Quick Enquiry Form
Categories
- Agile and Scrum (187)
- BigData (21)
- Business Analysis (87)
- Cirtix Client Administration (51)
- Cisco (57)
- Cloud Technology (71)
- Cyber Security (39)
- Data Science and Business Intelligence (35)
- Developement Courses (46)
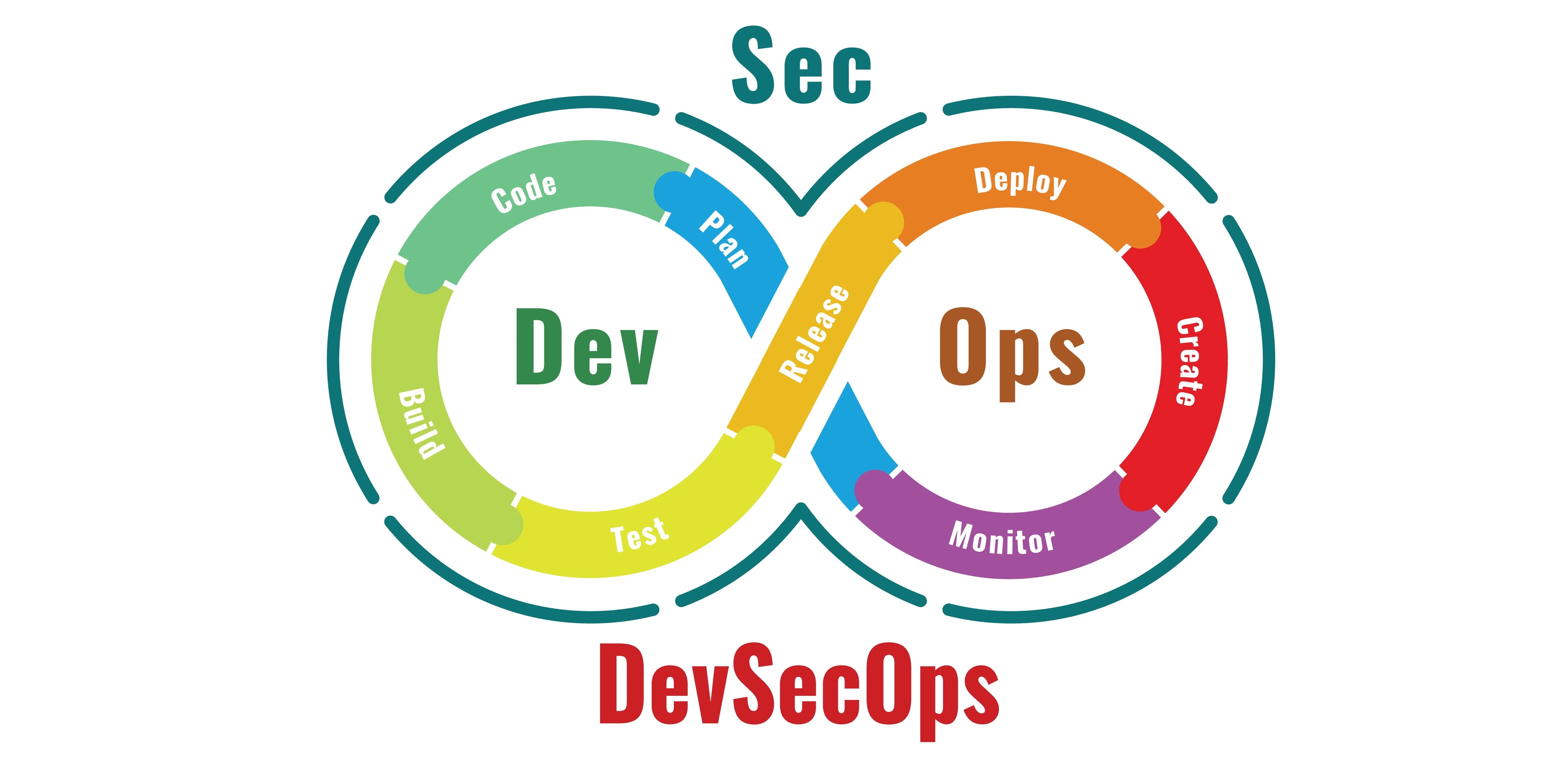
- DevOps (15)
- Digital Marketing (50)
- Emerging Technology (172)
- IT Service Management (70)
- Microsoft (52)
- Other (393)
- Project Management (471)
- Quality Management (127)
- salesforce (62)
Latest posts
Saving Money with Exin Cloud..
Mastering Salesforce Tips for Scalable..
Deep Learning Basics Unlocking Artificial..
Free Resources
Subscribe to Newsletter
Integration of Generative AI with RPA
Have you ever wondered how the integration of Generative AI with RPA can revolutionize the way businesses operate? This article will explore the benefits of combining these advanced technologies. It could streamline workflows, boost innovation, and improve efficiency.
What is Generative AI?
Generative AI, or GANs, is a branch of AI. It focuses on creating new content, like images, text, or audio, from existing data. This tech uses machine learning to find patterns in the input data. It then creates new content that mimics that data.
What is Robotic Process Automation (RPA)?
Robotic Process Automation (RPA) is a technology. It uses software robots, or "bots," to automate repetitive, rule-based tasks in business. RPA systems can mimic human actions and interact with digital systems. They can execute tasks with speed and accuracy. This frees employees to focus on more strategic, creative work.
The Benefits of Integrating Generative AI with RPA
Combining generative AI with RPA boosts automation. It lets bots do repetitive tasks, then adapt and learn from data patterns. This makes them more efficient and effective over time. This synergy enables more complex decisions. Generative AI can analyze unstructured data. It provides insights that inform the automated workflows. This leads to smarter, more responsive systems. Also, the combo streamlines operations, reduces manual work, and speeds up digital change in many industries.
Integrating generative AI with RPA offers big benefits. It enhances automation processes. This combo lets RPA bots use generative AI's advanced data analysis. It helps them adapt to changes and improve real-time decision-making. Organizations can be more efficient and cut costs. They can respond faster to market demands. This drives digital transformation across sectors.
-
Enhanced Data Processing: Merging Generative AI with RPA lets businesses use machine learning. It can analyze vast data quickly and accurately. This combo leads to faster decisions and a better grasp of complex data.
-
Improved Collaboration: Generative AI and RPA can work together. They can collaborate on tasks that need both data processing and automation. This collaboration can improve problem-solving and speed up tasks. It will boost productivity in the organization.
-
Tech Efficiency: Combining Generative AI with RPA can boost efficiency. It can automate repetitive tasks, reduce errors, and optimize processes. This blend of advanced technologies can improve operations and spark innovation in the organization.
Implementation of Generative AI and RPA in Business Processes
Businesses are using Generative AI and RPA to improve workflows. They want to combine both technologies for a seamless and efficient process. This integration requires careful planning and collaboration among data scientists, developers, and business stakeholders.
By integrating Generative AI with RPA, businesses can use advanced tech. It can transform operations, drive innovation, and boost productivity. This mix of AI and robotic automation can streamline workflows. It can improve decision-making and optimize resource use.
Generative AI and RPA are transforming business efficiency. They automate repetitive tasks and boost decision-making. Organizations can boost productivity and innovate workflows. They can do this by using RPA for automation and Generative AI for data analysis. This synergy streamlines operations. It also fosters an agile business. Companies can then adapt quickly to changing market demands.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, combining Generative AI with RPA can greatly benefit businesses. It can make them more efficient and effective. By using advanced technology, organizations can streamline operations and drive innovation. They can achieve excellence, too. Isn't it time for your business to embrace the power of Generative AI and RPA integration? Start exploring the possibilities today!
Contact Us For More Information:
Visit :www.icertglobal.com Email : 
Read More
Have you ever wondered how the integration of Generative AI with RPA can revolutionize the way businesses operate? This article will explore the benefits of combining these advanced technologies. It could streamline workflows, boost innovation, and improve efficiency.
What is Generative AI?
Generative AI, or GANs, is a branch of AI. It focuses on creating new content, like images, text, or audio, from existing data. This tech uses machine learning to find patterns in the input data. It then creates new content that mimics that data.
What is Robotic Process Automation (RPA)?
Robotic Process Automation (RPA) is a technology. It uses software robots, or "bots," to automate repetitive, rule-based tasks in business. RPA systems can mimic human actions and interact with digital systems. They can execute tasks with speed and accuracy. This frees employees to focus on more strategic, creative work.
The Benefits of Integrating Generative AI with RPA
Combining generative AI with RPA boosts automation. It lets bots do repetitive tasks, then adapt and learn from data patterns. This makes them more efficient and effective over time. This synergy enables more complex decisions. Generative AI can analyze unstructured data. It provides insights that inform the automated workflows. This leads to smarter, more responsive systems. Also, the combo streamlines operations, reduces manual work, and speeds up digital change in many industries.
Integrating generative AI with RPA offers big benefits. It enhances automation processes. This combo lets RPA bots use generative AI's advanced data analysis. It helps them adapt to changes and improve real-time decision-making. Organizations can be more efficient and cut costs. They can respond faster to market demands. This drives digital transformation across sectors.
-
Enhanced Data Processing: Merging Generative AI with RPA lets businesses use machine learning. It can analyze vast data quickly and accurately. This combo leads to faster decisions and a better grasp of complex data.
-
Improved Collaboration: Generative AI and RPA can work together. They can collaborate on tasks that need both data processing and automation. This collaboration can improve problem-solving and speed up tasks. It will boost productivity in the organization.
-
Tech Efficiency: Combining Generative AI with RPA can boost efficiency. It can automate repetitive tasks, reduce errors, and optimize processes. This blend of advanced technologies can improve operations and spark innovation in the organization.
Implementation of Generative AI and RPA in Business Processes
Businesses are using Generative AI and RPA to improve workflows. They want to combine both technologies for a seamless and efficient process. This integration requires careful planning and collaboration among data scientists, developers, and business stakeholders.
By integrating Generative AI with RPA, businesses can use advanced tech. It can transform operations, drive innovation, and boost productivity. This mix of AI and robotic automation can streamline workflows. It can improve decision-making and optimize resource use.
Generative AI and RPA are transforming business efficiency. They automate repetitive tasks and boost decision-making. Organizations can boost productivity and innovate workflows. They can do this by using RPA for automation and Generative AI for data analysis. This synergy streamlines operations. It also fosters an agile business. Companies can then adapt quickly to changing market demands.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, combining Generative AI with RPA can greatly benefit businesses. It can make them more efficient and effective. By using advanced technology, organizations can streamline operations and drive innovation. They can achieve excellence, too. Isn't it time for your business to embrace the power of Generative AI and RPA integration? Start exploring the possibilities today!
Contact Us For More Information:
Visit :www.icertglobal.com Email : 
CMMI Role in Minimizing Technical Debt in Software Projects
In software development, efficiency, quality, and speed are crucial. Technical debt is extra work. It arises when quick, easy software is chosen over better, but harder, options. It can slow down projects and reduce productivity. CMMI (Capability Maturity Model Integration) helps minimize technical debt. It is key to successful software projects.
What is CMMI? How Does it Work?
CMMI is a set of best practices and standards. They guide organizations in improving their development processes, project management, and quality. It provides guidelines and controls to manage technical debt in software development. CMMI lets organizations assess and adopt the best practices. This optimizes their software engineering, reduces risk, and ensures compliance with industry standards.
How Does CMMI Help Manage Technical Debt?
CMMI helps set maturity levels. They show an organization's ability to deliver quality software consistently. CMMI aims for high maturity levels to enable efficient software development. It does this by promoting improvement, governance, and performance measurement. This improves project planning, execution, and monitoring. It reduces technical debt and boosts software quality.
CMMI helps manage technical debt. It shows how to find, assess, and fix inefficiencies in software development and system management. CMMI promotes best practices in project planning and risk management. It also encourages continuous improvement. This minimizes and controls technical debt over time. This results in more sustainable software. It cuts the long-term costs and challenges of technical debt.
CMMI Implementation and Impact on Technical Debt
When organizations adopt CMMI, they prioritize software maintenance, optimizing processes, and managing risks. This leads to cost reduction, improved time-to-market, and enhanced product quality. Integrating CMMI into their processes can help organizations. It can streamline project planning, execution, and monitoring. This will reduce technical debt and ensure successful software delivery.
CMMI can cut technical debt. It promotes better processes and ongoing improvement in software development. CMMI helps teams find and fix issues early. It does this by stressing quality assurance, risk management, and clear workflows. This prevents technical debt from building up. So, organizations can sustain software, cut maintenance costs, and boost efficiency.
CMMI Best Practices for Technical Debt Mitigation
To reduce technical debt, follow these key CMMI best practices: document software, adhere to standards, test rigorously, and ensure strong security. By using these practices in their development cycle, organizations can improve software quality. This will reduce defects and boost product reliability.
Reducing technical debt is vital for long-term software success. CMMI offers best practices to tackle it proactively. CMMI's structured process improvement can help organizations. It can identify technical debt early, prioritize fixes, and allocate resources. This keeps quality high. It cuts costly rework and improves the software lifecycle.
CMMI and Continuous Improvement
CMMI is all about continuous improvement. It urges organizations to assess and enhance their processes. Regular CMMI assessments help organizations find areas to improve. They can then make changes and track progress over time. By optimizing and maturing, firms can stay ahead in the fast software industry.
CMMI (Capability Maturity Model Integration) is a framework. It helps organizations improve by setting clear, structured processes. CMMI helps businesses find inefficiencies by focusing on measurable outcomes. It guides them to make systematic changes for long-term success. This model promotes a culture of constant evaluation and refinement. It keeps organizations competitive and agile in changing markets.
How to obtain CMMI certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
By using CMMI's complete approach to software development, organizations can tackle technical debt. This lets them deliver high-quality software that meets customers' and industry's standards. CMMI is a vital tool for firms seeking to excel in today's software market.
In conclusion, CMMI is vital for reducing technical debt in software projects. It provides a framework for development, improvement, and quality management. CMMI guidelines and best practices can help organizations. They can optimize processes, reduce risk, and ensure efficient software delivery. CMMI boosts productivity, efficiency, and software performance for organizations. It leads to successful projects and happy stakeholders.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In software development, efficiency, quality, and speed are crucial. Technical debt is extra work. It arises when quick, easy software is chosen over better, but harder, options. It can slow down projects and reduce productivity. CMMI (Capability Maturity Model Integration) helps minimize technical debt. It is key to successful software projects.
What is CMMI? How Does it Work?
CMMI is a set of best practices and standards. They guide organizations in improving their development processes, project management, and quality. It provides guidelines and controls to manage technical debt in software development. CMMI lets organizations assess and adopt the best practices. This optimizes their software engineering, reduces risk, and ensures compliance with industry standards.
How Does CMMI Help Manage Technical Debt?
CMMI helps set maturity levels. They show an organization's ability to deliver quality software consistently. CMMI aims for high maturity levels to enable efficient software development. It does this by promoting improvement, governance, and performance measurement. This improves project planning, execution, and monitoring. It reduces technical debt and boosts software quality.
CMMI helps manage technical debt. It shows how to find, assess, and fix inefficiencies in software development and system management. CMMI promotes best practices in project planning and risk management. It also encourages continuous improvement. This minimizes and controls technical debt over time. This results in more sustainable software. It cuts the long-term costs and challenges of technical debt.
CMMI Implementation and Impact on Technical Debt
When organizations adopt CMMI, they prioritize software maintenance, optimizing processes, and managing risks. This leads to cost reduction, improved time-to-market, and enhanced product quality. Integrating CMMI into their processes can help organizations. It can streamline project planning, execution, and monitoring. This will reduce technical debt and ensure successful software delivery.
CMMI can cut technical debt. It promotes better processes and ongoing improvement in software development. CMMI helps teams find and fix issues early. It does this by stressing quality assurance, risk management, and clear workflows. This prevents technical debt from building up. So, organizations can sustain software, cut maintenance costs, and boost efficiency.
CMMI Best Practices for Technical Debt Mitigation
To reduce technical debt, follow these key CMMI best practices: document software, adhere to standards, test rigorously, and ensure strong security. By using these practices in their development cycle, organizations can improve software quality. This will reduce defects and boost product reliability.
Reducing technical debt is vital for long-term software success. CMMI offers best practices to tackle it proactively. CMMI's structured process improvement can help organizations. It can identify technical debt early, prioritize fixes, and allocate resources. This keeps quality high. It cuts costly rework and improves the software lifecycle.
CMMI and Continuous Improvement
CMMI is all about continuous improvement. It urges organizations to assess and enhance their processes. Regular CMMI assessments help organizations find areas to improve. They can then make changes and track progress over time. By optimizing and maturing, firms can stay ahead in the fast software industry.
CMMI (Capability Maturity Model Integration) is a framework. It helps organizations improve by setting clear, structured processes. CMMI helps businesses find inefficiencies by focusing on measurable outcomes. It guides them to make systematic changes for long-term success. This model promotes a culture of constant evaluation and refinement. It keeps organizations competitive and agile in changing markets.
How to obtain CMMI certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
By using CMMI's complete approach to software development, organizations can tackle technical debt. This lets them deliver high-quality software that meets customers' and industry's standards. CMMI is a vital tool for firms seeking to excel in today's software market.
In conclusion, CMMI is vital for reducing technical debt in software projects. It provides a framework for development, improvement, and quality management. CMMI guidelines and best practices can help organizations. They can optimize processes, reduce risk, and ensure efficient software delivery. CMMI boosts productivity, efficiency, and software performance for organizations. It leads to successful projects and happy stakeholders.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Google Cloud Architect vs AWS Solutions Architect
Are you considering a career in cloud architecture? Are you unsure whether to pursue a role as a Google Cloud Architect or an AWS Solutions Architect? This article will explore the key differences between these two roles. It will help you decide based on your career goals.
Cloud Architect Roles
Both Google Cloud Architects and AWS Solutions Architects must create cloud solutions for their platforms. Users disliked the last rewrite. They work closely with clients to understand their needs. Then, they develop scalable, secure cloud infrastructures.
A Cloud Architect is to design and build cloud infrastructures for organizations. They must be scalable, secure, and efficient. They work closely with stakeholders to identify business needs. Then, they translate those into technical solutions. This ensures optimal use of cloud resources. They also manage cloud service integration, migrations, and best practices for cloud security and cost.
Cloud Architect Responsibilities
A Google Cloud Architect and an AWS Solutions Architect have similar duties. They involve designing cloud solutions, ensuring security and scalability, and optimizing performance. They must guide and support development teams. They must troubleshoot issues and ensure compliance with industry standards.
A Cloud Architect is to design, implement, and manage an organization's cloud infrastructure. They make sure cloud solutions are scalable, secure, and fast. They also align them with business goals. They also collaborate with development teams. They oversee cloud migration and monitor system performance to maintain efficiency.
Cloud Architect Certification
To excel in cloud architecture, you must get relevant certifications. Google Cloud has the Professional Cloud Architect cert. AWS has the AWS Certified Solutions Architect cert. These certifications prove you are an expert in designing and building cloud solutions on their platforms.
A Cloud Architect Certification proves your skill in designing and managing strong cloud solutions. This certification gives professionals the skills to use cloud tech. It ensures they can design scalable, secure, high-performance systems. This certification is a smart investment in your career. It will boost your job prospects and deepen your tech skills.
Cloud Architect Job Descriptions
Google Cloud Architect and AWS Solutions Architect job descriptions may differ slightly. But, they generally require a strong cloud computing background. They also require excellent problem-solving skills and teamwork with cross-functional teams.
As a Cloud Architect, you will design and implement cloud solutions. They must be scalable, secure, and robust. They should meet the needs of our organization and clients. You will work with cross-functional teams. Your goal is to integrate cloud services and optimize existing infrastructures. Ensure they align with industry best practices and compliance requirements. The ideal candidate will have strong cloud platform skills and great problem-solving skills. They must also explain complex ideas to technical and non-technical stakeholders.
Cloud Architect Skills
Both Google Cloud Architects and AWS Solutions Architects need key skills. They must know cloud computing, networking, and security protocols. They must also design high-performance, cost-effective cloud solutions.
Cloud Architects must understand cloud computing and its service models: IaaS, PaaS, and SaaS. You must know cloud platforms like Google Cloud, AWS, or Azure. You should also know about networking, security, and compliance. This is key for designing scalable and secure solutions. Also, strong communication and teamwork skills are vital. Cloud Architects often work with cross-functional teams. They implement cloud strategies that align with business goals.
The salary for Google Cloud Architects and AWS Solutions Architects can vary based on factors such as experience, location, and company size. On average, Google Cloud Architects earn slightly more than AWS Solutions Architects.
Cloud Architect Career Path
Both Google Cloud Architects and AWS Solutions Architects have promising career paths with ample opportunities for growth and advancement. As cloud computing evolves, the demand for skilled cloud architects will rise.
Cloud Architect Interview Questions
In interviews for a Google Cloud Architect or AWS Solutions Architect role, you may get technical or scenario-based questions. They will test your knowledge and problem-solving skills. You must prepare well and show your expertise in cloud architecture.
How to obtain Google Cloud Architect certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, it doesn't matter if you become a Google Cloud Architect or an AWS Solutions Architect. The key is to update your skills. Stay updated on cloud computing trends. Adapt to the industry's changing needs. As a trusted cloud architect, you can build a successful career in this rewarding field.
Contact Us For More Information:
Visit :www.icertglobal.com Email : 
Read More
Are you considering a career in cloud architecture? Are you unsure whether to pursue a role as a Google Cloud Architect or an AWS Solutions Architect? This article will explore the key differences between these two roles. It will help you decide based on your career goals.
Cloud Architect Roles
Both Google Cloud Architects and AWS Solutions Architects must create cloud solutions for their platforms. Users disliked the last rewrite. They work closely with clients to understand their needs. Then, they develop scalable, secure cloud infrastructures.
A Cloud Architect is to design and build cloud infrastructures for organizations. They must be scalable, secure, and efficient. They work closely with stakeholders to identify business needs. Then, they translate those into technical solutions. This ensures optimal use of cloud resources. They also manage cloud service integration, migrations, and best practices for cloud security and cost.
Cloud Architect Responsibilities
A Google Cloud Architect and an AWS Solutions Architect have similar duties. They involve designing cloud solutions, ensuring security and scalability, and optimizing performance. They must guide and support development teams. They must troubleshoot issues and ensure compliance with industry standards.
A Cloud Architect is to design, implement, and manage an organization's cloud infrastructure. They make sure cloud solutions are scalable, secure, and fast. They also align them with business goals. They also collaborate with development teams. They oversee cloud migration and monitor system performance to maintain efficiency.
Cloud Architect Certification
To excel in cloud architecture, you must get relevant certifications. Google Cloud has the Professional Cloud Architect cert. AWS has the AWS Certified Solutions Architect cert. These certifications prove you are an expert in designing and building cloud solutions on their platforms.
A Cloud Architect Certification proves your skill in designing and managing strong cloud solutions. This certification gives professionals the skills to use cloud tech. It ensures they can design scalable, secure, high-performance systems. This certification is a smart investment in your career. It will boost your job prospects and deepen your tech skills.
Cloud Architect Job Descriptions
Google Cloud Architect and AWS Solutions Architect job descriptions may differ slightly. But, they generally require a strong cloud computing background. They also require excellent problem-solving skills and teamwork with cross-functional teams.
As a Cloud Architect, you will design and implement cloud solutions. They must be scalable, secure, and robust. They should meet the needs of our organization and clients. You will work with cross-functional teams. Your goal is to integrate cloud services and optimize existing infrastructures. Ensure they align with industry best practices and compliance requirements. The ideal candidate will have strong cloud platform skills and great problem-solving skills. They must also explain complex ideas to technical and non-technical stakeholders.
Cloud Architect Skills
Both Google Cloud Architects and AWS Solutions Architects need key skills. They must know cloud computing, networking, and security protocols. They must also design high-performance, cost-effective cloud solutions.
Cloud Architects must understand cloud computing and its service models: IaaS, PaaS, and SaaS. You must know cloud platforms like Google Cloud, AWS, or Azure. You should also know about networking, security, and compliance. This is key for designing scalable and secure solutions. Also, strong communication and teamwork skills are vital. Cloud Architects often work with cross-functional teams. They implement cloud strategies that align with business goals.
The salary for Google Cloud Architects and AWS Solutions Architects can vary based on factors such as experience, location, and company size. On average, Google Cloud Architects earn slightly more than AWS Solutions Architects.
Cloud Architect Career Path
Both Google Cloud Architects and AWS Solutions Architects have promising career paths with ample opportunities for growth and advancement. As cloud computing evolves, the demand for skilled cloud architects will rise.
Cloud Architect Interview Questions
In interviews for a Google Cloud Architect or AWS Solutions Architect role, you may get technical or scenario-based questions. They will test your knowledge and problem-solving skills. You must prepare well and show your expertise in cloud architecture.
How to obtain Google Cloud Architect certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, it doesn't matter if you become a Google Cloud Architect or an AWS Solutions Architect. The key is to update your skills. Stay updated on cloud computing trends. Adapt to the industry's changing needs. As a trusted cloud architect, you can build a successful career in this rewarding field.
Contact Us For More Information:
Visit :www.icertglobal.com Email : 
Exploring the Future of Data Processing
In today's digital age, data is a key asset for businesses. Collecting, analyzing, and gaining insights from vast data is vital. It helps make informed business decisions and gain a competitive edge. Big data, cloud computing, and real-time processing have risen. Traditional methods can’t handle the daily data's volume and speed. This is where Serverless Hadoop comes in. It offers a bright solution for the future of data processing.
Understanding Serverless Computing
Serverless computing, or Function as a Service (FaaS), is a cloud model. It lets developers run code without managing servers. Developers can now focus on writing and deploying code. Instead of managing servers, they use functions that run in response to events. This serverless approach offers various benefits, including scalability, cost-efficiency, and reduced operational burden.
Serverless computing is a cloud model. It lets developers run apps without managing the infrastructure. Users can deploy code in response to events. The cloud provider will handle the scaling and resource allocation. There is no need to provision or maintain servers. This approach boosts efficiency and cuts costs. It lets developers focus on coding, not server management.
The Power of Hadoop in Data Processing
Hadoop is an open-source framework. It enables distributed processing of large data sets across computer clusters. It has two main parts. The Hadoop Distributed File System (HDFS) stores data. The MapReduce programming model processes it. Hadoop is popular for data analytics and machine learning. It's also used for processing large data sets. However, traditional Hadoop deployments require managing infrastructure and configuring clusters. It can be complex and take time to monitor performance.
Hadoop has changed data processing. It lets firms store and analyze huge datasets on distributed systems. Its strong design allows for easy scalability. So, it is ideal for today's growing, diverse big data. Hadoop helps businesses find insights, make better decisions, and innovate. It can benefit many industries.
The Emergence of Serverless Hadoop
Serverless Hadoop combines Hadoop's power with serverless computing's benefits. It provides a more efficient, cost-effective way to process data. Organizations can run Hadoop workloads on serverless platforms like AWS, GCP, or Azure. They won't need to manage servers. It lets you scale on demand, cut costs, and easily integrate with other serverless services.
Serverless Hadoop is a big change in big data processing. It lets organizations run Hadoop apps without managing servers. This approach boosts scalability. It lets users handle varying workloads. It also optimizes resource use and cuts costs. With serverless architecture, businesses can focus on data analytics. This speeds up their time to value and boosts innovation in big data projects.
Benefits of Serverless Hadoop
-
Scalability: Serverless Hadoop auto-scales resources based on workload. It ensures peak performance and cost-efficiency.
-
Cost Optimization: With serverless computing, you pay only for the compute resources used. This is cheaper than traditional Hadoop deployments.
-
Serverless Hadoop supports real-time data processing. It helps organizations gain insights and make near real-time decisions.
-
Event-Driven Architecture: It uses event triggers to automate data tasks. Organizations can respond to events in real-time.
Use Cases of Serverless Hadoop
-
Data Engineering: Use serverless Hadoop for data engineering tasks. These include ETL (Extract, Transform, Load) and data orchestration and transformation.
-
Data Analytics: Organizations can use serverless Hadoop for data analytics and machine learning. They can also do real-time analytics.
-
Edge Computing: Serverless Hadoop can run at the edge. It will process data closer to its source. This reduces latency and boosts performance.
How to obtain Big Data and Hadoop certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Serverless Hadoop holds great promise for data processing. It combines the power of Hadoop with the benefits of serverless computing. Its scalability, cost optimization, and real-time processing can help organizations. They can now analyze and gain insights from data at scale. As the digital world evolves, Serverless Hadoop will shape data processing.
Contact Us For More Information:
Visit :www.icertglobal.com Email : 
Read More
In today's digital age, data is a key asset for businesses. Collecting, analyzing, and gaining insights from vast data is vital. It helps make informed business decisions and gain a competitive edge. Big data, cloud computing, and real-time processing have risen. Traditional methods can’t handle the daily data's volume and speed. This is where Serverless Hadoop comes in. It offers a bright solution for the future of data processing.
Understanding Serverless Computing
Serverless computing, or Function as a Service (FaaS), is a cloud model. It lets developers run code without managing servers. Developers can now focus on writing and deploying code. Instead of managing servers, they use functions that run in response to events. This serverless approach offers various benefits, including scalability, cost-efficiency, and reduced operational burden.
Serverless computing is a cloud model. It lets developers run apps without managing the infrastructure. Users can deploy code in response to events. The cloud provider will handle the scaling and resource allocation. There is no need to provision or maintain servers. This approach boosts efficiency and cuts costs. It lets developers focus on coding, not server management.
The Power of Hadoop in Data Processing
Hadoop is an open-source framework. It enables distributed processing of large data sets across computer clusters. It has two main parts. The Hadoop Distributed File System (HDFS) stores data. The MapReduce programming model processes it. Hadoop is popular for data analytics and machine learning. It's also used for processing large data sets. However, traditional Hadoop deployments require managing infrastructure and configuring clusters. It can be complex and take time to monitor performance.
Hadoop has changed data processing. It lets firms store and analyze huge datasets on distributed systems. Its strong design allows for easy scalability. So, it is ideal for today's growing, diverse big data. Hadoop helps businesses find insights, make better decisions, and innovate. It can benefit many industries.
The Emergence of Serverless Hadoop
Serverless Hadoop combines Hadoop's power with serverless computing's benefits. It provides a more efficient, cost-effective way to process data. Organizations can run Hadoop workloads on serverless platforms like AWS, GCP, or Azure. They won't need to manage servers. It lets you scale on demand, cut costs, and easily integrate with other serverless services.
Serverless Hadoop is a big change in big data processing. It lets organizations run Hadoop apps without managing servers. This approach boosts scalability. It lets users handle varying workloads. It also optimizes resource use and cuts costs. With serverless architecture, businesses can focus on data analytics. This speeds up their time to value and boosts innovation in big data projects.
Benefits of Serverless Hadoop
-
Scalability: Serverless Hadoop auto-scales resources based on workload. It ensures peak performance and cost-efficiency.
-
Cost Optimization: With serverless computing, you pay only for the compute resources used. This is cheaper than traditional Hadoop deployments.
-
Serverless Hadoop supports real-time data processing. It helps organizations gain insights and make near real-time decisions.
-
Event-Driven Architecture: It uses event triggers to automate data tasks. Organizations can respond to events in real-time.
Use Cases of Serverless Hadoop
-
Data Engineering: Use serverless Hadoop for data engineering tasks. These include ETL (Extract, Transform, Load) and data orchestration and transformation.
-
Data Analytics: Organizations can use serverless Hadoop for data analytics and machine learning. They can also do real-time analytics.
-
Edge Computing: Serverless Hadoop can run at the edge. It will process data closer to its source. This reduces latency and boosts performance.
How to obtain Big Data and Hadoop certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Serverless Hadoop holds great promise for data processing. It combines the power of Hadoop with the benefits of serverless computing. Its scalability, cost optimization, and real-time processing can help organizations. They can now analyze and gain insights from data at scale. As the digital world evolves, Serverless Hadoop will shape data processing.
Contact Us For More Information:
Visit :www.icertglobal.com Email : 
Immersive Marketing in the Metaverse
In today's digital age, marketing strategies must evolve. They must keep up with changing technology and consumer behavior. One of the latest trends gaining traction in the marketing world is immersive marketing in the metaverse. This advanced method uses virtual reality (VR), augmented reality (AR), and other immersive tech. It creates unique, engaging experiences for consumers. This article will explore immersive marketing in the metaverse. It will cover its impact on future advertising. We will also discuss how businesses can use it to engage their target audiences in new ways.
What is the Metaverse?
The metaverse is a virtual space. It is created by digital technologies. Users can interact with each other and digital objects in real-time. It is a parallel digital universe. Users can immerse in a variety of experiences. They can socialize with friends, attend virtual events, and shop at virtual stores. The metaverse is a creative, exploratory space. It is perfect for brands to connect with consumers in a more interactive and personal way.
The Rise of Immersive Experiences
Immersive experiences are now very popular. Advances in technology have made virtual environments more realistic and interactive. Brands can use VR and AR to create immersive experiences. These will transport consumers to virtual worlds. There, they can engage with products and services in a new way. Immersive marketing in the metaverse offers endless opportunities for brands. It includes VR shopping, AR ads, and 3D product tours. These methods can captivate audiences and help brands stand out in a crowded digital space.
Immersive experiences in digital marketing are on the rise. They are reshaping how brands engage with consumers. They allow for deeper emotional connections and better storytelling. VR and AR let businesses create interactive environments. Users can explore products and services in a more engaging way. As consumers seek unique experiences, brands must embrace immersive marketing. It can capture attention and build loyalty in a competitive landscape.
Benefits of Immersive Marketing in the Metaverse
There are many benefits to using immersive marketing in your overall marketing plan. Immersive marketing in the metaverse can boost brand experiences. It can also increase customer engagement and drive sales. It can help businesses achieve their marketing goals more effectively. Some of the key benefits include:
-
Increased Brand Awareness: Brands can increase visibility by creating unique, interactive experiences in the metaverse. This will reach a wider audience.
-
Immersive experiences boost customer engagement. They capture consumers' attention and keep them interested in your brand longer.
-
Improved Brand Loyalty: Brands can build loyalty by providing immersive, fun, and informative experiences. These can strengthen customer relationships.
-
Higher Conversion Rates: Immersive marketing drives higher conversion rates. Consumers are more likely to buy after experiencing a product or service in a virtual environment.
How Businesses Can Leverage Immersive Marketing
To use immersive marketing in the metaverse, businesses must think creatively. They need a strategic plan to add immersive experiences to their marketing. Here are some tips for businesses looking to get started with immersive marketing:
-
Know Your Audience: Before using immersive marketing, understand your target audience. Find out what experiences will resonate with them.
-
Partner with Experts: Consider working with agencies or experts in immersive tech to help bring your ideas to life.
-
Experiment with Different Formats: Try immersive formats like VR ads or AR stories. See what resonates best with your audience.
-
Measure and Analyze Results: Use analytics tools to assess your immersive marketing campaigns. Adjust them to optimize performance.
The Future of Advertising is Immersive
As technology advances and consumers change, immersive marketing in the metaverse will be key. It will help brands stand out in a competitive market. Engaging virtual experiences can immerse consumers in a brand's story. This can help businesses connect with their audience and build brand loyalty. As we enter the next generation of marketing, the possibilities for immersive ads are limitless.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, immersive marketing in the metaverse is an exciting, new way to advertise. It offers brands endless opportunities to engage consumers in immersive ways. Using VR, AR, and other immersive tech, businesses can create memorable brand experiences. This will drive customer engagement and keep them ahead in the fast-changing digital world. To embrace the future of advertising, we must embrace the metaverse. It offers limitless possibilities for creativity and connection through immersive marketing.
Contact Us For More Information:
Visit :www.icertglobal.com Email : 
Read More
In today's digital age, marketing strategies must evolve. They must keep up with changing technology and consumer behavior. One of the latest trends gaining traction in the marketing world is immersive marketing in the metaverse. This advanced method uses virtual reality (VR), augmented reality (AR), and other immersive tech. It creates unique, engaging experiences for consumers. This article will explore immersive marketing in the metaverse. It will cover its impact on future advertising. We will also discuss how businesses can use it to engage their target audiences in new ways.
What is the Metaverse?
The metaverse is a virtual space. It is created by digital technologies. Users can interact with each other and digital objects in real-time. It is a parallel digital universe. Users can immerse in a variety of experiences. They can socialize with friends, attend virtual events, and shop at virtual stores. The metaverse is a creative, exploratory space. It is perfect for brands to connect with consumers in a more interactive and personal way.
The Rise of Immersive Experiences
Immersive experiences are now very popular. Advances in technology have made virtual environments more realistic and interactive. Brands can use VR and AR to create immersive experiences. These will transport consumers to virtual worlds. There, they can engage with products and services in a new way. Immersive marketing in the metaverse offers endless opportunities for brands. It includes VR shopping, AR ads, and 3D product tours. These methods can captivate audiences and help brands stand out in a crowded digital space.
Immersive experiences in digital marketing are on the rise. They are reshaping how brands engage with consumers. They allow for deeper emotional connections and better storytelling. VR and AR let businesses create interactive environments. Users can explore products and services in a more engaging way. As consumers seek unique experiences, brands must embrace immersive marketing. It can capture attention and build loyalty in a competitive landscape.
Benefits of Immersive Marketing in the Metaverse
There are many benefits to using immersive marketing in your overall marketing plan. Immersive marketing in the metaverse can boost brand experiences. It can also increase customer engagement and drive sales. It can help businesses achieve their marketing goals more effectively. Some of the key benefits include:
-
Increased Brand Awareness: Brands can increase visibility by creating unique, interactive experiences in the metaverse. This will reach a wider audience.
-
Immersive experiences boost customer engagement. They capture consumers' attention and keep them interested in your brand longer.
-
Improved Brand Loyalty: Brands can build loyalty by providing immersive, fun, and informative experiences. These can strengthen customer relationships.
-
Higher Conversion Rates: Immersive marketing drives higher conversion rates. Consumers are more likely to buy after experiencing a product or service in a virtual environment.
How Businesses Can Leverage Immersive Marketing
To use immersive marketing in the metaverse, businesses must think creatively. They need a strategic plan to add immersive experiences to their marketing. Here are some tips for businesses looking to get started with immersive marketing:
-
Know Your Audience: Before using immersive marketing, understand your target audience. Find out what experiences will resonate with them.
-
Partner with Experts: Consider working with agencies or experts in immersive tech to help bring your ideas to life.
-
Experiment with Different Formats: Try immersive formats like VR ads or AR stories. See what resonates best with your audience.
-
Measure and Analyze Results: Use analytics tools to assess your immersive marketing campaigns. Adjust them to optimize performance.
The Future of Advertising is Immersive
As technology advances and consumers change, immersive marketing in the metaverse will be key. It will help brands stand out in a competitive market. Engaging virtual experiences can immerse consumers in a brand's story. This can help businesses connect with their audience and build brand loyalty. As we enter the next generation of marketing, the possibilities for immersive ads are limitless.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, immersive marketing in the metaverse is an exciting, new way to advertise. It offers brands endless opportunities to engage consumers in immersive ways. Using VR, AR, and other immersive tech, businesses can create memorable brand experiences. This will drive customer engagement and keep them ahead in the fast-changing digital world. To embrace the future of advertising, we must embrace the metaverse. It offers limitless possibilities for creativity and connection through immersive marketing.
Contact Us For More Information:
Visit :www.icertglobal.com Email : 
Program Risk Management PgMP Tools and Techniques
In today's fast-paced business world, program managers must manage risks. This is vital to their programs' success. Program Risk Management is key to program management. PgMP tools and techniques are vital. They help us manage risks throughout the program lifecycle.
Understanding Program Risk Management
Program Risk Management is the process of managing risks. These risks may affect a program's success. It uses a systematic approach to assess and manage risks. This ensures the program meets its goals within limits on time, cost, quality, and scope.
Program risk management is vital. It identifies, analyzes, and mitigates risks that could harm a program's success. Program managers manage risks. This ensures projects finish on time, within budget, and meet their goals. Effective risk management protects against negative outcomes. It also enables better decisions and resource use throughout the program's lifecycle.
Importance of Program Risk Management
Effective Program Risk Management is key. It minimizes uncertainties' impact on outcomes and boosts the chances of success. By spotting risks early, program managers can create plans to reduce them. This will help to limit their impact on the program.
Program risk management is key. It identifies, assesses, and mitigates risks that could harm large-scale programs. PgMP-certified pros can meet program goals on time and within budget. They do this by addressing risks. This minimizes disruptions. Effective risk management protects resources. It also builds trust in stakeholders and improves outcomes.
Key Components of Program Risk Management
-
Risk Assessment: This means finding and evaluating risks. They may affect the program's goals.
-
Risk Analysis: This means assessing known risks to the program. It involves their likelihood and impact.
-
Risk Identification: This is about finding potential risks in the program's lifecycle.
-
Risk Mitigation: This means making plans to lessen known risks.
-
Risk Monitoring: This is tracking known risks throughout the program. It ensures they are managed well.
-
Risk Planning: This involves developing a plan to address and manage risks proactively.
-
Risk Response: This involves implementing planned responses to address identified risks.
-
Risk Control: This means monitoring and controlling risks. They must not affect the program's goals.
-
Risk Evaluation: This means assessing risk management strategies. Adjust them as needed.
Program Risk Management Process
The Program Risk Management process involves the following key steps:
-
Risk Management Framework: Establishing a framework for managing risks within the program.
-
Risk Management Plan: Create a plan to identify, analyze, and respond to risks.
-
Risk Management Strategy: Defining the overall approach to managing risks within the program.
-
Risk Tolerance: Determining the level of risk that the program is willing to accept.
-
Risk Culture: Build a culture that values risk management in the program.
-
Risk Governance: Establishing governance structures to oversee and manage risks effectively.
-
Risk Appetite: Defining the program's appetite for risk-taking.
-
Risk Exposure: Identifying the level of exposure to risks within the program. Program Risk Management Tools & Techniques Program managers can use some tools and techniques to manage risks. Some of the most common tools and techniques include:
-
Risk Register: A document that tracks all identified program risks.
-
Risk Matrix: A visual representation of risks based on their likelihood and impact.
-
Risk Communication: The process of sharing risk information with stakeholders.
-
Risk Reporting: Providing regular updates on the status of risks within the program.
-
Risk Workshop: A collaborative session for identifying and analyzing risks.
-
Risk Workshop Facilitation: Guiding participants through the risk identification and analysis process. Effective use of these tools can help program managers. It can address risks and position the program for success.
How to obtain PgMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Program Risk Management is vital to program management. It needs a systematic approach to identify, analyze, and respond to risks. Effective use of PgMP tools and techniques can help program managers. It can reduce uncertainties' impact on program outcomes. It can also increase the chances of success. Program managers must proactively manage risks to ensure success. This is vital throughout the program lifecycle.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's fast-paced business world, program managers must manage risks. This is vital to their programs' success. Program Risk Management is key to program management. PgMP tools and techniques are vital. They help us manage risks throughout the program lifecycle.
Understanding Program Risk Management
Program Risk Management is the process of managing risks. These risks may affect a program's success. It uses a systematic approach to assess and manage risks. This ensures the program meets its goals within limits on time, cost, quality, and scope.
Program risk management is vital. It identifies, analyzes, and mitigates risks that could harm a program's success. Program managers manage risks. This ensures projects finish on time, within budget, and meet their goals. Effective risk management protects against negative outcomes. It also enables better decisions and resource use throughout the program's lifecycle.
Importance of Program Risk Management
Effective Program Risk Management is key. It minimizes uncertainties' impact on outcomes and boosts the chances of success. By spotting risks early, program managers can create plans to reduce them. This will help to limit their impact on the program.
Program risk management is key. It identifies, assesses, and mitigates risks that could harm large-scale programs. PgMP-certified pros can meet program goals on time and within budget. They do this by addressing risks. This minimizes disruptions. Effective risk management protects resources. It also builds trust in stakeholders and improves outcomes.
Key Components of Program Risk Management
-
Risk Assessment: This means finding and evaluating risks. They may affect the program's goals.
-
Risk Analysis: This means assessing known risks to the program. It involves their likelihood and impact.
-
Risk Identification: This is about finding potential risks in the program's lifecycle.
-
Risk Mitigation: This means making plans to lessen known risks.
-
Risk Monitoring: This is tracking known risks throughout the program. It ensures they are managed well.
-
Risk Planning: This involves developing a plan to address and manage risks proactively.
-
Risk Response: This involves implementing planned responses to address identified risks.
-
Risk Control: This means monitoring and controlling risks. They must not affect the program's goals.
-
Risk Evaluation: This means assessing risk management strategies. Adjust them as needed.
Program Risk Management Process
The Program Risk Management process involves the following key steps:
-
Risk Management Framework: Establishing a framework for managing risks within the program.
-
Risk Management Plan: Create a plan to identify, analyze, and respond to risks.
-
Risk Management Strategy: Defining the overall approach to managing risks within the program.
-
Risk Tolerance: Determining the level of risk that the program is willing to accept.
-
Risk Culture: Build a culture that values risk management in the program.
-
Risk Governance: Establishing governance structures to oversee and manage risks effectively.
-
Risk Appetite: Defining the program's appetite for risk-taking.
-
Risk Exposure: Identifying the level of exposure to risks within the program. Program Risk Management Tools & Techniques Program managers can use some tools and techniques to manage risks. Some of the most common tools and techniques include:
-
Risk Register: A document that tracks all identified program risks.
-
Risk Matrix: A visual representation of risks based on their likelihood and impact.
-
Risk Communication: The process of sharing risk information with stakeholders.
-
Risk Reporting: Providing regular updates on the status of risks within the program.
-
Risk Workshop: A collaborative session for identifying and analyzing risks.
-
Risk Workshop Facilitation: Guiding participants through the risk identification and analysis process. Effective use of these tools can help program managers. It can address risks and position the program for success.
How to obtain PgMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Program Risk Management is vital to program management. It needs a systematic approach to identify, analyze, and respond to risks. Effective use of PgMP tools and techniques can help program managers. It can reduce uncertainties' impact on program outcomes. It can also increase the chances of success. Program managers must proactively manage risks to ensure success. This is vital throughout the program lifecycle.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Creating a Personal Brand as a Certified CBAP Business Analyst
In the competitive world of business analysis, establishing a strong personal brand is essential for standing out from the crowd and showcasing your expertise. As a Certified CBAP (Certified Business Analysis Professional) Business Analyst, you have already proven your skills and knowledge in the field. Now, it's time to take your career to the next level by building a personal brand that reflects your unique identity and sets you apart as a thought leader in your industry.
Understanding the Importance of Personal Branding
Personal branding is the process of creating a distinct image and reputation for yourself in the professional world. It involves defining who you are, what you stand for, and what sets you apart from others in your field. As a Certified CBAP Business Analyst, your brand reflects your skills and reputation.
Developing Your Brand Strategy
To build a strong personal brand as a Certified CBAP Business Analyst, you must create a clear brand strategy. It should outline your goals, values, and target audience. Your brand strategy should align with your career goals. It should showcase your unique skills as a business analyst.
Developing your brand strategy is essential for creating a clear and consistent identity that resonates with your target audience. It involves defining your brand’s core values, messaging, and visual identity to establish a unique presence in the market. A strong brand strategy not only builds trust and recognition but also helps drive long-term business growth by aligning with your audience's needs and preferences.
Utilizing Branding Techniques
There are various branding techniques that you can use to enhance your personal brand as a Certified CBAP Business Analyst. These may include: a personal marketing plan, a strong online presence, and effective brand communication. They should showcase your expertise and credibility.
Branding techniques create a strong, cohesive identity. It must resonate with your target audience and set you apart from competitors. Consistent use of visuals, messages, and values builds brand trust and recognition. Effective branding builds emotional connections. It turns customers into loyal brand advocates.
Building Your Brand Identity
Your brand identity is the visual representation of your personal brand as a Certified CBAP Business Analyst. This may include your personal branding statement, brand story, logo, and messaging. A consistent brand identity will boost recognition and trust with your audience.
Building your brand identity is about defining how you want your audience to perceive your business. It means creating a consistent message, design, and tone. They must reflect your values, mission, and your unique offerings. A strong brand identity sets you apart from competitors. It also builds trust and recognition with your audience.
Leveraging Brand Management
Brand management is crucial for maintaining a strong personal brand as a Certified CBAP Business Analyst. It involves monitoring and controlling how others perceive your brand. It also means keeping brand consistency and adapting to industry changes. This ensures your brand remains relevant and impactful.
Using brand management is key. It creates a consistent, memorable brand identity that resonates with your audience. It means managing your brand, from visuals to customer experiences. Ensure they align with your company's values and goals. Strong brand equity boosts customer loyalty, market share, and growth.
Positioning Yourself as a Branding Expert
As a Certified CBAP Business Analyst, you have the opportunity to position yourself as a branding expert in your field. Sharing your insights on personal branding can build your authority. It can also attract new career growth opportunities.
To be seen as a branding expert, show your unique view on brand strategy. Use insightful content, like blog posts, podcasts, or webinars. Engage your audience. Share case studies and success stories. They show your expertise and results-driven approach. Also, network with branding professionals. Use social media to boost your visibility and credibility in the industry.
Seeking Professional Guidance
To boost your personal brand, consider hiring a branding coach. These experts can help you. They can improve your brand image, develop your brand story, and build a strong personal brand. It should resonate with your target audience.
Career development is complex and daunting. That's why seeking expert help is vital. Mentors and coaches offer insights. They help you find your strengths and align your goals with industry demands. Invest in professional support. It will boost your skills, expand your network, and advance your career. You'll do it with confidence.
Embracing Brand Authenticity
Authenticity is key when it comes to personal branding as a Certified CBAP Business Analyst. Your brand values, mission, and messaging should reflect who you truly are and what you stand for in your professional life. By staying true to yourself and your beliefs, you can build a genuine and trustworthy personal brand that resonates with others.
In today's market, consumers want genuine connections with brands. So, embracing brand authenticity is essential. Businesses can build trust and loyalty by being transparent. They should show their values and real stories. Ultimately, an authentic brand not only resonates more deeply with customers but also stands out in a crowded marketplace."
How to obtain CBAP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, a personal brand as a Certified CBAP Business Analyst is key to your career success. It is a valuable investment. Develop a strong brand strategy. Use effective branding techniques. Position yourself as a branding expert. This will establish you as a thought leader in business analysis. It will attract new opportunities for career advancement. Don't hesitate to take the necessary steps to build your personal brand and showcase your expertise to the world.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In the competitive world of business analysis, establishing a strong personal brand is essential for standing out from the crowd and showcasing your expertise. As a Certified CBAP (Certified Business Analysis Professional) Business Analyst, you have already proven your skills and knowledge in the field. Now, it's time to take your career to the next level by building a personal brand that reflects your unique identity and sets you apart as a thought leader in your industry.
Understanding the Importance of Personal Branding
Personal branding is the process of creating a distinct image and reputation for yourself in the professional world. It involves defining who you are, what you stand for, and what sets you apart from others in your field. As a Certified CBAP Business Analyst, your brand reflects your skills and reputation.
Developing Your Brand Strategy
To build a strong personal brand as a Certified CBAP Business Analyst, you must create a clear brand strategy. It should outline your goals, values, and target audience. Your brand strategy should align with your career goals. It should showcase your unique skills as a business analyst.
Developing your brand strategy is essential for creating a clear and consistent identity that resonates with your target audience. It involves defining your brand’s core values, messaging, and visual identity to establish a unique presence in the market. A strong brand strategy not only builds trust and recognition but also helps drive long-term business growth by aligning with your audience's needs and preferences.
Utilizing Branding Techniques
There are various branding techniques that you can use to enhance your personal brand as a Certified CBAP Business Analyst. These may include: a personal marketing plan, a strong online presence, and effective brand communication. They should showcase your expertise and credibility.
Branding techniques create a strong, cohesive identity. It must resonate with your target audience and set you apart from competitors. Consistent use of visuals, messages, and values builds brand trust and recognition. Effective branding builds emotional connections. It turns customers into loyal brand advocates.
Building Your Brand Identity
Your brand identity is the visual representation of your personal brand as a Certified CBAP Business Analyst. This may include your personal branding statement, brand story, logo, and messaging. A consistent brand identity will boost recognition and trust with your audience.
Building your brand identity is about defining how you want your audience to perceive your business. It means creating a consistent message, design, and tone. They must reflect your values, mission, and your unique offerings. A strong brand identity sets you apart from competitors. It also builds trust and recognition with your audience.
Leveraging Brand Management
Brand management is crucial for maintaining a strong personal brand as a Certified CBAP Business Analyst. It involves monitoring and controlling how others perceive your brand. It also means keeping brand consistency and adapting to industry changes. This ensures your brand remains relevant and impactful.
Using brand management is key. It creates a consistent, memorable brand identity that resonates with your audience. It means managing your brand, from visuals to customer experiences. Ensure they align with your company's values and goals. Strong brand equity boosts customer loyalty, market share, and growth.
Positioning Yourself as a Branding Expert
As a Certified CBAP Business Analyst, you have the opportunity to position yourself as a branding expert in your field. Sharing your insights on personal branding can build your authority. It can also attract new career growth opportunities.
To be seen as a branding expert, show your unique view on brand strategy. Use insightful content, like blog posts, podcasts, or webinars. Engage your audience. Share case studies and success stories. They show your expertise and results-driven approach. Also, network with branding professionals. Use social media to boost your visibility and credibility in the industry.
Seeking Professional Guidance
To boost your personal brand, consider hiring a branding coach. These experts can help you. They can improve your brand image, develop your brand story, and build a strong personal brand. It should resonate with your target audience.
Career development is complex and daunting. That's why seeking expert help is vital. Mentors and coaches offer insights. They help you find your strengths and align your goals with industry demands. Invest in professional support. It will boost your skills, expand your network, and advance your career. You'll do it with confidence.
Embracing Brand Authenticity
Authenticity is key when it comes to personal branding as a Certified CBAP Business Analyst. Your brand values, mission, and messaging should reflect who you truly are and what you stand for in your professional life. By staying true to yourself and your beliefs, you can build a genuine and trustworthy personal brand that resonates with others.
In today's market, consumers want genuine connections with brands. So, embracing brand authenticity is essential. Businesses can build trust and loyalty by being transparent. They should show their values and real stories. Ultimately, an authentic brand not only resonates more deeply with customers but also stands out in a crowded marketplace."
How to obtain CBAP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, a personal brand as a Certified CBAP Business Analyst is key to your career success. It is a valuable investment. Develop a strong brand strategy. Use effective branding techniques. Position yourself as a branding expert. This will establish you as a thought leader in business analysis. It will attract new opportunities for career advancement. Don't hesitate to take the necessary steps to build your personal brand and showcase your expertise to the world.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Future Trends in IT Governance The Evolution of COBIT
In the fast-paced IT world, governance has become vital. Organizations must align their IT systems with business goals. They must also comply with regulations and secure against cyber threats. As technology continues to evolve, so do the best practices and frameworks that guide IT governance. One framework at the forefront of IT governance is COBIT. It stands for Control Objectives for Information and Related Technologies.
Evolution of COBIT
COBIT, developed by ISACA, has been continuously evolving to keep pace with the changing IT landscape. COBIT, released in 1996, has been updated several times. These updates align it with industry trends, best practices, and regulations. COBIT 2019 builds on the success of COBIT 5. It adds new features to help organizations meet their governance goals.
COBIT's evolution reflects changes in IT governance. It shifted from a focus on IT control to a broader framework. This new approach emphasizes aligning IT with business goals. COBIT 5 integrated principles from various methodologies, including ITIL and ISO standards. It aimed to provide a comprehensive approach to governance, risk management, and compliance.
Importance of COBIT
COBIT is a framework. It helps organizations to align IT with business strategies. It does this by improving processes and establishing IT governance best practices. It enables organizations to manage risks, ensure compliance, and optimize IT resources. As IT environments grow more complex, so do cyber threats. COBIT is vital. It helps organizations with digital transformation and cybersecurity.
COBIT (Control Objectives for Information and Related Technologies) is vital for firms. It helps align IT strategies with business goals. It ensures governance and management practices are in sync. It offers a framework for organizations. It helps them manage risk and improve performance. It does this with defined processes and best practices. It also optimizes resources. Also, COBIT fosters a culture of accountability and transparency. It gives stakeholders confidence in the governance of IT investments.
COBIT Framework
The COBIT framework is built on five key principles: 1. Meet stakeholders' needs. 2. Cover the enterprise end-to-end. 3. Apply a single, integrated framework. 4. Enable a holistic approach. 5. Separate governance from management. These principles guide organizations in designing, implementing, and monitoring effective IT governance practices. COBIT has a maturity model. It helps organizations assess and improve their IT governance. The model consists of five maturity levels, ranging from ad hoc processes to optimized processes. Organizations can improve their IT governance by assessing their maturity. This will identify areas for improvement.
COBIT stands for Control Objectives for Information and Related Technologies. It is a framework of guidelines. They help organizations manage and govern their IT assets. It stresses aligning IT goals with business objectives. IT must deliver value, manage risk, and optimize resources.
COBIT vs. ITIL
COBIT focuses on IT governance and risk management. ITIL, however, is about IT service management. Both frameworks address different aspects of IT. Organizations can benefit from implementing them together. This will create a more holistic approach to IT governance and service delivery.
COBIT and ITIL are two key IT management frameworks. Each has a distinct but complementary purpose. COBIT stands for Control Objectives for Information and Related Technologies. It is for IT governance, risk management, and compliance. It is ideal for organizations needing to align IT with business goals and regulations. In contrast, ITIL (Information Technology Infrastructure Library) is about managing IT services. It offers best practices for delivering high-quality IT services. They must meet customers' and businesses' needs.
COBIT Compliance and Benefits
Compliance with COBIT standards can benefit organizations in many ways. It can improve risk management and decision-making. It can also increase efficiency and align IT with business goals. The COBIT framework can help organizations improve their governance. It will help them succeed in the fast-changing IT world.
COBIT compliance gives organizations a framework to improve IT governance. It aligns business goals with IT strategies. By adopting COBIT, organizations can improve risk management and resource use. It will help them make better decisions. This will boost efficiency and ensure compliance with regulations. Also, organizations that follow COBIT principles gain stakeholders' trust. This enhances business relationships and gives a competitive edge.
How to obtain COBIT 5 Foundation certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, as technology advances, IT governance is vital. It helps organizations manage IT resources, reduce risks, and meet business goals. By using frameworks like COBIT, organizations can thrive in the digital age. They can confidently navigate its complexities.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In the fast-paced IT world, governance has become vital. Organizations must align their IT systems with business goals. They must also comply with regulations and secure against cyber threats. As technology continues to evolve, so do the best practices and frameworks that guide IT governance. One framework at the forefront of IT governance is COBIT. It stands for Control Objectives for Information and Related Technologies.
Evolution of COBIT
COBIT, developed by ISACA, has been continuously evolving to keep pace with the changing IT landscape. COBIT, released in 1996, has been updated several times. These updates align it with industry trends, best practices, and regulations. COBIT 2019 builds on the success of COBIT 5. It adds new features to help organizations meet their governance goals.
COBIT's evolution reflects changes in IT governance. It shifted from a focus on IT control to a broader framework. This new approach emphasizes aligning IT with business goals. COBIT 5 integrated principles from various methodologies, including ITIL and ISO standards. It aimed to provide a comprehensive approach to governance, risk management, and compliance.
Importance of COBIT
COBIT is a framework. It helps organizations to align IT with business strategies. It does this by improving processes and establishing IT governance best practices. It enables organizations to manage risks, ensure compliance, and optimize IT resources. As IT environments grow more complex, so do cyber threats. COBIT is vital. It helps organizations with digital transformation and cybersecurity.
COBIT (Control Objectives for Information and Related Technologies) is vital for firms. It helps align IT strategies with business goals. It ensures governance and management practices are in sync. It offers a framework for organizations. It helps them manage risk and improve performance. It does this with defined processes and best practices. It also optimizes resources. Also, COBIT fosters a culture of accountability and transparency. It gives stakeholders confidence in the governance of IT investments.
COBIT Framework
The COBIT framework is built on five key principles: 1. Meet stakeholders' needs. 2. Cover the enterprise end-to-end. 3. Apply a single, integrated framework. 4. Enable a holistic approach. 5. Separate governance from management. These principles guide organizations in designing, implementing, and monitoring effective IT governance practices. COBIT has a maturity model. It helps organizations assess and improve their IT governance. The model consists of five maturity levels, ranging from ad hoc processes to optimized processes. Organizations can improve their IT governance by assessing their maturity. This will identify areas for improvement.
COBIT stands for Control Objectives for Information and Related Technologies. It is a framework of guidelines. They help organizations manage and govern their IT assets. It stresses aligning IT goals with business objectives. IT must deliver value, manage risk, and optimize resources.
COBIT vs. ITIL
COBIT focuses on IT governance and risk management. ITIL, however, is about IT service management. Both frameworks address different aspects of IT. Organizations can benefit from implementing them together. This will create a more holistic approach to IT governance and service delivery.
COBIT and ITIL are two key IT management frameworks. Each has a distinct but complementary purpose. COBIT stands for Control Objectives for Information and Related Technologies. It is for IT governance, risk management, and compliance. It is ideal for organizations needing to align IT with business goals and regulations. In contrast, ITIL (Information Technology Infrastructure Library) is about managing IT services. It offers best practices for delivering high-quality IT services. They must meet customers' and businesses' needs.
COBIT Compliance and Benefits
Compliance with COBIT standards can benefit organizations in many ways. It can improve risk management and decision-making. It can also increase efficiency and align IT with business goals. The COBIT framework can help organizations improve their governance. It will help them succeed in the fast-changing IT world.
COBIT compliance gives organizations a framework to improve IT governance. It aligns business goals with IT strategies. By adopting COBIT, organizations can improve risk management and resource use. It will help them make better decisions. This will boost efficiency and ensure compliance with regulations. Also, organizations that follow COBIT principles gain stakeholders' trust. This enhances business relationships and gives a competitive edge.
How to obtain COBIT 5 Foundation certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, as technology advances, IT governance is vital. It helps organizations manage IT resources, reduce risks, and meet business goals. By using frameworks like COBIT, organizations can thrive in the digital age. They can confidently navigate its complexities.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
The Future of Lean Six Sigma in the Digital Age
In today's fast-changing digital world, Lean Six Sigma is vital. It drives success and fosters a culture of improvement. As businesses adopt digital transformation and Industry 4.0, Lean Six Sigma is more relevant than ever. Let's explore how Lean Six Sigma is shaping quality management in the digital age.
Embracing Technology and Automation
One of the key pillars of Lean Six Sigma is a focus on leveraging technology and automation to drive efficiency and productivity. In the digital age, data analytics and AI have advanced. They help organizations improve decision-making and streamline operations. By merging Lean Six Sigma with new technology, businesses can optimize processes and cut costs.
Organizations must embrace technology and automation. It's key to boosting efficiency and driving innovation. AI and machine learning can help businesses. They can streamline operations, reduce errors, and improve decisions. Also, automation boosts productivity. It lets employees focus on higher-value tasks. This leads to greater job satisfaction and growth for the organization.
Continuous Improvement and Innovation
Lean Six Sigma is founded on the principles of continuous improvement and innovation. In the digital age, organizations must adapt to shifting markets and consumer preferences. Adopting Lean Six Sigma can foster innovation and drive growth. Using data and Lean Six Sigma tools, organizations can find and remove waste. This will boost customer satisfaction and help them beat the competition.
Continuous improvement and innovation are vital to an organization's success. They drive efficiency and adaptability in a fast-changing business world. Organizations can improve processes and find better solutions. They should create a culture that encourages feedback and testing to meet customer needs. Using methods like Lean Six Sigma can streamline operations. They can also promote sustainable growth. This will make innovation a key part of the company's culture.
Enhancing Quality Management
Quality management is at the core of Lean Six Sigma. In the digital age, high-quality standards are vital for business success. Lean Six Sigma practices can help organizations ensure consistent quality. This leads to greater customer loyalty and satisfaction. Lean Six Sigma tools can help businesses fix quality issues in real-time. This will boost their efficiency.
To improve quality management, implement processes. They must ensure products and services meet customer and regulatory standards. Techniques like continuous improvement and employee training are key. So are quality standards, like ISO 9001. They are vital for achieving operational excellence. A culture of quality can boost customer satisfaction. It can also improve efficiency and cut costs.
Maximizing Efficiency and Productivity
Efficiency and productivity are vital for an organization's success. Lean Six Sigma offers a way to achieve operational excellence. Businesses can boost efficiency, cut costs, and improve productivity. They can do this by optimizing processes and eliminating waste. In the digital age, Lean Six Sigma helps organizations. It lets them use tech and data to boost efficiency. It aims for continuous improvement and streamlined operations.
For organizations, it's vital to maximize efficiency and productivity. This helps them achieve their goals while using resources wisely. Teams can use Lean Six Sigma to streamline processes, cut waste, and boost performance. Also, a culture of continuous improvement encourages employees to find and fix inefficiencies. This will drive better results for the organization.
Building a Lean Culture
A Lean culture is vital for success in Lean Six Sigma. In the digital age, organizations must embrace a culture of learning. They need to improve constantly to stay competitive. Applying Lean principles to all parts of the business can create a culture of transparency, accountability, and collaboration. This applies to everyone, from leaders to front-line employees. This Lean culture will drive innovation, empower employees, and grow the business. It will do so sustainably.
A lean culture is key to continuous improvement and excellence. It fosters them in an organization. This culture values employee engagement. Team members should identify waste, suggest improvements, and help solve problems. Applying Lean principles at all levels can help companies. It can create a sustainable, efficient, and responsive environment for customers.
How to obtain LSSYB certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the future of Lean Six Sigma is bright. There are many opportunities for organizations to excel in quality and process. By embracing technology and improving continuously, businesses can use Lean Six Sigma. It will boost efficiency and productivity. This will drive innovation and help them outpace competitors. As we enter a digital age, Lean Six Sigma will be key for organizations. It will help them thrive in a fast-changing business landscape.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's fast-changing digital world, Lean Six Sigma is vital. It drives success and fosters a culture of improvement. As businesses adopt digital transformation and Industry 4.0, Lean Six Sigma is more relevant than ever. Let's explore how Lean Six Sigma is shaping quality management in the digital age.
Embracing Technology and Automation
One of the key pillars of Lean Six Sigma is a focus on leveraging technology and automation to drive efficiency and productivity. In the digital age, data analytics and AI have advanced. They help organizations improve decision-making and streamline operations. By merging Lean Six Sigma with new technology, businesses can optimize processes and cut costs.
Organizations must embrace technology and automation. It's key to boosting efficiency and driving innovation. AI and machine learning can help businesses. They can streamline operations, reduce errors, and improve decisions. Also, automation boosts productivity. It lets employees focus on higher-value tasks. This leads to greater job satisfaction and growth for the organization.
Continuous Improvement and Innovation
Lean Six Sigma is founded on the principles of continuous improvement and innovation. In the digital age, organizations must adapt to shifting markets and consumer preferences. Adopting Lean Six Sigma can foster innovation and drive growth. Using data and Lean Six Sigma tools, organizations can find and remove waste. This will boost customer satisfaction and help them beat the competition.
Continuous improvement and innovation are vital to an organization's success. They drive efficiency and adaptability in a fast-changing business world. Organizations can improve processes and find better solutions. They should create a culture that encourages feedback and testing to meet customer needs. Using methods like Lean Six Sigma can streamline operations. They can also promote sustainable growth. This will make innovation a key part of the company's culture.
Enhancing Quality Management
Quality management is at the core of Lean Six Sigma. In the digital age, high-quality standards are vital for business success. Lean Six Sigma practices can help organizations ensure consistent quality. This leads to greater customer loyalty and satisfaction. Lean Six Sigma tools can help businesses fix quality issues in real-time. This will boost their efficiency.
To improve quality management, implement processes. They must ensure products and services meet customer and regulatory standards. Techniques like continuous improvement and employee training are key. So are quality standards, like ISO 9001. They are vital for achieving operational excellence. A culture of quality can boost customer satisfaction. It can also improve efficiency and cut costs.
Maximizing Efficiency and Productivity
Efficiency and productivity are vital for an organization's success. Lean Six Sigma offers a way to achieve operational excellence. Businesses can boost efficiency, cut costs, and improve productivity. They can do this by optimizing processes and eliminating waste. In the digital age, Lean Six Sigma helps organizations. It lets them use tech and data to boost efficiency. It aims for continuous improvement and streamlined operations.
For organizations, it's vital to maximize efficiency and productivity. This helps them achieve their goals while using resources wisely. Teams can use Lean Six Sigma to streamline processes, cut waste, and boost performance. Also, a culture of continuous improvement encourages employees to find and fix inefficiencies. This will drive better results for the organization.
Building a Lean Culture
A Lean culture is vital for success in Lean Six Sigma. In the digital age, organizations must embrace a culture of learning. They need to improve constantly to stay competitive. Applying Lean principles to all parts of the business can create a culture of transparency, accountability, and collaboration. This applies to everyone, from leaders to front-line employees. This Lean culture will drive innovation, empower employees, and grow the business. It will do so sustainably.
A lean culture is key to continuous improvement and excellence. It fosters them in an organization. This culture values employee engagement. Team members should identify waste, suggest improvements, and help solve problems. Applying Lean principles at all levels can help companies. It can create a sustainable, efficient, and responsive environment for customers.
How to obtain LSSYB certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the future of Lean Six Sigma is bright. There are many opportunities for organizations to excel in quality and process. By embracing technology and improving continuously, businesses can use Lean Six Sigma. It will boost efficiency and productivity. This will drive innovation and help them outpace competitors. As we enter a digital age, Lean Six Sigma will be key for organizations. It will help them thrive in a fast-changing business landscape.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
The Impact of RPA on the Gig Economy and Freelance Work
In today's rapidly changing job market, the rise of Robotic Process Automation (RPA) is having a profound impact on the gig economy and freelance work. As automation technology and artificial intelligence continue to advance, more and more tasks that were once performed by humans are now being taken over by robots. This shift is reshaping the way freelancers and gig workers operate, creating both challenges and opportunities in the digital workforce landscape.
How is RPA Changing the Freelance Work Landscape?
With the implementation of RPA in various industries, many routine and repetitive tasks are now being automated, leading to increased efficiency and productivity. This automation allows freelancers and gig workers to focus on more complex and creative work, rather than spending time on mundane tasks. Additionally, RPA can help freelance workers streamline their workflows, reduce errors, and deliver high-quality results in a shorter amount of time.
RPA is transforming the freelance work landscape by automating routine tasks, allowing freelancers to focus on more complex and creative projects. With automation tools handling administrative duties like invoicing, scheduling, and data entry, freelancers can manage their time more efficiently and increase productivity. Additionally, RPA is enabling freelancers to offer new services, such as automating workflows for clients, further expanding their skillsets and market opportunities.
What Does This Mean for the Future of Freelancing?
The integration of RPA into the freelance economy is expected to bring about significant changes in the coming years. As more companies use automation, the demand for skilled freelancers who can work with robots will likely rise. Freelancers skilled in machine learning and AI will be in high demand. They can help companies use automation to drive innovation and growth.
RPA (Robotic Process Automation) is changing freelancing. It automates repetitive tasks. This lets freelancers focus on more creative, strategic work. This shift could raise demand for skilled freelancers. Their work would be in RPA, AI, and workflow optimization. However, it may reduce opportunities for freelancers in easily automated roles. This creates a need for upskilling and adaptability.
How Can Freelancers Adapt to the Rise of Automation Technology?
With RPA on the rise, freelancers must upgrade their skills to thrive. They need to stay ahead of the curve. Freelancers must invest in training on automation, machine learning, and AI. It will be key to staying competitive in the digital workforce. Also, freelancers can use gig economy sites to find clients seeking automation experts.
As automation changes industries, freelancers must adapt. They should upskill in data analysis, AI, and RPA to stay competitive. Automation tools can help freelancers. They can streamline repetitive tasks. This boosts productivity and allows for more creative work. Also, freelancers should track automation trends. They should align their services to complement these technologies. It will help them succeed in a fast-changing market.
The Benefits of RPA for Freelancers
The rise of automation may scare freelancers. But, it also offers chances for growth and success. By embracing RPA and learning to work with robots, freelancers can be more efficient. They can also expand their skills and take on tougher projects. Also, automation can help freelancers attract high-paying clients. It can help them get long-term contracts. This leads to a more stable and lucrative freelance career.
RPA (Robotic Process Automation) helps freelancers by automating repetitive tasks. It handles invoicing, data entry, and project tracking. This allows freelancers to focus on creative, high-value work. It cuts human errors. It speeds up, and makes tasks more accurate. This boosts productivity. Also, by streamlining admin work, freelancers can manage their time better. They can take on more clients without a heavier workload.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the impact of RPA on the gig economy and freelance work is undeniable. As automation technology advances, freelancers must adapt. They must embrace the new opportunities it brings.
Freelancers can succeed in an automated world by:
-
Staying updated on automation trends.
-
Upgrading their skills.
-
Using online platforms to connect with clients.
The future of freelancing is changing. Those who embrace it will thrive in the new digital workforce.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's rapidly changing job market, the rise of Robotic Process Automation (RPA) is having a profound impact on the gig economy and freelance work. As automation technology and artificial intelligence continue to advance, more and more tasks that were once performed by humans are now being taken over by robots. This shift is reshaping the way freelancers and gig workers operate, creating both challenges and opportunities in the digital workforce landscape.
How is RPA Changing the Freelance Work Landscape?
With the implementation of RPA in various industries, many routine and repetitive tasks are now being automated, leading to increased efficiency and productivity. This automation allows freelancers and gig workers to focus on more complex and creative work, rather than spending time on mundane tasks. Additionally, RPA can help freelance workers streamline their workflows, reduce errors, and deliver high-quality results in a shorter amount of time.
RPA is transforming the freelance work landscape by automating routine tasks, allowing freelancers to focus on more complex and creative projects. With automation tools handling administrative duties like invoicing, scheduling, and data entry, freelancers can manage their time more efficiently and increase productivity. Additionally, RPA is enabling freelancers to offer new services, such as automating workflows for clients, further expanding their skillsets and market opportunities.
What Does This Mean for the Future of Freelancing?
The integration of RPA into the freelance economy is expected to bring about significant changes in the coming years. As more companies use automation, the demand for skilled freelancers who can work with robots will likely rise. Freelancers skilled in machine learning and AI will be in high demand. They can help companies use automation to drive innovation and growth.
RPA (Robotic Process Automation) is changing freelancing. It automates repetitive tasks. This lets freelancers focus on more creative, strategic work. This shift could raise demand for skilled freelancers. Their work would be in RPA, AI, and workflow optimization. However, it may reduce opportunities for freelancers in easily automated roles. This creates a need for upskilling and adaptability.
How Can Freelancers Adapt to the Rise of Automation Technology?
With RPA on the rise, freelancers must upgrade their skills to thrive. They need to stay ahead of the curve. Freelancers must invest in training on automation, machine learning, and AI. It will be key to staying competitive in the digital workforce. Also, freelancers can use gig economy sites to find clients seeking automation experts.
As automation changes industries, freelancers must adapt. They should upskill in data analysis, AI, and RPA to stay competitive. Automation tools can help freelancers. They can streamline repetitive tasks. This boosts productivity and allows for more creative work. Also, freelancers should track automation trends. They should align their services to complement these technologies. It will help them succeed in a fast-changing market.
The Benefits of RPA for Freelancers
The rise of automation may scare freelancers. But, it also offers chances for growth and success. By embracing RPA and learning to work with robots, freelancers can be more efficient. They can also expand their skills and take on tougher projects. Also, automation can help freelancers attract high-paying clients. It can help them get long-term contracts. This leads to a more stable and lucrative freelance career.
RPA (Robotic Process Automation) helps freelancers by automating repetitive tasks. It handles invoicing, data entry, and project tracking. This allows freelancers to focus on creative, high-value work. It cuts human errors. It speeds up, and makes tasks more accurate. This boosts productivity. Also, by streamlining admin work, freelancers can manage their time better. They can take on more clients without a heavier workload.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the impact of RPA on the gig economy and freelance work is undeniable. As automation technology advances, freelancers must adapt. They must embrace the new opportunities it brings.
Freelancers can succeed in an automated world by:
-
Staying updated on automation trends.
-
Upgrading their skills.
-
Using online platforms to connect with clients.
The future of freelancing is changing. Those who embrace it will thrive in the new digital workforce.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Python in Cybersecurity Key Libraries and Tools
Cybersecurity is an ever-evolving field that demands constant vigilance and innovation. As cyber threats become more sophisticated, the need for powerful and flexible programming tools grows. Python has emerged as one of the most widely used languages in cybersecurity due to its simplicity, readability, and rich ecosystem of libraries and frameworks. Whether for penetration testing, malware analysis, network security, or digital forensics, Python provides cybersecurity professionals with a versatile toolkit to tackle modern challenges.
This blog will explore the role of Python in cybersecurity and dive deep into some of the most critical libraries and tools that professionals use to protect systems and data. We'll cover libraries for network security, web vulnerability testing, cryptography, malware analysis, and more, shedding light on why Python is an essential part of a cybersecurity professional's arsenal.
Why Python in Cybersecurity?
Python's role in cybersecurity is significant for several reasons:
1. Ease of Learning: Python is one of the easiest programming languages to learn, even for those new to coding. Its clean and straightforward syntax allows security professionals to quickly develop scripts and tools for various tasks.
2. Cross-Platform Compatibility: Python works seamlessly across different platforms, including Windows, Linux, and macOS, making it ideal for writing security tools that need to function in diverse environments.
3. Extensive Library Support: Python's vast range of libraries simplifies complex tasks such as network scanning, vulnerability detection, data encryption, and malware analysis.
4. Strong Community: Python has a large, active community of developers and security professionals, which means that new tools, tutorials, and libraries are continually being developed and shared.
1. Network Security and Penetration Testing
Scapy : is a powerful Python library for network packet manipulation. It allows you to craft, send, receive, and manipulate network packets at a very low level. Scapy is widely used for tasks like network scanning, packet sniffing, and even attacks such as ARP spoofing and Denial of Service (DoS) simulations.
Key Features:
- Packet crafting and injection.
- Network scanning and protocol testing.
- Built-in tools for tracerouting, scanning, and spoofing.
Example:
python
from scapy.all import *
Craft a simple ICMP packet and send it
icmp_packet = IP(dst="8.8.8.8")/ICMP()
send(icmp_packet)
Scapy’s flexibility makes it an essential tool for network analysts and penetration testers who need to simulate various attack scenarios and analyze network traffic.
Nmap (via python-nmap)
Nmap is a well-known network scanner used for discovering hosts and services on a network. While Nmap itself is written in C, the `python-nmap` library allows Python developers to interface with Nmap’s functionality programmatically. This combination is ideal for automating network scans and integrating them into larger cybersecurity workflows.
Key Features:
- Host discovery and port scanning.
- Version detection for services.
- Integration with Python for automation.
Example:
python
import nmap
nm = nmap.PortScanner()
nm.scan('192.168.1.0/24', '22-443')
print(nm.all_hosts())
python-nmap` is particularly useful for penetration testers who need to automate network scanning and incorporate it into scripts for vulnerability assessments.
2. Web Vulnerability Testing
SQLMap (via sqlmap-api)
SQL injection is one of the most common vulnerabilities in web applications. SQLMap is a powerful tool for automating the detection and exploitation of SQL injection flaws. Python’s `sqlmap-api` provides a Python interface to this tool, allowing cybersecurity professionals to integrate SQL injection testing into their automated workflows.
Key Features:
- Automatic detection and exploitation of SQL injection vulnerabilities.
- Database fingerprinting and data extraction.
- Support for various DBMS like MySQL, PostgreSQL, and MSSQL.
Example:
python
import requests
from sqlmapapi.sqlmap import Sqlmap
Initialize sqlmap API client
sqlmap = Sqlmap()
Launch SQL injection scan on target
sqlmap.scan(target="http://example.com", data="username=admin'--")
Using SQLMap’s API, testers can easily automate vulnerability scanning as part of a larger web application security testing suite.
W3af: is an open-source web application security scanner that helps find and exploit web application vulnerabilities. Written in Python, it provides both a graphical user interface (GUI) and command-line interface (CLI) for performing security tests. It has built-in modules for scanning for common vulnerabilities like Cross-Site Scripting (XSS), SQL Injection, and CSRF.
Key Features:
- Modular architecture with plugins for specific vulnerability types.
- Comprehensive web vulnerability scanning and exploitation.
- Extensible through Python scripting.
W3af is ideal for web application testers who want an all-in-one solution for detecting web vulnerabilities.
3. Cryptography and Secure Communications
Cryptography Library
Python’s `cryptography` package is a robust toolkit for implementing encryption, decryption, and secure communication protocols. It provides cryptographic recipes and low-level interfaces to common algorithms such as AES, RSA, and ECC (Elliptic Curve Cryptography).
Key Features:
- Symmetric and asymmetric encryption algorithms.
- Key management and generation.
- Secure hashing and digital signatures.
Example:
python
from cryptography.fernet import Fernet
Generate a key for encryption
key = Fernet.generate_key()
cipher = Fernet(key)
Encrypt and decrypt a message
encrypted_message = cipher.encrypt(b"Sensitive Data")
decrypted_message = cipher.decrypt(encrypted_message)
print(decrypted_message.decode())
The `cryptography` library is widely used in secure data transmission, password storage, and encryption-related tasks across cybersecurity solutions.
PyCryptodome: is a self-contained Python package of cryptographic tools that includes support for encryption algorithms, message authentication codes, and hashing functions. It’s a fork of the original PyCrypto library and is commonly used in cybersecurity projects that need robust cryptographic functions.
Key Features:
- Encryption algorithms like AES, DES, and RSA.
- Hashing functions like SHA256.
- Digital signatures and random number generation.
PyCryptodome is frequently used in building encryption tools, ensuring data integrity, and securing communication protocols in Python-based security applications.
4. Malware Analysis and Reverse Engineering
Yara (via yara-python)
Yara is a popular tool for identifying and classifying malware based on pattern matching. The `yara-python` library provides a Python interface to Yara, allowing malware analysts to integrate Yara’s pattern-matching capabilities directly into their Python scripts.
Key Features:
- Pattern-based matching for malware detection.
- Flexible rule creation for identifying specific malware families.
- Integration with Python for automated malware analysis.
Example:
python
import yara
Define a YARA rule for detecting a specific malware pattern
rule = """
rule MyMalware {
strings:
$a = "malicious_pattern"
condition:
$a
}
"""
# Compile and run the YARA rule
compiled_rule = yara.compile(source=rule)
matches = compiled_rule.match(filepath="/path/to/suspected/file")
print(matches)
`yara-python` is widely used in malware research, forensic investigations, and threat detection to identify known malicious patterns in files and executables.
Volatility: Volatility is a Python-based memory forensics framework that enables analysts to extract information from memory dumps. It is used in digital forensics to investigate running processes, extract cryptographic keys, and detect hidden malware.
Key Features:
- Extraction of digital artifacts from RAM.
- Detection of malware and rootkits in memory dumps.
- Analysis of live systems or offline memory images.
Volatility is a must-have tool for forensic investigators who need to perform detailed memory analysis on compromised systems.
5. Additional Tools and Frameworks
Paramiko: is a Python library for SSH communication that allows secure connections between machines. It is often used for remote system administration, secure file transfers, and automated command execution on remote servers, making it essential for penetration testers and system administrators.
Key Features:
- SSH client and server capabilities.
- Secure file transfers via SFTP.
- Automated remote command execution.
Paramiko simplifies remote access to servers during security testing and post-exploitation activities.
Requests
While not specifically a cybersecurity library, Requests is a widely-used Python library for making HTTP requests. In cybersecurity, it’s commonly used for interacting with web servers, testing APIs, and automating tasks like form submission and vulnerability testing.
Key Features:
- Simple HTTP requests (GET, POST, PUT, etc.).
- Support for SSL/TLS verification.
- Integration with proxies for anonymizing requests.
Requests is often used in web vulnerability testing, scraping, and automation tasks related to web security.
How to obtain Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Python has firmly established itself as one of the most versatile and powerful programming languages for cybersecurity professionals. Its ease of use, combined with a vast range of libraries and frameworks, makes it an indispensable tool for tasks such as network security, web vulnerability testing, cryptography, and malware analysis.
From tools like Scapy and Nmap for network security to Yara for malware detection and Volatility for memory forensics, Python offers solutions for almost every aspect of modern cybersecurity challenges. By leveraging these libraries and frameworks, cybersecurity professionals can stay ahead of emerging threats and protect critical systems from malicious attacks.
As cybersecurity threats continue to grow in complexity, the flexibility and power of Python ensure that it will remain a key player in the fight to secure networks, data, and applications in the years to come.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
Cybersecurity is an ever-evolving field that demands constant vigilance and innovation. As cyber threats become more sophisticated, the need for powerful and flexible programming tools grows. Python has emerged as one of the most widely used languages in cybersecurity due to its simplicity, readability, and rich ecosystem of libraries and frameworks. Whether for penetration testing, malware analysis, network security, or digital forensics, Python provides cybersecurity professionals with a versatile toolkit to tackle modern challenges.
This blog will explore the role of Python in cybersecurity and dive deep into some of the most critical libraries and tools that professionals use to protect systems and data. We'll cover libraries for network security, web vulnerability testing, cryptography, malware analysis, and more, shedding light on why Python is an essential part of a cybersecurity professional's arsenal.
Why Python in Cybersecurity?
Python's role in cybersecurity is significant for several reasons:
1. Ease of Learning: Python is one of the easiest programming languages to learn, even for those new to coding. Its clean and straightforward syntax allows security professionals to quickly develop scripts and tools for various tasks.
2. Cross-Platform Compatibility: Python works seamlessly across different platforms, including Windows, Linux, and macOS, making it ideal for writing security tools that need to function in diverse environments.
3. Extensive Library Support: Python's vast range of libraries simplifies complex tasks such as network scanning, vulnerability detection, data encryption, and malware analysis.
4. Strong Community: Python has a large, active community of developers and security professionals, which means that new tools, tutorials, and libraries are continually being developed and shared.
1. Network Security and Penetration Testing
Scapy : is a powerful Python library for network packet manipulation. It allows you to craft, send, receive, and manipulate network packets at a very low level. Scapy is widely used for tasks like network scanning, packet sniffing, and even attacks such as ARP spoofing and Denial of Service (DoS) simulations.
Key Features:
- Packet crafting and injection.
- Network scanning and protocol testing.
- Built-in tools for tracerouting, scanning, and spoofing.
Example:
python
from scapy.all import *
Craft a simple ICMP packet and send it
icmp_packet = IP(dst="8.8.8.8")/ICMP()
send(icmp_packet)
Scapy’s flexibility makes it an essential tool for network analysts and penetration testers who need to simulate various attack scenarios and analyze network traffic.
Nmap (via python-nmap)
Nmap is a well-known network scanner used for discovering hosts and services on a network. While Nmap itself is written in C, the `python-nmap` library allows Python developers to interface with Nmap’s functionality programmatically. This combination is ideal for automating network scans and integrating them into larger cybersecurity workflows.
Key Features:
- Host discovery and port scanning.
- Version detection for services.
- Integration with Python for automation.
Example:
python
import nmap
nm = nmap.PortScanner()
nm.scan('192.168.1.0/24', '22-443')
print(nm.all_hosts())
python-nmap` is particularly useful for penetration testers who need to automate network scanning and incorporate it into scripts for vulnerability assessments.
2. Web Vulnerability Testing
SQLMap (via sqlmap-api)
SQL injection is one of the most common vulnerabilities in web applications. SQLMap is a powerful tool for automating the detection and exploitation of SQL injection flaws. Python’s `sqlmap-api` provides a Python interface to this tool, allowing cybersecurity professionals to integrate SQL injection testing into their automated workflows.
Key Features:
- Automatic detection and exploitation of SQL injection vulnerabilities.
- Database fingerprinting and data extraction.
- Support for various DBMS like MySQL, PostgreSQL, and MSSQL.
Example:
python
import requests
from sqlmapapi.sqlmap import Sqlmap
Initialize sqlmap API client
sqlmap = Sqlmap()
Launch SQL injection scan on target
sqlmap.scan(target="http://example.com", data="username=admin'--")
Using SQLMap’s API, testers can easily automate vulnerability scanning as part of a larger web application security testing suite.
W3af: is an open-source web application security scanner that helps find and exploit web application vulnerabilities. Written in Python, it provides both a graphical user interface (GUI) and command-line interface (CLI) for performing security tests. It has built-in modules for scanning for common vulnerabilities like Cross-Site Scripting (XSS), SQL Injection, and CSRF.
Key Features:
- Modular architecture with plugins for specific vulnerability types.
- Comprehensive web vulnerability scanning and exploitation.
- Extensible through Python scripting.
W3af is ideal for web application testers who want an all-in-one solution for detecting web vulnerabilities.
3. Cryptography and Secure Communications
Cryptography Library
Python’s `cryptography` package is a robust toolkit for implementing encryption, decryption, and secure communication protocols. It provides cryptographic recipes and low-level interfaces to common algorithms such as AES, RSA, and ECC (Elliptic Curve Cryptography).
Key Features:
- Symmetric and asymmetric encryption algorithms.
- Key management and generation.
- Secure hashing and digital signatures.
Example:
python
from cryptography.fernet import Fernet
Generate a key for encryption
key = Fernet.generate_key()
cipher = Fernet(key)
Encrypt and decrypt a message
encrypted_message = cipher.encrypt(b"Sensitive Data")
decrypted_message = cipher.decrypt(encrypted_message)
print(decrypted_message.decode())
The `cryptography` library is widely used in secure data transmission, password storage, and encryption-related tasks across cybersecurity solutions.
PyCryptodome: is a self-contained Python package of cryptographic tools that includes support for encryption algorithms, message authentication codes, and hashing functions. It’s a fork of the original PyCrypto library and is commonly used in cybersecurity projects that need robust cryptographic functions.
Key Features:
- Encryption algorithms like AES, DES, and RSA.
- Hashing functions like SHA256.
- Digital signatures and random number generation.
PyCryptodome is frequently used in building encryption tools, ensuring data integrity, and securing communication protocols in Python-based security applications.
4. Malware Analysis and Reverse Engineering
Yara (via yara-python)
Yara is a popular tool for identifying and classifying malware based on pattern matching. The `yara-python` library provides a Python interface to Yara, allowing malware analysts to integrate Yara’s pattern-matching capabilities directly into their Python scripts.
Key Features:
- Pattern-based matching for malware detection.
- Flexible rule creation for identifying specific malware families.
- Integration with Python for automated malware analysis.
Example:
python
import yara
Define a YARA rule for detecting a specific malware pattern
rule = """
rule MyMalware {
strings:
$a = "malicious_pattern"
condition:
$a
}
"""
# Compile and run the YARA rule
compiled_rule = yara.compile(source=rule)
matches = compiled_rule.match(filepath="/path/to/suspected/file")
print(matches)
`yara-python` is widely used in malware research, forensic investigations, and threat detection to identify known malicious patterns in files and executables.
Volatility: Volatility is a Python-based memory forensics framework that enables analysts to extract information from memory dumps. It is used in digital forensics to investigate running processes, extract cryptographic keys, and detect hidden malware.
Key Features:
- Extraction of digital artifacts from RAM.
- Detection of malware and rootkits in memory dumps.
- Analysis of live systems or offline memory images.
Volatility is a must-have tool for forensic investigators who need to perform detailed memory analysis on compromised systems.
5. Additional Tools and Frameworks
Paramiko: is a Python library for SSH communication that allows secure connections between machines. It is often used for remote system administration, secure file transfers, and automated command execution on remote servers, making it essential for penetration testers and system administrators.
Key Features:
- SSH client and server capabilities.
- Secure file transfers via SFTP.
- Automated remote command execution.
Paramiko simplifies remote access to servers during security testing and post-exploitation activities.
Requests
While not specifically a cybersecurity library, Requests is a widely-used Python library for making HTTP requests. In cybersecurity, it’s commonly used for interacting with web servers, testing APIs, and automating tasks like form submission and vulnerability testing.
Key Features:
- Simple HTTP requests (GET, POST, PUT, etc.).
- Support for SSL/TLS verification.
- Integration with proxies for anonymizing requests.
Requests is often used in web vulnerability testing, scraping, and automation tasks related to web security.
How to obtain Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Python has firmly established itself as one of the most versatile and powerful programming languages for cybersecurity professionals. Its ease of use, combined with a vast range of libraries and frameworks, makes it an indispensable tool for tasks such as network security, web vulnerability testing, cryptography, and malware analysis.
From tools like Scapy and Nmap for network security to Yara for malware detection and Volatility for memory forensics, Python offers solutions for almost every aspect of modern cybersecurity challenges. By leveraging these libraries and frameworks, cybersecurity professionals can stay ahead of emerging threats and protect critical systems from malicious attacks.
As cybersecurity threats continue to grow in complexity, the flexibility and power of Python ensure that it will remain a key player in the fight to secure networks, data, and applications in the years to come.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Automating Data Analysis in Minitab
Do you want to speed up your data analysis and make your stats work more efficient? Minitab is a powerful software tool. It automates many data analysis tasks. This article will explore how automating data analysis in Minitab can help you. It can save you time, reduce manual work, and improve your analysis.
The Benefits of Minitab Data Analysis Automation
Minitab automates data analysis. It helps businesses by streamlining repetitive tasks. This reduces human error and increases efficiency. It lets users quickly process large datasets. This provides faster insights and enables timely decisions. Also, automation in Minitab improves consistency in statistical analysis. It ensures accuracy and reliability across projects.
Automating data analysis in Minitab has many benefits. It can greatly improve your data analysis workflows. By leveraging automation techniques in Minitab, you can:
-
Automate data entry, cleaning, manipulation, and transformation. This will cut tedious work and free up time for more strategic analysis.
-
Improve Data Accuracy: Use Minitab's automation tools. They can reduce errors and ensure your analysis is based on reliable data.
-
Increase Efficiency: Automating repetitive tasks can greatly improve your data analysis. This includes data processing, statistical tests, and analyses. These are regression, cluster, and time series. It also includes data mining.
-
Minitab automation can improve your data analysis. It can find trends, patterns, correlations, and outliers in your data. It will also give you deeper insights.
-
Automating statistical processes in Minitab can help you. It will speed up your analysis and boost your skills. You'll make data-driven decisions faster.
Using Minitab Data Analysis Automation Tools
Learn how Minitab's tools can automate data analysis. They can greatly improve your workflow and efficiency. Automate tasks like data cleaning and reporting. Then, you can focus on finding insights and making decisions. Explore Minitab's features and techniques to improve your data analysis. They will give you faster, more accurate results.
Minitab has many automation tools. They can simplify your data analysis workflows. Some of the key automation features in Minitab include:
-
Automated Reporting: Generate automated reports to communicate your data analysis results more efficiently.
-
Data Analysis Insights: Use your analysis to make better business decisions.
-
Data Analysis Trends: Identify and analyze data trends to better understand your data.
-
Data Analysis Expertise: Use automated tools to sharpen your data analysis and stats skills.
How to Implement Minitab Data Analysis Automation Techniques
In today's fast-paced data world, automating Minitab's data analysis can save time and improve accuracy. This blog explores key automation techniques. It focuses on Minitab's macros and scripts to streamline repetitive tasks and analyses. These strategies can help organizations find insights. They will save time and cut human error in data-driven decisions.
To get started with automating data analysis in Minitab, follow these simple steps:
-
Set Objectives: Define your goals for data analysis. Identify tasks to automate to achieve them.
-
Choose Automation Tools: Explore the automation features in Minitab and select the tools that best meet your needs.
-
Automate your data analysis. This will improve accuracy and speed up statistical analysis.
-
Monitor Results: Track your automated data analysis's performance. Find areas to improve, and adjust to boost efficiency. Use Minitab's automation features to simplify your data analysis. Follow these steps. This will boost efficiency and help you gain insights from your data.
How to obtain Minitab certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, automating data analysis in Minitab can improve your work. It will make your statistical tasks faster and more accurate. It will also help you make better, data-driven business decisions. Explore Minitab's automation tools today. They'll optimize your data analysis and unlock your data's full potential.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
Do you want to speed up your data analysis and make your stats work more efficient? Minitab is a powerful software tool. It automates many data analysis tasks. This article will explore how automating data analysis in Minitab can help you. It can save you time, reduce manual work, and improve your analysis.
The Benefits of Minitab Data Analysis Automation
Minitab automates data analysis. It helps businesses by streamlining repetitive tasks. This reduces human error and increases efficiency. It lets users quickly process large datasets. This provides faster insights and enables timely decisions. Also, automation in Minitab improves consistency in statistical analysis. It ensures accuracy and reliability across projects.
Automating data analysis in Minitab has many benefits. It can greatly improve your data analysis workflows. By leveraging automation techniques in Minitab, you can:
-
Automate data entry, cleaning, manipulation, and transformation. This will cut tedious work and free up time for more strategic analysis.
-
Improve Data Accuracy: Use Minitab's automation tools. They can reduce errors and ensure your analysis is based on reliable data.
-
Increase Efficiency: Automating repetitive tasks can greatly improve your data analysis. This includes data processing, statistical tests, and analyses. These are regression, cluster, and time series. It also includes data mining.
-
Minitab automation can improve your data analysis. It can find trends, patterns, correlations, and outliers in your data. It will also give you deeper insights.
-
Automating statistical processes in Minitab can help you. It will speed up your analysis and boost your skills. You'll make data-driven decisions faster.
Using Minitab Data Analysis Automation Tools
Learn how Minitab's tools can automate data analysis. They can greatly improve your workflow and efficiency. Automate tasks like data cleaning and reporting. Then, you can focus on finding insights and making decisions. Explore Minitab's features and techniques to improve your data analysis. They will give you faster, more accurate results.
Minitab has many automation tools. They can simplify your data analysis workflows. Some of the key automation features in Minitab include:
-
Automated Reporting: Generate automated reports to communicate your data analysis results more efficiently.
-
Data Analysis Insights: Use your analysis to make better business decisions.
-
Data Analysis Trends: Identify and analyze data trends to better understand your data.
-
Data Analysis Expertise: Use automated tools to sharpen your data analysis and stats skills.
How to Implement Minitab Data Analysis Automation Techniques
In today's fast-paced data world, automating Minitab's data analysis can save time and improve accuracy. This blog explores key automation techniques. It focuses on Minitab's macros and scripts to streamline repetitive tasks and analyses. These strategies can help organizations find insights. They will save time and cut human error in data-driven decisions.
To get started with automating data analysis in Minitab, follow these simple steps:
-
Set Objectives: Define your goals for data analysis. Identify tasks to automate to achieve them.
-
Choose Automation Tools: Explore the automation features in Minitab and select the tools that best meet your needs.
-
Automate your data analysis. This will improve accuracy and speed up statistical analysis.
-
Monitor Results: Track your automated data analysis's performance. Find areas to improve, and adjust to boost efficiency. Use Minitab's automation features to simplify your data analysis. Follow these steps. This will boost efficiency and help you gain insights from your data.
How to obtain Minitab certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, automating data analysis in Minitab can improve your work. It will make your statistical tasks faster and more accurate. It will also help you make better, data-driven business decisions. Explore Minitab's automation tools today. They'll optimize your data analysis and unlock your data's full potential.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Evolving Trends in Information Security Management
In a time of rapid tech growth, information security management is changing fast. As businesses rely more on digital systems, data security is vital. They use data to make decisions. So, we must protect sensitive information. This blog explores trends in information security management. It highlights the need for organizations to adapt and innovate their security strategies. We will examine key trends. They are the rise of cybersecurity frameworks, the impact of AI, and a growing focus on compliance. Our goal is to predict the future of information security management.
The Shift Toward Proactive Security Measures
Many organizations have a reactive approach to info security. They address threats only after they arise. However, this mindset is shifting toward a more proactive stance. Companies are investing more in advanced threat detection. They want to predict and prevent breaches, not just respond to them.
Threat Intelligence and Predictive Analytics
Threat intelligence is the study of data on potential threats to an organization's systems. Using predictive analytics, organizations can find patterns that may signal attacks. This trend is becoming essential as cybercriminals develop increasingly sophisticated tactics.
For example, the Cyber Threat Intelligence (CTI) landscape is evolving rapidly. A Cybersecurity Ventures report says global cybersecurity spending will exceed $1 trillion from 2017 to 2021. This shows a growing awareness of the need for strong threat intelligence.
Continuous Monitoring and Response
Continuous monitoring systems let organizations track their networks and systems in real time. Users disliked that rewrite. These systems use automated tools to detect unusual activity. They respond quickly to potential threats. This approach helps an organization reduce risks from cyber incidents.
Integration of Artificial Intelligence and Machine Learning
AI and ML are transforming information security management. They automate processes and improve threat detection. These technologies let organizations quickly analyze vast data. They can find patterns that may indicate security flaws or attacks.
Automated Threat Detection
AI tools can analyze user behavior and system activities. They can spot anomalies that traditional security measures might miss. For instance, machine learning can detect unusual login patterns or data access requests. It alerts security teams to potential breaches.
Enhanced Incident Response
AI can also enhance incident response by automating the containment and remediation of threats. With rules and algorithms, organizations can respond to incidents faster and more accurately. This reduces the damage from security breaches
The Importance of Compliance and Regulatory Frameworks
As data protection rules tighten, compliance is vital for info security. Organizations must follow regulations like the GDPR, HIPAA, and PCI DSS.
Navigating Regulatory Complexity
The complexity of compliance can pose challenges for organizations. The evolving regulatory landscape, though, offers a chance to improve security practices. By adopting compliance as a guiding principle, companies can protect sensitive data. This will build trust with stakeholders. It will also create a strong security framework.
Implementing Security Frameworks
Organizations are adopting security frameworks more and more. These include the NIST Cybersecurity Framework and ISO standards. These frameworks provide guidelines for managing cybersecurity risks. They ensure organizations use security measures that align with industry best practices.
Cloud Security and the Shift to Remote Work
The COVID-19 pandemic sped up cloud computing and remote work. It changed how organizations approach information security. As businesses move to the cloud, data storage and access concerns are rising.
Cloud Security Challenges
While cloud computing offers numerous benefits, it also introduces new security challenges. Data breaches, misconfigured cloud settings, and poor access controls can harm organizations. So, organizations must prioritize cloud security. They must protect sensitive data in the cloud with strong measures.
Zero Trust Security Model
The Zero Trust security model is gaining traction. It's due to the rise of remote work and cloud solutions. This model assumes that no user or device can be trusted by default, regardless of their location. Requiring verification for every access request can improve security. It reduces the risk of unauthorized access
The Rise of Cybersecurity Awareness Training
As cyber threats grow, organizations see the need for human factors in security. Employees are often the weakest link in security. So, we must invest in cybersecurity awareness training.
Building a Security Culture
Organizations are increasingly prioritizing the establishment of a security-aware culture. Regular training sessions can educate employees about new threats. They can also teach best practices for protecting sensitive information. This approach empowers employees to spot threats and respond. It reduces the chance of successful attacks.
Phishing Simulations and Social Engineering Awareness
Phishing is a common tactic used by cybercriminals to steal sensitive information. To combat this threat, organizations are using phishing simulations. They test employees' awareness and response to phishing attempts. By doing these simulations regularly, organizations can find weaknesses and improve training
How to obtain CISM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
As the security landscape changes, organizations must stay alert. They must adapt to new trends. Information security management is fast-changing. It brings both challenges and opportunities. It requires proactive security, AI, and a focus on compliance and cybersecurity training.
To protect sensitive information, organizations must adopt a complete security approach. It must combine technology, processes, and people. By keeping up with trends, organizations can better resist cyber threats. They can then navigate the complex digital landscape with confidence.
In conclusion, the future of information security will be shaped by organizations. They must prioritize proactive security, use advanced technology, and foster a security-aware culture. This will protect their assets and build trust with customers and stakeholders. It will also help create a safer digital world.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In a time of rapid tech growth, information security management is changing fast. As businesses rely more on digital systems, data security is vital. They use data to make decisions. So, we must protect sensitive information. This blog explores trends in information security management. It highlights the need for organizations to adapt and innovate their security strategies. We will examine key trends. They are the rise of cybersecurity frameworks, the impact of AI, and a growing focus on compliance. Our goal is to predict the future of information security management.
The Shift Toward Proactive Security Measures
Many organizations have a reactive approach to info security. They address threats only after they arise. However, this mindset is shifting toward a more proactive stance. Companies are investing more in advanced threat detection. They want to predict and prevent breaches, not just respond to them.
Threat Intelligence and Predictive Analytics
Threat intelligence is the study of data on potential threats to an organization's systems. Using predictive analytics, organizations can find patterns that may signal attacks. This trend is becoming essential as cybercriminals develop increasingly sophisticated tactics.
For example, the Cyber Threat Intelligence (CTI) landscape is evolving rapidly. A Cybersecurity Ventures report says global cybersecurity spending will exceed $1 trillion from 2017 to 2021. This shows a growing awareness of the need for strong threat intelligence.
Continuous Monitoring and Response
Continuous monitoring systems let organizations track their networks and systems in real time. Users disliked that rewrite. These systems use automated tools to detect unusual activity. They respond quickly to potential threats. This approach helps an organization reduce risks from cyber incidents.
Integration of Artificial Intelligence and Machine Learning
AI and ML are transforming information security management. They automate processes and improve threat detection. These technologies let organizations quickly analyze vast data. They can find patterns that may indicate security flaws or attacks.
Automated Threat Detection
AI tools can analyze user behavior and system activities. They can spot anomalies that traditional security measures might miss. For instance, machine learning can detect unusual login patterns or data access requests. It alerts security teams to potential breaches.
Enhanced Incident Response
AI can also enhance incident response by automating the containment and remediation of threats. With rules and algorithms, organizations can respond to incidents faster and more accurately. This reduces the damage from security breaches
The Importance of Compliance and Regulatory Frameworks
As data protection rules tighten, compliance is vital for info security. Organizations must follow regulations like the GDPR, HIPAA, and PCI DSS.
Navigating Regulatory Complexity
The complexity of compliance can pose challenges for organizations. The evolving regulatory landscape, though, offers a chance to improve security practices. By adopting compliance as a guiding principle, companies can protect sensitive data. This will build trust with stakeholders. It will also create a strong security framework.
Implementing Security Frameworks
Organizations are adopting security frameworks more and more. These include the NIST Cybersecurity Framework and ISO standards. These frameworks provide guidelines for managing cybersecurity risks. They ensure organizations use security measures that align with industry best practices.
Cloud Security and the Shift to Remote Work
The COVID-19 pandemic sped up cloud computing and remote work. It changed how organizations approach information security. As businesses move to the cloud, data storage and access concerns are rising.
Cloud Security Challenges
While cloud computing offers numerous benefits, it also introduces new security challenges. Data breaches, misconfigured cloud settings, and poor access controls can harm organizations. So, organizations must prioritize cloud security. They must protect sensitive data in the cloud with strong measures.
Zero Trust Security Model
The Zero Trust security model is gaining traction. It's due to the rise of remote work and cloud solutions. This model assumes that no user or device can be trusted by default, regardless of their location. Requiring verification for every access request can improve security. It reduces the risk of unauthorized access
The Rise of Cybersecurity Awareness Training
As cyber threats grow, organizations see the need for human factors in security. Employees are often the weakest link in security. So, we must invest in cybersecurity awareness training.
Building a Security Culture
Organizations are increasingly prioritizing the establishment of a security-aware culture. Regular training sessions can educate employees about new threats. They can also teach best practices for protecting sensitive information. This approach empowers employees to spot threats and respond. It reduces the chance of successful attacks.
Phishing Simulations and Social Engineering Awareness
Phishing is a common tactic used by cybercriminals to steal sensitive information. To combat this threat, organizations are using phishing simulations. They test employees' awareness and response to phishing attempts. By doing these simulations regularly, organizations can find weaknesses and improve training
How to obtain CISM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
As the security landscape changes, organizations must stay alert. They must adapt to new trends. Information security management is fast-changing. It brings both challenges and opportunities. It requires proactive security, AI, and a focus on compliance and cybersecurity training.
To protect sensitive information, organizations must adopt a complete security approach. It must combine technology, processes, and people. By keeping up with trends, organizations can better resist cyber threats. They can then navigate the complex digital landscape with confidence.
In conclusion, the future of information security will be shaped by organizations. They must prioritize proactive security, use advanced technology, and foster a security-aware culture. This will protect their assets and build trust with customers and stakeholders. It will also help create a safer digital world.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Unit Testing Angular 4 Ensuring Code in Quality
Unit testing is an essential aspect of software development that helps ensure the quality and reliability of the code. In Angular 4, unit testing plays a crucial role in verifying that individual components and services work as intended. Writing unit tests for your Angular 4 app can catch bugs early. It will improve code maintainability, too. This will help you deliver a better product to your users.
Why Should You Unit Test Your Angular 4 Code?
Unit testing your Angular 4 code checks that components and functions work as expected. It helps you catch bugs early in development. It makes your app easier to maintain. Tests ensure that updates and refactoring don't introduce new issues. Also, unit tests improve code quality and reliability. They ensure your app will perform well in different conditions.
Unit testing in Angular 4 helps create a more reliable codebase. It detects issues before they reach production. This reduces the chances of critical bugs slipping through. It also speeds up the development cycle, as automated tests can quickly verify changes without the need for manual testing. Unit tests encourage modular design. This makes your code easier to understand and modify. It also improves scalability and long-term maintenance of the app.
Unit testing is a best practice in software development that offers a multitude of benefits. By writing unit tests for your Angular 4 code, you can:
-
Detect bugs early in the development process, which leads to faster bug resolution and overall savings in time and resources.
-
Improve code maintainability by ensuring that changes to one part of your codebase do not inadvertently break other components.
-
Increase confidence in the quality and reliability of your code, which ultimately leads to a better user experience.
-
Facilitate collaboration among team members by providing clear documentation and examples of how different parts of your application are expected to work.
How to Write Unit Tests in Angular 4
Writing unit tests in Angular 4 ensures that individual components, services, and modules function correctly in isolation. By using the Angular testing framework, along with Jasmine and Karma, developers can create and run test cases to validate the behavior of their code. This not only improves code reliability but also makes debugging easier by catching issues early in development.
Unit testing in Angular 4 follows a structured approach, starting with configuring the TestBed to set up the environment for your components and services. Using Jasmine's `describe`, `it`, and `expect` syntax, you can define various test scenarios to validate expected outcomes. Running these tests with Karma provides immediate feedback, helping ensure the stability and performance of the application as changes are made.
Writing unit tests in Angular 4 is made easy thanks to the built-in testing utilities provided by the framework. Here are the basic steps to get started with unit testing in Angular 4:
-
Set Up Your Testing Environment: Install the necessary testing dependencies using npm, such as Jasmine and Karma, which are commonly used for writing and running unit tests in Angular applications.
-
Create Test Spec Files: In your Angular 4 project, create spec files for each component or service that you want to test. These spec files will contain the actual unit tests for your code.
-
Write Your Unit Tests: Use Jasmine's testing syntax to write descriptive and thorough unit tests for your Angular 4 components and services. Make sure to test both the expected behavior and edge cases of your code.
-
Run Your Tests: Use the Karma test runner to execute your unit tests and verify that your code behaves as expected. Make sure to run your tests regularly to catch any regressions or new bugs.
-
Refactor and Improve: Use the feedback from your unit tests to refactor and improve your code. Better unit tests can find areas for improvement. They will ensure your code is reliable and well-tested.
How to obtain Angular JS 4 certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Unit testing in Angular 4 is a great way to ensure code quality. It helps make your apps more reliable. Writing thorough unit tests for your components and services can catch bugs early. It also improves code maintainability and delivers a better product to your users. Follow best practices to do this. Start writing unit tests for your Angular 4 code today. You'll see a boost in code quality and developer productivity.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
Unit testing is an essential aspect of software development that helps ensure the quality and reliability of the code. In Angular 4, unit testing plays a crucial role in verifying that individual components and services work as intended. Writing unit tests for your Angular 4 app can catch bugs early. It will improve code maintainability, too. This will help you deliver a better product to your users.
Why Should You Unit Test Your Angular 4 Code?
Unit testing your Angular 4 code checks that components and functions work as expected. It helps you catch bugs early in development. It makes your app easier to maintain. Tests ensure that updates and refactoring don't introduce new issues. Also, unit tests improve code quality and reliability. They ensure your app will perform well in different conditions.
Unit testing in Angular 4 helps create a more reliable codebase. It detects issues before they reach production. This reduces the chances of critical bugs slipping through. It also speeds up the development cycle, as automated tests can quickly verify changes without the need for manual testing. Unit tests encourage modular design. This makes your code easier to understand and modify. It also improves scalability and long-term maintenance of the app.
Unit testing is a best practice in software development that offers a multitude of benefits. By writing unit tests for your Angular 4 code, you can:
-
Detect bugs early in the development process, which leads to faster bug resolution and overall savings in time and resources.
-
Improve code maintainability by ensuring that changes to one part of your codebase do not inadvertently break other components.
-
Increase confidence in the quality and reliability of your code, which ultimately leads to a better user experience.
-
Facilitate collaboration among team members by providing clear documentation and examples of how different parts of your application are expected to work.
How to Write Unit Tests in Angular 4
Writing unit tests in Angular 4 ensures that individual components, services, and modules function correctly in isolation. By using the Angular testing framework, along with Jasmine and Karma, developers can create and run test cases to validate the behavior of their code. This not only improves code reliability but also makes debugging easier by catching issues early in development.
Unit testing in Angular 4 follows a structured approach, starting with configuring the TestBed to set up the environment for your components and services. Using Jasmine's `describe`, `it`, and `expect` syntax, you can define various test scenarios to validate expected outcomes. Running these tests with Karma provides immediate feedback, helping ensure the stability and performance of the application as changes are made.
Writing unit tests in Angular 4 is made easy thanks to the built-in testing utilities provided by the framework. Here are the basic steps to get started with unit testing in Angular 4:
-
Set Up Your Testing Environment: Install the necessary testing dependencies using npm, such as Jasmine and Karma, which are commonly used for writing and running unit tests in Angular applications.
-
Create Test Spec Files: In your Angular 4 project, create spec files for each component or service that you want to test. These spec files will contain the actual unit tests for your code.
-
Write Your Unit Tests: Use Jasmine's testing syntax to write descriptive and thorough unit tests for your Angular 4 components and services. Make sure to test both the expected behavior and edge cases of your code.
-
Run Your Tests: Use the Karma test runner to execute your unit tests and verify that your code behaves as expected. Make sure to run your tests regularly to catch any regressions or new bugs.
-
Refactor and Improve: Use the feedback from your unit tests to refactor and improve your code. Better unit tests can find areas for improvement. They will ensure your code is reliable and well-tested.
How to obtain Angular JS 4 certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Unit testing in Angular 4 is a great way to ensure code quality. It helps make your apps more reliable. Writing thorough unit tests for your components and services can catch bugs early. It also improves code maintainability and delivers a better product to your users. Follow best practices to do this. Start writing unit tests for your Angular 4 code today. You'll see a boost in code quality and developer productivity.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
DNS and DHCP Essential Services for CCNA Professionals
In the world of networking, two essential services that every CCNA professional should be familiar with are DNS (Domain Name System) and DHCP (Dynamic Host Configuration Protocol). These services play a crucial role in the setup and management of networks, ensuring seamless communication between devices and servers. Let's dive into the world of DNS and DHCP and understand why they are considered essential for CCNA professionals.
What is DNS?
DNS, or Domain Name System, is a protocol used to translate human-readable domain names into IP addresses that computers can understand. Without DNS, we would have to remember complex strings of numbers to access websites, making the internet a much less user-friendly place. DNS serves as the "phone book" of the internet, allowing us to easily navigate to different websites and servers.
How Does DNS Work?
When you type a domain name into your web browser, your computer sends a request to a DNS server to resolve the domain name to an IP address. The DNS server then responds with the corresponding IP address, allowing your computer to connect to the desired website. This process runs in the background every time you visit a website. So, DNS is critical for internet communication.
DNS (Domain Name System) translates human-readable domain names into IP addresses. Computers use these to identify each other on the network. When a user enters a URL in their browser, the DNS server searches its database for the matching IP address. It then directs the request to the correct server. It takes milliseconds. This lets users access websites without remembering complex IP addresses.
What is DHCP?
DHCP, or Dynamic Host Configuration Protocol, is a protocol. It automatically allocates IP addresses to devices on a network. DHCP lets devices request and receive IP addresses. This simplifies network management and troubleshooting. It is better than manually configuring each device with an IP address.
Why is DHCP Important?
DHCP plays a crucial role in network configuration by automating the process of IP address allocation. This not only saves time and effort for network administrators but also reduces the chances of human error in IP address assignment. DHCP lets devices quickly connect to a network. It assigns them the needed settings, like IP address, subnet mask, and gateway.
Dynamic Host Configuration Protocol (DHCP) is essential. It automates assigning IP addresses and network settings to devices on a network. This reduces the chance of human error. DHCP manages IP addresses from a central point. It prevents conflicts and ensures efficient use of available addresses. This streamlines network admin. Also, DHCP simplifies onboarding new devices. It lets them connect to the network without manual setup.
Why are DNS and DHCP Essential for CCNA Professionals?
CCNA professionals should know networking concepts and protocols, like DNS and DHCP. By mastering these services, CCNA professionals can configure and manage networks. They can also troubleshoot connectivity issues. This will ensure reliable communication between devices and servers.
DNS and DHCP are crucial for CCNA professionals. They enable smooth network communication and management. DNS translates domain names into IP addresses. It lets users access websites easily. DHCP automates IP address assignment, simplifying network setup for devices. Networking pros must understand and manage these services. It is key to network reliability and efficiency.
What are the Benefits of Learning DNS and DHCP?
-
Improved Network Performance: By knowing how DNS and DHCP work, CCNA pros can optimize networks. This ensures smooth communication between devices.
-
Enhanced Security: Properly configuring DNS and DHCP servers can help prevent cyber threats. It can also ensure the integrity of network communication.
-
CCNA professionals know DNS and DHCP. They can quickly fix network issues, minimizing downtime.
How to obtain CCNA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, DNS and DHCP are vital for CCNA pros. They help in enhancing networking skills and expertise. By mastering these protocols, CCNA professionals can configure, manage, and troubleshoot network infrastructure. They can do this with confidence and efficiency. To succeed in networking, you must know DNS and DHCP. They are key for a certification exam and for improving your networking skills.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In the world of networking, two essential services that every CCNA professional should be familiar with are DNS (Domain Name System) and DHCP (Dynamic Host Configuration Protocol). These services play a crucial role in the setup and management of networks, ensuring seamless communication between devices and servers. Let's dive into the world of DNS and DHCP and understand why they are considered essential for CCNA professionals.
What is DNS?
DNS, or Domain Name System, is a protocol used to translate human-readable domain names into IP addresses that computers can understand. Without DNS, we would have to remember complex strings of numbers to access websites, making the internet a much less user-friendly place. DNS serves as the "phone book" of the internet, allowing us to easily navigate to different websites and servers.
How Does DNS Work?
When you type a domain name into your web browser, your computer sends a request to a DNS server to resolve the domain name to an IP address. The DNS server then responds with the corresponding IP address, allowing your computer to connect to the desired website. This process runs in the background every time you visit a website. So, DNS is critical for internet communication.
DNS (Domain Name System) translates human-readable domain names into IP addresses. Computers use these to identify each other on the network. When a user enters a URL in their browser, the DNS server searches its database for the matching IP address. It then directs the request to the correct server. It takes milliseconds. This lets users access websites without remembering complex IP addresses.
What is DHCP?
DHCP, or Dynamic Host Configuration Protocol, is a protocol. It automatically allocates IP addresses to devices on a network. DHCP lets devices request and receive IP addresses. This simplifies network management and troubleshooting. It is better than manually configuring each device with an IP address.
Why is DHCP Important?
DHCP plays a crucial role in network configuration by automating the process of IP address allocation. This not only saves time and effort for network administrators but also reduces the chances of human error in IP address assignment. DHCP lets devices quickly connect to a network. It assigns them the needed settings, like IP address, subnet mask, and gateway.
Dynamic Host Configuration Protocol (DHCP) is essential. It automates assigning IP addresses and network settings to devices on a network. This reduces the chance of human error. DHCP manages IP addresses from a central point. It prevents conflicts and ensures efficient use of available addresses. This streamlines network admin. Also, DHCP simplifies onboarding new devices. It lets them connect to the network without manual setup.
Why are DNS and DHCP Essential for CCNA Professionals?
CCNA professionals should know networking concepts and protocols, like DNS and DHCP. By mastering these services, CCNA professionals can configure and manage networks. They can also troubleshoot connectivity issues. This will ensure reliable communication between devices and servers.
DNS and DHCP are crucial for CCNA professionals. They enable smooth network communication and management. DNS translates domain names into IP addresses. It lets users access websites easily. DHCP automates IP address assignment, simplifying network setup for devices. Networking pros must understand and manage these services. It is key to network reliability and efficiency.
What are the Benefits of Learning DNS and DHCP?
-
Improved Network Performance: By knowing how DNS and DHCP work, CCNA pros can optimize networks. This ensures smooth communication between devices.
-
Enhanced Security: Properly configuring DNS and DHCP servers can help prevent cyber threats. It can also ensure the integrity of network communication.
-
CCNA professionals know DNS and DHCP. They can quickly fix network issues, minimizing downtime.
How to obtain CCNA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, DNS and DHCP are vital for CCNA pros. They help in enhancing networking skills and expertise. By mastering these protocols, CCNA professionals can configure, manage, and troubleshoot network infrastructure. They can do this with confidence and efficiency. To succeed in networking, you must know DNS and DHCP. They are key for a certification exam and for improving your networking skills.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Trends in Application Delivery Controllers ADCs
In tech's fast-changing world, trends in application delivery controllers (ADCs) are vital. They ensure smooth, efficient app delivery across networks. As organizations adopt digital transformation, the demand for ADCs is rising. They must handle the complexities of modern IT. This article will explore the latest trends in ADCs. We will see how they impact performance, security, and scalability.
The Evolution of Application Delivery Controllers
Application delivery controllers (ADCs) have evolved. They are now advanced devices. They manage traffic, optimize app performance, and provide security. They are more than simple load balancers. ADCs were once used to balance network traffic across servers and prevent overload. Now, they offer many functions to meet the needs of today's dynamic IT environments.
Application Delivery Controllers (ADCs) started as simple load balancers. They have now evolved into complex devices. They enhance application performance and security. Modern ADCs now have features like SSL offloading and web app firewalls. They also have advanced traffic management. This helps organizations optimize app delivery while ensuring security. As cloud computing and microservices grow, ADCs are adapting. They must support hybrid environments and connect diverse infrastructures.
Key Trends in ADCs
-
Cloud Migration: We now deploy ADCs in the cloud to optimize app delivery and scalability. This trend lets organizations migrate their apps to the cloud. It keeps performance and security.
-
SDN: Integrating ADCs with SDN tech helps organizations optimize and agile their networks. SDN decouples the control plane from the infrastructure. It simplifies ADC management and boosts their scalability.
-
Application Security: ADCs now have advanced security features. They include SSL offloading, content caching, and an application firewall. These protect against cyber threats and ensure data privacy. These security upgrades are vital. They protect sensitive data and stop unauthorized app access.
-
Multi-Cloud Environment: As firms adopt multi-cloud strategies, ADCs are key. They ensure smooth app delivery across different cloud platforms. ADCs optimize performance and reliability in multi-cloud setups. They do this by managing traffic and balancing loads.
-
Application Scalability: A key trend is to scale applications based on demand. ADCs must be able to scale them for peak performance and availability. They should do this either horizontally or vertically. ADCs support application scalability and improve user experience. They do this by adjusting resources to handle fluctuating traffic levels.
Benefits of Advanced ADC Features
Advanced Application Delivery Controllers (ADCs) boost performance. They optimize app traffic, reduce latency, and speed up load times. These features provide strong security. They include firewalls and DDoS protection. They safeguard apps from various threats. Also, advanced ADCs allow for better traffic management. They enable real-time monitoring of performance and user experience. This improves efficiency.
-
Application Acceleration: ADCs boost app performance. They speed up data traffic and reduce latency. This leads to faster response times and happier users.
-
SSL Encryption: ADCs use built-in SSL encryption. It ensures secure communication between clients and servers. This protects sensitive data from cyber threats and unauthorized access.
-
ADCs boost app availability. They monitor server health, find network bottlenecks, and route traffic to avoid downtime. This ensures uninterrupted service.
-
Traffic Optimization: ADCs optimize network performance by managing app traffic. They prioritize critical data. This improves efficiency and saves costs.
Future of Application Delivery Controllers
As organizations adopt new technologies, ADCs will be crucial. They will ensure optimal application delivery across networks. ADCs will be vital to future, complex IT systems. They have advanced features. They include: intelligent traffic management, scalable apps, and better security.
The future of ADCs is in their ability to integrate advanced technologies. AI and machine learning can enhance their traffic management and security. As businesses move to the cloud, ADCs will evolve. They will support multi-cloud and hybrid-cloud setups. This will optimize app performance across different infrastructures. Also, automation and orchestration will let ADCs adapt to changing networks. This will ensure high availability and a better user experience.
How to obtain NetScaler certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, ADC trends show organizations' changing needs in today's digital age. ADCs will revolutionize app delivery and management. They will do this by migrating to the cloud, using SDN, boosting app security, and ensuring app scalability. Stay tuned for more ADC innovations as technology advances. We aim for a more efficient and secure app delivery.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In tech's fast-changing world, trends in application delivery controllers (ADCs) are vital. They ensure smooth, efficient app delivery across networks. As organizations adopt digital transformation, the demand for ADCs is rising. They must handle the complexities of modern IT. This article will explore the latest trends in ADCs. We will see how they impact performance, security, and scalability.
The Evolution of Application Delivery Controllers
Application delivery controllers (ADCs) have evolved. They are now advanced devices. They manage traffic, optimize app performance, and provide security. They are more than simple load balancers. ADCs were once used to balance network traffic across servers and prevent overload. Now, they offer many functions to meet the needs of today's dynamic IT environments.
Application Delivery Controllers (ADCs) started as simple load balancers. They have now evolved into complex devices. They enhance application performance and security. Modern ADCs now have features like SSL offloading and web app firewalls. They also have advanced traffic management. This helps organizations optimize app delivery while ensuring security. As cloud computing and microservices grow, ADCs are adapting. They must support hybrid environments and connect diverse infrastructures.
Key Trends in ADCs
-
Cloud Migration: We now deploy ADCs in the cloud to optimize app delivery and scalability. This trend lets organizations migrate their apps to the cloud. It keeps performance and security.
-
SDN: Integrating ADCs with SDN tech helps organizations optimize and agile their networks. SDN decouples the control plane from the infrastructure. It simplifies ADC management and boosts their scalability.
-
Application Security: ADCs now have advanced security features. They include SSL offloading, content caching, and an application firewall. These protect against cyber threats and ensure data privacy. These security upgrades are vital. They protect sensitive data and stop unauthorized app access.
-
Multi-Cloud Environment: As firms adopt multi-cloud strategies, ADCs are key. They ensure smooth app delivery across different cloud platforms. ADCs optimize performance and reliability in multi-cloud setups. They do this by managing traffic and balancing loads.
-
Application Scalability: A key trend is to scale applications based on demand. ADCs must be able to scale them for peak performance and availability. They should do this either horizontally or vertically. ADCs support application scalability and improve user experience. They do this by adjusting resources to handle fluctuating traffic levels.
Benefits of Advanced ADC Features
Advanced Application Delivery Controllers (ADCs) boost performance. They optimize app traffic, reduce latency, and speed up load times. These features provide strong security. They include firewalls and DDoS protection. They safeguard apps from various threats. Also, advanced ADCs allow for better traffic management. They enable real-time monitoring of performance and user experience. This improves efficiency.
-
Application Acceleration: ADCs boost app performance. They speed up data traffic and reduce latency. This leads to faster response times and happier users.
-
SSL Encryption: ADCs use built-in SSL encryption. It ensures secure communication between clients and servers. This protects sensitive data from cyber threats and unauthorized access.
-
ADCs boost app availability. They monitor server health, find network bottlenecks, and route traffic to avoid downtime. This ensures uninterrupted service.
-
Traffic Optimization: ADCs optimize network performance by managing app traffic. They prioritize critical data. This improves efficiency and saves costs.
Future of Application Delivery Controllers
As organizations adopt new technologies, ADCs will be crucial. They will ensure optimal application delivery across networks. ADCs will be vital to future, complex IT systems. They have advanced features. They include: intelligent traffic management, scalable apps, and better security.
The future of ADCs is in their ability to integrate advanced technologies. AI and machine learning can enhance their traffic management and security. As businesses move to the cloud, ADCs will evolve. They will support multi-cloud and hybrid-cloud setups. This will optimize app performance across different infrastructures. Also, automation and orchestration will let ADCs adapt to changing networks. This will ensure high availability and a better user experience.
How to obtain NetScaler certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, ADC trends show organizations' changing needs in today's digital age. ADCs will revolutionize app delivery and management. They will do this by migrating to the cloud, using SDN, boosting app security, and ensuring app scalability. Stay tuned for more ADC innovations as technology advances. We aim for a more efficient and secure app delivery.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Optimizing Machine Creation Services MCS with XenServer
Do you want to boost your virtualization platform? Efficient VMs and automated VM deployment can help. Look no further than optimizing Machine Creation Services (MCS) with XenServer. This article will explore key strategies to optimize MCS with XenServer. This will ensure a smooth virtual desktop infrastructure for your organization.
Understanding XenServer Architecture
Before delving into the optimization techniques, let's first understand the architecture of XenServer. XenServer is a powerful hypervisor. It lets organizations easily create and manage virtual machines. XenServer's provisioning services let organizations create machine catalogs and delivery groups. This will streamline virtualization.
Virtualization Platform Optimization
To optimize your XenServer virtual environment, tune your VMs for better performance. Hypervisor management can benefit Citrix XenApp and XenDesktop. It allows for efficient remote desktop services and virtualization. A virtual desktop infrastructure (VDI) with XenServer can boost your IT systems.
Virtualization Platform Optimization means improving virtualized environments. The goal is to boost performance and efficiency to maximize resource use. By implementing best practices in configuration, monitoring, and management, organizations can reduce costs. They can also improve scalability and ensure high availability. This optimization boosts performance. It also helps deploy apps and services in the cloud.
Best Practices for Machine Creation Services Optimization
When configuring Machine Creation Services with XenServer, focus on workload and IT efficiency. Best practices for optimizing Xenserver can boost your VMs' performance. They will also ensure a smooth desktop-as-a-service experience.
Optimizing machine creation services means using best practices. They boost efficiency and cut resource use. Key strategies are: automate workflows, use the cloud, and track metrics to find bottlenecks. A culture of regular feedback and improvement can boost productivity and scalability.
Enhancing VDI Performance with XenServer
One of the key aspects of virtualization optimization is enhancing VDI performance. Optimizing XenServer and Citrix hypervisor settings can boost VM performance. To improve the virtual desktop experience, manage desktop provisioning and automate VDI deployment.
To boost VDI performance with XenServer, optimize resource use. This will ensure a seamless user experience. Organizations can cut latency and boost app responsiveness. They should use advanced features like dynamic memory management and storage optimization. Best practices in configuration and monitoring will maximize XenServer's benefits. This will create a more efficient, reliable VDI environment.
Securing Your Virtual Environment
It's crucial to secure your virtual environment, along with optimizing performance. Tuning XenServer settings and optimizing VDI can improve VDI security. XenServer's virtualization security features can provide added layers of protection against potential threats.
In today's digital world, cyber threats are more sophisticated. So, securing your virtual environment is essential. Strong security measures can help protect sensitive data and systems. Use firewalls, encryption, and regular updates. Also, train your team on best practices. Monitor for unusual activity. These steps are crucial to safeguarding your virtual assets.
Deploying Machine Creation Services with XenServer
To optimize Machine Creation Services with XenServer, organizations should manage settings and ensure scalability. By using best practices for virtualization and infrastructure, organizations can efficiently manage and provision machines. Improving virtual machine performance can boost resource use and IT efficiency.
Using Machine Creation Services (MCS) with XenServer simplifies VM management. It boosts efficiency in desktop and app delivery. MCS lets admins quickly create, manage, and scale virtual desktops. This ensures a seamless user experience. This approach reduces costs and improves resource use. It is key for organizations that want to optimize their virtual environments.
How to obtain XenServer certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, to get peak virtualization performance, optimize Machine Creation Services with XenServer. To improve their virtual environments, organizations can use XenServer. They should focus on three areas: 1. Optimizing virtual desktops. 2. Deploying machine creation services. 3. Scaling VDI. With the right strategies, organizations can create machines and manage virtualizations. They can do this efficiently. Are you ready to optimize your virtual infrastructure with XenServer? Start using these techniques today. They will make your virtual environment more efficient and secure.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
Do you want to boost your virtualization platform? Efficient VMs and automated VM deployment can help. Look no further than optimizing Machine Creation Services (MCS) with XenServer. This article will explore key strategies to optimize MCS with XenServer. This will ensure a smooth virtual desktop infrastructure for your organization.
Understanding XenServer Architecture
Before delving into the optimization techniques, let's first understand the architecture of XenServer. XenServer is a powerful hypervisor. It lets organizations easily create and manage virtual machines. XenServer's provisioning services let organizations create machine catalogs and delivery groups. This will streamline virtualization.
Virtualization Platform Optimization
To optimize your XenServer virtual environment, tune your VMs for better performance. Hypervisor management can benefit Citrix XenApp and XenDesktop. It allows for efficient remote desktop services and virtualization. A virtual desktop infrastructure (VDI) with XenServer can boost your IT systems.
Virtualization Platform Optimization means improving virtualized environments. The goal is to boost performance and efficiency to maximize resource use. By implementing best practices in configuration, monitoring, and management, organizations can reduce costs. They can also improve scalability and ensure high availability. This optimization boosts performance. It also helps deploy apps and services in the cloud.
Best Practices for Machine Creation Services Optimization
When configuring Machine Creation Services with XenServer, focus on workload and IT efficiency. Best practices for optimizing Xenserver can boost your VMs' performance. They will also ensure a smooth desktop-as-a-service experience.
Optimizing machine creation services means using best practices. They boost efficiency and cut resource use. Key strategies are: automate workflows, use the cloud, and track metrics to find bottlenecks. A culture of regular feedback and improvement can boost productivity and scalability.
Enhancing VDI Performance with XenServer
One of the key aspects of virtualization optimization is enhancing VDI performance. Optimizing XenServer and Citrix hypervisor settings can boost VM performance. To improve the virtual desktop experience, manage desktop provisioning and automate VDI deployment.
To boost VDI performance with XenServer, optimize resource use. This will ensure a seamless user experience. Organizations can cut latency and boost app responsiveness. They should use advanced features like dynamic memory management and storage optimization. Best practices in configuration and monitoring will maximize XenServer's benefits. This will create a more efficient, reliable VDI environment.
Securing Your Virtual Environment
It's crucial to secure your virtual environment, along with optimizing performance. Tuning XenServer settings and optimizing VDI can improve VDI security. XenServer's virtualization security features can provide added layers of protection against potential threats.
In today's digital world, cyber threats are more sophisticated. So, securing your virtual environment is essential. Strong security measures can help protect sensitive data and systems. Use firewalls, encryption, and regular updates. Also, train your team on best practices. Monitor for unusual activity. These steps are crucial to safeguarding your virtual assets.
Deploying Machine Creation Services with XenServer
To optimize Machine Creation Services with XenServer, organizations should manage settings and ensure scalability. By using best practices for virtualization and infrastructure, organizations can efficiently manage and provision machines. Improving virtual machine performance can boost resource use and IT efficiency.
Using Machine Creation Services (MCS) with XenServer simplifies VM management. It boosts efficiency in desktop and app delivery. MCS lets admins quickly create, manage, and scale virtual desktops. This ensures a seamless user experience. This approach reduces costs and improves resource use. It is key for organizations that want to optimize their virtual environments.
How to obtain XenServer certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, to get peak virtualization performance, optimize Machine Creation Services with XenServer. To improve their virtual environments, organizations can use XenServer. They should focus on three areas: 1. Optimizing virtual desktops. 2. Deploying machine creation services. 3. Scaling VDI. With the right strategies, organizations can create machines and manage virtualizations. They can do this efficiently. Are you ready to optimize your virtual infrastructure with XenServer? Start using these techniques today. They will make your virtual environment more efficient and secure.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Generative Deep Learning Powering Creative AI Applications
In the fast-changing world of AI, generative deep learning has emerged as a powerful tool. It drives creativity and innovation in many applications. Generative models use deep neural networks and advanced algorithms. They let AI systems create content, designs, and solutions that were once unthinkable. Let's explore how generative deep learning is changing AI. It's powering a new wave of creative apps.
Understanding Generative Deep Learning
Generative deep learning is a type of machine learning. It creates new data instead of just analyzing existing data. Generative models use deep neural networks with complex architectures. They can learn patterns in datasets and generate new outputs that mimic the original data. These deep learning techniques enable AI to create new solutions. They are better than traditional machine learning algorithms.
"Generative deep learning uses neural networks to create new data. This data mimics patterns in existing data, such as images, text, or audio." Generative deep learning can create realistic content using models like GANs and VAEs. The content is indistinguishable from real-world examples. This tech is advancing AI creativity. It now generates art and music, and creates deepfakes and synthetic data to train other models."
The Power of Generative AI Technology
Generative AI is at the forefront of AI applications. It pushes the limits of creativity and innovation. Deep learning-trained neural networks can create realistic images, music, and text. This can apply to many industries. Generative AI is transforming our tech interactions. It creates unique designs and personalized recommendations.
Generative AI is transforming industries. It lets machines create original content, including text, images, music, and code. This new tech uses GANs and transformers. It sparks creativity and automation in design, marketing, and entertainment. As generative AI evolves, it has the potential to change how businesses innovate and interact with digital content.
Advancements in Deep Learning Solutions
Advancements in deep learning are making generative AI more powerful and sophisticated. Deep neural networks now power creative algorithms. They can generate art, music, and even stories with great realism and creativity. We are training machine learning models to think creatively. They must find new solutions to complex problems. This could expand AI innovation in ways we never thought possible.
Deep learning has made great strides in recent years. It has driven innovation in healthcare, finance, and autonomous systems. New advancements in neural networks and model architectures are enabling more accurate predictions. They are also improving processing speed and real-time decision-making. Deep learning is transforming businesses and daily life. Research in unsupervised learning and AI explainability is ongoing.
Creative Applications of AI Technology
AI technology has endless creative uses. It can generate unique designs and develop innovative solutions to real-world problems. Generative AI is used in fashion, gaming, music, and visual arts. It aims to boost creativity and provide new insights into the creative process. AI systems can use deep learning and machine learning. They can create inspiring work that challenges our view of AI's limits.
AI is unlocking new creativity across industries. It generates realistic art and music. It also enhances film production with visual effects. Tools like generative adversarial networks (GANs) let artists and designers push their imaginations. They can create content that has never been seen before. AI can analyze trends and automate tasks. It is revolutionizing marketing, fashion, and game development. This is making creativity more accessible and scalable.
The Future of Generative AI
As generative AI evolves, we will see more groundbreaking apps and creative solutions. AI systems using deep learning will soon create complex, original content. This will spark a new era of creative innovation. From generative art to AI design tools, the possibilities are endless. Generative deep learning will shape the future of AI.
How to obtain Deep Learning certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, generative deep learning drives creative AI. It pushes the limits of AI. Generative AI is using deep neural networks and advanced algorithms. It is changing how we view creativity and innovation. As we explore generative deep learning, we will see new, exciting apps. They will transform AI technology for years to come.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In the fast-changing world of AI, generative deep learning has emerged as a powerful tool. It drives creativity and innovation in many applications. Generative models use deep neural networks and advanced algorithms. They let AI systems create content, designs, and solutions that were once unthinkable. Let's explore how generative deep learning is changing AI. It's powering a new wave of creative apps.
Understanding Generative Deep Learning
Generative deep learning is a type of machine learning. It creates new data instead of just analyzing existing data. Generative models use deep neural networks with complex architectures. They can learn patterns in datasets and generate new outputs that mimic the original data. These deep learning techniques enable AI to create new solutions. They are better than traditional machine learning algorithms.
"Generative deep learning uses neural networks to create new data. This data mimics patterns in existing data, such as images, text, or audio." Generative deep learning can create realistic content using models like GANs and VAEs. The content is indistinguishable from real-world examples. This tech is advancing AI creativity. It now generates art and music, and creates deepfakes and synthetic data to train other models."
The Power of Generative AI Technology
Generative AI is at the forefront of AI applications. It pushes the limits of creativity and innovation. Deep learning-trained neural networks can create realistic images, music, and text. This can apply to many industries. Generative AI is transforming our tech interactions. It creates unique designs and personalized recommendations.
Generative AI is transforming industries. It lets machines create original content, including text, images, music, and code. This new tech uses GANs and transformers. It sparks creativity and automation in design, marketing, and entertainment. As generative AI evolves, it has the potential to change how businesses innovate and interact with digital content.
Advancements in Deep Learning Solutions
Advancements in deep learning are making generative AI more powerful and sophisticated. Deep neural networks now power creative algorithms. They can generate art, music, and even stories with great realism and creativity. We are training machine learning models to think creatively. They must find new solutions to complex problems. This could expand AI innovation in ways we never thought possible.
Deep learning has made great strides in recent years. It has driven innovation in healthcare, finance, and autonomous systems. New advancements in neural networks and model architectures are enabling more accurate predictions. They are also improving processing speed and real-time decision-making. Deep learning is transforming businesses and daily life. Research in unsupervised learning and AI explainability is ongoing.
Creative Applications of AI Technology
AI technology has endless creative uses. It can generate unique designs and develop innovative solutions to real-world problems. Generative AI is used in fashion, gaming, music, and visual arts. It aims to boost creativity and provide new insights into the creative process. AI systems can use deep learning and machine learning. They can create inspiring work that challenges our view of AI's limits.
AI is unlocking new creativity across industries. It generates realistic art and music. It also enhances film production with visual effects. Tools like generative adversarial networks (GANs) let artists and designers push their imaginations. They can create content that has never been seen before. AI can analyze trends and automate tasks. It is revolutionizing marketing, fashion, and game development. This is making creativity more accessible and scalable.
The Future of Generative AI
As generative AI evolves, we will see more groundbreaking apps and creative solutions. AI systems using deep learning will soon create complex, original content. This will spark a new era of creative innovation. From generative art to AI design tools, the possibilities are endless. Generative deep learning will shape the future of AI.
How to obtain Deep Learning certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, generative deep learning drives creative AI. It pushes the limits of AI. Generative AI is using deep neural networks and advanced algorithms. It is changing how we view creativity and innovation. As we explore generative deep learning, we will see new, exciting apps. They will transform AI technology for years to come.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
How Salesforce Admins Can Improve CRM User Adoption
In today's fast-paced business world, companies must adopt a CRM system. It's key to boosting efficiency and engaging customers. Salesforce is a top CRM used by businesses worldwide. Salesforce Admins are key to ensuring users adopt the system. This article will explore strategies and best practices for Salesforce Admins. They can use them to boost CRM user adoption and drive success in their organizations.
Strategies for Improving CRM User Adoption
1. Training and Communication
One of the key factors in ensuring successful CRM adoption is providing users with thorough training on how to use the platform effectively. Salesforce Admins should create user-friendly training materials. They should also conduct training sessions to familiarize users with the system's features. Also, it's vital to communicate with users about the CRM system. They need to know its benefits and how it can help with their daily tasks. This is key to driving adoption.
2. Platform Integration and Data Management
Integrating the CRM platform with other systems used within the organization can streamline workflows and enhance the user experience. Salesforce Admins should work towards optimizing data management processes within the CRM system to ensure that users have access to accurate and up-to-date information.
Integrating platforms and managing data are key. They create seamless workflows across business apps. By connecting different platforms, businesses can ensure data consistency, reduce manual data entry, and improve decision-making. Effective data management strategies enhance data accuracy, security, and accessibility, enabling organizations to optimize their operations and gain deeper insights.
3. Adoption Rate Monitoring and Feedback
Monitoring the adoption rate of the CRM system and collecting feedback from users are crucial for understanding user behavior and identifying areas for improvement. Salesforce Admins should use tools and analytics to track user engagement and satisfaction levels, and use this data to continuously refine the system to meet the evolving needs of users.
Adoption rate monitoring involves tracking how effectively users are utilizing a new system or tool, providing key insights into its success. By regularly gathering user feedback, organizations can identify pain points and areas for improvement. This process helps in refining the system and ensuring long-term user engagement and satisfaction.
Techniques for Driving User Engagement
1. Workflow Automation
Implementing workflow automation within the CRM system can help users streamline repetitive tasks and focus on more strategic activities. Salesforce Admins should work towards automating routine processes to optimize efficiency and enhance user productivity.
2. Reports and Dashboards Customization
Customizing reports and dashboards within the CRM system can provide users with actionable insights and help them make informed decisions. Salesforce Admins should collaborate with users to understand their reporting needs and customize dashboards to display relevant data in a clear and concise manner.
3. Onboarding and Support
Providing robust onboarding support to new users and offering ongoing support to existing users can boost CRM adoption rates. Salesforce Admins should invest in creating comprehensive onboarding materials and providing round-the-clock support to address user queries and challenges.
Best Practices for Enhancing User Experience
1. Collaboration and Feedback
Encouraging collaboration among users and creating channels for feedback can foster a sense of community and engagement within the CRM system. Salesforce Admins should facilitate collaboration through features such as chat rooms, discussion boards, and feedback forms to promote user interaction.
2. Implementation of User-Centric Design
Designing the CRM system with a user-centric approach in mind can improve user satisfaction and drive adoption. Salesforce Admins should prioritize users when customizing the system. They should create a seamless user experience.
3. Performance Metrics and Mobile Optimization
Tracking metrics in the CRM and optimizing it for mobile can boost user productivity and satisfaction. Salesforce Admins should use analytics to monitor user performance. They must ensure the system works on various devices for users' convenience.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Salesforce Admins are vital for boosting CRM user adoption in organizations. By using the methods in this article, Salesforce Admins can drive success. They will help users maximize the CRM's capabilities. Salesforce Admins can boost efficiency and user satisfaction. They should focus on training, communication, and platform integration. Also, they should engage users and improve the user experience.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced business world, companies must adopt a CRM system. It's key to boosting efficiency and engaging customers. Salesforce is a top CRM used by businesses worldwide. Salesforce Admins are key to ensuring users adopt the system. This article will explore strategies and best practices for Salesforce Admins. They can use them to boost CRM user adoption and drive success in their organizations.
Strategies for Improving CRM User Adoption
1. Training and Communication
One of the key factors in ensuring successful CRM adoption is providing users with thorough training on how to use the platform effectively. Salesforce Admins should create user-friendly training materials. They should also conduct training sessions to familiarize users with the system's features. Also, it's vital to communicate with users about the CRM system. They need to know its benefits and how it can help with their daily tasks. This is key to driving adoption.
2. Platform Integration and Data Management
Integrating the CRM platform with other systems used within the organization can streamline workflows and enhance the user experience. Salesforce Admins should work towards optimizing data management processes within the CRM system to ensure that users have access to accurate and up-to-date information.
Integrating platforms and managing data are key. They create seamless workflows across business apps. By connecting different platforms, businesses can ensure data consistency, reduce manual data entry, and improve decision-making. Effective data management strategies enhance data accuracy, security, and accessibility, enabling organizations to optimize their operations and gain deeper insights.
3. Adoption Rate Monitoring and Feedback
Monitoring the adoption rate of the CRM system and collecting feedback from users are crucial for understanding user behavior and identifying areas for improvement. Salesforce Admins should use tools and analytics to track user engagement and satisfaction levels, and use this data to continuously refine the system to meet the evolving needs of users.
Adoption rate monitoring involves tracking how effectively users are utilizing a new system or tool, providing key insights into its success. By regularly gathering user feedback, organizations can identify pain points and areas for improvement. This process helps in refining the system and ensuring long-term user engagement and satisfaction.
Techniques for Driving User Engagement
1. Workflow Automation
Implementing workflow automation within the CRM system can help users streamline repetitive tasks and focus on more strategic activities. Salesforce Admins should work towards automating routine processes to optimize efficiency and enhance user productivity.
2. Reports and Dashboards Customization
Customizing reports and dashboards within the CRM system can provide users with actionable insights and help them make informed decisions. Salesforce Admins should collaborate with users to understand their reporting needs and customize dashboards to display relevant data in a clear and concise manner.
3. Onboarding and Support
Providing robust onboarding support to new users and offering ongoing support to existing users can boost CRM adoption rates. Salesforce Admins should invest in creating comprehensive onboarding materials and providing round-the-clock support to address user queries and challenges.
Best Practices for Enhancing User Experience
1. Collaboration and Feedback
Encouraging collaboration among users and creating channels for feedback can foster a sense of community and engagement within the CRM system. Salesforce Admins should facilitate collaboration through features such as chat rooms, discussion boards, and feedback forms to promote user interaction.
2. Implementation of User-Centric Design
Designing the CRM system with a user-centric approach in mind can improve user satisfaction and drive adoption. Salesforce Admins should prioritize users when customizing the system. They should create a seamless user experience.
3. Performance Metrics and Mobile Optimization
Tracking metrics in the CRM and optimizing it for mobile can boost user productivity and satisfaction. Salesforce Admins should use analytics to monitor user performance. They must ensure the system works on various devices for users' convenience.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Salesforce Admins are vital for boosting CRM user adoption in organizations. By using the methods in this article, Salesforce Admins can drive success. They will help users maximize the CRM's capabilities. Salesforce Admins can boost efficiency and user satisfaction. They should focus on training, communication, and platform integration. Also, they should engage users and improve the user experience.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Microsofts Investments in Quantum Cryptography
In the fast-changing world of digital security, Microsoft leads in quantum cryptography. It is the most innovative in that field. As quantum computing rises and cyber threats grow, we need better security. Microsoft's investments in quantum cryptography have led to quantum-safe cybersecurity. This technology revolutionizes data security in the digital age.
What is Quantum Cryptography?
Quantum cryptography uses quantum mechanics to secure communication and data. Unlike traditional encryption, which can be cracked over time, quantum cryptography is secure. It uses quantum protocols and algorithms based on quantum physics. This tech will change computer security. It will provide quantum-resistant encryption that is nearly unbreakable.
How Does Quantum Cryptography Work?
Quantum cryptography is based on qubits. They are the building blocks of quantum information. Quantum encryption uses qubits' unique properties, like superposition and entanglement. It can create secure communication channels that are immune to eavesdropping and hacking. Quantum key distribution is a key part of quantum cryptography. It uses quantum mechanics to enable secure key exchange between parties.
Microsoft’s Quantum Initiatives
Microsoft leads in quantum computing research. A team of experts is developing quantum communication and encryption technologies. The company's quantum network and encryption tech set the standard for secure quantum communication. Microsoft is investing in quantum-safe encryption and quantum cryptographic protocols. This will secure data in the future.
Microsoft's Quantum Initiatives aim to speed up quantum computing. They do this through research, software, and partnerships. Microsoft is using Azure Quantum to solve complex problems. This includes work in cryptography, materials science, and AI. These efforts make Microsoft a leader in practical quantum solutions. Industries seek to solve problems that classical computers cannot.
Advancements in Quantum Security
Quantum computing is making traditional encryption methods vulnerable to cyber attacks. Quantum-resistant algorithms and quantum-safe cryptography can help. They create secure channels that resist quantum decryption. Microsoft's quantum security measures are the best. They are pioneering quantum encryption solutions. These will secure data transmission and protect sensitive information in the quantum era.
Quantum security is a critical field. It uses quantum computing to create new, unbreakable encryption methods. As advanced computing weakens traditional cryptography, quantum security offers a solution. It will protect sensitive data from future threats. These advancements are paving the way for secure digital communications and financial transactions. They will also improve government data protection.
The Future of Quantum Cryptography
As quantum technology continues to advance, the possibilities for quantum cryptography are limitless. Quantum encryption has many uses. They range from quantum secure data transmission to quantum-resistant cryptography. Microsoft's work in quantum tech is advancing secure quantum communication. This will shape the future of cybersecurity.
Quantum cryptography is a major advance in secure digital communication. It uses quantum mechanics to protect data from future threats. Quantum computing advances threaten traditional encryption methods. Quantum cryptography promises unbreakable encryption and the highest security. As quantum technology matures, quantum cryptography will be vital. It will protect sensitive information in industries like finance and government.
How to obtain Microsoft certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Microsoft's work in quantum cryptography has made it a leader in digital security. Microsoft is using quantum mechanics and encryption. This will fight new cybersecurity threats and create a safer digital future. With quantum advancements on the horizon, quantum cryptography could revolutionize data security. Its potential is both exciting and promising.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In the fast-changing world of digital security, Microsoft leads in quantum cryptography. It is the most innovative in that field. As quantum computing rises and cyber threats grow, we need better security. Microsoft's investments in quantum cryptography have led to quantum-safe cybersecurity. This technology revolutionizes data security in the digital age.
What is Quantum Cryptography?
Quantum cryptography uses quantum mechanics to secure communication and data. Unlike traditional encryption, which can be cracked over time, quantum cryptography is secure. It uses quantum protocols and algorithms based on quantum physics. This tech will change computer security. It will provide quantum-resistant encryption that is nearly unbreakable.
How Does Quantum Cryptography Work?
Quantum cryptography is based on qubits. They are the building blocks of quantum information. Quantum encryption uses qubits' unique properties, like superposition and entanglement. It can create secure communication channels that are immune to eavesdropping and hacking. Quantum key distribution is a key part of quantum cryptography. It uses quantum mechanics to enable secure key exchange between parties.
Microsoft’s Quantum Initiatives
Microsoft leads in quantum computing research. A team of experts is developing quantum communication and encryption technologies. The company's quantum network and encryption tech set the standard for secure quantum communication. Microsoft is investing in quantum-safe encryption and quantum cryptographic protocols. This will secure data in the future.
Microsoft's Quantum Initiatives aim to speed up quantum computing. They do this through research, software, and partnerships. Microsoft is using Azure Quantum to solve complex problems. This includes work in cryptography, materials science, and AI. These efforts make Microsoft a leader in practical quantum solutions. Industries seek to solve problems that classical computers cannot.
Advancements in Quantum Security
Quantum computing is making traditional encryption methods vulnerable to cyber attacks. Quantum-resistant algorithms and quantum-safe cryptography can help. They create secure channels that resist quantum decryption. Microsoft's quantum security measures are the best. They are pioneering quantum encryption solutions. These will secure data transmission and protect sensitive information in the quantum era.
Quantum security is a critical field. It uses quantum computing to create new, unbreakable encryption methods. As advanced computing weakens traditional cryptography, quantum security offers a solution. It will protect sensitive data from future threats. These advancements are paving the way for secure digital communications and financial transactions. They will also improve government data protection.
The Future of Quantum Cryptography
As quantum technology continues to advance, the possibilities for quantum cryptography are limitless. Quantum encryption has many uses. They range from quantum secure data transmission to quantum-resistant cryptography. Microsoft's work in quantum tech is advancing secure quantum communication. This will shape the future of cybersecurity.
Quantum cryptography is a major advance in secure digital communication. It uses quantum mechanics to protect data from future threats. Quantum computing advances threaten traditional encryption methods. Quantum cryptography promises unbreakable encryption and the highest security. As quantum technology matures, quantum cryptography will be vital. It will protect sensitive information in industries like finance and government.
How to obtain Microsoft certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Microsoft's work in quantum cryptography has made it a leader in digital security. Microsoft is using quantum mechanics and encryption. This will fight new cybersecurity threats and create a safer digital future. With quantum advancements on the horizon, quantum cryptography could revolutionize data security. Its potential is both exciting and promising.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Agile Metrics and KPIs for Scrum Teams
In Agile project management, metrics and KPIs are key. They assess the performance of Scrum teams. Agile practitioners can gain insights by measuring the team's progress and productivity. They can spot inefficiencies and areas for improvement. This article will explore Agile metrics and KPIs for Scrum teams. We will discuss best practices for measuring and analyzing team performance.
Understanding Agile Metrics
Agile metrics are numbers that measure progress, performance, and quality in Agile development. These metrics show the project's status. They help teams make data-driven decisions to ensure project success. Some common Agile metrics include sprint velocity, team performance, and backlog management.
Agile metrics are key to measuring team performance and project progress in Scrum. Metrics like velocity, sprint burndown, and lead time provide insights. They help Scrum Masters and teams find areas to improve and make decisions. The right metrics can boost collaboration, accountability, and goal achievement.
Sprint Velocity: This metric measures the amount of work completed by a Scrum team during a sprint. It helps teams estimate how much work they can accomplish in future sprints and provides insights into the team's overall productivity.
Team Performance: These metrics assess a Scrum team's ability to meet its goals and deliver value to stakeholders. Metrics can include sprint burndown charts. They show the work left in a sprint. Also, there is sprint progress tracking. It evaluates the team's efficiency and effectiveness.
Backlog Management: This metric measures a team's management of its product backlog. It ensures that the most valuable items are prioritized and delivered on time. Effective backlog management is essential for Agile project success.
Key Performance Indicators for Scrum Teams
Key performance indicators (KPIs) are metrics. They evaluate Agile practices and Scrum teams' performance. These KPIs provide objective data on the team's progress and help identify areas for improvement. Common KPIs for Scrum teams are: sprint efficiency, stakeholder engagement, and team empowerment.
Scrum teams need Key Performance Indicators (KPIs). They measure progress and success in delivering value.
Common KPIs include velocity and burn-down charts.
Velocity tracks the work completed in a sprint. Burn-down charts show the remaining work over time. They help teams stay on track.
Also, monitoring team engagement can reveal dynamics and improvement areas. This fosters a more collaborative environment.
Sprint Efficiency: Sprint efficiency measures how well a team is able to deliver work within the allocated time frame. It tests the team's ability to meet sprint goals. And, it checks their efficiency and effectiveness in delivering value to stakeholders.
Stakeholder Engagement: This KPI measures how satisfied stakeholders are with the team's work and their level of involvement. Strong stakeholder engagement is key to project success. It ensures the team delivers value to its customers.
Team Empowerment: It measures how much autonomy and decision-making power teams have. Empowered teams are more motivated and productive. This leads to better work and happier customers.
Best Practices for Agile Measurement and Reporting
To measure and report Agile metrics and KPIs, teams must follow best practices. This ensures accurate, meaningful data. Some best practices include:
-
Define Clear Objectives: Clearly define the goals of the metrics and KPIs. They should align with the team's project objectives.
-
Use Agile Tools: Use Agile tools to collect and analyze data. This includes burndown charts, sprint backlogs, and reporting tools.
-
Regularly review and update Agile metrics and KPIs. This will keep them relevant and aligned with the team's objectives. By using Agile metrics and KPIs, Scrum teams can boost their performance. They can improve project outcomes and drive continuous improvement in their Agile practices.
How to obtain CSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Agile metrics and KPIs are essential tools for evaluating the performance and effectiveness of Scrum teams. By measuring key aspects of team performance, Agile practitioners can gain insights. They can find ways to improve their team's efficiency. Agile measurement and reporting best practices can help teams. They can ensure they are on track to deliver value to stakeholders and succeed.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In Agile project management, metrics and KPIs are key. They assess the performance of Scrum teams. Agile practitioners can gain insights by measuring the team's progress and productivity. They can spot inefficiencies and areas for improvement. This article will explore Agile metrics and KPIs for Scrum teams. We will discuss best practices for measuring and analyzing team performance.
Understanding Agile Metrics
Agile metrics are numbers that measure progress, performance, and quality in Agile development. These metrics show the project's status. They help teams make data-driven decisions to ensure project success. Some common Agile metrics include sprint velocity, team performance, and backlog management.
Agile metrics are key to measuring team performance and project progress in Scrum. Metrics like velocity, sprint burndown, and lead time provide insights. They help Scrum Masters and teams find areas to improve and make decisions. The right metrics can boost collaboration, accountability, and goal achievement.
Sprint Velocity: This metric measures the amount of work completed by a Scrum team during a sprint. It helps teams estimate how much work they can accomplish in future sprints and provides insights into the team's overall productivity.
Team Performance: These metrics assess a Scrum team's ability to meet its goals and deliver value to stakeholders. Metrics can include sprint burndown charts. They show the work left in a sprint. Also, there is sprint progress tracking. It evaluates the team's efficiency and effectiveness.
Backlog Management: This metric measures a team's management of its product backlog. It ensures that the most valuable items are prioritized and delivered on time. Effective backlog management is essential for Agile project success.
Key Performance Indicators for Scrum Teams
Key performance indicators (KPIs) are metrics. They evaluate Agile practices and Scrum teams' performance. These KPIs provide objective data on the team's progress and help identify areas for improvement. Common KPIs for Scrum teams are: sprint efficiency, stakeholder engagement, and team empowerment.
Scrum teams need Key Performance Indicators (KPIs). They measure progress and success in delivering value.
Common KPIs include velocity and burn-down charts.
Velocity tracks the work completed in a sprint. Burn-down charts show the remaining work over time. They help teams stay on track.
Also, monitoring team engagement can reveal dynamics and improvement areas. This fosters a more collaborative environment.
Sprint Efficiency: Sprint efficiency measures how well a team is able to deliver work within the allocated time frame. It tests the team's ability to meet sprint goals. And, it checks their efficiency and effectiveness in delivering value to stakeholders.
Stakeholder Engagement: This KPI measures how satisfied stakeholders are with the team's work and their level of involvement. Strong stakeholder engagement is key to project success. It ensures the team delivers value to its customers.
Team Empowerment: It measures how much autonomy and decision-making power teams have. Empowered teams are more motivated and productive. This leads to better work and happier customers.
Best Practices for Agile Measurement and Reporting
To measure and report Agile metrics and KPIs, teams must follow best practices. This ensures accurate, meaningful data. Some best practices include:
-
Define Clear Objectives: Clearly define the goals of the metrics and KPIs. They should align with the team's project objectives.
-
Use Agile Tools: Use Agile tools to collect and analyze data. This includes burndown charts, sprint backlogs, and reporting tools.
-
Regularly review and update Agile metrics and KPIs. This will keep them relevant and aligned with the team's objectives. By using Agile metrics and KPIs, Scrum teams can boost their performance. They can improve project outcomes and drive continuous improvement in their Agile practices.
How to obtain CSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Agile metrics and KPIs are essential tools for evaluating the performance and effectiveness of Scrum teams. By measuring key aspects of team performance, Agile practitioners can gain insights. They can find ways to improve their team's efficiency. Agile measurement and reporting best practices can help teams. They can ensure they are on track to deliver value to stakeholders and succeed.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Integrating Kafka with Serverless Functions
Are you looking to optimize real-time data processing in your cloud-native microservices architecture? If so, using Apache Kafka with serverless functions could be ideal for your needs. It would be great for event-driven processing. This article will discuss the benefits of using Kafka. It is a high-throughput messaging system. It will focus on its use with serverless computing, like AWS Lambda. Let's explore how this integration can improve your data pipelines. It can also enable scalable architecture in your cloud apps. It will streamline event-driven design, too.
The Power of Kafka in Event Streaming
Apache Kafka is a distributed event streaming platform. It excels at handling high volumes of real-time data. It is a reliable message queue for async microservice communication. It is ideal for event-driven programming in modern cloud architectures. Kafka ensures seamless data flow across your distributed systems. It supports your applications' growth and scalability.
Apache Kafka has changed event streaming. It offers a scalable, fault-tolerant platform for handling vast amounts of real-time data. Its distributed architecture allows seamless data integration across different systems. It supports event-driven microservices and real-time analytics. With Kafka, organizations can build apps that react to data changes instantly. This enhances decision-making and efficiency.
Leveraging Serverless Functions for Event-Driven Architecture
Serverless computing, like AWS Lambda, lets you run code. You don't have to manage servers. Serverless functions let you run event handlers in response to Kafka messages. This is a cheap, dynamic way to process real-time data. This integration lets you build serverless apps. They will react to events in your Kafka topics. It will trigger functions to process data on demand.
Serverless functions provide a flexible, scalable way to use event-driven architectures. They let developers process events in real-time without managing servers. Businesses can respond to data streams, user actions, and system events. They can do this by connecting to event sources like AWS Lambda and Azure Functions. This approach cuts costs, simplifies deployment, and boosts agility. It helps handle unpredictable workloads or demand spikes.
Enhancing Data Pipelines with Scalable Architecture
Combine Kafka with serverless functions. Then, you can design a scalable architecture. It should process data in real time and do so efficiently. Serverless frameworks like SAM and the Serverless Framework provide tools to deploy functions. These functions are triggered by Kafka events. They are event-driven and serverless. This approach simplifies the development and deployment of serverless apps with Kafka integration. It enhances the resiliency and flexibility of your data pipelines.
Data pipelines must have a scalable architecture. It will ensure systems can handle growing data volumes efficiently, without losing performance. Organizations can scale their data pipelines as needs grow. They can do this by using distributed processing, cloud-native tools, and modular design. This approach boosts reliability and throughput. It also enables real-time data analytics and seamless integration across multiple data sources.
Optimizing Event-Driven Workloads with Kafka
Using Kafka with serverless functions can improve your cloud apps' event-driven workloads. You can build a fast, efficient event-driven system. Use Kafka for real-time streams and serverless functions for on-demand data. Combining both technologies lets you build resilient, scalable apps. They can meet changing data needs in real time.
To optimize event-driven workloads with Apache Kafka, you must fine-tune some key components. These include producer configurations, partitioning strategies, and consumer parallelism. Organizations can improve real-time event processing. They should balance load across Kafka brokers and reduce latency. Also, Kafka's fault tolerance and scalability ensure it can handle high-throughput event streams. This makes it ideal for mission-critical systems.
How to obtain Apache Kafka certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Apache Kafka with serverless functions can boost your microservices' event-driven processing. They are cloud-native. Use Kafka for real-time event streams and serverless functions for on-demand data processing. This will help you build scalable, resilient, and cost-effective apps. This integration allows you to build efficient data pipelines. It will also streamline event-driven design and boost your cloud architecture's performance. Consider using Kafka with serverless functions. It will maximize your event-driven processing.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to optimize real-time data processing in your cloud-native microservices architecture? If so, using Apache Kafka with serverless functions could be ideal for your needs. It would be great for event-driven processing. This article will discuss the benefits of using Kafka. It is a high-throughput messaging system. It will focus on its use with serverless computing, like AWS Lambda. Let's explore how this integration can improve your data pipelines. It can also enable scalable architecture in your cloud apps. It will streamline event-driven design, too.
The Power of Kafka in Event Streaming
Apache Kafka is a distributed event streaming platform. It excels at handling high volumes of real-time data. It is a reliable message queue for async microservice communication. It is ideal for event-driven programming in modern cloud architectures. Kafka ensures seamless data flow across your distributed systems. It supports your applications' growth and scalability.
Apache Kafka has changed event streaming. It offers a scalable, fault-tolerant platform for handling vast amounts of real-time data. Its distributed architecture allows seamless data integration across different systems. It supports event-driven microservices and real-time analytics. With Kafka, organizations can build apps that react to data changes instantly. This enhances decision-making and efficiency.
Leveraging Serverless Functions for Event-Driven Architecture
Serverless computing, like AWS Lambda, lets you run code. You don't have to manage servers. Serverless functions let you run event handlers in response to Kafka messages. This is a cheap, dynamic way to process real-time data. This integration lets you build serverless apps. They will react to events in your Kafka topics. It will trigger functions to process data on demand.
Serverless functions provide a flexible, scalable way to use event-driven architectures. They let developers process events in real-time without managing servers. Businesses can respond to data streams, user actions, and system events. They can do this by connecting to event sources like AWS Lambda and Azure Functions. This approach cuts costs, simplifies deployment, and boosts agility. It helps handle unpredictable workloads or demand spikes.
Enhancing Data Pipelines with Scalable Architecture
Combine Kafka with serverless functions. Then, you can design a scalable architecture. It should process data in real time and do so efficiently. Serverless frameworks like SAM and the Serverless Framework provide tools to deploy functions. These functions are triggered by Kafka events. They are event-driven and serverless. This approach simplifies the development and deployment of serverless apps with Kafka integration. It enhances the resiliency and flexibility of your data pipelines.
Data pipelines must have a scalable architecture. It will ensure systems can handle growing data volumes efficiently, without losing performance. Organizations can scale their data pipelines as needs grow. They can do this by using distributed processing, cloud-native tools, and modular design. This approach boosts reliability and throughput. It also enables real-time data analytics and seamless integration across multiple data sources.
Optimizing Event-Driven Workloads with Kafka
Using Kafka with serverless functions can improve your cloud apps' event-driven workloads. You can build a fast, efficient event-driven system. Use Kafka for real-time streams and serverless functions for on-demand data. Combining both technologies lets you build resilient, scalable apps. They can meet changing data needs in real time.
To optimize event-driven workloads with Apache Kafka, you must fine-tune some key components. These include producer configurations, partitioning strategies, and consumer parallelism. Organizations can improve real-time event processing. They should balance load across Kafka brokers and reduce latency. Also, Kafka's fault tolerance and scalability ensure it can handle high-throughput event streams. This makes it ideal for mission-critical systems.
How to obtain Apache Kafka certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Apache Kafka with serverless functions can boost your microservices' event-driven processing. They are cloud-native. Use Kafka for real-time event streams and serverless functions for on-demand data processing. This will help you build scalable, resilient, and cost-effective apps. This integration allows you to build efficient data pipelines. It will also streamline event-driven design and boost your cloud architecture's performance. Consider using Kafka with serverless functions. It will maximize your event-driven processing.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
How AI and Automation are Impacting CISA Audits
In today's fast-changing digital world, AI and automation are vital in CISA audits. New technologies are making audits faster, more accurate, and more effective. This article explores AI and automation's impact on CISA audits. It highlights the benefits, challenges, and future trends in the industry.
AI in CISA Audits
AI has changed how CISA audits are done. It provides advanced analytics, predictive modeling, and anomaly detection. Auditors can use machine learning to analyze data in real-time. It can find patterns and detect risks and fraud. It lets organizations improve audits, decisions, and risk management.
Automation in CISA Audits
Automation is key. It streamlines repetitive tasks, reduces errors, and boosts audit efficiency. Automation of routine tasks, like data collection and reporting, can help. It allows auditors to focus on strategic work that needs human judgment. It saves time and resources. It also ensures more accurate, consistent audits.
Impact of AI on CISA Audits
AI and automation in CISA audits have greatly improved their quality, speed, and cost. AI tools can help auditors. They can find insights in complex data, spot new risks, and give better advice to clients. This ultimately enhances the credibility and value of the audit process.
CISA Audit Process Automation
Automating the CISA audit process has greatly helped organizations. They seek to improve their internal controls, compliance, and risk management. Automated audit tools can help auditors. They can speed up audit planning, execution, and reporting. This leads to faster results and better audits. This enables organizations to achieve greater transparency, accountability, and governance in their operations.
The CISA audit process automation revolutionizes how auditors work. It boosts their efficiency and accuracy in assessing information systems. Auditors can automate repetitive tasks using AI and machine learning. This lets them focus on higher-level analysis and decision-making. This automation speeds up audits. It also ensures compliance with changing regulations and boosts security.
CISA Audit Technology Trends
CISA audits now focus on using advanced tech to improve them. This includes data analytics, AI, and robotic process automation. These innovative tools give auditors more flexibility and speed. They help tackle complex challenges, like cybersecurity, compliance, and data privacy. By keeping up with these trends, auditors can navigate the changing audit landscape. They can then deliver value-added services to their clients.
CISA professionals must stay updated on the latest audit tech trends. The digital world is fast-changing. It will make them more effective and efficient. Emerging technologies like AI, machine learning, and data analytics are revolutionizing audits. They enable more thorough and insightful evaluations. By embracing these advancements, CISA auditors can improve risk assessment. They can also drive strategic decision-making in their organizations.
Enhancing CISA Audits with AI
Integrating AI into the CISA audit process can help auditors. It can improve audit planning, risk assessment, and fraud detection. AI tools let auditors analyze vast amounts of data. They can find anomalies and generate insights in real time. It helps auditors make informed decisions and prioritize tasks. They can then focus on the highest-risk areas.
AI is revolutionizing CISA audits. It automates routine tasks like data analysis, anomaly detection, and compliance checks. This lets auditors focus on high-level decision-making. AI tools can quickly analyze vast data. They can find risks and patterns that traditional methods might miss. This improves accuracy and efficiency. Integrating AI into CISA audits can boost cybersecurity. It can also cut audit time and costs.
Automation Tools for CISA Audits
Many automation tools can streamline the CISA audit process and improve efficiency. These tools include software for data extraction and analysis. They also include platforms for risk assessment and compliance monitoring. These automation tools can help auditors. They can: standardize procedures, ensure consistent findings, and improve team collaboration. This ultimately leads to more effective and value-driven audit engagements.
Automation tools are revolutionizing CISA audits. They streamline complex tasks like data collection, risk assessment, and compliance checks. These tools improve accuracy and efficiency. They let auditors focus on strategic analysis and decision-making. CISA professionals can use automation to speed up audits. It will make them more reliable and reduce human error.
How to obtain CISA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, using AI and automation in CISA audits is a game changer. It shifts how audits are done, managed, and reported. Organizations can boost audits, decisions, and growth by using advanced technologies. As the audit industry evolves, auditors must innovate and adapt. They must use technology to stay ahead.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-changing digital world, AI and automation are vital in CISA audits. New technologies are making audits faster, more accurate, and more effective. This article explores AI and automation's impact on CISA audits. It highlights the benefits, challenges, and future trends in the industry.
AI in CISA Audits
AI has changed how CISA audits are done. It provides advanced analytics, predictive modeling, and anomaly detection. Auditors can use machine learning to analyze data in real-time. It can find patterns and detect risks and fraud. It lets organizations improve audits, decisions, and risk management.
Automation in CISA Audits
Automation is key. It streamlines repetitive tasks, reduces errors, and boosts audit efficiency. Automation of routine tasks, like data collection and reporting, can help. It allows auditors to focus on strategic work that needs human judgment. It saves time and resources. It also ensures more accurate, consistent audits.
Impact of AI on CISA Audits
AI and automation in CISA audits have greatly improved their quality, speed, and cost. AI tools can help auditors. They can find insights in complex data, spot new risks, and give better advice to clients. This ultimately enhances the credibility and value of the audit process.
CISA Audit Process Automation
Automating the CISA audit process has greatly helped organizations. They seek to improve their internal controls, compliance, and risk management. Automated audit tools can help auditors. They can speed up audit planning, execution, and reporting. This leads to faster results and better audits. This enables organizations to achieve greater transparency, accountability, and governance in their operations.
The CISA audit process automation revolutionizes how auditors work. It boosts their efficiency and accuracy in assessing information systems. Auditors can automate repetitive tasks using AI and machine learning. This lets them focus on higher-level analysis and decision-making. This automation speeds up audits. It also ensures compliance with changing regulations and boosts security.
CISA Audit Technology Trends
CISA audits now focus on using advanced tech to improve them. This includes data analytics, AI, and robotic process automation. These innovative tools give auditors more flexibility and speed. They help tackle complex challenges, like cybersecurity, compliance, and data privacy. By keeping up with these trends, auditors can navigate the changing audit landscape. They can then deliver value-added services to their clients.
CISA professionals must stay updated on the latest audit tech trends. The digital world is fast-changing. It will make them more effective and efficient. Emerging technologies like AI, machine learning, and data analytics are revolutionizing audits. They enable more thorough and insightful evaluations. By embracing these advancements, CISA auditors can improve risk assessment. They can also drive strategic decision-making in their organizations.
Enhancing CISA Audits with AI
Integrating AI into the CISA audit process can help auditors. It can improve audit planning, risk assessment, and fraud detection. AI tools let auditors analyze vast amounts of data. They can find anomalies and generate insights in real time. It helps auditors make informed decisions and prioritize tasks. They can then focus on the highest-risk areas.
AI is revolutionizing CISA audits. It automates routine tasks like data analysis, anomaly detection, and compliance checks. This lets auditors focus on high-level decision-making. AI tools can quickly analyze vast data. They can find risks and patterns that traditional methods might miss. This improves accuracy and efficiency. Integrating AI into CISA audits can boost cybersecurity. It can also cut audit time and costs.
Automation Tools for CISA Audits
Many automation tools can streamline the CISA audit process and improve efficiency. These tools include software for data extraction and analysis. They also include platforms for risk assessment and compliance monitoring. These automation tools can help auditors. They can: standardize procedures, ensure consistent findings, and improve team collaboration. This ultimately leads to more effective and value-driven audit engagements.
Automation tools are revolutionizing CISA audits. They streamline complex tasks like data collection, risk assessment, and compliance checks. These tools improve accuracy and efficiency. They let auditors focus on strategic analysis and decision-making. CISA professionals can use automation to speed up audits. It will make them more reliable and reduce human error.
How to obtain CISA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, using AI and automation in CISA audits is a game changer. It shifts how audits are done, managed, and reported. Organizations can boost audits, decisions, and growth by using advanced technologies. As the audit industry evolves, auditors must innovate and adapt. They must use technology to stay ahead.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
RPA Impact on Workforce Dynamics
Robotic Process Automation (RPA) is changing how businesses work. It automates dull tasks and streamlines workflows. In this article, we will explore how RPA is reshaping workforce dynamics and the future of work.
The Role of RPA in Workforce Transformation
RPA technology uses software robots to do repetitive tasks. These tasks were once done by humans. This automation lets employees focus on more creative, strategic tasks. It boosts workplace efficiency and productivity.
Efficiency and Productivity
By automating time-consuming processes, RPA allows employees to work more efficiently and effectively. This technology can do boring tasks fast and accurately. It will boost productivity across the organization.
RPA greatly boosts efficiency. It automates repetitive tasks, letting employees focus on more valuable work. Automating routine tasks can help organizations. It speeds up processes, reduces errors, and improves efficiency. It saves costs and engages employees. They can focus on strategic work.
Machine Learning and Workforce Automation
RPA, powered by machine learning, can adapt to new tasks. It improves its efficiency by learning as it works. This lets organizations keep up with fast-changing business needs and market demands.
Machine learning is changing workforce automation. It lets systems learn from data, adapt to new inputs, and improve decision-making. As businesses adopt these technologies, they can automate routine tasks. This lets employees focus on more strategic, creative work. It will improve productivity and job satisfaction. This shift raises concerns about adapting the workforce, reskilling, and job losses.
The Impact of RPA on Work Environment
RPA is changing the work environment. It enables humans and robots to work together seamlessly. This collaboration enhances workforce agility and adaptability in an ever-evolving digital landscape.
RPA changes the work environment by automating repetitive tasks. This lets employees focus on more strategic, creative work. It boosts job satisfaction and productivity. RPA creates a collaborative space for humans and bots to work together. It boosts efficiency and reduces errors.
Workforce Development and Skills Enhancement
RPA technology lets employees develop new skills and enhance their abilities. RPA can handle routine tasks. This lets employees focus on strategy, problem-solving, and innovation.
We must develop the workforce and enhance skills. This is key to a competitive, adaptable labor market amid rapid tech advances. Organizations must invest in programs for continuous learning and development. They must equip employees with the skills to thrive in evolving roles. This will ensure a skilled workforce that can meet changing business demands. Companies that prioritize upskilling and reskilling boost productivity. They also improve employee satisfaction and retention. This leads to long-term success.
Overcoming Workforce Challenges with RPA
As organizations face workforce challenges like skills gaps, RPA offers a solution. It can help with evolving job roles. By automating repetitive tasks, RPA allows employees to upskill and reskill for the jobs of the future.
Robotic Process Automation (RPA) is a powerful tool. It automates repetitive, time-consuming tasks. This lets employees focus on higher-value work. RPA can reduce workforce stress and boost job satisfaction. It does this by streamlining operations and improving productivity. This leads to a more engaged and efficient team. Also, RPA helps firms with skill shortages. It optimizes existing resources. This lets them adapt quickly to changing business needs.
The Future of Work with RPA
As RPA continues to evolve, the future of work will be defined by human-robot collaboration, innovation, and efficiency. Organizations that embrace RPA will lead the way in workforce optimization and performance.
RPA will transform the future of work. It will make organizations more efficient and productive. RPA automates repetitive tasks. It frees employees to focus on more strategic, creative work. This boosts innovation and job satisfaction. As businesses adopt cloud-based, collaborative RPA, the workforce will shift to a hybrid model. Humans and bots will work together seamlessly.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Robotic Process Automation is not just a tech trend. It is a tool that is shaping the future workforce. RPA can help organizations innovate, boost productivity, and adapt to the digital era.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Robotic Process Automation (RPA) is changing how businesses work. It automates dull tasks and streamlines workflows. In this article, we will explore how RPA is reshaping workforce dynamics and the future of work.
The Role of RPA in Workforce Transformation
RPA technology uses software robots to do repetitive tasks. These tasks were once done by humans. This automation lets employees focus on more creative, strategic tasks. It boosts workplace efficiency and productivity.
Efficiency and Productivity
By automating time-consuming processes, RPA allows employees to work more efficiently and effectively. This technology can do boring tasks fast and accurately. It will boost productivity across the organization.
RPA greatly boosts efficiency. It automates repetitive tasks, letting employees focus on more valuable work. Automating routine tasks can help organizations. It speeds up processes, reduces errors, and improves efficiency. It saves costs and engages employees. They can focus on strategic work.
Machine Learning and Workforce Automation
RPA, powered by machine learning, can adapt to new tasks. It improves its efficiency by learning as it works. This lets organizations keep up with fast-changing business needs and market demands.
Machine learning is changing workforce automation. It lets systems learn from data, adapt to new inputs, and improve decision-making. As businesses adopt these technologies, they can automate routine tasks. This lets employees focus on more strategic, creative work. It will improve productivity and job satisfaction. This shift raises concerns about adapting the workforce, reskilling, and job losses.
The Impact of RPA on Work Environment
RPA is changing the work environment. It enables humans and robots to work together seamlessly. This collaboration enhances workforce agility and adaptability in an ever-evolving digital landscape.
RPA changes the work environment by automating repetitive tasks. This lets employees focus on more strategic, creative work. It boosts job satisfaction and productivity. RPA creates a collaborative space for humans and bots to work together. It boosts efficiency and reduces errors.
Workforce Development and Skills Enhancement
RPA technology lets employees develop new skills and enhance their abilities. RPA can handle routine tasks. This lets employees focus on strategy, problem-solving, and innovation.
We must develop the workforce and enhance skills. This is key to a competitive, adaptable labor market amid rapid tech advances. Organizations must invest in programs for continuous learning and development. They must equip employees with the skills to thrive in evolving roles. This will ensure a skilled workforce that can meet changing business demands. Companies that prioritize upskilling and reskilling boost productivity. They also improve employee satisfaction and retention. This leads to long-term success.
Overcoming Workforce Challenges with RPA
As organizations face workforce challenges like skills gaps, RPA offers a solution. It can help with evolving job roles. By automating repetitive tasks, RPA allows employees to upskill and reskill for the jobs of the future.
Robotic Process Automation (RPA) is a powerful tool. It automates repetitive, time-consuming tasks. This lets employees focus on higher-value work. RPA can reduce workforce stress and boost job satisfaction. It does this by streamlining operations and improving productivity. This leads to a more engaged and efficient team. Also, RPA helps firms with skill shortages. It optimizes existing resources. This lets them adapt quickly to changing business needs.
The Future of Work with RPA
As RPA continues to evolve, the future of work will be defined by human-robot collaboration, innovation, and efficiency. Organizations that embrace RPA will lead the way in workforce optimization and performance.
RPA will transform the future of work. It will make organizations more efficient and productive. RPA automates repetitive tasks. It frees employees to focus on more strategic, creative work. This boosts innovation and job satisfaction. As businesses adopt cloud-based, collaborative RPA, the workforce will shift to a hybrid model. Humans and bots will work together seamlessly.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Robotic Process Automation is not just a tech trend. It is a tool that is shaping the future workforce. RPA can help organizations innovate, boost productivity, and adapt to the digital era.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Getting Started with AWS Machine Learning
Are you interested in diving into the world of artificial intelligence and machine learning with Amazon Web Services (AWS)? This article will guide you on getting started with AWS Machine Learning. We will explore the AWS tools and services for data science, predictive modeling, and deep learning.
Introduction to AWS Machine Learning
Amazon Web Services (AWS) has a complete platform for building, training, and deploying machine learning models at scale. AWS Machine Learning lets you use the cloud to analyze large datasets, develop predictive models, and uncover insights.
What is AWS Machine Learning?
AWS Machine Learning is a cloud platform. It offers many tools and services for data scientists, developers, and businesses. They want to add machine learning to their apps. AWS Machine Learning has it all. It covers model training, deployment, data analysis, and visualization. Use it to build advanced AI solutions.
How can AWS Machine Learning help you?
Use AWS Machine Learning to automate tasks, make decisions, and improve your apps. Whether you are working on natural language processing, computer vision, anomaly detection, or recommendation systems, AWS Machine Learning has the tools and infrastructure to support your projects.
Getting Started with AWS Machine Learning
1. Set up your AWS Account
The first step in getting started with AWS Machine Learning is to create an AWS account. Simply visit the AWS website, sign up for an account, and choose a plan that best suits your needs. Once your account is set up, you can access a wide range of AWS services, including AWS Sagemaker, which is a fully managed service for building, training, and deploying machine learning models.
2. Explore AWS Machine Learning Services
Once you have set up your AWS account, it's time to explore the various machine learning services offered by AWS. From deep learning and neural networks to predictive modeling and data analysis, AWS has a diverse range of services to support your machine learning projects. Take some time to familiarize yourself with AWS Sagemaker, AWS Lambda, and other key services for model training and deployment.
3. Build and Train Your Models
With AWS Machine Learning, you can easily build and train machine learning models using a variety of algorithms, including decision trees, random forest, logistic regression, support vector machines, and deep neural networks. Leverage feature engineering, hyperparameter tuning, and data preprocessing to optimize your models for performance and accuracy.
Building and training your models is a key step in machine learning. It turns raw data into actionable insights. This phase usually involves choosing algorithms, tuning hyperparameters, and testing the model. This ensures it works well on unseen data. Using platforms like AWS SageMaker or Google Cloud AI can streamline this process. They provide tools to improve your model's accuracy and efficiency.
4. Deploy and Monitor Your Models
Once your machine learning models are trained and optimized, it's time to deploy them in a production environment. With AWS Machine Learning, you can easily deploy your models. Use AWS Lambda, SageMaker endpoints, and other services for batch and real-time predictions. Monitor the performance of your models using AWS CloudWatch and AWS CloudTrail for insights and analytics.
It's crucial to deploy and monitor your ML models. This ensures their effectiveness and reliability in real-world use. This process involves creating a strong deployment pipeline for model updates. It also requires monitoring tools to track performance, detect anomalies, and alert for issues. Continuously evaluate your models after deployment. This will keep them accurate and adapt to new data patterns. It will also improve decision-making.
5. Optimize and Scale Your Models
To ensure your machine learning models are scalable and efficient, optimize them for cost and performance. Use AWS services for data engineering, storage, and serverless apps. Use AWS Glue, AWS databases, and AWS Elastic Beanstalk. Use best practices for versioning, managing, and scaling models. This will maximize the impact of your AI solutions.
To achieve peak performance in machine learning, we must optimize two things. They are the model's architecture and its hyperparameters. This is key to maximizing accuracy and efficiency. Techniques like feature engineering, pruning, and advanced algorithms can boost model performance. They also ensure the model can scale with increased data loads. Using strategies like distributed training and cloud resources, organizations can scale their models. This meets growing demands while keeping speed and robustness in production.
How to obtain AWS Solution Architect certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, AWS Machine Learning is a rewarding but challenging journey for data scientists and developers. You can build advanced machine learning models with AWS cloud computing. It can automate tasks and help you make confident, data-driven decisions. Explore the various services and tools offered by AWS Machine Learning, and embark on your AI journey with Amazon Web Services today!
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you interested in diving into the world of artificial intelligence and machine learning with Amazon Web Services (AWS)? This article will guide you on getting started with AWS Machine Learning. We will explore the AWS tools and services for data science, predictive modeling, and deep learning.
Introduction to AWS Machine Learning
Amazon Web Services (AWS) has a complete platform for building, training, and deploying machine learning models at scale. AWS Machine Learning lets you use the cloud to analyze large datasets, develop predictive models, and uncover insights.
What is AWS Machine Learning?
AWS Machine Learning is a cloud platform. It offers many tools and services for data scientists, developers, and businesses. They want to add machine learning to their apps. AWS Machine Learning has it all. It covers model training, deployment, data analysis, and visualization. Use it to build advanced AI solutions.
How can AWS Machine Learning help you?
Use AWS Machine Learning to automate tasks, make decisions, and improve your apps. Whether you are working on natural language processing, computer vision, anomaly detection, or recommendation systems, AWS Machine Learning has the tools and infrastructure to support your projects.
Getting Started with AWS Machine Learning
1. Set up your AWS Account
The first step in getting started with AWS Machine Learning is to create an AWS account. Simply visit the AWS website, sign up for an account, and choose a plan that best suits your needs. Once your account is set up, you can access a wide range of AWS services, including AWS Sagemaker, which is a fully managed service for building, training, and deploying machine learning models.
2. Explore AWS Machine Learning Services
Once you have set up your AWS account, it's time to explore the various machine learning services offered by AWS. From deep learning and neural networks to predictive modeling and data analysis, AWS has a diverse range of services to support your machine learning projects. Take some time to familiarize yourself with AWS Sagemaker, AWS Lambda, and other key services for model training and deployment.
3. Build and Train Your Models
With AWS Machine Learning, you can easily build and train machine learning models using a variety of algorithms, including decision trees, random forest, logistic regression, support vector machines, and deep neural networks. Leverage feature engineering, hyperparameter tuning, and data preprocessing to optimize your models for performance and accuracy.
Building and training your models is a key step in machine learning. It turns raw data into actionable insights. This phase usually involves choosing algorithms, tuning hyperparameters, and testing the model. This ensures it works well on unseen data. Using platforms like AWS SageMaker or Google Cloud AI can streamline this process. They provide tools to improve your model's accuracy and efficiency.
4. Deploy and Monitor Your Models
Once your machine learning models are trained and optimized, it's time to deploy them in a production environment. With AWS Machine Learning, you can easily deploy your models. Use AWS Lambda, SageMaker endpoints, and other services for batch and real-time predictions. Monitor the performance of your models using AWS CloudWatch and AWS CloudTrail for insights and analytics.
It's crucial to deploy and monitor your ML models. This ensures their effectiveness and reliability in real-world use. This process involves creating a strong deployment pipeline for model updates. It also requires monitoring tools to track performance, detect anomalies, and alert for issues. Continuously evaluate your models after deployment. This will keep them accurate and adapt to new data patterns. It will also improve decision-making.
5. Optimize and Scale Your Models
To ensure your machine learning models are scalable and efficient, optimize them for cost and performance. Use AWS services for data engineering, storage, and serverless apps. Use AWS Glue, AWS databases, and AWS Elastic Beanstalk. Use best practices for versioning, managing, and scaling models. This will maximize the impact of your AI solutions.
To achieve peak performance in machine learning, we must optimize two things. They are the model's architecture and its hyperparameters. This is key to maximizing accuracy and efficiency. Techniques like feature engineering, pruning, and advanced algorithms can boost model performance. They also ensure the model can scale with increased data loads. Using strategies like distributed training and cloud resources, organizations can scale their models. This meets growing demands while keeping speed and robustness in production.
How to obtain AWS Solution Architect certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, AWS Machine Learning is a rewarding but challenging journey for data scientists and developers. You can build advanced machine learning models with AWS cloud computing. It can automate tasks and help you make confident, data-driven decisions. Explore the various services and tools offered by AWS Machine Learning, and embark on your AI journey with Amazon Web Services today!
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Scrum and DevOps The Synergy of Agile and DevOps
In software development, two methodologies have gained prominence: Scrum and DevOps. They have risen to fame in recent years. These two methodologies are often seen as distinct. But, they actually complement each other. This synergy can boost teams' productivity and efficiency. This article will explore the key principles of Scrum and DevOps. It will cover how they work together and the benefits of combining them in your development processes.
What is Agile Development?
Agile development is a method. It values adaptability, collaboration, and flexibility in software development. It values iterative development, frequent feedback, and quick responses to changes in requirements or priorities. Agile methods, like Scrum, help organize and manage projects. They aim to maximize efficiency and productivity.
What is DevOps?
DevOps is a set of practices. They aim to improve collaboration between software development and IT operations teams. DevOps aims to improve software delivery speed and quality. It does this by breaking down silos and encouraging cross-departmental teamwork. DevOps principles stress automation, CI, and CD. They let teams deploy code more often and reliably.
The Synergy of Scrum and DevOps:
Scrum and DevOps, when combined, create a powerful synergy. It can supercharge your development process. Scrum is a framework for organizing development projects. DevOps practices ensure smooth, efficient deployment and operations. Integrating the two methods will help teams. They will gain Scrum's agility and DevOps' efficiency.
"Scrum and DevOps work well together. They deliver high-quality software faster and more efficiently." Scrum is about iterative development and team collaboration. DevOps is about automation, continuous integration, and seamless deployment. They bridge the gap between development and operations. This enhances agility, reduces bottlenecks, and ensures quick delivery of value to customers."
1. "Scrum's iterative approach, and DevOps' automation, speed up development."" Scrum boosts team communication and adaptability. DevOps optimizes the infrastructure and processes for efficiency. This synergy accelerates delivery, reduces errors, and enhances product quality."
2. "Scrum and DevOps complement each other. They foster collaboration between development and operations teams." Scrum's focus on sprints and team roles fits with DevOps' push for continuous feedback, automated testing, and integration. Their work creates a streamlined workflow. It boosts innovation, speeds up releases, and improves productivity."
3. "Scrum and DevOps together promote a culture of constant improvement. In it, iterative planning and rapid feedback loops thrive." Scrum's task management and DevOps' automation both enable a quick response to changes. This fusion drives greater collaboration, agility, and operational efficiency across teams."
Benefits of Combining Scrum and DevOps:
Scrum and DevOps, when combined, create a strong synergy. It boosts both speed and quality in software development. Scrum's iterative approach ensures continuous feedback and improvement. DevOps aims to automate deployments and reduce bottlenecks. They help teams deliver features faster. They improve collaboration between development and operations. They ensure faster time-to-market with high-quality, reliable products.
Scrum and DevOps, when combined, create a seamless workflow. They integrate development, testing, and operations into an agile framework. Scrum ensures regular progress with feedback. DevOps speeds up deployment with automation and streamlined processes. This combo boosts teamwork, productivity, and release speed. It ensures faster value delivery to customers.
-
Improved collaboration between development and operations teams
-
Faster time to market for new features and products
-
Increased productivity and efficiency through automation and continuous integration
-
Better quality software through frequent feedback and testing
-
Enhanced visibility and transparency into the development process
How to obtain Agile and Scrum certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the blend of Scrum and DevOps can transform software development teams. It is a powerful combination. By combining the agile principles of Scrum with the automation and efficiency of DevOps, teams can achieve new levels of productivity, quality, and collaboration. If you're new to agile or want to improve, combining Scrum and DevOps can be a game-changer for your team.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In software development, two methodologies have gained prominence: Scrum and DevOps. They have risen to fame in recent years. These two methodologies are often seen as distinct. But, they actually complement each other. This synergy can boost teams' productivity and efficiency. This article will explore the key principles of Scrum and DevOps. It will cover how they work together and the benefits of combining them in your development processes.
What is Agile Development?
Agile development is a method. It values adaptability, collaboration, and flexibility in software development. It values iterative development, frequent feedback, and quick responses to changes in requirements or priorities. Agile methods, like Scrum, help organize and manage projects. They aim to maximize efficiency and productivity.
What is DevOps?
DevOps is a set of practices. They aim to improve collaboration between software development and IT operations teams. DevOps aims to improve software delivery speed and quality. It does this by breaking down silos and encouraging cross-departmental teamwork. DevOps principles stress automation, CI, and CD. They let teams deploy code more often and reliably.
The Synergy of Scrum and DevOps:
Scrum and DevOps, when combined, create a powerful synergy. It can supercharge your development process. Scrum is a framework for organizing development projects. DevOps practices ensure smooth, efficient deployment and operations. Integrating the two methods will help teams. They will gain Scrum's agility and DevOps' efficiency.
"Scrum and DevOps work well together. They deliver high-quality software faster and more efficiently." Scrum is about iterative development and team collaboration. DevOps is about automation, continuous integration, and seamless deployment. They bridge the gap between development and operations. This enhances agility, reduces bottlenecks, and ensures quick delivery of value to customers."
1. "Scrum's iterative approach, and DevOps' automation, speed up development."" Scrum boosts team communication and adaptability. DevOps optimizes the infrastructure and processes for efficiency. This synergy accelerates delivery, reduces errors, and enhances product quality."
2. "Scrum and DevOps complement each other. They foster collaboration between development and operations teams." Scrum's focus on sprints and team roles fits with DevOps' push for continuous feedback, automated testing, and integration. Their work creates a streamlined workflow. It boosts innovation, speeds up releases, and improves productivity."
3. "Scrum and DevOps together promote a culture of constant improvement. In it, iterative planning and rapid feedback loops thrive." Scrum's task management and DevOps' automation both enable a quick response to changes. This fusion drives greater collaboration, agility, and operational efficiency across teams."
Benefits of Combining Scrum and DevOps:
Scrum and DevOps, when combined, create a strong synergy. It boosts both speed and quality in software development. Scrum's iterative approach ensures continuous feedback and improvement. DevOps aims to automate deployments and reduce bottlenecks. They help teams deliver features faster. They improve collaboration between development and operations. They ensure faster time-to-market with high-quality, reliable products.
Scrum and DevOps, when combined, create a seamless workflow. They integrate development, testing, and operations into an agile framework. Scrum ensures regular progress with feedback. DevOps speeds up deployment with automation and streamlined processes. This combo boosts teamwork, productivity, and release speed. It ensures faster value delivery to customers.
-
Improved collaboration between development and operations teams
-
Faster time to market for new features and products
-
Increased productivity and efficiency through automation and continuous integration
-
Better quality software through frequent feedback and testing
-
Enhanced visibility and transparency into the development process
How to obtain Agile and Scrum certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the blend of Scrum and DevOps can transform software development teams. It is a powerful combination. By combining the agile principles of Scrum with the automation and efficiency of DevOps, teams can achieve new levels of productivity, quality, and collaboration. If you're new to agile or want to improve, combining Scrum and DevOps can be a game-changer for your team.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Wearable IoT Devices Trends and Applications
In today's fast-paced world, technology is advancing at an unprecedented rate. One of the most exciting developments in recent years is the rise of wearable IoT devices. These gadgets are revolutionizing our lives. They give us access to real-time data and insights like never before. This article will explore the latest trends in wearable IoT devices. We will look at their uses in health, fitness, and lifestyle industries, and more.
The Rise of Smart Technology
Smart technology has become an integral part of our daily lives, with wearable IoT devices leading the way in innovation. These devices have sensors that track data, like heart rate, sleep, and activity. By collecting and analyzing this data, users can gain valuable insights into their health and lifestyle habits.
The Internet of Things in Health and Fitness Monitoring
The integration of IoT technology in health and fitness monitoring has opened up a world of possibilities for users. Fitness trackers and smartwatches can provide real-time feedback on activity and calories burned. They can even recommend workouts. With the rise of wearable IoT devices, users can take control of their health and make more informed decisions about their wellness.
Connected Data and Innovation in Lifestyle
Wearable IoT devices connect to the internet. They let users use data in their daily lives. Smartwatches and fitness trackers aim to improve the user experience. They do this by sending notifications and tracking sleep patterns. Also, the innovation in lifestyle apps for wearable IoT devices is endless. They range from smart clothing to accessories that monitor your body temperature and hydration.
Connected data is changing our lives. It integrates smart devices and services. This makes them more convenient and personalized. Wearable health monitors track fitness. Smart home systems automate routines. This innovation is changing how we interact with our environment. With connected data, we will get a more personalized lifestyle. It will focus on efficiency, well-being, and connectivity.
The Future of Wearable Tech
As technology continues to evolve, so do wearable IoT devices. The future of wearable tech is bright. Advances in sensors, healthcare, connectivity, and tracking drive this. From smart gadgets to connected wearables, the possibilities are endless for how these devices can improve our lives.
The future of wearable tech is set to revolutionize how we interact with health, fitness, and everyday activities. Wearables will use smart fabrics, biometric sensors, and AI. They will provide better health monitoring and personalized experiences. Wearable tech will advance wellness, medical diagnostics, and AR apps. As devices shrink and merge with clothing and accessories, it will.
The Impact of Wearable Healthcare IoT Applications
Wearable IoT devices have greatly impacted healthcare. They provide pros with valuable data about patients' health. These devices are vital. They monitor vital signs and track medication use. They improve patient outcomes and cut healthcare costs. Wearable healthcare IoT apps are evolving. The future of healthcare looks promising.
Wearable healthcare IoT apps are changing patient care. They allow continuous health monitoring and real-time data collection. Devices like smartwatches and fitness trackers empower people. They can track vital signs, detect anomalies, and manage chronic conditions better. Wearable IoT devices improve preventive care and diagnosis. They do this by giving healthcare professionals remote access to patient data. This also reduces hospital visits.
Enhancing Fashion with Smart Health and Fitness Trackers
Fashion and technology have merged in wearable IoT devices. Smart health and fitness trackers are the leaders. These stylish devices can track your steps and calories burned. They can also remind you to stay active. With a mix of fashion and tech, users can now be stylish and track their health goals.
Smart health and fitness trackers are changing fashion. They blend tech with stylish accessories. These wearable devices monitor vital health metrics. They are also fashion statements, fitting into daily outfits. As tech advances, fashion brands are teaming up with tech firms. They aim to make stylish, functional smart wearables. This will give consumers a health-conscious, trendy look.
The Evolution of Wearable Sensors and Smart Wearables
Wearable sensors and smart wearables have improved a lot in recent years. They now provide users with more accurate and reliable data. These devices can provide real-time feedback on various health metrics. They include heart rate monitors and blood pressure sensors. With the continuous innovation in sensor technology, the future of wearable devices looks promising.
How to obtain IOT certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, wearable IoT devices are changing our lives. They give us access to real-time data and insights like never before. From health and fitness tracking to lifestyle apps, the possibilities are endless. These devices can enhance our daily routines. As technology evolves, the future of wearable tech looks bright. Advances in sensors, healthcare, connectivity, and tracking drive this. Embrace the future of wearable IoT devices, and experience a new level of connectivity and convenience in your daily life.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced world, technology is advancing at an unprecedented rate. One of the most exciting developments in recent years is the rise of wearable IoT devices. These gadgets are revolutionizing our lives. They give us access to real-time data and insights like never before. This article will explore the latest trends in wearable IoT devices. We will look at their uses in health, fitness, and lifestyle industries, and more.
The Rise of Smart Technology
Smart technology has become an integral part of our daily lives, with wearable IoT devices leading the way in innovation. These devices have sensors that track data, like heart rate, sleep, and activity. By collecting and analyzing this data, users can gain valuable insights into their health and lifestyle habits.
The Internet of Things in Health and Fitness Monitoring
The integration of IoT technology in health and fitness monitoring has opened up a world of possibilities for users. Fitness trackers and smartwatches can provide real-time feedback on activity and calories burned. They can even recommend workouts. With the rise of wearable IoT devices, users can take control of their health and make more informed decisions about their wellness.
Connected Data and Innovation in Lifestyle
Wearable IoT devices connect to the internet. They let users use data in their daily lives. Smartwatches and fitness trackers aim to improve the user experience. They do this by sending notifications and tracking sleep patterns. Also, the innovation in lifestyle apps for wearable IoT devices is endless. They range from smart clothing to accessories that monitor your body temperature and hydration.
Connected data is changing our lives. It integrates smart devices and services. This makes them more convenient and personalized. Wearable health monitors track fitness. Smart home systems automate routines. This innovation is changing how we interact with our environment. With connected data, we will get a more personalized lifestyle. It will focus on efficiency, well-being, and connectivity.
The Future of Wearable Tech
As technology continues to evolve, so do wearable IoT devices. The future of wearable tech is bright. Advances in sensors, healthcare, connectivity, and tracking drive this. From smart gadgets to connected wearables, the possibilities are endless for how these devices can improve our lives.
The future of wearable tech is set to revolutionize how we interact with health, fitness, and everyday activities. Wearables will use smart fabrics, biometric sensors, and AI. They will provide better health monitoring and personalized experiences. Wearable tech will advance wellness, medical diagnostics, and AR apps. As devices shrink and merge with clothing and accessories, it will.
The Impact of Wearable Healthcare IoT Applications
Wearable IoT devices have greatly impacted healthcare. They provide pros with valuable data about patients' health. These devices are vital. They monitor vital signs and track medication use. They improve patient outcomes and cut healthcare costs. Wearable healthcare IoT apps are evolving. The future of healthcare looks promising.
Wearable healthcare IoT apps are changing patient care. They allow continuous health monitoring and real-time data collection. Devices like smartwatches and fitness trackers empower people. They can track vital signs, detect anomalies, and manage chronic conditions better. Wearable IoT devices improve preventive care and diagnosis. They do this by giving healthcare professionals remote access to patient data. This also reduces hospital visits.
Enhancing Fashion with Smart Health and Fitness Trackers
Fashion and technology have merged in wearable IoT devices. Smart health and fitness trackers are the leaders. These stylish devices can track your steps and calories burned. They can also remind you to stay active. With a mix of fashion and tech, users can now be stylish and track their health goals.
Smart health and fitness trackers are changing fashion. They blend tech with stylish accessories. These wearable devices monitor vital health metrics. They are also fashion statements, fitting into daily outfits. As tech advances, fashion brands are teaming up with tech firms. They aim to make stylish, functional smart wearables. This will give consumers a health-conscious, trendy look.
The Evolution of Wearable Sensors and Smart Wearables
Wearable sensors and smart wearables have improved a lot in recent years. They now provide users with more accurate and reliable data. These devices can provide real-time feedback on various health metrics. They include heart rate monitors and blood pressure sensors. With the continuous innovation in sensor technology, the future of wearable devices looks promising.
How to obtain IOT certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, wearable IoT devices are changing our lives. They give us access to real-time data and insights like never before. From health and fitness tracking to lifestyle apps, the possibilities are endless. These devices can enhance our daily routines. As technology evolves, the future of wearable tech looks bright. Advances in sensors, healthcare, connectivity, and tracking drive this. Embrace the future of wearable IoT devices, and experience a new level of connectivity and convenience in your daily life.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Intersection of Big Data and Blockchain Technology
Big data and blockchain are revolutionizing data management in the digital age. A merger of these two technologies could greatly improve data security, transparency, and efficiency in many industries. This article will explore the link between big data and blockchain. It will discuss their benefits and challenges.
In today's data-driven world, businesses seek better ways to handle vast data. They want to collect, store, and analyze it. Big data is the huge daily data from many sources, like social media, sensors, and mobile devices. It includes both structured and unstructured data. Blockchain is a decentralized digital ledger. It securely records transactions across multiple computers. It is tamper-proof and transparent.
What is big data, and how is it transforming the way we process information in the digital age?
Big data refers to vast amounts of data. It is generated at an unprecedented rate. This data can come from many sources. They include social media, sensors, and mobile devices. The challenge is to analyze this data. We must extract insights to drive better decisions.
Big data is the huge amount of data created every second. It includes both structured and unstructured data. Traditional tools can't process it efficiently. In the digital age, big data is changing information processing. It lets organizations analyze large datasets and find valuable insights. This leads to better decisions and improved customer experiences. This change is helping businesses find trends, predict outcomes, and innovate quickly. It's reshaping industries and boosting economic growth.
How does blockchain technology work? What key features make it valuable for data management?
Blockchain is a decentralized, distributed ledger. It records transactions across multiple computers in a secure, transparent way. Network participants verify each transaction. This makes it nearly impossible to alter or tamper with the data. This high security and transparency make blockchain valuable for data management.
Blockchain is a decentralized, distributed ledger. It records transactions across multiple computers. This ensures the data is secure and cannot be changed. Its key features are transparency and cryptographic security. Transparency lets all participants access the same information. Cryptographic security protects data from unauthorized changes. These traits make blockchain valuable for data management. They build trust, cut fraud, and boost accountability in many areas, from finance to supply chains.
Benefits of the Intersection of Big Data and Blockchain Technology
Big Data and blockchain technology intersect. It offers major benefits. It boosts data security and integrity. Blockchain's decentralized and immutable nature can protect data. It can prevent tampering and unauthorized access. Also, this synergy improves data transparency and traceability. It fosters trust among stakeholders and streamlines processes across industries.
-
Enhanced Data Security: Blockchain technology securely stores and transmits data. It is tamper-proof. By combining big data and blockchain, organizations can protect their data. They can ensure its integrity and confidentiality.
-
Improved Data Transparency: Blockchain technology keeps a public, decentralized ledger of all transactions. This level of transparency can help organizations trace data throughout its lifecycle.
-
Efficient Data Processing: Blockchain can improve big data analytics. It enables faster, more accurate data processing. This can lead to quicker decision-making and improved operational efficiency.
-
Smart Contracts: Blockchain technology enables smart contracts. They are self-executing contracts with set rules and conditions. Smart contracts can automate and streamline agreements. They save time and reduce errors.
Challenges of the Intersection of Big Data and Blockchain Technology
Big data and blockchain tech intersect. It poses unique challenges, especially in data scalability and storage. Blockchain ensures data integrity and security. But, its decentralized design can complicate handling big data apps. Also, organizations must solve tough problems to use both technologies. They need to connect traditional data systems with blockchain networks.
-
Scalability: Both big data and blockchain require high processing power and storage. Scaling these technologies to handle large data can be a challenge for organizations.
-
Data Integration: Merging big data analytics with blockchain can be complex. It requires careful planning. A seamless data flow between these two technologies is crucial. It is key to their successful implementation.
-
Regulatory Compliance: As blockchain evolves, so must data privacy and security laws. Organizations using big data and blockchain must obey relevant laws.
-
Data Privacy: Blockchain technology is secure, but it raises data privacy issues. It's vital to protect sensitive data. Only authorized parties should access it. This is key to maintaining trust.
How to obtain Big Data certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, big data and blockchain have great potential. They could transform data management and use in many industries. Using these two technologies can help organizations. It can boost data security, transparency, and efficiency in a fast-changing digital world. The key is to overcome the challenges. Then, maximize the benefits. We must integrate big data and blockchain technology seamlessly.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Big data and blockchain are revolutionizing data management in the digital age. A merger of these two technologies could greatly improve data security, transparency, and efficiency in many industries. This article will explore the link between big data and blockchain. It will discuss their benefits and challenges.
In today's data-driven world, businesses seek better ways to handle vast data. They want to collect, store, and analyze it. Big data is the huge daily data from many sources, like social media, sensors, and mobile devices. It includes both structured and unstructured data. Blockchain is a decentralized digital ledger. It securely records transactions across multiple computers. It is tamper-proof and transparent.
What is big data, and how is it transforming the way we process information in the digital age?
Big data refers to vast amounts of data. It is generated at an unprecedented rate. This data can come from many sources. They include social media, sensors, and mobile devices. The challenge is to analyze this data. We must extract insights to drive better decisions.
Big data is the huge amount of data created every second. It includes both structured and unstructured data. Traditional tools can't process it efficiently. In the digital age, big data is changing information processing. It lets organizations analyze large datasets and find valuable insights. This leads to better decisions and improved customer experiences. This change is helping businesses find trends, predict outcomes, and innovate quickly. It's reshaping industries and boosting economic growth.
How does blockchain technology work? What key features make it valuable for data management?
Blockchain is a decentralized, distributed ledger. It records transactions across multiple computers in a secure, transparent way. Network participants verify each transaction. This makes it nearly impossible to alter or tamper with the data. This high security and transparency make blockchain valuable for data management.
Blockchain is a decentralized, distributed ledger. It records transactions across multiple computers. This ensures the data is secure and cannot be changed. Its key features are transparency and cryptographic security. Transparency lets all participants access the same information. Cryptographic security protects data from unauthorized changes. These traits make blockchain valuable for data management. They build trust, cut fraud, and boost accountability in many areas, from finance to supply chains.
Benefits of the Intersection of Big Data and Blockchain Technology
Big Data and blockchain technology intersect. It offers major benefits. It boosts data security and integrity. Blockchain's decentralized and immutable nature can protect data. It can prevent tampering and unauthorized access. Also, this synergy improves data transparency and traceability. It fosters trust among stakeholders and streamlines processes across industries.
-
Enhanced Data Security: Blockchain technology securely stores and transmits data. It is tamper-proof. By combining big data and blockchain, organizations can protect their data. They can ensure its integrity and confidentiality.
-
Improved Data Transparency: Blockchain technology keeps a public, decentralized ledger of all transactions. This level of transparency can help organizations trace data throughout its lifecycle.
-
Efficient Data Processing: Blockchain can improve big data analytics. It enables faster, more accurate data processing. This can lead to quicker decision-making and improved operational efficiency.
-
Smart Contracts: Blockchain technology enables smart contracts. They are self-executing contracts with set rules and conditions. Smart contracts can automate and streamline agreements. They save time and reduce errors.
Challenges of the Intersection of Big Data and Blockchain Technology
Big data and blockchain tech intersect. It poses unique challenges, especially in data scalability and storage. Blockchain ensures data integrity and security. But, its decentralized design can complicate handling big data apps. Also, organizations must solve tough problems to use both technologies. They need to connect traditional data systems with blockchain networks.
-
Scalability: Both big data and blockchain require high processing power and storage. Scaling these technologies to handle large data can be a challenge for organizations.
-
Data Integration: Merging big data analytics with blockchain can be complex. It requires careful planning. A seamless data flow between these two technologies is crucial. It is key to their successful implementation.
-
Regulatory Compliance: As blockchain evolves, so must data privacy and security laws. Organizations using big data and blockchain must obey relevant laws.
-
Data Privacy: Blockchain technology is secure, but it raises data privacy issues. It's vital to protect sensitive data. Only authorized parties should access it. This is key to maintaining trust.
How to obtain Big Data certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, big data and blockchain have great potential. They could transform data management and use in many industries. Using these two technologies can help organizations. It can boost data security, transparency, and efficiency in a fast-changing digital world. The key is to overcome the challenges. Then, maximize the benefits. We must integrate big data and blockchain technology seamlessly.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Power of Webinars in Digital Marketing
In today's fast-paced digital world, businesses seek new ways to engage their target audience. One highly effective tool that has gained popularity in recent years is the webinar. Webinars let businesses connect with their audience in a personal, interactive way. They are a powerful tool in digital marketing.
Why Are Webinars Important in Digital Marketing?
Webinars are a powerful digital marketing tool. They let brands showcase their expertise and engage with their audience. They enable real-time interaction. Q&A sessions can deepen connections and understanding of customer needs. Also, webinars are valuable. They can be repurposed for lead generation, nurturing, and marketing. This boosts brand visibility and authority.
Webinars offer many benefits for businesses. They can improve their digital marketing. Some key advantages of incorporating webinars into your marketing plan include:
Lead Generation
Webinars are a great way to generate leads for your business. Provide valuable content in the webinar. This will help you capture attendees' contact info and grow your email list.
Lead generation is a crucial process for businesses looking to expand their customer base and drive sales. Companies can attract and nurture potential customers. They can do this by using targeted strategies like content marketing, social media, and email campaigns. Knowing your audience and providing valuable resources can boost lead generation. This can turn prospects into loyal clients.
Engagement
Webinars are highly engaging, allowing you to interact with your audience in real-time. This interaction builds trust and credibility. It leads to stronger relationships and greater brand loyalty.
Audience Interaction
Webinars allow two-way communication between presenters and attendees. They enable live Q&A, polls, and surveys. This level of audience interaction can provide valuable insights and feedback for your business.
Audience interaction is key to connecting brands with customers. Engaging your audience through comments, polls, and social media stories improves user experience. It also gives you valuable insights into their preferences. Brands can build a community by fostering a two-way dialogue. This will boost loyalty and engagement.
Brand Awareness
Hosting webinars can help increase brand awareness and visibility within your target market. By sharing your expertise and knowledge, you can position your brand as a leader in your industry and attract new customers.
How Can You Use Webinars in Your Digital Strategy?
Webinars are a key part of your digital strategy. They let you engage your audience through live presentations and discussions. You can position your brand as an industry authority. To do this, offer valuable insights and expert knowledge. This will generate leads and build relationships. Also, recorded webinars can become on-demand content. This extends their reach and provides ongoing value to your audience.
To maximize your webinars' impact in digital marketing, consider these tips:
-
Create Compelling Content: Your webinar must engage your target audience. It must be valuable and relevant.
-
Promote Your Webinar: Use a mix of online and offline channels to promote your webinar and attract attendees.
-
Use Social Media: Promote your webinar on social media. Engage with your audience before, during, and after the event.
-
Optimize Your Registration Page: Create a clear, concise registration page. It should make it easy for attendees to register for your webinar.
-
Follow-Up: After your webinar, thank attendees for joining. Then, share valuable resources.
What Are Some Key Metrics to Measure Webinar Success?
To measure webinar success, track key metrics. They show participant engagement and effectiveness. Key metrics include the attendance rate and engagement rate. The former shows how many registered participants joined. The latter reflects how much they interacted with the content through polls, Q&A sessions, and chats. Also, follow-up actions can help assess the webinar's impact. Check how many participants downloaded resources or signed up for more info.
To assess your webinars' success, track these key performance indicators (KPIs):
-
Attendance Rate: Measure the number of registrants who actually attend the webinar.
-
Engagement Metrics: Track audience engagement in the webinar. This includes questions asked, polls answered, and comments made.
-
Conversion Rate: Measure the number of leads or sales generated as a result of the webinar.
-
Audience Retention: Measure how long attendees stay engaged with the webinar content.
-
Feedback and Testimonials: Collect feedback and testimonials from attendees. This will gauge satisfaction and find areas to improve.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Webinars can boost your digital marketing. They enhance engagement, generate leads, and raise brand awareness. They do this in a more personal, interactive way. With the right planning, webinars can drive success in the digital world.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced digital world, businesses seek new ways to engage their target audience. One highly effective tool that has gained popularity in recent years is the webinar. Webinars let businesses connect with their audience in a personal, interactive way. They are a powerful tool in digital marketing.
Why Are Webinars Important in Digital Marketing?
Webinars are a powerful digital marketing tool. They let brands showcase their expertise and engage with their audience. They enable real-time interaction. Q&A sessions can deepen connections and understanding of customer needs. Also, webinars are valuable. They can be repurposed for lead generation, nurturing, and marketing. This boosts brand visibility and authority.
Webinars offer many benefits for businesses. They can improve their digital marketing. Some key advantages of incorporating webinars into your marketing plan include:
Lead Generation
Webinars are a great way to generate leads for your business. Provide valuable content in the webinar. This will help you capture attendees' contact info and grow your email list.
Lead generation is a crucial process for businesses looking to expand their customer base and drive sales. Companies can attract and nurture potential customers. They can do this by using targeted strategies like content marketing, social media, and email campaigns. Knowing your audience and providing valuable resources can boost lead generation. This can turn prospects into loyal clients.
Engagement
Webinars are highly engaging, allowing you to interact with your audience in real-time. This interaction builds trust and credibility. It leads to stronger relationships and greater brand loyalty.
Audience Interaction
Webinars allow two-way communication between presenters and attendees. They enable live Q&A, polls, and surveys. This level of audience interaction can provide valuable insights and feedback for your business.
Audience interaction is key to connecting brands with customers. Engaging your audience through comments, polls, and social media stories improves user experience. It also gives you valuable insights into their preferences. Brands can build a community by fostering a two-way dialogue. This will boost loyalty and engagement.
Brand Awareness
Hosting webinars can help increase brand awareness and visibility within your target market. By sharing your expertise and knowledge, you can position your brand as a leader in your industry and attract new customers.
How Can You Use Webinars in Your Digital Strategy?
Webinars are a key part of your digital strategy. They let you engage your audience through live presentations and discussions. You can position your brand as an industry authority. To do this, offer valuable insights and expert knowledge. This will generate leads and build relationships. Also, recorded webinars can become on-demand content. This extends their reach and provides ongoing value to your audience.
To maximize your webinars' impact in digital marketing, consider these tips:
-
Create Compelling Content: Your webinar must engage your target audience. It must be valuable and relevant.
-
Promote Your Webinar: Use a mix of online and offline channels to promote your webinar and attract attendees.
-
Use Social Media: Promote your webinar on social media. Engage with your audience before, during, and after the event.
-
Optimize Your Registration Page: Create a clear, concise registration page. It should make it easy for attendees to register for your webinar.
-
Follow-Up: After your webinar, thank attendees for joining. Then, share valuable resources.
What Are Some Key Metrics to Measure Webinar Success?
To measure webinar success, track key metrics. They show participant engagement and effectiveness. Key metrics include the attendance rate and engagement rate. The former shows how many registered participants joined. The latter reflects how much they interacted with the content through polls, Q&A sessions, and chats. Also, follow-up actions can help assess the webinar's impact. Check how many participants downloaded resources or signed up for more info.
To assess your webinars' success, track these key performance indicators (KPIs):
-
Attendance Rate: Measure the number of registrants who actually attend the webinar.
-
Engagement Metrics: Track audience engagement in the webinar. This includes questions asked, polls answered, and comments made.
-
Conversion Rate: Measure the number of leads or sales generated as a result of the webinar.
-
Audience Retention: Measure how long attendees stay engaged with the webinar content.
-
Feedback and Testimonials: Collect feedback and testimonials from attendees. This will gauge satisfaction and find areas to improve.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
Webinars can boost your digital marketing. They enhance engagement, generate leads, and raise brand awareness. They do this in a more personal, interactive way. With the right planning, webinars can drive success in the digital world.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Building a Project Management Career with CAPM
Are you looking to build a successful career in project management? Have you considered obtaining the CAPM certification to help you reach your goals? This article will explore how to build a project management career with CAPM certification. It covers entry-level jobs and advancement opportunities.
What is CAPM?
The CAPM certification is a valuable credential from the PMI. It shows your grasp of basic project management concepts. It is a great start for those seeking a project management career.
Steps to Building a Project Management Career with CAPM
To build a project management career with CAPM, start with its structured curriculum. It will give you a solid grasp of key project management concepts. After certification, candidates can seek entry-level roles. They can apply for project coordinator or assistant jobs to gain experience. With ongoing development and use, CAPM holders can move up to senior project management roles.
-
Obtain the CAPM Certification: To build a project management career, first pass the CAPM exam. This certification will prove your project management skills. It will make you a more competitive job candidate.
-
Gain Project Management Experience: The CAPM certification is a great start. But, hands-on experience in project management is crucial for career growth. Look for opportunities to work as a project coordinator or assistant to gain valuable experience.
-
Update Your Resume: Be sure to highlight your CAPM certification and project management experience on your resume. Tailor your resume to the specific job you are applying for to increase your chances of landing a project management role.
-
Set Career Goals: Define your career goals in project management and create a plan to achieve them. Whether you want to be a project manager or an industry expert, clear goals will keep you focused and motivated.
-
Continue Your Education and Training: Stay up to date on project management trends. Attend training programs, workshops, and seminars. Consider advanced certifications like the PMP to boost your skills.
Tips for Building a Successful Project Management Career
To succeed in project management, master both technical and people skills. These include communication, leadership, and problem-solving. Pursuing certifications like CAPM and PMP can boost your credentials. Staying updated on industry trends keeps you relevant. Also, managing diverse projects and learning from mentors will boost your career.
-
Develop Strong Leadership Skills: As a project manager, you must lead well. Strong leadership skills are key to managing projects and teams. Develop your leadership abilities through training and on-the-job experience.
-
Enhance Your Project Management Skills: Always improve your skills. Focus on communication, risk management, and time management. These skills will help you effectively lead projects and achieve successful outcomes.
-
Network with Other Professionals: Attend industry events and join project management groups. Connect with other professionals to build a strong network. Networking can lead to new opportunities and valuable connections.
-
Seek Mentorship: Find a mentor with project management experience. They can guide you as you navigate your career. A mentor can offer valuable insights and help you avoid common pitfalls.
-
Stay Committed to Growth: To succeed in project management, be eager to learn. Stay motivated and focused on your goals to achieve success in the field.
How to obtain CAPM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the CAPM certification is a great way to begin your career in project management. It will unlock many opportunities. This article's steps and tips can help you. They will build a strong base for a rewarding career in project management. Start your journey to a successful project management career with CAPM. Take the first step toward your goals today.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to build a successful career in project management? Have you considered obtaining the CAPM certification to help you reach your goals? This article will explore how to build a project management career with CAPM certification. It covers entry-level jobs and advancement opportunities.
What is CAPM?
The CAPM certification is a valuable credential from the PMI. It shows your grasp of basic project management concepts. It is a great start for those seeking a project management career.
Steps to Building a Project Management Career with CAPM
To build a project management career with CAPM, start with its structured curriculum. It will give you a solid grasp of key project management concepts. After certification, candidates can seek entry-level roles. They can apply for project coordinator or assistant jobs to gain experience. With ongoing development and use, CAPM holders can move up to senior project management roles.
-
Obtain the CAPM Certification: To build a project management career, first pass the CAPM exam. This certification will prove your project management skills. It will make you a more competitive job candidate.
-
Gain Project Management Experience: The CAPM certification is a great start. But, hands-on experience in project management is crucial for career growth. Look for opportunities to work as a project coordinator or assistant to gain valuable experience.
-
Update Your Resume: Be sure to highlight your CAPM certification and project management experience on your resume. Tailor your resume to the specific job you are applying for to increase your chances of landing a project management role.
-
Set Career Goals: Define your career goals in project management and create a plan to achieve them. Whether you want to be a project manager or an industry expert, clear goals will keep you focused and motivated.
-
Continue Your Education and Training: Stay up to date on project management trends. Attend training programs, workshops, and seminars. Consider advanced certifications like the PMP to boost your skills.
Tips for Building a Successful Project Management Career
To succeed in project management, master both technical and people skills. These include communication, leadership, and problem-solving. Pursuing certifications like CAPM and PMP can boost your credentials. Staying updated on industry trends keeps you relevant. Also, managing diverse projects and learning from mentors will boost your career.
-
Develop Strong Leadership Skills: As a project manager, you must lead well. Strong leadership skills are key to managing projects and teams. Develop your leadership abilities through training and on-the-job experience.
-
Enhance Your Project Management Skills: Always improve your skills. Focus on communication, risk management, and time management. These skills will help you effectively lead projects and achieve successful outcomes.
-
Network with Other Professionals: Attend industry events and join project management groups. Connect with other professionals to build a strong network. Networking can lead to new opportunities and valuable connections.
-
Seek Mentorship: Find a mentor with project management experience. They can guide you as you navigate your career. A mentor can offer valuable insights and help you avoid common pitfalls.
-
Stay Committed to Growth: To succeed in project management, be eager to learn. Stay motivated and focused on your goals to achieve success in the field.
How to obtain CAPM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the CAPM certification is a great way to begin your career in project management. It will unlock many opportunities. This article's steps and tips can help you. They will build a strong base for a rewarding career in project management. Start your journey to a successful project management career with CAPM. Take the first step toward your goals today.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Impact of AI on the Future of Business Analysis
Artificial Intelligence (AI) is revolutionizing the way businesses analyze data and make strategic decisions. The integration of AI technology in business analysis processes is reshaping the future of this field. In this article, we will explore the key trends, benefits, challenges, and future implications of AI in business analysis.
AI Impact on Business Analysis
AI can transform business analysis. It can improve data processing speed, accuracy, and efficiency. AI tools let businesses analyze huge data sets in real-time. They can find insights and make better decisions. This technology helps analysts find trends and anomalies that manual methods might miss.
AI is changing business analysis. It automates data collection and improves predictive analytics. It also gives better insights for decision-making. AI tools help analysts find patterns in large datasets. They make complex analyses faster. As AI evolves, business analysts will be key. They will interpret AI data to align it with business goals.
Future of Business Analysis with AI
The future of business analysis is in integrating AI, machine learning, and advanced analytics. AI systems will evolve. They will have better data processing, predictive modeling, and decision support. As AI technology advances, business analysts will get better insights. These will help them solve complex problems and drive business growth.
The future of business analysis with AI is set to revolutionize how data is interpreted and decisions are made. AI tools will help a business analyst automate tasks, predict outcomes, and provide better insights. As AI evolves, business analysts must adapt. They should focus on strategic thinking, data-driven decisions, and better collaboration with AI.
AI Applications in Business Analysis
AI applications in business analysis have a wide range of uses. They include data collection, cleansing, visualization, predictive modeling, and performance monitoring. AI tools can help business analysts. They can streamline workflows, automate tasks, and focus on high-value work. These apps help businesses gain a competitive edge. They provide insights and improve efficiency.
AI applications in business analysis are transforming how organizations handle data-driven decision-making. AI automates repetitive tasks, like data collection and analysis. This lets business analysts focus on more strategic work. AI tools also boost predictive modeling. They help analysts better forecast trends and optimize processes.
Benefits of AI in Business Analysis
The benefits of incorporating AI into business analysis are manifold. AI can enhance decisions, forecasts, and efficiency. It can also optimize resource use. Using AI, businesses can unlock insights from their data. They can spot new opportunities, reduce risks, and outpace competitors.
AI boosts business analysis by automating data collection and processing. Analysts can then focus on higher-level decision-making and strategy. It enables better predictive analytics. It helps businesses to forecast trends and make data-driven decisions with greater precision. Also, AI tools boost efficiency. They provide real-time insights and reduce human error in complex analyses.
Challenges of Integrating AI in Business Analysis
AI can benefit business analysis. But, it has implementation challenges. These challenges may include data privacy, technical issues, integration issues, and a need for specialized skills. We must use a strategic approach to overcome these challenges. We need proper planning and a commitment to learning in AI.
Integrating AI in business analysis poses challenges. These include managing vast, unstructured data and ensuring its accuracy for decision-making. Also, business analysts may struggle with a steep learning curve in using AI tools and algorithms. This can hurt their analysis. Aligning AI insights with business goals is a key hurdle. It must address ethics and data privacy.
The Role of AI in Business Analysis
AI is key to business analysis today. It helps firms use their data assets fully. AI tools can help business analysts. They can extract insights from large, complex datasets, find trends, and make data-driven decisions. AI fuels innovation. It transforms businesses and sharpens decision-making.
How to obtain Business Analysis certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the impact of AI on the future of business analysis is profound. This tech is changing how businesses analyze data and make decisions. It helps them gain a competitive edge. By using AI solutions and keeping up with trends, businesses can unlock new opportunities. They can drive growth and achieve success in a fast-changing digital world.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Artificial Intelligence (AI) is revolutionizing the way businesses analyze data and make strategic decisions. The integration of AI technology in business analysis processes is reshaping the future of this field. In this article, we will explore the key trends, benefits, challenges, and future implications of AI in business analysis.
AI Impact on Business Analysis
AI can transform business analysis. It can improve data processing speed, accuracy, and efficiency. AI tools let businesses analyze huge data sets in real-time. They can find insights and make better decisions. This technology helps analysts find trends and anomalies that manual methods might miss.
AI is changing business analysis. It automates data collection and improves predictive analytics. It also gives better insights for decision-making. AI tools help analysts find patterns in large datasets. They make complex analyses faster. As AI evolves, business analysts will be key. They will interpret AI data to align it with business goals.
Future of Business Analysis with AI
The future of business analysis is in integrating AI, machine learning, and advanced analytics. AI systems will evolve. They will have better data processing, predictive modeling, and decision support. As AI technology advances, business analysts will get better insights. These will help them solve complex problems and drive business growth.
The future of business analysis with AI is set to revolutionize how data is interpreted and decisions are made. AI tools will help a business analyst automate tasks, predict outcomes, and provide better insights. As AI evolves, business analysts must adapt. They should focus on strategic thinking, data-driven decisions, and better collaboration with AI.
AI Applications in Business Analysis
AI applications in business analysis have a wide range of uses. They include data collection, cleansing, visualization, predictive modeling, and performance monitoring. AI tools can help business analysts. They can streamline workflows, automate tasks, and focus on high-value work. These apps help businesses gain a competitive edge. They provide insights and improve efficiency.
AI applications in business analysis are transforming how organizations handle data-driven decision-making. AI automates repetitive tasks, like data collection and analysis. This lets business analysts focus on more strategic work. AI tools also boost predictive modeling. They help analysts better forecast trends and optimize processes.
Benefits of AI in Business Analysis
The benefits of incorporating AI into business analysis are manifold. AI can enhance decisions, forecasts, and efficiency. It can also optimize resource use. Using AI, businesses can unlock insights from their data. They can spot new opportunities, reduce risks, and outpace competitors.
AI boosts business analysis by automating data collection and processing. Analysts can then focus on higher-level decision-making and strategy. It enables better predictive analytics. It helps businesses to forecast trends and make data-driven decisions with greater precision. Also, AI tools boost efficiency. They provide real-time insights and reduce human error in complex analyses.
Challenges of Integrating AI in Business Analysis
AI can benefit business analysis. But, it has implementation challenges. These challenges may include data privacy, technical issues, integration issues, and a need for specialized skills. We must use a strategic approach to overcome these challenges. We need proper planning and a commitment to learning in AI.
Integrating AI in business analysis poses challenges. These include managing vast, unstructured data and ensuring its accuracy for decision-making. Also, business analysts may struggle with a steep learning curve in using AI tools and algorithms. This can hurt their analysis. Aligning AI insights with business goals is a key hurdle. It must address ethics and data privacy.
The Role of AI in Business Analysis
AI is key to business analysis today. It helps firms use their data assets fully. AI tools can help business analysts. They can extract insights from large, complex datasets, find trends, and make data-driven decisions. AI fuels innovation. It transforms businesses and sharpens decision-making.
How to obtain Business Analysis certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the impact of AI on the future of business analysis is profound. This tech is changing how businesses analyze data and make decisions. It helps them gain a competitive edge. By using AI solutions and keeping up with trends, businesses can unlock new opportunities. They can drive growth and achieve success in a fast-changing digital world.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Innovations in Six Sigma Training and Development
In today's fast-paced business world, you must innovate to stay ahead of the competition. Organizations are always trying to improve their training programs, especially in Six Sigma. Six Sigma is a data-driven method. It aims to improve efficiency and reduce defects in processes. As technology and best practices evolve, so do the methods for training in Six Sigma. Let's explore the latest innovations in Six Sigma training. They are revolutionizing how organizations approach process improvement.
Online Six Sigma Courses
A major advancement in Six Sigma training is the shift to online courses. Remote work and digital learning have risen. Now, organizations can offer high-quality, global Six Sigma training to employees. Online courses are flexible and accessible. They let people learn at their own pace and schedule.
Lean Six Sigma Training Methods
Lean Six Sigma combines Six Sigma and Lean methods. It is a powerful way to improve processes. Lean-based training methods aim to eliminate waste and maximize value. They lead to more efficient, streamlined processes. Integrating Lean practices into Six Sigma training can yield even better results.
Modern Six Sigma Tools
New technology has created tools and software that improve Six Sigma training. These tools can better analyze data, track progress, and find areas for improvement. These tools can help organizations improve and speed up training.
Best Practices in Six Sigma Training
As Six Sigma evolves, best practices in training are being updated. Organizations are using new methods to train employees. They offer interactive workshops and customized solutions. This ensures employees have the knowledge and skills to succeed. Best practices in Six Sigma training can help organizations. They can maximize the impact of process improvement initiatives.
When implementing Six Sigma training, some best practices can boost its effectiveness. First, it's crucial to get a strong commitment from top leaders. Without their full support, the initiative may fail. Additionally, training is essential. But, it must be paired with ongoing project work. This will apply the learned concepts. It will ensure that process improvements yield results.
Interactive Six Sigma Workshops
Interactive workshops offer a hands-on, engaging learning experience. They reinforce key concepts. Using activities, simulations, and real-world case studies can make training more engaging. Organizations should use them. Interactive workshops help participants apply Six Sigma principles. This leads to a deeper understanding of the methodology.
Interactive Six Sigma Workshops offer a dynamic learning environment. Participants engage in hands-on activities to apply Six Sigma methods in real-time scenarios. These workshops use simulations, discussions, and exercises to boost understanding. They help attendees grasp complex concepts. These workshops foster collaboration. They build skills and promote a culture of continuous improvement.
Agile Six Sigma Training
Agile methodologies focus on adaptability, collaboration, and iterative improvement. Agile principles in Six Sigma training can help. They can make process improvements respond to changing business needs. Agile Six Sigma training stresses teamwork and fast feedback. It helps firms improve continuously in a fast-paced world.
Agile Six Sigma training merges Agile's flexible approach with Six Sigma's structure. It aims to improve processes and project management. This training gives participants skills for data-driven decision-making. They must also respond to changing customer needs. This will improve business outcomes. Agile Six Sigma boosts efficiency, cuts waste, and improves quality. So, it is a good investment for teams in a fast-paced world.
Customized Six Sigma Training Solutions
Every organization has unique challenges and goals. So, customized training is in demand. Organizations can ensure employees get the best training. They should tailor programs to specific needs and goals. Custom Six Sigma training helps organizations fix specific issues and improve.
Customized Six Sigma training solutions meet organizations' specific needs. They ensure teams gain the skills to improve processes. These solutions improve engagement and retention. They do this by aligning training with industry and organizational goals. Companies that use customized training often see big gains. They get higher productivity, better quality, and a stronger culture of improvement.
How to obtain Six Sigma Black Belt certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, new ideas in Six Sigma training are shaping process improvement's future. Organizations are using new methods to improve employees' skills. They are adopting online courses, lean methodologies, and modern tools. To succeed in a fast-changing business world, organizations must stay current on the latest trends in Six Sigma training.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced business world, you must innovate to stay ahead of the competition. Organizations are always trying to improve their training programs, especially in Six Sigma. Six Sigma is a data-driven method. It aims to improve efficiency and reduce defects in processes. As technology and best practices evolve, so do the methods for training in Six Sigma. Let's explore the latest innovations in Six Sigma training. They are revolutionizing how organizations approach process improvement.
Online Six Sigma Courses
A major advancement in Six Sigma training is the shift to online courses. Remote work and digital learning have risen. Now, organizations can offer high-quality, global Six Sigma training to employees. Online courses are flexible and accessible. They let people learn at their own pace and schedule.
Lean Six Sigma Training Methods
Lean Six Sigma combines Six Sigma and Lean methods. It is a powerful way to improve processes. Lean-based training methods aim to eliminate waste and maximize value. They lead to more efficient, streamlined processes. Integrating Lean practices into Six Sigma training can yield even better results.
Modern Six Sigma Tools
New technology has created tools and software that improve Six Sigma training. These tools can better analyze data, track progress, and find areas for improvement. These tools can help organizations improve and speed up training.
Best Practices in Six Sigma Training
As Six Sigma evolves, best practices in training are being updated. Organizations are using new methods to train employees. They offer interactive workshops and customized solutions. This ensures employees have the knowledge and skills to succeed. Best practices in Six Sigma training can help organizations. They can maximize the impact of process improvement initiatives.
When implementing Six Sigma training, some best practices can boost its effectiveness. First, it's crucial to get a strong commitment from top leaders. Without their full support, the initiative may fail. Additionally, training is essential. But, it must be paired with ongoing project work. This will apply the learned concepts. It will ensure that process improvements yield results.
Interactive Six Sigma Workshops
Interactive workshops offer a hands-on, engaging learning experience. They reinforce key concepts. Using activities, simulations, and real-world case studies can make training more engaging. Organizations should use them. Interactive workshops help participants apply Six Sigma principles. This leads to a deeper understanding of the methodology.
Interactive Six Sigma Workshops offer a dynamic learning environment. Participants engage in hands-on activities to apply Six Sigma methods in real-time scenarios. These workshops use simulations, discussions, and exercises to boost understanding. They help attendees grasp complex concepts. These workshops foster collaboration. They build skills and promote a culture of continuous improvement.
Agile Six Sigma Training
Agile methodologies focus on adaptability, collaboration, and iterative improvement. Agile principles in Six Sigma training can help. They can make process improvements respond to changing business needs. Agile Six Sigma training stresses teamwork and fast feedback. It helps firms improve continuously in a fast-paced world.
Agile Six Sigma training merges Agile's flexible approach with Six Sigma's structure. It aims to improve processes and project management. This training gives participants skills for data-driven decision-making. They must also respond to changing customer needs. This will improve business outcomes. Agile Six Sigma boosts efficiency, cuts waste, and improves quality. So, it is a good investment for teams in a fast-paced world.
Customized Six Sigma Training Solutions
Every organization has unique challenges and goals. So, customized training is in demand. Organizations can ensure employees get the best training. They should tailor programs to specific needs and goals. Custom Six Sigma training helps organizations fix specific issues and improve.
Customized Six Sigma training solutions meet organizations' specific needs. They ensure teams gain the skills to improve processes. These solutions improve engagement and retention. They do this by aligning training with industry and organizational goals. Companies that use customized training often see big gains. They get higher productivity, better quality, and a stronger culture of improvement.
How to obtain Six Sigma Black Belt certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, new ideas in Six Sigma training are shaping process improvement's future. Organizations are using new methods to improve employees' skills. They are adopting online courses, lean methodologies, and modern tools. To succeed in a fast-changing business world, organizations must stay current on the latest trends in Six Sigma training.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Resurgence of Configuration Management Databases
In IT infrastructure management, CMDBs are becoming popular again. These tools are vital for the smooth operation and security of IT systems. Let's explore the benefits, use, best practices, and trends of CMDB in IT.
Understanding CMDB and Its Importance
A Configuration Management Database is a central repository. It holds info on all components in an IT environment. It helps organizations track and manage configuration items. It also helps them understand their relationships. It sets a baseline for best practices in configuration management. CMDB is essential for maintaining the integrity and consistency of IT infrastructure.
A Configuration Management Database (CMDB) is key in IT service management. It is a central store of an organization's IT assets, their configs, and their relationships. A CMDB gives visibility into the IT infrastructure. So, it is essential to understand it. It helps with decision-making, risk management, and meeting regulations. By managing configuration items and their dependencies, organizations can improve. It will help incident response times, change management, and service delivery.
Benefits of CMDB Implementation
-
Improved visibility and control over IT assets.
-
Enhanced change management and risk reduction.
-
Automation of configuration management processes.
-
Facilitation of compliance audits and reporting.
-
Integration with other IT service management tools for seamless operations.
-
Greater scalability and data quality in configuration management.
CMDB Deployment and Tools
Implementing a CMDB solution involves careful planning, deployment, and maintenance. Organizations can choose from many CMDB tools on the market. Each offers unique features and capabilities. Deploying a CMDB requires a clear strategy and governance. It also needs ongoing monitoring to ensure its effectiveness.
A Configuration Management Database (CMDB) is vital for IT Service Management (ITSM). It is a central repository for all IT assets and their relationships. So, configuring and deploying a CMDB is essential. Modern CMDB tools allow real-time updates. They help organizations keep accurate records and make informed decisions. This is vital in fast-changing environments.
Modern CMDB Trends and Technology
CMDB technology has evolved. It has led to better, easier tools. Modern CMDBs use automation, AI, and machine learning. They streamline config management processes. They also support cloud-based deployment and scalability. They optimize datacenters for better performance and efficiency.
Modern CMDBs are using AI and machine learning. They aim to automate data collection and improve accuracy. This helps organizations maintain real-time visibility into their IT environments. AI-driven solutions improve incident response and service management. They provide context and insights into asset dependencies.
CMDB Integration and Automation
Integrating the CMDB with other IT tools is vital. It provides a complete view of the IT environment. Automation is key to CMDB accuracy. It reduces manual work and improves data correlation. CMDB integration and automation can help organizations. They can streamline operations, save costs, and ensure data consistency.
CMDB integration and automation are key to IT service management. They provide a central repository of IT assets and their relationships. This integration streamlines processes. It enables real-time visibility into infrastructure changes. It also improves decision-making on service delivery and risk management.
Challenges and Solutions in CMDB Implementation
While CMDB offers numerous benefits, organizations often face challenges during its implementation. Common issues include data synchronization, accuracy, scalability, and governance. Best practices, docs, and process control can help fix these issues. They can ensure CMDB initiatives succeed.
A Configuration Management Database (CMDB) can be hard to implement. It may have issues with data accuracy, system integration, and user adoption. Organizations often struggle to keep their CMDB data up to date. Real-time changes often lead to inaccuracies that undermine its effectiveness.
Future Benefits and Business Value of CMDB
As CMDB continues to evolve, its future holds promising benefits for organizations. The CMDB's automation, data modeling, metrics, and ROI should enhance config management. They should improve efficiency and innovation. Integrating CMDB with ITSM, asset management, and other systems can greatly benefit businesses. It can help them achieve operational excellence.
A Configuration Management Database (CMDB) is key for organizations. It helps improve IT service management. A CMDB is a central place to manage IT assets and their relationships. This tool helps businesses make better decisions. It improves visibility of asset dependencies. This leads to better resource use and risk management.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, CMDBs are a big step in IT infrastructure management. Using CMDB best practices and modern tech, organizations can unlock its full potential. This will boost efficiency, compliance, and business value. They must also address implementation challenges.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In IT infrastructure management, CMDBs are becoming popular again. These tools are vital for the smooth operation and security of IT systems. Let's explore the benefits, use, best practices, and trends of CMDB in IT.
Understanding CMDB and Its Importance
A Configuration Management Database is a central repository. It holds info on all components in an IT environment. It helps organizations track and manage configuration items. It also helps them understand their relationships. It sets a baseline for best practices in configuration management. CMDB is essential for maintaining the integrity and consistency of IT infrastructure.
A Configuration Management Database (CMDB) is key in IT service management. It is a central store of an organization's IT assets, their configs, and their relationships. A CMDB gives visibility into the IT infrastructure. So, it is essential to understand it. It helps with decision-making, risk management, and meeting regulations. By managing configuration items and their dependencies, organizations can improve. It will help incident response times, change management, and service delivery.
Benefits of CMDB Implementation
-
Improved visibility and control over IT assets.
-
Enhanced change management and risk reduction.
-
Automation of configuration management processes.
-
Facilitation of compliance audits and reporting.
-
Integration with other IT service management tools for seamless operations.
-
Greater scalability and data quality in configuration management.
CMDB Deployment and Tools
Implementing a CMDB solution involves careful planning, deployment, and maintenance. Organizations can choose from many CMDB tools on the market. Each offers unique features and capabilities. Deploying a CMDB requires a clear strategy and governance. It also needs ongoing monitoring to ensure its effectiveness.
A Configuration Management Database (CMDB) is vital for IT Service Management (ITSM). It is a central repository for all IT assets and their relationships. So, configuring and deploying a CMDB is essential. Modern CMDB tools allow real-time updates. They help organizations keep accurate records and make informed decisions. This is vital in fast-changing environments.
Modern CMDB Trends and Technology
CMDB technology has evolved. It has led to better, easier tools. Modern CMDBs use automation, AI, and machine learning. They streamline config management processes. They also support cloud-based deployment and scalability. They optimize datacenters for better performance and efficiency.
Modern CMDBs are using AI and machine learning. They aim to automate data collection and improve accuracy. This helps organizations maintain real-time visibility into their IT environments. AI-driven solutions improve incident response and service management. They provide context and insights into asset dependencies.
CMDB Integration and Automation
Integrating the CMDB with other IT tools is vital. It provides a complete view of the IT environment. Automation is key to CMDB accuracy. It reduces manual work and improves data correlation. CMDB integration and automation can help organizations. They can streamline operations, save costs, and ensure data consistency.
CMDB integration and automation are key to IT service management. They provide a central repository of IT assets and their relationships. This integration streamlines processes. It enables real-time visibility into infrastructure changes. It also improves decision-making on service delivery and risk management.
Challenges and Solutions in CMDB Implementation
While CMDB offers numerous benefits, organizations often face challenges during its implementation. Common issues include data synchronization, accuracy, scalability, and governance. Best practices, docs, and process control can help fix these issues. They can ensure CMDB initiatives succeed.
A Configuration Management Database (CMDB) can be hard to implement. It may have issues with data accuracy, system integration, and user adoption. Organizations often struggle to keep their CMDB data up to date. Real-time changes often lead to inaccuracies that undermine its effectiveness.
Future Benefits and Business Value of CMDB
As CMDB continues to evolve, its future holds promising benefits for organizations. The CMDB's automation, data modeling, metrics, and ROI should enhance config management. They should improve efficiency and innovation. Integrating CMDB with ITSM, asset management, and other systems can greatly benefit businesses. It can help them achieve operational excellence.
A Configuration Management Database (CMDB) is key for organizations. It helps improve IT service management. A CMDB is a central place to manage IT assets and their relationships. This tool helps businesses make better decisions. It improves visibility of asset dependencies. This leads to better resource use and risk management.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, CMDBs are a big step in IT infrastructure management. Using CMDB best practices and modern tech, organizations can unlock its full potential. This will boost efficiency, compliance, and business value. They must also address implementation challenges.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Top 5 Skills You ll Master with PgMP Certification in 2024
In today's fast-changing business world, effective program management is vital. It helps organizations achieve their strategic goals. The Project Management Institute (PMI) offers the PgMP certification. It is one of the most prestigious certifications for program managers. It shows you can manage complex projects and align them with goals. In 2024, earning a PgMP certification is not about knowing program management. It's about mastering skills that make you a standout leader in your field.
This article covers the top five skills that PgMP certification can help you master. These skills will boost your value to your organization.
Strategic Alignment and Business Acumen
A key skill of PgMP certification is to align projects with a group's long-term strategy. Program management is more than managing projects. It focuses on how related projects can work together to achieve the company's goals.
- Strategic thinking: You'll learn to align programs with broader goals. You'll define, install, and adjust them.
- PgMP teaches you to check business goals. It ensures your program's work supports the mission.
- Value realization: You'll learn to assess your program's value to the organization. This will ensure optimal resource use and alignment with business goals.
In today's fast-changing business world, success requires strategic thinking and adaptability.
Stakeholder Management and Communication Skills
Effective communication and stakeholder engagement are critical for any program manager. PgMP certification places a strong emphasis on developing robust stakeholder management skills.
- You'll learn to identify key stakeholders at all levels of the organization. Then, rank their needs and expectations.
- Effective communication: PgMP helps you craft clear, concise messages. They should suit various stakeholders, from project teams to executives.
- Conflict resolution: Managing stakeholder expectations and resolving conflicts is crucial for program success. You’ll master techniques for handling disputes with diplomacy and ensuring stakeholder satisfaction.
Strong communication skills foster collaboration and buy-in from stakeholders. This leads to smoother execution of programs and initiatives.
Leadership and Team Management
A successful program manager must be an effective leader. They must inspire and guide teams to achieve shared goals. PgMP certification improves your leadership and team management skills.
- Motivational leadership: You'll learn to motivate teams on many projects in a program. This will keep them focused on the program's goals.
- Building high-performing teams: PgMP teaches team dynamics. It helps you build teams that function with high efficiency and cooperation.
- PgMP certification improves your ability to delegate and empower your team. It teaches you to delegate tasks and to let your team take ownership. It teaches you to manage a program's many layers without micromanaging. This fosters autonomy and trust among team members.
Strong leadership skills are vital for managing complex projects. They make you a more effective program manager. You can then lead diverse teams to success.
Risk Management and Problem Solving
In any program, risks are inevitable. But the best program managers can manage and reduce these risks. This skill sets them apart. PgMP certification gives you the tools and techniques to manage risks.
- Risk identification and assessment: You'll learn to spot risks early in the program. You'll also assess their impact on its success.
- Mitigation strategies: PgMP offers a framework to create risk mitigation strategies. It helps you manage risks before they become critical issues.
- Adaptive problem-solving: PgMP certification builds your critical thinking skills. It helps you handle surprises and adjust your approach to keep the program on track.
Master risk management. You'll then navigate the complexities and uncertainties of program execution. This will ensure that we deliver programs on time and within budget.
Governance and Performance Management
Governance is key in program management. PgMP certification teaches you to govern your programs well.
- Establishing governance structures: You'll learn to design governance structures. They must align program objectives with business goals.
- Performance monitoring: PgMP helps you develop KPIs. Use them to track program performance against goals.
- Accountability and compliance: You will learn to ensure accountability and meet standards.
Good governance and performance management skills ensure programs operate without issues. They must follow protocols and deliver expected results to stakeholders.
How to obtain PgMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
PgMP certification is more than a credential. It shows mastery of the skills needed to excel in program management. In 2024, organizations will face complex challenges and opportunities. So, the demand for skilled program managers will grow. By earning your PgMP, you will be able to align programs with business strategy. You will manage stakeholders, lead teams, mitigate risks, and ensure strong governance.
Anyone who wants to be a high-performing program manager must have five skills. They are: strategic alignment, stakeholder management, leadership, risk management, and governance. These skills will boost your portfolio. They'll also help your organization achieve its goals.
As program management evolves, PgMP-certified professionals will be in high demand. They can drive success in complex program environments. Now is the time to invest in your career. Gain these critical skills through the PgMP certification.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-changing business world, effective program management is vital. It helps organizations achieve their strategic goals. The Project Management Institute (PMI) offers the PgMP certification. It is one of the most prestigious certifications for program managers. It shows you can manage complex projects and align them with goals. In 2024, earning a PgMP certification is not about knowing program management. It's about mastering skills that make you a standout leader in your field.
This article covers the top five skills that PgMP certification can help you master. These skills will boost your value to your organization.
Strategic Alignment and Business Acumen
A key skill of PgMP certification is to align projects with a group's long-term strategy. Program management is more than managing projects. It focuses on how related projects can work together to achieve the company's goals.
- Strategic thinking: You'll learn to align programs with broader goals. You'll define, install, and adjust them.
- PgMP teaches you to check business goals. It ensures your program's work supports the mission.
- Value realization: You'll learn to assess your program's value to the organization. This will ensure optimal resource use and alignment with business goals.
In today's fast-changing business world, success requires strategic thinking and adaptability.
Stakeholder Management and Communication Skills
Effective communication and stakeholder engagement are critical for any program manager. PgMP certification places a strong emphasis on developing robust stakeholder management skills.
- You'll learn to identify key stakeholders at all levels of the organization. Then, rank their needs and expectations.
- Effective communication: PgMP helps you craft clear, concise messages. They should suit various stakeholders, from project teams to executives.
- Conflict resolution: Managing stakeholder expectations and resolving conflicts is crucial for program success. You’ll master techniques for handling disputes with diplomacy and ensuring stakeholder satisfaction.
Strong communication skills foster collaboration and buy-in from stakeholders. This leads to smoother execution of programs and initiatives.
Leadership and Team Management
A successful program manager must be an effective leader. They must inspire and guide teams to achieve shared goals. PgMP certification improves your leadership and team management skills.
- Motivational leadership: You'll learn to motivate teams on many projects in a program. This will keep them focused on the program's goals.
- Building high-performing teams: PgMP teaches team dynamics. It helps you build teams that function with high efficiency and cooperation.
- PgMP certification improves your ability to delegate and empower your team. It teaches you to delegate tasks and to let your team take ownership. It teaches you to manage a program's many layers without micromanaging. This fosters autonomy and trust among team members.
Strong leadership skills are vital for managing complex projects. They make you a more effective program manager. You can then lead diverse teams to success.
Risk Management and Problem Solving
In any program, risks are inevitable. But the best program managers can manage and reduce these risks. This skill sets them apart. PgMP certification gives you the tools and techniques to manage risks.
- Risk identification and assessment: You'll learn to spot risks early in the program. You'll also assess their impact on its success.
- Mitigation strategies: PgMP offers a framework to create risk mitigation strategies. It helps you manage risks before they become critical issues.
- Adaptive problem-solving: PgMP certification builds your critical thinking skills. It helps you handle surprises and adjust your approach to keep the program on track.
Master risk management. You'll then navigate the complexities and uncertainties of program execution. This will ensure that we deliver programs on time and within budget.
Governance and Performance Management
Governance is key in program management. PgMP certification teaches you to govern your programs well.
- Establishing governance structures: You'll learn to design governance structures. They must align program objectives with business goals.
- Performance monitoring: PgMP helps you develop KPIs. Use them to track program performance against goals.
- Accountability and compliance: You will learn to ensure accountability and meet standards.
Good governance and performance management skills ensure programs operate without issues. They must follow protocols and deliver expected results to stakeholders.
How to obtain PgMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
PgMP certification is more than a credential. It shows mastery of the skills needed to excel in program management. In 2024, organizations will face complex challenges and opportunities. So, the demand for skilled program managers will grow. By earning your PgMP, you will be able to align programs with business strategy. You will manage stakeholders, lead teams, mitigate risks, and ensure strong governance.
Anyone who wants to be a high-performing program manager must have five skills. They are: strategic alignment, stakeholder management, leadership, risk management, and governance. These skills will boost your portfolio. They'll also help your organization achieve its goals.
As program management evolves, PgMP-certified professionals will be in high demand. They can drive success in complex program environments. Now is the time to invest in your career. Gain these critical skills through the PgMP certification.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Minitab Macros Automating Your Data Analysis
In the era of big data, organizations are overwhelmed with vast amounts of information. So, data analysis is now more critical than ever. Minitab is powerful statistical software. It has tools to help users analyze data. Of these tools, macros are the best. They automate repetitive tasks and improve efficiency. Macros can help analysts. They can streamline workflows, reduce errors, and ensure consistency in data analysis. This article covers Minitab macros. It covers their benefits, how to create them, common uses, and best practices for effective use.
Understanding Minitab Macros
Minitab macros are scripts that automate a sequence of commands in the software. Users can create these macros using Minitab's macro language. It allows scripts to run tasks automatically, without manual input. This feature helps with tasks that need repeated execution. For example, it can run the same analysis on different datasets. Or, it can apply the same settings across many projects.
Key Features of Minitab Macros:
- Automation: Streamline repetitive tasks to boost efficiency and minimize mistakes.
- Reusability: Once created, macros can be reused across different projects, enhancing efficiency.
- Customization: Users can customize macros for specific analyses. This allows for tailored workflows.
Creating Minitab macros
Creating a macro in Minitab involves a few straightforward steps. Users must learn the macro syntax and commands to write their scripts. Generally, the procedure involves the following steps:
Step-by-Step Process:
- Open the Minitab Macro Editor: Access the macro editor by selecting “File” > “New” > “Macro.”
- Write the Macro Script: Use Minitab's macro commands to define the macro's actions. This might include commands for data manipulation, statistical analysis, or generating reports.
- Save the Macro: After the script is complete, save the macro. Choose a name that clearly reflects its function.
- Run the macro: Use the Minitab interface to run the macro. It will perform the automated tasks.
Example of a Simple Macro:
plaintext
- This example reads data from a CSV file. It describes a column, does regression analysis, and saves the results.
Common Applications of Minitab Macros
Minitab macros can be applied in various scenarios to enhance data analysis processes. Some common applications include:
- Repeated analysis : For analysts who need to run the same tests on multiple datasets, macros can automate this. They streamline processes and deliver reliable outcomes.
- Report Generation : Macros can automatically generate reports. They compile analysis results and present them in a user-friendly format. This is particularly useful for stakeholders who require regular updates on project progress.
- Data Cleaning and Preparation : Before analysis, data often requires cleaning and preparation. Macros can automate preprocessing steps. This includes removing outliers, filling in missing values, and transforming variables.
- Customized Analyses : For organizations with unique analytical needs, macros can be tailored. They can perform specific analyses that align with business goals. This ensures the right insights are generated.
- Batch Processing : Macros enable batch processing of analyses on large datasets. They let users efficiently apply the same methods across many datasets.
Best Practices for Using Minitab Macros
To get the most from Minitab macros, users should follow some best practices.
- Keep It Simple : While Minitab allows for complex macros, simplicity should be prioritized. Simple, well-documented macros are easier to understand and maintain. This reduces errors.
- Document your code : Including comments within the macro code can greatly aid in understanding its functionality. This is crucial for users who may return to the code later. It's also important for those who share macros with colleagues.
- Test thoroughly : Before using a macro, test it. It must perform as expected. This includes testing on different datasets. It is to confirm that the macro works across various scenarios.
- Regular Updates : As data analysis needs evolve, so should the macros. Regularly review and update the macros. This keeps them effective for current tasks.
- Leverage Community Resources : The Minitab community has many resources. It includes forums, tutorials, and example macros. These resources can offer insights. They can help users improve their macro-writing skills.
How to obtain MiniTab certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Minitab macros are a powerful tool for automating data analysis. They help users streamline repetitive tasks, improve accuracy, and boost productivity. By learning to create and use macros, analysts can automate tasks. This lets them focus on extracting insights from their data, not on manual work. As organizations rely more on data for decisions, Minitab macros can help. They can improve analytical workflows. It lets teams respond quickly to business challenges and opportunities. Whether you're a seasoned Minitab user or just starting, use macros in your data analysis. It's a smart way to boost efficiency and effectiveness.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In the era of big data, organizations are overwhelmed with vast amounts of information. So, data analysis is now more critical than ever. Minitab is powerful statistical software. It has tools to help users analyze data. Of these tools, macros are the best. They automate repetitive tasks and improve efficiency. Macros can help analysts. They can streamline workflows, reduce errors, and ensure consistency in data analysis. This article covers Minitab macros. It covers their benefits, how to create them, common uses, and best practices for effective use.
Understanding Minitab Macros
Minitab macros are scripts that automate a sequence of commands in the software. Users can create these macros using Minitab's macro language. It allows scripts to run tasks automatically, without manual input. This feature helps with tasks that need repeated execution. For example, it can run the same analysis on different datasets. Or, it can apply the same settings across many projects.
Key Features of Minitab Macros:
- Automation: Streamline repetitive tasks to boost efficiency and minimize mistakes.
- Reusability: Once created, macros can be reused across different projects, enhancing efficiency.
- Customization: Users can customize macros for specific analyses. This allows for tailored workflows.
Creating Minitab macros
Creating a macro in Minitab involves a few straightforward steps. Users must learn the macro syntax and commands to write their scripts. Generally, the procedure involves the following steps:
Step-by-Step Process:
- Open the Minitab Macro Editor: Access the macro editor by selecting “File” > “New” > “Macro.”
- Write the Macro Script: Use Minitab's macro commands to define the macro's actions. This might include commands for data manipulation, statistical analysis, or generating reports.
- Save the Macro: After the script is complete, save the macro. Choose a name that clearly reflects its function.
- Run the macro: Use the Minitab interface to run the macro. It will perform the automated tasks.
Example of a Simple Macro:
plaintext
- This example reads data from a CSV file. It describes a column, does regression analysis, and saves the results.
Common Applications of Minitab Macros
Minitab macros can be applied in various scenarios to enhance data analysis processes. Some common applications include:
- Repeated analysis : For analysts who need to run the same tests on multiple datasets, macros can automate this. They streamline processes and deliver reliable outcomes.
- Report Generation : Macros can automatically generate reports. They compile analysis results and present them in a user-friendly format. This is particularly useful for stakeholders who require regular updates on project progress.
- Data Cleaning and Preparation : Before analysis, data often requires cleaning and preparation. Macros can automate preprocessing steps. This includes removing outliers, filling in missing values, and transforming variables.
- Customized Analyses : For organizations with unique analytical needs, macros can be tailored. They can perform specific analyses that align with business goals. This ensures the right insights are generated.
- Batch Processing : Macros enable batch processing of analyses on large datasets. They let users efficiently apply the same methods across many datasets.
Best Practices for Using Minitab Macros
To get the most from Minitab macros, users should follow some best practices.
- Keep It Simple : While Minitab allows for complex macros, simplicity should be prioritized. Simple, well-documented macros are easier to understand and maintain. This reduces errors.
- Document your code : Including comments within the macro code can greatly aid in understanding its functionality. This is crucial for users who may return to the code later. It's also important for those who share macros with colleagues.
- Test thoroughly : Before using a macro, test it. It must perform as expected. This includes testing on different datasets. It is to confirm that the macro works across various scenarios.
- Regular Updates : As data analysis needs evolve, so should the macros. Regularly review and update the macros. This keeps them effective for current tasks.
- Leverage Community Resources : The Minitab community has many resources. It includes forums, tutorials, and example macros. These resources can offer insights. They can help users improve their macro-writing skills.
How to obtain MiniTab certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Minitab macros are a powerful tool for automating data analysis. They help users streamline repetitive tasks, improve accuracy, and boost productivity. By learning to create and use macros, analysts can automate tasks. This lets them focus on extracting insights from their data, not on manual work. As organizations rely more on data for decisions, Minitab macros can help. They can improve analytical workflows. It lets teams respond quickly to business challenges and opportunities. Whether you're a seasoned Minitab user or just starting, use macros in your data analysis. It's a smart way to boost efficiency and effectiveness.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Balancing Data Privacy and SMAC Strategies in 2024
In our hyper-connected world, SMAC (Social, Mobile, Analytics, and Cloud) strategies are vital. They help businesses innovate and thrive in a digital-first landscape. However, these technologies come with significant challenges, primarily around data privacy. With more sensitive data flowing through these channels, businesses must balance their SMAC-driven initiatives with strong data privacy measures.
2024 is poised to be a pivotal year for organizations as they navigate this balancing act. As data protection laws like the GDPR and CCPA evolve, we must comply. We must also maximize the benefits of SMAC. This article will examine the trade-off. It's about using SMAC for a competitive edge. But, there are privacy concerns about customer data.
The Rise of SMAC Technologies in 2024
SMAC has changed how businesses operate. It offers new ways to engage customers and streamline operations. It also helps to gain insights from vast data. Each component of SMAC plays a key role in business transformation:
- Social: Social media platforms are powerful tools for customer engagement and brand building. In 2024, businesses will use social channels for better customer insights. They want to create more personalized marketing strategies.
- Mobile: Mobile technology connects us. It gives instant access to products, services, and information. Companies are focusing on optimizing mobile experiences to meet rising consumer expectations.
- Analytics: Big Data analytics is critical for turning raw data into actionable insights. Advanced analytics help organizations understand consumer behavior, predict market trends, and improve decision-making.
- Cloud: Cloud computing enables scalability, flexibility, and cost-efficiency. In 2024, more organizations will move their data and operations to the cloud. They want to be more agile and drive innovation.
However, with the growth of SMAC comes an influx of data, much of which is personal and sensitive. We urgently need strong data privacy measures to ensure trust and compliance.
Challenges in Data Privacy with SMAC
The integration of SMAC technologies into business processes introduces several data privacy challenges. As organizations collect more customer data, they must protect it. Key challenges include:
- Increased Data Collection: Social platforms, apps, and cloud services generate vast data. Organizations must be clear about the data they collect. They should state its purpose and how it will be used.
- Data Sharing Across Platforms: SMAC needs collaboration across multiple platforms. This often requires data sharing. It raises the risk of data breaches if third-party partners don't meet strict privacy standards.
- Regulatory Compliance: Laws like the GDPR and CCPA mandate stringent data protection requirements. Noncompliance can result in heavy fines and damage to reputation.
- Consumer Trust: Data privacy worries make consumers hesitant to share information. Organizations need to build trust by demonstrating strong privacy practices.
Regulatory Landscape for Data Privacy in 2024
The regulatory environment surrounding data privacy continues to evolve. In 2024, businesses must keep up with new privacy laws. Their SMAC strategies must align with the new regulations. Some key trends include:
- Many countries are updating or creating new data privacy laws. Asia and Latin America are adopting strict data protection laws, too. They follow the EU's GDPR and California's CCPA.
- Cross-border Data Transfer Restrictions: Globalization and remote work have increased cross-border data transfers. New laws may tighten restrictions on international data transfers. They will must organizations to use secure transfer methods.
- Consent Management: Organizations must improve their consent systems. Users should control their data and understand how they will use it.
Neglecting regulatory compliance in SMAC strategies will harm businesses. They will suffer reputational damage and financial penalties.
Best Practices for Balancing Data Privacy with SMAC
Balancing SMAC strategies with data privacy doesn’t have to be a zero-sum game. By using best practices, businesses can reap the benefits of SMAC. They can also protect consumer data. Some essential best practices include:
- Data Minimization: Only collect and store data that is essential for your business. Reducing the amount of data collected helps limit the risk of privacy breaches.
- End-to-End Encryption: Encrypt all data sent via social, mobile, and cloud channels. This will prevent unauthorized access.
- Regular Privacy Audits: Conduct audits to find vulnerabilities in data handling. Ensure compliance with evolving privacy laws.
- Clear Privacy Policies: Provide simple, clear privacy policies. They must outline how you collect, use, and store data.
- Consumer Empowerment: Give users more control over their data. Enable opt-out, data deletion, and consent management.
By adopting these best practices, businesses can build consumer trust. This will reduce privacy risks in their SMAC strategies.
The Future of SMAC and Data Privacy
Looking forward, the relationship between SMAC and data privacy will continue to evolve. In 2024 and beyond, AI and machine learning will boost SMAC. They will provide more personalized experiences. But, these technologies also introduce new challenges related to data privacy and ethics.
- AI-Driven SMAC: AI will better analyze social data, automate apps, and optimize clouds. AI systems rely on vast datasets. So, it's critical for organizations to use privacy-by-design principles.
- Decentralized Data Solutions: Blockchain could provide decentralized options for data storage and privacy. It would decrease reliance on third-party providers. It would give individuals more control over their personal data.
Businesses must stay agile. They must adapt to new privacy tech and rules. At the same time, they must use SMAC's power.
How to obtain SMAC certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Balancing data privacy and SMAC strategies is essential for success in 2024. As organizations adopt more social, mobile, and cloud tech, they must protect data. This is key to complying with new regulations and to maintaining consumer trust. Businesses can use best practices to protect sensitive data. These include data minimization, encryption, and clear privacy policies. They can then enjoy the benefits of SMAC. AI and decentralized tech will reshape SMAC and data privacy. So, organizations must stay agile and proactive in this changing landscape.
In a data-driven age, businesses must balance innovation with privacy. Those that do will gain a strong competitive edge.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In our hyper-connected world, SMAC (Social, Mobile, Analytics, and Cloud) strategies are vital. They help businesses innovate and thrive in a digital-first landscape. However, these technologies come with significant challenges, primarily around data privacy. With more sensitive data flowing through these channels, businesses must balance their SMAC-driven initiatives with strong data privacy measures.
2024 is poised to be a pivotal year for organizations as they navigate this balancing act. As data protection laws like the GDPR and CCPA evolve, we must comply. We must also maximize the benefits of SMAC. This article will examine the trade-off. It's about using SMAC for a competitive edge. But, there are privacy concerns about customer data.
The Rise of SMAC Technologies in 2024
SMAC has changed how businesses operate. It offers new ways to engage customers and streamline operations. It also helps to gain insights from vast data. Each component of SMAC plays a key role in business transformation:
- Social: Social media platforms are powerful tools for customer engagement and brand building. In 2024, businesses will use social channels for better customer insights. They want to create more personalized marketing strategies.
- Mobile: Mobile technology connects us. It gives instant access to products, services, and information. Companies are focusing on optimizing mobile experiences to meet rising consumer expectations.
- Analytics: Big Data analytics is critical for turning raw data into actionable insights. Advanced analytics help organizations understand consumer behavior, predict market trends, and improve decision-making.
- Cloud: Cloud computing enables scalability, flexibility, and cost-efficiency. In 2024, more organizations will move their data and operations to the cloud. They want to be more agile and drive innovation.
However, with the growth of SMAC comes an influx of data, much of which is personal and sensitive. We urgently need strong data privacy measures to ensure trust and compliance.
Challenges in Data Privacy with SMAC
The integration of SMAC technologies into business processes introduces several data privacy challenges. As organizations collect more customer data, they must protect it. Key challenges include:
- Increased Data Collection: Social platforms, apps, and cloud services generate vast data. Organizations must be clear about the data they collect. They should state its purpose and how it will be used.
- Data Sharing Across Platforms: SMAC needs collaboration across multiple platforms. This often requires data sharing. It raises the risk of data breaches if third-party partners don't meet strict privacy standards.
- Regulatory Compliance: Laws like the GDPR and CCPA mandate stringent data protection requirements. Noncompliance can result in heavy fines and damage to reputation.
- Consumer Trust: Data privacy worries make consumers hesitant to share information. Organizations need to build trust by demonstrating strong privacy practices.
Regulatory Landscape for Data Privacy in 2024
The regulatory environment surrounding data privacy continues to evolve. In 2024, businesses must keep up with new privacy laws. Their SMAC strategies must align with the new regulations. Some key trends include:
- Many countries are updating or creating new data privacy laws. Asia and Latin America are adopting strict data protection laws, too. They follow the EU's GDPR and California's CCPA.
- Cross-border Data Transfer Restrictions: Globalization and remote work have increased cross-border data transfers. New laws may tighten restrictions on international data transfers. They will must organizations to use secure transfer methods.
- Consent Management: Organizations must improve their consent systems. Users should control their data and understand how they will use it.
Neglecting regulatory compliance in SMAC strategies will harm businesses. They will suffer reputational damage and financial penalties.
Best Practices for Balancing Data Privacy with SMAC
Balancing SMAC strategies with data privacy doesn’t have to be a zero-sum game. By using best practices, businesses can reap the benefits of SMAC. They can also protect consumer data. Some essential best practices include:
- Data Minimization: Only collect and store data that is essential for your business. Reducing the amount of data collected helps limit the risk of privacy breaches.
- End-to-End Encryption: Encrypt all data sent via social, mobile, and cloud channels. This will prevent unauthorized access.
- Regular Privacy Audits: Conduct audits to find vulnerabilities in data handling. Ensure compliance with evolving privacy laws.
- Clear Privacy Policies: Provide simple, clear privacy policies. They must outline how you collect, use, and store data.
- Consumer Empowerment: Give users more control over their data. Enable opt-out, data deletion, and consent management.
By adopting these best practices, businesses can build consumer trust. This will reduce privacy risks in their SMAC strategies.
The Future of SMAC and Data Privacy
Looking forward, the relationship between SMAC and data privacy will continue to evolve. In 2024 and beyond, AI and machine learning will boost SMAC. They will provide more personalized experiences. But, these technologies also introduce new challenges related to data privacy and ethics.
- AI-Driven SMAC: AI will better analyze social data, automate apps, and optimize clouds. AI systems rely on vast datasets. So, it's critical for organizations to use privacy-by-design principles.
- Decentralized Data Solutions: Blockchain could provide decentralized options for data storage and privacy. It would decrease reliance on third-party providers. It would give individuals more control over their personal data.
Businesses must stay agile. They must adapt to new privacy tech and rules. At the same time, they must use SMAC's power.
How to obtain SMAC certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Balancing data privacy and SMAC strategies is essential for success in 2024. As organizations adopt more social, mobile, and cloud tech, they must protect data. This is key to complying with new regulations and to maintaining consumer trust. Businesses can use best practices to protect sensitive data. These include data minimization, encryption, and clear privacy policies. They can then enjoy the benefits of SMAC. AI and decentralized tech will reshape SMAC and data privacy. So, organizations must stay agile and proactive in this changing landscape.
In a data-driven age, businesses must balance innovation with privacy. Those that do will gain a strong competitive edge.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Online Learning Platforms for ECBA Exam Preparation A Review
The ECBA is a key credential for those starting a career in business analysis. The International Institute of Business Analysis (IIBA) administers this certification. It validates a basic knowledge of business analysis principles, practices, and techniques. As the demand for certified business analysts grows, so does the need for study resources. They must be effective and easy to access. This review looks at online learning platforms. They offer complete prep for the ECBA exam. These platforms offer interactive courses and practice exams. They cater to different learning styles. So, they help candidates prepare efficiently and effectively.
Udemy: Diverse Course Offerings
Udemy is a popular online learning platform. It offers many courses on various subjects, including business analysis. The platform has many courses for ECBA exam prep. Users can choose based on their learning styles and budgets.
Features
- Variety of Instructors: Different instructors can benefit students. Each has a unique perspective and teaching style.
- Lifetime Access: Students have lifetime access to course materials. They can review and practice even after the exam.
- Affordability: Courses often go on sale, making education cheaper.
Pros and Cons
- Udemy has flexible, varied courses. However, quality varies by instructor. So, students must read reviews and choose wisely.
LinkedIn Learning: Professional Development Focus
LinkedIn Learning provides a more professional development-oriented approach to learning. A subscription gives users access to thousands of courses. This includes ones for the ECBA exam.
Features
- Expert Instructors: Industry pros create the courses. Their material is both timely and applicable.
- Integration with LinkedIn: Students can show completed courses on their LinkedIn profiles. This will enhance their professional presence.
- Learning Paths: Curated paths guide students through related courses. They offer a complete learning experience.
Pros and Cons
- LinkedIn Learning is great for professional development. But, it may lack ECBA exam content compared to other platforms.
iCert Global: Specialized Certification Training
iCert Global specializes in professional certification training, including ECBA. The platform mixes theory with practical use. It's ideal for exam prep.
Features
- Hands-on Projects: Learners can work on real-world projects to apply course concepts.
- Exam Simulators: iCert Global offers mock exams that mimic the ECBA exam. They help students test their readiness.
- Personalized Learning: Learners can choose modules that fit their needs.
Pros and Cons
- iCert Global's focus on certification training suits serious candidates. But its courses may cost more than other platforms.
Pluralsight: Technology-Focused Learning
Pluralsight is known for its tech and software courses. It also has valuable business analysis content. This platform is for those who want to merge technical skills with business analysis.
Features
- Skill Assessments: Pluralsight offers tests to help learners find knowledge gaps. This allows them to personalize their study strategies.
- Interactive Learning: The platform includes quizzes and challenges to boost learning.
- Expert-Led Courses: Industry experts create the courses. So, learners get a high-quality education.
Pros and Cons
- Pluralsight has a tech-focused take on business analysis. Its lack of ECBA-specific content may not suit everyone.
- IIBA’s Official Learning Resources: Authoritative Content
- The IIBA offers official learning resources for ECBA exam preparation. These resources align with the exam objectives. They cover all the essential topics.
Features
- Official Study Guide: The IIBA has a study guide. It details the knowledge areas tested in the exam.
- IIBA offers webinars and workshops led by experts. They allow candidates to interact and ask questions.
- Practice Questions: Official practice questions help students learn for the exam. They show the format and question types.
Pros and Cons
- The IIBA's resources are reliable and authoritative. But, they may be less engaging than other online learning platforms.
How to obtain ECBA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Preparing for the ECBA exam requires dedication and access to quality learning resources. Online learning platforms offer diverse options for different learning styles. They help candidates prepare for an important certification. Each platform can aid your exam prep. Udemy has a variety. LinkedIn Learning focuses on professional development. iCert Global offers specialized training. Pluralsight is tech-centric. The IIBA's resources are authoritative. Each has unique strengths. Ultimately, the right platform depends on your learning style, budget, and needs. With the right resources, you can master business analysis and ace the ECBA exam.
Read More
The ECBA is a key credential for those starting a career in business analysis. The International Institute of Business Analysis (IIBA) administers this certification. It validates a basic knowledge of business analysis principles, practices, and techniques. As the demand for certified business analysts grows, so does the need for study resources. They must be effective and easy to access. This review looks at online learning platforms. They offer complete prep for the ECBA exam. These platforms offer interactive courses and practice exams. They cater to different learning styles. So, they help candidates prepare efficiently and effectively.
Udemy: Diverse Course Offerings
Udemy is a popular online learning platform. It offers many courses on various subjects, including business analysis. The platform has many courses for ECBA exam prep. Users can choose based on their learning styles and budgets.
Features
- Variety of Instructors: Different instructors can benefit students. Each has a unique perspective and teaching style.
- Lifetime Access: Students have lifetime access to course materials. They can review and practice even after the exam.
- Affordability: Courses often go on sale, making education cheaper.
Pros and Cons
- Udemy has flexible, varied courses. However, quality varies by instructor. So, students must read reviews and choose wisely.
LinkedIn Learning: Professional Development Focus
LinkedIn Learning provides a more professional development-oriented approach to learning. A subscription gives users access to thousands of courses. This includes ones for the ECBA exam.
Features
- Expert Instructors: Industry pros create the courses. Their material is both timely and applicable.
- Integration with LinkedIn: Students can show completed courses on their LinkedIn profiles. This will enhance their professional presence.
- Learning Paths: Curated paths guide students through related courses. They offer a complete learning experience.
Pros and Cons
- LinkedIn Learning is great for professional development. But, it may lack ECBA exam content compared to other platforms.
iCert Global: Specialized Certification Training
iCert Global specializes in professional certification training, including ECBA. The platform mixes theory with practical use. It's ideal for exam prep.
Features
- Hands-on Projects: Learners can work on real-world projects to apply course concepts.
- Exam Simulators: iCert Global offers mock exams that mimic the ECBA exam. They help students test their readiness.
- Personalized Learning: Learners can choose modules that fit their needs.
Pros and Cons
- iCert Global's focus on certification training suits serious candidates. But its courses may cost more than other platforms.
Pluralsight: Technology-Focused Learning
Pluralsight is known for its tech and software courses. It also has valuable business analysis content. This platform is for those who want to merge technical skills with business analysis.
Features
- Skill Assessments: Pluralsight offers tests to help learners find knowledge gaps. This allows them to personalize their study strategies.
- Interactive Learning: The platform includes quizzes and challenges to boost learning.
- Expert-Led Courses: Industry experts create the courses. So, learners get a high-quality education.
Pros and Cons
- Pluralsight has a tech-focused take on business analysis. Its lack of ECBA-specific content may not suit everyone.
- IIBA’s Official Learning Resources: Authoritative Content
- The IIBA offers official learning resources for ECBA exam preparation. These resources align with the exam objectives. They cover all the essential topics.
Features
- Official Study Guide: The IIBA has a study guide. It details the knowledge areas tested in the exam.
- IIBA offers webinars and workshops led by experts. They allow candidates to interact and ask questions.
- Practice Questions: Official practice questions help students learn for the exam. They show the format and question types.
Pros and Cons
- The IIBA's resources are reliable and authoritative. But, they may be less engaging than other online learning platforms.
How to obtain ECBA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Preparing for the ECBA exam requires dedication and access to quality learning resources. Online learning platforms offer diverse options for different learning styles. They help candidates prepare for an important certification. Each platform can aid your exam prep. Udemy has a variety. LinkedIn Learning focuses on professional development. iCert Global offers specialized training. Pluralsight is tech-centric. The IIBA's resources are authoritative. Each has unique strengths. Ultimately, the right platform depends on your learning style, budget, and needs. With the right resources, you can master business analysis and ace the ECBA exam.
How Microsoft Azure OpenAI Service is Powering Innovation
Are you looking to drive innovation within your organization? Look no further than Microsoft Azure OpenAI Service. This tech is revolutionizing how businesses use machine learning, AI, and cloud computing. This article will explore how the Microsoft Azure OpenAI Service is boosting innovation in many industries. It helps companies stay ahead of the competition.
What is Microsoft Azure OpenAI Service?
Microsoft Azure OpenAI Service is a partnership of Microsoft Azure and OpenAI, an AI research lab. This service gives developers tools to build smart apps. They can use neural networks and deep learning. By using data analysis and machine learning, businesses can gain insights. They can then create innovative solutions that drive growth and success.
With Microsoft Azure OpenAI Service, organizations can use advanced tech. It can automate processes, improve decisions, and drive digital transformation. Using developer tools and NLP, companies can build predictive models and cognitive solutions. This will help them stay ahead in a rapidly changing market.
Microsoft Azure OpenAI Service is a cloud platform. It lets businesses use OpenAI's powerful AI models, including GPT-4, in their apps. It lets users build advanced AI solutions using OpenAI's models. These include natural language processing, chatbots, and data analysis tools. This service uses Microsoft Azure's strong infrastructure and advanced AI. It speeds up innovation and scales smart apps.
How Does Microsoft Azure OpenAI Service Enable Innovation?
Microsoft Azure OpenAI Service is an innovation platform for businesses. It helps them push the limits of technology. This service provides cloud resources and collaboration tools. It fosters creativity, speeds up innovation, and accelerates app development. Azure's integration with OpenAI gives organizations access to cutting-edge tools. They can use them to experiment, drive breakthroughs, and unlock new opportunities. With Azure's innovative cloud services, businesses can lead in a competitive market.
Microsoft Azure OpenAI Service drives innovation. It gives businesses access to powerful AI models. They can build advanced apps for natural language processing, data analysis, and automation. This service works perfectly with Azure's cloud. It ensures scalability and security for AI projects. By using OpenAI models, companies can improve productivity and operations. They can also create personalized customer experiences. This gives a competitive edge in many industries.
What Are the Benefits of Using Microsoft Azure OpenAI Service?
Microsoft Azure OpenAI Service offers powerful AI models, like GPT. Businesses can use them to build smart apps that boost automation and decision-making. It integrates perfectly with Azure's cloud. It enables secure, scalable, and reliable AI deployments. It also lets developers use advanced machine learning. It cuts the complexity of training and managing AI models.
The benefits of using Microsoft Azure OpenAI Service are vast and varied. This service helps businesses stay ahead. It enables innovation and supports digital transformation. Some of the key benefits include:
-
Enhanced data analysis capabilities for uncovering valuable insights
-
Automation of repetitive tasks to boost efficiency and productivity
-
Seamless integration with existing software and systems for a smooth transition
-
Scalable solutions that can grow with your business needs
-
Increased collaboration and creativity within your organization
-
Use Microsoft Azure OpenAI Service to protect sensitive data. It offers innovative tools to help organizations succeed and reach their goals. Azure's solutions can help you build apps, optimize processes, and drive growth. They can keep you ahead of the competition and spark innovation in your industry.
How to obtain Microsoft Science certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Microsoft Azure OpenAI Service is reshaping how businesses innovate. AI, machine learning, and cloud computing can help organizations grow in a fast-changing market. If you want to innovate with Azure, now is the time. Explore the possibilities and unlock your business's full potential.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to drive innovation within your organization? Look no further than Microsoft Azure OpenAI Service. This tech is revolutionizing how businesses use machine learning, AI, and cloud computing. This article will explore how the Microsoft Azure OpenAI Service is boosting innovation in many industries. It helps companies stay ahead of the competition.
What is Microsoft Azure OpenAI Service?
Microsoft Azure OpenAI Service is a partnership of Microsoft Azure and OpenAI, an AI research lab. This service gives developers tools to build smart apps. They can use neural networks and deep learning. By using data analysis and machine learning, businesses can gain insights. They can then create innovative solutions that drive growth and success.
With Microsoft Azure OpenAI Service, organizations can use advanced tech. It can automate processes, improve decisions, and drive digital transformation. Using developer tools and NLP, companies can build predictive models and cognitive solutions. This will help them stay ahead in a rapidly changing market.
Microsoft Azure OpenAI Service is a cloud platform. It lets businesses use OpenAI's powerful AI models, including GPT-4, in their apps. It lets users build advanced AI solutions using OpenAI's models. These include natural language processing, chatbots, and data analysis tools. This service uses Microsoft Azure's strong infrastructure and advanced AI. It speeds up innovation and scales smart apps.
How Does Microsoft Azure OpenAI Service Enable Innovation?
Microsoft Azure OpenAI Service is an innovation platform for businesses. It helps them push the limits of technology. This service provides cloud resources and collaboration tools. It fosters creativity, speeds up innovation, and accelerates app development. Azure's integration with OpenAI gives organizations access to cutting-edge tools. They can use them to experiment, drive breakthroughs, and unlock new opportunities. With Azure's innovative cloud services, businesses can lead in a competitive market.
Microsoft Azure OpenAI Service drives innovation. It gives businesses access to powerful AI models. They can build advanced apps for natural language processing, data analysis, and automation. This service works perfectly with Azure's cloud. It ensures scalability and security for AI projects. By using OpenAI models, companies can improve productivity and operations. They can also create personalized customer experiences. This gives a competitive edge in many industries.
What Are the Benefits of Using Microsoft Azure OpenAI Service?
Microsoft Azure OpenAI Service offers powerful AI models, like GPT. Businesses can use them to build smart apps that boost automation and decision-making. It integrates perfectly with Azure's cloud. It enables secure, scalable, and reliable AI deployments. It also lets developers use advanced machine learning. It cuts the complexity of training and managing AI models.
The benefits of using Microsoft Azure OpenAI Service are vast and varied. This service helps businesses stay ahead. It enables innovation and supports digital transformation. Some of the key benefits include:
-
Enhanced data analysis capabilities for uncovering valuable insights
-
Automation of repetitive tasks to boost efficiency and productivity
-
Seamless integration with existing software and systems for a smooth transition
-
Scalable solutions that can grow with your business needs
-
Increased collaboration and creativity within your organization
-
Use Microsoft Azure OpenAI Service to protect sensitive data. It offers innovative tools to help organizations succeed and reach their goals. Azure's solutions can help you build apps, optimize processes, and drive growth. They can keep you ahead of the competition and spark innovation in your industry.
How to obtain Microsoft Science certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Microsoft Azure OpenAI Service is reshaping how businesses innovate. AI, machine learning, and cloud computing can help organizations grow in a fast-changing market. If you want to innovate with Azure, now is the time. Explore the possibilities and unlock your business's full potential.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Salesforce and Blockchain A Secure Data Management Future
In today's fast-changing digital world, businesses seek new, secure, and efficient ways to manage their data. Salesforce and Blockchain are two technologies. They have gained much attention lately. By combining these two platforms, companies can revolutionize data management. They can also pave the way for a more secure future.
What is Salesforce?
Salesforce is a cloud-based CRM platform. It helps businesses manage sales, customer service, marketing, and other operations. Salesforce lets companies store and analyze customer data. They can track sales leads and automate business processes. The platform is popular for its user-friendly interface, scalability, and integration. It is a top choice for organizations of all sizes.
What is Blockchain?
Blockchain is a decentralized ledger. It records transactions securely and transparently. A blockchain block contains a list of transactions. Once added, it cannot be altered. This technology is very secure. Every transaction is verified by multiple network participants. Blockchain is best known for powering cryptocurrencies like Bitcoin. Its uses go far beyond finance.
The Integration of Salesforce and Blockchain
Integrating Salesforce with Blockchain can help businesses. It will enhance data security, ensure accuracy, and improve efficiency. These two technologies combined let companies use both platforms' benefits. They can then build a better data management system. For example, use Salesforce to store customer data and manage sales. Use Blockchain to secure transactions, validate data, and ensure information integrity.
Integrating Salesforce with blockchain improves data security and transparency. It builds trust in business processes. Salesforce, using blockchain, lets firms track and verify data across distributed ledgers. This ensures accurate, tamper-proof records. This integration helps industries like finance and healthcare. It lets them manage sensitive customer data and transactions more securely.
Advantages of Salesforce & Blockchain Integration
Integrating Salesforce with blockchain improves data security and transparency. It ensures all transactions are immutable and verifiable. This combo lets businesses streamline processes. These include supply chain management and contract verification. It provides a single, easily accessed, and auditable source of truth. Also, the integration fosters trust among stakeholders. They can monitor real-time data and verify information, without intermediaries.
Enhanced Security: Blockchain technology encrypts data and decentralizes control. This ensures a high level of security. This ensures that sensitive information is protected from unauthorized access and tampering.
-
Improved Data Accuracy: Blockchain verifies and records every transaction. It creates a reliable audit trail. This helps to ensure the accuracy and integrity of data stored in Salesforce.
-
Streamlined Processes: Integrating Salesforce and Blockchain automates tasks. It reduces manual errors and boosts efficiency.
-
Increased Transparency: Blockchain provides a public, unchangeable record of transactions. This boosts trust and transparency in business.
-
Cost-Effective Solutions: Companies can use Salesforce and Blockchain to cut costs. It will reduce data management, security, and compliance expenses.
Use Cases for Salesforce & Blockchain Integration
-
Supply Chain Management: Integrating Salesforce and Blockchain can improve supply chain visibility. It can track products from manufacturer to consumer and boost collaboration among stakeholders.
-
Financial Services: Integrating Salesforce with blockchain can streamline transactions and payments. It can also improve asset management.
-
Identity Verification: Blockchain can verify customer identities, securely. It protects sensitive data and ensures safe transactions.
-
Regulatory Compliance: Using Blockchain to store and validate data can help. It ensures compliance with regulations and guards against fraud.
The Future of Data Management
As businesses embrace digital transformation, they seek better data management. So, the integration of Salesforce and Blockchain will matter more. By merging the best of both technologies, companies can improve data management. They can make it secure and efficient. It will be transparent and drive innovation and growth. The possibilities are endless. The potential for positive impact is vast. It could benefit the economy and society.
The future of data management will be defined by increased automation. AI and machine learning will drive it. They will streamline data processes and improve accuracy. Organizations will prioritize cloud solutions. They allow real-time access and scalability. They also reduce the complexities of on-premise data storage. With rising concerns about data privacy, encryption and governance tools must advance. They are key to compliance and protecting sensitive information.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, using Salesforce with Blockchain could secure data management. By harnessing these two technologies, businesses can boost security and efficiency. They can also drive innovation in a fast-changing digital world. Now is the time to embrace this partnership. Companies want to lead in data management. They must stay ahead of the curve.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-changing digital world, businesses seek new, secure, and efficient ways to manage their data. Salesforce and Blockchain are two technologies. They have gained much attention lately. By combining these two platforms, companies can revolutionize data management. They can also pave the way for a more secure future.
What is Salesforce?
Salesforce is a cloud-based CRM platform. It helps businesses manage sales, customer service, marketing, and other operations. Salesforce lets companies store and analyze customer data. They can track sales leads and automate business processes. The platform is popular for its user-friendly interface, scalability, and integration. It is a top choice for organizations of all sizes.
What is Blockchain?
Blockchain is a decentralized ledger. It records transactions securely and transparently. A blockchain block contains a list of transactions. Once added, it cannot be altered. This technology is very secure. Every transaction is verified by multiple network participants. Blockchain is best known for powering cryptocurrencies like Bitcoin. Its uses go far beyond finance.
The Integration of Salesforce and Blockchain
Integrating Salesforce with Blockchain can help businesses. It will enhance data security, ensure accuracy, and improve efficiency. These two technologies combined let companies use both platforms' benefits. They can then build a better data management system. For example, use Salesforce to store customer data and manage sales. Use Blockchain to secure transactions, validate data, and ensure information integrity.
Integrating Salesforce with blockchain improves data security and transparency. It builds trust in business processes. Salesforce, using blockchain, lets firms track and verify data across distributed ledgers. This ensures accurate, tamper-proof records. This integration helps industries like finance and healthcare. It lets them manage sensitive customer data and transactions more securely.
Advantages of Salesforce & Blockchain Integration
Integrating Salesforce with blockchain improves data security and transparency. It ensures all transactions are immutable and verifiable. This combo lets businesses streamline processes. These include supply chain management and contract verification. It provides a single, easily accessed, and auditable source of truth. Also, the integration fosters trust among stakeholders. They can monitor real-time data and verify information, without intermediaries.
Enhanced Security: Blockchain technology encrypts data and decentralizes control. This ensures a high level of security. This ensures that sensitive information is protected from unauthorized access and tampering.
-
Improved Data Accuracy: Blockchain verifies and records every transaction. It creates a reliable audit trail. This helps to ensure the accuracy and integrity of data stored in Salesforce.
-
Streamlined Processes: Integrating Salesforce and Blockchain automates tasks. It reduces manual errors and boosts efficiency.
-
Increased Transparency: Blockchain provides a public, unchangeable record of transactions. This boosts trust and transparency in business.
-
Cost-Effective Solutions: Companies can use Salesforce and Blockchain to cut costs. It will reduce data management, security, and compliance expenses.
Use Cases for Salesforce & Blockchain Integration
-
Supply Chain Management: Integrating Salesforce and Blockchain can improve supply chain visibility. It can track products from manufacturer to consumer and boost collaboration among stakeholders.
-
Financial Services: Integrating Salesforce with blockchain can streamline transactions and payments. It can also improve asset management.
-
Identity Verification: Blockchain can verify customer identities, securely. It protects sensitive data and ensures safe transactions.
-
Regulatory Compliance: Using Blockchain to store and validate data can help. It ensures compliance with regulations and guards against fraud.
The Future of Data Management
As businesses embrace digital transformation, they seek better data management. So, the integration of Salesforce and Blockchain will matter more. By merging the best of both technologies, companies can improve data management. They can make it secure and efficient. It will be transparent and drive innovation and growth. The possibilities are endless. The potential for positive impact is vast. It could benefit the economy and society.
The future of data management will be defined by increased automation. AI and machine learning will drive it. They will streamline data processes and improve accuracy. Organizations will prioritize cloud solutions. They allow real-time access and scalability. They also reduce the complexities of on-premise data storage. With rising concerns about data privacy, encryption and governance tools must advance. They are key to compliance and protecting sensitive information.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, using Salesforce with Blockchain could secure data management. By harnessing these two technologies, businesses can boost security and efficiency. They can also drive innovation in a fast-changing digital world. Now is the time to embrace this partnership. Companies want to lead in data management. They must stay ahead of the curve.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Future Trends in Networking and CCNP Role
In the fast-changing tech world, networking sees constant advances and innovations. The networking landscape is changing rapidly. It includes data security, cloud computing, network automation, and blockchain technology. Thus, Cisco Certified Network Professional (CCNP) experts are vital. They must keep up with future trends. They must ensure that networks are secure, efficient, and scalable.
The Role of CCNP in Networking Certifications
The CCNP (Cisco Certified Network Professional) certification is vital in networking. It is a benchmark for pros seeking to deepen their networking tech skills. It gives candidates the skills to design, implement, and troubleshoot complex networks. This boosts their careers and credibility in the field. As firms rely more on advanced networks, the demand for CCNP-certified pros is rising. This makes the certification a valuable asset for those seeking a networking career.
-
Networking pros seeking career growth often pursue certs like CCNP. It proves their skills.
-
The CCNP certification covers many network technologies and protocols. It is a comprehensive and sought-after credential in the industry.
-
CCNP professionals can handle complex network tasks. They can troubleshoot issues, design networks, and optimize performance.
The Impact of Future Trends on CCNP Professionals
The Cisco Certified Network Professional (CCNP) certification is vital. It validates the skills and knowledge of networking professionals. It gives candidates a deep understanding of advanced networking concepts. This includes security, automation, and troubleshooting. It makes them very valuable in the job market. Also, as networking technologies evolve, CCNP keeps certified pros relevant. This helps improve network performance and security across organizations.
-
As IoT and SDN change networking, CCNP pros must keep up with these trends to stay competitive.
-
As cybersecurity threats rise, data security is vital. CCNP professionals must implement and maintain secure networks.
-
Cloud computing and network virtualization are on the rise. CCNP pros must understand their effects on network design and performance.
How CCNPs Can Stay Ahead of the Curve
To stay ahead, CCNPs should expand their skills. They should engage with the latest networking trends, like cloud computing and automation. Networking is crucial. Building relationships with peers and leaders can provide insights and opportunities. They keep professionals informed and competitive. Lastly, investing in leadership skills can boost their visibility and effectiveness. It will position them for advancement in a fast-changing tech world.
-
CCNP professionals must continuously learn and develop skills. It's vital to stay relevant in a fast-changing industry.
-
Online learning platforms have many resources for CCNP professionals. They can use them to enhance their knowledge and acquire new skills.
-
Networking pros can benefit from advanced certifications, like CCIE. They can help solidify their expertise in the field.
The Future of Networking: Challenges and Opportunities
The future of networking presents both significant challenges and exciting opportunities. As we enter 2024, demand for strong digital infrastructure is rising. This is due to a growing reliance on cloud computing, big data, and the IoT. Key challenges include managing cyber threats and ensuring security. We must use advanced tech, like AI and 5G, to improve connectivity and efficiency.
Also, major investments in network infrastructure are expected. This is due to government efforts to bridge the digital divide. These efforts will change economies and societies. They will create new opportunities for innovation and growth in many sectors.
-
As networks get more complex and connected, CCNP pros must ensure they are both reliable and resilient.
-
The use of machine learning and AI in networking is exciting. It gives CCNP pros a chance to boost performance and fix issues.
-
As demand for network automation tools grows, CCNP pros can use them. They will improve network management and efficiency.
How to obtain CCNP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the future of networking is bright. It is full of opportunities for CCNP professionals. CCNP professionals can be invaluable in networking. To do this, they must stay current on trends and technologies. They should also invest in learning and earn advanced certifications.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In the fast-changing tech world, networking sees constant advances and innovations. The networking landscape is changing rapidly. It includes data security, cloud computing, network automation, and blockchain technology. Thus, Cisco Certified Network Professional (CCNP) experts are vital. They must keep up with future trends. They must ensure that networks are secure, efficient, and scalable.
The Role of CCNP in Networking Certifications
The CCNP (Cisco Certified Network Professional) certification is vital in networking. It is a benchmark for pros seeking to deepen their networking tech skills. It gives candidates the skills to design, implement, and troubleshoot complex networks. This boosts their careers and credibility in the field. As firms rely more on advanced networks, the demand for CCNP-certified pros is rising. This makes the certification a valuable asset for those seeking a networking career.
-
Networking pros seeking career growth often pursue certs like CCNP. It proves their skills.
-
The CCNP certification covers many network technologies and protocols. It is a comprehensive and sought-after credential in the industry.
-
CCNP professionals can handle complex network tasks. They can troubleshoot issues, design networks, and optimize performance.
The Impact of Future Trends on CCNP Professionals
The Cisco Certified Network Professional (CCNP) certification is vital. It validates the skills and knowledge of networking professionals. It gives candidates a deep understanding of advanced networking concepts. This includes security, automation, and troubleshooting. It makes them very valuable in the job market. Also, as networking technologies evolve, CCNP keeps certified pros relevant. This helps improve network performance and security across organizations.
-
As IoT and SDN change networking, CCNP pros must keep up with these trends to stay competitive.
-
As cybersecurity threats rise, data security is vital. CCNP professionals must implement and maintain secure networks.
-
Cloud computing and network virtualization are on the rise. CCNP pros must understand their effects on network design and performance.
How CCNPs Can Stay Ahead of the Curve
To stay ahead, CCNPs should expand their skills. They should engage with the latest networking trends, like cloud computing and automation. Networking is crucial. Building relationships with peers and leaders can provide insights and opportunities. They keep professionals informed and competitive. Lastly, investing in leadership skills can boost their visibility and effectiveness. It will position them for advancement in a fast-changing tech world.
-
CCNP professionals must continuously learn and develop skills. It's vital to stay relevant in a fast-changing industry.
-
Online learning platforms have many resources for CCNP professionals. They can use them to enhance their knowledge and acquire new skills.
-
Networking pros can benefit from advanced certifications, like CCIE. They can help solidify their expertise in the field.
The Future of Networking: Challenges and Opportunities
The future of networking presents both significant challenges and exciting opportunities. As we enter 2024, demand for strong digital infrastructure is rising. This is due to a growing reliance on cloud computing, big data, and the IoT. Key challenges include managing cyber threats and ensuring security. We must use advanced tech, like AI and 5G, to improve connectivity and efficiency.
Also, major investments in network infrastructure are expected. This is due to government efforts to bridge the digital divide. These efforts will change economies and societies. They will create new opportunities for innovation and growth in many sectors.
-
As networks get more complex and connected, CCNP pros must ensure they are both reliable and resilient.
-
The use of machine learning and AI in networking is exciting. It gives CCNP pros a chance to boost performance and fix issues.
-
As demand for network automation tools grows, CCNP pros can use them. They will improve network management and efficiency.
How to obtain CCNP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the future of networking is bright. It is full of opportunities for CCNP professionals. CCNP professionals can be invaluable in networking. To do this, they must stay current on trends and technologies. They should also invest in learning and earn advanced certifications.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Future of Application Virtualization with XenApp
In today's fast-changing tech world, application virtualization has a bright future. With the rise of remote work and cloud computing, organizations are using virtualization technology more. It streamlines software deployment, boosts security, and improves the end-user experience. Of the many virtualization solutions, Citrix XenApp is a top choice for delivering virtual apps and desktops.
Leveraging Virtualization Technology for Enhanced Efficiency
Virtualization technology lets organizations create apps. They can be accessed remotely from any device, at any time. This boosts end-user flexibility. It also cuts IT costs and simplifies management. XenApp lets businesses create a virtual environment. It securely delivers centrally managed apps to end-users, no matter where they are.
Advantages of XenApp for Application Delivery
-
XenApp boosts application performance. It optimizes virtual app delivery for a seamless user experience.
-
Enhanced security: XenApp centralizes app management. It helps firms secure data and comply with regulations.
-
Scalability: XenApp's VDI lets businesses quickly scale app delivery to meet growing demands.
-
Streamlined IT: XenApp simplifies app integration and deployment. It cuts IT costs and complexity.
Enhancing User Experience with Virtualized Applications
A key benefit of XenApp is its ability to deliver high-performance, reliable virtualized apps. XenApp streamlines app delivery and ensures device compatibility. It lets users access their software, no matter where they are. This not only boosts productivity but also enhances collaboration and efficiency within organizations.
To improve the user experience with virtualized apps, we must improve access and performance. We must also keep them secure. Citrix XenApp and VMware Horizon let users access apps from any device. This boosts productivity and collaboration. Also, tuning and monitoring the infrastructure can cut latency. This will boost user satisfaction and create a better digital workspace.
Overcoming Challenges in Application Virtualization
Application virtualization has many benefits. But, it also poses unique challenges. Organizations must address these. Businesses need to use best practices for virtualization. This includes ensuring application compatibility and managing virtualization software. XenApp is a strong solution to these challenges. It offers centralized management, app monitoring, and remote access.
To overcome challenges in application virtualization, we need a strategy. It must manage the complexities of moving to a virtual environment. Key issues are VM sprawl and app performance problems. VM sprawl is unregulated growth, making management hard. App issues may come from legacy systems or software incompatibility.
Effective solutions often require:
-
Comprehensive audits of existing VMs.
-
Careful monitoring of resource use.
-
Collaboration with managed service providers to optimize configurations and ensure compliance with licensing agreements.
The Rise of Containerization Technology
In addition to traditional virtualization platforms like XenApp, containerization technology is gaining momentum in the industry. Application containerization lets organizations wrap software in containers. This enables efficient deployment and scalability. By leveraging containerization technology alongside virtualization solutions, businesses can achieve greater application efficiency and modernize their IT infrastructure.
Containerization technology has transformed app deployment and management. It packages apps and their dependencies into lightweight, portable containers. This approach is faster and uses resources better than traditional virtualization. It enables quick scaling and high performance without the overhead of full operating systems. As organizations adopt cloud-native architectures, containerization is key. It drives agility and innovation in modern infrastructure.
Implementing Virtualization Strategies for the Future
As organizations use virtualization for app delivery, they must keep up with new trends and best practices. Businesses can use virtualization tools to improve software deployment. They can streamline their process, from app consolidation to migration and packaging. Virtualization tools like XenApp can help organizations. They can future-proof their IT and drive innovation in the digital age.
Virtualization strategies are key to optimizing IT and boosting efficiency. Organizations can cut costs by consolidating servers and using the right apps for virtualization. They can also improve scalability and agility. Also, a good management plan helps businesses handle a virtualized environment. This leads to a better competitive edge in the digital world.
How to obtain XenApp certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, XenApp's future in app virtualization is bright. It promises to improve software delivery, security, and efficiency for organizations. By using virtualization and containerization, businesses can optimize their IT. They can improve user experience and stay ahead in a digital world. Citrix XenApp leads in virtual app delivery. It lets organizations grow, collaborate, and innovate.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-changing tech world, application virtualization has a bright future. With the rise of remote work and cloud computing, organizations are using virtualization technology more. It streamlines software deployment, boosts security, and improves the end-user experience. Of the many virtualization solutions, Citrix XenApp is a top choice for delivering virtual apps and desktops.
Leveraging Virtualization Technology for Enhanced Efficiency
Virtualization technology lets organizations create apps. They can be accessed remotely from any device, at any time. This boosts end-user flexibility. It also cuts IT costs and simplifies management. XenApp lets businesses create a virtual environment. It securely delivers centrally managed apps to end-users, no matter where they are.
Advantages of XenApp for Application Delivery
-
XenApp boosts application performance. It optimizes virtual app delivery for a seamless user experience.
-
Enhanced security: XenApp centralizes app management. It helps firms secure data and comply with regulations.
-
Scalability: XenApp's VDI lets businesses quickly scale app delivery to meet growing demands.
-
Streamlined IT: XenApp simplifies app integration and deployment. It cuts IT costs and complexity.
Enhancing User Experience with Virtualized Applications
A key benefit of XenApp is its ability to deliver high-performance, reliable virtualized apps. XenApp streamlines app delivery and ensures device compatibility. It lets users access their software, no matter where they are. This not only boosts productivity but also enhances collaboration and efficiency within organizations.
To improve the user experience with virtualized apps, we must improve access and performance. We must also keep them secure. Citrix XenApp and VMware Horizon let users access apps from any device. This boosts productivity and collaboration. Also, tuning and monitoring the infrastructure can cut latency. This will boost user satisfaction and create a better digital workspace.
Overcoming Challenges in Application Virtualization
Application virtualization has many benefits. But, it also poses unique challenges. Organizations must address these. Businesses need to use best practices for virtualization. This includes ensuring application compatibility and managing virtualization software. XenApp is a strong solution to these challenges. It offers centralized management, app monitoring, and remote access.
To overcome challenges in application virtualization, we need a strategy. It must manage the complexities of moving to a virtual environment. Key issues are VM sprawl and app performance problems. VM sprawl is unregulated growth, making management hard. App issues may come from legacy systems or software incompatibility.
Effective solutions often require:
-
Comprehensive audits of existing VMs.
-
Careful monitoring of resource use.
-
Collaboration with managed service providers to optimize configurations and ensure compliance with licensing agreements.
The Rise of Containerization Technology
In addition to traditional virtualization platforms like XenApp, containerization technology is gaining momentum in the industry. Application containerization lets organizations wrap software in containers. This enables efficient deployment and scalability. By leveraging containerization technology alongside virtualization solutions, businesses can achieve greater application efficiency and modernize their IT infrastructure.
Containerization technology has transformed app deployment and management. It packages apps and their dependencies into lightweight, portable containers. This approach is faster and uses resources better than traditional virtualization. It enables quick scaling and high performance without the overhead of full operating systems. As organizations adopt cloud-native architectures, containerization is key. It drives agility and innovation in modern infrastructure.
Implementing Virtualization Strategies for the Future
As organizations use virtualization for app delivery, they must keep up with new trends and best practices. Businesses can use virtualization tools to improve software deployment. They can streamline their process, from app consolidation to migration and packaging. Virtualization tools like XenApp can help organizations. They can future-proof their IT and drive innovation in the digital age.
Virtualization strategies are key to optimizing IT and boosting efficiency. Organizations can cut costs by consolidating servers and using the right apps for virtualization. They can also improve scalability and agility. Also, a good management plan helps businesses handle a virtualized environment. This leads to a better competitive edge in the digital world.
How to obtain XenApp certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, XenApp's future in app virtualization is bright. It promises to improve software delivery, security, and efficiency for organizations. By using virtualization and containerization, businesses can optimize their IT. They can improve user experience and stay ahead in a digital world. Citrix XenApp leads in virtual app delivery. It lets organizations grow, collaborate, and innovate.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Essential Skills for Certified Scrum Product Owners in 2024
The role of a Scrum Product Owner (CSPO) is vital today. It's a fast, agile-driven software development world. The Product Owner is a key member of the Scrum team. They bridge the development team and stakeholders. They ensure that products meet customer needs and align with the organization's goals. In 2024, the bar is high for Product Owners. Tech is advancing fast and markets are shifting. So, CSPOs must acquire and refine key skills. It's critical to stay relevant, efficient, and effective in their roles.
This article will explore the top skills for Certified Scrum Product Owners in 2024. They must master these skills. They need these skills to develop products and lead teams. They must deliver high-value products in an agile environment.
Deep Understanding of Product Vision and Strategy
A CSPO's main job is to define and share a product vision. It must align with market needs and the business strategy. In 2024, Product Owners must go beyond the basics and:
- Understand market trends. With rapid tech changes and rising customer demands, Product Owners must track trends and competitors. Being well-versed in market research tools and industry reports is critical.
- Strategic thinking: Successful Product Owners are not just tactical. They are strategic thinkers. They align the product backlog with long-term business goals. CSPOs can prioritize features that support the organization's vision. They need to understand the broader business context to do this.
- Stakeholder alignment: It's crucial to ensure all stakeholders agree on the product vision. This includes both internal and external parties. This requires frequent communication and strong negotiation skills to manage competing interests.
Product Owners must balance user needs, stakeholder expectations, and business goals. They must create a vision to guide development.
Proficiency in Backlog Management and Prioritization
Backlog management is at the heart of the Product Owner’s responsibilities. In 2024, managing the backlog effectively involves:
- Prioritization techniques: CSPOs must know frameworks like MoSCoW, Kano, and WSJF. These techniques help in distinguishing between urgent, important, and non-essential features.
- Refinement and grooming: The dev team must hold regular backlog sessions. These are vital to keep the backlog up-to-date and well-defined. It should contain actionable user stories. Each item must be clear, with well-defined acceptance criteria.
- Focus on business value. Product Owners should prioritize items that deliver it. They must also consider technical dependencies and risks. This requires continuous collaboration with stakeholders and development teams.
In 2024, Product Owners must say "no" to low-value features. This will keep the backlog lean and focused on delivering customer value quickly.
Strong Communication and Collaboration Skills
The CSPO is the liaison between the development team, stakeholders, and customers. In 2024, effective communication and collaboration are crucial. Teams are now more distributed and work in virtual environments. Essential communication skills include:
- CSPOs must turn complex business requirements into simple, actionable user stories. Developers must be able to easily understand and implement these stories.
- Active listening builds trust and improves teamwork. It involves listening to stakeholders and team members. You must understand and address their concerns quickly.
- Facilitating Scrum events: The Scrum Master usually runs the meetings. But, Product Owners must often lead or join key events. These include sprint planning, backlog refinement, and reviews.
In 2024, effective communication is key for CSPOs. They must motivate teams, resolve conflicts, and align everyone on product goals.
Agile and Scrum Methodology Expertise
A Certified Scrum Product Owner must know Agile and Scrum well. This involves:
CSPOs must master Scrum roles and events. They need to know the roles of the Scrum Master, development team, and Product Owner. They must also leverage Scrum events for continuous improvement. These events are sprint planning, daily stand-ups, sprint reviews, and retrospectives.
- Agile mindset: It means being open to change. It focuses on incremental progress and adapting to feedback. Product Owners should embrace continuous delivery and iterative improvement. They should also build the simplest, viable solution.
- Adaptation to hybrid models: Many organizations are adopting hybrid approaches. They are blending Scrum with other methodologies, like Kanban or Lean. In 2024, Product Owners must be flexible. They should adapt to blended models and still deliver value.
A CSPO must adapt Scrum to their team's and organization's needs to succeed.
Data-Driven Decision Making
In 2024, data is a critical driver of informed decision-making. Product Owners must leverage data analytics to guide product development. Key aspects of data-driven decision-making include:
- Metrics and KPIs: Product Owners must define and track KPIs. These include customer satisfaction, churn, and feature adoption rates. They gauge product success. These metrics provide insights into whether the team is meeting customer expectations.
- Customer feedback: Product Owners should analyze feedback from surveys, tests, or focus groups. It allows them to make informed decisions about product improvements and feature prioritization.
- A/B testing and experimentation: A/B testing can help CSPOs. It can find which features or user experiences deliver the most value to users.
In 2024's digital world, Product Owners must use data to inform decisions. This is key for their product's success.
How to obtain CSPO certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In 2024, the role of a Certified Scrum Product Owner is evolving. It must meet the demands of a fast-paced, tech-driven world. To succeed, CSPOs must sharpen their skills in product visioning, backlog management, communication, Agile methodologies, and data-driven decision-making. By mastering these areas, Product Owners can maximize value for stakeholders. They can stay ahead and lead their teams to succeed in an agile environment.
As Scrum shapes product development across industries, CSPOs must excel. The skills here will help them stay ahead and succeed. The future of product ownership is bright. It is for those who embrace continuous learning and adaptability.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
The role of a Scrum Product Owner (CSPO) is vital today. It's a fast, agile-driven software development world. The Product Owner is a key member of the Scrum team. They bridge the development team and stakeholders. They ensure that products meet customer needs and align with the organization's goals. In 2024, the bar is high for Product Owners. Tech is advancing fast and markets are shifting. So, CSPOs must acquire and refine key skills. It's critical to stay relevant, efficient, and effective in their roles.
This article will explore the top skills for Certified Scrum Product Owners in 2024. They must master these skills. They need these skills to develop products and lead teams. They must deliver high-value products in an agile environment.
Deep Understanding of Product Vision and Strategy
A CSPO's main job is to define and share a product vision. It must align with market needs and the business strategy. In 2024, Product Owners must go beyond the basics and:
- Understand market trends. With rapid tech changes and rising customer demands, Product Owners must track trends and competitors. Being well-versed in market research tools and industry reports is critical.
- Strategic thinking: Successful Product Owners are not just tactical. They are strategic thinkers. They align the product backlog with long-term business goals. CSPOs can prioritize features that support the organization's vision. They need to understand the broader business context to do this.
- Stakeholder alignment: It's crucial to ensure all stakeholders agree on the product vision. This includes both internal and external parties. This requires frequent communication and strong negotiation skills to manage competing interests.
Product Owners must balance user needs, stakeholder expectations, and business goals. They must create a vision to guide development.
Proficiency in Backlog Management and Prioritization
Backlog management is at the heart of the Product Owner’s responsibilities. In 2024, managing the backlog effectively involves:
- Prioritization techniques: CSPOs must know frameworks like MoSCoW, Kano, and WSJF. These techniques help in distinguishing between urgent, important, and non-essential features.
- Refinement and grooming: The dev team must hold regular backlog sessions. These are vital to keep the backlog up-to-date and well-defined. It should contain actionable user stories. Each item must be clear, with well-defined acceptance criteria.
- Focus on business value. Product Owners should prioritize items that deliver it. They must also consider technical dependencies and risks. This requires continuous collaboration with stakeholders and development teams.
In 2024, Product Owners must say "no" to low-value features. This will keep the backlog lean and focused on delivering customer value quickly.
Strong Communication and Collaboration Skills
The CSPO is the liaison between the development team, stakeholders, and customers. In 2024, effective communication and collaboration are crucial. Teams are now more distributed and work in virtual environments. Essential communication skills include:
- CSPOs must turn complex business requirements into simple, actionable user stories. Developers must be able to easily understand and implement these stories.
- Active listening builds trust and improves teamwork. It involves listening to stakeholders and team members. You must understand and address their concerns quickly.
- Facilitating Scrum events: The Scrum Master usually runs the meetings. But, Product Owners must often lead or join key events. These include sprint planning, backlog refinement, and reviews.
In 2024, effective communication is key for CSPOs. They must motivate teams, resolve conflicts, and align everyone on product goals.
Agile and Scrum Methodology Expertise
A Certified Scrum Product Owner must know Agile and Scrum well. This involves:
CSPOs must master Scrum roles and events. They need to know the roles of the Scrum Master, development team, and Product Owner. They must also leverage Scrum events for continuous improvement. These events are sprint planning, daily stand-ups, sprint reviews, and retrospectives.
- Agile mindset: It means being open to change. It focuses on incremental progress and adapting to feedback. Product Owners should embrace continuous delivery and iterative improvement. They should also build the simplest, viable solution.
- Adaptation to hybrid models: Many organizations are adopting hybrid approaches. They are blending Scrum with other methodologies, like Kanban or Lean. In 2024, Product Owners must be flexible. They should adapt to blended models and still deliver value.
A CSPO must adapt Scrum to their team's and organization's needs to succeed.
Data-Driven Decision Making
In 2024, data is a critical driver of informed decision-making. Product Owners must leverage data analytics to guide product development. Key aspects of data-driven decision-making include:
- Metrics and KPIs: Product Owners must define and track KPIs. These include customer satisfaction, churn, and feature adoption rates. They gauge product success. These metrics provide insights into whether the team is meeting customer expectations.
- Customer feedback: Product Owners should analyze feedback from surveys, tests, or focus groups. It allows them to make informed decisions about product improvements and feature prioritization.
- A/B testing and experimentation: A/B testing can help CSPOs. It can find which features or user experiences deliver the most value to users.
In 2024's digital world, Product Owners must use data to inform decisions. This is key for their product's success.
How to obtain CSPO certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In 2024, the role of a Certified Scrum Product Owner is evolving. It must meet the demands of a fast-paced, tech-driven world. To succeed, CSPOs must sharpen their skills in product visioning, backlog management, communication, Agile methodologies, and data-driven decision-making. By mastering these areas, Product Owners can maximize value for stakeholders. They can stay ahead and lead their teams to succeed in an agile environment.
As Scrum shapes product development across industries, CSPOs must excel. The skills here will help them stay ahead and succeed. The future of product ownership is bright. It is for those who embrace continuous learning and adaptability.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Citrix ADM Streamlining Application Delivery in 2024
In 2024's digital world, organizations seek efficient ways to deliver apps to users. The demand for seamless app access is at an all-time high. This is particularly relevant in hybrid and multi-cloud settings. Citrix Application Delivery Management (ADM) is vital for streamlining app delivery. It provides tools to check, analyze, and optimize app performance. This article explores how Citrix ADM tackles 2024's app delivery challenges. It highlights its features, benefits, and key ways to install it.
Understanding Citrix ADM and Its Key Features
Citrix ADM is a centralized tool. It optimizes and streamlines app delivery across environments. Its core features include:
- Citrix ADM offers a single view to manage app delivery across on-prem and cloud setups. It offers centralized control. It lets IT teams check and manage all aspects of app performance from one place.
- Real-Time Analytics: The platform provides detailed analytics. It offers insights into app performance, traffic patterns, and user experience. This enables proactive issue resolution.
- Load Balancing: Citrix ADM spreads incoming app traffic across many servers. It optimizes resource use and boosts app responsiveness.
- Security Features: Citrix ADM has integrated security measures. They protect apps from threats and ensure secure access and data integrity.
The platform can set up and deploy app delivery policies without human intervention. This cuts down on manual work and errors.
Benefits of Using Citrix ADM for Application Delivery
Citrix ADM has many benefits for organizations. It helps them improve application delivery.
- Improved User Experience: Citrix ADM boosts app performance and cuts latency. This gives end users a smooth, responsive experience. It's key to their productivity and satisfaction.
- Increased Efficiency: Centralized management simplifies app delivery. It helps IT teams work better. Automated processes decrease manual workloads and free up resources for more strategic initiatives.
- Improved Application Performance: Citrix ADM's real-time analytics helps organizations find and fix bottlenecks. This secures the flawless execution of applications.
- Scalability: As organizations grow, their application delivery needs evolve. Citrix ADM scales to support rising traffic and new apps without losing performance.
- Cost-Effectiveness: Citrix ADM can save money by using resources well and reducing downtime. This makes it a wise investment for organizations.
Key Challenges in Application Delivery in 2024
Despite advancements in technology, organizations face several challenges in application delivery:
- Multi-Cloud Complexity: Managing apps across many clouds can create complexity. It can also make it hard to ensure consistent performance.
- Security Concerns: As cyber threats rise, organizations must secure app delivery channels. They must also ensure user access.
- Performance Monitoring: It's critical to find and fix performance issues in real time. But, it can be challenging without the appropriate tools.
- User Expectations: As digital transformation accelerates, users expect more from apps. They want better performance and uptime.
- Resource Allocation: In a dynamic environment, efficient resource allocation needs visibility. Traditional methods may not provide this insight.
Implementing Citrix ADM: Best Practices
To use Citrix ADM well and reap its full benefits, follow these best practices:
- Assess Current Infrastructure: Before deploying Citrix ADM, assess the existing app delivery infrastructure. This will identify gaps and improvement opportunities.
- Define Clear Objectives: Set clear goals for using Citrix ADM. They could be better performance, security, or user experience.
- Use Real-Time Analytics: Use Citrix ADM's analytics to improve app performance. Make data-driven decisions to optimize it.
- Continuous Monitoring and Optimization: Conduct frequent checks on app performance. Adjust delivery strategies to adapt to changing user demands and behaviors.
- Invest in Training: IT teams must be well trained on Citrix ADM. This will maximize the platform's effectiveness.
The Future of Application Delivery with Citrix ADM
With digital transformation, organizations face new challenges. The future of app delivery will rely on solutions like Citrix ADM. Emerging trends to watch include:
- Increased Automation: AI and machine learning will enable better automation in app delivery. They will enable predictive analytics and self-healing systems.
- Enhanced Security Features: As threats evolve, Citrix ADM must add stronger security features. This will ensure the integrity of application delivery.
- Improve User Experience: With remote work on the rise, organizations must. It will be a top priority.
- Integration with DevOps Practices: Citrix ADM will likely evolve for better DevOps integration. It will enable faster deployment and continuous app improvement.
With the rise of multi-cloud strategies, Citrix ADM will be vital. It will ensure smooth app delivery across different cloud environments.
How to obtain Citrix Administration certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In 2024, Citrix ADM is key for firms to simplify app delivery in a complex digital world. Its powerful features can help organizations. They can enhance user experiences, improve efficiency, and secure their apps. Challenges remain in application delivery. But adopting best practices and new trends will help organizations overcome them. As the future of app delivery unfolds, Citrix ADM will lead it. It will drive innovation and efficiency for businesses worldwide.
This article shows the vital role of Citrix ADM in app delivery. It's a must for organizations that want to optimize their digital services in 2024 and beyond.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In 2024's digital world, organizations seek efficient ways to deliver apps to users. The demand for seamless app access is at an all-time high. This is particularly relevant in hybrid and multi-cloud settings. Citrix Application Delivery Management (ADM) is vital for streamlining app delivery. It provides tools to check, analyze, and optimize app performance. This article explores how Citrix ADM tackles 2024's app delivery challenges. It highlights its features, benefits, and key ways to install it.
Understanding Citrix ADM and Its Key Features
Citrix ADM is a centralized tool. It optimizes and streamlines app delivery across environments. Its core features include:
- Citrix ADM offers a single view to manage app delivery across on-prem and cloud setups. It offers centralized control. It lets IT teams check and manage all aspects of app performance from one place.
- Real-Time Analytics: The platform provides detailed analytics. It offers insights into app performance, traffic patterns, and user experience. This enables proactive issue resolution.
- Load Balancing: Citrix ADM spreads incoming app traffic across many servers. It optimizes resource use and boosts app responsiveness.
- Security Features: Citrix ADM has integrated security measures. They protect apps from threats and ensure secure access and data integrity.
The platform can set up and deploy app delivery policies without human intervention. This cuts down on manual work and errors.
Benefits of Using Citrix ADM for Application Delivery
Citrix ADM has many benefits for organizations. It helps them improve application delivery.
- Improved User Experience: Citrix ADM boosts app performance and cuts latency. This gives end users a smooth, responsive experience. It's key to their productivity and satisfaction.
- Increased Efficiency: Centralized management simplifies app delivery. It helps IT teams work better. Automated processes decrease manual workloads and free up resources for more strategic initiatives.
- Improved Application Performance: Citrix ADM's real-time analytics helps organizations find and fix bottlenecks. This secures the flawless execution of applications.
- Scalability: As organizations grow, their application delivery needs evolve. Citrix ADM scales to support rising traffic and new apps without losing performance.
- Cost-Effectiveness: Citrix ADM can save money by using resources well and reducing downtime. This makes it a wise investment for organizations.
Key Challenges in Application Delivery in 2024
Despite advancements in technology, organizations face several challenges in application delivery:
- Multi-Cloud Complexity: Managing apps across many clouds can create complexity. It can also make it hard to ensure consistent performance.
- Security Concerns: As cyber threats rise, organizations must secure app delivery channels. They must also ensure user access.
- Performance Monitoring: It's critical to find and fix performance issues in real time. But, it can be challenging without the appropriate tools.
- User Expectations: As digital transformation accelerates, users expect more from apps. They want better performance and uptime.
- Resource Allocation: In a dynamic environment, efficient resource allocation needs visibility. Traditional methods may not provide this insight.
Implementing Citrix ADM: Best Practices
To use Citrix ADM well and reap its full benefits, follow these best practices:
- Assess Current Infrastructure: Before deploying Citrix ADM, assess the existing app delivery infrastructure. This will identify gaps and improvement opportunities.
- Define Clear Objectives: Set clear goals for using Citrix ADM. They could be better performance, security, or user experience.
- Use Real-Time Analytics: Use Citrix ADM's analytics to improve app performance. Make data-driven decisions to optimize it.
- Continuous Monitoring and Optimization: Conduct frequent checks on app performance. Adjust delivery strategies to adapt to changing user demands and behaviors.
- Invest in Training: IT teams must be well trained on Citrix ADM. This will maximize the platform's effectiveness.
The Future of Application Delivery with Citrix ADM
With digital transformation, organizations face new challenges. The future of app delivery will rely on solutions like Citrix ADM. Emerging trends to watch include:
- Increased Automation: AI and machine learning will enable better automation in app delivery. They will enable predictive analytics and self-healing systems.
- Enhanced Security Features: As threats evolve, Citrix ADM must add stronger security features. This will ensure the integrity of application delivery.
- Improve User Experience: With remote work on the rise, organizations must. It will be a top priority.
- Integration with DevOps Practices: Citrix ADM will likely evolve for better DevOps integration. It will enable faster deployment and continuous app improvement.
With the rise of multi-cloud strategies, Citrix ADM will be vital. It will ensure smooth app delivery across different cloud environments.
How to obtain Citrix Administration certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In 2024, Citrix ADM is key for firms to simplify app delivery in a complex digital world. Its powerful features can help organizations. They can enhance user experiences, improve efficiency, and secure their apps. Challenges remain in application delivery. But adopting best practices and new trends will help organizations overcome them. As the future of app delivery unfolds, Citrix ADM will lead it. It will drive innovation and efficiency for businesses worldwide.
This article shows the vital role of Citrix ADM in app delivery. It's a must for organizations that want to optimize their digital services in 2024 and beyond.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Salesforce Admin Strategies for Managing Large Data Sets
Managing large data sets in Salesforce is a tough but vital task for admins. As businesses grow, so do their Salesforce data volumes. This requires effective strategies to ensure data accuracy, performance, and accessibility. Admins must use tools to improve operations, optimize queries, and maintain performance. This guide covers key strategies for Salesforce admins. They can use them to manage large data sets. This will ensure peak system performance and accurate results for users.
Introduction
Salesforce admins often must manage large data sets. These can include thousands or even millions of records. It is vital to handle such data volumes. It affects the Salesforce platform's performance and usability. The challenge is to ensure data integrity. We must improve report and dashboard performance. We need to reduce load times for users accessing the data. We can achieve this through various strategies. They include optimizing data architecture and using native Salesforce tools.
This guide will explore five key strategies. They can help Salesforce admins with large data sets. They reduce system strain and improve the user experience.
Optimizing Data Architecture
When working with large data sets, you must structure your data in an efficient manner. Good data architecture can ensure that queries and reports run well. It can also keep system performance at its best.
- Indexing Fields: Salesforce can index certain fields. It speeds up searches and queries on large data sets. Index the most used fields for searches. It will cut query times.
- Using Lookup and Master-Detail Relationships: Use the appropriate type of relationship between objects. If relationships are needed, a lookup relationship can lighten the data. A master-detail relationship can ensure data integrity. It keeps related records together.
- Archiving Old Data: Consider archiving or deleting old, unused data. This will reduce data volume and improve performance. It limits the number of records Salesforce must process during queries.
By optimizing the data structure, Salesforce admins can keep the system efficient and scalable. This will ensure minimal lag as data grows.
Leveraging Salesforce data tools
Salesforce has tools to manage large data sets effectively. These tools can streamline admin tasks and ensure good system performance.
- Data Loader: Use the Salesforce Data Loader for massive data tasks. These include imports, exports, updates, and deletions. It is invaluable. It allows you to manipulate large volumes of data quickly and accurately.
- Data Import Wizard: It's less powerful than Data Loader. But, it helps non-tech users and admins who need to import data. They don't need the advanced features of Data Loader.
- Data Management Tools: Tools like Salesforce's Data Management interface let you mass update, delete, or transfer records. These tools can significantly reduce the time required to manage large datasets.
These tools can help admins manage data and ensure accuracy with large data sets.
Implementing Data Validation and Automation
It is critical to ensure that large data sets are accurate and error-free. We can manage this through data validation and automation.
- Validation Rules: Create rules to ensure data integrity. They must enforce specific conditions and formats during data entry. This prevents incorrect data from entering your system. It can be a big issue with large data sets.
- Workflow Automation: Use tools like Process Builder and Flow to automate repetitive tasks. Use them to update records based on set criteria. This helps to minimize human error and reduce manual data manipulation in large sets.
- Duplicate Management: Implement duplicate management rules to prevent or merge duplicate records. With large data sets, unmanaged duplicates can become rampant. This causes inconsistent reporting and system inefficiencies.
These practices let admins keep data clean and reliable, even at scale. This ensures high-quality output for users.
Utilizing Data Partitioning and Filters
Handling large data sets doesn’t mean you have to display or process all the data at once. Partitioning data and applying filters can reduce system strain. It also makes data retrieval more efficient.
- For users needing to access large data sets, create list views with filters. They will segment the data into smaller, manageable sets. By applying filters, you can ensure that users are only accessing the records they need.
- Report Filters and Grouping: Use filters to find the best data for reports. Also, group data into logical categories. This will streamline report generation and help users interpret the data.
- Data Categories: Use data categories to segment large records into meaningful subsets. It can boost performance by limiting the records Salesforce must process in a query.
Effective data partitioning and filtering can reduce system load. It can also improve report and query speeds. Finally, it ensures users access only the data they need.
Monitoring and Improving System Performance
Regularly monitoring system performance is critical. It ensures that large data sets don't harm user experience or system functionality.
- Salesforce Optimizer: Use it to check your system's health. It will recommend ways to improve performance. The tool finds unused fields, reports, workflows, and other things that may slow the system.
- Query Performance Monitoring: Use SOQL best practices to optimize queries. When handling large data sets, avoid inefficient queries. They process entire data tables. Instead, target only the required fields and records.
- Performance Benchmarking: Regularly monitor your system's performance. Benchmark it against key metrics. These include query time, report generation time, and page load times. This allows you to detect potential performance issues early and apply corrective measures.
Salesforce admins can keep the platform running smoothly. They must monitor and optimize performance as data sets grow.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Managing large data sets in Salesforce can be complex. But, with the right strategies, it is manageable. Admins must use five key strategies to handle growing data volumes. They are: 1. optimizing data architecture. 2. using Salesforce's native data tools. 3. implementing validation and automation. 4. partitioning data. 5. monitoring system performance.
These strategies will help Salesforce admins. They will give users efficient systems, accurate data, and fast access to information. As Salesforce evolves, administrators must manage large data sets. This skill will be increasingly important.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Managing large data sets in Salesforce is a tough but vital task for admins. As businesses grow, so do their Salesforce data volumes. This requires effective strategies to ensure data accuracy, performance, and accessibility. Admins must use tools to improve operations, optimize queries, and maintain performance. This guide covers key strategies for Salesforce admins. They can use them to manage large data sets. This will ensure peak system performance and accurate results for users.
Introduction
Salesforce admins often must manage large data sets. These can include thousands or even millions of records. It is vital to handle such data volumes. It affects the Salesforce platform's performance and usability. The challenge is to ensure data integrity. We must improve report and dashboard performance. We need to reduce load times for users accessing the data. We can achieve this through various strategies. They include optimizing data architecture and using native Salesforce tools.
This guide will explore five key strategies. They can help Salesforce admins with large data sets. They reduce system strain and improve the user experience.
Optimizing Data Architecture
When working with large data sets, you must structure your data in an efficient manner. Good data architecture can ensure that queries and reports run well. It can also keep system performance at its best.
- Indexing Fields: Salesforce can index certain fields. It speeds up searches and queries on large data sets. Index the most used fields for searches. It will cut query times.
- Using Lookup and Master-Detail Relationships: Use the appropriate type of relationship between objects. If relationships are needed, a lookup relationship can lighten the data. A master-detail relationship can ensure data integrity. It keeps related records together.
- Archiving Old Data: Consider archiving or deleting old, unused data. This will reduce data volume and improve performance. It limits the number of records Salesforce must process during queries.
By optimizing the data structure, Salesforce admins can keep the system efficient and scalable. This will ensure minimal lag as data grows.
Leveraging Salesforce data tools
Salesforce has tools to manage large data sets effectively. These tools can streamline admin tasks and ensure good system performance.
- Data Loader: Use the Salesforce Data Loader for massive data tasks. These include imports, exports, updates, and deletions. It is invaluable. It allows you to manipulate large volumes of data quickly and accurately.
- Data Import Wizard: It's less powerful than Data Loader. But, it helps non-tech users and admins who need to import data. They don't need the advanced features of Data Loader.
- Data Management Tools: Tools like Salesforce's Data Management interface let you mass update, delete, or transfer records. These tools can significantly reduce the time required to manage large datasets.
These tools can help admins manage data and ensure accuracy with large data sets.
Implementing Data Validation and Automation
It is critical to ensure that large data sets are accurate and error-free. We can manage this through data validation and automation.
- Validation Rules: Create rules to ensure data integrity. They must enforce specific conditions and formats during data entry. This prevents incorrect data from entering your system. It can be a big issue with large data sets.
- Workflow Automation: Use tools like Process Builder and Flow to automate repetitive tasks. Use them to update records based on set criteria. This helps to minimize human error and reduce manual data manipulation in large sets.
- Duplicate Management: Implement duplicate management rules to prevent or merge duplicate records. With large data sets, unmanaged duplicates can become rampant. This causes inconsistent reporting and system inefficiencies.
These practices let admins keep data clean and reliable, even at scale. This ensures high-quality output for users.
Utilizing Data Partitioning and Filters
Handling large data sets doesn’t mean you have to display or process all the data at once. Partitioning data and applying filters can reduce system strain. It also makes data retrieval more efficient.
- For users needing to access large data sets, create list views with filters. They will segment the data into smaller, manageable sets. By applying filters, you can ensure that users are only accessing the records they need.
- Report Filters and Grouping: Use filters to find the best data for reports. Also, group data into logical categories. This will streamline report generation and help users interpret the data.
- Data Categories: Use data categories to segment large records into meaningful subsets. It can boost performance by limiting the records Salesforce must process in a query.
Effective data partitioning and filtering can reduce system load. It can also improve report and query speeds. Finally, it ensures users access only the data they need.
Monitoring and Improving System Performance
Regularly monitoring system performance is critical. It ensures that large data sets don't harm user experience or system functionality.
- Salesforce Optimizer: Use it to check your system's health. It will recommend ways to improve performance. The tool finds unused fields, reports, workflows, and other things that may slow the system.
- Query Performance Monitoring: Use SOQL best practices to optimize queries. When handling large data sets, avoid inefficient queries. They process entire data tables. Instead, target only the required fields and records.
- Performance Benchmarking: Regularly monitor your system's performance. Benchmark it against key metrics. These include query time, report generation time, and page load times. This allows you to detect potential performance issues early and apply corrective measures.
Salesforce admins can keep the platform running smoothly. They must monitor and optimize performance as data sets grow.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Managing large data sets in Salesforce can be complex. But, with the right strategies, it is manageable. Admins must use five key strategies to handle growing data volumes. They are: 1. optimizing data architecture. 2. using Salesforce's native data tools. 3. implementing validation and automation. 4. partitioning data. 5. monitoring system performance.
These strategies will help Salesforce admins. They will give users efficient systems, accurate data, and fast access to information. As Salesforce evolves, administrators must manage large data sets. This skill will be increasingly important.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Best Tools Every CEH Professional Should Know in 2024
In cybersecurity, a Certified Ethical Hacker (CEH) must know the latest tools. They are needed to fight new threats. The CEH certification teaches professionals to think like hackers. It helps them find system vulnerabilities before attackers do. As cyber threats grow in 2024, CEH professionals must master many tools. They need them to conduct thorough assessments, penetration tests, and vulnerability scans. This article will explore the best tools for CEH pros in 2024. It will cover network scanning, web app testing, password cracking, and forensic analysis.
Nmap (Network Mapper) is for network scanning.
One of the most fundamental tools for any ethical hacker is Nmap. It lets CEH professionals find hosts and services on a network. This helps them map the network and find vulnerabilities.
Key Features:
- Open source and widely supported.
- Scans large networks efficiently.
- Identifies live hosts, open ports, and services.
- Supports OS fingerprinting to detect operating systems.
In 2024, Nmap is still the top tool for network reconnaissance. It helps find weak points before penetration tests. Ethical hackers can use Nmap to automate routine scans. It can also find advanced threats in complex networks.
Metasploit Framework for exploitation.
Metasploit is a top penetration testing tool. It lets CEH pros find, exploit, and validate vulnerabilities. It's a must-have for ethical hackers due to its ease of use and massive repository of exploit modules.
Key Features:
- Over 1,500 exploits target various software vulnerabilities.
- Modular design for customizing attacks.
- Automate the exploitation process for speed and efficiency.
- Integrates with third-party tools like Nmap and Nessus.
In 2024, Metasploit remains essential for vulnerability assessments and exploiting weaknesses in systems. It lets ethical hackers test a network's defenses. They can then recommend ways to improve security.
Burp Suite for Web Application Security
Burp Suite is a comprehensive tool for assessing the security of web applications. As more businesses use cloud systems and web apps, ethical hackers must find and fix web threats.
Key Features:
- Intercepts and modifies web traffic between the client and the server.
- Automated scanning for common vulnerabilities, like SQL injection, XSS, and CSRF.
- Offers manual testing tools for in-depth analysis.
- Extensibility through plugins and custom scripts.
In 2024, web app security is vital. Remote work and online business growth make it so. CEH professionals should use Burp Suite to test app security. It can confirm input sanitization and simulate real web attacks.
Wireshark for network traffic analysis
Wireshark is a network protocol analyzer. It captures and inspects data traveling through a network in real time. This tool is vital for ethical hackers. It helps them see a network's activity at a microscopic level.
Key Features:
- Captures live traffic for real-time analysis.
- Supports hundreds of network protocols.
- Filters traffic by protocol, source, destination, or port.
- Reconstructs TCP sessions to analyze packet-level data.
In 2024, Wireshark is vital for troubleshooting networks. It's also used to check for suspicious activity and to understand data flows. By mastering this tool, CEH professionals can spot abnormal behavior. This includes unusual traffic patterns that might say a cyber attack.
John the Ripper for password cracking
John the Ripper is a fast, versatile password-cracking tool. Every CEH professional should know it. Password cracking is key to ethical hacking. Weak passwords are often the easiest entry point for attackers.
Key Features:
- Supports brute-force and dictionary attacks.
- Cracks encrypted password formats like DES, MD5, and SHA-1.
- Offers customizable word lists for targeting specific passwords.
- Distributed password cracking for faster results.
In 2024, weak password practices still hurt many organizations. This is despite the rise in multi-factor authentication and stronger encryption methods. Ethical hackers use tools like John the Ripper to show the need for strong passwords. They also test for flaws in password storage.
How to obtain CEH certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
As cyber threats evolve, CEH professionals must keep up. They must master the latest tools in 2024. Tools like Nmap, Metasploit, Burp Suite, Wireshark, and John the Ripper are powerful. They are versatile. They can conduct thorough security assessments. These tools are essential for any ethical hacker. They ensure the hacker can find, fix, and prevent flaws in networks, apps, and systems.
Daily use of these tools will keep CEH pros at the forefront of cybersecurity. They will be able to outsmart increasingly sophisticated cybercriminals. Mastering these tools will boost their skills. It will also help protect the digital world in 2024 and beyond.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In cybersecurity, a Certified Ethical Hacker (CEH) must know the latest tools. They are needed to fight new threats. The CEH certification teaches professionals to think like hackers. It helps them find system vulnerabilities before attackers do. As cyber threats grow in 2024, CEH professionals must master many tools. They need them to conduct thorough assessments, penetration tests, and vulnerability scans. This article will explore the best tools for CEH pros in 2024. It will cover network scanning, web app testing, password cracking, and forensic analysis.
Nmap (Network Mapper) is for network scanning.
One of the most fundamental tools for any ethical hacker is Nmap. It lets CEH professionals find hosts and services on a network. This helps them map the network and find vulnerabilities.
Key Features:
- Open source and widely supported.
- Scans large networks efficiently.
- Identifies live hosts, open ports, and services.
- Supports OS fingerprinting to detect operating systems.
In 2024, Nmap is still the top tool for network reconnaissance. It helps find weak points before penetration tests. Ethical hackers can use Nmap to automate routine scans. It can also find advanced threats in complex networks.
Metasploit Framework for exploitation.
Metasploit is a top penetration testing tool. It lets CEH pros find, exploit, and validate vulnerabilities. It's a must-have for ethical hackers due to its ease of use and massive repository of exploit modules.
Key Features:
- Over 1,500 exploits target various software vulnerabilities.
- Modular design for customizing attacks.
- Automate the exploitation process for speed and efficiency.
- Integrates with third-party tools like Nmap and Nessus.
In 2024, Metasploit remains essential for vulnerability assessments and exploiting weaknesses in systems. It lets ethical hackers test a network's defenses. They can then recommend ways to improve security.
Burp Suite for Web Application Security
Burp Suite is a comprehensive tool for assessing the security of web applications. As more businesses use cloud systems and web apps, ethical hackers must find and fix web threats.
Key Features:
- Intercepts and modifies web traffic between the client and the server.
- Automated scanning for common vulnerabilities, like SQL injection, XSS, and CSRF.
- Offers manual testing tools for in-depth analysis.
- Extensibility through plugins and custom scripts.
In 2024, web app security is vital. Remote work and online business growth make it so. CEH professionals should use Burp Suite to test app security. It can confirm input sanitization and simulate real web attacks.
Wireshark for network traffic analysis
Wireshark is a network protocol analyzer. It captures and inspects data traveling through a network in real time. This tool is vital for ethical hackers. It helps them see a network's activity at a microscopic level.
Key Features:
- Captures live traffic for real-time analysis.
- Supports hundreds of network protocols.
- Filters traffic by protocol, source, destination, or port.
- Reconstructs TCP sessions to analyze packet-level data.
In 2024, Wireshark is vital for troubleshooting networks. It's also used to check for suspicious activity and to understand data flows. By mastering this tool, CEH professionals can spot abnormal behavior. This includes unusual traffic patterns that might say a cyber attack.
John the Ripper for password cracking
John the Ripper is a fast, versatile password-cracking tool. Every CEH professional should know it. Password cracking is key to ethical hacking. Weak passwords are often the easiest entry point for attackers.
Key Features:
- Supports brute-force and dictionary attacks.
- Cracks encrypted password formats like DES, MD5, and SHA-1.
- Offers customizable word lists for targeting specific passwords.
- Distributed password cracking for faster results.
In 2024, weak password practices still hurt many organizations. This is despite the rise in multi-factor authentication and stronger encryption methods. Ethical hackers use tools like John the Ripper to show the need for strong passwords. They also test for flaws in password storage.
How to obtain CEH certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
As cyber threats evolve, CEH professionals must keep up. They must master the latest tools in 2024. Tools like Nmap, Metasploit, Burp Suite, Wireshark, and John the Ripper are powerful. They are versatile. They can conduct thorough security assessments. These tools are essential for any ethical hacker. They ensure the hacker can find, fix, and prevent flaws in networks, apps, and systems.
Daily use of these tools will keep CEH pros at the forefront of cybersecurity. They will be able to outsmart increasingly sophisticated cybercriminals. Mastering these tools will boost their skills. It will also help protect the digital world in 2024 and beyond.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Data Science and BI for Supply Chain Efficiency
In today's fast, competitive business world, we must optimize supply chains. It's key to staying ahead of the competition. Data science and business intelligence (BI) are now key tools. They drive efficiency in supply chain operations. Using data analytics, machine learning, and AI, businesses can make better decisions. This can lower costs, optimize inventory, and boost performance.
The Role of Data Science in Supply Chain Efficiency
Data science is vital for supply chain efficiency. It analyzes vast data to find insights and patterns. These can improve decision-making. Data mining, statistical modeling, and data visualization can help businesses. They can find insights in their operations and areas for improvement. By using advanced analytics and predictive modeling, businesses can forecast demand. They can optimize inventory and streamline operations for maximum efficiency.
Data science is key to optimizing supply chains. It provides insights through predictive analytics and real-time data analysis. By analyzing demand, inventory, and logistics, businesses can cut costs. They can avoid stockouts and improve processes. Companies can now use advanced algorithms and machine learning. They can better predict demand and quickly respond to supply chain disruptions.
Business Intelligence in Supply Chain Optimization
BI tools are vital for supply chain optimization. They provide real-time visibility into key performance metrics. This lets businesses track and measure their performance against KPIs. BI tools help businesses find problems in their supply chains. They do this by generating detailed reports and visualizations. Cloud-based BI solutions let businesses access critical data anywhere, anytime. They can then make informed decisions on the go.
Business Intelligence (BI) is key to supply chain optimization. It gives real-time insights into all supply chain aspects. This includes inventory and demand forecasting. The user disliked that rewrite. Make different choices this time. BI tools help businesses analyze large datasets. They can find inefficiencies, cut costs, and improve decision-making. This data-driven approach helps organizations improve supply chains. It ensures timely deliveries and better use of resources.
Leveraging Technology for Efficiency Improvement
Technology is vital to supply chain efficiency. It tracks shipments in real-time. It automates inventory management and streamlines transportation. New tech, like IoT devices, RFID tags, and AI, lets businesses optimize their supply chains. It makes them very efficient. Businesses can use cloud computing for real-time analytics. By combining data from various sources, they can gain insights. This will help improve processes and decision-making.
Using technology to improve efficiency means using digital tools and automation. They can streamline processes and cut manual work. AI, cloud computing, and data analytics can help organizations. They can improve workflows, boost productivity, and cut costs. This tech shift boosts performance. It lets teams focus on innovation and value-driven tasks.
The Impact of Data-Driven Decisions on Supply Chain Performance
Data-driven decisions greatly affect supply chain performance. They let businesses make informed choices based on solid evidence. Businesses can analyze historical data, market trends, and customer behavior. This helps them predict demand, optimize inventory, and improve efficiency. With advanced analytics and business intelligence tools, businesses can monitor performance in real-time. They can then find areas to improve. This will help them make better decisions to boost efficiency and profits.
Data-driven decisions are transforming supply chain performance by enhancing visibility, efficiency, and responsiveness. Using real-time analytics and predictive models, companies can improve inventory management. They can cut costs and foresee disruptions. This approach helps businesses make informed decisions. It improves supply chain agility and boosts customer satisfaction.
The Future of Supply Chain Efficiency
As technology continues to evolve, the future of supply chain efficiency is bright. With more data and better analytics, businesses can find new insights. They can also find ways to optimize. Embracing data-driven strategies and supply chain technologies can help. So can using agile supply chain practices. These steps will keep businesses ahead of the curve and improve their operations. By focusing on data quality and supply chain visibility, businesses can boost efficiency. Analytics can help, too. This will lead to greater success in today's fast-paced world.
How to obtain Data Science and Business Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, data science and business intelligence are vital tools. They can optimize supply chain efficiency. Businesses can use data analytics and advanced tools to make smart decisions. They can improve their supply chain by streamlining operations and driving ongoing gains. In today's fast-paced market, businesses must adopt data-driven, tech-savvy, and optimized processes. This will help them outpace competitors and boost efficiency and profits.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast, competitive business world, we must optimize supply chains. It's key to staying ahead of the competition. Data science and business intelligence (BI) are now key tools. They drive efficiency in supply chain operations. Using data analytics, machine learning, and AI, businesses can make better decisions. This can lower costs, optimize inventory, and boost performance.
The Role of Data Science in Supply Chain Efficiency
Data science is vital for supply chain efficiency. It analyzes vast data to find insights and patterns. These can improve decision-making. Data mining, statistical modeling, and data visualization can help businesses. They can find insights in their operations and areas for improvement. By using advanced analytics and predictive modeling, businesses can forecast demand. They can optimize inventory and streamline operations for maximum efficiency.
Data science is key to optimizing supply chains. It provides insights through predictive analytics and real-time data analysis. By analyzing demand, inventory, and logistics, businesses can cut costs. They can avoid stockouts and improve processes. Companies can now use advanced algorithms and machine learning. They can better predict demand and quickly respond to supply chain disruptions.
Business Intelligence in Supply Chain Optimization
BI tools are vital for supply chain optimization. They provide real-time visibility into key performance metrics. This lets businesses track and measure their performance against KPIs. BI tools help businesses find problems in their supply chains. They do this by generating detailed reports and visualizations. Cloud-based BI solutions let businesses access critical data anywhere, anytime. They can then make informed decisions on the go.
Business Intelligence (BI) is key to supply chain optimization. It gives real-time insights into all supply chain aspects. This includes inventory and demand forecasting. The user disliked that rewrite. Make different choices this time. BI tools help businesses analyze large datasets. They can find inefficiencies, cut costs, and improve decision-making. This data-driven approach helps organizations improve supply chains. It ensures timely deliveries and better use of resources.
Leveraging Technology for Efficiency Improvement
Technology is vital to supply chain efficiency. It tracks shipments in real-time. It automates inventory management and streamlines transportation. New tech, like IoT devices, RFID tags, and AI, lets businesses optimize their supply chains. It makes them very efficient. Businesses can use cloud computing for real-time analytics. By combining data from various sources, they can gain insights. This will help improve processes and decision-making.
Using technology to improve efficiency means using digital tools and automation. They can streamline processes and cut manual work. AI, cloud computing, and data analytics can help organizations. They can improve workflows, boost productivity, and cut costs. This tech shift boosts performance. It lets teams focus on innovation and value-driven tasks.
The Impact of Data-Driven Decisions on Supply Chain Performance
Data-driven decisions greatly affect supply chain performance. They let businesses make informed choices based on solid evidence. Businesses can analyze historical data, market trends, and customer behavior. This helps them predict demand, optimize inventory, and improve efficiency. With advanced analytics and business intelligence tools, businesses can monitor performance in real-time. They can then find areas to improve. This will help them make better decisions to boost efficiency and profits.
Data-driven decisions are transforming supply chain performance by enhancing visibility, efficiency, and responsiveness. Using real-time analytics and predictive models, companies can improve inventory management. They can cut costs and foresee disruptions. This approach helps businesses make informed decisions. It improves supply chain agility and boosts customer satisfaction.
The Future of Supply Chain Efficiency
As technology continues to evolve, the future of supply chain efficiency is bright. With more data and better analytics, businesses can find new insights. They can also find ways to optimize. Embracing data-driven strategies and supply chain technologies can help. So can using agile supply chain practices. These steps will keep businesses ahead of the curve and improve their operations. By focusing on data quality and supply chain visibility, businesses can boost efficiency. Analytics can help, too. This will lead to greater success in today's fast-paced world.
How to obtain Data Science and Business Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, data science and business intelligence are vital tools. They can optimize supply chain efficiency. Businesses can use data analytics and advanced tools to make smart decisions. They can improve their supply chain by streamlining operations and driving ongoing gains. In today's fast-paced market, businesses must adopt data-driven, tech-savvy, and optimized processes. This will help them outpace competitors and boost efficiency and profits.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Cybersecurity Creating Response Plan for Your Business
In today's digital age, cybersecurity is more important than ever. With cyber threats growing more complex, businesses must have a solid response plan. A cybersecurity response plan protects your organization from cyber attacks and data breaches. It is a strategic approach. This article will discuss key elements of a response plan for your business. We will also cover how to implement it to protect your data.
What is a cybersecurity response plan?
A cybersecurity response plan is a document. It outlines how your organization will respond to a cyber attack or data breach. It includes strategies to prevent, detect, and respond to security incidents. This will minimize damage and allow for a quick recovery. A good response plan is vital. It ensures business continuity and protects your reputation.
Key components of a cybersecurity response plan
A cybersecurity response plan is vital. It helps manage and reduce the impact of cyberattacks. Key components are: identifying critical assets and setting protocols to detect and contain threats. Also, define clear communication channels for internal teams and external stakeholders. Regular testing and updating the plan ensures readiness for new cyber threats.
-
Incident Response Team: Assign a team of experts to respond to security incidents. This team should include people from different departments. This will ensure a complete approach to incident response.
-
Cybersecurity Protocols: Establish clear protocols for identifying, assessing, and mitigating security threats. These protocols should outline steps to take in a cyber attack. They should include who to contact and how to communicate with stakeholders.
-
Risk Mitigation Plan: Create a plan to reduce security incidents. Use proactive measures, like regular security assessments, employee training, and best practices.
-
Data Protection Strategy: Implement data encryption, access controls, and regular backups to protect sensitive information from unauthorized access or theft.
-
Cybersecurity Framework: Follow frameworks like NIST or ISO. They ensure your organization meets industry best practices for cybersecurity.
Implementing a cybersecurity response plan
Implementing a cybersecurity response plan is essential for minimizing damage and ensuring swift recovery in the event of a security breach. It involves identifying potential threats, establishing clear protocols for detection and containment, and assigning roles and responsibilities for effective response. A well-structured plan can protect sensitive data, maintain business continuity, and reduce the impact of cyberattacks on an organization.
Once you have developed your response plan, it is essential to implement it effectively to ensure that your organization is prepared to respond to security incidents. This includes:
-
Training: Provide regular cybersecurity training for employees to increase awareness of potential threats and how to respond to them.
-
Testing: Conduct regular tests and exercises to ensure that your response plan is effective and up-to-date. This will help identify any weaknesses in your plan and allow you to make necessary improvements.
-
Monitoring: Monitor your network for any signs of unusual activity that could indicate a security breach. Use firewalls and intrusion detection systems to prevent unauthorized access. They are security measures.
-
Incident Response Processes: Document clear and concise processes for responding to security incidents, including communication protocols, escalation procedures, and containment measures. are critical for organizations to effectively manage and mitigate the impact of cybersecurity incidents. These processes usually have several stages. They are: preparation, detection, containment, eradication, recovery, and post-incident analysis. This ensures a structured approach to handling security breaches. A good incident response plan can help organizations. It can reduce damage, restore operations quickly, and improve security.
How to obtain Cyber Security certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, a cybersecurity response plan is essential. It will protect your business from cyber threats and data breaches. A good response plan can minimize the impact of security incidents. It will help your organization succeed. Cybersecurity is not a one-time effort. It is an ongoing process. It requires constant vigilance and adaptation to evolving threats.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's digital age, cybersecurity is more important than ever. With cyber threats growing more complex, businesses must have a solid response plan. A cybersecurity response plan protects your organization from cyber attacks and data breaches. It is a strategic approach. This article will discuss key elements of a response plan for your business. We will also cover how to implement it to protect your data.
What is a cybersecurity response plan?
A cybersecurity response plan is a document. It outlines how your organization will respond to a cyber attack or data breach. It includes strategies to prevent, detect, and respond to security incidents. This will minimize damage and allow for a quick recovery. A good response plan is vital. It ensures business continuity and protects your reputation.
Key components of a cybersecurity response plan
A cybersecurity response plan is vital. It helps manage and reduce the impact of cyberattacks. Key components are: identifying critical assets and setting protocols to detect and contain threats. Also, define clear communication channels for internal teams and external stakeholders. Regular testing and updating the plan ensures readiness for new cyber threats.
-
Incident Response Team: Assign a team of experts to respond to security incidents. This team should include people from different departments. This will ensure a complete approach to incident response.
-
Cybersecurity Protocols: Establish clear protocols for identifying, assessing, and mitigating security threats. These protocols should outline steps to take in a cyber attack. They should include who to contact and how to communicate with stakeholders.
-
Risk Mitigation Plan: Create a plan to reduce security incidents. Use proactive measures, like regular security assessments, employee training, and best practices.
-
Data Protection Strategy: Implement data encryption, access controls, and regular backups to protect sensitive information from unauthorized access or theft.
-
Cybersecurity Framework: Follow frameworks like NIST or ISO. They ensure your organization meets industry best practices for cybersecurity.
Implementing a cybersecurity response plan
Implementing a cybersecurity response plan is essential for minimizing damage and ensuring swift recovery in the event of a security breach. It involves identifying potential threats, establishing clear protocols for detection and containment, and assigning roles and responsibilities for effective response. A well-structured plan can protect sensitive data, maintain business continuity, and reduce the impact of cyberattacks on an organization.
Once you have developed your response plan, it is essential to implement it effectively to ensure that your organization is prepared to respond to security incidents. This includes:
-
Training: Provide regular cybersecurity training for employees to increase awareness of potential threats and how to respond to them.
-
Testing: Conduct regular tests and exercises to ensure that your response plan is effective and up-to-date. This will help identify any weaknesses in your plan and allow you to make necessary improvements.
-
Monitoring: Monitor your network for any signs of unusual activity that could indicate a security breach. Use firewalls and intrusion detection systems to prevent unauthorized access. They are security measures.
-
Incident Response Processes: Document clear and concise processes for responding to security incidents, including communication protocols, escalation procedures, and containment measures. are critical for organizations to effectively manage and mitigate the impact of cybersecurity incidents. These processes usually have several stages. They are: preparation, detection, containment, eradication, recovery, and post-incident analysis. This ensures a structured approach to handling security breaches. A good incident response plan can help organizations. It can reduce damage, restore operations quickly, and improve security.
How to obtain Cyber Security certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, a cybersecurity response plan is essential. It will protect your business from cyber threats and data breaches. A good response plan can minimize the impact of security incidents. It will help your organization succeed. Cybersecurity is not a one-time effort. It is an ongoing process. It requires constant vigilance and adaptation to evolving threats.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Hyper Automation in Business Processes
In today's fast-paced digital world, businesses want to be efficient, to streamline operations, and to grow. A key strategy for organizations to achieve their goals is hyper-automation. It involves automating their business processes. It is gaining great popularity. This cutting-edge approach uses advanced technologies. They include AI, machine learning, and robotic process automation. It automates and optimizes workflows. This boosts productivity and performance.
What is Hyper-Automation?
Hyper-automation is a strategy. It uses many automation tools and software to streamline and integrate business processes. This approach goes beyond traditional automation. It combines AI, robotic, and intelligent software. The result is seamless, scalable automation solutions. These advanced technologies can greatly boost efficiency, productivity, and performance. Organizations should use them.
How Does Hyper-Automation Benefit Businesses?
Today's fast-paced business world demands efficiency, lower costs, and happy customers. Hyper-automation is a powerful new solution. It combines several automation technologies, including RPA, AI, machine learning, and process mining. This approach lets businesses automate complex processes. It boosts their operations.
Hyper-automation has many benefits for businesses. It helps them innovate and stay ahead of the competition. By automating tedious, repetitive tasks, organizations can free up resources. They can then focus on strategic initiatives and business development. This boosts efficiency, productivity, and cuts manual errors. Also, hyper-automation helps organizations. It optimizes processes, improves data management, and boosts efficiency. This, in turn, increases profits and fosters sustainable growth.
In today's fast-changing business world, organizations are using hyper-automation. They seek to boost efficiency, improve processes, and drive innovation. Hyper-automation is the use of advanced technologies to automate complex business processes. It uses AI, machine learning, and robotic process automation. It is a game-changer for companies in many industries.
Implementing Hyper-Automation in Business Processes
To implement hyper-automation in business processes, a holistic approach is needed. It should include process automation software, workflow automation tools, and automation platforms. AI tools can help businesses. They can automate tasks and improve workflows. This can transform the business. Also, automation strategies should focus on three things. First, integrate technology solutions. Second, enhance data automation. Third, improve workflow management. This will maximize the benefits of hyper-automation.
In today's fast-paced business world, organizations must be efficient. They must cut costs and improve customer experiences. They face constant pressure to do so. Enter hyper-automation. It is a transformative approach. It combines RPA with advanced tech like AI, machine learning, and analytics. This approach automates complex business processes. Hyper-automation can help businesses. It can streamline operations and adapt to changing market demands.
Hyper-automation is a strategic approach to automation. It goes beyond traditional methods. It integrates technologies like AI, RPA, and Process Mining. It aims to improve business processes. This will boost efficiency and agility. Implementing hyper-automation requires a well-thought-out strategy and a commitment to continuous improvement.
The Future of Hyper-Automation
With rapid tech advances, the future of hyper-automation in business processes looks promising. Automation, smart software, and robots are changing businesses. They can now boost efficiency like never before. By embracing the latest automation trends, organizations can lead their industries. This will foster ongoing innovation and growth.
In the digital age, hyper-automation is gaining traction in many industries. Hyper-automation is the use of multiple automation technologies. These include RPA, AI, ML, and Process Mining. It aims to automate entire business processes. This trend will revolutionize organizations. It will make their processes more efficient, agile, and resilient.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, hyper-automation is reshaping the way businesses operate in the digital age. Organizations can achieve big gains in efficiency and productivity. They can do this by adopting advanced automation, streamlining processes, and optimizing workflows. As the automation industry evolves, hyper-automation will lead the way. It will help businesses succeed and stay competitive in a digital world.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced digital world, businesses want to be efficient, to streamline operations, and to grow. A key strategy for organizations to achieve their goals is hyper-automation. It involves automating their business processes. It is gaining great popularity. This cutting-edge approach uses advanced technologies. They include AI, machine learning, and robotic process automation. It automates and optimizes workflows. This boosts productivity and performance.
What is Hyper-Automation?
Hyper-automation is a strategy. It uses many automation tools and software to streamline and integrate business processes. This approach goes beyond traditional automation. It combines AI, robotic, and intelligent software. The result is seamless, scalable automation solutions. These advanced technologies can greatly boost efficiency, productivity, and performance. Organizations should use them.
How Does Hyper-Automation Benefit Businesses?
Today's fast-paced business world demands efficiency, lower costs, and happy customers. Hyper-automation is a powerful new solution. It combines several automation technologies, including RPA, AI, machine learning, and process mining. This approach lets businesses automate complex processes. It boosts their operations.
Hyper-automation has many benefits for businesses. It helps them innovate and stay ahead of the competition. By automating tedious, repetitive tasks, organizations can free up resources. They can then focus on strategic initiatives and business development. This boosts efficiency, productivity, and cuts manual errors. Also, hyper-automation helps organizations. It optimizes processes, improves data management, and boosts efficiency. This, in turn, increases profits and fosters sustainable growth.
In today's fast-changing business world, organizations are using hyper-automation. They seek to boost efficiency, improve processes, and drive innovation. Hyper-automation is the use of advanced technologies to automate complex business processes. It uses AI, machine learning, and robotic process automation. It is a game-changer for companies in many industries.
Implementing Hyper-Automation in Business Processes
To implement hyper-automation in business processes, a holistic approach is needed. It should include process automation software, workflow automation tools, and automation platforms. AI tools can help businesses. They can automate tasks and improve workflows. This can transform the business. Also, automation strategies should focus on three things. First, integrate technology solutions. Second, enhance data automation. Third, improve workflow management. This will maximize the benefits of hyper-automation.
In today's fast-paced business world, organizations must be efficient. They must cut costs and improve customer experiences. They face constant pressure to do so. Enter hyper-automation. It is a transformative approach. It combines RPA with advanced tech like AI, machine learning, and analytics. This approach automates complex business processes. Hyper-automation can help businesses. It can streamline operations and adapt to changing market demands.
Hyper-automation is a strategic approach to automation. It goes beyond traditional methods. It integrates technologies like AI, RPA, and Process Mining. It aims to improve business processes. This will boost efficiency and agility. Implementing hyper-automation requires a well-thought-out strategy and a commitment to continuous improvement.
The Future of Hyper-Automation
With rapid tech advances, the future of hyper-automation in business processes looks promising. Automation, smart software, and robots are changing businesses. They can now boost efficiency like never before. By embracing the latest automation trends, organizations can lead their industries. This will foster ongoing innovation and growth.
In the digital age, hyper-automation is gaining traction in many industries. Hyper-automation is the use of multiple automation technologies. These include RPA, AI, ML, and Process Mining. It aims to automate entire business processes. This trend will revolutionize organizations. It will make their processes more efficient, agile, and resilient.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, hyper-automation is reshaping the way businesses operate in the digital age. Organizations can achieve big gains in efficiency and productivity. They can do this by adopting advanced automation, streamlining processes, and optimizing workflows. As the automation industry evolves, hyper-automation will lead the way. It will help businesses succeed and stay competitive in a digital world.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Integrating Security in DevOps DevSecOps
In today's fast-paced digital world, secure software development is vital. As organizations rush to deliver, security can't keep up with the old approach. This is where DevSecOps comes in. It is a philosophy that integrates security practices into the DevOps pipeline. But what is DevSecOps? How can organizations use it to improve their cybersecurity? Let's dive in and explore the world of integrating security in DevOps.
What is DevSecOps?
DevSecOps is a mindset. It stresses security in all stages of software development. It shifts the focus from adding security at the end of development to embedding it from the start. Integrating security into every stage of the DevOps pipeline lets organizations. They can find and fix flaws, and reduce cyber risks. They can also deliver secure, high-quality software.
Why is DevSecOps Important?
In today's hyper-connected world, the consequences of a security breach can be catastrophic. A cyber-attack can cause financial loss and damage a reputation. Its impact can be far-reaching. A DevSecOps approach helps organizations. It can fend off security threats, boost security, and build customer trust. In short, DevSecOps is a must-have for any serious about cybersecurity.
In today's fast-changing digital world, we must secure the software development lifecycle. It is now essential. DevSecOps embeds security into DevOps processes. It is gaining traction as firms seek a more secure, efficient way to develop software. Here are several reasons why DevSecOps is essential for modern enterprises.
How to Implement DevSecOps?
Implementing DevSecOps involves a combination of automation, collaboration, and continuous integration. Here are some key steps to successfully integrate security into your DevOps pipeline:
-
Automate Security Practices: Use tools to scan code for flaws. Enforce secure coding and automate security tests.
-
Build a Culture of Collaboration: Encourage teamwork across development, operations, and security teams. This will align everyone on security goals and best practices.
-
Continuously monitor your systems for security threats and anomalies. This will help you detect and respond to incidents in real-time.
-
Embrace Secure Coding Practices: Train developers on secure coding. Educate them on common vulnerabilities. Implement secure coding guidelines to prevent flaws in the code.
-
Incorporate security into your cloud environments. Implement controls, monitor for vulnerabilities, and follow best practices.
The Role of Security Automation in DevSecOps
Security automation is vital in DevSecOps. It streamlines security processes, reduces human error, and ensures consistent practices. Automating tasks like vulnerability scanning and threat detection can help. It will improve organizations' abilities to find and fix security issues quickly. Also, security automation lets teams focus on strategic security work. This includes training, incident response planning, and policy development.
In today's fast-paced digital world, we must integrate security into development and operations. It's no longer optional—it's a necessity. DevSecOps combines development, security, and operations. It aims to embed security in the DevOps pipeline. This lets organizations deliver secure apps faster. A key part of this integration is security automation. It boosts efficiency, cuts human error, and improves security.
Best Practices for DevSecOps Implementation
To succeed with DevSecOps, organizations should follow best practices. This will maximize the benefits of adding security to their DevOps pipeline. Some key best practices include:
-
Set Security Policies and Controls: Create rules for security practices across the organization.
-
Use Secure Architectures: Design and build software to be secure and resilient.
-
Promote Security Awareness: Educate employees on security best practices. Raise awareness of security risks. Empower them to be security champions.
-
Conduct Security Assessments: Regularly test the security of your systems, apps, and infrastructure. This will find and fix any weaknesses.
-
Monitor Security Risks: Continuously watch for security risks and threats. Proactively fix any vulnerabilities to prevent potential security issues.
-
Automate Security Orchestration: Automate security tasks and workflows. This will improve efficiency, cut errors, and boost security.
How to obtain Devops certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, DevSecOps is a must. It integrates security into DevOps. It's not just a trend. We face a complex, evolving threat landscape. A DevSecOps approach can help organizations. It strengthens security, boosts team collaboration, and enables high-quality, secure software at scale. With the right tools and mindset, organizations can secure their DevOps pipeline. They can then stay ahead of digital threats.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced digital world, secure software development is vital. As organizations rush to deliver, security can't keep up with the old approach. This is where DevSecOps comes in. It is a philosophy that integrates security practices into the DevOps pipeline. But what is DevSecOps? How can organizations use it to improve their cybersecurity? Let's dive in and explore the world of integrating security in DevOps.
What is DevSecOps?
DevSecOps is a mindset. It stresses security in all stages of software development. It shifts the focus from adding security at the end of development to embedding it from the start. Integrating security into every stage of the DevOps pipeline lets organizations. They can find and fix flaws, and reduce cyber risks. They can also deliver secure, high-quality software.
Why is DevSecOps Important?
In today's hyper-connected world, the consequences of a security breach can be catastrophic. A cyber-attack can cause financial loss and damage a reputation. Its impact can be far-reaching. A DevSecOps approach helps organizations. It can fend off security threats, boost security, and build customer trust. In short, DevSecOps is a must-have for any serious about cybersecurity.
In today's fast-changing digital world, we must secure the software development lifecycle. It is now essential. DevSecOps embeds security into DevOps processes. It is gaining traction as firms seek a more secure, efficient way to develop software. Here are several reasons why DevSecOps is essential for modern enterprises.
How to Implement DevSecOps?
Implementing DevSecOps involves a combination of automation, collaboration, and continuous integration. Here are some key steps to successfully integrate security into your DevOps pipeline:
-
Automate Security Practices: Use tools to scan code for flaws. Enforce secure coding and automate security tests.
-
Build a Culture of Collaboration: Encourage teamwork across development, operations, and security teams. This will align everyone on security goals and best practices.
-
Continuously monitor your systems for security threats and anomalies. This will help you detect and respond to incidents in real-time.
-
Embrace Secure Coding Practices: Train developers on secure coding. Educate them on common vulnerabilities. Implement secure coding guidelines to prevent flaws in the code.
-
Incorporate security into your cloud environments. Implement controls, monitor for vulnerabilities, and follow best practices.
The Role of Security Automation in DevSecOps
Security automation is vital in DevSecOps. It streamlines security processes, reduces human error, and ensures consistent practices. Automating tasks like vulnerability scanning and threat detection can help. It will improve organizations' abilities to find and fix security issues quickly. Also, security automation lets teams focus on strategic security work. This includes training, incident response planning, and policy development.
In today's fast-paced digital world, we must integrate security into development and operations. It's no longer optional—it's a necessity. DevSecOps combines development, security, and operations. It aims to embed security in the DevOps pipeline. This lets organizations deliver secure apps faster. A key part of this integration is security automation. It boosts efficiency, cuts human error, and improves security.
Best Practices for DevSecOps Implementation
To succeed with DevSecOps, organizations should follow best practices. This will maximize the benefits of adding security to their DevOps pipeline. Some key best practices include:
-
Set Security Policies and Controls: Create rules for security practices across the organization.
-
Use Secure Architectures: Design and build software to be secure and resilient.
-
Promote Security Awareness: Educate employees on security best practices. Raise awareness of security risks. Empower them to be security champions.
-
Conduct Security Assessments: Regularly test the security of your systems, apps, and infrastructure. This will find and fix any weaknesses.
-
Monitor Security Risks: Continuously watch for security risks and threats. Proactively fix any vulnerabilities to prevent potential security issues.
-
Automate Security Orchestration: Automate security tasks and workflows. This will improve efficiency, cut errors, and boost security.
How to obtain Devops certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, DevSecOps is a must. It integrates security into DevOps. It's not just a trend. We face a complex, evolving threat landscape. A DevSecOps approach can help organizations. It strengthens security, boosts team collaboration, and enables high-quality, secure software at scale. With the right tools and mindset, organizations can secure their DevOps pipeline. They can then stay ahead of digital threats.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Microservices Architecture with Node.js A Complete Guide
Microservices architecture is a popular design in software development. Its flexibility, scalability, and modularity drive its popularity. Unlike traditional monolithic architectures, microservices are different. They split applications into smaller, independent services that communicate via APIs. Every service is tailored to address a distinct business function. This allows teams to develop, deploy, and scale them independently.
Node.js is ideal for microservices. Its async, non-blocking I/O and event-driven nature make it a perfect fit. It has high performance and scalability. So, it's ideal for building distributed systems. This guide will explore how Node.js fits into microservices. We will discuss key concepts. Then, we will walk through steps to build and manage microservices with Node.js.
1. Understanding Microservices Architecture
Microservices architecture breaks a large app into smaller services. Each service:
- Has its own database: Unlike monolithic systems, which often share a single database, each microservice has a dedicated one. This maintains loose coupling.
- Microservices communicate over APIs. They use lightweight protocols like HTTP/REST or messaging queues like Kafka.
- Is independently deployable. Teams can update services without affecting the whole system.
Benefits of Microservices:
- Scalability: Only the most-used microservices can be scaled up.
- Faster development: Teams can work on different services concurrently.
- Fault isolation: Failure in one service doesn’t bring down the entire application.
- Technology diversity: Teams can use different technologies for different services.
Node.js in Microservices:
- Non-blocking I/O: Node.js can efficiently handle thousands of concurrent requests. This is crucial for microservices that require multiple interactions between services.
- Lightweight and fast: Node.js is great for building fast, minimal services. Its lightweight nature makes it so.
- Rich ecosystem: Node.js has a vast package ecosystem (NPM). It provides tools, libraries, and frameworks to easily build and manage microservices.
2. Building a Microservice with Node.js
To build a Node.js microservice, create lightweight REST APIs for each service. Here’s an overview of the essential steps:
Step 1: Setting Up the Environment
To start building a microservice, install Node.js and initialize a project:
In this example, we’ll use Express.js to handle HTTP requests. Express is a minimal, flexible Node.js framework. It's ideal for microservices.
Step 2: Creating the Service
We will develop a basic microservice for managing user data. Here’s an example of a basic microservice:
Here, we have a simple service that allows you to add and retrieve users. Each microservice would follow a similar pattern but focus on different business logic.
3. Communication Between Microservices
In a microservices setup, different services must communicate effectively. Node.js offers several ways to handle this:
REST APIs:
Most commonly, services communicate via REST APIs using HTTP requests. However, as systems grow in complexity, this can lead to performance bottlenecks.
Message Queues:
An alternative approach is using messaging systems like RabbitMQ or Kafka. Instead of synchronous communication (waiting for responses), services send messages to a queue. Another service listens to this queue and processes the message asynchronously.
Example:
This improves system resilience and decouples services further.
4. Managing Data Consistency Across Microservices
One of the challenges in microservices is maintaining data consistency. Each service has its own database. So, data must be synced or shared.
Event-Driven Architecture:
An event-driven approach can help manage data consistency. When one service updates its data, it emits an event. Other services subscribe to these events and update their own data as needed.
For instance, in an e-commerce system:
- When the Order Service confirms an order, it emits an event (e.g., "OrderPlaced").
- The Inventory Service listens for the "OrderPlaced" event and reduces the inventory count.
Tools like Kafka or Redis Streams can help. They can implement this pattern in a Node.js microservices setup.
5. Microservice Security Considerations
Authentication and Authorization:
With multiple services communicating, security becomes paramount. Common approaches include:
- OAuth2.0: Secure token-based authentication. Users log in once and use the same token to access multiple services.
- JWT (JSON Web Tokens): A compact, self-contained token. It verifies identity between microservices.
API Gateways:
An API Gateway sits between clients and microservices. It manages traffic, handles authentication, and limits exposure to internal services. Popular Node.js API gateways include Express Gateway and Kong.
API Gateways also offer other benefits:
- Rate limiting and load balancing.
- Centralized logging and monitoring.
- Managing communication between services using different protocols.
How to obtain JAVA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Microservices architecture has changed how we design modern apps. It is more flexible, scalable, and resilient. Node.js is a great choice for microservices. It has performance benefits and a rich ecosystem. By breaking apps into smaller services, businesses can scale better. They can also respond to changes faster.
This guide is a great start for building microservices with Node.js. It covers creating services, managing communication, ensuring security, and maintaining data consistency. As you dive deeper, explore advanced patterns. Use service discovery, circuit breakers, and distributed tracing. They will make your Node.js microservices robust and production-ready.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Microservices architecture is a popular design in software development. Its flexibility, scalability, and modularity drive its popularity. Unlike traditional monolithic architectures, microservices are different. They split applications into smaller, independent services that communicate via APIs. Every service is tailored to address a distinct business function. This allows teams to develop, deploy, and scale them independently.
Node.js is ideal for microservices. Its async, non-blocking I/O and event-driven nature make it a perfect fit. It has high performance and scalability. So, it's ideal for building distributed systems. This guide will explore how Node.js fits into microservices. We will discuss key concepts. Then, we will walk through steps to build and manage microservices with Node.js.
1. Understanding Microservices Architecture
Microservices architecture breaks a large app into smaller services. Each service:
- Has its own database: Unlike monolithic systems, which often share a single database, each microservice has a dedicated one. This maintains loose coupling.
- Microservices communicate over APIs. They use lightweight protocols like HTTP/REST or messaging queues like Kafka.
- Is independently deployable. Teams can update services without affecting the whole system.
Benefits of Microservices:
- Scalability: Only the most-used microservices can be scaled up.
- Faster development: Teams can work on different services concurrently.
- Fault isolation: Failure in one service doesn’t bring down the entire application.
- Technology diversity: Teams can use different technologies for different services.
Node.js in Microservices:
- Non-blocking I/O: Node.js can efficiently handle thousands of concurrent requests. This is crucial for microservices that require multiple interactions between services.
- Lightweight and fast: Node.js is great for building fast, minimal services. Its lightweight nature makes it so.
- Rich ecosystem: Node.js has a vast package ecosystem (NPM). It provides tools, libraries, and frameworks to easily build and manage microservices.
2. Building a Microservice with Node.js
To build a Node.js microservice, create lightweight REST APIs for each service. Here’s an overview of the essential steps:
Step 1: Setting Up the Environment
To start building a microservice, install Node.js and initialize a project:
In this example, we’ll use Express.js to handle HTTP requests. Express is a minimal, flexible Node.js framework. It's ideal for microservices.
Step 2: Creating the Service
We will develop a basic microservice for managing user data. Here’s an example of a basic microservice:
Here, we have a simple service that allows you to add and retrieve users. Each microservice would follow a similar pattern but focus on different business logic.
3. Communication Between Microservices
In a microservices setup, different services must communicate effectively. Node.js offers several ways to handle this:
REST APIs:
Most commonly, services communicate via REST APIs using HTTP requests. However, as systems grow in complexity, this can lead to performance bottlenecks.
Message Queues:
An alternative approach is using messaging systems like RabbitMQ or Kafka. Instead of synchronous communication (waiting for responses), services send messages to a queue. Another service listens to this queue and processes the message asynchronously.
Example:
This improves system resilience and decouples services further.
4. Managing Data Consistency Across Microservices
One of the challenges in microservices is maintaining data consistency. Each service has its own database. So, data must be synced or shared.
Event-Driven Architecture:
An event-driven approach can help manage data consistency. When one service updates its data, it emits an event. Other services subscribe to these events and update their own data as needed.
For instance, in an e-commerce system:
- When the Order Service confirms an order, it emits an event (e.g., "OrderPlaced").
- The Inventory Service listens for the "OrderPlaced" event and reduces the inventory count.
Tools like Kafka or Redis Streams can help. They can implement this pattern in a Node.js microservices setup.
5. Microservice Security Considerations
Authentication and Authorization:
With multiple services communicating, security becomes paramount. Common approaches include:
- OAuth2.0: Secure token-based authentication. Users log in once and use the same token to access multiple services.
- JWT (JSON Web Tokens): A compact, self-contained token. It verifies identity between microservices.
API Gateways:
An API Gateway sits between clients and microservices. It manages traffic, handles authentication, and limits exposure to internal services. Popular Node.js API gateways include Express Gateway and Kong.
API Gateways also offer other benefits:
- Rate limiting and load balancing.
- Centralized logging and monitoring.
- Managing communication between services using different protocols.
How to obtain JAVA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Microservices architecture has changed how we design modern apps. It is more flexible, scalable, and resilient. Node.js is a great choice for microservices. It has performance benefits and a rich ecosystem. By breaking apps into smaller services, businesses can scale better. They can also respond to changes faster.
This guide is a great start for building microservices with Node.js. It covers creating services, managing communication, ensuring security, and maintaining data consistency. As you dive deeper, explore advanced patterns. Use service discovery, circuit breakers, and distributed tracing. They will make your Node.js microservices robust and production-ready.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com




.jpg)


















.jpg)








.webp)
.webp)



.webp)