insights and strategies to foster adaptability and responsiveness. From embracing iterative development cycles to quick response mechanisms for changing project requirements, the segment guides project managers through the implementation of agile methodologies in diverse project scenarios. Furthermore, it sheds light on the role of agile project management software in facilitating seamless collaboration and communication within agile teams. By emphasizing the importance of adaptability, this segment equips project managers with the tools and methodologies needed to lead with resilience and agility, ultimately enhancing project outcomes in today's dynamic project management landscape.
Google Project Management: Unleashing Collaboration and Innovation
"Google Project Management: Unleashing Collaboration and Innovation" offers a deep dive into the collaborative potential of Google's project management tools, providing project managers with insights into fostering creativity and innovation within their teams. This sub-topic explores the unique features of Google Project Management tools and their integration capabilities, showcasing how G Suite applications complement project management processes. From real-time collaboration on documents to efficient communication through tools like Google Meet, the segment highlights the collaborative power inherent in Google's suite. Strategies for leveraging Google Project Management alongside other tools for enhanced productivity are also discussed, emphasizing its role in streamlining workflows and driving innovation. For project managers seeking a holistic approach to collaboration and project execution, this segment serves as a guide to harnessing the collaborative and innovative capacities of Google Project Management.
Professional Development with the Project Management Institute (PMI)
"Professional Development with the Project Management Institute (PMI)" illuminates the pivotal role that the Project Management Institute plays in shaping the growth and proficiency of project managers. This sub-topic provides an insightful overview of PMI, underscoring its significance as a premier organization in the project management domain. Exploring the multitude of resources, certifications, and best practices offered by PMI, the segment encourages project managers to embark on a journey of continuous learning and skill enhancement. By delving into PMI's certifications and highlighting its commitment to professional development, the segment empowers project managers to stay abreast of industry trends, refine their skills, and align themselves with global standards. For project management professionals seeking to elevate their expertise and advance their careers, this segment serves as a compass for navigating the enriching landscape of opportunities provided by the Project Management Institute.
Conclusion
In conclusion, these five sub-topics collectively form a comprehensive guide for project managers aiming to enhance their efficiency and effectiveness in the ever-evolving landscape of project management. From unlocking the full potential of Microsoft Project to navigating the diverse world of task and project management software, adopting agile methodologies, leveraging Google Project Management for collaboration, and embracing continuous professional development with the Project Management Institute (PMI), each segment provides valuable insights and practical tips. By implementing the strategies outlined in these sub-topics, project managers can not only optimize their use of cutting-edge tools but also cultivate adaptive leadership skills, fostering innovation and resilience in the face of change. In the dynamic field of project management, staying informed, agile, and focused on professional development is key to achieving success, and this guide aims to empower project managers with the knowledge and strategies needed to navigate challenges and drive projects to successful outcomes.
How to Become a Microsoft Azure Architect?
Embarking on the journey to become a Microsoft Azure Architect is an ambitious and rewarding endeavor in the ever-evolving landscape of cloud computing. As organizations increasingly rely on cloud solutions, the role of an Azure Architect has become pivotal in designing robust, scalable, and secure infrastructures on the Microsoft Azure platform. This comprehensive guide aims to provide an in-depth overview of the steps, skills, and certifications necessary to carve a successful path toward this coveted role.
Whether you are an aspiring IT professional, a seasoned developer, or a system administrator looking to transition into the cloud realm, understanding the intricacies of becoming a Microsoft Azure Architect is crucial. This guide will navigate you through the Azure certification landscape, offering insights into the requisite skills, recommended best practices, and the certification roadmap to achieve the esteemed Microsoft Certified: Azure Solutions Architect Expert designation.
From mastering cloud infrastructure design principles to honing your expertise in Azure services and technologies, each step in this journey plays a crucial role in shaping your proficiency as an Azure Architect. We will delve into the core responsibilities of an Azure Architect, explore the key areas of expertise required, and provide valuable resources to aid you in your learning and certification preparation.
Prepare to unlock a world of opportunities as we embark on this complete overview, unraveling the roadmap to becoming a Microsoft Azure Architect. Whether you're starting from scratch or enhancing your existing skills, this guide is designed to be your compass in navigating the dynamic landscape of cloud architecture and ensuring a successful ascent in your career.
Table of contents
-
Azure Certification Pathway: Navigating the Landscape
-
Essential Skills for Azure Architects: Building a Strong Foundation
-
Day in the Life of an Azure Architect: Responsibilities and Challenges
-
Strategies for Effective Azure Exam Preparation: Acing the Certification
-
Career Advancement and Growth Opportunities: Beyond Certification
-
Conclusion
Azure Certification Pathway: Navigating the Landscape
Navigating the Azure Certification Pathway is a crucial first step in the journey to becoming a Microsoft Azure Architect. This subtopic provides a detailed exploration of the diverse certification landscape offered by Microsoft, unraveling the tiers and exams that lead to the coveted Microsoft Certified: Azure Solutions Architect Expert designation. Aspiring architects will gain insights into the prerequisites and recommended experience for each certification level, empowering them to make informed decisions about their learning journey. From foundational certifications to specialized exams focusing on architecture and design, this segment serves as a roadmap for individuals looking to validate their expertise and proficiency in Azure technologies. Additionally, the subtopic emphasizes the importance of continuous learning, staying updated on Azure advancements, and strategically planning certification paths to align with individual career goals. By navigating this landscape effectively, aspiring Azure Architects can chart a course towards a comprehensive and robust skill set that is highly valued in the dynamic field of cloud computing.
Essential Skills for Azure Architects: Building a Strong Foundation
Building a strong foundation as a Microsoft Azure Architect requires the acquisition of essential skills that form the bedrock of success in the dynamic world of cloud computing. This subtopic delves into the core technical competencies crucial for architects designing solutions on the Azure platform. It encompasses a comprehensive exploration of cloud infrastructure design principles, emphasizing best practices to ensure scalability, security, and efficiency. The aspiring Azure Architect will gain insights into mastering Azure services, spanning compute, storage, networking, and beyond, while also developing proficiency in security measures and hybrid cloud solutions. This segment serves as a guide for honing the expertise necessary to navigate the complexities of architecting robust and resilient Azure solutions. From understanding the intricacies of virtualization to implementing effective networking strategies, building a strong foundation in these skills is imperative for those seeking to excel in the role of a Microsoft Azure Architect.
Day in the Life of an Azure Architect: Responsibilities and Challenges
A day in the life of a Microsoft Azure Architect is marked by dynamic and multifaceted responsibilities, reflecting the critical role they play in shaping an organization's cloud infrastructure. This subtopic offers a comprehensive overview of the typical tasks and challenges faced by Azure Architects. Architects are tasked with designing and implementing Azure solutions tailored to meet diverse business requirements, encompassing considerations for scalability, security, and cost-effectiveness. From collaborating with cross-functional teams to understanding the unique needs of stakeholders, Azure Architects navigate a complex landscape. This subtopic also explores real-world scenarios and case studies, shedding light on the practical challenges encountered in architecting solutions for various industries and business domains. Whether it involves optimizing resource utilization, ensuring data integrity, or addressing evolving security concerns, the day-to-day responsibilities of an Azure Architect demand a versatile skill set and an ability to adapt to the evolving demands of the cloud computing landscape. Understanding these responsibilities and challenges provides valuable insights for individuals aspiring to embark on this dynamic career path.
Strategies for Effective Azure Exam Preparation: Acing the Certification
Successfully navigating the Azure certification landscape requires strategic and effective exam preparation. This subtopic offers a detailed guide on formulating winning strategies to ace Microsoft Azure exams. Aspiring Azure Architects will benefit from practical tips and insights on structuring their study approach, including leveraging official Microsoft documentation, practice tests, and hands-on labs. Emphasis is placed on the importance of gaining practical experience, not only to pass exams but also to enhance real-world problem-solving skills. The paragraph covers the significance of understanding the exam objectives, time management during the test, and how to approach different types of questions. Additionally, it explores the value of community resources, study groups, and mentorship in enhancing the overall preparation experience. By adopting these strategies, individuals can confidently approach Azure certification exams, ensuring a comprehensive understanding of the material and increasing their chances of success in achieving certification as a Microsoft Azure Architect.
Career Advancement and Growth Opportunities: Beyond Certification
Beyond the realm of certifications, a Microsoft Azure Architect's journey extends into a landscape of abundant career advancement and growth opportunities. This subtopic explores the various pathways available to certified Azure Architects, emphasizing the transformative impact of achieving the Microsoft Certified: Azure Solutions Architect Expert designation. Aspiring architects will gain insights into how certifications can be leveraged to enhance career prospects, opening doors to roles such as Cloud Solutions Architect, IT Manager, or even executive positions within technology-driven organizations. The paragraph also delves into the importance of continued learning, staying abreast of evolving Azure technologies, and potential areas for specialization, ensuring architects remain at the forefront of innovation. Whether it's through leadership roles, consulting opportunities, or entrepreneurship, the skills honed in the journey to becoming an Azure Architect pave the way for a dynamic and rewarding career trajectory in the ever-evolving landscape of cloud computing. This segment serves as a guide for individuals looking not just to achieve certification but to strategically navigate a path toward sustained career growth and success.
Conclusion
In conclusion, the path to becoming a Microsoft Azure Architect is a multifaceted journey that encompasses certification, skill development, and real-world application. This guide has provided a comprehensive overview, starting with the navigation of the Azure Certification Pathway, highlighting the essential skills required to build a strong foundation as an architect, and offering insights into the responsibilities and challenges encountered in the day-to-day life of an Azure Architect. Additionally, we explored effective strategies for exam preparation, emphasizing the importance of practical experience and community engagement. Finally, we delved into the expansive realm of career advancement and growth opportunities beyond certification.
Aspiring Azure Architects are encouraged to approach this journey with a commitment to continuous learning, adaptability, and a proactive mindset. The dynamic nature of cloud computing demands not only technical expertise but also the ability to innovate and address evolving challenges. By leveraging the knowledge and resources provided in this guide, individuals can navigate the complexities of the Azure landscape, positioning themselves for success in a role that is integral to the digital transformation of organizations. Whether it's through achieving certifications, mastering essential skills, or embracing ongoing professional development, the pursuit of excellence as a Microsoft Azure Architect promises a fulfilling and impactful career in the ever-expanding world of cloud technology.
Read More
Embarking on the journey to become a Microsoft Azure Architect is an ambitious and rewarding endeavor in the ever-evolving landscape of cloud computing. As organizations increasingly rely on cloud solutions, the role of an Azure Architect has become pivotal in designing robust, scalable, and secure infrastructures on the Microsoft Azure platform. This comprehensive guide aims to provide an in-depth overview of the steps, skills, and certifications necessary to carve a successful path toward this coveted role.
Whether you are an aspiring IT professional, a seasoned developer, or a system administrator looking to transition into the cloud realm, understanding the intricacies of becoming a Microsoft Azure Architect is crucial. This guide will navigate you through the Azure certification landscape, offering insights into the requisite skills, recommended best practices, and the certification roadmap to achieve the esteemed Microsoft Certified: Azure Solutions Architect Expert designation.
From mastering cloud infrastructure design principles to honing your expertise in Azure services and technologies, each step in this journey plays a crucial role in shaping your proficiency as an Azure Architect. We will delve into the core responsibilities of an Azure Architect, explore the key areas of expertise required, and provide valuable resources to aid you in your learning and certification preparation.
Prepare to unlock a world of opportunities as we embark on this complete overview, unraveling the roadmap to becoming a Microsoft Azure Architect. Whether you're starting from scratch or enhancing your existing skills, this guide is designed to be your compass in navigating the dynamic landscape of cloud architecture and ensuring a successful ascent in your career.
Table of contents
-
Azure Certification Pathway: Navigating the Landscape
-
Essential Skills for Azure Architects: Building a Strong Foundation
-
Day in the Life of an Azure Architect: Responsibilities and Challenges
-
Strategies for Effective Azure Exam Preparation: Acing the Certification
-
Career Advancement and Growth Opportunities: Beyond Certification
-
Conclusion
Azure Certification Pathway: Navigating the Landscape
Navigating the Azure Certification Pathway is a crucial first step in the journey to becoming a Microsoft Azure Architect. This subtopic provides a detailed exploration of the diverse certification landscape offered by Microsoft, unraveling the tiers and exams that lead to the coveted Microsoft Certified: Azure Solutions Architect Expert designation. Aspiring architects will gain insights into the prerequisites and recommended experience for each certification level, empowering them to make informed decisions about their learning journey. From foundational certifications to specialized exams focusing on architecture and design, this segment serves as a roadmap for individuals looking to validate their expertise and proficiency in Azure technologies. Additionally, the subtopic emphasizes the importance of continuous learning, staying updated on Azure advancements, and strategically planning certification paths to align with individual career goals. By navigating this landscape effectively, aspiring Azure Architects can chart a course towards a comprehensive and robust skill set that is highly valued in the dynamic field of cloud computing.
Essential Skills for Azure Architects: Building a Strong Foundation
Building a strong foundation as a Microsoft Azure Architect requires the acquisition of essential skills that form the bedrock of success in the dynamic world of cloud computing. This subtopic delves into the core technical competencies crucial for architects designing solutions on the Azure platform. It encompasses a comprehensive exploration of cloud infrastructure design principles, emphasizing best practices to ensure scalability, security, and efficiency. The aspiring Azure Architect will gain insights into mastering Azure services, spanning compute, storage, networking, and beyond, while also developing proficiency in security measures and hybrid cloud solutions. This segment serves as a guide for honing the expertise necessary to navigate the complexities of architecting robust and resilient Azure solutions. From understanding the intricacies of virtualization to implementing effective networking strategies, building a strong foundation in these skills is imperative for those seeking to excel in the role of a Microsoft Azure Architect.
Day in the Life of an Azure Architect: Responsibilities and Challenges
A day in the life of a Microsoft Azure Architect is marked by dynamic and multifaceted responsibilities, reflecting the critical role they play in shaping an organization's cloud infrastructure. This subtopic offers a comprehensive overview of the typical tasks and challenges faced by Azure Architects. Architects are tasked with designing and implementing Azure solutions tailored to meet diverse business requirements, encompassing considerations for scalability, security, and cost-effectiveness. From collaborating with cross-functional teams to understanding the unique needs of stakeholders, Azure Architects navigate a complex landscape. This subtopic also explores real-world scenarios and case studies, shedding light on the practical challenges encountered in architecting solutions for various industries and business domains. Whether it involves optimizing resource utilization, ensuring data integrity, or addressing evolving security concerns, the day-to-day responsibilities of an Azure Architect demand a versatile skill set and an ability to adapt to the evolving demands of the cloud computing landscape. Understanding these responsibilities and challenges provides valuable insights for individuals aspiring to embark on this dynamic career path.
Strategies for Effective Azure Exam Preparation: Acing the Certification
Successfully navigating the Azure certification landscape requires strategic and effective exam preparation. This subtopic offers a detailed guide on formulating winning strategies to ace Microsoft Azure exams. Aspiring Azure Architects will benefit from practical tips and insights on structuring their study approach, including leveraging official Microsoft documentation, practice tests, and hands-on labs. Emphasis is placed on the importance of gaining practical experience, not only to pass exams but also to enhance real-world problem-solving skills. The paragraph covers the significance of understanding the exam objectives, time management during the test, and how to approach different types of questions. Additionally, it explores the value of community resources, study groups, and mentorship in enhancing the overall preparation experience. By adopting these strategies, individuals can confidently approach Azure certification exams, ensuring a comprehensive understanding of the material and increasing their chances of success in achieving certification as a Microsoft Azure Architect.
Career Advancement and Growth Opportunities: Beyond Certification
Beyond the realm of certifications, a Microsoft Azure Architect's journey extends into a landscape of abundant career advancement and growth opportunities. This subtopic explores the various pathways available to certified Azure Architects, emphasizing the transformative impact of achieving the Microsoft Certified: Azure Solutions Architect Expert designation. Aspiring architects will gain insights into how certifications can be leveraged to enhance career prospects, opening doors to roles such as Cloud Solutions Architect, IT Manager, or even executive positions within technology-driven organizations. The paragraph also delves into the importance of continued learning, staying abreast of evolving Azure technologies, and potential areas for specialization, ensuring architects remain at the forefront of innovation. Whether it's through leadership roles, consulting opportunities, or entrepreneurship, the skills honed in the journey to becoming an Azure Architect pave the way for a dynamic and rewarding career trajectory in the ever-evolving landscape of cloud computing. This segment serves as a guide for individuals looking not just to achieve certification but to strategically navigate a path toward sustained career growth and success.
Conclusion
In conclusion, the path to becoming a Microsoft Azure Architect is a multifaceted journey that encompasses certification, skill development, and real-world application. This guide has provided a comprehensive overview, starting with the navigation of the Azure Certification Pathway, highlighting the essential skills required to build a strong foundation as an architect, and offering insights into the responsibilities and challenges encountered in the day-to-day life of an Azure Architect. Additionally, we explored effective strategies for exam preparation, emphasizing the importance of practical experience and community engagement. Finally, we delved into the expansive realm of career advancement and growth opportunities beyond certification.
Aspiring Azure Architects are encouraged to approach this journey with a commitment to continuous learning, adaptability, and a proactive mindset. The dynamic nature of cloud computing demands not only technical expertise but also the ability to innovate and address evolving challenges. By leveraging the knowledge and resources provided in this guide, individuals can navigate the complexities of the Azure landscape, positioning themselves for success in a role that is integral to the digital transformation of organizations. Whether it's through achieving certifications, mastering essential skills, or embracing ongoing professional development, the pursuit of excellence as a Microsoft Azure Architect promises a fulfilling and impactful career in the ever-expanding world of cloud technology.
vCISO: A Cybersecurity Leadership Career Path for Tech Pros
In today's rapidly evolving digital landscape, the role of a Chief Information Security Officer (CISO) is more critical than ever. However, for many organizations, especially those in the tech industry, the traditional model of having an in-house CISO may not be the most practical or cost-effective solution. Enter the era of vCISO (Virtual Chief Information Security Officer) – a revolutionary approach to cybersecurity leadership that leverages virtual CISO services.
This emerging trend, often referred to as CISO as a Service or VCISO as a Service, presents a dynamic and flexible career path for tech professionals seeking to make a significant impact in the cybersecurity domain. From understanding the nuances of VCISO pricing and rates to exploring the responsibilities associated with being a virtual information security officer, this innovative model offers an array of opportunities for both individuals and organizations.
In this exploration of the vCISO landscape, we delve into the meaning of VCISO, dissecting the roles and responsibilities of a virtual chief information security officer. We will also examine the pricing models associated with VCISO services and the cost-effectiveness of adopting a virtual CISO, providing insights into the growing list of virtual CISO companies that are shaping the future of cybersecurity leadership.
Whether you are a seasoned cybersecurity professional or a tech enthusiast curious about the evolution of CISO roles, join us on this journey to unravel the intricacies of the virtual CISO career path and discover the immense potential it holds in fortifying organizations against the ever-present cyber threats.
Table of contents
-
The Rise of vCISO Services: Transforming Cybersecurity Leadership
-
Decoding VCISO Pricing Models: Navigating Cost and Value
-
Virtual CISO Responsibilities: Charting the Course for Cybersecurity Success
-
Virtual CISO Companies: Pioneers Shaping the Future of Cybersecurity Leadership
-
The Skill Set of a vCISO: Qualifications and Expertise for Cybersecurity Excellence
-
Conclusion
The Rise of vCISO Services: Transforming Cybersecurity Leadership
The rise of vCISO services marks a transformative shift in the realm of cybersecurity leadership, particularly within the dynamic landscape of the technology sector. In an era where cyber threats constantly evolve and traditional approaches to information security may fall short, organizations are increasingly turning to Virtual Chief Information Security Officers (vCISOs) to navigate this complex terrain. This sub-topic delves into the factors propelling the ascent of vCISO services, examining the unique challenges faced by tech companies and how a virtual CISO can offer tailored solutions. From the flexibility of service delivery to the ability to scale resources as needed, vCISO services provide an adaptive and cost-effective alternative to the conventional in-house CISO model. By exploring the nuances of this emerging trend, we aim to shed light on how vCISO services are not merely meeting but reshaping the expectations for effective cybersecurity leadership in the fast-paced and ever-evolving world of technology.
Decoding VCISO Pricing Models: Navigating Cost and Value
Decoding vCISO pricing models is essential in navigating the delicate balance between cost considerations and the strategic value that Virtual Chief Information Security Officers (vCISOs) bring to the cybersecurity landscape. In this sub-topic, we embark on an exploration of the various pricing structures associated with vCISO services, uncovering the intricacies that organizations must navigate to make informed decisions. From hourly rates to subscription-based models, understanding the nuances of vCISO pricing is crucial for businesses seeking effective cybersecurity leadership without compromising fiscal prudence. By delving into this aspect, we aim to provide insights into the cost-effectiveness of vCISO solutions compared to traditional, in-house CISO roles, ultimately offering a comprehensive guide for tech professionals and organizations alike in optimizing their cybersecurity investment while ensuring robust protection against evolving cyber threats.
Virtual CISO Responsibilities: Charting the Course for Cybersecurity Success
In the dynamic landscape of cybersecurity, the responsibilities of a Virtual Chief Information Security Officer (vCISO) play a pivotal role in charting the course for organizational success in the realm of digital defense. This sub-topic delves into the multifaceted role of a vCISO, exploring their key responsibilities and duties. A virtual CISO is tasked with developing and implementing a comprehensive cybersecurity strategy, aligning it with the organization's overall business objectives. From risk management and compliance oversight to incident response planning, the vCISO shoulders the responsibility of fortifying the organization's defenses against an ever-evolving threat landscape.
Moreover, the vCISO is instrumental in fostering a cybersecurity-aware culture within the organization, ensuring that employees are well-versed in security best practices. They collaborate with various departments to integrate security measures seamlessly into business processes while staying abreast of the latest technological advancements and emerging threats. By analyzing the critical responsibilities shouldered by vCISOs, this exploration aims to underscore the strategic importance of their role in steering organizations towards cybersecurity excellence and resilience.
Virtual CISO Companies: Pioneers Shaping the Future of Cybersecurity Leadership
In the ever-evolving landscape of cybersecurity, Virtual Chief Information Security Officer (vCISO) companies stand out as pioneers shaping the future of leadership in digital defense. This sub-topic delves into the profiles of leading vCISO companies that have pioneered innovative solutions and contributed significantly to the advancement of cybersecurity practices. These trailblazing organizations specialize in offering virtual CISO services, providing a spectrum of expertise that ranges from strategic planning to tactical execution in the face of diverse cyber threats.
By profiling these vCISO companies, we aim to showcase the varied approaches and methodologies they employ to fortify organizations against potential breaches. Case studies will shed light on successful implementations and highlight how these companies have become instrumental in enhancing the cybersecurity posture of their clients. Whether through groundbreaking technologies, adaptive methodologies, or strategic insights, the featured vCISO companies are at the forefront of driving resilience and excellence in the cybersecurity domain.
This exploration not only recognizes these companies as leaders in the field but also offers valuable insights into the evolving landscape of cybersecurity services, providing a roadmap for organizations seeking to partner with industry trailblazers to bolster their digital defenses effectively.
The Skill Set of a vCISO: Qualifications and Expertise for Cybersecurity Excellence
The role of a Virtual Chief Information Security Officer (vCISO) demands a unique and comprehensive skill set, making it imperative for individuals aspiring to this position to possess qualifications and expertise that align with the complexities of modern cybersecurity. This sub-topic dives into the specific skill set required for a vCISO to excel in their role, highlighting the multifaceted nature of their responsibilities. A strong foundation in cybersecurity fundamentals, including knowledge of threat landscapes, risk management, and compliance standards, serves as the cornerstone of a vCISO's proficiency.
In addition to technical acumen, effective communication skills are crucial for a vCISO to articulate complex security concepts and strategies to both technical and non-technical stakeholders. Leadership qualities, such as strategic thinking and decision-making abilities, are equally vital as vCISOs play a pivotal role in guiding organizations through cybersecurity challenges. Furthermore, staying abreast of the latest advancements in technology and cybersecurity trends is essential for a vCISO to provide proactive and adaptive security solutions.
This exploration aims to delineate the qualifications and expertise required for individuals seeking a career as a vCISO, shedding light on the educational background, certifications, and practical experiences that contribute to cybersecurity excellence in this dynamic leadership role. By understanding the skill set of a vCISO, aspiring professionals can tailor their career paths to meet the demands of this pivotal position in the ever-evolving landscape of cybersecurity.
Conclusion
In conclusion, the advent of Virtual Chief Information Security Officer (vCISO) services represents a paradigm shift in cybersecurity leadership, especially within the dynamic framework of the technology sector. As organizations grapple with the evolving threat landscape, the flexibility and adaptability offered by vCISOs emerge as instrumental factors in fortifying digital defenses. This exploration has delved into key aspects of the vCISO landscape, from decoding pricing models and understanding responsibilities to profiling pioneering companies and delineating the essential skill set for individuals aspiring to this role.
The rise of vCISO services not only addresses the unique challenges faced by tech organizations but also presents a cost-effective and strategic alternative to traditional, in-house CISO models. By strategically navigating pricing models, businesses can optimize their cybersecurity investments while reaping the benefits of tailored and scalable security solutions.
In essence, the exploration of vCISO as a cybersecurity leadership career path for tech professionals signifies not only a response to the current challenges but also a proactive stance in shaping the future of cybersecurity excellence. As organizations continue to navigate the complexities of the digital landscape, the vCISO model stands as a beacon, offering strategic guidance and adaptive solutions to fortify against the ever-present cyber threats.
Read More
In today's rapidly evolving digital landscape, the role of a Chief Information Security Officer (CISO) is more critical than ever. However, for many organizations, especially those in the tech industry, the traditional model of having an in-house CISO may not be the most practical or cost-effective solution. Enter the era of vCISO (Virtual Chief Information Security Officer) – a revolutionary approach to cybersecurity leadership that leverages virtual CISO services.
This emerging trend, often referred to as CISO as a Service or VCISO as a Service, presents a dynamic and flexible career path for tech professionals seeking to make a significant impact in the cybersecurity domain. From understanding the nuances of VCISO pricing and rates to exploring the responsibilities associated with being a virtual information security officer, this innovative model offers an array of opportunities for both individuals and organizations.
In this exploration of the vCISO landscape, we delve into the meaning of VCISO, dissecting the roles and responsibilities of a virtual chief information security officer. We will also examine the pricing models associated with VCISO services and the cost-effectiveness of adopting a virtual CISO, providing insights into the growing list of virtual CISO companies that are shaping the future of cybersecurity leadership.
Whether you are a seasoned cybersecurity professional or a tech enthusiast curious about the evolution of CISO roles, join us on this journey to unravel the intricacies of the virtual CISO career path and discover the immense potential it holds in fortifying organizations against the ever-present cyber threats.
Table of contents
-
The Rise of vCISO Services: Transforming Cybersecurity Leadership
-
Decoding VCISO Pricing Models: Navigating Cost and Value
-
Virtual CISO Responsibilities: Charting the Course for Cybersecurity Success
-
Virtual CISO Companies: Pioneers Shaping the Future of Cybersecurity Leadership
-
The Skill Set of a vCISO: Qualifications and Expertise for Cybersecurity Excellence
-
Conclusion
The Rise of vCISO Services: Transforming Cybersecurity Leadership
The rise of vCISO services marks a transformative shift in the realm of cybersecurity leadership, particularly within the dynamic landscape of the technology sector. In an era where cyber threats constantly evolve and traditional approaches to information security may fall short, organizations are increasingly turning to Virtual Chief Information Security Officers (vCISOs) to navigate this complex terrain. This sub-topic delves into the factors propelling the ascent of vCISO services, examining the unique challenges faced by tech companies and how a virtual CISO can offer tailored solutions. From the flexibility of service delivery to the ability to scale resources as needed, vCISO services provide an adaptive and cost-effective alternative to the conventional in-house CISO model. By exploring the nuances of this emerging trend, we aim to shed light on how vCISO services are not merely meeting but reshaping the expectations for effective cybersecurity leadership in the fast-paced and ever-evolving world of technology.
Decoding VCISO Pricing Models: Navigating Cost and Value
Decoding vCISO pricing models is essential in navigating the delicate balance between cost considerations and the strategic value that Virtual Chief Information Security Officers (vCISOs) bring to the cybersecurity landscape. In this sub-topic, we embark on an exploration of the various pricing structures associated with vCISO services, uncovering the intricacies that organizations must navigate to make informed decisions. From hourly rates to subscription-based models, understanding the nuances of vCISO pricing is crucial for businesses seeking effective cybersecurity leadership without compromising fiscal prudence. By delving into this aspect, we aim to provide insights into the cost-effectiveness of vCISO solutions compared to traditional, in-house CISO roles, ultimately offering a comprehensive guide for tech professionals and organizations alike in optimizing their cybersecurity investment while ensuring robust protection against evolving cyber threats.
Virtual CISO Responsibilities: Charting the Course for Cybersecurity Success
In the dynamic landscape of cybersecurity, the responsibilities of a Virtual Chief Information Security Officer (vCISO) play a pivotal role in charting the course for organizational success in the realm of digital defense. This sub-topic delves into the multifaceted role of a vCISO, exploring their key responsibilities and duties. A virtual CISO is tasked with developing and implementing a comprehensive cybersecurity strategy, aligning it with the organization's overall business objectives. From risk management and compliance oversight to incident response planning, the vCISO shoulders the responsibility of fortifying the organization's defenses against an ever-evolving threat landscape.
Moreover, the vCISO is instrumental in fostering a cybersecurity-aware culture within the organization, ensuring that employees are well-versed in security best practices. They collaborate with various departments to integrate security measures seamlessly into business processes while staying abreast of the latest technological advancements and emerging threats. By analyzing the critical responsibilities shouldered by vCISOs, this exploration aims to underscore the strategic importance of their role in steering organizations towards cybersecurity excellence and resilience.
Virtual CISO Companies: Pioneers Shaping the Future of Cybersecurity Leadership
In the ever-evolving landscape of cybersecurity, Virtual Chief Information Security Officer (vCISO) companies stand out as pioneers shaping the future of leadership in digital defense. This sub-topic delves into the profiles of leading vCISO companies that have pioneered innovative solutions and contributed significantly to the advancement of cybersecurity practices. These trailblazing organizations specialize in offering virtual CISO services, providing a spectrum of expertise that ranges from strategic planning to tactical execution in the face of diverse cyber threats.
By profiling these vCISO companies, we aim to showcase the varied approaches and methodologies they employ to fortify organizations against potential breaches. Case studies will shed light on successful implementations and highlight how these companies have become instrumental in enhancing the cybersecurity posture of their clients. Whether through groundbreaking technologies, adaptive methodologies, or strategic insights, the featured vCISO companies are at the forefront of driving resilience and excellence in the cybersecurity domain.
This exploration not only recognizes these companies as leaders in the field but also offers valuable insights into the evolving landscape of cybersecurity services, providing a roadmap for organizations seeking to partner with industry trailblazers to bolster their digital defenses effectively.
The Skill Set of a vCISO: Qualifications and Expertise for Cybersecurity Excellence
The role of a Virtual Chief Information Security Officer (vCISO) demands a unique and comprehensive skill set, making it imperative for individuals aspiring to this position to possess qualifications and expertise that align with the complexities of modern cybersecurity. This sub-topic dives into the specific skill set required for a vCISO to excel in their role, highlighting the multifaceted nature of their responsibilities. A strong foundation in cybersecurity fundamentals, including knowledge of threat landscapes, risk management, and compliance standards, serves as the cornerstone of a vCISO's proficiency.
In addition to technical acumen, effective communication skills are crucial for a vCISO to articulate complex security concepts and strategies to both technical and non-technical stakeholders. Leadership qualities, such as strategic thinking and decision-making abilities, are equally vital as vCISOs play a pivotal role in guiding organizations through cybersecurity challenges. Furthermore, staying abreast of the latest advancements in technology and cybersecurity trends is essential for a vCISO to provide proactive and adaptive security solutions.
This exploration aims to delineate the qualifications and expertise required for individuals seeking a career as a vCISO, shedding light on the educational background, certifications, and practical experiences that contribute to cybersecurity excellence in this dynamic leadership role. By understanding the skill set of a vCISO, aspiring professionals can tailor their career paths to meet the demands of this pivotal position in the ever-evolving landscape of cybersecurity.
Conclusion
In conclusion, the advent of Virtual Chief Information Security Officer (vCISO) services represents a paradigm shift in cybersecurity leadership, especially within the dynamic framework of the technology sector. As organizations grapple with the evolving threat landscape, the flexibility and adaptability offered by vCISOs emerge as instrumental factors in fortifying digital defenses. This exploration has delved into key aspects of the vCISO landscape, from decoding pricing models and understanding responsibilities to profiling pioneering companies and delineating the essential skill set for individuals aspiring to this role.
The rise of vCISO services not only addresses the unique challenges faced by tech organizations but also presents a cost-effective and strategic alternative to traditional, in-house CISO models. By strategically navigating pricing models, businesses can optimize their cybersecurity investments while reaping the benefits of tailored and scalable security solutions.
In essence, the exploration of vCISO as a cybersecurity leadership career path for tech professionals signifies not only a response to the current challenges but also a proactive stance in shaping the future of cybersecurity excellence. As organizations continue to navigate the complexities of the digital landscape, the vCISO model stands as a beacon, offering strategic guidance and adaptive solutions to fortify against the ever-present cyber threats.
Top 10 Most Popular Open Source Projects on GitHub
In the ever-evolving landscape of software development, GitHub stands out as a central hub for collaboration, hosting a plethora of open source projects that drive innovation across various domains. From powerful code editors like GitHub Copilot to seamless automation with GitHub Actions, the platform has become synonymous with cutting-edge technologies and collaborative coding practices.
In this compilation, we delve into the "Top 10 Most Popular Open Source Projects on GitHub," exploring the diverse realms of software development that have captured the attention and contributions of the global developer community. From GitHub Pages facilitating effortless website hosting to GitBucket offering a flexible Git platform, these projects showcase the versatility and impact of open source collaboration.
As we navigate through the list, we'll explore not only the functionality and features of these projects but also touch upon essential aspects such as GitHub pricing, repository management, and the significance of a well-maintained GitHub account. Whether you're a seasoned developer seeking new tools or a newcomer eager to explore the world of open source, this compilation serves as a guide to the vibrant and dynamic ecosystem that GitHub fosters. Let's embark on a journey through the top GitHub projects that have shaped and continue to shape the future of software development.
Table of contents
-
GitHub Copilot: Revolutionizing Code Assistance
-
GitHub Actions: Automating Workflows for Efficiency
-
GitHub Pages: Simplifying Web Hosting for Developers
-
GitBucket vs. GitHub: A Comparative Analysis
-
GitHub for Beginners: Navigating Repositories and Best Practices
-
Conclusion
GitHub Copilot: Revolutionizing Code Assistance
GitHub Copilot has emerged as a groundbreaking force in the realm of code assistance, ushering in a new era of productivity for developers. Developed in collaboration with OpenAI, Copilot is an AI-powered code completion tool integrated directly into the code editor, providing real-time suggestions and snippets as developers type. This revolutionary approach not only accelerates coding speed but also enhances the quality of code produced. By leveraging machine learning models trained on vast repositories of open-source code, GitHub Copilot understands context, enabling it to generate accurate and contextually relevant code snippets. Its ability to anticipate and complete entire lines or blocks of code based on natural language prompts has transformed the way developers approach coding challenges. GitHub Copilot has quickly become an indispensable companion for programmers, offering a dynamic and intuitive coding experience that pushes the boundaries of what's possible in code assistance tools. As developers continue to embrace this innovative technology, GitHub Copilot stands as a testament to the transformative potential of artificial intelligence in shaping the future of software development.
GitHub Actions: Automating Workflows for Efficiency
GitHub Actions has emerged as a game-changing solution in the software development landscape, providing developers with a robust platform to automate workflows and streamline the development lifecycle. This powerful tool, seamlessly integrated into the GitHub platform, allows developers to define custom workflows directly in their code repositories. GitHub Actions goes beyond traditional CI/CD (Continuous Integration/Continuous Deployment) by offering a versatile automation framework that can be tailored to various tasks, from code testing and building to deployment and beyond. With a vast library of pre-built actions and the flexibility to create custom actions, developers can orchestrate complex processes with ease. The ability to trigger actions based on events, such as code pushes or pull requests, ensures that development teams can maintain a continuous and efficient integration process. GitHub Actions not only accelerates development cycles but also enhances collaboration by automating repetitive tasks, enabling teams to focus on innovation and code quality. As developers embrace the power of automation, GitHub Actions stands as a key player in optimizing workflows for efficiency and scalability in modern software development.
GitHub Pages: Simplifying Web Hosting for Developers
GitHub Pages has become a go-to solution for developers seeking a straightforward and efficient way to host their websites directly from their GitHub repositories. This service, seamlessly integrated into the GitHub ecosystem, simplifies the process of showcasing and sharing static web content. With GitHub Pages, developers can effortlessly turn their repositories into live websites, eliminating the need for complex server configurations and external hosting services. Whether it's a personal portfolio, documentation, or a project homepage, GitHub Pages provides a user-friendly platform that aligns with the collaborative nature of GitHub. The service supports custom domains, allowing developers to showcase their work under their own branding. Additionally, GitHub Pages offers built-in Jekyll support for those who prefer static site generators. As an accessible and free hosting solution, GitHub Pages has played a pivotal role in democratizing web hosting for developers, enabling them to focus on content creation and code development without the hassle of managing intricate hosting setups.
GitBucket vs GitHub: A Comparative Analysis
In the realm of version control and collaborative software development, the choice between GitBucket and GitHub sparks a significant debate among developers seeking the most suitable platform for their projects. GitBucket, an open-source alternative to GitHub, shares the fundamental Git functionality but diverges in certain features and user experience. GitHub, a proprietary platform, has established itself as the industry standard for hosting Git repositories and fostering collaborative development. While GitBucket offers a self-hosted, customizable solution, GitHub provides an extensive ecosystem with features like GitHub Actions, GitHub Pages, and a vast marketplace for integrations. Developers often weigh factors such as community support, ease of use, and the additional features offered when deciding between GitBucket and GitHub. This comparative analysis aims to dissect the strengths and weaknesses of each platform, aiding developers in making an informed choice based on their specific needs and preferences in version control and collaborative coding environments.
GitHub for Beginners: Navigating Repositories and Best Practices
For beginners venturing into the expansive world of collaborative coding, GitHub serves as an essential platform, and understanding its foundational elements is crucial. Navigating repositories on GitHub involves creating, cloning, and collaborating on projects effectively. A repository houses the project's files, history, and documentation, serving as a central hub for collaboration. Forking allows beginners to create a personal copy of a repository to experiment without affecting the original project. Learning to manage branches, pull requests, and issues is vital for seamless collaboration. Best practices include committing changes with clear messages, regularly updating local repositories, and utilizing Gitignore files to exclude unnecessary files from version control. Establishing a well-maintained GitHub account, with a clear profile and contribution history, fosters a positive online presence within the developer community. As beginners navigate the GitHub landscape, grasping these fundamentals and adopting best practices ensures a smooth entry into the collaborative and open-source coding culture.
Conclusion
In conclusion, the "Top 10 Most Popular Open Source Projects on GitHub" encapsulates the dynamic and innovative spirit of the global developer community. From the revolutionary GitHub Copilot redefining code assistance to the robust automation capabilities offered by GitHub Actions, each project contributes uniquely to the ever-evolving landscape of software development. GitHub Pages simplifies web hosting, enabling developers to showcase their work effortlessly, while the comparative analysis of GitBucket versus GitHub sheds light on the choices available for version control and collaborative coding. For beginners, GitHub serves as a gateway to collaborative coding, providing essential tools and best practices for effective project management.
In this interconnected world of repositories, forks, and pull requests, the Top 10 GitHub projects showcase the potential for transformative change and collective progress. Whether you are an experienced developer harnessing the latest tools or a newcomer navigating the basics, the GitHub ecosystem stands as a testament to the collaborative spirit that propels the software development industry forward. Embracing these projects not only enhances individual coding capabilities but contributes to the collective evolution of technology, shaping the future of open source software development.
Read More
In the ever-evolving landscape of software development, GitHub stands out as a central hub for collaboration, hosting a plethora of open source projects that drive innovation across various domains. From powerful code editors like GitHub Copilot to seamless automation with GitHub Actions, the platform has become synonymous with cutting-edge technologies and collaborative coding practices.
In this compilation, we delve into the "Top 10 Most Popular Open Source Projects on GitHub," exploring the diverse realms of software development that have captured the attention and contributions of the global developer community. From GitHub Pages facilitating effortless website hosting to GitBucket offering a flexible Git platform, these projects showcase the versatility and impact of open source collaboration.
As we navigate through the list, we'll explore not only the functionality and features of these projects but also touch upon essential aspects such as GitHub pricing, repository management, and the significance of a well-maintained GitHub account. Whether you're a seasoned developer seeking new tools or a newcomer eager to explore the world of open source, this compilation serves as a guide to the vibrant and dynamic ecosystem that GitHub fosters. Let's embark on a journey through the top GitHub projects that have shaped and continue to shape the future of software development.
Table of contents
-
GitHub Copilot: Revolutionizing Code Assistance
-
GitHub Actions: Automating Workflows for Efficiency
-
GitHub Pages: Simplifying Web Hosting for Developers
-
GitBucket vs. GitHub: A Comparative Analysis
-
GitHub for Beginners: Navigating Repositories and Best Practices
-
Conclusion
GitHub Copilot: Revolutionizing Code Assistance
GitHub Copilot has emerged as a groundbreaking force in the realm of code assistance, ushering in a new era of productivity for developers. Developed in collaboration with OpenAI, Copilot is an AI-powered code completion tool integrated directly into the code editor, providing real-time suggestions and snippets as developers type. This revolutionary approach not only accelerates coding speed but also enhances the quality of code produced. By leveraging machine learning models trained on vast repositories of open-source code, GitHub Copilot understands context, enabling it to generate accurate and contextually relevant code snippets. Its ability to anticipate and complete entire lines or blocks of code based on natural language prompts has transformed the way developers approach coding challenges. GitHub Copilot has quickly become an indispensable companion for programmers, offering a dynamic and intuitive coding experience that pushes the boundaries of what's possible in code assistance tools. As developers continue to embrace this innovative technology, GitHub Copilot stands as a testament to the transformative potential of artificial intelligence in shaping the future of software development.
GitHub Actions: Automating Workflows for Efficiency
GitHub Actions has emerged as a game-changing solution in the software development landscape, providing developers with a robust platform to automate workflows and streamline the development lifecycle. This powerful tool, seamlessly integrated into the GitHub platform, allows developers to define custom workflows directly in their code repositories. GitHub Actions goes beyond traditional CI/CD (Continuous Integration/Continuous Deployment) by offering a versatile automation framework that can be tailored to various tasks, from code testing and building to deployment and beyond. With a vast library of pre-built actions and the flexibility to create custom actions, developers can orchestrate complex processes with ease. The ability to trigger actions based on events, such as code pushes or pull requests, ensures that development teams can maintain a continuous and efficient integration process. GitHub Actions not only accelerates development cycles but also enhances collaboration by automating repetitive tasks, enabling teams to focus on innovation and code quality. As developers embrace the power of automation, GitHub Actions stands as a key player in optimizing workflows for efficiency and scalability in modern software development.
GitHub Pages: Simplifying Web Hosting for Developers
GitHub Pages has become a go-to solution for developers seeking a straightforward and efficient way to host their websites directly from their GitHub repositories. This service, seamlessly integrated into the GitHub ecosystem, simplifies the process of showcasing and sharing static web content. With GitHub Pages, developers can effortlessly turn their repositories into live websites, eliminating the need for complex server configurations and external hosting services. Whether it's a personal portfolio, documentation, or a project homepage, GitHub Pages provides a user-friendly platform that aligns with the collaborative nature of GitHub. The service supports custom domains, allowing developers to showcase their work under their own branding. Additionally, GitHub Pages offers built-in Jekyll support for those who prefer static site generators. As an accessible and free hosting solution, GitHub Pages has played a pivotal role in democratizing web hosting for developers, enabling them to focus on content creation and code development without the hassle of managing intricate hosting setups.
GitBucket vs GitHub: A Comparative Analysis
In the realm of version control and collaborative software development, the choice between GitBucket and GitHub sparks a significant debate among developers seeking the most suitable platform for their projects. GitBucket, an open-source alternative to GitHub, shares the fundamental Git functionality but diverges in certain features and user experience. GitHub, a proprietary platform, has established itself as the industry standard for hosting Git repositories and fostering collaborative development. While GitBucket offers a self-hosted, customizable solution, GitHub provides an extensive ecosystem with features like GitHub Actions, GitHub Pages, and a vast marketplace for integrations. Developers often weigh factors such as community support, ease of use, and the additional features offered when deciding between GitBucket and GitHub. This comparative analysis aims to dissect the strengths and weaknesses of each platform, aiding developers in making an informed choice based on their specific needs and preferences in version control and collaborative coding environments.
GitHub for Beginners: Navigating Repositories and Best Practices
For beginners venturing into the expansive world of collaborative coding, GitHub serves as an essential platform, and understanding its foundational elements is crucial. Navigating repositories on GitHub involves creating, cloning, and collaborating on projects effectively. A repository houses the project's files, history, and documentation, serving as a central hub for collaboration. Forking allows beginners to create a personal copy of a repository to experiment without affecting the original project. Learning to manage branches, pull requests, and issues is vital for seamless collaboration. Best practices include committing changes with clear messages, regularly updating local repositories, and utilizing Gitignore files to exclude unnecessary files from version control. Establishing a well-maintained GitHub account, with a clear profile and contribution history, fosters a positive online presence within the developer community. As beginners navigate the GitHub landscape, grasping these fundamentals and adopting best practices ensures a smooth entry into the collaborative and open-source coding culture.
Conclusion
In conclusion, the "Top 10 Most Popular Open Source Projects on GitHub" encapsulates the dynamic and innovative spirit of the global developer community. From the revolutionary GitHub Copilot redefining code assistance to the robust automation capabilities offered by GitHub Actions, each project contributes uniquely to the ever-evolving landscape of software development. GitHub Pages simplifies web hosting, enabling developers to showcase their work effortlessly, while the comparative analysis of GitBucket versus GitHub sheds light on the choices available for version control and collaborative coding. For beginners, GitHub serves as a gateway to collaborative coding, providing essential tools and best practices for effective project management.
In this interconnected world of repositories, forks, and pull requests, the Top 10 GitHub projects showcase the potential for transformative change and collective progress. Whether you are an experienced developer harnessing the latest tools or a newcomer navigating the basics, the GitHub ecosystem stands as a testament to the collaborative spirit that propels the software development industry forward. Embracing these projects not only enhances individual coding capabilities but contributes to the collective evolution of technology, shaping the future of open source software development.
Understanding COBIT 5 Foundation: A Comprehensive Overview
In the ever-evolving landscape of information technology, effective governance and management are paramount for organizations to thrive and succeed. One framework that stands out in this context is COBIT 5 Foundation. COBIT, which stands for Control Objectives for Information and Related Technologies, is a globally recognized framework designed to help organizations govern and manage their IT effectively.
COBIT has a rich history of evolution, adapting to the changing needs of the IT industry. From its inception to the present COBIT 5 Foundation, it has become a standard bearer for organizations seeking to align their IT strategies with their business goals. This framework provides a structured approach to IT governance and management, ensuring that enterprises can achieve optimal outcomes and manage risks effectively.
Whether you're new to COBIT 5 or looking to refresh your understanding, this comprehensive overview aims to be your guide to mastering the core concepts and practical applications of COBIT 5 Foundation. So, let's begin our exploration of COBIT 5 Foundation and its role in shaping the future of IT governance.
Table of contents
-
Historical Evolution of COBIT
-
COBIT 5 Framework Components
-
Key Concepts in COBIT 5
-
Benefits of Implementing COBIT 5 Foundation
-
COBIT 5 Principles
-
COBIT 5 Domains
-
COBIT 5 Process Reference Model
-
COBIT 5 Enablers
-
COBIT 5 Implementation Challenges
-
Real-Life Examples of COBIT 5 Success Stories
-
Conclusion
Historical Evolution of COBIT
The historical evolution of COBIT (Control Objectives for Information and Related Technologies) is a fascinating journey that showcases its development from a simple set of IT control objectives into a globally recognized framework for IT governance and management. Let's take a closer look at the key milestones in the history of COBIT:
COBIT 1.0 (1996): COBIT was initially introduced by ISACA (Information Systems Audit and Control Association) in 1996 as a set of IT control objectives to help organizations manage their IT processes and risks. This first version provided a basic structure for IT governance.
COBIT 2.0 (1998): The framework was updated in 1998 as COBIT 2.0. This version included a more comprehensive set of control objectives, making it a valuable tool for IT audit and control professionals.
COBIT 3.0 (2000): In the year 2000, COBIT 3.0 was released with a significant expansion in scope. This version integrated IT governance and management practices, helping organizations align IT with business goals more effectively.
COBIT 4.0 (2005): COBIT 4.0 introduced the concept of domains, processes, and IT-related goals, making it more structured and easier to apply in organizations. It was a pivotal step toward broader acceptance.
COBIT 4.1 (2007): This version, released in 2007, brought some refinements and updates to COBIT 4.0, making it more practical for implementation in real-world scenarios.
COBIT 5.0 Updates (2019): In 2019, COBIT was updated to further align with the evolving IT landscape and address contemporary challenges. This update included guidance on digital transformation and emerging technologies.
The historical evolution of COBIT reflects the changing landscape of IT governance, from a focus on control objectives to a comprehensive framework for aligning IT with business strategy, managing risks, and achieving operational excellence.
COBIT 5 Framework Components
The COBIT 5 framework consists of several key components, each of which plays a crucial role in helping organizations govern and manage their information and technology effectively. Understanding these components is essential for implementing COBIT 5 successfully. Here are the main components of the COBIT 5 framework:
Principles:
Meeting Stakeholder Needs: The first principle of COBIT 5 emphasizes the importance of aligning IT with the needs and expectations of stakeholders, whether they are internal or external to the organization.
Applying a Single Integrated Framework: COBIT 5 promotes the use of a single integrated framework to harmonize and simplify the governance of IT.
Enablers:
Processes: COBIT 5 defines a set of governance and management processes that help organizations achieve their objectives. These processes cover areas such as risk management, resource management, and performance management.
Principles, Policies, and Frameworks: These enablers provide the foundation for governance and management. They include the principles mentioned earlier, as well as policies, standards, and guidelines.
Information: Information is a key enabler, and COBIT 5 provides guidance on managing and optimizing the use of information in decision-making processes.
Services, Infrastructure, and Applications: These enablers relate to the physical and logical resources required to deliver IT services.
Governance and Management Processes:
COBIT 5 defines a comprehensive set of governance and management processes that organizations can use to align their IT with business goals, manage risks, and deliver value. Some of the processes include:
Evaluate, Direct, and Monitor (EDM) processes: These processes are primarily related to governance activities.
Align, Plan, and Organize (APO) processes: These processes focus on strategic planning and organizational structure.
Monitor, Evaluate, and Assess (MEA) processes: These processes assess the effectiveness of governance and management.
COBIT 5 Framework Model:
The COBIT 5 framework model provides a graphical representation of the principles, enablers, and processes, helping organizations visualize how they interact and support the achievement of objectives.
These components work together to provide a structured and holistic approach to IT governance and management. COBIT 5's principles guide decision-making, the enablers provide the resources and tools, and the governance and management processes offer a practical roadmap for implementation. By leveraging these components effectively, organizations can improve their IT practices, mitigate risks, and deliver value to stakeholders
Key Concepts in COBIT 5
COBIT 5, a comprehensive framework for governing and managing enterprise IT, is built upon several key concepts that are fundamental to understanding and implementing the framework effectively. Here are the key concepts in COBIT 5:
Governance and Management: COBIT 5 distinguishes between governance and management. Governance is primarily concerned with decision-making and ensuring that IT aligns with business goals. Management, on the other hand, involves the execution of those decisions and the day-to-day operation of IT processes.
End-to-End Coverage: COBIT 5 advocates for a holistic approach to IT governance, covering all aspects of the enterprise. It's not limited to specific processes or departments; rather, it spans the entire organization.
Framework for the Governance and Management of Enterprise IT: COBIT 5 provides a structured framework that encompasses IT governance and management practices. This framework offers a systematic approach to achieving organizational goals.
Enabler: Enablers in COBIT 5 are the factors that facilitate or support the implementation of governance and management. These include processes, principles, policies, organizational structures, culture, ethics, and behavior, among others.
Principles: COBIT 5 is guided by seven key principles:
Meeting Stakeholder Needs
Covering the Enterprise End-to-End
Separating Governance from Management
Tailoring to the Enterprise
Implementing a Governance System
Domains: COBIT 5 defines four domains, each encompassing a set of processes and activities:
Lifecycle Approach: COBIT 5 advocates for a lifecycle approach to IT governance and management, emphasizing that governance and management are continuous and cyclical processes rather than one-time events.
Information Governance: Information is a critical asset in IT governance, and COBIT 5 underscores the importance of effectively managing and using information in decision-making processes.
Understanding these key concepts in COBIT 5 is essential for organizations looking to enhance their IT governance and management practices. These concepts provide the foundation for implementing the framework and aligning IT with business objectives while meeting the needs of various stakeholders.
Benefits of Implementing COBIT 5 Foundation
Implementing COBIT 5 Foundation can bring a wide range of benefits to organizations. Here are some of the key advantages of adopting the COBIT 5 framework for IT governance and management:
Enhanced IT Governance: COBIT 5 provides a structured and holistic approach to IT governance, helping organizations make informed decisions and align IT strategies with business objectives. This results in more effective governance practices.
Improved Risk Management: COBIT 5 offers guidelines and practices for identifying, assessing, and managing IT-related risks. Implementing COBIT 5 can enhance an organization's ability to mitigate and respond to risks effectively.
Alignment with Stakeholder Needs: COBIT 5 emphasizes the importance of meeting the needs and expectations of stakeholders. By aligning IT activities with stakeholder requirements, organizations can enhance their reputation and relationships.
Increased Efficiency and Effectiveness: COBIT 5 provides a clear framework for organizing and optimizing IT processes. This leads to increased efficiency in IT operations and the delivery of services, ultimately resulting in cost savings.
Better Compliance: COBIT 5 includes guidelines for ensuring regulatory compliance and adherence to industry standards. Implementing COBIT 5 can help organizations avoid non-compliance issues and associated penalties.
Optimized Resource Management: COBIT 5 enables organizations to manage IT resources efficiently, including people, technology, and information. This ensures that resources are used effectively to achieve business goals.
Enhanced Decision-Making: COBIT 5 offers a structured framework for decision-making, promoting evidence-based choices. This leads to better decision quality and more favorable outcomes.
Continuous Improvement: COBIT 5 promotes a culture of continual improvement in IT governance and management. Organizations can adapt to changing circumstances and stay agile in the face of evolving technology and business needs.
Mitigation of IT-related Failures: By following COBIT 5's best practices, organizations can reduce the likelihood of IT-related failures, such as system outages or security breaches.
In summary, implementing COBIT 5 Foundation offers organizations a structured and comprehensive approach to IT governance and management. It not only helps align IT with business goals but also results in better risk management, stakeholder satisfaction, and overall organizational performance.
COBIT 5 Principles
COBIT 5 is built upon seven key principles, which provide the foundation for effective IT governance and management. Here are five of those principles:
Meeting Stakeholder Needs: The first principle emphasizes the importance of aligning IT with the needs and expectations of stakeholders, both internal and external. Organizations should prioritize understanding and addressing the unique requirements of these stakeholders to ensure their satisfaction and support.
Covering the Enterprise End-to-End: This principle advocates for a holistic approach to IT governance and management. It highlights the need to consider all aspects of the enterprise, from strategy and planning to daily operations, to ensure that IT aligns with the entire organization.
Applying a Single Integrated Framework: COBIT 5 promotes the use of a single, integrated framework for IT governance and management. By applying a unified framework, organizations can avoid duplication, inconsistencies, and confusion, making IT governance more efficient and effective.
Enabling a Holistic Approach: This principle underscores the importance of adopting a comprehensive and integrated approach to IT governance. Organizations should consider the full spectrum of factors, including processes, culture, organizational structures, and information, to achieve effective governance and management.
These principles serve as guiding tenets for organizations looking to establish effective IT governance and management practices using the COBIT 5 framework. They provide a strategic and philosophical basis for decision-making and implementation, helping organizations meet their objectives and deliver value to stakeholders.
COBIT 5 Domains
COBIT 5 organizes its guidance and processes into four primary domains, each of which represents a distinct area of IT governance and management. These domains are designed to help organizations address various aspects of IT effectively. The four domains in COBIT 5 are as follows:
Governance (EDM - Evaluate, Direct, and Monitor): The Governance domain focuses on the high-level, strategic aspects of IT governance. It is responsible for ensuring that stakeholder needs and expectations are met, and that the enterprise's strategic objectives are aligned with IT. This domain includes processes related to evaluating the current state of IT, directing IT to achieve its goals, and monitoring IT performance. Key processes within this domain include:
Evaluate, Direct, and Monitor (EDM)
Ensure Governance Framework Setting and Maintenance
Ensure Stakeholder Value Delivery
Ensure Performance Optimization
Management (APO - Align, Plan, and Organize, BAI - Build, Acquire, and Implement, DSS - Deliver, Service, and Support): The Management domain encompasses the processes that support the actual planning, implementation, and operation of IT within the organization. It ensures that IT resources are organized and deployed effectively. The Management domain is divided into three subdomains:
Align, Plan, and Organize (APO): This subdomain is responsible for aligning IT with the organization's strategic objectives and planning IT activities. Key processes include strategic planning, portfolio management, and IT budgeting.
Build, Acquire, and Implement (BAI): This subdomain covers the processes related to developing, acquiring, and implementing IT solutions and services. It includes processes like project management, system development, and IT procurement.
Information (MEA - Monitor, Evaluate, and Assess): The Information domain is responsible for ensuring the effective management of information as an asset. It involves processes for monitoring and assessing the quality and security of information. Key processes within this domain include:
Monitor, Evaluate, and Assess (MEA)
Ensure Stakeholder Value Delivery
Ensure Risk Optimization
Supporting Processes (APO - Align, Plan, and Organize, BAI - Build, Acquire, and Implement, DSS - Deliver, Service, and Support, MEA - Monitor, Evaluate, and Assess): These processes are common to multiple domains and provide support for the primary processes in Governance, Management, and Information. They are not standalone domains but are essential for the smooth operation of IT governance and management. These supporting processes include areas like compliance, human resources, and knowledge management.
These four domains, along with their respective processes, help organizations implement comprehensive IT governance and management practices using the COBIT 5 framework. Each domain addresses specific aspects of IT, ensuring that IT aligns with business goals, delivers value, and is governed effectively.
COBIT 5 Process Reference Model
The COBIT 5 Process Reference Model is a core component of the COBIT 5 framework. It provides a structured and comprehensive framework for understanding and implementing IT governance and management processes within an organization. The model is designed to be flexible and scalable, allowing organizations to tailor it to their specific needs and requirements. Here's an overview of the COBIT 5 Process Reference Model:
Processes: The model is organized into a set of processes that cover various aspects of IT governance and management. These processes are divided into five domains: Evaluate, Direct, and Monitor (EDM); Align, Plan, and Organize (APO); Build, Acquire, and Implement (BAI); Deliver, Service, and Support (DSS); and Monitor, Evaluate, and Assess (MEA).
Processes and Activities: Within each domain, the COBIT 5 Process Reference Model defines specific processes and associated activities. These activities provide detailed guidance on how to implement and execute each process effectively.
Inputs and Outputs: The model also specifies the inputs and outputs of each process, helping organizations understand what information, resources, and deliverables are required to execute a process and what is generated as a result.
Responsibilities: The model identifies the roles and responsibilities associated with each process, ensuring that organizations have clear lines of accountability.
Interactions: It illustrates how processes within different domains interact with each other. This promotes a holistic and integrated approach to IT governance and management.
Maturity and Capability: COBIT 5 includes maturity and capability models to assess the maturity of an organization's processes and its capability to manage them effectively.
The COBIT 5 Process Reference Model serves as a practical tool for organizations to assess, plan, and improve their IT governance and management practices. It promotes transparency, alignment with business objectives, and the continuous improvement of IT processes, ultimately leading to better governance, risk management, and value delivery.
COBIT 5 Enablers
COBIT 5 emphasizes the importance of enablers as factors that support effective IT governance and management within an organization. These enablers provide the resources, tools, and structures necessary to achieve organizational objectives. COBIT 5 identifies seven primary categories of enablers that work together to facilitate the implementation of IT governance and management practices. Here are the COBIT 5 enablers:
Processes: COBIT 5 identifies a set of IT governance and management processes that are essential for aligning IT with business goals and objectives. These processes provide the practical steps and activities for governing and managing IT effectively.
Organizational Structures: Organizational structures and roles are enablers that define how responsibilities are distributed and delegated within the organization. They include roles, responsibilities, and reporting lines, ensuring clear accountability.
Information: Information is a critical enabler as it provides the data and knowledge necessary for making informed decisions. Effective information management, data quality, and information security are important aspects of this enabler.
Services, Infrastructure, and Applications: This enabler includes the physical and logical resources required to support IT services and applications. It covers areas such as infrastructure, applications, and IT service management tools.
People, Skills, and Competencies: People are at the heart of IT governance and management. This enabler focuses on ensuring that the organization has the right people with the right skills and competencies to support IT activities effectively.
These seven enablers collectively provide the framework and resources required for organizations to align their IT with business goals, manage risks, deliver value, and govern IT effectively. COBIT 5 emphasizes that these enablers are interrelated, and the successful implementation of IT governance and management practices requires a harmonious integration of all enablers. The specific application of these enablers will vary based on an organization's unique context and objectives.
COBIT 5 Implementation Challenges
Implementing COBIT 5 in an organization can bring numerous benefits, but it also presents several challenges. These challenges can vary depending on the organization's size, industry, and existing IT governance practices. Here are some common challenges associated with COBIT 5 implementation:
Resistance to Change: One of the most significant challenges is getting buy-in from all levels of the organization. Employees and management may be resistant to adopting new governance and management practices.
Resource Allocation: Implementing COBIT 5 requires dedicating time, people, and financial resources. Finding the necessary resources can be a challenge, especially for smaller organizations with limited budgets.
Skills and Training: Implementing COBIT 5 may require training and skill development for employees. Ensuring that staff has the necessary competencies can be a challenge, especially in rapidly changing IT environments.
Customization: COBIT 5 is a framework, and it needs to be tailored to the specific needs and context of each organization. Finding the right balance between customization and adherence to COBIT 5's principles can be challenging.
Measuring Success: Defining and measuring Key Performance Indicators (KPIs) and Critical Success Factors (CSFs) to evaluate the success of COBIT 5 implementation can be challenging. Identifying meaningful metrics and benchmarks for improvement is essential.
Top-Down vs. Bottom-Up Approach: Deciding whether to implement COBIT 5 top-down (starting with governance) or bottom-up (starting with management processes) is a strategic challenge that organizations must address.
Sustainability: Maintaining the momentum and ensuring that COBIT 5 practices continue to be effective over the long term can be challenging. Often, organizations face the risk of reverting to old practices after initial enthusiasm wanes.
Risk Management: While COBIT 5 provides guidance on risk management, identifying and addressing potential risks associated with implementation itself is a challenge.
To overcome these challenges, organizations should develop a well-defined implementation plan, engage with stakeholders, provide adequate training and support, and continuously monitor and adapt their COBIT 5 implementation as needed. It's also essential to recognize that COBIT 5 implementation is an ongoing process that requires commitment and adaptability to achieve its intended benefits.
Real-Life Examples of COBIT 5 Success Stories
COBIT 5 has been successfully implemented in numerous organizations across various industries, helping them achieve their IT governance and management objectives. Here are some real-life examples of organizations that have experienced success with COBIT 5:
ExxonMobil: ExxonMobil, one of the world's largest multinational oil and gas corporations, used COBIT 5 to enhance its IT governance and risk management. They successfully implemented COBIT 5's principles and processes to align IT with business objectives and improve risk mitigation strategies.
Dubai Customs: Dubai Customs, a government agency responsible for facilitating trade in the Emirate of Dubai, implemented COBIT 5 to enhance its IT service management practices. They used COBIT 5 to streamline IT processes, resulting in improved service delivery and customer satisfaction.
Walmart: Walmart, a global retail giant, leveraged COBIT 5 to optimize IT governance and management processes across its vast network of stores and data centers. COBIT 5 helped Walmart improve the efficiency of IT operations, reduce risks, and enhance customer experiences through effective supply chain management and data security.
US Department of Defense (DoD): The US DoD adopted COBIT 5 as part of its approach to IT governance and cybersecurity. COBIT 5 helped the DoD establish a standardized framework for managing and securing its IT assets, ultimately improving its information security posture.
AXA Group: AXA, a multinational insurance company, implemented COBIT 5 to align IT processes with business needs. By using COBIT 5, AXA improved risk management, IT performance, and the overall quality of IT services.
Government of Malaysia: The Malaysian government adopted COBIT 5 to enhance IT governance practices across various government agencies. This initiative has led to improved transparency, accountability, and effectiveness in IT management.
University of Waterloo: The University of Waterloo in Canada used COBIT 5 to optimize its IT governance practices. The implementation of COBIT 5 led to more effective IT service management, streamlined IT processes, and improved alignment with academic and administrative goals.
South African Revenue Service (SARS): SARS, the tax collection agency in South Africa, adopted COBIT 5 to enhance its IT governance and risk management practices. The use of COBIT 5 has resulted in better control over taxpayer data and improved compliance with tax regulations.
Vattenfall: Vattenfall, a Swedish multinational energy company, implemented COBIT 5 to enhance its IT governance and cybersecurity practices. COBIT 5 helped Vattenfall align its IT strategies with business objectives and strengthen its defenses against cyber threats.
Central Bank of Nigeria: The Central Bank of Nigeria utilized COBIT 5 to improve its IT governance practices and enhance the security and integrity of the country's financial systems. COBIT 5 has played a critical role in ensuring the stability and resilience of Nigeria's financial infrastructure.
These examples illustrate the versatility and effectiveness of COBIT 5 across various industries and sectors. Organizations have leveraged COBIT 5 to align IT with their strategic goals, enhance IT governance, manage risks, and deliver better services to their stakeholders. These success stories showcase the framework's adaptability and its ability to drive positive outcomes in diverse organizational contexts
Conclusion
In conclusion, COBIT 5 is a comprehensive and widely recognized framework for IT governance and management that provides organizations with the tools and guidance they need to align their IT functions with business objectives, manage risks, and deliver value to stakeholders. It is built on a foundation of key principles, a well-structured process reference model, and seven enablers that collectively support effective governance and management.
As technology continues to play a pivotal role in the success of organizations, COBIT 5 remains a valuable framework for those seeking a structured and systematic approach to IT governance and management. By adopting and customizing COBIT 5 to their specific needs, organizations can navigate the complexities of the digital landscape and ensure that their IT functions are aligned with their broader business strategies.
Read More
In the ever-evolving landscape of information technology, effective governance and management are paramount for organizations to thrive and succeed. One framework that stands out in this context is COBIT 5 Foundation. COBIT, which stands for Control Objectives for Information and Related Technologies, is a globally recognized framework designed to help organizations govern and manage their IT effectively.
COBIT has a rich history of evolution, adapting to the changing needs of the IT industry. From its inception to the present COBIT 5 Foundation, it has become a standard bearer for organizations seeking to align their IT strategies with their business goals. This framework provides a structured approach to IT governance and management, ensuring that enterprises can achieve optimal outcomes and manage risks effectively.
Whether you're new to COBIT 5 or looking to refresh your understanding, this comprehensive overview aims to be your guide to mastering the core concepts and practical applications of COBIT 5 Foundation. So, let's begin our exploration of COBIT 5 Foundation and its role in shaping the future of IT governance.
Table of contents
-
Historical Evolution of COBIT
-
COBIT 5 Framework Components
-
Key Concepts in COBIT 5
-
Benefits of Implementing COBIT 5 Foundation
-
COBIT 5 Principles
-
COBIT 5 Domains
-
COBIT 5 Process Reference Model
-
COBIT 5 Enablers
-
COBIT 5 Implementation Challenges
-
Real-Life Examples of COBIT 5 Success Stories
-
Conclusion
Historical Evolution of COBIT
The historical evolution of COBIT (Control Objectives for Information and Related Technologies) is a fascinating journey that showcases its development from a simple set of IT control objectives into a globally recognized framework for IT governance and management. Let's take a closer look at the key milestones in the history of COBIT:
COBIT 1.0 (1996): COBIT was initially introduced by ISACA (Information Systems Audit and Control Association) in 1996 as a set of IT control objectives to help organizations manage their IT processes and risks. This first version provided a basic structure for IT governance.
COBIT 2.0 (1998): The framework was updated in 1998 as COBIT 2.0. This version included a more comprehensive set of control objectives, making it a valuable tool for IT audit and control professionals.
COBIT 3.0 (2000): In the year 2000, COBIT 3.0 was released with a significant expansion in scope. This version integrated IT governance and management practices, helping organizations align IT with business goals more effectively.
COBIT 4.0 (2005): COBIT 4.0 introduced the concept of domains, processes, and IT-related goals, making it more structured and easier to apply in organizations. It was a pivotal step toward broader acceptance.
COBIT 4.1 (2007): This version, released in 2007, brought some refinements and updates to COBIT 4.0, making it more practical for implementation in real-world scenarios.
COBIT 5.0 Updates (2019): In 2019, COBIT was updated to further align with the evolving IT landscape and address contemporary challenges. This update included guidance on digital transformation and emerging technologies.
The historical evolution of COBIT reflects the changing landscape of IT governance, from a focus on control objectives to a comprehensive framework for aligning IT with business strategy, managing risks, and achieving operational excellence.
COBIT 5 Framework Components
The COBIT 5 framework consists of several key components, each of which plays a crucial role in helping organizations govern and manage their information and technology effectively. Understanding these components is essential for implementing COBIT 5 successfully. Here are the main components of the COBIT 5 framework:
Principles:
Meeting Stakeholder Needs: The first principle of COBIT 5 emphasizes the importance of aligning IT with the needs and expectations of stakeholders, whether they are internal or external to the organization.
Applying a Single Integrated Framework: COBIT 5 promotes the use of a single integrated framework to harmonize and simplify the governance of IT.
Enablers:
Processes: COBIT 5 defines a set of governance and management processes that help organizations achieve their objectives. These processes cover areas such as risk management, resource management, and performance management.
Principles, Policies, and Frameworks: These enablers provide the foundation for governance and management. They include the principles mentioned earlier, as well as policies, standards, and guidelines.
Information: Information is a key enabler, and COBIT 5 provides guidance on managing and optimizing the use of information in decision-making processes.
Services, Infrastructure, and Applications: These enablers relate to the physical and logical resources required to deliver IT services.
Governance and Management Processes:
COBIT 5 defines a comprehensive set of governance and management processes that organizations can use to align their IT with business goals, manage risks, and deliver value. Some of the processes include:
Evaluate, Direct, and Monitor (EDM) processes: These processes are primarily related to governance activities.
Align, Plan, and Organize (APO) processes: These processes focus on strategic planning and organizational structure.
Monitor, Evaluate, and Assess (MEA) processes: These processes assess the effectiveness of governance and management.
COBIT 5 Framework Model:
The COBIT 5 framework model provides a graphical representation of the principles, enablers, and processes, helping organizations visualize how they interact and support the achievement of objectives.
These components work together to provide a structured and holistic approach to IT governance and management. COBIT 5's principles guide decision-making, the enablers provide the resources and tools, and the governance and management processes offer a practical roadmap for implementation. By leveraging these components effectively, organizations can improve their IT practices, mitigate risks, and deliver value to stakeholders
Key Concepts in COBIT 5
COBIT 5, a comprehensive framework for governing and managing enterprise IT, is built upon several key concepts that are fundamental to understanding and implementing the framework effectively. Here are the key concepts in COBIT 5:
Governance and Management: COBIT 5 distinguishes between governance and management. Governance is primarily concerned with decision-making and ensuring that IT aligns with business goals. Management, on the other hand, involves the execution of those decisions and the day-to-day operation of IT processes.
End-to-End Coverage: COBIT 5 advocates for a holistic approach to IT governance, covering all aspects of the enterprise. It's not limited to specific processes or departments; rather, it spans the entire organization.
Framework for the Governance and Management of Enterprise IT: COBIT 5 provides a structured framework that encompasses IT governance and management practices. This framework offers a systematic approach to achieving organizational goals.
Enabler: Enablers in COBIT 5 are the factors that facilitate or support the implementation of governance and management. These include processes, principles, policies, organizational structures, culture, ethics, and behavior, among others.
Principles: COBIT 5 is guided by seven key principles:
Meeting Stakeholder Needs
Covering the Enterprise End-to-End
Separating Governance from Management
Tailoring to the Enterprise
Implementing a Governance System
Domains: COBIT 5 defines four domains, each encompassing a set of processes and activities:
Lifecycle Approach: COBIT 5 advocates for a lifecycle approach to IT governance and management, emphasizing that governance and management are continuous and cyclical processes rather than one-time events.
Information Governance: Information is a critical asset in IT governance, and COBIT 5 underscores the importance of effectively managing and using information in decision-making processes.
Understanding these key concepts in COBIT 5 is essential for organizations looking to enhance their IT governance and management practices. These concepts provide the foundation for implementing the framework and aligning IT with business objectives while meeting the needs of various stakeholders.
Benefits of Implementing COBIT 5 Foundation
Implementing COBIT 5 Foundation can bring a wide range of benefits to organizations. Here are some of the key advantages of adopting the COBIT 5 framework for IT governance and management:
Enhanced IT Governance: COBIT 5 provides a structured and holistic approach to IT governance, helping organizations make informed decisions and align IT strategies with business objectives. This results in more effective governance practices.
Improved Risk Management: COBIT 5 offers guidelines and practices for identifying, assessing, and managing IT-related risks. Implementing COBIT 5 can enhance an organization's ability to mitigate and respond to risks effectively.
Alignment with Stakeholder Needs: COBIT 5 emphasizes the importance of meeting the needs and expectations of stakeholders. By aligning IT activities with stakeholder requirements, organizations can enhance their reputation and relationships.
Increased Efficiency and Effectiveness: COBIT 5 provides a clear framework for organizing and optimizing IT processes. This leads to increased efficiency in IT operations and the delivery of services, ultimately resulting in cost savings.
Better Compliance: COBIT 5 includes guidelines for ensuring regulatory compliance and adherence to industry standards. Implementing COBIT 5 can help organizations avoid non-compliance issues and associated penalties.
Optimized Resource Management: COBIT 5 enables organizations to manage IT resources efficiently, including people, technology, and information. This ensures that resources are used effectively to achieve business goals.
Enhanced Decision-Making: COBIT 5 offers a structured framework for decision-making, promoting evidence-based choices. This leads to better decision quality and more favorable outcomes.
Continuous Improvement: COBIT 5 promotes a culture of continual improvement in IT governance and management. Organizations can adapt to changing circumstances and stay agile in the face of evolving technology and business needs.
Mitigation of IT-related Failures: By following COBIT 5's best practices, organizations can reduce the likelihood of IT-related failures, such as system outages or security breaches.
In summary, implementing COBIT 5 Foundation offers organizations a structured and comprehensive approach to IT governance and management. It not only helps align IT with business goals but also results in better risk management, stakeholder satisfaction, and overall organizational performance.
COBIT 5 Principles
COBIT 5 is built upon seven key principles, which provide the foundation for effective IT governance and management. Here are five of those principles:
Meeting Stakeholder Needs: The first principle emphasizes the importance of aligning IT with the needs and expectations of stakeholders, both internal and external. Organizations should prioritize understanding and addressing the unique requirements of these stakeholders to ensure their satisfaction and support.
Covering the Enterprise End-to-End: This principle advocates for a holistic approach to IT governance and management. It highlights the need to consider all aspects of the enterprise, from strategy and planning to daily operations, to ensure that IT aligns with the entire organization.
Applying a Single Integrated Framework: COBIT 5 promotes the use of a single, integrated framework for IT governance and management. By applying a unified framework, organizations can avoid duplication, inconsistencies, and confusion, making IT governance more efficient and effective.
Enabling a Holistic Approach: This principle underscores the importance of adopting a comprehensive and integrated approach to IT governance. Organizations should consider the full spectrum of factors, including processes, culture, organizational structures, and information, to achieve effective governance and management.
These principles serve as guiding tenets for organizations looking to establish effective IT governance and management practices using the COBIT 5 framework. They provide a strategic and philosophical basis for decision-making and implementation, helping organizations meet their objectives and deliver value to stakeholders.
COBIT 5 Domains
COBIT 5 organizes its guidance and processes into four primary domains, each of which represents a distinct area of IT governance and management. These domains are designed to help organizations address various aspects of IT effectively. The four domains in COBIT 5 are as follows:
Governance (EDM - Evaluate, Direct, and Monitor): The Governance domain focuses on the high-level, strategic aspects of IT governance. It is responsible for ensuring that stakeholder needs and expectations are met, and that the enterprise's strategic objectives are aligned with IT. This domain includes processes related to evaluating the current state of IT, directing IT to achieve its goals, and monitoring IT performance. Key processes within this domain include:
Evaluate, Direct, and Monitor (EDM)
Ensure Governance Framework Setting and Maintenance
Ensure Stakeholder Value Delivery
Ensure Performance Optimization
Management (APO - Align, Plan, and Organize, BAI - Build, Acquire, and Implement, DSS - Deliver, Service, and Support): The Management domain encompasses the processes that support the actual planning, implementation, and operation of IT within the organization. It ensures that IT resources are organized and deployed effectively. The Management domain is divided into three subdomains:
Align, Plan, and Organize (APO): This subdomain is responsible for aligning IT with the organization's strategic objectives and planning IT activities. Key processes include strategic planning, portfolio management, and IT budgeting.
Build, Acquire, and Implement (BAI): This subdomain covers the processes related to developing, acquiring, and implementing IT solutions and services. It includes processes like project management, system development, and IT procurement.
Information (MEA - Monitor, Evaluate, and Assess): The Information domain is responsible for ensuring the effective management of information as an asset. It involves processes for monitoring and assessing the quality and security of information. Key processes within this domain include:
Monitor, Evaluate, and Assess (MEA)
Ensure Stakeholder Value Delivery
Ensure Risk Optimization
Supporting Processes (APO - Align, Plan, and Organize, BAI - Build, Acquire, and Implement, DSS - Deliver, Service, and Support, MEA - Monitor, Evaluate, and Assess): These processes are common to multiple domains and provide support for the primary processes in Governance, Management, and Information. They are not standalone domains but are essential for the smooth operation of IT governance and management. These supporting processes include areas like compliance, human resources, and knowledge management.
These four domains, along with their respective processes, help organizations implement comprehensive IT governance and management practices using the COBIT 5 framework. Each domain addresses specific aspects of IT, ensuring that IT aligns with business goals, delivers value, and is governed effectively.
COBIT 5 Process Reference Model
The COBIT 5 Process Reference Model is a core component of the COBIT 5 framework. It provides a structured and comprehensive framework for understanding and implementing IT governance and management processes within an organization. The model is designed to be flexible and scalable, allowing organizations to tailor it to their specific needs and requirements. Here's an overview of the COBIT 5 Process Reference Model:
Processes: The model is organized into a set of processes that cover various aspects of IT governance and management. These processes are divided into five domains: Evaluate, Direct, and Monitor (EDM); Align, Plan, and Organize (APO); Build, Acquire, and Implement (BAI); Deliver, Service, and Support (DSS); and Monitor, Evaluate, and Assess (MEA).
Processes and Activities: Within each domain, the COBIT 5 Process Reference Model defines specific processes and associated activities. These activities provide detailed guidance on how to implement and execute each process effectively.
Inputs and Outputs: The model also specifies the inputs and outputs of each process, helping organizations understand what information, resources, and deliverables are required to execute a process and what is generated as a result.
Responsibilities: The model identifies the roles and responsibilities associated with each process, ensuring that organizations have clear lines of accountability.
Interactions: It illustrates how processes within different domains interact with each other. This promotes a holistic and integrated approach to IT governance and management.
Maturity and Capability: COBIT 5 includes maturity and capability models to assess the maturity of an organization's processes and its capability to manage them effectively.
The COBIT 5 Process Reference Model serves as a practical tool for organizations to assess, plan, and improve their IT governance and management practices. It promotes transparency, alignment with business objectives, and the continuous improvement of IT processes, ultimately leading to better governance, risk management, and value delivery.
COBIT 5 Enablers
COBIT 5 emphasizes the importance of enablers as factors that support effective IT governance and management within an organization. These enablers provide the resources, tools, and structures necessary to achieve organizational objectives. COBIT 5 identifies seven primary categories of enablers that work together to facilitate the implementation of IT governance and management practices. Here are the COBIT 5 enablers:
Processes: COBIT 5 identifies a set of IT governance and management processes that are essential for aligning IT with business goals and objectives. These processes provide the practical steps and activities for governing and managing IT effectively.
Organizational Structures: Organizational structures and roles are enablers that define how responsibilities are distributed and delegated within the organization. They include roles, responsibilities, and reporting lines, ensuring clear accountability.
Information: Information is a critical enabler as it provides the data and knowledge necessary for making informed decisions. Effective information management, data quality, and information security are important aspects of this enabler.
Services, Infrastructure, and Applications: This enabler includes the physical and logical resources required to support IT services and applications. It covers areas such as infrastructure, applications, and IT service management tools.
People, Skills, and Competencies: People are at the heart of IT governance and management. This enabler focuses on ensuring that the organization has the right people with the right skills and competencies to support IT activities effectively.
These seven enablers collectively provide the framework and resources required for organizations to align their IT with business goals, manage risks, deliver value, and govern IT effectively. COBIT 5 emphasizes that these enablers are interrelated, and the successful implementation of IT governance and management practices requires a harmonious integration of all enablers. The specific application of these enablers will vary based on an organization's unique context and objectives.
COBIT 5 Implementation Challenges
Implementing COBIT 5 in an organization can bring numerous benefits, but it also presents several challenges. These challenges can vary depending on the organization's size, industry, and existing IT governance practices. Here are some common challenges associated with COBIT 5 implementation:
Resistance to Change: One of the most significant challenges is getting buy-in from all levels of the organization. Employees and management may be resistant to adopting new governance and management practices.
Resource Allocation: Implementing COBIT 5 requires dedicating time, people, and financial resources. Finding the necessary resources can be a challenge, especially for smaller organizations with limited budgets.
Skills and Training: Implementing COBIT 5 may require training and skill development for employees. Ensuring that staff has the necessary competencies can be a challenge, especially in rapidly changing IT environments.
Customization: COBIT 5 is a framework, and it needs to be tailored to the specific needs and context of each organization. Finding the right balance between customization and adherence to COBIT 5's principles can be challenging.
Measuring Success: Defining and measuring Key Performance Indicators (KPIs) and Critical Success Factors (CSFs) to evaluate the success of COBIT 5 implementation can be challenging. Identifying meaningful metrics and benchmarks for improvement is essential.
Top-Down vs. Bottom-Up Approach: Deciding whether to implement COBIT 5 top-down (starting with governance) or bottom-up (starting with management processes) is a strategic challenge that organizations must address.
Sustainability: Maintaining the momentum and ensuring that COBIT 5 practices continue to be effective over the long term can be challenging. Often, organizations face the risk of reverting to old practices after initial enthusiasm wanes.
Risk Management: While COBIT 5 provides guidance on risk management, identifying and addressing potential risks associated with implementation itself is a challenge.
To overcome these challenges, organizations should develop a well-defined implementation plan, engage with stakeholders, provide adequate training and support, and continuously monitor and adapt their COBIT 5 implementation as needed. It's also essential to recognize that COBIT 5 implementation is an ongoing process that requires commitment and adaptability to achieve its intended benefits.
Real-Life Examples of COBIT 5 Success Stories
COBIT 5 has been successfully implemented in numerous organizations across various industries, helping them achieve their IT governance and management objectives. Here are some real-life examples of organizations that have experienced success with COBIT 5:
ExxonMobil: ExxonMobil, one of the world's largest multinational oil and gas corporations, used COBIT 5 to enhance its IT governance and risk management. They successfully implemented COBIT 5's principles and processes to align IT with business objectives and improve risk mitigation strategies.
Dubai Customs: Dubai Customs, a government agency responsible for facilitating trade in the Emirate of Dubai, implemented COBIT 5 to enhance its IT service management practices. They used COBIT 5 to streamline IT processes, resulting in improved service delivery and customer satisfaction.
Walmart: Walmart, a global retail giant, leveraged COBIT 5 to optimize IT governance and management processes across its vast network of stores and data centers. COBIT 5 helped Walmart improve the efficiency of IT operations, reduce risks, and enhance customer experiences through effective supply chain management and data security.
US Department of Defense (DoD): The US DoD adopted COBIT 5 as part of its approach to IT governance and cybersecurity. COBIT 5 helped the DoD establish a standardized framework for managing and securing its IT assets, ultimately improving its information security posture.
AXA Group: AXA, a multinational insurance company, implemented COBIT 5 to align IT processes with business needs. By using COBIT 5, AXA improved risk management, IT performance, and the overall quality of IT services.
Government of Malaysia: The Malaysian government adopted COBIT 5 to enhance IT governance practices across various government agencies. This initiative has led to improved transparency, accountability, and effectiveness in IT management.
University of Waterloo: The University of Waterloo in Canada used COBIT 5 to optimize its IT governance practices. The implementation of COBIT 5 led to more effective IT service management, streamlined IT processes, and improved alignment with academic and administrative goals.
South African Revenue Service (SARS): SARS, the tax collection agency in South Africa, adopted COBIT 5 to enhance its IT governance and risk management practices. The use of COBIT 5 has resulted in better control over taxpayer data and improved compliance with tax regulations.
Vattenfall: Vattenfall, a Swedish multinational energy company, implemented COBIT 5 to enhance its IT governance and cybersecurity practices. COBIT 5 helped Vattenfall align its IT strategies with business objectives and strengthen its defenses against cyber threats.
Central Bank of Nigeria: The Central Bank of Nigeria utilized COBIT 5 to improve its IT governance practices and enhance the security and integrity of the country's financial systems. COBIT 5 has played a critical role in ensuring the stability and resilience of Nigeria's financial infrastructure.
These examples illustrate the versatility and effectiveness of COBIT 5 across various industries and sectors. Organizations have leveraged COBIT 5 to align IT with their strategic goals, enhance IT governance, manage risks, and deliver better services to their stakeholders. These success stories showcase the framework's adaptability and its ability to drive positive outcomes in diverse organizational contexts
Conclusion
In conclusion, COBIT 5 is a comprehensive and widely recognized framework for IT governance and management that provides organizations with the tools and guidance they need to align their IT functions with business objectives, manage risks, and deliver value to stakeholders. It is built on a foundation of key principles, a well-structured process reference model, and seven enablers that collectively support effective governance and management.
As technology continues to play a pivotal role in the success of organizations, COBIT 5 remains a valuable framework for those seeking a structured and systematic approach to IT governance and management. By adopting and customizing COBIT 5 to their specific needs, organizations can navigate the complexities of the digital landscape and ensure that their IT functions are aligned with their broader business strategies.
The Benefits of Earning a CCNA Certification for Your Networking Career
In the fast-paced world of information technology, staying ahead in the networking industry is an ever-evolving challenge. Networking professionals must continually adapt to emerging technologies, understand complex systems, and demonstrate their skills to prospective employers. Among the various certifications available, the Cisco Certified Network Associate (CCNA) certification stands out as a prestigious and highly regarded credential that opens doors to numerous opportunities in the field.
This article explores the significant benefits of earning a CCNA certification for your networking career. Whether you are a seasoned IT professional looking to advance your skills or someone considering a career in networking, understanding the advantages of CCNA can help you make informed decisions about your professional development. From enhanced career prospects and higher earning potential to industry recognition and skill development, the CCNA certification offers a multitude of rewards that can positively impact your networking journey. In the pages that follow, we will delve into these benefits and illustrate how CCNA can be a pivotal asset in achieving your career aspirations.
Table of contents
-
Enhanced Career Opportunities: How CCNA Opens Doors
-
Higher Earning Potential: The Financial Benefits of CCNA Certification
-
Industry Recognition: Why Employers Value CCNA Certified Professionals
-
Skill Development: What You'll Learn During CCNA Training
-
A Foundation for Advanced Certifications: How CCNA Paves the Way
-
Global Reach: The Portability of CCNA Certification
-
Staying Current in Networking: The Importance of CCNA in a Dynamic Field
-
Job Security: How CCNA Certification Mitigates Career Risks
-
Networking Community and Support: CCNA's Role in Building Connections
-
Real-World Application: Success Stories of CCNA Professionals
-
Conclusion
Enhanced Career Opportunities: How CCNA Opens Doors
In the ever-evolving realm of networking, professionals are constantly seeking ways to enhance their careers and remain competitive. The Cisco Certified Network Associate (CCNA) certification has emerged as a game-changer in this regard, offering a clear pathway to enhanced career opportunities and professional growth.
Versatility in Networking Roles
CCNA certification is designed to equip professionals with a broad spectrum of networking skills. Whether you are interested in network administration, security, or wireless networking, CCNA provides a foundational understanding of these domains. This versatility makes CCNA holders attractive candidates for a wide range of networking roles, from network engineers to security specialists.
Immediate Recognition
When your resume bears the CCNA logo, it serves as an instant indicator of your networking proficiency to potential employers. Many organizations value CCNA certification as a prerequisite for hiring, as it validates your knowledge and commitment to the field. This immediate recognition can significantly reduce the time it takes to land your dream job.
Entry into Cisco's Ecosystem
Cisco is a global leader in networking technologies, and CCNA is your entry ticket to their ecosystem. Gaining a CCNA certification allows you to interact with Cisco's products and solutions more effectively. This deepens your understanding of their offerings, making you a more valuable asset to any organization that relies on Cisco networking equipment.
Better Networking Skills and Problem-Solving Abilities
The CCNA curriculum focuses on both theoretical knowledge and hands-on skills. As a CCNA candidate, you'll learn how to configure, troubleshoot, and manage network devices effectively. This not only enhances your networking expertise but also hones your problem-solving abilities, which are highly valued in IT roles.
Career Advancement
For networking professionals looking to climb the career ladder, CCNA certification is an invaluable stepping stone. Many companies prioritize employees with CCNA credentials when considering candidates for leadership and managerial positions. The knowledge and skills acquired through CCNA training can help you stand out and qualify for promotions.
Global Opportunities
Networking is a universal language in the IT world, and CCNA certification is recognized internationally. Whether you aspire to work in your home country or abroad, CCNA opens doors to a wealth of global career opportunities. It's a passport to working in diverse and exciting environments.
Higher Earning Potential: The Financial Benefits of CCNA Certification
In today's competitive job market, financial rewards play a significant role in career decisions. For networking professionals, the Cisco Certified Network Associate (CCNA) certification not only opens doors to exciting opportunities but also brings tangible financial benefits. In this section, we'll delve into how CCNA can lead to a substantial increase in earning potential.
Competitive Edge in Salary Negotiations
CCNA certification immediately sets you apart from non-certified peers. Employers often recognize the commitment, knowledge, and skills required to earn the CCNA credential. As a result, CCNA-certified professionals are in a better position to negotiate higher starting salaries, more significant pay raises, and more lucrative job offers.
Increased Starting Salaries
For entry-level positions, CCNA certification can significantly boost your starting salary. Employers are willing to pay more for professionals who have proven their expertise and commitment to the networking field through certification. This premium can help you secure a higher income from the outset of your career.
Expanded Career Options
CCNA certification opens the door to a wider range of career options, many of which come with higher earning potential. Specializations like network security, data center networking, and collaboration technologies are in high demand and often offer more competitive salaries than general networking roles.
Opportunities for Consulting and Contract Work
CCNA-certified professionals may have the option to work as network consultants or on a contract basis. These roles often come with higher hourly rates or project-based pay, allowing you to maximize your earnings.
Industry Recognition and Rewards
Several organizations and industries offer bonuses or recognition for employees who earn certifications such as CCNA. Government agencies, defense contractors, and technology companies may offer financial incentives or recognition for achieving and maintaining certifications.
In summary, CCNA certification not only enriches your knowledge and skills but also significantly enhances your financial prospects in the networking field. Whether you're just starting your career or looking to accelerate your earning potential, CCNA is a valuable investment that can lead to higher starting salaries, faster salary progression, job security, and access to a broader range of well-paying career opportunities. In the next sections, we'll explore how CCNA certification brings industry recognition and fosters skill development, making it a comprehensive asset for your networking career.
Industry Recognition: Why Employers Value CCNA Certified Professionals
In the competitive world of networking and information technology, industry recognition plays a crucial role in determining an individual's career trajectory. The Cisco Certified Network Associate (CCNA) certification is highly esteemed by employers for a multitude of reasons. In this section, we'll explore why CCNA-certified professionals are highly sought after in the job market.
Validation of Networking Skills
CCNA certification serves as tangible proof of your networking knowledge and skills. Employers value this validation because it minimizes the risk associated with hiring someone who may lack the essential competencies needed for the job. CCNA-certified professionals have demonstrated their ability to design, configure, troubleshoot, and manage network systems, making them a valuable asset to any organization.
Cisco's Global Reputation
Cisco, the organization behind CCNA certification, is a global leader in networking technology. Its products and solutions are widely used in businesses worldwide. Therefore, employers place immense trust in Cisco's certifications, including CCNA. Holding a CCNA certification not only demonstrates your knowledge but also aligns you with a globally recognized and respected brand in the networking industry.
Adaptability and Staying Current
CCNA certification requires candidates to stay updated with the latest networking technologies. Employers appreciate CCNA-certified professionals' adaptability and commitment to ongoing learning. In the rapidly evolving field of networking, the ability to stay current is highly valuable, as it ensures that organizations can keep pace with technological advancements.
Standardized Skillset
CCNA certification ensures a standardized skillset among professionals. This consistency is vital for organizations, as it allows them to establish a baseline of expectations for their networking staff. It simplifies the recruitment process and provides assurance that CCNA-certified professionals possess a certain level of proficiency.
Enhanced Troubleshooting Abilities
CCNA certification places a strong emphasis on troubleshooting network issues. This skill is invaluable in maintaining network uptime and resolving problems swiftly. Employers appreciate CCNA-certified professionals' ability to identify and address network challenges effectively, which can prevent costly downtime.
Reduced Training Costs
Hiring CCNA-certified professionals can save organizations money on training and onboarding. New hires who already possess the certification require less investment in additional training, which is particularly appealing to businesses with budget constraints.
CCNA-certified individuals are seen as standardized, efficient, and cost-effective contributors to their organizations. In the subsequent sections, we will explore how CCNA certification contributes to skill development, career advancement, and even international opportunities in the world of networking.
Skill Development: What You'll Learn During CCNA Training
Earning the Cisco Certified Network Associate (CCNA) certification is not just about acquiring a piece of paper for your resume; it's about developing a comprehensive set of skills that are highly valued in the networking industry. In this section, we'll explore the key skills you'll acquire during CCNA training.
Network Fundamentals
CCNA training starts with the fundamentals of networking, covering topics such as the OSI model, IP addressing, subnets, and basic network protocols. This foundational knowledge is essential for understanding more advanced networking concepts.
Network Security
CCNA training emphasizes network security, teaching you how to identify and mitigate security threats. You'll learn about access control, firewalls, and security best practices to protect network infrastructure.
Wireless Networking
Wireless technology is integral to modern networks. CCNA training covers wireless networking concepts, including how to configure and secure wireless access points and controllers.
Network Troubleshooting
One of the most valuable skills you'll develop is network troubleshooting. You'll learn how to identify and resolve common network issues efficiently, minimizing downtime and ensuring network reliability.
WAN Technologies
Wide Area Networks (WANs) are crucial for connecting remote offices and ensuring data transfer between locations. CCNA training covers WAN technologies like Frame Relay, PPP, and VPNs.
Network Design
CCNA explores network design principles, teaching you how to plan and design network architectures that meet specific business requirements.
IP Telephony
In CCNA Voice or Collaboration tracks, you'll gain skills related to Voice over IP (VoIP) technologies. This includes configuring and managing IP telephony systems.
Data Center Networking
For those pursuing the Data Center track, you'll develop expertise in data center networking, including technologies like virtualization and storage.
Automation and Programmability
CCNA has evolved to include topics related to automation and programmability, introducing you to network automation and scripting. These skills are increasingly valuable in modern network management.
Real-World Lab Experience
CCNA training often involves hands-on lab exercises where you'll configure and troubleshoot network devices. This practical experience is invaluable for applying your knowledge in real-world scenarios.
A Foundation for Advanced Certifications: How CCNA Paves the Way
Earning the Cisco Certified Network Associate (CCNA) certification isn't just an endpoint; it serves as a stepping stone for networking professionals to explore more advanced certifications. In this section, we'll discuss how CCNA provides a strong foundation and paves the way for pursuing higher-level certifications.
In-Depth Networking Knowledge
CCNA covers a broad range of networking concepts, ensuring that candidates have a solid understanding of the fundamentals. This knowledge is essential for tackling more advanced certifications. Without a strong foundation, pursuing higher-level certifications can be significantly more challenging.
Prerequisite for Advanced Certifications
Many advanced Cisco certifications require CCNA as a prerequisite. For example, to pursue the Cisco Certified Network Professional (CCNP) certification, you typically need to have a valid CCNA certification. CCNP certifications focus on more complex networking topics, such as advanced routing and switching, wireless, or security. CCNA ensures that candidates are prepared for the in-depth knowledge required at the professional level.
Seamless Progression
The content covered in CCNA provides a logical progression to advanced certifications. CCNA introduces key concepts in routing and switching, network security, and other fundamental areas. This foundational knowledge aligns well with the content covered in CCNP and other Cisco certifications.
Enhanced Career Opportunities
Having a CCNA certification on your resume can open doors to better job opportunities. Once you've earned your CCNA, you can apply for positions that require CCNA certification, gain more experience, and work towards your next certification. Advanced certifications can lead to even more lucrative roles and further career advancement.
Increased Technical Proficiency
CCNA offers hands-on experience with networking devices and technologies. This practical experience not only prepares you for the CCNA exam but also ensures that you are technically proficient. This proficiency will be valuable when pursuing more advanced certifications, where the expectations for hands-on skills are higher.
Recognition in the Networking Community
The CCNA certification is well-recognized in the networking community. Earning it demonstrates your commitment to the field and your readiness to take on more challenging certifications. Networking professionals who hold CCNA certifications are often well-regarded by peers and employers.
Preparation for Specializations
Cisco offers various specialization certifications, such as CCNA Security, CCNA Collaboration, and CCNA Data Center. These specializations allow you to focus on areas that interest you most. The foundational knowledge provided by CCNA is crucial for building expertise in these specialized fields.
Global Reach: The Portability of CCNA Certification
One of the distinct advantages of earning the Cisco Certified Network Associate (CCNA) certification is its global recognition and portability. CCNA is not confined to a specific geographical region or job market; it offers networking professionals the opportunity to work and thrive on a worldwide scale. In this section, we'll explore the portability of CCNA certification and how it opens doors to international opportunities.
Universal Networking Knowledge
CCNA covers fundamental networking concepts that apply universally, regardless of geographic location. Networking protocols, routing and switching principles, and security best practices are applicable worldwide. This means your CCNA knowledge is relevant wherever networking infrastructure exists.
Cisco's International Presence
Cisco, the organization behind CCNA certification, is a global technology leader with a presence in almost every corner of the world. This international footprint ensures that CCNA is recognized and respected globally, and Cisco's products and solutions are used in diverse international markets.
Industry Demand Worldwide
The demand for skilled networking professionals is not limited to a single region; it's a global need. Organizations around the world require network administrators, engineers, and technicians who can maintain and optimize their network infrastructure. Having a CCNA certification makes you an attractive candidate in any job market.
Career Mobility
CCNA certification provides networking professionals with the flexibility to move and work in different countries and regions. Many multinational companies value CCNA certification when hiring for their global IT teams. It can open doors to exciting international opportunities, allowing you to gain experience in various environments and cultures.
International Certifications
In addition to the standard CCNA certification, Cisco offers specialized CCNA tracks, such as CCNA Security, CCNA Collaboration, and CCNA Data Center. These tracks are valuable for professionals interested in specific fields and can enhance your international employability by focusing on in-demand areas.
Networking Community Connections
The CCNA community is vast and diverse, with professionals from all over the world. Engaging with this community can lead to international networking opportunities, collaboration, and exposure to different industry practices and trends.
Consulting and Contract Work
CCNA-certified professionals may have the option to work as network consultants or on a contract basis. These roles often come with flexibility and opportunities to work on international projects, further expanding your horizons.
Its universal networking knowledge, recognition by Cisco, and high demand in the IT industry make CCNA professionals sought after worldwide. Whether you aspire to work in your home country, gain international experience, or explore career opportunities in various regions, CCNA certification equips you with the skills and recognition needed for success in the global networking arena.
Staying Current in Networking: The Importance of CCNA in a Dynamic Field
In the ever-evolving world of networking, it's crucial for professionals to stay current with the latest technologies and industry trends. The Cisco Certified Network Associate (CCNA) certification is not just a one-time achievement; it plays a pivotal role in helping networking experts keep pace with the dynamic nature of their field. In this section, we'll discuss why CCNA is essential for professionals looking to stay current in networking.
Ongoing Skill Development
CCNA certification requires individuals to acquire a broad range of foundational skills. However, these skills are not stagnant; they form the building blocks for more advanced networking knowledge. CCNA serves as the first step in a lifelong journey of skill development, encouraging professionals to continue learning and staying up-to-date with the latest advancements.
Regular Certification Updates
Cisco periodically updates its certification exams to ensure they remain relevant in an ever-changing industry. CCNA-certified professionals are encouraged to recertify and take the latest versions of the exam to maintain the currency of their knowledge. This process reinforces the importance of staying current in networking.
Exposure to Emerging Technologies
CCNA training introduces candidates to emerging technologies and trends in networking, such as cloud computing, software-defined networking (SDN), and automation. This exposure not only prepares professionals for current challenges but also equips them to adapt to future developments in the field.
Foundation for Advanced Certifications
CCNA serves as a foundational certification for more advanced Cisco certifications, such as the Cisco Certified Network Professional (CCNP) and Cisco Certified Internetwork Expert (CCIE). These advanced certifications delve deeper into complex networking topics and require professionals to continually update their knowledge and skills.
Troubleshooting and Adaptability
One of the primary skills emphasized in CCNA training is network troubleshooting. This skill is invaluable in a dynamic field where new challenges and issues regularly arise. CCNA-certified professionals are adept at identifying and resolving network problems, which is critical for maintaining network reliability.
Security Awareness
Security is an evergreen concern in networking. CCNA training covers network security principles, but professionals must continuously stay informed about evolving security threats and solutions to protect network infrastructure effectively.
Industry Engagement
Cisco's extensive networking community and resources provide opportunities to engage with professionals and experts from around the world. Networking conferences, webinars, and forums keep CCNA-certified professionals connected to the latest industry insights and best practices.
Job Relevance
Staying current in networking ensures that your skills remain relevant to the job market. As new technologies and practices emerge, employers seek professionals who can apply these innovations to improve network performance, security, and efficiency.
the dynamic nature of networking demands continuous learning and adaptation. CCNA certification serves as a reminder that networking professionals must remain vigilant, embrace ongoing skill development, and engage with emerging technologies to stay current in their field. Whether through recertification, advanced certifications, or active participation in the networking community, CCNA paves the way for a career that thrives in a constantly evolving networking landscape.
Job Security: How CCNA Certification Mitigates Career Risks
In an ever-changing job market, job security is a critical concern for professionals in any field. Cisco Certified Network Associate (CCNA) certification can significantly mitigate career risks and provide a level of job security that is highly valuable. In this section, we'll discuss how CCNA certification contributes to job security in the networking industry.
Industry Demand for Networking Professionals
The demand for skilled networking professionals is a constant in the IT industry. Networks are the backbone of businesses, and their proper functioning is essential. As a result, organizations consistently seek professionals with networking expertise, creating a continuous demand for CCNA-certified individuals.
Demonstrated Skills and Knowledge
CCNA certification is a clear demonstration of your networking skills and knowledge. Employers prefer candidates with certifications because they provide tangible evidence of competency. CCNA-certified professionals are more likely to be retained, promoted, and entrusted with critical network responsibilities.
Ongoing Skill Development
CCNA requires professionals to continue developing their skills to stay current. This continuous learning process ensures that CCNA-certified individuals remain valuable assets to their employers, adapting to new technologies and maintaining network efficiency and security.
Troubleshooting Abilities
CCNA training emphasizes troubleshooting skills, equipping professionals with the ability to identify and resolve network issues quickly. This skill is invaluable in ensuring network reliability and reducing costly downtime.
Network Security Expertise
Security is a top priority for organizations, and CCNA certification includes essential network security knowledge. CCNA-certified professionals can help protect network infrastructure from security threats, which is a crucial aspect of job security.
Recognition by Employers
Many employers specifically seek CCNA-certified professionals for networking roles. Having the certification on your resume often increases your chances of being selected for interviews and job offers.
Career Advancement Opportunities
CCNA certification is a solid foundation for career advancement. It opens doors to roles with more responsibility, better compensation, and job stability. CCNA-certified professionals are often well-positioned to move up the career ladder.
Adaptability to Industry Changes
CCNA certification equips professionals with the adaptability needed to embrace industry changes. The networking field continually evolves with new technologies and practices. CCNA-certified individuals can easily adapt to these changes, mitigating the risk of becoming obsolete in their roles.
Strong Networking Community
The CCNA community is extensive and supportive. Engaging with this community can lead to networking opportunities, job referrals, and career advice, further enhancing job security.
Portfolio for Job Flexibility
A CCNA certification is transferable across different industries and geographic locations. This flexibility provides job security as it enables professionals to explore various career options and adapt to changes in personal circumstances or job markets.
Networking Community and Support: CCNA's Role in Building Connections
The world of networking is not just about cables and configurations; it's also about building connections with fellow professionals and experts. The Cisco Certified Network Associate (CCNA) certification extends beyond the technical aspects of networking; it fosters a sense of community and support that can significantly benefit networking professionals. In this section, we'll discuss how CCNA plays a role in building connections within the networking community.
CCNA Community Forums
Cisco provides official forums and online communities specifically for CCNA-certified professionals. These platforms are a space for individuals to ask questions, share insights, and seek advice from peers who have a similar background and expertise. They can be valuable sources of information and support.
Networking Events and Conferences
CCNA-certified professionals often participate in networking events and conferences. These gatherings provide opportunities to connect with fellow professionals, engage in discussions, and learn from experts in the field. Building relationships at such events can lead to new job opportunities and collaboration.
Online Study Groups
Many CCNA candidates form online study groups to prepare for the certification. These groups not only aid in exam preparation but also serve as a networking platform. Interacting with study partners can lead to long-lasting professional relationships.
Job Referrals and Recommendations
Being part of the CCNA community can lead to job referrals and recommendations. Networking professionals often hear about job openings or have colleagues in need of talent. Being connected to this network can make it easier to find new job opportunities.
Support in Exam Preparation
Preparing for the CCNA exam can be a challenging endeavor. Many CCNA candidates find support and motivation from the community. Connecting with others who are pursuing the same certification can provide encouragement and help you overcome obstacles.
Real-World Application: Success Stories of CCNA Professionals
The Cisco Certified Network Associate (CCNA) certification is more than just an academic achievement; it's a testament to practical networking skills and knowledge. In this section, we'll explore real-world success stories of CCNA professionals who have leveraged their certification to achieve remarkable career milestones and make a tangible impact in the field of networking.
Expertise in Network Troubleshooting
CCNA-certified professionals often excel in network troubleshooting, a skill they gain during their certification training. This expertise enables them to quickly identify and resolve network issues, reducing downtime and ensuring network reliability. As a result, their employers appreciate their ability to maintain network efficiency.
Network Security Specialists
CCNA Security specialization equips professionals with the knowledge and skills to handle network security. These CCNA-certified individuals often go on to become network security specialists, safeguarding their organizations' critical data from cyber threats.
Networking Entrepreneurship
Some CCNA professionals have leveraged their certification to start their own networking businesses. They provide services such as network design, installation, and maintenance to clients in need of networking solutions. The CCNA certification provides credibility and trust to their customers.
Specialized Career Paths
CCNA opens doors to specialized career paths, such as data center networking, collaboration technologies, and wireless networking. Professionals who pursue these specialized tracks often find themselves in high-demand roles that offer both financial rewards and job satisfaction.
Promotions in Multinational Companies
CCNA certification provides a strong foundation for working in multinational corporations. Success stories often include professionals who secure positions in global organizations, where they manage international networks and collaborate with teams across different countries.
Success in IT Management
Some CCNA professionals ascend to IT management positions, overseeing entire network infrastructures and leading teams of networking professionals. Their strong technical backgrounds, combined with leadership skills, make them valuable assets in management roles.
Building Resilient Networks
CCNA professionals are well-versed in building resilient and efficient network infrastructures. Success stories often involve individuals who design and manage networks for critical industries, such as healthcare or finance, where network reliability is paramount.
International Opportunities
CCNA certification's global recognition allows professionals to explore international career opportunities. Success stories may include individuals who land positions in different countries, gaining unique cultural experiences and expanding their professional horizons.
Conclusion
The Cisco Certified Network Associate (CCNA) certification is a transformative credential for networking professionals, offering a multitude of benefits and opportunities for those who pursue it. This article has explored the various facets of CCNA, from its role in enhancing career opportunities and increasing earning potential to its importance in maintaining job security and staying current in the ever-evolving field of networking.
Real-world success stories of CCNA professionals underscore the tangible impact that this certification has on careers, from career advancements to specialized roles, entrepreneurship, and international opportunities.
In sum, CCNA is a testament to the dedication and skills of networking professionals and serves as a versatile tool in their professional journey. It not only represents a strong foundation but also opens doors, enriches careers, and provides a network of support that transcends borders. As the networking industry continues to evolve, CCNA remains a constant in empowering professionals to navigate the ever-changing landscape with confidence and success.
Read More
In the fast-paced world of information technology, staying ahead in the networking industry is an ever-evolving challenge. Networking professionals must continually adapt to emerging technologies, understand complex systems, and demonstrate their skills to prospective employers. Among the various certifications available, the Cisco Certified Network Associate (CCNA) certification stands out as a prestigious and highly regarded credential that opens doors to numerous opportunities in the field.
This article explores the significant benefits of earning a CCNA certification for your networking career. Whether you are a seasoned IT professional looking to advance your skills or someone considering a career in networking, understanding the advantages of CCNA can help you make informed decisions about your professional development. From enhanced career prospects and higher earning potential to industry recognition and skill development, the CCNA certification offers a multitude of rewards that can positively impact your networking journey. In the pages that follow, we will delve into these benefits and illustrate how CCNA can be a pivotal asset in achieving your career aspirations.
Table of contents
-
Enhanced Career Opportunities: How CCNA Opens Doors
-
Higher Earning Potential: The Financial Benefits of CCNA Certification
-
Industry Recognition: Why Employers Value CCNA Certified Professionals
-
Skill Development: What You'll Learn During CCNA Training
-
A Foundation for Advanced Certifications: How CCNA Paves the Way
-
Global Reach: The Portability of CCNA Certification
-
Staying Current in Networking: The Importance of CCNA in a Dynamic Field
-
Job Security: How CCNA Certification Mitigates Career Risks
-
Networking Community and Support: CCNA's Role in Building Connections
-
Real-World Application: Success Stories of CCNA Professionals
-
Conclusion
Enhanced Career Opportunities: How CCNA Opens Doors
In the ever-evolving realm of networking, professionals are constantly seeking ways to enhance their careers and remain competitive. The Cisco Certified Network Associate (CCNA) certification has emerged as a game-changer in this regard, offering a clear pathway to enhanced career opportunities and professional growth.
Versatility in Networking Roles
CCNA certification is designed to equip professionals with a broad spectrum of networking skills. Whether you are interested in network administration, security, or wireless networking, CCNA provides a foundational understanding of these domains. This versatility makes CCNA holders attractive candidates for a wide range of networking roles, from network engineers to security specialists.
Immediate Recognition
When your resume bears the CCNA logo, it serves as an instant indicator of your networking proficiency to potential employers. Many organizations value CCNA certification as a prerequisite for hiring, as it validates your knowledge and commitment to the field. This immediate recognition can significantly reduce the time it takes to land your dream job.
Entry into Cisco's Ecosystem
Cisco is a global leader in networking technologies, and CCNA is your entry ticket to their ecosystem. Gaining a CCNA certification allows you to interact with Cisco's products and solutions more effectively. This deepens your understanding of their offerings, making you a more valuable asset to any organization that relies on Cisco networking equipment.
Better Networking Skills and Problem-Solving Abilities
The CCNA curriculum focuses on both theoretical knowledge and hands-on skills. As a CCNA candidate, you'll learn how to configure, troubleshoot, and manage network devices effectively. This not only enhances your networking expertise but also hones your problem-solving abilities, which are highly valued in IT roles.
Career Advancement
For networking professionals looking to climb the career ladder, CCNA certification is an invaluable stepping stone. Many companies prioritize employees with CCNA credentials when considering candidates for leadership and managerial positions. The knowledge and skills acquired through CCNA training can help you stand out and qualify for promotions.
Global Opportunities
Networking is a universal language in the IT world, and CCNA certification is recognized internationally. Whether you aspire to work in your home country or abroad, CCNA opens doors to a wealth of global career opportunities. It's a passport to working in diverse and exciting environments.
Higher Earning Potential: The Financial Benefits of CCNA Certification
In today's competitive job market, financial rewards play a significant role in career decisions. For networking professionals, the Cisco Certified Network Associate (CCNA) certification not only opens doors to exciting opportunities but also brings tangible financial benefits. In this section, we'll delve into how CCNA can lead to a substantial increase in earning potential.
Competitive Edge in Salary Negotiations
CCNA certification immediately sets you apart from non-certified peers. Employers often recognize the commitment, knowledge, and skills required to earn the CCNA credential. As a result, CCNA-certified professionals are in a better position to negotiate higher starting salaries, more significant pay raises, and more lucrative job offers.
Increased Starting Salaries
For entry-level positions, CCNA certification can significantly boost your starting salary. Employers are willing to pay more for professionals who have proven their expertise and commitment to the networking field through certification. This premium can help you secure a higher income from the outset of your career.
Expanded Career Options
CCNA certification opens the door to a wider range of career options, many of which come with higher earning potential. Specializations like network security, data center networking, and collaboration technologies are in high demand and often offer more competitive salaries than general networking roles.
Opportunities for Consulting and Contract Work
CCNA-certified professionals may have the option to work as network consultants or on a contract basis. These roles often come with higher hourly rates or project-based pay, allowing you to maximize your earnings.
Industry Recognition and Rewards
Several organizations and industries offer bonuses or recognition for employees who earn certifications such as CCNA. Government agencies, defense contractors, and technology companies may offer financial incentives or recognition for achieving and maintaining certifications.
In summary, CCNA certification not only enriches your knowledge and skills but also significantly enhances your financial prospects in the networking field. Whether you're just starting your career or looking to accelerate your earning potential, CCNA is a valuable investment that can lead to higher starting salaries, faster salary progression, job security, and access to a broader range of well-paying career opportunities. In the next sections, we'll explore how CCNA certification brings industry recognition and fosters skill development, making it a comprehensive asset for your networking career.
Industry Recognition: Why Employers Value CCNA Certified Professionals
In the competitive world of networking and information technology, industry recognition plays a crucial role in determining an individual's career trajectory. The Cisco Certified Network Associate (CCNA) certification is highly esteemed by employers for a multitude of reasons. In this section, we'll explore why CCNA-certified professionals are highly sought after in the job market.
Validation of Networking Skills
CCNA certification serves as tangible proof of your networking knowledge and skills. Employers value this validation because it minimizes the risk associated with hiring someone who may lack the essential competencies needed for the job. CCNA-certified professionals have demonstrated their ability to design, configure, troubleshoot, and manage network systems, making them a valuable asset to any organization.
Cisco's Global Reputation
Cisco, the organization behind CCNA certification, is a global leader in networking technology. Its products and solutions are widely used in businesses worldwide. Therefore, employers place immense trust in Cisco's certifications, including CCNA. Holding a CCNA certification not only demonstrates your knowledge but also aligns you with a globally recognized and respected brand in the networking industry.
Adaptability and Staying Current
CCNA certification requires candidates to stay updated with the latest networking technologies. Employers appreciate CCNA-certified professionals' adaptability and commitment to ongoing learning. In the rapidly evolving field of networking, the ability to stay current is highly valuable, as it ensures that organizations can keep pace with technological advancements.
Standardized Skillset
CCNA certification ensures a standardized skillset among professionals. This consistency is vital for organizations, as it allows them to establish a baseline of expectations for their networking staff. It simplifies the recruitment process and provides assurance that CCNA-certified professionals possess a certain level of proficiency.
Enhanced Troubleshooting Abilities
CCNA certification places a strong emphasis on troubleshooting network issues. This skill is invaluable in maintaining network uptime and resolving problems swiftly. Employers appreciate CCNA-certified professionals' ability to identify and address network challenges effectively, which can prevent costly downtime.
Reduced Training Costs
Hiring CCNA-certified professionals can save organizations money on training and onboarding. New hires who already possess the certification require less investment in additional training, which is particularly appealing to businesses with budget constraints.
CCNA-certified individuals are seen as standardized, efficient, and cost-effective contributors to their organizations. In the subsequent sections, we will explore how CCNA certification contributes to skill development, career advancement, and even international opportunities in the world of networking.
Skill Development: What You'll Learn During CCNA Training
Earning the Cisco Certified Network Associate (CCNA) certification is not just about acquiring a piece of paper for your resume; it's about developing a comprehensive set of skills that are highly valued in the networking industry. In this section, we'll explore the key skills you'll acquire during CCNA training.
Network Fundamentals
CCNA training starts with the fundamentals of networking, covering topics such as the OSI model, IP addressing, subnets, and basic network protocols. This foundational knowledge is essential for understanding more advanced networking concepts.
Network Security
CCNA training emphasizes network security, teaching you how to identify and mitigate security threats. You'll learn about access control, firewalls, and security best practices to protect network infrastructure.
Wireless Networking
Wireless technology is integral to modern networks. CCNA training covers wireless networking concepts, including how to configure and secure wireless access points and controllers.
Network Troubleshooting
One of the most valuable skills you'll develop is network troubleshooting. You'll learn how to identify and resolve common network issues efficiently, minimizing downtime and ensuring network reliability.
WAN Technologies
Wide Area Networks (WANs) are crucial for connecting remote offices and ensuring data transfer between locations. CCNA training covers WAN technologies like Frame Relay, PPP, and VPNs.
Network Design
CCNA explores network design principles, teaching you how to plan and design network architectures that meet specific business requirements.
IP Telephony
In CCNA Voice or Collaboration tracks, you'll gain skills related to Voice over IP (VoIP) technologies. This includes configuring and managing IP telephony systems.
Data Center Networking
For those pursuing the Data Center track, you'll develop expertise in data center networking, including technologies like virtualization and storage.
Automation and Programmability
CCNA has evolved to include topics related to automation and programmability, introducing you to network automation and scripting. These skills are increasingly valuable in modern network management.
Real-World Lab Experience
CCNA training often involves hands-on lab exercises where you'll configure and troubleshoot network devices. This practical experience is invaluable for applying your knowledge in real-world scenarios.
A Foundation for Advanced Certifications: How CCNA Paves the Way
Earning the Cisco Certified Network Associate (CCNA) certification isn't just an endpoint; it serves as a stepping stone for networking professionals to explore more advanced certifications. In this section, we'll discuss how CCNA provides a strong foundation and paves the way for pursuing higher-level certifications.
In-Depth Networking Knowledge
CCNA covers a broad range of networking concepts, ensuring that candidates have a solid understanding of the fundamentals. This knowledge is essential for tackling more advanced certifications. Without a strong foundation, pursuing higher-level certifications can be significantly more challenging.
Prerequisite for Advanced Certifications
Many advanced Cisco certifications require CCNA as a prerequisite. For example, to pursue the Cisco Certified Network Professional (CCNP) certification, you typically need to have a valid CCNA certification. CCNP certifications focus on more complex networking topics, such as advanced routing and switching, wireless, or security. CCNA ensures that candidates are prepared for the in-depth knowledge required at the professional level.
Seamless Progression
The content covered in CCNA provides a logical progression to advanced certifications. CCNA introduces key concepts in routing and switching, network security, and other fundamental areas. This foundational knowledge aligns well with the content covered in CCNP and other Cisco certifications.
Enhanced Career Opportunities
Having a CCNA certification on your resume can open doors to better job opportunities. Once you've earned your CCNA, you can apply for positions that require CCNA certification, gain more experience, and work towards your next certification. Advanced certifications can lead to even more lucrative roles and further career advancement.
Increased Technical Proficiency
CCNA offers hands-on experience with networking devices and technologies. This practical experience not only prepares you for the CCNA exam but also ensures that you are technically proficient. This proficiency will be valuable when pursuing more advanced certifications, where the expectations for hands-on skills are higher.
Recognition in the Networking Community
The CCNA certification is well-recognized in the networking community. Earning it demonstrates your commitment to the field and your readiness to take on more challenging certifications. Networking professionals who hold CCNA certifications are often well-regarded by peers and employers.
Preparation for Specializations
Cisco offers various specialization certifications, such as CCNA Security, CCNA Collaboration, and CCNA Data Center. These specializations allow you to focus on areas that interest you most. The foundational knowledge provided by CCNA is crucial for building expertise in these specialized fields.
Global Reach: The Portability of CCNA Certification
One of the distinct advantages of earning the Cisco Certified Network Associate (CCNA) certification is its global recognition and portability. CCNA is not confined to a specific geographical region or job market; it offers networking professionals the opportunity to work and thrive on a worldwide scale. In this section, we'll explore the portability of CCNA certification and how it opens doors to international opportunities.
Universal Networking Knowledge
CCNA covers fundamental networking concepts that apply universally, regardless of geographic location. Networking protocols, routing and switching principles, and security best practices are applicable worldwide. This means your CCNA knowledge is relevant wherever networking infrastructure exists.
Cisco's International Presence
Cisco, the organization behind CCNA certification, is a global technology leader with a presence in almost every corner of the world. This international footprint ensures that CCNA is recognized and respected globally, and Cisco's products and solutions are used in diverse international markets.
Industry Demand Worldwide
The demand for skilled networking professionals is not limited to a single region; it's a global need. Organizations around the world require network administrators, engineers, and technicians who can maintain and optimize their network infrastructure. Having a CCNA certification makes you an attractive candidate in any job market.
Career Mobility
CCNA certification provides networking professionals with the flexibility to move and work in different countries and regions. Many multinational companies value CCNA certification when hiring for their global IT teams. It can open doors to exciting international opportunities, allowing you to gain experience in various environments and cultures.
International Certifications
In addition to the standard CCNA certification, Cisco offers specialized CCNA tracks, such as CCNA Security, CCNA Collaboration, and CCNA Data Center. These tracks are valuable for professionals interested in specific fields and can enhance your international employability by focusing on in-demand areas.
Networking Community Connections
The CCNA community is vast and diverse, with professionals from all over the world. Engaging with this community can lead to international networking opportunities, collaboration, and exposure to different industry practices and trends.
Consulting and Contract Work
CCNA-certified professionals may have the option to work as network consultants or on a contract basis. These roles often come with flexibility and opportunities to work on international projects, further expanding your horizons.
Its universal networking knowledge, recognition by Cisco, and high demand in the IT industry make CCNA professionals sought after worldwide. Whether you aspire to work in your home country, gain international experience, or explore career opportunities in various regions, CCNA certification equips you with the skills and recognition needed for success in the global networking arena.
Staying Current in Networking: The Importance of CCNA in a Dynamic Field
In the ever-evolving world of networking, it's crucial for professionals to stay current with the latest technologies and industry trends. The Cisco Certified Network Associate (CCNA) certification is not just a one-time achievement; it plays a pivotal role in helping networking experts keep pace with the dynamic nature of their field. In this section, we'll discuss why CCNA is essential for professionals looking to stay current in networking.
Ongoing Skill Development
CCNA certification requires individuals to acquire a broad range of foundational skills. However, these skills are not stagnant; they form the building blocks for more advanced networking knowledge. CCNA serves as the first step in a lifelong journey of skill development, encouraging professionals to continue learning and staying up-to-date with the latest advancements.
Regular Certification Updates
Cisco periodically updates its certification exams to ensure they remain relevant in an ever-changing industry. CCNA-certified professionals are encouraged to recertify and take the latest versions of the exam to maintain the currency of their knowledge. This process reinforces the importance of staying current in networking.
Exposure to Emerging Technologies
CCNA training introduces candidates to emerging technologies and trends in networking, such as cloud computing, software-defined networking (SDN), and automation. This exposure not only prepares professionals for current challenges but also equips them to adapt to future developments in the field.
Foundation for Advanced Certifications
CCNA serves as a foundational certification for more advanced Cisco certifications, such as the Cisco Certified Network Professional (CCNP) and Cisco Certified Internetwork Expert (CCIE). These advanced certifications delve deeper into complex networking topics and require professionals to continually update their knowledge and skills.
Troubleshooting and Adaptability
One of the primary skills emphasized in CCNA training is network troubleshooting. This skill is invaluable in a dynamic field where new challenges and issues regularly arise. CCNA-certified professionals are adept at identifying and resolving network problems, which is critical for maintaining network reliability.
Security Awareness
Security is an evergreen concern in networking. CCNA training covers network security principles, but professionals must continuously stay informed about evolving security threats and solutions to protect network infrastructure effectively.
Industry Engagement
Cisco's extensive networking community and resources provide opportunities to engage with professionals and experts from around the world. Networking conferences, webinars, and forums keep CCNA-certified professionals connected to the latest industry insights and best practices.
Job Relevance
Staying current in networking ensures that your skills remain relevant to the job market. As new technologies and practices emerge, employers seek professionals who can apply these innovations to improve network performance, security, and efficiency.
the dynamic nature of networking demands continuous learning and adaptation. CCNA certification serves as a reminder that networking professionals must remain vigilant, embrace ongoing skill development, and engage with emerging technologies to stay current in their field. Whether through recertification, advanced certifications, or active participation in the networking community, CCNA paves the way for a career that thrives in a constantly evolving networking landscape.
Job Security: How CCNA Certification Mitigates Career Risks
In an ever-changing job market, job security is a critical concern for professionals in any field. Cisco Certified Network Associate (CCNA) certification can significantly mitigate career risks and provide a level of job security that is highly valuable. In this section, we'll discuss how CCNA certification contributes to job security in the networking industry.
Industry Demand for Networking Professionals
The demand for skilled networking professionals is a constant in the IT industry. Networks are the backbone of businesses, and their proper functioning is essential. As a result, organizations consistently seek professionals with networking expertise, creating a continuous demand for CCNA-certified individuals.
Demonstrated Skills and Knowledge
CCNA certification is a clear demonstration of your networking skills and knowledge. Employers prefer candidates with certifications because they provide tangible evidence of competency. CCNA-certified professionals are more likely to be retained, promoted, and entrusted with critical network responsibilities.
Ongoing Skill Development
CCNA requires professionals to continue developing their skills to stay current. This continuous learning process ensures that CCNA-certified individuals remain valuable assets to their employers, adapting to new technologies and maintaining network efficiency and security.
Troubleshooting Abilities
CCNA training emphasizes troubleshooting skills, equipping professionals with the ability to identify and resolve network issues quickly. This skill is invaluable in ensuring network reliability and reducing costly downtime.
Network Security Expertise
Security is a top priority for organizations, and CCNA certification includes essential network security knowledge. CCNA-certified professionals can help protect network infrastructure from security threats, which is a crucial aspect of job security.
Recognition by Employers
Many employers specifically seek CCNA-certified professionals for networking roles. Having the certification on your resume often increases your chances of being selected for interviews and job offers.
Career Advancement Opportunities
CCNA certification is a solid foundation for career advancement. It opens doors to roles with more responsibility, better compensation, and job stability. CCNA-certified professionals are often well-positioned to move up the career ladder.
Adaptability to Industry Changes
CCNA certification equips professionals with the adaptability needed to embrace industry changes. The networking field continually evolves with new technologies and practices. CCNA-certified individuals can easily adapt to these changes, mitigating the risk of becoming obsolete in their roles.
Strong Networking Community
The CCNA community is extensive and supportive. Engaging with this community can lead to networking opportunities, job referrals, and career advice, further enhancing job security.
Portfolio for Job Flexibility
A CCNA certification is transferable across different industries and geographic locations. This flexibility provides job security as it enables professionals to explore various career options and adapt to changes in personal circumstances or job markets.
Networking Community and Support: CCNA's Role in Building Connections
The world of networking is not just about cables and configurations; it's also about building connections with fellow professionals and experts. The Cisco Certified Network Associate (CCNA) certification extends beyond the technical aspects of networking; it fosters a sense of community and support that can significantly benefit networking professionals. In this section, we'll discuss how CCNA plays a role in building connections within the networking community.
CCNA Community Forums
Cisco provides official forums and online communities specifically for CCNA-certified professionals. These platforms are a space for individuals to ask questions, share insights, and seek advice from peers who have a similar background and expertise. They can be valuable sources of information and support.
Networking Events and Conferences
CCNA-certified professionals often participate in networking events and conferences. These gatherings provide opportunities to connect with fellow professionals, engage in discussions, and learn from experts in the field. Building relationships at such events can lead to new job opportunities and collaboration.
Online Study Groups
Many CCNA candidates form online study groups to prepare for the certification. These groups not only aid in exam preparation but also serve as a networking platform. Interacting with study partners can lead to long-lasting professional relationships.
Job Referrals and Recommendations
Being part of the CCNA community can lead to job referrals and recommendations. Networking professionals often hear about job openings or have colleagues in need of talent. Being connected to this network can make it easier to find new job opportunities.
Support in Exam Preparation
Preparing for the CCNA exam can be a challenging endeavor. Many CCNA candidates find support and motivation from the community. Connecting with others who are pursuing the same certification can provide encouragement and help you overcome obstacles.
Real-World Application: Success Stories of CCNA Professionals
The Cisco Certified Network Associate (CCNA) certification is more than just an academic achievement; it's a testament to practical networking skills and knowledge. In this section, we'll explore real-world success stories of CCNA professionals who have leveraged their certification to achieve remarkable career milestones and make a tangible impact in the field of networking.
Expertise in Network Troubleshooting
CCNA-certified professionals often excel in network troubleshooting, a skill they gain during their certification training. This expertise enables them to quickly identify and resolve network issues, reducing downtime and ensuring network reliability. As a result, their employers appreciate their ability to maintain network efficiency.
Network Security Specialists
CCNA Security specialization equips professionals with the knowledge and skills to handle network security. These CCNA-certified individuals often go on to become network security specialists, safeguarding their organizations' critical data from cyber threats.
Networking Entrepreneurship
Some CCNA professionals have leveraged their certification to start their own networking businesses. They provide services such as network design, installation, and maintenance to clients in need of networking solutions. The CCNA certification provides credibility and trust to their customers.
Specialized Career Paths
CCNA opens doors to specialized career paths, such as data center networking, collaboration technologies, and wireless networking. Professionals who pursue these specialized tracks often find themselves in high-demand roles that offer both financial rewards and job satisfaction.
Promotions in Multinational Companies
CCNA certification provides a strong foundation for working in multinational corporations. Success stories often include professionals who secure positions in global organizations, where they manage international networks and collaborate with teams across different countries.
Success in IT Management
Some CCNA professionals ascend to IT management positions, overseeing entire network infrastructures and leading teams of networking professionals. Their strong technical backgrounds, combined with leadership skills, make them valuable assets in management roles.
Building Resilient Networks
CCNA professionals are well-versed in building resilient and efficient network infrastructures. Success stories often involve individuals who design and manage networks for critical industries, such as healthcare or finance, where network reliability is paramount.
International Opportunities
CCNA certification's global recognition allows professionals to explore international career opportunities. Success stories may include individuals who land positions in different countries, gaining unique cultural experiences and expanding their professional horizons.
Conclusion
The Cisco Certified Network Associate (CCNA) certification is a transformative credential for networking professionals, offering a multitude of benefits and opportunities for those who pursue it. This article has explored the various facets of CCNA, from its role in enhancing career opportunities and increasing earning potential to its importance in maintaining job security and staying current in the ever-evolving field of networking.
Real-world success stories of CCNA professionals underscore the tangible impact that this certification has on careers, from career advancements to specialized roles, entrepreneurship, and international opportunities.
In sum, CCNA is a testament to the dedication and skills of networking professionals and serves as a versatile tool in their professional journey. It not only represents a strong foundation but also opens doors, enriches careers, and provides a network of support that transcends borders. As the networking industry continues to evolve, CCNA remains a constant in empowering professionals to navigate the ever-changing landscape with confidence and success.
The Role of a Certified Scrum Product Owner (CSPO):Responsibilities and Challenges
In the dynamic landscape of modern project management and Agile development, the role of a Certified Scrum Product Owner (CSPO) has emerged as a linchpin for success. In a world where adaptability, responsiveness, and delivering value are paramount, the CSPO is at the helm, steering the ship towards project excellence.
In this blog post, we'll embark on a journey through the multifaceted role of a Certified Scrum Product Owner, uncovering the essential responsibilities they undertake and the challenges they must overcome. Whether you're a CSPO looking to refine your skills or someone curious about this pivotal role in Agile development, this exploration will provide you with valuable insights.
So, whether you're considering a career as a CSPO, working alongside one, or simply keen to expand your knowledge of Agile practices, join us as we navigate the exciting world of CSPOs and uncover the responsibilities and challenges that define their role.
Table of contents
-
Understanding the CSPO Role
-
Effective Backlog Management
-
Collaborating with Stakeholders
-
Balancing Priorities
-
The Decision-Making Dilemma
-
User-Centric Product Development
-
Adapting to Change
-
Managing Expectations and Feedback
-
Overcoming Challenges and Obstacles
-
Continuous Improvement for CSPOs
-
Conclusion
Understanding the CSPO Role
The Certified Scrum Product Owner (CSPO) plays a pivotal role in the Scrum framework, acting as the linchpin between development teams and stakeholders. To truly appreciate the impact of a CSPO, it's essential to understand their multifaceted role. Here, we delve into the key aspects that define the CSPO's responsibilities:
Product Visionary: The CSPO is the visionary of the product, tasked with developing a clear understanding of what needs to be built and why. They must communicate this vision to the team and stakeholders.
Prioritization Guru: One of the CSPO's most critical responsibilities is to prioritize the items in the product backlog. This involves understanding the market, customer needs, and business goals to ensure the most valuable features are developed first.
Stakeholder Liaison: The CSPO acts as the bridge between the development team and various stakeholders, including customers, business leaders, and end-users. They must effectively gather and communicate requirements while managing expectations.
Team Support: CSPOs are there to support the development team in understanding the product vision, clarifying requirements, and answering questions, ensuring the team can work efficiently.
Continuous Improvement: A great CSPO is also dedicated to continuous improvement. They should regularly review their own performance and seek ways to enhance the product development process.
Understanding the CSPO role goes beyond a job description; it requires a blend of leadership, communication, and problem-solving skills. It's about championing the product's success by aligning it with business objectives and delivering value to customers.
In the following sections, we'll delve deeper into the challenges and strategies that CSPOs encounter in these various facets of their role.
Effective Backlog Management
The product backlog is the beating heart of Agile product development, and the Certified Scrum Product Owner (CSPO) is its custodian. Backlog management is a vital aspect of the CSPO's role, encompassing the organization, prioritization, and continuous refinement of tasks and requirements. Here, we will break down the components of effective backlog management:
Organization:Creating a Clear Structure: The CSPO is responsible for maintaining a well-organized backlog. This involves creating user stories, epics, and tasks in a structured manner, making it easier for the development team to understand and prioritize work.
Managing Dependencies: Identifying and managing dependencies between backlog items to ensure efficient development and delivery.
Prioritization:Value-Driven Prioritization: The CSPO must prioritize backlog items based on their value to the customer, business, and project objectives.
Alignment with Business Goals: Ensuring that the prioritization aligns with the broader business goals and strategies.
Continuous Refinement:Regular Grooming: Holding backlog grooming sessions to review, update, and refine items. This process helps in maintaining the relevance of items and keeping the backlog manageable.
Responding to Feedback: Being responsive to feedback from stakeholders and the development team, which might lead to changes in the backlog.
Communication:Effective Communication: The CSPO should be able to effectively communicate the priorities and requirements of the backlog to the development team and stakeholders.
Transparency: Maintaining transparency in the backlog to ensure everyone involved understands its status and contents.
Adaptability:Embracing Change: Acknowledging that changes in market conditions, customer feedback, and other factors may require adapting the backlog. The CSPO should be ready to pivot as needed.
Backlog Size:Right-Sizing the Backlog: Striking a balance between having a backlog that is too large (overwhelming) and too small (insufficient to support the team's work).
Effective backlog management is a dynamic process. It involves a constant reassessment of priorities, responsiveness to change, and a commitment to delivering the most valuable features to the customer. The CSPO plays a critical role in ensuring that the backlog remains a powerful tool for Agile development, guiding the team towards success.
Collaborating with Stakeholders
In the realm of Agile product development, collaboration is not just a buzzword; it's a fundamental principle. For a Certified Scrum Product Owner (CSPO), collaboration with stakeholders is a core responsibility. This involves a delicate dance of communication, feedback, and alignment. Let's explore the nuances of collaborating effectively with stakeholders:
Identifying Stakeholders:Cast a Wide Net: The CSPO's first step is identifying all potential stakeholders. This may include customers, business executives, end-users, and anyone who has a vested interest in the product's success.
Engaging in Continuous Communication:Open Channels: Establish and maintain open channels of communication with stakeholders. Regular meetings, emails, and project management tools are vital for keeping everyone informed.
Active Listening: Paying close attention to the needs and concerns of stakeholders. Encourage and embrace their feedback and input.
Managing Expectations:Transparency: Being transparent about what can and cannot be delivered in a given time frame. Setting realistic expectations is crucial to avoiding disappointment.
Alignment with Goals: Ensuring that stakeholder expectations are aligned with project goals and objectives.
Gathering and Prioritizing Feedback:Feedback Loops: Establishing structured feedback loops to collect input from stakeholders. This feedback should be considered when prioritizing and refining the product backlog.
Feedback Processing: Effective processing and incorporation of feedback into the product development process.
Conflict Resolution:Handling Conflicts: Dealing with conflicting interests or opinions among stakeholders. The CSPO must be adept at finding compromises that benefit the project.
Regular Updates:Progress Reporting: Keeping stakeholders informed about the project's progress, roadblocks, and successes. This keeps them engaged and aligned with the team's efforts.
Collaborating effectively with stakeholders is a complex task that involves not only effective communication but also the ability to navigate potentially conflicting interests. The CSPO's role is not just to manage relationships but to ensure that stakeholder feedback is translated into value-added product features and that everyone involved understands the product's direction.
Balancing Priorities
As a Certified Scrum Product Owner (CSPO), one of the most significant challenges is striking the right balance between multiple, often competing, priorities. The CSPO must be a master of prioritization, ensuring that the development team is working on the most valuable tasks. Let's explore the complexities of balancing priorities:
Value-Based Prioritization:Customer Value: Prioritizing items that bring the most value to the end customer or user. This ensures that the product remains competitive and addresses user needs effectively.
Business Value: Identifying and prioritizing tasks that align with the broader business objectives. These might include revenue generation, cost reduction, or strategic goals.
Alignment with Strategy:Strategic Objectives: Ensuring that the prioritization of tasks is in line with the organization's strategic goals. A CSPO must be aware of the big picture and ensure that daily tasks contribute to the long-term vision.
Managing Changing Requirements:Embracing Change: Being adaptable and open to changing priorities. Market conditions, customer feedback, and new opportunities might necessitate changes in what gets worked on first.
Stakeholder Expectations:Managing Stakeholder Demands: Dealing with multiple stakeholders with their own ideas about what should be prioritized. It's essential to balance these often conflicting demands.
Capacity Planning:Understanding Team Capacity: Having a clear understanding of the development team's capacity and ensuring that the workload aligns with this capacity. Overloading the team can lead to burnout and decreased quality.
Impact Assessment:Data-Driven Decisions: Making decisions based on data and analysis. Assessing the potential impact of different tasks and using this analysis to guide prioritization.
Balancing priorities is a delicate act of constant reassessment and adaptation. The CSPO must be flexible and responsive to change while maintaining a clear understanding of the overarching objectives. This skill is what ensures that the most valuable work is continually delivered and that the product remains competitive and aligned with the market.
The Decision-Making Dilemma
The role of a Certified Scrum Product Owner (CSPO) is fraught with decisions. Each decision has the potential to shape the course of the project and the product's success. However, decision-making in the Agile landscape is far from straightforward. Let's explore the CSPO's decision-making dilemmas:
Feature Selection:What to Build First: Deciding which features to prioritize for development, considering customer needs, market demands, and business goals.
What to Leave Out: Equally important is deciding what not to build. Not every idea or feature can be accommodated, and decisions must be made about what doesn't make the cut.
Scope Changes:Evaluating Change Requests: When stakeholders request scope changes or additions, the CSPO must evaluate the impact on the project's timeline, budget, and goals.
Balancing Flexibility and Stability: Deciding how much flexibility can be accommodated within the project without compromising stability and predictability.
Trade-Offs:Balancing Quality and Speed: Decisions often revolve around the trade-off between delivering quickly and maintaining high product quality.
Resource Allocation: Deciding how to allocate resources, including time and team capacity, to different tasks.
User Feedback and Prioritization:Incorporating User Feedback: Deciding how to prioritize and implement user feedback while maintaining alignment with the project's objectives.
Managing Expectations: Communicating decisions regarding the implementation of feedback to stakeholders and end-users.
Resource Constraints:Budget and Time Decisions: Deciding how to allocate budget and time resources, particularly when faced with constraints.
Long-Term Vision:Balancing Short-Term and Long-Term Goals: Making decisions that align with the long-term vision of the product, even when short-term demands might pull in a different direction.
The CSPO's decision-making is a constant juggling act that requires a deep understanding of the project's goals and the ability to adapt to changing circumstances. Decisions must be made in a manner that maximizes value while minimizing risks and conflicts.
User-Centric Product Development
In the Agile world, where the focus is on delivering value and responding to change, user-centricity is at the heart of successful product development. As a Certified Scrum Product Owner (CSPO), understanding and advocating for the needs and desires of the end-users is paramount. Let's dive into the principles of user-centric product development:
User Empathy:Putting Yourself in the User's Shoes: The CSPO must strive to understand the user's perspective, their goals, and the problems they need the product to solve.
Listening Actively: Engaging in user feedback sessions and actively listening to what users have to say about the product.
User Story Creation:Creating User Stories: Formulating user stories that represent the user's requirements and needs. These stories become the basis for development tasks.
Prioritizing User Stories: Prioritizing user stories based on user value and business objectives.
Usability and User Experience:Usability Testing: Ensuring the product is user-friendly and easy to navigate. Usability testing helps identify and address user interface and experience issues.
User-Centered Design: Integrating user-centered design principles into the development process to create intuitive and user-friendly interfaces.
Feedback Integration:Feedback Loops: Establishing feedback loops that allow for the continuous integration of user feedback into the product development cycle.
Iterative Improvement: Recognizing that user feedback often leads to iterative product improvements and being open to these changes.
Aligning with User Goals:Connecting with User Objectives: Making sure the product aligns with the users' goals and is instrumental in solving their problems.
Continuous Value Delivery: Ensuring that each development iteration delivers tangible value to the user.
User Advocacy:Advocating for the User: As the user's representative, the CSPO must advocate for their needs and ensure that these needs are met in the product's development.
Balancing User Interests: Balancing user needs with business goals and technical constraints.
User-centric product development ensures that the product remains relevant and valuable to its intended audience. It's about making the user's life easier, more efficient, and more enjoyable. As a CSPO, embracing these principles is pivotal to your role.
Adapting to Change
In the fast-paced world of Agile product development, change is the only constant. As a Certified Scrum Product Owner (CSPO), your ability to adapt to change is vital for the success of your projects. Let's delve into the challenges and strategies for effectively adapting to change:
Embracing Flexibility:Change as a Norm: Recognizing that change is an inherent part of Agile development. Being open to and prepared for changes in requirements, priorities, and even project goals.
Agile Mindset: Adopting an Agile mindset that values adaptability and welcomes change as a means of improvement.
Iterative Development:Sprints and Iterations: Leveraging the Agile framework's iterative nature to accommodate changes within specific timeframes, such as sprints.
Feedback Integration: Using the end of each iteration to incorporate feedback and adjust the product's direction accordingly.
Managing Scope Changes:Change Requests: Handling scope changes and additions with a structured change management process. This includes assessing their impact and aligning them with the project's objectives.
Balancing Scope and Schedule: Ensuring that scope changes don't jeopardize project timelines.
Agile Tools and Techniques:Backlog Refinement: Regularly refining the product backlog to adjust to changing requirements and priorities.
Burndown Charts and Velocity Tracking: Using tools like burndown charts and velocity tracking to monitor progress and adapt plans as needed.
Continual Improvement:Retrospectives: Conducting regular retrospectives to identify areas for improvement in the development process, fostering a culture of learning and adaptability.
Adapting Based on Feedback: Using feedback from retrospectives and other sources to make process changes.
Adapting to change in Agile development is not just a matter of reacting; it's a proactive approach to ensuring that the product remains aligned with customer needs and market demands. It's about using change as an opportunity for improvement rather than a disruptive force.
Managing Expectations and Feedback
As a Certified Scrum Product Owner (CSPO), your role extends beyond managing the product backlog. You are also responsible for effectively managing stakeholder expectations and feedback, a task that requires finesse and communication skills. Let's explore the intricacies of this responsibility:
Clear Communication:
Open Dialogue: Establishing open and transparent lines of communication with stakeholders. This creates an environment where expectations can be effectively managed.
Setting Realistic Expectations: Communicating what can and cannot be achieved within specific timeframes and resources.
Regular Updates:
Progress Reporting: Providing stakeholders with regular updates on the project's progress. This keeps them informed and engaged in the development process.
Highlighting Achievements: Sharing successes and milestones reached, reinforcing the value being delivered.
Gathering Feedback:
Feedback Loops: Setting up structured feedback loops that allow stakeholders to provide input and voice their concerns.
Actively Listening: Actively listening to feedback, even if it is critical, and demonstrating that it is being taken seriously.
Handling Conflicting Feedback:
Mediation: Resolving conflicts or contradictions within feedback from different stakeholders. The CSPO must make balanced decisions that serve the project's goals.
Responding to Change:
Change Management: Effectively communicating and managing changes in project direction, scope, or objectives to stakeholders.
Risk Communication: Sharing information about potential project risks or challenges and discussing strategies for mitigation.
Documentation:
Feedback Records: Maintaining records of feedback and its resolution to ensure that it is tracked and addressed.
Expectations Documentation: Documenting agreed-upon expectations, priorities, and objectives for reference.
Managing expectations and feedback requires a combination of excellent communication, empathy, and a deep understanding of the project's objectives. The CSPO's role in this aspect is to bridge the gap between stakeholders, development teams, and end-users, ensuring that everyone is on the same page and that feedback is integrated for continuous improvement.
Overcoming Challenges and Obstacles
In the role of a Certified Scrum Product Owner (CSPO), you're likely to encounter a range of challenges and obstacles. However, these challenges are not roadblocks; they're opportunities for growth and improvement. Let's explore some common challenges and strategies for overcoming them:
Conflicting Priorities:
Challenge: Balancing the priorities of different stakeholders can be challenging. Conflicting interests can lead to ambiguity in decision-making.
Strategy: Engage stakeholders in discussions to align their priorities with the project's objectives. Use data and clear communication to make informed decisions.
Changing Requirements:
Challenge: Requirements can change frequently, making it challenging to maintain a stable product backlog and plan.
Strategy: Embrace change as an opportunity for improvement. Implement change management processes to assess and integrate new requirements effectively.
Unrealistic Expectations:
Challenge: Managing stakeholder expectations can be difficult when they expect immediate results or don't fully grasp Agile principles.
Strategy: Educate stakeholders about Agile principles, setting realistic expectations, and providing regular updates to manage their understanding of the project's progress.
Resource Constraints:
Challenge: Limited resources, such as time, budget, or team capacity, can hinder your ability to meet stakeholder demands.
Strategy: Prioritize tasks based on their impact and feasibility within resource constraints. Communicate openly about resource limitations and adjust priorities accordingly.
Resistance to Change:
Challenge: Team members or stakeholders may resist adopting Agile practices or new ways of working.
Strategy: Lead by example, communicate the benefits of Agile, and involve team members in decision-making. Foster a culture of continuous improvement to encourage adaptation.
Incomplete Feedback:
Challenge: Stakeholder feedback may be vague or incomplete, making it challenging to act upon.
Strategy: Engage stakeholders in conversations to elicit more detailed feedback. Use techniques like "Five Whys" to dig deeper into their needs and concerns.
Managing Expectations:
Challenge: Managing stakeholder expectations while maintaining a user-centric approach can be challenging when interests diverge.
Strategy: Balance the needs of users with business goals and technical constraints. Clearly communicate the rationale behind decisions to manage expectations effectively.
Overcoming challenges and obstacles is a fundamental aspect of the CSPO role. It requires a combination of effective communication, adaptability, and strategic decision-making. By addressing these challenges with the right mindset and techniques, you can facilitate a more successful and resilient Agile product development process.
Continuous Improvement for CSPOs
In the dynamic world of Agile product development, the journey of a Certified Scrum Product Owner (CSPO) is one of continual growth and refinement. Continuous improvement is not just a practice; it's a mindset. Let's explore the principles and strategies for ongoing improvement as a CSPO:
Self-Assessment:Reflect on Your Role: Regularly assess your performance and the impact you're making as a CSPO. This self-assessment helps you identify areas for improvement.
Professional Development:Stay Informed: Keep abreast of the latest trends, tools, and best practices in Agile and product management. Attend training, workshops, and conferences to expand your knowledge.
Certification: Consider advanced certifications or training courses to enhance your skills and knowledge.
Feedback Integration:Seek Feedback: Actively seek feedback from team members, stakeholders, and Scrum Masters. Constructive criticism can be a valuable source of insights.
Feedback Processing: Process feedback by identifying actionable areas for improvement and taking steps to address them.
Scrum Master Collaboration:Work Closely with Scrum Masters: Collaborate with Scrum Masters to learn from their experiences and gain a better understanding of the Scrum framework.
Continuous Learning: Be open to sharing your experiences and insights, fostering mutual growth.
Experimentation:Embrace Experimentation: Be open to trying new tools, techniques, or approaches in your role. Experimentation can lead to innovative improvements.
Learn from Failures: Embrace failures as learning opportunities, understanding that not every experiment will yield the desired results.
Collaborative Learning:Learning from Peers: Engage with other CSPOs and product owners to exchange insights, challenges, and best practices.
Cross-Functional Collaboration: Collaborate with developers, designers, and other roles to expand your understanding of the product development process.
Goal Setting:Set Goals for Improvement: Establish clear goals for your own improvement and growth as a CSPO. Regularly review and adjust these goals as you progress.
Continuous improvement as a CSPO is about embracing a growth mindset, actively seeking ways to enhance your skills, and consistently applying new knowledge and insights. It's an ongoing journey of becoming a more effective, adaptable, and valuable product owner within the Agile landscape.
Conclusion
Becoming a Certified Scrum Product Owner (CSPO) is not just about a title; it's a journey of embracing responsibilities, overcoming challenges, and continuously improving. In this comprehensive exploration of the role of a CSPO, we've delved into the core responsibilities and the myriad challenges you might encounter in this dynamic position.
Effective backlog management, stakeholder collaboration, balancing priorities, and decision-making are just some of the intricate facets of your role. Managing expectations and feedback, adapting to change, and overcoming challenges are continuous endeavors that require a blend of skills, including effective communication, empathy, and adaptability.
The role of a CSPO is not for the faint of heart, but for those willing to embrace the challenges and opportunities it presents, it can be a rewarding and fulfilling journey. Remember, your dedication to this role contributes not only to the success of your projects but also to the broader Agile community.
In closing, the role of a CSPO is a journey of perpetual growth and a commitment to delivering value to customers while embracing the principles of Agile. Whether you're an aspiring CSPO or an experienced one, this role offers an ongoing opportunity to make a meaningful impact in the world of product development.
Thank you for accompanying us on this exploration of the CSPO role. May your journey as a Certified Scrum Product Owner be filled with continuous improvement, successful projects, and valuable product deliveries.
Read More
In the dynamic landscape of modern project management and Agile development, the role of a Certified Scrum Product Owner (CSPO) has emerged as a linchpin for success. In a world where adaptability, responsiveness, and delivering value are paramount, the CSPO is at the helm, steering the ship towards project excellence.
In this blog post, we'll embark on a journey through the multifaceted role of a Certified Scrum Product Owner, uncovering the essential responsibilities they undertake and the challenges they must overcome. Whether you're a CSPO looking to refine your skills or someone curious about this pivotal role in Agile development, this exploration will provide you with valuable insights.
So, whether you're considering a career as a CSPO, working alongside one, or simply keen to expand your knowledge of Agile practices, join us as we navigate the exciting world of CSPOs and uncover the responsibilities and challenges that define their role.
Table of contents
-
Understanding the CSPO Role
-
Effective Backlog Management
-
Collaborating with Stakeholders
-
Balancing Priorities
-
The Decision-Making Dilemma
-
User-Centric Product Development
-
Adapting to Change
-
Managing Expectations and Feedback
-
Overcoming Challenges and Obstacles
-
Continuous Improvement for CSPOs
-
Conclusion
Understanding the CSPO Role
The Certified Scrum Product Owner (CSPO) plays a pivotal role in the Scrum framework, acting as the linchpin between development teams and stakeholders. To truly appreciate the impact of a CSPO, it's essential to understand their multifaceted role. Here, we delve into the key aspects that define the CSPO's responsibilities:
Product Visionary: The CSPO is the visionary of the product, tasked with developing a clear understanding of what needs to be built and why. They must communicate this vision to the team and stakeholders.
Prioritization Guru: One of the CSPO's most critical responsibilities is to prioritize the items in the product backlog. This involves understanding the market, customer needs, and business goals to ensure the most valuable features are developed first.
Stakeholder Liaison: The CSPO acts as the bridge between the development team and various stakeholders, including customers, business leaders, and end-users. They must effectively gather and communicate requirements while managing expectations.
Team Support: CSPOs are there to support the development team in understanding the product vision, clarifying requirements, and answering questions, ensuring the team can work efficiently.
Continuous Improvement: A great CSPO is also dedicated to continuous improvement. They should regularly review their own performance and seek ways to enhance the product development process.
Understanding the CSPO role goes beyond a job description; it requires a blend of leadership, communication, and problem-solving skills. It's about championing the product's success by aligning it with business objectives and delivering value to customers.
In the following sections, we'll delve deeper into the challenges and strategies that CSPOs encounter in these various facets of their role.
Effective Backlog Management
The product backlog is the beating heart of Agile product development, and the Certified Scrum Product Owner (CSPO) is its custodian. Backlog management is a vital aspect of the CSPO's role, encompassing the organization, prioritization, and continuous refinement of tasks and requirements. Here, we will break down the components of effective backlog management:
Organization:Creating a Clear Structure: The CSPO is responsible for maintaining a well-organized backlog. This involves creating user stories, epics, and tasks in a structured manner, making it easier for the development team to understand and prioritize work.
Managing Dependencies: Identifying and managing dependencies between backlog items to ensure efficient development and delivery.
Prioritization:Value-Driven Prioritization: The CSPO must prioritize backlog items based on their value to the customer, business, and project objectives.
Alignment with Business Goals: Ensuring that the prioritization aligns with the broader business goals and strategies.
Continuous Refinement:Regular Grooming: Holding backlog grooming sessions to review, update, and refine items. This process helps in maintaining the relevance of items and keeping the backlog manageable.
Responding to Feedback: Being responsive to feedback from stakeholders and the development team, which might lead to changes in the backlog.
Communication:Effective Communication: The CSPO should be able to effectively communicate the priorities and requirements of the backlog to the development team and stakeholders.
Transparency: Maintaining transparency in the backlog to ensure everyone involved understands its status and contents.
Adaptability:Embracing Change: Acknowledging that changes in market conditions, customer feedback, and other factors may require adapting the backlog. The CSPO should be ready to pivot as needed.
Backlog Size:Right-Sizing the Backlog: Striking a balance between having a backlog that is too large (overwhelming) and too small (insufficient to support the team's work).
Effective backlog management is a dynamic process. It involves a constant reassessment of priorities, responsiveness to change, and a commitment to delivering the most valuable features to the customer. The CSPO plays a critical role in ensuring that the backlog remains a powerful tool for Agile development, guiding the team towards success.
Collaborating with Stakeholders
In the realm of Agile product development, collaboration is not just a buzzword; it's a fundamental principle. For a Certified Scrum Product Owner (CSPO), collaboration with stakeholders is a core responsibility. This involves a delicate dance of communication, feedback, and alignment. Let's explore the nuances of collaborating effectively with stakeholders:
Identifying Stakeholders:Cast a Wide Net: The CSPO's first step is identifying all potential stakeholders. This may include customers, business executives, end-users, and anyone who has a vested interest in the product's success.
Engaging in Continuous Communication:Open Channels: Establish and maintain open channels of communication with stakeholders. Regular meetings, emails, and project management tools are vital for keeping everyone informed.
Active Listening: Paying close attention to the needs and concerns of stakeholders. Encourage and embrace their feedback and input.
Managing Expectations:Transparency: Being transparent about what can and cannot be delivered in a given time frame. Setting realistic expectations is crucial to avoiding disappointment.
Alignment with Goals: Ensuring that stakeholder expectations are aligned with project goals and objectives.
Gathering and Prioritizing Feedback:Feedback Loops: Establishing structured feedback loops to collect input from stakeholders. This feedback should be considered when prioritizing and refining the product backlog.
Feedback Processing: Effective processing and incorporation of feedback into the product development process.
Conflict Resolution:Handling Conflicts: Dealing with conflicting interests or opinions among stakeholders. The CSPO must be adept at finding compromises that benefit the project.
Regular Updates:Progress Reporting: Keeping stakeholders informed about the project's progress, roadblocks, and successes. This keeps them engaged and aligned with the team's efforts.
Collaborating effectively with stakeholders is a complex task that involves not only effective communication but also the ability to navigate potentially conflicting interests. The CSPO's role is not just to manage relationships but to ensure that stakeholder feedback is translated into value-added product features and that everyone involved understands the product's direction.
Balancing Priorities
As a Certified Scrum Product Owner (CSPO), one of the most significant challenges is striking the right balance between multiple, often competing, priorities. The CSPO must be a master of prioritization, ensuring that the development team is working on the most valuable tasks. Let's explore the complexities of balancing priorities:
Value-Based Prioritization:Customer Value: Prioritizing items that bring the most value to the end customer or user. This ensures that the product remains competitive and addresses user needs effectively.
Business Value: Identifying and prioritizing tasks that align with the broader business objectives. These might include revenue generation, cost reduction, or strategic goals.
Alignment with Strategy:Strategic Objectives: Ensuring that the prioritization of tasks is in line with the organization's strategic goals. A CSPO must be aware of the big picture and ensure that daily tasks contribute to the long-term vision.
Managing Changing Requirements:Embracing Change: Being adaptable and open to changing priorities. Market conditions, customer feedback, and new opportunities might necessitate changes in what gets worked on first.
Stakeholder Expectations:Managing Stakeholder Demands: Dealing with multiple stakeholders with their own ideas about what should be prioritized. It's essential to balance these often conflicting demands.
Capacity Planning:Understanding Team Capacity: Having a clear understanding of the development team's capacity and ensuring that the workload aligns with this capacity. Overloading the team can lead to burnout and decreased quality.
Impact Assessment:Data-Driven Decisions: Making decisions based on data and analysis. Assessing the potential impact of different tasks and using this analysis to guide prioritization.
Balancing priorities is a delicate act of constant reassessment and adaptation. The CSPO must be flexible and responsive to change while maintaining a clear understanding of the overarching objectives. This skill is what ensures that the most valuable work is continually delivered and that the product remains competitive and aligned with the market.
The Decision-Making Dilemma
The role of a Certified Scrum Product Owner (CSPO) is fraught with decisions. Each decision has the potential to shape the course of the project and the product's success. However, decision-making in the Agile landscape is far from straightforward. Let's explore the CSPO's decision-making dilemmas:
Feature Selection:What to Build First: Deciding which features to prioritize for development, considering customer needs, market demands, and business goals.
What to Leave Out: Equally important is deciding what not to build. Not every idea or feature can be accommodated, and decisions must be made about what doesn't make the cut.
Scope Changes:Evaluating Change Requests: When stakeholders request scope changes or additions, the CSPO must evaluate the impact on the project's timeline, budget, and goals.
Balancing Flexibility and Stability: Deciding how much flexibility can be accommodated within the project without compromising stability and predictability.
Trade-Offs:Balancing Quality and Speed: Decisions often revolve around the trade-off between delivering quickly and maintaining high product quality.
Resource Allocation: Deciding how to allocate resources, including time and team capacity, to different tasks.
User Feedback and Prioritization:Incorporating User Feedback: Deciding how to prioritize and implement user feedback while maintaining alignment with the project's objectives.
Managing Expectations: Communicating decisions regarding the implementation of feedback to stakeholders and end-users.
Resource Constraints:Budget and Time Decisions: Deciding how to allocate budget and time resources, particularly when faced with constraints.
Long-Term Vision:Balancing Short-Term and Long-Term Goals: Making decisions that align with the long-term vision of the product, even when short-term demands might pull in a different direction.
The CSPO's decision-making is a constant juggling act that requires a deep understanding of the project's goals and the ability to adapt to changing circumstances. Decisions must be made in a manner that maximizes value while minimizing risks and conflicts.
User-Centric Product Development
In the Agile world, where the focus is on delivering value and responding to change, user-centricity is at the heart of successful product development. As a Certified Scrum Product Owner (CSPO), understanding and advocating for the needs and desires of the end-users is paramount. Let's dive into the principles of user-centric product development:
User Empathy:Putting Yourself in the User's Shoes: The CSPO must strive to understand the user's perspective, their goals, and the problems they need the product to solve.
Listening Actively: Engaging in user feedback sessions and actively listening to what users have to say about the product.
User Story Creation:Creating User Stories: Formulating user stories that represent the user's requirements and needs. These stories become the basis for development tasks.
Prioritizing User Stories: Prioritizing user stories based on user value and business objectives.
Usability and User Experience:Usability Testing: Ensuring the product is user-friendly and easy to navigate. Usability testing helps identify and address user interface and experience issues.
User-Centered Design: Integrating user-centered design principles into the development process to create intuitive and user-friendly interfaces.
Feedback Integration:Feedback Loops: Establishing feedback loops that allow for the continuous integration of user feedback into the product development cycle.
Iterative Improvement: Recognizing that user feedback often leads to iterative product improvements and being open to these changes.
Aligning with User Goals:Connecting with User Objectives: Making sure the product aligns with the users' goals and is instrumental in solving their problems.
Continuous Value Delivery: Ensuring that each development iteration delivers tangible value to the user.
User Advocacy:Advocating for the User: As the user's representative, the CSPO must advocate for their needs and ensure that these needs are met in the product's development.
Balancing User Interests: Balancing user needs with business goals and technical constraints.
User-centric product development ensures that the product remains relevant and valuable to its intended audience. It's about making the user's life easier, more efficient, and more enjoyable. As a CSPO, embracing these principles is pivotal to your role.
Adapting to Change
In the fast-paced world of Agile product development, change is the only constant. As a Certified Scrum Product Owner (CSPO), your ability to adapt to change is vital for the success of your projects. Let's delve into the challenges and strategies for effectively adapting to change:
Embracing Flexibility:Change as a Norm: Recognizing that change is an inherent part of Agile development. Being open to and prepared for changes in requirements, priorities, and even project goals.
Agile Mindset: Adopting an Agile mindset that values adaptability and welcomes change as a means of improvement.
Iterative Development:Sprints and Iterations: Leveraging the Agile framework's iterative nature to accommodate changes within specific timeframes, such as sprints.
Feedback Integration: Using the end of each iteration to incorporate feedback and adjust the product's direction accordingly.
Managing Scope Changes:Change Requests: Handling scope changes and additions with a structured change management process. This includes assessing their impact and aligning them with the project's objectives.
Balancing Scope and Schedule: Ensuring that scope changes don't jeopardize project timelines.
Agile Tools and Techniques:Backlog Refinement: Regularly refining the product backlog to adjust to changing requirements and priorities.
Burndown Charts and Velocity Tracking: Using tools like burndown charts and velocity tracking to monitor progress and adapt plans as needed.
Continual Improvement:Retrospectives: Conducting regular retrospectives to identify areas for improvement in the development process, fostering a culture of learning and adaptability.
Adapting Based on Feedback: Using feedback from retrospectives and other sources to make process changes.
Adapting to change in Agile development is not just a matter of reacting; it's a proactive approach to ensuring that the product remains aligned with customer needs and market demands. It's about using change as an opportunity for improvement rather than a disruptive force.
Managing Expectations and Feedback
As a Certified Scrum Product Owner (CSPO), your role extends beyond managing the product backlog. You are also responsible for effectively managing stakeholder expectations and feedback, a task that requires finesse and communication skills. Let's explore the intricacies of this responsibility:
Clear Communication:
Open Dialogue: Establishing open and transparent lines of communication with stakeholders. This creates an environment where expectations can be effectively managed.
Setting Realistic Expectations: Communicating what can and cannot be achieved within specific timeframes and resources.
Regular Updates:
Progress Reporting: Providing stakeholders with regular updates on the project's progress. This keeps them informed and engaged in the development process.
Highlighting Achievements: Sharing successes and milestones reached, reinforcing the value being delivered.
Gathering Feedback:
Feedback Loops: Setting up structured feedback loops that allow stakeholders to provide input and voice their concerns.
Actively Listening: Actively listening to feedback, even if it is critical, and demonstrating that it is being taken seriously.
Handling Conflicting Feedback:
Mediation: Resolving conflicts or contradictions within feedback from different stakeholders. The CSPO must make balanced decisions that serve the project's goals.
Responding to Change:
Change Management: Effectively communicating and managing changes in project direction, scope, or objectives to stakeholders.
Risk Communication: Sharing information about potential project risks or challenges and discussing strategies for mitigation.
Documentation:
Feedback Records: Maintaining records of feedback and its resolution to ensure that it is tracked and addressed.
Expectations Documentation: Documenting agreed-upon expectations, priorities, and objectives for reference.
Managing expectations and feedback requires a combination of excellent communication, empathy, and a deep understanding of the project's objectives. The CSPO's role in this aspect is to bridge the gap between stakeholders, development teams, and end-users, ensuring that everyone is on the same page and that feedback is integrated for continuous improvement.
Overcoming Challenges and Obstacles
In the role of a Certified Scrum Product Owner (CSPO), you're likely to encounter a range of challenges and obstacles. However, these challenges are not roadblocks; they're opportunities for growth and improvement. Let's explore some common challenges and strategies for overcoming them:
Conflicting Priorities:
Challenge: Balancing the priorities of different stakeholders can be challenging. Conflicting interests can lead to ambiguity in decision-making.
Strategy: Engage stakeholders in discussions to align their priorities with the project's objectives. Use data and clear communication to make informed decisions.
Changing Requirements:
Challenge: Requirements can change frequently, making it challenging to maintain a stable product backlog and plan.
Strategy: Embrace change as an opportunity for improvement. Implement change management processes to assess and integrate new requirements effectively.
Unrealistic Expectations:
Challenge: Managing stakeholder expectations can be difficult when they expect immediate results or don't fully grasp Agile principles.
Strategy: Educate stakeholders about Agile principles, setting realistic expectations, and providing regular updates to manage their understanding of the project's progress.
Resource Constraints:
Challenge: Limited resources, such as time, budget, or team capacity, can hinder your ability to meet stakeholder demands.
Strategy: Prioritize tasks based on their impact and feasibility within resource constraints. Communicate openly about resource limitations and adjust priorities accordingly.
Resistance to Change:
Challenge: Team members or stakeholders may resist adopting Agile practices or new ways of working.
Strategy: Lead by example, communicate the benefits of Agile, and involve team members in decision-making. Foster a culture of continuous improvement to encourage adaptation.
Incomplete Feedback:
Challenge: Stakeholder feedback may be vague or incomplete, making it challenging to act upon.
Strategy: Engage stakeholders in conversations to elicit more detailed feedback. Use techniques like "Five Whys" to dig deeper into their needs and concerns.
Managing Expectations:
Challenge: Managing stakeholder expectations while maintaining a user-centric approach can be challenging when interests diverge.
Strategy: Balance the needs of users with business goals and technical constraints. Clearly communicate the rationale behind decisions to manage expectations effectively.
Overcoming challenges and obstacles is a fundamental aspect of the CSPO role. It requires a combination of effective communication, adaptability, and strategic decision-making. By addressing these challenges with the right mindset and techniques, you can facilitate a more successful and resilient Agile product development process.
Continuous Improvement for CSPOs
In the dynamic world of Agile product development, the journey of a Certified Scrum Product Owner (CSPO) is one of continual growth and refinement. Continuous improvement is not just a practice; it's a mindset. Let's explore the principles and strategies for ongoing improvement as a CSPO:
Self-Assessment:Reflect on Your Role: Regularly assess your performance and the impact you're making as a CSPO. This self-assessment helps you identify areas for improvement.
Professional Development:Stay Informed: Keep abreast of the latest trends, tools, and best practices in Agile and product management. Attend training, workshops, and conferences to expand your knowledge.
Certification: Consider advanced certifications or training courses to enhance your skills and knowledge.
Feedback Integration:Seek Feedback: Actively seek feedback from team members, stakeholders, and Scrum Masters. Constructive criticism can be a valuable source of insights.
Feedback Processing: Process feedback by identifying actionable areas for improvement and taking steps to address them.
Scrum Master Collaboration:Work Closely with Scrum Masters: Collaborate with Scrum Masters to learn from their experiences and gain a better understanding of the Scrum framework.
Continuous Learning: Be open to sharing your experiences and insights, fostering mutual growth.
Experimentation:Embrace Experimentation: Be open to trying new tools, techniques, or approaches in your role. Experimentation can lead to innovative improvements.
Learn from Failures: Embrace failures as learning opportunities, understanding that not every experiment will yield the desired results.
Collaborative Learning:Learning from Peers: Engage with other CSPOs and product owners to exchange insights, challenges, and best practices.
Cross-Functional Collaboration: Collaborate with developers, designers, and other roles to expand your understanding of the product development process.
Goal Setting:Set Goals for Improvement: Establish clear goals for your own improvement and growth as a CSPO. Regularly review and adjust these goals as you progress.
Continuous improvement as a CSPO is about embracing a growth mindset, actively seeking ways to enhance your skills, and consistently applying new knowledge and insights. It's an ongoing journey of becoming a more effective, adaptable, and valuable product owner within the Agile landscape.
Conclusion
Becoming a Certified Scrum Product Owner (CSPO) is not just about a title; it's a journey of embracing responsibilities, overcoming challenges, and continuously improving. In this comprehensive exploration of the role of a CSPO, we've delved into the core responsibilities and the myriad challenges you might encounter in this dynamic position.
Effective backlog management, stakeholder collaboration, balancing priorities, and decision-making are just some of the intricate facets of your role. Managing expectations and feedback, adapting to change, and overcoming challenges are continuous endeavors that require a blend of skills, including effective communication, empathy, and adaptability.
The role of a CSPO is not for the faint of heart, but for those willing to embrace the challenges and opportunities it presents, it can be a rewarding and fulfilling journey. Remember, your dedication to this role contributes not only to the success of your projects but also to the broader Agile community.
In closing, the role of a CSPO is a journey of perpetual growth and a commitment to delivering value to customers while embracing the principles of Agile. Whether you're an aspiring CSPO or an experienced one, this role offers an ongoing opportunity to make a meaningful impact in the world of product development.
Thank you for accompanying us on this exploration of the CSPO role. May your journey as a Certified Scrum Product Owner be filled with continuous improvement, successful projects, and valuable product deliveries.
Benefits of CTFL Certification
In the ever-evolving landscape of software development, quality assurance and testing play a pivotal role in ensuring that applications and systems perform flawlessly. The Certified Tester Foundation Level (CTFL) certification stands as a beacon for those aspiring to excel in the field of software testing. It is a globally recognized and respected certification that opens doors to a world of opportunities in the realms of quality assurance and software testing. In this article, we will explore the numerous benefits of CTFL certification, shedding light on how it can empower individuals and organizations alike in their quest for excellence in software testing.
CTFL certification, like a well-constructed test plan, is structured to validate the skills and knowledge of aspiring software testers. It offers a multitude of advantages that extend beyond simply adding a prestigious credential to your name. This certification has the potential to reshape your career, enhance your skills, and contribute significantly to the quality and reliability of the software you are responsible for testing.
Let's dive deeper into the benefits of CTFL certification, from improved career prospects to enhanced testing capabilities, and discover why this certification is a game-changer in the world of software testing.
Table of Contents
-
Career Advancement
-
Global Recognition
-
Skill Enhancement
-
Quality Assurance Impact
-
Increased Marketability
-
Career Transition
-
Knowledge Expansion
-
Professional Networking
-
Organizational Benefits
-
Long-Term Career Growth
-
Conclusion
Career Advancement
In today's competitive job market, professionals are constantly seeking ways to distinguish themselves and achieve career growth. One powerful strategy to achieve career advancement, especially in the realm of software testing and quality assurance, is obtaining the Certified Tester Foundation Level (CTFL) certification. This certification offers a myriad of benefits that can significantly impact your career trajectory. Here's how:
Increased Employability: CTFL certification makes you a more attractive candidate to employers. It demonstrates your commitment to your field and validates your knowledge and skills in software testing. As a result, you become a preferred choice for hiring managers when filling positions related to quality assurance.
Career Opportunities: CTFL opens doors to a broader range of job opportunities. Whether you are seeking a new position, looking to switch industries, or aiming for a promotion within your current organization, having CTFL on your resume can make a substantial difference. Many job postings explicitly require or prefer candidates with testing certifications.
Salary Advancement: It's no secret that certified professionals often command higher salaries. CTFL certification can lead to better compensation packages, including increased base pay, bonuses, and benefits. Employers are willing to pay more for professionals who bring demonstrable skills and expertise to the table.
Career Progression: Career advancement isn't just about securing a job; it's also about climbing the career ladder. CTFL certification provides a solid foundation for further career progression. It can serve as a stepping stone to more advanced certifications and senior roles within the software testing domain.
Improved Job Security: With the increasing demand for quality software, CTFL-certified professionals tend to enjoy more job security. In times of economic uncertainty, organizations are less likely to let go of employees who are essential to ensuring the quality of their products.
CTFL certification is a strategic investment in your career. It enhances your employability, increases your career opportunities, and can lead to higher earnings. Beyond the financial aspects, it also nurtures your professional growth, offering job security and the potential for leadership roles. In the dynamic field of software testing, CTFL certification is a pathway to a rewarding and successful career.
Global Recognition
In an increasingly interconnected world, the value of professional certifications extends far beyond local or regional boundaries. The Certified Tester Foundation Level (CTFL) certification is a prime example of a qualification that enjoys widespread global recognition and respect. This recognition has several significant implications for those who hold the CTFL certification:
International Employability: One of the most compelling benefits of CTFL certification is that it's universally recognized. Whether you are looking to work in your home country or explore opportunities abroad, having CTFL on your resume assures potential employers of your standardized expertise in software testing. This opens doors to a diverse range of international job markets.
Consistency in Skill Set: CTFL's global recognition means that certified professionals share a common knowledge base and understanding of software testing practices. This consistency ensures that employers, regardless of their location, can rely on the skills and competencies of CTFL-certified individuals.
Trust and Credibility: CTFL is endorsed by a variety of prominent organizations and industry bodies. This certification carries an assurance of quality and reliability. Employers often trust the certification as a benchmark of excellence in software testing.
Cross-Industry Applicability: The principles and best practices in software testing are universal and relevant across various industries. CTFL's global recognition allows certified professionals to transition seamlessly between different sectors, such as healthcare, finance, automotive, and more.
Alignment with Industry Standards: CTFL aligns with international testing and quality standards, including those defined by the International Software Testing Qualifications Board (ISTQB). This alignment ensures that CTFL-certified individuals have a strong foundation in globally accepted testing methodologies.
International Collaboration: Being part of the CTFL-certified community provides opportunities for international collaboration. You can connect with professionals from diverse backgrounds, share knowledge, and stay updated on global testing trends and practices.
Competitive Advantage: When competing for job roles or promotions, CTFL certification can give you a significant competitive advantage. Employers often prioritize candidates with internationally recognized certifications to ensure their teams adhere to global testing standards.
In summary, the global recognition of CTFL certification is not just a label; it's a powerful testament to your skills and expertise in software testing that transcends borders. This recognition facilitates international career opportunities, provides a foundation for consistent quality, and positions you as a credible and trusted professional in the ever-expanding global software testing community.
Skill Enhancement
Certainly, let's delve into the subtopic of "Skill Enhancement" and explore how the Certified Tester Foundation Level (CTFL) certification can significantly enhance one's skills in the field of software testing:
Skill Enhancement with CTFL Certification
In the dynamic and ever-evolving realm of software testing, the ability to adapt, learn, and master new skills is essential for professional growth. CTFL certification is a gateway to skill enhancement, providing individuals with a structured and comprehensive foundation in software testing. Here's how CTFL enhances one's skills:
Comprehensive Understanding of Software Testing: CTFL certification equips professionals with a holistic understanding of software testing concepts, methodologies, and techniques. This includes knowledge of test planning, test design, test execution, and test management. By mastering these fundamentals, CTFL-certified individuals can contribute more effectively to the testing process.
Practical Testing Techniques: CTFL covers practical testing techniques that are essential for efficient software testing. It includes topics like boundary value analysis, equivalence partitioning, and decision table testing. These techniques enable testers to design and execute test cases that identify defects and improve software quality.
Test Documentation: Effective communication and documentation are key skills in software testing. CTFL certification emphasizes the creation of clear and well-organized test documentation, including test plans, test cases, and test reports. This skill enhances transparency and collaboration within testing teams.
Test Management: CTFL provides insights into test management practices, which involve planning, monitoring, and controlling testing activities. Understanding test management allows professionals to ensure that testing efforts align with project goals and timelines.
Effective Communication: Effective communication is vital for collaborating with development teams, stakeholders, and fellow testers. CTFL training encourages clear and concise communication, improving teamwork and understanding of testing objectives.
CTFL certification is a powerful catalyst for skill enhancement in the software testing domain. It imparts a strong foundation of knowledge and practical skills, enabling professionals to excel in their testing roles. By continually honing their abilities and staying up-to-date with industry best practices, CTFL-certified individuals can contribute significantly to the quality and reliability of the software they test.
Quality Assurance Impact
Quality assurance (QA) is at the heart of delivering reliable and high-quality software products. CTFL certification plays a pivotal role in enhancing and contributing to the overall quality assurance process. Here's how CTFL certification can impact quality assurance:
Early Defect Detection: CTFL emphasizes the importance of detecting defects at an early stage of the software development life cycle. CTFL-certified testers are trained to create test cases that catch defects before they propagate to later phases, reducing the cost and effort required for fixing them.
Enhanced Test Coverage: Quality assurance is closely linked to comprehensive test coverage. CTFL-certified individuals are skilled in various testing techniques and approaches that ensure a wider range of scenarios are considered during testing. This increased coverage leads to better assurance of software quality.
Consistency in Testing: Standardized testing practices and terminology are emphasized in CTFL training. This consistency across testing efforts enhances collaboration within QA teams and between development and testing teams, resulting in higher quality products.
Reduced Software Defects: CTFL-certified professionals are well-versed in identifying, reporting, and managing software defects. This leads to a decrease in the number of critical defects that reach the production phase, ultimately improving the end-user experience.
Collaboration and Communication: Effective communication is vital in quality assurance. CTFL training promotes clear and concise communication among team members, including developers, stakeholders, and fellow testers. This enhances collaboration and understanding of quality objectives.
CTFL certification has a profound impact on quality assurance within the software development process. It empowers professionals to adopt best practices, improve defect detection, and ensure the consistency and reliability of the software being tested. The result is higher-quality software products that meet or exceed user expectations, ultimately contributing to the success of software projects and the satisfaction of end-users.
Increased Marketability
In today's competitive job market, having a strong skill set and relevant certifications can significantly boost your marketability. The CTFL certification, with its global recognition and focus on fundamental software testing knowledge, can make you a more attractive candidate to employers. Here's how CTFL certification increases your marketability:
Attractiveness to Employers: CTFL certification on your resume immediately sets you apart from other candidates. Employers often receive a large number of applications for job openings, and having a recognized certification demonstrates your commitment and expertise in software testing.
Wider Job Opportunities: CTFL certification opens the door to a broader range of job opportunities. Many job postings explicitly require or prefer candidates with testing certifications, giving you access to a variety of roles in different industries and sectors.
Industry Recognition: CTFL is internationally recognized and respected in the software testing industry. This recognition carries weight and establishes your credibility as a competent tester, regardless of your prior experience.
Confidence Boost: Being CTFL-certified boosts your self-confidence. Knowing that you have achieved a globally recognized certification enhances your self-assurance, making you more convincing in job interviews and discussions with potential employers.
Networking Opportunities: CTFL certification often connects you to a community of certified professionals. This network can provide valuable mentorship, guidance, and opportunities for collaboration, helping you expand your professional connections and discover new career possibilities.
CTFL certification significantly enhances your marketability in the software testing industry. It makes you a more appealing candidate for job opportunities, increases your earning potential, and positions you as a credible and proficient tester. This certification serves as a valuable investment in your career, providing long-term benefits in a competitive job market.
Career Transition
Changing careers can be a challenging and rewarding journey, and the CTFL certification can be a valuable asset in facilitating a transition into the field of software testing. Here's how CTFL certification can help individuals navigate a successful career transition:
Establishing Credibility: Career transitions often involve moving into a field where you may have limited prior experience. CTFL certification establishes your credibility and competence as a software tester, which can be reassuring to potential employers who may have concerns about your background.
Fundamental Knowledge: CTFL provides a foundational understanding of software testing principles and practices. It equips you with essential knowledge and skills, even if you are new to the field, giving you the confidence to contribute effectively in a testing role.
Career Entry: Many employers look for CTFL-certified individuals when hiring entry-level testers. This certification can be a foot in the door, making it easier to secure your first job in the software testing industry.
Networking Opportunities: CTFL certification often connects you with a community of certified professionals. This network can provide mentorship, guidance, and job leads, making your transition smoother and more informed.
Continuous Learning: CTFL certification instills a mindset of continuous learning. As you transition into a new career, this mindset will serve you well as you adapt to changing industry trends and technologies.
CTFL certification is an excellent resource for those seeking to make a career transition into the software testing field. It helps establish your credibility, provides foundational knowledge, and connects you to a supportive community. This certification is an invaluable tool to help you embark on a new and promising career in software testing, regardless of your prior professional background.
Knowledge Expansion
Continuous learning is a cornerstone of professional growth, especially in the dynamic field of software testing. CTFL certification not only validates existing knowledge but also serves as a catalyst for knowledge expansion. Here's how CTFL certification contributes to knowledge expansion:
Fundamental Knowledge: CTFL certification provides a solid foundation in software testing principles, methodologies, and terminology. This foundational knowledge is essential for building a comprehensive understanding of the field.
Test Automation: CTFL touches on test automation, providing an introduction to automation concepts and tools. This knowledge is particularly valuable in today's testing landscape, where automation is a key focus.
Risk Assessment: CTFL teaches you to assess risks in the software testing process. Understanding risk allows you to make informed decisions about where to focus your testing efforts, expanding your capacity to address high-impact areas.
Quality Standards: CTFL aligns with international quality and testing standards, including those defined by the International Software Testing Qualifications Board (ISTQB). Familiarity with these standards ensures your work is in line with recognized benchmarks.
Documentation Skills: Effective communication and documentation are vital in software testing. CTFL places importance on clear and structured test documentation, fostering your documentation skills.
Problem-Solving: Software testing often requires critical thinking and creative problem-solving. CTFL certification hones these skills as you learn to identify defects, investigate their causes, and suggest effective solutions.
Networking: CTFL certification often connects you with a community of certified professionals. This network provides opportunities for knowledge sharing, collaboration, and mentorship, expanding your knowledge base through the experiences of others.
CTFL certification is not just a static credential; it's a journey of knowledge expansion. It introduces you to the core concepts and practices in software testing, setting the stage for ongoing learning and growth in the field. As you apply what you've learned and continue to explore new horizons, your knowledge and expertise in software testing will naturally expand, making you a more valuable asset in the industry.
Professional Networking
Networking is an essential aspect of career development, and CTFL certification can significantly enhance your professional networking opportunities in the field of software testing. Here's how CTFL certification contributes to professional networking:
Access to a Certified Community: CTFL certification often connects you to a global community of certified professionals. This community provides a valuable network of like-minded individuals who share your passion for software testing and quality assurance.
Career Opportunities: Your network of CTFL-certified professionals can serve as a valuable resource for job leads and career opportunities. You may learn about job openings, referrals, or recommendations through your network.
Conferences and Events: Many software testing conferences and events host gatherings for certified professionals. Attending these events provides you with in-person networking opportunities, where you can meet and connect with fellow CTFL-certified individuals.
Local Chapters and Associations: CTFL certification is often associated with local and national testing associations and chapters. Joining these associations provides opportunities to network with professionals in your region and get involved in community activities.
Job References and Recommendations: Your professional network can serve as references and provide recommendations when you seek new opportunities or career growth. Having a strong network of colleagues who can vouch for your skills and work ethic can be invaluable.
CTFL certification extends beyond validating your skills; it connects you with a community of professionals who share your passion for software testing. The network you build through CTFL certification can offer knowledge sharing, mentorship, collaboration, job opportunities, and valuable career insights, ultimately enriching your career in the software testing industry.
Organizational Benefits
Enhanced Software Quality: CTFL-certified professionals possess a strong understanding of testing principles and best practices. Their expertise leads to improved software quality, reducing the number of defects and ensuring that the software meets or exceeds user expectations.
Reduced Defects and Costs: Early defect detection by CTFL-certified testers results in a reduction of defects that reach the production phase. This leads to cost savings by minimizing the need for post-release bug fixes and patches, which can be expensive and time-consuming.
Efficient Testing Processes: CTFL certification ensures that testing processes are optimized and aligned with industry best practices. This efficiency streamlines testing efforts, reduces redundancy, and enhances productivity within the organization.
Consistency and Standardization: CTFL-certified professionals adhere to standardized terminology and practices. This consistency improves communication within the testing team and fosters a unified approach to software testing.
Risk Mitigation: CTFL certification equips professionals with skills in risk assessment. They can identify high-risk areas within projects and allocate testing resources accordingly, reducing the likelihood of critical issues going unnoticed.
Alignment with Industry Standards: CTFL certification aligns with internationally recognized testing standards, including those defined by the International Software Testing Qualifications Board (ISTQB). This alignment ensures that the organization's testing practices conform to industry-recognized benchmarks.
Enhanced Test Documentation: Effective communication and documentation are vital in software testing. CTFL certification promotes clear and structured test documentation, enhancing transparency and facilitating project management.
Adaptability to Industry Changes: CTFL-certified professionals are well-prepared to adapt to industry changes, such as new technologies and methodologies. This adaptability allows the organization to stay competitive and relevant in the evolving field of software testing.
CTFL certification brings numerous organizational benefits, including improved software quality, cost savings, efficient testing processes, and a competitive advantage in the market. Organizations that invest in CTFL-certified professionals can deliver higher-quality software products, reduce risks, and gain a reputation for reliability and excellence in the field of software testing.
Long-Term Career Growth
CTFL certification serves as a foundational stepping stone for professionals in the software testing field, providing numerous opportunities for long-term career growth. Here's how CTFL certification can contribute to your career advancement over time:
Foundation for Advanced Certifications: CTFL is often the first step in a series of software testing certifications. Building upon CTFL, you can pursue more advanced certifications such as Certified Tester Advanced Level (CTAL) or specialized certifications in areas like test automation, security testing, or performance testing. These advanced certifications can open doors to higher-level roles and increased earning potential.
Expanded Skill Set: As you gain practical experience and advance in your career, the knowledge and skills acquired through CTFL certification continue to benefit you. The foundational principles and best practices you've learned serve as a solid base for acquiring new and more specialized skills over time.
Leadership Opportunities: CTFL-certified professionals are often well-positioned to take on leadership roles within their organizations. With experience and additional training, you can move into positions such as Test Manager or Test Lead, where you'll be responsible for managing testing teams and overseeing testing efforts.
Consulting and Training: With advanced certifications and substantial experience, you may choose to venture into consulting or training. Becoming a testing consultant or trainer can be a rewarding career path, offering opportunities to work with various organizations and share your expertise.
Industry Involvement: Many CTFL-certified professionals actively participate in industry associations, forums, and conferences. Involvement in industry organizations can expand your network, expose you to emerging trends, and provide opportunities for thought leadership.
Job Security: As the demand for high-quality software continues to grow, CTFL-certified professionals often enjoy job security. Organizations value individuals who can ensure software quality, making your career in software testing more resilient.
CTFL certification is not just a one-time achievement; it's a foundation for long-term career growth in the software testing and quality assurance field. Whether you choose to specialize, pursue advanced certifications, or take on leadership roles, CTFL certification provides the knowledge and credibility necessary to support your journey to success in the ever-evolving world of software testing.
Conclusion
In conclusion, the Certified Tester Foundation Level (CTFL) certification offers a wide range of benefits for individuals, organizations, and the software testing industry as a whole.
For individuals, CTFL certification serves as a valuable credential that enhances their skills, employability, and marketability.CTFL-certified professionals often find themselves well-prepared for various roles, from entry-level positions to more advanced, specialized, and leadership roles. This certification not only validates their expertise but also fosters a culture of continuous learning and adaptability, ensuring long-term career growth.
For organizations, CTFL-certified professionals bring a wealth of advantages. They contribute to improved software quality, reduced defects, cost savings, and efficient testing processes. CTFL certification aligns with industry standards and promotes consistency in testing practices, mitigating risks and enhancing documentation and communication. As a result, organizations benefit from higher client satisfaction, a competitive edge, and a reputation for reliability and quality in the software testing domain.
In essence, CTFL certification is not just a single achievement; it's a dynamic and evolving journey. It supports the growth and success of individuals and organizations in the field of software testing, ensuring that software products are of high quality, meet user expectations, and contribute to the advancement of the software industry as a whole.
Read More
In the ever-evolving landscape of software development, quality assurance and testing play a pivotal role in ensuring that applications and systems perform flawlessly. The Certified Tester Foundation Level (CTFL) certification stands as a beacon for those aspiring to excel in the field of software testing. It is a globally recognized and respected certification that opens doors to a world of opportunities in the realms of quality assurance and software testing. In this article, we will explore the numerous benefits of CTFL certification, shedding light on how it can empower individuals and organizations alike in their quest for excellence in software testing.
CTFL certification, like a well-constructed test plan, is structured to validate the skills and knowledge of aspiring software testers. It offers a multitude of advantages that extend beyond simply adding a prestigious credential to your name. This certification has the potential to reshape your career, enhance your skills, and contribute significantly to the quality and reliability of the software you are responsible for testing.
Let's dive deeper into the benefits of CTFL certification, from improved career prospects to enhanced testing capabilities, and discover why this certification is a game-changer in the world of software testing.
Table of Contents
-
Career Advancement
-
Global Recognition
-
Skill Enhancement
-
Quality Assurance Impact
-
Increased Marketability
-
Career Transition
-
Knowledge Expansion
-
Professional Networking
-
Organizational Benefits
-
Long-Term Career Growth
-
Conclusion
Career Advancement
In today's competitive job market, professionals are constantly seeking ways to distinguish themselves and achieve career growth. One powerful strategy to achieve career advancement, especially in the realm of software testing and quality assurance, is obtaining the Certified Tester Foundation Level (CTFL) certification. This certification offers a myriad of benefits that can significantly impact your career trajectory. Here's how:
Increased Employability: CTFL certification makes you a more attractive candidate to employers. It demonstrates your commitment to your field and validates your knowledge and skills in software testing. As a result, you become a preferred choice for hiring managers when filling positions related to quality assurance.
Career Opportunities: CTFL opens doors to a broader range of job opportunities. Whether you are seeking a new position, looking to switch industries, or aiming for a promotion within your current organization, having CTFL on your resume can make a substantial difference. Many job postings explicitly require or prefer candidates with testing certifications.
Salary Advancement: It's no secret that certified professionals often command higher salaries. CTFL certification can lead to better compensation packages, including increased base pay, bonuses, and benefits. Employers are willing to pay more for professionals who bring demonstrable skills and expertise to the table.
Career Progression: Career advancement isn't just about securing a job; it's also about climbing the career ladder. CTFL certification provides a solid foundation for further career progression. It can serve as a stepping stone to more advanced certifications and senior roles within the software testing domain.
Improved Job Security: With the increasing demand for quality software, CTFL-certified professionals tend to enjoy more job security. In times of economic uncertainty, organizations are less likely to let go of employees who are essential to ensuring the quality of their products.
CTFL certification is a strategic investment in your career. It enhances your employability, increases your career opportunities, and can lead to higher earnings. Beyond the financial aspects, it also nurtures your professional growth, offering job security and the potential for leadership roles. In the dynamic field of software testing, CTFL certification is a pathway to a rewarding and successful career.
Global Recognition
In an increasingly interconnected world, the value of professional certifications extends far beyond local or regional boundaries. The Certified Tester Foundation Level (CTFL) certification is a prime example of a qualification that enjoys widespread global recognition and respect. This recognition has several significant implications for those who hold the CTFL certification:
International Employability: One of the most compelling benefits of CTFL certification is that it's universally recognized. Whether you are looking to work in your home country or explore opportunities abroad, having CTFL on your resume assures potential employers of your standardized expertise in software testing. This opens doors to a diverse range of international job markets.
Consistency in Skill Set: CTFL's global recognition means that certified professionals share a common knowledge base and understanding of software testing practices. This consistency ensures that employers, regardless of their location, can rely on the skills and competencies of CTFL-certified individuals.
Trust and Credibility: CTFL is endorsed by a variety of prominent organizations and industry bodies. This certification carries an assurance of quality and reliability. Employers often trust the certification as a benchmark of excellence in software testing.
Cross-Industry Applicability: The principles and best practices in software testing are universal and relevant across various industries. CTFL's global recognition allows certified professionals to transition seamlessly between different sectors, such as healthcare, finance, automotive, and more.
Alignment with Industry Standards: CTFL aligns with international testing and quality standards, including those defined by the International Software Testing Qualifications Board (ISTQB). This alignment ensures that CTFL-certified individuals have a strong foundation in globally accepted testing methodologies.
International Collaboration: Being part of the CTFL-certified community provides opportunities for international collaboration. You can connect with professionals from diverse backgrounds, share knowledge, and stay updated on global testing trends and practices.
Competitive Advantage: When competing for job roles or promotions, CTFL certification can give you a significant competitive advantage. Employers often prioritize candidates with internationally recognized certifications to ensure their teams adhere to global testing standards.
In summary, the global recognition of CTFL certification is not just a label; it's a powerful testament to your skills and expertise in software testing that transcends borders. This recognition facilitates international career opportunities, provides a foundation for consistent quality, and positions you as a credible and trusted professional in the ever-expanding global software testing community.
Skill Enhancement
Certainly, let's delve into the subtopic of "Skill Enhancement" and explore how the Certified Tester Foundation Level (CTFL) certification can significantly enhance one's skills in the field of software testing:
Skill Enhancement with CTFL Certification
In the dynamic and ever-evolving realm of software testing, the ability to adapt, learn, and master new skills is essential for professional growth. CTFL certification is a gateway to skill enhancement, providing individuals with a structured and comprehensive foundation in software testing. Here's how CTFL enhances one's skills:
Comprehensive Understanding of Software Testing: CTFL certification equips professionals with a holistic understanding of software testing concepts, methodologies, and techniques. This includes knowledge of test planning, test design, test execution, and test management. By mastering these fundamentals, CTFL-certified individuals can contribute more effectively to the testing process.
Practical Testing Techniques: CTFL covers practical testing techniques that are essential for efficient software testing. It includes topics like boundary value analysis, equivalence partitioning, and decision table testing. These techniques enable testers to design and execute test cases that identify defects and improve software quality.
Test Documentation: Effective communication and documentation are key skills in software testing. CTFL certification emphasizes the creation of clear and well-organized test documentation, including test plans, test cases, and test reports. This skill enhances transparency and collaboration within testing teams.
Test Management: CTFL provides insights into test management practices, which involve planning, monitoring, and controlling testing activities. Understanding test management allows professionals to ensure that testing efforts align with project goals and timelines.
Effective Communication: Effective communication is vital for collaborating with development teams, stakeholders, and fellow testers. CTFL training encourages clear and concise communication, improving teamwork and understanding of testing objectives.
CTFL certification is a powerful catalyst for skill enhancement in the software testing domain. It imparts a strong foundation of knowledge and practical skills, enabling professionals to excel in their testing roles. By continually honing their abilities and staying up-to-date with industry best practices, CTFL-certified individuals can contribute significantly to the quality and reliability of the software they test.
Quality Assurance Impact
Quality assurance (QA) is at the heart of delivering reliable and high-quality software products. CTFL certification plays a pivotal role in enhancing and contributing to the overall quality assurance process. Here's how CTFL certification can impact quality assurance:
Early Defect Detection: CTFL emphasizes the importance of detecting defects at an early stage of the software development life cycle. CTFL-certified testers are trained to create test cases that catch defects before they propagate to later phases, reducing the cost and effort required for fixing them.
Enhanced Test Coverage: Quality assurance is closely linked to comprehensive test coverage. CTFL-certified individuals are skilled in various testing techniques and approaches that ensure a wider range of scenarios are considered during testing. This increased coverage leads to better assurance of software quality.
Consistency in Testing: Standardized testing practices and terminology are emphasized in CTFL training. This consistency across testing efforts enhances collaboration within QA teams and between development and testing teams, resulting in higher quality products.
Reduced Software Defects: CTFL-certified professionals are well-versed in identifying, reporting, and managing software defects. This leads to a decrease in the number of critical defects that reach the production phase, ultimately improving the end-user experience.
Collaboration and Communication: Effective communication is vital in quality assurance. CTFL training promotes clear and concise communication among team members, including developers, stakeholders, and fellow testers. This enhances collaboration and understanding of quality objectives.
CTFL certification has a profound impact on quality assurance within the software development process. It empowers professionals to adopt best practices, improve defect detection, and ensure the consistency and reliability of the software being tested. The result is higher-quality software products that meet or exceed user expectations, ultimately contributing to the success of software projects and the satisfaction of end-users.
Increased Marketability
In today's competitive job market, having a strong skill set and relevant certifications can significantly boost your marketability. The CTFL certification, with its global recognition and focus on fundamental software testing knowledge, can make you a more attractive candidate to employers. Here's how CTFL certification increases your marketability:
Attractiveness to Employers: CTFL certification on your resume immediately sets you apart from other candidates. Employers often receive a large number of applications for job openings, and having a recognized certification demonstrates your commitment and expertise in software testing.
Wider Job Opportunities: CTFL certification opens the door to a broader range of job opportunities. Many job postings explicitly require or prefer candidates with testing certifications, giving you access to a variety of roles in different industries and sectors.
Industry Recognition: CTFL is internationally recognized and respected in the software testing industry. This recognition carries weight and establishes your credibility as a competent tester, regardless of your prior experience.
Confidence Boost: Being CTFL-certified boosts your self-confidence. Knowing that you have achieved a globally recognized certification enhances your self-assurance, making you more convincing in job interviews and discussions with potential employers.
Networking Opportunities: CTFL certification often connects you to a community of certified professionals. This network can provide valuable mentorship, guidance, and opportunities for collaboration, helping you expand your professional connections and discover new career possibilities.
CTFL certification significantly enhances your marketability in the software testing industry. It makes you a more appealing candidate for job opportunities, increases your earning potential, and positions you as a credible and proficient tester. This certification serves as a valuable investment in your career, providing long-term benefits in a competitive job market.
Career Transition
Changing careers can be a challenging and rewarding journey, and the CTFL certification can be a valuable asset in facilitating a transition into the field of software testing. Here's how CTFL certification can help individuals navigate a successful career transition:
Establishing Credibility: Career transitions often involve moving into a field where you may have limited prior experience. CTFL certification establishes your credibility and competence as a software tester, which can be reassuring to potential employers who may have concerns about your background.
Fundamental Knowledge: CTFL provides a foundational understanding of software testing principles and practices. It equips you with essential knowledge and skills, even if you are new to the field, giving you the confidence to contribute effectively in a testing role.
Career Entry: Many employers look for CTFL-certified individuals when hiring entry-level testers. This certification can be a foot in the door, making it easier to secure your first job in the software testing industry.
Networking Opportunities: CTFL certification often connects you with a community of certified professionals. This network can provide mentorship, guidance, and job leads, making your transition smoother and more informed.
Continuous Learning: CTFL certification instills a mindset of continuous learning. As you transition into a new career, this mindset will serve you well as you adapt to changing industry trends and technologies.
CTFL certification is an excellent resource for those seeking to make a career transition into the software testing field. It helps establish your credibility, provides foundational knowledge, and connects you to a supportive community. This certification is an invaluable tool to help you embark on a new and promising career in software testing, regardless of your prior professional background.
Knowledge Expansion
Continuous learning is a cornerstone of professional growth, especially in the dynamic field of software testing. CTFL certification not only validates existing knowledge but also serves as a catalyst for knowledge expansion. Here's how CTFL certification contributes to knowledge expansion:
Fundamental Knowledge: CTFL certification provides a solid foundation in software testing principles, methodologies, and terminology. This foundational knowledge is essential for building a comprehensive understanding of the field.
Test Automation: CTFL touches on test automation, providing an introduction to automation concepts and tools. This knowledge is particularly valuable in today's testing landscape, where automation is a key focus.
Risk Assessment: CTFL teaches you to assess risks in the software testing process. Understanding risk allows you to make informed decisions about where to focus your testing efforts, expanding your capacity to address high-impact areas.
Quality Standards: CTFL aligns with international quality and testing standards, including those defined by the International Software Testing Qualifications Board (ISTQB). Familiarity with these standards ensures your work is in line with recognized benchmarks.
Documentation Skills: Effective communication and documentation are vital in software testing. CTFL places importance on clear and structured test documentation, fostering your documentation skills.
Problem-Solving: Software testing often requires critical thinking and creative problem-solving. CTFL certification hones these skills as you learn to identify defects, investigate their causes, and suggest effective solutions.
Networking: CTFL certification often connects you with a community of certified professionals. This network provides opportunities for knowledge sharing, collaboration, and mentorship, expanding your knowledge base through the experiences of others.
CTFL certification is not just a static credential; it's a journey of knowledge expansion. It introduces you to the core concepts and practices in software testing, setting the stage for ongoing learning and growth in the field. As you apply what you've learned and continue to explore new horizons, your knowledge and expertise in software testing will naturally expand, making you a more valuable asset in the industry.
Professional Networking
Networking is an essential aspect of career development, and CTFL certification can significantly enhance your professional networking opportunities in the field of software testing. Here's how CTFL certification contributes to professional networking:
Access to a Certified Community: CTFL certification often connects you to a global community of certified professionals. This community provides a valuable network of like-minded individuals who share your passion for software testing and quality assurance.
Career Opportunities: Your network of CTFL-certified professionals can serve as a valuable resource for job leads and career opportunities. You may learn about job openings, referrals, or recommendations through your network.
Conferences and Events: Many software testing conferences and events host gatherings for certified professionals. Attending these events provides you with in-person networking opportunities, where you can meet and connect with fellow CTFL-certified individuals.
Local Chapters and Associations: CTFL certification is often associated with local and national testing associations and chapters. Joining these associations provides opportunities to network with professionals in your region and get involved in community activities.
Job References and Recommendations: Your professional network can serve as references and provide recommendations when you seek new opportunities or career growth. Having a strong network of colleagues who can vouch for your skills and work ethic can be invaluable.
CTFL certification extends beyond validating your skills; it connects you with a community of professionals who share your passion for software testing. The network you build through CTFL certification can offer knowledge sharing, mentorship, collaboration, job opportunities, and valuable career insights, ultimately enriching your career in the software testing industry.
Organizational Benefits
Enhanced Software Quality: CTFL-certified professionals possess a strong understanding of testing principles and best practices. Their expertise leads to improved software quality, reducing the number of defects and ensuring that the software meets or exceeds user expectations.
Reduced Defects and Costs: Early defect detection by CTFL-certified testers results in a reduction of defects that reach the production phase. This leads to cost savings by minimizing the need for post-release bug fixes and patches, which can be expensive and time-consuming.
Efficient Testing Processes: CTFL certification ensures that testing processes are optimized and aligned with industry best practices. This efficiency streamlines testing efforts, reduces redundancy, and enhances productivity within the organization.
Consistency and Standardization: CTFL-certified professionals adhere to standardized terminology and practices. This consistency improves communication within the testing team and fosters a unified approach to software testing.
Risk Mitigation: CTFL certification equips professionals with skills in risk assessment. They can identify high-risk areas within projects and allocate testing resources accordingly, reducing the likelihood of critical issues going unnoticed.
Alignment with Industry Standards: CTFL certification aligns with internationally recognized testing standards, including those defined by the International Software Testing Qualifications Board (ISTQB). This alignment ensures that the organization's testing practices conform to industry-recognized benchmarks.
Enhanced Test Documentation: Effective communication and documentation are vital in software testing. CTFL certification promotes clear and structured test documentation, enhancing transparency and facilitating project management.
Adaptability to Industry Changes: CTFL-certified professionals are well-prepared to adapt to industry changes, such as new technologies and methodologies. This adaptability allows the organization to stay competitive and relevant in the evolving field of software testing.
CTFL certification brings numerous organizational benefits, including improved software quality, cost savings, efficient testing processes, and a competitive advantage in the market. Organizations that invest in CTFL-certified professionals can deliver higher-quality software products, reduce risks, and gain a reputation for reliability and excellence in the field of software testing.
Long-Term Career Growth
CTFL certification serves as a foundational stepping stone for professionals in the software testing field, providing numerous opportunities for long-term career growth. Here's how CTFL certification can contribute to your career advancement over time:
Foundation for Advanced Certifications: CTFL is often the first step in a series of software testing certifications. Building upon CTFL, you can pursue more advanced certifications such as Certified Tester Advanced Level (CTAL) or specialized certifications in areas like test automation, security testing, or performance testing. These advanced certifications can open doors to higher-level roles and increased earning potential.
Expanded Skill Set: As you gain practical experience and advance in your career, the knowledge and skills acquired through CTFL certification continue to benefit you. The foundational principles and best practices you've learned serve as a solid base for acquiring new and more specialized skills over time.
Leadership Opportunities: CTFL-certified professionals are often well-positioned to take on leadership roles within their organizations. With experience and additional training, you can move into positions such as Test Manager or Test Lead, where you'll be responsible for managing testing teams and overseeing testing efforts.
Consulting and Training: With advanced certifications and substantial experience, you may choose to venture into consulting or training. Becoming a testing consultant or trainer can be a rewarding career path, offering opportunities to work with various organizations and share your expertise.
Industry Involvement: Many CTFL-certified professionals actively participate in industry associations, forums, and conferences. Involvement in industry organizations can expand your network, expose you to emerging trends, and provide opportunities for thought leadership.
Job Security: As the demand for high-quality software continues to grow, CTFL-certified professionals often enjoy job security. Organizations value individuals who can ensure software quality, making your career in software testing more resilient.
CTFL certification is not just a one-time achievement; it's a foundation for long-term career growth in the software testing and quality assurance field. Whether you choose to specialize, pursue advanced certifications, or take on leadership roles, CTFL certification provides the knowledge and credibility necessary to support your journey to success in the ever-evolving world of software testing.
Conclusion
In conclusion, the Certified Tester Foundation Level (CTFL) certification offers a wide range of benefits for individuals, organizations, and the software testing industry as a whole.
For individuals, CTFL certification serves as a valuable credential that enhances their skills, employability, and marketability.CTFL-certified professionals often find themselves well-prepared for various roles, from entry-level positions to more advanced, specialized, and leadership roles. This certification not only validates their expertise but also fosters a culture of continuous learning and adaptability, ensuring long-term career growth.
For organizations, CTFL-certified professionals bring a wealth of advantages. They contribute to improved software quality, reduced defects, cost savings, and efficient testing processes. CTFL certification aligns with industry standards and promotes consistency in testing practices, mitigating risks and enhancing documentation and communication. As a result, organizations benefit from higher client satisfaction, a competitive edge, and a reputation for reliability and quality in the software testing domain.
In essence, CTFL certification is not just a single achievement; it's a dynamic and evolving journey. It supports the growth and success of individuals and organizations in the field of software testing, ensuring that software products are of high quality, meet user expectations, and contribute to the advancement of the software industry as a whole.
Cisco's Strategic Investment in Cybersecurity Skills Certifications to Tackle the Shortage of Experts
Introduction
In today's digital landscape, cybersecurity has become a top priority for organizations around the world. The increasing frequency and sophistication of cyber threats have highlighted the critical need for skilled cybersecurity professionals. However, there is a shortage of experts in this field, making it challenging for businesses to protect their sensitive data and systems effectively. Cisco, a global technology leader, has recognized this gap and has taken a proactive approach to address the shortage of cybersecurity experts. With a focus on future skills certifications, Cisco is committed to providing the necessary education and training to develop a strong cybersecurity workforce.
Cisco Cybersecurity Investments
Cisco, a renowned name in the technology industry, has dedicated significant investments to enhance cybersecurity education and training. By leveraging its expertise in networking and security, Cisco aims to empower individuals with the knowledge and skills required to combat emerging cyber threats.
Through initiatives such as the Cisco Networking Academy, the company has been able to reach millions of students worldwide. The Networking Academy offers comprehensive training programs, including courses focused on cybersecurity. Students have the opportunity to gain hands-on experience and learn from industry experts, preparing them for real-world challenges.
Additionally, Cisco actively collaborates with educational institutions, government organizations, and businesses to promote cybersecurity awareness and education. By working together, these partnerships aim to create a more secure digital environment and bridge the cybersecurity skills gap.
Future Skills Certifications
Cisco has recognized the need for industry-recognized certifications that go beyond traditional qualifications. Future skills certifications focus on preparing individuals for the evolving landscape of cybersecurity, equipping them with the necessary skills to address emerging threats.
One of the notable future skills certifications offered by Cisco is the Cisco Certified CyberOps Associate. This certification validates an individual's knowledge in areas such as security concepts, security monitoring, and host-based analysis. By obtaining this certification, professionals can demonstrate their expertise in threat detection and response, essential skills in an increasingly complex cybersecurity landscape.
Cisco's commitment to future skills certifications extends beyond technical knowledge. The company also places emphasis on developing professionals with a holistic understanding of cybersecurity. This includes areas such as risk mitigation, governance, and compliance. By providing comprehensive training in these domains, Cisco ensures that cybersecurity experts are well-rounded and equipped to handle the multifaceted challenges of the digital age.
Addressing the Cybersecurity Expert Shortage
The shortage of cybersecurity experts is a global concern that affects organizations across various industries. Cisco understands the urgency of addressing this shortage and is actively working towards bridging the gap.
By investing in future skills certifications, Cisco is enabling individuals to acquire specialized knowledge and practical skills that are in high demand. These certifications not only prepare professionals for entry-level cybersecurity roles but also provide a pathway for career advancement and specialization.
Through its collaboration with educational institutions, Cisco aims to promote cybersecurity education from an early stage. By introducing students to cybersecurity concepts at the school level, Cisco is nurturing the next generation of cybersecurity experts, ensuring a sustainable pipeline of skilled professionals for the future.
Cisco's Commitment to Cybersecurity Education
Cisco's dedication to addressing the shortage of cybersecurity experts extends beyond certifications and training programs. The company places a strong emphasis on fostering a culture of cybersecurity education and awareness.
Through initiatives like the Cisco Security Ambassador Program, employees are encouraged to become advocates for cybersecurity. They are provided with resources and educational materials to help them stay informed about the latest threats and best practices. By empowering employees to take an active role in cybersecurity, Cisco strengthens its overall security posture and creates a more resilient organization.
Conclusion
As the digital landscape continues to evolve, the need for cybersecurity experts has never been more critical. Cisco's investments in future skills certifications and commitment to cybersecurity education demonstrate its commitment to addressing the shortage of experts in this field. By equipping individuals with the necessary knowledge and skills, Cisco is empowering a new generation of cybersecurity professionals who are ready to face the challenges of the digital age.
Read More
Introduction
In today's digital landscape, cybersecurity has become a top priority for organizations around the world. The increasing frequency and sophistication of cyber threats have highlighted the critical need for skilled cybersecurity professionals. However, there is a shortage of experts in this field, making it challenging for businesses to protect their sensitive data and systems effectively. Cisco, a global technology leader, has recognized this gap and has taken a proactive approach to address the shortage of cybersecurity experts. With a focus on future skills certifications, Cisco is committed to providing the necessary education and training to develop a strong cybersecurity workforce.
Cisco Cybersecurity Investments
Cisco, a renowned name in the technology industry, has dedicated significant investments to enhance cybersecurity education and training. By leveraging its expertise in networking and security, Cisco aims to empower individuals with the knowledge and skills required to combat emerging cyber threats.
Through initiatives such as the Cisco Networking Academy, the company has been able to reach millions of students worldwide. The Networking Academy offers comprehensive training programs, including courses focused on cybersecurity. Students have the opportunity to gain hands-on experience and learn from industry experts, preparing them for real-world challenges.
Additionally, Cisco actively collaborates with educational institutions, government organizations, and businesses to promote cybersecurity awareness and education. By working together, these partnerships aim to create a more secure digital environment and bridge the cybersecurity skills gap.
Future Skills Certifications
Cisco has recognized the need for industry-recognized certifications that go beyond traditional qualifications. Future skills certifications focus on preparing individuals for the evolving landscape of cybersecurity, equipping them with the necessary skills to address emerging threats.
One of the notable future skills certifications offered by Cisco is the Cisco Certified CyberOps Associate. This certification validates an individual's knowledge in areas such as security concepts, security monitoring, and host-based analysis. By obtaining this certification, professionals can demonstrate their expertise in threat detection and response, essential skills in an increasingly complex cybersecurity landscape.
Cisco's commitment to future skills certifications extends beyond technical knowledge. The company also places emphasis on developing professionals with a holistic understanding of cybersecurity. This includes areas such as risk mitigation, governance, and compliance. By providing comprehensive training in these domains, Cisco ensures that cybersecurity experts are well-rounded and equipped to handle the multifaceted challenges of the digital age.
Addressing the Cybersecurity Expert Shortage
The shortage of cybersecurity experts is a global concern that affects organizations across various industries. Cisco understands the urgency of addressing this shortage and is actively working towards bridging the gap.
By investing in future skills certifications, Cisco is enabling individuals to acquire specialized knowledge and practical skills that are in high demand. These certifications not only prepare professionals for entry-level cybersecurity roles but also provide a pathway for career advancement and specialization.
Through its collaboration with educational institutions, Cisco aims to promote cybersecurity education from an early stage. By introducing students to cybersecurity concepts at the school level, Cisco is nurturing the next generation of cybersecurity experts, ensuring a sustainable pipeline of skilled professionals for the future.
Cisco's Commitment to Cybersecurity Education
Cisco's dedication to addressing the shortage of cybersecurity experts extends beyond certifications and training programs. The company places a strong emphasis on fostering a culture of cybersecurity education and awareness.
Through initiatives like the Cisco Security Ambassador Program, employees are encouraged to become advocates for cybersecurity. They are provided with resources and educational materials to help them stay informed about the latest threats and best practices. By empowering employees to take an active role in cybersecurity, Cisco strengthens its overall security posture and creates a more resilient organization.
Conclusion
As the digital landscape continues to evolve, the need for cybersecurity experts has never been more critical. Cisco's investments in future skills certifications and commitment to cybersecurity education demonstrate its commitment to addressing the shortage of experts in this field. By equipping individuals with the necessary knowledge and skills, Cisco is empowering a new generation of cybersecurity professionals who are ready to face the challenges of the digital age.
OpenAI partners with ASU, granting full ChatGPT access
In a groundbreaking collaboration, OpenAI has joined forces with Arizona State University (ASU), ushering in a new era of advanced language models with full access to ChatGPT. As the next evolution in artificial intelligence, this partnership signifies a pivotal moment, leveraging the powerful capabilities of GPT-3 and paving the way for the highly anticipated GPT-4. OpenAI's commitment to innovation in the realm of AI chatbots is further exemplified by this collaboration, which not only grants unprecedented access to ChatGPT but also propels the conversation towards the future with a fusion of cutting-edge technologies like Azure OpenAI.
As OpenAI continues to make waves in the tech industry, the stock market is closely watching the developments in OpenAI stock. The integration of OpenAI's chatbots, including GPT-3 and the much-anticipated GPT-4, reflects the organization's dedication to pushing the boundaries of artificial intelligence. This collaboration not only showcases OpenAI's prowess in the field of text generation but also introduces users to the transformative potential of AI chatbots, including OpenAI Whisper.
With OpenAI ChatGPT at the forefront, users can now experience the unparalleled capabilities of OpenAI's text generators. The partnership with ASU not only expands the horizons of OpenAI's research but also underscores the company's commitment to democratizing access to advanced AI technologies. This milestone collaboration sets the stage for a future where openai.com remains synonymous with cutting-edge AI, empowering users to explore and harness the full potential of AI chatbots like never before. OpenAI's journey into the realms of language models and chatbot technology continues to captivate the industry, with GPT-4 on the horizon and the legacy of GPT-3 paving the way for a new era of artificial intelligence.
Table of contents
-
Collaborative Innovation in AI Research
-
Unlocking the Potential: GPT-4 and Beyond
-
Democratizing Access to Advanced AI
-
Stock Market Buzz: OpenAI's Impact on the Industry
-
Educational Partnerships in AI
-
Conclusion
Collaborative Innovation in AI Research
The partnership between OpenAI and Arizona State University marks a significant leap in collaborative innovation within the realm of AI research. By granting full ChatGPT access to ASU, both entities are poised to harness the collective expertise and resources to push the boundaries of artificial intelligence. This collaboration signifies a shared commitment to advancing the field, fostering an environment where researchers from OpenAI and ASU can collaborate seamlessly. With access to the powerful ChatGPT model, researchers can delve into new frontiers of natural language processing, explore innovative applications, and contribute to the ongoing evolution of AI technologies. The partnership embodies a synergistic approach, combining the strengths of a leading AI research organization with the academic prowess of a renowned university, ultimately aiming to drive groundbreaking advancements in the field of artificial intelligence.
Unlocking the Potential: GPT-4 and Beyond
The collaboration between OpenAI and Arizona State University, marked by the granting of full ChatGPT access, holds the key to unlocking the vast potential of the next-generation language models, notably GPT-4 and beyond. This partnership signifies a strategic effort to propel the evolution of AI text generation, allowing researchers to harness the full capabilities of ChatGPT and contribute to the development of more advanced models. With ASU's involvement, the collaborative efforts aim to push the boundaries of what is achievable in natural language processing, offering a glimpse into the future of AI technologies. As the anticipation for GPT-4 builds, this collaboration positions OpenAI at the forefront of cutting-edge research, with the potential to shape the trajectory of language models and redefine the benchmarks for AI capabilities in the years to come.
Democratizing Access to Advanced AI
The collaboration between OpenAI and Arizona State University, which grants full ChatGPT access, underscores a pivotal commitment to democratizing access to advanced AI technologies. By providing broader access to the powerful ChatGPT model, OpenAI aims to empower a diverse range of users, from researchers and developers to businesses and enthusiasts, allowing them to explore and harness the capabilities of sophisticated language models. This strategic move aligns with OpenAI's mission to make cutting-edge AI tools accessible to a wider audience, fostering inclusivity in the rapidly evolving field of artificial intelligence. The collaboration with ASU not only signifies a technological milestone but also represents a conscious effort to bridge the gap between AI innovation and user accessibility, democratizing the benefits of advanced AI for the benefit of society at large.
Stock Market Buzz: OpenAI's Impact on the Industry
The announcement of OpenAI's partnership with Arizona State University, granting full ChatGPT access, has generated a notable buzz within the stock market, reflecting the industry's keen interest in the organization's role in shaping the future of artificial intelligence. As OpenAI continues to pioneer advancements in language models, investors are closely monitoring the potential impact on OpenAI's stock. The collaboration with ASU signals not only technological innovation but also strategic foresight, potentially influencing the market's perception of OpenAI's position in the AI landscape. With the anticipation of GPT-4 and the broader implications for AI applications, the stock market response serves as a barometer for how investors view OpenAI's trajectory and its potential influence on the broader technology industry.
Educational Partnerships in AI
The collaboration between OpenAI and Arizona State University, marked by the full access to ChatGPT, underscores the increasingly vital role of educational partnerships in advancing the field of artificial intelligence. This collaboration goes beyond technological innovation, representing a bridge between industry leaders like OpenAI and academic institutions like ASU. By integrating advanced AI technologies into educational initiatives, the partnership holds the potential to shape the curriculum and research opportunities for students interested in AI. The collaboration not only enriches the academic landscape but also serves as a testament to the importance of fostering synergies between industry and academia, ensuring that the next generation of AI professionals has access to cutting-edge tools and knowledge, ultimately contributing to the continued growth and evolution of the field.
Conclusion
In conclusion, the partnership between OpenAI and Arizona State University, marked by the granting of full ChatGPT access, represents a significant stride in collaborative innovation within the realm of artificial intelligence. The commitment to unlocking the potential of GPT-4 and democratizing access to advanced AI technologies signals a forward-thinking approach that goes beyond mere technological advancements. As the stock market reacts to OpenAI's pivotal role in shaping the future of AI, the partnership highlights the intersection of academia and industry, showcasing the importance of educational collaborations in propelling the field forward. This milestone not only sets the stage for groundbreaking advancements in natural language processing but also emphasizes the broader societal impact of integrating advanced AI tools into educational frameworks. As the collaboration continues to unfold, it stands as a testament to the shared vision of OpenAI and ASU in pushing the boundaries of what is possible in the exciting and rapidly evolving field of artificial intelligence.
Read More
In a groundbreaking collaboration, OpenAI has joined forces with Arizona State University (ASU), ushering in a new era of advanced language models with full access to ChatGPT. As the next evolution in artificial intelligence, this partnership signifies a pivotal moment, leveraging the powerful capabilities of GPT-3 and paving the way for the highly anticipated GPT-4. OpenAI's commitment to innovation in the realm of AI chatbots is further exemplified by this collaboration, which not only grants unprecedented access to ChatGPT but also propels the conversation towards the future with a fusion of cutting-edge technologies like Azure OpenAI.
As OpenAI continues to make waves in the tech industry, the stock market is closely watching the developments in OpenAI stock. The integration of OpenAI's chatbots, including GPT-3 and the much-anticipated GPT-4, reflects the organization's dedication to pushing the boundaries of artificial intelligence. This collaboration not only showcases OpenAI's prowess in the field of text generation but also introduces users to the transformative potential of AI chatbots, including OpenAI Whisper.
With OpenAI ChatGPT at the forefront, users can now experience the unparalleled capabilities of OpenAI's text generators. The partnership with ASU not only expands the horizons of OpenAI's research but also underscores the company's commitment to democratizing access to advanced AI technologies. This milestone collaboration sets the stage for a future where openai.com remains synonymous with cutting-edge AI, empowering users to explore and harness the full potential of AI chatbots like never before. OpenAI's journey into the realms of language models and chatbot technology continues to captivate the industry, with GPT-4 on the horizon and the legacy of GPT-3 paving the way for a new era of artificial intelligence.
Table of contents
-
Collaborative Innovation in AI Research
-
Unlocking the Potential: GPT-4 and Beyond
-
Democratizing Access to Advanced AI
-
Stock Market Buzz: OpenAI's Impact on the Industry
-
Educational Partnerships in AI
-
Conclusion
Collaborative Innovation in AI Research
The partnership between OpenAI and Arizona State University marks a significant leap in collaborative innovation within the realm of AI research. By granting full ChatGPT access to ASU, both entities are poised to harness the collective expertise and resources to push the boundaries of artificial intelligence. This collaboration signifies a shared commitment to advancing the field, fostering an environment where researchers from OpenAI and ASU can collaborate seamlessly. With access to the powerful ChatGPT model, researchers can delve into new frontiers of natural language processing, explore innovative applications, and contribute to the ongoing evolution of AI technologies. The partnership embodies a synergistic approach, combining the strengths of a leading AI research organization with the academic prowess of a renowned university, ultimately aiming to drive groundbreaking advancements in the field of artificial intelligence.
Unlocking the Potential: GPT-4 and Beyond
The collaboration between OpenAI and Arizona State University, marked by the granting of full ChatGPT access, holds the key to unlocking the vast potential of the next-generation language models, notably GPT-4 and beyond. This partnership signifies a strategic effort to propel the evolution of AI text generation, allowing researchers to harness the full capabilities of ChatGPT and contribute to the development of more advanced models. With ASU's involvement, the collaborative efforts aim to push the boundaries of what is achievable in natural language processing, offering a glimpse into the future of AI technologies. As the anticipation for GPT-4 builds, this collaboration positions OpenAI at the forefront of cutting-edge research, with the potential to shape the trajectory of language models and redefine the benchmarks for AI capabilities in the years to come.
Democratizing Access to Advanced AI
The collaboration between OpenAI and Arizona State University, which grants full ChatGPT access, underscores a pivotal commitment to democratizing access to advanced AI technologies. By providing broader access to the powerful ChatGPT model, OpenAI aims to empower a diverse range of users, from researchers and developers to businesses and enthusiasts, allowing them to explore and harness the capabilities of sophisticated language models. This strategic move aligns with OpenAI's mission to make cutting-edge AI tools accessible to a wider audience, fostering inclusivity in the rapidly evolving field of artificial intelligence. The collaboration with ASU not only signifies a technological milestone but also represents a conscious effort to bridge the gap between AI innovation and user accessibility, democratizing the benefits of advanced AI for the benefit of society at large.
Stock Market Buzz: OpenAI's Impact on the Industry
The announcement of OpenAI's partnership with Arizona State University, granting full ChatGPT access, has generated a notable buzz within the stock market, reflecting the industry's keen interest in the organization's role in shaping the future of artificial intelligence. As OpenAI continues to pioneer advancements in language models, investors are closely monitoring the potential impact on OpenAI's stock. The collaboration with ASU signals not only technological innovation but also strategic foresight, potentially influencing the market's perception of OpenAI's position in the AI landscape. With the anticipation of GPT-4 and the broader implications for AI applications, the stock market response serves as a barometer for how investors view OpenAI's trajectory and its potential influence on the broader technology industry.
Educational Partnerships in AI
The collaboration between OpenAI and Arizona State University, marked by the full access to ChatGPT, underscores the increasingly vital role of educational partnerships in advancing the field of artificial intelligence. This collaboration goes beyond technological innovation, representing a bridge between industry leaders like OpenAI and academic institutions like ASU. By integrating advanced AI technologies into educational initiatives, the partnership holds the potential to shape the curriculum and research opportunities for students interested in AI. The collaboration not only enriches the academic landscape but also serves as a testament to the importance of fostering synergies between industry and academia, ensuring that the next generation of AI professionals has access to cutting-edge tools and knowledge, ultimately contributing to the continued growth and evolution of the field.
Conclusion
In conclusion, the partnership between OpenAI and Arizona State University, marked by the granting of full ChatGPT access, represents a significant stride in collaborative innovation within the realm of artificial intelligence. The commitment to unlocking the potential of GPT-4 and democratizing access to advanced AI technologies signals a forward-thinking approach that goes beyond mere technological advancements. As the stock market reacts to OpenAI's pivotal role in shaping the future of AI, the partnership highlights the intersection of academia and industry, showcasing the importance of educational collaborations in propelling the field forward. This milestone not only sets the stage for groundbreaking advancements in natural language processing but also emphasizes the broader societal impact of integrating advanced AI tools into educational frameworks. As the collaboration continues to unfold, it stands as a testament to the shared vision of OpenAI and ASU in pushing the boundaries of what is possible in the exciting and rapidly evolving field of artificial intelligence.
Pen Tester: Growing Opportunities for a Cybersecurity Career Path
Introduction
Are you interested in a career that allows you to combine your passion for technology with your desire to make the digital world a safer place? Look no further than becoming a pen tester. With the ever-increasing threats of cyber attacks and data breaches, there has never been a more critical time for professionals who can help safeguard our digital infrastructure. In this article, we will explore the exciting world of pen testing, the growing opportunities it presents in the cybersecurity industry, and why this career path is worth considering.
The Role of a Pen Tester
What exactly is a pen tester?
A pen tester, short for penetration tester, is a cybersecurity professional whose main responsibility is to identify vulnerabilities in a computer system, network, or application. By simulating potential attacks, pen testers assess the security measures already in place, determine weaknesses, and provide actionable recommendations to fortify the defenses.
Why is pen testing important?
With cyber attacks becoming increasingly sophisticated and prevalent, organizations across all industries are grappling with the need for robust security measures. By conducting regular pen tests, businesses can proactively identify and address vulnerabilities, thereby minimizing their risk of falling victim to malicious activities. Pen testers play a vital role in helping organizations stay one step ahead of potential threats.
Growing Career Opportunities
Increasing Demand for Cybersecurity Professionals
As technology continues to advance, the need for skilled cybersecurity professionals, including pen testers, continues to grow. According to the Bureau of Labor Statistics, the employment of information security analysts, which includes pen testers, is projected to grow at a much faster than average rate of 31% from 2019 to 2029. This demand makes pen testing an excellent career choice for those seeking stability and long-term opportunities.
Varied Industry Options
One of the greatest advantages of a career in pen testing is the wide range of industries that require these services. From financial institutions to government agencies, healthcare providers to e-commerce giants, every sector relies on robust cybersecurity measures. This diversity of opportunities ensures that pen testers can choose a path that aligns with their personal interests and passion.
Competitive Salaries
Due to the high demand and specialized nature of their work, pen testers enjoy highly competitive salaries. According to Indeed, the average annual salary for a pen tester in the United States is $93,000. However, with experience and additional certifications, it is not uncommon for professionals in this field to earn six-figure yearly incomes. Furthermore, as the demand for skilled pen testers continues to rise, salaries are expected to further increase.
Opportunities for Pen Testers
Constant Learning and Growth
Technology is ever-evolving, and so are the techniques used by cybercriminals. As a pen tester, you will be at the forefront of the battle against emerging threats, constantly learning and adapting your skills to stay ahead. This continuous learning curve ensures that your work remains challenging, engaging, and rewarding.
Networking and Collaboration
The field of cybersecurity is built on collaboration and shared knowledge. Pen testers often work closely with security analysts, network administrators, and software developers, collaborating to strengthen overall security measures. This collaborative environment provides ample opportunities to network with professionals from diverse backgrounds and expand your professional connections.
Progression into Leadership Roles
As you gain experience and expertise in pen testing, you can progress into leadership positions within the cybersecurity field. Whether it's leading a team of pen testers, managing complex security projects, or contributing to strategic decisions, this career path offers avenues for growth and advancement.
Conclusion
In a world where cyber threats are a daily concern, the role of a pen tester has never been more vital. With growing opportunities, competitive salaries, and the chance to make a real impact, a career in pen testing promises a bright future. So, if you're passionate about technology, have a strong interest in cybersecurity, and enjoy solving complex puzzles, consider exploring the exciting career path of a pen tester. Your expertise and contribution in safeguarding digital infrastructures will be invaluable in protecting our increasingly interconnected world.
Read More
Introduction
Are you interested in a career that allows you to combine your passion for technology with your desire to make the digital world a safer place? Look no further than becoming a pen tester. With the ever-increasing threats of cyber attacks and data breaches, there has never been a more critical time for professionals who can help safeguard our digital infrastructure. In this article, we will explore the exciting world of pen testing, the growing opportunities it presents in the cybersecurity industry, and why this career path is worth considering.
The Role of a Pen Tester
What exactly is a pen tester?
A pen tester, short for penetration tester, is a cybersecurity professional whose main responsibility is to identify vulnerabilities in a computer system, network, or application. By simulating potential attacks, pen testers assess the security measures already in place, determine weaknesses, and provide actionable recommendations to fortify the defenses.
Why is pen testing important?
With cyber attacks becoming increasingly sophisticated and prevalent, organizations across all industries are grappling with the need for robust security measures. By conducting regular pen tests, businesses can proactively identify and address vulnerabilities, thereby minimizing their risk of falling victim to malicious activities. Pen testers play a vital role in helping organizations stay one step ahead of potential threats.
Growing Career Opportunities
Increasing Demand for Cybersecurity Professionals
As technology continues to advance, the need for skilled cybersecurity professionals, including pen testers, continues to grow. According to the Bureau of Labor Statistics, the employment of information security analysts, which includes pen testers, is projected to grow at a much faster than average rate of 31% from 2019 to 2029. This demand makes pen testing an excellent career choice for those seeking stability and long-term opportunities.
Varied Industry Options
One of the greatest advantages of a career in pen testing is the wide range of industries that require these services. From financial institutions to government agencies, healthcare providers to e-commerce giants, every sector relies on robust cybersecurity measures. This diversity of opportunities ensures that pen testers can choose a path that aligns with their personal interests and passion.
Competitive Salaries
Due to the high demand and specialized nature of their work, pen testers enjoy highly competitive salaries. According to Indeed, the average annual salary for a pen tester in the United States is $93,000. However, with experience and additional certifications, it is not uncommon for professionals in this field to earn six-figure yearly incomes. Furthermore, as the demand for skilled pen testers continues to rise, salaries are expected to further increase.
Opportunities for Pen Testers
Constant Learning and Growth
Technology is ever-evolving, and so are the techniques used by cybercriminals. As a pen tester, you will be at the forefront of the battle against emerging threats, constantly learning and adapting your skills to stay ahead. This continuous learning curve ensures that your work remains challenging, engaging, and rewarding.
Networking and Collaboration
The field of cybersecurity is built on collaboration and shared knowledge. Pen testers often work closely with security analysts, network administrators, and software developers, collaborating to strengthen overall security measures. This collaborative environment provides ample opportunities to network with professionals from diverse backgrounds and expand your professional connections.
Progression into Leadership Roles
As you gain experience and expertise in pen testing, you can progress into leadership positions within the cybersecurity field. Whether it's leading a team of pen testers, managing complex security projects, or contributing to strategic decisions, this career path offers avenues for growth and advancement.
Conclusion
In a world where cyber threats are a daily concern, the role of a pen tester has never been more vital. With growing opportunities, competitive salaries, and the chance to make a real impact, a career in pen testing promises a bright future. So, if you're passionate about technology, have a strong interest in cybersecurity, and enjoy solving complex puzzles, consider exploring the exciting career path of a pen tester. Your expertise and contribution in safeguarding digital infrastructures will be invaluable in protecting our increasingly interconnected world.
The Benefits of Implementing RPA in Your Business
In today's fast-paced and highly competitive business landscape, organizations are constantly seeking innovative ways to enhance their operations, reduce costs, and drive growth. Robotic Process Automation (RPA) has emerged as a transformative solution, offering a plethora of benefits that can revolutionize the way businesses operate.
RPA is more than just a buzzword; it's a game-changer. It leverages the capabilities of software robots to automate repetitive, rule-based tasks that were once performed by humans. From data entry and invoicing to customer support and HR processes, RPA is redefining the modern business landscape in a profound way.
In this blog post, we'll explore the incredible advantages of implementing RPA in your business. We'll delve into the ways it can boost productivity, cut operational costs, and empower your employees to focus on more strategic, value-added tasks. We'll also discuss how RPA enables your organization to adapt to ever-changing workloads and market demands while ensuring compliance and enhancing customer satisfaction.
Join us on this journey to uncover the true potential of RPA and learn how it can be a key driver of success in your business.Let's embark on this automation adventure together.
Table of contents
-
Increased Productivity: How RPA Streamlines Repetitive Tasks
-
Cost Savings: The Financial Benefits of RPA Implementation
-
Error Reduction: Enhancing Accuracy Through Automation
-
24/7 Operations: The Advantage of RPA in Workflow Continuity
-
Scalability: Adapting Your Business to Changing Workloads with RPA
-
Employee Satisfaction: Empowering Workers with RPA
-
Data Insights: Leveraging RPA for Improved Decision-Making
-
Customer Experience Improvement: RPA's Impact on Service Quality
-
Compliance and Audit Readiness: Meeting Regulatory Requirements with RPA
-
Competitive Advantage: Staying Ahead in Your Industry with RPA
-
Conclusion
Increased Productivity: How RPA Streamlines Repetitive Tasks
In the relentless pursuit of operational excellence, businesses are increasingly turning to Robotic Process Automation (RPA) to revolutionize the way they handle repetitive and time-consuming tasks. Imagine a world where your workforce is liberated from mundane, repetitive chores, and your business can redirect its human talent towards creative and strategic endeavors. That's the promise of RPA, and in this article, we'll explore how it supercharges productivity by streamlining those monotonous tasks.
Automating the Mundane: RPA is the unsung hero of the business world. It excels at handling rule-based, repetitive tasks with precision and consistency. From data entry and report generation to invoice processing and email sorting, RPA tirelessly executes these activities, freeing up your human workforce for more meaningful, challenging, and engaging work.
24/7 Operations: Unlike human employees, RPA bots don't need breaks, sleep, or holidays. They work around the clock, ensuring that critical processes continue without interruption. This 24/7 availability not only accelerates task completion but also enhances customer service and response times.
Error Elimination: Human errors can be costly in terms of both time and money. RPA reduces the risk of errors to near zero. Bots follow predefined rules meticulously, resulting in accurate and consistent outcomes. This not only saves resources but also enhances the quality of your operations.
Scalability: As your business grows, so does the volume of repetitive tasks. RPA scales effortlessly, accommodating increased workloads without the need for lengthy recruitment and training processes. It's a flexible solution that grows with your business, allowing you to adapt to changing demands seamlessly.
Rapid Task Execution: With RPA, tasks that would take hours or days to complete manually can be executed in seconds or minutes. This expedited task execution enables your business to respond quickly to customer needs, market shifts, and other time-sensitive factors.
Enhanced Employee Satisfaction: Imagine your employees no longer bogged down by mind-numbing, repetitive work. RPA liberates your workforce from the most tedious aspects of their jobs, leading to increased job satisfaction and the ability to focus on tasks that require human creativity, decision-making, and critical thinking.
Cost Savings: The Financial Benefits of RPA Implementation
In an era where cost efficiency is paramount for businesses of all sizes, Robotic Process Automation (RPA) stands out as a formidable ally. It's not just about automation for the sake of it; it's about achieving substantial financial benefits through intelligent, rule-based processes. In this article, we'll explore how RPA can translate into real cost savings for your organization.
Reduced Labor Costs: The most immediate and noticeable cost savings with RPA come from a decreased reliance on human labor for repetitive tasks. RPA bots work tirelessly, without breaks or holidays, and do not require salaries, benefits, or overtime pay. This not only reduces labor costs but also eliminates the need for temporary staff during peak workloads.
Error Minimization: Human errors can be costly, leading to rework, customer dissatisfaction, and sometimes even regulatory fines. RPA dramatically reduces the risk of errors, ensuring that tasks are executed with a high degree of accuracy. This, in turn, mitigates the costs associated with correcting mistakes.
Improved Efficiency: RPA streamlines processes, making them more efficient and faster. Tasks that once took hours or days to complete manually can be accomplished in a fraction of the time with RPA. This increased efficiency allows your workforce to focus on higher-value tasks and revenue-generating activities.
Scalability Without Additional Costs: As your business grows, you may need to handle more transactions or process more data. Scaling up with human employees can be expensive, involving recruitment, training, and office space costs. RPA, on the other hand, scales easily without incurring additional costs.
Reduced Operational Costs: RPA can optimize various operational costs. It can help in inventory management, supply chain optimization, and other processes, reducing costs associated with excess inventory, carrying costs, and logistics.
Energy and Resource Savings: Automation doesn't just save labor costs; it can also lead to reduced energy consumption. RPA bots run on servers and data centers, which can be more energy-efficient than maintaining large office spaces with numerous employees.
the financial benefits of RPA implementation are substantial. It's not just about cutting costs; it's about doing so while improving operational efficiency, reducing errors, and allowing your employees to focus on strategic, value-adding tasks. RPA isn't an expense; it's an investment that pays off by delivering significant cost savings and contributing to the overall financial health of your organization. It's time to embrace RPA as a key driver of fiscal prudence and financial success.
Error Reduction: Enhancing Accuracy Through Automation
In the world of business, accuracy is not a mere aspiration; it's a prerequisite for success. Mistakes can be costly, resulting in financial losses, customer dissatisfaction, and even reputational damage. Fortunately, automation, specifically Robotic Process Automation (RPA), has emerged as a powerful tool for enhancing accuracy by minimizing errors. In this article, we'll explore how RPA's precision transforms the operational landscape of businesses.
Perfect Consistency: RPA bots are meticulously programmed to follow predefined rules and instructions. They execute tasks with unwavering consistency, ensuring that the same standard is upheld for every transaction, every time. This perfect consistency is a stark contrast to human work, which can be influenced by factors like fatigue, distractions, or oversight.
Reduction in Human Error: Human errors, no matter how diligent the employees, are an inherent part of manual processes. RPA mitigates this risk by automating rule-based tasks. Whether it's data entry, order processing, or calculations, RPA eliminates the potential for common errors such as typos, miscalculations, and missed steps.
Elimination of Repetitive Mistakes: Over time, repetitive tasks can become mundane, leading to inattentiveness and a higher likelihood of errors. RPA doesn't suffer from such lapses in attention. It tirelessly performs tasks with precision, without being influenced by factors that can lead to mistakes.
Error Monitoring and Reporting: RPA systems are equipped with error monitoring and reporting capabilities. If an issue arises, the system can detect it quickly and often correct it automatically. In cases where human intervention is required, the error is flagged for attention, reducing the chances of unnoticed errors that can compound over time.
24/7 Operations: The Advantage of RPA in Workflow Continuity
In a globalized and interconnected world, business operations are expected to run seamlessly around the clock. However, the human workforce has its limitations, including the need for rest and downtime. This is where Robotic Process Automation (RPA) steps in, offering a substantial advantage in workflow continuity through its ability to operate 24/7. In this article, we will delve into how RPA empowers businesses to break free from the constraints of traditional working hours.
Non-Stop Productivity: One of the most compelling advantages of RPA is its capacity for non-stop, 24/7 operations. RPA bots are not bound by the constraints of the human workday, allowing tasks to be executed continuously, even during evenings, weekends, and holidays. This round-the-clock productivity enhances the efficiency of critical business processes.
Reduced Response Times: With 24/7 RPA, customer inquiries, orders, and requests can be addressed instantly. This reduction in response times not only enhances customer satisfaction but can also give your business a competitive edge in industries where responsiveness is crucial.
No Overtime or Shift Work: Employing human workers for continuous operations typically involves overtime pay, shift differentials, and the associated costs of additional personnel management. RPA eliminates these costs while maintaining consistent, uninterrupted operations.
High Availability: RPA systems are designed for high availability. They can be configured to run on redundant servers or in the cloud, ensuring that operations continue even in the event of technical failures. This minimizes downtime and ensures uninterrupted workflow.
Enhanced Operational Efficiency: 24/7 RPA doesn't just mean working more hours; it means working more efficiently. Tasks are executed consistently and without the fluctuations in performance that can occur during late shifts or overnight hours.
The advantage of RPA in enabling 24/7 operations is a transformative element in the modern business landscape. It ensures that critical processes continue seamlessly, improves responsiveness, and reduces the costs associated with shift work and downtime. RPA's ability to work tirelessly and without interruption is a crucial factor in maintaining workflow continuity and meeting the demands of a 24/7 global economy.
Scalability: Adapting Your Business to Changing Workloads with RPA
In the dynamic and ever-evolving world of business, the ability to adapt to changing workloads is paramount for success. Robotic Process Automation (RPA) emerges as a pivotal solution, offering businesses the flexibility to scale their operations efficiently. In this article, we'll explore how RPA empowers organizations to seamlessly adjust to fluctuating demands, ensuring agility and sustained growth.
Handling Workload Peaks: Workload fluctuations are a common challenge for businesses. Seasonal spikes, promotions, or unforeseen events can cause a sudden surge in operational demands. RPA's scalability enables organizations to effortlessly address these peaks without the need for extensive human resource adjustments.
Speed and Accuracy: RPA bots can handle tasks with exceptional speed and accuracy. This not only ensures that tasks are completed on time during high-demand periods but also minimizes the risk of errors, contributing to a smoother scaling process.
Continuous Operation: RPA operates 24/7, providing continuous support for scaling efforts. Whether your business operates in multiple time zones or faces constant demand, RPA ensures that the scalability process can be ongoing and uninterrupted.
Improved Resource Allocation: The scalability offered by RPA allows human employees to focus on tasks that require creativity, decision-making, and critical thinking. This improved resource allocation not only enhances the quality of work but also promotes employee job satisfaction.
Rapid Deployment: Deploying additional RPA bots or reconfiguring existing ones can be achieved quickly. This agility is particularly valuable when responding to unexpected changes in workload, such as market fluctuations or emerging business opportunities.
Scalability Planning: RPA's analytics and data-driven insights can assist in proactive scalability planning. By analyzing historical data, businesses can anticipate workload fluctuations and adjust their RPA deployments accordingly.
The scalability that RPA offers is a strategic asset for businesses looking to adapt to changing workloads and seize growth opportunities. Whether you're aiming to respond to seasonal variations, sudden market shifts, or simply improve the efficiency of your daily operations, RPA provides a scalable solution that optimizes your resources and ensures that your business can remain agile and competitive in an ever-changing business landscape.
Employee Satisfaction: Empowering Workers with RPA
In the quest for business success, employee satisfaction is a critical factor that should never be underestimated. Satisfied and empowered employees are more productive, creative, and loyal to their organizations. Robotic Process Automation (RPA) plays a vital role in achieving these goals by relieving employees of mundane, repetitive tasks and giving them the opportunity to focus on higher-value, more fulfilling work. In this article, we'll explore how RPA empowers workers, leading to greater job satisfaction and overall success.
Skill Development: Employees empowered by RPA have the opportunity to develop new skills. As they transition to more complex, strategic roles, they can acquire valuable competencies that benefit both their personal growth and the organization.
Increased Job Satisfaction: By eliminating the least satisfying aspects of a job, RPA contributes to higher job satisfaction. Employees who find their work engaging and fulfilling are more likely to be committed to their roles and remain with the company for the long term.
Work-Life Balance: RPA's ability to handle tasks 24/7 ensures that employees are not burdened with late-night or weekend work to meet deadlines. This supports a healthier work-life balance, reducing stress and enhancing overall well-being.
Employee Empowerment: Employees often feel more empowered and valued when their employers invest in technologies like RPA to improve the work environment. This empowerment can boost morale and motivation.
Fostering Innovation: Employees freed from routine tasks can focus on more innovative and creative work. This not only benefits the company by driving innovation but also leads to a more fulfilling work experience for employees.
Consistency and Quality: RPA's ability to perform tasks with a high degree of accuracy ensures that employees can rely on consistent and error-free results in their work. This consistency reduces frustration and the need for rework.
Employee Feedback: RPA can be used to gather and process employee feedback more efficiently. By automating the data collection and analysis, it allows management to respond more effectively to concerns and suggestions, further boosting employee satisfaction.
RPA is a powerful tool for empowering employees and enhancing their job satisfaction. By automating repetitive tasks, it frees up time for more meaningful and challenging work, allows for skill development, and fosters a positive work environment. This not only benefits individual employees but also contributes to the overall success and competitiveness of the organization. It's a win-win scenario where both employees and the business thrive.
Data Insights: Leveraging RPA for Improved Decision-Making
In today's data-driven business landscape, making informed decisions is paramount for success. Fortunately, Robotic Process Automation (RPA) goes beyond task automation – it's a powerful tool for unlocking valuable data insights that can transform the way organizations make decisions. In this article, we'll explore how RPA can be harnessed to collect, process, and leverage data for more informed and strategic decision-making.
Data Collection and Aggregation: RPA can collect and aggregate data from various sources, including databases, spreadsheets, and online platforms. By automating the data collection process, it ensures data integrity and reduces the risk of human errors.
Real-Time Data Processing: RPA can process data in real-time, providing up-to-the-minute information that's crucial for making timely decisions. This real-time processing is especially valuable in fast-paced industries and competitive markets.
Data Cleansing and Quality Assurance: RPA can be programmed to cleanse and validate data, ensuring that it's accurate and reliable. This step is essential for high-quality decision-making, as inaccurate data can lead to poor judgments.
Predictive Analytics: RPA can be combined with predictive analytics models to forecast trends, identify potential issues, and recommend actions. This empowers decision-makers to proactively address challenges and seize opportunities.
Customized Reports and Dashboards: RPA can generate customized reports and dashboards that present data in a clear and actionable format. Decision-makers can quickly access the information they need, facilitating faster and more informed choices.
Exception Handling: RPA can identify exceptions or anomalies in data. When exceptions occur, RPA can alert decision-makers, enabling them to investigate and respond promptly to issues.
Compliance and Audit Trail: RPA ensures that tasks are executed according to predefined rules, creating a robust audit trail. This audit trail is invaluable for compliance with regulatory requirements and is a valuable resource for decision-making during audits.
RPA is not just about automating tasks; it's a key enabler of data-driven decision-making. By collecting, processing, and providing valuable data insights, RPA equips organizations to make informed, strategic decisions that can drive growth, efficiency, and competitive advantage. The ability to harness the power of data is a transformative asset in the modern business world, and RPA plays a central role in unlocking its potential.
Customer Experience Improvement: RPA's Impact on Service Quality
In an era where customer satisfaction can make or break a business, delivering an exceptional customer experience is a top priority. Robotic Process Automation (RPA) has emerged as a powerful tool for improving service quality and ensuring a seamless, satisfying customer journey. In this article, we'll explore how RPA positively impacts the customer experience and contributes to the success of businesses.
Faster Response Times: RPA can respond to customer inquiries and requests in real-time. This immediate response ensures that customers don't have to wait, enhancing their perception of your service quality.
Error Reduction: RPA minimizes errors in tasks such as order processing and data entry. Fewer mistakes mean fewer issues for customers to deal with, resulting in a smoother, more reliable experience.
24/7 Availability: RPA operates around the clock, ensuring that customers can interact with your business at any time. This high availability caters to diverse schedules and time zones, providing a more customer-centric experience.
Enhanced Data Security: RPA's robust security measures protect customer data and sensitive information. By safeguarding their data, you build trust and confidence, further improving the customer experience.
Proactive Issue Resolution: RPA can monitor systems for issues and exceptions in real-time. When issues arise, RPA can alert human staff to take corrective action promptly, minimizing customer disruption.
RPA is a game-changer in improving the customer experience. By reducing response times, minimizing errors, ensuring availability, and enhancing data security, RPA contributes to a higher level of customer satisfaction. Businesses that leverage RPA for service quality enhancements not only retain loyal customers but also gain a competitive edge in an environment where customer experience is a defining factor in success. RPA isn't just about efficiency; it's about enhancing the human touch in customer service and ensuring that customers receive the best service possible.
Compliance and Audit Readiness: Meeting Regulatory Requirements with RPA
In today's highly regulated business environment, compliance with industry-specific and government-mandated regulations is a non-negotiable aspect of operation. The failure to meet regulatory requirements can lead to significant legal consequences, fines, and damage to a company's reputation. Robotic Process Automation (RPA) offers a powerful solution for ensuring compliance and audit readiness. In this article, we'll explore how RPA can help businesses meet regulatory requirements and prepare for audits effectively.
Rule-Based Consistency: RPA excels at executing tasks following predefined rules and standards. This inherent consistency ensures that business processes are executed in a compliant manner every time.
Automated Data Logging: RPA can automatically record and log all actions taken during its processes. This comprehensive data logging provides a transparent audit trail, ensuring that regulators and auditors can easily review and verify compliance.
Real-Time Monitoring: RPA systems can monitor processes in real-time, identifying and rectifying deviations from compliance standards as they occur. This proactive approach minimizes the risk of non-compliance issues going unnoticed.
Data Security and Privacy: RPA is designed to protect sensitive data. By automating data handling and storage, it reduces the risk of data breaches and ensures that personally identifiable information (PII) and other sensitive data are handled in a compliant manner.
Regulatory Reporting: RPA can automate the collection and preparation of reports required for regulatory compliance. This not only reduces the time and effort required for reporting but also minimizes the risk of errors in these critical documents.
Controlled Access: RPA allows for controlled access to sensitive systems and data. By limiting access to authorized personnel and automating role-based permissions, it enhances security and compliance with access control regulations.
Reducing Human Error: Many compliance issues arise from human error. RPA minimizes these errors, which can lead to non-compliance, fines, and other penalties.
RPA is a vital tool for meeting regulatory requirements and achieving audit readiness. It not only protects businesses from legal consequences and fines but also allows them to focus on their core operations, knowing that they are operating within the boundaries of the law. RPA doesn't just streamline processes; it safeguards businesses and enhances their ability to navigate complex regulatory landscapes with confidence.
Competitive Advantage: Staying Ahead in Your Industry with RPA
In the fast-paced and ever-evolving world of business, staying ahead of the competition is a constant challenge. To gain a competitive edge, organizations must be agile, efficient, and innovative. Robotic Process Automation (RPA) offers a significant advantage by providing the tools to streamline operations, reduce costs, and make data-driven decisions. In this article, we'll explore how RPA can be a catalyst for achieving a competitive advantage in your industry.
Operational Efficiency: RPA optimizes business processes by automating repetitive and rule-based tasks. This increased efficiency enables your organization to deliver products and services more quickly and cost-effectively, giving you an edge in the market.
Cost Reduction: By automating tasks and minimizing errors, RPA reduces operational costs. This allows your business to allocate resources strategically, invest in growth, and potentially offer competitive pricing to customers.
Customer Satisfaction: RPA enhances the customer experience by ensuring faster response times, personalized interactions, and error-free service. Satisfied customers are more likely to remain loyal and recommend your business to others.
Real-Time Data Insights: RPA collects and processes data in real-time, providing valuable insights into market trends, customer behavior, and operational performance. These insights can be leveraged to make informed decisions and stay ahead of market shifts.
Innovation and Creativity: By automating routine tasks, RPA liberates your workforce from the mundane, allowing them to focus on creative, strategic, and value-added activities. This fosters a culture of innovation and provides a competitive advantage in product and service development.
Strategic Decision-Making: With RPA, your organization can make data-driven decisions more efficiently. This strategic approach to decision-making allows you to anticipate market trends, spot opportunities, and outmaneuver competitors.
RPA is a game-changer for businesses seeking to gain a competitive advantage in their industries. By increasing operational efficiency, reducing costs, enhancing customer satisfaction, and providing real-time insights, RPA empowers organizations to stay ahead in rapidly changing markets. It's not just about streamlining processes; it's about positioning your business to lead, innovate, and thrive in a highly competitive world. RPA is the key to not just keeping pace but setting the pace in your industry.
Conclusion
In conclusion, Robotic Process Automation (RPA) is a transformative force in the modern business landscape, offering a multitude of benefits that can revolutionize the way organizations operate. Throughout this series of articles, we've explored the diverse advantages of RPA and how it can be harnessed to enhance different aspects of business operations.
RPA's ability to operate 24/7 ensures workflow continuity, allowing businesses to adapt to fluctuating workloads, meet global demands, and maintain a competitive edge. It offers employees the opportunity to focus on more meaningful tasks, fostering job satisfaction, skill development, and innovation.
RPA leverages data insights to facilitate data-driven decision-making, enabling businesses to respond to market changes and opportunities with agility and precision. It improves the customer experience through faster response times, reduced errors, and personalized interactions, leading to higher customer satisfaction and loyalty.
In a world where efficiency, agility, and customer satisfaction are paramount, RPA is more than a tool for automation; it's a strategic asset that empowers businesses to thrive and excel. Embracing the automation revolution is not just a choice; it's a necessity for organizations that aim to remain competitive, innovative, and successful in the ever-evolving business landscape.
Read More
In today's fast-paced and highly competitive business landscape, organizations are constantly seeking innovative ways to enhance their operations, reduce costs, and drive growth. Robotic Process Automation (RPA) has emerged as a transformative solution, offering a plethora of benefits that can revolutionize the way businesses operate.
RPA is more than just a buzzword; it's a game-changer. It leverages the capabilities of software robots to automate repetitive, rule-based tasks that were once performed by humans. From data entry and invoicing to customer support and HR processes, RPA is redefining the modern business landscape in a profound way.
In this blog post, we'll explore the incredible advantages of implementing RPA in your business. We'll delve into the ways it can boost productivity, cut operational costs, and empower your employees to focus on more strategic, value-added tasks. We'll also discuss how RPA enables your organization to adapt to ever-changing workloads and market demands while ensuring compliance and enhancing customer satisfaction.
Join us on this journey to uncover the true potential of RPA and learn how it can be a key driver of success in your business.Let's embark on this automation adventure together.
Table of contents
-
Increased Productivity: How RPA Streamlines Repetitive Tasks
-
Cost Savings: The Financial Benefits of RPA Implementation
-
Error Reduction: Enhancing Accuracy Through Automation
-
24/7 Operations: The Advantage of RPA in Workflow Continuity
-
Scalability: Adapting Your Business to Changing Workloads with RPA
-
Employee Satisfaction: Empowering Workers with RPA
-
Data Insights: Leveraging RPA for Improved Decision-Making
-
Customer Experience Improvement: RPA's Impact on Service Quality
-
Compliance and Audit Readiness: Meeting Regulatory Requirements with RPA
-
Competitive Advantage: Staying Ahead in Your Industry with RPA
-
Conclusion
Increased Productivity: How RPA Streamlines Repetitive Tasks
In the relentless pursuit of operational excellence, businesses are increasingly turning to Robotic Process Automation (RPA) to revolutionize the way they handle repetitive and time-consuming tasks. Imagine a world where your workforce is liberated from mundane, repetitive chores, and your business can redirect its human talent towards creative and strategic endeavors. That's the promise of RPA, and in this article, we'll explore how it supercharges productivity by streamlining those monotonous tasks.
Automating the Mundane: RPA is the unsung hero of the business world. It excels at handling rule-based, repetitive tasks with precision and consistency. From data entry and report generation to invoice processing and email sorting, RPA tirelessly executes these activities, freeing up your human workforce for more meaningful, challenging, and engaging work.
24/7 Operations: Unlike human employees, RPA bots don't need breaks, sleep, or holidays. They work around the clock, ensuring that critical processes continue without interruption. This 24/7 availability not only accelerates task completion but also enhances customer service and response times.
Error Elimination: Human errors can be costly in terms of both time and money. RPA reduces the risk of errors to near zero. Bots follow predefined rules meticulously, resulting in accurate and consistent outcomes. This not only saves resources but also enhances the quality of your operations.
Scalability: As your business grows, so does the volume of repetitive tasks. RPA scales effortlessly, accommodating increased workloads without the need for lengthy recruitment and training processes. It's a flexible solution that grows with your business, allowing you to adapt to changing demands seamlessly.
Rapid Task Execution: With RPA, tasks that would take hours or days to complete manually can be executed in seconds or minutes. This expedited task execution enables your business to respond quickly to customer needs, market shifts, and other time-sensitive factors.
Enhanced Employee Satisfaction: Imagine your employees no longer bogged down by mind-numbing, repetitive work. RPA liberates your workforce from the most tedious aspects of their jobs, leading to increased job satisfaction and the ability to focus on tasks that require human creativity, decision-making, and critical thinking.
Cost Savings: The Financial Benefits of RPA Implementation
In an era where cost efficiency is paramount for businesses of all sizes, Robotic Process Automation (RPA) stands out as a formidable ally. It's not just about automation for the sake of it; it's about achieving substantial financial benefits through intelligent, rule-based processes. In this article, we'll explore how RPA can translate into real cost savings for your organization.
Reduced Labor Costs: The most immediate and noticeable cost savings with RPA come from a decreased reliance on human labor for repetitive tasks. RPA bots work tirelessly, without breaks or holidays, and do not require salaries, benefits, or overtime pay. This not only reduces labor costs but also eliminates the need for temporary staff during peak workloads.
Error Minimization: Human errors can be costly, leading to rework, customer dissatisfaction, and sometimes even regulatory fines. RPA dramatically reduces the risk of errors, ensuring that tasks are executed with a high degree of accuracy. This, in turn, mitigates the costs associated with correcting mistakes.
Improved Efficiency: RPA streamlines processes, making them more efficient and faster. Tasks that once took hours or days to complete manually can be accomplished in a fraction of the time with RPA. This increased efficiency allows your workforce to focus on higher-value tasks and revenue-generating activities.
Scalability Without Additional Costs: As your business grows, you may need to handle more transactions or process more data. Scaling up with human employees can be expensive, involving recruitment, training, and office space costs. RPA, on the other hand, scales easily without incurring additional costs.
Reduced Operational Costs: RPA can optimize various operational costs. It can help in inventory management, supply chain optimization, and other processes, reducing costs associated with excess inventory, carrying costs, and logistics.
Energy and Resource Savings: Automation doesn't just save labor costs; it can also lead to reduced energy consumption. RPA bots run on servers and data centers, which can be more energy-efficient than maintaining large office spaces with numerous employees.
the financial benefits of RPA implementation are substantial. It's not just about cutting costs; it's about doing so while improving operational efficiency, reducing errors, and allowing your employees to focus on strategic, value-adding tasks. RPA isn't an expense; it's an investment that pays off by delivering significant cost savings and contributing to the overall financial health of your organization. It's time to embrace RPA as a key driver of fiscal prudence and financial success.
Error Reduction: Enhancing Accuracy Through Automation
In the world of business, accuracy is not a mere aspiration; it's a prerequisite for success. Mistakes can be costly, resulting in financial losses, customer dissatisfaction, and even reputational damage. Fortunately, automation, specifically Robotic Process Automation (RPA), has emerged as a powerful tool for enhancing accuracy by minimizing errors. In this article, we'll explore how RPA's precision transforms the operational landscape of businesses.
Perfect Consistency: RPA bots are meticulously programmed to follow predefined rules and instructions. They execute tasks with unwavering consistency, ensuring that the same standard is upheld for every transaction, every time. This perfect consistency is a stark contrast to human work, which can be influenced by factors like fatigue, distractions, or oversight.
Reduction in Human Error: Human errors, no matter how diligent the employees, are an inherent part of manual processes. RPA mitigates this risk by automating rule-based tasks. Whether it's data entry, order processing, or calculations, RPA eliminates the potential for common errors such as typos, miscalculations, and missed steps.
Elimination of Repetitive Mistakes: Over time, repetitive tasks can become mundane, leading to inattentiveness and a higher likelihood of errors. RPA doesn't suffer from such lapses in attention. It tirelessly performs tasks with precision, without being influenced by factors that can lead to mistakes.
Error Monitoring and Reporting: RPA systems are equipped with error monitoring and reporting capabilities. If an issue arises, the system can detect it quickly and often correct it automatically. In cases where human intervention is required, the error is flagged for attention, reducing the chances of unnoticed errors that can compound over time.
24/7 Operations: The Advantage of RPA in Workflow Continuity
In a globalized and interconnected world, business operations are expected to run seamlessly around the clock. However, the human workforce has its limitations, including the need for rest and downtime. This is where Robotic Process Automation (RPA) steps in, offering a substantial advantage in workflow continuity through its ability to operate 24/7. In this article, we will delve into how RPA empowers businesses to break free from the constraints of traditional working hours.
Non-Stop Productivity: One of the most compelling advantages of RPA is its capacity for non-stop, 24/7 operations. RPA bots are not bound by the constraints of the human workday, allowing tasks to be executed continuously, even during evenings, weekends, and holidays. This round-the-clock productivity enhances the efficiency of critical business processes.
Reduced Response Times: With 24/7 RPA, customer inquiries, orders, and requests can be addressed instantly. This reduction in response times not only enhances customer satisfaction but can also give your business a competitive edge in industries where responsiveness is crucial.
No Overtime or Shift Work: Employing human workers for continuous operations typically involves overtime pay, shift differentials, and the associated costs of additional personnel management. RPA eliminates these costs while maintaining consistent, uninterrupted operations.
High Availability: RPA systems are designed for high availability. They can be configured to run on redundant servers or in the cloud, ensuring that operations continue even in the event of technical failures. This minimizes downtime and ensures uninterrupted workflow.
Enhanced Operational Efficiency: 24/7 RPA doesn't just mean working more hours; it means working more efficiently. Tasks are executed consistently and without the fluctuations in performance that can occur during late shifts or overnight hours.
The advantage of RPA in enabling 24/7 operations is a transformative element in the modern business landscape. It ensures that critical processes continue seamlessly, improves responsiveness, and reduces the costs associated with shift work and downtime. RPA's ability to work tirelessly and without interruption is a crucial factor in maintaining workflow continuity and meeting the demands of a 24/7 global economy.
Scalability: Adapting Your Business to Changing Workloads with RPA
In the dynamic and ever-evolving world of business, the ability to adapt to changing workloads is paramount for success. Robotic Process Automation (RPA) emerges as a pivotal solution, offering businesses the flexibility to scale their operations efficiently. In this article, we'll explore how RPA empowers organizations to seamlessly adjust to fluctuating demands, ensuring agility and sustained growth.
Handling Workload Peaks: Workload fluctuations are a common challenge for businesses. Seasonal spikes, promotions, or unforeseen events can cause a sudden surge in operational demands. RPA's scalability enables organizations to effortlessly address these peaks without the need for extensive human resource adjustments.
Speed and Accuracy: RPA bots can handle tasks with exceptional speed and accuracy. This not only ensures that tasks are completed on time during high-demand periods but also minimizes the risk of errors, contributing to a smoother scaling process.
Continuous Operation: RPA operates 24/7, providing continuous support for scaling efforts. Whether your business operates in multiple time zones or faces constant demand, RPA ensures that the scalability process can be ongoing and uninterrupted.
Improved Resource Allocation: The scalability offered by RPA allows human employees to focus on tasks that require creativity, decision-making, and critical thinking. This improved resource allocation not only enhances the quality of work but also promotes employee job satisfaction.
Rapid Deployment: Deploying additional RPA bots or reconfiguring existing ones can be achieved quickly. This agility is particularly valuable when responding to unexpected changes in workload, such as market fluctuations or emerging business opportunities.
Scalability Planning: RPA's analytics and data-driven insights can assist in proactive scalability planning. By analyzing historical data, businesses can anticipate workload fluctuations and adjust their RPA deployments accordingly.
The scalability that RPA offers is a strategic asset for businesses looking to adapt to changing workloads and seize growth opportunities. Whether you're aiming to respond to seasonal variations, sudden market shifts, or simply improve the efficiency of your daily operations, RPA provides a scalable solution that optimizes your resources and ensures that your business can remain agile and competitive in an ever-changing business landscape.
Employee Satisfaction: Empowering Workers with RPA
In the quest for business success, employee satisfaction is a critical factor that should never be underestimated. Satisfied and empowered employees are more productive, creative, and loyal to their organizations. Robotic Process Automation (RPA) plays a vital role in achieving these goals by relieving employees of mundane, repetitive tasks and giving them the opportunity to focus on higher-value, more fulfilling work. In this article, we'll explore how RPA empowers workers, leading to greater job satisfaction and overall success.
Skill Development: Employees empowered by RPA have the opportunity to develop new skills. As they transition to more complex, strategic roles, they can acquire valuable competencies that benefit both their personal growth and the organization.
Increased Job Satisfaction: By eliminating the least satisfying aspects of a job, RPA contributes to higher job satisfaction. Employees who find their work engaging and fulfilling are more likely to be committed to their roles and remain with the company for the long term.
Work-Life Balance: RPA's ability to handle tasks 24/7 ensures that employees are not burdened with late-night or weekend work to meet deadlines. This supports a healthier work-life balance, reducing stress and enhancing overall well-being.
Employee Empowerment: Employees often feel more empowered and valued when their employers invest in technologies like RPA to improve the work environment. This empowerment can boost morale and motivation.
Fostering Innovation: Employees freed from routine tasks can focus on more innovative and creative work. This not only benefits the company by driving innovation but also leads to a more fulfilling work experience for employees.
Consistency and Quality: RPA's ability to perform tasks with a high degree of accuracy ensures that employees can rely on consistent and error-free results in their work. This consistency reduces frustration and the need for rework.
Employee Feedback: RPA can be used to gather and process employee feedback more efficiently. By automating the data collection and analysis, it allows management to respond more effectively to concerns and suggestions, further boosting employee satisfaction.
RPA is a powerful tool for empowering employees and enhancing their job satisfaction. By automating repetitive tasks, it frees up time for more meaningful and challenging work, allows for skill development, and fosters a positive work environment. This not only benefits individual employees but also contributes to the overall success and competitiveness of the organization. It's a win-win scenario where both employees and the business thrive.
Data Insights: Leveraging RPA for Improved Decision-Making
In today's data-driven business landscape, making informed decisions is paramount for success. Fortunately, Robotic Process Automation (RPA) goes beyond task automation – it's a powerful tool for unlocking valuable data insights that can transform the way organizations make decisions. In this article, we'll explore how RPA can be harnessed to collect, process, and leverage data for more informed and strategic decision-making.
Data Collection and Aggregation: RPA can collect and aggregate data from various sources, including databases, spreadsheets, and online platforms. By automating the data collection process, it ensures data integrity and reduces the risk of human errors.
Real-Time Data Processing: RPA can process data in real-time, providing up-to-the-minute information that's crucial for making timely decisions. This real-time processing is especially valuable in fast-paced industries and competitive markets.
Data Cleansing and Quality Assurance: RPA can be programmed to cleanse and validate data, ensuring that it's accurate and reliable. This step is essential for high-quality decision-making, as inaccurate data can lead to poor judgments.
Predictive Analytics: RPA can be combined with predictive analytics models to forecast trends, identify potential issues, and recommend actions. This empowers decision-makers to proactively address challenges and seize opportunities.
Customized Reports and Dashboards: RPA can generate customized reports and dashboards that present data in a clear and actionable format. Decision-makers can quickly access the information they need, facilitating faster and more informed choices.
Exception Handling: RPA can identify exceptions or anomalies in data. When exceptions occur, RPA can alert decision-makers, enabling them to investigate and respond promptly to issues.
Compliance and Audit Trail: RPA ensures that tasks are executed according to predefined rules, creating a robust audit trail. This audit trail is invaluable for compliance with regulatory requirements and is a valuable resource for decision-making during audits.
RPA is not just about automating tasks; it's a key enabler of data-driven decision-making. By collecting, processing, and providing valuable data insights, RPA equips organizations to make informed, strategic decisions that can drive growth, efficiency, and competitive advantage. The ability to harness the power of data is a transformative asset in the modern business world, and RPA plays a central role in unlocking its potential.
Customer Experience Improvement: RPA's Impact on Service Quality
In an era where customer satisfaction can make or break a business, delivering an exceptional customer experience is a top priority. Robotic Process Automation (RPA) has emerged as a powerful tool for improving service quality and ensuring a seamless, satisfying customer journey. In this article, we'll explore how RPA positively impacts the customer experience and contributes to the success of businesses.
Faster Response Times: RPA can respond to customer inquiries and requests in real-time. This immediate response ensures that customers don't have to wait, enhancing their perception of your service quality.
Error Reduction: RPA minimizes errors in tasks such as order processing and data entry. Fewer mistakes mean fewer issues for customers to deal with, resulting in a smoother, more reliable experience.
24/7 Availability: RPA operates around the clock, ensuring that customers can interact with your business at any time. This high availability caters to diverse schedules and time zones, providing a more customer-centric experience.
Enhanced Data Security: RPA's robust security measures protect customer data and sensitive information. By safeguarding their data, you build trust and confidence, further improving the customer experience.
Proactive Issue Resolution: RPA can monitor systems for issues and exceptions in real-time. When issues arise, RPA can alert human staff to take corrective action promptly, minimizing customer disruption.
RPA is a game-changer in improving the customer experience. By reducing response times, minimizing errors, ensuring availability, and enhancing data security, RPA contributes to a higher level of customer satisfaction. Businesses that leverage RPA for service quality enhancements not only retain loyal customers but also gain a competitive edge in an environment where customer experience is a defining factor in success. RPA isn't just about efficiency; it's about enhancing the human touch in customer service and ensuring that customers receive the best service possible.
Compliance and Audit Readiness: Meeting Regulatory Requirements with RPA
In today's highly regulated business environment, compliance with industry-specific and government-mandated regulations is a non-negotiable aspect of operation. The failure to meet regulatory requirements can lead to significant legal consequences, fines, and damage to a company's reputation. Robotic Process Automation (RPA) offers a powerful solution for ensuring compliance and audit readiness. In this article, we'll explore how RPA can help businesses meet regulatory requirements and prepare for audits effectively.
Rule-Based Consistency: RPA excels at executing tasks following predefined rules and standards. This inherent consistency ensures that business processes are executed in a compliant manner every time.
Automated Data Logging: RPA can automatically record and log all actions taken during its processes. This comprehensive data logging provides a transparent audit trail, ensuring that regulators and auditors can easily review and verify compliance.
Real-Time Monitoring: RPA systems can monitor processes in real-time, identifying and rectifying deviations from compliance standards as they occur. This proactive approach minimizes the risk of non-compliance issues going unnoticed.
Data Security and Privacy: RPA is designed to protect sensitive data. By automating data handling and storage, it reduces the risk of data breaches and ensures that personally identifiable information (PII) and other sensitive data are handled in a compliant manner.
Regulatory Reporting: RPA can automate the collection and preparation of reports required for regulatory compliance. This not only reduces the time and effort required for reporting but also minimizes the risk of errors in these critical documents.
Controlled Access: RPA allows for controlled access to sensitive systems and data. By limiting access to authorized personnel and automating role-based permissions, it enhances security and compliance with access control regulations.
Reducing Human Error: Many compliance issues arise from human error. RPA minimizes these errors, which can lead to non-compliance, fines, and other penalties.
RPA is a vital tool for meeting regulatory requirements and achieving audit readiness. It not only protects businesses from legal consequences and fines but also allows them to focus on their core operations, knowing that they are operating within the boundaries of the law. RPA doesn't just streamline processes; it safeguards businesses and enhances their ability to navigate complex regulatory landscapes with confidence.
Competitive Advantage: Staying Ahead in Your Industry with RPA
In the fast-paced and ever-evolving world of business, staying ahead of the competition is a constant challenge. To gain a competitive edge, organizations must be agile, efficient, and innovative. Robotic Process Automation (RPA) offers a significant advantage by providing the tools to streamline operations, reduce costs, and make data-driven decisions. In this article, we'll explore how RPA can be a catalyst for achieving a competitive advantage in your industry.
Operational Efficiency: RPA optimizes business processes by automating repetitive and rule-based tasks. This increased efficiency enables your organization to deliver products and services more quickly and cost-effectively, giving you an edge in the market.
Cost Reduction: By automating tasks and minimizing errors, RPA reduces operational costs. This allows your business to allocate resources strategically, invest in growth, and potentially offer competitive pricing to customers.
Customer Satisfaction: RPA enhances the customer experience by ensuring faster response times, personalized interactions, and error-free service. Satisfied customers are more likely to remain loyal and recommend your business to others.
Real-Time Data Insights: RPA collects and processes data in real-time, providing valuable insights into market trends, customer behavior, and operational performance. These insights can be leveraged to make informed decisions and stay ahead of market shifts.
Innovation and Creativity: By automating routine tasks, RPA liberates your workforce from the mundane, allowing them to focus on creative, strategic, and value-added activities. This fosters a culture of innovation and provides a competitive advantage in product and service development.
Strategic Decision-Making: With RPA, your organization can make data-driven decisions more efficiently. This strategic approach to decision-making allows you to anticipate market trends, spot opportunities, and outmaneuver competitors.
RPA is a game-changer for businesses seeking to gain a competitive advantage in their industries. By increasing operational efficiency, reducing costs, enhancing customer satisfaction, and providing real-time insights, RPA empowers organizations to stay ahead in rapidly changing markets. It's not just about streamlining processes; it's about positioning your business to lead, innovate, and thrive in a highly competitive world. RPA is the key to not just keeping pace but setting the pace in your industry.
Conclusion
In conclusion, Robotic Process Automation (RPA) is a transformative force in the modern business landscape, offering a multitude of benefits that can revolutionize the way organizations operate. Throughout this series of articles, we've explored the diverse advantages of RPA and how it can be harnessed to enhance different aspects of business operations.
RPA's ability to operate 24/7 ensures workflow continuity, allowing businesses to adapt to fluctuating workloads, meet global demands, and maintain a competitive edge. It offers employees the opportunity to focus on more meaningful tasks, fostering job satisfaction, skill development, and innovation.
RPA leverages data insights to facilitate data-driven decision-making, enabling businesses to respond to market changes and opportunities with agility and precision. It improves the customer experience through faster response times, reduced errors, and personalized interactions, leading to higher customer satisfaction and loyalty.
In a world where efficiency, agility, and customer satisfaction are paramount, RPA is more than a tool for automation; it's a strategic asset that empowers businesses to thrive and excel. Embracing the automation revolution is not just a choice; it's a necessity for organizations that aim to remain competitive, innovative, and successful in the ever-evolving business landscape.
Citrix Cloud Administration: A Comprehensive Guide
In today's rapidly evolving digital landscape, businesses and organizations are continually seeking agile, secure, and efficient solutions to manage their virtual applications and desktops. Citrix Cloud, a game-changing platform, has emerged as the answer to this growing demand. As a Citrix administrator or IT professional, mastering the art of Citrix Cloud administration is an essential skillset.
Welcome to our comprehensive guide on Citrix Cloud Administration. Whether you're a seasoned Citrix expert looking to transition to the cloud or a newcomer eager to explore the vast potential of Citrix's cloud-based offerings, this guide is your roadmap to navigating the intricacies of Citrix Cloud.
Citrix Cloud introduces a new paradigm for managing your virtual apps and desktops. It brings flexibility, scalability, and simplified infrastructure management to the forefront. From resource provisioning to user management, networking, security, and much more, Citrix Cloud is a versatile toolbox waiting to be harnessed.
Table of contents
-
Getting Started with Citrix Cloud: An Introduction to the Platform
-
Citrix Cloud Connector Installation and Configuration: Steps and Best Practices
-
Citrix Virtual Apps and Desktops Service: Setting Up and Managing Resources
-
User Management in Citrix Cloud: User Authentication and Access Control
-
Citrix Cloud Networking: Configuring Secure Connectivity
-
Citrix Cloud Monitoring and Analytics: Tools and Techniques
-
Citrix Cloud Updates and Maintenance: Best Practices for Staying Current
-
Integrating Citrix Cloud with On-Premises Deployments: Hybrid Configuration
-
Citrix Cloud Workspaces: Creating and Managing Digital Workspaces
-
Citrix Cloud Security: Strategies for Data Protection and Compliance
-
Conclusion
Getting Started with Citrix Cloud: An Introduction to the Platform
Citrix Cloud is a transformative platform that brings the power of Citrix solutions to the cloud, providing a new level of flexibility and efficiency in managing virtual applications and desktops. Whether you're an IT professional seeking to streamline your organization's workspace or a Citrix administrator looking to expand your skill set, understanding the fundamentals of Citrix Cloud is the first step to harnessing its potential.
In this introductory article, we'll explore the core concepts of Citrix Cloud, its benefits, and the foundational elements that make it a compelling choice for organizations of all sizes. We'll break down the key components of the platform, its architecture, and the advantages it offers in terms of agility, scalability, and simplified infrastructure management.
By the end of this article, you'll have a solid grasp of what Citrix Cloud is, why it's a game-changer in the world of virtualization and cloud computing, and how it can empower your organization to deliver a superior digital workspace experience.
Citrix Cloud Connector Installation and Configuration: Steps and Best Practices
The Citrix Cloud Connector serves as the bridge between your on-premises infrastructure and the Citrix Cloud platform, enabling a seamless connection for managing virtual applications and desktops. In this guide, we'll walk you through the essential steps for installing and configuring the Citrix Cloud Connector, while highlighting best practices to ensure a secure and efficient connection.
Installing and configuring the Citrix Cloud Connector is a critical phase in your Citrix Cloud deployment. It enables your on-premises resources to be managed and extended into the Citrix Cloud, creating a unified, cohesive environment. Whether you're setting up your connector for the first time or looking to optimize an existing installation, this guide will provide the necessary insights.
We'll cover the prerequisites, installation process, and post-installation configuration steps in a clear and concise manner, ensuring that you have a comprehensive understanding of the tasks involved. Additionally, we'll share best practices that will help you maintain a reliable connection to the Citrix Cloud, enhance security, and streamline management.
By the end of this guide, you'll be well-equipped to confidently install and configure the Citrix Cloud Connector, facilitating a smooth and efficient link between your on-premises infrastructure and the Citrix Cloud platform. Let's dive in and get started on this important journey of connecting your environment to the cloud.
Citrix Virtual Apps and Desktops Service: Setting Up and Managing Resources
The Citrix Virtual Apps and Desktops Service, part of the Citrix Cloud platform, empowers organizations to deliver virtual applications and desktops to users across the globe. In this guide, we will explore the essential steps and best practices for setting up and managing resources within this service.
Citrix Virtual Apps and Desktops Service offers a powerful, cloud-based solution for creating, delivering, and managing virtualized applications and desktops. With this service, you can streamline resource provisioning, enhance user experiences, and simplify administration.
We'll take you through the process of creating and configuring virtual app and desktop resources, including machine catalogs and delivery groups. We'll also cover resource management, scaling, and optimizing your environment for peak performance. Additionally, we'll discuss user access, policies, and how to ensure a secure and productive workspace.
By the end of this guide, you'll have the knowledge and insights needed to effectively set up and manage resources within the Citrix Virtual Apps and Desktops Service, providing your users with a seamless and feature-rich virtual workspace. Let's begin the journey of optimizing your virtualization infrastructure in the cloud.
User Management in Citrix Cloud: User Authentication and Access Control
User management is a fundamental aspect of any Citrix Cloud deployment, as it directly impacts the security and accessibility of your virtual applications and desktops. In this guide, we will delve into the intricacies of user management within Citrix Cloud, focusing on user authentication and access control.
Ensuring the right individuals have access to your Citrix Cloud resources while maintaining a secure environment is paramount. In this guide, we'll explore the various methods of user authentication, from single sign-on (SSO) to multi-factor authentication (MFA), and discuss the best practices for implementing these solutions effectively.
We will also dive into access control mechanisms, such as role-based access control (RBAC) and user group management. You'll learn how to define and assign user roles and permissions to control what actions users can perform within your Citrix Cloud environment, whether it's managing resources, configuring settings, or simply accessing applications and desktops.
By the end of this guide, you'll have a comprehensive understanding of user management in Citrix Cloud, ensuring that your users are authenticated securely and that access control is finely tuned to meet your organization's specific needs. Let's explore the key elements of user authentication and access control in the world of Citrix Cloud.
Citrix Cloud Networking: Configuring Secure Connectivity
Networking forms the backbone of any successful Citrix Cloud deployment, as it directly influences the performance, reliability, and security of your virtualized resources. In this comprehensive guide, we will delve into the critical aspects of Citrix Cloud networking, focusing on configuring secure connectivity.
Citrix Cloud networking is about more than just connecting your virtual applications and desktops to the cloud—it's about creating a robust and secure infrastructure that ensures seamless access for users, no matter where they are. In this guide, we'll explore the key considerations, best practices, and steps to configure secure connectivity.
We'll cover topics such as setting up Virtual Private Networks (VPNs), leveraging Citrix Gateway for secure access, and optimizing network performance. We'll also delve into strategies for load balancing, content switching, and SSL offloading to create a seamless and secure experience for your users.
By the end of this guide, you'll be well-versed in the art of configuring secure connectivity in Citrix Cloud, ensuring that your virtualized resources are not only easily accessible but also well-protected from potential threats. Let's embark on this journey to create a robust and secure networking foundation for your Citrix Cloud environment.
Citrix Cloud Monitoring and Analytics: Tools and Techniques
In the dynamic world of Citrix Cloud administration, monitoring and analytics play a pivotal role in ensuring the optimal performance, availability, and security of your virtual applications and desktops. This guide will delve into the essential tools and techniques you need to effectively monitor and analyze your Citrix Cloud environment.
Citrix Cloud monitoring and analytics provide insights that help administrators proactively address issues, optimize resource utilization, and enhance the end-user experience. With the right tools and techniques, you can gain a deeper understanding of your environment and make data-driven decisions.
In this guide, we will explore the various monitoring and analytics solutions available within Citrix Cloud, including Citrix Director, Citrix Analytics, and third-party integrations. You'll learn how to set up and configure these tools, interpret the data they provide, and take action based on the insights gained.
We'll also cover best practices for proactive monitoring, performance tuning, and troubleshooting common issues. By the end of this guide, you'll have a clear roadmap for implementing monitoring and analytics within your Citrix Cloud environment, ensuring that it runs smoothly and efficiently. Let's dive into the world of Citrix Cloud monitoring and analytics to empower your administration efforts.
Citrix Cloud Updates and Maintenance: Best Practices for Staying Current
In the ever-evolving landscape of Citrix Cloud, staying up-to-date is essential for maintaining the security, performance, and functionality of your virtual applications and desktops. This guide is dedicated to helping you understand the best practices for managing updates and maintenance in your Citrix Cloud environment.
Citrix Cloud, like any other software platform, undergoes periodic updates and maintenance to address vulnerabilities, introduce new features, and improve overall performance. Staying current with these updates is crucial to ensure a reliable and secure environment.
In this guide, we will walk you through the essential steps of managing Citrix Cloud updates, including understanding the update release cycle, planning for updates, and testing updates in a safe environment before deploying them to your production environment.
We'll also explore maintenance practices that extend beyond software updates, such as resource optimization, backup strategies, and disaster recovery planning. You'll gain insights into strategies for minimizing downtime and potential disruptions.
By the end of this guide, you'll have a clear understanding of how to maintain your Citrix Cloud environment effectively, ensuring that it remains up-to-date, secure, and aligned with your organization's evolving needs. Let's delve into the world of Citrix Cloud updates and maintenance, and ensure your environment remains resilient and reliable.
Integrating Citrix Cloud with On-Premises Deployments: Hybrid Configuration
The hybrid configuration, bridging the gap between Citrix Cloud and on-premises deployments, offers a powerful solution that combines the advantages of both worlds. In this guide, we'll explore the intricacies of integrating Citrix Cloud with your on-premises infrastructure to create a seamless, versatile, and efficient virtualization environment.
As organizations often have a mix of on-premises and cloud-based resources, integrating Citrix Cloud with your existing infrastructure can optimize the utilization of resources, enhance flexibility, and simplify administration. This guide will provide you with a step-by-step approach to create a harmonious coexistence.
We'll delve into key topics, including connecting your on-premises Virtual Apps and Desktops to Citrix Cloud, leveraging resource location flexibility, and ensuring a consistent user experience. You'll learn how to configure the necessary components for a successful hybrid deployment and how to manage resources and user access across both environments.
By the end of this guide, you'll have a solid understanding of how to implement a hybrid configuration that streamlines your virtualization infrastructure, enabling your organization to make the most of both on-premises and cloud resources. Let's embark on this journey of integrating Citrix Cloud with your on-premises deployments for enhanced versatility and efficiency.
Citrix Cloud Workspaces: Creating and Managing Digital Workspaces
Digital workspaces have become the cornerstone of modern business environments, offering a unified platform for accessing applications, data, and resources from anywhere, at any time. In this guide, we will delve into the creation and management of digital workspaces using Citrix Cloud, empowering organizations to deliver a flexible and productive workspace experience.
Citrix Cloud workspaces bring together applications, desktops, and data in a secure and user-friendly manner. They offer seamless access on various devices, enhancing productivity and user satisfaction. This guide will provide you with the knowledge and techniques required to create and manage Citrix Cloud workspaces effectively.
We'll explore the fundamental concepts of workspace creation, including the setup of storefronts, application provisioning, and customization options. Additionally, we'll cover user profile management, personalization, and the integration of collaboration tools to create a holistic digital workspace experience.
By the end of this guide, you'll be well-equipped to design, create, and manage Citrix Cloud workspaces that cater to the specific needs of your organization, ensuring a productive and efficient digital workspace for your users. Let's embark on the journey of crafting dynamic and user-friendly digital workspaces using Citrix Cloud.
Citrix Cloud Security: Strategies for Data Protection and Compliance
In today's digital landscape, the security of your Citrix Cloud environment is of paramount importance. Protecting sensitive data and ensuring compliance with industry regulations are crucial aspects of Citrix Cloud administration. This guide is dedicated to exploring robust security strategies that will help safeguard your data and maintain compliance within Citrix Cloud.
Citrix Cloud Security is a multi-faceted approach that involves protecting your virtual applications, desktops, and the data that flows through them. We'll delve into various strategies and best practices that address security concerns, focusing on data protection and regulatory compliance.
Throughout this guide, you'll learn about the importance of encryption, access controls, and user authentication. We'll also discuss methods for securing data in transit and at rest, as well as strategies for addressing data governance and compliance requirements specific to your industry.
By the end of this guide, you'll have a clear understanding of how to implement effective security strategies in your Citrix Cloud environment, ensuring that your data remains protected, and your organization complies with relevant regulations. Let's embark on the journey of bolstering the security of your Citrix Cloud deployment.
Conclusion
In conclusion, this comprehensive guide has taken you on a journey through the world of Citrix Cloud administration, covering a wide range of critical topics and best practices. We've explored the fundamental concepts of Citrix Cloud, from its initial setup and resource management to user authentication, secure networking, and monitoring and analytics.
We've also discussed the importance of staying current with updates and maintenance and the benefits of integrating Citrix Cloud with on-premises deployments. Additionally, we delved into the creation and management of digital workspaces, empowering organizations to provide a productive and flexible workspace experience for their users.
Lastly, we highlighted the critical aspect of Citrix Cloud security, emphasizing data protection and compliance strategies to keep your environment safe and in adherence with industry regulations.
As you continue your Citrix Cloud administration journey, remember that technology and best practices are continually evolving. Staying informed, exploring new solutions, and adapting to the changing landscape will help you navigate the complex world of Citrix Cloud effectively.
We hope this guide has provided you with valuable insights, and we encourage you to put this knowledge into practice to optimize your Citrix Cloud environment, enhance security, and provide an exceptional digital workspace experience for your users. Thank you for joining us on this journey, and we wish you every success in your Citrix Cloud administration endeavors.
Read More
In today's rapidly evolving digital landscape, businesses and organizations are continually seeking agile, secure, and efficient solutions to manage their virtual applications and desktops. Citrix Cloud, a game-changing platform, has emerged as the answer to this growing demand. As a Citrix administrator or IT professional, mastering the art of Citrix Cloud administration is an essential skillset.
Welcome to our comprehensive guide on Citrix Cloud Administration. Whether you're a seasoned Citrix expert looking to transition to the cloud or a newcomer eager to explore the vast potential of Citrix's cloud-based offerings, this guide is your roadmap to navigating the intricacies of Citrix Cloud.
Citrix Cloud introduces a new paradigm for managing your virtual apps and desktops. It brings flexibility, scalability, and simplified infrastructure management to the forefront. From resource provisioning to user management, networking, security, and much more, Citrix Cloud is a versatile toolbox waiting to be harnessed.
Table of contents
-
Getting Started with Citrix Cloud: An Introduction to the Platform
-
Citrix Cloud Connector Installation and Configuration: Steps and Best Practices
-
Citrix Virtual Apps and Desktops Service: Setting Up and Managing Resources
-
User Management in Citrix Cloud: User Authentication and Access Control
-
Citrix Cloud Networking: Configuring Secure Connectivity
-
Citrix Cloud Monitoring and Analytics: Tools and Techniques
-
Citrix Cloud Updates and Maintenance: Best Practices for Staying Current
-
Integrating Citrix Cloud with On-Premises Deployments: Hybrid Configuration
-
Citrix Cloud Workspaces: Creating and Managing Digital Workspaces
-
Citrix Cloud Security: Strategies for Data Protection and Compliance
-
Conclusion
Getting Started with Citrix Cloud: An Introduction to the Platform
Citrix Cloud is a transformative platform that brings the power of Citrix solutions to the cloud, providing a new level of flexibility and efficiency in managing virtual applications and desktops. Whether you're an IT professional seeking to streamline your organization's workspace or a Citrix administrator looking to expand your skill set, understanding the fundamentals of Citrix Cloud is the first step to harnessing its potential.
In this introductory article, we'll explore the core concepts of Citrix Cloud, its benefits, and the foundational elements that make it a compelling choice for organizations of all sizes. We'll break down the key components of the platform, its architecture, and the advantages it offers in terms of agility, scalability, and simplified infrastructure management.
By the end of this article, you'll have a solid grasp of what Citrix Cloud is, why it's a game-changer in the world of virtualization and cloud computing, and how it can empower your organization to deliver a superior digital workspace experience.
Citrix Cloud Connector Installation and Configuration: Steps and Best Practices
The Citrix Cloud Connector serves as the bridge between your on-premises infrastructure and the Citrix Cloud platform, enabling a seamless connection for managing virtual applications and desktops. In this guide, we'll walk you through the essential steps for installing and configuring the Citrix Cloud Connector, while highlighting best practices to ensure a secure and efficient connection.
Installing and configuring the Citrix Cloud Connector is a critical phase in your Citrix Cloud deployment. It enables your on-premises resources to be managed and extended into the Citrix Cloud, creating a unified, cohesive environment. Whether you're setting up your connector for the first time or looking to optimize an existing installation, this guide will provide the necessary insights.
We'll cover the prerequisites, installation process, and post-installation configuration steps in a clear and concise manner, ensuring that you have a comprehensive understanding of the tasks involved. Additionally, we'll share best practices that will help you maintain a reliable connection to the Citrix Cloud, enhance security, and streamline management.
By the end of this guide, you'll be well-equipped to confidently install and configure the Citrix Cloud Connector, facilitating a smooth and efficient link between your on-premises infrastructure and the Citrix Cloud platform. Let's dive in and get started on this important journey of connecting your environment to the cloud.
Citrix Virtual Apps and Desktops Service: Setting Up and Managing Resources
The Citrix Virtual Apps and Desktops Service, part of the Citrix Cloud platform, empowers organizations to deliver virtual applications and desktops to users across the globe. In this guide, we will explore the essential steps and best practices for setting up and managing resources within this service.
Citrix Virtual Apps and Desktops Service offers a powerful, cloud-based solution for creating, delivering, and managing virtualized applications and desktops. With this service, you can streamline resource provisioning, enhance user experiences, and simplify administration.
We'll take you through the process of creating and configuring virtual app and desktop resources, including machine catalogs and delivery groups. We'll also cover resource management, scaling, and optimizing your environment for peak performance. Additionally, we'll discuss user access, policies, and how to ensure a secure and productive workspace.
By the end of this guide, you'll have the knowledge and insights needed to effectively set up and manage resources within the Citrix Virtual Apps and Desktops Service, providing your users with a seamless and feature-rich virtual workspace. Let's begin the journey of optimizing your virtualization infrastructure in the cloud.
User Management in Citrix Cloud: User Authentication and Access Control
User management is a fundamental aspect of any Citrix Cloud deployment, as it directly impacts the security and accessibility of your virtual applications and desktops. In this guide, we will delve into the intricacies of user management within Citrix Cloud, focusing on user authentication and access control.
Ensuring the right individuals have access to your Citrix Cloud resources while maintaining a secure environment is paramount. In this guide, we'll explore the various methods of user authentication, from single sign-on (SSO) to multi-factor authentication (MFA), and discuss the best practices for implementing these solutions effectively.
We will also dive into access control mechanisms, such as role-based access control (RBAC) and user group management. You'll learn how to define and assign user roles and permissions to control what actions users can perform within your Citrix Cloud environment, whether it's managing resources, configuring settings, or simply accessing applications and desktops.
By the end of this guide, you'll have a comprehensive understanding of user management in Citrix Cloud, ensuring that your users are authenticated securely and that access control is finely tuned to meet your organization's specific needs. Let's explore the key elements of user authentication and access control in the world of Citrix Cloud.
Citrix Cloud Networking: Configuring Secure Connectivity
Networking forms the backbone of any successful Citrix Cloud deployment, as it directly influences the performance, reliability, and security of your virtualized resources. In this comprehensive guide, we will delve into the critical aspects of Citrix Cloud networking, focusing on configuring secure connectivity.
Citrix Cloud networking is about more than just connecting your virtual applications and desktops to the cloud—it's about creating a robust and secure infrastructure that ensures seamless access for users, no matter where they are. In this guide, we'll explore the key considerations, best practices, and steps to configure secure connectivity.
We'll cover topics such as setting up Virtual Private Networks (VPNs), leveraging Citrix Gateway for secure access, and optimizing network performance. We'll also delve into strategies for load balancing, content switching, and SSL offloading to create a seamless and secure experience for your users.
By the end of this guide, you'll be well-versed in the art of configuring secure connectivity in Citrix Cloud, ensuring that your virtualized resources are not only easily accessible but also well-protected from potential threats. Let's embark on this journey to create a robust and secure networking foundation for your Citrix Cloud environment.
Citrix Cloud Monitoring and Analytics: Tools and Techniques
In the dynamic world of Citrix Cloud administration, monitoring and analytics play a pivotal role in ensuring the optimal performance, availability, and security of your virtual applications and desktops. This guide will delve into the essential tools and techniques you need to effectively monitor and analyze your Citrix Cloud environment.
Citrix Cloud monitoring and analytics provide insights that help administrators proactively address issues, optimize resource utilization, and enhance the end-user experience. With the right tools and techniques, you can gain a deeper understanding of your environment and make data-driven decisions.
In this guide, we will explore the various monitoring and analytics solutions available within Citrix Cloud, including Citrix Director, Citrix Analytics, and third-party integrations. You'll learn how to set up and configure these tools, interpret the data they provide, and take action based on the insights gained.
We'll also cover best practices for proactive monitoring, performance tuning, and troubleshooting common issues. By the end of this guide, you'll have a clear roadmap for implementing monitoring and analytics within your Citrix Cloud environment, ensuring that it runs smoothly and efficiently. Let's dive into the world of Citrix Cloud monitoring and analytics to empower your administration efforts.
Citrix Cloud Updates and Maintenance: Best Practices for Staying Current
In the ever-evolving landscape of Citrix Cloud, staying up-to-date is essential for maintaining the security, performance, and functionality of your virtual applications and desktops. This guide is dedicated to helping you understand the best practices for managing updates and maintenance in your Citrix Cloud environment.
Citrix Cloud, like any other software platform, undergoes periodic updates and maintenance to address vulnerabilities, introduce new features, and improve overall performance. Staying current with these updates is crucial to ensure a reliable and secure environment.
In this guide, we will walk you through the essential steps of managing Citrix Cloud updates, including understanding the update release cycle, planning for updates, and testing updates in a safe environment before deploying them to your production environment.
We'll also explore maintenance practices that extend beyond software updates, such as resource optimization, backup strategies, and disaster recovery planning. You'll gain insights into strategies for minimizing downtime and potential disruptions.
By the end of this guide, you'll have a clear understanding of how to maintain your Citrix Cloud environment effectively, ensuring that it remains up-to-date, secure, and aligned with your organization's evolving needs. Let's delve into the world of Citrix Cloud updates and maintenance, and ensure your environment remains resilient and reliable.
Integrating Citrix Cloud with On-Premises Deployments: Hybrid Configuration
The hybrid configuration, bridging the gap between Citrix Cloud and on-premises deployments, offers a powerful solution that combines the advantages of both worlds. In this guide, we'll explore the intricacies of integrating Citrix Cloud with your on-premises infrastructure to create a seamless, versatile, and efficient virtualization environment.
As organizations often have a mix of on-premises and cloud-based resources, integrating Citrix Cloud with your existing infrastructure can optimize the utilization of resources, enhance flexibility, and simplify administration. This guide will provide you with a step-by-step approach to create a harmonious coexistence.
We'll delve into key topics, including connecting your on-premises Virtual Apps and Desktops to Citrix Cloud, leveraging resource location flexibility, and ensuring a consistent user experience. You'll learn how to configure the necessary components for a successful hybrid deployment and how to manage resources and user access across both environments.
By the end of this guide, you'll have a solid understanding of how to implement a hybrid configuration that streamlines your virtualization infrastructure, enabling your organization to make the most of both on-premises and cloud resources. Let's embark on this journey of integrating Citrix Cloud with your on-premises deployments for enhanced versatility and efficiency.
Citrix Cloud Workspaces: Creating and Managing Digital Workspaces
Digital workspaces have become the cornerstone of modern business environments, offering a unified platform for accessing applications, data, and resources from anywhere, at any time. In this guide, we will delve into the creation and management of digital workspaces using Citrix Cloud, empowering organizations to deliver a flexible and productive workspace experience.
Citrix Cloud workspaces bring together applications, desktops, and data in a secure and user-friendly manner. They offer seamless access on various devices, enhancing productivity and user satisfaction. This guide will provide you with the knowledge and techniques required to create and manage Citrix Cloud workspaces effectively.
We'll explore the fundamental concepts of workspace creation, including the setup of storefronts, application provisioning, and customization options. Additionally, we'll cover user profile management, personalization, and the integration of collaboration tools to create a holistic digital workspace experience.
By the end of this guide, you'll be well-equipped to design, create, and manage Citrix Cloud workspaces that cater to the specific needs of your organization, ensuring a productive and efficient digital workspace for your users. Let's embark on the journey of crafting dynamic and user-friendly digital workspaces using Citrix Cloud.
Citrix Cloud Security: Strategies for Data Protection and Compliance
In today's digital landscape, the security of your Citrix Cloud environment is of paramount importance. Protecting sensitive data and ensuring compliance with industry regulations are crucial aspects of Citrix Cloud administration. This guide is dedicated to exploring robust security strategies that will help safeguard your data and maintain compliance within Citrix Cloud.
Citrix Cloud Security is a multi-faceted approach that involves protecting your virtual applications, desktops, and the data that flows through them. We'll delve into various strategies and best practices that address security concerns, focusing on data protection and regulatory compliance.
Throughout this guide, you'll learn about the importance of encryption, access controls, and user authentication. We'll also discuss methods for securing data in transit and at rest, as well as strategies for addressing data governance and compliance requirements specific to your industry.
By the end of this guide, you'll have a clear understanding of how to implement effective security strategies in your Citrix Cloud environment, ensuring that your data remains protected, and your organization complies with relevant regulations. Let's embark on the journey of bolstering the security of your Citrix Cloud deployment.
Conclusion
In conclusion, this comprehensive guide has taken you on a journey through the world of Citrix Cloud administration, covering a wide range of critical topics and best practices. We've explored the fundamental concepts of Citrix Cloud, from its initial setup and resource management to user authentication, secure networking, and monitoring and analytics.
We've also discussed the importance of staying current with updates and maintenance and the benefits of integrating Citrix Cloud with on-premises deployments. Additionally, we delved into the creation and management of digital workspaces, empowering organizations to provide a productive and flexible workspace experience for their users.
Lastly, we highlighted the critical aspect of Citrix Cloud security, emphasizing data protection and compliance strategies to keep your environment safe and in adherence with industry regulations.
As you continue your Citrix Cloud administration journey, remember that technology and best practices are continually evolving. Staying informed, exploring new solutions, and adapting to the changing landscape will help you navigate the complex world of Citrix Cloud effectively.
We hope this guide has provided you with valuable insights, and we encourage you to put this knowledge into practice to optimize your Citrix Cloud environment, enhance security, and provide an exceptional digital workspace experience for your users. Thank you for joining us on this journey, and we wish you every success in your Citrix Cloud administration endeavors.
Overview of Digital Marketing Certification Programs
In the rapidly evolving landscape of digital marketing, staying ahead of the curve is crucial for professionals aspiring to make a mark in the industry. Digital marketing certification programs have emerged as invaluable tools for individuals seeking to enhance their skills, validate their expertise, and gain a competitive edge in the job market. In this comprehensive overview, we'll delve into the world of digital marketing certifications, exploring the myriad options available and shedding light on the significance of these programs in today's dynamic business environment.
Digital marketing certifications encompass a diverse range of modules, each designed to cover essential aspects of online marketing, from search engine optimization (SEO) and social media marketing to analytics and content strategy. These programs not only serve as structured learning paths but also provide a standardized means of assessment, ensuring that certified professionals possess a well-rounded understanding of the multifaceted realm of digital marketing.
This overview will guide you through the considerations involved in choosing a certification program, whether you're a seasoned professional looking to upskill or a newcomer eager to establish a foothold in the industry. From exploring the content and structure of popular certification courses to understanding the broader implications of being certified, this series aims to be your go-to resource for navigating the diverse landscape of digital marketing certifications. Join us on this journey as we unravel the opportunities, challenges, and transformative potential of digital marketing certification programs.
Table of contents
-
Key Digital Marketing Certification Providers
-
Choosing the Right Certification for Your Career Goals
-
Examining the Curriculum
-
Certification Levels and Specializations
-
Industry Recognition and Credibility
-
Online vs In-Person Certification Programs
-
Practical Application and Real-World Projects
-
Cost and Time Considerations
-
Success Stories and Testimonials
-
Maintaining Certification Relevance in a Changing Landscape
-
Conclusion
Key Digital Marketing Certification Providers
In the dynamic landscape of digital marketing, several reputable certification providers offer comprehensive programs designed to equip professionals with the skills needed to thrive in the ever-evolving online space. Here are key digital marketing certification providers
Google Digital Garage:Google offers a range of free courses through its Digital Garage platform. Courses cover various aspects of digital marketing, including search engine optimization (SEO), social media, and analytics.
HubSpot Academy:HubSpot provides a comprehensive set of free certification courses on inbound marketing, content marketing, social media strategy, and more. Their certifications are well-regarded in the marketing community.
LinkedIn Learning (formerly Lynda.com):LinkedIn Learning provides a variety of courses on digital marketing, with a focus on skill development. Courses cover SEO, content marketing, email marketing, and more.
Semrush Academy:Semrush, a tool for SEO and online visibility management, provides a certification program covering the use of their platform as well as broader digital marketing topics.
Content Marketing Institute (CMI):CMI offers a content marketing certification program that covers content strategy, creation, and distribution. It's ideal for professionals looking to specialize in content marketing.
Simplilearn:Simplilearn offers a variety of digital marketing courses and certification programs. They cover topics like SEO, social media, pay-per-click (PPC), and digital strategy.
Microsoft Advertising Certification:Microsoft Advertising offers a certification program covering their advertising platform. It includes topics such as search engine marketing (SEM), display advertising, and analytics.
Choosing the Right Certification for Your Career Goals
Embarking on a journey to choose the right digital marketing certification is a crucial step in shaping a successful career in the ever-evolving landscape of online marketing. To navigate this decision effectively, it's essential to align your certification choice with your unique career goals and aspirations within the diverse field of digital marketing.
As you delve into the myriad of certification options available, carefully research the specializations offered by each program. Certifications often cater to specific aspects of digital marketing, and understanding the content focus will help you pinpoint the most relevant and impactful certification for your chosen path. Platforms like Facebook Blueprint or Hootsuite Academy may be particularly beneficial for those seeking expertise in social media marketing, while broader certifications from reputable providers like Google Digital Garage cover a spectrum of digital marketing disciplines.
Consider the industry recognition and reputation of the certification programs under consideration. Opting for certifications from well-established providers, such as Google Digital Garage, HubSpot, or Digital Marketing Institute, can enhance your credibility in the eyes of potential employers. A certification's standing within the industry is a valuable asset, opening doors to opportunities and signaling a commitment to excellence in the field.
Evaluate the structure and format of the certification programs to ensure they align with your preferred learning style and schedule. Whether you thrive in self-paced online courses or prefer the structure of live sessions, choosing a format that suits your needs is crucial for a successful learning experience. Additionally, assess whether the program incorporates practical, hands-on components, as these can significantly enhance your ability to apply learned skills in real-world scenarios.
Certification levels also play a pivotal role in the decision-making process. Some programs offer different levels, catering to individuals at various stages of their careers. Assess your current skill level and opt for a certification that matches your expertise, with the flexibility to progress to more advanced levels as you gain experience.
Budget constraints and accessibility are practical considerations that should not be overlooked. While some certifications, such as those from Google Digital Garage, offer free courses, others may involve costs. Ensure that the chosen certification aligns with your budget and is accessible in terms of time commitment and scheduling.
By thoughtfully considering these factors, you can make a well-informed decision when choosing the right digital marketing certification for your career goals. Remember that the certification you select should not only enhance your skill set but also align with your professional aspirations, setting the stage for a fulfilling and successful career in digital marketing.
Examining the Curriculum
Examining the curriculum of a digital marketing certification program is a critical step in ensuring that the educational content aligns with your learning objectives and professional aspirations. Begin by exploring the breadth and depth of the topics covered within the program. A well-rounded curriculum should encompass key aspects of digital marketing, including search engine optimization (SEO), social media marketing, email marketing, content strategy, and analytics.
Delve into the specifics of each module to understand the depth of coverage. For instance, in SEO, examine whether the curriculum addresses both on-page and off-page optimization techniques, keyword research strategies, and the latest trends in search engine algorithms. Similarly, in social media marketing, assess whether the program covers platforms comprehensively, explores paid advertising strategies, and includes insights into audience engagement and analytics.
In summary, scrutinizing the curriculum of a digital marketing certification program is a meticulous process that involves assessing the comprehensiveness, practicality, currency, flexibility, and continuous learning aspects of the educational content. By ensuring that the curriculum aligns with your specific learning objectives and industry demands, you can make an informed decision that propels you toward a successful and fulfilling career in digital marketing.
Certification Levels and Specializations
Understanding the certification levels and specializations within digital marketing is crucial for professionals seeking to tailor their learning experience to their specific career goals and expertise. Digital marketing certification programs often offer different levels of proficiency and opportunities for specialization to cater to the diverse needs of learners.
Certification levels typically range from foundational or beginner to intermediate and advanced. These levels are designed to accommodate individuals at different stages of their careers, ensuring that the content is relevant to their knowledge and experience. Beginners may start with foundational certifications, covering essential concepts and strategies, while experienced marketers may pursue advanced certifications that delve into intricate, specialized areas.
Foundational certifications often introduce learners to the fundamental principles of digital marketing. This may include an overview of key channels such as SEO, social media, email marketing, and basic analytics. These certifications provide a solid understanding of the digital marketing landscape, making them suitable for newcomers or those looking to establish a broad foundation.
Intermediate certifications build upon the foundational knowledge and delve deeper into specific areas of digital marketing. Learners may choose to specialize in disciplines like content marketing, paid advertising, or social media strategy. These certifications aim to enhance expertise in targeted domains while maintaining a comprehensive view of the broader digital marketing ecosystem.
When selecting a digital marketing certification, it's essential to consider both the certification level and any available specializations. Assess your current skill level, career aspirations, and the areas of digital marketing that align with your interests. Choosing a program that offers the right combination of certification level and specialization will ensure a tailored learning experience that adds significant value to your professional journey.
Industry Recognition and Credibility
Industry recognition and credibility are paramount considerations when selecting a digital marketing certification, as these factors play a pivotal role in how your qualifications are perceived by employers, clients, and peers within the competitive landscape of digital marketing. A certification from a recognized and respected institution enhances your professional standing and can open doors to opportunities within the industry.
One key aspect of industry recognition is the reputation of the certification provider. Certifications from well-established and reputable organizations are more likely to be acknowledged and valued by employers. Recognized providers, such as Google Digital Garage, HubSpot, and Digital Marketing Institute, have a track record of delivering high-quality content and staying abreast of industry trends.
Employers often use industry-recognized certifications as a benchmark for evaluating the skills and expertise of candidates. Having a certification from a reputable institution can serve as a tangible demonstration of your commitment to continuous learning and professional development. It provides assurance to employers that you possess a standardized set of skills and knowledge, which is particularly important in a field as dynamic as digital marketing.
Ultimately, the goal is to choose a digital marketing certification that not only imparts valuable knowledge but also holds weight in the eyes of employers and peers. Industry recognition and credibility are powerful assets that can boost your career prospects, increase your employability, and position you as a credible and competent digital marketing professional within the competitive landscape of the industry.
Online vs In-Person Certification Programs
The choice between online and in-person certification programs in digital marketing is a significant decision that depends on various factors, including personal preferences, learning styles, and logistical considerations.
Online Certification Programs:
Flexibility: One of the primary advantages of online certification programs is the flexibility they offer. Learners can access course materials at their own pace and schedule, making it suitable for individuals with varying commitments such as full-time jobs or other responsibilities.
Accessibility: Online programs provide access to a global pool of resources and instructors. Learners can engage with content from industry experts and connect with peers from around the world, fostering a diverse learning environment.
Cost-Effectiveness: Online programs often have lower tuition costs compared to in-person options. Additionally, learners can save on travel, accommodation, and other expenses associated with attending in-person classes.
Diverse Learning Formats: Online programs often incorporate a variety of multimedia elements, such as video lectures, interactive quizzes, and discussion forums, catering to different learning styles.
In-Person Certification Programs:
Real-Time Interaction: In-person programs provide the opportunity for immediate interaction with instructors and fellow learners. This can facilitate a more dynamic learning experience with real-time feedback and discussions.
Structured Learning Environment: Classroom settings offer a structured learning environment with set schedules, which can be beneficial for individuals who thrive in a more regimented and organized setting.
Networking Opportunities: In-person programs provide valuable networking opportunities. Engaging with instructors and classmates face-to-face can lead to meaningful professional connections and collaborations.
Hands-On Experience: Some in-person programs incorporate hands-on activities, workshops, and group projects that may be challenging to replicate in an online format.
Ultimately, the choice between online and in-person certification programs depends on individual preferences, lifestyle, and learning preferences. Some learners may thrive in the flexibility of online programs, while others may benefit more from the structure and personal interaction offered by in-person options. Consider your own learning style, time constraints, and budget when making this decision.
Practical Application and Real-World Projects
Integrating practical application and real-world projects into a digital marketing certification program is a cornerstone in bridging the gap between theoretical knowledge and practical skills. This hands-on approach serves as a catalyst for a more immersive and impactful learning experience, offering learners the opportunity to directly apply acquired concepts in scenarios reflective of the challenges encountered in professional digital marketing environments.
Real-world projects, such as case studies, play a pivotal role in grounding learners in the complexities of the digital marketing landscape. By dissecting and solving actual business challenges, learners gain a nuanced understanding of how theoretical concepts manifest in practical situations. This process not only reinforces theoretical knowledge but also hones problem-solving skills, preparing individuals to navigate the dynamic and ever-evolving field of digital marketing.
Hands-on exercises, ranging from creating and optimizing digital campaigns to analyzing performance metrics, offer learners tangible experiences that mirror the tasks they will encounter in real-world professional settings. These exercises not only develop technical proficiency but also instill a sense of confidence in learners as they apply their knowledge to concrete, actionable projects.
In summary, the inclusion of practical application and real-world projects in a digital marketing certification program is more than a supplement to theoretical learning; it is a cornerstone for cultivating a holistic and industry-ready skill set. These experiences not only prepare learners for the demands of the professional realm but also empower them to confidently navigate the multifaceted landscape of digital marketing upon completion of their certification.
Cost and Time Considerations
Considering the cost and time implications of a digital marketing certification program is crucial for individuals seeking to strike a balance between their educational aspirations, budget constraints, and personal commitments. Both factors play significant roles in shaping the overall feasibility and effectiveness of the certification journey.
Cost Considerations:The cost of a digital marketing certification program varies widely based on factors such as the institution, the level of the certification, and the inclusion of additional features like real-world projects or instructor-led sessions. Some certifications, like those offered by Google Digital Garage, are available for free, providing an accessible entry point for learners on a budget. On the other hand, certifications from well-known institutions or those with specialized content may come with a higher price tag.
In addition to tuition fees, learners should factor in potential additional costs such as study materials, textbooks, or software tools that may be required for the program. Travel expenses, particularly for in-person programs, should also be considered, as attending physical classes or workshops may incur additional costs.
Time Considerations:The time required to complete a digital marketing certification program can vary based on factors such as the level of the certification, the learning format (self-paced or instructor-led), and the individual learner's pace. Some certifications can be completed in a matter of weeks, while others may take several months.
Self-paced online programs offer flexibility in terms of scheduling, allowing learners to balance certification studies with other commitments such as work or family responsibilities. In contrast, in-person or live online programs with fixed schedules may require a more structured time commitment.
Balancing Cost and Time:Ultimately, finding the right balance between cost and time requires careful consideration of personal circumstances and educational goals. While a more affordable program may suit a tight budget, learners should ensure that it still meets their learning objectives and provides a reputable certification. Similarly, an intensive program that demands significant time commitments may be worthwhile for those seeking a comprehensive and immersive learning experience.
Before committing to a digital marketing certification program, individuals should thoroughly research the program's cost structure, available resources, and time requirements. This informed approach ensures that learners can make a strategic investment in their professional development, aligning their educational choices with both budgetary constraints and career aspirations.
Success Stories and Testimonials
Exploring success stories and testimonials is a valuable step in assessing the impact and effectiveness of a digital marketing certification program. Learning from the experiences of individuals who have completed the program provides insights into the tangible benefits, career advancements, and transformative outcomes that others have achieved. Success stories and testimonials offer a glimpse into the real-world impact of the certification on professional journeys.
Gaining Insight into Real-World Application: Success stories often highlight how individuals have applied the knowledge and skills acquired through the certification in their professional roles. These narratives provide concrete examples of how the certification program translated theoretical concepts into practical solutions, campaigns, or strategies within the dynamic field of digital marketing.
Understanding Career Progression: Testimonials frequently shed light on the career progression of individuals who completed the certification. They may detail how the certification acted as a catalyst for job promotions, career transitions, or enhanced job responsibilities. Such insights offer a tangible understanding of the certification's role in career development and marketability within the industry.
Identifying Diverse Perspectives: Testimonials come from a diverse range of individuals with varied backgrounds, experiences, and career goals. Examining testimonials from professionals with different profiles can provide a holistic view of the certification program's applicability across various industry sectors and roles.
Validating Program Quality: Success stories and testimonials serve as endorsements of the program's quality and effectiveness. Positive feedback from those who have successfully navigated the certification adds credibility to the program's curriculum, instructors, and overall educational approach.
Before enrolling in a digital marketing certification program, individuals should actively seek out success stories and testimonials on official program websites, forums, or professional networking platforms. Analyzing these narratives enables prospective learners to make informed decisions based on the real-world experiences of their peers and validates the potential impact of the certification on their own professional journey.
Maintaining Certification Relevance in a Changing Landscape
Maintaining the relevance of a digital marketing certification in a constantly evolving landscape is a critical consideration for both certification providers and professionals seeking to stay abreast of industry advancements. The field of digital marketing is dynamic, with technology, consumer behaviors, and platforms undergoing frequent changes. Ensuring that certification programs adapt to these changes is essential for professionals to acquire skills that align with current industry demands.
Integration of practical, hands-on experiences is another crucial element. Real-world projects, case studies, and simulations should mirror the challenges professionals face in contemporary digital marketing roles. This not only enhances the practical application of knowledge but also ensures that the skills gained are directly transferable to the current industry landscape.
Establishing partnerships with industry leaders and organizations can also contribute to certification relevance. Collaboration with companies at the forefront of digital marketing ensures that certification programs are informed by real-world practices and insights. Industry partnerships can facilitate access to cutting-edge tools, case studies, and expertise that enhance the overall quality and relevance of the certification.
In summary, maintaining certification relevance in the ever-changing digital marketing landscape requires a proactive and adaptive approach. Certification providers must commit to regular updates, modular learning structures, practical experiences, community engagement, industry partnerships, and feedback mechanisms. Simultaneously, professionals should embrace a mindset of continuous learning, leveraging these certification programs as a foundation for ongoing professional development in the dynamic world of digital marketing.
Conclusion
In conclusion, the world of digital marketing is marked by its constant evolution, with technologies, trends, and consumer behaviors continuously shaping the industry's landscape. The pursuit of a digital marketing certification is not merely a one-time achievement but a commitment to ongoing learning and adaptation. As professionals seek to navigate this dynamic environment, choosing a certification program that prioritizes relevance and adaptability is paramount.
Certification providers play a pivotal role in maintaining the currency and effectiveness of their programs. By regularly updating content, embracing modular learning structures, integrating practical experiences, fostering a culture of continuous learning, establishing industry partnerships, and actively seeking feedback from professionals, certification providers can ensure that their offerings remain at the forefront of the digital marketing field.
Read More
In the rapidly evolving landscape of digital marketing, staying ahead of the curve is crucial for professionals aspiring to make a mark in the industry. Digital marketing certification programs have emerged as invaluable tools for individuals seeking to enhance their skills, validate their expertise, and gain a competitive edge in the job market. In this comprehensive overview, we'll delve into the world of digital marketing certifications, exploring the myriad options available and shedding light on the significance of these programs in today's dynamic business environment.
Digital marketing certifications encompass a diverse range of modules, each designed to cover essential aspects of online marketing, from search engine optimization (SEO) and social media marketing to analytics and content strategy. These programs not only serve as structured learning paths but also provide a standardized means of assessment, ensuring that certified professionals possess a well-rounded understanding of the multifaceted realm of digital marketing.
This overview will guide you through the considerations involved in choosing a certification program, whether you're a seasoned professional looking to upskill or a newcomer eager to establish a foothold in the industry. From exploring the content and structure of popular certification courses to understanding the broader implications of being certified, this series aims to be your go-to resource for navigating the diverse landscape of digital marketing certifications. Join us on this journey as we unravel the opportunities, challenges, and transformative potential of digital marketing certification programs.
Table of contents
-
Key Digital Marketing Certification Providers
-
Choosing the Right Certification for Your Career Goals
-
Examining the Curriculum
-
Certification Levels and Specializations
-
Industry Recognition and Credibility
-
Online vs In-Person Certification Programs
-
Practical Application and Real-World Projects
-
Cost and Time Considerations
-
Success Stories and Testimonials
-
Maintaining Certification Relevance in a Changing Landscape
-
Conclusion
Key Digital Marketing Certification Providers
In the dynamic landscape of digital marketing, several reputable certification providers offer comprehensive programs designed to equip professionals with the skills needed to thrive in the ever-evolving online space. Here are key digital marketing certification providers
Google Digital Garage:Google offers a range of free courses through its Digital Garage platform. Courses cover various aspects of digital marketing, including search engine optimization (SEO), social media, and analytics.
HubSpot Academy:HubSpot provides a comprehensive set of free certification courses on inbound marketing, content marketing, social media strategy, and more. Their certifications are well-regarded in the marketing community.
LinkedIn Learning (formerly Lynda.com):LinkedIn Learning provides a variety of courses on digital marketing, with a focus on skill development. Courses cover SEO, content marketing, email marketing, and more.
Semrush Academy:Semrush, a tool for SEO and online visibility management, provides a certification program covering the use of their platform as well as broader digital marketing topics.
Content Marketing Institute (CMI):CMI offers a content marketing certification program that covers content strategy, creation, and distribution. It's ideal for professionals looking to specialize in content marketing.
Simplilearn:Simplilearn offers a variety of digital marketing courses and certification programs. They cover topics like SEO, social media, pay-per-click (PPC), and digital strategy.
Microsoft Advertising Certification:Microsoft Advertising offers a certification program covering their advertising platform. It includes topics such as search engine marketing (SEM), display advertising, and analytics.
Choosing the Right Certification for Your Career Goals
Embarking on a journey to choose the right digital marketing certification is a crucial step in shaping a successful career in the ever-evolving landscape of online marketing. To navigate this decision effectively, it's essential to align your certification choice with your unique career goals and aspirations within the diverse field of digital marketing.
As you delve into the myriad of certification options available, carefully research the specializations offered by each program. Certifications often cater to specific aspects of digital marketing, and understanding the content focus will help you pinpoint the most relevant and impactful certification for your chosen path. Platforms like Facebook Blueprint or Hootsuite Academy may be particularly beneficial for those seeking expertise in social media marketing, while broader certifications from reputable providers like Google Digital Garage cover a spectrum of digital marketing disciplines.
Consider the industry recognition and reputation of the certification programs under consideration. Opting for certifications from well-established providers, such as Google Digital Garage, HubSpot, or Digital Marketing Institute, can enhance your credibility in the eyes of potential employers. A certification's standing within the industry is a valuable asset, opening doors to opportunities and signaling a commitment to excellence in the field.
Evaluate the structure and format of the certification programs to ensure they align with your preferred learning style and schedule. Whether you thrive in self-paced online courses or prefer the structure of live sessions, choosing a format that suits your needs is crucial for a successful learning experience. Additionally, assess whether the program incorporates practical, hands-on components, as these can significantly enhance your ability to apply learned skills in real-world scenarios.
Certification levels also play a pivotal role in the decision-making process. Some programs offer different levels, catering to individuals at various stages of their careers. Assess your current skill level and opt for a certification that matches your expertise, with the flexibility to progress to more advanced levels as you gain experience.
Budget constraints and accessibility are practical considerations that should not be overlooked. While some certifications, such as those from Google Digital Garage, offer free courses, others may involve costs. Ensure that the chosen certification aligns with your budget and is accessible in terms of time commitment and scheduling.
By thoughtfully considering these factors, you can make a well-informed decision when choosing the right digital marketing certification for your career goals. Remember that the certification you select should not only enhance your skill set but also align with your professional aspirations, setting the stage for a fulfilling and successful career in digital marketing.
Examining the Curriculum
Examining the curriculum of a digital marketing certification program is a critical step in ensuring that the educational content aligns with your learning objectives and professional aspirations. Begin by exploring the breadth and depth of the topics covered within the program. A well-rounded curriculum should encompass key aspects of digital marketing, including search engine optimization (SEO), social media marketing, email marketing, content strategy, and analytics.
Delve into the specifics of each module to understand the depth of coverage. For instance, in SEO, examine whether the curriculum addresses both on-page and off-page optimization techniques, keyword research strategies, and the latest trends in search engine algorithms. Similarly, in social media marketing, assess whether the program covers platforms comprehensively, explores paid advertising strategies, and includes insights into audience engagement and analytics.
In summary, scrutinizing the curriculum of a digital marketing certification program is a meticulous process that involves assessing the comprehensiveness, practicality, currency, flexibility, and continuous learning aspects of the educational content. By ensuring that the curriculum aligns with your specific learning objectives and industry demands, you can make an informed decision that propels you toward a successful and fulfilling career in digital marketing.
Certification Levels and Specializations
Understanding the certification levels and specializations within digital marketing is crucial for professionals seeking to tailor their learning experience to their specific career goals and expertise. Digital marketing certification programs often offer different levels of proficiency and opportunities for specialization to cater to the diverse needs of learners.
Certification levels typically range from foundational or beginner to intermediate and advanced. These levels are designed to accommodate individuals at different stages of their careers, ensuring that the content is relevant to their knowledge and experience. Beginners may start with foundational certifications, covering essential concepts and strategies, while experienced marketers may pursue advanced certifications that delve into intricate, specialized areas.
Foundational certifications often introduce learners to the fundamental principles of digital marketing. This may include an overview of key channels such as SEO, social media, email marketing, and basic analytics. These certifications provide a solid understanding of the digital marketing landscape, making them suitable for newcomers or those looking to establish a broad foundation.
Intermediate certifications build upon the foundational knowledge and delve deeper into specific areas of digital marketing. Learners may choose to specialize in disciplines like content marketing, paid advertising, or social media strategy. These certifications aim to enhance expertise in targeted domains while maintaining a comprehensive view of the broader digital marketing ecosystem.
When selecting a digital marketing certification, it's essential to consider both the certification level and any available specializations. Assess your current skill level, career aspirations, and the areas of digital marketing that align with your interests. Choosing a program that offers the right combination of certification level and specialization will ensure a tailored learning experience that adds significant value to your professional journey.
Industry Recognition and Credibility
Industry recognition and credibility are paramount considerations when selecting a digital marketing certification, as these factors play a pivotal role in how your qualifications are perceived by employers, clients, and peers within the competitive landscape of digital marketing. A certification from a recognized and respected institution enhances your professional standing and can open doors to opportunities within the industry.
One key aspect of industry recognition is the reputation of the certification provider. Certifications from well-established and reputable organizations are more likely to be acknowledged and valued by employers. Recognized providers, such as Google Digital Garage, HubSpot, and Digital Marketing Institute, have a track record of delivering high-quality content and staying abreast of industry trends.
Employers often use industry-recognized certifications as a benchmark for evaluating the skills and expertise of candidates. Having a certification from a reputable institution can serve as a tangible demonstration of your commitment to continuous learning and professional development. It provides assurance to employers that you possess a standardized set of skills and knowledge, which is particularly important in a field as dynamic as digital marketing.
Ultimately, the goal is to choose a digital marketing certification that not only imparts valuable knowledge but also holds weight in the eyes of employers and peers. Industry recognition and credibility are powerful assets that can boost your career prospects, increase your employability, and position you as a credible and competent digital marketing professional within the competitive landscape of the industry.
Online vs In-Person Certification Programs
The choice between online and in-person certification programs in digital marketing is a significant decision that depends on various factors, including personal preferences, learning styles, and logistical considerations.
Online Certification Programs:
Flexibility: One of the primary advantages of online certification programs is the flexibility they offer. Learners can access course materials at their own pace and schedule, making it suitable for individuals with varying commitments such as full-time jobs or other responsibilities.
Accessibility: Online programs provide access to a global pool of resources and instructors. Learners can engage with content from industry experts and connect with peers from around the world, fostering a diverse learning environment.
Cost-Effectiveness: Online programs often have lower tuition costs compared to in-person options. Additionally, learners can save on travel, accommodation, and other expenses associated with attending in-person classes.
Diverse Learning Formats: Online programs often incorporate a variety of multimedia elements, such as video lectures, interactive quizzes, and discussion forums, catering to different learning styles.
In-Person Certification Programs:
Real-Time Interaction: In-person programs provide the opportunity for immediate interaction with instructors and fellow learners. This can facilitate a more dynamic learning experience with real-time feedback and discussions.
Structured Learning Environment: Classroom settings offer a structured learning environment with set schedules, which can be beneficial for individuals who thrive in a more regimented and organized setting.
Networking Opportunities: In-person programs provide valuable networking opportunities. Engaging with instructors and classmates face-to-face can lead to meaningful professional connections and collaborations.
Hands-On Experience: Some in-person programs incorporate hands-on activities, workshops, and group projects that may be challenging to replicate in an online format.
Ultimately, the choice between online and in-person certification programs depends on individual preferences, lifestyle, and learning preferences. Some learners may thrive in the flexibility of online programs, while others may benefit more from the structure and personal interaction offered by in-person options. Consider your own learning style, time constraints, and budget when making this decision.
Practical Application and Real-World Projects
Integrating practical application and real-world projects into a digital marketing certification program is a cornerstone in bridging the gap between theoretical knowledge and practical skills. This hands-on approach serves as a catalyst for a more immersive and impactful learning experience, offering learners the opportunity to directly apply acquired concepts in scenarios reflective of the challenges encountered in professional digital marketing environments.
Real-world projects, such as case studies, play a pivotal role in grounding learners in the complexities of the digital marketing landscape. By dissecting and solving actual business challenges, learners gain a nuanced understanding of how theoretical concepts manifest in practical situations. This process not only reinforces theoretical knowledge but also hones problem-solving skills, preparing individuals to navigate the dynamic and ever-evolving field of digital marketing.
Hands-on exercises, ranging from creating and optimizing digital campaigns to analyzing performance metrics, offer learners tangible experiences that mirror the tasks they will encounter in real-world professional settings. These exercises not only develop technical proficiency but also instill a sense of confidence in learners as they apply their knowledge to concrete, actionable projects.
In summary, the inclusion of practical application and real-world projects in a digital marketing certification program is more than a supplement to theoretical learning; it is a cornerstone for cultivating a holistic and industry-ready skill set. These experiences not only prepare learners for the demands of the professional realm but also empower them to confidently navigate the multifaceted landscape of digital marketing upon completion of their certification.
Cost and Time Considerations
Considering the cost and time implications of a digital marketing certification program is crucial for individuals seeking to strike a balance between their educational aspirations, budget constraints, and personal commitments. Both factors play significant roles in shaping the overall feasibility and effectiveness of the certification journey.
Cost Considerations:The cost of a digital marketing certification program varies widely based on factors such as the institution, the level of the certification, and the inclusion of additional features like real-world projects or instructor-led sessions. Some certifications, like those offered by Google Digital Garage, are available for free, providing an accessible entry point for learners on a budget. On the other hand, certifications from well-known institutions or those with specialized content may come with a higher price tag.
In addition to tuition fees, learners should factor in potential additional costs such as study materials, textbooks, or software tools that may be required for the program. Travel expenses, particularly for in-person programs, should also be considered, as attending physical classes or workshops may incur additional costs.
Time Considerations:The time required to complete a digital marketing certification program can vary based on factors such as the level of the certification, the learning format (self-paced or instructor-led), and the individual learner's pace. Some certifications can be completed in a matter of weeks, while others may take several months.
Self-paced online programs offer flexibility in terms of scheduling, allowing learners to balance certification studies with other commitments such as work or family responsibilities. In contrast, in-person or live online programs with fixed schedules may require a more structured time commitment.
Balancing Cost and Time:Ultimately, finding the right balance between cost and time requires careful consideration of personal circumstances and educational goals. While a more affordable program may suit a tight budget, learners should ensure that it still meets their learning objectives and provides a reputable certification. Similarly, an intensive program that demands significant time commitments may be worthwhile for those seeking a comprehensive and immersive learning experience.
Before committing to a digital marketing certification program, individuals should thoroughly research the program's cost structure, available resources, and time requirements. This informed approach ensures that learners can make a strategic investment in their professional development, aligning their educational choices with both budgetary constraints and career aspirations.
Success Stories and Testimonials
Exploring success stories and testimonials is a valuable step in assessing the impact and effectiveness of a digital marketing certification program. Learning from the experiences of individuals who have completed the program provides insights into the tangible benefits, career advancements, and transformative outcomes that others have achieved. Success stories and testimonials offer a glimpse into the real-world impact of the certification on professional journeys.
Gaining Insight into Real-World Application: Success stories often highlight how individuals have applied the knowledge and skills acquired through the certification in their professional roles. These narratives provide concrete examples of how the certification program translated theoretical concepts into practical solutions, campaigns, or strategies within the dynamic field of digital marketing.
Understanding Career Progression: Testimonials frequently shed light on the career progression of individuals who completed the certification. They may detail how the certification acted as a catalyst for job promotions, career transitions, or enhanced job responsibilities. Such insights offer a tangible understanding of the certification's role in career development and marketability within the industry.
Identifying Diverse Perspectives: Testimonials come from a diverse range of individuals with varied backgrounds, experiences, and career goals. Examining testimonials from professionals with different profiles can provide a holistic view of the certification program's applicability across various industry sectors and roles.
Validating Program Quality: Success stories and testimonials serve as endorsements of the program's quality and effectiveness. Positive feedback from those who have successfully navigated the certification adds credibility to the program's curriculum, instructors, and overall educational approach.
Before enrolling in a digital marketing certification program, individuals should actively seek out success stories and testimonials on official program websites, forums, or professional networking platforms. Analyzing these narratives enables prospective learners to make informed decisions based on the real-world experiences of their peers and validates the potential impact of the certification on their own professional journey.
Maintaining Certification Relevance in a Changing Landscape
Maintaining the relevance of a digital marketing certification in a constantly evolving landscape is a critical consideration for both certification providers and professionals seeking to stay abreast of industry advancements. The field of digital marketing is dynamic, with technology, consumer behaviors, and platforms undergoing frequent changes. Ensuring that certification programs adapt to these changes is essential for professionals to acquire skills that align with current industry demands.
Integration of practical, hands-on experiences is another crucial element. Real-world projects, case studies, and simulations should mirror the challenges professionals face in contemporary digital marketing roles. This not only enhances the practical application of knowledge but also ensures that the skills gained are directly transferable to the current industry landscape.
Establishing partnerships with industry leaders and organizations can also contribute to certification relevance. Collaboration with companies at the forefront of digital marketing ensures that certification programs are informed by real-world practices and insights. Industry partnerships can facilitate access to cutting-edge tools, case studies, and expertise that enhance the overall quality and relevance of the certification.
In summary, maintaining certification relevance in the ever-changing digital marketing landscape requires a proactive and adaptive approach. Certification providers must commit to regular updates, modular learning structures, practical experiences, community engagement, industry partnerships, and feedback mechanisms. Simultaneously, professionals should embrace a mindset of continuous learning, leveraging these certification programs as a foundation for ongoing professional development in the dynamic world of digital marketing.
Conclusion
In conclusion, the world of digital marketing is marked by its constant evolution, with technologies, trends, and consumer behaviors continuously shaping the industry's landscape. The pursuit of a digital marketing certification is not merely a one-time achievement but a commitment to ongoing learning and adaptation. As professionals seek to navigate this dynamic environment, choosing a certification program that prioritizes relevance and adaptability is paramount.
Certification providers play a pivotal role in maintaining the currency and effectiveness of their programs. By regularly updating content, embracing modular learning structures, integrating practical experiences, fostering a culture of continuous learning, establishing industry partnerships, and actively seeking feedback from professionals, certification providers can ensure that their offerings remain at the forefront of the digital marketing field.
Machine Learning Algorithms Demystified
"Machine Learning Algorithms Demystified" is an insightful journey into the intricate world of machine learning, where complex algorithms are unraveled and explained with clarity. In this enlightening exploration, readers are guided through the fundamental concepts and principles that underpin various machine learning algorithms. The book serves as a beacon for both beginners and seasoned enthusiasts, demystifying the intricate mechanisms that empower machines to learn from data and make intelligent decisions.
This comprehensive guide begins by establishing a strong foundation in the core concepts of machine learning, providing readers with a solid understanding of key terminologies and principles. It then delves into a diverse array of machine learning algorithms, ranging from the foundational supervised learning methods to advanced unsupervised and reinforcement learning techniques. The narrative is enriched with real-world examples and case studies, making abstract concepts tangible and fostering a deeper comprehension of the algorithms' applications across diverse domains.
Whether you're a curious novice seeking an introduction to machine learning or a seasoned professional aiming to deepen your understanding, this book promises to be an invaluable resource. With its accessible language, illustrative examples, and comprehensive coverage, "Machine Learning Algorithms Demystified" paves the way for a meaningful exploration of the algorithms driving the future of intelligent systems.
Table of contents
-
Foundations of Machine Learning
-
Linear Models and Regression Analysis
-
Decision Trees and Random Forests
-
Support Vector Machines (SVM)
-
Clustering Techniques
-
Neural Networks and Deep Learning Architectures
-
Gradient Boosting and XGBoost
-
Reinforcement Learning Essentials
-
Time Series Analysis and Forecasting
-
Interpretable Machine Learning
-
Conclusion
Foundations of Machine Learning
The foundations of machine learning are rooted in the fundamental principles that define this transformative field. At its core, machine learning represents a paradigm shift from traditional programming, where computers are not explicitly programmed to perform a task, but rather learn from data and experiences. This shift introduces a dynamic approach, enabling machines to improve their performance over time as they encounter more information.
One of the foundational distinctions in machine learning lies in its types: supervised learning, unsupervised learning, and reinforcement learning. Supervised learning involves training models on labeled datasets, where the algorithm learns to make predictions or classifications. Unsupervised learning, on the other hand, deals with unlabeled data, seeking patterns and structures within the information. Reinforcement learning revolves around agents interacting with an environment, learning optimal actions through a system of rewards and penalties.
Overcoming challenges like overfitting and underfitting involves the application of techniques like cross-validation, which ensures a more robust estimation of model capabilities. Feature scaling and normalization contribute to model stability, enhancing convergence during the training process. Ethical considerations, including bias mitigation, transparency, and accountability, are integral components of the foundations of machine learning, emphasizing the importance of responsible AI practices in the development and deployment of models. These foundational principles provide a solid base for further exploration into the diverse and dynamic world of machine learning algorithms.
Linear Models and Regression Analysis
Linear models and regression analysis constitute a cornerstone in the realm of machine learning, offering a powerful and interpretable approach to understand and predict relationships within data. At its essence, linear regression is a foundational technique used for modeling the relationship between a dependent variable and one or more independent variables.
Linear regression finds widespread application in scenarios where understanding the linear relationship between variables is essential. For instance, it is frequently employed in economics to model the impact of independent variables on a dependent variable, such as predicting housing prices based on features like square footage and location.
While linear regression assumes a linear relationship between variables, its simplicity and interpretability make it an invaluable tool. However, it's essential to recognize its limitations, particularly when dealing with complex, nonlinear relationships. In such cases, more advanced models, including polynomial regression or other nonlinear models, may be warranted.
In summary, linear models and regression analysis provide a solid foundation for understanding and predicting relationships within datasets. From predicting stock prices to analyzing marketing trends, the versatility of linear regression makes it a fundamental tool in the machine learning toolkit, offering a clear and intuitive way to model and interpret data patterns.
Decision Trees and Random Forests
Decision trees and random forests represent powerful and versatile tools in machine learning, particularly in the domain of predictive modeling and classification tasks. These algorithms excel at capturing complex decision-making processes and are highly interpretable, making them valuable assets in various applications.
Decision Trees:At the core of decision trees is a tree-like model where each internal node represents a decision based on the value of a particular feature, each branch represents the outcome of that decision, and each leaf node represents the final prediction. The construction of a decision tree involves recursively partitioning the data based on the most informative features, resulting in a tree structure that can be easily visualized and interpreted.
Decision trees are capable of handling both categorical and numerical data, making them flexible for a wide range of tasks. They are particularly adept at capturing non-linear relationships and interactions within the data. However, decision trees are prone to overfitting, capturing noise in the training data, which can be addressed through techniques like pruning.
Random Forests:Random forests extend the power of decision trees by combining multiple trees into an ensemble model. Instead of relying on the decision of a single tree, random forests aggregate predictions from numerous decision trees, providing a more robust and accurate outcome. Each tree in the forest is trained on a random subset of the data and may consider only a random subset of features at each decision point, introducing diversity and mitigating overfitting.
In summary, decision trees and random forests offer a dynamic duo in machine learning, where decision trees provide transparency and interpretability, and random forests enhance predictive accuracy and robustness. Their versatility and effectiveness make them go-to choices for a myriad of applications, striking a balance between complexity and interpretability in the pursuit of accurate and reliable predictions.
Support Vector Machines (SVM)
Support Vector Machines (SVM) represent a powerful class of supervised learning algorithms with applications in both classification and regression tasks. Developed by Vladimir Vapnik and his colleagues in the 1990s, SVM has garnered widespread popularity due to its effectiveness in handling complex data structures and its solid theoretical foundation.
At the heart of SVM is the concept of finding an optimal hyperplane that maximally separates data points of different classes in the feature space. In a two-dimensional space, this hyperplane is a line, while in higher dimensions, it becomes a hyperplane. The uniqueness of SVM lies in its focus on the margin, the distance between the hyperplane and the nearest data points of each class. The goal is to maximize this margin, leading to a robust and generalizable model.
SVM's versatility in handling non-linear relationships is facilitated by the use of kernels. Kernels transform the original feature space into a higher-dimensional space, enabling SVM to find complex decision boundaries. Commonly used kernels include the linear kernel for linearly separable data, the polynomial kernel for capturing polynomial relationships, and the radial basis function (RBF) kernel for handling intricate, non-linear patterns.
In scenarios where perfect separation is not feasible, SVM introduces the concept of a soft margin. The soft margin allows for a controlled degree of misclassification, providing flexibility in handling real-world datasets with inherent noise or overlapping classes. The trade-off between maximizing the margin and minimizing misclassification errors is governed by a regularization parameter, denoted as C.
Read More
"Machine Learning Algorithms Demystified" is an insightful journey into the intricate world of machine learning, where complex algorithms are unraveled and explained with clarity. In this enlightening exploration, readers are guided through the fundamental concepts and principles that underpin various machine learning algorithms. The book serves as a beacon for both beginners and seasoned enthusiasts, demystifying the intricate mechanisms that empower machines to learn from data and make intelligent decisions.
This comprehensive guide begins by establishing a strong foundation in the core concepts of machine learning, providing readers with a solid understanding of key terminologies and principles. It then delves into a diverse array of machine learning algorithms, ranging from the foundational supervised learning methods to advanced unsupervised and reinforcement learning techniques. The narrative is enriched with real-world examples and case studies, making abstract concepts tangible and fostering a deeper comprehension of the algorithms' applications across diverse domains.
Whether you're a curious novice seeking an introduction to machine learning or a seasoned professional aiming to deepen your understanding, this book promises to be an invaluable resource. With its accessible language, illustrative examples, and comprehensive coverage, "Machine Learning Algorithms Demystified" paves the way for a meaningful exploration of the algorithms driving the future of intelligent systems.
Table of contents
-
Foundations of Machine Learning
-
Linear Models and Regression Analysis
-
Decision Trees and Random Forests
-
Support Vector Machines (SVM)
-
Clustering Techniques
-
Neural Networks and Deep Learning Architectures
-
Gradient Boosting and XGBoost
-
Reinforcement Learning Essentials
-
Time Series Analysis and Forecasting
-
Interpretable Machine Learning
-
Conclusion
Foundations of Machine Learning
The foundations of machine learning are rooted in the fundamental principles that define this transformative field. At its core, machine learning represents a paradigm shift from traditional programming, where computers are not explicitly programmed to perform a task, but rather learn from data and experiences. This shift introduces a dynamic approach, enabling machines to improve their performance over time as they encounter more information.
One of the foundational distinctions in machine learning lies in its types: supervised learning, unsupervised learning, and reinforcement learning. Supervised learning involves training models on labeled datasets, where the algorithm learns to make predictions or classifications. Unsupervised learning, on the other hand, deals with unlabeled data, seeking patterns and structures within the information. Reinforcement learning revolves around agents interacting with an environment, learning optimal actions through a system of rewards and penalties.
Overcoming challenges like overfitting and underfitting involves the application of techniques like cross-validation, which ensures a more robust estimation of model capabilities. Feature scaling and normalization contribute to model stability, enhancing convergence during the training process. Ethical considerations, including bias mitigation, transparency, and accountability, are integral components of the foundations of machine learning, emphasizing the importance of responsible AI practices in the development and deployment of models. These foundational principles provide a solid base for further exploration into the diverse and dynamic world of machine learning algorithms.
Linear Models and Regression Analysis
Linear models and regression analysis constitute a cornerstone in the realm of machine learning, offering a powerful and interpretable approach to understand and predict relationships within data. At its essence, linear regression is a foundational technique used for modeling the relationship between a dependent variable and one or more independent variables.
Linear regression finds widespread application in scenarios where understanding the linear relationship between variables is essential. For instance, it is frequently employed in economics to model the impact of independent variables on a dependent variable, such as predicting housing prices based on features like square footage and location.
While linear regression assumes a linear relationship between variables, its simplicity and interpretability make it an invaluable tool. However, it's essential to recognize its limitations, particularly when dealing with complex, nonlinear relationships. In such cases, more advanced models, including polynomial regression or other nonlinear models, may be warranted.
In summary, linear models and regression analysis provide a solid foundation for understanding and predicting relationships within datasets. From predicting stock prices to analyzing marketing trends, the versatility of linear regression makes it a fundamental tool in the machine learning toolkit, offering a clear and intuitive way to model and interpret data patterns.
Decision Trees and Random Forests
Decision trees and random forests represent powerful and versatile tools in machine learning, particularly in the domain of predictive modeling and classification tasks. These algorithms excel at capturing complex decision-making processes and are highly interpretable, making them valuable assets in various applications.
Decision Trees:At the core of decision trees is a tree-like model where each internal node represents a decision based on the value of a particular feature, each branch represents the outcome of that decision, and each leaf node represents the final prediction. The construction of a decision tree involves recursively partitioning the data based on the most informative features, resulting in a tree structure that can be easily visualized and interpreted.
Decision trees are capable of handling both categorical and numerical data, making them flexible for a wide range of tasks. They are particularly adept at capturing non-linear relationships and interactions within the data. However, decision trees are prone to overfitting, capturing noise in the training data, which can be addressed through techniques like pruning.
Random Forests:Random forests extend the power of decision trees by combining multiple trees into an ensemble model. Instead of relying on the decision of a single tree, random forests aggregate predictions from numerous decision trees, providing a more robust and accurate outcome. Each tree in the forest is trained on a random subset of the data and may consider only a random subset of features at each decision point, introducing diversity and mitigating overfitting.
In summary, decision trees and random forests offer a dynamic duo in machine learning, where decision trees provide transparency and interpretability, and random forests enhance predictive accuracy and robustness. Their versatility and effectiveness make them go-to choices for a myriad of applications, striking a balance between complexity and interpretability in the pursuit of accurate and reliable predictions.
Support Vector Machines (SVM)
Support Vector Machines (SVM) represent a powerful class of supervised learning algorithms with applications in both classification and regression tasks. Developed by Vladimir Vapnik and his colleagues in the 1990s, SVM has garnered widespread popularity due to its effectiveness in handling complex data structures and its solid theoretical foundation.
At the heart of SVM is the concept of finding an optimal hyperplane that maximally separates data points of different classes in the feature space. In a two-dimensional space, this hyperplane is a line, while in higher dimensions, it becomes a hyperplane. The uniqueness of SVM lies in its focus on the margin, the distance between the hyperplane and the nearest data points of each class. The goal is to maximize this margin, leading to a robust and generalizable model.
SVM's versatility in handling non-linear relationships is facilitated by the use of kernels. Kernels transform the original feature space into a higher-dimensional space, enabling SVM to find complex decision boundaries. Commonly used kernels include the linear kernel for linearly separable data, the polynomial kernel for capturing polynomial relationships, and the radial basis function (RBF) kernel for handling intricate, non-linear patterns.
In scenarios where perfect separation is not feasible, SVM introduces the concept of a soft margin. The soft margin allows for a controlled degree of misclassification, providing flexibility in handling real-world datasets with inherent noise or overlapping classes. The trade-off between maximizing the margin and minimizing misclassification errors is governed by a regularization parameter, denoted as C.
Benefits of Implementing CMMI in Your Organization
Implementing the Capability Maturity Model Integration (CMMI) in your organization can bring about a myriad of benefits, enhancing its overall efficiency and competitiveness in today's dynamic business landscape. CMMI serves as a comprehensive framework designed to elevate and optimize an organization's processes, thereby ensuring higher levels of performance, quality, and productivity.
One of the primary advantages of implementing CMMI lies in its ability to provide a structured approach to process improvement. By adopting CMMI practices, organizations can systematically identify, evaluate, and refine their existing processes. This structured methodology not only streamlines operations but also fosters a culture of continuous improvement, ensuring that the organization remains adaptable and responsive to evolving market demands.
CMMI is not merely a tool for process improvement; it also plays a pivotal role in risk management. By identifying and addressing potential risks at early stages, organizations can proactively mitigate challenges that may arise during project execution. This risk mitigation approach not only safeguards project timelines and budgets but also contributes to a more resilient and sustainable business model.
In addition to these operational advantages, implementing CMMI can also enhance communication and collaboration within an organization. The framework encourages cross-functional teams to work cohesively towards common objectives, fostering a collaborative culture that promotes knowledge sharing and innovation. This collaborative mindset is crucial in today's interconnected business environment, where agility and adaptability are key to success.
The benefits of implementing CMMI in an organization are multi-faceted, ranging from improved process efficiency and product quality to enhanced risk management and competitive advantage. As businesses navigate the complexities of a rapidly changing landscape, CMMI stands as a valuable framework that empowers organizations to not only meet current challenges but also to thrive in the future.
Table of contents
-
Enhanced Process Efficiency
-
Quality Assurance and Product Excellence
-
Risk Mitigation Strategies
-
Standardization of Best Practices
-
Collaborative Team Culture
-
Strategic Alignment and Competitive Edge
-
Continuous Improvement Mindset
-
Resource Optimization and Cost Management
-
Employee Development and Engagement
-
Measurable Performance Metrics
-
Conclusion
Enhanced Process Efficiency
Enhanced process efficiency is a key benefit of implementing the Capability Maturity Model Integration (CMMI) in an organization. This aspect revolves around the systematic improvement and optimization of existing processes, leading to increased effectiveness and streamlined workflows.
CMMI provides a structured framework for organizations to assess, refine, and standardize their processes across various departments. Through the identification of best practices and the elimination of redundancies or bottlenecks, CMMI helps organizations achieve a higher level of efficiency in their day-to-day operations.
One way CMMI enhances process efficiency is by promoting a clear understanding of roles, responsibilities, and workflows within the organization. By defining and documenting processes, teams can work more cohesively, reducing the likelihood of misunderstandings or delays. This clarity contributes to smoother collaboration and improved overall efficiency.
Furthermore, CMMI encourages organizations to continuously monitor and evaluate their processes. This ongoing assessment allows for the identification of areas for improvement. By addressing inefficiencies and optimizing processes iteratively, organizations can adapt to changing circumstances and maintain a competitive edge in their respective industries.
Enhanced process efficiency, facilitated by CMMI, involves the systematic improvement of organizational processes through clear documentation, continuous monitoring, and the establishment of performance metrics. By embracing this aspect of CMMI, organizations position themselves to operate more smoothly, respond to challenges more effectively, and deliver high-quality products or services with greater consistency.
Quality Assurance and Product Excellence
Quality assurance and product excellence are fundamental outcomes of implementing the Capability Maturity Model Integration (CMMI) in an organization. CMMI provides a structured framework that not only ensures the consistency of processes but also places a strong emphasis on delivering high-quality products and services.
CMMI encourages organizations to adopt rigorous quality assurance practices throughout the product or service development lifecycle. This involves defining clear quality standards, conducting thorough reviews, and implementing robust testing procedures. By adhering to these practices, organizations can identify and rectify defects early in the process, preventing issues from escalating and ultimately ensuring the delivery of superior products or services.
One of the ways CMMI contributes to product excellence is through its focus on continuous improvement. The model prompts organizations to regularly assess their processes and make necessary adjustments to enhance efficiency and quality. This iterative approach ensures that products and services evolve over time, meeting or exceeding customer expectations.
CMMI's impact on quality assurance and product excellence is evident through its emphasis on rigorous testing, continuous improvement, customer-centric practices, and the establishment of measurable quality metrics. By integrating these principles into their processes, organizations can consistently produce high-quality products, build customer trust, and gain a competitive advantage in the marketplace.
Risk Mitigation Strategies
Risk mitigation strategies are essential components of effective project and organizational management, and the implementation of the Capability Maturity Model Integration (CMMI) plays a pivotal role in shaping these strategies. One key aspect of risk mitigation within the CMMI framework is the emphasis on early identification. By encouraging organizations to identify risks at the outset of a project or process, CMMI enables teams to assess potential challenges before they escalate. This proactive approach sets the stage for comprehensive risk management throughout the project lifecycle.
CMMI goes beyond qualitative assessments by promoting quantitative risk analysis techniques. Assigning numerical values to risks and their potential impacts allows organizations to prioritize and address the most critical issues. This data-driven approach ensures that resources are allocated efficiently, focusing on mitigating risks that pose the greatest threat to project success.
Effective communication is highlighted within CMMI's risk mitigation strategies. Transparent and open communication about identified risks ensures that relevant stakeholders are informed and can contribute to mitigation efforts. This inclusive communication approach fosters a sense of shared responsibility and promotes a collective effort in addressing and overcoming challenges.
Finally, CMMI promotes a culture of continuous improvement, extending to the organization's risk management processes. Through regular assessments and feedback loops, organizations refine their risk management approaches. This commitment to ongoing improvement ensures that risk mitigation strategies evolve and remain effective in the face of changing circumstances, contributing to overall organizational resilience. In essence, CMMI's risk mitigation strategies provide a comprehensive and adaptable framework for organizations to navigate challenges successfully and enhance project and organizational outcomes.
Standardization of Best Practices
The standardization of best practices is a key benefit derived from implementing the Capability Maturity Model Integration (CMMI) in an organization. CMMI provides a structured framework that emphasizes the identification, documentation, and adherence to proven methodologies across various business functions. This standardization contributes significantly to the overall efficiency, consistency, and quality of organizational processes.
CMMI guides organizations in defining and documenting their best practices, ensuring a clear understanding of established methods and procedures. This documentation serves as a valuable resource for employees, providing a reference point for how tasks and processes should be executed. Standardizing best practices in this manner fosters a shared understanding and promotes consistency across teams, reducing the likelihood of errors or variations in execution.
The standardization of best practices facilitated by CMMI is a cornerstone of organizational excellence. It provides a systematic approach to defining, documenting, and implementing proven methodologies, fostering consistency, efficiency, and quality across the organization. This standardized foundation not only enhances day-to-day operations but also establishes a framework for continuous improvement and organizational resilience.
Collaborative Team Culture
Collaborative team culture is a critical aspect of a thriving and high-performing organization. When teams work together seamlessly and share a common purpose, it not only enhances the quality of work but also contributes to a positive and engaging work environment. In a collaborative team culture, individuals come together, leveraging their diverse skills and experiences to achieve shared goals.
Effective communication lies at the heart of collaborative team culture. It's about more than just conveying information; it's about creating an environment where team members feel comfortable expressing ideas, asking questions, and providing feedback. A culture that values open communication fosters transparency and ensures that everyone is on the same page, reducing the likelihood of misunderstandings and promoting a sense of unity.
Cross-functional collaboration is a key element of collaborative team culture. When individuals from different departments or disciplines collaborate, it brings a richness of perspectives to problem-solving and decision-making. This interdisciplinary approach often leads to innovative solutions that may not have been possible within the confines of a single function. Cross-functional collaboration also breaks down silos, promoting a more holistic understanding of the organization's objectives.
Continuous improvement is a core principle of collaborative team culture. Teams that embrace a mindset of ongoing learning and adaptation are better equipped to navigate challenges and capitalize on opportunities. Regular reflections on successes and setbacks, coupled with a commitment to refining processes, contribute to a culture of growth and development.
In essence, a collaborative team culture is a catalyst for organizational success. It builds a foundation of trust, encourages innovation, and empowers individuals to contribute their best efforts toward shared objectives. As organizations embrace and cultivate collaborative team cultures, they position themselves for sustained excellence and adaptability in a dynamic and ever-evolving landscape.
Strategic Alignment and Competitive Edge
Strategic alignment and gaining a competitive edge are two significant outcomes of implementing the Capability Maturity Model Integration (CMMI) in an organization. CMMI provides a structured framework that aligns the organization's processes with its strategic objectives, fostering a cohesive approach that enhances competitiveness in the marketplace.
CMMI emphasizes strategic alignment by encouraging organizations to integrate their processes with overarching business goals. This alignment ensures that every process and activity within the organization contributes directly to the strategic objectives. As a result, teams work cohesively towards common goals, minimizing the risk of disjointed efforts and optimizing resources for maximum impact.
CMMI's focus on continuous improvement contributes to sustaining a competitive edge over time. The framework encourages organizations to regularly reassess their processes, incorporating lessons learned and adapting to evolving market conditions. This commitment to ongoing improvement ensures that the organization remains dynamic and responsive, staying ahead of competitors who may be slower to adapt.
Strategic alignment also plays a crucial role in decision-making. When processes are aligned with strategic objectives, decision-makers have a clear understanding of how choices impact overall goals. This clarity reduces the likelihood of decisions that may deviate from the strategic path and ensures that resources are allocated in ways that maximize value.
CMMI's emphasis on strategic alignment helps organizations create a seamless connection between their processes and overarching business objectives. This alignment enhances organizational agility, fosters a data-driven approach to performance measurement, and ultimately contributes to gaining and sustaining a competitive edge in the marketplace. As organizations implement and mature through the CMMI framework, they are better positioned to navigate the complexities of the business landscape while achieving strategic success.
Continuous Improvement Mindset
The continuous improvement mindset is a fundamental principle embedded in the Capability Maturity Model Integration (CMMI) and serves as a guiding philosophy for organizations seeking to enhance their processes and overall performance. CMMI encourages a culture where the pursuit of excellence is ongoing, and teams are committed to refining their practices incrementally over time.
CMMI's continuous improvement mindset involves the systematic identification and implementation of enhancements. Organizations are encouraged to gather data, feedback, and lessons learned from ongoing projects. This information is then analyzed to identify patterns and trends, providing insights that inform strategic decisions for improvement. The focus is not only on fixing immediate issues but on creating a foundation for sustained and long-term advancement.
CMMI's commitment to continuous improvement extends beyond individual projects to encompass the entire organization. It advocates for the establishment of metrics and key performance indicators (KPIs) that provide quantifiable insights into process effectiveness. Regular reviews of these metrics enable organizations to track progress, measure success, and identify areas for further enhancement.
The continuous improvement mindset advocated by CMMI is a cornerstone of organizational success. It instills a culture of reflection, learning, and proactive refinement. By embracing this mindset, organizations position themselves to not only address current challenges but also to navigate future uncertainties with resilience and agility. Continuous improvement becomes a journey, ingrained in the organizational DNA, driving sustained excellence and innovation.
Resource Optimization and Cost Management
Resource optimization and cost management are integral components of implementing the Capability Maturity Model Integration (CMMI) in an organization. CMMI provides a structured framework that guides organizations in efficiently managing their resources and controlling costs, contributing to improved overall performance and sustainability.
CMMI emphasizes the importance of optimizing resources by aligning them with organizational objectives. This involves a systematic evaluation of available human, financial, and technological resources and ensuring that they are strategically allocated to projects and processes. By optimizing resource utilization, organizations can enhance productivity, reduce waste, and achieve better outcomes without unnecessary expenditures.
Cost management, within the context of CMMI, involves controlling and optimizing expenses throughout the project lifecycle. This includes not only direct project costs but also indirect costs associated with supporting processes. CMMI encourages organizations to establish clear cost management practices, such as budgeting, monitoring expenditures, and implementing cost-saving measures.
CMMI promotes a proactive approach to resource optimization by emphasizing risk management. By identifying potential risks early in the project or process, organizations can develop contingency plans to address resource-related challenges. This proactive risk management contributes to avoiding cost overruns and disruptions, enhancing the organization's ability to stay within budgetary constraints.
Resource optimization and cost management, as guided by CMMI, are essential for organizations aiming to achieve efficiency, control expenses, and enhance overall performance. The framework's emphasis on quantitative metrics, risk management, standardization of best practices, and continuous improvement contributes to a systematic and strategic approach to resource utilization and cost control. By implementing these principles, organizations can navigate resource challenges effectively, control costs, and position themselves for sustained success in a competitive business environment.
Employee Development and Engagement
Employee development and engagement, as guided by the Capability Maturity Model Integration (CMMI), encompasses various strategic initiatives aimed at fostering a skilled and motivated workforce. CMMI emphasizes the establishment of structured professional development programs, ensuring that employees continuously enhance their skills and stay abreast of industry trends. This commitment to ongoing learning contributes to the organization's adaptability and the individual growth of its employees.
CMMI also advocates for a culture of knowledge sharing and collaboration. Organizations are encouraged to create platforms for employees to share their expertise, fostering a collaborative environment where collective learning is prioritized. This collaborative culture not only enhances employee development but also strengthens the overall knowledge base within the organization.
Recognition and rewards play a pivotal role in employee engagement within CMMI. By establishing systems that acknowledge and reward employees for their contributions, organizations boost morale and reinforce a positive and engaged workforce. This recognition creates a sense of value and appreciation among employees, strengthening their commitment to the organization's success.
Employee involvement in decision-making processes is another key principle of CMMI's approach to engagement. Seeking input from employees at various levels fosters a participatory environment where individuals feel their voices are heard. This inclusion not only improves the quality of decisions but also instills a sense of ownership and commitment among employees.
Measurable Performance Metrics
Implementing measurable performance metrics is a key component of the Capability Maturity Model Integration (CMMI) framework. CMMI emphasizes the importance of quantifiable indicators to assess and improve various aspects of an organization's processes. Measurable performance metrics provide valuable insights into efficiency, effectiveness, and overall success, guiding data-driven decision-making and continuous improvement efforts.
CMMI encourages organizations to define key performance indicators (KPIs) that align with their strategic objectives. These metrics should be specific, measurable, achievable, relevant, and time-bound (SMART), ensuring clarity in measurement and facilitating accurate assessments of performance. Examples of measurable performance metrics may include project completion time, defect rates, customer satisfaction scores, and adherence to schedule and budget.
Measurable performance metrics, as advocated by CMMI, provide a structured and data-driven approach to evaluating organizational processes. By defining clear, SMART indicators, establishing baselines, incorporating both quantitative and qualitative measures, and conducting regular reviews, organizations can gain valuable insights into their performance. These metrics not only guide decision-making but also support a culture of continuous improvement, fostering organizational maturity and resilience in a competitive landscape.
Conclusion
In conclusion, the Capability Maturity Model Integration (CMMI) serves as a comprehensive and structured framework that empowers organizations to achieve higher levels of performance, maturity, and success. The principles and practices outlined by CMMI touch on various critical aspects of organizational functioning, including process improvement, risk management, quality assurance, and team collaboration.
CMMI's emphasis on measurable performance metrics underscores the importance of data-driven decision-making. By defining clear and SMART key performance indicators, organizations gain the ability to objectively assess their processes and outcomes. This not only facilitates a deeper understanding of current performance but also provides a solid foundation for continuous improvement initiatives.
In essence, CMMI provides organizations with a roadmap for achieving maturity in their processes, fostering a culture of excellence, adaptability, and continuous growth. As organizations embrace and implement the principles of CMMI, they position themselves to navigate complexities, optimize performance, and thrive in an ever-evolving business landscape.
Read More
Implementing the Capability Maturity Model Integration (CMMI) in your organization can bring about a myriad of benefits, enhancing its overall efficiency and competitiveness in today's dynamic business landscape. CMMI serves as a comprehensive framework designed to elevate and optimize an organization's processes, thereby ensuring higher levels of performance, quality, and productivity.
One of the primary advantages of implementing CMMI lies in its ability to provide a structured approach to process improvement. By adopting CMMI practices, organizations can systematically identify, evaluate, and refine their existing processes. This structured methodology not only streamlines operations but also fosters a culture of continuous improvement, ensuring that the organization remains adaptable and responsive to evolving market demands.
CMMI is not merely a tool for process improvement; it also plays a pivotal role in risk management. By identifying and addressing potential risks at early stages, organizations can proactively mitigate challenges that may arise during project execution. This risk mitigation approach not only safeguards project timelines and budgets but also contributes to a more resilient and sustainable business model.
In addition to these operational advantages, implementing CMMI can also enhance communication and collaboration within an organization. The framework encourages cross-functional teams to work cohesively towards common objectives, fostering a collaborative culture that promotes knowledge sharing and innovation. This collaborative mindset is crucial in today's interconnected business environment, where agility and adaptability are key to success.
The benefits of implementing CMMI in an organization are multi-faceted, ranging from improved process efficiency and product quality to enhanced risk management and competitive advantage. As businesses navigate the complexities of a rapidly changing landscape, CMMI stands as a valuable framework that empowers organizations to not only meet current challenges but also to thrive in the future.
Table of contents
-
Enhanced Process Efficiency
-
Quality Assurance and Product Excellence
-
Risk Mitigation Strategies
-
Standardization of Best Practices
-
Collaborative Team Culture
-
Strategic Alignment and Competitive Edge
-
Continuous Improvement Mindset
-
Resource Optimization and Cost Management
-
Employee Development and Engagement
-
Measurable Performance Metrics
-
Conclusion
Enhanced Process Efficiency
Enhanced process efficiency is a key benefit of implementing the Capability Maturity Model Integration (CMMI) in an organization. This aspect revolves around the systematic improvement and optimization of existing processes, leading to increased effectiveness and streamlined workflows.
CMMI provides a structured framework for organizations to assess, refine, and standardize their processes across various departments. Through the identification of best practices and the elimination of redundancies or bottlenecks, CMMI helps organizations achieve a higher level of efficiency in their day-to-day operations.
One way CMMI enhances process efficiency is by promoting a clear understanding of roles, responsibilities, and workflows within the organization. By defining and documenting processes, teams can work more cohesively, reducing the likelihood of misunderstandings or delays. This clarity contributes to smoother collaboration and improved overall efficiency.
Furthermore, CMMI encourages organizations to continuously monitor and evaluate their processes. This ongoing assessment allows for the identification of areas for improvement. By addressing inefficiencies and optimizing processes iteratively, organizations can adapt to changing circumstances and maintain a competitive edge in their respective industries.
Enhanced process efficiency, facilitated by CMMI, involves the systematic improvement of organizational processes through clear documentation, continuous monitoring, and the establishment of performance metrics. By embracing this aspect of CMMI, organizations position themselves to operate more smoothly, respond to challenges more effectively, and deliver high-quality products or services with greater consistency.
Quality Assurance and Product Excellence
Quality assurance and product excellence are fundamental outcomes of implementing the Capability Maturity Model Integration (CMMI) in an organization. CMMI provides a structured framework that not only ensures the consistency of processes but also places a strong emphasis on delivering high-quality products and services.
CMMI encourages organizations to adopt rigorous quality assurance practices throughout the product or service development lifecycle. This involves defining clear quality standards, conducting thorough reviews, and implementing robust testing procedures. By adhering to these practices, organizations can identify and rectify defects early in the process, preventing issues from escalating and ultimately ensuring the delivery of superior products or services.
One of the ways CMMI contributes to product excellence is through its focus on continuous improvement. The model prompts organizations to regularly assess their processes and make necessary adjustments to enhance efficiency and quality. This iterative approach ensures that products and services evolve over time, meeting or exceeding customer expectations.
CMMI's impact on quality assurance and product excellence is evident through its emphasis on rigorous testing, continuous improvement, customer-centric practices, and the establishment of measurable quality metrics. By integrating these principles into their processes, organizations can consistently produce high-quality products, build customer trust, and gain a competitive advantage in the marketplace.
Risk Mitigation Strategies
Risk mitigation strategies are essential components of effective project and organizational management, and the implementation of the Capability Maturity Model Integration (CMMI) plays a pivotal role in shaping these strategies. One key aspect of risk mitigation within the CMMI framework is the emphasis on early identification. By encouraging organizations to identify risks at the outset of a project or process, CMMI enables teams to assess potential challenges before they escalate. This proactive approach sets the stage for comprehensive risk management throughout the project lifecycle.
CMMI goes beyond qualitative assessments by promoting quantitative risk analysis techniques. Assigning numerical values to risks and their potential impacts allows organizations to prioritize and address the most critical issues. This data-driven approach ensures that resources are allocated efficiently, focusing on mitigating risks that pose the greatest threat to project success.
Effective communication is highlighted within CMMI's risk mitigation strategies. Transparent and open communication about identified risks ensures that relevant stakeholders are informed and can contribute to mitigation efforts. This inclusive communication approach fosters a sense of shared responsibility and promotes a collective effort in addressing and overcoming challenges.
Finally, CMMI promotes a culture of continuous improvement, extending to the organization's risk management processes. Through regular assessments and feedback loops, organizations refine their risk management approaches. This commitment to ongoing improvement ensures that risk mitigation strategies evolve and remain effective in the face of changing circumstances, contributing to overall organizational resilience. In essence, CMMI's risk mitigation strategies provide a comprehensive and adaptable framework for organizations to navigate challenges successfully and enhance project and organizational outcomes.
Standardization of Best Practices
The standardization of best practices is a key benefit derived from implementing the Capability Maturity Model Integration (CMMI) in an organization. CMMI provides a structured framework that emphasizes the identification, documentation, and adherence to proven methodologies across various business functions. This standardization contributes significantly to the overall efficiency, consistency, and quality of organizational processes.
CMMI guides organizations in defining and documenting their best practices, ensuring a clear understanding of established methods and procedures. This documentation serves as a valuable resource for employees, providing a reference point for how tasks and processes should be executed. Standardizing best practices in this manner fosters a shared understanding and promotes consistency across teams, reducing the likelihood of errors or variations in execution.
The standardization of best practices facilitated by CMMI is a cornerstone of organizational excellence. It provides a systematic approach to defining, documenting, and implementing proven methodologies, fostering consistency, efficiency, and quality across the organization. This standardized foundation not only enhances day-to-day operations but also establishes a framework for continuous improvement and organizational resilience.
Collaborative Team Culture
Collaborative team culture is a critical aspect of a thriving and high-performing organization. When teams work together seamlessly and share a common purpose, it not only enhances the quality of work but also contributes to a positive and engaging work environment. In a collaborative team culture, individuals come together, leveraging their diverse skills and experiences to achieve shared goals.
Effective communication lies at the heart of collaborative team culture. It's about more than just conveying information; it's about creating an environment where team members feel comfortable expressing ideas, asking questions, and providing feedback. A culture that values open communication fosters transparency and ensures that everyone is on the same page, reducing the likelihood of misunderstandings and promoting a sense of unity.
Cross-functional collaboration is a key element of collaborative team culture. When individuals from different departments or disciplines collaborate, it brings a richness of perspectives to problem-solving and decision-making. This interdisciplinary approach often leads to innovative solutions that may not have been possible within the confines of a single function. Cross-functional collaboration also breaks down silos, promoting a more holistic understanding of the organization's objectives.
Continuous improvement is a core principle of collaborative team culture. Teams that embrace a mindset of ongoing learning and adaptation are better equipped to navigate challenges and capitalize on opportunities. Regular reflections on successes and setbacks, coupled with a commitment to refining processes, contribute to a culture of growth and development.
In essence, a collaborative team culture is a catalyst for organizational success. It builds a foundation of trust, encourages innovation, and empowers individuals to contribute their best efforts toward shared objectives. As organizations embrace and cultivate collaborative team cultures, they position themselves for sustained excellence and adaptability in a dynamic and ever-evolving landscape.
Strategic Alignment and Competitive Edge
Strategic alignment and gaining a competitive edge are two significant outcomes of implementing the Capability Maturity Model Integration (CMMI) in an organization. CMMI provides a structured framework that aligns the organization's processes with its strategic objectives, fostering a cohesive approach that enhances competitiveness in the marketplace.
CMMI emphasizes strategic alignment by encouraging organizations to integrate their processes with overarching business goals. This alignment ensures that every process and activity within the organization contributes directly to the strategic objectives. As a result, teams work cohesively towards common goals, minimizing the risk of disjointed efforts and optimizing resources for maximum impact.
CMMI's focus on continuous improvement contributes to sustaining a competitive edge over time. The framework encourages organizations to regularly reassess their processes, incorporating lessons learned and adapting to evolving market conditions. This commitment to ongoing improvement ensures that the organization remains dynamic and responsive, staying ahead of competitors who may be slower to adapt.
Strategic alignment also plays a crucial role in decision-making. When processes are aligned with strategic objectives, decision-makers have a clear understanding of how choices impact overall goals. This clarity reduces the likelihood of decisions that may deviate from the strategic path and ensures that resources are allocated in ways that maximize value.
CMMI's emphasis on strategic alignment helps organizations create a seamless connection between their processes and overarching business objectives. This alignment enhances organizational agility, fosters a data-driven approach to performance measurement, and ultimately contributes to gaining and sustaining a competitive edge in the marketplace. As organizations implement and mature through the CMMI framework, they are better positioned to navigate the complexities of the business landscape while achieving strategic success.
Continuous Improvement Mindset
The continuous improvement mindset is a fundamental principle embedded in the Capability Maturity Model Integration (CMMI) and serves as a guiding philosophy for organizations seeking to enhance their processes and overall performance. CMMI encourages a culture where the pursuit of excellence is ongoing, and teams are committed to refining their practices incrementally over time.
CMMI's continuous improvement mindset involves the systematic identification and implementation of enhancements. Organizations are encouraged to gather data, feedback, and lessons learned from ongoing projects. This information is then analyzed to identify patterns and trends, providing insights that inform strategic decisions for improvement. The focus is not only on fixing immediate issues but on creating a foundation for sustained and long-term advancement.
CMMI's commitment to continuous improvement extends beyond individual projects to encompass the entire organization. It advocates for the establishment of metrics and key performance indicators (KPIs) that provide quantifiable insights into process effectiveness. Regular reviews of these metrics enable organizations to track progress, measure success, and identify areas for further enhancement.
The continuous improvement mindset advocated by CMMI is a cornerstone of organizational success. It instills a culture of reflection, learning, and proactive refinement. By embracing this mindset, organizations position themselves to not only address current challenges but also to navigate future uncertainties with resilience and agility. Continuous improvement becomes a journey, ingrained in the organizational DNA, driving sustained excellence and innovation.
Resource Optimization and Cost Management
Resource optimization and cost management are integral components of implementing the Capability Maturity Model Integration (CMMI) in an organization. CMMI provides a structured framework that guides organizations in efficiently managing their resources and controlling costs, contributing to improved overall performance and sustainability.
CMMI emphasizes the importance of optimizing resources by aligning them with organizational objectives. This involves a systematic evaluation of available human, financial, and technological resources and ensuring that they are strategically allocated to projects and processes. By optimizing resource utilization, organizations can enhance productivity, reduce waste, and achieve better outcomes without unnecessary expenditures.
Cost management, within the context of CMMI, involves controlling and optimizing expenses throughout the project lifecycle. This includes not only direct project costs but also indirect costs associated with supporting processes. CMMI encourages organizations to establish clear cost management practices, such as budgeting, monitoring expenditures, and implementing cost-saving measures.
CMMI promotes a proactive approach to resource optimization by emphasizing risk management. By identifying potential risks early in the project or process, organizations can develop contingency plans to address resource-related challenges. This proactive risk management contributes to avoiding cost overruns and disruptions, enhancing the organization's ability to stay within budgetary constraints.
Resource optimization and cost management, as guided by CMMI, are essential for organizations aiming to achieve efficiency, control expenses, and enhance overall performance. The framework's emphasis on quantitative metrics, risk management, standardization of best practices, and continuous improvement contributes to a systematic and strategic approach to resource utilization and cost control. By implementing these principles, organizations can navigate resource challenges effectively, control costs, and position themselves for sustained success in a competitive business environment.
Employee Development and Engagement
Employee development and engagement, as guided by the Capability Maturity Model Integration (CMMI), encompasses various strategic initiatives aimed at fostering a skilled and motivated workforce. CMMI emphasizes the establishment of structured professional development programs, ensuring that employees continuously enhance their skills and stay abreast of industry trends. This commitment to ongoing learning contributes to the organization's adaptability and the individual growth of its employees.
CMMI also advocates for a culture of knowledge sharing and collaboration. Organizations are encouraged to create platforms for employees to share their expertise, fostering a collaborative environment where collective learning is prioritized. This collaborative culture not only enhances employee development but also strengthens the overall knowledge base within the organization.
Recognition and rewards play a pivotal role in employee engagement within CMMI. By establishing systems that acknowledge and reward employees for their contributions, organizations boost morale and reinforce a positive and engaged workforce. This recognition creates a sense of value and appreciation among employees, strengthening their commitment to the organization's success.
Employee involvement in decision-making processes is another key principle of CMMI's approach to engagement. Seeking input from employees at various levels fosters a participatory environment where individuals feel their voices are heard. This inclusion not only improves the quality of decisions but also instills a sense of ownership and commitment among employees.
Measurable Performance Metrics
Implementing measurable performance metrics is a key component of the Capability Maturity Model Integration (CMMI) framework. CMMI emphasizes the importance of quantifiable indicators to assess and improve various aspects of an organization's processes. Measurable performance metrics provide valuable insights into efficiency, effectiveness, and overall success, guiding data-driven decision-making and continuous improvement efforts.
CMMI encourages organizations to define key performance indicators (KPIs) that align with their strategic objectives. These metrics should be specific, measurable, achievable, relevant, and time-bound (SMART), ensuring clarity in measurement and facilitating accurate assessments of performance. Examples of measurable performance metrics may include project completion time, defect rates, customer satisfaction scores, and adherence to schedule and budget.
Measurable performance metrics, as advocated by CMMI, provide a structured and data-driven approach to evaluating organizational processes. By defining clear, SMART indicators, establishing baselines, incorporating both quantitative and qualitative measures, and conducting regular reviews, organizations can gain valuable insights into their performance. These metrics not only guide decision-making but also support a culture of continuous improvement, fostering organizational maturity and resilience in a competitive landscape.
Conclusion
In conclusion, the Capability Maturity Model Integration (CMMI) serves as a comprehensive and structured framework that empowers organizations to achieve higher levels of performance, maturity, and success. The principles and practices outlined by CMMI touch on various critical aspects of organizational functioning, including process improvement, risk management, quality assurance, and team collaboration.
CMMI's emphasis on measurable performance metrics underscores the importance of data-driven decision-making. By defining clear and SMART key performance indicators, organizations gain the ability to objectively assess their processes and outcomes. This not only facilitates a deeper understanding of current performance but also provides a solid foundation for continuous improvement initiatives.
In essence, CMMI provides organizations with a roadmap for achieving maturity in their processes, fostering a culture of excellence, adaptability, and continuous growth. As organizations embrace and implement the principles of CMMI, they position themselves to navigate complexities, optimize performance, and thrive in an ever-evolving business landscape.
Exploring Cloud Security in CompTIA Cloud Essentials
"Exploring Cloud Security in CompTIA Cloud Essentials" delves into the critical aspects of securing cloud environments, a fundamental component of the CompTIA Cloud Essentials certification. As organizations increasingly migrate their operations to the cloud, understanding and implementing robust security measures becomes paramount. This comprehensive exploration addresses the unique challenges and solutions associated with securing data, applications, and infrastructure in the cloud landscape.
The exploration begins by laying the groundwork for understanding the core principles of cloud computing. By establishing a solid foundation, participants are better prepared to grasp the nuances of securing cloud-based resources. From shared responsibility models to identity and access management, the course systematically covers the essential components of cloud security. Participants will gain insights into the intricacies of securing data during transit and at rest, as well as the implementation of encryption protocols to safeguard sensitive information.
"Exploring Cloud Security in CompTIA Cloud Essentials" offers a comprehensive and practical approach to understanding and implementing security measures in cloud environments. With a focus on real-world applications and industry-relevant scenarios, participants will emerge from this course equipped with the knowledge and skills necessary to navigate the dynamic landscape of cloud security and contribute to the resilient and secure operation of cloud-based systems.
Table of contents
-
Introduction to Cloud Security
-
Shared Responsibility Model
-
Identity and Access Management (IAM)
-
Data Security in the Cloud
-
Network Security in Cloud Environments
-
Compliance and Legal Considerations
-
Security Best Practices for Cloud Deployments
-
Incident Response and Disaster Recovery in the Cloud
-
Cloud Security Monitoring and Auditing
-
Emerging Trends in Cloud Security
-
Conclusion
Introduction to Cloud Security
In the dynamic landscape of contemporary IT infrastructure, where organizations increasingly rely on cloud computing services, the importance of robust cloud security cannot be overstated. Cloud security encompasses a set of practices, technologies, and policies designed to safeguard data, applications, and infrastructure hosted in cloud environments. As businesses migrate their operations to the cloud, they encounter unique challenges and opportunities, making a comprehensive understanding of cloud security paramount.
Cloud security operates on the foundational principle of the shared responsibility model, where both cloud service providers and their customers play integral roles in maintaining a secure ecosystem. This shared responsibility extends across various service models, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). By delineating these responsibilities, organizations can effectively implement security measures and mitigate potential risks.
One of the central pillars of cloud security is identity and access management (IAM). Ensuring that only authorized individuals or systems have access to resources in the cloud is fundamental to preventing unauthorized access and data breaches. Encryption also plays a crucial role, safeguarding data both in transit and at rest, providing an additional layer of protection against cyber threats.
As organizations navigate the complex landscape of cloud security, compliance with industry regulations and legal frameworks becomes a pressing concern. Meeting these standards not only mitigates legal risks but also fosters a culture of trust among customers and stakeholders.
Shared Responsibility Model
The Shared Responsibility Model is a fundamental framework within the realm of cloud computing, delineating the specific responsibilities between cloud service providers (CSPs) and their customers. This model serves as a crucial guide, ensuring clarity and accountability for security measures in the dynamic landscape of cloud environments. In the context of Infrastructure as a Service (IaaS), the onus of securing the foundational infrastructure, encompassing data centers, networking, and hardware, falls upon the cloud provider. Meanwhile, customers are tasked with securing their virtual machines, operating systems, applications, and data within this shared space.
Moving to Platform as a Service (PaaS), the Shared Responsibility Model adapts to the unique characteristics of this service model. Cloud providers extend their responsibilities to include the underlying platform, including runtime, middleware, and development frameworks. Customers, in turn, focus their attention on securing their applications and data, with a reduced emphasis on the lower-level infrastructure components, reflecting a more specialized division of labor.
In the realm of Software as a Service (SaaS), the Shared Responsibility Model takes another form. Cloud providers assume the comprehensive responsibility of managing and securing the entire software application, spanning infrastructure, middleware, and application layers. Customers, on the other hand, are entrusted with securing their data and controlling access to the application, acknowledging the shared commitment to maintaining a secure SaaS environment.
Central to this model are the common areas of shared responsibility. The security of the cloud, encompassing aspects such as physical security of data centers, network infrastructure, and hypervisor security, is a responsibility shouldered by the cloud provider. Conversely, security in the cloud, including data protection, encryption, access management, and application-level security, rests in the hands of the customer. This clear demarcation fosters collaboration, allowing customers to adapt security measures to their specific needs while leveraging the provider's expertise in managing the underlying infrastructure.
Identity and Access Management (IAM)
Identity and Access Management (IAM) is a critical component of cybersecurity that plays a pivotal role in securing digital assets and ensuring that the right individuals or systems have appropriate access to resources within an organization's IT infrastructure. IAM encompasses a set of policies, processes, and technologies designed to manage and control user identities, their access rights, and permissions. This multifaceted approach is fundamental for maintaining the confidentiality, integrity, and availability of sensitive data and applications.
IAM involves several key aspects:
User Authentication: IAM systems implement various authentication methods to verify the identity of users before granting access. This can include traditional username/password combinations, multi-factor authentication (MFA), biometrics, and more. Strong authentication mechanisms enhance overall security.
Authorization and Access Control: Authorization mechanisms within IAM dictate what actions users are allowed to perform and what resources they can access. Role-Based Access Control (RBAC) is commonly employed, assigning specific roles and permissions to individuals based on their responsibilities within the organization.
User Provisioning and De-provisioning: IAM systems facilitate the automated creation, modification, and removal of user accounts, ensuring that employees have the appropriate access during their tenure and that access is promptly revoked upon departure or role changes.
Single Sign-On (SSO): SSO enables users to log in once and gain access to multiple applications or systems without the need to reauthenticate for each one. This enhances user experience while simplifying the management of access credentials.
Audit and Compliance: IAM solutions provide auditing capabilities to track user activities and changes to access rights. This is crucial for compliance purposes, enabling organizations to meet regulatory requirements and conduct internal assessments of security policies.
Password Management: IAM systems often include features for password policy enforcement, password resets, and periodic rotation. These measures contribute to overall security hygiene by mitigating the risk of compromised credentials.
Federation: Federation enables secure and seamless access to resources across different systems, applications, or organizations. This is particularly important in scenarios where users need access to resources beyond their organization's boundaries.
Data Security in the Cloud
Data security in the cloud is a paramount concern as organizations entrust their sensitive information to third-party cloud service providers. The dynamic nature of cloud computing introduces unique challenges and opportunities for safeguarding data, both at rest and in transit. Encryption, a fundamental aspect of data security, plays a crucial role in protecting information from unauthorized access, ensuring that even if data is intercepted, it remains unintelligible to malicious actors.
Securing data at rest involves implementing encryption measures for stored information within the cloud infrastructure. Cloud service providers typically offer robust encryption mechanisms, allowing organizations to protect their data using encryption keys. This ensures that, even in the event of a security breach or unauthorized access, the data remains encrypted and unreadable without the corresponding decryption keys.
Access controls and identity management also play a pivotal role in data security in the cloud. Ensuring that only authorized individuals or systems have access to specific data sets is essential for preventing unauthorized data exposure. Identity and Access Management (IAM) solutions help organizations manage user access, enforce least privilege principles, and monitor user activities to detect and mitigate potential security threats.
Regular audits and compliance checks are essential to verify that data security measures align with industry regulations and organizational policies. Cloud service providers often undergo third-party audits and certifications, providing organizations with assurances regarding the security practices implemented in their cloud environments.
Effective data security in the cloud requires a comprehensive approach that encompasses encryption, access controls, identity management, and ongoing compliance efforts. As organizations continue to leverage the benefits of cloud computing, prioritizing robust data security measures is indispensable to instill trust, mitigate risks, and ensure the confidentiality and integrity of sensitive information in the cloud.
Network Security in Cloud Environments
Network security in cloud environments is a critical facet of ensuring the integrity, confidentiality, and availability of data and applications hosted in the cloud. As organizations increasingly migrate their operations to the cloud, the traditional perimeter-based network security models undergo transformation to adapt to the dynamic and distributed nature of cloud computing. In this evolving landscape, securing cloud networks involves a combination of advanced technologies, robust policies, and continuous monitoring.
Cloud service providers offer virtualized environments where customers can deploy and manage their resources. Securing these environments necessitates the implementation of comprehensive network security measures. Virtual Private Clouds (VPCs) play a pivotal role, allowing organizations to create isolated network spaces within the cloud infrastructure, segregating workloads and enhancing overall security. This isolation prevents unauthorized access and limits the potential impact of security incidents.
Firewalls, both traditional and cloud-native, are fundamental components of network security in the cloud. They act as gatekeepers, monitoring and controlling incoming and outgoing traffic based on predetermined security rules. Cloud providers often offer scalable and dynamically configurable firewall solutions, enabling organizations to adapt their security policies to changing operational requirements.
Monitoring and logging are integral to maintaining network security in the cloud. Cloud providers offer tools that enable real-time monitoring of network activities, allowing organizations to detect and respond to potential threats promptly. Comprehensive logging ensures that security incidents can be investigated thoroughly, contributing to continuous improvement of security postures.
Network security in cloud environments requires a holistic and adaptive approach. Organizations must leverage a combination of traditional and cloud-native security measures, employ isolation and segmentation strategies, and embrace advanced monitoring and response capabilities. By doing so, they can establish resilient and secure network architectures that align with the dynamic nature of cloud computing.
Compliance and Legal Considerations
Compliance and legal considerations are pivotal aspects that organizations must carefully navigate when adopting cloud computing solutions. In the dynamic and interconnected digital landscape, adherence to regulatory frameworks and legal standards is crucial for safeguarding data, ensuring privacy, and maintaining trust among stakeholders.
Data sovereignty and localization requirements add another layer of complexity to compliance considerations. Some jurisdictions have strict laws governing where data can be stored and processed. Organizations must carefully assess these requirements to choose cloud data centers that comply with data residency regulations, thereby mitigating legal risks associated with cross-border data transfers.
Contracts and agreements between organizations and cloud service providers are critical components of compliance efforts. Carefully drafted Service Level Agreements (SLAs) and Terms of Service should outline the responsibilities of both parties, specifying how security measures will be implemented, monitored, and maintained. This contractual clarity is essential for legal transparency and accountability.
Privacy laws, such as the General Data Protection Regulation (GDPR), are increasingly shaping the legal landscape for cloud computing. GDPR, for example, imposes stringent requirements on the processing and protection of personal data. Organizations must adopt measures to ensure compliance with privacy laws, including transparent data processing practices, robust consent mechanisms, and timely data breach notifications.
Compliance and legal considerations are integral to the success and sustainability of cloud adoption. Organizations that prioritize a comprehensive understanding of relevant regulations, engage with compliant cloud service providers, and establish transparent contractual agreements are better positioned to leverage the benefits of cloud computing while navigating the complex landscape of compliance and legal requirements.
Security Best Practices for Cloud Deployments
Implementing robust security practices is essential when deploying applications and data in cloud environments, where the dynamic nature of cloud computing introduces both opportunities and challenges. One critical best practice is the adoption of comprehensive data encryption strategies. This involves encrypting data at rest and in transit, employing industry-standard algorithms, and implementing strong key management practices. By doing so, organizations can safeguard sensitive information from unauthorized access and potential data breaches.
Identity and Access Management (IAM) is another cornerstone of cloud security best practices. Organizations should adhere to the principle of least privilege, ensuring that users have only the minimum access required for their roles. Strong authentication mechanisms, such as multi-factor authentication (MFA), further enhance identity verification, adding an additional layer of security to cloud deployments.
Network security plays a pivotal role in creating a secure cloud environment. Utilizing Virtual Private Clouds (VPCs) helps isolate and segment resources, while configuring firewalls and security groups enables precise control over inbound and outbound traffic. Continuous monitoring and auditing of network activities contribute to the early detection of anomalies, allowing for swift response to potential security incidents.
Regular audits and assessments are integral components of a robust security strategy for cloud deployments. Conducting security audits, penetration testing, and vulnerability scanning helps identify and remediate vulnerabilities before they can be exploited. Additionally, implementing a comprehensive backup strategy ensures data integrity and availability, with backups stored securely in a separate location from the primary data.
Employee training and awareness programs are vital in creating a security-conscious culture within the organization. Ongoing security training ensures that employees are aware of best practices and potential threats, fostering a collective responsibility for security. Finally, organizations should leverage built-in security features provided by cloud service providers and stay informed about updates and new security features to continuously enhance the security posture of their cloud deployments.
Incident Response and Disaster Recovery in the Cloud
Incident response and disaster recovery are integral components of a comprehensive cybersecurity strategy, and when it comes to cloud environments, these processes take on a unique set of considerations. Incident response in the cloud involves the systematic approach to identifying, managing, and mitigating security incidents such as data breaches or unauthorized access. In a cloud context, organizations must be adept at recognizing the dynamic nature of cloud infrastructure and responding swiftly to incidents that may impact data, applications, or the overall security of cloud-hosted resources.
Cloud environments introduce specific challenges to incident response, including the distributed nature of data and the diverse array of services provided by cloud service providers. A well-defined incident response plan tailored for cloud deployments is essential. This plan should include clear roles and responsibilities, communication strategies, and predefined steps to assess, contain, eradicate, recover, and learn from security incidents. Continuous testing and updating of the incident response plan ensure its effectiveness in the rapidly evolving cloud landscape.
Disaster recovery in the cloud extends beyond traditional backup and restoration processes. It involves planning for the restoration of critical systems and data in the event of a catastrophic failure, whether due to natural disasters, cyber-attacks, or other unforeseen circumstances. Cloud-based disaster recovery solutions leverage the flexibility and scalability of cloud infrastructure, allowing organizations to replicate and store data in geographically dispersed locations. This approach enhances data resilience and minimizes downtime, providing a more robust strategy for recovering from significant disruptions.
Incident response and disaster recovery in the cloud require a proactive and adaptive approach. Organizations must develop and regularly test comprehensive plans that address the unique challenges posed by cloud environments. By leveraging automation, fostering clear communication, and staying abreast of evolving threats, organizations can enhance their resilience in the face of security incidents and catastrophic events, ensuring the continuity of business operations in the cloud.
Cloud Security Monitoring and Auditing
Cloud security monitoring and auditing are pivotal components of a robust cybersecurity strategy, especially in the context of organizations leveraging cloud services for their operations. Security monitoring in the cloud involves continuous surveillance and analysis of activities within the cloud environment. This real-time scrutiny aims to detect and respond to potential security threats promptly. By employing monitoring tools and intrusion detection systems, organizations can identify unusual patterns or anomalies in network traffic, user behavior, and system activities. Centralized logging ensures that detailed information about user activities and system events is captured, facilitating comprehensive analysis. Automation plays a crucial role in incident response, allowing organizations to respond swiftly to predefined security incidents, ultimately enhancing the overall security posture.
Identity and access audits are essential in the cloud environment, where user access privileges and roles need meticulous scrutiny. Continuous assessment of identity and access management ensures that permissions are accurate and align with security policies. Furthermore, data protection audits evaluate encryption measures and validate the proper handling of sensitive data. Organizations also engage in third-party assessments to undergo independent evaluations, providing an additional layer of assurance about the security practices both within the organization and from the cloud service provider.
Continuous improvement is a fundamental principle underpinning effective cloud security monitoring and auditing. Regular reviews of monitoring findings and audit outcomes contribute to a dynamic cybersecurity strategy. Learning from security incidents, adjusting security strategies, and staying abreast of emerging threats foster a culture of ongoing enhancement. This iterative approach ensures that organizations not only meet compliance requirements but also adapt and strengthen their security measures in response to the evolving threat landscape in cloud environments.
Cloud security monitoring and auditing form a comprehensive and dynamic duo in the realm of cybersecurity. By embracing real-time threat detection, automated incident response, and rigorous auditing practices, organizations can fortify their cloud environments against an ever-evolving array of security challenges. This proactive approach not only safeguards sensitive data but also ensures the resilience and adaptability of cloud security strategies.
Emerging Trends in Cloud Security
Cloud security is a rapidly evolving domain, shaped by technological advancements, evolving threat landscapes, and the need for more robust protection in an increasingly interconnected digital environment. One prominent trend is the adoption of Zero Trust Architecture, reflecting a shift away from traditional perimeter-based security models. Zero Trust emphasizes continuous verification of identities and stringent access controls, aligning with the dynamic nature of cloud environments where trust is not assumed even among entities within the network perimeter.
As organizations increasingly embrace containerization technologies like Docker and Kubernetes, the need for robust container security is on the rise. Emerging solutions focus on securing containerized applications, ensuring the integrity and safety of workloads in cloud environments. Secure Access Service Edge (SASE) is gaining prominence, particularly in the context of remote work. This integrated security framework combines network security functions with WAN capabilities to accommodate the dynamic and secure access needs of modern organizations.
Artificial intelligence (AI) and machine learning (ML) are playing an expanding role in cloud security. These technologies are employed for threat detection, anomaly analysis, and automated response mechanisms, enhancing the ability to identify and mitigate security incidents in real-time. DevSecOps, the integration of security into the DevOps process, has become a standard practice. By treating security as a shared responsibility throughout the software development lifecycle, organizations can achieve faster and more secure deployment of applications in cloud environments.
Multi-cloud security is gaining traction as organizations adopt multi-cloud strategies to avoid vendor lock-in and enhance resilience. Securing data and applications across multiple cloud providers necessitates specialized security solutions and a consistent security posture. Homomorphic encryption is emerging as a promising technology for secure data processing in the cloud. This encryption technique allows computations on encrypted data without the need for decryption, addressing concerns about maintaining the confidentiality of sensitive information.
Staying informed about these emerging trends is crucial for organizations seeking to fortify their cloud security strategies. As the cloud landscape evolves, security measures must adapt to address new challenges and leverage innovative solutions. The combination of these trends reflects a concerted effort to enhance protection, detection, and response capabilities in the ever-changing landscape of cloud security.
Conclusion
In conclusion, the evolving landscape of cloud security is characterized by a dynamic interplay of technological advancements, emerging threats, and innovative strategies to safeguard digital assets. The adoption of Zero Trust Architecture reflects a paradigm shift towards continuous verification and stringent access controls, acknowledging the dynamic nature of cloud environments. The rise of cloud-native security solutions underscores the need for seamlessly integrated tools that can effectively manage the distributed nature of cloud infrastructures.
As organizations continue to embrace the benefits of cloud computing, a proactive and adaptive approach to security becomes imperative. By staying abreast of these emerging trends and adopting a holistic security posture, organizations can mitigate risks, enhance resilience, and ensure the integrity, confidentiality, and availability of their data and applications in the dynamic realm of cloud computing.
Read More
"Exploring Cloud Security in CompTIA Cloud Essentials" delves into the critical aspects of securing cloud environments, a fundamental component of the CompTIA Cloud Essentials certification. As organizations increasingly migrate their operations to the cloud, understanding and implementing robust security measures becomes paramount. This comprehensive exploration addresses the unique challenges and solutions associated with securing data, applications, and infrastructure in the cloud landscape.
The exploration begins by laying the groundwork for understanding the core principles of cloud computing. By establishing a solid foundation, participants are better prepared to grasp the nuances of securing cloud-based resources. From shared responsibility models to identity and access management, the course systematically covers the essential components of cloud security. Participants will gain insights into the intricacies of securing data during transit and at rest, as well as the implementation of encryption protocols to safeguard sensitive information.
"Exploring Cloud Security in CompTIA Cloud Essentials" offers a comprehensive and practical approach to understanding and implementing security measures in cloud environments. With a focus on real-world applications and industry-relevant scenarios, participants will emerge from this course equipped with the knowledge and skills necessary to navigate the dynamic landscape of cloud security and contribute to the resilient and secure operation of cloud-based systems.
Table of contents
-
Introduction to Cloud Security
-
Shared Responsibility Model
-
Identity and Access Management (IAM)
-
Data Security in the Cloud
-
Network Security in Cloud Environments
-
Compliance and Legal Considerations
-
Security Best Practices for Cloud Deployments
-
Incident Response and Disaster Recovery in the Cloud
-
Cloud Security Monitoring and Auditing
-
Emerging Trends in Cloud Security
-
Conclusion
Introduction to Cloud Security
In the dynamic landscape of contemporary IT infrastructure, where organizations increasingly rely on cloud computing services, the importance of robust cloud security cannot be overstated. Cloud security encompasses a set of practices, technologies, and policies designed to safeguard data, applications, and infrastructure hosted in cloud environments. As businesses migrate their operations to the cloud, they encounter unique challenges and opportunities, making a comprehensive understanding of cloud security paramount.
Cloud security operates on the foundational principle of the shared responsibility model, where both cloud service providers and their customers play integral roles in maintaining a secure ecosystem. This shared responsibility extends across various service models, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). By delineating these responsibilities, organizations can effectively implement security measures and mitigate potential risks.
One of the central pillars of cloud security is identity and access management (IAM). Ensuring that only authorized individuals or systems have access to resources in the cloud is fundamental to preventing unauthorized access and data breaches. Encryption also plays a crucial role, safeguarding data both in transit and at rest, providing an additional layer of protection against cyber threats.
As organizations navigate the complex landscape of cloud security, compliance with industry regulations and legal frameworks becomes a pressing concern. Meeting these standards not only mitigates legal risks but also fosters a culture of trust among customers and stakeholders.
Shared Responsibility Model
The Shared Responsibility Model is a fundamental framework within the realm of cloud computing, delineating the specific responsibilities between cloud service providers (CSPs) and their customers. This model serves as a crucial guide, ensuring clarity and accountability for security measures in the dynamic landscape of cloud environments. In the context of Infrastructure as a Service (IaaS), the onus of securing the foundational infrastructure, encompassing data centers, networking, and hardware, falls upon the cloud provider. Meanwhile, customers are tasked with securing their virtual machines, operating systems, applications, and data within this shared space.
Moving to Platform as a Service (PaaS), the Shared Responsibility Model adapts to the unique characteristics of this service model. Cloud providers extend their responsibilities to include the underlying platform, including runtime, middleware, and development frameworks. Customers, in turn, focus their attention on securing their applications and data, with a reduced emphasis on the lower-level infrastructure components, reflecting a more specialized division of labor.
In the realm of Software as a Service (SaaS), the Shared Responsibility Model takes another form. Cloud providers assume the comprehensive responsibility of managing and securing the entire software application, spanning infrastructure, middleware, and application layers. Customers, on the other hand, are entrusted with securing their data and controlling access to the application, acknowledging the shared commitment to maintaining a secure SaaS environment.
Central to this model are the common areas of shared responsibility. The security of the cloud, encompassing aspects such as physical security of data centers, network infrastructure, and hypervisor security, is a responsibility shouldered by the cloud provider. Conversely, security in the cloud, including data protection, encryption, access management, and application-level security, rests in the hands of the customer. This clear demarcation fosters collaboration, allowing customers to adapt security measures to their specific needs while leveraging the provider's expertise in managing the underlying infrastructure.
Identity and Access Management (IAM)
Identity and Access Management (IAM) is a critical component of cybersecurity that plays a pivotal role in securing digital assets and ensuring that the right individuals or systems have appropriate access to resources within an organization's IT infrastructure. IAM encompasses a set of policies, processes, and technologies designed to manage and control user identities, their access rights, and permissions. This multifaceted approach is fundamental for maintaining the confidentiality, integrity, and availability of sensitive data and applications.
IAM involves several key aspects:
User Authentication: IAM systems implement various authentication methods to verify the identity of users before granting access. This can include traditional username/password combinations, multi-factor authentication (MFA), biometrics, and more. Strong authentication mechanisms enhance overall security.
Authorization and Access Control: Authorization mechanisms within IAM dictate what actions users are allowed to perform and what resources they can access. Role-Based Access Control (RBAC) is commonly employed, assigning specific roles and permissions to individuals based on their responsibilities within the organization.
User Provisioning and De-provisioning: IAM systems facilitate the automated creation, modification, and removal of user accounts, ensuring that employees have the appropriate access during their tenure and that access is promptly revoked upon departure or role changes.
Single Sign-On (SSO): SSO enables users to log in once and gain access to multiple applications or systems without the need to reauthenticate for each one. This enhances user experience while simplifying the management of access credentials.
Audit and Compliance: IAM solutions provide auditing capabilities to track user activities and changes to access rights. This is crucial for compliance purposes, enabling organizations to meet regulatory requirements and conduct internal assessments of security policies.
Password Management: IAM systems often include features for password policy enforcement, password resets, and periodic rotation. These measures contribute to overall security hygiene by mitigating the risk of compromised credentials.
Federation: Federation enables secure and seamless access to resources across different systems, applications, or organizations. This is particularly important in scenarios where users need access to resources beyond their organization's boundaries.
Data Security in the Cloud
Data security in the cloud is a paramount concern as organizations entrust their sensitive information to third-party cloud service providers. The dynamic nature of cloud computing introduces unique challenges and opportunities for safeguarding data, both at rest and in transit. Encryption, a fundamental aspect of data security, plays a crucial role in protecting information from unauthorized access, ensuring that even if data is intercepted, it remains unintelligible to malicious actors.
Securing data at rest involves implementing encryption measures for stored information within the cloud infrastructure. Cloud service providers typically offer robust encryption mechanisms, allowing organizations to protect their data using encryption keys. This ensures that, even in the event of a security breach or unauthorized access, the data remains encrypted and unreadable without the corresponding decryption keys.
Access controls and identity management also play a pivotal role in data security in the cloud. Ensuring that only authorized individuals or systems have access to specific data sets is essential for preventing unauthorized data exposure. Identity and Access Management (IAM) solutions help organizations manage user access, enforce least privilege principles, and monitor user activities to detect and mitigate potential security threats.
Regular audits and compliance checks are essential to verify that data security measures align with industry regulations and organizational policies. Cloud service providers often undergo third-party audits and certifications, providing organizations with assurances regarding the security practices implemented in their cloud environments.
Effective data security in the cloud requires a comprehensive approach that encompasses encryption, access controls, identity management, and ongoing compliance efforts. As organizations continue to leverage the benefits of cloud computing, prioritizing robust data security measures is indispensable to instill trust, mitigate risks, and ensure the confidentiality and integrity of sensitive information in the cloud.
Network Security in Cloud Environments
Network security in cloud environments is a critical facet of ensuring the integrity, confidentiality, and availability of data and applications hosted in the cloud. As organizations increasingly migrate their operations to the cloud, the traditional perimeter-based network security models undergo transformation to adapt to the dynamic and distributed nature of cloud computing. In this evolving landscape, securing cloud networks involves a combination of advanced technologies, robust policies, and continuous monitoring.
Cloud service providers offer virtualized environments where customers can deploy and manage their resources. Securing these environments necessitates the implementation of comprehensive network security measures. Virtual Private Clouds (VPCs) play a pivotal role, allowing organizations to create isolated network spaces within the cloud infrastructure, segregating workloads and enhancing overall security. This isolation prevents unauthorized access and limits the potential impact of security incidents.
Firewalls, both traditional and cloud-native, are fundamental components of network security in the cloud. They act as gatekeepers, monitoring and controlling incoming and outgoing traffic based on predetermined security rules. Cloud providers often offer scalable and dynamically configurable firewall solutions, enabling organizations to adapt their security policies to changing operational requirements.
Monitoring and logging are integral to maintaining network security in the cloud. Cloud providers offer tools that enable real-time monitoring of network activities, allowing organizations to detect and respond to potential threats promptly. Comprehensive logging ensures that security incidents can be investigated thoroughly, contributing to continuous improvement of security postures.
Network security in cloud environments requires a holistic and adaptive approach. Organizations must leverage a combination of traditional and cloud-native security measures, employ isolation and segmentation strategies, and embrace advanced monitoring and response capabilities. By doing so, they can establish resilient and secure network architectures that align with the dynamic nature of cloud computing.
Compliance and Legal Considerations
Compliance and legal considerations are pivotal aspects that organizations must carefully navigate when adopting cloud computing solutions. In the dynamic and interconnected digital landscape, adherence to regulatory frameworks and legal standards is crucial for safeguarding data, ensuring privacy, and maintaining trust among stakeholders.
Data sovereignty and localization requirements add another layer of complexity to compliance considerations. Some jurisdictions have strict laws governing where data can be stored and processed. Organizations must carefully assess these requirements to choose cloud data centers that comply with data residency regulations, thereby mitigating legal risks associated with cross-border data transfers.
Contracts and agreements between organizations and cloud service providers are critical components of compliance efforts. Carefully drafted Service Level Agreements (SLAs) and Terms of Service should outline the responsibilities of both parties, specifying how security measures will be implemented, monitored, and maintained. This contractual clarity is essential for legal transparency and accountability.
Privacy laws, such as the General Data Protection Regulation (GDPR), are increasingly shaping the legal landscape for cloud computing. GDPR, for example, imposes stringent requirements on the processing and protection of personal data. Organizations must adopt measures to ensure compliance with privacy laws, including transparent data processing practices, robust consent mechanisms, and timely data breach notifications.
Compliance and legal considerations are integral to the success and sustainability of cloud adoption. Organizations that prioritize a comprehensive understanding of relevant regulations, engage with compliant cloud service providers, and establish transparent contractual agreements are better positioned to leverage the benefits of cloud computing while navigating the complex landscape of compliance and legal requirements.
Security Best Practices for Cloud Deployments
Implementing robust security practices is essential when deploying applications and data in cloud environments, where the dynamic nature of cloud computing introduces both opportunities and challenges. One critical best practice is the adoption of comprehensive data encryption strategies. This involves encrypting data at rest and in transit, employing industry-standard algorithms, and implementing strong key management practices. By doing so, organizations can safeguard sensitive information from unauthorized access and potential data breaches.
Identity and Access Management (IAM) is another cornerstone of cloud security best practices. Organizations should adhere to the principle of least privilege, ensuring that users have only the minimum access required for their roles. Strong authentication mechanisms, such as multi-factor authentication (MFA), further enhance identity verification, adding an additional layer of security to cloud deployments.
Network security plays a pivotal role in creating a secure cloud environment. Utilizing Virtual Private Clouds (VPCs) helps isolate and segment resources, while configuring firewalls and security groups enables precise control over inbound and outbound traffic. Continuous monitoring and auditing of network activities contribute to the early detection of anomalies, allowing for swift response to potential security incidents.
Regular audits and assessments are integral components of a robust security strategy for cloud deployments. Conducting security audits, penetration testing, and vulnerability scanning helps identify and remediate vulnerabilities before they can be exploited. Additionally, implementing a comprehensive backup strategy ensures data integrity and availability, with backups stored securely in a separate location from the primary data.
Employee training and awareness programs are vital in creating a security-conscious culture within the organization. Ongoing security training ensures that employees are aware of best practices and potential threats, fostering a collective responsibility for security. Finally, organizations should leverage built-in security features provided by cloud service providers and stay informed about updates and new security features to continuously enhance the security posture of their cloud deployments.
Incident Response and Disaster Recovery in the Cloud
Incident response and disaster recovery are integral components of a comprehensive cybersecurity strategy, and when it comes to cloud environments, these processes take on a unique set of considerations. Incident response in the cloud involves the systematic approach to identifying, managing, and mitigating security incidents such as data breaches or unauthorized access. In a cloud context, organizations must be adept at recognizing the dynamic nature of cloud infrastructure and responding swiftly to incidents that may impact data, applications, or the overall security of cloud-hosted resources.
Cloud environments introduce specific challenges to incident response, including the distributed nature of data and the diverse array of services provided by cloud service providers. A well-defined incident response plan tailored for cloud deployments is essential. This plan should include clear roles and responsibilities, communication strategies, and predefined steps to assess, contain, eradicate, recover, and learn from security incidents. Continuous testing and updating of the incident response plan ensure its effectiveness in the rapidly evolving cloud landscape.
Disaster recovery in the cloud extends beyond traditional backup and restoration processes. It involves planning for the restoration of critical systems and data in the event of a catastrophic failure, whether due to natural disasters, cyber-attacks, or other unforeseen circumstances. Cloud-based disaster recovery solutions leverage the flexibility and scalability of cloud infrastructure, allowing organizations to replicate and store data in geographically dispersed locations. This approach enhances data resilience and minimizes downtime, providing a more robust strategy for recovering from significant disruptions.
Incident response and disaster recovery in the cloud require a proactive and adaptive approach. Organizations must develop and regularly test comprehensive plans that address the unique challenges posed by cloud environments. By leveraging automation, fostering clear communication, and staying abreast of evolving threats, organizations can enhance their resilience in the face of security incidents and catastrophic events, ensuring the continuity of business operations in the cloud.
Cloud Security Monitoring and Auditing
Cloud security monitoring and auditing are pivotal components of a robust cybersecurity strategy, especially in the context of organizations leveraging cloud services for their operations. Security monitoring in the cloud involves continuous surveillance and analysis of activities within the cloud environment. This real-time scrutiny aims to detect and respond to potential security threats promptly. By employing monitoring tools and intrusion detection systems, organizations can identify unusual patterns or anomalies in network traffic, user behavior, and system activities. Centralized logging ensures that detailed information about user activities and system events is captured, facilitating comprehensive analysis. Automation plays a crucial role in incident response, allowing organizations to respond swiftly to predefined security incidents, ultimately enhancing the overall security posture.
Identity and access audits are essential in the cloud environment, where user access privileges and roles need meticulous scrutiny. Continuous assessment of identity and access management ensures that permissions are accurate and align with security policies. Furthermore, data protection audits evaluate encryption measures and validate the proper handling of sensitive data. Organizations also engage in third-party assessments to undergo independent evaluations, providing an additional layer of assurance about the security practices both within the organization and from the cloud service provider.
Continuous improvement is a fundamental principle underpinning effective cloud security monitoring and auditing. Regular reviews of monitoring findings and audit outcomes contribute to a dynamic cybersecurity strategy. Learning from security incidents, adjusting security strategies, and staying abreast of emerging threats foster a culture of ongoing enhancement. This iterative approach ensures that organizations not only meet compliance requirements but also adapt and strengthen their security measures in response to the evolving threat landscape in cloud environments.
Cloud security monitoring and auditing form a comprehensive and dynamic duo in the realm of cybersecurity. By embracing real-time threat detection, automated incident response, and rigorous auditing practices, organizations can fortify their cloud environments against an ever-evolving array of security challenges. This proactive approach not only safeguards sensitive data but also ensures the resilience and adaptability of cloud security strategies.
Emerging Trends in Cloud Security
Cloud security is a rapidly evolving domain, shaped by technological advancements, evolving threat landscapes, and the need for more robust protection in an increasingly interconnected digital environment. One prominent trend is the adoption of Zero Trust Architecture, reflecting a shift away from traditional perimeter-based security models. Zero Trust emphasizes continuous verification of identities and stringent access controls, aligning with the dynamic nature of cloud environments where trust is not assumed even among entities within the network perimeter.
As organizations increasingly embrace containerization technologies like Docker and Kubernetes, the need for robust container security is on the rise. Emerging solutions focus on securing containerized applications, ensuring the integrity and safety of workloads in cloud environments. Secure Access Service Edge (SASE) is gaining prominence, particularly in the context of remote work. This integrated security framework combines network security functions with WAN capabilities to accommodate the dynamic and secure access needs of modern organizations.
Artificial intelligence (AI) and machine learning (ML) are playing an expanding role in cloud security. These technologies are employed for threat detection, anomaly analysis, and automated response mechanisms, enhancing the ability to identify and mitigate security incidents in real-time. DevSecOps, the integration of security into the DevOps process, has become a standard practice. By treating security as a shared responsibility throughout the software development lifecycle, organizations can achieve faster and more secure deployment of applications in cloud environments.
Multi-cloud security is gaining traction as organizations adopt multi-cloud strategies to avoid vendor lock-in and enhance resilience. Securing data and applications across multiple cloud providers necessitates specialized security solutions and a consistent security posture. Homomorphic encryption is emerging as a promising technology for secure data processing in the cloud. This encryption technique allows computations on encrypted data without the need for decryption, addressing concerns about maintaining the confidentiality of sensitive information.
Staying informed about these emerging trends is crucial for organizations seeking to fortify their cloud security strategies. As the cloud landscape evolves, security measures must adapt to address new challenges and leverage innovative solutions. The combination of these trends reflects a concerted effort to enhance protection, detection, and response capabilities in the ever-changing landscape of cloud security.
Conclusion
In conclusion, the evolving landscape of cloud security is characterized by a dynamic interplay of technological advancements, emerging threats, and innovative strategies to safeguard digital assets. The adoption of Zero Trust Architecture reflects a paradigm shift towards continuous verification and stringent access controls, acknowledging the dynamic nature of cloud environments. The rise of cloud-native security solutions underscores the need for seamlessly integrated tools that can effectively manage the distributed nature of cloud infrastructures.
As organizations continue to embrace the benefits of cloud computing, a proactive and adaptive approach to security becomes imperative. By staying abreast of these emerging trends and adopting a holistic security posture, organizations can mitigate risks, enhance resilience, and ensure the integrity, confidentiality, and availability of their data and applications in the dynamic realm of cloud computing.
Unlocking Ethical Hacking: Use Your Digital Superpowers Responsibly
Introduction
In today's digital age, where cyber threats loom large, ethical hacking has emerged as a powerful tool to combat cybercrime. Ethical hackers, with their digital superpowers, play a crucial role in safeguarding sensitive information and protecting individuals and organizations from malicious attacks. However, ethical hacking must always be approached with responsibility and a strong sense of ethics. This article explores the world of ethical hacking, the importance of responsible hacking, and the role it plays in cybersecurity.
Ethical Hacking: An Overview
Ethical hacking, also known as penetration testing or white-hat hacking, involves systematically identifying vulnerabilities in computer systems, networks, or applications. It is a legal and authorized practice aimed at assessing the security posture of an organization's digital infrastructure. Ethical hackers use their technical skills and knowledge to simulate real-world cyberattacks and exploit weaknesses, all with the goal of helping organizations strengthen their security measures.
Digital Superpowers: The Skills of an Ethical Hacker
To excel in the field of ethical hacking, one must possess a diverse range of digital superpowers. These powers include expertise in programming languages, network protocols, operating systems, and web applications. Ethical hackers must also have the ability to think outside the box, identify potential vulnerabilities, and exploit them in a controlled manner. They often use sophisticated tools and techniques, such as password cracking, social engineering, and vulnerability scanning, to uncover weaknesses in systems and networks.
Responsible Hacking: The Ethical Compass
While ethical hackers have the power to crack into systems, it is important to remember that power comes with responsibility. Responsible hacking is about conducting security assessments and penetration testing with integrity, ethics, and respect for the law. It means adhering to a strict code of conduct, obtaining proper authorization before performing any testing, and ensuring that any vulnerabilities discovered are reported promptly and confidentially to the organization. Responsible hackers prioritize the protection of sensitive data and strive to make the digital world a safer place.
The Importance of Hacking Responsibly in Cybersecurity
Hacking responsibly is more than just a moral duty; it is a critical component of effective cybersecurity. By uncovering vulnerabilities, ethical hackers help organizations identify and fix security weaknesses before malicious actors exploit them. This proactive approach to security can save organizations significant financial losses, reputational damage, and legal trouble. Responsible hacking plays a crucial role in creating robust defense mechanisms and building resilience against cyber threats.
Conclusion
Ethical hacking, when used responsibly, serves as a powerful weapon in the fight against cybercrime. The digital superpowers of ethical hackers enable them to uncover vulnerabilities and protect individuals and organizations from malicious attacks. It is our ethical duty to ensure these superpowers are used responsibly, following a strict code of conduct and respecting the law. By embracing responsible hacking, we can create a safer digital world and unlock the full potential of ethical hacking in the realm of cybersecurity.
Read More
Introduction
In today's digital age, where cyber threats loom large, ethical hacking has emerged as a powerful tool to combat cybercrime. Ethical hackers, with their digital superpowers, play a crucial role in safeguarding sensitive information and protecting individuals and organizations from malicious attacks. However, ethical hacking must always be approached with responsibility and a strong sense of ethics. This article explores the world of ethical hacking, the importance of responsible hacking, and the role it plays in cybersecurity.
Ethical Hacking: An Overview
Ethical hacking, also known as penetration testing or white-hat hacking, involves systematically identifying vulnerabilities in computer systems, networks, or applications. It is a legal and authorized practice aimed at assessing the security posture of an organization's digital infrastructure. Ethical hackers use their technical skills and knowledge to simulate real-world cyberattacks and exploit weaknesses, all with the goal of helping organizations strengthen their security measures.
Digital Superpowers: The Skills of an Ethical Hacker
To excel in the field of ethical hacking, one must possess a diverse range of digital superpowers. These powers include expertise in programming languages, network protocols, operating systems, and web applications. Ethical hackers must also have the ability to think outside the box, identify potential vulnerabilities, and exploit them in a controlled manner. They often use sophisticated tools and techniques, such as password cracking, social engineering, and vulnerability scanning, to uncover weaknesses in systems and networks.
Responsible Hacking: The Ethical Compass
While ethical hackers have the power to crack into systems, it is important to remember that power comes with responsibility. Responsible hacking is about conducting security assessments and penetration testing with integrity, ethics, and respect for the law. It means adhering to a strict code of conduct, obtaining proper authorization before performing any testing, and ensuring that any vulnerabilities discovered are reported promptly and confidentially to the organization. Responsible hackers prioritize the protection of sensitive data and strive to make the digital world a safer place.
The Importance of Hacking Responsibly in Cybersecurity
Hacking responsibly is more than just a moral duty; it is a critical component of effective cybersecurity. By uncovering vulnerabilities, ethical hackers help organizations identify and fix security weaknesses before malicious actors exploit them. This proactive approach to security can save organizations significant financial losses, reputational damage, and legal trouble. Responsible hacking plays a crucial role in creating robust defense mechanisms and building resilience against cyber threats.
Conclusion
Ethical hacking, when used responsibly, serves as a powerful weapon in the fight against cybercrime. The digital superpowers of ethical hackers enable them to uncover vulnerabilities and protect individuals and organizations from malicious attacks. It is our ethical duty to ensure these superpowers are used responsibly, following a strict code of conduct and respecting the law. By embracing responsible hacking, we can create a safer digital world and unlock the full potential of ethical hacking in the realm of cybersecurity.
Integrating Apache Kafka with Machine Learning Pipelines
The integration of Apache Kafka with machine learning pipelines represents a powerful synergy between two transformative technologies, each playing a pivotal role in the modern data-driven landscape. Apache Kafka, a distributed streaming platform, has gained widespread recognition for its ability to handle real-time data streams at scale, ensuring reliable and efficient communication between disparate systems. On the other hand, machine learning pipelines have emerged as a cornerstone of advanced analytics, enabling organizations to extract valuable insights and predictions from vast datasets. The convergence of these technologies holds the promise of creating a seamless and dynamic ecosystem where real-time data flows seamlessly through machine learning workflows, fostering enhanced decision-making and operational efficiency.
At its core, Apache Kafka facilitates the seamless exchange of data across diverse applications, making it an ideal candidate for bridging the gap between data producers and consumers within machine learning pipelines. The event-driven architecture of Kafka aligns seamlessly with the iterative and continuous nature of machine learning processes, allowing organizations to ingest, process, and disseminate data in real-time. This integration not only addresses the challenges of handling large volumes of data but also establishes a foundation for responsive, adaptive machine learning models capable of evolving with dynamic data streams.
As organizations increasingly recognize the value of real-time insights, the integration of Apache Kafka with machine learning pipelines becomes imperative for staying competitive in today's data-centric landscape. This introduction sets the stage for exploring the various facets of this integration, delving into the technical nuances, practical applications, and potential benefits that arise from combining the strengths of Apache Kafka and machine learning. From streamlining data ingestion to facilitating model deployment and monitoring, this synergy opens up new avenues for organizations to leverage the power of real-time data in enhancing their machine learning capabilities.
Table of contents
-
Data Ingestion and Integration
-
Event-Driven Architecture for Machine Learning
-
Real-time Data Processing in Machine Learning Workflows
-
Ensuring Data Quality and Consistency
-
Monitoring and Management of Integrated Systems
-
Security and Data Privacy in Integrated Systems
-
Future Trends and Innovations
-
Conclusion
Data Ingestion and Integration
Data ingestion and integration form the foundational steps in the symbiotic relationship between Apache Kafka and machine learning pipelines. Apache Kafka, renowned for its distributed streaming capabilities, serves as a robust conduit for ingesting data from disparate sources into the machine learning ecosystem. The platform's ability to handle high-throughput, real-time data streams positions it as a key player in facilitating seamless data flow, acting as a bridge that connects various components within the integrated system.
In this context, data ingestion involves the process of collecting, importing, and organizing data from diverse origins into Kafka topics. These topics act as logical channels where data is partitioned and made available for consumption by downstream components, including machine learning models. Kafka's distributed architecture ensures that the ingestion process is scalable and fault-tolerant, allowing organizations to handle vast volumes of data with reliability and efficiency.
Integration, on the other hand, delves into the orchestration of data movement between Kafka and machine learning components. The integrated system leverages Kafka Connect, a framework that simplifies the development of connectors to bridge Kafka with various data sources and sinks. This integration framework enables a seamless and continuous flow of data, ensuring that machine learning pipelines receive timely updates from the incoming data streams. As a result, organizations can maintain a dynamic and responsive connection between their data sources and the machine learning algorithms that rely on them.
Event-Driven Architecture for Machine Learning
The integration of Apache Kafka with machine learning pipelines brings forth a transformative shift towards an event-driven architecture, redefining the landscape of how data is processed and utilized in the context of machine learning. At its core, event-driven architecture embraces the philosophy of responding to events or changes in real-time, aligning seamlessly with the iterative nature of machine learning processes. This architectural paradigm capitalizes on Kafka's distributed streaming capabilities, offering an efficient and scalable solution to handle the continuous flow of events within the machine learning ecosystem.
In the context of machine learning, events can encompass a spectrum of activities, ranging from data updates and model training triggers to the deployment of updated models. Apache Kafka acts as the backbone of this event-driven approach, serving as the central nervous system that facilitates the communication and coordination of these events. This real-time, bidirectional communication ensures that machine learning models are not only trained on the latest data but also respond dynamically to changing conditions, resulting in more adaptive and accurate predictions.
The event-driven architecture enables a decoupled and modularized system, where components within the machine learning pipeline react autonomously to specific events. This modularity enhances the scalability and maintainability of the overall system, allowing organizations to evolve and scale their machine learning infrastructure with greater agility. As data events propagate through Kafka topics, machine learning algorithms subscribe to these topics, ensuring they are continuously updated and refined based on the latest information.
The adoption of an event-driven architecture, powered by Apache Kafka, propels machine learning pipelines into a realm of responsiveness and adaptability that aligns with the dynamic nature of contemporary data ecosystems. This approach not only optimizes the performance of machine learning models but also paves the way for innovative applications and use cases in the rapidly evolving landscape of data-driven technologies.
Real-time Data Processing in Machine Learning Workflows
Real-time data processing stands as a cornerstone in the integration of Apache Kafka with machine learning workflows, revolutionizing the traditional paradigm of batch processing. Unlike batch processing, which handles data in chunks at scheduled intervals, real-time data processing leverages the continuous flow of data, enabling machine learning models to operate on the freshest information available. Apache Kafka plays a pivotal role in this context, acting as the conduit that seamlessly facilitates the flow of real-time data through the machine learning pipeline.
In a machine learning workflow, real-time data processing begins with the ingestion of data into Kafka topics. These topics serve as dynamic channels where data is partitioned and made available for immediate consumption by downstream machine learning components. The distributed nature of Kafka ensures that data can be processed in parallel across multiple nodes, enhancing the scalability and speed of real-time data processing.
Machine learning algorithms within the integrated system subscribe to these Kafka topics, allowing them to receive and process data updates as soon as they occur. This real-time responsiveness is particularly crucial in applications where the value of predictions diminishes rapidly over time, such as in financial trading, fraud detection, or dynamic pricing models. By continuously processing and updating models in real-time, organizations can derive insights and make decisions at the pace demanded by today's fast-paced and data-intensive environments.
Despite the advantages, real-time data processing in machine learning workflows comes with its set of challenges. Ensuring low-latency data processing, managing data consistency, and handling potential bottlenecks are critical considerations. However, the integration of Apache Kafka provides a robust infrastructure to address these challenges, laying the foundation for organizations to harness the full potential of real-time data processing in their machine learning endeavors. As the demand for timely insights continues to grow, the synergy between Apache Kafka and real-time machine learning processing emerges as a strategic asset for organizations seeking to gain a competitive edge in today's data-centric landscape.
Ensuring Data Quality and Consistency
In the integration of Apache Kafka with machine learning pipelines, the assurance of data quality and consistency emerges as a fundamental imperative. As data traverses the distributed architecture facilitated by Kafka, maintaining the integrity and reliability of information becomes pivotal for the accuracy and effectiveness of downstream machine learning processes.
Ensuring data quality encompasses several key facets, beginning with the validation and cleansing of incoming data streams. Apache Kafka's ability to handle real-time data influxes must be complemented by robust data validation mechanisms to identify and address anomalies, outliers, or inconsistencies in the data. This initial quality check is crucial to prevent inaccuracies from propagating through the machine learning pipeline, ensuring that models are trained on reliable and representative datasets.
Consistency, on the other hand, involves harmonizing data formats, schemas, and semantics across diverse sources and destinations. Kafka's schema registry, a component that manages the evolution of data schemas, plays a pivotal role in maintaining consistency within the data ecosystem. By enforcing schema compatibility and versioning, organizations can navigate changes in data structures without compromising downstream processes, thereby promoting a consistent interpretation of data across the entire machine learning workflow.
Data quality and consistency are also influenced by factors such as data drift and schema evolution, common challenges in dynamic environments. Data drift occurs when the statistical properties of the incoming data change over time, impacting the performance of machine learning models. Apache Kafka's ability to capture and version data enables organizations to monitor and adapt to such drift, allowing for the recalibration of models as needed.
Ensuring data quality and consistency in the context of Apache Kafka and machine learning integration is a multifaceted endeavor. By implementing rigorous validation processes, leveraging schema management capabilities, and addressing challenges like data drift, organizations can cultivate a reliable and coherent data foundation. This, in turn, enhances the robustness of machine learning models, fortifying the integration against potential pitfalls and reinforcing the value derived from real-time, high-throughput data streams.
Monitoring and Management of Integrated Systems
The integration of Apache Kafka with machine learning pipelines necessitates robust monitoring and management practices to ensure the efficiency, reliability, and security of the amalgamated system. In the intricate landscape where real-time data streams converge with machine learning algorithms, effective monitoring serves as a linchpin for maintaining operational integrity.
Central to the monitoring of integrated systems is the meticulous examination of infrastructure performance. Monitoring tools track key metrics within Apache Kafka clusters and machine learning components, providing administrators with real-time insights into throughput, latency, and resource utilization. This visibility enables proactive identification and resolution of potential bottlenecks, allowing for the optimization of configurations to meet the demands of both real-time data processing and machine learning workloads.
Security monitoring and auditing constitute foundational elements in the well-managed integrated system. Monitoring tools diligently track access, authentication, and authorization events within Apache Kafka and machine learning components. The utilization of Security Information and Event Management (SIEM) solutions aids in aggregating and analyzing security-related data, ensuring compliance, and offering insights into potential threats or vulnerabilities.
A comprehensive monitoring and management strategy is imperative for organizations navigating the intricacies of integrating Apache Kafka with machine learning pipelines. Addressing infrastructure performance, data flow tracking, security monitoring, and capacity planning collectively contribute to fostering a resilient and efficient integrated ecosystem, unlocking the full potential of real-time data processing and machine learning capabilities.
Security and Data Privacy in Integrated Systems
The integration of Apache Kafka with machine learning pipelines introduces a complex interplay of real-time data flows and advanced analytics, underscoring the critical need for robust security measures and data privacy safeguards within the integrated environment. As information traverses the interconnected architecture, safeguarding the confidentiality and integrity of data becomes paramount, demanding a comprehensive approach to address potential vulnerabilities and ensure compliance with data protection regulations.
Fundamental to the security framework of integrated systems is the implementation of stringent access controls and authentication mechanisms. Apache Kafka, as the central hub for data exchange, requires meticulous user authentication protocols and encryption methods to control and secure access, mitigating the risk of unauthorized parties infiltrating the system.
Authorization mechanisms play an equally vital role, defining and enforcing fine-grained permissions to ensure that users and components have access only to the data and functionalities essential to their specific roles. This approach minimizes the likelihood of unauthorized data access or manipulation, contributing to a more secure integrated system.
Encryption, both for data in transit and at rest, emerges as a linchpin in securing sensitive information within the integrated environment. The application of encryption protocols ensures that even if intercepted, the data remains indecipherable to unauthorized entities, fortifying the overall security posture of the integrated system.
Securing Apache Kafka and machine learning pipelines within integrated systems requires a multifaceted strategy encompassing authentication, encryption, privacy-preserving techniques, regulatory compliance, and incident response planning. By addressing these aspects, organizations can fortify their integrated environments against security threats while upholding the confidentiality and privacy of sensitive data.
Future Trends and Innovations
The integration of Apache Kafka with machine learning pipelines sets the stage for a landscape of continuous evolution, marked by emerging trends and innovations that promise to reshape the future of data processing and analytics. As organizations strive to extract greater value from their data, several key trajectories are poised to define the future of this dynamic integration.
Decentralized Machine Learning Architectures: Future trends indicate a shift towards decentralized machine learning architectures within integrated systems. This approach distributes the machine learning processing across multiple nodes, enabling more efficient and scalable models. Decentralization not only enhances performance but also aligns with the principles of edge computing, allowing for real-time processing closer to the data source.
Integration with Advanced Analytics: The future holds a convergence of Apache Kafka with advanced analytics techniques, including artificial intelligence (AI) and deep learning. The integration of these technologies within machine learning pipelines promises to unlock new levels of predictive and prescriptive analytics, enabling organizations to make more informed decisions and uncover hidden patterns within their data.
Exponential Growth in Data Governance Solutions: As the volume and complexity of data continue to surge, future trends point to the exponential growth of data governance solutions within integrated systems. Innovations in metadata management, data lineage tracking, and automated governance frameworks will become integral for ensuring data quality, compliance, and accountability across the entire data lifecycle.
Enhanced Security and Privacy Measures: Future innovations in the integration of Apache Kafka and machine learning pipelines will be closely intertwined with heightened security and privacy measures. As the regulatory landscape evolves, organizations will invest in advanced encryption techniques, secure access controls, and privacy-preserving methodologies to safeguard sensitive information and ensure compliance with data protection regulations.
How to obtain Data Science and Business Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the integration of Apache Kafka with machine learning pipelines represents a transformative synergy that propels data processing and analytics into a new era. This amalgamation not only addresses the challenges of handling real-time data streams but also unleashes the potential for organizations to derive actionable insights and drive innovation through advanced machine learning techniques.
The journey from data ingestion and integration to event-driven architectures and real-time data processing underscores the dynamic nature of this integration. As organizations navigate the complexities of monitoring, management, and ensuring data quality, the robust capabilities of Apache Kafka emerge as a linchpin for creating resilient, scalable, and efficient integrated systems.
Furthermore, the emphasis on security and data privacy within integrated systems is paramount. As the regulatory landscape evolves, the integration of Apache Kafka and machine learning pipelines must adhere to stringent security measures, encryption protocols, and privacy-preserving techniques to safeguard sensitive information and ensure compliance.
The integration of Apache Kafka with machine learning pipelines signifies more than just a technological collaboration; it represents a strategic imperative for organizations seeking to thrive in a data-driven world. As this integration continues to evolve, organizations stand to benefit from real-time insights, adaptive machine learning models, and a future-ready infrastructure that positions them at the forefront of innovation in the rapidly changing landscape of data and analytics.
Read More
The integration of Apache Kafka with machine learning pipelines represents a powerful synergy between two transformative technologies, each playing a pivotal role in the modern data-driven landscape. Apache Kafka, a distributed streaming platform, has gained widespread recognition for its ability to handle real-time data streams at scale, ensuring reliable and efficient communication between disparate systems. On the other hand, machine learning pipelines have emerged as a cornerstone of advanced analytics, enabling organizations to extract valuable insights and predictions from vast datasets. The convergence of these technologies holds the promise of creating a seamless and dynamic ecosystem where real-time data flows seamlessly through machine learning workflows, fostering enhanced decision-making and operational efficiency.
At its core, Apache Kafka facilitates the seamless exchange of data across diverse applications, making it an ideal candidate for bridging the gap between data producers and consumers within machine learning pipelines. The event-driven architecture of Kafka aligns seamlessly with the iterative and continuous nature of machine learning processes, allowing organizations to ingest, process, and disseminate data in real-time. This integration not only addresses the challenges of handling large volumes of data but also establishes a foundation for responsive, adaptive machine learning models capable of evolving with dynamic data streams.
As organizations increasingly recognize the value of real-time insights, the integration of Apache Kafka with machine learning pipelines becomes imperative for staying competitive in today's data-centric landscape. This introduction sets the stage for exploring the various facets of this integration, delving into the technical nuances, practical applications, and potential benefits that arise from combining the strengths of Apache Kafka and machine learning. From streamlining data ingestion to facilitating model deployment and monitoring, this synergy opens up new avenues for organizations to leverage the power of real-time data in enhancing their machine learning capabilities.
Table of contents
-
Data Ingestion and Integration
-
Event-Driven Architecture for Machine Learning
-
Real-time Data Processing in Machine Learning Workflows
-
Ensuring Data Quality and Consistency
-
Monitoring and Management of Integrated Systems
-
Security and Data Privacy in Integrated Systems
-
Future Trends and Innovations
-
Conclusion
Data Ingestion and Integration
Data ingestion and integration form the foundational steps in the symbiotic relationship between Apache Kafka and machine learning pipelines. Apache Kafka, renowned for its distributed streaming capabilities, serves as a robust conduit for ingesting data from disparate sources into the machine learning ecosystem. The platform's ability to handle high-throughput, real-time data streams positions it as a key player in facilitating seamless data flow, acting as a bridge that connects various components within the integrated system.
In this context, data ingestion involves the process of collecting, importing, and organizing data from diverse origins into Kafka topics. These topics act as logical channels where data is partitioned and made available for consumption by downstream components, including machine learning models. Kafka's distributed architecture ensures that the ingestion process is scalable and fault-tolerant, allowing organizations to handle vast volumes of data with reliability and efficiency.
Integration, on the other hand, delves into the orchestration of data movement between Kafka and machine learning components. The integrated system leverages Kafka Connect, a framework that simplifies the development of connectors to bridge Kafka with various data sources and sinks. This integration framework enables a seamless and continuous flow of data, ensuring that machine learning pipelines receive timely updates from the incoming data streams. As a result, organizations can maintain a dynamic and responsive connection between their data sources and the machine learning algorithms that rely on them.
Event-Driven Architecture for Machine Learning
The integration of Apache Kafka with machine learning pipelines brings forth a transformative shift towards an event-driven architecture, redefining the landscape of how data is processed and utilized in the context of machine learning. At its core, event-driven architecture embraces the philosophy of responding to events or changes in real-time, aligning seamlessly with the iterative nature of machine learning processes. This architectural paradigm capitalizes on Kafka's distributed streaming capabilities, offering an efficient and scalable solution to handle the continuous flow of events within the machine learning ecosystem.
In the context of machine learning, events can encompass a spectrum of activities, ranging from data updates and model training triggers to the deployment of updated models. Apache Kafka acts as the backbone of this event-driven approach, serving as the central nervous system that facilitates the communication and coordination of these events. This real-time, bidirectional communication ensures that machine learning models are not only trained on the latest data but also respond dynamically to changing conditions, resulting in more adaptive and accurate predictions.
The event-driven architecture enables a decoupled and modularized system, where components within the machine learning pipeline react autonomously to specific events. This modularity enhances the scalability and maintainability of the overall system, allowing organizations to evolve and scale their machine learning infrastructure with greater agility. As data events propagate through Kafka topics, machine learning algorithms subscribe to these topics, ensuring they are continuously updated and refined based on the latest information.
The adoption of an event-driven architecture, powered by Apache Kafka, propels machine learning pipelines into a realm of responsiveness and adaptability that aligns with the dynamic nature of contemporary data ecosystems. This approach not only optimizes the performance of machine learning models but also paves the way for innovative applications and use cases in the rapidly evolving landscape of data-driven technologies.
Real-time Data Processing in Machine Learning Workflows
Real-time data processing stands as a cornerstone in the integration of Apache Kafka with machine learning workflows, revolutionizing the traditional paradigm of batch processing. Unlike batch processing, which handles data in chunks at scheduled intervals, real-time data processing leverages the continuous flow of data, enabling machine learning models to operate on the freshest information available. Apache Kafka plays a pivotal role in this context, acting as the conduit that seamlessly facilitates the flow of real-time data through the machine learning pipeline.
In a machine learning workflow, real-time data processing begins with the ingestion of data into Kafka topics. These topics serve as dynamic channels where data is partitioned and made available for immediate consumption by downstream machine learning components. The distributed nature of Kafka ensures that data can be processed in parallel across multiple nodes, enhancing the scalability and speed of real-time data processing.
Machine learning algorithms within the integrated system subscribe to these Kafka topics, allowing them to receive and process data updates as soon as they occur. This real-time responsiveness is particularly crucial in applications where the value of predictions diminishes rapidly over time, such as in financial trading, fraud detection, or dynamic pricing models. By continuously processing and updating models in real-time, organizations can derive insights and make decisions at the pace demanded by today's fast-paced and data-intensive environments.
Despite the advantages, real-time data processing in machine learning workflows comes with its set of challenges. Ensuring low-latency data processing, managing data consistency, and handling potential bottlenecks are critical considerations. However, the integration of Apache Kafka provides a robust infrastructure to address these challenges, laying the foundation for organizations to harness the full potential of real-time data processing in their machine learning endeavors. As the demand for timely insights continues to grow, the synergy between Apache Kafka and real-time machine learning processing emerges as a strategic asset for organizations seeking to gain a competitive edge in today's data-centric landscape.
Ensuring Data Quality and Consistency
In the integration of Apache Kafka with machine learning pipelines, the assurance of data quality and consistency emerges as a fundamental imperative. As data traverses the distributed architecture facilitated by Kafka, maintaining the integrity and reliability of information becomes pivotal for the accuracy and effectiveness of downstream machine learning processes.
Ensuring data quality encompasses several key facets, beginning with the validation and cleansing of incoming data streams. Apache Kafka's ability to handle real-time data influxes must be complemented by robust data validation mechanisms to identify and address anomalies, outliers, or inconsistencies in the data. This initial quality check is crucial to prevent inaccuracies from propagating through the machine learning pipeline, ensuring that models are trained on reliable and representative datasets.
Consistency, on the other hand, involves harmonizing data formats, schemas, and semantics across diverse sources and destinations. Kafka's schema registry, a component that manages the evolution of data schemas, plays a pivotal role in maintaining consistency within the data ecosystem. By enforcing schema compatibility and versioning, organizations can navigate changes in data structures without compromising downstream processes, thereby promoting a consistent interpretation of data across the entire machine learning workflow.
Data quality and consistency are also influenced by factors such as data drift and schema evolution, common challenges in dynamic environments. Data drift occurs when the statistical properties of the incoming data change over time, impacting the performance of machine learning models. Apache Kafka's ability to capture and version data enables organizations to monitor and adapt to such drift, allowing for the recalibration of models as needed.
Ensuring data quality and consistency in the context of Apache Kafka and machine learning integration is a multifaceted endeavor. By implementing rigorous validation processes, leveraging schema management capabilities, and addressing challenges like data drift, organizations can cultivate a reliable and coherent data foundation. This, in turn, enhances the robustness of machine learning models, fortifying the integration against potential pitfalls and reinforcing the value derived from real-time, high-throughput data streams.
Monitoring and Management of Integrated Systems
The integration of Apache Kafka with machine learning pipelines necessitates robust monitoring and management practices to ensure the efficiency, reliability, and security of the amalgamated system. In the intricate landscape where real-time data streams converge with machine learning algorithms, effective monitoring serves as a linchpin for maintaining operational integrity.
Central to the monitoring of integrated systems is the meticulous examination of infrastructure performance. Monitoring tools track key metrics within Apache Kafka clusters and machine learning components, providing administrators with real-time insights into throughput, latency, and resource utilization. This visibility enables proactive identification and resolution of potential bottlenecks, allowing for the optimization of configurations to meet the demands of both real-time data processing and machine learning workloads.
Security monitoring and auditing constitute foundational elements in the well-managed integrated system. Monitoring tools diligently track access, authentication, and authorization events within Apache Kafka and machine learning components. The utilization of Security Information and Event Management (SIEM) solutions aids in aggregating and analyzing security-related data, ensuring compliance, and offering insights into potential threats or vulnerabilities.
A comprehensive monitoring and management strategy is imperative for organizations navigating the intricacies of integrating Apache Kafka with machine learning pipelines. Addressing infrastructure performance, data flow tracking, security monitoring, and capacity planning collectively contribute to fostering a resilient and efficient integrated ecosystem, unlocking the full potential of real-time data processing and machine learning capabilities.
Security and Data Privacy in Integrated Systems
The integration of Apache Kafka with machine learning pipelines introduces a complex interplay of real-time data flows and advanced analytics, underscoring the critical need for robust security measures and data privacy safeguards within the integrated environment. As information traverses the interconnected architecture, safeguarding the confidentiality and integrity of data becomes paramount, demanding a comprehensive approach to address potential vulnerabilities and ensure compliance with data protection regulations.
Fundamental to the security framework of integrated systems is the implementation of stringent access controls and authentication mechanisms. Apache Kafka, as the central hub for data exchange, requires meticulous user authentication protocols and encryption methods to control and secure access, mitigating the risk of unauthorized parties infiltrating the system.
Authorization mechanisms play an equally vital role, defining and enforcing fine-grained permissions to ensure that users and components have access only to the data and functionalities essential to their specific roles. This approach minimizes the likelihood of unauthorized data access or manipulation, contributing to a more secure integrated system.
Encryption, both for data in transit and at rest, emerges as a linchpin in securing sensitive information within the integrated environment. The application of encryption protocols ensures that even if intercepted, the data remains indecipherable to unauthorized entities, fortifying the overall security posture of the integrated system.
Securing Apache Kafka and machine learning pipelines within integrated systems requires a multifaceted strategy encompassing authentication, encryption, privacy-preserving techniques, regulatory compliance, and incident response planning. By addressing these aspects, organizations can fortify their integrated environments against security threats while upholding the confidentiality and privacy of sensitive data.
Future Trends and Innovations
The integration of Apache Kafka with machine learning pipelines sets the stage for a landscape of continuous evolution, marked by emerging trends and innovations that promise to reshape the future of data processing and analytics. As organizations strive to extract greater value from their data, several key trajectories are poised to define the future of this dynamic integration.
Decentralized Machine Learning Architectures: Future trends indicate a shift towards decentralized machine learning architectures within integrated systems. This approach distributes the machine learning processing across multiple nodes, enabling more efficient and scalable models. Decentralization not only enhances performance but also aligns with the principles of edge computing, allowing for real-time processing closer to the data source.
Integration with Advanced Analytics: The future holds a convergence of Apache Kafka with advanced analytics techniques, including artificial intelligence (AI) and deep learning. The integration of these technologies within machine learning pipelines promises to unlock new levels of predictive and prescriptive analytics, enabling organizations to make more informed decisions and uncover hidden patterns within their data.
Exponential Growth in Data Governance Solutions: As the volume and complexity of data continue to surge, future trends point to the exponential growth of data governance solutions within integrated systems. Innovations in metadata management, data lineage tracking, and automated governance frameworks will become integral for ensuring data quality, compliance, and accountability across the entire data lifecycle.
Enhanced Security and Privacy Measures: Future innovations in the integration of Apache Kafka and machine learning pipelines will be closely intertwined with heightened security and privacy measures. As the regulatory landscape evolves, organizations will invest in advanced encryption techniques, secure access controls, and privacy-preserving methodologies to safeguard sensitive information and ensure compliance with data protection regulations.
How to obtain Data Science and Business Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the integration of Apache Kafka with machine learning pipelines represents a transformative synergy that propels data processing and analytics into a new era. This amalgamation not only addresses the challenges of handling real-time data streams but also unleashes the potential for organizations to derive actionable insights and drive innovation through advanced machine learning techniques.
The journey from data ingestion and integration to event-driven architectures and real-time data processing underscores the dynamic nature of this integration. As organizations navigate the complexities of monitoring, management, and ensuring data quality, the robust capabilities of Apache Kafka emerge as a linchpin for creating resilient, scalable, and efficient integrated systems.
Furthermore, the emphasis on security and data privacy within integrated systems is paramount. As the regulatory landscape evolves, the integration of Apache Kafka and machine learning pipelines must adhere to stringent security measures, encryption protocols, and privacy-preserving techniques to safeguard sensitive information and ensure compliance.
The integration of Apache Kafka with machine learning pipelines signifies more than just a technological collaboration; it represents a strategic imperative for organizations seeking to thrive in a data-driven world. As this integration continues to evolve, organizations stand to benefit from real-time insights, adaptive machine learning models, and a future-ready infrastructure that positions them at the forefront of innovation in the rapidly changing landscape of data and analytics.
Machine Learning Integration with MongoDB: Certification Implications
In the rapidly evolving landscape of technology, the integration of Machine Learning (ML) with databases has emerged as a transformative force, unlocking new possibilities for data-driven decision-making and automation. One such pivotal integration lies in the fusion of Machine Learning with MongoDB, a leading NoSQL database platform known for its flexibility and scalability. This convergence not only addresses the challenges of handling vast and complex datasets but also opens avenues for harnessing the power of predictive analytics and pattern recognition.
Machine Learning Integration with MongoDB holds significant implications for professionals seeking to validate their expertise and stay abreast of cutting-edge developments in the field. As organizations increasingly recognize the value of data-driven insights, the demand for skilled individuals capable of seamlessly integrating ML algorithms with databases like MongoDB is on the rise. This burgeoning need has led to the establishment of certification programs that serve as a testament to an individual's proficiency in both machine learning principles and the intricacies of MongoDB implementation.
Certification in Machine Learning Integration with MongoDB signifies a comprehensive understanding of the symbiotic relationship between these two domains. It not only demonstrates mastery over ML algorithms but also validates the ability to leverage MongoDB's document-oriented structure for efficient data storage and retrieval. This certification becomes a badge of competence for professionals aspiring to play pivotal roles in data engineering, business intelligence, and application development, where the amalgamation of ML and MongoDB can propel innovation and drive strategic decision-making.
Table of contents
-
Overview of Machine Learning Integration with MongoDB
-
Certification Importance in the Data Science Landscape
-
Designing ML Models for MongoDB Compatibility
-
Hands-On Practical Exercises in ML-MongoDB Integration
-
Addressing Ethical Considerations in ML-MongoDB Integration
-
Certification Versatility and Career Opportunities
-
Continuous Learning and Upkeep of Certification
-
Conclusion
Overview of Machine Learning Integration with MongoDB
The integration of Machine Learning (ML) with MongoDB represents a pivotal advancement in the realm of data science and database management. At its core, this integration aims to synergize the power of predictive analytics and pattern recognition facilitated by ML with the flexible and scalable architecture of MongoDB, a prominent NoSQL database platform. Unlike traditional relational databases, MongoDB's document-oriented structure proves to be highly compatible with the diverse and unstructured nature of data commonly encountered in ML applications.
MongoDB's versatility in handling large volumes of data and its capacity to scale horizontally make it an ideal companion for ML tasks that often involve processing and analyzing massive datasets. The document-based storage model, where data is stored in BSON (Binary JSON) format, aligns well with the flexible schema requirements of machine learning applications, allowing for seamless adaptation to evolving data structures.
The overview of Machine Learning Integration with MongoDB underscores the symbiotic relationship between two powerful technological domains. It sets the stage for exploring the potential applications, challenges, and transformative implications of combining machine learning capabilities with the robust features of MongoDB, ushering in a new era of data-centric innovation and insight generation.
Certification Importance in the Data Science Landscape
Certifications play a crucial role in the dynamic and rapidly evolving landscape of data science, where the amalgamation of technical skills and domain knowledge is imperative for professional success. In this context, certifications specific to Machine Learning Integration with MongoDB hold particular significance. As organizations increasingly recognize the strategic importance of data-driven decision-making, the need for qualified and proficient individuals capable of navigating the complexities of both machine learning and advanced database management is more pronounced than ever.
Certifications in the field of data science serve as tangible proof of an individual's expertise and competence. They validate not only theoretical knowledge but also practical skills, ensuring that professionals are equipped to handle the intricacies of real-world scenarios. In the context of Machine Learning Integration with MongoDB, certification becomes a testament to an individual's ability to harness the synergies between these two domains, demonstrating proficiency in implementing machine learning models within the MongoDB ecosystem.
The importance of certifications in the data science landscape, particularly in the context of Machine Learning Integration with MongoDB, cannot be overstated. They not only serve as a validation of expertise but also provide professionals with a competitive edge, opening doors to exciting career opportunities in a field that continues to shape the future of technology and decision-making.
Designing ML Models for MongoDB Compatibility
Designing machine learning (ML) models for seamless compatibility with MongoDB involves a thoughtful and strategic approach that considers both the nuances of ML algorithms and the document-oriented nature of MongoDB. The fundamental principles revolve around optimizing the structure of the ML model to align with MongoDB's storage and retrieval capabilities, enhancing overall performance and efficiency.
One key consideration is the representation of data within the ML model. Given MongoDB's BSON format, which is a binary representation of JSON-like documents, designing models with features that naturally map to this structure is essential. This may involve transforming data into a format that aligns with MongoDB's document-based storage, ensuring that the model's output can be easily integrated into the database.
Another crucial aspect is the scalability of ML models, particularly when dealing with large datasets. MongoDB's horizontal scalability allows for the distribution of data across multiple servers, and ML models should be designed to handle parallel processing efficiently. This involves optimizing algorithms and workflows to exploit the parallelization capabilities of MongoDB, ensuring that the integration remains performant as the dataset grows.
Ultimately, designing ML models for MongoDB compatibility necessitates a holistic understanding of both the intricacies of ML algorithms and the unique features of MongoDB. It involves an iterative process of refinement, testing, and optimization to achieve a harmonious integration that maximizes the strengths of both technologies. The goal is to create a symbiotic relationship where ML models leverage MongoDB's scalability and flexibility, resulting in a powerful combination for handling and deriving insights from diverse and voluminous datasets.
Hands-On Practical Exercises in ML-MongoDB Integration
Hands-on practical exercises are essential for mastering the intricacies of integrating Machine Learning (ML) with MongoDB, providing practitioners with a tangible understanding of the integration process. To embark on this journey, the initial exercise involves setting up a MongoDB environment. This includes the installation and configuration of MongoDB on a local machine or a cloud-based platform, offering an introduction to fundamental database commands for data manipulation and retrieval.
A critical aspect of ML-MongoDB integration involves data preprocessing within MongoDB using its aggregation framework. Practitioners can engage in exercises where they filter, transform, and clean data directly within the database, optimizing the information for integration with ML models.
Optimizing for performance, practitioners can experiment with indexing strategies within MongoDB. This exercise sheds light on the impact of indexing on query efficiency, offering insights into how to fine-tune the retrieval of data for ML tasks.
Security implementation exercises address the crucial aspect of safeguarding both the MongoDB database and the integrated ML models. Practitioners gain hands-on experience in implementing access controls, encryption measures, and other security protocols to protect sensitive data.
Model deployment and monitoring exercises simulate real-world scenarios by deploying ML models integrated with MongoDB into a production-like environment. This holistic exercise includes monitoring the performance of deployed models and understanding the considerations for maintaining and updating models over time.
Addressing Ethical Considerations in ML-MongoDB Integration
Addressing ethical considerations in the integration of Machine Learning (ML) with MongoDB is paramount in the era of data-driven technologies. As organizations leverage the power of ML to extract insights from vast datasets stored in MongoDB, ethical concerns arise around issues such as data privacy, transparency, and potential biases embedded in algorithms. An essential first step in addressing these considerations is recognizing the responsibility of practitioners to ensure that the integration aligns with ethical standards and safeguards the rights and privacy of individuals whose data is involved.
One critical ethical consideration is data privacy, as MongoDB may store sensitive information that can be utilized by ML models. Practitioners must implement robust security measures, including encryption and access controls, to protect against unauthorized access and potential breaches. Additionally, transparent communication with users about data collection and utilization becomes imperative, fostering trust and compliance with privacy regulations.
Transparency and interpretability are key ethical principles in ML-MongoDB integration. Practitioners should strive to make ML models and the integration process understandable to stakeholders, promoting accountability and trust. Providing clear documentation on data sources, preprocessing steps, and model decisions contributes to transparency and enables users to comprehend and question the decisions made by the system.
Addressing ethical considerations in ML-MongoDB integration is a multifaceted task that demands a proactive and ongoing commitment to ethical practices. As the technological landscape evolves, practitioners must prioritize transparency, fairness, and privacy to ensure that ML models integrated with MongoDB align with ethical standards, contribute positively to society, and foster trust among users and stakeholders. By upholding these ethical principles, organizations can harness the benefits of ML-MongoDB integration while minimizing the potential risks and ethical pitfalls.
Certification Versatility and Career Opportunities
Certification in Machine Learning Integration with MongoDB opens up a realm of versatility and diverse career opportunities for professionals seeking to carve a niche in the dynamic intersection of data science and database management. The versatility of this certification lies in its ability to equip individuals with a comprehensive skill set, blending the proficiency in machine learning principles with the intricacies of MongoDB implementation. This unique combination positions certified professionals as valuable assets capable of addressing the evolving needs of organizations grappling with complex data challenges.
The certification's versatility is reflected in its applicability across various industries, where the integration of machine learning with MongoDB is becoming increasingly integral to decision-making processes. From healthcare and finance to e-commerce and beyond, certified individuals can leverage their expertise to drive innovation, optimize business operations, and extract meaningful insights from diverse datasets. The adaptability of this certification across sectors ensures that professionals possess skills that remain relevant and in-demand across a spectrum of industries.
In a competitive job market, certification in Machine Learning Integration with MongoDB becomes a valuable asset, enhancing a professional's marketability and employability. It not only demonstrates technical prowess but also underscores a commitment to staying abreast of cutting-edge developments in data science and database management. As organizations increasingly seek individuals with a diverse skill set, the certification opens doors to career advancements and positions certified professionals as leaders in the rapidly evolving landscape of technology.
The versatility and career opportunities associated with certification in Machine Learning Integration with MongoDB position it as a strategic investment for professionals aspiring to thrive in the data-driven era. Beyond imparting technical proficiency, the certification serves as a gateway to a myriad of career paths, where certified individuals can make impactful contributions and shape the future of data science and database management.
Continuous Learning and Upkeep of Certification
Continuous learning and the upkeep of certification in Machine Learning Integration with MongoDB are essential components for professionals aiming to stay at the forefront of the rapidly evolving landscape of data science and database management. In this dynamic field, where technologies and methodologies are in a perpetual state of evolution, the commitment to ongoing learning is paramount. Certified individuals recognize that the journey towards mastery is continuous and extends beyond the initial acquisition of skills.
The field of Machine Learning Integration with MongoDB is marked by constant innovation and emerging best practices. Therefore, professionals holding certifications must engage in continuous learning to stay updated with the latest developments, industry trends, and advancements in both machine learning and MongoDB. This commitment to ongoing education ensures that certified individuals remain well-informed about new tools, frameworks, and methodologies that may enhance their efficiency and efficacy in integrating ML with MongoDB.
Continuous learning and the upkeep of certification are inseparable components of a successful career in Machine Learning Integration with MongoDB. Embracing a mindset of lifelong learning ensures that certified professionals are well-equipped to navigate the complexities of the field, adapt to technological advancements, and contribute meaningfully to the ongoing transformation of data science and database management. By staying curious, connected, and committed to growth, individuals with certifications in ML-MongoDB integration position themselves as agile and resilient professionals in the ever-evolving landscape of technology.
How to obtain MONGODB DEVELOPER AND ADMINISTRATOR CERTIFICATION
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the integration of Machine Learning with MongoDB presents a compelling synergy that has transformative implications across diverse industries. The certification in Machine Learning Integration with MongoDB emerges as a key enabler for professionals seeking to navigate this dynamic intersection of data science and database management. As highlighted in the exploration of foundational concepts, practical exercises, and ethical considerations, this certification equips individuals with the knowledge and skills necessary to harness the full potential of both technologies.
The certification's importance in the data science landscape is underscored by the increasing demand for adept professionals capable of seamlessly integrating machine learning algorithms with MongoDB's flexible and scalable architecture. This recognition positions certified individuals as valuable assets in the data-driven era, where organizations prioritize actionable insights and strategic decision-making.
Addressing ethical considerations in ML-MongoDB integration is a critical aspect of the certification, emphasizing the responsibility of practitioners to uphold privacy, transparency, and fairness. By integrating ethical practices into the certification process, professionals ensure that their contributions align with societal expectations and contribute positively to the evolving landscape of technology.
The journey doesn't end with certification; instead, it is a stepping stone to a commitment to continuous learning. In the ever-evolving field of ML-MongoDB integration, staying informed, engaging in collaborative forums, and upkeeping the certification through ongoing education are crucial for maintaining relevance and competence. This dedication to continuous learning positions certified professionals as adaptable leaders in the face of evolving challenges and opportunities.
In essence, the Machine Learning Integration with MongoDB certification encapsulates not only technical proficiency but also a commitment to ethical practices, continuous learning, and a versatile skill set. As professionals embark on this certification journey, they position themselves at the forefront of innovation, ready to make impactful contributions to the transformative intersection of machine learning and MongoDB.
Read More
In the rapidly evolving landscape of technology, the integration of Machine Learning (ML) with databases has emerged as a transformative force, unlocking new possibilities for data-driven decision-making and automation. One such pivotal integration lies in the fusion of Machine Learning with MongoDB, a leading NoSQL database platform known for its flexibility and scalability. This convergence not only addresses the challenges of handling vast and complex datasets but also opens avenues for harnessing the power of predictive analytics and pattern recognition.
Machine Learning Integration with MongoDB holds significant implications for professionals seeking to validate their expertise and stay abreast of cutting-edge developments in the field. As organizations increasingly recognize the value of data-driven insights, the demand for skilled individuals capable of seamlessly integrating ML algorithms with databases like MongoDB is on the rise. This burgeoning need has led to the establishment of certification programs that serve as a testament to an individual's proficiency in both machine learning principles and the intricacies of MongoDB implementation.
Certification in Machine Learning Integration with MongoDB signifies a comprehensive understanding of the symbiotic relationship between these two domains. It not only demonstrates mastery over ML algorithms but also validates the ability to leverage MongoDB's document-oriented structure for efficient data storage and retrieval. This certification becomes a badge of competence for professionals aspiring to play pivotal roles in data engineering, business intelligence, and application development, where the amalgamation of ML and MongoDB can propel innovation and drive strategic decision-making.
Table of contents
-
Overview of Machine Learning Integration with MongoDB
-
Certification Importance in the Data Science Landscape
-
Designing ML Models for MongoDB Compatibility
-
Hands-On Practical Exercises in ML-MongoDB Integration
-
Addressing Ethical Considerations in ML-MongoDB Integration
-
Certification Versatility and Career Opportunities
-
Continuous Learning and Upkeep of Certification
-
Conclusion
Overview of Machine Learning Integration with MongoDB
The integration of Machine Learning (ML) with MongoDB represents a pivotal advancement in the realm of data science and database management. At its core, this integration aims to synergize the power of predictive analytics and pattern recognition facilitated by ML with the flexible and scalable architecture of MongoDB, a prominent NoSQL database platform. Unlike traditional relational databases, MongoDB's document-oriented structure proves to be highly compatible with the diverse and unstructured nature of data commonly encountered in ML applications.
MongoDB's versatility in handling large volumes of data and its capacity to scale horizontally make it an ideal companion for ML tasks that often involve processing and analyzing massive datasets. The document-based storage model, where data is stored in BSON (Binary JSON) format, aligns well with the flexible schema requirements of machine learning applications, allowing for seamless adaptation to evolving data structures.
The overview of Machine Learning Integration with MongoDB underscores the symbiotic relationship between two powerful technological domains. It sets the stage for exploring the potential applications, challenges, and transformative implications of combining machine learning capabilities with the robust features of MongoDB, ushering in a new era of data-centric innovation and insight generation.
Certification Importance in the Data Science Landscape
Certifications play a crucial role in the dynamic and rapidly evolving landscape of data science, where the amalgamation of technical skills and domain knowledge is imperative for professional success. In this context, certifications specific to Machine Learning Integration with MongoDB hold particular significance. As organizations increasingly recognize the strategic importance of data-driven decision-making, the need for qualified and proficient individuals capable of navigating the complexities of both machine learning and advanced database management is more pronounced than ever.
Certifications in the field of data science serve as tangible proof of an individual's expertise and competence. They validate not only theoretical knowledge but also practical skills, ensuring that professionals are equipped to handle the intricacies of real-world scenarios. In the context of Machine Learning Integration with MongoDB, certification becomes a testament to an individual's ability to harness the synergies between these two domains, demonstrating proficiency in implementing machine learning models within the MongoDB ecosystem.
The importance of certifications in the data science landscape, particularly in the context of Machine Learning Integration with MongoDB, cannot be overstated. They not only serve as a validation of expertise but also provide professionals with a competitive edge, opening doors to exciting career opportunities in a field that continues to shape the future of technology and decision-making.
Designing ML Models for MongoDB Compatibility
Designing machine learning (ML) models for seamless compatibility with MongoDB involves a thoughtful and strategic approach that considers both the nuances of ML algorithms and the document-oriented nature of MongoDB. The fundamental principles revolve around optimizing the structure of the ML model to align with MongoDB's storage and retrieval capabilities, enhancing overall performance and efficiency.
One key consideration is the representation of data within the ML model. Given MongoDB's BSON format, which is a binary representation of JSON-like documents, designing models with features that naturally map to this structure is essential. This may involve transforming data into a format that aligns with MongoDB's document-based storage, ensuring that the model's output can be easily integrated into the database.
Another crucial aspect is the scalability of ML models, particularly when dealing with large datasets. MongoDB's horizontal scalability allows for the distribution of data across multiple servers, and ML models should be designed to handle parallel processing efficiently. This involves optimizing algorithms and workflows to exploit the parallelization capabilities of MongoDB, ensuring that the integration remains performant as the dataset grows.
Ultimately, designing ML models for MongoDB compatibility necessitates a holistic understanding of both the intricacies of ML algorithms and the unique features of MongoDB. It involves an iterative process of refinement, testing, and optimization to achieve a harmonious integration that maximizes the strengths of both technologies. The goal is to create a symbiotic relationship where ML models leverage MongoDB's scalability and flexibility, resulting in a powerful combination for handling and deriving insights from diverse and voluminous datasets.
Hands-On Practical Exercises in ML-MongoDB Integration
Hands-on practical exercises are essential for mastering the intricacies of integrating Machine Learning (ML) with MongoDB, providing practitioners with a tangible understanding of the integration process. To embark on this journey, the initial exercise involves setting up a MongoDB environment. This includes the installation and configuration of MongoDB on a local machine or a cloud-based platform, offering an introduction to fundamental database commands for data manipulation and retrieval.
A critical aspect of ML-MongoDB integration involves data preprocessing within MongoDB using its aggregation framework. Practitioners can engage in exercises where they filter, transform, and clean data directly within the database, optimizing the information for integration with ML models.
Optimizing for performance, practitioners can experiment with indexing strategies within MongoDB. This exercise sheds light on the impact of indexing on query efficiency, offering insights into how to fine-tune the retrieval of data for ML tasks.
Security implementation exercises address the crucial aspect of safeguarding both the MongoDB database and the integrated ML models. Practitioners gain hands-on experience in implementing access controls, encryption measures, and other security protocols to protect sensitive data.
Model deployment and monitoring exercises simulate real-world scenarios by deploying ML models integrated with MongoDB into a production-like environment. This holistic exercise includes monitoring the performance of deployed models and understanding the considerations for maintaining and updating models over time.
Addressing Ethical Considerations in ML-MongoDB Integration
Addressing ethical considerations in the integration of Machine Learning (ML) with MongoDB is paramount in the era of data-driven technologies. As organizations leverage the power of ML to extract insights from vast datasets stored in MongoDB, ethical concerns arise around issues such as data privacy, transparency, and potential biases embedded in algorithms. An essential first step in addressing these considerations is recognizing the responsibility of practitioners to ensure that the integration aligns with ethical standards and safeguards the rights and privacy of individuals whose data is involved.
One critical ethical consideration is data privacy, as MongoDB may store sensitive information that can be utilized by ML models. Practitioners must implement robust security measures, including encryption and access controls, to protect against unauthorized access and potential breaches. Additionally, transparent communication with users about data collection and utilization becomes imperative, fostering trust and compliance with privacy regulations.
Transparency and interpretability are key ethical principles in ML-MongoDB integration. Practitioners should strive to make ML models and the integration process understandable to stakeholders, promoting accountability and trust. Providing clear documentation on data sources, preprocessing steps, and model decisions contributes to transparency and enables users to comprehend and question the decisions made by the system.
Addressing ethical considerations in ML-MongoDB integration is a multifaceted task that demands a proactive and ongoing commitment to ethical practices. As the technological landscape evolves, practitioners must prioritize transparency, fairness, and privacy to ensure that ML models integrated with MongoDB align with ethical standards, contribute positively to society, and foster trust among users and stakeholders. By upholding these ethical principles, organizations can harness the benefits of ML-MongoDB integration while minimizing the potential risks and ethical pitfalls.
Certification Versatility and Career Opportunities
Certification in Machine Learning Integration with MongoDB opens up a realm of versatility and diverse career opportunities for professionals seeking to carve a niche in the dynamic intersection of data science and database management. The versatility of this certification lies in its ability to equip individuals with a comprehensive skill set, blending the proficiency in machine learning principles with the intricacies of MongoDB implementation. This unique combination positions certified professionals as valuable assets capable of addressing the evolving needs of organizations grappling with complex data challenges.
The certification's versatility is reflected in its applicability across various industries, where the integration of machine learning with MongoDB is becoming increasingly integral to decision-making processes. From healthcare and finance to e-commerce and beyond, certified individuals can leverage their expertise to drive innovation, optimize business operations, and extract meaningful insights from diverse datasets. The adaptability of this certification across sectors ensures that professionals possess skills that remain relevant and in-demand across a spectrum of industries.
In a competitive job market, certification in Machine Learning Integration with MongoDB becomes a valuable asset, enhancing a professional's marketability and employability. It not only demonstrates technical prowess but also underscores a commitment to staying abreast of cutting-edge developments in data science and database management. As organizations increasingly seek individuals with a diverse skill set, the certification opens doors to career advancements and positions certified professionals as leaders in the rapidly evolving landscape of technology.
The versatility and career opportunities associated with certification in Machine Learning Integration with MongoDB position it as a strategic investment for professionals aspiring to thrive in the data-driven era. Beyond imparting technical proficiency, the certification serves as a gateway to a myriad of career paths, where certified individuals can make impactful contributions and shape the future of data science and database management.
Continuous Learning and Upkeep of Certification
Continuous learning and the upkeep of certification in Machine Learning Integration with MongoDB are essential components for professionals aiming to stay at the forefront of the rapidly evolving landscape of data science and database management. In this dynamic field, where technologies and methodologies are in a perpetual state of evolution, the commitment to ongoing learning is paramount. Certified individuals recognize that the journey towards mastery is continuous and extends beyond the initial acquisition of skills.
The field of Machine Learning Integration with MongoDB is marked by constant innovation and emerging best practices. Therefore, professionals holding certifications must engage in continuous learning to stay updated with the latest developments, industry trends, and advancements in both machine learning and MongoDB. This commitment to ongoing education ensures that certified individuals remain well-informed about new tools, frameworks, and methodologies that may enhance their efficiency and efficacy in integrating ML with MongoDB.
Continuous learning and the upkeep of certification are inseparable components of a successful career in Machine Learning Integration with MongoDB. Embracing a mindset of lifelong learning ensures that certified professionals are well-equipped to navigate the complexities of the field, adapt to technological advancements, and contribute meaningfully to the ongoing transformation of data science and database management. By staying curious, connected, and committed to growth, individuals with certifications in ML-MongoDB integration position themselves as agile and resilient professionals in the ever-evolving landscape of technology.
How to obtain MONGODB DEVELOPER AND ADMINISTRATOR CERTIFICATION
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the integration of Machine Learning with MongoDB presents a compelling synergy that has transformative implications across diverse industries. The certification in Machine Learning Integration with MongoDB emerges as a key enabler for professionals seeking to navigate this dynamic intersection of data science and database management. As highlighted in the exploration of foundational concepts, practical exercises, and ethical considerations, this certification equips individuals with the knowledge and skills necessary to harness the full potential of both technologies.
The certification's importance in the data science landscape is underscored by the increasing demand for adept professionals capable of seamlessly integrating machine learning algorithms with MongoDB's flexible and scalable architecture. This recognition positions certified individuals as valuable assets in the data-driven era, where organizations prioritize actionable insights and strategic decision-making.
Addressing ethical considerations in ML-MongoDB integration is a critical aspect of the certification, emphasizing the responsibility of practitioners to uphold privacy, transparency, and fairness. By integrating ethical practices into the certification process, professionals ensure that their contributions align with societal expectations and contribute positively to the evolving landscape of technology.
The journey doesn't end with certification; instead, it is a stepping stone to a commitment to continuous learning. In the ever-evolving field of ML-MongoDB integration, staying informed, engaging in collaborative forums, and upkeeping the certification through ongoing education are crucial for maintaining relevance and competence. This dedication to continuous learning positions certified professionals as adaptable leaders in the face of evolving challenges and opportunities.
In essence, the Machine Learning Integration with MongoDB certification encapsulates not only technical proficiency but also a commitment to ethical practices, continuous learning, and a versatile skill set. As professionals embark on this certification journey, they position themselves at the forefront of innovation, ready to make impactful contributions to the transformative intersection of machine learning and MongoDB.
Understanding the Core Concepts of Capability Maturity Model Integration (CMMI)
In the dynamic landscape of today's global business environment, organizations face the perpetual challenge of delivering high-quality products and services while striving for operational efficiency. To navigate this complex terrain, many enterprises turn to established frameworks and models that provide a structured approach to process improvement. One such powerful and widely adopted framework is the Capability Maturity Model Integration (CMMI).
CMMI stands as a beacon for organizations aspiring to enhance their capabilities and achieve a higher level of maturity in their processes. It offers a comprehensive and integrated set of best practices that guide organizations in developing and improving their processes, ultimately leading to increased performance, reliability, and customer satisfaction.
This exploration delves into the core concepts of CMMI, unraveling its intricacies and shedding light on the transformative journey that organizations embark upon when embracing this model. From understanding the fundamental principles that underpin CMMI to exploring its maturity levels and process areas, we will navigate through the key components that make CMMI a cornerstone in the pursuit of organizational excellence.
As we embark on this journey, we will demystify the terminology, delve into the rationale behind CMMI, and highlight the practical implications for organizations seeking to elevate their capabilities. Join us in unraveling the layers of CMMI, as we uncover the essence of this model and its profound impact on shaping robust, resilient, and high-performance organizations in the modern business landscape.
Table Of Contents
-
Foundations of CMMI: Defining Capability and Maturity
-
CMMI Framework Components: Processes, Practices, and Goals
-
Maturity Levels Demystified: Progressing from Chaos to Continual Improvement
-
Process Areas: Building Blocks for Effective Performance
-
Continuous and Staged Representations: Tailoring CMMI to Organizational Needs
-
CMMI Models for Different Domains: Customizing Excellence
-
Appraisals in CMMI: Evaluating and Improving Organizational Capability
-
Measuring Success: Key Performance Indicators in CMMI
-
CMMI and Agile: Bridging the Gap for Dynamic Environments
-
Challenges and Best Practices in CMMI Implementation: Lessons from the Field
-
Conclusion
Foundations of CMMI: Defining Capability and Maturity
The foundations of the Capability Maturity Model Integration (CMMI) lie in its dual emphasis on capability and maturity, which together form the bedrock of organizational excellence. In the CMMI context, capability refers to an organization's inherent ability to reliably and predictably achieve its business objectives through well-defined processes. This involves understanding and harnessing the organization's resources, processes, and technology to consistently produce desired outcomes. On the other hand, maturity signifies the evolutionary progression of an organization's processes from ad-hoc and chaotic states to well-defined, measured, and optimized levels. It encapsulates the organization's journey toward process improvement and the establishment of best practices. By defining capability and maturity as intertwined aspects, CMMI provides a holistic framework that empowers organizations to assess, enhance, and continually evolve their processes, ensuring they are not only capable of meeting current demands but are also on a trajectory of continual improvement. This foundational understanding sets the stage for organizations to embark on a purposeful journey towards operational excellence and sustained success.
CMMI Framework Components: Processes, Practices, and Goals
The Capability Maturity Model Integration (CMMI) is a robust framework built upon key components, each playing a pivotal role in guiding organizations toward process improvement and excellence. At its core are processes, the dynamic sequences of activities that transform inputs into valuable outputs. CMMI emphasizes the definition, implementation, and continuous refinement of these processes to ensure consistency, efficiency, and adaptability within an organization.
Embedded within the framework are best practices, collectively known as practices, which encapsulate the distilled wisdom of successful processes. Practices serve as guidelines, outlining the specific activities, methods, and techniques that contribute to the effective execution of processes. They provide organizations with a roadmap for achieving desired outcomes and for adapting to evolving business needs.
Furthermore, CMMI incorporates the concept of goals, which represent the high-level objectives that organizations aspire to achieve. Goals guide the selection and implementation of practices, aligning them with the organization's strategic objectives. These goals serve as benchmarks, enabling organizations to measure their progress and maturity levels across different areas.
In essence, the synergy among processes, practices, and goals within the CMMI framework forms a dynamic triad. Processes provide the operational backbone, practices offer actionable insights, and goals steer organizations towards overarching excellence. Understanding and optimizing this interconnected framework empowers organizations to systematically elevate their capabilities and achieve maturity in a structured and sustainable manner.
Maturity Levels Demystified: Progressing from Chaos to Continual Improvement
Navigating through the Maturity Levels within the Capability Maturity Model Integration (CMMI) unveils a transformative journey, guiding organizations from the tumultuous realm of chaos towards a state of perpetual enhancement. Commencing at Level 1, organizations grapple with ad-hoc processes, characterized by unpredictability and disorder. The transition to Level 2 signifies a pivotal step, introducing foundational project management practices and instilling a semblance of control.
As organizations ascend to Level 3, a culture of standardization emerges. Processes become not only defined but also tailored to specific project needs, fostering a proactive approach to process management. The journey intensifies at Level 4, where organizations employ quantitative techniques, utilizing data to gain insights and enhance predictability. This meticulous control sets the stage for the pinnacle, Level 5, characterized by an unwavering commitment to continual improvement.
At Level 5, organizations go beyond control to actively monitor, adapt, and innovate. A culture of perpetual enhancement becomes ingrained, enabling organizations not only to navigate complexity but to thrive amidst change. The narrative of progression through these maturity levels encapsulates more than a refinement of processes; it signifies a profound organizational evolution, positioning entities as dynamic and resilient contributors to the ever-evolving business landscape.
Process Areas: Building Blocks for Effective Performance
Process areas stand as the foundational building blocks within the Capability Maturity Model Integration (CMMI), forming the essential elements that underpin an organization's capability to deliver effective performance. These areas define clusters of related activities that, when executed cohesively, contribute to the achievement of specific objectives and the overall success of the organization.
Each process area within CMMI encapsulates a set of best practices and guidelines tailored to address particular aspects of an organization's operations. They serve as a roadmap, providing a structured approach for organizations to develop, implement, and continually improve their processes. These building blocks are instrumental in aligning organizational goals with practical, actionable steps, fostering consistency, efficiency, and ultimately, superior performance.
By focusing on process areas, organizations can systematically enhance their capabilities in critical areas such as project management, requirements development, and process improvement. The comprehensive nature of these areas ensures that organizations not only meet their immediate objectives but also cultivate a culture of continuous improvement, adaptability, and resilience.
Process areas within CMMI are the linchpin of effective performance. They enable organizations to elevate their processes beyond mere compliance to standards, driving them towards operational excellence and ensuring sustained success in today's dynamic and competitive business environment.
Continuous and Staged Representations: Tailoring CMMI to Organizational Needs
In the realm of Capability Maturity Model Integration (CMMI), organizations are presented with two distinct yet flexible approaches: the Continuous Representation and the Staged Representation. These representations serve as adaptable frameworks, allowing organizations to tailor their CMMI adoption to align precisely with their unique operational needs, preferences, and strategic objectives.
The Staged Representation offers a structured, milestone-oriented approach, where maturity levels are attained sequentially. This method provides a clear roadmap, guiding organizations from one level to the next, each level building upon the achievements of the previous one. It is particularly beneficial for organizations seeking a well-defined, step-by-step approach to maturity.
Conversely, the Continuous Representation allows for a more tailored and flexible adoption. Instead of following a strict sequence of maturity levels, organizations can choose to focus on specific process areas that align with their immediate priorities. This approach provides the freedom to address targeted areas of improvement without the constraint of a predetermined sequence.
The decision between these representations hinges on an organization's unique context, goals, and existing processes. The Staged Representation may be preferable for those seeking a systematic, comprehensive approach to maturity, while the Continuous Representation offers a more agile and customizable route.
Ultimately, whether an organization opts for the Staged or Continuous Representation, the key lies in aligning CMMI adoption with organizational needs. This strategic alignment empowers organizations to leverage the power of CMMI in a way that not only improves processes but also seamlessly integrates with their broader business objectives and operational landscape.
CMMI Models for Different Domains: Customizing Excellence
In the dynamic landscape of industries spanning from software development to manufacturing and beyond, a one-size-fits-all approach to process improvement may not be optimal. Recognizing this diversity, the Capability Maturity Model Integration (CMMI) provides specialized models tailored to meet the unique challenges and nuances of different domains. These domain-specific adaptations empower organizations to customize their journey toward excellence, aligning CMMI principles with the specific requirements of their industry.
For software and systems engineering, the CMMI for Development (CMMI-DEV) model offers a targeted framework. It emphasizes best practices for managing and improving development processes, ensuring the delivery of high-quality software and systems.
In the realm of services, the CMMI for Services (CMMI-SVC) model takes center stage. It addresses the distinctive aspects of service delivery, focusing on processes that enhance customer satisfaction, manage service delivery risks, and optimize service provider performance.
For organizations in the acquisition and supply chain domain, the CMMI for Acquisition (CMMI-ACQ) model becomes instrumental. It provides guidelines for effective acquisition processes, ensuring that organizations can seamlessly integrate suppliers and acquisitions into their overall improvement strategy.
The adaptability of CMMI models for different domains extends beyond these examples, encompassing areas such as product development, people management, and cybersecurity. Each tailored model incorporates industry-specific best practices while retaining the core CMMI principles, allowing organizations to reap the benefits of a proven framework while addressing the unique challenges within their domain.
Appraisals in CMMI: Evaluating and Improving Organizational Capability
In the realm of Capability Maturity Model Integration (CMMI), appraisals serve as pivotal mechanisms for evaluating and enhancing an organization's capability and maturity levels. An appraisal is a structured and rigorous assessment process conducted by certified professionals, providing organizations with insights into the effectiveness of their processes and identifying areas for improvement.
The CMMI appraisal process follows a systematic approach, examining how well an organization's processes align with the CMMI model's best practices. There are various types of appraisals, with the Standard CMMI Appraisal Method for Process Improvement (SCAMPI) being one of the most widely utilized. SCAMPI appraisals can be Class A, B, or C, each differing in scope, depth, and purpose.
Crucially, the insights gained from appraisals contribute to a continuous improvement cycle. Organizations can leverage appraisal findings to refine their processes, enhance capabilities, and align with strategic objectives. By identifying and addressing areas for improvement, organizations can systematically progress through the maturity levels of CMMI, ultimately enhancing their ability to deliver high-quality products and services.
CMMI appraisals play a dual role in evaluating and improving organizational capability. They offer a comprehensive assessment of an organization's adherence to CMMI best practices and provide a roadmap for continual enhancement, fostering a culture of proactive improvement and ensuring sustained success in today's competitive business landscape.
Measuring Success: Key Performance Indicators in CMMI
In the dynamic landscape of process improvement, the Capability Maturity Model Integration (CMMI) places a significant emphasis on quantifiable success through the use of Key Performance Indicators (KPIs). KPIs in CMMI act as essential metrics, offering organizations tangible and measurable insights into the effectiveness of their processes, the achievement of goals, and the overall progress in their journey towards maturity.
Key Performance Indicators within the CMMI framework are diverse and tailored to specific process areas. They are designed to provide a clear picture of an organization's performance, allowing for informed decision-making and targeted improvements. Some common KPIs include metrics related to project schedule adherence, defect density, and customer satisfaction.
The strategic use of KPIs extends beyond mere measurement; it serves as a catalyst for continuous improvement. By regularly assessing and analyzing these indicators, organizations can identify trends, areas of excellence, and potential challenges. This proactive approach enables them to make data-driven decisions, refine processes, and address issues promptly, fostering a culture of continual enhancement.
In summary, measuring success in CMMI relies on the strategic implementation of Key Performance Indicators. These metrics not only gauge the effectiveness of processes but also drive continuous improvement, enabling organizations to navigate the complexities of their industries with precision and ensuring a sustained trajectory of success.
CMMI and Agile: Bridging the Gap for Dynamic Environments
In the ever-evolving landscape of software development and project management, the integration of Capability Maturity Model Integration (CMMI) and Agile methodologies represents a strategic synergy aimed at addressing the challenges of dynamic and rapidly changing environments.
Agile, known for its flexibility, collaboration, and iterative approach, is favored in environments where responsiveness to change is paramount. CMMI, on the other hand, provides a structured framework for process improvement and maturity. Bridging the gap between these two seemingly distinct approaches holds the key to unlocking a holistic and adaptive model for organizational success.
Agile practices are inherently compatible with certain CMMI principles, particularly in the areas of continuous improvement, stakeholder engagement, and incremental development. By integrating Agile practices with CMMI, organizations can harness the iterative nature of Agile for rapid development cycles while leveraging CMMI's structure to ensure robust processes, measurement, and organizational learning.
This integration is not about compromising the agility of Agile or stifling innovation with rigid processes. Instead, it involves tailoring and adapting CMMI practices to complement and enhance Agile methodologies. The goal is to create a dynamic and resilient organizational culture that embraces change, values collaboration, and continually improves processes.
Ultimately, the combination of CMMI and Agile represents a powerful approach for organizations operating in dynamic environments. It harmonizes the best of both worlds, providing the structure needed for maturity and process improvement while preserving the agility required to navigate the uncertainties of today's fast-paced business landscape.
Challenges and Best Practices in CMMI Implementation: Lessons from the Field
Embarking on the journey of implementing Capability Maturity Model Integration (CMMI) is a transformative endeavor for any organization, and it comes with its unique set of challenges and valuable lessons. Drawing insights from real-world experiences, we explore both the common challenges faced during CMMI implementation and the best practices that organizations have employed to navigate these hurdles successfully.
Challenges:
Resistance to Change:
Challenge: Employees may resist changes to established processes and workflows.
Lesson: Clear communication about the benefits of CMMI, coupled with employee involvement in the process, helps alleviate resistance.
Resource Constraints:
Challenge: Limited time, budget, and personnel resources can hinder implementation efforts.
Lesson: Prioritize initiatives based on their impact and feasibility, and seek executive support for resource allocation.
Tailoring the Model:
Challenge: Adapting CMMI practices to the specific needs of the organization can be challenging.
Lesson: Tailor CMMI to fit the organization's context, ensuring relevance without compromising the integrity of the model.
Documentation Overload:
Challenge: Excessive documentation requirements can be perceived as burdensome.
Lesson: Streamline documentation processes, focusing on value-added documentation and avoiding unnecessary bureaucracy.
Lack of Organizational Buy-In:
Challenge: If the entire organization does not buy into the CMMI initiative, implementation may face resistance.
Lesson: Engage key stakeholders early, demonstrate the benefits, and foster a culture that values continuous improvement.
Best Practices:
Executive Sponsorship:
Practice: Secure executive sponsorship to drive commitment and allocate necessary resources.
Pilot Projects:
Practice: Start with pilot projects to test CMMI practices in a controlled environment before full-scale implementation.
Training and Skill Development:
Practice: Invest in training programs to enhance the skills of employees and build a competent workforce.
Continuous Communication:
Practice: Maintain open and continuous communication channels to address concerns, share successes, and reinforce the importance of CMMI.
Iterative Implementation:
Practice: Adopt an iterative approach to implementation, allowing for incremental improvements and learning from each cycle.
By acknowledging these challenges and implementing best practices derived from real-world experiences, organizations can not only overcome obstacles in their CMMI journey but also cultivate a culture of continuous improvement and excellence. These lessons from the field serve as a guide for organizations aspiring to enhance their processes and achieve greater maturity.
How to obtain Project Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
Conclusion
In conclusion, the Capability Maturity Model Integration (CMMI) stands as a powerful framework for organizations seeking to enhance their processes, achieve higher maturity levels, and thrive in today's competitive business landscape. Our exploration into the core concepts of CMMI has unveiled its foundational principles, the significance of maturity levels, the importance of process areas, and the adaptability of representations.
As organizations progress through the maturity levels, transitioning from chaos to continual improvement, they gain not only a structured approach to process enhancement but also a cultural transformation that fosters resilience and adaptability. The tailored CMMI models for different domains further emphasize the versatility of this framework, allowing organizations to customize their pursuit of excellence.
Appraisals serve as crucial checkpoints, evaluating and refining organizational capabilities. Key Performance Indicators provide tangible metrics, offering a clear gauge of success and driving continuous improvement. Integrating CMMI with Agile methodologies creates a harmonious balance between structure and agility, vital for success in dynamic environments.
The challenges and best practices discussed reflect the real-world lessons learned by organizations navigating the CMMI implementation journey. Overcoming resistance to change, addressing resource constraints, and ensuring organizational buy-in are pivotal elements, while executive sponsorship, iterative implementation, and effective communication emerge as best practices for success.
As organizations embrace CMMI, they embark on a transformative journey towards operational maturity, guided by a framework that not only elevates their processes but also instills a culture of excellence and adaptability. By leveraging the core concepts, overcoming challenges, and embracing best practices, organizations can position themselves as industry leaders, capable of navigating the complexities of today's ever-changing business environment with confidence and success.
Read More
In the dynamic landscape of today's global business environment, organizations face the perpetual challenge of delivering high-quality products and services while striving for operational efficiency. To navigate this complex terrain, many enterprises turn to established frameworks and models that provide a structured approach to process improvement. One such powerful and widely adopted framework is the Capability Maturity Model Integration (CMMI).
CMMI stands as a beacon for organizations aspiring to enhance their capabilities and achieve a higher level of maturity in their processes. It offers a comprehensive and integrated set of best practices that guide organizations in developing and improving their processes, ultimately leading to increased performance, reliability, and customer satisfaction.
This exploration delves into the core concepts of CMMI, unraveling its intricacies and shedding light on the transformative journey that organizations embark upon when embracing this model. From understanding the fundamental principles that underpin CMMI to exploring its maturity levels and process areas, we will navigate through the key components that make CMMI a cornerstone in the pursuit of organizational excellence.
As we embark on this journey, we will demystify the terminology, delve into the rationale behind CMMI, and highlight the practical implications for organizations seeking to elevate their capabilities. Join us in unraveling the layers of CMMI, as we uncover the essence of this model and its profound impact on shaping robust, resilient, and high-performance organizations in the modern business landscape.
Table Of Contents
-
Foundations of CMMI: Defining Capability and Maturity
-
CMMI Framework Components: Processes, Practices, and Goals
-
Maturity Levels Demystified: Progressing from Chaos to Continual Improvement
-
Process Areas: Building Blocks for Effective Performance
-
Continuous and Staged Representations: Tailoring CMMI to Organizational Needs
-
CMMI Models for Different Domains: Customizing Excellence
-
Appraisals in CMMI: Evaluating and Improving Organizational Capability
-
Measuring Success: Key Performance Indicators in CMMI
-
CMMI and Agile: Bridging the Gap for Dynamic Environments
-
Challenges and Best Practices in CMMI Implementation: Lessons from the Field
-
Conclusion
Foundations of CMMI: Defining Capability and Maturity
The foundations of the Capability Maturity Model Integration (CMMI) lie in its dual emphasis on capability and maturity, which together form the bedrock of organizational excellence. In the CMMI context, capability refers to an organization's inherent ability to reliably and predictably achieve its business objectives through well-defined processes. This involves understanding and harnessing the organization's resources, processes, and technology to consistently produce desired outcomes. On the other hand, maturity signifies the evolutionary progression of an organization's processes from ad-hoc and chaotic states to well-defined, measured, and optimized levels. It encapsulates the organization's journey toward process improvement and the establishment of best practices. By defining capability and maturity as intertwined aspects, CMMI provides a holistic framework that empowers organizations to assess, enhance, and continually evolve their processes, ensuring they are not only capable of meeting current demands but are also on a trajectory of continual improvement. This foundational understanding sets the stage for organizations to embark on a purposeful journey towards operational excellence and sustained success.
CMMI Framework Components: Processes, Practices, and Goals
The Capability Maturity Model Integration (CMMI) is a robust framework built upon key components, each playing a pivotal role in guiding organizations toward process improvement and excellence. At its core are processes, the dynamic sequences of activities that transform inputs into valuable outputs. CMMI emphasizes the definition, implementation, and continuous refinement of these processes to ensure consistency, efficiency, and adaptability within an organization.
Embedded within the framework are best practices, collectively known as practices, which encapsulate the distilled wisdom of successful processes. Practices serve as guidelines, outlining the specific activities, methods, and techniques that contribute to the effective execution of processes. They provide organizations with a roadmap for achieving desired outcomes and for adapting to evolving business needs.
Furthermore, CMMI incorporates the concept of goals, which represent the high-level objectives that organizations aspire to achieve. Goals guide the selection and implementation of practices, aligning them with the organization's strategic objectives. These goals serve as benchmarks, enabling organizations to measure their progress and maturity levels across different areas.
In essence, the synergy among processes, practices, and goals within the CMMI framework forms a dynamic triad. Processes provide the operational backbone, practices offer actionable insights, and goals steer organizations towards overarching excellence. Understanding and optimizing this interconnected framework empowers organizations to systematically elevate their capabilities and achieve maturity in a structured and sustainable manner.
Maturity Levels Demystified: Progressing from Chaos to Continual Improvement
Navigating through the Maturity Levels within the Capability Maturity Model Integration (CMMI) unveils a transformative journey, guiding organizations from the tumultuous realm of chaos towards a state of perpetual enhancement. Commencing at Level 1, organizations grapple with ad-hoc processes, characterized by unpredictability and disorder. The transition to Level 2 signifies a pivotal step, introducing foundational project management practices and instilling a semblance of control.
As organizations ascend to Level 3, a culture of standardization emerges. Processes become not only defined but also tailored to specific project needs, fostering a proactive approach to process management. The journey intensifies at Level 4, where organizations employ quantitative techniques, utilizing data to gain insights and enhance predictability. This meticulous control sets the stage for the pinnacle, Level 5, characterized by an unwavering commitment to continual improvement.
At Level 5, organizations go beyond control to actively monitor, adapt, and innovate. A culture of perpetual enhancement becomes ingrained, enabling organizations not only to navigate complexity but to thrive amidst change. The narrative of progression through these maturity levels encapsulates more than a refinement of processes; it signifies a profound organizational evolution, positioning entities as dynamic and resilient contributors to the ever-evolving business landscape.
Process Areas: Building Blocks for Effective Performance
Process areas stand as the foundational building blocks within the Capability Maturity Model Integration (CMMI), forming the essential elements that underpin an organization's capability to deliver effective performance. These areas define clusters of related activities that, when executed cohesively, contribute to the achievement of specific objectives and the overall success of the organization.
Each process area within CMMI encapsulates a set of best practices and guidelines tailored to address particular aspects of an organization's operations. They serve as a roadmap, providing a structured approach for organizations to develop, implement, and continually improve their processes. These building blocks are instrumental in aligning organizational goals with practical, actionable steps, fostering consistency, efficiency, and ultimately, superior performance.
By focusing on process areas, organizations can systematically enhance their capabilities in critical areas such as project management, requirements development, and process improvement. The comprehensive nature of these areas ensures that organizations not only meet their immediate objectives but also cultivate a culture of continuous improvement, adaptability, and resilience.
Process areas within CMMI are the linchpin of effective performance. They enable organizations to elevate their processes beyond mere compliance to standards, driving them towards operational excellence and ensuring sustained success in today's dynamic and competitive business environment.
Continuous and Staged Representations: Tailoring CMMI to Organizational Needs
In the realm of Capability Maturity Model Integration (CMMI), organizations are presented with two distinct yet flexible approaches: the Continuous Representation and the Staged Representation. These representations serve as adaptable frameworks, allowing organizations to tailor their CMMI adoption to align precisely with their unique operational needs, preferences, and strategic objectives.
The Staged Representation offers a structured, milestone-oriented approach, where maturity levels are attained sequentially. This method provides a clear roadmap, guiding organizations from one level to the next, each level building upon the achievements of the previous one. It is particularly beneficial for organizations seeking a well-defined, step-by-step approach to maturity.
Conversely, the Continuous Representation allows for a more tailored and flexible adoption. Instead of following a strict sequence of maturity levels, organizations can choose to focus on specific process areas that align with their immediate priorities. This approach provides the freedom to address targeted areas of improvement without the constraint of a predetermined sequence.
The decision between these representations hinges on an organization's unique context, goals, and existing processes. The Staged Representation may be preferable for those seeking a systematic, comprehensive approach to maturity, while the Continuous Representation offers a more agile and customizable route.
Ultimately, whether an organization opts for the Staged or Continuous Representation, the key lies in aligning CMMI adoption with organizational needs. This strategic alignment empowers organizations to leverage the power of CMMI in a way that not only improves processes but also seamlessly integrates with their broader business objectives and operational landscape.
CMMI Models for Different Domains: Customizing Excellence
In the dynamic landscape of industries spanning from software development to manufacturing and beyond, a one-size-fits-all approach to process improvement may not be optimal. Recognizing this diversity, the Capability Maturity Model Integration (CMMI) provides specialized models tailored to meet the unique challenges and nuances of different domains. These domain-specific adaptations empower organizations to customize their journey toward excellence, aligning CMMI principles with the specific requirements of their industry.
For software and systems engineering, the CMMI for Development (CMMI-DEV) model offers a targeted framework. It emphasizes best practices for managing and improving development processes, ensuring the delivery of high-quality software and systems.
In the realm of services, the CMMI for Services (CMMI-SVC) model takes center stage. It addresses the distinctive aspects of service delivery, focusing on processes that enhance customer satisfaction, manage service delivery risks, and optimize service provider performance.
For organizations in the acquisition and supply chain domain, the CMMI for Acquisition (CMMI-ACQ) model becomes instrumental. It provides guidelines for effective acquisition processes, ensuring that organizations can seamlessly integrate suppliers and acquisitions into their overall improvement strategy.
The adaptability of CMMI models for different domains extends beyond these examples, encompassing areas such as product development, people management, and cybersecurity. Each tailored model incorporates industry-specific best practices while retaining the core CMMI principles, allowing organizations to reap the benefits of a proven framework while addressing the unique challenges within their domain.
Appraisals in CMMI: Evaluating and Improving Organizational Capability
In the realm of Capability Maturity Model Integration (CMMI), appraisals serve as pivotal mechanisms for evaluating and enhancing an organization's capability and maturity levels. An appraisal is a structured and rigorous assessment process conducted by certified professionals, providing organizations with insights into the effectiveness of their processes and identifying areas for improvement.
The CMMI appraisal process follows a systematic approach, examining how well an organization's processes align with the CMMI model's best practices. There are various types of appraisals, with the Standard CMMI Appraisal Method for Process Improvement (SCAMPI) being one of the most widely utilized. SCAMPI appraisals can be Class A, B, or C, each differing in scope, depth, and purpose.
Crucially, the insights gained from appraisals contribute to a continuous improvement cycle. Organizations can leverage appraisal findings to refine their processes, enhance capabilities, and align with strategic objectives. By identifying and addressing areas for improvement, organizations can systematically progress through the maturity levels of CMMI, ultimately enhancing their ability to deliver high-quality products and services.
CMMI appraisals play a dual role in evaluating and improving organizational capability. They offer a comprehensive assessment of an organization's adherence to CMMI best practices and provide a roadmap for continual enhancement, fostering a culture of proactive improvement and ensuring sustained success in today's competitive business landscape.
Measuring Success: Key Performance Indicators in CMMI
In the dynamic landscape of process improvement, the Capability Maturity Model Integration (CMMI) places a significant emphasis on quantifiable success through the use of Key Performance Indicators (KPIs). KPIs in CMMI act as essential metrics, offering organizations tangible and measurable insights into the effectiveness of their processes, the achievement of goals, and the overall progress in their journey towards maturity.
Key Performance Indicators within the CMMI framework are diverse and tailored to specific process areas. They are designed to provide a clear picture of an organization's performance, allowing for informed decision-making and targeted improvements. Some common KPIs include metrics related to project schedule adherence, defect density, and customer satisfaction.
The strategic use of KPIs extends beyond mere measurement; it serves as a catalyst for continuous improvement. By regularly assessing and analyzing these indicators, organizations can identify trends, areas of excellence, and potential challenges. This proactive approach enables them to make data-driven decisions, refine processes, and address issues promptly, fostering a culture of continual enhancement.
In summary, measuring success in CMMI relies on the strategic implementation of Key Performance Indicators. These metrics not only gauge the effectiveness of processes but also drive continuous improvement, enabling organizations to navigate the complexities of their industries with precision and ensuring a sustained trajectory of success.
CMMI and Agile: Bridging the Gap for Dynamic Environments
In the ever-evolving landscape of software development and project management, the integration of Capability Maturity Model Integration (CMMI) and Agile methodologies represents a strategic synergy aimed at addressing the challenges of dynamic and rapidly changing environments.
Agile, known for its flexibility, collaboration, and iterative approach, is favored in environments where responsiveness to change is paramount. CMMI, on the other hand, provides a structured framework for process improvement and maturity. Bridging the gap between these two seemingly distinct approaches holds the key to unlocking a holistic and adaptive model for organizational success.
Agile practices are inherently compatible with certain CMMI principles, particularly in the areas of continuous improvement, stakeholder engagement, and incremental development. By integrating Agile practices with CMMI, organizations can harness the iterative nature of Agile for rapid development cycles while leveraging CMMI's structure to ensure robust processes, measurement, and organizational learning.
This integration is not about compromising the agility of Agile or stifling innovation with rigid processes. Instead, it involves tailoring and adapting CMMI practices to complement and enhance Agile methodologies. The goal is to create a dynamic and resilient organizational culture that embraces change, values collaboration, and continually improves processes.
Ultimately, the combination of CMMI and Agile represents a powerful approach for organizations operating in dynamic environments. It harmonizes the best of both worlds, providing the structure needed for maturity and process improvement while preserving the agility required to navigate the uncertainties of today's fast-paced business landscape.
Challenges and Best Practices in CMMI Implementation: Lessons from the Field
Embarking on the journey of implementing Capability Maturity Model Integration (CMMI) is a transformative endeavor for any organization, and it comes with its unique set of challenges and valuable lessons. Drawing insights from real-world experiences, we explore both the common challenges faced during CMMI implementation and the best practices that organizations have employed to navigate these hurdles successfully.
Challenges:
Resistance to Change:
Challenge: Employees may resist changes to established processes and workflows.
Lesson: Clear communication about the benefits of CMMI, coupled with employee involvement in the process, helps alleviate resistance.
Resource Constraints:
Challenge: Limited time, budget, and personnel resources can hinder implementation efforts.
Lesson: Prioritize initiatives based on their impact and feasibility, and seek executive support for resource allocation.
Tailoring the Model:
Challenge: Adapting CMMI practices to the specific needs of the organization can be challenging.
Lesson: Tailor CMMI to fit the organization's context, ensuring relevance without compromising the integrity of the model.
Documentation Overload:
Challenge: Excessive documentation requirements can be perceived as burdensome.
Lesson: Streamline documentation processes, focusing on value-added documentation and avoiding unnecessary bureaucracy.
Lack of Organizational Buy-In:
Challenge: If the entire organization does not buy into the CMMI initiative, implementation may face resistance.
Lesson: Engage key stakeholders early, demonstrate the benefits, and foster a culture that values continuous improvement.
Best Practices:
Executive Sponsorship:
Practice: Secure executive sponsorship to drive commitment and allocate necessary resources.
Pilot Projects:
Practice: Start with pilot projects to test CMMI practices in a controlled environment before full-scale implementation.
Training and Skill Development:
Practice: Invest in training programs to enhance the skills of employees and build a competent workforce.
Continuous Communication:
Practice: Maintain open and continuous communication channels to address concerns, share successes, and reinforce the importance of CMMI.
Iterative Implementation:
Practice: Adopt an iterative approach to implementation, allowing for incremental improvements and learning from each cycle.
By acknowledging these challenges and implementing best practices derived from real-world experiences, organizations can not only overcome obstacles in their CMMI journey but also cultivate a culture of continuous improvement and excellence. These lessons from the field serve as a guide for organizations aspiring to enhance their processes and achieve greater maturity.
How to obtain Project Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
Conclusion
In conclusion, the Capability Maturity Model Integration (CMMI) stands as a powerful framework for organizations seeking to enhance their processes, achieve higher maturity levels, and thrive in today's competitive business landscape. Our exploration into the core concepts of CMMI has unveiled its foundational principles, the significance of maturity levels, the importance of process areas, and the adaptability of representations.
As organizations progress through the maturity levels, transitioning from chaos to continual improvement, they gain not only a structured approach to process enhancement but also a cultural transformation that fosters resilience and adaptability. The tailored CMMI models for different domains further emphasize the versatility of this framework, allowing organizations to customize their pursuit of excellence.
Appraisals serve as crucial checkpoints, evaluating and refining organizational capabilities. Key Performance Indicators provide tangible metrics, offering a clear gauge of success and driving continuous improvement. Integrating CMMI with Agile methodologies creates a harmonious balance between structure and agility, vital for success in dynamic environments.
The challenges and best practices discussed reflect the real-world lessons learned by organizations navigating the CMMI implementation journey. Overcoming resistance to change, addressing resource constraints, and ensuring organizational buy-in are pivotal elements, while executive sponsorship, iterative implementation, and effective communication emerge as best practices for success.
As organizations embrace CMMI, they embark on a transformative journey towards operational maturity, guided by a framework that not only elevates their processes but also instills a culture of excellence and adaptability. By leveraging the core concepts, overcoming challenges, and embracing best practices, organizations can position themselves as industry leaders, capable of navigating the complexities of today's ever-changing business environment with confidence and success.
5G and IoT: A Powerful Combination for Connectivity
The advent of 5G technology has marked a transformative era in the realm of connectivity, promising unprecedented speed, low latency, and enhanced network capabilities. This fifth-generation wireless technology goes beyond merely improving our browsing experiences; it forms the backbone of a digital revolution that extends its influence to various industries and technologies. One of the most promising synergies emerging from the 5G landscape is its integration with the Internet of Things (IoT), creating a powerful alliance that has the potential to redefine how devices communicate, share data, and contribute to a seamlessly connected world.
As we delve into the intersection of 5G and IoT, it becomes evident that their combined capabilities unlock a new dimension of possibilities. The Internet of Things, characterized by interconnected devices exchanging information and performing tasks autonomously, gains a significant boost with the high-speed, low-latency nature of 5G networks. This synergy is poised to propel the growth of smart cities, autonomous vehicles, industrial automation, and countless other applications that demand rapid and reliable data transmission.
Moreover, the amalgamation of 5G and IoT is not confined to elevating the speed of data transfer. It brings forth a paradigm shift in how devices interact and collaborate, fostering an environment where real-time communication becomes the norm rather than the exception. This real-time connectivity has far-reaching implications, from enabling critical applications in healthcare to enhancing the efficiency of supply chain management. The seamless integration of 5G and IoT creates a robust foundation for innovation, paving the way for novel solutions and services that were once constrained by the limitations of previous-generation networks.
In this exploration of the powerful combination of 5G and IoT, it is essential to recognize the potential challenges and considerations that come with such technological advancements. From security concerns to the need for standardized protocols, navigating the intricacies of this evolving landscape requires a holistic understanding of the implications and a commitment to addressing the associated complexities. As we navigate this transformative journey, the fusion of 5G and IoT stands as a beacon guiding us toward a future where connectivity transcends its current boundaries, opening doors to unparalleled possibilities in the digital age.
Table of contents
-
Technical Foundations of 5G and IoT Integration
-
Enhancing Industrial Processes with 5G and IoT
-
Smart Cities and Urban Connectivity
-
Security Challenges and Solutions
-
Consumer Electronics and 5G
-
Edge Computing in the 5G-IoT Ecosystem
-
Conclusion
Technical Foundations of 5G and IoT Integration
The integration of 5G and the Internet of Things (IoT) is underpinned by a robust set of technical foundations that collectively redefine the landscape of connectivity. At the core of this integration lies the high-speed data transfer capabilities of 5G networks. With significantly increased data rates compared to its predecessors, 5G facilitates the rapid exchange of information between IoT devices, enabling them to communicate seamlessly and efficiently. This enhanced data transfer speed is a critical factor in supporting the diverse range of applications and services that rely on real-time data processing.
Low latency, another key element of 5G's technical prowess, plays a pivotal role in the integration with IoT. The near-instantaneous response times achieved by 5G networks reduce communication delays between devices, a crucial requirement for applications demanding real-time interactions. This is particularly relevant in scenarios such as autonomous vehicles, where split-second decision-making is imperative for safety and efficiency. The low-latency aspect of 5G is thus instrumental in unlocking the full potential of IoT applications that necessitate swift and reliable communication.
The technical foundations of 5G and IoT integration rest upon the pillars of high-speed data transfer, low latency, and the adaptability afforded by network slicing. This synergy not only addresses the connectivity needs of current IoT applications but also lays the groundwork for the emergence of innovative and transformative technologies that will shape the future of interconnected devices and services.
Enhancing Industrial Processes with 5G and IoT
The integration of 5G and the Internet of Things (IoT) holds profound implications for the industrial landscape, ushering in a new era marked by heightened efficiency, precision, and automation. One of the primary ways this synergy enhances industrial processes is through the concept of smart factories. With 5G's high-speed data transfer and low latency, IoT-enabled devices within manufacturing plants can communicate in real-time, optimizing production processes and reducing downtime. From predictive maintenance of machinery to the coordination of robotic systems, the integration of 5G and IoT empowers industries to operate with unprecedented levels of agility and responsiveness.
Predictive maintenance, enabled by the continuous monitoring and analysis of equipment through IoT sensors, stands as a transformative application in industrial settings. The timely detection of potential issues allows for proactive maintenance, minimizing unplanned downtime and extending the lifespan of machinery. The real-time insights provided by 5G-connected IoT devices contribute to a paradigm shift from reactive to proactive maintenance strategies, fundamentally altering how industries manage their assets.
The marriage of 5G and IoT is a catalyst for the transformation of industrial processes. The seamless connectivity, high data speeds, and low latency provided by 5G empower IoT devices to revolutionize manufacturing and operational practices. As industries continue to embrace these technologies, the prospect of smart factories and agile, data-driven decision-making emerges as a cornerstone in the evolution of modern industrial processes.
Smart Cities and Urban Connectivity
The fusion of 5G and the Internet of Things (IoT) is reshaping the urban landscape, giving rise to the concept of smart cities characterized by interconnected and intelligent infrastructure. This transformative synergy addresses the growing challenges faced by urban centers and propels cities into a future where efficiency, sustainability, and quality of life are paramount. At the heart of this evolution is the enhancement of urban connectivity through the deployment of 5G networks and the integration of IoT devices.
In the realm of smart cities, 5G's high-speed data transfer capabilities and low latency redefine the way urban systems operate. From traffic management and public safety to energy distribution and waste management, the integration of IoT sensors and devices leverages 5G connectivity to enable real-time data collection and analysis. This real-time responsiveness facilitates adaptive urban planning, allowing city authorities to make informed decisions promptly and address emerging challenges swiftly.
The collaboration between 5G and IoT is at the forefront of revolutionizing urban connectivity, giving rise to smart cities that are efficient, sustainable, and responsive to the needs of their residents. As this integration continues to evolve, the vision of interconnected urban environments holds the promise of enhancing the quality of life, promoting sustainability, and addressing the complex challenges faced by modern cities.
Security Challenges and Solutions
The integration of 5G and the Internet of Things (IoT) brings forth a myriad of opportunities, but it also introduces a complex array of security challenges that demand careful consideration and innovative solutions. As the number of interconnected devices increases exponentially, so does the attack surface, making the entire ecosystem susceptible to various cyber threats. One prominent challenge is the vulnerability of IoT devices, often characterized by limited computational capabilities and inadequate security measures. These devices, ranging from smart home appliances to industrial sensors, can become entry points for malicious actors if not adequately protected.
The nature of 5G networks introduces additional security concerns, particularly in the context of their virtualized and software-driven architecture. The reliance on software-defined processes and virtualized network functions creates potential points of entry for cyber threats. Moreover, the increased complexity of 5G networks amplifies the difficulty of monitoring and securing the vast number of connections and devices, making it essential to fortify the network against potential breaches.
While the integration of 5G and IoT brings unprecedented connectivity, addressing security challenges is paramount to ensuring the reliability and integrity of these advanced networks. By adopting a holistic and collaborative approach that encompasses encryption, authentication, secure development practices, and ongoing vigilance, stakeholders can build a resilient foundation for the secure coexistence of 5G and IoT technologies.
Consumer Electronics and 5G
The marriage of 5G technology with the Internet of Things (IoT) is reshaping the landscape of consumer electronics, ushering in a new era of connectivity and innovation. 5G's high-speed data transfer capabilities and low latency are revolutionizing the way consumers interact with their electronic devices, from smart homes to wearables and beyond. In the realm of consumer electronics, the integration of 5G brings forth a paradigm shift, offering enhanced experiences, increased device interactivity, and a broader scope of applications.
One of the notable impacts of 5G on consumer electronics is evident in the realm of smart homes. With the proliferation of IoT devices within households, ranging from smart thermostats and security cameras to connected appliances, 5G provides the bandwidth and responsiveness required for these devices to communicate seamlessly. Home automation becomes more sophisticated, allowing users to control and monitor various aspects of their homes remotely. The integration of 5G enables near-instantaneous responses, creating a more responsive and interactive smart home environment.
Entertainment experiences are elevated through 5G connectivity in consumer electronics. Streaming high-definition content, immersive virtual reality (VR), and augmented reality (AR) applications become more seamless and responsive, offering users a more immersive and engaging entertainment landscape. The integration of 5G enables faster downloads, reduced lag, and an overall improvement in the quality of multimedia experiences.
The fusion of 5G and consumer electronics marks a transformative moment in the way individuals interact with their devices. The high-speed, low-latency capabilities of 5G contribute to the evolution of smart homes, wearables, and entertainment systems, offering users enhanced connectivity, responsiveness, and a plethora of innovative applications. As consumer electronics continue to evolve within this interconnected ecosystem, the synergy between 5G and IoT is poised to redefine the possibilities of daily technological interactions.
Edge Computing in the 5G-IoT Ecosystem
Edge computing plays a pivotal role in the seamless integration of 5G and the Internet of Things (IoT), ushering in a paradigm shift in how data is processed and utilized within this dynamic ecosystem. At its core, edge computing involves the decentralization of computing resources, bringing data processing closer to the source of data generation. In the context of the 5G-IoT ecosystem, this approach becomes increasingly critical as it addresses the need for real-time data analysis, reduced latency, and efficient bandwidth utilization.
One of the key advantages of edge computing in the 5G-IoT landscape is its ability to alleviate latency concerns. By processing data closer to where it is generated, edge computing significantly reduces the time it takes for information to travel from IoT devices to centralized data centers and back. This is particularly crucial for applications that demand near-instantaneous responses, such as autonomous vehicles, smart grids, and industrial automation. The low-latency benefits of edge computing contribute to enhanced system responsiveness and overall efficiency.
The security implications of edge computing in the 5G-IoT ecosystem are noteworthy as well. By processing sensitive data locally, at the edge, organizations can mitigate potential risks associated with transmitting sensitive information across networks. This localized approach to data processing enhances privacy and security, aligning with the growing concerns surrounding the protection of IoT-generated data.
How to obtain Devops certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the intersection of 5G and the Internet of Things (IoT) represents a powerful symbiosis that is reshaping the landscape of connectivity and technological innovation. The technical foundations of 5G, including high-speed data transfer, low latency, and network slicing, provide the essential framework for the seamless integration of IoT devices, unlocking a new realm of possibilities across various industries and applications.
The enhanced connectivity facilitated by 5G and IoT is particularly evident in key domains such as industrial processes, where smart factories and predictive maintenance redefine efficiency, and in the development of smart cities, where urban connectivity is transforming the way cities operate, plan, and evolve. In healthcare, consumer electronics, and transportation, the amalgamation of 5G and IoT is driving advancements that were once constrained by the limitations of previous-generation networks.
As the integration of 5G and IoT continues to evolve, the promise of real-time connectivity, advanced automation, and data-driven decision-making comes to the forefront. Edge computing emerges as a critical enabler, addressing the need for reduced latency and efficient bandwidth utilization, while also enhancing the security posture of the interconnected ecosystem.
Looking forward, the collaborative efforts of industry stakeholders, ongoing research, and a commitment to addressing challenges will be instrumental in realizing the full potential of the 5G-IoT ecosystem. The journey towards a connected, intelligent, and responsive world is well underway, driven by the powerful combination of 5G and the Internet of Things. As these technologies continue to mature, the possibilities for innovation and positive societal impact are boundless, heralding a future where connectivity transcends current limitations, creating a foundation for a truly interconnected and intelligent world.
Read More
The advent of 5G technology has marked a transformative era in the realm of connectivity, promising unprecedented speed, low latency, and enhanced network capabilities. This fifth-generation wireless technology goes beyond merely improving our browsing experiences; it forms the backbone of a digital revolution that extends its influence to various industries and technologies. One of the most promising synergies emerging from the 5G landscape is its integration with the Internet of Things (IoT), creating a powerful alliance that has the potential to redefine how devices communicate, share data, and contribute to a seamlessly connected world.
As we delve into the intersection of 5G and IoT, it becomes evident that their combined capabilities unlock a new dimension of possibilities. The Internet of Things, characterized by interconnected devices exchanging information and performing tasks autonomously, gains a significant boost with the high-speed, low-latency nature of 5G networks. This synergy is poised to propel the growth of smart cities, autonomous vehicles, industrial automation, and countless other applications that demand rapid and reliable data transmission.
Moreover, the amalgamation of 5G and IoT is not confined to elevating the speed of data transfer. It brings forth a paradigm shift in how devices interact and collaborate, fostering an environment where real-time communication becomes the norm rather than the exception. This real-time connectivity has far-reaching implications, from enabling critical applications in healthcare to enhancing the efficiency of supply chain management. The seamless integration of 5G and IoT creates a robust foundation for innovation, paving the way for novel solutions and services that were once constrained by the limitations of previous-generation networks.
In this exploration of the powerful combination of 5G and IoT, it is essential to recognize the potential challenges and considerations that come with such technological advancements. From security concerns to the need for standardized protocols, navigating the intricacies of this evolving landscape requires a holistic understanding of the implications and a commitment to addressing the associated complexities. As we navigate this transformative journey, the fusion of 5G and IoT stands as a beacon guiding us toward a future where connectivity transcends its current boundaries, opening doors to unparalleled possibilities in the digital age.
Table of contents
-
Technical Foundations of 5G and IoT Integration
-
Enhancing Industrial Processes with 5G and IoT
-
Smart Cities and Urban Connectivity
-
Security Challenges and Solutions
-
Consumer Electronics and 5G
-
Edge Computing in the 5G-IoT Ecosystem
-
Conclusion
Technical Foundations of 5G and IoT Integration
The integration of 5G and the Internet of Things (IoT) is underpinned by a robust set of technical foundations that collectively redefine the landscape of connectivity. At the core of this integration lies the high-speed data transfer capabilities of 5G networks. With significantly increased data rates compared to its predecessors, 5G facilitates the rapid exchange of information between IoT devices, enabling them to communicate seamlessly and efficiently. This enhanced data transfer speed is a critical factor in supporting the diverse range of applications and services that rely on real-time data processing.
Low latency, another key element of 5G's technical prowess, plays a pivotal role in the integration with IoT. The near-instantaneous response times achieved by 5G networks reduce communication delays between devices, a crucial requirement for applications demanding real-time interactions. This is particularly relevant in scenarios such as autonomous vehicles, where split-second decision-making is imperative for safety and efficiency. The low-latency aspect of 5G is thus instrumental in unlocking the full potential of IoT applications that necessitate swift and reliable communication.
The technical foundations of 5G and IoT integration rest upon the pillars of high-speed data transfer, low latency, and the adaptability afforded by network slicing. This synergy not only addresses the connectivity needs of current IoT applications but also lays the groundwork for the emergence of innovative and transformative technologies that will shape the future of interconnected devices and services.
Enhancing Industrial Processes with 5G and IoT
The integration of 5G and the Internet of Things (IoT) holds profound implications for the industrial landscape, ushering in a new era marked by heightened efficiency, precision, and automation. One of the primary ways this synergy enhances industrial processes is through the concept of smart factories. With 5G's high-speed data transfer and low latency, IoT-enabled devices within manufacturing plants can communicate in real-time, optimizing production processes and reducing downtime. From predictive maintenance of machinery to the coordination of robotic systems, the integration of 5G and IoT empowers industries to operate with unprecedented levels of agility and responsiveness.
Predictive maintenance, enabled by the continuous monitoring and analysis of equipment through IoT sensors, stands as a transformative application in industrial settings. The timely detection of potential issues allows for proactive maintenance, minimizing unplanned downtime and extending the lifespan of machinery. The real-time insights provided by 5G-connected IoT devices contribute to a paradigm shift from reactive to proactive maintenance strategies, fundamentally altering how industries manage their assets.
The marriage of 5G and IoT is a catalyst for the transformation of industrial processes. The seamless connectivity, high data speeds, and low latency provided by 5G empower IoT devices to revolutionize manufacturing and operational practices. As industries continue to embrace these technologies, the prospect of smart factories and agile, data-driven decision-making emerges as a cornerstone in the evolution of modern industrial processes.
Smart Cities and Urban Connectivity
The fusion of 5G and the Internet of Things (IoT) is reshaping the urban landscape, giving rise to the concept of smart cities characterized by interconnected and intelligent infrastructure. This transformative synergy addresses the growing challenges faced by urban centers and propels cities into a future where efficiency, sustainability, and quality of life are paramount. At the heart of this evolution is the enhancement of urban connectivity through the deployment of 5G networks and the integration of IoT devices.
In the realm of smart cities, 5G's high-speed data transfer capabilities and low latency redefine the way urban systems operate. From traffic management and public safety to energy distribution and waste management, the integration of IoT sensors and devices leverages 5G connectivity to enable real-time data collection and analysis. This real-time responsiveness facilitates adaptive urban planning, allowing city authorities to make informed decisions promptly and address emerging challenges swiftly.
The collaboration between 5G and IoT is at the forefront of revolutionizing urban connectivity, giving rise to smart cities that are efficient, sustainable, and responsive to the needs of their residents. As this integration continues to evolve, the vision of interconnected urban environments holds the promise of enhancing the quality of life, promoting sustainability, and addressing the complex challenges faced by modern cities.
Security Challenges and Solutions
The integration of 5G and the Internet of Things (IoT) brings forth a myriad of opportunities, but it also introduces a complex array of security challenges that demand careful consideration and innovative solutions. As the number of interconnected devices increases exponentially, so does the attack surface, making the entire ecosystem susceptible to various cyber threats. One prominent challenge is the vulnerability of IoT devices, often characterized by limited computational capabilities and inadequate security measures. These devices, ranging from smart home appliances to industrial sensors, can become entry points for malicious actors if not adequately protected.
The nature of 5G networks introduces additional security concerns, particularly in the context of their virtualized and software-driven architecture. The reliance on software-defined processes and virtualized network functions creates potential points of entry for cyber threats. Moreover, the increased complexity of 5G networks amplifies the difficulty of monitoring and securing the vast number of connections and devices, making it essential to fortify the network against potential breaches.
While the integration of 5G and IoT brings unprecedented connectivity, addressing security challenges is paramount to ensuring the reliability and integrity of these advanced networks. By adopting a holistic and collaborative approach that encompasses encryption, authentication, secure development practices, and ongoing vigilance, stakeholders can build a resilient foundation for the secure coexistence of 5G and IoT technologies.
Consumer Electronics and 5G
The marriage of 5G technology with the Internet of Things (IoT) is reshaping the landscape of consumer electronics, ushering in a new era of connectivity and innovation. 5G's high-speed data transfer capabilities and low latency are revolutionizing the way consumers interact with their electronic devices, from smart homes to wearables and beyond. In the realm of consumer electronics, the integration of 5G brings forth a paradigm shift, offering enhanced experiences, increased device interactivity, and a broader scope of applications.
One of the notable impacts of 5G on consumer electronics is evident in the realm of smart homes. With the proliferation of IoT devices within households, ranging from smart thermostats and security cameras to connected appliances, 5G provides the bandwidth and responsiveness required for these devices to communicate seamlessly. Home automation becomes more sophisticated, allowing users to control and monitor various aspects of their homes remotely. The integration of 5G enables near-instantaneous responses, creating a more responsive and interactive smart home environment.
Entertainment experiences are elevated through 5G connectivity in consumer electronics. Streaming high-definition content, immersive virtual reality (VR), and augmented reality (AR) applications become more seamless and responsive, offering users a more immersive and engaging entertainment landscape. The integration of 5G enables faster downloads, reduced lag, and an overall improvement in the quality of multimedia experiences.
The fusion of 5G and consumer electronics marks a transformative moment in the way individuals interact with their devices. The high-speed, low-latency capabilities of 5G contribute to the evolution of smart homes, wearables, and entertainment systems, offering users enhanced connectivity, responsiveness, and a plethora of innovative applications. As consumer electronics continue to evolve within this interconnected ecosystem, the synergy between 5G and IoT is poised to redefine the possibilities of daily technological interactions.
Edge Computing in the 5G-IoT Ecosystem
Edge computing plays a pivotal role in the seamless integration of 5G and the Internet of Things (IoT), ushering in a paradigm shift in how data is processed and utilized within this dynamic ecosystem. At its core, edge computing involves the decentralization of computing resources, bringing data processing closer to the source of data generation. In the context of the 5G-IoT ecosystem, this approach becomes increasingly critical as it addresses the need for real-time data analysis, reduced latency, and efficient bandwidth utilization.
One of the key advantages of edge computing in the 5G-IoT landscape is its ability to alleviate latency concerns. By processing data closer to where it is generated, edge computing significantly reduces the time it takes for information to travel from IoT devices to centralized data centers and back. This is particularly crucial for applications that demand near-instantaneous responses, such as autonomous vehicles, smart grids, and industrial automation. The low-latency benefits of edge computing contribute to enhanced system responsiveness and overall efficiency.
The security implications of edge computing in the 5G-IoT ecosystem are noteworthy as well. By processing sensitive data locally, at the edge, organizations can mitigate potential risks associated with transmitting sensitive information across networks. This localized approach to data processing enhances privacy and security, aligning with the growing concerns surrounding the protection of IoT-generated data.
How to obtain Devops certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the intersection of 5G and the Internet of Things (IoT) represents a powerful symbiosis that is reshaping the landscape of connectivity and technological innovation. The technical foundations of 5G, including high-speed data transfer, low latency, and network slicing, provide the essential framework for the seamless integration of IoT devices, unlocking a new realm of possibilities across various industries and applications.
The enhanced connectivity facilitated by 5G and IoT is particularly evident in key domains such as industrial processes, where smart factories and predictive maintenance redefine efficiency, and in the development of smart cities, where urban connectivity is transforming the way cities operate, plan, and evolve. In healthcare, consumer electronics, and transportation, the amalgamation of 5G and IoT is driving advancements that were once constrained by the limitations of previous-generation networks.
As the integration of 5G and IoT continues to evolve, the promise of real-time connectivity, advanced automation, and data-driven decision-making comes to the forefront. Edge computing emerges as a critical enabler, addressing the need for reduced latency and efficient bandwidth utilization, while also enhancing the security posture of the interconnected ecosystem.
Looking forward, the collaborative efforts of industry stakeholders, ongoing research, and a commitment to addressing challenges will be instrumental in realizing the full potential of the 5G-IoT ecosystem. The journey towards a connected, intelligent, and responsive world is well underway, driven by the powerful combination of 5G and the Internet of Things. As these technologies continue to mature, the possibilities for innovation and positive societal impact are boundless, heralding a future where connectivity transcends current limitations, creating a foundation for a truly interconnected and intelligent world.
COBIT® 5 Foundation and IT Service Management (ITSM): Achieving Synergy
The convergence of COBIT® 5 Foundation and IT Service Management (ITSM) represents a dynamic and synergistic approach to enhancing organizational governance and optimizing IT service delivery. COBIT® 5, developed by the Information Systems Audit and Control Association (ISACA), is a globally recognized framework that provides a comprehensive set of principles, practices, and analytical tools for the effective governance and management of enterprise IT. On the other hand, IT Service Management focuses on aligning IT services with the needs of the business, emphasizing the delivery of high-quality services that meet customer expectations.
In recent years, organizations have increasingly recognized the need to integrate and harmonize their governance and service management practices. The collaboration between COBIT® 5 Foundation and ITSM offers a strategic alignment that enables businesses to achieve a more seamless and efficient IT environment. This integration is particularly crucial in today's complex and rapidly evolving digital landscape, where organizations must navigate challenges such as cybersecurity threats, regulatory compliance, and the ever-growing demand for innovative IT services.
The foundational principles of COBIT® 5, which include a focus on stakeholder value, risk management, and continual improvement, align seamlessly with the core objectives of IT Service Management. By combining these frameworks, organizations can establish a robust foundation for achieving not only compliance and risk mitigation but also the delivery of high-quality, customer-centric IT services. This synergy empowers businesses to streamline their processes, enhance decision-making, and foster a culture of collaboration across different functional areas.
Table of contents
-
Overview of COBIT® 5 Foundation
-
Essentials of IT Service Management (ITSM)
-
Governance and Risk Management Integration
-
Implementing the Synergy: Step-by-Step Guide
-
Measuring Success: Key Performance Indicators (KPIs)
-
Conclusion
Overview of COBIT® 5 Foundation
COBIT® 5 Foundation serves as a comprehensive framework developed by the Information Systems Audit and Control Association (ISACA) to guide organizations in achieving effective governance and management of information technology (IT). At its core, COBIT® (Control Objectives for Information and Related Technologies) emphasizes the importance of aligning IT processes with business objectives, ensuring that IT activities contribute directly to organizational success. The framework provides a set of principles, practices, and enablers that support enterprises in optimizing their IT capabilities while managing associated risks and ensuring the delivery of value to stakeholders.
The COBIT® 5 Foundation framework is structured around five key principles, each contributing to the achievement of effective IT governance. These principles include meeting stakeholder needs, covering the enterprise end-to-end, applying a single integrated framework, enabling a holistic approach, and separating governance from management. Together, these principles guide organizations in establishing a governance and management system that is both efficient and adaptable to the evolving landscape of IT and business.
COBIT® 5 Foundation offers a structured and comprehensive approach to IT governance, emphasizing stakeholder value, principled practices, and adaptability to the ever-changing IT landscape. By leveraging this framework, organizations can establish a robust foundation for effective governance, risk management, and the continuous improvement of their IT processes, ultimately contributing to enhanced overall business performance.
Essentials of IT Service Management (ITSM)
Essentials of IT Service Management (ITSM) form the foundational principles and practices that organizations adopt to ensure the effective delivery and support of IT services aligned with business objectives. At its core, ITSM revolves around meeting the needs of users, optimizing service quality, and enhancing overall organizational efficiency. The following components encapsulate the key essentials of ITSM:
Service Strategy constitutes a critical pillar of ITSM, involving the development of a comprehensive strategy aligned with business goals. This phase entails understanding customer needs, defining service offerings, and formulating a strategic roadmap for delivering IT services that contribute directly to the success of the organization.
In the Service Design phase, the focus shifts to creating service solutions that meet the requirements outlined in the service strategy. This encompasses designing processes, technologies, and other essential elements necessary for the efficient and effective delivery of high-quality services. Service design ensures that IT services are not only functional but also meet the broader objectives of the organization.
Service Transition is a crucial aspect of ITSM that involves planning and managing changes to services and service management processes. This phase ensures a smooth transition of new or modified services into the operational environment while minimizing disruptions. It encompasses activities such as change management, release and deployment management, and knowledge management.
Continual Service Improvement (CSI) serves as a guiding principle within ITSM, emphasizing the necessity of ongoing enhancement and optimization of services and processes. Through regular assessments, feedback mechanisms, and a commitment to learning from experiences, organizations practicing ITSM can identify areas for improvement and ensure a cycle of continuous enhancement in service delivery and operational efficiency. Together, these essentials form a holistic framework for organizations seeking to align their IT services with business goals, enhance customer satisfaction, and adapt to the dynamic landscape of technology and user expectations.
Governance and Risk Management Integration
In the realm of governance and risk management integration, organizations benefit from fostering a culture of risk awareness and accountability. This cultural shift encourages employees at all levels to recognize and report risks, fostering a collective responsibility for risk mitigation. By incorporating risk considerations into the organization's values and day-to-day operations, companies can create a more proactive and resilient stance toward potential challenges.
Integration also involves the development and implementation of robust risk management frameworks that seamlessly align with governance structures. This includes defining clear roles and responsibilities for risk management at various levels of the organization, establishing effective communication channels for sharing risk information, and integrating risk assessments into strategic planning processes. Such frameworks not only identify potential risks but also provide a structured approach to managing and monitoring these risks over time.
Continuous learning and improvement are inherent components of successful integration. Organizations should conduct periodic reviews and audits to evaluate the effectiveness of their integrated governance and risk management approach. Lessons learned from incidents and successes should be incorporated into future strategies, fostering a dynamic and adaptive governance structure that evolves in tandem with the changing risk landscape.
Governance and risk management integration is a multifaceted and ongoing process that requires a commitment to cultural change, technological innovation, and continuous improvement. By weaving risk considerations into the fabric of governance structures, organizations can enhance their resilience, make more informed decisions, and navigate an increasingly complex and uncertain business environment.
Implementing the Synergy: Step-by-Step Guide
Implementing the synergy between COBIT® 5 Foundation and IT Service Management (ITSM) is a strategic imperative that demands a methodical and well-coordinated approach. Commencing with a thorough assessment of the current state of IT governance and service management, organizations gain a foundational understanding of existing processes and their maturity. This assessment sets the stage for subsequent integration efforts, providing valuable insights into the organization's strengths and areas for improvement.
Precise definition of integration objectives and scope follows, as organizations articulate the desired outcomes and benefits to be derived from the amalgamation of COBIT® 5 Foundation and ITSM. A clear scope ensures that efforts remain focused on specific goals, preventing potential deviations and ensuring a streamlined implementation process. Stakeholder engagement becomes paramount, involving key representatives from IT and business units to gather diverse perspectives and ensure alignment with overarching organizational goals. This collaborative engagement fosters buy-in and support crucial for the successful integration.
Key performance indicators (KPIs) are established to measure the success of the integration, encompassing governance effectiveness, service delivery efficiency, and overall alignment with organizational objectives. Regular monitoring and assessment of these indicators offer valuable insights into the performance and impact of the integrated framework, guiding ongoing improvements.
Implementation efforts extend to training programs and change management initiatives, ensuring that teams are equipped with the necessary knowledge and skills to operate within the integrated framework. Pilot programs may be initiated in specific departments or business units to test the integrated framework in a controlled environment, allowing for the identification and resolution of potential challenges before full-scale deployment. Continuous monitoring and evaluation mechanisms are established to assess the ongoing effectiveness of the integrated COBIT® 5 Foundation and ITSM framework, incorporating feedback from users and stakeholders to drive necessary adjustments.
Cultivating a culture of continuous improvement is emphasized, encouraging teams to identify opportunities for enhancement and establishing mechanisms for regular reviews and refinements to the integrated framework. This adaptive approach ensures the sustained success of the integration, aligning IT services seamlessly with business objectives while fostering a dynamic and resilient organizational environment. In conclusion, this step-by-step guide serves as a comprehensive and structured approach to implementing the synergy between COBIT® 5 Foundation and IT Service Management, ultimately enhancing governance practices and optimizing the delivery of IT services.
Measuring Success: Key Performance Indicators (KPIs)
Measuring the success of the integration between COBIT® 5 Foundation and IT Service Management (ITSM) relies on a thoughtful selection of Key Performance Indicators (KPIs) that encompass various aspects critical to the alignment of governance and service delivery. One pivotal category of KPIs revolves around strategic alignment, evaluating how effectively the integrated framework contributes to organizational objectives. These indicators provide a holistic view of whether the governance practices and IT service delivery align with and support the broader strategic vision of the organization, emphasizing the symbiotic relationship between IT initiatives and overall business goals.
Governance effectiveness serves as another crucial dimension for assessing success. KPIs within this category focus on evaluating the efficiency and efficacy of governance processes. Metrics such as the speed of decision-making, compliance levels, and the responsiveness of governance structures offer insights into how well the organization is managing its IT resources and risks. These indicators serve as a barometer for the overall health and effectiveness of the governance component within the integrated framework.
User satisfaction and experience KPIs form a vital component, providing insights into the impact of the integrated framework on end-users. Metrics such as user satisfaction surveys, feedback on service quality, and user adoption rates offer a qualitative assessment of how well the integrated approach meets stakeholder expectations. These indicators are crucial for ensuring a positive and productive user experience, as the success of the integration is ultimately measured by the satisfaction and engagement of the end-users.
A continuous improvement mindset is integral to sustained success, and corresponding KPIs focus on the organization's ability to adapt and refine the integrated framework over time. Metrics related to the frequency and effectiveness of updates and refinements, as well as the organization's agility in responding to emerging challenges, highlight the dynamic nature of governance and service management integration. Success, in this context, is not merely a destination but an ongoing journey of refinement and adaptation to ensure that governance and service management practices evolve in tandem with organizational goals and the evolving IT landscape.
How to obtain COBIT® 5 Foundation certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the pursuit of synergy between COBIT® 5 Foundation and IT Service Management (ITSM) stands as a transformative endeavor, poised to elevate organizational effectiveness in IT governance and service delivery. This convergence represents a strategic alignment that, when carefully implemented, holds the promise of harmonizing IT processes, optimizing risk management, and enhancing the delivery of IT services in line with business objectives.
The step-by-step guide provided for achieving this synergy emphasizes the importance of a systematic and collaborative approach. From the initial assessment of the current state to the establishment of key performance indicators (KPIs) for ongoing measurement, the guide offers a structured pathway for organizations to navigate the integration process. Defining clear objectives, engaging stakeholders, and fostering a culture of continuous improvement emerge as pivotal elements, ensuring that the integration is purposeful, inclusive, and adaptable to the evolving landscape of IT and business dynamics.
The seamless alignment of COBIT® 5 Foundation and ITSM processes contributes not only to operational efficiency but also to a more resilient and responsive IT ecosystem. By integrating governance and service management, organizations are better equipped to meet the ever-changing needs of stakeholders, enhance risk mitigation strategies, and cultivate a customer-centric approach to IT services.
As organizations embark on this journey of achieving synergy between COBIT® 5 Foundation and ITSM, the ultimate goal is to create a dynamic and adaptive IT environment. This integration is not a static achievement but a continuous process of refinement and optimization. Success is measured not just by the integration itself but by the sustained ability to deliver value, align with strategic goals, and proactively respond to the challenges and opportunities inherent in the digital landscape. In essence, achieving synergy between COBIT® 5 Foundation and ITSM is a strategic imperative that positions organizations to thrive in an era where effective governance and agile service management are essential for sustained success.
Read More
The convergence of COBIT® 5 Foundation and IT Service Management (ITSM) represents a dynamic and synergistic approach to enhancing organizational governance and optimizing IT service delivery. COBIT® 5, developed by the Information Systems Audit and Control Association (ISACA), is a globally recognized framework that provides a comprehensive set of principles, practices, and analytical tools for the effective governance and management of enterprise IT. On the other hand, IT Service Management focuses on aligning IT services with the needs of the business, emphasizing the delivery of high-quality services that meet customer expectations.
In recent years, organizations have increasingly recognized the need to integrate and harmonize their governance and service management practices. The collaboration between COBIT® 5 Foundation and ITSM offers a strategic alignment that enables businesses to achieve a more seamless and efficient IT environment. This integration is particularly crucial in today's complex and rapidly evolving digital landscape, where organizations must navigate challenges such as cybersecurity threats, regulatory compliance, and the ever-growing demand for innovative IT services.
The foundational principles of COBIT® 5, which include a focus on stakeholder value, risk management, and continual improvement, align seamlessly with the core objectives of IT Service Management. By combining these frameworks, organizations can establish a robust foundation for achieving not only compliance and risk mitigation but also the delivery of high-quality, customer-centric IT services. This synergy empowers businesses to streamline their processes, enhance decision-making, and foster a culture of collaboration across different functional areas.
Table of contents
-
Overview of COBIT® 5 Foundation
-
Essentials of IT Service Management (ITSM)
-
Governance and Risk Management Integration
-
Implementing the Synergy: Step-by-Step Guide
-
Measuring Success: Key Performance Indicators (KPIs)
-
Conclusion
Overview of COBIT® 5 Foundation
COBIT® 5 Foundation serves as a comprehensive framework developed by the Information Systems Audit and Control Association (ISACA) to guide organizations in achieving effective governance and management of information technology (IT). At its core, COBIT® (Control Objectives for Information and Related Technologies) emphasizes the importance of aligning IT processes with business objectives, ensuring that IT activities contribute directly to organizational success. The framework provides a set of principles, practices, and enablers that support enterprises in optimizing their IT capabilities while managing associated risks and ensuring the delivery of value to stakeholders.
The COBIT® 5 Foundation framework is structured around five key principles, each contributing to the achievement of effective IT governance. These principles include meeting stakeholder needs, covering the enterprise end-to-end, applying a single integrated framework, enabling a holistic approach, and separating governance from management. Together, these principles guide organizations in establishing a governance and management system that is both efficient and adaptable to the evolving landscape of IT and business.
COBIT® 5 Foundation offers a structured and comprehensive approach to IT governance, emphasizing stakeholder value, principled practices, and adaptability to the ever-changing IT landscape. By leveraging this framework, organizations can establish a robust foundation for effective governance, risk management, and the continuous improvement of their IT processes, ultimately contributing to enhanced overall business performance.
Essentials of IT Service Management (ITSM)
Essentials of IT Service Management (ITSM) form the foundational principles and practices that organizations adopt to ensure the effective delivery and support of IT services aligned with business objectives. At its core, ITSM revolves around meeting the needs of users, optimizing service quality, and enhancing overall organizational efficiency. The following components encapsulate the key essentials of ITSM:
Service Strategy constitutes a critical pillar of ITSM, involving the development of a comprehensive strategy aligned with business goals. This phase entails understanding customer needs, defining service offerings, and formulating a strategic roadmap for delivering IT services that contribute directly to the success of the organization.
In the Service Design phase, the focus shifts to creating service solutions that meet the requirements outlined in the service strategy. This encompasses designing processes, technologies, and other essential elements necessary for the efficient and effective delivery of high-quality services. Service design ensures that IT services are not only functional but also meet the broader objectives of the organization.
Service Transition is a crucial aspect of ITSM that involves planning and managing changes to services and service management processes. This phase ensures a smooth transition of new or modified services into the operational environment while minimizing disruptions. It encompasses activities such as change management, release and deployment management, and knowledge management.
Continual Service Improvement (CSI) serves as a guiding principle within ITSM, emphasizing the necessity of ongoing enhancement and optimization of services and processes. Through regular assessments, feedback mechanisms, and a commitment to learning from experiences, organizations practicing ITSM can identify areas for improvement and ensure a cycle of continuous enhancement in service delivery and operational efficiency. Together, these essentials form a holistic framework for organizations seeking to align their IT services with business goals, enhance customer satisfaction, and adapt to the dynamic landscape of technology and user expectations.
Governance and Risk Management Integration
In the realm of governance and risk management integration, organizations benefit from fostering a culture of risk awareness and accountability. This cultural shift encourages employees at all levels to recognize and report risks, fostering a collective responsibility for risk mitigation. By incorporating risk considerations into the organization's values and day-to-day operations, companies can create a more proactive and resilient stance toward potential challenges.
Integration also involves the development and implementation of robust risk management frameworks that seamlessly align with governance structures. This includes defining clear roles and responsibilities for risk management at various levels of the organization, establishing effective communication channels for sharing risk information, and integrating risk assessments into strategic planning processes. Such frameworks not only identify potential risks but also provide a structured approach to managing and monitoring these risks over time.
Continuous learning and improvement are inherent components of successful integration. Organizations should conduct periodic reviews and audits to evaluate the effectiveness of their integrated governance and risk management approach. Lessons learned from incidents and successes should be incorporated into future strategies, fostering a dynamic and adaptive governance structure that evolves in tandem with the changing risk landscape.
Governance and risk management integration is a multifaceted and ongoing process that requires a commitment to cultural change, technological innovation, and continuous improvement. By weaving risk considerations into the fabric of governance structures, organizations can enhance their resilience, make more informed decisions, and navigate an increasingly complex and uncertain business environment.
Implementing the Synergy: Step-by-Step Guide
Implementing the synergy between COBIT® 5 Foundation and IT Service Management (ITSM) is a strategic imperative that demands a methodical and well-coordinated approach. Commencing with a thorough assessment of the current state of IT governance and service management, organizations gain a foundational understanding of existing processes and their maturity. This assessment sets the stage for subsequent integration efforts, providing valuable insights into the organization's strengths and areas for improvement.
Precise definition of integration objectives and scope follows, as organizations articulate the desired outcomes and benefits to be derived from the amalgamation of COBIT® 5 Foundation and ITSM. A clear scope ensures that efforts remain focused on specific goals, preventing potential deviations and ensuring a streamlined implementation process. Stakeholder engagement becomes paramount, involving key representatives from IT and business units to gather diverse perspectives and ensure alignment with overarching organizational goals. This collaborative engagement fosters buy-in and support crucial for the successful integration.
Key performance indicators (KPIs) are established to measure the success of the integration, encompassing governance effectiveness, service delivery efficiency, and overall alignment with organizational objectives. Regular monitoring and assessment of these indicators offer valuable insights into the performance and impact of the integrated framework, guiding ongoing improvements.
Implementation efforts extend to training programs and change management initiatives, ensuring that teams are equipped with the necessary knowledge and skills to operate within the integrated framework. Pilot programs may be initiated in specific departments or business units to test the integrated framework in a controlled environment, allowing for the identification and resolution of potential challenges before full-scale deployment. Continuous monitoring and evaluation mechanisms are established to assess the ongoing effectiveness of the integrated COBIT® 5 Foundation and ITSM framework, incorporating feedback from users and stakeholders to drive necessary adjustments.
Cultivating a culture of continuous improvement is emphasized, encouraging teams to identify opportunities for enhancement and establishing mechanisms for regular reviews and refinements to the integrated framework. This adaptive approach ensures the sustained success of the integration, aligning IT services seamlessly with business objectives while fostering a dynamic and resilient organizational environment. In conclusion, this step-by-step guide serves as a comprehensive and structured approach to implementing the synergy between COBIT® 5 Foundation and IT Service Management, ultimately enhancing governance practices and optimizing the delivery of IT services.
Measuring Success: Key Performance Indicators (KPIs)
Measuring the success of the integration between COBIT® 5 Foundation and IT Service Management (ITSM) relies on a thoughtful selection of Key Performance Indicators (KPIs) that encompass various aspects critical to the alignment of governance and service delivery. One pivotal category of KPIs revolves around strategic alignment, evaluating how effectively the integrated framework contributes to organizational objectives. These indicators provide a holistic view of whether the governance practices and IT service delivery align with and support the broader strategic vision of the organization, emphasizing the symbiotic relationship between IT initiatives and overall business goals.
Governance effectiveness serves as another crucial dimension for assessing success. KPIs within this category focus on evaluating the efficiency and efficacy of governance processes. Metrics such as the speed of decision-making, compliance levels, and the responsiveness of governance structures offer insights into how well the organization is managing its IT resources and risks. These indicators serve as a barometer for the overall health and effectiveness of the governance component within the integrated framework.
User satisfaction and experience KPIs form a vital component, providing insights into the impact of the integrated framework on end-users. Metrics such as user satisfaction surveys, feedback on service quality, and user adoption rates offer a qualitative assessment of how well the integrated approach meets stakeholder expectations. These indicators are crucial for ensuring a positive and productive user experience, as the success of the integration is ultimately measured by the satisfaction and engagement of the end-users.
A continuous improvement mindset is integral to sustained success, and corresponding KPIs focus on the organization's ability to adapt and refine the integrated framework over time. Metrics related to the frequency and effectiveness of updates and refinements, as well as the organization's agility in responding to emerging challenges, highlight the dynamic nature of governance and service management integration. Success, in this context, is not merely a destination but an ongoing journey of refinement and adaptation to ensure that governance and service management practices evolve in tandem with organizational goals and the evolving IT landscape.
How to obtain COBIT® 5 Foundation certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the pursuit of synergy between COBIT® 5 Foundation and IT Service Management (ITSM) stands as a transformative endeavor, poised to elevate organizational effectiveness in IT governance and service delivery. This convergence represents a strategic alignment that, when carefully implemented, holds the promise of harmonizing IT processes, optimizing risk management, and enhancing the delivery of IT services in line with business objectives.
The step-by-step guide provided for achieving this synergy emphasizes the importance of a systematic and collaborative approach. From the initial assessment of the current state to the establishment of key performance indicators (KPIs) for ongoing measurement, the guide offers a structured pathway for organizations to navigate the integration process. Defining clear objectives, engaging stakeholders, and fostering a culture of continuous improvement emerge as pivotal elements, ensuring that the integration is purposeful, inclusive, and adaptable to the evolving landscape of IT and business dynamics.
The seamless alignment of COBIT® 5 Foundation and ITSM processes contributes not only to operational efficiency but also to a more resilient and responsive IT ecosystem. By integrating governance and service management, organizations are better equipped to meet the ever-changing needs of stakeholders, enhance risk mitigation strategies, and cultivate a customer-centric approach to IT services.
As organizations embark on this journey of achieving synergy between COBIT® 5 Foundation and ITSM, the ultimate goal is to create a dynamic and adaptive IT environment. This integration is not a static achievement but a continuous process of refinement and optimization. Success is measured not just by the integration itself but by the sustained ability to deliver value, align with strategic goals, and proactively respond to the challenges and opportunities inherent in the digital landscape. In essence, achieving synergy between COBIT® 5 Foundation and ITSM is a strategic imperative that positions organizations to thrive in an era where effective governance and agile service management are essential for sustained success.
Unlock New Career Opportunities with CBAP Certification
Introduction
Are you looking to enhance your career as a business analyst? Do you want to stand out from the competition and unlock new opportunities in the field? Look no further than the Certified Business Analysis Professional Certification (CBAP). This prestigious certification not only validates your expertise and knowledge but also opens doors to exciting career advancements. In this article, we will explore what the CBAP certification is all about and how it can benefit aspiring business analysts like yourself.
What is the CBAP Certification?
The CBAP certification, also known as the Certified Business Analysis Professional Certification, is a globally recognized credential for business analysts. It is offered by the International Institute of Business Analysis (IIBA), the leading professional association for business analysts worldwide. This certification demonstrates your commitment to the field and showcases your proficiency in various business analysis tasks and techniques.
Benefits of the CBAP Certification
1. Enhanced Career Opportunities
Obtaining the CBAP certification can significantly enhance your career opportunities. Many organizations value and seek professionals who possess this esteemed credential. It distinguishes you from other candidates and increases your chances of securing high-level positions in the industry. This certification serves as proof of your skills, experience, and dedication to professional development.
2. Industry Recognition and Credibility
The CBAP certification is widely recognized in the business analysis community. It establishes your credibility as a professional business analyst, earning the trust of employers, clients, and colleagues alike. It demonstrates that you have met rigorous standards set by the IIBA and have the knowledge and expertise required to excel in the field.
3. Expanded Skill Set
Preparing for the CBAP certification requires you to delve deep into various aspects of business analysis. As a result, you gain an expanded skill set that covers essential areas such as requirements management, business analysis planning, stakeholder engagement, and solution evaluation. This comprehensive knowledge equips you to tackle complex business challenges and deliver effective solutions.
How to Become a CBAP
To become a CBAP, you must fulfill certain eligibility criteria and pass a rigorous examination. Here are the steps you need to follow:
Eligibility Criteria: You must have a minimum of 7,500 hours of business analysis experience in the past 10 years, along with a minimum of 900 hours across at least 4 of the 6 knowledge areas defined by the IIBA BABOK Guide. Additionally, you must have completed at least 35 hours of professional development in the field of business analysis.
Submit Your Application: Once you meet the eligibility criteria, you need to submit an application to the IIBA for review. This application includes details of your work experience, education, and professional development activities.
Prepare for the Examination: After your application is approved, you can start preparing for the CBAP examination. The examination tests your knowledge and comprehension of the BABOK Guide and assesses your ability to apply business analysis principles and techniques.
Pass the Examination: Passing the CBAP examination demonstrates your competence in business analysis. It signifies that you have the necessary skills and knowledge to excel in your role as a business analyst.
Maintain Your Certification: Once you have obtained your CBAP certification, you need to maintain it by earning Continuing Development Units (CDUs) every three years. This ensures that you stay up-to-date with evolving industry practices and trends.
Conclusion
The CBAP certification is much more than just a piece of paper. It is a testament to your expertise, commitment, and dedication to the field of business analysis. Unlocking new career opportunities becomes a reality as you showcase your skills and gain industry recognition. So, if you are an aspiring business analyst looking to take your career to new heights, consider pursuing the Certified Business Analysis Professional Certification. Take the leap and embrace the endless possibilities that await you!
Read More
Introduction
Are you looking to enhance your career as a business analyst? Do you want to stand out from the competition and unlock new opportunities in the field? Look no further than the Certified Business Analysis Professional Certification (CBAP). This prestigious certification not only validates your expertise and knowledge but also opens doors to exciting career advancements. In this article, we will explore what the CBAP certification is all about and how it can benefit aspiring business analysts like yourself.
What is the CBAP Certification?
The CBAP certification, also known as the Certified Business Analysis Professional Certification, is a globally recognized credential for business analysts. It is offered by the International Institute of Business Analysis (IIBA), the leading professional association for business analysts worldwide. This certification demonstrates your commitment to the field and showcases your proficiency in various business analysis tasks and techniques.
Benefits of the CBAP Certification
1. Enhanced Career Opportunities
Obtaining the CBAP certification can significantly enhance your career opportunities. Many organizations value and seek professionals who possess this esteemed credential. It distinguishes you from other candidates and increases your chances of securing high-level positions in the industry. This certification serves as proof of your skills, experience, and dedication to professional development.
2. Industry Recognition and Credibility
The CBAP certification is widely recognized in the business analysis community. It establishes your credibility as a professional business analyst, earning the trust of employers, clients, and colleagues alike. It demonstrates that you have met rigorous standards set by the IIBA and have the knowledge and expertise required to excel in the field.
3. Expanded Skill Set
Preparing for the CBAP certification requires you to delve deep into various aspects of business analysis. As a result, you gain an expanded skill set that covers essential areas such as requirements management, business analysis planning, stakeholder engagement, and solution evaluation. This comprehensive knowledge equips you to tackle complex business challenges and deliver effective solutions.
How to Become a CBAP
To become a CBAP, you must fulfill certain eligibility criteria and pass a rigorous examination. Here are the steps you need to follow:
Eligibility Criteria: You must have a minimum of 7,500 hours of business analysis experience in the past 10 years, along with a minimum of 900 hours across at least 4 of the 6 knowledge areas defined by the IIBA BABOK Guide. Additionally, you must have completed at least 35 hours of professional development in the field of business analysis.
Submit Your Application: Once you meet the eligibility criteria, you need to submit an application to the IIBA for review. This application includes details of your work experience, education, and professional development activities.
Prepare for the Examination: After your application is approved, you can start preparing for the CBAP examination. The examination tests your knowledge and comprehension of the BABOK Guide and assesses your ability to apply business analysis principles and techniques.
Pass the Examination: Passing the CBAP examination demonstrates your competence in business analysis. It signifies that you have the necessary skills and knowledge to excel in your role as a business analyst.
Maintain Your Certification: Once you have obtained your CBAP certification, you need to maintain it by earning Continuing Development Units (CDUs) every three years. This ensures that you stay up-to-date with evolving industry practices and trends.
Conclusion
The CBAP certification is much more than just a piece of paper. It is a testament to your expertise, commitment, and dedication to the field of business analysis. Unlocking new career opportunities becomes a reality as you showcase your skills and gain industry recognition. So, if you are an aspiring business analyst looking to take your career to new heights, consider pursuing the Certified Business Analysis Professional Certification. Take the leap and embrace the endless possibilities that await you!
Quality Management: Definition, Importance, Components
Introduction
Quality management plays a crucial role in ensuring the success of businesses across various industries. It involves a systematic approach to maintaining and improving the quality of products, services, and processes. In this article, we will explore the definition, importance, and components of quality management and delve into the concept of Total Quality Management.
Quality Management System (QMS)
A Quality Management System (QMS) is the framework that enables organizations to establish and uphold their commitment to quality. It encompasses the policies, procedures, and processes that guide the organization in achieving its quality objectives. The QMS serves as the backbone of quality management, providing a structured framework for identifying, controlling, and improving quality-related activities.
Importance of Quality Management
Quality management is of utmost importance for businesses, as it offers several significant benefits. Let's take a closer look at why quality management is vital:
1. Customer Satisfaction
In today's competitive market, customer satisfaction is a top priority for businesses. Quality management ensures that products and services meet or exceed customer expectations, leading to increased satisfaction and loyalty. Satisfied customers not only become repeat customers but also act as brand advocates, attracting new customers through positive word-of-mouth.
2. Cost Reduction
Implementing quality management practices can result in cost reductions for businesses. By identifying and eliminating inefficiencies, defects, and non-value-added activities, organizations can streamline their processes and improve overall productivity. This, in turn, leads to lower production costs, reduced waste, and increased profitability.
3. Brand Reputation
Maintaining a strong brand reputation is vital for businesses to thrive in today's competitive landscape. Quality management helps organizations consistently deliver high-quality products and services, earning them a favorable reputation among customers, partners, and stakeholders. A positive brand image fosters trust, credibility, and long-term success.
4. Compliance and Risk Mitigation
Compliance with industry standards, regulations, and quality requirements is critical for businesses to avoid legal liabilities and penalties. Quality management ensures adherence to these standards, reducing the risk of non-compliance and associated risks. By identifying and mitigating potential risks, organizations can proactively protect their interests and reputation.
Quality Components
Quality management involves various components that collectively contribute to achieving high standards of quality. Let's explore some key quality components:
1. Quality Planning
Quality planning involves defining quality standards, setting objectives, and determining the processes required to meet those standards. It includes identifying customer requirements, establishing quality metrics, and establishing a framework for continuous improvement.
2. Quality Assurance
Quality assurance focuses on preventing defects and ensuring compliance with established quality standards. It involves the implementation of processes, procedures, and controls to verify that products and services meet quality requirements. Quality audits are often conducted to assess the effectiveness of quality assurance activities.
3. Quality Control
Quality control is the process of monitoring and inspecting products, services, and processes to ensure they meet predetermined quality standards. It involves activities such as inspections, testing, and data analysis to detect and correct any deviations from the desired quality level.
4. Continuous Improvement
Continuous improvement is a fundamental concept in quality management, aiming to enhance processes, products, and services over time. It involves regular evaluation, identification of areas for improvement, and the implementation of measures to drive ongoing progress. Continuous improvement fosters innovation, efficiency, and customer satisfaction.
Total Quality Management (TQM)
Total Quality Management (TQM) is a comprehensive approach to quality management that emphasizes the involvement of every individual in an organization. It integrates all aspects of quality management, focusing on meeting customer needs and achieving organizational goals. TQM encourages a culture of continuous improvement, teamwork, and employee empowerment.
How to obtain Quality Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
- Salesforce : SALESFORCE PLATFORM DEVELOPER
Conclusion
Quality management is a critical aspect of business success, ensuring customer satisfaction, cost reduction, brand reputation, and compliance. By implementing a robust Quality Management System and focusing on key quality components, organizations can maintain high standards and drive continuous improvement. Embracing the principles of Total Quality Management further enhances the effectiveness of quality management practices. Upholding quality as a top priority is essential for businesses aiming to thrive in today's competitive market landscape.
Read More
Introduction
Quality management plays a crucial role in ensuring the success of businesses across various industries. It involves a systematic approach to maintaining and improving the quality of products, services, and processes. In this article, we will explore the definition, importance, and components of quality management and delve into the concept of Total Quality Management.
Quality Management System (QMS)
A Quality Management System (QMS) is the framework that enables organizations to establish and uphold their commitment to quality. It encompasses the policies, procedures, and processes that guide the organization in achieving its quality objectives. The QMS serves as the backbone of quality management, providing a structured framework for identifying, controlling, and improving quality-related activities.
Importance of Quality Management
Quality management is of utmost importance for businesses, as it offers several significant benefits. Let's take a closer look at why quality management is vital:
1. Customer Satisfaction
In today's competitive market, customer satisfaction is a top priority for businesses. Quality management ensures that products and services meet or exceed customer expectations, leading to increased satisfaction and loyalty. Satisfied customers not only become repeat customers but also act as brand advocates, attracting new customers through positive word-of-mouth.
2. Cost Reduction
Implementing quality management practices can result in cost reductions for businesses. By identifying and eliminating inefficiencies, defects, and non-value-added activities, organizations can streamline their processes and improve overall productivity. This, in turn, leads to lower production costs, reduced waste, and increased profitability.
3. Brand Reputation
Maintaining a strong brand reputation is vital for businesses to thrive in today's competitive landscape. Quality management helps organizations consistently deliver high-quality products and services, earning them a favorable reputation among customers, partners, and stakeholders. A positive brand image fosters trust, credibility, and long-term success.
4. Compliance and Risk Mitigation
Compliance with industry standards, regulations, and quality requirements is critical for businesses to avoid legal liabilities and penalties. Quality management ensures adherence to these standards, reducing the risk of non-compliance and associated risks. By identifying and mitigating potential risks, organizations can proactively protect their interests and reputation.
Quality Components
Quality management involves various components that collectively contribute to achieving high standards of quality. Let's explore some key quality components:
1. Quality Planning
Quality planning involves defining quality standards, setting objectives, and determining the processes required to meet those standards. It includes identifying customer requirements, establishing quality metrics, and establishing a framework for continuous improvement.
2. Quality Assurance
Quality assurance focuses on preventing defects and ensuring compliance with established quality standards. It involves the implementation of processes, procedures, and controls to verify that products and services meet quality requirements. Quality audits are often conducted to assess the effectiveness of quality assurance activities.
3. Quality Control
Quality control is the process of monitoring and inspecting products, services, and processes to ensure they meet predetermined quality standards. It involves activities such as inspections, testing, and data analysis to detect and correct any deviations from the desired quality level.
4. Continuous Improvement
Continuous improvement is a fundamental concept in quality management, aiming to enhance processes, products, and services over time. It involves regular evaluation, identification of areas for improvement, and the implementation of measures to drive ongoing progress. Continuous improvement fosters innovation, efficiency, and customer satisfaction.
Total Quality Management (TQM)
Total Quality Management (TQM) is a comprehensive approach to quality management that emphasizes the involvement of every individual in an organization. It integrates all aspects of quality management, focusing on meeting customer needs and achieving organizational goals. TQM encourages a culture of continuous improvement, teamwork, and employee empowerment.
How to obtain Quality Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
- Salesforce : SALESFORCE PLATFORM DEVELOPER
Conclusion
Quality management is a critical aspect of business success, ensuring customer satisfaction, cost reduction, brand reputation, and compliance. By implementing a robust Quality Management System and focusing on key quality components, organizations can maintain high standards and drive continuous improvement. Embracing the principles of Total Quality Management further enhances the effectiveness of quality management practices. Upholding quality as a top priority is essential for businesses aiming to thrive in today's competitive market landscape.
Boost your cloud career with EXIN Cloud Certification!
Cloud computing has become an integral part of the IT industry, revolutionizing the way businesses operate and organize their data. As more and more companies migrate their operations to the cloud, there is an increasing demand for skilled professionals who can effectively manage and implement cloud solutions. This is where EXIN Cloud Computing Certification comes into play.
EXIN Cloud Computing Certification: What is it?
EXIN Cloud Computing Certification is a globally recognized certification that validates your knowledge and expertise in cloud computing. It covers a wide range of topics, including cloud infrastructure, deployment models, security, and governance. By obtaining this certification, you demonstrate your commitment to professional development and your ability to handle complex cloud projects.
Why Choose EXIN Cloud Computing Certification?
Enhance Your Skills: By pursuing EXIN Cloud Computing Certification, you can enhance your skills and stay ahead of the curve in this rapidly evolving field. The comprehensive curriculum covers all aspects of cloud computing, ensuring that you develop a solid foundation and become well-versed in the latest industry trends and best practices.
Gain Industry Recognition: EXIN is a renowned provider of IT certifications, trusted by professionals and employers worldwide. With EXIN Cloud Computing Certification on your resume, you gain instant industry recognition and significantly increase your marketability. Employers are more likely to consider candidates with relevant certifications, giving you a competitive edge in the job market.
Expand Your Career Opportunities: Cloud computing is reshaping the future of IT, and skilled professionals in this domain are in high demand. By obtaining EXIN Cloud Computing Certification, you open up a world of exciting career opportunities. Whether you are looking to advance in your current organization or explore new horizons, this certification can pave the way for lucrative positions and roles with greater responsibilities.
Stay Updated with the Latest Technologies: The EXIN Cloud Computing Certification program is designed to equip you with up-to-date knowledge and skills. As part of the certification process, you will learn about the latest cloud technologies, industry standards, and emerging trends. This ensures that you stay relevant in the fast-paced and ever-changing world of cloud computing.
How to Obtain EXIN Cloud Computing Certification
To obtain the EXIN Cloud Computing Certification, you need to pass the relevant exam. The exam consists of multiple-choice questions that test your understanding of cloud computing concepts, architecture, and implementation. It also evaluates your ability to analyze and troubleshoot cloud-related issues.
It is recommended to enroll in a training program or study guide to prepare for the certification exam. These resources provide in-depth coverage of the exam syllabus and offer practice tests to assess your knowledge and readiness. Additionally, hands-on experience with cloud platforms and tools can greatly enhance your chances of success.
How to obtain Exin Cloud Computing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
-
Salesforce : SALESFORCE PLATFORM DEVELOPER
Conclusion
In conclusion, if you are looking to level up your career in the cloud, EXIN Cloud Computing Certification is the key. By obtaining this certification, you not only enhance your skills and gain industry recognition but also open up a world of exciting career opportunities. Don't miss out on the chance to become a certified professional in cloud computing and take your career to new heights!
Read More
Cloud computing has become an integral part of the IT industry, revolutionizing the way businesses operate and organize their data. As more and more companies migrate their operations to the cloud, there is an increasing demand for skilled professionals who can effectively manage and implement cloud solutions. This is where EXIN Cloud Computing Certification comes into play.
EXIN Cloud Computing Certification: What is it?
EXIN Cloud Computing Certification is a globally recognized certification that validates your knowledge and expertise in cloud computing. It covers a wide range of topics, including cloud infrastructure, deployment models, security, and governance. By obtaining this certification, you demonstrate your commitment to professional development and your ability to handle complex cloud projects.
Why Choose EXIN Cloud Computing Certification?
Enhance Your Skills: By pursuing EXIN Cloud Computing Certification, you can enhance your skills and stay ahead of the curve in this rapidly evolving field. The comprehensive curriculum covers all aspects of cloud computing, ensuring that you develop a solid foundation and become well-versed in the latest industry trends and best practices.
Gain Industry Recognition: EXIN is a renowned provider of IT certifications, trusted by professionals and employers worldwide. With EXIN Cloud Computing Certification on your resume, you gain instant industry recognition and significantly increase your marketability. Employers are more likely to consider candidates with relevant certifications, giving you a competitive edge in the job market.
Expand Your Career Opportunities: Cloud computing is reshaping the future of IT, and skilled professionals in this domain are in high demand. By obtaining EXIN Cloud Computing Certification, you open up a world of exciting career opportunities. Whether you are looking to advance in your current organization or explore new horizons, this certification can pave the way for lucrative positions and roles with greater responsibilities.
Stay Updated with the Latest Technologies: The EXIN Cloud Computing Certification program is designed to equip you with up-to-date knowledge and skills. As part of the certification process, you will learn about the latest cloud technologies, industry standards, and emerging trends. This ensures that you stay relevant in the fast-paced and ever-changing world of cloud computing.
How to Obtain EXIN Cloud Computing Certification
To obtain the EXIN Cloud Computing Certification, you need to pass the relevant exam. The exam consists of multiple-choice questions that test your understanding of cloud computing concepts, architecture, and implementation. It also evaluates your ability to analyze and troubleshoot cloud-related issues.
It is recommended to enroll in a training program or study guide to prepare for the certification exam. These resources provide in-depth coverage of the exam syllabus and offer practice tests to assess your knowledge and readiness. Additionally, hands-on experience with cloud platforms and tools can greatly enhance your chances of success.
How to obtain Exin Cloud Computing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
-
Salesforce : SALESFORCE PLATFORM DEVELOPER
Conclusion
In conclusion, if you are looking to level up your career in the cloud, EXIN Cloud Computing Certification is the key. By obtaining this certification, you not only enhance your skills and gain industry recognition but also open up a world of exciting career opportunities. Don't miss out on the chance to become a certified professional in cloud computing and take your career to new heights!
Mastering Data Science with R: Unlocking Certification Success
If you are interested in the field of data science, becoming proficient in the R programming language can unlock a world of opportunities. With its powerful capabilities in data analysis, visualization, statistical modeling, and machine learning, R is widely recognized as one of the most popular programming languages for data scientists. In this article, we will explore how mastering data science with the power of R can lead to certification success and help you advance in your career.
The Importance of Data Analysis:
Data analysis is at the core of any data science project. By leveraging the power of R, you can efficiently analyze large datasets, identify patterns, and draw meaningful insights. R provides a rich variety of packages and libraries that offer a wide range of statistical and analytical tools. With R, you can handle data preprocessing, perform exploratory data analysis, and apply advanced statistical techniques to uncover hidden patterns in your data.
Visualization Made Easy with R:
Data visualization plays a crucial role in communicating complex data insights effectively. R offers a plethora of visualization tools and packages, such as ggplot2 and plotly, that make it easy to create visually appealing and interactive plots and charts. Whether you need to create bar charts, scatter plots, or even interactive dashboards, R provides the versatility and flexibility to transform your data into compelling visual representations.
Statistical Modeling with R:
Statistical modeling is a key component of data science, allowing you to build models that can predict outcomes and make data-driven decisions. R provides a comprehensive set of packages, like caret and glmnet, that facilitate the implementation of various statistical modeling techniques. Whether you need to perform regression analysis, build decision trees, or conduct time series forecasting, R has the tools and libraries to support your statistical modeling needs.
Unlocking Machine Learning Capabilities with R:
Machine learning is revolutionizing many industries, and R is an excellent language for implementing machine learning algorithms. R provides popular machine learning libraries, such as caret and randomForest, that enable you to train and evaluate models for classification, regression, and clustering tasks. Additionally, R offers seamless integration with other machine learning frameworks like TensorFlow and Keras, allowing you to leverage the power of deep learning.
Efficient Data Manipulation with R:
Manipulating and transforming data is a fundamental step in any data science project. R's data manipulation capabilities make it easy to preprocess, clean, and reshape data to fit the requirements of your analysis. R provides intuitive functions like dplyr and tidyr that enable you to filter, sort, join, and reshape datasets with ease. With R, you can efficiently handle missing values, perform data aggregation, and create new variables to enhance your data analysis workflow.
How to obtain Data Science With R certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
-
Salesforce : SALESFORCE PLATFORM DEVELOPER
-
Data Science and Business Intelligence: Data Science with R Programming
Conclusion:
Mastering data science with the power of R is a surefire way to unlock your certification success. With its unmatched capabilities in data analysis, visualization, statistical modeling, machine learning, and data manipulation, R equips you with the necessary tools to excel in the field of data science. As you embark on your journey to become a certified data scientist, make sure to invest time and effort in enhancing your R programming skills. The possibilities are endless, and the rewards are immense for those who embrace the power of R in their data science journey.
Read More
If you are interested in the field of data science, becoming proficient in the R programming language can unlock a world of opportunities. With its powerful capabilities in data analysis, visualization, statistical modeling, and machine learning, R is widely recognized as one of the most popular programming languages for data scientists. In this article, we will explore how mastering data science with the power of R can lead to certification success and help you advance in your career.
The Importance of Data Analysis:
Data analysis is at the core of any data science project. By leveraging the power of R, you can efficiently analyze large datasets, identify patterns, and draw meaningful insights. R provides a rich variety of packages and libraries that offer a wide range of statistical and analytical tools. With R, you can handle data preprocessing, perform exploratory data analysis, and apply advanced statistical techniques to uncover hidden patterns in your data.
Visualization Made Easy with R:
Data visualization plays a crucial role in communicating complex data insights effectively. R offers a plethora of visualization tools and packages, such as ggplot2 and plotly, that make it easy to create visually appealing and interactive plots and charts. Whether you need to create bar charts, scatter plots, or even interactive dashboards, R provides the versatility and flexibility to transform your data into compelling visual representations.
Statistical Modeling with R:
Statistical modeling is a key component of data science, allowing you to build models that can predict outcomes and make data-driven decisions. R provides a comprehensive set of packages, like caret and glmnet, that facilitate the implementation of various statistical modeling techniques. Whether you need to perform regression analysis, build decision trees, or conduct time series forecasting, R has the tools and libraries to support your statistical modeling needs.
Unlocking Machine Learning Capabilities with R:
Machine learning is revolutionizing many industries, and R is an excellent language for implementing machine learning algorithms. R provides popular machine learning libraries, such as caret and randomForest, that enable you to train and evaluate models for classification, regression, and clustering tasks. Additionally, R offers seamless integration with other machine learning frameworks like TensorFlow and Keras, allowing you to leverage the power of deep learning.
Efficient Data Manipulation with R:
Manipulating and transforming data is a fundamental step in any data science project. R's data manipulation capabilities make it easy to preprocess, clean, and reshape data to fit the requirements of your analysis. R provides intuitive functions like dplyr and tidyr that enable you to filter, sort, join, and reshape datasets with ease. With R, you can efficiently handle missing values, perform data aggregation, and create new variables to enhance your data analysis workflow.
How to obtain Data Science With R certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
-
Salesforce : SALESFORCE PLATFORM DEVELOPER
-
Data Science and Business Intelligence: Data Science with R Programming
Conclusion:
Mastering data science with the power of R is a surefire way to unlock your certification success. With its unmatched capabilities in data analysis, visualization, statistical modeling, machine learning, and data manipulation, R equips you with the necessary tools to excel in the field of data science. As you embark on your journey to become a certified data scientist, make sure to invest time and effort in enhancing your R programming skills. The possibilities are endless, and the rewards are immense for those who embrace the power of R in their data science journey.
Project Documentation and Its Importance in 2024
In the world of project management, documentation plays a crucial role in ensuring the success and smooth execution of projects. In 2024, with the advancements in technology and the increasing complexity of projects, the importance of project documentation has become even more significant. This article will delve into the importance of documentation, best practices, and the role it plays in project success.
Importance of Documentation
Documentation is the backbone of any project. It serves as a reference point for all the critical information related to the project, including project objectives, timelines, resources, and deliverables. It provides a clear roadmap for the project team and stakeholders, helping them stay aligned and remain focused on the project goals.
One of the primary reasons documentation is essential is that it acts as a knowledge repository. It captures lessons learned, best practices, and key insights gained during the project's lifecycle. This knowledge can be valuable for future projects, helping teams avoid repeating mistakes and leveraging successful strategies.
Documentation in 2024
With the rapid advancements in technology, the way documentation is created and managed has changed significantly. In 2024, project documentation is largely digital, with traditional paper-based documentation becoming obsolete. This shift has brought about numerous benefits, including increased accessibility, improved collaboration, and enhanced security.
Document control has also become more streamlined with the use of centralized document management systems. These systems allow project teams to manage and control document versions, ensuring everyone is working with the most up-to-date information. Furthermore, information management has become more efficient, with easy searchability and retrieval of documents.
Documentation Best Practices
To ensure effective documentation, project managers should follow a set of best practices. Firstly, it is essential to have a well-defined project planning phase where project objectives, scope, and deliverables are clearly outlined. This lays the foundation for documentation and ensures all key aspects of the project are captured.
Secondly, project managers should establish a document control process. This includes defining naming conventions, file structures, and version control protocols to maintain consistency and allow for easy retrieval of documents. Additionally, regular document reviews should be conducted to validate the accuracy and relevance of information.
Project Communication and Collaboration
Documentation plays a crucial role in project communication and collaboration. It serves as a common reference point for all project stakeholders, ensuring everyone is on the same page. By documenting project updates, milestones, and decisions, project managers can effectively communicate progress and changes to the team and other stakeholders.
Collaboration tools have become instrumental in enhancing project documentation and communication. These tools facilitate real-time collaboration, document sharing, and feedback exchange, even for geographically dispersed teams. This not only improves efficiency but also fosters a collaborative and engaged project environment.
Knowledge Sharing and Documentation Trends
In 2024, knowledge sharing has become an essential aspect of project documentation. Project teams are encouraged to document their experiences, challenges, and successes, which can be shared with other teams within the organization. This promotes organizational learning and the continuous improvement of project management practices.
Additionally, new trends in documentation have emerged, such as digital documentation. This includes the use of multimedia formats like videos and interactive presentations to enhance the documentation experience. Digital documentation also allows for easier integration with other organizational systems, such as analytics tools, making data-driven decision-making more accessible.
Document Workflow and Project Success Factors
A well-defined document workflow is crucial for the success of a project. This workflow outlines the process of creating, reviewing, approving, and archiving project documentation. By following a standardized workflow, project teams can ensure consistency, traceability, and compliance with organizational standards.
Several factors contribute to project success, and proper documentation is one of them. Clear and concise documentation helps mitigate risks, improves communication, and facilitates efficient decision-making. It enables project teams to effectively manage scope changes, identify bottlenecks, and monitor progress towards project goals.
How to obtain A.I certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, project documentation plays a vital role in the success and smooth execution of projects in 2024. It acts as a knowledge repository, enables effective communication, and supports collaboration among project stakeholders. By following best practices, leveraging collaboration tools, and embracing digital trends, project teams can maximize the benefits of documentation and set themselves up for success. So, investing time and effort in creating comprehensive and well-structured project documentation is crucial for project managers in 2024.
Read More
In the world of project management, documentation plays a crucial role in ensuring the success and smooth execution of projects. In 2024, with the advancements in technology and the increasing complexity of projects, the importance of project documentation has become even more significant. This article will delve into the importance of documentation, best practices, and the role it plays in project success.
Importance of Documentation
Documentation is the backbone of any project. It serves as a reference point for all the critical information related to the project, including project objectives, timelines, resources, and deliverables. It provides a clear roadmap for the project team and stakeholders, helping them stay aligned and remain focused on the project goals.
One of the primary reasons documentation is essential is that it acts as a knowledge repository. It captures lessons learned, best practices, and key insights gained during the project's lifecycle. This knowledge can be valuable for future projects, helping teams avoid repeating mistakes and leveraging successful strategies.
Documentation in 2024
With the rapid advancements in technology, the way documentation is created and managed has changed significantly. In 2024, project documentation is largely digital, with traditional paper-based documentation becoming obsolete. This shift has brought about numerous benefits, including increased accessibility, improved collaboration, and enhanced security.
Document control has also become more streamlined with the use of centralized document management systems. These systems allow project teams to manage and control document versions, ensuring everyone is working with the most up-to-date information. Furthermore, information management has become more efficient, with easy searchability and retrieval of documents.
Documentation Best Practices
To ensure effective documentation, project managers should follow a set of best practices. Firstly, it is essential to have a well-defined project planning phase where project objectives, scope, and deliverables are clearly outlined. This lays the foundation for documentation and ensures all key aspects of the project are captured.
Secondly, project managers should establish a document control process. This includes defining naming conventions, file structures, and version control protocols to maintain consistency and allow for easy retrieval of documents. Additionally, regular document reviews should be conducted to validate the accuracy and relevance of information.
Project Communication and Collaboration
Documentation plays a crucial role in project communication and collaboration. It serves as a common reference point for all project stakeholders, ensuring everyone is on the same page. By documenting project updates, milestones, and decisions, project managers can effectively communicate progress and changes to the team and other stakeholders.
Collaboration tools have become instrumental in enhancing project documentation and communication. These tools facilitate real-time collaboration, document sharing, and feedback exchange, even for geographically dispersed teams. This not only improves efficiency but also fosters a collaborative and engaged project environment.
Knowledge Sharing and Documentation Trends
In 2024, knowledge sharing has become an essential aspect of project documentation. Project teams are encouraged to document their experiences, challenges, and successes, which can be shared with other teams within the organization. This promotes organizational learning and the continuous improvement of project management practices.
Additionally, new trends in documentation have emerged, such as digital documentation. This includes the use of multimedia formats like videos and interactive presentations to enhance the documentation experience. Digital documentation also allows for easier integration with other organizational systems, such as analytics tools, making data-driven decision-making more accessible.
Document Workflow and Project Success Factors
A well-defined document workflow is crucial for the success of a project. This workflow outlines the process of creating, reviewing, approving, and archiving project documentation. By following a standardized workflow, project teams can ensure consistency, traceability, and compliance with organizational standards.
Several factors contribute to project success, and proper documentation is one of them. Clear and concise documentation helps mitigate risks, improves communication, and facilitates efficient decision-making. It enables project teams to effectively manage scope changes, identify bottlenecks, and monitor progress towards project goals.
How to obtain A.I certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, project documentation plays a vital role in the success and smooth execution of projects in 2024. It acts as a knowledge repository, enables effective communication, and supports collaboration among project stakeholders. By following best practices, leveraging collaboration tools, and embracing digital trends, project teams can maximize the benefits of documentation and set themselves up for success. So, investing time and effort in creating comprehensive and well-structured project documentation is crucial for project managers in 2024.
Cybersecurity Predictions for 2024: 5 Trends to Watch
In an era dominated by rapidly evolving technological landscapes, the realm of cybersecurity stands as an ever-vigilant guardian against the escalating threats in the digital domain. As we usher in 2024, the spotlight on cybersecurity intensifies, prompting a keen examination of the forthcoming trends that will shape the landscape of digital defense. This exploration navigates through the intricate web of cyber threats, with a focus on the role of cyber security companies, the dynamic world of cyber threat intelligence, and the pivotal contributions of institutions like the Cybersecurity and Infrastructure Security Agency (CISA).
In this insightful journey, we will delve into the nuances of cyber security online, exploring the strategies employed by top cyber security companies to safeguard individuals, businesses, and governments alike. A particular emphasis will be placed on the ever-expanding sphere of cloud computing security, considering its integral role in the contemporary digital infrastructure.
As we embark on this exploration, we cannot overlook the influence of tech giants like Google on the cyber security landscape. With a specific focus on Google Cyber Security initiatives, we will analyze their contributions to fortifying online defenses and shaping the trajectory of cyber resilience.
Join us in uncovering the Cyber security Predictions for 2024, where five key trends will be meticulously examined, offering invaluable insights into the future of digital defense. In a world where information is both power and vulnerability, understanding and anticipating these trends is essential for staying one step ahead in the ever-evolving battle against cyber threats.
Table of contents
-
AI and Machine Learning in Cybersecurity: Advancements and Challenges
-
Emergence of Quantum-Safe Cryptography: A Paradigm Shift in Security
-
Rise of Zero Trust Architecture: Shifting Security Perimeters
-
Securing the Cloud: Evolving Strategies in Cloud Computing Security
-
Cybersecurity Workforce Development: Bridging the Skills Gap
-
Conclusion
AI and Machine Learning in Cybersecurity: Advancements and Challenges
In the dynamic landscape of cybersecurity, the integration of artificial intelligence (AI) and machine learning (ML) stands as a transformative force, promising advancements in threat detection, response, and mitigation. As we delve into the realm of 2024, the role of AI and ML in cyber security becomes increasingly pivotal. These technologies enable the analysis of vast datasets at speeds unattainable by traditional methods, allowing for real-time identification of anomalous activities and potential threats. Moreover, AI-driven solutions contribute to the automation of routine tasks, freeing up cybersecurity professionals to focus on more complex and strategic aspects of defense. However, this integration is not without its challenges. The evolving nature of cyber threats demands constant adaptation, and adversaries are quick to exploit any vulnerabilities in AI and ML systems. Moreover, ethical considerations, interpretability of AI-driven decisions, and the potential for adversarial attacks pose significant challenges. As organizations embrace AI and ML as key components of their cybersecurity arsenal, a delicate balance must be struck between harnessing the power of these technologies and addressing the inherent complexities and risks they bring to the ever-evolving cybersecurity landscape.
Emergence of Quantum-Safe Cryptography: A Paradigm Shift in Security
The imminent era of quantum computing has ushered in a paradigm shift in the field of cybersecurity, compelling a proactive response in the form of quantum-safe cryptography. As we progress into 2024, the realization of quantum computers poses a substantial threat to traditional cryptographic methods, rendering widely-used encryption vulnerable to rapid decryption by quantum algorithms. The emergence of quantum-safe cryptography represents a fundamental rethinking and restructuring of cryptographic protocols to withstand the computational power of quantum machines. This paradigm shift involves the development and adoption of quantum-resistant algorithms that can secure sensitive data and communications against the unprecedented computing capabilities of quantum adversaries. The integration of quantum-safe cryptography is not only a technological necessity but also a strategic imperative for organizations seeking to maintain the confidentiality and integrity of their digital assets in the face of the quantum revolution. This trend signifies a pivotal transition in the cybersecurity landscape, where anticipating and preparing for quantum threats becomes an integral aspect of securing the digital future.
Rise of Zero Trust Architecture: Shifting Security Perimeters
The cybersecurity landscape is undergoing a significant transformation with the ascendance of the Zero Trust Architecture (ZTA) paradigm, marking a departure from traditional security models. In 2024, the rise of Zero Trust Architecture reflects a fundamental shift in how organizations approach network security. Unlike conventional models that operate on the assumption of trust within established perimeters, ZTA challenges these assumptions by treating every user and device as potentially untrusted, regardless of their location within or outside the network. This approach acknowledges the dynamic and evolving nature of cyber threats, necessitating a continuous verification process for users, devices, and applications. By dismantling the concept of implicit trust, Zero Trust Architecture provides a more robust defense mechanism against sophisticated cyberattacks, limiting lateral movement and minimizing the potential impact of breaches. As organizations increasingly embrace ZTA, the security perimeters are redefined, reinforcing the notion that trust must be earned continuously, and security measures must adapt dynamically to the evolving threat landscape.
Securing the Cloud: Evolving Strategies in Cloud Computing Security
In the ever-expanding digital landscape of 2024, the significance of securing the cloud has become paramount, prompting a continuous evolution in strategies for cloud computing security. As organizations increasingly migrate their data, applications, and infrastructure to cloud environments, the dynamic nature of this shift introduces new challenges and opportunities for cybersecurity. The focus on securing the cloud involves the implementation of innovative strategies by cyber security companies, aiming to safeguard sensitive information and ensure the resilience of cloud-based systems. From robust encryption protocols to advanced identity and access management solutions, the evolving strategies in cloud computing security address concerns related to data breaches, unauthorized access, and other cyber threats that may compromise the integrity and confidentiality of digital assets stored in the cloud. The integration of artificial intelligence and machine learning further enhances the detection and response capabilities within cloud environments, contributing to a more adaptive and proactive approach to cybersecurity in the rapidly advancing realm of cloud computing.
Cybersecurity Workforce Development: Bridging the Skills Gap
As we navigate the intricate landscape of cybersecurity in 2024, the critical importance of Cybersecurity Workforce Development emerges as a pivotal focus in bridging the ever-widening skills gap. With the relentless evolution of cyber threats, the demand for skilled cybersecurity professionals has reached unprecedented levels. The paragraph explores the dynamic intersection of education and cyber defense, highlighting the need for specialized training programs to cultivate a proficient workforce capable of tackling the multifaceted challenges of the digital era. In this context, emphasis is placed on understanding the initiatives and strategies implemented to nurture a robust cybersecurity workforce, ensuring that professionals possess the requisite skills to stay ahead of emerging threats and safeguard the digital infrastructure effectively.
How to obtain CyberSecurity certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
As we peer into the future of cyber security in 2024, it becomes evident that the landscape is marked by a confluence of technological advancements, paradigm shifts, and an unwavering commitment to fortify digital defenses. The trends explored, from the integration of artificial intelligence and machine learning to the emergence of quantum-safe cryptography, the adoption of Zero Trust Architecture, evolving strategies in cloud computing security, and the imperative focus on workforce development, collectively paint a comprehensive picture of the challenges and opportunities that lie ahead. The intricate dance between innovation and security underscores the dynamic nature of the cybersecurity domain. As organizations navigate this complex terrain, a proactive and adaptive mindset is paramount. The convergence of these trends underscores the need for a holistic approach to cybersecurity, one that leverages cutting-edge technologies, redefines traditional paradigms, and invests in nurturing a skilled workforce capable of safeguarding our digital future. In the relentless pursuit of cyber resilience, collaboration, innovation, and a commitment to continuous learning will remain the guiding principles, ensuring that we not only anticipate and adapt to the evolving threat landscape but emerge stronger and more secure in the face of unprecedented challenges.
Read More
In an era dominated by rapidly evolving technological landscapes, the realm of cybersecurity stands as an ever-vigilant guardian against the escalating threats in the digital domain. As we usher in 2024, the spotlight on cybersecurity intensifies, prompting a keen examination of the forthcoming trends that will shape the landscape of digital defense. This exploration navigates through the intricate web of cyber threats, with a focus on the role of cyber security companies, the dynamic world of cyber threat intelligence, and the pivotal contributions of institutions like the Cybersecurity and Infrastructure Security Agency (CISA).
In this insightful journey, we will delve into the nuances of cyber security online, exploring the strategies employed by top cyber security companies to safeguard individuals, businesses, and governments alike. A particular emphasis will be placed on the ever-expanding sphere of cloud computing security, considering its integral role in the contemporary digital infrastructure.
As we embark on this exploration, we cannot overlook the influence of tech giants like Google on the cyber security landscape. With a specific focus on Google Cyber Security initiatives, we will analyze their contributions to fortifying online defenses and shaping the trajectory of cyber resilience.
Join us in uncovering the Cyber security Predictions for 2024, where five key trends will be meticulously examined, offering invaluable insights into the future of digital defense. In a world where information is both power and vulnerability, understanding and anticipating these trends is essential for staying one step ahead in the ever-evolving battle against cyber threats.
Table of contents
-
AI and Machine Learning in Cybersecurity: Advancements and Challenges
-
Emergence of Quantum-Safe Cryptography: A Paradigm Shift in Security
-
Rise of Zero Trust Architecture: Shifting Security Perimeters
-
Securing the Cloud: Evolving Strategies in Cloud Computing Security
-
Cybersecurity Workforce Development: Bridging the Skills Gap
-
Conclusion
AI and Machine Learning in Cybersecurity: Advancements and Challenges
In the dynamic landscape of cybersecurity, the integration of artificial intelligence (AI) and machine learning (ML) stands as a transformative force, promising advancements in threat detection, response, and mitigation. As we delve into the realm of 2024, the role of AI and ML in cyber security becomes increasingly pivotal. These technologies enable the analysis of vast datasets at speeds unattainable by traditional methods, allowing for real-time identification of anomalous activities and potential threats. Moreover, AI-driven solutions contribute to the automation of routine tasks, freeing up cybersecurity professionals to focus on more complex and strategic aspects of defense. However, this integration is not without its challenges. The evolving nature of cyber threats demands constant adaptation, and adversaries are quick to exploit any vulnerabilities in AI and ML systems. Moreover, ethical considerations, interpretability of AI-driven decisions, and the potential for adversarial attacks pose significant challenges. As organizations embrace AI and ML as key components of their cybersecurity arsenal, a delicate balance must be struck between harnessing the power of these technologies and addressing the inherent complexities and risks they bring to the ever-evolving cybersecurity landscape.
Emergence of Quantum-Safe Cryptography: A Paradigm Shift in Security
The imminent era of quantum computing has ushered in a paradigm shift in the field of cybersecurity, compelling a proactive response in the form of quantum-safe cryptography. As we progress into 2024, the realization of quantum computers poses a substantial threat to traditional cryptographic methods, rendering widely-used encryption vulnerable to rapid decryption by quantum algorithms. The emergence of quantum-safe cryptography represents a fundamental rethinking and restructuring of cryptographic protocols to withstand the computational power of quantum machines. This paradigm shift involves the development and adoption of quantum-resistant algorithms that can secure sensitive data and communications against the unprecedented computing capabilities of quantum adversaries. The integration of quantum-safe cryptography is not only a technological necessity but also a strategic imperative for organizations seeking to maintain the confidentiality and integrity of their digital assets in the face of the quantum revolution. This trend signifies a pivotal transition in the cybersecurity landscape, where anticipating and preparing for quantum threats becomes an integral aspect of securing the digital future.
Rise of Zero Trust Architecture: Shifting Security Perimeters
The cybersecurity landscape is undergoing a significant transformation with the ascendance of the Zero Trust Architecture (ZTA) paradigm, marking a departure from traditional security models. In 2024, the rise of Zero Trust Architecture reflects a fundamental shift in how organizations approach network security. Unlike conventional models that operate on the assumption of trust within established perimeters, ZTA challenges these assumptions by treating every user and device as potentially untrusted, regardless of their location within or outside the network. This approach acknowledges the dynamic and evolving nature of cyber threats, necessitating a continuous verification process for users, devices, and applications. By dismantling the concept of implicit trust, Zero Trust Architecture provides a more robust defense mechanism against sophisticated cyberattacks, limiting lateral movement and minimizing the potential impact of breaches. As organizations increasingly embrace ZTA, the security perimeters are redefined, reinforcing the notion that trust must be earned continuously, and security measures must adapt dynamically to the evolving threat landscape.
Securing the Cloud: Evolving Strategies in Cloud Computing Security
In the ever-expanding digital landscape of 2024, the significance of securing the cloud has become paramount, prompting a continuous evolution in strategies for cloud computing security. As organizations increasingly migrate their data, applications, and infrastructure to cloud environments, the dynamic nature of this shift introduces new challenges and opportunities for cybersecurity. The focus on securing the cloud involves the implementation of innovative strategies by cyber security companies, aiming to safeguard sensitive information and ensure the resilience of cloud-based systems. From robust encryption protocols to advanced identity and access management solutions, the evolving strategies in cloud computing security address concerns related to data breaches, unauthorized access, and other cyber threats that may compromise the integrity and confidentiality of digital assets stored in the cloud. The integration of artificial intelligence and machine learning further enhances the detection and response capabilities within cloud environments, contributing to a more adaptive and proactive approach to cybersecurity in the rapidly advancing realm of cloud computing.
Cybersecurity Workforce Development: Bridging the Skills Gap
As we navigate the intricate landscape of cybersecurity in 2024, the critical importance of Cybersecurity Workforce Development emerges as a pivotal focus in bridging the ever-widening skills gap. With the relentless evolution of cyber threats, the demand for skilled cybersecurity professionals has reached unprecedented levels. The paragraph explores the dynamic intersection of education and cyber defense, highlighting the need for specialized training programs to cultivate a proficient workforce capable of tackling the multifaceted challenges of the digital era. In this context, emphasis is placed on understanding the initiatives and strategies implemented to nurture a robust cybersecurity workforce, ensuring that professionals possess the requisite skills to stay ahead of emerging threats and safeguard the digital infrastructure effectively.
How to obtain CyberSecurity certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
As we peer into the future of cyber security in 2024, it becomes evident that the landscape is marked by a confluence of technological advancements, paradigm shifts, and an unwavering commitment to fortify digital defenses. The trends explored, from the integration of artificial intelligence and machine learning to the emergence of quantum-safe cryptography, the adoption of Zero Trust Architecture, evolving strategies in cloud computing security, and the imperative focus on workforce development, collectively paint a comprehensive picture of the challenges and opportunities that lie ahead. The intricate dance between innovation and security underscores the dynamic nature of the cybersecurity domain. As organizations navigate this complex terrain, a proactive and adaptive mindset is paramount. The convergence of these trends underscores the need for a holistic approach to cybersecurity, one that leverages cutting-edge technologies, redefines traditional paradigms, and invests in nurturing a skilled workforce capable of safeguarding our digital future. In the relentless pursuit of cyber resilience, collaboration, innovation, and a commitment to continuous learning will remain the guiding principles, ensuring that we not only anticipate and adapt to the evolving threat landscape but emerge stronger and more secure in the face of unprecedented challenges.
Microsoft Introduces ARM-Native Toolkit at BUILD
In an effort to revolutionize software development for the ARM architecture, Microsoft has made a groundbreaking announcement at its annual BUILD conference. The tech giant unveiled a game-changing tool, the ARM-Native Toolkit, which aims to empower developers and enhance application compatibility for Windows 10. This exciting development opens up new possibilities for app development and solidifies Microsoft's authority and expertise in the field. Let's explore the features and benefits of this innovative toolkit.
The ARM Architecture and its Significance
The ARM architecture, known for its power efficiency and widespread use in mobile devices, has gained significant traction in recent years. As more Windows devices, including tablets and laptops, adopt ARM processors, it has become crucial to provide developers with the tools to create ARM-native apps. With the ARM-Native Toolkit, Microsoft is addressing this need and enabling developers to tap into the full potential of ARM technology.
Empowering App Development with ARM-Native Toolkit
The ARM-Native Toolkit streamlines the app development process, making it easier than ever for developers to create ARM-native applications. By optimizing the toolkit for ARM architecture, Microsoft ensures that apps built with this tool are faster and more efficient. Developers can harness the power of ARM processors to deliver optimal performance and an enhanced user experience.
Enhancing Application Compatibility
One of the significant challenges faced by developers working with ARM architecture is ensuring application compatibility across different platforms. With the ARM-Native Toolkit, Microsoft tackles this issue head-on. Developers can build apps that seamlessly adapt to multiple devices, regardless of their underlying architecture. This level of compatibility is crucial for promoting widespread adoption and allowing developers to reach a broader audience.
Windows 10 Integration
The ARM-Native Toolkit is fully integrated with Windows 10, Microsoft's flagship operating system. With the toolkit's native support for ARM architecture, developers can unleash the true potential of their apps on Windows 10 devices. This integration further strengthens Microsoft's commitment to creating a seamless ecosystem for developers and users alike.
Leveraging the Power of the ARM-Native Toolkit
The ARM-Native Toolkit empowers developers to create high-performance apps, enabling them to take advantage of the unique features offered by ARM architecture. Whether it's building resource-intensive applications, leveraging hardware accelerators, or optimizing power consumption, the toolkit provides developers with the necessary tools to bring their ideas to life.
Achieving Application Optimization
With the ARM-Native Toolkit, developers can optimize their applications specifically for ARM architecture. This allows for improved performance and efficiency, leading to faster load times, smoother user interfaces, and reduced battery consumption. By capitalizing on the features of the underlying architecture, developers can deliver applications that stand out in terms of both functionality and user experience.
The Future of Software Development with Microsoft
The introduction of the ARM-Native Toolkit at BUILD showcases Microsoft's commitment to providing cutting-edge tools and technologies for software development. With this groundbreaking toolkit, developers have the means to create ARM-native applications with ease, ensuring broad compatibility and exceptional performance across Windows 10 devices.
How to obtain Microsoft certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
Microsoft's ARM-Native Toolkit represents a significant leap forward in software development for the ARM architecture. By addressing the challenges faced by developers and facilitating app compatibility, Microsoft solidifies its position as an industry leader. With seamless integration into Windows 10 and the ability to leverage the unique capabilities of ARM architecture, developers now have the tools they need to create optimized applications. The ARM-Native Toolkit paves the way for a future where ARM-powered devices become the norm, and Microsoft continues to lead the way in innovative software development.
Read More
In an effort to revolutionize software development for the ARM architecture, Microsoft has made a groundbreaking announcement at its annual BUILD conference. The tech giant unveiled a game-changing tool, the ARM-Native Toolkit, which aims to empower developers and enhance application compatibility for Windows 10. This exciting development opens up new possibilities for app development and solidifies Microsoft's authority and expertise in the field. Let's explore the features and benefits of this innovative toolkit.
The ARM Architecture and its Significance
The ARM architecture, known for its power efficiency and widespread use in mobile devices, has gained significant traction in recent years. As more Windows devices, including tablets and laptops, adopt ARM processors, it has become crucial to provide developers with the tools to create ARM-native apps. With the ARM-Native Toolkit, Microsoft is addressing this need and enabling developers to tap into the full potential of ARM technology.
Empowering App Development with ARM-Native Toolkit
The ARM-Native Toolkit streamlines the app development process, making it easier than ever for developers to create ARM-native applications. By optimizing the toolkit for ARM architecture, Microsoft ensures that apps built with this tool are faster and more efficient. Developers can harness the power of ARM processors to deliver optimal performance and an enhanced user experience.
Enhancing Application Compatibility
One of the significant challenges faced by developers working with ARM architecture is ensuring application compatibility across different platforms. With the ARM-Native Toolkit, Microsoft tackles this issue head-on. Developers can build apps that seamlessly adapt to multiple devices, regardless of their underlying architecture. This level of compatibility is crucial for promoting widespread adoption and allowing developers to reach a broader audience.
Windows 10 Integration
The ARM-Native Toolkit is fully integrated with Windows 10, Microsoft's flagship operating system. With the toolkit's native support for ARM architecture, developers can unleash the true potential of their apps on Windows 10 devices. This integration further strengthens Microsoft's commitment to creating a seamless ecosystem for developers and users alike.
Leveraging the Power of the ARM-Native Toolkit
The ARM-Native Toolkit empowers developers to create high-performance apps, enabling them to take advantage of the unique features offered by ARM architecture. Whether it's building resource-intensive applications, leveraging hardware accelerators, or optimizing power consumption, the toolkit provides developers with the necessary tools to bring their ideas to life.
Achieving Application Optimization
With the ARM-Native Toolkit, developers can optimize their applications specifically for ARM architecture. This allows for improved performance and efficiency, leading to faster load times, smoother user interfaces, and reduced battery consumption. By capitalizing on the features of the underlying architecture, developers can deliver applications that stand out in terms of both functionality and user experience.
The Future of Software Development with Microsoft
The introduction of the ARM-Native Toolkit at BUILD showcases Microsoft's commitment to providing cutting-edge tools and technologies for software development. With this groundbreaking toolkit, developers have the means to create ARM-native applications with ease, ensuring broad compatibility and exceptional performance across Windows 10 devices.
How to obtain Microsoft certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
Microsoft's ARM-Native Toolkit represents a significant leap forward in software development for the ARM architecture. By addressing the challenges faced by developers and facilitating app compatibility, Microsoft solidifies its position as an industry leader. With seamless integration into Windows 10 and the ability to leverage the unique capabilities of ARM architecture, developers now have the tools they need to create optimized applications. The ARM-Native Toolkit paves the way for a future where ARM-powered devices become the norm, and Microsoft continues to lead the way in innovative software development.
The Role of AI in IT Service Management
Are you looking to streamline your IT service management processes and improve efficiency? Look no further than the integration of artificial intelligence (AI) into your IT service management strategy. AI has revolutionized the way IT services are delivered and managed, offering a wide range of benefits that can help organizations operate more effectively and provide better service to their customers.
AI in IT Service Management
AI refers to the use of intelligent machines and algorithms that can perform tasks that typically require human intelligence, such as learning, reasoning, problem-solving, and understanding natural language. In the context of IT service management, AI can be used to automate repetitive tasks, predict and prevent IT issues, and analyze vast amounts of data to make informed decisions.
Artificial Intelligence for IT Service Management
By leveraging AI technologies, IT service management teams can work smarter, not harder. AI-powered systems can handle routine tasks like ticket routing, categorization, and resolution, freeing up IT professionals to focus on more critical issues that require human intervention. This not only increases efficiency but also improves employee satisfaction and reduces burnout.
Machine Learning in IT Service Management
Machine learning, a subset of AI, enables IT service management systems to learn from past data and experiences to improve future outcomes. By analyzing historical data, machine learning algorithms can identify patterns and trends that humans might overlook, leading to more accurate predictions and proactive problem resolution. This can result in fewer service disruptions, reduced downtime, and improved overall performance.
IT Service Management Automation
Automation is a key component of AI in IT service management. By automating routine tasks and processes, organizations can reduce manual errors, speed up service delivery, and provide a consistent and reliable experience for users. From automated incident response to self-service portals, AI-driven automation can revolutionize the way IT services are delivered.
Benefits of AI in IT Service Management
The use of AI in IT service management offers a wide range of benefits for organizations, including:
Enhanced efficiency: AI can handle tasks faster and more accurately than humans, leading to increased productivity and reduced operational costs.
Improved decision-making: AI algorithms can analyze data in real-time and provide valuable insights that can help organizations make informed decisions.
Better customer satisfaction: By automating routine tasks and providing faster service delivery, organizations can enhance the customer experience and build loyalty.
Proactive problem resolution: AI can predict and prevent IT issues before they occur, reducing downtime and minimizing impact on business operations.
Scalability: AI-powered systems can scale up or down based on demand, allowing organizations to adapt to changing business needs quickly.
Role of Artificial Intelligence in IT Service
The role of artificial intelligence in IT service is to augment and optimize the capabilities of IT service management teams. By automating routine tasks, analyzing data, and making predictions, AI can help organizations operate more efficiently, reduce costs, and deliver better service to their customers. From predicting system failures to optimizing resource allocation, AI can transform the way IT services are managed and delivered.
IT Service Management Optimization with AI
To optimize IT service management with AI, organizations should:
Identify areas where AI can have the most significant impact, such as incident management, problem resolution, and service desk operations.
Invest in AI technologies that align with organizational goals and objectives, ensuring a seamless integration with existing IT systems.
Train IT staff on how to leverage AI tools and technologies effectively, empowering them to work more efficiently and effectively.
Continuously monitor and evaluate the performance of AI-powered systems, making adjustments as needed to maximize benefits and ROI.
How to obtain IT Service Management & Governace certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, AI plays a crucial role in IT service management by improving efficiency, automating routine tasks, and helping organizations deliver better service to their customers. By embracing AI technologies and incorporating them into their IT service management strategy, organizations can stay ahead of the curve and drive innovation in the fast-paced world of IT services.
Read More
Are you looking to streamline your IT service management processes and improve efficiency? Look no further than the integration of artificial intelligence (AI) into your IT service management strategy. AI has revolutionized the way IT services are delivered and managed, offering a wide range of benefits that can help organizations operate more effectively and provide better service to their customers.
AI in IT Service Management
AI refers to the use of intelligent machines and algorithms that can perform tasks that typically require human intelligence, such as learning, reasoning, problem-solving, and understanding natural language. In the context of IT service management, AI can be used to automate repetitive tasks, predict and prevent IT issues, and analyze vast amounts of data to make informed decisions.
Artificial Intelligence for IT Service Management
By leveraging AI technologies, IT service management teams can work smarter, not harder. AI-powered systems can handle routine tasks like ticket routing, categorization, and resolution, freeing up IT professionals to focus on more critical issues that require human intervention. This not only increases efficiency but also improves employee satisfaction and reduces burnout.
Machine Learning in IT Service Management
Machine learning, a subset of AI, enables IT service management systems to learn from past data and experiences to improve future outcomes. By analyzing historical data, machine learning algorithms can identify patterns and trends that humans might overlook, leading to more accurate predictions and proactive problem resolution. This can result in fewer service disruptions, reduced downtime, and improved overall performance.
IT Service Management Automation
Automation is a key component of AI in IT service management. By automating routine tasks and processes, organizations can reduce manual errors, speed up service delivery, and provide a consistent and reliable experience for users. From automated incident response to self-service portals, AI-driven automation can revolutionize the way IT services are delivered.
Benefits of AI in IT Service Management
The use of AI in IT service management offers a wide range of benefits for organizations, including:
Enhanced efficiency: AI can handle tasks faster and more accurately than humans, leading to increased productivity and reduced operational costs.
Improved decision-making: AI algorithms can analyze data in real-time and provide valuable insights that can help organizations make informed decisions.
Better customer satisfaction: By automating routine tasks and providing faster service delivery, organizations can enhance the customer experience and build loyalty.
Proactive problem resolution: AI can predict and prevent IT issues before they occur, reducing downtime and minimizing impact on business operations.
Scalability: AI-powered systems can scale up or down based on demand, allowing organizations to adapt to changing business needs quickly.
Role of Artificial Intelligence in IT Service
The role of artificial intelligence in IT service is to augment and optimize the capabilities of IT service management teams. By automating routine tasks, analyzing data, and making predictions, AI can help organizations operate more efficiently, reduce costs, and deliver better service to their customers. From predicting system failures to optimizing resource allocation, AI can transform the way IT services are managed and delivered.
IT Service Management Optimization with AI
To optimize IT service management with AI, organizations should:
Identify areas where AI can have the most significant impact, such as incident management, problem resolution, and service desk operations.
Invest in AI technologies that align with organizational goals and objectives, ensuring a seamless integration with existing IT systems.
Train IT staff on how to leverage AI tools and technologies effectively, empowering them to work more efficiently and effectively.
Continuously monitor and evaluate the performance of AI-powered systems, making adjustments as needed to maximize benefits and ROI.
How to obtain IT Service Management & Governace certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, AI plays a crucial role in IT service management by improving efficiency, automating routine tasks, and helping organizations deliver better service to their customers. By embracing AI technologies and incorporating them into their IT service management strategy, organizations can stay ahead of the curve and drive innovation in the fast-paced world of IT services.
Agile ITSM: Adapting to Rapid Changes
In today's fast-paced world, traditional IT Service Management (ITSM) practices are no longer sufficient to meet the demands of modern businesses. With technology innovation happening at breakneck speed, organizations need to be responsive, efficient, and adaptable to stay ahead of the curve. This is where Agile ITSM comes into play, offering a more flexible and dynamic approach that allows businesses to quickly adapt to rapid changes in the IT landscape.
What is Agile ITSM?
Agile ITSM is a methodology that combines the principles of Agile software development with IT Service Management best practices. It focuses on delivering value to customers through iterative and incremental improvements, rather than following a rigid, linear process. By breaking down work into smaller, manageable chunks, Agile ITSM enables teams to respond quickly to changing requirements and priorities.
How does Agile ITSM differ from traditional ITSM?
Traditional ITSM is often characterized by strict processes and procedures that can be slow to adapt to changing circumstances. In contrast, Agile ITSM encourages collaboration, flexibility, and continuous improvement. Teams work together in cross-functional units, with a shared goal of delivering high-quality services that meet the needs of the business.
The Benefits of Agile ITSM
-
Increased Flexibility: Agile ITSM allows teams to respond quickly to changing requirements, ensuring that IT services remain aligned with business goals.
-
Faster Time to Market: By breaking work down into smaller increments, Agile ITSM enables organizations to deliver value to customers more quickly.
-
Improved Customer Satisfaction: Agile ITSM focuses on delivering value to customers, resulting in higher levels of satisfaction and loyalty.
-
Enhanced Collaboration: Agile ITSM encourages cross-functional teams to work together, fostering a culture of collaboration and innovation.
-
Continuous Improvement: Agile ITSM emphasizes the importance of learning from experience and making ongoing improvements to processes and services.
How to Implement Agile ITSM
-
Define Clear Goals: Start by setting clear goals and objectives for your Agile ITSM implementation. What do you hope to achieve? How will you measure success?
-
Build Cross-Functional Teams: Create cross-functional teams with the right mix of skills and expertise to deliver value to customers.
-
Implement Agile Practices: Adopt Agile practices such as Scrum, Kanban, and Lean to manage work effectively and efficiently.
-
Embrace a Culture of Collaboration: Encourage open communication, feedback, and collaboration among team members to drive innovation and continuous improvement.
-
Measure and Adapt: Continuously monitor and measure your progress, making adjustments as needed to ensure that you are meeting your goals.
How to obtain Agile & Scrum certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, Agile ITSM offers a more flexible and adaptable approach to IT Service Management, enabling organizations to respond quickly to rapid changes in technology and business requirements. By embracing Agile principles and practices, businesses can deliver value to customers more effectively, improve collaboration and innovation, and drive continuous improvement. Are you ready to take your ITSM practices to the next level with Agile?
Read More
In today's fast-paced world, traditional IT Service Management (ITSM) practices are no longer sufficient to meet the demands of modern businesses. With technology innovation happening at breakneck speed, organizations need to be responsive, efficient, and adaptable to stay ahead of the curve. This is where Agile ITSM comes into play, offering a more flexible and dynamic approach that allows businesses to quickly adapt to rapid changes in the IT landscape.
What is Agile ITSM?
Agile ITSM is a methodology that combines the principles of Agile software development with IT Service Management best practices. It focuses on delivering value to customers through iterative and incremental improvements, rather than following a rigid, linear process. By breaking down work into smaller, manageable chunks, Agile ITSM enables teams to respond quickly to changing requirements and priorities.
How does Agile ITSM differ from traditional ITSM?
Traditional ITSM is often characterized by strict processes and procedures that can be slow to adapt to changing circumstances. In contrast, Agile ITSM encourages collaboration, flexibility, and continuous improvement. Teams work together in cross-functional units, with a shared goal of delivering high-quality services that meet the needs of the business.
The Benefits of Agile ITSM
-
Increased Flexibility: Agile ITSM allows teams to respond quickly to changing requirements, ensuring that IT services remain aligned with business goals.
-
Faster Time to Market: By breaking work down into smaller increments, Agile ITSM enables organizations to deliver value to customers more quickly.
-
Improved Customer Satisfaction: Agile ITSM focuses on delivering value to customers, resulting in higher levels of satisfaction and loyalty.
-
Enhanced Collaboration: Agile ITSM encourages cross-functional teams to work together, fostering a culture of collaboration and innovation.
-
Continuous Improvement: Agile ITSM emphasizes the importance of learning from experience and making ongoing improvements to processes and services.
How to Implement Agile ITSM
-
Define Clear Goals: Start by setting clear goals and objectives for your Agile ITSM implementation. What do you hope to achieve? How will you measure success?
-
Build Cross-Functional Teams: Create cross-functional teams with the right mix of skills and expertise to deliver value to customers.
-
Implement Agile Practices: Adopt Agile practices such as Scrum, Kanban, and Lean to manage work effectively and efficiently.
-
Embrace a Culture of Collaboration: Encourage open communication, feedback, and collaboration among team members to drive innovation and continuous improvement.
-
Measure and Adapt: Continuously monitor and measure your progress, making adjustments as needed to ensure that you are meeting your goals.
How to obtain Agile & Scrum certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, Agile ITSM offers a more flexible and adaptable approach to IT Service Management, enabling organizations to respond quickly to rapid changes in technology and business requirements. By embracing Agile principles and practices, businesses can deliver value to customers more effectively, improve collaboration and innovation, and drive continuous improvement. Are you ready to take your ITSM practices to the next level with Agile?
How artificial intelligence is transforming digital marketing
In today's fast-paced digital world, technology continues to evolve and revolutionize how businesses market their products and services. One of the most significant advancements in recent years is the integration of artificial intelligence (AI) into digital marketing strategies. AI has become a game-changer for marketers, providing powerful tools and capabilities to optimize campaigns, analyze data, and personalize customer experiences like never before.
AI in Digital Marketing
Artificial intelligence technology is reshaping the landscape of digital marketing in various ways. From automation in marketing to machine learning algorithms, AI is empowering marketers to streamline processes, enhance decision-making, and deliver more targeted and personalized campaigns to their audiences. With AI, marketers can leverage predictive analytics to forecast trends, identify opportunities, and optimize their strategies for maximum impact.
Digital Marketing Trends
The use of AI in digital marketing has opened up new possibilities and trends that are shaping how businesses engage with their customers. From chatbots and personalized marketing to digital advertising and customer segmentation, AI-driven solutions are driving growth and innovation across industries. As businesses continue to invest in digital transformation, AI will play a crucial role in driving success and maintaining a competitive edge in the market.
Automation in Marketing
Automation has become a cornerstone of modern marketing strategies, allowing businesses to streamline processes and scale their efforts efficiently. AI-powered tools enable marketers to automate repetitive tasks, such as email marketing automation, targeted advertising, and social media management. By automating these processes, marketers can focus on higher-value tasks, such as creating compelling content and analyzing campaign performance.
Marketing Strategies
Artificial intelligence is redefining marketing strategies by providing insights and intelligence that help businesses make data-driven decisions. With AI, marketers can optimize online campaigns, analyze customer behavior, and measure the effectiveness of their marketing efforts in real-time. By leveraging AI-driven insights, businesses can adjust their strategies on-the-go, ensuring they stay relevant and engaging to their target audience.
Personalized Marketing
Personalization has become a critical component of successful marketing strategies, as customers demand more personalized experiences from brands. AI enables marketers to create tailored experiences for each customer, based on their preferences, behavior, and interactions with the brand. By delivering personalized content, recommendations, and offers, businesses can enhance customer engagement, drive loyalty, and increase conversions.
Digital Transformation
Digital transformation is the process of integrating digital technologies into all aspects of a business, fundamentally changing how they operate and deliver value to customers. AI is at the forefront of this transformation, empowering businesses to leverage data analytics, marketing intelligence, and automation tools to drive growth and innovation. By embracing AI, businesses can stay ahead of the curve, adapt to changing market dynamics, and deliver exceptional customer experiences.
How to obtain Emerging Technology certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, artificial intelligence is revolutionizing digital marketing by empowering businesses to leverage data, automation, and intelligence to optimize their strategies and engage with customers in more meaningful ways. As AI continues to evolve and advance, businesses that embrace this technology will have a competitive advantage, driving growth and success in the digital landscape.
Read More
In today's fast-paced digital world, technology continues to evolve and revolutionize how businesses market their products and services. One of the most significant advancements in recent years is the integration of artificial intelligence (AI) into digital marketing strategies. AI has become a game-changer for marketers, providing powerful tools and capabilities to optimize campaigns, analyze data, and personalize customer experiences like never before.
AI in Digital Marketing
Artificial intelligence technology is reshaping the landscape of digital marketing in various ways. From automation in marketing to machine learning algorithms, AI is empowering marketers to streamline processes, enhance decision-making, and deliver more targeted and personalized campaigns to their audiences. With AI, marketers can leverage predictive analytics to forecast trends, identify opportunities, and optimize their strategies for maximum impact.
Digital Marketing Trends
The use of AI in digital marketing has opened up new possibilities and trends that are shaping how businesses engage with their customers. From chatbots and personalized marketing to digital advertising and customer segmentation, AI-driven solutions are driving growth and innovation across industries. As businesses continue to invest in digital transformation, AI will play a crucial role in driving success and maintaining a competitive edge in the market.
Automation in Marketing
Automation has become a cornerstone of modern marketing strategies, allowing businesses to streamline processes and scale their efforts efficiently. AI-powered tools enable marketers to automate repetitive tasks, such as email marketing automation, targeted advertising, and social media management. By automating these processes, marketers can focus on higher-value tasks, such as creating compelling content and analyzing campaign performance.
Marketing Strategies
Artificial intelligence is redefining marketing strategies by providing insights and intelligence that help businesses make data-driven decisions. With AI, marketers can optimize online campaigns, analyze customer behavior, and measure the effectiveness of their marketing efforts in real-time. By leveraging AI-driven insights, businesses can adjust their strategies on-the-go, ensuring they stay relevant and engaging to their target audience.
Personalized Marketing
Personalization has become a critical component of successful marketing strategies, as customers demand more personalized experiences from brands. AI enables marketers to create tailored experiences for each customer, based on their preferences, behavior, and interactions with the brand. By delivering personalized content, recommendations, and offers, businesses can enhance customer engagement, drive loyalty, and increase conversions.
Digital Transformation
Digital transformation is the process of integrating digital technologies into all aspects of a business, fundamentally changing how they operate and deliver value to customers. AI is at the forefront of this transformation, empowering businesses to leverage data analytics, marketing intelligence, and automation tools to drive growth and innovation. By embracing AI, businesses can stay ahead of the curve, adapt to changing market dynamics, and deliver exceptional customer experiences.
How to obtain Emerging Technology certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, artificial intelligence is revolutionizing digital marketing by empowering businesses to leverage data, automation, and intelligence to optimize their strategies and engage with customers in more meaningful ways. As AI continues to evolve and advance, businesses that embrace this technology will have a competitive advantage, driving growth and success in the digital landscape.
Building a Culture of Service Excellence in IT
In today's fast-paced and competitive business environment, it is crucial for IT companies to prioritize service excellence. Building a culture of service excellence in IT can lead to increased customer satisfaction, improved employee morale, and ultimately, enhanced business growth. In this article, we will explore the importance of service excellence in the IT industry and provide valuable insights on how to cultivate a culture of service excellence within your organization.
Why is Service Excellence Important in IT?
Service excellence is essential in the IT industry as it allows companies to differentiate themselves from competitors and deliver exceptional value to customers. In a highly competitive market, providing outstanding service can be a key differentiator that sets your company apart and attracts new customers. Additionally, focusing on service excellence can help improve customer retention rates, increase customer loyalty, and drive repeat business.
How to Build a Culture of Service Excellence in IT
Lead by Example: Cultivating a culture of service excellence starts at the top. Leaders within the organization should demonstrate a commitment to providing exceptional service and set a positive example for their teams to follow.
Empower Employees: Empowering employees to take ownership of the customer experience can lead to improved service delivery. Provide training, resources, and support to help employees excel in their roles and deliver outstanding service to customers.
Foster a Customer-Centric Mindset: Encourage employees to always prioritize the needs and preferences of customers. By focusing on understanding and meeting customer expectations, employees can deliver personalized service that exceeds customer satisfaction.
Establish Clear Service Standards: Define clear service standards and expectations to guide employees in their interactions with customers. Regularly review and update these standards to ensure they align with the company's values and goals.
Encourage Feedback and Continuous Improvement: Create a culture of continuous improvement by actively seeking feedback from customers and employees. Use this feedback to identify areas for improvement and implement changes to enhance the overall customer experience.
Benefits of Building a Culture of Service Excellence in IT
Increased Customer Satisfaction: By prioritizing service excellence, IT companies can enhance customer satisfaction levels and build strong relationships with their clients.
Improved Employee Morale: Employees who feel empowered to deliver exceptional service are more engaged, motivated, and satisfied in their roles.
Enhanced Business Growth: A culture of service excellence can drive business growth by attracting new customers, increasing customer loyalty, and generating positive word-of-mouth referrals.
How to obtain ITServices & Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
Building a culture of service excellence in IT is essential for companies looking to thrive in today's competitive business landscape. By prioritizing service excellence, empowering employees, and fostering a customer-centric mindset, IT organizations can differentiate themselves from competitors, drive business growth, and create lasting customer relationships. Embrace service excellence as a core value within your organization and watch as it transforms the way you do business.
Read More
In today's fast-paced and competitive business environment, it is crucial for IT companies to prioritize service excellence. Building a culture of service excellence in IT can lead to increased customer satisfaction, improved employee morale, and ultimately, enhanced business growth. In this article, we will explore the importance of service excellence in the IT industry and provide valuable insights on how to cultivate a culture of service excellence within your organization.
Why is Service Excellence Important in IT?
Service excellence is essential in the IT industry as it allows companies to differentiate themselves from competitors and deliver exceptional value to customers. In a highly competitive market, providing outstanding service can be a key differentiator that sets your company apart and attracts new customers. Additionally, focusing on service excellence can help improve customer retention rates, increase customer loyalty, and drive repeat business.
How to Build a Culture of Service Excellence in IT
Lead by Example: Cultivating a culture of service excellence starts at the top. Leaders within the organization should demonstrate a commitment to providing exceptional service and set a positive example for their teams to follow.
Empower Employees: Empowering employees to take ownership of the customer experience can lead to improved service delivery. Provide training, resources, and support to help employees excel in their roles and deliver outstanding service to customers.
Foster a Customer-Centric Mindset: Encourage employees to always prioritize the needs and preferences of customers. By focusing on understanding and meeting customer expectations, employees can deliver personalized service that exceeds customer satisfaction.
Establish Clear Service Standards: Define clear service standards and expectations to guide employees in their interactions with customers. Regularly review and update these standards to ensure they align with the company's values and goals.
Encourage Feedback and Continuous Improvement: Create a culture of continuous improvement by actively seeking feedback from customers and employees. Use this feedback to identify areas for improvement and implement changes to enhance the overall customer experience.
Benefits of Building a Culture of Service Excellence in IT
Increased Customer Satisfaction: By prioritizing service excellence, IT companies can enhance customer satisfaction levels and build strong relationships with their clients.
Improved Employee Morale: Employees who feel empowered to deliver exceptional service are more engaged, motivated, and satisfied in their roles.
Enhanced Business Growth: A culture of service excellence can drive business growth by attracting new customers, increasing customer loyalty, and generating positive word-of-mouth referrals.
How to obtain ITServices & Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
Building a culture of service excellence in IT is essential for companies looking to thrive in today's competitive business landscape. By prioritizing service excellence, empowering employees, and fostering a customer-centric mindset, IT organizations can differentiate themselves from competitors, drive business growth, and create lasting customer relationships. Embrace service excellence as a core value within your organization and watch as it transforms the way you do business.
R Programming Language Predictions of Its Death Premature
In the world of programming languages, the death of a language is often predicted with the emergence of new and more popular alternatives. Such predictions have been made about the R programming language, but are they premature? This article dives into the relevance of R in the era of data analysis, statistical computing, data science, and software development.
Is R Programming Losing Its Relevance?
The first question that arises is whether R programming is losing its relevance in today's fast-paced world. With the rise of languages like Python and its extensive libraries, it is natural to question the future of R. However, it is important to remember that R was specifically designed for statistical computing and data analysis. It has a rich ecosystem of packages and functions that make it a preferred choice for many data scientists and statisticians.
While Python certainly has its merits, it cannot match the depth and breadth of functionality that R provides in the field of data analysis. R's extensive library of statistical packages, such as "ggplot2" for data visualization and "caret" for machine learning, showcases its expertise and authority in this domain.
The Role of R Programming in Data Science
When it comes to data science, R continues to play a crucial role. The language excels in handling and manipulating large datasets, performing advanced statistical analyses, and building sophisticated models. Its flexibility allows data scientists to explore and experiment with different approaches, making it an integral part of the data science workflow.
R's popularity among data scientists can be attributed to its ease of use and the wide range of statistical techniques it supports. From linear regression to time series analysis, R has tools and packages to address various data science challenges. Its robustness in handling complex statistical computations further showcases why the predictions of its death may be premature.
R Programming in Software Development
While R is closely associated with data science, it also finds utility in software development. Its ability to integrate with other programming languages, such as C++ and Java, expands its applicability beyond statistical analysis. R's strength lies in its ability to bridge the gap between scientific computations and software engineering, enabling developers to build efficient and scalable solutions.
Moreover, R's popularity in academia and research communities fosters a collaborative environment for software development. There are numerous packages in R, developed and maintained by the community, that cater to various domains of software development. From building web applications to implementing machine learning algorithms, R provides a rich ecosystem of tools for software engineers.
The Importance of R in Statistical Computing
Statistical computing heavily relies on R due to its extensive capabilities. R provides a vast array of built-in functions and packages for conducting statistical operations, such as hypothesis testing, probability distributions, and data visualization. These features make it an ideal choice for statisticians and researchers who require a powerful toolset for their analyses.
R's emphasis on reproducibility and transparency further strengthens its position in statistical computing. The ability to document and share code, along with the integrated development environment (IDE) like RStudio, simplifies the process of performing complex statistical computations. This makes R an indispensable tool in the field of statistical computing.+
How to obtain Data Science certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the predictions of the death of the R programming language are premature. R continues to demonstrate its expertise, authority, and relevance in the domains of data analysis, statistical computing, data science, and software development. Its comprehensive package ecosystem, coupled with its statistical prowess, solidifies its position as a language of choice for many professionals in the industry. So, if you are considering venturing into the world of data science or statistical computing, don't underestimate the power of R. It may just be the missing piece in your toolkit.
Read More
In the world of programming languages, the death of a language is often predicted with the emergence of new and more popular alternatives. Such predictions have been made about the R programming language, but are they premature? This article dives into the relevance of R in the era of data analysis, statistical computing, data science, and software development.
Is R Programming Losing Its Relevance?
The first question that arises is whether R programming is losing its relevance in today's fast-paced world. With the rise of languages like Python and its extensive libraries, it is natural to question the future of R. However, it is important to remember that R was specifically designed for statistical computing and data analysis. It has a rich ecosystem of packages and functions that make it a preferred choice for many data scientists and statisticians.
While Python certainly has its merits, it cannot match the depth and breadth of functionality that R provides in the field of data analysis. R's extensive library of statistical packages, such as "ggplot2" for data visualization and "caret" for machine learning, showcases its expertise and authority in this domain.
The Role of R Programming in Data Science
When it comes to data science, R continues to play a crucial role. The language excels in handling and manipulating large datasets, performing advanced statistical analyses, and building sophisticated models. Its flexibility allows data scientists to explore and experiment with different approaches, making it an integral part of the data science workflow.
R's popularity among data scientists can be attributed to its ease of use and the wide range of statistical techniques it supports. From linear regression to time series analysis, R has tools and packages to address various data science challenges. Its robustness in handling complex statistical computations further showcases why the predictions of its death may be premature.
R Programming in Software Development
While R is closely associated with data science, it also finds utility in software development. Its ability to integrate with other programming languages, such as C++ and Java, expands its applicability beyond statistical analysis. R's strength lies in its ability to bridge the gap between scientific computations and software engineering, enabling developers to build efficient and scalable solutions.
Moreover, R's popularity in academia and research communities fosters a collaborative environment for software development. There are numerous packages in R, developed and maintained by the community, that cater to various domains of software development. From building web applications to implementing machine learning algorithms, R provides a rich ecosystem of tools for software engineers.
The Importance of R in Statistical Computing
Statistical computing heavily relies on R due to its extensive capabilities. R provides a vast array of built-in functions and packages for conducting statistical operations, such as hypothesis testing, probability distributions, and data visualization. These features make it an ideal choice for statisticians and researchers who require a powerful toolset for their analyses.
R's emphasis on reproducibility and transparency further strengthens its position in statistical computing. The ability to document and share code, along with the integrated development environment (IDE) like RStudio, simplifies the process of performing complex statistical computations. This makes R an indispensable tool in the field of statistical computing.+
How to obtain Data Science certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the predictions of the death of the R programming language are premature. R continues to demonstrate its expertise, authority, and relevance in the domains of data analysis, statistical computing, data science, and software development. Its comprehensive package ecosystem, coupled with its statistical prowess, solidifies its position as a language of choice for many professionals in the industry. So, if you are considering venturing into the world of data science or statistical computing, don't underestimate the power of R. It may just be the missing piece in your toolkit.
What is Git Rebase, and How Do You Use It?
Git has become an essential tool for software development and version control. With its vast array of commands and features, it allows developers to effectively manage, collaborate on, and track changes within their codebase. One such command that plays a crucial role in code organization and collaboration is Git Rebase. In this article, we will explore what Git Rebase is, why it is important, and how to use it effectively.
Understanding Git Rebase:
Git Rebase is a powerful command that allows developers to integrate changes from one branch into another. This process involves moving or combining a sequence of commits to a new base commit, resulting in a cleaner, more linear branch history. It is particularly useful when multiple developers are working on a project simultaneously, as it helps in maintaining a clear and organized codebase.
The Importance of Git Rebase:
1. Code Management and Organization:
Git Rebase plays a significant role in code management and organization. By integrating changes from one branch to another, it helps in maintaining a clean and linear commit history. This makes it easier to understand the evolution of the codebase and trace back any issues or bugs that may arise.
2. Code Collaboration and Versioning:
In a collaborative development environment, multiple developers work on different branches simultaneously. Git Rebase allows these changes to be seamlessly integrated into a single branch, ensuring that the codebase remains up to date and all changes are accounted for. This promotes efficient collaboration and helps in avoiding conflicts during the merging process.
3. Streamlined Git Workflow:
Git Rebase simplifies the Git workflow by eliminating unnecessary branch merges. Instead of merging branches, it allows you to apply changes in a streamlined manner directly onto the desired branch. This reduces the clutter in the commit history and makes it easier to review and understand the changes made.
How to Use Git Rebase:
Using Git Rebase effectively requires a clear understanding of the workflow and the desired outcome. Here is a step-by-step guide on how to use Git Rebase:
Step 1: Create a New Branch:
Before starting the rebase process, create a new branch from the branch you wish to incorporate changes into. This ensures that you have a separate branch to work on without affecting the original codebase.
Step 2: Initiate the Rebase:
To initiate the rebase process, use the following command:
git rebase
Replace with the name of the branch you want to integrate changes from.
Step 3: Resolve Conflicts:
During the rebase process, conflicts may arise if there are conflicting changes between the two branches. Git will prompt you to resolve these conflicts manually. Use a text editor or a merge tool to resolve the conflicts, save the changes, and continue with the rebase process.
Step 4: Complete the Rebase:
Once all conflicts have been resolved, complete the rebase process by using the command:
git rebase --continue
This will apply all the changes from the specified branch onto the new branch you created.
Step 5: Push the Changes:
Finally, push the changes to the remote repository using the command:
git push origin
Replace with the name of the new branch you created.
How to obtain Development certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion:
In conclusion, Git Rebase is a powerful command that allows for efficient code management, collaboration, and versioning in software development. By understanding how to use Git Rebase effectively, developers can maintain a clean and organized codebase, streamline their Git workflow, and enhance collaboration among team members. So, the next time you find yourself needing to integrate changes from one branch to another, remember the power of Git Rebase and how it can simplify your development process. Happy rebasing!
Read More
Git has become an essential tool for software development and version control. With its vast array of commands and features, it allows developers to effectively manage, collaborate on, and track changes within their codebase. One such command that plays a crucial role in code organization and collaboration is Git Rebase. In this article, we will explore what Git Rebase is, why it is important, and how to use it effectively.
Understanding Git Rebase:
Git Rebase is a powerful command that allows developers to integrate changes from one branch into another. This process involves moving or combining a sequence of commits to a new base commit, resulting in a cleaner, more linear branch history. It is particularly useful when multiple developers are working on a project simultaneously, as it helps in maintaining a clear and organized codebase.
The Importance of Git Rebase:
1. Code Management and Organization:
Git Rebase plays a significant role in code management and organization. By integrating changes from one branch to another, it helps in maintaining a clean and linear commit history. This makes it easier to understand the evolution of the codebase and trace back any issues or bugs that may arise.
2. Code Collaboration and Versioning:
In a collaborative development environment, multiple developers work on different branches simultaneously. Git Rebase allows these changes to be seamlessly integrated into a single branch, ensuring that the codebase remains up to date and all changes are accounted for. This promotes efficient collaboration and helps in avoiding conflicts during the merging process.
3. Streamlined Git Workflow:
Git Rebase simplifies the Git workflow by eliminating unnecessary branch merges. Instead of merging branches, it allows you to apply changes in a streamlined manner directly onto the desired branch. This reduces the clutter in the commit history and makes it easier to review and understand the changes made.
How to Use Git Rebase:
Using Git Rebase effectively requires a clear understanding of the workflow and the desired outcome. Here is a step-by-step guide on how to use Git Rebase:
Step 1: Create a New Branch:
Before starting the rebase process, create a new branch from the branch you wish to incorporate changes into. This ensures that you have a separate branch to work on without affecting the original codebase.
Step 2: Initiate the Rebase:
To initiate the rebase process, use the following command:
git rebase
Replace with the name of the branch you want to integrate changes from.
Step 3: Resolve Conflicts:
During the rebase process, conflicts may arise if there are conflicting changes between the two branches. Git will prompt you to resolve these conflicts manually. Use a text editor or a merge tool to resolve the conflicts, save the changes, and continue with the rebase process.
Step 4: Complete the Rebase:
Once all conflicts have been resolved, complete the rebase process by using the command:
git rebase --continue
This will apply all the changes from the specified branch onto the new branch you created.
Step 5: Push the Changes:
Finally, push the changes to the remote repository using the command:
git push origin
Replace with the name of the new branch you created.
How to obtain Development certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion:
In conclusion, Git Rebase is a powerful command that allows for efficient code management, collaboration, and versioning in software development. By understanding how to use Git Rebase effectively, developers can maintain a clean and organized codebase, streamline their Git workflow, and enhance collaboration among team members. So, the next time you find yourself needing to integrate changes from one branch to another, remember the power of Git Rebase and how it can simplify your development process. Happy rebasing!
The rise of 5G technology and its implications
The world of technology is constantly evolving, and one of the most significant developments in recent years has been the rise of 5G technology. This next generation of wireless technology promises to revolutionize the way we connect, communicate, and consume information. In this article, we will explore the implications of 5G technology, its benefits, and what the future holds for this cutting-edge innovation.
What is 5G Technology?
5G technology is the fifth generation of wireless technology, succeeding 4G. It promises faster internet speeds, lower latency, and increased capacity, paving the way for a more connected and efficient world. With speeds up to 100 times faster than 4G, 5G technology is set to transform industries and enable new possibilities in telemedicine, autonomous vehicles, and the Internet of Things (IoT).
Implications of 5G
The implications of 5G technology are profound and far-reaching. From improved network connectivity to enhanced communication capabilities, 5G has the potential to reshape the way we interact with technology. With its lower latency and higher capacity, 5G can support a wide range of applications, including virtual reality, augmented reality, and real-time gaming experiences.
Benefits of 5G
One of the key benefits of 5G technology is its lightning-fast speed. This means faster download and upload speeds, seamless streaming, and quicker access to information. In addition, 5G offers lower latency, which reduces the delay between sending and receiving data, making it ideal for real-time applications like video calls and online gaming. Furthermore, the increased capacity of 5G networks can support a higher number of connected devices, making it perfect for smart homes and smart cities.
The Future of 5G
The future of 5G is bright, with continued advancements and innovations on the horizon. As more countries deploy 5G infrastructure and manufacturers develop compatible devices, the possibilities for this technology are endless. From improved healthcare services to enhanced transportation systems, 5G has the potential to revolutionize industries and improve people's lives around the world.
5G Technology Explained
At its core, 5G technology operates on higher frequency bands than previous generations, allowing for faster data transmission and reduced latency. This technology utilizes advanced antennas and beamforming techniques to deliver a more reliable and efficient network. In addition, 5G networks use network slicing to allocate resources based on specific user needs, ensuring optimal performance for each connected device.
5G Connectivity
5G connectivity is more than just faster internet speeds. It offers improved reliability, enhanced security, and seamless connectivity across devices. With the ability to support massive IoT deployments and mission-critical applications, 5G connectivity is poised to drive digital transformation and unlock new opportunities for businesses and consumers alike.
5G Speed
The speed of 5G technology is unparalleled, with peak speeds reaching up to 10 gigabits per second. This ultra-fast speed enables instant downloads, buffer-free streaming, and lag-free gaming experiences. Whether you're downloading a movie in seconds or participating in a virtual meeting with crystal-clear video quality, 5G speed is sure to impress even the most demanding users.
Impact of 5G
The impact of 5G technology extends beyond just faster internet speeds. It has the potential to drive economic growth, spur innovation, and create new opportunities for businesses and individuals. With its ability to support emerging technologies like AI, cloud computing, and edge computing, 5G is shaping the digital landscape and fueling the Fourth Industrial Revolution.
How to obtain Development certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the rise of 5G technology is ushering in a new era of connectivity and innovation. With its incredible speed, low latency, and high capacity, 5G has the power to transform industries, improve communication, and enhance the way we live and work. As we continue to explore the possibilities of this groundbreaking technology, the future looks brighter than ever before.
Read More
The world of technology is constantly evolving, and one of the most significant developments in recent years has been the rise of 5G technology. This next generation of wireless technology promises to revolutionize the way we connect, communicate, and consume information. In this article, we will explore the implications of 5G technology, its benefits, and what the future holds for this cutting-edge innovation.
What is 5G Technology?
5G technology is the fifth generation of wireless technology, succeeding 4G. It promises faster internet speeds, lower latency, and increased capacity, paving the way for a more connected and efficient world. With speeds up to 100 times faster than 4G, 5G technology is set to transform industries and enable new possibilities in telemedicine, autonomous vehicles, and the Internet of Things (IoT).
Implications of 5G
The implications of 5G technology are profound and far-reaching. From improved network connectivity to enhanced communication capabilities, 5G has the potential to reshape the way we interact with technology. With its lower latency and higher capacity, 5G can support a wide range of applications, including virtual reality, augmented reality, and real-time gaming experiences.
Benefits of 5G
One of the key benefits of 5G technology is its lightning-fast speed. This means faster download and upload speeds, seamless streaming, and quicker access to information. In addition, 5G offers lower latency, which reduces the delay between sending and receiving data, making it ideal for real-time applications like video calls and online gaming. Furthermore, the increased capacity of 5G networks can support a higher number of connected devices, making it perfect for smart homes and smart cities.
The Future of 5G
The future of 5G is bright, with continued advancements and innovations on the horizon. As more countries deploy 5G infrastructure and manufacturers develop compatible devices, the possibilities for this technology are endless. From improved healthcare services to enhanced transportation systems, 5G has the potential to revolutionize industries and improve people's lives around the world.
5G Technology Explained
At its core, 5G technology operates on higher frequency bands than previous generations, allowing for faster data transmission and reduced latency. This technology utilizes advanced antennas and beamforming techniques to deliver a more reliable and efficient network. In addition, 5G networks use network slicing to allocate resources based on specific user needs, ensuring optimal performance for each connected device.
5G Connectivity
5G connectivity is more than just faster internet speeds. It offers improved reliability, enhanced security, and seamless connectivity across devices. With the ability to support massive IoT deployments and mission-critical applications, 5G connectivity is poised to drive digital transformation and unlock new opportunities for businesses and consumers alike.
5G Speed
The speed of 5G technology is unparalleled, with peak speeds reaching up to 10 gigabits per second. This ultra-fast speed enables instant downloads, buffer-free streaming, and lag-free gaming experiences. Whether you're downloading a movie in seconds or participating in a virtual meeting with crystal-clear video quality, 5G speed is sure to impress even the most demanding users.
Impact of 5G
The impact of 5G technology extends beyond just faster internet speeds. It has the potential to drive economic growth, spur innovation, and create new opportunities for businesses and individuals. With its ability to support emerging technologies like AI, cloud computing, and edge computing, 5G is shaping the digital landscape and fueling the Fourth Industrial Revolution.
How to obtain Development certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the rise of 5G technology is ushering in a new era of connectivity and innovation. With its incredible speed, low latency, and high capacity, 5G has the power to transform industries, improve communication, and enhance the way we live and work. As we continue to explore the possibilities of this groundbreaking technology, the future looks brighter than ever before.
Virtual team-building activities
In today's digital age, more and more teams are working remotely, making virtual team-building activities an essential component of fostering camaraderie, collaboration, and communication among team members. From online team building games to virtual icebreakers, there are a plethora of activities that can bring remote teams closer together and boost morale. Let's explore some virtual team-building ideas and strategies to enhance team cohesion and engagement in a virtual setting.
The Importance of Virtual Team-Building Activities
Remote work can often lead to feelings of isolation and disconnection among team members. Virtual team-building activities play a crucial role in bridging the physical gap between team members and creating a sense of belonging and camaraderie. By engaging in team-building exercises, remote teams can build trust, improve communication, and strengthen relationships, ultimately leading to a more cohesive and productive team.
Virtual Team-Building Ideas
Virtual Team Challenges: Organize fun and interactive challenges such as virtual scavenger hunts or trivia contests to encourage teamwork and collaboration.
Virtual Team-Building Workshops: Schedule workshops on topics such as effective communication or conflict resolution to enhance team dynamics and skills.
Virtual Team-Building Games: Play online games like virtual escape rooms or team-building simulations to promote problem-solving and collaboration.
Virtual Team-Building Strategies
Regular Check-Ins: Schedule regular video calls or virtual coffee breaks to check in with team members and maintain open communication.
Encourage Feedback: Create a culture of feedback where team members can freely share their thoughts and ideas to foster a culture of continuous improvement.
Recognition and Rewards: Acknowledge and appreciate the efforts of team members through virtual shoutouts, awards, or incentives to boost morale and motivation.
Virtual Team-Building Tips
Set Clear Objectives: Clearly define the goals and objectives of each virtual team-building activity to ensure alignment and engagement.
Mix It Up: Keep virtual team-building activities fresh and exciting by trying out a variety of activities to cater to different interests and preferences.
Encourage Participation: Create a safe and inclusive environment where all team members feel comfortable participating and sharing their thoughts and ideas.
Conclusion
In conclusion, virtual team-building activities are an essential tool for fostering collaboration, communication, and camaraderie among remote teams. By incorporating a variety of virtual team-building exercises, workshops, and games, teams can strengthen relationships, boost morale, and enhance overall team performance. Embrace the power of virtual team-building to create a more connected and engaged remote team.
Read More
In today's digital age, more and more teams are working remotely, making virtual team-building activities an essential component of fostering camaraderie, collaboration, and communication among team members. From online team building games to virtual icebreakers, there are a plethora of activities that can bring remote teams closer together and boost morale. Let's explore some virtual team-building ideas and strategies to enhance team cohesion and engagement in a virtual setting.
The Importance of Virtual Team-Building Activities
Remote work can often lead to feelings of isolation and disconnection among team members. Virtual team-building activities play a crucial role in bridging the physical gap between team members and creating a sense of belonging and camaraderie. By engaging in team-building exercises, remote teams can build trust, improve communication, and strengthen relationships, ultimately leading to a more cohesive and productive team.
Virtual Team-Building Ideas
Virtual Team Challenges: Organize fun and interactive challenges such as virtual scavenger hunts or trivia contests to encourage teamwork and collaboration.
Virtual Team-Building Workshops: Schedule workshops on topics such as effective communication or conflict resolution to enhance team dynamics and skills.
Virtual Team-Building Games: Play online games like virtual escape rooms or team-building simulations to promote problem-solving and collaboration.
Virtual Team-Building Strategies
Regular Check-Ins: Schedule regular video calls or virtual coffee breaks to check in with team members and maintain open communication.
Encourage Feedback: Create a culture of feedback where team members can freely share their thoughts and ideas to foster a culture of continuous improvement.
Recognition and Rewards: Acknowledge and appreciate the efforts of team members through virtual shoutouts, awards, or incentives to boost morale and motivation.
Virtual Team-Building Tips
Set Clear Objectives: Clearly define the goals and objectives of each virtual team-building activity to ensure alignment and engagement.
Mix It Up: Keep virtual team-building activities fresh and exciting by trying out a variety of activities to cater to different interests and preferences.
Encourage Participation: Create a safe and inclusive environment where all team members feel comfortable participating and sharing their thoughts and ideas.
Conclusion
In conclusion, virtual team-building activities are an essential tool for fostering collaboration, communication, and camaraderie among remote teams. By incorporating a variety of virtual team-building exercises, workshops, and games, teams can strengthen relationships, boost morale, and enhance overall team performance. Embrace the power of virtual team-building to create a more connected and engaged remote team.
Augmented reality (AR) and virtual reality (VR) applications
In today's digital age, technology is rapidly advancing, offering innovative solutions to everyday challenges. Augmented Reality (AR) and Virtual Reality (VR) are two prominent technologies that have gained significant traction in various industries. From entertainment and gaming to healthcare and education, AR and VR applications are revolutionizing the way we interact with our surroundings and experiences.
What are Augmented Reality (AR) and Virtual Reality (VR) Applications?
Augmented Reality (AR) is a technology that overlays digital information onto the real world, enhancing our perception of reality. On the other hand, Virtual Reality (VR) creates a completely immersive digital environment, allowing users to interact with a virtual world. Both AR and VR applications utilize advanced technologies such as sensors, cameras, and display devices to create interactive and engaging experiences.
Augmented Reality Apps
AR applications are designed to enhance the user's perception of reality by integrating digital information into the physical world. Popular AR apps include Pokemon Go, which allows users to capture virtual creatures in real-world locations, and Snapchat filters, which add playful animations to selfies. These applications showcase the potential of AR technology in creating interactive and engaging experiences for users.
Virtual Reality Apps
VR applications immerse users in a virtual environment, allowing them to interact with and explore digital worlds. Popular VR apps include Google Earth VR, which enables users to explore the world in 3D, and Beat Saber, a rhythm game that combines music and virtual reality. These applications provide users with a unique and immersive experience that transports them to new and exciting realities.
The Impact of AR and VR Technology
AR and VR technology has the potential to revolutionize various industries by providing unique and engaging experiences for users. From healthcare simulation to training and education, AR and VR applications are transforming the way we learn, work, and play. With the continuous development of AR and VR solutions, the possibilities are endless.
AR Solutions
AR solutions offer businesses and organizations innovative ways to engage with their customers and employees. For example, AR shopping experiences allow customers to visualize products in their own space before making a purchase, while AR training simulations provide hands-on learning experiences for employees. These solutions enhance productivity and efficiency while creating memorable experiences for users.
VR Solutions
VR solutions are revolutionizing industries such as healthcare, architecture, and entertainment by offering immersive experiences for users. For example, VR medical simulations enable healthcare professionals to practice complex procedures in a safe and controlled environment, while VR architectural visualizations provide clients with a realistic preview of their future projects. These solutions enhance decision-making processes and improve user engagement.
The Future of AR and VR Technology
As technology continues to evolve, the future of AR and VR applications looks promising. From advancements in wearable devices to the development of interactive storytelling experiences, AR and VR technologies are constantly evolving to meet the needs of users in various industries. With the incorporation of artificial intelligence and machine learning, the possibilities for AR and VR innovation are limitless.
AR Companies
Several companies are at the forefront of AR technology, including Apple, Google, and Microsoft. These companies are developing innovative AR solutions that enhance user experiences in various fields, such as gaming, navigation, and communication. With the integration of AR technologies into everyday devices, the adoption of AR applications is expected to increase significantly in the coming years.
VR Companies
Similarly, VR companies such as Oculus, HTC, and Sony are driving innovation in the virtual reality market. These companies are developing advanced VR solutions that offer realistic and immersive experiences for users. From interactive games to virtual meetings, VR technology is reshaping the way we interact with digital content and each other. With the continuous development of VR devices and software, the adoption of VR applications is expected to grow substantially in the near future.
How to obtain Artificial Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, Augmented Reality (AR) and Virtual Reality (VR) applications are transforming the way we interact with technology and the world around us. From immersive gaming experiences to innovative training simulations, AR and VR technologies offer limitless possibilities for users in various industries. As these technologies continue to evolve and advance, the future of AR and VR applications looks bright, promising innovative solutions and engaging experiences for users worldwide.
Read More
In today's digital age, technology is rapidly advancing, offering innovative solutions to everyday challenges. Augmented Reality (AR) and Virtual Reality (VR) are two prominent technologies that have gained significant traction in various industries. From entertainment and gaming to healthcare and education, AR and VR applications are revolutionizing the way we interact with our surroundings and experiences.
What are Augmented Reality (AR) and Virtual Reality (VR) Applications?
Augmented Reality (AR) is a technology that overlays digital information onto the real world, enhancing our perception of reality. On the other hand, Virtual Reality (VR) creates a completely immersive digital environment, allowing users to interact with a virtual world. Both AR and VR applications utilize advanced technologies such as sensors, cameras, and display devices to create interactive and engaging experiences.
Augmented Reality Apps
AR applications are designed to enhance the user's perception of reality by integrating digital information into the physical world. Popular AR apps include Pokemon Go, which allows users to capture virtual creatures in real-world locations, and Snapchat filters, which add playful animations to selfies. These applications showcase the potential of AR technology in creating interactive and engaging experiences for users.
Virtual Reality Apps
VR applications immerse users in a virtual environment, allowing them to interact with and explore digital worlds. Popular VR apps include Google Earth VR, which enables users to explore the world in 3D, and Beat Saber, a rhythm game that combines music and virtual reality. These applications provide users with a unique and immersive experience that transports them to new and exciting realities.
The Impact of AR and VR Technology
AR and VR technology has the potential to revolutionize various industries by providing unique and engaging experiences for users. From healthcare simulation to training and education, AR and VR applications are transforming the way we learn, work, and play. With the continuous development of AR and VR solutions, the possibilities are endless.
AR Solutions
AR solutions offer businesses and organizations innovative ways to engage with their customers and employees. For example, AR shopping experiences allow customers to visualize products in their own space before making a purchase, while AR training simulations provide hands-on learning experiences for employees. These solutions enhance productivity and efficiency while creating memorable experiences for users.
VR Solutions
VR solutions are revolutionizing industries such as healthcare, architecture, and entertainment by offering immersive experiences for users. For example, VR medical simulations enable healthcare professionals to practice complex procedures in a safe and controlled environment, while VR architectural visualizations provide clients with a realistic preview of their future projects. These solutions enhance decision-making processes and improve user engagement.
The Future of AR and VR Technology
As technology continues to evolve, the future of AR and VR applications looks promising. From advancements in wearable devices to the development of interactive storytelling experiences, AR and VR technologies are constantly evolving to meet the needs of users in various industries. With the incorporation of artificial intelligence and machine learning, the possibilities for AR and VR innovation are limitless.
AR Companies
Several companies are at the forefront of AR technology, including Apple, Google, and Microsoft. These companies are developing innovative AR solutions that enhance user experiences in various fields, such as gaming, navigation, and communication. With the integration of AR technologies into everyday devices, the adoption of AR applications is expected to increase significantly in the coming years.
VR Companies
Similarly, VR companies such as Oculus, HTC, and Sony are driving innovation in the virtual reality market. These companies are developing advanced VR solutions that offer realistic and immersive experiences for users. From interactive games to virtual meetings, VR technology is reshaping the way we interact with digital content and each other. With the continuous development of VR devices and software, the adoption of VR applications is expected to grow substantially in the near future.
How to obtain Artificial Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, Augmented Reality (AR) and Virtual Reality (VR) applications are transforming the way we interact with technology and the world around us. From immersive gaming experiences to innovative training simulations, AR and VR technologies offer limitless possibilities for users in various industries. As these technologies continue to evolve and advance, the future of AR and VR applications looks bright, promising innovative solutions and engaging experiences for users worldwide.
Hybrid Project Management Models: Blending Traditional and Agile Approaches
In the dynamic world of project management, organizations are constantly seeking ways to improve efficiency, collaboration, and adaptability. Traditional project management approaches have long been relied upon for their structured processes and predictability, while agile project management has gained popularity for its flexibility and iterative nature. However, in today's fast-paced business environment, many organizations are turning to hybrid project management models to combine the best of both worlds. By blending traditional and agile approaches, companies can harness the strengths of each to achieve successful project outcomes.
Understanding Hybrid Project Management
Hybrid project management is a strategic approach that combines elements of both traditional and agile project management methodologies. This model allows organizations to tailor their project management approach to fit the unique needs of each project. By using a hybrid approach, teams can maintain the structure and control of traditional project management while also incorporating the flexibility and responsiveness of agile practices. This blending of methodologies enables organizations to deliver projects more efficiently, adapt to changing requirements, and drive innovation.
Benefits of Hybrid Project Management
Enhanced flexibility: By integrating traditional and agile practices, teams can adapt to evolving project requirements and stakeholder needs.
Improved project outcomes: The combination of structured processes and iterative development leads to higher quality deliverables and increased customer satisfaction.
Better risk management: Hybrid project management allows teams to proactively identify and address risks throughout the project lifecycle.
Increased collaboration: By using a hybrid approach, teams are encouraged to work together more closely, fostering stronger communication and alignment.
Traditional vs. Agile Project Management
Traditional project management is characterized by its linear, sequential approach, with a focus on detailed planning and control. In contrast, agile project management emphasizes adaptability, collaboration, and continuous improvement. While traditional project management is well-suited for projects with defined requirements and stable scope, agile methodologies excel in situations where requirements are uncertain or likely to change.
When comparing traditional and agile project management, it's important to recognize that each approach has its strengths and weaknesses. Traditional project management provides a clear roadmap for project execution and is valuable for projects with well-defined objectives. On the other hand, agile project management allows teams to adapt to changing circumstances and deliver value incrementally.
Combining Traditional and Agile Methodologies
The key to successful hybrid project management is finding the right balance between traditional and agile methodologies. Organizations can customize their approach to fit the specific needs of each project, taking into account factors such as project size, complexity, and stakeholder requirements.
By integrating traditional and agile practices, teams can leverage the strengths of each approach to optimize project performance. For example, teams may use traditional project management techniques for initial planning and risk assessment, while adopting agile practices for iterative development and testing. This hybrid approach allows teams to maintain control and visibility while also embracing change and innovation.
Best Practices for Hybrid Project Management
Tailor your approach: Customize your project management methodology to fit the unique characteristics of each project.
Foster collaboration: Encourage open communication and collaboration among team members to promote alignment and shared goals.
Embrace change: Be open to adapting your project management approach in response to changing requirements or stakeholder feedback.
Continuously improve: Regularly review and evaluate your project management practices to identify opportunities for optimization and enhancement.
How to obtain Project Management Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, hybrid project management models offer a flexible and effective approach to project execution in today's fast-paced business environment. By blending traditional and agile methodologies, organizations can leverage the strengths of each approach to deliver successful project outcomes. Through careful planning, collaboration, and adaptability, teams can harness the power of hybrid project management to drive innovation and achieve project success.
Read More
In the dynamic world of project management, organizations are constantly seeking ways to improve efficiency, collaboration, and adaptability. Traditional project management approaches have long been relied upon for their structured processes and predictability, while agile project management has gained popularity for its flexibility and iterative nature. However, in today's fast-paced business environment, many organizations are turning to hybrid project management models to combine the best of both worlds. By blending traditional and agile approaches, companies can harness the strengths of each to achieve successful project outcomes.
Understanding Hybrid Project Management
Hybrid project management is a strategic approach that combines elements of both traditional and agile project management methodologies. This model allows organizations to tailor their project management approach to fit the unique needs of each project. By using a hybrid approach, teams can maintain the structure and control of traditional project management while also incorporating the flexibility and responsiveness of agile practices. This blending of methodologies enables organizations to deliver projects more efficiently, adapt to changing requirements, and drive innovation.
Benefits of Hybrid Project Management
Enhanced flexibility: By integrating traditional and agile practices, teams can adapt to evolving project requirements and stakeholder needs.
Improved project outcomes: The combination of structured processes and iterative development leads to higher quality deliverables and increased customer satisfaction.
Better risk management: Hybrid project management allows teams to proactively identify and address risks throughout the project lifecycle.
Increased collaboration: By using a hybrid approach, teams are encouraged to work together more closely, fostering stronger communication and alignment.
Traditional vs. Agile Project Management
Traditional project management is characterized by its linear, sequential approach, with a focus on detailed planning and control. In contrast, agile project management emphasizes adaptability, collaboration, and continuous improvement. While traditional project management is well-suited for projects with defined requirements and stable scope, agile methodologies excel in situations where requirements are uncertain or likely to change.
When comparing traditional and agile project management, it's important to recognize that each approach has its strengths and weaknesses. Traditional project management provides a clear roadmap for project execution and is valuable for projects with well-defined objectives. On the other hand, agile project management allows teams to adapt to changing circumstances and deliver value incrementally.
Combining Traditional and Agile Methodologies
The key to successful hybrid project management is finding the right balance between traditional and agile methodologies. Organizations can customize their approach to fit the specific needs of each project, taking into account factors such as project size, complexity, and stakeholder requirements.
By integrating traditional and agile practices, teams can leverage the strengths of each approach to optimize project performance. For example, teams may use traditional project management techniques for initial planning and risk assessment, while adopting agile practices for iterative development and testing. This hybrid approach allows teams to maintain control and visibility while also embracing change and innovation.
Best Practices for Hybrid Project Management
Tailor your approach: Customize your project management methodology to fit the unique characteristics of each project.
Foster collaboration: Encourage open communication and collaboration among team members to promote alignment and shared goals.
Embrace change: Be open to adapting your project management approach in response to changing requirements or stakeholder feedback.
Continuously improve: Regularly review and evaluate your project management practices to identify opportunities for optimization and enhancement.
How to obtain Project Management Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, hybrid project management models offer a flexible and effective approach to project execution in today's fast-paced business environment. By blending traditional and agile methodologies, organizations can leverage the strengths of each approach to deliver successful project outcomes. Through careful planning, collaboration, and adaptability, teams can harness the power of hybrid project management to drive innovation and achieve project success.
Discuss the legal aspects of ethical hacking and cybersecurity
In today's digital age, cybersecurity has become more important than ever before. With the rise in cybercrimes and data breaches, organizations are constantly looking for ways to protect their assets and secure their information. One method that has gained popularity in recent years is ethical hacking. Ethical hackers, also known as white-hat hackers, work to identify vulnerabilities in a system before malicious hackers can exploit them.
Ethical Hacking Laws and Regulations
Ethical hacking falls under the umbrella of cybersecurity, and as such, there are legal frameworks that govern its practice. In many countries, including the United States, there are laws that protect ethical hackers from legal action as long as they are acting in good faith and with the permission of the system owner. For example, the Computer Fraud and Abuse Act (CFAA) in the U.S. prohibits unauthorized access to computer systems, but it also includes a provision that exempts ethical hackers who have permission to test a system's security.
Cyber Laws for Ethical Hacking
The legality of ethical hacking is also governed by cyber laws specific to each country. For instance, the United Kingdom's Computer Misuse Act outlines offenses related to unauthorized access to computer systems, but it contains exceptions for those who are conducting ethical hacking with the owner's consent. Similarly, the European Union's General Data Protection Regulation (GDPR) requires organizations to protect the personal data of individuals, which can also impact how ethical hacking is conducted.
Ethical Hacking and Data Protection
One of the main concerns surrounding ethical hacking is data protection. As ethical hackers test the security of a system, they may come across sensitive information or personal data. It is crucial that ethical hackers follow data protection laws and guidelines to ensure that this information is not compromised or misused. In the event that data is accessed during an ethical hacking exercise, it is important to have procedures in place to handle and report any breaches in compliance with data protection regulations.
Regulatory Framework for Cybersecurity
In addition to legal considerations for ethical hacking, organizations must also adhere to regulatory frameworks for cybersecurity. These standards, such as the ISO/IEC 27001 or the NIST Cybersecurity Framework, provide guidelines for implementing effective cybersecurity measures. Ethical hackers play a vital role in helping organizations meet these standards by identifying vulnerabilities and weaknesses that could be exploited by malicious actors.
Ethical Hacking Policies and Procedures
To ensure compliance with legal and regulatory requirements, organizations should establish clear policies and procedures for ethical hacking. These documents should outline the scope of ethical hacking activities, the rules of engagement, and the steps to take in the event of a security breach. By having robust policies in place, organizations can mitigate legal risks and demonstrate a commitment to cybersecurity best practices.
How to obtain Ethical Hacking Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, ethical hacking is a valuable tool for enhancing cybersecurity, but it is essential to understand the legal aspects and requirements associated with this practice. By following the laws and regulations related to ethical hacking, organizations can protect themselves from legal liabilities and ensure the integrity of their cybersecurity efforts. By maintaining compliance with data protection laws, regulatory frameworks, and internal policies, organizations can leverage ethical hacking as a proactive measure to safeguard their assets and information.
Read More
In today's digital age, cybersecurity has become more important than ever before. With the rise in cybercrimes and data breaches, organizations are constantly looking for ways to protect their assets and secure their information. One method that has gained popularity in recent years is ethical hacking. Ethical hackers, also known as white-hat hackers, work to identify vulnerabilities in a system before malicious hackers can exploit them.
Ethical Hacking Laws and Regulations
Ethical hacking falls under the umbrella of cybersecurity, and as such, there are legal frameworks that govern its practice. In many countries, including the United States, there are laws that protect ethical hackers from legal action as long as they are acting in good faith and with the permission of the system owner. For example, the Computer Fraud and Abuse Act (CFAA) in the U.S. prohibits unauthorized access to computer systems, but it also includes a provision that exempts ethical hackers who have permission to test a system's security.
Cyber Laws for Ethical Hacking
The legality of ethical hacking is also governed by cyber laws specific to each country. For instance, the United Kingdom's Computer Misuse Act outlines offenses related to unauthorized access to computer systems, but it contains exceptions for those who are conducting ethical hacking with the owner's consent. Similarly, the European Union's General Data Protection Regulation (GDPR) requires organizations to protect the personal data of individuals, which can also impact how ethical hacking is conducted.
Ethical Hacking and Data Protection
One of the main concerns surrounding ethical hacking is data protection. As ethical hackers test the security of a system, they may come across sensitive information or personal data. It is crucial that ethical hackers follow data protection laws and guidelines to ensure that this information is not compromised or misused. In the event that data is accessed during an ethical hacking exercise, it is important to have procedures in place to handle and report any breaches in compliance with data protection regulations.
Regulatory Framework for Cybersecurity
In addition to legal considerations for ethical hacking, organizations must also adhere to regulatory frameworks for cybersecurity. These standards, such as the ISO/IEC 27001 or the NIST Cybersecurity Framework, provide guidelines for implementing effective cybersecurity measures. Ethical hackers play a vital role in helping organizations meet these standards by identifying vulnerabilities and weaknesses that could be exploited by malicious actors.
Ethical Hacking Policies and Procedures
To ensure compliance with legal and regulatory requirements, organizations should establish clear policies and procedures for ethical hacking. These documents should outline the scope of ethical hacking activities, the rules of engagement, and the steps to take in the event of a security breach. By having robust policies in place, organizations can mitigate legal risks and demonstrate a commitment to cybersecurity best practices.
How to obtain Ethical Hacking Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, ethical hacking is a valuable tool for enhancing cybersecurity, but it is essential to understand the legal aspects and requirements associated with this practice. By following the laws and regulations related to ethical hacking, organizations can protect themselves from legal liabilities and ensure the integrity of their cybersecurity efforts. By maintaining compliance with data protection laws, regulatory frameworks, and internal policies, organizations can leverage ethical hacking as a proactive measure to safeguard their assets and information.
Discover Cisco’s social and environmental initiatives
In today's rapidly evolving world, companies are being pushed to think beyond profits and focus on their social and environmental impact. Cisco, a global leader in technology and networking, is one such company that has taken corporate responsibility to heart. Their commitment to sustainability, community engagement, and innovation is reflected in a range of initiatives aimed at making a positive impact on society and the planet. Let's dive into some of the key social and environmental programs that Cisco has implemented to make a difference.
Cisco's Social Responsibility Initiatives
Cisco's social impact initiatives are centered around community outreach and fostering a sustainable future for all. Through various programs, the company aims to leverage technology solutions for the betterment of society. One such initiative is their focus on digital transformation in underserved communities, providing access to education and healthcare through innovative technology solutions. By using their expertise in networking and technology, Cisco is empowering communities and driving positive change.
Community Engagement
Cisco's community engagement programs are designed to create lasting relationships with local communities and drive societal impact. Through partnerships with non-profit organizations and local governments, Cisco is able to address key social issues such as access to education, healthcare, and job opportunities. By actively engaging with communities around the world, Cisco is building a network of support and collaboration that goes beyond business goals.
Corporate Ethics and Values
At the core of Cisco's social responsibility initiatives are their company values of integrity, transparency, and respect for all individuals. By adhering to strong ethical practices and promoting global citizenship, Cisco is setting a standard for corporate ethics in the technology industry. Their commitment to ethical business practices and environmental conservation is evident in every aspect of their operations, from supply chain management to employee relations.
Cisco's Environmental Sustainability Efforts
In addition to their social responsibility initiatives, Cisco is also dedicated to reducing their environmental footprint and promoting eco-friendly practices. With a focus on green technology and sustainable business practices, Cisco is leading the way in addressing climate change and environmental awareness.
Green Initiatives
Cisco's green initiatives are aimed at reducing their carbon footprint and promoting energy efficiency in all aspects of their operations. From eco-friendly office practices to sustainable product design, Cisco is committed to minimizing their impact on the environment. By promoting the use of green technology and renewable energy sources, Cisco is taking steps towards a more sustainable future for our planet.
Technology for Good
Cisco's commitment to environmental sustainability extends to their products and services, with a focus on developing technology solutions that promote sustainability and reduce waste. By incorporating green technology into their products, Cisco is helping customers reduce their own environmental impact and move towards a more sustainable future. Through innovation and collaboration, Cisco is driving positive change and setting a new standard for corporate environmental responsibility.
How to obtain Cisco certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, Cisco's social and environmental initiatives are a testament to their commitment to making a positive impact on society and the planet. By focusing on sustainability, corporate responsibility, and community engagement, Cisco is setting a standard for ethical business practices and environmental conservation in the technology industry. Through their innovative programs and green initiatives, Cisco is driving positive change and working towards a more sustainable future for all.
Read More
In today's rapidly evolving world, companies are being pushed to think beyond profits and focus on their social and environmental impact. Cisco, a global leader in technology and networking, is one such company that has taken corporate responsibility to heart. Their commitment to sustainability, community engagement, and innovation is reflected in a range of initiatives aimed at making a positive impact on society and the planet. Let's dive into some of the key social and environmental programs that Cisco has implemented to make a difference.
Cisco's Social Responsibility Initiatives
Cisco's social impact initiatives are centered around community outreach and fostering a sustainable future for all. Through various programs, the company aims to leverage technology solutions for the betterment of society. One such initiative is their focus on digital transformation in underserved communities, providing access to education and healthcare through innovative technology solutions. By using their expertise in networking and technology, Cisco is empowering communities and driving positive change.
Community Engagement
Cisco's community engagement programs are designed to create lasting relationships with local communities and drive societal impact. Through partnerships with non-profit organizations and local governments, Cisco is able to address key social issues such as access to education, healthcare, and job opportunities. By actively engaging with communities around the world, Cisco is building a network of support and collaboration that goes beyond business goals.
Corporate Ethics and Values
At the core of Cisco's social responsibility initiatives are their company values of integrity, transparency, and respect for all individuals. By adhering to strong ethical practices and promoting global citizenship, Cisco is setting a standard for corporate ethics in the technology industry. Their commitment to ethical business practices and environmental conservation is evident in every aspect of their operations, from supply chain management to employee relations.
Cisco's Environmental Sustainability Efforts
In addition to their social responsibility initiatives, Cisco is also dedicated to reducing their environmental footprint and promoting eco-friendly practices. With a focus on green technology and sustainable business practices, Cisco is leading the way in addressing climate change and environmental awareness.
Green Initiatives
Cisco's green initiatives are aimed at reducing their carbon footprint and promoting energy efficiency in all aspects of their operations. From eco-friendly office practices to sustainable product design, Cisco is committed to minimizing their impact on the environment. By promoting the use of green technology and renewable energy sources, Cisco is taking steps towards a more sustainable future for our planet.
Technology for Good
Cisco's commitment to environmental sustainability extends to their products and services, with a focus on developing technology solutions that promote sustainability and reduce waste. By incorporating green technology into their products, Cisco is helping customers reduce their own environmental impact and move towards a more sustainable future. Through innovation and collaboration, Cisco is driving positive change and setting a new standard for corporate environmental responsibility.
How to obtain Cisco certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, Cisco's social and environmental initiatives are a testament to their commitment to making a positive impact on society and the planet. By focusing on sustainability, corporate responsibility, and community engagement, Cisco is setting a standard for ethical business practices and environmental conservation in the technology industry. Through their innovative programs and green initiatives, Cisco is driving positive change and working towards a more sustainable future for all.
Explore ethical hackers improving biometric security
In today's digital age, cybersecurity is more important than ever. With the rise of biometric technology for data protection, it has become crucial to ensure that biometric security systems are secure from cyber threats. Ethical hackers play a vital role in improving biometric security by identifying vulnerabilities and implementing measures to enhance digital security.
How do Ethical Hackers Improve Biometric Security?
Ethical hackers utilize a variety of hacker tools and techniques to test the security of biometric authentication systems. By mimicking cyber threats, they can identify weaknesses in security protocols and develop strategies to prevent unauthorized access to biometric data.
What is Ethical Hacking?
Ethical hacking is the practice of testing and improving the security of computer systems and networks. Ethical hackers, also known as "white hat" hackers, use their skills to identify vulnerabilities and protect against cyber attacks.
Ethical Hacking Techniques for Biometric Security:
-
Penetration Testing: Ethical hackers conduct penetration tests to identify weaknesses in biometric security systems.
-
Social Engineering: They use social engineering techniques to test the human factor of security protocols.
-
Code Analysis: Ethical hackers analyze the code of biometric authentication systems to identify vulnerabilities.
Cybersecurity Measures for Biometric Data Protection:
-
Encryption: Encrypting biometric data helps protect it from unauthorized access.
-
Multi-factor Authentication: Implementing multi-factor authentication adds an extra layer of security to biometric verification.
-
Regular Security Audits: Conducting regular security audits helps identify and address any security vulnerabilities in biometric systems.
Advancements in Biometric Security:
With the advancement of biometric technology, biometric authentication has become more secure and reliable. Ethical hackers play a crucial role in ensuring that these systems are protected from cyber threats.
The Role of Ethical Hackers in Enhancing Biometric Security:
Ethical hackers in the hacker community work tirelessly to improve the security of biometric verification systems. Their expertise in hacking prevention techniques and biometric authentication helps enhance the overall security of digital systems.
Ethical Hacking Services for Improving Security Systems:
Many organizations offer ethical hacking services to help businesses improve their security systems. These services include vulnerability assessments, penetration testing, and security audits to identify and address security vulnerabilities.
Secure Biometric Solutions:
By working with ethical hackers, businesses can implement secure biometric solutions that protect sensitive data from cyber threats. Ethical hackers provide valuable insights into the best practices for biometric security.
How to obtain Ethical Hacking Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, ethical hackers play a crucial role in improving biometric security by identifying vulnerabilities, implementing cybersecurity measures, and enhancing biometric authentication systems. With their expertise and skills, ethical hackers help businesses protect their data and secure their digital systems from cyber threats.
Read More
In today's digital age, cybersecurity is more important than ever. With the rise of biometric technology for data protection, it has become crucial to ensure that biometric security systems are secure from cyber threats. Ethical hackers play a vital role in improving biometric security by identifying vulnerabilities and implementing measures to enhance digital security.
How do Ethical Hackers Improve Biometric Security?
Ethical hackers utilize a variety of hacker tools and techniques to test the security of biometric authentication systems. By mimicking cyber threats, they can identify weaknesses in security protocols and develop strategies to prevent unauthorized access to biometric data.
What is Ethical Hacking?
Ethical hacking is the practice of testing and improving the security of computer systems and networks. Ethical hackers, also known as "white hat" hackers, use their skills to identify vulnerabilities and protect against cyber attacks.
Ethical Hacking Techniques for Biometric Security:
-
Penetration Testing: Ethical hackers conduct penetration tests to identify weaknesses in biometric security systems.
-
Social Engineering: They use social engineering techniques to test the human factor of security protocols.
-
Code Analysis: Ethical hackers analyze the code of biometric authentication systems to identify vulnerabilities.
Cybersecurity Measures for Biometric Data Protection:
-
Encryption: Encrypting biometric data helps protect it from unauthorized access.
-
Multi-factor Authentication: Implementing multi-factor authentication adds an extra layer of security to biometric verification.
-
Regular Security Audits: Conducting regular security audits helps identify and address any security vulnerabilities in biometric systems.
Advancements in Biometric Security:
With the advancement of biometric technology, biometric authentication has become more secure and reliable. Ethical hackers play a crucial role in ensuring that these systems are protected from cyber threats.
The Role of Ethical Hackers in Enhancing Biometric Security:
Ethical hackers in the hacker community work tirelessly to improve the security of biometric verification systems. Their expertise in hacking prevention techniques and biometric authentication helps enhance the overall security of digital systems.
Ethical Hacking Services for Improving Security Systems:
Many organizations offer ethical hacking services to help businesses improve their security systems. These services include vulnerability assessments, penetration testing, and security audits to identify and address security vulnerabilities.
Secure Biometric Solutions:
By working with ethical hackers, businesses can implement secure biometric solutions that protect sensitive data from cyber threats. Ethical hackers provide valuable insights into the best practices for biometric security.
How to obtain Ethical Hacking Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, ethical hackers play a crucial role in improving biometric security by identifying vulnerabilities, implementing cybersecurity measures, and enhancing biometric authentication systems. With their expertise and skills, ethical hackers help businesses protect their data and secure their digital systems from cyber threats.
Explore Azure monitoring tools and diagnostic solutions
Are you looking to enhance the performance and security of your Azure cloud environment? Explore Azure monitoring tools and diagnostic solutions to gain valuable insights into your infrastructure, applications, and network.
Introduction to Azure Monitoring and Diagnostic Solutions
Azure offers a comprehensive suite of monitoring and diagnostic tools to help you monitor, detect, and troubleshoot issues in real-time. From performance monitoring to log analytics, Azure provides a range of solutions to ensure the health and security of your cloud environment.
Azure Monitoring Services
Azure monitoring services allow you to collect and analyze data from various sources to gain insights into the health and performance of your applications and infrastructure. These services include:
-
Azure Monitor: A unified platform for monitoring your Azure resources and applications.
-
Azure Application Insights: Provides real-time insights into the performance and usage of your applications.
-
Azure Log Analytics: Collects and analyzes log data from various sources for troubleshooting and monitoring.
Azure Diagnostic Solutions
Azure diagnostic solutions enable you to diagnose issues, monitor performance, and capture diagnostics data across your Azure resources. Some key diagnostic solutions include:
-
Network Monitoring Tools: Monitor network traffic, connectivity, and performance.
-
Azure Resource Monitoring: Track the performance and health of your Azure resources.
-
Azure Infrastructure Monitoring: Monitor the infrastructure components of your Azure environment.
-
Azure Security Monitoring: Detect and respond to security threats in real-time.
Azure Performance Monitoring
Monitoring the performance of your Azure environment is crucial to ensure optimal operation and user experience. Azure offers a range of tools for performance monitoring, including:
-
Azure Log Monitoring: Monitor and analyze log data to identify performance issues.
-
Azure Application Monitoring: Track the performance of your applications and services.
-
Server Monitoring Tools: Monitor the performance and health of servers in your Azure environment.
Azure Troubleshooting Tools
In the event of performance issues or system failures, Azure troubleshooting tools can help you quickly diagnose and resolve issues. These tools include:
Azure Health Monitoring: Check the health status of your resources and applications.
Application Performance Monitoring: Monitor the performance metrics of your applications.
Azure Alerting Tools: Set up alerts to notify you of critical issues in real-time.
Best Practices for Azure Monitoring
To maximize the benefits of Azure monitoring tools and diagnostic solutions, consider the following best practices:
Ensure proper configuration of monitoring tools to capture relevant data.
Regularly review and analyze monitoring data to identify performance trends and anomalies.
Set up alerts and notifications to proactively address issues before they impact operations.
Azure Monitoring Integration
Azure monitoring tools can be integrated with third-party monitoring solutions for enhanced visibility and analysis. Explore the possibilities of integrating Azure monitoring services for a comprehensive monitoring strategy.
Azure Monitoring Services Comparison
When choosing monitoring solutions for your Azure environment, consider the unique capabilities and features of each service. Compare Azure monitoring services to select the options that best meet your monitoring requirements.
How to obtain MicroSoft Azure certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
1. Certified Information Systems Security Professional® (CISSP)
2. AWS Certified Solutions Architect
3. Google Certified Professional Cloud Architect
4. Big Data Certification
5. Data Science Certification
6. Certified In Risk And Information Systems Control (CRISC)
7. Certified Information Security Manager(CISM)
8. Project Management Professional (PMP)® Certification
9. Certified Ethical Hacker (CEH)
10. Certified Scrum Master (CSM)
Conclusion
Exploring Azure monitoring tools and diagnostic solutions is essential for maintaining the performance, security, and reliability of your cloud environment. With a range of monitoring services and diagnostic solutions available, Azure provides the tools you need to monitor, diagnose, and troubleshoot issues in real-time. Take advantage of these solutions to optimize the performance of your Azure infrastructure and applications.
Read More
Are you looking to enhance the performance and security of your Azure cloud environment? Explore Azure monitoring tools and diagnostic solutions to gain valuable insights into your infrastructure, applications, and network.
Introduction to Azure Monitoring and Diagnostic Solutions
Azure offers a comprehensive suite of monitoring and diagnostic tools to help you monitor, detect, and troubleshoot issues in real-time. From performance monitoring to log analytics, Azure provides a range of solutions to ensure the health and security of your cloud environment.
Azure Monitoring Services
Azure monitoring services allow you to collect and analyze data from various sources to gain insights into the health and performance of your applications and infrastructure. These services include:
-
Azure Monitor: A unified platform for monitoring your Azure resources and applications.
-
Azure Application Insights: Provides real-time insights into the performance and usage of your applications.
-
Azure Log Analytics: Collects and analyzes log data from various sources for troubleshooting and monitoring.
Azure Diagnostic Solutions
Azure diagnostic solutions enable you to diagnose issues, monitor performance, and capture diagnostics data across your Azure resources. Some key diagnostic solutions include:
-
Network Monitoring Tools: Monitor network traffic, connectivity, and performance.
-
Azure Resource Monitoring: Track the performance and health of your Azure resources.
-
Azure Infrastructure Monitoring: Monitor the infrastructure components of your Azure environment.
-
Azure Security Monitoring: Detect and respond to security threats in real-time.
Azure Performance Monitoring
Monitoring the performance of your Azure environment is crucial to ensure optimal operation and user experience. Azure offers a range of tools for performance monitoring, including:
-
Azure Log Monitoring: Monitor and analyze log data to identify performance issues.
-
Azure Application Monitoring: Track the performance of your applications and services.
-
Server Monitoring Tools: Monitor the performance and health of servers in your Azure environment.
Azure Troubleshooting Tools
In the event of performance issues or system failures, Azure troubleshooting tools can help you quickly diagnose and resolve issues. These tools include:
Azure Health Monitoring: Check the health status of your resources and applications.
Application Performance Monitoring: Monitor the performance metrics of your applications.
Azure Alerting Tools: Set up alerts to notify you of critical issues in real-time.
Best Practices for Azure Monitoring
To maximize the benefits of Azure monitoring tools and diagnostic solutions, consider the following best practices:
Ensure proper configuration of monitoring tools to capture relevant data.
Regularly review and analyze monitoring data to identify performance trends and anomalies.
Set up alerts and notifications to proactively address issues before they impact operations.
Azure Monitoring Integration
Azure monitoring tools can be integrated with third-party monitoring solutions for enhanced visibility and analysis. Explore the possibilities of integrating Azure monitoring services for a comprehensive monitoring strategy.
Azure Monitoring Services Comparison
When choosing monitoring solutions for your Azure environment, consider the unique capabilities and features of each service. Compare Azure monitoring services to select the options that best meet your monitoring requirements.
How to obtain MicroSoft Azure certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
1. Certified Information Systems Security Professional® (CISSP)
2. AWS Certified Solutions Architect
3. Google Certified Professional Cloud Architect
4. Big Data Certification
5. Data Science Certification
6. Certified In Risk And Information Systems Control (CRISC)
7. Certified Information Security Manager(CISM)
8. Project Management Professional (PMP)® Certification
9. Certified Ethical Hacker (CEH)
10. Certified Scrum Master (CSM)
Conclusion
Exploring Azure monitoring tools and diagnostic solutions is essential for maintaining the performance, security, and reliability of your cloud environment. With a range of monitoring services and diagnostic solutions available, Azure provides the tools you need to monitor, diagnose, and troubleshoot issues in real-time. Take advantage of these solutions to optimize the performance of your Azure infrastructure and applications.
CISSP Certification and Government Security Roles: A Deep Dive
Are you interested in advancing your career in cybersecurity and securing a government IT role? If so, obtaining a Certified Information Systems Security Professional (CISSP) certification could be the key to unlocking new opportunities in the field of information security. In this article, we will delve into the importance of CISSP certification in government security roles and explore the various aspects of cybersecurity that this certification covers.
What is a CISSP Certification?
A CISSP certification is a globally recognized certification in the field of information security. It demonstrates that an individual has the expertise and knowledge required to effectively design, implement, and manage a secure business environment. Obtaining a CISSP certification requires passing a rigorous certification exam that covers various domains of information security.
What are the Domains Covered in the CISSP Certification Exam?
The CISSP certification exam covers eight domains of information security, including:
-
Security and Risk Management
-
Asset Security
-
Security Architecture and Engineering
-
Communication and Network Security
-
Identity and Access Management
-
Security Assessment and Testing
-
Security Operations
-
Software Development Security
Government Security Roles and CISSP Certification
Government organizations hold a vast amount of sensitive data that must be protected from cybersecurity threats. Therefore, they often require professionals with CISSP certification to ensure the security of their IT infrastructures. By obtaining a CISSP certification, you can qualify for various government security roles such as:
-
Cyber Defense Analyst
-
Information Assurance Specialist
-
Security Architect
-
Security Engineer
-
Security Operations Manager
Advantages of CISSP Certification in Government Security Roles
Obtaining a CISSP certification can provide you with numerous benefits when pursuing government security roles, including:
-
Enhanced Knowledge: The certification covers a wide range of cybersecurity domains, equipping you with the necessary skills to protect government IT environments.
-
Career Advancement: CISSP certification can open up new career opportunities and lead to higher-paying positions within government organizations.
-
Enhanced Security Policies: By understanding security policies, risk management, and asset security, you can help improve the overall security posture of government agencies.
-
Incident Response: With expertise in incident response and disaster recovery planning, you can effectively mitigate security incidents and protect government data.
-
Ethical Hacking Skills: CISSP certification includes knowledge of ethical hacking, allowing you to identify and address vulnerabilities in government systems.
How to obtain CISSP Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, CISSP certification plays a crucial role in securing government IT environments and advancing careers in cybersecurity. By obtaining this certification, you can demonstrate your expertise in various cybersecurity domains and qualify for prestigious government security roles. If you are considering a career in government cybersecurity, pursuing a CISSP certification could be the first step towards achieving your goals.
Read More
Are you interested in advancing your career in cybersecurity and securing a government IT role? If so, obtaining a Certified Information Systems Security Professional (CISSP) certification could be the key to unlocking new opportunities in the field of information security. In this article, we will delve into the importance of CISSP certification in government security roles and explore the various aspects of cybersecurity that this certification covers.
What is a CISSP Certification?
A CISSP certification is a globally recognized certification in the field of information security. It demonstrates that an individual has the expertise and knowledge required to effectively design, implement, and manage a secure business environment. Obtaining a CISSP certification requires passing a rigorous certification exam that covers various domains of information security.
What are the Domains Covered in the CISSP Certification Exam?
The CISSP certification exam covers eight domains of information security, including:
-
Security and Risk Management
-
Asset Security
-
Security Architecture and Engineering
-
Communication and Network Security
-
Identity and Access Management
-
Security Assessment and Testing
-
Security Operations
-
Software Development Security
Government Security Roles and CISSP Certification
Government organizations hold a vast amount of sensitive data that must be protected from cybersecurity threats. Therefore, they often require professionals with CISSP certification to ensure the security of their IT infrastructures. By obtaining a CISSP certification, you can qualify for various government security roles such as:
-
Cyber Defense Analyst
-
Information Assurance Specialist
-
Security Architect
-
Security Engineer
-
Security Operations Manager
Advantages of CISSP Certification in Government Security Roles
Obtaining a CISSP certification can provide you with numerous benefits when pursuing government security roles, including:
-
Enhanced Knowledge: The certification covers a wide range of cybersecurity domains, equipping you with the necessary skills to protect government IT environments.
-
Career Advancement: CISSP certification can open up new career opportunities and lead to higher-paying positions within government organizations.
-
Enhanced Security Policies: By understanding security policies, risk management, and asset security, you can help improve the overall security posture of government agencies.
-
Incident Response: With expertise in incident response and disaster recovery planning, you can effectively mitigate security incidents and protect government data.
-
Ethical Hacking Skills: CISSP certification includes knowledge of ethical hacking, allowing you to identify and address vulnerabilities in government systems.
How to obtain CISSP Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, CISSP certification plays a crucial role in securing government IT environments and advancing careers in cybersecurity. By obtaining this certification, you can demonstrate your expertise in various cybersecurity domains and qualify for prestigious government security roles. If you are considering a career in government cybersecurity, pursuing a CISSP certification could be the first step towards achieving your goals.
The Ultimate Minitab Certification Study Plan: Structuring Your Preparation
Are you looking to boost your career in data analysis and statistics? Obtaining a Minitab certification can be a great way to demonstrate your expertise and proficiency in using this powerful statistical software. However, preparing for the Minitab certification exam can be a daunting task. That's why it's essential to have a structured study plan in place to ensure success. In this article, we'll provide you with a comprehensive guide on how to create the ultimate Minitab certification study plan to help you ace the exam with confidence.
Understanding the Minitab Certification Process
Before diving into your study plan, it's crucial to first understand the Minitab certification process. The Minitab certification exam tests your knowledge and skills in using the software for statistical analysis, quality improvement, and process optimization. To become certified, you must pass the exam, which consists of multiple-choice questions designed to assess your proficiency in various aspects of Minitab.
Creating a Study Schedule
The key to success in preparing for the Minitab certification exam is to create a well-structured study schedule. Start by assessing your current knowledge and skills in using Minitab and identify areas where you need to improve. Divide your study schedule into manageable sections, focusing on different topics such as data analysis, hypothesis testing, regression analysis, and more.
Minitab Certification Exam Tips
To help you prepare effectively for the Minitab certification exam, here are some valuable tips to keep in mind:
-
Familiarize yourself with the Minitab interface and features
-
Practice using the software regularly to enhance your proficiency
-
Review sample exam questions to understand the format and types of questions
-
Join a study group or online course to supplement your studying
-
Utilize resources such as study guides, practice exams, and tutorials
-
Stay organized and track your progress to ensure you cover all necessary topics
Best Practices for Minitab Certification
In addition to creating a study schedule and following exam tips, here are some best practices to consider when preparing for the Minitab certification:
-
Set realistic goals and timelines for your study plan
-
Take breaks and allow yourself time to rest and recharge
-
Seek guidance from experienced professionals or mentors in the field
-
Stay motivated and committed to your study plan
-
Practice problem-solving and critical thinking skills
-
Stay updated on the latest trends and developments in data analysis and statistics
Minitab Certification Study Materials
As you prepare for the Minitab certification exam, you'll need access to a variety of study materials to help you review and practice. Some essential resources to consider include:
-
Official Minitab study guides and practice exams
-
Online tutorials and video tutorials
-
Reference books on statistics and data analysis
-
Interactive online courses and workshops
-
Study aids such as flashcards and cheat sheets
How to obtain Quality Management Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Top 10 – Certification Cources in 2024
Conclusion
In conclusion, preparing for the Minitab certification exam requires dedication, commitment, and a well-structured study plan. By following the tips, best practices, and utilizing the right study materials, you can enhance your chances of success and achieve your goal of becoming Minitab certified.
Read More
Are you looking to boost your career in data analysis and statistics? Obtaining a Minitab certification can be a great way to demonstrate your expertise and proficiency in using this powerful statistical software. However, preparing for the Minitab certification exam can be a daunting task. That's why it's essential to have a structured study plan in place to ensure success. In this article, we'll provide you with a comprehensive guide on how to create the ultimate Minitab certification study plan to help you ace the exam with confidence.
Understanding the Minitab Certification Process
Before diving into your study plan, it's crucial to first understand the Minitab certification process. The Minitab certification exam tests your knowledge and skills in using the software for statistical analysis, quality improvement, and process optimization. To become certified, you must pass the exam, which consists of multiple-choice questions designed to assess your proficiency in various aspects of Minitab.
Creating a Study Schedule
The key to success in preparing for the Minitab certification exam is to create a well-structured study schedule. Start by assessing your current knowledge and skills in using Minitab and identify areas where you need to improve. Divide your study schedule into manageable sections, focusing on different topics such as data analysis, hypothesis testing, regression analysis, and more.
Minitab Certification Exam Tips
To help you prepare effectively for the Minitab certification exam, here are some valuable tips to keep in mind:
-
Familiarize yourself with the Minitab interface and features
-
Practice using the software regularly to enhance your proficiency
-
Review sample exam questions to understand the format and types of questions
-
Join a study group or online course to supplement your studying
-
Utilize resources such as study guides, practice exams, and tutorials
-
Stay organized and track your progress to ensure you cover all necessary topics
Best Practices for Minitab Certification
In addition to creating a study schedule and following exam tips, here are some best practices to consider when preparing for the Minitab certification:
-
Set realistic goals and timelines for your study plan
-
Take breaks and allow yourself time to rest and recharge
-
Seek guidance from experienced professionals or mentors in the field
-
Stay motivated and committed to your study plan
-
Practice problem-solving and critical thinking skills
-
Stay updated on the latest trends and developments in data analysis and statistics
Minitab Certification Study Materials
As you prepare for the Minitab certification exam, you'll need access to a variety of study materials to help you review and practice. Some essential resources to consider include:
-
Official Minitab study guides and practice exams
-
Online tutorials and video tutorials
-
Reference books on statistics and data analysis
-
Interactive online courses and workshops
-
Study aids such as flashcards and cheat sheets
How to obtain Quality Management Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Top 10 – Certification Cources in 2024
Conclusion
In conclusion, preparing for the Minitab certification exam requires dedication, commitment, and a well-structured study plan. By following the tips, best practices, and utilizing the right study materials, you can enhance your chances of success and achieve your goal of becoming Minitab certified.
NetScaler Certification: Benefits for IT Professionals and Employers
Are you an IT professional looking to advance your career and stand out in the competitive job market? Or are you an employer seeking skilled professionals to enhance your organization's technological capabilities? Look no further than the NetScaler certification program offered by Citrix.
What is NetScaler Certification?
NetScaler certification is a validation of one's expertise in networking, virtualization, and cloud computing technologies. It demonstrates that an individual possesses the necessary skills to design, implement, and manage Citrix NetScaler solutions effectively.
Benefits for IT Professionals
-
Career Advancement: Holding a NetScaler certification can open doors to new job opportunities and career growth within the IT industry. Employers value certified professionals for their specialized skills and expertise.
-
Skills Validation: By obtaining a NetScaler certification, IT professionals can demonstrate their proficiency in network security, load balancing, and application delivery control. This validation can boost their credibility and reputation in the industry.
-
Professional Development: Certification programs provide structured learning paths that help professionals stay current with the latest technologies and trends. Continuous learning and skill development are essential for staying competitive in today's rapidly evolving IT landscape.
-
Remote Work: In an era where remote work is becoming increasingly prevalent, having a NetScaler certification can give IT professionals a competitive edge. Employers are seeking individuals who can effectively manage and secure remote access to corporate networks.
Benefits for Employers
-
Industry Recognition: Employers who hire certified IT professionals with NetScaler credentials can gain industry recognition for employing skilled individuals with specialized knowledge in networking and virtualization technologies.
-
Workforce Development: Investing in certification training for employees can enhance the overall skill level of the workforce and improve the organization's technological capabilities. Well-trained professionals can contribute to increased productivity and efficiency.
-
Certification Worth It: The benefits of hiring certified IT professionals often outweigh the costs associated with certification training. Organizations can reap the rewards of having skilled employees who can drive innovation and technological advancement within the company.
How to obtain Citrix Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Top 10 – Certification Cources in 2024
Conclusion
In conclusion, NetScaler certification offers numerous benefits for both IT professionals and employers. Whether you are looking to enhance your career prospects or strengthen your organization's technological capabilities, investing in certification training can be a wise decision. Stay ahead of the curve in the ever-evolving IT industry by acquiring the knowledge and skills needed to succeed with a NetScaler certification.
Read More
Are you an IT professional looking to advance your career and stand out in the competitive job market? Or are you an employer seeking skilled professionals to enhance your organization's technological capabilities? Look no further than the NetScaler certification program offered by Citrix.
What is NetScaler Certification?
NetScaler certification is a validation of one's expertise in networking, virtualization, and cloud computing technologies. It demonstrates that an individual possesses the necessary skills to design, implement, and manage Citrix NetScaler solutions effectively.
Benefits for IT Professionals
-
Career Advancement: Holding a NetScaler certification can open doors to new job opportunities and career growth within the IT industry. Employers value certified professionals for their specialized skills and expertise.
-
Skills Validation: By obtaining a NetScaler certification, IT professionals can demonstrate their proficiency in network security, load balancing, and application delivery control. This validation can boost their credibility and reputation in the industry.
-
Professional Development: Certification programs provide structured learning paths that help professionals stay current with the latest technologies and trends. Continuous learning and skill development are essential for staying competitive in today's rapidly evolving IT landscape.
-
Remote Work: In an era where remote work is becoming increasingly prevalent, having a NetScaler certification can give IT professionals a competitive edge. Employers are seeking individuals who can effectively manage and secure remote access to corporate networks.
Benefits for Employers
-
Industry Recognition: Employers who hire certified IT professionals with NetScaler credentials can gain industry recognition for employing skilled individuals with specialized knowledge in networking and virtualization technologies.
-
Workforce Development: Investing in certification training for employees can enhance the overall skill level of the workforce and improve the organization's technological capabilities. Well-trained professionals can contribute to increased productivity and efficiency.
-
Certification Worth It: The benefits of hiring certified IT professionals often outweigh the costs associated with certification training. Organizations can reap the rewards of having skilled employees who can drive innovation and technological advancement within the company.
How to obtain Citrix Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Top 10 – Certification Cources in 2024
Conclusion
In conclusion, NetScaler certification offers numerous benefits for both IT professionals and employers. Whether you are looking to enhance your career prospects or strengthen your organization's technological capabilities, investing in certification training can be a wise decision. Stay ahead of the curve in the ever-evolving IT industry by acquiring the knowledge and skills needed to succeed with a NetScaler certification.
Understanding Quality Control and Process Improvement with Minitab
In today's competitive business environment, ensuring quality control and process improvement is essential for organizations to stay ahead of the curve. One powerful tool that has gained widespread popularity for statistical analysis and data-driven decision-making is Minitab. This article will explore how Minitab software can help businesses enhance their quality management, optimize processes, and drive continuous improvement.
What is Minitab and How Does it Work?
Minitab is a powerful statistical software that provides a wide range of tools and features for quality control and process improvement. With Minitab, users can perform statistical analysis, data visualization, and hypothesis testing to identify trends, patterns, and insights in their data. From quality assurance to process optimization, Minitab offers a comprehensive suite of statistical tools to help businesses make informed decisions and drive performance improvements.
Key Features of Minitab:
Some key features of Minitab software include:
-
Statistical techniques: Minitab offers a wide range of statistical tools and techniques for analyzing data and making data-driven decisions.
-
Process monitoring: With Minitab, users can monitor processes in real-time and identify any deviations or abnormalities that may impact quality.
-
Quality inspection: Minitab allows users to conduct thorough quality inspections and ensure that products meet the required quality standards.
-
Process optimization: Minitab helps businesses identify process inefficiencies and bottlenecks, leading to process enhancement and improved productivity.
-
Continuous improvement: Minitab enables organizations to implement a culture of continuous improvement, driving efficiency and innovation in their processes.
Minitab in Action: Case Study
To better understand how companies can benefit from Minitab, let's look at a case study of a manufacturing company that utilized Minitab for quality control and process improvement. The company was experiencing high defect rates in their production line, leading to increased rework and customer complaints. By implementing Minitab for statistical analysis and process optimization, the company was able to identify the root causes of defects, implement corrective actions, and reduce defect rates by 20% within six months. This resulted in cost savings, improved customer satisfaction, and enhanced process efficiency.
Training and Resources:
For organizations looking to maximize the benefits of Minitab, training and resources are essential. Minitab offers a range of training programs, tutorials, and certifications to help users master the software and apply statistical techniques effectively. From basic Minitab techniques to advanced statistical tools, organizations can leverage Minitab's capabilities to enhance their quality management and process optimization initiatives.
How to obtain Minitab certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion:
In conclusion, Minitab is a powerful tool for quality control and process improvement, offering a wide range of statistical tools and techniques to help businesses drive performance improvements. From quality inspection to process monitoring, Minitab can help organizations optimize their processes, ensure quality standards, and achieve continuous improvement. By leveraging Minitab's capabilities and training resources, businesses can enhance their quality management practices, boost efficiency, and stay ahead of the competition in today's dynamic business landscape.
Read More
In today's competitive business environment, ensuring quality control and process improvement is essential for organizations to stay ahead of the curve. One powerful tool that has gained widespread popularity for statistical analysis and data-driven decision-making is Minitab. This article will explore how Minitab software can help businesses enhance their quality management, optimize processes, and drive continuous improvement.
What is Minitab and How Does it Work?
Minitab is a powerful statistical software that provides a wide range of tools and features for quality control and process improvement. With Minitab, users can perform statistical analysis, data visualization, and hypothesis testing to identify trends, patterns, and insights in their data. From quality assurance to process optimization, Minitab offers a comprehensive suite of statistical tools to help businesses make informed decisions and drive performance improvements.
Key Features of Minitab:
Some key features of Minitab software include:
-
Statistical techniques: Minitab offers a wide range of statistical tools and techniques for analyzing data and making data-driven decisions.
-
Process monitoring: With Minitab, users can monitor processes in real-time and identify any deviations or abnormalities that may impact quality.
-
Quality inspection: Minitab allows users to conduct thorough quality inspections and ensure that products meet the required quality standards.
-
Process optimization: Minitab helps businesses identify process inefficiencies and bottlenecks, leading to process enhancement and improved productivity.
-
Continuous improvement: Minitab enables organizations to implement a culture of continuous improvement, driving efficiency and innovation in their processes.
Minitab in Action: Case Study
To better understand how companies can benefit from Minitab, let's look at a case study of a manufacturing company that utilized Minitab for quality control and process improvement. The company was experiencing high defect rates in their production line, leading to increased rework and customer complaints. By implementing Minitab for statistical analysis and process optimization, the company was able to identify the root causes of defects, implement corrective actions, and reduce defect rates by 20% within six months. This resulted in cost savings, improved customer satisfaction, and enhanced process efficiency.
Training and Resources:
For organizations looking to maximize the benefits of Minitab, training and resources are essential. Minitab offers a range of training programs, tutorials, and certifications to help users master the software and apply statistical techniques effectively. From basic Minitab techniques to advanced statistical tools, organizations can leverage Minitab's capabilities to enhance their quality management and process optimization initiatives.
How to obtain Minitab certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion:
In conclusion, Minitab is a powerful tool for quality control and process improvement, offering a wide range of statistical tools and techniques to help businesses drive performance improvements. From quality inspection to process monitoring, Minitab can help organizations optimize their processes, ensure quality standards, and achieve continuous improvement. By leveraging Minitab's capabilities and training resources, businesses can enhance their quality management practices, boost efficiency, and stay ahead of the competition in today's dynamic business landscape.
Visualizing Data with Charts and Graphs: Excel 2024 Certification Tips
In today's data-driven world, the ability to effectively visualize and analyze data is a crucial skill for professionals in any industry. Excel, with its powerful charting and graphing features, is a popular tool for creating visual representations of data. If you are looking to enhance your Excel skills and earn certification in 2024, you've come to the right place. In this article, we will explore some tips and best practices for visualizing data with charts and graphs in Excel, as well as how to prepare for Excel certification in 2024.
Excel Charts and Graphs
One of the key features of Excel is its ability to create a wide variety of charts and graphs to visually represent data. From simple bar charts and line graphs to more complex pie charts and scatter plots, Excel offers a range of options for displaying data in a clear and informative way. By choosing the right chart type for your data, you can easily communicate trends, patterns, and insights to your audience.
Data Visualization Techniques
When creating charts and graphs in Excel, it's important to consider the best practices for data visualization. This includes choosing the right colors, fonts, and labels to make your charts easy to read and understand. You should also pay attention to the use of whitespace and gridlines to help guide the viewer's eyes across the chart. By following these techniques, you can create professional-looking visualizations that effectively convey your message.
Excel Certification Tips
If you are aiming to become certified in Excel in 2024, it's important to start preparing early and familiarize yourself with the exam requirements. Excel certification exams typically test your knowledge of chart creation, graph design, data analysis, and formula use. By practicing with sample questions and completing mock exams, you can identify areas where you need to improve and focus your study efforts accordingly.
Excel Data Analysis Skills
Excel certification exams often include questions that require you to analyze data sets and interpret the results using charts and graphs. To excel in this aspect of the exam, you should be familiar with common data analysis techniques such as sorting, filtering, and pivot tables. You should also have a good understanding of how to use Excel formulas to perform calculations and create dynamic visualizations.
Excel Chart Design
When designing charts in Excel, it's important to consider the visual representation of your data. Choosing the right chart type and formatting options can make a big difference in how effectively your message is communicated. By experimenting with different chart styles and layouts, you can find the best design that enhances the readability and impact of your data visualizations.
How to obtain Microsoft Excel 2013 Foundation Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, mastering the art of visualizing data with charts and graphs in Excel is a valuable skill for anyone looking to excel in data analysis and presentation. By following these tips and best practices, you can enhance your Excel skills, prepare for certification in 2024, and create compelling visualizations that tell a compelling story.
Read More
In today's data-driven world, the ability to effectively visualize and analyze data is a crucial skill for professionals in any industry. Excel, with its powerful charting and graphing features, is a popular tool for creating visual representations of data. If you are looking to enhance your Excel skills and earn certification in 2024, you've come to the right place. In this article, we will explore some tips and best practices for visualizing data with charts and graphs in Excel, as well as how to prepare for Excel certification in 2024.
Excel Charts and Graphs
One of the key features of Excel is its ability to create a wide variety of charts and graphs to visually represent data. From simple bar charts and line graphs to more complex pie charts and scatter plots, Excel offers a range of options for displaying data in a clear and informative way. By choosing the right chart type for your data, you can easily communicate trends, patterns, and insights to your audience.
Data Visualization Techniques
When creating charts and graphs in Excel, it's important to consider the best practices for data visualization. This includes choosing the right colors, fonts, and labels to make your charts easy to read and understand. You should also pay attention to the use of whitespace and gridlines to help guide the viewer's eyes across the chart. By following these techniques, you can create professional-looking visualizations that effectively convey your message.
Excel Certification Tips
If you are aiming to become certified in Excel in 2024, it's important to start preparing early and familiarize yourself with the exam requirements. Excel certification exams typically test your knowledge of chart creation, graph design, data analysis, and formula use. By practicing with sample questions and completing mock exams, you can identify areas where you need to improve and focus your study efforts accordingly.
Excel Data Analysis Skills
Excel certification exams often include questions that require you to analyze data sets and interpret the results using charts and graphs. To excel in this aspect of the exam, you should be familiar with common data analysis techniques such as sorting, filtering, and pivot tables. You should also have a good understanding of how to use Excel formulas to perform calculations and create dynamic visualizations.
Excel Chart Design
When designing charts in Excel, it's important to consider the visual representation of your data. Choosing the right chart type and formatting options can make a big difference in how effectively your message is communicated. By experimenting with different chart styles and layouts, you can find the best design that enhances the readability and impact of your data visualizations.
How to obtain Microsoft Excel 2013 Foundation Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, mastering the art of visualizing data with charts and graphs in Excel is a valuable skill for anyone looking to excel in data analysis and presentation. By following these tips and best practices, you can enhance your Excel skills, prepare for certification in 2024, and create compelling visualizations that tell a compelling story.
Salesforce Automation: Simplifying Repetitive Tasks and Boosting Efficiency
In today's fast-paced business world, time is of the essence. Every second counts, and any opportunity to streamline processes and increase efficiency is considered a valuable asset. This is where Salesforce automation comes into play. By automating repetitive tasks and optimizing workflows, businesses can save time, reduce errors, and ultimately boost their overall productivity.
What is Salesforce Automation?
Salesforce automation is the practice of using technology to automate manual tasks within the Salesforce platform. This can include anything from automatically updating customer records to sending out follow-up emails based on predefined criteria. By leveraging automation tools, businesses can free up their employees to focus on more strategic tasks, while also ensuring that routine processes are completed efficiently and consistently.
How Does Salesforce Automation Work?
At its core, Salesforce automation relies on a set of rules and triggers that determine when certain actions should be taken. For example, a sales representative may set up a rule that triggers an automated email to be sent to a customer after a certain amount of time has passed since their last interaction. This not only saves the sales rep time but also ensures that no leads slip through the cracks.
Benefits of Salesforce Automation
-
Time Savings: By automating repetitive tasks, employees can focus their time and energy on higher-value activities that require a human touch.
-
Increased Efficiency: Automation helps streamline processes, reduce errors, and ensure consistent results.
-
Improved Customer Experience: By automating follow-up communication and personalized outreach, businesses can provide a better experience for their customers.
-
Data Accuracy: Automation helps keep customer records up to date and ensures that information is entered correctly every time.
-
Scalability: As businesses grow, automation can help them handle larger volumes of leads, customers, and data without sacrificing quality.
Implementing Salesforce Automation
Implementing Salesforce automation is a strategic process that involves analyzing existing workflows, identifying areas for improvement, and designing automation rules that align with business goals. It's important to involve key stakeholders from various departments to ensure that the automation process meets everyone's needs and expectations.
Best Practices for Salesforce Automation
-
Start Small: Begin by automating simple, repetitive tasks before moving on to more complex processes.
-
Test and Iterate: Continuously monitor and tweak your automation rules to ensure they are producing the desired results.
-
Train Your Team: Provide training and support to employees to ensure they understand how automation works and how it can benefit them in their daily tasks.
How to obtain Salesforce Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Salesforce automation is a powerful tool that can help businesses simplify repetitive tasks, boost efficiency, and ultimately drive success. By embracing automation and leveraging the capabilities of the Salesforce platform, businesses can stay ahead of the curve and deliver exceptional value to their customers.
Read More
In today's fast-paced business world, time is of the essence. Every second counts, and any opportunity to streamline processes and increase efficiency is considered a valuable asset. This is where Salesforce automation comes into play. By automating repetitive tasks and optimizing workflows, businesses can save time, reduce errors, and ultimately boost their overall productivity.
What is Salesforce Automation?
Salesforce automation is the practice of using technology to automate manual tasks within the Salesforce platform. This can include anything from automatically updating customer records to sending out follow-up emails based on predefined criteria. By leveraging automation tools, businesses can free up their employees to focus on more strategic tasks, while also ensuring that routine processes are completed efficiently and consistently.
How Does Salesforce Automation Work?
At its core, Salesforce automation relies on a set of rules and triggers that determine when certain actions should be taken. For example, a sales representative may set up a rule that triggers an automated email to be sent to a customer after a certain amount of time has passed since their last interaction. This not only saves the sales rep time but also ensures that no leads slip through the cracks.
Benefits of Salesforce Automation
-
Time Savings: By automating repetitive tasks, employees can focus their time and energy on higher-value activities that require a human touch.
-
Increased Efficiency: Automation helps streamline processes, reduce errors, and ensure consistent results.
-
Improved Customer Experience: By automating follow-up communication and personalized outreach, businesses can provide a better experience for their customers.
-
Data Accuracy: Automation helps keep customer records up to date and ensures that information is entered correctly every time.
-
Scalability: As businesses grow, automation can help them handle larger volumes of leads, customers, and data without sacrificing quality.
Implementing Salesforce Automation
Implementing Salesforce automation is a strategic process that involves analyzing existing workflows, identifying areas for improvement, and designing automation rules that align with business goals. It's important to involve key stakeholders from various departments to ensure that the automation process meets everyone's needs and expectations.
Best Practices for Salesforce Automation
-
Start Small: Begin by automating simple, repetitive tasks before moving on to more complex processes.
-
Test and Iterate: Continuously monitor and tweak your automation rules to ensure they are producing the desired results.
-
Train Your Team: Provide training and support to employees to ensure they understand how automation works and how it can benefit them in their daily tasks.
How to obtain Salesforce Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Salesforce automation is a powerful tool that can help businesses simplify repetitive tasks, boost efficiency, and ultimately drive success. By embracing automation and leveraging the capabilities of the Salesforce platform, businesses can stay ahead of the curve and deliver exceptional value to their customers.
The Role of Agile in Digital Transformation Strategies
In today's fast-paced and ever-changing business landscape, companies are constantly looking for ways to adapt and stay ahead of the competition. One of the key strategies that businesses are turning to is Agile methodology. Agile is a project management approach that emphasizes flexibility, collaboration, and continuous improvement. But what exactly is the role of Agile in digital transformation strategies?
What is Agile?
Agile is a set of principles and practices that prioritize adaptability and responsiveness in project management. It was originally developed for software development teams but has since been adopted by a wide range of industries. Agile teams work in short, iterative cycles called sprints, where they deliver small pieces of functionality quickly and regularly. This allows teams to respond to feedback, change priorities, and make adjustments as needed.
Why is Agile Important for Digital Transformation?
Digital transformation is the process of using digital technologies to fundamentally change business operations and create new value for customers. In today's digital world, companies are under increasing pressure to innovate quickly and deliver products and services that meet the demands of modern consumers. Agile methodology provides a framework for companies to navigate the complexities of digital transformation by enabling them to:
Respond to Change Quickly: Agile allows companies to adapt to changing market conditions, customer preferences, and technological advancements. This flexibility is crucial in the fast-paced digital landscape.
Prioritize Customer Value: By breaking projects into small, manageable pieces, Agile helps businesses focus on delivering value to customers quickly and consistently. This customer-centric approach is key to successful digital transformation.
Improve Collaboration: Agile encourages cross-functional teams to work together closely and communicate effectively. This fosters innovation, creativity, and a shared sense of ownership over project outcomes.
How Does Agile Drive Digital Transformation Success?
Agile methodology is a powerful tool for driving digital transformation success in several ways:
Faster Time to Market: Agile's iterative approach enables companies to release new products and features more quickly, allowing them to stay ahead of the competition and respond to changing customer needs.
Better Quality: By focusing on continuous improvement and regular feedback loops, Agile teams can identify and address issues early on, resulting in higher-quality products and services.
Increased Innovation: Agile encourages experimentation and risk-taking, which leads to greater innovation and the development of cutting-edge solutions that set companies apart in the digital marketplace.
How to obtain Agile & Scrum Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Agile methodology plays a crucial role in digital transformation strategies by providing companies with the flexibility, adaptability, and customer-centric focus needed to succeed in today's rapidly evolving business landscape. By embracing Agile principles and practices, companies can drive innovation, deliver value to customers, and achieve sustainable competitive advantage.
Read More
In today's fast-paced and ever-changing business landscape, companies are constantly looking for ways to adapt and stay ahead of the competition. One of the key strategies that businesses are turning to is Agile methodology. Agile is a project management approach that emphasizes flexibility, collaboration, and continuous improvement. But what exactly is the role of Agile in digital transformation strategies?
What is Agile?
Agile is a set of principles and practices that prioritize adaptability and responsiveness in project management. It was originally developed for software development teams but has since been adopted by a wide range of industries. Agile teams work in short, iterative cycles called sprints, where they deliver small pieces of functionality quickly and regularly. This allows teams to respond to feedback, change priorities, and make adjustments as needed.
Why is Agile Important for Digital Transformation?
Digital transformation is the process of using digital technologies to fundamentally change business operations and create new value for customers. In today's digital world, companies are under increasing pressure to innovate quickly and deliver products and services that meet the demands of modern consumers. Agile methodology provides a framework for companies to navigate the complexities of digital transformation by enabling them to:
Respond to Change Quickly: Agile allows companies to adapt to changing market conditions, customer preferences, and technological advancements. This flexibility is crucial in the fast-paced digital landscape.
Prioritize Customer Value: By breaking projects into small, manageable pieces, Agile helps businesses focus on delivering value to customers quickly and consistently. This customer-centric approach is key to successful digital transformation.
Improve Collaboration: Agile encourages cross-functional teams to work together closely and communicate effectively. This fosters innovation, creativity, and a shared sense of ownership over project outcomes.
How Does Agile Drive Digital Transformation Success?
Agile methodology is a powerful tool for driving digital transformation success in several ways:
Faster Time to Market: Agile's iterative approach enables companies to release new products and features more quickly, allowing them to stay ahead of the competition and respond to changing customer needs.
Better Quality: By focusing on continuous improvement and regular feedback loops, Agile teams can identify and address issues early on, resulting in higher-quality products and services.
Increased Innovation: Agile encourages experimentation and risk-taking, which leads to greater innovation and the development of cutting-edge solutions that set companies apart in the digital marketplace.
How to obtain Agile & Scrum Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Agile methodology plays a crucial role in digital transformation strategies by providing companies with the flexibility, adaptability, and customer-centric focus needed to succeed in today's rapidly evolving business landscape. By embracing Agile principles and practices, companies can drive innovation, deliver value to customers, and achieve sustainable competitive advantage.
The Role of Technology in Quality Management Processes
In today's fast-paced and highly competitive business environment, organizations are constantly looking for ways to improve efficiency and ensure high-quality products and services. One way in which technology has significantly impacted the field of quality management is through the use of sophisticated tools and systems that help streamline processes, detect defects early on, and ultimately deliver better outcomes for customers. Let's explore the various ways in which technology plays a crucial role in enhancing quality management processes.
How Does Technology Improve Quality Management?
With the advent of advanced software and automation tools, organizations can now track and monitor every stage of the production process in real-time. This level of visibility allows for early detection of any potential issues or defects, enabling companies to take corrective action before the problem escalates. Additionally, technology-driven quality management systems can analyze large datasets to identify patterns and trends that may not be apparent to human eyes, leading to more informed decision-making and improved overall quality.
What are the Benefits of Using Technology in Quality Management?
One of the key benefits of incorporating technology into quality management processes is the ability to standardize procedures and ensure consistency across all operations. By automating manual tasks and implementing digital workflows, companies can reduce the risk of human error and minimize variability in product output. Furthermore, technology enables real-time collaboration and communication among team members, facilitating faster problem-solving and decision-making.
The Role of Artificial Intelligence in Quality Management
Artificial intelligence (AI) is revolutionizing the field of quality management by providing advanced analytics and predictive capabilities that help organizations proactively address quality issues. AI-powered tools can analyze complex data sets to identify potential risks, recommend corrective actions, and even predict future quality trends. By leveraging AI, companies can enhance their quality control processes and continuously improve their products and services.
How can AI Improve Quality Control?
AI algorithms can process vast amounts of data from multiple sources, including sensors, IoT devices, and production equipment, to identify anomalies and deviations from established quality standards. This enables organizations to detect quality issues in real-time and take immediate action to rectify them. Moreover, AI can learn from past quality incidents and continuously optimize quality control processes, leading to higher levels of efficiency and accuracy.
Integrating Technology into Quality Management Systems
To fully leverage the benefits of technology in quality management, organizations must invest in modern quality management systems that are equipped with advanced features and functionalities. These systems should be flexible, scalable, and easy to integrate with existing IT infrastructure to ensure seamless operations. By centralizing quality data and processes in a digital platform, companies can enhance visibility, transparency, and traceability throughout the supply chain.
How to obtain Quality Management Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
Technology plays a vital role in enhancing quality management processes by enabling better data analysis, standardizing procedures, and improving collaboration among team members. By embracing advanced technologies such as AI, organizations can proactively address quality issues, optimize production processes, and deliver superior products and services to customers. As the business landscape continues to evolve, leveraging technology will be essential for staying competitive and meeting the ever-increasing demands for quality and efficiency.
Read More
In today's fast-paced and highly competitive business environment, organizations are constantly looking for ways to improve efficiency and ensure high-quality products and services. One way in which technology has significantly impacted the field of quality management is through the use of sophisticated tools and systems that help streamline processes, detect defects early on, and ultimately deliver better outcomes for customers. Let's explore the various ways in which technology plays a crucial role in enhancing quality management processes.
How Does Technology Improve Quality Management?
With the advent of advanced software and automation tools, organizations can now track and monitor every stage of the production process in real-time. This level of visibility allows for early detection of any potential issues or defects, enabling companies to take corrective action before the problem escalates. Additionally, technology-driven quality management systems can analyze large datasets to identify patterns and trends that may not be apparent to human eyes, leading to more informed decision-making and improved overall quality.
What are the Benefits of Using Technology in Quality Management?
One of the key benefits of incorporating technology into quality management processes is the ability to standardize procedures and ensure consistency across all operations. By automating manual tasks and implementing digital workflows, companies can reduce the risk of human error and minimize variability in product output. Furthermore, technology enables real-time collaboration and communication among team members, facilitating faster problem-solving and decision-making.
The Role of Artificial Intelligence in Quality Management
Artificial intelligence (AI) is revolutionizing the field of quality management by providing advanced analytics and predictive capabilities that help organizations proactively address quality issues. AI-powered tools can analyze complex data sets to identify potential risks, recommend corrective actions, and even predict future quality trends. By leveraging AI, companies can enhance their quality control processes and continuously improve their products and services.
How can AI Improve Quality Control?
AI algorithms can process vast amounts of data from multiple sources, including sensors, IoT devices, and production equipment, to identify anomalies and deviations from established quality standards. This enables organizations to detect quality issues in real-time and take immediate action to rectify them. Moreover, AI can learn from past quality incidents and continuously optimize quality control processes, leading to higher levels of efficiency and accuracy.
Integrating Technology into Quality Management Systems
To fully leverage the benefits of technology in quality management, organizations must invest in modern quality management systems that are equipped with advanced features and functionalities. These systems should be flexible, scalable, and easy to integrate with existing IT infrastructure to ensure seamless operations. By centralizing quality data and processes in a digital platform, companies can enhance visibility, transparency, and traceability throughout the supply chain.
How to obtain Quality Management Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
Technology plays a vital role in enhancing quality management processes by enabling better data analysis, standardizing procedures, and improving collaboration among team members. By embracing advanced technologies such as AI, organizations can proactively address quality issues, optimize production processes, and deliver superior products and services to customers. As the business landscape continues to evolve, leveraging technology will be essential for staying competitive and meeting the ever-increasing demands for quality and efficiency.
The Impact of AI & ML on Cybersecurity
In our modern digital world, the threat of cyber attacks is constantly looming. As hackers become more sophisticated, traditional security measures are no longer enough to protect sensitive data and information. This is where artificial intelligence (AI) and machine learning (ML) come into play, revolutionizing the field of cybersecurity.
How Can Artificial Intelligence Improve Cyber Security?
Artificial intelligence has the ability to quickly analyze vast amounts of data and identify patterns that may indicate a potential threat. By using AI algorithms, cybersecurity professionals can detect anomalies and potential security breaches in real-time, allowing for a more proactive approach to cybersecurity.
- AI can help improve threat detection by continuously monitoring network activity and flagging suspicious behavior.
- AI-powered systems can also automate threat response, minimizing the time between detection and mitigation of a cyber attack.
- Machine learning can be used to train AI algorithms to recognize new types of cyber threats, making cybersecurity systems more adaptive and resilient.
How Does Machine Learning Enhance Cyber Security?
Machine learning algorithms can learn from past cyber attacks and adapt to new threats, making them invaluable tools in the fight against cybercrime. By analyzing historical data and trends, ML algorithms can predict future attacks and prevent them from occurring.
- ML algorithms can classify and prioritize security alerts, reducing false positives and allowing cybersecurity professionals to focus on the most critical threats.
- ML can also be used to improve user authentication processes, detecting unauthorized access attempts and strengthening password security.
- With the ability to perform continuous monitoring and analysis, machine learning can help organizations stay one step ahead of cyber attackers.
What Are the Benefits of Using AI and ML in Cyber Security?
When it comes to cybersecurity, staying ahead of the curve is essential. By leveraging the power of artificial intelligence and machine learning, organizations can enhance their security measures and protect sensitive data more effectively.
- Improved threat detection and response times can help minimize the impact of cyber attacks and reduce downtime.
- AI and ML can help organizations predict and prevent future security breaches, saving time and resources.
- By automating routine cybersecurity tasks, AI and ML free up cybersecurity professionals to focus on more strategic initiatives.
How to obtain Cybersecurity Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
Artificial intelligence and machine learning are powerful tools that can revolutionize the field of cybersecurity. By harnessing the capabilities of AI and ML, organizations can better protect themselves against cyber threats and safeguard their valuable data and assets. Embracing these technologies is essential in today's digital landscape to stay one step ahead of cyber attackers.
Read More
In our modern digital world, the threat of cyber attacks is constantly looming. As hackers become more sophisticated, traditional security measures are no longer enough to protect sensitive data and information. This is where artificial intelligence (AI) and machine learning (ML) come into play, revolutionizing the field of cybersecurity.
How Can Artificial Intelligence Improve Cyber Security?
Artificial intelligence has the ability to quickly analyze vast amounts of data and identify patterns that may indicate a potential threat. By using AI algorithms, cybersecurity professionals can detect anomalies and potential security breaches in real-time, allowing for a more proactive approach to cybersecurity.
- AI can help improve threat detection by continuously monitoring network activity and flagging suspicious behavior.
- AI-powered systems can also automate threat response, minimizing the time between detection and mitigation of a cyber attack.
- Machine learning can be used to train AI algorithms to recognize new types of cyber threats, making cybersecurity systems more adaptive and resilient.
How Does Machine Learning Enhance Cyber Security?
Machine learning algorithms can learn from past cyber attacks and adapt to new threats, making them invaluable tools in the fight against cybercrime. By analyzing historical data and trends, ML algorithms can predict future attacks and prevent them from occurring.
- ML algorithms can classify and prioritize security alerts, reducing false positives and allowing cybersecurity professionals to focus on the most critical threats.
- ML can also be used to improve user authentication processes, detecting unauthorized access attempts and strengthening password security.
- With the ability to perform continuous monitoring and analysis, machine learning can help organizations stay one step ahead of cyber attackers.
What Are the Benefits of Using AI and ML in Cyber Security?
When it comes to cybersecurity, staying ahead of the curve is essential. By leveraging the power of artificial intelligence and machine learning, organizations can enhance their security measures and protect sensitive data more effectively.
- Improved threat detection and response times can help minimize the impact of cyber attacks and reduce downtime.
- AI and ML can help organizations predict and prevent future security breaches, saving time and resources.
- By automating routine cybersecurity tasks, AI and ML free up cybersecurity professionals to focus on more strategic initiatives.
How to obtain Cybersecurity Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
Artificial intelligence and machine learning are powerful tools that can revolutionize the field of cybersecurity. By harnessing the capabilities of AI and ML, organizations can better protect themselves against cyber threats and safeguard their valuable data and assets. Embracing these technologies is essential in today's digital landscape to stay one step ahead of cyber attackers.
Automating Cybersecurity: Streamlining Operations
In today's digital age, cyber security has become more critical than ever before. With the increasing number of cyber threats and attacks targeting businesses and individuals, it is essential to have robust security measures in place to protect sensitive data and information. One of the most effective ways to enhance cyber security is through automation and orchestration.
What is Cyber security Automation?
Cyber security automation involves the use of technology to streamline and automate security tasks and processes. By leveraging automation tools, organizations can reduce manual intervention, minimize human errors, and enhance the overall efficiency of their security operations. From threat detection to incident response, automation can play a crucial role in strengthening an organization's cyber security posture.
Automation can be applied to various aspects of cyber security, such as:
- Vulnerability Management: Automatically scanning systems for vulnerabilities and prioritizing remediation efforts based on risk levels.
- Endpoint Security: Automatically updating and patching endpoints to ensure they are protected against the latest threats.
- Threat Intelligence: Automatically aggregating and analyzing threat intelligence data to identify potential security threats.
- Incident Response: Automating the response to security incidents, such as isolating affected systems and containing the threat.
The Benefits of Cyber security Automation
There are several benefits to implementing cyber security automation within an organization, including:
- Improved efficiency: Automation can help security teams respond to incidents faster and more effectively, reducing the time and resources needed to address security threats.
- Enhanced accuracy: By automating routine security tasks, organizations can minimize the risk of human error and ensure consistent security practices.
- Increased scalability: Automation can help organizations scale their security operations to address the growing volume and complexity of cyber threats.
- Cost savings: By reducing manual intervention and streamlining processes, automation can help organizations save on operational costs and resources.
What is Cybe rsecurity Orchestration?
Cybersecurity orchestration is the process of integrating and coordinating various security tools and technologies to improve the overall effectiveness of security operations. By orchestrating security processes, organizations can ensure that different security solutions work together seamlessly to detect, respond to, and mitigate security threats.
Orchestration can help organizations achieve:
- Centralized visibility: Orchestration solutions provide a centralized view of the organization's security posture, enabling security teams to better understand and respond to security incidents.
- Automated workflows: Orchestration tools enable organizations to automate security workflows, such as incident response processes, to ensure a swift and coordinated response to security incidents.
- Integration of security tools: Orchestration allows organizations to integrate different security tools and technologies, creating a more comprehensive and interconnected security ecosystem.
The Benefits of Cybersecurity Orchestration
The benefits of cybersecurity orchestration include:
- Improved threat detection and response: By orchestrating security tools and processes, organizations can enhance their ability to detect and respond to security threats in real-time.
- Increased efficiency: Orchestration can help streamline security operations and reduce the time and effort required to manage security incidents.
- Enhanced collaboration: Orchestration fosters collaboration between different security teams and departments, ensuring a coordinated and unified response to security incidents.
How to obtain Cybersecurity Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
Cyber security automation and orchestration are essential components of a robust cyber security strategy. By leveraging automation and orchestration technologies, organizations can enhance their security posture, improve operational efficiency, and better protect against evolving cyber threats. Investing in cyber security automation and orchestration is essential for organizations looking to stay ahead of cyber threats and safeguard their sensitive data and assets.
Read More
In today's digital age, cyber security has become more critical than ever before. With the increasing number of cyber threats and attacks targeting businesses and individuals, it is essential to have robust security measures in place to protect sensitive data and information. One of the most effective ways to enhance cyber security is through automation and orchestration.
What is Cyber security Automation?
Cyber security automation involves the use of technology to streamline and automate security tasks and processes. By leveraging automation tools, organizations can reduce manual intervention, minimize human errors, and enhance the overall efficiency of their security operations. From threat detection to incident response, automation can play a crucial role in strengthening an organization's cyber security posture.
Automation can be applied to various aspects of cyber security, such as:
- Vulnerability Management: Automatically scanning systems for vulnerabilities and prioritizing remediation efforts based on risk levels.
- Endpoint Security: Automatically updating and patching endpoints to ensure they are protected against the latest threats.
- Threat Intelligence: Automatically aggregating and analyzing threat intelligence data to identify potential security threats.
- Incident Response: Automating the response to security incidents, such as isolating affected systems and containing the threat.
The Benefits of Cyber security Automation
There are several benefits to implementing cyber security automation within an organization, including:
- Improved efficiency: Automation can help security teams respond to incidents faster and more effectively, reducing the time and resources needed to address security threats.
- Enhanced accuracy: By automating routine security tasks, organizations can minimize the risk of human error and ensure consistent security practices.
- Increased scalability: Automation can help organizations scale their security operations to address the growing volume and complexity of cyber threats.
- Cost savings: By reducing manual intervention and streamlining processes, automation can help organizations save on operational costs and resources.
What is Cybe rsecurity Orchestration?
Cybersecurity orchestration is the process of integrating and coordinating various security tools and technologies to improve the overall effectiveness of security operations. By orchestrating security processes, organizations can ensure that different security solutions work together seamlessly to detect, respond to, and mitigate security threats.
Orchestration can help organizations achieve:
- Centralized visibility: Orchestration solutions provide a centralized view of the organization's security posture, enabling security teams to better understand and respond to security incidents.
- Automated workflows: Orchestration tools enable organizations to automate security workflows, such as incident response processes, to ensure a swift and coordinated response to security incidents.
- Integration of security tools: Orchestration allows organizations to integrate different security tools and technologies, creating a more comprehensive and interconnected security ecosystem.
The Benefits of Cybersecurity Orchestration
The benefits of cybersecurity orchestration include:
- Improved threat detection and response: By orchestrating security tools and processes, organizations can enhance their ability to detect and respond to security threats in real-time.
- Increased efficiency: Orchestration can help streamline security operations and reduce the time and effort required to manage security incidents.
- Enhanced collaboration: Orchestration fosters collaboration between different security teams and departments, ensuring a coordinated and unified response to security incidents.
How to obtain Cybersecurity Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
Cyber security automation and orchestration are essential components of a robust cyber security strategy. By leveraging automation and orchestration technologies, organizations can enhance their security posture, improve operational efficiency, and better protect against evolving cyber threats. Investing in cyber security automation and orchestration is essential for organizations looking to stay ahead of cyber threats and safeguard their sensitive data and assets.
Citrix Workspace: Revolutionizing Productivity in the Digital Era
In today's fast-paced digital era, where technology continues to evolve at a rapid pace, businesses are constantly seeking innovative solutions to enhance productivity and efficiency. One such groundbreaking technology that is revolutionizing the way we work is Citrix Workspace. With its advanced collaboration tools, remote work capabilities, virtual desktop infrastructure, cloud computing integration, and mobility features, Citrix Workspace is transforming the traditional work environment and empowering employees to work smarter, not harder.
What is Citrix Workspace?
Citrix Workspace is a digital workspace solution that allows users to access their applications, desktops, and data securely from any device, anywhere in the world. By leveraging cloud technology, Citrix Workspace provides a seamless and efficient way for employees to collaborate, communicate, and work on the go. Whether you're in the office, at home, or on the road, Citrix Workspace ensures that you have access to all the tools and resources you need to stay productive and connected.
The Benefits of Citrix Workspace
-
Enhanced Collaboration: With Citrix Workspace, teams can easily collaborate on projects in real-time, regardless of their physical location. By enabling secure communication and file sharing, Citrix Workspace fosters a culture of teamwork and innovation.
-
Increased Productivity: Citrix Workspace streamlines workflows and eliminates manual tasks, allowing employees to focus on high-value work. By providing access to productivity tools and resources, Citrix Workspace helps boost efficiency and output.
-
Work from Anywhere: Thanks to its virtual desktop capabilities, Citrix Workspace enables employees to work from anywhere, whether it's in the office, at home, or on the go. This flexibility not only improves work-life balance but also enhances employee satisfaction.
-
Seamless Integration: Citrix Workspace seamlessly integrates with existing business systems and applications, making it easy to adopt and implement within your organization. This level of integration ensures a smooth transition and minimal disruption to your operations.
How Citrix Workspace is Transforming the Modern Workplace
In today's digital age, where remote work and flexible work arrangements are becoming increasingly common, Citrix Workspace provides the tools and technology needed to thrive in this new era of work. By empowering employees to access their work resources from anywhere, on any device, Citrix Workspace enables organizations to adapt to changing work trends and optimizes workflows for maximum efficiency.
With Citrix Workspace, employees can enjoy a user-friendly experience that prioritizes accessibility and productivity. From secure remote access to flexible workspace options, Citrix Workspace offers a comprehensive solution for businesses looking to embrace the future of work.
How to obtain Citrix Client Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Citrix Workspace is revolutionizing productivity in the digital era by providing advanced technology solutions that empower employees, streamline workflows, and enhance communication. By leveraging cutting-edge technology and innovation, Citrix Workspace is setting the standard for modern workplace solutions that prioritize efficiency, flexibility, and collaboration.
Read More
In today's fast-paced digital era, where technology continues to evolve at a rapid pace, businesses are constantly seeking innovative solutions to enhance productivity and efficiency. One such groundbreaking technology that is revolutionizing the way we work is Citrix Workspace. With its advanced collaboration tools, remote work capabilities, virtual desktop infrastructure, cloud computing integration, and mobility features, Citrix Workspace is transforming the traditional work environment and empowering employees to work smarter, not harder.
What is Citrix Workspace?
Citrix Workspace is a digital workspace solution that allows users to access their applications, desktops, and data securely from any device, anywhere in the world. By leveraging cloud technology, Citrix Workspace provides a seamless and efficient way for employees to collaborate, communicate, and work on the go. Whether you're in the office, at home, or on the road, Citrix Workspace ensures that you have access to all the tools and resources you need to stay productive and connected.
The Benefits of Citrix Workspace
-
Enhanced Collaboration: With Citrix Workspace, teams can easily collaborate on projects in real-time, regardless of their physical location. By enabling secure communication and file sharing, Citrix Workspace fosters a culture of teamwork and innovation.
-
Increased Productivity: Citrix Workspace streamlines workflows and eliminates manual tasks, allowing employees to focus on high-value work. By providing access to productivity tools and resources, Citrix Workspace helps boost efficiency and output.
-
Work from Anywhere: Thanks to its virtual desktop capabilities, Citrix Workspace enables employees to work from anywhere, whether it's in the office, at home, or on the go. This flexibility not only improves work-life balance but also enhances employee satisfaction.
-
Seamless Integration: Citrix Workspace seamlessly integrates with existing business systems and applications, making it easy to adopt and implement within your organization. This level of integration ensures a smooth transition and minimal disruption to your operations.
How Citrix Workspace is Transforming the Modern Workplace
In today's digital age, where remote work and flexible work arrangements are becoming increasingly common, Citrix Workspace provides the tools and technology needed to thrive in this new era of work. By empowering employees to access their work resources from anywhere, on any device, Citrix Workspace enables organizations to adapt to changing work trends and optimizes workflows for maximum efficiency.
With Citrix Workspace, employees can enjoy a user-friendly experience that prioritizes accessibility and productivity. From secure remote access to flexible workspace options, Citrix Workspace offers a comprehensive solution for businesses looking to embrace the future of work.
How to obtain Citrix Client Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Citrix Workspace is revolutionizing productivity in the digital era by providing advanced technology solutions that empower employees, streamline workflows, and enhance communication. By leveraging cutting-edge technology and innovation, Citrix Workspace is setting the standard for modern workplace solutions that prioritize efficiency, flexibility, and collaboration.
The Power of Storytelling in Digital Marketing: Crafting Compelling Brand Stories
In today's fast-paced digital world, it has become increasingly important for brands to cut through the noise and grab the attention of consumers. One effective way to do this is through the power of storytelling in digital marketing. By crafting compelling brand stories, companies can create an emotional connection with their audience, drive engagement, and ultimately build customer loyalty.
The Impact of Storytelling in Digital Marketing
Storytelling is a powerful tool in digital marketing because it allows brands to communicate their values, mission, and purpose in a way that resonates with consumers. When done effectively, storytelling can make a brand more relatable, humanize its message, and differentiate it from competitors.
By crafting a compelling brand narrative, companies can create a cohesive story that ties together all aspects of their marketing campaigns. This narrative helps to establish brand identity, build trust with consumers, and drive customer loyalty.
Crafting Compelling Brand Stories
When crafting a brand story, it is important to consider the emotional impact it will have on your audience. By tapping into the emotions of your target market, you can create a connection that goes beyond the transactional nature of business. This emotional connection is what drives engagement and fosters customer loyalty.
To create a compelling brand story, consider the following storytelling techniques:
Online Branding: Use your online presence to tell your brand story through your website, social media channels, and email marketing campaigns.
Creative Storytelling: Think outside the box and use innovative storytelling techniques to capture the attention of your audience.
Storytelling in Advertising: Incorporate storytelling into your advertising campaigns to make them more memorable and impactful.
Examples of Brand Storytelling
Many brands have successfully used storytelling to connect with their audience and drive engagement. One example is Nike, which tells compelling stories of athletes overcoming obstacles to achieve greatness. By showcasing real-life struggles and triumphs, Nike creates a powerful emotional connection with consumers.
Another example is Coca-Cola, which has built a brand around the idea of happiness and togetherness. By telling stories of people coming together over a Coke, Coca-Cola creates a warm and inviting brand image.
The Future of Storytelling in Digital Marketing
As technology continues to evolve, the ways in which brands can tell their story will also change. From visual storytelling to social media storytelling, the possibilities are endless. The key is to stay authentic and true to your brand identity while using storytelling to captivate and engage your audience.
How to obtain Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the power of storytelling in digital marketing cannot be underestimated. By crafting compelling brand stories, companies can create an emotional connection with their audience, drive engagement, and build customer loyalty. As the digital landscape continues to evolve, brands that master the art of storytelling will be the ones that stand out from the crowd and leave a lasting impression on consumers.
Read More
In today's fast-paced digital world, it has become increasingly important for brands to cut through the noise and grab the attention of consumers. One effective way to do this is through the power of storytelling in digital marketing. By crafting compelling brand stories, companies can create an emotional connection with their audience, drive engagement, and ultimately build customer loyalty.
The Impact of Storytelling in Digital Marketing
Storytelling is a powerful tool in digital marketing because it allows brands to communicate their values, mission, and purpose in a way that resonates with consumers. When done effectively, storytelling can make a brand more relatable, humanize its message, and differentiate it from competitors.
By crafting a compelling brand narrative, companies can create a cohesive story that ties together all aspects of their marketing campaigns. This narrative helps to establish brand identity, build trust with consumers, and drive customer loyalty.
Crafting Compelling Brand Stories
When crafting a brand story, it is important to consider the emotional impact it will have on your audience. By tapping into the emotions of your target market, you can create a connection that goes beyond the transactional nature of business. This emotional connection is what drives engagement and fosters customer loyalty.
To create a compelling brand story, consider the following storytelling techniques:
Online Branding: Use your online presence to tell your brand story through your website, social media channels, and email marketing campaigns.
Creative Storytelling: Think outside the box and use innovative storytelling techniques to capture the attention of your audience.
Storytelling in Advertising: Incorporate storytelling into your advertising campaigns to make them more memorable and impactful.
Examples of Brand Storytelling
Many brands have successfully used storytelling to connect with their audience and drive engagement. One example is Nike, which tells compelling stories of athletes overcoming obstacles to achieve greatness. By showcasing real-life struggles and triumphs, Nike creates a powerful emotional connection with consumers.
Another example is Coca-Cola, which has built a brand around the idea of happiness and togetherness. By telling stories of people coming together over a Coke, Coca-Cola creates a warm and inviting brand image.
The Future of Storytelling in Digital Marketing
As technology continues to evolve, the ways in which brands can tell their story will also change. From visual storytelling to social media storytelling, the possibilities are endless. The key is to stay authentic and true to your brand identity while using storytelling to captivate and engage your audience.
How to obtain Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the power of storytelling in digital marketing cannot be underestimated. By crafting compelling brand stories, companies can create an emotional connection with their audience, drive engagement, and build customer loyalty. As the digital landscape continues to evolve, brands that master the art of storytelling will be the ones that stand out from the crowd and leave a lasting impression on consumers.
The Role of Business Analysis in Digital Transformation Strategies
In today's fast-paced and ever-changing business landscape, companies must adapt to new technologies and trends to stay competitive. One crucial aspect of this adaptation is digital transformation, which involves leveraging digital technologies to streamline processes, improve customer experiences, and drive growth. And at the heart of successful digital transformation strategies lies business analysis.
What is Business Analysis?
Business analysis is the practice of identifying business needs and finding solutions to address them. It involves analyzing processes, gathering requirements, and recommending changes to improve efficiency and effectiveness. Business analysts play a crucial role in driving organizational change and ensuring that projects align with business goals.
Business analysis encompasses a wide range of activities, including:
-
Conducting market research to identify trends and opportunities
-
Collaborating with stakeholders to gather requirements
-
Analyzing data to uncover insights and make informed decisions
-
Developing business cases to justify investments
-
Facilitating communication between business and IT teams
How Does Business Analysis Support Digital Transformation?
In the context of digital transformation, business analysis is essential for several reasons:
-
Identifying Opportunities: Business analysts help organizations identify new opportunities for innovation and growth by analyzing market trends, customer needs, and competitive landscapes.
-
Defining Requirements: Business analysts work closely with stakeholders to gather and document requirements for digital initiatives. This ensures that projects meet business needs and deliver value to customers.
-
Driving Process Improvements: Business analysts analyze existing processes to identify inefficiencies and bottlenecks. By proposing changes and new technologies, they help organizations streamline operations and enhance productivity.
-
Ensuring Alignment: Business analysts play a key role in ensuring that digital projects align with business goals and objectives. By defining clear objectives and success criteria, they help organizations measure the impact of their digital initiatives.
Case Study: Digital Transformation at Company X
Company X, a leading retail chain, embarked on a digital transformation journey to enhance its online presence and improve customer experiences. Business analysts played a critical role in this initiative by:
-
Conducting market research to understand customer preferences and buying behaviors
-
Collaborating with IT teams to define requirements for a new e-commerce platform
-
Analyzing data to personalize marketing campaigns and improve customer engagement
-
Developing a business case to justify investments in digital technologies.
-
Facilitating communication between business leaders and project teams to ensure alignment
As a result of these efforts, Company X successfully launched a new e-commerce platform that boosted online sales and improved customer satisfaction.
The Future of Business Analysis in Digital Transformation
As digital technologies continue to evolve, the role of business analysis in digital transformation will become even more critical. Companies that invest in skilled business analysts and robust analysis practices will be better positioned to drive innovation, adapt to market changes, and achieve sustainable growth.
How to obtain Business Analysis certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Business analysis is a key driver of successful digital transformation strategies. By identifying opportunities, defining requirements, driving process improvements, and ensuring alignment, business analysts help organizations navigate the complexities of digital change and emerge as leaders in the digital economy.
Read More
In today's fast-paced and ever-changing business landscape, companies must adapt to new technologies and trends to stay competitive. One crucial aspect of this adaptation is digital transformation, which involves leveraging digital technologies to streamline processes, improve customer experiences, and drive growth. And at the heart of successful digital transformation strategies lies business analysis.
What is Business Analysis?
Business analysis is the practice of identifying business needs and finding solutions to address them. It involves analyzing processes, gathering requirements, and recommending changes to improve efficiency and effectiveness. Business analysts play a crucial role in driving organizational change and ensuring that projects align with business goals.
Business analysis encompasses a wide range of activities, including:
-
Conducting market research to identify trends and opportunities
-
Collaborating with stakeholders to gather requirements
-
Analyzing data to uncover insights and make informed decisions
-
Developing business cases to justify investments
-
Facilitating communication between business and IT teams
How Does Business Analysis Support Digital Transformation?
In the context of digital transformation, business analysis is essential for several reasons:
-
Identifying Opportunities: Business analysts help organizations identify new opportunities for innovation and growth by analyzing market trends, customer needs, and competitive landscapes.
-
Defining Requirements: Business analysts work closely with stakeholders to gather and document requirements for digital initiatives. This ensures that projects meet business needs and deliver value to customers.
-
Driving Process Improvements: Business analysts analyze existing processes to identify inefficiencies and bottlenecks. By proposing changes and new technologies, they help organizations streamline operations and enhance productivity.
-
Ensuring Alignment: Business analysts play a key role in ensuring that digital projects align with business goals and objectives. By defining clear objectives and success criteria, they help organizations measure the impact of their digital initiatives.
Case Study: Digital Transformation at Company X
Company X, a leading retail chain, embarked on a digital transformation journey to enhance its online presence and improve customer experiences. Business analysts played a critical role in this initiative by:
-
Conducting market research to understand customer preferences and buying behaviors
-
Collaborating with IT teams to define requirements for a new e-commerce platform
-
Analyzing data to personalize marketing campaigns and improve customer engagement
-
Developing a business case to justify investments in digital technologies.
-
Facilitating communication between business leaders and project teams to ensure alignment
As a result of these efforts, Company X successfully launched a new e-commerce platform that boosted online sales and improved customer satisfaction.
The Future of Business Analysis in Digital Transformation
As digital technologies continue to evolve, the role of business analysis in digital transformation will become even more critical. Companies that invest in skilled business analysts and robust analysis practices will be better positioned to drive innovation, adapt to market changes, and achieve sustainable growth.
How to obtain Business Analysis certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Business analysis is a key driver of successful digital transformation strategies. By identifying opportunities, defining requirements, driving process improvements, and ensuring alignment, business analysts help organizations navigate the complexities of digital change and emerge as leaders in the digital economy.
Unlocking the Power of Data with Cisco's Analytics and Insights Solutions
Are you looking for innovative ways to leverage the vast amounts of data within your organization? Look no further than Cisco's Analytics and Insights Solutions. With their cutting-edge technology and expertise in data analytics, Cisco can help you unlock the full potential of your data, allowing you to make informed decisions and drive your business forward.
The Importance of Data Analytics
In today's digital age, data is king. Businesses generate massive amounts of data every day, from customer interactions to operational metrics. However, without the right tools and strategies in place, all that data is nothing more than a collection of ones and zeros. This is where data analytics comes in.Data analytics is the process of analyzing raw data to extract valuable insights, trends, and patterns. By harnessing the power of data analytics, businesses can gain a deeper understanding of their operations, customers, and market trends. This, in turn, allows them to make more informed decisions that drive growth and success.
How Cisco's Analytics and Insights Solutions Can Help
Cisco's Analytics and Insights Solutions are designed to help businesses make sense of their data and turn it into actionable intelligence. With a comprehensive suite of tools and services, Cisco can help you unlock the full potential of your data and drive innovation within your organization.One of the key features of Cisco's Analytics and Insights Solutions is their ability to provide real-time insights into your data. With the power of real-time analytics, you can make quick decisions based on up-to-the-minute information, giving you a competitive edge in today's fast-paced business environment.
Another key benefit of Cisco's Analytics and Insights Solutions is their scalability. Whether you're a small startup or a large enterprise, Cisco has solutions that can grow with your business and adapt to your changing needs. This scalability ensures that you always have access to the data analytics tools you need, no matter how much your business grows.
The Future of Data Analytics
As we move into the future, the importance of data analytics will only continue to grow. With the rise of technologies like artificial intelligence and machine learning, businesses will have access to even more advanced tools for analyzing and interpreting their data. By embracing these technologies and partnering with innovative companies like Cisco, businesses can stay ahead of the curve and unlock the full power of their data.
How to obtain Cisco certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Data analytics is a powerful tool that can help businesses unlock the full potential of their data, driving growth and success. With Cisco's Analytics and Insights Solutions, you can harness the power of data analytics and make informed decisions that propel your business forward. Don't let your data go to waste – unlock its power with Cisco today.
Read More
Are you looking for innovative ways to leverage the vast amounts of data within your organization? Look no further than Cisco's Analytics and Insights Solutions. With their cutting-edge technology and expertise in data analytics, Cisco can help you unlock the full potential of your data, allowing you to make informed decisions and drive your business forward.
The Importance of Data Analytics
In today's digital age, data is king. Businesses generate massive amounts of data every day, from customer interactions to operational metrics. However, without the right tools and strategies in place, all that data is nothing more than a collection of ones and zeros. This is where data analytics comes in.Data analytics is the process of analyzing raw data to extract valuable insights, trends, and patterns. By harnessing the power of data analytics, businesses can gain a deeper understanding of their operations, customers, and market trends. This, in turn, allows them to make more informed decisions that drive growth and success.
How Cisco's Analytics and Insights Solutions Can Help
Cisco's Analytics and Insights Solutions are designed to help businesses make sense of their data and turn it into actionable intelligence. With a comprehensive suite of tools and services, Cisco can help you unlock the full potential of your data and drive innovation within your organization.One of the key features of Cisco's Analytics and Insights Solutions is their ability to provide real-time insights into your data. With the power of real-time analytics, you can make quick decisions based on up-to-the-minute information, giving you a competitive edge in today's fast-paced business environment.
Another key benefit of Cisco's Analytics and Insights Solutions is their scalability. Whether you're a small startup or a large enterprise, Cisco has solutions that can grow with your business and adapt to your changing needs. This scalability ensures that you always have access to the data analytics tools you need, no matter how much your business grows.
The Future of Data Analytics
As we move into the future, the importance of data analytics will only continue to grow. With the rise of technologies like artificial intelligence and machine learning, businesses will have access to even more advanced tools for analyzing and interpreting their data. By embracing these technologies and partnering with innovative companies like Cisco, businesses can stay ahead of the curve and unlock the full power of their data.
How to obtain Cisco certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Data analytics is a powerful tool that can help businesses unlock the full potential of their data, driving growth and success. With Cisco's Analytics and Insights Solutions, you can harness the power of data analytics and make informed decisions that propel your business forward. Don't let your data go to waste – unlock its power with Cisco today.
Securing the Digital Frontier: Cisco's Latest Innovations in Cyber security
In today's fast-paced digital world, the need for robust cyber security solutions has never been greater. With cyber threats becoming increasingly sophisticated, organizations must stay one step ahead to protect their sensitive data and infrastructure. Cisco, a global leader in networking and cyber security, has been at the forefront of innovation, continuously developing cutting-edge technologies to secure the digital frontier.
The Importance of Cyber security in the Digital Age
In an era where cyber attacks are becoming more frequent and severe, cyber security has become a top priority for businesses of all sizes. From ran so m ware and phishing scams to data breaches and D Do S attacks, the threats facing organizations are varied and ever-evolving. Without strong cyber security measures in place, companies risk not only financial losses but also damage to their reputation and customer trust.
Cisco's Comprehensive Approach to Cyber security
Cisco understands the importance of a comprehensive approach to cyber security, which is why they offer a range of innovative solutions to protect organizations from a wide range of threats. From network security and cloud security to endpoint protection and threat intelligence, Cisco's cyber security portfolio is designed to address the most pressing security challenges facing businesses today.One of Cisco's latest innovations in cyber security is their Secure X platform, a cloud-native, built-in platform that unifies visibility, enables automation, and strengthens security across your network, endpoints, cloud, and applications. By providing a centralized view of your organization's security posture and enabling seamless integration with Cisco's security products, Secure X helps organizations streamline their security operations and better respond to threats in real-time.
Leveraging Artificial Intelligence and Machine Learning
Artificial intelligence and machine learning are two technologies that are revolutionizing the field of cyber security. By leveraging the power of AI and ML, Cisco is able to detect and respond to threats with greater speed and accuracy than ever before. Through the use of advanced analytics and behavioral modeling, Cisco's security solutions can proactively identify and mitigate potential threats before they cause harm to your organization.
Securing the Future of Cyberspace
As the digital landscape continues to evolve, so too must our approach to cyber security. Cisco remains committed to staying at the forefront of innovation, developing new technologies and solutions to help organizations secure their digital assets and protect against cyber threats. With Cisco's latest innovations in cyber security, businesses can rest assured that they are equipped with the tools and expertise needed to defend against even the most sophisticated attacks.
How to obtain Cisco certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Securing the digital frontier is no easy task, but with Cisco's latest innovations in cyber security, organizations can strengthen their defenses and stay one step ahead of cyber threats. By leveraging cutting-edge technologies such as AI and ML, Cisco is helping businesses protect their data, infrastructure, and reputation in an increasingly connected world. With Cisco as your trusted cyber security partner, you can navigate the digital landscape with confidence and peace of mind.
Read More
In today's fast-paced digital world, the need for robust cyber security solutions has never been greater. With cyber threats becoming increasingly sophisticated, organizations must stay one step ahead to protect their sensitive data and infrastructure. Cisco, a global leader in networking and cyber security, has been at the forefront of innovation, continuously developing cutting-edge technologies to secure the digital frontier.
The Importance of Cyber security in the Digital Age
In an era where cyber attacks are becoming more frequent and severe, cyber security has become a top priority for businesses of all sizes. From ran so m ware and phishing scams to data breaches and D Do S attacks, the threats facing organizations are varied and ever-evolving. Without strong cyber security measures in place, companies risk not only financial losses but also damage to their reputation and customer trust.
Cisco's Comprehensive Approach to Cyber security
Cisco understands the importance of a comprehensive approach to cyber security, which is why they offer a range of innovative solutions to protect organizations from a wide range of threats. From network security and cloud security to endpoint protection and threat intelligence, Cisco's cyber security portfolio is designed to address the most pressing security challenges facing businesses today.One of Cisco's latest innovations in cyber security is their Secure X platform, a cloud-native, built-in platform that unifies visibility, enables automation, and strengthens security across your network, endpoints, cloud, and applications. By providing a centralized view of your organization's security posture and enabling seamless integration with Cisco's security products, Secure X helps organizations streamline their security operations and better respond to threats in real-time.
Leveraging Artificial Intelligence and Machine Learning
Artificial intelligence and machine learning are two technologies that are revolutionizing the field of cyber security. By leveraging the power of AI and ML, Cisco is able to detect and respond to threats with greater speed and accuracy than ever before. Through the use of advanced analytics and behavioral modeling, Cisco's security solutions can proactively identify and mitigate potential threats before they cause harm to your organization.
Securing the Future of Cyberspace
As the digital landscape continues to evolve, so too must our approach to cyber security. Cisco remains committed to staying at the forefront of innovation, developing new technologies and solutions to help organizations secure their digital assets and protect against cyber threats. With Cisco's latest innovations in cyber security, businesses can rest assured that they are equipped with the tools and expertise needed to defend against even the most sophisticated attacks.
How to obtain Cisco certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Securing the digital frontier is no easy task, but with Cisco's latest innovations in cyber security, organizations can strengthen their defenses and stay one step ahead of cyber threats. By leveraging cutting-edge technologies such as AI and ML, Cisco is helping businesses protect their data, infrastructure, and reputation in an increasingly connected world. With Cisco as your trusted cyber security partner, you can navigate the digital landscape with confidence and peace of mind.
Effective Change Management in IT Service Delivery
Introduction
In the ever-evolving world of Information Technology (IT), change is inevitable. With advancements in technology and shifting business needs, organizations must adapt to stay competitive. Effective change management in IT service delivery is crucial for ensuring that changes are implemented smoothly, with minimal disruption to operations. In this article, we will explore the key components of effective change management in IT service delivery and how organizations can navigate these changes successfully.
The Importance of Change Management
Change management is the process of managing changes to IT systems, processes, and infrastructure in a controlled and systematic manner. It involves planning, implementing, and monitoring changes to ensure that they are aligned with business goals and do not negatively impact operations. Effective change management is essential for organizations to minimize risks, optimize resources, and drive innovation.
Key Components of Effective Change Management
Clear Communication: Communication is key to successful change management. Stakeholders must be informed about the reasons for the change, the expected outcomes, and their roles and responsibilities. Clear and transparent communication helps build trust and ensures that everyone is on the same page.
Risk Assessment: Before implementing any changes, organizations must conduct a thorough risk assessment to identify potential risks and develop mitigation strategies. Understanding the impact of the changes allows organizations to proactively address any issues that may arise.
Change Control: Establishing a formal change control process helps organizations maintain control over changes and ensures that they are implemented in a structured manner. Change control involves documenting changes, obtaining approval from stakeholders, and tracking progress throughout the implementation process.
Training and Support: Providing training and support to employees is essential for successful change management. Employees need to understand how the changes will affect their roles and responsibilities and receive the necessary training to adapt to new processes and technologies.
Monitoring and Evaluation: Once changes are implemented, organizations must monitor and evaluate their impact on operations. Regular assessment helps identify any issues or bottlenecks and allows organizations to make adjustments as needed.
Overcoming Challenges in Change Management
Change management is not without its challenges. Resistance to change, lack of resources, and poor planning can derail even the most well-thought-out change management strategy. To overcome these challenges, organizations must prioritize open communication, engage stakeholders early in the process, and allocate sufficient resources to support the change management initiative.
How to obtain IT Service Management and Governance certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Effective change management is essential for organizations looking to stay ahead in today's fast-paced IT landscape. By implementing clear communication strategies, conducting thorough risk assessments, establishing change control processes, providing training and support to employees, and monitoring and evaluating changes, organizations can successfully navigate the complexities of change management in IT service delivery. Embracing change as an opportunity for growth and innovation can position organizations for success in the digital age.
Read More
Introduction
In the ever-evolving world of Information Technology (IT), change is inevitable. With advancements in technology and shifting business needs, organizations must adapt to stay competitive. Effective change management in IT service delivery is crucial for ensuring that changes are implemented smoothly, with minimal disruption to operations. In this article, we will explore the key components of effective change management in IT service delivery and how organizations can navigate these changes successfully.
The Importance of Change Management
Change management is the process of managing changes to IT systems, processes, and infrastructure in a controlled and systematic manner. It involves planning, implementing, and monitoring changes to ensure that they are aligned with business goals and do not negatively impact operations. Effective change management is essential for organizations to minimize risks, optimize resources, and drive innovation.
Key Components of Effective Change Management
Clear Communication: Communication is key to successful change management. Stakeholders must be informed about the reasons for the change, the expected outcomes, and their roles and responsibilities. Clear and transparent communication helps build trust and ensures that everyone is on the same page.
Risk Assessment: Before implementing any changes, organizations must conduct a thorough risk assessment to identify potential risks and develop mitigation strategies. Understanding the impact of the changes allows organizations to proactively address any issues that may arise.
Change Control: Establishing a formal change control process helps organizations maintain control over changes and ensures that they are implemented in a structured manner. Change control involves documenting changes, obtaining approval from stakeholders, and tracking progress throughout the implementation process.
Training and Support: Providing training and support to employees is essential for successful change management. Employees need to understand how the changes will affect their roles and responsibilities and receive the necessary training to adapt to new processes and technologies.
Monitoring and Evaluation: Once changes are implemented, organizations must monitor and evaluate their impact on operations. Regular assessment helps identify any issues or bottlenecks and allows organizations to make adjustments as needed.
Overcoming Challenges in Change Management
Change management is not without its challenges. Resistance to change, lack of resources, and poor planning can derail even the most well-thought-out change management strategy. To overcome these challenges, organizations must prioritize open communication, engage stakeholders early in the process, and allocate sufficient resources to support the change management initiative.
How to obtain IT Service Management and Governance certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Effective change management is essential for organizations looking to stay ahead in today's fast-paced IT landscape. By implementing clear communication strategies, conducting thorough risk assessments, establishing change control processes, providing training and support to employees, and monitoring and evaluating changes, organizations can successfully navigate the complexities of change management in IT service delivery. Embracing change as an opportunity for growth and innovation can position organizations for success in the digital age.
Managing Citrix Client Updates: Strategies for Smooth Deployment
In today's rapidly evolving technological landscape, it is imperative to keep software current in order to maintain security, performance, and compatibility. When it comes to handling updates for Citrix clients, implementing effective deployment strategies is crucial for a seamless and efficient process. This article delves into the best practices for updating Citrix clients, covering aspects such as scheduling, automation, integration, and coordination.
Recognizing the Significance of Updating Citrix Clients
Citrix software is widely utilized in businesses globally for enabling remote access and virtualization. Updating client software is essential to address vulnerabilities, fix bugs, and introduce new features. Nevertheless, managing these updates can be a challenging task, particularly in large organizations with numerous users and devices.
Why is efficient deployment important for updating Citrix clients?
Efficient deployment of Citrix client updates is critical to ensuring that all devices are running the most recent software versions. This helps to minimize security risks, enhance performance, and improve user experience. Without effective deployment strategies in place, organizations may encounter compatibility issues, security breaches, and downtime.
Strategies for Handling Citrix Client Updates
1. Scheduling Updates
Thoughtful scheduling of Citrix client updates is vital to minimize disruptions and guarantee timely updates for all devices. Develop a comprehensive update schedule considering peak usage times, maintenance windows, and critical business operations.
2. Automating Updates
Automation can streamline the update process by automatically deploying patches and software updates to Citrix clients. Implementing automation tools can reduce manual errors, save time, and ensure consistency across all devices.
3. Integrating Updates
Integrating Citrix client updates with other software deployment processes can enhance the efficiency of the overall update management workflow. Ensure updates are tested for compatibility with other applications before deployment to prevent any issues.
4. Coordinating Updates
Effective coordination between IT teams, system administrators, and end-users is crucial for successful update deployment. Clearly communicate the update schedule, potential impacts, and any actions required from users to ensure a smooth transition.
Best Practices for Deploying Citrix Client Updates
1. Establish a standardized update process encompassing testing, deployment, and monitoring.
2. Develop a backup and rollback plan in case of issues during the update process.
3. Maintain a log of all updates and modifications made to Citrix clients for reference and auditing purposes.
4. Regularly assess and update your update management strategy to align with evolving security threats and software requirements.
How to obtain Citrix Client certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, By adhering to these strategies and best practices for managing Citrix client updates, organizations can ensure a seamless and efficient deployment process that minimizes disruptions and maximizes the benefits of the latest software versions. Stay proactive in keeping your Citrix clients up to date to safeguard your business and enhance productivity.
Read More
In today's rapidly evolving technological landscape, it is imperative to keep software current in order to maintain security, performance, and compatibility. When it comes to handling updates for Citrix clients, implementing effective deployment strategies is crucial for a seamless and efficient process. This article delves into the best practices for updating Citrix clients, covering aspects such as scheduling, automation, integration, and coordination.
Recognizing the Significance of Updating Citrix Clients
Citrix software is widely utilized in businesses globally for enabling remote access and virtualization. Updating client software is essential to address vulnerabilities, fix bugs, and introduce new features. Nevertheless, managing these updates can be a challenging task, particularly in large organizations with numerous users and devices.
Why is efficient deployment important for updating Citrix clients?
Efficient deployment of Citrix client updates is critical to ensuring that all devices are running the most recent software versions. This helps to minimize security risks, enhance performance, and improve user experience. Without effective deployment strategies in place, organizations may encounter compatibility issues, security breaches, and downtime.
Strategies for Handling Citrix Client Updates
1. Scheduling Updates
Thoughtful scheduling of Citrix client updates is vital to minimize disruptions and guarantee timely updates for all devices. Develop a comprehensive update schedule considering peak usage times, maintenance windows, and critical business operations.
2. Automating Updates
Automation can streamline the update process by automatically deploying patches and software updates to Citrix clients. Implementing automation tools can reduce manual errors, save time, and ensure consistency across all devices.
3. Integrating Updates
Integrating Citrix client updates with other software deployment processes can enhance the efficiency of the overall update management workflow. Ensure updates are tested for compatibility with other applications before deployment to prevent any issues.
4. Coordinating Updates
Effective coordination between IT teams, system administrators, and end-users is crucial for successful update deployment. Clearly communicate the update schedule, potential impacts, and any actions required from users to ensure a smooth transition.
Best Practices for Deploying Citrix Client Updates
1. Establish a standardized update process encompassing testing, deployment, and monitoring.
2. Develop a backup and rollback plan in case of issues during the update process.
3. Maintain a log of all updates and modifications made to Citrix clients for reference and auditing purposes.
4. Regularly assess and update your update management strategy to align with evolving security threats and software requirements.
How to obtain Citrix Client certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, By adhering to these strategies and best practices for managing Citrix client updates, organizations can ensure a seamless and efficient deployment process that minimizes disruptions and maximizes the benefits of the latest software versions. Stay proactive in keeping your Citrix clients up to date to safeguard your business and enhance productivity.
Securing Citrix Client Connections with SSL/TLS
In today's digital age, ensuring the security of data transfer between clients and servers is of utmost importance. With the rise in cyber threats and data breaches, organizations need to employ robust security measures to protect their sensitive information. One such technology that can help in securing Citrix client connections is SSL/TLS.
Understanding SSL/TLS
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are cryptographic protocols that provide secure communication over a computer network. These protocols encrypt the data transmitted between a client and a server, ensuring that it cannot be intercepted or tampered with by unauthorized parties.
How does SSL/TLS work?
When a client connects to a server using SSL/TLS, a secure connection is established through a process called the SSL/TLS handshake. During this handshake, the client and server exchange cryptographic keys to encrypt and decrypt the data they send to each other. This encryption ensures that even if the data is intercepted, it cannot be understood without the proper decryption key.
Importance of Securing Citrix Client Connections
Citrix is a popular technology used by organizations to provide remote access to applications and desktops. With employees accessing corporate resources from various locations and devices, securing Citrix client connections becomes crucial to prevent unauthorized access and data breaches.
Why is SSL/TLS important for Citrix?
By implementing SSL/TLS for Citrix client connections, organizations can ensure that the data transmitted between the client devices and the Citrix servers is encrypted and secure. This encryption protects sensitive information such as login credentials, financial data, and proprietary business information from being intercepted by hackers.
Best Practices for Securing Citrix Client Connections with SSL/TLS
Implementing SSL/TLS for Citrix client connections is a multi-step process that involves configuring the Citrix server and client devices to use secure protocols and encryption algorithms. Here are some best practices to ensure the security of Citrix client connections:
-
Enable SSL/TLS on Citrix Servers: Ensure that SSL/TLS is enabled on the Citrix servers to secure the communication between clients and servers.
-
Use Strong Encryption Algorithms: Choose strong encryption algorithms such as AES (Advanced Encryption Standard) to encrypt the data transmitted over Citrix client connections.
-
Regularly Update SSL/TLS Certificates: Keep the SSL/TLS certificates up to date to prevent security vulnerabilities and ensure the integrity of the encryption.
How can organizations benefit from SSL/TLS for Citrix?
By implementing SSL/TLS for Citrix client connections, organizations can enhance the security of their remote access infrastructure and protect sensitive data from unauthorized access. This can help in maintaining the trust of customers and stakeholders and complying with data protection regulations.
How to obtain Citrix Client Administration Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Securing Citrix client connections with SSL/TLS is essential for organizations looking to safeguard their sensitive data and prevent unauthorized access. By implementing robust encryption protocols and best practices, organizations can ensure the security of their Citrix infrastructure and protect their valuable information from cyber threats. Embracing SSL/TLS for Citrix client connections is a proactive step towards enhancing data security and maintaining the trust of clients and stakeholders in today's digital world.
Read More
In today's digital age, ensuring the security of data transfer between clients and servers is of utmost importance. With the rise in cyber threats and data breaches, organizations need to employ robust security measures to protect their sensitive information. One such technology that can help in securing Citrix client connections is SSL/TLS.
Understanding SSL/TLS
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are cryptographic protocols that provide secure communication over a computer network. These protocols encrypt the data transmitted between a client and a server, ensuring that it cannot be intercepted or tampered with by unauthorized parties.
How does SSL/TLS work?
When a client connects to a server using SSL/TLS, a secure connection is established through a process called the SSL/TLS handshake. During this handshake, the client and server exchange cryptographic keys to encrypt and decrypt the data they send to each other. This encryption ensures that even if the data is intercepted, it cannot be understood without the proper decryption key.
Importance of Securing Citrix Client Connections
Citrix is a popular technology used by organizations to provide remote access to applications and desktops. With employees accessing corporate resources from various locations and devices, securing Citrix client connections becomes crucial to prevent unauthorized access and data breaches.
Why is SSL/TLS important for Citrix?
By implementing SSL/TLS for Citrix client connections, organizations can ensure that the data transmitted between the client devices and the Citrix servers is encrypted and secure. This encryption protects sensitive information such as login credentials, financial data, and proprietary business information from being intercepted by hackers.
Best Practices for Securing Citrix Client Connections with SSL/TLS
Implementing SSL/TLS for Citrix client connections is a multi-step process that involves configuring the Citrix server and client devices to use secure protocols and encryption algorithms. Here are some best practices to ensure the security of Citrix client connections:
-
Enable SSL/TLS on Citrix Servers: Ensure that SSL/TLS is enabled on the Citrix servers to secure the communication between clients and servers.
-
Use Strong Encryption Algorithms: Choose strong encryption algorithms such as AES (Advanced Encryption Standard) to encrypt the data transmitted over Citrix client connections.
-
Regularly Update SSL/TLS Certificates: Keep the SSL/TLS certificates up to date to prevent security vulnerabilities and ensure the integrity of the encryption.
How can organizations benefit from SSL/TLS for Citrix?
By implementing SSL/TLS for Citrix client connections, organizations can enhance the security of their remote access infrastructure and protect sensitive data from unauthorized access. This can help in maintaining the trust of customers and stakeholders and complying with data protection regulations.
How to obtain Citrix Client Administration Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Securing Citrix client connections with SSL/TLS is essential for organizations looking to safeguard their sensitive data and prevent unauthorized access. By implementing robust encryption protocols and best practices, organizations can ensure the security of their Citrix infrastructure and protect their valuable information from cyber threats. Embracing SSL/TLS for Citrix client connections is a proactive step towards enhancing data security and maintaining the trust of clients and stakeholders in today's digital world.
Democratizing Data Science: Empowering Everyone with Data
In today's data-driven world, access to data is more important than ever. The concept of "democratizing data science" is all about making data accessible to everyone, regardless of their background or expertise. This movement towards data democratization is revolutionizing the way we use and understand data, empowering individuals to make better decisions and drive innovation. In this article, we will explore the importance of data accessibility, the rise of citizen data scientists, and the benefits of inclusive analytics for all.
What is Data Democratization?
Data democratization is the idea that data should be accessible and understandable to everyone, not just data scientists or experts. By breaking down traditional barriers to data access, organizations can empower employees at all levels to make data-driven decisions. This shift towards data inclusivity allows for greater collaboration, innovation, and efficiency within an organization.
Why is Data Accessibility Important?
Data accessibility is crucial for organizations looking to stay competitive in today's fast-paced economy. By providing employees with access to relevant data, businesses can foster a culture of data-driven decision-making. This not only leads to better outcomes but also ensures that all voices within the organization are heard and valued. Data accessibility empowers employees to take ownership of their work and make informed decisions based on data.
The Rise of Citizen Data Scientists
Citizen data scientists are non-experts who use data analysis tools to uncover insights and make recommendations. These individuals may not have a formal background in data science but have the curiosity and drive to explore data on their own. By empowering citizen data scientists, organizations can tap into a wealth of untapped potential and drive innovation from the ground up.
How can Organizations Support Citizen Data Scientists?
Organizations can support citizen data scientists by providing training and resources to help them develop their data literacy skills. By investing in the education and empowerment of all employees, organizations can foster a culture of data-driven decision-making and innovation.
The Benefits of Inclusive Analytics
Inclusive analytics is a key component of data democratization, ensuring that data is accessible and understandable to all. By incorporating diverse perspectives and voices into the data analysis process, organizations can uncover new insights and drive innovation. Inclusive analytics leads to better decision-making, improved collaboration, and a more engaged workforce.
How to obtain DataScience and Business Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, democratizing data science is about more than just making data accessible—it's about driving innovation, empowerment, and inclusion for all. By breaking down traditional barriers to data access and empowering individuals at all levels, organizations can unlock the full potential of data and drive better decision-making. Data for all means data for everyone, regardless of their background or expertise.
Read More
In today's data-driven world, access to data is more important than ever. The concept of "democratizing data science" is all about making data accessible to everyone, regardless of their background or expertise. This movement towards data democratization is revolutionizing the way we use and understand data, empowering individuals to make better decisions and drive innovation. In this article, we will explore the importance of data accessibility, the rise of citizen data scientists, and the benefits of inclusive analytics for all.
What is Data Democratization?
Data democratization is the idea that data should be accessible and understandable to everyone, not just data scientists or experts. By breaking down traditional barriers to data access, organizations can empower employees at all levels to make data-driven decisions. This shift towards data inclusivity allows for greater collaboration, innovation, and efficiency within an organization.
Why is Data Accessibility Important?
Data accessibility is crucial for organizations looking to stay competitive in today's fast-paced economy. By providing employees with access to relevant data, businesses can foster a culture of data-driven decision-making. This not only leads to better outcomes but also ensures that all voices within the organization are heard and valued. Data accessibility empowers employees to take ownership of their work and make informed decisions based on data.
The Rise of Citizen Data Scientists
Citizen data scientists are non-experts who use data analysis tools to uncover insights and make recommendations. These individuals may not have a formal background in data science but have the curiosity and drive to explore data on their own. By empowering citizen data scientists, organizations can tap into a wealth of untapped potential and drive innovation from the ground up.
How can Organizations Support Citizen Data Scientists?
Organizations can support citizen data scientists by providing training and resources to help them develop their data literacy skills. By investing in the education and empowerment of all employees, organizations can foster a culture of data-driven decision-making and innovation.
The Benefits of Inclusive Analytics
Inclusive analytics is a key component of data democratization, ensuring that data is accessible and understandable to all. By incorporating diverse perspectives and voices into the data analysis process, organizations can uncover new insights and drive innovation. Inclusive analytics leads to better decision-making, improved collaboration, and a more engaged workforce.
How to obtain DataScience and Business Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, democratizing data science is about more than just making data accessible—it's about driving innovation, empowerment, and inclusion for all. By breaking down traditional barriers to data access and empowering individuals at all levels, organizations can unlock the full potential of data and drive better decision-making. Data for all means data for everyone, regardless of their background or expertise.
The Role of ISO 20000 in Ensuring Cybersecurity in IT Service Management
In today's digital age, where cyber threats are constantly evolving, organizations need to prioritize cybersecurity in their IT service management practices. One essential tool in this fight against cyber threats is the ISO/IEC 20000 standard. ISO 20000 is a globally recognized standard that outlines best practices for IT service management, including cybersecurity measures to protect valuable data and systems. Let's explore the role of ISO 20000 in ensuring cyber security in IT service management.
What is ISO 20000?
ISO 20000 is an international standard for IT service management that helps organizations ensure the effective delivery of IT services to meet the needs of their customers. It provides a framework for establishing, implementing, maintaining, and continually improving an IT service management system. By adhering to the requirements of ISO 20000, organizations can enhance the quality of their IT services and demonstrate their commitment to excellence in IT service delivery.
The Role of ISO 20000 in Cybersecurity
One of the key benefits of implementing ISO 20000 is its emphasis on information security. The standard includes specific requirements for managing information security risks and protecting sensitive data from cyber threats. By following the guidelines set forth in ISO 20000, organizations can establish robust controls and processes to safeguard their IT infrastructure and systems from potential security breaches.
Certification and Compliance
Achieving ISO 20000 certification demonstrates an organization's commitment to cybersecurity and best practices in IT service management. By undergoing a rigorous audit process, organizations can prove their compliance with the standard and showcase their dedication to maintaining a secure and reliable IT environment. ISO 20000 certification not only enhances an organization's reputation but also instills confidence in customers and stakeholders regarding the security of their information assets.
Incident Response and Risk Management
ISO 20000 also emphasizes the importance of incident response and risk management in IT service management. By establishing clear procedures for identifying, assessing, and mitigating cybersecurity risks, organizations can proactively manage potential threats and prevent security incidents from occurring. Additionally, ISO 20000 promotes a structured approach to incident response, ensuring that organizations can effectively respond to and recover from cybersecurity incidents in a timely manner.
Best Practices and Continuous Improvement
ISO 20000 encompasses a set of best practices for IT service management, including cybersecurity measures such as vulnerability management, asset management, and business continuity planning. By following these best practices, organizations can enhance their cybersecurity posture and improve the overall quality of their IT services. Furthermore, ISO 20000 promotes a culture of continuous improvement, encouraging organizations to regularly review and enhance their cybersecurity practices to adapt to evolving cyber threats.
How to obtain IT Service Management and Governance certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, ISO 20000 plays a crucial role in ensuring cybersecurity in IT service management by providing organizations with a comprehensive framework for implementing robust security controls and processes. By adhering to the requirements of ISO 20000, organizations can enhance the quality of their IT services, protect sensitive data from cyber threats, and demonstrate their commitment to excellence in IT service delivery. Ultimately, ISO 20000 certification can help organizations build trust with customers and stakeholders, showcasing their dedication to maintaining a secure and reliable IT environment.
Read More
In today's digital age, where cyber threats are constantly evolving, organizations need to prioritize cybersecurity in their IT service management practices. One essential tool in this fight against cyber threats is the ISO/IEC 20000 standard. ISO 20000 is a globally recognized standard that outlines best practices for IT service management, including cybersecurity measures to protect valuable data and systems. Let's explore the role of ISO 20000 in ensuring cyber security in IT service management.
What is ISO 20000?
ISO 20000 is an international standard for IT service management that helps organizations ensure the effective delivery of IT services to meet the needs of their customers. It provides a framework for establishing, implementing, maintaining, and continually improving an IT service management system. By adhering to the requirements of ISO 20000, organizations can enhance the quality of their IT services and demonstrate their commitment to excellence in IT service delivery.
The Role of ISO 20000 in Cybersecurity
One of the key benefits of implementing ISO 20000 is its emphasis on information security. The standard includes specific requirements for managing information security risks and protecting sensitive data from cyber threats. By following the guidelines set forth in ISO 20000, organizations can establish robust controls and processes to safeguard their IT infrastructure and systems from potential security breaches.
Certification and Compliance
Achieving ISO 20000 certification demonstrates an organization's commitment to cybersecurity and best practices in IT service management. By undergoing a rigorous audit process, organizations can prove their compliance with the standard and showcase their dedication to maintaining a secure and reliable IT environment. ISO 20000 certification not only enhances an organization's reputation but also instills confidence in customers and stakeholders regarding the security of their information assets.
Incident Response and Risk Management
ISO 20000 also emphasizes the importance of incident response and risk management in IT service management. By establishing clear procedures for identifying, assessing, and mitigating cybersecurity risks, organizations can proactively manage potential threats and prevent security incidents from occurring. Additionally, ISO 20000 promotes a structured approach to incident response, ensuring that organizations can effectively respond to and recover from cybersecurity incidents in a timely manner.
Best Practices and Continuous Improvement
ISO 20000 encompasses a set of best practices for IT service management, including cybersecurity measures such as vulnerability management, asset management, and business continuity planning. By following these best practices, organizations can enhance their cybersecurity posture and improve the overall quality of their IT services. Furthermore, ISO 20000 promotes a culture of continuous improvement, encouraging organizations to regularly review and enhance their cybersecurity practices to adapt to evolving cyber threats.
How to obtain IT Service Management and Governance certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, ISO 20000 plays a crucial role in ensuring cybersecurity in IT service management by providing organizations with a comprehensive framework for implementing robust security controls and processes. By adhering to the requirements of ISO 20000, organizations can enhance the quality of their IT services, protect sensitive data from cyber threats, and demonstrate their commitment to excellence in IT service delivery. Ultimately, ISO 20000 certification can help organizations build trust with customers and stakeholders, showcasing their dedication to maintaining a secure and reliable IT environment.
Exploring the World of Natural Language Processing (NLP) with Python
Are you curious about the fascinating world of Natural Language Processing (NLP) and how Python is used to delve deep into the realms of text analysis and machine learning? In this article, we will take a comprehensive look at the vast landscape of NLP and how Python serves as a powerful tool for data scientists, artificial intelligence enthusiasts, and anyone interested in understanding and manipulating human language through the lens of computer programming.
Introduction to Natural Language Processing (NLP)
Natural Language Processing (NLP) is a field of study that focuses on the interaction between computers and human language. With the advancement of machine learning and artificial intelligence, NLP has gained immense popularity in recent years. From sentiment analysis to text classification, and from named entity recognition to language modeling, NLP encompasses a wide range of applications that are revolutionizing the way we interact with machines.
Why Python for NLP?
Python has emerged as the go-to programming language for NLP due to its simplicity, readability, and extensive libraries tailored for text processing tasks. Libraries such as spaCy, NLTK, gensim, and Word2Vec are widely used for various NLP applications. Python's versatility and ease of use make it the ideal choice for both beginners and seasoned professionals in the field of NLP.
Key Components of NLP with Python
Let's delve into some of the key components of NLP with Python that are essential for understanding and working with textual data:
Tokenization
Tokenization is the process of breaking down text into smaller units, such as words or sentences. Python libraries like NLTK and spaCy offer efficient tokenization tools that help extract meaningful information from text data.
Part-of-Speech Tagging
Part-of-speech tagging involves assigning grammatical tags to words in a sentence, such as nouns, verbs, adjectives, and adverbs. This information is crucial for understanding the syntactic structure of text, and tools like spaCy excel at part-of-speech tagging.
Named Entity Recognition
Named Entity Recognition (NER) is the task of identifying named entities in text, such as names of people, organizations, locations, and dates. Python libraries like NLTK and spaCy offer robust NER capabilities that aid in extracting meaningful information from unstructured text.
Sentiment Analysis
Sentiment analysis is the process of determining the sentiment or emotion expressed in text, such as positive, negative, or neutral. Python libraries like NLTK and TextBlob provide sentiment analysis tools that help analyze the tone and sentiment of text data.
Text Classification
Text classification involves categorizing text into predefined categories, such as spam detection, sentiment analysis, or topic classification. Python libraries like scikit-learn and Keras offer powerful tools for text classification tasks.
Language Modeling
Language modeling is the task of predicting the next word in a sequence of words, based on the context of the text. Python libraries like TensorFlow and PyTorch provide efficient tools for building language models that can generate coherent and contextually relevant text.
Topic Modeling
Topic modeling is a technique for discovering the hidden topics present in a collection of text documents. Python libraries like Gensim and LDA offer powerful tools for performing topic modeling on textual data.
Information Extraction
Information extraction involves extracting structured information from unstructured text, such as extracting entities, relationships, and events. Python libraries like spaCy and NLTK provide tools for information extraction tasks.
Word Embeddings
Word embeddings are dense vector representations of words that capture semantic relationships between words. Python libraries like Word2Vec and GloVe offer pretrained word embeddings that can be used for a variety of NLP tasks.
How to obtain Development Course in Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the world of Natural Language Processing (NLP) with Python is an exciting and dynamic field that offers endless possibilities for exploring and analyzing textual data. With a wide range of libraries and tools available, Python provides a versatile platform for building sophisticated NLP applications that can revolutionize the way we interact with and understand human language.
Read More
Are you curious about the fascinating world of Natural Language Processing (NLP) and how Python is used to delve deep into the realms of text analysis and machine learning? In this article, we will take a comprehensive look at the vast landscape of NLP and how Python serves as a powerful tool for data scientists, artificial intelligence enthusiasts, and anyone interested in understanding and manipulating human language through the lens of computer programming.
Introduction to Natural Language Processing (NLP)
Natural Language Processing (NLP) is a field of study that focuses on the interaction between computers and human language. With the advancement of machine learning and artificial intelligence, NLP has gained immense popularity in recent years. From sentiment analysis to text classification, and from named entity recognition to language modeling, NLP encompasses a wide range of applications that are revolutionizing the way we interact with machines.
Why Python for NLP?
Python has emerged as the go-to programming language for NLP due to its simplicity, readability, and extensive libraries tailored for text processing tasks. Libraries such as spaCy, NLTK, gensim, and Word2Vec are widely used for various NLP applications. Python's versatility and ease of use make it the ideal choice for both beginners and seasoned professionals in the field of NLP.
Key Components of NLP with Python
Let's delve into some of the key components of NLP with Python that are essential for understanding and working with textual data:
Tokenization
Tokenization is the process of breaking down text into smaller units, such as words or sentences. Python libraries like NLTK and spaCy offer efficient tokenization tools that help extract meaningful information from text data.
Part-of-Speech Tagging
Part-of-speech tagging involves assigning grammatical tags to words in a sentence, such as nouns, verbs, adjectives, and adverbs. This information is crucial for understanding the syntactic structure of text, and tools like spaCy excel at part-of-speech tagging.
Named Entity Recognition
Named Entity Recognition (NER) is the task of identifying named entities in text, such as names of people, organizations, locations, and dates. Python libraries like NLTK and spaCy offer robust NER capabilities that aid in extracting meaningful information from unstructured text.
Sentiment Analysis
Sentiment analysis is the process of determining the sentiment or emotion expressed in text, such as positive, negative, or neutral. Python libraries like NLTK and TextBlob provide sentiment analysis tools that help analyze the tone and sentiment of text data.
Text Classification
Text classification involves categorizing text into predefined categories, such as spam detection, sentiment analysis, or topic classification. Python libraries like scikit-learn and Keras offer powerful tools for text classification tasks.
Language Modeling
Language modeling is the task of predicting the next word in a sequence of words, based on the context of the text. Python libraries like TensorFlow and PyTorch provide efficient tools for building language models that can generate coherent and contextually relevant text.
Topic Modeling
Topic modeling is a technique for discovering the hidden topics present in a collection of text documents. Python libraries like Gensim and LDA offer powerful tools for performing topic modeling on textual data.
Information Extraction
Information extraction involves extracting structured information from unstructured text, such as extracting entities, relationships, and events. Python libraries like spaCy and NLTK provide tools for information extraction tasks.
Word Embeddings
Word embeddings are dense vector representations of words that capture semantic relationships between words. Python libraries like Word2Vec and GloVe offer pretrained word embeddings that can be used for a variety of NLP tasks.
How to obtain Development Course in Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the world of Natural Language Processing (NLP) with Python is an exciting and dynamic field that offers endless possibilities for exploring and analyzing textual data. With a wide range of libraries and tools available, Python provides a versatile platform for building sophisticated NLP applications that can revolutionize the way we interact with and understand human language.
5 Key Concepts to Ace Your COBIT 5 Foundation Certification Exam
Are you preparing for your COBIT® 5 Foundation certification exam and looking for ways to ensure success? Achieving this certification can open up new opportunities for career advancement and professional development in the field of IT governance. To help you pass your exam with flying colors, here are 5 key concepts to focus on in your study guide and exam preparation:
Understanding the COBIT® 5 Framework
The COBIT® 5 framework is a globally recognized standard for IT governance that helps organizations align their IT strategies with their business goals. By understanding the framework's core principles and control objectives, you will be better equipped to answer exam questions related to implementing best practices for effective IT governance.
Mastering IT Governance Strategies
IT governance is essential for ensuring that an organization's IT infrastructure supports its overall business objectives. By grasping the various strategies and principles outlined in COBIT® 5, you will be able to demonstrate your knowledge of how to align IT with business goals and drive value through effective governance practices.
Familiarizing Yourself with Control Objectives
Control objectives in the COBIT® 5 framework provide a set of guidelines for implementing IT governance processes and controls. By studying the control objectives relevant to your exam, you can gain a deeper understanding of how to manage risks, ensure compliance, and optimize IT resources to achieve organizational objectives.
Practicing with Mock Tests
Mock tests are a valuable tool for assessing your knowledge and readiness for the COBIT® 5 Foundation exam. By taking practice exams online, you can familiarize yourself with the exam format, test questions, and time constraints, allowing you to identify areas where you may need additional study and practice.
Creating a Study Plan
A well-structured study plan is essential for effective exam preparation. By creating a study schedule that includes review of study materials, completion of online courses, and practice with mock tests, you can ensure that you cover all the necessary topics and concepts before exam day. Consider enrolling in accredited training programs to gain access to expert guidance and resources for a comprehensive study experience.
How to obtain IT Service Management and Governance in COBIT certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, by focusing on these key concepts and following a strategic study plan, you can increase your chances of acing your COBIT® 5 Foundation certification exam. Remember to stay focused, prioritize your study time, and leverage resources such as mock tests and study materials to maximize your preparation efforts.
Read More
Are you preparing for your COBIT® 5 Foundation certification exam and looking for ways to ensure success? Achieving this certification can open up new opportunities for career advancement and professional development in the field of IT governance. To help you pass your exam with flying colors, here are 5 key concepts to focus on in your study guide and exam preparation:
Understanding the COBIT® 5 Framework
The COBIT® 5 framework is a globally recognized standard for IT governance that helps organizations align their IT strategies with their business goals. By understanding the framework's core principles and control objectives, you will be better equipped to answer exam questions related to implementing best practices for effective IT governance.
Mastering IT Governance Strategies
IT governance is essential for ensuring that an organization's IT infrastructure supports its overall business objectives. By grasping the various strategies and principles outlined in COBIT® 5, you will be able to demonstrate your knowledge of how to align IT with business goals and drive value through effective governance practices.
Familiarizing Yourself with Control Objectives
Control objectives in the COBIT® 5 framework provide a set of guidelines for implementing IT governance processes and controls. By studying the control objectives relevant to your exam, you can gain a deeper understanding of how to manage risks, ensure compliance, and optimize IT resources to achieve organizational objectives.
Practicing with Mock Tests
Mock tests are a valuable tool for assessing your knowledge and readiness for the COBIT® 5 Foundation exam. By taking practice exams online, you can familiarize yourself with the exam format, test questions, and time constraints, allowing you to identify areas where you may need additional study and practice.
Creating a Study Plan
A well-structured study plan is essential for effective exam preparation. By creating a study schedule that includes review of study materials, completion of online courses, and practice with mock tests, you can ensure that you cover all the necessary topics and concepts before exam day. Consider enrolling in accredited training programs to gain access to expert guidance and resources for a comprehensive study experience.
How to obtain IT Service Management and Governance in COBIT certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, by focusing on these key concepts and following a strategic study plan, you can increase your chances of acing your COBIT® 5 Foundation certification exam. Remember to stay focused, prioritize your study time, and leverage resources such as mock tests and study materials to maximize your preparation efforts.
Exploring the Relationship Between ISO 20000 and ITIL Frameworks
In the world of IT service management, two prominent frameworks often come into play: ISO 20000 and ITIL. These frameworks play a crucial role in shaping how organizations deliver services to their customers. However, many people are still unclear about the relationship between ISO 20000 and ITIL frameworks. In this article, we will explore the key similarities, differences, benefits, and implementation strategies of these frameworks to help you better understand their connection.
ISO 20000 and ITIL: A Comparative Analysis
Understanding ISO 20000
ISO 20000 is an international standard that specifies requirements for an organization to establish, implement, maintain, and continually improve a service management system. It focuses on the processes needed to deliver effective services to customers and meet their requirements.
Decoding ITIL Framework
ITIL, on the other hand, stands for Information Technology Infrastructure Library and is a set of detailed practices for IT service management (ITSM) that focuses on aligning IT services with the needs of business. It provides a framework for organizations to manage their IT services effectively and efficiently.
Exploring the Relationship Between ISO 20000 and ITIL
While ISO 20000 and ITIL are distinct frameworks, they are not mutually exclusive. In fact, many organizations find that implementing both standards can lead to a more holistic approach to service management. ISO 20000 provides a set of requirements that organizations must meet to achieve certification, while ITIL offers best practices and guidelines for implementing IT service management processes.
Benefits of Integrating ISO 20000 and ITIL
-
Improved Service Quality: By aligning with both frameworks, organizations can enhance the quality of their services and ensure they meet industry standards.
-
Enhanced Efficiency: The integration of ISO 20000 and ITIL can help streamline processes and increase operational efficiency.
-
Better Customer Satisfaction: Meeting the requirements of both frameworks can lead to improved customer satisfaction and loyalty.
-
Compliance and Certification: Implementing both standards can help organizations achieve ISO 20000 certification and adhere to ITIL best practices.
Implementation Strategies and Approaches
When integrating ISO 20000 and ITIL frameworks, organizations should focus on aligning their processes, procedures, and documentation to meet the requirements of both standards. This may involve conducting a gap analysis, identifying areas for improvement, and creating a roadmap for implementation.
The Impact on Organizations
The integration of ISO 20000 and ITIL frameworks can have a significant impact on organizations, leading to improved service delivery, increased efficiency, and enhanced customer satisfaction. It can also help organizations stay competitive in the market and meet the growing demands of customers.
Key Points to Remember
-
ISO 20000 and ITIL are complementary frameworks that can be integrated to improve service management.
-
Organizations can benefit from aligning with both standards to enhance service quality and efficiency.
-
Implementing both frameworks requires careful planning, analysis, and continuous improvement.
How to obtain IT Service Management and Governance certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, understanding the relationship between ISO 20000 and ITIL frameworks is essential for organizations looking to improve their service management practices. By integrating these frameworks, organizations can achieve certification, improve service quality, and enhance customer satisfaction. The synergy between ISO 20000 and ITIL offers a comprehensive approach to IT service management that can benefit organizations of all sizes.
Read More
In the world of IT service management, two prominent frameworks often come into play: ISO 20000 and ITIL. These frameworks play a crucial role in shaping how organizations deliver services to their customers. However, many people are still unclear about the relationship between ISO 20000 and ITIL frameworks. In this article, we will explore the key similarities, differences, benefits, and implementation strategies of these frameworks to help you better understand their connection.
ISO 20000 and ITIL: A Comparative Analysis
Understanding ISO 20000
ISO 20000 is an international standard that specifies requirements for an organization to establish, implement, maintain, and continually improve a service management system. It focuses on the processes needed to deliver effective services to customers and meet their requirements.
Decoding ITIL Framework
ITIL, on the other hand, stands for Information Technology Infrastructure Library and is a set of detailed practices for IT service management (ITSM) that focuses on aligning IT services with the needs of business. It provides a framework for organizations to manage their IT services effectively and efficiently.
Exploring the Relationship Between ISO 20000 and ITIL
While ISO 20000 and ITIL are distinct frameworks, they are not mutually exclusive. In fact, many organizations find that implementing both standards can lead to a more holistic approach to service management. ISO 20000 provides a set of requirements that organizations must meet to achieve certification, while ITIL offers best practices and guidelines for implementing IT service management processes.
Benefits of Integrating ISO 20000 and ITIL
-
Improved Service Quality: By aligning with both frameworks, organizations can enhance the quality of their services and ensure they meet industry standards.
-
Enhanced Efficiency: The integration of ISO 20000 and ITIL can help streamline processes and increase operational efficiency.
-
Better Customer Satisfaction: Meeting the requirements of both frameworks can lead to improved customer satisfaction and loyalty.
-
Compliance and Certification: Implementing both standards can help organizations achieve ISO 20000 certification and adhere to ITIL best practices.
Implementation Strategies and Approaches
When integrating ISO 20000 and ITIL frameworks, organizations should focus on aligning their processes, procedures, and documentation to meet the requirements of both standards. This may involve conducting a gap analysis, identifying areas for improvement, and creating a roadmap for implementation.
The Impact on Organizations
The integration of ISO 20000 and ITIL frameworks can have a significant impact on organizations, leading to improved service delivery, increased efficiency, and enhanced customer satisfaction. It can also help organizations stay competitive in the market and meet the growing demands of customers.
Key Points to Remember
-
ISO 20000 and ITIL are complementary frameworks that can be integrated to improve service management.
-
Organizations can benefit from aligning with both standards to enhance service quality and efficiency.
-
Implementing both frameworks requires careful planning, analysis, and continuous improvement.
How to obtain IT Service Management and Governance certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, understanding the relationship between ISO 20000 and ITIL frameworks is essential for organizations looking to improve their service management practices. By integrating these frameworks, organizations can achieve certification, improve service quality, and enhance customer satisfaction. The synergy between ISO 20000 and ITIL offers a comprehensive approach to IT service management that can benefit organizations of all sizes.
Voice Search Revolutionizing Digital Marketing
In the fast-paced world of digital marketing, staying ahead of the latest trends and technologies is crucial to success. One of the most groundbreaking developments in recent years has been the rise of voice search technology. This revolutionary innovation is changing the way businesses connect with consumers and revolutionizing the digital marketing landscape.
The Power of Voice Search
Voice search utilizes artificial intelligence to enable users to perform searches and access information using voice commands rather than traditional text input. This technology has quickly gained popularity, especially with the widespread use of virtual assistants like Siri, Alexa, and Google Assistant on mobile devices and smart speakers. As a result, optimizing for voice search has become a key strategy for businesses looking to enhance their online presence and reach a broader audience.
Benefits of Voice Search Optimization
-
Convenience: Voice search offers a more convenient and hands-free way for users to interact with technology and access information on-the-go.
-
Improved User Experience: By providing quick and accurate responses to user queries, businesses can enhance the overall user experience and increase engagement.
-
Data Analysis: Voice search allows businesses to gather valuable data on user behavior and preferences, enabling them to tailor their marketing strategies more effectively.
Incorporating Voice Search into Marketing Strategy
To harness the power of voice search and maximize its impact on digital marketing efforts, businesses must adapt their strategies accordingly. Here are some key considerations for integrating voice search optimization into your marketing plan
1. Content Innovation
Creating high-quality, voice-friendly content is essential for attracting voice search users. Focus on crafting conversational and informative content that answers common user queries and incorporates relevant keywords for voice search optimization.
2. Mobile Optimization
Given the prevalence of voice search on mobile devices, ensuring your website is mobile-friendly is crucial. Mobile optimization helps improve the user experience and ensures your content is easy to access and navigate via voice commands.
3. Keyword Targeting
Identifying and targeting long-tail keywords and phrases that are likely to be used in voice search queries can help boost your visibility in voice search results. Tailor your content to align with natural language patterns and user intent for optimal performance.
The Future of Voice Search in Digital Marketing
As voice recognition technology continues to advance and become more integrated into everyday life, the role of voice search in digital marketing is only expected to grow. Businesses that embrace voice search optimization early on will be better positioned to capitalize on this trend and stay ahead of the competition.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the voice search revolution is transforming the way businesses approach digital marketing, offering new opportunities to engage with consumers and enhance their online presence. By adapting to the changing landscape and incorporating voice search optimization strategies into their marketing efforts, businesses can position themselves for success in the digital age.
Read More
In the fast-paced world of digital marketing, staying ahead of the latest trends and technologies is crucial to success. One of the most groundbreaking developments in recent years has been the rise of voice search technology. This revolutionary innovation is changing the way businesses connect with consumers and revolutionizing the digital marketing landscape.
The Power of Voice Search
Voice search utilizes artificial intelligence to enable users to perform searches and access information using voice commands rather than traditional text input. This technology has quickly gained popularity, especially with the widespread use of virtual assistants like Siri, Alexa, and Google Assistant on mobile devices and smart speakers. As a result, optimizing for voice search has become a key strategy for businesses looking to enhance their online presence and reach a broader audience.
Benefits of Voice Search Optimization
-
Convenience: Voice search offers a more convenient and hands-free way for users to interact with technology and access information on-the-go.
-
Improved User Experience: By providing quick and accurate responses to user queries, businesses can enhance the overall user experience and increase engagement.
-
Data Analysis: Voice search allows businesses to gather valuable data on user behavior and preferences, enabling them to tailor their marketing strategies more effectively.
Incorporating Voice Search into Marketing Strategy
To harness the power of voice search and maximize its impact on digital marketing efforts, businesses must adapt their strategies accordingly. Here are some key considerations for integrating voice search optimization into your marketing plan
1. Content Innovation
Creating high-quality, voice-friendly content is essential for attracting voice search users. Focus on crafting conversational and informative content that answers common user queries and incorporates relevant keywords for voice search optimization.
2. Mobile Optimization
Given the prevalence of voice search on mobile devices, ensuring your website is mobile-friendly is crucial. Mobile optimization helps improve the user experience and ensures your content is easy to access and navigate via voice commands.
3. Keyword Targeting
Identifying and targeting long-tail keywords and phrases that are likely to be used in voice search queries can help boost your visibility in voice search results. Tailor your content to align with natural language patterns and user intent for optimal performance.
The Future of Voice Search in Digital Marketing
As voice recognition technology continues to advance and become more integrated into everyday life, the role of voice search in digital marketing is only expected to grow. Businesses that embrace voice search optimization early on will be better positioned to capitalize on this trend and stay ahead of the competition.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the voice search revolution is transforming the way businesses approach digital marketing, offering new opportunities to engage with consumers and enhance their online presence. By adapting to the changing landscape and incorporating voice search optimization strategies into their marketing efforts, businesses can position themselves for success in the digital age.
Monitoring Hadoop Clusters: Tools
Have you ever wondered how to effectively monitor your Hadoop clusters to ensure optimal performance and efficient management? In this article, we will explore the best tools and strategies for monitoring Hadoop clusters, so you can stay on top of your big data ecosystem.
Introduction
Monitoring a Hadoop cluster is crucial for maintaining its health and performance. With the volume of data processed by Hadoop clusters continuously increasing, it is essential to have reliable monitoring tools in place to prevent any downtime or performance bottlenecks.
Hadoop Cluster Monitoring Tools
There are several tools available in the market that can help you monitor your Hadoop clusters effectively. These tools offer real-time monitoring, centralized dashboard views, alerts, and performance metrics. Some popular Hadoop monitoring tools include:
-
Ambari: Ambari is an open-source software for provisioning, managing, and monitoring Hadoop clusters. It provides an intuitive web interface for monitoring cluster health, managing services, and configuring alerts.
-
Ganglia: Ganglia is another widely used monitoring tool for Hadoop clusters. It offers scalable monitoring and distributed monitoring capabilities, making it a popular choice for monitoring large-scale clusters.
-
Nagios: Nagios is a powerful monitoring tool that can be used to monitor various aspects of Hadoop clusters, including infrastructure, services, and applications. It offers customizable alerts, dashboards, and reporting features.
-
Cloudera Manager: Cloudera Manager is a comprehensive platform for managing and monitoring Hadoop clusters. It provides centralized administration, monitoring, and diagnostics for Hadoop clusters running on Cloudera's distribution.
Hadoop Monitoring Strategies
Monitoring a Hadoop cluster involves tracking various metrics, such as cluster resource utilization, job status, node health, and network activity. To effectively monitor your Hadoop cluster, consider the following strategies:
-
Real-time Monitoring: Implement tools that offer real-time monitoring capabilities to promptly identify any issues or bottlenecks.
-
Automated Alerts: Configure alerts for critical metrics to receive notifications when thresholds are exceeded.
-
Cluster Health Dashboard: Use a centralized dashboard to visualize the health and performance of your Hadoop cluster.
-
Job Monitoring: Monitor Hadoop job execution to ensure timely completion and optimal resource utilization.
-
Infrastructure Monitoring: Track the performance of individual nodes, network connectivity, and storage utilization.
Hadoop Cluster Monitoring Best Practices
To ensure effective monitoring of your Hadoop cluster, follow these best practices:
-
Regularly monitor cluster metrics and performance to identify any anomalies or bottlenecks.
-
Set up automated alerts for critical events to take proactive actions.
-
Implement a centralized monitoring solution for easy access to cluster health and performance data.
-
Conduct regular performance tuning and optimization to enhance cluster efficiency.
-
Regularly review and update monitoring configurations to adapt to changing workload requirements.
How to obtain Big data and Hadoop Administrator certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, monitoring Hadoop clusters is essential for ensuring optimal performance, efficient management, and timely issue resolution. By leveraging the right monitoring tools and strategies, you can effectively monitor your Hadoop cluster and maintain its health and performance.
Read More
Have you ever wondered how to effectively monitor your Hadoop clusters to ensure optimal performance and efficient management? In this article, we will explore the best tools and strategies for monitoring Hadoop clusters, so you can stay on top of your big data ecosystem.
Introduction
Monitoring a Hadoop cluster is crucial for maintaining its health and performance. With the volume of data processed by Hadoop clusters continuously increasing, it is essential to have reliable monitoring tools in place to prevent any downtime or performance bottlenecks.
Hadoop Cluster Monitoring Tools
There are several tools available in the market that can help you monitor your Hadoop clusters effectively. These tools offer real-time monitoring, centralized dashboard views, alerts, and performance metrics. Some popular Hadoop monitoring tools include:
-
Ambari: Ambari is an open-source software for provisioning, managing, and monitoring Hadoop clusters. It provides an intuitive web interface for monitoring cluster health, managing services, and configuring alerts.
-
Ganglia: Ganglia is another widely used monitoring tool for Hadoop clusters. It offers scalable monitoring and distributed monitoring capabilities, making it a popular choice for monitoring large-scale clusters.
-
Nagios: Nagios is a powerful monitoring tool that can be used to monitor various aspects of Hadoop clusters, including infrastructure, services, and applications. It offers customizable alerts, dashboards, and reporting features.
-
Cloudera Manager: Cloudera Manager is a comprehensive platform for managing and monitoring Hadoop clusters. It provides centralized administration, monitoring, and diagnostics for Hadoop clusters running on Cloudera's distribution.
Hadoop Monitoring Strategies
Monitoring a Hadoop cluster involves tracking various metrics, such as cluster resource utilization, job status, node health, and network activity. To effectively monitor your Hadoop cluster, consider the following strategies:
-
Real-time Monitoring: Implement tools that offer real-time monitoring capabilities to promptly identify any issues or bottlenecks.
-
Automated Alerts: Configure alerts for critical metrics to receive notifications when thresholds are exceeded.
-
Cluster Health Dashboard: Use a centralized dashboard to visualize the health and performance of your Hadoop cluster.
-
Job Monitoring: Monitor Hadoop job execution to ensure timely completion and optimal resource utilization.
-
Infrastructure Monitoring: Track the performance of individual nodes, network connectivity, and storage utilization.
Hadoop Cluster Monitoring Best Practices
To ensure effective monitoring of your Hadoop cluster, follow these best practices:
-
Regularly monitor cluster metrics and performance to identify any anomalies or bottlenecks.
-
Set up automated alerts for critical events to take proactive actions.
-
Implement a centralized monitoring solution for easy access to cluster health and performance data.
-
Conduct regular performance tuning and optimization to enhance cluster efficiency.
-
Regularly review and update monitoring configurations to adapt to changing workload requirements.
How to obtain Big data and Hadoop Administrator certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, monitoring Hadoop clusters is essential for ensuring optimal performance, efficient management, and timely issue resolution. By leveraging the right monitoring tools and strategies, you can effectively monitor your Hadoop cluster and maintain its health and performance.
Natural Language Processing (NLP): Revolutionizing the Way We Interact with Technology
Natural Language Processing (NLP) is a fascinating field of artificial intelligence that focuses on enabling computers to understand, interpret, and generate human language in a way that is both meaningful and useful. From virtual assistants like Siri and Alexa to chatbots and language translation tools, NLP is revolutionizing the way we interact with technology and enhancing the user experience in countless applications.
What is Natural Language Processing (NLP)?
Natural Language Processing (NLP) is a branch of artificial intelligence that enables computers to understand, interpret, and generate human language in a way that is both meaningful and useful. By combining computational linguistics with computer science, NLP allows machines to process, analyze, and respond to text and speech data in a manner that mimics human communication.
How Does NLP Work?
NLP leverages algorithms and models to analyze the structure and meaning of language in order to perform tasks like text classification, sentiment analysis, speech recognition, and language translation. By breaking down language into its constituent parts, NLP algorithms can identify patterns, extract information, and generate responses that are contextually relevant and accurate.?
The Impact of NLP on Communication?
The advancement of NLP technology has significantly improved the way we communicate with machines. Virtual assistants like Siri, Alexa, and Google Assistant utilize NLP to understand voice commands, answer questions, and perform tasks on behalf of users. Chatbots powered by NLP can engage in natural language conversations with customers, providing personalized assistance and support in real-time. Language translation tools powered by NLP make it easier to communicate across linguistic barriers, enabling seamless global interaction.?
Emerging Trends in NLP?
As NLP continues to evolve, we are seeing exciting advancements in areas such as emotion recognition, dialect understanding, and context-aware language processing. Emotion recognition technologies allow machines to detect and respond to human emotions in text and speech, enabling more empathetic and personalized interactions. Dialect understanding algorithms can decipher regional accents and dialects, improving the accuracy of speech recognition and language translation. Context-aware language processing models can analyze the context of a conversation to generate more relevant and coherent responses.?
The Future of NLP?
The future of NLP holds immense potential for transforming the way we interact with technology and each other. As NLP algorithms become more sophisticated and capable, we can expect to see even greater improvements in areas such as conversational AI, sentiment analysis, and language understanding. From enhancing customer service experiences to enabling more intuitive human-machine communication, NLP is poised to revolutionize the way we engage with the digital world.
How to obtain Emerging Technology certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Natural Language Processing (NLP) is a groundbreaking field of artificial intelligence that is reshaping the way we interact with technology. By enabling machines to understand, interpret, and generate human language, NLP is opening up new possibilities for more intuitive and seamless communication experiences. As NLP technology continues to advance, we can look forward to a future where machines not only understand what we say but also how we feel and what we need. Get ready for a world where human-machine interaction is more natural, empathetic, and engaging than ever before.
Read More
Natural Language Processing (NLP) is a fascinating field of artificial intelligence that focuses on enabling computers to understand, interpret, and generate human language in a way that is both meaningful and useful. From virtual assistants like Siri and Alexa to chatbots and language translation tools, NLP is revolutionizing the way we interact with technology and enhancing the user experience in countless applications.
What is Natural Language Processing (NLP)?
Natural Language Processing (NLP) is a branch of artificial intelligence that enables computers to understand, interpret, and generate human language in a way that is both meaningful and useful. By combining computational linguistics with computer science, NLP allows machines to process, analyze, and respond to text and speech data in a manner that mimics human communication.
How Does NLP Work?
NLP leverages algorithms and models to analyze the structure and meaning of language in order to perform tasks like text classification, sentiment analysis, speech recognition, and language translation. By breaking down language into its constituent parts, NLP algorithms can identify patterns, extract information, and generate responses that are contextually relevant and accurate.?
The Impact of NLP on Communication?
The advancement of NLP technology has significantly improved the way we communicate with machines. Virtual assistants like Siri, Alexa, and Google Assistant utilize NLP to understand voice commands, answer questions, and perform tasks on behalf of users. Chatbots powered by NLP can engage in natural language conversations with customers, providing personalized assistance and support in real-time. Language translation tools powered by NLP make it easier to communicate across linguistic barriers, enabling seamless global interaction.?
Emerging Trends in NLP?
As NLP continues to evolve, we are seeing exciting advancements in areas such as emotion recognition, dialect understanding, and context-aware language processing. Emotion recognition technologies allow machines to detect and respond to human emotions in text and speech, enabling more empathetic and personalized interactions. Dialect understanding algorithms can decipher regional accents and dialects, improving the accuracy of speech recognition and language translation. Context-aware language processing models can analyze the context of a conversation to generate more relevant and coherent responses.?
The Future of NLP?
The future of NLP holds immense potential for transforming the way we interact with technology and each other. As NLP algorithms become more sophisticated and capable, we can expect to see even greater improvements in areas such as conversational AI, sentiment analysis, and language understanding. From enhancing customer service experiences to enabling more intuitive human-machine communication, NLP is poised to revolutionize the way we engage with the digital world.
How to obtain Emerging Technology certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Natural Language Processing (NLP) is a groundbreaking field of artificial intelligence that is reshaping the way we interact with technology. By enabling machines to understand, interpret, and generate human language, NLP is opening up new possibilities for more intuitive and seamless communication experiences. As NLP technology continues to advance, we can look forward to a future where machines not only understand what we say but also how we feel and what we need. Get ready for a world where human-machine interaction is more natural, empathetic, and engaging than ever before.
The Rise of Self-Service Portals in IT Service Management
In today's fast-paced digital landscape, businesses are constantly seeking ways to streamline processes and enhance efficiency. One key area where significant advancements have been made is in IT service management, with the rise of self-service portals revolutionizing the way organizations deliver support to their users.
Self-Service Portals and IT Service Management
Self-service portals have quickly become a cornerstone of modern IT service management. These portals empower users to find solutions to their problems independently, without the need to rely on IT support staff. By providing users with a centralized hub where they can access knowledge articles, submit service requests, and track the status of their tickets, self-service portals offer a level of convenience and autonomy that was previously unheard of.
The Benefits of Automation
Automation lies at the heart of self-service portals, enabling organizations to streamline repetitive tasks and free up their IT teams to focus on more strategic initiatives. By automating routine processes such as ticket routing, incident categorization, and request fulfillment, organizations can significantly reduce response times and improve overall service delivery.
Enhanced User Experience
Self-service portals also play a critical role in enhancing the user experience. By providing users with a user-friendly interface and intuitive navigation, organizations can ensure that users can easily find the information they need and quickly resolve their issues. This not only boosts user satisfaction but also contributes to higher productivity levels across the organization.
Driving Digital Transformation
The rise of self-service portals is closely aligned with the broader trend of digital transformation. By leveraging technologies such as cloud computing and software integration, organizations can create seamless and connected experiences for their users. Self-service portals serve as the gateway to this digital ecosystem, providing users with a centralized platform to access a wide range of services and resources.
Key Features of Self-Service Portals
-
Ticketing System: Enables users to report issues and track the status of their requests.
-
Service Desk: Provides a central point of contact for users to seek assistance.
-
Remote Assistance: Allows support staff to troubleshoot and resolve issues remotely.
-
Knowledge Base: Offers a repository of articles and FAQs to help users find solutions independently.
-
Access Control: Ensures that users have the appropriate permissions to access specific resources.
-
Authentication and Authorization: Verify the identity of users and determine their level of access.
-
Service Catalog: Displays a catalog of available services that users can request.
-
Incident Management: Handles the reporting and resolution of incidents in a structured manner.
-
Request Fulfillment: Manages service requests from initiation to completion.
-
Problem Management: Addresses the root causes of recurring incidents to prevent future disruptions.
-
Change Management: Controls changes to IT infrastructure to minimize risks and disruptions.
Empowering Users and Boosting Productivity
Self-service portals empower users to take control of their IT needs, reducing their reliance on support staff and enabling them to resolve issues more quickly. This not only leads to cost-effective solutions but also enhances scalability and productivity across the organization. By providing users with the tools they need to find solutions independently, self-service portals drive user empowerment and pave the way for a more efficient and effective IT service management framework.
How to obtain IT Service Management and Governance certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the rise of self-service portals in IT service management represents a significant advancement in the way organizations deliver support to their users. By leveraging automation, technology, and user-centric design principles, self-service portals offer a seamless and efficient way for users to access the support they need. As businesses continue to embrace digital transformation, self-service portals will play an increasingly crucial role in driving efficiency, productivity enhancements, and user empowerment within organizations
Read More
In today's fast-paced digital landscape, businesses are constantly seeking ways to streamline processes and enhance efficiency. One key area where significant advancements have been made is in IT service management, with the rise of self-service portals revolutionizing the way organizations deliver support to their users.
Self-Service Portals and IT Service Management
Self-service portals have quickly become a cornerstone of modern IT service management. These portals empower users to find solutions to their problems independently, without the need to rely on IT support staff. By providing users with a centralized hub where they can access knowledge articles, submit service requests, and track the status of their tickets, self-service portals offer a level of convenience and autonomy that was previously unheard of.
The Benefits of Automation
Automation lies at the heart of self-service portals, enabling organizations to streamline repetitive tasks and free up their IT teams to focus on more strategic initiatives. By automating routine processes such as ticket routing, incident categorization, and request fulfillment, organizations can significantly reduce response times and improve overall service delivery.
Enhanced User Experience
Self-service portals also play a critical role in enhancing the user experience. By providing users with a user-friendly interface and intuitive navigation, organizations can ensure that users can easily find the information they need and quickly resolve their issues. This not only boosts user satisfaction but also contributes to higher productivity levels across the organization.
Driving Digital Transformation
The rise of self-service portals is closely aligned with the broader trend of digital transformation. By leveraging technologies such as cloud computing and software integration, organizations can create seamless and connected experiences for their users. Self-service portals serve as the gateway to this digital ecosystem, providing users with a centralized platform to access a wide range of services and resources.
Key Features of Self-Service Portals
-
Ticketing System: Enables users to report issues and track the status of their requests.
-
Service Desk: Provides a central point of contact for users to seek assistance.
-
Remote Assistance: Allows support staff to troubleshoot and resolve issues remotely.
-
Knowledge Base: Offers a repository of articles and FAQs to help users find solutions independently.
-
Access Control: Ensures that users have the appropriate permissions to access specific resources.
-
Authentication and Authorization: Verify the identity of users and determine their level of access.
-
Service Catalog: Displays a catalog of available services that users can request.
-
Incident Management: Handles the reporting and resolution of incidents in a structured manner.
-
Request Fulfillment: Manages service requests from initiation to completion.
-
Problem Management: Addresses the root causes of recurring incidents to prevent future disruptions.
-
Change Management: Controls changes to IT infrastructure to minimize risks and disruptions.
Empowering Users and Boosting Productivity
Self-service portals empower users to take control of their IT needs, reducing their reliance on support staff and enabling them to resolve issues more quickly. This not only leads to cost-effective solutions but also enhances scalability and productivity across the organization. By providing users with the tools they need to find solutions independently, self-service portals drive user empowerment and pave the way for a more efficient and effective IT service management framework.
How to obtain IT Service Management and Governance certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the rise of self-service portals in IT service management represents a significant advancement in the way organizations deliver support to their users. By leveraging automation, technology, and user-centric design principles, self-service portals offer a seamless and efficient way for users to access the support they need. As businesses continue to embrace digital transformation, self-service portals will play an increasingly crucial role in driving efficiency, productivity enhancements, and user empowerment within organizations
Exploring the Core Principles of COBIT 5: A Comprehensive Guide blog
Are you looking to enhance your understanding of IT governance and information technology best practices? Look no further than COBIT® 5, a globally recognized framework that provides a comprehensive guide to achieving effective IT governance. In this article, we will delve into the core principles of COBIT® 5, exploring its key concepts, implementation strategies, and the numerous benefits it can offer to organizations of all sizes.
What is COBIT® 5?
COBIT® 5, developed by ISACA, is a leading framework for the governance and management of enterprise IT. It helps organizations create optimal value from IT by maintaining a balance between realizing benefits and optimizing risk levels and resource use. By aligning business goals with IT goals, COBIT® 5 enables enterprises to implement effective IT processes and controls.
Core Principles of COBIT® 5
-
COBIT Principles: The framework is built on five core principles: meeting stakeholder needs, covering the enterprise end-to-end, applying a single integrated framework, enabling a holistic approach, and separating governance from management.
-
COBIT Implementation: Organizations can implement COBIT® 5 by following a structured methodology that includes assessing current IT processes, defining improvement opportunities, and aligning IT goals with business objectives.
-
COBIT Best Practices: COBIT® 5 offers best practices for IT governance, risk management, and compliance, providing a roadmap for organizations to achieve operational excellence and regulatory compliance.
-
COBIT Training and Certification: Professionals can enhance their expertise in IT governance by undergoing COBIT® training and obtaining certification, which validates their knowledge and skills in implementing the framework.
The Benefits of COBIT® 5
-
Efficiency: By streamlining IT processes and controls, COBIT® 5 improves operational efficiency and reduces the risk of errors and inefficiencies.
-
Effectiveness: The framework helps organizations achieve their strategic objectives by aligning IT with business goals and ensuring optimal resource allocation.
-
Accountability: COBIT® 5 promotes transparency and accountability in IT governance, ensuring that stakeholders are informed and involved in decision-making processes.
COBIT® 5 Processes and Controls
COBIT® 5 defines a set of processes and controls that organizations can use to manage and govern their IT functions effectively. Some of the key processes include:
-
Governance Framework Implementation
-
Risk Management
-
Business-IT Alignment
-
IT Security
-
Compliance
-
Efficiency and Effectiveness
-
Strategy Implementation
Assessing COBIT® Maturity
Organizations can assess their maturity in implementing COBIT® 5 by using the maturity model provided by the framework. This assessment helps identify areas for improvement and prioritize initiatives to enhance IT governance practices.
Conducting a COBIT® Audit
A COBIT® audit involves evaluating the effectiveness of IT processes and controls against the framework's standards. By conducting regular audits, organizations can ensure compliance with regulatory requirements and identify areas of non-compliance.
How to obtain Cobit 5 Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, COBIT® 5 is a robust framework that provides organizations with the tools and guidance needed to achieve excellence in IT governance. By understanding the core principles of COBIT® 5 and implementing best practices, organizations can enhance their operational efficiency, effectiveness, and accountability in managing their IT assets. Invest in COBIT® 5 training and certification to elevate your IT governance capabilities and drive sustainable value for your organization.
Read More
Are you looking to enhance your understanding of IT governance and information technology best practices? Look no further than COBIT® 5, a globally recognized framework that provides a comprehensive guide to achieving effective IT governance. In this article, we will delve into the core principles of COBIT® 5, exploring its key concepts, implementation strategies, and the numerous benefits it can offer to organizations of all sizes.
What is COBIT® 5?
COBIT® 5, developed by ISACA, is a leading framework for the governance and management of enterprise IT. It helps organizations create optimal value from IT by maintaining a balance between realizing benefits and optimizing risk levels and resource use. By aligning business goals with IT goals, COBIT® 5 enables enterprises to implement effective IT processes and controls.
Core Principles of COBIT® 5
-
COBIT Principles: The framework is built on five core principles: meeting stakeholder needs, covering the enterprise end-to-end, applying a single integrated framework, enabling a holistic approach, and separating governance from management.
-
COBIT Implementation: Organizations can implement COBIT® 5 by following a structured methodology that includes assessing current IT processes, defining improvement opportunities, and aligning IT goals with business objectives.
-
COBIT Best Practices: COBIT® 5 offers best practices for IT governance, risk management, and compliance, providing a roadmap for organizations to achieve operational excellence and regulatory compliance.
-
COBIT Training and Certification: Professionals can enhance their expertise in IT governance by undergoing COBIT® training and obtaining certification, which validates their knowledge and skills in implementing the framework.
The Benefits of COBIT® 5
-
Efficiency: By streamlining IT processes and controls, COBIT® 5 improves operational efficiency and reduces the risk of errors and inefficiencies.
-
Effectiveness: The framework helps organizations achieve their strategic objectives by aligning IT with business goals and ensuring optimal resource allocation.
-
Accountability: COBIT® 5 promotes transparency and accountability in IT governance, ensuring that stakeholders are informed and involved in decision-making processes.
COBIT® 5 Processes and Controls
COBIT® 5 defines a set of processes and controls that organizations can use to manage and govern their IT functions effectively. Some of the key processes include:
-
Governance Framework Implementation
-
Risk Management
-
Business-IT Alignment
-
IT Security
-
Compliance
-
Efficiency and Effectiveness
-
Strategy Implementation
Assessing COBIT® Maturity
Organizations can assess their maturity in implementing COBIT® 5 by using the maturity model provided by the framework. This assessment helps identify areas for improvement and prioritize initiatives to enhance IT governance practices.
Conducting a COBIT® Audit
A COBIT® audit involves evaluating the effectiveness of IT processes and controls against the framework's standards. By conducting regular audits, organizations can ensure compliance with regulatory requirements and identify areas of non-compliance.
How to obtain Cobit 5 Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, COBIT® 5 is a robust framework that provides organizations with the tools and guidance needed to achieve excellence in IT governance. By understanding the core principles of COBIT® 5 and implementing best practices, organizations can enhance their operational efficiency, effectiveness, and accountability in managing their IT assets. Invest in COBIT® 5 training and certification to elevate your IT governance capabilities and drive sustainable value for your organization.
10 Key Benefits of Achieving CMMI Certification for Your Organization
Are you looking to take your organization to the next level of excellence and efficiency? Achieving Capability Maturity Model Integration (CMMI) certification could be the key to unlocking a wide range of benefits for your business. In this article, we will explore the 10 key benefits of achieving CMMI certification for your organization, and why it matters in today's competitive business landscape.
What is CMMI Certification?
Before diving into the benefits, let's first understand what CMMI certification is all about. CMMI is a globally recognized framework that helps organizations improve their processes and performance. By achieving CMMI certification, organizations demonstrate their commitment to maintaining high standards of quality and efficiency in everything they do.
1. Improved Organizational Performance
One of the main benefits of achieving CMMI certification is the significant improvement in organizational performance. By implementing best practices recommended by CMMI, organizations can streamline their processes, reduce errors, and increase productivity.
2. Enhanced Customer Satisfaction
With CMMI certification, organizations can better meet customer expectations and deliver high-quality products and services consistently. This leads to increased customer satisfaction and loyalty, ultimately helping the business retain existing customers and attract new ones.
3. Increased Efficiency and Cost Savings
CMMI certification helps organizations identify and eliminate wasteful practices, leading to increased efficiency and cost savings. By optimizing processes and reducing errors, organizations can reduce rework and improve overall operational efficiency.
4. Better Risk Management
Achieving CMMI certification enables organizations to establish robust risk management processes. By identifying potential risks and implementing proactive measures to mitigate them, organizations can safeguard against potential disruptions and ensure business continuity.
5. Enhanced Employee Morale and Engagement
By establishing a culture of continuous improvement and professional development, CMMI certification can boost employee morale and engagement. Employees feel valued and empowered to contribute to the organization's success, leading to higher job satisfaction and retention rates.
6. Competitive Advantage
In today's competitive market, having CMMI certification can give organizations a significant edge over their competitors. CMMI-certified organizations are seen as more reliable, efficient, and quality-focused, which can attract new customers and business opportunities.
7. Sustainable Growth and Scalability
CMMI certification provides organizations with a solid foundation for sustainable growth and scalability. By standardizing processes and establishing best practices, organizations can expand their operations and adapt to changing market demands more effectively.
8. Regulatory Compliance
Achieving CMMI certification ensures that organizations comply with industry standards and regulations. This critical aspect helps organizations avoid fines, penalties, and legal issues, demonstrating a commitment to ethical business practices.
9. Improved Decision-Making
With a data-driven approach to process improvement, organizations can make informed decisions based on accurate data and metrics. CMMI certification equips organizations with the tools and insights needed to drive strategic decision-making and achieve business objectives.
10. International Recognition and Reputation
Lastly, achieving CMMI certification provides organizations with international recognition and a positive reputation in the industry. CMMI-certified organizations are perceived as reliable and trustworthy partners, opening doors to global opportunities and collaborations.
How to obtain CMMI Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, achieving CMMI certification for your organization can deliver a wide range of benefits, from improved organizational performance to enhanced customer satisfaction and competitive advantage. By investing in CMMI certification, organizations can drive sustainable growth, mitigate risks, and establish themselves as industry leaders. Don't miss out on the opportunity to take your organization to the next level of excellence with CMMI certification.
Read More
Are you looking to take your organization to the next level of excellence and efficiency? Achieving Capability Maturity Model Integration (CMMI) certification could be the key to unlocking a wide range of benefits for your business. In this article, we will explore the 10 key benefits of achieving CMMI certification for your organization, and why it matters in today's competitive business landscape.
What is CMMI Certification?
Before diving into the benefits, let's first understand what CMMI certification is all about. CMMI is a globally recognized framework that helps organizations improve their processes and performance. By achieving CMMI certification, organizations demonstrate their commitment to maintaining high standards of quality and efficiency in everything they do.
1. Improved Organizational Performance
One of the main benefits of achieving CMMI certification is the significant improvement in organizational performance. By implementing best practices recommended by CMMI, organizations can streamline their processes, reduce errors, and increase productivity.
2. Enhanced Customer Satisfaction
With CMMI certification, organizations can better meet customer expectations and deliver high-quality products and services consistently. This leads to increased customer satisfaction and loyalty, ultimately helping the business retain existing customers and attract new ones.
3. Increased Efficiency and Cost Savings
CMMI certification helps organizations identify and eliminate wasteful practices, leading to increased efficiency and cost savings. By optimizing processes and reducing errors, organizations can reduce rework and improve overall operational efficiency.
4. Better Risk Management
Achieving CMMI certification enables organizations to establish robust risk management processes. By identifying potential risks and implementing proactive measures to mitigate them, organizations can safeguard against potential disruptions and ensure business continuity.
5. Enhanced Employee Morale and Engagement
By establishing a culture of continuous improvement and professional development, CMMI certification can boost employee morale and engagement. Employees feel valued and empowered to contribute to the organization's success, leading to higher job satisfaction and retention rates.
6. Competitive Advantage
In today's competitive market, having CMMI certification can give organizations a significant edge over their competitors. CMMI-certified organizations are seen as more reliable, efficient, and quality-focused, which can attract new customers and business opportunities.
7. Sustainable Growth and Scalability
CMMI certification provides organizations with a solid foundation for sustainable growth and scalability. By standardizing processes and establishing best practices, organizations can expand their operations and adapt to changing market demands more effectively.
8. Regulatory Compliance
Achieving CMMI certification ensures that organizations comply with industry standards and regulations. This critical aspect helps organizations avoid fines, penalties, and legal issues, demonstrating a commitment to ethical business practices.
9. Improved Decision-Making
With a data-driven approach to process improvement, organizations can make informed decisions based on accurate data and metrics. CMMI certification equips organizations with the tools and insights needed to drive strategic decision-making and achieve business objectives.
10. International Recognition and Reputation
Lastly, achieving CMMI certification provides organizations with international recognition and a positive reputation in the industry. CMMI-certified organizations are perceived as reliable and trustworthy partners, opening doors to global opportunities and collaborations.
How to obtain CMMI Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, achieving CMMI certification for your organization can deliver a wide range of benefits, from improved organizational performance to enhanced customer satisfaction and competitive advantage. By investing in CMMI certification, organizations can drive sustainable growth, mitigate risks, and establish themselves as industry leaders. Don't miss out on the opportunity to take your organization to the next level of excellence with CMMI certification.
5 Emerging Digital Marketing Strategies for 2024
In the fast-paced world of digital marketing, staying ahead of the curve is essential to success. As we look towards 2024, it's vital for businesses to adopt innovative marketing strategies to reach their target audience effectively. To help you navigate the ever-evolving landscape of digital marketing, here are five emerging strategies that will shape the industry in the coming years.
Next-Gen Marketing Tactics
One of the key trends we can expect to see in 2024 is the rise of next-generation marketing tactics. This includes leveraging advanced technologies such as artificial intelligence and machine learning to personalize marketing campaigns and create highly targeted and engaging content. By harnessing the power of data analytics, businesses can better understand their customers' needs and preferences, allowing them to deliver more relevant and impactful messaging.
Disruptive Digital Marketing
Another emerging trend in digital marketing is the concept of disruptive marketing. This involves thinking outside the box and taking bold risks to stand out in a crowded marketplace. Whether it's through unconventional advertising methods or creating viral campaigns that capture audiences' attention, disruptive marketing can help brands make a lasting impression and drive significant results.
Groundbreaking Marketing Ideas
To succeed in 2024 and beyond, businesses will need to embrace groundbreaking marketing ideas that challenge the status quo. This could involve exploring new platforms and channels, experimenting with interactive content formats, or collaborating with influencers and thought leaders in their industry. By pushing boundaries and thinking creatively, brands can differentiate themselves from competitors and connect with consumers in meaningful ways.
Innovative Promotional Tactics
Innovative promotional tactics will also play a crucial role in the future of digital marketing. This includes exploring new ways to engage with audiences, such as gamification, virtual reality experiences, or interactive live streams. By creating memorable and immersive brand experiences, businesses can drive customer engagement and loyalty to new heights.
Futuristic Marketing Campaigns
Looking ahead to 2024, businesses should also consider investing in futuristic marketing campaigns that embrace cutting-edge technologies and trends. This could involve leveraging advancements in augmented reality, voice search, or 5G connectivity to create seamless and integrated brand experiences. By staying ahead of the curve and embracing the latest tools and platforms, businesses can position themselves as industry leaders and drive significant growth.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the digital marketing landscape is constantly evolving, and businesses must adapt to stay competitive. By adopting these five emerging strategies in 2024 and beyond, brands can connect with consumers in new and innovative ways, drive engagement and loyalty, and ultimately achieve their marketing goals. The future of digital marketing is bright, and those who embrace change and innovation will be best positioned for success.
Read More
In the fast-paced world of digital marketing, staying ahead of the curve is essential to success. As we look towards 2024, it's vital for businesses to adopt innovative marketing strategies to reach their target audience effectively. To help you navigate the ever-evolving landscape of digital marketing, here are five emerging strategies that will shape the industry in the coming years.
Next-Gen Marketing Tactics
One of the key trends we can expect to see in 2024 is the rise of next-generation marketing tactics. This includes leveraging advanced technologies such as artificial intelligence and machine learning to personalize marketing campaigns and create highly targeted and engaging content. By harnessing the power of data analytics, businesses can better understand their customers' needs and preferences, allowing them to deliver more relevant and impactful messaging.
Disruptive Digital Marketing
Another emerging trend in digital marketing is the concept of disruptive marketing. This involves thinking outside the box and taking bold risks to stand out in a crowded marketplace. Whether it's through unconventional advertising methods or creating viral campaigns that capture audiences' attention, disruptive marketing can help brands make a lasting impression and drive significant results.
Groundbreaking Marketing Ideas
To succeed in 2024 and beyond, businesses will need to embrace groundbreaking marketing ideas that challenge the status quo. This could involve exploring new platforms and channels, experimenting with interactive content formats, or collaborating with influencers and thought leaders in their industry. By pushing boundaries and thinking creatively, brands can differentiate themselves from competitors and connect with consumers in meaningful ways.
Innovative Promotional Tactics
Innovative promotional tactics will also play a crucial role in the future of digital marketing. This includes exploring new ways to engage with audiences, such as gamification, virtual reality experiences, or interactive live streams. By creating memorable and immersive brand experiences, businesses can drive customer engagement and loyalty to new heights.
Futuristic Marketing Campaigns
Looking ahead to 2024, businesses should also consider investing in futuristic marketing campaigns that embrace cutting-edge technologies and trends. This could involve leveraging advancements in augmented reality, voice search, or 5G connectivity to create seamless and integrated brand experiences. By staying ahead of the curve and embracing the latest tools and platforms, businesses can position themselves as industry leaders and drive significant growth.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the digital marketing landscape is constantly evolving, and businesses must adapt to stay competitive. By adopting these five emerging strategies in 2024 and beyond, brands can connect with consumers in new and innovative ways, drive engagement and loyalty, and ultimately achieve their marketing goals. The future of digital marketing is bright, and those who embrace change and innovation will be best positioned for success.
Navigating the Complexities of IoT: Why Certification Matters
In today's fast-paced digital world, the Internet of Things (IoT) has revolutionized the way we interact with technology. From smart homes to industrial automation, IoT devices are becoming increasingly prevalent in our daily lives. However, with the rise of IoT comes a host of complexities and challenges. One crucial aspect that must not be overlooked is certification. In this article, we will explore why certification matters in the realm of IoT, the importance of certification, and how it can benefit both individuals and organizations operating in this space.
The Importance of Certification in IoT
Certification in IoT is vital for ensuring that devices and networks operate securely and efficiently. With the proliferation of IoT devices, industry standards and regulations have become increasingly important to guarantee interoperability and security. By obtaining certification, professionals can demonstrate their expertise and commitment to upholding these standards.
Why IoT Certification Matters
-
Ensuring Security: IoT devices are vulnerable to cyber threats, making security a top priority. Certification ensures that devices meet stringent security guidelines, protecting against potential breaches and data leaks.
-
Compliance: Certification demonstrates compliance with industry regulations and standards, giving organizations a competitive edge in the market.
-
Professional Development: Becoming a certified IoT professional can open up new career opportunities and enhance one's skill set in this rapidly evolving field.
-
Quality Assurance: Certification signifies that devices and solutions have undergone rigorous testing and meet the highest quality standards, instilling confidence in users and stakeholders.
-
Risk Mitigation: By adhering to certification requirements, organizations can mitigate the risks associated with non-compliance and potential legal consequences.
Benefits of IoT Certification
-
Enhanced Credibility: Certified professionals and organizations have increased credibility in the industry, positioning them as trusted experts in the field of IoT.
-
Improved Performance: Certified devices and networks are more reliable and perform better, leading to enhanced user experience and customer satisfaction.
-
Streamlined Processes: Certification streamlines the development and implementation of IoT solutions, ensuring seamless integration and compatibility across different platforms.
-
Competitive Advantage: Organizations that invest in certification gain a competitive advantage, attracting more customers and partners who value security and reliability.
The Certification Process in IoT
Obtaining certification in IoT involves rigorous training, testing, and evaluation of devices and solutions. Professionals can enroll in certification programs that cover a wide range of topics, including IoT standards, security protocols, and compliance requirements. By completing these programs, individuals can become certified IoT specialists, demonstrating their proficiency in the field.
How to obtain Internet of Things Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, navigating the complexities of IoT requires a deep understanding of industry standards and regulations. Certification plays a crucial role in ensuring the security, compliance, and performance of IoT devices and networks. By investing in certification, professionals and organizations can stay ahead of the curve, mitigate risks, and unlock new opportunities in the ever-expanding world of IoT.
Read More
In today's fast-paced digital world, the Internet of Things (IoT) has revolutionized the way we interact with technology. From smart homes to industrial automation, IoT devices are becoming increasingly prevalent in our daily lives. However, with the rise of IoT comes a host of complexities and challenges. One crucial aspect that must not be overlooked is certification. In this article, we will explore why certification matters in the realm of IoT, the importance of certification, and how it can benefit both individuals and organizations operating in this space.
The Importance of Certification in IoT
Certification in IoT is vital for ensuring that devices and networks operate securely and efficiently. With the proliferation of IoT devices, industry standards and regulations have become increasingly important to guarantee interoperability and security. By obtaining certification, professionals can demonstrate their expertise and commitment to upholding these standards.
Why IoT Certification Matters
-
Ensuring Security: IoT devices are vulnerable to cyber threats, making security a top priority. Certification ensures that devices meet stringent security guidelines, protecting against potential breaches and data leaks.
-
Compliance: Certification demonstrates compliance with industry regulations and standards, giving organizations a competitive edge in the market.
-
Professional Development: Becoming a certified IoT professional can open up new career opportunities and enhance one's skill set in this rapidly evolving field.
-
Quality Assurance: Certification signifies that devices and solutions have undergone rigorous testing and meet the highest quality standards, instilling confidence in users and stakeholders.
-
Risk Mitigation: By adhering to certification requirements, organizations can mitigate the risks associated with non-compliance and potential legal consequences.
Benefits of IoT Certification
-
Enhanced Credibility: Certified professionals and organizations have increased credibility in the industry, positioning them as trusted experts in the field of IoT.
-
Improved Performance: Certified devices and networks are more reliable and perform better, leading to enhanced user experience and customer satisfaction.
-
Streamlined Processes: Certification streamlines the development and implementation of IoT solutions, ensuring seamless integration and compatibility across different platforms.
-
Competitive Advantage: Organizations that invest in certification gain a competitive advantage, attracting more customers and partners who value security and reliability.
The Certification Process in IoT
Obtaining certification in IoT involves rigorous training, testing, and evaluation of devices and solutions. Professionals can enroll in certification programs that cover a wide range of topics, including IoT standards, security protocols, and compliance requirements. By completing these programs, individuals can become certified IoT specialists, demonstrating their proficiency in the field.
How to obtain Internet of Things Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, navigating the complexities of IoT requires a deep understanding of industry standards and regulations. Certification plays a crucial role in ensuring the security, compliance, and performance of IoT devices and networks. By investing in certification, professionals and organizations can stay ahead of the curve, mitigate risks, and unlock new opportunities in the ever-expanding world of IoT.
XenServer Cloud: Virtualization for Scalability
In today's fast-paced digital world, businesses are constantly looking for ways to stay ahead of the competition by improving their infrastructure and maximizing efficiency. Cloud computing has revolutionized the way companies manage their data and applications, offering a flexible and scalable solution for all their IT needs. XenServer Cloud, a virtualization platform designed for scalability, is an excellent choice for businesses looking to optimize their resources and streamline their operations.
What is XenServer Cloud?
XenServer Cloud is a powerful virtualization platform that allows businesses to create and manage virtual machines on a single physical server. By using a hypervisor to partition the server's resources, XenServer Cloud enables companies to run multiple virtual machines simultaneously, maximizing the efficiency of their infrastructure. This cutting-edge technology makes it easy for businesses to deploy and manage their applications in the cloud, reducing the need for costly hardware upgrades and maintenance.
How Does XenServer Cloud Enable Scalability?
XenServer Cloud is specifically designed to accommodate the growing needs of businesses, offering a scalable infrastructure that can easily adapt to changing workloads. By creating virtual servers on-demand, companies can quickly scale up or down their resources based on demand, ensuring that they always have the computing power they need to support their operations. This flexibility is essential for businesses looking to expand their operations and reach new markets without the constraints of traditional IT infrastructure.
Benefits of Using XenServer Cloud for Business Scalability
-
Cost-Effective Solution: XenServer Cloud allows businesses to reduce their hardware and maintenance costs by virtualizing their infrastructure. This cost-effective solution enables companies to allocate resources more efficiently, saving money in the long run.
-
Improved Performance: By running multiple virtual machines on a single server, XenServer Cloud can improve the performance of applications and services, ensuring that businesses can meet the demands of their customers effectively.
-
Enhanced Security: XenServer Cloud offers robust security features to protect sensitive data and prevent unauthorized access to virtual servers. This enhanced security is critical for businesses looking to maintain the integrity of their operations.
-
Streamlined Management: With XenServer Cloud, businesses can easily manage their virtual machines through a centralized interface, simplifying the process of deploying and monitoring applications in the cloud. This streamlined management approach saves time and resources, allowing businesses to focus on their core competencies.
How to obtain Citrix Client Administration Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, XenServer Cloud is a valuable virtualization platform that offers businesses the scalability and flexibility they need to thrive in today's competitive market. By leveraging cloud technology, companies can optimize their infrastructure, enhance their performance, and improve their security posture, ultimately driving growth and success. With XenServer Cloud, businesses can unlock the full potential of their data center and achieve unparalleled efficiency in their operations.
Read More
In today's fast-paced digital world, businesses are constantly looking for ways to stay ahead of the competition by improving their infrastructure and maximizing efficiency. Cloud computing has revolutionized the way companies manage their data and applications, offering a flexible and scalable solution for all their IT needs. XenServer Cloud, a virtualization platform designed for scalability, is an excellent choice for businesses looking to optimize their resources and streamline their operations.
What is XenServer Cloud?
XenServer Cloud is a powerful virtualization platform that allows businesses to create and manage virtual machines on a single physical server. By using a hypervisor to partition the server's resources, XenServer Cloud enables companies to run multiple virtual machines simultaneously, maximizing the efficiency of their infrastructure. This cutting-edge technology makes it easy for businesses to deploy and manage their applications in the cloud, reducing the need for costly hardware upgrades and maintenance.
How Does XenServer Cloud Enable Scalability?
XenServer Cloud is specifically designed to accommodate the growing needs of businesses, offering a scalable infrastructure that can easily adapt to changing workloads. By creating virtual servers on-demand, companies can quickly scale up or down their resources based on demand, ensuring that they always have the computing power they need to support their operations. This flexibility is essential for businesses looking to expand their operations and reach new markets without the constraints of traditional IT infrastructure.
Benefits of Using XenServer Cloud for Business Scalability
-
Cost-Effective Solution: XenServer Cloud allows businesses to reduce their hardware and maintenance costs by virtualizing their infrastructure. This cost-effective solution enables companies to allocate resources more efficiently, saving money in the long run.
-
Improved Performance: By running multiple virtual machines on a single server, XenServer Cloud can improve the performance of applications and services, ensuring that businesses can meet the demands of their customers effectively.
-
Enhanced Security: XenServer Cloud offers robust security features to protect sensitive data and prevent unauthorized access to virtual servers. This enhanced security is critical for businesses looking to maintain the integrity of their operations.
-
Streamlined Management: With XenServer Cloud, businesses can easily manage their virtual machines through a centralized interface, simplifying the process of deploying and monitoring applications in the cloud. This streamlined management approach saves time and resources, allowing businesses to focus on their core competencies.
How to obtain Citrix Client Administration Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, XenServer Cloud is a valuable virtualization platform that offers businesses the scalability and flexibility they need to thrive in today's competitive market. By leveraging cloud technology, companies can optimize their infrastructure, enhance their performance, and improve their security posture, ultimately driving growth and success. With XenServer Cloud, businesses can unlock the full potential of their data center and achieve unparalleled efficiency in their operations.
Integrating ISO 20000 with Other Quality Management Systems (QMS)
In today's fast-paced business environment, organizations are constantly seeking ways to improve their processes and ensure the highest quality of service delivery. One way to achieve this is by integrating ISO 20000 with other Quality Management Systems (QMS) to create a seamless and efficient system that aligns with industry standards and best practices.
Understanding ISO 20000
ISO 20000 is an international standard for IT Service Management that outlines the requirements for an organization to effectively deliver quality IT services. It focuses on ensuring the alignment of IT services with the needs of the business and the continuous improvement of service delivery processes.
Benefits of Integrating ISO 20000 with QMS
Integrating ISO 20000 with other Quality Management Systems offers several benefits to organizations, including:
-
Improved efficiency and effectiveness of processes
-
Enhanced service delivery and customer satisfaction
-
Greater alignment with industry standards and best practices
-
Streamlined compliance with regulatory requirements
-
Increased visibility and control over service performance
-
Enhanced risk management and mitigation strategies
Strategies for Integration
When integrating ISO 20000 with other Quality Management Systems, organizations should consider the following strategies:
-
Conduct a gap analysis to identify areas of overlap and areas that require alignment.
-
Develop a roadmap for integration that outlines the steps, timelines, and responsibilities.
-
Engage stakeholders from different departments to ensure buy-in and collaboration.
-
Monitor and measure the performance of the integrated system to identify areas for improvement.
Best Practices for Integration
To ensure a successful integration of ISO 20000 with QMS, organizations should consider the following best practices:
-
Ensure compatibility between systems to avoid conflicts and ensure seamless integration.
-
Align QMS standards with ISO 20000 requirements to create a unified approach to quality management.
-
Implement a framework for continuous improvement to drive efficiencies and enhance service delivery.
-
Focus on improving QMS processes to meet the requirements of ISO 20000 and enhance overall performance.
-
Establish guidelines and protocols for service delivery integration to ensure consistency and quality.
Achieving Certification and Compliance
By integrating ISO 20000 with other Quality Management Systems, organizations can enhance their chances of achieving certification and compliance with industry standards. This not only demonstrates a commitment to quality and excellence but also opens doors to new business opportunities and partnerships.
How to obtain ISO 20000 Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, Integrating ISO 20000 with other Quality Management Systems is a strategic approach to improving service delivery, enhancing quality assurance, and driving efficiencies within an organization. By following best practices, engaging stakeholders, and focusing on continuous improvement, organizations can create a seamless and effective system that aligns with industry standards and best practices. Start integrating your ISO 20000 with QMS today to experience the benefits firsthand.
Read More
In today's fast-paced business environment, organizations are constantly seeking ways to improve their processes and ensure the highest quality of service delivery. One way to achieve this is by integrating ISO 20000 with other Quality Management Systems (QMS) to create a seamless and efficient system that aligns with industry standards and best practices.
Understanding ISO 20000
ISO 20000 is an international standard for IT Service Management that outlines the requirements for an organization to effectively deliver quality IT services. It focuses on ensuring the alignment of IT services with the needs of the business and the continuous improvement of service delivery processes.
Benefits of Integrating ISO 20000 with QMS
Integrating ISO 20000 with other Quality Management Systems offers several benefits to organizations, including:
-
Improved efficiency and effectiveness of processes
-
Enhanced service delivery and customer satisfaction
-
Greater alignment with industry standards and best practices
-
Streamlined compliance with regulatory requirements
-
Increased visibility and control over service performance
-
Enhanced risk management and mitigation strategies
Strategies for Integration
When integrating ISO 20000 with other Quality Management Systems, organizations should consider the following strategies:
-
Conduct a gap analysis to identify areas of overlap and areas that require alignment.
-
Develop a roadmap for integration that outlines the steps, timelines, and responsibilities.
-
Engage stakeholders from different departments to ensure buy-in and collaboration.
-
Monitor and measure the performance of the integrated system to identify areas for improvement.
Best Practices for Integration
To ensure a successful integration of ISO 20000 with QMS, organizations should consider the following best practices:
-
Ensure compatibility between systems to avoid conflicts and ensure seamless integration.
-
Align QMS standards with ISO 20000 requirements to create a unified approach to quality management.
-
Implement a framework for continuous improvement to drive efficiencies and enhance service delivery.
-
Focus on improving QMS processes to meet the requirements of ISO 20000 and enhance overall performance.
-
Establish guidelines and protocols for service delivery integration to ensure consistency and quality.
Achieving Certification and Compliance
By integrating ISO 20000 with other Quality Management Systems, organizations can enhance their chances of achieving certification and compliance with industry standards. This not only demonstrates a commitment to quality and excellence but also opens doors to new business opportunities and partnerships.
How to obtain ISO 20000 Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, Integrating ISO 20000 with other Quality Management Systems is a strategic approach to improving service delivery, enhancing quality assurance, and driving efficiencies within an organization. By following best practices, engaging stakeholders, and focusing on continuous improvement, organizations can create a seamless and effective system that aligns with industry standards and best practices. Start integrating your ISO 20000 with QMS today to experience the benefits firsthand.
The Role of Cybersecurity in Safeguarding Digital Identities
In today's digital age, where most of our personal and sensitive information is stored online, cybersecurity plays a crucial role in safeguarding our digital identities. From protecting our online accounts to securing our digital transactions, cybersecurity is essential in ensuring that our data remains safe from cyber threats and identity theft.
The Importance of Cybersecurity in Safeguarding Digital Identities
Cybersecurity is vital in protecting our digital identities from various online threats, such as hackers, phishing scams, and malware attacks. By implementing robust cybersecurity measures, individuals can prevent unauthorized access to their personal data and sensitive information.
Digital Identity Protection Measures
There are several digital security measures that individuals can take to protect their digital identities. These include using strong and unique passwords for each online account, enabling two-factor authentication, and regularly updating security software on their devices. Additionally, individuals should be cautious about sharing personal information online and avoid clicking on suspicious links or attachments in emails.
Cybersecurity Strategies for Safeguarding Digital Identities
To enhance cybersecurity and protect digital identities, individuals can adopt various strategies. These may include regularly monitoring their digital footprints, limiting the amount of personal information shared on social media, and being vigilant against identity theft scams. By staying informed about the latest cyber threats and best practices, individuals can better safeguard their online identities.
Cyber Defense for Identities
Implementing strong cyber defense mechanisms, such as firewalls, antivirus software, and encryption, can help protect digital identities from cyber attacks. By securing personal information with encryption technologies, individuals can prevent unauthorized access and ensure the confidentiality of their data.
Protecting Digital Footprints Online
Our online activities leave behind digital footprints that can be used to track our behavior and identity. To protect digital footprints, individuals should be mindful of the information they share and the websites they visit. By using privacy settings and regularly deleting browsing history and cookies, individuals can reduce the visibility of their digital footprint online.
Internet Security Measures for Safeguarding Personal Data
Internet security measures, such as using secure networks, avoiding public Wi-Fi for sensitive transactions, and encrypting data transmission, are essential for protecting personal data online. By taking precautions when accessing the internet, individuals can minimize the risk of data breaches and unauthorized access to their information.
Cybersecurity Solutions for Safeguarding Personal Data
Various cyber security solutions, such as identity theft protection services, secure online storage platforms, and data encryption tools, can help individuals safeguard their personal data. By investing in reputable cybersecurity solutions, individuals can better protect their digital identities and minimize the risk of cyber threats.
Data Protection Strategies for Secure Online Identities
Developing data protection strategies, such as regularly backing up data, implementing access controls, and conducting security audits, can help secure online identities. By proactively managing and protecting personal data, individuals can mitigate the impact of data breaches and unauthorized access to their information.
Cyber Threats Prevention for Digital Privacy Safeguards
Preventing cyber threats, such as malware infections, phishing attacks, and social engineering scams, is essential for safeguarding digital privacy. By practicing safe browsing habits, avoiding suspicious websites, and being cautious about sharing personal information online, individuals can reduce the risk of falling victim to cyber threats.
Identity Theft Prevention Through Cybersecurity Best Practices
Adopting cybersecurity best practices, such as regularly updating security software, using strong passwords, and being vigilant against social engineering tactics, can help prevent identity theft. By staying informed about the latest cybersecurity trends and following best practices, individuals can protect themselves from becoming victims of identity theft.
How to obtain Cyber Security Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, cyber security plays a crucial role in safeguarding our digital identities in the digital age. By implementing robust cybersecurity measures, individuals can protect their personal data, secure online accounts, and prevent identity theft. By staying informed about cyber threats and best practices, individuals can better safeguard their digital identities and maintain their privacy and security online.
Read More
In today's digital age, where most of our personal and sensitive information is stored online, cybersecurity plays a crucial role in safeguarding our digital identities. From protecting our online accounts to securing our digital transactions, cybersecurity is essential in ensuring that our data remains safe from cyber threats and identity theft.
The Importance of Cybersecurity in Safeguarding Digital Identities
Cybersecurity is vital in protecting our digital identities from various online threats, such as hackers, phishing scams, and malware attacks. By implementing robust cybersecurity measures, individuals can prevent unauthorized access to their personal data and sensitive information.
Digital Identity Protection Measures
There are several digital security measures that individuals can take to protect their digital identities. These include using strong and unique passwords for each online account, enabling two-factor authentication, and regularly updating security software on their devices. Additionally, individuals should be cautious about sharing personal information online and avoid clicking on suspicious links or attachments in emails.
Cybersecurity Strategies for Safeguarding Digital Identities
To enhance cybersecurity and protect digital identities, individuals can adopt various strategies. These may include regularly monitoring their digital footprints, limiting the amount of personal information shared on social media, and being vigilant against identity theft scams. By staying informed about the latest cyber threats and best practices, individuals can better safeguard their online identities.
Cyber Defense for Identities
Implementing strong cyber defense mechanisms, such as firewalls, antivirus software, and encryption, can help protect digital identities from cyber attacks. By securing personal information with encryption technologies, individuals can prevent unauthorized access and ensure the confidentiality of their data.
Protecting Digital Footprints Online
Our online activities leave behind digital footprints that can be used to track our behavior and identity. To protect digital footprints, individuals should be mindful of the information they share and the websites they visit. By using privacy settings and regularly deleting browsing history and cookies, individuals can reduce the visibility of their digital footprint online.
Internet Security Measures for Safeguarding Personal Data
Internet security measures, such as using secure networks, avoiding public Wi-Fi for sensitive transactions, and encrypting data transmission, are essential for protecting personal data online. By taking precautions when accessing the internet, individuals can minimize the risk of data breaches and unauthorized access to their information.
Cybersecurity Solutions for Safeguarding Personal Data
Various cyber security solutions, such as identity theft protection services, secure online storage platforms, and data encryption tools, can help individuals safeguard their personal data. By investing in reputable cybersecurity solutions, individuals can better protect their digital identities and minimize the risk of cyber threats.
Data Protection Strategies for Secure Online Identities
Developing data protection strategies, such as regularly backing up data, implementing access controls, and conducting security audits, can help secure online identities. By proactively managing and protecting personal data, individuals can mitigate the impact of data breaches and unauthorized access to their information.
Cyber Threats Prevention for Digital Privacy Safeguards
Preventing cyber threats, such as malware infections, phishing attacks, and social engineering scams, is essential for safeguarding digital privacy. By practicing safe browsing habits, avoiding suspicious websites, and being cautious about sharing personal information online, individuals can reduce the risk of falling victim to cyber threats.
Identity Theft Prevention Through Cybersecurity Best Practices
Adopting cybersecurity best practices, such as regularly updating security software, using strong passwords, and being vigilant against social engineering tactics, can help prevent identity theft. By staying informed about the latest cybersecurity trends and following best practices, individuals can protect themselves from becoming victims of identity theft.
How to obtain Cyber Security Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, cyber security plays a crucial role in safeguarding our digital identities in the digital age. By implementing robust cybersecurity measures, individuals can protect their personal data, secure online accounts, and prevent identity theft. By staying informed about cyber threats and best practices, individuals can better safeguard their digital identities and maintain their privacy and security online.
Mastering Citrix Virtual Apps and Desktops
In today's rapidly evolving IT landscape, mastering Citrix Virtual Apps and Desktops has become essential for IT professionals looking to stay competitive and advance in their careers. As remote work becomes the new norm, businesses are increasingly relying on virtualization technologies like Citrix to enable secure remote access to applications and desktops. By investing in training courses and certification in Citrix Virtual Apps and Desktops, IT professionals can enhance their skills, improve productivity, and streamline IT operations.
The Importance of Citrix Virtual Apps and Desktops
Citrix Virtual Apps and Desktops, formerly known as Citrix XenApp and Citrix XenDesktop, are leading virtualization solutions that allow organizations to deliver applications and desktops to employees on any device, anywhere. With Citrix Virtual Apps, users can access their applications from a centralized server, while Citrix Desktops provide a full virtual desktop experience. These technologies are essential for businesses looking to optimize their IT infrastructure, improve efficiency, and enhance security.
Benefits of Mastering Citrix Virtual Apps and Desktops
By mastering Citrix Virtual Apps and Desktops, IT professionals can gain a competitive edge in the job market and unlock a wide range of career opportunities. With Citrix certification, professionals can demonstrate their expertise in implementing, troubleshooting, and optimizing Citrix technologies, making them valuable assets to any organization. Additionally, mastering Citrix Virtual Apps and Desktops can lead to increased productivity, streamlined management, and enhanced security for businesses relying on virtualization.
How to Master Citrix Virtual Apps and Desktops
To master Citrix Virtual Apps and Desktops, IT professionals can take advantage of online learning platforms that offer comprehensive training courses and certification programs. These courses cover a range of topics, including software implementation, troubleshooting, configurations, best practices, and optimization techniques. By completing these courses and obtaining Citrix certification, professionals can demonstrate their advanced skills in desktop virtualization and gain the expertise needed to excel in their careers.
Online Learning for Citrix Virtual Apps and Desktops
Online learning has become increasingly popular for IT professionals looking to enhance their skills and stay up to date with the latest technologies. With Citrix Virtual Apps and Desktops training courses available online, professionals can learn at their own pace, from anywhere in the world. Online learning provides flexibility, convenience, and cost-effective training options for IT professionals seeking to improve their knowledge and expertise in Citrix technologies.
Certification for Citrix Virtual Apps and Desktops
Obtaining Citrix certification in Virtual Apps and Desktops is a valuable investment for IT professionals looking to advance their careers. Citrix certification validates an individual's expertise in implementing and managing Citrix technologies, demonstrating their proficiency to potential employers. With Citrix certification, professionals can enhance their job prospects, increase their earning potential, and gain recognition as trusted experts in virtualization technology.
How to obtain Citrix Administration Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, mastering Citrix Virtual Apps and Desktops is essential for IT professionals looking to succeed in today's competitive job market. By investing in training courses, certification, and online learning opportunities, professionals can enhance their skills, advance their careers, and become trusted experts in Citrix technologies. With the increasing demand for remote access, cloud computing, and efficient IT management, mastering Citrix Virtual Apps and Desktops has never been more important for IT professionals seeking to stay ahead of the curve.
Read More
In today's rapidly evolving IT landscape, mastering Citrix Virtual Apps and Desktops has become essential for IT professionals looking to stay competitive and advance in their careers. As remote work becomes the new norm, businesses are increasingly relying on virtualization technologies like Citrix to enable secure remote access to applications and desktops. By investing in training courses and certification in Citrix Virtual Apps and Desktops, IT professionals can enhance their skills, improve productivity, and streamline IT operations.
The Importance of Citrix Virtual Apps and Desktops
Citrix Virtual Apps and Desktops, formerly known as Citrix XenApp and Citrix XenDesktop, are leading virtualization solutions that allow organizations to deliver applications and desktops to employees on any device, anywhere. With Citrix Virtual Apps, users can access their applications from a centralized server, while Citrix Desktops provide a full virtual desktop experience. These technologies are essential for businesses looking to optimize their IT infrastructure, improve efficiency, and enhance security.
Benefits of Mastering Citrix Virtual Apps and Desktops
By mastering Citrix Virtual Apps and Desktops, IT professionals can gain a competitive edge in the job market and unlock a wide range of career opportunities. With Citrix certification, professionals can demonstrate their expertise in implementing, troubleshooting, and optimizing Citrix technologies, making them valuable assets to any organization. Additionally, mastering Citrix Virtual Apps and Desktops can lead to increased productivity, streamlined management, and enhanced security for businesses relying on virtualization.
How to Master Citrix Virtual Apps and Desktops
To master Citrix Virtual Apps and Desktops, IT professionals can take advantage of online learning platforms that offer comprehensive training courses and certification programs. These courses cover a range of topics, including software implementation, troubleshooting, configurations, best practices, and optimization techniques. By completing these courses and obtaining Citrix certification, professionals can demonstrate their advanced skills in desktop virtualization and gain the expertise needed to excel in their careers.
Online Learning for Citrix Virtual Apps and Desktops
Online learning has become increasingly popular for IT professionals looking to enhance their skills and stay up to date with the latest technologies. With Citrix Virtual Apps and Desktops training courses available online, professionals can learn at their own pace, from anywhere in the world. Online learning provides flexibility, convenience, and cost-effective training options for IT professionals seeking to improve their knowledge and expertise in Citrix technologies.
Certification for Citrix Virtual Apps and Desktops
Obtaining Citrix certification in Virtual Apps and Desktops is a valuable investment for IT professionals looking to advance their careers. Citrix certification validates an individual's expertise in implementing and managing Citrix technologies, demonstrating their proficiency to potential employers. With Citrix certification, professionals can enhance their job prospects, increase their earning potential, and gain recognition as trusted experts in virtualization technology.
How to obtain Citrix Administration Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, mastering Citrix Virtual Apps and Desktops is essential for IT professionals looking to succeed in today's competitive job market. By investing in training courses, certification, and online learning opportunities, professionals can enhance their skills, advance their careers, and become trusted experts in Citrix technologies. With the increasing demand for remote access, cloud computing, and efficient IT management, mastering Citrix Virtual Apps and Desktops has never been more important for IT professionals seeking to stay ahead of the curve.
Microsoft's Initiatives in EdTech and Remote Learning
In recent years, the education sector has witnessed a significant transformation with the integration of technology in traditional classroom settings. Microsoft, a global leader in technology, has taken numerous initiatives to revolutionize education through the use of EdTech and remote learning solutions. In this article, we will explore Microsoft's innovative approaches in reshaping the way students learn and teachers teach in the digital age.
Microsoft Education: Empowering Students and Teachers
Microsoft Education, a dedicated division of the tech giant, focuses on empowering students and educators through the use of digital tools and resources. From virtual classrooms to learning management systems, Microsoft has been at the forefront of driving innovation in the education sector. By providing cutting-edge technology solutions, Microsoft aims to enhance the learning experience and improve academic outcomes for students worldwide.
Microsoft Teams: A Hub for Collaboration and Communication
One of Microsoft's flagship products in the education sector is Microsoft Teams, a versatile platform that enables seamless collaboration and communication among students and teachers. With features such as virtual meetings, file sharing, and chat functionality, Microsoft Teams has become a go-to tool for educators to engage with their students in the virtual classroom. Additionally, the integration of learning management systems in Teams allows for a more streamlined educational experience.
Leveraging Cloud Computing for Enhanced Learning
Microsoft's Azure cloud computing platform has been instrumental in enabling remote learning and virtual classrooms. By leveraging the power of cloud computing, schools and universities can easily access educational resources and software from anywhere, at any time. This flexibility has revolutionized the way students engage with course materials and collaborate with their peers, making learning more dynamic and interactive.
Integrating Microsoft Office Tools for Productivity
Another key aspect of Microsoft's initiatives in EdTech and remote learning is the integration of Microsoft Office tools such as Outlook, Word, Excel, and PowerPoint. These familiar software applications allow teachers to create engaging lesson plans, students to complete assignments, and collaboration on group projects seamlessly. The versatility of Microsoft Office tools makes them essential for enhancing productivity in the digital classroom.
Continuous Innovation in Educational Technology
Microsoft's commitment to education goes beyond providing tools and resources; the company is continuously innovating to meet the evolving needs of students and educators. Whether it's developing new e-learning solutions or enhancing existing software, Microsoft's focus on educational technology has resulted in a more engaging and efficient learning experience for all stakeholders.
How to obtain Microsoft Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Microsoft's initiatives in EdTech and remote learning have significantly impacted the education sector, helping to create a more dynamic and engaging learning environment. By leveraging technology such as Microsoft Teams, Azure cloud computing, and Office tools, students and teachers can collaborate effectively and access educational resources with ease. Microsoft's dedication to innovation in educational technology ensures that the future of learning remains bright and promising for all.
Read More
In recent years, the education sector has witnessed a significant transformation with the integration of technology in traditional classroom settings. Microsoft, a global leader in technology, has taken numerous initiatives to revolutionize education through the use of EdTech and remote learning solutions. In this article, we will explore Microsoft's innovative approaches in reshaping the way students learn and teachers teach in the digital age.
Microsoft Education: Empowering Students and Teachers
Microsoft Education, a dedicated division of the tech giant, focuses on empowering students and educators through the use of digital tools and resources. From virtual classrooms to learning management systems, Microsoft has been at the forefront of driving innovation in the education sector. By providing cutting-edge technology solutions, Microsoft aims to enhance the learning experience and improve academic outcomes for students worldwide.
Microsoft Teams: A Hub for Collaboration and Communication
One of Microsoft's flagship products in the education sector is Microsoft Teams, a versatile platform that enables seamless collaboration and communication among students and teachers. With features such as virtual meetings, file sharing, and chat functionality, Microsoft Teams has become a go-to tool for educators to engage with their students in the virtual classroom. Additionally, the integration of learning management systems in Teams allows for a more streamlined educational experience.
Leveraging Cloud Computing for Enhanced Learning
Microsoft's Azure cloud computing platform has been instrumental in enabling remote learning and virtual classrooms. By leveraging the power of cloud computing, schools and universities can easily access educational resources and software from anywhere, at any time. This flexibility has revolutionized the way students engage with course materials and collaborate with their peers, making learning more dynamic and interactive.
Integrating Microsoft Office Tools for Productivity
Another key aspect of Microsoft's initiatives in EdTech and remote learning is the integration of Microsoft Office tools such as Outlook, Word, Excel, and PowerPoint. These familiar software applications allow teachers to create engaging lesson plans, students to complete assignments, and collaboration on group projects seamlessly. The versatility of Microsoft Office tools makes them essential for enhancing productivity in the digital classroom.
Continuous Innovation in Educational Technology
Microsoft's commitment to education goes beyond providing tools and resources; the company is continuously innovating to meet the evolving needs of students and educators. Whether it's developing new e-learning solutions or enhancing existing software, Microsoft's focus on educational technology has resulted in a more engaging and efficient learning experience for all stakeholders.
How to obtain Microsoft Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Microsoft's initiatives in EdTech and remote learning have significantly impacted the education sector, helping to create a more dynamic and engaging learning environment. By leveraging technology such as Microsoft Teams, Azure cloud computing, and Office tools, students and teachers can collaborate effectively and access educational resources with ease. Microsoft's dedication to innovation in educational technology ensures that the future of learning remains bright and promising for all.
IT Service Management Trends to Watch in 2024 and Beyond
In today's rapidly evolving technological landscape, staying abreast of the latest IT service management trends is essential for businesses to remain competitive and efficient. As we look ahead to 2024 and beyond, several key trends are poised to shape the future of IT service management, incorporating advancements in technology, innovation, automation, cybersecurity, artificial intelligence, data analytics, cloud computing, digital transformation, customer experience, agile methodologies, remote work, and more.
Embracing Emerging Technologies
One of the most prominent trends in IT service management is the increasing adoption of emerging technologies. From artificial intelligence and machine learning to data analytics and cloud computing, businesses are leveraging these technologies to optimize their IT operations and deliver scalable solutions to their customers. By embracing these cutting-edge technologies, organizations can streamline their processes, improve efficiency, and enhance the overall customer experience.
Shifting Towards Automation
Automation is another key trend that is transforming the field of IT service management. By automating routine tasks and processes, businesses can reduce manual errors, increase productivity, and free up their IT teams to focus on more strategic initiatives. From automating incident response and change management to implementing the ITIL framework for continuous improvement, automation is revolutionizing how IT services are delivered and managed.
Enhancing Cybersecurity Measures
With the increasing threat of cyberattacks and data breaches, cybersecurity continues to be a top priority for businesses. In 2024 and beyond, organizations will need to invest in robust cybersecurity measures to protect their data, systems, and networks from evolving threats. This includes implementing best practices for IT security, vendor management, and mobile device security, as well as ensuring compliance with IT governance standards to safeguard sensitive information.
Enabling Remote Work Capabilities
The rise of remote work has become a permanent fixture in the modern workplace, driven by the global pandemic and the need for flexibility and collaboration. As businesses continue to support remote work environments, IT service management will need to adapt to meet the changing needs of a distributed workforce. This includes providing secure access to IT resources, supporting remote collaboration tools, and implementing agile methodologies to enhance productivity and communication.
Leveraging Predictive Analytics
Predictive analytics is playing an increasingly important role in IT service management, enabling organizations to anticipate and prevent potential issues before they occur. By analyzing historical data and trends, businesses can identify patterns, forecast future events, and make data-driven decisions to optimize their IT infrastructure and operations. This proactive approach helps businesses to mitigate risks, improve performance, and deliver superior customer service.
How to obtain IT Service Management and Governance Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, IT service management is undergoing a significant transformation as we look ahead to 2024 and beyond. By embracing emerging technologies, shifting towards automation, enhancing cybersecurity measures, enabling remote work capabilities, and leveraging predictive analytics, businesses can position themselves for success in the digital age. As technology continues to evolve, staying ahead of these key trends will be crucial for organizations to drive innovation, improve efficiency, and deliver exceptional IT services to their customers.
Read More
In today's rapidly evolving technological landscape, staying abreast of the latest IT service management trends is essential for businesses to remain competitive and efficient. As we look ahead to 2024 and beyond, several key trends are poised to shape the future of IT service management, incorporating advancements in technology, innovation, automation, cybersecurity, artificial intelligence, data analytics, cloud computing, digital transformation, customer experience, agile methodologies, remote work, and more.
Embracing Emerging Technologies
One of the most prominent trends in IT service management is the increasing adoption of emerging technologies. From artificial intelligence and machine learning to data analytics and cloud computing, businesses are leveraging these technologies to optimize their IT operations and deliver scalable solutions to their customers. By embracing these cutting-edge technologies, organizations can streamline their processes, improve efficiency, and enhance the overall customer experience.
Shifting Towards Automation
Automation is another key trend that is transforming the field of IT service management. By automating routine tasks and processes, businesses can reduce manual errors, increase productivity, and free up their IT teams to focus on more strategic initiatives. From automating incident response and change management to implementing the ITIL framework for continuous improvement, automation is revolutionizing how IT services are delivered and managed.
Enhancing Cybersecurity Measures
With the increasing threat of cyberattacks and data breaches, cybersecurity continues to be a top priority for businesses. In 2024 and beyond, organizations will need to invest in robust cybersecurity measures to protect their data, systems, and networks from evolving threats. This includes implementing best practices for IT security, vendor management, and mobile device security, as well as ensuring compliance with IT governance standards to safeguard sensitive information.
Enabling Remote Work Capabilities
The rise of remote work has become a permanent fixture in the modern workplace, driven by the global pandemic and the need for flexibility and collaboration. As businesses continue to support remote work environments, IT service management will need to adapt to meet the changing needs of a distributed workforce. This includes providing secure access to IT resources, supporting remote collaboration tools, and implementing agile methodologies to enhance productivity and communication.
Leveraging Predictive Analytics
Predictive analytics is playing an increasingly important role in IT service management, enabling organizations to anticipate and prevent potential issues before they occur. By analyzing historical data and trends, businesses can identify patterns, forecast future events, and make data-driven decisions to optimize their IT infrastructure and operations. This proactive approach helps businesses to mitigate risks, improve performance, and deliver superior customer service.
How to obtain IT Service Management and Governance Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, IT service management is undergoing a significant transformation as we look ahead to 2024 and beyond. By embracing emerging technologies, shifting towards automation, enhancing cybersecurity measures, enabling remote work capabilities, and leveraging predictive analytics, businesses can position themselves for success in the digital age. As technology continues to evolve, staying ahead of these key trends will be crucial for organizations to drive innovation, improve efficiency, and deliver exceptional IT services to their customers.
Unleashing the World Stage: Digital Marketing Certifications as Keys to International Careers
The digital marketing landscape is no longer confined by borders. Today's marketers navigate a globalized marketplace, where consumer demographics transcend geographic limitations. To capitalize on this interconnected world, equipping yourself with the right tools is paramount. Enter the realm of digital marketing certifications – specialized programs that validate your proficiency in the ever-evolving digital marketing sphere. These credentials, particularly for internationally recognized certifications, can be your golden ticket to a rewarding international career.
Why Digital Marketing Certifications Matter?
In a competitive job market, certifications act as a potent differentiator. They demonstrate your commitment to continuous learning and mastery of specific digital marketing skills. Renowned certifications like Google Analytics Individual Qualification (IQ) or HubSpot Inbound Marketing Certification showcase your expertise to potential employers worldwide. These programs often incorporate a global perspective, ensuring you understand the nuances of marketing across diverse cultures and languages.
International Appeal of Digital Marketing Skills
The beauty of digital marketing lies in its universality. Fundamental marketing principles – understanding customer needs, crafting compelling content, and leveraging data-driven insights – remain constant across borders. However, a skilled international marketer tailors these strategies to resonate with local audiences. Certifications often equip you with this cultural competency, making you a valuable asset to companies seeking to expand their global reach.
Exploring International Career Opportunities
Digital marketing certifications open doors to a plethora of exciting international careers. With the rise of e-commerce, multinational corporations are constantly seeking talent to manage their online presence in overseas markets. Here are some potential career paths:
-
Global Marketing Manager: Overseeing the development and execution of marketing strategies for international markets.
-
Localization Specialist: Adapting marketing materials to resonate with specific cultural contexts.
-
International SEO Specialist: Optimizing websites for global search engines, ensuring discoverability in targeted regions.
-
Social Media Strategist: Crafting engaging social media campaigns that cater to diverse audiences across the globe.
The Power of Continuous Learning
The digital marketing landscape is a dynamic one. To stay ahead of the curve, continuous learning is imperative. Many certification programs offer ongoing educational resources and opportunities to stay updated on the latest trends and technologies. This ensures you remain a valuable asset in the international job market.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion:
In today's interconnected world, the digital landscape transcends geographical boundaries. By acquiring recognized digital marketing certifications, ambitious professionals can unlock a treasure trove of international career opportunities. These credentials validate a marketer's proficiency in the ever-evolving digital realm, fostering trust and marketability across borders.
Digital marketing certifications equip individuals with the necessary skills to navigate the complexities of global marketing campaigns. From understanding cultural nuances and tailoring content for diverse audiences to mastering data analysis for international market insights, these qualifications empower marketers to excel on the world stage.
Furthermore, certifications demonstrate a commitment to continuous learning, a quality highly sought-after by international employers. They signal a marketer's ability to adapt to the dynamic digital landscape, ensuring they remain competitive in the global marketplace.
As the digital world continues to shrink distances, embracing digital marketing certifications is no longer an option, but a strategic imperative. These credentials empower individuals to not only navigate the international marketing landscape but to thrive within it. So for those seeking a fulfilling career on the world stage, the key lies in unlocking the potential of digital marketing certifications.
Read More
The digital marketing landscape is no longer confined by borders. Today's marketers navigate a globalized marketplace, where consumer demographics transcend geographic limitations. To capitalize on this interconnected world, equipping yourself with the right tools is paramount. Enter the realm of digital marketing certifications – specialized programs that validate your proficiency in the ever-evolving digital marketing sphere. These credentials, particularly for internationally recognized certifications, can be your golden ticket to a rewarding international career.
Why Digital Marketing Certifications Matter?
In a competitive job market, certifications act as a potent differentiator. They demonstrate your commitment to continuous learning and mastery of specific digital marketing skills. Renowned certifications like Google Analytics Individual Qualification (IQ) or HubSpot Inbound Marketing Certification showcase your expertise to potential employers worldwide. These programs often incorporate a global perspective, ensuring you understand the nuances of marketing across diverse cultures and languages.
International Appeal of Digital Marketing Skills
The beauty of digital marketing lies in its universality. Fundamental marketing principles – understanding customer needs, crafting compelling content, and leveraging data-driven insights – remain constant across borders. However, a skilled international marketer tailors these strategies to resonate with local audiences. Certifications often equip you with this cultural competency, making you a valuable asset to companies seeking to expand their global reach.
Exploring International Career Opportunities
Digital marketing certifications open doors to a plethora of exciting international careers. With the rise of e-commerce, multinational corporations are constantly seeking talent to manage their online presence in overseas markets. Here are some potential career paths:
-
Global Marketing Manager: Overseeing the development and execution of marketing strategies for international markets.
-
Localization Specialist: Adapting marketing materials to resonate with specific cultural contexts.
-
International SEO Specialist: Optimizing websites for global search engines, ensuring discoverability in targeted regions.
-
Social Media Strategist: Crafting engaging social media campaigns that cater to diverse audiences across the globe.
The Power of Continuous Learning
The digital marketing landscape is a dynamic one. To stay ahead of the curve, continuous learning is imperative. Many certification programs offer ongoing educational resources and opportunities to stay updated on the latest trends and technologies. This ensures you remain a valuable asset in the international job market.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion:
In today's interconnected world, the digital landscape transcends geographical boundaries. By acquiring recognized digital marketing certifications, ambitious professionals can unlock a treasure trove of international career opportunities. These credentials validate a marketer's proficiency in the ever-evolving digital realm, fostering trust and marketability across borders.
Digital marketing certifications equip individuals with the necessary skills to navigate the complexities of global marketing campaigns. From understanding cultural nuances and tailoring content for diverse audiences to mastering data analysis for international market insights, these qualifications empower marketers to excel on the world stage.
Furthermore, certifications demonstrate a commitment to continuous learning, a quality highly sought-after by international employers. They signal a marketer's ability to adapt to the dynamic digital landscape, ensuring they remain competitive in the global marketplace.
As the digital world continues to shrink distances, embracing digital marketing certifications is no longer an option, but a strategic imperative. These credentials empower individuals to not only navigate the international marketing landscape but to thrive within it. So for those seeking a fulfilling career on the world stage, the key lies in unlocking the potential of digital marketing certifications.
Efficient Data Cleaning and Validation with SAS Base
In today's data-driven world, ensuring the accuracy and quality of data is paramount for any organization. Data cleaning and validation are crucial steps in the data management process, as they help in improving data quality, making informed decisions, and ensuring compliance with regulatory requirements. In this article, we will explore the importance of efficient data cleaning and validation with SAS Base, a powerful tool for data processing, analysis, and manipulation.
What is data cleaning?
Data cleaning, also known as data scrubbing, is the process of detecting and correcting errors in datasets to improve data quality. It involves identifying inconsistencies, missing values, and outliers in the data, and correcting or removing them to ensure that the data is accurate and reliable for analysis.
With SAS Base, data cleaning is made easier through a variety of data cleansing tools and techniques that can be used to clean raw data, identify and remove duplicate records, fill in missing values, and standardize data formats.
Cleaning raw data
Cleaning raw data involves identifying and removing inconsistencies, errors, and missing values in the dataset. This can be done by using SAS programming to apply data cleaning techniques such as removing duplicates, correcting data entry errors, and filling in missing values with imputed data.
Data scrubbing methods
Data scrubbing methods in SAS Base include data profiling, data structure validation, and data preprocessing.
Data profiling involves analyzing the data to identify patterns, correlations, and inconsistencies that may need to be addressed during the data cleaning process. Data structure validation ensures that the data is properly formatted and structured according to predefined rules and standards. Data preprocessing involves transforming the data into a format that is suitable for analysis, such as normalizing variables or creating new variables based on existing data.
What is data validation?
Data validation is the process of ensuring that the data meets certain quality standards and is free from errors and inconsistencies. It involves performing checks and validations on the data to detect anomalies, outliers, and discrepancies that may affect the integrity of the data.
With SAS Base, data validation techniques such as error detection, data profiling, and data integrity checks can be used to identify and resolve issues in the data before it is used for analysis.
Error detection in datasets
Error detection in datasets involves identifying and correcting errors, inconsistencies, and outliers that may affect the accuracy of the data. This can be done by using SAS programming to perform data validation checks such as range validations, format validations, and logic validations to ensure that the data is accurate and reliable for analysis.
Data profiling in SAS
Data profiling in SAS involves analyzing the data to understand its structure, quality, and content. This can help in identifying patterns, correlations, and anomalies in the data that may need to be addressed during the data cleaning and validation process. Data profiling can also help in identifying data quality issues such as missing values, outliers, and duplicate records, which can be resolved to improve data quality.
How to obtain SAS Base Programmer Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, efficient data cleaning and validation with SAS Base is essential for ensuring the accuracy, reliability, and quality of data in today's data-driven world. By following best practices and leveraging the tools and techniques available in SAS Base, organizations can improve data quality, make informed decisions, and stay compliant with regulatory requirements.
Read More
In today's data-driven world, ensuring the accuracy and quality of data is paramount for any organization. Data cleaning and validation are crucial steps in the data management process, as they help in improving data quality, making informed decisions, and ensuring compliance with regulatory requirements. In this article, we will explore the importance of efficient data cleaning and validation with SAS Base, a powerful tool for data processing, analysis, and manipulation.
What is data cleaning?
Data cleaning, also known as data scrubbing, is the process of detecting and correcting errors in datasets to improve data quality. It involves identifying inconsistencies, missing values, and outliers in the data, and correcting or removing them to ensure that the data is accurate and reliable for analysis.
With SAS Base, data cleaning is made easier through a variety of data cleansing tools and techniques that can be used to clean raw data, identify and remove duplicate records, fill in missing values, and standardize data formats.
Cleaning raw data
Cleaning raw data involves identifying and removing inconsistencies, errors, and missing values in the dataset. This can be done by using SAS programming to apply data cleaning techniques such as removing duplicates, correcting data entry errors, and filling in missing values with imputed data.
Data scrubbing methods
Data scrubbing methods in SAS Base include data profiling, data structure validation, and data preprocessing.
Data profiling involves analyzing the data to identify patterns, correlations, and inconsistencies that may need to be addressed during the data cleaning process. Data structure validation ensures that the data is properly formatted and structured according to predefined rules and standards. Data preprocessing involves transforming the data into a format that is suitable for analysis, such as normalizing variables or creating new variables based on existing data.
What is data validation?
Data validation is the process of ensuring that the data meets certain quality standards and is free from errors and inconsistencies. It involves performing checks and validations on the data to detect anomalies, outliers, and discrepancies that may affect the integrity of the data.
With SAS Base, data validation techniques such as error detection, data profiling, and data integrity checks can be used to identify and resolve issues in the data before it is used for analysis.
Error detection in datasets
Error detection in datasets involves identifying and correcting errors, inconsistencies, and outliers that may affect the accuracy of the data. This can be done by using SAS programming to perform data validation checks such as range validations, format validations, and logic validations to ensure that the data is accurate and reliable for analysis.
Data profiling in SAS
Data profiling in SAS involves analyzing the data to understand its structure, quality, and content. This can help in identifying patterns, correlations, and anomalies in the data that may need to be addressed during the data cleaning and validation process. Data profiling can also help in identifying data quality issues such as missing values, outliers, and duplicate records, which can be resolved to improve data quality.
How to obtain SAS Base Programmer Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, efficient data cleaning and validation with SAS Base is essential for ensuring the accuracy, reliability, and quality of data in today's data-driven world. By following best practices and leveraging the tools and techniques available in SAS Base, organizations can improve data quality, make informed decisions, and stay compliant with regulatory requirements.
Tokenization of Assets: How Blockchain is Disrupting Traditional Asset Management
In today's ever-evolving digital landscape, the concept of tokenization has emerged as a game-changer in the world of asset management. With the rise of blockchain technology, traditional asset management practices are being revolutionized by the tokenization of assets. This innovative approach holds the potential to reshape the way we think about investments, finance, and security. Let's explore how blockchain is disrupting traditional asset management through the tokenization of assets.
Understanding Tokenization of Assets
Tokenization refers to the process of converting real-world assets into digital tokens on a blockchain. These tokens represent ownership of the underlying asset and can be traded or transferred in a secure and transparent manner. By tokenizing assets, traditional barriers to investment are removed, allowing for greater access to a wider range of asset classes.
One of the key advantages of tokenization is the ability to fractionalize ownership. This means that high-value assets, such as real estate properties or fine art collections, can be divided into smaller, more affordable units. Investors can then purchase fractions of these assets, opening up new opportunities for diversification and portfolio optimization.
How Blockchain Facilitates Asset Tokenization
Blockchain technology plays a crucial role in enabling the tokenization of assets. By leveraging smart contracts, assets can be digitized and represented as tokens on a decentralized ledger. These smart contracts automate the process of issuance, transfer, and tracking of tokenized assets, providing increased efficiency and security.
Additionally, blockchain offers enhanced transparency and immutability, ensuring that ownership rights are securely recorded and tamper-proof. This level of trust and accountability is a significant improvement over traditional asset management systems, which often rely on manual processes and intermediaries.
The Rise of Tokenized Securities
Security tokens are a subset of tokenized assets that represent ownership in real-world securities, such as stocks, bonds, and funds. These security tokens adhere to regulatory compliance standards and can offer investors the benefits of traditional securities, such as dividends and voting rights.
The issuance of security tokens is governed by token standards, which define the rules and protocols for creating and trading these tokens. By complying with these standards, issuers can ensure the legitimacy and transferability of their tokenized assets.
The Future of Asset Management
The tokenization of assets represents a paradigm shift in the way we approach investments and finance. This innovative approach offers greater liquidity, transparency, and accessibility to a wider range of investors, democratizing the world of finance.
As blockchain technology continues to mature and regulatory frameworks evolve, we can expect to see an increasing number of assets being tokenized. From real estate properties to fine art collections, the potential for asset tokenization is vast and promising.
How to obtain Blockchain Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the tokenization of assets through blockchain technology is disrupting traditional asset management practices and opening up new possibilities for investors. By leveraging the power of tokenization, we can expect to see a more efficient, secure, and inclusive financial ecosystem in the years to come.
Read More
In today's ever-evolving digital landscape, the concept of tokenization has emerged as a game-changer in the world of asset management. With the rise of blockchain technology, traditional asset management practices are being revolutionized by the tokenization of assets. This innovative approach holds the potential to reshape the way we think about investments, finance, and security. Let's explore how blockchain is disrupting traditional asset management through the tokenization of assets.
Understanding Tokenization of Assets
Tokenization refers to the process of converting real-world assets into digital tokens on a blockchain. These tokens represent ownership of the underlying asset and can be traded or transferred in a secure and transparent manner. By tokenizing assets, traditional barriers to investment are removed, allowing for greater access to a wider range of asset classes.
One of the key advantages of tokenization is the ability to fractionalize ownership. This means that high-value assets, such as real estate properties or fine art collections, can be divided into smaller, more affordable units. Investors can then purchase fractions of these assets, opening up new opportunities for diversification and portfolio optimization.
How Blockchain Facilitates Asset Tokenization
Blockchain technology plays a crucial role in enabling the tokenization of assets. By leveraging smart contracts, assets can be digitized and represented as tokens on a decentralized ledger. These smart contracts automate the process of issuance, transfer, and tracking of tokenized assets, providing increased efficiency and security.
Additionally, blockchain offers enhanced transparency and immutability, ensuring that ownership rights are securely recorded and tamper-proof. This level of trust and accountability is a significant improvement over traditional asset management systems, which often rely on manual processes and intermediaries.
The Rise of Tokenized Securities
Security tokens are a subset of tokenized assets that represent ownership in real-world securities, such as stocks, bonds, and funds. These security tokens adhere to regulatory compliance standards and can offer investors the benefits of traditional securities, such as dividends and voting rights.
The issuance of security tokens is governed by token standards, which define the rules and protocols for creating and trading these tokens. By complying with these standards, issuers can ensure the legitimacy and transferability of their tokenized assets.
The Future of Asset Management
The tokenization of assets represents a paradigm shift in the way we approach investments and finance. This innovative approach offers greater liquidity, transparency, and accessibility to a wider range of investors, democratizing the world of finance.
As blockchain technology continues to mature and regulatory frameworks evolve, we can expect to see an increasing number of assets being tokenized. From real estate properties to fine art collections, the potential for asset tokenization is vast and promising.
How to obtain Blockchain Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the tokenization of assets through blockchain technology is disrupting traditional asset management practices and opening up new possibilities for investors. By leveraging the power of tokenization, we can expect to see a more efficient, secure, and inclusive financial ecosystem in the years to come.
Unlocking Automation with Process Builder and Flow Builder
Salesforce is a powerful CRM platform, but manual data entry and repetitive tasks can bog down productivity. Process Builder and Flow Builder are two automation tools that can empower you to streamline workflows and unleash the true potential of Salesforce. This blog will guide you through their capabilities and how they can revolutionize your Sales force experience.
Process Builder: The Power of Simplicity
Process Builder is a user-friendly tool designed for automating common workflows. Think of it as a set of "if-then" rules that fire automatically based on specific criteria. Here are some of its strengths:
-
Easy to Use: Process Builder offers a drag-and-drop interface, making it ideal for users with minimal coding experience.
-
Common Use Cases: It excels at automating tasks like sending email notifications, updating fields, and triggering field validations.
Flow Builder: Unveiling Complex Automation
Flow Builder extends Process Builder's capabilities for intricate automations. It provides a visual interface for building sophisticated logic flows, incorporating features like:
-
Conditional Logic: Flows allow for branching paths based on various conditions, enabling you to create highly customized workflows.
-
Data Manipulation: You can manipulate and transform data within the flow itself, eliminating the need for separate tools.
-
User Interaction: Flows can include user interface elements like screens and prompts, creating a guided user experience during the automation process.
Choosing the Right Tool
When deciding between Process Builder and Flow Builder, consider the complexity of your automation needs:
-
Simple Workflows: Process Builder is the perfect choice for straightforward tasks with pre-defined actions.
-
Complex Processes: Flow Builder shines for intricate automations with conditional logic, data manipulation, or user interaction.
Working Together: A Dynamic Duo
Process Builder and Flow Builder can be a powerful combination. You can leverage Process Builder to trigger a Flow for more advanced automation when needed. This allows you to build modular workflows, maintaining simplicity while achieving complex results.
Getting Started with Automation
Salesforce offers a wealth of resources to get you started with Process Builder and Flow Builder, including tutorials, documentation, and training videos. Consider these steps:
-
Identify Automation Opportunities: Look for repetitive tasks or manual processes that can be automated.
-
Define Your Requirements: Clearly outline the triggers, actions, and desired outcomes of your automation.
-
Choose the Right Tool: Based on your requirements, select Process Builder or Flow Builder (or potentially both).
-
Build and Test: Utilize the drag-and-drop interface to create your automation and thoroughly test it before deployment.
Unlocking Efficiency with Automation
By embracing Process Builder and Flow Builder, you can significantly boost your Sales force efficiency. These tools can:
-
Save Time: Automate repetitive tasks, freeing up valuable time for strategic work.
-
Reduce Errors: Eliminate human error from manual data entry and processes.
-
Improve User Productivity: Streamline workflows and provide a more intuitive user experience.
-
Enhance Data Consistency: Ensure data accuracy and consistency across Sales force.
How to obtain Salesforce Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, Process Builder and Flow Builder are powerful tools that can transform the way you work with Sales force. By leveraging their capabilities, you can unlock new levels of efficiency, accuracy, and productivity within your organization. So, start exploring these automation tools and discover the potential they hold for your Sales force success!
Read More
Salesforce is a powerful CRM platform, but manual data entry and repetitive tasks can bog down productivity. Process Builder and Flow Builder are two automation tools that can empower you to streamline workflows and unleash the true potential of Salesforce. This blog will guide you through their capabilities and how they can revolutionize your Sales force experience.
Process Builder: The Power of Simplicity
Process Builder is a user-friendly tool designed for automating common workflows. Think of it as a set of "if-then" rules that fire automatically based on specific criteria. Here are some of its strengths:
-
Easy to Use: Process Builder offers a drag-and-drop interface, making it ideal for users with minimal coding experience.
-
Common Use Cases: It excels at automating tasks like sending email notifications, updating fields, and triggering field validations.
Flow Builder: Unveiling Complex Automation
Flow Builder extends Process Builder's capabilities for intricate automations. It provides a visual interface for building sophisticated logic flows, incorporating features like:
-
Conditional Logic: Flows allow for branching paths based on various conditions, enabling you to create highly customized workflows.
-
Data Manipulation: You can manipulate and transform data within the flow itself, eliminating the need for separate tools.
-
User Interaction: Flows can include user interface elements like screens and prompts, creating a guided user experience during the automation process.
Choosing the Right Tool
When deciding between Process Builder and Flow Builder, consider the complexity of your automation needs:
-
Simple Workflows: Process Builder is the perfect choice for straightforward tasks with pre-defined actions.
-
Complex Processes: Flow Builder shines for intricate automations with conditional logic, data manipulation, or user interaction.
Working Together: A Dynamic Duo
Process Builder and Flow Builder can be a powerful combination. You can leverage Process Builder to trigger a Flow for more advanced automation when needed. This allows you to build modular workflows, maintaining simplicity while achieving complex results.
Getting Started with Automation
Salesforce offers a wealth of resources to get you started with Process Builder and Flow Builder, including tutorials, documentation, and training videos. Consider these steps:
-
Identify Automation Opportunities: Look for repetitive tasks or manual processes that can be automated.
-
Define Your Requirements: Clearly outline the triggers, actions, and desired outcomes of your automation.
-
Choose the Right Tool: Based on your requirements, select Process Builder or Flow Builder (or potentially both).
-
Build and Test: Utilize the drag-and-drop interface to create your automation and thoroughly test it before deployment.
Unlocking Efficiency with Automation
By embracing Process Builder and Flow Builder, you can significantly boost your Sales force efficiency. These tools can:
-
Save Time: Automate repetitive tasks, freeing up valuable time for strategic work.
-
Reduce Errors: Eliminate human error from manual data entry and processes.
-
Improve User Productivity: Streamline workflows and provide a more intuitive user experience.
-
Enhance Data Consistency: Ensure data accuracy and consistency across Sales force.
How to obtain Salesforce Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, Process Builder and Flow Builder are powerful tools that can transform the way you work with Sales force. By leveraging their capabilities, you can unlock new levels of efficiency, accuracy, and productivity within your organization. So, start exploring these automation tools and discover the potential they hold for your Sales force success!
Implementing End-to-End Security in AWS Architectures
In today's digital landscape, security is a top priority for businesses of all sizes. With the increasing adoption of cloud services, such as Amazon Web Services (AWS), implementing end-to-end security in AWS architectures has become crucial to protect valuable data and ensure regulatory compliance. In this article, we will explore the best practices for securing your AWS environment, from data protection to threat detection, encryption methods to incident response plans.
Main Keyword Heading: Implementing End-to-End Security in AWS Architectures
Data Protection
One of the fundamental aspects of securing your AWS architecture is data protection. By implementing strong encryption methods, you can ensure that your sensitive data is protected both in transit and at rest. AWS offers a range of security services, such as AWS Key Management Service (KMS), which allows you to easily manage encryption keys and protect your data.
Network Security
Another essential component of securing your AWS environment is network security. By implementing security protocols and secure architecture designs, you can create a secure network infrastructure that prevents unauthorized access and protects against cyber threats. Utilizing AWS security services like Amazon Virtual Private Cloud (VPC) and AWS WAF (Web Application Firewall) can enhance your network security posture.
Threat Detection
In today's cyber landscape, it's not a matter of if but when a security incident will occur. By implementing threat detection capabilities in your AWS environment, you can quickly identify and respond to security threats. Tools like AWS GuardDuty and Amazon Inspector can help you detect and respond to potential security issues before they escalate.
Incident Response Plan
Having an effective incident response plan is critical to a successful security strategy. By outlining clear procedures and protocols for responding to security incidents, you can minimize the impact of a breach and mitigate potential damage. Ensure that your incident response plan aligns with compliance standards and includes mechanisms for security automation and monitoring.
Access Control and Identity Management
Implementing strong access control and identity management policies is essential for securing your AWS environment. By leveraging AWS security features like AWS IAM (Identity and Access Management) and AWS SSO (Single Sign-On), you can ensure that only authorized users have access to sensitive resources and data. Regularly review and update your access control policies to maintain a secure environment.
Security Monitoring
Continuous security monitoring is key to detecting and responding to security incidents in real-time. By leveraging tools like AWS CloudTrail and Amazon CloudWatch, you can monitor security events, track user activity, and ensure compliance with security policies. Establishing a robust security monitoring strategy is essential for maintaining the integrity of your AWS architecture.
How to obtain Cloud Technology Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Implementing end-to-end security in AWS architectures is essential for protecting your data, maintaining compliance, and mitigating security risks. By following best practices, such as data protection, network security, threat detection, and access control, you can create a secure environment that safeguards your valuable assets. Remember to regularly assess your security posture, implement security frameworks, and stay updated on the latest security trends to stay ahead of emerging threats.
Read More
In today's digital landscape, security is a top priority for businesses of all sizes. With the increasing adoption of cloud services, such as Amazon Web Services (AWS), implementing end-to-end security in AWS architectures has become crucial to protect valuable data and ensure regulatory compliance. In this article, we will explore the best practices for securing your AWS environment, from data protection to threat detection, encryption methods to incident response plans.
Main Keyword Heading: Implementing End-to-End Security in AWS Architectures
Data Protection
One of the fundamental aspects of securing your AWS architecture is data protection. By implementing strong encryption methods, you can ensure that your sensitive data is protected both in transit and at rest. AWS offers a range of security services, such as AWS Key Management Service (KMS), which allows you to easily manage encryption keys and protect your data.
Network Security
Another essential component of securing your AWS environment is network security. By implementing security protocols and secure architecture designs, you can create a secure network infrastructure that prevents unauthorized access and protects against cyber threats. Utilizing AWS security services like Amazon Virtual Private Cloud (VPC) and AWS WAF (Web Application Firewall) can enhance your network security posture.
Threat Detection
In today's cyber landscape, it's not a matter of if but when a security incident will occur. By implementing threat detection capabilities in your AWS environment, you can quickly identify and respond to security threats. Tools like AWS GuardDuty and Amazon Inspector can help you detect and respond to potential security issues before they escalate.
Incident Response Plan
Having an effective incident response plan is critical to a successful security strategy. By outlining clear procedures and protocols for responding to security incidents, you can minimize the impact of a breach and mitigate potential damage. Ensure that your incident response plan aligns with compliance standards and includes mechanisms for security automation and monitoring.
Access Control and Identity Management
Implementing strong access control and identity management policies is essential for securing your AWS environment. By leveraging AWS security features like AWS IAM (Identity and Access Management) and AWS SSO (Single Sign-On), you can ensure that only authorized users have access to sensitive resources and data. Regularly review and update your access control policies to maintain a secure environment.
Security Monitoring
Continuous security monitoring is key to detecting and responding to security incidents in real-time. By leveraging tools like AWS CloudTrail and Amazon CloudWatch, you can monitor security events, track user activity, and ensure compliance with security policies. Establishing a robust security monitoring strategy is essential for maintaining the integrity of your AWS architecture.
How to obtain Cloud Technology Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Implementing end-to-end security in AWS architectures is essential for protecting your data, maintaining compliance, and mitigating security risks. By following best practices, such as data protection, network security, threat detection, and access control, you can create a secure environment that safeguards your valuable assets. Remember to regularly assess your security posture, implement security frameworks, and stay updated on the latest security trends to stay ahead of emerging threats.
The Role of Automation in IT Service Management
Are you looking to streamline your IT service management processes and improve overall efficiency? Look no further than automation! Automation plays a crucial role in IT service management, offering a wide range of benefits and opportunities for organizations looking to optimize their operations. In this article, we will explore the various aspects of automation in IT service management, including its implementation, challenges, best practices, and future developments.
What is Automation in IT Service Management?
Automation in IT service management refers to the use of technology to perform manual tasks, processes, and workflows automatically. This can include automating routine tasks such as incident management, problem resolution, change management, and asset management. By leveraging automation tools and technologies, organizations can reduce human error, improve productivity, and enhance the overall quality of IT services.
Benefits of Automation in IT Service Management
-
Improved efficiency and productivity: By automating repetitive tasks, IT teams can focus on more strategic initiatives and projects.
-
Enhanced accuracy: Automation reduces the risk of human error, leading to higher data accuracy and consistency.
-
Faster response times: Automated workflows can respond to incidents and requests in real-time, leading to quicker resolution times.
-
Cost savings: Automation helps reduce operational costs by minimizing the need for manual intervention and streamlining processes.
-
Better scalability: With automation, IT service management processes can easily scale to support growing business needs and requirements.
Automation Tools in IT Service Management
Several automation tools are available in the market to support IT service management processes. These tools offer features such as workflow automation, ticket routing, alerting, and reporting capabilities. Some popular automation tools in IT service management include:
-
ServiceNow
-
BMC Helix
-
Cherwell
-
SolarWinds
-
Freshservice
Automation Strategies and Practices in IT Service Management
When implementing automation in IT service management, organizations should consider the following strategies and practices:
-
Identify key processes and tasks that can be automated to improve efficiency.
-
Establish clear objectives and goals for automation initiatives.
-
Train employees on how to use automation tools effectively.
-
Monitor and measure the impact of automation on IT service management processes.
-
Continuously optimize and improve automation workflows to adapt to changing business needs.
Automation Challenges and Solutions in IT Service Management
While automation offers numerous benefits, organizations may face challenges during implementation. Some common challenges include:
-
Resistance to change from employees.
-
Integration issues with existing systems.
-
Complexity of defining automation workflows.
-
Ensuring data security and compliance.
To overcome these challenges, organizations should focus on:
-
Communicating the benefits of automation to employees.
-
Investing in integration tools to connect different systems.
-
Collaborating with IT and business stakeholders to define automation workflows.
-
Implementing robust security measures to protect sensitive data.
Future of Automation in IT Service Management
The future of automation in IT service management looks promising, with advancements in technologies such as artificial intelligence, machine learning, and robotic process automation. These technologies will further enhance automation capabilities, enabling organizations to achieve higher levels of efficiency, agility, and innovation in their IT service management processes.
How to obtain IT Service Management and Governance Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, automation plays a critical role in IT service management, offering a wide range of benefits and opportunities for organizations. By leveraging automation tools, strategies, and practices, organizations can streamline their operations, improve efficiency, and deliver higher quality IT services to their customers. Embrace automation today and stay ahead in the rapidly evolving world of IT service management!
Read More
Are you looking to streamline your IT service management processes and improve overall efficiency? Look no further than automation! Automation plays a crucial role in IT service management, offering a wide range of benefits and opportunities for organizations looking to optimize their operations. In this article, we will explore the various aspects of automation in IT service management, including its implementation, challenges, best practices, and future developments.
What is Automation in IT Service Management?
Automation in IT service management refers to the use of technology to perform manual tasks, processes, and workflows automatically. This can include automating routine tasks such as incident management, problem resolution, change management, and asset management. By leveraging automation tools and technologies, organizations can reduce human error, improve productivity, and enhance the overall quality of IT services.
Benefits of Automation in IT Service Management
-
Improved efficiency and productivity: By automating repetitive tasks, IT teams can focus on more strategic initiatives and projects.
-
Enhanced accuracy: Automation reduces the risk of human error, leading to higher data accuracy and consistency.
-
Faster response times: Automated workflows can respond to incidents and requests in real-time, leading to quicker resolution times.
-
Cost savings: Automation helps reduce operational costs by minimizing the need for manual intervention and streamlining processes.
-
Better scalability: With automation, IT service management processes can easily scale to support growing business needs and requirements.
Automation Tools in IT Service Management
Several automation tools are available in the market to support IT service management processes. These tools offer features such as workflow automation, ticket routing, alerting, and reporting capabilities. Some popular automation tools in IT service management include:
-
ServiceNow
-
BMC Helix
-
Cherwell
-
SolarWinds
-
Freshservice
Automation Strategies and Practices in IT Service Management
When implementing automation in IT service management, organizations should consider the following strategies and practices:
-
Identify key processes and tasks that can be automated to improve efficiency.
-
Establish clear objectives and goals for automation initiatives.
-
Train employees on how to use automation tools effectively.
-
Monitor and measure the impact of automation on IT service management processes.
-
Continuously optimize and improve automation workflows to adapt to changing business needs.
Automation Challenges and Solutions in IT Service Management
While automation offers numerous benefits, organizations may face challenges during implementation. Some common challenges include:
-
Resistance to change from employees.
-
Integration issues with existing systems.
-
Complexity of defining automation workflows.
-
Ensuring data security and compliance.
To overcome these challenges, organizations should focus on:
-
Communicating the benefits of automation to employees.
-
Investing in integration tools to connect different systems.
-
Collaborating with IT and business stakeholders to define automation workflows.
-
Implementing robust security measures to protect sensitive data.
Future of Automation in IT Service Management
The future of automation in IT service management looks promising, with advancements in technologies such as artificial intelligence, machine learning, and robotic process automation. These technologies will further enhance automation capabilities, enabling organizations to achieve higher levels of efficiency, agility, and innovation in their IT service management processes.
How to obtain IT Service Management and Governance Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, automation plays a critical role in IT service management, offering a wide range of benefits and opportunities for organizations. By leveraging automation tools, strategies, and practices, organizations can streamline their operations, improve efficiency, and deliver higher quality IT services to their customers. Embrace automation today and stay ahead in the rapidly evolving world of IT service management!
Trends Shaping the Future of Business Analysis in a Digital World
In today's fast-paced digital world, the field of business analysis is constantly evolving to keep up with the latest trends and technologies. As businesses seek to stay competitive and innovative, it is crucial for business analysts to stay ahead of the curve. Let's explore some of the key trends that are shaping the future of business analysis in a digital world.
Digital Transformation
One of the most significant trends impacting business analysis is digital transformation. Companies are increasingly embracing digital technologies to streamline operations, improve customer experiences, and drive growth. Business analysts play a crucial role in helping organizations navigate this digital transformation by identifying opportunities for process improvement, analyzing data trends, and recommending strategic initiatives.
Data Analytics
Data analytics is another key trend shaping the future of business analysis. With the proliferation of data from various sources, businesses are now able to gather valuable insights to make informed decisions. Business analysts with expertise in data analytics can help organizations unlock the power of their data, whether it's through advanced analytics, predictive modeling, or business intelligence tools.
Technology Trends
Advancements in technology are constantly reshaping the business landscape and presenting new opportunities for growth and innovation. Business analysts need to stay abreast of the latest technology trends, such as artificial intelligence, machine learning, and big data, to help organizations leverage these technologies effectively. By understanding how emerging technologies can impact business operations, analysts can drive strategic initiatives that position their companies for success.
Agile Methodology
Agile methodology is becoming increasingly popular in the world of business analysis. This iterative approach to project management emphasizes collaboration, flexibility, and continuous improvement. Business analysts who are well-versed in agile methodology can help organizations adapt to changing market conditions, deliver projects more efficiently, and respond quickly to customer feedback.
Data Visualization
Data visualization is an essential tool for business analysts to communicate complex information in a clear and visually appealing manner. By using charts, graphs, and interactive dashboards, analysts can help stakeholders make sense of large datasets and identify trends and patterns. Effective data visualization enhances decision-making processes and enables organizations to act upon insights more effectively.
Artificial Intelligence
Artificial intelligence (AI) is revolutionizing the way businesses operate by automating tasks, predicting outcomes, and personalizing customer experiences. Business analysts with expertise in AI can help organizations harness the power of this technology to drive innovation and efficiency. Whether it's implementing chatbots for customer service or using machine learning algorithms for predictive analytics, AI is transforming how business analysis is conducted.
Digital Disruption
Digital disruption is reshaping industries and challenging traditional business models. Business analysts play a critical role in helping organizations navigate this disruption by identifying threats and opportunities, conducting competitive intelligence, and recommending strategic responses. By staying ahead of digital trends and understanding how they impact the market, analysts can help businesses adapt and thrive in a rapidly changing environment.
How to obtain Business Analysis Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the future of business analysis in a digital world is filled with exciting opportunities and challenges. By staying abreast of the latest trends in digital transformation, data analytics, technology, and agile methodology, business analysts can position themselves as trusted advisors who drive strategic innovation and growth. As businesses continue to evolve in response to digital disruption, the role of the business analyst will remain essential in helping organizations make informed decisions and stay competitive in the marketplace.
Read More
In today's fast-paced digital world, the field of business analysis is constantly evolving to keep up with the latest trends and technologies. As businesses seek to stay competitive and innovative, it is crucial for business analysts to stay ahead of the curve. Let's explore some of the key trends that are shaping the future of business analysis in a digital world.
Digital Transformation
One of the most significant trends impacting business analysis is digital transformation. Companies are increasingly embracing digital technologies to streamline operations, improve customer experiences, and drive growth. Business analysts play a crucial role in helping organizations navigate this digital transformation by identifying opportunities for process improvement, analyzing data trends, and recommending strategic initiatives.
Data Analytics
Data analytics is another key trend shaping the future of business analysis. With the proliferation of data from various sources, businesses are now able to gather valuable insights to make informed decisions. Business analysts with expertise in data analytics can help organizations unlock the power of their data, whether it's through advanced analytics, predictive modeling, or business intelligence tools.
Technology Trends
Advancements in technology are constantly reshaping the business landscape and presenting new opportunities for growth and innovation. Business analysts need to stay abreast of the latest technology trends, such as artificial intelligence, machine learning, and big data, to help organizations leverage these technologies effectively. By understanding how emerging technologies can impact business operations, analysts can drive strategic initiatives that position their companies for success.
Agile Methodology
Agile methodology is becoming increasingly popular in the world of business analysis. This iterative approach to project management emphasizes collaboration, flexibility, and continuous improvement. Business analysts who are well-versed in agile methodology can help organizations adapt to changing market conditions, deliver projects more efficiently, and respond quickly to customer feedback.
Data Visualization
Data visualization is an essential tool for business analysts to communicate complex information in a clear and visually appealing manner. By using charts, graphs, and interactive dashboards, analysts can help stakeholders make sense of large datasets and identify trends and patterns. Effective data visualization enhances decision-making processes and enables organizations to act upon insights more effectively.
Artificial Intelligence
Artificial intelligence (AI) is revolutionizing the way businesses operate by automating tasks, predicting outcomes, and personalizing customer experiences. Business analysts with expertise in AI can help organizations harness the power of this technology to drive innovation and efficiency. Whether it's implementing chatbots for customer service or using machine learning algorithms for predictive analytics, AI is transforming how business analysis is conducted.
Digital Disruption
Digital disruption is reshaping industries and challenging traditional business models. Business analysts play a critical role in helping organizations navigate this disruption by identifying threats and opportunities, conducting competitive intelligence, and recommending strategic responses. By staying ahead of digital trends and understanding how they impact the market, analysts can help businesses adapt and thrive in a rapidly changing environment.
How to obtain Business Analysis Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the future of business analysis in a digital world is filled with exciting opportunities and challenges. By staying abreast of the latest trends in digital transformation, data analytics, technology, and agile methodology, business analysts can position themselves as trusted advisors who drive strategic innovation and growth. As businesses continue to evolve in response to digital disruption, the role of the business analyst will remain essential in helping organizations make informed decisions and stay competitive in the marketplace.
Mastering AWS Networking for Solution Architects
Are you a solution architect looking to enhance your networking skills within Amazon Web Services (AWS)? If so, mastering AWS networking is essential for designing effective and secure solutions in the cloud. In this article, we will explore the fundamentals of AWS networking, best practices for network design, and tips for optimizing your network architecture. Let's dive in and learn how to become a master of AWS networking for solution architects.
AWS Networking Fundamentals
Before diving into the advanced aspects of AWS networking, it's crucial to understand the fundamentals. At the core of AWS networking is the Virtual Private Cloud (VPC), which allows you to create isolated virtual networks within the AWS cloud. By designing your solution architecture within a VPC, you can control network security, IP addressing, routing, and other networking aspects.
AWS Architecture for Solution Design
As a solutions architect, you must design AWS solutions that are scalable, secure, and optimized for performance. When it comes to networking, you need to consider factors such as network security, high availability, and efficient data transfer. By leveraging AWS networking services such as Amazon VPC, AWS Direct Connect, and Route 53, you can build robust and reliable architectures that meet your clients' needs.
Network Security in AWS
One of the biggest concerns for solution architects is network security. With AWS, you have access to a wide range of tools and features to secure your network infrastructure, including security groups, network ACLs, and encryption. By implementing best practices for network security, you can protect your data and applications from unauthorized access and cyber threats.
Best Practices for AWS Networking
When designing and implementing networking in AWS, it's essential to follow best practices to ensure optimal performance and reliability. Some key best practices include proper routing and switching configurations, utilizing AWS Direct Connect for dedicated network connections, and implementing network optimization techniques to enhance the efficiency of data transfer.
AWS Networking Certification and Training
To truly master AWS networking, consider pursuing certifications such as the AWS Certified Solutions Architect - Associate or Professional. These certifications will validate your expertise in designing and implementing AWS solutions, including networking components. Additionally, enrolling in AWS networking training courses can provide you with the knowledge and skills needed to excel in this field.
Network Design and Optimization
Effective network design is crucial for ensuring high performance and scalability in the cloud. By applying best practices for scaling AWS networking, you can design architectures that can handle increased traffic and workloads. Optimization techniques such as load balancing, caching, and content delivery networks (CDNs) can further enhance the performance of your network infrastructure.
How to obtain Cloud Technology Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, mastering AWS networking is essential for solution architects looking to design secure, scalable, and efficient solutions in the cloud. By following best practices, obtaining certifications, and continuously improving your networking skills, you can become a trusted expert in AWS networking. So, are you ready to take your networking skills to the next level in AWS? Start mastering AWS networking today.
Read More
Are you a solution architect looking to enhance your networking skills within Amazon Web Services (AWS)? If so, mastering AWS networking is essential for designing effective and secure solutions in the cloud. In this article, we will explore the fundamentals of AWS networking, best practices for network design, and tips for optimizing your network architecture. Let's dive in and learn how to become a master of AWS networking for solution architects.
AWS Networking Fundamentals
Before diving into the advanced aspects of AWS networking, it's crucial to understand the fundamentals. At the core of AWS networking is the Virtual Private Cloud (VPC), which allows you to create isolated virtual networks within the AWS cloud. By designing your solution architecture within a VPC, you can control network security, IP addressing, routing, and other networking aspects.
AWS Architecture for Solution Design
As a solutions architect, you must design AWS solutions that are scalable, secure, and optimized for performance. When it comes to networking, you need to consider factors such as network security, high availability, and efficient data transfer. By leveraging AWS networking services such as Amazon VPC, AWS Direct Connect, and Route 53, you can build robust and reliable architectures that meet your clients' needs.
Network Security in AWS
One of the biggest concerns for solution architects is network security. With AWS, you have access to a wide range of tools and features to secure your network infrastructure, including security groups, network ACLs, and encryption. By implementing best practices for network security, you can protect your data and applications from unauthorized access and cyber threats.
Best Practices for AWS Networking
When designing and implementing networking in AWS, it's essential to follow best practices to ensure optimal performance and reliability. Some key best practices include proper routing and switching configurations, utilizing AWS Direct Connect for dedicated network connections, and implementing network optimization techniques to enhance the efficiency of data transfer.
AWS Networking Certification and Training
To truly master AWS networking, consider pursuing certifications such as the AWS Certified Solutions Architect - Associate or Professional. These certifications will validate your expertise in designing and implementing AWS solutions, including networking components. Additionally, enrolling in AWS networking training courses can provide you with the knowledge and skills needed to excel in this field.
Network Design and Optimization
Effective network design is crucial for ensuring high performance and scalability in the cloud. By applying best practices for scaling AWS networking, you can design architectures that can handle increased traffic and workloads. Optimization techniques such as load balancing, caching, and content delivery networks (CDNs) can further enhance the performance of your network infrastructure.
How to obtain Cloud Technology Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, mastering AWS networking is essential for solution architects looking to design secure, scalable, and efficient solutions in the cloud. By following best practices, obtaining certifications, and continuously improving your networking skills, you can become a trusted expert in AWS networking. So, are you ready to take your networking skills to the next level in AWS? Start mastering AWS networking today.
Effective Strategies for Root Cause Analysis in Quality Management
In the realm of quality management, identifying and addressing the root cause of issues is crucial for ensuring continuous improvement and optimal performance. Root cause analysis (RCA) is a systematic approach used to uncover the underlying reasons behind problems or defects within a process or system. By implementing effective strategies for RCA, organizations can proactively tackle issues, prevent future recurrences, and enhance overall quality control.
What is Root Cause Analysis?
Root cause analysis is a methodical process that involves investigating and identifying the primary cause of a problem, rather than just addressing its symptoms. By digging deeper into the root cause of an issue, organizations can implement targeted solutions that address the underlying issues and prevent them from resurfacing in the future. This approach is essential for achieving sustainable quality improvement and operational excellence.
The Importance of Root Cause Analysis in Quality Management
Root cause analysis plays a critical role in quality management by helping organizations:
-
Problem-Solving: RCA helps organizations solve complex problems by getting to the heart of the issue and implementing effective solutions.
-
Continuous Improvement: By identifying and addressing root causes, organizations can continuously improve processes and systems to enhance quality and efficiency.
-
Data Analysis: RCA involves analyzing data to pinpoint the underlying cause of problems, enabling data-driven decision-making.
-
Corrective Action: Once the root cause is identified, organizations can take corrective action to prevent future issues from occurring.
-
Process Optimization: RCA helps organizations optimize processes by eliminating inefficiencies and streamlining operations.
Strategies for Effective Root Cause Analysis
When conducting root cause analysis in quality management, it is essential to employ the following strategies to ensure accurate and actionable results:
-
Utilize Six Sigma and Lean Methodology: Incorporate Six Sigma and Lean principles to streamline processes, reduce waste, and enhance quality control.
-
Root Cause Identification: Thoroughly investigate and analyze the problem to determine the underlying cause, rather than focusing solely on symptoms.
-
Quality Assurance: Implement quality assurance measures to maintain high standards and identify deviations from the norm.
-
Quality Improvement: Continuously strive to improve quality by addressing root causes and implementing effective solutions.
-
Defect Prevention: Focus on preventing defects rather than just correcting them, to ensure long-term quality and efficiency.
Techniques for Root Cause Analysis
There are various techniques and tools that can be used for root cause analysis in quality management, including:
-
Cause and Effect Analysis: Also known as the Fishbone Diagram, this tool helps visualize the potential causes of a problem and identify the root cause.
-
Failure Analysis: Investigate past failures to uncover the underlying reasons and prevent similar issues from occurring in the future.
-
System Analysis: Analyze the entire system to understand how different components interact and influence the overall performance.
-
Critical Thinking: Encourage critical thinking to delve deep into the problem and explore all possible causes and solutions.
-
Problem Resolution: Develop a systematic approach for resolving problems and preventing their recurrence.
How to obtain Quality Management Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, By utilizing these strategies and techniques for root cause analysis in quality management, organizations can enhance their problem-solving capabilities, drive continuous improvement, and achieve optimal performance and quality standards.
Remember, effective root cause analysis is not just about identifying problems but also about implementing sustainable solutions that prevent future issues from arising. By investing time and resources into RCA, organizations can proactively address challenges, optimize processes, and maintain high levels of quality and performance.
Read More
In the realm of quality management, identifying and addressing the root cause of issues is crucial for ensuring continuous improvement and optimal performance. Root cause analysis (RCA) is a systematic approach used to uncover the underlying reasons behind problems or defects within a process or system. By implementing effective strategies for RCA, organizations can proactively tackle issues, prevent future recurrences, and enhance overall quality control.
What is Root Cause Analysis?
Root cause analysis is a methodical process that involves investigating and identifying the primary cause of a problem, rather than just addressing its symptoms. By digging deeper into the root cause of an issue, organizations can implement targeted solutions that address the underlying issues and prevent them from resurfacing in the future. This approach is essential for achieving sustainable quality improvement and operational excellence.
The Importance of Root Cause Analysis in Quality Management
Root cause analysis plays a critical role in quality management by helping organizations:
-
Problem-Solving: RCA helps organizations solve complex problems by getting to the heart of the issue and implementing effective solutions.
-
Continuous Improvement: By identifying and addressing root causes, organizations can continuously improve processes and systems to enhance quality and efficiency.
-
Data Analysis: RCA involves analyzing data to pinpoint the underlying cause of problems, enabling data-driven decision-making.
-
Corrective Action: Once the root cause is identified, organizations can take corrective action to prevent future issues from occurring.
-
Process Optimization: RCA helps organizations optimize processes by eliminating inefficiencies and streamlining operations.
Strategies for Effective Root Cause Analysis
When conducting root cause analysis in quality management, it is essential to employ the following strategies to ensure accurate and actionable results:
-
Utilize Six Sigma and Lean Methodology: Incorporate Six Sigma and Lean principles to streamline processes, reduce waste, and enhance quality control.
-
Root Cause Identification: Thoroughly investigate and analyze the problem to determine the underlying cause, rather than focusing solely on symptoms.
-
Quality Assurance: Implement quality assurance measures to maintain high standards and identify deviations from the norm.
-
Quality Improvement: Continuously strive to improve quality by addressing root causes and implementing effective solutions.
-
Defect Prevention: Focus on preventing defects rather than just correcting them, to ensure long-term quality and efficiency.
Techniques for Root Cause Analysis
There are various techniques and tools that can be used for root cause analysis in quality management, including:
-
Cause and Effect Analysis: Also known as the Fishbone Diagram, this tool helps visualize the potential causes of a problem and identify the root cause.
-
Failure Analysis: Investigate past failures to uncover the underlying reasons and prevent similar issues from occurring in the future.
-
System Analysis: Analyze the entire system to understand how different components interact and influence the overall performance.
-
Critical Thinking: Encourage critical thinking to delve deep into the problem and explore all possible causes and solutions.
-
Problem Resolution: Develop a systematic approach for resolving problems and preventing their recurrence.
How to obtain Quality Management Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, By utilizing these strategies and techniques for root cause analysis in quality management, organizations can enhance their problem-solving capabilities, drive continuous improvement, and achieve optimal performance and quality standards.
Remember, effective root cause analysis is not just about identifying problems but also about implementing sustainable solutions that prevent future issues from arising. By investing time and resources into RCA, organizations can proactively address challenges, optimize processes, and maintain high levels of quality and performance.
An Overview with CompTIA Cloud Essentials Certification
Are you looking to advance your career in IT and elevate your expertise in cloud computing? If so, obtaining the CompTIA Cloud Essentials certification could be a valuable investment in your professional development. In this article, we will provide you with an overview of the CompTIA Cloud Essentials certification, including the benefits, skills, and career opportunities it can bring.
Certification Overview
The CompTIA Cloud Essentials certification is designed to validate the foundational knowledge and understanding of cloud computing concepts. It covers essential cloud computing principles, including cloud computing basics, cloud concepts, and cloud fundamentals. This certification is ideal for IT professionals who want to demonstrate their expertise in cloud technology and services.
Cloud Essentials Certification
Achieving the CompTIA Cloud Essentials certification demonstrates that you have the necessary skills to understand cloud deployment models, cloud management, and cloud governance. It also signifies that you can navigate cloud migration, cloud integration, and cloud storage effectively. This certification showcases your proficiency in cloud infrastructure, cloud virtualization, and cloud implementation.
IT Certification
The CompTIA Cloud Essentials certification is a valuable addition to your IT certification portfolio. It showcases your expertise in cloud technology and your ability to implement cloud best practices. With this certification, you can demonstrate your understanding of cloud benefits, cloud risks, and cloud adoption strategies.
CompTIA Cloud
By obtaining the CompTIA Cloud Essentials certification, you can enhance your knowledge and skills in cloud computing. This certification equips you with the necessary tools to excel in cloud technology and stand out in the competitive IT industry. It opens up a world of opportunities for you to explore cloud services, cloud security, and cloud career prospects.
Cloud Technology
In today's digital age, cloud technology plays a critical role in driving innovation and transforming businesses. With the CompTIA Cloud Essentials certification, you can gain a deeper understanding of cloud services, cloud deployment models, and cloud management practices. This certification empowers you to leverage cloud technology effectively and enhance your contribution to your organization.
Cloud Services
As a certified professional with the CompTIA Cloud Essentials certification, you are equipped to handle various cloud services and solutions. Whether it's cloud migration, cloud integration, or cloud storage, you have the knowledge and skills to navigate complex cloud environments. This certification enables you to provide value to your organization by optimizing cloud services and maximizing efficiency.
Cloud Security
One of the key components of the CompTIA Cloud Essentials certification is cloud security. This certification emphasizes the importance of maintaining a secure cloud environment and implementing robust security measures. By mastering cloud security concepts, you can safeguard your organization's data, protect against cyber threats, and ensure compliance with industry regulations.
Cloud Career Opportunities
Earning the CompTIA Cloud Essentials certification opens up a plethora of career opportunities in the IT industry. Whether you aspire to become a cloud architect, cloud administrator, or cloud consultant, this certification can pave the way for a successful and rewarding career. With the demand for cloud professionals on the rise, possessing this certification gives you a competitive edge in the job market.
How to obtain Cloud Technology Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the CompTIA Cloud Essentials certification is a valuable asset for IT professionals looking to enhance their expertise in cloud computing. By obtaining this certification, you can demonstrate your proficiency in cloud technology, advance your career prospects, and stay ahead of the curve in the rapidly evolving IT landscape. So, why wait? Take the next step in your professional journey and unlock a world of opportunities with CompTIA Cloud Essentials certification.
Read More
Are you looking to advance your career in IT and elevate your expertise in cloud computing? If so, obtaining the CompTIA Cloud Essentials certification could be a valuable investment in your professional development. In this article, we will provide you with an overview of the CompTIA Cloud Essentials certification, including the benefits, skills, and career opportunities it can bring.
Certification Overview
The CompTIA Cloud Essentials certification is designed to validate the foundational knowledge and understanding of cloud computing concepts. It covers essential cloud computing principles, including cloud computing basics, cloud concepts, and cloud fundamentals. This certification is ideal for IT professionals who want to demonstrate their expertise in cloud technology and services.
Cloud Essentials Certification
Achieving the CompTIA Cloud Essentials certification demonstrates that you have the necessary skills to understand cloud deployment models, cloud management, and cloud governance. It also signifies that you can navigate cloud migration, cloud integration, and cloud storage effectively. This certification showcases your proficiency in cloud infrastructure, cloud virtualization, and cloud implementation.
IT Certification
The CompTIA Cloud Essentials certification is a valuable addition to your IT certification portfolio. It showcases your expertise in cloud technology and your ability to implement cloud best practices. With this certification, you can demonstrate your understanding of cloud benefits, cloud risks, and cloud adoption strategies.
CompTIA Cloud
By obtaining the CompTIA Cloud Essentials certification, you can enhance your knowledge and skills in cloud computing. This certification equips you with the necessary tools to excel in cloud technology and stand out in the competitive IT industry. It opens up a world of opportunities for you to explore cloud services, cloud security, and cloud career prospects.
Cloud Technology
In today's digital age, cloud technology plays a critical role in driving innovation and transforming businesses. With the CompTIA Cloud Essentials certification, you can gain a deeper understanding of cloud services, cloud deployment models, and cloud management practices. This certification empowers you to leverage cloud technology effectively and enhance your contribution to your organization.
Cloud Services
As a certified professional with the CompTIA Cloud Essentials certification, you are equipped to handle various cloud services and solutions. Whether it's cloud migration, cloud integration, or cloud storage, you have the knowledge and skills to navigate complex cloud environments. This certification enables you to provide value to your organization by optimizing cloud services and maximizing efficiency.
Cloud Security
One of the key components of the CompTIA Cloud Essentials certification is cloud security. This certification emphasizes the importance of maintaining a secure cloud environment and implementing robust security measures. By mastering cloud security concepts, you can safeguard your organization's data, protect against cyber threats, and ensure compliance with industry regulations.
Cloud Career Opportunities
Earning the CompTIA Cloud Essentials certification opens up a plethora of career opportunities in the IT industry. Whether you aspire to become a cloud architect, cloud administrator, or cloud consultant, this certification can pave the way for a successful and rewarding career. With the demand for cloud professionals on the rise, possessing this certification gives you a competitive edge in the job market.
How to obtain Cloud Technology Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the CompTIA Cloud Essentials certification is a valuable asset for IT professionals looking to enhance their expertise in cloud computing. By obtaining this certification, you can demonstrate your proficiency in cloud technology, advance your career prospects, and stay ahead of the curve in the rapidly evolving IT landscape. So, why wait? Take the next step in your professional journey and unlock a world of opportunities with CompTIA Cloud Essentials certification.
Exploring the Role of Cisco in IoT and Smart Cities
In today's rapidly evolving digital landscape, the Internet of Things (IoT) and smart cities have become integral components of urban development and efficiency. As technology continues to advance, companies like Cisco are playing a pivotal role in shaping the way cities operate and function. So, what exactly is Cisco's role in IoT and smart cities, and how is their technology revolutionizing urban development?
Cisco: A Leader in Connectivity Solutions
Cisco is a renowned global technology company that specializes in networking, communication, and automation solutions. With a strong focus on innovation and digital transformation, Cisco has positioned itself as a leader in providing connectivity solutions for IoT and smart city initiatives.
One of the key areas where Cisco excels is in providing infrastructure and networking solutions that enable seamless connectivity between sensors, devices, and cloud computing platforms. By leveraging their expertise in data analysis and security, Cisco is able to create robust and reliable networks that support the growing demands of smart cities.
The Power of IoT and Smart Technology
IoT technology is revolutionizing the way we interact with our surroundings. By connecting everyday devices to the internet, cities can collect real-time data and analyze it to make more informed decisions. This data-driven approach allows for greater efficiency, sustainability, and overall improvement in the quality of life for residents.
Cisco's IoT solutions enable cities to implement smart infrastructure that can monitor and manage various aspects of urban life, such as transportation, energy usage, and public safety. By integrating sensors, devices, and cloud computing capabilities, Cisco helps cities optimize their operations and deliver services more effectively.
Cisco Services for Smart Cities
Cisco offers a wide range of services designed specifically for smart cities, including:
-
Security Solutions: Cisco provides robust security solutions to protect data and infrastructure from cyber threats.
-
Partnerships and Collaborations: Cisco partners with other technology companies to create integrated solutions that address the unique needs of smart cities.
-
Artificial Intelligence and Big Data: Cisco leverages AI and big data analytics to help cities make sense of the vast amount of data generated by IoT devices.
-
Industry 4.0: Cisco is at the forefront of the Industry 4.0 revolution, helping cities embrace automation and digitalization for increased efficiency.
-
Remote Monitoring: Cisco's remote monitoring solutions enable cities to track assets and infrastructure in real-time, ensuring smooth operations.
The Future of Smart Cities with Cisco
As we look to the future, the role of Cisco in IoT and smart cities will only continue to grow. By providing innovative connectivity solutions and leveraging cutting-edge technologies, Cisco is helping to shape the cities of tomorrow. With a focus on efficiency, sustainability, and connectivity, Cisco is driving urban development forward and creating a more connected world.
How to obtain Cisco Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Cisco's expertise and authority in IoT and smart cities technology make them a key player in the digital transformation of urban environments. Their commitment to innovation, connectivity solutions, and security is paving the way for smarter, more efficient cities around the globe.
Read More
In today's rapidly evolving digital landscape, the Internet of Things (IoT) and smart cities have become integral components of urban development and efficiency. As technology continues to advance, companies like Cisco are playing a pivotal role in shaping the way cities operate and function. So, what exactly is Cisco's role in IoT and smart cities, and how is their technology revolutionizing urban development?
Cisco: A Leader in Connectivity Solutions
Cisco is a renowned global technology company that specializes in networking, communication, and automation solutions. With a strong focus on innovation and digital transformation, Cisco has positioned itself as a leader in providing connectivity solutions for IoT and smart city initiatives.
One of the key areas where Cisco excels is in providing infrastructure and networking solutions that enable seamless connectivity between sensors, devices, and cloud computing platforms. By leveraging their expertise in data analysis and security, Cisco is able to create robust and reliable networks that support the growing demands of smart cities.
The Power of IoT and Smart Technology
IoT technology is revolutionizing the way we interact with our surroundings. By connecting everyday devices to the internet, cities can collect real-time data and analyze it to make more informed decisions. This data-driven approach allows for greater efficiency, sustainability, and overall improvement in the quality of life for residents.
Cisco's IoT solutions enable cities to implement smart infrastructure that can monitor and manage various aspects of urban life, such as transportation, energy usage, and public safety. By integrating sensors, devices, and cloud computing capabilities, Cisco helps cities optimize their operations and deliver services more effectively.
Cisco Services for Smart Cities
Cisco offers a wide range of services designed specifically for smart cities, including:
-
Security Solutions: Cisco provides robust security solutions to protect data and infrastructure from cyber threats.
-
Partnerships and Collaborations: Cisco partners with other technology companies to create integrated solutions that address the unique needs of smart cities.
-
Artificial Intelligence and Big Data: Cisco leverages AI and big data analytics to help cities make sense of the vast amount of data generated by IoT devices.
-
Industry 4.0: Cisco is at the forefront of the Industry 4.0 revolution, helping cities embrace automation and digitalization for increased efficiency.
-
Remote Monitoring: Cisco's remote monitoring solutions enable cities to track assets and infrastructure in real-time, ensuring smooth operations.
The Future of Smart Cities with Cisco
As we look to the future, the role of Cisco in IoT and smart cities will only continue to grow. By providing innovative connectivity solutions and leveraging cutting-edge technologies, Cisco is helping to shape the cities of tomorrow. With a focus on efficiency, sustainability, and connectivity, Cisco is driving urban development forward and creating a more connected world.
How to obtain Cisco Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Cisco's expertise and authority in IoT and smart cities technology make them a key player in the digital transformation of urban environments. Their commitment to innovation, connectivity solutions, and security is paving the way for smarter, more efficient cities around the globe.
Shield Your Business: Proven IT Risk Management Tactics for a Secure Future
In today's rapidly evolving digital landscape, businesses of all sizes face a multitude of IT risks that can pose significant threats to their operations, finances, and reputation. From cyber attract and data breaches to hardware failures and natural disasters, the potential risks are diverse and ever-present. To safeguard your business and ensure a secure future, it is essential to implement robust IT risk management strategies. In this article, we will explore proven tactics for mitigating IT risks and protecting your business from potential vulnerabilities.
Understanding IT Risk Management
IT risk management is the process of identifying, assessing, and mitigating risks related to the use of information technology within an organization. By taking proactive steps to identify and address potential threats, businesses can minimize the impact of IT-related incidents and ensure continuity of operations. Effective IT risk management involves a combination of policies, procedures, technologies, and employee training to create a secure and resilient IT environment.
Assessing IT Risks
The first step in effective IT risk management is to conduct a comprehensive assessment of potential risks facing your business. This involves identifying all possible threats, vulnerabilities, and potential impacts on your organization. By understanding the specific risks you face, you can prioritize your efforts and allocate resources effectively to address the most critical areas of concern.
What are the key benefits of conducting an IT risk assessment?
A thorough IT risk assessment can help you identify vulnerabilities in your systems, prioritize remediation efforts, and ensure compliance with regulatory requirements.
How can businesses conduct an IT risk assessment?
Businesses can conduct an IT risk assessment by using a combination of automated tools, manual inspections, vulnerability scans, and risk analysis techniques.
Implementing Risk Mitigation Strategies
Once you have identified and assessed the IT risks facing your business, the next step is to implement mitigation strategies to address these vulnerabilities. This may involve implementing security controls, updating software and hardware, and establishing backup and recovery processes to minimize the impact of potential incidents.
What are some effective risk mitigation strategies for businesses?
Some effective risk mitigation strategies include implementing robust access controls, encrypting sensitive data, conducting regular security audits, and providing ongoing staff training on cyber security best practices.
Monitoring and Continuous Improvement
Effective IT risk management is an ongoing process that requires constant vigilance and monitoring to ensure the security and resilience of your IT systems. By regularly monitoring for potential risks, implementing updates and patches, and conducting regular security assessments, businesses can adapt to evolving threats and maintain a strong security posture.
How can businesses ensure continuous improvement in their IT risk management practices?
Businesses can ensure continuous improvement by staying informed about the latest cyber security trends, investing in advanced security technologies, and conducting regular reviews of their IT risk management policies and procedures.
How to obtain IT Service Management & Governace Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Protecting your business from IT risks requires a proactive and comprehensive approach to risk management. By understanding the specific risks facing your organization, implementing effective mitigation strategies, and continuously monitoring for potential threats, you can shield your business from harm and ensure a secure future.
Read More
In today's rapidly evolving digital landscape, businesses of all sizes face a multitude of IT risks that can pose significant threats to their operations, finances, and reputation. From cyber attract and data breaches to hardware failures and natural disasters, the potential risks are diverse and ever-present. To safeguard your business and ensure a secure future, it is essential to implement robust IT risk management strategies. In this article, we will explore proven tactics for mitigating IT risks and protecting your business from potential vulnerabilities.
Understanding IT Risk Management
IT risk management is the process of identifying, assessing, and mitigating risks related to the use of information technology within an organization. By taking proactive steps to identify and address potential threats, businesses can minimize the impact of IT-related incidents and ensure continuity of operations. Effective IT risk management involves a combination of policies, procedures, technologies, and employee training to create a secure and resilient IT environment.
Assessing IT Risks
The first step in effective IT risk management is to conduct a comprehensive assessment of potential risks facing your business. This involves identifying all possible threats, vulnerabilities, and potential impacts on your organization. By understanding the specific risks you face, you can prioritize your efforts and allocate resources effectively to address the most critical areas of concern.
What are the key benefits of conducting an IT risk assessment?
A thorough IT risk assessment can help you identify vulnerabilities in your systems, prioritize remediation efforts, and ensure compliance with regulatory requirements.
How can businesses conduct an IT risk assessment?
Businesses can conduct an IT risk assessment by using a combination of automated tools, manual inspections, vulnerability scans, and risk analysis techniques.
Implementing Risk Mitigation Strategies
Once you have identified and assessed the IT risks facing your business, the next step is to implement mitigation strategies to address these vulnerabilities. This may involve implementing security controls, updating software and hardware, and establishing backup and recovery processes to minimize the impact of potential incidents.
What are some effective risk mitigation strategies for businesses?
Some effective risk mitigation strategies include implementing robust access controls, encrypting sensitive data, conducting regular security audits, and providing ongoing staff training on cyber security best practices.
Monitoring and Continuous Improvement
Effective IT risk management is an ongoing process that requires constant vigilance and monitoring to ensure the security and resilience of your IT systems. By regularly monitoring for potential risks, implementing updates and patches, and conducting regular security assessments, businesses can adapt to evolving threats and maintain a strong security posture.
How can businesses ensure continuous improvement in their IT risk management practices?
Businesses can ensure continuous improvement by staying informed about the latest cyber security trends, investing in advanced security technologies, and conducting regular reviews of their IT risk management policies and procedures.
How to obtain IT Service Management & Governace Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Protecting your business from IT risks requires a proactive and comprehensive approach to risk management. By understanding the specific risks facing your organization, implementing effective mitigation strategies, and continuously monitoring for potential threats, you can shield your business from harm and ensure a secure future.
Navigating the Digital Landscape: A Beginner's Guide to IT Governance Frameworks
In today's fast-paced digital world, it is more important than ever for organizations to have a solid IT governance framework in place. Navigating the complex digital landscape can be overwhelming for beginners, but with the right guidance and knowledge, you can successfully implement an effective IT governance framework to protect your organization from potential cyber threats and ensure compliance with regulations.
Understanding IT Governance Frameworks
IT governance frameworks are essentially a set of guidelines and practices that organizations follow to ensure that their IT systems and processes are aligned with business objectives. These frameworks help organizations make informed decisions regarding technology strategy, cybersecurity policies, compliance, risk management, data protection, information technology controls, and best practices.
Why is IT Governance Important for Beginners?
As a beginner in the digital landscape, it is crucial to understand the importance of IT governance. Without a proper framework in place, organizations are vulnerable to cyber-attacks, data breaches, and other IT-related risks. By implementing an IT governance framework, beginners can ensure that their organization's IT systems are secure, compliant, and aligned with business goals.
Key Components of IT Governance Frameworks
-
Regulations: IT governance frameworks help organizations comply with industry regulations and standards to avoid legal consequences.
-
Framework Implementation: Beginners can use frameworks such as COBIT, ITIL, or NIST to implement IT governance best practices.
-
Audit Trails: Keeping detailed audit trails helps organizations track changes and monitor system activities effectively.
-
Guidelines and Procedures: Following established guidelines and procedures ensures consistency and efficiency in IT operations.
-
Software, Hardware, Network Security: Implementing robust security measures across software, hardware, and networks is essential for protecting sensitive data.
-
Incident Response: Having a well-defined incident response plan in place can help organizations mitigate the impact of cybersecurity incidents.
-
Training and Documentation: Training employees on IT governance practices and documenting processes are critical for successful framework implementation.
Choosing the Right Governance Structure
There are various governance models and practices to choose from, depending on the organization's size, industry, and specific needs. Beginners should carefully assess different governance standards before selecting a framework that best suits their organization.
Common Governance Models
-
Centralized Governance: In this model, decision-making authority is centralized, allowing for consistency and control over IT operations.
-
Decentralized Governance: Decentralized governance allows individual departments to make decisions based on their specific requirements.
-
Hybrid Governance: A combination of centralized and decentralized governance models can offer flexibility and efficiency in IT management.
How to obtain IT Service Management & Governance Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, Navigating the digital landscape as a beginner can be challenging, but with a solid IT governance framework in place, you can effectively manage risks, ensure compliance, and align technology with business objectives. By following best practices, implementing robust security measures, and choosing the right governance structure, beginners can successfully navigate the complex world of IT governance.
Read More
In today's fast-paced digital world, it is more important than ever for organizations to have a solid IT governance framework in place. Navigating the complex digital landscape can be overwhelming for beginners, but with the right guidance and knowledge, you can successfully implement an effective IT governance framework to protect your organization from potential cyber threats and ensure compliance with regulations.
Understanding IT Governance Frameworks
IT governance frameworks are essentially a set of guidelines and practices that organizations follow to ensure that their IT systems and processes are aligned with business objectives. These frameworks help organizations make informed decisions regarding technology strategy, cybersecurity policies, compliance, risk management, data protection, information technology controls, and best practices.
Why is IT Governance Important for Beginners?
As a beginner in the digital landscape, it is crucial to understand the importance of IT governance. Without a proper framework in place, organizations are vulnerable to cyber-attacks, data breaches, and other IT-related risks. By implementing an IT governance framework, beginners can ensure that their organization's IT systems are secure, compliant, and aligned with business goals.
Key Components of IT Governance Frameworks
-
Regulations: IT governance frameworks help organizations comply with industry regulations and standards to avoid legal consequences.
-
Framework Implementation: Beginners can use frameworks such as COBIT, ITIL, or NIST to implement IT governance best practices.
-
Audit Trails: Keeping detailed audit trails helps organizations track changes and monitor system activities effectively.
-
Guidelines and Procedures: Following established guidelines and procedures ensures consistency and efficiency in IT operations.
-
Software, Hardware, Network Security: Implementing robust security measures across software, hardware, and networks is essential for protecting sensitive data.
-
Incident Response: Having a well-defined incident response plan in place can help organizations mitigate the impact of cybersecurity incidents.
-
Training and Documentation: Training employees on IT governance practices and documenting processes are critical for successful framework implementation.
Choosing the Right Governance Structure
There are various governance models and practices to choose from, depending on the organization's size, industry, and specific needs. Beginners should carefully assess different governance standards before selecting a framework that best suits their organization.
Common Governance Models
-
Centralized Governance: In this model, decision-making authority is centralized, allowing for consistency and control over IT operations.
-
Decentralized Governance: Decentralized governance allows individual departments to make decisions based on their specific requirements.
-
Hybrid Governance: A combination of centralized and decentralized governance models can offer flexibility and efficiency in IT management.
How to obtain IT Service Management & Governance Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, Navigating the digital landscape as a beginner can be challenging, but with a solid IT governance framework in place, you can effectively manage risks, ensure compliance, and align technology with business objectives. By following best practices, implementing robust security measures, and choosing the right governance structure, beginners can successfully navigate the complex world of IT governance.
IT Project Management Methodologies: Finding the Right Approach for Your Team
In the world of information technology, project management methodologies play a crucial role in ensuring the successful completion of projects. From Agile to Waterfall to Hybrid approaches, choosing the right methodology can greatly impact the outcome of your IT projects. In this article, we will explore the different IT project management methodologies available and how you can determine which one is best suited for your team.
What are IT Project Management Methodologies?
IT project management methodologies are frameworks that guide the planning, execution, and monitoring of IT projects. These methodologies provide structure and guidelines for how projects should be managed from start to finish. By following a defined methodology, project managers can ensure that projects are completed on time, within budget, and meet the desired quality standards.
Agile Methodology
Agile is a popular iterative approach to project management that emphasizes flexibility and adaptability. In Agile methodology, projects are broken down into smaller, manageable tasks known as sprints. Teams work collaboratively, responding to changes and feedback quickly throughout the project. Agile is ideal for projects where requirements are likely to change or evolve over time.
Waterfall Methodology
Waterfall is a more traditional project management approach that follows a linear, sequential process. In this methodology, each phase of the project must be completed before moving on to the next phase. Waterfall is best suited for projects with well-defined requirements and a clear scope. While it may lack the flexibility of Agile, Waterfall can be effective for projects where change is minimal.
Hybrid Methodology
Hybrid methodology combines elements of both Agile and Waterfall approaches. This flexible approach allows teams to tailor the project management process to meet the specific needs of the project. For example, teams may choose to use Agile for certain phases of the project and then switch to a more Waterfall-like approach for other phases. Hybrid methodology is ideal for teams that require a mix of flexibility and structure.
How to Choose the Right Methodology for Your Team
When selecting an IT project management methodology for your team, it's essential to consider factors such as the project's scope, requirements, and team dynamics. Here are some tips to help you choose the right methodology:
-
Assess Your Project: Evaluate the size, complexity, and uncertainty of your project to determine which methodology aligns best with your needs.
-
Understand Your Team: Consider your team's experience, skills, and working style to ensure that the chosen methodology is a good fit.
-
Client Requirements: Take into account any specific requirements or preferences of your clients or stakeholders when deciding on a methodology.
-
Iterate and Adapt: Don't be afraid to experiment with different methodologies and adapt them to better suit your team and project needs.
By carefully considering these factors, you can select the IT project management methodology that will set your team up for success.
How to obtain IT Service Mangement & Governance Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, Choosing the right IT project management methodology is crucial for the success of your projects. Whether you opt for Agile, Waterfall, Hybrid, or another approach altogether, selecting the methodology that aligns best with your team's needs and project requirements is key. By following the guidelines outlined in this article, you can confidently navigate the world of IT project management and lead your team to project success.
Read More
In the world of information technology, project management methodologies play a crucial role in ensuring the successful completion of projects. From Agile to Waterfall to Hybrid approaches, choosing the right methodology can greatly impact the outcome of your IT projects. In this article, we will explore the different IT project management methodologies available and how you can determine which one is best suited for your team.
What are IT Project Management Methodologies?
IT project management methodologies are frameworks that guide the planning, execution, and monitoring of IT projects. These methodologies provide structure and guidelines for how projects should be managed from start to finish. By following a defined methodology, project managers can ensure that projects are completed on time, within budget, and meet the desired quality standards.
Agile Methodology
Agile is a popular iterative approach to project management that emphasizes flexibility and adaptability. In Agile methodology, projects are broken down into smaller, manageable tasks known as sprints. Teams work collaboratively, responding to changes and feedback quickly throughout the project. Agile is ideal for projects where requirements are likely to change or evolve over time.
Waterfall Methodology
Waterfall is a more traditional project management approach that follows a linear, sequential process. In this methodology, each phase of the project must be completed before moving on to the next phase. Waterfall is best suited for projects with well-defined requirements and a clear scope. While it may lack the flexibility of Agile, Waterfall can be effective for projects where change is minimal.
Hybrid Methodology
Hybrid methodology combines elements of both Agile and Waterfall approaches. This flexible approach allows teams to tailor the project management process to meet the specific needs of the project. For example, teams may choose to use Agile for certain phases of the project and then switch to a more Waterfall-like approach for other phases. Hybrid methodology is ideal for teams that require a mix of flexibility and structure.
How to Choose the Right Methodology for Your Team
When selecting an IT project management methodology for your team, it's essential to consider factors such as the project's scope, requirements, and team dynamics. Here are some tips to help you choose the right methodology:
-
Assess Your Project: Evaluate the size, complexity, and uncertainty of your project to determine which methodology aligns best with your needs.
-
Understand Your Team: Consider your team's experience, skills, and working style to ensure that the chosen methodology is a good fit.
-
Client Requirements: Take into account any specific requirements or preferences of your clients or stakeholders when deciding on a methodology.
-
Iterate and Adapt: Don't be afraid to experiment with different methodologies and adapt them to better suit your team and project needs.
By carefully considering these factors, you can select the IT project management methodology that will set your team up for success.
How to obtain IT Service Mangement & Governance Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, Choosing the right IT project management methodology is crucial for the success of your projects. Whether you opt for Agile, Waterfall, Hybrid, or another approach altogether, selecting the methodology that aligns best with your team's needs and project requirements is key. By following the guidelines outlined in this article, you can confidently navigate the world of IT project management and lead your team to project success.
Maximizing ROI with Data-Driven Marketing Strategies
Are you looking to boost your return on investment (ROI) through effective marketing tactics? In today's digital age, harnessing the power of data-driven strategies is essential for maximizing your marketing efforts. By utilizing data analysis, conversion rate optimization, and targeted advertising, businesses can enhance customer engagement and drive successful marketing campaigns. In this article, we will explore how incorporating data-driven marketing strategies can help you achieve a higher ROI and ensure the success of your marketing initiatives.
Data Analysis and Customer Segmentation
Data analysis is the cornerstone of data-driven marketing strategies. By leveraging market research, customer behavior analysis, and performance tracking, businesses can gain valuable insights into their target audience. Customer segmentation allows businesses to categorize their customers based on demographics, interests, and buying behavior. This segmentation enables personalized marketing campaigns that resonate with specific customer groups, leading to higher conversion rates and increased ROI.
Conversion Rate Optimization and A/B Testing
Conversion rate optimization (CRO) focuses on improving the percentage of website visitors who take a desired action, such as making a purchase or signing up for a newsletter. By conducting A/B testing, businesses can compare different versions of their marketing campaigns to determine which one yields the best results. This iterative process helps businesses refine their marketing tactics and optimize their conversion rates, ultimately increasing ROI.
How can A/B testing benefit your marketing campaigns?
A/B testing allows businesses to experiment with different elements of their marketing campaigns, such as headlines, images, and calls to action. By testing these variations on a sample of their audience, businesses can identify which elements drive the most conversions. This data-driven approach enables businesses to make informed decisions about their marketing strategies and continually improve their ROI.
Predictive Modeling and Marketing Analytics
Predictive modeling uses historical data to forecast future trends and behaviors. By analyzing past performance and customer data, businesses can predict which marketing strategies will be most effective in the future. Marketing analytics provides real-time insights into the performance of marketing campaigns, allowing businesses to adjust their tactics as needed. With predictive modeling and marketing analytics, businesses can make strategic decisions that maximize ROI and drive business growth.
How can predictive modeling improve your marketing efforts?
Predictive modeling helps businesses identify patterns and trends in their data, allowing them to anticipate customer behavior and preferences. By leveraging predictive insights, businesses can tailor their marketing campaigns to meet the specific needs of their target audience, resulting in higher engagement and conversion rates. This data-driven approach empowers businesses to make informed decisions that drive success and maximize ROI.
Data Visualization and Marketing Optimization
Data visualization transforms complex data sets into easy-to-understand visualizations, such as charts and graphs. By visualizing data insights, businesses can quickly identify trends and opportunities for optimization. This visual representation of data enables businesses to track the performance of their marketing campaigns and make data-driven decisions to improve ROI.
How does data visualization impact marketing optimization?
Data visualization provides businesses with a clear and concise view of their marketing performance, allowing them to identify areas for improvement and optimization. By visualizing key metrics, such as conversion rates and customer engagement, businesses can quickly assess the effectiveness of their marketing tactics and make adjustments as needed. This data-driven approach to marketing optimization enables businesses to maximize ROI and achieve their marketing goals.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, data-driven marketing strategies offer businesses a powerful tool for maximizing ROI and driving successful marketing campaigns. By combining data analysis, customer segmentation, and predictive modeling, businesses can optimize their marketing efforts and achieve higher conversion rates. With the right tools and techniques, businesses can harness the power of data to drive strategic decision-making and achieve sustainable growth. Don't miss out on the opportunity to leverage data-driven marketing strategies and unlock your business's full potential. Start maximizing your ROI today.
Read More
Are you looking to boost your return on investment (ROI) through effective marketing tactics? In today's digital age, harnessing the power of data-driven strategies is essential for maximizing your marketing efforts. By utilizing data analysis, conversion rate optimization, and targeted advertising, businesses can enhance customer engagement and drive successful marketing campaigns. In this article, we will explore how incorporating data-driven marketing strategies can help you achieve a higher ROI and ensure the success of your marketing initiatives.
Data Analysis and Customer Segmentation
Data analysis is the cornerstone of data-driven marketing strategies. By leveraging market research, customer behavior analysis, and performance tracking, businesses can gain valuable insights into their target audience. Customer segmentation allows businesses to categorize their customers based on demographics, interests, and buying behavior. This segmentation enables personalized marketing campaigns that resonate with specific customer groups, leading to higher conversion rates and increased ROI.
Conversion Rate Optimization and A/B Testing
Conversion rate optimization (CRO) focuses on improving the percentage of website visitors who take a desired action, such as making a purchase or signing up for a newsletter. By conducting A/B testing, businesses can compare different versions of their marketing campaigns to determine which one yields the best results. This iterative process helps businesses refine their marketing tactics and optimize their conversion rates, ultimately increasing ROI.
How can A/B testing benefit your marketing campaigns?
A/B testing allows businesses to experiment with different elements of their marketing campaigns, such as headlines, images, and calls to action. By testing these variations on a sample of their audience, businesses can identify which elements drive the most conversions. This data-driven approach enables businesses to make informed decisions about their marketing strategies and continually improve their ROI.
Predictive Modeling and Marketing Analytics
Predictive modeling uses historical data to forecast future trends and behaviors. By analyzing past performance and customer data, businesses can predict which marketing strategies will be most effective in the future. Marketing analytics provides real-time insights into the performance of marketing campaigns, allowing businesses to adjust their tactics as needed. With predictive modeling and marketing analytics, businesses can make strategic decisions that maximize ROI and drive business growth.
How can predictive modeling improve your marketing efforts?
Predictive modeling helps businesses identify patterns and trends in their data, allowing them to anticipate customer behavior and preferences. By leveraging predictive insights, businesses can tailor their marketing campaigns to meet the specific needs of their target audience, resulting in higher engagement and conversion rates. This data-driven approach empowers businesses to make informed decisions that drive success and maximize ROI.
Data Visualization and Marketing Optimization
Data visualization transforms complex data sets into easy-to-understand visualizations, such as charts and graphs. By visualizing data insights, businesses can quickly identify trends and opportunities for optimization. This visual representation of data enables businesses to track the performance of their marketing campaigns and make data-driven decisions to improve ROI.
How does data visualization impact marketing optimization?
Data visualization provides businesses with a clear and concise view of their marketing performance, allowing them to identify areas for improvement and optimization. By visualizing key metrics, such as conversion rates and customer engagement, businesses can quickly assess the effectiveness of their marketing tactics and make adjustments as needed. This data-driven approach to marketing optimization enables businesses to maximize ROI and achieve their marketing goals.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, data-driven marketing strategies offer businesses a powerful tool for maximizing ROI and driving successful marketing campaigns. By combining data analysis, customer segmentation, and predictive modeling, businesses can optimize their marketing efforts and achieve higher conversion rates. With the right tools and techniques, businesses can harness the power of data to drive strategic decision-making and achieve sustainable growth. Don't miss out on the opportunity to leverage data-driven marketing strategies and unlock your business's full potential. Start maximizing your ROI today.
Unveiling Cyber Threats and Criminal Activities
In today's digital age, cyber threats and criminal activities have become a growing concern for individuals and businesses alike. With the rise of technology, the internet has become a breeding ground for malicious actors looking to exploit vulnerabilities and steal sensitive information. From data breaches and malware attacks to phishing scams and identity theft, the world of cybersecurity is constantly evolving to stay one step ahead of cybercriminals.
The Landscape of Cyber Threats
Cyber threats come in many forms, each posing a unique risk to our online security. Hackers, often operating from the dark web, are constantly scanning for weaknesses to infiltrate systems and networks. Once inside, they may deploy malware to gain access to sensitive data or launch phishing attacks to trick individuals into revealing personal information. The growing trend of ransomware has also become a significant threat, with cybercriminals locking users out of their own systems until a ransom is paid.
One of the most prevalent forms of cybercrime is online fraud, where criminals use various tactics to deceive individuals into giving up their money or personal information. Whether through fake websites, fraudulent emails, or social engineering techniques, online fraudsters are constantly looking for new ways to exploit unsuspecting victims.
Protecting Against Cyber Attacks
To combat the ever-evolving landscape of cyber threats, organizations must prioritize cybersecurity measures to protect sensitive data and prevent unauthorized access. Implementing robust network security protocols, conducting regular vulnerability assessments, and investing in threat intelligence are essential steps in safeguarding against cyber attacks.
Furthermore, fostering a culture of cybersecurity awareness among employees is crucial in preventing insider threats and ensuring that all staff members are vigilant in detecting potential risks. By educating users on best practices for online safety and implementing strong password policies, businesses can reduce the likelihood of falling victim to cybercriminal activities.
Responding to Cyber Incidents
In the event of a cyber incident, having a well-defined incident response plan in place is essential for minimizing the impact and restoring normal operations promptly. A swift and coordinated response to a data breach or malware attack can mean the difference between containing the damage and suffering widespread repercussions.
Cyber defense strategies such as cyber risk management and cyber resilience are also essential components of an effective cybersecurity program. By proactively identifying vulnerabilities, preparing for potential attacks, and promptly responding to incidents, organizations can bolster their defenses and mitigate the impact of cyber threats.
How to obtain Cyber Security Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, As cyber threats and criminal activities continue to pose significant risks in the digital landscape, staying informed and proactive in cybersecurity practices is more critical than ever. By understanding the various forms of cyber threats, implementing robust security measures, and maintaining a vigilant stance against malicious actors, individuals and businesses can better protect themselves from falling victim to cybercrime. Remember, when it comes to cybersecurity, prevention is always better than cure.
Read More
In today's digital age, cyber threats and criminal activities have become a growing concern for individuals and businesses alike. With the rise of technology, the internet has become a breeding ground for malicious actors looking to exploit vulnerabilities and steal sensitive information. From data breaches and malware attacks to phishing scams and identity theft, the world of cybersecurity is constantly evolving to stay one step ahead of cybercriminals.
The Landscape of Cyber Threats
Cyber threats come in many forms, each posing a unique risk to our online security. Hackers, often operating from the dark web, are constantly scanning for weaknesses to infiltrate systems and networks. Once inside, they may deploy malware to gain access to sensitive data or launch phishing attacks to trick individuals into revealing personal information. The growing trend of ransomware has also become a significant threat, with cybercriminals locking users out of their own systems until a ransom is paid.
One of the most prevalent forms of cybercrime is online fraud, where criminals use various tactics to deceive individuals into giving up their money or personal information. Whether through fake websites, fraudulent emails, or social engineering techniques, online fraudsters are constantly looking for new ways to exploit unsuspecting victims.
Protecting Against Cyber Attacks
To combat the ever-evolving landscape of cyber threats, organizations must prioritize cybersecurity measures to protect sensitive data and prevent unauthorized access. Implementing robust network security protocols, conducting regular vulnerability assessments, and investing in threat intelligence are essential steps in safeguarding against cyber attacks.
Furthermore, fostering a culture of cybersecurity awareness among employees is crucial in preventing insider threats and ensuring that all staff members are vigilant in detecting potential risks. By educating users on best practices for online safety and implementing strong password policies, businesses can reduce the likelihood of falling victim to cybercriminal activities.
Responding to Cyber Incidents
In the event of a cyber incident, having a well-defined incident response plan in place is essential for minimizing the impact and restoring normal operations promptly. A swift and coordinated response to a data breach or malware attack can mean the difference between containing the damage and suffering widespread repercussions.
Cyber defense strategies such as cyber risk management and cyber resilience are also essential components of an effective cybersecurity program. By proactively identifying vulnerabilities, preparing for potential attacks, and promptly responding to incidents, organizations can bolster their defenses and mitigate the impact of cyber threats.
How to obtain Cyber Security Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, As cyber threats and criminal activities continue to pose significant risks in the digital landscape, staying informed and proactive in cybersecurity practices is more critical than ever. By understanding the various forms of cyber threats, implementing robust security measures, and maintaining a vigilant stance against malicious actors, individuals and businesses can better protect themselves from falling victim to cybercrime. Remember, when it comes to cybersecurity, prevention is always better than cure.
Salesforce Data Migration Best Practices: Ensuring a Smooth Transition
Are you considering migrating data to Salesforce? Whether you are moving from another CRM system or upgrading from an older version of Salesforce, data migration can be a complex process. However, with the right strategies and tools in place, you can ensure a smooth transition. In this article, we will discuss the best practices for Salesforce data migration to help you avoid common pitfalls and achieve a successful migration.
Understanding the Salesforce Data Migration Process
Before diving into the data migration process, it is important to have a clear understanding of the steps involved. Here are the key stages of Salesforce data migration:
-
Assessment: Evaluate your current data, identify what needs to be migrated, and assess the quality of your data.
-
Planning: Develop a detailed migration plan, including timelines, responsibilities, and resources required.
-
Data Mapping: Map out how your existing data will align with Salesforce fields and objects.
-
Data Cleansing: Cleanse and de-duplicate your data to ensure accuracy and consistency.
-
Testing: Test the migration process with a small subset of data to identify any issues before the full migration.
-
Execution: Migrate your data to Salesforce according to the migration plan.
-
Validation: Validate the migrated data to ensure it is accurate and complete.
Key Strategies for Successful Data Migration
To ensure a successful data migration to Salesforce, consider the following best practices:
-
Engage Stakeholders: Involve key stakeholders from different departments in the migration process to ensure all requirements are met.
-
Train Users: Provide training to users on how to use Salesforce effectively after the migration.
-
Use Data Migration Tools: Utilize data migration tools such as Salesforce Data Loader or Dataloader.io to streamline the migration process.
-
Monitor Progress: Keep track of the migration progress and address any issues promptly.
-
Backup Data: Make sure to back up your data before the migration to avoid any loss.
Common Challenges and Risks
Despite following best practices, data migration can still pose challenges and risks. Some common challenges to watch out for include:
-
Data Mapping Errors: Incorrectly mapping data fields can lead to data loss or inaccuracies.
-
Integration Issues: Ensuring seamless integration with other systems can be challenging.
-
Data Security: Protecting sensitive data during the migration process is crucial.
To mitigate these risks, it is important to plan meticulously, test thoroughly, and monitor the migration closely.
How to obtain Salesforce Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, Data migration to Salesforce can be a daunting task, but with proper planning and execution, you can ensure a smooth transition. By following best practices, utilizing the right tools, and addressing challenges proactively, you can achieve a successful data migration that sets you up for long-term success in Salesforce. Make sure to stay informed about the latest data migration techniques and tools to stay ahead of the curve.
Read More
Are you considering migrating data to Salesforce? Whether you are moving from another CRM system or upgrading from an older version of Salesforce, data migration can be a complex process. However, with the right strategies and tools in place, you can ensure a smooth transition. In this article, we will discuss the best practices for Salesforce data migration to help you avoid common pitfalls and achieve a successful migration.
Understanding the Salesforce Data Migration Process
Before diving into the data migration process, it is important to have a clear understanding of the steps involved. Here are the key stages of Salesforce data migration:
-
Assessment: Evaluate your current data, identify what needs to be migrated, and assess the quality of your data.
-
Planning: Develop a detailed migration plan, including timelines, responsibilities, and resources required.
-
Data Mapping: Map out how your existing data will align with Salesforce fields and objects.
-
Data Cleansing: Cleanse and de-duplicate your data to ensure accuracy and consistency.
-
Testing: Test the migration process with a small subset of data to identify any issues before the full migration.
-
Execution: Migrate your data to Salesforce according to the migration plan.
-
Validation: Validate the migrated data to ensure it is accurate and complete.
Key Strategies for Successful Data Migration
To ensure a successful data migration to Salesforce, consider the following best practices:
-
Engage Stakeholders: Involve key stakeholders from different departments in the migration process to ensure all requirements are met.
-
Train Users: Provide training to users on how to use Salesforce effectively after the migration.
-
Use Data Migration Tools: Utilize data migration tools such as Salesforce Data Loader or Dataloader.io to streamline the migration process.
-
Monitor Progress: Keep track of the migration progress and address any issues promptly.
-
Backup Data: Make sure to back up your data before the migration to avoid any loss.
Common Challenges and Risks
Despite following best practices, data migration can still pose challenges and risks. Some common challenges to watch out for include:
-
Data Mapping Errors: Incorrectly mapping data fields can lead to data loss or inaccuracies.
-
Integration Issues: Ensuring seamless integration with other systems can be challenging.
-
Data Security: Protecting sensitive data during the migration process is crucial.
To mitigate these risks, it is important to plan meticulously, test thoroughly, and monitor the migration closely.
How to obtain Salesforce Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, Data migration to Salesforce can be a daunting task, but with proper planning and execution, you can ensure a smooth transition. By following best practices, utilizing the right tools, and addressing challenges proactively, you can achieve a successful data migration that sets you up for long-term success in Salesforce. Make sure to stay informed about the latest data migration techniques and tools to stay ahead of the curve.
Agile Project Management Revolution: Microsoft Project 2024's Agile Capabilities
In today's fast-paced and ever-changing business landscape, traditional project management approaches are proving to be inadequate in meeting the demands of the modern world. This is where agile project management comes in, offering a more flexible and iterative approach to project management that focuses on delivering value to customers quickly and efficiently. Microsoft Project 2024 has revolutionized the way project teams work by incorporating agile capabilities into its platform, allowing for more efficient and collaborative project delivery.
The Rise of Agile Methodologies
Agile methodologies have gained widespread popularity in the software development industry due to their focus on adapting to change, fostering teamwork, and promoting continuous improvement. By breaking projects down into smaller, manageable chunks called sprints, teams can deliver value to customers more frequently and respond to feedback in real-time. This ensures that projects stay on track and meet the needs of stakeholders throughout the development process.
Enhancing Project Planning and Tracking
With Microsoft Project 2024's agile capabilities, project teams can now benefit from enhanced project planning and tracking features. By using the scrum framework, teams can prioritize tasks, set project milestones, and track progress in real-time. This level of visibility allows for better decision-making and ensures that projects are delivered on time and within budget.
Fostering Project Collaboration and Efficiency
One of the key benefits of agile project management is its focus on collaboration and teamwork. Microsoft Project 2024's agile tools allow team members to work together seamlessly, share knowledge, and leverage each other's strengths. This leads to improved project efficiency and allows teams to deliver high-quality results consistently.
Embracing Lean Project Management Principles
Lean project management is another key aspect of agile methodologies that Microsoft Project 2024 has incorporated into its platform. By eliminating waste, optimizing processes, and continually seeking ways to improve project delivery, teams can achieve greater success and drive innovation within their organizations. This Lean mindset fosters a culture of continuous improvement and ensures that projects are delivered with the highest level of quality and efficiency.
Leading the Agile Transformation
Project leaders play a crucial role in the agile transformation process. By embracing agile principles and techniques, project managers can guide their teams towards greater organizational agility and success. This requires a shift in mindset from traditional project leadership to a more adaptive and collaborative approach that focuses on delivering value to customers and stakeholders.
Ensuring Project Governance and Integration
Effective project governance is essential for the success of any project, regardless of its size or complexity. Microsoft Project 2024's agile integration features ensure that projects are managed in a transparent and accountable manner, with clear roles, responsibilities, and accountability. This promotes effective decision-making and ensures that projects are aligned with organizational goals and objectives.
Driving Project Innovation and Success
In today's competitive business environment, innovation is key to driving project success. By leveraging agile methodologies and Microsoft Project 2024's advanced capabilities, project teams can drive innovation, foster creativity, and deliver cutting-edge solutions to customers. This level of agility and adaptability ensures that projects stay ahead of the curve and continue to meet the ever-changing needs of the marketplace.
Agile project management is more than just a trend - it's a proven methodology that is revolutionizing the way projects are delivered. With Microsoft Project 2024's agile capabilities, project teams can benefit from enhanced project planning, teamwork, collaboration, and efficiency. By embracing agile principles and techniques, organizations can drive greater innovation, success, and project delivery. Are you ready to join the agile revolution and take your projects to the next level?
How to obtain Microsoft Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Microsoft Project 2024's agile capabilities are shaping the future of project management by incorporating agile methodologies, fostering teamwork, enhancing project planning and tracking, promoting project collaboration and efficiency, embracing Lean project management principles, leading the agile transformation, ensuring project governance and integration, and driving project innovation and success.
Read More
In today's fast-paced and ever-changing business landscape, traditional project management approaches are proving to be inadequate in meeting the demands of the modern world. This is where agile project management comes in, offering a more flexible and iterative approach to project management that focuses on delivering value to customers quickly and efficiently. Microsoft Project 2024 has revolutionized the way project teams work by incorporating agile capabilities into its platform, allowing for more efficient and collaborative project delivery.
The Rise of Agile Methodologies
Agile methodologies have gained widespread popularity in the software development industry due to their focus on adapting to change, fostering teamwork, and promoting continuous improvement. By breaking projects down into smaller, manageable chunks called sprints, teams can deliver value to customers more frequently and respond to feedback in real-time. This ensures that projects stay on track and meet the needs of stakeholders throughout the development process.
Enhancing Project Planning and Tracking
With Microsoft Project 2024's agile capabilities, project teams can now benefit from enhanced project planning and tracking features. By using the scrum framework, teams can prioritize tasks, set project milestones, and track progress in real-time. This level of visibility allows for better decision-making and ensures that projects are delivered on time and within budget.
Fostering Project Collaboration and Efficiency
One of the key benefits of agile project management is its focus on collaboration and teamwork. Microsoft Project 2024's agile tools allow team members to work together seamlessly, share knowledge, and leverage each other's strengths. This leads to improved project efficiency and allows teams to deliver high-quality results consistently.
Embracing Lean Project Management Principles
Lean project management is another key aspect of agile methodologies that Microsoft Project 2024 has incorporated into its platform. By eliminating waste, optimizing processes, and continually seeking ways to improve project delivery, teams can achieve greater success and drive innovation within their organizations. This Lean mindset fosters a culture of continuous improvement and ensures that projects are delivered with the highest level of quality and efficiency.
Leading the Agile Transformation
Project leaders play a crucial role in the agile transformation process. By embracing agile principles and techniques, project managers can guide their teams towards greater organizational agility and success. This requires a shift in mindset from traditional project leadership to a more adaptive and collaborative approach that focuses on delivering value to customers and stakeholders.
Ensuring Project Governance and Integration
Effective project governance is essential for the success of any project, regardless of its size or complexity. Microsoft Project 2024's agile integration features ensure that projects are managed in a transparent and accountable manner, with clear roles, responsibilities, and accountability. This promotes effective decision-making and ensures that projects are aligned with organizational goals and objectives.
Driving Project Innovation and Success
In today's competitive business environment, innovation is key to driving project success. By leveraging agile methodologies and Microsoft Project 2024's advanced capabilities, project teams can drive innovation, foster creativity, and deliver cutting-edge solutions to customers. This level of agility and adaptability ensures that projects stay ahead of the curve and continue to meet the ever-changing needs of the marketplace.
Agile project management is more than just a trend - it's a proven methodology that is revolutionizing the way projects are delivered. With Microsoft Project 2024's agile capabilities, project teams can benefit from enhanced project planning, teamwork, collaboration, and efficiency. By embracing agile principles and techniques, organizations can drive greater innovation, success, and project delivery. Are you ready to join the agile revolution and take your projects to the next level?
How to obtain Microsoft Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Microsoft Project 2024's agile capabilities are shaping the future of project management by incorporating agile methodologies, fostering teamwork, enhancing project planning and tracking, promoting project collaboration and efficiency, embracing Lean project management principles, leading the agile transformation, ensuring project governance and integration, and driving project innovation and success.
The Role of Google Cloud Platform Fundamentals CP100A in Digital Transformation Strategies
Are you looking to enhance your digital transformation strategies with the power of Google Cloud Platform? If so, the Google Cloud Platform Fundamentals CP100A certification may be the perfect tool for you. In this article, we will explore the role of CP100A in digital transformation strategies and how it can help propel your business
Google Cloud Platform Fundamentals CP100A
Google Cloud Platform Fundamentals CP100A is a training course designed to provide individuals with a solid foundation in cloud computing and the capabilities of Google Cloud Platform. This course covers key concepts such as cloud infrastructure, data storage, networking, and security, providing participants with the knowledge and skills they need to leverage Google Cloud Platform effectively.
The Benefits of Google Cloud Platform in Digital Transformation
Google Cloud Platform offers a wide range of benefits for businesses looking to undergo digital transformation. From improved scalability and flexibility to enhanced security and reliability, Google Cloud Platform can help organizations streamline their operations, cut costs, and drive innovation.
By obtaining the CP100A certification, individuals can demonstrate their proficiency in Google Cloud Platform and showcase their ability to harness its capabilities for digital transformation initiatives. This certification can open up new opportunities for career advancement and help professionals stand out in a competitive job market.
How CP100A Can Impact Business Strategies
In today's fast-paced digital landscape, businesses need to be agile and adaptive to stay ahead of the competition. The CP100A certification equips individuals with the skills and knowledge they need to drive digital transformation within their organizations, helping them harness the power of cloud technology to drive innovation and growth.
By leveraging the capabilities of Google Cloud Platform, businesses can optimize their operations, improve collaboration and communication, and deliver better experiences for their customers. With the CP100A certification, individuals can play a key role in shaping digital transformation initiatives and driving business success.
Getting Started with Google Cloud Platform Fundamentals CP100A
If you're ready to take your digital transformation strategies to the next level, the CP100A certification is a great place to start. With comprehensive training materials, hands-on labs, and expert guidance, this course will equip you with the skills and knowledge you need to succeed in the world of cloud computing.
Don't wait any longer to unlock the full potential of Google Cloud Platform for your business. Enroll in the CP100A certification course today and take the first step towards transforming your organization for the digital age.
How to obtain Cloud Technology Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the role of Google Cloud Platform Fundamentals CP100A in digital transformation strategies cannot be overstated. By obtaining this certification, individuals can position themselves as experts in cloud computing and drive impactful change within their organizations. Don't miss out on the opportunity to elevate your digital transformation initiatives with Google Cloud Platform – enroll in the CP100A certification course today and unlock a world of possibilities for your business.
Read More
Are you looking to enhance your digital transformation strategies with the power of Google Cloud Platform? If so, the Google Cloud Platform Fundamentals CP100A certification may be the perfect tool for you. In this article, we will explore the role of CP100A in digital transformation strategies and how it can help propel your business
Google Cloud Platform Fundamentals CP100A
Google Cloud Platform Fundamentals CP100A is a training course designed to provide individuals with a solid foundation in cloud computing and the capabilities of Google Cloud Platform. This course covers key concepts such as cloud infrastructure, data storage, networking, and security, providing participants with the knowledge and skills they need to leverage Google Cloud Platform effectively.
The Benefits of Google Cloud Platform in Digital Transformation
Google Cloud Platform offers a wide range of benefits for businesses looking to undergo digital transformation. From improved scalability and flexibility to enhanced security and reliability, Google Cloud Platform can help organizations streamline their operations, cut costs, and drive innovation.
By obtaining the CP100A certification, individuals can demonstrate their proficiency in Google Cloud Platform and showcase their ability to harness its capabilities for digital transformation initiatives. This certification can open up new opportunities for career advancement and help professionals stand out in a competitive job market.
How CP100A Can Impact Business Strategies
In today's fast-paced digital landscape, businesses need to be agile and adaptive to stay ahead of the competition. The CP100A certification equips individuals with the skills and knowledge they need to drive digital transformation within their organizations, helping them harness the power of cloud technology to drive innovation and growth.
By leveraging the capabilities of Google Cloud Platform, businesses can optimize their operations, improve collaboration and communication, and deliver better experiences for their customers. With the CP100A certification, individuals can play a key role in shaping digital transformation initiatives and driving business success.
Getting Started with Google Cloud Platform Fundamentals CP100A
If you're ready to take your digital transformation strategies to the next level, the CP100A certification is a great place to start. With comprehensive training materials, hands-on labs, and expert guidance, this course will equip you with the skills and knowledge you need to succeed in the world of cloud computing.
Don't wait any longer to unlock the full potential of Google Cloud Platform for your business. Enroll in the CP100A certification course today and take the first step towards transforming your organization for the digital age.
How to obtain Cloud Technology Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the role of Google Cloud Platform Fundamentals CP100A in digital transformation strategies cannot be overstated. By obtaining this certification, individuals can position themselves as experts in cloud computing and drive impactful change within their organizations. Don't miss out on the opportunity to elevate your digital transformation initiatives with Google Cloud Platform – enroll in the CP100A certification course today and unlock a world of possibilities for your business.
Exploring GSLB (Global Server Load Balancing) with Netscaler
Are you looking to optimize your network performance and ensure high availability for your applications? In this article, we will delve into the world of Global Server Load Balancing (GSLB) with Netscaler, a powerful solution for distributing traffic across multiple servers and data centers. Let's explore the features, benefits, deployment steps, and best practices of GSLB with Netscaler.
What is GSLB and how does it work?
Global Server Load Balancing (GSLB) is a technology that enables organizations to distribute incoming network traffic across multiple servers in different geographical locations. By using GSLB, organizations can achieve better performance, higher availability, and improved scalability for their applications.
With GSLB, traffic is intelligently routed to the most optimal server based on factors such as server load, network latency, and geographical proximity. This helps in minimizing downtime, reducing response time, and ensuring a seamless user experience.
GSLB features with Netscaler
Netscaler is a leading application delivery controller that offers robust GSLB capabilities. Some key features of GSLB with Netscaler include:
-
Intelligent traffic distribution based on real-time server and network conditions
-
Seamless failover and high availability for applications
-
Global server health monitoring and automatic failover mechanisms
-
Built-in DNS load balancing for efficient traffic management
-
Scalable architecture to support growing network demands
Setting up GSLB with Netscaler
Setting up GSLB with Netscaler is a straightforward process that involves configuring the GSLB virtual server, services, and monitors. Here are some basic steps to deploy GSLB with Netscaler:
-
Configure GSLB virtual server with appropriate settings
-
Add GSLB services representing the backend servers
-
Configure health monitors to check the availability of servers
-
Define GSLB domains and geographic locations for traffic routing
-
Test the GSLB setup for functionality and performance
Benefits of GSLB with Netscaler
The use of GSLB with Netscaler offers several advantages for organizations:
-
Improved application performance and user experience
-
Enhanced availability and fault tolerance for critical applications
-
Efficient traffic management and distribution across servers
-
Simplified network configuration and maintenance
-
Scalability to support growing traffic loads and expanding infrastructure
GSLB deployment best practices
When deploying GSLB with Netscaler, it is essential to follow best practices to ensure optimal performance and reliability:
-
Regularly monitor server health and network conditions
-
Implement a comprehensive failover strategy for seamless recovery
-
Test GSLB configuration for load balancing accuracy and efficiency
-
Keep GSLB configurations up to date with changing network requirements
-
Consider using GSLB in conjunction with other load balancing methods for enhanced performance.
How to obtain Citrix Client Administration Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, GSLB with Netscaler is a powerful solution for achieving high availability, scalability, and performance optimization for applications in a distributed network environment. By understanding the features, benefits, and best practices of GSLB, organizations can leverage this technology to improve their network infrastructure and deliver a superior user experience.
Read More
Are you looking to optimize your network performance and ensure high availability for your applications? In this article, we will delve into the world of Global Server Load Balancing (GSLB) with Netscaler, a powerful solution for distributing traffic across multiple servers and data centers. Let's explore the features, benefits, deployment steps, and best practices of GSLB with Netscaler.
What is GSLB and how does it work?
Global Server Load Balancing (GSLB) is a technology that enables organizations to distribute incoming network traffic across multiple servers in different geographical locations. By using GSLB, organizations can achieve better performance, higher availability, and improved scalability for their applications.
With GSLB, traffic is intelligently routed to the most optimal server based on factors such as server load, network latency, and geographical proximity. This helps in minimizing downtime, reducing response time, and ensuring a seamless user experience.
GSLB features with Netscaler
Netscaler is a leading application delivery controller that offers robust GSLB capabilities. Some key features of GSLB with Netscaler include:
-
Intelligent traffic distribution based on real-time server and network conditions
-
Seamless failover and high availability for applications
-
Global server health monitoring and automatic failover mechanisms
-
Built-in DNS load balancing for efficient traffic management
-
Scalable architecture to support growing network demands
Setting up GSLB with Netscaler
Setting up GSLB with Netscaler is a straightforward process that involves configuring the GSLB virtual server, services, and monitors. Here are some basic steps to deploy GSLB with Netscaler:
-
Configure GSLB virtual server with appropriate settings
-
Add GSLB services representing the backend servers
-
Configure health monitors to check the availability of servers
-
Define GSLB domains and geographic locations for traffic routing
-
Test the GSLB setup for functionality and performance
Benefits of GSLB with Netscaler
The use of GSLB with Netscaler offers several advantages for organizations:
-
Improved application performance and user experience
-
Enhanced availability and fault tolerance for critical applications
-
Efficient traffic management and distribution across servers
-
Simplified network configuration and maintenance
-
Scalability to support growing traffic loads and expanding infrastructure
GSLB deployment best practices
When deploying GSLB with Netscaler, it is essential to follow best practices to ensure optimal performance and reliability:
-
Regularly monitor server health and network conditions
-
Implement a comprehensive failover strategy for seamless recovery
-
Test GSLB configuration for load balancing accuracy and efficiency
-
Keep GSLB configurations up to date with changing network requirements
-
Consider using GSLB in conjunction with other load balancing methods for enhanced performance.
How to obtain Citrix Client Administration Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, GSLB with Netscaler is a powerful solution for achieving high availability, scalability, and performance optimization for applications in a distributed network environment. By understanding the features, benefits, and best practices of GSLB, organizations can leverage this technology to improve their network infrastructure and deliver a superior user experience.
Implementing Lean Principles for Improved Quality Management
In today's competitive business environment, companies are constantly seeking ways to enhance operational efficiency, minimize waste, and improve overall quality management. One highly effective approach that has gained widespread popularity in recent years is the implementation of lean principles. By adopting lean methodologies and tools, organizations can streamline processes, drive continuous improvement, and ultimately deliver higher-quality products and services to their customers.
What are Lean Principles?
Lean principles are centered around the concept of maximizing customer value while minimizing waste. This philosophy is rooted in the idea that every process should add value for the customer, and any activities that do not contribute to this value should be considered wasteful and eliminated. By focusing on process optimization and waste reduction, lean organizations are able to deliver higher-quality products and services in a more efficient and cost-effective manner.
Lean Methodologies and Tools
There are several key methodologies and tools that are commonly used in lean practices. These include:
-
Value stream mapping: A tool used to visualize and analyze the flow of materials and information through a process, helping to identify areas of waste and inefficiency.
-
Kaizen: A philosophy of continuous improvement that encourages small, incremental changes to improve quality and efficiency over time.
-
Six Sigma: A data-driven approach to process improvement that focuses on reducing defects and variation in processes.
-
Lean production: A method of manufacturing that focuses on producing goods in the most efficient and cost-effective way possible.
-
Lean culture: A shared set of values, beliefs, and behaviors that promote a culture of continuous improvement and waste reduction.
The Benefits of Lean Implementation
Implementing lean principles can have a wide range of benefits for organizations looking to improve their quality management practices. Some of the key benefits include:
-
Improved quality control: By focusing on eliminating waste and optimizing processes, organizations can deliver higher-quality products and services to their customers.
-
Increased operational efficiency: Lean practices help to streamline processes, reduce cycle times, and improve overall efficiency in the organization.
-
Enhanced customer satisfaction: By delivering higher-quality products and services in a more efficient manner, organizations can enhance customer satisfaction and loyalty.
-
Greater employee engagement: Lean practices encourage collaboration, problem-solving, and continuous improvement, leading to higher levels of employee engagement and satisfaction.
Lean Strategies for Success
To successfully implement lean principles and realize the benefits of improved quality management, organizations should focus on the following strategies:
-
Foster a lean mindset: Encourage employees at all levels of the organization to embrace lean thinking and actively seek out opportunities for improvement.
-
Invest in lean training: Provide employees with the training and tools they need to effectively implement lean practices and drive continuous improvement.
-
Establish lean teams: Create cross-functional teams dedicated to implementing lean methodologies and driving quality improvement initiatives.
-
Embrace lean leadership: Develop leaders who can champion lean principles, inspire employees, and drive a culture of continuous improvement.
How to obtain Quality Management Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, implementing lean principles is a powerful strategy for organizations looking to enhance their quality management practices and deliver higher-quality products and services to their customers. By adopting lean methodologies, tools, and strategies, organizations can drive process optimization, waste reduction, and continuous improvement, ultimately leading to greater operational efficiency and customer satisfaction. By fostering a lean culture, investing in lean training, and embracing lean leadership, organizations can position themselves for long-term success in today's competitive market. So, are you ready to take your quality management to the next level by implementing lean principles?
Read More
In today's competitive business environment, companies are constantly seeking ways to enhance operational efficiency, minimize waste, and improve overall quality management. One highly effective approach that has gained widespread popularity in recent years is the implementation of lean principles. By adopting lean methodologies and tools, organizations can streamline processes, drive continuous improvement, and ultimately deliver higher-quality products and services to their customers.
What are Lean Principles?
Lean principles are centered around the concept of maximizing customer value while minimizing waste. This philosophy is rooted in the idea that every process should add value for the customer, and any activities that do not contribute to this value should be considered wasteful and eliminated. By focusing on process optimization and waste reduction, lean organizations are able to deliver higher-quality products and services in a more efficient and cost-effective manner.
Lean Methodologies and Tools
There are several key methodologies and tools that are commonly used in lean practices. These include:
-
Value stream mapping: A tool used to visualize and analyze the flow of materials and information through a process, helping to identify areas of waste and inefficiency.
-
Kaizen: A philosophy of continuous improvement that encourages small, incremental changes to improve quality and efficiency over time.
-
Six Sigma: A data-driven approach to process improvement that focuses on reducing defects and variation in processes.
-
Lean production: A method of manufacturing that focuses on producing goods in the most efficient and cost-effective way possible.
-
Lean culture: A shared set of values, beliefs, and behaviors that promote a culture of continuous improvement and waste reduction.
The Benefits of Lean Implementation
Implementing lean principles can have a wide range of benefits for organizations looking to improve their quality management practices. Some of the key benefits include:
-
Improved quality control: By focusing on eliminating waste and optimizing processes, organizations can deliver higher-quality products and services to their customers.
-
Increased operational efficiency: Lean practices help to streamline processes, reduce cycle times, and improve overall efficiency in the organization.
-
Enhanced customer satisfaction: By delivering higher-quality products and services in a more efficient manner, organizations can enhance customer satisfaction and loyalty.
-
Greater employee engagement: Lean practices encourage collaboration, problem-solving, and continuous improvement, leading to higher levels of employee engagement and satisfaction.
Lean Strategies for Success
To successfully implement lean principles and realize the benefits of improved quality management, organizations should focus on the following strategies:
-
Foster a lean mindset: Encourage employees at all levels of the organization to embrace lean thinking and actively seek out opportunities for improvement.
-
Invest in lean training: Provide employees with the training and tools they need to effectively implement lean practices and drive continuous improvement.
-
Establish lean teams: Create cross-functional teams dedicated to implementing lean methodologies and driving quality improvement initiatives.
-
Embrace lean leadership: Develop leaders who can champion lean principles, inspire employees, and drive a culture of continuous improvement.
How to obtain Quality Management Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, implementing lean principles is a powerful strategy for organizations looking to enhance their quality management practices and deliver higher-quality products and services to their customers. By adopting lean methodologies, tools, and strategies, organizations can drive process optimization, waste reduction, and continuous improvement, ultimately leading to greater operational efficiency and customer satisfaction. By fostering a lean culture, investing in lean training, and embracing lean leadership, organizations can position themselves for long-term success in today's competitive market. So, are you ready to take your quality management to the next level by implementing lean principles?
Optimizing Sales Processes with Salesforce Workflow Automation
In today's fast-paced business environment, optimizing sales processes is crucial for staying ahead of the competition and driving revenue growth. One of the most effective ways to streamline sales operations and enhance sales efficiency is through the use of Salesforce workflow automation. By leveraging sales automation software and workflow automation tools, businesses can automate mundane tasks, improve sales productivity, and ultimately boost sales performance.
The Benefits of Salesforce Workflow Automation
Salesforce automation solutions offer a wide range of benefits for organizations looking to optimize their sales operations. By implementing sales workflow automation, businesses can:
-
Streamline sales processes: Automating repetitive tasks such as data entry, lead nurturing, and follow-up emails can help sales teams focus on high-value activities.
-
Enhance sales efficiency: By reducing manual work and increasing automation, sales teams can work more efficiently and effectively.
-
Improve sales productivity: Automated sales workflows ensure that leads are promptly followed up on, resulting in higher conversion rates and increased revenue.
-
Optimize sales operations: By standardizing processes and eliminating bottlenecks, sales workflow automation helps organizations run more smoothly and efficiently.
Implementing Salesforce Automation Best Practices
To get the most out of Salesforce workflow automation, it's important to follow best practices and strategies for optimizing sales processes. Some key best practices include:
-
Defining clear objectives: Before implementing automation, clearly define your sales goals and objectives to ensure that your workflows align with your business needs.
-
Mapping out your sales process: Create a visual representation of your sales process and identify areas where automation can be most beneficial.
-
Leveraging workflow rules: Use Salesforce workflow rules to automate repetitive tasks, trigger notifications, and enforce data quality standards.
-
Using automation features: Take advantage of Salesforce's automation features such as process builder, flow, and approvals to streamline sales processes and improve efficiency.
Optimizing Sales Strategy with Salesforce Workflow Automation
Sales workflow automation can play a crucial role in optimizing your sales strategy and improving overall business performance. By automating sales tasks, increasing sales effectiveness, and implementing best practices, businesses can drive revenue growth and achieve their sales goals.
How to obtain Salesforce Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Salesforce workflow automation offers a powerful solution for optimizing sales processes and enhancing sales performance. By leveraging sales automation software and implementing best practices, businesses can streamline operations, improve efficiency, and drive revenue growth.
Read More
In today's fast-paced business environment, optimizing sales processes is crucial for staying ahead of the competition and driving revenue growth. One of the most effective ways to streamline sales operations and enhance sales efficiency is through the use of Salesforce workflow automation. By leveraging sales automation software and workflow automation tools, businesses can automate mundane tasks, improve sales productivity, and ultimately boost sales performance.
The Benefits of Salesforce Workflow Automation
Salesforce automation solutions offer a wide range of benefits for organizations looking to optimize their sales operations. By implementing sales workflow automation, businesses can:
-
Streamline sales processes: Automating repetitive tasks such as data entry, lead nurturing, and follow-up emails can help sales teams focus on high-value activities.
-
Enhance sales efficiency: By reducing manual work and increasing automation, sales teams can work more efficiently and effectively.
-
Improve sales productivity: Automated sales workflows ensure that leads are promptly followed up on, resulting in higher conversion rates and increased revenue.
-
Optimize sales operations: By standardizing processes and eliminating bottlenecks, sales workflow automation helps organizations run more smoothly and efficiently.
Implementing Salesforce Automation Best Practices
To get the most out of Salesforce workflow automation, it's important to follow best practices and strategies for optimizing sales processes. Some key best practices include:
-
Defining clear objectives: Before implementing automation, clearly define your sales goals and objectives to ensure that your workflows align with your business needs.
-
Mapping out your sales process: Create a visual representation of your sales process and identify areas where automation can be most beneficial.
-
Leveraging workflow rules: Use Salesforce workflow rules to automate repetitive tasks, trigger notifications, and enforce data quality standards.
-
Using automation features: Take advantage of Salesforce's automation features such as process builder, flow, and approvals to streamline sales processes and improve efficiency.
Optimizing Sales Strategy with Salesforce Workflow Automation
Sales workflow automation can play a crucial role in optimizing your sales strategy and improving overall business performance. By automating sales tasks, increasing sales effectiveness, and implementing best practices, businesses can drive revenue growth and achieve their sales goals.
How to obtain Salesforce Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Salesforce workflow automation offers a powerful solution for optimizing sales processes and enhancing sales performance. By leveraging sales automation software and implementing best practices, businesses can streamline operations, improve efficiency, and drive revenue growth.
The Impact of Digital Transformation on Business Analysis Practices
In today's rapidly evolving business landscape, the concept of digital transformation has become a key driver of change for organizations seeking to stay competitive and relevant. But what exactly is digital transformation, and how does it impact business analysis practices? In this article, we will explore the implications of digital transformation on business analysis, including the role of technology, data analytics, automation, innovation, strategic planning, decision-making, market research, process improvement, efficiency, competitive advantage, organizational change, digital tools, business strategy, adaptation, digitalization, industry trends, data management, project management, agile methodologies, customer experience, performance metrics, transformational leadership, digital solutions, communication strategies, change management, and workforce optimization.
What is Digital Transformation?
Digital transformation is the integration of digital technology into all aspects of a business, fundamentally changing how the organization operates and delivers value to its customers. This can involve the adoption of new digital tools and technologies, the implementation of innovative processes and systems, and the cultivation of a digital-first mindset across the organization.
The Role of Technology in Business Analysis
Technology plays a crucial role in the field of business analysis, enabling analysts to gather, analyze, and interpret data more efficiently and effectively than ever before. With the advent of advanced data analytics tools and automation technologies, business analysts can uncover valuable insights and trends that can inform strategic decision-making and drive business growth.
Leveraging Data Analytics for Business Insights
One of the key benefits of digital transformation for business analysis practices is the ability to leverage data analytics to gain valuable insights into customer behavior, market trends, and operational performance. By harnessing the power of data, organizations can make more informed decisions, identify opportunities for improvement, and stay ahead of the competition.
Driving Innovation and Strategic Planning
Digital transformation also enables organizations to drive innovation and strategic planning by leveraging cutting-edge technologies and digital solutions. By embracing digital tools and methodologies, businesses can develop new products and services, streamline processes, and optimize their operations for maximum efficiency and effectiveness.
Enhancing Decision-Making and Market Research
In the digital age, the ability to make informed decisions based on data-driven insights is essential for business success. Through digital transformation, organizations can enhance their decision-making processes by utilizing advanced analytics tools, conducting comprehensive market research, and staying attuned to industry trends and customer preferences.
Improving Process Efficiency and Competitive Advantage
Another key impact of digital transformation on business analysis practices is the improvement of process efficiency and the creation of a competitive advantage. By streamlining operations, eliminating inefficiencies, and embracing a culture of continuous improvement, organizations can enhance their overall performance and achieve sustainable growth in a rapidly changing market.
Navigating Organizational Change and Adaptation
Digital transformation often requires organizations to undergo significant changes in order to adapt to new technologies, systems, and ways of working. Business analysts play a critical role in facilitating this transition by identifying areas of improvement, developing change management strategies, and supporting the organization in its journey towards digital maturity.
How to obtain Business Analysis Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the impact of digital transformation on business analysis practices is profound and far-reaching. By embracing digital technologies, leveraging data analytics, driving innovation, enhancing decision-making, improving efficiency, and navigating organizational change, organizations can position themselves for success in an increasingly digital world. Business analysts play a crucial role in this transformative process, serving as catalysts for change and driving strategic decision-making based on data-driven insights and market intelligence. As organizations continue to adapt to the challenges and opportunities of the digital age, business analysis practices will play an ever more critical role in shaping the future of business.
Read More
In today's rapidly evolving business landscape, the concept of digital transformation has become a key driver of change for organizations seeking to stay competitive and relevant. But what exactly is digital transformation, and how does it impact business analysis practices? In this article, we will explore the implications of digital transformation on business analysis, including the role of technology, data analytics, automation, innovation, strategic planning, decision-making, market research, process improvement, efficiency, competitive advantage, organizational change, digital tools, business strategy, adaptation, digitalization, industry trends, data management, project management, agile methodologies, customer experience, performance metrics, transformational leadership, digital solutions, communication strategies, change management, and workforce optimization.
What is Digital Transformation?
Digital transformation is the integration of digital technology into all aspects of a business, fundamentally changing how the organization operates and delivers value to its customers. This can involve the adoption of new digital tools and technologies, the implementation of innovative processes and systems, and the cultivation of a digital-first mindset across the organization.
The Role of Technology in Business Analysis
Technology plays a crucial role in the field of business analysis, enabling analysts to gather, analyze, and interpret data more efficiently and effectively than ever before. With the advent of advanced data analytics tools and automation technologies, business analysts can uncover valuable insights and trends that can inform strategic decision-making and drive business growth.
Leveraging Data Analytics for Business Insights
One of the key benefits of digital transformation for business analysis practices is the ability to leverage data analytics to gain valuable insights into customer behavior, market trends, and operational performance. By harnessing the power of data, organizations can make more informed decisions, identify opportunities for improvement, and stay ahead of the competition.
Driving Innovation and Strategic Planning
Digital transformation also enables organizations to drive innovation and strategic planning by leveraging cutting-edge technologies and digital solutions. By embracing digital tools and methodologies, businesses can develop new products and services, streamline processes, and optimize their operations for maximum efficiency and effectiveness.
Enhancing Decision-Making and Market Research
In the digital age, the ability to make informed decisions based on data-driven insights is essential for business success. Through digital transformation, organizations can enhance their decision-making processes by utilizing advanced analytics tools, conducting comprehensive market research, and staying attuned to industry trends and customer preferences.
Improving Process Efficiency and Competitive Advantage
Another key impact of digital transformation on business analysis practices is the improvement of process efficiency and the creation of a competitive advantage. By streamlining operations, eliminating inefficiencies, and embracing a culture of continuous improvement, organizations can enhance their overall performance and achieve sustainable growth in a rapidly changing market.
Navigating Organizational Change and Adaptation
Digital transformation often requires organizations to undergo significant changes in order to adapt to new technologies, systems, and ways of working. Business analysts play a critical role in facilitating this transition by identifying areas of improvement, developing change management strategies, and supporting the organization in its journey towards digital maturity.
How to obtain Business Analysis Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the impact of digital transformation on business analysis practices is profound and far-reaching. By embracing digital technologies, leveraging data analytics, driving innovation, enhancing decision-making, improving efficiency, and navigating organizational change, organizations can position themselves for success in an increasingly digital world. Business analysts play a crucial role in this transformative process, serving as catalysts for change and driving strategic decision-making based on data-driven insights and market intelligence. As organizations continue to adapt to the challenges and opportunities of the digital age, business analysis practices will play an ever more critical role in shaping the future of business.
Preparing for the AWS Solutions Architect Certification: Best Practices and Resources
One of the best ways to showcase your expertise in Amazon Web Services (AWS) is by obtaining the AWS Solutions Architect certification. This prestigious certification demonstrates your ability to design and deploy scalable, secure, and reliable applications on AWS infrastructure. In this article, we will explore the best practices and resources to help you prepare for the AWS Solutions Architect certification exam.
Preparing for AWS Solutions Architect
Preparing for the AWS Solutions Architect certification exam requires dedication, time, and effort. Here are some best practices to help you get ready for the exam:
-
Understand the Exam Blueprint: Familiarize yourself with the exam blueprint provided by AWS. This will give you insight into the topics covered on the exam and help you create a study plan.
-
Hands-On Experience: Practice, practice, practice! Ensure you have hands-on experience working with AWS services and solutions. Create and deploy projects on AWS to gain practical knowledge.
-
Study Materials: Invest in quality study materials such as AWS whitepapers, documentation, and online courses. There are many resources available online to help you prepare for the exam.
-
Join Study Groups: Joining a study group or forum can be beneficial. You can exchange knowledge and tips with other candidates preparing for the exam.
Best Practices for AWS Certification
When preparing for the AWS Solutions Architect certification, keep these best practices in mind:
-
Start Early: Give yourself enough time to study and prepare for the exam. Cramming at the last minute is not effective.
-
Set Realistic Goals: Break down the topics into manageable sections and set goals for each study session.
-
Take Practice Exams: Practice exams are a great way to test your knowledge and familiarize yourself with the exam format.
-
Stay Updated: AWS constantly updates its services and features. Stay informed about the latest changes to ensure you are studying relevant information.
-
Stay Motivated: Maintain a positive attitude and stay motivated throughout your preparation journey.
Resources for AWS Solutions Architect
To ace the AWS Solutions Architect certification exam, utilize the following resources:
-
AWS Training and Certification: AWS offers training courses tailored to help you prepare for certification exams.
-
Online Courses: Platforms like Coursera, Udemy, and A Cloud Guru offer online courses specifically designed for AWS certification preparation.
-
Practice Exams: Take advantage of practice exams to assess your knowledge and identify areas that need improvement.
-
Whitepapers and Documentation: Dive into AWS whitepapers and documentation to gain a deeper understanding of AWS services.
-
Study Guides: Look for study guides and books that cover the topics tested on the exam.
How to Pass AWS Certification
To pass the AWS Solutions Architect certification exam, follow these tips:
-
Create a Study Plan: Set aside dedicated time each day to study and stick to your plan.
-
Understand Core Concepts: Ensure you have a solid understanding of core AWS concepts such as EC2, S3, IAM, and VPC.
-
Hands-On Practice: Apply your knowledge by working on real-world projects using AWS services.
-
Review Your Weaknesses: Focus on areas where you feel less confident and review them thoroughly.
-
Stay Calm During the Exam: On the day of the exam, stay calm, read each question carefully, and manage your time effectively.
How to obtain AWS Solution Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, Earning the AWS Solutions Architect certification can open up exciting opportunities in the field of cloud computing. By following best practices, utilizing resources effectively, and staying committed to your study plan, you can increase your chances of passing the certification exam with flying colors.
Read More
One of the best ways to showcase your expertise in Amazon Web Services (AWS) is by obtaining the AWS Solutions Architect certification. This prestigious certification demonstrates your ability to design and deploy scalable, secure, and reliable applications on AWS infrastructure. In this article, we will explore the best practices and resources to help you prepare for the AWS Solutions Architect certification exam.
Preparing for AWS Solutions Architect
Preparing for the AWS Solutions Architect certification exam requires dedication, time, and effort. Here are some best practices to help you get ready for the exam:
-
Understand the Exam Blueprint: Familiarize yourself with the exam blueprint provided by AWS. This will give you insight into the topics covered on the exam and help you create a study plan.
-
Hands-On Experience: Practice, practice, practice! Ensure you have hands-on experience working with AWS services and solutions. Create and deploy projects on AWS to gain practical knowledge.
-
Study Materials: Invest in quality study materials such as AWS whitepapers, documentation, and online courses. There are many resources available online to help you prepare for the exam.
-
Join Study Groups: Joining a study group or forum can be beneficial. You can exchange knowledge and tips with other candidates preparing for the exam.
Best Practices for AWS Certification
When preparing for the AWS Solutions Architect certification, keep these best practices in mind:
-
Start Early: Give yourself enough time to study and prepare for the exam. Cramming at the last minute is not effective.
-
Set Realistic Goals: Break down the topics into manageable sections and set goals for each study session.
-
Take Practice Exams: Practice exams are a great way to test your knowledge and familiarize yourself with the exam format.
-
Stay Updated: AWS constantly updates its services and features. Stay informed about the latest changes to ensure you are studying relevant information.
-
Stay Motivated: Maintain a positive attitude and stay motivated throughout your preparation journey.
Resources for AWS Solutions Architect
To ace the AWS Solutions Architect certification exam, utilize the following resources:
-
AWS Training and Certification: AWS offers training courses tailored to help you prepare for certification exams.
-
Online Courses: Platforms like Coursera, Udemy, and A Cloud Guru offer online courses specifically designed for AWS certification preparation.
-
Practice Exams: Take advantage of practice exams to assess your knowledge and identify areas that need improvement.
-
Whitepapers and Documentation: Dive into AWS whitepapers and documentation to gain a deeper understanding of AWS services.
-
Study Guides: Look for study guides and books that cover the topics tested on the exam.
How to Pass AWS Certification
To pass the AWS Solutions Architect certification exam, follow these tips:
-
Create a Study Plan: Set aside dedicated time each day to study and stick to your plan.
-
Understand Core Concepts: Ensure you have a solid understanding of core AWS concepts such as EC2, S3, IAM, and VPC.
-
Hands-On Practice: Apply your knowledge by working on real-world projects using AWS services.
-
Review Your Weaknesses: Focus on areas where you feel less confident and review them thoroughly.
-
Stay Calm During the Exam: On the day of the exam, stay calm, read each question carefully, and manage your time effectively.
How to obtain AWS Solution Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, Earning the AWS Solutions Architect certification can open up exciting opportunities in the field of cloud computing. By following best practices, utilizing resources effectively, and staying committed to your study plan, you can increase your chances of passing the certification exam with flying colors.
Java for Android Development: Mastering App Development with the Latest Android SDK
Are you looking to become a master in Android app development using Java with the latest Android SDK? In this article, we will explore the essential tools, libraries, and techniques to help you excel in building innovative and user-friendly mobile applications. Let's dive into the world of Java for Android development and become an expert in creating cutting-edge apps.
Introduction to Java for Android Development
Java is the primary programming language used for Android app development. It offers a robust and versatile platform for building mobile applications with the latest Android software development kit (SDK). By mastering Java, you can leverage the power of Google's Android Studio and create high-quality apps that stand out in the competitive app market.
Why Choose Java for Android Development?
Java is a popular choice for Android app development due to its simplicity, flexibility, and scalability. It offers a wide range of tools and libraries that make it easy to develop feature-rich applications with a clean and intuitive user interface (UI). With Java, you can also take advantage of the Android architecture components and support libraries to enhance your app's functionality and performance.
Getting Started with Java for Android Development
To start your journey in mastering Java for Android development, you need to have a basic understanding of Java programming concepts and syntax. Familiarize yourself with the Android Studio IDE, which provides a comprehensive development environment for creating and testing Android apps. You can also explore Kotlin, a modern programming language that works seamlessly with Java for building Android applications.
Essential Tools and Techniques for Android App Development
Android Manifest and Gradle Build Tools
The Android manifest file is a key component of every Android app, as it contains essential information about the app's structure and requirements. Gradle build tools, on the other hand, automate the process of building, testing, and deploying Android apps. By mastering these tools, you can streamline your app development process and ensure smooth integration with the latest Android SDK.
Android UI/UX Design and Integration
User experience (UX) and user interface (UI) design are crucial aspects of Android app development. Create visually appealing and intuitive interfaces that provide a seamless user experience. Leverage the Firebase platform for backend integration, real-time data synchronization, and cloud messaging to enhance your app's functionality and reach a wider audience.
Debugging and Testing with Android Studio
Effective debugging and testing are essential for ensuring the reliability and performance of your Android apps. Use Android Studio's built-in debugging tools to identify and fix errors in your code, as well as run comprehensive tests to validate your app's functionality across different devices and screen sizes. By mastering debugging and testing techniques, you can deliver high-quality apps to your users.
How to obtain Java Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Mastering Java for Android development with the latest Android SDK is a rewarding journey that offers endless possibilities for creating innovative and user-friendly mobile applications. By leveraging essential tools, libraries, and techniques, you can enhance your app development skills and become a proficient Android app developer. Start exploring Java for Android development today and unlock the full potential of the Android platform.
Read More
Are you looking to become a master in Android app development using Java with the latest Android SDK? In this article, we will explore the essential tools, libraries, and techniques to help you excel in building innovative and user-friendly mobile applications. Let's dive into the world of Java for Android development and become an expert in creating cutting-edge apps.
Introduction to Java for Android Development
Java is the primary programming language used for Android app development. It offers a robust and versatile platform for building mobile applications with the latest Android software development kit (SDK). By mastering Java, you can leverage the power of Google's Android Studio and create high-quality apps that stand out in the competitive app market.
Why Choose Java for Android Development?
Java is a popular choice for Android app development due to its simplicity, flexibility, and scalability. It offers a wide range of tools and libraries that make it easy to develop feature-rich applications with a clean and intuitive user interface (UI). With Java, you can also take advantage of the Android architecture components and support libraries to enhance your app's functionality and performance.
Getting Started with Java for Android Development
To start your journey in mastering Java for Android development, you need to have a basic understanding of Java programming concepts and syntax. Familiarize yourself with the Android Studio IDE, which provides a comprehensive development environment for creating and testing Android apps. You can also explore Kotlin, a modern programming language that works seamlessly with Java for building Android applications.
Essential Tools and Techniques for Android App Development
Android Manifest and Gradle Build Tools
The Android manifest file is a key component of every Android app, as it contains essential information about the app's structure and requirements. Gradle build tools, on the other hand, automate the process of building, testing, and deploying Android apps. By mastering these tools, you can streamline your app development process and ensure smooth integration with the latest Android SDK.
Android UI/UX Design and Integration
User experience (UX) and user interface (UI) design are crucial aspects of Android app development. Create visually appealing and intuitive interfaces that provide a seamless user experience. Leverage the Firebase platform for backend integration, real-time data synchronization, and cloud messaging to enhance your app's functionality and reach a wider audience.
Debugging and Testing with Android Studio
Effective debugging and testing are essential for ensuring the reliability and performance of your Android apps. Use Android Studio's built-in debugging tools to identify and fix errors in your code, as well as run comprehensive tests to validate your app's functionality across different devices and screen sizes. By mastering debugging and testing techniques, you can deliver high-quality apps to your users.
How to obtain Java Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Mastering Java for Android development with the latest Android SDK is a rewarding journey that offers endless possibilities for creating innovative and user-friendly mobile applications. By leveraging essential tools, libraries, and techniques, you can enhance your app development skills and become a proficient Android app developer. Start exploring Java for Android development today and unlock the full potential of the Android platform.
The Evolution of Citrix Certification: Trends and Predictions for the Next Decade
In the ever-evolving world of technology and IT, certifications play a crucial role in advancing one's career and expertise. Citrix Certification has been a benchmark for professionals looking to specialize in virtualization, remote work, and cloud computing. Let's delve into the evolution of Citrix Certification and explore the trends and predictions for the next decade.
Citrix Certification: A Brief Overview
Citrix Certification is a renowned program that validates a professional's skills in Citrix technologies and solutions. It covers a wide range of topics, including networking, software, and cloud computing. Over the years, Citrix Certification has adapted to the changing landscape of technology, offering specialized tracks to meet the demands of the industry.
Evolution of Citrix Certification
Citrix Certification has evolved significantly since its inception. Initially focusing on basic skills and knowledge, it has now expanded to include advanced topics such as virtualization, digital transformation, and networking. The curriculum has been updated regularly to align with industry standards and innovations.
Trends in Citrix Certification
The future of Citrix Certification looks promising, with a growing emphasis on specialized skills and qualifications. As technology continues to advance, professionals need to stay ahead of the curve by obtaining the latest certifications. Remote work and virtualization have become integral parts of the workforce, making Citrix Certification more relevant than ever.
Predictions for the Next Decade
Looking ahead, Citrix Certification is expected to focus on cutting-edge technologies such as AI, cybersecurity, and hybrid cloud solutions. Professionals will need to enhance their expertise in these areas to remain competitive in the job market. Certification renewal will also play a crucial role in ensuring that professionals stay up-to-date with the latest advancements in technology.
Advancement in Citrix Certification
The advancement of Citrix Certification is essential for professionals looking to grow their careers. By obtaining specialized certifications, individuals can demonstrate their expertise and stand out in a crowded job market. Online learning has made it easier for professionals to acquire new skills and pave the way for career growth.
Expertise and Skills Development
Citrix Certification offers professionals the opportunity to develop their expertise in specific areas of technology. By acquiring in-depth knowledge through certification programs, individuals can increase their value in the workforce and become sought-after specialists. The skills obtained through Citrix Certification are invaluable in today's digital age.
How to obtain Citrix Client Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion:
In conclusion, the evolution of Citrix Certification has been shaped by the ever-changing landscape of technology. As we look towards the next decade, professionals can expect to see a continued emphasis on specialization, innovation, and expertise. By staying ahead of the trends and predictions, individuals can secure their future in the technology industry. Citrix Certification remains a key component of professional development and career growth in the digital era.
Read More
In the ever-evolving world of technology and IT, certifications play a crucial role in advancing one's career and expertise. Citrix Certification has been a benchmark for professionals looking to specialize in virtualization, remote work, and cloud computing. Let's delve into the evolution of Citrix Certification and explore the trends and predictions for the next decade.
Citrix Certification: A Brief Overview
Citrix Certification is a renowned program that validates a professional's skills in Citrix technologies and solutions. It covers a wide range of topics, including networking, software, and cloud computing. Over the years, Citrix Certification has adapted to the changing landscape of technology, offering specialized tracks to meet the demands of the industry.
Evolution of Citrix Certification
Citrix Certification has evolved significantly since its inception. Initially focusing on basic skills and knowledge, it has now expanded to include advanced topics such as virtualization, digital transformation, and networking. The curriculum has been updated regularly to align with industry standards and innovations.
Trends in Citrix Certification
The future of Citrix Certification looks promising, with a growing emphasis on specialized skills and qualifications. As technology continues to advance, professionals need to stay ahead of the curve by obtaining the latest certifications. Remote work and virtualization have become integral parts of the workforce, making Citrix Certification more relevant than ever.
Predictions for the Next Decade
Looking ahead, Citrix Certification is expected to focus on cutting-edge technologies such as AI, cybersecurity, and hybrid cloud solutions. Professionals will need to enhance their expertise in these areas to remain competitive in the job market. Certification renewal will also play a crucial role in ensuring that professionals stay up-to-date with the latest advancements in technology.
Advancement in Citrix Certification
The advancement of Citrix Certification is essential for professionals looking to grow their careers. By obtaining specialized certifications, individuals can demonstrate their expertise and stand out in a crowded job market. Online learning has made it easier for professionals to acquire new skills and pave the way for career growth.
Expertise and Skills Development
Citrix Certification offers professionals the opportunity to develop their expertise in specific areas of technology. By acquiring in-depth knowledge through certification programs, individuals can increase their value in the workforce and become sought-after specialists. The skills obtained through Citrix Certification are invaluable in today's digital age.
How to obtain Citrix Client Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion:
In conclusion, the evolution of Citrix Certification has been shaped by the ever-changing landscape of technology. As we look towards the next decade, professionals can expect to see a continued emphasis on specialization, innovation, and expertise. By staying ahead of the trends and predictions, individuals can secure their future in the technology industry. Citrix Certification remains a key component of professional development and career growth in the digital era.
The Benefits of Pursuing a CCBA Certification for Business Analysts
In the dynamic world of business analysis, staying ahead of the curve is essential to success. One way to demonstrate your expertise and commitment to the field is by pursuing a CCBA certification. This article will explore the various benefits of obtaining a CCBA certification for business analysts, including career advancement, professional development, industry recognition, and enhanced job opportunities.
What is a CCBA Certification?
A CCBA certification, or Certification of Competency in Business Analysis, is a widely recognized credential that validates a business analyst's skills and expertise. It is designed for individuals with a minimum of 3750 hours of hands-on business analysis experience and provides a thorough understanding of business analysis techniques, tools, and best practices.
Why Pursue a CCBA Certification?
-
Career Advancement: Obtaining a CCBA certification can open doors to new career opportunities and higher salary potential. Employers value professionals who have demonstrated a commitment to their field through certification.
-
Professional Development: The process of preparing for the certification exam allows business analysts to deepen their knowledge and skills in areas such as project management, business process improvement, data analysis, critical thinking, and decision-making.
-
Industry Recognition: Holding a CCBA certification demonstrates to employers and peers that you have met the rigorous eligibility requirements and passed a comprehensive exam. This can enhance your reputation in the industry and boost your credibility as a business analyst.
-
Skills Enhancement: The CCBA certification process involves studying a wide range of business analysis techniques, tools, and best practices. This helps business analysts develop a comprehensive skill set that can be applied to a variety of projects and scenarios.
-
Job Opportunities: Many companies actively seek out CCBA certified professionals when hiring for business analyst roles. Having this certification on your resume can give you a competitive edge in the job market.
How to Prepare for the CCBA Certification Exam
To qualify for the CCBA exam, candidates must meet certain eligibility requirements, including a minimum of 3750 hours of business analysis work experience. Study materials such as a CCBA study guide, analysis tools, and study resources are available to help prepare for the exam. It is recommended to invest in CCBA training to ensure a thorough understanding of business requirements, stakeholders engagement, business strategy, and performance evaluation.
Exam Cost and Application Process
The cost of the CCBA exam varies depending on whether you are a member of the International Institute of Business Analysis (IIBA). The application process involves submitting proof of eligibility, completing the online application, and scheduling your exam date. Be sure to review the CCBA exam syllabus and familiarize yourself with the topics that will be covered on the exam.
How to obtain Business Analysis Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, pursuing a CCBA certification for business analysts can bring a wealth of benefits, including career advancement, professional development, industry recognition, skills enhancement, and job opportunities. By investing time and effort into preparing for the certification exam, business analysts can demonstrate their expertise and commitment to the field of business analysis
Read More
In the dynamic world of business analysis, staying ahead of the curve is essential to success. One way to demonstrate your expertise and commitment to the field is by pursuing a CCBA certification. This article will explore the various benefits of obtaining a CCBA certification for business analysts, including career advancement, professional development, industry recognition, and enhanced job opportunities.
What is a CCBA Certification?
A CCBA certification, or Certification of Competency in Business Analysis, is a widely recognized credential that validates a business analyst's skills and expertise. It is designed for individuals with a minimum of 3750 hours of hands-on business analysis experience and provides a thorough understanding of business analysis techniques, tools, and best practices.
Why Pursue a CCBA Certification?
-
Career Advancement: Obtaining a CCBA certification can open doors to new career opportunities and higher salary potential. Employers value professionals who have demonstrated a commitment to their field through certification.
-
Professional Development: The process of preparing for the certification exam allows business analysts to deepen their knowledge and skills in areas such as project management, business process improvement, data analysis, critical thinking, and decision-making.
-
Industry Recognition: Holding a CCBA certification demonstrates to employers and peers that you have met the rigorous eligibility requirements and passed a comprehensive exam. This can enhance your reputation in the industry and boost your credibility as a business analyst.
-
Skills Enhancement: The CCBA certification process involves studying a wide range of business analysis techniques, tools, and best practices. This helps business analysts develop a comprehensive skill set that can be applied to a variety of projects and scenarios.
-
Job Opportunities: Many companies actively seek out CCBA certified professionals when hiring for business analyst roles. Having this certification on your resume can give you a competitive edge in the job market.
How to Prepare for the CCBA Certification Exam
To qualify for the CCBA exam, candidates must meet certain eligibility requirements, including a minimum of 3750 hours of business analysis work experience. Study materials such as a CCBA study guide, analysis tools, and study resources are available to help prepare for the exam. It is recommended to invest in CCBA training to ensure a thorough understanding of business requirements, stakeholders engagement, business strategy, and performance evaluation.
Exam Cost and Application Process
The cost of the CCBA exam varies depending on whether you are a member of the International Institute of Business Analysis (IIBA). The application process involves submitting proof of eligibility, completing the online application, and scheduling your exam date. Be sure to review the CCBA exam syllabus and familiarize yourself with the topics that will be covered on the exam.
How to obtain Business Analysis Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, pursuing a CCBA certification for business analysts can bring a wealth of benefits, including career advancement, professional development, industry recognition, skills enhancement, and job opportunities. By investing time and effort into preparing for the certification exam, business analysts can demonstrate their expertise and commitment to the field of business analysis
The CCNP Advantage: How It Opens Doors to High-Paying Networking Jobs
Are you looking to advance your career in the field of networking and secure a high-paying job? If so, obtaining the Cisco Certified Network Professional (CCNP) certification could be your key to success. In this article, we will explore how the CCNP advantage can open doors to lucrative networking opportunities and provide you with the skills and expertise needed to excel in the ever-evolving technology industry.
What is the CCNP Certification?
The CCNP certification is a professional credential that demonstrates a networking professional's expertise in designing, implementing, and troubleshooting both local and wide area networks. This certification is recognized globally and is highly valued in the industry for its comprehensive coverage of networking concepts and technologies.
How Does the CCNP Advantage Benefit Your Career?
With the CCNP certification under your belt, you will be equipped with the knowledge and skills required to excel in the networking field. Employers value CCNP-certified professionals for their ability to design and implement complex network solutions, troubleshoot network issues effectively, and stay up-to-date with the latest technologies and advancements in the industry.
Networking Jobs with Better Pay
One of the main advantages of obtaining the CCNP certification is the potential for significantly higher salaries. CCNP-certified professionals often command better pay compared to their non-certified counterparts due to their specialized skills and expertise in networking. In fact, many companies are willing to offer higher salaries to CCNP-certified individuals to ensure that their networks are designed and maintained by qualified professionals.
Job Opportunities and Career Growth
The CCNP certification opens doors to a wide range of job opportunities in the networking field. From network engineer to IT networking specialist, CCNP-certified professionals are in high demand across various industries. With the rapid advancement of technology, the need for skilled networking professionals continues to grow, providing ample opportunities for career development and growth.
Industry Recognition and Employability
Earning the CCNP certification is a testament to your dedication and commitment to your profession. This industry-recognized credential enhances your credibility as a networking professional and increases your employability in the job market. Employers value CCNP-certified individuals for their proven expertise and reliability in managing and maintaining complex network infrastructures.
How to obtain CCNP Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the CCNP advantage is undeniable when it comes to boosting your career prospects in the networking field. From better pay to increased job opportunities and industry recognition, the CCNP certification can pave the way for a successful and rewarding career as a networking professional. So why wait? Invest in your future today and unlock the doors to high-paying networking jobs with the CCNP certification.
Read More
Are you looking to advance your career in the field of networking and secure a high-paying job? If so, obtaining the Cisco Certified Network Professional (CCNP) certification could be your key to success. In this article, we will explore how the CCNP advantage can open doors to lucrative networking opportunities and provide you with the skills and expertise needed to excel in the ever-evolving technology industry.
What is the CCNP Certification?
The CCNP certification is a professional credential that demonstrates a networking professional's expertise in designing, implementing, and troubleshooting both local and wide area networks. This certification is recognized globally and is highly valued in the industry for its comprehensive coverage of networking concepts and technologies.
How Does the CCNP Advantage Benefit Your Career?
With the CCNP certification under your belt, you will be equipped with the knowledge and skills required to excel in the networking field. Employers value CCNP-certified professionals for their ability to design and implement complex network solutions, troubleshoot network issues effectively, and stay up-to-date with the latest technologies and advancements in the industry.
Networking Jobs with Better Pay
One of the main advantages of obtaining the CCNP certification is the potential for significantly higher salaries. CCNP-certified professionals often command better pay compared to their non-certified counterparts due to their specialized skills and expertise in networking. In fact, many companies are willing to offer higher salaries to CCNP-certified individuals to ensure that their networks are designed and maintained by qualified professionals.
Job Opportunities and Career Growth
The CCNP certification opens doors to a wide range of job opportunities in the networking field. From network engineer to IT networking specialist, CCNP-certified professionals are in high demand across various industries. With the rapid advancement of technology, the need for skilled networking professionals continues to grow, providing ample opportunities for career development and growth.
Industry Recognition and Employability
Earning the CCNP certification is a testament to your dedication and commitment to your profession. This industry-recognized credential enhances your credibility as a networking professional and increases your employability in the job market. Employers value CCNP-certified individuals for their proven expertise and reliability in managing and maintaining complex network infrastructures.
How to obtain CCNP Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the CCNP advantage is undeniable when it comes to boosting your career prospects in the networking field. From better pay to increased job opportunities and industry recognition, the CCNP certification can pave the way for a successful and rewarding career as a networking professional. So why wait? Invest in your future today and unlock the doors to high-paying networking jobs with the CCNP certification.
How To Use Your CRM For Advertising and Digital Marketing Campaigns
In today's digital age, leveraging Customer Relationship Management (CRM) systems for advertising and digital marketing campaigns is crucial for businesses looking to stay ahead of the competition. By integrating CRM into marketing strategies, companies can personalize their messaging, optimize their advertising efforts, and maximize their return on investment. In this article, we will explore the various ways in which businesses can use their CRM system for effective advertising and digital marketing campaigns.
Using CRM for Marketing Campaigns:
One of the key benefits of using a CRM system for marketing campaigns is the ability to segment and target specific customer groups. By analyzing customer data stored in the CRM, businesses can create personalized marketing messages that resonate with their target audience. Whether it's sending targeted email campaigns, running social media ads, or creating personalized landing pages, CRM software provides the tools needed to tailor marketing efforts to individual customer preferences.
CRM Integration in Marketing:
CRM integration with marketing automation platforms allows businesses to streamline their marketing efforts and track the effectiveness of their campaigns. By syncing CRM data with marketing automation tools, businesses can automate lead generation, nurture leads through the sales funnel, and track customer interactions across multiple channels. This integration enables businesses to create cohesive marketing campaigns that deliver personalized messages at the right time and on the right channel.
CRM Digital Advertising Strategy:
When it comes to digital advertising, CRM can help businesses create targeted ads, measure campaign performance, and optimize advertising spend. By using CRM data to create custom audiences, businesses can target their ads to specific customer segments based on demographics, interests, and behavior. This targeted approach not only increases the effectiveness of digital advertising campaigns but also helps businesses reduce wasted ad spend on irrelevant audiences.
Advertising Campaigns with CRM:
CRM software provides businesses with valuable insights into customer behavior, preferences, and purchasing history, which can be used to inform advertising campaigns. By analyzing CRM data, businesses can identify trends, predict customer behavior, and tailor their advertising campaigns to meet customer needs. Whether it's creating personalized ad copy, designing targeted display ads, or retargeting customers who have shown interest in a product or service, CRM can help businesses create impactful advertising campaigns that drive results.
CRM Advertising Solutions:
There are various CRM advertising tools and platforms available in the market that can help businesses create, manage, and optimize their advertising campaigns. From CRM software with built-in advertising capabilities to third-party integrations with popular advertising platforms like Google Ads and Facebook Ads, businesses have a wide range of solutions to choose from. These tools provide businesses with the flexibility and scalability needed to create successful advertising campaigns that reach the right audience at the right time.
CRM Advertising Best Practices:
To make the most of CRM for advertising and digital marketing campaigns, businesses should follow best practices to ensure they are maximizing their ROI. Some best practices include:
- Regularly updating and maintaining CRM data to ensure accuracy and relevance
- Segmenting customer data to create targeted advertising campaigns
- Integrating CRM with marketing automation tools for seamless campaign management
- Analyzing campaign performance metrics to optimize advertising spend
- Personalizing messaging and ad creative to resonate with target audiences
- Testing and iterating on campaigns to identify what works best for your business.
How to obtain Salesforce Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion:
In conclusion, using CRM for advertising and digital marketing campaigns can provide businesses with a competitive edge in today's digital landscape. By leveraging CRM data, integrating CRM with marketing automation tools, and following best practices, businesses can create personalized, targeted advertising campaigns that drive results. With the right CRM advertising solutions and strategies in place, businesses can maximize their marketing efforts and achieve success in the digital marketplace.
Read More
In today's digital age, leveraging Customer Relationship Management (CRM) systems for advertising and digital marketing campaigns is crucial for businesses looking to stay ahead of the competition. By integrating CRM into marketing strategies, companies can personalize their messaging, optimize their advertising efforts, and maximize their return on investment. In this article, we will explore the various ways in which businesses can use their CRM system for effective advertising and digital marketing campaigns.
Using CRM for Marketing Campaigns:
One of the key benefits of using a CRM system for marketing campaigns is the ability to segment and target specific customer groups. By analyzing customer data stored in the CRM, businesses can create personalized marketing messages that resonate with their target audience. Whether it's sending targeted email campaigns, running social media ads, or creating personalized landing pages, CRM software provides the tools needed to tailor marketing efforts to individual customer preferences.
CRM Integration in Marketing:
CRM integration with marketing automation platforms allows businesses to streamline their marketing efforts and track the effectiveness of their campaigns. By syncing CRM data with marketing automation tools, businesses can automate lead generation, nurture leads through the sales funnel, and track customer interactions across multiple channels. This integration enables businesses to create cohesive marketing campaigns that deliver personalized messages at the right time and on the right channel.
CRM Digital Advertising Strategy:
When it comes to digital advertising, CRM can help businesses create targeted ads, measure campaign performance, and optimize advertising spend. By using CRM data to create custom audiences, businesses can target their ads to specific customer segments based on demographics, interests, and behavior. This targeted approach not only increases the effectiveness of digital advertising campaigns but also helps businesses reduce wasted ad spend on irrelevant audiences.
Advertising Campaigns with CRM:
CRM software provides businesses with valuable insights into customer behavior, preferences, and purchasing history, which can be used to inform advertising campaigns. By analyzing CRM data, businesses can identify trends, predict customer behavior, and tailor their advertising campaigns to meet customer needs. Whether it's creating personalized ad copy, designing targeted display ads, or retargeting customers who have shown interest in a product or service, CRM can help businesses create impactful advertising campaigns that drive results.
CRM Advertising Solutions:
There are various CRM advertising tools and platforms available in the market that can help businesses create, manage, and optimize their advertising campaigns. From CRM software with built-in advertising capabilities to third-party integrations with popular advertising platforms like Google Ads and Facebook Ads, businesses have a wide range of solutions to choose from. These tools provide businesses with the flexibility and scalability needed to create successful advertising campaigns that reach the right audience at the right time.
CRM Advertising Best Practices:
To make the most of CRM for advertising and digital marketing campaigns, businesses should follow best practices to ensure they are maximizing their ROI. Some best practices include:
- Regularly updating and maintaining CRM data to ensure accuracy and relevance
- Segmenting customer data to create targeted advertising campaigns
- Integrating CRM with marketing automation tools for seamless campaign management
- Analyzing campaign performance metrics to optimize advertising spend
- Personalizing messaging and ad creative to resonate with target audiences
- Testing and iterating on campaigns to identify what works best for your business.
How to obtain Salesforce Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion:
In conclusion, using CRM for advertising and digital marketing campaigns can provide businesses with a competitive edge in today's digital landscape. By leveraging CRM data, integrating CRM with marketing automation tools, and following best practices, businesses can create personalized, targeted advertising campaigns that drive results. With the right CRM advertising solutions and strategies in place, businesses can maximize their marketing efforts and achieve success in the digital marketplace.
The rise of the metaverse and its implications for marketing
The concept of the metaverse has been gaining traction in recent years, fueled by advancements in virtual reality and digital world technology. As we move towards a more connected and immersive online experience, the implications for marketing are profound. In this article, we will explore the rise of the metaverse and its impact on brands, consumer behavior, and the future of digital marketing.
What is the Metaverse?
The metaverse is a collective virtual shared space, created by the convergence of physical and digital environments. It allows users to interact with a computer-generated environment and other users in a 3D virtual space. In the metaverse, individuals can engage in various activities, from socializing to shopping and gaming, all within a digital world that blurs the lines between reality and imagination.
Implications for Marketing
1. Enhanced Brand Presence : In the metaverse, brands have the opportunity to create interactive and immersive experiences for their customers. By establishing a presence in virtual platforms, companies can engage with their audience in new and innovative ways, driving customer engagement and loyalty.
2. Targeted Advertising : The rise of the metaverse, brands can use augmented reality and virtual experiences to deliver targeted advertising to consumers. By leveraging the interactive nature of the metaverse, companies can create personalized marketing campaigns that resonate with their target audience.
3. Changing Consumer Behavior : As consumers spend more time in virtual environments, their behavior and preferences are evolving. Brands that understand these shifts in consumer behavior can adapt their marketing strategies to better connect with their audience in the metaverse.
4. SEO and Content Creation : In the metaverse, SEO and content creation play a crucial role in driving traffic and engagement. By optimizing their digital presence for virtual platforms, brands can improve their visibility and reach in the online world.
5. E-commerce Opportunities : The metaverse presents new opportunities for e-commerce, allowing brands to sell products and services in a virtual environment. By creating virtual storefronts and immersive shopping experiences, companies can tap into the growing trend of online shopping in the metaverse.
The Future of Digital Marketing
As we move towards a more interconnected and interactive digital landscape, the future of marketing will be shaped by the metaverse. Brands that embrace this new paradigm and adapt their strategies to the virtual world will have a competitive edge in the evolving digital marketplace.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the rise of the metaverse is revolutionizing the way we connect, engage, and interact online. For marketers, the implications of this shift are significant, presenting new opportunities for innovation and customer engagement. By understanding the trends and possibilities of the metaverse, brands can position themselves for success in the digital world of tomorrow.
Read More
The concept of the metaverse has been gaining traction in recent years, fueled by advancements in virtual reality and digital world technology. As we move towards a more connected and immersive online experience, the implications for marketing are profound. In this article, we will explore the rise of the metaverse and its impact on brands, consumer behavior, and the future of digital marketing.
What is the Metaverse?
The metaverse is a collective virtual shared space, created by the convergence of physical and digital environments. It allows users to interact with a computer-generated environment and other users in a 3D virtual space. In the metaverse, individuals can engage in various activities, from socializing to shopping and gaming, all within a digital world that blurs the lines between reality and imagination.
Implications for Marketing
1. Enhanced Brand Presence : In the metaverse, brands have the opportunity to create interactive and immersive experiences for their customers. By establishing a presence in virtual platforms, companies can engage with their audience in new and innovative ways, driving customer engagement and loyalty.
2. Targeted Advertising : The rise of the metaverse, brands can use augmented reality and virtual experiences to deliver targeted advertising to consumers. By leveraging the interactive nature of the metaverse, companies can create personalized marketing campaigns that resonate with their target audience.
3. Changing Consumer Behavior : As consumers spend more time in virtual environments, their behavior and preferences are evolving. Brands that understand these shifts in consumer behavior can adapt their marketing strategies to better connect with their audience in the metaverse.
4. SEO and Content Creation : In the metaverse, SEO and content creation play a crucial role in driving traffic and engagement. By optimizing their digital presence for virtual platforms, brands can improve their visibility and reach in the online world.
5. E-commerce Opportunities : The metaverse presents new opportunities for e-commerce, allowing brands to sell products and services in a virtual environment. By creating virtual storefronts and immersive shopping experiences, companies can tap into the growing trend of online shopping in the metaverse.
The Future of Digital Marketing
As we move towards a more interconnected and interactive digital landscape, the future of marketing will be shaped by the metaverse. Brands that embrace this new paradigm and adapt their strategies to the virtual world will have a competitive edge in the evolving digital marketplace.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the rise of the metaverse is revolutionizing the way we connect, engage, and interact online. For marketers, the implications of this shift are significant, presenting new opportunities for innovation and customer engagement. By understanding the trends and possibilities of the metaverse, brands can position themselves for success in the digital world of tomorrow.
Minitab for Lean Management: Improving Efficiency and Reducing Waste
In today's competitive business environment, companies are constantly striving to improve efficiency and reduce waste in their processes. Lean management is a methodology that focuses on maximizing value while minimizing waste. One powerful tool that has been instrumental in helping organizations achieve these goals is Minitab statistical software. In this article, we will explore how Minitab can be used to enhance lean management practices and drive process improvement.
What is Lean Management?
Lean management is a systematic approach to identifying and eliminating waste within a process. It is based on the principles of continuous improvement and respect for people. By streamlining processes and optimizing workflows, organizations can achieve higher levels of productivity and customer satisfaction.
How Does Minitab Fit into Lean Management?
Minitab is a data analysis software that is widely used in various industries for process improvement and quality control. It provides powerful statistical tools that enable users to analyze data, identify patterns, and make data-driven decisions. By leveraging Minitab, lean practitioners can gain valuable insights into their processes and drive continuous improvement initiatives.
The Benefits of Using Minitab for Lean Management
-
Lean Productivity: Minitab enables organizations to identify bottlenecks and inefficiencies in their processes, allowing them to streamline operations and improve productivity.
-
Lean Workflow: By using Minitab, organizations can visualize their workflow and identify areas for improvement, leading to smoother and more efficient processes.
Minitab Tools for Lean Management
Minitab offers a wide range of tools and features that are specifically designed to support lean management practices. Some of the key tools include:
-
Statistical Analysis: Minitab allows users to perform statistical analysis on data sets, helping them uncover trends and patterns that may not be visible to the naked eye.
-
Lean Six Sigma: Minitab is often used in conjunction with lean six sigma methodologies to drive process optimization and quality improvement initiatives.
How to Use Minitab for Lean Management
-
Data Analysis: Utilize Minitab to analyze and interpret data to gain valuable insights into process performance and identify areas for improvement.
-
Lean Principles: Apply lean principles such as value stream mapping and 5S with the help of Minitab to streamline processes and reduce waste.
Minitab Training for Lean Management
To fully leverage the capabilities of Minitab for lean management, organizations should invest in Minitab training for their employees. Training programs can help users become proficient in using the software and applying lean techniques to drive process improvement initiatives.
How to obtain Minitab Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Minitab is a powerful tool that can significantly enhance lean management practices by providing valuable insights into processes and enabling data-driven decision-making. By leveraging Minitab for lean management, organizations can improve efficiency, reduce waste, and drive continuous improvement initiatives. Investing in Minitab training for employees can further enhance the benefits of using this software for process optimization and quality improvement.
Read More
In today's competitive business environment, companies are constantly striving to improve efficiency and reduce waste in their processes. Lean management is a methodology that focuses on maximizing value while minimizing waste. One powerful tool that has been instrumental in helping organizations achieve these goals is Minitab statistical software. In this article, we will explore how Minitab can be used to enhance lean management practices and drive process improvement.
What is Lean Management?
Lean management is a systematic approach to identifying and eliminating waste within a process. It is based on the principles of continuous improvement and respect for people. By streamlining processes and optimizing workflows, organizations can achieve higher levels of productivity and customer satisfaction.
How Does Minitab Fit into Lean Management?
Minitab is a data analysis software that is widely used in various industries for process improvement and quality control. It provides powerful statistical tools that enable users to analyze data, identify patterns, and make data-driven decisions. By leveraging Minitab, lean practitioners can gain valuable insights into their processes and drive continuous improvement initiatives.
The Benefits of Using Minitab for Lean Management
-
Lean Productivity: Minitab enables organizations to identify bottlenecks and inefficiencies in their processes, allowing them to streamline operations and improve productivity.
-
Lean Workflow: By using Minitab, organizations can visualize their workflow and identify areas for improvement, leading to smoother and more efficient processes.
Minitab Tools for Lean Management
Minitab offers a wide range of tools and features that are specifically designed to support lean management practices. Some of the key tools include:
-
Statistical Analysis: Minitab allows users to perform statistical analysis on data sets, helping them uncover trends and patterns that may not be visible to the naked eye.
-
Lean Six Sigma: Minitab is often used in conjunction with lean six sigma methodologies to drive process optimization and quality improvement initiatives.
How to Use Minitab for Lean Management
-
Data Analysis: Utilize Minitab to analyze and interpret data to gain valuable insights into process performance and identify areas for improvement.
-
Lean Principles: Apply lean principles such as value stream mapping and 5S with the help of Minitab to streamline processes and reduce waste.
Minitab Training for Lean Management
To fully leverage the capabilities of Minitab for lean management, organizations should invest in Minitab training for their employees. Training programs can help users become proficient in using the software and applying lean techniques to drive process improvement initiatives.
How to obtain Minitab Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Minitab is a powerful tool that can significantly enhance lean management practices by providing valuable insights into processes and enabling data-driven decision-making. By leveraging Minitab for lean management, organizations can improve efficiency, reduce waste, and drive continuous improvement initiatives. Investing in Minitab training for employees can further enhance the benefits of using this software for process optimization and quality improvement.
Minitab in Academia :Enhancing Statistical Learning and Research
In the world of academia, the ability to analyze data effectively is crucial for student learning and faculty research. One tool that has become indispensable in this endeavor is Minitab, a powerful statistical software that offers a wide range of analytical tools for data exploration, hypothesis testing, and data visualization. In this article, we will explore how Minitab is enhancing statistical learning and research in higher education institutions.
The Role of Minitab in Academia
Minitab serves as an essential educational tool in universities and colleges worldwide, providing students and faculty members with the means to conduct in-depth data analysis and statistical modeling. By utilizing Minitab, students can gain hands-on experience with statistical techniques, enabling them to make data-driven decisions and enhance their academic success.
Benefits of Using Minitab in Academia
-
Enhanced Data Interpretation: Minitab allows users to easily manipulate data and perform complex statistical analyses, enabling them to interpret results accurately and draw meaningful conclusions from their research.
-
Improved Data Presentation: With Minitab's data visualization capabilities, users can create informative graphs and charts to present their findings in a clear and concise manner, making it easier for others to understand and interpret the data.
-
Facilitating Student Projects: Minitab provides students with a valuable tool for conducting research projects, allowing them to design experiments, analyze data, and present their findings effectively. This empowers students to take ownership of their learning and develop critical thinking and analytical skills.
Minitab in Faculty Research
In addition to benefiting students, Minitab also plays a crucial role in faculty research endeavors. By using Minitab to analyze data, faculty members can conduct rigorous research studies, explore new research methods, and make groundbreaking discoveries in their respective fields of study.
Case Study: University X Incorporates Minitab in Research Methods Course
At University X, the Department of Statistics has integrated Minitab into its research methods course to enhance student learning and research skills. By utilizing Minitab, students have been able to delve into the intricacies of experimental design, data manipulation, and statistical analysis, leading to a deeper understanding of research methodologies.
The Future of Minitab in Academia
As educational technology continues to evolve, Minitab remains at the forefront of statistical software, providing users with innovative tools for data analysis and interpretation. With its user-friendly interface and robust features, Minitab is poised to revolutionize statistical learning and research in academia for years to come.
How to obtain Minitab Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Minitab is a valuable asset in the academic realm, offering students and faculty members the tools they need to excel in data analysis, statistical learning, and research. By incorporating Minitab into their academic pursuits, individuals can enhance their understanding of statistical concepts, improve their research methodologies, and ultimately contribute to the advancement of knowledge in their respective fields.
Read More
In the world of academia, the ability to analyze data effectively is crucial for student learning and faculty research. One tool that has become indispensable in this endeavor is Minitab, a powerful statistical software that offers a wide range of analytical tools for data exploration, hypothesis testing, and data visualization. In this article, we will explore how Minitab is enhancing statistical learning and research in higher education institutions.
The Role of Minitab in Academia
Minitab serves as an essential educational tool in universities and colleges worldwide, providing students and faculty members with the means to conduct in-depth data analysis and statistical modeling. By utilizing Minitab, students can gain hands-on experience with statistical techniques, enabling them to make data-driven decisions and enhance their academic success.
Benefits of Using Minitab in Academia
-
Enhanced Data Interpretation: Minitab allows users to easily manipulate data and perform complex statistical analyses, enabling them to interpret results accurately and draw meaningful conclusions from their research.
-
Improved Data Presentation: With Minitab's data visualization capabilities, users can create informative graphs and charts to present their findings in a clear and concise manner, making it easier for others to understand and interpret the data.
-
Facilitating Student Projects: Minitab provides students with a valuable tool for conducting research projects, allowing them to design experiments, analyze data, and present their findings effectively. This empowers students to take ownership of their learning and develop critical thinking and analytical skills.
Minitab in Faculty Research
In addition to benefiting students, Minitab also plays a crucial role in faculty research endeavors. By using Minitab to analyze data, faculty members can conduct rigorous research studies, explore new research methods, and make groundbreaking discoveries in their respective fields of study.
Case Study: University X Incorporates Minitab in Research Methods Course
At University X, the Department of Statistics has integrated Minitab into its research methods course to enhance student learning and research skills. By utilizing Minitab, students have been able to delve into the intricacies of experimental design, data manipulation, and statistical analysis, leading to a deeper understanding of research methodologies.
The Future of Minitab in Academia
As educational technology continues to evolve, Minitab remains at the forefront of statistical software, providing users with innovative tools for data analysis and interpretation. With its user-friendly interface and robust features, Minitab is poised to revolutionize statistical learning and research in academia for years to come.
How to obtain Minitab Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Minitab is a valuable asset in the academic realm, offering students and faculty members the tools they need to excel in data analysis, statistical learning, and research. By incorporating Minitab into their academic pursuits, individuals can enhance their understanding of statistical concepts, improve their research methodologies, and ultimately contribute to the advancement of knowledge in their respective fields.
Blockchain in Identity Management: Redefining Digital Identity and Authentication
In today's digital world, the need for secure online identity verification is more important than ever before. With the rise of cyber threats and identity theft, traditional methods of authentication are no longer sufficient to protect users' personal information. This is where blockchain technology comes into play, revolutionizing the way we manage digital identities and authenticate users online.
The Role of Blockchain in Identity Management
Blockchain technology offers a decentralized and tamper-proof way to store and verify digital identities. By leveraging cryptographic principles and distributed consensus mechanisms, blockchain ensures that users' identity information is secure and cannot be altered without their consent. This makes blockchain an ideal solution for identity management systems that require high levels of security and trust.
Why is Blockchain Authentication Important?
Blockchain authentication provides a secure and transparent way to verify the identity of users online. With blockchain, users can prove their identity without the need for a central authority, such as a government or financial institution. This eliminates the risk of identity theft and fraud, as well as reduces the likelihood of data breaches.
How Does Blockchain Ensure Secure Digital Identity?
Blockchain uses advanced encryption algorithms and digital signatures to secure users' identity information. Each user is assigned a unique cryptographic key that allows them to access their digital identity securely. This key is stored on the blockchain, making it immutable and resistant to tampering. This ensures that users' identity information is protected from unauthorized access and cyber attacks.
Implementing Blockchain in Identity Management
The implementation of blockchain in identity management involves creating a decentralized system that allows users to control their own identity information. This empowers users to share only the information they choose to disclose, while keeping the rest of their data secure and private. This model of self-sovereign identity puts users in control of their digital identities, enhancing privacy and security online.
What are the Benefits of Blockchain for Identity Security?
- Enhanced security: Blockchain provides a secure and tamper-proof way to store and verify users' identity information.
- Decentralization: Users have full control over their digital identities, reducing the risk of data breaches and identity theft.
- Privacy: Users can choose what information to share and with whom, maintaining their privacy and confidentiality online.
- Trust: Blockchain authentication builds trust between users and service providers, as it ensures that identity information is reliable and verifiable.
How Can Organizations Leverage Blockchain for Identity Management?
Organizations can leverage blockchain technology to enhance their identity management systems and provide a more secure and reliable authentication process for users. By implementing blockchain-based identity verification solutions, organizations can streamline their onboarding process, reduce fraud, and improve the overall customer experience. This not only enhances security but also builds trust and credibility with users.
How to obtain Blockchain Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Blockchain technology is redefining the way we manage digital identities and authenticate users online. By providing a secure and decentralized solution for identity management, blockchain offers a more reliable and trustworthy way to verify users' identities. As organizations continue to adopt blockchain in their identity management systems, we can expect to see a more secure and privacy-focused online environment for users worldwide.
Read More
In today's digital world, the need for secure online identity verification is more important than ever before. With the rise of cyber threats and identity theft, traditional methods of authentication are no longer sufficient to protect users' personal information. This is where blockchain technology comes into play, revolutionizing the way we manage digital identities and authenticate users online.
The Role of Blockchain in Identity Management
Blockchain technology offers a decentralized and tamper-proof way to store and verify digital identities. By leveraging cryptographic principles and distributed consensus mechanisms, blockchain ensures that users' identity information is secure and cannot be altered without their consent. This makes blockchain an ideal solution for identity management systems that require high levels of security and trust.
Why is Blockchain Authentication Important?
Blockchain authentication provides a secure and transparent way to verify the identity of users online. With blockchain, users can prove their identity without the need for a central authority, such as a government or financial institution. This eliminates the risk of identity theft and fraud, as well as reduces the likelihood of data breaches.
How Does Blockchain Ensure Secure Digital Identity?
Blockchain uses advanced encryption algorithms and digital signatures to secure users' identity information. Each user is assigned a unique cryptographic key that allows them to access their digital identity securely. This key is stored on the blockchain, making it immutable and resistant to tampering. This ensures that users' identity information is protected from unauthorized access and cyber attacks.
Implementing Blockchain in Identity Management
The implementation of blockchain in identity management involves creating a decentralized system that allows users to control their own identity information. This empowers users to share only the information they choose to disclose, while keeping the rest of their data secure and private. This model of self-sovereign identity puts users in control of their digital identities, enhancing privacy and security online.
What are the Benefits of Blockchain for Identity Security?
- Enhanced security: Blockchain provides a secure and tamper-proof way to store and verify users' identity information.
- Decentralization: Users have full control over their digital identities, reducing the risk of data breaches and identity theft.
- Privacy: Users can choose what information to share and with whom, maintaining their privacy and confidentiality online.
- Trust: Blockchain authentication builds trust between users and service providers, as it ensures that identity information is reliable and verifiable.
How Can Organizations Leverage Blockchain for Identity Management?
Organizations can leverage blockchain technology to enhance their identity management systems and provide a more secure and reliable authentication process for users. By implementing blockchain-based identity verification solutions, organizations can streamline their onboarding process, reduce fraud, and improve the overall customer experience. This not only enhances security but also builds trust and credibility with users.
How to obtain Blockchain Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Blockchain technology is redefining the way we manage digital identities and authenticate users online. By providing a secure and decentralized solution for identity management, blockchain offers a more reliable and trustworthy way to verify users' identities. As organizations continue to adopt blockchain in their identity management systems, we can expect to see a more secure and privacy-focused online environment for users worldwide.
Mastering Agile Project Management with PMP Principles
In today's fast-paced business environment, mastering agile project management with PMP principles is essential for success. Agile project management is a methodology that focuses on flexibility, collaboration, and continuous improvement. By combining agile practices with PMP principles, project managers can effectively plan, execute, and deliver projects with speed and efficiency.
Agile Project Management: A Winning Strategy
Agile project management involves breaking down projects into smaller, manageable tasks that can be completed in short iterations. This approach allows teams to adapt to changes quickly and deliver value to stakeholders in a timely manner. By embracing agile practices, project managers can improve project delivery and achieve better outcomes for their organizations.
One of the key benefits of agile project management is its focus on collaboration and communication. By fostering a culture of teamwork and transparency, project managers can ensure that all team members are aligned on project goals and working towards a common purpose. This leads to improved efficiency, higher quality deliverables, and increased customer satisfaction.
PMP Principles: The Foundation of Project Management Success
PMP principles, on the other hand, provide project managers with a comprehensive framework for planning, executing, and monitoring projects. By obtaining a project management certification such as the PMP certification, professionals can demonstrate their expertise in project management and enhance their career prospects.
Project management training is essential for mastering PMP principles and acquiring the necessary skills to lead successful projects. Through project management courses and PMP exam preparation, professionals can gain a deep understanding of project management best practices, techniques, and tools.
Combining Agile and PMP: Best of Both Worlds
By combining agile project management with PMP principles, project managers can leverage the strengths of both methodologies to achieve project success. Agile project planning allows for quick adaptation to changing requirements, while PMP principles provide a solid foundation for project governance and control.
Agile project leadership is another key aspect of mastering agile project management with PMP principles. Agile project managers must inspire and motivate their teams to deliver high-quality results in a fast-paced environment. By applying PMP principles, project managers can ensure that projects are completed on time, within budget, and to the satisfaction of stakeholders.
Key Strategies for Agile Project Success
To ensure agile project success, project managers must focus on effective project management strategies that align with agile practices and PMP principles. This includes establishing clear project goals, defining project scope, and continuously monitoring project progress.
Agile project development and implementation require a collaborative and iterative approach. By breaking down projects into smaller tasks and delivering incremental value, project managers can respond quickly to changing requirements and deliver projects more efficiently.
How to obtain PMP Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, mastering agile project management with PMP principles is a winning strategy for project managers looking to enhance their project management skills and deliver successful projects. By combining agile practices with PMP principles, project managers can achieve greater project success, improve stakeholder satisfaction, and drive business results.
Read More
In today's fast-paced business environment, mastering agile project management with PMP principles is essential for success. Agile project management is a methodology that focuses on flexibility, collaboration, and continuous improvement. By combining agile practices with PMP principles, project managers can effectively plan, execute, and deliver projects with speed and efficiency.
Agile Project Management: A Winning Strategy
Agile project management involves breaking down projects into smaller, manageable tasks that can be completed in short iterations. This approach allows teams to adapt to changes quickly and deliver value to stakeholders in a timely manner. By embracing agile practices, project managers can improve project delivery and achieve better outcomes for their organizations.
One of the key benefits of agile project management is its focus on collaboration and communication. By fostering a culture of teamwork and transparency, project managers can ensure that all team members are aligned on project goals and working towards a common purpose. This leads to improved efficiency, higher quality deliverables, and increased customer satisfaction.
PMP Principles: The Foundation of Project Management Success
PMP principles, on the other hand, provide project managers with a comprehensive framework for planning, executing, and monitoring projects. By obtaining a project management certification such as the PMP certification, professionals can demonstrate their expertise in project management and enhance their career prospects.
Project management training is essential for mastering PMP principles and acquiring the necessary skills to lead successful projects. Through project management courses and PMP exam preparation, professionals can gain a deep understanding of project management best practices, techniques, and tools.
Combining Agile and PMP: Best of Both Worlds
By combining agile project management with PMP principles, project managers can leverage the strengths of both methodologies to achieve project success. Agile project planning allows for quick adaptation to changing requirements, while PMP principles provide a solid foundation for project governance and control.
Agile project leadership is another key aspect of mastering agile project management with PMP principles. Agile project managers must inspire and motivate their teams to deliver high-quality results in a fast-paced environment. By applying PMP principles, project managers can ensure that projects are completed on time, within budget, and to the satisfaction of stakeholders.
Key Strategies for Agile Project Success
To ensure agile project success, project managers must focus on effective project management strategies that align with agile practices and PMP principles. This includes establishing clear project goals, defining project scope, and continuously monitoring project progress.
Agile project development and implementation require a collaborative and iterative approach. By breaking down projects into smaller tasks and delivering incremental value, project managers can respond quickly to changing requirements and deliver projects more efficiently.
How to obtain PMP Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, mastering agile project management with PMP principles is a winning strategy for project managers looking to enhance their project management skills and deliver successful projects. By combining agile practices with PMP principles, project managers can achieve greater project success, improve stakeholder satisfaction, and drive business results.
Harnessing the Power of AI in Digital Marketing Campaigns
Are you looking to revolutionize your digital marketing efforts and stay ahead of the competition? Harnessing the power of Artificial Intelligence (AI) in your digital marketing campaigns is the key to achieving unparalleled success in today's fast-paced digital landscape. AI has completely transformed the way businesses approach marketing, enabling them to leverage data-driven insights, automate processes, personalize content, and engage with customers in a more meaningful way.
The Role of AI in Digital Marketing
AI plays a crucial role in digital marketing by enabling businesses to streamline their marketing efforts, make data-driven decisions, and deliver personalized experiences to their target audience. By leveraging AI technology, marketers can analyze vast amounts of data, identify trends and patterns, and gain valuable insights into consumer behavior. This allows them to create highly targeted and effective marketing campaigns that resonate with their audience.
Marketing Automation
One of the key benefits of AI in digital marketing is marketing automation. AI-powered tools and platforms can automate repetitive tasks such as email marketing, social media management, and content scheduling, allowing marketers to focus on more strategic initiatives. By automating these processes, businesses can save time and resources while delivering more personalized and timely communications to their customers.
Data Analytics
AI technology enables businesses to gather, analyze, and interpret large sets of data in real-time. This allows marketers to track the performance of their campaigns, measure key metrics, and optimize their strategies for better results. By harnessing the power of AI in data analytics, businesses can gain valuable insights into customer behavior, preferences, and trends, allowing them to tailor their marketing efforts for maximum impact.
Personalized Content
AI-driven personalization is a game-changer in digital marketing. By leveraging machine learning algorithms, businesses can create personalized content that is tailored to the individual preferences and interests of their target audience. This not only enhances customer engagement but also increases the likelihood of conversion. Personalized content resonates with customers on a deeper level, making them more likely to take action and make a purchase.
Customer Engagement
AI-powered chatbots are revolutionizing the way businesses engage with their customers. These intelligent virtual assistants can provide instant support, answer customer queries, and guide users through the purchasing process. By implementing chatbots in their digital marketing strategies, businesses can deliver a seamless and personalized customer experience that fosters loyalty and drives sales.
Predictive Analytics
Predictive analytics is another powerful application of AI in digital marketing. By analyzing historical data and trends, businesses can predict future outcomes, trends, and behaviors. This allows marketers to anticipate customer needs, tailor their messaging, and create targeted campaigns that yield higher ROI. Predictive analytics enables businesses to stay ahead of the competition and capitalize on emerging opportunities in the market.
Leveraging AI Tools for Marketing Success
There are a plethora of AI tools available in the market that can help businesses enhance their digital marketing efforts. From email marketing platforms to social media management tools to SEO tactics, AI-powered tools can streamline processes, optimize campaigns, and drive results. By leveraging these tools, businesses can stay competitive, improve their marketing strategies, and achieve greater success in the digital landscape.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, harnessing the power of AI in digital marketing campaigns is essential for businesses looking to stay ahead in today's competitive landscape. From marketing automation to personalized content to predictive analytics, AI offers endless opportunities for businesses to enhance their marketing efforts, engage with customers, and drive ROI. By leveraging AI tools and strategies, businesses can optimize their campaigns, gain valuable insights, and deliver personalized experiences that resonate with their audience. Embrace the power of AI in your digital marketing efforts and watch your business soar to new heights.
Read More
Are you looking to revolutionize your digital marketing efforts and stay ahead of the competition? Harnessing the power of Artificial Intelligence (AI) in your digital marketing campaigns is the key to achieving unparalleled success in today's fast-paced digital landscape. AI has completely transformed the way businesses approach marketing, enabling them to leverage data-driven insights, automate processes, personalize content, and engage with customers in a more meaningful way.
The Role of AI in Digital Marketing
AI plays a crucial role in digital marketing by enabling businesses to streamline their marketing efforts, make data-driven decisions, and deliver personalized experiences to their target audience. By leveraging AI technology, marketers can analyze vast amounts of data, identify trends and patterns, and gain valuable insights into consumer behavior. This allows them to create highly targeted and effective marketing campaigns that resonate with their audience.
Marketing Automation
One of the key benefits of AI in digital marketing is marketing automation. AI-powered tools and platforms can automate repetitive tasks such as email marketing, social media management, and content scheduling, allowing marketers to focus on more strategic initiatives. By automating these processes, businesses can save time and resources while delivering more personalized and timely communications to their customers.
Data Analytics
AI technology enables businesses to gather, analyze, and interpret large sets of data in real-time. This allows marketers to track the performance of their campaigns, measure key metrics, and optimize their strategies for better results. By harnessing the power of AI in data analytics, businesses can gain valuable insights into customer behavior, preferences, and trends, allowing them to tailor their marketing efforts for maximum impact.
Personalized Content
AI-driven personalization is a game-changer in digital marketing. By leveraging machine learning algorithms, businesses can create personalized content that is tailored to the individual preferences and interests of their target audience. This not only enhances customer engagement but also increases the likelihood of conversion. Personalized content resonates with customers on a deeper level, making them more likely to take action and make a purchase.
Customer Engagement
AI-powered chatbots are revolutionizing the way businesses engage with their customers. These intelligent virtual assistants can provide instant support, answer customer queries, and guide users through the purchasing process. By implementing chatbots in their digital marketing strategies, businesses can deliver a seamless and personalized customer experience that fosters loyalty and drives sales.
Predictive Analytics
Predictive analytics is another powerful application of AI in digital marketing. By analyzing historical data and trends, businesses can predict future outcomes, trends, and behaviors. This allows marketers to anticipate customer needs, tailor their messaging, and create targeted campaigns that yield higher ROI. Predictive analytics enables businesses to stay ahead of the competition and capitalize on emerging opportunities in the market.
Leveraging AI Tools for Marketing Success
There are a plethora of AI tools available in the market that can help businesses enhance their digital marketing efforts. From email marketing platforms to social media management tools to SEO tactics, AI-powered tools can streamline processes, optimize campaigns, and drive results. By leveraging these tools, businesses can stay competitive, improve their marketing strategies, and achieve greater success in the digital landscape.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, harnessing the power of AI in digital marketing campaigns is essential for businesses looking to stay ahead in today's competitive landscape. From marketing automation to personalized content to predictive analytics, AI offers endless opportunities for businesses to enhance their marketing efforts, engage with customers, and drive ROI. By leveraging AI tools and strategies, businesses can optimize their campaigns, gain valuable insights, and deliver personalized experiences that resonate with their audience. Embrace the power of AI in your digital marketing efforts and watch your business soar to new heights.
The Future of Software Testing How CTFL Fits In
In today's fast-paced and constantly evolving technology landscape, the future of software testing is more critical than ever. As software continues to play a vital role in our daily lives, the need for efficient and reliable testing processes has become paramount. This is where the Certified Tester Foundation Level (CTFL) certification comes in.
The Importance of Software Testing in Today's World
Software testing is an essential component of the software development lifecycle. It ensures that the final product meets the desired quality standards, functions as intended, and is free of defects. Without proper testing, software projects can result in costly errors, delays, and ultimately, dissatisfied users.
What is CTFL and Why is it Important?
CTFL is a certification designed for software testers who want to demonstrate their knowledge and skills in testing processes, agile testing, quality assurance, and more. By obtaining a CTFL certification, professionals can showcase their expertise in the field and enhance their career opportunities.
Benefits of CTFL Certification
- Demonstrates mastery of testing methodologies and best practices
- Enhances credibility and trustworthiness in the software industry
- Opens doors for career advancement and higher-paying opportunities
- Equips professionals with the skills needed to excel in software testing roles
How CTFL Fits into the Software Development Lifecycle
CTFL plays a crucial role in ensuring the quality and reliability of software products. From test automation to test management, CTFL-certified professionals are well-versed in the latest tools and techniques needed to execute effective testing strategies throughout the software lifecycle.
When it comes to continuous testing and innovation in testing, CTFL certification provides professionals with the knowledge and expertise needed to stay ahead of the curve. By keeping up with the latest trends and advancements in the industry, CTFL-certified individuals can contribute to the success of software projects and drive digital transformation.
CTFL Training and Syllabus
To obtain a CTFL certification, professionals must undergo rigorous training and preparation. The CTFL course covers a wide range of topics, including test cases, test strategy, software quality, and more. By mastering these key concepts, individuals can enhance their testing skills and become valuable assets to their organizations.
How to obtain CTFL Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, the future of software testing relies heavily on qualified and skilled professionals who can effectively navigate the complexities of the industry. With CTFL certification, software testers can set themselves apart from the competition and position themselves as leaders in the field. It's time to invest in your future and take your software testing career to the next level with CTFL.
Read More
In today's fast-paced and constantly evolving technology landscape, the future of software testing is more critical than ever. As software continues to play a vital role in our daily lives, the need for efficient and reliable testing processes has become paramount. This is where the Certified Tester Foundation Level (CTFL) certification comes in.
The Importance of Software Testing in Today's World
Software testing is an essential component of the software development lifecycle. It ensures that the final product meets the desired quality standards, functions as intended, and is free of defects. Without proper testing, software projects can result in costly errors, delays, and ultimately, dissatisfied users.
What is CTFL and Why is it Important?
CTFL is a certification designed for software testers who want to demonstrate their knowledge and skills in testing processes, agile testing, quality assurance, and more. By obtaining a CTFL certification, professionals can showcase their expertise in the field and enhance their career opportunities.
Benefits of CTFL Certification
- Demonstrates mastery of testing methodologies and best practices
- Enhances credibility and trustworthiness in the software industry
- Opens doors for career advancement and higher-paying opportunities
- Equips professionals with the skills needed to excel in software testing roles
How CTFL Fits into the Software Development Lifecycle
CTFL plays a crucial role in ensuring the quality and reliability of software products. From test automation to test management, CTFL-certified professionals are well-versed in the latest tools and techniques needed to execute effective testing strategies throughout the software lifecycle.
When it comes to continuous testing and innovation in testing, CTFL certification provides professionals with the knowledge and expertise needed to stay ahead of the curve. By keeping up with the latest trends and advancements in the industry, CTFL-certified individuals can contribute to the success of software projects and drive digital transformation.
CTFL Training and Syllabus
To obtain a CTFL certification, professionals must undergo rigorous training and preparation. The CTFL course covers a wide range of topics, including test cases, test strategy, software quality, and more. By mastering these key concepts, individuals can enhance their testing skills and become valuable assets to their organizations.
How to obtain CTFL Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, the future of software testing relies heavily on qualified and skilled professionals who can effectively navigate the complexities of the industry. With CTFL certification, software testers can set themselves apart from the competition and position themselves as leaders in the field. It's time to invest in your future and take your software testing career to the next level with CTFL.
The Role of Big Data in Smart Cities Enhancing Urban Infrastructure and Services
In today's rapidly evolving world, the emergence of smart cities has revolutionized the way urban areas are managed and developed. One of the key drivers behind the success of smart cities is the utilization of big data to enhance urban infrastructure and services. From data analytics and technology to IoT sensors and artificial intelligence, big data is playing a crucial role in shaping the future of urban planning and sustainable development.
Urban Infrastructure and Smart City Services
Urban infrastructure is the backbone of any city, encompassing everything from transportation systems and energy grids to water supply networks and waste management facilities. By harnessing the power of big data, city management authorities can optimize the efficiency and effectiveness of these infrastructure systems, leading to improved quality of life for residents.
Smart city services, on the other hand, rely on real-time data insights to deliver innovative solutions to urban challenges. From smart sensors that monitor air quality and traffic flow to digital platforms that enable predictive analytics and data-driven decision making, the integration of big data technologies is revolutionizing the way cities operate.
Data Analytics and Technology in Urban Planning
Data analytics plays a crucial role in urban planning by providing city officials with valuable insights into population trends, infrastructure usage, and environmental impact. By leveraging advanced analytics tools, urban planners can make informed decisions about infrastructure development, resource allocation, and policy implementation.
Moreover, technology such as IoT sensors and cloud computing are transforming the way cities collect, manage, and analyze data. These technologies enable real-time monitoring of key urban metrics, allowing city officials to respond quickly to emerging issues and opportunities.
Artificial Intelligence and Urban Governance
Artificial intelligence (AI) is another powerful tool in the smart city arsenal, enabling city officials to harness the power of machine learning and predictive analytics to optimize urban governance. AI-powered solutions can help streamline city operations, improve service delivery, and enhance urban sustainability.
Through the deployment of smart sensors and IoT sensors, city authorities can collect vast amounts of data on various aspects of city life, from traffic patterns and energy consumption to waste disposal and public health. This data can then be analyzed using AI algorithms to identify trends, patterns, and anomalies, enabling city officials to make data-driven decisions that benefit residents and businesses alike.
Innovation and Smart City Projects
Innovative projects that leverage big data technologies are transforming the way cities are planned, managed, and developed. From smart mobility solutions that optimize transportation systems to smart grids that enhance energy efficiency, the possibilities for innovation are endless.
By embracing digital transformation and adopting cutting-edge technologies, cities can unlock new opportunities for growth, efficiency, and sustainability. Through collaboration with technology partners and investment in smart city projects, urban areas can become more resilient, competitive, and livable for their residents.
How to obtain Big Data Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the role of big data in smart cities is undeniable. By enhancing urban infrastructure and services through data analytics, technology, and innovation, cities can achieve unprecedented levels of efficiency, sustainability, and quality of life for their residents. As we look to the future, the continued integration of big data technologies will be essential in shaping the cities of tomorrow.Remember, the future of urban development lies in the hands of those who harness the power of big data to create smarter, more livable cities for all.
Read More
In today's rapidly evolving world, the emergence of smart cities has revolutionized the way urban areas are managed and developed. One of the key drivers behind the success of smart cities is the utilization of big data to enhance urban infrastructure and services. From data analytics and technology to IoT sensors and artificial intelligence, big data is playing a crucial role in shaping the future of urban planning and sustainable development.
Urban Infrastructure and Smart City Services
Urban infrastructure is the backbone of any city, encompassing everything from transportation systems and energy grids to water supply networks and waste management facilities. By harnessing the power of big data, city management authorities can optimize the efficiency and effectiveness of these infrastructure systems, leading to improved quality of life for residents.
Smart city services, on the other hand, rely on real-time data insights to deliver innovative solutions to urban challenges. From smart sensors that monitor air quality and traffic flow to digital platforms that enable predictive analytics and data-driven decision making, the integration of big data technologies is revolutionizing the way cities operate.
Data Analytics and Technology in Urban Planning
Data analytics plays a crucial role in urban planning by providing city officials with valuable insights into population trends, infrastructure usage, and environmental impact. By leveraging advanced analytics tools, urban planners can make informed decisions about infrastructure development, resource allocation, and policy implementation.
Moreover, technology such as IoT sensors and cloud computing are transforming the way cities collect, manage, and analyze data. These technologies enable real-time monitoring of key urban metrics, allowing city officials to respond quickly to emerging issues and opportunities.
Artificial Intelligence and Urban Governance
Artificial intelligence (AI) is another powerful tool in the smart city arsenal, enabling city officials to harness the power of machine learning and predictive analytics to optimize urban governance. AI-powered solutions can help streamline city operations, improve service delivery, and enhance urban sustainability.
Through the deployment of smart sensors and IoT sensors, city authorities can collect vast amounts of data on various aspects of city life, from traffic patterns and energy consumption to waste disposal and public health. This data can then be analyzed using AI algorithms to identify trends, patterns, and anomalies, enabling city officials to make data-driven decisions that benefit residents and businesses alike.
Innovation and Smart City Projects
Innovative projects that leverage big data technologies are transforming the way cities are planned, managed, and developed. From smart mobility solutions that optimize transportation systems to smart grids that enhance energy efficiency, the possibilities for innovation are endless.
By embracing digital transformation and adopting cutting-edge technologies, cities can unlock new opportunities for growth, efficiency, and sustainability. Through collaboration with technology partners and investment in smart city projects, urban areas can become more resilient, competitive, and livable for their residents.
How to obtain Big Data Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the role of big data in smart cities is undeniable. By enhancing urban infrastructure and services through data analytics, technology, and innovation, cities can achieve unprecedented levels of efficiency, sustainability, and quality of life for their residents. As we look to the future, the continued integration of big data technologies will be essential in shaping the cities of tomorrow.Remember, the future of urban development lies in the hands of those who harness the power of big data to create smarter, more livable cities for all.
Integrating CMMI with Other Quality Models ISO Six Sigma and More
In today's fast-paced and highly competitive business environment, organizations are constantly seeking ways to improve their processes, enhance product quality, and increase customer satisfaction. One of the most effective ways to achieve these goals is by integrating different quality models such as CMMI, ISO, and Six Sigma. By combining the strengths of each model, companies can create a robust quality management system that is tailored to their specific needs and requirements.
CMMI and ISO: A Comparison
Both CMMI (Capability Maturity Model Integration) and ISO (International Organization for Standardization) are widely used quality models that provide guidelines for improving processes and ensuring product quality. While CMMI focuses on process improvement and organizational maturity, ISO standards are more focused on setting standards for quality management systems.
Are CMMI and ISO compatible?
Yes, CMMI and ISO can be compatible and complementary. Many companies have successfully integrated both models to create a more comprehensive quality management system that addresses both process improvement and compliance with international standards.
CMMI and Six Sigma: Finding Common Ground
Six Sigma is another popular quality improvement methodology that focuses on reducing defects and variations in processes. While CMMI and Six Sigma have different approaches, they can be aligned to achieve common goals such as improving product quality and customer satisfaction.
How can CMMI and Six Sigma be integrated?
By combining the process improvement capabilities of CMMI with the statistical tools and methodologies of Six Sigma, companies can create a powerful quality management system that is capable of driving continuous improvement and enhancing efficiency.
Integrating CMMI with Other Quality Models
In addition to ISO and Six Sigma, there are other quality models that can be integrated with CMMI to further enhance the effectiveness of a company's quality management system. These may include Lean, TQM (Total Quality Management), and Agile methodologies.
What are the benefits of integrating multiple quality models?
By integrating multiple quality models, companies can leverage the strengths of each model and tailor their quality management system to meet the specific needs and requirements of their organization. This can result in improved process efficiency, higher product quality, and increased customer satisfaction.
How to obtain CMMI Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, integrating CMMI with other quality models such as ISO, Six Sigma, and more can provide companies with a comprehensive and robust quality management system that drives continuous improvement and ensures customer satisfaction. By combining the strengths of different models and methodologies, companies can create a tailored approach to quality management that meets their unique business needs. So, don't hesitate to explore the possibilities of integrating CMMI with other quality models to take your organization's quality management to the next level.
Read More
In today's fast-paced and highly competitive business environment, organizations are constantly seeking ways to improve their processes, enhance product quality, and increase customer satisfaction. One of the most effective ways to achieve these goals is by integrating different quality models such as CMMI, ISO, and Six Sigma. By combining the strengths of each model, companies can create a robust quality management system that is tailored to their specific needs and requirements.
CMMI and ISO: A Comparison
Both CMMI (Capability Maturity Model Integration) and ISO (International Organization for Standardization) are widely used quality models that provide guidelines for improving processes and ensuring product quality. While CMMI focuses on process improvement and organizational maturity, ISO standards are more focused on setting standards for quality management systems.
Are CMMI and ISO compatible?
Yes, CMMI and ISO can be compatible and complementary. Many companies have successfully integrated both models to create a more comprehensive quality management system that addresses both process improvement and compliance with international standards.
CMMI and Six Sigma: Finding Common Ground
Six Sigma is another popular quality improvement methodology that focuses on reducing defects and variations in processes. While CMMI and Six Sigma have different approaches, they can be aligned to achieve common goals such as improving product quality and customer satisfaction.
How can CMMI and Six Sigma be integrated?
By combining the process improvement capabilities of CMMI with the statistical tools and methodologies of Six Sigma, companies can create a powerful quality management system that is capable of driving continuous improvement and enhancing efficiency.
Integrating CMMI with Other Quality Models
In addition to ISO and Six Sigma, there are other quality models that can be integrated with CMMI to further enhance the effectiveness of a company's quality management system. These may include Lean, TQM (Total Quality Management), and Agile methodologies.
What are the benefits of integrating multiple quality models?
By integrating multiple quality models, companies can leverage the strengths of each model and tailor their quality management system to meet the specific needs and requirements of their organization. This can result in improved process efficiency, higher product quality, and increased customer satisfaction.
How to obtain CMMI Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, integrating CMMI with other quality models such as ISO, Six Sigma, and more can provide companies with a comprehensive and robust quality management system that drives continuous improvement and ensures customer satisfaction. By combining the strengths of different models and methodologies, companies can create a tailored approach to quality management that meets their unique business needs. So, don't hesitate to explore the possibilities of integrating CMMI with other quality models to take your organization's quality management to the next level.
Salesforce for Nonprofits Empowering Social Impact Organizations
In today's fast-paced and digital world, social impact organizations face unique challenges when it comes to managing their operations, engaging with donors and volunteers, and maximizing their impact. However, with the advent of cloud technology and nonprofit-focused software solutions like Salesforce, nonprofits now have access to powerful tools that can help streamline their processes, improve communication, and drive greater efficiency. In this article, we will explore how Salesforce for nonprofits is empowering social impact organizations to achieve their missions more effectively and efficiently.
What is Salesforce for Nonprofits?
Salesforce for nonprofits is a specialized version of the popular CRM platform that is designed to meet the unique needs of social impact organizations. This powerful tool provides nonprofits with a comprehensive suite of features, including donor management, fundraising software, volunteer management, nonprofit CRM, and more. By leveraging the power of cloud technology, nonprofits can access their data from anywhere, at any time, and streamline their operations for maximum efficiency.
How Does Salesforce Empower Nonprofits?
One of the key benefits of using Salesforce for nonprofits is its ability to automate many of the tedious tasks that can consume valuable time and resources. From managing donor relationships to tracking fundraising campaigns, Salesforce can handle it all, allowing nonprofit staff to focus on what truly matters - making a difference in the community. Additionally, Salesforce provides powerful reporting and analytics tools that can help nonprofits track their progress, measure their impact, and make data-driven decisions moving forward.
What Are Some Key Features of Salesforce for Nonprofits?
-
Donor Management: Easily track and manage donor relationships, communications, and contributions.
-
Fundraising Software: Create and track fundraising campaigns, events, and appeals with ease.
-
Volunteer Management: Recruit, schedule, and communicate with volunteers efficiently.
-
Nonprofit CRM: Centralize all your nonprofit's data in one secure and accessible location.
-
Cloud Technology for Nonprofits: Access your data and tools from anywhere, at any time.
How Does Salesforce Drive Digital Transformation for Nonprofits?
By implementing Salesforce for nonprofits, social impact organizations can undergo a digital transformation that revolutionizes the way they operate. With automated workflows, streamlined communication tools, and integrated software solutions, nonprofits can work more efficiently and effectively than ever before. Salesforce helps nonprofits leverage technology to scale their operations, engage with donors and volunteers, and track their impact in real-time.
Why Should Nonprofits Consider Salesforce?
Nonprofits that are looking to optimize their operations, improve their communication, and enhance their fundraising efforts should consider implementing Salesforce. With its user-friendly interface, customizable features, and powerful integrations, Salesforce offers a comprehensive solution for nonprofits of all sizes. By investing in Salesforce, nonprofits can boost their efficiency, drive their impact, and empower their team to achieve greater success.
How to obtain Salesforce Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Salesforce for nonprofits is a game-changer for social impact organizations looking to increase their efficiency, engage with donors and volunteers, and maximize their impact. By harnessing the power of cloud technology and nonprofit-focused software solutions, nonprofits can transform the way they operate, drive greater impact, and make a difference in their communities. If your nonprofit is ready to take its operations to the next level, consider leveraging Salesforce to empower your organization and achieve your mission more effectively and efficiently.
Read More
In today's fast-paced and digital world, social impact organizations face unique challenges when it comes to managing their operations, engaging with donors and volunteers, and maximizing their impact. However, with the advent of cloud technology and nonprofit-focused software solutions like Salesforce, nonprofits now have access to powerful tools that can help streamline their processes, improve communication, and drive greater efficiency. In this article, we will explore how Salesforce for nonprofits is empowering social impact organizations to achieve their missions more effectively and efficiently.
What is Salesforce for Nonprofits?
Salesforce for nonprofits is a specialized version of the popular CRM platform that is designed to meet the unique needs of social impact organizations. This powerful tool provides nonprofits with a comprehensive suite of features, including donor management, fundraising software, volunteer management, nonprofit CRM, and more. By leveraging the power of cloud technology, nonprofits can access their data from anywhere, at any time, and streamline their operations for maximum efficiency.
How Does Salesforce Empower Nonprofits?
One of the key benefits of using Salesforce for nonprofits is its ability to automate many of the tedious tasks that can consume valuable time and resources. From managing donor relationships to tracking fundraising campaigns, Salesforce can handle it all, allowing nonprofit staff to focus on what truly matters - making a difference in the community. Additionally, Salesforce provides powerful reporting and analytics tools that can help nonprofits track their progress, measure their impact, and make data-driven decisions moving forward.
What Are Some Key Features of Salesforce for Nonprofits?
-
Donor Management: Easily track and manage donor relationships, communications, and contributions.
-
Fundraising Software: Create and track fundraising campaigns, events, and appeals with ease.
-
Volunteer Management: Recruit, schedule, and communicate with volunteers efficiently.
-
Nonprofit CRM: Centralize all your nonprofit's data in one secure and accessible location.
-
Cloud Technology for Nonprofits: Access your data and tools from anywhere, at any time.
How Does Salesforce Drive Digital Transformation for Nonprofits?
By implementing Salesforce for nonprofits, social impact organizations can undergo a digital transformation that revolutionizes the way they operate. With automated workflows, streamlined communication tools, and integrated software solutions, nonprofits can work more efficiently and effectively than ever before. Salesforce helps nonprofits leverage technology to scale their operations, engage with donors and volunteers, and track their impact in real-time.
Why Should Nonprofits Consider Salesforce?
Nonprofits that are looking to optimize their operations, improve their communication, and enhance their fundraising efforts should consider implementing Salesforce. With its user-friendly interface, customizable features, and powerful integrations, Salesforce offers a comprehensive solution for nonprofits of all sizes. By investing in Salesforce, nonprofits can boost their efficiency, drive their impact, and empower their team to achieve greater success.
How to obtain Salesforce Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Salesforce for nonprofits is a game-changer for social impact organizations looking to increase their efficiency, engage with donors and volunteers, and maximize their impact. By harnessing the power of cloud technology and nonprofit-focused software solutions, nonprofits can transform the way they operate, drive greater impact, and make a difference in their communities. If your nonprofit is ready to take its operations to the next level, consider leveraging Salesforce to empower your organization and achieve your mission more effectively and efficiently.
The Ultimate Salesforce Admin Productivity Hacks
In today's fast-paced working environment, Salesforce admins are constantly striving to find ways to increase productivity and efficiency. With the right tools, tips, and tricks, admins can streamline their workflow, automate repetitive tasks, and optimize their performance. In this article, we will explore the ultimate Salesforce admin productivity hacks to help you work smarter, not harder.
Salesforce Admin Productivity Tips
-
Utilize Dashboard Customization: Customize your dashboards to display the most important data at a glance. This will help you make informed decisions quickly and efficiently.
-
Automate Reporting: Set up automated reports to save time on manual data gathering and analysis. Schedule reports to be delivered directly to your inbox at regular intervals.
-
Optimize Workflows: Streamline your workflows by identifying bottlenecks and eliminating unnecessary steps. Use approval processes and validation rules to automate tasks and improve efficiency.
-
Effective Data Management: Keep your Salesforce data clean and organized. Regularly deduplicate records, update outdated information, and use data loaders to mass update data.
-
Task Management Tools: Use task management tools such as Salesforce Inbox to prioritize tasks, set reminders, and track progress. Stay organized and focused on what matters most.
-
Efficiency Tools Integration: Integrate efficiency tools such as Slack, Trello, or Asana with Salesforce to centralize communication and streamline collaboration.
Boost Your Productivity with Advanced Tips
-
Customize your Salesforce homepage for quick access to frequently used features.
-
Create keyboard shortcuts to navigate Salesforce faster.
-
Leverage Salesforce mobile app for on-the-go access to CRM data.
-
Implement Einstein AI features for predictive analytics and automation.
-
Use Salesforce Trailhead to stay updated on new features and best practices.
Enhance Performance with Admin Strategies
-
Create reusable templates for common tasks and reports.
-
Standardize naming conventions for consistency and easy search.
-
Collaborate with other admins to share tips and best practices.
-
Regularly review and optimize your Salesforce setup for performance improvements.
-
Invest in ongoing training and certifications to stay ahead of the curve.
How to obtain Salesforce Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion , By implementing these Salesforce admin productivity hacks, you can enhance your performance, increase efficiency, and boost productivity. Work smarter, not harder, with these tips and tricks to streamline your workflow, automate tasks, and optimize your Salesforce experience. Stay organized, stay focused, and watch your productivity soar.
Read More
In today's fast-paced working environment, Salesforce admins are constantly striving to find ways to increase productivity and efficiency. With the right tools, tips, and tricks, admins can streamline their workflow, automate repetitive tasks, and optimize their performance. In this article, we will explore the ultimate Salesforce admin productivity hacks to help you work smarter, not harder.
Salesforce Admin Productivity Tips
-
Utilize Dashboard Customization: Customize your dashboards to display the most important data at a glance. This will help you make informed decisions quickly and efficiently.
-
Automate Reporting: Set up automated reports to save time on manual data gathering and analysis. Schedule reports to be delivered directly to your inbox at regular intervals.
-
Optimize Workflows: Streamline your workflows by identifying bottlenecks and eliminating unnecessary steps. Use approval processes and validation rules to automate tasks and improve efficiency.
-
Effective Data Management: Keep your Salesforce data clean and organized. Regularly deduplicate records, update outdated information, and use data loaders to mass update data.
-
Task Management Tools: Use task management tools such as Salesforce Inbox to prioritize tasks, set reminders, and track progress. Stay organized and focused on what matters most.
-
Efficiency Tools Integration: Integrate efficiency tools such as Slack, Trello, or Asana with Salesforce to centralize communication and streamline collaboration.
Boost Your Productivity with Advanced Tips
-
Customize your Salesforce homepage for quick access to frequently used features.
-
Create keyboard shortcuts to navigate Salesforce faster.
-
Leverage Salesforce mobile app for on-the-go access to CRM data.
-
Implement Einstein AI features for predictive analytics and automation.
-
Use Salesforce Trailhead to stay updated on new features and best practices.
Enhance Performance with Admin Strategies
-
Create reusable templates for common tasks and reports.
-
Standardize naming conventions for consistency and easy search.
-
Collaborate with other admins to share tips and best practices.
-
Regularly review and optimize your Salesforce setup for performance improvements.
-
Invest in ongoing training and certifications to stay ahead of the curve.
How to obtain Salesforce Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion , By implementing these Salesforce admin productivity hacks, you can enhance your performance, increase efficiency, and boost productivity. Work smarter, not harder, with these tips and tricks to streamline your workflow, automate tasks, and optimize your Salesforce experience. Stay organized, stay focused, and watch your productivity soar.
Building Microservices Architecture with Apache Kafka
In today's digital age, businesses are constantly seeking ways to innovate and stay ahead of the competition. One way to achieve this is by adopting a microservices architecture with Apache Kafka. This powerful combination allows for the development of scalable, reliable, and efficient systems that can handle the complexities of modern applications.
What is Apache Kafka?
Apache Kafka is an open-source distributed event streaming platform that is designed for high-performance data pipelines, streaming analytics, data integration, and mission-critical applications. It is built on the principles of fault tolerance, scalability, and durability, making it ideal for handling large volumes of data in real-time.
Kafka Integration in Microservices Architecture
When building a microservices architecture, Kafka plays a crucial role in enabling communication between services. By using Kafka as a message broker, microservices can communicate asynchronously, allowing for greater flexibility and resilience in the system. This event-driven architecture ensures that services remain decoupled and can scale independently, leading to a more robust and reliable system overall.
Distributed Systems with Kafka
Kafka's distributed nature makes it well-suited for building scalable architectures. By leveraging Kafka topics, which act as message queues, microservices can communicate with each other in a seamless and efficient manner. This ensures that data can be processed and delivered in real-time, even in the face of system failures or network issues.
Microservices Communication Using Kafka
In a microservices environment, communication between services is essential for the smooth operation of the system. Kafka enables microservices to communicate through its streaming capabilities, allowing for the seamless transfer of data between services. This ensures that services can work together harmoniously to deliver value to the end-users.
Kafka Producers and Consumers
In Kafka, producers are responsible for publishing messages to topics, while consumers subscribe to these topics to receive and process messages. This producer-consumer model ensures that data can be efficiently distributed across services, enabling real-time processing and analysis of information. By leveraging Kafka producers and consumers, microservices can achieve a high level of fault tolerance and scalability within their architecture.
When it comes to deploying microservices with Kafka, it is essential to consider the architecture's scalability and fault tolerance. By utilizing Kafka's messaging capabilities, microservices can communicate asynchronously, ensuring that data can be processed in real-time. Additionally, Kafka's support for event sourcing and stream processing enables microservices to handle large volumes of data with ease, making it an ideal choice for building scalable and reliable architectures.
Kafka Ecosystem and Deployment Options
The Kafka ecosystem offers a wide range of tools and connectors that can be used to integrate Kafka into various applications. From Kafka connectors to message brokers, the Kafka ecosystem provides the necessary components to build robust and resilient systems. Additionally, Kafka can be deployed using Docker containers, making it easy to create cloud-native applications that can scale dynamically based on demand.
How to obtain Apache Kafka Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and contact us
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, Apache Kafka is a powerful tool for building microservices architectures that are scalable, reliable, and efficient. By leveraging Kafka's messaging capabilities, microservices can communicate asynchronously, handle large volumes of data in real-time, and scale effortlessly. With Kafka at the core of their architecture, businesses can achieve a competitive edge in today's fast-paced digital landscape..
Read More
In today's digital age, businesses are constantly seeking ways to innovate and stay ahead of the competition. One way to achieve this is by adopting a microservices architecture with Apache Kafka. This powerful combination allows for the development of scalable, reliable, and efficient systems that can handle the complexities of modern applications.
What is Apache Kafka?
Apache Kafka is an open-source distributed event streaming platform that is designed for high-performance data pipelines, streaming analytics, data integration, and mission-critical applications. It is built on the principles of fault tolerance, scalability, and durability, making it ideal for handling large volumes of data in real-time.
Kafka Integration in Microservices Architecture
When building a microservices architecture, Kafka plays a crucial role in enabling communication between services. By using Kafka as a message broker, microservices can communicate asynchronously, allowing for greater flexibility and resilience in the system. This event-driven architecture ensures that services remain decoupled and can scale independently, leading to a more robust and reliable system overall.
Distributed Systems with Kafka
Kafka's distributed nature makes it well-suited for building scalable architectures. By leveraging Kafka topics, which act as message queues, microservices can communicate with each other in a seamless and efficient manner. This ensures that data can be processed and delivered in real-time, even in the face of system failures or network issues.
Microservices Communication Using Kafka
In a microservices environment, communication between services is essential for the smooth operation of the system. Kafka enables microservices to communicate through its streaming capabilities, allowing for the seamless transfer of data between services. This ensures that services can work together harmoniously to deliver value to the end-users.
Kafka Producers and Consumers
In Kafka, producers are responsible for publishing messages to topics, while consumers subscribe to these topics to receive and process messages. This producer-consumer model ensures that data can be efficiently distributed across services, enabling real-time processing and analysis of information. By leveraging Kafka producers and consumers, microservices can achieve a high level of fault tolerance and scalability within their architecture.
When it comes to deploying microservices with Kafka, it is essential to consider the architecture's scalability and fault tolerance. By utilizing Kafka's messaging capabilities, microservices can communicate asynchronously, ensuring that data can be processed in real-time. Additionally, Kafka's support for event sourcing and stream processing enables microservices to handle large volumes of data with ease, making it an ideal choice for building scalable and reliable architectures.
Kafka Ecosystem and Deployment Options
The Kafka ecosystem offers a wide range of tools and connectors that can be used to integrate Kafka into various applications. From Kafka connectors to message brokers, the Kafka ecosystem provides the necessary components to build robust and resilient systems. Additionally, Kafka can be deployed using Docker containers, making it easy to create cloud-native applications that can scale dynamically based on demand.
How to obtain Apache Kafka Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and contact us
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, Apache Kafka is a powerful tool for building microservices architectures that are scalable, reliable, and efficient. By leveraging Kafka's messaging capabilities, microservices can communicate asynchronously, handle large volumes of data in real-time, and scale effortlessly. With Kafka at the core of their architecture, businesses can achieve a competitive edge in today's fast-paced digital landscape..
Game-changing assets: Making concept art with Google Cloud's generative AI
In today's rapidly evolving digital landscape, the intersection of technology and art has given rise to groundbreaking innovations in the creative industry. One such innovation is the use of generative AI by Google Cloud to revolutionize the process of creating concept art. By leveraging the power of machine learning and artificial intelligence, artists are able to unlock new possibilities in game art and design, paving the way for a future where creativity knows no bounds.
Artificial intelligence transforming the creative process
Artificial intelligence has become a game-changer in the world of digital art, offering artists new tools and techniques to enhance their creative process. With Google Cloud's generative AI, creatives can now explore a realm where machine creativity meets human ingenuity, resulting in dynamic artwork that pushes the boundaries of traditional artistic expression.
Breaking barriers with advanced technology
The fusion of AI and design has opened up a world of possibilities for artists looking to push the limits of their creativity. Through Google Cloud's generative AI, artists can tap into neural networks and algorithmic design to create innovative and visually stunning concept art that captivates audiences and redefines the future of art in the digital age.
Unleashing the potential of automated creation
By harnessing the power of cloud computing and machine learning, artists are able to unlock a new level of creative freedom and flexibility in their work. With Google Cloud's generative AI, the process of creating concept art becomes more streamlined and efficient, allowing artists to focus on the artistic expression rather than the technical aspects of design.
The future of art and design
As technology continues to evolve, the role of AI in the creative process will only become more prominent, revolutionizing the way we think about art and design. Google Cloud's generative AI is leading the charge in this creative evolution, empowering artists to explore new frontiers in digital innovation and artistic expression.
Enhancing visual effects and virtual reality
In the gaming industry, the use of generative AI is transforming the way visual effects are created and implemented in games. By leveraging advanced technology and AI-powered tools, game developers can now push the boundaries of realism and interactivity, creating immersive experiences that blur the line between reality and virtual worlds.
Empowering artists with cutting-edge tools
Google Cloud's generative AI is not only revolutionizing the way concept art is created, but also empowering artists with a new set of tools and techniques to level up their creative process. By embracing AI and machine creativity, artists can explore new avenues of artistic expression and interactive media, leading to a more dynamic and engaging art form.
How to obtain Cloud Technology Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and Contact Us
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion,As we move towards a future where technology and creativity intersect, the role of AI in the creative process will continue to expand and redefine the way we think about art and design. Google Cloud's generative AI is at the forefront of this creative revolution, offering artists a powerful platform to explore new possibilities in artistic expression and innovation. With advanced technology and cutting-edge tools, the future of art is limitless, and the only barrier to creativity is our own imagination.
Read More
In today's rapidly evolving digital landscape, the intersection of technology and art has given rise to groundbreaking innovations in the creative industry. One such innovation is the use of generative AI by Google Cloud to revolutionize the process of creating concept art. By leveraging the power of machine learning and artificial intelligence, artists are able to unlock new possibilities in game art and design, paving the way for a future where creativity knows no bounds.
Artificial intelligence transforming the creative process
Artificial intelligence has become a game-changer in the world of digital art, offering artists new tools and techniques to enhance their creative process. With Google Cloud's generative AI, creatives can now explore a realm where machine creativity meets human ingenuity, resulting in dynamic artwork that pushes the boundaries of traditional artistic expression.
Breaking barriers with advanced technology
The fusion of AI and design has opened up a world of possibilities for artists looking to push the limits of their creativity. Through Google Cloud's generative AI, artists can tap into neural networks and algorithmic design to create innovative and visually stunning concept art that captivates audiences and redefines the future of art in the digital age.
Unleashing the potential of automated creation
By harnessing the power of cloud computing and machine learning, artists are able to unlock a new level of creative freedom and flexibility in their work. With Google Cloud's generative AI, the process of creating concept art becomes more streamlined and efficient, allowing artists to focus on the artistic expression rather than the technical aspects of design.
The future of art and design
As technology continues to evolve, the role of AI in the creative process will only become more prominent, revolutionizing the way we think about art and design. Google Cloud's generative AI is leading the charge in this creative evolution, empowering artists to explore new frontiers in digital innovation and artistic expression.
Enhancing visual effects and virtual reality
In the gaming industry, the use of generative AI is transforming the way visual effects are created and implemented in games. By leveraging advanced technology and AI-powered tools, game developers can now push the boundaries of realism and interactivity, creating immersive experiences that blur the line between reality and virtual worlds.
Empowering artists with cutting-edge tools
Google Cloud's generative AI is not only revolutionizing the way concept art is created, but also empowering artists with a new set of tools and techniques to level up their creative process. By embracing AI and machine creativity, artists can explore new avenues of artistic expression and interactive media, leading to a more dynamic and engaging art form.
How to obtain Cloud Technology Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and Contact Us
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion,As we move towards a future where technology and creativity intersect, the role of AI in the creative process will continue to expand and redefine the way we think about art and design. Google Cloud's generative AI is at the forefront of this creative revolution, offering artists a powerful platform to explore new possibilities in artistic expression and innovation. With advanced technology and cutting-edge tools, the future of art is limitless, and the only barrier to creativity is our own imagination.
PMP for Startups Improving Business with Project Management
In today's fast-paced and competitive business landscape, startups face numerous challenges in managing their projects effectively. From lack of resources to tight budgets, startups often struggle to keep up with the demands of their growing business. This is where Project Management Professional (PMP) certification can make a significant impact on the success and growth of a startup.
What is PMP Certification?
PMP certification is a globally recognized professional designation offered by the Project Management Institute (PMI). It demonstrates a project manager's expertise, experience, and skills in leading and directing projects. By obtaining PMP certification, individuals can enhance their project management knowledge, improve their leadership skills, and increase their job prospects in the competitive business world.
Why is PMP Important for Startups?
Project management plays a crucial role in the success of any organization, including startups. Implementing PMP principles can help startups improve their organizational structure, strategy, and efficiency. It allows them to plan and execute projects more effectively, communicate with stakeholders, and ultimately achieve success in their ventures.
How Can PMP Benefit Startups?
-
Improved Planning and Execution: PMP certification equips project managers with the necessary skills and tools to plan and execute projects efficiently. This leads to better time management, resource allocation, and risk mitigation, ultimately increasing the chances of project success.
-
Enhanced Communication: Effective communication is key to the success of any project. With PMP certification, project managers can improve their communication skills, ensuring that team members, stakeholders, and clients are on the same page throughout the project lifecycle.
-
Increased Productivity: By implementing PMP best practices, startups can streamline their project management processes, leading to increased productivity and faster project delivery. This allows startups to meet deadlines, satisfy clients, and drive business growth.
-
Encourages Collaboration and Innovation: PMP certification promotes teamwork and collaboration among project team members. By fostering a culture of innovation and creativity, startups can develop unique solutions to complex problems and stay ahead of the competition.
How to Implement PMP in a Startup Setting?
-
Identify Project Management Needs: Assess the current project management practices within the startup and identify areas that need improvement. Determine the project management framework that best fits the startup's needs and goals.
-
Invest in Project Management Tools: Utilize technology and project management tools to streamline project processes, improve communication, and enhance project visibility. Tools such as Trello, Asana, and Microsoft Project can help startups stay organized and on track.
-
Develop PMP Skills: Encourage project managers and team members to pursue PMP certification and enhance their project management skills. This will not only benefit the individual but also the startup as a whole, leading to improved project outcomes.
-
Seek Professional Consulting: Consider hiring a project management consultant with PMP certification to provide expert guidance and support in implementing PMP best practices within the startup. This external perspective can help startups overcome project management challenges and achieve success.
How to obtain Project Management Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and contact us
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, PMP certification can greatly benefit startups by improving their project management capabilities, enhancing organization, promoting efficiency, and ultimately driving business success. By investing in PMP skills and best practices, startups can position themselves for growth, development, and innovation in today's competitive business environment. Don't wait any longer - start incorporating PMP principles into your startup today and watch your business thrive!
Read More
In today's fast-paced and competitive business landscape, startups face numerous challenges in managing their projects effectively. From lack of resources to tight budgets, startups often struggle to keep up with the demands of their growing business. This is where Project Management Professional (PMP) certification can make a significant impact on the success and growth of a startup.
What is PMP Certification?
PMP certification is a globally recognized professional designation offered by the Project Management Institute (PMI). It demonstrates a project manager's expertise, experience, and skills in leading and directing projects. By obtaining PMP certification, individuals can enhance their project management knowledge, improve their leadership skills, and increase their job prospects in the competitive business world.
Why is PMP Important for Startups?
Project management plays a crucial role in the success of any organization, including startups. Implementing PMP principles can help startups improve their organizational structure, strategy, and efficiency. It allows them to plan and execute projects more effectively, communicate with stakeholders, and ultimately achieve success in their ventures.
How Can PMP Benefit Startups?
-
Improved Planning and Execution: PMP certification equips project managers with the necessary skills and tools to plan and execute projects efficiently. This leads to better time management, resource allocation, and risk mitigation, ultimately increasing the chances of project success.
-
Enhanced Communication: Effective communication is key to the success of any project. With PMP certification, project managers can improve their communication skills, ensuring that team members, stakeholders, and clients are on the same page throughout the project lifecycle.
-
Increased Productivity: By implementing PMP best practices, startups can streamline their project management processes, leading to increased productivity and faster project delivery. This allows startups to meet deadlines, satisfy clients, and drive business growth.
-
Encourages Collaboration and Innovation: PMP certification promotes teamwork and collaboration among project team members. By fostering a culture of innovation and creativity, startups can develop unique solutions to complex problems and stay ahead of the competition.
How to Implement PMP in a Startup Setting?
-
Identify Project Management Needs: Assess the current project management practices within the startup and identify areas that need improvement. Determine the project management framework that best fits the startup's needs and goals.
-
Invest in Project Management Tools: Utilize technology and project management tools to streamline project processes, improve communication, and enhance project visibility. Tools such as Trello, Asana, and Microsoft Project can help startups stay organized and on track.
-
Develop PMP Skills: Encourage project managers and team members to pursue PMP certification and enhance their project management skills. This will not only benefit the individual but also the startup as a whole, leading to improved project outcomes.
-
Seek Professional Consulting: Consider hiring a project management consultant with PMP certification to provide expert guidance and support in implementing PMP best practices within the startup. This external perspective can help startups overcome project management challenges and achieve success.
How to obtain Project Management Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and contact us
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, PMP certification can greatly benefit startups by improving their project management capabilities, enhancing organization, promoting efficiency, and ultimately driving business success. By investing in PMP skills and best practices, startups can position themselves for growth, development, and innovation in today's competitive business environment. Don't wait any longer - start incorporating PMP principles into your startup today and watch your business thrive!
How to Transition from Project Manager to PMO Leader
Are you a seasoned project manager looking to make the leap to a PMO leadership role? Transitioning from a project manager to a PMO leader can be a challenging but rewarding career progression. In this article, we will discuss the steps you can take to successfully navigate this transition and become a successful PMO leader.
Project Manager to PMO Leader Transition Path
Making the transition from a project manager to a PMO leader requires a strategic approach and the development of specific skills and competencies. Here are some steps you can take to make a seamless transition:
-
Develop Leadership Skills: PMO leaders are responsible for overseeing a team of project managers and ensuring that projects are executed successfully. Developing strong leadership skills, such as communication, team building, and strategic thinking, is essential for success in a PMO leadership role.
-
Understand the PMO: Take the time to fully understand the role of the PMO within your organization. Familiarize yourself with the processes, tools, and methodologies that the PMO uses to support project delivery.
-
Build Your Network: Networking is crucial for career advancement. Connect with other PMO leaders, attend industry events, and seek out mentorship opportunities to help broaden your perspective and build valuable relationships.
-
Seek Professional Development: Consider pursuing additional certifications or training in PMO leadership to strengthen your skills and knowledge in this area. This can help set you apart as a candidate for PMO leadership roles.
PMO Leader Responsibilities
As a PMO leader, you will be responsible for overseeing the project management office and ensuring that projects are delivered on time, within budget, and meet the organization's strategic objectives. Some of the key responsibilities of a PMO leader include:
-
Developing and implementing project management processes and methodologies
-
Providing guidance and support to project managers
-
Monitoring project performance and identifying areas for improvement
-
Ensuring alignment between projects and organizational goals
-
Managing stakeholder relationships and communication
Difference Between Project Manager and PMO Leader
While project managers are focused on the execution of individual projects, PMO leaders take a more strategic and holistic approach to project management. PMO leaders are responsible for setting the overall project management direction for the organization and ensuring that projects align with the organization's objectives. They are also tasked with developing and implementing standardized processes and methodologies to improve project delivery across the organization.
How to obtain Project Management Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and Contact Us
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, transitioning from a project manager to a PMO leader requires a combination of leadership skills, industry knowledge, and strategic thinking. By following these steps and actively seeking out opportunities for growth and development, you can successfully make the transition to a PMO leadership role and advance your career in project management
Read More
Are you a seasoned project manager looking to make the leap to a PMO leadership role? Transitioning from a project manager to a PMO leader can be a challenging but rewarding career progression. In this article, we will discuss the steps you can take to successfully navigate this transition and become a successful PMO leader.
Project Manager to PMO Leader Transition Path
Making the transition from a project manager to a PMO leader requires a strategic approach and the development of specific skills and competencies. Here are some steps you can take to make a seamless transition:
-
Develop Leadership Skills: PMO leaders are responsible for overseeing a team of project managers and ensuring that projects are executed successfully. Developing strong leadership skills, such as communication, team building, and strategic thinking, is essential for success in a PMO leadership role.
-
Understand the PMO: Take the time to fully understand the role of the PMO within your organization. Familiarize yourself with the processes, tools, and methodologies that the PMO uses to support project delivery.
-
Build Your Network: Networking is crucial for career advancement. Connect with other PMO leaders, attend industry events, and seek out mentorship opportunities to help broaden your perspective and build valuable relationships.
-
Seek Professional Development: Consider pursuing additional certifications or training in PMO leadership to strengthen your skills and knowledge in this area. This can help set you apart as a candidate for PMO leadership roles.
PMO Leader Responsibilities
As a PMO leader, you will be responsible for overseeing the project management office and ensuring that projects are delivered on time, within budget, and meet the organization's strategic objectives. Some of the key responsibilities of a PMO leader include:
-
Developing and implementing project management processes and methodologies
-
Providing guidance and support to project managers
-
Monitoring project performance and identifying areas for improvement
-
Ensuring alignment between projects and organizational goals
-
Managing stakeholder relationships and communication
Difference Between Project Manager and PMO Leader
While project managers are focused on the execution of individual projects, PMO leaders take a more strategic and holistic approach to project management. PMO leaders are responsible for setting the overall project management direction for the organization and ensuring that projects align with the organization's objectives. They are also tasked with developing and implementing standardized processes and methodologies to improve project delivery across the organization.
How to obtain Project Management Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and Contact Us
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, transitioning from a project manager to a PMO leader requires a combination of leadership skills, industry knowledge, and strategic thinking. By following these steps and actively seeking out opportunities for growth and development, you can successfully make the transition to a PMO leadership role and advance your career in project management
Benefits of Cloud Computing and Preparing IT Team for Cloud
In today's fast-paced and technologically advanced world, cloud computing has become a crucial part of every business operation. From increased flexibility to cost savings, the benefits of moving to the cloud are undeniable. However, in order to fully realize these benefits, it is essential for your IT team to be prepared for the transition. Let's dive into the advantages of cloud computing and how you can ensure your IT team is ready for the shift.
Benefits of Cloud Computing
-
Cost Savings: One of the most significant benefits of cloud computing is the cost savings it offers. By moving to the cloud, businesses can eliminate the need for costly hardware and maintenance, leading to reduced operational expenses.
-
Scalability: Cloud computing allows for easy scalability, enabling businesses to quickly adjust their resources based on demand. This flexibility ensures that businesses can easily adapt to changing needs without incurring additional costs.
-
Increased Efficiency: With cloud technology, employees can access data and applications from anywhere, at any time, leading to increased collaboration and productivity. This level of accessibility can greatly enhance overall efficiency within the organization.
Preparing Your IT Team for Cloud
-
Cloud Migration Benefits: Before migrating to the cloud, it is crucial for your IT team to understand the benefits of cloud migration. This includes improved security, reduced maintenance, and enhanced scalability, all of which can positively impact business operations.
-
Cloud Computing Training: Providing your IT team with proper cloud computing training is essential for a smooth transition. This training should cover the basics of cloud technology, best practices for cloud adoption, and security protocols to ensure data protection.
-
Cloud Readiness for IT Team: Assessing the readiness of your IT team for cloud adoption is crucial. Identify any skills gaps within the team and provide training and resources to bridge these gaps. This will ensure that your IT team can effectively manage cloud solutions.
Cloud Computing Advantages
-
Cloud Computing Skills Development: By investing in cloud computing training for your IT team, you are not only preparing them for the shift to the cloud but also enhancing their skills and knowledge in the latest technology trends. This can greatly benefit your organization in the long run.
-
Importance of Cloud Computing Training: Training your IT team in cloud computing is essential for staying competitive in today's digital landscape. By equipping your team with the necessary skills and knowledge, you are positioning your organization for success in the age of cloud technology.
-
Cloud Transformation Benefits: Embracing cloud technology can lead to transformative benefits for your organization. From improved collaboration to enhanced security, the advantages of cloud computing are vast and can greatly impact your business operations.
How to obtain Cloud Technology Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and contact us
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the benefits of cloud computing are undeniable, but in order to fully realize these advantages, it is essential to prepare your IT team for the transition. By providing proper training, assessing readiness, and investing in skills development, you can ensure that your IT team is equipped to handle the shift to the cloud. Ultimately, preparing your IT team for cloud technology is key to unlocking the full potential of cloud computing for your organization.
Contact Us :
Read More
In today's fast-paced and technologically advanced world, cloud computing has become a crucial part of every business operation. From increased flexibility to cost savings, the benefits of moving to the cloud are undeniable. However, in order to fully realize these benefits, it is essential for your IT team to be prepared for the transition. Let's dive into the advantages of cloud computing and how you can ensure your IT team is ready for the shift.
Benefits of Cloud Computing
-
Cost Savings: One of the most significant benefits of cloud computing is the cost savings it offers. By moving to the cloud, businesses can eliminate the need for costly hardware and maintenance, leading to reduced operational expenses.
-
Scalability: Cloud computing allows for easy scalability, enabling businesses to quickly adjust their resources based on demand. This flexibility ensures that businesses can easily adapt to changing needs without incurring additional costs.
-
Increased Efficiency: With cloud technology, employees can access data and applications from anywhere, at any time, leading to increased collaboration and productivity. This level of accessibility can greatly enhance overall efficiency within the organization.
Preparing Your IT Team for Cloud
-
Cloud Migration Benefits: Before migrating to the cloud, it is crucial for your IT team to understand the benefits of cloud migration. This includes improved security, reduced maintenance, and enhanced scalability, all of which can positively impact business operations.
-
Cloud Computing Training: Providing your IT team with proper cloud computing training is essential for a smooth transition. This training should cover the basics of cloud technology, best practices for cloud adoption, and security protocols to ensure data protection.
-
Cloud Readiness for IT Team: Assessing the readiness of your IT team for cloud adoption is crucial. Identify any skills gaps within the team and provide training and resources to bridge these gaps. This will ensure that your IT team can effectively manage cloud solutions.
Cloud Computing Advantages
-
Cloud Computing Skills Development: By investing in cloud computing training for your IT team, you are not only preparing them for the shift to the cloud but also enhancing their skills and knowledge in the latest technology trends. This can greatly benefit your organization in the long run.
-
Importance of Cloud Computing Training: Training your IT team in cloud computing is essential for staying competitive in today's digital landscape. By equipping your team with the necessary skills and knowledge, you are positioning your organization for success in the age of cloud technology.
-
Cloud Transformation Benefits: Embracing cloud technology can lead to transformative benefits for your organization. From improved collaboration to enhanced security, the advantages of cloud computing are vast and can greatly impact your business operations.
How to obtain Cloud Technology Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and contact us
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the benefits of cloud computing are undeniable, but in order to fully realize these advantages, it is essential to prepare your IT team for the transition. By providing proper training, assessing readiness, and investing in skills development, you can ensure that your IT team is equipped to handle the shift to the cloud. Ultimately, preparing your IT team for cloud technology is key to unlocking the full potential of cloud computing for your organization.
Contact Us :
CBAP Certification Benefits and Career Opportunities
Are you considering taking the next step in your business analysis career? Obtaining your CBAP certification could be the perfect way to advance your skills and open up new opportunities in the field of business analysis. In this article, we will explore the benefits of CBAP certification and the various career opportunities that come with being a certified business analysis professional.
What is CBAP Certification?
The Certified Business Analysis Professional (CBAP) certification is a globally recognized designation offered by the International Institute of Business Analysis (IIBA). This certification is designed for experienced business analysts who have demonstrated their expertise in the field through education, work experience, and passing a rigorous exam.
Benefits of CBAP Certification
-
Enhanced Credibility: CBAP certification demonstrates to employers and colleagues that you have the knowledge and skills required to excel in the field of business analysis.
-
Increased Salary: On average, CBAP-certified professionals earn higher salaries than their non-certified counterparts. This certification can open the door to higher-paying opportunities in the field.
-
Career Growth: CBAP certification can help you stand out in a competitive job market and qualify for advanced positions in business analysis.
-
Global Recognition: The CBAP certification is recognized worldwide, allowing you to pursue opportunities on a global scale.
Career Opportunities with CBAP Certification
-
Business Analyst: With CBAP certification, you can pursue roles such as Senior Business Analyst, Lead Business Analyst, or Business Analysis Manager.
-
Project Manager: Many CBAP-certified professionals go on to become project managers, overseeing business analysis projects and ensuring successful outcomes.
-
Consultant: CBAP certification can open up opportunities to work as a business analysis consultant, helping organizations improve their processes and achieve their goals.
-
Entrepreneur: With the skills and knowledge gained through CBAP certification, you may choose to start your own business as a business analysis expert.
CBAP Exam Preparation
To obtain your CBAP certification, you must first meet the eligibility requirements set by the IIBA and pass a 3.5-hour exam consisting of 120 multiple-choice questions. Preparation is key to success, and there are various resources available to help you study, including CBAP training courses, study guides, and online practice exams.
Is CBAP Certification Worth It?
Absolutely! CBAP certification not only validates your expertise in business analysis but also opens up a world of opportunities for career growth and advancement. The benefits of CBAP certification far outweigh the time and effort required to obtain it, making it a valuable investment in your future.
How to obtain CBAP Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and contact us
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, pursuing your CBAP certification is a smart move for anyone looking to advance their career in business analysis. From enhanced credibility and increased salary potential to a wide range of career opportunities, CBAP certification can provide you with the skills and recognition needed to succeed in this dynamic field. So, why wait? Start your journey towards becoming a Certified Business Analysis Professional today!
Contact Us :
Read More
Are you considering taking the next step in your business analysis career? Obtaining your CBAP certification could be the perfect way to advance your skills and open up new opportunities in the field of business analysis. In this article, we will explore the benefits of CBAP certification and the various career opportunities that come with being a certified business analysis professional.
What is CBAP Certification?
The Certified Business Analysis Professional (CBAP) certification is a globally recognized designation offered by the International Institute of Business Analysis (IIBA). This certification is designed for experienced business analysts who have demonstrated their expertise in the field through education, work experience, and passing a rigorous exam.
Benefits of CBAP Certification
-
Enhanced Credibility: CBAP certification demonstrates to employers and colleagues that you have the knowledge and skills required to excel in the field of business analysis.
-
Increased Salary: On average, CBAP-certified professionals earn higher salaries than their non-certified counterparts. This certification can open the door to higher-paying opportunities in the field.
-
Career Growth: CBAP certification can help you stand out in a competitive job market and qualify for advanced positions in business analysis.
-
Global Recognition: The CBAP certification is recognized worldwide, allowing you to pursue opportunities on a global scale.
Career Opportunities with CBAP Certification
-
Business Analyst: With CBAP certification, you can pursue roles such as Senior Business Analyst, Lead Business Analyst, or Business Analysis Manager.
-
Project Manager: Many CBAP-certified professionals go on to become project managers, overseeing business analysis projects and ensuring successful outcomes.
-
Consultant: CBAP certification can open up opportunities to work as a business analysis consultant, helping organizations improve their processes and achieve their goals.
-
Entrepreneur: With the skills and knowledge gained through CBAP certification, you may choose to start your own business as a business analysis expert.
CBAP Exam Preparation
To obtain your CBAP certification, you must first meet the eligibility requirements set by the IIBA and pass a 3.5-hour exam consisting of 120 multiple-choice questions. Preparation is key to success, and there are various resources available to help you study, including CBAP training courses, study guides, and online practice exams.
Is CBAP Certification Worth It?
Absolutely! CBAP certification not only validates your expertise in business analysis but also opens up a world of opportunities for career growth and advancement. The benefits of CBAP certification far outweigh the time and effort required to obtain it, making it a valuable investment in your future.
How to obtain CBAP Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and contact us
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, pursuing your CBAP certification is a smart move for anyone looking to advance their career in business analysis. From enhanced credibility and increased salary potential to a wide range of career opportunities, CBAP certification can provide you with the skills and recognition needed to succeed in this dynamic field. So, why wait? Start your journey towards becoming a Certified Business Analysis Professional today!
Contact Us :
Understanding the Impact of 5G on Digital Marketing
In today's fast-paced digital world, technology is constantly evolving to meet the demands of consumers and businesses alike. One of the most anticipated advancements in recent years has been the roll-out of 5G technology. This next-generation wireless network promises lightning-fast speeds, ultra-low latency, and massive connectivity - all of which have the potential to revolutionize the way we approach digital marketing.
Evolution of Digital Marketing Trends with 5G Technology
As 5G technology becomes more widespread, digital marketing trends are expected to shift in response to its capabilities. With faster internet speeds and improved network reliability, marketers will have the opportunity to deliver richer, more engaging content to consumers in real-time. This opens up new possibilities for interactive and immersive marketing experiences that were previously not feasible with slower network speeds.
Improved Mobile Marketing Strategies in the 5G Era
Mobile marketing is set to benefit significantly from the introduction of 5G technology. With faster data speeds and reduced latency, marketers can deliver more personalized and location-based messages to consumers on their mobile devices. This level of targeted advertising has the potential to enhance customer engagement and drive higher conversion rates for businesses operating in the mobile space.
Enhancing Digital Advertising with 5G
The advent of 5G technology will also transform the way digital advertising is delivered to consumers. Marketers can leverage the benefits of 5G network speeds to serve high-quality video ads seamlessly across multiple devices. Additionally, improved connectivity will enable more targeted and relevant advertising placements, leading to better performance and ROI for digital advertising campaigns.
Leveraging Marketing Automation in the 5G Era
With 5G network capabilities, marketing automation tools will become even more powerful and efficient. Marketers can streamline their processes and workflows, allowing for real-time data analysis and personalized marketing experiences on a large scale. This level of automation will enable businesses to deliver more timely and relevant content to their target audience, ultimately driving greater engagement and conversion rates.
Harnessing Data Analytics in the Age of 5G
The increased data speeds and capacity of 5G networks will provide marketers with a wealth of valuable consumer data to analyze and interpret. This data can be used to gain deeper insights into consumer behavior and preferences, allowing marketers to tailor their strategies more effectively. Data analytics in the 5G era will empower businesses to make data-driven decisions and optimize their marketing campaigns for better results.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the impact of 5G on digital marketing is poised to be transformative. From improved internet speed and connectivity to enhanced marketing automation and data analytics capabilities, businesses that embrace 5G technology will have a competitive advantage in engaging with consumers in new and innovative ways. As we continue to see the evolution of digital marketing in the 5G era, it is essential for businesses to adapt and leverage these emerging technologies to stay ahead of the curve and drive success in the digital landscape
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced digital world, technology is constantly evolving to meet the demands of consumers and businesses alike. One of the most anticipated advancements in recent years has been the roll-out of 5G technology. This next-generation wireless network promises lightning-fast speeds, ultra-low latency, and massive connectivity - all of which have the potential to revolutionize the way we approach digital marketing.
Evolution of Digital Marketing Trends with 5G Technology
As 5G technology becomes more widespread, digital marketing trends are expected to shift in response to its capabilities. With faster internet speeds and improved network reliability, marketers will have the opportunity to deliver richer, more engaging content to consumers in real-time. This opens up new possibilities for interactive and immersive marketing experiences that were previously not feasible with slower network speeds.
Improved Mobile Marketing Strategies in the 5G Era
Mobile marketing is set to benefit significantly from the introduction of 5G technology. With faster data speeds and reduced latency, marketers can deliver more personalized and location-based messages to consumers on their mobile devices. This level of targeted advertising has the potential to enhance customer engagement and drive higher conversion rates for businesses operating in the mobile space.
Enhancing Digital Advertising with 5G
The advent of 5G technology will also transform the way digital advertising is delivered to consumers. Marketers can leverage the benefits of 5G network speeds to serve high-quality video ads seamlessly across multiple devices. Additionally, improved connectivity will enable more targeted and relevant advertising placements, leading to better performance and ROI for digital advertising campaigns.
Leveraging Marketing Automation in the 5G Era
With 5G network capabilities, marketing automation tools will become even more powerful and efficient. Marketers can streamline their processes and workflows, allowing for real-time data analysis and personalized marketing experiences on a large scale. This level of automation will enable businesses to deliver more timely and relevant content to their target audience, ultimately driving greater engagement and conversion rates.
Harnessing Data Analytics in the Age of 5G
The increased data speeds and capacity of 5G networks will provide marketers with a wealth of valuable consumer data to analyze and interpret. This data can be used to gain deeper insights into consumer behavior and preferences, allowing marketers to tailor their strategies more effectively. Data analytics in the 5G era will empower businesses to make data-driven decisions and optimize their marketing campaigns for better results.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the impact of 5G on digital marketing is poised to be transformative. From improved internet speed and connectivity to enhanced marketing automation and data analytics capabilities, businesses that embrace 5G technology will have a competitive advantage in engaging with consumers in new and innovative ways. As we continue to see the evolution of digital marketing in the 5G era, it is essential for businesses to adapt and leverage these emerging technologies to stay ahead of the curve and drive success in the digital landscape
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
New agent capabilities in Microsoft Copilot unlock business value
Microsoft Copilot is a revolutionary AI technology that is transforming the way businesses operate. With its advanced agent capabilities and seamless integration with Microsoft AI productivity tools, Copilot empowers businesses to achieve enhanced productivity, streamline operations, and drive digital transformation.
Agent capabilities
The agent capabilities within Microsoft Copilot enable intelligent agents to assist users in various tasks, providing AI-driven insights, automating processes, and enhancing business efficiency. These agents are equipped with the latest technologies to deliver top-notch performance and help businesses achieve their goals effectively.
Business value
The incorporation of agent capabilities in Microsoft Copilot brings immense business value to organizations of all sizes. By leveraging AI automation and intelligent agents, businesses can optimize workflows, boost productivity, and stay ahead of the competition in today's fast-paced business environment.
AI productivity tools
Microsoft Copilot is equipped with a wide range of AI productivity tools that empower users to work smarter, not harder. From AI-driven insights to business automation tools, Copilot offers a comprehensive suite of solutions that enhance productivity and efficiency across various business functions.
Enterprise solutions
With Copilot's seamless integration with Microsoft business tools, enterprises can harness the power of AI for business transformation. These enterprise solutions enable organizations to unlock new opportunities, streamline operations, and achieve enhanced business outcomes.
AI integration
The integration of AI technology within Copilot enables businesses to access cutting-edge capabilities that drive innovation and efficiency. By leveraging AI-driven insights and intelligent agents, organizations can make informed decisions, automate processes, and accelerate their digital transformation journey.
Business automation
Microsoft Copilot's advanced business automation tools revolutionize how businesses operate by automating repetitive tasks, reducing errors, and improving overall efficiency. These automation capabilities allow organizations to focus on high-value activities, fuel growth, and achieve sustainable success.
Microsoft AI
As a leader in AI technology, Microsoft continues to push boundaries with Copilot, offering businesses access to state-of-the-art AI solutions that drive enhanced productivity and business outcomes. With Microsoft AI at the core of Copilot, businesses can leverage cutting-edge technology for unprecedented success.
Copilot features
Copilot comes packed with a host of features that empower businesses to unlock their full potential. From intelligent agents to AI-driven insights, Copilot offers a comprehensive set of tools that enable organizations to achieve business excellence and drive sustainable growth.
Digital transformation
Microsoft Copilot plays a pivotal role in facilitating digital transformation within organizations by integrating AI technology seamlessly into business operations. By embracing Copilot's innovative features, businesses can embark on a digital transformation journey that revolutionizes how they operate and deliver value to customers.
Intelligent agents
One of the key components of Microsoft Copilot is its intelligent agents, which are designed to assist users in various tasks, provide valuable insights, and drive business efficiency. These intelligent agents streamline workflows, improve decision-making, and empower businesses to achieve their objectives effectively.
Microsoft business tools
Microsoft Copilot seamlessly integrates with a wide range of Microsoft business tools, allowing organizations to leverage the full potential of AI technology for enhanced productivity and efficiency. By combining Copilot with Microsoft business tools, businesses can unlock new possibilities and achieve sustainable growth.
Copilot updates
Microsoft continuously updates Copilot with new features, enhancements, and capabilities to ensure that businesses have access to the latest technology advancements. These updates enable organizations to stay ahead of the curve, adapt to changing market conditions, and drive innovation in their operations.
Copilot innovations
Microsoft is committed to driving innovation in AI technology through Copilot, delivering groundbreaking features and capabilities that redefine how businesses operate. With Copilot's continuous innovations, organizations can leverage cutting-edge technology to solve complex challenges, capitalize on opportunities, and achieve unprecedented success.
Microsoft technology advancements
Microsoft continues to push the boundaries of technology advancements with Copilot, providing businesses with access to state-of-the-art solutions that drive digital transformation and business growth. By embracing Microsoft technology advancements, organizations can stay ahead of the curve, adapt to changing market dynamics, and drive innovation in their operations.
How to obtain Microsoft Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php .
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, the new agent capabilities in Microsoft Copilot unlock significant business value by empowering organizations to achieve enhanced productivity, streamline operations, and drive digital transformation. By leveraging Copilot's advanced AI technology, intelligent agents, and business automation tools, businesses can optimize workflows, boost efficiency, and stay ahead of the competition in today's fast-paced business environment. Embrace the power of Copilot and embark on a transformative journey towards business excellence and sustainable success.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Microsoft Copilot is a revolutionary AI technology that is transforming the way businesses operate. With its advanced agent capabilities and seamless integration with Microsoft AI productivity tools, Copilot empowers businesses to achieve enhanced productivity, streamline operations, and drive digital transformation.
Agent capabilities
The agent capabilities within Microsoft Copilot enable intelligent agents to assist users in various tasks, providing AI-driven insights, automating processes, and enhancing business efficiency. These agents are equipped with the latest technologies to deliver top-notch performance and help businesses achieve their goals effectively.
Business value
The incorporation of agent capabilities in Microsoft Copilot brings immense business value to organizations of all sizes. By leveraging AI automation and intelligent agents, businesses can optimize workflows, boost productivity, and stay ahead of the competition in today's fast-paced business environment.
AI productivity tools
Microsoft Copilot is equipped with a wide range of AI productivity tools that empower users to work smarter, not harder. From AI-driven insights to business automation tools, Copilot offers a comprehensive suite of solutions that enhance productivity and efficiency across various business functions.
Enterprise solutions
With Copilot's seamless integration with Microsoft business tools, enterprises can harness the power of AI for business transformation. These enterprise solutions enable organizations to unlock new opportunities, streamline operations, and achieve enhanced business outcomes.
AI integration
The integration of AI technology within Copilot enables businesses to access cutting-edge capabilities that drive innovation and efficiency. By leveraging AI-driven insights and intelligent agents, organizations can make informed decisions, automate processes, and accelerate their digital transformation journey.
Business automation
Microsoft Copilot's advanced business automation tools revolutionize how businesses operate by automating repetitive tasks, reducing errors, and improving overall efficiency. These automation capabilities allow organizations to focus on high-value activities, fuel growth, and achieve sustainable success.
Microsoft AI
As a leader in AI technology, Microsoft continues to push boundaries with Copilot, offering businesses access to state-of-the-art AI solutions that drive enhanced productivity and business outcomes. With Microsoft AI at the core of Copilot, businesses can leverage cutting-edge technology for unprecedented success.
Copilot features
Copilot comes packed with a host of features that empower businesses to unlock their full potential. From intelligent agents to AI-driven insights, Copilot offers a comprehensive set of tools that enable organizations to achieve business excellence and drive sustainable growth.
Digital transformation
Microsoft Copilot plays a pivotal role in facilitating digital transformation within organizations by integrating AI technology seamlessly into business operations. By embracing Copilot's innovative features, businesses can embark on a digital transformation journey that revolutionizes how they operate and deliver value to customers.
Intelligent agents
One of the key components of Microsoft Copilot is its intelligent agents, which are designed to assist users in various tasks, provide valuable insights, and drive business efficiency. These intelligent agents streamline workflows, improve decision-making, and empower businesses to achieve their objectives effectively.
Microsoft business tools
Microsoft Copilot seamlessly integrates with a wide range of Microsoft business tools, allowing organizations to leverage the full potential of AI technology for enhanced productivity and efficiency. By combining Copilot with Microsoft business tools, businesses can unlock new possibilities and achieve sustainable growth.
Copilot updates
Microsoft continuously updates Copilot with new features, enhancements, and capabilities to ensure that businesses have access to the latest technology advancements. These updates enable organizations to stay ahead of the curve, adapt to changing market conditions, and drive innovation in their operations.
Copilot innovations
Microsoft is committed to driving innovation in AI technology through Copilot, delivering groundbreaking features and capabilities that redefine how businesses operate. With Copilot's continuous innovations, organizations can leverage cutting-edge technology to solve complex challenges, capitalize on opportunities, and achieve unprecedented success.
Microsoft technology advancements
Microsoft continues to push the boundaries of technology advancements with Copilot, providing businesses with access to state-of-the-art solutions that drive digital transformation and business growth. By embracing Microsoft technology advancements, organizations can stay ahead of the curve, adapt to changing market dynamics, and drive innovation in their operations.
How to obtain Microsoft Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php .
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, the new agent capabilities in Microsoft Copilot unlock significant business value by empowering organizations to achieve enhanced productivity, streamline operations, and drive digital transformation. By leveraging Copilot's advanced AI technology, intelligent agents, and business automation tools, businesses can optimize workflows, boost efficiency, and stay ahead of the competition in today's fast-paced business environment. Embrace the power of Copilot and embark on a transformative journey towards business excellence and sustainable success.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Empowering Your Sales Team with Power BI Analytics
Are you looking to take your sales team to the next level and drive increased revenue for your business? Empowering your sales team with Power BI analytics could be the key to unlocking valuable insights and enhancing sales performance. In this article, we will explore how leveraging data visualization, business intelligence, and interactive dashboards through Power BI can empower your sales team to make data-driven decisions, optimize sales strategies, and ultimately improve sales productivity.
What is Power BI Analytics?
Power BI is a powerful business analytics tool by Microsoft that enables organizations to visualize their data and share insights across the organization. With Power BI, businesses can connect to a wide range of data sources, create interactive reports and dashboards, and easily share them with stakeholders. This tool provides a comprehensive view of your sales performance through visualizations that are easy to understand and act upon.
Benefits of Empowering Your Sales Team with Power BI Analytics
-
Data Analysis: By harnessing the power of Power BI analytics, your sales team can analyze sales data in real-time, identify trends, and uncover opportunities for growth. This enables them to make informed decisions and focus their efforts on strategies that drive results.
-
Performance Tracking: Power BI allows you to track key sales metrics and performance indicators in one centralized dashboard. This provides visibility into individual and team performance, making it easier to identify areas for improvement and celebrate successes.
-
Sales Insights: With Power BI, your sales team can gain valuable insights into customer behavior, market trends, and sales patterns. This knowledge can help them tailor their approach, prioritize leads, and deliver more personalized experiences to customers.
-
Interactive Reports: Power BI enables interactive reporting, allowing users to drill down into data to uncover more detailed insights. This level of interactivity empowers your sales team to explore data from different angles, identify patterns, and make data-driven decisions on the fly.
How Power BI Can Empower Your Sales Team
Empowering your sales team with Power BI analytics can transform the way they operate, leading to increased efficiency, productivity, and revenue generation. By leveraging visualization tools, performance tracking features, and interactive reports, your team can:
-
Improve Sales: Through data-driven decision-making, your sales team can target the right customers, engage with them more effectively, and close more deals. This can result in increased sales and revenue for your business.
-
Enhance Sales Productivity: Power BI streamlines the sales process by providing quick access to relevant data and insights. This saves time for your sales team, allowing them to focus on selling and building relationships with customers.
-
Optimize Sales Strategies: By analyzing sales data and monitoring performance metrics, your sales team can identify what works and what doesn't. This knowledge empowers them to refine their strategies, prioritize activities, and allocate resources more effectively.
How to obtain Power Business Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, empowering your sales team with Power BI analytics is a strategic investment that can drive significant value for your business. By leveraging data visualization, business intelligence, and interactive dashboards, your sales team can make smarter decisions, optimize strategies, and ultimately increase revenue. So why wait? Take the first step towards empowering your sales team with Power BI analytics today and unlock the full potential of your sales organization.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to take your sales team to the next level and drive increased revenue for your business? Empowering your sales team with Power BI analytics could be the key to unlocking valuable insights and enhancing sales performance. In this article, we will explore how leveraging data visualization, business intelligence, and interactive dashboards through Power BI can empower your sales team to make data-driven decisions, optimize sales strategies, and ultimately improve sales productivity.
What is Power BI Analytics?
Power BI is a powerful business analytics tool by Microsoft that enables organizations to visualize their data and share insights across the organization. With Power BI, businesses can connect to a wide range of data sources, create interactive reports and dashboards, and easily share them with stakeholders. This tool provides a comprehensive view of your sales performance through visualizations that are easy to understand and act upon.
Benefits of Empowering Your Sales Team with Power BI Analytics
-
Data Analysis: By harnessing the power of Power BI analytics, your sales team can analyze sales data in real-time, identify trends, and uncover opportunities for growth. This enables them to make informed decisions and focus their efforts on strategies that drive results.
-
Performance Tracking: Power BI allows you to track key sales metrics and performance indicators in one centralized dashboard. This provides visibility into individual and team performance, making it easier to identify areas for improvement and celebrate successes.
-
Sales Insights: With Power BI, your sales team can gain valuable insights into customer behavior, market trends, and sales patterns. This knowledge can help them tailor their approach, prioritize leads, and deliver more personalized experiences to customers.
-
Interactive Reports: Power BI enables interactive reporting, allowing users to drill down into data to uncover more detailed insights. This level of interactivity empowers your sales team to explore data from different angles, identify patterns, and make data-driven decisions on the fly.
How Power BI Can Empower Your Sales Team
Empowering your sales team with Power BI analytics can transform the way they operate, leading to increased efficiency, productivity, and revenue generation. By leveraging visualization tools, performance tracking features, and interactive reports, your team can:
-
Improve Sales: Through data-driven decision-making, your sales team can target the right customers, engage with them more effectively, and close more deals. This can result in increased sales and revenue for your business.
-
Enhance Sales Productivity: Power BI streamlines the sales process by providing quick access to relevant data and insights. This saves time for your sales team, allowing them to focus on selling and building relationships with customers.
-
Optimize Sales Strategies: By analyzing sales data and monitoring performance metrics, your sales team can identify what works and what doesn't. This knowledge empowers them to refine their strategies, prioritize activities, and allocate resources more effectively.
How to obtain Power Business Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, empowering your sales team with Power BI analytics is a strategic investment that can drive significant value for your business. By leveraging data visualization, business intelligence, and interactive dashboards, your sales team can make smarter decisions, optimize strategies, and ultimately increase revenue. So why wait? Take the first step towards empowering your sales team with Power BI analytics today and unlock the full potential of your sales organization.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
DevOps Engineer Job Description Skills Roles and Responsibilities
Are you interested in becoming a DevOps Engineer but not sure what the job entails? In this article, we will explore the role of a DevOps Engineer, the skills required, and the responsibilities involved in this exciting and fast-paced career.
Introduction to DevOps Engineer
A DevOps Engineer plays a crucial role in software development and infrastructure management. They are responsible for implementing and managing processes that streamline the software development lifecycle, including continuous integration, continuous delivery, and automation.
What are the Skills Required for a DevOps Engineer?
-
Programming: DevOps Engineers should have a strong foundation in programming languages such as Python, Java, or Ruby.
-
Scripting: Proficiency in scripting languages like Bash or PowerShell is essential for automating tasks.
-
Troubleshooting: Being able to quickly identify and resolve issues is a key skill for a DevOps Engineer.
-
Monitoring: DevOps Engineers should be skilled in monitoring tools to ensure the stability and performance of systems.
-
Configuration Management: Knowledge of tools like Ansible, Puppet, or Chef is necessary for managing infrastructure configurations.
-
Deployment: Experience with tools like Jenkins or Docker for deploying applications.
-
Agile Methodology: Understanding of agile practices to collaborate effectively with cross-functional teams.
What are the Roles and Responsibilities of a DevOps Engineer?
-
Version Control: Using tools like Git to manage code changes and track revisions.
-
Server Administration: Managing servers, deploying updates, and ensuring system security.
-
Network Security: Implementing security measures to protect data and systems from cyber threats.
-
System Architecture: Designing and maintaining system architecture to support business goals.
-
Cloud Computing: Experience with cloud platforms like AWS, Azure, or Google Cloud for scalable infrastructure.
-
Collaboration: Working closely with developers, operations teams, and other stakeholders to achieve project goals.
-
Communication Skills: Effective communication is essential for coordinating tasks and sharing updates with the team.
-
Problem-Solving: DevOps Engineers must be able to think critically and creatively to solve complex issues.
-
Team Player: Being a team player and collaborating with others to achieve common objectives.
-
Innovation: Continuously seeking new and innovative solutions to improve processes and systems.
-
Technology Stack: Knowledge of a variety of technologies and tools to support software development and deployment.
How to obtain DevOps certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, a DevOps Engineer plays a vital role in bridging the gap between software development and IT operations. With a diverse skill set, strong technical abilities, and a collaborative mindset, a DevOps Engineer can drive efficiency and innovation in any organization. If you are passionate about technology and enjoy solving complex problems, a career as a DevOps Engineer may be the perfect fit for you. Start honing your skills today and embark on an exciting and rewarding career in DevOps engineering.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you interested in becoming a DevOps Engineer but not sure what the job entails? In this article, we will explore the role of a DevOps Engineer, the skills required, and the responsibilities involved in this exciting and fast-paced career.
Introduction to DevOps Engineer
A DevOps Engineer plays a crucial role in software development and infrastructure management. They are responsible for implementing and managing processes that streamline the software development lifecycle, including continuous integration, continuous delivery, and automation.
What are the Skills Required for a DevOps Engineer?
-
Programming: DevOps Engineers should have a strong foundation in programming languages such as Python, Java, or Ruby.
-
Scripting: Proficiency in scripting languages like Bash or PowerShell is essential for automating tasks.
-
Troubleshooting: Being able to quickly identify and resolve issues is a key skill for a DevOps Engineer.
-
Monitoring: DevOps Engineers should be skilled in monitoring tools to ensure the stability and performance of systems.
-
Configuration Management: Knowledge of tools like Ansible, Puppet, or Chef is necessary for managing infrastructure configurations.
-
Deployment: Experience with tools like Jenkins or Docker for deploying applications.
-
Agile Methodology: Understanding of agile practices to collaborate effectively with cross-functional teams.
What are the Roles and Responsibilities of a DevOps Engineer?
-
Version Control: Using tools like Git to manage code changes and track revisions.
-
Server Administration: Managing servers, deploying updates, and ensuring system security.
-
Network Security: Implementing security measures to protect data and systems from cyber threats.
-
System Architecture: Designing and maintaining system architecture to support business goals.
-
Cloud Computing: Experience with cloud platforms like AWS, Azure, or Google Cloud for scalable infrastructure.
-
Collaboration: Working closely with developers, operations teams, and other stakeholders to achieve project goals.
-
Communication Skills: Effective communication is essential for coordinating tasks and sharing updates with the team.
-
Problem-Solving: DevOps Engineers must be able to think critically and creatively to solve complex issues.
-
Team Player: Being a team player and collaborating with others to achieve common objectives.
-
Innovation: Continuously seeking new and innovative solutions to improve processes and systems.
-
Technology Stack: Knowledge of a variety of technologies and tools to support software development and deployment.
How to obtain DevOps certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, a DevOps Engineer plays a vital role in bridging the gap between software development and IT operations. With a diverse skill set, strong technical abilities, and a collaborative mindset, a DevOps Engineer can drive efficiency and innovation in any organization. If you are passionate about technology and enjoy solving complex problems, a career as a DevOps Engineer may be the perfect fit for you. Start honing your skills today and embark on an exciting and rewarding career in DevOps engineering.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Difference between traditional and digital marketing
Traditional marketing and digital marketing differ fundamentally in their approaches and mediums. Traditional marketing utilizes offline channels like print ads, billboards, and television, aiming to reach a broad audience through mass communication. In contrast, digital marketing leverages online platforms such as social media, search engines, and email to target specific demographics with personalized, interactive content.
Traditional Marketing and Digital Marketing
Traditional marketing refers to conventional marketing strategies used before the rise of the internet and digital technologies. It includes print ads, billboards, TV commercials, radio spots, and direct mail. the other hand, digital marketing encompasses online methods such as social media marketing, email, SEO, content marketing, and pay-per-click advertising.
Marketing Strategies Comparison
Traditional marketing focuses on reaching a broad audience through mass media channels. It relies heavily on one-way communication, where the message is broadcasted to the target market. Conversely, digital marketing allows for targeted advertising based on user behavior, demographics, and interests. It enables two-way communication between businesses and customers.
Offline vs Online Marketing
Offline marketing involves physical interactions with customers, such as in-store promotions or event sponsorships. Online marketing, on the other hand, leverages digital platforms to engage with potential customers through websites, social media, and search engines.
Advertising Techniques Differences
Traditional marketing uses traditional advertising channels like print, TV, and radio to convey brand messages. Digital marketing employs online tools like social media ads, Google AdWords, and influencer partnerships to connect with audiences in a more targeted and interactive manner.
Digital Marketing Advantages
-
Greater Reach: Digital marketing allows businesses to reach a global audience through various online channels.
-
Data-driven Strategies: Digital marketing provides access to real-time data and analytics, enabling businesses to optimize their campaigns for better results.
-
Cost-effective: Compared to traditional marketing, digital marketing is often more affordable, making it accessible to businesses of all sizes.
Traditional Marketing Advantages
-
Tangible Presence: Traditional marketing tactics like direct mail or brochures provide a physical presence that can resonate with audiences.
-
Brand Familiarity: Traditional marketing has been around for decades, making it a familiar and trusted form of advertising among consumers.
-
Local Targeting: Traditional marketing allows businesses to target local markets effectively through tactics like flyers or local newspapers.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php.
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, both traditional and digital marketing have their own set of advantages and capabilities. While traditional marketing offers a tangible presence and local targeting, digital marketing provides greater reach, data-driven strategies, and cost-effective solutions. By combining the strengths of both approaches, businesses can create comprehensive marketing strategies that effectively engage audiences in today's digital age.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Traditional marketing and digital marketing differ fundamentally in their approaches and mediums. Traditional marketing utilizes offline channels like print ads, billboards, and television, aiming to reach a broad audience through mass communication. In contrast, digital marketing leverages online platforms such as social media, search engines, and email to target specific demographics with personalized, interactive content.
Traditional Marketing and Digital Marketing
Traditional marketing refers to conventional marketing strategies used before the rise of the internet and digital technologies. It includes print ads, billboards, TV commercials, radio spots, and direct mail. the other hand, digital marketing encompasses online methods such as social media marketing, email, SEO, content marketing, and pay-per-click advertising.
Marketing Strategies Comparison
Traditional marketing focuses on reaching a broad audience through mass media channels. It relies heavily on one-way communication, where the message is broadcasted to the target market. Conversely, digital marketing allows for targeted advertising based on user behavior, demographics, and interests. It enables two-way communication between businesses and customers.
Offline vs Online Marketing
Offline marketing involves physical interactions with customers, such as in-store promotions or event sponsorships. Online marketing, on the other hand, leverages digital platforms to engage with potential customers through websites, social media, and search engines.
Advertising Techniques Differences
Traditional marketing uses traditional advertising channels like print, TV, and radio to convey brand messages. Digital marketing employs online tools like social media ads, Google AdWords, and influencer partnerships to connect with audiences in a more targeted and interactive manner.
Digital Marketing Advantages
-
Greater Reach: Digital marketing allows businesses to reach a global audience through various online channels.
-
Data-driven Strategies: Digital marketing provides access to real-time data and analytics, enabling businesses to optimize their campaigns for better results.
-
Cost-effective: Compared to traditional marketing, digital marketing is often more affordable, making it accessible to businesses of all sizes.
Traditional Marketing Advantages
-
Tangible Presence: Traditional marketing tactics like direct mail or brochures provide a physical presence that can resonate with audiences.
-
Brand Familiarity: Traditional marketing has been around for decades, making it a familiar and trusted form of advertising among consumers.
-
Local Targeting: Traditional marketing allows businesses to target local markets effectively through tactics like flyers or local newspapers.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php.
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, both traditional and digital marketing have their own set of advantages and capabilities. While traditional marketing offers a tangible presence and local targeting, digital marketing provides greater reach, data-driven strategies, and cost-effective solutions. By combining the strengths of both approaches, businesses can create comprehensive marketing strategies that effectively engage audiences in today's digital age.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Migrating Legacy Java Applications to Modern Architectures
In today's rapidly changing technological landscape, businesses are constantly looking for ways to stay ahead of the curve and remain competitive. One key aspect of this is ensuring that their software applications are up to date and able to meet the demands of modern users. This is especially true when it comes to legacy Java applications, which may have been built using outdated technologies and frameworks that are no longer supported or efficient.
Challenges of Legacy Java Applications
Legacy Java applications present a number of challenges when it comes to modernizing them. These applications are often built on monolithic architectures, which can be difficult to scale and maintain. Additionally, the codebase of these applications may be outdated and cumbersome, making it hard to add new features or fix bugs.
The Benefits of Modern Architectures
Modern architectures, on the other hand, offer a number of benefits that can help businesses improve their software applications. These architectures are typically based on microservices, which allow for greater scalability, flexibility, and agility. By breaking down applications into smaller, more modular components, businesses can easily add new features, scale their applications, and respond to changing market demands.
Strategies for Migrating Legacy Java Applications
When it comes to migrating legacy Java applications to modern architectures, there are several strategies that businesses can use. One common approach is application refactoring, which involves restructuring the codebase of the application to make it more modular and easier to maintain. Another strategy is software redevelopment, which involves rebuilding the application from scratch using modern technologies and frameworks.
Best Practices for Application Migration
To ensure a successful migration, businesses should follow best practices for application migration. This includes conducting a thorough assessment of the legacy system to understand its strengths and weaknesses, developing a migration plan that outlines the steps needed to modernize the application, and executing the migration with minimal downtime and disruption to users.
How to obtain JAVA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, migrating legacy Java applications to modern architectures is a complex process that requires careful planning and execution. By following best practices and using the right strategies, businesses can successfully modernize their applications and stay ahead of the competition. With the right approach, legacy Java applications can be transformed into modern, agile, and efficient software solutions that meet the needs of today's users.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's rapidly changing technological landscape, businesses are constantly looking for ways to stay ahead of the curve and remain competitive. One key aspect of this is ensuring that their software applications are up to date and able to meet the demands of modern users. This is especially true when it comes to legacy Java applications, which may have been built using outdated technologies and frameworks that are no longer supported or efficient.
Challenges of Legacy Java Applications
Legacy Java applications present a number of challenges when it comes to modernizing them. These applications are often built on monolithic architectures, which can be difficult to scale and maintain. Additionally, the codebase of these applications may be outdated and cumbersome, making it hard to add new features or fix bugs.
The Benefits of Modern Architectures
Modern architectures, on the other hand, offer a number of benefits that can help businesses improve their software applications. These architectures are typically based on microservices, which allow for greater scalability, flexibility, and agility. By breaking down applications into smaller, more modular components, businesses can easily add new features, scale their applications, and respond to changing market demands.
Strategies for Migrating Legacy Java Applications
When it comes to migrating legacy Java applications to modern architectures, there are several strategies that businesses can use. One common approach is application refactoring, which involves restructuring the codebase of the application to make it more modular and easier to maintain. Another strategy is software redevelopment, which involves rebuilding the application from scratch using modern technologies and frameworks.
Best Practices for Application Migration
To ensure a successful migration, businesses should follow best practices for application migration. This includes conducting a thorough assessment of the legacy system to understand its strengths and weaknesses, developing a migration plan that outlines the steps needed to modernize the application, and executing the migration with minimal downtime and disruption to users.
How to obtain JAVA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, migrating legacy Java applications to modern architectures is a complex process that requires careful planning and execution. By following best practices and using the right strategies, businesses can successfully modernize their applications and stay ahead of the competition. With the right approach, legacy Java applications can be transformed into modern, agile, and efficient software solutions that meet the needs of today's users.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
The Benefits of Agile Marketing
In today's fast-paced digital landscape, traditional marketing strategies may no longer be as effective as they once were. As the marketing world continues to evolve, businesses are turning to agile marketing to stay ahead of the curve. Agile marketing is a customer-centric, data-driven approach that emphasizes adaptability, flexibility, and quick response to market trends. In this article, we will explore the numerous benefits of agile marketing and why businesses should consider implementing this innovative strategy.
What is Agile Marketing?
Agile marketing is a methodology inspired by the principles of agile software development. It focuses on collaboration, iteration, and customer feedback to deliver targeted campaigns with maximum efficiency and impact. Unlike traditional marketing methods that follow a linear, long-term plan, agile marketing allows businesses to adapt to rapid changes in the market and consumer behavior.
Customer-Centric Approach
Agile marketing puts the customer at the center of every decision. By continuously gathering and analyzing real-time data, businesses can create personalized campaigns that resonate with their target audience. This customer-centric approach leads to higher customer satisfaction and loyalty, ultimately driving brand growth and development.
Improved Communication and Collaboration
One of the key benefits of agile marketing is improved communication and collaboration among cross-functional teams. By breaking down silos and fostering a culture of transparency and accountability, businesses can streamline project management and ensure that everyone is working towards the same goal.
The Advantages of Agile Marketing
-
Competitive Advantage : By embracing agile marketing, businesses can gain a competitive advantage in today's crowded marketplace. With the ability to quickly adapt to changing market conditions and consumer preferences, agile teams can stay ahead of the competition and capitalize on emerging opportunities.
-
Scalability and ROI : Agile marketing allows businesses to scale their campaigns based on performance data and customer feedback. This results in higher ROI as businesses can allocate resources more effectively and focus on strategies that deliver the best results.
-
Continuous Improvement : One of the hallmarks of agile marketing is the commitment to continuous improvement. By regularly reviewing and analyzing campaign data, businesses can identify areas for optimization and make data-driven decisions to drive performance and results.
How to obtain Agile & Scrum Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php .
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, agile marketing offers numerous benefits for businesses looking to stay ahead in today's dynamic digital landscape. By embracing flexibility, adaptability, and innovation, businesses can create targeted campaigns that drive customer engagement, satisfaction, and ultimately, business growth. Whether you're a startup or an established brand, incorporating agile marketing into your strategy can help you achieve long-term success and establish a stronger market presence.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced digital landscape, traditional marketing strategies may no longer be as effective as they once were. As the marketing world continues to evolve, businesses are turning to agile marketing to stay ahead of the curve. Agile marketing is a customer-centric, data-driven approach that emphasizes adaptability, flexibility, and quick response to market trends. In this article, we will explore the numerous benefits of agile marketing and why businesses should consider implementing this innovative strategy.
What is Agile Marketing?
Agile marketing is a methodology inspired by the principles of agile software development. It focuses on collaboration, iteration, and customer feedback to deliver targeted campaigns with maximum efficiency and impact. Unlike traditional marketing methods that follow a linear, long-term plan, agile marketing allows businesses to adapt to rapid changes in the market and consumer behavior.
Customer-Centric Approach
Agile marketing puts the customer at the center of every decision. By continuously gathering and analyzing real-time data, businesses can create personalized campaigns that resonate with their target audience. This customer-centric approach leads to higher customer satisfaction and loyalty, ultimately driving brand growth and development.
Improved Communication and Collaboration
One of the key benefits of agile marketing is improved communication and collaboration among cross-functional teams. By breaking down silos and fostering a culture of transparency and accountability, businesses can streamline project management and ensure that everyone is working towards the same goal.
The Advantages of Agile Marketing
-
Competitive Advantage : By embracing agile marketing, businesses can gain a competitive advantage in today's crowded marketplace. With the ability to quickly adapt to changing market conditions and consumer preferences, agile teams can stay ahead of the competition and capitalize on emerging opportunities.
-
Scalability and ROI : Agile marketing allows businesses to scale their campaigns based on performance data and customer feedback. This results in higher ROI as businesses can allocate resources more effectively and focus on strategies that deliver the best results.
-
Continuous Improvement : One of the hallmarks of agile marketing is the commitment to continuous improvement. By regularly reviewing and analyzing campaign data, businesses can identify areas for optimization and make data-driven decisions to drive performance and results.
How to obtain Agile & Scrum Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php .
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, agile marketing offers numerous benefits for businesses looking to stay ahead in today's dynamic digital landscape. By embracing flexibility, adaptability, and innovation, businesses can create targeted campaigns that drive customer engagement, satisfaction, and ultimately, business growth. Whether you're a startup or an established brand, incorporating agile marketing into your strategy can help you achieve long-term success and establish a stronger market presence.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
The Role of Leadership in Quality Management
In the world of quality management, leadership plays a crucial role in ensuring that organizations meet their quality goals and deliver exceptional products and services to customers. Effective leadership in quality management is essential for creating a culture of accountability, continuous improvement, and innovation. Leaders in quality management must possess certain qualities and skills to drive success in their organization's quality initiatives.
Importance of Leadership in Quality
Leadership in quality management is vital for setting the vision, goals, and direction for the organization's quality programs. Good leadership can inspire teams to strive for excellence and consistently meet quality standards. Without strong leadership, quality management programs may lack direction, motivation, and oversight, leading to subpar results and customer satisfaction.
Leadership Qualities for Quality Management
Effective leaders in quality management exhibit certain key qualities that set them apart from others. These qualities include strong communication skills, a results-driven mindset, the ability to empower and inspire others, strategic thinking, and a commitment to continuous learning and improvement. Leaders must also be able to make tough decisions, prioritize tasks effectively, and build strong relationships with their teams.
Effective Leadership in Quality
Effective leadership in quality management involves setting clear goals and expectations, providing support and resources to team members, and holding everyone accountable for their performance. Leaders must create a positive work environment where employees feel motivated and engaged in their work. By fostering a culture of quality and continuous improvement, leaders can drive success in their organization's quality management efforts.
Leadership Role in Quality Assurance
Quality assurance is a critical aspect of quality management, and leaders play a significant role in ensuring that QA processes are effective and efficient. Leaders must establish quality standards, develop QA procedures, monitor performance metrics, and implement corrective actions when necessary. By championing quality assurance initiatives, leaders can demonstrate their commitment to delivering high-quality products and services to customers.
Quality Management and Leadership
Quality management and leadership go hand in hand, as effective leadership is essential for implementing and sustaining quality management systems. Leaders must be proactive in identifying opportunities for improvement, addressing quality issues, and promoting a culture of quality throughout the organization. By providing guidance, support, and resources, leaders can help their teams achieve excellence in quality management.
Leadership Skills in Quality Control
Leadership skills in quality control involve the ability to analyze data, identify trends, and make informed decisions based on quality indicators. Leaders must be able to lead cross-functional teams, coordinate quality control activities, and drive continuous improvement initiatives. By fostering collaboration and communication among team members, leaders can ensure that quality control processes are effective and efficient.
Leadership Impact on Quality
The impact of leadership on quality is profound, as leaders set the tone for the organization's quality culture and performance. Strong leadership can inspire employees to strive for excellence, take ownership of quality initiatives, and deliver exceptional results. By leading by example and demonstrating a commitment to quality, leaders can positively influence the organization's overall quality performance.
How to obtain Quality Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, leadership plays a critical role in quality management, driving success, and sustainable results in organizations. Effective leaders in quality management must possess the right qualities, skills, and competencies to inspire, empower, and align teams towards achieving quality goals. By investing in leadership development, fostering a culture of quality, and promoting ethical leadership practices, organizations can enhance their quality management efforts and deliver exceptional products and services to customers.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In the world of quality management, leadership plays a crucial role in ensuring that organizations meet their quality goals and deliver exceptional products and services to customers. Effective leadership in quality management is essential for creating a culture of accountability, continuous improvement, and innovation. Leaders in quality management must possess certain qualities and skills to drive success in their organization's quality initiatives.
Importance of Leadership in Quality
Leadership in quality management is vital for setting the vision, goals, and direction for the organization's quality programs. Good leadership can inspire teams to strive for excellence and consistently meet quality standards. Without strong leadership, quality management programs may lack direction, motivation, and oversight, leading to subpar results and customer satisfaction.
Leadership Qualities for Quality Management
Effective leaders in quality management exhibit certain key qualities that set them apart from others. These qualities include strong communication skills, a results-driven mindset, the ability to empower and inspire others, strategic thinking, and a commitment to continuous learning and improvement. Leaders must also be able to make tough decisions, prioritize tasks effectively, and build strong relationships with their teams.
Effective Leadership in Quality
Effective leadership in quality management involves setting clear goals and expectations, providing support and resources to team members, and holding everyone accountable for their performance. Leaders must create a positive work environment where employees feel motivated and engaged in their work. By fostering a culture of quality and continuous improvement, leaders can drive success in their organization's quality management efforts.
Leadership Role in Quality Assurance
Quality assurance is a critical aspect of quality management, and leaders play a significant role in ensuring that QA processes are effective and efficient. Leaders must establish quality standards, develop QA procedures, monitor performance metrics, and implement corrective actions when necessary. By championing quality assurance initiatives, leaders can demonstrate their commitment to delivering high-quality products and services to customers.
Quality Management and Leadership
Quality management and leadership go hand in hand, as effective leadership is essential for implementing and sustaining quality management systems. Leaders must be proactive in identifying opportunities for improvement, addressing quality issues, and promoting a culture of quality throughout the organization. By providing guidance, support, and resources, leaders can help their teams achieve excellence in quality management.
Leadership Skills in Quality Control
Leadership skills in quality control involve the ability to analyze data, identify trends, and make informed decisions based on quality indicators. Leaders must be able to lead cross-functional teams, coordinate quality control activities, and drive continuous improvement initiatives. By fostering collaboration and communication among team members, leaders can ensure that quality control processes are effective and efficient.
Leadership Impact on Quality
The impact of leadership on quality is profound, as leaders set the tone for the organization's quality culture and performance. Strong leadership can inspire employees to strive for excellence, take ownership of quality initiatives, and deliver exceptional results. By leading by example and demonstrating a commitment to quality, leaders can positively influence the organization's overall quality performance.
How to obtain Quality Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, leadership plays a critical role in quality management, driving success, and sustainable results in organizations. Effective leaders in quality management must possess the right qualities, skills, and competencies to inspire, empower, and align teams towards achieving quality goals. By investing in leadership development, fostering a culture of quality, and promoting ethical leadership practices, organizations can enhance their quality management efforts and deliver exceptional products and services to customers.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Welcome the New 2024 Citrix Technology Advocates (CTAs)!
Are you a tech enthusiast looking to join a community of like-minded individuals dedicated to innovation, collaboration, and industry leadership? Look no further than the Citrix Technology Advocates (CTAs) network!
What is the Citrix Technology Advocates Program?
The Citrix Technology Advocates program is a prestigious community of technology experts who are passionate about Citrix solutions. These individuals are industry leaders in their respective fields and are committed to driving growth, supporting empowerment, and fostering connections within the tech community.
Join the Network of Innovation Experts
By becoming a Citrix Technology Advocate, you will have the opportunity to collaborate with a diverse group of technology experts from around the world. You will have access to exclusive events, webinars, and resources that will help you stay on the cutting edge of industry trends and advancements.
Grow Your Skills and Knowledge
As a Citrix Technology Advocate, you will have the chance to expand your skills and knowledge through engaging with fellow members, participating in training sessions, and accessing expert-led workshops. This will not only enhance your professional development but also set you up for success in your career.
Empowerment and Support
The Citrix Technology Advocates program is more than just a network - it is a support system. You will have the opportunity to connect with like-minded individuals who are passionate about technology and are eager to help each other succeed. Whether you have a question about a new technology or need advice on a project, the CTA community is there to support you.
Engage with Industry Leaders
One of the key benefits of being a Citrix Technology Advocate is the opportunity to engage with industry leaders and influencers. You will have the chance to learn from the best in the business, share your own insights and expertise, and make valuable connections that can propel your career forward.
Celebrate Success and Impact
As a member of the Citrix Technology Advocates program, you will have the opportunity to celebrate your successes and the impact you have made in the tech community. From virtual events to recognition programs, the CTAs program is designed to highlight the achievements of its members and inspire others to reach new heights.
How to obtain Citrix Client Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php .
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, If you are looking to join a community of tech experts, collaborate with industry leaders, and grow your skills and knowledge, then the Citrix Technology Advocates program is the perfect fit for you. Join us today and welcome the new 2024 CTAs to our thriving community of innovation and success.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you a tech enthusiast looking to join a community of like-minded individuals dedicated to innovation, collaboration, and industry leadership? Look no further than the Citrix Technology Advocates (CTAs) network!
What is the Citrix Technology Advocates Program?
The Citrix Technology Advocates program is a prestigious community of technology experts who are passionate about Citrix solutions. These individuals are industry leaders in their respective fields and are committed to driving growth, supporting empowerment, and fostering connections within the tech community.
Join the Network of Innovation Experts
By becoming a Citrix Technology Advocate, you will have the opportunity to collaborate with a diverse group of technology experts from around the world. You will have access to exclusive events, webinars, and resources that will help you stay on the cutting edge of industry trends and advancements.
Grow Your Skills and Knowledge
As a Citrix Technology Advocate, you will have the chance to expand your skills and knowledge through engaging with fellow members, participating in training sessions, and accessing expert-led workshops. This will not only enhance your professional development but also set you up for success in your career.
Empowerment and Support
The Citrix Technology Advocates program is more than just a network - it is a support system. You will have the opportunity to connect with like-minded individuals who are passionate about technology and are eager to help each other succeed. Whether you have a question about a new technology or need advice on a project, the CTA community is there to support you.
Engage with Industry Leaders
One of the key benefits of being a Citrix Technology Advocate is the opportunity to engage with industry leaders and influencers. You will have the chance to learn from the best in the business, share your own insights and expertise, and make valuable connections that can propel your career forward.
Celebrate Success and Impact
As a member of the Citrix Technology Advocates program, you will have the opportunity to celebrate your successes and the impact you have made in the tech community. From virtual events to recognition programs, the CTAs program is designed to highlight the achievements of its members and inspire others to reach new heights.
How to obtain Citrix Client Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php .
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, If you are looking to join a community of tech experts, collaborate with industry leaders, and grow your skills and knowledge, then the Citrix Technology Advocates program is the perfect fit for you. Join us today and welcome the new 2024 CTAs to our thriving community of innovation and success.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Artificial Intelligence With Python
In today's rapidly evolving digital landscape, artificial intelligence (AI) has become a game-changer in various industries. Particularly, the integration of Python programming language into AI development has paved the way for groundbreaking advancements in machine learning, data science, and deep learning. Let's explore how the combination of AI and Python is shaping the future of technology.
What is Artificial Intelligence with Python?
Artificial intelligence, often abbreviated as AI, refers to the simulation of human intelligence processes by machines, primarily computer systems. With Python being a versatile and powerful programming language, it has become the go-to choice for developing AI applications due to its simplicity, readability, and extensive libraries designed for data manipulation and analysis.
Why Use Python for AI Development?
Python's popularity in the AI community can be attributed to its user-friendly syntax, dynamic typing, and high-level data structures, making it easier for developers to prototype and deploy AI models quickly. Additionally, Python's robust libraries, such as TensorFlow, facilitate the implementation of complex neural networks and algorithms essential for machine learning tasks.
Machine Learning and Data Science in Python
Machine learning, a subset of AI, empowers systems to learn and improve from experience without being explicitly programmed. Python's rich ecosystem of libraries, including scikit-learn and pandas, provides developers with the tools to build predictive models, perform data analysis, and extract valuable insights from large datasets efficiently.
In the realm of data science, Python's versatility enables professionals to leverage statistical techniques, visualization tools, and machine learning algorithms to unravel patterns and trends within vast amounts of data. This aids organizations in making informed decisions and driving innovation through data-driven strategies.
Deep Learning and Neural Networks
Deep learning, a sophisticated form of machine learning, involves the use of artificial neural networks to model complex patterns and relationships within data. Python, with libraries like Keras and PyTorch, empowers developers to construct deep learning models for tasks such as image recognition, natural language processing, and speech recognition effectively.
Neural networks, inspired by the human brain's structure, consist of interconnected nodes that process and transmit information. Python's flexibility and scalability make it the ideal choice for implementing neural networks, enabling the development of intelligent systems capable of autonomous decision-making and cognitive computing.
Automation and Computer Vision
The marriage of AI and Python has revolutionized automation processes across industries by streamlining repetitive tasks and enhancing operational efficiency. Computer vision, a subfield of AI, focuses on enabling machines to interpret and analyze visual information from the environment using digital images or videos.
With Python libraries like OpenCV, developers can implement computer vision algorithms for tasks such as object detection, image recognition, and pattern recognition. This technology finds applications in autonomous vehicles, surveillance systems, and medical imaging, demonstrating the transformative impact of AI-driven automation in various sectors.
Natural Language Processing and Chatbots
Natural language processing (NLP) empowers machines to understand, interpret, and generate human language. Python's NLTK and spaCy libraries provide developers with tools to process textual data, build sentiment analysis models, and create chatbots capable of engaging in meaningful conversations with users.
Chatbots, powered by AI and Python, are used in customer service, e-commerce, and personal assistants to deliver personalized experiences and streamline communication channels. By harnessing the capabilities of NLP, chatbots can understand user queries, provide relevant responses, and handle interactions seamlessly, enhancing customer satisfaction and engagement.
Decision Making and Predictive Analytics
The integration of AI and Python enables organizations to leverage predictive analytics to forecast trends, identify patterns, and make data-driven decisions. Through supervised learning, unsupervised learning, and ensemble learning techniques, Python facilitates the development of predictive models that provide insights into future outcomes and behavior.
Reinforcement learning, a branch of machine learning, focuses on learning optimal decision-making strategies through trial and error. Python frameworks like RLlib enable developers to build reinforcement learning agents that learn and adapt in dynamic environments, paving the way for intelligent systems capable of autonomous decision-making and adaptive behavior.
How to obtain Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the synergy between artificial intelligence and Python has transformed the technological landscape, enabling developers to create innovative solutions across diverse domains. By harnessing the power of AI, machine learning, and deep learning in conjunction with Python's robust programming capabilities, organizations can unlock new possibilities for automation, data analysis, decision-making, and cognitive computing. As the demand for intelligent systems continues to rise, mastering the fusion of AI and Python will be crucial for staying ahead in the digital age.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's rapidly evolving digital landscape, artificial intelligence (AI) has become a game-changer in various industries. Particularly, the integration of Python programming language into AI development has paved the way for groundbreaking advancements in machine learning, data science, and deep learning. Let's explore how the combination of AI and Python is shaping the future of technology.
What is Artificial Intelligence with Python?
Artificial intelligence, often abbreviated as AI, refers to the simulation of human intelligence processes by machines, primarily computer systems. With Python being a versatile and powerful programming language, it has become the go-to choice for developing AI applications due to its simplicity, readability, and extensive libraries designed for data manipulation and analysis.
Why Use Python for AI Development?
Python's popularity in the AI community can be attributed to its user-friendly syntax, dynamic typing, and high-level data structures, making it easier for developers to prototype and deploy AI models quickly. Additionally, Python's robust libraries, such as TensorFlow, facilitate the implementation of complex neural networks and algorithms essential for machine learning tasks.
Machine Learning and Data Science in Python
Machine learning, a subset of AI, empowers systems to learn and improve from experience without being explicitly programmed. Python's rich ecosystem of libraries, including scikit-learn and pandas, provides developers with the tools to build predictive models, perform data analysis, and extract valuable insights from large datasets efficiently.
In the realm of data science, Python's versatility enables professionals to leverage statistical techniques, visualization tools, and machine learning algorithms to unravel patterns and trends within vast amounts of data. This aids organizations in making informed decisions and driving innovation through data-driven strategies.
Deep Learning and Neural Networks
Deep learning, a sophisticated form of machine learning, involves the use of artificial neural networks to model complex patterns and relationships within data. Python, with libraries like Keras and PyTorch, empowers developers to construct deep learning models for tasks such as image recognition, natural language processing, and speech recognition effectively.
Neural networks, inspired by the human brain's structure, consist of interconnected nodes that process and transmit information. Python's flexibility and scalability make it the ideal choice for implementing neural networks, enabling the development of intelligent systems capable of autonomous decision-making and cognitive computing.
Automation and Computer Vision
The marriage of AI and Python has revolutionized automation processes across industries by streamlining repetitive tasks and enhancing operational efficiency. Computer vision, a subfield of AI, focuses on enabling machines to interpret and analyze visual information from the environment using digital images or videos.
With Python libraries like OpenCV, developers can implement computer vision algorithms for tasks such as object detection, image recognition, and pattern recognition. This technology finds applications in autonomous vehicles, surveillance systems, and medical imaging, demonstrating the transformative impact of AI-driven automation in various sectors.
Natural Language Processing and Chatbots
Natural language processing (NLP) empowers machines to understand, interpret, and generate human language. Python's NLTK and spaCy libraries provide developers with tools to process textual data, build sentiment analysis models, and create chatbots capable of engaging in meaningful conversations with users.
Chatbots, powered by AI and Python, are used in customer service, e-commerce, and personal assistants to deliver personalized experiences and streamline communication channels. By harnessing the capabilities of NLP, chatbots can understand user queries, provide relevant responses, and handle interactions seamlessly, enhancing customer satisfaction and engagement.
Decision Making and Predictive Analytics
The integration of AI and Python enables organizations to leverage predictive analytics to forecast trends, identify patterns, and make data-driven decisions. Through supervised learning, unsupervised learning, and ensemble learning techniques, Python facilitates the development of predictive models that provide insights into future outcomes and behavior.
Reinforcement learning, a branch of machine learning, focuses on learning optimal decision-making strategies through trial and error. Python frameworks like RLlib enable developers to build reinforcement learning agents that learn and adapt in dynamic environments, paving the way for intelligent systems capable of autonomous decision-making and adaptive behavior.
How to obtain Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the synergy between artificial intelligence and Python has transformed the technological landscape, enabling developers to create innovative solutions across diverse domains. By harnessing the power of AI, machine learning, and deep learning in conjunction with Python's robust programming capabilities, organizations can unlock new possibilities for automation, data analysis, decision-making, and cognitive computing. As the demand for intelligent systems continues to rise, mastering the fusion of AI and Python will be crucial for staying ahead in the digital age.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Transform your SD-WAN with IOS-XE
Look no further than IOS-XE, the cutting-edge network operating system that can revolutionize your SD-WAN deployment. In this article, we will explore how IOS-XE can transform your SD-WAN, the benefits it offers, and how it can enhance the performance and security of your network.
Upgrading Your SD-WAN with IOS-XE
When it comes to upgrading your SD-WAN, IOS-XE is the perfect choice. With its seamless integration capabilities, IOS-XE can easily be configured to work with your existing SD-WAN solution, providing a smooth and efficient transition. The features of IOS-XE are specifically designed to enhance SD-WAN performance and management, making it the ideal choice for businesses looking to optimize their network.
The Benefits of Using IOS-XE for SD-WAN
One of the key benefits of using IOS-XE for SD-WAN is the advanced features it offers. From enhanced security capabilities to improved network automation, IOS-XE provides a wide range of benefits that can help take your SD-WAN to the next level. Additionally, IOS-XE is known for its reliability and scalability, making it a smart choice for businesses of all sizes.
Enhancing SD-WAN Performance with IOS-XE
When it comes to optimizing SD-WAN performance, IOS-XE is the solution. With its advanced capabilities and efficient architecture, IOS-XE can significantly boost the performance of your SD-WAN, providing faster and more reliable network connectivity. Additionally, IOS-XE offers regular updates and advancements in SD-WAN technology, ensuring that your network stays ahead of the curve.
Improving SD-WAN Security with IOS-XE
Security is a top priority for businesses, especially when it comes to network connectivity. IOS-XE offers robust security features that can help protect your SD-WAN from potential threats and vulnerabilities. With IOS-XE, you can rest assured that your network is secure and protected at all times, giving you peace of mind and allowing you to focus on your business operations.
Simplifying SD-WAN Deployment with IOS-XE
Deploying a new SD-WAN solution can be a complex and time-consuming process. However, with IOS-XE, SD-WAN deployment is made easy. IOS-XE offers simplified configuration options, compatibility with a wide range of SD-WAN solutions, and efficient management capabilities, making it the perfect choice for businesses looking to streamline their network deployment.
How to obtain Cisco Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php .
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, IOS-XE is transforming the way businesses implement and manage their SD-WAN solutions. With its advanced features, enhanced performance, and top-notch security capabilities, IOS-XE is revolutionizing the way businesses connect and communicate. If you're ready to take your SD-WAN to the next level, consider upgrading to IOS-XE today and experience the future of networking technology.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Look no further than IOS-XE, the cutting-edge network operating system that can revolutionize your SD-WAN deployment. In this article, we will explore how IOS-XE can transform your SD-WAN, the benefits it offers, and how it can enhance the performance and security of your network.
Upgrading Your SD-WAN with IOS-XE
When it comes to upgrading your SD-WAN, IOS-XE is the perfect choice. With its seamless integration capabilities, IOS-XE can easily be configured to work with your existing SD-WAN solution, providing a smooth and efficient transition. The features of IOS-XE are specifically designed to enhance SD-WAN performance and management, making it the ideal choice for businesses looking to optimize their network.
The Benefits of Using IOS-XE for SD-WAN
One of the key benefits of using IOS-XE for SD-WAN is the advanced features it offers. From enhanced security capabilities to improved network automation, IOS-XE provides a wide range of benefits that can help take your SD-WAN to the next level. Additionally, IOS-XE is known for its reliability and scalability, making it a smart choice for businesses of all sizes.
Enhancing SD-WAN Performance with IOS-XE
When it comes to optimizing SD-WAN performance, IOS-XE is the solution. With its advanced capabilities and efficient architecture, IOS-XE can significantly boost the performance of your SD-WAN, providing faster and more reliable network connectivity. Additionally, IOS-XE offers regular updates and advancements in SD-WAN technology, ensuring that your network stays ahead of the curve.
Improving SD-WAN Security with IOS-XE
Security is a top priority for businesses, especially when it comes to network connectivity. IOS-XE offers robust security features that can help protect your SD-WAN from potential threats and vulnerabilities. With IOS-XE, you can rest assured that your network is secure and protected at all times, giving you peace of mind and allowing you to focus on your business operations.
Simplifying SD-WAN Deployment with IOS-XE
Deploying a new SD-WAN solution can be a complex and time-consuming process. However, with IOS-XE, SD-WAN deployment is made easy. IOS-XE offers simplified configuration options, compatibility with a wide range of SD-WAN solutions, and efficient management capabilities, making it the perfect choice for businesses looking to streamline their network deployment.
How to obtain Cisco Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php .
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, IOS-XE is transforming the way businesses implement and manage their SD-WAN solutions. With its advanced features, enhanced performance, and top-notch security capabilities, IOS-XE is revolutionizing the way businesses connect and communicate. If you're ready to take your SD-WAN to the next level, consider upgrading to IOS-XE today and experience the future of networking technology.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Creating Interactive Data Visualizations with Plotly and Dash
Have you ever wanted to create stunning and interactive data visualizations for your web applications or dashboards? Well, look no further than Plotly and Dash. These powerful Python libraries allow you to effortlessly build interactive charts, graphs, and dashboards for data analysis, visualization, and presentation. In this article, we will explore how you can leverage Plotly and Dash to create visually appealing and engaging data visualizations that will impress your audience.
What is Plotly?
Plotly is a data visualization library that allows you to create interactive plots, charts, and graphs. It provides a wide range of chart types, including scatter plots, bar charts, line charts, and more. With Plotly, you can easily customize the appearance of your charts and add interactive elements such as tooltips, zooming, panning, and more. Plotly is widely used in data science, engineering, finance, and other fields for data visualization and analysis.
What is Dash?
Dash is a web application framework that allows you to build interactive web applications with Plotly visualizations. With Dash, you can create dynamic dashboards that update in real-time based on user input. You can combine multiple Plotly charts and graphs into a single dashboard, allowing users to explore data interactively. Dash is designed to be easy to use and requires minimal coding, making it ideal for both beginners and advanced users.
Getting Started with Plotly and Dash
To get started with Plotly and Dash, you first need to install the libraries in your Python environment. You can do this using pip, the Python package manager. Once you have installed Plotly and Dash, you can start creating interactive data visualizations.
How to obtain Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php .
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Plotly and Dash are powerful tools for creating interactive data visualizations for web applications, dashboards, and presentations. Whether you are a data scientist, developer, or analyst, Plotly and Dash can help you visualize and communicate your data effectively. By leveraging the capabilities of Plotly and Dash, you can create stunning and interactive charts, graphs, and dashboards that will impress your audience and provide valuable insights. So why wait? Start exploring Plotly and Dash today and take your data visualizations to the next level!
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Have you ever wanted to create stunning and interactive data visualizations for your web applications or dashboards? Well, look no further than Plotly and Dash. These powerful Python libraries allow you to effortlessly build interactive charts, graphs, and dashboards for data analysis, visualization, and presentation. In this article, we will explore how you can leverage Plotly and Dash to create visually appealing and engaging data visualizations that will impress your audience.
What is Plotly?
Plotly is a data visualization library that allows you to create interactive plots, charts, and graphs. It provides a wide range of chart types, including scatter plots, bar charts, line charts, and more. With Plotly, you can easily customize the appearance of your charts and add interactive elements such as tooltips, zooming, panning, and more. Plotly is widely used in data science, engineering, finance, and other fields for data visualization and analysis.
What is Dash?
Dash is a web application framework that allows you to build interactive web applications with Plotly visualizations. With Dash, you can create dynamic dashboards that update in real-time based on user input. You can combine multiple Plotly charts and graphs into a single dashboard, allowing users to explore data interactively. Dash is designed to be easy to use and requires minimal coding, making it ideal for both beginners and advanced users.
Getting Started with Plotly and Dash
To get started with Plotly and Dash, you first need to install the libraries in your Python environment. You can do this using pip, the Python package manager. Once you have installed Plotly and Dash, you can start creating interactive data visualizations.
How to obtain Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php .
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Plotly and Dash are powerful tools for creating interactive data visualizations for web applications, dashboards, and presentations. Whether you are a data scientist, developer, or analyst, Plotly and Dash can help you visualize and communicate your data effectively. By leveraging the capabilities of Plotly and Dash, you can create stunning and interactive charts, graphs, and dashboards that will impress your audience and provide valuable insights. So why wait? Start exploring Plotly and Dash today and take your data visualizations to the next level!
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
The Impact of Edge Computing on Data Processing and Security
In today's digital age, the amount of data generated by devices and applications has grown exponentially. This has led to the need for more efficient and secure ways of processing and storing data. Edge computing has emerged as a revolutionary technology that addresses these challenges by bringing computation and data storage closer to the source of data generation – the edge devices. In this article, we will delve into the impact of edge computing on data processing and security, and how this innovative technology is transforming the way data is managed in various industries.
Edge Computing: A Game-Changer in Data Processing
Edge computing is a distributed computing paradigm that brings computation and data storage closer to the source of data generation. By processing data near the edge devices, edge computing reduces network latency and enables real-time data processing. This not only improves the efficiency of data processing but also allows for faster decision-making and response times. With the proliferation of IoT devices and the increasing demand for real-time data analytics, edge computing has become an indispensable technology for organizations looking to gain a competitive edge.
How does edge computing improve data processing efficiency?
Edge computing enhances data processing efficiency by reducing the need to transfer data back and forth between edge devices and centralized cloud infrastructure. By processing data locally, edge devices can perform computations faster and with lower network latency, resulting in quicker response times and improved overall performance.
Enhancing Security with Edge Computing
Security is a top priority for organizations handling sensitive data, and edge computing plays a crucial role in enhancing data security. By processing data locally on edge devices, organizations can reduce the risk of data breaches and unauthorized access to sensitive information. Edge computing also allows for data to be encrypted and securely transmitted to centralized servers, ensuring that data remains protected throughout the processing and storage process.
How does edge computing improve data security?
Edge computing enhances data security by reducing the exposure of sensitive data to potential threats. By processing data locally on edge devices, organizations can minimize the risk of data breaches and unauthorized access, ensuring that data remains secure throughout the processing and storage process.
Revolutionizing Data Management with Edge Analytics
Edge analytics is a key component of edge computing that enables real-time data processing and analysis at the edge of the network. By leveraging machine learning algorithms and AI technologies, edge analytics can extract valuable insights from data collected by edge devices. This allows organizations to make informed decisions quickly and efficiently, leading to improved operational efficiency and innovation.
How does edge analytics support data management?
Edge analytics enables real-time data processing and analysis at the edge of the network, allowing organizations to extract valuable insights from data collected by edge devices. By leveraging machine learning algorithms and AI technologies, edge analytics supports data-driven decision-making and enables organizations to optimize their operations and drive innovation.
The Future of Edge Computing
As the demand for real-time data processing and secure data management continues to rise, edge computing is set to play a central role in shaping the future of technology. From edge servers and edge architecture to edge security and data privacy, organizations are increasingly adopting edge computing solutions to drive efficiency, scalability, and innovation. With its ability to process data closer to the source and enhance security measures, edge computing is transforming the way data is managed across industries.
How to obtain Emerging Technologies certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the impact of edge computing on data processing and security is undeniable. By bringing computation and data storage closer to the edge devices, organizations can achieve greater efficiency, security, and scalability in managing their data. As technology continues to evolve, edge computing will undoubtedly play a critical role in driving innovation and reshaping the future of data processing and security.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's digital age, the amount of data generated by devices and applications has grown exponentially. This has led to the need for more efficient and secure ways of processing and storing data. Edge computing has emerged as a revolutionary technology that addresses these challenges by bringing computation and data storage closer to the source of data generation – the edge devices. In this article, we will delve into the impact of edge computing on data processing and security, and how this innovative technology is transforming the way data is managed in various industries.
Edge Computing: A Game-Changer in Data Processing
Edge computing is a distributed computing paradigm that brings computation and data storage closer to the source of data generation. By processing data near the edge devices, edge computing reduces network latency and enables real-time data processing. This not only improves the efficiency of data processing but also allows for faster decision-making and response times. With the proliferation of IoT devices and the increasing demand for real-time data analytics, edge computing has become an indispensable technology for organizations looking to gain a competitive edge.
How does edge computing improve data processing efficiency?
Edge computing enhances data processing efficiency by reducing the need to transfer data back and forth between edge devices and centralized cloud infrastructure. By processing data locally, edge devices can perform computations faster and with lower network latency, resulting in quicker response times and improved overall performance.
Enhancing Security with Edge Computing
Security is a top priority for organizations handling sensitive data, and edge computing plays a crucial role in enhancing data security. By processing data locally on edge devices, organizations can reduce the risk of data breaches and unauthorized access to sensitive information. Edge computing also allows for data to be encrypted and securely transmitted to centralized servers, ensuring that data remains protected throughout the processing and storage process.
How does edge computing improve data security?
Edge computing enhances data security by reducing the exposure of sensitive data to potential threats. By processing data locally on edge devices, organizations can minimize the risk of data breaches and unauthorized access, ensuring that data remains secure throughout the processing and storage process.
Revolutionizing Data Management with Edge Analytics
Edge analytics is a key component of edge computing that enables real-time data processing and analysis at the edge of the network. By leveraging machine learning algorithms and AI technologies, edge analytics can extract valuable insights from data collected by edge devices. This allows organizations to make informed decisions quickly and efficiently, leading to improved operational efficiency and innovation.
How does edge analytics support data management?
Edge analytics enables real-time data processing and analysis at the edge of the network, allowing organizations to extract valuable insights from data collected by edge devices. By leveraging machine learning algorithms and AI technologies, edge analytics supports data-driven decision-making and enables organizations to optimize their operations and drive innovation.
The Future of Edge Computing
As the demand for real-time data processing and secure data management continues to rise, edge computing is set to play a central role in shaping the future of technology. From edge servers and edge architecture to edge security and data privacy, organizations are increasingly adopting edge computing solutions to drive efficiency, scalability, and innovation. With its ability to process data closer to the source and enhance security measures, edge computing is transforming the way data is managed across industries.
How to obtain Emerging Technologies certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the impact of edge computing on data processing and security is undeniable. By bringing computation and data storage closer to the edge devices, organizations can achieve greater efficiency, security, and scalability in managing their data. As technology continues to evolve, edge computing will undoubtedly play a critical role in driving innovation and reshaping the future of data processing and security.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Maximizing ROI through Identity Management and Cybersecurity
In today's digital landscape, the need for robust identity management and cybersecurity measures has never been greater. With the increasing frequency and sophistication of cyber threats, organizations must prioritize their cyber defense strategies to protect sensitive data and mitigate risks. One crucial aspect of this defense strategy is the concept of Return on Investment (ROI) when it comes to identity management and cybersecurity initiatives. By effectively managing identities and implementing strong cybersecurity measures, organizations can not only enhance their security posture but also maximize their ROI.
Identity Management: A Key Component of Cybersecurity Strategy
Identity Access Management (IAM):
Identity Management is the foundation of a strong cybersecurity strategy. IAM is the process of managing digital identities, including user authentication and authorization. By implementing IAM solutions, organizations can ensure that only authorized users have access to sensitive information and resources.
Authentication and Access Control:
Authentication is the process of verifying a user's identity, typically through passwords, biometrics, or multi-factor authentication. Access control, on the other hand, is the practice of restricting access to authorized users only. By implementing strong authentication and access control measures, organizations can prevent unauthorized access and reduce the risk of data breaches.
Cybersecurity: Protecting Against Threats
Data Security:
Data security is paramount in the digital age, with cyber threats constantly evolving. By implementing encryption, data loss prevention, and secure data storage practices, organizations can protect their sensitive information from unauthorized access and cyber attacks.
Threat Detection and Incident Response:
Threat detection involves identifying and responding to potential cyber threats in real-time. Incident response, on the other hand, is the process of mitigating the impact of a cyber attack and restoring normal operations. By implementing robust threat detection and incident response protocols, organizations can minimize the damage caused by cyber attacks and recover quickly.
Security Compliance and Risk Management:
Compliance with security standards and regulations is essential for organizations to protect their data and maintain customer trust. By implementing robust security compliance measures and risk management practices, organizations can minimize the likelihood of security breaches and financial penalties.
Cybersecurity Awareness and Training:
Employee training and cybersecurity awareness programs are crucial components of a strong cybersecurity posture. By educating employees about cybersecurity best practices and potential threats, organizations can reduce the risk of human error leading to security incidents.
Cybersecurity Solutions and Best Practices:
Implementing cybersecurity solutions such as firewalls, antivirus software, and intrusion detection systems, along with adherence to cybersecurity best practices, can significantly enhance an organization's security posture. By leveraging the right tools and practices, organizations can protect their data and assets from cyber threats effectively.
Network Security and Privacy Protection:
Network security involves securing an organization's network infrastructure and monitoring network traffic for potential threats. Data privacy protection, on the other hand, focuses on safeguarding personal and sensitive information from unauthorized access. By implementing robust network security and privacy protection measures, organizations can protect their data and user information from cyber threats.
How to obtain Cyber Security certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, effective identity management and cybersecurity measures are essential components of a strong defense strategy against cyber threats. By prioritizing security compliance, implementing robust cybersecurity solutions, and educating employees about best practices, organizations can enhance their security posture and maximize their ROI. Investing in identity management and cybersecurity is not just about protecting data and assets; it's about building a secure future for the organization and its stakeholders.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's digital landscape, the need for robust identity management and cybersecurity measures has never been greater. With the increasing frequency and sophistication of cyber threats, organizations must prioritize their cyber defense strategies to protect sensitive data and mitigate risks. One crucial aspect of this defense strategy is the concept of Return on Investment (ROI) when it comes to identity management and cybersecurity initiatives. By effectively managing identities and implementing strong cybersecurity measures, organizations can not only enhance their security posture but also maximize their ROI.
Identity Management: A Key Component of Cybersecurity Strategy
Identity Access Management (IAM):
Identity Management is the foundation of a strong cybersecurity strategy. IAM is the process of managing digital identities, including user authentication and authorization. By implementing IAM solutions, organizations can ensure that only authorized users have access to sensitive information and resources.
Authentication and Access Control:
Authentication is the process of verifying a user's identity, typically through passwords, biometrics, or multi-factor authentication. Access control, on the other hand, is the practice of restricting access to authorized users only. By implementing strong authentication and access control measures, organizations can prevent unauthorized access and reduce the risk of data breaches.
Cybersecurity: Protecting Against Threats
Data Security:
Data security is paramount in the digital age, with cyber threats constantly evolving. By implementing encryption, data loss prevention, and secure data storage practices, organizations can protect their sensitive information from unauthorized access and cyber attacks.
Threat Detection and Incident Response:
Threat detection involves identifying and responding to potential cyber threats in real-time. Incident response, on the other hand, is the process of mitigating the impact of a cyber attack and restoring normal operations. By implementing robust threat detection and incident response protocols, organizations can minimize the damage caused by cyber attacks and recover quickly.
Security Compliance and Risk Management:
Compliance with security standards and regulations is essential for organizations to protect their data and maintain customer trust. By implementing robust security compliance measures and risk management practices, organizations can minimize the likelihood of security breaches and financial penalties.
Cybersecurity Awareness and Training:
Employee training and cybersecurity awareness programs are crucial components of a strong cybersecurity posture. By educating employees about cybersecurity best practices and potential threats, organizations can reduce the risk of human error leading to security incidents.
Cybersecurity Solutions and Best Practices:
Implementing cybersecurity solutions such as firewalls, antivirus software, and intrusion detection systems, along with adherence to cybersecurity best practices, can significantly enhance an organization's security posture. By leveraging the right tools and practices, organizations can protect their data and assets from cyber threats effectively.
Network Security and Privacy Protection:
Network security involves securing an organization's network infrastructure and monitoring network traffic for potential threats. Data privacy protection, on the other hand, focuses on safeguarding personal and sensitive information from unauthorized access. By implementing robust network security and privacy protection measures, organizations can protect their data and user information from cyber threats.
How to obtain Cyber Security certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, effective identity management and cybersecurity measures are essential components of a strong defense strategy against cyber threats. By prioritizing security compliance, implementing robust cybersecurity solutions, and educating employees about best practices, organizations can enhance their security posture and maximize their ROI. Investing in identity management and cybersecurity is not just about protecting data and assets; it's about building a secure future for the organization and its stakeholders.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Integrating Minitab with Other Software Tools
Are you looking to streamline your data analysis process and improve decision-making within your organization? If so, integrating Minitab with other software tools could be the solution you have been searching for. Minitab, a powerful statistical analysis software, offers a wide range of features that can help you make informed decisions based on data-driven insights. In this article, we will explore the benefits of integrating Minitab with other tools, the various options available for integration, and best practices to ensure a seamless collaboration between different software platforms.
Why Integrate Minitab with Other Software Tools?
Integrating Minitab with Excel, quality control tools, process optimization software, and other data analysis tools can significantly enhance your data analysis capabilities. By combining the features of Minitab with other tools, you can create a more comprehensive data analysis workflow that allows for deeper insights and more accurate results. Additionally, integrating Minitab with other software tools can help improve the efficiency of your data analysis process, saving time and resources in the long run.
Minitab Integration Options
There are several options available for integrating Minitab with other software tools. Some common integration strategies include using Minitab add-ins, data visualization software, and plugins that allow for seamless collaboration between different platforms. Additionally, Minitab offers compatibility with various business intelligence tools, process control software, and lean six sigma software, making it easy to incorporate Minitab into your existing data analysis workflow.
Collaboration with Minitab Software
When integrating Minitab with other software tools, it is important to ensure that the different platforms can work together seamlessly. This may require data manipulation to ensure compatibility between systems, as well as setting up integration best practices to streamline the workflow. By collaborating with Minitab software experts, you can learn how to link Minitab with other tools effectively and optimize your data analysis process for better results.
Enhancing Data Analysis with Minitab
By integrating Minitab with other software tools, you can enhance your data analysis capabilities and achieve more accurate and meaningful insights. Minitab offers a wide range of statistical tools that can help you make informed decisions based on real-time data. Whether you are performing process optimization, quality assurance, or statistical modeling, Minitab provides the features you need to succeed in today's data-driven business environment.
Minitab and Lean Six Sigma Software
One area where Minitab excels is in its compatibility with lean six sigma software. By integrating Minitab with lean six sigma tools, you can streamline your process improvement efforts and identify areas for optimization more efficiently. Minitab's interoperability with lean six sigma software allows for a seamless collaboration between the two platforms, enabling you to achieve greater results in your quality control initiatives.
How to obtain Minitab certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, integrating Minitab with other software tools can greatly enhance your data analysis capabilities and improve decision-making within your organization. By leveraging the features of Minitab and collaborating with other software platforms, you can streamline your data analysis process, achieve more accurate results, and make informed decisions based on real-time insights. So why wait? Start integrating Minitab with other tools today and take your data analysis to the next level!
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to streamline your data analysis process and improve decision-making within your organization? If so, integrating Minitab with other software tools could be the solution you have been searching for. Minitab, a powerful statistical analysis software, offers a wide range of features that can help you make informed decisions based on data-driven insights. In this article, we will explore the benefits of integrating Minitab with other tools, the various options available for integration, and best practices to ensure a seamless collaboration between different software platforms.
Why Integrate Minitab with Other Software Tools?
Integrating Minitab with Excel, quality control tools, process optimization software, and other data analysis tools can significantly enhance your data analysis capabilities. By combining the features of Minitab with other tools, you can create a more comprehensive data analysis workflow that allows for deeper insights and more accurate results. Additionally, integrating Minitab with other software tools can help improve the efficiency of your data analysis process, saving time and resources in the long run.
Minitab Integration Options
There are several options available for integrating Minitab with other software tools. Some common integration strategies include using Minitab add-ins, data visualization software, and plugins that allow for seamless collaboration between different platforms. Additionally, Minitab offers compatibility with various business intelligence tools, process control software, and lean six sigma software, making it easy to incorporate Minitab into your existing data analysis workflow.
Collaboration with Minitab Software
When integrating Minitab with other software tools, it is important to ensure that the different platforms can work together seamlessly. This may require data manipulation to ensure compatibility between systems, as well as setting up integration best practices to streamline the workflow. By collaborating with Minitab software experts, you can learn how to link Minitab with other tools effectively and optimize your data analysis process for better results.
Enhancing Data Analysis with Minitab
By integrating Minitab with other software tools, you can enhance your data analysis capabilities and achieve more accurate and meaningful insights. Minitab offers a wide range of statistical tools that can help you make informed decisions based on real-time data. Whether you are performing process optimization, quality assurance, or statistical modeling, Minitab provides the features you need to succeed in today's data-driven business environment.
Minitab and Lean Six Sigma Software
One area where Minitab excels is in its compatibility with lean six sigma software. By integrating Minitab with lean six sigma tools, you can streamline your process improvement efforts and identify areas for optimization more efficiently. Minitab's interoperability with lean six sigma software allows for a seamless collaboration between the two platforms, enabling you to achieve greater results in your quality control initiatives.
How to obtain Minitab certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, integrating Minitab with other software tools can greatly enhance your data analysis capabilities and improve decision-making within your organization. By leveraging the features of Minitab and collaborating with other software platforms, you can streamline your data analysis process, achieve more accurate results, and make informed decisions based on real-time insights. So why wait? Start integrating Minitab with other tools today and take your data analysis to the next level!
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
What Is Lean Methodology? and its Principles
What Is Lean Methodology?
Lean methodology is a systematic approach to continuous process improvement through the elimination of waste. It originated in the manufacturing industry, specifically within Toyota, in the mid-20th century as part of the Toyota Production System (TPS), which sought to maximize value for the customer through the optimal use of resources. The principles of Lean have since been adapted and applied across various sectors, including healthcare, software development, and service industries
Principles of Lean Methodology
Lean methodology principles are fundamental guidelines that help organizations focus on value creation while minimizing waste. The five core principles of Lean methodology are designed to improve efficiency, quality, and customer satisfaction. They are:
-
Define Value: The starting point of Lean is to specify value from the standpoint of the end customer. Understanding what the customer values in a product or service allows organizations to streamline their processes, ensuring that every action contributes towards fulfilling the customer's needs and expectations.
-
Map the Value Stream: This principle involves identifying and mapping all the steps involved in delivering a product or service, from raw materials to the final delivery to the customer. The goal is to visualize the flow of materials and information throughout the organization. This mapping helps identify and eliminate non-value-adding activities (waste), ensuring that every step in the process adds value to the product or service.
-
Create Flow: Once the value stream is identified, the next step is to ensure that the value-creating steps occur in a tight sequence, allowing the product or service to flow smoothly toward the customer without interruptions, delays, or bottlenecks. This can involve reconfiguring production steps, leveling workload, creating cross-functional teams, or adopting new technologies to enable a seamless flow of products and services.
-
Establish Pull: Instead of pushing products through production based on forecasted demand, Lean dictates that production should be based on actual customer demand, thereby minimizing waste associated with overproduction and excess inventory. A pull-based system allows for a more responsive and flexible production scheduling and inventory management approach.
-
Pursue Perfection: Lean is an ongoing process of continuous improvement. Pursuing perfection involves continually seeking ways to reduce waste and improve processes, thereby maximizing value for the customer. This principle encourages a culture of continuous learning and improvement, where employees at all levels identify inefficiencies and suggest improvements.
How to obtain Lean Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
From manufacturing to healthcare and software development to retail, Lean principles empower organizations to streamline operations, enhance efficiency, and deliver unparalleled value to customers. Lean methodology optimizes processes and fosters a culture of excellence and innovation by focusing on waste elimination, continuous improvement, and value creation.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
What Is Lean Methodology?
Lean methodology is a systematic approach to continuous process improvement through the elimination of waste. It originated in the manufacturing industry, specifically within Toyota, in the mid-20th century as part of the Toyota Production System (TPS), which sought to maximize value for the customer through the optimal use of resources. The principles of Lean have since been adapted and applied across various sectors, including healthcare, software development, and service industries
Principles of Lean Methodology
Lean methodology principles are fundamental guidelines that help organizations focus on value creation while minimizing waste. The five core principles of Lean methodology are designed to improve efficiency, quality, and customer satisfaction. They are:
-
Define Value: The starting point of Lean is to specify value from the standpoint of the end customer. Understanding what the customer values in a product or service allows organizations to streamline their processes, ensuring that every action contributes towards fulfilling the customer's needs and expectations.
-
Map the Value Stream: This principle involves identifying and mapping all the steps involved in delivering a product or service, from raw materials to the final delivery to the customer. The goal is to visualize the flow of materials and information throughout the organization. This mapping helps identify and eliminate non-value-adding activities (waste), ensuring that every step in the process adds value to the product or service.
-
Create Flow: Once the value stream is identified, the next step is to ensure that the value-creating steps occur in a tight sequence, allowing the product or service to flow smoothly toward the customer without interruptions, delays, or bottlenecks. This can involve reconfiguring production steps, leveling workload, creating cross-functional teams, or adopting new technologies to enable a seamless flow of products and services.
-
Establish Pull: Instead of pushing products through production based on forecasted demand, Lean dictates that production should be based on actual customer demand, thereby minimizing waste associated with overproduction and excess inventory. A pull-based system allows for a more responsive and flexible production scheduling and inventory management approach.
-
Pursue Perfection: Lean is an ongoing process of continuous improvement. Pursuing perfection involves continually seeking ways to reduce waste and improve processes, thereby maximizing value for the customer. This principle encourages a culture of continuous learning and improvement, where employees at all levels identify inefficiencies and suggest improvements.
How to obtain Lean Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
From manufacturing to healthcare and software development to retail, Lean principles empower organizations to streamline operations, enhance efficiency, and deliver unparalleled value to customers. Lean methodology optimizes processes and fosters a culture of excellence and innovation by focusing on waste elimination, continuous improvement, and value creation.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
The Impact of Artificial Intelligence on Quality Management Systems
In today's fast-paced and competitive business environment, companies are constantly looking for ways to improve their operations and stay ahead of the curve. One key technology that is revolutionizing the way organizations manage quality is artificial intelligence (AI). By leveraging AI, companies can streamline their quality management systems, enhance efficiency, and drive innovation like never before.
How Does Artificial Intelligence Impact Quality Management Systems?
-
Automation: AI enables the automation of repetitive tasks and processes in quality management systems, freeing up employees to focus on more strategic initiatives.
-
Data Analysis: With AI-powered analytics tools, businesses can gather and analyze vast amounts of data to identify trends, patterns, and anomalies in quality metrics.
-
Machine Learning: AI algorithms can learn from data and improve over time, allowing quality management systems to become more accurate and efficient.
-
Optimization: By utilizing AI, organizations can optimize their quality control processes and make real-time adjustments to ensure product quality.
The Advantages of Integrating AI into Quality Management Systems
-
Performance: AI can enhance the overall performance of quality management systems by maximizing efficiency and minimizing errors.
-
Process Improvement: With AI, companies can identify areas for improvement in their quality management processes and make strategic changes.
-
Predictive Maintenance: AI can predict equipment failures and maintenance needs, helping companies prevent quality issues before they occur.
How AI is Transforming Quality Control
-
Risk Management: AI tools can help companies identify potential risks in their quality management systems and take proactive measures to mitigate them.
-
Productivity: By automating tasks and processes, AI can boost productivity and streamline quality control workflows.
-
Advancements: AI is driving advancements in quality management systems, leading to more innovative solutions and practices.
The Future of Quality Management Systems with AI
-
Digital Transformation: AI is at the forefront of digital transformation, reshaping the way companies approach quality management.
-
Sustainability: By improving efficiency and reducing waste, AI can help companies achieve sustainability goals in their quality management processes.
-
Workflow: AI can optimize workflows and streamline quality control procedures, making operations more seamless and efficient.
Benefits of AI in Quality Management Systems
-
Smart Solutions: AI offers smart solutions for quality management, enabling companies to make data-driven decisions and enhance quality assurance.
-
Business Intelligence: With AI-powered tools, companies can gain valuable insights into their quality metrics and make informed decisions.
-
Best Practices: AI can help organizations establish and maintain best practices in quality management, ensuring consistent product quality.
How to obtain Quality Management Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php.
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the impact of artificial intelligence on quality management systems is undeniable. By leveraging AI technology, companies can improve efficiency, drive innovation, and enhance overall quality control processes. As AI continues to evolve, the possibilities for quality management systems are endless, opening up new opportunities for companies to achieve operational excellence and deliver high-quality products and services to their customers.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced and competitive business environment, companies are constantly looking for ways to improve their operations and stay ahead of the curve. One key technology that is revolutionizing the way organizations manage quality is artificial intelligence (AI). By leveraging AI, companies can streamline their quality management systems, enhance efficiency, and drive innovation like never before.
How Does Artificial Intelligence Impact Quality Management Systems?
-
Automation: AI enables the automation of repetitive tasks and processes in quality management systems, freeing up employees to focus on more strategic initiatives.
-
Data Analysis: With AI-powered analytics tools, businesses can gather and analyze vast amounts of data to identify trends, patterns, and anomalies in quality metrics.
-
Machine Learning: AI algorithms can learn from data and improve over time, allowing quality management systems to become more accurate and efficient.
-
Optimization: By utilizing AI, organizations can optimize their quality control processes and make real-time adjustments to ensure product quality.
The Advantages of Integrating AI into Quality Management Systems
-
Performance: AI can enhance the overall performance of quality management systems by maximizing efficiency and minimizing errors.
-
Process Improvement: With AI, companies can identify areas for improvement in their quality management processes and make strategic changes.
-
Predictive Maintenance: AI can predict equipment failures and maintenance needs, helping companies prevent quality issues before they occur.
How AI is Transforming Quality Control
-
Risk Management: AI tools can help companies identify potential risks in their quality management systems and take proactive measures to mitigate them.
-
Productivity: By automating tasks and processes, AI can boost productivity and streamline quality control workflows.
-
Advancements: AI is driving advancements in quality management systems, leading to more innovative solutions and practices.
The Future of Quality Management Systems with AI
-
Digital Transformation: AI is at the forefront of digital transformation, reshaping the way companies approach quality management.
-
Sustainability: By improving efficiency and reducing waste, AI can help companies achieve sustainability goals in their quality management processes.
-
Workflow: AI can optimize workflows and streamline quality control procedures, making operations more seamless and efficient.
Benefits of AI in Quality Management Systems
-
Smart Solutions: AI offers smart solutions for quality management, enabling companies to make data-driven decisions and enhance quality assurance.
-
Business Intelligence: With AI-powered tools, companies can gain valuable insights into their quality metrics and make informed decisions.
-
Best Practices: AI can help organizations establish and maintain best practices in quality management, ensuring consistent product quality.
How to obtain Quality Management Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php.
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the impact of artificial intelligence on quality management systems is undeniable. By leveraging AI technology, companies can improve efficiency, drive innovation, and enhance overall quality control processes. As AI continues to evolve, the possibilities for quality management systems are endless, opening up new opportunities for companies to achieve operational excellence and deliver high-quality products and services to their customers.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Salesforce for Mobile: Developing with Salesforce Mobile SDK
Are you looking to create mobile applications that are seamlessly integrated with Salesforce? Look no further than the Salesforce Mobile SDK. This powerful tool allows developers to build custom mobile apps that connect directly to the Salesforce platform, enabling companies to streamline their processes and provide a more seamless user experience. In this article, we will explore the benefits of using Salesforce Mobile SDK for mobile app development and how you can leverage this tool to create innovative solutions for your business.
What is Salesforce Mobile SDK?
Salesforce Mobile SDK is a collection of tools and resources that allow developers to create custom mobile applications that are tightly integrated with the Salesforce platform. This SDK provides a set of libraries and APIs that make it easy to build mobile apps that can access Salesforce data, interact with Salesforce processes, and provide a seamless user experience. With Salesforce Mobile SDK, developers can create native iOS and Android apps, as well as hybrid apps using popular frameworks like React Native.
Why Use Salesforce Mobile SDK for Mobile Development?
There are several reasons why companies choose to use Salesforce Mobile SDK for their mobile development projects. One of the main benefits is the ability to seamlessly integrate with Salesforce data and processes. This allows developers to create apps that provide real-time access to customer data, sales information, and other key business metrics. By leveraging the power of Salesforce Mobile SDK, companies can streamline their processes, improve productivity, and provide a more personalized experience for their customers.
Another key advantage of using Salesforce Mobile SDK is the ability to create custom features and functionality that are tailored to the specific needs of your business. Whether you need to create a mobile app for field service employees, sales representatives, or customer service agents, Salesforce Mobile SDK provides the flexibility to build apps that meet your unique requirements. With a wide range of tools and resources available, developers can create apps that are robust, scalable, and easy to maintain.
How to Get Started with Salesforce Mobile SDK?
Getting started with Salesforce Mobile SDK is easier than you might think. The first step is to sign up for a Salesforce developer account, which will give you access to all the tools and resources you need to start building mobile apps. From there, you can download the Salesforce Mobile SDK and begin exploring the various libraries and APIs that are available.
Once you have familiarized yourself with the Salesforce Mobile SDK, you can start building your mobile app. Whether you are developing a native iOS app, an Android app, or a hybrid app, Salesforce Mobile SDK provides everything you need to create a seamless integration with the Salesforce platform. With a robust set of tools and resources at your disposal, you can build custom features, connect to Salesforce data, and deliver a mobile app that meets the needs of your business.
How to obtain Salesforce Platform Developer certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Salesforce Mobile SDK is a powerful tool for building custom mobile applications that are seamlessly integrated with the Salesforce platform. With a wide range of tools and resources available, developers can create apps that provide real-time access to Salesforce data, streamline business processes, and provide a more personalized experience for users. Whether you are looking to create a mobile app for sales, customer service, or field service, Salesforce Mobile SDK offers the flexibility and scalability you need to build innovative solutions for your business. Start exploring the possibilities of Salesforce Mobile SDK today and take your mobile development projects to the next level.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to create mobile applications that are seamlessly integrated with Salesforce? Look no further than the Salesforce Mobile SDK. This powerful tool allows developers to build custom mobile apps that connect directly to the Salesforce platform, enabling companies to streamline their processes and provide a more seamless user experience. In this article, we will explore the benefits of using Salesforce Mobile SDK for mobile app development and how you can leverage this tool to create innovative solutions for your business.
What is Salesforce Mobile SDK?
Salesforce Mobile SDK is a collection of tools and resources that allow developers to create custom mobile applications that are tightly integrated with the Salesforce platform. This SDK provides a set of libraries and APIs that make it easy to build mobile apps that can access Salesforce data, interact with Salesforce processes, and provide a seamless user experience. With Salesforce Mobile SDK, developers can create native iOS and Android apps, as well as hybrid apps using popular frameworks like React Native.
Why Use Salesforce Mobile SDK for Mobile Development?
There are several reasons why companies choose to use Salesforce Mobile SDK for their mobile development projects. One of the main benefits is the ability to seamlessly integrate with Salesforce data and processes. This allows developers to create apps that provide real-time access to customer data, sales information, and other key business metrics. By leveraging the power of Salesforce Mobile SDK, companies can streamline their processes, improve productivity, and provide a more personalized experience for their customers.
Another key advantage of using Salesforce Mobile SDK is the ability to create custom features and functionality that are tailored to the specific needs of your business. Whether you need to create a mobile app for field service employees, sales representatives, or customer service agents, Salesforce Mobile SDK provides the flexibility to build apps that meet your unique requirements. With a wide range of tools and resources available, developers can create apps that are robust, scalable, and easy to maintain.
How to Get Started with Salesforce Mobile SDK?
Getting started with Salesforce Mobile SDK is easier than you might think. The first step is to sign up for a Salesforce developer account, which will give you access to all the tools and resources you need to start building mobile apps. From there, you can download the Salesforce Mobile SDK and begin exploring the various libraries and APIs that are available.
Once you have familiarized yourself with the Salesforce Mobile SDK, you can start building your mobile app. Whether you are developing a native iOS app, an Android app, or a hybrid app, Salesforce Mobile SDK provides everything you need to create a seamless integration with the Salesforce platform. With a robust set of tools and resources at your disposal, you can build custom features, connect to Salesforce data, and deliver a mobile app that meets the needs of your business.
How to obtain Salesforce Platform Developer certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Salesforce Mobile SDK is a powerful tool for building custom mobile applications that are seamlessly integrated with the Salesforce platform. With a wide range of tools and resources available, developers can create apps that provide real-time access to Salesforce data, streamline business processes, and provide a more personalized experience for users. Whether you are looking to create a mobile app for sales, customer service, or field service, Salesforce Mobile SDK offers the flexibility and scalability you need to build innovative solutions for your business. Start exploring the possibilities of Salesforce Mobile SDK today and take your mobile development projects to the next level.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
E-commerce Trends and Digital Marketing
In today's fast-paced digital world, e-commerce trends and digital marketing strategies are constantly evolving to meet the ever-changing needs of consumers. With online shopping, internet sales, social media, and mobile commerce continuing to shape the way we shop, businesses must adapt and stay ahead of the competition to succeed. Let's explore some of the key trends and strategies that are shaping the e-commerce landscape today.
The Rise of Online Shopping
Online shopping has become increasingly popular in recent years, with more and more consumers turning to the internet to make their purchases. The convenience of shopping from the comfort of your own home, the wide variety of products available online, and the ease of comparison shopping have all contributed to the growth of e-commerce. As a result, businesses must have a strong online presence to attract and retain customers in this competitive market.
Leveraging Social Media for Marketing Success
Social media has become an invaluable tool for businesses looking to connect with their customers and reach a wider audience. Platforms like Facebook, Instagram, and Twitter allow companies to engage with customers, showcase their products, and drive traffic to their e-commerce websites. By creating engaging content, running targeted ads, and collaborating with influencers, businesses can leverage social media to increase brand awareness and drive sales.
The Importance of Mobile Commerce
With more and more consumers using their smartphones and tablets to shop online, mobile commerce has become a crucial aspect of e-commerce. Businesses must optimize their websites for mobile devices, create mobile-friendly shopping experiences, and offer convenient payment options to cater to the growing number of mobile shoppers. By embracing mobile commerce, businesses can reach a wider audience and increase sales.
Enhancing Customer Experience
Providing a seamless and personalized customer experience is essential for e-commerce success. Businesses must prioritize user-friendly website design, fast loading times, easy navigation, and secure payment options to create a positive shopping experience for customers. By investing in customer service, feedback mechanisms, and loyalty programs, businesses can build trust and loyalty with their customers, leading to repeat purchases and increased sales.
Harnessing the Power of Online Advertising
Online advertising is a powerful tool for e-commerce businesses looking to reach their target audience and drive sales. Whether through pay-per-click ads, display ads, or social media ads, businesses can effectively promote their products and services to potential customers. By analyzing data, targeting specific demographics, and tracking results, businesses can optimize their online advertising campaigns for maximum impact.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, staying ahead of e-commerce trends and leveraging digital marketing strategies are essential for businesses looking to succeed in today's competitive market. By embracing online shopping, social media marketing, mobile commerce, and customer experience enhancements, businesses can attract and retain customers, drive sales, and stay ahead of the competition. By adapting to new technologies and trends, businesses can position themselves for long-term success in the ever-changing e-commerce landscape.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced digital world, e-commerce trends and digital marketing strategies are constantly evolving to meet the ever-changing needs of consumers. With online shopping, internet sales, social media, and mobile commerce continuing to shape the way we shop, businesses must adapt and stay ahead of the competition to succeed. Let's explore some of the key trends and strategies that are shaping the e-commerce landscape today.
The Rise of Online Shopping
Online shopping has become increasingly popular in recent years, with more and more consumers turning to the internet to make their purchases. The convenience of shopping from the comfort of your own home, the wide variety of products available online, and the ease of comparison shopping have all contributed to the growth of e-commerce. As a result, businesses must have a strong online presence to attract and retain customers in this competitive market.
Leveraging Social Media for Marketing Success
Social media has become an invaluable tool for businesses looking to connect with their customers and reach a wider audience. Platforms like Facebook, Instagram, and Twitter allow companies to engage with customers, showcase their products, and drive traffic to their e-commerce websites. By creating engaging content, running targeted ads, and collaborating with influencers, businesses can leverage social media to increase brand awareness and drive sales.
The Importance of Mobile Commerce
With more and more consumers using their smartphones and tablets to shop online, mobile commerce has become a crucial aspect of e-commerce. Businesses must optimize their websites for mobile devices, create mobile-friendly shopping experiences, and offer convenient payment options to cater to the growing number of mobile shoppers. By embracing mobile commerce, businesses can reach a wider audience and increase sales.
Enhancing Customer Experience
Providing a seamless and personalized customer experience is essential for e-commerce success. Businesses must prioritize user-friendly website design, fast loading times, easy navigation, and secure payment options to create a positive shopping experience for customers. By investing in customer service, feedback mechanisms, and loyalty programs, businesses can build trust and loyalty with their customers, leading to repeat purchases and increased sales.
Harnessing the Power of Online Advertising
Online advertising is a powerful tool for e-commerce businesses looking to reach their target audience and drive sales. Whether through pay-per-click ads, display ads, or social media ads, businesses can effectively promote their products and services to potential customers. By analyzing data, targeting specific demographics, and tracking results, businesses can optimize their online advertising campaigns for maximum impact.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, staying ahead of e-commerce trends and leveraging digital marketing strategies are essential for businesses looking to succeed in today's competitive market. By embracing online shopping, social media marketing, mobile commerce, and customer experience enhancements, businesses can attract and retain customers, drive sales, and stay ahead of the competition. By adapting to new technologies and trends, businesses can position themselves for long-term success in the ever-changing e-commerce landscape.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
PgMP Certification: Is It Worth It in 2024?
Are you considering pursuing a PgMP certification in 2024, but wondering if it's worth the time, effort, and cost? In this article, we will explore the benefits, requirements, and validity of PgMP certification to help you make an informed decision. Let's dive in!
What is PgMP Certification?
The Program Management Professional (PgMP) certification is a globally recognized credential offered by the Project Management Institute (PMI). It is designed for experienced program managers who want to demonstrate their expertise, skills, and ability to oversee multiple projects and programs.
PgMP Certification Requirements
To be eligible for the PgMP exam, candidates must meet specific requirements, including:
-
A minimum of four years of project management experience
-
A minimum of four years of program management experience
-
A high school diploma or equivalent
-
35 hours of project management education
Is PgMP Certification Worth It in 2024?
Benefits of PgMP Certification
-
Enhanced Career Opportunities: PgMP certification can open doors to new career opportunities and advancement in the field of program management.
-
Increased Salary Potential: Certified PgMP professionals often command higher salaries than their non-certified counterparts.
-
Global Recognition: PgMP certification is globally recognized and respected in the industry, showcasing your expertise and credibility.
PgMP Certification Cost
The cost of obtaining a PgMP certification can vary depending on your PMI membership status and exam location. On average, the cost ranges from $800 to $1,500.
PgMP Certification Salary
According to the PMI's Earning Power Salary Survey, PgMP certified professionals earn an average salary of $150,000 per year, demonstrating the financial benefits of obtaining this credential.
PgMP Certification vs. PMP Certification
While both PgMP and PMP certifications focus on project management, PgMP is geared towards program managers overseeing multiple projects, while PMP is for project managers handling individual projects.
PgMP Certification Validity
PgMP certification is valid for three years. To maintain your certification, you must earn 60 professional development units (PDUs) during the three-year cycle and undergo a renewal process.
How to obtain PgMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, PgMP certification can be a valuable investment in your career in program management. With its global recognition, potential salary increase, and career advancement opportunities, obtaining PgMP certification in 2024 could be well worth the effort. Make sure to carefully weigh the benefits against the costs and requirements to determine if it aligns with your career goals. Good luck on your certification journey!
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you considering pursuing a PgMP certification in 2024, but wondering if it's worth the time, effort, and cost? In this article, we will explore the benefits, requirements, and validity of PgMP certification to help you make an informed decision. Let's dive in!
What is PgMP Certification?
The Program Management Professional (PgMP) certification is a globally recognized credential offered by the Project Management Institute (PMI). It is designed for experienced program managers who want to demonstrate their expertise, skills, and ability to oversee multiple projects and programs.
PgMP Certification Requirements
To be eligible for the PgMP exam, candidates must meet specific requirements, including:
-
A minimum of four years of project management experience
-
A minimum of four years of program management experience
-
A high school diploma or equivalent
-
35 hours of project management education
Is PgMP Certification Worth It in 2024?
Benefits of PgMP Certification
-
Enhanced Career Opportunities: PgMP certification can open doors to new career opportunities and advancement in the field of program management.
-
Increased Salary Potential: Certified PgMP professionals often command higher salaries than their non-certified counterparts.
-
Global Recognition: PgMP certification is globally recognized and respected in the industry, showcasing your expertise and credibility.
PgMP Certification Cost
The cost of obtaining a PgMP certification can vary depending on your PMI membership status and exam location. On average, the cost ranges from $800 to $1,500.
PgMP Certification Salary
According to the PMI's Earning Power Salary Survey, PgMP certified professionals earn an average salary of $150,000 per year, demonstrating the financial benefits of obtaining this credential.
PgMP Certification vs. PMP Certification
While both PgMP and PMP certifications focus on project management, PgMP is geared towards program managers overseeing multiple projects, while PMP is for project managers handling individual projects.
PgMP Certification Validity
PgMP certification is valid for three years. To maintain your certification, you must earn 60 professional development units (PDUs) during the three-year cycle and undergo a renewal process.
How to obtain PgMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, PgMP certification can be a valuable investment in your career in program management. With its global recognition, potential salary increase, and career advancement opportunities, obtaining PgMP certification in 2024 could be well worth the effort. Make sure to carefully weigh the benefits against the costs and requirements to determine if it aligns with your career goals. Good luck on your certification journey!
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
IoT Security: Challenges and Solutions
In this digital age, the Internet of Things (IoT) has become an integral part of our daily lives. From smart homes to industrial applications, IoT devices play a crucial role in enhancing efficiency and convenience. However, with the rapid proliferation of IoT devices, the need for robust security measures has never been more critical. In this article, we will delve into the challenges of IoT security and explore effective solutions to safeguard these interconnected devices.
IoT Security Challenges
-
Vulnerabilities in Devices: IoT devices often have limited processing power and memory, making them vulnerable to cyber attacks.
-
Inadequate Protection: Many IoT devices lack basic security features such as encryption and authentication, leaving them susceptible to breaches.
-
Weak Network Security: IoT devices are often connected to the internet via insecure networks, making them easy targets for hackers.
-
Data Privacy Concerns: The vast amount of data collected by IoT devices raises concerns about privacy and potential data breaches.
Solutions to IoT Security Challenges
-
Implementation of Encryption: Encrypting data transmitted between IoT devices and networks can prevent unauthorized access and ensure data privacy.
-
Strong Authentication: Implementing two-factor authentication and biometric security measures can enhance the security of IoT devices.
-
Firewall Protection: Installing firewalls on IoT networks can help monitor and control incoming and outgoing traffic to prevent cyber attacks.
-
Best Practices: Following cybersecurity best practices such as regular software updates and password management can mitigate security risks.
-
Regulatory Compliance: Adhering to industry regulations and standards can ensure that IoT devices meet security requirements.
-
Automation and Integration: Using automated security solutions and integrating them with existing systems can enhance the overall security of IoT networks.
-
Remote Monitoring: Implementing remote monitoring tools can help identify security threats in real-time and respond proactively.
-
Cloud Security: Securing data stored in the cloud and implementing access controls can prevent unauthorized data breaches.
-
Artificial Intelligence: Leveraging AI technology can help detect and respond to security incidents faster and more effectively.
-
Safeguarding Against Malware: Deploying anti-malware solutions on IoT devices can detect and remove malicious software.
How to obtain IoT certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
As IoT devices continue to proliferate across various industries, ensuring robust security measures is essential to protect against cyber threats. By implementing encryption, strong authentication, firewall protection, and following best practices, organizations can safeguard their IoT networks and data from potential breaches. Additionally, staying compliant with regulations and leveraging innovative technologies such as AI can further enhance the security posture of IoT systems. By addressing these challenges and implementing effective security measures, we can harness the full potential of IoT technology while mitigating security risks.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In this digital age, the Internet of Things (IoT) has become an integral part of our daily lives. From smart homes to industrial applications, IoT devices play a crucial role in enhancing efficiency and convenience. However, with the rapid proliferation of IoT devices, the need for robust security measures has never been more critical. In this article, we will delve into the challenges of IoT security and explore effective solutions to safeguard these interconnected devices.
IoT Security Challenges
-
Vulnerabilities in Devices: IoT devices often have limited processing power and memory, making them vulnerable to cyber attacks.
-
Inadequate Protection: Many IoT devices lack basic security features such as encryption and authentication, leaving them susceptible to breaches.
-
Weak Network Security: IoT devices are often connected to the internet via insecure networks, making them easy targets for hackers.
-
Data Privacy Concerns: The vast amount of data collected by IoT devices raises concerns about privacy and potential data breaches.
Solutions to IoT Security Challenges
-
Implementation of Encryption: Encrypting data transmitted between IoT devices and networks can prevent unauthorized access and ensure data privacy.
-
Strong Authentication: Implementing two-factor authentication and biometric security measures can enhance the security of IoT devices.
-
Firewall Protection: Installing firewalls on IoT networks can help monitor and control incoming and outgoing traffic to prevent cyber attacks.
-
Best Practices: Following cybersecurity best practices such as regular software updates and password management can mitigate security risks.
-
Regulatory Compliance: Adhering to industry regulations and standards can ensure that IoT devices meet security requirements.
-
Automation and Integration: Using automated security solutions and integrating them with existing systems can enhance the overall security of IoT networks.
-
Remote Monitoring: Implementing remote monitoring tools can help identify security threats in real-time and respond proactively.
-
Cloud Security: Securing data stored in the cloud and implementing access controls can prevent unauthorized data breaches.
-
Artificial Intelligence: Leveraging AI technology can help detect and respond to security incidents faster and more effectively.
-
Safeguarding Against Malware: Deploying anti-malware solutions on IoT devices can detect and remove malicious software.
How to obtain IoT certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
As IoT devices continue to proliferate across various industries, ensuring robust security measures is essential to protect against cyber threats. By implementing encryption, strong authentication, firewall protection, and following best practices, organizations can safeguard their IoT networks and data from potential breaches. Additionally, staying compliant with regulations and leveraging innovative technologies such as AI can further enhance the security posture of IoT systems. By addressing these challenges and implementing effective security measures, we can harness the full potential of IoT technology while mitigating security risks.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Key Duties and Responsibilities of an Azure Administrator
Are you considering a career as an Azure Administrator? Curious about the key duties and responsibilities involved in this role? Look no further! In this article, we will delve into the essential aspects of being an Azure Administrator, including security management, resource monitoring, data migration, troubleshooting, automation, and much more.
Introduction to Azure Administrator
Azure Administrator is a crucial role in the realm of cloud computing, particularly with Microsoft's Azure services. As an Azure Administrator, you will be responsible for overseeing various aspects of Azure, such as security management, user management, identity management, virtual machines, backup and recovery, patch management, compliance, scripting, and more. Your primary goal is to ensure the smooth operation of Azure services and maintain high levels of performance and security.
Security Management
One of the key duties of an Azure Administrator is security management. This involves implementing security measures to protect Azure services from cyber threats and unauthorized access. You will be responsible for configuring security policies, monitoring security events, performing security assessments, and ensuring compliance with security standards.
-
Implementing security measures to protect Azure services.
-
Configuring security policies and monitoring security events.
-
Performing security assessments and ensuring compliance with security standards.
Resource Monitoring
Another essential responsibility of an Azure Administrator is resource monitoring. You will need to monitor the performance and availability of Azure resources, identify any issues or anomalies, and take proactive measures to optimize resource utilization. This includes monitoring resource usage, performance metrics, and service health.
-
Monitoring the performance and availability of Azure resources.
-
Identifying issues or anomalies and taking proactive measures to optimize resource utilization.
-
Monitoring resource usage, performance metrics, and service health.
User Management
As an Azure Administrator, you will be responsible for managing user accounts and access permissions. This includes creating user accounts, assigning roles and permissions, managing user groups, and enforcing access control policies. You will also be responsible for ensuring that users have the appropriate level of access to Azure services.
-
Managing user accounts and access permissions.
-
Creating user accounts, assigning roles and permissions, managing user groups.
-
Enforcing access control policies and ensuring appropriate access to Azure services..
Troubleshooting
Troubleshooting is a crucial skill for an Azure Administrator. You will need to identify and resolve technical issues, troubleshoot system failures, and provide technical support to users. This includes analyzing system logs, performing root cause analysis, and implementing solutions to prevent recurring issues.
-
Identifying and resolving technical issues, troubleshooting system failures.
-
Providing technical support to users and analyzing system logs.
-
Performing root cause analysis and implementing solutions to prevent recurring issues.
Automation
Automation is key to streamlining Azure operations and increasing efficiency. As an Azure Administrator, you will be responsible for automating routine tasks, deploying automation scripts, and implementing workflow automation. This includes using automation tools, scripting languages, and Azure automation services to improve operational efficiency.
-
Automating routine tasks and deploying automation scripts.
-
Implementing workflow automation using automation tools and scripting languages.
-
Using Azure automation services to improve operational efficiency.
Networking
Networking is an essential aspect of Azure administration. You will be responsible for configuring and managing network resources, establishing network connectivity, and optimizing network performance. This includes setting up virtual networks, configuring network security groups, and managing network traffic.
-
Configuring and managing network resources, establishing network connectivity.
-
Optimizing network performance, setting up virtual networks, configuring security groups.
-
Managing network traffic and ensuring network security.
Identity Management
Identity management is crucial for controlling access to Azure resources. As an Azure Administrator, you will be responsible for managing user identities, enforcing authentication mechanisms, and implementing identity and access management solutions. This includes setting up Azure Active Directory, configuring single sign-on, and managing user authentication.
-
Managing user identities, enforcing authentication mechanisms.
-
Implementing identity and access management solutions, setting up Azure Active Directory.
-
Configuring single sign-on and managing user authentication.
Virtual Machines
Virtual machines play a significant role in Azure services. As an Azure Administrator, you will be responsible for provisioning, managing, and monitoring virtual machines. This includes deploying virtual machines, configuring virtual machine settings, and monitoring virtual machine performance.
-
Provisioning, managing, and monitoring virtual machines.
-
Deploying virtual machines, configuring settings, monitoring performance.
Backup and Recovery
Backup and recovery are vital for ensuring data protection and business continuity. As an Azure Administrator, you will be responsible for creating backup plans, scheduling backups, and performing data recovery operations. This includes configuring backup policies, monitoring backup jobs, and testing data recovery procedures.
-
Creating backup plans, scheduling backups, performing data recovery operations.
-
Configuring backup policies, monitoring backup jobs, testing recovery procedures.
Patch Management
Patch management is crucial for keeping systems up to date and secure. As an Azure Administrator, you will be responsible for applying patches and updates to Azure services, ensuring that systems are protected against security vulnerabilities. This includes evaluating patch releases, testing patches, and deploying patches to production environments.
-
Applying patches and updates to Azure services, protecting against security vulnerabilities.
-
Evaluating patch releases, testing patches, deploying patches to production environments.
Log Analysis
Log analysis is essential for monitoring system activity and identifying security incidents. As an Azure Administrator, you will be responsible for analyzing system logs, detecting anomalies, and investigating security events. This includes using log analysis tools, correlating log data, and generating reports on system activity.
-
Analyzing system logs, detecting anomalies, investigating security events.
-
Using log analysis tools, correlating log data, generating activity reports.
Performance Tuning
Performance tuning is essential for optimizing system performance and resource utilization. As an Azure Administrator, you will be responsible for analyzing system performance, identifying bottlenecks, and implementing performance improvements. This includes monitoring system metrics, tuning system settings, and optimizing resource allocation.
-
Analyzing system performance, identifying bottlenecks, implementing improvements.
-
Monitoring metrics, tuning settings, optimizing resource allocation.
Access Control
Access control is vital for managing user access to Azure resources. As an Azure Administrator, you will be responsible for defining access policies, assigning access permissions, and enforcing access controls. This includes implementing role-based access control, configuring access rules, and monitoring user access.
-
Defining access policies, assigning permissions, enforcing controls.
-
Implementing role-based access control, configuring rules, monitoring access.
Software Updates
Software updates are crucial for keeping systems secure and up to date. As an Azure Administrator, you will be responsible for applying software updates, testing updates, and monitoring update releases. This includes evaluating software patches, scheduling update deployments, and ensuring that systems are updated promptly.
-
Applying updates, testing releases, monitoring patches.
-
Evaluating patches, scheduling deployments, ensuring prompt updates.
How to obtain Cloud Technology certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, being an Azure Administrator comes with a diverse range of responsibilities and duties that are critical for the smooth operation of Azure services. Whether it's security management, resource monitoring, user management, data migration, troubleshooting, or any other aspect of Azure administration, your expertise and attention to detail will be instrumental in ensuring the success of Azure environments. So, if you're considering a career in Azure administration, rest assured that your contributions are valuable and necessary for organizations leveraging Azure services.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you considering a career as an Azure Administrator? Curious about the key duties and responsibilities involved in this role? Look no further! In this article, we will delve into the essential aspects of being an Azure Administrator, including security management, resource monitoring, data migration, troubleshooting, automation, and much more.
Introduction to Azure Administrator
Azure Administrator is a crucial role in the realm of cloud computing, particularly with Microsoft's Azure services. As an Azure Administrator, you will be responsible for overseeing various aspects of Azure, such as security management, user management, identity management, virtual machines, backup and recovery, patch management, compliance, scripting, and more. Your primary goal is to ensure the smooth operation of Azure services and maintain high levels of performance and security.
Security Management
One of the key duties of an Azure Administrator is security management. This involves implementing security measures to protect Azure services from cyber threats and unauthorized access. You will be responsible for configuring security policies, monitoring security events, performing security assessments, and ensuring compliance with security standards.
-
Implementing security measures to protect Azure services.
-
Configuring security policies and monitoring security events.
-
Performing security assessments and ensuring compliance with security standards.
Resource Monitoring
Another essential responsibility of an Azure Administrator is resource monitoring. You will need to monitor the performance and availability of Azure resources, identify any issues or anomalies, and take proactive measures to optimize resource utilization. This includes monitoring resource usage, performance metrics, and service health.
-
Monitoring the performance and availability of Azure resources.
-
Identifying issues or anomalies and taking proactive measures to optimize resource utilization.
-
Monitoring resource usage, performance metrics, and service health.
User Management
As an Azure Administrator, you will be responsible for managing user accounts and access permissions. This includes creating user accounts, assigning roles and permissions, managing user groups, and enforcing access control policies. You will also be responsible for ensuring that users have the appropriate level of access to Azure services.
-
Managing user accounts and access permissions.
-
Creating user accounts, assigning roles and permissions, managing user groups.
-
Enforcing access control policies and ensuring appropriate access to Azure services..
Troubleshooting
Troubleshooting is a crucial skill for an Azure Administrator. You will need to identify and resolve technical issues, troubleshoot system failures, and provide technical support to users. This includes analyzing system logs, performing root cause analysis, and implementing solutions to prevent recurring issues.
-
Identifying and resolving technical issues, troubleshooting system failures.
-
Providing technical support to users and analyzing system logs.
-
Performing root cause analysis and implementing solutions to prevent recurring issues.
Automation
Automation is key to streamlining Azure operations and increasing efficiency. As an Azure Administrator, you will be responsible for automating routine tasks, deploying automation scripts, and implementing workflow automation. This includes using automation tools, scripting languages, and Azure automation services to improve operational efficiency.
-
Automating routine tasks and deploying automation scripts.
-
Implementing workflow automation using automation tools and scripting languages.
-
Using Azure automation services to improve operational efficiency.
Networking
Networking is an essential aspect of Azure administration. You will be responsible for configuring and managing network resources, establishing network connectivity, and optimizing network performance. This includes setting up virtual networks, configuring network security groups, and managing network traffic.
-
Configuring and managing network resources, establishing network connectivity.
-
Optimizing network performance, setting up virtual networks, configuring security groups.
-
Managing network traffic and ensuring network security.
Identity Management
Identity management is crucial for controlling access to Azure resources. As an Azure Administrator, you will be responsible for managing user identities, enforcing authentication mechanisms, and implementing identity and access management solutions. This includes setting up Azure Active Directory, configuring single sign-on, and managing user authentication.
-
Managing user identities, enforcing authentication mechanisms.
-
Implementing identity and access management solutions, setting up Azure Active Directory.
-
Configuring single sign-on and managing user authentication.
Virtual Machines
Virtual machines play a significant role in Azure services. As an Azure Administrator, you will be responsible for provisioning, managing, and monitoring virtual machines. This includes deploying virtual machines, configuring virtual machine settings, and monitoring virtual machine performance.
-
Provisioning, managing, and monitoring virtual machines.
-
Deploying virtual machines, configuring settings, monitoring performance.
Backup and Recovery
Backup and recovery are vital for ensuring data protection and business continuity. As an Azure Administrator, you will be responsible for creating backup plans, scheduling backups, and performing data recovery operations. This includes configuring backup policies, monitoring backup jobs, and testing data recovery procedures.
-
Creating backup plans, scheduling backups, performing data recovery operations.
-
Configuring backup policies, monitoring backup jobs, testing recovery procedures.
Patch Management
Patch management is crucial for keeping systems up to date and secure. As an Azure Administrator, you will be responsible for applying patches and updates to Azure services, ensuring that systems are protected against security vulnerabilities. This includes evaluating patch releases, testing patches, and deploying patches to production environments.
-
Applying patches and updates to Azure services, protecting against security vulnerabilities.
-
Evaluating patch releases, testing patches, deploying patches to production environments.
Log Analysis
Log analysis is essential for monitoring system activity and identifying security incidents. As an Azure Administrator, you will be responsible for analyzing system logs, detecting anomalies, and investigating security events. This includes using log analysis tools, correlating log data, and generating reports on system activity.
-
Analyzing system logs, detecting anomalies, investigating security events.
-
Using log analysis tools, correlating log data, generating activity reports.
Performance Tuning
Performance tuning is essential for optimizing system performance and resource utilization. As an Azure Administrator, you will be responsible for analyzing system performance, identifying bottlenecks, and implementing performance improvements. This includes monitoring system metrics, tuning system settings, and optimizing resource allocation.
-
Analyzing system performance, identifying bottlenecks, implementing improvements.
-
Monitoring metrics, tuning settings, optimizing resource allocation.
Access Control
Access control is vital for managing user access to Azure resources. As an Azure Administrator, you will be responsible for defining access policies, assigning access permissions, and enforcing access controls. This includes implementing role-based access control, configuring access rules, and monitoring user access.
-
Defining access policies, assigning permissions, enforcing controls.
-
Implementing role-based access control, configuring rules, monitoring access.
Software Updates
Software updates are crucial for keeping systems secure and up to date. As an Azure Administrator, you will be responsible for applying software updates, testing updates, and monitoring update releases. This includes evaluating software patches, scheduling update deployments, and ensuring that systems are updated promptly.
-
Applying updates, testing releases, monitoring patches.
-
Evaluating patches, scheduling deployments, ensuring prompt updates.
How to obtain Cloud Technology certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, being an Azure Administrator comes with a diverse range of responsibilities and duties that are critical for the smooth operation of Azure services. Whether it's security management, resource monitoring, user management, data migration, troubleshooting, or any other aspect of Azure administration, your expertise and attention to detail will be instrumental in ensuring the success of Azure environments. So, if you're considering a career in Azure administration, rest assured that your contributions are valuable and necessary for organizations leveraging Azure services.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Migrating from Citrix XenServer to Open Source XenServer
Are you looking to transition from Citrix XenServer to an open-source alternative like XenServer? In this article, we will discuss the migration process, benefits of virtualization, and important considerations when converting to a new hypervisor. Whether you're looking to switch to open source for cost-effective solutions or better system performance, we've got you covered with a comprehensive migration checklist and deployment strategy.
Understanding the Migration Process
Migrating from Citrix XenServer to Open Source XenServer involves transferring your virtualized workloads, network configurations, and backup and recovery integration. It's essential to have a clear transition plan in place to ensure a smooth migration without disrupting your operations. By choosing the right migration tools and following a structured approach, you can minimize downtime and ensure system compatibility during the migration process.
Benefits of Virtualization and Cloud Computing
Virtualization allows you to consolidate your servers, optimize resource utilization, and improve scalability in your virtual environment. By migrating from a legacy system like Citrix XenServer to an open-source solution, you can take advantage of cost-effective cloud computing services and seamless software integration. With the right infrastructure upgrade and deployment strategy, you can enhance your system performance and streamline your IT operations for better efficiency.
Considerations for Data Migration and Virtual Machine Migration
When migrating workloads from Citrix XenServer to Open Source XenServer, it's crucial to consider data migration and virtual machine migration. Ensure that your migration checklist includes a detailed plan for transferring your data securely and efficiently. By assessing xenserver alternatives and evaluating open source solutions, you can choose the best option for your organization's needs. Keep in mind factors such as system performance, technical support, and server consolidation to make the most out of your migration process.
Switching to Open Source XenServer: A Cost-Effective Solution
By switching to Open Source XenServer, you can enjoy the benefits of a cost-effective virtualization platform with robust features and reliable performance. With the right migration strategy and deployment plan, you can seamlessly transition from Citrix XenServer to an open-source alternative without compromising on system integrity or data security. Take advantage of the latest migration tools and system performance enhancements to optimize your virtual environment for better efficiency and scalability.
Leveraging Technical Support and Backup Integration
During the migration process, it's essential to leverage technical support resources and backup and recovery integration to ensure a seamless transition. By working with experienced professionals and utilizing reliable backup solutions, you can minimize risks and address any challenges that may arise during the migration process. With proper network configuration and system compatibility testing, you can guarantee a successful migration from Citrix XenServer to Open Source XenServer.
How to obtain Xenserver certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, migrating from Citrix XenServer to Open Source XenServer offers a cost-effective and efficient solution for organizations looking to enhance their virtual environment. By following a structured migration plan, leveraging the right tools, and considering important factors such as system performance and data migration, you can successfully switch to an open-source alternative. With the right deployment strategy and technical support, you can optimize your virtualization platform for better efficiency and scalability. Make the transition today and experience the benefits of open-source virtualization with XenServer.
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to transition from Citrix XenServer to an open-source alternative like XenServer? In this article, we will discuss the migration process, benefits of virtualization, and important considerations when converting to a new hypervisor. Whether you're looking to switch to open source for cost-effective solutions or better system performance, we've got you covered with a comprehensive migration checklist and deployment strategy.
Understanding the Migration Process
Migrating from Citrix XenServer to Open Source XenServer involves transferring your virtualized workloads, network configurations, and backup and recovery integration. It's essential to have a clear transition plan in place to ensure a smooth migration without disrupting your operations. By choosing the right migration tools and following a structured approach, you can minimize downtime and ensure system compatibility during the migration process.
Benefits of Virtualization and Cloud Computing
Virtualization allows you to consolidate your servers, optimize resource utilization, and improve scalability in your virtual environment. By migrating from a legacy system like Citrix XenServer to an open-source solution, you can take advantage of cost-effective cloud computing services and seamless software integration. With the right infrastructure upgrade and deployment strategy, you can enhance your system performance and streamline your IT operations for better efficiency.
Considerations for Data Migration and Virtual Machine Migration
When migrating workloads from Citrix XenServer to Open Source XenServer, it's crucial to consider data migration and virtual machine migration. Ensure that your migration checklist includes a detailed plan for transferring your data securely and efficiently. By assessing xenserver alternatives and evaluating open source solutions, you can choose the best option for your organization's needs. Keep in mind factors such as system performance, technical support, and server consolidation to make the most out of your migration process.
Switching to Open Source XenServer: A Cost-Effective Solution
By switching to Open Source XenServer, you can enjoy the benefits of a cost-effective virtualization platform with robust features and reliable performance. With the right migration strategy and deployment plan, you can seamlessly transition from Citrix XenServer to an open-source alternative without compromising on system integrity or data security. Take advantage of the latest migration tools and system performance enhancements to optimize your virtual environment for better efficiency and scalability.
Leveraging Technical Support and Backup Integration
During the migration process, it's essential to leverage technical support resources and backup and recovery integration to ensure a seamless transition. By working with experienced professionals and utilizing reliable backup solutions, you can minimize risks and address any challenges that may arise during the migration process. With proper network configuration and system compatibility testing, you can guarantee a successful migration from Citrix XenServer to Open Source XenServer.
How to obtain Xenserver certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, migrating from Citrix XenServer to Open Source XenServer offers a cost-effective and efficient solution for organizations looking to enhance their virtual environment. By following a structured migration plan, leveraging the right tools, and considering important factors such as system performance and data migration, you can successfully switch to an open-source alternative. With the right deployment strategy and technical support, you can optimize your virtualization platform for better efficiency and scalability. Make the transition today and experience the benefits of open-source virtualization with XenServer.
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
The Importance of Network Security in the CCNA Curriculum
With the rise of cyber threats and attacks in today's digital age, network security has become a critical aspect of IT infrastructure. This is especially true in the context of the CCNA curriculum, where understanding the importance of network security is essential for students looking to pursue a career in networking. In this article, we will delve into the significance of network security within the CCNA curriculum and how it plays a vital role in cybersecurity and information protection.
Why is Network Security Important in the CCNA Curriculum?
Network security forms the foundation of cybersecurity, aiming to protect networks, devices, and data from unauthorized access or malicious attacks. In the CCNA curriculum, students learn about various security protocols and practices to secure network infrastructures effectively. This knowledge is crucial in today's interconnected world, where online threats and cyber attacks pose a constant risk to businesses and individuals.
What role does Network Security play in Cybersecurity?
Network security is a fundamental component of cybersecurity, as it focuses on safeguarding networks and data from breaches and intrusions. By understanding network security principles and technologies, CCNA students can enhance their cybersecurity skills and contribute to building secure and resilient IT environments. This knowledge is invaluable in combating cyber threats and ensuring the confidentiality, integrity, and availability of information.
How does Network Security enhance Information Security?
Information security revolves around protecting sensitive data from unauthorized access, disclosure, alteration, or destruction. By incorporating network security into the CCNA curriculum, students gain the necessary knowledge and tools to implement data protection measures effectively. This not only ensures the privacy and confidentiality of information but also reinforces the overall security posture of organizations.
What are the Benefits of Integrating Network Security into Networking Certification?
Integrating network security into the CCNA curriculum offers several benefits to aspiring network professionals. These include acquiring in-depth knowledge of threat prevention, network defense, and secure networking practices. By obtaining a CCNA certification with a strong focus on network security, students can demonstrate their expertise in mitigating online threats and securing network infrastructures effectively.
How does Network Security Training prepare for Cyber Attacks?
Network security training equips individuals with the necessary skills and knowledge to identify, prevent, and respond to cyber attacks. By understanding network vulnerabilities, security protocols, and network monitoring techniques, CCNA students can proactively defend against potential threats and breaches. This proactive approach is crucial in maintaining network safety and protecting sensitive data from malicious actors.
What is the Role of Network Security Practices in Data Protection?
Network security practices play a crucial role in ensuring the protection of data transmitted over networks. By implementing firewall protection, encryption technologies, and network monitoring tools, organizations can safeguard their data from unauthorized access and interception. CCNA students learn how to adopt best practices for data privacy and integrity, thereby enhancing the overall security of network communications.
How to obtain CCNA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the importance of network security in the CCNA curriculum cannot be overstated. By integrating network security principles and practices into networking certification programs, students can develop essential cybersecurity skills and expertise. This not only prepares them for the challenges of today's digital landscape but also enables them to become effective network administrators capable of maintaining secure and resilient networks. Emphasizing network security in the CCNA curriculum is essential for building a workforce equipped to counter cyber threats and protect critical information assets.
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
With the rise of cyber threats and attacks in today's digital age, network security has become a critical aspect of IT infrastructure. This is especially true in the context of the CCNA curriculum, where understanding the importance of network security is essential for students looking to pursue a career in networking. In this article, we will delve into the significance of network security within the CCNA curriculum and how it plays a vital role in cybersecurity and information protection.
Why is Network Security Important in the CCNA Curriculum?
Network security forms the foundation of cybersecurity, aiming to protect networks, devices, and data from unauthorized access or malicious attacks. In the CCNA curriculum, students learn about various security protocols and practices to secure network infrastructures effectively. This knowledge is crucial in today's interconnected world, where online threats and cyber attacks pose a constant risk to businesses and individuals.
What role does Network Security play in Cybersecurity?
Network security is a fundamental component of cybersecurity, as it focuses on safeguarding networks and data from breaches and intrusions. By understanding network security principles and technologies, CCNA students can enhance their cybersecurity skills and contribute to building secure and resilient IT environments. This knowledge is invaluable in combating cyber threats and ensuring the confidentiality, integrity, and availability of information.
How does Network Security enhance Information Security?
Information security revolves around protecting sensitive data from unauthorized access, disclosure, alteration, or destruction. By incorporating network security into the CCNA curriculum, students gain the necessary knowledge and tools to implement data protection measures effectively. This not only ensures the privacy and confidentiality of information but also reinforces the overall security posture of organizations.
What are the Benefits of Integrating Network Security into Networking Certification?
Integrating network security into the CCNA curriculum offers several benefits to aspiring network professionals. These include acquiring in-depth knowledge of threat prevention, network defense, and secure networking practices. By obtaining a CCNA certification with a strong focus on network security, students can demonstrate their expertise in mitigating online threats and securing network infrastructures effectively.
How does Network Security Training prepare for Cyber Attacks?
Network security training equips individuals with the necessary skills and knowledge to identify, prevent, and respond to cyber attacks. By understanding network vulnerabilities, security protocols, and network monitoring techniques, CCNA students can proactively defend against potential threats and breaches. This proactive approach is crucial in maintaining network safety and protecting sensitive data from malicious actors.
What is the Role of Network Security Practices in Data Protection?
Network security practices play a crucial role in ensuring the protection of data transmitted over networks. By implementing firewall protection, encryption technologies, and network monitoring tools, organizations can safeguard their data from unauthorized access and interception. CCNA students learn how to adopt best practices for data privacy and integrity, thereby enhancing the overall security of network communications.
How to obtain CCNA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the importance of network security in the CCNA curriculum cannot be overstated. By integrating network security principles and practices into networking certification programs, students can develop essential cybersecurity skills and expertise. This not only prepares them for the challenges of today's digital landscape but also enables them to become effective network administrators capable of maintaining secure and resilient networks. Emphasizing network security in the CCNA curriculum is essential for building a workforce equipped to counter cyber threats and protect critical information assets.
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
Zero Trust Security Models: What You Need to Know
In today's ever-evolving digital landscape, cybersecurity has become a top priority for organizations of all sizes. With the rising number of data breaches and malicious threats, it's crucial to implement robust security measures to safeguard sensitive information. One such approach that has gained traction in recent years is the zero trust security model.
What is Zero Trust?
Zero trust is a security concept based on the principle of "never trust, always verify." Unlike traditional security models that operate on the assumption that everything inside a network can be trusted, zero trust challenges this notion by implementing strict identity verification and access controls for all users and devices, both inside and outside the network perimeter.
Network Security
Zero trust architecture focuses on securing every network endpoint, regardless of its location. This approach ensures that only authorized users and devices can access sensitive data, reducing the risk of data breaches and unauthorized access.
Data Protection
By implementing zero trust principles, organizations can protect their data from external threats and insider attacks. Data encryption and network segmentation play a crucial role in ensuring that sensitive information remains secure and confidential.
Identity Verification
Identity and access management are key components of the zero trust model. By verifying the identities of users and devices before granting access to resources, organizations can prevent unauthorized access and minimize security risks.
Access Control
Least privilege is a fundamental principle of zero trust security, ensuring that users and devices have access only to the resources they need to perform their tasks. This helps reduce the attack surface and mitigate the impact of potential security breaches.
Micro-Segmentation
Microsegmentation further enhances network security by dividing the network into smaller, isolated segments. This limits the lateral movement of threats within the network and contains potential security incidents.
Endpoint Security
Protecting endpoint devices is essential in a zero trust environment. By implementing robust endpoint security measures, organizations can prevent malware infections and unauthorized access to critical systems.
Cloud Security
As more organizations migrate their data and applications to the cloud, ensuring cloud security is paramount. Zero trust principles can be applied to cloud environments to secure data and applications from external threats and insider attacks.
Defense in Depth
The defense-in-depth strategy complements the zero trust model by incorporating multiple layers of security controls. By combining proactive threat detection, adaptive authentication, and data encryption, organizations can enhance their security posture and minimize the risk of data breaches.
Secure Communication
Establishing secure communication channels is essential for maintaining trust boundaries in a zero trust environment. By encrypting data in transit and implementing secure access service edge (SASE) solutions, organizations can ensure that sensitive information remains protected from unauthorized access.
Security Best Practices
Adopting a comprehensive security framework that incorporates zero trust principles is essential for mitigating security risks and ensuring regulatory compliance. By implementing security protocols and regularly monitoring network activity, organizations can strengthen their security posture and protect against emerging cyber threats.
How to obtain Cyber Security certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, zero trust security models offer a proactive approach to cybersecurity by challenging traditional security paradigms and emphasizing strict access controls and authentication mechanisms. By implementing zero trust principles, organizations can reduce the risk of data breaches, enhance network security, and protect their critical assets from malicious threats. Embracing a zero trust mindset is essential in today's interconnected world to maintain trust boundaries and safeguard sensitive information from potential security threats.
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's ever-evolving digital landscape, cybersecurity has become a top priority for organizations of all sizes. With the rising number of data breaches and malicious threats, it's crucial to implement robust security measures to safeguard sensitive information. One such approach that has gained traction in recent years is the zero trust security model.
What is Zero Trust?
Zero trust is a security concept based on the principle of "never trust, always verify." Unlike traditional security models that operate on the assumption that everything inside a network can be trusted, zero trust challenges this notion by implementing strict identity verification and access controls for all users and devices, both inside and outside the network perimeter.
Network Security
Zero trust architecture focuses on securing every network endpoint, regardless of its location. This approach ensures that only authorized users and devices can access sensitive data, reducing the risk of data breaches and unauthorized access.
Data Protection
By implementing zero trust principles, organizations can protect their data from external threats and insider attacks. Data encryption and network segmentation play a crucial role in ensuring that sensitive information remains secure and confidential.
Identity Verification
Identity and access management are key components of the zero trust model. By verifying the identities of users and devices before granting access to resources, organizations can prevent unauthorized access and minimize security risks.
Access Control
Least privilege is a fundamental principle of zero trust security, ensuring that users and devices have access only to the resources they need to perform their tasks. This helps reduce the attack surface and mitigate the impact of potential security breaches.
Micro-Segmentation
Microsegmentation further enhances network security by dividing the network into smaller, isolated segments. This limits the lateral movement of threats within the network and contains potential security incidents.
Endpoint Security
Protecting endpoint devices is essential in a zero trust environment. By implementing robust endpoint security measures, organizations can prevent malware infections and unauthorized access to critical systems.
Cloud Security
As more organizations migrate their data and applications to the cloud, ensuring cloud security is paramount. Zero trust principles can be applied to cloud environments to secure data and applications from external threats and insider attacks.
Defense in Depth
The defense-in-depth strategy complements the zero trust model by incorporating multiple layers of security controls. By combining proactive threat detection, adaptive authentication, and data encryption, organizations can enhance their security posture and minimize the risk of data breaches.
Secure Communication
Establishing secure communication channels is essential for maintaining trust boundaries in a zero trust environment. By encrypting data in transit and implementing secure access service edge (SASE) solutions, organizations can ensure that sensitive information remains protected from unauthorized access.
Security Best Practices
Adopting a comprehensive security framework that incorporates zero trust principles is essential for mitigating security risks and ensuring regulatory compliance. By implementing security protocols and regularly monitoring network activity, organizations can strengthen their security posture and protect against emerging cyber threats.
How to obtain Cyber Security certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, zero trust security models offer a proactive approach to cybersecurity by challenging traditional security paradigms and emphasizing strict access controls and authentication mechanisms. By implementing zero trust principles, organizations can reduce the risk of data breaches, enhance network security, and protect their critical assets from malicious threats. Embracing a zero trust mindset is essential in today's interconnected world to maintain trust boundaries and safeguard sensitive information from potential security threats.
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
What Advantages Come with Earning a Scrum Master Certification?
Are you considering taking your career to the next level in project management and Agile methodologies? If so, earning a Scrum Master certification could be the key to unlocking a world of opportunities and career growth. In this article, we'll explore the numerous benefits and advantages of obtaining a Scrum Master certification and why it's worth the time, effort, and investment.
Advantages of Scrum Master Certification
-
Enhanced Job Opportunities: With a Scrum Master certification, you open yourself up to a wide range of job opportunities in various industries and companies that are adopting Agile practices. This certification can make you stand out in a competitive job market and increase your employability.
-
Higher Salary Potential: Studies have shown that professionals with Scrum Master certifications earn higher salaries than those without certification. This is due to the increased demand for certified Scrum Masters in the industry.
-
Improved Project Performance: As a certified Scrum Master, you will have the knowledge and skills to effectively lead Agile teams, resulting in improved project performance, faster delivery, and higher quality outcomes.
-
Career Growth: Having a Scrum Master certification on your resume demonstrates your commitment to continuous learning and professional development. This can open doors to higher-level positions and more challenging projects.
-
Professional Credibility: Certification validates your expertise in Scrum principles and practices, giving you credibility among colleagues, employers, and clients. It shows that you have the knowledge and skills to successfully navigate the challenges of Agile project management.
-
Networking Opportunities: Joining the community of certified Scrum Masters can provide you with valuable networking opportunities, allowing you to connect with industry experts, thought leaders, and potential collaborators.
Why Get Scrum Master Certified?
When considering whether to pursue a Scrum Master certification, it's essential to weigh the benefits against the investment of time and resources. Here are a few reasons why getting certified is a smart career move:
-
Increased Job Security: With the rising popularity of Agile methodologies, companies are looking for professionals who can lead Agile teams effectively. Having a Scrum Master certification can increase your job security and marketability.
-
Stay Competitive: In today's fast-paced business environment, continuous learning and upskilling are essential to staying competitive. Earning a Scrum Master certification demonstrates your commitment to professional development and innovation.
-
Unlock Global Opportunities: The demand for certified Scrum Masters is not limited to any specific region or industry. With a Scrum Master certification, you can pursue job opportunities worldwide and work in diverse and exciting organizations.
-
Personal Growth: Mastering the skills and practices of Scrum not only benefits your career but also promotes personal growth and self-improvement. As a Scrum Master, you will develop leadership, communication, and problem-solving skills that are valuable in any professional setting.
How to obtain Scrum certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, earning a Scrum Master certification comes with a myriad of advantages and benefits for your career, professional development, and personal growth. Whether you're a seasoned project manager looking to upskill or a newcomer to Agile methodologies, obtaining this certification can propel your career to new heights. Don't miss out on the opportunities that await you as a certified Scrum Master
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you considering taking your career to the next level in project management and Agile methodologies? If so, earning a Scrum Master certification could be the key to unlocking a world of opportunities and career growth. In this article, we'll explore the numerous benefits and advantages of obtaining a Scrum Master certification and why it's worth the time, effort, and investment.
Advantages of Scrum Master Certification
-
Enhanced Job Opportunities: With a Scrum Master certification, you open yourself up to a wide range of job opportunities in various industries and companies that are adopting Agile practices. This certification can make you stand out in a competitive job market and increase your employability.
-
Higher Salary Potential: Studies have shown that professionals with Scrum Master certifications earn higher salaries than those without certification. This is due to the increased demand for certified Scrum Masters in the industry.
-
Improved Project Performance: As a certified Scrum Master, you will have the knowledge and skills to effectively lead Agile teams, resulting in improved project performance, faster delivery, and higher quality outcomes.
-
Career Growth: Having a Scrum Master certification on your resume demonstrates your commitment to continuous learning and professional development. This can open doors to higher-level positions and more challenging projects.
-
Professional Credibility: Certification validates your expertise in Scrum principles and practices, giving you credibility among colleagues, employers, and clients. It shows that you have the knowledge and skills to successfully navigate the challenges of Agile project management.
-
Networking Opportunities: Joining the community of certified Scrum Masters can provide you with valuable networking opportunities, allowing you to connect with industry experts, thought leaders, and potential collaborators.
Why Get Scrum Master Certified?
When considering whether to pursue a Scrum Master certification, it's essential to weigh the benefits against the investment of time and resources. Here are a few reasons why getting certified is a smart career move:
-
Increased Job Security: With the rising popularity of Agile methodologies, companies are looking for professionals who can lead Agile teams effectively. Having a Scrum Master certification can increase your job security and marketability.
-
Stay Competitive: In today's fast-paced business environment, continuous learning and upskilling are essential to staying competitive. Earning a Scrum Master certification demonstrates your commitment to professional development and innovation.
-
Unlock Global Opportunities: The demand for certified Scrum Masters is not limited to any specific region or industry. With a Scrum Master certification, you can pursue job opportunities worldwide and work in diverse and exciting organizations.
-
Personal Growth: Mastering the skills and practices of Scrum not only benefits your career but also promotes personal growth and self-improvement. As a Scrum Master, you will develop leadership, communication, and problem-solving skills that are valuable in any professional setting.
How to obtain Scrum certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, earning a Scrum Master certification comes with a myriad of advantages and benefits for your career, professional development, and personal growth. Whether you're a seasoned project manager looking to upskill or a newcomer to Agile methodologies, obtaining this certification can propel your career to new heights. Don't miss out on the opportunities that await you as a certified Scrum Master
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
ITSM and DevOps: Bridging the Gap for Better Collaboration
In today's fast-paced world of technology and information, the collaboration between ITSM (IT Service Management) and DevOps is crucial for success. By bridging the gap between these two key areas, organizations can improve efficiency, communication, and innovation in their IT operations. In this article, we will explore how ITSM and DevOps can work together to create a culture of collaboration and drive continuous improvement.
ITSM and DevOps: A Winning Combination
For many years, ITSM and DevOps have been viewed as separate entities within organizations. ITSM focuses on the delivery of quality IT services, while DevOps is centered around the rapid and continuous delivery of software. However, by integrating these two approaches, organizations can achieve greater alignment, efficiency, and innovation.
Why is Collaboration Important?
Collaboration between ITSM and DevOps is essential for ensuring that IT operations run smoothly and effectively. By working together, teams can streamline processes, improve workflows, and enhance overall productivity. Additionally, collaboration can help organizations respond more quickly to changing business needs and market demands.
Bridging the Gap: How to Foster Collaboration
To bridge the gap between ITSM and DevOps, organizations must focus on building a culture of teamwork and communication. This can be achieved by:
-
Implementing Agile Practices: Agile methodologies can help teams work together more effectively by promoting flexibility, adaptability, and transparency.
-
Embracing Automation: Automation tools can streamline processes and eliminate manual tasks, allowing teams to focus on higher-value work.
-
Encouraging Open Communication: Regular communication between ITSM and DevOps teams is crucial for sharing information, resolving issues, and aligning priorities.
-
Investing in Training and Development: Training programs can help team members develop new skills, stay up-to-date on the latest technologies, and foster a culture of continuous learning.
By adopting these strategies, organizations can create a collaborative environment where ITSM and DevOps teams can work together seamlessly to drive innovation and deliver value to the business.
Improving Efficiency and Performance
When ITSM and DevOps collaborate effectively, organizations can achieve significant improvements in efficiency and performance. By aligning processes, tools, and practices, teams can work more cohesively and deliver results faster. This leads to greater customer satisfaction, increased agility, and reduced time-to-market for new products and services.
Aligning Culture and Strategy
Collaboration between ITSM and DevOps also requires a shift in culture and strategy. Organizations must prioritize collaboration, innovation, and continuous improvement to succeed in today's competitive landscape. By fostering a culture of teamwork, trust, and experimentation, teams can drive positive change and achieve better results.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, bridging the gap between ITSM and DevOps is essential for organizations looking to maximize the benefits of technology, information, and innovation. By fostering collaboration, improving communication, and aligning processes, organizations can create a culture of teamwork and drive continuous improvement in their IT operations. It is time for organizations to embrace the power of collaboration between ITSM and DevOps and unlock the full potential of their technology investments.
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced world of technology and information, the collaboration between ITSM (IT Service Management) and DevOps is crucial for success. By bridging the gap between these two key areas, organizations can improve efficiency, communication, and innovation in their IT operations. In this article, we will explore how ITSM and DevOps can work together to create a culture of collaboration and drive continuous improvement.
ITSM and DevOps: A Winning Combination
For many years, ITSM and DevOps have been viewed as separate entities within organizations. ITSM focuses on the delivery of quality IT services, while DevOps is centered around the rapid and continuous delivery of software. However, by integrating these two approaches, organizations can achieve greater alignment, efficiency, and innovation.
Why is Collaboration Important?
Collaboration between ITSM and DevOps is essential for ensuring that IT operations run smoothly and effectively. By working together, teams can streamline processes, improve workflows, and enhance overall productivity. Additionally, collaboration can help organizations respond more quickly to changing business needs and market demands.
Bridging the Gap: How to Foster Collaboration
To bridge the gap between ITSM and DevOps, organizations must focus on building a culture of teamwork and communication. This can be achieved by:
-
Implementing Agile Practices: Agile methodologies can help teams work together more effectively by promoting flexibility, adaptability, and transparency.
-
Embracing Automation: Automation tools can streamline processes and eliminate manual tasks, allowing teams to focus on higher-value work.
-
Encouraging Open Communication: Regular communication between ITSM and DevOps teams is crucial for sharing information, resolving issues, and aligning priorities.
-
Investing in Training and Development: Training programs can help team members develop new skills, stay up-to-date on the latest technologies, and foster a culture of continuous learning.
By adopting these strategies, organizations can create a collaborative environment where ITSM and DevOps teams can work together seamlessly to drive innovation and deliver value to the business.
Improving Efficiency and Performance
When ITSM and DevOps collaborate effectively, organizations can achieve significant improvements in efficiency and performance. By aligning processes, tools, and practices, teams can work more cohesively and deliver results faster. This leads to greater customer satisfaction, increased agility, and reduced time-to-market for new products and services.
Aligning Culture and Strategy
Collaboration between ITSM and DevOps also requires a shift in culture and strategy. Organizations must prioritize collaboration, innovation, and continuous improvement to succeed in today's competitive landscape. By fostering a culture of teamwork, trust, and experimentation, teams can drive positive change and achieve better results.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, bridging the gap between ITSM and DevOps is essential for organizations looking to maximize the benefits of technology, information, and innovation. By fostering collaboration, improving communication, and aligning processes, organizations can create a culture of teamwork and drive continuous improvement in their IT operations. It is time for organizations to embrace the power of collaboration between ITSM and DevOps and unlock the full potential of their technology investments.
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
Mastering Project Quality: Detailed Steps
Are you ready to take your project quality management skills to the next level? In this comprehensive guide, we will walk you through a step-by-step process to help you master project quality management from start to finish. From quality assurance to quality control, project planning to quality management techniques, we've got you covered. Let's dive in and explore the world of project quality management together!
Introduction to Project Quality Management
Project quality management is a crucial aspect of any successful project. It involves ensuring that the project meets the specified quality standards set forth by the stakeholders. By implementing quality management processes, you can optimize project outcomes, minimize risks, and deliver a high-quality end product.
What is Project Quality Management?
Project quality management is the process of ensuring that a project meets the specified quality standards throughout its lifecycle. This involves careful planning, implementation, and monitoring of quality control measures to ensure that the project delivers the desired results.
Why is Project Quality Management Important?
Quality management is vital for the success of any project. By focusing on quality assurance, control, and improvement, you can enhance customer satisfaction, reduce rework, and increase overall project efficiency.
The Project Quality Management Process
To master project quality management, you need to follow a structured process. Here is a step-by-step guide to help you navigate the quality management framework successfully:
-
Project Quality Planning: Define the quality standards and establish a plan to achieve them.
-
Quality Assurance: Implement processes to ensure quality standards are met throughout the project.
-
Quality Control: Monitor and validate project deliverables to meet quality requirements.
-
Quality Improvement: Continuously assess and enhance project processes to improve quality outcomes.
Strategies for Project Quality Management
To excel in project quality management, consider the following strategies:
-
Set Clear Objectives: Define quality goals and expectations from the outset.
-
Empower Team Members: Equip your team with the resources and training needed to achieve quality standards.
-
Utilize Quality Metrics: Measure and analyze key quality indicators to track performance.
-
Continuous Improvement: Foster a culture of quality improvement to drive project success.
How to obtain Quality Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
By mastering project quality management, you can elevate your project outcomes and build a reputation for delivering high-quality results. Use the step-by-step guide, tools, and strategies outlined in this comprehensive article to enhance your quality management skills and excel in your project endeavors. Remember, quality is not an act, it is a habit. Start building your quality management habits today!
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you ready to take your project quality management skills to the next level? In this comprehensive guide, we will walk you through a step-by-step process to help you master project quality management from start to finish. From quality assurance to quality control, project planning to quality management techniques, we've got you covered. Let's dive in and explore the world of project quality management together!
Introduction to Project Quality Management
Project quality management is a crucial aspect of any successful project. It involves ensuring that the project meets the specified quality standards set forth by the stakeholders. By implementing quality management processes, you can optimize project outcomes, minimize risks, and deliver a high-quality end product.
What is Project Quality Management?
Project quality management is the process of ensuring that a project meets the specified quality standards throughout its lifecycle. This involves careful planning, implementation, and monitoring of quality control measures to ensure that the project delivers the desired results.
Why is Project Quality Management Important?
Quality management is vital for the success of any project. By focusing on quality assurance, control, and improvement, you can enhance customer satisfaction, reduce rework, and increase overall project efficiency.
The Project Quality Management Process
To master project quality management, you need to follow a structured process. Here is a step-by-step guide to help you navigate the quality management framework successfully:
-
Project Quality Planning: Define the quality standards and establish a plan to achieve them.
-
Quality Assurance: Implement processes to ensure quality standards are met throughout the project.
-
Quality Control: Monitor and validate project deliverables to meet quality requirements.
-
Quality Improvement: Continuously assess and enhance project processes to improve quality outcomes.
Strategies for Project Quality Management
To excel in project quality management, consider the following strategies:
-
Set Clear Objectives: Define quality goals and expectations from the outset.
-
Empower Team Members: Equip your team with the resources and training needed to achieve quality standards.
-
Utilize Quality Metrics: Measure and analyze key quality indicators to track performance.
-
Continuous Improvement: Foster a culture of quality improvement to drive project success.
How to obtain Quality Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
By mastering project quality management, you can elevate your project outcomes and build a reputation for delivering high-quality results. Use the step-by-step guide, tools, and strategies outlined in this comprehensive article to enhance your quality management skills and excel in your project endeavors. Remember, quality is not an act, it is a habit. Start building your quality management habits today!
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
CRISC Certification: A Guide for Aspiring IT Professionals
Are you an aspiring IT professional looking to advance your career in IT security, risk management, cybersecurity, IT auditing, IT governance, or information assurance? If so, obtaining the CRISC certification could be the key to unlocking new job opportunities and professional development in the information technology industry. In this comprehensive guide, we will explore everything you need to know about the CRISC certification process, exam preparation, benefits, study materials, certification costs, job prospects, and more.
What is CRISC Certification?
CRISC stands for Certified in Risk and Information Systems Control. It is a globally recognized certification designed for IT professionals who have experience in IT risk management, information systems control, and IT governance. The CRISC certification validates your skills and expertise in identifying and managing IT risks within an organization, making you a valuable asset in today's competitive IT industry.
Why Should You Pursue CRISC Certification?
-
Career Advancement: CRISC certification can open doors to new job opportunities and higher salary potential as employers value professionals with specialized skills in IT risk management.
-
Professional Development: By obtaining the CRISC certification, you demonstrate a commitment to continuous learning and professional growth in the field of information technology.
-
Increased Job Security: With the rise of cybersecurity threats and data breaches, organizations are increasingly looking for skilled professionals who can help them protect their information assets.
How to Become CRISC Certified?
To become CRISC certified, you must meet certain requirements and pass the CRISC certification exam. Here is a step-by-step guide to help you navigate the certification process:
-
Meet Eligibility Requirements: To be eligible for the CRISC certification, you must have at least three years of cumulative work experience in IT risk management and pass the CRISC exam.
-
Prepare for the Exam: Use study materials such as review courses, practice exams, and study guides to prepare for the CRISC exam. Familiarize yourself with IT skills, concepts, and best practices related to risk management and information systems control.
-
Take the Certification Exam: Register for the CRISC exam, which consists of 150 multiple-choice questions and tests your knowledge of IT risk management, information systems control, and IT governance.
-
Maintain Your Certification: Once you have passed the CRISC exam, you must adhere to ISACA's Code of Professional Ethics and meet continuing professional education (CPE) requirements to maintain your certification validity.
What Are the Benefits of CRISC Certification?
-
Validation of Expertise: CRISC certification demonstrates your expertise in IT risk management and information systems control, making you a trusted professional in the industry.
-
Career Growth: With CRISC certification, you can pursue specialized roles such as IT risk manager, information security analyst, IT auditor, or IT governance specialist in various organizations.
-
Networking Opportunities: Join a global community of CRISC certified professionals and expand your professional network for future career opportunities.
How to obtain CRISC certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, obtaining the CRISC certification can enhance your credibility, knowledge, and skills in IT risk management, cybersecurity, and information systems control. Whether you are a seasoned IT professional or just starting your career in the industry, CRISC certification can help you stand out in a competitive job market and secure rewarding job opportunities. Take the first step towards advancing your career by pursuing CRISC certification today!.
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you an aspiring IT professional looking to advance your career in IT security, risk management, cybersecurity, IT auditing, IT governance, or information assurance? If so, obtaining the CRISC certification could be the key to unlocking new job opportunities and professional development in the information technology industry. In this comprehensive guide, we will explore everything you need to know about the CRISC certification process, exam preparation, benefits, study materials, certification costs, job prospects, and more.
What is CRISC Certification?
CRISC stands for Certified in Risk and Information Systems Control. It is a globally recognized certification designed for IT professionals who have experience in IT risk management, information systems control, and IT governance. The CRISC certification validates your skills and expertise in identifying and managing IT risks within an organization, making you a valuable asset in today's competitive IT industry.
Why Should You Pursue CRISC Certification?
-
Career Advancement: CRISC certification can open doors to new job opportunities and higher salary potential as employers value professionals with specialized skills in IT risk management.
-
Professional Development: By obtaining the CRISC certification, you demonstrate a commitment to continuous learning and professional growth in the field of information technology.
-
Increased Job Security: With the rise of cybersecurity threats and data breaches, organizations are increasingly looking for skilled professionals who can help them protect their information assets.
How to Become CRISC Certified?
To become CRISC certified, you must meet certain requirements and pass the CRISC certification exam. Here is a step-by-step guide to help you navigate the certification process:
-
Meet Eligibility Requirements: To be eligible for the CRISC certification, you must have at least three years of cumulative work experience in IT risk management and pass the CRISC exam.
-
Prepare for the Exam: Use study materials such as review courses, practice exams, and study guides to prepare for the CRISC exam. Familiarize yourself with IT skills, concepts, and best practices related to risk management and information systems control.
-
Take the Certification Exam: Register for the CRISC exam, which consists of 150 multiple-choice questions and tests your knowledge of IT risk management, information systems control, and IT governance.
-
Maintain Your Certification: Once you have passed the CRISC exam, you must adhere to ISACA's Code of Professional Ethics and meet continuing professional education (CPE) requirements to maintain your certification validity.
What Are the Benefits of CRISC Certification?
-
Validation of Expertise: CRISC certification demonstrates your expertise in IT risk management and information systems control, making you a trusted professional in the industry.
-
Career Growth: With CRISC certification, you can pursue specialized roles such as IT risk manager, information security analyst, IT auditor, or IT governance specialist in various organizations.
-
Networking Opportunities: Join a global community of CRISC certified professionals and expand your professional network for future career opportunities.
How to obtain CRISC certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, obtaining the CRISC certification can enhance your credibility, knowledge, and skills in IT risk management, cybersecurity, and information systems control. Whether you are a seasoned IT professional or just starting your career in the industry, CRISC certification can help you stand out in a competitive job market and secure rewarding job opportunities. Take the first step towards advancing your career by pursuing CRISC certification today!.
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
Agile PM and Scrum Ex with Step-by-Step Help
Are you looking to enhance your project management skills and streamline your workflow? Agile project management and Scrum methodology might be the solution you've been searching for. In this article, we will explore the step-by-step process of implementing Agile project management and Scrum, with real-world examples to help you grasp the concepts easily.
Introduction to Agile Project Management and Scrum
Agile project management is a flexible and iterative approach to managing projects. It focuses on breaking down the project into smaller, more manageable tasks, allowing teams to adapt to changes quickly. Scrum, on the other hand, is a specific framework within Agile that defines roles, events, and artifacts to guide the project's execution. By combining Agile project management with Scrum methodology, teams can deliver high-quality products in a more efficient manner.
Agile Project Planning
The first step in Agile project management is project planning. This involves defining the project scope, setting goals and objectives, and creating a roadmap for implementation. In Agile, project planning is done in iterations, with frequent check-ins and adjustments as needed. By breaking down the project into smaller increments, teams can stay focused and on track throughout the project's lifecycle.
Sprint Planning
Once the project plan is in place, the team moves on to sprint planning. A sprint is a short, time-boxed period during which a specific set of tasks is completed. During sprint planning, the team decides which tasks to work on and how to accomplish them within the sprint timeframe. This collaborative effort ensures that everyone is on the same page and working towards a common goal.
Product Backlog
The product backlog is a list of all the tasks, features, and enhancements that need to be completed throughout the project. It serves as a roadmap for the team, guiding them on what needs to be prioritized and when. By maintaining a well-organized product backlog, teams can stay focused and deliver value to the customer in a timely manner.
Agile Team
The Agile team is a cross-functional group of individuals with different skills and expertise who work together to deliver the project. Each team member has a specific role and responsibility, contributing to the success of the project. By fostering collaboration and communication within the team, Agile project management encourages creativity and innovation.
User Stories
User stories are short, simple descriptions of a feature or functionality from the end-user's perspective. They help teams understand what the user needs and why the feature is important. By writing user stories, teams can prioritize tasks and focus on delivering value to the customer with each sprint.
Agile Development
During the sprint, the team works on developing the features and functionalities outlined in the user stories. By using Agile development practices such as test-driven development and continuous integration, teams can ensure that the product meets the customer's requirements and is of high quality. Agile development promotes flexibility and adaptability, allowing teams to make changes quickly based on feedback.
Sprint Review
At the end of the sprint, the team holds a sprint review meeting to demonstrate the completed work to the stakeholders. This allows the stakeholders to provide feedback and suggestions for improvement. By incorporating feedback into the next sprint, teams can continuously improve the product and deliver value to the customer.
Agile Practices
Agile project management is guided by a set of practices that help teams work more effectively. These practices include daily stand-up meetings, retrospectives, and continuous improvement. By following these practices, teams can identify issues early on and address them before they become major obstacles to project success.
Agile Framework
The Agile framework provides a structured approach to Agile project management, outlining the roles, events, and artifacts that are essential for project success. By following the Agile framework, teams can ensure that they are following best practices and delivering value to the customer in a timely manner.
Agile Principles
Agile project management is based on a set of principles that promote collaboration, flexibility, and customer satisfaction. These principles emphasize individuals and interactions over processes and tools, working software over comprehensive documentation, customer collaboration over contract negotiation, and responding to change over following a plan. By embracing these principles, teams can deliver high-quality products that meet the customer's needs.
Scrum Master
The Scrum Master is a key role in the Scrum framework, responsible for ensuring that the team follows Scrum practices and principles. The Scrum Master acts as a facilitator, coach, and mentor to the team, helping them overcome obstacles and achieve their goals. By providing guidance and support, the Scrum Master ensures that the team stays focused, motivated, and on track throughout the project.
Scrum Events
Scrum events are key ceremonies in the Scrum framework that help teams collaborate and communicate effectively. These events include sprint planning, daily stand-up meetings, sprint review, and sprint retrospective. By following the Scrum events, teams can stay on track, identify issues early on, and make improvements based on feedback.
Agile Tools
Agile project management relies on a variety of tools and software to facilitate communication, collaboration, and project tracking. These tools include project management software, communication platforms, version control systems, and testing tools. By using Agile tools, teams can streamline their workflow, improve productivity, and deliver high-quality products to the customer.
Agile Project Monitoring
Agile project monitoring involves tracking progress, identifying issues, and making adjustments as needed to ensure project success. By monitoring key performance indicators, such as sprint velocity, burndown rate, and stakeholder satisfaction, teams can stay on track and deliver value to the customer. Agile project monitoring promotes transparency, visibility, and accountability, ensuring that the project stays on track and meets the customer's requirements.
Agile Project Control
Agile project control involves managing risks, resolving issues, and making decisions to keep the project on track. By establishing clear roles, responsibilities, and communication channels, teams can maintain control over the project and make informed decisions based on data and feedback. Agile project control promotes accountability, adaptability, and continuous improvement, ensuring that the project stays on track and delivers value to the customer.
Agile Project Communication
Agile project communication involves sharing information, updates, and feedback with team members and stakeholders. By using a variety of communication channels, such as meetings, emails, and collaboration tools, teams can ensure that everyone is on the same page and working towards a common goal. Agile project communication promotes transparency, clarity, and collaboration, ensuring that the project stays on track and delivers value to the customer.
Agile Project Collaboration
Agile project collaboration involves working together as a team to achieve shared goals and objectives. By fostering a culture of trust, respect, and openness, teams can collaborate effectively and deliver high-quality products to the customer. Agile project collaboration promotes creativity, innovation, and continuous improvement, ensuring that the project meets the customer's requirements and expectations.
How to obtain Agile and Scrum certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Agile project management and Scrum methodology offer a structured and efficient approach to managing projects. By following the step-by-step process outlined in this article and incorporating real-world examples, you can enhance your project management skills and deliver high-quality products to the customer. Embrace Agile project management and Scrum methodology to streamline your workflow, increase productivity, and achieve project success..
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to enhance your project management skills and streamline your workflow? Agile project management and Scrum methodology might be the solution you've been searching for. In this article, we will explore the step-by-step process of implementing Agile project management and Scrum, with real-world examples to help you grasp the concepts easily.
Introduction to Agile Project Management and Scrum
Agile project management is a flexible and iterative approach to managing projects. It focuses on breaking down the project into smaller, more manageable tasks, allowing teams to adapt to changes quickly. Scrum, on the other hand, is a specific framework within Agile that defines roles, events, and artifacts to guide the project's execution. By combining Agile project management with Scrum methodology, teams can deliver high-quality products in a more efficient manner.
Agile Project Planning
The first step in Agile project management is project planning. This involves defining the project scope, setting goals and objectives, and creating a roadmap for implementation. In Agile, project planning is done in iterations, with frequent check-ins and adjustments as needed. By breaking down the project into smaller increments, teams can stay focused and on track throughout the project's lifecycle.
Sprint Planning
Once the project plan is in place, the team moves on to sprint planning. A sprint is a short, time-boxed period during which a specific set of tasks is completed. During sprint planning, the team decides which tasks to work on and how to accomplish them within the sprint timeframe. This collaborative effort ensures that everyone is on the same page and working towards a common goal.
Product Backlog
The product backlog is a list of all the tasks, features, and enhancements that need to be completed throughout the project. It serves as a roadmap for the team, guiding them on what needs to be prioritized and when. By maintaining a well-organized product backlog, teams can stay focused and deliver value to the customer in a timely manner.
Agile Team
The Agile team is a cross-functional group of individuals with different skills and expertise who work together to deliver the project. Each team member has a specific role and responsibility, contributing to the success of the project. By fostering collaboration and communication within the team, Agile project management encourages creativity and innovation.
User Stories
User stories are short, simple descriptions of a feature or functionality from the end-user's perspective. They help teams understand what the user needs and why the feature is important. By writing user stories, teams can prioritize tasks and focus on delivering value to the customer with each sprint.
Agile Development
During the sprint, the team works on developing the features and functionalities outlined in the user stories. By using Agile development practices such as test-driven development and continuous integration, teams can ensure that the product meets the customer's requirements and is of high quality. Agile development promotes flexibility and adaptability, allowing teams to make changes quickly based on feedback.
Sprint Review
At the end of the sprint, the team holds a sprint review meeting to demonstrate the completed work to the stakeholders. This allows the stakeholders to provide feedback and suggestions for improvement. By incorporating feedback into the next sprint, teams can continuously improve the product and deliver value to the customer.
Agile Practices
Agile project management is guided by a set of practices that help teams work more effectively. These practices include daily stand-up meetings, retrospectives, and continuous improvement. By following these practices, teams can identify issues early on and address them before they become major obstacles to project success.
Agile Framework
The Agile framework provides a structured approach to Agile project management, outlining the roles, events, and artifacts that are essential for project success. By following the Agile framework, teams can ensure that they are following best practices and delivering value to the customer in a timely manner.
Agile Principles
Agile project management is based on a set of principles that promote collaboration, flexibility, and customer satisfaction. These principles emphasize individuals and interactions over processes and tools, working software over comprehensive documentation, customer collaboration over contract negotiation, and responding to change over following a plan. By embracing these principles, teams can deliver high-quality products that meet the customer's needs.
Scrum Master
The Scrum Master is a key role in the Scrum framework, responsible for ensuring that the team follows Scrum practices and principles. The Scrum Master acts as a facilitator, coach, and mentor to the team, helping them overcome obstacles and achieve their goals. By providing guidance and support, the Scrum Master ensures that the team stays focused, motivated, and on track throughout the project.
Scrum Events
Scrum events are key ceremonies in the Scrum framework that help teams collaborate and communicate effectively. These events include sprint planning, daily stand-up meetings, sprint review, and sprint retrospective. By following the Scrum events, teams can stay on track, identify issues early on, and make improvements based on feedback.
Agile Tools
Agile project management relies on a variety of tools and software to facilitate communication, collaboration, and project tracking. These tools include project management software, communication platforms, version control systems, and testing tools. By using Agile tools, teams can streamline their workflow, improve productivity, and deliver high-quality products to the customer.
Agile Project Monitoring
Agile project monitoring involves tracking progress, identifying issues, and making adjustments as needed to ensure project success. By monitoring key performance indicators, such as sprint velocity, burndown rate, and stakeholder satisfaction, teams can stay on track and deliver value to the customer. Agile project monitoring promotes transparency, visibility, and accountability, ensuring that the project stays on track and meets the customer's requirements.
Agile Project Control
Agile project control involves managing risks, resolving issues, and making decisions to keep the project on track. By establishing clear roles, responsibilities, and communication channels, teams can maintain control over the project and make informed decisions based on data and feedback. Agile project control promotes accountability, adaptability, and continuous improvement, ensuring that the project stays on track and delivers value to the customer.
Agile Project Communication
Agile project communication involves sharing information, updates, and feedback with team members and stakeholders. By using a variety of communication channels, such as meetings, emails, and collaboration tools, teams can ensure that everyone is on the same page and working towards a common goal. Agile project communication promotes transparency, clarity, and collaboration, ensuring that the project stays on track and delivers value to the customer.
Agile Project Collaboration
Agile project collaboration involves working together as a team to achieve shared goals and objectives. By fostering a culture of trust, respect, and openness, teams can collaborate effectively and deliver high-quality products to the customer. Agile project collaboration promotes creativity, innovation, and continuous improvement, ensuring that the project meets the customer's requirements and expectations.
How to obtain Agile and Scrum certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Agile project management and Scrum methodology offer a structured and efficient approach to managing projects. By following the step-by-step process outlined in this article and incorporating real-world examples, you can enhance your project management skills and deliver high-quality products to the customer. Embrace Agile project management and Scrum methodology to streamline your workflow, increase productivity, and achieve project success..
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
The Role of Blockchain in Enhancing Security
In today's digital age, security is more important than ever before. With the increasing amount of data being generated and shared online, the need for robust security measures has become paramount. One technology that has been at the forefront of enhancing security is blockchain. In this article, we will explore the role of blockchain in enhancing security and how it is revolutionizing the way we protect sensitive information.
What is Blockchain?
Blockchain is a decentralized, distributed ledger technology that stores data in a secure and tamper-proof manner. The data is stored in blocks, which are linked together in a chain using cryptographic techniques. This makes it virtually impossible for hackers to alter or corrupt the data stored on the blockchain.
Blockchain technology was originally developed for the cryptocurrency Bitcoin, but its applications extend far beyond just digital currencies. It has the potential to revolutionize industries such as cybersecurity, data protection, and secure transactions.
How Does Blockchain Enhance Security?
Secure Data Storage
One of the key ways in which blockchain enhances security is through secure data storage. Traditional databases are vulnerable to hacking and data breaches, as they are stored on centralized servers. In contrast, blockchain stores data in a decentralized manner across a network of computers, making it virtually impossible for hackers to gain unauthorized access.
Encryption
Blockchain uses advanced encryption techniques to secure data stored on the network. Each block of data is encrypted using cryptographic algorithms, making it extremely difficult for hackers to decipher the information. This ensures that sensitive data remains protected at all times.
Smart Contracts
Smart contracts are self-executing contracts with the terms of the agreement between parties directly written into code. These contracts are stored on the blockchain and automatically execute when predefined conditions are met. This eliminates the need for intermediaries and provides a secure and transparent way to conduct transactions.
The Benefits of Blockchain Security
-
Improved Data Privacy
-
Secure Transactions
-
Tamper-proof Data Storage
-
Decentralized Network
-
Enhanced Data Integrity
By leveraging blockchain technology, organizations can enhance their security measures and protect sensitive information from cyber threats. Whether it's securing financial transactions, protecting personal data, or enhancing network security, blockchain offers a revolutionary solution to today's security challenges.
Blockchain Innovation and Solutions
Blockchain is continuously evolving, with innovative solutions being developed to address various security concerns. From secure communication channels to authentication protocols, blockchain offers a wide range of tools and technologies to enhance security in the digital landscape.
The Blockchain Ecosystem
The blockchain ecosystem is a complex network of technologies, platforms, and applications that work together to ensure the security and integrity of data. From the underlying architecture of the blockchain to the applications built on top of it, every component plays a crucial role in enhancing security and protecting digital assets.
How to obtain Blockchain certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the role of blockchain in enhancing security cannot be understated. With its decentralized network, secure data storage, and advanced encryption techniques, blockchain offers a robust solution to the security challenges faced by organizations today. By leveraging blockchain technology, organizations can not only protect sensitive information but also revolutionize the way security is approached in the digital age.
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's digital age, security is more important than ever before. With the increasing amount of data being generated and shared online, the need for robust security measures has become paramount. One technology that has been at the forefront of enhancing security is blockchain. In this article, we will explore the role of blockchain in enhancing security and how it is revolutionizing the way we protect sensitive information.
What is Blockchain?
Blockchain is a decentralized, distributed ledger technology that stores data in a secure and tamper-proof manner. The data is stored in blocks, which are linked together in a chain using cryptographic techniques. This makes it virtually impossible for hackers to alter or corrupt the data stored on the blockchain.
Blockchain technology was originally developed for the cryptocurrency Bitcoin, but its applications extend far beyond just digital currencies. It has the potential to revolutionize industries such as cybersecurity, data protection, and secure transactions.
How Does Blockchain Enhance Security?
Secure Data Storage
One of the key ways in which blockchain enhances security is through secure data storage. Traditional databases are vulnerable to hacking and data breaches, as they are stored on centralized servers. In contrast, blockchain stores data in a decentralized manner across a network of computers, making it virtually impossible for hackers to gain unauthorized access.
Encryption
Blockchain uses advanced encryption techniques to secure data stored on the network. Each block of data is encrypted using cryptographic algorithms, making it extremely difficult for hackers to decipher the information. This ensures that sensitive data remains protected at all times.
Smart Contracts
Smart contracts are self-executing contracts with the terms of the agreement between parties directly written into code. These contracts are stored on the blockchain and automatically execute when predefined conditions are met. This eliminates the need for intermediaries and provides a secure and transparent way to conduct transactions.
The Benefits of Blockchain Security
-
Improved Data Privacy
-
Secure Transactions
-
Tamper-proof Data Storage
-
Decentralized Network
-
Enhanced Data Integrity
By leveraging blockchain technology, organizations can enhance their security measures and protect sensitive information from cyber threats. Whether it's securing financial transactions, protecting personal data, or enhancing network security, blockchain offers a revolutionary solution to today's security challenges.
Blockchain Innovation and Solutions
Blockchain is continuously evolving, with innovative solutions being developed to address various security concerns. From secure communication channels to authentication protocols, blockchain offers a wide range of tools and technologies to enhance security in the digital landscape.
The Blockchain Ecosystem
The blockchain ecosystem is a complex network of technologies, platforms, and applications that work together to ensure the security and integrity of data. From the underlying architecture of the blockchain to the applications built on top of it, every component plays a crucial role in enhancing security and protecting digital assets.
How to obtain Blockchain certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the role of blockchain in enhancing security cannot be understated. With its decentralized network, secure data storage, and advanced encryption techniques, blockchain offers a robust solution to the security challenges faced by organizations today. By leveraging blockchain technology, organizations can not only protect sensitive information but also revolutionize the way security is approached in the digital age.
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
Agile Methodology: Its Evolution and Impact on History
In today's fast-paced and ever-changing business landscape, the need for flexibility, adaptability, and efficiency is more important than ever. This is where Agile methodology comes into play, revolutionizing the way organizations approach project management and software development. Let's delve into the history of Agile, its evolution over the years, and its profound impact on history.
History of Agile
The roots of Agile methodology can be traced back to the early 2000s when a group of software developers came together to discuss more flexible and collaborative approaches to software development. This led to the creation of the Agile Manifesto, a set of principles that prioritized individuals and interactions over processes and tools, working software over comprehensive documentation, customer collaboration over contract negotiation, and responding to change over following a plan.
Evolution of Agile
Over the years, Agile methodology has evolved and grown in popularity across various industries, not just limited to software development. Its principles and practices have been adopted by organizations looking to increase productivity, improve communication, and deliver value to customers more efficiently. From Agile project management to Agile software development, the methodology has become a cornerstone of modern business practices.
Agile Impact on History
The impact of Agile methodology on history cannot be overstated. Its emphasis on continuous improvement, collaboration, and adaptability has revolutionized the way projects are managed and executed. By breaking down silos, fostering cross-functional teams, and promoting iterative development, Agile has helped organizations achieve faster time-to-market, higher customer satisfaction, and greater overall success.
Agile Practices
There are several key practices that define Agile methodology, including:
-
Scrum Methodology: A framework for Agile project management that emphasizes short development cycles called sprints.
-
Lean Agile: Combining Agile principles with lean manufacturing concepts to streamline processes and reduce waste.
-
Agile Software Development: A set of software development principles and practices that emphasize adaptability and customer collaboration.
-
Agile Principles: The core values and principles outlined in the Agile Manifesto that guide Agile development projects.
-
Kanban Methodology: A visual management tool that helps teams visualize work in progress and improve workflow efficiency.
Agile Frameworks
There are various Agile frameworks that organizations can adopt, including:
-
Scrum: A popular Agile framework for managing complex projects through incremental development.
-
Kanban: A visual framework for managing work in progress and optimizing workflow.
-
Lean: A framework based on lean manufacturing principles that focuses on maximizing customer value and minimizing waste.
Agile Teams
Agile methodology emphasizes the importance of cross-functional teams that work collaboratively to deliver value to customers. These teams are self-organizing, empowered to make decisions, and focused on achieving shared goals.
Agile Transformation
Many organizations are undergoing Agile transformations to become more flexible, adaptive, and customer-focused. This involves a shift in mindset, culture, and practices to embrace Agile principles and ways of working.
Modern Agile
Modern Agile is an evolution of traditional Agile methodology that focuses on simplicity, safety, and delivering value to customers. It emphasizes four guiding principles: Make People Awesome, Make Safety a Prerequisite, Experiment and Learn Rapidly, and Deliver Value Continuously.
Agile Methodologies Comparison
There are several Agile methodologies that organizations can choose from, each with its own strengths and weaknesses. By understanding the differences between them, organizations can select the methodology that best aligns with their goals, values, and project requirements.
Agile Evolution Timeline
The evolution of Agile methodology can be traced through a timeline of key events, from the creation of the Agile Manifesto in 2001 to the emergence of modern Agile frameworks and practices. This timeline reflects the ongoing evolution and refinement of Agile principles in response to changing market demands and technological advancements.
Agile Adaptive
Agile methodology is inherently adaptive, allowing teams to respond quickly to changing requirements, market conditions, and customer feedback. By embracing change and prioritizing flexibility, organizations can stay ahead of the curve and deliver value to customers more effectively.
Agile Mindset
Having an Agile mindset is essential for success in today's fast-paced and competitive business environment. This mindset involves being open to change, embracing collaboration, and focusing on continuous improvement. By cultivating an Agile mindset, organizations can foster innovation, creativity, and resilience in the face of uncertainty.
Agile Success Stories
There are numerous success stories of organizations that have embraced Agile methodology and achieved remarkable results. From increased productivity and profitability to higher customer satisfaction and employee engagement, these success stories highlight the transformative power of Agile in driving business success.
Agile Culture
Creating an Agile culture involves fostering a mindset of continuous improvement, collaboration, and innovation throughout the organization. By promoting transparency, trust, and empowerment, organizations can build a culture that values adaptability, resilience, and customer focus, ultimately driving success and growth.
Agile Innovation
Agile methodology promotes a culture of experimentation, creativity, and risk-taking, which are essential for fostering innovation and driving business growth. By embracing Agile practices and principles, organizations can unlock new opportunities, drive change, and stay ahead of the competition in an increasingly dynamic and competitive market.
How to obtain Agile certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Agile methodology has come a long way since its inception, evolving and adapting to meet the changing needs and challenges of modern business. Its impact on history is profound, reshaping the way organizations approach project management, software development, and customer collaboration. By embracing Agile practices, frameworks, and principles, organizations can drive innovation, agility, and success in today's rapidly evolving business landscape.
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced and ever-changing business landscape, the need for flexibility, adaptability, and efficiency is more important than ever. This is where Agile methodology comes into play, revolutionizing the way organizations approach project management and software development. Let's delve into the history of Agile, its evolution over the years, and its profound impact on history.
History of Agile
The roots of Agile methodology can be traced back to the early 2000s when a group of software developers came together to discuss more flexible and collaborative approaches to software development. This led to the creation of the Agile Manifesto, a set of principles that prioritized individuals and interactions over processes and tools, working software over comprehensive documentation, customer collaboration over contract negotiation, and responding to change over following a plan.
Evolution of Agile
Over the years, Agile methodology has evolved and grown in popularity across various industries, not just limited to software development. Its principles and practices have been adopted by organizations looking to increase productivity, improve communication, and deliver value to customers more efficiently. From Agile project management to Agile software development, the methodology has become a cornerstone of modern business practices.
Agile Impact on History
The impact of Agile methodology on history cannot be overstated. Its emphasis on continuous improvement, collaboration, and adaptability has revolutionized the way projects are managed and executed. By breaking down silos, fostering cross-functional teams, and promoting iterative development, Agile has helped organizations achieve faster time-to-market, higher customer satisfaction, and greater overall success.
Agile Practices
There are several key practices that define Agile methodology, including:
-
Scrum Methodology: A framework for Agile project management that emphasizes short development cycles called sprints.
-
Lean Agile: Combining Agile principles with lean manufacturing concepts to streamline processes and reduce waste.
-
Agile Software Development: A set of software development principles and practices that emphasize adaptability and customer collaboration.
-
Agile Principles: The core values and principles outlined in the Agile Manifesto that guide Agile development projects.
-
Kanban Methodology: A visual management tool that helps teams visualize work in progress and improve workflow efficiency.
Agile Frameworks
There are various Agile frameworks that organizations can adopt, including:
-
Scrum: A popular Agile framework for managing complex projects through incremental development.
-
Kanban: A visual framework for managing work in progress and optimizing workflow.
-
Lean: A framework based on lean manufacturing principles that focuses on maximizing customer value and minimizing waste.
Agile Teams
Agile methodology emphasizes the importance of cross-functional teams that work collaboratively to deliver value to customers. These teams are self-organizing, empowered to make decisions, and focused on achieving shared goals.
Agile Transformation
Many organizations are undergoing Agile transformations to become more flexible, adaptive, and customer-focused. This involves a shift in mindset, culture, and practices to embrace Agile principles and ways of working.
Modern Agile
Modern Agile is an evolution of traditional Agile methodology that focuses on simplicity, safety, and delivering value to customers. It emphasizes four guiding principles: Make People Awesome, Make Safety a Prerequisite, Experiment and Learn Rapidly, and Deliver Value Continuously.
Agile Methodologies Comparison
There are several Agile methodologies that organizations can choose from, each with its own strengths and weaknesses. By understanding the differences between them, organizations can select the methodology that best aligns with their goals, values, and project requirements.
Agile Evolution Timeline
The evolution of Agile methodology can be traced through a timeline of key events, from the creation of the Agile Manifesto in 2001 to the emergence of modern Agile frameworks and practices. This timeline reflects the ongoing evolution and refinement of Agile principles in response to changing market demands and technological advancements.
Agile Adaptive
Agile methodology is inherently adaptive, allowing teams to respond quickly to changing requirements, market conditions, and customer feedback. By embracing change and prioritizing flexibility, organizations can stay ahead of the curve and deliver value to customers more effectively.
Agile Mindset
Having an Agile mindset is essential for success in today's fast-paced and competitive business environment. This mindset involves being open to change, embracing collaboration, and focusing on continuous improvement. By cultivating an Agile mindset, organizations can foster innovation, creativity, and resilience in the face of uncertainty.
Agile Success Stories
There are numerous success stories of organizations that have embraced Agile methodology and achieved remarkable results. From increased productivity and profitability to higher customer satisfaction and employee engagement, these success stories highlight the transformative power of Agile in driving business success.
Agile Culture
Creating an Agile culture involves fostering a mindset of continuous improvement, collaboration, and innovation throughout the organization. By promoting transparency, trust, and empowerment, organizations can build a culture that values adaptability, resilience, and customer focus, ultimately driving success and growth.
Agile Innovation
Agile methodology promotes a culture of experimentation, creativity, and risk-taking, which are essential for fostering innovation and driving business growth. By embracing Agile practices and principles, organizations can unlock new opportunities, drive change, and stay ahead of the competition in an increasingly dynamic and competitive market.
How to obtain Agile certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Agile methodology has come a long way since its inception, evolving and adapting to meet the changing needs and challenges of modern business. Its impact on history is profound, reshaping the way organizations approach project management, software development, and customer collaboration. By embracing Agile practices, frameworks, and principles, organizations can drive innovation, agility, and success in today's rapidly evolving business landscape.
Contact Us For More Information
Visit : www.icertglobal.com Email : info@icertglobal.com
Integrating Salesforce with External Systems
Are you looking to streamline your business processes by integrating Salesforce with external systems? This article will provide you with insights into the benefits, challenges, and best practices of integrating Salesforce with external systems such as data integration, API integration, and third-party integration solutions.
Benefits of Salesforce Integration with External Systems
Integrating Salesforce with external systems offers numerous benefits for businesses of all sizes. Some of the key advantages include:
1. Improved Data Accuracy: By integrating Salesforce with external systems, you can ensure that all data is synchronized and up-to-date across platforms.
2. Enhanced Efficiency: Automation through integration can help streamline processes and reduce manual tasks, freeing up valuable time for your team.
3. Better Decision Making: Access to real-time data from external systems within Salesforce can help improve decision-making processes.
4. Enhanced Customer Experience: Integrating external systems with Salesforce can provide a 360-degree view of customer interactions, leading to a more personalized and seamless experience for your customers.
Challenges of Integrating Salesforce with External Systems
While there are many benefits to integrating Salesforce with external systems,there are also some challenges that businesses may face:
1. Complexity: Integrating multiple systems can be complex and require careful planning and execution.
2. Security Concerns: Integrating external systems with Salesforce can raise security concerns, especially when dealing with sensitive data.
3. Compatibility Issues: Ensuring compatibility between different systems and platforms can be a challenge, particularly when dealing with legacy systems.
4. Cost: Integration projects can be costly, both in terms of time and resources, so it's essential to carefully consider the ROI.
Best Practices for Salesforce Integration with External Systems
To ensure a successful integration project, consider the following best practices:
1. Define Clear Objectives: Clearly define your integration objectives and goals to ensure alignment with your business requirements.
2. Choose the Right Integration Tools: Select tools and platforms that are compatible with Salesforce and your external systems to streamline the integration process.
3. Secure Data Integration: Implement robust security measures to protect sensitive data during the integration process.
4. Test Thoroughly: Conduct thorough testing to identify and address any issues before deploying the integrated solution.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
• Project Management: PMP, CAPM ,PMI RMP
• Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
• Business Analysis: CBAP, CCBA, ECBA
• Agile Training: PMI-ACP , CSM , CSPO
• Scrum Training: CSM
• DevOps
• Program Management: PgMP
• Cloud Technology: Exin Cloud Computing
• Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
• Certified Information Systems Security Professional® (CISSP)
• AWS Certified Solutions Architect
• Google Certified Professional Cloud Architect
• Big Data Certification
• Data Science Certification
• Certified In Risk And Information Systems Control (CRISC)
• Certified Information Security Manager(CISM)
• Project Management Professional (PMP)® Certification
• Certified Ethical Hacker (CEH)
• Certified Scrum Master (CSM)
Conclusion
In conclusion, integrating Salesforce with external systems can provide numerous benefits for businesses looking to streamline processes and enhance efficiency. By following best practices and addressing challenges proactively, businesses can leverage the power of Salesforce integration to drive growth and improve customer satisfaction.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to streamline your business processes by integrating Salesforce with external systems? This article will provide you with insights into the benefits, challenges, and best practices of integrating Salesforce with external systems such as data integration, API integration, and third-party integration solutions.
Benefits of Salesforce Integration with External Systems
Integrating Salesforce with external systems offers numerous benefits for businesses of all sizes. Some of the key advantages include:
1. Improved Data Accuracy: By integrating Salesforce with external systems, you can ensure that all data is synchronized and up-to-date across platforms.
2. Enhanced Efficiency: Automation through integration can help streamline processes and reduce manual tasks, freeing up valuable time for your team.
3. Better Decision Making: Access to real-time data from external systems within Salesforce can help improve decision-making processes.
4. Enhanced Customer Experience: Integrating external systems with Salesforce can provide a 360-degree view of customer interactions, leading to a more personalized and seamless experience for your customers.
Challenges of Integrating Salesforce with External Systems
While there are many benefits to integrating Salesforce with external systems,there are also some challenges that businesses may face:
1. Complexity: Integrating multiple systems can be complex and require careful planning and execution.
2. Security Concerns: Integrating external systems with Salesforce can raise security concerns, especially when dealing with sensitive data.
3. Compatibility Issues: Ensuring compatibility between different systems and platforms can be a challenge, particularly when dealing with legacy systems.
4. Cost: Integration projects can be costly, both in terms of time and resources, so it's essential to carefully consider the ROI.
Best Practices for Salesforce Integration with External Systems
To ensure a successful integration project, consider the following best practices:
1. Define Clear Objectives: Clearly define your integration objectives and goals to ensure alignment with your business requirements.
2. Choose the Right Integration Tools: Select tools and platforms that are compatible with Salesforce and your external systems to streamline the integration process.
3. Secure Data Integration: Implement robust security measures to protect sensitive data during the integration process.
4. Test Thoroughly: Conduct thorough testing to identify and address any issues before deploying the integrated solution.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
• Project Management: PMP, CAPM ,PMI RMP
• Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
• Business Analysis: CBAP, CCBA, ECBA
• Agile Training: PMI-ACP , CSM , CSPO
• Scrum Training: CSM
• DevOps
• Program Management: PgMP
• Cloud Technology: Exin Cloud Computing
• Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
• Certified Information Systems Security Professional® (CISSP)
• AWS Certified Solutions Architect
• Google Certified Professional Cloud Architect
• Big Data Certification
• Data Science Certification
• Certified In Risk And Information Systems Control (CRISC)
• Certified Information Security Manager(CISM)
• Project Management Professional (PMP)® Certification
• Certified Ethical Hacker (CEH)
• Certified Scrum Master (CSM)
Conclusion
In conclusion, integrating Salesforce with external systems can provide numerous benefits for businesses looking to streamline processes and enhance efficiency. By following best practices and addressing challenges proactively, businesses can leverage the power of Salesforce integration to drive growth and improve customer satisfaction.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Integrating SAS Base with Other Data Systems and Platforms
In today's data-driven world, organizations rely on various data systems and platforms to store, manage, and analyze their data. One of the most popular tools for data analysis is SAS Base, a powerful software suite used by data analysts and data scientists worldwide. Integrating SAS Base with other data systems and platforms is crucial for organizations looking to streamline their data processes, increase efficiency, and make better-informed decisions. This article will explore the importance of integrating SAS Base with other data systems and platforms, the benefits it can bring, and some best practices for successful integration.
Why Integrate SAS Base with Other Data Systems and Platforms?
Integrating SAS Base with other data systems and platforms allows organizations to leverage the power of SAS Base while accessing data stored in different systems. This integration enables seamless data exchange, sharing, and analysis across various platforms, reducing silos and ensuring data consistency. By integrating SAS Base with other systems, organizations can also automate workflows, improve data accuracy, and enhance decision-making processes.
Benefits of Integration
-
Streamlined Data Processes: Integration of SAS Base with other data systems simplifies data access and processing, saving time and effort for data analysts.
-
Increased Efficiency: By automating data exchange and analysis, integration helps organizations work more efficiently and make quicker decisions.
-
Improved Data Quality: Integrating SAS Base with other systems ensures data consistency and accuracy, leading to better insights and outcomes.
Best Practices for Integrating SAS Base with Other Systems
Successful integration of SAS Base with other data systems and platforms requires careful planning and execution. Here are some best practices to consider:
1. Identify Integration Goals
Before starting the integration process, define clear integration goals and objectives. Understand what you aim to achieve through integration and how it will benefit your organization.
2. Assess Data Compatibility
Ensure compatibility between SAS Base and other data systems in terms of data formats, protocols, and security requirements. This will help prevent data loss or corruption during integration.
3. Design an Integration Strategy
Develop a comprehensive integration strategy that outlines the steps, tools, and resources needed for successful integration. Consider factors such as data mapping, transformation, and synchronization.
4. Test Integration
Before fully implementing the integration, conduct thorough testing to identify and address any potential issues or errors. Test data exchange, analysis, and reporting functionalities to ensure seamless operation.
5. Monitor and Maintain Integration
Once integration is complete, monitor its performance regularly to ensure data integrity and system stability. Implement regular maintenance and updates to keep the integration running smoothly.
6. Seek Expert Consultation
If you are unsure about how to integrate SAS Base with other systems, consider seeking expert consultation from a data integration specialist. They can provide guidance and support to ensure successful integration.
How to obtain SAS Base Programmer certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, integrating SAS Base with other data systems and platforms is essential for organizations looking to optimize their data processes, improve efficiency, and enhance decision-making capabilities. By following best practices and carefully planning integration, organizations can unlock the full potential of SAS Base and maximize the value of their data assets. Start integrating SAS Base with other data systems and platforms today to take your data analysis to the next level.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's data-driven world, organizations rely on various data systems and platforms to store, manage, and analyze their data. One of the most popular tools for data analysis is SAS Base, a powerful software suite used by data analysts and data scientists worldwide. Integrating SAS Base with other data systems and platforms is crucial for organizations looking to streamline their data processes, increase efficiency, and make better-informed decisions. This article will explore the importance of integrating SAS Base with other data systems and platforms, the benefits it can bring, and some best practices for successful integration.
Why Integrate SAS Base with Other Data Systems and Platforms?
Integrating SAS Base with other data systems and platforms allows organizations to leverage the power of SAS Base while accessing data stored in different systems. This integration enables seamless data exchange, sharing, and analysis across various platforms, reducing silos and ensuring data consistency. By integrating SAS Base with other systems, organizations can also automate workflows, improve data accuracy, and enhance decision-making processes.
Benefits of Integration
-
Streamlined Data Processes: Integration of SAS Base with other data systems simplifies data access and processing, saving time and effort for data analysts.
-
Increased Efficiency: By automating data exchange and analysis, integration helps organizations work more efficiently and make quicker decisions.
-
Improved Data Quality: Integrating SAS Base with other systems ensures data consistency and accuracy, leading to better insights and outcomes.
Best Practices for Integrating SAS Base with Other Systems
Successful integration of SAS Base with other data systems and platforms requires careful planning and execution. Here are some best practices to consider:
1. Identify Integration Goals
Before starting the integration process, define clear integration goals and objectives. Understand what you aim to achieve through integration and how it will benefit your organization.
2. Assess Data Compatibility
Ensure compatibility between SAS Base and other data systems in terms of data formats, protocols, and security requirements. This will help prevent data loss or corruption during integration.
3. Design an Integration Strategy
Develop a comprehensive integration strategy that outlines the steps, tools, and resources needed for successful integration. Consider factors such as data mapping, transformation, and synchronization.
4. Test Integration
Before fully implementing the integration, conduct thorough testing to identify and address any potential issues or errors. Test data exchange, analysis, and reporting functionalities to ensure seamless operation.
5. Monitor and Maintain Integration
Once integration is complete, monitor its performance regularly to ensure data integrity and system stability. Implement regular maintenance and updates to keep the integration running smoothly.
6. Seek Expert Consultation
If you are unsure about how to integrate SAS Base with other systems, consider seeking expert consultation from a data integration specialist. They can provide guidance and support to ensure successful integration.
How to obtain SAS Base Programmer certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, integrating SAS Base with other data systems and platforms is essential for organizations looking to optimize their data processes, improve efficiency, and enhance decision-making capabilities. By following best practices and carefully planning integration, organizations can unlock the full potential of SAS Base and maximize the value of their data assets. Start integrating SAS Base with other data systems and platforms today to take your data analysis to the next level.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Digital Marketing Guide for Beginners
Are you new to the world of digital marketing and feeling overwhelmed by the plethora of information out there? Don't worry, we've got you covered! In this comprehensive guide, we will walk you through the basics of digital marketing, provide you with essential tips and strategies, and help you kickstart your journey towards mastering online marketing.
What is Digital Marketing?
Digital marketing encompasses all marketing efforts that use an electronic device or the internet. It involves leveraging various online channels such as social media, search engines, email, and websites to connect with current and prospective customers.
Digital Marketing Basics
-
Understanding your target audience and their needs is key to a successful digital marketing strategy.
-
Create a strong online presence through a professional website and active social media profiles.
-
Utilize SEO (Search Engine Optimization) to improve your website's visibility on search engines.
-
Email marketing can be a powerful tool for engaging with your audience and driving conversions.
Getting Started with Digital Marketing
If you are just starting out in the world of digital marketing, here are some beginner tips to help you navigate this exciting and ever-evolving field:
-
Educate Yourself: Take advantage of online resources, courses, and tutorials to build your knowledge and skills.
-
Set Clear Goals: Define what you want to achieve with your digital marketing efforts and create a plan to reach those goals.
-
Experiment and Learn: Don't be afraid to try new strategies and tactics. Test different approaches to see what works best for your business.
-
Stay Updated: The digital marketing landscape is constantly evolving. Stay informed about the latest trends and technologies to stay ahead of the competition.
Digital Marketing Strategies for Beginners
Here are some effective digital marketing strategies that beginners can implement to drive traffic and increase brand awareness:
-
Social Media Marketing: Engage with your audience on platforms like Facebook, Instagram, and Twitter.
-
Content Marketing: Create valuable and relevant content to attract and retain customers.
-
PPC Advertising: Use pay-per-click ads to target specific keywords and demographics.
-
Video Marketing: Leverage the power of video to showcase your products or services.
Beginner's Digital Marketing Course
If you are looking to deepen your knowledge and skills in digital marketing, consider enrolling in a beginner's course. These courses cover a wide range of topics, including SEO, social media marketing, email marketing, and more.
Beginner-Friendly Digital Marketing Tips
-
Focus on building a strong brand identity that resonates with your target audience.
-
Utilize analytics tools to track and measure the success of your campaigns.
-
Don't underestimate the power of word-of-mouth marketing. Encourage satisfied customers to spread the word about your business.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion,digital marketing can seem daunting at first, but with the right guidance and strategies, you can successfully promote your business online and reach a wider audience. Remember to stay curious, experiment, and continuously educate yourself to stay ahead in the ever-changing digital landscape.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you new to the world of digital marketing and feeling overwhelmed by the plethora of information out there? Don't worry, we've got you covered! In this comprehensive guide, we will walk you through the basics of digital marketing, provide you with essential tips and strategies, and help you kickstart your journey towards mastering online marketing.
What is Digital Marketing?
Digital marketing encompasses all marketing efforts that use an electronic device or the internet. It involves leveraging various online channels such as social media, search engines, email, and websites to connect with current and prospective customers.
Digital Marketing Basics
-
Understanding your target audience and their needs is key to a successful digital marketing strategy.
-
Create a strong online presence through a professional website and active social media profiles.
-
Utilize SEO (Search Engine Optimization) to improve your website's visibility on search engines.
-
Email marketing can be a powerful tool for engaging with your audience and driving conversions.
Getting Started with Digital Marketing
If you are just starting out in the world of digital marketing, here are some beginner tips to help you navigate this exciting and ever-evolving field:
-
Educate Yourself: Take advantage of online resources, courses, and tutorials to build your knowledge and skills.
-
Set Clear Goals: Define what you want to achieve with your digital marketing efforts and create a plan to reach those goals.
-
Experiment and Learn: Don't be afraid to try new strategies and tactics. Test different approaches to see what works best for your business.
-
Stay Updated: The digital marketing landscape is constantly evolving. Stay informed about the latest trends and technologies to stay ahead of the competition.
Digital Marketing Strategies for Beginners
Here are some effective digital marketing strategies that beginners can implement to drive traffic and increase brand awareness:
-
Social Media Marketing: Engage with your audience on platforms like Facebook, Instagram, and Twitter.
-
Content Marketing: Create valuable and relevant content to attract and retain customers.
-
PPC Advertising: Use pay-per-click ads to target specific keywords and demographics.
-
Video Marketing: Leverage the power of video to showcase your products or services.
Beginner's Digital Marketing Course
If you are looking to deepen your knowledge and skills in digital marketing, consider enrolling in a beginner's course. These courses cover a wide range of topics, including SEO, social media marketing, email marketing, and more.
Beginner-Friendly Digital Marketing Tips
-
Focus on building a strong brand identity that resonates with your target audience.
-
Utilize analytics tools to track and measure the success of your campaigns.
-
Don't underestimate the power of word-of-mouth marketing. Encourage satisfied customers to spread the word about your business.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion,digital marketing can seem daunting at first, but with the right guidance and strategies, you can successfully promote your business online and reach a wider audience. Remember to stay curious, experiment, and continuously educate yourself to stay ahead in the ever-changing digital landscape.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
ECBA in Digital Transformation & Agile Settings
In this article, we will explore the importance of the ECBA™ certification in digital transformation and agile settings, and how it can benefit business analysts in navigating the complexities of today's fast-paced and ever-changing business landscape.
Introduction to ECBA™ Certification
The ECBA™ (Entry Certificate in Business Analysis) certification is a valuable credential offered by the International Institute of Business Analysis (IIBA). It is designed for entry-level business analysts who are looking to enhance their skills and knowledge in the field of business analysis. The ECBA™ certification covers a wide range of topics, including requirements management, stakeholder engagement, data analysis, and decision-making.
Digital Transformation and Agile Methodologies
With the rapid advancements in technology and changing customer demands, organizations are increasingly turning towards digital transformation to stay competitive in the market. Agile methodologies, such as Scrum and Lean Six Sigma, have become essential tools for organizations looking to streamline their product development and project management processes.
How can ECBA™ Help in Digital Transformation?
-
Requirements Management: Business analysts with the ECBA™ certification are equipped with the skills to effectively gather and analyze requirements for digital transformation projects.
-
Stakeholder Engagement: ECBA™ certified professionals are trained in stakeholder engagement, ensuring that all key stakeholders are involved throughout the digital transformation process.
-
Process Improvement: The knowledge of business processes gained through ECBA™ certification can help business analysts identify areas for improvement and optimization in digital transformation projects.
The Role of Business Analysts in Agile Settings
In agile settings, business analysts play a crucial role in facilitating communication and collaboration between cross-functional teams. They are responsible for translating business requirements into actionable user stories, and working closely with agile teams to ensure project delivery aligns with the organization's business strategy.
How do ECBA™ Certified Professionals Contribute to Agile Teams?
-
Decision-Making: ECBA™ certified professionals are trained in making data-driven decisions, helping agile teams prioritize and focus on delivering value to the organization.
-
Change Management: Business analysts with the ECBA™ certification are well-versed in change management principles, assisting agile teams in smoothly navigating organizational change.
-
Collaboration: ECBA™ certified professionals excel in fostering collaboration among team members, ensuring that everyone is aligned towards a common goal in agile settings
How to obtain ECBA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the ECBA™ certification is a valuable asset for business analysts operating in digital transformation and agile settings. By equipping professionals with the knowledge and skills needed to navigate the complexities of modern business environments, the ECBA™ certification sets them up for success in delivering value to organizations through effective business analysis practices.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In this article, we will explore the importance of the ECBA™ certification in digital transformation and agile settings, and how it can benefit business analysts in navigating the complexities of today's fast-paced and ever-changing business landscape.
Introduction to ECBA™ Certification
The ECBA™ (Entry Certificate in Business Analysis) certification is a valuable credential offered by the International Institute of Business Analysis (IIBA). It is designed for entry-level business analysts who are looking to enhance their skills and knowledge in the field of business analysis. The ECBA™ certification covers a wide range of topics, including requirements management, stakeholder engagement, data analysis, and decision-making.
Digital Transformation and Agile Methodologies
With the rapid advancements in technology and changing customer demands, organizations are increasingly turning towards digital transformation to stay competitive in the market. Agile methodologies, such as Scrum and Lean Six Sigma, have become essential tools for organizations looking to streamline their product development and project management processes.
How can ECBA™ Help in Digital Transformation?
-
Requirements Management: Business analysts with the ECBA™ certification are equipped with the skills to effectively gather and analyze requirements for digital transformation projects.
-
Stakeholder Engagement: ECBA™ certified professionals are trained in stakeholder engagement, ensuring that all key stakeholders are involved throughout the digital transformation process.
-
Process Improvement: The knowledge of business processes gained through ECBA™ certification can help business analysts identify areas for improvement and optimization in digital transformation projects.
The Role of Business Analysts in Agile Settings
In agile settings, business analysts play a crucial role in facilitating communication and collaboration between cross-functional teams. They are responsible for translating business requirements into actionable user stories, and working closely with agile teams to ensure project delivery aligns with the organization's business strategy.
How do ECBA™ Certified Professionals Contribute to Agile Teams?
-
Decision-Making: ECBA™ certified professionals are trained in making data-driven decisions, helping agile teams prioritize and focus on delivering value to the organization.
-
Change Management: Business analysts with the ECBA™ certification are well-versed in change management principles, assisting agile teams in smoothly navigating organizational change.
-
Collaboration: ECBA™ certified professionals excel in fostering collaboration among team members, ensuring that everyone is aligned towards a common goal in agile settings
How to obtain ECBA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the ECBA™ certification is a valuable asset for business analysts operating in digital transformation and agile settings. By equipping professionals with the knowledge and skills needed to navigate the complexities of modern business environments, the ECBA™ certification sets them up for success in delivering value to organizations through effective business analysis practices.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Creating Efficient Workspaces with the 5S Methodology
Are you looking to optimize your workspace for maximum efficiency and productivity? Implementing the 5S methodology is a proven way to declutter, organize, and streamline your workspace. In this article, we will explore how you can use the 5S principles to transform your workplace into a well-organized and highly efficient environment.
What is the 5S Methodology?
The 5S methodology is a workplace organization system that originated in Japan. The 5S stands for Sort, Set in Order, Shine, Standardize, and Sustain. It is based on five simple principles that, when implemented correctly, can lead to a more productive and efficient work environment.
Sort
The first step in the 5S methodology is to sort through all the items in your workspace and eliminate anything that is unnecessary. This includes getting rid of clutter, unused equipment, and outdated documents. By reducing the number of items in your workspace, you can create a more organized and streamlined environment.
Set in Order
After sorting through your workspace, the next step is to set everything in its proper place. This involves creating designated storage areas for tools, supplies, and documents. By having a designated spot for everything, you can easily find what you need when you need it, leading to increased efficiency and productivity.
Shine
The shine step of the 5S methodology involves cleaning and maintaining your workspace on a regular basis. A clean and organized workspace not only looks better but also creates a more enjoyable and productive work environment. By implementing regular cleaning and maintenance routines, you can ensure that your workspace remains clutter-free and efficient.
Standardize
Standardizing your workspace involves creating consistent processes and procedures for maintaining organization and cleanliness. This includes developing standard operating procedures for tasks, creating visual cues for where items should be stored, and implementing regular audits to ensure compliance. By standardizing your processes, you can maintain an efficient and productive workspace over the long term.
Sustain
The final step in the 5S methodology is to sustain the improvements made in your workspace. This involves creating a culture of continuous improvement and maintaining the discipline to follow the 5S principles on a daily basis. By sustaining the changes made to your workspace, you can ensure that your organization remains efficient and productive in the long run.
Benefits of Implementing the 5S Methodology
Implementing the 5S methodology in your workspace can lead to a wide range of benefits, including:
-
Increased workplace efficiency
-
Improved productivity
-
Enhanced workplace safety
-
Better employee morale
-
Reduced waste and costs
-
Improved quality of work
By following the 5S principles and creating an organized and efficient workspace, you can create a more enjoyable and productive work environment for yourself and your employees.
Tools and Resources for Implementing the 5S Methodology
There are a variety of tools and resources available to help you implement the 5S methodology in your workspace. Some common tools include:
-
5S checklists
-
Visual management boards
-
Shadow boards
-
Lean management software
-
Kaizen events
By utilizing these tools and resources, you can streamline your workspace, reduce clutter, and increase productivity and efficiency.
How to obtain Quality management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, implementing the 5S methodology in your workspace can lead to significant improvements in efficiency, productivity, and overall workplace organization. By following the 5S principles of Sort, Set in Order, Shine, Standardize, and Sustain, you can create a well-organized and highly efficient work environment that promotes productivity and employee satisfaction. So why wait? Start implementing the 5S methodology in your workspace today and reap the benefits of a more efficient and productive workplace!
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to optimize your workspace for maximum efficiency and productivity? Implementing the 5S methodology is a proven way to declutter, organize, and streamline your workspace. In this article, we will explore how you can use the 5S principles to transform your workplace into a well-organized and highly efficient environment.
What is the 5S Methodology?
The 5S methodology is a workplace organization system that originated in Japan. The 5S stands for Sort, Set in Order, Shine, Standardize, and Sustain. It is based on five simple principles that, when implemented correctly, can lead to a more productive and efficient work environment.
Sort
The first step in the 5S methodology is to sort through all the items in your workspace and eliminate anything that is unnecessary. This includes getting rid of clutter, unused equipment, and outdated documents. By reducing the number of items in your workspace, you can create a more organized and streamlined environment.
Set in Order
After sorting through your workspace, the next step is to set everything in its proper place. This involves creating designated storage areas for tools, supplies, and documents. By having a designated spot for everything, you can easily find what you need when you need it, leading to increased efficiency and productivity.
Shine
The shine step of the 5S methodology involves cleaning and maintaining your workspace on a regular basis. A clean and organized workspace not only looks better but also creates a more enjoyable and productive work environment. By implementing regular cleaning and maintenance routines, you can ensure that your workspace remains clutter-free and efficient.
Standardize
Standardizing your workspace involves creating consistent processes and procedures for maintaining organization and cleanliness. This includes developing standard operating procedures for tasks, creating visual cues for where items should be stored, and implementing regular audits to ensure compliance. By standardizing your processes, you can maintain an efficient and productive workspace over the long term.
Sustain
The final step in the 5S methodology is to sustain the improvements made in your workspace. This involves creating a culture of continuous improvement and maintaining the discipline to follow the 5S principles on a daily basis. By sustaining the changes made to your workspace, you can ensure that your organization remains efficient and productive in the long run.
Benefits of Implementing the 5S Methodology
Implementing the 5S methodology in your workspace can lead to a wide range of benefits, including:
-
Increased workplace efficiency
-
Improved productivity
-
Enhanced workplace safety
-
Better employee morale
-
Reduced waste and costs
-
Improved quality of work
By following the 5S principles and creating an organized and efficient workspace, you can create a more enjoyable and productive work environment for yourself and your employees.
Tools and Resources for Implementing the 5S Methodology
There are a variety of tools and resources available to help you implement the 5S methodology in your workspace. Some common tools include:
-
5S checklists
-
Visual management boards
-
Shadow boards
-
Lean management software
-
Kaizen events
By utilizing these tools and resources, you can streamline your workspace, reduce clutter, and increase productivity and efficiency.
How to obtain Quality management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, implementing the 5S methodology in your workspace can lead to significant improvements in efficiency, productivity, and overall workplace organization. By following the 5S principles of Sort, Set in Order, Shine, Standardize, and Sustain, you can create a well-organized and highly efficient work environment that promotes productivity and employee satisfaction. So why wait? Start implementing the 5S methodology in your workspace today and reap the benefits of a more efficient and productive workplace!
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Mastering Statistical Process Control (SPC) with Minitab
Have you ever wondered how you can improve the quality of your manufacturing processes? Statistical Process Control (SPC) with Minitab is the key to achieving process optimization and ensuring high-quality products. In this article, we will delve into the world of SPC techniques, statistical analysis, and quality control using Minitab software.
What is Statistical Process Control (SPC)?
Statistical Process Control (SPC) is a method of quality control that uses statistical methods to monitor and control a process. SPC techniques involve analyzing data to understand the process variation, identifying trends, and making data-driven decisions for process improvement. By implementing SPC, organizations can achieve process optimization and ensure consistent quality in their products and services.
How can Minitab help with SPC?
Minitab is a powerful statistical software that is widely used for process monitoring and analysis. With Minitab, you can easily create control charts, perform statistical analysis, and conduct capability analysis to assess the performance of your processes. The software provides a user-friendly interface and a wide range of statistical tools that make it easier to implement SPC techniques and drive continuous improvement.
The Benefits of SPC with Minitab
-
Process Optimization: By using Minitab for SPC, organizations can identify process variations and make data-driven decisions to optimize their processes for better performance.
-
Quality Management: SPC with Minitab enables organizations to maintain high-quality standards in their products and services by monitoring process performance and ensuring consistency.
-
SPC Implementation: Minitab provides the necessary tools and resources for implementing SPC techniques effectively, leading to improved process stability and product quality.
How to Master SPC Techniques with Minitab
To master SPC techniques with Minitab, it is essential to undergo proper training and certification in statistical quality control. Organizations can invest in SPC training programs that focus on the fundamentals of SPC principles, process monitoring, and statistical process control tools. By mastering SPC techniques with Minitab, organizations can enhance their process optimization efforts and drive continuous improvement in their operations.
How to obtain Minitab certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Mastering Statistical Process Control (SPC) with Minitab is essential for organizations looking to achieve process optimization, quality management, and continuous improvement. By leveraging the power of SPC techniques and statistical analysis with Minitab software, organizations can ensure high-quality products and services, improve process performance, and drive business success.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Have you ever wondered how you can improve the quality of your manufacturing processes? Statistical Process Control (SPC) with Minitab is the key to achieving process optimization and ensuring high-quality products. In this article, we will delve into the world of SPC techniques, statistical analysis, and quality control using Minitab software.
What is Statistical Process Control (SPC)?
Statistical Process Control (SPC) is a method of quality control that uses statistical methods to monitor and control a process. SPC techniques involve analyzing data to understand the process variation, identifying trends, and making data-driven decisions for process improvement. By implementing SPC, organizations can achieve process optimization and ensure consistent quality in their products and services.
How can Minitab help with SPC?
Minitab is a powerful statistical software that is widely used for process monitoring and analysis. With Minitab, you can easily create control charts, perform statistical analysis, and conduct capability analysis to assess the performance of your processes. The software provides a user-friendly interface and a wide range of statistical tools that make it easier to implement SPC techniques and drive continuous improvement.
The Benefits of SPC with Minitab
-
Process Optimization: By using Minitab for SPC, organizations can identify process variations and make data-driven decisions to optimize their processes for better performance.
-
Quality Management: SPC with Minitab enables organizations to maintain high-quality standards in their products and services by monitoring process performance and ensuring consistency.
-
SPC Implementation: Minitab provides the necessary tools and resources for implementing SPC techniques effectively, leading to improved process stability and product quality.
How to Master SPC Techniques with Minitab
To master SPC techniques with Minitab, it is essential to undergo proper training and certification in statistical quality control. Organizations can invest in SPC training programs that focus on the fundamentals of SPC principles, process monitoring, and statistical process control tools. By mastering SPC techniques with Minitab, organizations can enhance their process optimization efforts and drive continuous improvement in their operations.
How to obtain Minitab certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Mastering Statistical Process Control (SPC) with Minitab is essential for organizations looking to achieve process optimization, quality management, and continuous improvement. By leveraging the power of SPC techniques and statistical analysis with Minitab software, organizations can ensure high-quality products and services, improve process performance, and drive business success.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
The Environmental Impact of RPA: Sustainability and Efficiency
In today's digital age, companies are constantly seeking ways to improve efficiency, reduce costs, and minimize their environmental impact. Robotic Process Automation (RPA) has emerged as a powerful tool that can help organizations achieve these goals. By automating repetitive tasks and workflows, RPA can streamline operations, increase productivity, and lower costs. But what is the environmental impact of RPA? How can organizations ensure that they are using this technology in a sustainable and responsible manner?
Environmental Impact of RPA:
Reduced Carbon Footprint: RPA can help reduce the carbon footprint of organizations by minimizing the need for manual intervention in repetitive processes. By automating tasks that would otherwise require human intervention, companies can lower their energy consumption and greenhouse gas emissions.
Waste Reduction: Automation tools can help companies minimize waste production by optimizing processes and reducing errors. This can result in less paper usage, lower energy consumption, and overall reduced waste generation.
Energy Efficiency: RPA can improve energy efficiency by optimizing processes and reducing the amount of energy required to complete tasks. By automating workflows, companies can lower their energy consumption and operate more sustainably.
Renewable Energy: Organizations can further enhance the environmental impact of RPA by powering their automation tools with renewable energy sources. By using clean energy to fuel their operations, companies can reduce their carbon footprint and contribute to a more sustainable future.
Sustainability Measures with RPA:
Environmental Responsibility: Companies using RPA have a responsibility to ensure that their automation initiatives align with environmental sustainability goals. By incorporating green initiatives into their RPA strategies, organizations can demonstrate their commitment to environmental responsibility.
Sustainable Development: RPA can play a key role in driving sustainable development by enabling organizations to operate more efficiently and reduce their environmental impact. By implementing sustainable practices, companies can contribute to a more sustainable future.
Sustainable Solutions: By leveraging RPA technologies, companies can implement sustainable solutions that help them achieve their environmental goals. From waste reduction to energy efficiency, RPA can enable organizations to adopt sustainable business practices and drive positive change.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the environmental impact of RPA is significant and can help organizations improve sustainability and efficiency. By reducing carbon footprint, minimizing waste, and increasing energy efficiency, companies can use automation tools to drive environmental responsibility and sustainable practices. As the world continues to grapple with climate change and environmental awareness, RPA offers a powerful solution for organizations looking to reduce their impact on the planet. By embracing sustainable innovation and eco-friendly practices, companies can harness the power of RPA to create a more sustainable future for all.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's digital age, companies are constantly seeking ways to improve efficiency, reduce costs, and minimize their environmental impact. Robotic Process Automation (RPA) has emerged as a powerful tool that can help organizations achieve these goals. By automating repetitive tasks and workflows, RPA can streamline operations, increase productivity, and lower costs. But what is the environmental impact of RPA? How can organizations ensure that they are using this technology in a sustainable and responsible manner?
Environmental Impact of RPA:
Reduced Carbon Footprint: RPA can help reduce the carbon footprint of organizations by minimizing the need for manual intervention in repetitive processes. By automating tasks that would otherwise require human intervention, companies can lower their energy consumption and greenhouse gas emissions.
Waste Reduction: Automation tools can help companies minimize waste production by optimizing processes and reducing errors. This can result in less paper usage, lower energy consumption, and overall reduced waste generation.
Energy Efficiency: RPA can improve energy efficiency by optimizing processes and reducing the amount of energy required to complete tasks. By automating workflows, companies can lower their energy consumption and operate more sustainably.
Renewable Energy: Organizations can further enhance the environmental impact of RPA by powering their automation tools with renewable energy sources. By using clean energy to fuel their operations, companies can reduce their carbon footprint and contribute to a more sustainable future.
Sustainability Measures with RPA:
Environmental Responsibility: Companies using RPA have a responsibility to ensure that their automation initiatives align with environmental sustainability goals. By incorporating green initiatives into their RPA strategies, organizations can demonstrate their commitment to environmental responsibility.
Sustainable Development: RPA can play a key role in driving sustainable development by enabling organizations to operate more efficiently and reduce their environmental impact. By implementing sustainable practices, companies can contribute to a more sustainable future.
Sustainable Solutions: By leveraging RPA technologies, companies can implement sustainable solutions that help them achieve their environmental goals. From waste reduction to energy efficiency, RPA can enable organizations to adopt sustainable business practices and drive positive change.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the environmental impact of RPA is significant and can help organizations improve sustainability and efficiency. By reducing carbon footprint, minimizing waste, and increasing energy efficiency, companies can use automation tools to drive environmental responsibility and sustainable practices. As the world continues to grapple with climate change and environmental awareness, RPA offers a powerful solution for organizations looking to reduce their impact on the planet. By embracing sustainable innovation and eco-friendly practices, companies can harness the power of RPA to create a more sustainable future for all.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Leveraging Business Analysis Tools for a Competitive Advantage
In today's rapidly evolving business landscape, organizations are constantly seeking ways to gain a competitive edge over their rivals. One of the most effective strategies for achieving this is by leveraging business analysis tools to gain valuable insights and make informed decisions. By utilizing a combination of business analysis techniques, strategies, and tools, companies can enhance their strategic planning, optimize their processes, and ultimately drive business performance.
The Benefits of Business Analysis
Business analysis involves the process of identifying business needs, evaluating options, and delivering value to stakeholders. By conducting thorough business analysis, organizations can uncover opportunities for improvement, identify potential risks, and make data-driven decisions. Some of the key benefits of leveraging business analysis tools include:
-
Improved decision-making: Business analysis tools provide organizations with the information they need to make informed decisions that align with their strategic objectives.
-
Enhanced strategic planning: By conducting competitor analysis, SWOT analysis, PESTLE analysis, and other strategic analysis techniques, companies can better understand their position in the market and develop effective strategies to outperform their competitors.
-
Optimized processes: Business analysis tools help organizations identify inefficiencies in their processes and implement improvements that drive operational excellence.
-
Better business performance: With the help of data analysis, market analysis, and trend analysis, organizations can monitor their performance, identify areas for growth, and make strategic adjustments to achieve their goals.
Leveraging Business Analysis Tools for Success
When it comes to leveraging business analysis tools for a competitive advantage, there are several key strategies that organizations can employ. These include:
-
Data Visualization: By using data visualization tools, organizations can transform complex data sets into visually appealing and easy-to-understand graphics. This enables stakeholders to quickly interpret the data and make informed decisions based on the insights gained.
-
Market Research: Conducting thorough market research is essential for understanding consumer preferences, market trends, and competitive landscapes. By leveraging market analysis tools, organizations can gather relevant data and gain a competitive advantage in their industry.
-
Cost Analysis: Analyzing costs is crucial for optimizing business operations and maximizing profitability. By using cost analysis tools, organizations can identify cost-saving opportunities, streamline processes, and improve overall financial performance.
-
Risk Assessment: Identifying and mitigating risks is essential for minimizing potential threats to the business. By leveraging risk assessment tools, organizations can assess potential risks, develop risk mitigation strategies, and ensure business continuity.
-
Financial Analysis: Analyzing financial data is key to understanding the financial health of the organization. By using financial analysis tools, organizations can track key performance indicators, analyze financial statements, and make data-driven decisions to drive business success.
How to obtain Business Analysis certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, leveraging business analysis tools is a powerful strategy for gaining a competitive advantage in today's business environment. By implementing the right combination of business analysis techniques, organizations can enhance their strategic planning, optimize processes, and drive business performance. From competitor analysis and SWOT analysis to data visualization and market research, there are a wide variety of tools available to help organizations achieve their business goals. By embracing business analysis and making it a core part of their decision-making process, organizations can position themselves for long-term success in an increasingly competitive marketplace.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's rapidly evolving business landscape, organizations are constantly seeking ways to gain a competitive edge over their rivals. One of the most effective strategies for achieving this is by leveraging business analysis tools to gain valuable insights and make informed decisions. By utilizing a combination of business analysis techniques, strategies, and tools, companies can enhance their strategic planning, optimize their processes, and ultimately drive business performance.
The Benefits of Business Analysis
Business analysis involves the process of identifying business needs, evaluating options, and delivering value to stakeholders. By conducting thorough business analysis, organizations can uncover opportunities for improvement, identify potential risks, and make data-driven decisions. Some of the key benefits of leveraging business analysis tools include:
-
Improved decision-making: Business analysis tools provide organizations with the information they need to make informed decisions that align with their strategic objectives.
-
Enhanced strategic planning: By conducting competitor analysis, SWOT analysis, PESTLE analysis, and other strategic analysis techniques, companies can better understand their position in the market and develop effective strategies to outperform their competitors.
-
Optimized processes: Business analysis tools help organizations identify inefficiencies in their processes and implement improvements that drive operational excellence.
-
Better business performance: With the help of data analysis, market analysis, and trend analysis, organizations can monitor their performance, identify areas for growth, and make strategic adjustments to achieve their goals.
Leveraging Business Analysis Tools for Success
When it comes to leveraging business analysis tools for a competitive advantage, there are several key strategies that organizations can employ. These include:
-
Data Visualization: By using data visualization tools, organizations can transform complex data sets into visually appealing and easy-to-understand graphics. This enables stakeholders to quickly interpret the data and make informed decisions based on the insights gained.
-
Market Research: Conducting thorough market research is essential for understanding consumer preferences, market trends, and competitive landscapes. By leveraging market analysis tools, organizations can gather relevant data and gain a competitive advantage in their industry.
-
Cost Analysis: Analyzing costs is crucial for optimizing business operations and maximizing profitability. By using cost analysis tools, organizations can identify cost-saving opportunities, streamline processes, and improve overall financial performance.
-
Risk Assessment: Identifying and mitigating risks is essential for minimizing potential threats to the business. By leveraging risk assessment tools, organizations can assess potential risks, develop risk mitigation strategies, and ensure business continuity.
-
Financial Analysis: Analyzing financial data is key to understanding the financial health of the organization. By using financial analysis tools, organizations can track key performance indicators, analyze financial statements, and make data-driven decisions to drive business success.
How to obtain Business Analysis certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, leveraging business analysis tools is a powerful strategy for gaining a competitive advantage in today's business environment. By implementing the right combination of business analysis techniques, organizations can enhance their strategic planning, optimize processes, and drive business performance. From competitor analysis and SWOT analysis to data visualization and market research, there are a wide variety of tools available to help organizations achieve their business goals. By embracing business analysis and making it a core part of their decision-making process, organizations can position themselves for long-term success in an increasingly competitive marketplace.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Habits of Highly Effective DevOps Professionals
In the fast-paced world of software development and system administration, DevOps plays a crucial role in ensuring efficiency, reliability, and innovation. Highly effective DevOps professionals possess a unique set of habits that enable them to thrive in this dynamic environment. Let's explore some of the key habits that set them apart from the rest.
The Importance of Automation
One of the fundamental habits of highly effective DevOps professionals is a strong emphasis on automation. By automating repetitive tasks and processes, they are able to save time, reduce errors, and increase productivity. Automation also allows them to focus on more important tasks that require human creativity and problem-solving skills.
Embracing Continuous Integration and Deployment
Effective DevOps teams prioritize continuous integration and deployment to ensure that code changes are quickly and seamlessly integrated into the production environment. This practice not only accelerates the development cycle but also helps to identify and fix issues early on, leading to a more stable and reliable software release.
Collaboration and Teamwork
DevOps is all about breaking down silos and fostering collaboration between development, operations, and other relevant teams. Highly effective DevOps professionals excel at working together towards a common goal, sharing knowledge and expertise, and leveraging each other's strengths to deliver exceptional results.
Clear Communication and Feedback
Effective communication is essential for successful DevOps practices. Highly effective professionals are diligent in sharing information, providing feedback, and actively listening to their team members. Clear and effective communication helps to avoid misunderstandings, resolve conflicts, and keep everyone aligned towards the common objective.
Continuous Improvement
DevOps is a journey of continuous improvement. Highly effective professionals are always looking for ways to enhance processes, tools, and workflows. They are open to feedback, embrace change, and strive to optimize every aspect of their work to deliver better results with each iteration.
Following Best Practices
Highly effective DevOps professionals adhere to industry best practices and standards. By following established guidelines and principles, they ensure consistency, stability, and security in their environments. This commitment to best practices also demonstrates their dedication to quality and excellence in their work.
Embracing Innovation
Innovation is at the core of DevOps. Highly effective professionals are not afraid to challenge the status quo, experiment with new ideas, and push the boundaries of what is possible. By embracing innovation, they drive progress, spark creativity, and stay ahead of the curve in a rapidly evolving industry.
Effective Problem-Solving
DevOps professionals encounter challenges and obstacles on a daily basis. Highly effective professionals excel at problem-solving, approaching issues with a systematic and analytical mindset. They are proactive in identifying root causes, developing solutions, and implementing fixes to ensure smooth operations.
Scalability and Agility
Highly effective DevOps professionals design systems and workflows that are scalable and agile. They anticipate growth, plan for flexibility, and build resilience into their infrastructure. This enables them to adapt to changing requirements, handle increased workload, and maintain high performance levels under varying conditions.
Cultivating a Culture of Learning
Continuous learning is a hallmark of highly effective DevOps professionals. They are committed to expanding their knowledge, acquiring new skills, and staying updated on the latest technologies and trends. By fostering a culture of learning, they remain relevant, adaptable, and competitive in a dynamic and fast-evolving industry.
Perseverance and Efficiency
DevOps is a demanding field that requires perseverance and efficiency. Highly effective professionals are disciplined, focused, and persistent in their pursuit of goals. They prioritize tasks, manage time effectively, and deliver results with speed and accuracy.
Leveraging the Right Tools and Workflows
Highly effective DevOps professionals understand the importance of using the right tools and workflows to streamline processes and maximize productivity. They are well-versed in a variety of tools and technologies, select the most suitable ones for each task, and tailor workflows to suit specific requirements.
How to obtain Devops certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the habits of highly effective DevOps professionals encompass a wide range of skills, practices, and mindsets that enable them to excel in a challenging and dynamic industry. By embracing automation, continuous integration, collaboration, communication, feedback, improvement, best practices, innovation, problem-solving, scalability, agility, resilience, monitoring, optimization, culture, learning, perseverance, efficiency, tools, workflows, software development, system administration, cloud computing, security, and performance, they are able to drive innovation, deliver quality results, and stay ahead of the curve. By cultivating these habits, aspiring DevOps professionals can set themselves on the path to success in this exciting and rewarding field.
Read More
In the fast-paced world of software development and system administration, DevOps plays a crucial role in ensuring efficiency, reliability, and innovation. Highly effective DevOps professionals possess a unique set of habits that enable them to thrive in this dynamic environment. Let's explore some of the key habits that set them apart from the rest.
The Importance of Automation
One of the fundamental habits of highly effective DevOps professionals is a strong emphasis on automation. By automating repetitive tasks and processes, they are able to save time, reduce errors, and increase productivity. Automation also allows them to focus on more important tasks that require human creativity and problem-solving skills.
Embracing Continuous Integration and Deployment
Effective DevOps teams prioritize continuous integration and deployment to ensure that code changes are quickly and seamlessly integrated into the production environment. This practice not only accelerates the development cycle but also helps to identify and fix issues early on, leading to a more stable and reliable software release.
Collaboration and Teamwork
DevOps is all about breaking down silos and fostering collaboration between development, operations, and other relevant teams. Highly effective DevOps professionals excel at working together towards a common goal, sharing knowledge and expertise, and leveraging each other's strengths to deliver exceptional results.
Clear Communication and Feedback
Effective communication is essential for successful DevOps practices. Highly effective professionals are diligent in sharing information, providing feedback, and actively listening to their team members. Clear and effective communication helps to avoid misunderstandings, resolve conflicts, and keep everyone aligned towards the common objective.
Continuous Improvement
DevOps is a journey of continuous improvement. Highly effective professionals are always looking for ways to enhance processes, tools, and workflows. They are open to feedback, embrace change, and strive to optimize every aspect of their work to deliver better results with each iteration.
Following Best Practices
Highly effective DevOps professionals adhere to industry best practices and standards. By following established guidelines and principles, they ensure consistency, stability, and security in their environments. This commitment to best practices also demonstrates their dedication to quality and excellence in their work.
Embracing Innovation
Innovation is at the core of DevOps. Highly effective professionals are not afraid to challenge the status quo, experiment with new ideas, and push the boundaries of what is possible. By embracing innovation, they drive progress, spark creativity, and stay ahead of the curve in a rapidly evolving industry.
Effective Problem-Solving
DevOps professionals encounter challenges and obstacles on a daily basis. Highly effective professionals excel at problem-solving, approaching issues with a systematic and analytical mindset. They are proactive in identifying root causes, developing solutions, and implementing fixes to ensure smooth operations.
Scalability and Agility
Highly effective DevOps professionals design systems and workflows that are scalable and agile. They anticipate growth, plan for flexibility, and build resilience into their infrastructure. This enables them to adapt to changing requirements, handle increased workload, and maintain high performance levels under varying conditions.
Cultivating a Culture of Learning
Continuous learning is a hallmark of highly effective DevOps professionals. They are committed to expanding their knowledge, acquiring new skills, and staying updated on the latest technologies and trends. By fostering a culture of learning, they remain relevant, adaptable, and competitive in a dynamic and fast-evolving industry.
Perseverance and Efficiency
DevOps is a demanding field that requires perseverance and efficiency. Highly effective professionals are disciplined, focused, and persistent in their pursuit of goals. They prioritize tasks, manage time effectively, and deliver results with speed and accuracy.
Leveraging the Right Tools and Workflows
Highly effective DevOps professionals understand the importance of using the right tools and workflows to streamline processes and maximize productivity. They are well-versed in a variety of tools and technologies, select the most suitable ones for each task, and tailor workflows to suit specific requirements.
How to obtain Devops certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the habits of highly effective DevOps professionals encompass a wide range of skills, practices, and mindsets that enable them to excel in a challenging and dynamic industry. By embracing automation, continuous integration, collaboration, communication, feedback, improvement, best practices, innovation, problem-solving, scalability, agility, resilience, monitoring, optimization, culture, learning, perseverance, efficiency, tools, workflows, software development, system administration, cloud computing, security, and performance, they are able to drive innovation, deliver quality results, and stay ahead of the curve. By cultivating these habits, aspiring DevOps professionals can set themselves on the path to success in this exciting and rewarding field.
Leading IT Service Management Tools of 2024
Are you looking for the best IT service management tools that will help your business stay ahead in 2024? Look no further! In this article, we will explore the leading IT service management tools that are shaping the future of IT solutions and services.
Introduction to IT Service Management Tools
IT service management tools are crucial for businesses to effectively manage their IT infrastructure, processes, and operations. These tools help streamline IT services, enhance operational efficiency, and improve overall productivity. With the rapid advancement in technology, it is essential for businesses to leverage the latest IT service management tools to stay competitive in the market.
Best IT Tools for 2024
-
ServiceNow: ServiceNow is a cloud-based IT service management software that offers a comprehensive suite of IT solutions. It provides advanced IT services including IT asset management, IT operations management, and IT governance. With ServiceNow, businesses can enhance their IT service delivery and improve customer satisfaction.
-
BMC Helix: BMC Helix is a top IT management tool that offers innovative IT solutions for businesses. It provides cutting-edge IT services such as predictive analytics, IT automation, and AI-driven IT operations. BMC Helix helps businesses achieve digital transformation and drive operational excellence.
-
Zendesk: Zendesk is a leading IT service desk software that helps businesses streamline their IT support services. It offers remote IT tools, IT asset management, and scalable IT solutions. Zendesk is known for its user-friendly interface and exceptional customer support.
-
Splunk: Splunk is a powerful IT monitoring tool that provides real-time visibility into IT infrastructure and operations. It offers advanced features such as artificial intelligence in IT, predictive analytics, and IT automation. Splunk helps businesses proactively manage IT incidents and ensure optimal performance.
Emerging IT Tools for the Future
As we look towards the future of IT service management, there are several emerging IT tools that are set to revolutionize the industry. These tools focus on enhancing IT service delivery, improving IT processes, and driving digital transformation. Some of the key emerging IT tools include:
-
AI-powered IT automation tools
-
Cloud-based IT infrastructure solutions
-
Predictive analytics tools for IT operations
-
Cybersecurity tools for advanced threat detection
-
IT governance tools for compliance management
With these innovative IT solutions, businesses can stay ahead of the curve and adapt to the ever-changing IT landscape. By leveraging the latest IT tools, businesses can improve operational efficiency, enhance customer satisfaction, and drive business growth.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the leading IT service management tools of 2024 offer a wide range of advanced features and capabilities that can help businesses thrive in the digital age. From cloud-based IT tools to AI-driven solutions, these tools are shaping the future of IT service delivery. By investing in the right IT tools, businesses can stay competitive, drive innovation, and achieve success in a rapidly evolving IT environment. Embrace the future of IT service management with the best tools available in 2024.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking for the best IT service management tools that will help your business stay ahead in 2024? Look no further! In this article, we will explore the leading IT service management tools that are shaping the future of IT solutions and services.
Introduction to IT Service Management Tools
IT service management tools are crucial for businesses to effectively manage their IT infrastructure, processes, and operations. These tools help streamline IT services, enhance operational efficiency, and improve overall productivity. With the rapid advancement in technology, it is essential for businesses to leverage the latest IT service management tools to stay competitive in the market.
Best IT Tools for 2024
-
ServiceNow: ServiceNow is a cloud-based IT service management software that offers a comprehensive suite of IT solutions. It provides advanced IT services including IT asset management, IT operations management, and IT governance. With ServiceNow, businesses can enhance their IT service delivery and improve customer satisfaction.
-
BMC Helix: BMC Helix is a top IT management tool that offers innovative IT solutions for businesses. It provides cutting-edge IT services such as predictive analytics, IT automation, and AI-driven IT operations. BMC Helix helps businesses achieve digital transformation and drive operational excellence.
-
Zendesk: Zendesk is a leading IT service desk software that helps businesses streamline their IT support services. It offers remote IT tools, IT asset management, and scalable IT solutions. Zendesk is known for its user-friendly interface and exceptional customer support.
-
Splunk: Splunk is a powerful IT monitoring tool that provides real-time visibility into IT infrastructure and operations. It offers advanced features such as artificial intelligence in IT, predictive analytics, and IT automation. Splunk helps businesses proactively manage IT incidents and ensure optimal performance.
Emerging IT Tools for the Future
As we look towards the future of IT service management, there are several emerging IT tools that are set to revolutionize the industry. These tools focus on enhancing IT service delivery, improving IT processes, and driving digital transformation. Some of the key emerging IT tools include:
-
AI-powered IT automation tools
-
Cloud-based IT infrastructure solutions
-
Predictive analytics tools for IT operations
-
Cybersecurity tools for advanced threat detection
-
IT governance tools for compliance management
With these innovative IT solutions, businesses can stay ahead of the curve and adapt to the ever-changing IT landscape. By leveraging the latest IT tools, businesses can improve operational efficiency, enhance customer satisfaction, and drive business growth.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the leading IT service management tools of 2024 offer a wide range of advanced features and capabilities that can help businesses thrive in the digital age. From cloud-based IT tools to AI-driven solutions, these tools are shaping the future of IT service delivery. By investing in the right IT tools, businesses can stay competitive, drive innovation, and achieve success in a rapidly evolving IT environment. Embrace the future of IT service management with the best tools available in 2024.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
PgMP Networking and Growth Opportunities
In today's competitive business environment, professionals in project management are constantly looking for ways to enhance their skills, advance their careers, and stay ahead of the curve. One powerful tool that can help individuals achieve these goals is the Program Management Professional (PgMP) certification. By earning this prestigious certification, professionals not only demonstrate their expertise in program management but also open up a world of networking and growth opportunities.
What is PgMP?
The PgMP certification, offered by the Project Management Institute (PMI), is designed for experienced program managers who want to demonstrate their proficiency in managing multiple, related projects and achieving strategic business goals. This certification is recognized globally and is highly regarded in the industry for showcasing an individual's ability to lead and direct program teams.
With PgMP certification, professionals gain a deep understanding of program governance, stakeholder management, team leadership, change management, and continuous improvement. These skills are vital for ensuring the successful delivery of complex programs and driving organizational growth and success.
How does PgMP Certification Lead to Professional Networking?
One of the key benefits of earning a PgMP certification is the opportunity to expand professional networking. By being part of a select group of certified program managers, individuals gain access to exclusive networking events, industry connections, and career opportunities. These networking opportunities can lead to collaborations, partnerships, and mentorships that can accelerate career growth and open doors to new challenges and experiences.
How does PgMP Certification Create Growth Opportunities?
Earning a PgMP certification not only enhances an individual's skills and knowledge but also demonstrates a commitment to professional development and excellence. This commitment is highly valued by organizations looking for leaders who can drive strategic planning, execute business strategies, and deliver successful outcomes. With PgMP certification, professionals position themselves for career advancement, executive leadership roles, and opportunities in project portfolio management and organizational development.
Professional Growth with PgMP Certification
Professionals who hold a PgMP certification not only demonstrate their expertise in program management but also showcase their leadership abilities, strategic thinking, and commitment to continuous improvement. These qualities are highly sought after by organizations looking to drive project success, foster innovation, and achieve sustainable growth.
By investing in PgMP certification, professionals invest in their future success and create opportunities for personal and professional growth. Whether individuals are looking to advance their careers, expand their skill sets, or make a difference in their organizations, PgMP certification is a powerful tool that can help them achieve their goals.
How to obtain PgMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, PgMP certification is not just about gaining a credential; it is about unlocking a world of networking and growth opportunities that can lead to career advancement, success, and fulfillment. By earning this prestigious certification, professionals demonstrate their expertise, leadership, and commitment to excellence, setting themselves apart as leaders in the field of program management. With PgMP certification, the possibilities are endless, and the potential for growth and success is limitless.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's competitive business environment, professionals in project management are constantly looking for ways to enhance their skills, advance their careers, and stay ahead of the curve. One powerful tool that can help individuals achieve these goals is the Program Management Professional (PgMP) certification. By earning this prestigious certification, professionals not only demonstrate their expertise in program management but also open up a world of networking and growth opportunities.
What is PgMP?
The PgMP certification, offered by the Project Management Institute (PMI), is designed for experienced program managers who want to demonstrate their proficiency in managing multiple, related projects and achieving strategic business goals. This certification is recognized globally and is highly regarded in the industry for showcasing an individual's ability to lead and direct program teams.
With PgMP certification, professionals gain a deep understanding of program governance, stakeholder management, team leadership, change management, and continuous improvement. These skills are vital for ensuring the successful delivery of complex programs and driving organizational growth and success.
How does PgMP Certification Lead to Professional Networking?
One of the key benefits of earning a PgMP certification is the opportunity to expand professional networking. By being part of a select group of certified program managers, individuals gain access to exclusive networking events, industry connections, and career opportunities. These networking opportunities can lead to collaborations, partnerships, and mentorships that can accelerate career growth and open doors to new challenges and experiences.
How does PgMP Certification Create Growth Opportunities?
Earning a PgMP certification not only enhances an individual's skills and knowledge but also demonstrates a commitment to professional development and excellence. This commitment is highly valued by organizations looking for leaders who can drive strategic planning, execute business strategies, and deliver successful outcomes. With PgMP certification, professionals position themselves for career advancement, executive leadership roles, and opportunities in project portfolio management and organizational development.
Professional Growth with PgMP Certification
Professionals who hold a PgMP certification not only demonstrate their expertise in program management but also showcase their leadership abilities, strategic thinking, and commitment to continuous improvement. These qualities are highly sought after by organizations looking to drive project success, foster innovation, and achieve sustainable growth.
By investing in PgMP certification, professionals invest in their future success and create opportunities for personal and professional growth. Whether individuals are looking to advance their careers, expand their skill sets, or make a difference in their organizations, PgMP certification is a powerful tool that can help them achieve their goals.
How to obtain PgMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, PgMP certification is not just about gaining a credential; it is about unlocking a world of networking and growth opportunities that can lead to career advancement, success, and fulfillment. By earning this prestigious certification, professionals demonstrate their expertise, leadership, and commitment to excellence, setting themselves apart as leaders in the field of program management. With PgMP certification, the possibilities are endless, and the potential for growth and success is limitless.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Explaining Apache Spark: Spark Cluster Architecture
Do you want to dive deep into the world of Apache Spark and understand how it works within a distributed computing environment? In this article, we will break down the intricate details of Apache Spark, focusing on its cluster architecture, components, and processing capabilities. Let's explore the inner workings of this powerful data processing framework and how it enables real-time analytics, scalable processing, and efficient data engineering.
What is Apache Spark and Why is it Important?
Apache Spark is a popular open-source framework for big data analytics that provides in-memory computing capabilities for lightning-fast data processing. It is a cluster computing system that offers high-level APIs in languages like Java, Scala, Python, and R, making it accessible to a wide range of users. Spark is known for its fault tolerance, parallel processing, and ability to handle large-scale data processing tasks with ease.
Spark Cluster Architecture Overview
At the heart of Apache Spark is its cluster architecture, which consists of a Master node and multiple Worker nodes. The Master node is responsible for managing the overall execution of Spark applications, while the Worker nodes perform the actual data processing tasks. This master-slave architecture allows Spark to distribute computing tasks across multiple nodes in a cluster, enabling efficient parallel processing of data.
Spark Components
Spark Core: This is the foundation of Apache Spark and provides basic functionality for distributed data processing. It includes the resilient distributed dataset (RDD) abstraction, which allows data to be stored in memory and processed in parallel.
Spark SQL: This module enables Spark to perform SQL queries on structured data, making it easier for users to work with relational data sources.
Spark Streaming: With this component, Spark can process real-time data streams from sources like Kafka, Flume, and Twitter in mini-batches.
Spark MLlib: This library provides machine learning algorithms for data analysis tasks, allowing users to build and train predictive models.
Spark GraphX: This component enables graph processing capabilities, making it easy to analyze and visualize graph data.
Spark Data Processing and Transformation
Apache Spark excels at processing and transforming data through its powerful set of APIs and libraries. It can handle complex data pipelines, perform data transformations, and execute machine learning algorithms in a scalable and efficient manner. By leveraging in-memory computing and distributed systems, Spark can process massive amounts of data quickly and accurately.
Are you intrigued by the capabilities of Apache Spark when it comes to data processing and analytics? Let's take a closer look at how Spark job scheduling works and how data is transformed within the Spark ecosystem.
Spark Job Scheduler and Executors
Spark uses a sophisticated job scheduler to allocate resources and manage job execution within a cluster. The scheduler assigns tasks to individual executors, which are responsible for processing data on worker nodes. By efficiently managing resources and tasks, Spark ensures optimal performance and resource utilization.
Spark RDDs and Data Structures
RDDs (Resilient Distributed Datasets) are at the core of Spark's data processing capabilities. These data structures allow Spark to store data in memory across multiple nodes in a cluster, enabling fast and fault-tolerant data processing. By using transformations and actions on RDDs, users can manipulate and analyze data in a distributed and parallel manner.
Spark Cluster Setup and Configuration
Setting up a Spark cluster involves configuring the Master and Worker nodes, installing the necessary dependencies, and launching the Spark application. By following the proper setup procedures, users can create a robust and efficient Spark cluster that meets their data processing needs.
How to obtain Data Science and Business Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Apache Spark's cluster architecture, components, and data processing capabilities make it a powerful tool for handling big data analytics and real-time processing tasks. By understanding how Spark works within a distributed computing environment, users can leverage its capabilities to perform complex data transformations, build machine learning models, and drive actionable insights from their data.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Do you want to dive deep into the world of Apache Spark and understand how it works within a distributed computing environment? In this article, we will break down the intricate details of Apache Spark, focusing on its cluster architecture, components, and processing capabilities. Let's explore the inner workings of this powerful data processing framework and how it enables real-time analytics, scalable processing, and efficient data engineering.
What is Apache Spark and Why is it Important?
Apache Spark is a popular open-source framework for big data analytics that provides in-memory computing capabilities for lightning-fast data processing. It is a cluster computing system that offers high-level APIs in languages like Java, Scala, Python, and R, making it accessible to a wide range of users. Spark is known for its fault tolerance, parallel processing, and ability to handle large-scale data processing tasks with ease.
Spark Cluster Architecture Overview
At the heart of Apache Spark is its cluster architecture, which consists of a Master node and multiple Worker nodes. The Master node is responsible for managing the overall execution of Spark applications, while the Worker nodes perform the actual data processing tasks. This master-slave architecture allows Spark to distribute computing tasks across multiple nodes in a cluster, enabling efficient parallel processing of data.
Spark Components
Spark Core: This is the foundation of Apache Spark and provides basic functionality for distributed data processing. It includes the resilient distributed dataset (RDD) abstraction, which allows data to be stored in memory and processed in parallel.
Spark SQL: This module enables Spark to perform SQL queries on structured data, making it easier for users to work with relational data sources.
Spark Streaming: With this component, Spark can process real-time data streams from sources like Kafka, Flume, and Twitter in mini-batches.
Spark MLlib: This library provides machine learning algorithms for data analysis tasks, allowing users to build and train predictive models.
Spark GraphX: This component enables graph processing capabilities, making it easy to analyze and visualize graph data.
Spark Data Processing and Transformation
Apache Spark excels at processing and transforming data through its powerful set of APIs and libraries. It can handle complex data pipelines, perform data transformations, and execute machine learning algorithms in a scalable and efficient manner. By leveraging in-memory computing and distributed systems, Spark can process massive amounts of data quickly and accurately.
Are you intrigued by the capabilities of Apache Spark when it comes to data processing and analytics? Let's take a closer look at how Spark job scheduling works and how data is transformed within the Spark ecosystem.
Spark Job Scheduler and Executors
Spark uses a sophisticated job scheduler to allocate resources and manage job execution within a cluster. The scheduler assigns tasks to individual executors, which are responsible for processing data on worker nodes. By efficiently managing resources and tasks, Spark ensures optimal performance and resource utilization.
Spark RDDs and Data Structures
RDDs (Resilient Distributed Datasets) are at the core of Spark's data processing capabilities. These data structures allow Spark to store data in memory across multiple nodes in a cluster, enabling fast and fault-tolerant data processing. By using transformations and actions on RDDs, users can manipulate and analyze data in a distributed and parallel manner.
Spark Cluster Setup and Configuration
Setting up a Spark cluster involves configuring the Master and Worker nodes, installing the necessary dependencies, and launching the Spark application. By following the proper setup procedures, users can create a robust and efficient Spark cluster that meets their data processing needs.
How to obtain Data Science and Business Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Apache Spark's cluster architecture, components, and data processing capabilities make it a powerful tool for handling big data analytics and real-time processing tasks. By understanding how Spark works within a distributed computing environment, users can leverage its capabilities to perform complex data transformations, build machine learning models, and drive actionable insights from their data.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Integrating IoT Solutions with Google Cloud
Are you looking to enhance your business operations with cutting-edge IoT technology? Look no further than integrating IoT solutions with Google Cloud! In this article, we will explore the benefits of integrating IoT solutions with Google Cloud, how it can revolutionize your business, and the key factors to consider when implementing this innovative technology.
What is IoT and Why is it Important?
IoT, or Internet of Things, refers to the interconnection of devices through the internet, allowing them to collect and exchange data seamlessly. This technology has revolutionized various industries by enabling smart devices, data analytics, and cloud services to work in harmony. By integrating IoT solutions with Google Cloud, businesses can harness the power of real-time data, improve connectivity, and enhance their overall operations.
Advantages of Integrating IoT Solutions with Google Cloud
-
Enhanced Connectivity: Google Cloud's robust network integration allows seamless connectivity between IoT devices, ensuring smooth data transmission and communication.
-
Data Analytics: By leveraging Google Cloud's data analytics capabilities, businesses can gain valuable insights from IoT devices, enabling informed decision-making and improved efficiency.
-
Cloud-Based Solutions: Google Cloud offers scalable and secure cloud services, providing businesses with the flexibility to adapt to changing market demands and enhance their operations.
-
Device Management: Simplify device management with Google Cloud's IoT Core, which enables businesses to monitor and control IoT devices effectively.
-
IoT Security: Protect your IoT infrastructure with Google Cloud's advanced security features, ensuring data privacy and compliance with industry regulations.
Key Considerations for Integrating IoT Solutions with Google Cloud
-
Google Cloud Architecture: Understand the architecture of Google Cloud and how it can support your IoT applications, ensuring a seamless integration process.
-
IoT Platforms: Choose the right IoT platform that aligns with your business needs and integrates seamlessly with Google Cloud for optimal performance.
-
Real-Time Data: Leverage Google Cloud's capabilities to process and analyze real-time data from IoT devices, enabling quick decision-making and improved responsiveness.
-
Sensor Technology: Implement advanced sensor technology to collect accurate data from IoT devices, ensuring reliable insights for your business operations.
-
Machine Learning: Utilize machine learning algorithms on Google Cloud to derive actionable insights from IoT data, improving predictive analytics and operational efficiency.
How to obtain Cloud Technology certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Integrating IoT solutions with Google Cloud opens up a world of possibilities for businesses looking to harness the power of data, connectivity, and cloud computing. By leveraging Google Cloud's advanced features and capabilities, businesses can streamline their operations, enhance security, and drive innovation in the digital age. So why wait? Start integrating IoT solutions with Google Cloud today and take your business to new heights.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to enhance your business operations with cutting-edge IoT technology? Look no further than integrating IoT solutions with Google Cloud! In this article, we will explore the benefits of integrating IoT solutions with Google Cloud, how it can revolutionize your business, and the key factors to consider when implementing this innovative technology.
What is IoT and Why is it Important?
IoT, or Internet of Things, refers to the interconnection of devices through the internet, allowing them to collect and exchange data seamlessly. This technology has revolutionized various industries by enabling smart devices, data analytics, and cloud services to work in harmony. By integrating IoT solutions with Google Cloud, businesses can harness the power of real-time data, improve connectivity, and enhance their overall operations.
Advantages of Integrating IoT Solutions with Google Cloud
-
Enhanced Connectivity: Google Cloud's robust network integration allows seamless connectivity between IoT devices, ensuring smooth data transmission and communication.
-
Data Analytics: By leveraging Google Cloud's data analytics capabilities, businesses can gain valuable insights from IoT devices, enabling informed decision-making and improved efficiency.
-
Cloud-Based Solutions: Google Cloud offers scalable and secure cloud services, providing businesses with the flexibility to adapt to changing market demands and enhance their operations.
-
Device Management: Simplify device management with Google Cloud's IoT Core, which enables businesses to monitor and control IoT devices effectively.
-
IoT Security: Protect your IoT infrastructure with Google Cloud's advanced security features, ensuring data privacy and compliance with industry regulations.
Key Considerations for Integrating IoT Solutions with Google Cloud
-
Google Cloud Architecture: Understand the architecture of Google Cloud and how it can support your IoT applications, ensuring a seamless integration process.
-
IoT Platforms: Choose the right IoT platform that aligns with your business needs and integrates seamlessly with Google Cloud for optimal performance.
-
Real-Time Data: Leverage Google Cloud's capabilities to process and analyze real-time data from IoT devices, enabling quick decision-making and improved responsiveness.
-
Sensor Technology: Implement advanced sensor technology to collect accurate data from IoT devices, ensuring reliable insights for your business operations.
-
Machine Learning: Utilize machine learning algorithms on Google Cloud to derive actionable insights from IoT data, improving predictive analytics and operational efficiency.
How to obtain Cloud Technology certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Integrating IoT solutions with Google Cloud opens up a world of possibilities for businesses looking to harness the power of data, connectivity, and cloud computing. By leveraging Google Cloud's advanced features and capabilities, businesses can streamline their operations, enhance security, and drive innovation in the digital age. So why wait? Start integrating IoT solutions with Google Cloud today and take your business to new heights.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Privacy and Data Security in Digital Marketing
In today's digital world, where personal information is constantly being shared online, privacy and data security have become major concerns for both consumers and businesses. In the realm of digital marketing, where companies collect vast amounts of data to tailor their marketing strategies, ensuring the protection of this data is crucial. Let's explore how privacy and data security play a vital role in digital marketing and what measures can be taken to safeguard sensitive information.
Importance of Privacy in Digital Marketing
In the age of targeted advertising and personalized marketing campaigns, consumers are becoming more aware of how their personal data is being used. Privacy concerns have led to the implementation of strict regulations, such as the General Data Protection Regulation (GDPR), which aims to protect the personal data of individuals within the European Union. Compliance with these regulations not only builds trust with customers but also helps in maintaining a positive brand reputation.
But what exactly is GDPR and how does it impact digital marketing strategies??
The GDPR is a comprehensive data privacy law that sets guidelines for the collection, processing, and storage of personal data. In the context of digital marketing, businesses must obtain explicit consent from individuals before collecting their data and must also provide transparent information on how this data will be used. Failure to comply with GDPR can result in hefty fines, highlighting the importance of incorporating privacy measures into digital marketing practices.
Data Security Measures in Digital Marketing
In addition to privacy concerns, data security is another crucial aspect of digital marketing. With cyber threats on the rise, businesses must implement robust security measures to protect their data from unauthorized access and breaches. Encryption, for example, is a powerful tool that can help safeguard sensitive information by encoding it in such a way that only authorized parties can access it.
How does data encryption enhance data security in digital marketing?
Data encryption involves converting data into a code that can only be deciphered with the appropriate encryption key. By encrypting sensitive information such as customer details and payment data, businesses can mitigate the risk of unauthorized access and protect their data from cyber threats. Implementing encryption technology not only helps in safeguarding data but also demonstrates a commitment to data security and consumer privacy.
Ensuring Compliance with Privacy Regulations
To ensure compliance with privacy regulations and maintain consumer trust, businesses must establish clear data privacy policies and guidelines. These policies should outline how data is collected, stored, and used, as well as provide individuals with options to control their data preferences. By being transparent about data handling practices, businesses can build trust with their customers and differentiate themselves in a competitive digital landscape.
How can businesses create effective data privacy policies and practices??
Businesses can start by conducting privacy assessments to identify potential risks and vulnerabilities in their data handling processes. By assessing the flow of data within the organization, businesses can identify areas where data security measures can be improved and privacy controls can be implemented. Furthermore, regular audits and reviews of data privacy policies are essential to ensure ongoing compliance with regulations and best practices.
The Future of Privacy and Data Security in Digital Marketing
As technology continues to evolve, the landscape of privacy and data security in digital marketing will also undergo significant changes. With advancements in artificial intelligence and data analytics, businesses will have access to even more data to personalize their marketing strategies. However, this also poses challenges in terms of data privacy and security.
To stay ahead of the curve, businesses must adopt a proactive approach to privacy and data security. By investing in technologies that enhance data protection, such as secure data storage solutions and advanced encryption tools, businesses can mitigate the risks associated with cyber threats and data breaches. Additionally, ongoing training and education for employees on data security best practices are essential to promote a culture of privacy and security awareness within the organization.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, privacy and data security are fundamental aspects of digital marketing that cannot be ignored. By prioritizing data protection, implementing robust security measures, and ensuring compliance with regulations, businesses can build trust with their customers and establish a strong foundation for successful marketing campaigns. Stay proactive, stay informed, and stay secure in the digital age.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's digital world, where personal information is constantly being shared online, privacy and data security have become major concerns for both consumers and businesses. In the realm of digital marketing, where companies collect vast amounts of data to tailor their marketing strategies, ensuring the protection of this data is crucial. Let's explore how privacy and data security play a vital role in digital marketing and what measures can be taken to safeguard sensitive information.
Importance of Privacy in Digital Marketing
In the age of targeted advertising and personalized marketing campaigns, consumers are becoming more aware of how their personal data is being used. Privacy concerns have led to the implementation of strict regulations, such as the General Data Protection Regulation (GDPR), which aims to protect the personal data of individuals within the European Union. Compliance with these regulations not only builds trust with customers but also helps in maintaining a positive brand reputation.
But what exactly is GDPR and how does it impact digital marketing strategies??
The GDPR is a comprehensive data privacy law that sets guidelines for the collection, processing, and storage of personal data. In the context of digital marketing, businesses must obtain explicit consent from individuals before collecting their data and must also provide transparent information on how this data will be used. Failure to comply with GDPR can result in hefty fines, highlighting the importance of incorporating privacy measures into digital marketing practices.
Data Security Measures in Digital Marketing
In addition to privacy concerns, data security is another crucial aspect of digital marketing. With cyber threats on the rise, businesses must implement robust security measures to protect their data from unauthorized access and breaches. Encryption, for example, is a powerful tool that can help safeguard sensitive information by encoding it in such a way that only authorized parties can access it.
How does data encryption enhance data security in digital marketing?
Data encryption involves converting data into a code that can only be deciphered with the appropriate encryption key. By encrypting sensitive information such as customer details and payment data, businesses can mitigate the risk of unauthorized access and protect their data from cyber threats. Implementing encryption technology not only helps in safeguarding data but also demonstrates a commitment to data security and consumer privacy.
Ensuring Compliance with Privacy Regulations
To ensure compliance with privacy regulations and maintain consumer trust, businesses must establish clear data privacy policies and guidelines. These policies should outline how data is collected, stored, and used, as well as provide individuals with options to control their data preferences. By being transparent about data handling practices, businesses can build trust with their customers and differentiate themselves in a competitive digital landscape.
How can businesses create effective data privacy policies and practices??
Businesses can start by conducting privacy assessments to identify potential risks and vulnerabilities in their data handling processes. By assessing the flow of data within the organization, businesses can identify areas where data security measures can be improved and privacy controls can be implemented. Furthermore, regular audits and reviews of data privacy policies are essential to ensure ongoing compliance with regulations and best practices.
The Future of Privacy and Data Security in Digital Marketing
As technology continues to evolve, the landscape of privacy and data security in digital marketing will also undergo significant changes. With advancements in artificial intelligence and data analytics, businesses will have access to even more data to personalize their marketing strategies. However, this also poses challenges in terms of data privacy and security.
To stay ahead of the curve, businesses must adopt a proactive approach to privacy and data security. By investing in technologies that enhance data protection, such as secure data storage solutions and advanced encryption tools, businesses can mitigate the risks associated with cyber threats and data breaches. Additionally, ongoing training and education for employees on data security best practices are essential to promote a culture of privacy and security awareness within the organization.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, privacy and data security are fundamental aspects of digital marketing that cannot be ignored. By prioritizing data protection, implementing robust security measures, and ensuring compliance with regulations, businesses can build trust with their customers and establish a strong foundation for successful marketing campaigns. Stay proactive, stay informed, and stay secure in the digital age.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Ethics and Professionalism in Information Security Management
In today's digital age, where cybersecurity threats are constantly evolving, the importance of ethics and professionalism in information security management cannot be overstated. As organizations strive to protect their sensitive data and information from cyber attacks, it is essential to uphold ethical behavior and professional standards within the realm of information security.
Ethics in Information Security
Ethics play a crucial role in information security, as professionals are tasked with safeguarding sensitive data and information from unauthorized access and malicious attacks. Ethical behavior in information security involves adhering to a code of conduct, maintaining confidentiality, and upholding the integrity of systems and data.
Ethical Decision Making
When faced with ethical dilemmas in information security, professionals must make decisions based on ethical considerations and principles. Ethical decision-making involves weighing the potential consequences of actions, considering the impact on data privacy and protection, and upholding ethical responsibilities.
Professionalism in Information Security
Professionalism in information security encompasses qualities such as trustworthiness, ethical leadership, and adherence to professional standards. Cybersecurity professionals are expected to demonstrate integrity in their work, follow ethical guidelines, and uphold a code of conduct that promotes ethical practices and behaviors.
Cyber Professionalism
Cyber professionalism involves maintaining a high level of professionalism and ethical standards in the field of information security. Professionals must demonstrate ethical awareness, adhere to security policies, and make decisions that reflect their commitment to ethical practices and behaviors.
Ethical Hacking and Data Privacy
Ethical hacking, also known as penetration testing, is a practice used to identify vulnerabilities in systems and networks to enhance cybersecurity. By conducting ethical hacking tests, organizations can proactively identify and address potential security risks, safeguarding data privacy and protecting sensitive information.
Data Protection
Protecting data is essential in maintaining the confidentiality and integrity of information. Professionals must implement robust security measures, adhere to data protection regulations, and ensure that sensitive data is safeguarded against unauthorized access and breaches.
Creating an Ethical Culture
Building an ethical culture within an organization is essential for promoting ethical behavior and professionalism in information security. By fostering a culture of integrity, transparency, and accountability, organizations can instill ethical values and principles that guide decision-making and behavior.
Ethical Framework
Developing an ethical framework for information security management involves defining ethical guidelines, establishing ethical responsibilities, and promoting ethical practices within the organization. By creating a framework that aligns with ethical principles, professionals can navigate ethical dilemmas and make informed decisions that uphold ethical standards.
How to obtain CISM certification?
We are an Education Technology company providingcertification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, ethics and professionalism are essential components of information security management. By upholding ethical guidelines, maintaining professional integrity, and promoting a culture of ethics, cybersecurity professionals can safeguard data, protect information, and mitigate cybersecurity risks effectively. Upholding ethical behavior and professional standards is not only a moral imperative but also a strategic imperative for organizations seeking to secure their digital assets and maintain trust with stakeholders.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's digital age, where cybersecurity threats are constantly evolving, the importance of ethics and professionalism in information security management cannot be overstated. As organizations strive to protect their sensitive data and information from cyber attacks, it is essential to uphold ethical behavior and professional standards within the realm of information security.
Ethics in Information Security
Ethics play a crucial role in information security, as professionals are tasked with safeguarding sensitive data and information from unauthorized access and malicious attacks. Ethical behavior in information security involves adhering to a code of conduct, maintaining confidentiality, and upholding the integrity of systems and data.
Ethical Decision Making
When faced with ethical dilemmas in information security, professionals must make decisions based on ethical considerations and principles. Ethical decision-making involves weighing the potential consequences of actions, considering the impact on data privacy and protection, and upholding ethical responsibilities.
Professionalism in Information Security
Professionalism in information security encompasses qualities such as trustworthiness, ethical leadership, and adherence to professional standards. Cybersecurity professionals are expected to demonstrate integrity in their work, follow ethical guidelines, and uphold a code of conduct that promotes ethical practices and behaviors.
Cyber Professionalism
Cyber professionalism involves maintaining a high level of professionalism and ethical standards in the field of information security. Professionals must demonstrate ethical awareness, adhere to security policies, and make decisions that reflect their commitment to ethical practices and behaviors.
Ethical Hacking and Data Privacy
Ethical hacking, also known as penetration testing, is a practice used to identify vulnerabilities in systems and networks to enhance cybersecurity. By conducting ethical hacking tests, organizations can proactively identify and address potential security risks, safeguarding data privacy and protecting sensitive information.
Data Protection
Protecting data is essential in maintaining the confidentiality and integrity of information. Professionals must implement robust security measures, adhere to data protection regulations, and ensure that sensitive data is safeguarded against unauthorized access and breaches.
Creating an Ethical Culture
Building an ethical culture within an organization is essential for promoting ethical behavior and professionalism in information security. By fostering a culture of integrity, transparency, and accountability, organizations can instill ethical values and principles that guide decision-making and behavior.
Ethical Framework
Developing an ethical framework for information security management involves defining ethical guidelines, establishing ethical responsibilities, and promoting ethical practices within the organization. By creating a framework that aligns with ethical principles, professionals can navigate ethical dilemmas and make informed decisions that uphold ethical standards.
How to obtain CISM certification?
We are an Education Technology company providingcertification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, ethics and professionalism are essential components of information security management. By upholding ethical guidelines, maintaining professional integrity, and promoting a culture of ethics, cybersecurity professionals can safeguard data, protect information, and mitigate cybersecurity risks effectively. Upholding ethical behavior and professional standards is not only a moral imperative but also a strategic imperative for organizations seeking to secure their digital assets and maintain trust with stakeholders.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Boost Your Career with Crucial Spark Skills in 2024
In the fast-paced and ever-evolving world of work, having the right skills is crucial to boost your career and stay ahead of the competition. As we look towards 2024, it's important to identify the essential skills that will set you up for success and help you thrive in the workplace. One such set of skills that is becoming increasingly important is Spark Skills. In this article, we will explore what Spark Skills are, why they are crucial for career development, and how you can enhance your professional growth by mastering them.
What are Spark Skills?
Spark Skills are a combination of soft skills and technical skills that ares essential for navigating the modern workplace. These skills not only help you excel in your current role but also equip you for future job opportunities and career advancement. Some examples of Spark Skills include communication, problem-solving, adaptability, creativity, and digital literacy. These skills are highly valued by employers as they enable employees to work effectively in diverse and dynamic environments.
Why are Spark Skills crucial for career development?
In today's competitive job market, having strong Spark Skills can set you apart from other candidates and make you more attractive to potential employers. Employers are looking for candidates who not only have the technical know-how but also possess the ability to collaborate, think critically, and adapt to change. By developing your Spark Skills, you can demonstrate your ability to work well with others, navigate challenges, and contribute to the success of your organization.
How can you enhance your professional growth with Spark Skills?
To boost your career in 2024 and beyond, it's essential to invest in developing your Spark Skills. One way to enhance your professional growth is to seek out training and skill-building opportunities that focus on communication, leadership, problem-solving, and other key Spark Skills. Additionally, you can take on new challenges at work, volunteer for leadership roles, and pursue continued education to expand your skill set and advance your career.
Advancing Your Career with Spark Skills in 2024
As the job market continues to evolve, having strong Spark Skills will be essential for career success. By focusing on developing these essential skills, you can position yourself for future job opportunities, workplace success, and career advancement. Invest in your personal development, master key Spark Skills, and watch your career soar to new heights in 2024 and beyond.
How to obtain Big Data certification?
We are an Education Technology company providingcertification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, to boost your career in 2024, it's crucial to prioritize the development of Spark Skills. These essential skills will not only enhance your professional growth but also position you for success in the ever-changing job market. By investing in skill training, advancing your career readiness, and mastering key Spark Skills, you can set yourself up for career success and achieve your career aspirations in the years to come.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In the fast-paced and ever-evolving world of work, having the right skills is crucial to boost your career and stay ahead of the competition. As we look towards 2024, it's important to identify the essential skills that will set you up for success and help you thrive in the workplace. One such set of skills that is becoming increasingly important is Spark Skills. In this article, we will explore what Spark Skills are, why they are crucial for career development, and how you can enhance your professional growth by mastering them.
What are Spark Skills?
Spark Skills are a combination of soft skills and technical skills that ares essential for navigating the modern workplace. These skills not only help you excel in your current role but also equip you for future job opportunities and career advancement. Some examples of Spark Skills include communication, problem-solving, adaptability, creativity, and digital literacy. These skills are highly valued by employers as they enable employees to work effectively in diverse and dynamic environments.
Why are Spark Skills crucial for career development?
In today's competitive job market, having strong Spark Skills can set you apart from other candidates and make you more attractive to potential employers. Employers are looking for candidates who not only have the technical know-how but also possess the ability to collaborate, think critically, and adapt to change. By developing your Spark Skills, you can demonstrate your ability to work well with others, navigate challenges, and contribute to the success of your organization.
How can you enhance your professional growth with Spark Skills?
To boost your career in 2024 and beyond, it's essential to invest in developing your Spark Skills. One way to enhance your professional growth is to seek out training and skill-building opportunities that focus on communication, leadership, problem-solving, and other key Spark Skills. Additionally, you can take on new challenges at work, volunteer for leadership roles, and pursue continued education to expand your skill set and advance your career.
Advancing Your Career with Spark Skills in 2024
As the job market continues to evolve, having strong Spark Skills will be essential for career success. By focusing on developing these essential skills, you can position yourself for future job opportunities, workplace success, and career advancement. Invest in your personal development, master key Spark Skills, and watch your career soar to new heights in 2024 and beyond.
How to obtain Big Data certification?
We are an Education Technology company providingcertification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, to boost your career in 2024, it's crucial to prioritize the development of Spark Skills. These essential skills will not only enhance your professional growth but also position you for success in the ever-changing job market. By investing in skill training, advancing your career readiness, and mastering key Spark Skills, you can set yourself up for career success and achieve your career aspirations in the years to come.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Citrix XenServer vs VMware vSphere
In the world of virtualization software, two of the biggest players are Citrix XenServer and VMware vSphere. Both offer powerful hypervisor platforms that enable businesses to create and manage virtual machines, but they have distinct differences in features, benefits, and performance. This article will delve into the key aspects of Citrix XenServer and VMware vSphere, comparing their strengths and weaknesses to help you make an informed decision for your virtual infrastructure needs.
Citrix XenServer: Features and Advantages
Citrix XenServer is a robust virtualization platform that offers a wide range of features for enterprise virtualization. Some of its key advantages include:
-
Server Virtualization: Citrix XenServer allows businesses to consolidate their servers onto fewer physical machines, reducing hardware costs and improving resource utilization.
-
Virtual Machine Management: With Citrix XenServer, administrators can easily create, deploy, and manage virtual machines, optimizing performance and scalability.
-
Citrix Products Integration:XenServer seamlessly integrates with other Citrix products, such as Citrix Cloud and Citrix Virtual Apps and Desktops, providing a comprehensive virtualization solution.
-
Network Virtualization: Citrix XenServer offers advanced networking capabilities, allowing for efficient traffic management and enhanced security within the virtual environment.
VMware vSphere: Benefits and Features
VMware vSphere is a leading virtualization solution that is known for its performance and reliability. Some of the benefits of using VMware vSphere include:
-
Enterprise Virtualization: VMware vSphere is designed for enterprise-level virtualization, providing scalable and high-performance solutions for large organizations.
-
Virtual Infrastructure: With VMware vSphere, businesses can build a robust virtual infrastructure that supports a wide range of applications and workloads.
-
Cloud Computing: VMware vSphere seamlessly integrates with VMware Cloud Foundation, enabling businesses to leverage cloud computing for greater flexibility and scalability.
-
Application Virtualization: VMware vSphere offers advanced application virtualization capabilities, allowing businesses to run and manage applications more efficiently.
Citrix vs VMware: A Head-to-Head Comparison
When comparing Citrix XenServer and VMware vSphere, there are several key differences to consider. Here is a comparison table outlining the main features and benefits of each platform.
How to obtain Citrix Client Administration certification?
We are an Education Technology company providingcertification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, both Citrix XenServer and VMware vSphere offer powerful virtualization solutions for businesses of all sizes. Whether you choose XenServer for its feature-rich platform or VMware vSphere for its performance and reliability, you can rest assured that you are investing in a top-notch virtualization solution. Consider your specific needs and requirements when making your decision, and leverage the strengths of each platform to maximize the benefits of virtualization in your organization.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In the world of virtualization software, two of the biggest players are Citrix XenServer and VMware vSphere. Both offer powerful hypervisor platforms that enable businesses to create and manage virtual machines, but they have distinct differences in features, benefits, and performance. This article will delve into the key aspects of Citrix XenServer and VMware vSphere, comparing their strengths and weaknesses to help you make an informed decision for your virtual infrastructure needs.
Citrix XenServer: Features and Advantages
Citrix XenServer is a robust virtualization platform that offers a wide range of features for enterprise virtualization. Some of its key advantages include:
-
Server Virtualization: Citrix XenServer allows businesses to consolidate their servers onto fewer physical machines, reducing hardware costs and improving resource utilization.
-
Virtual Machine Management: With Citrix XenServer, administrators can easily create, deploy, and manage virtual machines, optimizing performance and scalability.
-
Citrix Products Integration:XenServer seamlessly integrates with other Citrix products, such as Citrix Cloud and Citrix Virtual Apps and Desktops, providing a comprehensive virtualization solution.
-
Network Virtualization: Citrix XenServer offers advanced networking capabilities, allowing for efficient traffic management and enhanced security within the virtual environment.
VMware vSphere: Benefits and Features
VMware vSphere is a leading virtualization solution that is known for its performance and reliability. Some of the benefits of using VMware vSphere include:
-
Enterprise Virtualization: VMware vSphere is designed for enterprise-level virtualization, providing scalable and high-performance solutions for large organizations.
-
Virtual Infrastructure: With VMware vSphere, businesses can build a robust virtual infrastructure that supports a wide range of applications and workloads.
-
Cloud Computing: VMware vSphere seamlessly integrates with VMware Cloud Foundation, enabling businesses to leverage cloud computing for greater flexibility and scalability.
-
Application Virtualization: VMware vSphere offers advanced application virtualization capabilities, allowing businesses to run and manage applications more efficiently.
Citrix vs VMware: A Head-to-Head Comparison
When comparing Citrix XenServer and VMware vSphere, there are several key differences to consider. Here is a comparison table outlining the main features and benefits of each platform.
How to obtain Citrix Client Administration certification?
We are an Education Technology company providingcertification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, both Citrix XenServer and VMware vSphere offer powerful virtualization solutions for businesses of all sizes. Whether you choose XenServer for its feature-rich platform or VMware vSphere for its performance and reliability, you can rest assured that you are investing in a top-notch virtualization solution. Consider your specific needs and requirements when making your decision, and leverage the strengths of each platform to maximize the benefits of virtualization in your organization.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
CISM Certification: Benefits and Career Opportunities
Are you considering getting certified in Information Security Management? If so, obtaining a Certified Information Security Manager (CISM) certification could be a valuable step in advancing your career in the cybersecurity industry. In this article, we will explore the benefits and career opportunities that come with earning a CISM certification.
What is CISM Certification?
The Certified Information Security Manager (CISM) certification is a globally recognized credential for information security professionals. It is offered by the Information Systems Audit and Control Association (ISACA) and is designed for individuals who manage, design, oversee, and assess an enterprise's information security.
Benefits of CISM Certification
-
Increased earning potential: CISM-certified professionals often earn higher salaries compared to their non-certified counterparts.
-
Career advancement: Having a CISM certification can open doors to higher-level positions in information security management.
-
Industry recognition: Employers and peers acknowledge CISM certification as a mark of excellence in the field of information security.
-
Validation of skills: Holding a CISM certification demonstrates expertise in information security governance, risk management, and compliance.
CISM Certification Career Opportunities
With a CISM certification, you can pursue various roles in the cybersecurity industry. Some common job titles include:
-
Information Security Manager
-
IT Risk Manager
-
Cybersecurity Consultant
-
Chief Information Security Officer (CISO)
-
Security Analyst
CISM Certification Advantages
-
Job prospects: The demand for skilled information security professionals continues to grow, creating numerous job opportunities for CISM-certified individuals.
-
Salary: CISM certification holders typically command higher salaries than non-certified professionals in similar roles.
-
Professional development: CISM certification equips individuals with the knowledge and skills needed to succeed in the dynamic field of information security.
CISM Certification Job Market
The job market for CISM-certified professionals is robust, with a steady demand for skilled information security managers across various industries. Organizations are increasingly recognizing the value of hiring certified professionals to safeguard their sensitive information from cyber threats.
How to obtain CISM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, obtaining a CISM certification can significantly enhance your career prospects in the cybersecurity industry. By showcasing your expertise in information security management, you can position yourself as a valuable asset to organizations looking to strengthen their cybersecurity defenses. With the numerous benefits and career opportunities that come with a CISM certification, investing in your professional development through this credential is well worth it.
Contact Us For More Information:
Visit : www.icertglobal.comEmail : info@icertglobal.com
Read More
Are you considering getting certified in Information Security Management? If so, obtaining a Certified Information Security Manager (CISM) certification could be a valuable step in advancing your career in the cybersecurity industry. In this article, we will explore the benefits and career opportunities that come with earning a CISM certification.
What is CISM Certification?
The Certified Information Security Manager (CISM) certification is a globally recognized credential for information security professionals. It is offered by the Information Systems Audit and Control Association (ISACA) and is designed for individuals who manage, design, oversee, and assess an enterprise's information security.
Benefits of CISM Certification
-
Increased earning potential: CISM-certified professionals often earn higher salaries compared to their non-certified counterparts.
-
Career advancement: Having a CISM certification can open doors to higher-level positions in information security management.
-
Industry recognition: Employers and peers acknowledge CISM certification as a mark of excellence in the field of information security.
-
Validation of skills: Holding a CISM certification demonstrates expertise in information security governance, risk management, and compliance.
CISM Certification Career Opportunities
With a CISM certification, you can pursue various roles in the cybersecurity industry. Some common job titles include:
-
Information Security Manager
-
IT Risk Manager
-
Cybersecurity Consultant
-
Chief Information Security Officer (CISO)
-
Security Analyst
CISM Certification Advantages
-
Job prospects: The demand for skilled information security professionals continues to grow, creating numerous job opportunities for CISM-certified individuals.
-
Salary: CISM certification holders typically command higher salaries than non-certified professionals in similar roles.
-
Professional development: CISM certification equips individuals with the knowledge and skills needed to succeed in the dynamic field of information security.
CISM Certification Job Market
The job market for CISM-certified professionals is robust, with a steady demand for skilled information security managers across various industries. Organizations are increasingly recognizing the value of hiring certified professionals to safeguard their sensitive information from cyber threats.
How to obtain CISM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, obtaining a CISM certification can significantly enhance your career prospects in the cybersecurity industry. By showcasing your expertise in information security management, you can position yourself as a valuable asset to organizations looking to strengthen their cybersecurity defenses. With the numerous benefits and career opportunities that come with a CISM certification, investing in your professional development through this credential is well worth it.
Contact Us For More Information:
Visit : www.icertglobal.comEmail : info@icertglobal.com
Building Java Applications with GraalVM
In the ever-evolving landscape of software development, staying ahead of the curve is essential to success. One such cutting-edge technology that is transforming the way we build and deploy Java applications is GraalVM. This innovative tool offers a plethora of features and benefits that can significantly boost productivity, performance, and efficiency. Let's explore the possibilities of building Java applications with GraalVM.
Building Java Applications with GraalVM
GraalVM is a high-performance polyglot virtual machine that supports multiple programming languages, including Java, JavaScript, Ruby, R, and Python. By leveraging GraalVM, developers can write code in multiple languages within the same application, leading to increased productivity and flexibility. Moreover, GraalVM's native code compilation capabilities allow for faster execution and improved performance compared to traditional Java Virtual Machines (JVMs).
Efficiency and Optimization
One of the key advantages of using GraalVM for building Java applications is its ability to optimize the runtime performance of the code. By compiling Java bytecode into highly efficient native code, GraalVM eliminates the need for interpretation, resulting in faster execution times and reduced memory consumption. This optimization translates into improved efficiency and responsiveness, making GraalVM an ideal choice for high-performance applications.
Runtime Enhancements and Compatibility
GraalVM provides a range of runtime enhancements that further enhance the performance and compatibility of Java applications. The Ahead-of-Time (AOT) compilation feature allows developers to compile Java code into standalone executable binaries, eliminating the need for a separate JVM installation. Additionally, GraalVM offers seamless compatibility with existing Java frameworks and libraries, making it easy to integrate into existing projects without any major modifications.
Productivity and Innovation
By leveraging GraalVM's advanced capabilities, developers can unleash their creativity and build innovative Java applications that push the boundaries of traditional software development. GraalVM's support for microservices, cloud deployment, and virtualization enables developers to create scalable and efficient applications that meet the demands of modern computing environments. Furthermore, GraalVM's compatibility with popular tools and frameworks ensures a smooth and seamless development experience, leading to increased productivity and faster time-to-market.
Technology and Integration
GraalVM's integration capabilities extend beyond Java, allowing developers to incorporate a wide range of programming languages and tools into their applications. Whether you're building a web application, mobile app, or enterprise software, GraalVM provides the flexibility and versatility to meet your specific needs. With support for modernization frameworks and deployment options, GraalVM offers a comprehensive solution for building cutting-edge Java applications that stand out in today's competitive marketplace.
How to obtain JAVA certification?
We are an Education Technology company providingcertification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, GraalVM is a game-changer in the world of Java application development, offering a host of features and benefits that enhance performance, efficiency, and innovation. By embracing GraalVM's capabilities, developers can unlock new possibilities and build Java applications that are faster, more reliable, and more scalable than ever before. So, why wait? Dive into the world of GraalVM today and experience the future of Java development firsthand.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In the ever-evolving landscape of software development, staying ahead of the curve is essential to success. One such cutting-edge technology that is transforming the way we build and deploy Java applications is GraalVM. This innovative tool offers a plethora of features and benefits that can significantly boost productivity, performance, and efficiency. Let's explore the possibilities of building Java applications with GraalVM.
Building Java Applications with GraalVM
GraalVM is a high-performance polyglot virtual machine that supports multiple programming languages, including Java, JavaScript, Ruby, R, and Python. By leveraging GraalVM, developers can write code in multiple languages within the same application, leading to increased productivity and flexibility. Moreover, GraalVM's native code compilation capabilities allow for faster execution and improved performance compared to traditional Java Virtual Machines (JVMs).
Efficiency and Optimization
One of the key advantages of using GraalVM for building Java applications is its ability to optimize the runtime performance of the code. By compiling Java bytecode into highly efficient native code, GraalVM eliminates the need for interpretation, resulting in faster execution times and reduced memory consumption. This optimization translates into improved efficiency and responsiveness, making GraalVM an ideal choice for high-performance applications.
Runtime Enhancements and Compatibility
GraalVM provides a range of runtime enhancements that further enhance the performance and compatibility of Java applications. The Ahead-of-Time (AOT) compilation feature allows developers to compile Java code into standalone executable binaries, eliminating the need for a separate JVM installation. Additionally, GraalVM offers seamless compatibility with existing Java frameworks and libraries, making it easy to integrate into existing projects without any major modifications.
Productivity and Innovation
By leveraging GraalVM's advanced capabilities, developers can unleash their creativity and build innovative Java applications that push the boundaries of traditional software development. GraalVM's support for microservices, cloud deployment, and virtualization enables developers to create scalable and efficient applications that meet the demands of modern computing environments. Furthermore, GraalVM's compatibility with popular tools and frameworks ensures a smooth and seamless development experience, leading to increased productivity and faster time-to-market.
Technology and Integration
GraalVM's integration capabilities extend beyond Java, allowing developers to incorporate a wide range of programming languages and tools into their applications. Whether you're building a web application, mobile app, or enterprise software, GraalVM provides the flexibility and versatility to meet your specific needs. With support for modernization frameworks and deployment options, GraalVM offers a comprehensive solution for building cutting-edge Java applications that stand out in today's competitive marketplace.
How to obtain JAVA certification?
We are an Education Technology company providingcertification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, GraalVM is a game-changer in the world of Java application development, offering a host of features and benefits that enhance performance, efficiency, and innovation. By embracing GraalVM's capabilities, developers can unlock new possibilities and build Java applications that are faster, more reliable, and more scalable than ever before. So, why wait? Dive into the world of GraalVM today and experience the future of Java development firsthand.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
The Advantages and Challenges of Transitioning to the Cloud
In today's digital age, businesses are increasingly moving towards cloud services to enhance efficiency, scalability, and cost-effectiveness. However, transitioning to the cloud comes with its own set of advantages and challenges. In this article, we will explore the benefits of moving to the cloud as well as the obstacles that organizations may face during the migration process.
Advantages of Cloud Transition
-
Scalability: One of the key advantages of transitioning to the cloud is the ability to scale resources up or down based on demand. This flexibility allows businesses to adapt to changing needs without incurring unnecessary costs.
-
Cost Savings: By moving to the cloud, organizations can reduce the need for physical infrastructure and on-premises maintenance. This can lead to significant cost savings in the long run.
-
Enhanced Security: Cloud service providers invest heavily in security measures to protect data from cyber threats. By leveraging cloud technologies, businesses can benefit from robust security protocols without the need for additional resources.
Challenges of Cloud Migration
-
Data Security Concerns: While cloud providers offer stringent security measures, some organizations may still have concerns about storing sensitive data off-site. Addressing these concerns and ensuring compliance with data protection regulations is crucial during the migration process.
-
Integration Issues: Migrating to the cloud can be complex, especially when integrating existing systems and applications. Compatibility issues and data migration challenges may arise, requiring careful planning and execution.
-
Downtime Risk: During the transition period, businesses may experience downtime as data is transferred to the cloud. Minimizing downtime and ensuring business continuity are essential considerations for a successful migration.
Benefits of Moving to the Cloud
-
Increased Flexibility: Cloud services offer the flexibility to access data and applications from anywhere, at any time. This remote accessibility enables employees to collaborate more effectively and enhance productivity.
-
Improved Collaboration: Cloud-based tools and platforms facilitate seamless collaboration among team members, regardless of their physical location. Real-time communication and file sharing capabilities enhance teamwork and streamline workflows.
-
Automatic Updates: Cloud service providers regularly update their platforms with the latest features and security patches. This ensures that organizations always have access to the most up-to-date technologies without the need for manual updates.
Cloud Adoption Pros and Cons
-
Pros: Scalability, cost savings, enhanced security.
-
Cons: Data security concerns, integration issues, downtime risk.
Migrating to Cloud Computing
When migrating to cloud computing, organizations must carefully assess their needs, evaluate potential providers, and develop a comprehensive migration strategy. Consideration should be given to data migration, application compatibility, and training requirements to ensure a smooth transition.
Transitioning to Cloud Services
Transitioning to cloud services requires a phased approach, starting with an assessment of current infrastructure and applications. Organizations should prioritize workloads based on criticality and complexity, taking into account potential challenges and risks.
Cloud Migration Strategies
There are several migration strategies that organizations can employ, including rehosting, refactoring, and rearchitecting. Each approach has its own benefits and challenges, depending on the organization's specific requirements and goals.
Advantages of Cloud Integration
Integrating cloud services with existing systems can enhance productivity, streamline workflows, and improve data accessibility. By leveraging interoperable technologies, organizations can maximize the benefits of cloud integration and achieve a seamless transition.
Transitioning to Cloud-Based Systems
Moving from on-premises systems to cloud-based solutions can offer numerous advantages, including increased flexibility, scalability, and efficiency. However, organizations must carefully plan and execute the transition to avoid potential pitfalls and ensure a successful deployment.
Cloud Migration Best Practices
To optimize the migration process, organizations should follow best practices such as conducting thorough research, engaging key stakeholders, and implementing a robust testing plan. By adopting a structured approach, businesses can minimize risks and maximize the benefits of cloud migration.
Moving Data to the Cloud
Data migration is a critical aspect of transitioning to the cloud, requiring careful planning and execution. Organizations must ensure data integrity, security, and compliance throughout the migration process to safeguard sensitive information and prevent data loss.
Cloud Services Advantages
Cloud services offer numerous advantages, including on-demand scalability, cost-effective pricing models, and automatic updates. By leveraging cloud technologies, organizations can enhance operational efficiency, streamline processes, and drive innovation.
Cloud Adoption Challenges
While cloud adoption offers numerous benefits, organizations may face challenges such as resistance to change, skills gaps, and compliance issues. Overcoming these challenges requires a strategic approach, effective communication, and ongoing training and support.
Benefits of Cloud Deployment
Cloud deployment enables organizations to access resources and services on-demand, without the need for physical infrastructure. This flexibility allows businesses to allocate resources efficiently, scale operations rapidly, and adapt to changing market conditions.
Cloud Transition Planning
Effective cloud transition planning involves assessing business needs, identifying migration goals, and developing a roadmap for implementation. By creating a detailed plan and engaging key stakeholders, organizations can ensure a successful transition to the cloud.
Cloud Computing Challenges and Opportunities
While cloud computing offers numerous opportunities for innovation and growth, organizations must also be aware of potential challenges such as data security risks, compliance issues, and vendor lock-in. By addressing these challenges proactively, businesses can leverage cloud technologies to drive digital transformation and achieve competitive advantage.
Cloud Migration Considerations
When considering cloud migration, organizations should evaluate factors such as data security, compliance requirements, cost implications, and vendor reliability. Conducting a thorough assessment of these considerations can help businesses make informed decisions and mitigate potential risks associated with cloud transition.
Reasons for Cloud Transition
The primary reasons for transitioning to the cloud include improving scalability, enhancing security, reducing costs, and increasing flexibility. By leveraging cloud technologies, organizations can modernize their IT infrastructure, streamline operations, and drive business growth.
Advantages of Cloud Storage
Cloud storage provides organizations with a scalable, secure, and cost-effective solution for storing and accessing data. By leveraging cloud storage services, businesses can reduce reliance on physical infrastructure, enhance data availability, and improve disaster recovery capabilities.
Risks of Transitioning to the Cloud
While cloud transition offers numerous benefits, organizations must also consider potential risks such as data breaches, data loss, and service outages. Mitigating these risks requires implementing robust security measures, backup protocols, and disaster recovery plans.
Cloud Adoption Benefits
Cloud adoption offers benefits such as scalability, cost savings, enhanced security, and improved collaboration. By embracing cloud technologies, organizations can drive innovation, increase operational efficiency, and gain a competitive edge in the digital marketplace.
Cloud Migration Issues
During the cloud migration process, organizations may encounter issues such as data compatibility, performance bottlenecks, and application downtime. Addressing these issues requires careful planning, proactive monitoring, and timely intervention to ensure a seamless transition.
Transitioning Legacy Systems to the Cloud
Migrating legacy systems to the cloud can present unique challenges due to outdated technologies, complex dependencies, and legacy codebase. By following best practices, organizations can minimize disruption, optimize performance, and modernize legacy applications for the cloud environment.
How to obtain Cloud Technology certification?
We are an Education Technology company providingcertification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, transitioning to the cloud offers organizations a wide range of benefits, from increased flexibility and cost savings to enhanced security and collaboration. While cloud migration presents challenges, careful planning, and strategic execution can help businesses navigate the transition successfully and unlock the full potential of cloud technologies. By leveraging the advantages of cloud integration and addressing potential risks, organizations can drive digital transformation, streamline operations, and achieve sustainable growth in the rapidly evolving digital landscape.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's digital age, businesses are increasingly moving towards cloud services to enhance efficiency, scalability, and cost-effectiveness. However, transitioning to the cloud comes with its own set of advantages and challenges. In this article, we will explore the benefits of moving to the cloud as well as the obstacles that organizations may face during the migration process.
Advantages of Cloud Transition
-
Scalability: One of the key advantages of transitioning to the cloud is the ability to scale resources up or down based on demand. This flexibility allows businesses to adapt to changing needs without incurring unnecessary costs.
-
Cost Savings: By moving to the cloud, organizations can reduce the need for physical infrastructure and on-premises maintenance. This can lead to significant cost savings in the long run.
-
Enhanced Security: Cloud service providers invest heavily in security measures to protect data from cyber threats. By leveraging cloud technologies, businesses can benefit from robust security protocols without the need for additional resources.
Challenges of Cloud Migration
-
Data Security Concerns: While cloud providers offer stringent security measures, some organizations may still have concerns about storing sensitive data off-site. Addressing these concerns and ensuring compliance with data protection regulations is crucial during the migration process.
-
Integration Issues: Migrating to the cloud can be complex, especially when integrating existing systems and applications. Compatibility issues and data migration challenges may arise, requiring careful planning and execution.
-
Downtime Risk: During the transition period, businesses may experience downtime as data is transferred to the cloud. Minimizing downtime and ensuring business continuity are essential considerations for a successful migration.
Benefits of Moving to the Cloud
-
Increased Flexibility: Cloud services offer the flexibility to access data and applications from anywhere, at any time. This remote accessibility enables employees to collaborate more effectively and enhance productivity.
-
Improved Collaboration: Cloud-based tools and platforms facilitate seamless collaboration among team members, regardless of their physical location. Real-time communication and file sharing capabilities enhance teamwork and streamline workflows.
-
Automatic Updates: Cloud service providers regularly update their platforms with the latest features and security patches. This ensures that organizations always have access to the most up-to-date technologies without the need for manual updates.
Cloud Adoption Pros and Cons
-
Pros: Scalability, cost savings, enhanced security.
-
Cons: Data security concerns, integration issues, downtime risk.
Migrating to Cloud Computing
When migrating to cloud computing, organizations must carefully assess their needs, evaluate potential providers, and develop a comprehensive migration strategy. Consideration should be given to data migration, application compatibility, and training requirements to ensure a smooth transition.
Transitioning to Cloud Services
Transitioning to cloud services requires a phased approach, starting with an assessment of current infrastructure and applications. Organizations should prioritize workloads based on criticality and complexity, taking into account potential challenges and risks.
Cloud Migration Strategies
There are several migration strategies that organizations can employ, including rehosting, refactoring, and rearchitecting. Each approach has its own benefits and challenges, depending on the organization's specific requirements and goals.
Advantages of Cloud Integration
Integrating cloud services with existing systems can enhance productivity, streamline workflows, and improve data accessibility. By leveraging interoperable technologies, organizations can maximize the benefits of cloud integration and achieve a seamless transition.
Transitioning to Cloud-Based Systems
Moving from on-premises systems to cloud-based solutions can offer numerous advantages, including increased flexibility, scalability, and efficiency. However, organizations must carefully plan and execute the transition to avoid potential pitfalls and ensure a successful deployment.
Cloud Migration Best Practices
To optimize the migration process, organizations should follow best practices such as conducting thorough research, engaging key stakeholders, and implementing a robust testing plan. By adopting a structured approach, businesses can minimize risks and maximize the benefits of cloud migration.
Moving Data to the Cloud
Data migration is a critical aspect of transitioning to the cloud, requiring careful planning and execution. Organizations must ensure data integrity, security, and compliance throughout the migration process to safeguard sensitive information and prevent data loss.
Cloud Services Advantages
Cloud services offer numerous advantages, including on-demand scalability, cost-effective pricing models, and automatic updates. By leveraging cloud technologies, organizations can enhance operational efficiency, streamline processes, and drive innovation.
Cloud Adoption Challenges
While cloud adoption offers numerous benefits, organizations may face challenges such as resistance to change, skills gaps, and compliance issues. Overcoming these challenges requires a strategic approach, effective communication, and ongoing training and support.
Benefits of Cloud Deployment
Cloud deployment enables organizations to access resources and services on-demand, without the need for physical infrastructure. This flexibility allows businesses to allocate resources efficiently, scale operations rapidly, and adapt to changing market conditions.
Cloud Transition Planning
Effective cloud transition planning involves assessing business needs, identifying migration goals, and developing a roadmap for implementation. By creating a detailed plan and engaging key stakeholders, organizations can ensure a successful transition to the cloud.
Cloud Computing Challenges and Opportunities
While cloud computing offers numerous opportunities for innovation and growth, organizations must also be aware of potential challenges such as data security risks, compliance issues, and vendor lock-in. By addressing these challenges proactively, businesses can leverage cloud technologies to drive digital transformation and achieve competitive advantage.
Cloud Migration Considerations
When considering cloud migration, organizations should evaluate factors such as data security, compliance requirements, cost implications, and vendor reliability. Conducting a thorough assessment of these considerations can help businesses make informed decisions and mitigate potential risks associated with cloud transition.
Reasons for Cloud Transition
The primary reasons for transitioning to the cloud include improving scalability, enhancing security, reducing costs, and increasing flexibility. By leveraging cloud technologies, organizations can modernize their IT infrastructure, streamline operations, and drive business growth.
Advantages of Cloud Storage
Cloud storage provides organizations with a scalable, secure, and cost-effective solution for storing and accessing data. By leveraging cloud storage services, businesses can reduce reliance on physical infrastructure, enhance data availability, and improve disaster recovery capabilities.
Risks of Transitioning to the Cloud
While cloud transition offers numerous benefits, organizations must also consider potential risks such as data breaches, data loss, and service outages. Mitigating these risks requires implementing robust security measures, backup protocols, and disaster recovery plans.
Cloud Adoption Benefits
Cloud adoption offers benefits such as scalability, cost savings, enhanced security, and improved collaboration. By embracing cloud technologies, organizations can drive innovation, increase operational efficiency, and gain a competitive edge in the digital marketplace.
Cloud Migration Issues
During the cloud migration process, organizations may encounter issues such as data compatibility, performance bottlenecks, and application downtime. Addressing these issues requires careful planning, proactive monitoring, and timely intervention to ensure a seamless transition.
Transitioning Legacy Systems to the Cloud
Migrating legacy systems to the cloud can present unique challenges due to outdated technologies, complex dependencies, and legacy codebase. By following best practices, organizations can minimize disruption, optimize performance, and modernize legacy applications for the cloud environment.
How to obtain Cloud Technology certification?
We are an Education Technology company providingcertification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, transitioning to the cloud offers organizations a wide range of benefits, from increased flexibility and cost savings to enhanced security and collaboration. While cloud migration presents challenges, careful planning, and strategic execution can help businesses navigate the transition successfully and unlock the full potential of cloud technologies. By leveraging the advantages of cloud integration and addressing potential risks, organizations can drive digital transformation, streamline operations, and achieve sustainable growth in the rapidly evolving digital landscape.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
The Impact of Big Data on Urban Planning and Smart Cities
Since the advent of big data, urban planning and the development of smart cities have been revolutionized. With the help of data analytics, technology, and innovative solutions, urban areas are becoming more efficient, sustainable, and livable. In this article, we will explore the significant impact that big data has had on urban planning and the creation of smart cities, as well as the challenges and opportunities that come with it.
Big Data Revolutionizing Urban Development
The use of big data in urban development has completely transformed the way cities are designed, managed, and grown. By harnessing the power of data analytics, city planners can make more informed decisions about infrastructure, transportation, housing, and public services. This data-driven approach allows for better allocation of resources, improved efficiency, and enhanced quality of life for residents.
One of the key advantages of using big data in urban planning is the ability to analyze trends and patterns to predict future needs and challenges. By leveraging predictive analytics and machine learning algorithms, city planners can anticipate population growth, traffic congestion, and environmental risks, allowing them to proactively address these issues before they become major problems.
Advancements in Technology and Urban Infrastructure
The integration of technology into urban infrastructure has been instrumental in creating smart cities that are connected, sustainable, and efficient. The Internet of Things (IoT) has enabled the development of smart sensors and networks that can collect real-time data on various aspects of city life, from traffic flow to air quality. This data can then be used to optimize urban systems, reduce energy consumption, and improve overall sustainability.
Furthermore, the use of geospatial data has revolutionized urban planning by providing detailed insights into land use, demographic trends, and environmental conditions. With the help of geographic information systems (GIS), city planners can create more accurate maps, assess potential development sites, and make data-driven decisions about zoning and infrastructure projects.
Challenges and Opportunities in Urban Management
While big data has brought about significant benefits to urban planning and smart cities, it also poses several challenges that need to be addressed. One of the main issues is the collection and management of vast amounts of data, which can overwhelm city governments and lead to privacy concerns. Additionally, there is a need for skilled professionals who can analyze and interpret this data effectively to extract valuable insights and make informed decisions.On the other hand, the opportunities presented by big data in urban management are vast. By embracing digital transformation and adopting data-driven approaches, cities can become more resilient, inclusive, and sustainable. From optimizing transportation systems to reducing carbon emissions, the possibilities for leveraging big data to improve urban life are endless.
How to obtain Big Data Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the impact of big data on urban planning and smart cities cannot be overstated. By utilizing data analytics, technology, and innovative solutions, cities can become more efficient, sustainable, and livable for residents. While there are challenges to overcome, the opportunities presented by big data in urban management are vast, and the future of urban development looks brighter than ever before.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Since the advent of big data, urban planning and the development of smart cities have been revolutionized. With the help of data analytics, technology, and innovative solutions, urban areas are becoming more efficient, sustainable, and livable. In this article, we will explore the significant impact that big data has had on urban planning and the creation of smart cities, as well as the challenges and opportunities that come with it.
Big Data Revolutionizing Urban Development
The use of big data in urban development has completely transformed the way cities are designed, managed, and grown. By harnessing the power of data analytics, city planners can make more informed decisions about infrastructure, transportation, housing, and public services. This data-driven approach allows for better allocation of resources, improved efficiency, and enhanced quality of life for residents.
One of the key advantages of using big data in urban planning is the ability to analyze trends and patterns to predict future needs and challenges. By leveraging predictive analytics and machine learning algorithms, city planners can anticipate population growth, traffic congestion, and environmental risks, allowing them to proactively address these issues before they become major problems.
Advancements in Technology and Urban Infrastructure
The integration of technology into urban infrastructure has been instrumental in creating smart cities that are connected, sustainable, and efficient. The Internet of Things (IoT) has enabled the development of smart sensors and networks that can collect real-time data on various aspects of city life, from traffic flow to air quality. This data can then be used to optimize urban systems, reduce energy consumption, and improve overall sustainability.
Furthermore, the use of geospatial data has revolutionized urban planning by providing detailed insights into land use, demographic trends, and environmental conditions. With the help of geographic information systems (GIS), city planners can create more accurate maps, assess potential development sites, and make data-driven decisions about zoning and infrastructure projects.
Challenges and Opportunities in Urban Management
While big data has brought about significant benefits to urban planning and smart cities, it also poses several challenges that need to be addressed. One of the main issues is the collection and management of vast amounts of data, which can overwhelm city governments and lead to privacy concerns. Additionally, there is a need for skilled professionals who can analyze and interpret this data effectively to extract valuable insights and make informed decisions.On the other hand, the opportunities presented by big data in urban management are vast. By embracing digital transformation and adopting data-driven approaches, cities can become more resilient, inclusive, and sustainable. From optimizing transportation systems to reducing carbon emissions, the possibilities for leveraging big data to improve urban life are endless.
How to obtain Big Data Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the impact of big data on urban planning and smart cities cannot be overstated. By utilizing data analytics, technology, and innovative solutions, cities can become more efficient, sustainable, and livable for residents. While there are challenges to overcome, the opportunities presented by big data in urban management are vast, and the future of urban development looks brighter than ever before.
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Deep Learning for Image and Video Recognition
In today's digital world, the ability to accurately recognize and identify images and videos plays a crucial role in various fields such as security, healthcare, entertainment, and more. Deep learning, a subset of artificial intelligence, has revolutionized the way image and video recognition is approached, providing highly accurate results compared to traditional methods. This article will explore the evolution of deep learning in the realm of image and video recognition, its key applications, and the underlying technologies that drive its success.
Understanding Deep Learning
Deep learning is a form of machine learning that uses neural networks with multiple layers to extract features from data. These deep neural networks are inspired by the structure and function of the human brain, allowing them to learn complex patterns and relationships in data. In the context of image and video recognition, deep learning algorithms utilize convolutional neural networks (CNNs) to automatically learn hierarchical representations of images and videos.
Q: How does deep learning improve image and video recognition?
A: Deep learning excels at automatically learning intricate features from raw input data, enabling more accurate and robust image and video recognition compared to traditional methods.
Image Recognition
Image recognition is the process of identifying and categorizing objects and patterns within images. Deep learning techniques have significantly advanced the field of image recognition, enabling models to achieve state-of-the-art performance on tasks such as object detection, image classification, and image segmentation. By leveraging deep features extracted from CNNs, these models can accurately recognize objects in images with high precision.
Q: What are some common applications of image recognition?
A: Image recognition has various applications, including facial recognition for security systems, automated medical image analysis for healthcare, and content-based image retrieval for e-commerce platforms.
Video Recognition
Video recognition involves analyzing and interpreting the content of videos, which often contain temporal information in addition to spatial details. Deep learning models trained on video data can capture motion patterns, spatial relationships, and temporal dependencies to perform tasks such as action recognition, video classification, and video analysis. By applying deep convolutional networks and recurrent neural networks, these models can achieve remarkable accuracy in video recognition tasks.
Q: How does video recognition differ from image recognition?
A: Video recognition requires capturing temporal dynamics and motion patterns present in videos, in addition to spatial features, making it a more complex task compared to image recognition.
Q: What are some practical applications of video recognition?
A: Video recognition is used in surveillance systems for anomaly detection, video summarization for content analysis, and human activity recognition in sports analytics.
How to obtain Deep Learning certification?
We are an Education Technology company providingcertification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Deep learning has transformed the field of image and video recognition, offering unparalleled accuracy and efficiency in analyzing visual data. By leveraging neural network architectures, deep convolutional networks, and recurrent networks, deep learning models can extract meaningful features and patterns from images and videos, enabling a wide range of applications in computer vision. As technology continues to advance, the potential for deep learning in image and video recognition is limitless, paving the way for innovative solutions in various industries.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's digital world, the ability to accurately recognize and identify images and videos plays a crucial role in various fields such as security, healthcare, entertainment, and more. Deep learning, a subset of artificial intelligence, has revolutionized the way image and video recognition is approached, providing highly accurate results compared to traditional methods. This article will explore the evolution of deep learning in the realm of image and video recognition, its key applications, and the underlying technologies that drive its success.
Understanding Deep Learning
Deep learning is a form of machine learning that uses neural networks with multiple layers to extract features from data. These deep neural networks are inspired by the structure and function of the human brain, allowing them to learn complex patterns and relationships in data. In the context of image and video recognition, deep learning algorithms utilize convolutional neural networks (CNNs) to automatically learn hierarchical representations of images and videos.
Q: How does deep learning improve image and video recognition?
A: Deep learning excels at automatically learning intricate features from raw input data, enabling more accurate and robust image and video recognition compared to traditional methods.
Image Recognition
Image recognition is the process of identifying and categorizing objects and patterns within images. Deep learning techniques have significantly advanced the field of image recognition, enabling models to achieve state-of-the-art performance on tasks such as object detection, image classification, and image segmentation. By leveraging deep features extracted from CNNs, these models can accurately recognize objects in images with high precision.
Q: What are some common applications of image recognition?
A: Image recognition has various applications, including facial recognition for security systems, automated medical image analysis for healthcare, and content-based image retrieval for e-commerce platforms.
Video Recognition
Video recognition involves analyzing and interpreting the content of videos, which often contain temporal information in addition to spatial details. Deep learning models trained on video data can capture motion patterns, spatial relationships, and temporal dependencies to perform tasks such as action recognition, video classification, and video analysis. By applying deep convolutional networks and recurrent neural networks, these models can achieve remarkable accuracy in video recognition tasks.
Q: How does video recognition differ from image recognition?
A: Video recognition requires capturing temporal dynamics and motion patterns present in videos, in addition to spatial features, making it a more complex task compared to image recognition.
Q: What are some practical applications of video recognition?
A: Video recognition is used in surveillance systems for anomaly detection, video summarization for content analysis, and human activity recognition in sports analytics.
How to obtain Deep Learning certification?
We are an Education Technology company providingcertification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Deep learning has transformed the field of image and video recognition, offering unparalleled accuracy and efficiency in analyzing visual data. By leveraging neural network architectures, deep convolutional networks, and recurrent networks, deep learning models can extract meaningful features and patterns from images and videos, enabling a wide range of applications in computer vision. As technology continues to advance, the potential for deep learning in image and video recognition is limitless, paving the way for innovative solutions in various industries.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
5 Innovative Digital Marketing Strategies to Boost Your ROI in 2024
Are you looking to take your digital marketing efforts to the next level and maximize your return on investment in 2024? In today's fast-paced and ever-evolving digital landscape, it's crucial to stay ahead of the curve with innovative marketing strategies that drive results. Here are five cutting-edge tactics to help you supercharge your marketing efforts and boost your ROI in the upcoming year.
Digital Marketing Tactics for 2024
1. Personalized Marketing
Personalization is key in today's digital world. By tailoring your marketing efforts to specific individuals based on their preferences, behaviors, and demographics, you can create a more engaging and relevant experience for your audience. Utilize customer data and analytics to segment your target audience and deliver personalized content through email campaigns, social media, and website interactions.
2. Interactive Content
Interactive content is a game-changer when it comes to engaging your audience and capturing their attention. From quizzes and polls to interactive infographics and webinars, interactive content invites users to actively participate in the experience, making it more memorable and shareable. Incorporate interactive elements into your digital marketing strategy to drive higher levels of engagement and increase brand awareness.
3. Technology Integration
Embrace the latest technologies to enhance your digital marketing efforts and streamline your processes. From artificial intelligence and machine learning to marketing automation tools and chatbots, technology integration can help you deliver more personalized and efficient marketing campaigns. Invest in technology that empowers you to connect with your audience on a deeper level and stay ahead of the competition.
4. Video Marketing
Video has become one of the most powerful forms of content in the digital marketing landscape. With the rise of platforms like YouTube, TikTok, and Instagram Reels, video marketing offers a highly engaging and shareable way to communicate your brand message. Create compelling video content that showcases your products, tells your brand story, and connects with your audience on an emotional level to drive conversions and boost your ROI.
5. Influencer Partnerships
Collaborating with influencers who align with your brand values and target audience can help you reach new customers and expand your reach. Influencers have built loyal followings and credibility in their niches, making them valuable partners for promoting your products or services. Leverage influencer partnerships to amplify your brand message, drive traffic to your website, and increase customer engagement for a higher ROI.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, By implementing these innovative digital marketing strategies in 2024, you can elevate your brand's online presence, connect with your target audience on a deeper level, and ultimately boost your return on investment. Stay ahead of the curve with personalized marketing, interactive content, technology integration, video marketing, and influencer partnerships to drive success in the digital landscape. Are you ready to take your digital marketing to the next level and achieve impressive results in the coming year? Let's make 2024 your best year yet!
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to take your digital marketing efforts to the next level and maximize your return on investment in 2024? In today's fast-paced and ever-evolving digital landscape, it's crucial to stay ahead of the curve with innovative marketing strategies that drive results. Here are five cutting-edge tactics to help you supercharge your marketing efforts and boost your ROI in the upcoming year.
Digital Marketing Tactics for 2024
1. Personalized Marketing
Personalization is key in today's digital world. By tailoring your marketing efforts to specific individuals based on their preferences, behaviors, and demographics, you can create a more engaging and relevant experience for your audience. Utilize customer data and analytics to segment your target audience and deliver personalized content through email campaigns, social media, and website interactions.
2. Interactive Content
Interactive content is a game-changer when it comes to engaging your audience and capturing their attention. From quizzes and polls to interactive infographics and webinars, interactive content invites users to actively participate in the experience, making it more memorable and shareable. Incorporate interactive elements into your digital marketing strategy to drive higher levels of engagement and increase brand awareness.
3. Technology Integration
Embrace the latest technologies to enhance your digital marketing efforts and streamline your processes. From artificial intelligence and machine learning to marketing automation tools and chatbots, technology integration can help you deliver more personalized and efficient marketing campaigns. Invest in technology that empowers you to connect with your audience on a deeper level and stay ahead of the competition.
4. Video Marketing
Video has become one of the most powerful forms of content in the digital marketing landscape. With the rise of platforms like YouTube, TikTok, and Instagram Reels, video marketing offers a highly engaging and shareable way to communicate your brand message. Create compelling video content that showcases your products, tells your brand story, and connects with your audience on an emotional level to drive conversions and boost your ROI.
5. Influencer Partnerships
Collaborating with influencers who align with your brand values and target audience can help you reach new customers and expand your reach. Influencers have built loyal followings and credibility in their niches, making them valuable partners for promoting your products or services. Leverage influencer partnerships to amplify your brand message, drive traffic to your website, and increase customer engagement for a higher ROI.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, By implementing these innovative digital marketing strategies in 2024, you can elevate your brand's online presence, connect with your target audience on a deeper level, and ultimately boost your return on investment. Stay ahead of the curve with personalized marketing, interactive content, technology integration, video marketing, and influencer partnerships to drive success in the digital landscape. Are you ready to take your digital marketing to the next level and achieve impressive results in the coming year? Let's make 2024 your best year yet!
Contact Us For More Information :
Visit : www.icertglobal.com Email : info@icertglobal.com
Ensure IT Service Continuity Management Protects Your Infrastructure In today's fast-paced
In today's fast-paced digital world, IT service continuity management plays a crucial role in ensuring the protection and resilience of your organization's infrastructure. With the increasing reliance on technology for day-to-day operations, it is essential to have robust processes in place to prevent service interruptions and safeguard critical data and systems. Let's explore how you can effectively implement IT service continuity management to protect your infrastructure and ensure business continuity.
Importance of Infrastructure Protection in IT Service Management
IT service management encompasses various processes and practices aimed at delivering and supporting IT services to meet the needs of the organization. One of the key components of IT service management is continuity planning, which focuses on maintaining service availability and resilience in the face of disruptions. By implementing effective continuity planning, organizations can mitigate risks associated with service interruptions and ensure uninterrupted operations.
Data Protection and Disaster Recovery in IT Service Continuity Management
Data protection is a critical aspect of IT service continuity management, as it involves safeguarding sensitive information and ensuring its availability in case of data loss or corruption. Disaster recovery plans are essential for restoring IT systems and services in the event of a disaster or outage. By implementing robust data protection and disaster recovery measures, organizations can minimize downtime and mitigate the impact of potential disruptions on their operations.
Business Continuity and IT Infrastructure Security
Business continuity planning focuses on maintaining overall operational resilience and ensuring the continuity of critical business functions during unforeseen events. IT infrastructure security plays a vital role in protecting IT assets and preventing unauthorized access or data breaches. By integrating business continuity and IT infrastructure security measures, organizations can enhance their overall resilience and responsiveness to disruptions.
Implementing Service Continuity Framework and Incident Response
A comprehensive service continuity framework includes policies, procedures, and processes that support the organization's ability to maintain service availability and respond effectively to incidents. Incident response plans outline the steps to be taken in the event of a security breach, outage, or other disruptions. By proactively implementing a service continuity framework and incident response plans, organizations can minimize the impact of incidents on their operations and accelerate the recovery process.
Protecting IT Systems and Preventing Service Interruptions
Effective IT service continuity management involves implementing measures to protect IT systems from potential threats and vulnerabilities. By conducting regular infrastructure maintenance, organizations can enhance the stability and performance of their IT environment. Additionally, implementing robust security measures and continuity procedures can help prevent service interruptions and ensure the timely restoration of services in case of disruptions.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, ensuring IT service continuity management protects your infrastructure is essential for maintaining the resilience and reliability of your organization's IT operations. By implementing proactive measures to protect data, prevent service interruptions, and respond to incidents effectively, organizations can minimize downtime and ensure business continuity. With a holistic approach to IT service continuity management, organizations can enhance their infrastructure's security, reliability, and resilience in the face of potential risks and disruptions.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's fast-paced digital world, IT service continuity management plays a crucial role in ensuring the protection and resilience of your organization's infrastructure. With the increasing reliance on technology for day-to-day operations, it is essential to have robust processes in place to prevent service interruptions and safeguard critical data and systems. Let's explore how you can effectively implement IT service continuity management to protect your infrastructure and ensure business continuity.
Importance of Infrastructure Protection in IT Service Management
IT service management encompasses various processes and practices aimed at delivering and supporting IT services to meet the needs of the organization. One of the key components of IT service management is continuity planning, which focuses on maintaining service availability and resilience in the face of disruptions. By implementing effective continuity planning, organizations can mitigate risks associated with service interruptions and ensure uninterrupted operations.
Data Protection and Disaster Recovery in IT Service Continuity Management
Data protection is a critical aspect of IT service continuity management, as it involves safeguarding sensitive information and ensuring its availability in case of data loss or corruption. Disaster recovery plans are essential for restoring IT systems and services in the event of a disaster or outage. By implementing robust data protection and disaster recovery measures, organizations can minimize downtime and mitigate the impact of potential disruptions on their operations.
Business Continuity and IT Infrastructure Security
Business continuity planning focuses on maintaining overall operational resilience and ensuring the continuity of critical business functions during unforeseen events. IT infrastructure security plays a vital role in protecting IT assets and preventing unauthorized access or data breaches. By integrating business continuity and IT infrastructure security measures, organizations can enhance their overall resilience and responsiveness to disruptions.
Implementing Service Continuity Framework and Incident Response
A comprehensive service continuity framework includes policies, procedures, and processes that support the organization's ability to maintain service availability and respond effectively to incidents. Incident response plans outline the steps to be taken in the event of a security breach, outage, or other disruptions. By proactively implementing a service continuity framework and incident response plans, organizations can minimize the impact of incidents on their operations and accelerate the recovery process.
Protecting IT Systems and Preventing Service Interruptions
Effective IT service continuity management involves implementing measures to protect IT systems from potential threats and vulnerabilities. By conducting regular infrastructure maintenance, organizations can enhance the stability and performance of their IT environment. Additionally, implementing robust security measures and continuity procedures can help prevent service interruptions and ensure the timely restoration of services in case of disruptions.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, ensuring IT service continuity management protects your infrastructure is essential for maintaining the resilience and reliability of your organization's IT operations. By implementing proactive measures to protect data, prevent service interruptions, and respond to incidents effectively, organizations can minimize downtime and ensure business continuity. With a holistic approach to IT service continuity management, organizations can enhance their infrastructure's security, reliability, and resilience in the face of potential risks and disruptions.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Revolutionizing HR Operations with RPA Technology
In the fast-paced world of Human Resources, efficiency and accuracy are key to success. Robotic Process Automation (RPA) is a cutting-edge technology that is transforming the way HR departments operate. By automating repetitive tasks and streamlining processes, RPA is revolutionizing HR operations and optimizing workforce management.
RPA in Human Resources
Robotic Process Automation (RPA) is a game-changing technology that uses software robots to automate repetitive tasks and streamline workflows in HR departments. By eliminating manual data entry, processing times are reduced, freeing up HR professionals to focus on more strategic tasks.
Automation in HR
Automation in HR is simplifying and optimizing processes such as employee onboarding, payroll processing, and performance evaluations. RPA technology can handle these tasks with speed and accuracy, resulting in improved efficiency and productivity within the HR department.
Human Resources Optimization
With RPA technology, human resources optimization is achieved through enhanced workflow automation and task delegation. By implementing RPA solutions, HR departments can minimize errors, reduce costs, and improve overall operational efficiency.
RPA Benefits in HR
The benefits of incorporating RPA in HR are vast. From increased productivity to improved data accuracy, RPA technology enhances HR processes and ensures compliance with regulations. By leveraging RPA tools, HR professionals can focus on strategic decision-making and employee engagement.
HR Software Integration
Integrating RPA technology with HR software systems is essential for maximizing its benefits. By seamlessly connecting RPA tools with existing HR platforms, organizations can achieve a higher level of automation and efficiency in their HR processes.
RPA Technology in HR
The integration of RPA technology in HR is paving the way for digital transformation within organizations. By automating routine tasks and optimizing workflows, RPA technology is driving innovation and enhancing the overall employee experience.
Improving HR Efficiency
RPA technology plays a crucial role in improving HR efficiency by automating time-consuming and repetitive tasks. By streamlining HR operations and enhancing productivity, RPA enables HR departments to operate more efficiently and effectively.
Human Resources Automation
Human resources automation through RPA technology is streamlining HR operations and enabling organizations to achieve greater levels of efficiency. By automating manual processes and standardizing workflows, RPA is transforming the way HR tasks are performed.
RPA Implementation in HR
Successful RPA implementation in HR requires careful planning and collaboration between IT and HR departments. By identifying key areas for automation and selecting the right RPA tools, organizations can achieve significant improvements in HR processes.
HR Workflow Automation
RPA technology enables HR workflow automation by automating repetitive tasks, such as data entry, scheduling, and report generation. By implementing RPA solutions, HR departments can streamline workflow processes and enhance overall productivity..
RPA for HR Professionals
RPA technology empowers HR professionals to focus on strategic initiatives by automating routine tasks and optimizing workflow processes. By leveraging RPA solutions, HR professionals can drive innovation and enhance employee experiences within the organization.
Robotic HR Management
Robotic HR management through RPA technology is revolutionizing how HR departments operate and deliver value to the organization. By automating administrative tasks, standardizing workflows, and enhancing data accuracy, RPA is reshaping HR management practices.
RPA Applications in HR
RPA applications in HR are diverse, ranging from automating recruitment processes to optimizing employee onboarding and offboarding. By leveraging RPA technology, HR departments can achieve greater efficiency and deliver enhanced employee experiences.
HR Automation Strategy
Developing an HR automation strategy with RPA technology is essential for achieving operational excellence and driving organizational success. By identifying key areas for automation and implementing RPA solutions, organizations can optimize HR processes and deliver better outcomes.
HR Automation Tools
HR automation tools powered by RPA technology are transforming how HR departments operate and deliver value to the organization. By implementing RPA tools specifically designed for HR processes, organizations can achieve significant improvements in efficiency and productivity.
RPA Use Cases in Human Resources
RPA use cases in human resources are wide-ranging, from automating employee onboarding processes to optimizing payroll management and compliance monitoring. By leveraging RPA technology, organizations can streamline HR operations and enhance overall productivity.
HR Operational Efficiency with RPA
RPA technology enhances HR operational efficiency by automating routine tasks, optimizing workflows, and improving data accuracy. By incorporating RPA tools in HR operations, organizations can achieve greater efficiency and drive business performance.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, RPA technology is revolutionizing HR operations by automating repetitive tasks, streamlining workflows, and enhancing data accuracy. By integrating RPA tools into HR processes, organizations can achieve greater efficiency, productivity, and operational excellence. As the HR landscape continues to evolve, RPA technology will play a critical role in driving digital transformation and shaping the future of workforce management.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In the fast-paced world of Human Resources, efficiency and accuracy are key to success. Robotic Process Automation (RPA) is a cutting-edge technology that is transforming the way HR departments operate. By automating repetitive tasks and streamlining processes, RPA is revolutionizing HR operations and optimizing workforce management.
RPA in Human Resources
Robotic Process Automation (RPA) is a game-changing technology that uses software robots to automate repetitive tasks and streamline workflows in HR departments. By eliminating manual data entry, processing times are reduced, freeing up HR professionals to focus on more strategic tasks.
Automation in HR
Automation in HR is simplifying and optimizing processes such as employee onboarding, payroll processing, and performance evaluations. RPA technology can handle these tasks with speed and accuracy, resulting in improved efficiency and productivity within the HR department.
Human Resources Optimization
With RPA technology, human resources optimization is achieved through enhanced workflow automation and task delegation. By implementing RPA solutions, HR departments can minimize errors, reduce costs, and improve overall operational efficiency.
RPA Benefits in HR
The benefits of incorporating RPA in HR are vast. From increased productivity to improved data accuracy, RPA technology enhances HR processes and ensures compliance with regulations. By leveraging RPA tools, HR professionals can focus on strategic decision-making and employee engagement.
HR Software Integration
Integrating RPA technology with HR software systems is essential for maximizing its benefits. By seamlessly connecting RPA tools with existing HR platforms, organizations can achieve a higher level of automation and efficiency in their HR processes.
RPA Technology in HR
The integration of RPA technology in HR is paving the way for digital transformation within organizations. By automating routine tasks and optimizing workflows, RPA technology is driving innovation and enhancing the overall employee experience.
Improving HR Efficiency
RPA technology plays a crucial role in improving HR efficiency by automating time-consuming and repetitive tasks. By streamlining HR operations and enhancing productivity, RPA enables HR departments to operate more efficiently and effectively.
Human Resources Automation
Human resources automation through RPA technology is streamlining HR operations and enabling organizations to achieve greater levels of efficiency. By automating manual processes and standardizing workflows, RPA is transforming the way HR tasks are performed.
RPA Implementation in HR
Successful RPA implementation in HR requires careful planning and collaboration between IT and HR departments. By identifying key areas for automation and selecting the right RPA tools, organizations can achieve significant improvements in HR processes.
HR Workflow Automation
RPA technology enables HR workflow automation by automating repetitive tasks, such as data entry, scheduling, and report generation. By implementing RPA solutions, HR departments can streamline workflow processes and enhance overall productivity..
RPA for HR Professionals
RPA technology empowers HR professionals to focus on strategic initiatives by automating routine tasks and optimizing workflow processes. By leveraging RPA solutions, HR professionals can drive innovation and enhance employee experiences within the organization.
Robotic HR Management
Robotic HR management through RPA technology is revolutionizing how HR departments operate and deliver value to the organization. By automating administrative tasks, standardizing workflows, and enhancing data accuracy, RPA is reshaping HR management practices.
RPA Applications in HR
RPA applications in HR are diverse, ranging from automating recruitment processes to optimizing employee onboarding and offboarding. By leveraging RPA technology, HR departments can achieve greater efficiency and deliver enhanced employee experiences.
HR Automation Strategy
Developing an HR automation strategy with RPA technology is essential for achieving operational excellence and driving organizational success. By identifying key areas for automation and implementing RPA solutions, organizations can optimize HR processes and deliver better outcomes.
HR Automation Tools
HR automation tools powered by RPA technology are transforming how HR departments operate and deliver value to the organization. By implementing RPA tools specifically designed for HR processes, organizations can achieve significant improvements in efficiency and productivity.
RPA Use Cases in Human Resources
RPA use cases in human resources are wide-ranging, from automating employee onboarding processes to optimizing payroll management and compliance monitoring. By leveraging RPA technology, organizations can streamline HR operations and enhance overall productivity.
HR Operational Efficiency with RPA
RPA technology enhances HR operational efficiency by automating routine tasks, optimizing workflows, and improving data accuracy. By incorporating RPA tools in HR operations, organizations can achieve greater efficiency and drive business performance.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, RPA technology is revolutionizing HR operations by automating repetitive tasks, streamlining workflows, and enhancing data accuracy. By integrating RPA tools into HR processes, organizations can achieve greater efficiency, productivity, and operational excellence. As the HR landscape continues to evolve, RPA technology will play a critical role in driving digital transformation and shaping the future of workforce management.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Creating Effective Email Campaigns with Salesforce Pardot
In today's digital world, email marketing continues to be one of the most powerful tools for businesses to connect with their customers. With the right strategy and tools in place, you can create effective email campaigns that drive engagement, nurture leads, and ultimately boost your ROI. Salesforce Pardot is a leading marketing automation platform that can help you streamline your email marketing efforts and achieve your goals. In this article, we will explore how you can leverage Salesforce Pardot to create successful email campaigns that deliver results.
Introduction to Salesforce Pardot
Salesforce Pardot is a comprehensive marketing automation platform that allows businesses to create, manage, and analyze their email marketing campaigns with ease. With features such as lead nurturing, subscriber engagement, segmentation, personalization, drip campaigns, targeted emails, analytics, and more, Salesforce Pardot empowers marketers to reach their target audience effectively and efficiently.
Getting Started with Salesforce Pardot
Before you can start creating email campaigns with Salesforce Pardot, you need to set up your account and integrate it with your CRM system. Once you have done this, you can begin building your subscriber list and segmenting your audience based on various criteria such as demographics, behavior, and interests.
Building Your Subscriber List
One of the first steps in creating effective email campaigns is to build a robust subscriber list. You can do this by capturing leads through your website, social media channels, events, and other marketing channels. Salesforce Pardot allows you to easily import your contacts, create custom fields, and track their engagement with your emails.
Segmenting Your Audience
Segmentation is key to delivering personalized and relevant content to your subscribers. With Salesforce Pardot, you can create dynamic lists based on criteria such as location, industry, purchase history, and engagement level. By segmenting your audience, you can tailor your email campaigns to specific groups and increase the likelihood of conversion.
Designing Your Email Campaigns
Once you have built your subscriber list and segmented your audience, it's time to start designing your email campaigns. Salesforce Pardot offers a wide range of email templates that you can customize to match your brand and messaging. You can also schedule your emails to be sent at the optimal time for maximum impact.
Creating Engaging Content
The key to a successful email campaign is creating engaging and relevant content that resonates with your audience. Whether you are promoting a new product, sharing industry insights, or offering a special promotion, make sure your content is informative, engaging, and visually appealing.
A/B Testing
Testing is essential to optimizing your email campaigns for maximum effectiveness. With Salesforce Pardot, you can easily set up A/B tests to experiment with different subject lines, copy, images, and calls to action. By analyzing the results of these tests, you can identify what resonates with your audience and refine your email strategy accordingly.
Analyzing Your Results
After you have launched your email campaigns, it's important to analyze the results to determine their success. Salesforce Pardot provides detailed analytics on metrics such as open rates, click-through rates, conversion rates, and ROI tracking. By monitoring these metrics, you can gain valuable insights into the performance of your campaigns and make data-driven decisions for future optimizations.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, creating effective email campaigns with Salesforce Pardot is a powerful way to engage your audience, nurture leads, and drive conversions. By following best practices such as audience segmentation, personalized content, A/B testing, and analytics tracking, you can optimize your email campaigns for success. With the right strategy and tools at your disposal, you can take your email marketing efforts to the next level and achieve your business goals.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's digital world, email marketing continues to be one of the most powerful tools for businesses to connect with their customers. With the right strategy and tools in place, you can create effective email campaigns that drive engagement, nurture leads, and ultimately boost your ROI. Salesforce Pardot is a leading marketing automation platform that can help you streamline your email marketing efforts and achieve your goals. In this article, we will explore how you can leverage Salesforce Pardot to create successful email campaigns that deliver results.
Introduction to Salesforce Pardot
Salesforce Pardot is a comprehensive marketing automation platform that allows businesses to create, manage, and analyze their email marketing campaigns with ease. With features such as lead nurturing, subscriber engagement, segmentation, personalization, drip campaigns, targeted emails, analytics, and more, Salesforce Pardot empowers marketers to reach their target audience effectively and efficiently.
Getting Started with Salesforce Pardot
Before you can start creating email campaigns with Salesforce Pardot, you need to set up your account and integrate it with your CRM system. Once you have done this, you can begin building your subscriber list and segmenting your audience based on various criteria such as demographics, behavior, and interests.
Building Your Subscriber List
One of the first steps in creating effective email campaigns is to build a robust subscriber list. You can do this by capturing leads through your website, social media channels, events, and other marketing channels. Salesforce Pardot allows you to easily import your contacts, create custom fields, and track their engagement with your emails.
Segmenting Your Audience
Segmentation is key to delivering personalized and relevant content to your subscribers. With Salesforce Pardot, you can create dynamic lists based on criteria such as location, industry, purchase history, and engagement level. By segmenting your audience, you can tailor your email campaigns to specific groups and increase the likelihood of conversion.
Designing Your Email Campaigns
Once you have built your subscriber list and segmented your audience, it's time to start designing your email campaigns. Salesforce Pardot offers a wide range of email templates that you can customize to match your brand and messaging. You can also schedule your emails to be sent at the optimal time for maximum impact.
Creating Engaging Content
The key to a successful email campaign is creating engaging and relevant content that resonates with your audience. Whether you are promoting a new product, sharing industry insights, or offering a special promotion, make sure your content is informative, engaging, and visually appealing.
A/B Testing
Testing is essential to optimizing your email campaigns for maximum effectiveness. With Salesforce Pardot, you can easily set up A/B tests to experiment with different subject lines, copy, images, and calls to action. By analyzing the results of these tests, you can identify what resonates with your audience and refine your email strategy accordingly.
Analyzing Your Results
After you have launched your email campaigns, it's important to analyze the results to determine their success. Salesforce Pardot provides detailed analytics on metrics such as open rates, click-through rates, conversion rates, and ROI tracking. By monitoring these metrics, you can gain valuable insights into the performance of your campaigns and make data-driven decisions for future optimizations.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, creating effective email campaigns with Salesforce Pardot is a powerful way to engage your audience, nurture leads, and drive conversions. By following best practices such as audience segmentation, personalized content, A/B testing, and analytics tracking, you can optimize your email campaigns for success. With the right strategy and tools at your disposal, you can take your email marketing efforts to the next level and achieve your business goals.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
6 Reasons to Protect IT Systems
In today's digital world, protecting government IT systems is more important than ever. From cybersecurity threats to potential data breaches, government agencies must take proactive measures to ensure the security of sensitive information and safeguard their operations. Here are 6 reasons why protecting government IT systems is crucial:
1. Cybersecurity
Cyber threats are constantly evolving, becoming more sophisticated and complex with each passing day. Government IT systems house a wealth of sensitive information, making them prime targets for malicious actors looking to exploit vulnerabilities. By implementing robust cybersecurity measures, government agencies can mitigate the risk of cyber attacks and protect their digital assets.
2. Data Security
Government data is incredibly valuable and must be kept secure at all costs. Data breaches can have severe consequences, ranging from financial losses to damage to the government's reputation. Protecting government IT systems ensures that sensitive information remains safe from unauthorized access and potential exploitation.
3. Proactive Prevention
Prevention is key when it comes to protecting government IT systems. By implementing effective security measures and protocols, government agencies can proactively identify and address potential threats before they escalate into full-blown cyber attacks. This proactive approach helps mitigate risks and ensures the continuous functioning of critical government operations.
4. Cyber Resilience
In the event of a cyber attack or data breach, cyber resilience is crucial for government agencies to bounce back quickly and recover from the incident. By investing in robust IT infrastructure and risk management practices, government agencies can enhance their cyber resilience and minimize the impact of security breaches on their operations.
5. Threat Detection
Effective threat detection is essential for safeguarding government IT systems against cyber attacks. By deploying advanced security protocols and tools, government agencies can detect and respond to potential threats in real-time, preventing them from causing significant damage or compromising sensitive information.
6. Government Cybersecurity Solutions
There is a wide range of cybersecurity solutions available to help government agencies protect their IT systems effectively. From implementing encryption technologies to conducting regular security audits, these solutions can significantly enhance the overall security posture of government IT systems and safeguard critical infrastructure from cyber threats.
How to obtain Cyber Security certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, protecting government IT systems is imperative in today's digital age. By prioritizing cybersecurity, implementing proactive prevention measures, enhancing cyber resilience, focusing on threat detection, and leveraging cybersecurity solutions, government agencies can effectively safeguard their operations and ensure the security of sensitive information. With the increasing prevalence of cyber threats, investing in the protection of government IT systems is not only necessary but also critical for maintaining the trust and confidence of the public in government operations.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's digital world, protecting government IT systems is more important than ever. From cybersecurity threats to potential data breaches, government agencies must take proactive measures to ensure the security of sensitive information and safeguard their operations. Here are 6 reasons why protecting government IT systems is crucial:
1. Cybersecurity
Cyber threats are constantly evolving, becoming more sophisticated and complex with each passing day. Government IT systems house a wealth of sensitive information, making them prime targets for malicious actors looking to exploit vulnerabilities. By implementing robust cybersecurity measures, government agencies can mitigate the risk of cyber attacks and protect their digital assets.
2. Data Security
Government data is incredibly valuable and must be kept secure at all costs. Data breaches can have severe consequences, ranging from financial losses to damage to the government's reputation. Protecting government IT systems ensures that sensitive information remains safe from unauthorized access and potential exploitation.
3. Proactive Prevention
Prevention is key when it comes to protecting government IT systems. By implementing effective security measures and protocols, government agencies can proactively identify and address potential threats before they escalate into full-blown cyber attacks. This proactive approach helps mitigate risks and ensures the continuous functioning of critical government operations.
4. Cyber Resilience
In the event of a cyber attack or data breach, cyber resilience is crucial for government agencies to bounce back quickly and recover from the incident. By investing in robust IT infrastructure and risk management practices, government agencies can enhance their cyber resilience and minimize the impact of security breaches on their operations.
5. Threat Detection
Effective threat detection is essential for safeguarding government IT systems against cyber attacks. By deploying advanced security protocols and tools, government agencies can detect and respond to potential threats in real-time, preventing them from causing significant damage or compromising sensitive information.
6. Government Cybersecurity Solutions
There is a wide range of cybersecurity solutions available to help government agencies protect their IT systems effectively. From implementing encryption technologies to conducting regular security audits, these solutions can significantly enhance the overall security posture of government IT systems and safeguard critical infrastructure from cyber threats.
How to obtain Cyber Security certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, protecting government IT systems is imperative in today's digital age. By prioritizing cybersecurity, implementing proactive prevention measures, enhancing cyber resilience, focusing on threat detection, and leveraging cybersecurity solutions, government agencies can effectively safeguard their operations and ensure the security of sensitive information. With the increasing prevalence of cyber threats, investing in the protection of government IT systems is not only necessary but also critical for maintaining the trust and confidence of the public in government operations.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Vital Concepts of Big Data and Hadoop
In today's digital age, the amount of data being generated on a daily basis is staggering. From social media interactions to online transactions, every click, like, and share produces valuable data that can be used for insights and decision-making. This is where big data and Hadoop come into play. In this article, we will explore the vital concepts of big data and Hadoop, uncovering the key components that make this technology so essential in the world of data analytics and processing.
What is Big Data?
Big data refers to the vast volume of structured and unstructured data that is generated at a high velocity and requires innovative forms of processing for insights and decision-making. This data comes from a variety of sources, including social media, IoT devices, sensors, and more. Traditional data processing applications are not equipped to handle such large and complex datasets, which is where big data technologies like Hadoop come in.
Understanding Hadoop
Hadoop is an open-source framework that facilitates the distributed processing of large data sets across clusters of computers. It consists of two main components: MapReduce for data processing and HDFS (Hadoop Distributed File System) for data storage. Hadoop enables organizations to store, process, and analyze massive amounts of data in a cost-effective and scalable manner.
Key Concepts of Big Data and Hadoop
-
Data Processing: Big data technologies like Hadoop enable organizations to process large amounts of data quickly and efficiently. This is essential for tasks such as data cleansing, transformation, and analysis.
-
Data Analysis: Hadoop allows for sophisticated data analysis techniques, such as machine learning and real-time analytics, to be applied to large datasets. This helps organizations uncover valuable insights and trends from their data.
-
Distributed Computing: Hadoop uses a distributed computing model, where data is processed in parallel across multiple nodes in a cluster. This enables faster processing speeds and increased scalability.
-
Data Storage: HDFS, the storage component of Hadoop, allows organizations to store vast amounts of data across multiple nodes in a cluster. This provides redundancy and fault tolerance, ensuring data integrity.
-
Data Management: Hadoop offers tools for data management, such as data retrieval, data visualization, and data integration. These tools help organizations make sense of their data and derive actionable insights.
-
Scalability: Hadoop's distributed architecture enables organizations to scale their data processing and storage capabilities as their data volumes grow. This ensures that organizations can continue to derive value from their data as it expands.
-
Parallel Processing: Hadoop leverages parallel processing techniques to distribute data processing tasks across multiple nodes in a cluster. This speeds up processing times and increases efficiency.
-
Data Science: Hadoop is a key tool in the field of data science, enabling data scientists to work with large and complex datasets to uncover patterns, trends, and insights. This is essential for making data-driven decisions.
-
Machine Learning: Hadoop supports machine learning algorithms, allowing organizations to build predictive models and make accurate forecasts based on their data. This is invaluable for businesses looking to optimize processes and strategies.
-
Real-time Analytics: Hadoop enables real-time analytics by processing data as it is generated, rather than in batch processes. This allows organizations to make immediate decisions based on up-to-date information.
How to obtain Big Data certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the vital concepts of big data and Hadoop are essential for organizations looking to harness the power of data in today's digital age. By understanding the key components of big data and Hadoop, organizations can unlock valuable insights, improve decision-making, and drive innovation. With the right tools and techniques, organizations can leverage the power of big data to gain a competitive edge in their industry.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's digital age, the amount of data being generated on a daily basis is staggering. From social media interactions to online transactions, every click, like, and share produces valuable data that can be used for insights and decision-making. This is where big data and Hadoop come into play. In this article, we will explore the vital concepts of big data and Hadoop, uncovering the key components that make this technology so essential in the world of data analytics and processing.
What is Big Data?
Big data refers to the vast volume of structured and unstructured data that is generated at a high velocity and requires innovative forms of processing for insights and decision-making. This data comes from a variety of sources, including social media, IoT devices, sensors, and more. Traditional data processing applications are not equipped to handle such large and complex datasets, which is where big data technologies like Hadoop come in.
Understanding Hadoop
Hadoop is an open-source framework that facilitates the distributed processing of large data sets across clusters of computers. It consists of two main components: MapReduce for data processing and HDFS (Hadoop Distributed File System) for data storage. Hadoop enables organizations to store, process, and analyze massive amounts of data in a cost-effective and scalable manner.
Key Concepts of Big Data and Hadoop
-
Data Processing: Big data technologies like Hadoop enable organizations to process large amounts of data quickly and efficiently. This is essential for tasks such as data cleansing, transformation, and analysis.
-
Data Analysis: Hadoop allows for sophisticated data analysis techniques, such as machine learning and real-time analytics, to be applied to large datasets. This helps organizations uncover valuable insights and trends from their data.
-
Distributed Computing: Hadoop uses a distributed computing model, where data is processed in parallel across multiple nodes in a cluster. This enables faster processing speeds and increased scalability.
-
Data Storage: HDFS, the storage component of Hadoop, allows organizations to store vast amounts of data across multiple nodes in a cluster. This provides redundancy and fault tolerance, ensuring data integrity.
-
Data Management: Hadoop offers tools for data management, such as data retrieval, data visualization, and data integration. These tools help organizations make sense of their data and derive actionable insights.
-
Scalability: Hadoop's distributed architecture enables organizations to scale their data processing and storage capabilities as their data volumes grow. This ensures that organizations can continue to derive value from their data as it expands.
-
Parallel Processing: Hadoop leverages parallel processing techniques to distribute data processing tasks across multiple nodes in a cluster. This speeds up processing times and increases efficiency.
-
Data Science: Hadoop is a key tool in the field of data science, enabling data scientists to work with large and complex datasets to uncover patterns, trends, and insights. This is essential for making data-driven decisions.
-
Machine Learning: Hadoop supports machine learning algorithms, allowing organizations to build predictive models and make accurate forecasts based on their data. This is invaluable for businesses looking to optimize processes and strategies.
-
Real-time Analytics: Hadoop enables real-time analytics by processing data as it is generated, rather than in batch processes. This allows organizations to make immediate decisions based on up-to-date information.
How to obtain Big Data certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the vital concepts of big data and Hadoop are essential for organizations looking to harness the power of data in today's digital age. By understanding the key components of big data and Hadoop, organizations can unlock valuable insights, improve decision-making, and drive innovation. With the right tools and techniques, organizations can leverage the power of big data to gain a competitive edge in their industry.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Top Business Agility Trends to Watch in 2024
In today's fast-paced and ever-changing business landscape, staying ahead of the competition requires adaptability and agility. As we look towards 2024, it's essential for businesses to anticipate and embrace the upcoming trends that will shape the future of the market. Let's explore the top business agility trends to watch in 2024 and how organizations can prepare themselves for the challenges and opportunities that lie ahead.
Business Agility Trends 2024
1. Agile Business Strategies
Agile methodologies have become increasingly popular in recent years as businesses seek to improve efficiency and flexibility in their operations. In 2024, we can expect to see even more companies adopting agile business strategies to quickly respond to market changes and customer needs.
2. Organizational Flexibility
Organizational flexibility will be key for businesses to thrive in 2024. Companies that can easily pivot and adapt to new circumstances will have a competitive edge in the dynamic business environment.
3. Market Innovation
Innovation will continue to drive business success in 2024. Companies that prioritize innovation and invest in research and development will be better positioned to meet the evolving needs of customers and stay ahead of the competition.
4. Corporate Agility
Corporate agility will be crucial for businesses to navigate the complexities of the market in 2024. Companies that can quickly adjust their strategies and processes in response to changing market dynamics will be better equipped to succeed.
5. Business Resilience
Building resilience will be a top priority for businesses in 2024. With economic uncertainties and market disruptions on the horizon, companies must focus on creating robust business models that can withstand unexpected challenges.
Future of Business Agility
As we look towards the future of business agility, it's clear that organizations must stay ahead of the curve to remain competitive. By embracing agile practices, fostering innovation, and fostering a culture of adaptability, businesses can thrive in the dynamic market landscape of 2024.
Strategic Evolution
Strategic evolution will be essential for businesses to stay relevant in 2024. Companies must constantly review and refine their strategies to align with market trends and customer expectations.
Modern Business Practices
Embracing modern business practices, such as digital transformation and AI integration, will be crucial for companies looking to stay ahead of the curve in 2024. By leveraging technology and data analytics, businesses can drive innovation and improve efficiency.
Customer Experience Evolution
Customer experience will continue to be a top priority for businesses in 2024. Companies that prioritize delivering exceptional customer experiences will build brand loyalty and drive growth in a competitive market.
Remote Work Trends
As remote work becomes more prevalent, businesses must adapt their strategies to support a distributed workforce in 2024. Companies that can effectively manage and empower remote teams will have a competitive advantage in the evolving business landscape.
How to obtain Agile and Scrum certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the top business agility trends to watch in 2024 emphasize the importance of adaptability, innovation, and resilience for businesses looking to succeed in a dynamic market environment. By staying ahead of the curve and embracing the upcoming trends, organizations can position themselves for growth and success in the years to come.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's fast-paced and ever-changing business landscape, staying ahead of the competition requires adaptability and agility. As we look towards 2024, it's essential for businesses to anticipate and embrace the upcoming trends that will shape the future of the market. Let's explore the top business agility trends to watch in 2024 and how organizations can prepare themselves for the challenges and opportunities that lie ahead.
Business Agility Trends 2024
1. Agile Business Strategies
Agile methodologies have become increasingly popular in recent years as businesses seek to improve efficiency and flexibility in their operations. In 2024, we can expect to see even more companies adopting agile business strategies to quickly respond to market changes and customer needs.
2. Organizational Flexibility
Organizational flexibility will be key for businesses to thrive in 2024. Companies that can easily pivot and adapt to new circumstances will have a competitive edge in the dynamic business environment.
3. Market Innovation
Innovation will continue to drive business success in 2024. Companies that prioritize innovation and invest in research and development will be better positioned to meet the evolving needs of customers and stay ahead of the competition.
4. Corporate Agility
Corporate agility will be crucial for businesses to navigate the complexities of the market in 2024. Companies that can quickly adjust their strategies and processes in response to changing market dynamics will be better equipped to succeed.
5. Business Resilience
Building resilience will be a top priority for businesses in 2024. With economic uncertainties and market disruptions on the horizon, companies must focus on creating robust business models that can withstand unexpected challenges.
Future of Business Agility
As we look towards the future of business agility, it's clear that organizations must stay ahead of the curve to remain competitive. By embracing agile practices, fostering innovation, and fostering a culture of adaptability, businesses can thrive in the dynamic market landscape of 2024.
Strategic Evolution
Strategic evolution will be essential for businesses to stay relevant in 2024. Companies must constantly review and refine their strategies to align with market trends and customer expectations.
Modern Business Practices
Embracing modern business practices, such as digital transformation and AI integration, will be crucial for companies looking to stay ahead of the curve in 2024. By leveraging technology and data analytics, businesses can drive innovation and improve efficiency.
Customer Experience Evolution
Customer experience will continue to be a top priority for businesses in 2024. Companies that prioritize delivering exceptional customer experiences will build brand loyalty and drive growth in a competitive market.
Remote Work Trends
As remote work becomes more prevalent, businesses must adapt their strategies to support a distributed workforce in 2024. Companies that can effectively manage and empower remote teams will have a competitive advantage in the evolving business landscape.
How to obtain Agile and Scrum certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the top business agility trends to watch in 2024 emphasize the importance of adaptability, innovation, and resilience for businesses looking to succeed in a dynamic market environment. By staying ahead of the curve and embracing the upcoming trends, organizations can position themselves for growth and success in the years to come.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Deploying High Availability Solutions with XenServer
Are you looking to enhance the reliability and availability of your virtualized environment? Deploying high availability solutions with XenServer can help you achieve just that. XenServer, a powerful virtualization platform, offers a range of features and capabilities to support high availability deployment, disaster recovery, failover clustering, and more. In this article, we will explore how XenServer can help you build a robust and resilient IT infrastructure to ensure system availability, redundancy, and business continuity.
High Availability Deployment with XenServer
Deploying high availability solutions with XenServer involves setting up server clustering, failover mechanisms, and other features to ensure that your virtual machines are always available and operational. XenServer offers built-in tools for creating virtual environments that can withstand hardware failures and maximize uptime. By leveraging XenServer's hypervisor technology, you can achieve fault tolerance and reliability for your virtualized workloads.
One of the key benefits of deploying high availability solutions with XenServer is the ability to create scalable solutions that can grow with your business. Whether you are running virtual desktops, network infrastructure, or enterprise applications, XenServer provides the flexibility and performance you need to meet your IT operations requirements. By utilizing XenServer for server virtualization, you can avoid downtime, ensure data protection, and optimize your storage solutions.
Disaster Recovery and Business Continuity
In today's digital age, data protection and disaster recovery are critical components of any IT strategy. With XenServer, you can implement robust disaster recovery plans that minimize downtime and ensure the integrity of your data. By leveraging XenServer's high availability features, such as server clustering and failover mechanisms, you can achieve near-instantaneous recovery times and seamless failover in the event of hardware failures.
XenServer also offers support for load balancing, which enables you to distribute workloads across multiple servers for optimal performance and resource utilization. By balancing the load across your virtualized environment, you can prevent downtime and ensure that your applications and services remain available to your users. Additionally, XenServer's fault tolerance capabilities provide an added layer of protection against hardware failures, ensuring that your IT infrastructure remains operational at all times.
How to obtain XENSERVER certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, deploying high availability solutions with XenServer can help you build a resilient and reliable IT infrastructure that meets the demands of modern businesses. Whether you are looking to enhance system availability, ensure business continuity, or optimize your virtualized environment, XenServer offers the features and capabilities you need to achieve your goals. With XenServer's support for redundancy, server clustering, and disaster recovery, you can rest assured that your IT operations will remain operational and secure. So why wait? Start deploying high availability solutions with XenServer today and experience the benefits of a robust and resilient virtualized environment.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
Are you looking to enhance the reliability and availability of your virtualized environment? Deploying high availability solutions with XenServer can help you achieve just that. XenServer, a powerful virtualization platform, offers a range of features and capabilities to support high availability deployment, disaster recovery, failover clustering, and more. In this article, we will explore how XenServer can help you build a robust and resilient IT infrastructure to ensure system availability, redundancy, and business continuity.
High Availability Deployment with XenServer
Deploying high availability solutions with XenServer involves setting up server clustering, failover mechanisms, and other features to ensure that your virtual machines are always available and operational. XenServer offers built-in tools for creating virtual environments that can withstand hardware failures and maximize uptime. By leveraging XenServer's hypervisor technology, you can achieve fault tolerance and reliability for your virtualized workloads.
One of the key benefits of deploying high availability solutions with XenServer is the ability to create scalable solutions that can grow with your business. Whether you are running virtual desktops, network infrastructure, or enterprise applications, XenServer provides the flexibility and performance you need to meet your IT operations requirements. By utilizing XenServer for server virtualization, you can avoid downtime, ensure data protection, and optimize your storage solutions.
Disaster Recovery and Business Continuity
In today's digital age, data protection and disaster recovery are critical components of any IT strategy. With XenServer, you can implement robust disaster recovery plans that minimize downtime and ensure the integrity of your data. By leveraging XenServer's high availability features, such as server clustering and failover mechanisms, you can achieve near-instantaneous recovery times and seamless failover in the event of hardware failures.
XenServer also offers support for load balancing, which enables you to distribute workloads across multiple servers for optimal performance and resource utilization. By balancing the load across your virtualized environment, you can prevent downtime and ensure that your applications and services remain available to your users. Additionally, XenServer's fault tolerance capabilities provide an added layer of protection against hardware failures, ensuring that your IT infrastructure remains operational at all times.
How to obtain XENSERVER certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, deploying high availability solutions with XenServer can help you build a resilient and reliable IT infrastructure that meets the demands of modern businesses. Whether you are looking to enhance system availability, ensure business continuity, or optimize your virtualized environment, XenServer offers the features and capabilities you need to achieve your goals. With XenServer's support for redundancy, server clustering, and disaster recovery, you can rest assured that your IT operations will remain operational and secure. So why wait? Start deploying high availability solutions with XenServer today and experience the benefits of a robust and resilient virtualized environment.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
The Role of Digital Identity in Secure Online Transactions
In today's digital age, where online transactions have become the norm, ensuring secure and reliable processes is paramount. With the increasing prevalence of cyber threats and identity theft, the role of digital identity in securing online transactions has never been more crucial. Let's delve into the importance of digital identity in ensuring a safe and secure online environment.
What is Digital Identity and Its Importance in Online Transactions?
Digital identity refers to the unique representation of a person, organization, or device in the digital world. It is the online presence that defines who we are and establishes our credentials for online interactions. In the context of online transactions, digital identity plays a vital role in authenticating users, ensuring cybersecurity, protecting privacy, and preventing fraud.
Authentication and Fraud Prevention
One of the key functions of digital identity in online transactions is authentication. By verifying the identity of users through various means such as biometrics, two-factor authentication, or password protection, digital identity helps ensure that only authorized individuals have access to sensitive information and secure systems.
Additionally, digital identity plays a crucial role in fraud prevention. By establishing the legitimacy of users and monitoring their activities, digital identity solutions can detect and prevent unauthorized transactions, identity theft, and other fraudulent activities.
Data Protection and Privacy
Privacy and data protection are fundamental aspects of online transactions. Digital identity solutions enable users to control access to their personal information, safeguarding their privacy and ensuring that sensitive data is protected from unauthorized access.
By encrypting data and implementing secure protocols, digital identity technologies help safeguard personal information and prevent data breaches. This ensures that online transactions are conducted securely and that users' personal data is protected from cyber threats.
The Evolution of Identity Management in Online Transactions
Over the years, identity management has evolved to meet the growing demands of secure online transactions. From traditional methods such as username and password authentication to more advanced technologies like biometrics and digital signatures, identity management solutions have become increasingly sophisticated and secure.
Secure Banking and E-Commerce Security
In the realm of online banking and e-commerce, digital identity plays a crucial role in securing transactions and protecting sensitive financial information. By implementing secure login processes, encryption mechanisms, and identity verification protocols, banks and e-commerce platforms can ensure that transactions are conducted safely and securely.
Digital signatures also play a vital role in validating the authenticity of transactions and ensuring that documents are tamper-proof. By utilizing digital signatures, organizations can verify the integrity of transactions and establish a secure chain of trust between parties involved.
Transaction Security and Secure Authorization
Ensuring transaction security is essential in online transactions to protect against financial loss and fraud. Digital identity solutions provide secure authorization mechanisms that authenticate users and authorize transactions, ensuring that only authorized individuals can access sensitive information and conduct transactions.
By utilizing advanced encryption techniques and secure protocols, digital identity solutions help create a secure environment for online transactions, safeguarding against cyber threats and enhancing the overall security of online transactions.
How to obtain Emerging Technologies certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the role of digital identity in secure online transactions cannot be overstated. From authentication and fraud prevention to data protection and privacy, digital identity technologies play a crucial role in ensuring that online transactions are conducted securely and reliably.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's digital age, where online transactions have become the norm, ensuring secure and reliable processes is paramount. With the increasing prevalence of cyber threats and identity theft, the role of digital identity in securing online transactions has never been more crucial. Let's delve into the importance of digital identity in ensuring a safe and secure online environment.
What is Digital Identity and Its Importance in Online Transactions?
Digital identity refers to the unique representation of a person, organization, or device in the digital world. It is the online presence that defines who we are and establishes our credentials for online interactions. In the context of online transactions, digital identity plays a vital role in authenticating users, ensuring cybersecurity, protecting privacy, and preventing fraud.
Authentication and Fraud Prevention
One of the key functions of digital identity in online transactions is authentication. By verifying the identity of users through various means such as biometrics, two-factor authentication, or password protection, digital identity helps ensure that only authorized individuals have access to sensitive information and secure systems.
Additionally, digital identity plays a crucial role in fraud prevention. By establishing the legitimacy of users and monitoring their activities, digital identity solutions can detect and prevent unauthorized transactions, identity theft, and other fraudulent activities.
Data Protection and Privacy
Privacy and data protection are fundamental aspects of online transactions. Digital identity solutions enable users to control access to their personal information, safeguarding their privacy and ensuring that sensitive data is protected from unauthorized access.
By encrypting data and implementing secure protocols, digital identity technologies help safeguard personal information and prevent data breaches. This ensures that online transactions are conducted securely and that users' personal data is protected from cyber threats.
The Evolution of Identity Management in Online Transactions
Over the years, identity management has evolved to meet the growing demands of secure online transactions. From traditional methods such as username and password authentication to more advanced technologies like biometrics and digital signatures, identity management solutions have become increasingly sophisticated and secure.
Secure Banking and E-Commerce Security
In the realm of online banking and e-commerce, digital identity plays a crucial role in securing transactions and protecting sensitive financial information. By implementing secure login processes, encryption mechanisms, and identity verification protocols, banks and e-commerce platforms can ensure that transactions are conducted safely and securely.
Digital signatures also play a vital role in validating the authenticity of transactions and ensuring that documents are tamper-proof. By utilizing digital signatures, organizations can verify the integrity of transactions and establish a secure chain of trust between parties involved.
Transaction Security and Secure Authorization
Ensuring transaction security is essential in online transactions to protect against financial loss and fraud. Digital identity solutions provide secure authorization mechanisms that authenticate users and authorize transactions, ensuring that only authorized individuals can access sensitive information and conduct transactions.
By utilizing advanced encryption techniques and secure protocols, digital identity solutions help create a secure environment for online transactions, safeguarding against cyber threats and enhancing the overall security of online transactions.
How to obtain Emerging Technologies certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the role of digital identity in secure online transactions cannot be overstated. From authentication and fraud prevention to data protection and privacy, digital identity technologies play a crucial role in ensuring that online transactions are conducted securely and reliably.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Exploring the Reach of Digital Marketing in 2024
Are you curious about the future of digital marketing in the year 2024? As technology continues to evolve at a rapid pace, digital marketing is constantly adapting to new trends and strategies. In this article, we will delve into the various aspects of digital marketing and explore how it is projected to shape the marketing landscape in 2024.
Digital Marketing Trends 2024
The year 2024 is expected to bring about several key trends in digital marketing. One major trend is the increasing focus on personalized marketing approaches. Brands will leverage data analytics to create highly targeted and tailored marketing campaigns that resonate with individual consumers. Additionally, the rise of artificial intelligence (AI) in marketing will lead to more efficient and effective customer engagement strategies.
Future of Digital Marketing
The future of digital marketing lies in the seamless integration of various online advertising strategies. From social media marketing to SEO and content marketing, brands will need to utilize a combination of tactics to reach their target audience effectively. Additionally, the evolution of digital branding strategies will play a crucial role in establishing a strong brand presence in the digital space.
Online Advertising Strategies in 2024
In 2024, online advertising strategies will become more sophisticated and data-driven. Brands will increasingly rely on targeted marketing campaigns that leverage consumer behavior analysis to deliver relevant content to their audience. Furthermore, the use of influencer marketing will continue to grow as companies collaborate with popular influencers to promote their products or services.
The Role of Social Media Marketing
Social media marketing will remain a cornerstone of digital marketing in 2024. With the growing popularity of platforms like TikTok and Instagram, brands will need to stay ahead of the curve by creating engaging content that resonates with their target audience. Effective social media advertising will be key to driving brand awareness and customer engagement.
SEO and Content Marketing Evolution
Search engine optimization (SEO) will continue to be a vital component of digital marketing in 2024. Brands will focus on optimizing their websites and content for search engines to improve their visibility online. Content marketing will also evolve, with a greater emphasis on storytelling and creating valuable, engaging content that captures the attention of consumers.
Digital Marketing Innovations
As we look towards 2024, we can expect to see several digital marketing innovations take center stage. Video marketing strategies will become increasingly popular, as brands leverage the power of video content to engage with their audience. Mobile marketing will also play a significant role, with brands optimizing their campaigns for mobile devices to reach consumers on the go.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the reach of digital marketing in 2024 is poised to extend to new heights as brands continue to innovate and adapt to changing consumer behaviors. By staying ahead of the latest trends and leveraging the power of technology, businesses can position themselves for success in the digital marketing landscape of the future.
So, are you ready to embrace the possibilities of digital marketing in 2024? With the right strategies and innovative approaches, your brand can reach new heights and connect with your target audience like never before.
Read More
Are you curious about the future of digital marketing in the year 2024? As technology continues to evolve at a rapid pace, digital marketing is constantly adapting to new trends and strategies. In this article, we will delve into the various aspects of digital marketing and explore how it is projected to shape the marketing landscape in 2024.
Digital Marketing Trends 2024
The year 2024 is expected to bring about several key trends in digital marketing. One major trend is the increasing focus on personalized marketing approaches. Brands will leverage data analytics to create highly targeted and tailored marketing campaigns that resonate with individual consumers. Additionally, the rise of artificial intelligence (AI) in marketing will lead to more efficient and effective customer engagement strategies.
Future of Digital Marketing
The future of digital marketing lies in the seamless integration of various online advertising strategies. From social media marketing to SEO and content marketing, brands will need to utilize a combination of tactics to reach their target audience effectively. Additionally, the evolution of digital branding strategies will play a crucial role in establishing a strong brand presence in the digital space.
Online Advertising Strategies in 2024
In 2024, online advertising strategies will become more sophisticated and data-driven. Brands will increasingly rely on targeted marketing campaigns that leverage consumer behavior analysis to deliver relevant content to their audience. Furthermore, the use of influencer marketing will continue to grow as companies collaborate with popular influencers to promote their products or services.
The Role of Social Media Marketing
Social media marketing will remain a cornerstone of digital marketing in 2024. With the growing popularity of platforms like TikTok and Instagram, brands will need to stay ahead of the curve by creating engaging content that resonates with their target audience. Effective social media advertising will be key to driving brand awareness and customer engagement.
SEO and Content Marketing Evolution
Search engine optimization (SEO) will continue to be a vital component of digital marketing in 2024. Brands will focus on optimizing their websites and content for search engines to improve their visibility online. Content marketing will also evolve, with a greater emphasis on storytelling and creating valuable, engaging content that captures the attention of consumers.
Digital Marketing Innovations
As we look towards 2024, we can expect to see several digital marketing innovations take center stage. Video marketing strategies will become increasingly popular, as brands leverage the power of video content to engage with their audience. Mobile marketing will also play a significant role, with brands optimizing their campaigns for mobile devices to reach consumers on the go.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the reach of digital marketing in 2024 is poised to extend to new heights as brands continue to innovate and adapt to changing consumer behaviors. By staying ahead of the latest trends and leveraging the power of technology, businesses can position themselves for success in the digital marketing landscape of the future.
So, are you ready to embrace the possibilities of digital marketing in 2024? With the right strategies and innovative approaches, your brand can reach new heights and connect with your target audience like never before.
AES Encryption for Improved Data Security
In today's digital age, the need for robust data security measures has never been more critical. With cyber threats on the rise, companies and individuals must take proactive steps to safeguard their sensitive information. One of the most effective ways to enhance data security is through the use of AES encryption.
What is AES Encryption?
AES stands for Advanced Encryption Standard, which is a symmetric encryption algorithm that is used to secure data transmission and storage. This encryption technique is considered highly secure and is widely used for protecting confidential information. AES encryption involves the use of an encryption key to scramble the data, making it unreadable to anyone without the corresponding decryption key.
How Does AES Encryption Improve Data Security?
-
Secure Information Exchange: AES encryption ensures that only authorized parties can access the encrypted data, preventing unauthorized interception of sensitive information.
-
Secure Communication: By encrypting communication channels with AES, data exchanged between parties is protected from eavesdroppers and hackers.
-
Secure Storage: AES encryption can be used to encrypt data stored on devices or in the cloud, ensuring that even if the data is compromised, it remains encrypted and secure.
-
Encryption Strength: AES encryption offers a high level of encryption strength, making it extremely difficult for attackers to decrypt the data without the encryption key.
Why is AES Encryption Essential for Data Protection?
-
Cybersecurity: In today's digital landscape, cybersecurity threats are ever-present. AES encryption provides a strong defense against cyber attacks by securing data from unauthorized access.
-
Data Privacy: AES encryption helps to maintain the privacy of sensitive information, ensuring that only authorized users can access the data.
-
Secure Network: By encrypting data transmitted over networks, AES encryption helps to create a secure environment for data exchange and communication.
The use of AES encryption is essential for companies and individuals looking to enhance their data security measures. By incorporating AES encryption into their data protection strategies, organizations can safeguard sensitive information, maintain data integrity, and mitigate the risk of data breaches.
How to obtain Cyber Security certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, AES encryption is a powerful tool for improving data security in today's digital world. By utilizing the advanced encryption standard, organizations and individuals can protect their sensitive information, secure their communication channels, and safeguard their data from cyber threats. Implementing AES encryption as part of a comprehensive data security strategy is essential for ensuring the confidentiality, integrity, and availability of data in today's increasingly interconnected world.
Read More
In today's digital age, the need for robust data security measures has never been more critical. With cyber threats on the rise, companies and individuals must take proactive steps to safeguard their sensitive information. One of the most effective ways to enhance data security is through the use of AES encryption.
What is AES Encryption?
AES stands for Advanced Encryption Standard, which is a symmetric encryption algorithm that is used to secure data transmission and storage. This encryption technique is considered highly secure and is widely used for protecting confidential information. AES encryption involves the use of an encryption key to scramble the data, making it unreadable to anyone without the corresponding decryption key.
How Does AES Encryption Improve Data Security?
-
Secure Information Exchange: AES encryption ensures that only authorized parties can access the encrypted data, preventing unauthorized interception of sensitive information.
-
Secure Communication: By encrypting communication channels with AES, data exchanged between parties is protected from eavesdroppers and hackers.
-
Secure Storage: AES encryption can be used to encrypt data stored on devices or in the cloud, ensuring that even if the data is compromised, it remains encrypted and secure.
-
Encryption Strength: AES encryption offers a high level of encryption strength, making it extremely difficult for attackers to decrypt the data without the encryption key.
Why is AES Encryption Essential for Data Protection?
-
Cybersecurity: In today's digital landscape, cybersecurity threats are ever-present. AES encryption provides a strong defense against cyber attacks by securing data from unauthorized access.
-
Data Privacy: AES encryption helps to maintain the privacy of sensitive information, ensuring that only authorized users can access the data.
-
Secure Network: By encrypting data transmitted over networks, AES encryption helps to create a secure environment for data exchange and communication.
The use of AES encryption is essential for companies and individuals looking to enhance their data security measures. By incorporating AES encryption into their data protection strategies, organizations can safeguard sensitive information, maintain data integrity, and mitigate the risk of data breaches.
How to obtain Cyber Security certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, AES encryption is a powerful tool for improving data security in today's digital world. By utilizing the advanced encryption standard, organizations and individuals can protect their sensitive information, secure their communication channels, and safeguard their data from cyber threats. Implementing AES encryption as part of a comprehensive data security strategy is essential for ensuring the confidentiality, integrity, and availability of data in today's increasingly interconnected world.
Automating Network Management with NetScaler and Ansible
Are you looking to streamline your network management processes and increase efficiency within your IT operations? Look no further than NetScaler and Ansible, two powerful tools that can revolutionize the way you manage your network infrastructure.
Introduction to Network Automation
In today's fast-paced digital landscape, network automation has become essential for organizations looking to stay ahead of the curve. Automating network management tasks can help network administrators save time, reduce errors, and improve overall network performance.
With automated solutions like NetScaler and Ansible, IT teams can simplify complex network configurations, enhance network security, and optimize network scalability. By leveraging automation tools, organizations can ensure that their network infrastructure is running smoothly and efficiently at all times.
The Power of NetScaler
NetScaler is a leading application delivery controller that offers advanced load balancing, security, and optimization features for network administrators. By automating network provisioning, monitoring, and cloud networking tasks, NetScaler helps organizations improve network performance and efficiency.
With NetScaler, network administrators can easily configure network settings, manage network protocols, and streamline device management tasks. Additionally, NetScaler provides automated solutions for network deployment, allowing IT teams to quickly and effectively implement changes to their network infrastructure.
Streamlining Tasks with Ansible
Ansible is a powerful automation tool that simplifies configuration management, system automation, and network operations. By using Ansible playbooks and automation scripts, IT teams can automate repetitive network tasks, reduce manual errors, and enhance overall network efficiency.
With Ansible, network administrators can automate network configurations, deploy network resources, and manage network virtualization. Ansible's network automation framework allows organizations to standardize their network operations, leading to improved network architecture and enhanced network scalability.
Implementing Network Automation Solutions
To get started with automating your network management with NetScaler and Ansible, consider the following steps:
-
Evaluate your current network infrastructure and identify areas where automation can improve efficiency.
-
Set clear goals and objectives for your network automation project, such as reducing manual tasks, improving network security, or enhancing network performance.
-
Install and configure NetScaler and Ansible on your network infrastructure, ensuring that they are integrated seamlessly with your existing systems.
-
Develop automation workflows and playbooks that align with your organization's network management requirements and objectives.
-
Test and evaluate your automated solutions to ensure they are functioning as expected and delivering the desired results.
By implementing network automation solutions with NetScaler and Ansible, organizations can streamline their network management processes, increase productivity, and achieve greater agility in their IT operations. With the power of automation, network administrators can focus on strategic initiatives and innovation, rather than getting bogged down by manual network tasks.
How to obtain Netscaler certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, automating network management with NetScaler and Ansible offers organizations a cost-effective and efficient way to optimize their network infrastructure and improve overall network performance. By leveraging these powerful automation tools, IT teams can enhance network security, scalability, and efficiency, ultimately driving business success in today's digital world.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
Are you looking to streamline your network management processes and increase efficiency within your IT operations? Look no further than NetScaler and Ansible, two powerful tools that can revolutionize the way you manage your network infrastructure.
Introduction to Network Automation
In today's fast-paced digital landscape, network automation has become essential for organizations looking to stay ahead of the curve. Automating network management tasks can help network administrators save time, reduce errors, and improve overall network performance.
With automated solutions like NetScaler and Ansible, IT teams can simplify complex network configurations, enhance network security, and optimize network scalability. By leveraging automation tools, organizations can ensure that their network infrastructure is running smoothly and efficiently at all times.
The Power of NetScaler
NetScaler is a leading application delivery controller that offers advanced load balancing, security, and optimization features for network administrators. By automating network provisioning, monitoring, and cloud networking tasks, NetScaler helps organizations improve network performance and efficiency.
With NetScaler, network administrators can easily configure network settings, manage network protocols, and streamline device management tasks. Additionally, NetScaler provides automated solutions for network deployment, allowing IT teams to quickly and effectively implement changes to their network infrastructure.
Streamlining Tasks with Ansible
Ansible is a powerful automation tool that simplifies configuration management, system automation, and network operations. By using Ansible playbooks and automation scripts, IT teams can automate repetitive network tasks, reduce manual errors, and enhance overall network efficiency.
With Ansible, network administrators can automate network configurations, deploy network resources, and manage network virtualization. Ansible's network automation framework allows organizations to standardize their network operations, leading to improved network architecture and enhanced network scalability.
Implementing Network Automation Solutions
To get started with automating your network management with NetScaler and Ansible, consider the following steps:
-
Evaluate your current network infrastructure and identify areas where automation can improve efficiency.
-
Set clear goals and objectives for your network automation project, such as reducing manual tasks, improving network security, or enhancing network performance.
-
Install and configure NetScaler and Ansible on your network infrastructure, ensuring that they are integrated seamlessly with your existing systems.
-
Develop automation workflows and playbooks that align with your organization's network management requirements and objectives.
-
Test and evaluate your automated solutions to ensure they are functioning as expected and delivering the desired results.
By implementing network automation solutions with NetScaler and Ansible, organizations can streamline their network management processes, increase productivity, and achieve greater agility in their IT operations. With the power of automation, network administrators can focus on strategic initiatives and innovation, rather than getting bogged down by manual network tasks.
How to obtain Netscaler certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, automating network management with NetScaler and Ansible offers organizations a cost-effective and efficient way to optimize their network infrastructure and improve overall network performance. By leveraging these powerful automation tools, IT teams can enhance network security, scalability, and efficiency, ultimately driving business success in today's digital world.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Using COBIT 5 for Digital Transformation
In today's fast-paced and ever-changing business landscape, digital transformation is a crucial process that organizations need to undertake to stay competitive and relevant. One framework that can help businesses navigate this complex journey is COBIT® 5.
What is COBIT® 5?
COBIT® 5 is a comprehensive framework developed by ISACA that helps organizations effectively govern and manage their information and technology assets. It provides a set of best practices and guidelines that can be tailored to suit the specific needs of each organization.
Business Process
COBIT® 5 focuses on aligning IT goals with business objectives, ensuring that technology investments contribute to the overall success of the organization. By mapping out business processes and identifying areas for improvement, COBIT® 5 helps streamline operations and drive efficiency.
IT Governance
One of the key aspects of COBIT® 5 is IT governance, which involves setting clear roles and responsibilities, establishing decision-making processes, and ensuring accountability. This helps organizations make informed decisions about their IT investments and initiatives.
Risk Management
Risk management is another critical component of COBIT® 5. By identifying and assessing potential risks, organizations can take proactive measures to mitigate them and protect their assets. This proactive approach helps minimize disruptions and ensures continuity of operations.
Control Objectives
COBIT® 5 provides a set of control objectives that organizations can use to evaluate and monitor their IT processes. These objectives help ensure that technology systems are secure, reliable, and compliant with regulatory requirements.
Enterprise Architecture
COBIT® 5 also emphasizes the importance of building a solid enterprise architecture that supports the organization's strategic objectives. By aligning IT resources with business goals, organizations can drive innovation and create a competitive advantage.
Information Security
Information security is a top priority for organizations in the digital age. COBIT® 5 helps organizations implement robust security measures to protect their data and systems from cyber threats and breaches.
Compliance Requirements
Staying compliant with industry regulations and standards is crucial for organizations operating in highly regulated sectors. COBIT® 5 provides a roadmap for achieving compliance and maintaining a strong governance framework.
The Principles of COBIT® 5
The principles of COBIT® 5 are based on seven key factors that drive successful governance and management of IT assets. These principles include:
-
Aligning IT with business goals
-
Enabling a holistic approach to governance
-
Ensuring end-to-end coverage of IT processes
-
Applying a single integrated framework
-
Enabling a tailored approach to implementation
-
Focusing on organizational goals
-
Separating governance from management
By adhering to these principles, organizations can effectively leverage COBIT® 5 to drive digital transformation and achieve their strategic objectives.
COBIT® 5 Certification and Training
For professionals looking to enhance their knowledge and skills in IT governance and management, COBIT® 5 certification and training programs are available. These programs provide in-depth training on how to implement and leverage COBIT® 5 within an organization, enabling professionals to drive successful digital transformation initiatives.
How to obtain COBIT 5 certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, COBIT® 5 is a powerful framework that can help organizations navigate the complexities of digital transformation. By implementing COBIT® 5 principles and guidelines, organizations can maximize the value of their IT investments, drive innovation, and ensure long-term success in today's competitive business environment. Embracing COBIT® 5 is not just an option—it's a necessity for organizations looking to thrive in the digital age.
Read More
In today's fast-paced and ever-changing business landscape, digital transformation is a crucial process that organizations need to undertake to stay competitive and relevant. One framework that can help businesses navigate this complex journey is COBIT® 5.
What is COBIT® 5?
COBIT® 5 is a comprehensive framework developed by ISACA that helps organizations effectively govern and manage their information and technology assets. It provides a set of best practices and guidelines that can be tailored to suit the specific needs of each organization.
Business Process
COBIT® 5 focuses on aligning IT goals with business objectives, ensuring that technology investments contribute to the overall success of the organization. By mapping out business processes and identifying areas for improvement, COBIT® 5 helps streamline operations and drive efficiency.
IT Governance
One of the key aspects of COBIT® 5 is IT governance, which involves setting clear roles and responsibilities, establishing decision-making processes, and ensuring accountability. This helps organizations make informed decisions about their IT investments and initiatives.
Risk Management
Risk management is another critical component of COBIT® 5. By identifying and assessing potential risks, organizations can take proactive measures to mitigate them and protect their assets. This proactive approach helps minimize disruptions and ensures continuity of operations.
Control Objectives
COBIT® 5 provides a set of control objectives that organizations can use to evaluate and monitor their IT processes. These objectives help ensure that technology systems are secure, reliable, and compliant with regulatory requirements.
Enterprise Architecture
COBIT® 5 also emphasizes the importance of building a solid enterprise architecture that supports the organization's strategic objectives. By aligning IT resources with business goals, organizations can drive innovation and create a competitive advantage.
Information Security
Information security is a top priority for organizations in the digital age. COBIT® 5 helps organizations implement robust security measures to protect their data and systems from cyber threats and breaches.
Compliance Requirements
Staying compliant with industry regulations and standards is crucial for organizations operating in highly regulated sectors. COBIT® 5 provides a roadmap for achieving compliance and maintaining a strong governance framework.
The Principles of COBIT® 5
The principles of COBIT® 5 are based on seven key factors that drive successful governance and management of IT assets. These principles include:
-
Aligning IT with business goals
-
Enabling a holistic approach to governance
-
Ensuring end-to-end coverage of IT processes
-
Applying a single integrated framework
-
Enabling a tailored approach to implementation
-
Focusing on organizational goals
-
Separating governance from management
By adhering to these principles, organizations can effectively leverage COBIT® 5 to drive digital transformation and achieve their strategic objectives.
COBIT® 5 Certification and Training
For professionals looking to enhance their knowledge and skills in IT governance and management, COBIT® 5 certification and training programs are available. These programs provide in-depth training on how to implement and leverage COBIT® 5 within an organization, enabling professionals to drive successful digital transformation initiatives.
How to obtain COBIT 5 certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, COBIT® 5 is a powerful framework that can help organizations navigate the complexities of digital transformation. By implementing COBIT® 5 principles and guidelines, organizations can maximize the value of their IT investments, drive innovation, and ensure long-term success in today's competitive business environment. Embracing COBIT® 5 is not just an option—it's a necessity for organizations looking to thrive in the digital age.
Integrating Lean Six Sigma with Agile and Scrum Methodologies
In today's rapidly evolving business landscape, organizations are constantly seeking ways to improve their operational efficiency and deliver value to their customers. Two popular methodologies that have gained significant traction in recent years are Lean Six Sigma and Agile/Scrum. While these methodologies originated in different industries and serve distinct purposes, they can be integrated to create a powerful framework for driving process improvement and delivering high-quality products and services.
What is Lean Six Sigma?
Lean Six Sigma is a methodology that combines the principles of Lean manufacturing and Six Sigma to eliminate waste, reduce variation, and improve overall quality in a systematic and data-driven manner. Lean focuses on streamlining processes and eliminating non-value-added activities, while Six Sigma aims to reduce defects and variation in processes to achieve near-perfect quality. By integrating the principles of Lean and Six Sigma, organizations can achieve significant improvements in efficiency, productivity, and customer satisfaction.
What is Agile and Scrum?
Agile is a project management methodology that emphasizes flexibility, adaptability, and collaboration in the development of software and other products. Scrum, on the other hand, is a specific framework within Agile that defines roles, activities, and artifacts to facilitate the iterative and incremental development of products. Agile and Scrum are well-suited for projects that require frequent changes, rapid delivery, and close collaboration between cross-functional teams.
Benefits of Integrating Lean Six Sigma with Agile and Scrum:
-
Improved process efficiency and quality
-
Faster delivery of products and services
-
Enhanced collaboration and communication between teams
-
Better alignment of project objectives with customer needs
-
Increased flexibility and adaptability to changing market conditions
-
Reduced waste and variation in processes
-
Continuous improvement culture that drives innovation and growth
How to Integrate Lean Six Sigma with Agile and Scrum:
Integrating Lean Six Sigma with Agile and Scrum requires a deep understanding of both methodologies and how they complement each other. Organizations can start by aligning Lean Six Sigma principles with Agile values, such as customer focus, continuous improvement, and empowerment of teams. By incorporating Lean Six Sigma tools and techniques into Agile/Scrum processes, organizations can identify and eliminate waste, reduce defects, and improve overall process efficiency.
Success Factors for Lean Six Sigma with Agile and Scrum:
-
Strong leadership support and commitment to process improvement
-
Cross-functional collaboration and communication
-
Training and certification in Lean Six Sigma and Agile/Scrum methodologies
-
Clear alignment of project objectives with customer needs
-
Regular monitoring and evaluation of process performance
-
Continuous learning and adaptation based on feedback and data
How to obtain Lean Six Sigma Black Belt certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion:
Integrating Lean Six Sigma with Agile and Scrum methodologies can provide organizations with a powerful framework for driving process improvement, delivering high-quality products and services, and achieving sustainable growth. By combining the principles of Lean Six Sigma with the flexibility and adaptability of Agile/Scrum, organizations can create a culture of continuous improvement, innovation, and customer-centricity that sets them apart in today's competitive marketplace.
Read More
In today's rapidly evolving business landscape, organizations are constantly seeking ways to improve their operational efficiency and deliver value to their customers. Two popular methodologies that have gained significant traction in recent years are Lean Six Sigma and Agile/Scrum. While these methodologies originated in different industries and serve distinct purposes, they can be integrated to create a powerful framework for driving process improvement and delivering high-quality products and services.
What is Lean Six Sigma?
Lean Six Sigma is a methodology that combines the principles of Lean manufacturing and Six Sigma to eliminate waste, reduce variation, and improve overall quality in a systematic and data-driven manner. Lean focuses on streamlining processes and eliminating non-value-added activities, while Six Sigma aims to reduce defects and variation in processes to achieve near-perfect quality. By integrating the principles of Lean and Six Sigma, organizations can achieve significant improvements in efficiency, productivity, and customer satisfaction.
What is Agile and Scrum?
Agile is a project management methodology that emphasizes flexibility, adaptability, and collaboration in the development of software and other products. Scrum, on the other hand, is a specific framework within Agile that defines roles, activities, and artifacts to facilitate the iterative and incremental development of products. Agile and Scrum are well-suited for projects that require frequent changes, rapid delivery, and close collaboration between cross-functional teams.
Benefits of Integrating Lean Six Sigma with Agile and Scrum:
-
Improved process efficiency and quality
-
Faster delivery of products and services
-
Enhanced collaboration and communication between teams
-
Better alignment of project objectives with customer needs
-
Increased flexibility and adaptability to changing market conditions
-
Reduced waste and variation in processes
-
Continuous improvement culture that drives innovation and growth
How to Integrate Lean Six Sigma with Agile and Scrum:
Integrating Lean Six Sigma with Agile and Scrum requires a deep understanding of both methodologies and how they complement each other. Organizations can start by aligning Lean Six Sigma principles with Agile values, such as customer focus, continuous improvement, and empowerment of teams. By incorporating Lean Six Sigma tools and techniques into Agile/Scrum processes, organizations can identify and eliminate waste, reduce defects, and improve overall process efficiency.
Success Factors for Lean Six Sigma with Agile and Scrum:
-
Strong leadership support and commitment to process improvement
-
Cross-functional collaboration and communication
-
Training and certification in Lean Six Sigma and Agile/Scrum methodologies
-
Clear alignment of project objectives with customer needs
-
Regular monitoring and evaluation of process performance
-
Continuous learning and adaptation based on feedback and data
How to obtain Lean Six Sigma Black Belt certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion:
Integrating Lean Six Sigma with Agile and Scrum methodologies can provide organizations with a powerful framework for driving process improvement, delivering high-quality products and services, and achieving sustainable growth. By combining the principles of Lean Six Sigma with the flexibility and adaptability of Agile/Scrum, organizations can create a culture of continuous improvement, innovation, and customer-centricity that sets them apart in today's competitive marketplace.
Blockchain Certification for Business Leaders: Why It’s Essential
In today's fast-paced business world, staying ahead of the curve is essential. One way to ensure you are at the forefront of innovation and strategic decision-making is by obtaining a blockchain certification. But why is blockchain certification essential for business leaders, and how can it benefit your career and business? Let's explore the importance of blockchain certification and the impact it can have on your professional development.
Why Blockchain Certification is Essential
1. Stay Ahead in Emerging Technologies : With the rise of blockchain technology, businesses are increasingly looking for leaders who understand how to leverage this technology for strategic advantage. By obtaining a blockchain certification, you demonstrate your expertise in this emerging field and position yourself as a valuable asset to any organization looking to innovate and adapt to the future of business.
2. Enhance Your Leadership Skills : Blockchain certification programs not only teach you about the technical aspects of blockchain but also help you develop essential leadership skills. These programs focus on areas such as decision-making, problem-solving, and strategic thinking, all of which are crucial for effective leadership in today's competitive business environment.
3. Drive Business Innovation : Blockchain has the potential to revolutionize the way businesses operate, from increasing efficiency to enhancing security and transparency. With a blockchain certification, you can drive innovation within your organization by implementing blockchain solutions that improve processes, streamline operations, and create new opportunities for growth.
4. Adapt to Industry Disruption : As blockchain technology continues to disrupt traditional industries, businesses need leaders who can navigate and capitalize on these changes. By acquiring a blockchain certification, you demonstrate your ability to understand and adapt to industry disruption, positioning yourself as a forward-thinking leader who can drive your organization's success in the face of change.
The Benefits of Blockchain Certification for Business Leaders
-
Career Advancement: With a blockchain certification, you can differentiate yourself from your peers and stand out in a competitive job market. Employers are increasingly looking for candidates with expertise in blockchain, and having a certification can open up new opportunities for career advancement.
-
Expertise in Emerging Technology: Blockchain is one of the most exciting and transformative technologies of our time. By obtaining a blockchain certification, you can build expertise in this innovative technology and position yourself as a leader in the digital transformation landscape.
-
Strategic Decision-Making: Blockchain certification programs focus on teaching you how to strategically leverage blockchain technology to drive business success. With this knowledge, you can make informed, data-driven decisions that give your organization a competitive advantage.
-
Future-Proof Your Skills: As blockchain adoption continues to grow, having a certification in this field is essential for staying relevant and competitive in the evolving business landscape. By investing in blockchain education, you future-proof your skills and ensure long-term success in your career.
-
Competitive Advantage: By obtaining a blockchain certification, you set yourself apart from other business leaders and demonstrate your commitment to professional development and continuous learning. This competitive advantage can help you secure new opportunities, attract top talent, and drive business growth.
-
Upskilling Opportunities: Blockchain certification programs provide a valuable opportunity to upskill and expand your knowledge and expertise in a rapidly evolving field. By investing in your education and development, you can stay ahead of the curve and position yourself as a leader in blockchain technology.
How to obtain Block Chain Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, blockchain certification is essential for business leaders looking to stay ahead in today's competitive business landscape. By acquiring expertise in blockchain technology, you can drive innovation, enhance your leadership skills, and position yourself for career advancement and success. So, why wait? Invest in your professional development today and reap the benefits of blockchain certification for years to come.
Read More
In today's fast-paced business world, staying ahead of the curve is essential. One way to ensure you are at the forefront of innovation and strategic decision-making is by obtaining a blockchain certification. But why is blockchain certification essential for business leaders, and how can it benefit your career and business? Let's explore the importance of blockchain certification and the impact it can have on your professional development.
Why Blockchain Certification is Essential
1. Stay Ahead in Emerging Technologies : With the rise of blockchain technology, businesses are increasingly looking for leaders who understand how to leverage this technology for strategic advantage. By obtaining a blockchain certification, you demonstrate your expertise in this emerging field and position yourself as a valuable asset to any organization looking to innovate and adapt to the future of business.
2. Enhance Your Leadership Skills : Blockchain certification programs not only teach you about the technical aspects of blockchain but also help you develop essential leadership skills. These programs focus on areas such as decision-making, problem-solving, and strategic thinking, all of which are crucial for effective leadership in today's competitive business environment.
3. Drive Business Innovation : Blockchain has the potential to revolutionize the way businesses operate, from increasing efficiency to enhancing security and transparency. With a blockchain certification, you can drive innovation within your organization by implementing blockchain solutions that improve processes, streamline operations, and create new opportunities for growth.
4. Adapt to Industry Disruption : As blockchain technology continues to disrupt traditional industries, businesses need leaders who can navigate and capitalize on these changes. By acquiring a blockchain certification, you demonstrate your ability to understand and adapt to industry disruption, positioning yourself as a forward-thinking leader who can drive your organization's success in the face of change.
The Benefits of Blockchain Certification for Business Leaders
-
Career Advancement: With a blockchain certification, you can differentiate yourself from your peers and stand out in a competitive job market. Employers are increasingly looking for candidates with expertise in blockchain, and having a certification can open up new opportunities for career advancement.
-
Expertise in Emerging Technology: Blockchain is one of the most exciting and transformative technologies of our time. By obtaining a blockchain certification, you can build expertise in this innovative technology and position yourself as a leader in the digital transformation landscape.
-
Strategic Decision-Making: Blockchain certification programs focus on teaching you how to strategically leverage blockchain technology to drive business success. With this knowledge, you can make informed, data-driven decisions that give your organization a competitive advantage.
-
Future-Proof Your Skills: As blockchain adoption continues to grow, having a certification in this field is essential for staying relevant and competitive in the evolving business landscape. By investing in blockchain education, you future-proof your skills and ensure long-term success in your career.
-
Competitive Advantage: By obtaining a blockchain certification, you set yourself apart from other business leaders and demonstrate your commitment to professional development and continuous learning. This competitive advantage can help you secure new opportunities, attract top talent, and drive business growth.
-
Upskilling Opportunities: Blockchain certification programs provide a valuable opportunity to upskill and expand your knowledge and expertise in a rapidly evolving field. By investing in your education and development, you can stay ahead of the curve and position yourself as a leader in blockchain technology.
How to obtain Block Chain Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, blockchain certification is essential for business leaders looking to stay ahead in today's competitive business landscape. By acquiring expertise in blockchain technology, you can drive innovation, enhance your leadership skills, and position yourself for career advancement and success. So, why wait? Invest in your professional development today and reap the benefits of blockchain certification for years to come.
Understanding the Digital Marketing Certification Landscape: What Employers Look For
In today's competitive job market, having a digital marketing certification can give you a significant edge over other candidates. Employers are constantly on the lookout for candidates who possess the right skills and qualifications to excel in the fast-paced world of digital marketing. But what exactly are employers looking for when it comes to digital marketing certifications? Let's delve into the requirements, industry trends, and criteria that employers consider when hiring.
The Importance of Digital Marketing Certifications
Digital marketing certifications are a testament to your knowledge and expertise in the field. They show potential employers that you have put in the effort to deepen your understanding of digital marketing strategies and tactics. In a rapidly evolving industry like digital marketing, having up-to-date certifications can set you apart from the competition and demonstrate your commitment to professional growth.
What Employers Value in Digital Marketing Certifications
When hiring for digital marketing roles, employers look for certifications that are accredited and recognized within the industry. Certifications from reputable organizations signal to employers that you have received quality training and have demonstrated competency in key areas of digital marketing.
Additionally, employers value certifications that cover a broad range of digital marketing skills, including SEO, SEM, social media marketing, content marketing, and analytics. A well-rounded certification program will ensure that you have the knowledge and skills needed to succeed in various aspects of digital marketing.
Trends in Digital Marketing Certification
The digital marketing landscape is constantly evolving, and employers are looking for candidates who can keep up with the latest trends and technologies. As such, certifications that cover emerging trends such as AI-powered marketing, voice search optimization, and omnichannel marketing are particularly valuable in today's job market.
Career Qualifications and Competitive Edge
Obtaining a digital marketing certification can give you a significant competitive edge in your job search. In a field where industry trends and technologies are constantly changing, having the right certifications can make you a more attractive candidate to potential employers.
Employers are not only looking for candidates with the right skills and qualifications, but also those who are willing to invest in their professional development. By obtaining relevant certifications, you can demonstrate your commitment to staying current in the ever-changing world of digital marketing.
What to Consider Before Pursuing a Digital Marketing Certification
Before pursuing a digital marketing certification, it's important to research the specific requirements and criteria that employers in your industry are looking for. Consider the value that the certification will add to your skill set and how it aligns with your career goals. Additionally, assess the credibility of the certification program and ensure that it is recognized within the industry.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, digital marketing certifications play a crucial role in demonstrating your expertise and skills to potential employers. By staying informed about industry trends, investing in relevant certifications, and showcasing your commitment to professional growth, you can position yourself as a top candidate in the competitive field of digital marketing. Remember, employers are looking for candidates who can bring value to their organization, so make sure to choose certifications that align with your career goals and enhance your digital marketing skill set.
Read More
In today's competitive job market, having a digital marketing certification can give you a significant edge over other candidates. Employers are constantly on the lookout for candidates who possess the right skills and qualifications to excel in the fast-paced world of digital marketing. But what exactly are employers looking for when it comes to digital marketing certifications? Let's delve into the requirements, industry trends, and criteria that employers consider when hiring.
The Importance of Digital Marketing Certifications
Digital marketing certifications are a testament to your knowledge and expertise in the field. They show potential employers that you have put in the effort to deepen your understanding of digital marketing strategies and tactics. In a rapidly evolving industry like digital marketing, having up-to-date certifications can set you apart from the competition and demonstrate your commitment to professional growth.
What Employers Value in Digital Marketing Certifications
When hiring for digital marketing roles, employers look for certifications that are accredited and recognized within the industry. Certifications from reputable organizations signal to employers that you have received quality training and have demonstrated competency in key areas of digital marketing.
Additionally, employers value certifications that cover a broad range of digital marketing skills, including SEO, SEM, social media marketing, content marketing, and analytics. A well-rounded certification program will ensure that you have the knowledge and skills needed to succeed in various aspects of digital marketing.
Trends in Digital Marketing Certification
The digital marketing landscape is constantly evolving, and employers are looking for candidates who can keep up with the latest trends and technologies. As such, certifications that cover emerging trends such as AI-powered marketing, voice search optimization, and omnichannel marketing are particularly valuable in today's job market.
Career Qualifications and Competitive Edge
Obtaining a digital marketing certification can give you a significant competitive edge in your job search. In a field where industry trends and technologies are constantly changing, having the right certifications can make you a more attractive candidate to potential employers.
Employers are not only looking for candidates with the right skills and qualifications, but also those who are willing to invest in their professional development. By obtaining relevant certifications, you can demonstrate your commitment to staying current in the ever-changing world of digital marketing.
What to Consider Before Pursuing a Digital Marketing Certification
Before pursuing a digital marketing certification, it's important to research the specific requirements and criteria that employers in your industry are looking for. Consider the value that the certification will add to your skill set and how it aligns with your career goals. Additionally, assess the credibility of the certification program and ensure that it is recognized within the industry.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, digital marketing certifications play a crucial role in demonstrating your expertise and skills to potential employers. By staying informed about industry trends, investing in relevant certifications, and showcasing your commitment to professional growth, you can position yourself as a top candidate in the competitive field of digital marketing. Remember, employers are looking for candidates who can bring value to their organization, so make sure to choose certifications that align with your career goals and enhance your digital marketing skill set.
The Future of AWS Architecture: Trends and Predictions
In today's fast-paced digital world, cloud computing has become an integral part of how businesses operate. With the rise of technologies like AWS (Amazon Web Services), companies are able to scale their infrastructure, increase efficiency, and drive innovation like never before. As we look ahead to the future of AWS architecture, what trends can we expect to see, and what predictions can we make about the direction of cloud computing?
AWS Architecture in the Cloud Computing Landscape
AWS architecture plays a crucial role in the overall cloud computing landscape. It provides businesses with the tools and resources they need to build scalable, secure, and efficient IT infrastructure. With services like EC2, S3, and RDS, AWS offers a wide range of solutions for companies of all sizes and industries.
Innovations in Infrastructure
One of the key trends we can expect to see in the future of AWS architecture is a focus on innovation in infrastructure. As technology continues to evolve, AWS will likely introduce new services and features that allow businesses to build more resilient and scalable infrastructure. From improved storage solutions to advanced networking capabilities, AWS will continue to push the boundaries of what is possible in the cloud.
Scalability and Serverless Computing
Scalability is another important trend in the future of AWS architecture. With the increasing demand for flexible and agile infrastructure, AWS will continue to enhance its scalability features to meet the needs of growing businesses. Serverless computing, in particular, will play a significant role in this trend, allowing companies to run code without provisioning or managing servers.
Embracing Microservices and Containers
Microservices and containers have revolutionized the way applications are built and deployed. In the future, we can expect AWS to continue to support these innovative technologies, providing businesses with the tools they need to create modular and scalable applications. By embracing microservices and containers, companies can increase agility, reduce complexity, and improve efficiency in their IT operations.
Integration of Machine Learning and IoT
Machine learning and IoT (Internet of Things) are two rapidly growing fields that are driving innovation across industries. In the future of AWS architecture, we can expect to see a seamless integration of these technologies, enabling businesses to harness the power of data and analytics to drive decision-making and create new, personalized experiences for customers.
Focus on Security and Automation
Security will remain a top priority for AWS as more businesses transition to the cloud. With an increasing number of cyber threats, AWS will continue to enhance its security features, providing customers with the tools they need to protect their data and applications. Automation will also play a key role in the future of AWS architecture, allowing companies to streamline their operations and reduce manual tasks.
Multi-Cloud and Virtualization
As businesses increasingly adopt a multi-cloud strategy, AWS will need to provide solutions that enable seamless integration across different cloud platforms. Virtualization will also continue to be a key trend in the future of AWS architecture, allowing companies to optimize resources, reduce costs, and improve flexibility in their IT infrastructure.
The Rise of DevOps and Data Storage
DevOps practices have become essential for companies looking to accelerate software development and improve collaboration between teams. In the future, we can expect AWS to further support DevOps initiatives, providing tools and services that enable companies to automate processes and streamline workflows. Data storage will also be a key focus, with AWS offering innovative solutions for storing and managing large volumes of data efficiently.
Cost Optimization, Elasticity, and Sustainability
Cost optimization will be a critical factor in the future of AWS architecture, with businesses looking to reduce expenses while maximizing performance. AWS will continue to offer tools and services that help companies optimize their cloud spending, improve elasticity, and achieve sustainability goals. By leveraging AWS's cost optimization features, businesses can ensure that they are getting the most value out of their cloud investments.
Serverless Computing and Hybrid Cloud
Serverless computing is gaining popularity as companies look for ways to run applications more efficiently and cost-effectively. In the future, we can expect AWS to further enhance its serverless offerings, providing businesses with the tools they need to build and deploy applications without managing servers. Hybrid cloud integration will also be a key trend, with AWS offering solutions that enable seamless connectivity between on-premises infrastructure and the cloud.
Edge Computing and Artificial Intelligence
Edge computing is becoming increasingly important as businesses look for ways to process data closer to where it is generated. In the future of AWS architecture, we can expect to see a focus on edge computing solutions, enabling companies to process data faster and improve application performance. Artificial intelligence will also play a significant role, with AWS offering tools and services that enable businesses to leverage AI technologies for data analytics, machine vision, and more.
Data Analytics, Big Data, and Machine Translation
Data analytics and big data will continue to be key drivers of innovation in the future of AWS architecture. With tools like Amazon Redshift and AWS Glue, businesses can unlock valuable insights from their data and drive informed decision-making. Machine translation will also be an important trend, with AWS providing translation services that enable companies to communicate with customers and employees in multiple languages.
Blockchain, Cybersecurity, and Compliance
Blockchain technology has the potential to revolutionize industries like finance, healthcare, and supply chain management. In the future, we can expect AWS to support blockchain integration, providing businesses with secure and scalable solutions for storing and managing transactional data. Cybersecurity and compliance will also be top priorities, with AWS offering tools and services that help companies protect their data, meet regulatory requirements, and maintain trust with customers.
Data Governance, Containerization, and Lambda Functions
Data governance is essential for businesses looking to maintain data integrity, security, and privacy. In the future, we can expect AWS to offer enhanced data governance solutions, helping companies ensure that their data is protected and compliant with regulations. Containerization will also be a key trend, with AWS providing tools and services that enable companies to deploy and manage containers at scale. Lambda functions, which allow businesses to run code without provisioning or managing servers, will continue to be a popular choice for serverless computing in the future of AWS architecture.
Cloud-Native, Event-Driven, and High Availability
Cloud-native architecture is designed to take full advantage of the cloud environment, enabling businesses to build and deploy applications that are scalable, resilient, and agile. In the future, we can expect AWS to offer more cloud-native solutions, helping companies leverage the benefits of the cloud to drive innovation and growth. Event-driven architecture will also be a key trend, with AWS providing tools and services that enable real-time processing of events and data. High availability, which ensures that applications are always accessible and running smoothly, will continue to be a top priority for AWS as businesses rely on cloud services for critical operations.
Machine Vision, Hybrid Cloud, and Edge Computing
Machine vision technologies are rapidly advancing, enabling businesses to extract valuable insights from images and videos. In the future of AWS architecture, we can expect to see more machine vision solutions, allowing companies to analyze visual data and improve decision-making. Hybrid cloud integration will also be a key trend, with AWS offering services that enable seamless connectivity between on-premises infrastructure and the cloud. Edge computing, which processes data closer to where it is generated, will continue to gain traction as companies look for ways to improve performance and reduce latency in their applications.
How to obtain AWS Solution Architect certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the future of AWS architecture is bright and full of exciting opportunities for businesses looking to innovate and grow. With trends like scalability, serverless computing, microservices, and machine learning shaping the landscape of cloud computing, companies can expect to see continued advancements in infrastructure, security, and automation. By staying ahead of these trends and embracing new technologies, businesses can position themselves for success in the ever-evolving digital world.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's fast-paced digital world, cloud computing has become an integral part of how businesses operate. With the rise of technologies like AWS (Amazon Web Services), companies are able to scale their infrastructure, increase efficiency, and drive innovation like never before. As we look ahead to the future of AWS architecture, what trends can we expect to see, and what predictions can we make about the direction of cloud computing?
AWS Architecture in the Cloud Computing Landscape
AWS architecture plays a crucial role in the overall cloud computing landscape. It provides businesses with the tools and resources they need to build scalable, secure, and efficient IT infrastructure. With services like EC2, S3, and RDS, AWS offers a wide range of solutions for companies of all sizes and industries.
Innovations in Infrastructure
One of the key trends we can expect to see in the future of AWS architecture is a focus on innovation in infrastructure. As technology continues to evolve, AWS will likely introduce new services and features that allow businesses to build more resilient and scalable infrastructure. From improved storage solutions to advanced networking capabilities, AWS will continue to push the boundaries of what is possible in the cloud.
Scalability and Serverless Computing
Scalability is another important trend in the future of AWS architecture. With the increasing demand for flexible and agile infrastructure, AWS will continue to enhance its scalability features to meet the needs of growing businesses. Serverless computing, in particular, will play a significant role in this trend, allowing companies to run code without provisioning or managing servers.
Embracing Microservices and Containers
Microservices and containers have revolutionized the way applications are built and deployed. In the future, we can expect AWS to continue to support these innovative technologies, providing businesses with the tools they need to create modular and scalable applications. By embracing microservices and containers, companies can increase agility, reduce complexity, and improve efficiency in their IT operations.
Integration of Machine Learning and IoT
Machine learning and IoT (Internet of Things) are two rapidly growing fields that are driving innovation across industries. In the future of AWS architecture, we can expect to see a seamless integration of these technologies, enabling businesses to harness the power of data and analytics to drive decision-making and create new, personalized experiences for customers.
Focus on Security and Automation
Security will remain a top priority for AWS as more businesses transition to the cloud. With an increasing number of cyber threats, AWS will continue to enhance its security features, providing customers with the tools they need to protect their data and applications. Automation will also play a key role in the future of AWS architecture, allowing companies to streamline their operations and reduce manual tasks.
Multi-Cloud and Virtualization
As businesses increasingly adopt a multi-cloud strategy, AWS will need to provide solutions that enable seamless integration across different cloud platforms. Virtualization will also continue to be a key trend in the future of AWS architecture, allowing companies to optimize resources, reduce costs, and improve flexibility in their IT infrastructure.
The Rise of DevOps and Data Storage
DevOps practices have become essential for companies looking to accelerate software development and improve collaboration between teams. In the future, we can expect AWS to further support DevOps initiatives, providing tools and services that enable companies to automate processes and streamline workflows. Data storage will also be a key focus, with AWS offering innovative solutions for storing and managing large volumes of data efficiently.
Cost Optimization, Elasticity, and Sustainability
Cost optimization will be a critical factor in the future of AWS architecture, with businesses looking to reduce expenses while maximizing performance. AWS will continue to offer tools and services that help companies optimize their cloud spending, improve elasticity, and achieve sustainability goals. By leveraging AWS's cost optimization features, businesses can ensure that they are getting the most value out of their cloud investments.
Serverless Computing and Hybrid Cloud
Serverless computing is gaining popularity as companies look for ways to run applications more efficiently and cost-effectively. In the future, we can expect AWS to further enhance its serverless offerings, providing businesses with the tools they need to build and deploy applications without managing servers. Hybrid cloud integration will also be a key trend, with AWS offering solutions that enable seamless connectivity between on-premises infrastructure and the cloud.
Edge Computing and Artificial Intelligence
Edge computing is becoming increasingly important as businesses look for ways to process data closer to where it is generated. In the future of AWS architecture, we can expect to see a focus on edge computing solutions, enabling companies to process data faster and improve application performance. Artificial intelligence will also play a significant role, with AWS offering tools and services that enable businesses to leverage AI technologies for data analytics, machine vision, and more.
Data Analytics, Big Data, and Machine Translation
Data analytics and big data will continue to be key drivers of innovation in the future of AWS architecture. With tools like Amazon Redshift and AWS Glue, businesses can unlock valuable insights from their data and drive informed decision-making. Machine translation will also be an important trend, with AWS providing translation services that enable companies to communicate with customers and employees in multiple languages.
Blockchain, Cybersecurity, and Compliance
Blockchain technology has the potential to revolutionize industries like finance, healthcare, and supply chain management. In the future, we can expect AWS to support blockchain integration, providing businesses with secure and scalable solutions for storing and managing transactional data. Cybersecurity and compliance will also be top priorities, with AWS offering tools and services that help companies protect their data, meet regulatory requirements, and maintain trust with customers.
Data Governance, Containerization, and Lambda Functions
Data governance is essential for businesses looking to maintain data integrity, security, and privacy. In the future, we can expect AWS to offer enhanced data governance solutions, helping companies ensure that their data is protected and compliant with regulations. Containerization will also be a key trend, with AWS providing tools and services that enable companies to deploy and manage containers at scale. Lambda functions, which allow businesses to run code without provisioning or managing servers, will continue to be a popular choice for serverless computing in the future of AWS architecture.
Cloud-Native, Event-Driven, and High Availability
Cloud-native architecture is designed to take full advantage of the cloud environment, enabling businesses to build and deploy applications that are scalable, resilient, and agile. In the future, we can expect AWS to offer more cloud-native solutions, helping companies leverage the benefits of the cloud to drive innovation and growth. Event-driven architecture will also be a key trend, with AWS providing tools and services that enable real-time processing of events and data. High availability, which ensures that applications are always accessible and running smoothly, will continue to be a top priority for AWS as businesses rely on cloud services for critical operations.
Machine Vision, Hybrid Cloud, and Edge Computing
Machine vision technologies are rapidly advancing, enabling businesses to extract valuable insights from images and videos. In the future of AWS architecture, we can expect to see more machine vision solutions, allowing companies to analyze visual data and improve decision-making. Hybrid cloud integration will also be a key trend, with AWS offering services that enable seamless connectivity between on-premises infrastructure and the cloud. Edge computing, which processes data closer to where it is generated, will continue to gain traction as companies look for ways to improve performance and reduce latency in their applications.
How to obtain AWS Solution Architect certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the future of AWS architecture is bright and full of exciting opportunities for businesses looking to innovate and grow. With trends like scalability, serverless computing, microservices, and machine learning shaping the landscape of cloud computing, companies can expect to see continued advancements in infrastructure, security, and automation. By staying ahead of these trends and embracing new technologies, businesses can position themselves for success in the ever-evolving digital world.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
The Impact of Emerging Technologies on IT Service Management
In today's rapidly evolving digital landscape, the impact of emerging technologies on IT service management cannot be overlooked. With constant advancements in technology trends such as digital transformation, cloud computing, artificial intelligence, machine learning, cybersecurity, automation, big data, internet of things, data analytics, and more, IT service management professionals must adapt and evolve to meet the demands of the modern IT industry.
Evolution of IT Service Management
As technology continues to advance at a rapid pace, IT service management has undergone significant transformation. The traditional IT infrastructure is being replaced by innovative tech advancements, leading to the adoption of new and improved IT strategies. Organizations are increasingly leveraging emerging technologies to enhance their IT operations, driving the need for seamless technology integration and efficient change management practices.
Question: How has digital transformation impacted IT service management?
Answer: Digital transformation has revolutionized the way organizations approach IT service management, enabling them to streamline processes, improve efficiency, and enhance overall business performance.
The Role of IT Professionals
With the emergence of new technologies and tech disruptions, IT professionals are faced with a myriad of challenges. From ensuring business continuity to implementing effective IT governance practices, IT professionals must navigate the complexities of the modern IT landscape. This requires a deep understanding of IT best practices, the ability to adapt to evolving technology trends, and a proactive approach to IT risk management.
-
IT Challenges: What challenges do IT professionals face in the era of emerging technologies?
-
IT Trends: How can IT professionals stay ahead of the latest technology trends in IT service management?
-
IT Innovation: What role does innovation play in driving success for IT professionals in the digital age?
Enhancing IT Operations
In order to stay competitive in today's digital economy, organizations must prioritize IT modernization and implement adaptive IT practices. This includes leveraging emerging IT tools, optimizing IT infrastructure, and embracing new software development methodologies. By embracing tech advancements and staying ahead of the curve, organizations can effectively enhance their IT operations and drive business growth.
Benefits of Technology Integration
-
Improved efficiency and productivity
-
Enhanced collaboration and communication
-
Streamlined processes and workflows
Challenges of Change Management
-
Resistance to change from employees
-
Integration issues with legacy systems
-
Training and upskilling requirements for IT professionals
The Future of IT Service Management
As technology continues to evolve, the future of IT service management holds endless possibilities. From AI-driven solutions to advanced cybersecurity measures, the IT industry is constantly innovating to address the diverse needs of organizations worldwide. By staying informed about the latest technology trends and embracing a proactive approach to IT service management, organizations can pave the way for a successful digital future.
How to obtain IT Service Management and Governance certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the impact of emerging technologies on IT service management is undeniable. To thrive in today's fast-paced digital landscape, IT professionals must continuously adapt, innovate, and evolve in order to meet the demands of the modern IT industry. By prioritizing IT modernization, embracing adaptive IT practices, and staying ahead of the latest technology trends, organizations can position themselves for long-term success in the ever-changing world of IT service management.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's rapidly evolving digital landscape, the impact of emerging technologies on IT service management cannot be overlooked. With constant advancements in technology trends such as digital transformation, cloud computing, artificial intelligence, machine learning, cybersecurity, automation, big data, internet of things, data analytics, and more, IT service management professionals must adapt and evolve to meet the demands of the modern IT industry.
Evolution of IT Service Management
As technology continues to advance at a rapid pace, IT service management has undergone significant transformation. The traditional IT infrastructure is being replaced by innovative tech advancements, leading to the adoption of new and improved IT strategies. Organizations are increasingly leveraging emerging technologies to enhance their IT operations, driving the need for seamless technology integration and efficient change management practices.
Question: How has digital transformation impacted IT service management?
Answer: Digital transformation has revolutionized the way organizations approach IT service management, enabling them to streamline processes, improve efficiency, and enhance overall business performance.
The Role of IT Professionals
With the emergence of new technologies and tech disruptions, IT professionals are faced with a myriad of challenges. From ensuring business continuity to implementing effective IT governance practices, IT professionals must navigate the complexities of the modern IT landscape. This requires a deep understanding of IT best practices, the ability to adapt to evolving technology trends, and a proactive approach to IT risk management.
-
IT Challenges: What challenges do IT professionals face in the era of emerging technologies?
-
IT Trends: How can IT professionals stay ahead of the latest technology trends in IT service management?
-
IT Innovation: What role does innovation play in driving success for IT professionals in the digital age?
Enhancing IT Operations
In order to stay competitive in today's digital economy, organizations must prioritize IT modernization and implement adaptive IT practices. This includes leveraging emerging IT tools, optimizing IT infrastructure, and embracing new software development methodologies. By embracing tech advancements and staying ahead of the curve, organizations can effectively enhance their IT operations and drive business growth.
Benefits of Technology Integration
-
Improved efficiency and productivity
-
Enhanced collaboration and communication
-
Streamlined processes and workflows
Challenges of Change Management
-
Resistance to change from employees
-
Integration issues with legacy systems
-
Training and upskilling requirements for IT professionals
The Future of IT Service Management
As technology continues to evolve, the future of IT service management holds endless possibilities. From AI-driven solutions to advanced cybersecurity measures, the IT industry is constantly innovating to address the diverse needs of organizations worldwide. By staying informed about the latest technology trends and embracing a proactive approach to IT service management, organizations can pave the way for a successful digital future.
How to obtain IT Service Management and Governance certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the impact of emerging technologies on IT service management is undeniable. To thrive in today's fast-paced digital landscape, IT professionals must continuously adapt, innovate, and evolve in order to meet the demands of the modern IT industry. By prioritizing IT modernization, embracing adaptive IT practices, and staying ahead of the latest technology trends, organizations can position themselves for long-term success in the ever-changing world of IT service management.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Top AWS Services to Focus On for the Solution Architect Certification Exam
Are you aiming to become an AWS Certified Solution Architect? If so, you've come to the right place. This article will guide you through the top AWS services to focus on for the Solution Architect Certification Exam, helping you prepare effectively and ace the test with ease.
Why Choose AWS for Your Certification Exam?
Amazon Web Services (AWS) is a leading cloud services provider, offering a wide range of services to help businesses and individuals leverage the power of the cloud. AWS certification is highly valued in the IT industry, as it demonstrates your expertise in AWS services and best practices. By becoming an AWS Certified Solution Architect, you position yourself as a skilled professional with the knowledge and skills to design and deploy scalable, reliable, and cost-effective cloud solutions.
The Top AWS Services to Focus On
When preparing for the AWS Solution Architect Certification Exam, it's crucial to focus on the key AWS services that are commonly tested in the exam. Below are some of the top AWS services you should pay extra attention to:
1. Amazon EC2 (Elastic Compute Cloud) : Amazon EC2 is a fundamental AWS service that allows you to easily launch and manage virtual servers in the cloud. Understanding how to deploy, resize, and monitor EC2 instances is essential for the Solution Architect exam.
2. Amazon S3 (Simple Storage Service) : Amazon S3 is a scalable object storage service that enables you to store and retrieve data in the cloud. Knowing how to create S3 buckets, set up policies, and manage data lifecycle in S3 is key for the exam.
3. Amazon RDS (Relational Database Service) : Amazon RDS is a managed relational database service that makes it easy to set up, operate, and scale a relational database in the cloud. Familiarize yourself with different database engines supported by RDS and understand how to optimize performance and security.
4. Amazon VPC (Virtual Private Cloud) : Amazon VPC enables you to create a virtual network in the cloud, complete with subnets, route tables, and security groups. Mastering VPC networking concepts, such as IP addressing, routing, and peering, is vital for the exam.
5. AWS Lambda : AWS Lambda is a serverless computing service that allows you to run code without provisioning or managing servers. Learn how to create and deploy Lambda functions, set up triggers, and integrate with other AWS services.
How to Prepare for the AWS Solution Architect Certification Exam
To succeed in the AWS Solution Architect Certification Exam, you need to invest time and effort in studying and practicing with AWS services. Here are some tips to help you prepare effectively:
-
Enroll in AWS training courses or use study guides to deepen your understanding of AWS services and best practices.
-
Take practice exams to assess your knowledge and identify areas for improvement.
-
Hands-on experience with AWS services is crucial, so make sure to experiment with AWS solutions and implement best practices.
-
Stay updated with the latest AWS developments and updates by following AWS blogs, forums, and community channels.
By following these preparation tips and focusing on the top AWS services mentioned above, you'll be well on your way to becoming an AWS Certified Solution Architect.
How to obtain AWS SOLUTION ARCHITECT certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, Becoming an AWS Certified Solution Architect is a rewarding achievement that can open up new career opportunities in the cloud computing industry. By focusing on the top AWS services mentioned in this article and following the preparation tips provided, you'll be well-prepared to excel in the Solution Architect Certification Exam. Good luck on your AWS certification journey!
Read More
Are you aiming to become an AWS Certified Solution Architect? If so, you've come to the right place. This article will guide you through the top AWS services to focus on for the Solution Architect Certification Exam, helping you prepare effectively and ace the test with ease.
Why Choose AWS for Your Certification Exam?
Amazon Web Services (AWS) is a leading cloud services provider, offering a wide range of services to help businesses and individuals leverage the power of the cloud. AWS certification is highly valued in the IT industry, as it demonstrates your expertise in AWS services and best practices. By becoming an AWS Certified Solution Architect, you position yourself as a skilled professional with the knowledge and skills to design and deploy scalable, reliable, and cost-effective cloud solutions.
The Top AWS Services to Focus On
When preparing for the AWS Solution Architect Certification Exam, it's crucial to focus on the key AWS services that are commonly tested in the exam. Below are some of the top AWS services you should pay extra attention to:
1. Amazon EC2 (Elastic Compute Cloud) : Amazon EC2 is a fundamental AWS service that allows you to easily launch and manage virtual servers in the cloud. Understanding how to deploy, resize, and monitor EC2 instances is essential for the Solution Architect exam.
2. Amazon S3 (Simple Storage Service) : Amazon S3 is a scalable object storage service that enables you to store and retrieve data in the cloud. Knowing how to create S3 buckets, set up policies, and manage data lifecycle in S3 is key for the exam.
3. Amazon RDS (Relational Database Service) : Amazon RDS is a managed relational database service that makes it easy to set up, operate, and scale a relational database in the cloud. Familiarize yourself with different database engines supported by RDS and understand how to optimize performance and security.
4. Amazon VPC (Virtual Private Cloud) : Amazon VPC enables you to create a virtual network in the cloud, complete with subnets, route tables, and security groups. Mastering VPC networking concepts, such as IP addressing, routing, and peering, is vital for the exam.
5. AWS Lambda : AWS Lambda is a serverless computing service that allows you to run code without provisioning or managing servers. Learn how to create and deploy Lambda functions, set up triggers, and integrate with other AWS services.
How to Prepare for the AWS Solution Architect Certification Exam
To succeed in the AWS Solution Architect Certification Exam, you need to invest time and effort in studying and practicing with AWS services. Here are some tips to help you prepare effectively:
-
Enroll in AWS training courses or use study guides to deepen your understanding of AWS services and best practices.
-
Take practice exams to assess your knowledge and identify areas for improvement.
-
Hands-on experience with AWS services is crucial, so make sure to experiment with AWS solutions and implement best practices.
-
Stay updated with the latest AWS developments and updates by following AWS blogs, forums, and community channels.
By following these preparation tips and focusing on the top AWS services mentioned above, you'll be well on your way to becoming an AWS Certified Solution Architect.
How to obtain AWS SOLUTION ARCHITECT certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In Conclusion, Becoming an AWS Certified Solution Architect is a rewarding achievement that can open up new career opportunities in the cloud computing industry. By focusing on the top AWS services mentioned in this article and following the preparation tips provided, you'll be well-prepared to excel in the Solution Architect Certification Exam. Good luck on your AWS certification journey!
Benefits of AI (Artificial Intelligence) in Project Management
In today's fast-paced business environment, project managers are constantly seeking ways to improve efficiency, reduce costs, and deliver projects on time. Enter artificial intelligence (AI), a groundbreaking technology that is revolutionizing the field of project management. AI has the potential to transform how projects are planned, executed, monitored, and controlled. In this article, we will explore the many benefits of AI in project management and how it can help organizations achieve their project goals more effectively.
Artificial Intelligence in Project Management
AI involves the replication of human intelligence processes by machines, encompassing learning, reasoning, and self-correction.When applied to project management, AI can analyze data, make predictions, automate tasks, and provide valuable insights to help project managers make informed decisions.
AI Impact on Project Management
The influence of AI on project management is profound.By leveraging AI technologies, project managers can streamline workflows, optimize resource allocation, identify risks, and improve communication among team members. Additionally, AI can enhance project success rates by providing real-time feedback and recommendations to project managers.
Importance of AI in Project Management
The significance of AI in project management is unparalleled. AI has the potential to enhance project efficiency, reduce costs, minimize risks, and improve project outcomes. By harnessing the power of AI, project managers can gain a competitive edge in today's competitive business landscape.
AI Benefits for Project Management
There are numerous benefits of using AI in project management. Some of the key advantages include improved decision-making, enhanced productivity, better resource allocation, faster project completion times, and increased project success rates. AI can also help project managers identify patterns and trends in project data, leading to more informed planning and decision-making.
AI Applications in Project Management
AI has a wide range of applications in project management, including risk assessment, task automation, resource optimization, schedule management, and performance tracking. By leveraging AI tools and technologies, project managers can enhance project efficiency, minimize errors, and improve project outcomes.
Project Management AI Benefits
Some of the key benefits of using AI in project management include increased efficiency, reduced costs, improved decision-making, enhanced collaboration, and better project outcomes. AI can help project managers automate routine tasks, analyze large volumes of data, and identify opportunities for improvement.
Advantages of AI in Project Management
The advantages of AI in project management are manifold. AI can help project managers identify project risks, predict project outcomes, optimize resource allocation, and streamline project workflows. By harnessing the power of AI, project managers can achieve better results in less time.
AI Technology in Project Management
AI technology is rapidly transforming the field of project management. With AI-powered tools and solutions, project managers can automate repetitive tasks, analyze project data, and optimize project schedules. AI technology is revolutionizing how projects are planned, executed, monitored, and controlled.
How to obtain Project Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, AI has the potential to revolutionize the field of project management. By leveraging AI technologies, project managers can enhance efficiency, reduce costs, minimize risks, and improve project outcomes. The benefits of AI in project management are clear, and organizations that embrace this transformative technology will gain a competitive edge in today's dynamic business landscape.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's fast-paced business environment, project managers are constantly seeking ways to improve efficiency, reduce costs, and deliver projects on time. Enter artificial intelligence (AI), a groundbreaking technology that is revolutionizing the field of project management. AI has the potential to transform how projects are planned, executed, monitored, and controlled. In this article, we will explore the many benefits of AI in project management and how it can help organizations achieve their project goals more effectively.
Artificial Intelligence in Project Management
AI involves the replication of human intelligence processes by machines, encompassing learning, reasoning, and self-correction.When applied to project management, AI can analyze data, make predictions, automate tasks, and provide valuable insights to help project managers make informed decisions.
AI Impact on Project Management
The influence of AI on project management is profound.By leveraging AI technologies, project managers can streamline workflows, optimize resource allocation, identify risks, and improve communication among team members. Additionally, AI can enhance project success rates by providing real-time feedback and recommendations to project managers.
Importance of AI in Project Management
The significance of AI in project management is unparalleled. AI has the potential to enhance project efficiency, reduce costs, minimize risks, and improve project outcomes. By harnessing the power of AI, project managers can gain a competitive edge in today's competitive business landscape.
AI Benefits for Project Management
There are numerous benefits of using AI in project management. Some of the key advantages include improved decision-making, enhanced productivity, better resource allocation, faster project completion times, and increased project success rates. AI can also help project managers identify patterns and trends in project data, leading to more informed planning and decision-making.
AI Applications in Project Management
AI has a wide range of applications in project management, including risk assessment, task automation, resource optimization, schedule management, and performance tracking. By leveraging AI tools and technologies, project managers can enhance project efficiency, minimize errors, and improve project outcomes.
Project Management AI Benefits
Some of the key benefits of using AI in project management include increased efficiency, reduced costs, improved decision-making, enhanced collaboration, and better project outcomes. AI can help project managers automate routine tasks, analyze large volumes of data, and identify opportunities for improvement.
Advantages of AI in Project Management
The advantages of AI in project management are manifold. AI can help project managers identify project risks, predict project outcomes, optimize resource allocation, and streamline project workflows. By harnessing the power of AI, project managers can achieve better results in less time.
AI Technology in Project Management
AI technology is rapidly transforming the field of project management. With AI-powered tools and solutions, project managers can automate repetitive tasks, analyze project data, and optimize project schedules. AI technology is revolutionizing how projects are planned, executed, monitored, and controlled.
How to obtain Project Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, AI has the potential to revolutionize the field of project management. By leveraging AI technologies, project managers can enhance efficiency, reduce costs, minimize risks, and improve project outcomes. The benefits of AI in project management are clear, and organizations that embrace this transformative technology will gain a competitive edge in today's dynamic business landscape.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
The Role of Apache Kafka Certification in Data Streaming Architectures
Are you looking to advance your career in data streaming architectures? Have you considered the importance of obtaining an Apache Kafka certification? In this article, we will explore the benefits of Apache Kafka certification, the role it plays in data streaming architectures, and the impact it can have on your career in the data engineering industry.
Importance of Apache Kafka Certification
Earning an Apache Kafka certification can significantly enhance your skills and knowledge in data streaming technologies. By completing a Kafka certification program, you demonstrate your expertise in utilizing Apache Kafka to build real-time data pipelines and stream processing applications. This certification not only validates your proficiency in Kafka, but also showcases your commitment to continuous learning and professional development.
Benefits of Kafka Certification
-
Enhanced Skills: Apache Kafka training certification equips you with the necessary skills to design, implement, and manage scalable data streaming architectures.
-
Career Advancement: Kafka architect roles are in high demand in the data engineering industry. By obtaining a Kafka certification, you open up new opportunities for career growth and advancement.
-
Industry Recognition: Holding an Apache Kafka certification demonstrates to employers and peers that you have the expertise to excel in data streaming technologies.
Kafka Architect Certification Program
The Apache Kafka certification exam covers various topics related to data streaming, including Kafka architecture, configuration, monitoring, and performance tuning. By completing the Kafka certification program, you will gain a deep understanding of how Kafka can be used to build distributed systems for real-time data processing.
Kafka Certification Online
For those looking to obtain their Kafka certification online, there are several platforms that offer comprehensive training courses for aspiring Kafka architects. These online courses provide flexibility and convenience for busy professionals seeking to enhance their skills in data streaming technologies.
Apache Kafka Accreditation
Upon successfully passing the Apache Kafka certification exam, you will receive official accreditation as a certified Kafka architect. This accreditation not only adds credibility to your resume but also increases your value as a professional in the data streaming industry.
Data Streaming Career
With the rapid growth of data streaming technologies, professionals with Apache Kafka skills are in high demand across various industries. By pursuing a career in data streaming, you can leverage your Kafka certification to secure rewarding job opportunities and contribute to cutting-edge projects in real-time data processing.
Apache Kafka Course
If you are considering obtaining your Kafka certification, enrolling in an Apache Kafka course can provide you with the necessary knowledge and skills to excel in data streaming architectures. These courses cover a wide range of topics, including Kafka basics, architecture design, and performance optimization.
Data Streaming Specialists
As a certified Kafka architect, you will join a community of data streaming specialists who are at the forefront of innovation in real-time data processing. By networking with fellow Kafka experts, you can stay up-to-date on the latest trends and technologies in the data engineering industry.
How to obtain Apache kafka Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Apache Kafka certification plays a vital role in advancing your career in data streaming architectures. By obtaining your Kafka certification, you can enhance your skills, expand your career opportunities, and become a valuable asset in the rapidly evolving data engineering industry. Don't wait any longer - invest in your future today with Apache Kafka certification!
Read More
Are you looking to advance your career in data streaming architectures? Have you considered the importance of obtaining an Apache Kafka certification? In this article, we will explore the benefits of Apache Kafka certification, the role it plays in data streaming architectures, and the impact it can have on your career in the data engineering industry.
Importance of Apache Kafka Certification
Earning an Apache Kafka certification can significantly enhance your skills and knowledge in data streaming technologies. By completing a Kafka certification program, you demonstrate your expertise in utilizing Apache Kafka to build real-time data pipelines and stream processing applications. This certification not only validates your proficiency in Kafka, but also showcases your commitment to continuous learning and professional development.
Benefits of Kafka Certification
-
Enhanced Skills: Apache Kafka training certification equips you with the necessary skills to design, implement, and manage scalable data streaming architectures.
-
Career Advancement: Kafka architect roles are in high demand in the data engineering industry. By obtaining a Kafka certification, you open up new opportunities for career growth and advancement.
-
Industry Recognition: Holding an Apache Kafka certification demonstrates to employers and peers that you have the expertise to excel in data streaming technologies.
Kafka Architect Certification Program
The Apache Kafka certification exam covers various topics related to data streaming, including Kafka architecture, configuration, monitoring, and performance tuning. By completing the Kafka certification program, you will gain a deep understanding of how Kafka can be used to build distributed systems for real-time data processing.
Kafka Certification Online
For those looking to obtain their Kafka certification online, there are several platforms that offer comprehensive training courses for aspiring Kafka architects. These online courses provide flexibility and convenience for busy professionals seeking to enhance their skills in data streaming technologies.
Apache Kafka Accreditation
Upon successfully passing the Apache Kafka certification exam, you will receive official accreditation as a certified Kafka architect. This accreditation not only adds credibility to your resume but also increases your value as a professional in the data streaming industry.
Data Streaming Career
With the rapid growth of data streaming technologies, professionals with Apache Kafka skills are in high demand across various industries. By pursuing a career in data streaming, you can leverage your Kafka certification to secure rewarding job opportunities and contribute to cutting-edge projects in real-time data processing.
Apache Kafka Course
If you are considering obtaining your Kafka certification, enrolling in an Apache Kafka course can provide you with the necessary knowledge and skills to excel in data streaming architectures. These courses cover a wide range of topics, including Kafka basics, architecture design, and performance optimization.
Data Streaming Specialists
As a certified Kafka architect, you will join a community of data streaming specialists who are at the forefront of innovation in real-time data processing. By networking with fellow Kafka experts, you can stay up-to-date on the latest trends and technologies in the data engineering industry.
How to obtain Apache kafka Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Apache Kafka certification plays a vital role in advancing your career in data streaming architectures. By obtaining your Kafka certification, you can enhance your skills, expand your career opportunities, and become a valuable asset in the rapidly evolving data engineering industry. Don't wait any longer - invest in your future today with Apache Kafka certification!
Online vs. In-Person MINITAB Certification: Pros and Cons
Are you considering getting certified in MINITAB, but unsure whether to pursue online certification or attend in-person training? Let's break down the pros and cons of each option to help you make an informed decision.
MINITAB Certification Online
Pros:
-
Convenience: Online MINITAB certification allows you to study and complete the course at your own pace and schedule.
-
Cost-Effective: Online courses are often more affordable than in-person training, saving you money on travel and accommodation expenses.
-
Flexibility: You can access online resources from anywhere in the world, giving you the flexibility to learn from the comfort of your own home.
-
Self-Paced Learning: Online courses allow you to review materials at your own pace and focus on areas that need more attention.
Cons:
-
Lack of Hands-On Experience: Online certification may lack hands-on experience and practical application of MINITAB skills.
-
Limited Interaction: You may have limited interaction with instructors and other students in an online setting, leading to potential difficulties in clarifying doubts.
MINITAB Certification In-Person
Pros:
-
Hands-On Experience: In-person training provides hands-on experience and practical application of MINITAB skills.
-
Interactive Learning: In-person training allows for real-time interaction with instructors and other students, promoting a better understanding of the material.
-
Networking Opportunities: Attending in-person training sessions can help you build a professional network within the MINITAB community.
Cons:
-
Time-Costly: In-person training may require you to take time off work or travel to attend sessions, which can be time-consuming and costly.
-
Higher Costs: In-person training is often more expensive than online certification due to additional expenses such as travel and accommodation.
MINITAB Certification Comparison
Online MINITAB Certification:
-
Convenient
-
Cost-effective
-
Flexible
-
Self-paced learning
In-Person MINITAB Certification:
-
Hands-on experience
-
Interactive learning
-
Networking opportunities
-
Time-costly
How to obtain MINITAB certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, whether you choose online or in-person MINITAB certification depends on your preferences, learning style, and budget. Online certification offers flexibility and cost-effectiveness, while in-person training provides hands-on experience and networking opportunities. Consider your priorities and choose the option that aligns best with your goals and resources.
Read More
Are you considering getting certified in MINITAB, but unsure whether to pursue online certification or attend in-person training? Let's break down the pros and cons of each option to help you make an informed decision.
MINITAB Certification Online
Pros:
-
Convenience: Online MINITAB certification allows you to study and complete the course at your own pace and schedule.
-
Cost-Effective: Online courses are often more affordable than in-person training, saving you money on travel and accommodation expenses.
-
Flexibility: You can access online resources from anywhere in the world, giving you the flexibility to learn from the comfort of your own home.
-
Self-Paced Learning: Online courses allow you to review materials at your own pace and focus on areas that need more attention.
Cons:
-
Lack of Hands-On Experience: Online certification may lack hands-on experience and practical application of MINITAB skills.
-
Limited Interaction: You may have limited interaction with instructors and other students in an online setting, leading to potential difficulties in clarifying doubts.
MINITAB Certification In-Person
Pros:
-
Hands-On Experience: In-person training provides hands-on experience and practical application of MINITAB skills.
-
Interactive Learning: In-person training allows for real-time interaction with instructors and other students, promoting a better understanding of the material.
-
Networking Opportunities: Attending in-person training sessions can help you build a professional network within the MINITAB community.
Cons:
-
Time-Costly: In-person training may require you to take time off work or travel to attend sessions, which can be time-consuming and costly.
-
Higher Costs: In-person training is often more expensive than online certification due to additional expenses such as travel and accommodation.
MINITAB Certification Comparison
Online MINITAB Certification:
-
Convenient
-
Cost-effective
-
Flexible
-
Self-paced learning
In-Person MINITAB Certification:
-
Hands-on experience
-
Interactive learning
-
Networking opportunities
-
Time-costly
How to obtain MINITAB certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, whether you choose online or in-person MINITAB certification depends on your preferences, learning style, and budget. Online certification offers flexibility and cost-effectiveness, while in-person training provides hands-on experience and networking opportunities. Consider your priorities and choose the option that aligns best with your goals and resources.
The Impact of CISM Certification on Organizational Security Posture
As cyber threats continue to evolve and become more sophisticated, organizations are facing increasing challenges in ensuring the security of their systems and data. In this digital age, the protection of sensitive information and the prevention of cyber-attacks are paramount. One way that organizations are strengthening their security posture is by investing in Certified Information Security Manager (CISM) certification for their employees. This article will explore the impact of CISM certification on organizational security posture and why it is crucial for businesses in today's environment.
What is CISM Certification?
CISM is a globally recognized certification that validates the expertise of information security professionals. Offered by the Information Systems Audit and Control Association (ISACA), CISM is designed for individuals who manage, design, oversee, and assess an enterprise's information security. To earn the CISM designation, candidates must pass a rigorous exam and meet specific experience requirements in the field of information security management.
How Does CISM Certification Benefit Organizational Security?
-
Enhanced Security Awareness: CISM training equips professionals with the knowledge and skills to identify security risks and implement appropriate controls to mitigate them. This heightened security awareness can help organizations proactively address vulnerabilities and prevent security incidents.
-
Adherence to Security Standards: CISM certification ensures that security professionals are well-versed in industry best practices and standards. By following recognized security frameworks, organizations can strengthen their security posture and remain compliant with regulatory requirements.
-
Improved Risk Management: CISM professionals are trained to assess and manage risks effectively. By identifying potential threats and vulnerabilities, they can develop strategies to minimize the impact of security incidents and safeguard critical assets.
-
Effective Security Controls: CISM certification enables professionals to implement robust security controls that protect against unauthorized access, data breaches, and other security threats. By establishing and maintaining these controls, organizations can reduce the risk of cyber-attacks and minimize potential damage.
-
Strategic Security Planning: CISM professionals are skilled in developing security strategies that align with business objectives. By integrating security into the organization's overall strategy, they can ensure that security measures support the company's goals and protect its assets effectively.
Why is CISM Certification Important?
Obtaining CISM certification is essential for security professionals who wish to demonstrate their expertise and commitment to information security. In today's digital landscape, where cyber threats are constantly evolving, organizations need skilled professionals who can protect their sensitive data and systems effectively. CISM certification sets individuals apart as experts in information security management and gives them the credibility to lead security initiatives within their organizations.
How Does CISM Training Prepare Professionals for the Certification Exam?
CISM training provides professionals with the knowledge and skills needed to pass the certification exam successfully. The training covers all areas of information security management, including risk assessment, security governance, incident response, and compliance. By participating in CISM training, individuals can enhance their understanding of key concepts and best practices in information security, giving them the confidence to excel in the certification exam.
How to obtain CISM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, CISM certification plays a vital role in enhancing organizational security posture by equipping professionals with the expertise and skills needed to protect against cyber threats effectively. By investing in CISM certification for their employees, organizations can strengthen their security defenses, mitigate risks, and ensure the confidentiality, integrity, and availability of their critical information assets.
Read More
As cyber threats continue to evolve and become more sophisticated, organizations are facing increasing challenges in ensuring the security of their systems and data. In this digital age, the protection of sensitive information and the prevention of cyber-attacks are paramount. One way that organizations are strengthening their security posture is by investing in Certified Information Security Manager (CISM) certification for their employees. This article will explore the impact of CISM certification on organizational security posture and why it is crucial for businesses in today's environment.
What is CISM Certification?
CISM is a globally recognized certification that validates the expertise of information security professionals. Offered by the Information Systems Audit and Control Association (ISACA), CISM is designed for individuals who manage, design, oversee, and assess an enterprise's information security. To earn the CISM designation, candidates must pass a rigorous exam and meet specific experience requirements in the field of information security management.
How Does CISM Certification Benefit Organizational Security?
-
Enhanced Security Awareness: CISM training equips professionals with the knowledge and skills to identify security risks and implement appropriate controls to mitigate them. This heightened security awareness can help organizations proactively address vulnerabilities and prevent security incidents.
-
Adherence to Security Standards: CISM certification ensures that security professionals are well-versed in industry best practices and standards. By following recognized security frameworks, organizations can strengthen their security posture and remain compliant with regulatory requirements.
-
Improved Risk Management: CISM professionals are trained to assess and manage risks effectively. By identifying potential threats and vulnerabilities, they can develop strategies to minimize the impact of security incidents and safeguard critical assets.
-
Effective Security Controls: CISM certification enables professionals to implement robust security controls that protect against unauthorized access, data breaches, and other security threats. By establishing and maintaining these controls, organizations can reduce the risk of cyber-attacks and minimize potential damage.
-
Strategic Security Planning: CISM professionals are skilled in developing security strategies that align with business objectives. By integrating security into the organization's overall strategy, they can ensure that security measures support the company's goals and protect its assets effectively.
Why is CISM Certification Important?
Obtaining CISM certification is essential for security professionals who wish to demonstrate their expertise and commitment to information security. In today's digital landscape, where cyber threats are constantly evolving, organizations need skilled professionals who can protect their sensitive data and systems effectively. CISM certification sets individuals apart as experts in information security management and gives them the credibility to lead security initiatives within their organizations.
How Does CISM Training Prepare Professionals for the Certification Exam?
CISM training provides professionals with the knowledge and skills needed to pass the certification exam successfully. The training covers all areas of information security management, including risk assessment, security governance, incident response, and compliance. By participating in CISM training, individuals can enhance their understanding of key concepts and best practices in information security, giving them the confidence to excel in the certification exam.
How to obtain CISM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, CISM certification plays a vital role in enhancing organizational security posture by equipping professionals with the expertise and skills needed to protect against cyber threats effectively. By investing in CISM certification for their employees, organizations can strengthen their security defenses, mitigate risks, and ensure the confidentiality, integrity, and availability of their critical information assets.
Creating a Data Vis Strategy & Understanding Its Importance
In today's data-driven world, creating a solid data visualization strategy is crucial for businesses looking to make sense of the vast amount of information available to them. By understanding the importance of data visualization and how it can impact decision-making processes, organizations can unlock valuable insights that drive growth and success.
What is Data Visualization?
Data visualization is the graphical representation of information and data. By using visual elements such as charts, graphs, and maps, data visualization tools provide an accessible way to see and understand trends, outliers, and patterns in data. This visual representation helps organizations make informed decisions based on data insights rather than intuition.
The Importance of Visualization:
-
Data Interpretation: Visualizing data allows for easier interpretation of complex information. Patterns and trends that may not be apparent in raw data can be easily identified through visual representation.
-
Visual Storytelling: Effective data visualization can tell a story, making it easier for stakeholders to grasp complex concepts and make meaningful connections between data points.
-
Business Intelligence: Data visualization is a key component of business intelligence, providing a clear and concise way to present data insights to decision-makers.
-
Data-Driven Decisions: By visually representing data, organizations can make data-driven decisions that are backed by evidence and analysis rather than assumptions or gut feelings.
-
Developing a Data Vis Strategy:
When developing a data visualization strategy, it's important to consider the following key elements:
-
Data Interpretation: Understand the data you are working with and the story you want to tell.
-
Visualization Process: Plan out the steps involved in creating effective visualizations, from data collection to final presentation.
-
Techniques: Familiarize yourself with data visualization techniques and best practices to ensure clear and impactful visuals.
-
Tools: Utilize a variety of data visualization tools to create visually appealing and informative graphics.
-
Skills: Develop your skills in data visualization, including design thinking, data interpretation, and visual storytelling.
Visual Data Strategy
A visual data strategy involves the systematic approach to creating data visualizations that align with organizational goals and objectives. By outlining the steps involved in data visualization, including data collection, analysis, and presentation, organizations can ensure that their visualizations effectively communicate the intended message and drive actionable insights.
Data Visualization Best Practices
-
Simplicity: Keep visualizations simple and easy to understand.
-
Consistency: Use consistent design elements and color schemes throughout your visuals.
-
Interactivity: Incorporate interactive features to engage users and allow for further exploration of data.
-
Accuracy: Ensure that your visualizations accurately represent the underlying data to avoid misleading interpretations.
-
Relevance: Focus on the key insights and information that will drive decision-making processes.
How to obtain Big Data certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, creating a data visualization strategy is essential for organizations looking to harness the power of data and make informed decisions. By understanding the importance of data visualization and following best practices in visualization techniques, businesses can unlock valuable insights that drive success and growth. Start developing your data visualization strategy today to leverage the power of visual data analysis and drive smarter decision-making processes.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's data-driven world, creating a solid data visualization strategy is crucial for businesses looking to make sense of the vast amount of information available to them. By understanding the importance of data visualization and how it can impact decision-making processes, organizations can unlock valuable insights that drive growth and success.
What is Data Visualization?
Data visualization is the graphical representation of information and data. By using visual elements such as charts, graphs, and maps, data visualization tools provide an accessible way to see and understand trends, outliers, and patterns in data. This visual representation helps organizations make informed decisions based on data insights rather than intuition.
The Importance of Visualization:
-
Data Interpretation: Visualizing data allows for easier interpretation of complex information. Patterns and trends that may not be apparent in raw data can be easily identified through visual representation.
-
Visual Storytelling: Effective data visualization can tell a story, making it easier for stakeholders to grasp complex concepts and make meaningful connections between data points.
-
Business Intelligence: Data visualization is a key component of business intelligence, providing a clear and concise way to present data insights to decision-makers.
-
Data-Driven Decisions: By visually representing data, organizations can make data-driven decisions that are backed by evidence and analysis rather than assumptions or gut feelings.
-
Developing a Data Vis Strategy:
When developing a data visualization strategy, it's important to consider the following key elements:
-
Data Interpretation: Understand the data you are working with and the story you want to tell.
-
Visualization Process: Plan out the steps involved in creating effective visualizations, from data collection to final presentation.
-
Techniques: Familiarize yourself with data visualization techniques and best practices to ensure clear and impactful visuals.
-
Tools: Utilize a variety of data visualization tools to create visually appealing and informative graphics.
-
Skills: Develop your skills in data visualization, including design thinking, data interpretation, and visual storytelling.
Visual Data Strategy
A visual data strategy involves the systematic approach to creating data visualizations that align with organizational goals and objectives. By outlining the steps involved in data visualization, including data collection, analysis, and presentation, organizations can ensure that their visualizations effectively communicate the intended message and drive actionable insights.
Data Visualization Best Practices
-
Simplicity: Keep visualizations simple and easy to understand.
-
Consistency: Use consistent design elements and color schemes throughout your visuals.
-
Interactivity: Incorporate interactive features to engage users and allow for further exploration of data.
-
Accuracy: Ensure that your visualizations accurately represent the underlying data to avoid misleading interpretations.
-
Relevance: Focus on the key insights and information that will drive decision-making processes.
How to obtain Big Data certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, creating a data visualization strategy is essential for organizations looking to harness the power of data and make informed decisions. By understanding the importance of data visualization and following best practices in visualization techniques, businesses can unlock valuable insights that drive success and growth. Start developing your data visualization strategy today to leverage the power of visual data analysis and drive smarter decision-making processes.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
GitLab or GitHub: Which Will Lead for Developers in 2024?
In the ever-evolving world of software development, GitLab and GitHub have emerged as two of the most popular platforms for developers to collaborate, manage code, and streamline their workflows. As we look ahead to 2024, the question arises: which of these two giants will take the lead in shaping the future of software development?
A Look at GitLab
GitLab is a web-based Git repository manager that provides a complete DevOps platform for software development teams. With its robust set of features, including version control, issue tracking, continuous integration, and deployment pipelines, GitLab has become a favorite among developers looking for an all-in-one solution.
One of the key strengths of GitLab is its focus on collaboration. The platform allows developers to easily work together on projects, share code, and manage tasks seamlessly. By integrating all the necessary tools in one place, GitLab promotes efficiency and teamwork, making it ideal for both small startups and large enterprises.
A Look at GitHub
GitHub, on the other hand, is a code hosting platform that offers version control using Git. It has long been a go-to choice for software developers, boasting a vast community of users and repositories. GitHub is known for its user-friendly interface, social coding features, and extensive integration options.
GitHub's emphasis on open-source projects and community involvement has made it a hub for collaboration and innovation. Developers can easily fork and contribute to projects, track issues, and showcase their work to the world. GitHub's popularity and widespread adoption have cemented its position as a leader in the software development industry.
Comparison of GitLab and GitHub
When comparing GitLab and GitHub, several key differences emerge. While both platforms offer version control and collaboration tools, GitLab stands out for its comprehensive DevOps capabilities, including built-in CI/CD pipelines and Kubernetes integration. GitHub, on the other hand, excels in its social coding features and vast ecosystem of third-party integrations.
In terms of user experience, GitLab is praised for its clean interface and intuitive design, which allows developers to quickly navigate and access the features they need. GitHub, on the other hand, is known for its robust community support and extensive documentation, making it easy for developers to find help and resources.
The Future of Software Development
As we look ahead to 2024, the software development landscape is poised for further innovation and growth. Both GitLab and GitHub are expected to continue evolving and introducing new features to cater to the changing needs of developers. From advancements in AI-driven code recommendations to enhanced security measures and improved collaboration tools, the future of software development looks bright.
Main Keyword Heading: GitLab or GitHub: Which Will Lead for Developers in 2024?
As we look ahead to 2024, the question remains: which of these two leading platforms, GitLab or GitHub, will emerge as the dominant force in the world of software development? With their distinctive features and strengths, both GitLab and GitHub are well-positioned to continue driving innovation and collaboration among developers worldwide.
How to obtain Devops certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In the fast-paced world of software development, choosing between GitLab and GitHub can be a tough decision. Both platforms offer unique features and benefits that cater to the diverse needs of developers. Whether you're looking for a comprehensive DevOps solution or a community-driven platform for open-source projects, GitLab and GitHub have you covered. As we look ahead to 2024, the future of software development is bright, with GitLab and GitHub leading the way towards new innovations and possibilities.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In the ever-evolving world of software development, GitLab and GitHub have emerged as two of the most popular platforms for developers to collaborate, manage code, and streamline their workflows. As we look ahead to 2024, the question arises: which of these two giants will take the lead in shaping the future of software development?
A Look at GitLab
GitLab is a web-based Git repository manager that provides a complete DevOps platform for software development teams. With its robust set of features, including version control, issue tracking, continuous integration, and deployment pipelines, GitLab has become a favorite among developers looking for an all-in-one solution.
One of the key strengths of GitLab is its focus on collaboration. The platform allows developers to easily work together on projects, share code, and manage tasks seamlessly. By integrating all the necessary tools in one place, GitLab promotes efficiency and teamwork, making it ideal for both small startups and large enterprises.
A Look at GitHub
GitHub, on the other hand, is a code hosting platform that offers version control using Git. It has long been a go-to choice for software developers, boasting a vast community of users and repositories. GitHub is known for its user-friendly interface, social coding features, and extensive integration options.
GitHub's emphasis on open-source projects and community involvement has made it a hub for collaboration and innovation. Developers can easily fork and contribute to projects, track issues, and showcase their work to the world. GitHub's popularity and widespread adoption have cemented its position as a leader in the software development industry.
Comparison of GitLab and GitHub
When comparing GitLab and GitHub, several key differences emerge. While both platforms offer version control and collaboration tools, GitLab stands out for its comprehensive DevOps capabilities, including built-in CI/CD pipelines and Kubernetes integration. GitHub, on the other hand, excels in its social coding features and vast ecosystem of third-party integrations.
In terms of user experience, GitLab is praised for its clean interface and intuitive design, which allows developers to quickly navigate and access the features they need. GitHub, on the other hand, is known for its robust community support and extensive documentation, making it easy for developers to find help and resources.
The Future of Software Development
As we look ahead to 2024, the software development landscape is poised for further innovation and growth. Both GitLab and GitHub are expected to continue evolving and introducing new features to cater to the changing needs of developers. From advancements in AI-driven code recommendations to enhanced security measures and improved collaboration tools, the future of software development looks bright.
Main Keyword Heading: GitLab or GitHub: Which Will Lead for Developers in 2024?
As we look ahead to 2024, the question remains: which of these two leading platforms, GitLab or GitHub, will emerge as the dominant force in the world of software development? With their distinctive features and strengths, both GitLab and GitHub are well-positioned to continue driving innovation and collaboration among developers worldwide.
How to obtain Devops certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In the fast-paced world of software development, choosing between GitLab and GitHub can be a tough decision. Both platforms offer unique features and benefits that cater to the diverse needs of developers. Whether you're looking for a comprehensive DevOps solution or a community-driven platform for open-source projects, GitLab and GitHub have you covered. As we look ahead to 2024, the future of software development is bright, with GitLab and GitHub leading the way towards new innovations and possibilities.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Automating XenDesktop Management with Citrix ADM
Are you looking to streamline and simplify your XenDesktop management tasks? Look no further than Citrix ADM. This powerful platform offers a wide range of automation capabilities that can help you save time, reduce errors, and improve overall efficiency in managing your Citrix XenDesktop environment.
What is Citrix ADM?
Citrix ADM, short for Citrix Application Delivery Management, is a comprehensive management and monitoring solution designed to help organizations automate and streamline the management of their Citrix infrastructure. With features such as centralized management, policy enforcement, and reporting capabilities, Citrix ADM is the perfect tool for automating XenDesktop management tasks.
How does Citrix ADM integrate with XenDesktop?
Citrix ADM seamlessly integrates with Citrix XenDesktop, allowing you to automate a wide range of tasks such as XenDesktop configuration, deployment, monitoring, and security. By leveraging the automation capabilities of Citrix ADM, you can significantly reduce the time and effort required to manage your XenDesktop environment.
What are the benefits of automating Citrix XenDesktop with Citrix ADM?
-
Reduced manual efforts and errors in XenDesktop administration
-
Improved efficiency and productivity in managing XenDesktop infrastructure
-
Enhanced security through automated policy enforcement and security automation
-
Streamlined deployment and provisioning processes for XenDesktop virtualization
-
Simplified monitoring and optimization of XenDesktop performance
How can Citrix ADM help automate XenDesktop management tasks?
Citrix ADM offers a wide range of automation solutions tailored specifically for XenDesktop management. From automated provisioning and deployment to policy management and software updates, Citrix ADM can handle all aspects of XenDesktop administration with ease.
For example, with Citrix ADM, you can automate the configuration of XenDesktop virtual machines, ensuring consistency and compliance across your environment. You can also set up automated monitoring tasks to keep a close eye on the performance of your XenDesktop infrastructure and make real-time adjustments as needed.
What sets Citrix ADM apart as a XenDesktop automation platform?
One of the key advantages of Citrix ADM is its centralized management capabilities. With Citrix ADM, you can easily manage multiple XenDesktop deployments from a single, unified interface, allowing for greater visibility and control over your entire infrastructure.
Additionally, Citrix ADM offers advanced features such as workflow automation, self-service automation, and resource optimization tools that further enhance the automation capabilities of XenDesktop management. By leveraging these features, you can ensure that your XenDesktop environment is always running at peak performance with minimal manual intervention.
How to obtain XenDesktop certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, automating XenDesktop management with Citrix ADM is the key to unlocking greater efficiency, productivity, and security in managing your Citrix infrastructure. With its robust automation capabilities and seamless integration with XenDesktop, Citrix ADM is the perfect tool for simplifying and streamlining your XenDesktop administration tasks.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
Are you looking to streamline and simplify your XenDesktop management tasks? Look no further than Citrix ADM. This powerful platform offers a wide range of automation capabilities that can help you save time, reduce errors, and improve overall efficiency in managing your Citrix XenDesktop environment.
What is Citrix ADM?
Citrix ADM, short for Citrix Application Delivery Management, is a comprehensive management and monitoring solution designed to help organizations automate and streamline the management of their Citrix infrastructure. With features such as centralized management, policy enforcement, and reporting capabilities, Citrix ADM is the perfect tool for automating XenDesktop management tasks.
How does Citrix ADM integrate with XenDesktop?
Citrix ADM seamlessly integrates with Citrix XenDesktop, allowing you to automate a wide range of tasks such as XenDesktop configuration, deployment, monitoring, and security. By leveraging the automation capabilities of Citrix ADM, you can significantly reduce the time and effort required to manage your XenDesktop environment.
What are the benefits of automating Citrix XenDesktop with Citrix ADM?
-
Reduced manual efforts and errors in XenDesktop administration
-
Improved efficiency and productivity in managing XenDesktop infrastructure
-
Enhanced security through automated policy enforcement and security automation
-
Streamlined deployment and provisioning processes for XenDesktop virtualization
-
Simplified monitoring and optimization of XenDesktop performance
How can Citrix ADM help automate XenDesktop management tasks?
Citrix ADM offers a wide range of automation solutions tailored specifically for XenDesktop management. From automated provisioning and deployment to policy management and software updates, Citrix ADM can handle all aspects of XenDesktop administration with ease.
For example, with Citrix ADM, you can automate the configuration of XenDesktop virtual machines, ensuring consistency and compliance across your environment. You can also set up automated monitoring tasks to keep a close eye on the performance of your XenDesktop infrastructure and make real-time adjustments as needed.
What sets Citrix ADM apart as a XenDesktop automation platform?
One of the key advantages of Citrix ADM is its centralized management capabilities. With Citrix ADM, you can easily manage multiple XenDesktop deployments from a single, unified interface, allowing for greater visibility and control over your entire infrastructure.
Additionally, Citrix ADM offers advanced features such as workflow automation, self-service automation, and resource optimization tools that further enhance the automation capabilities of XenDesktop management. By leveraging these features, you can ensure that your XenDesktop environment is always running at peak performance with minimal manual intervention.
How to obtain XenDesktop certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, automating XenDesktop management with Citrix ADM is the key to unlocking greater efficiency, productivity, and security in managing your Citrix infrastructure. With its robust automation capabilities and seamless integration with XenDesktop, Citrix ADM is the perfect tool for simplifying and streamlining your XenDesktop administration tasks.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Blockchain Interoperability: Connecting Different Networks
In the ever-evolving world of blockchain technology, one of the key challenges that needs to be addressed is the interoperability of different networks. Blockchain interoperability refers to the ability of different blockchain networks to communicate and interact with each other seamlessly. It is essential for the advancement of the blockchain ecosystem as a whole, as it allows for cross-chain communication, enabling decentralized networks to work together efficiently.
What is Blockchain Interoperability?
Blockchain interoperability is the concept of connecting and enabling communication between different blockchain networks. This allows for the transfer of assets and data between disparate networks without the need for intermediaries. In simple terms, blockchain interoperability enables seamless interaction and collaboration between various blockchain platforms.
Why is Cross-Chain Communication Important?
Cross-chain communication is crucial for the growth and adoption of blockchain technology. It enables users to transfer assets and data across different blockchain networks, opening up a world of possibilities for decentralized applications and services. Without interoperability, blockchain networks operate in silos, limiting their potential and hindering innovation.
How Does Blockchain Connectivity Work?
Interoperable blockchain platforms use a variety of technologies and protocols to facilitate cross-network interactions. These platforms are designed to be compatible with multiple blockchain networks, allowing for inter-chain transactions and seamless network interoperability. Blockchain bridges, multi-chain solutions, and interoperable protocols are just some of the tools used to connect different networks.
Challenges of Interoperability
While blockchain interoperability offers numerous benefits, there are also challenges that need to be addressed. One of the main challenges is achieving seamless integration and compatibility between different blockchain networks. Bridging blockchain networks and ensuring protocol interoperability can be complex tasks that require careful planning and execution.
Solutions for Interoperability
To overcome the challenges of blockchain interoperability, various solutions have been proposed. These include developing standards for network interoperability, creating interoperable applications, and implementing protocols for cross-platform connectivity. By working together to address these issues, the blockchain community can unlock the full potential of interoperable technology.
The Future of Blockchain Interoperability
As blockchain technology continues to evolve, the need for network interoperability will only grow. Connecting decentralized networks and enabling cross-network transactions will be essential for driving innovation and growth in the blockchain ecosystem. By developing interoperable solutions and standards, we can ensure that blockchain networks work together seamlessly, benefiting users and developers alike.
How to obtain Blockchain certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, blockchain interoperability is a key factor in the advancement of blockchain technology. By connecting different networks, we can unlock new possibilities for decentralized applications and services. As we work towards creating interoperable blockchain solutions, we can pave the way for a more connected and collaborative blockchain ecosystem.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In the ever-evolving world of blockchain technology, one of the key challenges that needs to be addressed is the interoperability of different networks. Blockchain interoperability refers to the ability of different blockchain networks to communicate and interact with each other seamlessly. It is essential for the advancement of the blockchain ecosystem as a whole, as it allows for cross-chain communication, enabling decentralized networks to work together efficiently.
What is Blockchain Interoperability?
Blockchain interoperability is the concept of connecting and enabling communication between different blockchain networks. This allows for the transfer of assets and data between disparate networks without the need for intermediaries. In simple terms, blockchain interoperability enables seamless interaction and collaboration between various blockchain platforms.
Why is Cross-Chain Communication Important?
Cross-chain communication is crucial for the growth and adoption of blockchain technology. It enables users to transfer assets and data across different blockchain networks, opening up a world of possibilities for decentralized applications and services. Without interoperability, blockchain networks operate in silos, limiting their potential and hindering innovation.
How Does Blockchain Connectivity Work?
Interoperable blockchain platforms use a variety of technologies and protocols to facilitate cross-network interactions. These platforms are designed to be compatible with multiple blockchain networks, allowing for inter-chain transactions and seamless network interoperability. Blockchain bridges, multi-chain solutions, and interoperable protocols are just some of the tools used to connect different networks.
Challenges of Interoperability
While blockchain interoperability offers numerous benefits, there are also challenges that need to be addressed. One of the main challenges is achieving seamless integration and compatibility between different blockchain networks. Bridging blockchain networks and ensuring protocol interoperability can be complex tasks that require careful planning and execution.
Solutions for Interoperability
To overcome the challenges of blockchain interoperability, various solutions have been proposed. These include developing standards for network interoperability, creating interoperable applications, and implementing protocols for cross-platform connectivity. By working together to address these issues, the blockchain community can unlock the full potential of interoperable technology.
The Future of Blockchain Interoperability
As blockchain technology continues to evolve, the need for network interoperability will only grow. Connecting decentralized networks and enabling cross-network transactions will be essential for driving innovation and growth in the blockchain ecosystem. By developing interoperable solutions and standards, we can ensure that blockchain networks work together seamlessly, benefiting users and developers alike.
How to obtain Blockchain certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, blockchain interoperability is a key factor in the advancement of blockchain technology. By connecting different networks, we can unlock new possibilities for decentralized applications and services. As we work towards creating interoperable blockchain solutions, we can pave the way for a more connected and collaborative blockchain ecosystem.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
CAPM Exam: How to Approach Situational Questions
Are you preparing for the CAPM exam and feeling overwhelmed by the situational questions? Don't worry, you're not alone. Many test takers find these types of questions challenging, but with the right approach, you can navigate them successfully. In this article, we will discuss some tips and strategies to help you tackle situational questions with confidence and ace your CAPM exam.
Understanding CAPM Certification
Before we dive into how to approach situational questions, let's first understand what the CAPM certification is all about. CAPM stands for Certified Associate in Project Management, and it is a globally recognized certification for project management professionals. It is designed for individuals who are interested in entering and advancing in the field of project management.
CAPM Exam Format and Difficulty
The CAPM exam consists of 150 multiple-choice questions that you need to answer within a 3-hour time limit. The questions are based on the Project Management Body of Knowledge (PMBOK) guide, which is considered the standard for project management practices. The exam covers various aspects of project management, including initiating, planning, executing, monitoring and controlling, and closing projects.
One of the challenging aspects of the CAPM exam is the situational questions. These questions present you with a scenario or problem related to project management and ask you to choose the best course of action. It requires critical thinking, problem-solving, decision-making, and analytical skills to answer these questions effectively.
Tips for Approaching Situational Questions
-
Understand the Scenario: When you encounter a situational question, take the time to carefully read and understand the scenario presented. Pay attention to the details and try to identify the key issues or challenges involved.
-
Apply PMBOK Knowledge: Use your knowledge of the PMBOK guide to analyze the situation and determine the most appropriate action based on project management best practices. Consider how each option aligns with the processes and principles outlined in the guide.
-
Eliminate Wrong Choices: If you're unsure about the correct answer, try to eliminate the obviously wrong choices first. This can help narrow down your options and increase your chances of selecting the right answer.
-
Think Like a Project Manager: Put yourself in the shoes of a project manager facing a similar situation in the real world. Consider what steps you would take to address the issue and achieve the project objectives.
Practice and Preparation
To succeed in answering situational questions on the CAPM exam, practice is key. Utilize practice tests, study guides, and online resources to familiarize yourself with the types of questions you may encounter. This will help you sharpen your critical thinking and decision-making skills and improve your overall exam performance.
How to obtain CAPM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, approaching situational questions on the CAPM exam requires a combination of knowledge, skills, and strategic thinking. By understanding the exam format, practicing with sample questions, and applying project management principles, you can confidently tackle these challenging questions and boost your chances of passing the exam.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
Are you preparing for the CAPM exam and feeling overwhelmed by the situational questions? Don't worry, you're not alone. Many test takers find these types of questions challenging, but with the right approach, you can navigate them successfully. In this article, we will discuss some tips and strategies to help you tackle situational questions with confidence and ace your CAPM exam.
Understanding CAPM Certification
Before we dive into how to approach situational questions, let's first understand what the CAPM certification is all about. CAPM stands for Certified Associate in Project Management, and it is a globally recognized certification for project management professionals. It is designed for individuals who are interested in entering and advancing in the field of project management.
CAPM Exam Format and Difficulty
The CAPM exam consists of 150 multiple-choice questions that you need to answer within a 3-hour time limit. The questions are based on the Project Management Body of Knowledge (PMBOK) guide, which is considered the standard for project management practices. The exam covers various aspects of project management, including initiating, planning, executing, monitoring and controlling, and closing projects.
One of the challenging aspects of the CAPM exam is the situational questions. These questions present you with a scenario or problem related to project management and ask you to choose the best course of action. It requires critical thinking, problem-solving, decision-making, and analytical skills to answer these questions effectively.
Tips for Approaching Situational Questions
-
Understand the Scenario: When you encounter a situational question, take the time to carefully read and understand the scenario presented. Pay attention to the details and try to identify the key issues or challenges involved.
-
Apply PMBOK Knowledge: Use your knowledge of the PMBOK guide to analyze the situation and determine the most appropriate action based on project management best practices. Consider how each option aligns with the processes and principles outlined in the guide.
-
Eliminate Wrong Choices: If you're unsure about the correct answer, try to eliminate the obviously wrong choices first. This can help narrow down your options and increase your chances of selecting the right answer.
-
Think Like a Project Manager: Put yourself in the shoes of a project manager facing a similar situation in the real world. Consider what steps you would take to address the issue and achieve the project objectives.
Practice and Preparation
To succeed in answering situational questions on the CAPM exam, practice is key. Utilize practice tests, study guides, and online resources to familiarize yourself with the types of questions you may encounter. This will help you sharpen your critical thinking and decision-making skills and improve your overall exam performance.
How to obtain CAPM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, approaching situational questions on the CAPM exam requires a combination of knowledge, skills, and strategic thinking. By understanding the exam format, practicing with sample questions, and applying project management principles, you can confidently tackle these challenging questions and boost your chances of passing the exam.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Network Security Basics: A Guide to Protecting Your Network
In this digital age, network security is of utmost importance to ensure the safety of your information and data. Whether you are an individual user, a small business, or a large corporation, protecting your network from cyber threats is essential. This guide will provide you with the basic knowledge and tools needed to safeguard your network effectively.
What is Network Security?
Network security is the practice of securing a computer network infrastructure against unauthorized access, misuse, modification, or denial of service. It involves implementing various technologies and processes to protect the integrity, confidentiality, and availability of information transmitted over the network.
Why is Network Security Important?
Network security is crucial because it helps prevent unauthorized access to sensitive information, prevents cyber-attacks, ensures data privacy, and protects against financial losses resulting from data breaches. By implementing robust network security measures, you can safeguard your network from malicious actors and maintain the trust of your users and customers.
Key Components of Network Security
-
Firewall: A firewall acts as a barrier between your internal network and external networks, filtering incoming and outgoing traffic based on predefined security rules.
-
Encryption: Encryption converts data into a code to prevent unauthorized access. It ensures that even if data is intercepted, it remains protected.
-
Intrusion Detection Systems (IDS): IDS monitor network traffic for suspicious activity or patterns that may indicate a security breach.
-
Password Security: Strong passwords are essential for network security. Implementing password policies and multi-factor authentication can enhance your network's defense.
-
Network Monitoring: Regular monitoring of your network allows you to detect and respond to security incidents promptly.
Best Practices for Network Security
-
Implement Network Authentication: Use strong authentication methods such as biometrics or two-factor authentication to verify user identities.
-
Enforce Network Encryption: Encrypt sensitive data in transit and at rest to prevent unauthorized access.
-
Establish Network Policies: Define clear security policies for your network, including access control rules and data handling guidelines.
-
Manage Network Access Control: Restrict access to sensitive information based on user roles and responsibilities.
-
Conduct Network Audits: Regularly audit your network to identify vulnerabilities and compliance issues.
Network Security Solutions and Tools
There are various network security solutions and tools available to help you protect your network effectively. Some popular options include:
-
Firewalls: Hardware or software-based firewalls that monitor and control incoming and outgoing network traffic.
-
Antivirus Software: Programs that detect and remove malware and viruses from your network.
-
Intrusion Prevention Systems (IPS): Security appliances that monitor network traffic and block suspicious activity in real-time.
-
Virtual Private Networks (VPNs): Secure connections that allow users to access a private network over a public network securely.
How to obtain Cyber Security certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Network security is a critical aspect of maintaining the integrity and confidentiality of your data. By understanding the basics of network security, implementing best practices, and utilizing the right tools and solutions, you can protect your network from cyber threats effectively. Remember, staying informed about the latest trends and techniques in network security is essential to adapt to ever-evolving cyber threats and ensure the safety of your network.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In this digital age, network security is of utmost importance to ensure the safety of your information and data. Whether you are an individual user, a small business, or a large corporation, protecting your network from cyber threats is essential. This guide will provide you with the basic knowledge and tools needed to safeguard your network effectively.
What is Network Security?
Network security is the practice of securing a computer network infrastructure against unauthorized access, misuse, modification, or denial of service. It involves implementing various technologies and processes to protect the integrity, confidentiality, and availability of information transmitted over the network.
Why is Network Security Important?
Network security is crucial because it helps prevent unauthorized access to sensitive information, prevents cyber-attacks, ensures data privacy, and protects against financial losses resulting from data breaches. By implementing robust network security measures, you can safeguard your network from malicious actors and maintain the trust of your users and customers.
Key Components of Network Security
-
Firewall: A firewall acts as a barrier between your internal network and external networks, filtering incoming and outgoing traffic based on predefined security rules.
-
Encryption: Encryption converts data into a code to prevent unauthorized access. It ensures that even if data is intercepted, it remains protected.
-
Intrusion Detection Systems (IDS): IDS monitor network traffic for suspicious activity or patterns that may indicate a security breach.
-
Password Security: Strong passwords are essential for network security. Implementing password policies and multi-factor authentication can enhance your network's defense.
-
Network Monitoring: Regular monitoring of your network allows you to detect and respond to security incidents promptly.
Best Practices for Network Security
-
Implement Network Authentication: Use strong authentication methods such as biometrics or two-factor authentication to verify user identities.
-
Enforce Network Encryption: Encrypt sensitive data in transit and at rest to prevent unauthorized access.
-
Establish Network Policies: Define clear security policies for your network, including access control rules and data handling guidelines.
-
Manage Network Access Control: Restrict access to sensitive information based on user roles and responsibilities.
-
Conduct Network Audits: Regularly audit your network to identify vulnerabilities and compliance issues.
Network Security Solutions and Tools
There are various network security solutions and tools available to help you protect your network effectively. Some popular options include:
-
Firewalls: Hardware or software-based firewalls that monitor and control incoming and outgoing network traffic.
-
Antivirus Software: Programs that detect and remove malware and viruses from your network.
-
Intrusion Prevention Systems (IPS): Security appliances that monitor network traffic and block suspicious activity in real-time.
-
Virtual Private Networks (VPNs): Secure connections that allow users to access a private network over a public network securely.
How to obtain Cyber Security certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Network security is a critical aspect of maintaining the integrity and confidentiality of your data. By understanding the basics of network security, implementing best practices, and utilizing the right tools and solutions, you can protect your network from cyber threats effectively. Remember, staying informed about the latest trends and techniques in network security is essential to adapt to ever-evolving cyber threats and ensure the safety of your network.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Career Growth for Non-IT Pros with ECBA Certification
In today's competitive job market, professionals from non-IT backgrounds are constantly seeking ways to enhance their career prospects and open up new opportunities for growth. One such avenue that has gained popularity in recent years is obtaining the ECBA (Entry Certificate in Business Analysis) certification. This certification program is designed to provide individuals with the necessary skills and knowledge to excel in the field of business analysis, even if they do not have a background in IT.
What is ECBA Certification?
The ECBA certification is an entry-level certification offered by the International Institute of Business Analysis (IIBA). It is designed for individuals who are new to the field of business analysis and wish to establish a solid foundation of knowledge and skills. The certification program covers a wide range of topics, including business analysis fundamentals, business analysis planning and monitoring, elicitation and collaboration, requirements life cycle management, strategy analysis, and solution evaluation.
How Can ECBA Certification Benefit Non-IT Professionals?
-
Career Transition: Obtaining the ECBA certification can help non-IT professionals make a successful transition into a business analyst role. The certification demonstrates to employers that an individual possesses the necessary skills and knowledge to excel in the field.
-
Professional Development: The ECBA certification program provides non-IT professionals with the opportunity to enhance their skills and develop a deeper understanding of business analysis techniques and tools.
-
Career Advancement: With the ECBA certification, non-IT professionals can open up new opportunities for career advancement and growth within their current organization or in the job market.
-
Skill Enhancement: The certification program helps individuals develop critical business analysis skills, such as critical thinking, problem-solving, communication, and stakeholder management.
-
Business Acumen: Non-IT professionals can benefit from gaining a deeper understanding of business processes and domain knowledge, which can help them contribute more effectively to their organizations.
How to Prepare for the ECBA Exam?
Preparing for the ECBA exam requires dedication and commitment. It is essential to study the ECBA curriculum thoroughly, which includes understanding key business analysis concepts, techniques, and best practices. Additionally, utilizing ECBA study materials, attending ECBA training sessions, and practicing with ECBA exam preparation tools can help individuals feel more confident and prepared on exam day.
The Road to Career Growth with ECBA Certification
For non-IT professionals looking to advance their careers and explore new opportunities, obtaining the ECBA certification can be a game-changer. The certification program not only equips individuals with essential business analysis skills but also provides a pathway for career growth and development. With the right mix of dedication, hard work, and determination, non-IT professionals can leverage their ECBA credentials to make a successful career switch and unlock new possibilities in the job market.
How to obtain ECBA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the ECBA certification offers non-IT professionals a unique opportunity to enhance their career prospects, develop essential business skills, and explore new career paths. By investing in their professional growth and acquiring the necessary knowledge and expertise, individuals can position themselves for success in the dynamic field of business analysis.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's competitive job market, professionals from non-IT backgrounds are constantly seeking ways to enhance their career prospects and open up new opportunities for growth. One such avenue that has gained popularity in recent years is obtaining the ECBA (Entry Certificate in Business Analysis) certification. This certification program is designed to provide individuals with the necessary skills and knowledge to excel in the field of business analysis, even if they do not have a background in IT.
What is ECBA Certification?
The ECBA certification is an entry-level certification offered by the International Institute of Business Analysis (IIBA). It is designed for individuals who are new to the field of business analysis and wish to establish a solid foundation of knowledge and skills. The certification program covers a wide range of topics, including business analysis fundamentals, business analysis planning and monitoring, elicitation and collaboration, requirements life cycle management, strategy analysis, and solution evaluation.
How Can ECBA Certification Benefit Non-IT Professionals?
-
Career Transition: Obtaining the ECBA certification can help non-IT professionals make a successful transition into a business analyst role. The certification demonstrates to employers that an individual possesses the necessary skills and knowledge to excel in the field.
-
Professional Development: The ECBA certification program provides non-IT professionals with the opportunity to enhance their skills and develop a deeper understanding of business analysis techniques and tools.
-
Career Advancement: With the ECBA certification, non-IT professionals can open up new opportunities for career advancement and growth within their current organization or in the job market.
-
Skill Enhancement: The certification program helps individuals develop critical business analysis skills, such as critical thinking, problem-solving, communication, and stakeholder management.
-
Business Acumen: Non-IT professionals can benefit from gaining a deeper understanding of business processes and domain knowledge, which can help them contribute more effectively to their organizations.
How to Prepare for the ECBA Exam?
Preparing for the ECBA exam requires dedication and commitment. It is essential to study the ECBA curriculum thoroughly, which includes understanding key business analysis concepts, techniques, and best practices. Additionally, utilizing ECBA study materials, attending ECBA training sessions, and practicing with ECBA exam preparation tools can help individuals feel more confident and prepared on exam day.
The Road to Career Growth with ECBA Certification
For non-IT professionals looking to advance their careers and explore new opportunities, obtaining the ECBA certification can be a game-changer. The certification program not only equips individuals with essential business analysis skills but also provides a pathway for career growth and development. With the right mix of dedication, hard work, and determination, non-IT professionals can leverage their ECBA credentials to make a successful career switch and unlock new possibilities in the job market.
How to obtain ECBA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the ECBA certification offers non-IT professionals a unique opportunity to enhance their career prospects, develop essential business skills, and explore new career paths. By investing in their professional growth and acquiring the necessary knowledge and expertise, individuals can position themselves for success in the dynamic field of business analysis.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Java Methods: A Beginner's Guide with Examples
Are you a new aspiring programmer looking to learn Java? Understanding Java methods is a crucial aspect of mastering the language. In this comprehensive guide, we will walk you through the basics of Java methods, provide examples, and offer tips for beginners to enhance their learning experience.
Introduction to Java Methods
In Java programming, methods are used to define the behavior of objects. They are blocks of code that perform specific tasks and can be called upon to execute those tasks. Methods are essential for breaking down a program into smaller, manageable chunks, making code more readable and reusable.
Syntax and Implementation of Java Methods
The syntax of a method in Java is as follows:
public void myMethod() {
// code to be executed
}
Here, public is an access modifier, void is the return type (void means the method does not return a value), myMethod is the method name, and the code within the curly braces is the method body.
Example of a Simple Java Method
Let's look at an example of a simple Java method that prints a message to the console:
public void printMessage() {
System.out.println("Hello, World!");
}
In this example, we have created a method called printMessage that prints "Hello, World!" when called.
Parameters in Java Methods
Methods can also take parameters, allowing you to pass values to the method for processing. Here's an example of a method that takes a parameter:
public void greetUser(String name) {
System.out.println("Hello, " + name + "!");
}
In this example, the greetUser method takes a String parameter name and prints a personalized greeting.
Types of Java Methods
There are several types of methods in Java, including:
-
Static Methods: These methods are associated with the class rather than objects.
-
Instance Methods: These methods belong to objects of the class.
-
Constructor Methods: These methods are used to initialize objects.
-
Accessor Methods: These methods are used to access the value of an object's attributes.
-
Mutator Methods: These methods are used to modify the value of an object's attributes.
Best Practices for Java Methods
When writing Java methods, it's essential to follow best practices to ensure clean, efficient, and maintainable code. Some best practices include:
-
Giving methods descriptive names that accurately reflect their purpose.
-
Keeping methods short and focused on a single task.
-
Using parameters effectively to make methods more versatile.
-
Avoiding complex nesting and excessive branching within methods.
How to obtain JAVA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Java methods are a fundamental aspect of Java programming that allows for code organization, reusability, and modularity. By understanding the syntax, implementation, and usage of methods in Java, beginners can enhance their programming skills and develop efficient solutions to problems. With practice and dedication, mastering Java methods will open doors to endless possibilities in the world of software development.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you a new aspiring programmer looking to learn Java? Understanding Java methods is a crucial aspect of mastering the language. In this comprehensive guide, we will walk you through the basics of Java methods, provide examples, and offer tips for beginners to enhance their learning experience.
Introduction to Java Methods
In Java programming, methods are used to define the behavior of objects. They are blocks of code that perform specific tasks and can be called upon to execute those tasks. Methods are essential for breaking down a program into smaller, manageable chunks, making code more readable and reusable.
Syntax and Implementation of Java Methods
The syntax of a method in Java is as follows:
public void myMethod() {
// code to be executed
}
Here, public is an access modifier, void is the return type (void means the method does not return a value), myMethod is the method name, and the code within the curly braces is the method body.
Example of a Simple Java Method
Let's look at an example of a simple Java method that prints a message to the console:
public void printMessage() {
System.out.println("Hello, World!");
}
In this example, we have created a method called printMessage that prints "Hello, World!" when called.
Parameters in Java Methods
Methods can also take parameters, allowing you to pass values to the method for processing. Here's an example of a method that takes a parameter:
public void greetUser(String name) {
System.out.println("Hello, " + name + "!");
}
In this example, the greetUser method takes a String parameter name and prints a personalized greeting.
Types of Java Methods
There are several types of methods in Java, including:
-
Static Methods: These methods are associated with the class rather than objects.
-
Instance Methods: These methods belong to objects of the class.
-
Constructor Methods: These methods are used to initialize objects.
-
Accessor Methods: These methods are used to access the value of an object's attributes.
-
Mutator Methods: These methods are used to modify the value of an object's attributes.
Best Practices for Java Methods
When writing Java methods, it's essential to follow best practices to ensure clean, efficient, and maintainable code. Some best practices include:
-
Giving methods descriptive names that accurately reflect their purpose.
-
Keeping methods short and focused on a single task.
-
Using parameters effectively to make methods more versatile.
-
Avoiding complex nesting and excessive branching within methods.
How to obtain JAVA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Java methods are a fundamental aspect of Java programming that allows for code organization, reusability, and modularity. By understanding the syntax, implementation, and usage of methods in Java, beginners can enhance their programming skills and develop efficient solutions to problems. With practice and dedication, mastering Java methods will open doors to endless possibilities in the world of software development.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
CTFL Certification: Benefits for Developers and Managers
In today's competitive job market, having a CTFL certification can significantly boost your career prospects as a developer or manager. The Certified Tester Foundation Level (CTFL) certification is a globally recognized credential that demonstrates your expertise in software testing. In this article, we will explore the benefits of CTFL certification for both developers and managers, as well as the process of obtaining this valuable credential.
Benefits of CTFL Certification
-
Enhanced Skills: CTFL certification equips you with the essential skills and knowledge required to excel in software testing. This includes understanding different testing techniques, tools, and methodologies.
-
Career Advancement: Holding a CTFL certification can open up new job opportunities and help you advance in your career. Employers often prefer candidates with relevant certifications, as it demonstrates their commitment to professional development.
-
Increased Credibility: CTFL certification enhances your credibility as a software testing professional. It shows that you have met the rigorous standards set by the International Software Testing Qualifications Board (ISTQB).
-
Higher Salary: Certified professionals typically command higher salaries than their non-certified counterparts. CTFL certification can lead to increased earning potential and better job prospects.
CTFL Certification for Developers
For developers, CTFL certification offers several advantages. It provides a solid foundation in software testing principles and practices, helping developers to deliver high-quality code. By understanding the importance of testing early in the development process, developers can identify and fix issues more efficiently, resulting in a more robust and reliable product.
CTFL Certification for Managers
Managers who hold a CTFL certification can effectively lead their teams and ensure the successful completion of testing projects. They have the knowledge and skills needed to make informed decisions about testing strategies, resource allocation, and risk management. CTFL certification also allows managers to communicate more effectively with their technical teams, fostering collaboration and innovation.
CTFL Exam and Syllabus
The CTFL exam covers a wide range of topics related to software testing, including testing principles, test design techniques, and test management. It assesses your understanding of key concepts and your ability to apply them in real-world scenarios. The exam is administered by accredited training providers and consists of multiple-choice questions.
The CTFL syllabus includes the following areas:
-
Fundamentals of software testing
-
Testing levels and types
-
Static testing
-
Test design techniques
-
Test management
-
Tools support for testing
How to Get CTFL Certification
To obtain CTFL certification, you must pass the official exam administered by an accredited training provider. It is recommended to prepare for the exam by studying the CTFL syllabus and using practice tests to assess your knowledge. Once you pass the exam, you will receive your certification, which is valid for life.
How to obtain CTFL Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, CTFL certification offers numerous benefits for developers and managers alike. It enhances your skills, opens up new career opportunities, and increases your credibility in the field of software testing. Whether you are looking to advance your career or improve your team's testing capabilities, CTFL certification is a valuable asset that can help you achieve your goals.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's competitive job market, having a CTFL certification can significantly boost your career prospects as a developer or manager. The Certified Tester Foundation Level (CTFL) certification is a globally recognized credential that demonstrates your expertise in software testing. In this article, we will explore the benefits of CTFL certification for both developers and managers, as well as the process of obtaining this valuable credential.
Benefits of CTFL Certification
-
Enhanced Skills: CTFL certification equips you with the essential skills and knowledge required to excel in software testing. This includes understanding different testing techniques, tools, and methodologies.
-
Career Advancement: Holding a CTFL certification can open up new job opportunities and help you advance in your career. Employers often prefer candidates with relevant certifications, as it demonstrates their commitment to professional development.
-
Increased Credibility: CTFL certification enhances your credibility as a software testing professional. It shows that you have met the rigorous standards set by the International Software Testing Qualifications Board (ISTQB).
-
Higher Salary: Certified professionals typically command higher salaries than their non-certified counterparts. CTFL certification can lead to increased earning potential and better job prospects.
CTFL Certification for Developers
For developers, CTFL certification offers several advantages. It provides a solid foundation in software testing principles and practices, helping developers to deliver high-quality code. By understanding the importance of testing early in the development process, developers can identify and fix issues more efficiently, resulting in a more robust and reliable product.
CTFL Certification for Managers
Managers who hold a CTFL certification can effectively lead their teams and ensure the successful completion of testing projects. They have the knowledge and skills needed to make informed decisions about testing strategies, resource allocation, and risk management. CTFL certification also allows managers to communicate more effectively with their technical teams, fostering collaboration and innovation.
CTFL Exam and Syllabus
The CTFL exam covers a wide range of topics related to software testing, including testing principles, test design techniques, and test management. It assesses your understanding of key concepts and your ability to apply them in real-world scenarios. The exam is administered by accredited training providers and consists of multiple-choice questions.
The CTFL syllabus includes the following areas:
-
Fundamentals of software testing
-
Testing levels and types
-
Static testing
-
Test design techniques
-
Test management
-
Tools support for testing
How to Get CTFL Certification
To obtain CTFL certification, you must pass the official exam administered by an accredited training provider. It is recommended to prepare for the exam by studying the CTFL syllabus and using practice tests to assess your knowledge. Once you pass the exam, you will receive your certification, which is valid for life.
How to obtain CTFL Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, CTFL certification offers numerous benefits for developers and managers alike. It enhances your skills, opens up new career opportunities, and increases your credibility in the field of software testing. Whether you are looking to advance your career or improve your team's testing capabilities, CTFL certification is a valuable asset that can help you achieve your goals.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
User Experience (UX): A Crucial Element in Digital Marketing
In the fast-paced world of digital marketing, one crucial element stands out above the rest - user experience (UX). With the ever-evolving landscape of technology and consumer behavior, creating a seamless and user-friendly experience for website visitors has become more important than ever. Let's delve into the world of UX and explore why it is a key component of any successful digital marketing strategy.
What is User Experience (UX)?
User experience (UX) refers to the overall experience that a user has when interacting with a website or digital product. It encompasses everything from the user interface design to the interaction design, customer journey, and overall online presence. A positive user experience can lead to increased user engagement, improved website usability, higher conversion rates, and ultimately, happier customers.
Why is UX Important in Digital Marketing?
User experience plays a vital role in digital marketing for several reasons. Firstly, it directly impacts user behavior on a website. A well-designed and user-friendly website will encourage visitors to explore further, engage with content, and take desired actions such as making a purchase or filling out a form. On the other hand, a poorly designed website with a confusing user interface can lead to frustration and high bounce rates.
Secondly, user experience is closely tied to customer satisfaction. By prioritizing UX in website design and development, businesses can create a positive brand experience and build trust with their target audience. Satisfied customers are more likely to return to a website, make repeat purchases, and recommend the brand to others.
How to Improve User Experience in Digital Marketing?
There are several key strategies that businesses can implement to enhance user experience and drive digital marketing success:
-
Conduct User Research: By understanding the needs and preferences of your target audience, you can tailor your website design and content to meet their expectations.
-
Implement User Testing: Testing the usability of your website with real users can help identify areas for improvement and optimize the overall user experience.
-
Focus on Information Architecture: Well-organized and intuitive website navigation can make it easy for users to find what they are looking for and navigate the site efficiently.
-
Prioritize Responsive Design: With the increasing use of mobile devices, it is essential to ensure that your website is optimized for mobile users to provide a seamless browsing experience across all devices.
-
Create User Personas: Developing user personas can help you better understand your target audience and design a website that aligns with their needs and preferences.
By implementing these strategies and prioritizing user experience in digital marketing efforts, businesses can create a competitive advantage, drive website performance, and ultimately, achieve greater success in the online marketplace.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, user experience (UX) is a crucial element in digital marketing that should not be overlooked. By focusing on creating a seamless and user-friendly experience for website visitors, businesses can improve user engagement, drive conversions, and build long-lasting relationships with their customers. Embracing user-centered design principles and prioritizing UX in website development can lead to a more successful digital marketing strategy.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In the fast-paced world of digital marketing, one crucial element stands out above the rest - user experience (UX). With the ever-evolving landscape of technology and consumer behavior, creating a seamless and user-friendly experience for website visitors has become more important than ever. Let's delve into the world of UX and explore why it is a key component of any successful digital marketing strategy.
What is User Experience (UX)?
User experience (UX) refers to the overall experience that a user has when interacting with a website or digital product. It encompasses everything from the user interface design to the interaction design, customer journey, and overall online presence. A positive user experience can lead to increased user engagement, improved website usability, higher conversion rates, and ultimately, happier customers.
Why is UX Important in Digital Marketing?
User experience plays a vital role in digital marketing for several reasons. Firstly, it directly impacts user behavior on a website. A well-designed and user-friendly website will encourage visitors to explore further, engage with content, and take desired actions such as making a purchase or filling out a form. On the other hand, a poorly designed website with a confusing user interface can lead to frustration and high bounce rates.
Secondly, user experience is closely tied to customer satisfaction. By prioritizing UX in website design and development, businesses can create a positive brand experience and build trust with their target audience. Satisfied customers are more likely to return to a website, make repeat purchases, and recommend the brand to others.
How to Improve User Experience in Digital Marketing?
There are several key strategies that businesses can implement to enhance user experience and drive digital marketing success:
-
Conduct User Research: By understanding the needs and preferences of your target audience, you can tailor your website design and content to meet their expectations.
-
Implement User Testing: Testing the usability of your website with real users can help identify areas for improvement and optimize the overall user experience.
-
Focus on Information Architecture: Well-organized and intuitive website navigation can make it easy for users to find what they are looking for and navigate the site efficiently.
-
Prioritize Responsive Design: With the increasing use of mobile devices, it is essential to ensure that your website is optimized for mobile users to provide a seamless browsing experience across all devices.
-
Create User Personas: Developing user personas can help you better understand your target audience and design a website that aligns with their needs and preferences.
By implementing these strategies and prioritizing user experience in digital marketing efforts, businesses can create a competitive advantage, drive website performance, and ultimately, achieve greater success in the online marketplace.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, user experience (UX) is a crucial element in digital marketing that should not be overlooked. By focusing on creating a seamless and user-friendly experience for website visitors, businesses can improve user engagement, drive conversions, and build long-lasting relationships with their customers. Embracing user-centered design principles and prioritizing UX in website development can lead to a more successful digital marketing strategy.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Apache Kafka vs. RabbitMQ: Which One to Choose?
When it comes to choosing the right messaging system for your application, Apache Kafka and RabbitMQ are two popular options that come to mind. Both are powerful tools that offer various features and capabilities, but they have distinct differences that set them apart. In this article, we will compare Apache Kafka and RabbitMQ in terms of performance, scalability, architecture, features, use cases, and more to help you make an informed decision on which one to choose for your project.
Apache Kafka
Apache Kafka is a distributed streaming platform designed for handling real-time data feeds. It provides high throughput, low latency, fault tolerance, and scalability, making it suitable for use cases that require processing large volumes of data in real-time. Kafka is built as a distributed system that can be easily scaled horizontally to handle a high volume of data streams efficiently.
Key Features of Apache Kafka:
- Message Brokers: Kafka acts as a messaging queue where producers can send messages that are stored in topics and consumed by consumers.
- Event Streaming: Kafka allows for real-time event streaming, enabling applications to react to events as they occur.
- Message Ordering: Kafka guarantees message ordering within a partition, ensuring that messages are processed in the order they were produced.
- Distributed Systems: Kafka is designed to operate as a distributed system, providing fault tolerance and high availability.
- Compatibility: Kafka can be easily integrated with various systems and platforms, making it versatile for different use cases.
RabbitMQ
RabbitMQ is a messaging broker that implements the Advanced Message Queuing Protocol (AMQP). It is known for its ease of use, flexibility, and reliability, making it a popular choice for applications that require reliable asynchronous communication. RabbitMQ is designed to handle message queues efficiently, ensuring that messages are delivered reliably and in the correct order.
Key Features of RabbitMQ:
- Messaging Queue: RabbitMQ provides a message queue where producers can send messages that are stored until consumers are ready to process them.
- Data Consistency: RabbitMQ ensures data consistency by guaranteeing message delivery and order.
- Throughput: RabbitMQ offers high throughput for processing messages efficiently and quickly.
- Ease of Use: RabbitMQ is easy to set up and configure, making it ideal for developers who want a simple messaging solution.
- Integration: RabbitMQ can be integrated with various systems and platforms, allowing for seamless communication between different components.
Comparison
Now, let's compare Apache Kafka and RabbitMQ based on various factors to help you decide which one to choose for your project:
| Factors | Apache Kafka | RabbitMQ |
|------------------|-------------------------------------------|-----------------------------------------------|
| Performance | High throughput and low latency | Reliable message delivery and data consistency|
| Scalability | Easily scalable horizontally | Scalable with clustering capabilities |
| Architecture | Distributed system with fault tolerance | Message broker with support for different protocols|
| Features | Event streaming, message ordering | Messaging queue with data consistency |
| Use Cases | Real-time data processing, event streaming| Asynchronous communication, task queues |
So, which one to choose?
The answer to whether you should choose Apache Kafka or RabbitMQ depends on your specific use case and requirements. If you need a high-throughput, low-latency system for real-time data processing and event streaming, Apache Kafka would be the ideal choice. On the other hand, if you require reliable message delivery, data consistency, and ease of use for asynchronous communication, RabbitMQ may be more suitable for your project.
How to obtain Apache Kafka Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, both Apache Kafka and RabbitMQ are powerful messaging systems with unique features and capabilities. By understanding the differences between the two, you can make an informed decision on which one to choose based on your project's needs. Whether you choose Apache Kafka for its performance and scalability or RabbitMQ for its reliability and ease of use, both systems can help you build robust and efficient applications that meet your messaging requirements.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
When it comes to choosing the right messaging system for your application, Apache Kafka and RabbitMQ are two popular options that come to mind. Both are powerful tools that offer various features and capabilities, but they have distinct differences that set them apart. In this article, we will compare Apache Kafka and RabbitMQ in terms of performance, scalability, architecture, features, use cases, and more to help you make an informed decision on which one to choose for your project.
Apache Kafka
Apache Kafka is a distributed streaming platform designed for handling real-time data feeds. It provides high throughput, low latency, fault tolerance, and scalability, making it suitable for use cases that require processing large volumes of data in real-time. Kafka is built as a distributed system that can be easily scaled horizontally to handle a high volume of data streams efficiently.
Key Features of Apache Kafka:
- Message Brokers: Kafka acts as a messaging queue where producers can send messages that are stored in topics and consumed by consumers.
- Event Streaming: Kafka allows for real-time event streaming, enabling applications to react to events as they occur.
- Message Ordering: Kafka guarantees message ordering within a partition, ensuring that messages are processed in the order they were produced.
- Distributed Systems: Kafka is designed to operate as a distributed system, providing fault tolerance and high availability.
- Compatibility: Kafka can be easily integrated with various systems and platforms, making it versatile for different use cases.
RabbitMQ
RabbitMQ is a messaging broker that implements the Advanced Message Queuing Protocol (AMQP). It is known for its ease of use, flexibility, and reliability, making it a popular choice for applications that require reliable asynchronous communication. RabbitMQ is designed to handle message queues efficiently, ensuring that messages are delivered reliably and in the correct order.
Key Features of RabbitMQ:
- Messaging Queue: RabbitMQ provides a message queue where producers can send messages that are stored until consumers are ready to process them.
- Data Consistency: RabbitMQ ensures data consistency by guaranteeing message delivery and order.
- Throughput: RabbitMQ offers high throughput for processing messages efficiently and quickly.
- Ease of Use: RabbitMQ is easy to set up and configure, making it ideal for developers who want a simple messaging solution.
- Integration: RabbitMQ can be integrated with various systems and platforms, allowing for seamless communication between different components.
Comparison
Now, let's compare Apache Kafka and RabbitMQ based on various factors to help you decide which one to choose for your project:
| Factors | Apache Kafka | RabbitMQ |
|------------------|-------------------------------------------|-----------------------------------------------|
| Performance | High throughput and low latency | Reliable message delivery and data consistency|
| Scalability | Easily scalable horizontally | Scalable with clustering capabilities |
| Architecture | Distributed system with fault tolerance | Message broker with support for different protocols|
| Features | Event streaming, message ordering | Messaging queue with data consistency |
| Use Cases | Real-time data processing, event streaming| Asynchronous communication, task queues |
So, which one to choose?
The answer to whether you should choose Apache Kafka or RabbitMQ depends on your specific use case and requirements. If you need a high-throughput, low-latency system for real-time data processing and event streaming, Apache Kafka would be the ideal choice. On the other hand, if you require reliable message delivery, data consistency, and ease of use for asynchronous communication, RabbitMQ may be more suitable for your project.
How to obtain Apache Kafka Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, both Apache Kafka and RabbitMQ are powerful messaging systems with unique features and capabilities. By understanding the differences between the two, you can make an informed decision on which one to choose based on your project's needs. Whether you choose Apache Kafka for its performance and scalability or RabbitMQ for its reliability and ease of use, both systems can help you build robust and efficient applications that meet your messaging requirements.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Exploring the COBIT Framework
Do you want to enhance your organization's IT governance and ensure effective risk management and compliance practices? Look no further than the COBIT framework, a widely recognized and trusted set of guidelines designed to help businesses achieve their IT objectives while maintaining a high level of control over their systems and processes.
What is the COBIT Framework?
The COBIT framework, short for Control Objectives for Information and Related Technologies, is a comprehensive framework developed by ISACA to help organizations align their IT strategies with their business goals. It provides a structured approach to IT governance and helps organizations improve their overall performance by implementing best practices and controls.
COBIT Principles and Concepts
At the core of the COBIT framework are a set of principles that guide organizations in achieving their goals and objectives. These principles include aligning IT with business goals, providing value to the organization, managing risk effectively, and optimizing resource utilization.
Components of the COBIT Framework
The COBIT framework is divided into five key components: principles, processes, organizational structures, culture, and information. These components work together to ensure that IT governance practices are effectively implemented and maintained throughout the organization.
COBIT Governance and Domains
One of the key aspects of the COBIT framework is its focus on governance, which involves defining roles and responsibilities, establishing clear decision-making processes, and ensuring accountability. The framework also includes four domains: planning and organization, acquisition and implementation, delivery and support, and monitoring and evaluation.
COBIT Implementation and Best Practices
Implementing the COBIT framework involves following a set of best practices that are outlined in the framework. These practices include defining and communicating IT roles and responsibilities, establishing clear performance metrics, and regularly monitoring and evaluating the effectiveness of IT processes.
COBIT Controls and Benefits
The COBIT framework includes a set of controls that organizations can use to manage their IT processes effectively. These controls help organizations identify and mitigate risks, ensure compliance with regulations, and improve overall performance. By implementing the COBIT framework, organizations can benefit from improved IT governance, enhanced risk management practices, and increased transparency and accountability.
COBIT Certification and Training
For organizations looking to enhance their IT governance practices, COBIT certification and training programs are available. These programs help professionals gain a deeper understanding of the COBIT framework and learn how to implement it effectively within their organizations.
How to obtain COBIT certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the COBIT framework is an invaluable tool for organizations looking to improve their IT governance practices and achieve their business objectives. By following the principles, processes, and best practices outlined in the framework, organizations can enhance their overall performance, manage risks effectively, and ensure compliance with regulations. With its emphasis on governance, control, and risk management, the COBIT framework is a must-have for any organization looking to succeed in today's increasingly digital world.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
Do you want to enhance your organization's IT governance and ensure effective risk management and compliance practices? Look no further than the COBIT framework, a widely recognized and trusted set of guidelines designed to help businesses achieve their IT objectives while maintaining a high level of control over their systems and processes.
What is the COBIT Framework?
The COBIT framework, short for Control Objectives for Information and Related Technologies, is a comprehensive framework developed by ISACA to help organizations align their IT strategies with their business goals. It provides a structured approach to IT governance and helps organizations improve their overall performance by implementing best practices and controls.
COBIT Principles and Concepts
At the core of the COBIT framework are a set of principles that guide organizations in achieving their goals and objectives. These principles include aligning IT with business goals, providing value to the organization, managing risk effectively, and optimizing resource utilization.
Components of the COBIT Framework
The COBIT framework is divided into five key components: principles, processes, organizational structures, culture, and information. These components work together to ensure that IT governance practices are effectively implemented and maintained throughout the organization.
COBIT Governance and Domains
One of the key aspects of the COBIT framework is its focus on governance, which involves defining roles and responsibilities, establishing clear decision-making processes, and ensuring accountability. The framework also includes four domains: planning and organization, acquisition and implementation, delivery and support, and monitoring and evaluation.
COBIT Implementation and Best Practices
Implementing the COBIT framework involves following a set of best practices that are outlined in the framework. These practices include defining and communicating IT roles and responsibilities, establishing clear performance metrics, and regularly monitoring and evaluating the effectiveness of IT processes.
COBIT Controls and Benefits
The COBIT framework includes a set of controls that organizations can use to manage their IT processes effectively. These controls help organizations identify and mitigate risks, ensure compliance with regulations, and improve overall performance. By implementing the COBIT framework, organizations can benefit from improved IT governance, enhanced risk management practices, and increased transparency and accountability.
COBIT Certification and Training
For organizations looking to enhance their IT governance practices, COBIT certification and training programs are available. These programs help professionals gain a deeper understanding of the COBIT framework and learn how to implement it effectively within their organizations.
How to obtain COBIT certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the COBIT framework is an invaluable tool for organizations looking to improve their IT governance practices and achieve their business objectives. By following the principles, processes, and best practices outlined in the framework, organizations can enhance their overall performance, manage risks effectively, and ensure compliance with regulations. With its emphasis on governance, control, and risk management, the COBIT framework is a must-have for any organization looking to succeed in today's increasingly digital world.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
CTFL for Test Managers: Benefits and Insights
In today's fast-paced world of software development, test managers play a crucial role in ensuring the quality and reliability of the products being delivered to customers. The Certified Tester Foundation Level (CTFL) certification is designed specifically for test managers, providing them with the knowledge and skills needed to excel in their roles. In this article, we will explore the benefits and insights of CTFL for test managers, highlighting how this certification can enhance their abilities and drive success in their careers.
What is CTFL?
CTFL stands for Certified Tester Foundation Level, and it is a globally recognized certification that validates an individual's proficiency in software testing and quality assurance. The CTFL certification exam covers a wide range of topics related to test management, including test planning, test strategy, test design, test execution, defect management, test automation, and more. By obtaining the CTFL certification, test managers demonstrate their commitment to excellence and their dedication to continuous improvement in the field of software testing.
Benefits of CTFL for Test Managers
1. Enhanced Leadership Skills
Test managers with CTFL certification have a thorough understanding of best practices in test management, team management, and quality assurance. They are equipped with the knowledge and skills needed to lead their teams effectively, establish clear objectives, and drive performance excellence. CTFL certification helps test managers develop strong leadership skills that are essential for success in today's competitive software testing industry.
2. Improved Communication and Stakeholder Management
Effective communication is crucial in test management, as it ensures that all stakeholders are informed and aligned throughout the testing process. CTFL-certified test managers have the communication skills needed to interact with team members, developers, project managers, and customers effectively. They can articulate complex testing concepts in a clear and concise manner, building trust and rapport with stakeholders at all levels.
3. Strong Problem-Solving and Decision-Making Skills
Test managers often encounter complex challenges and critical decisions during the testing process. CTFL certification equips test managers with the problem-solving skills and analytical mindset needed to address issues efficiently and make informed decisions under pressure. By mastering critical thinking, time management, and decision-making skills, CTFL-certified test managers can navigate through obstacles and drive successful outcomes for their testing projects.
4. Career Advancement and Development Opportunities
CTFL certification opens doors to new career opportunities and advancement for test managers. Employers value professionals with recognized certifications, as they demonstrate a commitment to excellence and continuous learning. With CTFL certification, test managers can enhance their credibility, expand their skill set, and pursue higher-level roles in the software testing industry. CTFL certification serves as a valuable asset for career growth and development, providing test managers with the competitive edge needed to excel in their careers.
Insights from CTFL Certification
CTFL certification offers valuable insights and best practices for test managers, helping them improve their test processes, enhance quality assurance practices, and drive continuous improvement in their testing projects. By leveraging the knowledge and skills gained through CTFL certification, test managers can deliver high-quality products, mitigate risks effectively, and exceed customer expectations. CTFL-certified test managers are well-equipped to lead their teams to success, implement industry best practices, and achieve excellence in software testing.
How to obtain CTFL certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, CTFL certification is a valuable asset for test managers seeking to enhance their skills, advance their careers, and excel in the field of software testing. By obtaining CTFL certification, test managers can gain a competitive edge, demonstrate their expertise, and drive success in their testing projects. CTFL certification provides test managers with the knowledge, skills, and insights needed to lead their teams to success, deliver high-quality products, and achieve excellence in software testing.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's fast-paced world of software development, test managers play a crucial role in ensuring the quality and reliability of the products being delivered to customers. The Certified Tester Foundation Level (CTFL) certification is designed specifically for test managers, providing them with the knowledge and skills needed to excel in their roles. In this article, we will explore the benefits and insights of CTFL for test managers, highlighting how this certification can enhance their abilities and drive success in their careers.
What is CTFL?
CTFL stands for Certified Tester Foundation Level, and it is a globally recognized certification that validates an individual's proficiency in software testing and quality assurance. The CTFL certification exam covers a wide range of topics related to test management, including test planning, test strategy, test design, test execution, defect management, test automation, and more. By obtaining the CTFL certification, test managers demonstrate their commitment to excellence and their dedication to continuous improvement in the field of software testing.
Benefits of CTFL for Test Managers
1. Enhanced Leadership Skills
Test managers with CTFL certification have a thorough understanding of best practices in test management, team management, and quality assurance. They are equipped with the knowledge and skills needed to lead their teams effectively, establish clear objectives, and drive performance excellence. CTFL certification helps test managers develop strong leadership skills that are essential for success in today's competitive software testing industry.
2. Improved Communication and Stakeholder Management
Effective communication is crucial in test management, as it ensures that all stakeholders are informed and aligned throughout the testing process. CTFL-certified test managers have the communication skills needed to interact with team members, developers, project managers, and customers effectively. They can articulate complex testing concepts in a clear and concise manner, building trust and rapport with stakeholders at all levels.
3. Strong Problem-Solving and Decision-Making Skills
Test managers often encounter complex challenges and critical decisions during the testing process. CTFL certification equips test managers with the problem-solving skills and analytical mindset needed to address issues efficiently and make informed decisions under pressure. By mastering critical thinking, time management, and decision-making skills, CTFL-certified test managers can navigate through obstacles and drive successful outcomes for their testing projects.
4. Career Advancement and Development Opportunities
CTFL certification opens doors to new career opportunities and advancement for test managers. Employers value professionals with recognized certifications, as they demonstrate a commitment to excellence and continuous learning. With CTFL certification, test managers can enhance their credibility, expand their skill set, and pursue higher-level roles in the software testing industry. CTFL certification serves as a valuable asset for career growth and development, providing test managers with the competitive edge needed to excel in their careers.
Insights from CTFL Certification
CTFL certification offers valuable insights and best practices for test managers, helping them improve their test processes, enhance quality assurance practices, and drive continuous improvement in their testing projects. By leveraging the knowledge and skills gained through CTFL certification, test managers can deliver high-quality products, mitigate risks effectively, and exceed customer expectations. CTFL-certified test managers are well-equipped to lead their teams to success, implement industry best practices, and achieve excellence in software testing.
How to obtain CTFL certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, CTFL certification is a valuable asset for test managers seeking to enhance their skills, advance their careers, and excel in the field of software testing. By obtaining CTFL certification, test managers can gain a competitive edge, demonstrate their expertise, and drive success in their testing projects. CTFL certification provides test managers with the knowledge, skills, and insights needed to lead their teams to success, deliver high-quality products, and achieve excellence in software testing.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Understanding Apache Spark Architecture
In this article, we will delve into the intricate world of Apache Spark architecture and explore how this powerful framework enables big data processing through its unique design and components. By the end of this read, you will have a solid understanding of Spark's distributed computing model, memory processing capabilities, fault tolerance mechanisms, and much more.
What is Apache Spark?
Apache Spark is an open-source distributed computing framework that provides an efficient way to process large datasets across a cluster of machines. It offers a flexible and powerful programming model that supports a wide range of applications, from batch processing to real-time analytics. Understanding Apache Spark's architecture is essential for harnessing its full potential in data processing workflows.
Spark Cluster
At the heart of Apache Spark architecture lies the concept of a Spark cluster. A Spark cluster is a group of interconnected machines that work together to process data in parallel. It consists of a master node, which manages the cluster, and multiple worker nodes, where the actual processing takes place. Understanding how Spark clusters operate is crucial for scaling data processing tasks efficiently.
Spark Components
Apache Spark is composed of several key components that work together to enable distributed data processing. These components include the Spark driver, which controls the execution of Spark applications, Spark nodes, where data is processed in parallel, and various libraries and modules that facilitate tasks such as data transformations, actions, and job scheduling. Understanding the role of each component is essential for optimizing Spark applications.
Big Data Processing
Spark is designed to handle large-scale data processing tasks efficiently, making it an ideal choice for big data applications. By leveraging in-memory processing and parallel computing techniques, Spark can process massive datasets with ease. Understanding how Spark handles big data processing tasks is key to building robust and scalable data pipelines.
Spark Programming Model
One of the reasons for Apache Spark's popularity is its intuitive programming model, which allows developers to write complex data processing tasks with ease. Spark's programming model is based on the concept of resilient distributed datasets (RDDs), which are resilient, immutable distributed collections of data that can be transformed and manipulated in parallel. Understanding Spark's programming model is essential for writing efficient and scalable data processing workflows.
Fault Tolerance
Fault tolerance is a critical aspect of Apache Spark's architecture, ensuring that data processing tasks can recover from failures seamlessly. Spark achieves fault tolerance through mechanisms such as lineage tracking, data checkpointing, and task retrying. Understanding how Spark maintains fault tolerance is crucial for building reliable data pipelines that can withstand failures.
Resilient Distributed Dataset
Central to Apache Spark's fault tolerance mechanisms is the concept of resilient distributed datasets (RDDs). RDDs are fault-tolerant, parallel collections of data that can be operated on in a distributed manner. By storing lineage information and ensuring data durability, RDDs enable Spark to recover from failures and maintain data consistency. Understanding RDDs is essential for designing fault-tolerant data processing workflows.
Data Pipelines
Data pipelines are a fundamental building block of Apache Spark applications, enabling users to define and execute complex data processing tasks. Spark provides a rich set of APIs for building data pipelines, allowing users to transform, filter, and aggregate data sets efficiently. Understanding how data pipelines work in Spark is essential for orchestrating data processing workflows and optimizing job performance.
How to obtain Apache Spark certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, understanding Apache Spark's architecture is crucial for harnessing the full power of this versatile framework in big data processing. By grasping concepts such as Spark clusters, fault tolerance mechanisms, and data pipelines, users can design efficient and scalable data processing workflows. With its in-memory processing capabilities, parallel computing techniques, and flexible programming model, Apache Spark is a formidable tool for handling large-scale data processing tasks. So, dive into Apache Spark's architecture today and unlock its full potential for your data processing needs.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In this article, we will delve into the intricate world of Apache Spark architecture and explore how this powerful framework enables big data processing through its unique design and components. By the end of this read, you will have a solid understanding of Spark's distributed computing model, memory processing capabilities, fault tolerance mechanisms, and much more.
What is Apache Spark?
Apache Spark is an open-source distributed computing framework that provides an efficient way to process large datasets across a cluster of machines. It offers a flexible and powerful programming model that supports a wide range of applications, from batch processing to real-time analytics. Understanding Apache Spark's architecture is essential for harnessing its full potential in data processing workflows.
Spark Cluster
At the heart of Apache Spark architecture lies the concept of a Spark cluster. A Spark cluster is a group of interconnected machines that work together to process data in parallel. It consists of a master node, which manages the cluster, and multiple worker nodes, where the actual processing takes place. Understanding how Spark clusters operate is crucial for scaling data processing tasks efficiently.
Spark Components
Apache Spark is composed of several key components that work together to enable distributed data processing. These components include the Spark driver, which controls the execution of Spark applications, Spark nodes, where data is processed in parallel, and various libraries and modules that facilitate tasks such as data transformations, actions, and job scheduling. Understanding the role of each component is essential for optimizing Spark applications.
Big Data Processing
Spark is designed to handle large-scale data processing tasks efficiently, making it an ideal choice for big data applications. By leveraging in-memory processing and parallel computing techniques, Spark can process massive datasets with ease. Understanding how Spark handles big data processing tasks is key to building robust and scalable data pipelines.
Spark Programming Model
One of the reasons for Apache Spark's popularity is its intuitive programming model, which allows developers to write complex data processing tasks with ease. Spark's programming model is based on the concept of resilient distributed datasets (RDDs), which are resilient, immutable distributed collections of data that can be transformed and manipulated in parallel. Understanding Spark's programming model is essential for writing efficient and scalable data processing workflows.
Fault Tolerance
Fault tolerance is a critical aspect of Apache Spark's architecture, ensuring that data processing tasks can recover from failures seamlessly. Spark achieves fault tolerance through mechanisms such as lineage tracking, data checkpointing, and task retrying. Understanding how Spark maintains fault tolerance is crucial for building reliable data pipelines that can withstand failures.
Resilient Distributed Dataset
Central to Apache Spark's fault tolerance mechanisms is the concept of resilient distributed datasets (RDDs). RDDs are fault-tolerant, parallel collections of data that can be operated on in a distributed manner. By storing lineage information and ensuring data durability, RDDs enable Spark to recover from failures and maintain data consistency. Understanding RDDs is essential for designing fault-tolerant data processing workflows.
Data Pipelines
Data pipelines are a fundamental building block of Apache Spark applications, enabling users to define and execute complex data processing tasks. Spark provides a rich set of APIs for building data pipelines, allowing users to transform, filter, and aggregate data sets efficiently. Understanding how data pipelines work in Spark is essential for orchestrating data processing workflows and optimizing job performance.
How to obtain Apache Spark certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, understanding Apache Spark's architecture is crucial for harnessing the full power of this versatile framework in big data processing. By grasping concepts such as Spark clusters, fault tolerance mechanisms, and data pipelines, users can design efficient and scalable data processing workflows. With its in-memory processing capabilities, parallel computing techniques, and flexible programming model, Apache Spark is a formidable tool for handling large-scale data processing tasks. So, dive into Apache Spark's architecture today and unlock its full potential for your data processing needs.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Emerging Trends in Hadoop Security Best Practices for 2024
In the ever-evolving landscape of technology, data security remains a top priority for organizations across the globe. As more and more companies turn to big data analytics to drive business decisions, the need for robust security measures in technologies like Hadoop becomes increasingly crucial. Let's explore the emerging trends in Hadoop security and the best practices to ensure data protection in 2024.
Hadoop Security Landscape in 2024
With the rapid expansion of big data and Hadoop technology, cybersecurity threats have also become more sophisticated. Data protection is no longer just about securing data at rest and in transit, but also about protecting data during processing and analysis. This has led to a shift towards more holistic security approaches that encompass the entire Hadoop ecosystem.
Encryption and Authentication
One of the key trends in Hadoop security for 2024 is the widespread adoption of encryption and strong authentication mechanisms. Encryption helps protect data both in transit and at rest, ensuring that only authorized users can access sensitive information. Strong authentication practices, such as multi-factor authentication, further enhance data security by verifying the identity of users before granting access to the data.
Authorization and Data Privacy
Another important aspect of Hadoop security is authorization, which determines what actions users are allowed to perform on data within the Hadoop clusters. Implementing fine-grained access controls based on user roles and privileges helps prevent unauthorized access and data breaches. Data privacy regulations, such as GDPR, also play a significant role in shaping data security practices, requiring organizations to implement measures to protect user privacy and ensure compliance with data protection laws.
Threat Detection and Incident Response
In 2024, organizations are increasingly focusing on threat detection and incident response capabilities to proactively identify and mitigate security threats. Advanced security tools and technologies, such as machine learning algorithms and AI-powered analytics, are being leveraged to detect anomalies and potential security breaches in real-time. Having a robust incident response plan in place allows organizations to respond swiftly to security incidents and minimize the impact on their data and operations.
Best Practices for Hadoop Security in 2024
With the evolving landscape of cybersecurity threats, it's essential for organizations to implement best practices for securing their Hadoop environments. Here are some key practices to ensure robust data security in 2024:
- Implement encryption for data at rest and in transit to protect sensitive information from unauthorized access.
- Enforce strong authentication mechanisms, such as multi-factor authentication, to verify the identity of users before granting access to data.
- Set up fine-grained access controls based on user roles and privileges to prevent unauthorized access to sensitive data.
- Regularly monitor and audit access to Hadoop clusters to detect and prevent potential security breaches.
- Develop a comprehensive incident response plan to quickly respond to security incidents and mitigate their impact on data and operations.
- Stay updated on emerging cybersecurity threats and trends to proactively adapt security measures to protect against evolving risks.
By following these best practices and staying informed about the latest trends in Hadoop security, organizations can effectively safeguard their data and maintain the integrity of their Hadoop ecosystems in 2024 and beyond.
Security Solutions and Compliance
In addition to the best practices mentioned above, organizations can also leverage security solutions tailored specifically for Hadoop environments. These solutions offer comprehensive security functionalities, such as threat detection, compliance management, risk assessment, and vulnerability scanning, to ensure robust data protection. Compliance with industry regulations and data privacy laws is also critical for maintaining the security of Hadoop clusters and protecting sensitive information from potential threats.
How to obtain BigData and Hadoop certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, the evolving landscape of Hadoop security in 2024 presents both challenges and opportunities for organizations seeking to protect their data from cybersecurity threats. By adopting best practices such as encryption, authentication, access control, threat detection, and incident response, companies can strengthen their security posture and ensure the integrity of their Hadoop environments. Stay proactive, stay informed, and stay secure to safeguard your data in the rapidly changing world of technology.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In the ever-evolving landscape of technology, data security remains a top priority for organizations across the globe. As more and more companies turn to big data analytics to drive business decisions, the need for robust security measures in technologies like Hadoop becomes increasingly crucial. Let's explore the emerging trends in Hadoop security and the best practices to ensure data protection in 2024.
Hadoop Security Landscape in 2024
With the rapid expansion of big data and Hadoop technology, cybersecurity threats have also become more sophisticated. Data protection is no longer just about securing data at rest and in transit, but also about protecting data during processing and analysis. This has led to a shift towards more holistic security approaches that encompass the entire Hadoop ecosystem.
Encryption and Authentication
One of the key trends in Hadoop security for 2024 is the widespread adoption of encryption and strong authentication mechanisms. Encryption helps protect data both in transit and at rest, ensuring that only authorized users can access sensitive information. Strong authentication practices, such as multi-factor authentication, further enhance data security by verifying the identity of users before granting access to the data.
Authorization and Data Privacy
Another important aspect of Hadoop security is authorization, which determines what actions users are allowed to perform on data within the Hadoop clusters. Implementing fine-grained access controls based on user roles and privileges helps prevent unauthorized access and data breaches. Data privacy regulations, such as GDPR, also play a significant role in shaping data security practices, requiring organizations to implement measures to protect user privacy and ensure compliance with data protection laws.
Threat Detection and Incident Response
In 2024, organizations are increasingly focusing on threat detection and incident response capabilities to proactively identify and mitigate security threats. Advanced security tools and technologies, such as machine learning algorithms and AI-powered analytics, are being leveraged to detect anomalies and potential security breaches in real-time. Having a robust incident response plan in place allows organizations to respond swiftly to security incidents and minimize the impact on their data and operations.
Best Practices for Hadoop Security in 2024
With the evolving landscape of cybersecurity threats, it's essential for organizations to implement best practices for securing their Hadoop environments. Here are some key practices to ensure robust data security in 2024:
- Implement encryption for data at rest and in transit to protect sensitive information from unauthorized access.
- Enforce strong authentication mechanisms, such as multi-factor authentication, to verify the identity of users before granting access to data.
- Set up fine-grained access controls based on user roles and privileges to prevent unauthorized access to sensitive data.
- Regularly monitor and audit access to Hadoop clusters to detect and prevent potential security breaches.
- Develop a comprehensive incident response plan to quickly respond to security incidents and mitigate their impact on data and operations.
- Stay updated on emerging cybersecurity threats and trends to proactively adapt security measures to protect against evolving risks.
By following these best practices and staying informed about the latest trends in Hadoop security, organizations can effectively safeguard their data and maintain the integrity of their Hadoop ecosystems in 2024 and beyond.
Security Solutions and Compliance
In addition to the best practices mentioned above, organizations can also leverage security solutions tailored specifically for Hadoop environments. These solutions offer comprehensive security functionalities, such as threat detection, compliance management, risk assessment, and vulnerability scanning, to ensure robust data protection. Compliance with industry regulations and data privacy laws is also critical for maintaining the security of Hadoop clusters and protecting sensitive information from potential threats.
How to obtain BigData and Hadoop certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, the evolving landscape of Hadoop security in 2024 presents both challenges and opportunities for organizations seeking to protect their data from cybersecurity threats. By adopting best practices such as encryption, authentication, access control, threat detection, and incident response, companies can strengthen their security posture and ensure the integrity of their Hadoop environments. Stay proactive, stay informed, and stay secure to safeguard your data in the rapidly changing world of technology.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Citrix Virtual WAN Enhancing Network Performance
Are you looking for a solution to boost your network performance and efficiency? Look no further than Citrix Virtual WAN. In today's digital world, where businesses rely heavily on fast and secure network connections, Citrix Virtual WAN offers a comprehensive set of features to optimize your Wide Area Network (WAN) and elevate your network infrastructure to new heights.
Introduction to Citrix Virtual WAN
Citrix Virtual WAN is a cutting-edge technology that leverages software-defined networking to enhance network performance across geographically dispersed locations. By utilizing cloud networking and WAN optimization techniques, Citrix Virtual WAN delivers secure and reliable connectivity for a wide range of applications, including virtual desktop infrastructure, remote access, and data acceleration.
With Citrix Virtual WAN, organizations can streamline their network deployment process, reduce latency, and improve user experience. The platform offers advanced capabilities such as network visibility, network scalability, and intelligent routing, making it an ideal solution for businesses looking to enhance their network infrastructure.
Key Features and Benefits
1. Enhanced Network Security
Citrix Virtual WAN provides secure connectivity for branch offices and remote users, ensuring that data protection is always a top priority. By using firewall security and network segmentation techniques, Citrix Virtual WAN offers a secure access solution for organizations of all sizes.
2. Application Performance Optimization
With Citrix Virtual WAN, organizations can improve application delivery and performance through dynamic bandwidth allocation and traffic shaping. This ensures that critical applications receive the necessary resources to operate seamlessly, even during peak usage periods.
3. Network Efficiency and Reliability
By reducing network congestion and optimizing network throughput, Citrix Virtual WAN enhances network reliability and resilience. Organizations can rely on consistent network performance, even in the face of network challenges or increased traffic.
4. Cloud Migration and Data Center Consolidation
Citrix Virtual WAN offers seamless connectivity for organizations transitioning to the cloud or consolidating data center resources. By providing secure and efficient network connections, Citrix Virtual WAN simplifies the process of moving to a hybrid cloud environment.
How Does Citrix Virtual WAN Work?
Citrix Virtual WAN leverages virtualization technology to create a software-defined infrastructure that optimizes network performance. By using network monitoring tools and network segmentation, Citrix Virtual WAN ensures that network traffic is efficiently managed and controlled. Through intelligent routing and network congestion control, Citrix Virtual WAN offers a streamlined network architecture that can adapt to changing business needs.
Is Citrix Virtual WAN Right for Your Business?
If you are looking to improve network performance, reduce latency, and enhance network reliability, Citrix Virtual WAN may be the solution for you. With its robust set of features and benefits, Citrix Virtual WAN offers a comprehensive network optimization solution for businesses of all sizes.
How to obtain Citrix Administration certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Citrix Virtual WAN is a powerful tool for enhancing network performance and efficiency. By leveraging software-defined networking and cloud-based technologies, Citrix Virtual WAN provides organizations with the tools they need to optimize their network infrastructure and drive business success.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking for a solution to boost your network performance and efficiency? Look no further than Citrix Virtual WAN. In today's digital world, where businesses rely heavily on fast and secure network connections, Citrix Virtual WAN offers a comprehensive set of features to optimize your Wide Area Network (WAN) and elevate your network infrastructure to new heights.
Introduction to Citrix Virtual WAN
Citrix Virtual WAN is a cutting-edge technology that leverages software-defined networking to enhance network performance across geographically dispersed locations. By utilizing cloud networking and WAN optimization techniques, Citrix Virtual WAN delivers secure and reliable connectivity for a wide range of applications, including virtual desktop infrastructure, remote access, and data acceleration.
With Citrix Virtual WAN, organizations can streamline their network deployment process, reduce latency, and improve user experience. The platform offers advanced capabilities such as network visibility, network scalability, and intelligent routing, making it an ideal solution for businesses looking to enhance their network infrastructure.
Key Features and Benefits
1. Enhanced Network Security
Citrix Virtual WAN provides secure connectivity for branch offices and remote users, ensuring that data protection is always a top priority. By using firewall security and network segmentation techniques, Citrix Virtual WAN offers a secure access solution for organizations of all sizes.
2. Application Performance Optimization
With Citrix Virtual WAN, organizations can improve application delivery and performance through dynamic bandwidth allocation and traffic shaping. This ensures that critical applications receive the necessary resources to operate seamlessly, even during peak usage periods.
3. Network Efficiency and Reliability
By reducing network congestion and optimizing network throughput, Citrix Virtual WAN enhances network reliability and resilience. Organizations can rely on consistent network performance, even in the face of network challenges or increased traffic.
4. Cloud Migration and Data Center Consolidation
Citrix Virtual WAN offers seamless connectivity for organizations transitioning to the cloud or consolidating data center resources. By providing secure and efficient network connections, Citrix Virtual WAN simplifies the process of moving to a hybrid cloud environment.
How Does Citrix Virtual WAN Work?
Citrix Virtual WAN leverages virtualization technology to create a software-defined infrastructure that optimizes network performance. By using network monitoring tools and network segmentation, Citrix Virtual WAN ensures that network traffic is efficiently managed and controlled. Through intelligent routing and network congestion control, Citrix Virtual WAN offers a streamlined network architecture that can adapt to changing business needs.
Is Citrix Virtual WAN Right for Your Business?
If you are looking to improve network performance, reduce latency, and enhance network reliability, Citrix Virtual WAN may be the solution for you. With its robust set of features and benefits, Citrix Virtual WAN offers a comprehensive network optimization solution for businesses of all sizes.
How to obtain Citrix Administration certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Citrix Virtual WAN is a powerful tool for enhancing network performance and efficiency. By leveraging software-defined networking and cloud-based technologies, Citrix Virtual WAN provides organizations with the tools they need to optimize their network infrastructure and drive business success.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
How EXIN Cloud Certification Boosts Your Cloud Security Skills
Wondering how you can enhance your cloud security skills and advance your career in the ever-evolving field of technology? Look no further than the EXIN Cloud Certification. This certification is designed to provide you with the knowledge and expertise needed to navigate the complexities of cloud technology while ensuring the security of sensitive data. In this article, we will explore the benefits of obtaining an EXIN Cloud Certification and how it can boost your skills in cloud security.
What is EXIN Cloud Certification?
EXIN Cloud Certification is a globally recognized certification that validates your expertise in cloud technology and security. This certification equips you with the necessary skills to design, implement, and manage secure cloud solutions, making you a valuable asset to any organization looking to protect their data in the cloud.
How Does EXIN Cloud Certification Boost Your Cloud Security Skills?
-
Specialized Training: By undergoing EXIN Cloud Certification training, you will receive specialized instruction on cloud security best practices, data protection, and risk management. This training will give you a comprehensive understanding of how to secure cloud environments and mitigate potential threats.
-
Hands-On Experience: The certification program includes practical, hands-on experience that allows you to apply your knowledge in real-world scenarios. This hands-on experience will not only solidify your understanding of cloud security concepts but also give you the confidence to tackle security challenges effectively.
-
Career Advancement: Possessing an EXIN Cloud Certification demonstrates to employers that you have the skills and expertise needed to secure cloud environments effectively. This certification can open doors to new job opportunities and pave the way for career advancement in the field of cybersecurity.
-
Enhanced Skills: The knowledge and skills acquired through EXIN Cloud Certification training will enable you to enhance your cloud security skills and stay ahead of the curve in the fast-paced world of technology. You will be equipped to proactively identify and address security vulnerabilities in cloud environments, making you an indispensable asset to any organization.
-
Professional Development: Investing in professional development through EXIN Cloud Certification not only boosts your cloud security skills but also demonstrates your commitment to lifelong learning and continuous improvement. Employers value professionals who are dedicated to enhancing their skills and staying current with industry trends.
The Benefits of EXIN Cloud Certification
-
Increased Job Opportunities: With an EXIN Cloud Certification, you can qualify for a variety of positions in cloud security, cybersecurity, and information technology. This certification demonstrates your expertise in cloud security, making you a top candidate for roles that require advanced skills in securing cloud environments.
-
Industry Recognition: EXIN Cloud Certification is widely recognized in the industry as a symbol of excellence in cloud security. Holding this certification sets you apart from your peers and demonstrates your dedication to upholding high standards of security in cloud computing.
-
Expanded Knowledge: The comprehensive curriculum of the EXIN Cloud Certification program will expand your knowledge of cloud technology, security best practices, and risk management strategies. You will gain a deep understanding of how to protect sensitive data in cloud environments while optimizing performance and efficiency.
-
Networking Opportunities: When you obtain an EXIN Cloud Certification, you join a community of industry professionals who share your passion for cloud security. This network can provide valuable connections, resources, and opportunities for collaboration and professional growth.
How to obtain EXIN Cloud Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, obtaining an EXIN Cloud Certification is a valuable investment in your career that can significantly boost your cloud security skills. With specialized training, hands-on experience, and industry recognition, this certification will enhance your expertise in cloud technology and position you as a trusted professional in the field of cybersecurity. Take the next step in advancing your career and securing your future by pursuing an EXIN Cloud Certification today.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Wondering how you can enhance your cloud security skills and advance your career in the ever-evolving field of technology? Look no further than the EXIN Cloud Certification. This certification is designed to provide you with the knowledge and expertise needed to navigate the complexities of cloud technology while ensuring the security of sensitive data. In this article, we will explore the benefits of obtaining an EXIN Cloud Certification and how it can boost your skills in cloud security.
What is EXIN Cloud Certification?
EXIN Cloud Certification is a globally recognized certification that validates your expertise in cloud technology and security. This certification equips you with the necessary skills to design, implement, and manage secure cloud solutions, making you a valuable asset to any organization looking to protect their data in the cloud.
How Does EXIN Cloud Certification Boost Your Cloud Security Skills?
-
Specialized Training: By undergoing EXIN Cloud Certification training, you will receive specialized instruction on cloud security best practices, data protection, and risk management. This training will give you a comprehensive understanding of how to secure cloud environments and mitigate potential threats.
-
Hands-On Experience: The certification program includes practical, hands-on experience that allows you to apply your knowledge in real-world scenarios. This hands-on experience will not only solidify your understanding of cloud security concepts but also give you the confidence to tackle security challenges effectively.
-
Career Advancement: Possessing an EXIN Cloud Certification demonstrates to employers that you have the skills and expertise needed to secure cloud environments effectively. This certification can open doors to new job opportunities and pave the way for career advancement in the field of cybersecurity.
-
Enhanced Skills: The knowledge and skills acquired through EXIN Cloud Certification training will enable you to enhance your cloud security skills and stay ahead of the curve in the fast-paced world of technology. You will be equipped to proactively identify and address security vulnerabilities in cloud environments, making you an indispensable asset to any organization.
-
Professional Development: Investing in professional development through EXIN Cloud Certification not only boosts your cloud security skills but also demonstrates your commitment to lifelong learning and continuous improvement. Employers value professionals who are dedicated to enhancing their skills and staying current with industry trends.
The Benefits of EXIN Cloud Certification
-
Increased Job Opportunities: With an EXIN Cloud Certification, you can qualify for a variety of positions in cloud security, cybersecurity, and information technology. This certification demonstrates your expertise in cloud security, making you a top candidate for roles that require advanced skills in securing cloud environments.
-
Industry Recognition: EXIN Cloud Certification is widely recognized in the industry as a symbol of excellence in cloud security. Holding this certification sets you apart from your peers and demonstrates your dedication to upholding high standards of security in cloud computing.
-
Expanded Knowledge: The comprehensive curriculum of the EXIN Cloud Certification program will expand your knowledge of cloud technology, security best practices, and risk management strategies. You will gain a deep understanding of how to protect sensitive data in cloud environments while optimizing performance and efficiency.
-
Networking Opportunities: When you obtain an EXIN Cloud Certification, you join a community of industry professionals who share your passion for cloud security. This network can provide valuable connections, resources, and opportunities for collaboration and professional growth.
How to obtain EXIN Cloud Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, obtaining an EXIN Cloud Certification is a valuable investment in your career that can significantly boost your cloud security skills. With specialized training, hands-on experience, and industry recognition, this certification will enhance your expertise in cloud technology and position you as a trusted professional in the field of cybersecurity. Take the next step in advancing your career and securing your future by pursuing an EXIN Cloud Certification today.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Machine Learning on the Edge Opportunities and Challenges
In the ever-evolving landscape of technology, the convergence of machine learning and edge computing has opened up a world of opportunities for businesses and individuals alike. By bringing artificial intelligence to the edge devices of the Internet of Things (IoT), organizations can harness the power of data processing and real-time analytics like never before. However, with these opportunities come a unique set of challenges that must be addressed to fully realize the potential of edge AI.
The Rise of Edge Technology
Edge computing has revolutionized the way data is processed and analyzed. By moving computation closer to the source of data generation, edge devices can perform complex tasks without relying on cloud computing resources. This shift towards edge technology has paved the way for more efficient data processing, low latency, and improved performance for smart devices.
Opportunities in Machine Learning on the Edge
One of the key opportunities presented by machine learning on the edge is the ability to deploy machine learning models directly on edge devices. This allows for real-time data analysis and decision-making without the need for constant communication with the cloud. By leveraging sensor data and edge servers, organizations can implement predictive maintenance and anomaly detection functionalities to enhance operational efficiency. Additionally, edge computing allows for the deployment of edge applications that can perform tasks such as image recognition, natural language processing, and sentiment analysis locally on edge devices. This not only reduces latency but also ensures data security by keeping sensitive information within the confines of the device.
Challenges in Implementing Edge AI
While the opportunities presented by edge AI are abundant, there are several challenges that organizations must overcome to fully capitalize on this technology. One of the main challenges is the complexity of edge computing architecture, which requires careful planning and implementation to ensure seamless integration with existing infrastructure. Furthermore, the management of edge devices can prove to be a daunting task, especially in scenarios where thousands of devices are deployed across distributed environments. Ensuring the security and reliability of these devices is paramount to prevent potential vulnerabilities and data breaches.
Overcoming Challenges with Edge Solutions
To address these challenges, organizations can implement edge analytics and intelligence solutions that provide a centralized platform for managing edge devices and monitoring performance. By leveraging distributed computing capabilities, organizations can streamline the deployment of machine learning models and ensure consistent data processing across edge devices.
With the right edge solution in place, organizations can harness the full potential of machine learning on the edge and drive innovation in various industries. From predictive maintenance in manufacturing to real-time video analytics in retail, the possibilities are endless when it comes to leveraging edge AI for business growth.
How to obtain Machine Learning Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, machine learning on the edge presents a wealth of opportunities for organizations looking to transform their operations and drive digital transformation. By addressing the challenges associated with edge computing and implementing robust edge solutions, organizations can unlock the full potential of edge AI and stay ahead of the competition in today's fast-paced technological landscape.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In the ever-evolving landscape of technology, the convergence of machine learning and edge computing has opened up a world of opportunities for businesses and individuals alike. By bringing artificial intelligence to the edge devices of the Internet of Things (IoT), organizations can harness the power of data processing and real-time analytics like never before. However, with these opportunities come a unique set of challenges that must be addressed to fully realize the potential of edge AI.
The Rise of Edge Technology
Edge computing has revolutionized the way data is processed and analyzed. By moving computation closer to the source of data generation, edge devices can perform complex tasks without relying on cloud computing resources. This shift towards edge technology has paved the way for more efficient data processing, low latency, and improved performance for smart devices.
Opportunities in Machine Learning on the Edge
One of the key opportunities presented by machine learning on the edge is the ability to deploy machine learning models directly on edge devices. This allows for real-time data analysis and decision-making without the need for constant communication with the cloud. By leveraging sensor data and edge servers, organizations can implement predictive maintenance and anomaly detection functionalities to enhance operational efficiency. Additionally, edge computing allows for the deployment of edge applications that can perform tasks such as image recognition, natural language processing, and sentiment analysis locally on edge devices. This not only reduces latency but also ensures data security by keeping sensitive information within the confines of the device.
Challenges in Implementing Edge AI
While the opportunities presented by edge AI are abundant, there are several challenges that organizations must overcome to fully capitalize on this technology. One of the main challenges is the complexity of edge computing architecture, which requires careful planning and implementation to ensure seamless integration with existing infrastructure. Furthermore, the management of edge devices can prove to be a daunting task, especially in scenarios where thousands of devices are deployed across distributed environments. Ensuring the security and reliability of these devices is paramount to prevent potential vulnerabilities and data breaches.
Overcoming Challenges with Edge Solutions
To address these challenges, organizations can implement edge analytics and intelligence solutions that provide a centralized platform for managing edge devices and monitoring performance. By leveraging distributed computing capabilities, organizations can streamline the deployment of machine learning models and ensure consistent data processing across edge devices.
With the right edge solution in place, organizations can harness the full potential of machine learning on the edge and drive innovation in various industries. From predictive maintenance in manufacturing to real-time video analytics in retail, the possibilities are endless when it comes to leveraging edge AI for business growth.
How to obtain Machine Learning Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, machine learning on the edge presents a wealth of opportunities for organizations looking to transform their operations and drive digital transformation. By addressing the challenges associated with edge computing and implementing robust edge solutions, organizations can unlock the full potential of edge AI and stay ahead of the competition in today's fast-paced technological landscape.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Salesforce Integration with ERP Systems
Are you looking to streamline your business operations and improve efficiency? Integrating Salesforce with ERP systems can be the key to achieving this goal. In this article, we will discuss the benefits of Salesforce integration with ERP systems, best practices to follow, and examples of successful integration projects.
Introduction to Salesforce ERP Integration
Salesforce is a powerful customer relationship management (CRM) platform that helps businesses manage their relationships and interactions with customers. On the other hand, Enterprise Resource Planning (ERP) systems are software solutions that help organizations manage their core business processes, such as finance, HR, and supply chain management.
When Salesforce is integrated with ERP systems, it creates a seamless flow of data between sales, marketing, customer service, and other departments. This integration allows for real-time access to critical information, improved communication between teams, and enhanced reporting capabilities.
Benefits of Salesforce Integration with ERP Systems
-
Enhanced Data Synchronization: Integrating Salesforce with ERP systems ensures that all departments have access to the most up-to-date information, leading to improved decision-making and customer service.
-
Improved Reporting Capabilities: By combining data from Salesforce and ERP systems, businesses can generate comprehensive reports and analytics to gain insights into their performance and trends.
-
Streamlined Business Processes: Integration eliminates the need for manual data entry and reduces the risk of errors, allowing teams to focus on more strategic tasks.
-
Increased Efficiency and Productivity: With automated processes and seamless data flow, employees can work more efficiently and collaborate effectively across departments.
Best Practices for Salesforce ERP Integration
-
Define Clear Objectives: Before initiating the integration process, clearly outline your goals and objectives to ensure that the integration meets your business needs.
-
Choose the Right Integration Software: Select a reputable integration software that is compatible with both Salesforce and your ERP system to ensure a smooth implementation.
-
Engage Stakeholders: Involve key stakeholders from different departments in the integration process to ensure that their needs are met and to promote buy-in across the organization.
-
Test and Validate: Conduct thorough testing of the integration to identify any issues or discrepancies before fully implementing it in your business operations.
Successful Salesforce ERP Integration Examples
-
Salesforce Integration with SAP: By integrating Salesforce with SAP, businesses can leverage the strengths of both platforms to create a unified view of customer data and improve sales and marketing effectiveness.
-
Salesforce Integration with Oracle: Integration with Oracle ERP systems enables seamless data synchronization and streamlines financial and operational processes for improved efficiency.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Salesforce integration with ERP systems offers numerous benefits for businesses looking to streamline their operations and improve productivity. By following best practices and learning from successful integration examples, organizations can achieve a seamless and efficient data flow between Salesforce and ERP systems, leading to enhanced decision-making and business growth.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to streamline your business operations and improve efficiency? Integrating Salesforce with ERP systems can be the key to achieving this goal. In this article, we will discuss the benefits of Salesforce integration with ERP systems, best practices to follow, and examples of successful integration projects.
Introduction to Salesforce ERP Integration
Salesforce is a powerful customer relationship management (CRM) platform that helps businesses manage their relationships and interactions with customers. On the other hand, Enterprise Resource Planning (ERP) systems are software solutions that help organizations manage their core business processes, such as finance, HR, and supply chain management.
When Salesforce is integrated with ERP systems, it creates a seamless flow of data between sales, marketing, customer service, and other departments. This integration allows for real-time access to critical information, improved communication between teams, and enhanced reporting capabilities.
Benefits of Salesforce Integration with ERP Systems
-
Enhanced Data Synchronization: Integrating Salesforce with ERP systems ensures that all departments have access to the most up-to-date information, leading to improved decision-making and customer service.
-
Improved Reporting Capabilities: By combining data from Salesforce and ERP systems, businesses can generate comprehensive reports and analytics to gain insights into their performance and trends.
-
Streamlined Business Processes: Integration eliminates the need for manual data entry and reduces the risk of errors, allowing teams to focus on more strategic tasks.
-
Increased Efficiency and Productivity: With automated processes and seamless data flow, employees can work more efficiently and collaborate effectively across departments.
Best Practices for Salesforce ERP Integration
-
Define Clear Objectives: Before initiating the integration process, clearly outline your goals and objectives to ensure that the integration meets your business needs.
-
Choose the Right Integration Software: Select a reputable integration software that is compatible with both Salesforce and your ERP system to ensure a smooth implementation.
-
Engage Stakeholders: Involve key stakeholders from different departments in the integration process to ensure that their needs are met and to promote buy-in across the organization.
-
Test and Validate: Conduct thorough testing of the integration to identify any issues or discrepancies before fully implementing it in your business operations.
Successful Salesforce ERP Integration Examples
-
Salesforce Integration with SAP: By integrating Salesforce with SAP, businesses can leverage the strengths of both platforms to create a unified view of customer data and improve sales and marketing effectiveness.
-
Salesforce Integration with Oracle: Integration with Oracle ERP systems enables seamless data synchronization and streamlines financial and operational processes for improved efficiency.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Salesforce integration with ERP systems offers numerous benefits for businesses looking to streamline their operations and improve productivity. By following best practices and learning from successful integration examples, organizations can achieve a seamless and efficient data flow between Salesforce and ERP systems, leading to enhanced decision-making and business growth.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
RPA Certification Impact on Business Digital Transformation
In today's rapidly evolving business landscape, digital transformation has become a key priority for organizations looking to stay competitive and relevant. Robotic Process Automation (RPA) has emerged as a powerful tool in driving this transformation, enabling businesses to streamline processes, enhance efficiency, and reduce operational costs. In this article, we will explore the impact of RPA certification on business digital transformation and the benefits it brings to organizations.
RPA Certification: Upskilling for Business Success
RPA certification programs are designed to equip professionals with the necessary skills and knowledge to effectively implement and manage robotic process automation within their organizations. By obtaining RPA certification, individuals can enhance their automation skills, stay ahead of the technological curve, and contribute to workforce transformation within their organizations.
Advantages of RPA Certification
-
Enhanced Technology Skills: RPA certification provides professionals with a deep understanding of automation technologies, allowing them to optimize processes and drive efficiency.
-
Career Advancement: Individuals with RPA certification are better positioned for career growth and development, as they possess in-demand skills that are highly valuable in today's digital economy.
-
Industry Impact: Organizations that invest in RPA certification for their employees experience improved operational efficiency, process optimization, and increased productivity.
Strategic Integration of RPA into Business Processes
By incorporating RPA into their automation strategy, businesses can achieve workflow automation, operational excellence, and drive business growth. RPA certification plays a crucial role in enabling organizations to leverage the full potential of robotic process automation and gain a competitive advantage in the market.
The Role of RPA Certification in Digital Workforce Development
RPA certification programs not only benefit individual professionals but also contribute to the overall skill enhancement of the workforce. By upskilling employees through RPA training, organizations can build a digital workforce that is equipped to drive digital transformation and innovation within the company.
Unlocking Job Opportunities with RPA Certification
As businesses continue to adopt RPA to improve operational efficiency and streamline processes, the demand for professionals with RPA certification is on the rise. Individuals with RPA certification are well-positioned to capitalize on job opportunities in a variety of industries, as organizations seek to leverage automation technologies to stay competitive in the digital age.
How to obtain Emerging Technology Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, RPA certification plays a significant role in driving business digital transformation, enabling organizations to enhance efficiency, streamline processes, and achieve operational excellence. By investing in RPA certification for professionals, businesses can unlock a host of benefits, from improved productivity and process optimization to increased job opportunities and career advancement. Embracing RPA certification is key to staying ahead in today's rapidly evolving digital landscape.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's rapidly evolving business landscape, digital transformation has become a key priority for organizations looking to stay competitive and relevant. Robotic Process Automation (RPA) has emerged as a powerful tool in driving this transformation, enabling businesses to streamline processes, enhance efficiency, and reduce operational costs. In this article, we will explore the impact of RPA certification on business digital transformation and the benefits it brings to organizations.
RPA Certification: Upskilling for Business Success
RPA certification programs are designed to equip professionals with the necessary skills and knowledge to effectively implement and manage robotic process automation within their organizations. By obtaining RPA certification, individuals can enhance their automation skills, stay ahead of the technological curve, and contribute to workforce transformation within their organizations.
Advantages of RPA Certification
-
Enhanced Technology Skills: RPA certification provides professionals with a deep understanding of automation technologies, allowing them to optimize processes and drive efficiency.
-
Career Advancement: Individuals with RPA certification are better positioned for career growth and development, as they possess in-demand skills that are highly valuable in today's digital economy.
-
Industry Impact: Organizations that invest in RPA certification for their employees experience improved operational efficiency, process optimization, and increased productivity.
Strategic Integration of RPA into Business Processes
By incorporating RPA into their automation strategy, businesses can achieve workflow automation, operational excellence, and drive business growth. RPA certification plays a crucial role in enabling organizations to leverage the full potential of robotic process automation and gain a competitive advantage in the market.
The Role of RPA Certification in Digital Workforce Development
RPA certification programs not only benefit individual professionals but also contribute to the overall skill enhancement of the workforce. By upskilling employees through RPA training, organizations can build a digital workforce that is equipped to drive digital transformation and innovation within the company.
Unlocking Job Opportunities with RPA Certification
As businesses continue to adopt RPA to improve operational efficiency and streamline processes, the demand for professionals with RPA certification is on the rise. Individuals with RPA certification are well-positioned to capitalize on job opportunities in a variety of industries, as organizations seek to leverage automation technologies to stay competitive in the digital age.
How to obtain Emerging Technology Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, RPA certification plays a significant role in driving business digital transformation, enabling organizations to enhance efficiency, streamline processes, and achieve operational excellence. By investing in RPA certification for professionals, businesses can unlock a host of benefits, from improved productivity and process optimization to increased job opportunities and career advancement. Embracing RPA certification is key to staying ahead in today's rapidly evolving digital landscape.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Top 10 Tips for Passing the MINITAB Certification Exam
Are you looking to excel in the world of data analysis and statistical software? One key step to demonstrating your expertise in MINITAB is by passing the MINITAB Certification Exam. This certification is a valuable asset for anyone looking to showcase their proficiency in data analysis, statistical tools, and process improvement using MINITAB software. To help you succeed in this endeavor, here are top 10 tips for passing the MINITAB Certification Exam:
1. Start with a Strong Foundation
Before diving into exam preparation, ensure you have a solid understanding of the key concepts and techniques in MINITAB. Familiarize yourself with statistical analysis, data visualization, hypothesis testing, and data interpretation to build a strong foundation.
2. Utilize Study Guides and Resources
Make use of MINITAB training materials, study guides, and online resources to enhance your knowledge and skills. Practice using the software to manipulate data, perform statistical analysis, and apply quality control methods.
3. Focus on Statistics and Analysis Techniques
Pay special attention to statistical tools and analysis techniques commonly used in MINITAB. Brush up on topics such as six sigma, quality control, and data manipulation to ensure you are well-prepared for the exam.
4. Master MINITAB Techniques
Take the time to master MINITAB techniques such as generating graphs, conducting hypothesis tests, and interpreting results. Practice using the software to analyze data sets and draw meaningful insights from your findings.
5. Practice Exam Preparation
Set aside dedicated time for exam preparation and practice using sample questions and mock exams. This will help you familiarize yourself with the format of the exam and build confidence in your abilities.
6. Seek Expert Guidance
Consider seeking guidance from MINITAB experts or instructors who can provide valuable insights and tips for success. Their experience and expertise can help you navigate challenging concepts and refine your skills.
7. Stay Updated on MINITAB Developments
Stay informed about the latest developments and updates in MINITAB software. Familiarize yourself with new features and enhancements that may be relevant to the certification exam.
8. Focus on Practical Tips
In addition to theoretical knowledge, focus on practical tips for using MINITAB effectively. Learn shortcuts, best practices, and time-saving techniques that can help you navigate the software efficiently during the exam.
9. Embrace a Growth Mindset
Approach the MINITAB Certification Exam with a growth mindset, embracing challenges as opportunities for learning and growth. Stay positive and motivated throughout your preparation journey.
10. Visualize Exam Success
Visualize yourself achieving success in the MINITAB Certification Exam. Imagine yourself confidently answering questions, applying MINITAB techniques, and demonstrating your expertise in data analysis.
How to obtain Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
By following these top 10 tips for passing the MINITAB Certification Exam, you can enhance your chances of success and demonstrate your proficiency in MINITAB software. Remember to stay focused, dedicated, and motivated throughout your exam preparation journey. Good luck!
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to excel in the world of data analysis and statistical software? One key step to demonstrating your expertise in MINITAB is by passing the MINITAB Certification Exam. This certification is a valuable asset for anyone looking to showcase their proficiency in data analysis, statistical tools, and process improvement using MINITAB software. To help you succeed in this endeavor, here are top 10 tips for passing the MINITAB Certification Exam:
1. Start with a Strong Foundation
Before diving into exam preparation, ensure you have a solid understanding of the key concepts and techniques in MINITAB. Familiarize yourself with statistical analysis, data visualization, hypothesis testing, and data interpretation to build a strong foundation.
2. Utilize Study Guides and Resources
Make use of MINITAB training materials, study guides, and online resources to enhance your knowledge and skills. Practice using the software to manipulate data, perform statistical analysis, and apply quality control methods.
3. Focus on Statistics and Analysis Techniques
Pay special attention to statistical tools and analysis techniques commonly used in MINITAB. Brush up on topics such as six sigma, quality control, and data manipulation to ensure you are well-prepared for the exam.
4. Master MINITAB Techniques
Take the time to master MINITAB techniques such as generating graphs, conducting hypothesis tests, and interpreting results. Practice using the software to analyze data sets and draw meaningful insights from your findings.
5. Practice Exam Preparation
Set aside dedicated time for exam preparation and practice using sample questions and mock exams. This will help you familiarize yourself with the format of the exam and build confidence in your abilities.
6. Seek Expert Guidance
Consider seeking guidance from MINITAB experts or instructors who can provide valuable insights and tips for success. Their experience and expertise can help you navigate challenging concepts and refine your skills.
7. Stay Updated on MINITAB Developments
Stay informed about the latest developments and updates in MINITAB software. Familiarize yourself with new features and enhancements that may be relevant to the certification exam.
8. Focus on Practical Tips
In addition to theoretical knowledge, focus on practical tips for using MINITAB effectively. Learn shortcuts, best practices, and time-saving techniques that can help you navigate the software efficiently during the exam.
9. Embrace a Growth Mindset
Approach the MINITAB Certification Exam with a growth mindset, embracing challenges as opportunities for learning and growth. Stay positive and motivated throughout your preparation journey.
10. Visualize Exam Success
Visualize yourself achieving success in the MINITAB Certification Exam. Imagine yourself confidently answering questions, applying MINITAB techniques, and demonstrating your expertise in data analysis.
How to obtain Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
By following these top 10 tips for passing the MINITAB Certification Exam, you can enhance your chances of success and demonstrate your proficiency in MINITAB software. Remember to stay focused, dedicated, and motivated throughout your exam preparation journey. Good luck!
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Importance of SMAC Certification in Digital Marketing Strategies
Are you looking to take your digital marketing skills to the next level? If so, obtaining a SMAC certification could be the key to unlocking new opportunities and advancing your career in the ever-evolving world of online marketing. In this article, we will explore the importance of SMAC certification in digital marketing strategies, the benefits of obtaining this certification, and how it can help you stay ahead of the curve in the competitive landscape of digital marketing.
What is SMAC Certification and Why is it Important in Digital Marketing?
SMAC stands for Social, Mobile, Analytics, and Cloud – four key components that play a crucial role in today's digital marketing strategies. SMAC certification equips professionals with the knowledge and skills needed to leverage these components effectively in their marketing efforts. By obtaining a SMAC certification, individuals demonstrate their proficiency in utilizing social media, mobile technologies, analytics tools, and cloud computing to create impactful marketing campaigns that drive results.
The Benefits of SMAC Certification in Digital Marketing
-
Enhanced Skillset: With a SMAC certification, you will gain a deeper understanding of how to leverage social media platforms, mobile technologies, analytics tools, and cloud computing to optimize your marketing strategies. This enhanced skillset will make you a more valuable asset to any organization looking to succeed in the digital realm.
-
Stay Ahead of Trends: Digital marketing is a rapidly evolving field, with new trends and technologies emerging constantly. By obtaining a SMAC certification, you will stay ahead of the curve and be well-equipped to adapt to the latest trends in the industry.
-
Increase Your Job Opportunities: In today's competitive job market, having a SMAC certification can give you a competitive edge and open up new job opportunities in the digital marketing sector. Many employers look for candidates with specialized certifications that demonstrate their expertise in specific areas of marketing.
-
Boost Your Credibility: A SMAC certification is a testament to your expertise and commitment to excellence in digital marketing. By showcasing this certification on your resume and LinkedIn profile, you can boost your credibility and attract potential employers and clients.
How to Obtain a SMAC Certification
There are several options available for professionals looking to obtain a SMAC certification. Many online platforms and educational institutions offer digital marketing certification programs that include training on social media, mobile marketing, analytics, and cloud computing. These programs typically include coursework, exams, and hands-on projects that test your knowledge and skills in each component of SMAC.
How to obtain SMAC Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, obtaining a SMAC certification is essential for digital marketers looking to stay ahead of the competition, enhance their skillset, and increase their job opportunities in the fast-paced world of online marketing. By investing in a SMAC certification, you can gain the knowledge and expertise needed to succeed in today's digital landscape and elevate your career to new heights. So, are you ready to take your digital marketing skills to the next level with a SMAC certification?
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to take your digital marketing skills to the next level? If so, obtaining a SMAC certification could be the key to unlocking new opportunities and advancing your career in the ever-evolving world of online marketing. In this article, we will explore the importance of SMAC certification in digital marketing strategies, the benefits of obtaining this certification, and how it can help you stay ahead of the curve in the competitive landscape of digital marketing.
What is SMAC Certification and Why is it Important in Digital Marketing?
SMAC stands for Social, Mobile, Analytics, and Cloud – four key components that play a crucial role in today's digital marketing strategies. SMAC certification equips professionals with the knowledge and skills needed to leverage these components effectively in their marketing efforts. By obtaining a SMAC certification, individuals demonstrate their proficiency in utilizing social media, mobile technologies, analytics tools, and cloud computing to create impactful marketing campaigns that drive results.
The Benefits of SMAC Certification in Digital Marketing
-
Enhanced Skillset: With a SMAC certification, you will gain a deeper understanding of how to leverage social media platforms, mobile technologies, analytics tools, and cloud computing to optimize your marketing strategies. This enhanced skillset will make you a more valuable asset to any organization looking to succeed in the digital realm.
-
Stay Ahead of Trends: Digital marketing is a rapidly evolving field, with new trends and technologies emerging constantly. By obtaining a SMAC certification, you will stay ahead of the curve and be well-equipped to adapt to the latest trends in the industry.
-
Increase Your Job Opportunities: In today's competitive job market, having a SMAC certification can give you a competitive edge and open up new job opportunities in the digital marketing sector. Many employers look for candidates with specialized certifications that demonstrate their expertise in specific areas of marketing.
-
Boost Your Credibility: A SMAC certification is a testament to your expertise and commitment to excellence in digital marketing. By showcasing this certification on your resume and LinkedIn profile, you can boost your credibility and attract potential employers and clients.
How to Obtain a SMAC Certification
There are several options available for professionals looking to obtain a SMAC certification. Many online platforms and educational institutions offer digital marketing certification programs that include training on social media, mobile marketing, analytics, and cloud computing. These programs typically include coursework, exams, and hands-on projects that test your knowledge and skills in each component of SMAC.
How to obtain SMAC Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, obtaining a SMAC certification is essential for digital marketers looking to stay ahead of the competition, enhance their skillset, and increase their job opportunities in the fast-paced world of online marketing. By investing in a SMAC certification, you can gain the knowledge and expertise needed to succeed in today's digital landscape and elevate your career to new heights. So, are you ready to take your digital marketing skills to the next level with a SMAC certification?
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
How Ethical Hacking Cert Elevates Your Cybersecurity Career
Are you looking to advance your cybersecurity career and stay ahead of cyber threats in the industry? If so, obtaining an ethical hacking certification may be the key to boosting your skills, knowledge, and job opportunities in the field.
What is Ethical Hacking Certification?
Ethical hacking certification is a professional credential that demonstrates expertise in advanced techniques for identifying vulnerabilities, assessing security measures, and developing defensive strategies to protect information and data from cyber attacks. By passing a certification exam, individuals become certified ethical hackers, equipped with the necessary skills to secure networks and systems.
The Benefits of Ethical Hacking Certification
- Gain Practical Experience: Through hands-on training and real-world scenarios, individuals can gain practical experience in identifying and addressing security threats effectively. This experience is invaluable in the fast-paced world of cybersecurity.
- Enhance Professional Development: Certification in ethical hacking demonstrates a commitment to ongoing professional development and a dedication to staying current on the latest trends and threats in the industry. Employers value candidates who continuously seek to improve their skills.
- Increase Employment Opportunities: With the rise of cyber threats and the growing importance of online security, demand for skilled cybersecurity professionals is higher than ever. Holding an ethical hacking certification can open doors to new job opportunities and career advancement.
- Boost Salary Potential: Certified ethical hackers often command higher salaries than their non-certified counterparts. Employers recognize the value of certification and are willing to pay a premium for professionals with proven expertise in cybersecurity.
- Establish Credibility and Trust: By earning a recognized certification in ethical hacking, individuals establish themselves as experts in the field and build credibility with colleagues, clients, and employers. This trust can lead to increased opportunities for collaboration and advancement.
How to Get Started with Ethical Hacking Certification
If you are interested in enhancing your cybersecurity career through ethical hacking certification, there are several steps you can take to get started:
- Choose the Right Certification Program: Research different certification programs and select one that aligns with your career goals and interests. Popular certifications include Certified Ethical Hacker (CEH) and Certified Information Systems Security Professional (CISSP).
- Prepare for the Certification Exam: Study the exam objectives, practice with sample questions, and consider enrolling in a training course to ensure you are fully prepared to pass the certification exam on your first attempt.
- Gain Hands-On Experience: Seek opportunities to apply your skills in real-world scenarios, either through internships, volunteer work, or side projects. Practical experience is crucial for developing expertise in ethical hacking.
- Stay Current on Industry Trends: Stay informed about the latest developments in cybersecurity, attend industry conferences, and participate in online forums to engage with other cybersecurity professionals and expand your knowledge.
How to obtain Ethical Hacking certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, earning an ethical hacking certification can significantly enhance your cybersecurity career by providing you with the skills, knowledge, and expertise needed to protect networks and systems from cyber threats. By investing in certification, you can increase your employment opportunities, boost your salary potential, and establish yourself as a trusted professional in the field. Take the first step towards advancing your career in cybersecurity by pursuing ethical hacking certification today.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to advance your cybersecurity career and stay ahead of cyber threats in the industry? If so, obtaining an ethical hacking certification may be the key to boosting your skills, knowledge, and job opportunities in the field.
What is Ethical Hacking Certification?
Ethical hacking certification is a professional credential that demonstrates expertise in advanced techniques for identifying vulnerabilities, assessing security measures, and developing defensive strategies to protect information and data from cyber attacks. By passing a certification exam, individuals become certified ethical hackers, equipped with the necessary skills to secure networks and systems.
The Benefits of Ethical Hacking Certification
- Gain Practical Experience: Through hands-on training and real-world scenarios, individuals can gain practical experience in identifying and addressing security threats effectively. This experience is invaluable in the fast-paced world of cybersecurity.
- Enhance Professional Development: Certification in ethical hacking demonstrates a commitment to ongoing professional development and a dedication to staying current on the latest trends and threats in the industry. Employers value candidates who continuously seek to improve their skills.
- Increase Employment Opportunities: With the rise of cyber threats and the growing importance of online security, demand for skilled cybersecurity professionals is higher than ever. Holding an ethical hacking certification can open doors to new job opportunities and career advancement.
- Boost Salary Potential: Certified ethical hackers often command higher salaries than their non-certified counterparts. Employers recognize the value of certification and are willing to pay a premium for professionals with proven expertise in cybersecurity.
- Establish Credibility and Trust: By earning a recognized certification in ethical hacking, individuals establish themselves as experts in the field and build credibility with colleagues, clients, and employers. This trust can lead to increased opportunities for collaboration and advancement.
How to Get Started with Ethical Hacking Certification
If you are interested in enhancing your cybersecurity career through ethical hacking certification, there are several steps you can take to get started:
- Choose the Right Certification Program: Research different certification programs and select one that aligns with your career goals and interests. Popular certifications include Certified Ethical Hacker (CEH) and Certified Information Systems Security Professional (CISSP).
- Prepare for the Certification Exam: Study the exam objectives, practice with sample questions, and consider enrolling in a training course to ensure you are fully prepared to pass the certification exam on your first attempt.
- Gain Hands-On Experience: Seek opportunities to apply your skills in real-world scenarios, either through internships, volunteer work, or side projects. Practical experience is crucial for developing expertise in ethical hacking.
- Stay Current on Industry Trends: Stay informed about the latest developments in cybersecurity, attend industry conferences, and participate in online forums to engage with other cybersecurity professionals and expand your knowledge.
How to obtain Ethical Hacking certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, earning an ethical hacking certification can significantly enhance your cybersecurity career by providing you with the skills, knowledge, and expertise needed to protect networks and systems from cyber threats. By investing in certification, you can increase your employment opportunities, boost your salary potential, and establish yourself as a trusted professional in the field. Take the first step towards advancing your career in cybersecurity by pursuing ethical hacking certification today.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Data Mining: Uses and Benefits
In today's data-driven world, data mining plays a crucial role in extracting valuable insights from large datasets. This powerful technique involves the process of discovering patterns, trends, and relationships within data to help businesses make informed decisions. Let's explore the various uses and benefits of data mining in different applications and industries.
What is Data Mining?
Data mining is the process of analyzing large datasets to uncover hidden patterns, relationships, and insights that can be used to make strategic decisions. By using sophisticated algorithms and techniques, data mining helps businesses extract valuable information from complex datasets that would be impossible to analyze manually.
Uses of Data Mining
-
Business Intelligence: Data mining is widely used in business intelligence to analyze customer behavior patterns, market trends, and competitor strategies. By understanding these insights, businesses can optimize their operations, improve customer satisfaction, and drive growth.
-
Clustering and Classification: Data mining techniques such as clustering and classification help businesses categorize data into groups based on similarities or assign labels to new data points. This enables organizations to segment customers, detect fraud, and make predictions based on historical data.
-
Predictive Modeling: By leveraging predictive modeling techniques, data mining allows businesses to forecast future trends, identify potential risks, and make data-driven decisions. This helps organizations mitigate risks, maximize opportunities, and stay ahead of the competition.
-
Market Research: Data mining is essential in market research to analyze consumer preferences, buying patterns, and market trends. By understanding these insights, businesses can launch targeted marketing campaigns, develop new products, and enhance customer satisfaction.
-
Fraud Detection: Data mining techniques are instrumental in detecting fraudulent activities in various industries such as banking, insurance, and e-commerce. By analyzing patterns and anomalies in data, businesses can identify suspicious transactions, prevent fraud, and protect their assets.
Benefits of Data Mining
-
Improved Decision-Making: Data mining provides businesses with valuable insights and predictive analytics that help them make informed decisions. By leveraging these insights, organizations can identify opportunities, mitigate risks, and optimize performance.
-
Enhanced Customer Segmentation: Data mining allows businesses to segment customers based on their buying behaviors, preferences, and demographics. This enables organizations to personalize marketing campaigns, improve customer retention, and drive sales growth.
-
Optimized Operations: By analyzing data patterns and relationships, businesses can identify inefficiencies, bottlenecks, and areas for improvement in their operations. This helps organizations streamline processes, reduce costs, and increase productivity.
-
Data-Driven Strategies: Data mining enables businesses to develop data-driven strategies that are based on empirical evidence and statistical analysis. By leveraging these insights, organizations can optimize their marketing efforts, improve customer satisfaction, and drive business growth.
-
Competitive Advantage: By harnessing the power of data mining, businesses can gain a competitive advantage in their industry. By analyzing market trends, customer preferences, and competitor strategies, organizations can stay ahead of the curve and position themselves for success.
How to obtain Data Science and Business Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, data mining is a powerful tool that offers a wide range of uses and benefits for businesses across various industries. By using advanced techniques and algorithms, organizations can extract valuable insights, make informed decisions, and drive growth. As the volume of data continues to grow exponentially, data mining will become increasingly essential for businesses seeking to gain a competitive edge and thrive in the digital age.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's data-driven world, data mining plays a crucial role in extracting valuable insights from large datasets. This powerful technique involves the process of discovering patterns, trends, and relationships within data to help businesses make informed decisions. Let's explore the various uses and benefits of data mining in different applications and industries.
What is Data Mining?
Data mining is the process of analyzing large datasets to uncover hidden patterns, relationships, and insights that can be used to make strategic decisions. By using sophisticated algorithms and techniques, data mining helps businesses extract valuable information from complex datasets that would be impossible to analyze manually.
Uses of Data Mining
-
Business Intelligence: Data mining is widely used in business intelligence to analyze customer behavior patterns, market trends, and competitor strategies. By understanding these insights, businesses can optimize their operations, improve customer satisfaction, and drive growth.
-
Clustering and Classification: Data mining techniques such as clustering and classification help businesses categorize data into groups based on similarities or assign labels to new data points. This enables organizations to segment customers, detect fraud, and make predictions based on historical data.
-
Predictive Modeling: By leveraging predictive modeling techniques, data mining allows businesses to forecast future trends, identify potential risks, and make data-driven decisions. This helps organizations mitigate risks, maximize opportunities, and stay ahead of the competition.
-
Market Research: Data mining is essential in market research to analyze consumer preferences, buying patterns, and market trends. By understanding these insights, businesses can launch targeted marketing campaigns, develop new products, and enhance customer satisfaction.
-
Fraud Detection: Data mining techniques are instrumental in detecting fraudulent activities in various industries such as banking, insurance, and e-commerce. By analyzing patterns and anomalies in data, businesses can identify suspicious transactions, prevent fraud, and protect their assets.
Benefits of Data Mining
-
Improved Decision-Making: Data mining provides businesses with valuable insights and predictive analytics that help them make informed decisions. By leveraging these insights, organizations can identify opportunities, mitigate risks, and optimize performance.
-
Enhanced Customer Segmentation: Data mining allows businesses to segment customers based on their buying behaviors, preferences, and demographics. This enables organizations to personalize marketing campaigns, improve customer retention, and drive sales growth.
-
Optimized Operations: By analyzing data patterns and relationships, businesses can identify inefficiencies, bottlenecks, and areas for improvement in their operations. This helps organizations streamline processes, reduce costs, and increase productivity.
-
Data-Driven Strategies: Data mining enables businesses to develop data-driven strategies that are based on empirical evidence and statistical analysis. By leveraging these insights, organizations can optimize their marketing efforts, improve customer satisfaction, and drive business growth.
-
Competitive Advantage: By harnessing the power of data mining, businesses can gain a competitive advantage in their industry. By analyzing market trends, customer preferences, and competitor strategies, organizations can stay ahead of the curve and position themselves for success.
How to obtain Data Science and Business Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, data mining is a powerful tool that offers a wide range of uses and benefits for businesses across various industries. By using advanced techniques and algorithms, organizations can extract valuable insights, make informed decisions, and drive growth. As the volume of data continues to grow exponentially, data mining will become increasingly essential for businesses seeking to gain a competitive edge and thrive in the digital age.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Understanding XenApp Architecture A Certification Overview
Are you interested in becoming a Citrix certified professional and want to understand the ins and outs of XenApp architecture? This comprehensive guide will take you through the key aspects of XenApp, its architecture, certification overview, and much more. Let's dive into the world of virtualization, application delivery, and network security with Citrix XenApp.
What is XenApp Architecture?
XenApp architecture is designed to deliver applications to users securely, regardless of their location or device. It uses server infrastructure to host applications which are then streamed to the user's device. This enables remote access, enhances user experience, and ensures high availability of applications in a multi-user environment. By integrating with Active Directory, XenApp allows for seamless access to applications and data.
Certification Overview
Citrix certification in XenApp validates your skills in software deployment, IT infrastructure management, and system administration. It covers a wide range of topics including data center management, load balancing, scalability, and desktop virtualization. By obtaining Citrix certification, you demonstrate your expertise in application delivery, network security, and remote access solutions.
Benefits of Citrix Certification
-
Enhanced career opportunities in the field of IT
-
Demonstrated expertise in virtualization and cloud computing
-
Recognition of your skills by employers
-
Access to exclusive Citrix resources and tools for professionals
-
Opportunities for professional growth and development
Exam Preparation
When preparing for the Citrix XenApp certification exam, it is essential to cover all key topics such as application streaming, service virtualization, and virtual desktop infrastructure. Familiarize yourself with Citrix Receiver, application virtualization, and network optimization techniques. Practice performance monitoring, storage solutions, and system administration tasks to ensure you are ready for the exam.
How to obtain XenApp Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, understanding XenApp architecture is crucial for IT professionals looking to excel in the field of application delivery and virtualization. By obtaining Citrix certification, you demonstrate your expertise in server infrastructure, network security, and user experience management. Prepare for the exam by covering key topics such as desktop virtualization, high availability, and application streaming. Start your journey towards becoming a Citrix certified professional today!
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you interested in becoming a Citrix certified professional and want to understand the ins and outs of XenApp architecture? This comprehensive guide will take you through the key aspects of XenApp, its architecture, certification overview, and much more. Let's dive into the world of virtualization, application delivery, and network security with Citrix XenApp.
What is XenApp Architecture?
XenApp architecture is designed to deliver applications to users securely, regardless of their location or device. It uses server infrastructure to host applications which are then streamed to the user's device. This enables remote access, enhances user experience, and ensures high availability of applications in a multi-user environment. By integrating with Active Directory, XenApp allows for seamless access to applications and data.
Certification Overview
Citrix certification in XenApp validates your skills in software deployment, IT infrastructure management, and system administration. It covers a wide range of topics including data center management, load balancing, scalability, and desktop virtualization. By obtaining Citrix certification, you demonstrate your expertise in application delivery, network security, and remote access solutions.
Benefits of Citrix Certification
-
Enhanced career opportunities in the field of IT
-
Demonstrated expertise in virtualization and cloud computing
-
Recognition of your skills by employers
-
Access to exclusive Citrix resources and tools for professionals
-
Opportunities for professional growth and development
Exam Preparation
When preparing for the Citrix XenApp certification exam, it is essential to cover all key topics such as application streaming, service virtualization, and virtual desktop infrastructure. Familiarize yourself with Citrix Receiver, application virtualization, and network optimization techniques. Practice performance monitoring, storage solutions, and system administration tasks to ensure you are ready for the exam.
How to obtain XenApp Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, understanding XenApp architecture is crucial for IT professionals looking to excel in the field of application delivery and virtualization. By obtaining Citrix certification, you demonstrate your expertise in server infrastructure, network security, and user experience management. Prepare for the exam by covering key topics such as desktop virtualization, high availability, and application streaming. Start your journey towards becoming a Citrix certified professional today!
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Managing Async Operations in Angular 4 with RxJS
Are you struggling to manage asynchronous operations in your Angular 4 application? Handling async tasks can often be a challenge, but with the power of Reactive Extensions for JavaScript (RxJS), you can simplify your code and improve the performance of your application. In this article, we will explore how to efficiently manage async operations in Angular 4 using RxJS, ensuring a seamless user experience and optimized data flow.
What is RxJS and Why Use it in Angular 4?
RxJS is a popular library for reactive programming in JavaScript applications. It allows you to work with asynchronous data streams using observables, which are a powerful way to handle sequences of asynchronous events. In Angular 4, RxJS is used extensively to manage HTTP requests, services, components, and data streams.
Using RxJS in Angular 4 brings several benefits, including:
-
Simplifying the management of asynchronous operations
-
Improving the performance of your application
-
Enhancing the reactivity of your UI
-
Making it easier to handle complex data flows
In essence, RxJS provides a more elegant and efficient way to handle asynchronous tasks in Angular 4, leading to cleaner code and better user experience.
Handling Async Operations with RxJS in Angular 4
Observables in Angular
In Angular 4, observables are used to handle asynchronous data streams, such as HTTP requests or user interactions. With observables, you can subscribe to data streams and react to events as they occur. This reactive approach helps in managing async operations more effectively and ensuring timely updates to your UI.
Reactive Programming in Angular 4
Reactive programming is a paradigm that focuses on handling data flow and event propagation. In Angular 4, reactive programming with RxJS allows you to create observable sequences, apply operators to manipulate the data stream, and subscribe to the results. This enables you to build responsive and interactive applications that react to user inputs and external events.
Managing HTTP Requests and Services
In Angular 4, HTTP requests are common async operations that can be effectively managed using RxJS. By creating observables for HTTP requests and leveraging operators like map, filter, and mergeMap, you can handle data responses more efficiently and perform tasks such as error handling and data transformation.
Similarly, Angular services can benefit from RxJS by using observables to communicate between components, manage state, and handle data streams. By using observables for service interactions, you can ensure a consistent data flow and improve the overall performance of your application.
Handling Async Patterns and Data Flow
Asynchronous patterns in Angular 4, such as promises and async/await, can also be managed using RxJS. By converting promises to observables or using RxJS operators to await multiple async tasks, you can simplify your code and ensure a more predictable data flow.
With RxJS, you can easily implement common async patterns like debounce, throttle, retry, and switchMap to handle different scenarios in your Angular 4 application. These patterns help in managing async events, optimizing performance, and enhancing user experience.
Best Practices and Examples
To effectively manage async operations in Angular 4 with RxJS, it is essential to follow best practices and leverage examples from the Angular community. By understanding observable patterns, using operators effectively, and applying reactive programming principles, you can create efficient and responsive applications that handle async tasks seamlessly.
How to obtain Angular JS 4 certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, RxJS is a powerful tool for managing async operations in Angular 4. By using observables, operators, and reactive programming techniques, you can streamline your code, improve performance, and enhance the user experience of your application.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you struggling to manage asynchronous operations in your Angular 4 application? Handling async tasks can often be a challenge, but with the power of Reactive Extensions for JavaScript (RxJS), you can simplify your code and improve the performance of your application. In this article, we will explore how to efficiently manage async operations in Angular 4 using RxJS, ensuring a seamless user experience and optimized data flow.
What is RxJS and Why Use it in Angular 4?
RxJS is a popular library for reactive programming in JavaScript applications. It allows you to work with asynchronous data streams using observables, which are a powerful way to handle sequences of asynchronous events. In Angular 4, RxJS is used extensively to manage HTTP requests, services, components, and data streams.
Using RxJS in Angular 4 brings several benefits, including:
-
Simplifying the management of asynchronous operations
-
Improving the performance of your application
-
Enhancing the reactivity of your UI
-
Making it easier to handle complex data flows
In essence, RxJS provides a more elegant and efficient way to handle asynchronous tasks in Angular 4, leading to cleaner code and better user experience.
Handling Async Operations with RxJS in Angular 4
Observables in Angular
In Angular 4, observables are used to handle asynchronous data streams, such as HTTP requests or user interactions. With observables, you can subscribe to data streams and react to events as they occur. This reactive approach helps in managing async operations more effectively and ensuring timely updates to your UI.
Reactive Programming in Angular 4
Reactive programming is a paradigm that focuses on handling data flow and event propagation. In Angular 4, reactive programming with RxJS allows you to create observable sequences, apply operators to manipulate the data stream, and subscribe to the results. This enables you to build responsive and interactive applications that react to user inputs and external events.
Managing HTTP Requests and Services
In Angular 4, HTTP requests are common async operations that can be effectively managed using RxJS. By creating observables for HTTP requests and leveraging operators like map, filter, and mergeMap, you can handle data responses more efficiently and perform tasks such as error handling and data transformation.
Similarly, Angular services can benefit from RxJS by using observables to communicate between components, manage state, and handle data streams. By using observables for service interactions, you can ensure a consistent data flow and improve the overall performance of your application.
Handling Async Patterns and Data Flow
Asynchronous patterns in Angular 4, such as promises and async/await, can also be managed using RxJS. By converting promises to observables or using RxJS operators to await multiple async tasks, you can simplify your code and ensure a more predictable data flow.
With RxJS, you can easily implement common async patterns like debounce, throttle, retry, and switchMap to handle different scenarios in your Angular 4 application. These patterns help in managing async events, optimizing performance, and enhancing user experience.
Best Practices and Examples
To effectively manage async operations in Angular 4 with RxJS, it is essential to follow best practices and leverage examples from the Angular community. By understanding observable patterns, using operators effectively, and applying reactive programming principles, you can create efficient and responsive applications that handle async tasks seamlessly.
How to obtain Angular JS 4 certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, RxJS is a powerful tool for managing async operations in Angular 4. By using observables, operators, and reactive programming techniques, you can streamline your code, improve performance, and enhance the user experience of your application.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Angular 4 vs Angular 12 Certifications and Its Relevance in 2024
It is vital to remain in tune with the latest trends and tools in today’s fast-paced technology world and software development industry, which are essential for career advancement and success. Angular has seen significant updates and improvements during this period, making it one of the most popular frameworks for web developers. For example, a question often arises whether getting certified is still necessary even after extensive use of Angular 4 and Angular 12 in 2024. In this article, we will compare Angular 4 to Angular 12 among other things as well as explain why having certification in tech dynamic environment is so important.
Angular 4 vs Angular 12: The Difference
This version came with various enhancements over its predecessor, particularly with regard to architecture like new features that allowed for better performance optimization among others when compared against earlier iterations from three years ago up until now where we have reached technological advancements such as more advanced tooling options available at present like those introduced inside last few releases by Google’s team working on angularJs framework.. However, these are just some examples of changes made; there may be many others not specified here such as differences between various versions including their respective strengths/weaknesses concerning contemporary techniques applied during website construction etc., while sometimes speaking about backward compatibility issues either within particular company projects or throughout entire IT world (e.g. release). These days people still use old angularJs framework but most prefer the updated angularJs framework because it supports current web technology requirements.
Certification: Is It Still Relevant in 2024?
The matter of whether certification is still valuable in 2024 is a legitimate question, especially with the rapid development of technologies like Angular. Although certification can demonstrate some proficiency and knowledge in a specific version of Angular, it may not always represent the latest skills and expertise required by employers. In the battle between Angular 4 vs Angular 12, having a certification in Angular 4 might count less as compared to knowing Angular 12 well and its updated features. On the other hand, certifications can be helpful for showing that one is committed to learning and keeping up with current industry standards.
The Importance of Staying Updated With Angular Upgrades
For developers, it is mandatory to keep up with new updates on software technologies such as frameworks like angular as they continue to grow rapidly. Migrating to newer versions such as Angular 12 enables developers benefit from improved performance, enhanced security or even new functionality aimed at speeding up development processes. Developers can advance their skills, follow industry tendencies and remain competitive on the labor market by staying updated on changes in Angular.
The Future of Angular Certification
When looking forward to the years beyond 2023, it is vital to remember that the relevancy of angular certification may change with time as the framework itself develops. In case newer versions of Angular come up, these certification programs might have to go along with them in order to include all those new features or best practices. That being said, developers should not only be focused on getting a certificate in angular but also continuously updating their knowledge and skills, gaining practical experience and staying abreast with latest tools and technologies for web development.
How to obtain Angular JS 4 Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, comparing Angular 4 with Angular 12 reveals how the Angular framework has changed and why developers need to update themselves in order to grow professionally. Yet certifications can still be useful for indicating expertise and commitment to learning; working experience becomes more important when we assess its value from a developer’s point of view: always demanding continuous learning, adapting to industry trends which are related directly toward this process. Moving into future orientation concerning web development; angular certification could be significant even after many years as a means of proving competence and expertise in such evolving field.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
It is vital to remain in tune with the latest trends and tools in today’s fast-paced technology world and software development industry, which are essential for career advancement and success. Angular has seen significant updates and improvements during this period, making it one of the most popular frameworks for web developers. For example, a question often arises whether getting certified is still necessary even after extensive use of Angular 4 and Angular 12 in 2024. In this article, we will compare Angular 4 to Angular 12 among other things as well as explain why having certification in tech dynamic environment is so important.
Angular 4 vs Angular 12: The Difference
This version came with various enhancements over its predecessor, particularly with regard to architecture like new features that allowed for better performance optimization among others when compared against earlier iterations from three years ago up until now where we have reached technological advancements such as more advanced tooling options available at present like those introduced inside last few releases by Google’s team working on angularJs framework.. However, these are just some examples of changes made; there may be many others not specified here such as differences between various versions including their respective strengths/weaknesses concerning contemporary techniques applied during website construction etc., while sometimes speaking about backward compatibility issues either within particular company projects or throughout entire IT world (e.g. release). These days people still use old angularJs framework but most prefer the updated angularJs framework because it supports current web technology requirements.
Certification: Is It Still Relevant in 2024?
The matter of whether certification is still valuable in 2024 is a legitimate question, especially with the rapid development of technologies like Angular. Although certification can demonstrate some proficiency and knowledge in a specific version of Angular, it may not always represent the latest skills and expertise required by employers. In the battle between Angular 4 vs Angular 12, having a certification in Angular 4 might count less as compared to knowing Angular 12 well and its updated features. On the other hand, certifications can be helpful for showing that one is committed to learning and keeping up with current industry standards.
The Importance of Staying Updated With Angular Upgrades
For developers, it is mandatory to keep up with new updates on software technologies such as frameworks like angular as they continue to grow rapidly. Migrating to newer versions such as Angular 12 enables developers benefit from improved performance, enhanced security or even new functionality aimed at speeding up development processes. Developers can advance their skills, follow industry tendencies and remain competitive on the labor market by staying updated on changes in Angular.
The Future of Angular Certification
When looking forward to the years beyond 2023, it is vital to remember that the relevancy of angular certification may change with time as the framework itself develops. In case newer versions of Angular come up, these certification programs might have to go along with them in order to include all those new features or best practices. That being said, developers should not only be focused on getting a certificate in angular but also continuously updating their knowledge and skills, gaining practical experience and staying abreast with latest tools and technologies for web development.
How to obtain Angular JS 4 Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, comparing Angular 4 with Angular 12 reveals how the Angular framework has changed and why developers need to update themselves in order to grow professionally. Yet certifications can still be useful for indicating expertise and commitment to learning; working experience becomes more important when we assess its value from a developer’s point of view: always demanding continuous learning, adapting to industry trends which are related directly toward this process. Moving into future orientation concerning web development; angular certification could be significant even after many years as a means of proving competence and expertise in such evolving field.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
5 Key Types of Quality Management Systems
Quality management systems are essential for organizations to ensure that they meet customer requirements and continuously improve their processes. There are various types of quality management systems that companies can implement to achieve operational excellence and drive business efficiency. In this article, we will explore the 5 key types of quality management systems that are widely used in different industries.
ISO 9001
ISO 9001 is the most well-known quality management standard that focuses on meeting customer requirements and enhancing customer satisfaction. It provides a framework for organizations to establish a quality management system, set quality objectives, and monitor their performance. By implementing ISO 9001, companies can improve their processes, reduce errors, and enhance customer trust.
ISO 14001
ISO 14001 is a standard specifically for environmental management systems. It helps organizations to minimize their environmental impact, comply with environmental regulations, and improve sustainability. By implementing ISO 14001, companies can reduce waste, conserve resources, and demonstrate their commitment to environmental responsibility.
Total Quality Management
Total Quality Management (TQM) is a holistic approach to quality management that involves all employees in the continuous improvement of processes. TQM focuses on customer satisfaction, employee involvement, and process improvement. By implementing TQM principles, organizations can enhance product quality, reduce waste, and increase customer loyalty.
Six Sigma
Six Sigma is a data-driven approach to quality management that aims to reduce defects and variations in processes. It uses statistical methods to analyze data, identify root causes of problems, and implement solutions to improve process performance. By applying Six Sigma techniques, organizations can enhance quality, increase productivity, and achieve cost savings.
Lean Manufacturing
Lean Manufacturing is a systematic approach to eliminating waste and maximizing value in processes. It focuses on improving efficiency, reducing lead times, and increasing customer value. By implementing Lean principles, companies can optimize their operations, minimize costs, and enhance competitiveness in the market.
How to obtain Quality Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, quality management systems play a crucial role in ensuring that organizations deliver high-quality products and services to their customers. By implementing the 5 key types of quality management systems - ISO 9001, ISO 14001, Total Quality Management, Six Sigma, and Lean Manufacturing - companies can drive continuous improvement, increase efficiency, and achieve competitive advantage in the industry. It is important for organizations to select the right quality management system that aligns with their business goals and objectives to truly realize the benefits of quality management.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Quality management systems are essential for organizations to ensure that they meet customer requirements and continuously improve their processes. There are various types of quality management systems that companies can implement to achieve operational excellence and drive business efficiency. In this article, we will explore the 5 key types of quality management systems that are widely used in different industries.
ISO 9001
ISO 9001 is the most well-known quality management standard that focuses on meeting customer requirements and enhancing customer satisfaction. It provides a framework for organizations to establish a quality management system, set quality objectives, and monitor their performance. By implementing ISO 9001, companies can improve their processes, reduce errors, and enhance customer trust.
ISO 14001
ISO 14001 is a standard specifically for environmental management systems. It helps organizations to minimize their environmental impact, comply with environmental regulations, and improve sustainability. By implementing ISO 14001, companies can reduce waste, conserve resources, and demonstrate their commitment to environmental responsibility.
Total Quality Management
Total Quality Management (TQM) is a holistic approach to quality management that involves all employees in the continuous improvement of processes. TQM focuses on customer satisfaction, employee involvement, and process improvement. By implementing TQM principles, organizations can enhance product quality, reduce waste, and increase customer loyalty.
Six Sigma
Six Sigma is a data-driven approach to quality management that aims to reduce defects and variations in processes. It uses statistical methods to analyze data, identify root causes of problems, and implement solutions to improve process performance. By applying Six Sigma techniques, organizations can enhance quality, increase productivity, and achieve cost savings.
Lean Manufacturing
Lean Manufacturing is a systematic approach to eliminating waste and maximizing value in processes. It focuses on improving efficiency, reducing lead times, and increasing customer value. By implementing Lean principles, companies can optimize their operations, minimize costs, and enhance competitiveness in the market.
How to obtain Quality Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, quality management systems play a crucial role in ensuring that organizations deliver high-quality products and services to their customers. By implementing the 5 key types of quality management systems - ISO 9001, ISO 14001, Total Quality Management, Six Sigma, and Lean Manufacturing - companies can drive continuous improvement, increase efficiency, and achieve competitive advantage in the industry. It is important for organizations to select the right quality management system that aligns with their business goals and objectives to truly realize the benefits of quality management.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Maximizing Efficiency with Salesforce Lightning Tips for Admins
In today's fast-paced business world, efficiency is key to beating the competition. Salesforce admins can boost productivity by using all of Salesforce Lightning. It will also streamline workflows. This article will share tips to help admins optimize Salesforce Lightning. It will enhance their experience with the platform.
Salesforce Lightning Best Practices
To maximize efficiency with Salesforce Lightning, admins can use several best practices. Here are some key tips to keep in mind:
-
Customize Lightning Experience: Tailoring it to your needs can boost adoption and productivity. Customizing page layouts, profiles, and permissions can help. It can streamline processes and make navigation more intuitive.
-
Use Lightning Features: Use the features in Salesforce Lightning. These include the Lightning App Builder, Lightning Components, and Einstein AI. These tools can automate repetitive tasks. They can also provide insights and improve the user experience.
-
Optimize Dashboards: Create personalized dashboards with key metrics and reports. They should provide users with quick insights. Customizing dashboard components and filters can help. It can focus on key performance indicators and drive informed decisions.
-
Workflow Optimization: Streamline workflows by automating processes using Process Builder and Workflow Rules. Rules and triggers can save admins time. They ensure consistent data management.
Salesforce Lightning Strategies for Admins
To effectively maximize efficiency with Salesforce Lightning, admins can install the following strategies:
-
User Training and Support: Train users to use the Lightning Experience. Then, provide ongoing support. Conduct regular training sessions, create user guides, and offer help when needed.
-
Data Management Best Practices: Set data policies to ensure data security and integrity. Regularly clean up redundant or outdated data. Set up data validation rules. Install data backup strategies.
-
Use Admin Tools: Explore the admin tools in Salesforce Lightning. These include Data Loader, Workbench, and Salesforce admin. These tools can simplify tasks. They include importing, exporting, analyzing data, and managing users.
Enhancing Salesforce Lightning productivity.
To enhance productivity in Salesforce Lightning, admins can leverage the following techniques:
-
Automation: Use tools like Process Builder and Lightning Flows. They automate workflows and cut manual tasks.
-
Customization: Tailor layouts, record types, and fields to improve the user experience.
-
Collaboration: Encourage users to collaborate. Set up Chatter groups, share files, and work on projects in real time.
-
Analytics: Use Salesforce reports and dashboards to track key metrics. Analyze data trends to gain insights for better decisions.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, admins must maximize efficiency with Salesforce Lightning. It is key to driving success and productivity. By following this article's tips, admins can improve their Salesforce Lightning experience. They can also streamline workflows and boost productivity. Investigate emerging features, tools, and strategies on a regular basis. It's key to staying ahead in today's competitive business world.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced business world, efficiency is key to beating the competition. Salesforce admins can boost productivity by using all of Salesforce Lightning. It will also streamline workflows. This article will share tips to help admins optimize Salesforce Lightning. It will enhance their experience with the platform.
Salesforce Lightning Best Practices
To maximize efficiency with Salesforce Lightning, admins can use several best practices. Here are some key tips to keep in mind:
-
Customize Lightning Experience: Tailoring it to your needs can boost adoption and productivity. Customizing page layouts, profiles, and permissions can help. It can streamline processes and make navigation more intuitive.
-
Use Lightning Features: Use the features in Salesforce Lightning. These include the Lightning App Builder, Lightning Components, and Einstein AI. These tools can automate repetitive tasks. They can also provide insights and improve the user experience.
-
Optimize Dashboards: Create personalized dashboards with key metrics and reports. They should provide users with quick insights. Customizing dashboard components and filters can help. It can focus on key performance indicators and drive informed decisions.
-
Workflow Optimization: Streamline workflows by automating processes using Process Builder and Workflow Rules. Rules and triggers can save admins time. They ensure consistent data management.
Salesforce Lightning Strategies for Admins
To effectively maximize efficiency with Salesforce Lightning, admins can install the following strategies:
-
User Training and Support: Train users to use the Lightning Experience. Then, provide ongoing support. Conduct regular training sessions, create user guides, and offer help when needed.
-
Data Management Best Practices: Set data policies to ensure data security and integrity. Regularly clean up redundant or outdated data. Set up data validation rules. Install data backup strategies.
-
Use Admin Tools: Explore the admin tools in Salesforce Lightning. These include Data Loader, Workbench, and Salesforce admin. These tools can simplify tasks. They include importing, exporting, analyzing data, and managing users.
Enhancing Salesforce Lightning productivity.
To enhance productivity in Salesforce Lightning, admins can leverage the following techniques:
-
Automation: Use tools like Process Builder and Lightning Flows. They automate workflows and cut manual tasks.
-
Customization: Tailor layouts, record types, and fields to improve the user experience.
-
Collaboration: Encourage users to collaborate. Set up Chatter groups, share files, and work on projects in real time.
-
Analytics: Use Salesforce reports and dashboards to track key metrics. Analyze data trends to gain insights for better decisions.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, admins must maximize efficiency with Salesforce Lightning. It is key to driving success and productivity. By following this article's tips, admins can improve their Salesforce Lightning experience. They can also streamline workflows and boost productivity. Investigate emerging features, tools, and strategies on a regular basis. It's key to staying ahead in today's competitive business world.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Advantages of Networking with ECBA Candidates and Certified
Connecting and networking with ECBA candidates and certified professionals can provide a multitude of benefits and opportunities for those in the field of business analysis. Understanding the advantages of building connections within the ECBA community can help individuals enhance their careers, expand their knowledge, and increase their professional opportunities.
Networking Benefits with ECBA Candidates
When you network with ECBA candidates, you open yourself up to a world of possibilities. By connecting with like-minded individuals who are also pursuing the ECBA certification, you can gain valuable insights, share resources, and support each other on your journey to becoming certified. Networking with ECBA candidates can also provide you with a sense of community and belonging, as you work towards a common goal together.
ECBA Networking Advantages
There are numerous advantages to networking with ECBA candidates and certified professionals. Building connections within the ECBA community can lead to mentorship opportunities, collaboration on projects, and referrals for job opportunities. Additionally, networking with ECBA peers can help you stay up-to-date on industry trends, best practices, and new developments in the field of business analysis.
Networking with ECBA Professionals
Connecting with ECBA professionals can open doors to new career opportunities and professional growth. By networking with individuals who have already achieved the ECBA certification, you can learn from their experiences, gather valuable advice, and potentially secure referrals for job interviews. Building relationships with seasoned ECBA professionals can also help you establish yourself within the business analysis community and position yourself as a trusted and knowledgeable expert in the field.
ECBA Certification Benefits
Obtaining the ECBA certification can significantly enhance your credibility and marketability as a business analyst. Networking with other ECBA certified professionals can further solidify your reputation within the industry and increase your visibility among potential employers. By leveraging your connections within the ECBA community, you can showcase your expertise, build your professional network, and advance your career in business analysis.
Building Connections with ECBA Candidates
Networking with ECBA candidates and certified professionals offers a wealth of opportunities for building meaningful and mutually beneficial connections. By actively engaging with the ECBA community, you can establish rapport, exchange ideas, and form partnerships that can propel your career to new heights. Whether you are seeking mentorship, collaboration, or simply a supportive network of peers, networking with ECBA candidates can provide you with the resources and support you need to succeed in the field of business analysis.
How to obtain ECBA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, networking with ECBA candidates and certified professionals can have a transformative impact on your career and professional development. By building connections within the ECBA community, you can gain invaluable insights, expand your knowledge, and enhance your opportunities for growth and success in the field of business analysis. Take advantage of the networking opportunities available to you within the ECBA community and watch your career soar to new heights.
Remember, the key to success in business analysis lies not only in your technical skills and expertise but also in your ability to build and nurture relationships within the industry. By networking with ECBA candidates and certified professionals, you can position yourself as a respected and influential figure within the business analysis community, opening doors to endless possibilities for growth and advancement.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Connecting and networking with ECBA candidates and certified professionals can provide a multitude of benefits and opportunities for those in the field of business analysis. Understanding the advantages of building connections within the ECBA community can help individuals enhance their careers, expand their knowledge, and increase their professional opportunities.
Networking Benefits with ECBA Candidates
When you network with ECBA candidates, you open yourself up to a world of possibilities. By connecting with like-minded individuals who are also pursuing the ECBA certification, you can gain valuable insights, share resources, and support each other on your journey to becoming certified. Networking with ECBA candidates can also provide you with a sense of community and belonging, as you work towards a common goal together.
ECBA Networking Advantages
There are numerous advantages to networking with ECBA candidates and certified professionals. Building connections within the ECBA community can lead to mentorship opportunities, collaboration on projects, and referrals for job opportunities. Additionally, networking with ECBA peers can help you stay up-to-date on industry trends, best practices, and new developments in the field of business analysis.
Networking with ECBA Professionals
Connecting with ECBA professionals can open doors to new career opportunities and professional growth. By networking with individuals who have already achieved the ECBA certification, you can learn from their experiences, gather valuable advice, and potentially secure referrals for job interviews. Building relationships with seasoned ECBA professionals can also help you establish yourself within the business analysis community and position yourself as a trusted and knowledgeable expert in the field.
ECBA Certification Benefits
Obtaining the ECBA certification can significantly enhance your credibility and marketability as a business analyst. Networking with other ECBA certified professionals can further solidify your reputation within the industry and increase your visibility among potential employers. By leveraging your connections within the ECBA community, you can showcase your expertise, build your professional network, and advance your career in business analysis.
Building Connections with ECBA Candidates
Networking with ECBA candidates and certified professionals offers a wealth of opportunities for building meaningful and mutually beneficial connections. By actively engaging with the ECBA community, you can establish rapport, exchange ideas, and form partnerships that can propel your career to new heights. Whether you are seeking mentorship, collaboration, or simply a supportive network of peers, networking with ECBA candidates can provide you with the resources and support you need to succeed in the field of business analysis.
How to obtain ECBA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, networking with ECBA candidates and certified professionals can have a transformative impact on your career and professional development. By building connections within the ECBA community, you can gain invaluable insights, expand your knowledge, and enhance your opportunities for growth and success in the field of business analysis. Take advantage of the networking opportunities available to you within the ECBA community and watch your career soar to new heights.
Remember, the key to success in business analysis lies not only in your technical skills and expertise but also in your ability to build and nurture relationships within the industry. By networking with ECBA candidates and certified professionals, you can position yourself as a respected and influential figure within the business analysis community, opening doors to endless possibilities for growth and advancement.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Best Online Digital Marketing Certifications 2024
In digital marketing, staying ahead is key to success. As we enter 2024, demand for skilled digital marketers is rising. So, certifications are more valuable than ever. The best online digital marketing certifications in 2024 teach the latest trends and tools. They also cover new strategies. They give professionals the skills and credentials to excel in this competitive field. These certifications will help you thrive in digital marketing. They are for those who want to improve skills or enter the field.
Why Digital Marketing Certification Matters
In today's fast-paced digital world, staying ahead in digital marketing is vital. An online digital marketing certification can help. It suits both seasoned and new marketers. It will give you the latest insights, tools, and strategies. Digital marketing evolves rapidly. To succeed, keep up with trends and best practices. A certification gives you a deep knowledge of social media, SEO, and content marketing. It also boosts your professional credibility.
Top Online Digital Marketing Certifications for 2024
- Google Digital Marketing Certification: Google's program covers Google Ads and Analytics in depth. This certification can greatly boost your credibility. It shows you are skilled in key online marketing tools.
- HubSpot Content Marketing Certification: It's perfect for aspiring content marketers. It covers everything from content creation to promotion and analysis. It’s a valuable credential. It boosts your content's ability to resonate with your audience.
- Facebook Blueprint Certification: It's a must-have for social media marketers. It trains you to use Facebook and Instagram ads. It helps you optimize your campaigns and reach your target audience.
- Digital Marketing Institute Certification: It certifies in digital strategy, social media, and SEO. These top certifications can give you an edge in your digital marketing career.
Key Benefits of Pursuing an Online Digital Marketing Certification
- Upgrade Your Skills: Get vital, cutting-edge skills for success in today's competitive market.
- Increase Your Marketability: A certified skill boosts your appeal to employers. It proves your expertise and dedication.
- Boost Your Earning Potential: Certified pros earn more and get promoted more often.
- Network with Experts: Many certification programs connect you with industry leaders and peers.
- Stay Ahead of the Curve: Learn the latest tools and techniques. This will help you keep up with the fast-changing digital marketing world.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, investing in an online digital marketing certification is a smart move. It can boost your career. The right certification will boost your skills. It will also mark you as a leader in digital marketing. Enroll in a top certification program today. It will elevate your career in 2024. Don't miss the chance! Your future in digital marketing starts now!
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In digital marketing, staying ahead is key to success. As we enter 2024, demand for skilled digital marketers is rising. So, certifications are more valuable than ever. The best online digital marketing certifications in 2024 teach the latest trends and tools. They also cover new strategies. They give professionals the skills and credentials to excel in this competitive field. These certifications will help you thrive in digital marketing. They are for those who want to improve skills or enter the field.
Why Digital Marketing Certification Matters
In today's fast-paced digital world, staying ahead in digital marketing is vital. An online digital marketing certification can help. It suits both seasoned and new marketers. It will give you the latest insights, tools, and strategies. Digital marketing evolves rapidly. To succeed, keep up with trends and best practices. A certification gives you a deep knowledge of social media, SEO, and content marketing. It also boosts your professional credibility.
Top Online Digital Marketing Certifications for 2024
- Google Digital Marketing Certification: Google's program covers Google Ads and Analytics in depth. This certification can greatly boost your credibility. It shows you are skilled in key online marketing tools.
- HubSpot Content Marketing Certification: It's perfect for aspiring content marketers. It covers everything from content creation to promotion and analysis. It’s a valuable credential. It boosts your content's ability to resonate with your audience.
- Facebook Blueprint Certification: It's a must-have for social media marketers. It trains you to use Facebook and Instagram ads. It helps you optimize your campaigns and reach your target audience.
- Digital Marketing Institute Certification: It certifies in digital strategy, social media, and SEO. These top certifications can give you an edge in your digital marketing career.
Key Benefits of Pursuing an Online Digital Marketing Certification
- Upgrade Your Skills: Get vital, cutting-edge skills for success in today's competitive market.
- Increase Your Marketability: A certified skill boosts your appeal to employers. It proves your expertise and dedication.
- Boost Your Earning Potential: Certified pros earn more and get promoted more often.
- Network with Experts: Many certification programs connect you with industry leaders and peers.
- Stay Ahead of the Curve: Learn the latest tools and techniques. This will help you keep up with the fast-changing digital marketing world.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, investing in an online digital marketing certification is a smart move. It can boost your career. The right certification will boost your skills. It will also mark you as a leader in digital marketing. Enroll in a top certification program today. It will elevate your career in 2024. Don't miss the chance! Your future in digital marketing starts now!
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Improving ITSM with Process Mining and Automation
Are you looking to enhance the efficiency and effectiveness of your IT Service Management (ITSM) processes? If so, incorporating process mining and automation techniques can revolutionize the way your IT operations function. In this article, we will explore how these innovative solutions can streamline your IT processes, optimize service delivery, and drive operational excellence in your organization.
\
Leveraging Process Mining for Enhanced Data Analysis
Process mining involves analyzing event logs generated by IT systems to gain insights into the actual execution of business processes. By visualizing and analyzing these logs, organizations can identify inefficiencies, bottlenecks, and deviations from standard procedures. This data-driven approach enables IT teams to make informed decisions for process improvement and optimization.
With the help of process mining tools, IT departments can track the flow of activities within their IT processes, identify root causes of issues, and pinpoint areas for enhancement. By harnessing the power of data analysis, organizations can achieve a deeper understanding of their workflows and make strategic improvements to drive efficiency and effectiveness.
Automating IT Processes for Enhanced Workflow Management
Automation plays a crucial role in streamlining IT processes and enhancing operational efficiency. By automating repetitive tasks, IT teams can free up time and resources to focus on more strategic initiatives. Automation tools can be used to automate routine activities such as incident management, performance monitoring, and service desk operations.
Workflow automation not only reduces the risk of human error but also accelerates the execution of tasks, leading to faster resolution times and improved service quality. With the integration of artificial intelligence and machine learning technologies, organizations can leverage automation to drive digital transformation and deliver cost-effective solutions.
Benefits of Process Mining and Automation in ITSM
-
Enhanced Data Insights: By combining process mining and automation, organizations can gain valuable insights into their IT workflows and identify areas for improvement.
-
Improved Workflows: Automation streamlines IT processes, leading to increased productivity and efficiency.
-
Compliance and Governance: Automation ensures that IT processes adhere to industry regulations and internal governance policies.
-
Continuous Improvement: Process mining and automation facilitate ongoing process enhancements and optimization.
-
Service Efficiency: Automated workflows enable IT teams to deliver services more effectively and efficiently.
By investing in process mining and automation solutions, organizations can unlock a world of possibilities for their IT operations. From optimized IT workflows to streamlined processes and improved service delivery, these innovative technologies offer a blueprint for success in the digital age.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, improving ITSM with process mining and automation is essential for organizations looking to stay competitive in today's fast-paced digital landscape. By leveraging data-driven insights, automating workflows, and embracing innovative technologies, IT departments can achieve operational excellence, drive business efficiency, and deliver superior service quality. It's time to take your IT processes to the next level with process mining and automation.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to enhance the efficiency and effectiveness of your IT Service Management (ITSM) processes? If so, incorporating process mining and automation techniques can revolutionize the way your IT operations function. In this article, we will explore how these innovative solutions can streamline your IT processes, optimize service delivery, and drive operational excellence in your organization.
\
Leveraging Process Mining for Enhanced Data Analysis
Process mining involves analyzing event logs generated by IT systems to gain insights into the actual execution of business processes. By visualizing and analyzing these logs, organizations can identify inefficiencies, bottlenecks, and deviations from standard procedures. This data-driven approach enables IT teams to make informed decisions for process improvement and optimization.
With the help of process mining tools, IT departments can track the flow of activities within their IT processes, identify root causes of issues, and pinpoint areas for enhancement. By harnessing the power of data analysis, organizations can achieve a deeper understanding of their workflows and make strategic improvements to drive efficiency and effectiveness.
Automating IT Processes for Enhanced Workflow Management
Automation plays a crucial role in streamlining IT processes and enhancing operational efficiency. By automating repetitive tasks, IT teams can free up time and resources to focus on more strategic initiatives. Automation tools can be used to automate routine activities such as incident management, performance monitoring, and service desk operations.
Workflow automation not only reduces the risk of human error but also accelerates the execution of tasks, leading to faster resolution times and improved service quality. With the integration of artificial intelligence and machine learning technologies, organizations can leverage automation to drive digital transformation and deliver cost-effective solutions.
Benefits of Process Mining and Automation in ITSM
-
Enhanced Data Insights: By combining process mining and automation, organizations can gain valuable insights into their IT workflows and identify areas for improvement.
-
Improved Workflows: Automation streamlines IT processes, leading to increased productivity and efficiency.
-
Compliance and Governance: Automation ensures that IT processes adhere to industry regulations and internal governance policies.
-
Continuous Improvement: Process mining and automation facilitate ongoing process enhancements and optimization.
-
Service Efficiency: Automated workflows enable IT teams to deliver services more effectively and efficiently.
By investing in process mining and automation solutions, organizations can unlock a world of possibilities for their IT operations. From optimized IT workflows to streamlined processes and improved service delivery, these innovative technologies offer a blueprint for success in the digital age.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, improving ITSM with process mining and automation is essential for organizations looking to stay competitive in today's fast-paced digital landscape. By leveraging data-driven insights, automating workflows, and embracing innovative technologies, IT departments can achieve operational excellence, drive business efficiency, and deliver superior service quality. It's time to take your IT processes to the next level with process mining and automation.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Role of Hadoop in Hybrid Cloud Architectures
In today's data-driven world, businesses seek new ways to analyze vast amounts of data. Hadoop, a powerful open-source software, is key in hybrid cloud architecture.
What is Hadoop, and how does it fit into hybrid cloud architectures?
Hadoop is a distributed system for storage and processing. It is a low-cost way to handle huge datasets on cheap hardware clusters. It can scale from a single server to thousands of machines. Each machine offers local computation and storage. In hybrid cloud architectures, Hadoop can be integrated. This will leverage the benefits of both on-premises infrastructure and cloud services.
The Benefits of Incorporating Hadoop in Hybrid Cloud Environments
- Scalability: Hadoop's distributed design allows for easy scaling. It is ideal for processing large data volumes in hybrid cloud environments.
- Data Processing: Hadoop processes data efficiently. It helps organizations analyze their data and gain insights quickly.
- Big Data Solutions: Hadoop helps businesses manage and process big data. It enables them to make data-driven decisions.
- Data Analytics: Hadoop enables advanced analytics on large datasets. It allows organizations to run complex analytical tasks.
Hadoop Integration in Hybrid Cloud Environments
By using Hadoop in hybrid clouds, organizations can get the best of both worlds. They can enjoy the cloud's flexibility and on-premises control. It helps businesses optimize data management, boost security, and improve performance.
Hadoop Use Cases in Hybrid Cloud Environments
- Cloud Migration: Hadoop can move data and workloads to the cloud and back. It ensures data consistency and accessibility.
- Big Data Management: Hadoop helps manage big data in hybrid clouds. It provides tools to store, process, and analyze massive datasets.
- Security: Hadoop has strong security features. They protect sensitive data in hybrid clouds. They ensure data privacy and compliance with regulations.
The Future of Hadoop in Hybrid Cloud Architectures
As businesses embrace data-driven decisions, Hadoop's role in hybrid clouds will grow. Hadoop can handle vast data, enable advanced analytics, and scale. So, it will be key to the future of cloud computing.
How to obtain Big Data and Hadoop Administrator certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, Hadoop in hybrid clouds gives businesses a powerful tool. It enables efficient data management, processing, and analysis. Hadoop's distributed nature offers great benefits. It can help organizations manage and analyze data in today's fast-changing digital world.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's data-driven world, businesses seek new ways to analyze vast amounts of data. Hadoop, a powerful open-source software, is key in hybrid cloud architecture.
What is Hadoop, and how does it fit into hybrid cloud architectures?
Hadoop is a distributed system for storage and processing. It is a low-cost way to handle huge datasets on cheap hardware clusters. It can scale from a single server to thousands of machines. Each machine offers local computation and storage. In hybrid cloud architectures, Hadoop can be integrated. This will leverage the benefits of both on-premises infrastructure and cloud services.
The Benefits of Incorporating Hadoop in Hybrid Cloud Environments
- Scalability: Hadoop's distributed design allows for easy scaling. It is ideal for processing large data volumes in hybrid cloud environments.
- Data Processing: Hadoop processes data efficiently. It helps organizations analyze their data and gain insights quickly.
- Big Data Solutions: Hadoop helps businesses manage and process big data. It enables them to make data-driven decisions.
- Data Analytics: Hadoop enables advanced analytics on large datasets. It allows organizations to run complex analytical tasks.
Hadoop Integration in Hybrid Cloud Environments
By using Hadoop in hybrid clouds, organizations can get the best of both worlds. They can enjoy the cloud's flexibility and on-premises control. It helps businesses optimize data management, boost security, and improve performance.
Hadoop Use Cases in Hybrid Cloud Environments
- Cloud Migration: Hadoop can move data and workloads to the cloud and back. It ensures data consistency and accessibility.
- Big Data Management: Hadoop helps manage big data in hybrid clouds. It provides tools to store, process, and analyze massive datasets.
- Security: Hadoop has strong security features. They protect sensitive data in hybrid clouds. They ensure data privacy and compliance with regulations.
The Future of Hadoop in Hybrid Cloud Architectures
As businesses embrace data-driven decisions, Hadoop's role in hybrid clouds will grow. Hadoop can handle vast data, enable advanced analytics, and scale. So, it will be key to the future of cloud computing.
How to obtain Big Data and Hadoop Administrator certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, Hadoop in hybrid clouds gives businesses a powerful tool. It enables efficient data management, processing, and analysis. Hadoop's distributed nature offers great benefits. It can help organizations manage and analyze data in today's fast-changing digital world.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Role of a CSM in Facilitating Agile Procurement
In today's fast-paced business environment, agile procurement has become essential for organizations looking to stay competitive and adapt quickly to changing market conditions. Agile methodologies have revolutionized the way companies approach project management, product development, and now, procurement processes. As companies embrace agile principles and practices, the role of a Customer Success Manager (CSM) becomes crucial in facilitating agile procurement to drive efficiency, innovation, and collaboration in the procurement process.
Agile Procurement: A Paradigm Shift
Agile procurement involves applying agile project management principles to the procurement process, enabling organizations to respond rapidly to changing requirements and market dynamics. Unlike traditional procurement approaches, agile procurement focuses on flexibility, customer satisfaction, and continuous improvement rather than rigid processes and strict protocols. By embracing an agile framework, organizations can streamline their procurement operations, optimize efficiency, and drive innovation in sourcing and supplier management.
The Role of a CSM in Agile Procurement
As organizations transition to agile procurement, the role of a Customer Success Manager becomes pivotal in supporting procurement professionals and teams in adopting agile methodologies. The CSM acts as a bridge between the procurement function and agile practices, providing guidance, training, and support to ensure successful agile implementation. From understanding agile principles to enhancing procurement efficiency, the CSM plays a key role in driving agile transformation in the procurement function.
CSM Responsibilities in Agile Procurement
-
Providing agile training and guidance to procurement professionals.
-
Facilitating agile processes and collaboration among cross-functional teams.
-
Supporting procurement automation and integration of agile techniques.
-
Driving procurement innovation and improvement through agile practices.
-
Ensuring customer satisfaction and procurement efficiency in agile projects.
Agile Benefits in Procurement
Agile procurement offers a myriad of benefits for organizations looking to enhance their procurement efficiency and effectiveness. By adopting agile methodologies, organizations can:
-
Improve procurement collaboration and teamwork.
-
Enhance procurement efficiency and optimization.
-
Drive procurement innovation and integration of agile solutions.
-
Increase procurement visibility and insights for better decision-making.
-
Enhance procurement agility and responsiveness to market changes.
CSM Impact on Agile Procurement
The CSM's involvement in agile procurement is instrumental in driving success and maximizing the benefits of agile practices in the procurement function. As organizations strive to achieve procurement excellence and agility, the CSM's contribution is vital in ensuring smooth implementation of agile strategies, fostering collaboration among procurement professionals, and driving continuous improvement in procurement operations.
How to obtain CSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the role of a CSM in facilitating agile procurement is essential for organizations looking to embrace agile principles and practices in their procurement processes. By leveraging the expertise of a CSM in agile project management and customer success, organizations can drive efficiency, innovation, and collaboration in their procurement function, leading to tangible benefits and competitive advantages in the ever-evolving business landscape.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced business environment, agile procurement has become essential for organizations looking to stay competitive and adapt quickly to changing market conditions. Agile methodologies have revolutionized the way companies approach project management, product development, and now, procurement processes. As companies embrace agile principles and practices, the role of a Customer Success Manager (CSM) becomes crucial in facilitating agile procurement to drive efficiency, innovation, and collaboration in the procurement process.
Agile Procurement: A Paradigm Shift
Agile procurement involves applying agile project management principles to the procurement process, enabling organizations to respond rapidly to changing requirements and market dynamics. Unlike traditional procurement approaches, agile procurement focuses on flexibility, customer satisfaction, and continuous improvement rather than rigid processes and strict protocols. By embracing an agile framework, organizations can streamline their procurement operations, optimize efficiency, and drive innovation in sourcing and supplier management.
The Role of a CSM in Agile Procurement
As organizations transition to agile procurement, the role of a Customer Success Manager becomes pivotal in supporting procurement professionals and teams in adopting agile methodologies. The CSM acts as a bridge between the procurement function and agile practices, providing guidance, training, and support to ensure successful agile implementation. From understanding agile principles to enhancing procurement efficiency, the CSM plays a key role in driving agile transformation in the procurement function.
CSM Responsibilities in Agile Procurement
-
Providing agile training and guidance to procurement professionals.
-
Facilitating agile processes and collaboration among cross-functional teams.
-
Supporting procurement automation and integration of agile techniques.
-
Driving procurement innovation and improvement through agile practices.
-
Ensuring customer satisfaction and procurement efficiency in agile projects.
Agile Benefits in Procurement
Agile procurement offers a myriad of benefits for organizations looking to enhance their procurement efficiency and effectiveness. By adopting agile methodologies, organizations can:
-
Improve procurement collaboration and teamwork.
-
Enhance procurement efficiency and optimization.
-
Drive procurement innovation and integration of agile solutions.
-
Increase procurement visibility and insights for better decision-making.
-
Enhance procurement agility and responsiveness to market changes.
CSM Impact on Agile Procurement
The CSM's involvement in agile procurement is instrumental in driving success and maximizing the benefits of agile practices in the procurement function. As organizations strive to achieve procurement excellence and agility, the CSM's contribution is vital in ensuring smooth implementation of agile strategies, fostering collaboration among procurement professionals, and driving continuous improvement in procurement operations.
How to obtain CSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the role of a CSM in facilitating agile procurement is essential for organizations looking to embrace agile principles and practices in their procurement processes. By leveraging the expertise of a CSM in agile project management and customer success, organizations can drive efficiency, innovation, and collaboration in their procurement function, leading to tangible benefits and competitive advantages in the ever-evolving business landscape.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Impact of Web3 on Digital Marketing
In today's rapidly evolving digital landscape, the emergence of Web3 technology is revolutionizing the way businesses approach marketing strategies. From blockchain to augmented reality, Web3 is transforming the digital marketing landscape and opening up new opportunities for brands to engage with their target audience in innovative ways.
Impact on Marketing Strategy
Web3 technology is disrupting traditional marketing strategies by offering decentralized and transparent solutions that prioritize user privacy and data security. This shift towards a more user-centric approach is forcing marketers to rethink their tactics and focus on building authentic relationships with customers.
Marketing Trends in Web3
With the rise of Web3 technology, new marketing trends are emerging that prioritize immersive experiences, personalized interactions, and ethical practices. Brands are leveraging blockchain, NFTs, and augmented reality to create unique and engaging campaigns that resonate with their audience on a deeper level.
Web3 Technology in Marketing Solutions
Web3 technology is providing marketers with unique solutions to challenges such as data privacy, customer engagement, and content delivery. By harnessing the power of blockchain and smart contracts, brands can create secure and transparent campaigns that build trust and loyalty among consumers.
Coming up to the forefront, Web3 is reshaping digital marketing with its decentralized and innovative approach to engaging with customers. This new technology offers endless possibilities for brands to create immersive experiences, personalized interactions, and ethical marketing practices that resonate with their target audience.
In this article, we'll explore the various ways in which Web3 is transforming the digital marketing landscape and discuss the implications for brands looking to stay ahead of the curve. From blockchain to augmented reality, Web3 is revolutionizing the way businesses connect with their customers and driving the future of marketing in a more decentralized and user-centric direction.
So, how exactly is Web3 reshaping the world of digital marketing? Let's dive into the key areas where this technology is making a significant impact:
1. Decentralized Marketing
Web3 technology is enabling brands to bypass traditional intermediaries and connect directly with their target audience. By leveraging blockchain and smart contracts, marketers can create decentralized campaigns that prioritize transparency and trust, ultimately leading to a more authentic and engaging customer experience.
2. Personalized Marketing Experiences
With Web3 technology, brands can create personalized marketing experiences that cater to the unique preferences and interests of individual consumers. By utilizing data-driven insights and artificial intelligence, marketers can deliver hyper-targeted campaigns that resonate with their audience on a more personal level.
3. Ethical Marketing Practices
Web3 technology is putting a greater emphasis on ethical marketing practices by prioritizing user privacy, data security, and transparency. Brands that embrace these principles can build trust and credibility with their customers, ultimately leading to stronger brand loyalty and long-term success.
4. Immersive Marketing Techniques
From augmented reality to virtual reality, Web3 technology is enabling brands to create immersive marketing experiences that captivate and engage their audience. By leveraging these cutting-edge technologies, marketers can deliver unique and interactive campaigns that stand out in a crowded digital landscape.
5. Customer Engagement Strategies
Web3 technology is empowering brands to create innovative customer engagement strategies that prioritize authentic interactions and meaningful connections. By fostering two-way communication and encouraging user participation, marketers can build stronger relationships with their audience and drive brand loyalty.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Web3 technology is revolutionizing the digital marketing landscape by offering new solutions to age-old challenges and empowering brands to create more engaging, personalized, and ethical campaigns. By embracing these innovations and staying ahead of the curve, businesses can position themselves for success in an increasingly decentralized and user-centric digital world.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's rapidly evolving digital landscape, the emergence of Web3 technology is revolutionizing the way businesses approach marketing strategies. From blockchain to augmented reality, Web3 is transforming the digital marketing landscape and opening up new opportunities for brands to engage with their target audience in innovative ways.
Impact on Marketing Strategy
Web3 technology is disrupting traditional marketing strategies by offering decentralized and transparent solutions that prioritize user privacy and data security. This shift towards a more user-centric approach is forcing marketers to rethink their tactics and focus on building authentic relationships with customers.
Marketing Trends in Web3
With the rise of Web3 technology, new marketing trends are emerging that prioritize immersive experiences, personalized interactions, and ethical practices. Brands are leveraging blockchain, NFTs, and augmented reality to create unique and engaging campaigns that resonate with their audience on a deeper level.
Web3 Technology in Marketing Solutions
Web3 technology is providing marketers with unique solutions to challenges such as data privacy, customer engagement, and content delivery. By harnessing the power of blockchain and smart contracts, brands can create secure and transparent campaigns that build trust and loyalty among consumers.
Coming up to the forefront, Web3 is reshaping digital marketing with its decentralized and innovative approach to engaging with customers. This new technology offers endless possibilities for brands to create immersive experiences, personalized interactions, and ethical marketing practices that resonate with their target audience.
In this article, we'll explore the various ways in which Web3 is transforming the digital marketing landscape and discuss the implications for brands looking to stay ahead of the curve. From blockchain to augmented reality, Web3 is revolutionizing the way businesses connect with their customers and driving the future of marketing in a more decentralized and user-centric direction.
So, how exactly is Web3 reshaping the world of digital marketing? Let's dive into the key areas where this technology is making a significant impact:
1. Decentralized Marketing
Web3 technology is enabling brands to bypass traditional intermediaries and connect directly with their target audience. By leveraging blockchain and smart contracts, marketers can create decentralized campaigns that prioritize transparency and trust, ultimately leading to a more authentic and engaging customer experience.
2. Personalized Marketing Experiences
With Web3 technology, brands can create personalized marketing experiences that cater to the unique preferences and interests of individual consumers. By utilizing data-driven insights and artificial intelligence, marketers can deliver hyper-targeted campaigns that resonate with their audience on a more personal level.
3. Ethical Marketing Practices
Web3 technology is putting a greater emphasis on ethical marketing practices by prioritizing user privacy, data security, and transparency. Brands that embrace these principles can build trust and credibility with their customers, ultimately leading to stronger brand loyalty and long-term success.
4. Immersive Marketing Techniques
From augmented reality to virtual reality, Web3 technology is enabling brands to create immersive marketing experiences that captivate and engage their audience. By leveraging these cutting-edge technologies, marketers can deliver unique and interactive campaigns that stand out in a crowded digital landscape.
5. Customer Engagement Strategies
Web3 technology is empowering brands to create innovative customer engagement strategies that prioritize authentic interactions and meaningful connections. By fostering two-way communication and encouraging user participation, marketers can build stronger relationships with their audience and drive brand loyalty.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Web3 technology is revolutionizing the digital marketing landscape by offering new solutions to age-old challenges and empowering brands to create more engaging, personalized, and ethical campaigns. By embracing these innovations and staying ahead of the curve, businesses can position themselves for success in an increasingly decentralized and user-centric digital world.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Architecting for Sustainability Green Cloud Solutions with AWS
With rising awareness of environmental issues, companies must cut carbon emissions and focus on sustainability. A key way to do this is by using green cloud solutions in their IT. AWS launches innovative green initiatives in cloud computing technology.
The Rise of Sustainable Architecture
Sustainability is reshaping architecture. It needs designs that blend beauty with function and preserve nature. Amid climate change, architects seek to reduce energy use and carbon emissions. They aim to build greener structures.
What Makes Cloud Computing Green?
Green cloud computing focuses on minimizing the environmental impact of cloud services. This involves:
- Renewable Energy: Using energy from sustainable sources.
- Efficiency: Enhancing data center operations to reduce power usage.
- Emission Reduction: Lowering greenhouse gas emissions.

Green Cloud Solutions can cut energy costs and boost a company's green image.
Why AWS Leads in Green Cloud Solutions
AWS is not a top-tier cloud service provider; it is also a pioneer in sustainable practices. AWS reflects its commitment to environmental responsibility in its operations and services.
- Energy-Efficient Data Centers: AWS spends much on designing data centers. They must use less power and emit less.
- Renewable Energy Usage: AWS wants its data centers to run on 100% renewable energy. This will help businesses support green energy.
- Reduced Carbon Footprint: Moving to AWS lets firms shut down old, in-house data centers. This will cut energy use and emissions.
Key Practices for Green Cloud Integration with AWS
To build sustainable architecture with AWS, adopt these practices:
- Reduce Data Center Power Use: Use AWS's tech to optimize your data use.
- Support Renewable Energy: Use AWS services that run on renewable energy. This aligns your business with clean energy goals.
- Efficient Operations: Use server consolidation and virtualization to reduce energy waste.
AWS’s Role in Sustainable Innovation
AWS’s sustainability efforts extend beyond its operations. AWS helps businesses meet global sustainability goals. It supports projects that reduce environmental impact and invests in green technologies. Choosing AWS means supporting a leader in environmental stewardship. It can boost your own sustainability profile.
Embracing a Greener Future
Using AWS green cloud solutions for sustainable design has a dual benefit. It helps the environment and provides business advantages. These practices can help businesses. They can cut costs, boost efficiency, and promote sustainability.
How to obtain Cloud Technology Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, AWS's green cloud solutions increase productivity and promote environmental sustainability. It's a smart choice. Use these solutions to lead in sustainability and improve the tech industry.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
With rising awareness of environmental issues, companies must cut carbon emissions and focus on sustainability. A key way to do this is by using green cloud solutions in their IT. AWS launches innovative green initiatives in cloud computing technology.
The Rise of Sustainable Architecture
Sustainability is reshaping architecture. It needs designs that blend beauty with function and preserve nature. Amid climate change, architects seek to reduce energy use and carbon emissions. They aim to build greener structures.
What Makes Cloud Computing Green?
Green cloud computing focuses on minimizing the environmental impact of cloud services. This involves:
- Renewable Energy: Using energy from sustainable sources.
- Efficiency: Enhancing data center operations to reduce power usage.
- Emission Reduction: Lowering greenhouse gas emissions.
Green Cloud Solutions can cut energy costs and boost a company's green image.
Why AWS Leads in Green Cloud Solutions
AWS is not a top-tier cloud service provider; it is also a pioneer in sustainable practices. AWS reflects its commitment to environmental responsibility in its operations and services.
- Energy-Efficient Data Centers: AWS spends much on designing data centers. They must use less power and emit less.
- Renewable Energy Usage: AWS wants its data centers to run on 100% renewable energy. This will help businesses support green energy.
- Reduced Carbon Footprint: Moving to AWS lets firms shut down old, in-house data centers. This will cut energy use and emissions.
Key Practices for Green Cloud Integration with AWS
To build sustainable architecture with AWS, adopt these practices:
- Reduce Data Center Power Use: Use AWS's tech to optimize your data use.
- Support Renewable Energy: Use AWS services that run on renewable energy. This aligns your business with clean energy goals.
- Efficient Operations: Use server consolidation and virtualization to reduce energy waste.
AWS’s Role in Sustainable Innovation
AWS’s sustainability efforts extend beyond its operations. AWS helps businesses meet global sustainability goals. It supports projects that reduce environmental impact and invests in green technologies. Choosing AWS means supporting a leader in environmental stewardship. It can boost your own sustainability profile.
Embracing a Greener Future
Using AWS green cloud solutions for sustainable design has a dual benefit. It helps the environment and provides business advantages. These practices can help businesses. They can cut costs, boost efficiency, and promote sustainability.
How to obtain Cloud Technology Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, AWS's green cloud solutions increase productivity and promote environmental sustainability. It's a smart choice. Use these solutions to lead in sustainability and improve the tech industry.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Role of CRISC in Cloud Security and Risk Management
In today's digital age, cloud security and risk management have become crucial aspects of any organization's cybersecurity strategy. With the rapid adoption of cloud technology, the need for professionals who are skilled in managing cloud security risks has never been higher. This is where the Certified in Risk and Information Systems Control (CRISC) certification plays a vital role.
CRISC in Cloud Security and Risk Management
The CRISC certification is designed for IT professionals who have experience in identifying and managing IT and business risks. When it comes to cloud security, CRISC professionals are equipped with the knowledge and skills to assess and mitigate risks associated with cloud computing.
CRISC certification holders understand the unique challenges that come with securing cloud environments, such as data breaches, compliance issues, and data loss. By applying best practices and frameworks, CRISC professionals can help organizations enhance their cloud security posture and effectively manage risks.
Benefits of CRISC in Cloud Security
There are numerous benefits to having CRISC professionals leading cloud security and risk management efforts. Some of the key advantages include:
-
Enhanced risk assessment and management capabilities
-
Improved compliance with industry regulations and standards
-
Increased awareness of emerging cloud security threats
-
Better alignment of cloud security initiatives with business objectives
-
Enhanced decision-making processes related to cloud security
Importance of CRISC in Cloud Security
The importance of CRISC in cloud security cannot be overstated. With the ever-evolving threat landscape and the increasing complexity of cloud environments, organizations need skilled professionals who can effectively manage risks and secure their cloud infrastructure. CRISC certification demonstrates a professional's expertise in risk management and positions them as a valuable asset in safeguarding critical data and systems.
CRISC Cloud Security Certification
CRISC certification in cloud security signifies that a professional has the knowledge and skills to assess, mitigate, and manage risks in cloud environments. By earning this certification, individuals demonstrate their commitment to excellence in cloud security and risk management, making them stand out in a competitive job market.
How to obtain CRISC certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the role of CRISC in cloud security and risk management is essential for organizations looking to protect their valuable assets in the digital landscape. By leveraging the expertise of CRISC professionals, organizations can strengthen their cloud security defenses, mitigate risks effectively, and ensure business continuity. Investing in CRISC certification can lead to enhanced cybersecurity practices and a more secure cloud environment.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's digital age, cloud security and risk management have become crucial aspects of any organization's cybersecurity strategy. With the rapid adoption of cloud technology, the need for professionals who are skilled in managing cloud security risks has never been higher. This is where the Certified in Risk and Information Systems Control (CRISC) certification plays a vital role.
CRISC in Cloud Security and Risk Management
The CRISC certification is designed for IT professionals who have experience in identifying and managing IT and business risks. When it comes to cloud security, CRISC professionals are equipped with the knowledge and skills to assess and mitigate risks associated with cloud computing.
CRISC certification holders understand the unique challenges that come with securing cloud environments, such as data breaches, compliance issues, and data loss. By applying best practices and frameworks, CRISC professionals can help organizations enhance their cloud security posture and effectively manage risks.
Benefits of CRISC in Cloud Security
There are numerous benefits to having CRISC professionals leading cloud security and risk management efforts. Some of the key advantages include:
-
Enhanced risk assessment and management capabilities
-
Improved compliance with industry regulations and standards
-
Increased awareness of emerging cloud security threats
-
Better alignment of cloud security initiatives with business objectives
-
Enhanced decision-making processes related to cloud security
Importance of CRISC in Cloud Security
The importance of CRISC in cloud security cannot be overstated. With the ever-evolving threat landscape and the increasing complexity of cloud environments, organizations need skilled professionals who can effectively manage risks and secure their cloud infrastructure. CRISC certification demonstrates a professional's expertise in risk management and positions them as a valuable asset in safeguarding critical data and systems.
CRISC Cloud Security Certification
CRISC certification in cloud security signifies that a professional has the knowledge and skills to assess, mitigate, and manage risks in cloud environments. By earning this certification, individuals demonstrate their commitment to excellence in cloud security and risk management, making them stand out in a competitive job market.
How to obtain CRISC certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the role of CRISC in cloud security and risk management is essential for organizations looking to protect their valuable assets in the digital landscape. By leveraging the expertise of CRISC professionals, organizations can strengthen their cloud security defenses, mitigate risks effectively, and ensure business continuity. Investing in CRISC certification can lead to enhanced cybersecurity practices and a more secure cloud environment.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Top Citrix Administration Tools You Should Know in 2024
Are you looking to optimize your Citrix administration tasks in 2024? With tech evolving fast, it's vital to use the right tools for efficient management. This will help you stay ahead. This article will explore the best Citrix admin tools. They can streamline your operations and boost productivity.
Introduction to Citrix Administration Tools
Citrix administration tools are vital for managing Citrix environments. They simplify administrative tasks. These tools do many things. They track, deploy, secure, troubleshoot, and configure. The right Citrix admin tools can help organizations. They simplify complex tasks, reduce manual work, and ensure smooth operations.
Best Citrix Admin Tools in 2024
- Citrix Cloud: It is a platform for managing Citrix environments from the cloud.Citrix Cloud enables administrators to deploy, organize, and track their resources. It offers better flexibility and scalability.
- Citrix Workspace: Citrix Workspace is a unified digital workspace. It provides a secure, seamless user experience. Admins can use Citrix Workspace to deliver apps and desktops to users. They can manage access and ensure compliance with security policies.
- Citrix Director: It is a tool for monitoring and troubleshooting. It lets admins check their Citrix environment's performance in real time.
Admins can use Citrix Director to:
- Identify and fix issues.
- Optimize resource use.
- Improve the user experience.
Citrix ADC, once NetScaler, dominates application delivery through robust control mechanisms. It helps organizations improve application performance, ensure uptime, and boost security.
Admins can use Citrix ADC to:
- Load-balance traffic.
- Secure applications.
- Improve user experience.
Citrix Virtual Apps and Desktops is a virtualization tool. They were once called XenApp and XenDesktop. They deliver apps and desktops to users.
Admins can use Citrix Virtual Apps and Desktops to:
- Centralize management.
- Simplify app delivery.
- Improve mobility.
Must-Have Citrix Administration Tools for Every Admin
- Citrix Provisioning Services (PVS) is a tool for admins. It lets them stream OS and app images to virtual desktops and servers. This enables fast deployment and updates.
- Citrix Endpoint Management helps admins manage mobile devices, apps, and content. It encrypts data. This boosts productivity, and protects data.
- Citrix Hypervisor is a powerful virtualization platform. It lets admins create and manage virtual machines. This ensures high performance and resource usage.
How to obtain Citrix Administration Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, use these top Citrix admin tools in your strategy. They boost output, simplify workflows, and optimize your Citrix environment. With the right tools, you can stay ahead in the fast-changing tech world. This will help your business succeed.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to optimize your Citrix administration tasks in 2024? With tech evolving fast, it's vital to use the right tools for efficient management. This will help you stay ahead. This article will explore the best Citrix admin tools. They can streamline your operations and boost productivity.
Introduction to Citrix Administration Tools
Citrix administration tools are vital for managing Citrix environments. They simplify administrative tasks. These tools do many things. They track, deploy, secure, troubleshoot, and configure. The right Citrix admin tools can help organizations. They simplify complex tasks, reduce manual work, and ensure smooth operations.
Best Citrix Admin Tools in 2024
- Citrix Cloud: It is a platform for managing Citrix environments from the cloud.Citrix Cloud enables administrators to deploy, organize, and track their resources. It offers better flexibility and scalability.
- Citrix Workspace: Citrix Workspace is a unified digital workspace. It provides a secure, seamless user experience. Admins can use Citrix Workspace to deliver apps and desktops to users. They can manage access and ensure compliance with security policies.
- Citrix Director: It is a tool for monitoring and troubleshooting. It lets admins check their Citrix environment's performance in real time.
Admins can use Citrix Director to:
- Identify and fix issues.
- Optimize resource use.
- Improve the user experience.
Citrix ADC, once NetScaler, dominates application delivery through robust control mechanisms. It helps organizations improve application performance, ensure uptime, and boost security.
Admins can use Citrix ADC to:
- Load-balance traffic.
- Secure applications.
- Improve user experience.
Citrix Virtual Apps and Desktops is a virtualization tool. They were once called XenApp and XenDesktop. They deliver apps and desktops to users.
Admins can use Citrix Virtual Apps and Desktops to:
- Centralize management.
- Simplify app delivery.
- Improve mobility.
Must-Have Citrix Administration Tools for Every Admin
- Citrix Provisioning Services (PVS) is a tool for admins. It lets them stream OS and app images to virtual desktops and servers. This enables fast deployment and updates.
- Citrix Endpoint Management helps admins manage mobile devices, apps, and content. It encrypts data. This boosts productivity, and protects data.
- Citrix Hypervisor is a powerful virtualization platform. It lets admins create and manage virtual machines. This ensures high performance and resource usage.
How to obtain Citrix Administration Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, use these top Citrix admin tools in your strategy. They boost output, simplify workflows, and optimize your Citrix environment. With the right tools, you can stay ahead in the fast-changing tech world. This will help your business succeed.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Future of Digital Marketing Embracing Web3
Digital marketing has changed in recent years due to Web3. The decentralized web will change business-user interactions. This article will cover the effects of Web3 on digital marketing. We will discuss what businesses must do to stay ahead in a fast-changing world.
Understanding Web3: A New Era of the Internet
Web3 is the third version of the internet. Users control it. This makes it decentralized and more secure. It shifts control to them. Centralized platforms dominate Web2. Web3, unlike Web2, is on blockchain and decentralized tech. This change is a big step toward a more user-focused, transparent web. It will give people more control over their data and digital assets.
Web's transformative effects on digital marketing
Web3 gives users control over their personal info. It's a data privacy revolution. It challenges the data-driven marketing model. Marketers must adapt. They should use ethical, clear practices. They must protect user privacy. They must also find new ways to engage audiences. We must gather information but not harm privacy.
The Rise of Smart Contracts
Smart contracts are self-executing agreements. They have coded their own terms. They run on blockchain technology. These contracts can transform digital marketing. They can automate tasks, secure systems, and build trust. This will speed up transactions and remove middlemen.
Tokenization: A New Approach to Engagement
Web3 enables tokenizing digital assets. It lets businesses create new loyalty programs and perks. Using tokens in marketing can improve engagement and loyalty. They can reward users for participating in the ecosystem in new ways.

Decentralized Advertising Takes Center Stage
As Web3 evolves, decentralized ad platforms may replace the old ones. They rank user consent and fair rewards. These platforms empower creators and consumers. They reduce reliance on middlemen. They build a direct link between brands and their audiences.
Adapting to the Web3 Revolution: A Guide to Success
- Embrace Decentralized Marketing Strategies : To succeed in Web3, businesses must go to a decentralized model. They must focus on transparency, privacy, and data rights. Brands can use decentralized platforms to gain users' trust.
- Integrate blockchain into marketing campaigns : Blockchain technology offers many opportunities for marketers. It can verify products' authenticity. It can ensure a clear supply chain. Blockchain can help businesses. It can check reviews, improve security, and build trust.
- Cultivate Community Engagement : In the Web3 world, community is key. Businesses should engage with decentralized communities. They should share insights and connect with users. Joining these ecosystems can help brands. It can create loyal customers and boost their status in the web.
- Experiment with NFTs and digital collectibles : NFTs are unique digital assets. Use them for exclusive marketing campaigns. NFT promos and rare collectibles can excite fans. They can also offer virtual experiences. This will boost brand awareness and loyalty in the Web3 space.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion , The Web3 shift in digital marketing. Web3 revolutionizes digital marketing. This new paradigm can help businesses. It can give them an edge, build trust, and spark new marketing in a decentralized world. As the Web3 landscape evolves, agility will be key. It will spark new ideas in digital marketing.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Digital marketing has changed in recent years due to Web3. The decentralized web will change business-user interactions. This article will cover the effects of Web3 on digital marketing. We will discuss what businesses must do to stay ahead in a fast-changing world.
Understanding Web3: A New Era of the Internet
Web3 is the third version of the internet. Users control it. This makes it decentralized and more secure. It shifts control to them. Centralized platforms dominate Web2. Web3, unlike Web2, is on blockchain and decentralized tech. This change is a big step toward a more user-focused, transparent web. It will give people more control over their data and digital assets.
Web's transformative effects on digital marketing
Web3 gives users control over their personal info. It's a data privacy revolution. It challenges the data-driven marketing model. Marketers must adapt. They should use ethical, clear practices. They must protect user privacy. They must also find new ways to engage audiences. We must gather information but not harm privacy.
The Rise of Smart Contracts
Smart contracts are self-executing agreements. They have coded their own terms. They run on blockchain technology. These contracts can transform digital marketing. They can automate tasks, secure systems, and build trust. This will speed up transactions and remove middlemen.
Tokenization: A New Approach to Engagement
Web3 enables tokenizing digital assets. It lets businesses create new loyalty programs and perks. Using tokens in marketing can improve engagement and loyalty. They can reward users for participating in the ecosystem in new ways.
Decentralized Advertising Takes Center Stage
As Web3 evolves, decentralized ad platforms may replace the old ones. They rank user consent and fair rewards. These platforms empower creators and consumers. They reduce reliance on middlemen. They build a direct link between brands and their audiences.
Adapting to the Web3 Revolution: A Guide to Success
- Embrace Decentralized Marketing Strategies : To succeed in Web3, businesses must go to a decentralized model. They must focus on transparency, privacy, and data rights. Brands can use decentralized platforms to gain users' trust.
- Integrate blockchain into marketing campaigns : Blockchain technology offers many opportunities for marketers. It can verify products' authenticity. It can ensure a clear supply chain. Blockchain can help businesses. It can check reviews, improve security, and build trust.
- Cultivate Community Engagement : In the Web3 world, community is key. Businesses should engage with decentralized communities. They should share insights and connect with users. Joining these ecosystems can help brands. It can create loyal customers and boost their status in the web.
- Experiment with NFTs and digital collectibles : NFTs are unique digital assets. Use them for exclusive marketing campaigns. NFT promos and rare collectibles can excite fans. They can also offer virtual experiences. This will boost brand awareness and loyalty in the Web3 space.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion , The Web3 shift in digital marketing. Web3 revolutionizes digital marketing. This new paradigm can help businesses. It can give them an edge, build trust, and spark new marketing in a decentralized world. As the Web3 landscape evolves, agility will be key. It will spark new ideas in digital marketing.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
RPA in IT Ops Improving IT Service Support
Are you looking to enhance your IT service support and streamline operations? Robotic Process Automation (RPA) in IT Ops can be the solution you need. By leveraging automation tools and technology, you can improve efficiency, reduce costs, and boost productivity in your IT operations.
What is RPA in IT Ops?
RPA involves automating tasks and business processes by using software robots to mimic human actions. In the context of IT Ops, RPA can be used to automate repetitive and time-consuming tasks, such as data processing, infrastructure management, and service desk operations. This enables IT teams to focus on more strategic and high-value activities.
Benefits of RPA in IT Ops
-
Cost Reduction: By automating tasks, you can reduce the need for manual labor and save on operational costs.
-
Process Optimization: RPA can help streamline workflows and optimize business processes for better efficiency.
-
Improved Accuracy: Automation tools ensure consistent and error-free results, improving overall data accuracy.
-
Enhanced Customer Experience: With faster response times and proactive support, customer service can be greatly improved.
-
Resource Optimization: IT teams can allocate resources more effectively and focus on tasks that require human intervention.
How Does RPA Improve IT Service Support?
Implementing RPA in IT Ops can lead to a host of benefits for IT service support and delivery.
1. Enhanced Productivity
By automating routine tasks, IT professionals can focus on more strategic initiatives, leading to increased productivity and faster service delivery.
2. Streamlined Operations
RPA can help streamline workflows and eliminate bottlenecks in IT operations, leading to smoother and more efficient processes.
3. Task Automation
Routine tasks such as data entry, password resets, and system monitoring can be automated, reducing manual effort and freeing up time for more critical work.
4. Enhanced Customer Experience
With faster response times and improved service delivery, customers can experience better support and satisfaction.
5. Cost Reduction
By automating tasks, IT departments can reduce operational costs and allocate resources more effectively.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, RPA in IT Ops is a powerful technology that can revolutionize IT service support and operations management. By leveraging automation tools and software, IT teams can enhance efficiency, streamline workflows, and deliver superior service to customers. Embracing RPA is not just about technology; it's a strategic decision that can drive digital transformation and innovation in the modern IT landscape.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to enhance your IT service support and streamline operations? Robotic Process Automation (RPA) in IT Ops can be the solution you need. By leveraging automation tools and technology, you can improve efficiency, reduce costs, and boost productivity in your IT operations.
What is RPA in IT Ops?
RPA involves automating tasks and business processes by using software robots to mimic human actions. In the context of IT Ops, RPA can be used to automate repetitive and time-consuming tasks, such as data processing, infrastructure management, and service desk operations. This enables IT teams to focus on more strategic and high-value activities.
Benefits of RPA in IT Ops
-
Cost Reduction: By automating tasks, you can reduce the need for manual labor and save on operational costs.
-
Process Optimization: RPA can help streamline workflows and optimize business processes for better efficiency.
-
Improved Accuracy: Automation tools ensure consistent and error-free results, improving overall data accuracy.
-
Enhanced Customer Experience: With faster response times and proactive support, customer service can be greatly improved.
-
Resource Optimization: IT teams can allocate resources more effectively and focus on tasks that require human intervention.
How Does RPA Improve IT Service Support?
Implementing RPA in IT Ops can lead to a host of benefits for IT service support and delivery.
1. Enhanced Productivity
By automating routine tasks, IT professionals can focus on more strategic initiatives, leading to increased productivity and faster service delivery.
2. Streamlined Operations
RPA can help streamline workflows and eliminate bottlenecks in IT operations, leading to smoother and more efficient processes.
3. Task Automation
Routine tasks such as data entry, password resets, and system monitoring can be automated, reducing manual effort and freeing up time for more critical work.
4. Enhanced Customer Experience
With faster response times and improved service delivery, customers can experience better support and satisfaction.
5. Cost Reduction
By automating tasks, IT departments can reduce operational costs and allocate resources more effectively.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, RPA in IT Ops is a powerful technology that can revolutionize IT service support and operations management. By leveraging automation tools and software, IT teams can enhance efficiency, streamline workflows, and deliver superior service to customers. Embracing RPA is not just about technology; it's a strategic decision that can drive digital transformation and innovation in the modern IT landscape.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Enhancing Data Literacy with Power BI
Are you looking to improve your data literacy skills and make better data-driven decisions? Look no further than Power BI, a powerful data visualization and business intelligence tool that can help you interpret and analyze data effectively. In this article, we will explore how Power BI can enhance your data literacy and provide you with the necessary tools to excel in data analysis.
Understanding Data Literacy
Data literacy is the ability to read, work with, analyze, and communicate data effectively. It involves interpreting data, understanding the context in which it was collected, and making informed decisions based on the data. In today's data-driven world, data literacy is a crucial skill that can help individuals and organizations succeed.
The Importance of Data Literacy
Data literacy is essential for professionals in all industries, from marketing and finance to healthcare and education. It allows individuals to make sense of complex data sets, identify trends and patterns, and communicate findings to stakeholders effectively. With the rise of big data and advanced data analysis techniques, data literacy has become a valuable skill in the workplace.
Enhancing Data Literacy with Power BI
Power BI is a user-friendly data visualization tool that allows users to create interactive dashboards, reports, and data visualizations. With Power BI, you can easily explore and analyze data, gain insights, and share your findings with others. By using Power BI, you can improve your data literacy skills and become more proficient in data analysis.
Data Visualization Tools
Power BI offers a wide range of data visualization tools that can help you present data in a clear and visually appealing way. From bar charts and line graphs to maps and scatter plots, Power BI allows you to choose the best visualization for your data. With Power BI, you can create informative and engaging dashboards that convey complex information effectively.
Data Interpretation
Power BI helps you interpret data by providing visual representations of your data sets. By using Power BI's interactive features, you can explore your data, identify trends, and uncover insights. Power BI makes it easy to filter, sort, and drill down into your data, allowing you to extract valuable information and make data-driven decisions.
Data Storytelling
Power BI enables you to tell a compelling story with your data. By combining different visualizations and data sets, you can create a narrative that explains the key findings and insights from your data analysis. With Power BI, you can communicate complex data in a simple and engaging way, making it easier for others to understand and act on your findings.
Data Literacy Training
To enhance your data literacy skills with Power BI, consider enrolling in a data literacy training program. These programs provide hands-on experience with Power BI, teaching you how to use the tool effectively and interpret data accurately. By participating in a data literacy workshop or course, you can improve your data analysis skills and apply them in real-world scenarios.
How to obtain Power BI certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Power BI is a powerful tool for enhancing data literacy and improving data analysis skills. By using Power BI's data visualization tools, data interpretation features, and data storytelling capabilities, you can become more proficient in working with data and making informed decisions. Consider investing in data literacy training and exploring the full potential of Power BI to excel in data analysis and interpretation.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to improve your data literacy skills and make better data-driven decisions? Look no further than Power BI, a powerful data visualization and business intelligence tool that can help you interpret and analyze data effectively. In this article, we will explore how Power BI can enhance your data literacy and provide you with the necessary tools to excel in data analysis.
Understanding Data Literacy
Data literacy is the ability to read, work with, analyze, and communicate data effectively. It involves interpreting data, understanding the context in which it was collected, and making informed decisions based on the data. In today's data-driven world, data literacy is a crucial skill that can help individuals and organizations succeed.
The Importance of Data Literacy
Data literacy is essential for professionals in all industries, from marketing and finance to healthcare and education. It allows individuals to make sense of complex data sets, identify trends and patterns, and communicate findings to stakeholders effectively. With the rise of big data and advanced data analysis techniques, data literacy has become a valuable skill in the workplace.
Enhancing Data Literacy with Power BI
Power BI is a user-friendly data visualization tool that allows users to create interactive dashboards, reports, and data visualizations. With Power BI, you can easily explore and analyze data, gain insights, and share your findings with others. By using Power BI, you can improve your data literacy skills and become more proficient in data analysis.
Data Visualization Tools
Power BI offers a wide range of data visualization tools that can help you present data in a clear and visually appealing way. From bar charts and line graphs to maps and scatter plots, Power BI allows you to choose the best visualization for your data. With Power BI, you can create informative and engaging dashboards that convey complex information effectively.
Data Interpretation
Power BI helps you interpret data by providing visual representations of your data sets. By using Power BI's interactive features, you can explore your data, identify trends, and uncover insights. Power BI makes it easy to filter, sort, and drill down into your data, allowing you to extract valuable information and make data-driven decisions.
Data Storytelling
Power BI enables you to tell a compelling story with your data. By combining different visualizations and data sets, you can create a narrative that explains the key findings and insights from your data analysis. With Power BI, you can communicate complex data in a simple and engaging way, making it easier for others to understand and act on your findings.
Data Literacy Training
To enhance your data literacy skills with Power BI, consider enrolling in a data literacy training program. These programs provide hands-on experience with Power BI, teaching you how to use the tool effectively and interpret data accurately. By participating in a data literacy workshop or course, you can improve your data analysis skills and apply them in real-world scenarios.
How to obtain Power BI certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Power BI is a powerful tool for enhancing data literacy and improving data analysis skills. By using Power BI's data visualization tools, data interpretation features, and data storytelling capabilities, you can become more proficient in working with data and making informed decisions. Consider investing in data literacy training and exploring the full potential of Power BI to excel in data analysis and interpretation.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Multithreading and Concurrency Patterns in Java
In today's fast-paced world, where speed and efficiency are crucial in software development, multithreading and concurrency patterns in Java play a significant role in ensuring optimal performance. Let's explore the key concepts, best practices, and design patterns that can help you harness the power of multithreading and concurrency in Java programming.
Introduction to Multithreading and Concurrency in Java
Multithreading in Java refers to the ability of a program to execute multiple threads simultaneously, allowing for parallel execution of tasks. Concurrency, on the other hand, refers to the ability of multiple threads to coordinate and synchronize their operations to ensure data consistency and avoid race conditions.
With the rise of multi-core processors, multithreading and concurrency have become essential skills for Java developers looking to take full advantage of the hardware capabilities and improve application performance.
Java Threads and Synchronization
In Java, threads are lightweight processes that can be created and managed by the JVM to execute tasks concurrently. Synchronization is a mechanism provided by Java to control the access of multiple threads to shared resources and avoid data inconsistencies. By using synchronized blocks, locks, and other synchronization mechanisms, developers can ensure thread safety and prevent race conditions in their applications.
Concurrency Patterns and Best Practices
Several concurrency patterns and best practices can help developers design robust and efficient multithreaded applications in Java. Some of the common patterns include thread pools, executors, asynchronous programming, task scheduling, and parallel programming models. By leveraging these patterns, developers can improve the scalability, responsiveness, and performance of their applications.
Dealing with Deadlocks and Race Conditions
Deadlocks and race conditions are common pitfalls in multithreaded programming that can lead to application crashes and data corruption. By understanding the root causes of deadlocks and race conditions, developers can employ techniques such as deadlock prevention, thread coordination, and synchronized data structures to mitigate these issues and ensure the reliability of their applications.
Best Practices for Multithreading in Java
-
Use thread pools and executors for efficient thread management.
-
Avoid excessive synchronization to prevent performance bottlenecks.
-
Employ blocking queues for thread communication and coordination.
-
Implement thread-safe data structures to ensure data consistency.
-
Monitor and tune your multithreaded application for optimal performance.
How to obtain JAVA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Multithreading and concurrency patterns in Java offer developers the tools and techniques to harness the power of parallelism and maximize the performance of their applications. By following best practices, design patterns, and synchronization mechanisms, Java developers can create robust, efficient, and scalable multithreaded applications that take full advantage of modern hardware capabilities.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced world, where speed and efficiency are crucial in software development, multithreading and concurrency patterns in Java play a significant role in ensuring optimal performance. Let's explore the key concepts, best practices, and design patterns that can help you harness the power of multithreading and concurrency in Java programming.
Introduction to Multithreading and Concurrency in Java
Multithreading in Java refers to the ability of a program to execute multiple threads simultaneously, allowing for parallel execution of tasks. Concurrency, on the other hand, refers to the ability of multiple threads to coordinate and synchronize their operations to ensure data consistency and avoid race conditions.
With the rise of multi-core processors, multithreading and concurrency have become essential skills for Java developers looking to take full advantage of the hardware capabilities and improve application performance.
Java Threads and Synchronization
In Java, threads are lightweight processes that can be created and managed by the JVM to execute tasks concurrently. Synchronization is a mechanism provided by Java to control the access of multiple threads to shared resources and avoid data inconsistencies. By using synchronized blocks, locks, and other synchronization mechanisms, developers can ensure thread safety and prevent race conditions in their applications.
Concurrency Patterns and Best Practices
Several concurrency patterns and best practices can help developers design robust and efficient multithreaded applications in Java. Some of the common patterns include thread pools, executors, asynchronous programming, task scheduling, and parallel programming models. By leveraging these patterns, developers can improve the scalability, responsiveness, and performance of their applications.
Dealing with Deadlocks and Race Conditions
Deadlocks and race conditions are common pitfalls in multithreaded programming that can lead to application crashes and data corruption. By understanding the root causes of deadlocks and race conditions, developers can employ techniques such as deadlock prevention, thread coordination, and synchronized data structures to mitigate these issues and ensure the reliability of their applications.
Best Practices for Multithreading in Java
-
Use thread pools and executors for efficient thread management.
-
Avoid excessive synchronization to prevent performance bottlenecks.
-
Employ blocking queues for thread communication and coordination.
-
Implement thread-safe data structures to ensure data consistency.
-
Monitor and tune your multithreaded application for optimal performance.
How to obtain JAVA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Multithreading and concurrency patterns in Java offer developers the tools and techniques to harness the power of parallelism and maximize the performance of their applications. By following best practices, design patterns, and synchronization mechanisms, Java developers can create robust, efficient, and scalable multithreaded applications that take full advantage of modern hardware capabilities.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Generative AI Models Capabilities and Limitations
In today’s tech-savvy world, artificial intelligence (AI) has become essential for both businesses and individuals. One of the most thrilling advances in AI is the development of generative AI models. These models have the incredible ability to create new, unique data by learning from existing data. This opens up exciting possibilities for machine learning and creative content creation.
What Are Generative AI Models?
Generative AI models are a type of AI designed to produce new data that resembles the original data they were trained on. They use deep learning algorithms, specifically neural networks, to analyze and learn from large amounts of data. This ability to generate new, synthetic data is what drives innovations in areas like automated content creation, language generation, and creative algorithms.
How Generative AI Fits into Machine Learning
Generative AI models rely on machine learning techniques that allow them to improve and refine their outputs over time. By training these models on extensive datasets, they learn to recognize patterns, generate realistic results, and adapt to new situations. This makes generative AI incredibly versatile, applicable in fields like design, computer vision, and natural language processing.
What Generative AI Can Do
Generative AI models are showing incredible potential in various creative fields. They can generate text, create images, and even compose music, proving their versatility across different domains. As AI technology progresses, generative AI is paving the way for innovative solutions in data enhancement, model development, and customized content creation.
The Latest in Generative AI
Generative AI technology is evolving quickly, bringing new tools and techniques for creative content. From generative art to video creation and self-learning models, AI is transforming how we interact with technology and produce content. As generative AI advances, we can look forward to groundbreaking applications in decision-making, pattern recognition, and predictive modeling.
Challenges of Generative AI
Despite their impressive capabilities, generative AI models have limitations and challenges. Ethical issues like bias, data privacy, and interpretability raise important questions about the transparency and fairness of these algorithms. As we rely more on AI for creative tasks, it’s crucial to address these concerns to ensure generative AI remains trustworthy and reliable.
Tackling Ethical Concerns
To address the ethical challenges of generative AI, developers and researchers must focus on fairness, transparency, and accountability. By integrating ethical considerations into AI design and development, we can build more responsible technologies. Continued efforts to improve data privacy, interpretability, and fairness will help establish trust in generative AI.
Looking Ahead: The Future of Generative AI
As generative AI continues to advance, we can expect a wide range of new applications and innovations. From interactive storytelling to chatbots and virtual assistants, the possibilities are endless. By leveraging generative technology, we can unlock new creative opportunities, drive innovation, and enhance our interactions with AI.
How to obtain AI certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Generative AI models combine creativity, innovation, and technical expertise to shape the future of AI technology. By exploring the capabilities of generative AI while addressing its limitations and ethical concerns, we can create a more responsible and trustworthy AI ecosystem. As we continue to push the boundaries of generative AI, we’ll see exciting advancements that will revolutionize how we create, communicate, and interact with technology.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today’s tech-savvy world, artificial intelligence (AI) has become essential for both businesses and individuals. One of the most thrilling advances in AI is the development of generative AI models. These models have the incredible ability to create new, unique data by learning from existing data. This opens up exciting possibilities for machine learning and creative content creation.
What Are Generative AI Models?
Generative AI models are a type of AI designed to produce new data that resembles the original data they were trained on. They use deep learning algorithms, specifically neural networks, to analyze and learn from large amounts of data. This ability to generate new, synthetic data is what drives innovations in areas like automated content creation, language generation, and creative algorithms.
How Generative AI Fits into Machine Learning
Generative AI models rely on machine learning techniques that allow them to improve and refine their outputs over time. By training these models on extensive datasets, they learn to recognize patterns, generate realistic results, and adapt to new situations. This makes generative AI incredibly versatile, applicable in fields like design, computer vision, and natural language processing.
What Generative AI Can Do
Generative AI models are showing incredible potential in various creative fields. They can generate text, create images, and even compose music, proving their versatility across different domains. As AI technology progresses, generative AI is paving the way for innovative solutions in data enhancement, model development, and customized content creation.
The Latest in Generative AI
Generative AI technology is evolving quickly, bringing new tools and techniques for creative content. From generative art to video creation and self-learning models, AI is transforming how we interact with technology and produce content. As generative AI advances, we can look forward to groundbreaking applications in decision-making, pattern recognition, and predictive modeling.
Challenges of Generative AI
Despite their impressive capabilities, generative AI models have limitations and challenges. Ethical issues like bias, data privacy, and interpretability raise important questions about the transparency and fairness of these algorithms. As we rely more on AI for creative tasks, it’s crucial to address these concerns to ensure generative AI remains trustworthy and reliable.
Tackling Ethical Concerns
To address the ethical challenges of generative AI, developers and researchers must focus on fairness, transparency, and accountability. By integrating ethical considerations into AI design and development, we can build more responsible technologies. Continued efforts to improve data privacy, interpretability, and fairness will help establish trust in generative AI.
Looking Ahead: The Future of Generative AI
As generative AI continues to advance, we can expect a wide range of new applications and innovations. From interactive storytelling to chatbots and virtual assistants, the possibilities are endless. By leveraging generative technology, we can unlock new creative opportunities, drive innovation, and enhance our interactions with AI.
How to obtain AI certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Generative AI models combine creativity, innovation, and technical expertise to shape the future of AI technology. By exploring the capabilities of generative AI while addressing its limitations and ethical concerns, we can create a more responsible and trustworthy AI ecosystem. As we continue to push the boundaries of generative AI, we’ll see exciting advancements that will revolutionize how we create, communicate, and interact with technology.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Sustainable Agile Balancing Speed with Long Term Quality
In software development, Sustainable Agile is key. It's a fast-paced world. What is Sustainable Agile? How can organizations balance speed and quality in their agile work? They want both, but agile focuses on speed. It covers the principles of Sustainable Agile. It also covers its benefits and offers tips for use.
What is Sustainable Agile?
Sustainable Agile is an approach. It aims to balance speed and quality in coding. Quality should last long. It stresses on-time delivery of methods that add value to the business. Sustainable Agile helps teams unite and adapt. It keeps high product standards and adapts to market shifts.
Key Principles of Sustainable Agile
-
Sustainable Agile relies on iterative development cycles. Teams must break work into smaller tasks. They must be manageable. It allows for quick feedback and a fast response to changes.
-
In Sustainable Agile, cross-functional teams must team up as one. They must deliver value. Teams unite diverse skills to reach common goals.
-
Customer Collaboration: Sustainable Agile values customer collaboration. Involving stakeholders in development helps teams find out what users need. They can then deliver products that users expect or better.
-
Team Empowerment: Sustainable Agile promotes team empowerment. It gives individuals the power to make decisions and lead the project. It fosters a sense of ownership and accountability in the team.
Benefits of Sustainable Agility.
-
Touchable Agile forms teams that adapt to change. They merge efforts to craft high-quality products.
-
Technical Excellence: Sustainable Agile values technical excellence. It seeks to improve and ensure quality.
-
Sustainable Agile helps teams be nimble. It uses an adaptive approach. They can respond to market changes. This keeps products relevant and competitive.
Practical Tips for Implementing Sustainable Agile
-
Value delivery: Rank value delivery by its key features. Deliver it in small increments.
-
User stories take requirements and break them into small, easy bits. They ensure that they meet the end user's needs.
-
Stakeholder Engagement: Involve stakeholders in the process. Use regular feedback sessions and collaboration.
How to obtain Agile and Scrum certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Sustainable Agile is a balanced way to build software. It lets organizations be quick and still high quality.
Teams follow three key principles:
1. iterative development,
2. cross-functional teams,
3. customer collaboration.
They use efficient workflows to deliver value.
Sustainable Agile practices are good for business. They also ensure that projects succeed in the long run.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In software development, Sustainable Agile is key. It's a fast-paced world. What is Sustainable Agile? How can organizations balance speed and quality in their agile work? They want both, but agile focuses on speed. It covers the principles of Sustainable Agile. It also covers its benefits and offers tips for use.
What is Sustainable Agile?
Sustainable Agile is an approach. It aims to balance speed and quality in coding. Quality should last long. It stresses on-time delivery of methods that add value to the business. Sustainable Agile helps teams unite and adapt. It keeps high product standards and adapts to market shifts.
Key Principles of Sustainable Agile
-
Sustainable Agile relies on iterative development cycles. Teams must break work into smaller tasks. They must be manageable. It allows for quick feedback and a fast response to changes.
-
In Sustainable Agile, cross-functional teams must team up as one. They must deliver value. Teams unite diverse skills to reach common goals.
-
Customer Collaboration: Sustainable Agile values customer collaboration. Involving stakeholders in development helps teams find out what users need. They can then deliver products that users expect or better.
-
Team Empowerment: Sustainable Agile promotes team empowerment. It gives individuals the power to make decisions and lead the project. It fosters a sense of ownership and accountability in the team.
Benefits of Sustainable Agility.
-
Touchable Agile forms teams that adapt to change. They merge efforts to craft high-quality products.
-
Technical Excellence: Sustainable Agile values technical excellence. It seeks to improve and ensure quality.
-
Sustainable Agile helps teams be nimble. It uses an adaptive approach. They can respond to market changes. This keeps products relevant and competitive.
Practical Tips for Implementing Sustainable Agile
-
Value delivery: Rank value delivery by its key features. Deliver it in small increments.
-
User stories take requirements and break them into small, easy bits. They ensure that they meet the end user's needs.
-
Stakeholder Engagement: Involve stakeholders in the process. Use regular feedback sessions and collaboration.
How to obtain Agile and Scrum certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Sustainable Agile is a balanced way to build software. It lets organizations be quick and still high quality.
Teams follow three key principles:
1. iterative development,
2. cross-functional teams,
3. customer collaboration.
They use efficient workflows to deliver value.
Sustainable Agile practices are good for business. They also ensure that projects succeed in the long run.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Top Security Considerations for XenApp Deployments
As cyber threats become more advanced, securing your XenApp deployment is vital. It protects your organization's data and apps. This guide will cover key security strategies. They are vital for a safe, resilient XenApp environment.
Why Security Matters in XenApp Deployments
With the rise of cyber-attacks, it's crucial to secure your XenApp deployment. Good security measures keep your apps and data safe, intact, and available. By staying ahead of threats, you can protect your digital assets. This will shield your organization from costly security incidents.
Key Security Strategies for XenApp
- Robust Access Control: Ensure that only authorized personnel can access your XenApp environment. Use multi-factor authentication (MFA) and role-based access controls (RBAC). They will manage user permissions and reduce the risk of unauthorized access.
- Use strong encryption protocols to protect sensitive data. It must be secure in transit and at rest. Use SSL/TLS encryption for secure communication between clients and XenApp servers. It will keep your data private and secure.
- Timely Patch Management: Update your XenApp servers and apps. Use the latest security patches. Regular updates help address known vulnerabilities and prevent exploitation. Establish a robust patch management process to stay current with security updates.
- Network Segmentation: Create separate network segments for your XenApp deployment. This will isolate it from other critical systems. It lowers the risk of widespread damage from a breach. It also helps contain potential threats. Use firewalls and intrusion detection systems (IDS) to check and control network traffic.
- Secure Configuration Practices: Follow best practices for configuring your XenApp servers and applications. Disable unnecessary services and ports to cut your attack surface. Check your setup often to match industry security rules exactly.
How to obtain XenApp certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, prioritizing these security strategies in your XenApp deployment will help. They will protect your organization's digital assets from cyber threats. To secure your XenApp environment, focus on these areas:
- access control
- data encryption
- patch management
- network segmentation
- secure configurations
This will create a strong security posture. Stay vigilant and proactive to keep your systems safe and secure.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
As cyber threats become more advanced, securing your XenApp deployment is vital. It protects your organization's data and apps. This guide will cover key security strategies. They are vital for a safe, resilient XenApp environment.
Why Security Matters in XenApp Deployments
With the rise of cyber-attacks, it's crucial to secure your XenApp deployment. Good security measures keep your apps and data safe, intact, and available. By staying ahead of threats, you can protect your digital assets. This will shield your organization from costly security incidents.
Key Security Strategies for XenApp
- Robust Access Control: Ensure that only authorized personnel can access your XenApp environment. Use multi-factor authentication (MFA) and role-based access controls (RBAC). They will manage user permissions and reduce the risk of unauthorized access.
- Use strong encryption protocols to protect sensitive data. It must be secure in transit and at rest. Use SSL/TLS encryption for secure communication between clients and XenApp servers. It will keep your data private and secure.
- Timely Patch Management: Update your XenApp servers and apps. Use the latest security patches. Regular updates help address known vulnerabilities and prevent exploitation. Establish a robust patch management process to stay current with security updates.
- Network Segmentation: Create separate network segments for your XenApp deployment. This will isolate it from other critical systems. It lowers the risk of widespread damage from a breach. It also helps contain potential threats. Use firewalls and intrusion detection systems (IDS) to check and control network traffic.
- Secure Configuration Practices: Follow best practices for configuring your XenApp servers and applications. Disable unnecessary services and ports to cut your attack surface. Check your setup often to match industry security rules exactly.
How to obtain XenApp certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, prioritizing these security strategies in your XenApp deployment will help. They will protect your organization's digital assets from cyber threats. To secure your XenApp environment, focus on these areas:
- access control
- data encryption
- patch management
- network segmentation
- secure configurations
This will create a strong security posture. Stay vigilant and proactive to keep your systems safe and secure.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Rise of GitOps How Its Revolutionizing DevOps in 2024
In tech's fast-changing world, GitOps and DevOps are merging. This is changing how we develop and deploy software. GitOps is a new, cutting-edge approach. It uses version control systems, like Git. It automates integration, simplifies deployments, and manages infrastructure.
Understanding GitOps: A New Paradigm in Software Management
GitOps redefines infrastructure management. It uses Git repos as the source for all config and deployment settings. This method tracks every change. It boosts collaboration. It ensures deployments are consistent and transparent. Git workflows help developers manage infrastructure changes and do code reviews. They use pull requests for this. They can also use CI/CD pipelines to automate deployments. This will make their work more efficient.
Transforming DevOps through GitOps
GitOps in the DevOps framework has begun a new era in software development. This synergy lets teams deploy faster, work better, and collaborate more. Treating infrastructure as code and automating deployment can help. It can cut manual errors, simplify rollbacks, and ensure uniformity across development stages.
Enhancing Container Management with Kubernetes
A key feature of GitOps is its perfect fit with Kubernetes and other container tools. Storing deployment manifests in Git repos lets teams use Kubernetes. It automates scaling, load balancing, and fault tolerance. This integration lets developers focus on coding and adding value. It spares them the hassle of managing infrastructure.
Empowering Agile Teams with GitOps
GitOps gives agile teams a fast workflow. It supports quick iteration, feedback, and collaboration. With Git as the central hub for code and configs, teams can manage version control and track changes. They can also roll back if needed. It guarantees timely delivery of superior software with consistent results. It also maintains a complete audit trail.
Driving Efficiency and Innovation
In a competitive market, businesses want to be more efficient and reduce time to market. GitOps drives innovation. It automates deployments, manages infrastructure, and boosts teamwork between dev and ops teams. By embracing GitOps, organizations can stay ahead. They provide immediate answers to customer feedback, fine-tuning software delivery.
How to obtain DevOps certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, GitOps is set to transform DevOps as we enter 2024. It promises to make software development more agile, efficient, and reliable. It focuses on automation, infrastructure as code, and continuous delivery. GitOps, Kubernetes, and other new tools can help teams. They can build resilient, scalable, cloud-native apps. These apps will meet the demands of a fast-changing market. Adopting GitOps isn’t a trend—it’s a strategic move for organizations aiming to excel in the digital era.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In tech's fast-changing world, GitOps and DevOps are merging. This is changing how we develop and deploy software. GitOps is a new, cutting-edge approach. It uses version control systems, like Git. It automates integration, simplifies deployments, and manages infrastructure.
Understanding GitOps: A New Paradigm in Software Management
GitOps redefines infrastructure management. It uses Git repos as the source for all config and deployment settings. This method tracks every change. It boosts collaboration. It ensures deployments are consistent and transparent. Git workflows help developers manage infrastructure changes and do code reviews. They use pull requests for this. They can also use CI/CD pipelines to automate deployments. This will make their work more efficient.
Transforming DevOps through GitOps
GitOps in the DevOps framework has begun a new era in software development. This synergy lets teams deploy faster, work better, and collaborate more. Treating infrastructure as code and automating deployment can help. It can cut manual errors, simplify rollbacks, and ensure uniformity across development stages.
Enhancing Container Management with Kubernetes
A key feature of GitOps is its perfect fit with Kubernetes and other container tools. Storing deployment manifests in Git repos lets teams use Kubernetes. It automates scaling, load balancing, and fault tolerance. This integration lets developers focus on coding and adding value. It spares them the hassle of managing infrastructure.
Empowering Agile Teams with GitOps
GitOps gives agile teams a fast workflow. It supports quick iteration, feedback, and collaboration. With Git as the central hub for code and configs, teams can manage version control and track changes. They can also roll back if needed. It guarantees timely delivery of superior software with consistent results. It also maintains a complete audit trail.
Driving Efficiency and Innovation
In a competitive market, businesses want to be more efficient and reduce time to market. GitOps drives innovation. It automates deployments, manages infrastructure, and boosts teamwork between dev and ops teams. By embracing GitOps, organizations can stay ahead. They provide immediate answers to customer feedback, fine-tuning software delivery.
How to obtain DevOps certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In conclusion, GitOps is set to transform DevOps as we enter 2024. It promises to make software development more agile, efficient, and reliable. It focuses on automation, infrastructure as code, and continuous delivery. GitOps, Kubernetes, and other new tools can help teams. They can build resilient, scalable, cloud-native apps. These apps will meet the demands of a fast-changing market. Adopting GitOps isn’t a trend—it’s a strategic move for organizations aiming to excel in the digital era.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Role of Microsoft GitHub in Modern Software Development
Today, software development is vital to every industry. It's due to the fast pace of the world. As the demand for reliable software grows, developers want better tools. They seek to improve their workflow. Microsoft's GitHub is now a top site for sharing code and collaborating on software. Let's explore GitHub's key role in shaping the future of software development. It's owned by Microsoft.
Collaboration and Open Source: GitHub is for developers to collaborate and share code. They can also contribute to open-source projects. This open-source approach fosters creativity, knowledge sharing, and community-driven innovation. Developers fork projects, add changes, and discuss via issues and requests.
Version Control and Programming: GitHub has a robust version control system. It's a key feature. Developers can track changes, manage code versions, and collaborate with their team. It ensures a smooth, organized development process. It lets developers test new features, revert changes, and keep code quality.
Version control is vital in software development. It tracks changes and manages code. It lets developers collaborate and keeps a history of code changes. Version control systems like Git help teams. They can revise code, resolve conflicts, and document updates. They must make each update reversible. This boosts productivity and cuts errors.
Repository and Code Sharing: GitHub is a central place to store, manage, and share code. Developers can create repositories for their projects. They can organize code files and track changes over time. Work with team members. Review code. Ensure consistent software versions.
In today's software development world, teams must share code and repositories. This is key to improving workflows and productivity. GitHub and GitLab let developers share code, manage versions, and collaborate. This ensures that every team member aligns and stays up to date with the latest changes.
Developer Community and Agile Workflow: GitHub has a vibrant developer community. Developers can connect, learn, and share knowledge there. This community-driven approach promotes agility, continuous improvement, and rapid iteration. Developers can use agile methods, like Scrum and Kanban. They ease rapid software deployment with exceptional quality.
The developer community is key to agile workflows. It fosters collaboration and feedback, which speeds up development and innovation. Agile methods help developers adapt to changing requirements. This leads to better, more responsive software.
Software engineers and innovation: GitHub lets engineers innovate, experiment, and push tech's limits. GitHub fuels creativity. It does this by enabling idea-sharing, project collaboration, and learning from one another. Software engineers can explore new technologies, build innovative solutions, and drive industry advancements. GitHub has many tools to help developers with their work. GitHub has tools to streamline software development. They cover code review, project management, and continuous integration and deployment. Developers can leverage these tools to enhance productivity, efficiency, and collaboration.
In today's fast-paced digital world, technology is vital. It drives innovation and efficiency in many industries. From advanced data analytics platforms to productivity software, these tools are evolving. They aim to meet the demands of modern businesses and improve efficiency.
Software Platform and Coding: GitHub is a top software platform. It enables developers to integrate writing, testing, and deployment into one process. GitHub helps developers manage code, track changes, and collaborate. They can rely on it for small projects or large applications. This streamlined coding experience enhances developer productivity and code quality.
How to obtain Microsoft certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Microsoft's GitHub is vital to modern software development. It offers a collaborative, efficient, and innovative platform for developers. GitHub has tools to help developers with their projects. It supports version control, code sharing, collaboration, and community building. As software development evolves, GitHub leads the way. It drives innovation and excellence in the field.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Today, software development is vital to every industry. It's due to the fast pace of the world. As the demand for reliable software grows, developers want better tools. They seek to improve their workflow. Microsoft's GitHub is now a top site for sharing code and collaborating on software. Let's explore GitHub's key role in shaping the future of software development. It's owned by Microsoft.
Collaboration and Open Source: GitHub is for developers to collaborate and share code. They can also contribute to open-source projects. This open-source approach fosters creativity, knowledge sharing, and community-driven innovation. Developers fork projects, add changes, and discuss via issues and requests.
Version Control and Programming: GitHub has a robust version control system. It's a key feature. Developers can track changes, manage code versions, and collaborate with their team. It ensures a smooth, organized development process. It lets developers test new features, revert changes, and keep code quality.
Version control is vital in software development. It tracks changes and manages code. It lets developers collaborate and keeps a history of code changes. Version control systems like Git help teams. They can revise code, resolve conflicts, and document updates. They must make each update reversible. This boosts productivity and cuts errors.
Repository and Code Sharing: GitHub is a central place to store, manage, and share code. Developers can create repositories for their projects. They can organize code files and track changes over time. Work with team members. Review code. Ensure consistent software versions.
In today's software development world, teams must share code and repositories. This is key to improving workflows and productivity. GitHub and GitLab let developers share code, manage versions, and collaborate. This ensures that every team member aligns and stays up to date with the latest changes.
Developer Community and Agile Workflow: GitHub has a vibrant developer community. Developers can connect, learn, and share knowledge there. This community-driven approach promotes agility, continuous improvement, and rapid iteration. Developers can use agile methods, like Scrum and Kanban. They ease rapid software deployment with exceptional quality.
The developer community is key to agile workflows. It fosters collaboration and feedback, which speeds up development and innovation. Agile methods help developers adapt to changing requirements. This leads to better, more responsive software.
Software engineers and innovation: GitHub lets engineers innovate, experiment, and push tech's limits. GitHub fuels creativity. It does this by enabling idea-sharing, project collaboration, and learning from one another. Software engineers can explore new technologies, build innovative solutions, and drive industry advancements. GitHub has many tools to help developers with their work. GitHub has tools to streamline software development. They cover code review, project management, and continuous integration and deployment. Developers can leverage these tools to enhance productivity, efficiency, and collaboration.
In today's fast-paced digital world, technology is vital. It drives innovation and efficiency in many industries. From advanced data analytics platforms to productivity software, these tools are evolving. They aim to meet the demands of modern businesses and improve efficiency.
Software Platform and Coding: GitHub is a top software platform. It enables developers to integrate writing, testing, and deployment into one process. GitHub helps developers manage code, track changes, and collaborate. They can rely on it for small projects or large applications. This streamlined coding experience enhances developer productivity and code quality.
How to obtain Microsoft certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Microsoft's GitHub is vital to modern software development. It offers a collaborative, efficient, and innovative platform for developers. GitHub has tools to help developers with their projects. It supports version control, code sharing, collaboration, and community building. As software development evolves, GitHub leads the way. It drives innovation and excellence in the field.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Bitcoin vs Ethereum
When it comes to the world of cryptocurrency, two names stand out among the rest - Bitcoin and Ethereum. Both digital currencies are now very popular. They are key players in the fast-changing blockchain technology world. This article will explore the differences and similarities between Bitcoin and Ethereum. We will examine their features, uses, and investment potential.
What is Bitcoin?
Bitcoin is called the original cryptocurrency. It was created in 2009 by an unknown person or group using the name Satoshi Nakamoto. It runs on a decentralized network called blockchain. It allows peer-to-peer transactions without a central authority.
How does Bitcoin work?
Miners verify Bitcoin transactions. They use powerful computers to solve complex puzzles. Once a transaction is verified, it is added to a block on the blockchain, forming a permanent record that cannot be altered. This process, known as proof of work, ensures the security and integrity of the Bitcoin network.
What is Ethereum?
Ethereum is a decentralized platform. It lets developers build and deploy smart contracts and DApps. It was proposed by Vitalik Buterin in late 2013 and development was crowdfunded in 2014. The Ethereum network went live on July 30, 2015.
How does Ethereum work?
Ethereum operates on its own blockchain, which is powered by its native cryptocurrency called Ether (ETH). The network uses a consensus mechanism called proof of stake. Validators are chosen to create new blocks based on how much Ether they hold. This allows for faster transaction processing and lower energy consumption compared to Bitcoin's proof of work model.
Blockchain: Ethereum uses a blockchain. It is a distributed ledger that records all transactions and smart contract executions. Each block in the chain contains a record of transactions and is cryptographically linked to the previous block.
Smart Contracts: They are self-executing contracts. The agreement's terms are in code. These contracts automatically enforce and execute the terms of the agreement when predefined conditions are met. They run on the Ethereum Virtual Machine (EVM), which processes and executes the contract code.
Ethereum Virtual Machine (EVM): The EVM is a decentralized computing environment that allows smart contracts to be executed across all nodes in the Ethereum network. It ensures that smart contracts behave consistently and predictably, regardless of the node that executes them.
Ether (ETH) is the native cryptocurrency of the Ethereum network. It has two main uses: as a digital currency and as "gas." "Gas" pays for transaction fees and computing power on the network. Gas measures the work needed to run operations, like transactions and smart contracts.
Consensus Mechanism: Ethereum initially used Proof of Work (PoW) to validate transactions and secure the network. However, it has been transitioning to Proof of Stake (PoS) with Ethereum 2.0, where validators are chosen to create new blocks and confirm transactions based on the amount of ETH they "stake" as collateral.
Decentralization: Ethereum’s decentralized nature means that no single entity controls the network. Instead, a distributed network of nodes maintains it. They validate transactions and smart contract executions.
Technology Comparison
While both Bitcoin and Ethereum are based on blockchain technology, they serve different purposes. Bitcoin is a digital currency for peer-to-peer transactions and a store of value. Ethereum is a platform for building decentralized apps and running smart contracts.
Network
The Bitcoin network aims to process transactions and secure its blockchain. In contrast, the Ethereum network is more versatile and customizable. This allows developers to create a wide range of applications and tokens on the Ethereum platform.
Scalability
One of the key differences between Bitcoin and Ethereum is their approach to scalability. Bitcoin's block size limit and proof of work have caused slower transactions and higher fees during busy times. In contrast, Ethereum is working to implement sharding and Ethereum 2.0. These will improve scalability and reduce network congestion.
Decentralized Finance
Ethereum is now a hub for decentralized finance (DeFi) apps. They want to disrupt traditional finance. They will offer lending, borrowing, and trading without intermediaries. Bitcoin, on the other hand, is primarily used as a digital store of value and has a limited range of DeFi applications.
Investment Opportunity
Bitcoin and Ethereum are popular for diversifying portfolios. They offer growth potential in the crypto market. Bitcoin is seen as a safer investment, a digital gold. But, Ethereum has unique opportunities in decentralized finance.
How to obtain Blockchain certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Bitcoin and Ethereum are key players in crypto. Each has its strengths and weaknesses. If you want to invest in digital assets, or build apps, Bitcoin and Ethereum provide unique opportunities for growth. They are good for exploring blockchain too. You must know the differences between these two digital currencies. It will help you make informed investment decisions based on your goals and risk tolerance.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
When it comes to the world of cryptocurrency, two names stand out among the rest - Bitcoin and Ethereum. Both digital currencies are now very popular. They are key players in the fast-changing blockchain technology world. This article will explore the differences and similarities between Bitcoin and Ethereum. We will examine their features, uses, and investment potential.
What is Bitcoin?
Bitcoin is called the original cryptocurrency. It was created in 2009 by an unknown person or group using the name Satoshi Nakamoto. It runs on a decentralized network called blockchain. It allows peer-to-peer transactions without a central authority.
How does Bitcoin work?
Miners verify Bitcoin transactions. They use powerful computers to solve complex puzzles. Once a transaction is verified, it is added to a block on the blockchain, forming a permanent record that cannot be altered. This process, known as proof of work, ensures the security and integrity of the Bitcoin network.
What is Ethereum?
Ethereum is a decentralized platform. It lets developers build and deploy smart contracts and DApps. It was proposed by Vitalik Buterin in late 2013 and development was crowdfunded in 2014. The Ethereum network went live on July 30, 2015.
How does Ethereum work?
Ethereum operates on its own blockchain, which is powered by its native cryptocurrency called Ether (ETH). The network uses a consensus mechanism called proof of stake. Validators are chosen to create new blocks based on how much Ether they hold. This allows for faster transaction processing and lower energy consumption compared to Bitcoin's proof of work model.
Blockchain: Ethereum uses a blockchain. It is a distributed ledger that records all transactions and smart contract executions. Each block in the chain contains a record of transactions and is cryptographically linked to the previous block.
Smart Contracts: They are self-executing contracts. The agreement's terms are in code. These contracts automatically enforce and execute the terms of the agreement when predefined conditions are met. They run on the Ethereum Virtual Machine (EVM), which processes and executes the contract code.
Ethereum Virtual Machine (EVM): The EVM is a decentralized computing environment that allows smart contracts to be executed across all nodes in the Ethereum network. It ensures that smart contracts behave consistently and predictably, regardless of the node that executes them.
Ether (ETH) is the native cryptocurrency of the Ethereum network. It has two main uses: as a digital currency and as "gas." "Gas" pays for transaction fees and computing power on the network. Gas measures the work needed to run operations, like transactions and smart contracts.
Consensus Mechanism: Ethereum initially used Proof of Work (PoW) to validate transactions and secure the network. However, it has been transitioning to Proof of Stake (PoS) with Ethereum 2.0, where validators are chosen to create new blocks and confirm transactions based on the amount of ETH they "stake" as collateral.
Decentralization: Ethereum’s decentralized nature means that no single entity controls the network. Instead, a distributed network of nodes maintains it. They validate transactions and smart contract executions.
Technology Comparison
While both Bitcoin and Ethereum are based on blockchain technology, they serve different purposes. Bitcoin is a digital currency for peer-to-peer transactions and a store of value. Ethereum is a platform for building decentralized apps and running smart contracts.
Network
The Bitcoin network aims to process transactions and secure its blockchain. In contrast, the Ethereum network is more versatile and customizable. This allows developers to create a wide range of applications and tokens on the Ethereum platform.
Scalability
One of the key differences between Bitcoin and Ethereum is their approach to scalability. Bitcoin's block size limit and proof of work have caused slower transactions and higher fees during busy times. In contrast, Ethereum is working to implement sharding and Ethereum 2.0. These will improve scalability and reduce network congestion.
Decentralized Finance
Ethereum is now a hub for decentralized finance (DeFi) apps. They want to disrupt traditional finance. They will offer lending, borrowing, and trading without intermediaries. Bitcoin, on the other hand, is primarily used as a digital store of value and has a limited range of DeFi applications.
Investment Opportunity
Bitcoin and Ethereum are popular for diversifying portfolios. They offer growth potential in the crypto market. Bitcoin is seen as a safer investment, a digital gold. But, Ethereum has unique opportunities in decentralized finance.
How to obtain Blockchain certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Bitcoin and Ethereum are key players in crypto. Each has its strengths and weaknesses. If you want to invest in digital assets, or build apps, Bitcoin and Ethereum provide unique opportunities for growth. They are good for exploring blockchain too. You must know the differences between these two digital currencies. It will help you make informed investment decisions based on your goals and risk tolerance.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Understanding Java Security Best Practices for Secure Coding
As cyber threats grow more advanced, software security is vital. Java is a top target for attackers. It's one of the most used programming languages. They seek to exploit its vulnerabilities. Developers must know and apply Java security best practices. It's key to building robust, secure applications. This blog will cover key strategies for secure coding in Java. It will detail practices to protect your code from common threats and vulnerabilities. We will explore how to secure your apps and maintain user trust. This includes managing sensitive data and handling authentication and authorization.
Table Of Contents
- Secure Coding Fundamentals in Java
- Handling Sensitive Data Safely
- Implementing Robust Authentication and Authorization
- Defending Against Common Java Vulnerabilities
- Utilizing Java Security Libraries and Tools
- Conclusion
Secure Coding Fundamentals in Java:
Secure coding in Java starts with basic principles. They aim to reduce vulnerabilities. First, install strong input validation. It will ensure that we expect and keep incoming data safe. This will prevent common issues like SQL injection and XSS. Error handling is vital. Avoid exposing sensitive info in error messages. Use straightforward language in your messages. Also, practice secure coding. Follow the principle of least privilege. Limit your code's permissions to only what is necessary for its function. Library and framework updates cut down on security risks. They patch known vulnerabilities.
Handle sensitive data with the utmost care to prevent unauthorized access:
Use strong encryption to protect sensitive data in Java apps. It must be safe both at rest and in transit. Use encryption libraries, like Java's Cryptography Extension (JCE), to encrypt data. Do this before storing it or sending it over networks. Protect cryptographic keys with specialized management systems that control access. Also, do not hard-code sensitive data in source code or config files. Store sensitive info, like API keys and passwords, in secure vaults or env vars.
Implementing Robust Authentication and Authorization:
Effective authentication and authorization mechanisms are vital for securing Java applications. Use strong password policies. Use intricate passwords and hash them with robust algorithms such as bcrypt. Enhance security by adding multi-factor authentication (MFA). It adds protection beyond passwords. For authorization, use role-based access control (RBAC). It limits users to resources needed for their roles. Also, consider using best practices for session management. They prevent session hijacking and ensure proper logout.
Defending Against Common Java Vulnerabilities:
Java applications are prone to security flaws. These include deserialization attacks, insecure object references, and improper API usage. To reduce these risks, confirm and sanitize all input before processing. Also, do not deserialize untrusted data. Protect object references with robust security measures. This will prevent unauthorized access and exposure of sensitive objects. Refresh code with new insights and improvements often. Follow best practices and secure coding guidelines to prevent vulnerabilities. Use static code analysis tools to find security issues early in development.
Utilizing Java Security Libraries and Tools:
Java offers a range of security libraries and tools to enhance application security. Libraries like Apache Shiro and Spring Security offer strong solutions. They excel at authentication, authorization, and secure session management. For code analysis, tools like SonarQube and FindBugs can help. They can find potential security flaws in your codebase. Dependency management tools like OWASP Dependency-Check can identify vulnerabilities in third-party libraries. Using these tools in your workflow can automate security checks. It will improve the security of your Java apps.
How to obtain Java certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion:
In Conclusion, Securing Java apps requires a comprehensive approach. It must include secure coding, effective data management, and strong authentication and authorization. By using these best practices, developers can reduce security risks. They can build more resilient apps. Using security libraries and tools will help you find and fix vulnerabilities. This secures your apps amid shifting threats. Prioritizing security in development protects your apps. It also builds trust with users and stakeholders.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
As cyber threats grow more advanced, software security is vital. Java is a top target for attackers. It's one of the most used programming languages. They seek to exploit its vulnerabilities. Developers must know and apply Java security best practices. It's key to building robust, secure applications. This blog will cover key strategies for secure coding in Java. It will detail practices to protect your code from common threats and vulnerabilities. We will explore how to secure your apps and maintain user trust. This includes managing sensitive data and handling authentication and authorization.
Table Of Contents
- Secure Coding Fundamentals in Java
- Handling Sensitive Data Safely
- Implementing Robust Authentication and Authorization
- Defending Against Common Java Vulnerabilities
- Utilizing Java Security Libraries and Tools
- Conclusion
Secure Coding Fundamentals in Java:
Secure coding in Java starts with basic principles. They aim to reduce vulnerabilities. First, install strong input validation. It will ensure that we expect and keep incoming data safe. This will prevent common issues like SQL injection and XSS. Error handling is vital. Avoid exposing sensitive info in error messages. Use straightforward language in your messages. Also, practice secure coding. Follow the principle of least privilege. Limit your code's permissions to only what is necessary for its function. Library and framework updates cut down on security risks. They patch known vulnerabilities.
Handle sensitive data with the utmost care to prevent unauthorized access:
Use strong encryption to protect sensitive data in Java apps. It must be safe both at rest and in transit. Use encryption libraries, like Java's Cryptography Extension (JCE), to encrypt data. Do this before storing it or sending it over networks. Protect cryptographic keys with specialized management systems that control access. Also, do not hard-code sensitive data in source code or config files. Store sensitive info, like API keys and passwords, in secure vaults or env vars.
Implementing Robust Authentication and Authorization:
Effective authentication and authorization mechanisms are vital for securing Java applications. Use strong password policies. Use intricate passwords and hash them with robust algorithms such as bcrypt. Enhance security by adding multi-factor authentication (MFA). It adds protection beyond passwords. For authorization, use role-based access control (RBAC). It limits users to resources needed for their roles. Also, consider using best practices for session management. They prevent session hijacking and ensure proper logout.
Defending Against Common Java Vulnerabilities:
Java applications are prone to security flaws. These include deserialization attacks, insecure object references, and improper API usage. To reduce these risks, confirm and sanitize all input before processing. Also, do not deserialize untrusted data. Protect object references with robust security measures. This will prevent unauthorized access and exposure of sensitive objects. Refresh code with new insights and improvements often. Follow best practices and secure coding guidelines to prevent vulnerabilities. Use static code analysis tools to find security issues early in development.
Utilizing Java Security Libraries and Tools:
Java offers a range of security libraries and tools to enhance application security. Libraries like Apache Shiro and Spring Security offer strong solutions. They excel at authentication, authorization, and secure session management. For code analysis, tools like SonarQube and FindBugs can help. They can find potential security flaws in your codebase. Dependency management tools like OWASP Dependency-Check can identify vulnerabilities in third-party libraries. Using these tools in your workflow can automate security checks. It will improve the security of your Java apps.
How to obtain Java certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion:
In Conclusion, Securing Java apps requires a comprehensive approach. It must include secure coding, effective data management, and strong authentication and authorization. By using these best practices, developers can reduce security risks. They can build more resilient apps. Using security libraries and tools will help you find and fix vulnerabilities. This secures your apps amid shifting threats. Prioritizing security in development protects your apps. It also builds trust with users and stakeholders.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Service Level Agreements SLAs in IT Service Management
In IT Service Management (ITSM), SLAs are key. They define the expectations and responsibilities between service providers and customers. Let's explore SLAs. They are vital for efficient IT service delivery.
What are Service Level Agreements?
Service Level Agreements, or SLAs, are formal agreements. They outline the service levels a provider commits to delivering to its customers. These agreements define key metrics that the provider must meet. They include response times, resolution times, uptime, and performance.
Why are SLAs important in ITSM?
SLAs are essential in ITSM for several reasons:
1. SLAs define what the customer can expect from service levels. They help manage expectations and avoid misunderstandings.
2. Measuring Performance: SLAs set clear metrics and targets. They allow both the provider and customer to measure IT service performance.
3. Improving Service Quality: SLAs set a benchmark for service quality. They drive continuous improvement.
4. SLAs hold service providers accountable for agreed-upon service levels. This helps improve service reliability and customer satisfaction.
5. SLAs are crucial in ITSM. They set clear expectations for service delivery. They ensure both the provider and customer understand the performance standards and responsibilities. They also support accountability and improvement. They do this by setting targets, communication protocols, and dispute resolution methods. They also manage service quality.
6. SLAs are vital in ITSM. They set service expectations and performance metrics. This aligns the goals of the service provider and the customer. It boosts accountability, communication, and service. This raises customer satisfaction and IT reliability.
Components of an SLA
An SLA always has these core elements:
Service descriptions define what the vendor will deliver. Performance metrics quantify the service quality. Problem management outlines the process for issue resolution. Warranties and remediation specify penalties for non-compliance. Termination clauses state the conditions for agreement ending.
· Service Level Targets: Specific, measurable targets that the service provider commits to achieving.
· SLA Metrics: KPIs that measure IT service performance.
· Service Level Reporting: Regular reports on IT service performance vs. targets.
· SLA Enforcement: The process for enforcing the SLA, including penalties for non-compliance.
· SLA Reviews: Periodic reviews to assess and adjust the SLA's effectiveness.
· Monitoring and Reporting:
· Performance Monitoring: It is the tools that check service performance against the SLOs.
· Reporting Schedule: Frequency and format of performance reports provided to the customer.
· Penalties and Remedies:
Service Credits: Compensation to the customer if service levels are not met.
·Penalties: Consequences for failing to meet agreed-upon service levels.
· Review and Revision:
· Review Schedule: Frequency of SLA reviews to ensure they remain relevant and up-to-date.
· Amendment Process: Procedures for making changes to the SLA.
· Dispute Resolution:
· Resolution Mechanisms: Processes for settling disputes between the provider and the customer.
· Term and Termination:
· Contract Duration: Length of time the SLA is in effect.
·Termination Conditions: Conditions under which the SLA or service agreement can be terminated.
· Contact Information:
· Primary Contacts: Key contacts on both sides to manage the SLA.
Best Practices for SLAs in ITSM
To ensure the effectiveness of SLAs in ITSM, consider the following best practices:
· Align with Business Objectives: SLAs must support the organization's goals. They should match the business objectives.
Emphasize refining processes: Periodically reassess and refine service agreements. This will drive service improvement and keep them relevant.
·Monitor Performance: Use metrics and reports to check service levels. Address any deviations from the targets.
· Establish Clear Communication: Keep customers informed about the SLA and any changes.
Document Everything: Keep detailed records of SLA negotiations, agreements, and performance metrics. Also, record any disputes or exceptions. In conclusion, SLAs are vital to IT Service Management. They ensure providers deliver high-quality IT services that meet customers' expectations. Best practices and regular reviews of SLAs can improve services. This will boost customer satisfaction.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, SLAs are key to effective IT Service Management. They ensure providers deliver IT services that meet customer expectations. Organizations can drive service improvement and boost customer satisfaction. They should follow best practices and regularly update SLAs.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In IT Service Management (ITSM), SLAs are key. They define the expectations and responsibilities between service providers and customers. Let's explore SLAs. They are vital for efficient IT service delivery.
What are Service Level Agreements?
Service Level Agreements, or SLAs, are formal agreements. They outline the service levels a provider commits to delivering to its customers. These agreements define key metrics that the provider must meet. They include response times, resolution times, uptime, and performance.
Why are SLAs important in ITSM?
SLAs are essential in ITSM for several reasons:
1. SLAs define what the customer can expect from service levels. They help manage expectations and avoid misunderstandings.
2. Measuring Performance: SLAs set clear metrics and targets. They allow both the provider and customer to measure IT service performance.
3. Improving Service Quality: SLAs set a benchmark for service quality. They drive continuous improvement.
4. SLAs hold service providers accountable for agreed-upon service levels. This helps improve service reliability and customer satisfaction.
5. SLAs are crucial in ITSM. They set clear expectations for service delivery. They ensure both the provider and customer understand the performance standards and responsibilities. They also support accountability and improvement. They do this by setting targets, communication protocols, and dispute resolution methods. They also manage service quality.
6. SLAs are vital in ITSM. They set service expectations and performance metrics. This aligns the goals of the service provider and the customer. It boosts accountability, communication, and service. This raises customer satisfaction and IT reliability.
Components of an SLA
An SLA always has these core elements:
Service descriptions define what the vendor will deliver. Performance metrics quantify the service quality. Problem management outlines the process for issue resolution. Warranties and remediation specify penalties for non-compliance. Termination clauses state the conditions for agreement ending.
· Service Level Targets: Specific, measurable targets that the service provider commits to achieving.
· SLA Metrics: KPIs that measure IT service performance.
· Service Level Reporting: Regular reports on IT service performance vs. targets.
· SLA Enforcement: The process for enforcing the SLA, including penalties for non-compliance.
· SLA Reviews: Periodic reviews to assess and adjust the SLA's effectiveness.
· Monitoring and Reporting:
· Performance Monitoring: It is the tools that check service performance against the SLOs.
· Reporting Schedule: Frequency and format of performance reports provided to the customer.
· Penalties and Remedies:
Service Credits: Compensation to the customer if service levels are not met.
·Penalties: Consequences for failing to meet agreed-upon service levels.
· Review and Revision:
· Review Schedule: Frequency of SLA reviews to ensure they remain relevant and up-to-date.
· Amendment Process: Procedures for making changes to the SLA.
· Dispute Resolution:
· Resolution Mechanisms: Processes for settling disputes between the provider and the customer.
· Term and Termination:
· Contract Duration: Length of time the SLA is in effect.
·Termination Conditions: Conditions under which the SLA or service agreement can be terminated.
· Contact Information:
· Primary Contacts: Key contacts on both sides to manage the SLA.
Best Practices for SLAs in ITSM
To ensure the effectiveness of SLAs in ITSM, consider the following best practices:
· Align with Business Objectives: SLAs must support the organization's goals. They should match the business objectives.
Emphasize refining processes: Periodically reassess and refine service agreements. This will drive service improvement and keep them relevant.
·Monitor Performance: Use metrics and reports to check service levels. Address any deviations from the targets.
· Establish Clear Communication: Keep customers informed about the SLA and any changes.
Document Everything: Keep detailed records of SLA negotiations, agreements, and performance metrics. Also, record any disputes or exceptions. In conclusion, SLAs are vital to IT Service Management. They ensure providers deliver high-quality IT services that meet customers' expectations. Best practices and regular reviews of SLAs can improve services. This will boost customer satisfaction.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, SLAs are key to effective IT Service Management. They ensure providers deliver IT services that meet customer expectations. Organizations can drive service improvement and boost customer satisfaction. They should follow best practices and regularly update SLAs.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
What is Fuzzy Logic in AI and its uses?
In AI, fuzzy logic helps bridge the gap between human reasoning and machine processing. This new method is a flexible, nuanced way to handle complex, uncertain data. It is a valuable tool for many applications. But what exactly is fuzzy logic and how is it utilized in AI? Let's dive into the world of fuzzy logic and explore its uses in the field of artificial intelligence.
Understanding Fuzzy Logic
Fuzzy logic is a form of mathematical reasoning that deals with imprecise and vague information. Unlike traditional binary logic, which is absolute (true or false), fuzzy logic is more human-like. It represents uncertainty in a natural way. It uses "fuzzy sets" and "linguistic variables." They let the system work with degrees of truth, not rigid values. A key part of fuzzy logic is the "fuzzy inference system." It takes input variables, applies fuzzy logic rules, and outputs a fuzzy set. This process allows for more flexible decisions. It helps solve problems, especially with incomplete or unclear data.
Applications of Fuzzy Logic in AI
The versatility of fuzzy logic makes it applicable in a wide range of AI applications. Some of the key areas where fuzzy logic is used include:
-
Control Systems: Fuzzy logic is widely used in control systems. It handles complex, nonlinear processes. It enables better control strategies. They are more adaptive and intuitive. This boosts performance and efficiency.
-
Pattern Recognition: Fuzzy logic is used in pattern recognition, like image and speech recognition. It enables machines to recognize and interpret patterns in data with varying degrees of certainty.
-
Decision Making: Decision support systems use fuzzy logic. It helps to make decisions more like humans. It helps in weighing multiple factors and arriving at optimal decisions even in uncertain conditions.
-
Robotics: Fuzzy logic is vital in robotics. It helps with motion planning, navigation, and object manipulation. By incorporating fuzzy logic, robots can exhibit more intelligent and adaptive behavior.
-
Data Analysis: Fuzzy logic is used in data mining and predictive modeling. It helps deal with uncertainty in large datasets. It aids in extracting valuable insights and patterns from complex data.
Fuzzy logic is key to AI. It lets systems handle uncertainty and make decisions using approximate data, not precise data. It can improve control systems in cars. It can also enhance decision-making in finance and healthcare.
Fuzzy logic offers a flexible AI approach. It lets systems reason about imprecise or vague data, like humans do. Its applications are widespread. They include consumer electronics, like washing machines and air conditioners. They also include complex fields, like autonomous vehicles and medical diagnosis.
Benefits of Fuzzy Logic in AI
The application of fuzzy logic in AI offers several advantages, including:
-
Handling Uncertainty: Fuzzy logic handles uncertain, incomplete data well. It is ideal for real-world applications where data may not be precise.
-
Better Decisions: Fuzzy logic allows for more nuanced, context-aware decisions. It helps AI systems make better judgments.
-
Fuzzy logic is flexible. It can capture the complexities of human reasoning. This can lead to more adaptive AI systems.
Fuzzy logic can make control systems and automation more efficient. This increases their responsiveness and leads to better outcomes.
Fuzzy logic improves AI. It lets them handle uncertainty and imprecision, like human reasoning. This approach allows for better, more flexible decision-making. It helps the system adapt to complex, ambiguous situations.
Fuzzy logic greatly helps AI. It lets systems model and process uncertain, imprecise data. This capability makes AI apps more robust and adaptable. It improves their performance in real-world situations with no clear answers.
How to obtain AI certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, fuzzy logic in AI is a human-like way to handle uncertainty in decisions and problems. Its many uses show its role in advancing AI systems. Fuzzy logic can boost AI. It will make it smarter and more advanced.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In AI, fuzzy logic helps bridge the gap between human reasoning and machine processing. This new method is a flexible, nuanced way to handle complex, uncertain data. It is a valuable tool for many applications. But what exactly is fuzzy logic and how is it utilized in AI? Let's dive into the world of fuzzy logic and explore its uses in the field of artificial intelligence.
Understanding Fuzzy Logic
Fuzzy logic is a form of mathematical reasoning that deals with imprecise and vague information. Unlike traditional binary logic, which is absolute (true or false), fuzzy logic is more human-like. It represents uncertainty in a natural way. It uses "fuzzy sets" and "linguistic variables." They let the system work with degrees of truth, not rigid values. A key part of fuzzy logic is the "fuzzy inference system." It takes input variables, applies fuzzy logic rules, and outputs a fuzzy set. This process allows for more flexible decisions. It helps solve problems, especially with incomplete or unclear data.
Applications of Fuzzy Logic in AI
The versatility of fuzzy logic makes it applicable in a wide range of AI applications. Some of the key areas where fuzzy logic is used include:
-
Control Systems: Fuzzy logic is widely used in control systems. It handles complex, nonlinear processes. It enables better control strategies. They are more adaptive and intuitive. This boosts performance and efficiency.
-
Pattern Recognition: Fuzzy logic is used in pattern recognition, like image and speech recognition. It enables machines to recognize and interpret patterns in data with varying degrees of certainty.
-
Decision Making: Decision support systems use fuzzy logic. It helps to make decisions more like humans. It helps in weighing multiple factors and arriving at optimal decisions even in uncertain conditions.
-
Robotics: Fuzzy logic is vital in robotics. It helps with motion planning, navigation, and object manipulation. By incorporating fuzzy logic, robots can exhibit more intelligent and adaptive behavior.
-
Data Analysis: Fuzzy logic is used in data mining and predictive modeling. It helps deal with uncertainty in large datasets. It aids in extracting valuable insights and patterns from complex data.
Fuzzy logic is key to AI. It lets systems handle uncertainty and make decisions using approximate data, not precise data. It can improve control systems in cars. It can also enhance decision-making in finance and healthcare.
Fuzzy logic offers a flexible AI approach. It lets systems reason about imprecise or vague data, like humans do. Its applications are widespread. They include consumer electronics, like washing machines and air conditioners. They also include complex fields, like autonomous vehicles and medical diagnosis.
Benefits of Fuzzy Logic in AI
The application of fuzzy logic in AI offers several advantages, including:
-
Handling Uncertainty: Fuzzy logic handles uncertain, incomplete data well. It is ideal for real-world applications where data may not be precise.
-
Better Decisions: Fuzzy logic allows for more nuanced, context-aware decisions. It helps AI systems make better judgments.
-
Fuzzy logic is flexible. It can capture the complexities of human reasoning. This can lead to more adaptive AI systems.
Fuzzy logic can make control systems and automation more efficient. This increases their responsiveness and leads to better outcomes.
Fuzzy logic improves AI. It lets them handle uncertainty and imprecision, like human reasoning. This approach allows for better, more flexible decision-making. It helps the system adapt to complex, ambiguous situations.
Fuzzy logic greatly helps AI. It lets systems model and process uncertain, imprecise data. This capability makes AI apps more robust and adaptable. It improves their performance in real-world situations with no clear answers.
How to obtain AI certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, fuzzy logic in AI is a human-like way to handle uncertainty in decisions and problems. Its many uses show its role in advancing AI systems. Fuzzy logic can boost AI. It will make it smarter and more advanced.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Managing Technical Debt A CSPO Responsibility
In today's fast-paced software development environment, technical debt is an inevitable reality. Technical debt is the cost of rework. It comes from choosing a quick, limited solution now instead of a better, but longer, approach. The term is often linked to developers and tech teams. But, it's also a key concern for the Certified Scrum Product Owner (CSPO). The CSPO is the link between the business and the dev team. They must prioritize features, keep the backlog, and ensure the product is valuable to stakeholders. Managing technical debt is not just a technical task. It is a strategic one that the CSPO must embrace. It is key to long-term product success.
Table of Contents
Understanding Technical Debt
The Role of the CSPO in Managing Technical Debt
Prioritizing Technical Debt in the Product Backlog
Communicating the Impact of Technical Debt to Stakeholders
Strategies for Reducing Technical Debt
Conclusion
Understanding Technical Debt
The first step in managing technical debt is understanding what it is and how it manifests in the software development lifecycle. Technical debt can arise from various sources. They include rushed development, lack of documentation, poor code quality, and legacy systems. A CSPO must know that technical debt isn't always bad. Sometimes, it's a choice to meet deadlines or market demands. However, unchecked technical debt can accumulate. It can increase costs, slow development, and reduce product quality over time. The CSPO must work with the dev team to find technical debt, understand its impact on the product, and report this to stakeholders.
The Role of the CSPO in Managing Technical Debt
The CSPO plays a pivotal role in managing technical debt by prioritizing it within the product backlog. Unlike traditional project management, technical decisions are often left to developers. The CSPO must engage in discussions about technical debt. This involves balancing new feature development with addressing technical debt. It can be tough, especially when stakeholders want new features. The CSPO must advocate for reducing technical debt. It affects the product's long-term viability and the team's ability to deliver high-quality software.
Prioritizing Technical Debt in the Product Backlog
One of the most challenging aspects of managing technical debt is determining when and how to address it. The CSPO must prioritize technical debt. It is as important as new features, bug fixes, and other improvements. It requires a deep understanding of the product's state. It also needs knowledge of the team's capacity and the risks of ignoring technical debt. The CSPO should work with the dev team. They should estimate the effort to fix technical debt. Then, weigh it against the value of new features. In some cases, we may need to deprioritize new features. This is to reduce technical debt, especially if it risks the product's stability or performance.
Communicating the Impact of Technical Debt to Stakeholders
Effective communication is crucial in managing technical debt. This is especially true for stakeholders who may not grasp its implications. The CSPO must be able to articulate the long-term risks of accumulating technical debt and the benefits of addressing it early. It means to show how technical debt harms the product's value, the user experience, and the dev team's productivity. By framing technical debt in a business context, the CSPO can gain stakeholder support for initiatives to reduce it. This may require delaying new features or increasing short-term costs.
Strategies for Reducing Technical Debt
Finally, the CSPO must work with the development team to implement strategies for reducing technical debt. This may involve refactoring code, improving documentation, or upgrading legacy systems. The CSPO should foster a culture of continuous improvement. The team should see addressing technical debt as an ongoing process, not a one-time effort. Also, the CSPO can seek to include technical debt reduction in regular sprint planning. This will ensure the team allocates time and resources to this vital task. The CSPO can help ensure the product is maintainable and scalable. Integrating technical debt management into the product strategy will do this. It will also ensure the product delivers long-term value to stakeholders.
How to obtain CSPO certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Managing technical debt is a key duty of the CSPO. It affects the product's success and the team's ability to deliver quality software. The CSPO can ensure the product's long-term viability. They should know about technical debt. Prioritize it in the backlog. Communicate its impact to stakeholders. Also, they should implement strategies to reduce it. Reducing technical debt may require tough trade-offs. But, the benefits of reducing it far outweigh the risks of letting it grow unchecked. A CSPO must manage technical debt. This will make the product more resilient, adaptable, and successful.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced software development environment, technical debt is an inevitable reality. Technical debt is the cost of rework. It comes from choosing a quick, limited solution now instead of a better, but longer, approach. The term is often linked to developers and tech teams. But, it's also a key concern for the Certified Scrum Product Owner (CSPO). The CSPO is the link between the business and the dev team. They must prioritize features, keep the backlog, and ensure the product is valuable to stakeholders. Managing technical debt is not just a technical task. It is a strategic one that the CSPO must embrace. It is key to long-term product success.
Table of Contents
Understanding Technical Debt
The Role of the CSPO in Managing Technical Debt
Prioritizing Technical Debt in the Product Backlog
Communicating the Impact of Technical Debt to Stakeholders
Strategies for Reducing Technical Debt
Conclusion
Understanding Technical Debt
The first step in managing technical debt is understanding what it is and how it manifests in the software development lifecycle. Technical debt can arise from various sources. They include rushed development, lack of documentation, poor code quality, and legacy systems. A CSPO must know that technical debt isn't always bad. Sometimes, it's a choice to meet deadlines or market demands. However, unchecked technical debt can accumulate. It can increase costs, slow development, and reduce product quality over time. The CSPO must work with the dev team to find technical debt, understand its impact on the product, and report this to stakeholders.
The Role of the CSPO in Managing Technical Debt
The CSPO plays a pivotal role in managing technical debt by prioritizing it within the product backlog. Unlike traditional project management, technical decisions are often left to developers. The CSPO must engage in discussions about technical debt. This involves balancing new feature development with addressing technical debt. It can be tough, especially when stakeholders want new features. The CSPO must advocate for reducing technical debt. It affects the product's long-term viability and the team's ability to deliver high-quality software.
Prioritizing Technical Debt in the Product Backlog
One of the most challenging aspects of managing technical debt is determining when and how to address it. The CSPO must prioritize technical debt. It is as important as new features, bug fixes, and other improvements. It requires a deep understanding of the product's state. It also needs knowledge of the team's capacity and the risks of ignoring technical debt. The CSPO should work with the dev team. They should estimate the effort to fix technical debt. Then, weigh it against the value of new features. In some cases, we may need to deprioritize new features. This is to reduce technical debt, especially if it risks the product's stability or performance.
Communicating the Impact of Technical Debt to Stakeholders
Effective communication is crucial in managing technical debt. This is especially true for stakeholders who may not grasp its implications. The CSPO must be able to articulate the long-term risks of accumulating technical debt and the benefits of addressing it early. It means to show how technical debt harms the product's value, the user experience, and the dev team's productivity. By framing technical debt in a business context, the CSPO can gain stakeholder support for initiatives to reduce it. This may require delaying new features or increasing short-term costs.
Strategies for Reducing Technical Debt
Finally, the CSPO must work with the development team to implement strategies for reducing technical debt. This may involve refactoring code, improving documentation, or upgrading legacy systems. The CSPO should foster a culture of continuous improvement. The team should see addressing technical debt as an ongoing process, not a one-time effort. Also, the CSPO can seek to include technical debt reduction in regular sprint planning. This will ensure the team allocates time and resources to this vital task. The CSPO can help ensure the product is maintainable and scalable. Integrating technical debt management into the product strategy will do this. It will also ensure the product delivers long-term value to stakeholders.
How to obtain CSPO certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Managing technical debt is a key duty of the CSPO. It affects the product's success and the team's ability to deliver quality software. The CSPO can ensure the product's long-term viability. They should know about technical debt. Prioritize it in the backlog. Communicate its impact to stakeholders. Also, they should implement strategies to reduce it. Reducing technical debt may require tough trade-offs. But, the benefits of reducing it far outweigh the risks of letting it grow unchecked. A CSPO must manage technical debt. This will make the product more resilient, adaptable, and successful.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
IoT Standards Ensuring Interoperability in a Connected World
Today, the Internet of Things (IoT) is vital to our lives. It is revolutionizing industries, homes, and cities. The promise of IoT is its ability to create a network of devices that communicate with each other. This will lead to better efficiency, convenience, and innovation. The true potential of IoT is in devices working together. They should work together, regardless of their maker, protocol, or tech. This is where IoT standards play a critical role. IoT standards ensure interoperability, security, and scalability in a fast-growing ecosystem. They do this by setting a common framework for devices to communicate and exchange data. This article explores the need for IoT standards. It covers vital areas and the challenges of a fully connected, interoperable world.
The Importance of Interoperability in IoT
Interoperability is the cornerstone of a successful IoT ecosystem. Without it, the essence of IoT—a network of connected devices—would crumble. Interoperability allows devices from different makers to communicate. It lets users combine systems into one network. It is vital in healthcare, smart cities, and manufacturing. A lack of interoperability there can cause inefficiencies, higher costs, and safety risks. In a smart city, traffic systems, sensors, and transit must work together. They should optimize urban planning and resource use. IoT standards are needed to connect different systems. They ensure that these systems can work together. This will deliver the full benefits of a connected environment.
Key IoT Standards and Protocols
Many standards and protocols aim to improve IoT interoperability. These include:
IPv6 over Low-Power Wireless Personal Area Networks (6LoWPAN): This standard lets low-power, low-resource devices go online. It enables widespread IoT use.
Message Queuing Telemetry Transport (MQTT) is a lightweight messaging protocol. It's for constrained devices and low-bandwidth networks. MQTT is widely used in IoT apps for reliable, efficient communication.
Constrained Application Protocol (CoAP): It is like HTTP but optimized for constrained environments. CoAP is used in machine-to-machine (M2M) communication and IoT devices.
Zigbee and Z-Wave are wireless standards for low-power, home-automation devices. They provide a reliable mesh network for IoT devices to communicate.
OPC Unified Architecture (OPC UA) is a machine-to-machine protocol for industrial automation. It provides a secure, reliable way to connect industrial IoT devices.
Each standard addresses specific aspects of IoT communication. They ensure devices can operate efficiently and securely in various environments.
Challenges in Implementing IoT Standards
IoT standards are vital. But, applying them in a fast-changing, diverse ecosystem is tough. A key challenge is the diversity of IoT devices. They have different capabilities, power needs, and communication requirements. This diversity makes it hard to create a universal standard for all devices. Also, the IoT market's competition has led to many proprietary solutions. They create silos that hinder interoperability. Manufacturers often create their own protocols and standards. This locks users into their ecosystems. It makes it hard for devices from different vendors to work together. Also, no central body governs IoT standards. This has led to a fragmented landscape, with multiple groups creating competing standards. This can confuse developers and users, slowing IoT adoption.
The Role of Open Standards and Industry Collaboration
To overcome the challenges of interoperability, open standards and industry collaboration are essential. Open standards are publicly available. Anyone can implement them. This ensures that devices from different manufacturers can communicate. The OCF, IEEE, and ITU are working to develop and promote open IoT standards. These organizations unite industry stakeholders to develop IoT standards. They aim to meet the needs of the broader IoT ecosystem. Collaboration can spur innovation, cut costs, and speed up IoT adoption. Open standards can enable this. Also, governments can promote open standards. They should mandate their use in public projects. And, they should incentivize their use in the private sector.
Future Trends in IoT Standards and Interoperability
As the IoT ecosystem evolves, new trends are emerging. They will shape the future of IoT standards and interoperability. One trend is the rise of edge computing. It involves processing data closer to the source, not in centralized cloud servers. This shift requires new standards. They must support low-latency communication and data processing at the network's edge. Another trend is the increasing importance of security in IoT standards. As the number of connected devices rises, so do cyberattack risks. So, security is a top priority in IoT development. Future IoT standards must include strong security. This means using encryption, authentication, and access control. These measures will protect sensitive data and ensure IoT systems' integrity. Finally, we need new standards for IoT devices. AI and ML will be in them. They must support smart decision-making and autonomous operation in IoT networks. These trends show a need for ongoing innovation in IoT standards. They must ensure the ecosystem is interoperable, secure, and scalable.
How to obtain IOTcertification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, IoT standards will be the foundation of a connected, future world. They ensure that devices from different manufacturers can work together. This unlocks the full potential of IoT. True interoperability is a complex, ongoing challenge. It needs collaboration, innovation, and a commitment to open standards. As the IoT ecosystem grows, it needs strong standards. They are key to realizing IoT's benefits across industries and applications. IoT standards will solve interoperability, security, and scalability issues. They will create a smarter, more efficient, and more resilient connected world.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Today, the Internet of Things (IoT) is vital to our lives. It is revolutionizing industries, homes, and cities. The promise of IoT is its ability to create a network of devices that communicate with each other. This will lead to better efficiency, convenience, and innovation. The true potential of IoT is in devices working together. They should work together, regardless of their maker, protocol, or tech. This is where IoT standards play a critical role. IoT standards ensure interoperability, security, and scalability in a fast-growing ecosystem. They do this by setting a common framework for devices to communicate and exchange data. This article explores the need for IoT standards. It covers vital areas and the challenges of a fully connected, interoperable world.
The Importance of Interoperability in IoT
Interoperability is the cornerstone of a successful IoT ecosystem. Without it, the essence of IoT—a network of connected devices—would crumble. Interoperability allows devices from different makers to communicate. It lets users combine systems into one network. It is vital in healthcare, smart cities, and manufacturing. A lack of interoperability there can cause inefficiencies, higher costs, and safety risks. In a smart city, traffic systems, sensors, and transit must work together. They should optimize urban planning and resource use. IoT standards are needed to connect different systems. They ensure that these systems can work together. This will deliver the full benefits of a connected environment.
Key IoT Standards and Protocols
Many standards and protocols aim to improve IoT interoperability. These include:
IPv6 over Low-Power Wireless Personal Area Networks (6LoWPAN): This standard lets low-power, low-resource devices go online. It enables widespread IoT use.
Message Queuing Telemetry Transport (MQTT) is a lightweight messaging protocol. It's for constrained devices and low-bandwidth networks. MQTT is widely used in IoT apps for reliable, efficient communication.
Constrained Application Protocol (CoAP): It is like HTTP but optimized for constrained environments. CoAP is used in machine-to-machine (M2M) communication and IoT devices.
Zigbee and Z-Wave are wireless standards for low-power, home-automation devices. They provide a reliable mesh network for IoT devices to communicate.
OPC Unified Architecture (OPC UA) is a machine-to-machine protocol for industrial automation. It provides a secure, reliable way to connect industrial IoT devices.
Each standard addresses specific aspects of IoT communication. They ensure devices can operate efficiently and securely in various environments.
Challenges in Implementing IoT Standards
IoT standards are vital. But, applying them in a fast-changing, diverse ecosystem is tough. A key challenge is the diversity of IoT devices. They have different capabilities, power needs, and communication requirements. This diversity makes it hard to create a universal standard for all devices. Also, the IoT market's competition has led to many proprietary solutions. They create silos that hinder interoperability. Manufacturers often create their own protocols and standards. This locks users into their ecosystems. It makes it hard for devices from different vendors to work together. Also, no central body governs IoT standards. This has led to a fragmented landscape, with multiple groups creating competing standards. This can confuse developers and users, slowing IoT adoption.
The Role of Open Standards and Industry Collaboration
To overcome the challenges of interoperability, open standards and industry collaboration are essential. Open standards are publicly available. Anyone can implement them. This ensures that devices from different manufacturers can communicate. The OCF, IEEE, and ITU are working to develop and promote open IoT standards. These organizations unite industry stakeholders to develop IoT standards. They aim to meet the needs of the broader IoT ecosystem. Collaboration can spur innovation, cut costs, and speed up IoT adoption. Open standards can enable this. Also, governments can promote open standards. They should mandate their use in public projects. And, they should incentivize their use in the private sector.
Future Trends in IoT Standards and Interoperability
As the IoT ecosystem evolves, new trends are emerging. They will shape the future of IoT standards and interoperability. One trend is the rise of edge computing. It involves processing data closer to the source, not in centralized cloud servers. This shift requires new standards. They must support low-latency communication and data processing at the network's edge. Another trend is the increasing importance of security in IoT standards. As the number of connected devices rises, so do cyberattack risks. So, security is a top priority in IoT development. Future IoT standards must include strong security. This means using encryption, authentication, and access control. These measures will protect sensitive data and ensure IoT systems' integrity. Finally, we need new standards for IoT devices. AI and ML will be in them. They must support smart decision-making and autonomous operation in IoT networks. These trends show a need for ongoing innovation in IoT standards. They must ensure the ecosystem is interoperable, secure, and scalable.
How to obtain IOTcertification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, IoT standards will be the foundation of a connected, future world. They ensure that devices from different manufacturers can work together. This unlocks the full potential of IoT. True interoperability is a complex, ongoing challenge. It needs collaboration, innovation, and a commitment to open standards. As the IoT ecosystem grows, it needs strong standards. They are key to realizing IoT's benefits across industries and applications. IoT standards will solve interoperability, security, and scalability issues. They will create a smarter, more efficient, and more resilient connected world.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Value of CISM Certification for IT Managers and Executives
In today's digital age, information security is a key business issue, not a technical one. As organizations use more digital systems, the need for strong info security is clear. Cyber threats are evolving at an unprecedented pace. Security breaches can have catastrophic effects. They can cause financial loss, damage reputations, and lead to fines. IT managers and executives must now know information security management. It's a necessity, not an option. ISACA offers the Certified Information Security Manager (CISM) certification. It is a prestigious credential. It equips IT professionals to manage and govern enterprise information security. This article explores the value of CISM certification for IT managers and executives. It shows its impact on career growth and business success, and on security.
Table Of Contents
- Enhancing Leadership in Information Security
- Improving Organizational Security Posture
- Aligning Security with Business Objectives
- Enhancing Career Prospects and Professional Growth
- Ensuring compliance and regulatory adherence
- Conclusion
Enhancing Leadership in Information Security
The CISM certification is for managers. It focuses on the business side of info security. CISM differs from other certifications. It prepares IT managers and executives for leadership roles, not technical skills. It helps them design and manage security programs that align with their goals. CISM-certified pros know how to stress info security to business leaders. Their skills make them invaluable in boardrooms and exec meetings.
A CISM certification can boost IT managers' leadership skills. It will position them as key decision-makers in their organizations. They gain the confidence to advocate for security investments. These will protect the organization's assets and support its business goals. The certification gives executives a framework to oversee security. It ensures security measures are proactive. They should align with long-term business goals, not be reactive.
Improving Organizational Security Posture
A strong security posture is vital. It helps organizations defend against rising cyber threats. CISM certification teaches IT managers to build a strong, secure info security program. This includes developing security policies, managing risk, and following industry standards and regulations. CISM professionals assess an organization's security. They find vulnerabilities and reduce risks.
A key benefit of CISM-certified leaders is their broad view of security. They know that security is not about technology. It's also about processes, people, and governance. It lets them to create effective, sustainable, long-term security strategies. Also, CISM certification stresses continuous improvement. It urges IT managers and execs to update their security practices. They must combat evolving threats.
Aligning Security with Business Objectives
A major challenge in info security is aligning security efforts with business goals. Too often, people see security as a cost center instead of a business enabler. The CISM certification teaches IT managers to integrate security into the organization's strategy. It addresses a challenge. This alignment is vital. It will win senior leaders' support. It will show that security investments are key to the organization's success.
CISM-certified professionals can communicate security's value in business terms. This helps to secure funding for security projects. They excel at balancing security with business needs. They ensure security measures don't hinder innovation and growth. CISM-certified IT managers and execs can align security with business goals. This will help their organizations gain a competitive edge while protecting vital assets.
Enhancing Career Prospects and Professional Growth
The demand for skilled information security professionals is rising. All industries now see the need for strong security practices. The CISM certification offers IT managers a way to advance their careers. It is a globally recognized credential. It validates the individual's expertise in information security management. These individuals are in great demand by employers.
CISM certification improves job prospects and enables professional growth. ISACA's global community connects certified professionals with peers and experts. It helps them keep up with the latest trends and best practices in information security. Also, people view CISM-certified individuals as fit for leadership roles, like CISO. They can transform the organization's security strategy and catapult it to success.
Ensuring compliance and regulatory adherence
Today, compliance with information security standards is crucial. It helps organizations avoid legal penalties and maintain customer trust. The CISM certification trains IT managers and executives. They must ensure their organizations follow all relevant laws. This includes knowing and using frameworks like ISO/IEC 27001, NIST, and GDPR. They are vital for protecting sensitive data and ensuring compliance.
Professionals with CISM certification train to create and install security policies. They must meet regulations and support the organization's objectives. They are also skilled at conducting audits and assessments. They ensure compliance and reduce the risk of noncompliance penalties. CISM-certified leaders can show an organization's commitment to security. This can enhance its reputation and build customer trust.
How to obtain CISM Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, The CISM certification is valuable for IT managers and execs. It shows they can manage and govern their organization's info security programs. It gives them the skills and tools to align security with business goals. They can then improve security and meet regulatory requirements. CISM certification improves career prospects. It positions IT pros for key leadership roles that impact the organization's success. In a digital world, cyber threats are everywhere. So, the value of CISM certification for IT managers and executives is huge. It is not a certification. It is a vital investment in the organization's security and business success.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's digital age, information security is a key business issue, not a technical one. As organizations use more digital systems, the need for strong info security is clear. Cyber threats are evolving at an unprecedented pace. Security breaches can have catastrophic effects. They can cause financial loss, damage reputations, and lead to fines. IT managers and executives must now know information security management. It's a necessity, not an option. ISACA offers the Certified Information Security Manager (CISM) certification. It is a prestigious credential. It equips IT professionals to manage and govern enterprise information security. This article explores the value of CISM certification for IT managers and executives. It shows its impact on career growth and business success, and on security.
Table Of Contents
- Enhancing Leadership in Information Security
- Improving Organizational Security Posture
- Aligning Security with Business Objectives
- Enhancing Career Prospects and Professional Growth
- Ensuring compliance and regulatory adherence
- Conclusion
Enhancing Leadership in Information Security
The CISM certification is for managers. It focuses on the business side of info security. CISM differs from other certifications. It prepares IT managers and executives for leadership roles, not technical skills. It helps them design and manage security programs that align with their goals. CISM-certified pros know how to stress info security to business leaders. Their skills make them invaluable in boardrooms and exec meetings.
A CISM certification can boost IT managers' leadership skills. It will position them as key decision-makers in their organizations. They gain the confidence to advocate for security investments. These will protect the organization's assets and support its business goals. The certification gives executives a framework to oversee security. It ensures security measures are proactive. They should align with long-term business goals, not be reactive.
Improving Organizational Security Posture
A strong security posture is vital. It helps organizations defend against rising cyber threats. CISM certification teaches IT managers to build a strong, secure info security program. This includes developing security policies, managing risk, and following industry standards and regulations. CISM professionals assess an organization's security. They find vulnerabilities and reduce risks.
A key benefit of CISM-certified leaders is their broad view of security. They know that security is not about technology. It's also about processes, people, and governance. It lets them to create effective, sustainable, long-term security strategies. Also, CISM certification stresses continuous improvement. It urges IT managers and execs to update their security practices. They must combat evolving threats.
Aligning Security with Business Objectives
A major challenge in info security is aligning security efforts with business goals. Too often, people see security as a cost center instead of a business enabler. The CISM certification teaches IT managers to integrate security into the organization's strategy. It addresses a challenge. This alignment is vital. It will win senior leaders' support. It will show that security investments are key to the organization's success.
CISM-certified professionals can communicate security's value in business terms. This helps to secure funding for security projects. They excel at balancing security with business needs. They ensure security measures don't hinder innovation and growth. CISM-certified IT managers and execs can align security with business goals. This will help their organizations gain a competitive edge while protecting vital assets.
Enhancing Career Prospects and Professional Growth
The demand for skilled information security professionals is rising. All industries now see the need for strong security practices. The CISM certification offers IT managers a way to advance their careers. It is a globally recognized credential. It validates the individual's expertise in information security management. These individuals are in great demand by employers.
CISM certification improves job prospects and enables professional growth. ISACA's global community connects certified professionals with peers and experts. It helps them keep up with the latest trends and best practices in information security. Also, people view CISM-certified individuals as fit for leadership roles, like CISO. They can transform the organization's security strategy and catapult it to success.
Ensuring compliance and regulatory adherence
Today, compliance with information security standards is crucial. It helps organizations avoid legal penalties and maintain customer trust. The CISM certification trains IT managers and executives. They must ensure their organizations follow all relevant laws. This includes knowing and using frameworks like ISO/IEC 27001, NIST, and GDPR. They are vital for protecting sensitive data and ensuring compliance.
Professionals with CISM certification train to create and install security policies. They must meet regulations and support the organization's objectives. They are also skilled at conducting audits and assessments. They ensure compliance and reduce the risk of noncompliance penalties. CISM-certified leaders can show an organization's commitment to security. This can enhance its reputation and build customer trust.
How to obtain CISM Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, The CISM certification is valuable for IT managers and execs. It shows they can manage and govern their organization's info security programs. It gives them the skills and tools to align security with business goals. They can then improve security and meet regulatory requirements. CISM certification improves career prospects. It positions IT pros for key leadership roles that impact the organization's success. In a digital world, cyber threats are everywhere. So, the value of CISM certification for IT managers and executives is huge. It is not a certification. It is a vital investment in the organization's security and business success.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Top 5 Reasons to Get COBIT 5 Foundation Certified in 2024
In today's fast-changing digital world, businesses rely on strong IT governance and management. As organizations seek to align IT with business goals, COBIT® 5 is essential.COBIT® 5 represents Control Objectives for Information and Related Technologies. It is a global framework. It offers guidance for governing and managing enterprise IT. In 2024, there is a greater focus on compliance, risk, and IT investment. So, COBIT® 5 Foundation certification is now more relevant than ever.
This article will share the top five reasons to get COBIT® 5 Foundation certified in 2024. This opportunity can transform your career and revolutionize your organization. If you're an IT pro, a business manager, or into GRC, know the benefits of COBIT® 5 certification. It will help you navigate today's complex IT and drive business success.
Table Of Contents
- Enhances Your Understanding of IT Governance
- Strengthens Risk Management Capabilities
- Facilitates regulatory compliance
- Boosts Career Opportunities and Earning Potential
- Supports Continuous Improvement and Value Creation
- Conclusion
Enhances Your Understanding of IT Governance
In the digital age, IT governance is vital to corporate governance. It is no longer a niche concern. COBIT® 5 is a strong framework. It helps organizations meet their IT governance goals. It does this by aligning IT processes with business objectives. COBIT® 5 Foundation certification teaches you to improve IT governance in your organization.
The certification covers the core principles of COBIT® 5. They are:
- Meeting stakeholders' needs;
- covering the enterprise end to
- Applying a single integrated framework.
- Enabling a holistic approach.
- Separating governance from management.
This knowledge is invaluable for IT managers. They must use IT resources well, manage risks, and maximize returns on IT investments. In 2024, scrutiny of IT practices will rise. Your IT governance skills will set you apart in the job market.
Strengthens Risk Management Capabilities
Risk management is key to any organization's success. In IT, it is even more critical. COBIT® 5 offers comprehensive guidance on identifying, assessing, and mitigating IT-related risks. COBIT® 5 Foundation certification will equip you to manage risks. It will help protect your organization from potential threats.
In today's business world, it's vital to optimize risk, not avoid it. So, the framework's focus on this is very relevant. COBIT® 5 stresses the need to balance risk and opportunity. IT investments should add business value without exposing the organization to excess risk. In 2024, cyber threats will evolve, and regulations will tighten. So, the ability to manage IT risks will be a sought-after skill.
Facilitates regulatory compliance
With data breaches in the news, compliance is a top priority for organizations. COBIT® 5 ensures IT processes meet laws, regulations, and industry standards. Certification will teach you to design and install IT controls. They must meet regulations and support business goals.
The certification will let you help your organization with complex regulations. It includes data protection laws like GDPR and industry standards like HIPAA. It also includes various national and international laws. In 2024, new regulations and stricter enforcement may come. A COBIT® 5 certification will show you are an expert in IT compliance. It will allow you to guide your organization through these challenges.
Boosts Career Opportunities and Earning Potential
The demand for GRC professionals is growing. COBIT® 5 Foundation certification can boost your career. The certification is globally recognized. It demonstrates mastery of a popular development platform. Organizations of all sizes and industries adopt it.
In 2024, demand for IT pros with GRC skills will be high. Companies need help to navigate complex IT environments. COBIT® 5 certification will make you a more appealing job candidate. It is especially useful for IT governance, risk, and compliance. Also, for IT auditors. Also, certified professionals often earn more than their non-certified peers. This makes the certification a valuable investment in your future.
Supports Continuous Improvement and Value Creation
One of the key benefits of COBIT® 5 is its focus on continuous improvement and value creation. The framework guides how to measure and improve IT performance. It ensures that IT helps the organization's success. COBIT® 5 Foundation certification will teach you to apply these principles in practice. This will help your organization achieve its strategic goals.
COBIT® 5 promotes a holistic view of IT governance. It involves all stakeholders in decision-making. IT initiatives must align with business goals. This approach boosts IT performance. It also drives innovation and value. In 2024, organizations will want to maximize their IT investments. Your ability to help with improvement initiatives will make you invaluable.
How to obtain Cobit 5 Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, As we enter 2024, IT governance, risk management, and compliance are crucial. COBIT® 5 Foundation certification gives a deep understanding of these areas.COBIT® 5 certification can help you. It will boost your IT governance knowledge, improve risk management, and ensure compliance. It can also boost your career and support improvement efforts. The certification provides the tools you need to succeed.
In a world of rapid tech change, it's vital to stay ahead. Get COBIT® 5 Foundation certified in 2024. This will make you a leader in IT governance and a valuable asset to any organization. Make a real impact in IT management and governance.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-changing digital world, businesses rely on strong IT governance and management. As organizations seek to align IT with business goals, COBIT® 5 is essential.COBIT® 5 represents Control Objectives for Information and Related Technologies. It is a global framework. It offers guidance for governing and managing enterprise IT. In 2024, there is a greater focus on compliance, risk, and IT investment. So, COBIT® 5 Foundation certification is now more relevant than ever.
This article will share the top five reasons to get COBIT® 5 Foundation certified in 2024. This opportunity can transform your career and revolutionize your organization. If you're an IT pro, a business manager, or into GRC, know the benefits of COBIT® 5 certification. It will help you navigate today's complex IT and drive business success.
Table Of Contents
- Enhances Your Understanding of IT Governance
- Strengthens Risk Management Capabilities
- Facilitates regulatory compliance
- Boosts Career Opportunities and Earning Potential
- Supports Continuous Improvement and Value Creation
- Conclusion
Enhances Your Understanding of IT Governance
In the digital age, IT governance is vital to corporate governance. It is no longer a niche concern. COBIT® 5 is a strong framework. It helps organizations meet their IT governance goals. It does this by aligning IT processes with business objectives. COBIT® 5 Foundation certification teaches you to improve IT governance in your organization.
The certification covers the core principles of COBIT® 5. They are:
- Meeting stakeholders' needs;
- covering the enterprise end to
- Applying a single integrated framework.
- Enabling a holistic approach.
- Separating governance from management.
This knowledge is invaluable for IT managers. They must use IT resources well, manage risks, and maximize returns on IT investments. In 2024, scrutiny of IT practices will rise. Your IT governance skills will set you apart in the job market.
Strengthens Risk Management Capabilities
Risk management is key to any organization's success. In IT, it is even more critical. COBIT® 5 offers comprehensive guidance on identifying, assessing, and mitigating IT-related risks. COBIT® 5 Foundation certification will equip you to manage risks. It will help protect your organization from potential threats.
In today's business world, it's vital to optimize risk, not avoid it. So, the framework's focus on this is very relevant. COBIT® 5 stresses the need to balance risk and opportunity. IT investments should add business value without exposing the organization to excess risk. In 2024, cyber threats will evolve, and regulations will tighten. So, the ability to manage IT risks will be a sought-after skill.
Facilitates regulatory compliance
With data breaches in the news, compliance is a top priority for organizations. COBIT® 5 ensures IT processes meet laws, regulations, and industry standards. Certification will teach you to design and install IT controls. They must meet regulations and support business goals.
The certification will let you help your organization with complex regulations. It includes data protection laws like GDPR and industry standards like HIPAA. It also includes various national and international laws. In 2024, new regulations and stricter enforcement may come. A COBIT® 5 certification will show you are an expert in IT compliance. It will allow you to guide your organization through these challenges.
Boosts Career Opportunities and Earning Potential
The demand for GRC professionals is growing. COBIT® 5 Foundation certification can boost your career. The certification is globally recognized. It demonstrates mastery of a popular development platform. Organizations of all sizes and industries adopt it.
In 2024, demand for IT pros with GRC skills will be high. Companies need help to navigate complex IT environments. COBIT® 5 certification will make you a more appealing job candidate. It is especially useful for IT governance, risk, and compliance. Also, for IT auditors. Also, certified professionals often earn more than their non-certified peers. This makes the certification a valuable investment in your future.
Supports Continuous Improvement and Value Creation
One of the key benefits of COBIT® 5 is its focus on continuous improvement and value creation. The framework guides how to measure and improve IT performance. It ensures that IT helps the organization's success. COBIT® 5 Foundation certification will teach you to apply these principles in practice. This will help your organization achieve its strategic goals.
COBIT® 5 promotes a holistic view of IT governance. It involves all stakeholders in decision-making. IT initiatives must align with business goals. This approach boosts IT performance. It also drives innovation and value. In 2024, organizations will want to maximize their IT investments. Your ability to help with improvement initiatives will make you invaluable.
How to obtain Cobit 5 Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, As we enter 2024, IT governance, risk management, and compliance are crucial. COBIT® 5 Foundation certification gives a deep understanding of these areas.COBIT® 5 certification can help you. It will boost your IT governance knowledge, improve risk management, and ensure compliance. It can also boost your career and support improvement efforts. The certification provides the tools you need to succeed.
In a world of rapid tech change, it's vital to stay ahead. Get COBIT® 5 Foundation certified in 2024. This will make you a leader in IT governance and a valuable asset to any organization. Make a real impact in IT management and governance.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Role of Podcasts in Expanding Digital Marketing Reach
In today's fast-paced digital world, businesses want new ways to reach their audience. One powerful tool that has emerged as a game-changer in the world of marketing is podcasts. Podcasts are now very popular. They let brands reach and engage their audiences in a new, personal way. This article will explore podcasts' role in digital marketing. We'll discuss how businesses can use them to grow online and engage customers.
Podcasting Strategy: Engaging with Your Audience
Podcasts are a unique way for brands to connect with their audience via digital audio. By making informative and entertaining episodes, businesses can become industry thought leaders. They can also build brand awareness with their target audience. Podcasts connect with listeners on a personal level. This fosters brand loyalty and deeper engagement.
A well-crafted podcasting strategy is essential for building strong connections with your audience. Brands can build a loyal podcast community. They need to create content that resonates with listeners. They should encourage feedback and social media participation.
Building Brand Awareness through Audio Content Marketing
A key benefit of podcasting is its ability to boost brand visibility. Create high-quality, relevant content that resonates with your audience. It will position your brand as a trusted authority in your niche. Podcasts let you show your expertise. You can share insights and tell stories that resonate with your audience. This helps to strengthen your brand and build credibility.
In today's digital world, audio content marketing builds brand awareness. It's a very effective strategy. Brands can connect with their audience by creating engaging audio content. This includes podcasts, interviews, and audio blogs. This makes their message more memorable and impactful.
Leveraging Podcast Advertising for Business Growth
Podcast ads are a great way to reach a target audience and grow a business. Partnering with popular podcasts in your industry can help. Sponsoring niche-related episodes can also work. Both will reach a larger audience and drive traffic to your website. Podcast ads allow for very targeted messaging. This makes it easier to connect with potential customers and drive conversions.
Podcast ads are a powerful tool for business growth. They reach highly engaged audiences in a personalized, non-intrusive way. Targeted ads in relevant podcasts can help businesses connect with potential customers. This will raise brand awareness and boost conversions.
Harnessing the Power of Marketing Analytics
A key advantage of podcasting is its analytics. They let you track and measure your content's performance. Analyzing metrics like downloads and listens can provide insights. They reveal how your audience interacts with your content. You can then adjust your marketing strategy. Podcast analytics let you track your ads' effectiveness and measure your podcast's ROI.
Integrating Podcasts into Your Marketing Strategy
Using podcasts in your marketing can expand your audience and boost engagement. By creating relevant, compelling content, you can attract new listeners. It will build brand loyalty and drive customer retention. Podcasts are a cheap way to promote your products and services. They boost your brand's visibility and drive traffic to your website.
1. Building Brand Authority: Podcasts help brands become thought leaders in their field. Brands can build trust by sharing expert insights. This positions them as go-to sources for knowledge.
2. Niche Audiences: Podcasts cater to many interests and demographics. This helps brands target niche markets. This focused approach ensures that marketing efforts resonate with the right audience.
3. Enhancing Content Marketing: Repurpose podcast content into blogs, social media posts, and videos. This creates a multi-channel strategy that maximizes reach and engagement.
4. Fostering Audience Engagement: The conversational style of podcasts encourages audience interaction. This builds a loyal community.
5. Cost-Effective Advertising: Podcast ads are often cheaper than traditional media. They offer a cost-effective way for brands to reach potential customers.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, podcasts are key to boosting digital marketing and business growth. Using audio content marketing, businesses can connect with their audience. It builds brand awareness and engages customers in a personal way. Podcasts let brands showcase their expertise, tell stories, and connect with their audience. A good podcasting strategy can help businesses reach their target audience. It will engage them and drive success in digital marketing.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced digital world, businesses want new ways to reach their audience. One powerful tool that has emerged as a game-changer in the world of marketing is podcasts. Podcasts are now very popular. They let brands reach and engage their audiences in a new, personal way. This article will explore podcasts' role in digital marketing. We'll discuss how businesses can use them to grow online and engage customers.
Podcasting Strategy: Engaging with Your Audience
Podcasts are a unique way for brands to connect with their audience via digital audio. By making informative and entertaining episodes, businesses can become industry thought leaders. They can also build brand awareness with their target audience. Podcasts connect with listeners on a personal level. This fosters brand loyalty and deeper engagement.
A well-crafted podcasting strategy is essential for building strong connections with your audience. Brands can build a loyal podcast community. They need to create content that resonates with listeners. They should encourage feedback and social media participation.
Building Brand Awareness through Audio Content Marketing
A key benefit of podcasting is its ability to boost brand visibility. Create high-quality, relevant content that resonates with your audience. It will position your brand as a trusted authority in your niche. Podcasts let you show your expertise. You can share insights and tell stories that resonate with your audience. This helps to strengthen your brand and build credibility.
In today's digital world, audio content marketing builds brand awareness. It's a very effective strategy. Brands can connect with their audience by creating engaging audio content. This includes podcasts, interviews, and audio blogs. This makes their message more memorable and impactful.
Leveraging Podcast Advertising for Business Growth
Podcast ads are a great way to reach a target audience and grow a business. Partnering with popular podcasts in your industry can help. Sponsoring niche-related episodes can also work. Both will reach a larger audience and drive traffic to your website. Podcast ads allow for very targeted messaging. This makes it easier to connect with potential customers and drive conversions.
Podcast ads are a powerful tool for business growth. They reach highly engaged audiences in a personalized, non-intrusive way. Targeted ads in relevant podcasts can help businesses connect with potential customers. This will raise brand awareness and boost conversions.
Harnessing the Power of Marketing Analytics
A key advantage of podcasting is its analytics. They let you track and measure your content's performance. Analyzing metrics like downloads and listens can provide insights. They reveal how your audience interacts with your content. You can then adjust your marketing strategy. Podcast analytics let you track your ads' effectiveness and measure your podcast's ROI.
Integrating Podcasts into Your Marketing Strategy
Using podcasts in your marketing can expand your audience and boost engagement. By creating relevant, compelling content, you can attract new listeners. It will build brand loyalty and drive customer retention. Podcasts are a cheap way to promote your products and services. They boost your brand's visibility and drive traffic to your website.
1. Building Brand Authority: Podcasts help brands become thought leaders in their field. Brands can build trust by sharing expert insights. This positions them as go-to sources for knowledge.
2. Niche Audiences: Podcasts cater to many interests and demographics. This helps brands target niche markets. This focused approach ensures that marketing efforts resonate with the right audience.
3. Enhancing Content Marketing: Repurpose podcast content into blogs, social media posts, and videos. This creates a multi-channel strategy that maximizes reach and engagement.
4. Fostering Audience Engagement: The conversational style of podcasts encourages audience interaction. This builds a loyal community.
5. Cost-Effective Advertising: Podcast ads are often cheaper than traditional media. They offer a cost-effective way for brands to reach potential customers.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, podcasts are key to boosting digital marketing and business growth. Using audio content marketing, businesses can connect with their audience. It builds brand awareness and engages customers in a personal way. Podcasts let brands showcase their expertise, tell stories, and connect with their audience. A good podcasting strategy can help businesses reach their target audience. It will engage them and drive success in digital marketing.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Deep Learning in Cybersecurity Detecting Threats with AI
As data breaches and cyberattacks rise, AI is now key in cybersecurity. Traditional threat detection methods often fail against modern, complex attacks. So, a subset of AI, deep learning, is vital in the fight against cybercrime. The brain's neural networks inspire deep learning algorithms. They can analyze huge data sets, find patterns, and make decisions with little human input. This technology is reshaping cybersecurity. It offers better, faster, and more proactive threat detection.
This article explores the link between deep learning and cybersecurity. It focuses on using AI models to detect and reduce cyber threats. We will explore the basics of deep learning. We will look at its uses in cybersecurity. We will explore the hurdles and outlook for sophisticated cyber defense systems.
Table Of Contents
- Understanding Deep Learning and Its Role in Cybersecurity
- Applications of Deep Learning in Cybersecurity
- Challenges of Implementing Deep Learning in Cybersecurity
- Future Prospects and Innovations in AI-Driven Cybersecurity
- Case Studies: Real-World Examples of Deep Learning in Cybersecurity
- Conclusion
Understanding Deep Learning and Its Role in Cybersecurity
Deep learning is a branch of machine learning. It uses artificial neural networks with many layers. This allows it to process and learn from large datasets. These networks discover optimal classification representations on their own. They do this using raw data, such as images, text, or audio.
In cybersecurity, deep learning models can detect anomalies and threats in real time. They can also recognize patterns. Unlike traditional cybersecurity methods, deep learning models can adapt to new threats. They don't need explicit programming. Traditional methods rely on predefined rules and signatures. Their adaptability makes them effective against zero-day attacks. These are new, unknown vulnerabilities exploited by attackers.
Deep learning has a big advantage in cybersecurity. It can handle large-scale data. This is key for analyzing network traffic and user behavior. It helps spot digital footprints that may indicate malicious activity. Deep learning can learn from the data it processes. It can then provide predictive insights and proactive defenses. This slashes detection and response time for cyber threats.
Applications of Deep Learning in Cybersecurity
Deep learning has many uses in cybersecurity. Each offers unique benefits for threat detection and response.
Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) check network traffic for suspicious activity. They alert admins to potential breaches. Traditional IDS often use signature-based detection. It can miss new or evolving threats. Deep learning-enhanced IDS can detect anomalies in network traffic. They may signal an intrusion, even if the attack does not match any known signatures. These systems learn from normal and abnormal traffic. They improve over time and reduce false positives.
Malware Detection and Classification
Malware, like viruses, worms, ransomware, and trojans, is a big threat to digital systems. You can train deep learning models to spot and classify malware. They do this by analyzing the code or behavior of suspicious files. Deep learning can find unknown malware. It does this by spotting code or behavior similarities with known threats. Unlike signature-based methods, it does not rely on a database of known malware. This skill is vital in the fight against polymorphic malware. It often changes its code to evade traditional detection methods.
Phishing Detection
Phishing attacks are a common cyber threat. Attackers try to trick users into giving sensitive info. They pretend to be a trustworthy entity. Deep learning models can analyze emails and websites to detect phishing. They will check the content, structure, and origin. These models can spot subtle differences in real and fake emails. They learn from large datasets of both. These differences may elude humans. This achieves enhanced phishing detection.
Behavioral Analysis and User Authentication
User authentication and access control are critical components of cybersecurity. Attackers can target traditional methods such as passwords and 2FA. Deep learning can improve user authentication. It can analyze patterns in users' behavior, like typing speed and mouse movements. This creates a unique behavioral profile for each user. This method, called behavioral biometrics, can spot unusual user behavior. It may indicate a hacked account. This adds an extra layer of security.
Threat Intelligence and Predictive Analysis
Threat intelligence is about collecting and analyzing data on threats. It aims to prevent cyber attacks. Deep learning models can analyze vast threat data. This includes logs, threat feeds, and dark web info. They can find patterns and predict future attacks. These models can provide insights by understanding attackers' tactics, techniques, and procedures (TTPs). They can help organizations improve defenses against new threats.
Challenges of Implementing Deep Learning in Cybersecurity
Deep learning has big benefits for cybersecurity. But, it has challenges.
Data Privacy and Security Concerns
Deep learning models need a lot of data for training. This often includes sensitive information. The privacy and security of this data are vital. A breach could have severe consequences. Also, deep learning in cybersecurity raises fears of misuse. There is a risk of AI-driven cyberattacks that can learn and adapt to defenses.
Computational Requirements
Deep learning models demand robust processing, ample memory, and generous storage. For organizations with limited resources, this can be a barrier to adoption. We revise models regularly to combat new threats head-on. This adds to the computational burden.
Interpretability and Transparency
One of the major criticisms of deep learning is its lack of interpretability. Deep learning models are often seen as "black boxes." Unlike traditional rule-based systems, cybersecurity professionals find it hard to understand their decisions. This lack of transparency can be a problem. It is crucial to explain and justify security decisions to stakeholders or regulators.
False Positives and Model Drift
Deep learning models can cut false positives from traditional systems. But they can still make errors. Misidentification of benign activity as malicious triggers excessive warnings. They can also reduce trust in the system. Additionally, model drift can pose a challenge. It occurs when a model's performance degrades over time. Its training data becomes less representative of current conditions. Regular retraining with up-to-date data is necessary to maintain model accuracy.
Future Prospects and Innovations in AI-Driven Cybersecurity
AI and deep learning are tied to the future of cybersecurity. As cyber threats evolve, so too must the defenses against them. Several trends and innovations will likely shape the future of AI in cybersecurity.
Federated Learning for Enhanced Privacy
Federated learning trains models on many devices or servers. It keeps the data localized. This method protects privacy. It ensures that sensitive data is not sent to a central server for training. In cybersecurity, federated learning could help build strong deep learning models. They would learn from many data sources without harming privacy.
Adversarial Machine Learning
Adversarial machine learning trains models to defend against attacks. Attackers try to deceive AI systems by feeding them misleading data. As cyber attackers use AI for evil, adversarial machine learning will be vital. It will help ensure that deep learning models resist such attacks.
Integration with blockchain technology
Blockchain is secure and transparent. It can boost deep learning in cybersecurity. Using blockchain with AI can create unchangeable logs. They would track all data processed by deep learning models. This would enhance accountability and traceability. This integration could help secure supply chains. It could verify threat data and prevent tampering with cybersecurity systems.
Autonomous Security Systems
The goal of using AI and deep learning in cybersecurity is to create systems that run themselves. They must detect, respond to, and mitigate threats in real time, without human help. These systems would check networks. They would learn from new data and adapt to evolving threats. They would provide a dynamic, proactive defense against cyberattacks. Security automation still requires human oversight. But AI advances are bringing it closer to reality.
Case Studies: Real-World Examples of Deep Learning in Cybersecurity
Studying real-world uses of deep learning in cybersecurity shows its value and potential.
Google’s Use of AI in Gmail
Google uses deep learning to protect Gmail users from spam, phishing, and malware. These algorithms analyze hundreds of millions of emails daily. They find patterns that indicate malicious intent. Google claims to block over 99.9% of spam, phishing, and malware. This shows the power of AI-driven cybersecurity.
Darktrace’s Autonomous Response Technology
Darktrace, a leader in cybersecurity AI, has developed an AI. Employs deep learning to generate independent responses. This system can detect and respond to threats in real time, without humans. Darktrace’s technology analyzes network traffic and user behavior. It finds subtle deviations from normal patterns. This lets it neutralize threats before they can cause harm.
Microsoft’s Project InnerEye
Microsoft's Project InnerEye uses deep learning to secure its cloud services. The project seeks to find anomalies in Azure. It aims to spot unusual activity that might signal a security breach. Microsoft plans to use AI to improve security for its cloud customers. This is especially important in healthcare and finance. Regulators govern those industries.
How to obtain Deep Learning Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Deep learning is changing cybersecurity. It offers new tools to detect and reduce cyber threats. It can analyze vast data and adapt to new threats with little human input. So, it is vital in the fight against cybercrime. But the implementation of deep learning in cybersecurity is not without challenges.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
As data breaches and cyberattacks rise, AI is now key in cybersecurity. Traditional threat detection methods often fail against modern, complex attacks. So, a subset of AI, deep learning, is vital in the fight against cybercrime. The brain's neural networks inspire deep learning algorithms. They can analyze huge data sets, find patterns, and make decisions with little human input. This technology is reshaping cybersecurity. It offers better, faster, and more proactive threat detection.
This article explores the link between deep learning and cybersecurity. It focuses on using AI models to detect and reduce cyber threats. We will explore the basics of deep learning. We will look at its uses in cybersecurity. We will explore the hurdles and outlook for sophisticated cyber defense systems.
Table Of Contents
- Understanding Deep Learning and Its Role in Cybersecurity
- Applications of Deep Learning in Cybersecurity
- Challenges of Implementing Deep Learning in Cybersecurity
- Future Prospects and Innovations in AI-Driven Cybersecurity
- Case Studies: Real-World Examples of Deep Learning in Cybersecurity
- Conclusion
Understanding Deep Learning and Its Role in Cybersecurity
Deep learning is a branch of machine learning. It uses artificial neural networks with many layers. This allows it to process and learn from large datasets. These networks discover optimal classification representations on their own. They do this using raw data, such as images, text, or audio.
In cybersecurity, deep learning models can detect anomalies and threats in real time. They can also recognize patterns. Unlike traditional cybersecurity methods, deep learning models can adapt to new threats. They don't need explicit programming. Traditional methods rely on predefined rules and signatures. Their adaptability makes them effective against zero-day attacks. These are new, unknown vulnerabilities exploited by attackers.
Deep learning has a big advantage in cybersecurity. It can handle large-scale data. This is key for analyzing network traffic and user behavior. It helps spot digital footprints that may indicate malicious activity. Deep learning can learn from the data it processes. It can then provide predictive insights and proactive defenses. This slashes detection and response time for cyber threats.
Applications of Deep Learning in Cybersecurity
Deep learning has many uses in cybersecurity. Each offers unique benefits for threat detection and response.
Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) check network traffic for suspicious activity. They alert admins to potential breaches. Traditional IDS often use signature-based detection. It can miss new or evolving threats. Deep learning-enhanced IDS can detect anomalies in network traffic. They may signal an intrusion, even if the attack does not match any known signatures. These systems learn from normal and abnormal traffic. They improve over time and reduce false positives.
Malware Detection and Classification
Malware, like viruses, worms, ransomware, and trojans, is a big threat to digital systems. You can train deep learning models to spot and classify malware. They do this by analyzing the code or behavior of suspicious files. Deep learning can find unknown malware. It does this by spotting code or behavior similarities with known threats. Unlike signature-based methods, it does not rely on a database of known malware. This skill is vital in the fight against polymorphic malware. It often changes its code to evade traditional detection methods.
Phishing Detection
Phishing attacks are a common cyber threat. Attackers try to trick users into giving sensitive info. They pretend to be a trustworthy entity. Deep learning models can analyze emails and websites to detect phishing. They will check the content, structure, and origin. These models can spot subtle differences in real and fake emails. They learn from large datasets of both. These differences may elude humans. This achieves enhanced phishing detection.
Behavioral Analysis and User Authentication
User authentication and access control are critical components of cybersecurity. Attackers can target traditional methods such as passwords and 2FA. Deep learning can improve user authentication. It can analyze patterns in users' behavior, like typing speed and mouse movements. This creates a unique behavioral profile for each user. This method, called behavioral biometrics, can spot unusual user behavior. It may indicate a hacked account. This adds an extra layer of security.
Threat Intelligence and Predictive Analysis
Threat intelligence is about collecting and analyzing data on threats. It aims to prevent cyber attacks. Deep learning models can analyze vast threat data. This includes logs, threat feeds, and dark web info. They can find patterns and predict future attacks. These models can provide insights by understanding attackers' tactics, techniques, and procedures (TTPs). They can help organizations improve defenses against new threats.
Challenges of Implementing Deep Learning in Cybersecurity
Deep learning has big benefits for cybersecurity. But, it has challenges.
Data Privacy and Security Concerns
Deep learning models need a lot of data for training. This often includes sensitive information. The privacy and security of this data are vital. A breach could have severe consequences. Also, deep learning in cybersecurity raises fears of misuse. There is a risk of AI-driven cyberattacks that can learn and adapt to defenses.
Computational Requirements
Deep learning models demand robust processing, ample memory, and generous storage. For organizations with limited resources, this can be a barrier to adoption. We revise models regularly to combat new threats head-on. This adds to the computational burden.
Interpretability and Transparency
One of the major criticisms of deep learning is its lack of interpretability. Deep learning models are often seen as "black boxes." Unlike traditional rule-based systems, cybersecurity professionals find it hard to understand their decisions. This lack of transparency can be a problem. It is crucial to explain and justify security decisions to stakeholders or regulators.
False Positives and Model Drift
Deep learning models can cut false positives from traditional systems. But they can still make errors. Misidentification of benign activity as malicious triggers excessive warnings. They can also reduce trust in the system. Additionally, model drift can pose a challenge. It occurs when a model's performance degrades over time. Its training data becomes less representative of current conditions. Regular retraining with up-to-date data is necessary to maintain model accuracy.
Future Prospects and Innovations in AI-Driven Cybersecurity
AI and deep learning are tied to the future of cybersecurity. As cyber threats evolve, so too must the defenses against them. Several trends and innovations will likely shape the future of AI in cybersecurity.
Federated Learning for Enhanced Privacy
Federated learning trains models on many devices or servers. It keeps the data localized. This method protects privacy. It ensures that sensitive data is not sent to a central server for training. In cybersecurity, federated learning could help build strong deep learning models. They would learn from many data sources without harming privacy.
Adversarial Machine Learning
Adversarial machine learning trains models to defend against attacks. Attackers try to deceive AI systems by feeding them misleading data. As cyber attackers use AI for evil, adversarial machine learning will be vital. It will help ensure that deep learning models resist such attacks.
Integration with blockchain technology
Blockchain is secure and transparent. It can boost deep learning in cybersecurity. Using blockchain with AI can create unchangeable logs. They would track all data processed by deep learning models. This would enhance accountability and traceability. This integration could help secure supply chains. It could verify threat data and prevent tampering with cybersecurity systems.
Autonomous Security Systems
The goal of using AI and deep learning in cybersecurity is to create systems that run themselves. They must detect, respond to, and mitigate threats in real time, without human help. These systems would check networks. They would learn from new data and adapt to evolving threats. They would provide a dynamic, proactive defense against cyberattacks. Security automation still requires human oversight. But AI advances are bringing it closer to reality.
Case Studies: Real-World Examples of Deep Learning in Cybersecurity
Studying real-world uses of deep learning in cybersecurity shows its value and potential.
Google’s Use of AI in Gmail
Google uses deep learning to protect Gmail users from spam, phishing, and malware. These algorithms analyze hundreds of millions of emails daily. They find patterns that indicate malicious intent. Google claims to block over 99.9% of spam, phishing, and malware. This shows the power of AI-driven cybersecurity.
Darktrace’s Autonomous Response Technology
Darktrace, a leader in cybersecurity AI, has developed an AI. Employs deep learning to generate independent responses. This system can detect and respond to threats in real time, without humans. Darktrace’s technology analyzes network traffic and user behavior. It finds subtle deviations from normal patterns. This lets it neutralize threats before they can cause harm.
Microsoft’s Project InnerEye
Microsoft's Project InnerEye uses deep learning to secure its cloud services. The project seeks to find anomalies in Azure. It aims to spot unusual activity that might signal a security breach. Microsoft plans to use AI to improve security for its cloud customers. This is especially important in healthcare and finance. Regulators govern those industries.
How to obtain Deep Learning Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Deep learning is changing cybersecurity. It offers new tools to detect and reduce cyber threats. It can analyze vast data and adapt to new threats with little human input. So, it is vital in the fight against cybercrime. But the implementation of deep learning in cybersecurity is not without challenges.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
RPA and Cybersecurity Protecting Automated Systems
In today's digital world, businesses are using RPA. It helps to streamline operations, improve efficiency, and cut costs. RPA uses robots, machine learning, and AI to automate repetitive tasks. RPA has many benefits. But, it brings new cybersecurity risks. Organizations must address these to protect their automated systems.
Automation and the Risks of Cybersecurity
Automated processes powered by RPA can help organizations. They can transform and optimize their operations. However, these systems are vulnerable to cyber threats. These include data breaches, malware, and other attacks. It is crucial for businesses to have strong security measures. They protect automated processes and sensitive information from unauthorized access.
As organizations use automation to streamline operations, they must watch for cybersecurity risks. Automated systems can add vulnerabilities if not secured. So, businesses must use strong cybersecurity measures. They must also monitor their automated systems to prevent breaches.
Understanding the Importance of Data Security
Data security is vital to cybersecurity. It protects automated systems. To protect their data, organizations must implement IT security measures. These include threat detection, vulnerability management, and network and cloud security. They are vital for data confidentiality, integrity, and availability. Securing their data can help businesses. It can reduce cyber threats and prevent unauthorized access to their automated systems.
In an age of rising data breaches and cyber threats, understanding data security is vital. It protects sensitive information and ensures organizational integrity. Good data security measures prevent unauthorized access. They build trust with customers and stakeholders by protecting their data.
Implementing Security Measures and Compliance
Organizations must assess risks, comply with laws, and protect data. These are key to cybersecurity. They must also ensure privacy controls for their automated systems. Regular risk assessments and compliance with security standards can help. They can identify vulnerabilities in automated processes. Then, businesses can implement controls to reduce risks. Also, data protection measures and privacy controls can help. They can safeguard sensitive information and prevent data breaches.
Strong security and compliance are vital. They protect automated processes and sensitive data. Organizations can protect their automation investments. They can do this by using advanced security protocols and following regulations. This will reduce risks.
Enhancing Security with Automation
To boost security in automated systems, businesses can use:
-
Security software
-
Automated threat response
-
Security intelligence
-
Secure coding practices
Automating security processes helps organizations detect and respond to cyber threats. This reduces the risk of data breaches and other security incidents. Also, using security best practices and tools can help businesses. They can better protect their automated systems from cyber attacks.
"Enhancing security through automation is crucial in today’s rapidly evolving threat landscape. "By integrating advanced automated systems, organizations can find and fix security incidents. This will reduce vulnerabilities and improve protection against cyber threats.""
Ensuring Secure Networks and Access Control
Cybersecurity requires four key tools. They are: data encryption, access control, identity management, and security analytics. Organizations must use them to secure networks and control access in automated systems. By encrypting data, organizations can protect sensitive information. It prevents unauthorized access. Access control and identity management solutions can help manage user permissions. They can also stop unauthorized users from accessing automated processes. Also, security analytics can help organizations spot and respond to security incidents in real time. This will improve the security of their automated systems.
In today's digital world, strong network security is vital. It protects sensitive data from unauthorized access and cyber threats. Regular access reviews and strong security measures can greatly improve your organization's defenses. They will help protect your critical information from breaches.
Final Thoughts
In short, protecting automated systems from cyber threats requires a multi-faceted approach. It must combine data security, compliance, security measures, and access control. This will protect sensitive information and prevent unauthorized access to automated processes. Organizations can protect their automated systems. They should use security best practices, technologies, and a focus on cybersecurity. This will reduce the risk of cyber attacks.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, RPA can greatly benefit businesses. It helps automate processes and improve efficiency. Organizations must prioritize cybersecurity. They should implement strong measures to protect their automated systems from cyber threats. By knowing the risks of cybersecurity, businesses can improve their security. They can do this by using automation, and ensuring secure networks and access control. This will protect their automated processes from security breaches. By prioritizing cybersecurity, organizations can protect their automated systems. Strong security will lower the risk of cyber attacks today.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's digital world, businesses are using RPA. It helps to streamline operations, improve efficiency, and cut costs. RPA uses robots, machine learning, and AI to automate repetitive tasks. RPA has many benefits. But, it brings new cybersecurity risks. Organizations must address these to protect their automated systems.
Automation and the Risks of Cybersecurity
Automated processes powered by RPA can help organizations. They can transform and optimize their operations. However, these systems are vulnerable to cyber threats. These include data breaches, malware, and other attacks. It is crucial for businesses to have strong security measures. They protect automated processes and sensitive information from unauthorized access.
As organizations use automation to streamline operations, they must watch for cybersecurity risks. Automated systems can add vulnerabilities if not secured. So, businesses must use strong cybersecurity measures. They must also monitor their automated systems to prevent breaches.
Understanding the Importance of Data Security
Data security is vital to cybersecurity. It protects automated systems. To protect their data, organizations must implement IT security measures. These include threat detection, vulnerability management, and network and cloud security. They are vital for data confidentiality, integrity, and availability. Securing their data can help businesses. It can reduce cyber threats and prevent unauthorized access to their automated systems.
In an age of rising data breaches and cyber threats, understanding data security is vital. It protects sensitive information and ensures organizational integrity. Good data security measures prevent unauthorized access. They build trust with customers and stakeholders by protecting their data.
Implementing Security Measures and Compliance
Organizations must assess risks, comply with laws, and protect data. These are key to cybersecurity. They must also ensure privacy controls for their automated systems. Regular risk assessments and compliance with security standards can help. They can identify vulnerabilities in automated processes. Then, businesses can implement controls to reduce risks. Also, data protection measures and privacy controls can help. They can safeguard sensitive information and prevent data breaches.
Strong security and compliance are vital. They protect automated processes and sensitive data. Organizations can protect their automation investments. They can do this by using advanced security protocols and following regulations. This will reduce risks.
Enhancing Security with Automation
To boost security in automated systems, businesses can use:
-
Security software
-
Automated threat response
-
Security intelligence
-
Secure coding practices
Automating security processes helps organizations detect and respond to cyber threats. This reduces the risk of data breaches and other security incidents. Also, using security best practices and tools can help businesses. They can better protect their automated systems from cyber attacks.
"Enhancing security through automation is crucial in today’s rapidly evolving threat landscape. "By integrating advanced automated systems, organizations can find and fix security incidents. This will reduce vulnerabilities and improve protection against cyber threats.""
Ensuring Secure Networks and Access Control
Cybersecurity requires four key tools. They are: data encryption, access control, identity management, and security analytics. Organizations must use them to secure networks and control access in automated systems. By encrypting data, organizations can protect sensitive information. It prevents unauthorized access. Access control and identity management solutions can help manage user permissions. They can also stop unauthorized users from accessing automated processes. Also, security analytics can help organizations spot and respond to security incidents in real time. This will improve the security of their automated systems.
In today's digital world, strong network security is vital. It protects sensitive data from unauthorized access and cyber threats. Regular access reviews and strong security measures can greatly improve your organization's defenses. They will help protect your critical information from breaches.
Final Thoughts
In short, protecting automated systems from cyber threats requires a multi-faceted approach. It must combine data security, compliance, security measures, and access control. This will protect sensitive information and prevent unauthorized access to automated processes. Organizations can protect their automated systems. They should use security best practices, technologies, and a focus on cybersecurity. This will reduce the risk of cyber attacks.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, RPA can greatly benefit businesses. It helps automate processes and improve efficiency. Organizations must prioritize cybersecurity. They should implement strong measures to protect their automated systems from cyber threats. By knowing the risks of cybersecurity, businesses can improve their security. They can do this by using automation, and ensuring secure networks and access control. This will protect their automated processes from security breaches. By prioritizing cybersecurity, organizations can protect their automated systems. Strong security will lower the risk of cyber attacks today.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Impact of PgMP Certification on Change Initiatives
Are you considering pursuing a Program Management Professional (PgMP) certification? Could this prestigious certification help you lead change in your organization? Look no further! This article will explore the benefits of PgMP certification. It will cover the requirements, cost, salary potential, and more.
What is PgMP Certification?
PgMP certification is a globally recognized program management credential. It is offered by the Project Management Institute (PMI). It is for experienced program managers. They want to prove they can manage projects to meet business goals.
PgMP Certification Benefits
-
PgMP certification proves your program management skills. It shows your dedication to professional growth.
-
Career Advancement: PgMP certification can open new doors in program management. It can help you advance your career.
-
Higher Earning Potential: PgMP certified workers often earn more than non-certified ones.
-
Global Recognition: PgMP certification is respected worldwide. It gives you a competitive edge in the job market.
-
Improved Job Performance: The PgMP certification will boost your skills. This will improve your job performance and project success.
PgMP Certification Requirements
To be eligible for PgMP certification, you must meet the following requirements:
-
Education: You must have a secondary degree or higher. (a high school diploma or an associate's degree)
-
You must have at least four years of experience in both project and program management.
-
PgMP Exam: Pass the PgMP exam, which tests your knowledge and skills in program management.
PgMP Certification Cost
The cost of PgMP certification includes an exam and PMI membership fee. Exam fees depend on your PMI membership status and location. The membership fee is annual.
PgMP Certification Salary
PgMP certification can boost your earning potential Salary scales for PgMP holders can vary. They depend on experience, industry, and location.
Importance of PgMP Certification
PgMP certification is vital for program managers. It helps them prove their expertise and stand out in a tough job market. It boosts their careers.
PgMP vs PMP Certification
PgMP certification is for program management. PMP certification is for project management. Both certifications are valuable. But, PgMP is better for those managing multiple projects to achieve business goals.
When comparing PgMP and PMP certifications, it's vital to know the differences between program and project management. Also, each certification suits different career goals and job duties.
1. Scope and Focus:
-
PMP Certification:
-
Focuses on individual project management.
-
Emphasizes managing a single project from initiation to completion.
-
Involves knowledge of the Project Management Body of Knowledge (PMBOK® Guide).
-
PgMP Certification:
-
Focuses on managing multiple related projects, known as a program.
-
Emphasizes strategic alignment, coordinating multiple projects to achieve broader organizational goals.
-
It requires knowing how to manage project interdependencies. They must contribute to program goals.
2. Eligibility and Experience Requirements:
-
PMP Certification:
-
Requires a secondary degree and 5 years of project management experience. A high school diploma, an associate degree, or an equivalent are acceptable for the secondary degree.Requires 35 hours of project management education.
-
PgMP Certification:
-
Requires more experience: a degree and 6,000 hours each of project and program management. Or, a four-year degree with 6,000 hours in program management.
-
Demonstrates higher-level expertise in managing complex programs.
3. Target Audience:
-
PMP Certification:
-
Ideal for individuals managing single projects or working as project managers.
-
Suitable for professionals looking to solidify their project management skills.
-
PgMP Certification:
-
For senior program managers, directors, and those managing multiple, related projects.
-
Ideal for professionals looking to advance to higher strategic roles in program management.
4. Career Impact:
-
PMP Certification:
-
Recognized globally as a standard for project management professionals.
-
Can lead to roles like Project Manager, Senior Project Manager, or Project Consultant.
-
PgMP Certification:
-
Positions you as a strategic leader capable of managing complex, organization-wide initiatives.
-
Can lead to roles like Program Manager or VP of Program Management.
5. Exam Structure:
-
PMP Certification:
-
The exam has 180 questions. They include multiple-choice, multiple-response, matching, hotspot, and limited fill-in-the-blank types.
-
PgMP Certification:
-
The exam has 170 multiple-choice questions. They cover: program strategy, the program life cycle, benefits, stakeholders, and governance.
6. Maintenance of Certification:
-
PMP Certification:
-
Requires earning 60 Professional Development Units (PDUs) every three years to maintain certification.
-
PgMP Certification:
-
Must earn 60 PDUs every three years. They should focus on a strategic view of program management.
7. Market Demand and Salary:
-
PMP Certification:
-
High demand across various industries, with an increase in salary and job opportunities.
-
PgMP Certification:
-
It's more specialized. It often commands a higher salary due to the seniority and complexity of the roles it qualifies for.
How to obtain PgMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, a PgMP certification can boost your skills to lead change in your organization. It shows your expertise. It boosts your career and earning potential. If you are a seasoned program manager, consider PgMP certification. It may be the right choice to advance your career.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you considering pursuing a Program Management Professional (PgMP) certification? Could this prestigious certification help you lead change in your organization? Look no further! This article will explore the benefits of PgMP certification. It will cover the requirements, cost, salary potential, and more.
What is PgMP Certification?
PgMP certification is a globally recognized program management credential. It is offered by the Project Management Institute (PMI). It is for experienced program managers. They want to prove they can manage projects to meet business goals.
PgMP Certification Benefits
-
PgMP certification proves your program management skills. It shows your dedication to professional growth.
-
Career Advancement: PgMP certification can open new doors in program management. It can help you advance your career.
-
Higher Earning Potential: PgMP certified workers often earn more than non-certified ones.
-
Global Recognition: PgMP certification is respected worldwide. It gives you a competitive edge in the job market.
-
Improved Job Performance: The PgMP certification will boost your skills. This will improve your job performance and project success.
PgMP Certification Requirements
To be eligible for PgMP certification, you must meet the following requirements:
-
Education: You must have a secondary degree or higher. (a high school diploma or an associate's degree)
-
You must have at least four years of experience in both project and program management.
-
PgMP Exam: Pass the PgMP exam, which tests your knowledge and skills in program management.
PgMP Certification Cost
The cost of PgMP certification includes an exam and PMI membership fee. Exam fees depend on your PMI membership status and location. The membership fee is annual.
PgMP Certification Salary
PgMP certification can boost your earning potential Salary scales for PgMP holders can vary. They depend on experience, industry, and location.
Importance of PgMP Certification
PgMP certification is vital for program managers. It helps them prove their expertise and stand out in a tough job market. It boosts their careers.
PgMP vs PMP Certification
PgMP certification is for program management. PMP certification is for project management. Both certifications are valuable. But, PgMP is better for those managing multiple projects to achieve business goals.
When comparing PgMP and PMP certifications, it's vital to know the differences between program and project management. Also, each certification suits different career goals and job duties.
1. Scope and Focus:
-
PMP Certification:
-
Focuses on individual project management.
-
Emphasizes managing a single project from initiation to completion.
-
Involves knowledge of the Project Management Body of Knowledge (PMBOK® Guide).
-
-
PgMP Certification:
-
Focuses on managing multiple related projects, known as a program.
-
Emphasizes strategic alignment, coordinating multiple projects to achieve broader organizational goals.
-
It requires knowing how to manage project interdependencies. They must contribute to program goals.
-
2. Eligibility and Experience Requirements:
-
PMP Certification:
-
Requires a secondary degree and 5 years of project management experience. A high school diploma, an associate degree, or an equivalent are acceptable for the secondary degree.Requires 35 hours of project management education.
-
-
PgMP Certification:
-
Requires more experience: a degree and 6,000 hours each of project and program management. Or, a four-year degree with 6,000 hours in program management.
-
Demonstrates higher-level expertise in managing complex programs.
-
3. Target Audience:
-
PMP Certification:
-
Ideal for individuals managing single projects or working as project managers.
-
Suitable for professionals looking to solidify their project management skills.
-
-
PgMP Certification:
-
For senior program managers, directors, and those managing multiple, related projects.
-
Ideal for professionals looking to advance to higher strategic roles in program management.
-
4. Career Impact:
-
PMP Certification:
-
Recognized globally as a standard for project management professionals.
-
Can lead to roles like Project Manager, Senior Project Manager, or Project Consultant.
-
-
PgMP Certification:
-
Positions you as a strategic leader capable of managing complex, organization-wide initiatives.
-
Can lead to roles like Program Manager or VP of Program Management.
-
5. Exam Structure:
-
PMP Certification:
-
The exam has 180 questions. They include multiple-choice, multiple-response, matching, hotspot, and limited fill-in-the-blank types.
-
-
PgMP Certification:
-
The exam has 170 multiple-choice questions. They cover: program strategy, the program life cycle, benefits, stakeholders, and governance.
-
6. Maintenance of Certification:
-
PMP Certification:
-
Requires earning 60 Professional Development Units (PDUs) every three years to maintain certification.
-
-
PgMP Certification:
-
Must earn 60 PDUs every three years. They should focus on a strategic view of program management.
-
7. Market Demand and Salary:
-
PMP Certification:
-
High demand across various industries, with an increase in salary and job opportunities.
-
-
PgMP Certification:
-
It's more specialized. It often commands a higher salary due to the seniority and complexity of the roles it qualifies for.
-
How to obtain PgMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, a PgMP certification can boost your skills to lead change in your organization. It shows your expertise. It boosts your career and earning potential. If you are a seasoned program manager, consider PgMP certification. It may be the right choice to advance your career.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Deep Learning for Speech Recognition and Synthesis
In today's fast world, AI has advanced a lot, especially in deep learning. A thrilling use of deep learning is in speech recognition and synthesis. Here, neural networks process and interpret spoken language. This article will explore deep learning methods in speech technology. It will cover the techniques, algorithms, applications, and advancements.
What is Deep Learning?
Deep learning is a type of machine learning. It uses neural networks to find complex patterns in data. These deep neural networks can learn from data. So, they are ideal for tasks like speech recognition and synthesis. Deep learning models use multiple layers of connected nodes. They can find complex patterns in large datasets.
Speech Recognition with Deep Learning
Speech recognition, or automatic speech recognition (ASR), converts spoken language into text. Deep learning has changed speech recognition. It enabled the development of highly accurate, robust systems. Deep learning models for voice recognition can analyze audio signals. They can extract features that are crucial for understanding spoken language.
1. Introduction to Speech Recognition
Definition: Speech recognition is the process of converting spoken language into text. It involves capturing audio signals, processing them, and interpreting the linguistic content.
Historical Context: Early systems relied on rule-based algorithms and limited vocabulary. Modern systems use deep learning. It boosts accuracy and handles complex tasks.
2. Key Technologies in Speech Recognition
Acoustic Models: These models analyze audio signals. They show the link between phonetic units and audio features. Deep learning models like CNNs and RNNs are used to build these models.
Language Models: These models predict the probability of a sequence of words. Transformers, a type of deep learning, improve language models and context understanding.
End-to-End Systems: Recent advances involve end-to-end deep learning models. They combine acoustic and language modeling into one system. This simplifies the pipeline and often improves performance.
3. Deep Learning Architectures for Speech Recognition
Convolutional Neural Networks (CNNs) extract features from raw audio or spectrograms. CNNs help in identifying patterns and features in audio data.
RNNs, including LSTMs, capture time-based patterns in speech. They are useful for modeling sequences and predicting speech over time.
Transformer Models: Recent work uses Transformer-based models like BERT and GPT. They are good at handling long-range dependencies and context in speech recognition tasks.
Attention Mechanisms: They help the model focus on parts of the input sequence. This boosts its ability to interpret and transcribe speech accurately.
4. Training Deep Learning Models for Speech Recognition
Data Collection: Training requires large datasets of spoken language. Common datasets include LibriSpeech, TED-LIUM, and CommonVoice.
Preprocessing: Audio data is often turned into spectrograms or MFCCs. This converts raw audio into a format suitable for deep learning models.
Model Training: We train models using supervised learning. We use labeled audio and text pairs. Techniques like transfer learning and fine-tuning are used to improve performance.
5. Challenges and Solutions
Accent and Dialect Variability: Speech recognition systems may struggle with accents and dialects. Solutions include using diverse training data and incorporating adaptive models.
Background Noise: Noise can interfere with recognition accuracy. Techniques like noise reduction and robust feature extraction can help. So can noise-aware training.
Real-Time Processing: Efficient real-time processing is crucial for applications like voice assistants. To achieve low latency, we must optimize models and use faster hardware, like GPUs.
6. Applications of Speech Recognition
Virtual Assistants: Siri, Alexa, and Google Assistant are personal assistants. They use speech recognition to interact with users and perform tasks.
Transcription Services: Automated transcription of meetings, interviews, and lectures. It helps with records and accessibility.
Voice-Controlled Devices: Speech recognition allows hands-free control of devices. This includes smart home gadgets and tools for the disabled.
Customer Service: Automated support systems use speech recognition to respond to customer inquiries.
7. Future Directions
Multilingual and Cross-Lingual Models: Build models that can use and switch between many languages.
Improved Context Understanding: Bettering the model's grasp of context in complex chats.
Integration with Other Modalities: Combine speech recognition with other AI, like computer vision. This will create more advanced, interactive systems.
8. Key Papers and Resources
"Deep Speech: Scaling up end-to-end speech recognition" by Baidu. It's an influential paper on using end-to-end deep learning for speech recognition.
Listen, Attend and Spell: A paper on an attention-based model for speech recognition.
Open-source Libraries: Kaldi, Mozilla's DeepSpeech, and Hugging Face's Transformers are resources. They provide tools and pre-trained models for speech recognition.
Speech Synthesis with Deep Learning
On the other hand, speech synthesis involves generating spoken language from text. Deep learning has made synthetic voices that sound like humans. They mimic human speech patterns. Researchers have made great strides in synthetic voice quality and expressiveness. They used deep neural networks for speech synthesis.
Deep Learning Applications in Speech Technology
Deep learning has a wide range of uses in speech tech, including:
· Speech processing techniques
· Speech emotion recognition
· Speech feature extraction
· Voice cloning
· Speaker recognition
· End-to-end speech recognition
· Speech sentiment analysis By using deep learning, researchers can advance speech tech.
How to obtain Deep Learning certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, deep learning has transformed speech recognition and synthesis. It is a powerful tool. Researchers have used deep neural networks and advanced algorithms. They have developed systems that can process and understand spoken language. These systems are very accurate and efficient. As technology evolves, deep learning will drive exciting advances in speech tech.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast world, AI has advanced a lot, especially in deep learning. A thrilling use of deep learning is in speech recognition and synthesis. Here, neural networks process and interpret spoken language. This article will explore deep learning methods in speech technology. It will cover the techniques, algorithms, applications, and advancements.
What is Deep Learning?
Deep learning is a type of machine learning. It uses neural networks to find complex patterns in data. These deep neural networks can learn from data. So, they are ideal for tasks like speech recognition and synthesis. Deep learning models use multiple layers of connected nodes. They can find complex patterns in large datasets.
Speech Recognition with Deep Learning
Speech recognition, or automatic speech recognition (ASR), converts spoken language into text. Deep learning has changed speech recognition. It enabled the development of highly accurate, robust systems. Deep learning models for voice recognition can analyze audio signals. They can extract features that are crucial for understanding spoken language.
1. Introduction to Speech Recognition
Definition: Speech recognition is the process of converting spoken language into text. It involves capturing audio signals, processing them, and interpreting the linguistic content.
Historical Context: Early systems relied on rule-based algorithms and limited vocabulary. Modern systems use deep learning. It boosts accuracy and handles complex tasks.
2. Key Technologies in Speech Recognition
Acoustic Models: These models analyze audio signals. They show the link between phonetic units and audio features. Deep learning models like CNNs and RNNs are used to build these models.
Language Models: These models predict the probability of a sequence of words. Transformers, a type of deep learning, improve language models and context understanding.
End-to-End Systems: Recent advances involve end-to-end deep learning models. They combine acoustic and language modeling into one system. This simplifies the pipeline and often improves performance.
3. Deep Learning Architectures for Speech Recognition
Convolutional Neural Networks (CNNs) extract features from raw audio or spectrograms. CNNs help in identifying patterns and features in audio data.
RNNs, including LSTMs, capture time-based patterns in speech. They are useful for modeling sequences and predicting speech over time.
Transformer Models: Recent work uses Transformer-based models like BERT and GPT. They are good at handling long-range dependencies and context in speech recognition tasks.
Attention Mechanisms: They help the model focus on parts of the input sequence. This boosts its ability to interpret and transcribe speech accurately.
4. Training Deep Learning Models for Speech Recognition
Data Collection: Training requires large datasets of spoken language. Common datasets include LibriSpeech, TED-LIUM, and CommonVoice.
Preprocessing: Audio data is often turned into spectrograms or MFCCs. This converts raw audio into a format suitable for deep learning models.
Model Training: We train models using supervised learning. We use labeled audio and text pairs. Techniques like transfer learning and fine-tuning are used to improve performance.
5. Challenges and Solutions
Accent and Dialect Variability: Speech recognition systems may struggle with accents and dialects. Solutions include using diverse training data and incorporating adaptive models.
Background Noise: Noise can interfere with recognition accuracy. Techniques like noise reduction and robust feature extraction can help. So can noise-aware training.
Real-Time Processing: Efficient real-time processing is crucial for applications like voice assistants. To achieve low latency, we must optimize models and use faster hardware, like GPUs.
6. Applications of Speech Recognition
Virtual Assistants: Siri, Alexa, and Google Assistant are personal assistants. They use speech recognition to interact with users and perform tasks.
Transcription Services: Automated transcription of meetings, interviews, and lectures. It helps with records and accessibility.
Voice-Controlled Devices: Speech recognition allows hands-free control of devices. This includes smart home gadgets and tools for the disabled.
Customer Service: Automated support systems use speech recognition to respond to customer inquiries.
7. Future Directions
Multilingual and Cross-Lingual Models: Build models that can use and switch between many languages.
Improved Context Understanding: Bettering the model's grasp of context in complex chats.
Integration with Other Modalities: Combine speech recognition with other AI, like computer vision. This will create more advanced, interactive systems.
8. Key Papers and Resources
"Deep Speech: Scaling up end-to-end speech recognition" by Baidu. It's an influential paper on using end-to-end deep learning for speech recognition.
Listen, Attend and Spell: A paper on an attention-based model for speech recognition.
Open-source Libraries: Kaldi, Mozilla's DeepSpeech, and Hugging Face's Transformers are resources. They provide tools and pre-trained models for speech recognition.
Speech Synthesis with Deep Learning
On the other hand, speech synthesis involves generating spoken language from text. Deep learning has made synthetic voices that sound like humans. They mimic human speech patterns. Researchers have made great strides in synthetic voice quality and expressiveness. They used deep neural networks for speech synthesis.
Deep Learning Applications in Speech Technology
Deep learning has a wide range of uses in speech tech, including:
· Speech processing techniques
· Speech emotion recognition
· Speech feature extraction
· Voice cloning
· Speaker recognition
· End-to-end speech recognition
· Speech sentiment analysis By using deep learning, researchers can advance speech tech.
How to obtain Deep Learning certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, deep learning has transformed speech recognition and synthesis. It is a powerful tool. Researchers have used deep neural networks and advanced algorithms. They have developed systems that can process and understand spoken language. These systems are very accurate and efficient. As technology evolves, deep learning will drive exciting advances in speech tech.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Benefits of CAPM Certification for Non Project Managers
In today's competitive market, effective project management is vital. It's no longer the job of traditional project managers. Organizations now expect employees in all roles to know basic project management. The Project Management Institute (PMI) offers the CAPM certification. It is now a key credential for many aspiring project managers. For non-project managers, the CAPM certification can be very useful. It teaches key project management skills. It boosts their credibility and opens new career paths. This article explores the benefits of CAPM certification for non-project managers. It states it is a good investment for career growth and success.
Table Of Contents
- Understanding the CAPM certification
- Enhancing Cross-Functional Collaboration
- Improving Time Management and Efficiency
- Building Leadership and Decision-Making Skills
- Expanding Career Opportunities and Professional Growth
- Conclusion
Understanding the CAPM certification
The CAPM certification aims to teach professionals the basics of project management. The CAPM is easier to get than the advanced PMP. The PMP requires extensive project management experience. The CAPM is open to those with little or no experience in managing projects. It is an entry-level certification. It tests a person's knowledge of project management in the PMI's PMBOK Guide.
The CAPM cert gives non-project managers a full view of project management. It covers project scope, time, cost, quality, and more. It includes human resources, communications, risk, procurement, and stakeholder management. A basic knowledge of these areas will help non-project managers. They will then understand the context and requirements of their organization's projects. This will make them more effective contributors to project teams and initiatives.
Enhancing Cross-Functional Collaboration
In many organizations, projects must collaboration between various departments. These include marketing, finance, HR, and IT. Non-project managers with CAPM certification can help cross-functional collaboration. They can communicate better with project managers and team members. They know project management principles. This ensures their work aligns with the project's goals.
Knowing the project management framework will help non-project managers. They can better foresee challenges and risks. They can also be more proactive in solving problems. This leads to smoother projects, fewer misunderstandings, and a better team. In the end, good cross-departmental collaboration boosts project success. It also improves the organization's performance.
Improving Time Management and Efficiency
A key benefit of the CAPM certification is its focus on time management and efficiency. Non-project managers often juggle many tasks. So, they must manage their time well to stay productive. The CAPM certification teaches professionals to plan, schedule, and rank tasks in projects. These skills are useful in their daily work.
For example, non-project managers can use WBS and CPM. They help organize their work and find the most critical tasks. By adopting these practices, they can ensure their work is on time. This will help deliver projects on schedule. This efficiency helps both the individual and the organization.
Building Leadership and Decision-Making Skills
Leadership and decision-making are essential skills for any professional, regardless of their role. The CAPM certification helps non-project managers. It teaches them the project management decision-making processes. A non-project manager can lead and manage better. They should learn to assess risks and divide resources. They must also make decisions within a project framework.
A marketing manager with a CAPM may make better campaign decisions. They must work within time, budget, and scope limits. This skill can boost a non-project manager's leadership. It can make them a valuable asset to the organization. Apply project management principles to make informed decisions through critical thinking.
Expanding Career Opportunities and Professional Growth
Earning a CAPM certification boosts a non-project manager's career opportunities. In a tough job market, a recognized certification, like the CAPM, can help a candidate stand out. It shows a commitment to professional growth and a willingness to exceed their role.
For non-project managers seeking to advance, the CAPM certification can help. It can also be a stepping stone for job seekers. It opens doors to roles needing both skills: functional expertise and project management. These include program management, operations management, and strategic planning. Also, the CAPM certification can help non-project managers. It can enable them to take on more complex, challenging projects. This will further their professional growth.
How to obtain CAPM Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, The CAPM certification benefits non-project managers. It gives them the skills to excel in their current roles and beyond. By learning project management basics, non-project managers can collaborate better with project teams. They can also improve their time management and efficiency. They will develop their leadership and decision-making skills and expand their career opportunities. As organizations value project management, the CAPM certification is becoming more sought after. It is an asset for professionals in any field. Investing in CAPM certification boosts personal growth and the organization's success. The CAPM certification is a powerful tool. It can help you achieve your career goals, whether you want to improve your current job or explore new paths.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's competitive market, effective project management is vital. It's no longer the job of traditional project managers. Organizations now expect employees in all roles to know basic project management. The Project Management Institute (PMI) offers the CAPM certification. It is now a key credential for many aspiring project managers. For non-project managers, the CAPM certification can be very useful. It teaches key project management skills. It boosts their credibility and opens new career paths. This article explores the benefits of CAPM certification for non-project managers. It states it is a good investment for career growth and success.
Table Of Contents
- Understanding the CAPM certification
- Enhancing Cross-Functional Collaboration
- Improving Time Management and Efficiency
- Building Leadership and Decision-Making Skills
- Expanding Career Opportunities and Professional Growth
- Conclusion
Understanding the CAPM certification
The CAPM certification aims to teach professionals the basics of project management. The CAPM is easier to get than the advanced PMP. The PMP requires extensive project management experience. The CAPM is open to those with little or no experience in managing projects. It is an entry-level certification. It tests a person's knowledge of project management in the PMI's PMBOK Guide.
The CAPM cert gives non-project managers a full view of project management. It covers project scope, time, cost, quality, and more. It includes human resources, communications, risk, procurement, and stakeholder management. A basic knowledge of these areas will help non-project managers. They will then understand the context and requirements of their organization's projects. This will make them more effective contributors to project teams and initiatives.
Enhancing Cross-Functional Collaboration
In many organizations, projects must collaboration between various departments. These include marketing, finance, HR, and IT. Non-project managers with CAPM certification can help cross-functional collaboration. They can communicate better with project managers and team members. They know project management principles. This ensures their work aligns with the project's goals.
Knowing the project management framework will help non-project managers. They can better foresee challenges and risks. They can also be more proactive in solving problems. This leads to smoother projects, fewer misunderstandings, and a better team. In the end, good cross-departmental collaboration boosts project success. It also improves the organization's performance.
Improving Time Management and Efficiency
A key benefit of the CAPM certification is its focus on time management and efficiency. Non-project managers often juggle many tasks. So, they must manage their time well to stay productive. The CAPM certification teaches professionals to plan, schedule, and rank tasks in projects. These skills are useful in their daily work.
For example, non-project managers can use WBS and CPM. They help organize their work and find the most critical tasks. By adopting these practices, they can ensure their work is on time. This will help deliver projects on schedule. This efficiency helps both the individual and the organization.
Building Leadership and Decision-Making Skills
Leadership and decision-making are essential skills for any professional, regardless of their role. The CAPM certification helps non-project managers. It teaches them the project management decision-making processes. A non-project manager can lead and manage better. They should learn to assess risks and divide resources. They must also make decisions within a project framework.
A marketing manager with a CAPM may make better campaign decisions. They must work within time, budget, and scope limits. This skill can boost a non-project manager's leadership. It can make them a valuable asset to the organization. Apply project management principles to make informed decisions through critical thinking.
Expanding Career Opportunities and Professional Growth
Earning a CAPM certification boosts a non-project manager's career opportunities. In a tough job market, a recognized certification, like the CAPM, can help a candidate stand out. It shows a commitment to professional growth and a willingness to exceed their role.
For non-project managers seeking to advance, the CAPM certification can help. It can also be a stepping stone for job seekers. It opens doors to roles needing both skills: functional expertise and project management. These include program management, operations management, and strategic planning. Also, the CAPM certification can help non-project managers. It can enable them to take on more complex, challenging projects. This will further their professional growth.
How to obtain CAPM Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, The CAPM certification benefits non-project managers. It gives them the skills to excel in their current roles and beyond. By learning project management basics, non-project managers can collaborate better with project teams. They can also improve their time management and efficiency. They will develop their leadership and decision-making skills and expand their career opportunities. As organizations value project management, the CAPM certification is becoming more sought after. It is an asset for professionals in any field. Investing in CAPM certification boosts personal growth and the organization's success. The CAPM certification is a powerful tool. It can help you achieve your career goals, whether you want to improve your current job or explore new paths.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
5 Benefits of Completing Google Cloud Platform CP100A
In today's fast-paced world, cloud computing is crucial for businesses. It offers agility, scalability, and cost savings. Google Cloud Platform (GCP) is a top cloud provider. It offers a suite of services that help organizations innovate and thrive. Among its foundational courses, CP100A (Google Cloud Fundamentals: Core Infrastructure) is essential. It teaches learners the core concepts and services of GCP. This course instructs on mastering cloud navigation techniques. Completing the CP100A course opens up many opportunities. It offers benefits beyond technical skills. We explore five key benefits of completing the Google Cloud Platform CP100A. This course can boost your career and improve your organization. It can also foster innovation in the fast-changing tech world.
Table of Contents
- Comprehensive Understanding of Google Cloud Services
- Enhanced Career Opportunities and Job Prospects
- Boosting Organizational Efficiency and Innovation
- Hands-On Experience with Real-World Scenarios
- Building a Strong Network and Community Engagement
- Conclusion
Comprehensive Understanding of Google Cloud Services
A key benefit of the CP100A course is its deep knowledge of Google Cloud Platform's services. Participants learn about key services, like Compute Engine, Cloud Storage, and BigQuery. This knowledge is crucial for successful cloud solution installation.
- The course covers essential cloud concepts, networking, databases, and machine learning. It gives learners a holistic view of how GCP operates.
- Hands-on Labs and Demos: Interactive labs and demos let learners use real GCP services. This enhances their understanding through practical experience.
- Building Blocks for Expertise: This knowledge is a foundation. It gets you ready for advanced GCP certs and jobs, like Solutions Architect or Cloud Engineer.
By the end of the CP100A course, participants will know GCP's ecosystem. They will be able to contribute to cloud-based projects in their organizations.
Enhanced Career Opportunities and Job Prospects
Demand for cloud computing skills is surging. Many organizations seek experts in managing and deploying cloud solutions. The CP100A course boosts your job prospects. It shows your dedication to learning cloud technologies.
- High Demand for Cloud Professionals: Reports say cloud jobs are among the fastest-growing. CP100A provides a strong foundation, enhancing your job market prospects.
- Attractive Salaries: Professionals with cloud skills often earn more than others. The CP100A course shows employers you're ready to work with GCP. This could lead to high-paying job offers.
- Career Advancement: The CP100A certification can boost your career. With basic GCP skills, you can apply for jobs as a Cloud Architect, Data Engineer, or Cloud Consultant. This catapults your career to new heights.
The CP100A course trains learners for careers in cloud computing. It gives them the skills and confidence to succeed.
Boosting Organizational Efficiency and Innovation
For Google Cloud users, CP100A training can boost efficiency and spark innovation. The course trains people to install cloud strategies. These can streamline processes and improve service delivery.
- Improved Collaboration: Employees familiar with GCP can collaborate better across teams. They harness cloud tools to streamline their workflow. The course covers best practices for using GCP to ease teamwork and communication.
- Cost Optimization: Knowing GCP services can help cut cloud costs. CP100A participants learn about resource management and scaling. They also learn to design cost-effective architectures. This helps them manage budgets better.
- Driving Innovation: A solid GCP foundation helps employees innovate at their firms. They can use GCP's advanced tech, like machine learning, to create new products.
Investing in employee training via the CP100A course can help. It can foster a culture of improvement and innovation. This establishes a strong market presence for organizations.
Hands-On Experience with Real-World Scenarios
The CP100A course stresses hands-on experience. It lets participants tackle real-world, industry-like scenarios. This practical approach is vital. It builds confidence and competence in using cloud technologies.
- Interactive Learning Environment: The course has labs. They let learners use GCP services, fix issues, and create solutions. This hands-on experience is invaluable for reinforcing theoretical knowledge.
- Problem-Solving Skills: Solving real-world scenarios builds vital problem-solving skills. They are key for fixing cloud-related issues in future jobs. They install GCP tools to tackle particular business obstacles effectively.
- The CP100A course teaches practical skills. They are key for those seeking advanced GCP certification exams. The labs provide a solid basis for mastering complex cloud topics.
The CP100A course gives learners both theoretical and practical skills. They are then ready to succeed in cloud environments.
Building a Strong Network and Community Engagement
Another major benefit of the CP100A course is meeting like-minded cloud experts. Building a network can be instrumental for career growth and knowledge sharing.
- Access to a Global Community: Google Cloud has a vast user, developer, and expert community. The CP100A course will connect you to a global network. It will open doors to collaboration and knowledge sharing.
- Mentorship Opportunities: Engaging with instructors and peers can lead to mentorship. They can guide you in your cloud computing career. Mentors can offer valuable insights and advice based on their experiences.
- Various groups host events and meetups on Google Cloud. Completing the CP100A course can make you eligible for these gatherings. They offer networking and industry insights.
By using the connections from the CP100A course, participants can boost their careers. They can learn industry trends and build relationships for success.
How to obtain Google Cloud Platform CP100A Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Completing the CP100A course on Google Cloud Platform is a smart career move. It offers many benefits beyond basic cloud knowledge. This course offers many benefits. It provides a solid grasp of GCP services. It also boosts career prospects, efficiency, and community engagement. Plus, it gives hands-on experience. As cloud computing changes business, CP100A is vital. It gives people and organizations the skills to succeed in a competitive landscape. The CP100A course is crucial for your goals in cloud computing. It will boost your career, spark innovation, or improve your cloud skills. Seize the chance. Invest in your future. Unlock Google Cloud's potential.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced world, cloud computing is crucial for businesses. It offers agility, scalability, and cost savings. Google Cloud Platform (GCP) is a top cloud provider. It offers a suite of services that help organizations innovate and thrive. Among its foundational courses, CP100A (Google Cloud Fundamentals: Core Infrastructure) is essential. It teaches learners the core concepts and services of GCP. This course instructs on mastering cloud navigation techniques. Completing the CP100A course opens up many opportunities. It offers benefits beyond technical skills. We explore five key benefits of completing the Google Cloud Platform CP100A. This course can boost your career and improve your organization. It can also foster innovation in the fast-changing tech world.
Table of Contents
- Comprehensive Understanding of Google Cloud Services
- Enhanced Career Opportunities and Job Prospects
- Boosting Organizational Efficiency and Innovation
- Hands-On Experience with Real-World Scenarios
- Building a Strong Network and Community Engagement
- Conclusion
Comprehensive Understanding of Google Cloud Services
A key benefit of the CP100A course is its deep knowledge of Google Cloud Platform's services. Participants learn about key services, like Compute Engine, Cloud Storage, and BigQuery. This knowledge is crucial for successful cloud solution installation.
- The course covers essential cloud concepts, networking, databases, and machine learning. It gives learners a holistic view of how GCP operates.
- Hands-on Labs and Demos: Interactive labs and demos let learners use real GCP services. This enhances their understanding through practical experience.
- Building Blocks for Expertise: This knowledge is a foundation. It gets you ready for advanced GCP certs and jobs, like Solutions Architect or Cloud Engineer.
By the end of the CP100A course, participants will know GCP's ecosystem. They will be able to contribute to cloud-based projects in their organizations.
Enhanced Career Opportunities and Job Prospects
Demand for cloud computing skills is surging. Many organizations seek experts in managing and deploying cloud solutions. The CP100A course boosts your job prospects. It shows your dedication to learning cloud technologies.
- High Demand for Cloud Professionals: Reports say cloud jobs are among the fastest-growing. CP100A provides a strong foundation, enhancing your job market prospects.
- Attractive Salaries: Professionals with cloud skills often earn more than others. The CP100A course shows employers you're ready to work with GCP. This could lead to high-paying job offers.
- Career Advancement: The CP100A certification can boost your career. With basic GCP skills, you can apply for jobs as a Cloud Architect, Data Engineer, or Cloud Consultant. This catapults your career to new heights.
The CP100A course trains learners for careers in cloud computing. It gives them the skills and confidence to succeed.
Boosting Organizational Efficiency and Innovation
For Google Cloud users, CP100A training can boost efficiency and spark innovation. The course trains people to install cloud strategies. These can streamline processes and improve service delivery.
- Improved Collaboration: Employees familiar with GCP can collaborate better across teams. They harness cloud tools to streamline their workflow. The course covers best practices for using GCP to ease teamwork and communication.
- Cost Optimization: Knowing GCP services can help cut cloud costs. CP100A participants learn about resource management and scaling. They also learn to design cost-effective architectures. This helps them manage budgets better.
- Driving Innovation: A solid GCP foundation helps employees innovate at their firms. They can use GCP's advanced tech, like machine learning, to create new products.
Investing in employee training via the CP100A course can help. It can foster a culture of improvement and innovation. This establishes a strong market presence for organizations.
Hands-On Experience with Real-World Scenarios
The CP100A course stresses hands-on experience. It lets participants tackle real-world, industry-like scenarios. This practical approach is vital. It builds confidence and competence in using cloud technologies.
- Interactive Learning Environment: The course has labs. They let learners use GCP services, fix issues, and create solutions. This hands-on experience is invaluable for reinforcing theoretical knowledge.
- Problem-Solving Skills: Solving real-world scenarios builds vital problem-solving skills. They are key for fixing cloud-related issues in future jobs. They install GCP tools to tackle particular business obstacles effectively.
- The CP100A course teaches practical skills. They are key for those seeking advanced GCP certification exams. The labs provide a solid basis for mastering complex cloud topics.
The CP100A course gives learners both theoretical and practical skills. They are then ready to succeed in cloud environments.
Building a Strong Network and Community Engagement
Another major benefit of the CP100A course is meeting like-minded cloud experts. Building a network can be instrumental for career growth and knowledge sharing.
- Access to a Global Community: Google Cloud has a vast user, developer, and expert community. The CP100A course will connect you to a global network. It will open doors to collaboration and knowledge sharing.
- Mentorship Opportunities: Engaging with instructors and peers can lead to mentorship. They can guide you in your cloud computing career. Mentors can offer valuable insights and advice based on their experiences.
- Various groups host events and meetups on Google Cloud. Completing the CP100A course can make you eligible for these gatherings. They offer networking and industry insights.
By using the connections from the CP100A course, participants can boost their careers. They can learn industry trends and build relationships for success.
How to obtain Google Cloud Platform CP100A Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Completing the CP100A course on Google Cloud Platform is a smart career move. It offers many benefits beyond basic cloud knowledge. This course offers many benefits. It provides a solid grasp of GCP services. It also boosts career prospects, efficiency, and community engagement. Plus, it gives hands-on experience. As cloud computing changes business, CP100A is vital. It gives people and organizations the skills to succeed in a competitive landscape. The CP100A course is crucial for your goals in cloud computing. It will boost your career, spark innovation, or improve your cloud skills. Seize the chance. Invest in your future. Unlock Google Cloud's potential.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Lean Management and Digital Twin Technology
In today's fast, competitive business world, firms want to be more efficient and stay ahead. Two key technologies are transforming how businesses operate. They are Lean Management and Digital Twin Technology. Let's explore how these new methods are changing industries and creating success.
What is Lean Management?
Lean management is a method. It aims to maximize customer value and minimize waste. It aims to create more customer value with fewer resources. It is based on continuous improvement and waste reduction. Lean Management helps organizations excel and grow. It speeds up processes, reduces waste, and lets employees use data to decide.
How Does Digital Twin Technology Work?
Digital Twin Technology creates a virtual copy of a physical object, like a factory or a supply chain. Organizations can gain insights into their assets and processes. They can do this by combining real-time data with advanced analytics and simulations. It lets them optimize operations and predict maintenance needs. They can then make data-driven decisions that boost efficiency and productivity.
Digital twin technology creates a virtual copy of a physical thing. It can be an object, process, or system. It enables real-time monitoring, simulation, and analysis. Here’s a breakdown of how it works:
1. Data Collection
Sensors and IoT Devices: Physical objects or systems have sensors and IoT devices. They continuously collect data. This data can include temperature, pressure, vibration, and other operational metrics.
Data Sources: The data can come from various sources. These include machines, sensors, and enterprise systems (like ERP). It can also come from external factors, like the weather.
2. Data Integration
Data Aggregation: Collected data is aggregated from multiple sources. This may mean merging data from various sensors and systems into a central platform.
Data Processing: The data is processed and cleaned to ensure accuracy and relevance. This may involve filtering out noise, correcting errors, and normalizing data formats.
3. Digital Twin Creation
Model Development:A digital model or replica of the physical entity is created. This involves using CAD drawings, 3D modeling, and other tools to create a virtual model.
Simulation and Visualization: The digital twin is often visualized in 3D. It lets users see and interact with the model. It can also simulate the behavior of the physical object or system based on the collected data.
4. Real-Time Synchronization
Continuous Data Feed:The digital twin receives real-time data from its physical counterpart. This makes the virtual model match the physical object or system.
State Updates: The digital twin is updated in real-time to reflect changes in the real world. This synchronization allows for accurate monitoring and analysis.
5. Analysis and Insights
Performance Monitoring: Users can monitor the physical entity's health through the digital twin. This includes tracking key metrics, identifying anomalies, and assessing overall performance.
Predictive Analytics: Analyzing data from the digital twin can forecast issues. It can find potential failures before they occur. This helps in proactive maintenance and decision-making.
Scenario Testing: Users can run simulations in the digital twin. This will help them understand potential outcomes and impacts. This helps in optimizing processes and planning.
6. Feedback and Optimization
Use the digital twin to optimize the physical object or system. This can involve adjustments, better processes, or changes based on simulations.
Feedback Loop: Optimizations and changes are fed back into the digital twin. This keeps it an accurate representation of the physical entity. This creates a continuous loop of improvement and refinement.
Applications
Manufacturing: Monitoring and optimizing production processes, predicting equipment failures, and improving operational efficiency.
Healthcare: Creating virtual models of patients. This is for personalized treatments and monitoring medical devices.
Urban Planning:Simulating city infrastructure and services to improve urban design and management.
Automotive: Testing vehicle designs and performance under various conditions without physical prototypes.
Digital twin technology links the physical and digital worlds. It allows for better decisions, predictive maintenance, and process optimization.
The Intersection of Lean Management and Digital Twin Technology
Combining Lean Management with Digital Twin Technology can boost organizations. It can unlock new optimization and innovation. Using virtual modeling, real-time monitoring, and AI, companies can improve their processes. They can also make better decisions and boost performance. This lets businesses optimize operations, improve quality, and cut costs. They can also stay agile and respond to changing market demands.
Benefits of Implementing Lean Practices with Digital Twin Technology
-
Enhanced process optimization and efficiency
-
Improved quality and reliability of products and services
-
Real-time monitoring and data-driven decision-making
-
Predictive maintenance to prevent costly downtime
-
Seamless integration of IoT devices for enhanced connectivity
-
Enhanced lean culture and mindset among employees
-
Improved operational visibility and control
-
Streamlined production processes and reduced waste
-
Accelerated digital transformation and innovation
-
Facilitated lean training programs and continuous improvement initiatives
Case Study: Lean Manufacturing in Industry 4.0
One industry that has embraced Lean Management and Digital Twin Technology is manufacturing. By using lean practices and digital twin solutions, companies can create smart factories. These factories can optimize and automate processes in real time. This results in increased productivity, reduced operational costs, and improved quality control. Manufacturers can use advanced analytics, machine learning, and IoT. These tools can drive lean transformation and help them compete in the digital age.
How to obtain Lean Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, combining Lean Management with Digital Twin Technology is a game-changer. It helps businesses boost efficiency and innovation in today's digital era. Organizations can boost their operations and performance. They can do this by using lean principles and digital tools. They should also optimize their processes. They can also achieve sustainable growth. The future of lean management is in digital twin technology. It can create smart, agile, connected enterprises. They will thrive in the Fourth Industrial Revolution.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast, competitive business world, firms want to be more efficient and stay ahead. Two key technologies are transforming how businesses operate. They are Lean Management and Digital Twin Technology. Let's explore how these new methods are changing industries and creating success.
What is Lean Management?
Lean management is a method. It aims to maximize customer value and minimize waste. It aims to create more customer value with fewer resources. It is based on continuous improvement and waste reduction. Lean Management helps organizations excel and grow. It speeds up processes, reduces waste, and lets employees use data to decide.
How Does Digital Twin Technology Work?
Digital Twin Technology creates a virtual copy of a physical object, like a factory or a supply chain. Organizations can gain insights into their assets and processes. They can do this by combining real-time data with advanced analytics and simulations. It lets them optimize operations and predict maintenance needs. They can then make data-driven decisions that boost efficiency and productivity.
Digital twin technology creates a virtual copy of a physical thing. It can be an object, process, or system. It enables real-time monitoring, simulation, and analysis. Here’s a breakdown of how it works:
1. Data Collection
Sensors and IoT Devices: Physical objects or systems have sensors and IoT devices. They continuously collect data. This data can include temperature, pressure, vibration, and other operational metrics.
Data Sources: The data can come from various sources. These include machines, sensors, and enterprise systems (like ERP). It can also come from external factors, like the weather.
2. Data Integration
Data Aggregation: Collected data is aggregated from multiple sources. This may mean merging data from various sensors and systems into a central platform.
Data Processing: The data is processed and cleaned to ensure accuracy and relevance. This may involve filtering out noise, correcting errors, and normalizing data formats.
3. Digital Twin Creation
Model Development:A digital model or replica of the physical entity is created. This involves using CAD drawings, 3D modeling, and other tools to create a virtual model.
Simulation and Visualization: The digital twin is often visualized in 3D. It lets users see and interact with the model. It can also simulate the behavior of the physical object or system based on the collected data.
4. Real-Time Synchronization
Continuous Data Feed:The digital twin receives real-time data from its physical counterpart. This makes the virtual model match the physical object or system.
State Updates: The digital twin is updated in real-time to reflect changes in the real world. This synchronization allows for accurate monitoring and analysis.
5. Analysis and Insights
Performance Monitoring: Users can monitor the physical entity's health through the digital twin. This includes tracking key metrics, identifying anomalies, and assessing overall performance.
Predictive Analytics: Analyzing data from the digital twin can forecast issues. It can find potential failures before they occur. This helps in proactive maintenance and decision-making.
Scenario Testing: Users can run simulations in the digital twin. This will help them understand potential outcomes and impacts. This helps in optimizing processes and planning.
6. Feedback and Optimization
Use the digital twin to optimize the physical object or system. This can involve adjustments, better processes, or changes based on simulations.
Feedback Loop: Optimizations and changes are fed back into the digital twin. This keeps it an accurate representation of the physical entity. This creates a continuous loop of improvement and refinement.
Applications
Manufacturing: Monitoring and optimizing production processes, predicting equipment failures, and improving operational efficiency.
Healthcare: Creating virtual models of patients. This is for personalized treatments and monitoring medical devices.
Urban Planning:Simulating city infrastructure and services to improve urban design and management.
Automotive: Testing vehicle designs and performance under various conditions without physical prototypes.
Digital twin technology links the physical and digital worlds. It allows for better decisions, predictive maintenance, and process optimization.
The Intersection of Lean Management and Digital Twin Technology
Combining Lean Management with Digital Twin Technology can boost organizations. It can unlock new optimization and innovation. Using virtual modeling, real-time monitoring, and AI, companies can improve their processes. They can also make better decisions and boost performance. This lets businesses optimize operations, improve quality, and cut costs. They can also stay agile and respond to changing market demands.
Benefits of Implementing Lean Practices with Digital Twin Technology
-
Enhanced process optimization and efficiency
-
Improved quality and reliability of products and services
-
Real-time monitoring and data-driven decision-making
-
Predictive maintenance to prevent costly downtime
-
Seamless integration of IoT devices for enhanced connectivity
-
Enhanced lean culture and mindset among employees
-
Improved operational visibility and control
-
Streamlined production processes and reduced waste
-
Accelerated digital transformation and innovation
-
Facilitated lean training programs and continuous improvement initiatives
Case Study: Lean Manufacturing in Industry 4.0
One industry that has embraced Lean Management and Digital Twin Technology is manufacturing. By using lean practices and digital twin solutions, companies can create smart factories. These factories can optimize and automate processes in real time. This results in increased productivity, reduced operational costs, and improved quality control. Manufacturers can use advanced analytics, machine learning, and IoT. These tools can drive lean transformation and help them compete in the digital age.
How to obtain Lean Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, combining Lean Management with Digital Twin Technology is a game-changer. It helps businesses boost efficiency and innovation in today's digital era. Organizations can boost their operations and performance. They can do this by using lean principles and digital tools. They should also optimize their processes. They can also achieve sustainable growth. The future of lean management is in digital twin technology. It can create smart, agile, connected enterprises. They will thrive in the Fourth Industrial Revolution.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Integrating Citrix with Other IT Systems
Integrating Citrix with other IT systems can benefit organizations. It can increase efficiency, improve collaboration, and enhance security. This article will explore integrating Citrix with various IT systems. These include Citrix software, virtualization, data integration, and cloud computing.
Understanding Citrix Integration
Citrix is a top provider of virtualization, networking, and cloud services. Their tools help organizations improve their IT and boost productivity. Integrating Citrix with other IT systems will create a seamless, interconnected environment. It will enable the efficient sharing of resources and data.
Citrix Software Integration
Citrix offers many software solutions, like Citrix XenApp, XenDesktop, and Workspace. They help organizations virtualize apps, desktops, and networks. Integrating these software solutions with existing IT systems can create a unified platform. It will simplify management and enhance the user experience.
Integrating Citrix software with other IT systems can boost efficiency and user experience. By seamlessly connecting Citrix environments with applications, databases, and cloud services, organizations can streamline workflows and improve productivity. This integration simplifies administration. It also creates a more responsive IT infrastructure.
Integrating Citrix software with other IT systems offers numerous benefits for modern enterprises. It lets Citrix environments communicate with various apps, cloud services, and databases. This fosters a more efficient workflow. This integration improves the user experience. It provides a single access point. It simplifies management with centralized control. It optimizes performance across the IT infrastructure. This drives higher productivity and better operations.
Data Integration and Enterprise Systems
Data integration is vital for organizations. They want to sync data from various sources. Integrating Citrix with CRM and ERP will ensure seamless data flow across platforms. This will improve decision-making and efficiency.
Data integration is vital. It ensures smooth communication across systems. It helps organizations use their data fully. By merging different data sources, businesses can see their operations in one view. This will streamline processes and improve decision-making. Effective data integration strategies improve efficiency. They also support better data governance and analytics.
Data integration is the backbone of modern enterprise systems. It links various data sources to create a unified, actionable information ecosystem. Effective integration can eliminate data silos in organizations. It ensures that information flows smoothly across departments and apps. This unified approach boosts efficiency and reporting. It gives a complete view of operations. This drives better decision-making and planning.
Cloud Integration and Networking
Cloud integration lets organizations extend their IT to the cloud. It enables scalability, flexibility, and cost savings. Integrating Citrix with cloud services lets businesses use virtualization and automation. This will boost network performance, optimize resource use, and improve security.
Cloud integration and networking are vital today. They enable seamless communication and data flow between different systems. Cloud integration must be effective. It should let apps and services interact smoothly. This will boost efficiency and scalability. By using advanced networking, organizations can optimize their cloud infrastructure. They can boost security and support flexible, adaptive solutions.
Application Integration and Citrix Workspace
Citrix Workspace is a unified platform. It provides secure access to apps, data, and services from any device, anywhere. Integrating Citrix Workspace with other apps can boost collaboration, productivity, and user experience. It creates a better digital workspace.
Citrix Workspace boosts productivity by integrating business apps into a single digital workspace. This integration lets users access multiple apps from one interface. It streamlines workflows and boosts efficiency. By using Citrix's strong integration capabilities, organizations can optimize their IT. This will create a better, more user-friendly experience for their employees.
Benefits of Integrating Citrix with IT Systems
There are several benefits to integrating Citrix with other IT systems. They include:
-
Improved efficiency and productivity
-
Enhanced security and compliance
-
Simplified management and administration
-
Scalability and flexibility
-
Cost savings and ROI
Best Practices for Citrix Integration
When integrating Citrix with other IT systems, use best practices. They ensure a smooth, successful implementation. Some best practices include:
-
Conduct a thorough assessment of existing IT systems and infrastructure.
-
Define clear objectives and goals for the integration project.
-
Engage key stakeholders and obtain buy-in from all departments.
-
Develop a detailed integration plan with milestones and timelines.
-
Test the integration thoroughly before rollout to ensure compatibility and performance.
How to obtain Citrix Administrator certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Integrating Citrix with other IT systems is a smart move. It can help organizations streamline operations, improve collaboration, and enhance security. By using Citrix software and services, businesses can optimize their IT. This will help them succeed.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Integrating Citrix with other IT systems can benefit organizations. It can increase efficiency, improve collaboration, and enhance security. This article will explore integrating Citrix with various IT systems. These include Citrix software, virtualization, data integration, and cloud computing.
Understanding Citrix Integration
Citrix is a top provider of virtualization, networking, and cloud services. Their tools help organizations improve their IT and boost productivity. Integrating Citrix with other IT systems will create a seamless, interconnected environment. It will enable the efficient sharing of resources and data.
Citrix Software Integration
Citrix offers many software solutions, like Citrix XenApp, XenDesktop, and Workspace. They help organizations virtualize apps, desktops, and networks. Integrating these software solutions with existing IT systems can create a unified platform. It will simplify management and enhance the user experience.
Integrating Citrix software with other IT systems can boost efficiency and user experience. By seamlessly connecting Citrix environments with applications, databases, and cloud services, organizations can streamline workflows and improve productivity. This integration simplifies administration. It also creates a more responsive IT infrastructure.
Integrating Citrix software with other IT systems offers numerous benefits for modern enterprises. It lets Citrix environments communicate with various apps, cloud services, and databases. This fosters a more efficient workflow. This integration improves the user experience. It provides a single access point. It simplifies management with centralized control. It optimizes performance across the IT infrastructure. This drives higher productivity and better operations.
Data Integration and Enterprise Systems
Data integration is vital for organizations. They want to sync data from various sources. Integrating Citrix with CRM and ERP will ensure seamless data flow across platforms. This will improve decision-making and efficiency.
Data integration is vital. It ensures smooth communication across systems. It helps organizations use their data fully. By merging different data sources, businesses can see their operations in one view. This will streamline processes and improve decision-making. Effective data integration strategies improve efficiency. They also support better data governance and analytics.
Data integration is the backbone of modern enterprise systems. It links various data sources to create a unified, actionable information ecosystem. Effective integration can eliminate data silos in organizations. It ensures that information flows smoothly across departments and apps. This unified approach boosts efficiency and reporting. It gives a complete view of operations. This drives better decision-making and planning.
Cloud Integration and Networking
Cloud integration lets organizations extend their IT to the cloud. It enables scalability, flexibility, and cost savings. Integrating Citrix with cloud services lets businesses use virtualization and automation. This will boost network performance, optimize resource use, and improve security.
Cloud integration and networking are vital today. They enable seamless communication and data flow between different systems. Cloud integration must be effective. It should let apps and services interact smoothly. This will boost efficiency and scalability. By using advanced networking, organizations can optimize their cloud infrastructure. They can boost security and support flexible, adaptive solutions.
Application Integration and Citrix Workspace
Citrix Workspace is a unified platform. It provides secure access to apps, data, and services from any device, anywhere. Integrating Citrix Workspace with other apps can boost collaboration, productivity, and user experience. It creates a better digital workspace.
Citrix Workspace boosts productivity by integrating business apps into a single digital workspace. This integration lets users access multiple apps from one interface. It streamlines workflows and boosts efficiency. By using Citrix's strong integration capabilities, organizations can optimize their IT. This will create a better, more user-friendly experience for their employees.
Benefits of Integrating Citrix with IT Systems
There are several benefits to integrating Citrix with other IT systems. They include:
-
Improved efficiency and productivity
-
Enhanced security and compliance
-
Simplified management and administration
-
Scalability and flexibility
-
Cost savings and ROI
Best Practices for Citrix Integration
When integrating Citrix with other IT systems, use best practices. They ensure a smooth, successful implementation. Some best practices include:
-
Conduct a thorough assessment of existing IT systems and infrastructure.
-
Define clear objectives and goals for the integration project.
-
Engage key stakeholders and obtain buy-in from all departments.
-
Develop a detailed integration plan with milestones and timelines.
-
Test the integration thoroughly before rollout to ensure compatibility and performance.
How to obtain Citrix Administrator certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Integrating Citrix with other IT systems is a smart move. It can help organizations streamline operations, improve collaboration, and enhance security. By using Citrix software and services, businesses can optimize their IT. This will help them succeed.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Maximizing ROI with SMAC Strategies for Effective Integration
In today's fast-changing digital world, businesses seek to use new tech. They want to boost growth and ROI. The SMAC stack—Social, Mobile, Analytics, and Cloud—can help. It is a strong framework to achieve these goals. By combining these four pillars, organizations can boost efficiency. They can engage customers and gain insights to inform decisions. This article explores ways to maximize ROI by using SMAC. It also gives tips for businesses to harness their full potential.
Table Of Contents
- Leveraging Social Media for Enhanced Customer Engagement
- Harnessing Mobile Technology for Enhanced Accessibility and Convenience
- Utilizing Analytics for Data-Driven Decision-Making
- Leveraging Cloud Technology for Scalability and Flexibility
- Integrating SMAC Components for Comprehensive Solutions
- Conclusion
Leveraging Social Media for Enhanced Customer Engagement
Social media platforms are more than communication channels. They are vital for engaging customers and building brand loyalty. By using social media analytics and engagement tools, businesses can improve. They can better understand customer preferences, behavior, and sentiment. Implementing social media strategies can boost customer satisfaction and ROI. These should include targeted content, personal interactions, and quick responses.
Strategies:
- Data-Driven Social Media Campaigns: Use analytics tools to track engagement metrics. Identify trends and tailor campaigns to meet audience expectations.
- Influencer Partnerships: Work with influencers to broaden your audience and boost brand credibility.
- Customer Feedback Loop: Use surveys, polls, and chats to gather feedback. Engage with customers to refine strategies.
A retail brand that uses social media analytics can boost sales. By tailoring promotions to customer preferences, it can increase engagement.
Harnessing Mobile Technology for Enhanced Accessibility and Convenience
Mobile technology has transformed the way businesses operate and interact with customers. Companies construct optimized platforms and applications for mobile devices. This lets users access their services and products anywhere, anytime. To maximize ROI with mobile tech, rank users. Create experiences that are convenient and functional.
Strategies:
- Responsive Design: Optimize websites and apps for mobile devices. This ensures a consistent user experience.
- Mobile Payments: Use secure, easy payment options to boost sales.
- Push Notifications: Use them to inform users of promotions, updates, and new offerings.
A mobile-optimized e-commerce site with easy payments can boost conversions and retention.
Utilizing Analytics for Data-Driven Decision-Making
Analytics is a key part of the SMAC stack. It gives businesses insights to make informed decisions and drive initiatives. Big data and analytics let organizations find patterns, predict trends, and optimize operations. This boosts ROI.
Strategies:
- Real-Time Analytics: Use tools for real-time data. This helps you make quick decisions and respond to market changes.
- Predictive Analytics: Use models to forecast trends and prepare for challenges.
- Track key performance indicators at regular intervals. They measure our strategies' success and show where to improve.
A financial services company can boost revenue by using predictive analytics. It can identify customer needs and tailor offerings. This will improve client satisfaction.
Leveraging Cloud Technology for Scalability and Flexibility
Cloud computing has no rival in scalability and flexibility. It lets businesses adapt to changes and improve operations. Cloud-based solutions can help organizations. They cut costs, improve collaboration, and scale operations.
Strategies:
- Cloud Migration: Move to the cloud to cut IT costs and boost efficiency.
- Hybrid Cloud Models: Use a mix of public and private clouds to meet business needs and boost security.
- Collaboration Tools: Install cloud-based collaboration tools to ease communication and teamwork among employees.
A tech startup that uses cloud services can scale and manage costs. It fosters development and teamwork on time.
Integrating SMAC Components for Comprehensive Solutions
The true power of the SMAC stack lies in its integration. Combining social, mobile, analytics, and cloud tech lets businesses create solutions. These will drive innovation and add more value. An integrated approach ensures that each part supports the others. This leads to a better strategy and higher ROI.
Strategies:
- Unified Data Strategy: Integrate data from social media, mobile, and cloud sources. This will provide a complete view of customer interactions and preferences.
- Cross-Channel Marketing: Develop campaigns that use social, mobile, and cloud platforms. They should reach customers through multiple channels.
- Enhanced Security: Use strong security in all SMAC components. It will protect data and ensure compliance.
A global business can use social media insights to merge a cloud CRM and mobile apps. This can boost ROI and deliver a seamless customer experience.
How to obtain SMAC certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, A strategic approach is key to using SMAC to maximize ROI. It requires integrating social, mobile, analytics, and cloud technologies. By using these components, businesses can boost engagement. They can also streamline operations and make data-driven decisions to drive growth. Success requires a unified strategy. It must align with business goals. It should leverage the strengths of each SMAC component. It combines them into a unified whole. Using these strategies will help organizations unlock the SMAC stack. They will then achieve a higher ROI in today's competitive digital world.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-changing digital world, businesses seek to use new tech. They want to boost growth and ROI. The SMAC stack—Social, Mobile, Analytics, and Cloud—can help. It is a strong framework to achieve these goals. By combining these four pillars, organizations can boost efficiency. They can engage customers and gain insights to inform decisions. This article explores ways to maximize ROI by using SMAC. It also gives tips for businesses to harness their full potential.
Table Of Contents
- Leveraging Social Media for Enhanced Customer Engagement
- Harnessing Mobile Technology for Enhanced Accessibility and Convenience
- Utilizing Analytics for Data-Driven Decision-Making
- Leveraging Cloud Technology for Scalability and Flexibility
- Integrating SMAC Components for Comprehensive Solutions
- Conclusion
Leveraging Social Media for Enhanced Customer Engagement
Social media platforms are more than communication channels. They are vital for engaging customers and building brand loyalty. By using social media analytics and engagement tools, businesses can improve. They can better understand customer preferences, behavior, and sentiment. Implementing social media strategies can boost customer satisfaction and ROI. These should include targeted content, personal interactions, and quick responses.
Strategies:
- Data-Driven Social Media Campaigns: Use analytics tools to track engagement metrics. Identify trends and tailor campaigns to meet audience expectations.
- Influencer Partnerships: Work with influencers to broaden your audience and boost brand credibility.
- Customer Feedback Loop: Use surveys, polls, and chats to gather feedback. Engage with customers to refine strategies.
A retail brand that uses social media analytics can boost sales. By tailoring promotions to customer preferences, it can increase engagement.
Harnessing Mobile Technology for Enhanced Accessibility and Convenience
Mobile technology has transformed the way businesses operate and interact with customers. Companies construct optimized platforms and applications for mobile devices. This lets users access their services and products anywhere, anytime. To maximize ROI with mobile tech, rank users. Create experiences that are convenient and functional.
Strategies:
- Responsive Design: Optimize websites and apps for mobile devices. This ensures a consistent user experience.
- Mobile Payments: Use secure, easy payment options to boost sales.
- Push Notifications: Use them to inform users of promotions, updates, and new offerings.
A mobile-optimized e-commerce site with easy payments can boost conversions and retention.
Utilizing Analytics for Data-Driven Decision-Making
Analytics is a key part of the SMAC stack. It gives businesses insights to make informed decisions and drive initiatives. Big data and analytics let organizations find patterns, predict trends, and optimize operations. This boosts ROI.
Strategies:
- Real-Time Analytics: Use tools for real-time data. This helps you make quick decisions and respond to market changes.
- Predictive Analytics: Use models to forecast trends and prepare for challenges.
- Track key performance indicators at regular intervals. They measure our strategies' success and show where to improve.
A financial services company can boost revenue by using predictive analytics. It can identify customer needs and tailor offerings. This will improve client satisfaction.
Leveraging Cloud Technology for Scalability and Flexibility
Cloud computing has no rival in scalability and flexibility. It lets businesses adapt to changes and improve operations. Cloud-based solutions can help organizations. They cut costs, improve collaboration, and scale operations.
Strategies:
- Cloud Migration: Move to the cloud to cut IT costs and boost efficiency.
- Hybrid Cloud Models: Use a mix of public and private clouds to meet business needs and boost security.
- Collaboration Tools: Install cloud-based collaboration tools to ease communication and teamwork among employees.
A tech startup that uses cloud services can scale and manage costs. It fosters development and teamwork on time.
Integrating SMAC Components for Comprehensive Solutions
The true power of the SMAC stack lies in its integration. Combining social, mobile, analytics, and cloud tech lets businesses create solutions. These will drive innovation and add more value. An integrated approach ensures that each part supports the others. This leads to a better strategy and higher ROI.
Strategies:
- Unified Data Strategy: Integrate data from social media, mobile, and cloud sources. This will provide a complete view of customer interactions and preferences.
- Cross-Channel Marketing: Develop campaigns that use social, mobile, and cloud platforms. They should reach customers through multiple channels.
- Enhanced Security: Use strong security in all SMAC components. It will protect data and ensure compliance.
A global business can use social media insights to merge a cloud CRM and mobile apps. This can boost ROI and deliver a seamless customer experience.
How to obtain SMAC certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, A strategic approach is key to using SMAC to maximize ROI. It requires integrating social, mobile, analytics, and cloud technologies. By using these components, businesses can boost engagement. They can also streamline operations and make data-driven decisions to drive growth. Success requires a unified strategy. It must align with business goals. It should leverage the strengths of each SMAC component. It combines them into a unified whole. Using these strategies will help organizations unlock the SMAC stack. They will then achieve a higher ROI in today's competitive digital world.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
10 Essential Minitab Shortcuts Every Analyst Should Know
In the world of data analysis, efficiency is key. Minitab has powerful tools to help your workflow. Use it for statistical analyses, making charts, or managing large datasets. One way to boost your productivity in Minitab is to master keyboard shortcuts. These shortcuts can save you time. They can also reduce the strain of navigating menus and dialog boxes. In this article, we'll explore ten essential Minitab shortcuts every analyst should know. Using these shortcuts in your daily routine will help you. You can then work more efficiently and use Minitab's features.
Shortcuts:
Ctrl + E: Open the Editor
When working with data, the Editor is your go-to tool for editing data in your worksheet. The shortcut Ctrl + E opens the Data Editor. It lets you quickly edit your dataset without using the menu. This is particularly useful for quickly correcting data entries or making batch updates.
Ctrl + Q: Open the Query Dialog
The Ctrl + Q shortcut brings up the Query Dialog, which is used to create and manage queries in Minitab. Queries are essential for filtering and analyzing specific subsets of data. This shortcut lets you set up complex queries easily. There's no need for multiple steps in the menu system.
Ctrl + T: Create a t-test
A t-test is common in stats. Press Ctrl + T to start a t-test. This shortcut opens the T-Test dialog, where you can specify your data and settings. Frequent hypothesis testers reap significant time savings.
Ctrl + G: Generate a graph
Creating visual representations of data is crucial for analysis and presentations. Press Ctrl + G to access the Graph dialog immediately. This lets you customize a graph, like a histogram or scatter plot, without using the main menu.
Ctrl + M: Open the Manager
The Ctrl + M shortcut opens the Manager window. It shows all your ongoing analyses, including projects and data files. This window helps you manage your work and track progress. It grants instant access to various segments of your analysis.
Ctrl + A: Select All Data
Selecting all data in a worksheet can be cumbersome, especially with large datasets. The Ctrl + A shortcut makes this task easy by selecting all the cells in the current worksheet. This shortcut is useful when you need to copy, paste, or perform operations on the entire dataset.
Ctrl + Z: Undo Last Action
Errors occur, and reversing your previous step proves priceless. The Ctrl + Z shortcut undoes your last change in Minitab. It works for both data-entry errors and graph edits. This function helps prevent loss of work and reduces the need for repetitive steps.
Ctrl + Y: Redo Last Action
The Ctrl + Y shortcut redoes the last undone action. It complements the Undo function. This is useful if you’ve undone an action by mistake and want to revert to the previous state. Changes are recovered immediately, eliminating manual reapplication entirely.
Ctrl + F: Find and Replace
Searching for specific data or values in a large dataset can be time-consuming. The Ctrl + F shortcut opens the Find and Replace dialog. It enables swift location and alteration of dataset entries. This is especially handy for data cleaning and preparation.
Ctrl + P: Print Current View
Once your analysis is complete, you might need to print your results or graphs. The Ctrl + P shortcut opens the Print dialog for the current view, whether it’s a worksheet, graph, or report. It makes it easier to produce physical copies of your work for sharing or presentation.
How to obtain MiniTab Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Mastering Minitab's keyboard shortcuts can boost your productivity as an analyst. Use these ten shortcuts in your workflow. They will save you time, reduce repetitive tasks, and let you focus on the analysis. These shortcuts aim to make common tasks easier and help you navigate Minitab better. As you learn these shortcuts, your workflow will improve. It will be smoother and more efficient. Embrace these shortcuts. Make them a key part of your data analysis toolkit.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In the world of data analysis, efficiency is key. Minitab has powerful tools to help your workflow. Use it for statistical analyses, making charts, or managing large datasets. One way to boost your productivity in Minitab is to master keyboard shortcuts. These shortcuts can save you time. They can also reduce the strain of navigating menus and dialog boxes. In this article, we'll explore ten essential Minitab shortcuts every analyst should know. Using these shortcuts in your daily routine will help you. You can then work more efficiently and use Minitab's features.
Shortcuts:
Ctrl + E: Open the Editor
When working with data, the Editor is your go-to tool for editing data in your worksheet. The shortcut Ctrl + E opens the Data Editor. It lets you quickly edit your dataset without using the menu. This is particularly useful for quickly correcting data entries or making batch updates.
Ctrl + Q: Open the Query Dialog
The Ctrl + Q shortcut brings up the Query Dialog, which is used to create and manage queries in Minitab. Queries are essential for filtering and analyzing specific subsets of data. This shortcut lets you set up complex queries easily. There's no need for multiple steps in the menu system.
Ctrl + T: Create a t-test
A t-test is common in stats. Press Ctrl + T to start a t-test. This shortcut opens the T-Test dialog, where you can specify your data and settings. Frequent hypothesis testers reap significant time savings.
Ctrl + G: Generate a graph
Creating visual representations of data is crucial for analysis and presentations. Press Ctrl + G to access the Graph dialog immediately. This lets you customize a graph, like a histogram or scatter plot, without using the main menu.
Ctrl + M: Open the Manager
The Ctrl + M shortcut opens the Manager window. It shows all your ongoing analyses, including projects and data files. This window helps you manage your work and track progress. It grants instant access to various segments of your analysis.
Ctrl + A: Select All Data
Selecting all data in a worksheet can be cumbersome, especially with large datasets. The Ctrl + A shortcut makes this task easy by selecting all the cells in the current worksheet. This shortcut is useful when you need to copy, paste, or perform operations on the entire dataset.
Ctrl + Z: Undo Last Action
Errors occur, and reversing your previous step proves priceless. The Ctrl + Z shortcut undoes your last change in Minitab. It works for both data-entry errors and graph edits. This function helps prevent loss of work and reduces the need for repetitive steps.
Ctrl + Y: Redo Last Action
The Ctrl + Y shortcut redoes the last undone action. It complements the Undo function. This is useful if you’ve undone an action by mistake and want to revert to the previous state. Changes are recovered immediately, eliminating manual reapplication entirely.
Ctrl + F: Find and Replace
Searching for specific data or values in a large dataset can be time-consuming. The Ctrl + F shortcut opens the Find and Replace dialog. It enables swift location and alteration of dataset entries. This is especially handy for data cleaning and preparation.
Ctrl + P: Print Current View
Once your analysis is complete, you might need to print your results or graphs. The Ctrl + P shortcut opens the Print dialog for the current view, whether it’s a worksheet, graph, or report. It makes it easier to produce physical copies of your work for sharing or presentation.
How to obtain MiniTab Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Mastering Minitab's keyboard shortcuts can boost your productivity as an analyst. Use these ten shortcuts in your workflow. They will save you time, reduce repetitive tasks, and let you focus on the analysis. These shortcuts aim to make common tasks easier and help you navigate Minitab better. As you learn these shortcuts, your workflow will improve. It will be smoother and more efficient. Embrace these shortcuts. Make them a key part of your data analysis toolkit.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Role of AR and VR in Enhancing Digital Marketing Campaigns
Augmented Reality (AR) and Virtual Reality (VR) have revolutionized the digital marketing landscape. These technologies blend the physical and digital worlds. They design immersive experiences that envelop consumers completely. AR overlays digital content onto the real world. Virtual Reality envelops users in completely artificial worlds. Consumers crave personalized, interactive content. So, AR and VR are now key marketing tools. They drive engagement, improve brand perception, and boost conversions.
This article will explore the key roles of AR and VR in boosting digital marketing campaigns. We'll discuss using these technologies to create immersive experiences. They can also personalize content, prove products, boost brand stories, and engage customers.
Table Of Content
- Creating Immersive Experiences
- Offering Personalized Content
- Providing Interactive Product Demonstrations
- Enhancing Brand Storytelling
- Improving Customer Engagement
- Conclusion
Creating Immersive Experiences
A key benefit of AR and VR in digital marketing is their power to create immersive experiences. These technologies let brands connect with consumers. They craft surroundings that engage users and simulate real experiences. For instance, VR can take a user to a virtual store. They can browse products there as they would in a physical store. It improves the shopping experience and strengthens the emotional bond with the brand.
AR lets consumers, in real time, interact with products in their own environment. A furniture company can use AR to show customers how a piece of furniture would look in their home before they buy it. This immersive experience boosts conversion by reducing uncertainty. Consumers can see the product in their own context.
Offering Personalized Content
Personalization is a key trend in digital marketing. AR and VR are great tools for delivering tailored content to consumers. Marketers can use data to create personalized AR and VR experiences. These will resonate with individual users. For example, a beauty brand can use AR for a virtual try-on. Customers can see how different makeup products would look on their faces. This personalization improves the user experience. It also boosts conversion rates. Customers are more likely to buy products they have "tried on."
In VR, we can personalize experiences. We can match the virtual world to the user's preferences. A travel company could create a VR experience. Users could explore a destination before booking a trip. The company can improve its marketing by personalizing it to the user's interests. It will be more engaging. This could include highlighting specific activities or attractions.
Providing Interactive Product Demonstrations
AR and VR allow interactive product demos. Consumers can experience products in ways that traditional media cannot. For example, a car company could use VR to create a virtual test drive. Users could check the vehicle's performance and features from home. They provide a unique, memorable experience. They also help consumers make better buying decisions.
AR can create interactive product tutorials. Users can see how a product works in real time. For example, a tech company could create an AR app. It would show users how to set up a new device, step by step, with digital overlays guiding them. This interactive content helps customers understand the product. It also reduces post-purchase dissatisfaction and returns.
Enhancing Brand Storytelling
Storytelling is a powerful marketing tool. AR and VR offer new ways to tell compelling brand stories. These technologies can create a stronger bond with the brand. They do this by immersing users in a narrative. A charity could use VR to transport users to the field. They would see the impact of their donations firsthand. This immersive storytelling can be more impactful than traditional methods. It lets users experience the story in a more visceral, personal way.
AR can enhance storytelling by adding interactivity to traditional media. For instance, AR could bring a print ad to life. Users could scan the ad with their smartphones to see extra content, like videos or 3D animations. It makes the story more engaging. It also adds information. This can deepen the user's understanding of the brand's message.
Improving Customer Engagement
AR and VR can boost customer engagement. They create unique, memorable experiences that encourage users to interact with the brand. A retail brand could create a VR shopping experience. Users could explore a virtual store and interact with products in a game-like setting. It makes shopping more enjoyable. It also encourages users to engage with the brand. This boosts the chances of conversion.
AR can create engaging marketing campaigns that boost user participation. A fashion brand could run an AR-based social media campaign. Users could try on virtual outfits and share their looks with friends. This interactive content boosts engagement. It also creates user-generated content. Users can share it on social media, which extends the campaign's reach.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, AR and VR are changing digital marketing. They offer new ways to engage consumers and improve brand experiences. These technologies offer many ways for brands to connect with their audience. They can create immersive environments, provide personalized content, and enhance storytelling. They can also offer interactive product demos. As AR and VR evolve, they will play a bigger role in digital marketing. They will give marketers new tools to capture customers' attention and loyalty.
AR and VR are now a must in digital marketing. Brands must use them to stay competitive in today's fast-paced digital world. Using these technologies, marketers can create more engaging, personalized experiences. These will resonate with consumers and boost business success.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Augmented Reality (AR) and Virtual Reality (VR) have revolutionized the digital marketing landscape. These technologies blend the physical and digital worlds. They design immersive experiences that envelop consumers completely. AR overlays digital content onto the real world. Virtual Reality envelops users in completely artificial worlds. Consumers crave personalized, interactive content. So, AR and VR are now key marketing tools. They drive engagement, improve brand perception, and boost conversions.
This article will explore the key roles of AR and VR in boosting digital marketing campaigns. We'll discuss using these technologies to create immersive experiences. They can also personalize content, prove products, boost brand stories, and engage customers.
Table Of Content
- Creating Immersive Experiences
- Offering Personalized Content
- Providing Interactive Product Demonstrations
- Enhancing Brand Storytelling
- Improving Customer Engagement
- Conclusion
Creating Immersive Experiences
A key benefit of AR and VR in digital marketing is their power to create immersive experiences. These technologies let brands connect with consumers. They craft surroundings that engage users and simulate real experiences. For instance, VR can take a user to a virtual store. They can browse products there as they would in a physical store. It improves the shopping experience and strengthens the emotional bond with the brand.
AR lets consumers, in real time, interact with products in their own environment. A furniture company can use AR to show customers how a piece of furniture would look in their home before they buy it. This immersive experience boosts conversion by reducing uncertainty. Consumers can see the product in their own context.
Offering Personalized Content
Personalization is a key trend in digital marketing. AR and VR are great tools for delivering tailored content to consumers. Marketers can use data to create personalized AR and VR experiences. These will resonate with individual users. For example, a beauty brand can use AR for a virtual try-on. Customers can see how different makeup products would look on their faces. This personalization improves the user experience. It also boosts conversion rates. Customers are more likely to buy products they have "tried on."
In VR, we can personalize experiences. We can match the virtual world to the user's preferences. A travel company could create a VR experience. Users could explore a destination before booking a trip. The company can improve its marketing by personalizing it to the user's interests. It will be more engaging. This could include highlighting specific activities or attractions.
Providing Interactive Product Demonstrations
AR and VR allow interactive product demos. Consumers can experience products in ways that traditional media cannot. For example, a car company could use VR to create a virtual test drive. Users could check the vehicle's performance and features from home. They provide a unique, memorable experience. They also help consumers make better buying decisions.
AR can create interactive product tutorials. Users can see how a product works in real time. For example, a tech company could create an AR app. It would show users how to set up a new device, step by step, with digital overlays guiding them. This interactive content helps customers understand the product. It also reduces post-purchase dissatisfaction and returns.
Enhancing Brand Storytelling
Storytelling is a powerful marketing tool. AR and VR offer new ways to tell compelling brand stories. These technologies can create a stronger bond with the brand. They do this by immersing users in a narrative. A charity could use VR to transport users to the field. They would see the impact of their donations firsthand. This immersive storytelling can be more impactful than traditional methods. It lets users experience the story in a more visceral, personal way.
AR can enhance storytelling by adding interactivity to traditional media. For instance, AR could bring a print ad to life. Users could scan the ad with their smartphones to see extra content, like videos or 3D animations. It makes the story more engaging. It also adds information. This can deepen the user's understanding of the brand's message.
Improving Customer Engagement
AR and VR can boost customer engagement. They create unique, memorable experiences that encourage users to interact with the brand. A retail brand could create a VR shopping experience. Users could explore a virtual store and interact with products in a game-like setting. It makes shopping more enjoyable. It also encourages users to engage with the brand. This boosts the chances of conversion.
AR can create engaging marketing campaigns that boost user participation. A fashion brand could run an AR-based social media campaign. Users could try on virtual outfits and share their looks with friends. This interactive content boosts engagement. It also creates user-generated content. Users can share it on social media, which extends the campaign's reach.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, AR and VR are changing digital marketing. They offer new ways to engage consumers and improve brand experiences. These technologies offer many ways for brands to connect with their audience. They can create immersive environments, provide personalized content, and enhance storytelling. They can also offer interactive product demos. As AR and VR evolve, they will play a bigger role in digital marketing. They will give marketers new tools to capture customers' attention and loyalty.
AR and VR are now a must in digital marketing. Brands must use them to stay competitive in today's fast-paced digital world. Using these technologies, marketers can create more engaging, personalized experiences. These will resonate with consumers and boost business success.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Cisco UCS vs Competitors A 2024 Comparison for Enterprises
In the fast-changing world of enterprise IT, the right server architecture is crucial. It affects your organization's performance, scalability, and IT costs. Cisco Unified Computing System (UCS) has been a major player in this space. It offers integrated computing, networking, and storage in a unified platform. In 2024, Dell EMC VxRail and HPE Synergy will compete for market share. Enterprises must choose the best solution. This comparison will explore Cisco UCS's strengths and weaknesses versus its competitors. It will help decision-makers make informed choices.
Table Of Contents
- Architecture and Scalability
- Performance and Reliability
- Management and Automation
- Cost Efficiency and Total Cost of Ownership (TCO)
- Support and Ecosystem
- Conclusion
Architecture and Scalability
- Cisco UCS: It has a unified design. It combines computing, networking, and storage in one platform. The architecture's modular design allows easy scalability. It is ideal for growing enterprises. UCS Manager allows centralized management of all resources. It simplifies IT operations and cuts costs.
- Dell EMC VxRail: Dell EMC VxRail is a hyper-converged infrastructure solution. It has a scalable architecture. Yet, it focuses more on simplicity and ease of deployment. VxRail integrates VMware's vSAN. It lets enterprises add nodes to their infrastructure. So, it's a good choice for VMware-centric environments.
- HPE Synergy: HPE Synergy is a composable infrastructure. We allocate resources to match shifting work demands. This architecture is very flexible. It benefits firms with varied, fast-changing workloads. HPE OneView is the management tool used to oversee these resources.
- Lenovo ThinkSystem: It provides traditional and converged infrastructure options. It focuses on performance and reliability. The architecture allows for tailored modifications. This helps enterprises with specific hardware needs. Yet, it may not be as streamlined as Cisco UCS for unified management.
Comparison Summary: Cisco UCS excels in unified architecture and management. Dell EMC VxRail and HPE Synergy are strong alternatives. They concentrate on hyper-convergence. They focus on composability. Lenovo ThinkSystem stands out for its customization capabilities.
Performance and Reliability
- Cisco UCS is well-known for delivering strong performance and reliability. It uses Cisco's Nexus switching technology for high bandwidth and low latency. The tight integration of hardware and software ensures peak performance. It handles both general applications and demanding tasks like AI and machine learning.
- Dell EMC VxRail: VxRail, built on Dell's PowerEdge servers, excels in VMware. It supports many workloads. But its performance often depends on VMware's software. This may not suit all enterprises.
- HPE Synergy is for high performance. It excels in environments needing fast resource allocation. It supports many workloads. It tackles mixed, variable workloads with impressive workload management capabilities. This is essential for dynamic enterprise environments.
- Lenovo ThinkSystem: Lenovo’s ThinkSystem excels in raw performance, particularly in compute-intensive tasks. Its high reliability and strong support are well-known. So, it is a solid choice for enterprises that value these aspects.
Comparison Summary: Cisco UCS is a top choice for performance and reliability. It excels in diverse IT environments. Dell EMC VxRail and HPE Synergy excel within their frameworks. Lenovo ThinkSystem is best for those needing high performance and reliability.
Management and Automation
- Cisco UCS: Use UCS Manager and UCS Director to manage and automate Cisco UCS environments. These tools automate tasks. They reduce the time IT staff spend on routine work. Integration with third-party tools further enhances management capabilities.
- Dell EMC VxRail: VxRail Manager simplifies management in VMware environments. It provides a seamless management experience with automated integration. Yet, its tight integration with VMware could limit flexibility. It may hurt enterprises that need to manage non-VMware environments.
- HPE Synergy: HPE's OneView software is a great tool for managing Synergy environments. It enables extensive automation and simplifies the management of composable infrastructure. OneView's ability to manage diverse workloads and resources is a big plus. It makes the necessary changes.
- Lenovo ThinkSystem: Use Lenovo XClarity to manage ThinkSystem. It provides a single interface for managing infrastructure. It is effective. Yet, it may lack the features of Cisco or HPE's tools. This may must more manual management.
Comparison Summary: Cisco UCS excels with its strong management and automation tools. It provides great flexibility and integration options. HPE Synergy excels in managing dynamic workloads. Dell EMC VxRail is for VMware environments. Lenovo ThinkSystem provides solid management but may need more manual intervention.
Cost Efficiency and Total Cost of Ownership (TCO)
- Cisco UCS: Cisco UCS has low prices. It is fast, scalable, and easy to manage. The initial investment may be higher than some competitors. But, the unified architecture can lower costs and improve TCO over time.
- Dell EMC VxRail: VxRail's hyper-converged approach can be cost-efficient. It's a good option for organizations already invested in VMware. The appliance-based model simplifies procurement and deployment. It may cut upfront costs. But long-term costs depend on VMware licensing and support.
- The organization's specific requirements determine the value of HPE Synergy. It can be more expensive at first due to its composable infrastructure. Yet, it can save money over time. Its ability to optimize resource allocation can help, especially with variable workloads.
- Lenovo ThinkSystem: It has competitive pricing for high-performance hardware, especially for enterprises. Customization requirements drive significant cost differences. Extensive management or integration efforts may increase the TCO.
Summary: Cisco UCS balances performance and cost. It's a solid, long-term investment. Dell EMC VxRail and HPE Synergy can be cost-effective, depending on the use case. Lenovo ThinkSystem may need careful cost management to keep a good TCO.
Support and Ecosystem
- Cisco UCS: Cisco's global support and partner network is a key benefit for enterprises. UCS supports many software and hardware integrations. It can fit into almost any IT environment. So, it is a versatile choice.
- Dell EMC VxRail: VxRail has strong service options. Dell's global support network backs it. Its deep integration with VMware means extensive support from both Dell and VMware. This helps enterprises in VMware ecosystems.
- HPE Synergy: HPE's global support makes it a top choice for firms needing high support. The composable infrastructure model is well-supported. Many integrations meet diverse needs.
- Lenovo ThinkSystem: Lenovo has good global support. It may be less extensive than Cisco's or Dell's. The ecosystem is growing, with many partnerships and integrations. Yet, enterprises may find fewer resources than those of larger competitors.
Comparison Summary: Cisco UCS is best. It has a vast support network and a large ecosystem. This ensures compatibility and reliable help. Dell EMC VxRail and HPE Synergy offer strong support in their ecosystems. Lenovo ThinkSystem has solid support, but it's less extensive.
How to obtain Cisco certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In 2024, choosing between Cisco UCS and its rivals depends on an enterprise's needs. Cisco UCS is a top choice for many businesses. Its unified design, strong management tools, and vast support make it very versatile. Dell EMC VxRail is simple and efficient in VMware environments. HPE Synergy excels in flexible, composable infrastructure. Lenovo ThinkSystem offers strong performance and reliability. In this competitive landscape, firms must choose the best IT solution. They should assess their needs, current systems, and long-term goals.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In the fast-changing world of enterprise IT, the right server architecture is crucial. It affects your organization's performance, scalability, and IT costs. Cisco Unified Computing System (UCS) has been a major player in this space. It offers integrated computing, networking, and storage in a unified platform. In 2024, Dell EMC VxRail and HPE Synergy will compete for market share. Enterprises must choose the best solution. This comparison will explore Cisco UCS's strengths and weaknesses versus its competitors. It will help decision-makers make informed choices.
Table Of Contents
- Architecture and Scalability
- Performance and Reliability
- Management and Automation
- Cost Efficiency and Total Cost of Ownership (TCO)
- Support and Ecosystem
- Conclusion
Architecture and Scalability
- Cisco UCS: It has a unified design. It combines computing, networking, and storage in one platform. The architecture's modular design allows easy scalability. It is ideal for growing enterprises. UCS Manager allows centralized management of all resources. It simplifies IT operations and cuts costs.
- Dell EMC VxRail: Dell EMC VxRail is a hyper-converged infrastructure solution. It has a scalable architecture. Yet, it focuses more on simplicity and ease of deployment. VxRail integrates VMware's vSAN. It lets enterprises add nodes to their infrastructure. So, it's a good choice for VMware-centric environments.
- HPE Synergy: HPE Synergy is a composable infrastructure. We allocate resources to match shifting work demands. This architecture is very flexible. It benefits firms with varied, fast-changing workloads. HPE OneView is the management tool used to oversee these resources.
- Lenovo ThinkSystem: It provides traditional and converged infrastructure options. It focuses on performance and reliability. The architecture allows for tailored modifications. This helps enterprises with specific hardware needs. Yet, it may not be as streamlined as Cisco UCS for unified management.
Comparison Summary: Cisco UCS excels in unified architecture and management. Dell EMC VxRail and HPE Synergy are strong alternatives. They concentrate on hyper-convergence. They focus on composability. Lenovo ThinkSystem stands out for its customization capabilities.
Performance and Reliability
- Cisco UCS is well-known for delivering strong performance and reliability. It uses Cisco's Nexus switching technology for high bandwidth and low latency. The tight integration of hardware and software ensures peak performance. It handles both general applications and demanding tasks like AI and machine learning.
- Dell EMC VxRail: VxRail, built on Dell's PowerEdge servers, excels in VMware. It supports many workloads. But its performance often depends on VMware's software. This may not suit all enterprises.
- HPE Synergy is for high performance. It excels in environments needing fast resource allocation. It supports many workloads. It tackles mixed, variable workloads with impressive workload management capabilities. This is essential for dynamic enterprise environments.
- Lenovo ThinkSystem: Lenovo’s ThinkSystem excels in raw performance, particularly in compute-intensive tasks. Its high reliability and strong support are well-known. So, it is a solid choice for enterprises that value these aspects.
Comparison Summary: Cisco UCS is a top choice for performance and reliability. It excels in diverse IT environments. Dell EMC VxRail and HPE Synergy excel within their frameworks. Lenovo ThinkSystem is best for those needing high performance and reliability.
Management and Automation
- Cisco UCS: Use UCS Manager and UCS Director to manage and automate Cisco UCS environments. These tools automate tasks. They reduce the time IT staff spend on routine work. Integration with third-party tools further enhances management capabilities.
- Dell EMC VxRail: VxRail Manager simplifies management in VMware environments. It provides a seamless management experience with automated integration. Yet, its tight integration with VMware could limit flexibility. It may hurt enterprises that need to manage non-VMware environments.
- HPE Synergy: HPE's OneView software is a great tool for managing Synergy environments. It enables extensive automation and simplifies the management of composable infrastructure. OneView's ability to manage diverse workloads and resources is a big plus. It makes the necessary changes.
- Lenovo ThinkSystem: Use Lenovo XClarity to manage ThinkSystem. It provides a single interface for managing infrastructure. It is effective. Yet, it may lack the features of Cisco or HPE's tools. This may must more manual management.
Comparison Summary: Cisco UCS excels with its strong management and automation tools. It provides great flexibility and integration options. HPE Synergy excels in managing dynamic workloads. Dell EMC VxRail is for VMware environments. Lenovo ThinkSystem provides solid management but may need more manual intervention.
Cost Efficiency and Total Cost of Ownership (TCO)
- Cisco UCS: Cisco UCS has low prices. It is fast, scalable, and easy to manage. The initial investment may be higher than some competitors. But, the unified architecture can lower costs and improve TCO over time.
- Dell EMC VxRail: VxRail's hyper-converged approach can be cost-efficient. It's a good option for organizations already invested in VMware. The appliance-based model simplifies procurement and deployment. It may cut upfront costs. But long-term costs depend on VMware licensing and support.
- The organization's specific requirements determine the value of HPE Synergy. It can be more expensive at first due to its composable infrastructure. Yet, it can save money over time. Its ability to optimize resource allocation can help, especially with variable workloads.
- Lenovo ThinkSystem: It has competitive pricing for high-performance hardware, especially for enterprises. Customization requirements drive significant cost differences. Extensive management or integration efforts may increase the TCO.
Summary: Cisco UCS balances performance and cost. It's a solid, long-term investment. Dell EMC VxRail and HPE Synergy can be cost-effective, depending on the use case. Lenovo ThinkSystem may need careful cost management to keep a good TCO.
Support and Ecosystem
- Cisco UCS: Cisco's global support and partner network is a key benefit for enterprises. UCS supports many software and hardware integrations. It can fit into almost any IT environment. So, it is a versatile choice.
- Dell EMC VxRail: VxRail has strong service options. Dell's global support network backs it. Its deep integration with VMware means extensive support from both Dell and VMware. This helps enterprises in VMware ecosystems.
- HPE Synergy: HPE's global support makes it a top choice for firms needing high support. The composable infrastructure model is well-supported. Many integrations meet diverse needs.
- Lenovo ThinkSystem: Lenovo has good global support. It may be less extensive than Cisco's or Dell's. The ecosystem is growing, with many partnerships and integrations. Yet, enterprises may find fewer resources than those of larger competitors.
Comparison Summary: Cisco UCS is best. It has a vast support network and a large ecosystem. This ensures compatibility and reliable help. Dell EMC VxRail and HPE Synergy offer strong support in their ecosystems. Lenovo ThinkSystem has solid support, but it's less extensive.
How to obtain Cisco certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In 2024, choosing between Cisco UCS and its rivals depends on an enterprise's needs. Cisco UCS is a top choice for many businesses. Its unified design, strong management tools, and vast support make it very versatile. Dell EMC VxRail is simple and efficient in VMware environments. HPE Synergy excels in flexible, composable infrastructure. Lenovo ThinkSystem offers strong performance and reliability. In this competitive landscape, firms must choose the best IT solution. They should assess their needs, current systems, and long-term goals.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Ethical Hacking for Cloud Security Best Practices for 2024
With the rise of cloud use, securing cloud sites is now a top priority for organizations. The growth of cloud services raises security threats. So, ethical hacking is vital to protect cloud infrastructures. Ethical hacking, also known as penetration testing, simulates cyberattacks on systems. It aims to find vulnerabilities before malicious actors can exploit them. This approach helps organizations boost cloud security and meet standards.
In 2024, cloud environments will be complex, and hybrid models will be common. Ethical hacking must evolve to address new challenges. This article reviews the best practices for ethical hacking in cloud security. It highlights key areas for security professionals to protect their cloud assets.
Table Of Contents
- Understanding the Cloud Threat Landscape
- Leveraging Automation in Ethical Hacking
- Securing Cloud-Based DevOps Practices
- Enhancing Access Management and Identity Security
- Ensuring compliance with cloud security standards
- Conclusion
Understanding the Cloud Threat Landscape
First, ethical hackers must know the unique threats of cloud environments. Unlike traditional on-premises systems, cloud infrastructures are more dynamic. They share a responsibility model with cloud service providers (CSPs). Key threats include:
- Misconfigurations: a common cloud vulnerability, often due to human error. They expose data and services.
- Insider Threats: Employees or contractors with cloud access who may compromise security. This could be intentional or accidental.
- API vulnerabilities: exploitable flaws in the APIs used to manage cloud services.
- Data Breaches: Unauthorized access to sensitive data stored in the cloud.
- Denial of Service (DoS) attacks: Overloading cloud services to disrupt availability.
Ethical hackers must adapt to cloud-specific threats. They must find weaknesses in configurations, access controls, and data protection.
Leveraging Automation in Ethical Hacking
In 2024, automation is key to ethical hacking, especially in cloud security. Cloud environments are complex. Manual testing can't keep up with evolving threats. Automated tools and frameworks can:
- Conduct in-depth analysis: Use advanced scanning technology to reveal cloud weaknesses. It will detect threats in real time.
- Simulate Attacks: Tools like Metasploit and Burp Suite can simulate attacks. They can find potential security gaps.
- Automated scripts pinpoint misconfigurations in cloud resources with precision. They can detect open storage buckets and weak encryption settings.
- Use Automation: It can create detailed reports on findings. This helps security teams focus on their remediation efforts.
Automation boosts efficiency. But, it is vital to balance it with manual testing. Manual tests can find subtle bugs that automation may miss.
Securing Cloud-Based DevOps Practices
DevOps is now standard in cloud environments. It allows faster development and continuous deployment. Yet, the integration of DevOps in cloud environments introduces new security challenges. Ethical hacking in this context should focus on:
- Pipeline Security: Assess the CI/CD pipelines. Ensure that no malicious code gets into production environments.
- Container Security: Test for vulnerabilities in containerized apps. Ensure secure configurations of container orchestration tools, such as Kubernetes.
- Infrastructure as Code (IaC): Ethical hackers should test IaC scripts for flaws before deploying them to the cloud.
By focusing on these areas, ethical hackers can secure the DevOps lifecycle. This will lower the risk of cloud vulnerabilities from rapid development.
Enhancing Access Management and Identity Security
Access management and identity security are key to cloud security. Improper access controls can lead to unauthorized access to cloud resources. Ethical hacking efforts should include:
- Assessing IAM Policies: Check IAM policies. They must follow the principle of least privilege. This minimizes the risk of unauthorized access.
- Confirm Multi-Factor Authentication setup completion and accuracy. It should add security to cloud accounts.
- Monitoring Privileged Accounts: Conduct penetration tests on privileged accounts. They may have flaws that attackers could exploit.
Ethical hackers should also test for social engineering tactics to compromise cloud accounts. They must ensure that access management protocols are robust against such threats.
Ensuring compliance with cloud security standards
Compliance with industry standards and regulations is a critical aspect of cloud security. Ethical hackers should help organizations:
- Map Compliance: Align hacking with standards like GDPR, HIPAA, and ISO 27001. Ensure cloud environments meet the required security and privacy standards.
- Conduct Regular Audits: Include ethical hacking in regular security audits. It ensures compliance with evolving regulations.
- Encrypt Data: Test the encryption methods for data at rest and in transit. Ensure they protect sensitive information.
Ethical hackers can help organizations avoid fines and reputational damage. By focusing on compliance, they can also improve cloud security.
How to obtain Ethical Hacking Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, As cloud environments evolve, so must the strategies to secure them. Ethical hacking is key to cloud security. It identifies weaknesses and takes proactive measures to address them. Organizations can protect their cloud assets in 2024 and beyond. They must: know the cloud threat, automate, secure DevOps, and improve access management. They must also ensure compliance.
Ethical hackers are vital to this process. They have the skills to navigate the complexities of cloud security. As threats become more sophisticated, we must adopt best practices. One cannot overstate their importance. By staying ahead of risks, organizations can embrace cloud computing. They can protect their critical data and operations.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
With the rise of cloud use, securing cloud sites is now a top priority for organizations. The growth of cloud services raises security threats. So, ethical hacking is vital to protect cloud infrastructures. Ethical hacking, also known as penetration testing, simulates cyberattacks on systems. It aims to find vulnerabilities before malicious actors can exploit them. This approach helps organizations boost cloud security and meet standards.
In 2024, cloud environments will be complex, and hybrid models will be common. Ethical hacking must evolve to address new challenges. This article reviews the best practices for ethical hacking in cloud security. It highlights key areas for security professionals to protect their cloud assets.
Table Of Contents
- Understanding the Cloud Threat Landscape
- Leveraging Automation in Ethical Hacking
- Securing Cloud-Based DevOps Practices
- Enhancing Access Management and Identity Security
- Ensuring compliance with cloud security standards
- Conclusion
Understanding the Cloud Threat Landscape
First, ethical hackers must know the unique threats of cloud environments. Unlike traditional on-premises systems, cloud infrastructures are more dynamic. They share a responsibility model with cloud service providers (CSPs). Key threats include:
- Misconfigurations: a common cloud vulnerability, often due to human error. They expose data and services.
- Insider Threats: Employees or contractors with cloud access who may compromise security. This could be intentional or accidental.
- API vulnerabilities: exploitable flaws in the APIs used to manage cloud services.
- Data Breaches: Unauthorized access to sensitive data stored in the cloud.
- Denial of Service (DoS) attacks: Overloading cloud services to disrupt availability.
Ethical hackers must adapt to cloud-specific threats. They must find weaknesses in configurations, access controls, and data protection.
Leveraging Automation in Ethical Hacking
In 2024, automation is key to ethical hacking, especially in cloud security. Cloud environments are complex. Manual testing can't keep up with evolving threats. Automated tools and frameworks can:
- Conduct in-depth analysis: Use advanced scanning technology to reveal cloud weaknesses. It will detect threats in real time.
- Simulate Attacks: Tools like Metasploit and Burp Suite can simulate attacks. They can find potential security gaps.
- Automated scripts pinpoint misconfigurations in cloud resources with precision. They can detect open storage buckets and weak encryption settings.
- Use Automation: It can create detailed reports on findings. This helps security teams focus on their remediation efforts.
Automation boosts efficiency. But, it is vital to balance it with manual testing. Manual tests can find subtle bugs that automation may miss.
Securing Cloud-Based DevOps Practices
DevOps is now standard in cloud environments. It allows faster development and continuous deployment. Yet, the integration of DevOps in cloud environments introduces new security challenges. Ethical hacking in this context should focus on:
- Pipeline Security: Assess the CI/CD pipelines. Ensure that no malicious code gets into production environments.
- Container Security: Test for vulnerabilities in containerized apps. Ensure secure configurations of container orchestration tools, such as Kubernetes.
- Infrastructure as Code (IaC): Ethical hackers should test IaC scripts for flaws before deploying them to the cloud.
By focusing on these areas, ethical hackers can secure the DevOps lifecycle. This will lower the risk of cloud vulnerabilities from rapid development.
Enhancing Access Management and Identity Security
Access management and identity security are key to cloud security. Improper access controls can lead to unauthorized access to cloud resources. Ethical hacking efforts should include:
- Assessing IAM Policies: Check IAM policies. They must follow the principle of least privilege. This minimizes the risk of unauthorized access.
- Confirm Multi-Factor Authentication setup completion and accuracy. It should add security to cloud accounts.
- Monitoring Privileged Accounts: Conduct penetration tests on privileged accounts. They may have flaws that attackers could exploit.
Ethical hackers should also test for social engineering tactics to compromise cloud accounts. They must ensure that access management protocols are robust against such threats.
Ensuring compliance with cloud security standards
Compliance with industry standards and regulations is a critical aspect of cloud security. Ethical hackers should help organizations:
- Map Compliance: Align hacking with standards like GDPR, HIPAA, and ISO 27001. Ensure cloud environments meet the required security and privacy standards.
- Conduct Regular Audits: Include ethical hacking in regular security audits. It ensures compliance with evolving regulations.
- Encrypt Data: Test the encryption methods for data at rest and in transit. Ensure they protect sensitive information.
Ethical hackers can help organizations avoid fines and reputational damage. By focusing on compliance, they can also improve cloud security.
How to obtain Ethical Hacking Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, As cloud environments evolve, so must the strategies to secure them. Ethical hacking is key to cloud security. It identifies weaknesses and takes proactive measures to address them. Organizations can protect their cloud assets in 2024 and beyond. They must: know the cloud threat, automate, secure DevOps, and improve access management. They must also ensure compliance.
Ethical hackers are vital to this process. They have the skills to navigate the complexities of cloud security. As threats become more sophisticated, we must adopt best practices. One cannot overstate their importance. By staying ahead of risks, organizations can embrace cloud computing. They can protect their critical data and operations.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Service Management in the Era of Digital Transformation
In today's fast-changing tech world, service management is vital. It ensures success for organizations undergoing digital transformation. As businesses rely more on technology, service management has evolved. It now has many tools. They manage IT, deliver services, and improve customer experiences.
The Impact of Digital Transformation on Service Management
Digital transformation has changed how organizations operate. It uses cloud computing, automation, and agile methods. These technologies streamline processes, boost efficiency, and drive innovation. As businesses go digital, service management's role becomes vital. It must ensure a smooth tech integration into their operations. Digital technologies are growing. Organizations now face new challenges. They must manage their IT infrastructure, data analytics, cybersecurity, and IT service management. To solve these challenges, service management must evolve for the digital era. It should adopt best practices like DevOps, continuous improvement, and change management.
Digital transformation is reshaping service management. It integrates advanced tech, like AI, automation, and cloud solutions. These tools streamline processes and boost efficiency. This evolution lets organizations provide better, more responsive customer experiences. It also improves service delivery using real-time data and predictive analytics. As businesses adapt to the digital shift, they must embrace new tools and strategies. This is to stay competitive and meet their customers' complex demands.
Leveraging Technology for Service Management
A key to effective service management today is adopting new tech. This includes AI, IoT, and virtualization. These technologies help organizations. They enhance network management, improve IT operations, and drive innovation in service delivery.
In today's fast-changing digital world, using technology is key to improving service management. Advanced tools, like AI analytics and automation, can help organizations. They can streamline operations, improve service, and boost customer satisfaction. These new technologies boost efficiency. They also empower service teams to fix issues and adapt to change.
By using AI and IoT, organizations can automate routine tasks. They can also improve decision-making and optimize service delivery. It improves efficiency and scalability. It helps organizations improve customer experience with real-time, personalized insights and services.
Best Practices for Service Management in the Digital Era
To succeed in the digital era, organizations must use best practices in service management. These should focus on efficiency, adaptability, and scalability. This includes using agile methods, cloud services, and SaaS. It also includes adopting ITIL for service desk management.
In the digital era, we must use new tech and agile methods to improve service management. This will boost efficiency and responsiveness. Best practices are to automate routine tasks. Use data analytics for decisions. Focus on customers to meet their changing expectations. By using these strategies, organizations can excel in service. They can also adapt to the fast-paced digital world.
Best practices can help organizations. They improve service, cut costs, and reduce risks. These include: service optimization, process automation, and service virtualization. It also involves ensuring compliance with regulations. It requires robust incident management and problem-solving processes. We must also monitor performance metrics to gauge user satisfaction.
The Future of Service Management
As technology evolves, the future of service management will be shaped by trends. These include the digital workforce, service request automation, and predictive analytics. To thrive in the digital age, organizations must modernize their IT. They should improve their service design and transition processes. They must also optimize service performance.
As technology evolves, the future of service management looks bright. It promises big gains in efficiency and customer experience. AI, automation, and predictive analytics will change service delivery. They will enable proactive solutions instead of reactive ones. Organizations must embrace these innovations to stay competitive. They must also meet their customers' ever-changing expectations.
A shift to agile, flexible frameworks is shaping the future of service management. It is driven by a need to adapt to new technologies and changing customer demands. 5G and IoT will revolutionize service delivery. They will provide real-time data and improve connectivity. To thrive in a changing world, organizations must invest in new tools and strategies. These must prioritize efficiency and great customer experiences.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, service management is vital in the digital age. It helps organizations innovate, improve processes, and boost customer experiences. Using technology and best practices, organizations can succeed in the fast-changing digital world. They must also optimize their services.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-changing tech world, service management is vital. It ensures success for organizations undergoing digital transformation. As businesses rely more on technology, service management has evolved. It now has many tools. They manage IT, deliver services, and improve customer experiences.
The Impact of Digital Transformation on Service Management
Digital transformation has changed how organizations operate. It uses cloud computing, automation, and agile methods. These technologies streamline processes, boost efficiency, and drive innovation. As businesses go digital, service management's role becomes vital. It must ensure a smooth tech integration into their operations. Digital technologies are growing. Organizations now face new challenges. They must manage their IT infrastructure, data analytics, cybersecurity, and IT service management. To solve these challenges, service management must evolve for the digital era. It should adopt best practices like DevOps, continuous improvement, and change management.
Digital transformation is reshaping service management. It integrates advanced tech, like AI, automation, and cloud solutions. These tools streamline processes and boost efficiency. This evolution lets organizations provide better, more responsive customer experiences. It also improves service delivery using real-time data and predictive analytics. As businesses adapt to the digital shift, they must embrace new tools and strategies. This is to stay competitive and meet their customers' complex demands.
Leveraging Technology for Service Management
A key to effective service management today is adopting new tech. This includes AI, IoT, and virtualization. These technologies help organizations. They enhance network management, improve IT operations, and drive innovation in service delivery.
In today's fast-changing digital world, using technology is key to improving service management. Advanced tools, like AI analytics and automation, can help organizations. They can streamline operations, improve service, and boost customer satisfaction. These new technologies boost efficiency. They also empower service teams to fix issues and adapt to change.
By using AI and IoT, organizations can automate routine tasks. They can also improve decision-making and optimize service delivery. It improves efficiency and scalability. It helps organizations improve customer experience with real-time, personalized insights and services.
Best Practices for Service Management in the Digital Era
To succeed in the digital era, organizations must use best practices in service management. These should focus on efficiency, adaptability, and scalability. This includes using agile methods, cloud services, and SaaS. It also includes adopting ITIL for service desk management.
In the digital era, we must use new tech and agile methods to improve service management. This will boost efficiency and responsiveness. Best practices are to automate routine tasks. Use data analytics for decisions. Focus on customers to meet their changing expectations. By using these strategies, organizations can excel in service. They can also adapt to the fast-paced digital world.
Best practices can help organizations. They improve service, cut costs, and reduce risks. These include: service optimization, process automation, and service virtualization. It also involves ensuring compliance with regulations. It requires robust incident management and problem-solving processes. We must also monitor performance metrics to gauge user satisfaction.
The Future of Service Management
As technology evolves, the future of service management will be shaped by trends. These include the digital workforce, service request automation, and predictive analytics. To thrive in the digital age, organizations must modernize their IT. They should improve their service design and transition processes. They must also optimize service performance.
As technology evolves, the future of service management looks bright. It promises big gains in efficiency and customer experience. AI, automation, and predictive analytics will change service delivery. They will enable proactive solutions instead of reactive ones. Organizations must embrace these innovations to stay competitive. They must also meet their customers' ever-changing expectations.
A shift to agile, flexible frameworks is shaping the future of service management. It is driven by a need to adapt to new technologies and changing customer demands. 5G and IoT will revolutionize service delivery. They will provide real-time data and improve connectivity. To thrive in a changing world, organizations must invest in new tools and strategies. These must prioritize efficiency and great customer experiences.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, service management is vital in the digital age. It helps organizations innovate, improve processes, and boost customer experiences. Using technology and best practices, organizations can succeed in the fast-changing digital world. They must also optimize their services.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
CSPO Role in Aligning Product Strategy with Business Goals
In agile product development, speed is key. The CSPO ensures that the product strategy aligns with the business goals. The CSPO certification gives professionals skills for complex product management. It helps them manage projects and implement strategies in a fast-changing business world.
Agile Product Management and Business Alignment
A key duty of a CSPO is to connect the product team with business stakeholders. The CSPO works closely with stakeholders. This ensures the product vision and roadmap align with the organization's goals. This collaboration is vital. It will ensure the product adds value for both the business and the end-users.
Agile Product Management aligns business goals with product development. It ensures teams deliver value that meets strategic aims. Agile practices promote ongoing collaboration among product owners, stakeholders, and dev teams. This bridges the gap between business needs and tech work. It drives product success in fast-changing markets.
Stakeholder Collaboration and Product Vision
Effective stakeholder collaboration is at the core of the CSPO role. The CSPO gathers feedback from stakeholders through regular engagement. It helps shape the product vision. This feedback and refinement process ensures the product meets stakeholders' needs. It also aligns with the business goals.
Effective stakeholder collaboration is crucial for shaping and sustaining a clear product vision. CSPOs engage stakeholders early and often. This integrates diverse views into the product roadmap. It aligns the development team with business goals and customer needs.
· Stakeholder collaboration is essential for understanding customer needs and market trends?
· Regular engagement with stakeholders helps gather valuable feedback for product development?
· How does stakeholder collaboration help in shaping the product vision?
Sprint Planning and Requirement Analysis
Sprint planning is another critical aspect of the CSPO role. The CSPO works closely with the Scrum Master and dev team. They help prioritize the product backlog and define requirements for each sprint. This approach keeps the team focused on delivering value in each iteration.
Sprint planning and requirement analysis are critical in Agile. They ensure the team's work aligns with the project's goals. During sprint planning, teams must analyze requirements. This lets them prioritize tasks, manage resources, and set realistic expectations. It will drive successful project outcomes.
· How does the CSPO contribute to sprint planning in agile development?
· Why is requirement analysis crucial for product success in agile methodologies?
· What role does the CSPO play in prioritizing the product backlog?
Value Delivery and Strategic Planning
The CSPO must ensure the product is valuable to users and meets the organization's goals. The CSPO drives innovation and creates value for the business. They do this by constantly evaluating market demands, customer feedback, and competitors.
The key to lasting business success is a mix of value and strategy. Aligning goals with value delivery can boost growth, satisfaction, and competitiveness. Organizations should do this. This ensures every initiative helps.
· How does the CSPO contribute to value delivery in product development?
· Why is strategic planning essential for aligning the product strategy with business goals?
· What role does the CSPO play in driving innovation and value creation?
Team Collaboration and Agile Practices
Team collaboration is key to agile product development. The CSPO must foster a productive, collaborative team environment. The CSPO uses agile practices, like daily stand-ups and sprint reviews. These keep the team aligned with the product vision and focused on the goals.
Effective team collaboration is key to Agile success. It enables cross-functional teams to work together towards a common goal. Agile teams can adapt to change. They do this by fostering open communication, respect, and shared ownership. They will improve processes and deliver high-quality products that meet customers' needs.
· How does the CSPO foster team collaboration in agile development?
· What agile practices does the CSPO leverage to align the team with the product strategy?
· Why is team collaboration essential for achieving project success in agile methodologies?
How to obtain CSPO certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the CSPO is vital in agile product development. They align the product strategy with business goals. The CSPO ensures the product meets business needs. It focuses on delivering value to end-users. They do this by collaborating with stakeholders, sprint planning, and team work. The CSPO drives product success and business impact in today's competitive market. They focus on strategic alignment, innovation, and a customer-centric approach.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In agile product development, speed is key. The CSPO ensures that the product strategy aligns with the business goals. The CSPO certification gives professionals skills for complex product management. It helps them manage projects and implement strategies in a fast-changing business world.
Agile Product Management and Business Alignment
A key duty of a CSPO is to connect the product team with business stakeholders. The CSPO works closely with stakeholders. This ensures the product vision and roadmap align with the organization's goals. This collaboration is vital. It will ensure the product adds value for both the business and the end-users.
Agile Product Management aligns business goals with product development. It ensures teams deliver value that meets strategic aims. Agile practices promote ongoing collaboration among product owners, stakeholders, and dev teams. This bridges the gap between business needs and tech work. It drives product success in fast-changing markets.
Stakeholder Collaboration and Product Vision
Effective stakeholder collaboration is at the core of the CSPO role. The CSPO gathers feedback from stakeholders through regular engagement. It helps shape the product vision. This feedback and refinement process ensures the product meets stakeholders' needs. It also aligns with the business goals.
Effective stakeholder collaboration is crucial for shaping and sustaining a clear product vision. CSPOs engage stakeholders early and often. This integrates diverse views into the product roadmap. It aligns the development team with business goals and customer needs.
· Stakeholder collaboration is essential for understanding customer needs and market trends?
· Regular engagement with stakeholders helps gather valuable feedback for product development?
· How does stakeholder collaboration help in shaping the product vision?
Sprint Planning and Requirement Analysis
Sprint planning is another critical aspect of the CSPO role. The CSPO works closely with the Scrum Master and dev team. They help prioritize the product backlog and define requirements for each sprint. This approach keeps the team focused on delivering value in each iteration.
Sprint planning and requirement analysis are critical in Agile. They ensure the team's work aligns with the project's goals. During sprint planning, teams must analyze requirements. This lets them prioritize tasks, manage resources, and set realistic expectations. It will drive successful project outcomes.
· How does the CSPO contribute to sprint planning in agile development?
· Why is requirement analysis crucial for product success in agile methodologies?
· What role does the CSPO play in prioritizing the product backlog?
Value Delivery and Strategic Planning
The CSPO must ensure the product is valuable to users and meets the organization's goals. The CSPO drives innovation and creates value for the business. They do this by constantly evaluating market demands, customer feedback, and competitors.
The key to lasting business success is a mix of value and strategy. Aligning goals with value delivery can boost growth, satisfaction, and competitiveness. Organizations should do this. This ensures every initiative helps.
· How does the CSPO contribute to value delivery in product development?
· Why is strategic planning essential for aligning the product strategy with business goals?
· What role does the CSPO play in driving innovation and value creation?
Team Collaboration and Agile Practices
Team collaboration is key to agile product development. The CSPO must foster a productive, collaborative team environment. The CSPO uses agile practices, like daily stand-ups and sprint reviews. These keep the team aligned with the product vision and focused on the goals.
Effective team collaboration is key to Agile success. It enables cross-functional teams to work together towards a common goal. Agile teams can adapt to change. They do this by fostering open communication, respect, and shared ownership. They will improve processes and deliver high-quality products that meet customers' needs.
· How does the CSPO foster team collaboration in agile development?
· What agile practices does the CSPO leverage to align the team with the product strategy?
· Why is team collaboration essential for achieving project success in agile methodologies?
How to obtain CSPO certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the CSPO is vital in agile product development. They align the product strategy with business goals. The CSPO ensures the product meets business needs. It focuses on delivering value to end-users. They do this by collaborating with stakeholders, sprint planning, and team work. The CSPO drives product success and business impact in today's competitive market. They focus on strategic alignment, innovation, and a customer-centric approach.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
The Influence of Social Media Algorithms on Content Visibility
In today's digital age, social media algorithms decide what content is visible. They are crucial to visibility on various platforms. These algorithms analyze user behavior and trends. They ensure the most relevant content reaches the target audience. Social media algorithms greatly affect content visibility. They impact a brand's online reach, engagement, and success.
Understanding Social Media Algorithms
Social media algorithms are complex systems that determine the content that appears in users' feeds based on a variety of factors. These factors include user interactions, like likes, shares, and comments. They also include the content's relevance to the user's interests. Algorithms use data to tailor content for users. This maximizes engagement and personalizes their experience.
Knowing social media algorithms is key. It helps optimize your content's reach and engagement. By understanding how these algorithms prioritize and display content, you can tailor your posts. This will boost visibility and help you connect with your target audience.
Impact on Content Visibility
The influence of social media algorithms on content visibility is profound. With the growing content on social media, algorithms are key. They decide which posts to prioritize in users' feeds. Brands must understand how these algorithms work. They must optimize their content for maximum visibility.
Social media algorithms now prioritize engagement and relevance. They increasingly affect your content's visibility. Adapting to these algorithm changes can boost your content's reach and impact.
Engagement and Reach
Social media algorithms prioritize content that has high levels of engagement, such as likes, shares, and comments. Brands can boost their visibility on social media by creating content that sparks user interaction. Also, knowing each platform's algorithms can help brands. They can then tailor their content to boost engagement and reach.
For a successful digital marketing strategy, you must maximize engagement and reach. They are key to connecting with your target audience. Use data to improve your content for each platform. This will boost visibility and engagement with your brand.
Audience Targeting
Another key aspect of social media algorithms is audience targeting. Algorithms analyze user data. They find the most relevant content for each user. Brands can boost their visibility and engagement on social media. They should create targeted content for specific audience segments.
Effective audience targeting lets marketers tailor their messages. It ensures that content reaches those most likely to engage and convert. Using data analytics, businesses can improve their targeting and ROI. This will make their marketing more effective.
Organic vs. Paid Reach
Organic reach is key for brand awareness and credibility. But, paid reach can also boost content visibility. Targeted ads can help brands reach a larger audience. They ensure potential customers see their content. Brands can use a mix of organic and paid reach to maximize their visibility on social media.
Organic reach means gaining visibility through non-paid methods. These include engaging content and SEO. They build long-term trust and credibility with your audience. In contrast, paid reach uses ads to boost visibility. It targets specific demographics. It gives quick results but needs ongoing investment.
Maximizing Content Visibility
To maximize visibility on social media, brands must understand the algorithms. They must tailor their content strategy to them. Brands can boost their online visibility by creating engaging, relevant, and targeted content. Stay up-to-date on algorithm changes, trends, and best practices. This ensures your content stays visible to your target audience.
To maximize visibility, use SEO best practices. Also, promote your content on social media to reach the widest audience. Using data to optimize timing and targeting can boost your content's reach and impact.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the influence of social media algorithms on content visibility is undeniable. By understanding how these algorithms work, you can optimize your content. This will maximize your brand's online presence and reach a larger audience. To reach the right people, focus on engagement and targeting your audience. Use a mix of organic and paid reach.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's digital age, social media algorithms decide what content is visible. They are crucial to visibility on various platforms. These algorithms analyze user behavior and trends. They ensure the most relevant content reaches the target audience. Social media algorithms greatly affect content visibility. They impact a brand's online reach, engagement, and success.
Understanding Social Media Algorithms
Social media algorithms are complex systems that determine the content that appears in users' feeds based on a variety of factors. These factors include user interactions, like likes, shares, and comments. They also include the content's relevance to the user's interests. Algorithms use data to tailor content for users. This maximizes engagement and personalizes their experience.
Knowing social media algorithms is key. It helps optimize your content's reach and engagement. By understanding how these algorithms prioritize and display content, you can tailor your posts. This will boost visibility and help you connect with your target audience.
Impact on Content Visibility
The influence of social media algorithms on content visibility is profound. With the growing content on social media, algorithms are key. They decide which posts to prioritize in users' feeds. Brands must understand how these algorithms work. They must optimize their content for maximum visibility.
Social media algorithms now prioritize engagement and relevance. They increasingly affect your content's visibility. Adapting to these algorithm changes can boost your content's reach and impact.
Engagement and Reach
Social media algorithms prioritize content that has high levels of engagement, such as likes, shares, and comments. Brands can boost their visibility on social media by creating content that sparks user interaction. Also, knowing each platform's algorithms can help brands. They can then tailor their content to boost engagement and reach.
For a successful digital marketing strategy, you must maximize engagement and reach. They are key to connecting with your target audience. Use data to improve your content for each platform. This will boost visibility and engagement with your brand.
Audience Targeting
Another key aspect of social media algorithms is audience targeting. Algorithms analyze user data. They find the most relevant content for each user. Brands can boost their visibility and engagement on social media. They should create targeted content for specific audience segments.
Effective audience targeting lets marketers tailor their messages. It ensures that content reaches those most likely to engage and convert. Using data analytics, businesses can improve their targeting and ROI. This will make their marketing more effective.
Organic vs. Paid Reach
Organic reach is key for brand awareness and credibility. But, paid reach can also boost content visibility. Targeted ads can help brands reach a larger audience. They ensure potential customers see their content. Brands can use a mix of organic and paid reach to maximize their visibility on social media.
Organic reach means gaining visibility through non-paid methods. These include engaging content and SEO. They build long-term trust and credibility with your audience. In contrast, paid reach uses ads to boost visibility. It targets specific demographics. It gives quick results but needs ongoing investment.
Maximizing Content Visibility
To maximize visibility on social media, brands must understand the algorithms. They must tailor their content strategy to them. Brands can boost their online visibility by creating engaging, relevant, and targeted content. Stay up-to-date on algorithm changes, trends, and best practices. This ensures your content stays visible to your target audience.
To maximize visibility, use SEO best practices. Also, promote your content on social media to reach the widest audience. Using data to optimize timing and targeting can boost your content's reach and impact.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the influence of social media algorithms on content visibility is undeniable. By understanding how these algorithms work, you can optimize your content. This will maximize your brand's online presence and reach a larger audience. To reach the right people, focus on engagement and targeting your audience. Use a mix of organic and paid reach.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Key Trends in Information Systems Auditing for 2024
As we enter 2024, IS auditing is evolving. It must adapt to fast-changing tech, new rules, and emerging threats. Organizations are using stronger IS auditing practices more. They want to ensure their information systems are secure and reliable. This article looks at key trends in IS auditing for 2024. It offers insights on how auditors can adapt and improve their processes.
Table Of Contents
- Emphasis on Cybersecurity Audits
- Integration of Artificial Intelligence in Auditing
- Focus on data privacy and compliance.
- Expanding Role of IT Governance in Auditing
- Increased attention to ethical and social considerations.
- Conclusion
Emphasis on Cybersecurity Audits
Cybersecurity is a top priority for organizations. This focus shows in IS auditing practices. Cyberattacks are becoming more advanced. This has increased the demand for thorough cybersecurity audits. These audits go beyond perimeter security checks. They examine incident response, cloud security, and supply chain resilience.
- Cloud Security Audits: As cloud services rise, IS auditors must check their security. This includes evaluating encryption practices, access controls, and data sovereignty issues.
- Incident Response: Auditors now focus on the effectiveness of incident response plans. This involves evaluating the speed and success of responses to security breaches. It also includes the organization's ability to recover from them.
- Supply Chain Security: Supply chain attacks are rising. So, IS auditors are checking third-party vendors' security practices. This includes checking vendor risk management and suppliers' security.
Integration of Artificial Intelligence in Auditing
AI is transforming IS auditing. It automates routine tasks. It also helps auditors find anomalies and risks. AI tools are being used to analyze large data sets. They detect patterns and flag unusual activities. This may say security breaches or non-compliance.
- Automation of Routine Tasks: AI tools can automate repetitive tasks, like data collection. This lets auditors focus on more complex issues. This not only improves efficiency but also reduces the likelihood of human error.
- Anomaly Detection: AI algorithms find unusual data patterns. They may say fraud or system vulnerabilities. AI can analyze historical data. It can predict risks and provide auditors with useful insights.
- Continuous Auditing: AI allows continuous auditing. It enables real-time monitoring of systems and processes. This lets auditors find and fix issues as they arise instead of relying only on periodic audits.
Focus on data privacy and compliance.
Regulations like the GDPR and CCPA have made data privacy audits more important. In 2024, IS auditors must help firms follow regulations. They must protect customers' personal data.
- Compliance Audits: IS auditors must verify that organizations follow data privacy laws. This involves reviewing data practices, assessing protections, and checking consent.
- Data Encryption and Anonymization: Auditors are checking encryption and anonymization methods. They want to ensure sensitive data is well protected. This includes evaluating encryption protocols and the management of encryption keys.
- Cross-Border Data Transfers: IS auditors must assess the risks of cross-border data transfers. Organizations operate globally. This includes ensuring that data transfers follow international laws. Additionally, there must be adequate safeguards in place.
Expanding Role of IT Governance in Auditing
IT governance is now a key focus for IS auditors. Organizations see the need to align IT strategies with business goals. IT governance makes sure that IT investments align with the organization's goals. It also ensures that we manage risks well.
- Auditors are assessing the alignment of IT strategies with the organization's business goals. This includes assessing IT project management, resource use, and IT governance.
- Risk Management: IS auditors are more involved in assessing IT risk management. This involves evaluating how we identify, assess, and manage risks. It also includes the organization's risk appetite.
- IT Performance Measurement: Auditors are also focusing on the metrics for IT performance. This involves reviewing KPIs. They must reflect the IT goals and results.
Increased attention to ethical and social considerations.
As technology merges with society, ethics are vital in IS auditing. Auditors must now assess the ethics of IT practices. They hold organizations accountable for their actions.
- Ethical Auditing: IS auditors are checking the ethics of IT practices, like AI and data use. This includes checking whether these technologies respect human rights and avoid bias.
- Sustainability and Environmental Impact: Auditors are now assessing the environmental impact of IT. This includes evaluating data center sustainability and IT energy use. It also includes the organization's commitment to reducing its carbon footprint.
- Social Responsibility: IS auditors now focus on organizations' tech use and social responsibility. This means checking how technology affects communities and stakeholders. Organizations take ethical actions.
How to obtain CISA Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Information Systems auditing is changing. New technologies, rules, and ethics are driving this shift. In 2024, IS auditors must adapt to changes. They must embrace new tools, focus on cybersecurity, and follow data privacy laws. They also must consider the ethical and social impacts of IT practices. Staying ahead of these trends lets IS auditors help. Their insights can guide organizations through the complex, ever-changing world of information systems.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
As we enter 2024, IS auditing is evolving. It must adapt to fast-changing tech, new rules, and emerging threats. Organizations are using stronger IS auditing practices more. They want to ensure their information systems are secure and reliable. This article looks at key trends in IS auditing for 2024. It offers insights on how auditors can adapt and improve their processes.
Table Of Contents
- Emphasis on Cybersecurity Audits
- Integration of Artificial Intelligence in Auditing
- Focus on data privacy and compliance.
- Expanding Role of IT Governance in Auditing
- Increased attention to ethical and social considerations.
- Conclusion
Emphasis on Cybersecurity Audits
Cybersecurity is a top priority for organizations. This focus shows in IS auditing practices. Cyberattacks are becoming more advanced. This has increased the demand for thorough cybersecurity audits. These audits go beyond perimeter security checks. They examine incident response, cloud security, and supply chain resilience.
- Cloud Security Audits: As cloud services rise, IS auditors must check their security. This includes evaluating encryption practices, access controls, and data sovereignty issues.
- Incident Response: Auditors now focus on the effectiveness of incident response plans. This involves evaluating the speed and success of responses to security breaches. It also includes the organization's ability to recover from them.
- Supply Chain Security: Supply chain attacks are rising. So, IS auditors are checking third-party vendors' security practices. This includes checking vendor risk management and suppliers' security.
Integration of Artificial Intelligence in Auditing
AI is transforming IS auditing. It automates routine tasks. It also helps auditors find anomalies and risks. AI tools are being used to analyze large data sets. They detect patterns and flag unusual activities. This may say security breaches or non-compliance.
- Automation of Routine Tasks: AI tools can automate repetitive tasks, like data collection. This lets auditors focus on more complex issues. This not only improves efficiency but also reduces the likelihood of human error.
- Anomaly Detection: AI algorithms find unusual data patterns. They may say fraud or system vulnerabilities. AI can analyze historical data. It can predict risks and provide auditors with useful insights.
- Continuous Auditing: AI allows continuous auditing. It enables real-time monitoring of systems and processes. This lets auditors find and fix issues as they arise instead of relying only on periodic audits.
Focus on data privacy and compliance.
Regulations like the GDPR and CCPA have made data privacy audits more important. In 2024, IS auditors must help firms follow regulations. They must protect customers' personal data.
- Compliance Audits: IS auditors must verify that organizations follow data privacy laws. This involves reviewing data practices, assessing protections, and checking consent.
- Data Encryption and Anonymization: Auditors are checking encryption and anonymization methods. They want to ensure sensitive data is well protected. This includes evaluating encryption protocols and the management of encryption keys.
- Cross-Border Data Transfers: IS auditors must assess the risks of cross-border data transfers. Organizations operate globally. This includes ensuring that data transfers follow international laws. Additionally, there must be adequate safeguards in place.
Expanding Role of IT Governance in Auditing
IT governance is now a key focus for IS auditors. Organizations see the need to align IT strategies with business goals. IT governance makes sure that IT investments align with the organization's goals. It also ensures that we manage risks well.
- Auditors are assessing the alignment of IT strategies with the organization's business goals. This includes assessing IT project management, resource use, and IT governance.
- Risk Management: IS auditors are more involved in assessing IT risk management. This involves evaluating how we identify, assess, and manage risks. It also includes the organization's risk appetite.
- IT Performance Measurement: Auditors are also focusing on the metrics for IT performance. This involves reviewing KPIs. They must reflect the IT goals and results.
Increased attention to ethical and social considerations.
As technology merges with society, ethics are vital in IS auditing. Auditors must now assess the ethics of IT practices. They hold organizations accountable for their actions.
- Ethical Auditing: IS auditors are checking the ethics of IT practices, like AI and data use. This includes checking whether these technologies respect human rights and avoid bias.
- Sustainability and Environmental Impact: Auditors are now assessing the environmental impact of IT. This includes evaluating data center sustainability and IT energy use. It also includes the organization's commitment to reducing its carbon footprint.
- Social Responsibility: IS auditors now focus on organizations' tech use and social responsibility. This means checking how technology affects communities and stakeholders. Organizations take ethical actions.
How to obtain CISA Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Information Systems auditing is changing. New technologies, rules, and ethics are driving this shift. In 2024, IS auditors must adapt to changes. They must embrace new tools, focus on cybersecurity, and follow data privacy laws. They also must consider the ethical and social impacts of IT practices. Staying ahead of these trends lets IS auditors help. Their insights can guide organizations through the complex, ever-changing world of information systems.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Impact of Blockchain on Traditional Banking Systems
Blockchain technology has disrupted many industries, with banking being the most affected. Blockchain is a decentralized ledger. It records transactions across many computers. It promises improved security, transparency, and efficiency. As banks struggle to adapt to new technology, questions arise about their future. Does traditional banking have the agility to thrive in a flux?
This article explores the impact of blockchain on traditional banks. It focuses on transaction processing, customer trust, and regulatory challenges. It also covers costs and the future of banking in a blockchain world.
Table Of Contents
- Transforming Transaction Processing and Settlements
- Enhancing Security and Customer Trust
- Regulatory Challenges and Compliance Issues
- Reducing Operational Costs and Increasing Efficiency
- The Future of Banking in a Blockchain-Driven World
- Conclusion
Transforming Transaction Processing and Settlements
Blockchain's biggest impact on banking is its speed. It speeds up transactions and settlements. In traditional banking, transactions involve many intermediaries. This causes delays and higher costs. Blockchain enables peer-to-peer transactions. It reduces the need for intermediaries and speeds up the process.
- Blockchain transactions complete upon confirmation. In contrast, traditional systems can take days or even weeks.
- Cost Reduction: By eliminating intermediaries, blockchain reduces the costs associated with transaction processing.
- Blockchain is transparent. It records all transactions and makes them unchangeable. This reduces fraud and errors.
Enhancing Security and Customer Trust
Banking must prioritize security. Breaches can cause huge losses and damage customer trust. Blockchain technology enhances security through its decentralized and immutable ledger.
- Decentralization: Traditional banks rely on centralized databases. They are vulnerable to attacks. Blockchain is more secure against hacking because it is decentralized.
- Immutable Records: A transaction on the blockchain cannot be changed or deleted. This ensures data integrity.
- Increased Customer Trust: Better security may boost trust in a blockchain system.
Regulatory Challenges and Compliance Issues
Blockchain has many benefits, but it also poses regulatory challenges. Traditional banking is regulated to ensure stability and protect consumers. But, it's hard to apply those rules to blockchain's decentralized nature.
- Lack of Standardization: Blockchain is still evolving. There is no universal standard for its implementation, which creates regulatory uncertainty.
- KYC and AML Compliance: Traditional banks must follow KYC and AML rules. It's hard to enforce them on decentralized blockchain platforms.
- Jurisdictional Issues: Blockchain operates across borders, complicating the application of national regulations.
Reducing Operational Costs and Increasing Efficiency
Blockchain has the potential to drastically reduce the operational costs of traditional banks. By automating processes and using fewer middlemen, banks can cut costs. They can also be more efficient.
- Automation: Smart contracts can cut costs and errors. They automatically execute agreements when predefined conditions are met.
- Reduced Reconciliation Needs: Blockchain's transparency cuts the need for reconciliation. It saves time and resources.
- Streamlined Audits: All transactions are on a blockchain. This makes audits easier. It reduces time and costs.
The Future of Banking in a Blockchain-Driven World
The future of traditional banking in the blockchain era is uncertain. Some predict a complete industry overhaul. Others see a hybrid model where blockchain complements existing systems.
- Blockchain could disrupt traditional banking, especially in cross-border payments, loans, and trade finance.
- New Financial Services May Emerge: As blockchain tech matures, it may lead to new financial services.
- Hybrid Systems: Many experts believe the future will merge banks with blockchain systems. They expect banks to adopt blockchain to improve their services.
How to obtain Block Chain Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Blockchain technology revolutionizes traditional banking's established norms. It can improve processing, boost security, and cut costs. This poses risks and rewards for banks. It also challenges regulations. The tech is still in its early stages. But it could revolutionize banking. We must not ignore this potential. As banks test and adopt blockchain, the future of banking will likely blend old and new systems. This will offer customers the best of both worlds.
This transition will have challenges, especially with regulation. We need a clear, adaptable framework to protect consumers as new technologies emerge. But banks that embrace blockchain may lead the next generation of financial services.
Read More
Blockchain technology has disrupted many industries, with banking being the most affected. Blockchain is a decentralized ledger. It records transactions across many computers. It promises improved security, transparency, and efficiency. As banks struggle to adapt to new technology, questions arise about their future. Does traditional banking have the agility to thrive in a flux?
This article explores the impact of blockchain on traditional banks. It focuses on transaction processing, customer trust, and regulatory challenges. It also covers costs and the future of banking in a blockchain world.
Table Of Contents
- Transforming Transaction Processing and Settlements
- Enhancing Security and Customer Trust
- Regulatory Challenges and Compliance Issues
- Reducing Operational Costs and Increasing Efficiency
- The Future of Banking in a Blockchain-Driven World
- Conclusion
Transforming Transaction Processing and Settlements
Blockchain's biggest impact on banking is its speed. It speeds up transactions and settlements. In traditional banking, transactions involve many intermediaries. This causes delays and higher costs. Blockchain enables peer-to-peer transactions. It reduces the need for intermediaries and speeds up the process.
- Blockchain transactions complete upon confirmation. In contrast, traditional systems can take days or even weeks.
- Cost Reduction: By eliminating intermediaries, blockchain reduces the costs associated with transaction processing.
- Blockchain is transparent. It records all transactions and makes them unchangeable. This reduces fraud and errors.
Enhancing Security and Customer Trust
Banking must prioritize security. Breaches can cause huge losses and damage customer trust. Blockchain technology enhances security through its decentralized and immutable ledger.
- Decentralization: Traditional banks rely on centralized databases. They are vulnerable to attacks. Blockchain is more secure against hacking because it is decentralized.
- Immutable Records: A transaction on the blockchain cannot be changed or deleted. This ensures data integrity.
- Increased Customer Trust: Better security may boost trust in a blockchain system.
Regulatory Challenges and Compliance Issues
Blockchain has many benefits, but it also poses regulatory challenges. Traditional banking is regulated to ensure stability and protect consumers. But, it's hard to apply those rules to blockchain's decentralized nature.
- Lack of Standardization: Blockchain is still evolving. There is no universal standard for its implementation, which creates regulatory uncertainty.
- KYC and AML Compliance: Traditional banks must follow KYC and AML rules. It's hard to enforce them on decentralized blockchain platforms.
- Jurisdictional Issues: Blockchain operates across borders, complicating the application of national regulations.
Reducing Operational Costs and Increasing Efficiency
Blockchain has the potential to drastically reduce the operational costs of traditional banks. By automating processes and using fewer middlemen, banks can cut costs. They can also be more efficient.
- Automation: Smart contracts can cut costs and errors. They automatically execute agreements when predefined conditions are met.
- Reduced Reconciliation Needs: Blockchain's transparency cuts the need for reconciliation. It saves time and resources.
- Streamlined Audits: All transactions are on a blockchain. This makes audits easier. It reduces time and costs.
The Future of Banking in a Blockchain-Driven World
The future of traditional banking in the blockchain era is uncertain. Some predict a complete industry overhaul. Others see a hybrid model where blockchain complements existing systems.
- Blockchain could disrupt traditional banking, especially in cross-border payments, loans, and trade finance.
- New Financial Services May Emerge: As blockchain tech matures, it may lead to new financial services.
- Hybrid Systems: Many experts believe the future will merge banks with blockchain systems. They expect banks to adopt blockchain to improve their services.
How to obtain Block Chain Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Blockchain technology revolutionizes traditional banking's established norms. It can improve processing, boost security, and cut costs. This poses risks and rewards for banks. It also challenges regulations. The tech is still in its early stages. But it could revolutionize banking. We must not ignore this potential. As banks test and adopt blockchain, the future of banking will likely blend old and new systems. This will offer customers the best of both worlds.
This transition will have challenges, especially with regulation. We need a clear, adaptable framework to protect consumers as new technologies emerge. But banks that embrace blockchain may lead the next generation of financial services.
Azure NSG Overview Strengthening Your Cloud Security
In today's fast-changing cloud world, firms must rank security. They use cloud services like Microsoft Azure. Network Security Groups (NSGs) are key to Azure's security. They control network traffic to and from Azure resources. NSGs are a virtual firewall. They let you set and enforce security policies for the network and apps. This guide shows how Azure NSGs can boost your cloud security. It covers their features, best practices, and real-world uses.
Table Of Contents
- Understanding Azure NSGs: The Basics
- Best Practices for Configuring Azure NSGs
- Advanced Features of Azure NSGs
- Common Challenges and Solutions with Azure NSGs
- Case Studies: Real-World Applications of Azure NSGs
- Conclusion
Understanding Azure NSGs: The Basics
Azure NSGs are rule-based controls. They allow or deny network traffic to Azure resources. These controls can apply to network interfaces, VMs, or entire subnets in a virtual network. Here’s a breakdown of their core components:
- Inbound and Outbound Rules: NSGs have rules that control inbound and outbound traffic. These rules are defined by the source and destination IPs, ports, and protocols (TCP/UDP).
- Default Security Rules: Azure NSGs have default rules to ensure basic security. They allow all traffic within a virtual network and deny all from the internet by default.
- Custom Security Rules: Organizations can create rules for their specific security needs. These rules can override the default settings, providing flexibility in managing network security.
It's crucial to know these components. They are key to deploying and managing NSGs to protect your Azure environment.
Best Practices for Configuring Azure NSGs
To get the most security from Azure NSGs, follow best practices in their setup.
- Least Privilege Principle: Always configure NSGs with the least privilege principle in mind. Only allow the least necessary traffic and block all other traffic by default. This approach minimizes the attack surface and limits potential security breaches.
- Priority rules are processed by their numbers, from lowest to highest. Rank critical rules. Regularly review rules to avoid conflicts or redundancy.
- Regular Auditing and Monitoring: Check NSG rules continuously. Audit them regularly. This will ensure they meet current security and compliance requirements. Azure Check and Network Watcher tools can help with real-time monitoring and alerting.
- Service Tags and ASGs: Service Tags simplify NSG rule management. They group IPs by Azure services. ASGs let you group VMs and set security rules for those groups. This makes it easier to manage complex environments.
These best practices will optimize your NSG for security and efficiency.
Advanced Features of Azure NSGs
Azure NSGs offer several advanced features that can further enhance your network security:
- Augmented Security Rules: These rules allow complex rule sets. They support many IP addresses and ports. This simplifies security rule management in large-scale environments.
- Flow Logging and Diagnostics: NSGs support the logging of network traffic flow. It is invaluable for diagnosing issues and analyzing traffic patterns. It can also improve security policies. Integrate logs with Azure Check or third-party SIEM tools for full analysis.
- NSGs can work with Azure Firewall for layered security. NSGs manage access at the network interface and subnet level. Azure Firewall protects and logs network traffic across many VNets. It does this in a centralized way.
- Azure NSGs can integrate with Azure DDoS Protection for DDoS Protection Integration. This adds a layer of defense for critical resources against DDoS attacks.
These advanced features provide organizations with tools to improve their security. They ensure that their Azure environments are safe from many threats.
Common Challenges and Solutions with Azure NSGs
Azure NSGs have strong security features. But, organizations may struggle to install them. Here are some common challenges and solutions:
- In large setups, managing NSGs with many VMs and subnets can be complex. The solution is to use ASGs and Service Tags. They will simplify rule management and reduce the number of rules needed.
- Rule Conflicts: Conflicting NSG rules can cause issues. They may block legitimate traffic or allow unauthorized access. Regular audits and the use of tools like Azure Policy can help detect and resolve conflicts.
- Performance Impact: NSGs process traffic at the network level. This can cause latency if not configured properly. Optimize NSG rules. Remove unnecessary ones to reduce performance impact.
- Troubleshooting Issues: Diagnosing issues related to NSG rules can be challenging. Using tools like Azure Network Watcher can help. It shows traffic flow. This can help to find and fix problems.
By knowing these challenges and using the solutions, organizations can achieve an efficient and effective NSG configuration.
Case Studies: Real-World Applications of Azure NSGs
To illustrate the effectiveness of Azure NSGs, let’s look at a few real-world scenarios:
- Scenario 1: Securing a Multi-Tier Web App: NSGs must control traffic between the web, app, and database tiers of a cloud app. Only the web tier is exposed to the internet. NSG rules tightly control traffic to the app and database tiers.
- Scenario 2: Isolating Development and Production Environments. NSGs ensure isolation between dev and prod environments. They prevent dev resources from accessing or disrupting prod systems.
- Scenario 3: Protecting Sensitive Data. NSGs allow only certain IPs to access a database with sensitive data. This setup prevents unauthorized access and ensures compliance with data protection regulations.
These case studies show that Azure NSGs can meet diverse security needs. They apply to various industries and use cases.
How to obtain Microsoft Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Azure Network Security Groups are a powerful tool. They enhance your cloud environment's security. NSGs give fine control over network traffic. They help organizations enforce security policies to guard against many threats. NSGs secure modern cloud infrastructures. They are flexible and robust. They work from basic setups to advanced features and real-world applications. By using best practices and solving common problems, organizations can fully use NSGs. They will then have a secure, resilient Azure environment.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-changing cloud world, firms must rank security. They use cloud services like Microsoft Azure. Network Security Groups (NSGs) are key to Azure's security. They control network traffic to and from Azure resources. NSGs are a virtual firewall. They let you set and enforce security policies for the network and apps. This guide shows how Azure NSGs can boost your cloud security. It covers their features, best practices, and real-world uses.
Table Of Contents
- Understanding Azure NSGs: The Basics
- Best Practices for Configuring Azure NSGs
- Advanced Features of Azure NSGs
- Common Challenges and Solutions with Azure NSGs
- Case Studies: Real-World Applications of Azure NSGs
- Conclusion
Understanding Azure NSGs: The Basics
Azure NSGs are rule-based controls. They allow or deny network traffic to Azure resources. These controls can apply to network interfaces, VMs, or entire subnets in a virtual network. Here’s a breakdown of their core components:
- Inbound and Outbound Rules: NSGs have rules that control inbound and outbound traffic. These rules are defined by the source and destination IPs, ports, and protocols (TCP/UDP).
- Default Security Rules: Azure NSGs have default rules to ensure basic security. They allow all traffic within a virtual network and deny all from the internet by default.
- Custom Security Rules: Organizations can create rules for their specific security needs. These rules can override the default settings, providing flexibility in managing network security.
It's crucial to know these components. They are key to deploying and managing NSGs to protect your Azure environment.
Best Practices for Configuring Azure NSGs
To get the most security from Azure NSGs, follow best practices in their setup.
- Least Privilege Principle: Always configure NSGs with the least privilege principle in mind. Only allow the least necessary traffic and block all other traffic by default. This approach minimizes the attack surface and limits potential security breaches.
- Priority rules are processed by their numbers, from lowest to highest. Rank critical rules. Regularly review rules to avoid conflicts or redundancy.
- Regular Auditing and Monitoring: Check NSG rules continuously. Audit them regularly. This will ensure they meet current security and compliance requirements. Azure Check and Network Watcher tools can help with real-time monitoring and alerting.
- Service Tags and ASGs: Service Tags simplify NSG rule management. They group IPs by Azure services. ASGs let you group VMs and set security rules for those groups. This makes it easier to manage complex environments.
These best practices will optimize your NSG for security and efficiency.
Advanced Features of Azure NSGs
Azure NSGs offer several advanced features that can further enhance your network security:
- Augmented Security Rules: These rules allow complex rule sets. They support many IP addresses and ports. This simplifies security rule management in large-scale environments.
- Flow Logging and Diagnostics: NSGs support the logging of network traffic flow. It is invaluable for diagnosing issues and analyzing traffic patterns. It can also improve security policies. Integrate logs with Azure Check or third-party SIEM tools for full analysis.
- NSGs can work with Azure Firewall for layered security. NSGs manage access at the network interface and subnet level. Azure Firewall protects and logs network traffic across many VNets. It does this in a centralized way.
- Azure NSGs can integrate with Azure DDoS Protection for DDoS Protection Integration. This adds a layer of defense for critical resources against DDoS attacks.
These advanced features provide organizations with tools to improve their security. They ensure that their Azure environments are safe from many threats.
Common Challenges and Solutions with Azure NSGs
Azure NSGs have strong security features. But, organizations may struggle to install them. Here are some common challenges and solutions:
- In large setups, managing NSGs with many VMs and subnets can be complex. The solution is to use ASGs and Service Tags. They will simplify rule management and reduce the number of rules needed.
- Rule Conflicts: Conflicting NSG rules can cause issues. They may block legitimate traffic or allow unauthorized access. Regular audits and the use of tools like Azure Policy can help detect and resolve conflicts.
- Performance Impact: NSGs process traffic at the network level. This can cause latency if not configured properly. Optimize NSG rules. Remove unnecessary ones to reduce performance impact.
- Troubleshooting Issues: Diagnosing issues related to NSG rules can be challenging. Using tools like Azure Network Watcher can help. It shows traffic flow. This can help to find and fix problems.
By knowing these challenges and using the solutions, organizations can achieve an efficient and effective NSG configuration.
Case Studies: Real-World Applications of Azure NSGs
To illustrate the effectiveness of Azure NSGs, let’s look at a few real-world scenarios:
- Scenario 1: Securing a Multi-Tier Web App: NSGs must control traffic between the web, app, and database tiers of a cloud app. Only the web tier is exposed to the internet. NSG rules tightly control traffic to the app and database tiers.
- Scenario 2: Isolating Development and Production Environments. NSGs ensure isolation between dev and prod environments. They prevent dev resources from accessing or disrupting prod systems.
- Scenario 3: Protecting Sensitive Data. NSGs allow only certain IPs to access a database with sensitive data. This setup prevents unauthorized access and ensures compliance with data protection regulations.
These case studies show that Azure NSGs can meet diverse security needs. They apply to various industries and use cases.
How to obtain Microsoft Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Azure Network Security Groups are a powerful tool. They enhance your cloud environment's security. NSGs give fine control over network traffic. They help organizations enforce security policies to guard against many threats. NSGs secure modern cloud infrastructures. They are flexible and robust. They work from basic setups to advanced features and real-world applications. By using best practices and solving common problems, organizations can fully use NSGs. They will then have a secure, resilient Azure environment.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
RPA Vendor Lock In Strategies for Flexibility
In today's fast-changing business world, firms are using RPA to boost efficiency. It helps to streamline their operations. As businesses rely more on RPA vendors, they risk vendor lock-in. This is a key concern for those wanting to control their automation efforts. This article will explore ways to manage vendor lock-in. We will also look at how to ensure flexibility in RPA systems.
Understanding Vendor Lock-In in RPA
Vendor lock-in is when a business relies on a vendor for tech solutions. This makes it hard or costly to switch to another provider. In RPA, vendor lock-in can be risky. It can limit scalability, hinder integration, and reduce adaptability to changing business needs. To reduce these risks, organizations must tackle vendor lock-in in their RPA strategy.
Vendor lock-in in RPA happens when firms rely too much on a single RPA provider. This makes it hard to switch vendors or integrate with other systems. This can limit flexibility and innovation. So, it's crucial to carefully evaluate potential vendors. Consider strategies to avoid lock-in, like adopting open standards and ensuring tool compatibility.
Risk Mitigation and Scalability
A key aspect of managing vendor lock-in is to ensure that the RPA solution is scalable. It must meet the organization's evolving needs. This means checking the vendor's technology. It must align with the organization's long-term goals. Also, organizations should seek contracts that allow flexible scaling of the RPA solution. They should not be tied to a specific vendor.
Effective risk mitigation in RPA means finding vulnerabilities. Then, implement safeguards to prevent disruptions. To achieve scalability, organizations must design their automation for flexibility. This allows for seamless expansion as business needs change.
Vendor Relationship and Adaptability
Building a strong vendor relationship is essential for ensuring flexibility in RPA implementations. Organizations should engage with their RPA vendors. They must know the vendors' product roadmaps and how they align with their goals. This can help find areas for customization in the RPA solution. It will enable the organization to adapt to changing business needs.
In the fast-changing world of RPA, a flexible vendor relationship is vital. It helps adapt to new tech and shifting business needs. By fostering strong, adaptable partnerships with RPA vendors, organizations can stay agile. They can avoid vendor lock-in and optimize their automation strategies.
Vendor Selection and Migration
When choosing an RPA vendor, consider their partnerships and independence. Also, assess their agility in managing vendors. Using multiple vendors can reduce the risk of vendor lock-in. It does this by diversifying reliance on a single provider. Also, organizations should have a clear vendor migration strategy. It will help a smooth transition if a vendor changes or is terminated.
Choosing the right RPA vendor is key. It ensures a smooth integration and long-term success. Evaluating vendors on scalability, support, and flexibility can prevent costly migrations. It will ensure your automation strategy evolves with your business needs.
Continuous Improvement and Innovation
To keep RPA flexible, organizations should improve vendor management. They should focus on innovation. This may involve vendor evaluations, performance metrics, and audits. They ensure the vendor meets the organization's expectations. Collaborating with RPA vendors can help organizations innovate and gain an edge.
In today's fast-paced business world, a competitive edge is vital. So, continuous improvement and innovation are crucial. A culture of ongoing improvement and creativity can help organizations. It can help them adapt to changing markets, streamline processes, and succeed long-term.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, organizations must manage vendor lock-in when using RPA solutions. Flexible vendor management can reduce the risk of vendor lock-in. It can also keep automation efforts adaptable and scalable. Organizations must address vendor lock-in to maximize RPA's benefits. This will drive digital transformation in their business processes. They should do this from vendor evaluation to contract negotiation and improvement.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-changing business world, firms are using RPA to boost efficiency. It helps to streamline their operations. As businesses rely more on RPA vendors, they risk vendor lock-in. This is a key concern for those wanting to control their automation efforts. This article will explore ways to manage vendor lock-in. We will also look at how to ensure flexibility in RPA systems.
Understanding Vendor Lock-In in RPA
Vendor lock-in is when a business relies on a vendor for tech solutions. This makes it hard or costly to switch to another provider. In RPA, vendor lock-in can be risky. It can limit scalability, hinder integration, and reduce adaptability to changing business needs. To reduce these risks, organizations must tackle vendor lock-in in their RPA strategy.
Vendor lock-in in RPA happens when firms rely too much on a single RPA provider. This makes it hard to switch vendors or integrate with other systems. This can limit flexibility and innovation. So, it's crucial to carefully evaluate potential vendors. Consider strategies to avoid lock-in, like adopting open standards and ensuring tool compatibility.
Risk Mitigation and Scalability
A key aspect of managing vendor lock-in is to ensure that the RPA solution is scalable. It must meet the organization's evolving needs. This means checking the vendor's technology. It must align with the organization's long-term goals. Also, organizations should seek contracts that allow flexible scaling of the RPA solution. They should not be tied to a specific vendor.
Effective risk mitigation in RPA means finding vulnerabilities. Then, implement safeguards to prevent disruptions. To achieve scalability, organizations must design their automation for flexibility. This allows for seamless expansion as business needs change.
Vendor Relationship and Adaptability
Building a strong vendor relationship is essential for ensuring flexibility in RPA implementations. Organizations should engage with their RPA vendors. They must know the vendors' product roadmaps and how they align with their goals. This can help find areas for customization in the RPA solution. It will enable the organization to adapt to changing business needs.
In the fast-changing world of RPA, a flexible vendor relationship is vital. It helps adapt to new tech and shifting business needs. By fostering strong, adaptable partnerships with RPA vendors, organizations can stay agile. They can avoid vendor lock-in and optimize their automation strategies.
Vendor Selection and Migration
When choosing an RPA vendor, consider their partnerships and independence. Also, assess their agility in managing vendors. Using multiple vendors can reduce the risk of vendor lock-in. It does this by diversifying reliance on a single provider. Also, organizations should have a clear vendor migration strategy. It will help a smooth transition if a vendor changes or is terminated.
Choosing the right RPA vendor is key. It ensures a smooth integration and long-term success. Evaluating vendors on scalability, support, and flexibility can prevent costly migrations. It will ensure your automation strategy evolves with your business needs.
Continuous Improvement and Innovation
To keep RPA flexible, organizations should improve vendor management. They should focus on innovation. This may involve vendor evaluations, performance metrics, and audits. They ensure the vendor meets the organization's expectations. Collaborating with RPA vendors can help organizations innovate and gain an edge.
In today's fast-paced business world, a competitive edge is vital. So, continuous improvement and innovation are crucial. A culture of ongoing improvement and creativity can help organizations. It can help them adapt to changing markets, streamline processes, and succeed long-term.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, organizations must manage vendor lock-in when using RPA solutions. Flexible vendor management can reduce the risk of vendor lock-in. It can also keep automation efforts adaptable and scalable. Organizations must address vendor lock-in to maximize RPA's benefits. This will drive digital transformation in their business processes. They should do this from vendor evaluation to contract negotiation and improvement.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Building a CISM Centric Career Path in Cybersecurity
Do you want to advance your career in cybersecurity? Do you want to specialize in information security management? Building a CISM-centric career path could be the perfect choice for you. This article will explore the CISM certification's importance. It will cover the skills for a successful career in cybersecurity and the industry's opportunities.
What is CISM Certification?
The CISM certification is a global credential. It verifies the skills of info security managers. This certification shows a person's skill in designing, managing, and assessing an organization's info security systems.
Why Choose a Career in Cybersecurity?
Cybersecurity is now vital for all organizations. There are more cyber threats and data breaches. Cybersecurity experts are in high demand. So, it's a great field for a rewarding career.
A career in cybersecurity offers unique chances to make a big impact in a fast-growing field. Cyber threats are more sophisticated now. So, there is high demand for cybersecurity professionals. This offers job stability and high pay. Also, a career in cybersecurity puts you at tech's forefront. You must constantly learn and adapt to protect vital info and systems.
Advantages of CISM Certification
-
Career Advancement: A CISM certification can lead to higher-paying jobs and leadership roles.
-
Specialization: Focusing on information security management can build expertise in it.
-
Job Security: As our world goes digital, demand for cybersecurity experts will grow. This will provide job security for qualified individuals.
Building a Career in Cybersecurity with CISM
In a fast-changing field, CISM certification gives a career edge in cybersecurity. CISM certifies skills in managing an organization's info security program. It also boosts leadership skills needed for higher-level roles. As cybersecurity threats grow, demand for CISM-certified pros is rising. They protect and manage critical digital assets.
Developing CISM Skills and Expertise
To excel in a CISM-focused cybersecurity career, one must have many skills and a range of expertise. These may include:
-
Risk Management: Understanding and mitigating cybersecurity risks within an organization.
-
Security Governance: Establishing and overseeing information security policies and procedures.
-
Incident Response: Responding effectively to cybersecurity incidents and breaches.
-
Compliance: Ensuring that an organization complies with relevant cybersecurity laws and regulations.
CISM Training and Certification
To earn a CISM certification, you must pass the CISM exam. It tests your knowledge of information security management.
CISM Training and Certification gives info security pros the skills to run a cybersecurity program. This globally recognized certification is vital for advancing careers in information security. It focuses on risk management, security governance, and incident response. CISM validates a professional's expertise in managing an enterprise-level security program. It does so through rigorous training and exams.
CISM Exam Details
-
Duration: 4 hours
-
Format: Multiple choice questions
-
Passing Score: 450 out of 800. CISM training and certification can help professionals. It can boost their skills and careers. It keeps them competitive in the cybersecurity job market.
The Future of CISM in Cybersecurity
As the cybersecurity industry evolves, demand for CISM experts will rise. Organizations will rely on CISM-certified individuals to lead their security efforts and protect their data.
CISM's future in cybersecurity is vital. Organizations face more advanced, evolving threats. As cyber threats grow, CISM pros will shape security strategies and governance. With tech advances and new rules, CISM certification is a must for info security leaders.
CISM Career Opportunities
CISM professionals may take on roles like CISO, Security Consultant, or Information Security Manager. With the right skills and certs, the careers in cybersecurity are endless.
How to obtain CISM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, a CISM-focused path in cybersecurity can lead to a rewarding career. A CISM certification can help. It shows relevant skills and knowledge. Staying updated on trends is also key. With these, pros can have a bright future in cybersecurity.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Do you want to advance your career in cybersecurity? Do you want to specialize in information security management? Building a CISM-centric career path could be the perfect choice for you. This article will explore the CISM certification's importance. It will cover the skills for a successful career in cybersecurity and the industry's opportunities.
What is CISM Certification?
The CISM certification is a global credential. It verifies the skills of info security managers. This certification shows a person's skill in designing, managing, and assessing an organization's info security systems.
Why Choose a Career in Cybersecurity?
Cybersecurity is now vital for all organizations. There are more cyber threats and data breaches. Cybersecurity experts are in high demand. So, it's a great field for a rewarding career.
A career in cybersecurity offers unique chances to make a big impact in a fast-growing field. Cyber threats are more sophisticated now. So, there is high demand for cybersecurity professionals. This offers job stability and high pay. Also, a career in cybersecurity puts you at tech's forefront. You must constantly learn and adapt to protect vital info and systems.
Advantages of CISM Certification
-
Career Advancement: A CISM certification can lead to higher-paying jobs and leadership roles.
-
Specialization: Focusing on information security management can build expertise in it.
-
Job Security: As our world goes digital, demand for cybersecurity experts will grow. This will provide job security for qualified individuals.
Building a Career in Cybersecurity with CISM
In a fast-changing field, CISM certification gives a career edge in cybersecurity. CISM certifies skills in managing an organization's info security program. It also boosts leadership skills needed for higher-level roles. As cybersecurity threats grow, demand for CISM-certified pros is rising. They protect and manage critical digital assets.
Developing CISM Skills and Expertise
To excel in a CISM-focused cybersecurity career, one must have many skills and a range of expertise. These may include:
-
Risk Management: Understanding and mitigating cybersecurity risks within an organization.
-
Security Governance: Establishing and overseeing information security policies and procedures.
-
Incident Response: Responding effectively to cybersecurity incidents and breaches.
-
Compliance: Ensuring that an organization complies with relevant cybersecurity laws and regulations.
CISM Training and Certification
To earn a CISM certification, you must pass the CISM exam. It tests your knowledge of information security management.
CISM Training and Certification gives info security pros the skills to run a cybersecurity program. This globally recognized certification is vital for advancing careers in information security. It focuses on risk management, security governance, and incident response. CISM validates a professional's expertise in managing an enterprise-level security program. It does so through rigorous training and exams.
CISM Exam Details
-
Duration: 4 hours
-
Format: Multiple choice questions
-
Passing Score: 450 out of 800. CISM training and certification can help professionals. It can boost their skills and careers. It keeps them competitive in the cybersecurity job market.
The Future of CISM in Cybersecurity
As the cybersecurity industry evolves, demand for CISM experts will rise. Organizations will rely on CISM-certified individuals to lead their security efforts and protect their data.
CISM's future in cybersecurity is vital. Organizations face more advanced, evolving threats. As cyber threats grow, CISM pros will shape security strategies and governance. With tech advances and new rules, CISM certification is a must for info security leaders.
CISM Career Opportunities
CISM professionals may take on roles like CISO, Security Consultant, or Information Security Manager. With the right skills and certs, the careers in cybersecurity are endless.
How to obtain CISM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, a CISM-focused path in cybersecurity can lead to a rewarding career. A CISM certification can help. It shows relevant skills and knowledge. Staying updated on trends is also key. With these, pros can have a bright future in cybersecurity.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Creating Interactive Dashboards with Plotly in Python
Are you looking to create dynamic and engaging interactive dashboards for your data visualization projects? Look no further! In this article, we will explore how you can leverage the power of the Plotly library in Python to design stunning interactive charts and graphs for your data analysis needs.
Introduction to Plotly
Before we dive into the details of creating interactive dashboards with Plotly in Python, let's first understand what Plotly is. Plotly is a leading visualization tool that allows users to create interactive graphs and charts for data representation. It is widely used in various fields, including data science, web development, and python programming, to visualize data in a more engaging and meaningful way.
Plotly is a powerful open-source library for creating interactive and visually appealing data visualizations in Python. It offers a range of chart types and customization options, making it a popular choice for data scientists and analysts who need to present complex data insights. With Plotly’s intuitive syntax and integration capabilities, users can easily create dynamic dashboards and interactive plots that enhance data storytelling.
Getting Started with Plotly in Python
Plotly in Python enables interactive, dynamic data visualizations. It opens up a world of possibilities. This guide will cover the basics of Plotly. It will explain key features and give steps to create your first plots. Plotly's tools make it easy to create stunning visuals. Whether you're using simple charts or complex data sets, they are powerful and flexible.
To get started with Plotly in Python, you will need to install the Plotly library using the following command:
pip install plotly
Once you have installed Plotly, you can begin creating interactive graphs and charts using the Plotly Express API. Plotly Express is a high-level API for making charts. It uses minimal code. This makes it easy to create interactive visualizations quickly.
Creating Interactive Dashboards with Plotly Express
Plotly Express has many interactive charts. They include scatter plots, bar charts, line charts, and heatmaps. With Plotly Express, you can easily customize your charts. You can add annotations and create interactive features. These include zooming, panning, and hovering for more info on data points.
Plotly Express lets you create interactive dashboards. It's a simple way to visualize data. It helps you make dynamic, engaging interfaces with ease. With its intuitive API, you can easily create a variety of charts and graphs that respond to user inputs and interactions in real time. This blog will guide you on using Plotly Express. It will help you create interactive dashboards. They will present data well and improve user experience.
Dashboard Creation with Plotly Dash
To level up your data visualization and make custom, interactive dashboards, use Plotly Dash. It's the perfect tool for the job. Plotly Dash is a powerful framework for building interactive web-based dashboards with Python. With Plotly Dash, you can create custom layouts. You can add interactive components like sliders, dropdowns, and buttons. You can also make real-time updates for dynamic data visualization.
Creating interactive dashboards with Plotly Dash offers a powerful way to visualize data and gain insights. Plotly Dash has a user-friendly interface and strong features. It lets developers build customizable, responsive dashboards for various business needs. Whether you want to show real-time data or complex visuals, use Plotly Dash. It has the tools and flexibility to turn your data into useful insights.
Plotly Examples and Tutorials
To help you, there are many examples and tutorials online for creating interactive dashboards with Plotly in Python. The Plotly docs explain different chart types and dashboard layouts. They include code snippets, too. You can also explore Plotly's gallery of examples. It can inspire your data visualization projects.
How to obtain Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, using Plotly in Python to make interactive dashboards is a simple and powerful way to visualize data. It makes the data compelling and interactive. Use Plotly Express and Plotly Dash to create custom charts, graphs, and dashboards. They will engage your audience and reveal insights in your data. So why wait? Start creating stunning interactive dashboards with Plotly in Python today!
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to create dynamic and engaging interactive dashboards for your data visualization projects? Look no further! In this article, we will explore how you can leverage the power of the Plotly library in Python to design stunning interactive charts and graphs for your data analysis needs.
Introduction to Plotly
Before we dive into the details of creating interactive dashboards with Plotly in Python, let's first understand what Plotly is. Plotly is a leading visualization tool that allows users to create interactive graphs and charts for data representation. It is widely used in various fields, including data science, web development, and python programming, to visualize data in a more engaging and meaningful way.
Plotly is a powerful open-source library for creating interactive and visually appealing data visualizations in Python. It offers a range of chart types and customization options, making it a popular choice for data scientists and analysts who need to present complex data insights. With Plotly’s intuitive syntax and integration capabilities, users can easily create dynamic dashboards and interactive plots that enhance data storytelling.
Getting Started with Plotly in Python
Plotly in Python enables interactive, dynamic data visualizations. It opens up a world of possibilities. This guide will cover the basics of Plotly. It will explain key features and give steps to create your first plots. Plotly's tools make it easy to create stunning visuals. Whether you're using simple charts or complex data sets, they are powerful and flexible.
To get started with Plotly in Python, you will need to install the Plotly library using the following command:
pip install plotly
Once you have installed Plotly, you can begin creating interactive graphs and charts using the Plotly Express API. Plotly Express is a high-level API for making charts. It uses minimal code. This makes it easy to create interactive visualizations quickly.
Creating Interactive Dashboards with Plotly Express
Plotly Express has many interactive charts. They include scatter plots, bar charts, line charts, and heatmaps. With Plotly Express, you can easily customize your charts. You can add annotations and create interactive features. These include zooming, panning, and hovering for more info on data points.
Plotly Express lets you create interactive dashboards. It's a simple way to visualize data. It helps you make dynamic, engaging interfaces with ease. With its intuitive API, you can easily create a variety of charts and graphs that respond to user inputs and interactions in real time. This blog will guide you on using Plotly Express. It will help you create interactive dashboards. They will present data well and improve user experience.
Dashboard Creation with Plotly Dash
To level up your data visualization and make custom, interactive dashboards, use Plotly Dash. It's the perfect tool for the job. Plotly Dash is a powerful framework for building interactive web-based dashboards with Python. With Plotly Dash, you can create custom layouts. You can add interactive components like sliders, dropdowns, and buttons. You can also make real-time updates for dynamic data visualization.
Creating interactive dashboards with Plotly Dash offers a powerful way to visualize data and gain insights. Plotly Dash has a user-friendly interface and strong features. It lets developers build customizable, responsive dashboards for various business needs. Whether you want to show real-time data or complex visuals, use Plotly Dash. It has the tools and flexibility to turn your data into useful insights.
Plotly Examples and Tutorials
To help you, there are many examples and tutorials online for creating interactive dashboards with Plotly in Python. The Plotly docs explain different chart types and dashboard layouts. They include code snippets, too. You can also explore Plotly's gallery of examples. It can inspire your data visualization projects.
How to obtain Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, using Plotly in Python to make interactive dashboards is a simple and powerful way to visualize data. It makes the data compelling and interactive. Use Plotly Express and Plotly Dash to create custom charts, graphs, and dashboards. They will engage your audience and reveal insights in your data. So why wait? Start creating stunning interactive dashboards with Plotly in Python today!
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
How to Align Business Goals with IT Objectives Using COBIT® 5
In today's fast-paced business world, IT must align with business goals. It's vital for success. COBIT® 5 is a global IT governance and management framework. It provides a complete way to achieve this alignment. This framework links IT and business. It ensures tech investments support business goals, reduce risks, and maximize value. This guide shows how COBIT® 5 can help organizations. It aligns IT objectives with business goals. This drives better decisions and boosts performance.
Table Of Contents
- Understanding the Importance of IT-Business Alignment
- Leveraging COBIT® 5 principles for strategic alignment
- Implementing COBIT® 5 enablers for effective alignment
- Measuring and Monitoring Alignment with COBIT® 5
- Case Studies: Successful Alignment Using COBIT® 5
- Conclusion
Understanding the Importance of IT-Business Alignment
IT-business alignment is the sync of IT and business strategies to achieve goals. It's important. It ensures that IT investments and initiatives are directly contributing to business objectives.
- Challenges of Misalignment: Misalignment can lead to inefficiencies, wasted resources, and missed opportunities. Common challenges include communication gaps, conflicting priorities, and a lack of strategic oversight.
- Role of COBIT® 5: COBIT® 5 is a framework. It helps organizations align IT with the business. It does this by defining clear governance principles, processes, and enablers. It focuses on creating value through effective risk management and resource optimization.
IT-business alignment is vital for organizations aiming to remain competitive and innovative. When IT goals don't align with business ones, organizations face problems. They may become less efficient, incur higher costs, and miss growth opportunities. COBIT® 5, with its governance principles and processes, offers a solution. It ensures that IT initiatives align with business goals. This alignment leads to better decision-making, optimized resource utilization, and enhanced risk management.
Leveraging COBIT® 5 principles for strategic alignment
COBIT® 5 stresses the need to meet stakeholders. IT initiatives must support business goals.
- End-to-End Governance: The framework provides a full view of governance. It covers all IT activities and aligns them with business processes.
- Using a Single Integrated Framework: COBIT® 5 integrates with other frameworks and standards. It enables a consistent approach to governance and management across the organization.
COBIT® 5 is built on five principles that guide the alignment of IT with business goals. The first principle, "Meeting Stakeholder Needs," ensures IT projects meet the business's needs. By focusing on stakeholders' expectations, organizations can prioritize IT projects. This will provide the most value. The second principle, "End-to-End Governance," ensures all IT work aligns with business processes. It provides a holistic view of governance. COBIT® 5's third principle, 'Applying a Single Integrated Framework,' says to integrate it with other frameworks. It seeks a consistent, unified approach to governance.
Implementing COBIT® 5 enablers for effective alignment
COBIT® 5 outlines governance and management objectives. They align IT initiatives with business strategies. The focus is on value creation, risk management, and resource optimization.
- Enabler Models: The framework uses enabler models to align. These include processes, structures, and culture. These enablers support the achievement of governance and management objectives.
- Critical Enablers: The seven COBIT® 5 enablers are: principles, policies, frameworks, processes, structures, culture, information, services, infrastructure, applications, and skills. Also, infrastructure and competencies.
COBIT® 5 names enablers to help organizations align IT with business goals. These enablers include governance and management objectives. They aim for value creation, risk management, and resource optimization. The framework's enabler models, like processes and culture, provide the tools to align. By focusing on seven key enablers, organizations can align IT with business goals. This will improve performance and drive better outcomes.
Measuring and Monitoring Alignment with COBIT® 5
Performance Measurement: COBIT® 5 includes practices to measure performance. They help organizations track and assess how well IT aligns with business goals.
- Key Performance Indicators (KPIs): Use KPIs to assess IT governance and management. They should support business goals.
- Continuous Improvement: COBIT® 5 promotes a continuous improvement approach. Regularly reviewing and adjusting ensures that we maintain alignment over time.
Measuring and monitoring IT's alignment with business goals is vital for success. COBIT® 5 offers practices to measure performance. They enable organizations to track their IT governance and management. Organizations can use KPIs to see if IT projects are valuable and meeting goals. COBIT® 5 emphasizes continuous improvement. It calls for organizations to reassess their alignment strategies periodically. They must adapt to changing business needs.
Case Studies: Successful Alignment Using COBIT® 5
Real-World Examples: Study organizations that have used COBIT® 5. They aligned their IT and business goals.
- Lessons Learned: Key takeaways from the case studies. They include best practices and pitfalls to avoid.
- Scalability and Flexibility: Explain using COBIT® 5 in small to large businesses.
Case studies offer insights into how organizations used COBIT® 5. They aligned their IT and business goals. These examples show the framework's real-world use. They share best practices and lessons learned. The case studies teach us three key lessons. First, engage stakeholders. Second, have a clear governance structure. Monitor development and make adjustments as needed. Also, COBIT® 5 demonstrates scalability and flexibility. The framework can adapt to different organizations and sizes.
How to obtain COBIT 5 certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Aligning IT with business goals is key to success today. COBIT® 5 offers a strong framework for this alignment. It provides clear governance principles, enablers, and ways to measure performance. COBIT® 5 can help organizations. It ensures their IT investments support business goals. It also optimizes resources and manages risks. As a result, businesses can improve their strategies, efficiency, and growth.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced business world, IT must align with business goals. It's vital for success. COBIT® 5 is a global IT governance and management framework. It provides a complete way to achieve this alignment. This framework links IT and business. It ensures tech investments support business goals, reduce risks, and maximize value. This guide shows how COBIT® 5 can help organizations. It aligns IT objectives with business goals. This drives better decisions and boosts performance.
Table Of Contents
- Understanding the Importance of IT-Business Alignment
- Leveraging COBIT® 5 principles for strategic alignment
- Implementing COBIT® 5 enablers for effective alignment
- Measuring and Monitoring Alignment with COBIT® 5
- Case Studies: Successful Alignment Using COBIT® 5
- Conclusion
Understanding the Importance of IT-Business Alignment
IT-business alignment is the sync of IT and business strategies to achieve goals. It's important. It ensures that IT investments and initiatives are directly contributing to business objectives.
- Challenges of Misalignment: Misalignment can lead to inefficiencies, wasted resources, and missed opportunities. Common challenges include communication gaps, conflicting priorities, and a lack of strategic oversight.
- Role of COBIT® 5: COBIT® 5 is a framework. It helps organizations align IT with the business. It does this by defining clear governance principles, processes, and enablers. It focuses on creating value through effective risk management and resource optimization.
IT-business alignment is vital for organizations aiming to remain competitive and innovative. When IT goals don't align with business ones, organizations face problems. They may become less efficient, incur higher costs, and miss growth opportunities. COBIT® 5, with its governance principles and processes, offers a solution. It ensures that IT initiatives align with business goals. This alignment leads to better decision-making, optimized resource utilization, and enhanced risk management.
Leveraging COBIT® 5 principles for strategic alignment
COBIT® 5 stresses the need to meet stakeholders. IT initiatives must support business goals.
- End-to-End Governance: The framework provides a full view of governance. It covers all IT activities and aligns them with business processes.
- Using a Single Integrated Framework: COBIT® 5 integrates with other frameworks and standards. It enables a consistent approach to governance and management across the organization.
COBIT® 5 is built on five principles that guide the alignment of IT with business goals. The first principle, "Meeting Stakeholder Needs," ensures IT projects meet the business's needs. By focusing on stakeholders' expectations, organizations can prioritize IT projects. This will provide the most value. The second principle, "End-to-End Governance," ensures all IT work aligns with business processes. It provides a holistic view of governance. COBIT® 5's third principle, 'Applying a Single Integrated Framework,' says to integrate it with other frameworks. It seeks a consistent, unified approach to governance.
Implementing COBIT® 5 enablers for effective alignment
COBIT® 5 outlines governance and management objectives. They align IT initiatives with business strategies. The focus is on value creation, risk management, and resource optimization.
- Enabler Models: The framework uses enabler models to align. These include processes, structures, and culture. These enablers support the achievement of governance and management objectives.
- Critical Enablers: The seven COBIT® 5 enablers are: principles, policies, frameworks, processes, structures, culture, information, services, infrastructure, applications, and skills. Also, infrastructure and competencies.
COBIT® 5 names enablers to help organizations align IT with business goals. These enablers include governance and management objectives. They aim for value creation, risk management, and resource optimization. The framework's enabler models, like processes and culture, provide the tools to align. By focusing on seven key enablers, organizations can align IT with business goals. This will improve performance and drive better outcomes.
Measuring and Monitoring Alignment with COBIT® 5
Performance Measurement: COBIT® 5 includes practices to measure performance. They help organizations track and assess how well IT aligns with business goals.
- Key Performance Indicators (KPIs): Use KPIs to assess IT governance and management. They should support business goals.
- Continuous Improvement: COBIT® 5 promotes a continuous improvement approach. Regularly reviewing and adjusting ensures that we maintain alignment over time.
Measuring and monitoring IT's alignment with business goals is vital for success. COBIT® 5 offers practices to measure performance. They enable organizations to track their IT governance and management. Organizations can use KPIs to see if IT projects are valuable and meeting goals. COBIT® 5 emphasizes continuous improvement. It calls for organizations to reassess their alignment strategies periodically. They must adapt to changing business needs.
Case Studies: Successful Alignment Using COBIT® 5
Real-World Examples: Study organizations that have used COBIT® 5. They aligned their IT and business goals.
- Lessons Learned: Key takeaways from the case studies. They include best practices and pitfalls to avoid.
- Scalability and Flexibility: Explain using COBIT® 5 in small to large businesses.
Case studies offer insights into how organizations used COBIT® 5. They aligned their IT and business goals. These examples show the framework's real-world use. They share best practices and lessons learned. The case studies teach us three key lessons. First, engage stakeholders. Second, have a clear governance structure. Monitor development and make adjustments as needed. Also, COBIT® 5 demonstrates scalability and flexibility. The framework can adapt to different organizations and sizes.
How to obtain COBIT 5 certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Aligning IT with business goals is key to success today. COBIT® 5 offers a strong framework for this alignment. It provides clear governance principles, enablers, and ways to measure performance. COBIT® 5 can help organizations. It ensures their IT investments support business goals. It also optimizes resources and manages risks. As a result, businesses can improve their strategies, efficiency, and growth.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
ISO 20000 and Continuous Improvement in IT Services
In today's fast-paced digital world, IT services must be efficient and high-quality. They are vital to business success. ISO 20000 is the international standard for IT service management (ITSM). It provides a framework for managing and delivering quality IT services. A core principle is continuous improvement. It ensures that IT services meet changing business needs. And, it improves them. This article shows how ISO 20000 boosts IT service improvement. It provides a structured way to optimize IT operations.
Table Of Contents
- Understanding ISO 20000: A Brief Overview
- The Role of Continuous Improvement in ITSM
- Implementing ISO 20000: Key Steps for Success
- The Benefits of ISO 20000 and Continuous Improvement
- Challenges in Maintaining Continuous Improvement
- Conclusion
Understanding ISO 20000: A Brief Overview
ISO 20000 is the first international standard for IT service management. It harmonizes IT services with business requirements and provides efficient delivery. The standard integrates processes and mirrors ITIL's framework. It consists of two main parts:
- ISO 20000-1: A specification. It outlines what an organization must do to improve its IT service management system (SMS).
- ISO 20000-2: The code of practice that provides guidance on the application of the SMS.
ISO 20000 helps organizations manage risks, boost customer satisfaction, and improve services. The standard stresses the need to plan, install, and improve IT services. It also calls for monitoring and reviewing them.
The Role of Continuous Improvement in ITSM
Continuous improvement is key to ISO 20000 and IT service management. It uses a systematic method to find ways to improve. It then implements changes and measures their impact. ITSM's continuous improvement process revolves around the Plan-Do-Check-Act cycle.
- Plan: Identify areas for improvement and develop a plan to address them.
- Do: Install the planned changes.
- Check and test the results of the changes.
- Act: Take action based on the results to further refine and optimize the process.
This cycle is iterative. It means that improvement is ongoing, not a one-time event. Continuous improvement helps organizations adapt to change. It improves service quality and outcomes.
Implementing ISO 20000: Key Steps for Success
Implementing ISO 20000 involves several key steps. Each step aims at continuous improvement.
- Gap Analysis: Assess your IT service management processes against ISO 20000. Identify gaps and areas for improvement.
- Service Management Plan: Create a plan to install changes to meet ISO 20000. This plan should include clear objectives, roles, responsibilities, and timelines.
- Process Development and Documentation: Define and document the ISO 20000 ITSM processes. Align these processes with business needs. They should support continuous improvement.
- Training and Awareness: Train staff on the new processes. They must know their roles in continuous improvement.
- Internal Audits and Management Reviews: Conduct regular internal audits and management reviews. They will check compliance with ISO 20000 and find improvement opportunities.
These steps help organizations install ISO 20000. They also build a culture of continuous improvement in IT services.
The Benefits of ISO 20000 and Continuous Improvement
Implementing ISO 20000 and embracing continuous improvement offers many benefits to organizations:
- Continuous improvement leads to better IT services. This boosts customer satisfaction and reduces disruptions.
- Increased Efficiency: Streamlined processes and reviews cut inefficiencies and costs.
- Risk Management: ISO 20000's ITSM approach helps firms find and reduce risks. It leads to more reliable and secure IT services.
- ISO 20000 certification shows a commitment to quality and improvement. It enhances an organization's reputation and its competitive edge in the market.
- Employee Engagement: Involving employees in improvement projects boosts collaboration and innovation. This raises job satisfaction and productivity.
These benefits make ISO 20000 a wise investment. It helps organizations improve their IT services and succeed long-term.
Challenges in Maintaining Continuous Improvement
While continuous improvement is essential, it is not without challenges. Organizations may face several obstacles in IT services. They must maintain a culture of continuous improvement.
- Resistance to Change: Employees may resist new processes or role changes. This can hinder improvement efforts.
- Resource Constraints: Continuous improvement requires time, effort, and resources. Organizations must ensure they have the necessary support to sustain improvement initiatives.
- Complex IT environments are tough to improve. It's hard to find areas to fix and to make changes. Organizations must have a clear understanding of their IT infrastructure and processes.
- Measuring Improvement: It's hard to gauge the short-term impacts of improvement initiatives. Organizations need effective metrics and monitoring systems to track progress.
We must overcome these challenges. We need strong leadership, clear communication, and a commitment to learning and growth.
How to obtain ISO 20000 Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, ISO 20000 is a strong IT service management framework. It focuses on continuous improvement. ISO 20000 helps organizations improve their IT services. It ensures they meet the business's changing needs and deliver value to customers. Continuous improvement is not a one-time effort. It is an ongoing journey. It requires dedication, resources, and a willingness to adapt to change. It will help organizations excel and manage risks. They will stay competitive in today's fast-changing world.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced digital world, IT services must be efficient and high-quality. They are vital to business success. ISO 20000 is the international standard for IT service management (ITSM). It provides a framework for managing and delivering quality IT services. A core principle is continuous improvement. It ensures that IT services meet changing business needs. And, it improves them. This article shows how ISO 20000 boosts IT service improvement. It provides a structured way to optimize IT operations.
Table Of Contents
- Understanding ISO 20000: A Brief Overview
- The Role of Continuous Improvement in ITSM
- Implementing ISO 20000: Key Steps for Success
- The Benefits of ISO 20000 and Continuous Improvement
- Challenges in Maintaining Continuous Improvement
- Conclusion
Understanding ISO 20000: A Brief Overview
ISO 20000 is the first international standard for IT service management. It harmonizes IT services with business requirements and provides efficient delivery. The standard integrates processes and mirrors ITIL's framework. It consists of two main parts:
- ISO 20000-1: A specification. It outlines what an organization must do to improve its IT service management system (SMS).
- ISO 20000-2: The code of practice that provides guidance on the application of the SMS.
ISO 20000 helps organizations manage risks, boost customer satisfaction, and improve services. The standard stresses the need to plan, install, and improve IT services. It also calls for monitoring and reviewing them.
The Role of Continuous Improvement in ITSM
Continuous improvement is key to ISO 20000 and IT service management. It uses a systematic method to find ways to improve. It then implements changes and measures their impact. ITSM's continuous improvement process revolves around the Plan-Do-Check-Act cycle.
- Plan: Identify areas for improvement and develop a plan to address them.
- Do: Install the planned changes.
- Check and test the results of the changes.
- Act: Take action based on the results to further refine and optimize the process.
This cycle is iterative. It means that improvement is ongoing, not a one-time event. Continuous improvement helps organizations adapt to change. It improves service quality and outcomes.
Implementing ISO 20000: Key Steps for Success
Implementing ISO 20000 involves several key steps. Each step aims at continuous improvement.
- Gap Analysis: Assess your IT service management processes against ISO 20000. Identify gaps and areas for improvement.
- Service Management Plan: Create a plan to install changes to meet ISO 20000. This plan should include clear objectives, roles, responsibilities, and timelines.
- Process Development and Documentation: Define and document the ISO 20000 ITSM processes. Align these processes with business needs. They should support continuous improvement.
- Training and Awareness: Train staff on the new processes. They must know their roles in continuous improvement.
- Internal Audits and Management Reviews: Conduct regular internal audits and management reviews. They will check compliance with ISO 20000 and find improvement opportunities.
These steps help organizations install ISO 20000. They also build a culture of continuous improvement in IT services.
The Benefits of ISO 20000 and Continuous Improvement
Implementing ISO 20000 and embracing continuous improvement offers many benefits to organizations:
- Continuous improvement leads to better IT services. This boosts customer satisfaction and reduces disruptions.
- Increased Efficiency: Streamlined processes and reviews cut inefficiencies and costs.
- Risk Management: ISO 20000's ITSM approach helps firms find and reduce risks. It leads to more reliable and secure IT services.
- ISO 20000 certification shows a commitment to quality and improvement. It enhances an organization's reputation and its competitive edge in the market.
- Employee Engagement: Involving employees in improvement projects boosts collaboration and innovation. This raises job satisfaction and productivity.
These benefits make ISO 20000 a wise investment. It helps organizations improve their IT services and succeed long-term.
Challenges in Maintaining Continuous Improvement
While continuous improvement is essential, it is not without challenges. Organizations may face several obstacles in IT services. They must maintain a culture of continuous improvement.
- Resistance to Change: Employees may resist new processes or role changes. This can hinder improvement efforts.
- Resource Constraints: Continuous improvement requires time, effort, and resources. Organizations must ensure they have the necessary support to sustain improvement initiatives.
- Complex IT environments are tough to improve. It's hard to find areas to fix and to make changes. Organizations must have a clear understanding of their IT infrastructure and processes.
- Measuring Improvement: It's hard to gauge the short-term impacts of improvement initiatives. Organizations need effective metrics and monitoring systems to track progress.
We must overcome these challenges. We need strong leadership, clear communication, and a commitment to learning and growth.
How to obtain ISO 20000 Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, ISO 20000 is a strong IT service management framework. It focuses on continuous improvement. ISO 20000 helps organizations improve their IT services. It ensures they meet the business's changing needs and deliver value to customers. Continuous improvement is not a one-time effort. It is an ongoing journey. It requires dedication, resources, and a willingness to adapt to change. It will help organizations excel and manage risks. They will stay competitive in today's fast-changing world.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Microsoft Intune for Enterprise Mobility
In today's fast-paced business world, technology is vital. It ensures efficiency, security, and flexibility. As remote work and mobile devices increase, organizations must manage their digital assets. They must be comprehensive and effective. Microsoft Intune for Enterprise Mobility is a powerful tool. It helps businesses to manage devices, improve security, and boost productivity.
What is Microsoft Intune?
Microsoft Intune is a cloud service. It lets organizations manage their devices and apps from a single platform. It works perfectly with other Microsoft services, like Azure and Microsoft 365. It provides a complete solution for managing enterprise mobility. Intune has many features. They help IT teams secure data and simplify their work. They range from setting device policies to deploying corporate apps.
Enhancing Device Management with Intune
With Microsoft Intune, organizations can manage many devices, including Windows, Android, and iOS. It lets them easily configure policies and settings. Admins can use security measures to protect company data. These include data encryption and access control. Intune simplifies device management. It is a central portal to monitor and enforce compliance on the corporate network.
Microsoft Intune is changing device management. It offers a cloud-based solution that integrates with existing IT infrastructure. Its intuitive interface lets IT teams manage many devices from one platform. They can deploy, configure, and secure them. Using Intune, organizations can improve operations and security. They can also ensure a consistent user experience across all devices. This will boost productivity and lower admin costs.
Securing Data and Applications
A key benefit of Microsoft Intune is its focus on data protection and app management. Organizations can sync their data across devices. This ensures employees can access the latest info, no matter where they are. Strong authentication and permissions can restrict access to sensitive data and apps. Only authorized users can access them. Companies should use them. This enhances security.
In today's digital world, securing data and apps is vital. It protects sensitive info and maintains business integrity. Using strong security measures can reduce risks from data breaches and cyber-attacks. These measures include encryption, multi-factor authentication, and regular security audits. By prioritizing security, organizations can protect their assets. They can also ensure resilience against evolving cyber threats.
Simplifying Deployment and Administration
Intune has a user-friendly interface. It makes it easy to deploy devices, manage configurations, and monitor performance. Administrators can quickly set up devices with the needed software and services. There's no need for complex coding or manual configuration. The platform has reporting tools. They track device usage and find issues. They ensure optimal performance.
Simplifying deployment and administration is crucial for optimizing IT operations and reducing overhead. Using modern tools and automation, organizations can speed up deployments. This will ensure faster rollouts and fewer errors. Good admin practices save time. They also improve system reliability and scalability. This lets IT teams focus on strategy, not maintenance.
Ensuring Compliance and Control
Intune helps organizations enforce policies on their devices and apps. It ensures compliance with corporate and industry rules. The platform lets admins customize settings to meet compliance needs. It gives them greater control over device use within the organization. Intune secures corporate data and communication. It has data encryption, access control, and remote data wiping.
It's vital for organizations to ensure compliance and control. This helps to reduce risks and meet regulations. Strong policies and tech solutions can help. Compliance software and automated monitoring tools can streamline the process and improve oversight. Businesses can protect their reputation and ensure success. They should fix compliance issues and control internal processes.
Improving Productivity and Collaboration
Microsoft Intune aims to improve user experience and boost collaboration. Employees need to be productive and connected, wherever they are. Easy access to corporate apps and data helps with that. The platform lets users manage devices flexibly. They can enroll their own devices and access company resources easily.
In today's fast-paced work world, we must use tools to boost productivity and teamwork. They are key to success. Microsoft's productivity apps, like Teams, SharePoint, and OneDrive, work well together. They enable real-time communication. This helps teams work efficiently and stay connected. If used well, these tools can help organizations. They can streamline workflows, improve project management, and foster collaboration. This will drive innovation and growth.
How to obtain Microsoft certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Microsoft Intune for Enterprise Mobility is a powerful tool. It helps organizations manage devices, improve security, and boost productivity. Intune has a cloud-based platform and robust security. Its easy-to-use interface lets you manage the org's devices, apps, and data. Using Microsoft Intune, businesses can ensure efficient operations. It secures data and enables collaboration among employees.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced business world, technology is vital. It ensures efficiency, security, and flexibility. As remote work and mobile devices increase, organizations must manage their digital assets. They must be comprehensive and effective. Microsoft Intune for Enterprise Mobility is a powerful tool. It helps businesses to manage devices, improve security, and boost productivity.
What is Microsoft Intune?
Microsoft Intune is a cloud service. It lets organizations manage their devices and apps from a single platform. It works perfectly with other Microsoft services, like Azure and Microsoft 365. It provides a complete solution for managing enterprise mobility. Intune has many features. They help IT teams secure data and simplify their work. They range from setting device policies to deploying corporate apps.
Enhancing Device Management with Intune
With Microsoft Intune, organizations can manage many devices, including Windows, Android, and iOS. It lets them easily configure policies and settings. Admins can use security measures to protect company data. These include data encryption and access control. Intune simplifies device management. It is a central portal to monitor and enforce compliance on the corporate network.
Microsoft Intune is changing device management. It offers a cloud-based solution that integrates with existing IT infrastructure. Its intuitive interface lets IT teams manage many devices from one platform. They can deploy, configure, and secure them. Using Intune, organizations can improve operations and security. They can also ensure a consistent user experience across all devices. This will boost productivity and lower admin costs.
Securing Data and Applications
A key benefit of Microsoft Intune is its focus on data protection and app management. Organizations can sync their data across devices. This ensures employees can access the latest info, no matter where they are. Strong authentication and permissions can restrict access to sensitive data and apps. Only authorized users can access them. Companies should use them. This enhances security.
In today's digital world, securing data and apps is vital. It protects sensitive info and maintains business integrity. Using strong security measures can reduce risks from data breaches and cyber-attacks. These measures include encryption, multi-factor authentication, and regular security audits. By prioritizing security, organizations can protect their assets. They can also ensure resilience against evolving cyber threats.
Simplifying Deployment and Administration
Intune has a user-friendly interface. It makes it easy to deploy devices, manage configurations, and monitor performance. Administrators can quickly set up devices with the needed software and services. There's no need for complex coding or manual configuration. The platform has reporting tools. They track device usage and find issues. They ensure optimal performance.
Simplifying deployment and administration is crucial for optimizing IT operations and reducing overhead. Using modern tools and automation, organizations can speed up deployments. This will ensure faster rollouts and fewer errors. Good admin practices save time. They also improve system reliability and scalability. This lets IT teams focus on strategy, not maintenance.
Ensuring Compliance and Control
Intune helps organizations enforce policies on their devices and apps. It ensures compliance with corporate and industry rules. The platform lets admins customize settings to meet compliance needs. It gives them greater control over device use within the organization. Intune secures corporate data and communication. It has data encryption, access control, and remote data wiping.
It's vital for organizations to ensure compliance and control. This helps to reduce risks and meet regulations. Strong policies and tech solutions can help. Compliance software and automated monitoring tools can streamline the process and improve oversight. Businesses can protect their reputation and ensure success. They should fix compliance issues and control internal processes.
Improving Productivity and Collaboration
Microsoft Intune aims to improve user experience and boost collaboration. Employees need to be productive and connected, wherever they are. Easy access to corporate apps and data helps with that. The platform lets users manage devices flexibly. They can enroll their own devices and access company resources easily.
In today's fast-paced work world, we must use tools to boost productivity and teamwork. They are key to success. Microsoft's productivity apps, like Teams, SharePoint, and OneDrive, work well together. They enable real-time communication. This helps teams work efficiently and stay connected. If used well, these tools can help organizations. They can streamline workflows, improve project management, and foster collaboration. This will drive innovation and growth.
How to obtain Microsoft certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Microsoft Intune for Enterprise Mobility is a powerful tool. It helps organizations manage devices, improve security, and boost productivity. Intune has a cloud-based platform and robust security. Its easy-to-use interface lets you manage the org's devices, apps, and data. Using Microsoft Intune, businesses can ensure efficient operations. It secures data and enables collaboration among employees.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Integrating Salesforce with Social Media Platforms
Are you looking to take your sales and marketing efforts to the next level? Integrating Salesforce with social media is key. It will maximize your reach, engagement, and conversion rates. This article will explore the benefits of integrating Salesforce with social media. It will cover best practices for a seamless integration. Finally, it will show how to use this powerful combo to drive business growth.
Benefits of Integrating Salesforce with Social Media
Integrating Salesforce with social media helps businesses of all sizes. It offers many benefits. Some of the key advantages include:
-
Improved Customer Engagement: Use Salesforce to integrate with social media. It lets you connect with customers on their favorite channels. This builds stronger relationships and boosts brand loyalty.
-
Improved Lead Generation: Social media is a goldmine for leads. By integrating Salesforce, you can capture and nurture these leads in your CRM.
-
Efficient Marketing Campaigns: Salesforce CRM's social media integration lets you track and analyze your social media marketing campaigns. This helps you optimize your strategies for maximum impact.
-
Streamlined Data Management: Integrating Salesforce with social media centralizes all customer data and interactions. This gives a complete view of each customer's journey.
-
Enhanced Reporting and Analytics: Combining Salesforce and social media data gives insights into customer behavior, preferences, and trends. This enables data-driven decisions.
How to Integrate Salesforce with Social Media
Integrating Salesforce with social media platforms is easier than you might think. Here are some steps to help you get started:
-
Choose the Right Integration Tool: Many tools can help you connect Salesforce to social media. They include Salesforce Marketing Cloud, Social Studio, and Hootsuite.
-
Define Your Integration Goals: Before starting, clearly define your goals. Are you looking to increase brand awareness, drive website traffic, or boost sales?
-
Map Out Your Data: Identify the key data to sync between Salesforce and your social media. This includes customer profiles, leads, and engagement metrics.
-
Set Up Automation Rules: Automation is key to streamlining the integration process. Set up rules and workflows to ensure that data is synced automatically and accurately.
-
Monitor and Optimize: After the integration is live, check its performance. Use analytics to track ROI, engagement rates, and other key metrics, and make adjustments as needed.
Best Practices for Salesforce Social Media Integration
To ensure a successful integration of Salesforce with social media, consider these best practices:
-
Align Sales and Marketing Teams: Collaboration between sales and marketing teams is essential for effective integration. Ensure that both teams are aligned on goals, processes, and strategies.
-
Use Salesforce and social media data to personalize customer interactions. Deliver relevant content and offers.
-
Monitor Social Media Trends: Stay up-to-date on social media trends to optimize your integration strategy.
-
Implement Security Measures: Protect your data and ensure compliance. Use encryption, access controls, and user authentication.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, linking Salesforce with social media can boost engagement and generate leads. It will help grow the business. By following best practices and leveraging the right tools, you can unlock the full potential of this dynamic combination. Are you ready to boost your sales and marketing with Salesforce's social media tools? Start today and see the results for yourself!
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to take your sales and marketing efforts to the next level? Integrating Salesforce with social media is key. It will maximize your reach, engagement, and conversion rates. This article will explore the benefits of integrating Salesforce with social media. It will cover best practices for a seamless integration. Finally, it will show how to use this powerful combo to drive business growth.
Benefits of Integrating Salesforce with Social Media
Integrating Salesforce with social media helps businesses of all sizes. It offers many benefits. Some of the key advantages include:
-
Improved Customer Engagement: Use Salesforce to integrate with social media. It lets you connect with customers on their favorite channels. This builds stronger relationships and boosts brand loyalty.
-
Improved Lead Generation: Social media is a goldmine for leads. By integrating Salesforce, you can capture and nurture these leads in your CRM.
-
Efficient Marketing Campaigns: Salesforce CRM's social media integration lets you track and analyze your social media marketing campaigns. This helps you optimize your strategies for maximum impact.
-
Streamlined Data Management: Integrating Salesforce with social media centralizes all customer data and interactions. This gives a complete view of each customer's journey.
-
Enhanced Reporting and Analytics: Combining Salesforce and social media data gives insights into customer behavior, preferences, and trends. This enables data-driven decisions.
How to Integrate Salesforce with Social Media
Integrating Salesforce with social media platforms is easier than you might think. Here are some steps to help you get started:
-
Choose the Right Integration Tool: Many tools can help you connect Salesforce to social media. They include Salesforce Marketing Cloud, Social Studio, and Hootsuite.
-
Define Your Integration Goals: Before starting, clearly define your goals. Are you looking to increase brand awareness, drive website traffic, or boost sales?
-
Map Out Your Data: Identify the key data to sync between Salesforce and your social media. This includes customer profiles, leads, and engagement metrics.
-
Set Up Automation Rules: Automation is key to streamlining the integration process. Set up rules and workflows to ensure that data is synced automatically and accurately.
-
Monitor and Optimize: After the integration is live, check its performance. Use analytics to track ROI, engagement rates, and other key metrics, and make adjustments as needed.
Best Practices for Salesforce Social Media Integration
To ensure a successful integration of Salesforce with social media, consider these best practices:
-
Align Sales and Marketing Teams: Collaboration between sales and marketing teams is essential for effective integration. Ensure that both teams are aligned on goals, processes, and strategies.
-
Use Salesforce and social media data to personalize customer interactions. Deliver relevant content and offers.
-
Monitor Social Media Trends: Stay up-to-date on social media trends to optimize your integration strategy.
-
Implement Security Measures: Protect your data and ensure compliance. Use encryption, access controls, and user authentication.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, linking Salesforce with social media can boost engagement and generate leads. It will help grow the business. By following best practices and leveraging the right tools, you can unlock the full potential of this dynamic combination. Are you ready to boost your sales and marketing with Salesforce's social media tools? Start today and see the results for yourself!
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
The Role of Java in Serverless Architectures
Serverless architectures have changed how we develop and deploy cloud apps. Java is a key, versatile language. It powers serverless apps. This article will explore the importance of Java in serverless architectures. We will discuss its key features, benefits, and applications.
Why is Java Important in Serverless Architectures?
Java is a versatile, robust language. It is great for building complex, scalable apps. Its object-oriented nature, platform independence, and libraries make it ideal for serverless apps. Java lets developers use its vast ecosystem. They can create efficient, reliable serverless functions.
Java is key in serverless architectures. Its strength and ability to grow make it ideal for complex business logic in a serverless environment. Java has a mature ecosystem and many libraries. It lets developers build and deploy serverless functions efficiently. This ensures high performance and reliability. Also, Java's strong support for concurrency improves handling multiple requests at once. It is a great choice for responsive, efficient serverless apps.
Benefits of Using Java in Serverless Architectures:
Java's versatility and performance make it great for serverless architectures. It offers big benefits in this environment. Its strong ecosystem and mature libraries speed up development. They enable quick deployment and efficient handling of complex business logic. Also, Java's strong typing and compile-time checks improve code reliability. This is vital for scaling serverless applications.
1. Scalability: Java's strength makes it perfect for large workloads in serverless environments.
2. Efficiency: Java's runtime is very efficient. It runs serverless functions faster. This ensures optimal performance.
3. Integration: Java works well with other technologies. It simplifies building and deploying serverless apps.
4. Functionality: Java has many features that improve serverless apps.
5. Elasticity: Java can scale resources based on demand. This helps with resource use in serverless environments.
Applications of Java in Serverless Architectures:
Serverless architectures are changing how we develop and manage apps. Java is key to this shift. Java developers can use AWS Lambda and Azure Functions. They can build scalable, event-driven apps with them. They don't have to manage servers. This approach boosts flexibility, cuts costs, and speeds up development. It lets developers focus on writing code and delivering value, not managing infrastructure. Java lets developers build microservices. They can be easily deployed and scaled in a serverless environment.
· Backend Development: Java is often used to build the backend logic of serverless apps. It handles tasks like data processing and business logic.
· Event-Driven Integration: Java enables seamless integration with event triggers and other components in serverless architectures.
· Data Storage: Java enables fast data storage and retrieval in serverless apps. It ensures high performance and reliability.
Real-World Use Cases:
Real-world use cases demonstrate the practical applications of technology in various industries. These examples show technology's power to transform. They use AI to streamline operations and new software to improve customer experiences. Examining real-world cases can help organizations. They can learn to use these tools to boost efficiency, gain a competitive edge, and grow.
· Serverless Platform: You can use Java to deploy serverless functions on AWS Lambda. It is a scalable, cost-effective solution for app development.
· Automated Management: Java's ability to auto-scale makes it great for managing serverless functions in real-time.
· Dynamic Scaling: Java can scale resources to match workload demands. This ensures optimal performance in serverless architectures.
How to obtain JAVA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Java is vital to serverless architectures. It is a scalable, efficient, and reliable language for modern apps. Java's versatility and robustness keep it at the forefront of serverless development. It enables developers to create high-performance applications in the cloud.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Serverless architectures have changed how we develop and deploy cloud apps. Java is a key, versatile language. It powers serverless apps. This article will explore the importance of Java in serverless architectures. We will discuss its key features, benefits, and applications.
Why is Java Important in Serverless Architectures?
Java is a versatile, robust language. It is great for building complex, scalable apps. Its object-oriented nature, platform independence, and libraries make it ideal for serverless apps. Java lets developers use its vast ecosystem. They can create efficient, reliable serverless functions.
Java is key in serverless architectures. Its strength and ability to grow make it ideal for complex business logic in a serverless environment. Java has a mature ecosystem and many libraries. It lets developers build and deploy serverless functions efficiently. This ensures high performance and reliability. Also, Java's strong support for concurrency improves handling multiple requests at once. It is a great choice for responsive, efficient serverless apps.
Benefits of Using Java in Serverless Architectures:
Java's versatility and performance make it great for serverless architectures. It offers big benefits in this environment. Its strong ecosystem and mature libraries speed up development. They enable quick deployment and efficient handling of complex business logic. Also, Java's strong typing and compile-time checks improve code reliability. This is vital for scaling serverless applications.
1. Scalability: Java's strength makes it perfect for large workloads in serverless environments.
2. Efficiency: Java's runtime is very efficient. It runs serverless functions faster. This ensures optimal performance.
3. Integration: Java works well with other technologies. It simplifies building and deploying serverless apps.
4. Functionality: Java has many features that improve serverless apps.
5. Elasticity: Java can scale resources based on demand. This helps with resource use in serverless environments.
Applications of Java in Serverless Architectures:
Serverless architectures are changing how we develop and manage apps. Java is key to this shift. Java developers can use AWS Lambda and Azure Functions. They can build scalable, event-driven apps with them. They don't have to manage servers. This approach boosts flexibility, cuts costs, and speeds up development. It lets developers focus on writing code and delivering value, not managing infrastructure. Java lets developers build microservices. They can be easily deployed and scaled in a serverless environment.
· Backend Development: Java is often used to build the backend logic of serverless apps. It handles tasks like data processing and business logic.
· Event-Driven Integration: Java enables seamless integration with event triggers and other components in serverless architectures.
· Data Storage: Java enables fast data storage and retrieval in serverless apps. It ensures high performance and reliability.
Real-World Use Cases:
Real-world use cases demonstrate the practical applications of technology in various industries. These examples show technology's power to transform. They use AI to streamline operations and new software to improve customer experiences. Examining real-world cases can help organizations. They can learn to use these tools to boost efficiency, gain a competitive edge, and grow.
· Serverless Platform: You can use Java to deploy serverless functions on AWS Lambda. It is a scalable, cost-effective solution for app development.
· Automated Management: Java's ability to auto-scale makes it great for managing serverless functions in real-time.
· Dynamic Scaling: Java can scale resources to match workload demands. This ensures optimal performance in serverless architectures.
How to obtain JAVA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Java is vital to serverless architectures. It is a scalable, efficient, and reliable language for modern apps. Java's versatility and robustness keep it at the forefront of serverless development. It enables developers to create high-performance applications in the cloud.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
The Role of PMP in Digital Transformation Projects
In today's fast-paced world, businesses must adapt. Digital transformation is now vital for staying competitive and relevant. As technology advances quickly, businesses must adapt. They must meet their customers' and stakeholders' changing needs. PMP certification is vital for successful digital transformation projects. It gives project managers the skills to lead complex initiatives.
What is the Role of PMP in Digital Transformation Projects?
PMPs are vital to the success of digital transformation projects. Their role is multifaceted. PMP-certified project managers are experts in many areas. They excel in project management, agile methods, and leadership. They also know technology, strategic planning, business analysis, and change management. Plus, they communicate well with stakeholders. Their skills in risk management, project scope, and execution are vital. They ensure digital projects are on time, on budget, and satisfy stakeholders.
In digital transformation projects, the PMP certification is vital. It ensures a structured and efficient management of complex changes. PMP-certified project managers use proven methods to drive successful digital projects. They excel in risk management, stakeholder communication, and resource planning. Their expertise helps align project goals with business objectives. This helps organizations navigate the fast-evolving tech landscape. It minimizes disruptions and optimizes outcomes.
How does PMP Certification Benefit Digital Transformation Projects?
PMP certification brings a range of benefits to digital transformation projects, including:
PMP certification teaches project managers how to lead digital transformations. It ensures they can manage complex projects and align them with organizational goals. They must also navigate challenges like stakeholder management, resource allocation, and timeline adherence. PMP-certified professionals are better at driving digital transformation projects. They focus on structured processes and risk management to deliver lasting results.
-
PMP-certified project managers excel at leading and motivating teams. They can achieve project goals.
-
Effective Risk Management: PMPs excel at spotting and reducing risks to project success.
-
Strategic Planning: PMPs are great at making project plans. They align with the organization's strategic goals.
-
Stakeholder Communication: PMPs excel at communicating with stakeholders at all levels. This ensures alignment and buy-in for the project.
-
Project Monitoring and Control: PMPs use tools to track progress, find issues, and fix them.
Challenges and Opportunities in Digital Transformation Projects
Digital transformation projects present unique challenges and opportunities for organizations. Digital transformation has great benefits. But, integrating new technologies, processes, and systems can be daunting. PMP-certified project managers can tackle these challenges. They have the skills to use project management methods, tools, and techniques. They can deliver successful digital transformation projects.
Digital transformation projects can help organizations innovate and improve. But, they also pose major challenges. The key obstacles are: resistance to change, old systems, and cyber risks in complex digital environments. But, with a smart plan and good management, businesses can overcome these hurdles. They can then use digital transformation to drive growth and competitiveness.
Digital transformation projects present both significant challenges and immense opportunities for organizations. A key challenge is managing change. Teams often resist new technologies and processes, causing delays. However, if done right, digital transformation can help businesses. It can streamline operations, improve customer experiences, and drive innovation. This will give them an edge in a more digital world.
How to obtain PMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, PMP certification is vital to digital transformation projects. It gives project managers the skills and tools to lead complex initiatives. PMPs can help organizations succeed in digital transformation. They can navigate its challenges and seize its opportunities. They have expertise in project management, agile methods, leadership, and stakeholder communication. To ensure your next digital transformation project succeeds, hire a PMP-certified project manager.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced world, businesses must adapt. Digital transformation is now vital for staying competitive and relevant. As technology advances quickly, businesses must adapt. They must meet their customers' and stakeholders' changing needs. PMP certification is vital for successful digital transformation projects. It gives project managers the skills to lead complex initiatives.
What is the Role of PMP in Digital Transformation Projects?
PMPs are vital to the success of digital transformation projects. Their role is multifaceted. PMP-certified project managers are experts in many areas. They excel in project management, agile methods, and leadership. They also know technology, strategic planning, business analysis, and change management. Plus, they communicate well with stakeholders. Their skills in risk management, project scope, and execution are vital. They ensure digital projects are on time, on budget, and satisfy stakeholders.
In digital transformation projects, the PMP certification is vital. It ensures a structured and efficient management of complex changes. PMP-certified project managers use proven methods to drive successful digital projects. They excel in risk management, stakeholder communication, and resource planning. Their expertise helps align project goals with business objectives. This helps organizations navigate the fast-evolving tech landscape. It minimizes disruptions and optimizes outcomes.
How does PMP Certification Benefit Digital Transformation Projects?
PMP certification brings a range of benefits to digital transformation projects, including:
PMP certification teaches project managers how to lead digital transformations. It ensures they can manage complex projects and align them with organizational goals. They must also navigate challenges like stakeholder management, resource allocation, and timeline adherence. PMP-certified professionals are better at driving digital transformation projects. They focus on structured processes and risk management to deliver lasting results.
-
PMP-certified project managers excel at leading and motivating teams. They can achieve project goals.
-
Effective Risk Management: PMPs excel at spotting and reducing risks to project success.
-
Strategic Planning: PMPs are great at making project plans. They align with the organization's strategic goals.
-
Stakeholder Communication: PMPs excel at communicating with stakeholders at all levels. This ensures alignment and buy-in for the project.
-
Project Monitoring and Control: PMPs use tools to track progress, find issues, and fix them.
Challenges and Opportunities in Digital Transformation Projects
Digital transformation projects present unique challenges and opportunities for organizations. Digital transformation has great benefits. But, integrating new technologies, processes, and systems can be daunting. PMP-certified project managers can tackle these challenges. They have the skills to use project management methods, tools, and techniques. They can deliver successful digital transformation projects.
Digital transformation projects can help organizations innovate and improve. But, they also pose major challenges. The key obstacles are: resistance to change, old systems, and cyber risks in complex digital environments. But, with a smart plan and good management, businesses can overcome these hurdles. They can then use digital transformation to drive growth and competitiveness.
Digital transformation projects present both significant challenges and immense opportunities for organizations. A key challenge is managing change. Teams often resist new technologies and processes, causing delays. However, if done right, digital transformation can help businesses. It can streamline operations, improve customer experiences, and drive innovation. This will give them an edge in a more digital world.
How to obtain PMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, PMP certification is vital to digital transformation projects. It gives project managers the skills and tools to lead complex initiatives. PMPs can help organizations succeed in digital transformation. They can navigate its challenges and seize its opportunities. They have expertise in project management, agile methods, leadership, and stakeholder communication. To ensure your next digital transformation project succeeds, hire a PMP-certified project manager.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Implementing Multi Factor Authentication with Citrix Clients
MFA is vital. It protects sensitive data and stops unauthorized access. For Citrix clients, MFA adds security by authenticating users and protecting their logins. This article will explore the need for MFA with Citrix clients. We will also discuss Citrix's user authentication methods and its data security features.
Why Implement Multi-Factor Authentication with Citrix Clients?
Using MFA with Citrix clients is vital. It will boost security and stop unauthorized access to sensitive data. MFA requires users to verify their identity with multiple factors. These include passwords, biometrics, or security tokens. It adds protection against identity theft, data breaches, and other cyber threats. With the rise of sophisticated cyber attacks on user credentials, we must deploy MFA. It will secure user accounts and prevent unauthorized access to Citrix systems.
Using Multi-Factor Authentication (MFA) with Citrix clients greatly boosts security. It adds a verification step beyond just a password. This step helps protect sensitive data and access points from unauthorized users. It reduces breach risks and ensures compliance with industry standards. MFA can protect Citrix environments from evolving threats. It will also provide a more secure, reliable user experience.
How Does Multi-Factor Authentication Work with Citrix Clients?
If a user tries to access a Citrix workspace or app, they must provide extra authentication beyond their password. This could include a one-time passcode to their mobile, a fingerprint scan, or a security question. Citrix clients can ensure that only authorized users access sensitive data and connections. They require users to verify their identity using multiple factors.
MFA adds security to Citrix Clients. It requires users to verify their identity beyond just their password. This usually involves a mix of three things. They are: 1. Something the user knows, like a password. 2. Something they have, like a mobile device or security token. 3. Something they are, like a biometric verification. MFA boosts Citrix's protection against unauthorized access. It requires extra verification even if login credentials are compromised.
What Are the Benefits of Multi-Factor Authentication with Citrix Clients?
MFA greatly boosts security for Citrix clients. It adds a verification step beyond passwords. This cuts the risk of unauthorized access. If credentials are compromised, a second form of verification is still needed. MFA boosts security. It helps meet compliance and build user trust.
-
Enhanced Security: MFA boosts security. It requires users to verify their identity with multiple factors. This reduces the risk of unauthorized access.
-
User Verification: MFA checks users' identities before granting access. This prevents identity fraud and unauthorized logins.
-
Secure Login: MFA ensures only legitimate users can access Citrix clients. It protects sensitive data and prevents breaches.
-
Data Protection: MFA encrypts user credentials and data. It prevents data theft by ensuring secure transfer and storage of information.
How to obtain Citrix Client Administration certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
We must implement Multi-Factor Authentication with Citrix clients. It's key to security, user data, and preventing unauthorized access to sensitive info. MFA can help organizations. It boosts security, meets regulations, and protects against cyber threats. Citrix has advanced security and authentication solutions. They help organizations secure their environment and user accounts, and prevent identity fraud. Implement MFA with Citrix clients. It will protect your data from cybercriminals.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
MFA is vital. It protects sensitive data and stops unauthorized access. For Citrix clients, MFA adds security by authenticating users and protecting their logins. This article will explore the need for MFA with Citrix clients. We will also discuss Citrix's user authentication methods and its data security features.
Why Implement Multi-Factor Authentication with Citrix Clients?
Using MFA with Citrix clients is vital. It will boost security and stop unauthorized access to sensitive data. MFA requires users to verify their identity with multiple factors. These include passwords, biometrics, or security tokens. It adds protection against identity theft, data breaches, and other cyber threats. With the rise of sophisticated cyber attacks on user credentials, we must deploy MFA. It will secure user accounts and prevent unauthorized access to Citrix systems.
Using Multi-Factor Authentication (MFA) with Citrix clients greatly boosts security. It adds a verification step beyond just a password. This step helps protect sensitive data and access points from unauthorized users. It reduces breach risks and ensures compliance with industry standards. MFA can protect Citrix environments from evolving threats. It will also provide a more secure, reliable user experience.
How Does Multi-Factor Authentication Work with Citrix Clients?
If a user tries to access a Citrix workspace or app, they must provide extra authentication beyond their password. This could include a one-time passcode to their mobile, a fingerprint scan, or a security question. Citrix clients can ensure that only authorized users access sensitive data and connections. They require users to verify their identity using multiple factors.
MFA adds security to Citrix Clients. It requires users to verify their identity beyond just their password. This usually involves a mix of three things. They are: 1. Something the user knows, like a password. 2. Something they have, like a mobile device or security token. 3. Something they are, like a biometric verification. MFA boosts Citrix's protection against unauthorized access. It requires extra verification even if login credentials are compromised.
What Are the Benefits of Multi-Factor Authentication with Citrix Clients?
MFA greatly boosts security for Citrix clients. It adds a verification step beyond passwords. This cuts the risk of unauthorized access. If credentials are compromised, a second form of verification is still needed. MFA boosts security. It helps meet compliance and build user trust.
-
Enhanced Security: MFA boosts security. It requires users to verify their identity with multiple factors. This reduces the risk of unauthorized access.
-
User Verification: MFA checks users' identities before granting access. This prevents identity fraud and unauthorized logins.
-
Secure Login: MFA ensures only legitimate users can access Citrix clients. It protects sensitive data and prevents breaches.
-
Data Protection: MFA encrypts user credentials and data. It prevents data theft by ensuring secure transfer and storage of information.
How to obtain Citrix Client Administration certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
We must implement Multi-Factor Authentication with Citrix clients. It's key to security, user data, and preventing unauthorized access to sensitive info. MFA can help organizations. It boosts security, meets regulations, and protects against cyber threats. Citrix has advanced security and authentication solutions. They help organizations secure their environment and user accounts, and prevent identity fraud. Implement MFA with Citrix clients. It will protect your data from cybercriminals.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Strategies for Effective Quality Control in Manufacturing
In manufacturing, high-quality products are key to success. Good quality control can help companies. It can maintain consistency, meet regulations, and improve customer satisfaction. This article will discuss ways to ensure quality in manufacturing.
Importance of Quality Control in Manufacturing
Quality control is key in manufacturing. It ensures products meet customer and legal standards. Companies can reduce defects and improve efficiency by using effective quality control. It will also ensure consistent products. This ultimately leads to higher customer satisfaction and increased profitability.
Quality control in manufacturing is vital. It ensures product consistency and meets industry standards. This builds customer trust and satisfaction. QC minimizes waste, cuts costs, and boosts efficiency. It does this by finding and fixing defects early. Also, good quality control helps meet regulations. It builds a strong brand. This drives long-term success and competitiveness in the market.
Best Practices for Quality Control
-
Establish Quality Control Standards: First, set clear quality control standards. This is key to ensuring product consistency and reliability. These standards should detail the criteria for acceptable products.
-
Implement Quality Control Procedures: Develop standard tests to inspect for quality. This will ensure products meet the established standards. Regularly monitor and evaluate these procedures to identify areas for improvement.
-
Use Quality Control Tools: Give your team the tools to test and inspect products. This can include equipment for measurements, testing, and inspection software.
-
Develop a Quality Control Plan: Create a plan. It must detail how to implement quality control measures in manufacturing. This plan should detail responsibilities, procedures, and processes for quality control.
-
Train Your Team: Provide ongoing training for your quality control team. This will ensure they have the skills to do their jobs well. Regular training can help improve the accuracy and efficiency of quality control measures.
Quality Control Methods in Manufacturing
-
Statistical Process Control (SPC): SPC is a method to monitor and control processes. It ensures they stay within specifications. Manufacturers can find trends by analyzing data. They can then adjust to maintain product quality.
-
Six Sigma is a data-driven quality control method. It aims to reduce defects and variations in manufacturing processes. Six Sigma can help companies improve quality, cut costs, and boost customer satisfaction.
-
Lean Manufacturing: It aims to cut waste and boost efficiency in manufacturing. By streamlining operations, companies can improve product quality and cut lead times.
Quality Control Challenges
Manufacturing often faces quality control (QC) challenges. They can hurt product consistency and efficiency. QC efforts often face issues. They are: detecting defects early, standardizing processes, and ensuring compliance with laws. We must use a strategic approach to tackle these challenges. We should use advanced tech and ongoing training. They will improve accuracy and effectiveness in quality management.
Quality control is vital for manufacturing success. But, companies may face challenges in implementing it. Some common challenges include:
-
Ensuring consistency in product quality across different production lines and locations
-
Managing supplier quality control to ensure the reliability of raw materials
-
Adapting to changing regulations and industry standards is tough. It requires a complete quality control approach. This must include continuous improvement, communication, and collaboration across departments.
Implementing Effective Quality Control Measures
To ensure the success of quality control measures in manufacturing, companies must:
-
Invest in quality control training programs for employees
-
Regularly audit and evaluate quality control procedures
-
Utilize advanced quality control tools and technology
-
Foster a culture of quality and improvement across the organization. These quality control practices can help companies. They boost product quality, cut defects, and improve customer satisfaction. Quality control is not just a process. It is a mindset. It should be in every aspect of manufacturing. By prioritizing quality, companies can stand out from the competition. They can also build a reputation for excellence in the industry.
How to obtain Quality Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, quality control is vital in manufacturing. It affects product quality, customer satisfaction, and business success. Companies can boost profits by using quality control and best practices. They will then have consistent products with fewer defects. Remember, quality is not an act; it is a habit. It must be cultivated and maintained throughout the manufacturing process.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In manufacturing, high-quality products are key to success. Good quality control can help companies. It can maintain consistency, meet regulations, and improve customer satisfaction. This article will discuss ways to ensure quality in manufacturing.
Importance of Quality Control in Manufacturing
Quality control is key in manufacturing. It ensures products meet customer and legal standards. Companies can reduce defects and improve efficiency by using effective quality control. It will also ensure consistent products. This ultimately leads to higher customer satisfaction and increased profitability.
Quality control in manufacturing is vital. It ensures product consistency and meets industry standards. This builds customer trust and satisfaction. QC minimizes waste, cuts costs, and boosts efficiency. It does this by finding and fixing defects early. Also, good quality control helps meet regulations. It builds a strong brand. This drives long-term success and competitiveness in the market.
Best Practices for Quality Control
-
Establish Quality Control Standards: First, set clear quality control standards. This is key to ensuring product consistency and reliability. These standards should detail the criteria for acceptable products.
-
Implement Quality Control Procedures: Develop standard tests to inspect for quality. This will ensure products meet the established standards. Regularly monitor and evaluate these procedures to identify areas for improvement.
-
Use Quality Control Tools: Give your team the tools to test and inspect products. This can include equipment for measurements, testing, and inspection software.
-
Develop a Quality Control Plan: Create a plan. It must detail how to implement quality control measures in manufacturing. This plan should detail responsibilities, procedures, and processes for quality control.
-
Train Your Team: Provide ongoing training for your quality control team. This will ensure they have the skills to do their jobs well. Regular training can help improve the accuracy and efficiency of quality control measures.
Quality Control Methods in Manufacturing
-
Statistical Process Control (SPC): SPC is a method to monitor and control processes. It ensures they stay within specifications. Manufacturers can find trends by analyzing data. They can then adjust to maintain product quality.
-
Six Sigma is a data-driven quality control method. It aims to reduce defects and variations in manufacturing processes. Six Sigma can help companies improve quality, cut costs, and boost customer satisfaction.
-
Lean Manufacturing: It aims to cut waste and boost efficiency in manufacturing. By streamlining operations, companies can improve product quality and cut lead times.
Quality Control Challenges
Manufacturing often faces quality control (QC) challenges. They can hurt product consistency and efficiency. QC efforts often face issues. They are: detecting defects early, standardizing processes, and ensuring compliance with laws. We must use a strategic approach to tackle these challenges. We should use advanced tech and ongoing training. They will improve accuracy and effectiveness in quality management.
Quality control is vital for manufacturing success. But, companies may face challenges in implementing it. Some common challenges include:
-
Ensuring consistency in product quality across different production lines and locations
-
Managing supplier quality control to ensure the reliability of raw materials
-
Adapting to changing regulations and industry standards is tough. It requires a complete quality control approach. This must include continuous improvement, communication, and collaboration across departments.
Implementing Effective Quality Control Measures
To ensure the success of quality control measures in manufacturing, companies must:
-
Invest in quality control training programs for employees
-
Regularly audit and evaluate quality control procedures
-
Utilize advanced quality control tools and technology
-
Foster a culture of quality and improvement across the organization. These quality control practices can help companies. They boost product quality, cut defects, and improve customer satisfaction. Quality control is not just a process. It is a mindset. It should be in every aspect of manufacturing. By prioritizing quality, companies can stand out from the competition. They can also build a reputation for excellence in the industry.
How to obtain Quality Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, quality control is vital in manufacturing. It affects product quality, customer satisfaction, and business success. Companies can boost profits by using quality control and best practices. They will then have consistent products with fewer defects. Remember, quality is not an act; it is a habit. It must be cultivated and maintained throughout the manufacturing process.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Unstructured Data Uncovering Insights with Big Data Tools
In today's digital age, data is generated at an unprecedented rate. It comes from various sources, like social media, sensors, and logs. Much of this data is unstructured. It does not fit into traditional rows and columns like structured data. Unstructured data includes text, images, videos, and social media posts. It is hard to analyze with traditional methods. Big data tools can help organizations find insights in unstructured data. These insights can drive better decisions and spark innovation.
What is Unstructured Data?
Unstructured data is data that has no predefined model. It is not organized in a structured way. This data is often generated in real-time. It can come from many sources. This makes it hard to analyze with traditional databases. Unstructured data includes social media posts, emails, and customer reviews. It also includes video and audio files, and more. Unstructured data is tough to handle. But, it is very valuable. Organizations want it to gain a competitive edge. Big data tools let businesses find insights in unstructured data. These insights can guide decisions, improve customer experiences, and spur innovation.
Unstructured Data Sources
Unstructured data can come from a wide range of sources, including:
-
Social media platforms
-
Customer reviews
-
Emails
-
Sensor data
-
Images and videos
-
Log files
Leveraging Big Data Tools for Unstructured Data Analysis
Unstructured data, like text documents and social media posts, is a challenge for traditional data tools. Big data tools, like Hadoop and Apache Spark, help organizations. They quickly analyze a vast, complex data source. They also gain insights from it. These tools can help businesses find hidden patterns. They can boost decision-making and provide an edge in healthcare and e-commerce.
Big data tools are essential for processing and analyzing unstructured data at scale. These tools can handle huge amounts of data from various sources. They can run complex analyses to find patterns, trends, and insights. Some key capabilities of big data tools for unstructured data analysis include:
-
Data discovery
-
Data visualization
-
Data mining
-
Machine learning
-
Artificial intelligence
-
Predictive analytics. By using big data tools, organizations can turn unstructured data into valuable insights. These insights can drive business success. Big data tools help find insights in social media and sensor data. They let organizations confidently make data-driven decisions.
Key Benefits of Analyzing Unstructured Data with Big Data Tools
Big data tools can analyze unstructured data. This can give organizations insights that traditional methods might miss. Unstructured data, like emails and social media posts, often hides patterns and customer sentiments. So do videos. They can improve decision-making and business strategies. With the right big data tools, companies can mine this vast info. They can then enhance personalization, optimize operations, and stay ahead of market trends.
-
Better decisions: Organizations can make smarter choices by analyzing unstructured data. It offers real-time insights.
-
Enhanced customer experiences: Understanding customer sentiments and behaviors from unstructured data enables organizations to personalize interactions and anticipate needs.
-
Innovation: Analyzing unstructured data can find new opportunities. It can help develop products, improve processes, and expand markets. While there are numerous benefits to analyzing unstructured data with big data tools, it's essential to be aware of the challenges as well.
Challenges of Analyzing Unstructured Data
Analyzing unstructured data is hard. It has no set format or structure. Unstructured data, like emails, videos, and social media posts, is not in tables or databases. It needs advanced tools and algorithms for analysis. Cleaning, classifying, and extracting insights from this data is complex and costly. It often requires machine learning and natural language processing to overcome these hurdles.
-
Data quality: Unstructured data can be messy and inconsistent. It needs thorough cleansing and normalization.
-
Data integration: It's complex to merge unstructured data with structured data.
-
Data interpretation: To make sense of unstructured data, you need advanced analytics and expertise.
How to obtain Big Data certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, unstructured data presents both challenges and opportunities for organizations across industries. Big data tools can help. They can find insights in unstructured data. This can drive innovation, improve decisions, and enhance customer experiences. Big data tools help organizations use unstructured data. They turn it into a valuable, strategic asset for the future.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's digital age, data is generated at an unprecedented rate. It comes from various sources, like social media, sensors, and logs. Much of this data is unstructured. It does not fit into traditional rows and columns like structured data. Unstructured data includes text, images, videos, and social media posts. It is hard to analyze with traditional methods. Big data tools can help organizations find insights in unstructured data. These insights can drive better decisions and spark innovation.
What is Unstructured Data?
Unstructured data is data that has no predefined model. It is not organized in a structured way. This data is often generated in real-time. It can come from many sources. This makes it hard to analyze with traditional databases. Unstructured data includes social media posts, emails, and customer reviews. It also includes video and audio files, and more. Unstructured data is tough to handle. But, it is very valuable. Organizations want it to gain a competitive edge. Big data tools let businesses find insights in unstructured data. These insights can guide decisions, improve customer experiences, and spur innovation.
Unstructured Data Sources
Unstructured data can come from a wide range of sources, including:
-
Social media platforms
-
Customer reviews
-
Emails
-
Sensor data
-
Images and videos
-
Log files
Leveraging Big Data Tools for Unstructured Data Analysis
Unstructured data, like text documents and social media posts, is a challenge for traditional data tools. Big data tools, like Hadoop and Apache Spark, help organizations. They quickly analyze a vast, complex data source. They also gain insights from it. These tools can help businesses find hidden patterns. They can boost decision-making and provide an edge in healthcare and e-commerce.
Big data tools are essential for processing and analyzing unstructured data at scale. These tools can handle huge amounts of data from various sources. They can run complex analyses to find patterns, trends, and insights. Some key capabilities of big data tools for unstructured data analysis include:
-
Data discovery
-
Data visualization
-
Data mining
-
Machine learning
-
Artificial intelligence
-
Predictive analytics. By using big data tools, organizations can turn unstructured data into valuable insights. These insights can drive business success. Big data tools help find insights in social media and sensor data. They let organizations confidently make data-driven decisions.
Key Benefits of Analyzing Unstructured Data with Big Data Tools
Big data tools can analyze unstructured data. This can give organizations insights that traditional methods might miss. Unstructured data, like emails and social media posts, often hides patterns and customer sentiments. So do videos. They can improve decision-making and business strategies. With the right big data tools, companies can mine this vast info. They can then enhance personalization, optimize operations, and stay ahead of market trends.
-
Better decisions: Organizations can make smarter choices by analyzing unstructured data. It offers real-time insights.
-
Enhanced customer experiences: Understanding customer sentiments and behaviors from unstructured data enables organizations to personalize interactions and anticipate needs.
-
Innovation: Analyzing unstructured data can find new opportunities. It can help develop products, improve processes, and expand markets. While there are numerous benefits to analyzing unstructured data with big data tools, it's essential to be aware of the challenges as well.
Challenges of Analyzing Unstructured Data
Analyzing unstructured data is hard. It has no set format or structure. Unstructured data, like emails, videos, and social media posts, is not in tables or databases. It needs advanced tools and algorithms for analysis. Cleaning, classifying, and extracting insights from this data is complex and costly. It often requires machine learning and natural language processing to overcome these hurdles.
-
Data quality: Unstructured data can be messy and inconsistent. It needs thorough cleansing and normalization.
-
Data integration: It's complex to merge unstructured data with structured data.
-
Data interpretation: To make sense of unstructured data, you need advanced analytics and expertise.
How to obtain Big Data certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, unstructured data presents both challenges and opportunities for organizations across industries. Big data tools can help. They can find insights in unstructured data. This can drive innovation, improve decisions, and enhance customer experiences. Big data tools help organizations use unstructured data. They turn it into a valuable, strategic asset for the future.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Digital Marketing and Trust How Reviews Affect Credibility
In today's digital age, trust plays a crucial role in the success of any business. With the rise of online shopping and social media, consumers have more choices than ever before. As a result, building trust and credibility has become a key focus for businesses looking to stand out in a crowded marketplace. One of the most powerful tools for establishing trust in the digital landscape is customer reviews. This article will explore how reviews affect credibility in digital marketing. They are vital for building trust with consumers.
Understanding the Importance of Trust in Digital Marketing
Before we dive into reviews and their role in building credibility, we must understand why trust is vital in digital marketing. In today's hyper-connected world, consumers have access to a wealth of information at their fingertips. They can easily research products, compare prices, and read reviews before buying. As a result, businesses must work hard to earn and maintain the trust of their target audience. Without trust, consumers are unlikely to engage with a brand, let alone make a purchase. Trust is the key to any successful relationship. This includes those between friends, family, and businesses with their customers. In digital marketing, trust is earned. It comes from consistent messaging, quality products, and positive customer interactions.
Trust is key to effective digital marketing. It greatly affects consumer choices and brand loyalty. Building trust requires transparent communication and consistent messaging. It also needs delivering on promises. This fosters a strong relationship between brands and their audience. By prioritizing trust, businesses can boost customer satisfaction. This will drive conversions and foster long-term success in the digital world.
The Impact of Reviews on Credibility
Customer reviews are a powerful tool for building credibility and trust in the digital age. When a potential customer is considering making a purchase, they often turn to online reviews to help them make an informed decision. Positive reviews can boost confidence in a brand and its products. Negative reviews can raise red flags and hurt sales. Reviews provide social proof that a business is trustworthy and reliable. When a customer shares their experience with a product, it adds authenticity. It is more credible than any marketing tactic. Studies show that consumers trust online reviews as much as friends' recommendations.
Reviews are now vital for a brand's credibility. They greatly affect consumer trust and buying decisions. Positive reviews boost a brand's reputation and act as social proof. They can attract new customers. Negative reviews reveal areas for improvement. So, it's vital to manage and respond to reviews. It builds a strong, credible online presence and fosters customer loyalty.
Leveraging Reviews to Build Trust
So, how can businesses leverage reviews to build trust with their target audience? The key is to actively encourage and manage customer feedback. Businesses can show their commitment to customer satisfaction. They can do this by asking satisfied customers for reviews. They should also respond to feedback quickly and professionally. Responding to reviews shows a business values its customers. It cares to address any concerns. This approach helps businesses build customer loyalty and a strong reputation.
In today's digital world, customer reviews are vital. They build trust and credibility for brands. By showing real feedback, businesses can build trust. It shows they care about customer satisfaction. Using positive reviews in marketing boosts brand reputation. It also influences potential buyers, increasing conversions.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, customer reviews are vital in building trust in digital marketing. Businesses can build trust by showcasing real customers' experiences. It makes them reliable sources of products or services. Positive reviews can boost a brand's image and sales. Negative reviews offer feedback for improvement. In digital marketing, trust is key to long-term success. Businesses can use customer reviews to build a strong online reputation, gain brand loyalty, and stand out in a crowded market. To establish credibility in the digital age, value customer reviews. They're very impactful.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's digital age, trust plays a crucial role in the success of any business. With the rise of online shopping and social media, consumers have more choices than ever before. As a result, building trust and credibility has become a key focus for businesses looking to stand out in a crowded marketplace. One of the most powerful tools for establishing trust in the digital landscape is customer reviews. This article will explore how reviews affect credibility in digital marketing. They are vital for building trust with consumers.
Understanding the Importance of Trust in Digital Marketing
Before we dive into reviews and their role in building credibility, we must understand why trust is vital in digital marketing. In today's hyper-connected world, consumers have access to a wealth of information at their fingertips. They can easily research products, compare prices, and read reviews before buying. As a result, businesses must work hard to earn and maintain the trust of their target audience. Without trust, consumers are unlikely to engage with a brand, let alone make a purchase. Trust is the key to any successful relationship. This includes those between friends, family, and businesses with their customers. In digital marketing, trust is earned. It comes from consistent messaging, quality products, and positive customer interactions.
Trust is key to effective digital marketing. It greatly affects consumer choices and brand loyalty. Building trust requires transparent communication and consistent messaging. It also needs delivering on promises. This fosters a strong relationship between brands and their audience. By prioritizing trust, businesses can boost customer satisfaction. This will drive conversions and foster long-term success in the digital world.
The Impact of Reviews on Credibility
Customer reviews are a powerful tool for building credibility and trust in the digital age. When a potential customer is considering making a purchase, they often turn to online reviews to help them make an informed decision. Positive reviews can boost confidence in a brand and its products. Negative reviews can raise red flags and hurt sales. Reviews provide social proof that a business is trustworthy and reliable. When a customer shares their experience with a product, it adds authenticity. It is more credible than any marketing tactic. Studies show that consumers trust online reviews as much as friends' recommendations.
Reviews are now vital for a brand's credibility. They greatly affect consumer trust and buying decisions. Positive reviews boost a brand's reputation and act as social proof. They can attract new customers. Negative reviews reveal areas for improvement. So, it's vital to manage and respond to reviews. It builds a strong, credible online presence and fosters customer loyalty.
Leveraging Reviews to Build Trust
So, how can businesses leverage reviews to build trust with their target audience? The key is to actively encourage and manage customer feedback. Businesses can show their commitment to customer satisfaction. They can do this by asking satisfied customers for reviews. They should also respond to feedback quickly and professionally. Responding to reviews shows a business values its customers. It cares to address any concerns. This approach helps businesses build customer loyalty and a strong reputation.
In today's digital world, customer reviews are vital. They build trust and credibility for brands. By showing real feedback, businesses can build trust. It shows they care about customer satisfaction. Using positive reviews in marketing boosts brand reputation. It also influences potential buyers, increasing conversions.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, customer reviews are vital in building trust in digital marketing. Businesses can build trust by showcasing real customers' experiences. It makes them reliable sources of products or services. Positive reviews can boost a brand's image and sales. Negative reviews offer feedback for improvement. In digital marketing, trust is key to long-term success. Businesses can use customer reviews to build a strong online reputation, gain brand loyalty, and stand out in a crowded market. To establish credibility in the digital age, value customer reviews. They're very impactful.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
CISA Helps Manage New Threats and Vulnerabilities
In today's fast-changing tech world, organizations face many new cyber threats and weaknesses. As digital transformation accelerates, so do the sophistication and frequency of cyberattacks. In this tough environment, the CISA certification is now vital. It is for those dedicated to protecting IT systems. This blog explores CISA's key role in managing new threats. It provides a guide to its impact on modern cybersecurity practices.
1. Understanding the CISA Certification
The CISA certification, from ISACA, is a global credential. It validates expertise in IT auditing, control, and security. It is for those who monitor and control an organization's IT and business systems. A CISA certification shows that individuals can manage and reduce cybersecurity risks. It's a valuable asset for organizations that want to protect their digital assets.
2. The Evolution of Cyber Threats
Cyber threats are always changing. They evolve due to new tech and the growing complexity of IT systems. Historically, threats such as malware and phishing attacks were the primary concerns. Today, organizations face threats from APTs, ransomware, and complex social engineering attacks. CISA professionals have the skills to understand new threats. They can also implement strategies to counter them. This ensures organizations stay resilient against new challenges.
3. Identifying Emerging Vulnerabilities
As technology advances, new vulnerabilities are continuously discovered. Cybercriminals can exploit vulnerabilities. They can come from outdated software or misconfigured systems. CISA professionals are vital. They identify and assess vulnerabilities through rigorous audits and tests. CISA-certified individuals use tools to find weaknesses in IT systems. They help organizations fix risks before malicious actors can exploit them.
4. Implementing Effective Risk Management Strategies
Effective risk management is key. It reduces the impact of new threats and vulnerabilities. CISA professionals apply risk assessment methods. They evaluate the impact of threats and vulnerabilities on an organization's assets. They create and apply risk management strategies. These strategies prioritize remediation efforts based on risk levels. By tackling high-risk areas, organizations can lower their risk of security breaches. They can also build a stronger defense against cyber threats.
5. Enhancing Incident Response Capabilities
In a security incident, a quick, coordinated response is vital. It limits damage and aids recovery. CISA professionals are trained to improve incident response. They do this by developing and refining response plans. They ensure response teams are ready for incidents, like data breaches. CISA-certified individuals help organizations respond to and recover from security incidents. They do this by using best practices and conducting regular drills.
6. Leveraging CISA Best Practices for Continuous Improvement
The field of cybersecurity is dynamic, with new threats and vulnerabilities emerging regularly. CISA pros are committed to improvement. They regularly update their skills to stay ahead. They use industry best practices to keep organizations' security effective. CISA-certified individuals foster a culture of improvement. This helps organizations adapt to changing threats and stay secure.
How to obtain CISA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
As cyber threats grow more complex, CISA professionals are vital. CISA-certified individuals are vital to protecting organizations' IT systems. They do this by managing emerging threats, finding vulnerabilities, and using best practices. They also improve risk management and incident response. As technology evolves, CISA professionals will remain vital. Their skills will help organizations navigate the changing cybersecurity landscape with confidence.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-changing tech world, organizations face many new cyber threats and weaknesses. As digital transformation accelerates, so do the sophistication and frequency of cyberattacks. In this tough environment, the CISA certification is now vital. It is for those dedicated to protecting IT systems. This blog explores CISA's key role in managing new threats. It provides a guide to its impact on modern cybersecurity practices.
1. Understanding the CISA Certification
The CISA certification, from ISACA, is a global credential. It validates expertise in IT auditing, control, and security. It is for those who monitor and control an organization's IT and business systems. A CISA certification shows that individuals can manage and reduce cybersecurity risks. It's a valuable asset for organizations that want to protect their digital assets.
2. The Evolution of Cyber Threats
Cyber threats are always changing. They evolve due to new tech and the growing complexity of IT systems. Historically, threats such as malware and phishing attacks were the primary concerns. Today, organizations face threats from APTs, ransomware, and complex social engineering attacks. CISA professionals have the skills to understand new threats. They can also implement strategies to counter them. This ensures organizations stay resilient against new challenges.
3. Identifying Emerging Vulnerabilities
As technology advances, new vulnerabilities are continuously discovered. Cybercriminals can exploit vulnerabilities. They can come from outdated software or misconfigured systems. CISA professionals are vital. They identify and assess vulnerabilities through rigorous audits and tests. CISA-certified individuals use tools to find weaknesses in IT systems. They help organizations fix risks before malicious actors can exploit them.
4. Implementing Effective Risk Management Strategies
Effective risk management is key. It reduces the impact of new threats and vulnerabilities. CISA professionals apply risk assessment methods. They evaluate the impact of threats and vulnerabilities on an organization's assets. They create and apply risk management strategies. These strategies prioritize remediation efforts based on risk levels. By tackling high-risk areas, organizations can lower their risk of security breaches. They can also build a stronger defense against cyber threats.
5. Enhancing Incident Response Capabilities
In a security incident, a quick, coordinated response is vital. It limits damage and aids recovery. CISA professionals are trained to improve incident response. They do this by developing and refining response plans. They ensure response teams are ready for incidents, like data breaches. CISA-certified individuals help organizations respond to and recover from security incidents. They do this by using best practices and conducting regular drills.
6. Leveraging CISA Best Practices for Continuous Improvement
The field of cybersecurity is dynamic, with new threats and vulnerabilities emerging regularly. CISA pros are committed to improvement. They regularly update their skills to stay ahead. They use industry best practices to keep organizations' security effective. CISA-certified individuals foster a culture of improvement. This helps organizations adapt to changing threats and stay secure.
How to obtain CISA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
As cyber threats grow more complex, CISA professionals are vital. CISA-certified individuals are vital to protecting organizations' IT systems. They do this by managing emerging threats, finding vulnerabilities, and using best practices. They also improve risk management and incident response. As technology evolves, CISA professionals will remain vital. Their skills will help organizations navigate the changing cybersecurity landscape with confidence.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Visualizing Data Trends Minitabs Graphical Capabilities
Are you looking to gain valuable insights from your data analysis? Minitab's graphical capabilities provide a powerful tool for visualizing data trends and patterns. This article will explore how Minitab's graphs can help you. They can analyze data, interpret trends, and aid decision-making.
Introduction to Minitab and Data Visualization
Minitab is a top statistical software. It's widely used for data analysis and visualization. Its user-friendly interface and strong tools make it popular with researchers, analysts, and data scientists. A key feature of Minitab is its graphics. Users can create various graphs and charts to show data trends.
Analyzing Trends with Graphical Data Analysis
Graphical data analysis of trends uses visuals to find patterns and changes in data over time. Minitab offers a range of graphing tools, such as time series plots and control charts, to help users easily spot trends and anomalies. These tools can help you see your data better. You can then make better decisions based on the trends you find.
When it comes to data analysis, one of the most effective ways to identify trends and patterns is through visual representation. Minitab has many graph types, including line graphs, bar charts, and scatter plots. They can help you visualize your data and find relationships between variables. These graphs can deepen your understanding of your data. You can then make better decisions.
Interpreting Data Trends with Visual Analytics
Visual analytics is a data analysis method. It combines interactive visualization with analytical techniques. It helps to explore data, find trends, and gain insights. Minitab's graphical tools let you explore your data. You can find trends and hidden patterns that traditional analysis may miss. This visual method lets you quickly find outliers, anomalies, and correlations in your data. It leads to better, more reliable insights.
"Visual analytics in Minitab helps find data trends. It turns complex datasets into clear, actionable insights." By leveraging various charts and graphs, you can easily spot patterns, anomalies, and correlations that might be missed in raw data. "Using these visual tools improves your analysis and decision-making. It helps you make better decisions based on trend analysis.""
Trend Analysis and Data Visualization Techniques
Minitab's graphs include advanced data visualization techniques. They can help you analyze trends and patterns in your data. You can easily visualize data trends using trend graphs and charts. You can also compare data sets and track changes over time. Also, Minitab has many visualization tools. They let you customize your graphs and add annotations. You can also create interactive data displays for more engaging presentations.
Trend analysis and data visualization are key for finding patterns in large datasets. Use tools like Minitab to create visualizations. They include line charts, scatter plots, and control charts. They highlight trends and anomalies. These techniques improve your data analysis. They also help you communicate findings to stakeholders.
Exploring Data Trends with Minitab Software
With Minitab's graphical capabilities, exploring data trends has never been easier. Minitab's graphical tools can analyze sales data, customer feedback, or research. They help you visualize trends, interpret data, and present your findings clearly. Use Minitab's data visualization tools. They can unlock your data's full potential. They can also provide insights for better decision-making.
Unlock your data's potential. Explore trends with Minitab Software. It is a powerful tool for detailed statistical analysis. Minitab has strong graphics and statistical tools. It helps you find and see patterns. This makes it easier to uncover insights and make decisions. Minitab's trend analysis features reveal your data's story. They provide a clear, actionable view, whether you're analyzing sales or quality metrics.
How to obtain Minitab certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Minitab's graphs are a powerful tool. They help to visualize data trends, analyze patterns, and interpret data better. Minitab's graphical tools let you explore data trends. You can find relationships and generate insights. These can help you make data-driven decisions. Minitab's graphs can improve your data analysis workflow. They will show your data trends visually, which is valuable for researchers, analysts, and data scientists. So why wait? Use Minitab's graphical tools to analyze your data. Start visualizing your data trends today!
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to gain valuable insights from your data analysis? Minitab's graphical capabilities provide a powerful tool for visualizing data trends and patterns. This article will explore how Minitab's graphs can help you. They can analyze data, interpret trends, and aid decision-making.
Introduction to Minitab and Data Visualization
Minitab is a top statistical software. It's widely used for data analysis and visualization. Its user-friendly interface and strong tools make it popular with researchers, analysts, and data scientists. A key feature of Minitab is its graphics. Users can create various graphs and charts to show data trends.
Analyzing Trends with Graphical Data Analysis
Graphical data analysis of trends uses visuals to find patterns and changes in data over time. Minitab offers a range of graphing tools, such as time series plots and control charts, to help users easily spot trends and anomalies. These tools can help you see your data better. You can then make better decisions based on the trends you find.
When it comes to data analysis, one of the most effective ways to identify trends and patterns is through visual representation. Minitab has many graph types, including line graphs, bar charts, and scatter plots. They can help you visualize your data and find relationships between variables. These graphs can deepen your understanding of your data. You can then make better decisions.
Interpreting Data Trends with Visual Analytics
Visual analytics is a data analysis method. It combines interactive visualization with analytical techniques. It helps to explore data, find trends, and gain insights. Minitab's graphical tools let you explore your data. You can find trends and hidden patterns that traditional analysis may miss. This visual method lets you quickly find outliers, anomalies, and correlations in your data. It leads to better, more reliable insights.
"Visual analytics in Minitab helps find data trends. It turns complex datasets into clear, actionable insights." By leveraging various charts and graphs, you can easily spot patterns, anomalies, and correlations that might be missed in raw data. "Using these visual tools improves your analysis and decision-making. It helps you make better decisions based on trend analysis.""
Trend Analysis and Data Visualization Techniques
Minitab's graphs include advanced data visualization techniques. They can help you analyze trends and patterns in your data. You can easily visualize data trends using trend graphs and charts. You can also compare data sets and track changes over time. Also, Minitab has many visualization tools. They let you customize your graphs and add annotations. You can also create interactive data displays for more engaging presentations.
Trend analysis and data visualization are key for finding patterns in large datasets. Use tools like Minitab to create visualizations. They include line charts, scatter plots, and control charts. They highlight trends and anomalies. These techniques improve your data analysis. They also help you communicate findings to stakeholders.
Exploring Data Trends with Minitab Software
With Minitab's graphical capabilities, exploring data trends has never been easier. Minitab's graphical tools can analyze sales data, customer feedback, or research. They help you visualize trends, interpret data, and present your findings clearly. Use Minitab's data visualization tools. They can unlock your data's full potential. They can also provide insights for better decision-making.
Unlock your data's potential. Explore trends with Minitab Software. It is a powerful tool for detailed statistical analysis. Minitab has strong graphics and statistical tools. It helps you find and see patterns. This makes it easier to uncover insights and make decisions. Minitab's trend analysis features reveal your data's story. They provide a clear, actionable view, whether you're analyzing sales or quality metrics.
How to obtain Minitab certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Minitab's graphs are a powerful tool. They help to visualize data trends, analyze patterns, and interpret data better. Minitab's graphical tools let you explore data trends. You can find relationships and generate insights. These can help you make data-driven decisions. Minitab's graphs can improve your data analysis workflow. They will show your data trends visually, which is valuable for researchers, analysts, and data scientists. So why wait? Use Minitab's graphical tools to analyze your data. Start visualizing your data trends today!
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
The Evolution of RPA from Rule Based to Cognitive Automation
RPA has changed how businesses operate. It automates repetitive tasks and streamlines processes. RPA technology has evolved over the years. It moved from rule-based automation to cognitive automation. Now, it uses machine learning and AI to improve efficiency and decision-making. This article will explore the evolution of RPA. It will also discuss its impact on business digital transformation.
Evolution of RPA.
Initially, RPA systems were rule-based. They were programmed to follow a set of predefined rules to execute tasks. This approach saved money and improved efficiency. But, it could not adapt to change or handle complex tasks needing decision-making. Rule-Based Automation It involves creating a set of if-then rules. These rules guide the behavior of bots. These rules limit how tasks can be done. They restrict the flexibility of RPA systems.
Rule-based automation means programming software to follow set rules and workflows. It performs repetitive tasks with high precision. It works well for structured, repetitive tasks, like data entry or invoice processing. The rules must be clear and fixed. Rule-based automation is easy to implement. But, it is inflexible. It can't handle tasks that require judgment or adapt to change. Cognitive Automation Cognitive automation enhances RPA by adding AI and machine learning. This lets RPA systems learn from data, make decisions, and improve. They do this without human help.
Cognitive Automation is more advanced than traditional RPA.
It uses AI and machine learning to handle complex tasks. It enables systems to understand, learn from, and decide using unstructured data. It automates tasks at a level that mimics human thinking. This advancement lets businesses automate complex workflows, not just repetitive tasks. Those workflows require judgment and adaptation. Machine Learning in RPA Machine learning algorithms are vital for cognitive automation. They let RPA systems learn from data, find patterns, and make predictions. This enables RPA bots to handle complex tasks that require decision-making capabilities.
Machine learning in RPA is changing how automation systems learn.
They now adapt to complex tasks. It does this by using data-driven insights. This integration lets robots improve over time. They will make better decisions and handle exceptions more efficiently. Machine learning algorithms analyze patterns and outcomes. They let RPA systems evolve. They can now do more than simple, rule-based automation. They can now run sophisticated, intelligent processes. AI in Automation AI enables RPA to process unstructured data and understand natural language. It can also interact with users. It helps businesses automate more tasks and boost efficiency.
AI is revolutionizing automation.
It enables systems to do complex tasks with greater efficiency and adaptability. AI can help automation solutions. They can learn from data, make real-time decisions, and improve processes. They are better than old, rule-based methods. AI and automation are working together. This is driving innovation across industries. It is creating more intelligent, responsive systems.
Automation Tools.
Businesses can now use automation tools to streamline their operations. These tools have many functions. They automate processes, integrate data, and analyze it. Digital Transformation RPA is vital for digital transformation. It automates repetitive tasks. This frees up humans to focus on strategic initiatives. This leads to improved productivity, reduced errors, and enhanced customer satisfaction.
Benefits of RPA
RPA has many benefits. They include cost savings, and better efficiency, accuracy, and compliance. Automating routine tasks helps businesses excel and stay competitive today. RPA Implementation For success, use a strategic approach. Set clear goals. Get stakeholders' buy-in. Businesses must find the right processes to automate.
They must choose the right tools and monitor performance to ensure maximum ROI. Future of Automation RPA will evolve. We will see advances in cognitive automation, intelligent algorithms, and automation analytics. The future of automation is bright. It offers businesses endless ways to cut costs and beat the competition.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
RPA has evolved from rule-based to cognitive automation. This has transformed how businesses operate. RPA systems can automate complex tasks using machine learning and AI. They can make intelligent decisions and drive digital transformation. As businesses adopt RPA, the future of automation looks bright. There are endless opportunities for growth and innovation.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
RPA has changed how businesses operate. It automates repetitive tasks and streamlines processes. RPA technology has evolved over the years. It moved from rule-based automation to cognitive automation. Now, it uses machine learning and AI to improve efficiency and decision-making. This article will explore the evolution of RPA. It will also discuss its impact on business digital transformation.
Evolution of RPA.
Initially, RPA systems were rule-based. They were programmed to follow a set of predefined rules to execute tasks. This approach saved money and improved efficiency. But, it could not adapt to change or handle complex tasks needing decision-making. Rule-Based Automation It involves creating a set of if-then rules. These rules guide the behavior of bots. These rules limit how tasks can be done. They restrict the flexibility of RPA systems.
Rule-based automation means programming software to follow set rules and workflows. It performs repetitive tasks with high precision. It works well for structured, repetitive tasks, like data entry or invoice processing. The rules must be clear and fixed. Rule-based automation is easy to implement. But, it is inflexible. It can't handle tasks that require judgment or adapt to change. Cognitive Automation Cognitive automation enhances RPA by adding AI and machine learning. This lets RPA systems learn from data, make decisions, and improve. They do this without human help.
Cognitive Automation is more advanced than traditional RPA.
It uses AI and machine learning to handle complex tasks. It enables systems to understand, learn from, and decide using unstructured data. It automates tasks at a level that mimics human thinking. This advancement lets businesses automate complex workflows, not just repetitive tasks. Those workflows require judgment and adaptation. Machine Learning in RPA Machine learning algorithms are vital for cognitive automation. They let RPA systems learn from data, find patterns, and make predictions. This enables RPA bots to handle complex tasks that require decision-making capabilities.
Machine learning in RPA is changing how automation systems learn.
They now adapt to complex tasks. It does this by using data-driven insights. This integration lets robots improve over time. They will make better decisions and handle exceptions more efficiently. Machine learning algorithms analyze patterns and outcomes. They let RPA systems evolve. They can now do more than simple, rule-based automation. They can now run sophisticated, intelligent processes. AI in Automation AI enables RPA to process unstructured data and understand natural language. It can also interact with users. It helps businesses automate more tasks and boost efficiency.
AI is revolutionizing automation.
It enables systems to do complex tasks with greater efficiency and adaptability. AI can help automation solutions. They can learn from data, make real-time decisions, and improve processes. They are better than old, rule-based methods. AI and automation are working together. This is driving innovation across industries. It is creating more intelligent, responsive systems.
Automation Tools.
Businesses can now use automation tools to streamline their operations. These tools have many functions. They automate processes, integrate data, and analyze it. Digital Transformation RPA is vital for digital transformation. It automates repetitive tasks. This frees up humans to focus on strategic initiatives. This leads to improved productivity, reduced errors, and enhanced customer satisfaction.
Benefits of RPA
RPA has many benefits. They include cost savings, and better efficiency, accuracy, and compliance. Automating routine tasks helps businesses excel and stay competitive today. RPA Implementation For success, use a strategic approach. Set clear goals. Get stakeholders' buy-in. Businesses must find the right processes to automate.
They must choose the right tools and monitor performance to ensure maximum ROI. Future of Automation RPA will evolve. We will see advances in cognitive automation, intelligent algorithms, and automation analytics. The future of automation is bright. It offers businesses endless ways to cut costs and beat the competition.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
RPA has evolved from rule-based to cognitive automation. This has transformed how businesses operate. RPA systems can automate complex tasks using machine learning and AI. They can make intelligent decisions and drive digital transformation. As businesses adopt RPA, the future of automation looks bright. There are endless opportunities for growth and innovation.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Top Tools Every Digital Marketer Needs in 2024
In 2024, the digital marketing landscape is evolving faster than ever. To keep up, marketers must use the right tools. They should streamline their efforts, boost productivity, and maximize results. These tools are vital for creating effective strategies. They help with social media management and data analytics. This article lists the top tools every digital marketer needs in 2024. They must outpace the competition, adapt to new trends, and optimize performance.
Table Of Contents
- Social Media Management Tools: Enhance Your Social Strategy
- Email Marketing Tools: Optimize Your Campaigns
- SEO Tools: Master Search Engine Rankings
- Data Analytics Tools: Measure Your Success
- Content Creation Tools: Power Your Marketing Strategy
- Conclusion
Social Media Management Tools: Enhance Your Social Strategy
Social media platforms remain at the heart of digital marketing in 2024. With new networks and ever-changing algorithms, managing many accounts is key to success. Social media management tools let marketers schedule posts and track performance. They can also engage with their audience in real time.
Popular Tools:
- Hootsuite: Schedule, manage, and check all social accounts from one dashboard.
- Buffer: Streamline content distribution and access in-depth analytics.
- Sprout Social offers advanced analytics and social listening features to improve engagement.
These tools help marketers:
- Save time by automating posts.
- Check brand mentions and interactions across platforms.
- Analyze performance with detailed reports, helping to adjust strategy as needed.
In 2024, expect a focus on AI social listening tools. They will provide better insights into audience sentiment and trends.
Email Marketing Tools: Optimize Your Campaigns
Email marketing is a top way to nurture leads and keep customers. To compete in 2024, marketers must make their campaigns hyper-personalized and engaging. Email marketing tools are vital for automating, segmenting, and personalizing email outreach.
Popular Tools:
- Mailchimp offers robust automation features, audience segmentation, and advanced analytics.
- Constant Contact: It's perfect for small businesses. It has an easy-to-use, customizable platform.
- ActiveCampaign provides advanced customer experience automation and CRM integration.
Using these tools, digital marketers can:
- Classify audiences according to their behaviors, preferences, and demographic characteristics.
- A/B test campaigns to determine the most effective messaging.
- Automate follow-ups and lead-nurturing processes.
In 2024, AI-driven email marketing will grow. It will allow for dynamic content based on real-time user behavior.
SEO Tools: Master Search Engine Rankings
Optimizing for search engines is crucial for increasing organic website traffic. In 2024, SEO is vital to digital marketing. But it has grown more complex due to Google's updates and the rise of voice search and AI algorithms. Marketers need the latest SEO tools to stay competitive. They must ensure their content ranks well.
Popular Tools:
- SEMrush offers comprehensive SEO tools, from keyword research to competitor analysis.
- Ahrefs is known for its powerful backlink analysis and keyword ranking features.
- Moz provides in-depth SEO audits and keyword tracking to boost rankings.
SEO tools in 2024 will help marketers:
- Identify valuable keywords and content gaps.
- Analyze competitors’ strategies for backlinks and content.
- Track rankings across many search engines, including voice search.
Expect SEO tools to use AI. It will predict ranking factors and optimize content better.
Data Analytics Tools: Measure Your Success
Data-driven decision-making is at the core of successful digital marketing strategies in 2024. As conversion rates and ROI grow in importance, marketers need strong data tools. They must track and check their performance across all channels.
Popular Tools:
- Google Analytics: A must-have for tracking website traffic, user behavior, and conversion rates.
- Hotjar: It provides heatmaps and user recordings. They show how visitors interact with your website.
- Kissmetrics: It helps you improve marketing by focusing on customer engagement and value.
These tools allow marketers to:
- Understand user behavior and how visitors navigate their websites.
- Optimize conversion funnels by identifying weak points.
- Measure ROI across many campaigns to refine strategies.
In 2024, data analytics tools will have more predictive insights. They will help marketers forecast trends and adapt in real time.
Content Creation Tools: Power Your Marketing Strategy
Content is still king in 2024. But, it's hard to produce high-quality, engaging content consistently. Content creation tools help marketers stay productive. They share a steady stream of valuable content. This includes blog posts, social media updates, and visuals.
Popular Tools:
- Canva: A simple, powerful tool for designing social media graphics, presentations, and infographics.
- Grammarly ensures that written content is clear, concise, and free from grammatical errors.
- Adobe Spark allows marketers to create eye-catching visuals and videos for various platforms.
With these tools, digital marketers can:
- Create professional-grade graphics without needing a design team.
- Produce consistent, high-quality content across all platforms.
- Streamline video editing to create engaging video marketing content.
In 2024, expect AI to enhance content creation tools. It will suggest visuals, topics, and keywords based on current trends.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
The right tools can make a significant difference in a digital marketer’s success in 2024. The tools in this article are vital for marketing. They help with social media, SEO, and creating quality content. They will streamline processes and keep you ahead of the competition. As AI and automation advance, digital marketers must use them. They must adapt quickly and make data-driven, personalized campaigns. To thrive in digital marketing, stay updated on the latest trends. Then, integrate these tools into your workflow.
Embrace these tools. They will prepare you for the 2024 challenges and opportunities.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In 2024, the digital marketing landscape is evolving faster than ever. To keep up, marketers must use the right tools. They should streamline their efforts, boost productivity, and maximize results. These tools are vital for creating effective strategies. They help with social media management and data analytics. This article lists the top tools every digital marketer needs in 2024. They must outpace the competition, adapt to new trends, and optimize performance.
Table Of Contents
- Social Media Management Tools: Enhance Your Social Strategy
- Email Marketing Tools: Optimize Your Campaigns
- SEO Tools: Master Search Engine Rankings
- Data Analytics Tools: Measure Your Success
- Content Creation Tools: Power Your Marketing Strategy
- Conclusion
Social Media Management Tools: Enhance Your Social Strategy
Social media platforms remain at the heart of digital marketing in 2024. With new networks and ever-changing algorithms, managing many accounts is key to success. Social media management tools let marketers schedule posts and track performance. They can also engage with their audience in real time.
Popular Tools:
- Hootsuite: Schedule, manage, and check all social accounts from one dashboard.
- Buffer: Streamline content distribution and access in-depth analytics.
- Sprout Social offers advanced analytics and social listening features to improve engagement.
These tools help marketers:
- Save time by automating posts.
- Check brand mentions and interactions across platforms.
- Analyze performance with detailed reports, helping to adjust strategy as needed.
In 2024, expect a focus on AI social listening tools. They will provide better insights into audience sentiment and trends.
Email Marketing Tools: Optimize Your Campaigns
Email marketing is a top way to nurture leads and keep customers. To compete in 2024, marketers must make their campaigns hyper-personalized and engaging. Email marketing tools are vital for automating, segmenting, and personalizing email outreach.
Popular Tools:
- Mailchimp offers robust automation features, audience segmentation, and advanced analytics.
- Constant Contact: It's perfect for small businesses. It has an easy-to-use, customizable platform.
- ActiveCampaign provides advanced customer experience automation and CRM integration.
Using these tools, digital marketers can:
- Classify audiences according to their behaviors, preferences, and demographic characteristics.
- A/B test campaigns to determine the most effective messaging.
- Automate follow-ups and lead-nurturing processes.
In 2024, AI-driven email marketing will grow. It will allow for dynamic content based on real-time user behavior.
SEO Tools: Master Search Engine Rankings
Optimizing for search engines is crucial for increasing organic website traffic. In 2024, SEO is vital to digital marketing. But it has grown more complex due to Google's updates and the rise of voice search and AI algorithms. Marketers need the latest SEO tools to stay competitive. They must ensure their content ranks well.
Popular Tools:
- SEMrush offers comprehensive SEO tools, from keyword research to competitor analysis.
- Ahrefs is known for its powerful backlink analysis and keyword ranking features.
- Moz provides in-depth SEO audits and keyword tracking to boost rankings.
SEO tools in 2024 will help marketers:
- Identify valuable keywords and content gaps.
- Analyze competitors’ strategies for backlinks and content.
- Track rankings across many search engines, including voice search.
Expect SEO tools to use AI. It will predict ranking factors and optimize content better.
Data Analytics Tools: Measure Your Success
Data-driven decision-making is at the core of successful digital marketing strategies in 2024. As conversion rates and ROI grow in importance, marketers need strong data tools. They must track and check their performance across all channels.
Popular Tools:
- Google Analytics: A must-have for tracking website traffic, user behavior, and conversion rates.
- Hotjar: It provides heatmaps and user recordings. They show how visitors interact with your website.
- Kissmetrics: It helps you improve marketing by focusing on customer engagement and value.
These tools allow marketers to:
- Understand user behavior and how visitors navigate their websites.
- Optimize conversion funnels by identifying weak points.
- Measure ROI across many campaigns to refine strategies.
In 2024, data analytics tools will have more predictive insights. They will help marketers forecast trends and adapt in real time.
Content Creation Tools: Power Your Marketing Strategy
Content is still king in 2024. But, it's hard to produce high-quality, engaging content consistently. Content creation tools help marketers stay productive. They share a steady stream of valuable content. This includes blog posts, social media updates, and visuals.
Popular Tools:
- Canva: A simple, powerful tool for designing social media graphics, presentations, and infographics.
- Grammarly ensures that written content is clear, concise, and free from grammatical errors.
- Adobe Spark allows marketers to create eye-catching visuals and videos for various platforms.
With these tools, digital marketers can:
- Create professional-grade graphics without needing a design team.
- Produce consistent, high-quality content across all platforms.
- Streamline video editing to create engaging video marketing content.
In 2024, expect AI to enhance content creation tools. It will suggest visuals, topics, and keywords based on current trends.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
The right tools can make a significant difference in a digital marketer’s success in 2024. The tools in this article are vital for marketing. They help with social media, SEO, and creating quality content. They will streamline processes and keep you ahead of the competition. As AI and automation advance, digital marketers must use them. They must adapt quickly and make data-driven, personalized campaigns. To thrive in digital marketing, stay updated on the latest trends. Then, integrate these tools into your workflow.
Embrace these tools. They will prepare you for the 2024 challenges and opportunities.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Deploying XenApp in a Microservices Architecture
Do you want to improve your IT by deploying XenApp in a microservices architecture? This innovative approach to application delivery can greatly improve scalability, efficiency, and flexibility. This article will explore the benefits of using XenApp in a microservices architecture. It will cover best deployment practices and tools to streamline the process.
What is XenApp and Microservices Architecture?
First, let's break down what XenApp and microservices architecture are. XenApp is a popular app virtualization solution by Citrix. It lets users access Windows apps from any device. Microservices architecture, on the other hand, is a way to develop software. It breaks applications into smaller, independent services. They can be deployed, managed, and scaled on their own. Merging XenApp with a microservices architecture gives the best of both. Organizations can use both. They can create a more agile and scalable IT infrastructure.
XenApp is a Citrix solution. It virtualizes and delivers Windows apps to any device, no matter its OS. XenApp boosts scalability and flexibility in a microservices setup. It lets businesses deploy app components independently. This combo improves resource use, speeds updates, and boosts performance. It is ideal for modern enterprise environments.
Benefits of Deploying XenApp in a Microservices Architecture
Deploying XenApp in a microservices architecture allows for greater scalability and flexibility. It lets businesses efficiently manage and deliver apps across diverse environments. This approach decouples application components. It reduces downtime and simplifies updates or maintenance without affecting the entire system. It also optimizes workloads. This improves resource use, performance, and cuts costs for businesses.
1. Scalability: Microservices architecture lets you scale your app's parts independently. This gives you more control over resource use.
2. Containerization: Use tools like Docker to containerize your apps. This lets you deploy and manage them across different environments without compatibility issues.
3. Load Balancing: Microservices let you spread traffic across multiple app instances. This ensures peak performance and reliability.
4. Cloud Hosting: Use XenApp and microservices to deploy and manage your apps in the cloud. It is more efficient and cheaper.
5. Application Scalability: Microservices architecture lets your apps scale. You can add more instances to handle higher traffic and demand.
Deployment Best Practices for XenApp in a Microservices Architecture
Deploying XenApp in a microservices architecture needs a strategic approach. It ensures seamless app delivery and scalability. Best practices are to: containerize services, optimize networks, and load balance. These will help maintain high availability. Also, integrating XenApp with Kubernetes or Docker can boost resource management. It can also streamline updates. This ensures a smooth, efficient deployment.
When deploying XenApp in a microservices architecture, decouple services. This improves fault tolerance and scalability. Automation tools can streamline maintenance and reduce downtime during updates. It's vital to secure sensitive data in a distributed system. We must use container isolation and API management for this. They protect against threats and keep the system intact.
Before starting the deployment process, follow these best practices. They will ensure a smooth and successful implementation:
1. Automate Deployment: Use deployment tools to speed up the process and reduce errors.
2. Use Container Orchestration: Use tools like Kubernetes to manage and scale your containers.
3. Monitor and Test: Constantly check your apps' performance. Test them regularly to find and fix issues early.
4. Implement Security Measures: Secure your microservices. Use best practices for network and app security.
How to obtain XENAPP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Use these tools and best practices. You can then deploy XenApp in a microservicesarchitecture. This will create a more efficient and scalable IT infrastructure. So, are you ready to take your application delivery to the next level? Deploying XenApp in a microservices architecture is key. It will unlock a world of possibilities.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Do you want to improve your IT by deploying XenApp in a microservices architecture? This innovative approach to application delivery can greatly improve scalability, efficiency, and flexibility. This article will explore the benefits of using XenApp in a microservices architecture. It will cover best deployment practices and tools to streamline the process.
What is XenApp and Microservices Architecture?
First, let's break down what XenApp and microservices architecture are. XenApp is a popular app virtualization solution by Citrix. It lets users access Windows apps from any device. Microservices architecture, on the other hand, is a way to develop software. It breaks applications into smaller, independent services. They can be deployed, managed, and scaled on their own. Merging XenApp with a microservices architecture gives the best of both. Organizations can use both. They can create a more agile and scalable IT infrastructure.
XenApp is a Citrix solution. It virtualizes and delivers Windows apps to any device, no matter its OS. XenApp boosts scalability and flexibility in a microservices setup. It lets businesses deploy app components independently. This combo improves resource use, speeds updates, and boosts performance. It is ideal for modern enterprise environments.
Benefits of Deploying XenApp in a Microservices Architecture
Deploying XenApp in a microservices architecture allows for greater scalability and flexibility. It lets businesses efficiently manage and deliver apps across diverse environments. This approach decouples application components. It reduces downtime and simplifies updates or maintenance without affecting the entire system. It also optimizes workloads. This improves resource use, performance, and cuts costs for businesses.
1. Scalability: Microservices architecture lets you scale your app's parts independently. This gives you more control over resource use.
2. Containerization: Use tools like Docker to containerize your apps. This lets you deploy and manage them across different environments without compatibility issues.
3. Load Balancing: Microservices let you spread traffic across multiple app instances. This ensures peak performance and reliability.
4. Cloud Hosting: Use XenApp and microservices to deploy and manage your apps in the cloud. It is more efficient and cheaper.
5. Application Scalability: Microservices architecture lets your apps scale. You can add more instances to handle higher traffic and demand.
Deployment Best Practices for XenApp in a Microservices Architecture
Deploying XenApp in a microservices architecture needs a strategic approach. It ensures seamless app delivery and scalability. Best practices are to: containerize services, optimize networks, and load balance. These will help maintain high availability. Also, integrating XenApp with Kubernetes or Docker can boost resource management. It can also streamline updates. This ensures a smooth, efficient deployment.
When deploying XenApp in a microservices architecture, decouple services. This improves fault tolerance and scalability. Automation tools can streamline maintenance and reduce downtime during updates. It's vital to secure sensitive data in a distributed system. We must use container isolation and API management for this. They protect against threats and keep the system intact.
Before starting the deployment process, follow these best practices. They will ensure a smooth and successful implementation:
1. Automate Deployment: Use deployment tools to speed up the process and reduce errors.
2. Use Container Orchestration: Use tools like Kubernetes to manage and scale your containers.
3. Monitor and Test: Constantly check your apps' performance. Test them regularly to find and fix issues early.
4. Implement Security Measures: Secure your microservices. Use best practices for network and app security.
How to obtain XENAPP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Use these tools and best practices. You can then deploy XenApp in a microservicesarchitecture. This will create a more efficient and scalable IT infrastructure. So, are you ready to take your application delivery to the next level? Deploying XenApp in a microservices architecture is key. It will unlock a world of possibilities.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Hadoop in Hybrid Cloud Challenges and Opportunitie
As organizations pursue digital transformation, they are using hybrid clouds. This maximizes flexibility, scalability, and cost efficiency. Hadoop is a powerful, open-source framework. It stores and processes large datasets across many computers. It is now a key player in data analytics. But, running Hadoop in a hybrid cloud has its challenges and opportunities. Knowing these dynamics can help businesses. They can optimize their data strategies. They can then leverage the full potential of the hybrid cloud and Hadoop.
This article will explore the pros and cons of using Hadoop in hybrid clouds. It will also offer tips for organizations on how to navigate these challenges.
Table Of Contents
- The Hybrid Cloud Landscape and Why Hadoop Fits In
- Key Opportunities of Hadoop in Hybrid Cloud
- Key Challenges of Running Hadoop in a Hybrid Cloud
- Best Practices for Overcoming Hybrid Cloud Hadoop Challenges
- Real-World Use Cases of Hadoop in a Hybrid Cloud
- Conclusion
The Hybrid Cloud Landscape and Why Hadoop Fits In
Hybrid cloud is a computing environment. It combines on-premises infrastructure with public and private cloud services. Organizations use hybrid clouds to achieve greater control, flexibility, and scalability. This model offers several advantages for data-heavy applications, making Hadoop a natural fit.
- Scalability: Hadoop clusters can adjust to meet changing big data workloads.
- Cost Efficiency: Organizations can store sensitive data on-premises. They can use the cloud for extra storage or computing power, cutting costs.
- Flexibility: A hybrid approach lets organizations pick the best environments for different workloads.
Hadoop in hybrid clouds lets companies use cloud power. It keeps critical data close for better security and compliance.
Key Opportunities of Hadoop in Hybrid Cloud
A hybrid cloud deployment of Hadoop offers several benefits. It can help organizations improve their data analytics.
- On-Demand Resource Allocation: In a hybrid setup, firms can use cloud resources as needed. This enables cost-effective, on-demand scalability. This is useful for handling large seasonal spikes in data workloads.
- Data Security and Compliance: Sensitive data can be stored on-premise, in private clouds, or in compliant environments. Non-sensitive workloads can run in the public cloud.
- Disaster Recovery and Business Continuity: Hybrid cloud architectures use distributed storage. This reduces the risk of data loss. If an on-premise failure occurs, you can move workloads to the cloud. There will be no disruptions.
- Improved Performance with Data Locality: Data locality means processing data near its storage. Hadoop, with hybrid cloud, lets organizations process data in the cloud or on-premise. This optimizes performance based on workload.
These opportunities make Hadoop a versatile tool in hybrid clouds. It helps businesses manage their large-scale data analytics needs.
Key Challenges of Running Hadoop in a Hybrid Cloud
The opportunities are great. But deploying Hadoop in hybrid cloud environments has challenges. They must be addressed.
- Data Integration and Management: It's tough to manage data flows between on-premise systems and the cloud. Organizations often struggle with ensuring seamless integration of data storage, movement, and processing.
- Latency Issues: Hybrid cloud uses many environments. This can cause latency when transferring data between on-premises systems and the cloud. Real-time data analytics might suffer due to poor management.
- Security Concerns: Hybrid cloud keeps sensitive data on-premises. Organizations must ensure the security of data transferred between environments. Encryption, secure data transfer protocols, and proper authentication mechanisms are essential.
- Cost Management: Hybrid clouds can incur unexpected costs if not optimized. Businesses must watch and optimize their cloud usage to avoid budget overruns.
- Managing Hadoop clusters in a hybrid cloud is hard. Cluster management is complex. Organizations must ensure they have the right tools and skills. They need to manage clusters that span on-premise and cloud environments.
Each challenge needs a careful approach. It must balance performance, security, and cost for smooth operations.
Best Practices for Overcoming Hybrid Cloud Hadoop Challenges
To use Hadoop well in a hybrid cloud, organizations should follow some best practices:
- Optimize Data Placement: Decide which data to keep on-premise and what to move to the cloud. Keep frequently accessed data close to the processing location to reduce latency.
- Use Data Compression and Tiered Storage: Compress data before moving it to the cloud. Use tiered storage: cold for less critical data, hot for frequently accessed data. This can improve performance and reduce costs.
- Use Automation Tools: Use tools like Apache Ambari or Cloudera Manager. They can automate Hadoop clusters in hybrid environments. They can deploy, monitor, and manage them. Automation helps reduce human errors and ensures operational consistency.
- Ensure end-to-end security. Use strong encryption and secure access for data at rest and in transit. Multi-factor authentication and regular audits should be part of your security strategy.
- Regularly monitor cloud and on-premises resources to ensure efficiency. Setting up alerts for anomalies can help prevent budget overruns and underperformance.
These practices can help. They will ensure Hadoop runs well in a hybrid cloud.
Real-World Use Cases of Hadoop in a Hybrid Cloud
Several industries are already leveraging the power of Hadoop in hybrid cloud environments.
- Finance: Banks and financial institutions use Hadoop in hybrid clouds. They analyze large volumes of transactional data. For security and compliance, sensitive data stays on-premises.
- Healthcare: Hospitals use hybrid clouds to store sensitive patient data on-premises. They run non-sensitive workloads in the cloud for research.
- Retail: Retail companies use hybrid clouds to analyze customer data. They run real-time transactions on-premises and use the cloud for analytics and marketing.
- Manufacturers are using Hadoop in hybrid clouds to analyze IoT sensor data. This optimizes production while keeping critical data on-premises.
These applications show Hadoop's flexibility in hybrid environments. They let organizations balance performance, cost, and security based on their needs.
How to obtain BigData certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Deploying Hadoop in a hybrid cloud has great potential but also serious challenges. The hybrid cloud model is perfect for big data analytics. It is flexible, scalable, and cost-efficient. But, issues like data integration, latency, and security need careful planning. So does cost management.
Organizations can overcome obstacles and unlock Hadoop's full potential in hybrid clouds. They must understand the challenges and use best practices. These include optimizing data placement, implementing security protocols, and using automation tools. In the long run, Hadoop in hybrid clouds helps firms use data. It aids in making decisions and keeps control over sensitive information.
Read More
As organizations pursue digital transformation, they are using hybrid clouds. This maximizes flexibility, scalability, and cost efficiency. Hadoop is a powerful, open-source framework. It stores and processes large datasets across many computers. It is now a key player in data analytics. But, running Hadoop in a hybrid cloud has its challenges and opportunities. Knowing these dynamics can help businesses. They can optimize their data strategies. They can then leverage the full potential of the hybrid cloud and Hadoop.
This article will explore the pros and cons of using Hadoop in hybrid clouds. It will also offer tips for organizations on how to navigate these challenges.
Table Of Contents
- The Hybrid Cloud Landscape and Why Hadoop Fits In
- Key Opportunities of Hadoop in Hybrid Cloud
- Key Challenges of Running Hadoop in a Hybrid Cloud
- Best Practices for Overcoming Hybrid Cloud Hadoop Challenges
- Real-World Use Cases of Hadoop in a Hybrid Cloud
- Conclusion
The Hybrid Cloud Landscape and Why Hadoop Fits In
Hybrid cloud is a computing environment. It combines on-premises infrastructure with public and private cloud services. Organizations use hybrid clouds to achieve greater control, flexibility, and scalability. This model offers several advantages for data-heavy applications, making Hadoop a natural fit.
- Scalability: Hadoop clusters can adjust to meet changing big data workloads.
- Cost Efficiency: Organizations can store sensitive data on-premises. They can use the cloud for extra storage or computing power, cutting costs.
- Flexibility: A hybrid approach lets organizations pick the best environments for different workloads.
Hadoop in hybrid clouds lets companies use cloud power. It keeps critical data close for better security and compliance.
Key Opportunities of Hadoop in Hybrid Cloud
A hybrid cloud deployment of Hadoop offers several benefits. It can help organizations improve their data analytics.
- On-Demand Resource Allocation: In a hybrid setup, firms can use cloud resources as needed. This enables cost-effective, on-demand scalability. This is useful for handling large seasonal spikes in data workloads.
- Data Security and Compliance: Sensitive data can be stored on-premise, in private clouds, or in compliant environments. Non-sensitive workloads can run in the public cloud.
- Disaster Recovery and Business Continuity: Hybrid cloud architectures use distributed storage. This reduces the risk of data loss. If an on-premise failure occurs, you can move workloads to the cloud. There will be no disruptions.
- Improved Performance with Data Locality: Data locality means processing data near its storage. Hadoop, with hybrid cloud, lets organizations process data in the cloud or on-premise. This optimizes performance based on workload.
These opportunities make Hadoop a versatile tool in hybrid clouds. It helps businesses manage their large-scale data analytics needs.
Key Challenges of Running Hadoop in a Hybrid Cloud
The opportunities are great. But deploying Hadoop in hybrid cloud environments has challenges. They must be addressed.
- Data Integration and Management: It's tough to manage data flows between on-premise systems and the cloud. Organizations often struggle with ensuring seamless integration of data storage, movement, and processing.
- Latency Issues: Hybrid cloud uses many environments. This can cause latency when transferring data between on-premises systems and the cloud. Real-time data analytics might suffer due to poor management.
- Security Concerns: Hybrid cloud keeps sensitive data on-premises. Organizations must ensure the security of data transferred between environments. Encryption, secure data transfer protocols, and proper authentication mechanisms are essential.
- Cost Management: Hybrid clouds can incur unexpected costs if not optimized. Businesses must watch and optimize their cloud usage to avoid budget overruns.
- Managing Hadoop clusters in a hybrid cloud is hard. Cluster management is complex. Organizations must ensure they have the right tools and skills. They need to manage clusters that span on-premise and cloud environments.
Each challenge needs a careful approach. It must balance performance, security, and cost for smooth operations.
Best Practices for Overcoming Hybrid Cloud Hadoop Challenges
To use Hadoop well in a hybrid cloud, organizations should follow some best practices:
- Optimize Data Placement: Decide which data to keep on-premise and what to move to the cloud. Keep frequently accessed data close to the processing location to reduce latency.
- Use Data Compression and Tiered Storage: Compress data before moving it to the cloud. Use tiered storage: cold for less critical data, hot for frequently accessed data. This can improve performance and reduce costs.
- Use Automation Tools: Use tools like Apache Ambari or Cloudera Manager. They can automate Hadoop clusters in hybrid environments. They can deploy, monitor, and manage them. Automation helps reduce human errors and ensures operational consistency.
- Ensure end-to-end security. Use strong encryption and secure access for data at rest and in transit. Multi-factor authentication and regular audits should be part of your security strategy.
- Regularly monitor cloud and on-premises resources to ensure efficiency. Setting up alerts for anomalies can help prevent budget overruns and underperformance.
These practices can help. They will ensure Hadoop runs well in a hybrid cloud.
Real-World Use Cases of Hadoop in a Hybrid Cloud
Several industries are already leveraging the power of Hadoop in hybrid cloud environments.
- Finance: Banks and financial institutions use Hadoop in hybrid clouds. They analyze large volumes of transactional data. For security and compliance, sensitive data stays on-premises.
- Healthcare: Hospitals use hybrid clouds to store sensitive patient data on-premises. They run non-sensitive workloads in the cloud for research.
- Retail: Retail companies use hybrid clouds to analyze customer data. They run real-time transactions on-premises and use the cloud for analytics and marketing.
- Manufacturers are using Hadoop in hybrid clouds to analyze IoT sensor data. This optimizes production while keeping critical data on-premises.
These applications show Hadoop's flexibility in hybrid environments. They let organizations balance performance, cost, and security based on their needs.
How to obtain BigData certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Deploying Hadoop in a hybrid cloud has great potential but also serious challenges. The hybrid cloud model is perfect for big data analytics. It is flexible, scalable, and cost-efficient. But, issues like data integration, latency, and security need careful planning. So does cost management.
Organizations can overcome obstacles and unlock Hadoop's full potential in hybrid clouds. They must understand the challenges and use best practices. These include optimizing data placement, implementing security protocols, and using automation tools. In the long run, Hadoop in hybrid clouds helps firms use data. It aids in making decisions and keeps control over sensitive information.
Data Science with R Real World Applications in 2024
In 2024, data science continues to evolve. R is still a top data science tool. R is known for its stats skills and open-source nature. It is now popular for data analysis, visualization, and machine learning. R is widely used across industries to drive innovation. It handles huge datasets and builds predictive models to solve tough problems. This article explores R's real-world applications in data science in 2024. It examines its impact across various sectors.
Table Of Contents
- R in Healthcare: Predictive Analytics and Disease Prevention
- R in Finance: Risk Management and Fraud Detection
- R in Marketing: Customer Segmentation and Sentiment Analysis
- R in Environmental Science: Climate Modeling and Resource Management
- R in Retail: Demand Forecasting and Inventory Management
- Conclusion
R in Healthcare: Predictive Analytics and Disease Prevention
Healthcare is a data-rich industry. R is key to turning that data into insights. Predictive analytics using R is helping healthcare providers. It improves patient outcomes, reduces costs, and boosts efficiency.
- R is used to create models that predict diseases like diabetes, heart disease, and cancer. By analyzing patient histories and genetic data, these models enable early interventions.
- Personalized Medicine: R lets healthcare pros analyze large genetic and medical datasets. They can then create personalized treatment plans for patients.
- Drug Development: In pharma research, R helps with clinical trials. It analyzes data, optimizes dosages, and predicts patient responses. This speeds up and improves drug development.
R in Finance: Risk Management and Fraud Detection
The finance industry is using R to improve risk management and find fraud. In 2024, R is well-known for financial modeling, algorithmic trading, and credit scoring.
- Risk Management: R helps financial firms manage risks. It is used for portfolio optimization, VaR calculations, and stress tests. R's statistical models help firms forecast market risks. They can then use strong strategies to reduce those risks.
- Fraud Detection: Financial institutions employ R for anomaly detection to identify fraudulent transactions. R uses machine learning on large transaction datasets. It helps flag suspicious activities in real-time.
- Algorithmic Trading: In algorithmic trading, R is used for three tasks. They are: back-testing trading strategies, analyzing trends, and predicting asset prices.
R in Marketing: Customer Segmentation and Sentiment Analysis
Data-driven marketing is now vital for businesses. R is key to gaining insights from customer data. In 2024, marketing teams use R for advanced customer segmentation and sentiment analysis. They also use it for predictive modeling.
- Customer Segmentation: R helps marketers segment customers by demographics, behavior, and purchase history. It lets businesses make targeted marketing campaigns. These boost customer engagement and retention.
- Sentiment Analysis: R's NLP can analyze customer feedback, reviews, and social media posts. By identifying sentiments, businesses can refine their products. They can find positive, negative, and neutral feelings.
- Churn Prediction: R helps businesses predict customer churn. It lets them take steps to retain valuable customers.
R in Environmental Science: Climate Modeling and Resource Management
As concerns about the environment grow in 2024, R is key. It analyzes data for climate change, resource management, and biodiversity efforts.
- Climate Change Projections: Scientists use R to analyze data on global temperatures, greenhouse gas emissions, and rising seas. These models help in forecasting climate change impacts and informing policy decisions.
- Resource Management: R optimizes the management of natural resources, like water and energy. Data from sensors and satellite images are analyzed in R to develop sustainable resource allocation strategies.
- Wildlife Conservation: In wildlife conservation, R is used to analyze population data, migration patterns, and habitat changes, enabling conservationists to make data-driven decisions for protecting endangered species.
R in Retail: Demand Forecasting and Inventory Management
Retailers are using R to improve efficiency, optimize inventory, and understand demand. In 2024, R is used in retail. It's for demand forecasting, price optimization, and supply chain management.
- Demand Forecasting: Retailers use R to analyze past sales data and external factors. These include seasonality, the economy, and promotions. They do this to forecast future demand. It ensures products are available when customers need them. This reduces stockouts and overstock.
- Price Optimization: R is used to build pricing models. They consider competitors' prices, demand elasticity, and market trends. This helps retailers set optimal prices that maximize profits while maintaining customer satisfaction.
- Inventory Management: R helps businesses predict inventory needs from sales trends. This lowers costs and cuts the risk of obsolete products.
How to obtain Data Science with R certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In 2024, R's use in data science is broad and impactful across many industries. R is a versatile tool for solving real-world problems. It is used in many fields. These include healthcare, finance, marketing, and environmental science. Its strong statistical skills and machine learning libraries are vital. So are its visualization tools. They are key for data-driven decision-making. As industries embrace data science, R's relevance will grow. It will be a crucial skill for data scientists and analysts. R is key to success in today's data-driven world. It can unlock many opportunities for both new and seasoned data scientists.
Read More
In 2024, data science continues to evolve. R is still a top data science tool. R is known for its stats skills and open-source nature. It is now popular for data analysis, visualization, and machine learning. R is widely used across industries to drive innovation. It handles huge datasets and builds predictive models to solve tough problems. This article explores R's real-world applications in data science in 2024. It examines its impact across various sectors.
Table Of Contents
- R in Healthcare: Predictive Analytics and Disease Prevention
- R in Finance: Risk Management and Fraud Detection
- R in Marketing: Customer Segmentation and Sentiment Analysis
- R in Environmental Science: Climate Modeling and Resource Management
- R in Retail: Demand Forecasting and Inventory Management
- Conclusion
R in Healthcare: Predictive Analytics and Disease Prevention
Healthcare is a data-rich industry. R is key to turning that data into insights. Predictive analytics using R is helping healthcare providers. It improves patient outcomes, reduces costs, and boosts efficiency.
- R is used to create models that predict diseases like diabetes, heart disease, and cancer. By analyzing patient histories and genetic data, these models enable early interventions.
- Personalized Medicine: R lets healthcare pros analyze large genetic and medical datasets. They can then create personalized treatment plans for patients.
- Drug Development: In pharma research, R helps with clinical trials. It analyzes data, optimizes dosages, and predicts patient responses. This speeds up and improves drug development.
R in Finance: Risk Management and Fraud Detection
The finance industry is using R to improve risk management and find fraud. In 2024, R is well-known for financial modeling, algorithmic trading, and credit scoring.
- Risk Management: R helps financial firms manage risks. It is used for portfolio optimization, VaR calculations, and stress tests. R's statistical models help firms forecast market risks. They can then use strong strategies to reduce those risks.
- Fraud Detection: Financial institutions employ R for anomaly detection to identify fraudulent transactions. R uses machine learning on large transaction datasets. It helps flag suspicious activities in real-time.
- Algorithmic Trading: In algorithmic trading, R is used for three tasks. They are: back-testing trading strategies, analyzing trends, and predicting asset prices.
R in Marketing: Customer Segmentation and Sentiment Analysis
Data-driven marketing is now vital for businesses. R is key to gaining insights from customer data. In 2024, marketing teams use R for advanced customer segmentation and sentiment analysis. They also use it for predictive modeling.
- Customer Segmentation: R helps marketers segment customers by demographics, behavior, and purchase history. It lets businesses make targeted marketing campaigns. These boost customer engagement and retention.
- Sentiment Analysis: R's NLP can analyze customer feedback, reviews, and social media posts. By identifying sentiments, businesses can refine their products. They can find positive, negative, and neutral feelings.
- Churn Prediction: R helps businesses predict customer churn. It lets them take steps to retain valuable customers.
R in Environmental Science: Climate Modeling and Resource Management
As concerns about the environment grow in 2024, R is key. It analyzes data for climate change, resource management, and biodiversity efforts.
- Climate Change Projections: Scientists use R to analyze data on global temperatures, greenhouse gas emissions, and rising seas. These models help in forecasting climate change impacts and informing policy decisions.
- Resource Management: R optimizes the management of natural resources, like water and energy. Data from sensors and satellite images are analyzed in R to develop sustainable resource allocation strategies.
- Wildlife Conservation: In wildlife conservation, R is used to analyze population data, migration patterns, and habitat changes, enabling conservationists to make data-driven decisions for protecting endangered species.
R in Retail: Demand Forecasting and Inventory Management
Retailers are using R to improve efficiency, optimize inventory, and understand demand. In 2024, R is used in retail. It's for demand forecasting, price optimization, and supply chain management.
- Demand Forecasting: Retailers use R to analyze past sales data and external factors. These include seasonality, the economy, and promotions. They do this to forecast future demand. It ensures products are available when customers need them. This reduces stockouts and overstock.
- Price Optimization: R is used to build pricing models. They consider competitors' prices, demand elasticity, and market trends. This helps retailers set optimal prices that maximize profits while maintaining customer satisfaction.
- Inventory Management: R helps businesses predict inventory needs from sales trends. This lowers costs and cuts the risk of obsolete products.
How to obtain Data Science with R certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In 2024, R's use in data science is broad and impactful across many industries. R is a versatile tool for solving real-world problems. It is used in many fields. These include healthcare, finance, marketing, and environmental science. Its strong statistical skills and machine learning libraries are vital. So are its visualization tools. They are key for data-driven decision-making. As industries embrace data science, R's relevance will grow. It will be a crucial skill for data scientists and analysts. R is key to success in today's data-driven world. It can unlock many opportunities for both new and seasoned data scientists.
ITIL 4 and Its Role in Modern IT Governance
In today's fast-paced digital world, IT governance is vital for success. One popular framework that plays a key role in modern IT governance is ITIL 4. In this article, we will explore the significance of ITIL 4 and how it can benefit organizations in achieving their IT goals.
What is ITIL 4?
ITIL 4 stands for Information Technology Infrastructure Library. It is a set of best practices for IT service management. It gives organizations a way to manage IT services and operations.
Why is ITIL 4 Important for Modern IT Governance?
ITIL 4 is vital for modern IT governance. It helps align IT services with business goals, improve service delivery, and boost customer satisfaction. ITIL 4 practices help organizations run IT operations efficiently. They will then support their business goals.
ITIL 4 is key for IT governance. It aligns IT services with business needs and goals. It is a complete framework. By focusing on value creation, and service management, it ensures IT operations are efficient and effective. Integrating ITIL 4 practices can help organizations. It can improve governance, service quality, and adaptation to the digital world.
ITIL 4 is vital for modern IT governance. It offers a flexible, scalable way to manage IT services. It meets the demands of today's fast-paced digital world. The focus on the SVS and four dimensions model ensures a complete view of service management. It aligns IT with business goals and boosts efficiency. Also, ITIL 4 promotes a culture of improvement and agility. It helps organizations quickly adapt to changes and achieve lasting success.
How Does ITIL 4 Benefit Organizations?
ITIL 4 gives organizations a modern way to manage IT services. It emphasizes flexibility, collaboration, and continual improvement. By aligning IT services with business needs, it helps companies deliver value and adapt to change. ITIL 4 practices can help organizations. They improve service quality and streamline operations. This leads to better overall outcomes.
-
ITIL 4 helps organizations improve service management and delivery.
-
Improved Processes: Using ITIL 4 practices can optimize IT processes and boost efficiency.
-
Better Customer Experience: ITIL 4 aims for customer-focused service. This improves customer satisfaction.
-
Increased Productivity: ITIL 4 principles and practices boost productivity and results.
ITIL 4 Implementation and Challenges
ITIL 4 has great benefits. But, its implementation can be hard for organizations. Some common challenges include resistance to change, lack of awareness, and insufficient resources. With proper training, tools, and support, organizations can overcome these challenges. They can then reap the rewards of ITIL 4 implementation.
ITIL 4 can greatly improve IT service management. It offers a flexible, complete framework that aligns IT services with business needs. However, organizations often face challenges. These include resistance to change, adapting processes, and training all stakeholders. We must take a strategic approach to address these hurdles. It needs clear communication, phased implementation, and ongoing support to succeed.
ITIL 4 Best Practices
ITIL 4 takes a holistic approach to IT service management. It blends modern practices with traditional ITIL principles. It emphasizes value co-creation and continuous improvement. ITIL 4's best practices can help. They focus on the Service Value System (SVS) and use agile methods. This aligns IT services with business goals and customer needs. These practices help teams to improve service, efficiency, and innovation in a fast-changing tech world.
ITIL 4 encompasses a range of best practices that organizations can leverage to improve their IT service management. Some key ITIL 4 best practices include:
-
Incident Management: Resolving IT incidents promptly and efficiently to minimize downtime.
-
Change Management: Managing changes to IT systems in a controlled and systematic manner to reduce risks.
-
Service Level Management: Defining, monitoring, and improving service levels to meet business requirements.
-
Continual Improvement: Regularly reviewing and improving IT services and processes. This drives ongoing improvement.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, ITIL 4 is vital to modern IT governance. It gives a framework for managing IT services effectively. ITIL 4's principles and best practices can help organizations. They can improve service delivery, processes, and business outcomes. With the right approach and commitment, organizations can harness the power of ITIL 4 to drive success in today's digital age.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced digital world, IT governance is vital for success. One popular framework that plays a key role in modern IT governance is ITIL 4. In this article, we will explore the significance of ITIL 4 and how it can benefit organizations in achieving their IT goals.
What is ITIL 4?
ITIL 4 stands for Information Technology Infrastructure Library. It is a set of best practices for IT service management. It gives organizations a way to manage IT services and operations.
Why is ITIL 4 Important for Modern IT Governance?
ITIL 4 is vital for modern IT governance. It helps align IT services with business goals, improve service delivery, and boost customer satisfaction. ITIL 4 practices help organizations run IT operations efficiently. They will then support their business goals.
ITIL 4 is key for IT governance. It aligns IT services with business needs and goals. It is a complete framework. By focusing on value creation, and service management, it ensures IT operations are efficient and effective. Integrating ITIL 4 practices can help organizations. It can improve governance, service quality, and adaptation to the digital world.
ITIL 4 is vital for modern IT governance. It offers a flexible, scalable way to manage IT services. It meets the demands of today's fast-paced digital world. The focus on the SVS and four dimensions model ensures a complete view of service management. It aligns IT with business goals and boosts efficiency. Also, ITIL 4 promotes a culture of improvement and agility. It helps organizations quickly adapt to changes and achieve lasting success.
How Does ITIL 4 Benefit Organizations?
ITIL 4 gives organizations a modern way to manage IT services. It emphasizes flexibility, collaboration, and continual improvement. By aligning IT services with business needs, it helps companies deliver value and adapt to change. ITIL 4 practices can help organizations. They improve service quality and streamline operations. This leads to better overall outcomes.
-
ITIL 4 helps organizations improve service management and delivery.
-
Improved Processes: Using ITIL 4 practices can optimize IT processes and boost efficiency.
-
Better Customer Experience: ITIL 4 aims for customer-focused service. This improves customer satisfaction.
-
Increased Productivity: ITIL 4 principles and practices boost productivity and results.
ITIL 4 Implementation and Challenges
ITIL 4 has great benefits. But, its implementation can be hard for organizations. Some common challenges include resistance to change, lack of awareness, and insufficient resources. With proper training, tools, and support, organizations can overcome these challenges. They can then reap the rewards of ITIL 4 implementation.
ITIL 4 can greatly improve IT service management. It offers a flexible, complete framework that aligns IT services with business needs. However, organizations often face challenges. These include resistance to change, adapting processes, and training all stakeholders. We must take a strategic approach to address these hurdles. It needs clear communication, phased implementation, and ongoing support to succeed.
ITIL 4 Best Practices
ITIL 4 takes a holistic approach to IT service management. It blends modern practices with traditional ITIL principles. It emphasizes value co-creation and continuous improvement. ITIL 4's best practices can help. They focus on the Service Value System (SVS) and use agile methods. This aligns IT services with business goals and customer needs. These practices help teams to improve service, efficiency, and innovation in a fast-changing tech world.
ITIL 4 encompasses a range of best practices that organizations can leverage to improve their IT service management. Some key ITIL 4 best practices include:
-
Incident Management: Resolving IT incidents promptly and efficiently to minimize downtime.
-
Change Management: Managing changes to IT systems in a controlled and systematic manner to reduce risks.
-
Service Level Management: Defining, monitoring, and improving service levels to meet business requirements.
-
Continual Improvement: Regularly reviewing and improving IT services and processes. This drives ongoing improvement.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, ITIL 4 is vital to modern IT governance. It gives a framework for managing IT services effectively. ITIL 4's principles and best practices can help organizations. They can improve service delivery, processes, and business outcomes. With the right approach and commitment, organizations can harness the power of ITIL 4 to drive success in today's digital age.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
CMMI 2 0 Key Updates and Benefits
In software development, project management, and quality improvement, it's vital to stay current on the latest methods. They are key to success. One such framework is the Capability Maturity Model Integration (CMMI). It has recently undergone significant updates. In this article, we will explore the key updates and benefits of CMMI 2.0, the latest version of this renowned model.
What's New in CMMI 2.0?
CMMI 2.0 has many new features. They aim to help organizations improve their processes, quality, and maturity. Key changes include a more flexible framework, updated processes, and better appraisals.
CMMI 2.0 introduces faster, more efficient appraisal methods. It also emphasizes agile practices. This lets organizations combine CMMI with modern development methods. It also focuses on performance outcomes. So, process improvements must help achieve business goals.
Benefits of CMMI 2.0
Improved Process Efficiency
One of the main benefits of CMMI 2.0 is its focus on improving process efficiency. By implementing best practices and standardized processes, organizations can reduce waste, lower costs, and deliver higher quality products and services.
Enhanced Quality
With a strong emphasis on quality improvement, CMMI 2.0 helps organizations ensure that their products and services meet the highest standards. By following the guidelines and practices outlined in the framework, companies can enhance customer satisfaction and build a reputation for excellence.
Increased Maturity Levels
CMMI 2.0 offers a roadmap for organizations to increase their maturity levels and progress towards becoming high-performing entities. By following the guidelines and best practices, companies can mature their processes, improve performance, and drive continuous improvement.
Certification and Compliance
By achieving CMMI 2.0 certification, organizations can demonstrate their commitment to quality, efficiency, and continuous improvement. This certification can not only help companies attract new business and clients but also ensure compliance with industry standards and regulations.
CMMI 2.0 Features and Updates
CMMI 2.0 offers a flexible, scalable framework. It can be tailored to fit the needs of different organizations. The model now includes new process areas, appraisal methods, and maturity levels. It gives companies a complete guide to improving their processes and performance.
CMMI 2.0 has major updates. It has a new, simpler model structure. This makes it easier to use and implement. The new version stresses performance management. It focuses on results and outcomes, not just compliance with processes. Also, CMMI 2.0 adds digital transformation practices. It gives organizations new guidelines to navigate today's tech.
Advantages of CMMI 2.0
Tailored for Different Industries
CMMI 2.0 is designed to be flexible and adaptable, making it suitable for a wide range of industries and sectors. CMMI 2.0 can be customized to fit your organization's needs. This applies to software development, project management, and quality improvement.
Enhanced Project Management
CMMI 2.0's guidelines can help organizations improve project management. It will boost efficiency, cut risks, and improve results. The framework offers a method to manage projects. It ensures they finish on time and within budget.
Streamlined Processes
CMMI 2.0 helps organizations streamline their processes. It does this by providing a standardized set of practices and guidelines. These best practices can help companies. They will reduce waste, improve communication, and boost productivity. This will lead to better results and higher customer satisfaction.
Continuous Improvement
One of the key benefits of CMMI 2.0 is its focus on continuous improvement. By following the model's guidelines, organizations can improve. They can find areas for enhancement, implement changes, and measure their impact. This will create a culture of continuous learning and improvement.
How to obtain CMMI certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, CMMI 2.0 has many updates and benefits. They can help organizations improve processes, enhance quality, and boost performance. This framework will help companies. It will streamline operations, raise maturity levels, and drive improvement. In the end, it will boost their success and competitiveness in the market.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In software development, project management, and quality improvement, it's vital to stay current on the latest methods. They are key to success. One such framework is the Capability Maturity Model Integration (CMMI). It has recently undergone significant updates. In this article, we will explore the key updates and benefits of CMMI 2.0, the latest version of this renowned model.
What's New in CMMI 2.0?
CMMI 2.0 has many new features. They aim to help organizations improve their processes, quality, and maturity. Key changes include a more flexible framework, updated processes, and better appraisals.
CMMI 2.0 introduces faster, more efficient appraisal methods. It also emphasizes agile practices. This lets organizations combine CMMI with modern development methods. It also focuses on performance outcomes. So, process improvements must help achieve business goals.
Benefits of CMMI 2.0
Improved Process Efficiency
One of the main benefits of CMMI 2.0 is its focus on improving process efficiency. By implementing best practices and standardized processes, organizations can reduce waste, lower costs, and deliver higher quality products and services.
Enhanced Quality
With a strong emphasis on quality improvement, CMMI 2.0 helps organizations ensure that their products and services meet the highest standards. By following the guidelines and practices outlined in the framework, companies can enhance customer satisfaction and build a reputation for excellence.
Increased Maturity Levels
CMMI 2.0 offers a roadmap for organizations to increase their maturity levels and progress towards becoming high-performing entities. By following the guidelines and best practices, companies can mature their processes, improve performance, and drive continuous improvement.
Certification and Compliance
By achieving CMMI 2.0 certification, organizations can demonstrate their commitment to quality, efficiency, and continuous improvement. This certification can not only help companies attract new business and clients but also ensure compliance with industry standards and regulations.
CMMI 2.0 Features and Updates
CMMI 2.0 offers a flexible, scalable framework. It can be tailored to fit the needs of different organizations. The model now includes new process areas, appraisal methods, and maturity levels. It gives companies a complete guide to improving their processes and performance.
CMMI 2.0 has major updates. It has a new, simpler model structure. This makes it easier to use and implement. The new version stresses performance management. It focuses on results and outcomes, not just compliance with processes. Also, CMMI 2.0 adds digital transformation practices. It gives organizations new guidelines to navigate today's tech.
Advantages of CMMI 2.0
Tailored for Different Industries
CMMI 2.0 is designed to be flexible and adaptable, making it suitable for a wide range of industries and sectors. CMMI 2.0 can be customized to fit your organization's needs. This applies to software development, project management, and quality improvement.
Enhanced Project Management
CMMI 2.0's guidelines can help organizations improve project management. It will boost efficiency, cut risks, and improve results. The framework offers a method to manage projects. It ensures they finish on time and within budget.
Streamlined Processes
CMMI 2.0 helps organizations streamline their processes. It does this by providing a standardized set of practices and guidelines. These best practices can help companies. They will reduce waste, improve communication, and boost productivity. This will lead to better results and higher customer satisfaction.
Continuous Improvement
One of the key benefits of CMMI 2.0 is its focus on continuous improvement. By following the model's guidelines, organizations can improve. They can find areas for enhancement, implement changes, and measure their impact. This will create a culture of continuous learning and improvement.
How to obtain CMMI certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, CMMI 2.0 has many updates and benefits. They can help organizations improve processes, enhance quality, and boost performance. This framework will help companies. It will streamline operations, raise maturity levels, and drive improvement. In the end, it will boost their success and competitiveness in the market.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Key Benefits of Implementing COBIT® 5 in Your IT Organization
In today's fast-changing tech world, IT governance is vital. It ensures that technology meets organizational goals. COBIT® 5 is a framework by ISACA. It guides the management and governance of enterprise IT. COBIT® 5 can help organizations. It improves IT governance and management. It aligns IT with business goals. It drives better performance and risk management. This article explores the key benefits of adopting COBIT® 5 in your IT organization.
Table Of Contents
- Enhanced Alignment Between IT and Business Goals
- Improved Risk Management
- Enhanced IT process efficiency
- Strengthened IT governance
- Continuous Improvement and Adaptability
- Conclusion
Enhanced Alignment Between IT and Business Goals
A key benefit of COBIT® 5 is its focus on aligning IT with business goals. COBIT® 5 provides a way to ensure that IT work supports business goals.
- COBIT® 5 helps align IT with business goals. It ensures IT investments and projects deliver value to the organization. This alignment helps rank IT initiatives. Their contributions to business goals form the basis.
- Value Delivery: The framework emphasizes delivering measurable value from IT investments. It helps organizations manage the benefits, costs, and risks of IT projects. This ensures the effective use of IT resources.
Aligning IT strategies with business goals can boost performance. It helps organizations achieve their objectives with greater efficiency.
Improved Risk Management
Effective risk management is critical for protecting organizational assets and ensuring business continuity. COBIT® 5 offers a robust approach to managing IT-related risks.
- Risk Identification: The framework helps in identifying potential IT risks and vulnerabilities. COBIT® 5 provides a complete set of risk management practices. It ensures the identification, assessment, and mitigation of risks.
- Risk Response: COBIT® 5 offers guidance on developing and implementing risk response strategies. This includes defining risk tolerance levels, establishing controls, and monitoring risk management activities.
- Compliance and Security: The framework meets regulations and boosts IT security. Integrating risk management into IT processes helps protect sensitive data and ensures compliance.
COBIT® 5's risk management practices can help reduce IT risks. They can also protect assets.
Enhanced IT process efficiency
COBIT® 5 offers best practices and frameworks. They help organizations optimize their IT operations.
- Process Optimization: The framework outlines best practices for IT process management. It will make them more efficient and effective. This includes streamlining workflows, reducing redundancies, and enhancing process performance.
- Performance Measurement: COBIT® 5 has metrics to assess IT processes. By monitoring performance, organizations can find areas to improve. They can then make the necessary changes.
- Resource Management: The framework helps organizations manage IT resources: personnel, technology, and budgets. Effective resource management maximizes IT investments and ensures the efficient use of resources.
Using COBIT® 5 to improve IT processes boosts performance and saves costs.
Strengthened IT governance
COBIT® 5 offers a complete method for IT governance. It ensures that IT management aligns with corporate governance principles.
- Governance Framework: The framework sets clear IT management structures, roles, and responsibilities. This includes defining decision-making processes, accountability mechanisms, and oversight functions.
- Compliance Management: COBIT® 5 supports compliance with internal policies and external regulations. Governance practices in IT processes can ensure compliance with laws and regulations.
- Strategic Decision-Making: The framework helps with strategic decisions. It provides a structured way to test IT investments and initiatives. This helps in making informed decisions that support long-term business objectives.
Strengthening IT governance through COBIT® 5 enhances organizational control, accountability, and compliance.
Continuous Improvement and Adaptability
COBIT® 5 promotes a culture of continuous improvement and adaptability within IT organizations.
- Continuous Improvement: The framework encourages regular evaluation and improvement of IT processes. A mindset of continuous improvement helps organizations stay competitive. It allows them to respond to changes in business needs and new technologies.
- Adaptability: COBIT® 5 supports it with a flexible, customizable framework. It can fit different organizations and needs. This allows organizations to adjust their IT governance and management as needed.
- Benchmarking and Best Practices: The framework includes benchmarking techniques. They compare IT performance to industry standards and best practices. This helps organizations identify gaps and install improvements based on proven methods.
COBIT® 5 helps organizations stay agile in a fast-changing world. It does this by promoting a culture of continuous improvement and adaptability.
How to obtain Cobit 5 certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, COBIT® 5 has many benefits for IT organizations. It improves alignment between IT and business goals. It also boosts risk management and IT process efficiency. It strengthens IT governance and fosters a culture of continuous improvement. COBIT® 5 helps organizations align IT with business goals. It also manages risks, optimizes IT processes, and strengthens governance. As technology evolves, COBIT® 5 offers a framework. It helps manage complex IT and drives organizational success.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-changing tech world, IT governance is vital. It ensures that technology meets organizational goals. COBIT® 5 is a framework by ISACA. It guides the management and governance of enterprise IT. COBIT® 5 can help organizations. It improves IT governance and management. It aligns IT with business goals. It drives better performance and risk management. This article explores the key benefits of adopting COBIT® 5 in your IT organization.
Table Of Contents
- Enhanced Alignment Between IT and Business Goals
- Improved Risk Management
- Enhanced IT process efficiency
- Strengthened IT governance
- Continuous Improvement and Adaptability
- Conclusion
Enhanced Alignment Between IT and Business Goals
A key benefit of COBIT® 5 is its focus on aligning IT with business goals. COBIT® 5 provides a way to ensure that IT work supports business goals.
- COBIT® 5 helps align IT with business goals. It ensures IT investments and projects deliver value to the organization. This alignment helps rank IT initiatives. Their contributions to business goals form the basis.
- Value Delivery: The framework emphasizes delivering measurable value from IT investments. It helps organizations manage the benefits, costs, and risks of IT projects. This ensures the effective use of IT resources.
Aligning IT strategies with business goals can boost performance. It helps organizations achieve their objectives with greater efficiency.
Improved Risk Management
Effective risk management is critical for protecting organizational assets and ensuring business continuity. COBIT® 5 offers a robust approach to managing IT-related risks.
- Risk Identification: The framework helps in identifying potential IT risks and vulnerabilities. COBIT® 5 provides a complete set of risk management practices. It ensures the identification, assessment, and mitigation of risks.
- Risk Response: COBIT® 5 offers guidance on developing and implementing risk response strategies. This includes defining risk tolerance levels, establishing controls, and monitoring risk management activities.
- Compliance and Security: The framework meets regulations and boosts IT security. Integrating risk management into IT processes helps protect sensitive data and ensures compliance.
COBIT® 5's risk management practices can help reduce IT risks. They can also protect assets.
Enhanced IT process efficiency
COBIT® 5 offers best practices and frameworks. They help organizations optimize their IT operations.
- Process Optimization: The framework outlines best practices for IT process management. It will make them more efficient and effective. This includes streamlining workflows, reducing redundancies, and enhancing process performance.
- Performance Measurement: COBIT® 5 has metrics to assess IT processes. By monitoring performance, organizations can find areas to improve. They can then make the necessary changes.
- Resource Management: The framework helps organizations manage IT resources: personnel, technology, and budgets. Effective resource management maximizes IT investments and ensures the efficient use of resources.
Using COBIT® 5 to improve IT processes boosts performance and saves costs.
Strengthened IT governance
COBIT® 5 offers a complete method for IT governance. It ensures that IT management aligns with corporate governance principles.
- Governance Framework: The framework sets clear IT management structures, roles, and responsibilities. This includes defining decision-making processes, accountability mechanisms, and oversight functions.
- Compliance Management: COBIT® 5 supports compliance with internal policies and external regulations. Governance practices in IT processes can ensure compliance with laws and regulations.
- Strategic Decision-Making: The framework helps with strategic decisions. It provides a structured way to test IT investments and initiatives. This helps in making informed decisions that support long-term business objectives.
Strengthening IT governance through COBIT® 5 enhances organizational control, accountability, and compliance.
Continuous Improvement and Adaptability
COBIT® 5 promotes a culture of continuous improvement and adaptability within IT organizations.
- Continuous Improvement: The framework encourages regular evaluation and improvement of IT processes. A mindset of continuous improvement helps organizations stay competitive. It allows them to respond to changes in business needs and new technologies.
- Adaptability: COBIT® 5 supports it with a flexible, customizable framework. It can fit different organizations and needs. This allows organizations to adjust their IT governance and management as needed.
- Benchmarking and Best Practices: The framework includes benchmarking techniques. They compare IT performance to industry standards and best practices. This helps organizations identify gaps and install improvements based on proven methods.
COBIT® 5 helps organizations stay agile in a fast-changing world. It does this by promoting a culture of continuous improvement and adaptability.
How to obtain Cobit 5 certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, COBIT® 5 has many benefits for IT organizations. It improves alignment between IT and business goals. It also boosts risk management and IT process efficiency. It strengthens IT governance and fosters a culture of continuous improvement. COBIT® 5 helps organizations align IT with business goals. It also manages risks, optimizes IT processes, and strengthens governance. As technology evolves, COBIT® 5 offers a framework. It helps manage complex IT and drives organizational success.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Chatbots in Digital Marketing Enhancing Customer Engagement
In today's fast-paced digital world, customer engagement is key. It builds brand loyalty and drives business growth. Chatbots are now a top tool in digital marketing. They enhance customer interactions by offering instant support, personalized experiences, and seamless communication. Chatbots can handle many customer queries at once. They are reshaping how businesses engage with customers. This article explores how chatbots are revolutionizing digital marketing. They enhance customer experience and boost brand value.
Table Of Contents
- The Role of Chatbots in Customer Engagement
- Benefits of Using Chatbots in Digital Marketing
- Chatbot Best Practices for Enhancing Customer Engagement
- How Chatbots Enhance the Customer Journey
- Examples of chatbot success in digital marketing.
- Conclusion
The Role of Chatbots in Customer Engagement
Chatbots are now vital to digital marketing. They shape how brands interact with customers. Their AI powers businesses to engage customers 24/7 across many channels. Key aspects include:
- Chatbots provide immediate responses. Customers don't have to wait for help. This instant support fosters a positive customer experience and enhances engagement.
- Personalization: Modern chatbots use machine learning and NLP. They offer personalized interactions. They can recognize customer preferences and past interactions. They can also see buying behaviors. This lets them tailor responses to meet individual needs.
- Proactive Engagement: Chatbots can start chats, suggest products, or help. This makes customers feel valued and understood. This proactive approach often leads to higher conversion rates and customer satisfaction.
- Chatbots gather valuable customer data during interactions. We can analyze it to understand consumer behavior and preferences. This data can help businesses refine their marketing strategies for improved engagement.
Benefits of Using Chatbots in Digital Marketing
Chatbots in digital marketing can greatly boost customer engagement. Some of these advantages include:
- Cost-Effective Customer Support: Chatbots can handle many inquiries at once. They reduce the need for a large support team, as they are a cost-effective solution.
- 24/7 Availability: Unlike humans, chatbots can work 24/7. They provide support and answers whenever customers need them. This constant availability can build trust and improve customer loyalty.
- Lead Generation and Nurturing: Chatbots can qualify leads. They do this by asking questions and gathering info. They can also nurture these leads. They can do this by giving tailored product recommendations. They should also engage with customers during their buying journey.
- Multichannel Support: Chatbots can be on websites, social media, and messaging apps. This omnichannel presence lets businesses engage with customers on their preferred platforms.
- Scalability: Chatbots can handle many queries at once. This allows for easy scaling of support without losing quality.
Chatbot Best Practices for Enhancing Customer Engagement
To use chatbots in digital marketing, businesses must follow best practices. This will maximize customer engagement.
- A simple, intuitive chatbot will engage customers with greater effectiveness. Use clear language, easy navigation, and ensure quick responses to keep interactions smooth.
- Create Engaging Scripts: A chatbot's script should match the brand's voice and personality. Use a friendly tone. Add humor where fitting. Address customer concerns without delay. This will make interactions enjoyable.
- Use AI and NLP for personalization. They will help the chatbot understand customers' contexts and feelings. This enables more personalized and relevant responses, enhancing engagement.
- Integrate with CRM Systems: Connecting chatbots to CRM systems can improve tailored interactions. CRM integration allows chatbots to access customer data. It includes history, preferences, and past interactions. This enables more informed engagement.
- Use Human Handoff When Needed: Chatbots are efficient, but they can't handle everything. For complex queries, the chatbot must transfer the chat to a human. This will provide a better resolution.
How Chatbots Enhance the Customer Journey
Chatbots are crucial at every stage of the customer journey. They help from awareness to post-purchase support.
- Awareness Stage: At this stage, chatbots can introduce potential customers to the brand. They can highlight key products and answer common questions. They can also guide visitors to relevant pages on the site. This helps them explore without difficulty.
- Consideration Stage: In this phase, chatbots can compare products and show reviews. They can also give personalized recommendations based on user preferences. This personalized guidance helps customers make informed decisions.
- Buy Stage: At the point of sale, chatbots can assist with checkout. They can provide discount codes and address last-minute concerns. This can reduce cart abandonment and increase conversions.
- Post-Purchase Support: After the sale, chatbots can handle order, return, and refund queries. They can offer product tips and upsell items based on past purchases. This will improve the customer experience.
Examples of chatbot success in digital marketing.
Many brands have used chatbots to boost engagement and marketing. They have succeeded. Here are some real-world examples:
- Sephora: Sephora's chatbot on Facebook Messenger gives makeup tips and product recommendations. It also lets customers book in-store makeovers. This chatbot has helped Sephora boost sales by engaging customers with personalized chats.
- H&M: The clothing brand H&M uses a chatbot on its website and app. It helps customers browse outfits and make fashion choices. The bot asks about the customers' styles. It then suggests items. This improves the shopping experience.
- Domino's Pizza: Their "Dom" chatbot lets customers order and track pizza on social media. This chatbot has streamlined the ordering process, making it more convenient for customers.
- Bank of America: Its chatbot, Erica, helps customers with tasks. It can check balances, pay bills, and provide spending insights. By offering financial advice and support, Erica enhances customer engagement and satisfaction.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Chatbots are a game changer in digital marketing. They offer personalized, real-time interactions. They boost customer engagement at every stage of the journey. Chatbots can provide instant support. They gather data and offer personalized recommendations. They help businesses connect with their audience. Companies can improve customer experience by using best practices. They should also add chatbots to their marketing. They can build brand loyalty and grow in today's digital world. As chatbot technology evolves, it will impact customer engagement more.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced digital world, customer engagement is key. It builds brand loyalty and drives business growth. Chatbots are now a top tool in digital marketing. They enhance customer interactions by offering instant support, personalized experiences, and seamless communication. Chatbots can handle many customer queries at once. They are reshaping how businesses engage with customers. This article explores how chatbots are revolutionizing digital marketing. They enhance customer experience and boost brand value.
Table Of Contents
- The Role of Chatbots in Customer Engagement
- Benefits of Using Chatbots in Digital Marketing
- Chatbot Best Practices for Enhancing Customer Engagement
- How Chatbots Enhance the Customer Journey
- Examples of chatbot success in digital marketing.
- Conclusion
The Role of Chatbots in Customer Engagement
Chatbots are now vital to digital marketing. They shape how brands interact with customers. Their AI powers businesses to engage customers 24/7 across many channels. Key aspects include:
- Chatbots provide immediate responses. Customers don't have to wait for help. This instant support fosters a positive customer experience and enhances engagement.
- Personalization: Modern chatbots use machine learning and NLP. They offer personalized interactions. They can recognize customer preferences and past interactions. They can also see buying behaviors. This lets them tailor responses to meet individual needs.
- Proactive Engagement: Chatbots can start chats, suggest products, or help. This makes customers feel valued and understood. This proactive approach often leads to higher conversion rates and customer satisfaction.
- Chatbots gather valuable customer data during interactions. We can analyze it to understand consumer behavior and preferences. This data can help businesses refine their marketing strategies for improved engagement.
Benefits of Using Chatbots in Digital Marketing
Chatbots in digital marketing can greatly boost customer engagement. Some of these advantages include:
- Cost-Effective Customer Support: Chatbots can handle many inquiries at once. They reduce the need for a large support team, as they are a cost-effective solution.
- 24/7 Availability: Unlike humans, chatbots can work 24/7. They provide support and answers whenever customers need them. This constant availability can build trust and improve customer loyalty.
- Lead Generation and Nurturing: Chatbots can qualify leads. They do this by asking questions and gathering info. They can also nurture these leads. They can do this by giving tailored product recommendations. They should also engage with customers during their buying journey.
- Multichannel Support: Chatbots can be on websites, social media, and messaging apps. This omnichannel presence lets businesses engage with customers on their preferred platforms.
- Scalability: Chatbots can handle many queries at once. This allows for easy scaling of support without losing quality.
Chatbot Best Practices for Enhancing Customer Engagement
To use chatbots in digital marketing, businesses must follow best practices. This will maximize customer engagement.
- A simple, intuitive chatbot will engage customers with greater effectiveness. Use clear language, easy navigation, and ensure quick responses to keep interactions smooth.
- Create Engaging Scripts: A chatbot's script should match the brand's voice and personality. Use a friendly tone. Add humor where fitting. Address customer concerns without delay. This will make interactions enjoyable.
- Use AI and NLP for personalization. They will help the chatbot understand customers' contexts and feelings. This enables more personalized and relevant responses, enhancing engagement.
- Integrate with CRM Systems: Connecting chatbots to CRM systems can improve tailored interactions. CRM integration allows chatbots to access customer data. It includes history, preferences, and past interactions. This enables more informed engagement.
- Use Human Handoff When Needed: Chatbots are efficient, but they can't handle everything. For complex queries, the chatbot must transfer the chat to a human. This will provide a better resolution.
How Chatbots Enhance the Customer Journey
Chatbots are crucial at every stage of the customer journey. They help from awareness to post-purchase support.
- Awareness Stage: At this stage, chatbots can introduce potential customers to the brand. They can highlight key products and answer common questions. They can also guide visitors to relevant pages on the site. This helps them explore without difficulty.
- Consideration Stage: In this phase, chatbots can compare products and show reviews. They can also give personalized recommendations based on user preferences. This personalized guidance helps customers make informed decisions.
- Buy Stage: At the point of sale, chatbots can assist with checkout. They can provide discount codes and address last-minute concerns. This can reduce cart abandonment and increase conversions.
- Post-Purchase Support: After the sale, chatbots can handle order, return, and refund queries. They can offer product tips and upsell items based on past purchases. This will improve the customer experience.
Examples of chatbot success in digital marketing.
Many brands have used chatbots to boost engagement and marketing. They have succeeded. Here are some real-world examples:
- Sephora: Sephora's chatbot on Facebook Messenger gives makeup tips and product recommendations. It also lets customers book in-store makeovers. This chatbot has helped Sephora boost sales by engaging customers with personalized chats.
- H&M: The clothing brand H&M uses a chatbot on its website and app. It helps customers browse outfits and make fashion choices. The bot asks about the customers' styles. It then suggests items. This improves the shopping experience.
- Domino's Pizza: Their "Dom" chatbot lets customers order and track pizza on social media. This chatbot has streamlined the ordering process, making it more convenient for customers.
- Bank of America: Its chatbot, Erica, helps customers with tasks. It can check balances, pay bills, and provide spending insights. By offering financial advice and support, Erica enhances customer engagement and satisfaction.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Chatbots are a game changer in digital marketing. They offer personalized, real-time interactions. They boost customer engagement at every stage of the journey. Chatbots can provide instant support. They gather data and offer personalized recommendations. They help businesses connect with their audience. Companies can improve customer experience by using best practices. They should also add chatbots to their marketing. They can build brand loyalty and grow in today's digital world. As chatbot technology evolves, it will impact customer engagement more.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Balancing Profit with Social Responsibility
Ethical marketing is now vital in business. Companies are realizing they can't focus only on profit. It must be balanced with social responsibility. Ethical marketing is a tough balance. It must maximize profits and be socially responsible. This article will explore ethical marketing. It will show how companies can align their practices with ethical values.
What is Ethical Marketing?
Ethical marketing is a philosophy. It guides companies to decide based on fairness, transparency, and honesty. It involves promoting products and services in a way that is truthful and does not mislead consumers. Ethical marketing means considering the social and environmental impact of business. It requires that business activities benefit society as a whole.
The Importance of Social Responsibility
Social responsibility is a key component of ethical marketing. Companies must consider their actions' impact on society and the environment. Sustainable practices and ethical ads can build trust and enhance brands.
Balancing Profit and Social Responsibility
One of the challenges of ethical marketing is balancing the need to generate profits with the desire to act responsibly. Companies must find ways to maximize profits. They must also consider employees, customers, and the community. Companies can achieve this by using sustainable practices, responsible ads, and ethical business.
Sustainable Marketing Practices
Sustainable marketing promotes products and services. It must reduce harm to the environment and society. This can include using eco-friendly materials, reducing waste, and supporting fair labor practices. By using sustainability in their marketing, companies can attract eco-conscious consumers. It will also help them stand out in the market.
Sustainable marketing is key for businesses. It helps them to reduce their environmental impact and promote ethical values. Brands can attract eco-conscious consumers by using green strategies in their campaigns. They can also enhance their corporate reputation. Being transparent and committed to sustainability can build stronger customer connections. It can also help create a more responsible future.
Responsible Advertising
Responsible advertising is another key aspect of ethical marketing. Companies should avoid deceptive ads. Their marketing must be truthful and clear. Honest, ethical ads can build trust and long-term customer ties.
Responsible advertising means making campaigns that are truthful, clear, and respectful to all audiences. It means avoiding false claims, protecting privacy, and considering the message's social impact. By prioritizing ethical practices, brands build trust and foster long-term relationships with consumers.
Corporate Social Responsibility
Corporate social responsibility (CSR) is an important part of ethical marketing. Companies that do CSR, like donating to charities, care about society. Companies can boost their reputation by aligning with ethical values. This shows their commitment to positively impacting society.
Corporate Social Responsibility (CSR) is a business's duty. It must profit while benefiting society and the environment. Using ethical practices and sustainable strategies can boost a company's brand. It can build customer trust and drive long-term success. Good CSR initiatives solve social and environmental problems. They also create a positive corporate culture and make a real impact.
The Rise of Ethical Consumerism
Ethical consumerism is rising. More buyers now prioritize ethics in their purchases. Companies that use ethical marketing can attract loyal customers. They can tap into a growing trend. By promoting ethical values, companies can stand out in the market. It will build a strong brand reputation.
Consumers are prioritizing ethics in their buying decisions. They seek brands that align with their values on sustainability and social responsibility. The rise in ethical shopping is pushing companies to be more transparent. They must invest in sustainable products. Thus, businesses that embrace ethics gain consumer trust. They also positively impact society and the environment.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, ethical marketing is about more than just making a profit. It means balancing the need for profit with a duty to be responsible and sustainable. Companies can build trust with consumers by being ethical. They should do responsible advertising and adopt sustainable practices. This will differentiate them in the market and positively impact society. In today's competitive market, ethical marketing is a must, not a choice.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Ethical marketing is now vital in business. Companies are realizing they can't focus only on profit. It must be balanced with social responsibility. Ethical marketing is a tough balance. It must maximize profits and be socially responsible. This article will explore ethical marketing. It will show how companies can align their practices with ethical values.
What is Ethical Marketing?
Ethical marketing is a philosophy. It guides companies to decide based on fairness, transparency, and honesty. It involves promoting products and services in a way that is truthful and does not mislead consumers. Ethical marketing means considering the social and environmental impact of business. It requires that business activities benefit society as a whole.
The Importance of Social Responsibility
Social responsibility is a key component of ethical marketing. Companies must consider their actions' impact on society and the environment. Sustainable practices and ethical ads can build trust and enhance brands.
Balancing Profit and Social Responsibility
One of the challenges of ethical marketing is balancing the need to generate profits with the desire to act responsibly. Companies must find ways to maximize profits. They must also consider employees, customers, and the community. Companies can achieve this by using sustainable practices, responsible ads, and ethical business.
Sustainable Marketing Practices
Sustainable marketing promotes products and services. It must reduce harm to the environment and society. This can include using eco-friendly materials, reducing waste, and supporting fair labor practices. By using sustainability in their marketing, companies can attract eco-conscious consumers. It will also help them stand out in the market.
Sustainable marketing is key for businesses. It helps them to reduce their environmental impact and promote ethical values. Brands can attract eco-conscious consumers by using green strategies in their campaigns. They can also enhance their corporate reputation. Being transparent and committed to sustainability can build stronger customer connections. It can also help create a more responsible future.
Responsible Advertising
Responsible advertising is another key aspect of ethical marketing. Companies should avoid deceptive ads. Their marketing must be truthful and clear. Honest, ethical ads can build trust and long-term customer ties.
Responsible advertising means making campaigns that are truthful, clear, and respectful to all audiences. It means avoiding false claims, protecting privacy, and considering the message's social impact. By prioritizing ethical practices, brands build trust and foster long-term relationships with consumers.
Corporate Social Responsibility
Corporate social responsibility (CSR) is an important part of ethical marketing. Companies that do CSR, like donating to charities, care about society. Companies can boost their reputation by aligning with ethical values. This shows their commitment to positively impacting society.
Corporate Social Responsibility (CSR) is a business's duty. It must profit while benefiting society and the environment. Using ethical practices and sustainable strategies can boost a company's brand. It can build customer trust and drive long-term success. Good CSR initiatives solve social and environmental problems. They also create a positive corporate culture and make a real impact.
The Rise of Ethical Consumerism
Ethical consumerism is rising. More buyers now prioritize ethics in their purchases. Companies that use ethical marketing can attract loyal customers. They can tap into a growing trend. By promoting ethical values, companies can stand out in the market. It will build a strong brand reputation.
Consumers are prioritizing ethics in their buying decisions. They seek brands that align with their values on sustainability and social responsibility. The rise in ethical shopping is pushing companies to be more transparent. They must invest in sustainable products. Thus, businesses that embrace ethics gain consumer trust. They also positively impact society and the environment.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, ethical marketing is about more than just making a profit. It means balancing the need for profit with a duty to be responsible and sustainable. Companies can build trust with consumers by being ethical. They should do responsible advertising and adopt sustainable practices. This will differentiate them in the market and positively impact society. In today's competitive market, ethical marketing is a must, not a choice.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
CISSP Influence on Cybersecurity Duties
As cybersecurity threats grow more sophisticated, the need for experts is urgent. The CISSP certification is a top credential in the field. It is from (ISC)². It indicates a high level of skill and dedication to information security. This blog examines the CISSP's major impact on cybersecurity jobs. It looks at how it affects careers, job roles, and contributions to security.
1. Elevating Professional Expertise
The CISSP certification is known for its tough test of security principles. It covers many topics, including risk management and network security. For professionals, CISSP shows a deep understanding of these areas. It sets them apart from their peers. This advanced knowledge boosts their skills and credibility. It makes them more competitive for senior roles.
2. Advancing Career Opportunities
One major impact of getting a CISSP is more job options. The credential is highly regarded by employers and often required for senior-level positions. CISSP helps professionals advance to roles like Security Manager and CISO. It also helps them become IT Security Consultants. These roles require strategic decision-making, leadership, and oversight of security programs. They reflect the higher responsibility that comes with the certification.
3. Enhancing Strategic Decision-Making
CISSP-certified pros often set the security strategy for an organization. They can design security frameworks, assess risk, and create policies. Their work will align with business goals. This role requires technical knowledge. It also needs an understanding of how security affects business operations. CISSP professionals can bridge the gap between tech and business. They ensure that security strategies support organizational goals.
4. Broadening Responsibilities in Risk Management
Risk management is key to the CISSP certification. It also affects job roles. CISSP-certified professionals are responsible for managing risks to an organization's information systems. They must identify, assess, and reduce those risks. This responsibility includes developing risk assessment methodologies, implementing controls, and continuously monitoring for potential threats. CISSP professionals protect assets and ensure business continuity. They do this by mastering risk management.
5. Leadership and Management Responsibilities
The CISSP certification often leads to increased leadership and management responsibilities. Certified professionals often oversee security teams and projects. They coordinate with other departments to ensure cohesive security practices. They must mentor junior staff, develop training programs, and foster a security-aware culture. This leadership aspect of CISSP positions professionals as key contributors to both the strategic and operational sides of cybersecurity.
6. Driving Compliance and Governance
A key focus for CISSP-certified professionals is compliance with regulations and standards. They often ensure an organization's security practices comply with laws, like GDPR, HIPAA, and ISO/IEC 27001. CISSP professionals develop and enforce policies to ensure compliance. They conduct audits and address any gaps or deficiencies. Their governance skills help organizations avoid legal penalties and a bad reputation.
7. Influencing Incident Response and Management
Incident response is vital to cybersecurity. CISSP professionals usually lead in managing security incidents. They must develop and implement incident response plans. They lead response efforts and analyze incidents afterward. CISSP-certified individuals can use their vast knowledge. They can manage crises, reduce damage, and improve incident response. Their expertise ensures that organizations can respond swiftly and efficiently to security breaches.
How to obtain CISSP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
The impact of CISSP on cybersecurity job roles and responsibilities is profound and far-reaching. The certification boosts skills and opens doors to better jobs. CISSP-certified professionals are instrumental in shaping security strategies, managing risks, and ensuring compliance with regulations. Their skills help build strong security programs and a security-aware culture. As the cybersecurity landscape evolves, the CISSP certification is still valuable. It helps professionals make a big impact in information security.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
As cybersecurity threats grow more sophisticated, the need for experts is urgent. The CISSP certification is a top credential in the field. It is from (ISC)². It indicates a high level of skill and dedication to information security. This blog examines the CISSP's major impact on cybersecurity jobs. It looks at how it affects careers, job roles, and contributions to security.
1. Elevating Professional Expertise
The CISSP certification is known for its tough test of security principles. It covers many topics, including risk management and network security. For professionals, CISSP shows a deep understanding of these areas. It sets them apart from their peers. This advanced knowledge boosts their skills and credibility. It makes them more competitive for senior roles.
2. Advancing Career Opportunities
One major impact of getting a CISSP is more job options. The credential is highly regarded by employers and often required for senior-level positions. CISSP helps professionals advance to roles like Security Manager and CISO. It also helps them become IT Security Consultants. These roles require strategic decision-making, leadership, and oversight of security programs. They reflect the higher responsibility that comes with the certification.
3. Enhancing Strategic Decision-Making
CISSP-certified pros often set the security strategy for an organization. They can design security frameworks, assess risk, and create policies. Their work will align with business goals. This role requires technical knowledge. It also needs an understanding of how security affects business operations. CISSP professionals can bridge the gap between tech and business. They ensure that security strategies support organizational goals.
4. Broadening Responsibilities in Risk Management
Risk management is key to the CISSP certification. It also affects job roles. CISSP-certified professionals are responsible for managing risks to an organization's information systems. They must identify, assess, and reduce those risks. This responsibility includes developing risk assessment methodologies, implementing controls, and continuously monitoring for potential threats. CISSP professionals protect assets and ensure business continuity. They do this by mastering risk management.
5. Leadership and Management Responsibilities
The CISSP certification often leads to increased leadership and management responsibilities. Certified professionals often oversee security teams and projects. They coordinate with other departments to ensure cohesive security practices. They must mentor junior staff, develop training programs, and foster a security-aware culture. This leadership aspect of CISSP positions professionals as key contributors to both the strategic and operational sides of cybersecurity.
6. Driving Compliance and Governance
A key focus for CISSP-certified professionals is compliance with regulations and standards. They often ensure an organization's security practices comply with laws, like GDPR, HIPAA, and ISO/IEC 27001. CISSP professionals develop and enforce policies to ensure compliance. They conduct audits and address any gaps or deficiencies. Their governance skills help organizations avoid legal penalties and a bad reputation.
7. Influencing Incident Response and Management
Incident response is vital to cybersecurity. CISSP professionals usually lead in managing security incidents. They must develop and implement incident response plans. They lead response efforts and analyze incidents afterward. CISSP-certified individuals can use their vast knowledge. They can manage crises, reduce damage, and improve incident response. Their expertise ensures that organizations can respond swiftly and efficiently to security breaches.
How to obtain CISSP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
The impact of CISSP on cybersecurity job roles and responsibilities is profound and far-reaching. The certification boosts skills and opens doors to better jobs. CISSP-certified professionals are instrumental in shaping security strategies, managing risks, and ensuring compliance with regulations. Their skills help build strong security programs and a security-aware culture. As the cybersecurity landscape evolves, the CISSP certification is still valuable. It helps professionals make a big impact in information security.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com




.webp)
.jpg)













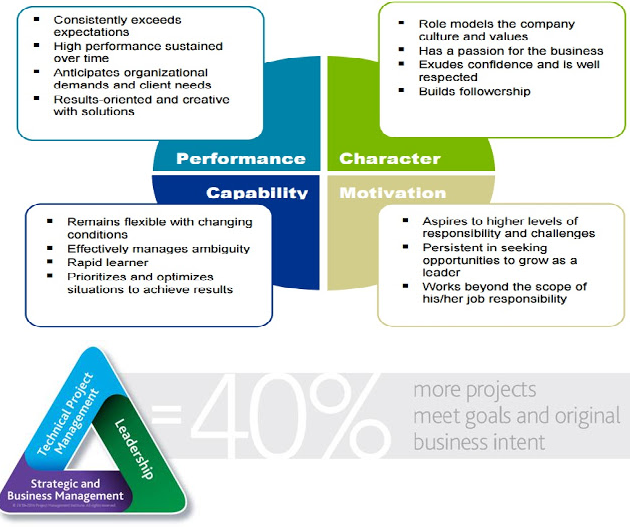

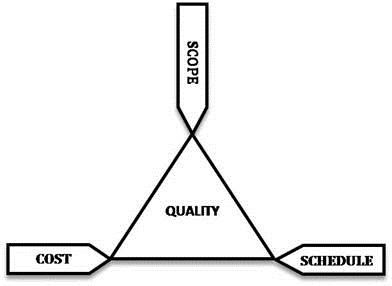

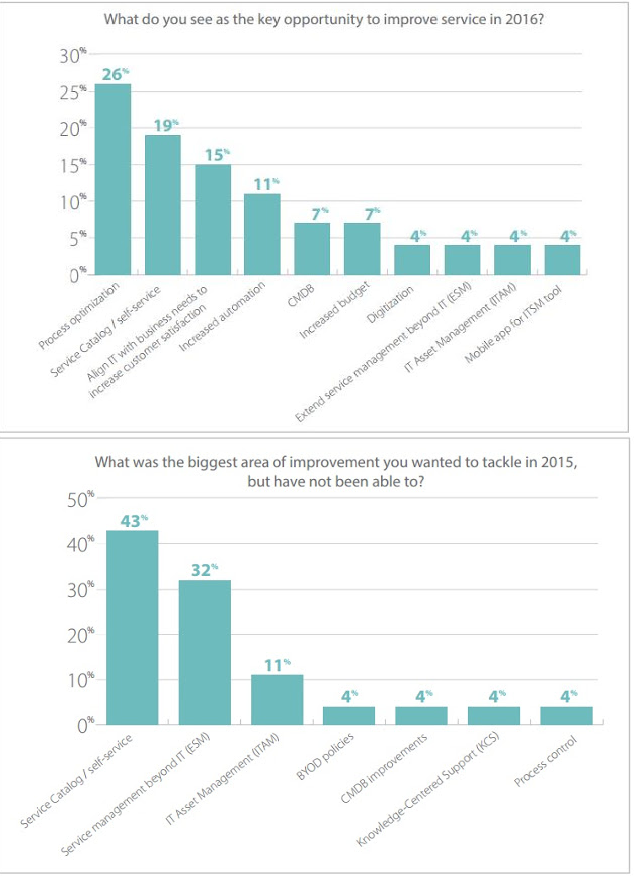


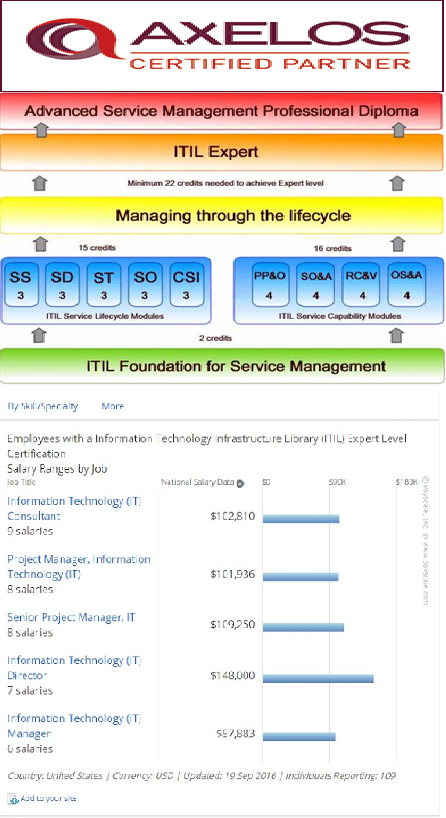




























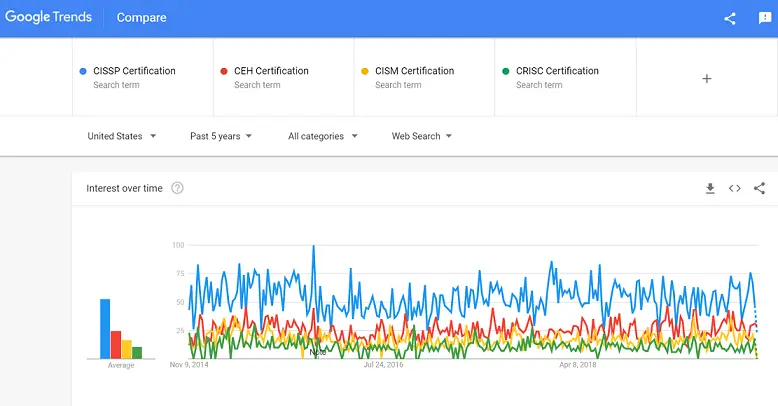
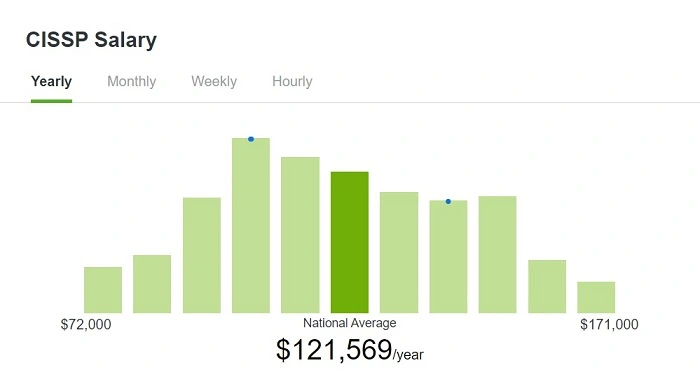
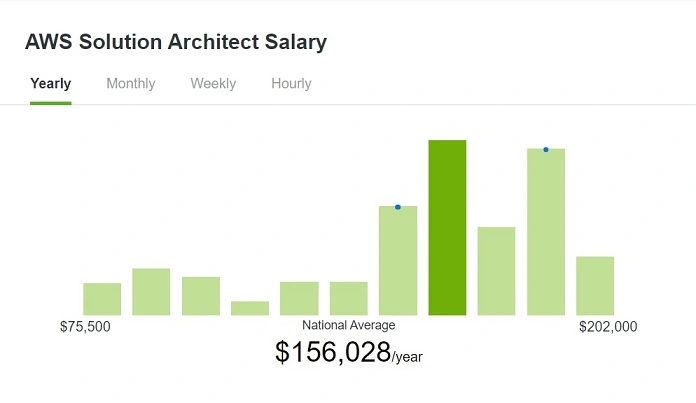
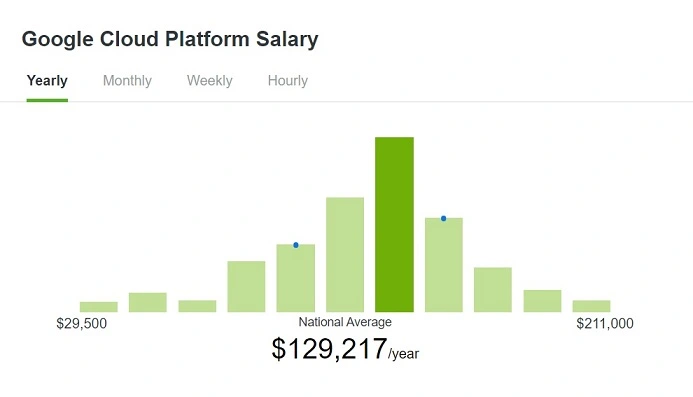


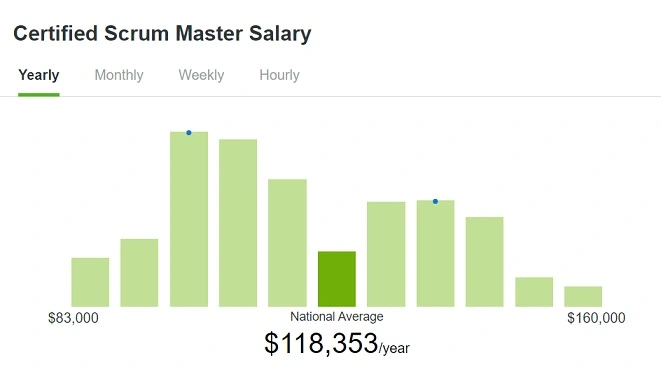




.jpg)



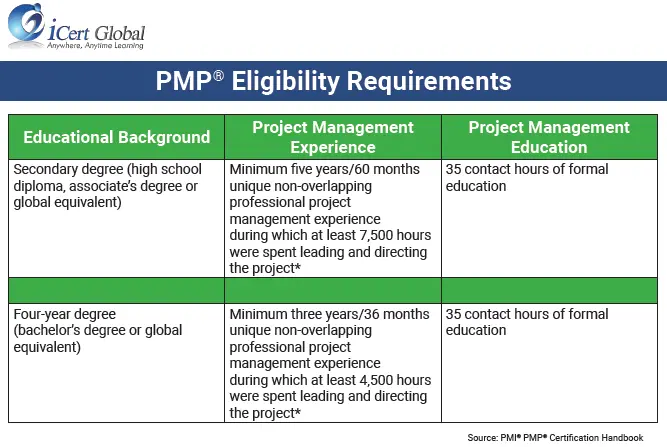
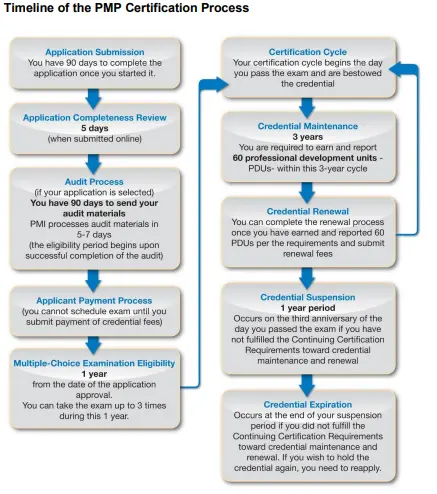
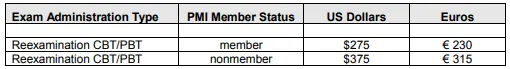
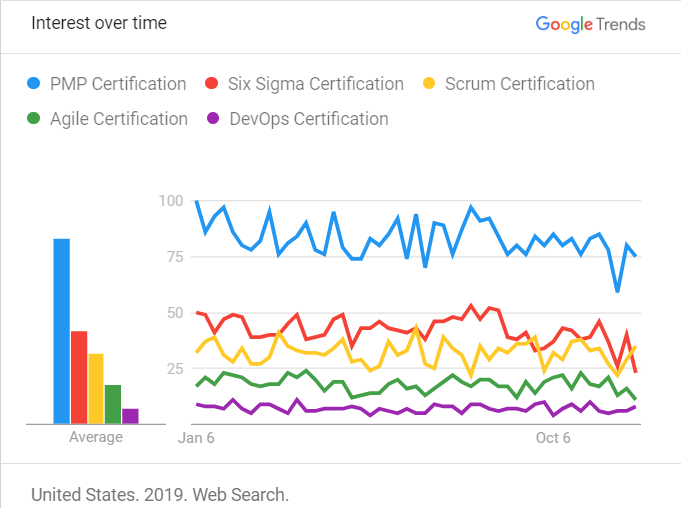




.jpg)
 (2).jpg)


























 Benefits in Today’s World.png)















.png)

 Enhance the Visual Learning Process.png)
.png)
.png)
.png)



.png)

.png)


.png)
.png)







.png)
.png)
.png)




.png)




























 [MConverter.eu].jpg)




.png)


 [MConverter.eu].jpg)
















.jpg)





 [MConverter.eu].jpg)






 [MConverter.eu].jpg)




















.webp)







.webp)




.webp)



























.webp)

















.webp)






!.webp)





























.webp)




















.webp)





.webp)




 (1).webp)















.webp)



















.webp)















.webp)



















.webp)











.webp)
.webp)



.png)